Patents
Literature
52 results about "Trusted components" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
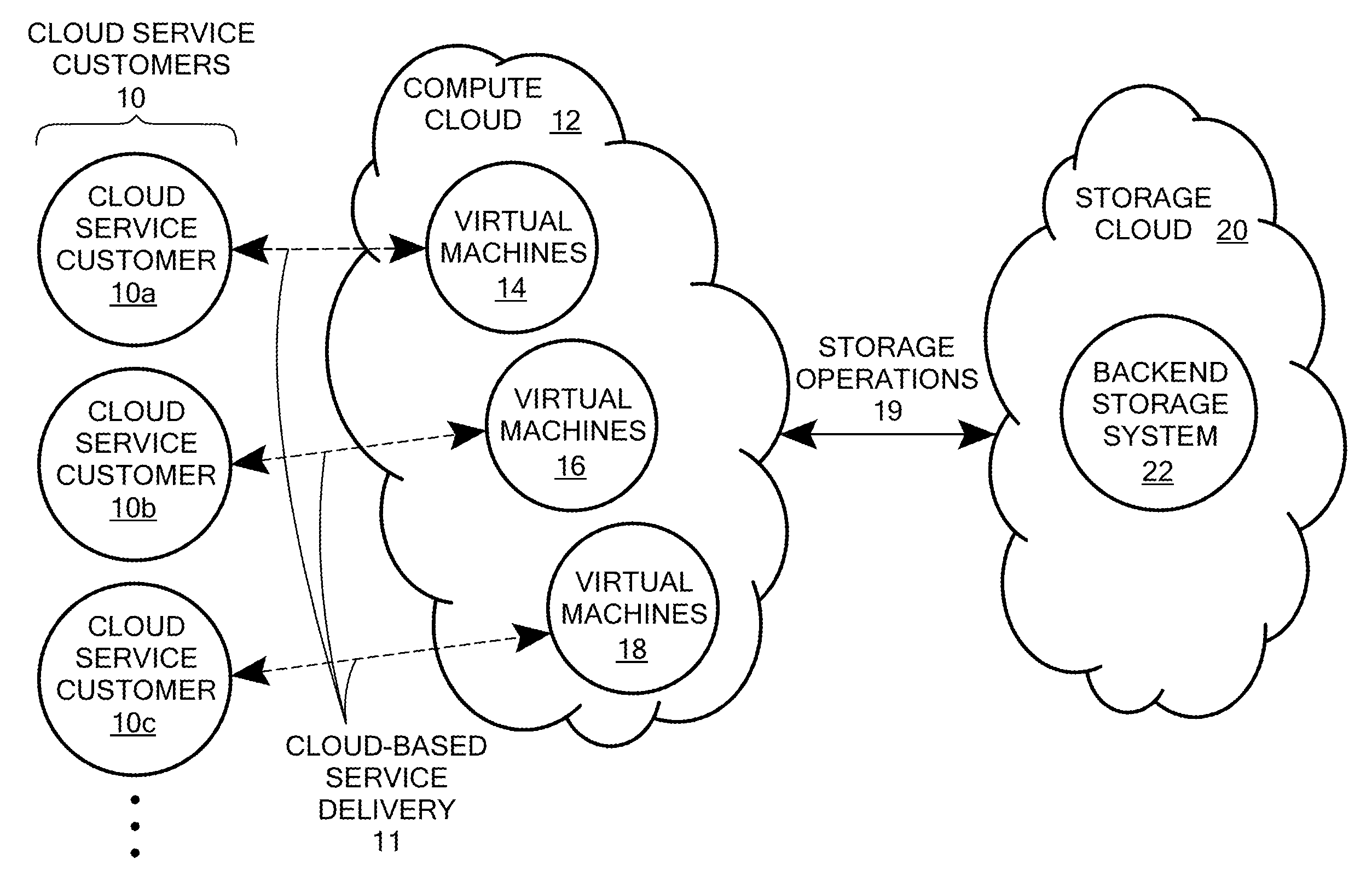
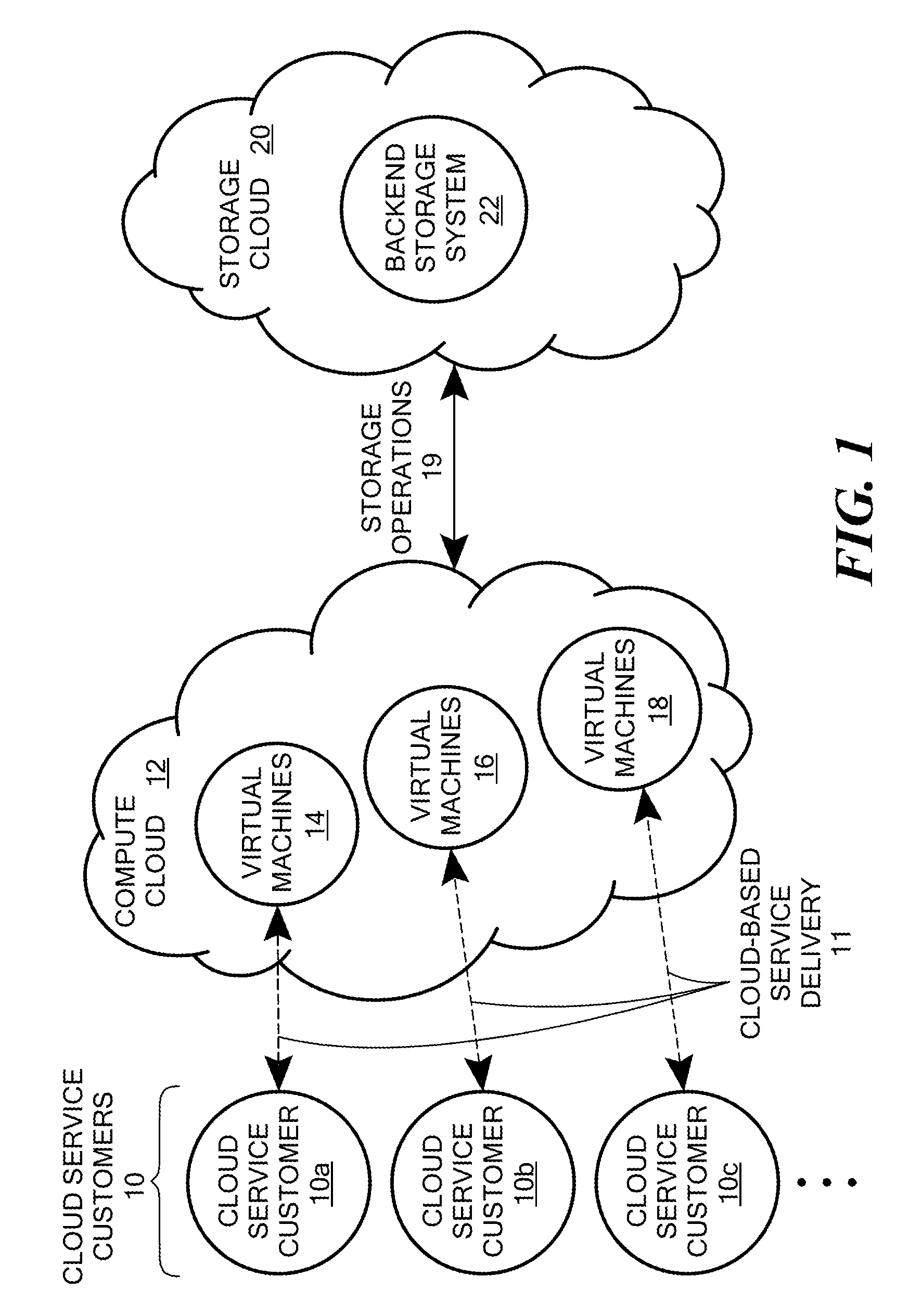
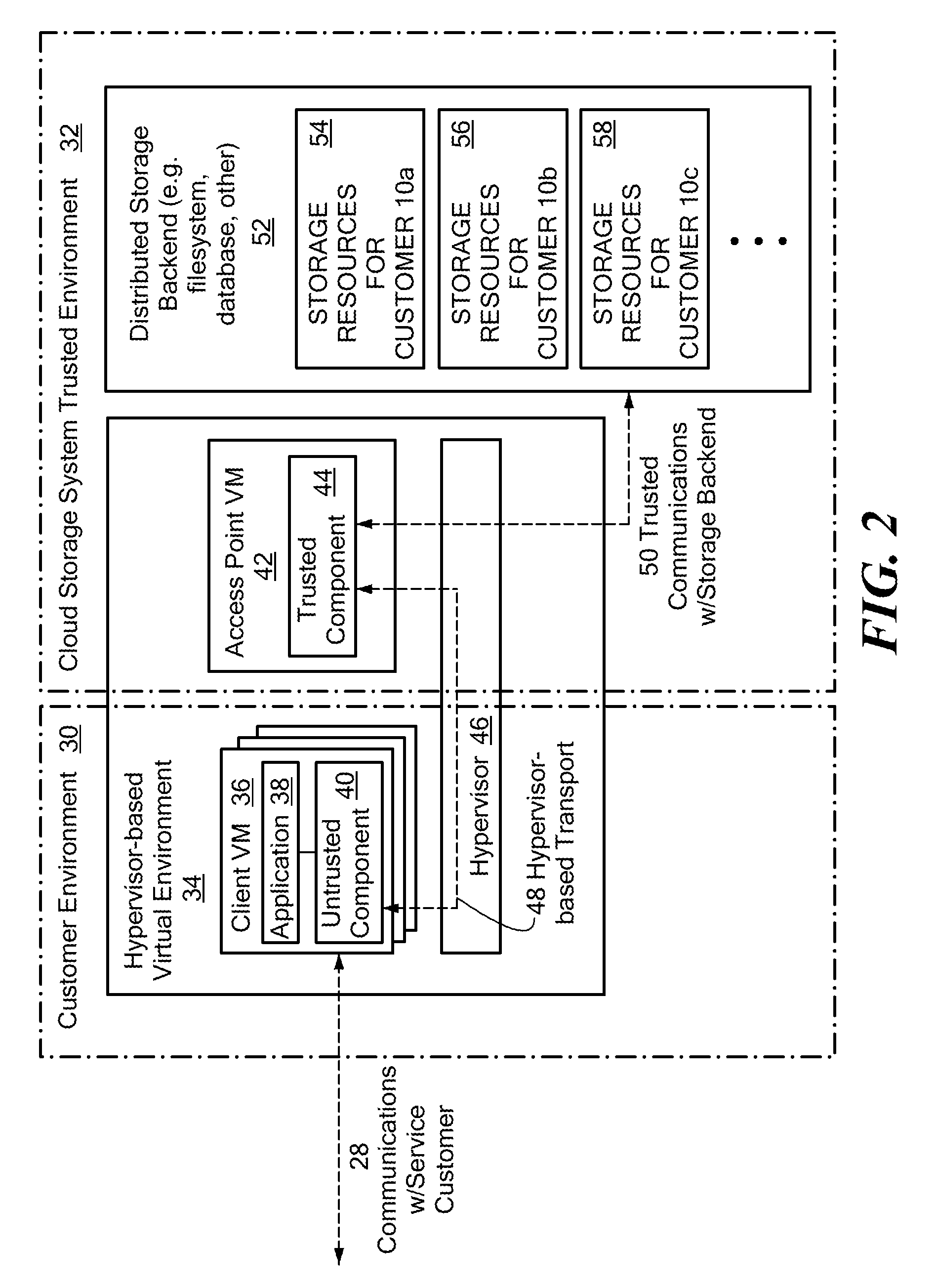
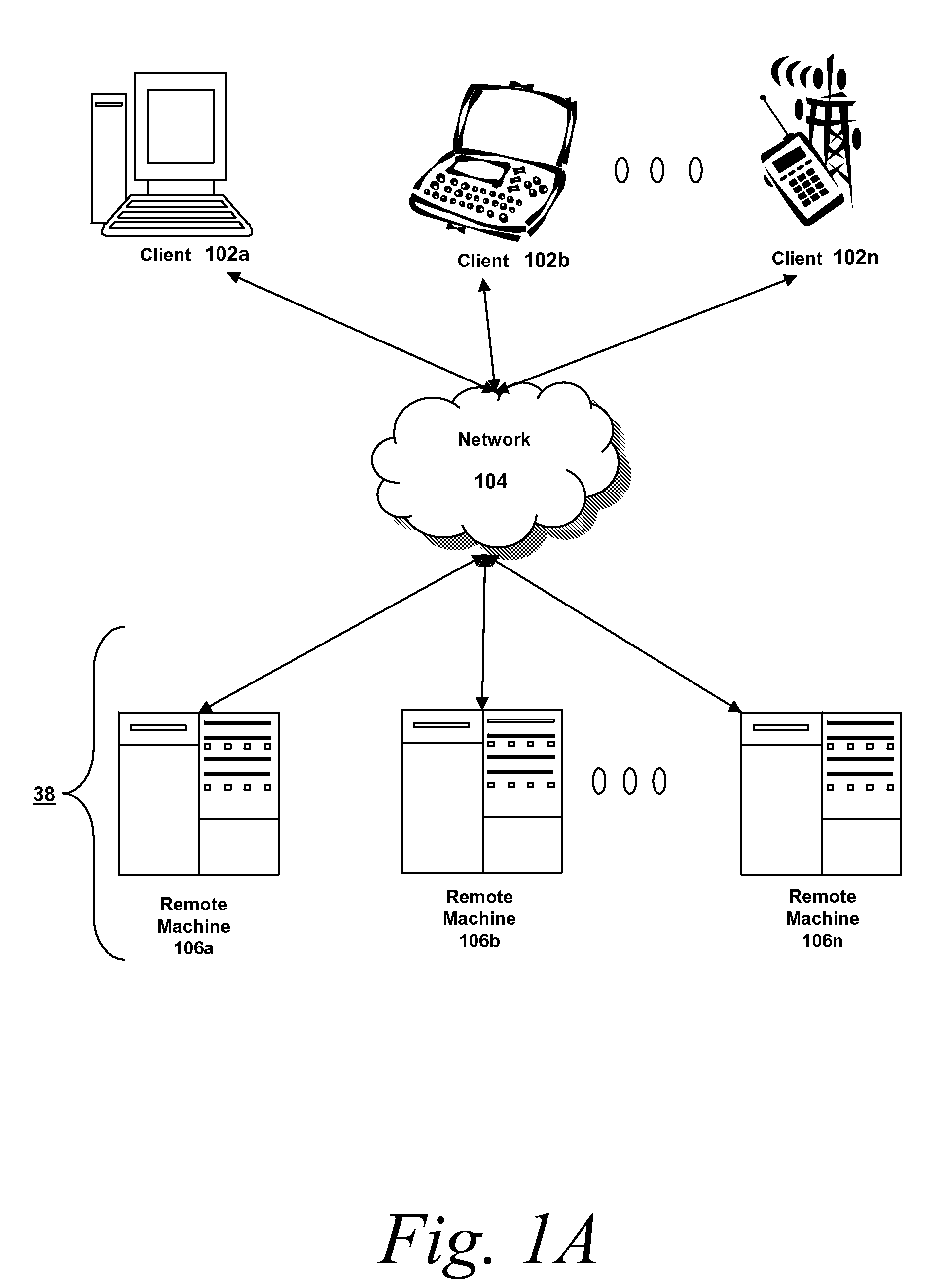
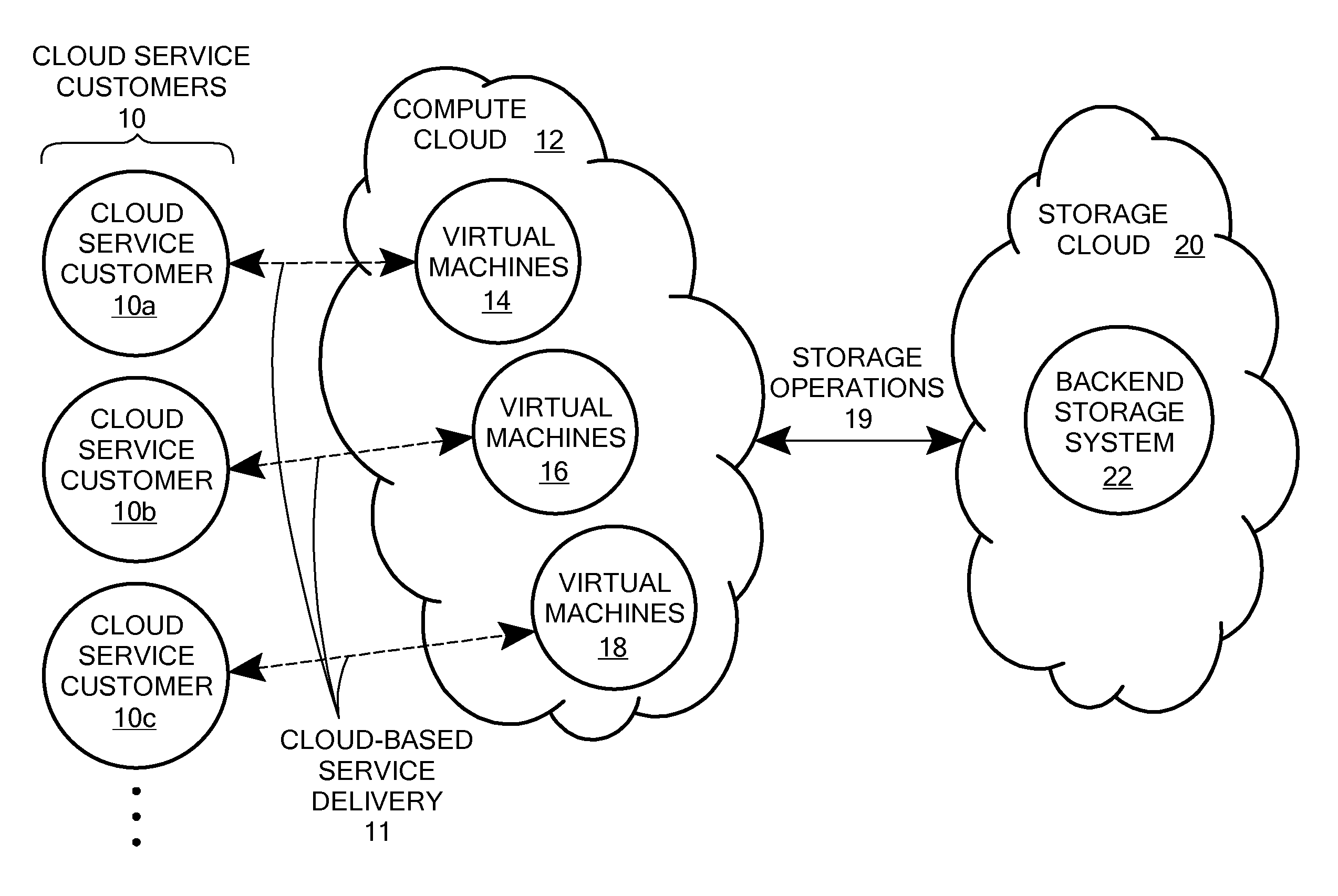
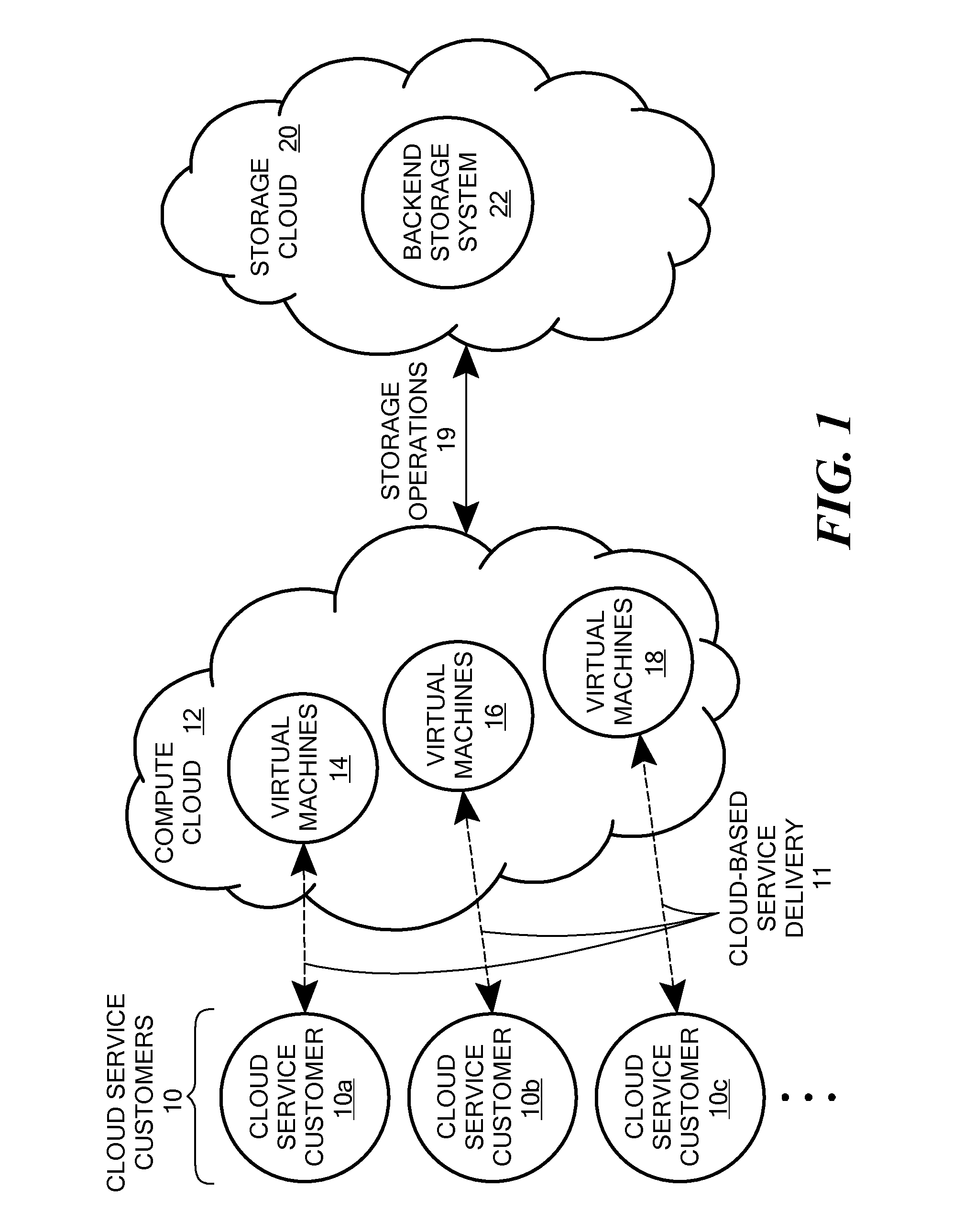
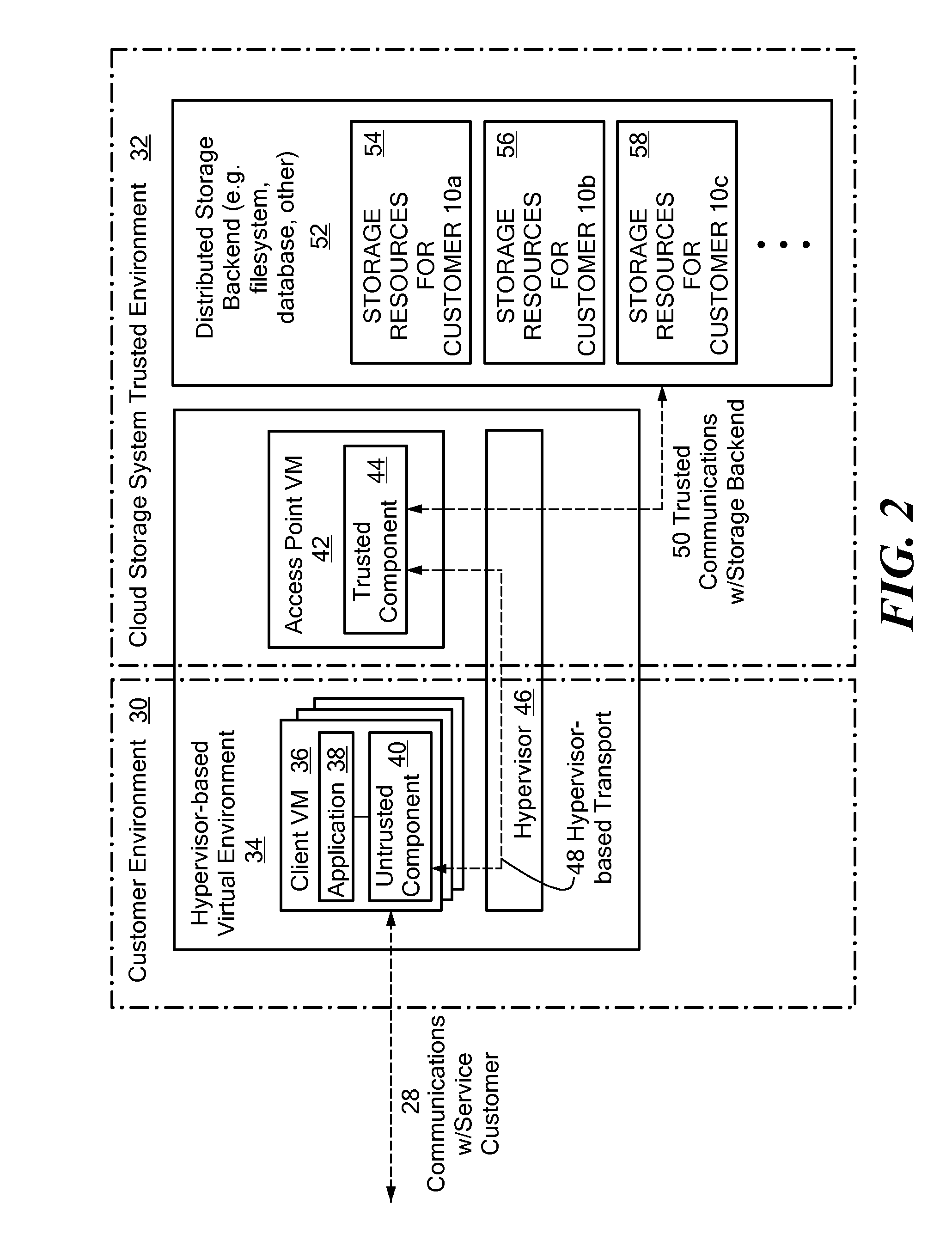
Scalable and secure high-level storage access for cloud computing platforms
ActiveUS8352941B1Effective segmentationImprove the level ofMultiprogramming arrangementsSoftware simulation/interpretation/emulationTrusted componentsTrust relationship
An untrusted component exposing a high level storage object interface within an untrusted client virtual machine accepts application level storage object operations. Responsive to a storage object operation, the untrusted component passes a message through the underlying hypervisor to an associated trusted component. The trusted component processes the message by authenticating the client virtual machine and locating an internal mapping between the client virtual machine and an associated customer-specific set of backend storage resources to which the requested storage object operation is to be applied. The trusted component uses a trust relationship with the backend storage system to securely communicate the storage object operation to the backend storage system, and passes the operation results through the hypervisor back to the untrusted component in the source client virtual machine from which the storage object request originated.
Owner:EMC IP HLDG CO LLC
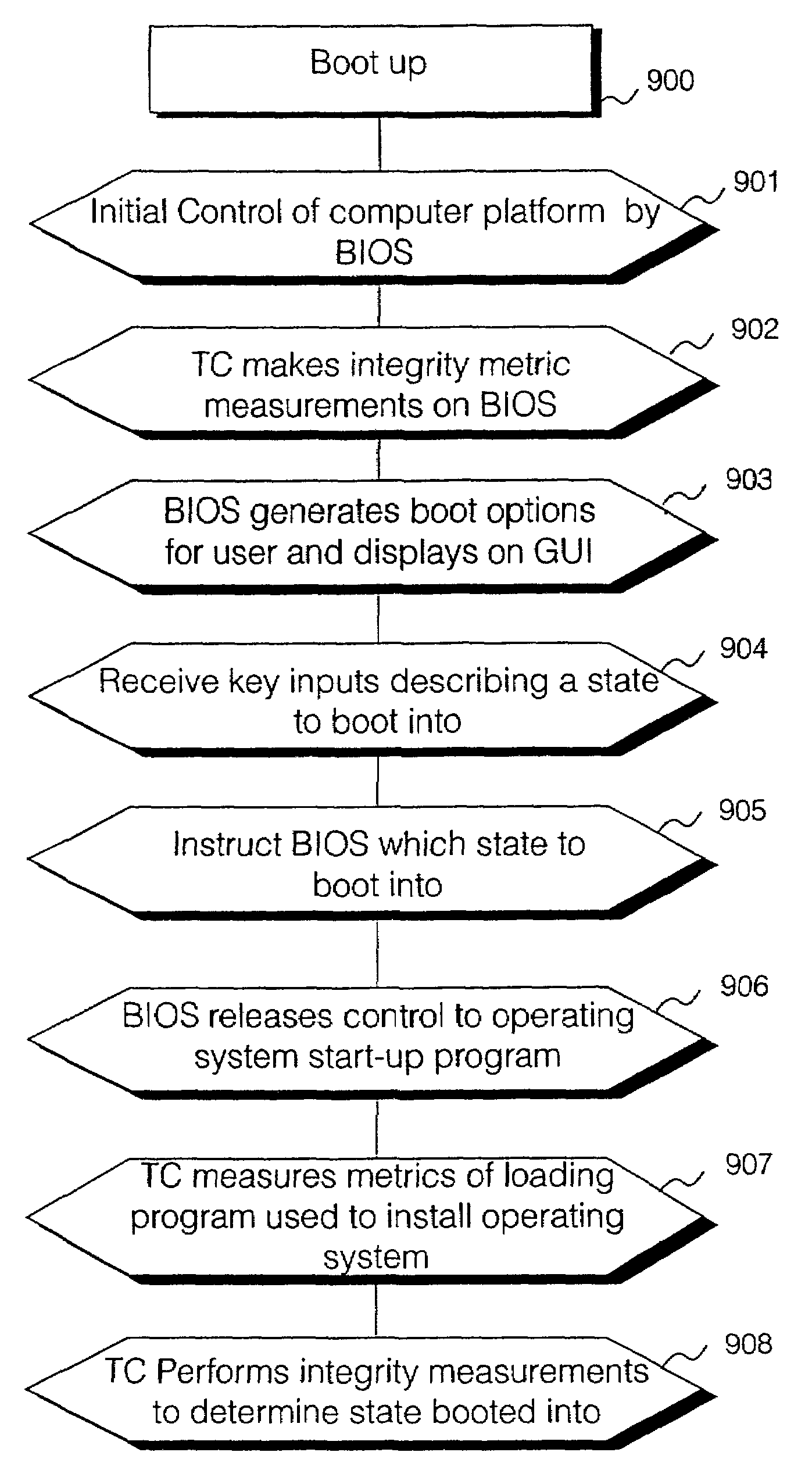
Operation of trusted state in computing platform
ActiveUS7302698B1Improve trustSimple taskDigital data processing detailsUser identity/authority verificationOperational systemModem device
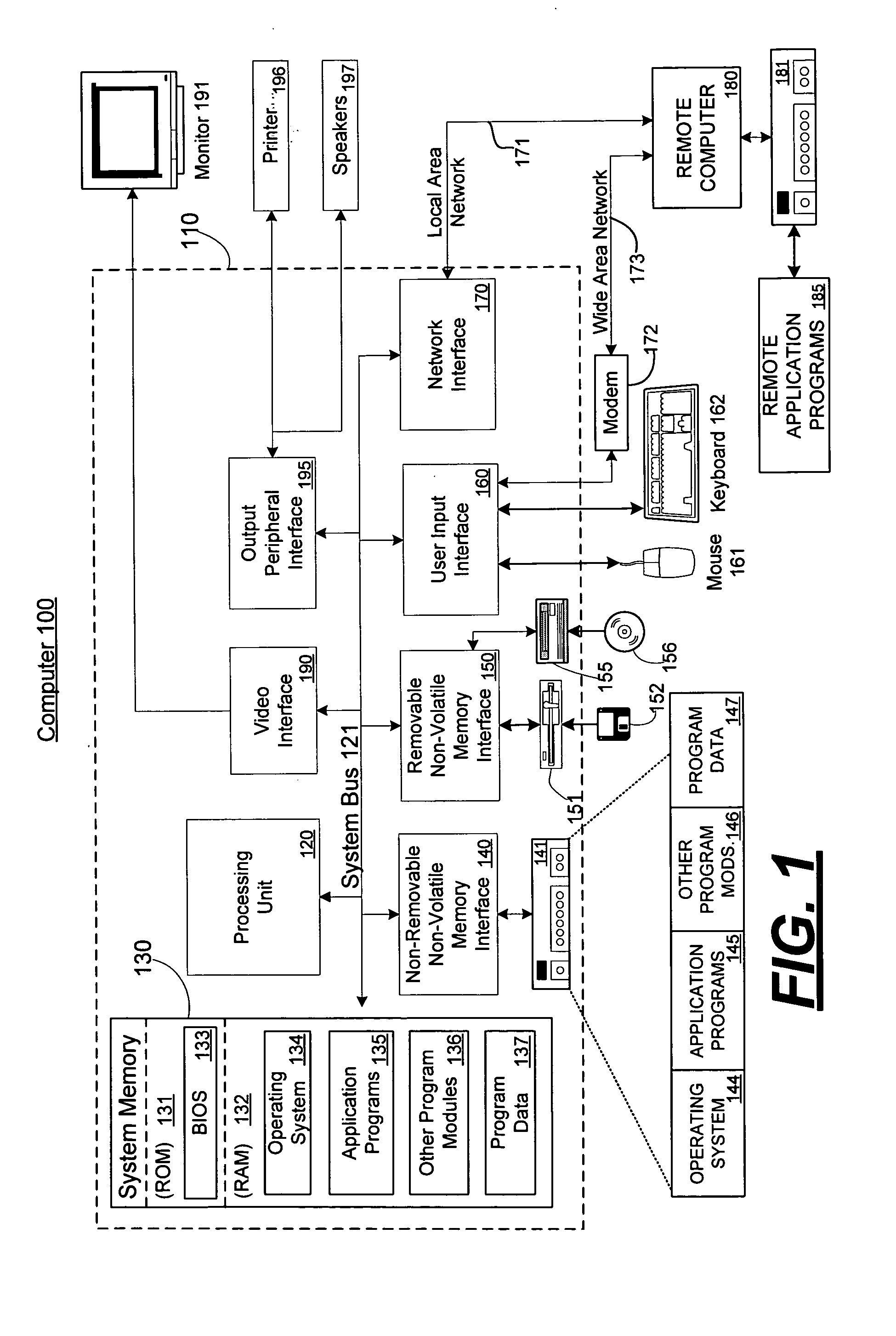
A computing entity comprises a trusted monitoring component having a first processing means and a first memory means, the trusted monitoring component being a self-contained autonomous data processing unit, and a computer platform having a main processing means and a main memory area, along with a plurality of associated physical and logical resources such as peripheral devices including printers, modems, application programs, operating systems and the like. The computer platform is capable of entering a plurality of different states of operation, each state of operation having a different level of security and trustworthiness. Selected ones of the states comprise trusted states in which a user can enter sensitive confidential information with a high degree of certainty that the computer platform has not been compromised by external influences such as viruses, hackers or hostile attacks. To enter a trusted state, references made automatically to the trusted component, and to exit a trusted state reference must be made to the trusted component. On exiting the trusted state, all references to the trusted state are deleted from the computer platform. On entering the trusted state, the state is entered in a reproducible and known manner, having a reproducible and known configuration which is confirmed by the trusted component.
Owner:META PLATFORMS INC
Data event logging in computing platform
InactiveUS7194623B1None of methods is secureDigital data processing detailsUser identity/authority verificationTrusted componentsData file
There is disclosed a computer entity having a trusted component which compiles an event log for events occurring on a computer platform. The event log contains event data of types which are pre-specified by a user by inputting details through a dialogue display generated by the trusted component. Items which can be monitored include data files, applications drivers and the like. The trusted component operates through a monitoring agent which may be launched onto the computer platform. The monitoring agent may be periodically interrogated to make sure that it is operating correctly and responding to interrogations by the trusted component.
Owner:HEWLETT PACKARD DEV CO LP
Data integrity monitoring in trusted computing entity
InactiveUS7457951B1Digital data processing detailsUnauthorized memory use protectionData integrityTrusted components
A method of security monitoring of data files in a computer platform is carried out by a trusted component having a processor and trusted memory area. The method comprises creating one or a plurality of data files in an untrusted memory area of said computing platform, for each created data file, periodically generating a digest data by applying a hash function to each data file, storing the digest data in a trusted memory area and for each file periodically comparing a current digest data of the file with a previously generated digest data of the file. Any differences between a previous and a current digest data indicate that a file in the untrusted memory area has been corrupted.
Owner:HEWLETT-PACKARD ENTERPRISE DEV LP
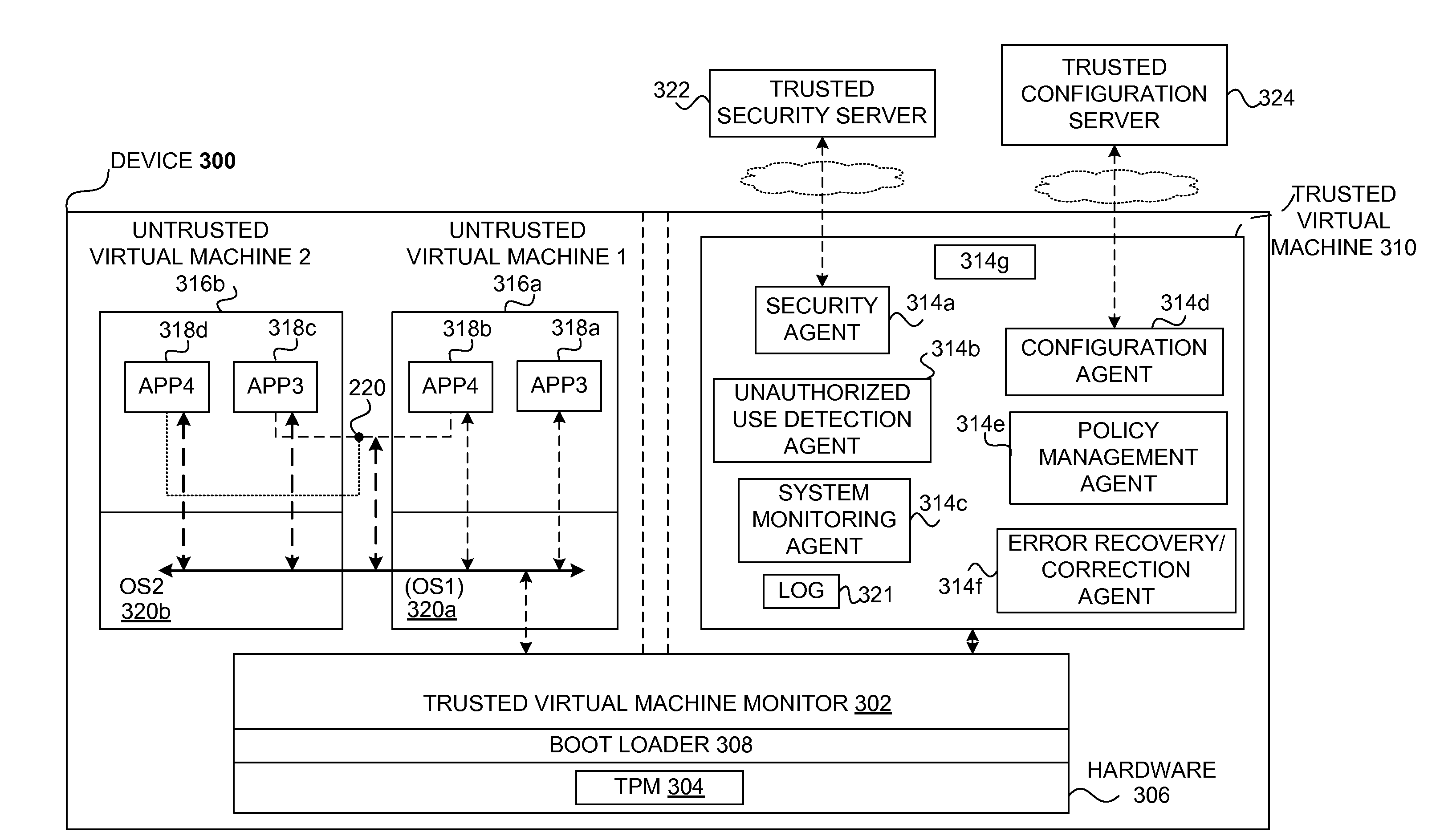
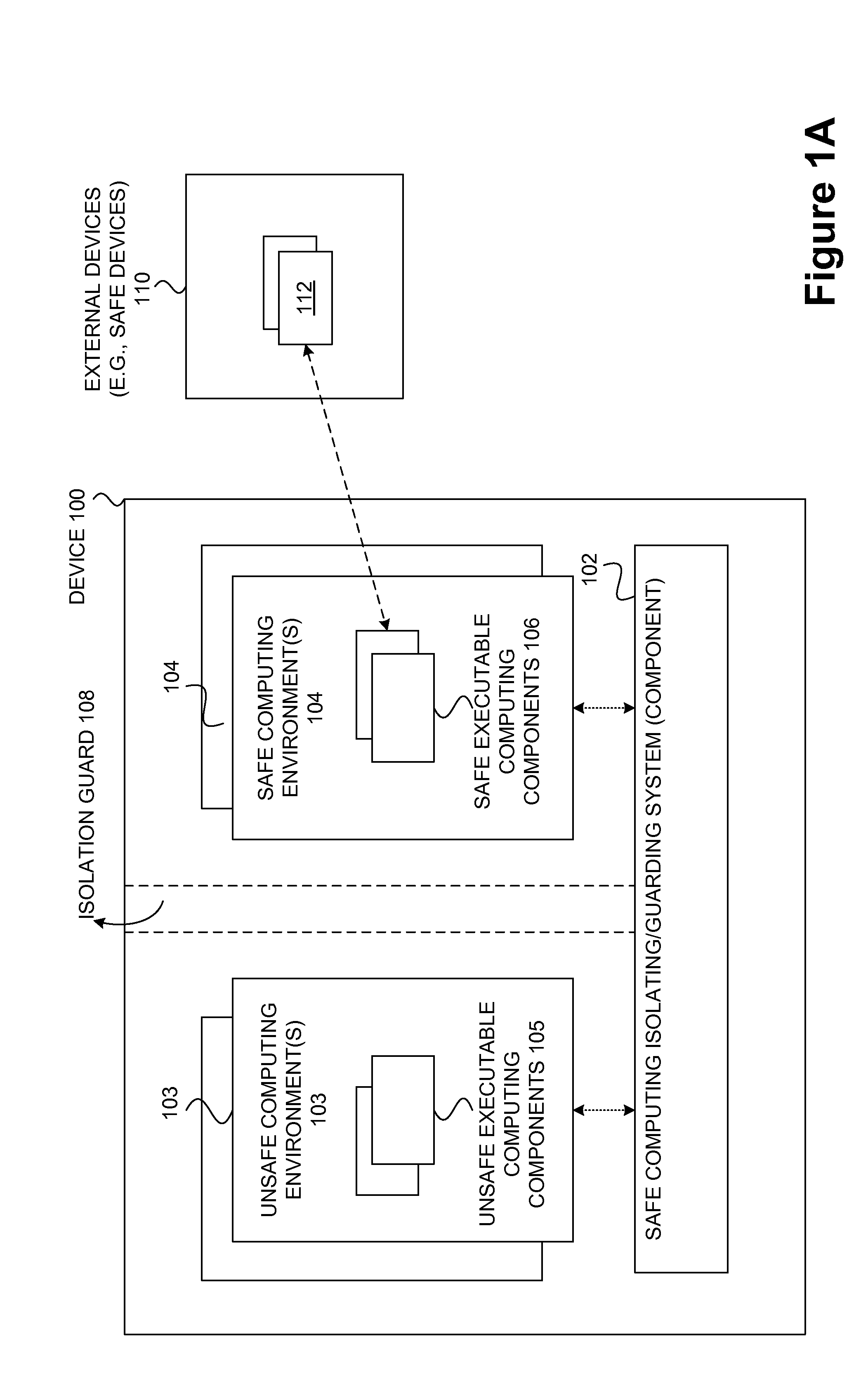
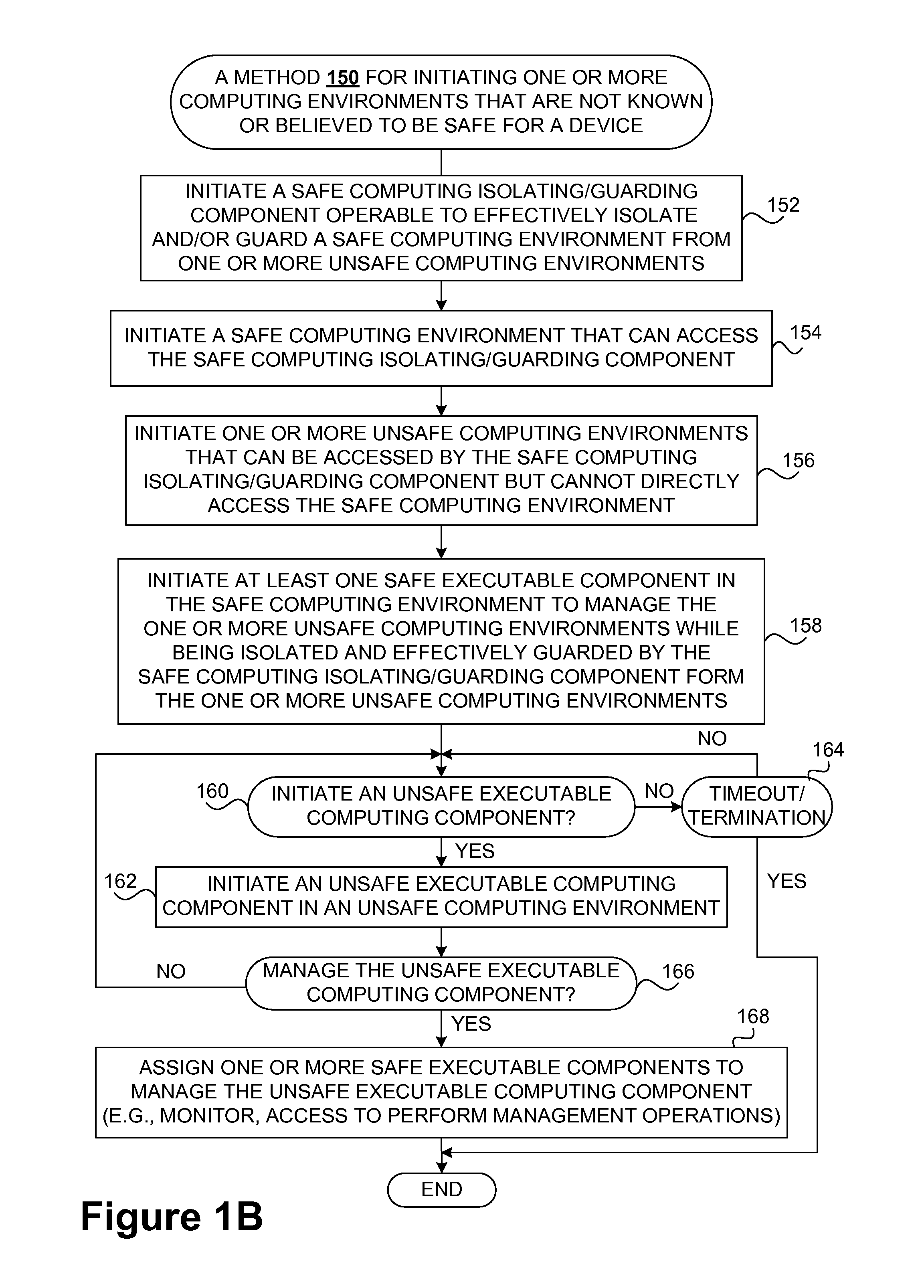
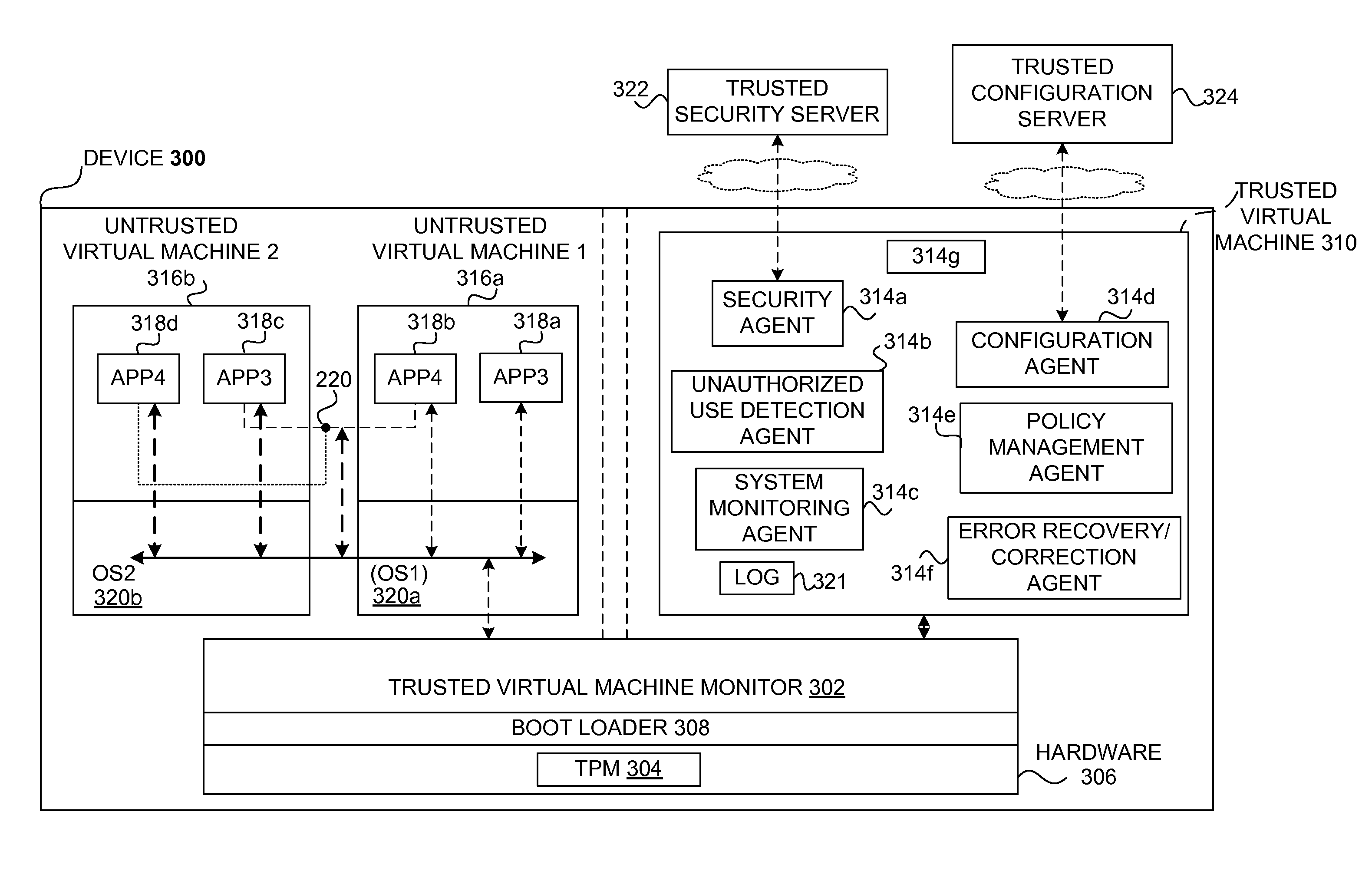
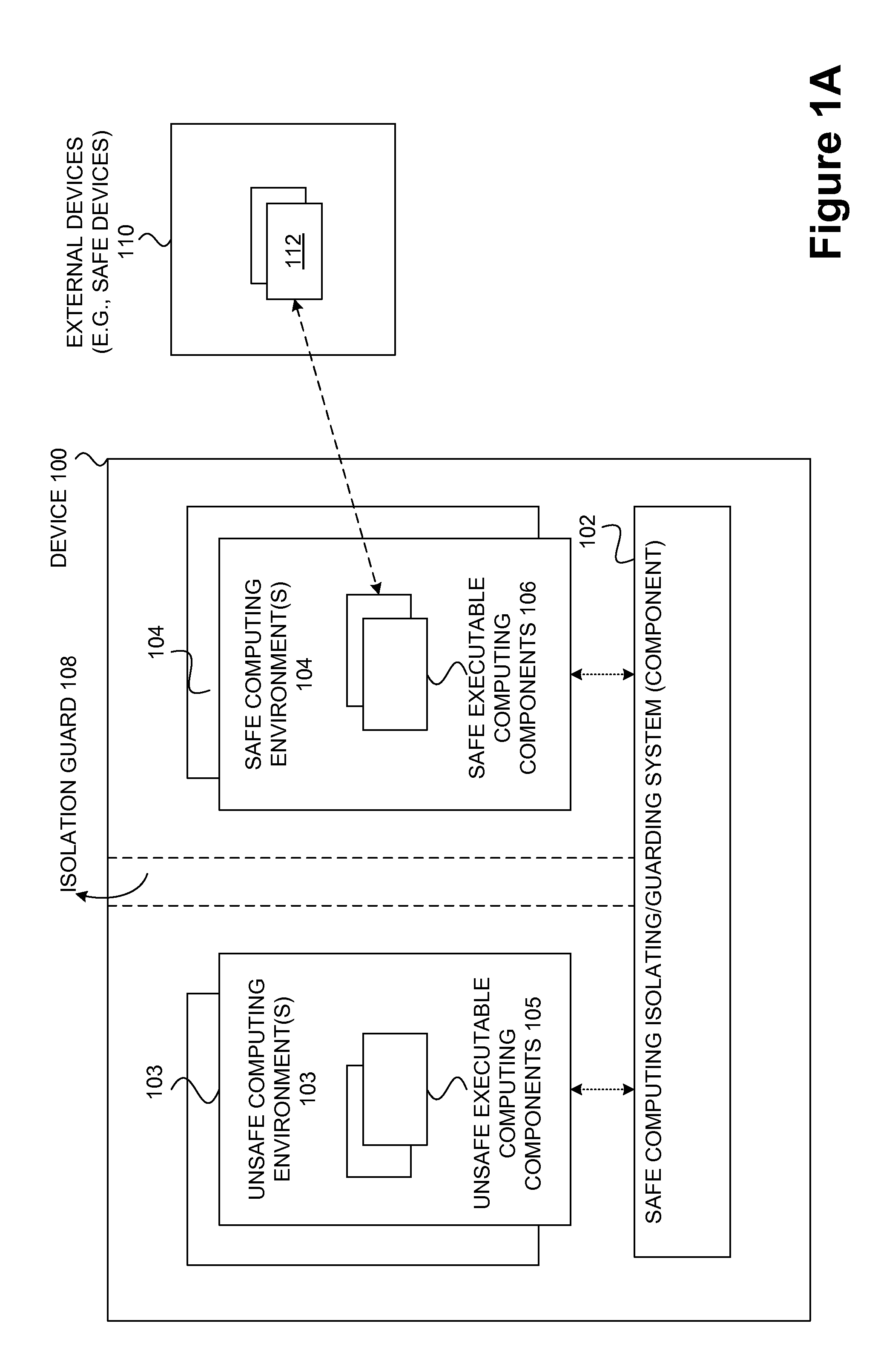
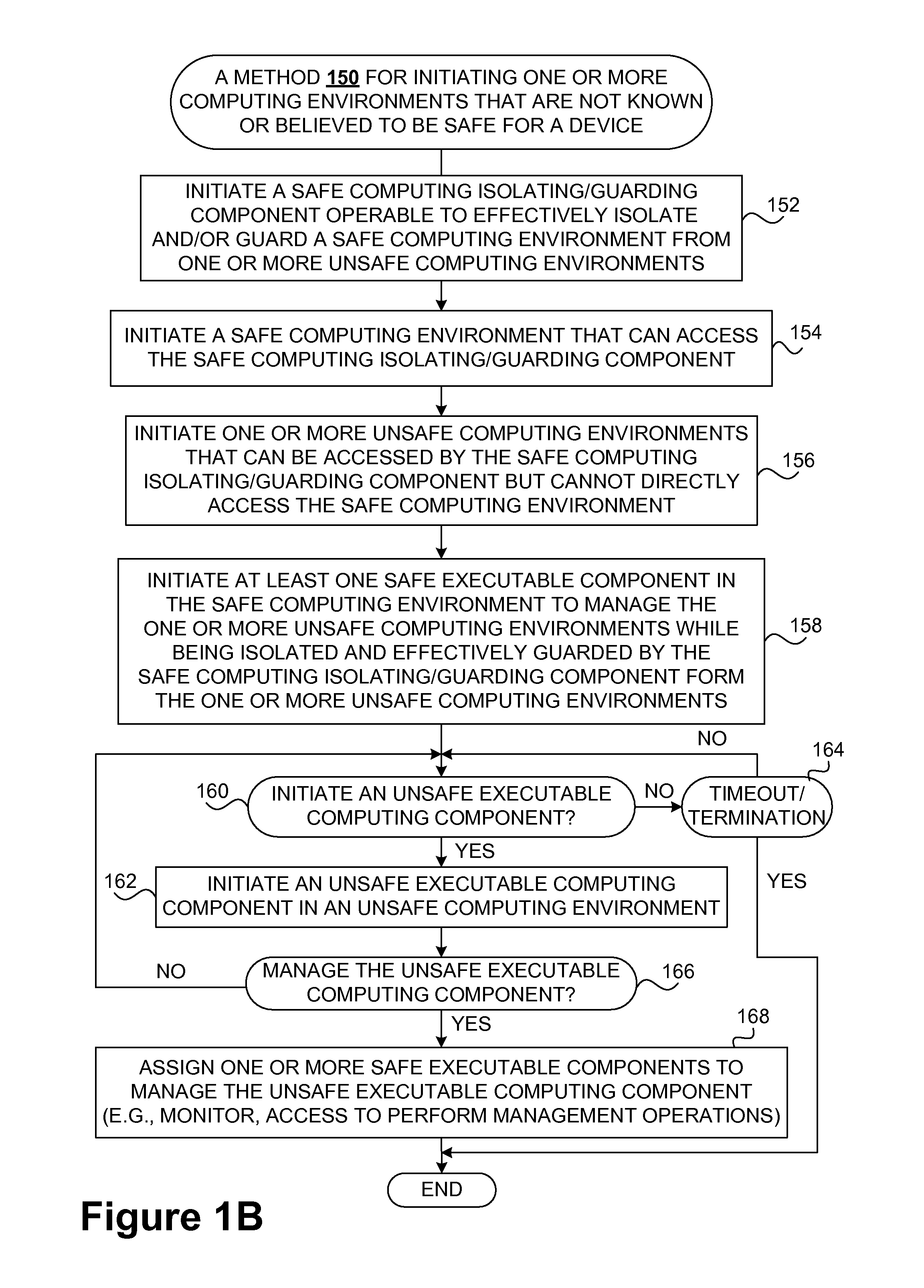
Safety and management of computing environments that may support unsafe components
InactiveUS20090265756A1Effectively guardEffective isolationMemory loss protectionError detection/correctionTrusted componentsTrusted Computing
Techniques for managing and protecting computing environments are disclosed. A safe computing environment can be provided for ensuring the safety and / or management of a device. The safe computing environment can be secured by a safe component that isolates and protects it from unsafe computing environments which may also be operating. As a result, various security and management activities can be securely performed from a safe computing environment. A safe computing environment can, for example, be provided on a device as a safe virtual computing environment (e.g., a safe virtual machine) protected by a safe virtual computing monitor (e.g., a safe virtual machine monitor) from one or more other virtual computing environments that are not known or not believed to be safe for the device. It will also be appreciated that the safe components can, for example, be provided as trusted components for a device. As such, various trusted components (or agent) can operate in a trusted computing environment secured from interference by components that many not be trusted and perform various security and / or management tasks alone or in connection, for example, with other trusted components (e.g., trusted serves).
Owner:SAMSUNG ELECTRONICS CO LTD
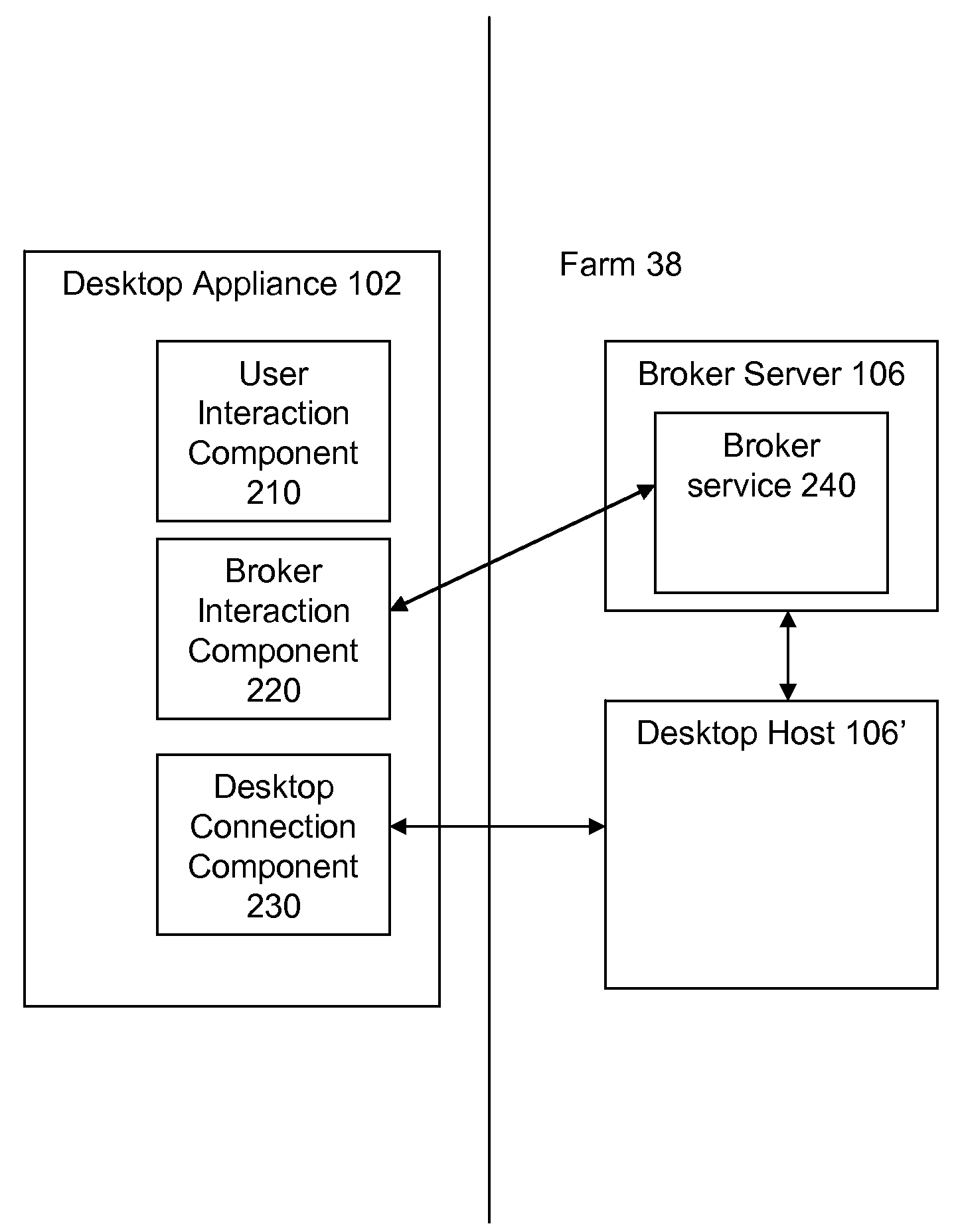
Systems and Methods for Secure Handling of Secure Attention Sequences
ActiveUS20090210934A1Digital data processing detailsUser identity/authority verificationTrusted componentsInternet privacy
A method for authenticating, by a trusted component, a user of a desktop appliance to a remote machine includes executing, by a desktop appliance, a user interaction component, responsive to receiving a secure attention sequence from a user. The user interaction component receives authentication credentials associated with the user. The desktop appliance transmits, to a broker service, the received authentication credentials. The broker service authenticates the user, responsive to the received authentication credentials. The broker service transmits, to a remote machine, authentication data associated with the received authentication credentials. The remote machine authenticates the user, responsive to the received authentication data. The remote machine provides, to the desktop appliance, access to a resource requested by the user. In another aspect, a trusted component provides, to a user of a desktop appliance, access to secure desktop functionality provided by a remote machine.
Owner:CITRIX SYST INC
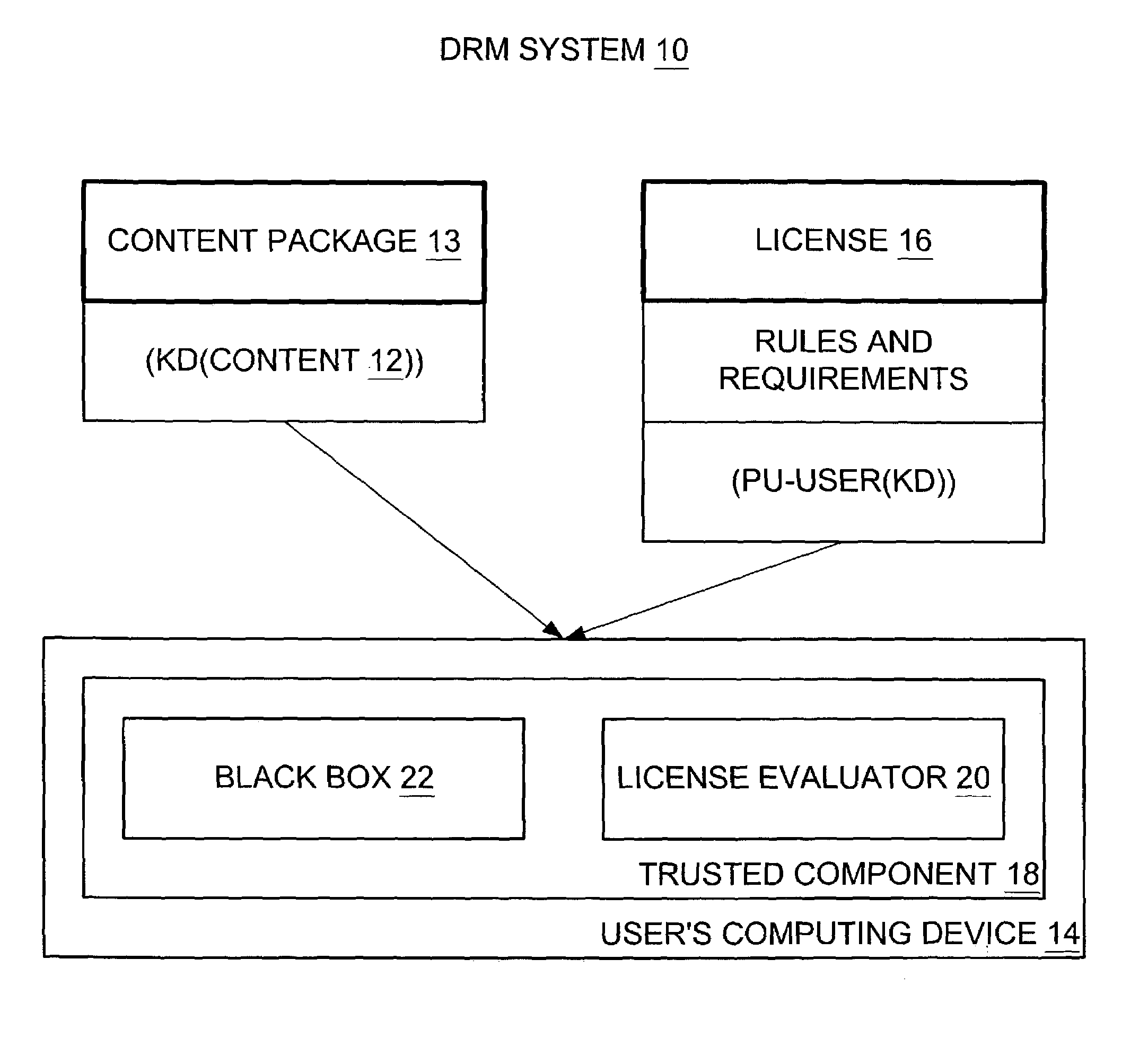
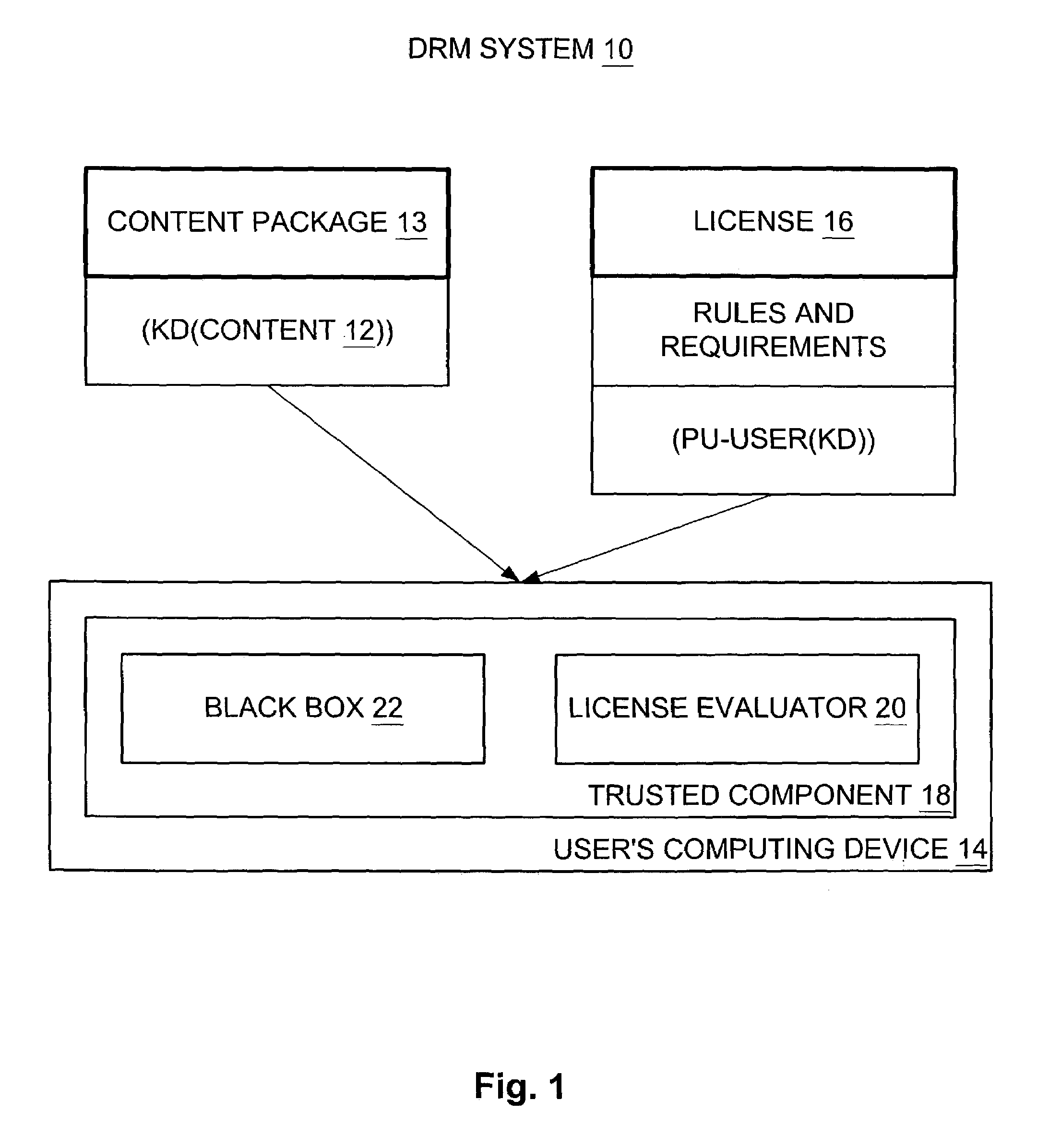
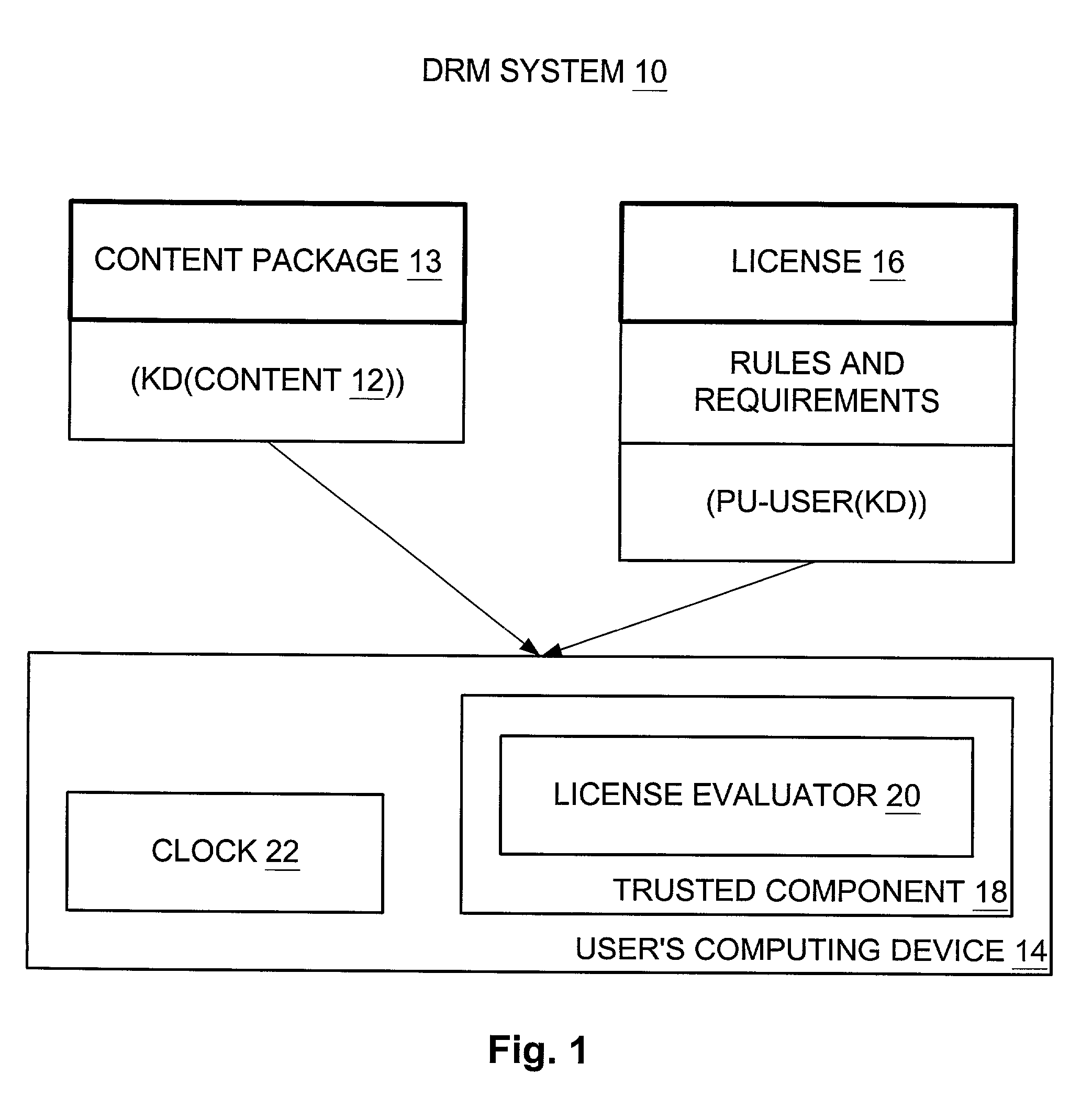
Tying a digital license to a user and tying the user to multiple computing devices in a digital rights management (DRM) system
InactiveUS7318236B2BronchoscopesKey distribution for secure communicationTrusted componentsDigital rights management
A first trusted component on a first computing device performs cryptography, evaluation, and enforcement and is tied thereto, and a first user-machine certificate associated with the first computing device is tied to a user. Correspondingly, a second trusted component on a second computing device performs cryptography, evaluation, and enforcement and is tied thereto, and a second user-machine certificate associated with the second computing device is also tied to the user. The first trusted component obtains the content for rendering on the first computing device by way of the first user-machine certificate and the license, and the second trusted component obtains the content for rendering on the second computing device by way of the second user-machine certificate and the same license.
Owner:MICROSOFT TECH LICENSING LLC
Association of host translations that are associated to an access control level on a PCI bridge that supports virtualization
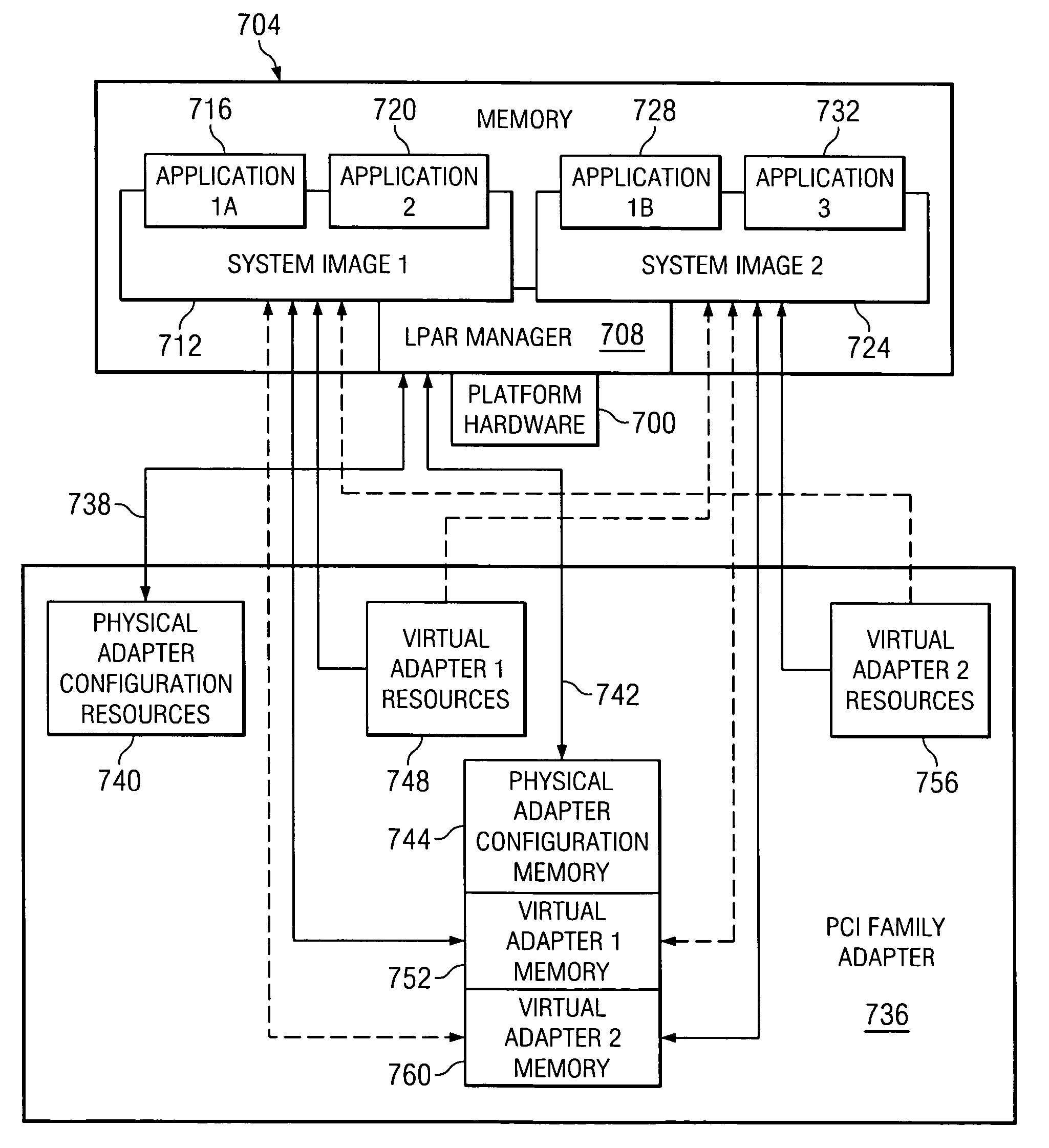
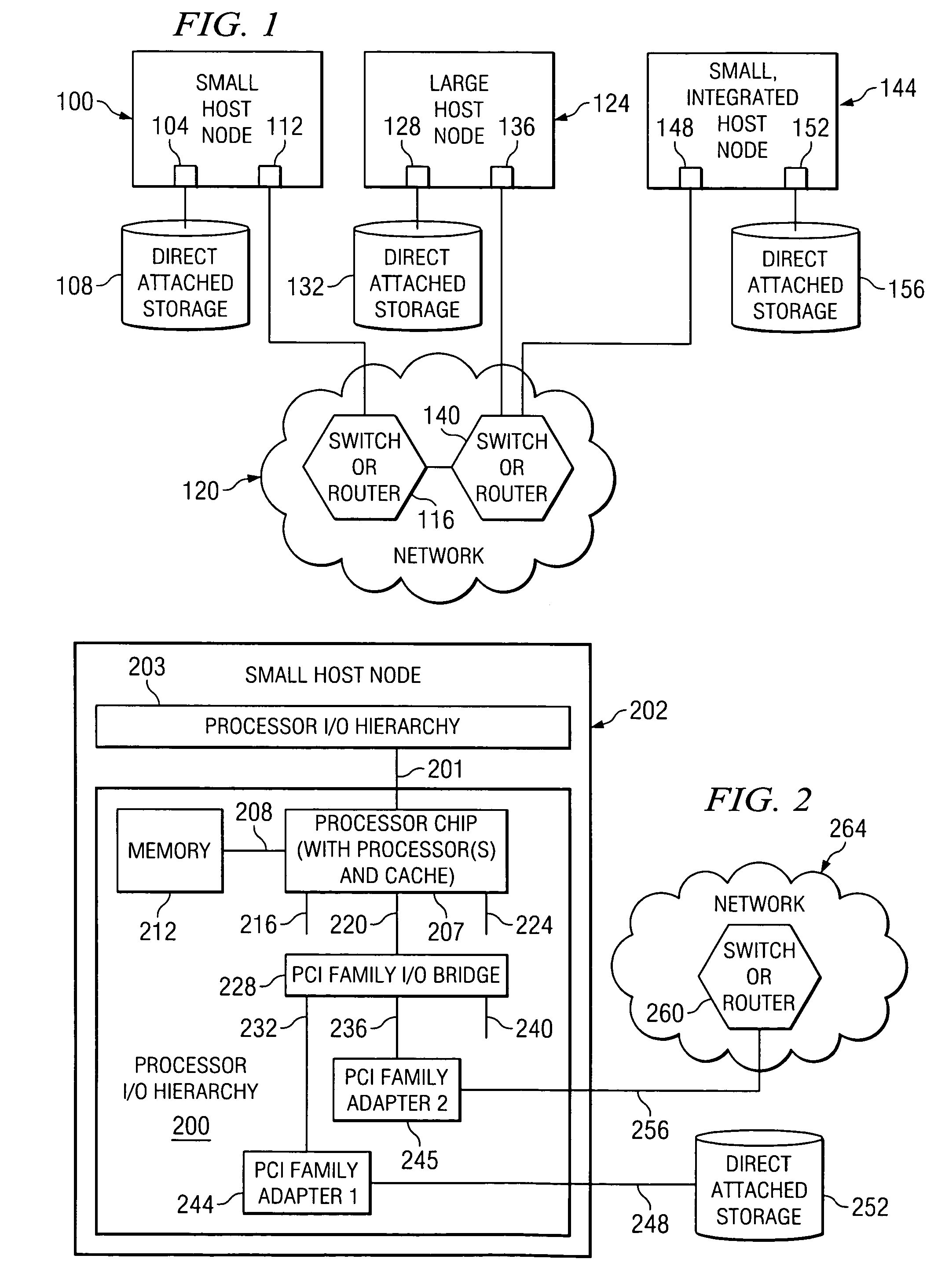
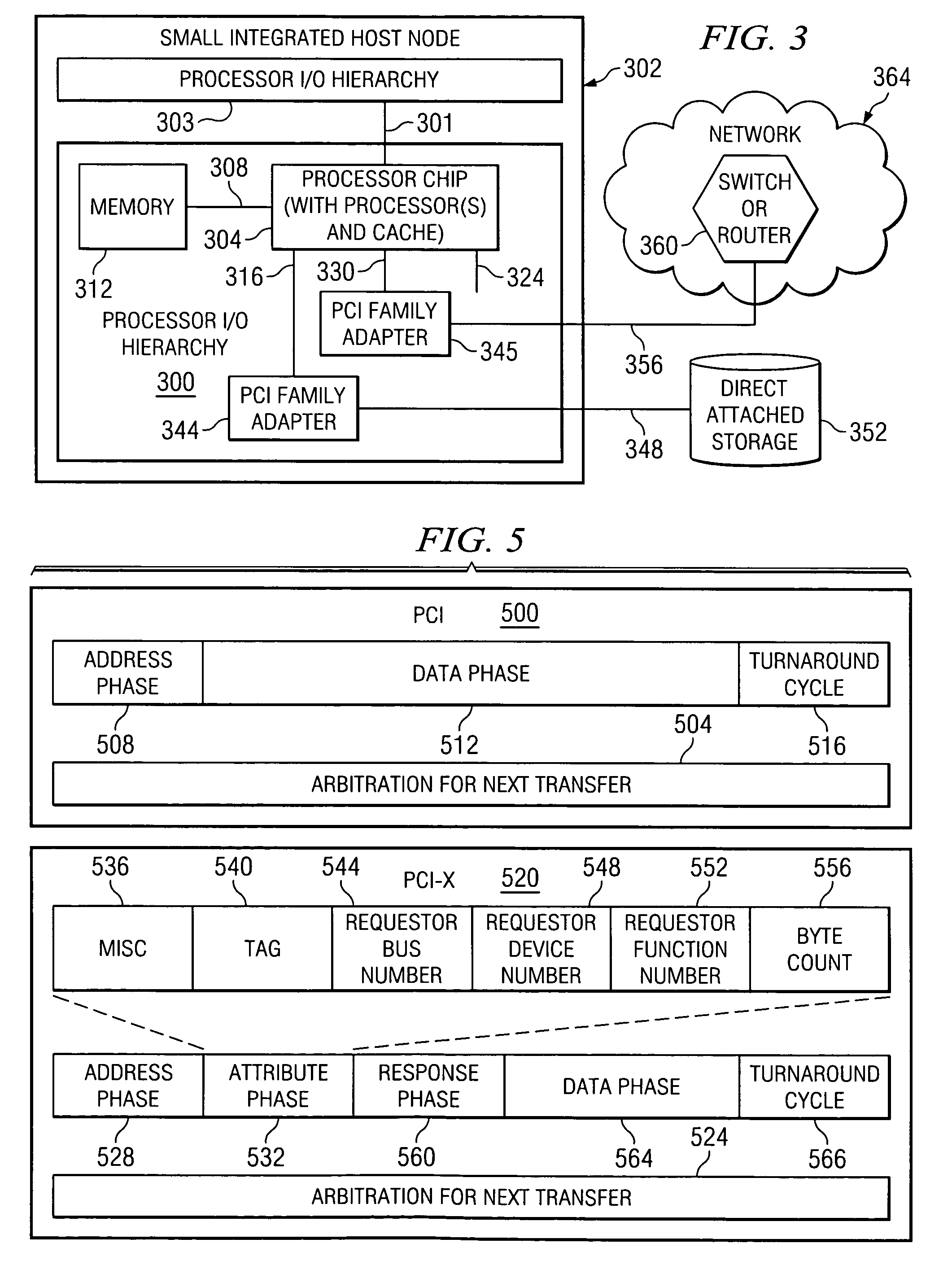
InactiveUS20060195675A1Memory adressing/allocation/relocationInput/output processes for data processingTrusted componentsPCI Express
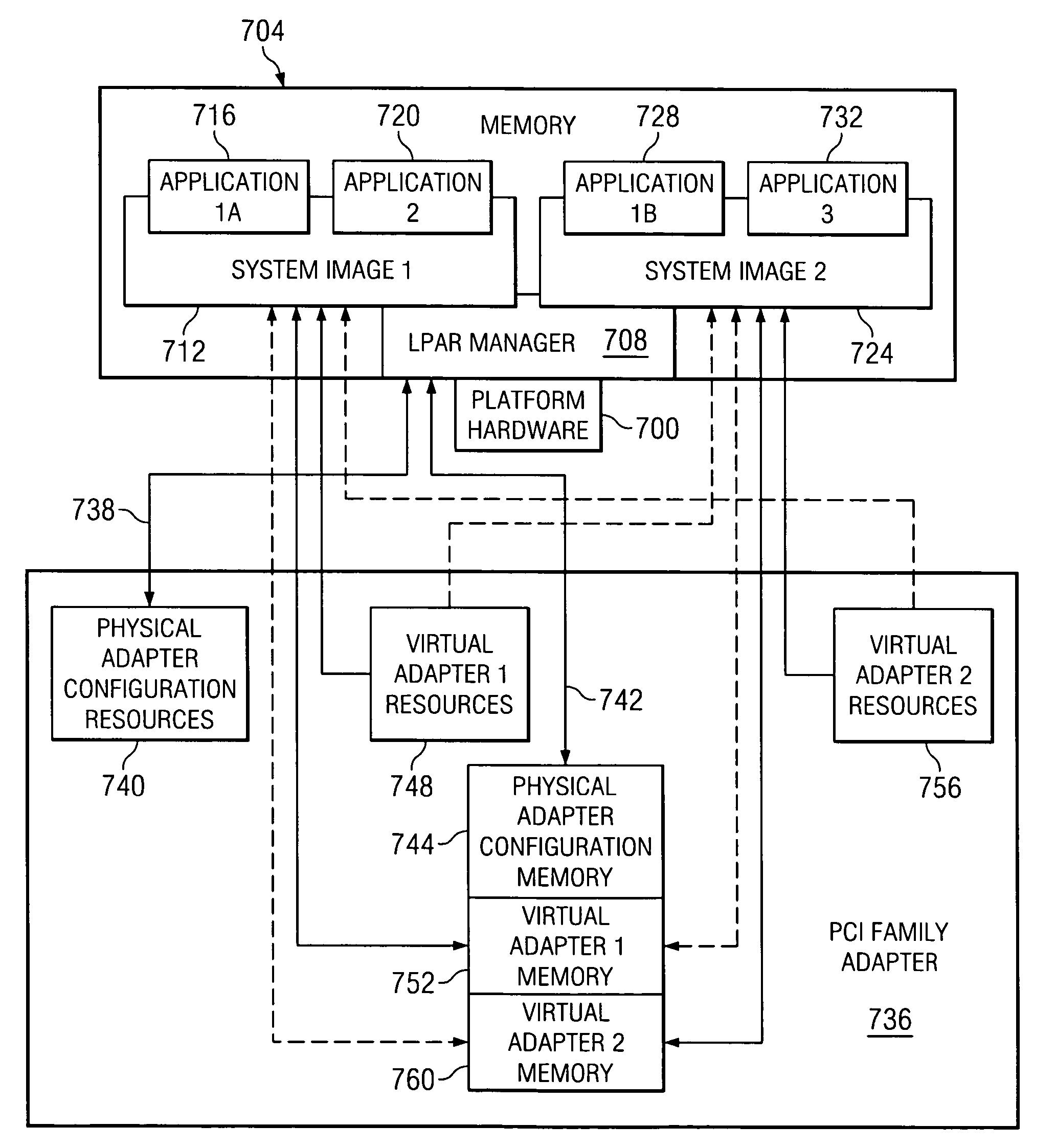
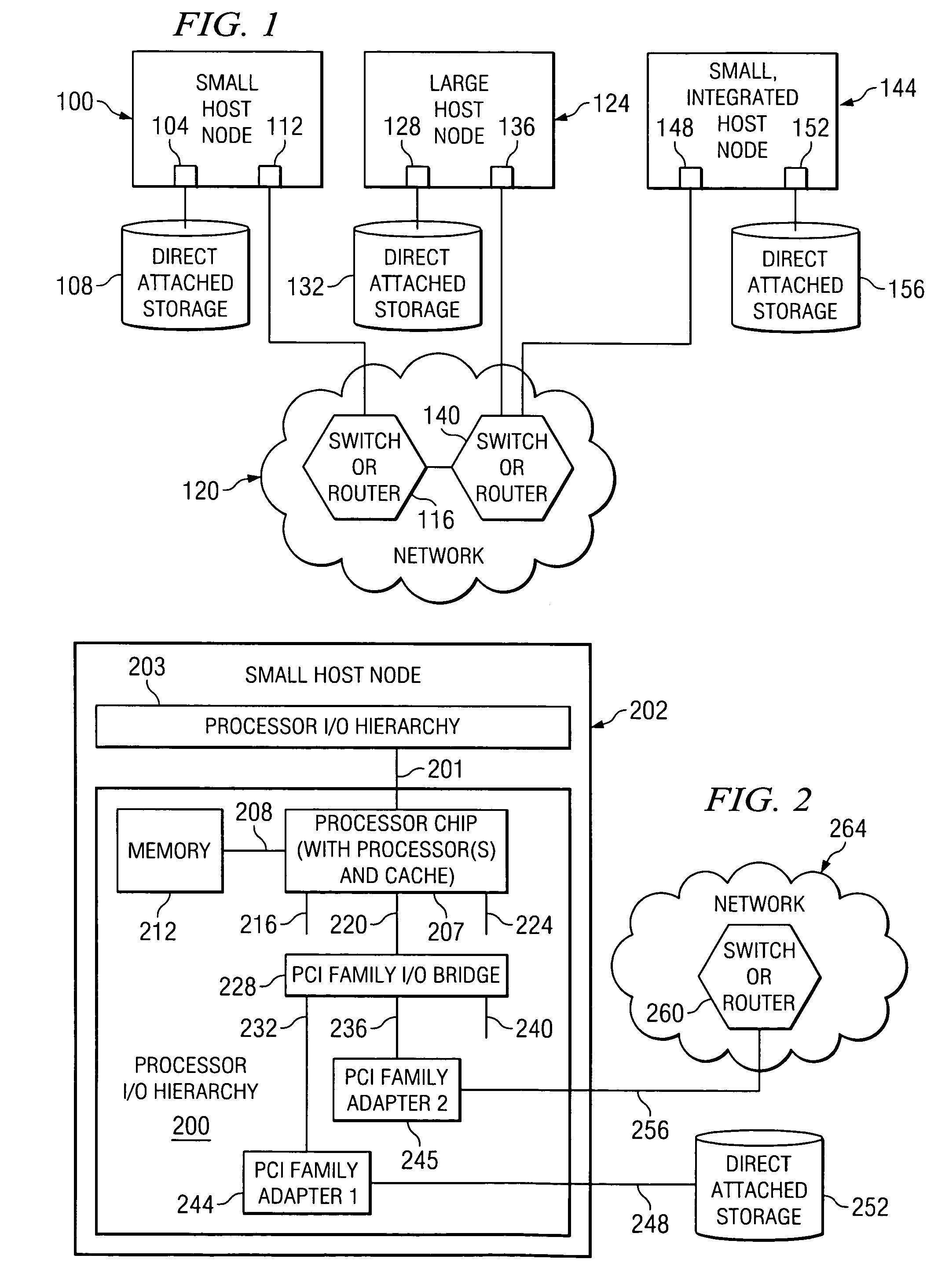
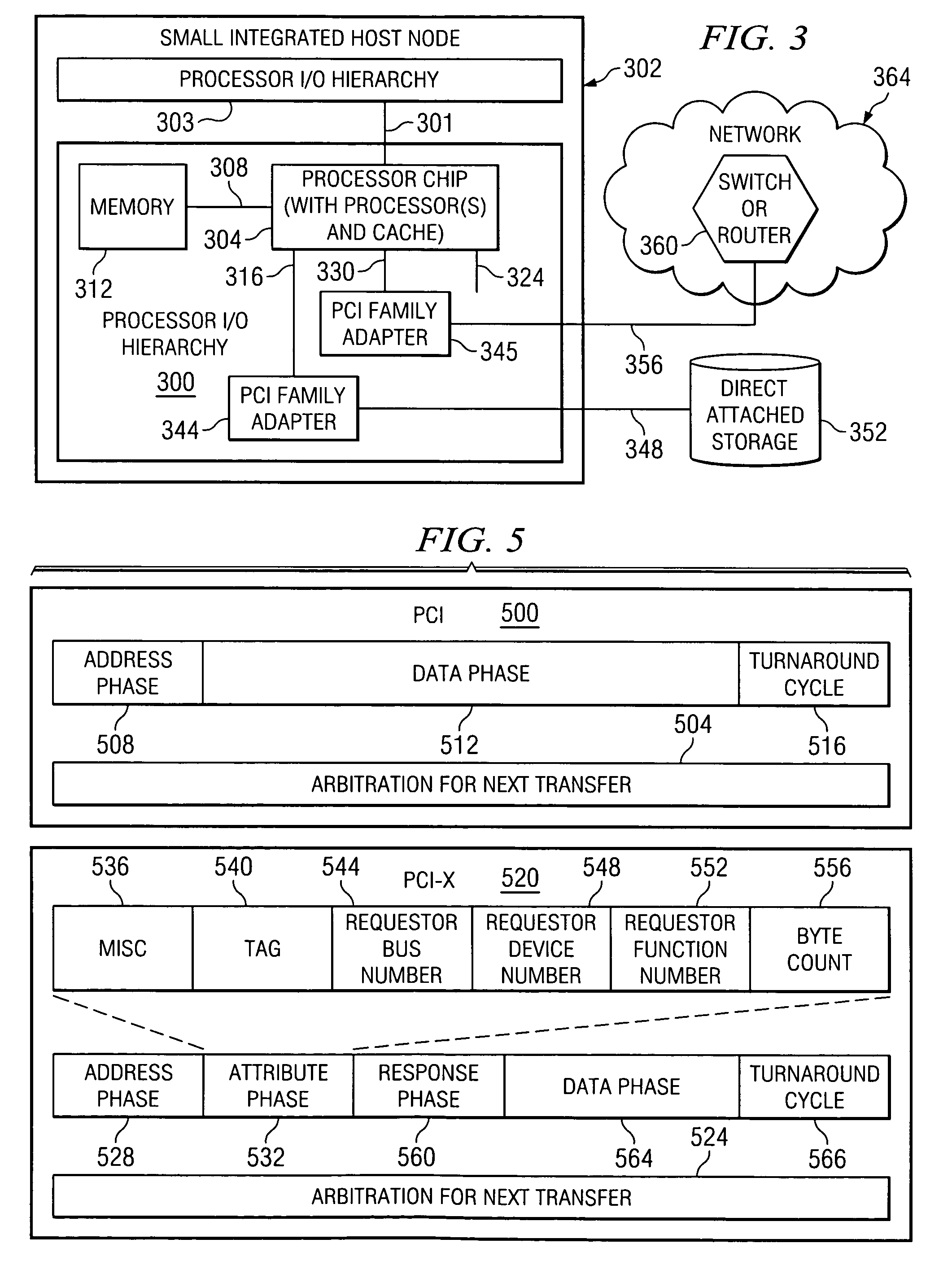
A method, computer program product, and distributed data processing system that allows a system image within a multiple system image virtual server to directly expose a portion, or all, of its associated system memory to a shared PCI adapter without having to go through a trusted component, such as a Hypervisor. Specifically, the present invention is directed to a mechanism for sharing conventional PCI I / O adapters, PCI-X I / O Adapters, PCI-Express I / O Adapters, and, in general, any I / O adapter that uses a memory mapped I / O interface for communications.
Owner:IBM CORP
Validation And/Or Authentication Of A Device For Communication With Network
InactiveUS20110099361A1Data taking preventionError detection/correctionThird partyTrusted components
A device may include a trusted component. The trusted component may be verified by a trusted third party and may have a certificate of verification stored therein based on the verification by the trusted third party. The trusted component may include a root of trust that may provide secure code and data storage and secure application execution. The root of trust may also be configured to verify an integrity of the trusted component via a secure boot and to prevent access to the certain information in the device if the integrity of the trusted component may not be verified.
Owner:INTERDIGITAL PATENT HLDG INC
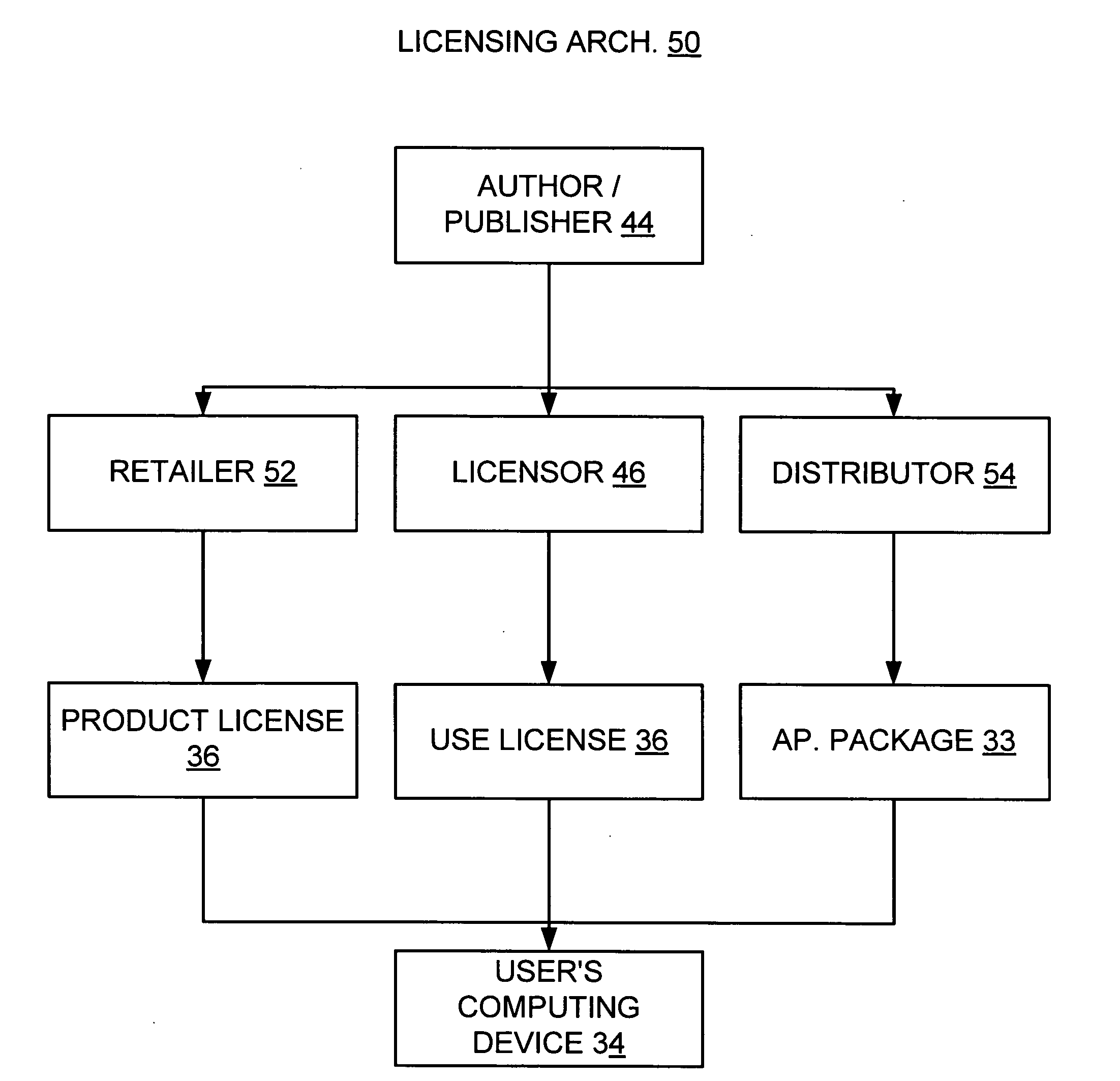
Flexible licensing architecture for licensing digital application
InactiveUS20060179002A1Satisfies needData processing applicationsWinding mechanismsTrusted componentsDistributor
An application includes a plurality of features. A transaction is engaged with a retailer to obtain a product license corresponding to the application. The product license defines at least one feature of the application that may be employed. A base copy of the application is obtained from a distributor and is actuated. A use license corresponding to the product license is acquired from a licensor by way of the actuated application sending the product license to the licensor along with an identification of at least one of a user, the computing device, and a trusted component operating on the computing device, where the use license includes feature policy granting rights to employ each feature defined in the product license.
Owner:MICROSOFT TECH LICENSING LLC
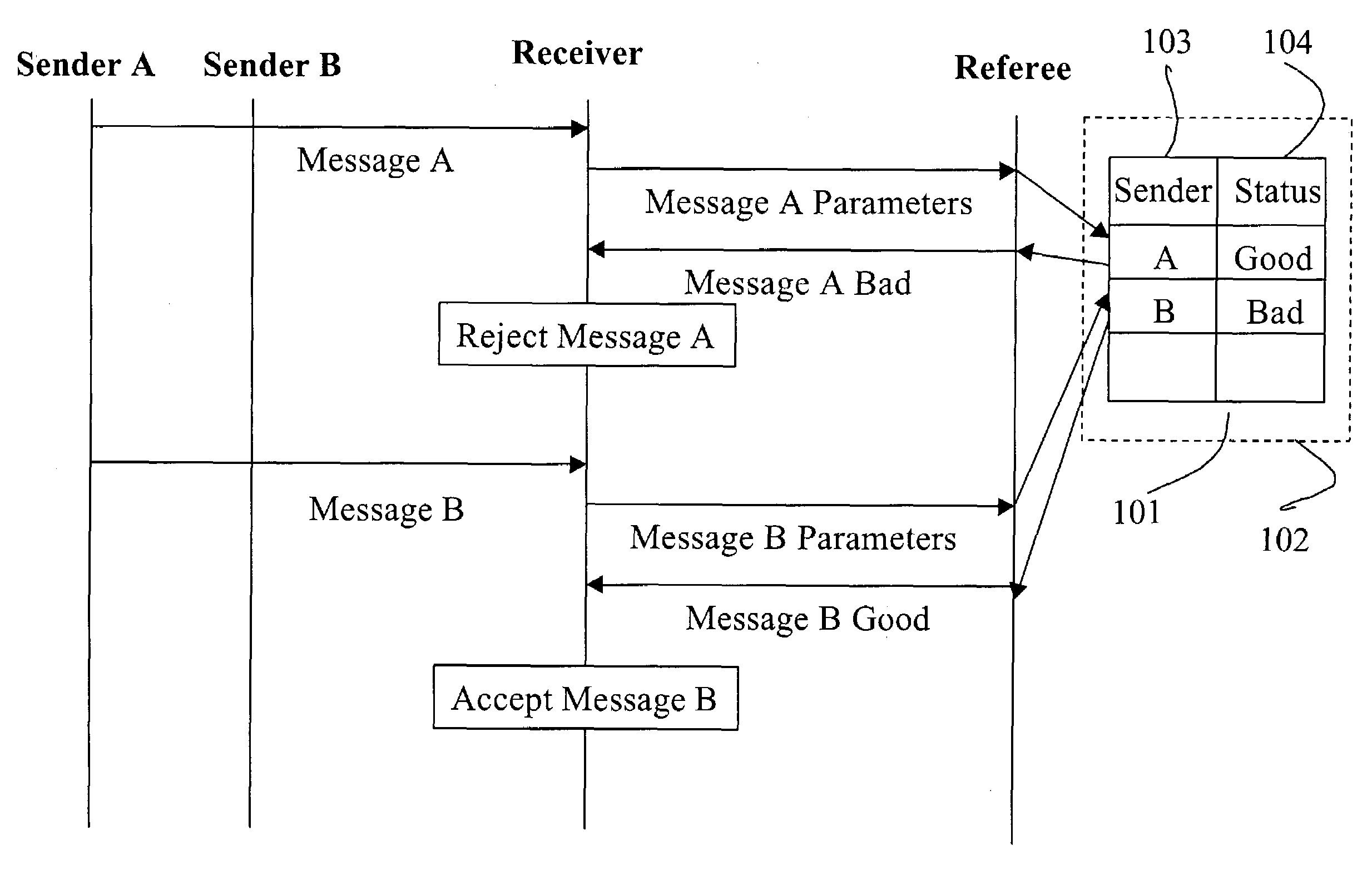
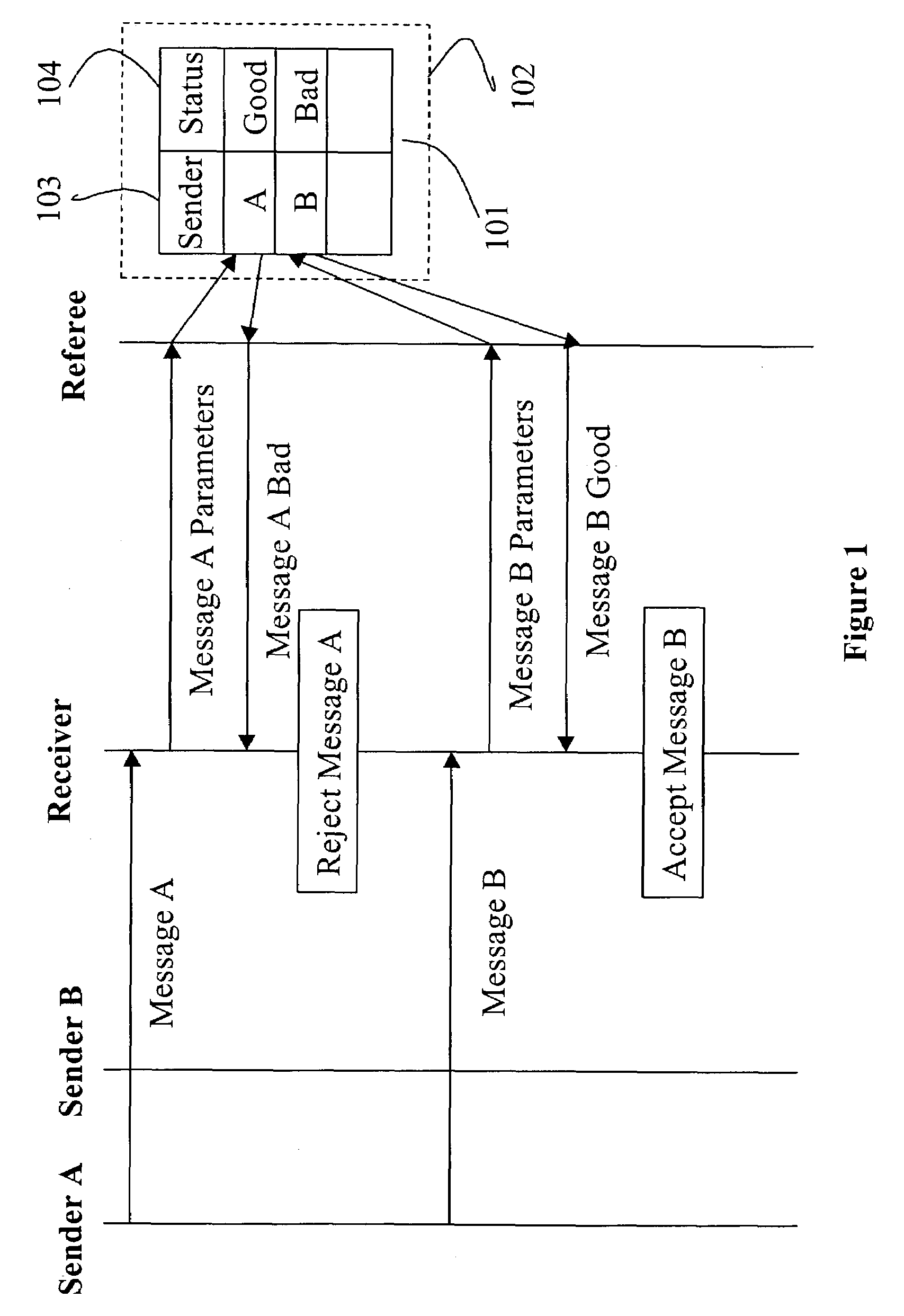
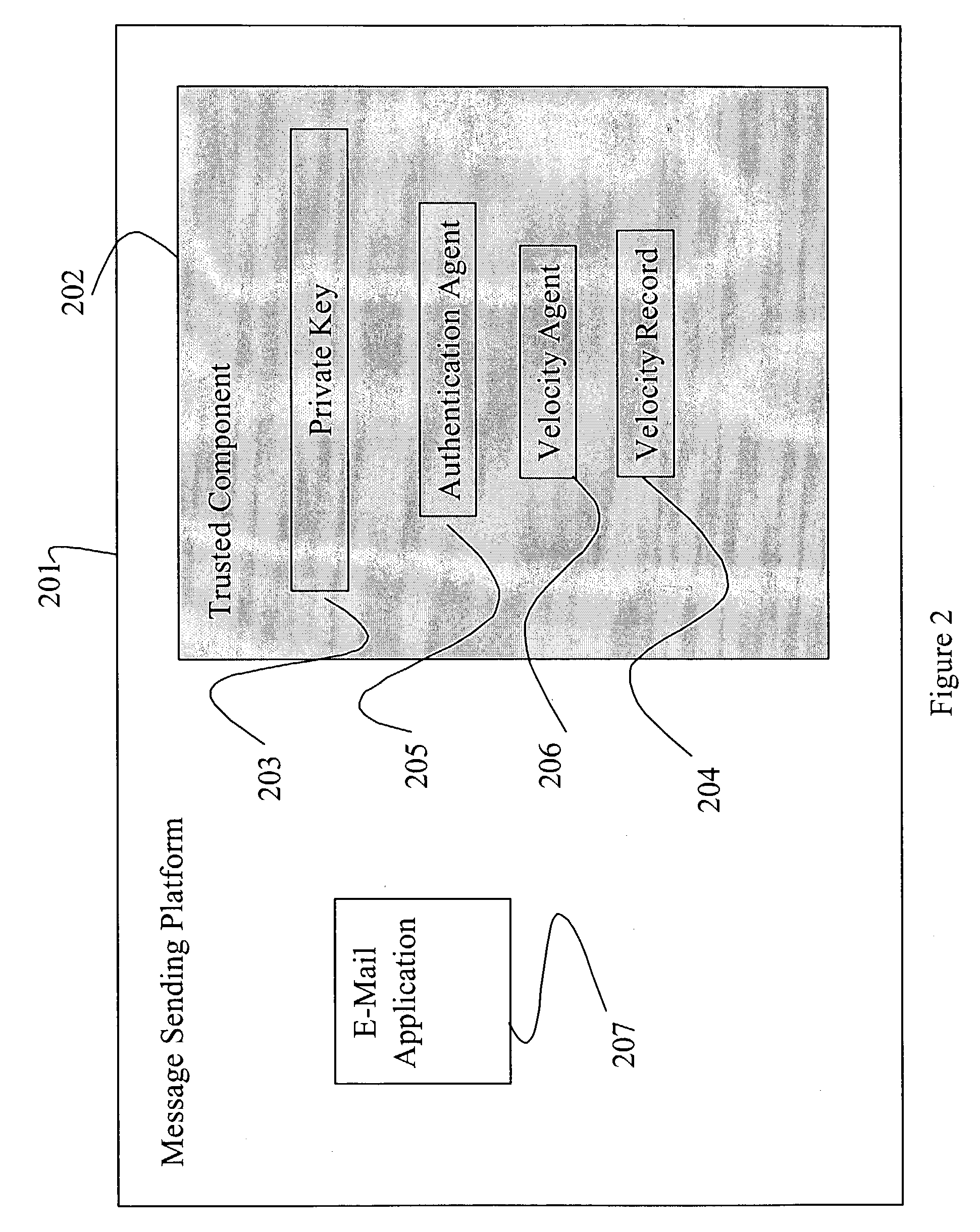
Verifying human interaction to a computer entity by way of a trusted component on a computing device or the like
InactiveUS20050278253A1Easy constructionDigital data processing detailsUser identity/authority verificationHuman interactionTrusted components
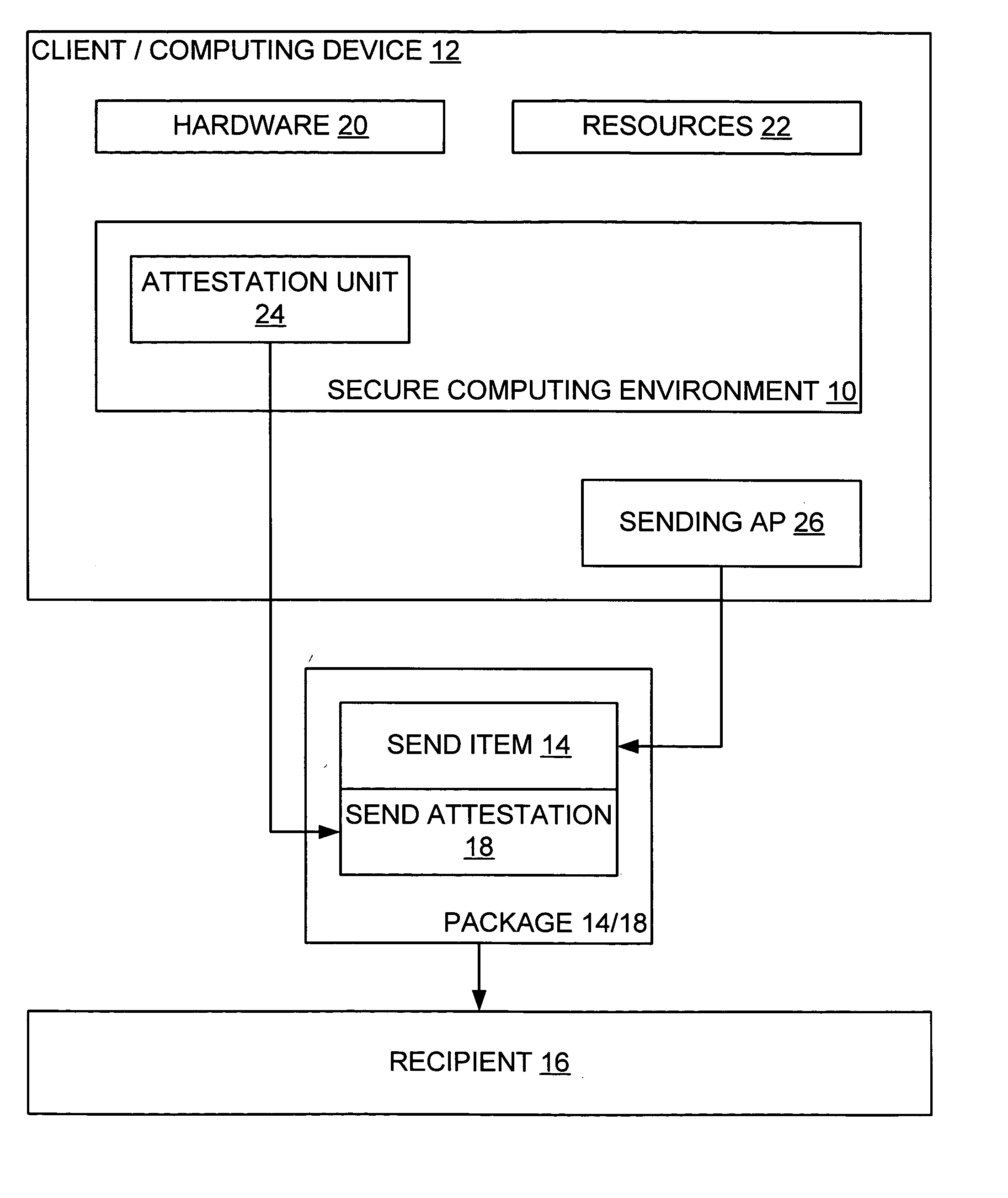
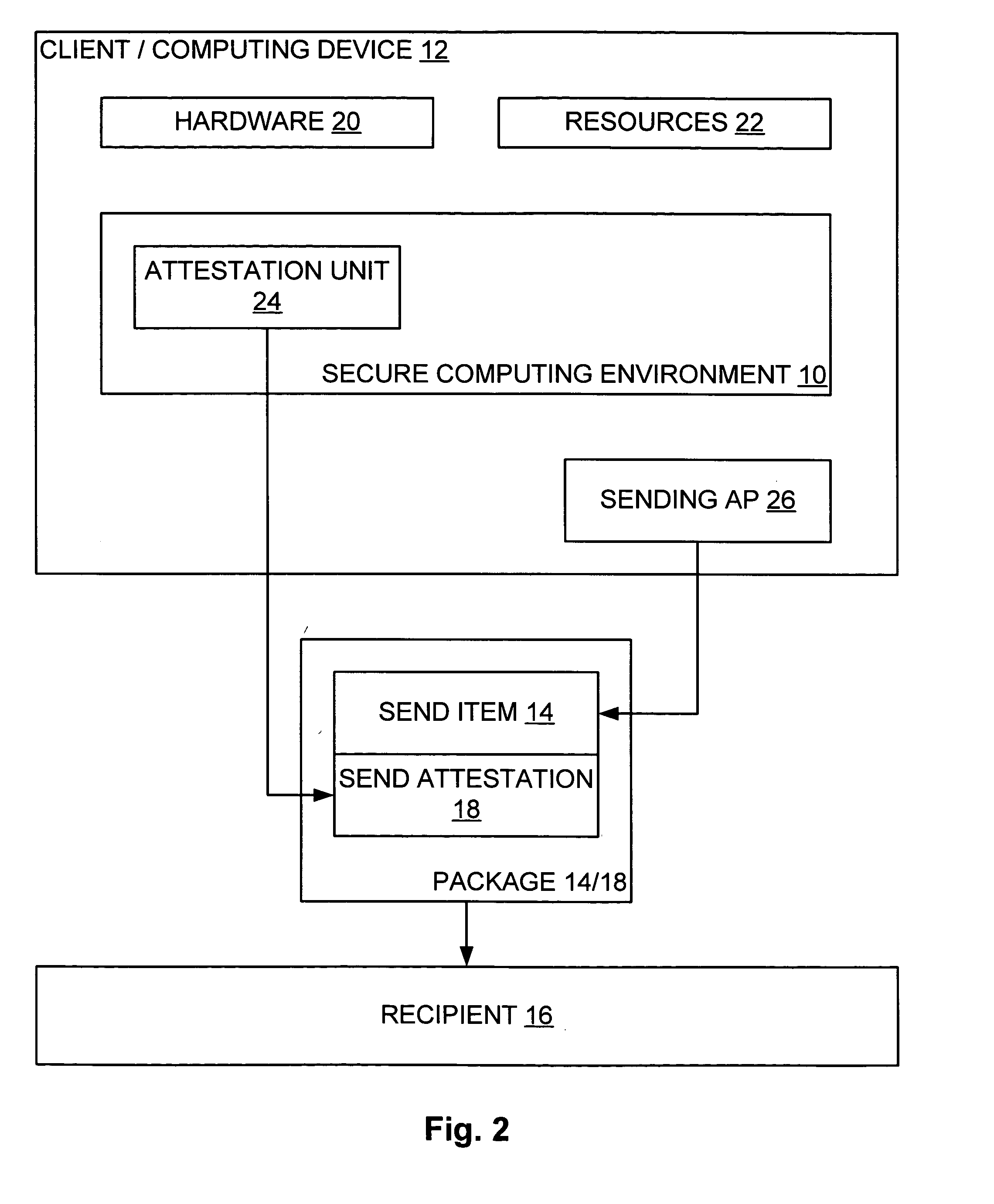
A method describes user interaction in combination with sending a send item from an application of a computing device to a recipient. The computing device has an attestation unit thereon for attesting to trustworthiness. The application facilitates a user in constructing the send item, and pre-determined indicia are monitored that can be employed to detect that the user is in fact expending effort to construct the send item. The attestation unit authenticates the application to impart trust thereto, and upon the user commanding the application to send, a send attestation is constructed to accompany the send item. The send attestation is based on the monitored indicia and the authentication of the application and thereby describes the user interaction. The constructed send attestation is packaged with the constructed send item and the package is sent to the recipient.
Owner:MICROSOFT TECH LICENSING LLC
Association of host translations that are associated to an access control level on a PCI bridge that supports virtualization
InactiveUS7398337B2Memory adressing/allocation/relocationInput/output processes for data processingTrusted componentsPCI Express
A method, computer program product, and distributed data processing system that allows a system image within a multiple system image virtual server to directly expose a portion, or all, of its associated system memory to a shared PCI adapter without having to go through a trusted component, such as a Hypervisor. Specifically, the present invention is directed to a mechanism for sharing conventional PCI I / O adapters, PCI-X I / O Adapters, PCI-Express I / O Adapters, and, in general, any I / O adapter that uses a memory mapped I / O interface for communications.
Owner:INT BUSINESS MASCH CORP
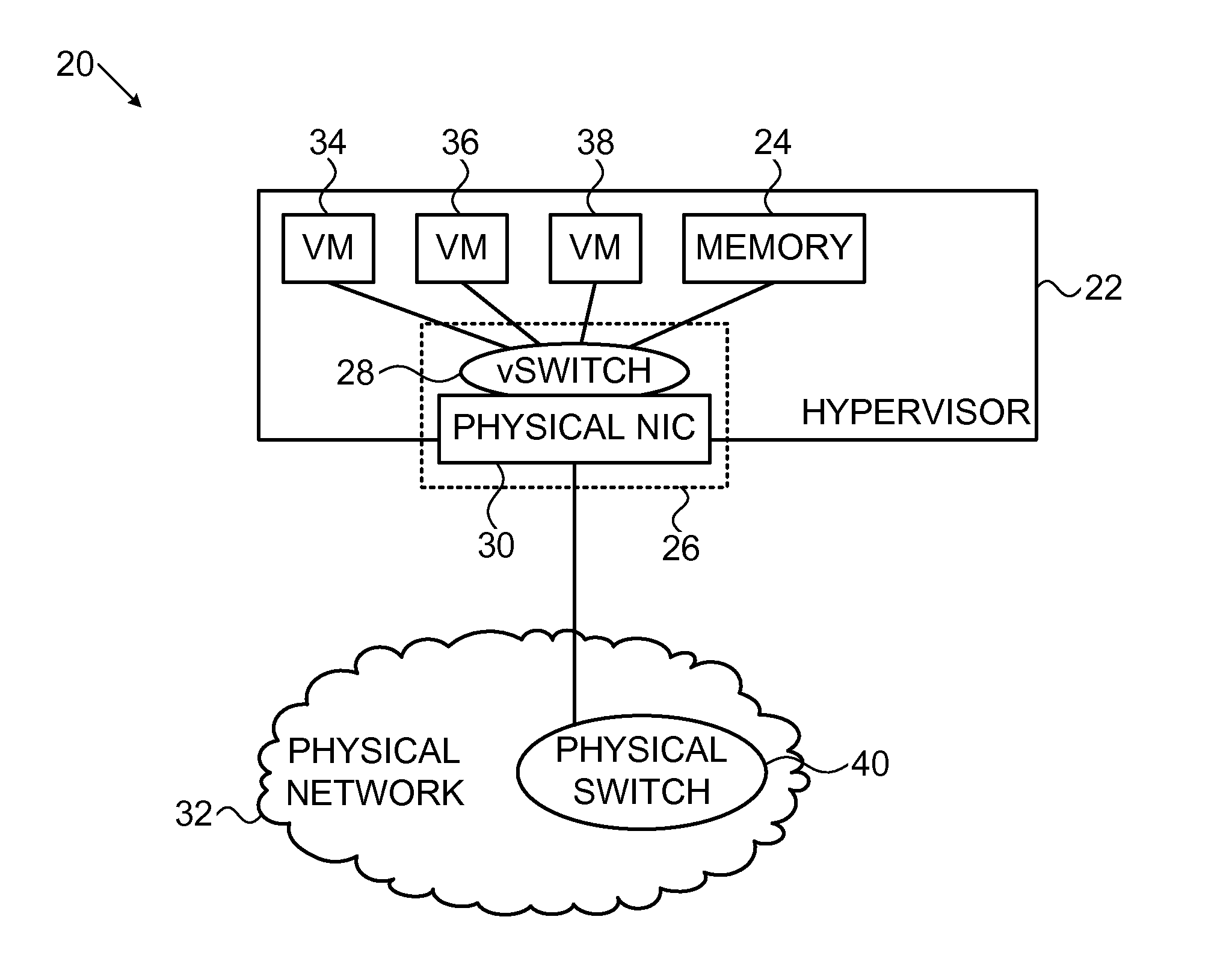
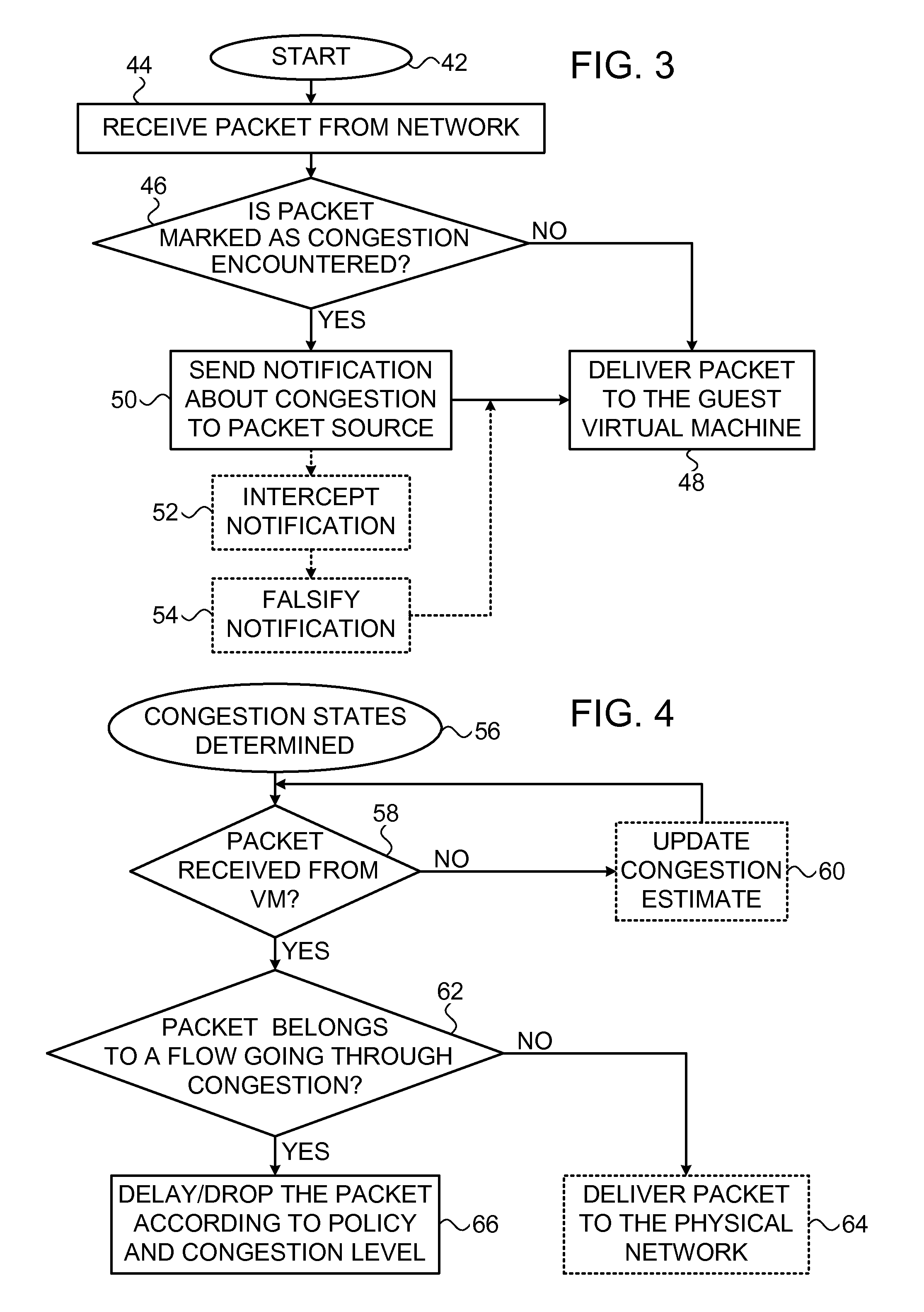
Congestion control enforcement in a virtualized environment
ActiveUS20150029853A1Facilitate transmissionImprove fairnessError preventionTransmission systemsTrusted componentsPacket loss
In a data network congestion control in a virtualized environment is enforced in packet flows to and from virtual machines in a host. A hypervisor and network interface hardware in the host are trusted components. Enforcement comprises estimating congestion states in the data network attributable to respective packet flows, recognizing a new packet that belongs to one of the data packet flows, and using one or more of the trusted components and to make a determination based on the congestion states that the new packet belongs to a congestion-producing packet flow. A congestion-control policy is applied by one or more of the trusted components to the new packet responsively to the determination.
Owner:MELLANOX TECHNOLOGIES LTD
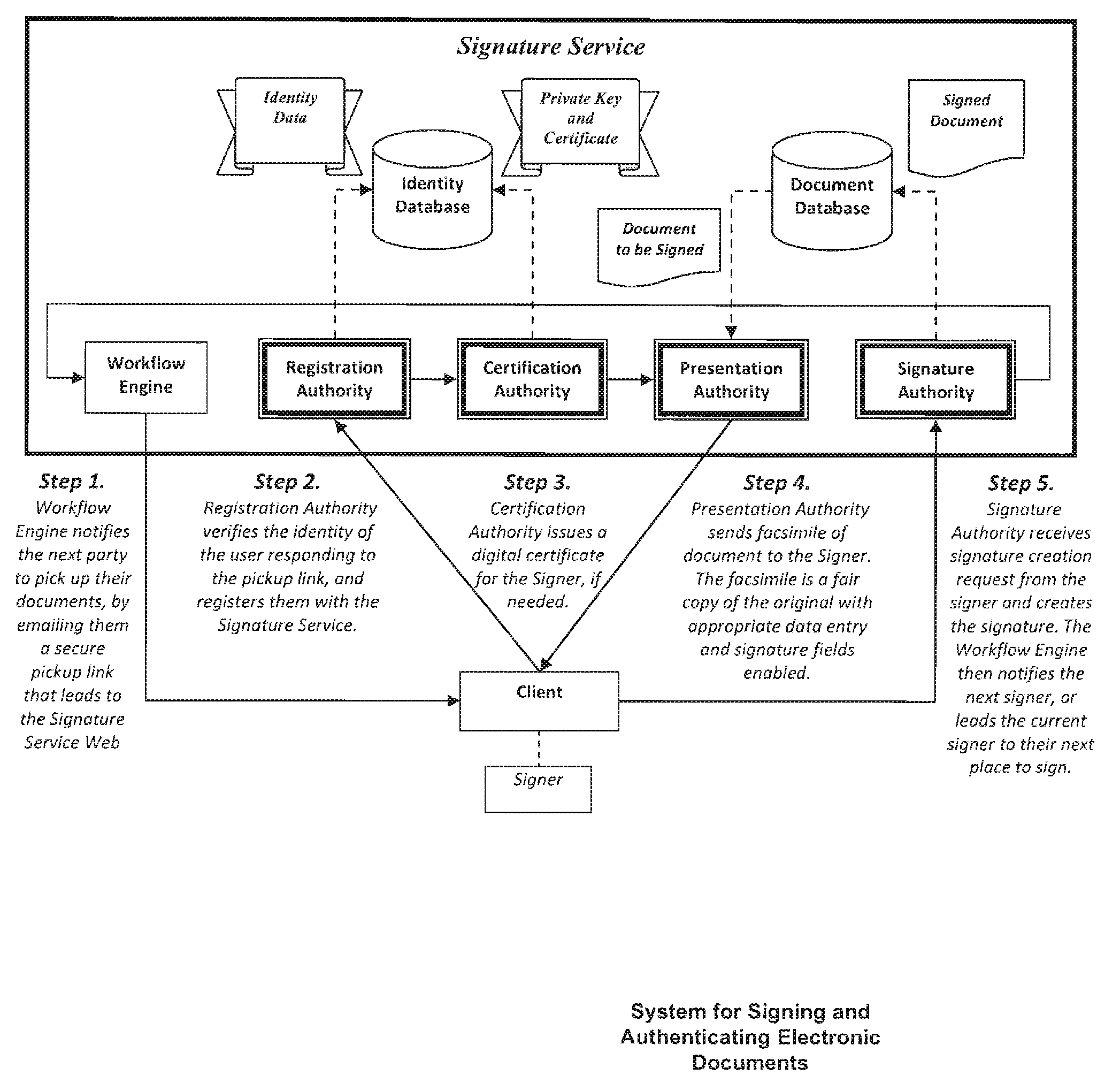
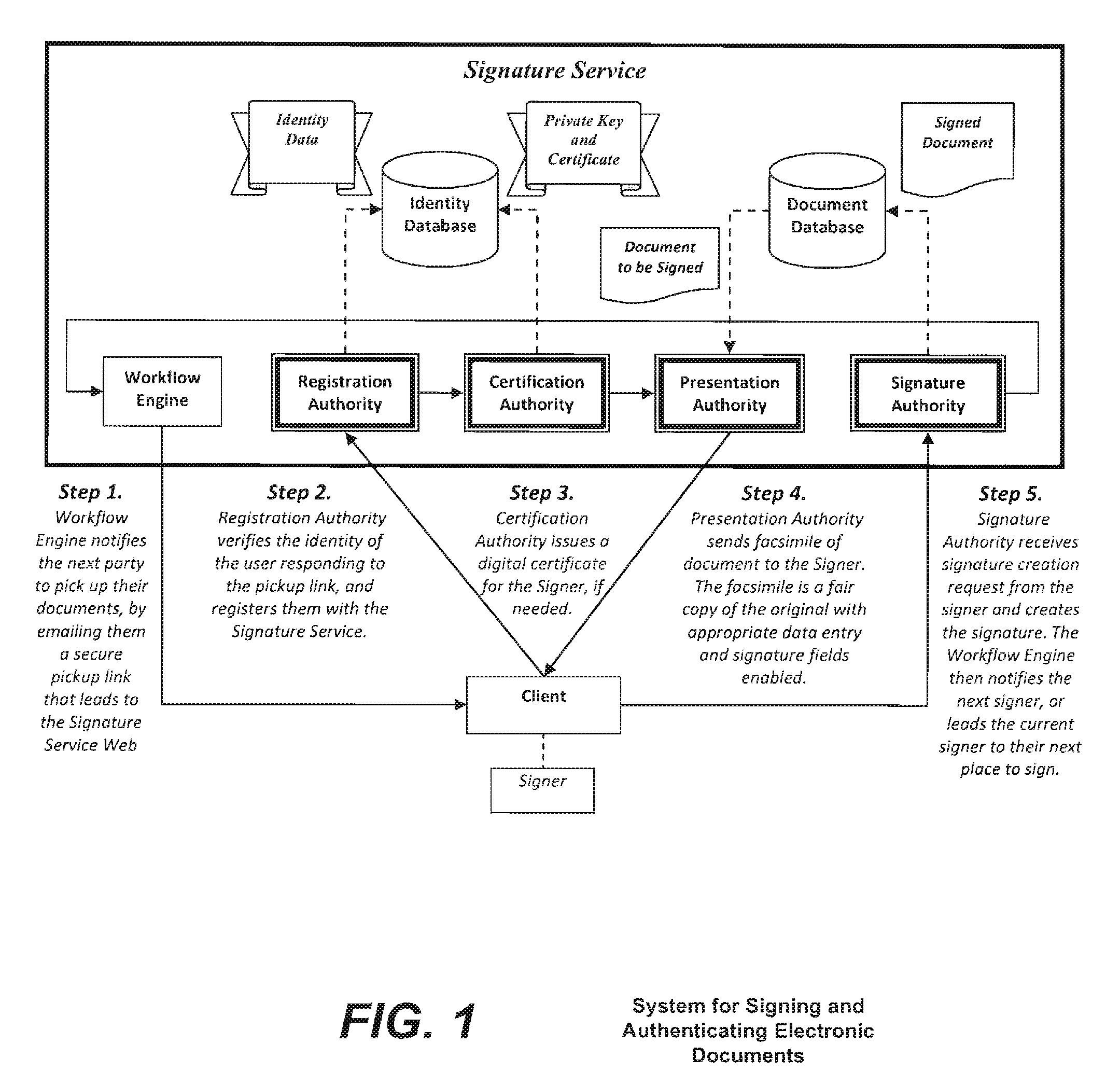
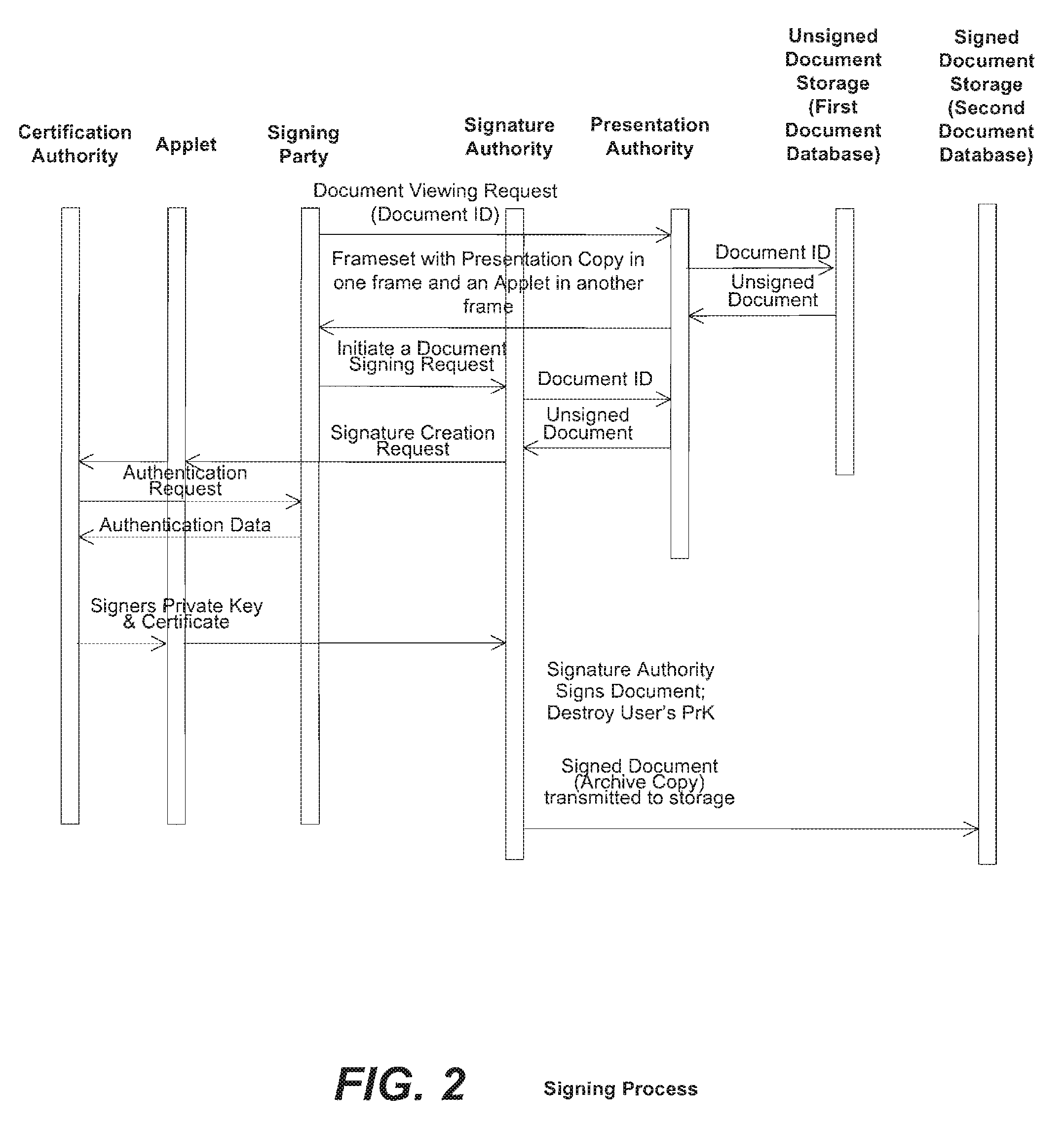
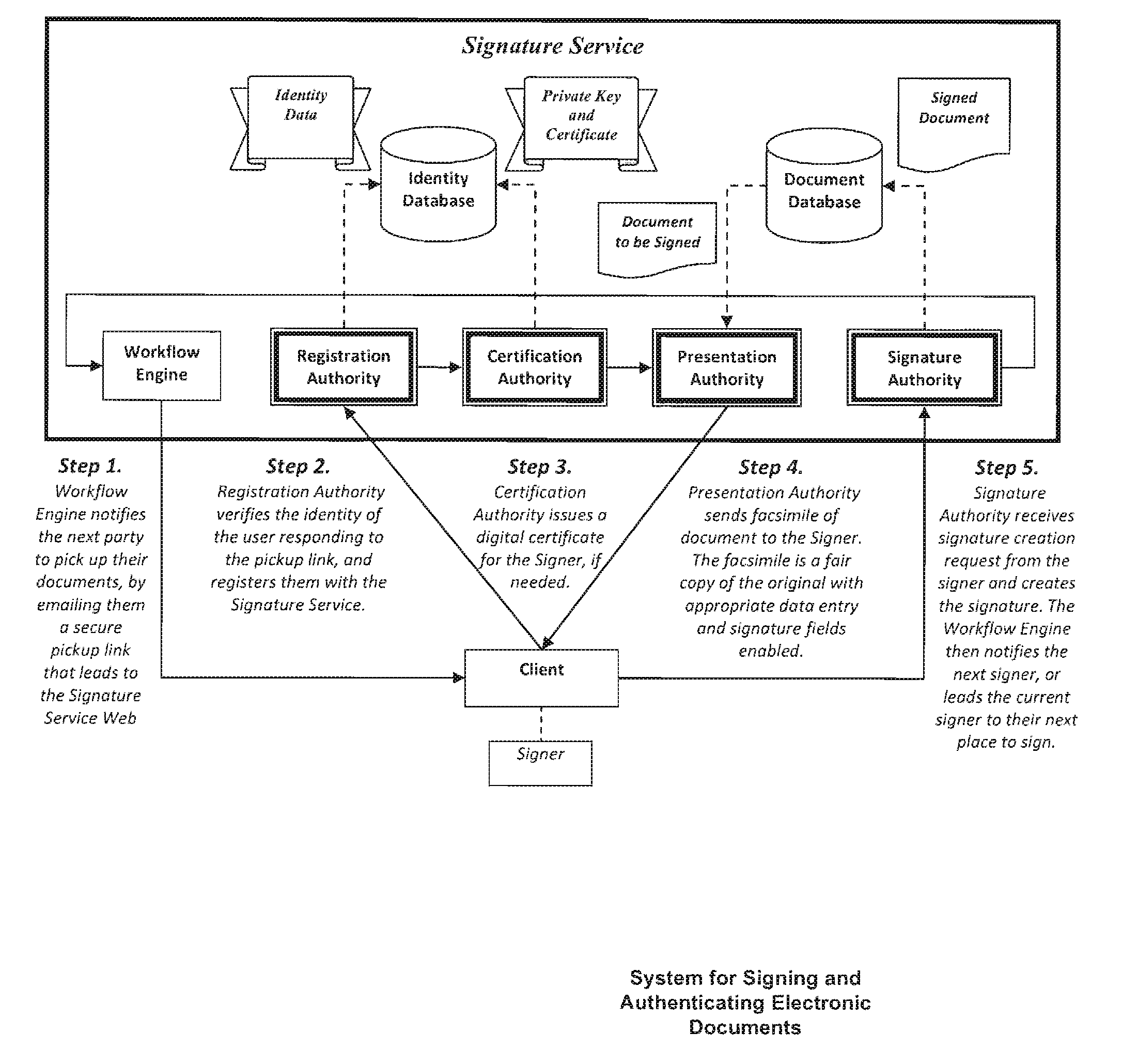
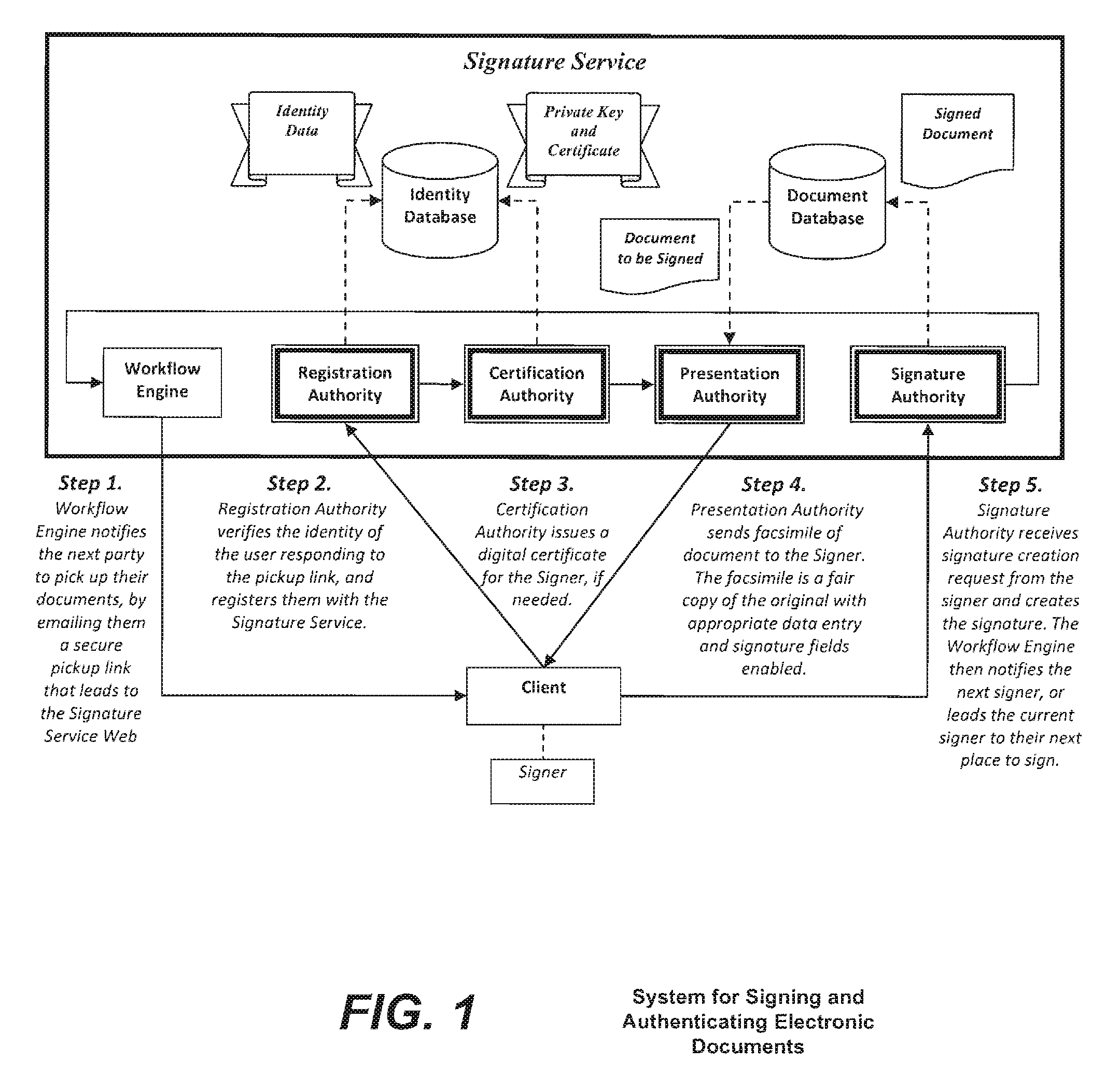
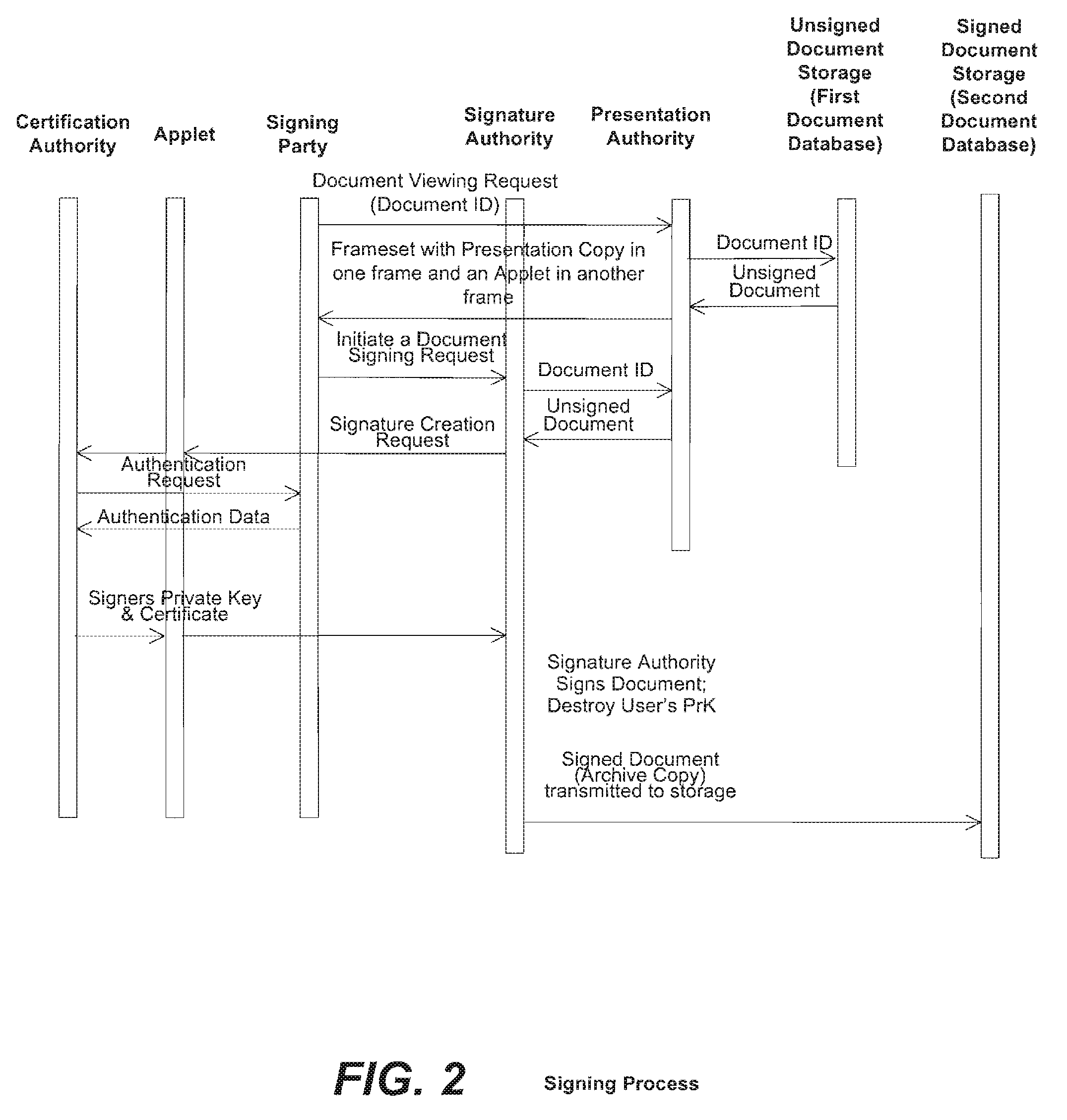
Method and system for signing and authenticating electronic documents via a signature authority which may act in concert with software controlled by the signer
ActiveUS20100313032A1Verify authenticityUser identity/authority verificationElectronic documentComputer cluster
A system and method for signing and authenticating electronic documents using public key cryptography applied by one or more server computer clusters operated in a trustworthy manner, which may act in cooperation with trusted components controlled and operated by the signer. The system employs a presentation authority for presenting an unsigned copy of an electronic document to a signing party and a signature authority for controlling a process for affixing an electronic signature to the unsigned document to create a signed electronic document. The system provides an applet for a signing party's computer that communicates with the signature authority.
Owner:SIGNIX
Memory isolation through address translation data edit control
InactiveUS7058768B2Address translation is avoidedInhibition of translationUnauthorized memory use protectionMicro-instruction address formationTrusted componentsOperating system
Owner:MICROSOFT TECH LICENSING LLC
Control and management of electronic messaging
ActiveUS7676546B2Easy to controlDigital data processing detailsUser identity/authority verificationTrusted componentsElectronic messaging
Owner:VERISIGN
Debugging and application that employs rights-managed content
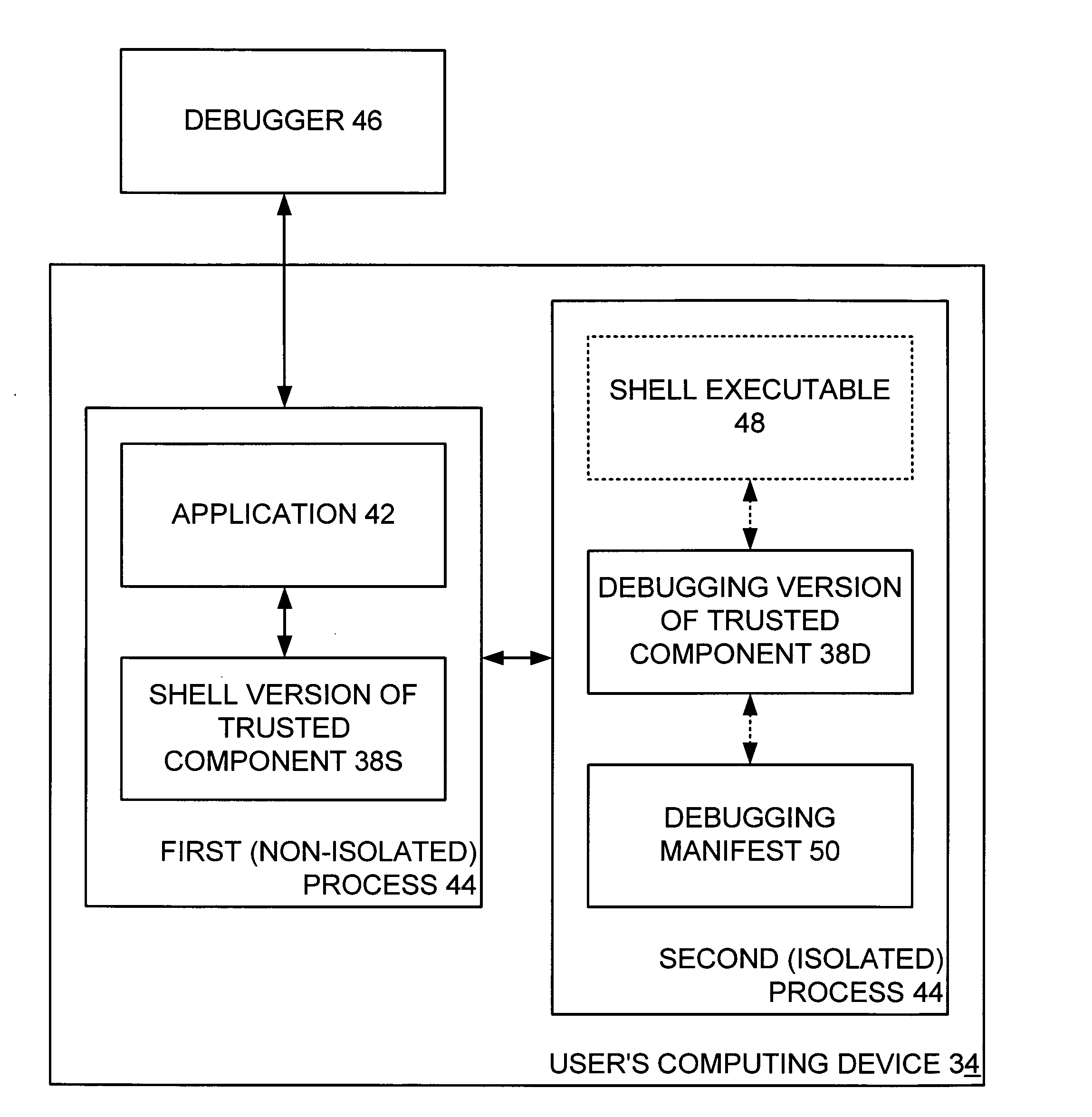
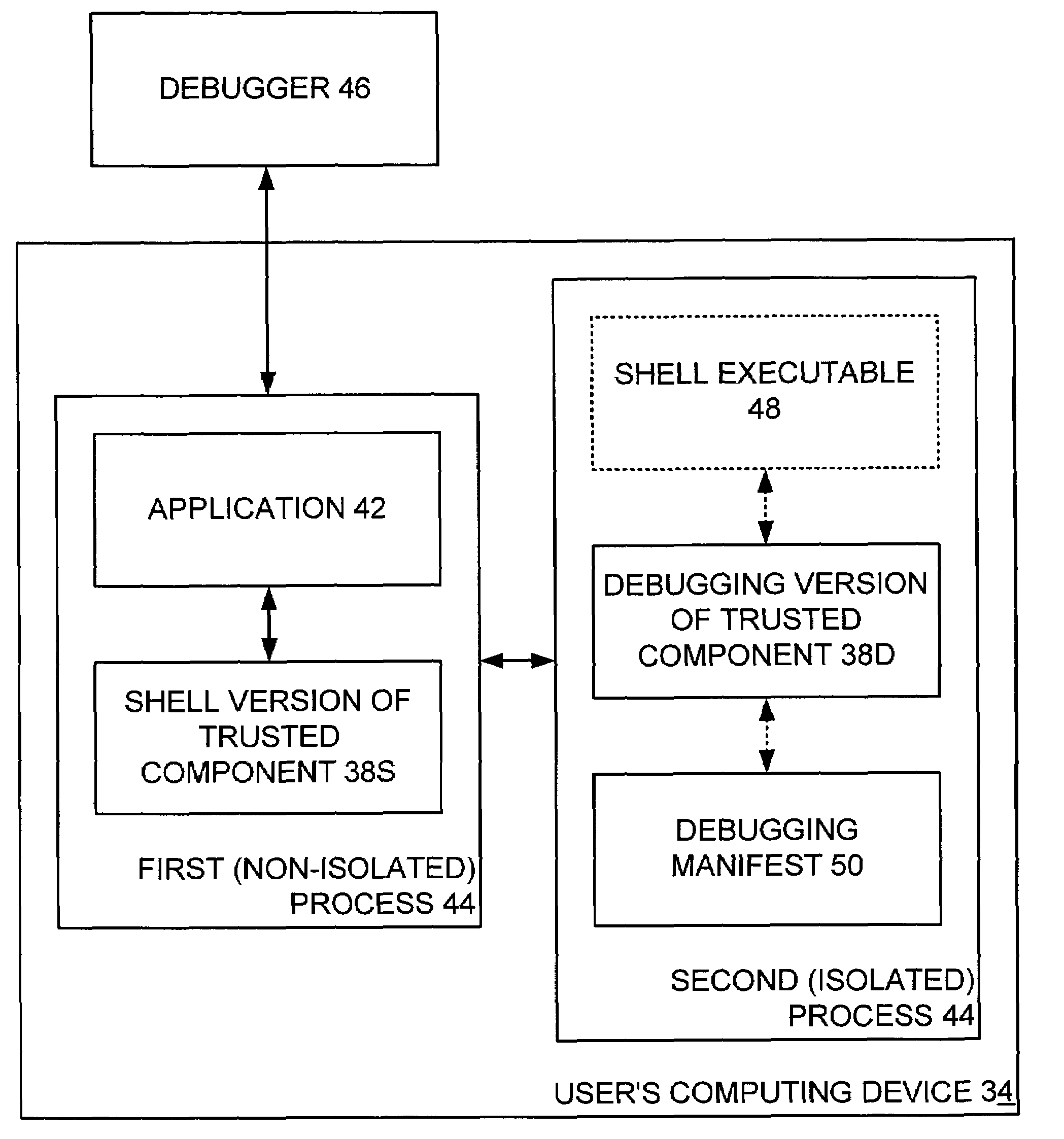
ActiveUS20050044534A1Satisfies needSoftware testing/debuggingSpecific program execution arrangementsTrusted componentsSoftware engineering
A system debugs a computer application that employs rights-managed (RM) content. A first, non-isolated process has the application and a shell version of the trusted component, where such shell version receives each request by the application for RM services. The shell version is unconcerned whether a debugger is monitoring the first process. A second, isolated process is separate from the first process and has a debugging version of the trusted component. The shell version in the first process forwards the received request to the debugging version in the second process, and such debugging version acts upon same. The debugging version ensures that the debugger is not monitoring the second process, but is unconcerned whether the debugger is monitoring the first process.
Owner:MICROSOFT TECH LICENSING LLC
Providing a secure hardware identifier (HWID) for use in connection with digital rights management (DRM) system
InactiveUS7152243B2Easy accessDigital data processing detailsUser identity/authority verificationComputer hardwareTrusted components
A trusted component on a device includes a secure HWID therein and is verified by obtaining a key from the device, and verifying each signed component of the operating system of the device therewith. A driver table is examined to locate a HWID driver which is verified as containing a pointer back to an address inside a kernel. The verified operating system is called to obtain the secure HWID from a HWID component by way of the HWID driver and to return same to the trusted component. Thereafter, the returned HWID is verified as matching the HWID included with the trusted component.
Owner:SZ DJI TECH CO LTD
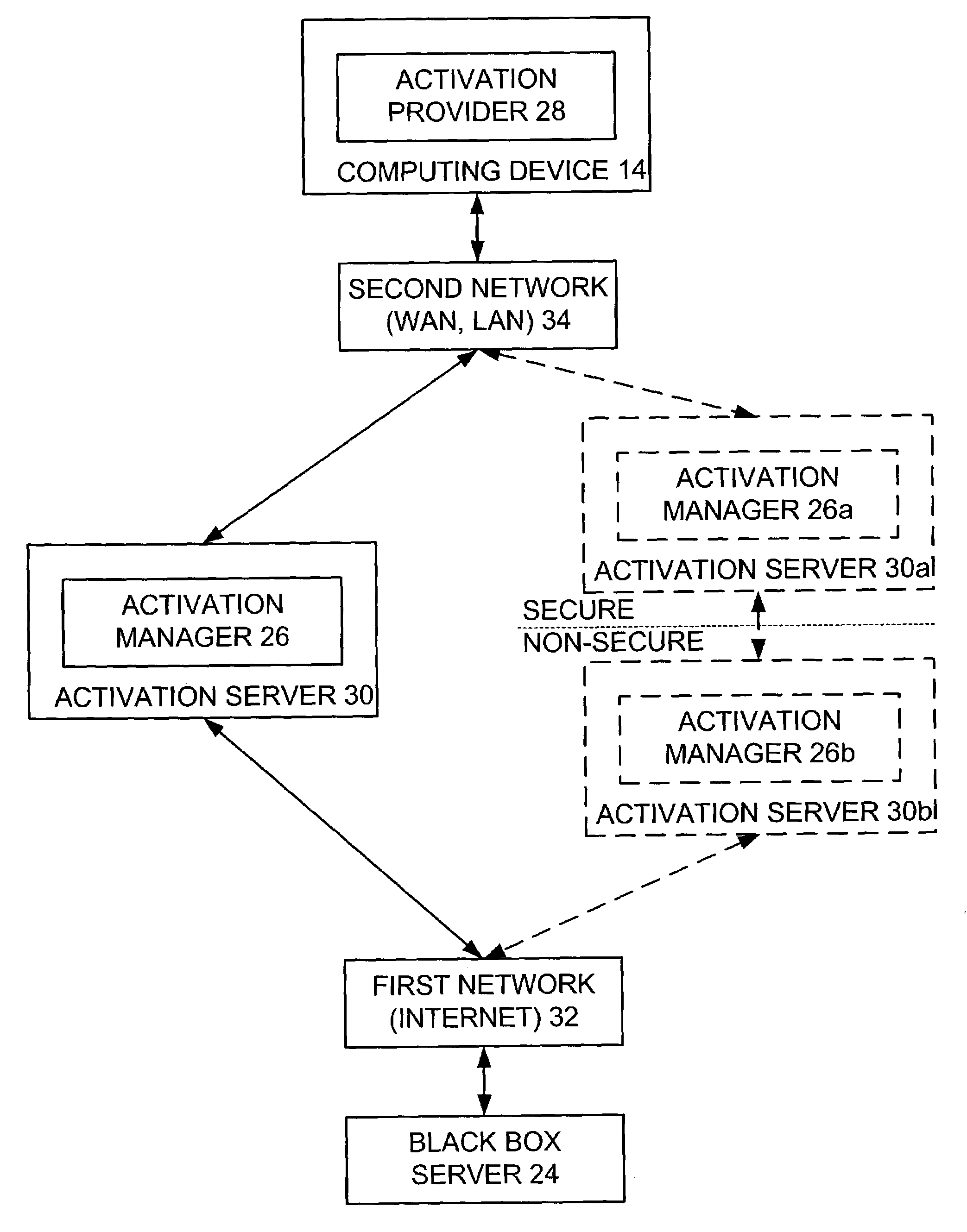
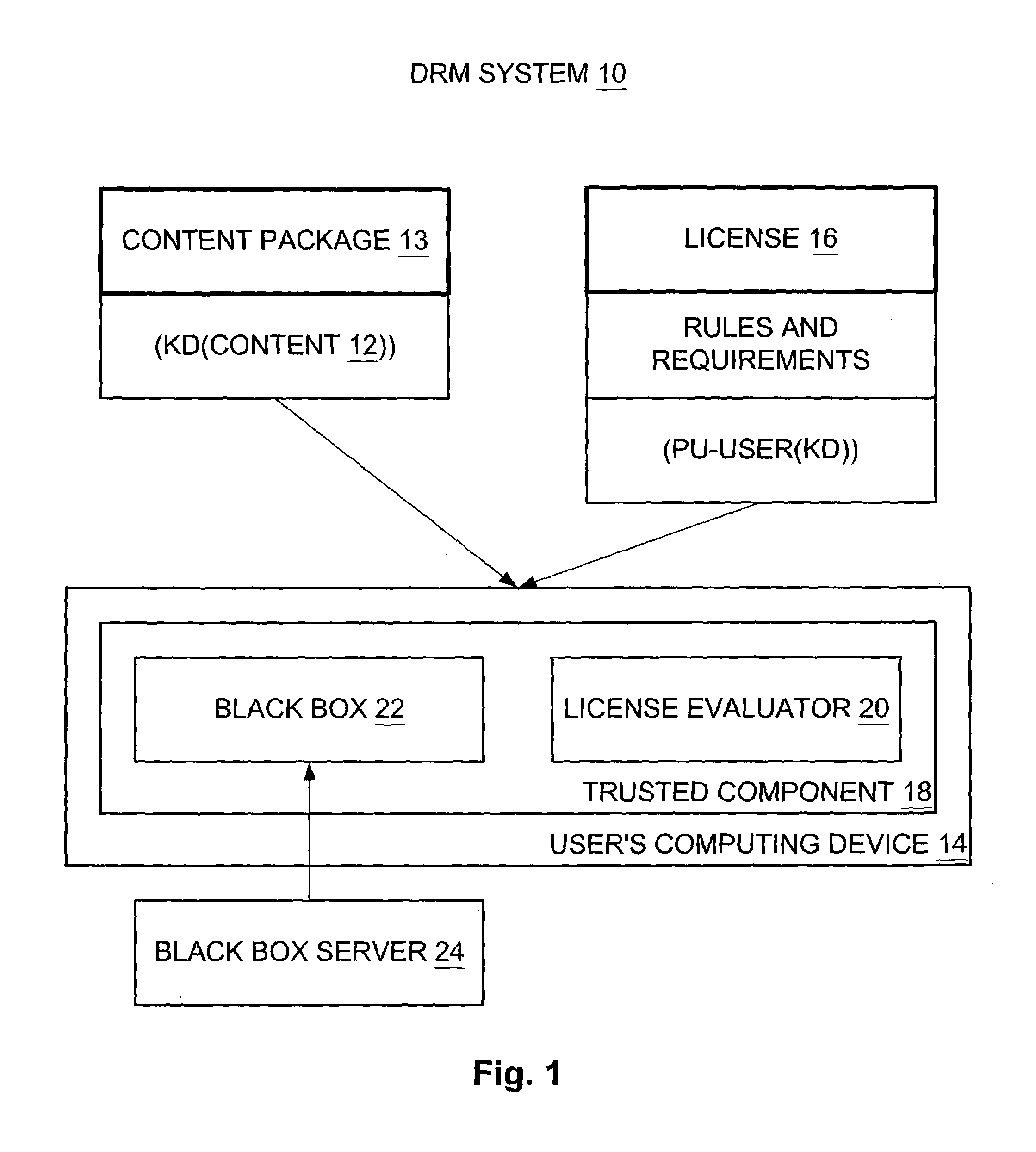
Installation of black box for trusted component for digital rights management (DRM) on computing device
InactiveUS7152245B2Satisfies needData processing applicationsDigital data processing detailsTrusted componentsDigital rights management
To install a black box on a computing device, an administrator has access to the computing device and queries same for machine properties thereof. The administrator sends the machine properties of the computing device to a black box server as part of a request for a new black box for the computing device. The black box server in response constructs the new black box based in part on the machine properties so as to tie the new black box to the computing device, and delivers the new black box to the administrator. The administrator thereafter installs the new black box on the computing device. The administrator may include an activation provider running on the computing device and an activation manager in communication with the activation provider. The administrator may also deactivate the black box if it determines that the black box is no longer trustworthy.
Owner:SZ DJI TECH CO LTD
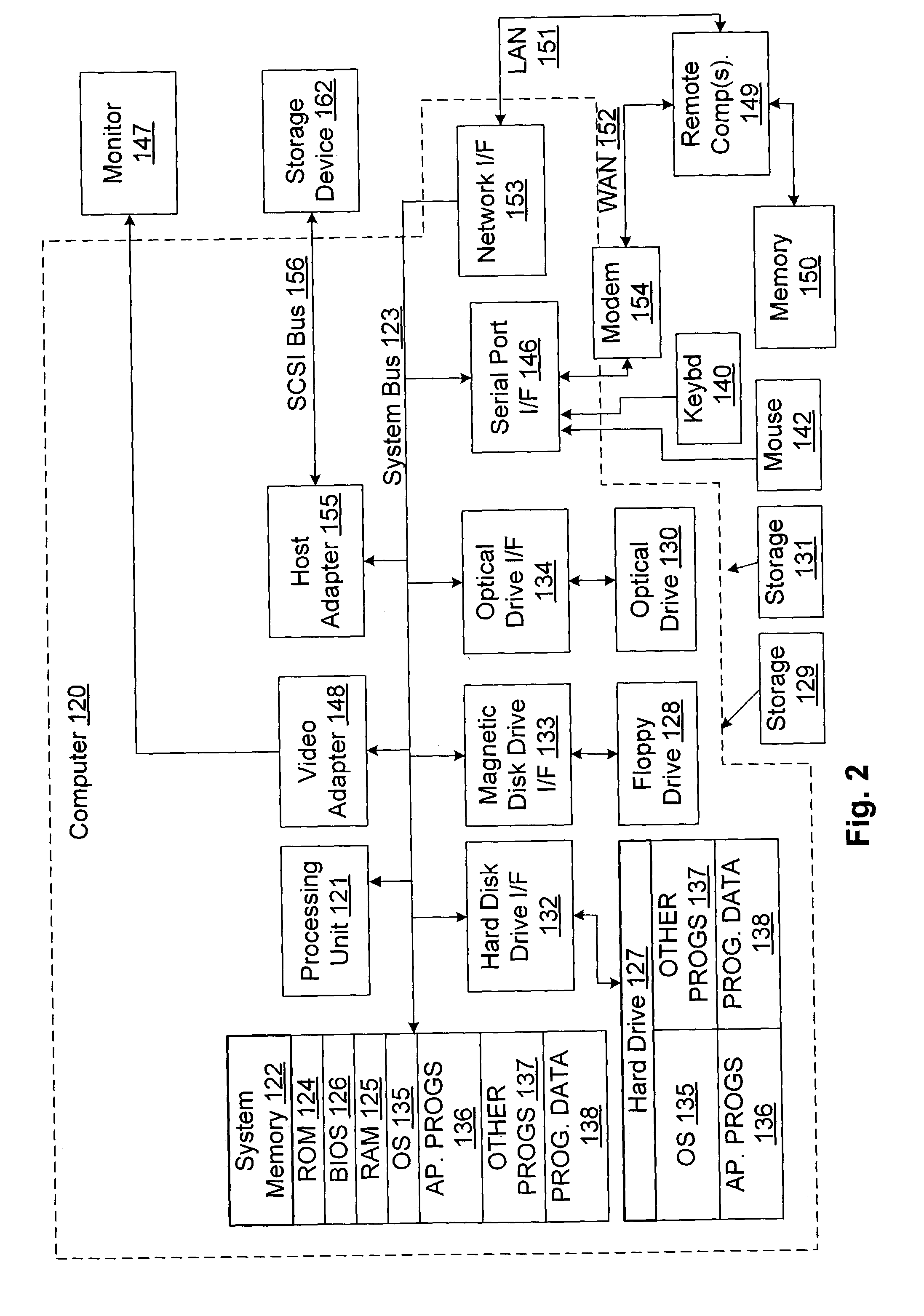
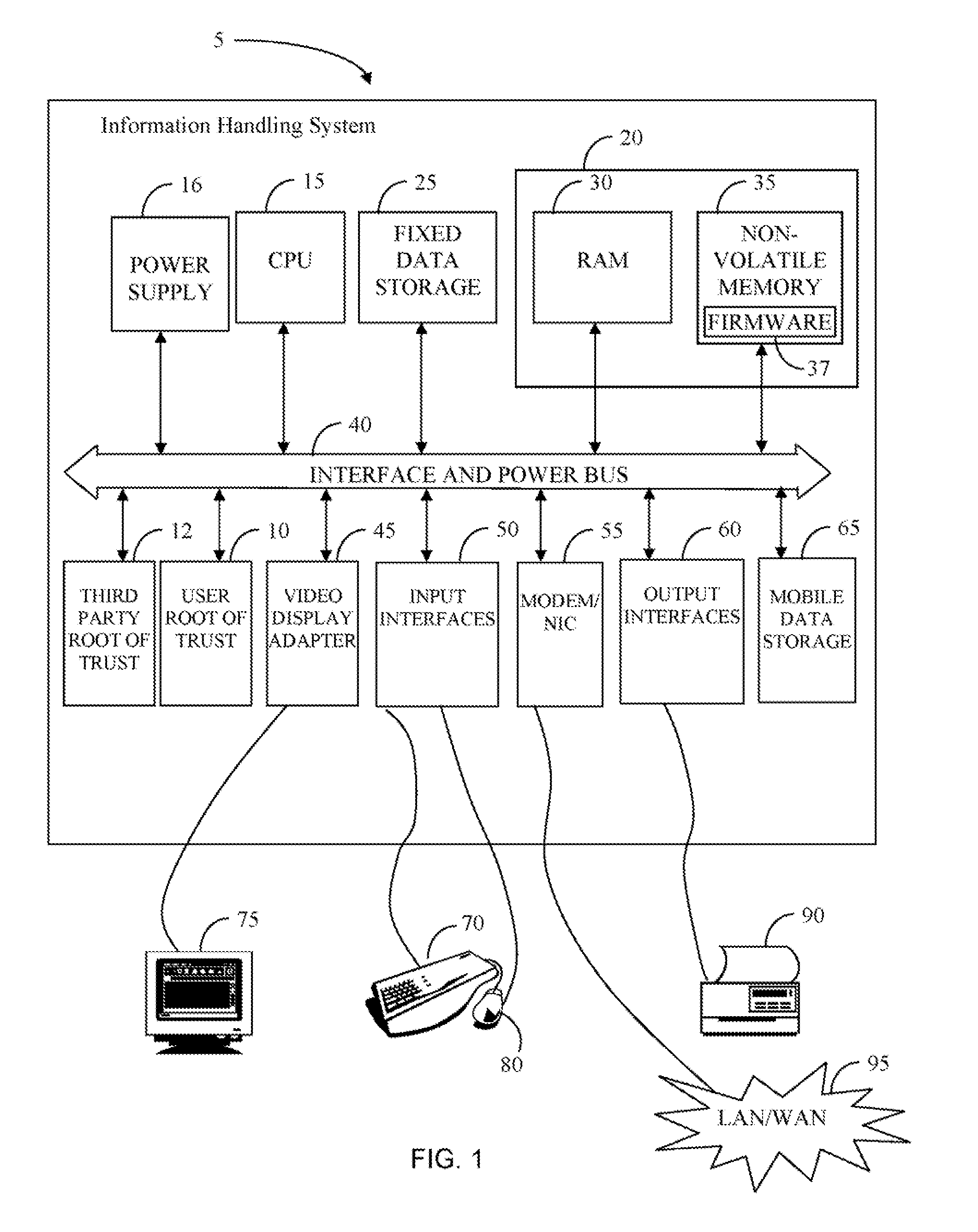
Methods, Apparatus and Products for Establishing a Trusted Information Handling System
InactiveUS20080184028A1Limit scopeUser identity/authority verificationInternal/peripheral component protectionThird partyTrusted components
A method for modifying a trusted information handling system (IHS) is disclosed that includes providing a trusted component (TC) on the IHS and providing at least one third party TC on the IHS. A trusted IHS is disclosed that includes a processor in data communication with memory, a user TC on the trusted IHS for receiving user data establishing a user foundation of trust (FOT) and at least one third party TC on the trusted IHS for establishing a third party FOT.
Owner:DELL PROD LP
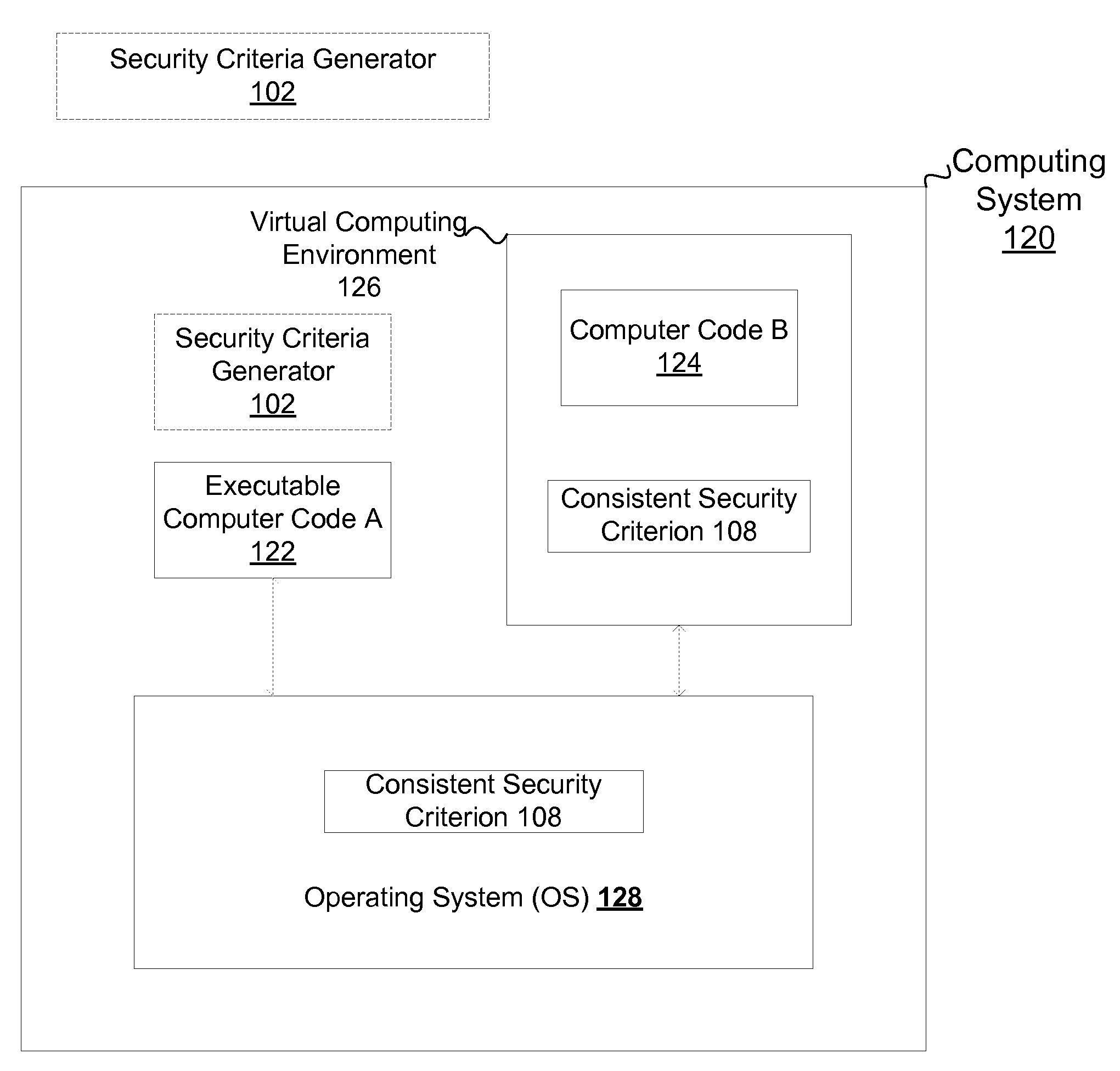
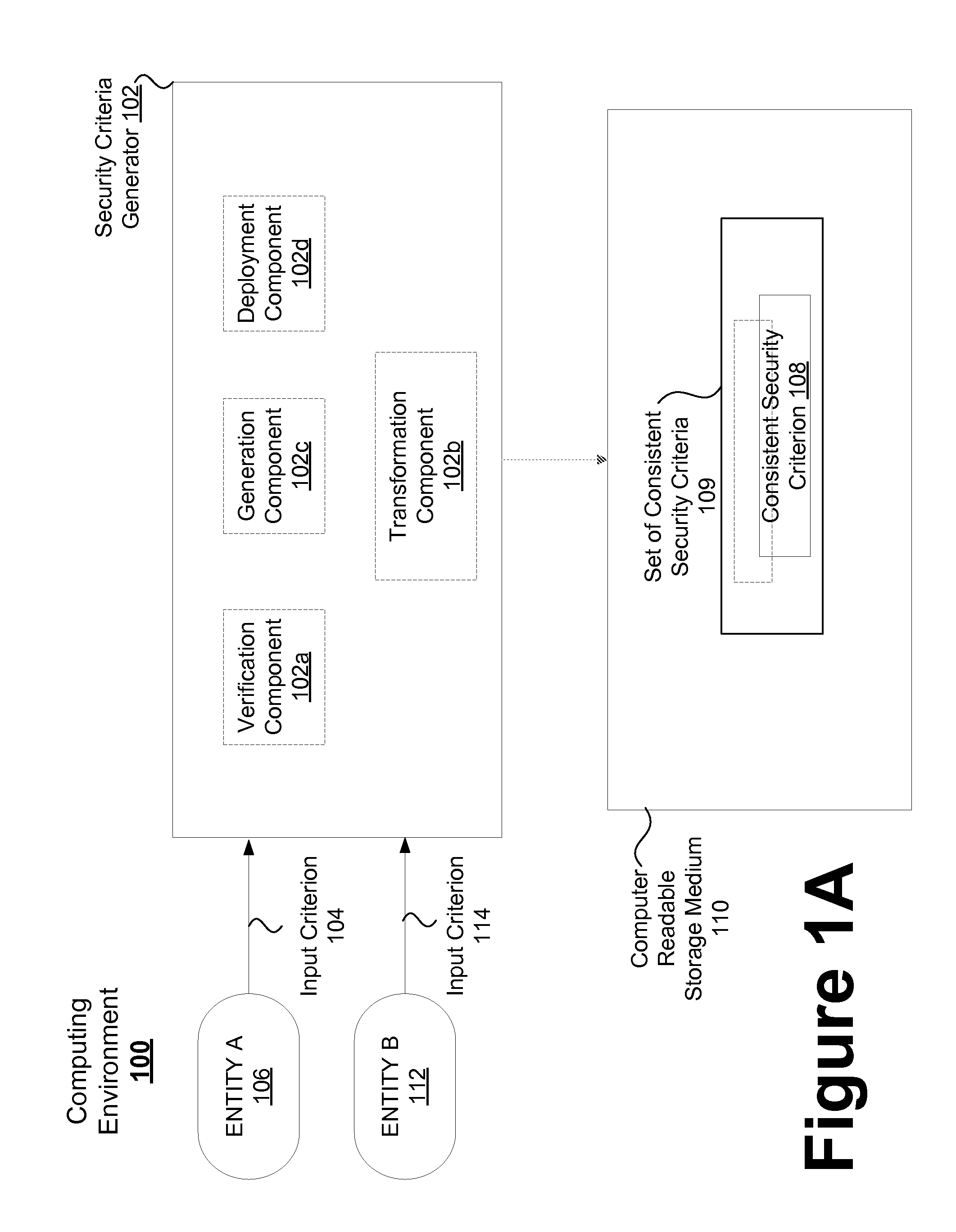
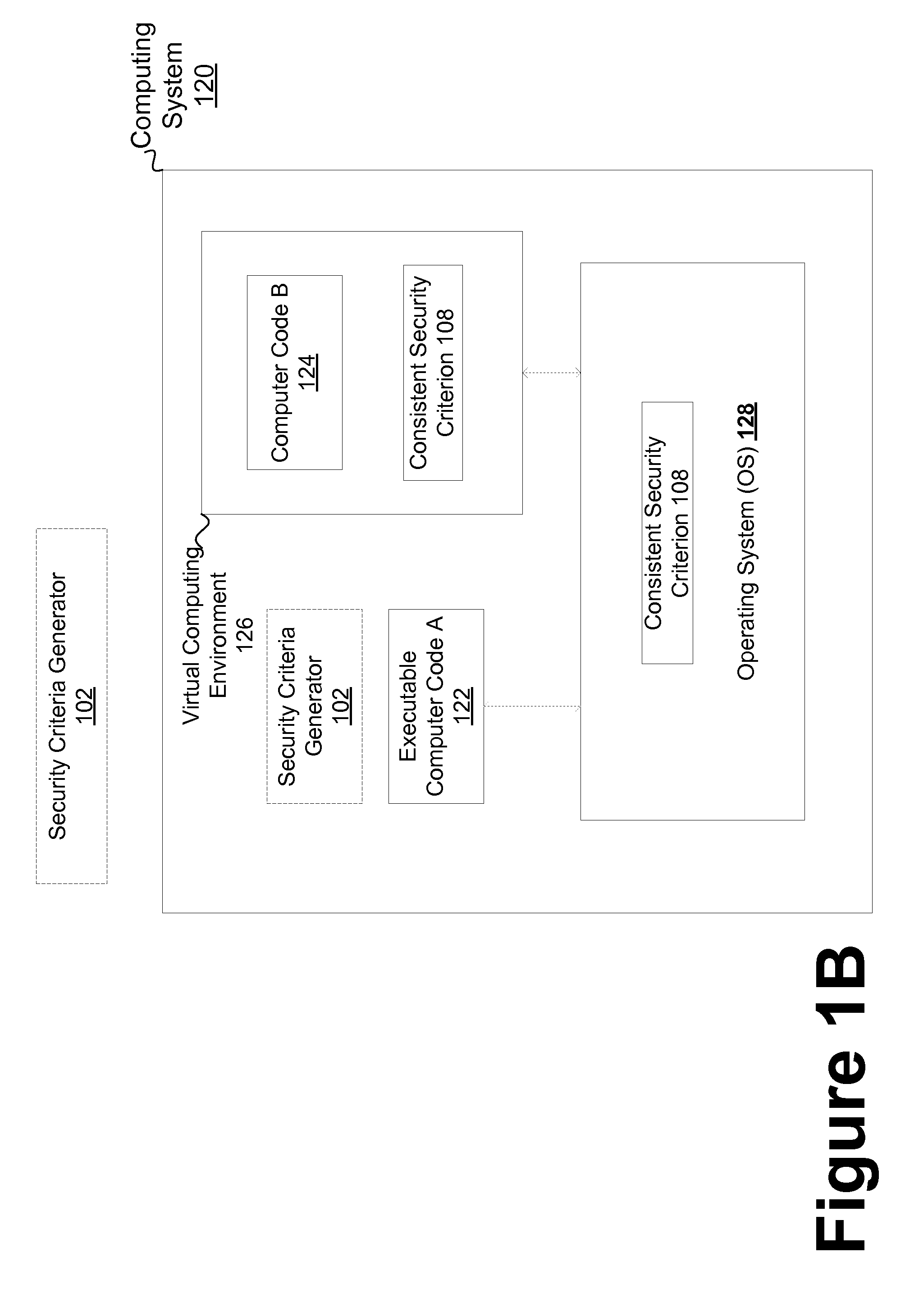
Consistent security enforcement for safer computing systems
InactiveUS20100162240A1Efficiently provideProvide securityComputer security arrangementsSoftware simulation/interpretation/emulationOperational systemTrusted components
Security can be enforced in a consistent manner with respect to various computing environments that may be operable in a computing system. Consistent security criteria can be generated, based on input security criterion, in a computer readable and storable form and stored in a computer readable storage medium, thereby allowing the consistent security criterion to be effectively provided to a computing system for enforcement of the input security criterion in a consistent manner with respect to, for example, (a) a first executable computer code effectively supported by an Operating System (OS), and (b) a second computer code effectively supported by the Virtual Computing Environment (VCE). A Trusted Component (TC) can effectively provide a consistent security criterion as a part and / or form that is suitable for a particular computing environment. The TC can, for example, be an automated tool that performs various functions including: verifying the consistency of security criteria, generation and deployment of consistent security criteria, and transformation of security criteria to parts and / or forms suitable for various computing environments. In addition, a Virtual Computing Environment (VCE) can obtain from the Operating System (OS) one or more security criteria. The Virtual Computing Environment (VCE) can be operable in a Trusted Computing Environment (TCE) and interface with a Trusted Operating System (TOS) that effectively enforces Mandatory Access Control (MAC), thereby allowing the Virtual Computing Environment (VCE) to leverage the security provided by the OS. The OS can, for example, be a Security-Enhanced Linux (SELinux) Operating System operating as a Trusted Component in a Trusted Environment that includes a Trusted Security Agent (TSA) operable to deploy consistent security criteria.
Owner:SAMSUNG ELECTRONICS CO LTD
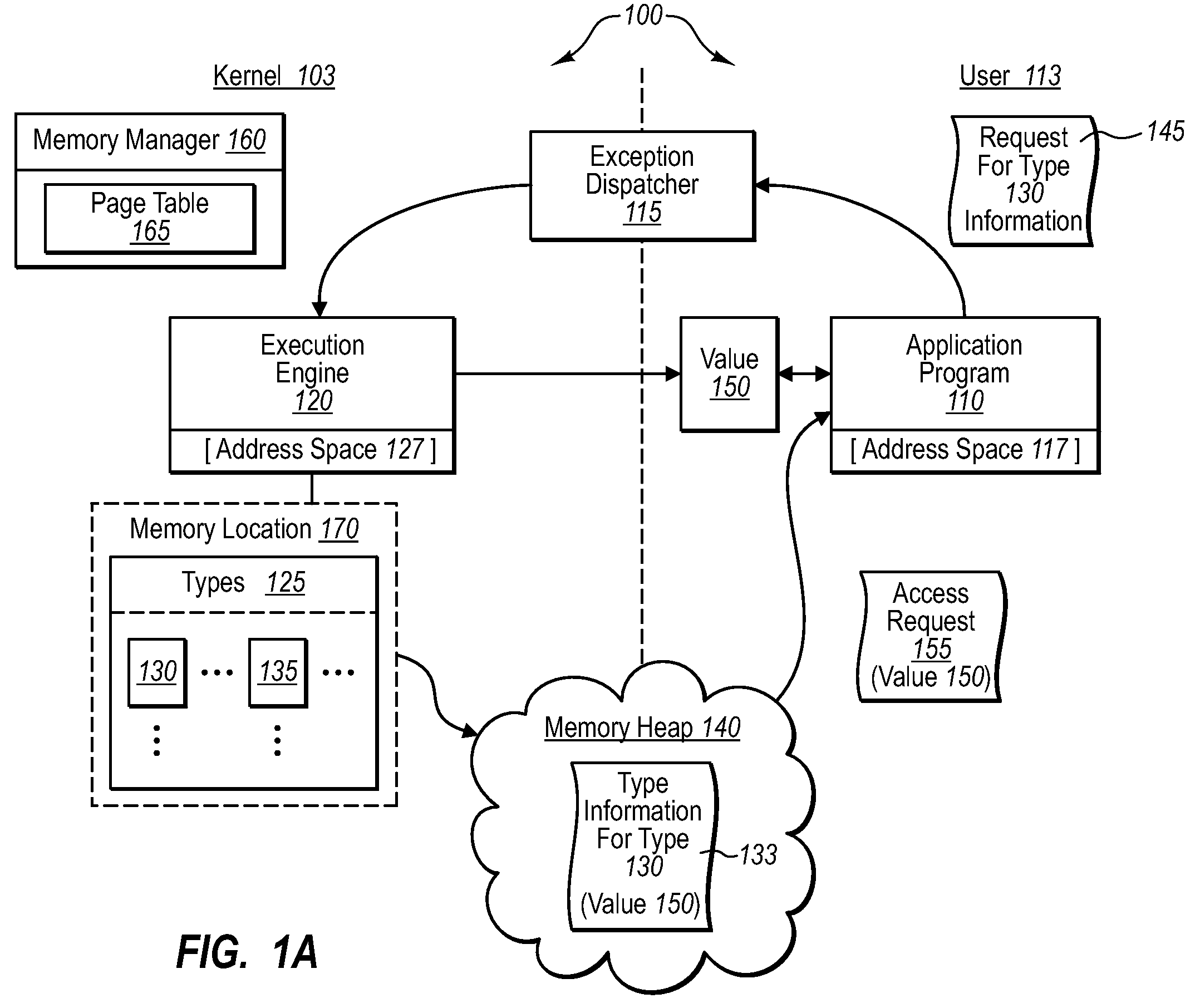
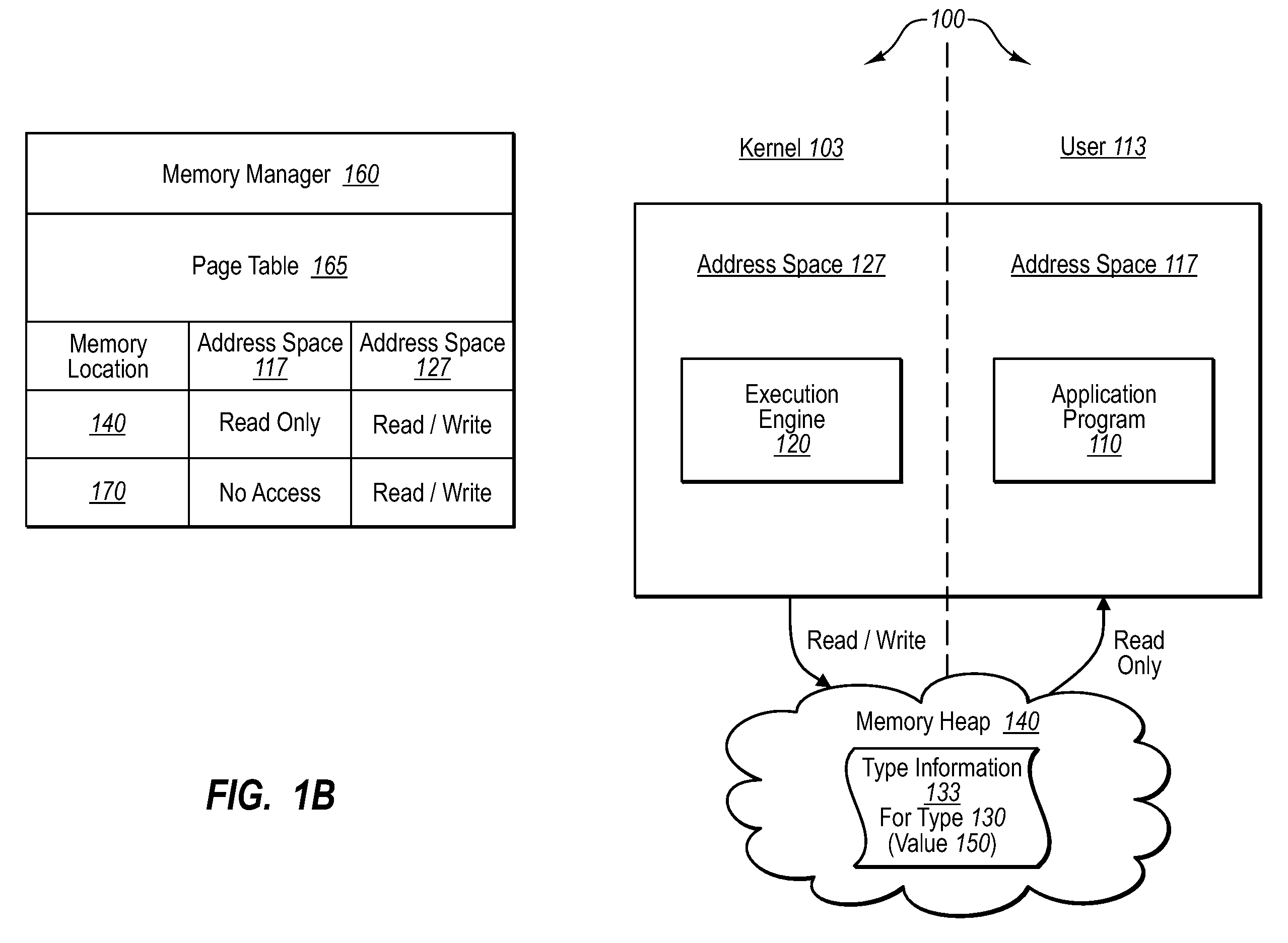
Restricting type access to high-trust components
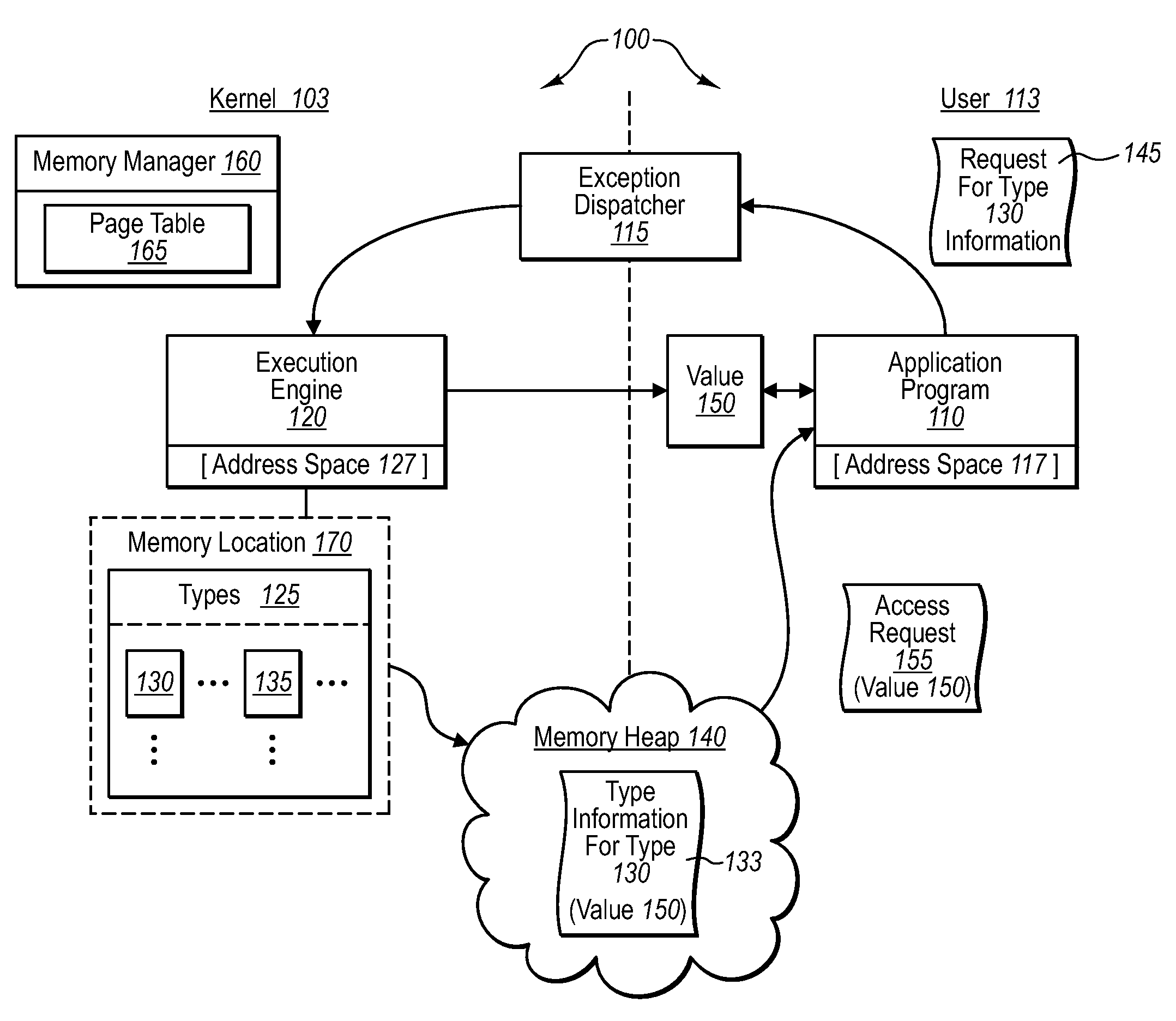
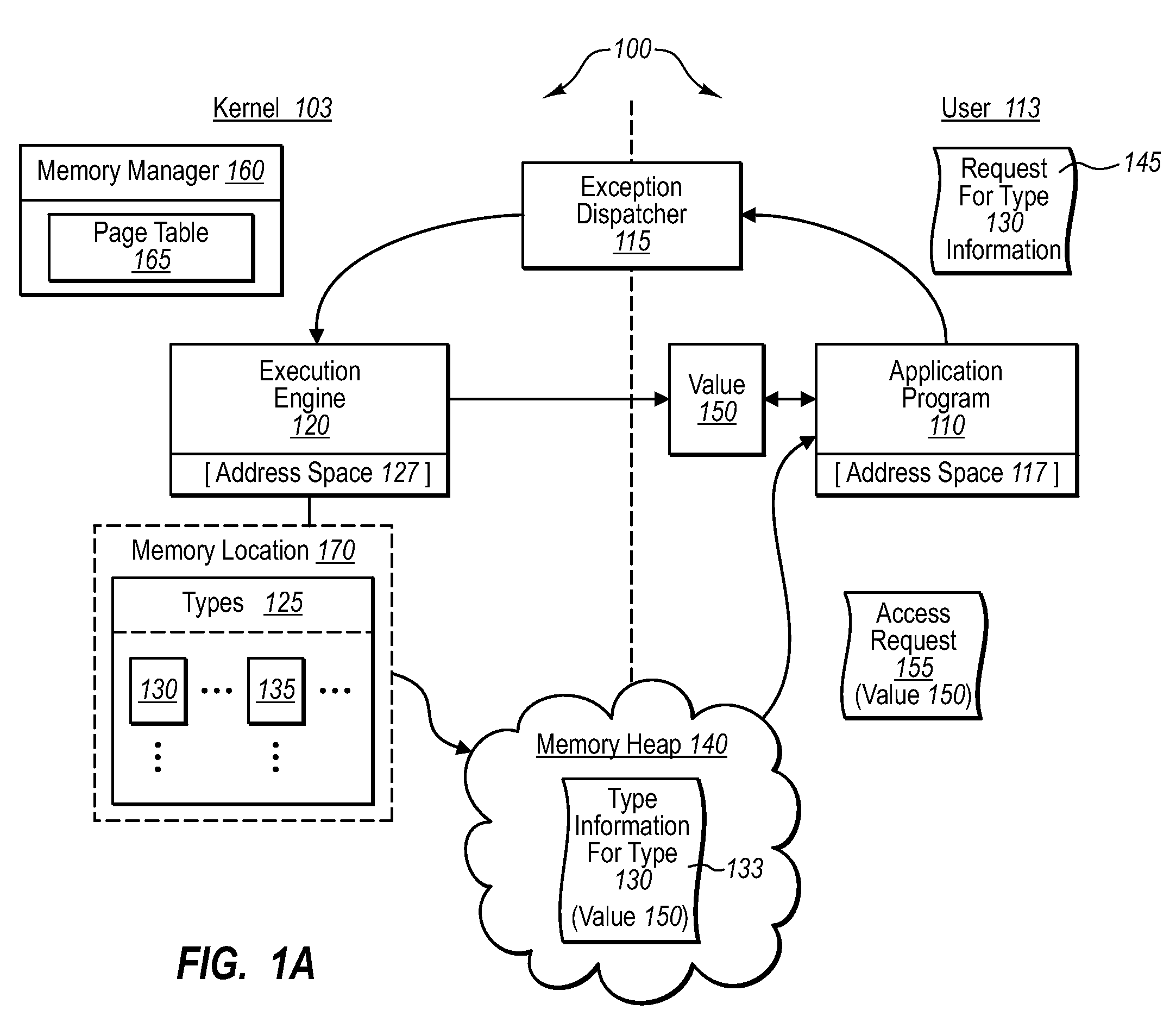
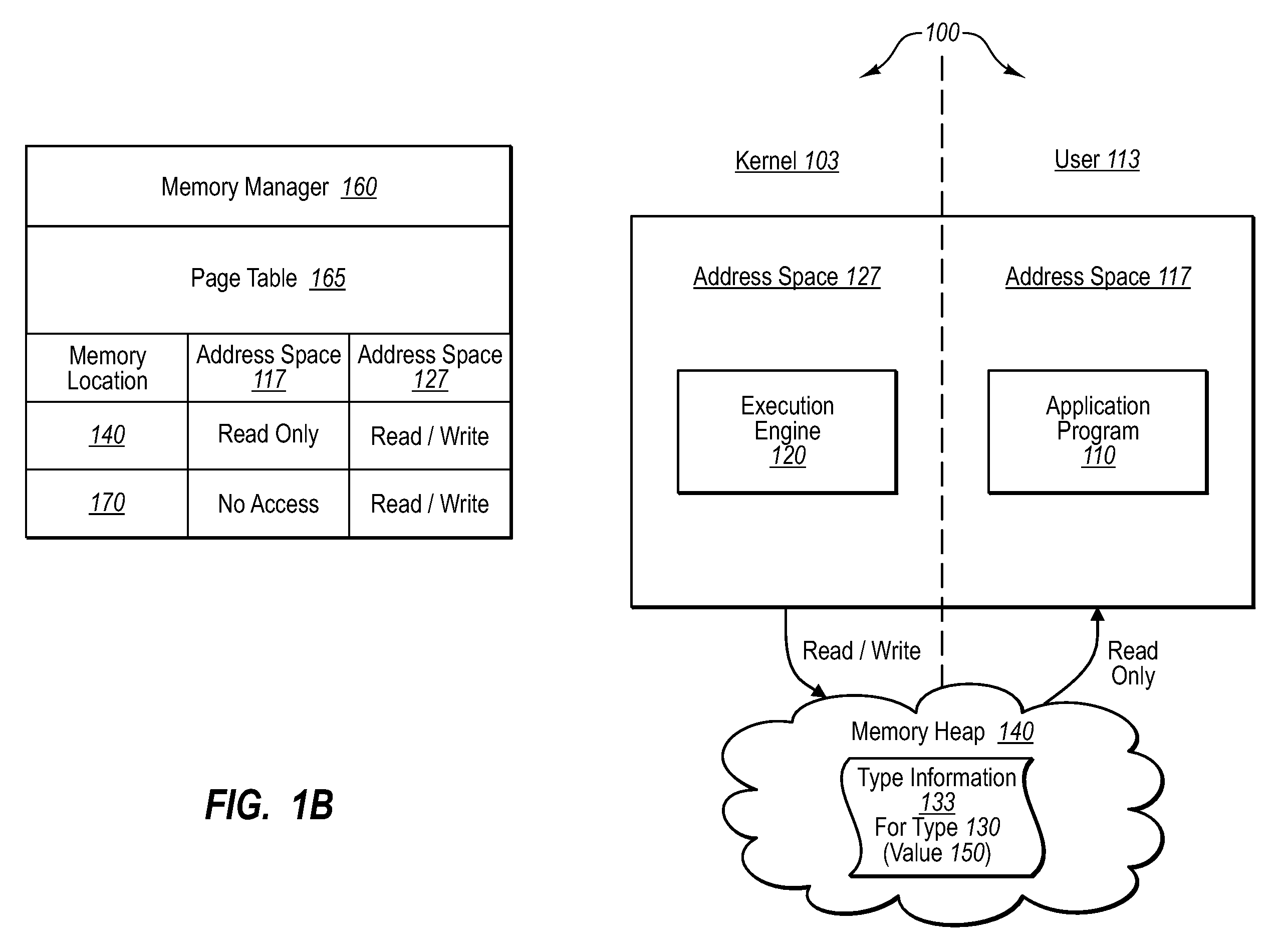
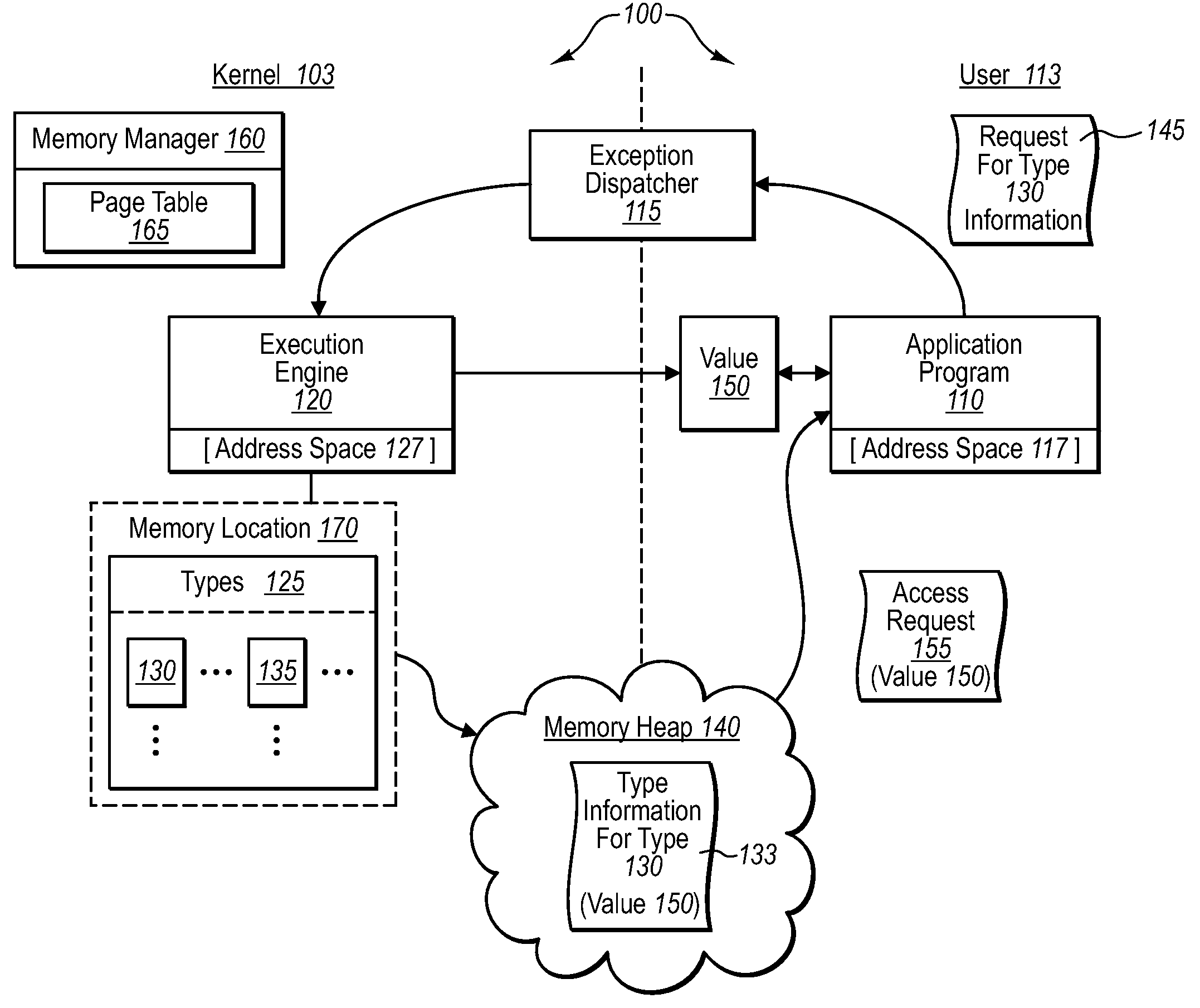
Sensitive data structures, such as type data structures, can be used by untrusted application programs without necessarily exposing the sensitive data structures directly. For example, untrusted components, such as application programs that may or may not be type safe, can be allowed to operate in a lower-privilege mode. In addition, the application programs can be associated with an address space with limited permissions (e.g., read-only) to a shared memory heap. Requests by the untrusted components for sensitive data structures can then be handled by trusted components operating in a higher-privilege mode, which may have broader permissions to the shared memory heap. If the requests by the untrusted components are deemed to be valid, the results of the requests can be shared with the lower-privilege mode components through the shared memory heap.
Owner:MICROSOFT TECH LICENSING LLC
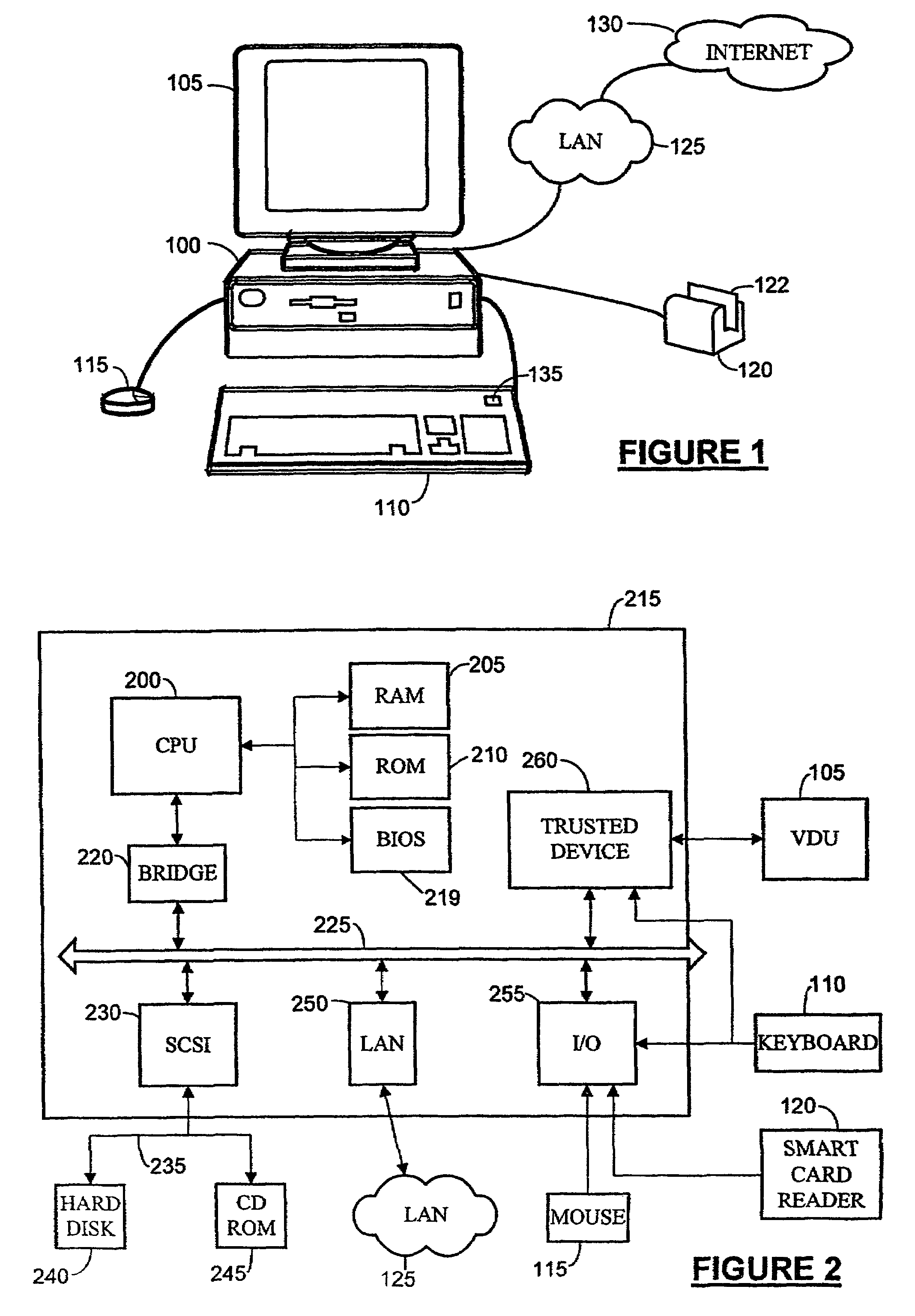
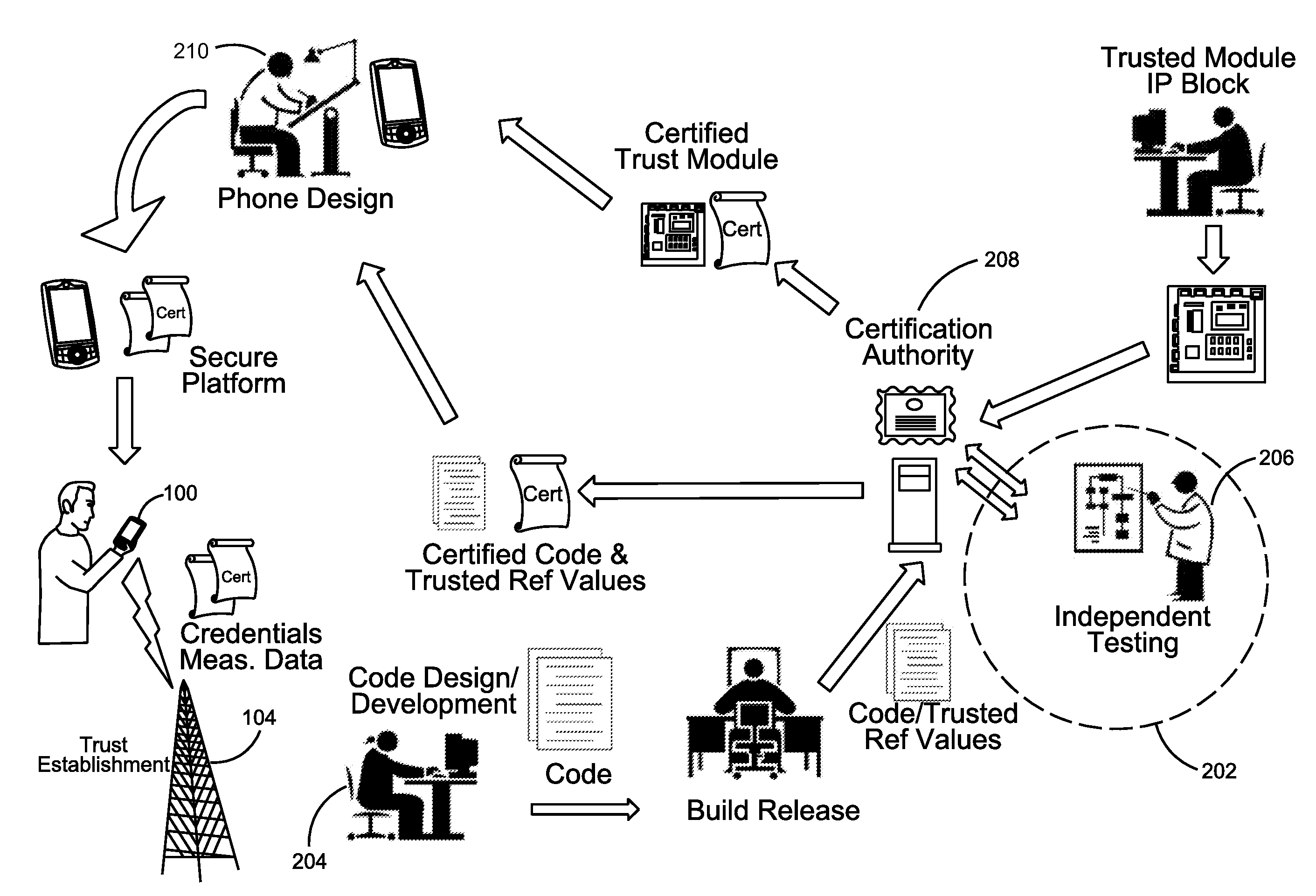
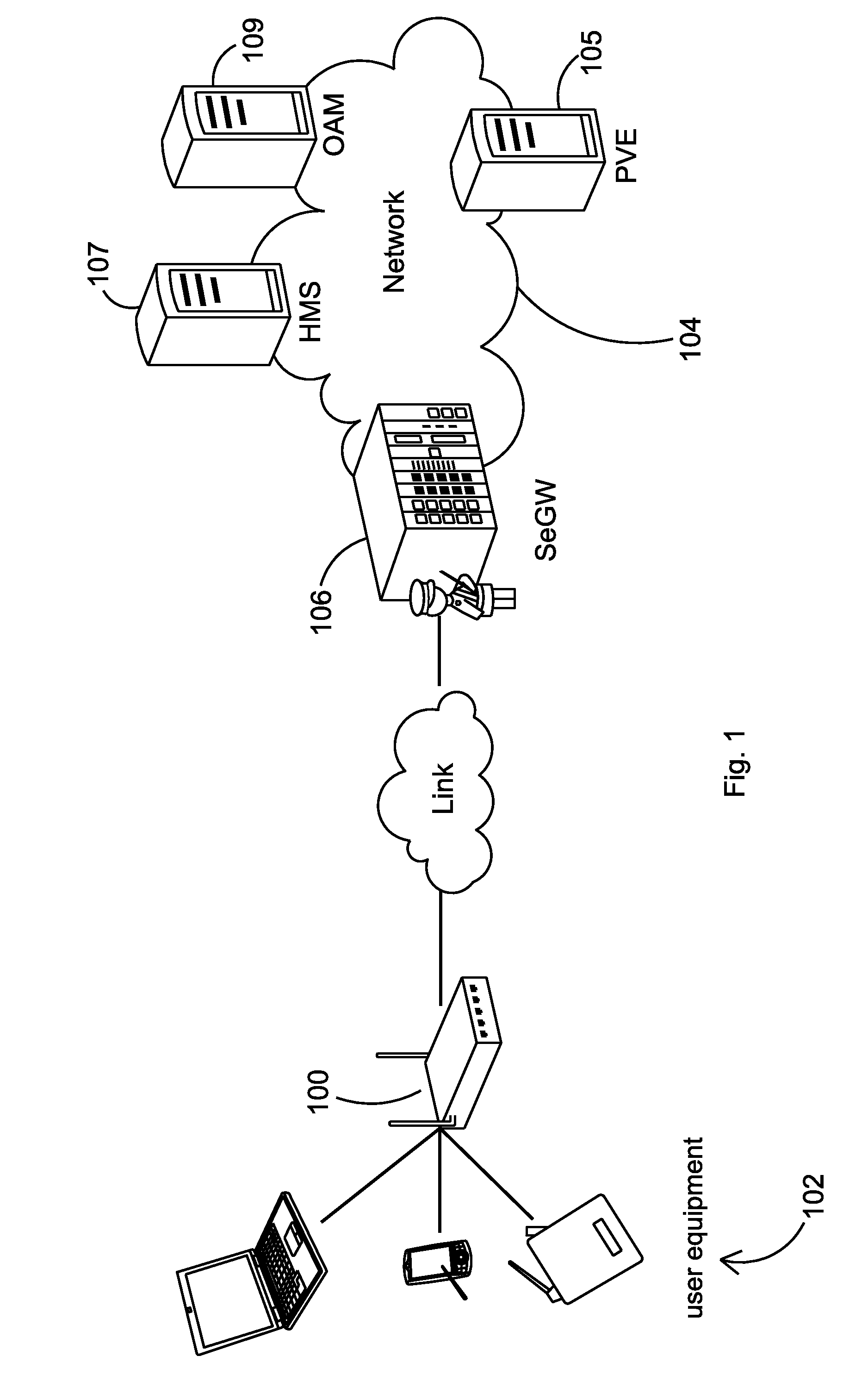
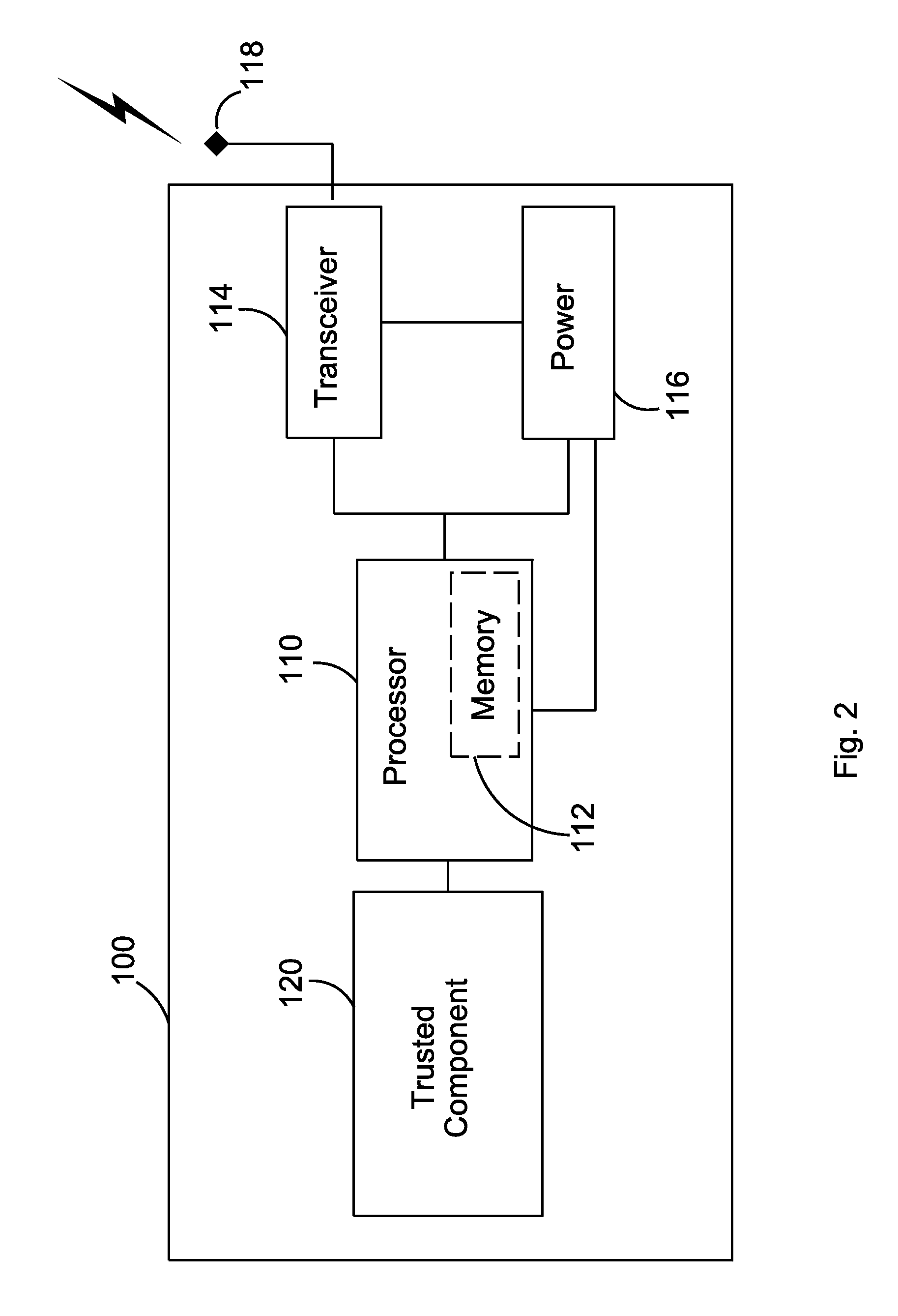
Scalable and secure high-level storage access for cloud computing platforms
ActiveUS8997096B1Effective segmentationHighly accessibleUser identity/authority verificationMultiple digital computer combinationsTrusted componentsTrust relationship
Owner:EMC IP HLDG CO LLC
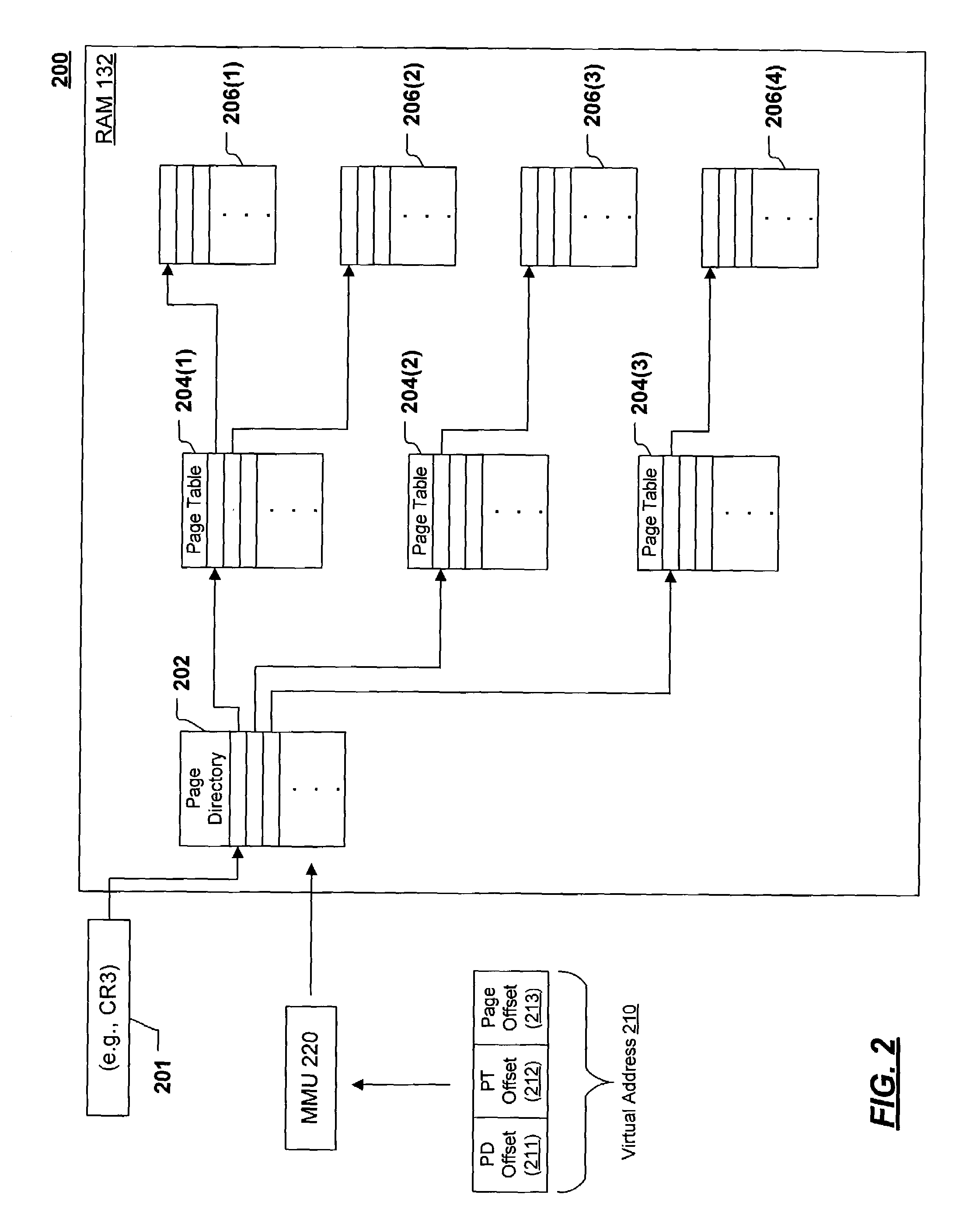
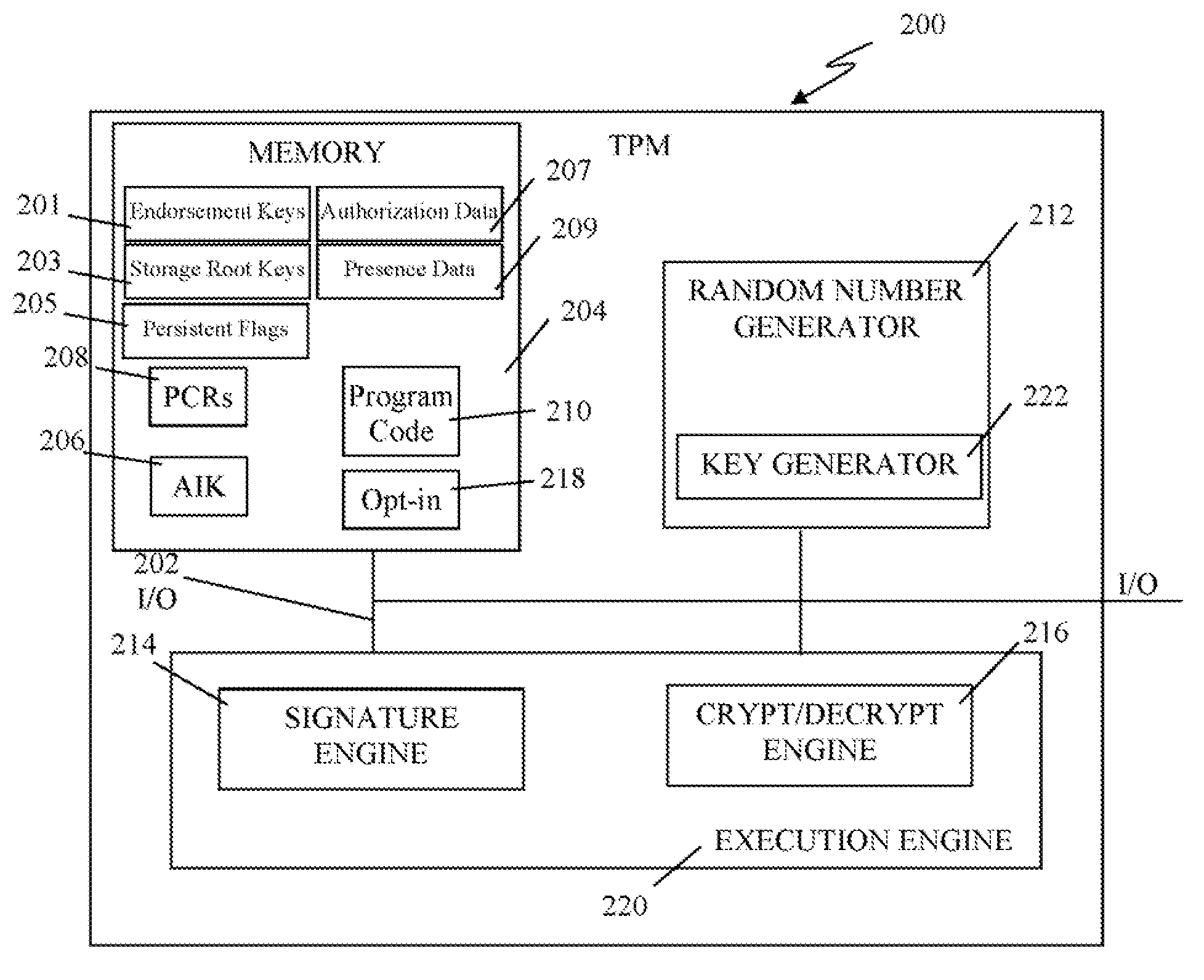
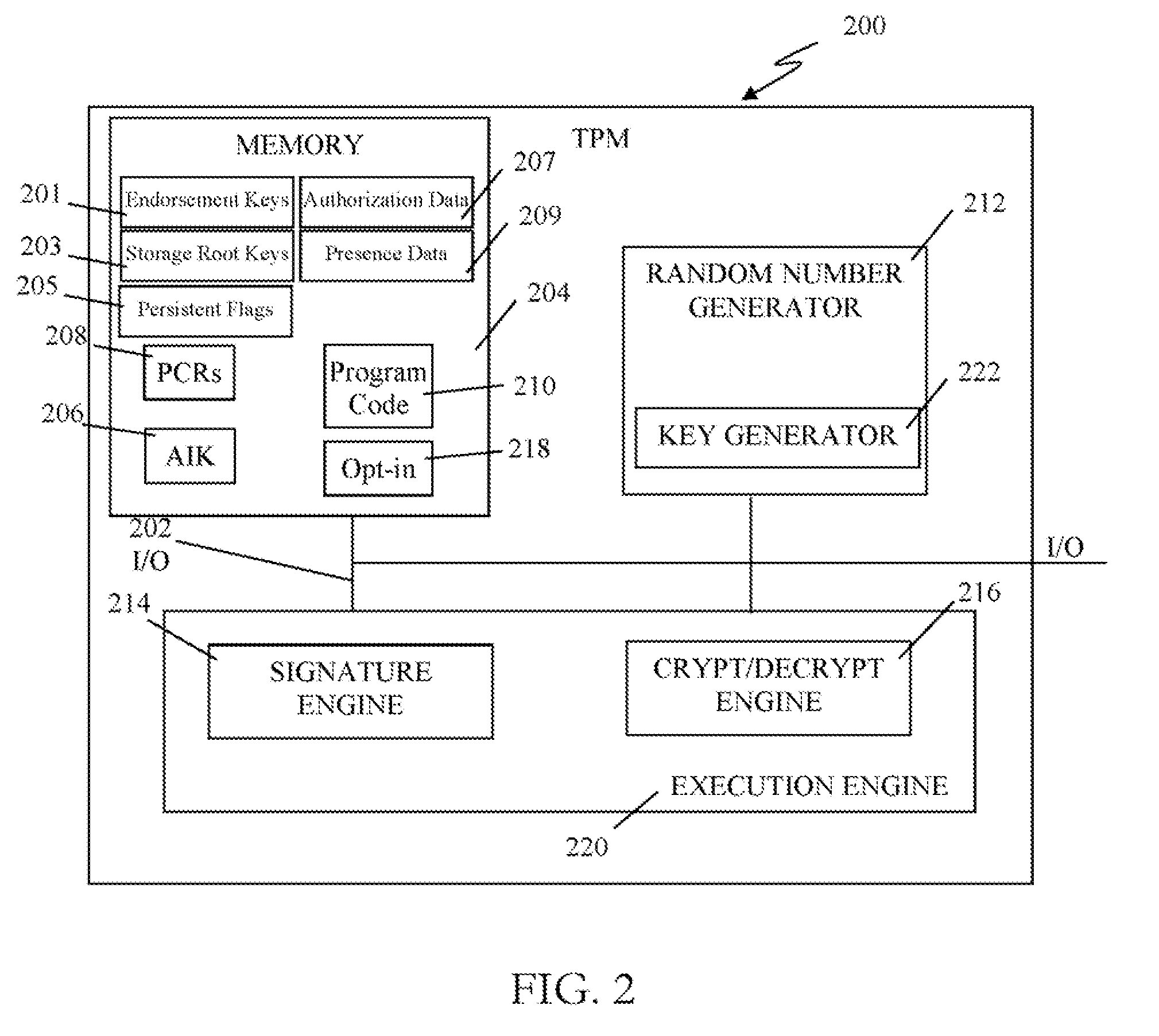
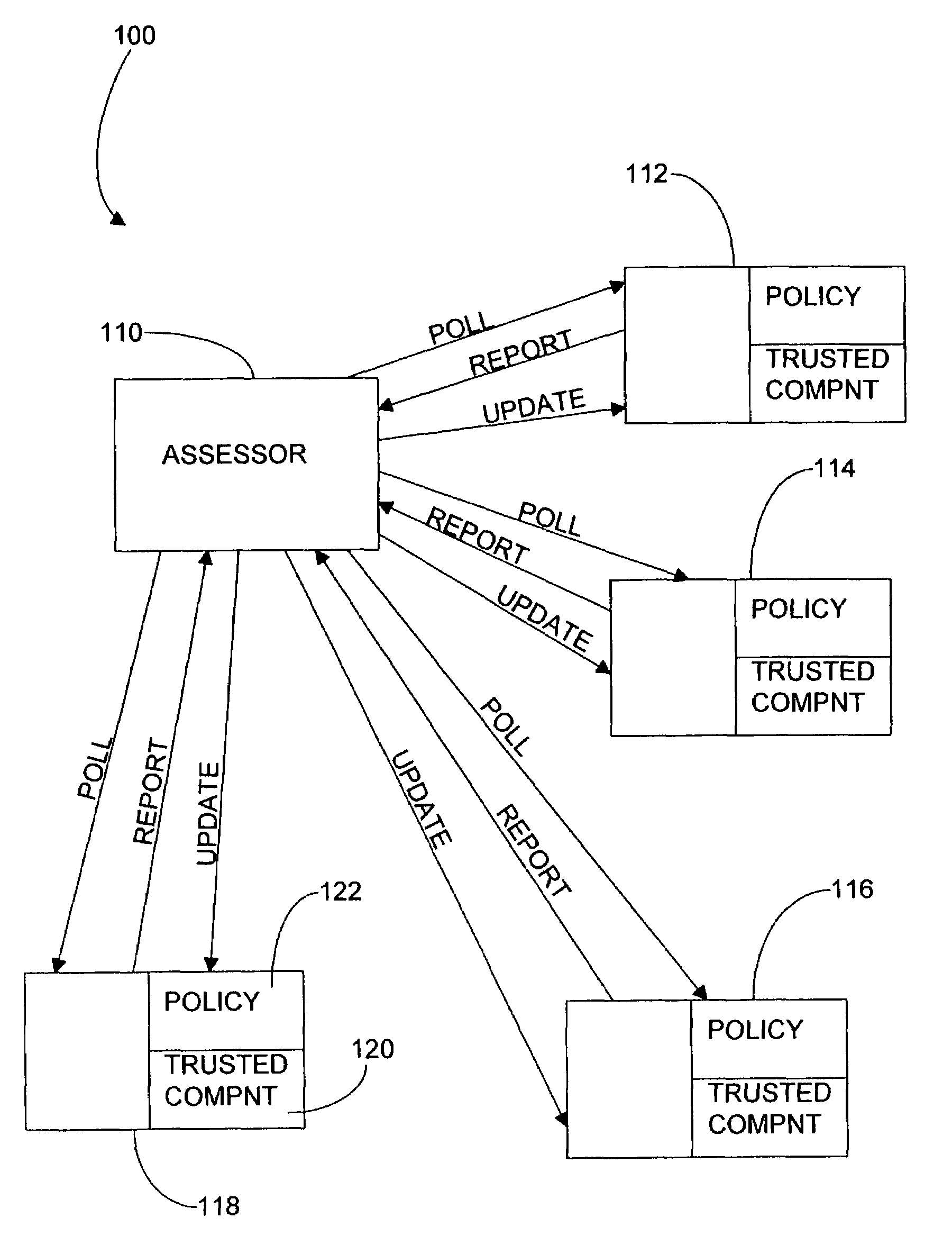
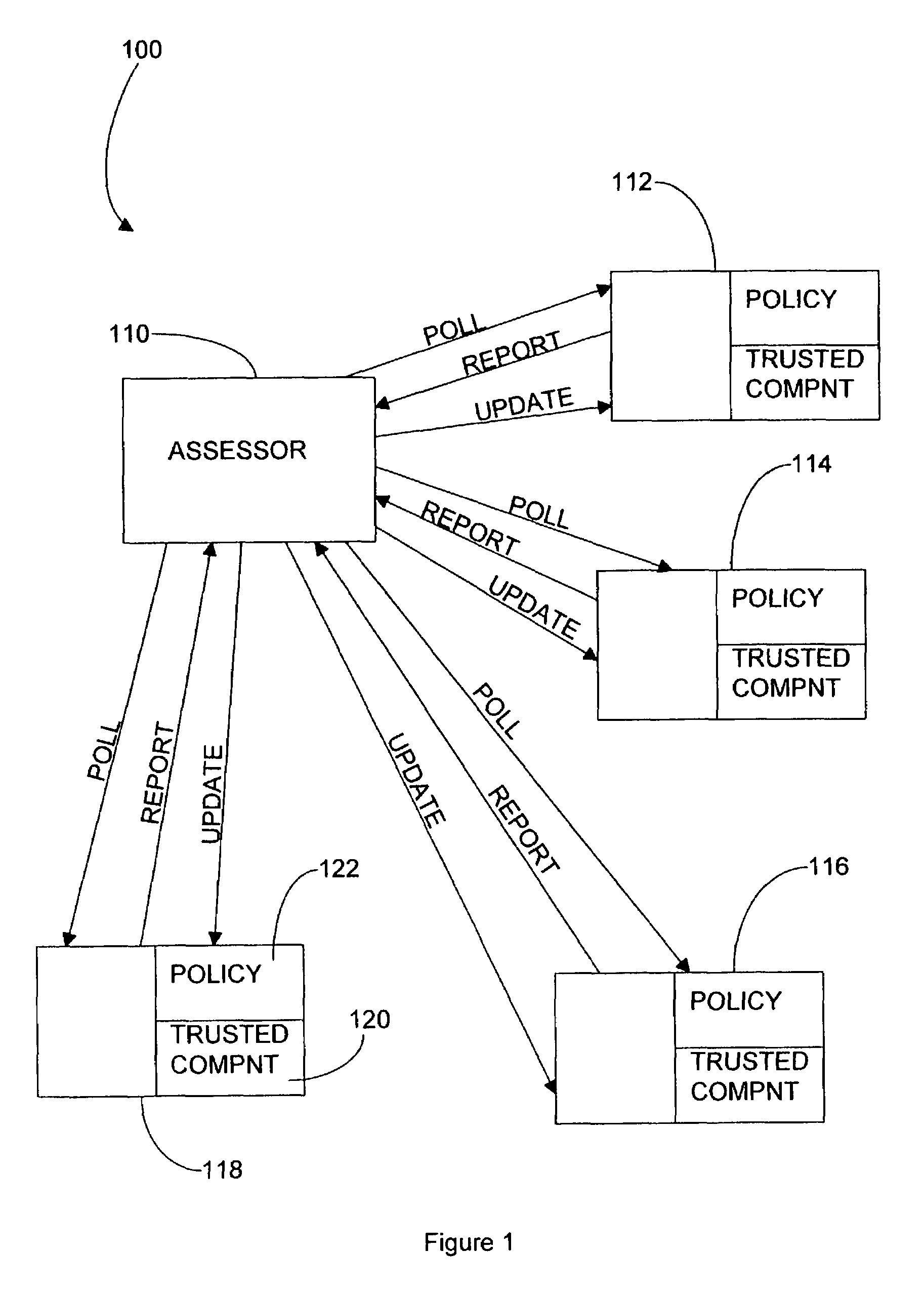
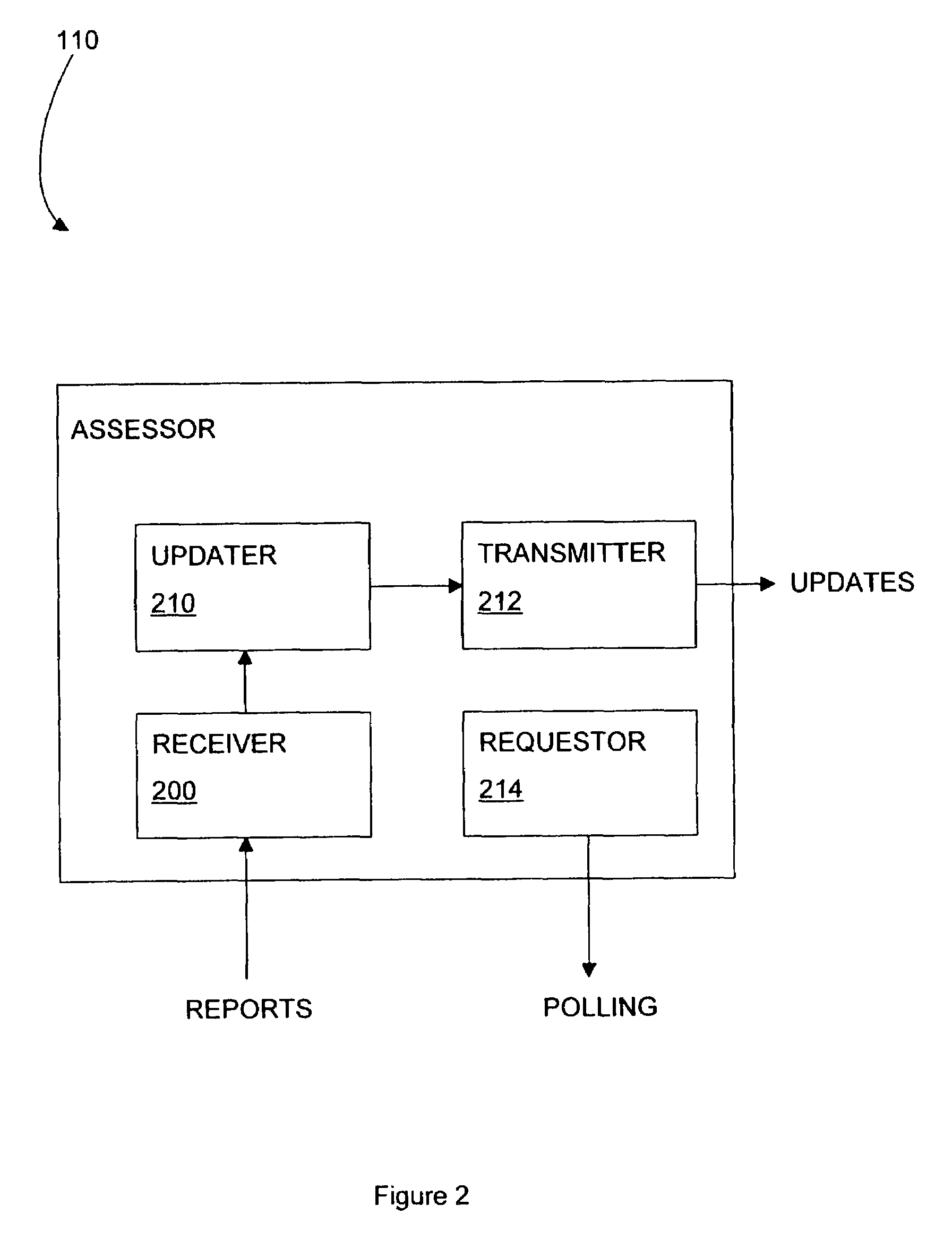
Trusted computing environment
ActiveUS7353531B2Efficiently informedSure of,Cosmonautic condition simulationsDigital data processing detailsTrusted componentsTrusted Computing
A trusted computing environment 100, wherein each computing device 112 to 118 holds a policy specifying the degree to which it can trust the other devices in the environment 100. The policies are updated by an assessor 110 which receives reports from trusted components 120 in the computing devices 112 to 118 which identify the trustworthiness of the computing devices 112 to 118.
Owner:HEWLETT-PACKARD ENTERPRISE DEV LP
Debugging an application that employs rights-managed content
ActiveUS7383537B2Software testing/debuggingSpecific program execution arrangementsTrusted componentsSoftware engineering
A system debugs a computer application that employs rights-managed (RM) content. A first, non-isolated process has the application and a shell version of the trusted component, where such shell version receives each request by the application for RM services. The shell version is unconcerned whether a debugger is monitoring the first process. A second, isolated process is separate from the first process and has a debugging version of the trusted component. The shell version in the first process forwards the received request to the debugging version in the second process, and such debugging version acts upon same. The debugging version ensures that the debugger is not monitoring the second process, but is unconcerned whether the debugger is monitoring the first process.
Owner:MICROSOFT TECH LICENSING LLC
Restricting type access to high-trust components
Owner:MICROSOFT TECH LICENSING LLC
Method and system for signing and authenticating electronic documents via a signature authority which may act in concert with software controlled by the signer
ActiveUS8484723B2Key distribution for secure communicationDigital data processing detailsElectronic documentTrusted components
A system and method for signing and authenticating electronic documents using public key cryptography applied by one or more server computer clusters operated in a trustworthy manner, which may act in cooperation with trusted components controlled and operated by the signer. The system employs a presentation authority for presenting an unsigned copy of an electronic document to a signing party and a signature authority for controlling a process for affixing an electronic signature to the unsigned document to create a signed electronic document. The system provides an applet for a signing party's computer that communicates with the signature authority.
Owner:SIGNIX
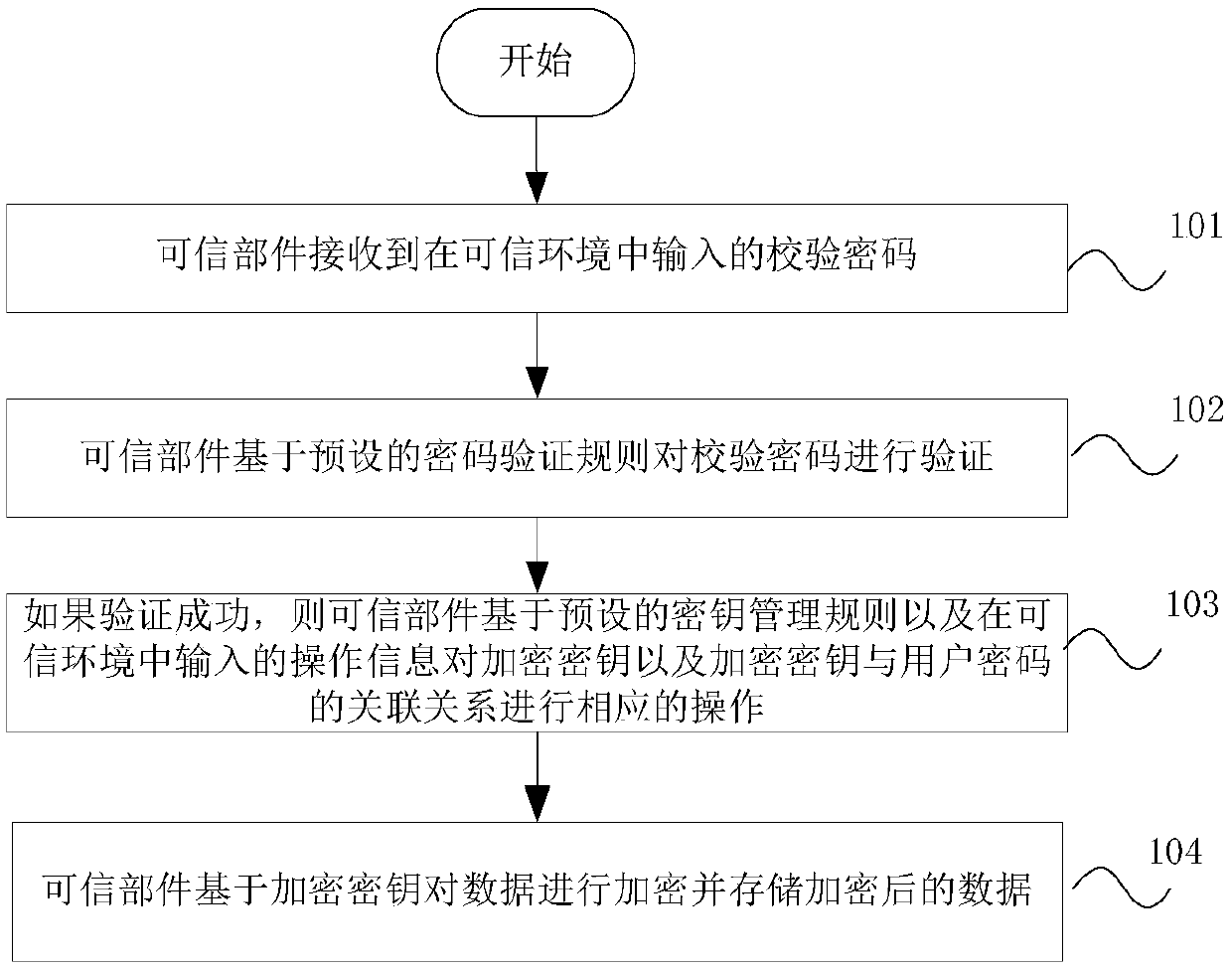
Data encryption method, system and terminal
ActiveCN110401538AImprove securityEnsure safetyKey distribution for secure communicationUser identity/authority verificationTrusted componentsPassword
The embodiment of the invention discloses a data encryption method, system and a terminal. The method comprises the following steps: a trusted component receiving a verification password input in a trusted environment; and if the verification password is successfully verified, performing corresponding operation on the encryption key and the association relationship between the encryption key and the user password based on a preset key management rule and operation information input in the trusted environment, encrypting the data based on the encryption key, and storing the encrypted data. According to the method, the system and the terminal, the user password can be input and verified in the trusted environment, and the password is prevented from being monitored, intercepted and leaked. Data is encrypted and stored in a trusted environment, so that the security is remarkably enhanced. A plurality of different encryption keys can be managed and protected by one password. The encryptionkey is not changed when the password is modified, the target data does not need to be encrypted again, and the security of the data can be ensured.
Owner:WATCHDATA SYST +1
Safety and management of computing environments that may support unsafe components
InactiveUS8621551B2Ensuring the safety of a deviceEffectively guardMemory loss protectionDigital data processing detailsTrusted componentsTrusted Computing
Techniques for managing and protecting computing environments are disclosed. A safe computing environment can be provided for ensuring the safety and / or management of a device. The safe computing environment can be secured by a safe component that isolates and protects it from unsafe computing environments which may also be operating. As a result, various security and management activities can be securely performed from a safe computing environment. A safe computing environment can, for example, be provided on a device as a safe virtual computing environment (e.g., a safe virtual machine) protected by a safe virtual computing monitor (e.g., a safe virtual machine monitor) from one or more other virtual computing environments that are not known or not believed to be safe for the device. It will also be appreciated that the safe components can, for example, be provided as trusted components for a device. As such, various trusted components (or agent) can operate in a trusted computing environment secured from interference by components that many not be trusted and perform various security and / or management tasks alone or in connection, for example, with other trusted components (e.g., trusted serves).
Owner:SAMSUNG ELECTRONICS CO LTD
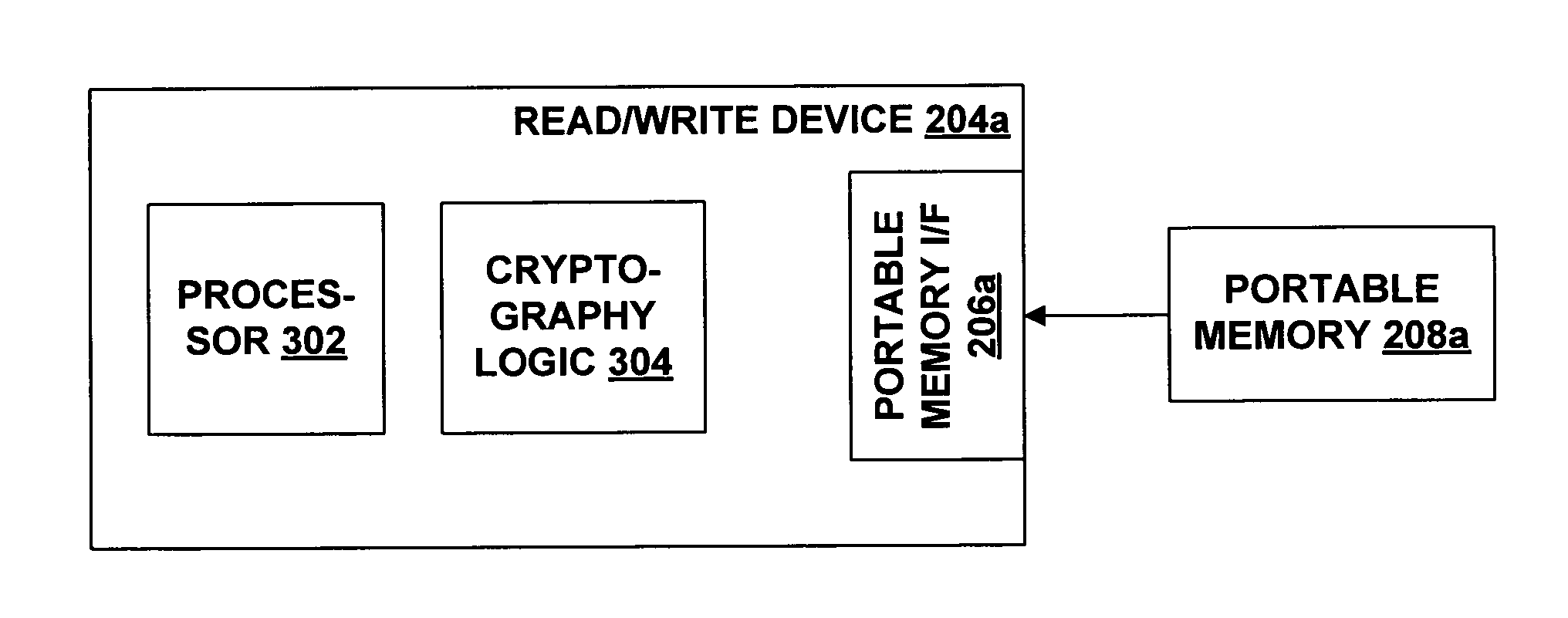
Protection of content stored on portable memory from unauthorized usage
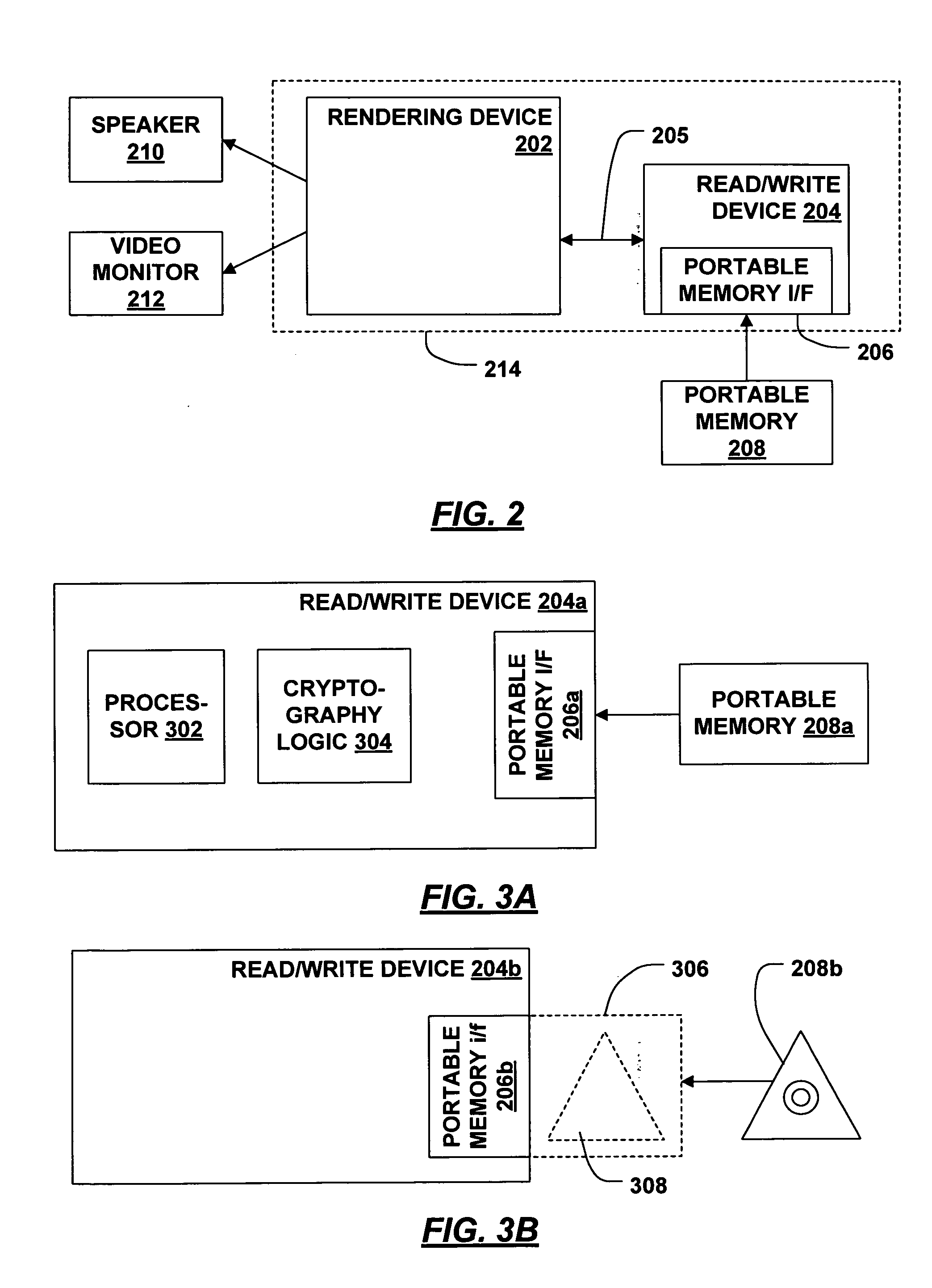
InactiveUS20050177694A1Spoofing becomes difficultReduce in quantityUnauthorized memory use protectionProgram/content distribution protectionComputer hardwareTrusted components
Owner:MICROSOFT TECH LICENSING LLC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com