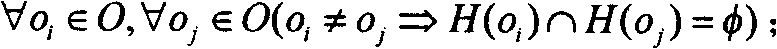Patents
Literature
300 results about "Mandatory access control" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
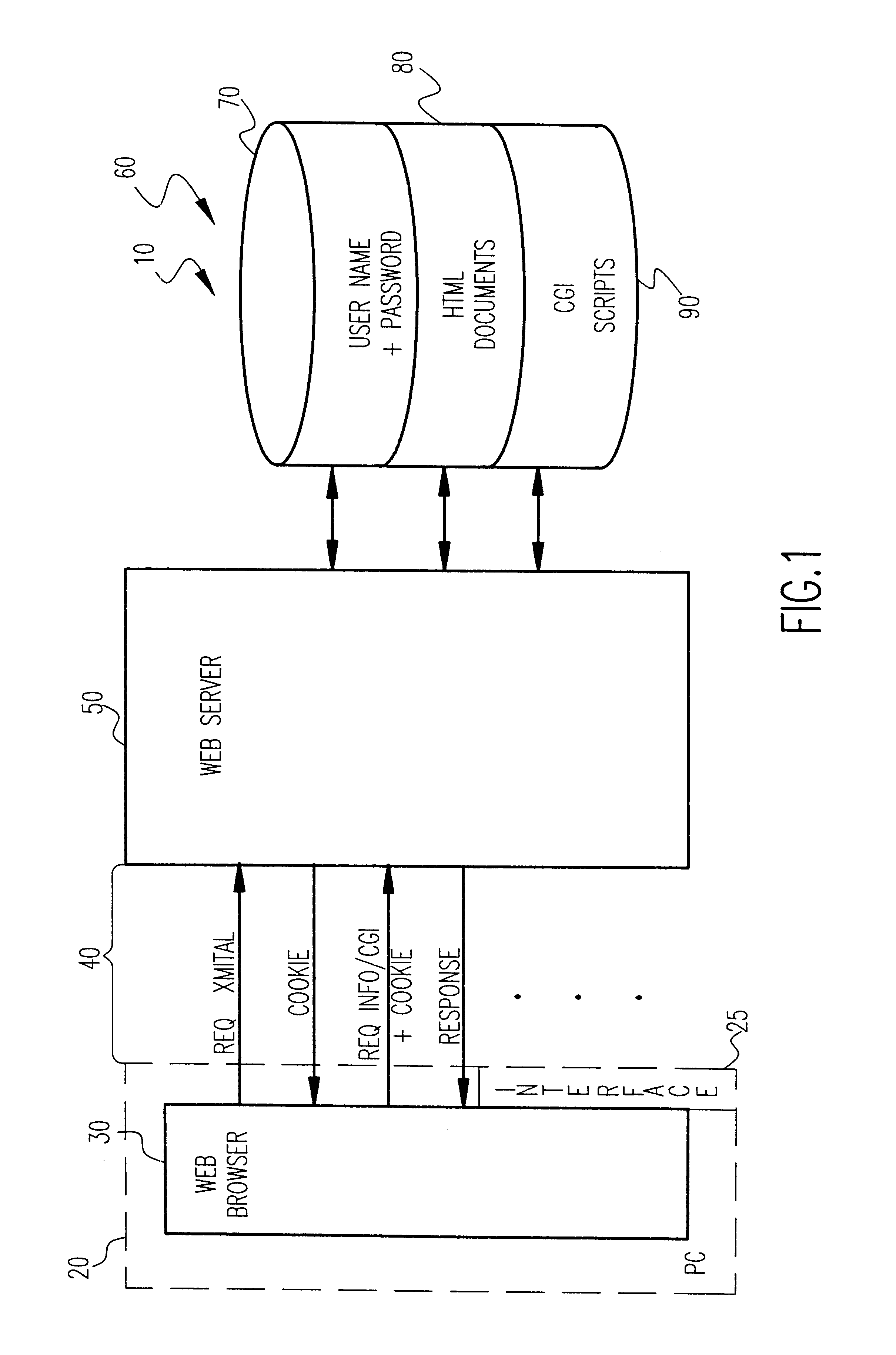
In computer security, mandatory access control (MAC) refers to a type of access control by which the operating system constrains the ability of a subject or initiator to access or generally perform some sort of operation on an object or target. In practice, a subject is usually a process or thread; objects are constructs such as files, directories, TCP/UDP ports, shared memory segments, IO devices, etc. Subjects and objects each have a set of security attributes. Whenever a subject attempts to access an object, an authorization rule enforced by the operating system kernel examines these security attributes and decides whether the access can take place. Any operation by any subject on any object is tested against the set of authorization rules (aka policy) to determine if the operation is allowed. A database management system, in its access control mechanism, can also apply mandatory access control; in this case, the objects are tables, views, procedures, etc.
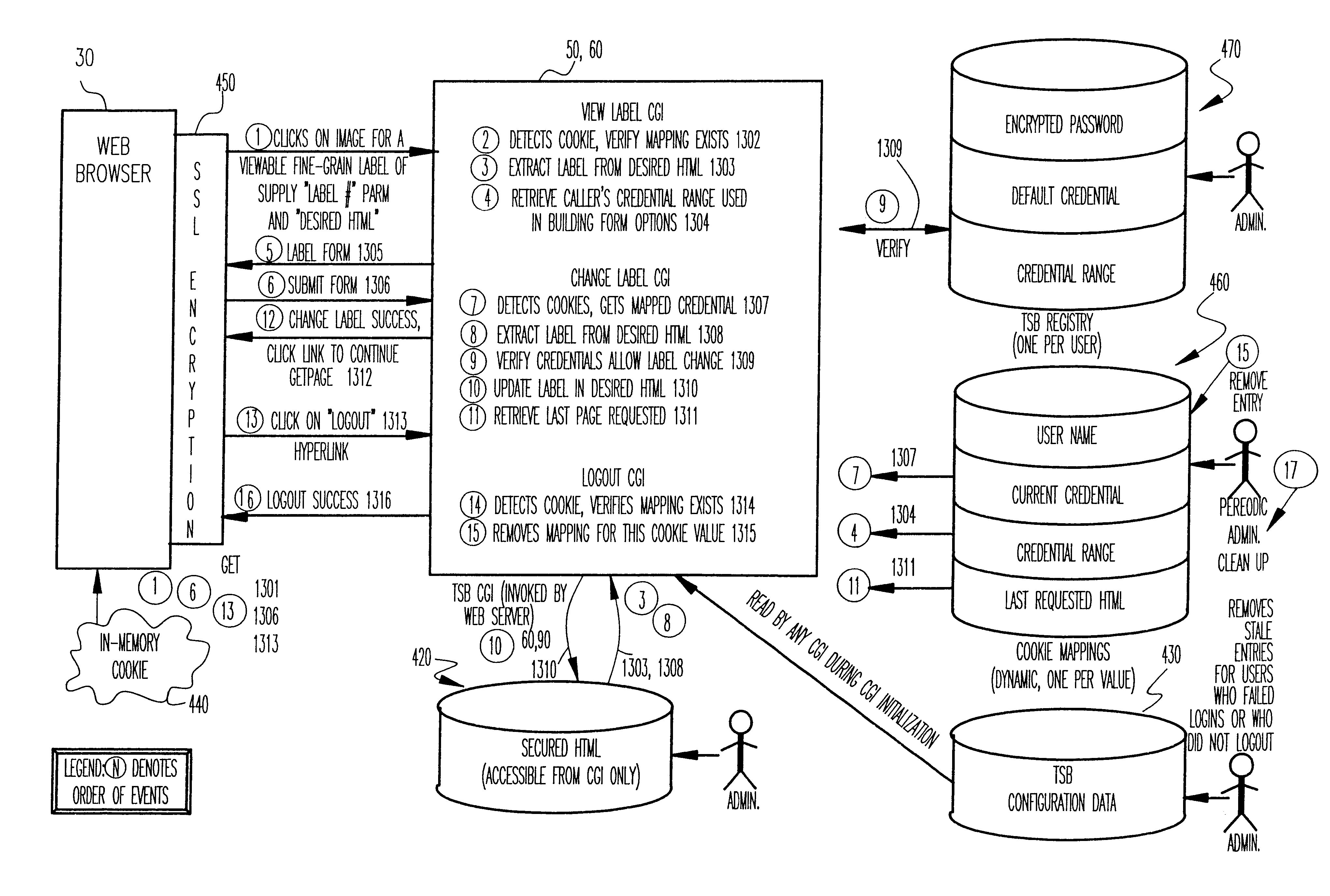
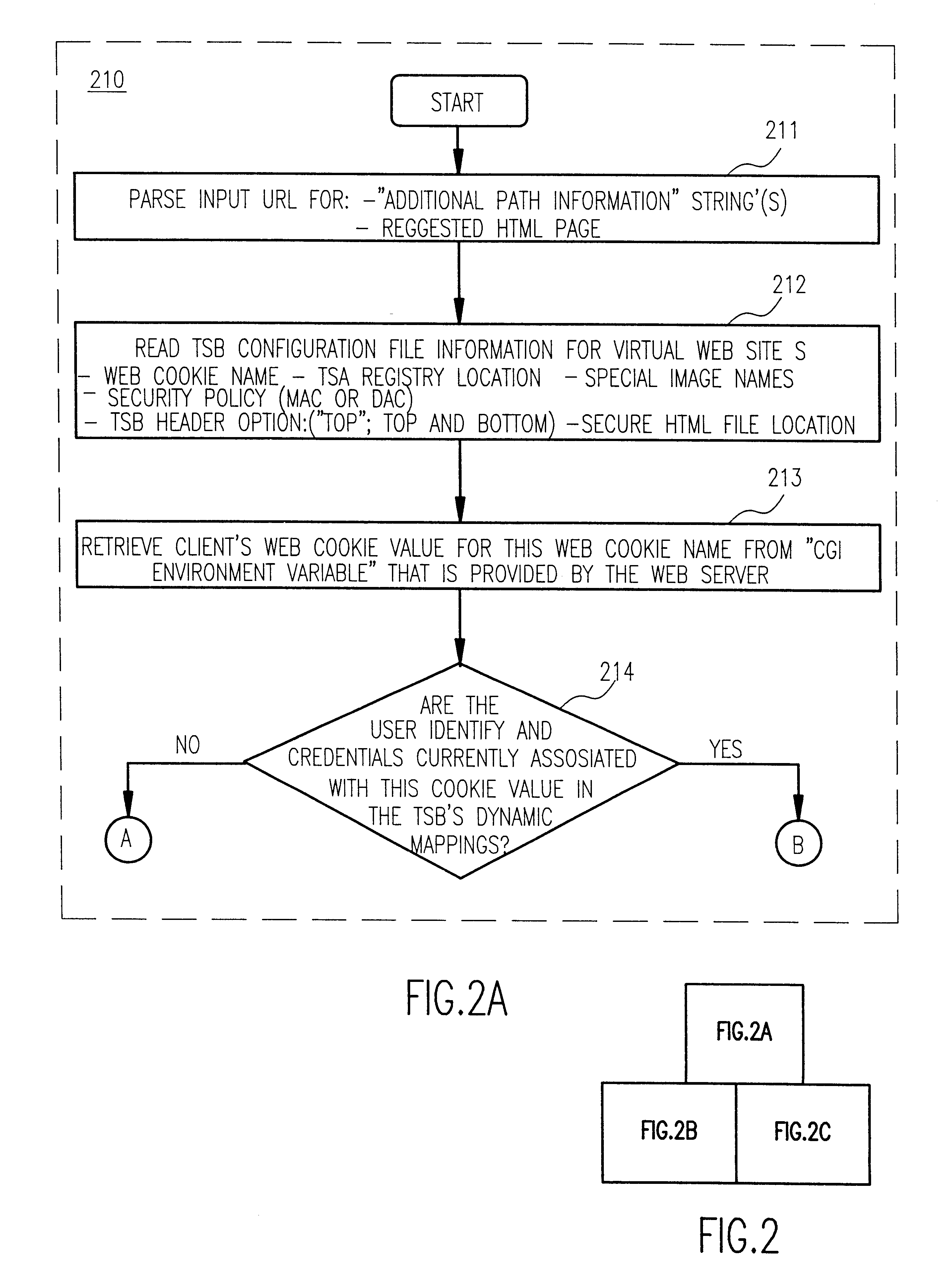
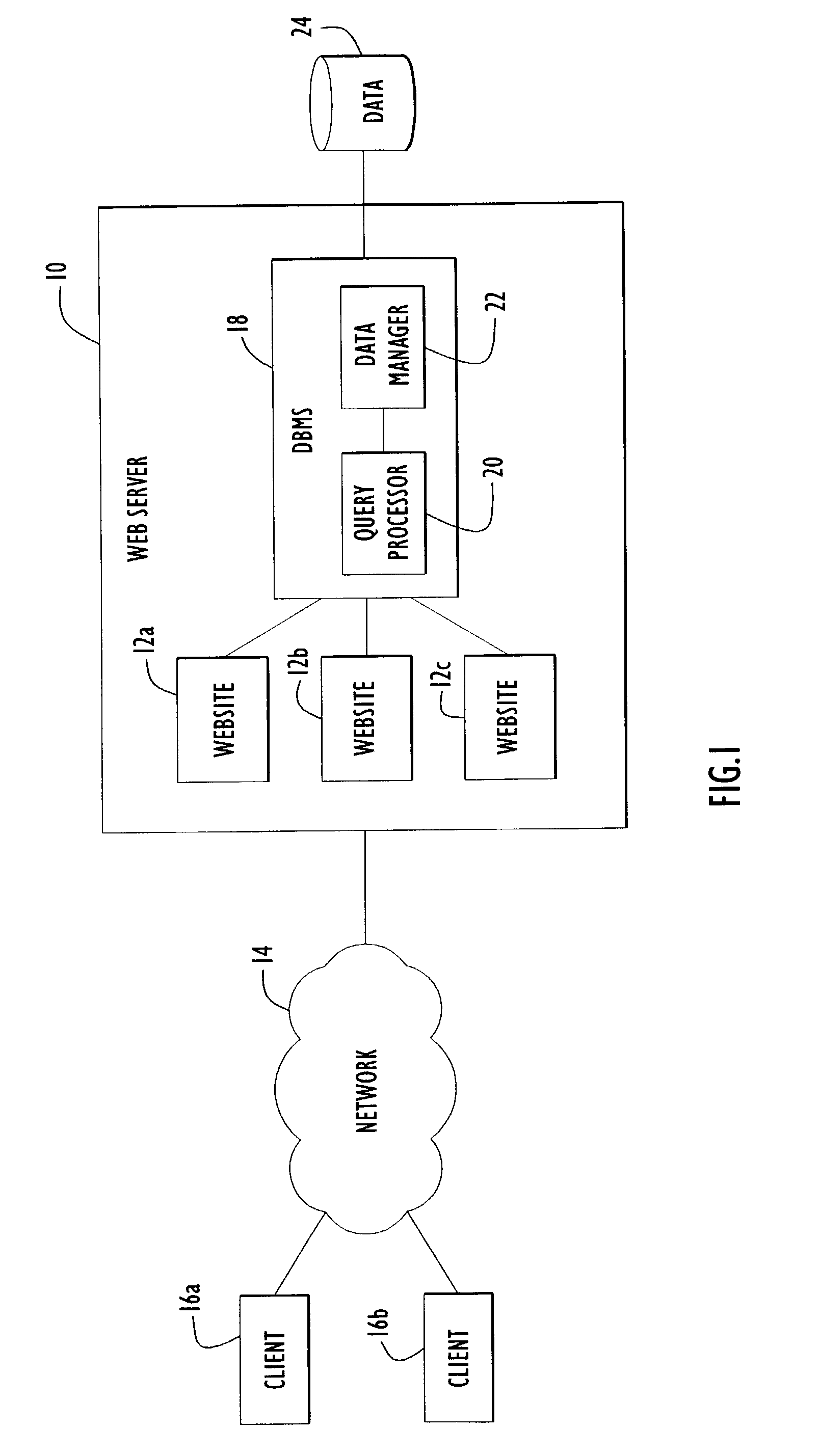
Trusted services broker for web page fine-grained security labeling
InactiveUS6311269B2Limit installationNeed to installWeb data retrievalDigital data processing detailsPasswordRandom assignment
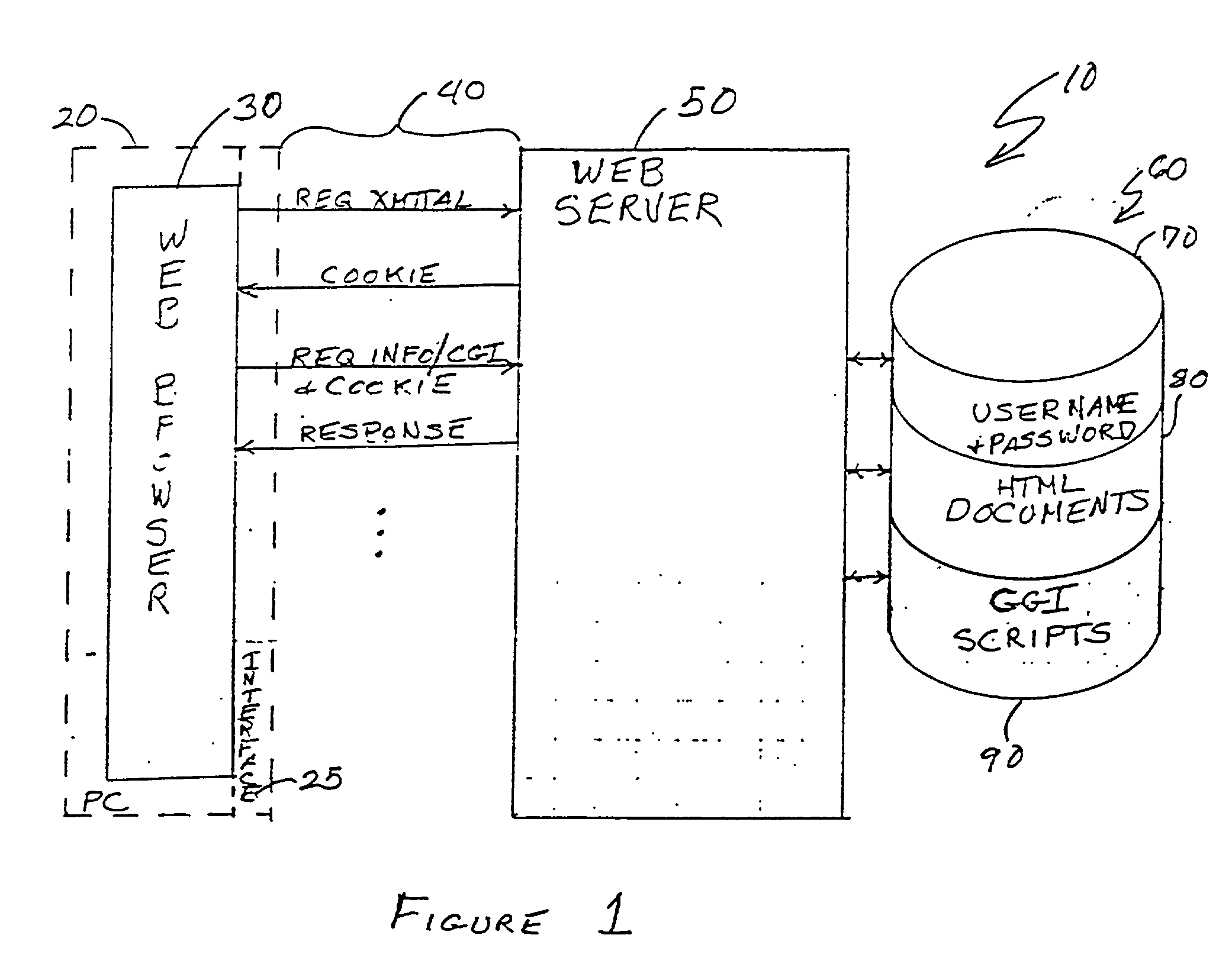
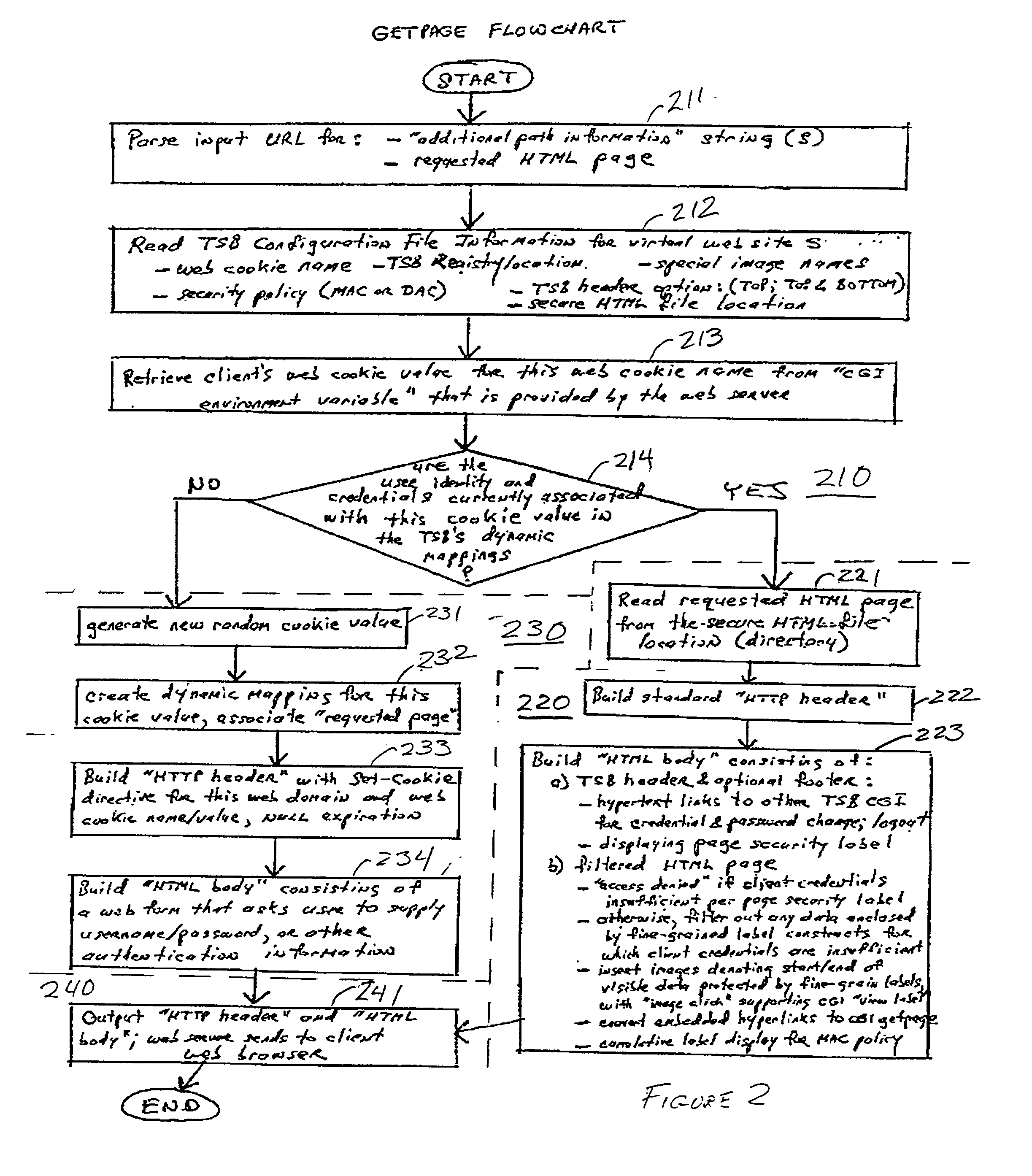
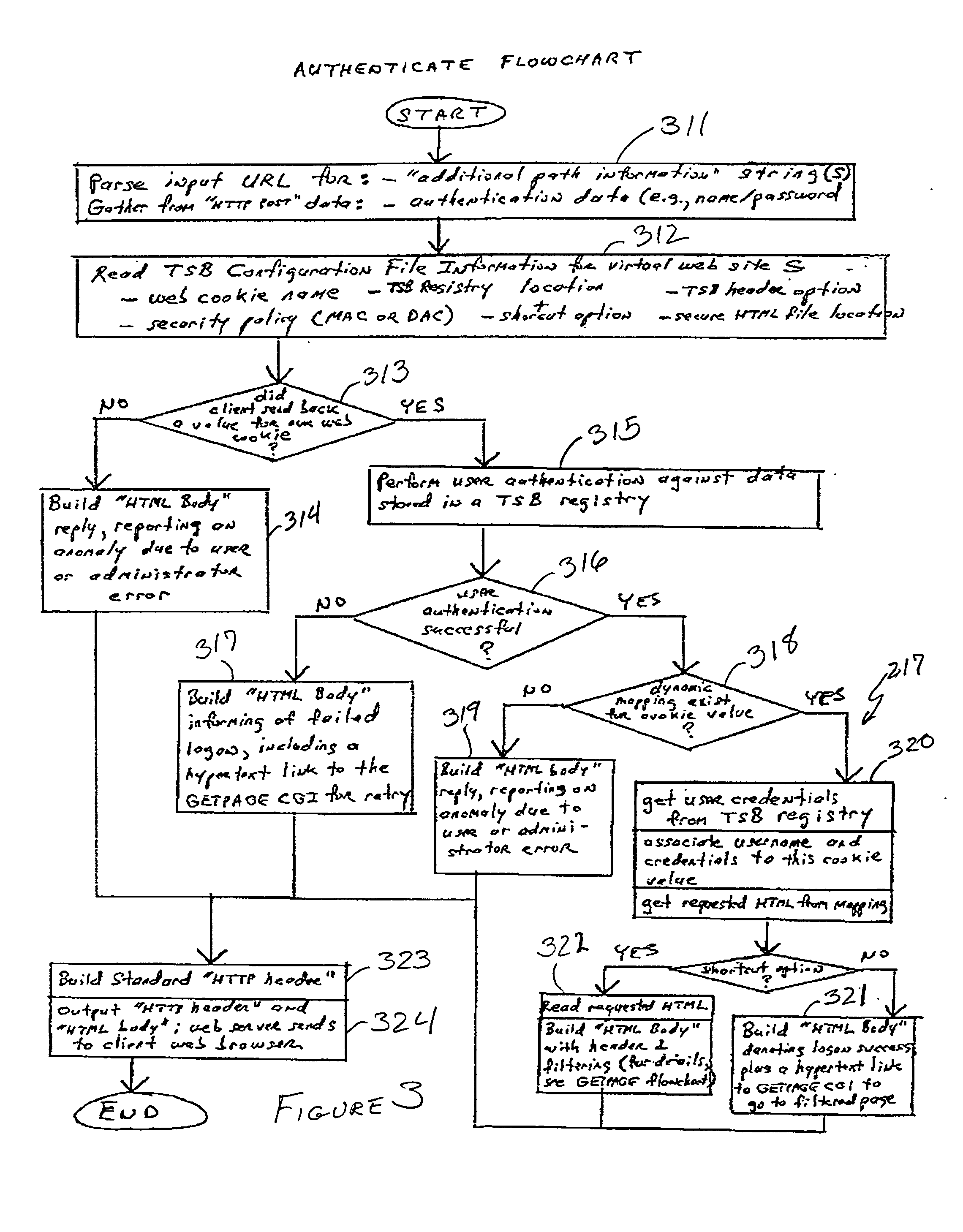
Arbitrarily fine-grained limitation of access to information stored in a resource of a data processor network is provided in a manner compatible with existing network browsers by mapping user identity and credentials with randomly assigned security cookie information which thus serves as a surrogate credential accompanying each user request during a session. Labels are imbedded within HTML files / text which may embody any desired security policy, including mandatory access control (MAC) arrangements which are not available through native browser functions. Data is retrieved in response to a user request which includes a security cookie from a location in the resource which is not directly accessible through use of a URL; the location being stored in a configuration file which is hidden from users. The retrieved data is then filtered in accordance with labels provided for each page and / or embedded in the text and used to build a response which may include hypertext links or other user interfaces for transmission to the user. Provision is made for viewing or changing of labels, credentials and passwords.
Owner:LEIDOS INNOVATIONS TECH INC
Mandatory access control label security
ActiveUS20080010233A1Ease of administrationEnsure effective implementationDigital data processing detailsComputer security arrangementsData setDatabase security
A secure database appliance leverages database security in a consistent framework provides consistent, flexible, and adaptable security using mandatory access controls in addition to user and role based security for access control and accountability. A database system comprises a plurality of datasets, each dataset including a plurality of data, and a plurality of database objects, each object having a security label comprising a security classification of the object, at least one database session, the database session having a security label indicating a security classification of the database session, wherein, the database system is operable to allow or deny access to data to a database session based on a security label of a database object and on a security label of the database session.
Owner:ORACLE INT CORP
Lattice-based security classification system and method
InactiveUS6922696B1Avoids overclassifyingDecrease overclassificationData processing applicationsDigital computer detailsInformation repositoryRelevant information
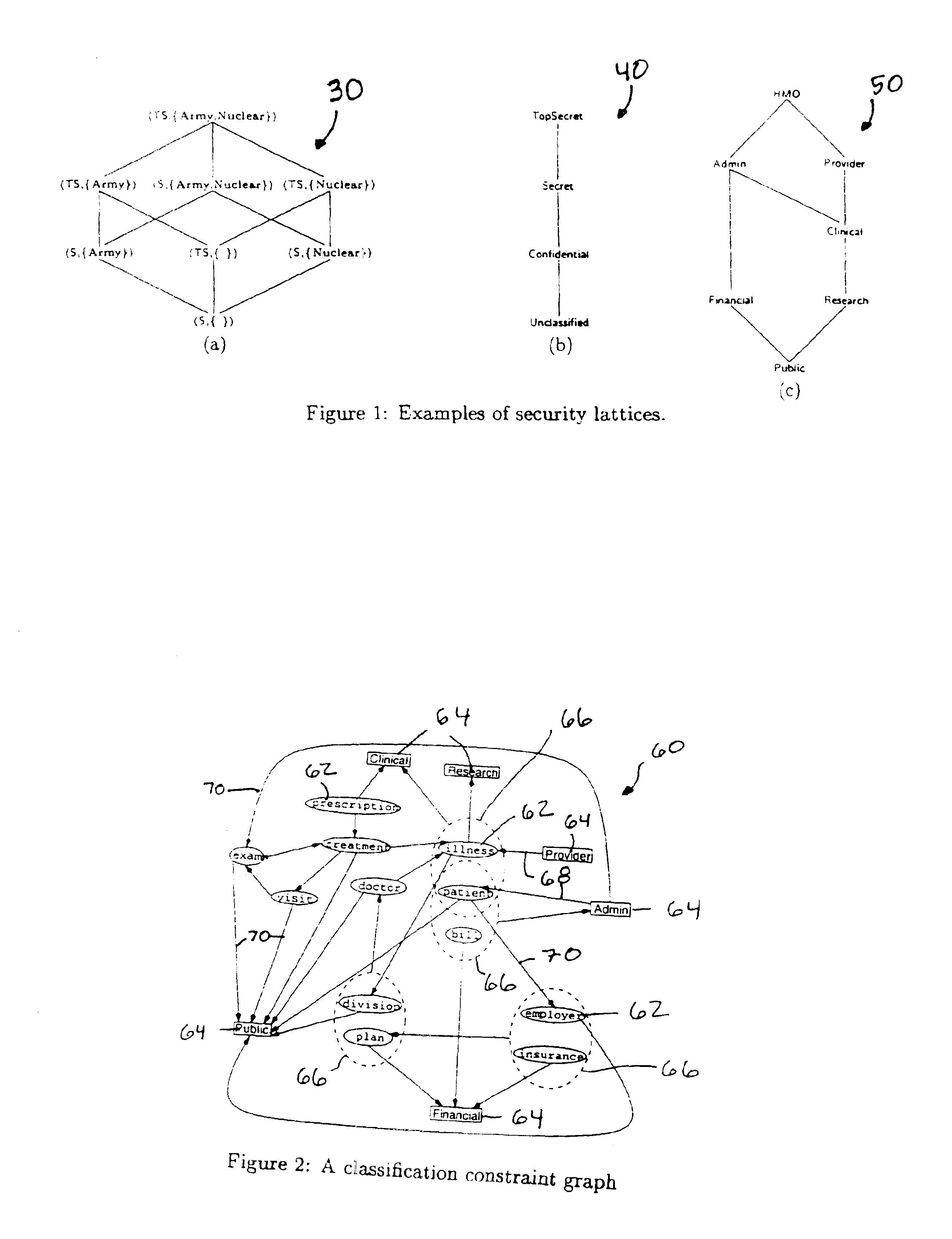
Despite advances in recent years in the area of mandatory access control in database systems, today's information repositories remain vulnerable to inference and data association attacks that can result in serious information leakage. Without support for coping against these attacks, sensitive information can be put at risk because of release of other (less sensitive) related information. The ability to protect information disclosure against such improper leakage would be of great benefit to governmental, public, and private institutions, which are, today more than ever, required to make portions of their data available for external release. In accordance with the invention, a solution to the problem of classifying information by enforcing explicit data classification as well as inference and association constraints is provided. We formulate the problem of determining a classification that ensures satisfaction of the constraints, while at the same time guaranteeing that information will not be unnecessarily overclassified.
Owner:SRI INTERNATIONAL
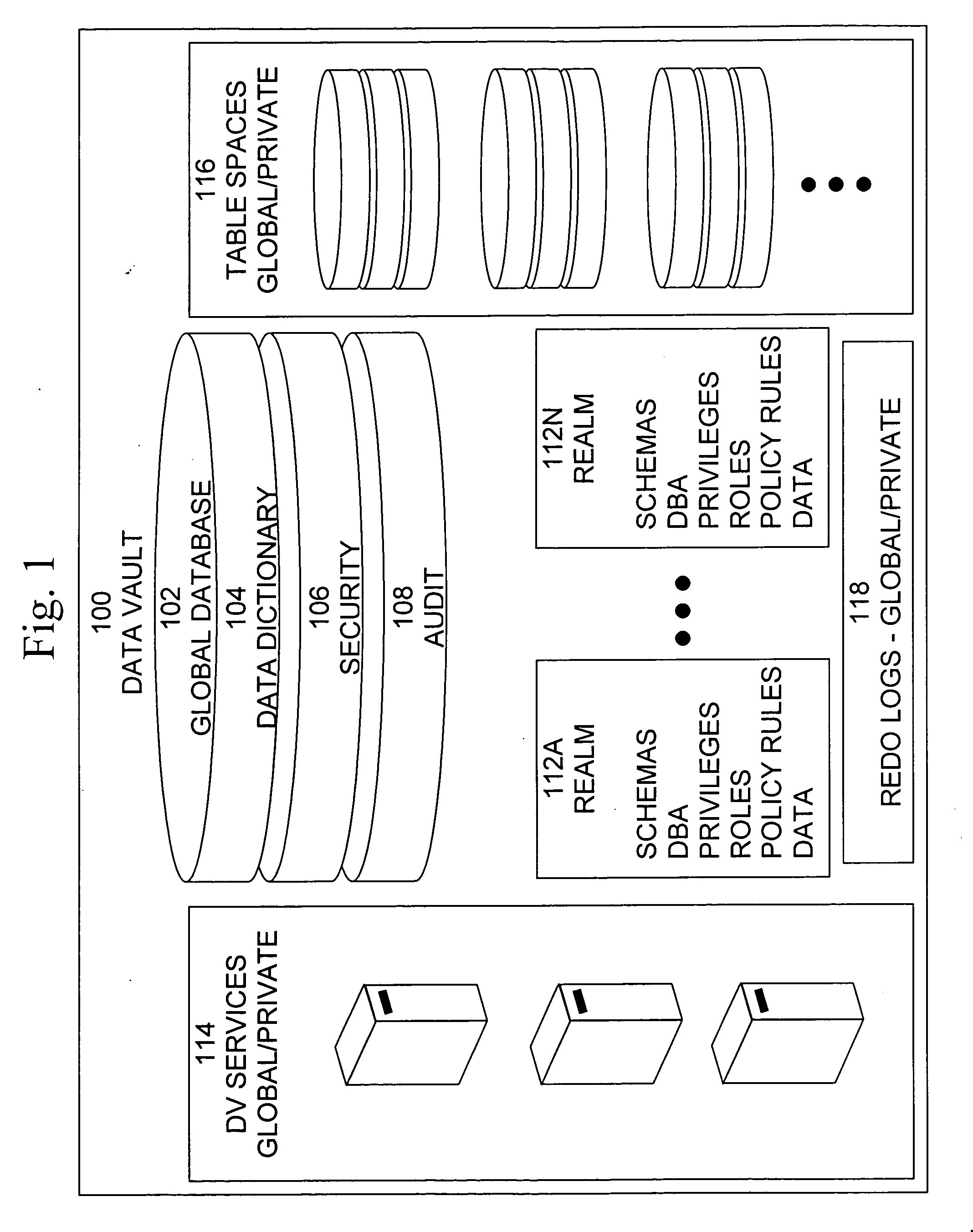
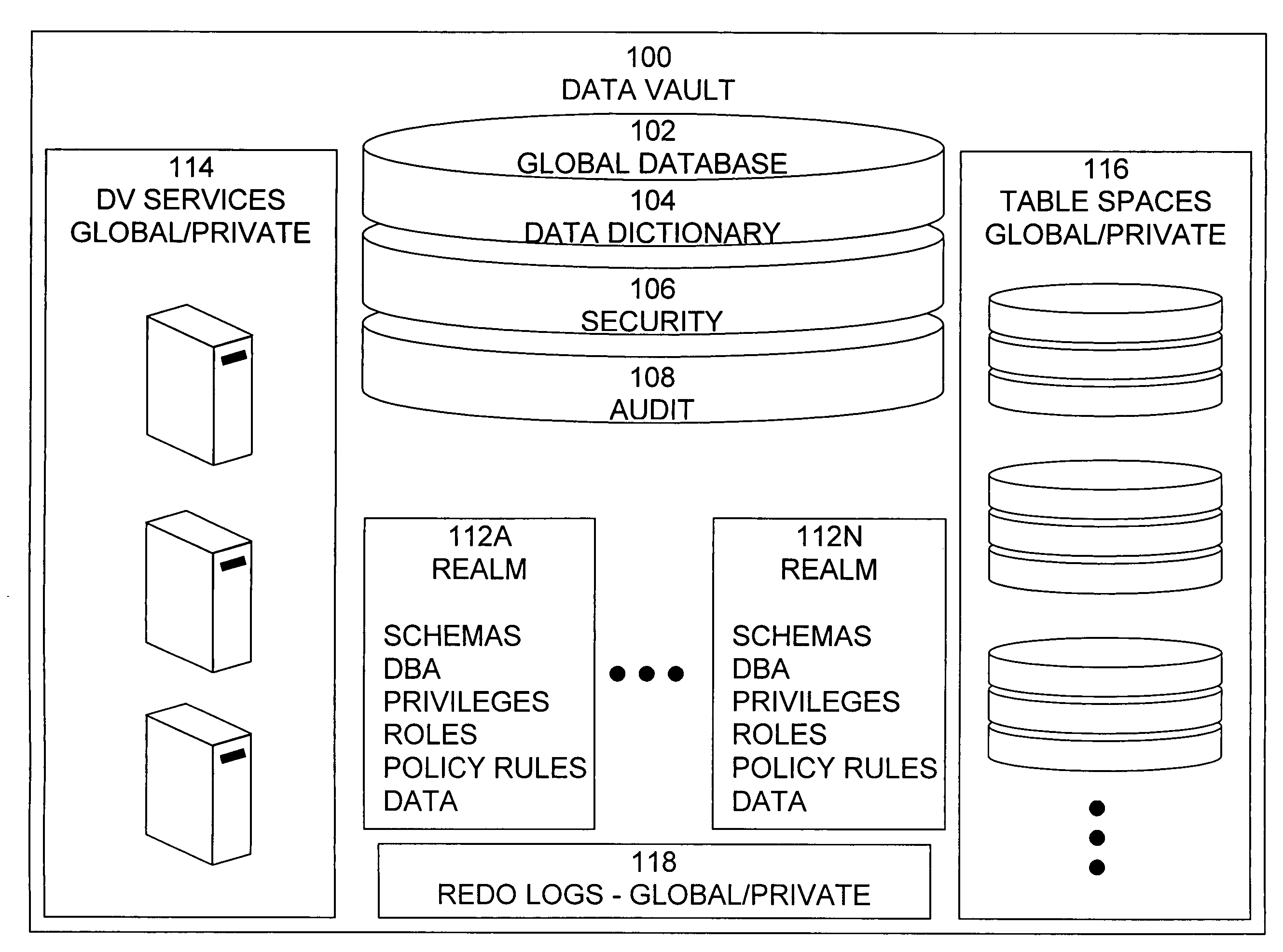
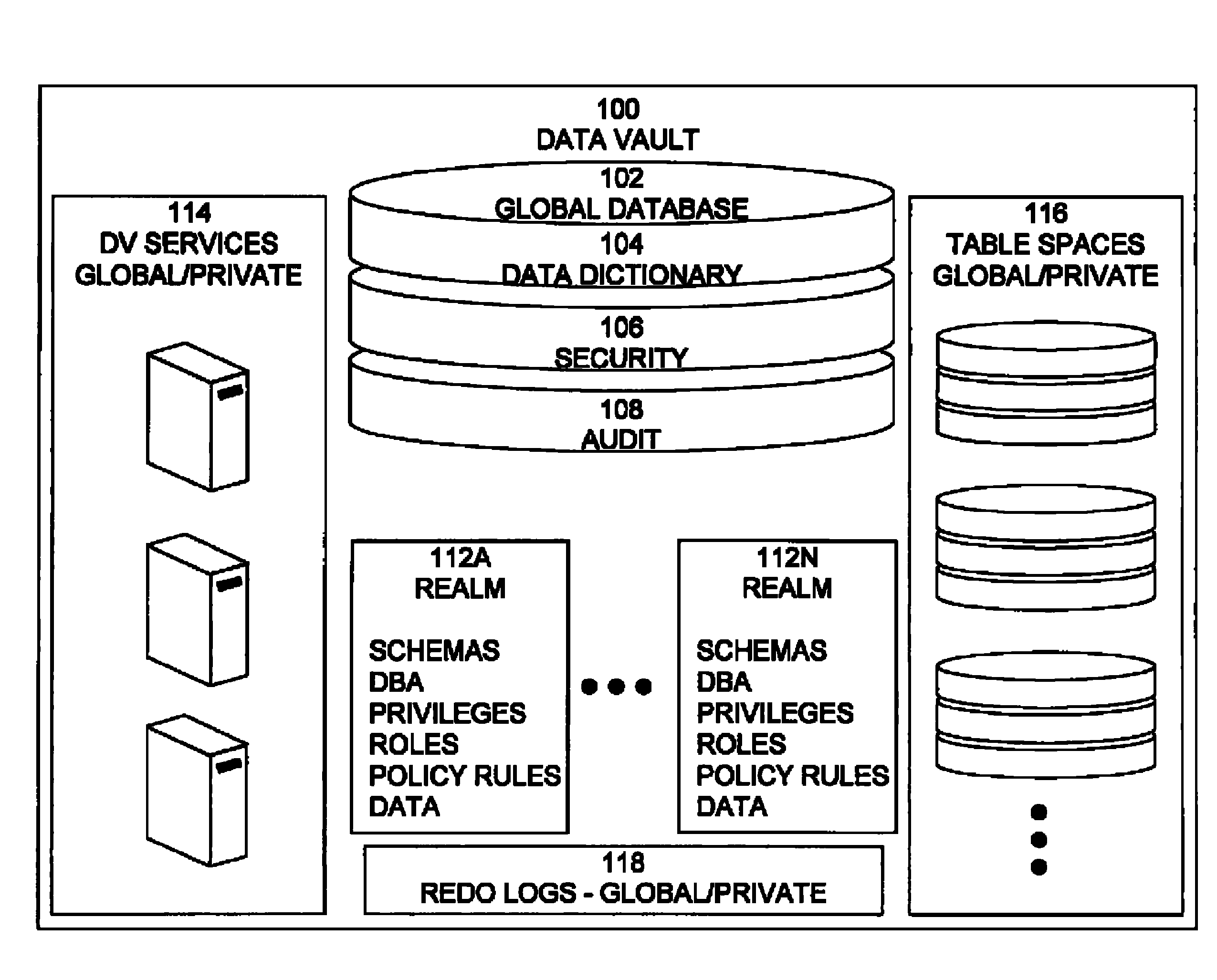
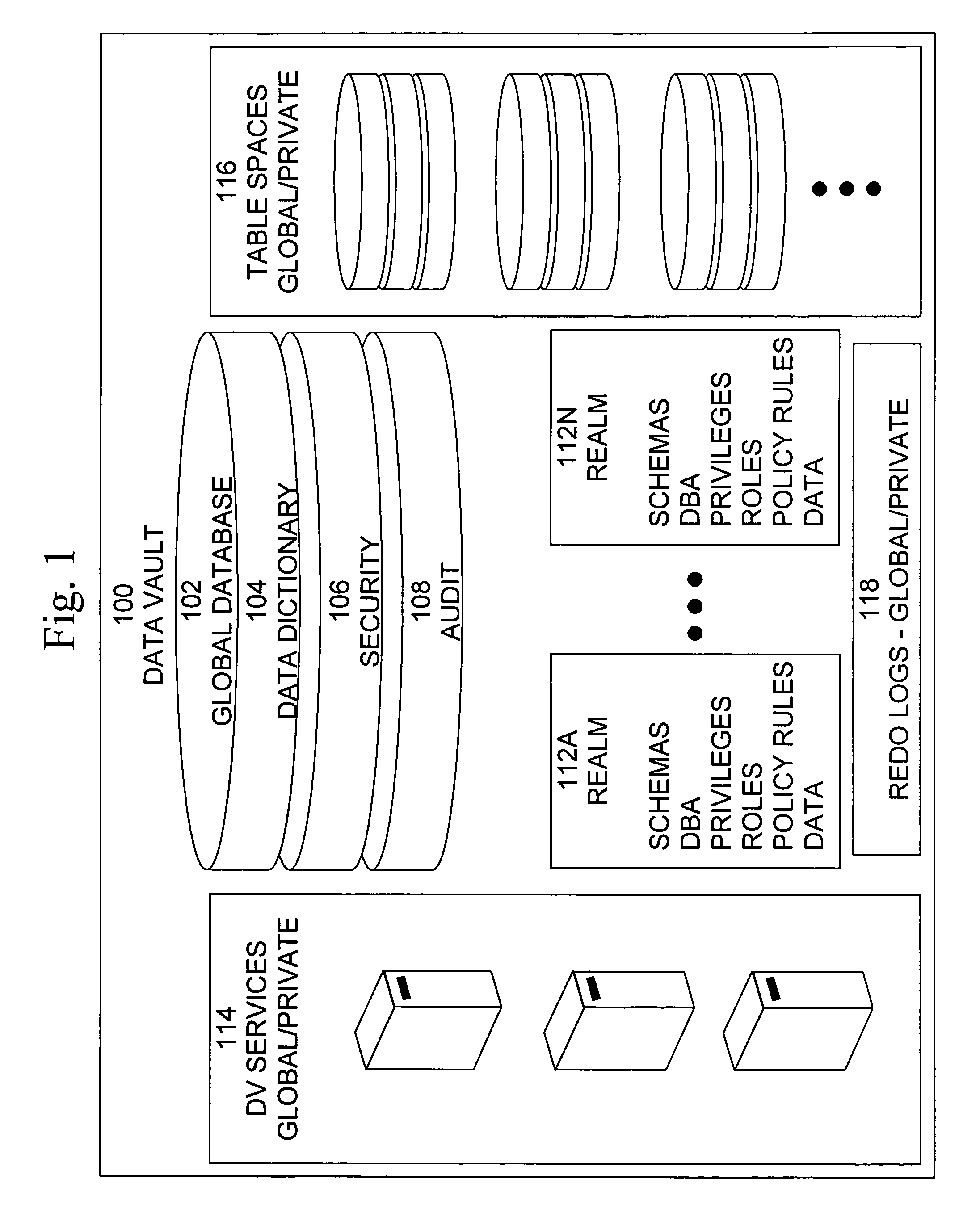
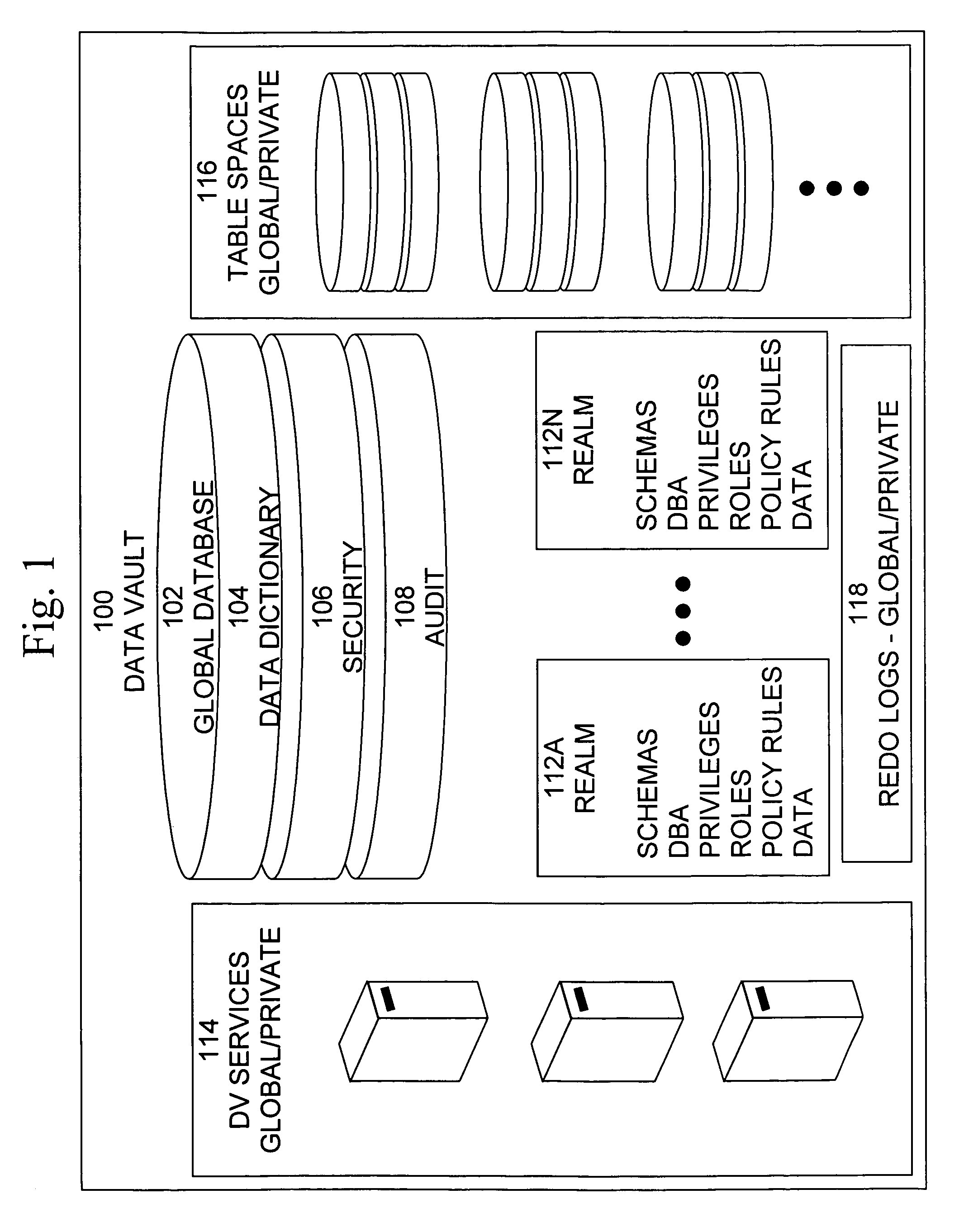
Cross-domain security for data vault
ActiveUS20060248599A1Ease of administrationEnsure effective implementationDigital data processing detailsUser identity/authority verificationDatabase securitySecurity level
A secure database appliance leverages database security in a consistent framework provides consistent, flexible, and adaptable security using mandatory access controls in addition to user and role based security for access control and accountability. A database system communicatively connected to a plurality of network domains, each network domain having a level of security, the database system comprises at least one database accessible from all of the plurality of network domains, the database comprising data, each unit of data having a level of security and access control security operable to provide access to a unit of data in the database to a network domain based on the level of security of the network domain and based on the level of security of the unit of data.
Owner:ORACLE INT CORP
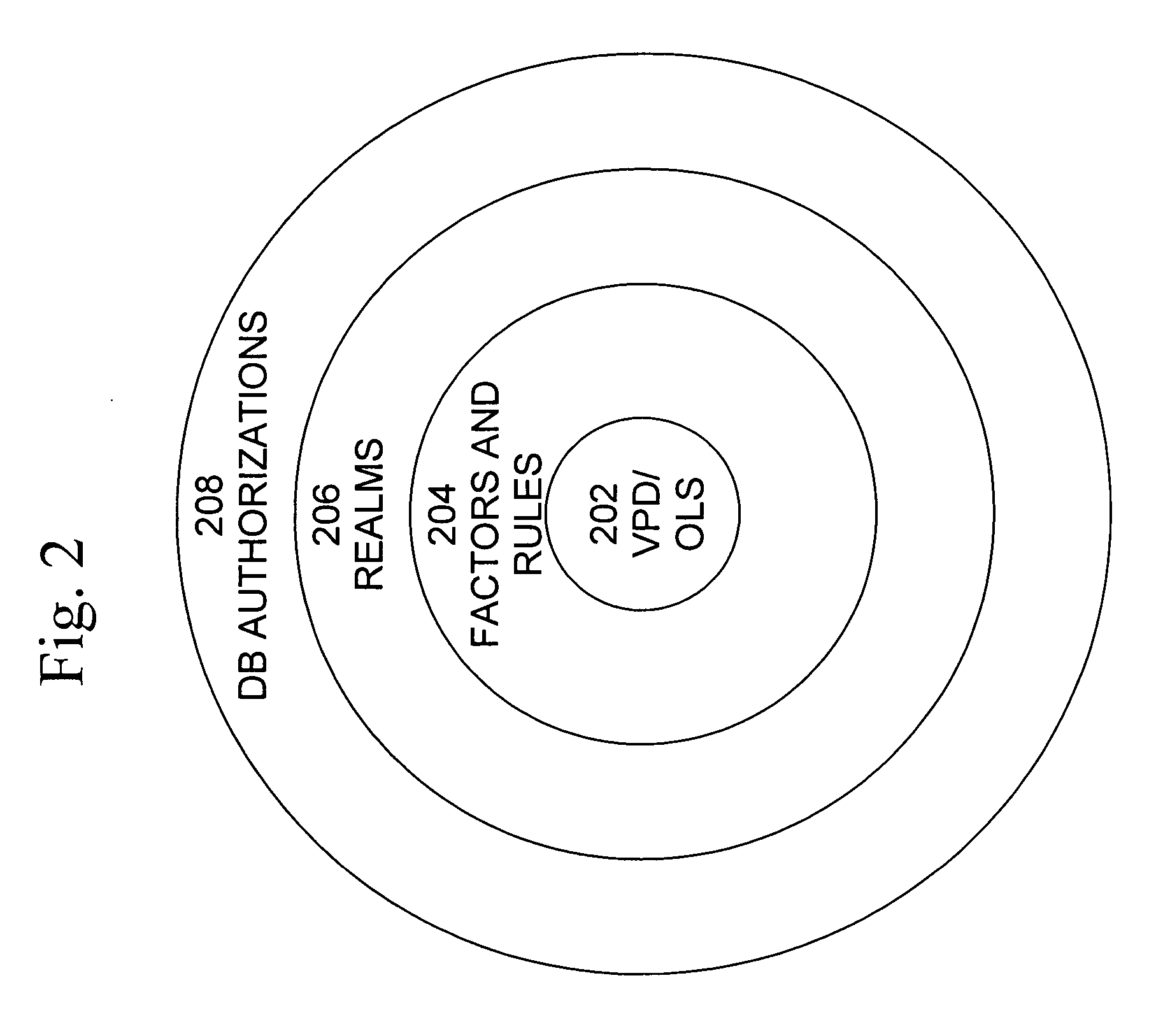
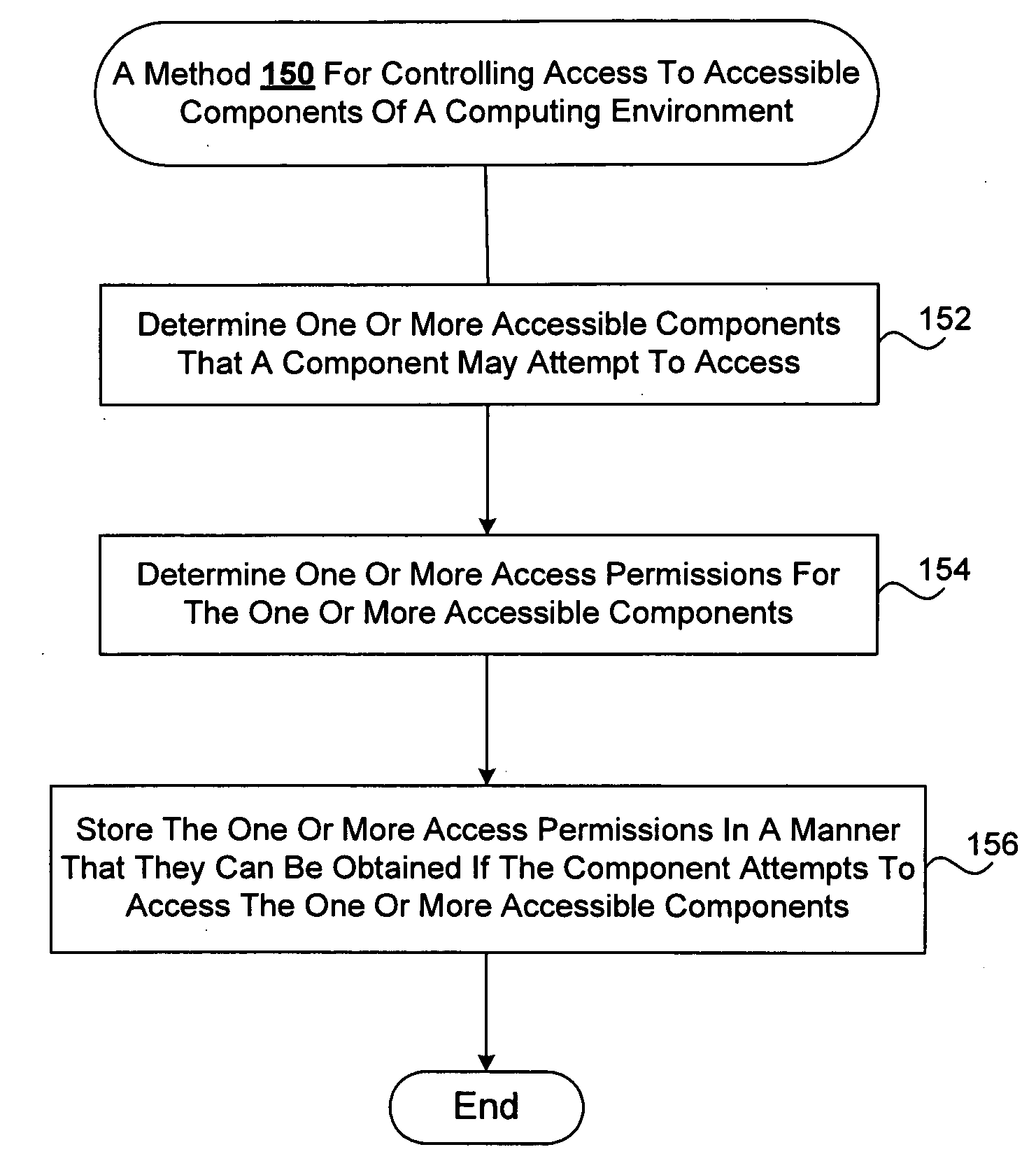
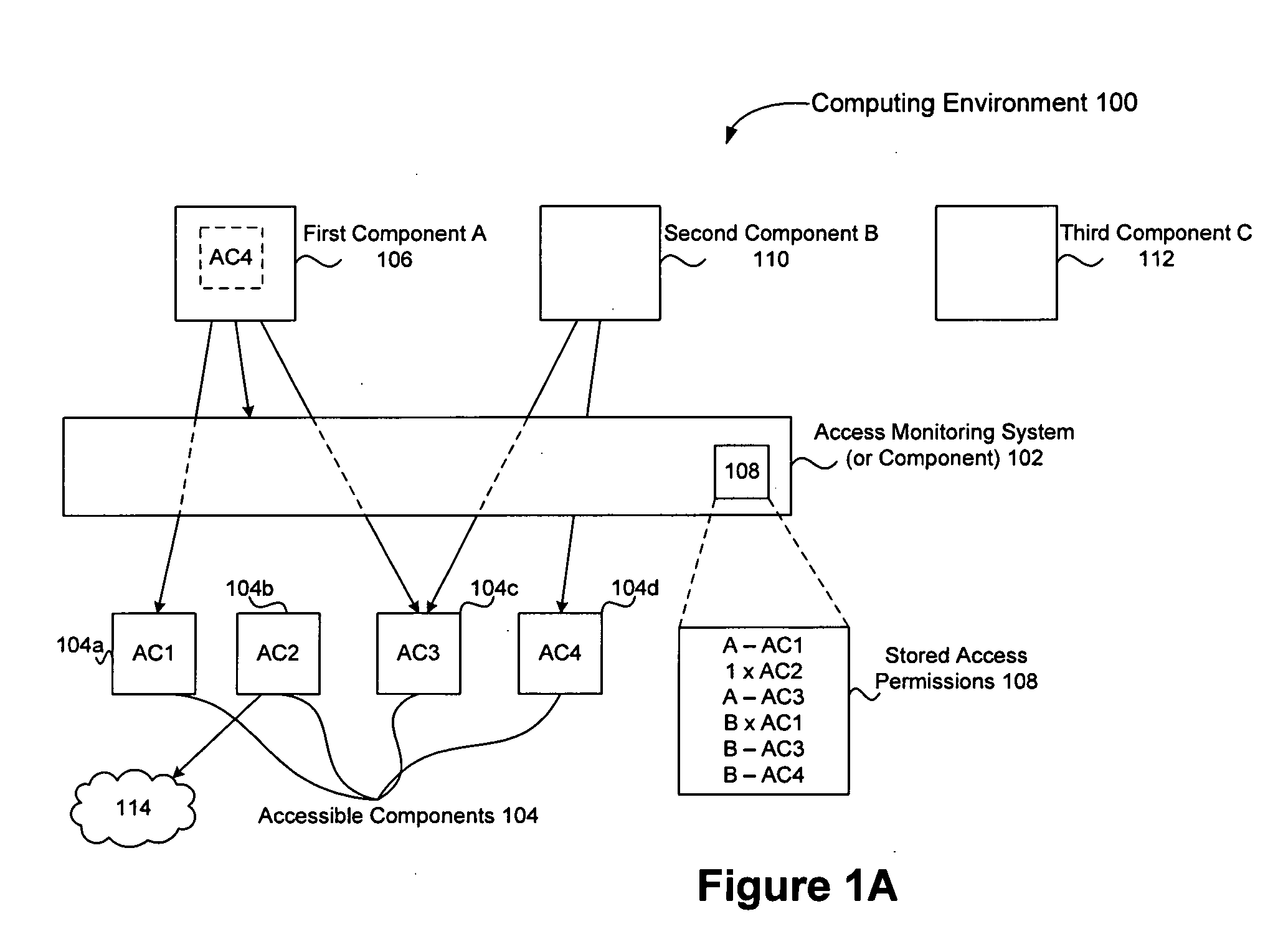
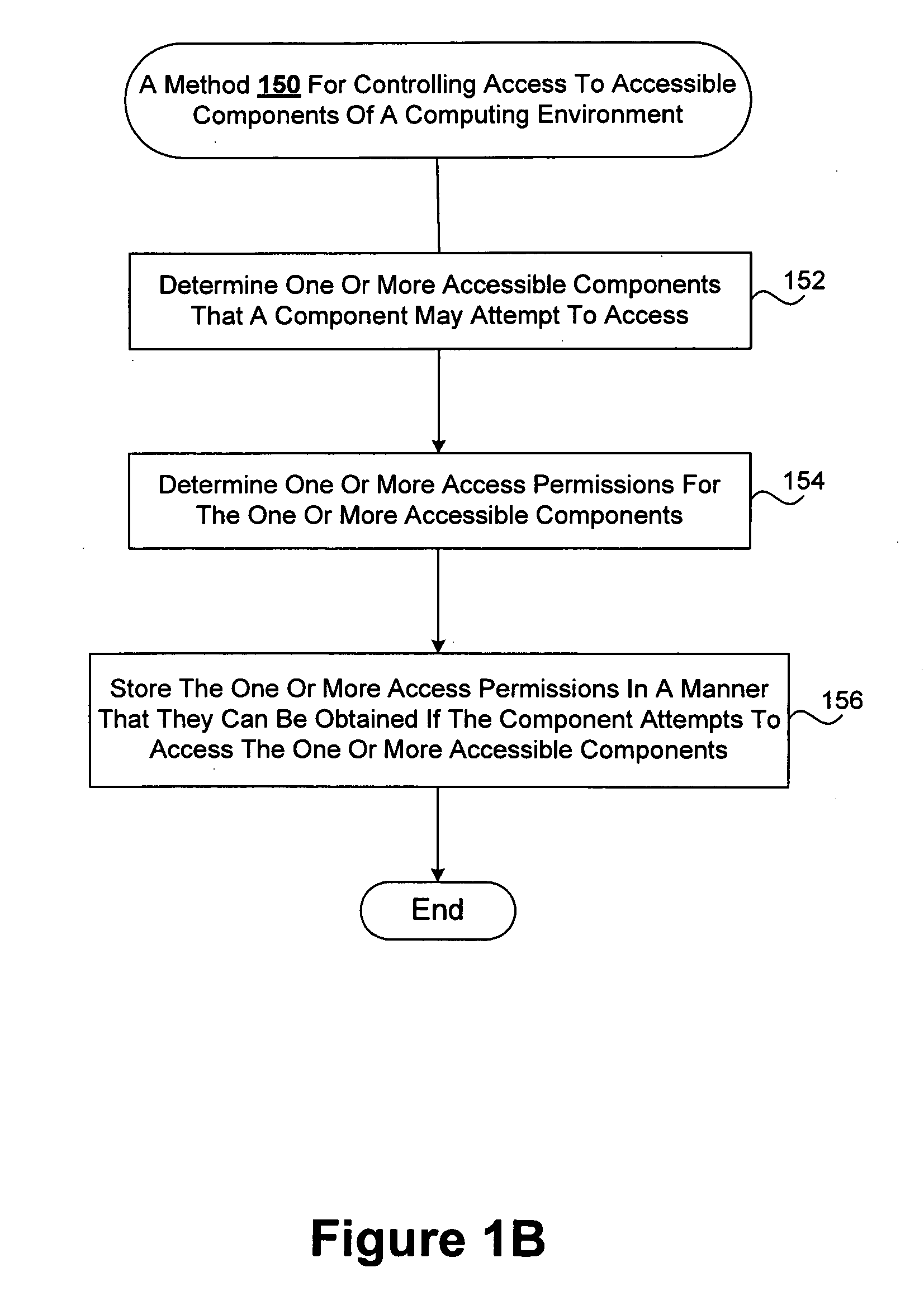
Safe and efficient access control mechanisms for computing environments
InactiveUS20090271844A1Save processing timeEffectively make good decisionDigital data processing detailsMultiple digital computer combinationsOperational systemMonitoring system
Improved techniques for controlling access to accessible components of computing environments are disclosed. The techniques, among other things, can be used to provide Mandatory Access Control (MAC) mechanisms for mobile and embedded systems. One or more accessible components (e.g., accessible resources) which a component may attempt to access are determined so that one or more access permissions can be stored in a manner that they can be obtained if the component attempts to access the one or more accessible components, thereby allowing access to the one or more accessible components to be determined based on access permissions that are readily available. Generally, access permissions can be identified and stored in anticipation of need. Access permissions can be identified, for example, based on the likelihood of use, or all possible access permissions can be determined and stored. A safe (e.g., a trusted) access controlling (or monitoring) system (or component) can control access to resources of a computing environment. For example, a trusted access monitoring system can be provided in a secure and trusted operating environment utilizing Mandatory Access Control (MAC) capabilities of a secure operating system (e.g., SELinux Operating System).
Owner:SAMSUNG ELECTRONICS CO LTD
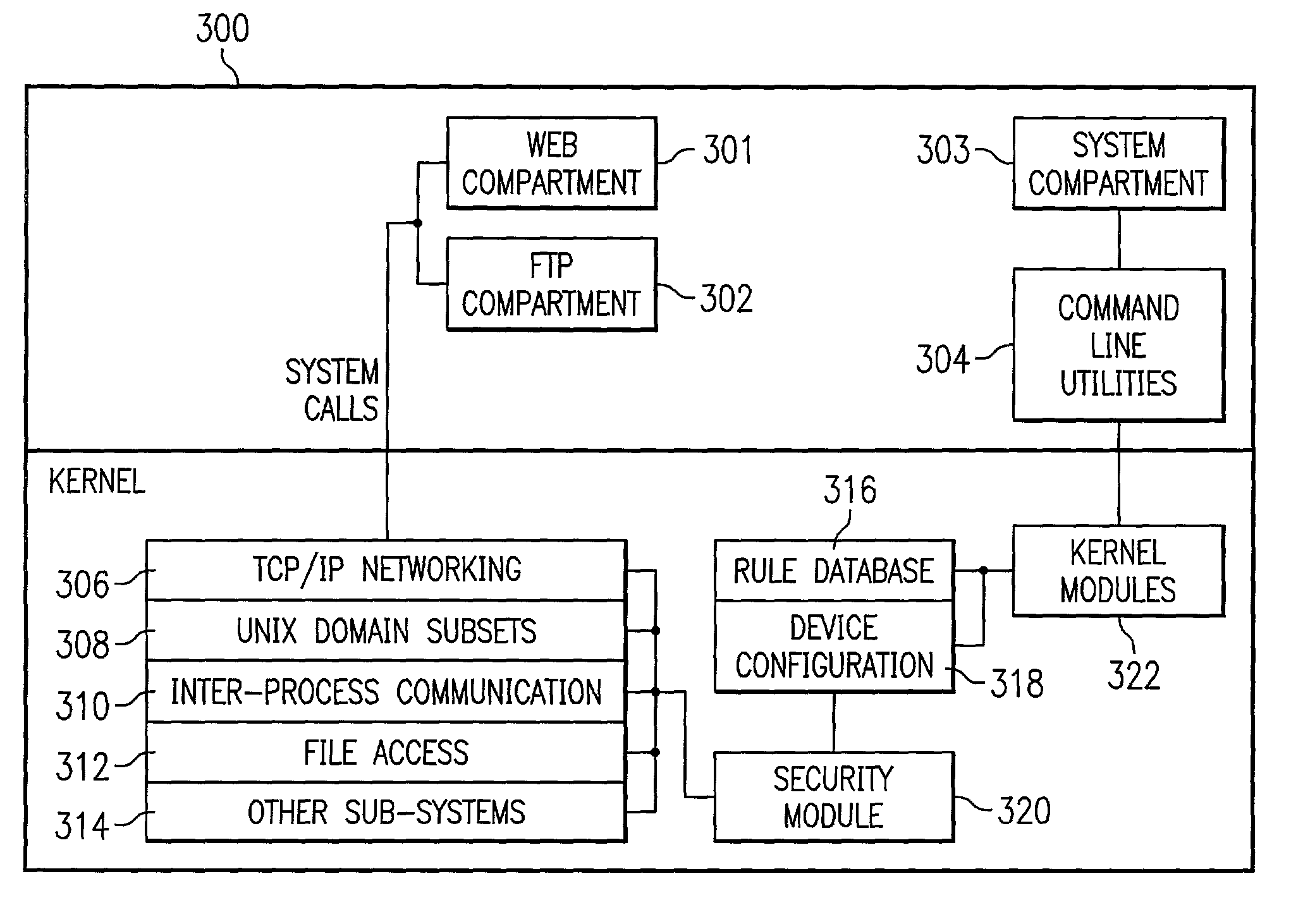
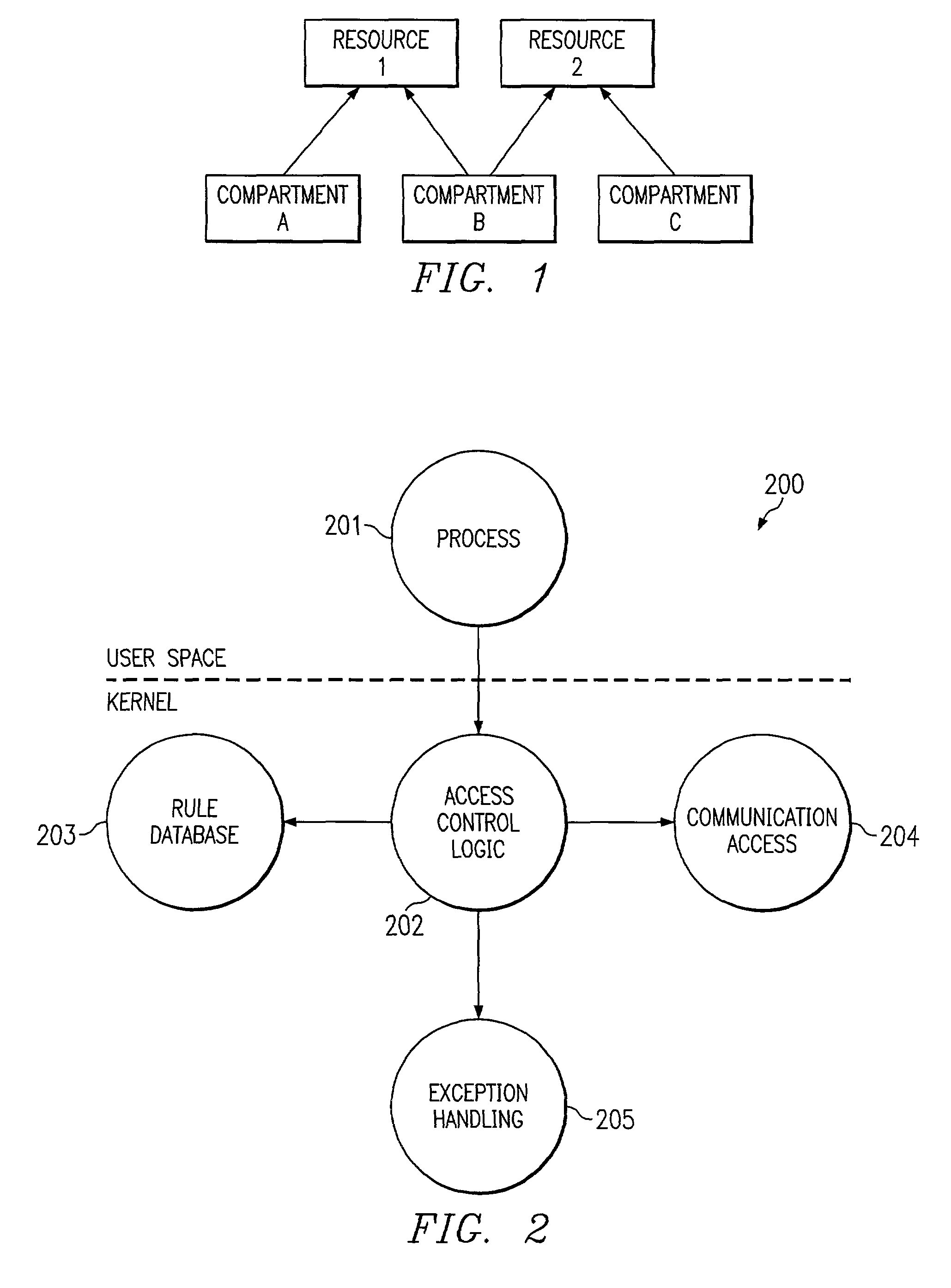
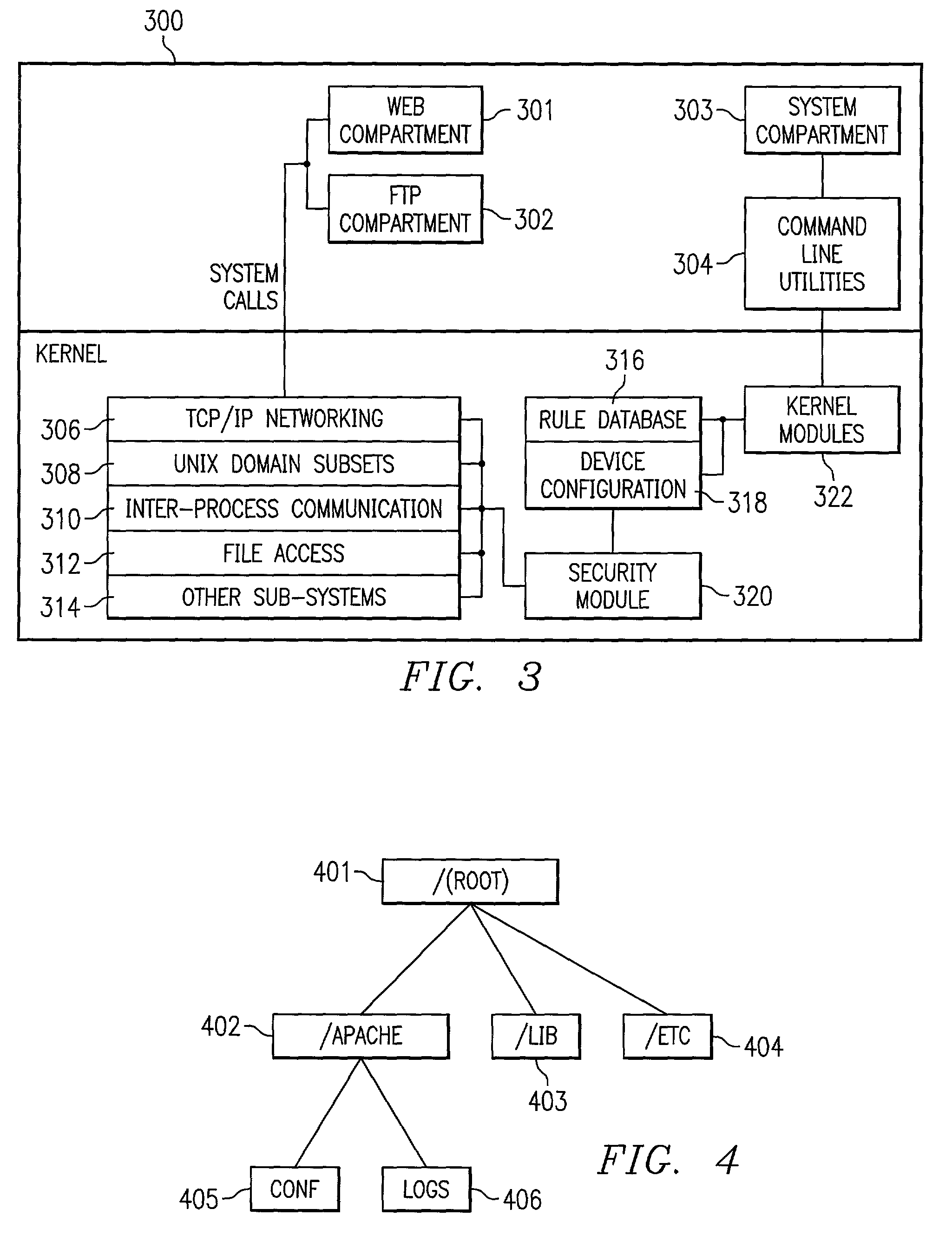
System and method for file system mandatory access control
InactiveUS7962950B2Digital data processing detailsAnalogue secracy/subscription systemsOperational systemFile system
In one embodiment, the present invention is related to a computer system including compartments implemented on an operating system. A database contains access rules with the access rules defining which compartments are authorized to access particular file resources. A kernel module receives a system call to access a file from a user space application belonging to a compartment. A security module determines whether the user space application is authorized to access the file utilizing access rules stored in the database.
Owner:MICRO FOCUS LLC
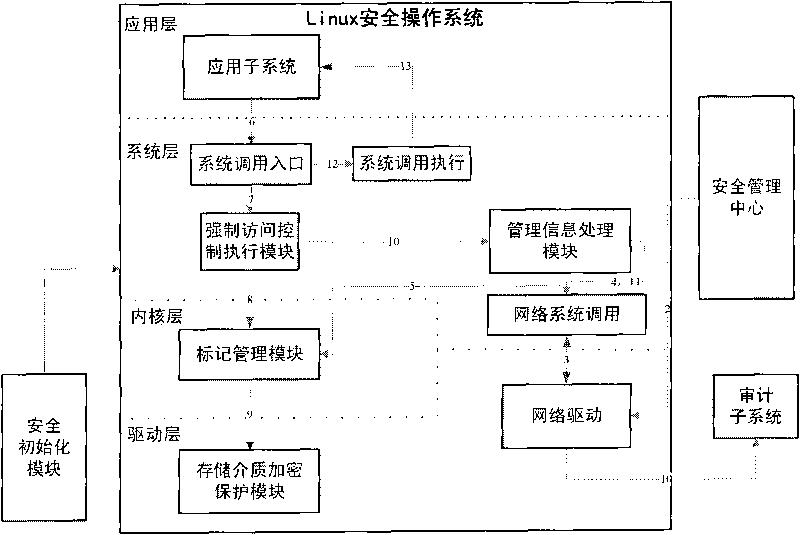
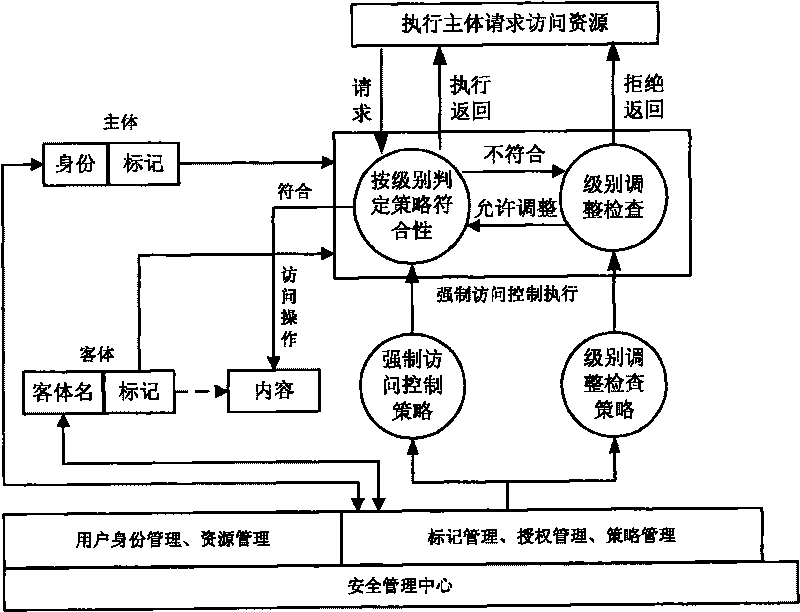
Method for implementing mandatory access control mechanism of security operating system
InactiveCN101727545ALower threshold requirementsInternal/peripheral component protectionInformation processingOperational system
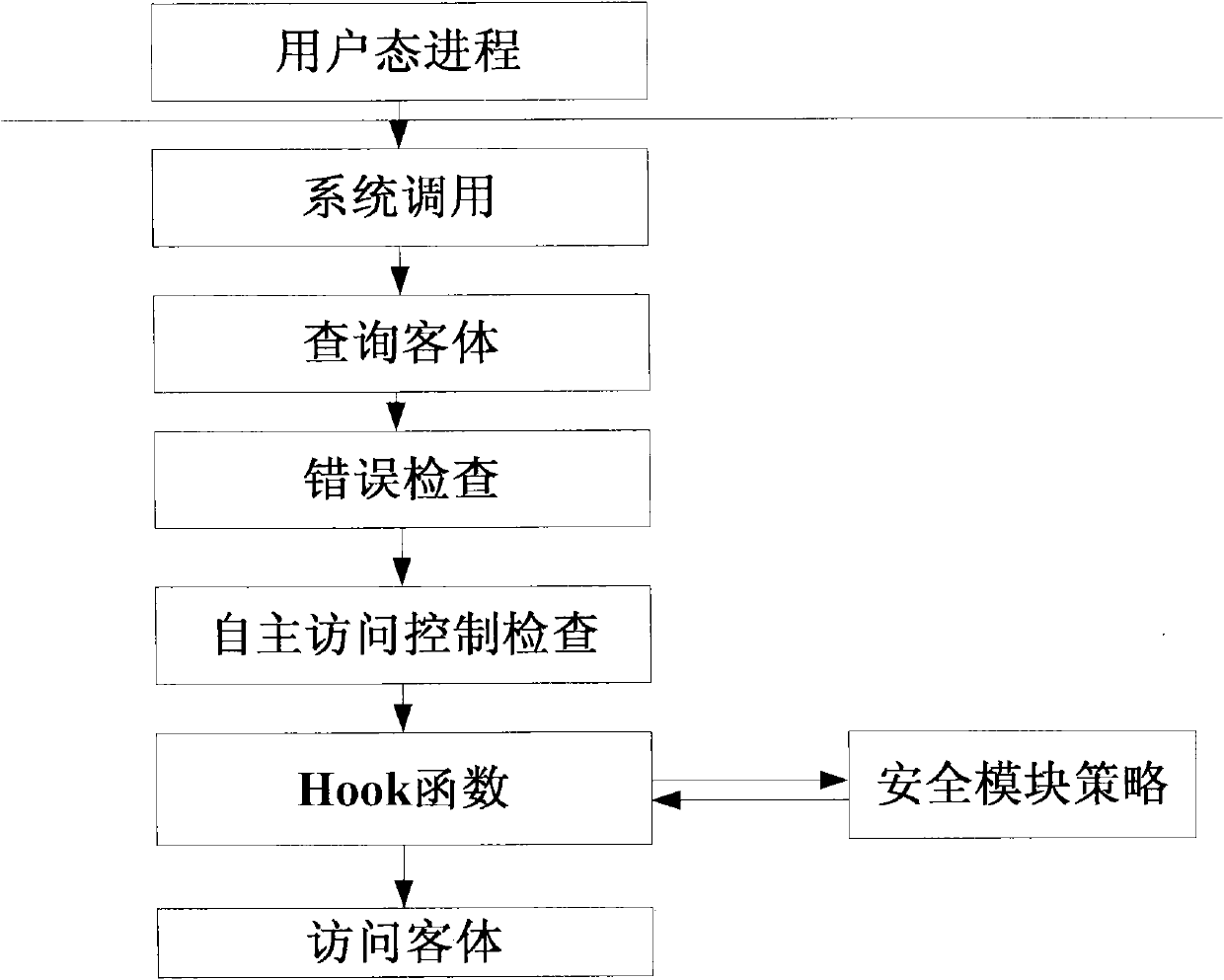
The invention relates to a method for implementing a mandatory access control mechanism of a security operating system, which belongs to the field of the design and implementation of a security operating system. The subject of the security operating system is a security system structure and an access control process. The security system structure requires an operation system to support the mandatory access control mechanism, describe the dependency relationship between hierarchical division and modules in design, be divided into a driving layer, an inner nuclear layer, a system layer and an application layer from the bottom to the top in implementation method and comprise a mandatory access control execution module, a mark management module, a management information processing module, a security initialization module and a storage medium encipherment protection module. The mandatory access control process determines the time and process precedence relationship for implementing the mandatory access control in the security operation system. A support model, a data structure and a hook function specify the details of the implementation. The mandatory access control mechanism is a necessary security function of a high-security operation system. The method can be widely used in the design of high-security operation system.
Owner:GRADUATE SCHOOL OF THE CHINESE ACAD OF SCI GSCAS
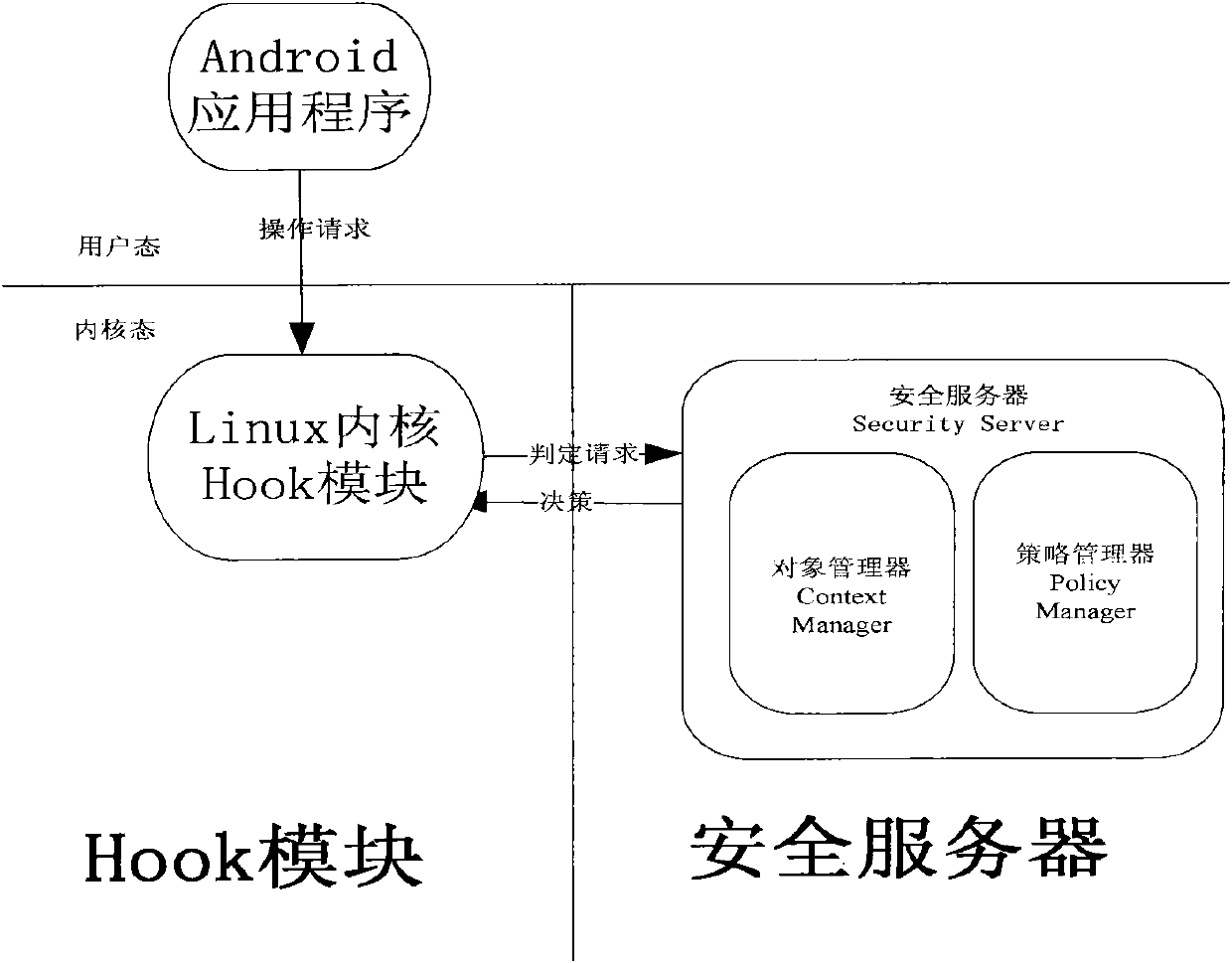
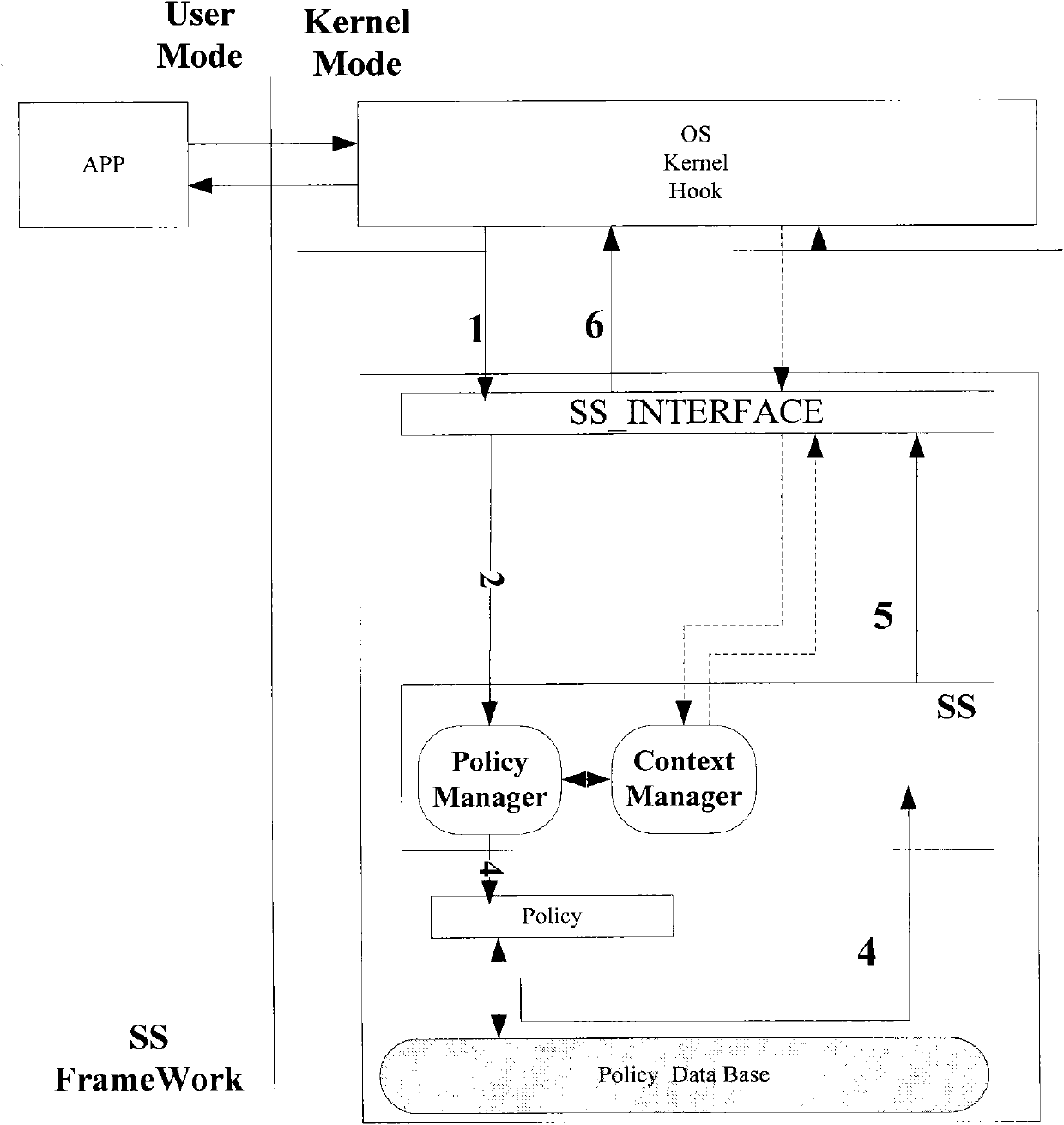
Mandatory access control device based on Android platform and control method thereof
InactiveCN101997912ADynamic Access Control MechanismReliable Access Control MechanismTransmissionProgram/content distribution protectionOperational systemComputer module
The invention discloses a mandatory access control device based on an Android platform and a control method thereof. The device comprises a security server and is characterized in that an HOOK module communicated with the security server is embedded in the kernel of the Android platform for intercepting an access request of an operation system process to a kernel object, and the access request is provided for the security server for security judgement; and the HOOK module controls whether the access request is permitted or not according to the security judgement result of the security server. The invention does not allow a subject to interfere an access control strategy, determines whether access is permitted or not by comparing the security label of the subject and an object and has higher security than own two-layer security mechanism of the Android system.
Owner:SUZHOU LINGXIAO TECH
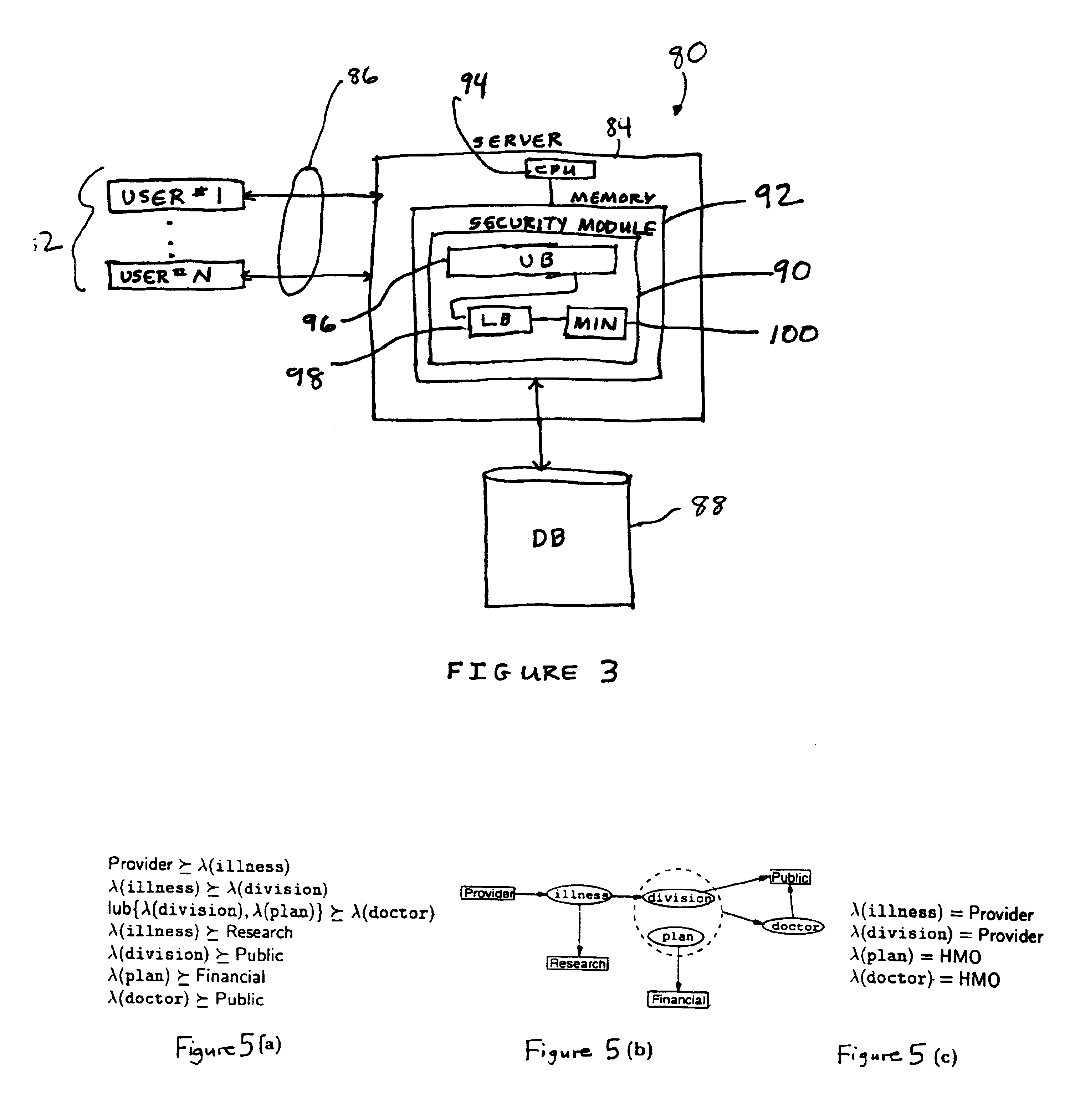
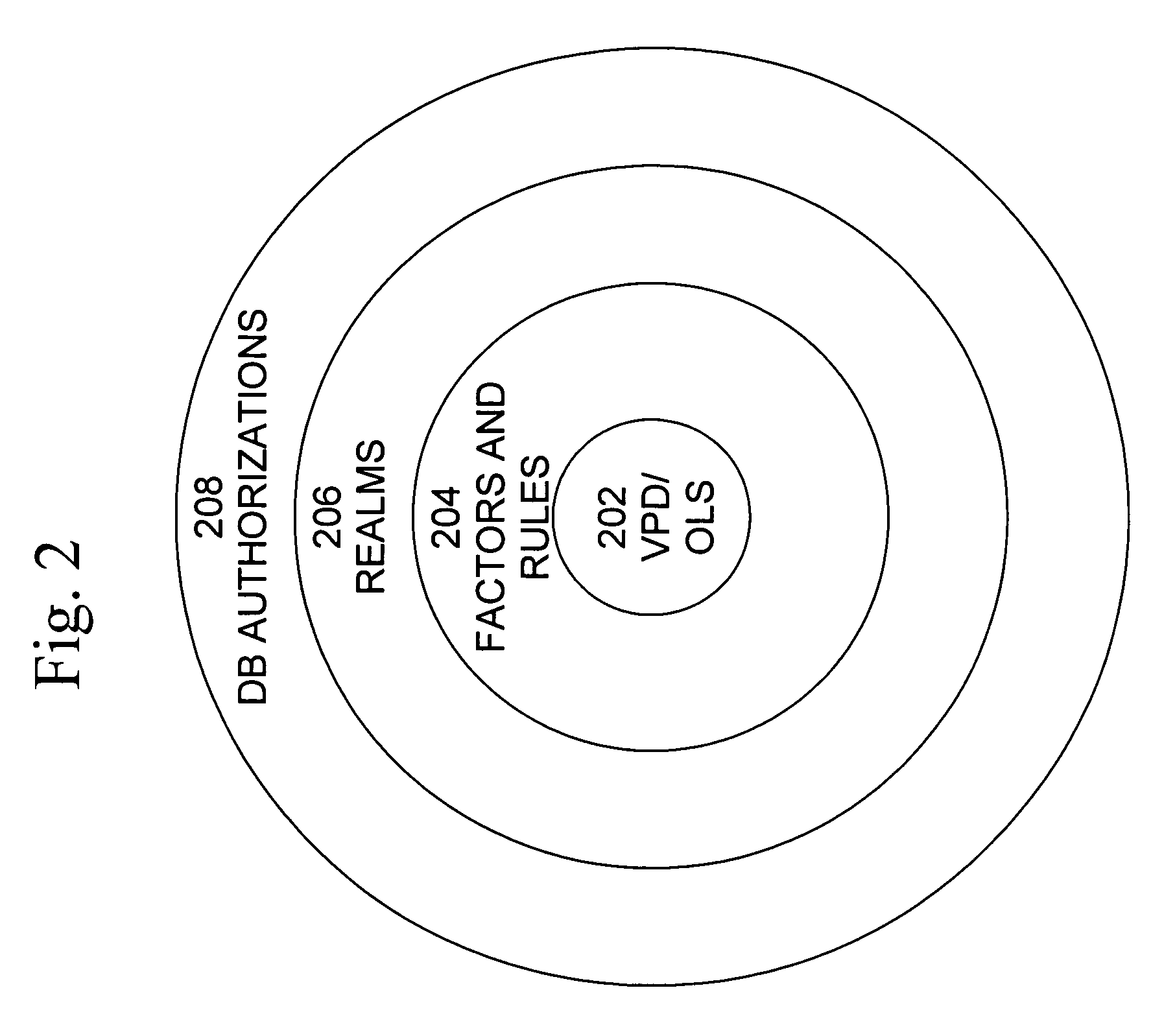
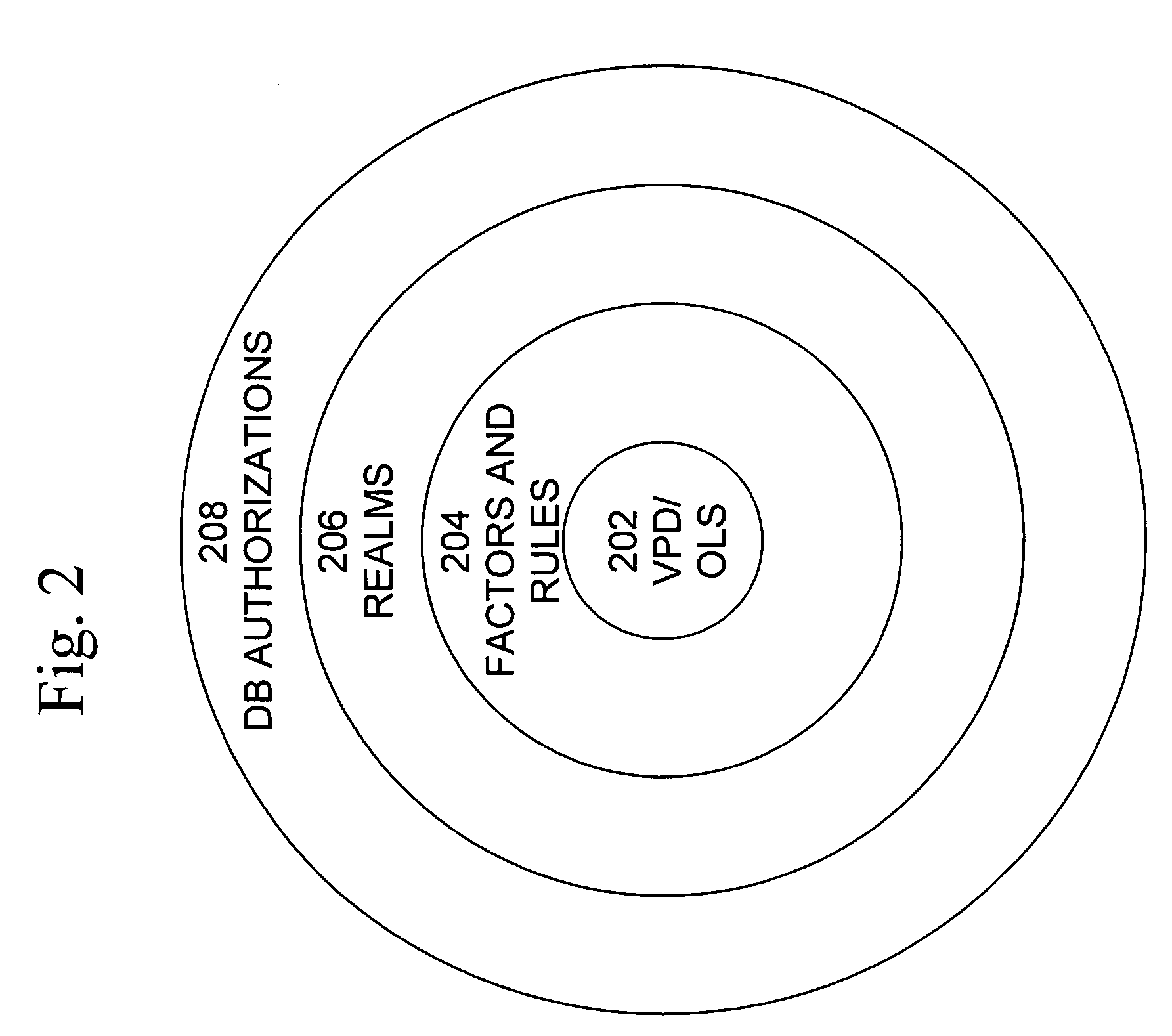
Mandatory access control base
ActiveUS20060248083A1Ease of administrationEnsure effective implementationComputer security arrangementsSpecial data processing applicationsData accessDatabase security
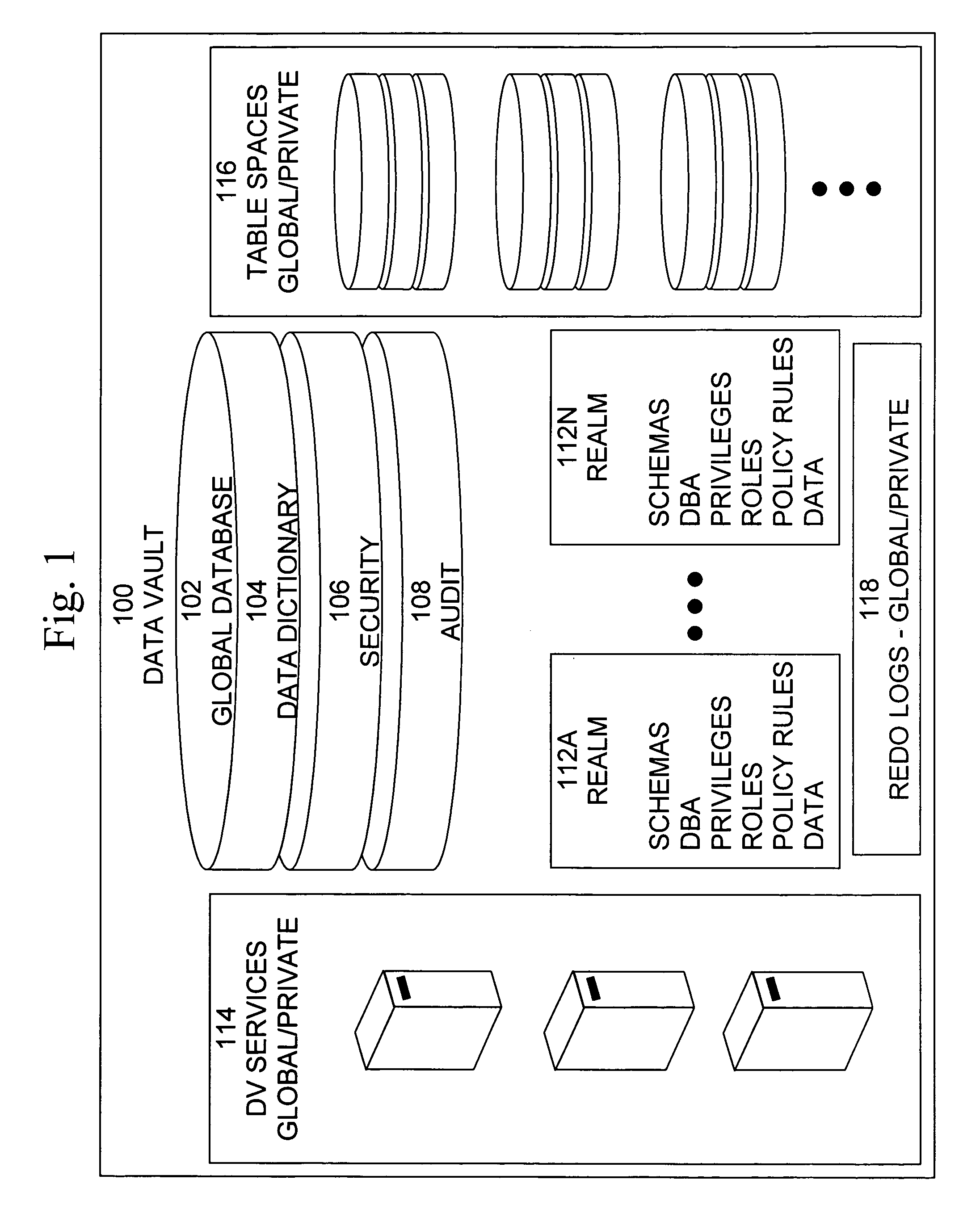
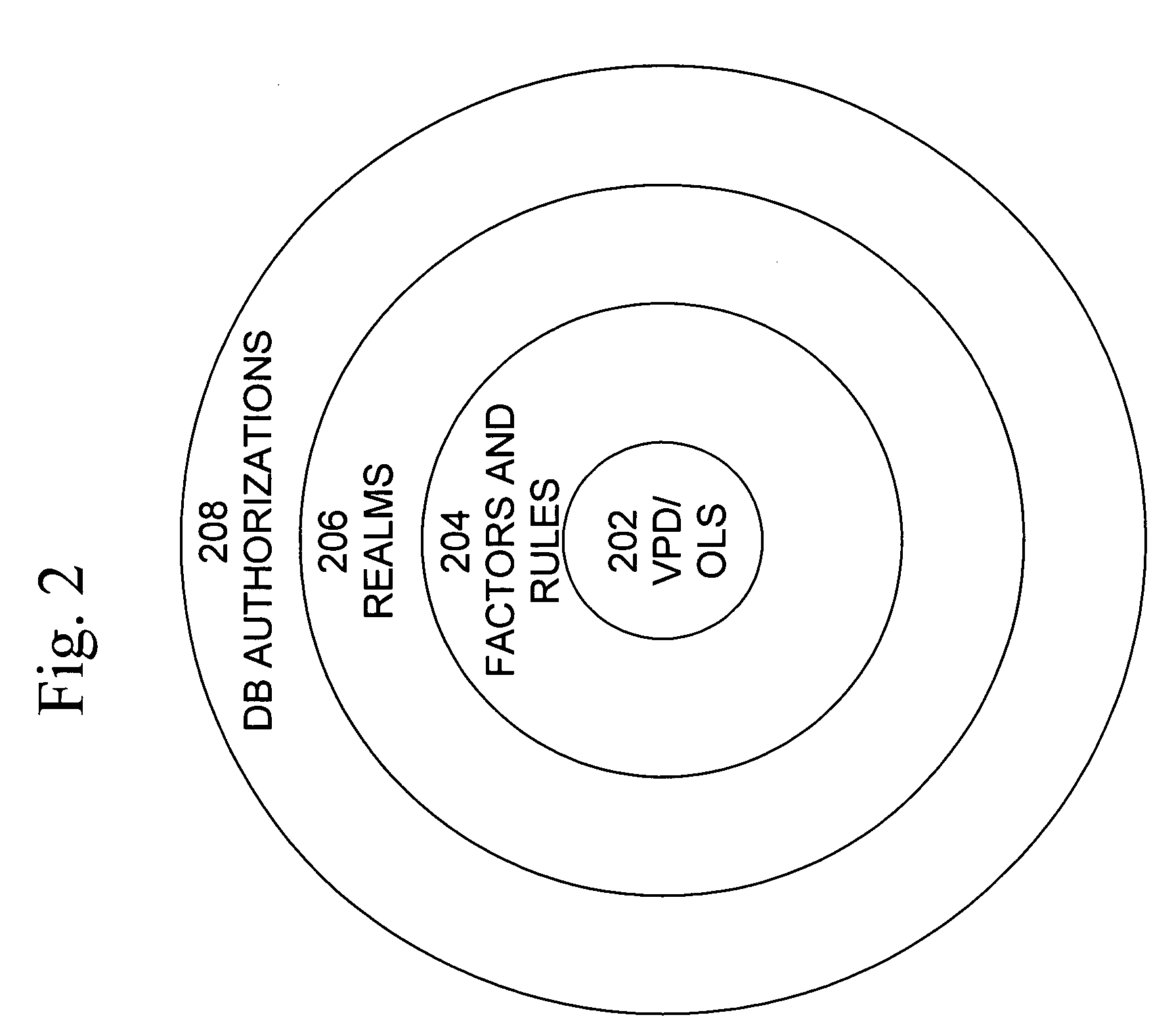
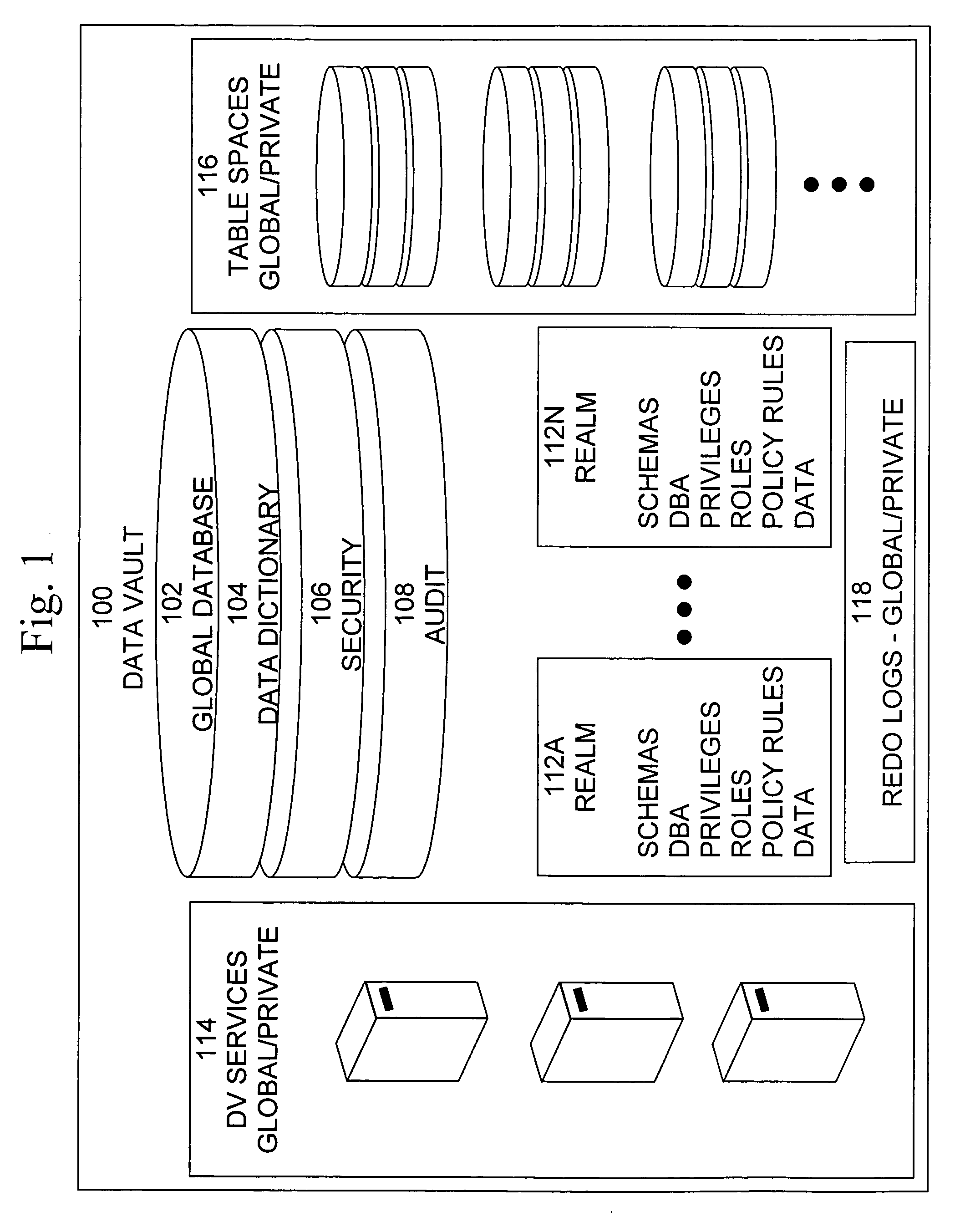
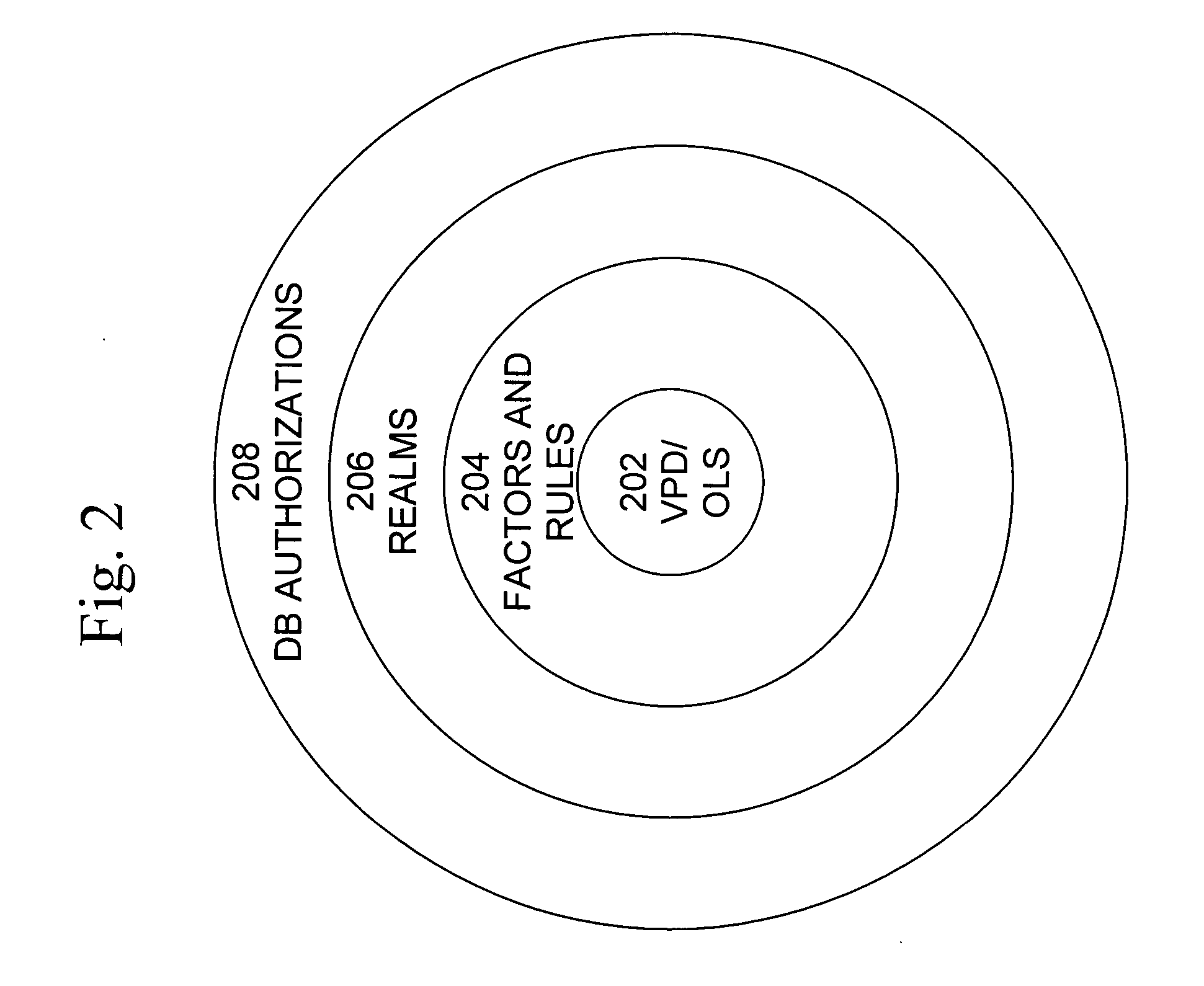
A secure database appliance leverages database security in a consistent framework provides consistent, flexible, and adaptable security using mandatory access controls in addition to user and role based security for access control and accountability. A database system comprises database objects having a level of security, factors representing a characteristic of a user of the database system, rules defining a limitation on operation of the database system by the user based on at least some of the plurality of factors and based on attributes of data to be operated on, including the level of security of the database object, and a plurality of realms defining a privilege of the user relative to a schema, the database system is operable to grant or deny access to data to a user based on the factors, the rules satisfied by the factors and the attributes of the data, and the realm associated with the user.
Owner:ORACLE INT CORP
Security data item level database encryption system
ActiveCN102236766ADigital data protectionSpecial data processing applicationsHash functionCiphertext
The invention relates to a security data item level database encryption method. Confidential data is encrypted by a data item level particle size; a hash function is used for deriving an encryption key of each data item according to a derived key and unique positioning information of the data item, even the data item encryption keys for encryption of all integral databases can be derived by using one key to reduce the using amount of the keys and facilitate key management; and a stream cipher algorithm is used for encrypting the data items to avoid filling. A ciphertext index is also encrypted by the stream cipher algorithm; each field (column) is encrypted by using the same key; therefore, searching keywords can be encrypted and then ciphertexts of corresponding fields are matched in spite of precise complete or incomplete searching. The method also has complete security functions of key management, secret sharing, security backup, mandatory access control, security connection and the like.
Owner:WANBANG CHARGING EQUIP CO LTD +1
Memory access control system and management method using access control ticket
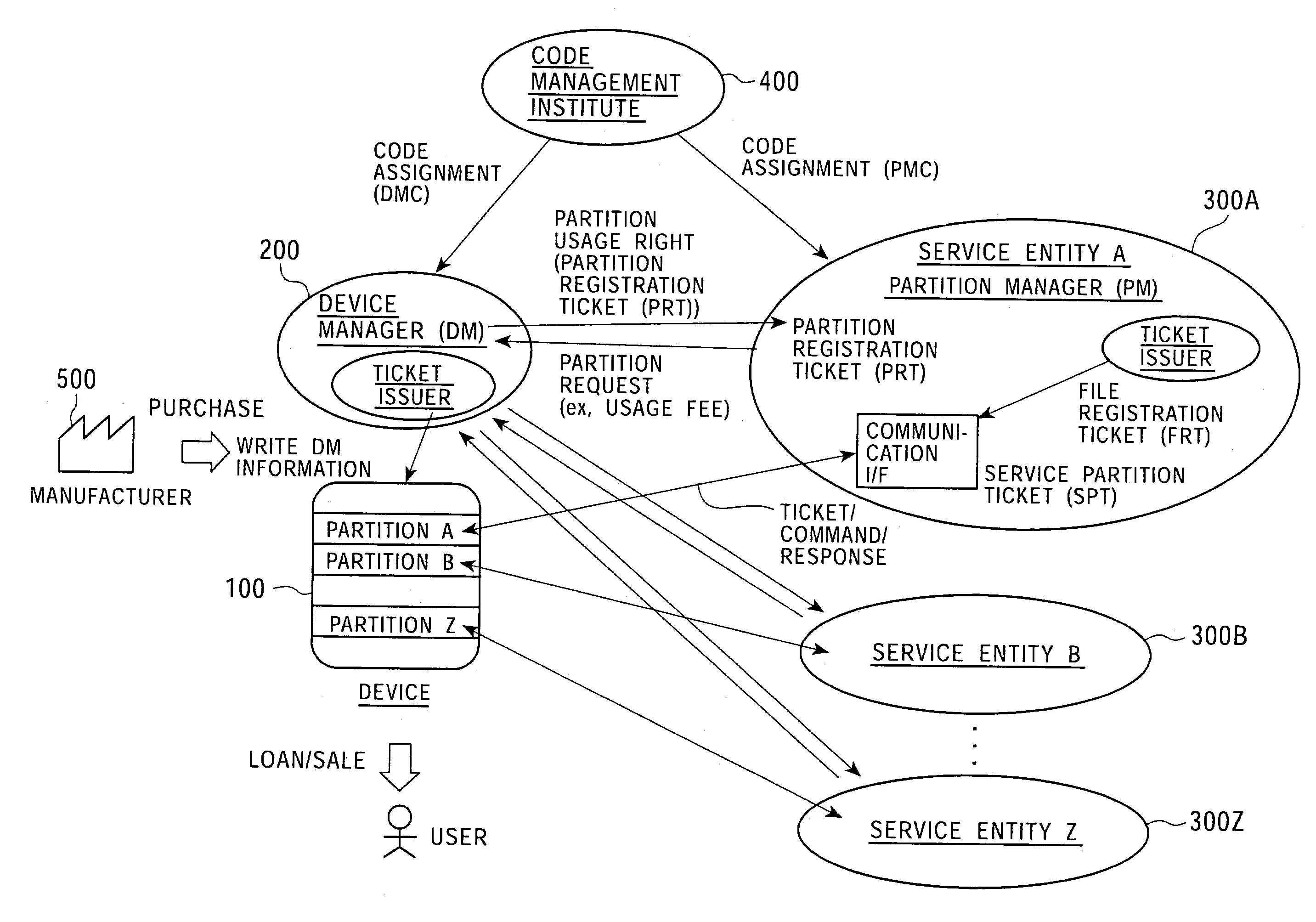
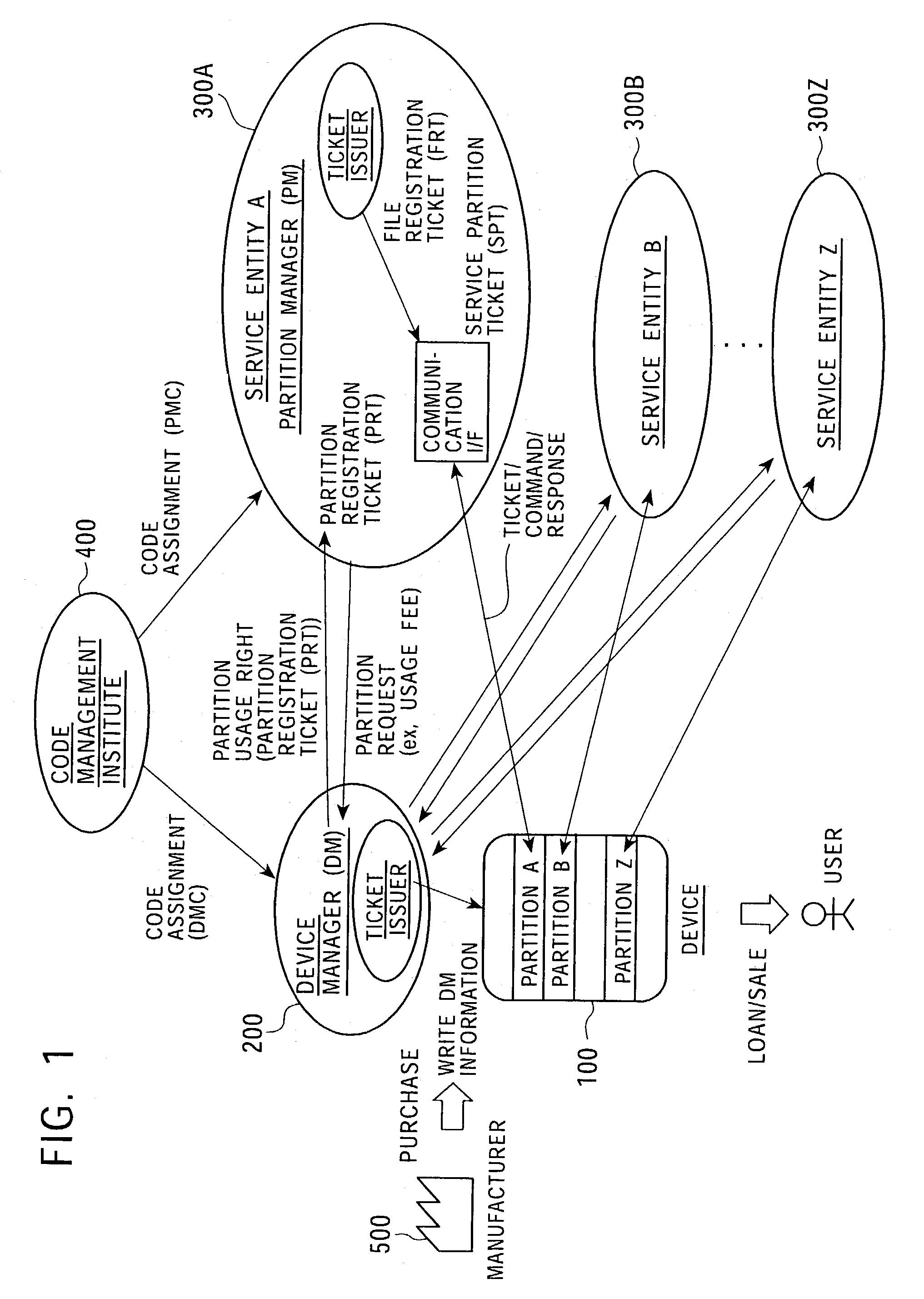
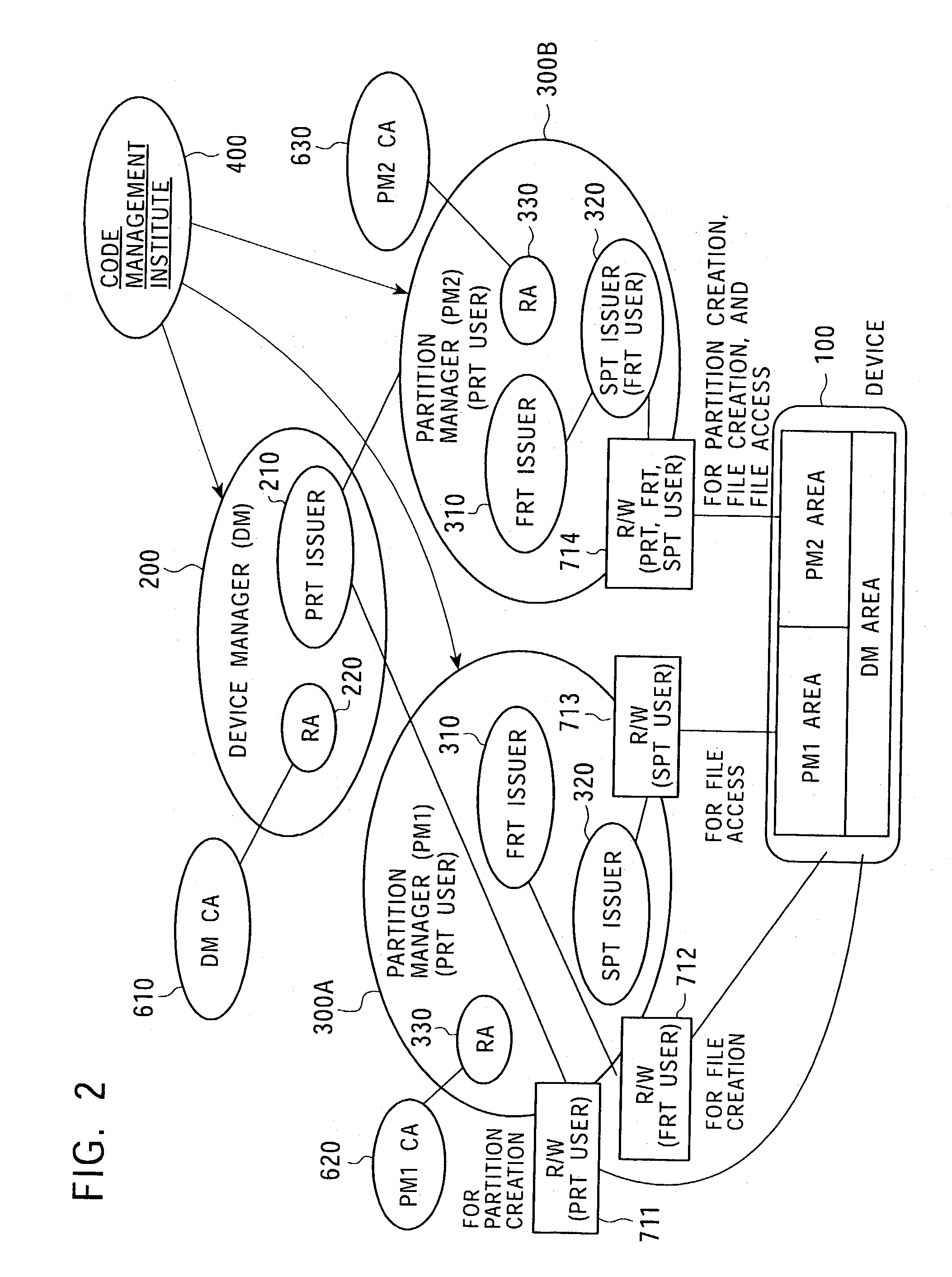
InactiveUS7225341B2Implement configurationUser identity/authority verificationUnauthorized memory use protectionComputer hardwareAccess control matrix
To provide a memory access control system in which partitions, which are divided memory areas generated in a device, can be independently managed. In response to access to the divided memory areas, which are a plurality of partitions, various types of access control tickets are issued under the management of each device or partition manager, and processing based on rules indicated in each ticket is performed in a memory-loaded device. A memory has a partition, which serves as a memory area managed by the partition manager, and a device manager management area managed by the device manager. Accordingly, partition authentication and device authentication can be executed according to either a public-key designation method or a common-key designation method.
Owner:SONY CORP
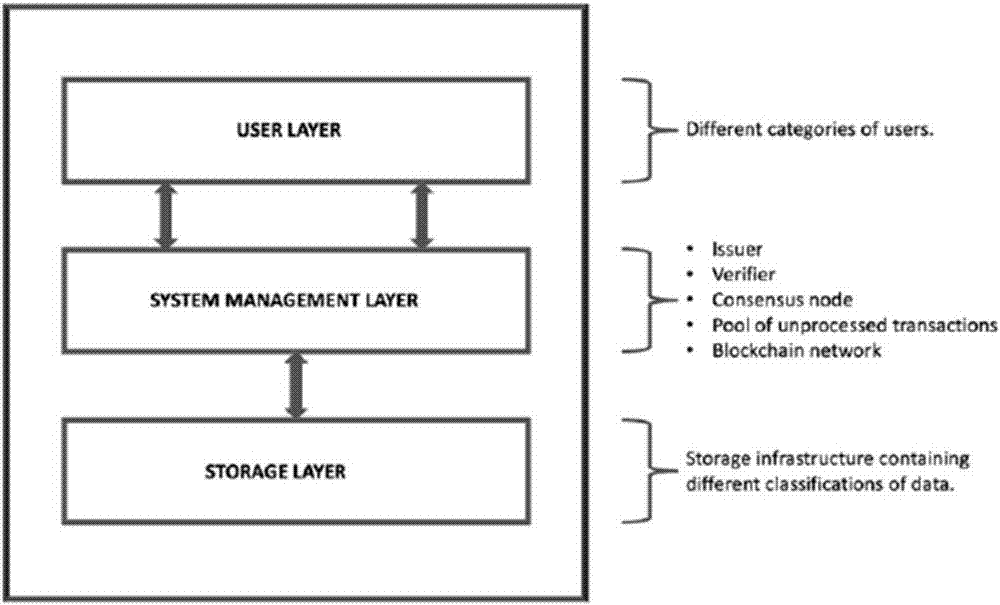
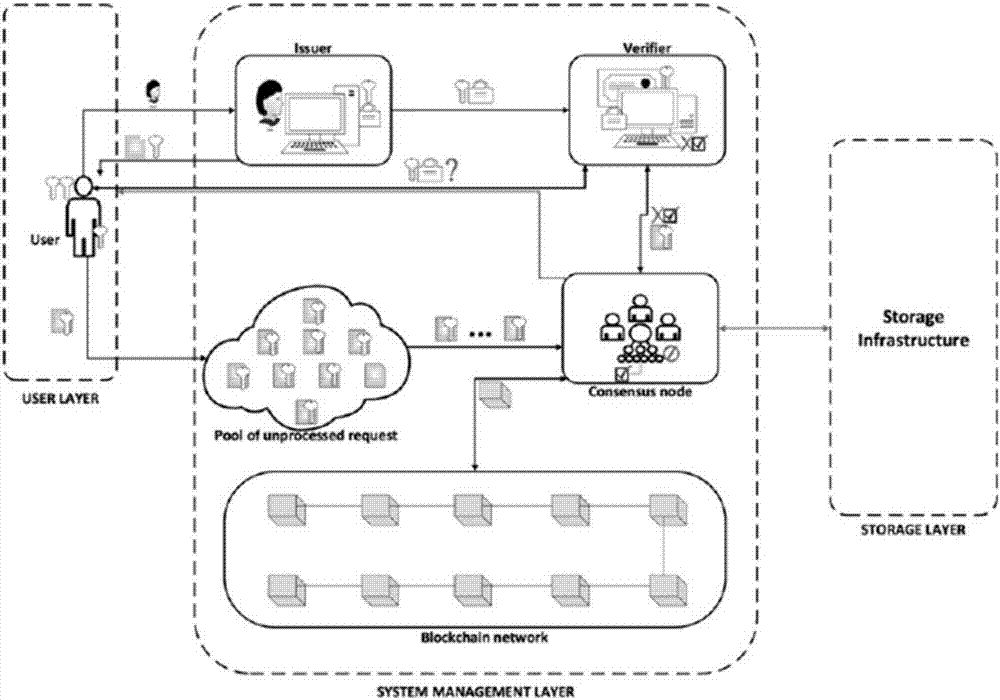
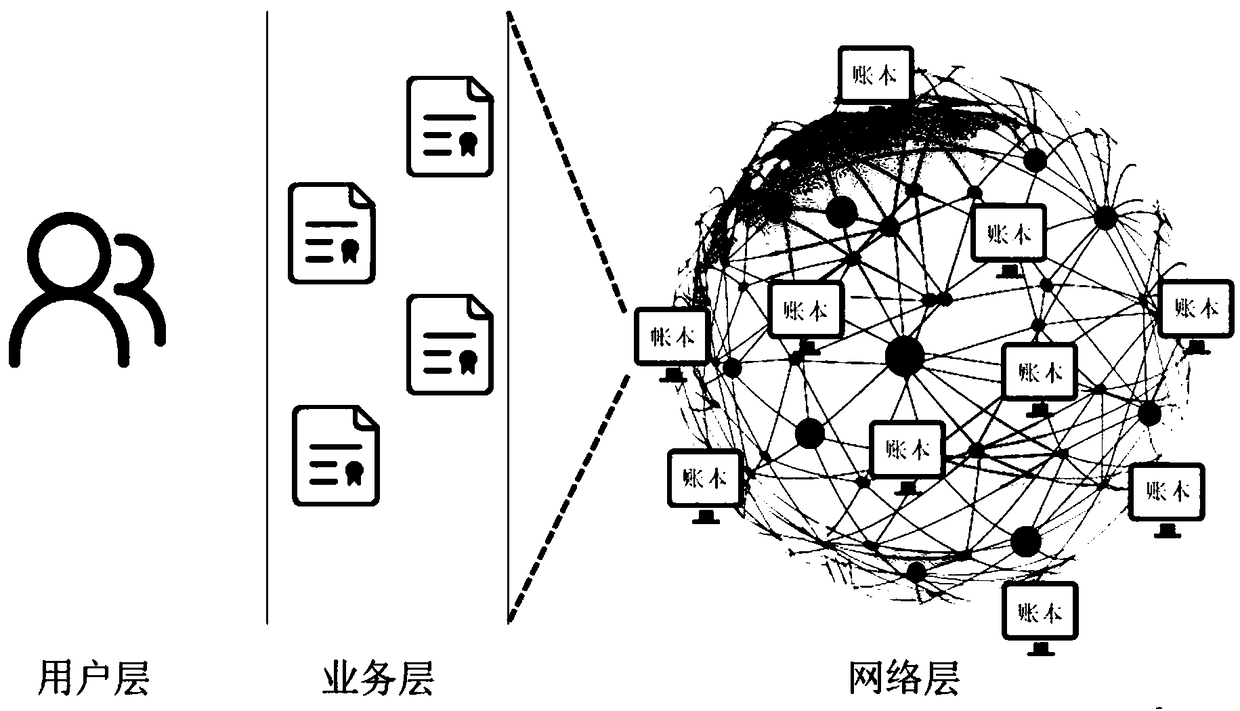
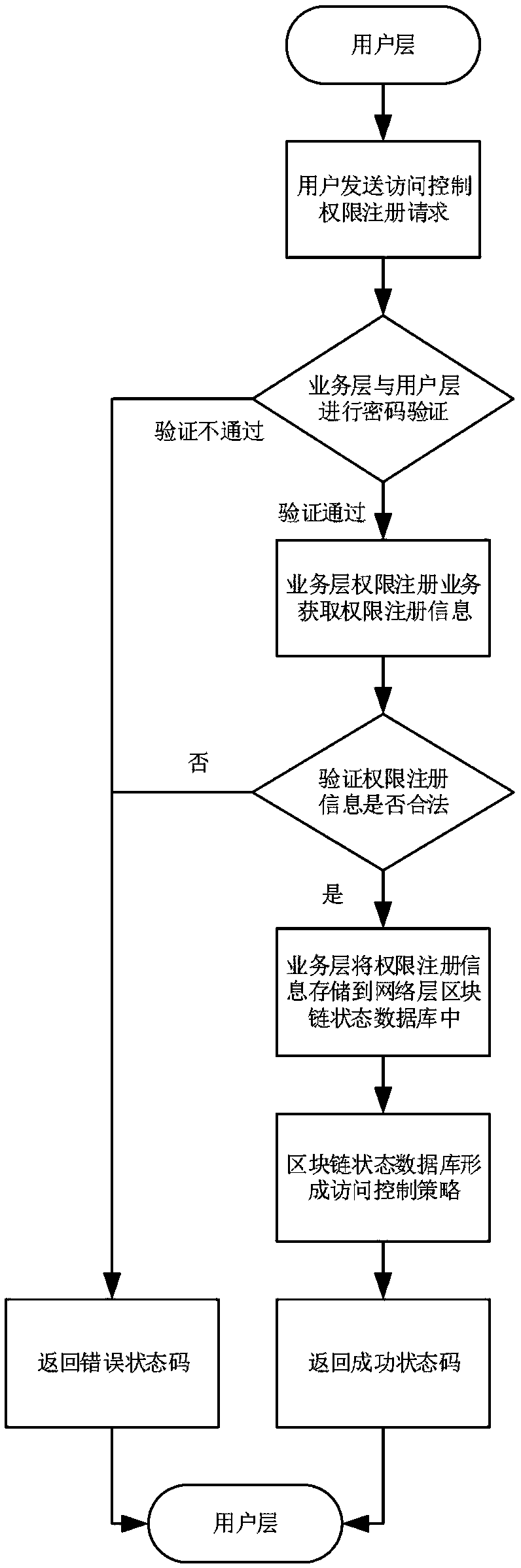
Block chain based data access control system
InactiveCN107070938AAchieve sharingSolve technical problems that are vulnerable to theftKey distribution for secure communicationUser identity/authority verificationSystems managementControl system
The invention discloses a block chain based data access control system. The block chain based data access control system comprises a user layer used for a user to send a registration application or a data access request to subordinates; a system management layer used for receiving the registration request or the data access request; and a storage layer used for the user layer to perform data access after the registration application and the data access request pass verification. When sending the registration application, password checking and verification between the system management layer and the user layer is carried out for three times, the system management layer generates a transaction public key and a transaction private key based on the last password and hands in the transaction public key to the system management layer for keeping; and when sending the data access request, the system management layer takes out and verifies a block of the data access request which is encrypted by the last password and signed by the transaction private key, and the user obtains the access permission of data stored in the storage layer after the successful verification. The block chain based data access control system solves the technical problem that user data are stolen easily due to adoption of a centralized deployment mode in the prior art.
Owner:UNIV OF ELECTRONICS SCI & TECH OF CHINA
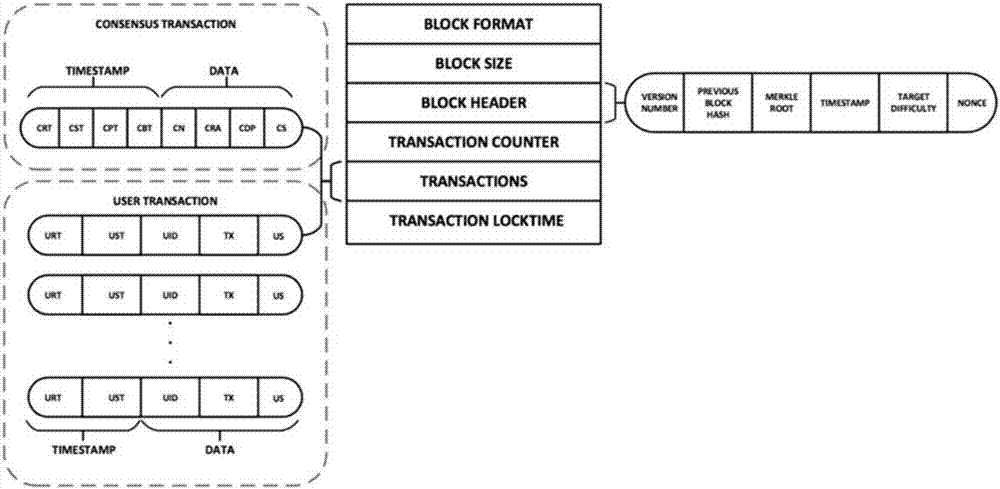
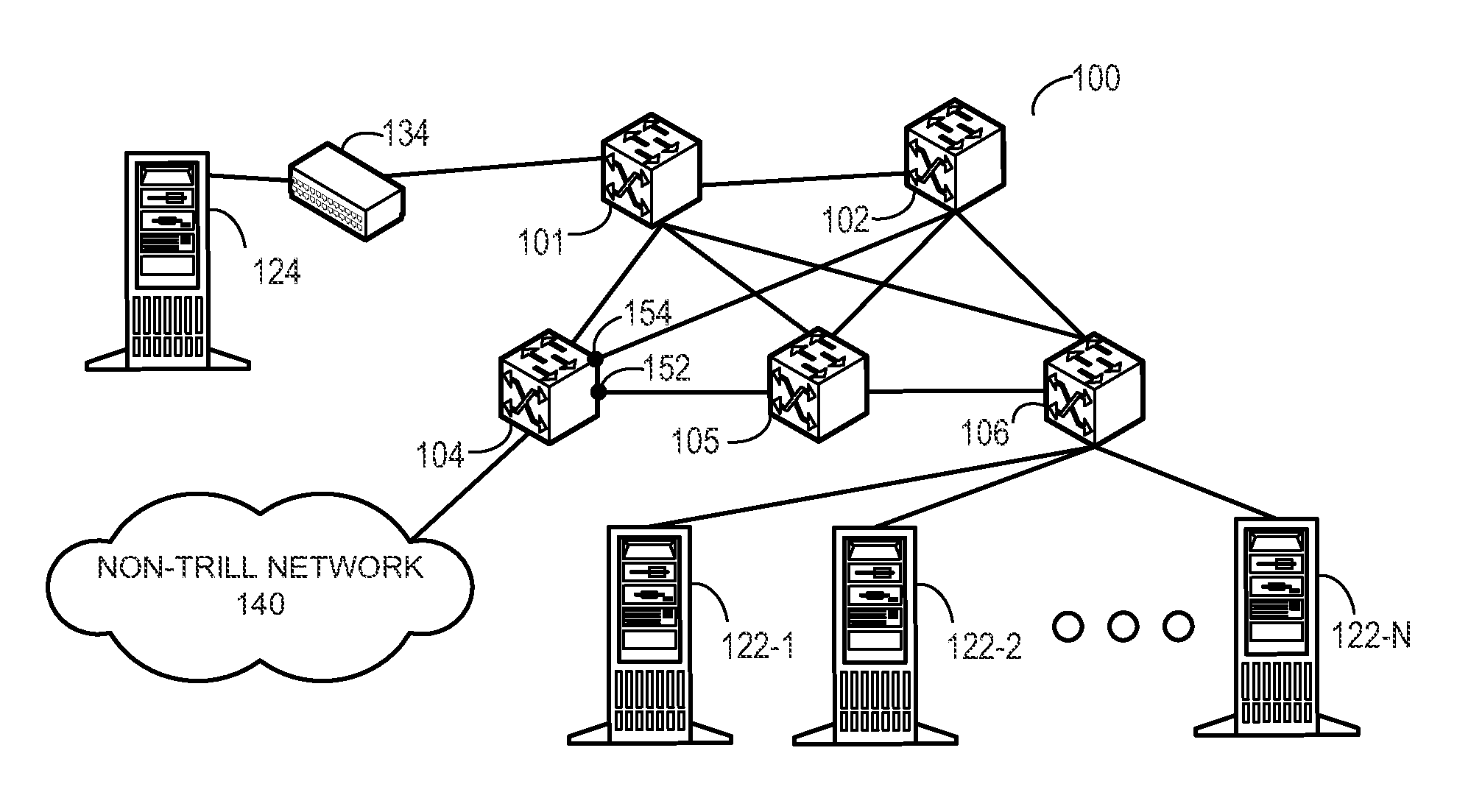
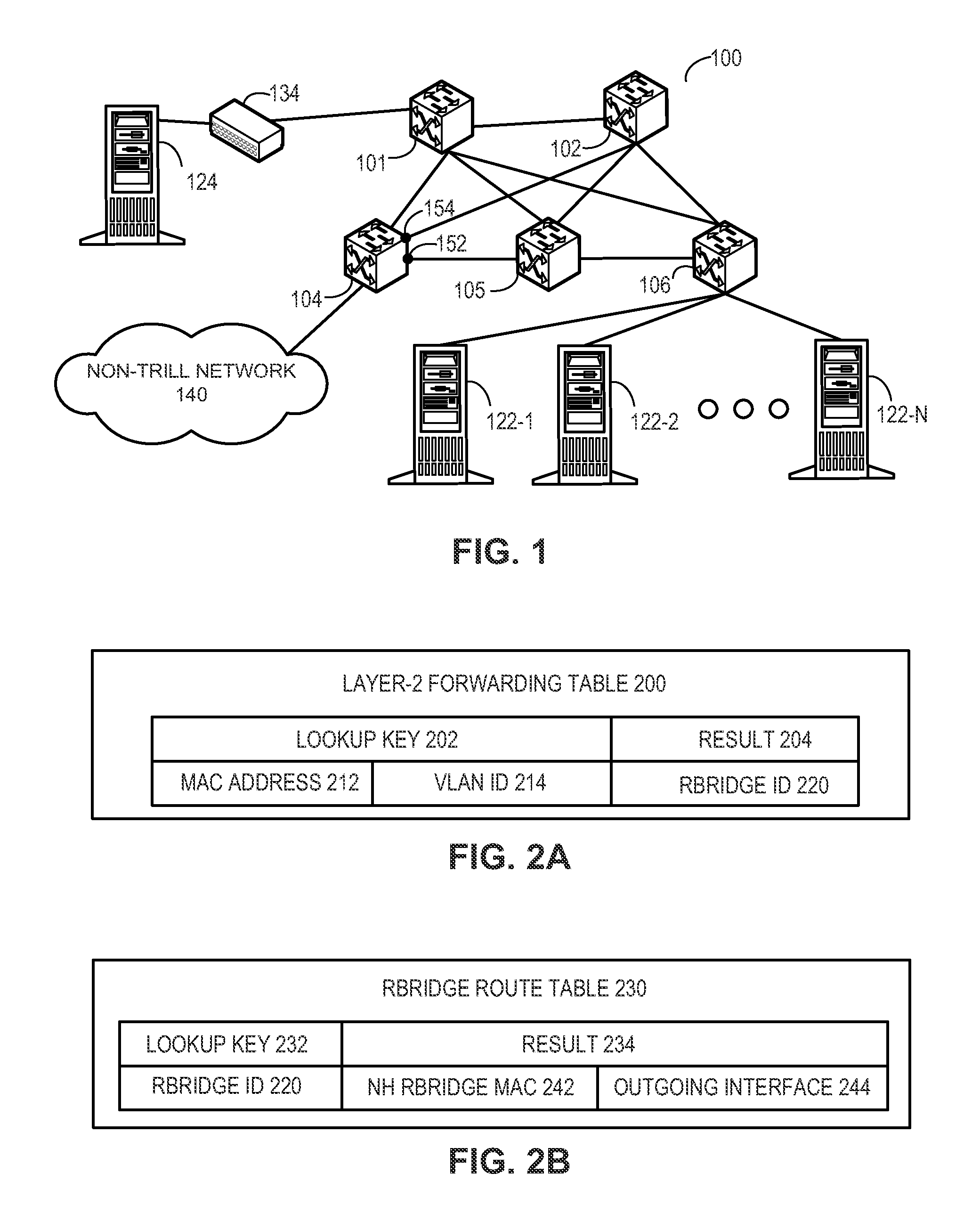
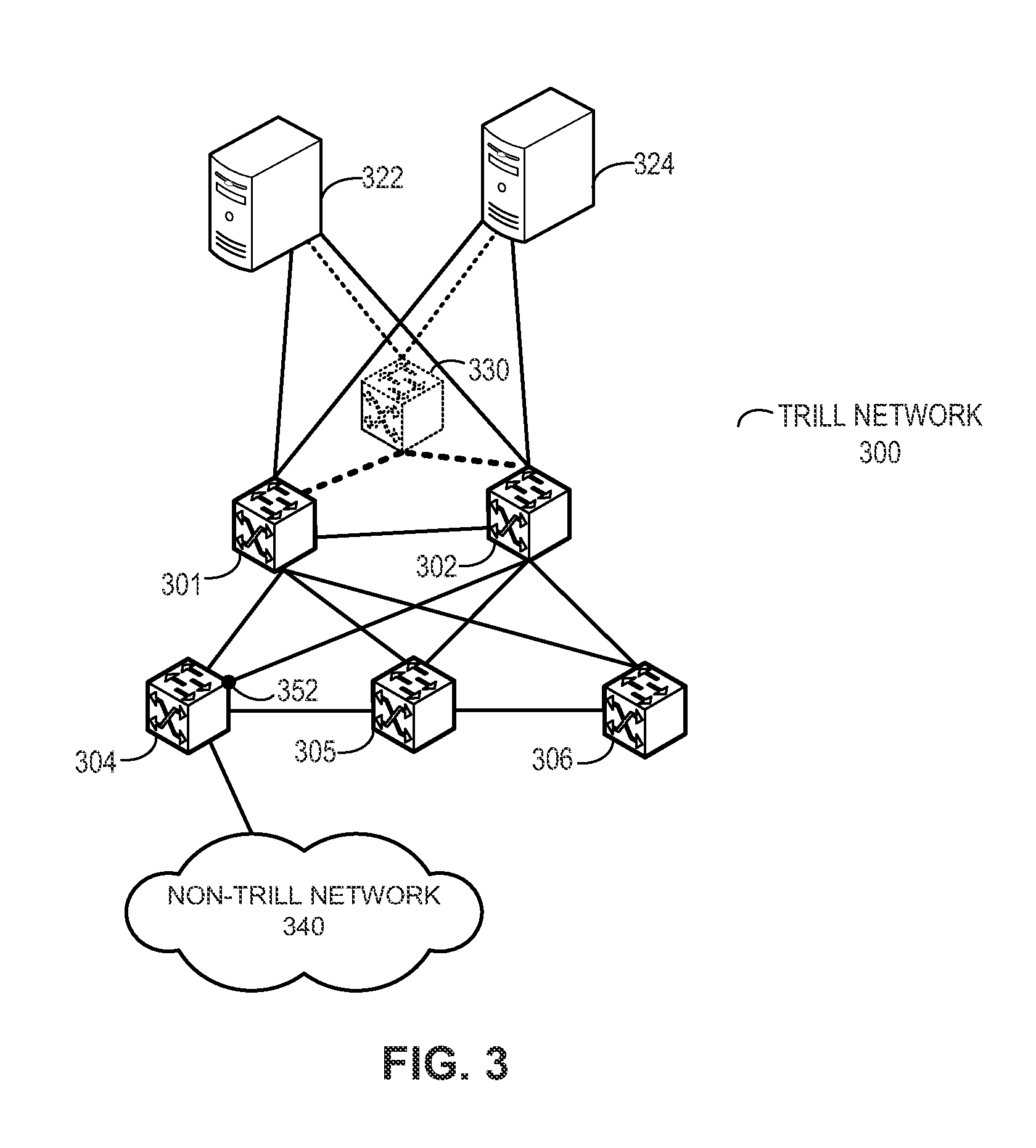
Efficient trill forwarding
One embodiment of the present invention provides a switch. The switch includes a storage and a lookup mechanism. The storage stores a first table that contains an entry corresponding to a media access control (MAC) address of a device and an identifier of a remote switch associated with the device. The storage also stores a second table that contains an entry indicating a local outgoing interface corresponding to the remote switch. The lookup mechanism identifies the local outgoing interface corresponding to the device based on the first table and the second table.
Owner:AVAGO TECH INT SALES PTE LTD
Trusted services broker for web page fine-grained security labeling
InactiveUS20010013096A1Need to installEnhance known web server functionsWeb data retrievalDigital data processing detailsPasswordRandom assignment
Arbitrarily fine-grained limitation of access to information stored in a resource of a data processor network is provided in a manner compatible with existing network browsers by mapping user identity and credentials with randomly assigned security cookie information which thus serves as a surrogate credential accompanying each user request during a session. Labels are imbedded within HTML files / text which may embody any desired security policy, including mandatory access control (MAC) arrangements which are not available through native browser functions. Data is retrieved in response to a user request which includes a security cookie from a location in the resource which is not directly accessible through use of a URL; the location being stored in a configuration file which is hidden from users. The retrieved data is then filtered in accordance with labels provided for each page and / or embedded in the text and used to build a response which may include hypertext links or other user interfaces for transmission to the user. Provision is made for viewing or changing of labels, credentials and passwords.
Owner:LEIDOS INNOVATIONS TECH INC
Dynamic auditing
ActiveUS20060248084A1Ease of administrationEnsure effective implementationDigital data processing detailsComputer security arrangementsDatabase securitySecurity level
A secure database appliance leverages database security in a consistent framework provides consistent, flexible, and adaptable security using mandatory access controls in addition to user and role based security for access control and accountability. A database system comprises a plurality of database objects, each database object having a level of security, a plurality of factors, each factor representing a characteristic of a user of the database system, at least one database session of the user in the database, the database session having a level of security, the user connected to the database with a network domain, each network domain having a level of security, wherein the database system is operable to grant or deny access to the data to a user based on the factors associated with the user, based on the level of security of the data, based on the level of security of the database session, and based on the level of security of the network domain.
Owner:ORACLE INT CORP
Multi-level and multi-category data labeling system
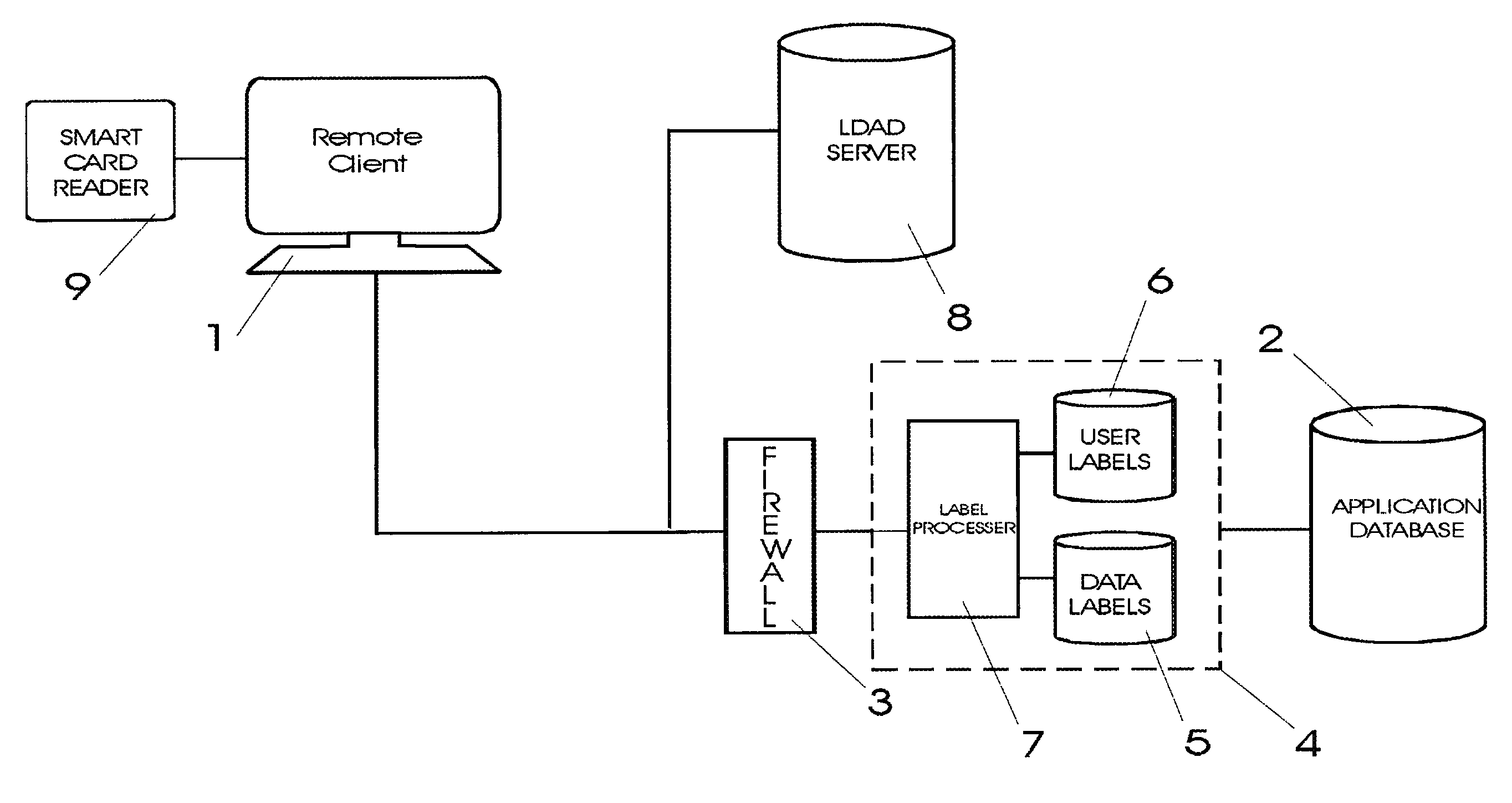
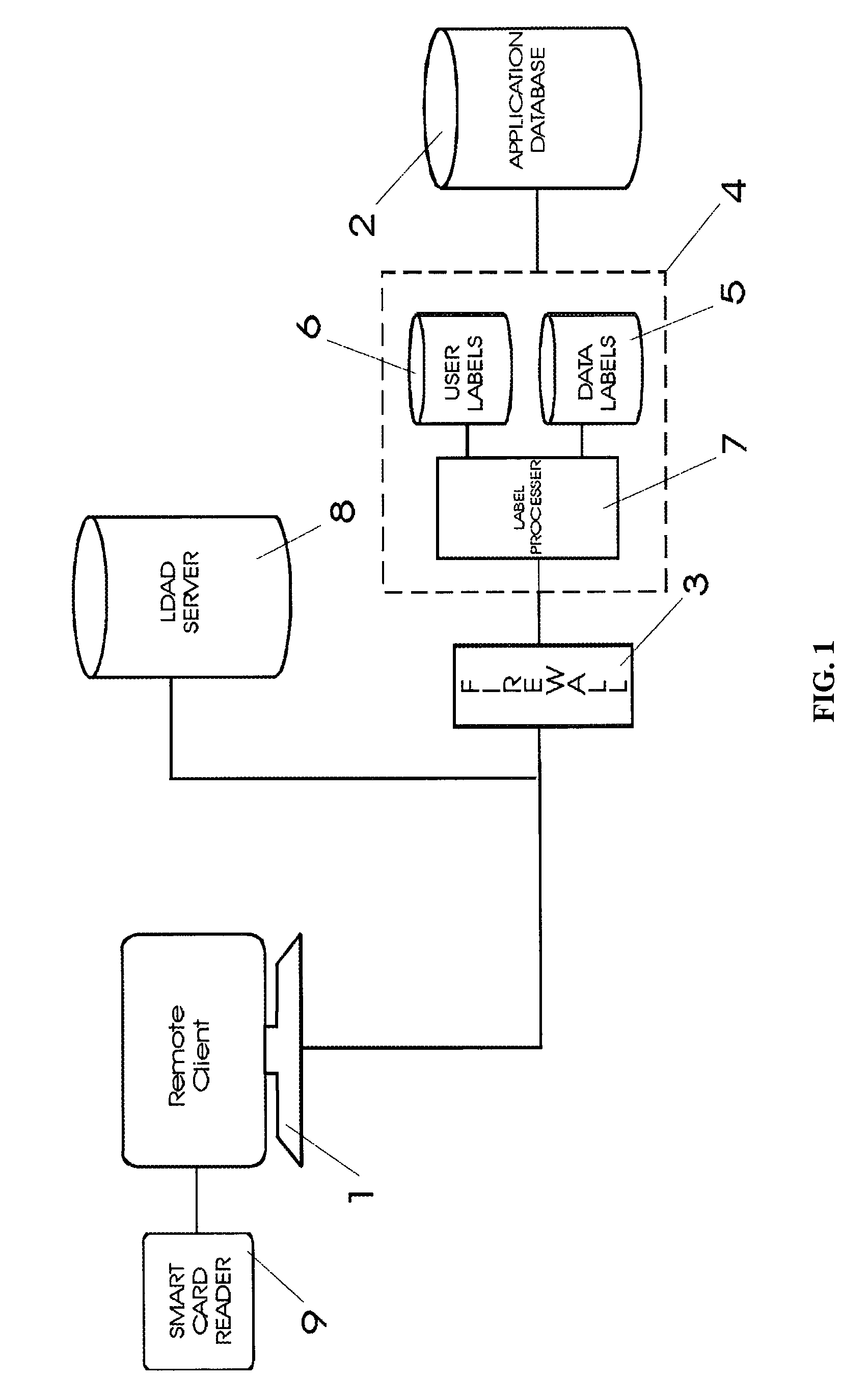
A security apparatus and method that provides Multi-Level and Multi-Category Mandatory Access Control (MAC) for controlling access to data within a database at the granularity of the data record. The access control mechanism is implemented so that it has no impact on the database. A standard labeling technology is used in which access to data is dependent on the label of the accessing entity and the label of the data being accessed. The data labels designate security access requirements for data within the database and are stored or generated in a label server that intercepts access requests to the database from remote users. User labels define user access rights and are retrieved or generated and linked to all access requests. The label server compares the user labels linked to an access request with the data label for the data requested to determine if user access is granted or denied.
Owner:FLYNTZ TERENCE T
Mandatory access control label security
ActiveUS7831570B2Ease of administrationEnsure effective implementationDigital data processing detailsComputer security arrangementsData setData access
A secure database appliance leverages database security in a consistent framework provides consistent, flexible, and adaptable security using mandatory access controls in addition to user and role based security for access control and accountability. A database system comprises a plurality of datasets, each dataset including a plurality of data, and a plurality of database objects, each object having a security label comprising a security classification of the object, at least one database session, the database session having a security label indicating a security classification of the database session, wherein, the database system is operable to allow or deny access to data to a database session based on a security label of a database object and on a security label of the database session.
Owner:ORACLE INT CORP
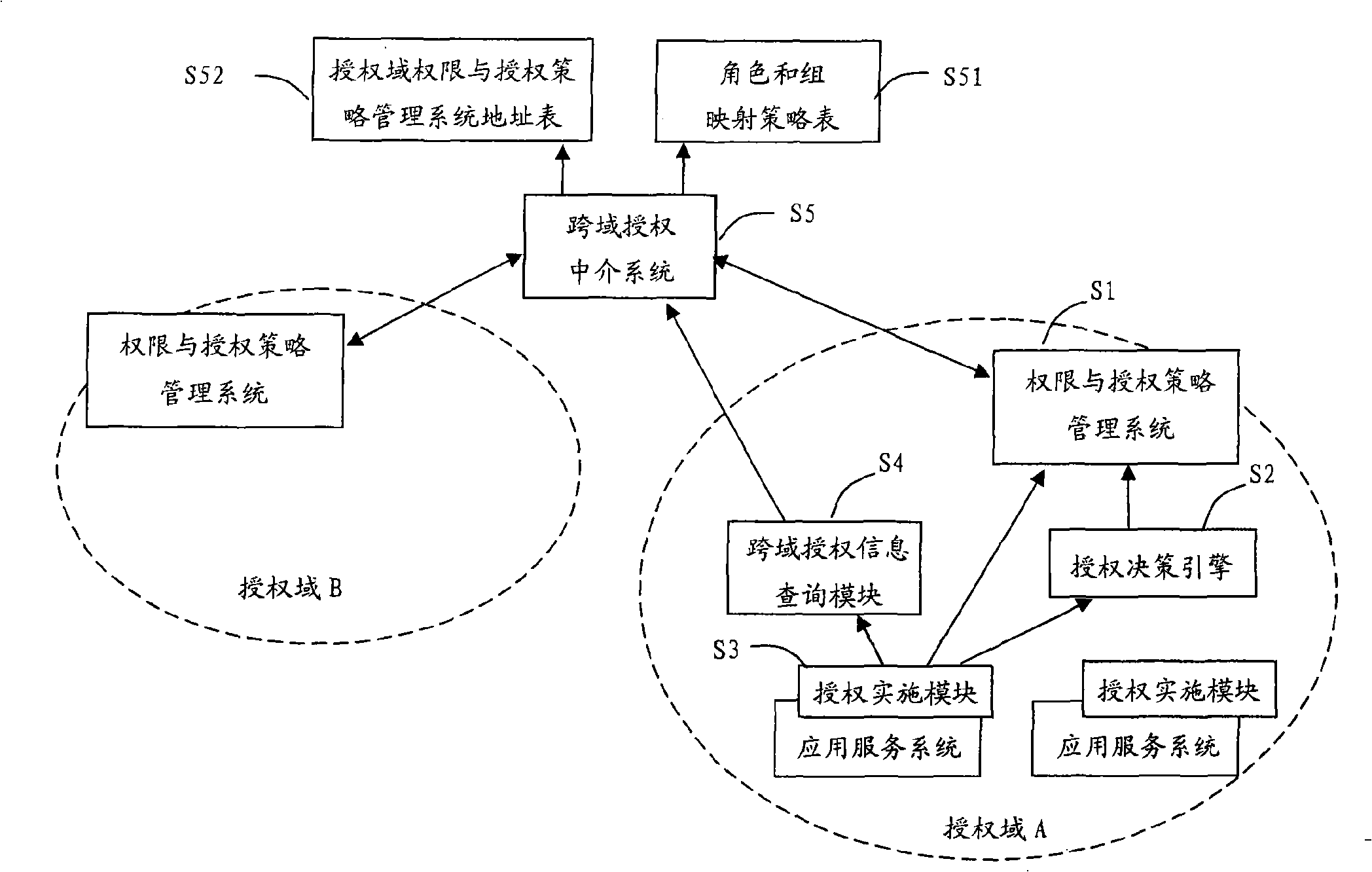
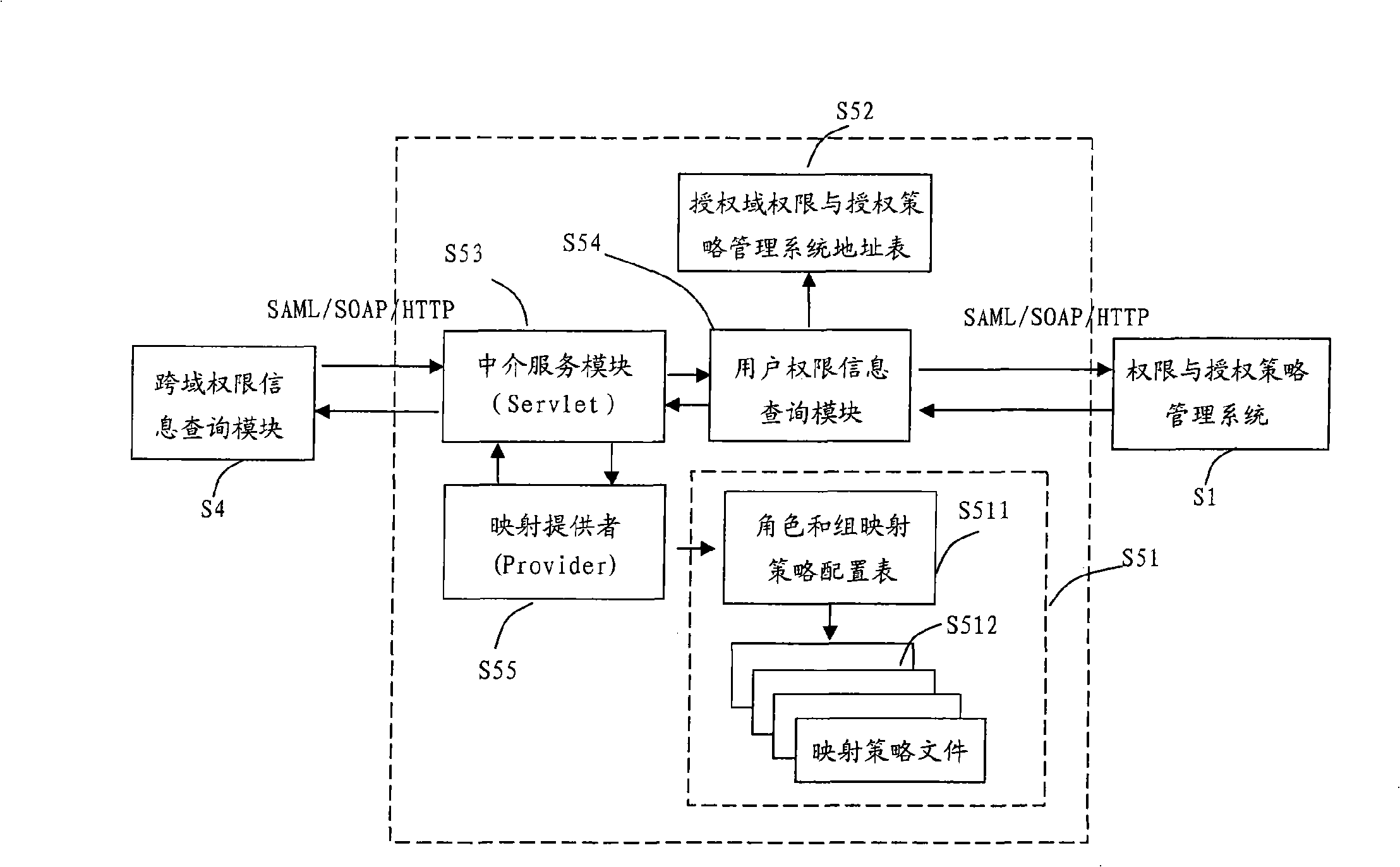
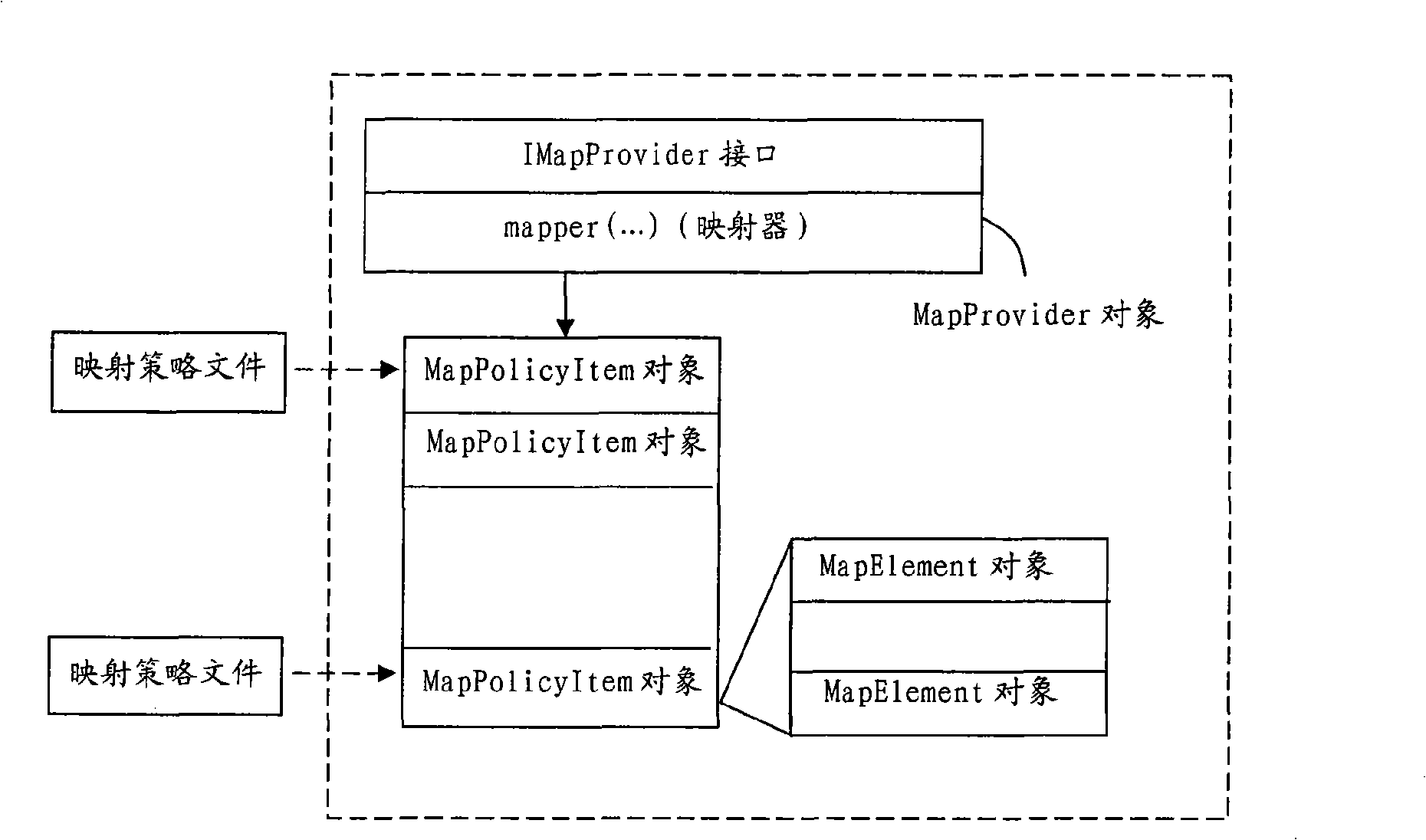
A cross-domain access control system for realizing role and group mapping based on cross-domain authorization
InactiveCN101262474ASuitable for cross-domain access controlUser identity/authority verificationControl systemSystem maintenance
The invention relates to a cross-domain access control system for role implementation and group mapping on the basis of cross-domain authorization medium. The cross-domain access control system of the invention maintains one role and group mapping strategy table through one cross-domain authorization medium system, wherein, the strategy table is provided with a serials of mapping strategies, and one mapping strategy defines the mapping relationship of roles and groups from one authorization domain to another. When the users of one authorization domain access another authorization domain, the medium system of cross-domain authorization provides roles and groups in the target authorization domain to be accessed, corresponding to the roles and groups in the original authorization domain and on the basis of roles and groups strategy, leading user limit of authorization in one domain to be converted or correspondingly matched to another domain, thereby realizing cross-domain access control based on RBAC or ACL. The cross-domain access control system of the invention is not only suitable for the cross-domain access control based on RBAC and based on ACL, but also suitable for the cross-domain access control based on inter-domain of RBAC and ACL.
Owner:WUHAN UNIV OF TECH +1
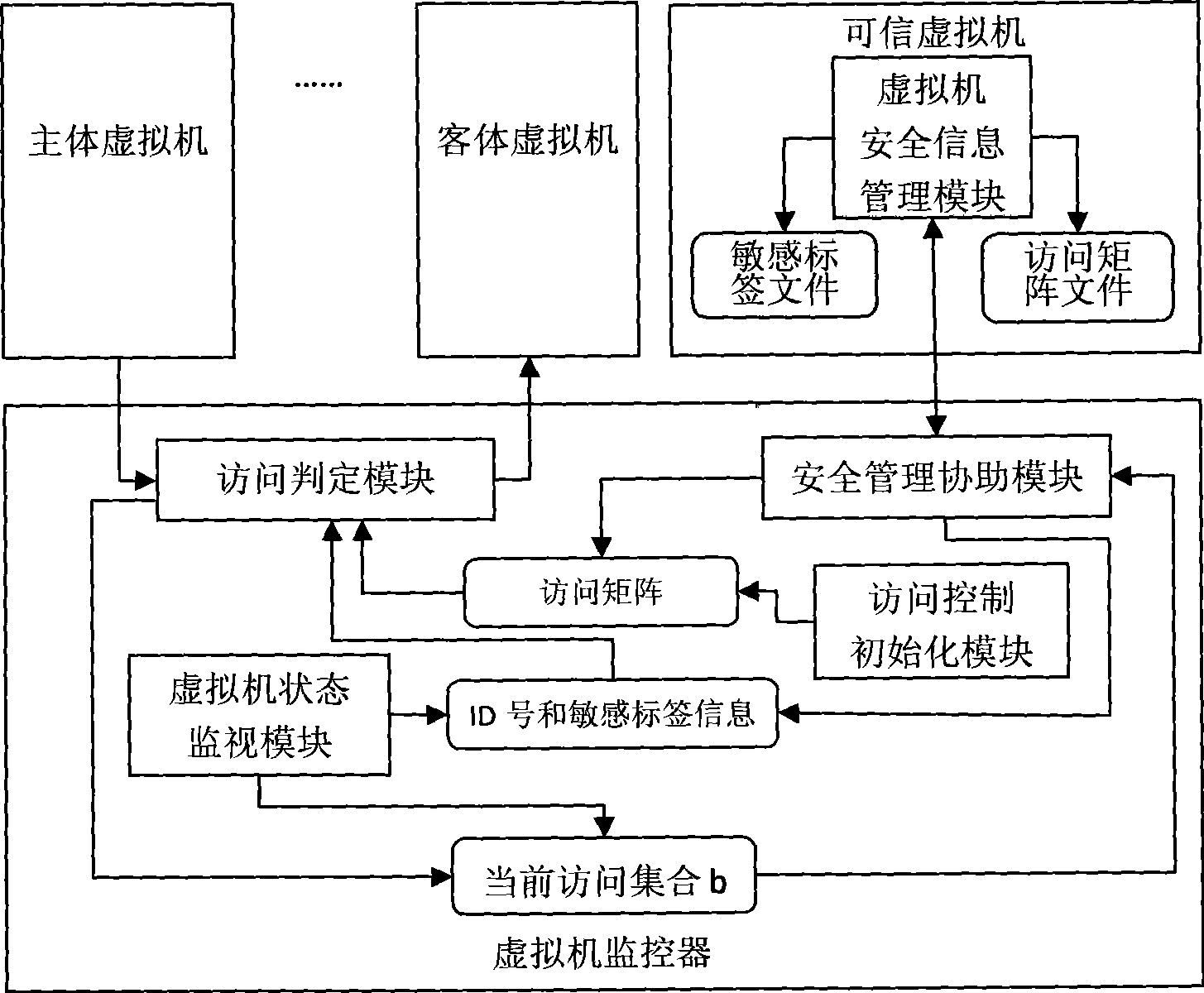
Forced access control method and apparatus in virtual environment
InactiveCN101452397AMeet security needsShare blockingSoftware simulation/interpretation/emulationVirtualizationSecurity level
The invention relates to a forced access control method and a device applied to a virtual environment in the technical field of computer application. The method comprises: designating a virtual machine in a virtual environment as a credible virtual machine with security management authority, in which, the credible virtual machine uses security classification and security category as a sensitive label to identify the security level of a single virtual machine; establishing an access matrix and setting the access type set of each virtual machine to other virtual machines; and when a certain virtual machine main body gets access to a certain virtual machine object in a certain access type, judging whether the access is permitted according to the sensitive label of both the main body and the object and the access type set of the main body to the object in the access matrix. The device comprises an access control initializing module, a virtual machine state monitoring module, an access judgment module, a security management assisting module and a virtual machine security information management module in the credible virtual machine. The forced access control method and the device can effectively control communication and resource sharing between virtual machines in a virtual environment of multilevel security.
Owner:SHANGHAI JIAO TONG UNIV
Access control method and system for object cloud storage
InactiveCN105357201AStorage supportPrivacy protectionTransmissionStructure of Management InformationClient-side
The invention discloses an access control method and system for object cloud storage. According to the method, data is stored at a cloud side in object storage structure, and the uploading and downloading of a file object are realized at a client side; when a server receives a request, the security level and security category of the request user are extracted, and the security levels and security categories of the user and the object file are judged through the mandatory access control method. The method and system can conveniently provide services for various clients and mobile terminals. As the two attributes, i.e. the security level and security category, are taken into consideration for the access control policy, the security of the object data is greatly improved. The method and system are capable of supporting the storage of large data volume, and effectively protecting the data privacy.
Owner:INST OF INFORMATION ENG CAS
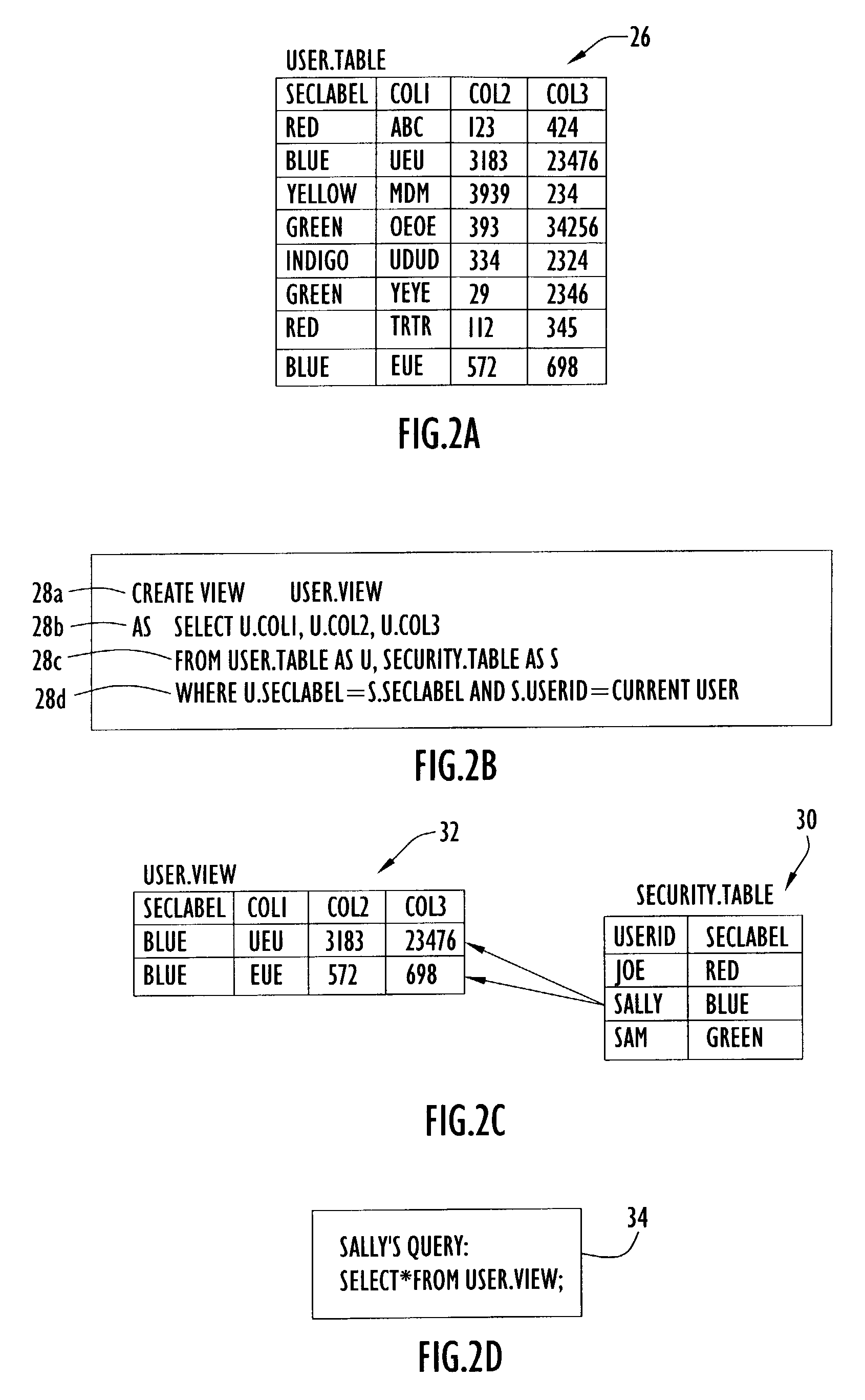
Row-level security in a relational database management system
ActiveUS7240046B2Minimize processing requirementMinimize elapsed time overheadData processing applicationsDigital data processing detailsControl systemInternet privacy
An access control system and access control methods provide multilevel and mandatory access control for a database management system. The access control techniques provide access control at the row level in a relational database table. The database table contains a security label column within which is recorded a security label that is defined within a hierarchical security scheme. A user's security label is encoded with security information concerning the user. When a user requests access to a row, a security mechanism compares the user's security information with the security information in the row. If the user's security dominates the row's security, the user is given access to the row.
Owner:IBM CORP
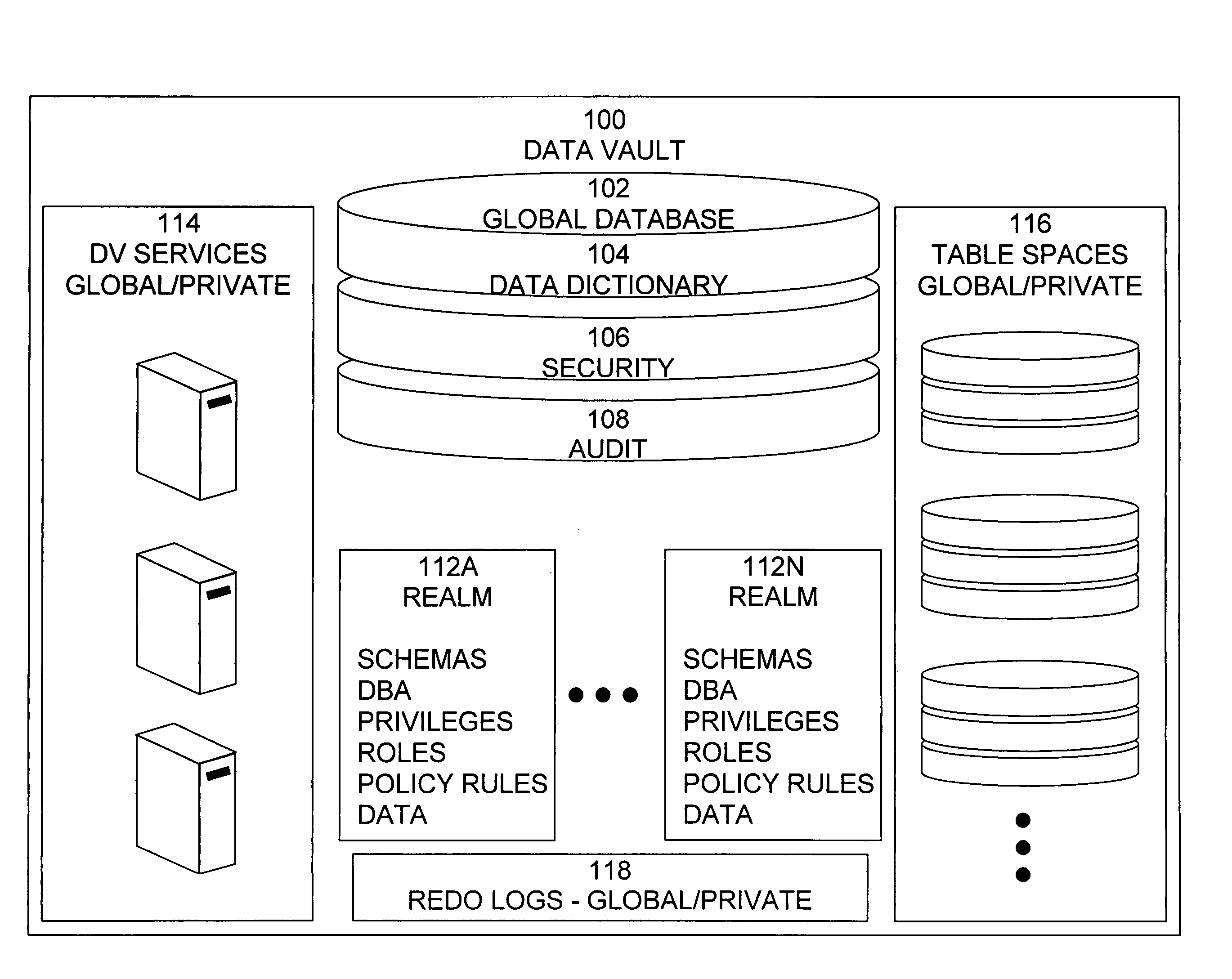
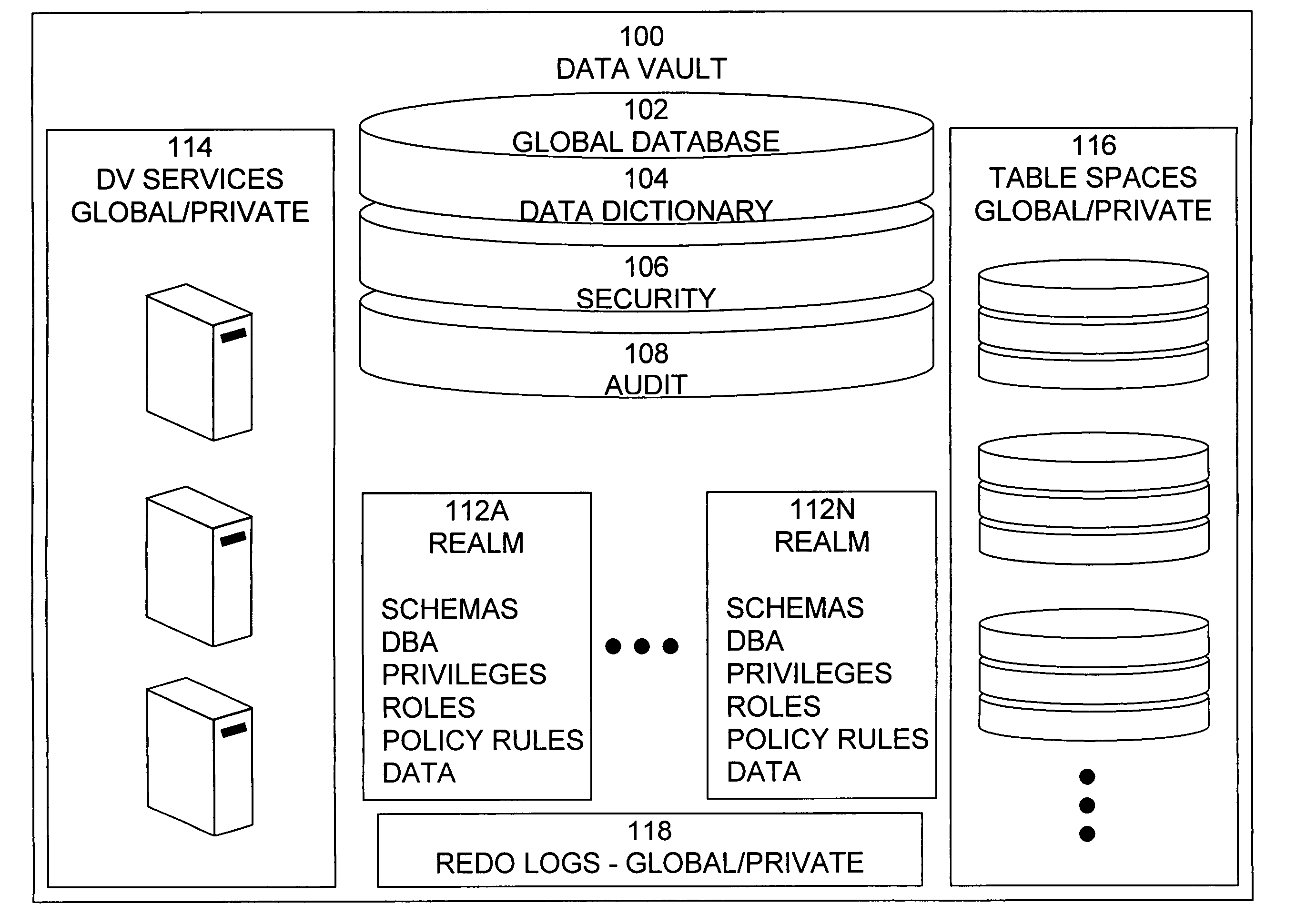
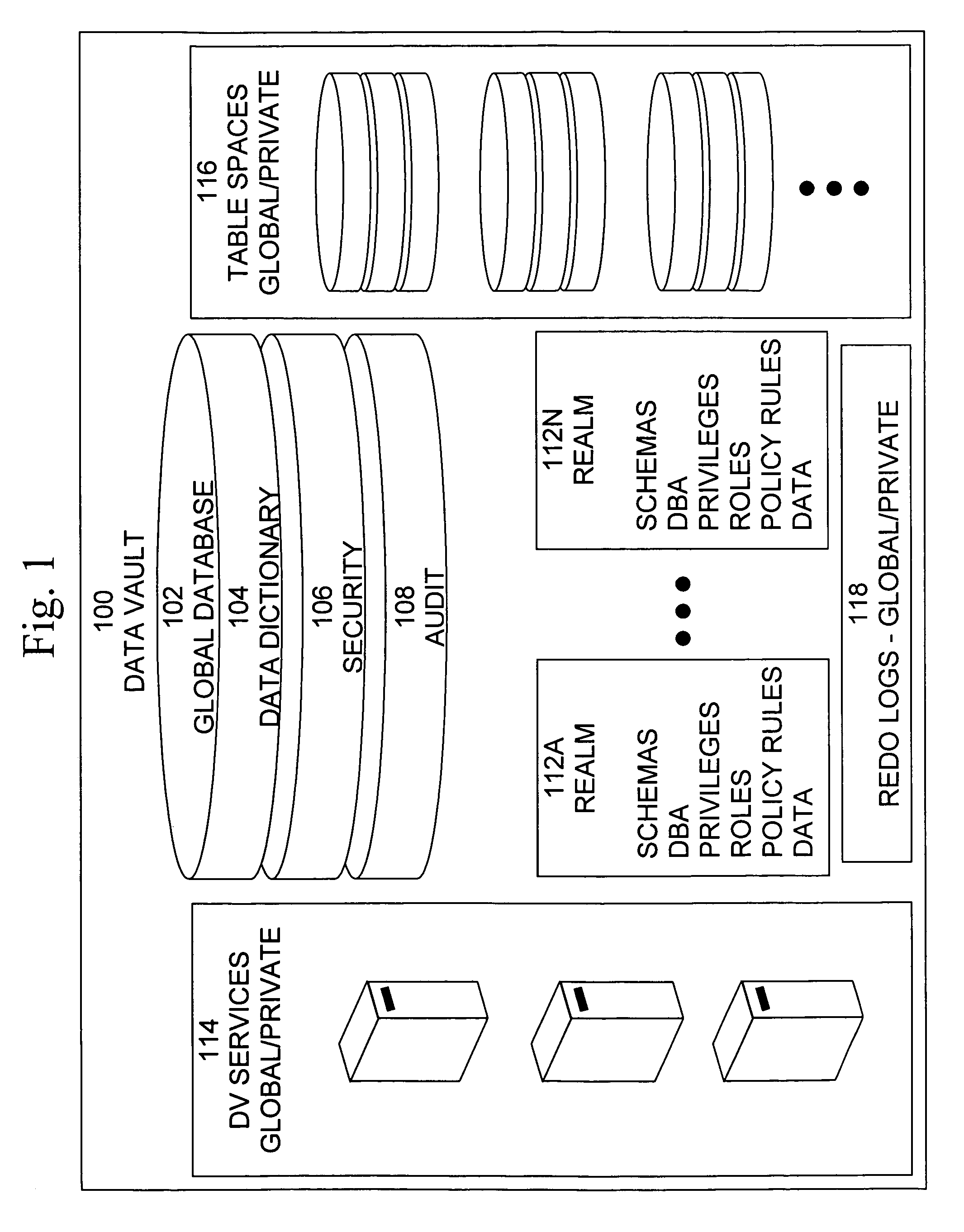
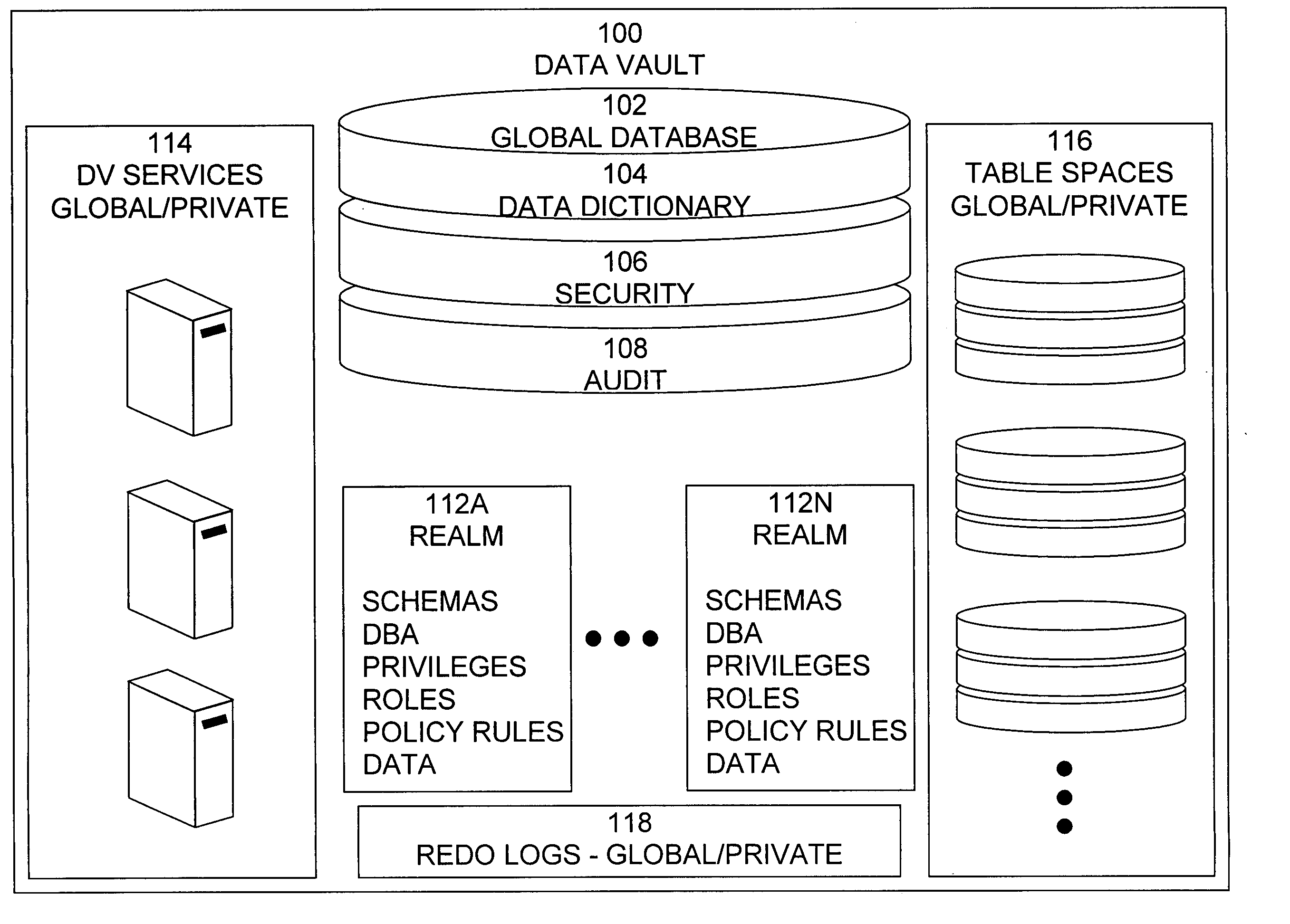
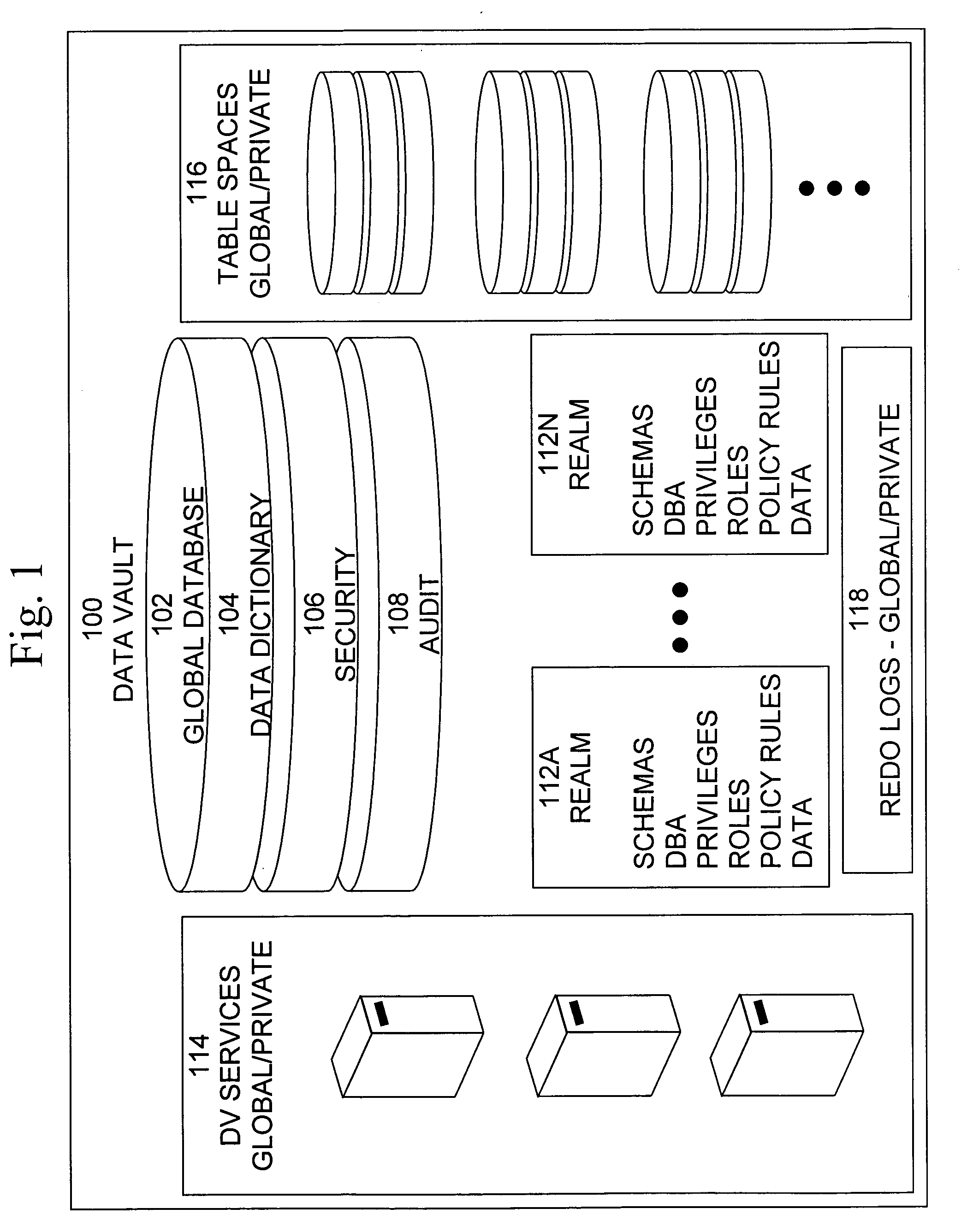
Data vault
ActiveUS20060248085A1Ease of administrationEnsure effective implementationDigital data processing detailsComputer security arrangementsDatabase securitySecurity level
A secure database appliance leverages database security in a consistent framework providwa consistent, flexible, and adaptable security using mandatory access controls in addition to user and role based security for access control and accountability. A database system comprises a plurality of database objects, each database object having a level of security, a plurality of factors, each factor representing a characteristic of a user of the database system, at least one database session of the user in the database, the database session having a level of security, the user connected to the database with a network domain, each network domain having a level of security, wherein the database system is operable to grant or deny access to the data to a user based on the factors associated with the user, based on the level of security of the data, based on the level of security of the database session, and based on the level of security of the network domain.
Owner:ORACLE INT CORP
Character constant weight method
InactiveCN1773413AVersatileGood security propertiesDigital data processing detailsManagement toolOperational system
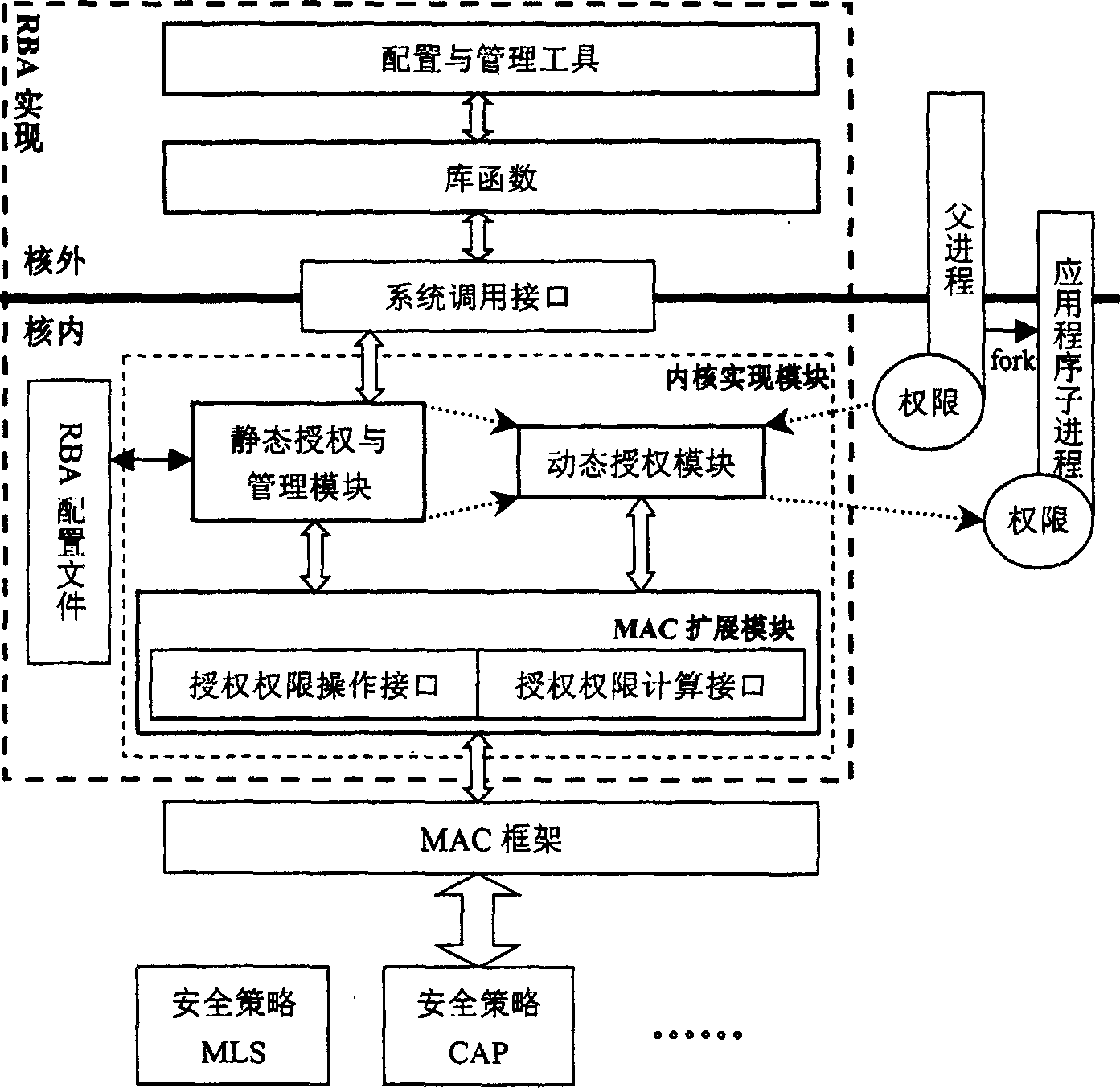
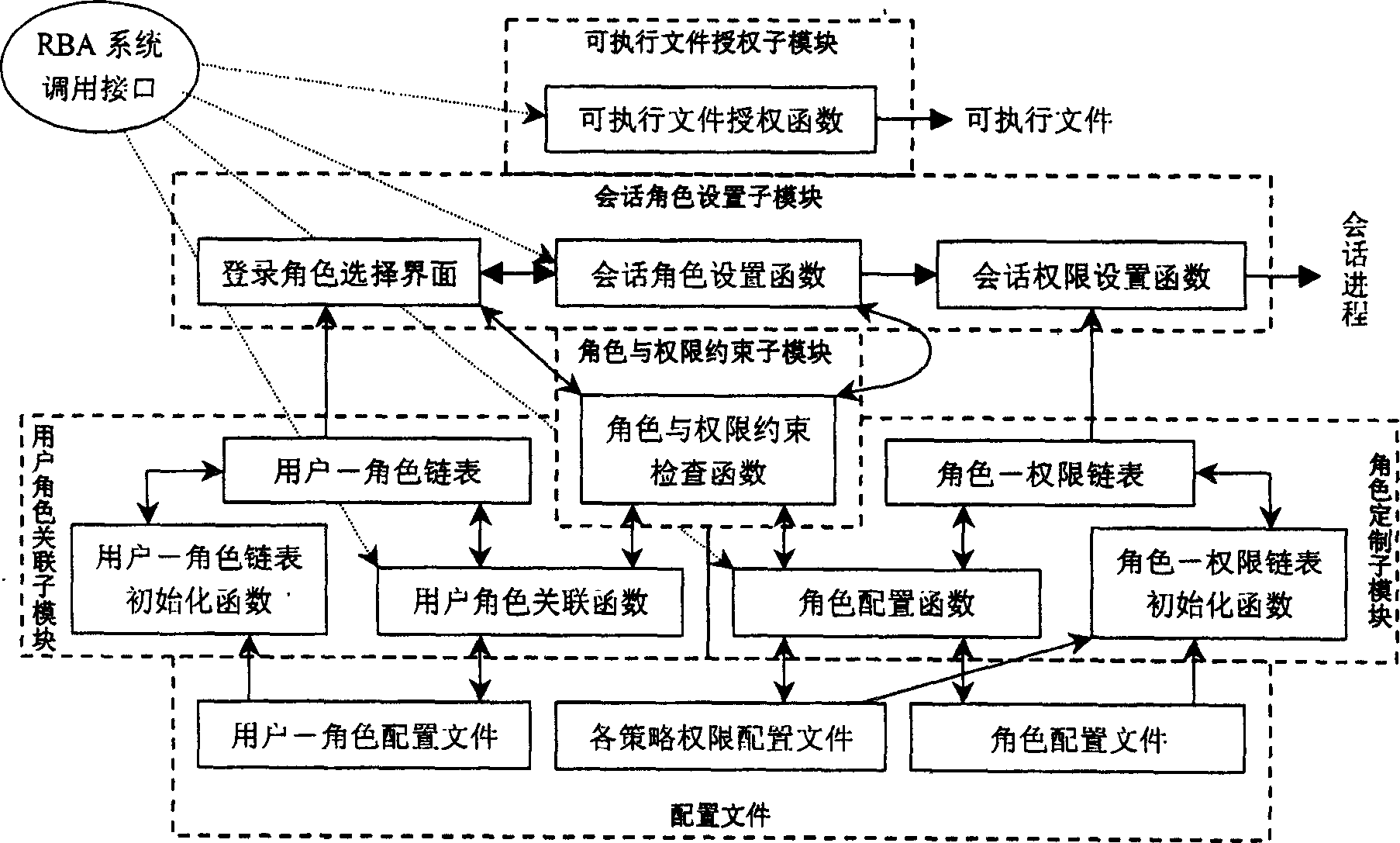
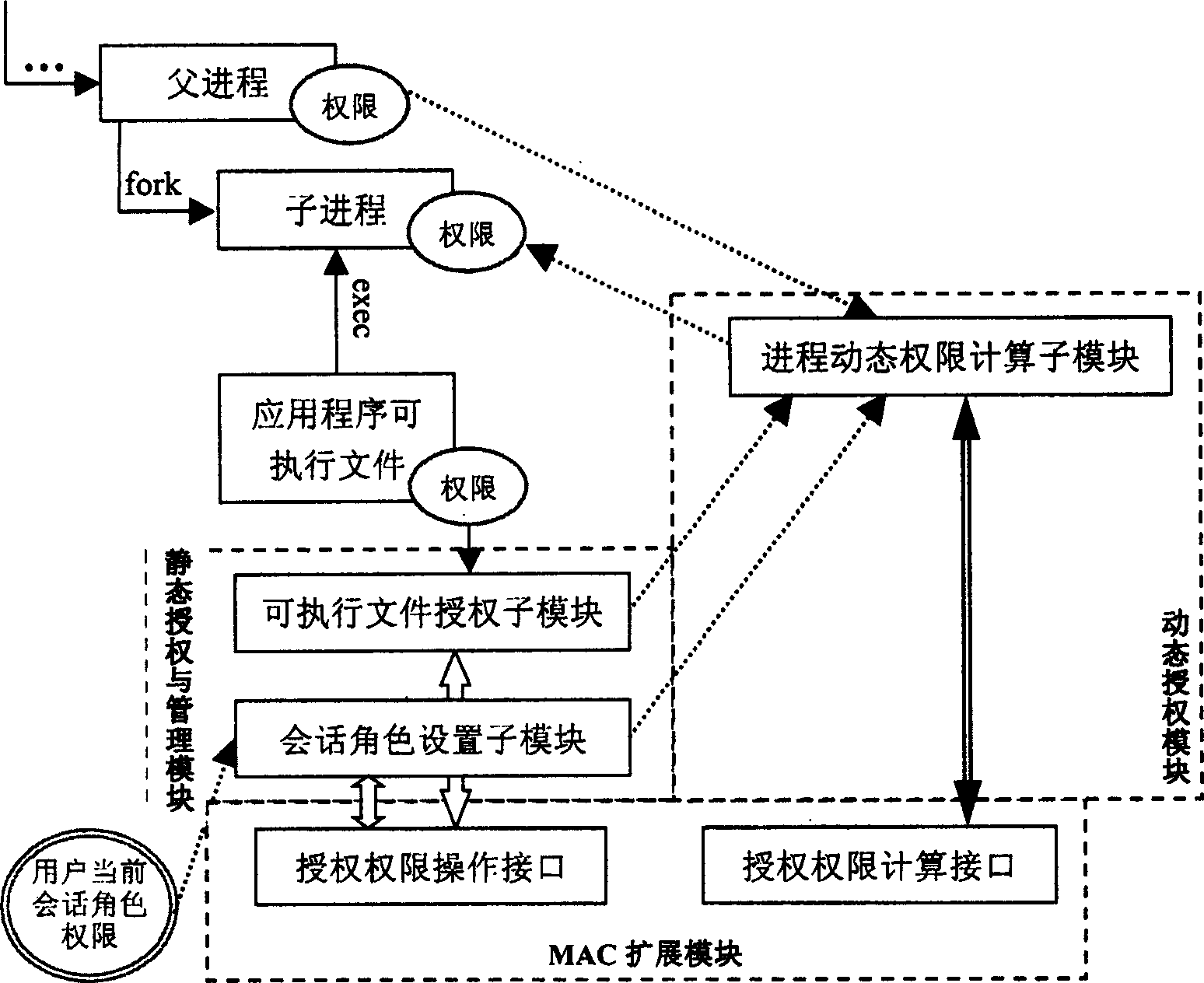
The present invention discloses an actor authority defining method. Its technical scheme includes the following contents: on the forced access frame MAC of operation system constructing a RBA implement system to make authorization for main body in safety operation system adopting forced access control MAC mechanism and configure management. The RBA implement system is formed from internal kernel implement module, RBA configuration file, system calling interface, library function and configuration and management tool. Besides, said invention also provides the concrete implement steps of said method by adopting said RBA implement system.
Owner:NAT UNIV OF DEFENSE TECH
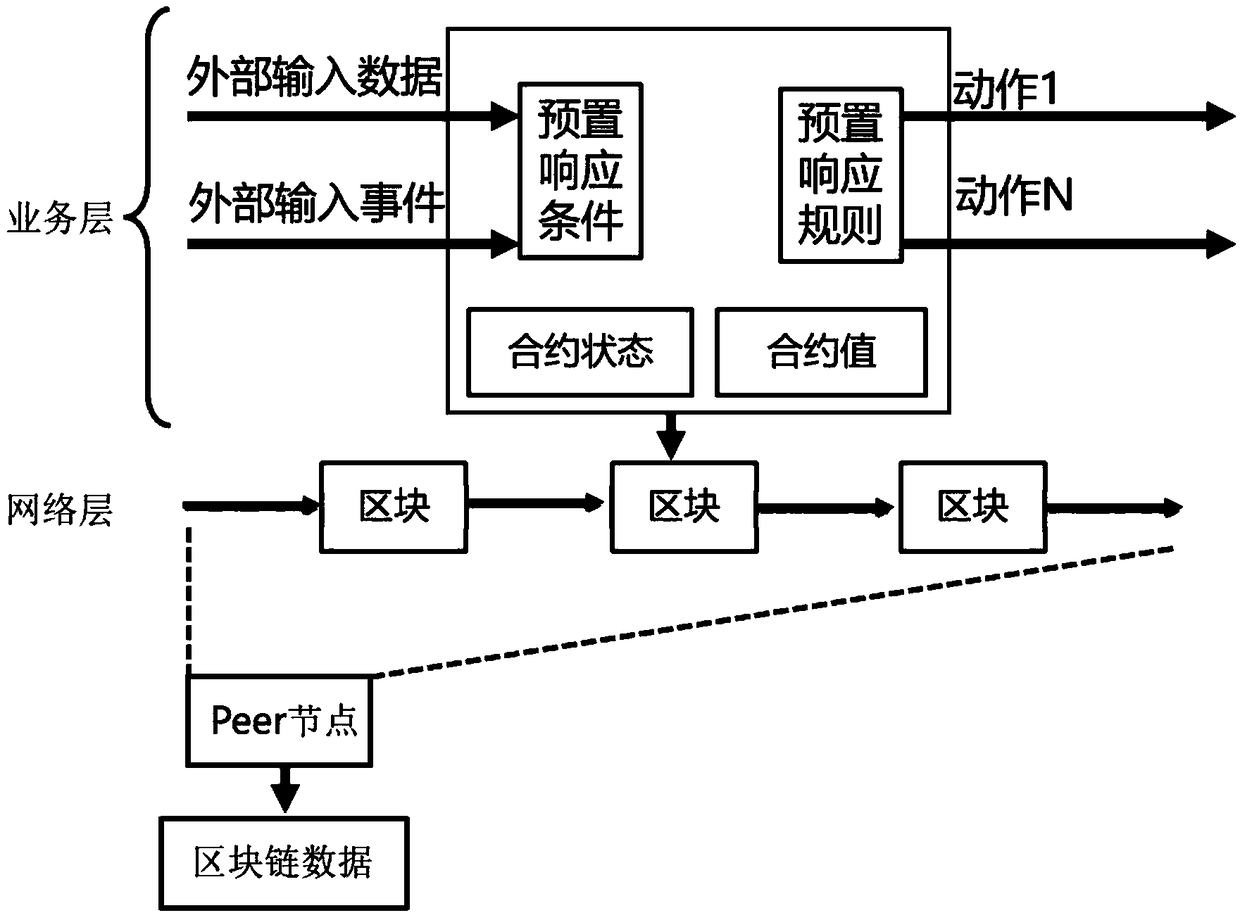
Internet of things multi-domain access control system and method based on block chain
ActiveCN108810073ARealize access control business functionsImprove securityTransmissionConfidentialityInteraction interface
The invention belongs to the field of the internet of things access and control, and discloses an internet of things multi-domain access control system and method based on a block chain. A network layer is a block chain network, and an alliance block chain with various domains respectively taking charge of network nodes; a service layer is a distributed application intelligent contract developed based on the block chain network and can be used for executing complete machine language; a user layer is a user interaction interface developed based on the node of each domain, and used for providingaccess control permission registration and initiating a trans-domain access request. The safe access control system based on the block chain can be realized, the distributed storage of the access control policy is realized, and the access control policy is recorded on the block chain in an account book way, thereby realizing tamper resistance; the confidentiality, the completeness and the repudiation resistance of the cryptology technique and the tamper-resistance of the distributed account book of the block chain technology are combined so as to promote the safe and sufficient sharing of theinternet of things data.
Owner:XIDIAN UNIV
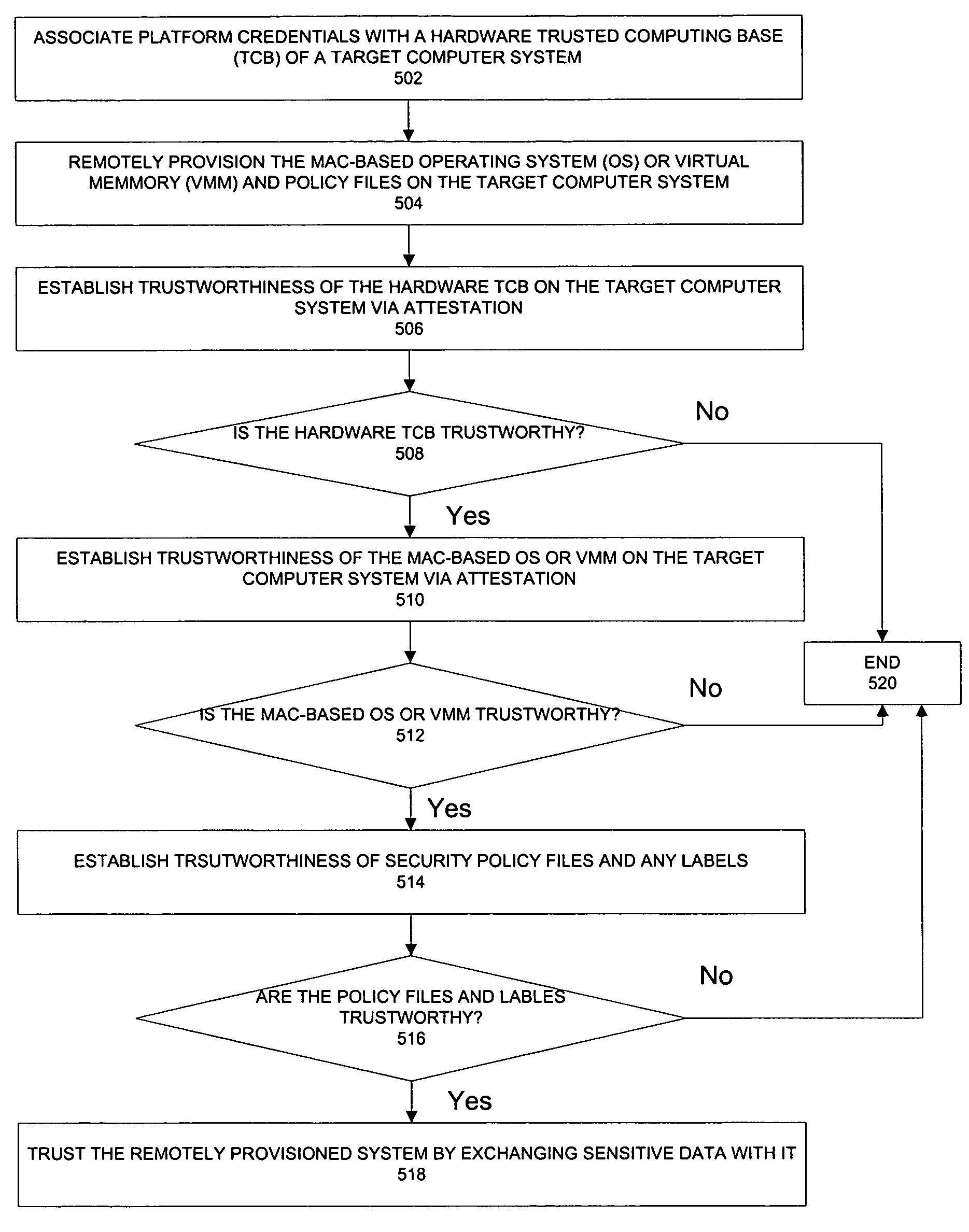
Remote provisioning of secure systems for mandatory control
InactiveUS7424610B2Memory loss protectionError detection/correctionOperational systemTrusted Computing
Owner:INTEL CORP
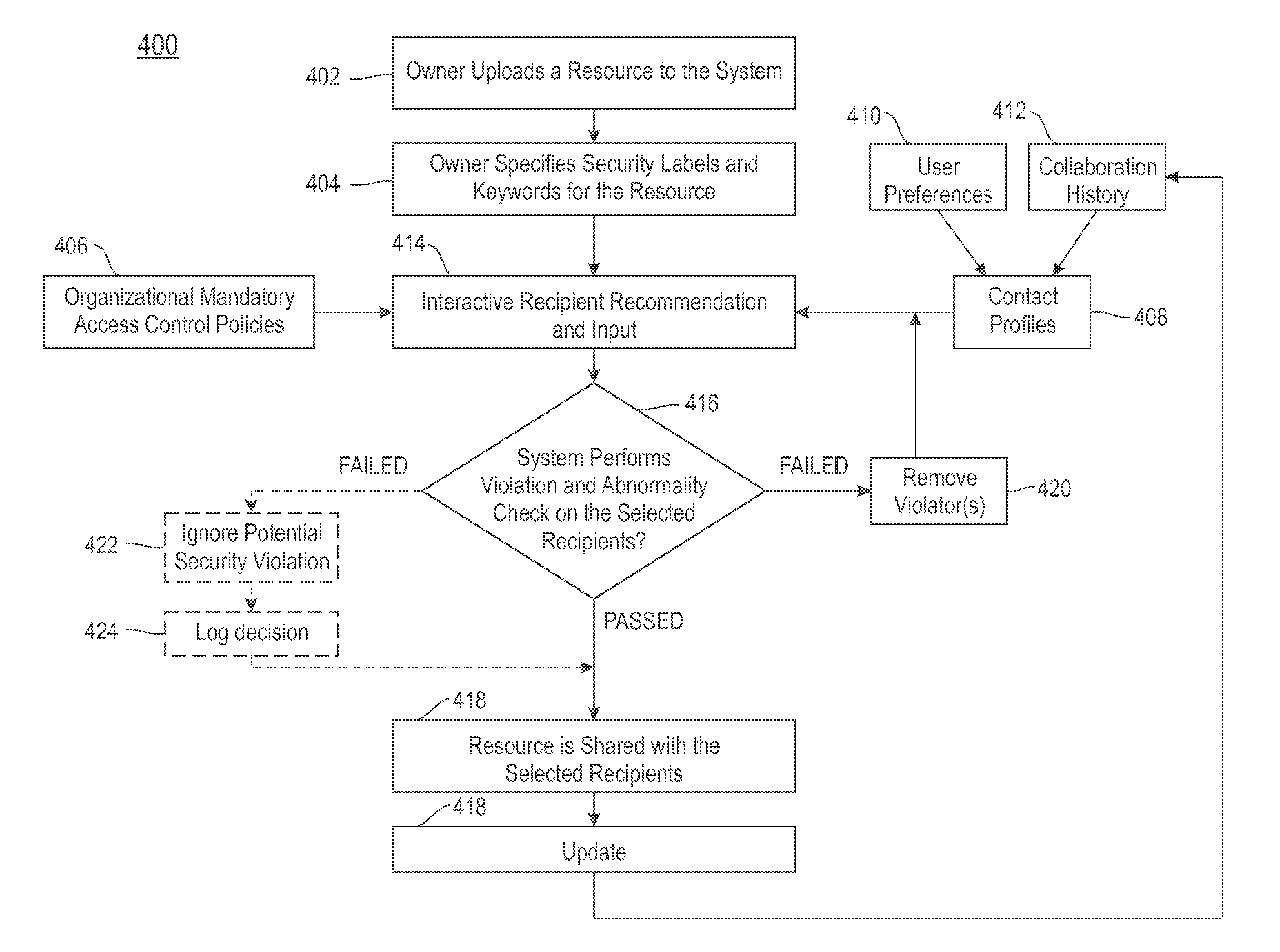
Mitigation of data leakage in a multi-site computing infrastructure
ActiveUS20120317135A1Avoid loweringDigital data information retrievalDigital data processing detailsMulti siteDecision taking
Embodiments of the invention relate to a method, system, and computer program product to dynamically mitigate data leakage in a file sharing environment. Mandatory access control policies are provided to address and maintain restrictions on file sharing both with respect to security rules of an organization and restrictions pertaining to discretionary sharing decisions. In addition, suggestions for potential recipients for file sharing are supported, as well as examination of abnormal recipients in response to the discretionary sharing decisions.
Owner:IBM CORP
Secure container and design method thereof
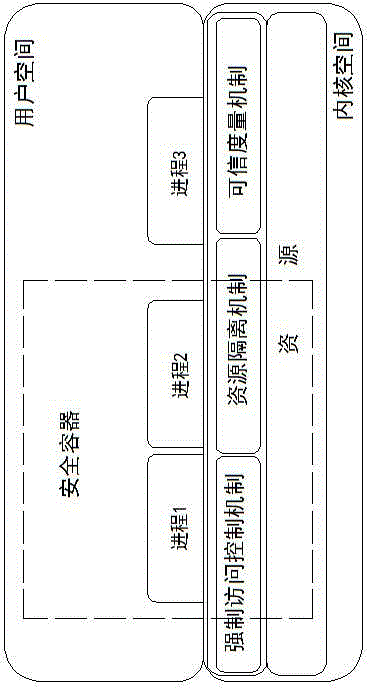
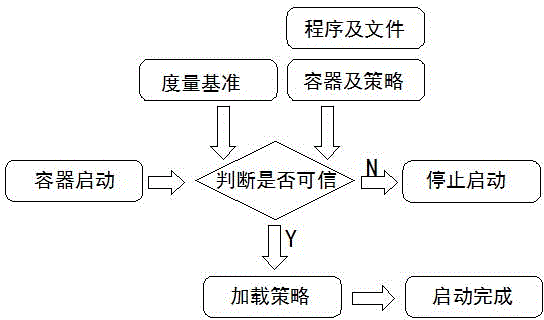
InactiveCN104573507AAvoid security issuesThe use does not affect each otherPlatform integrity maintainanceOperational systemResource isolation
The invention discloses a secure container and a design method thereof, belonging to the technical field of information safety. The secure container disclosed by the invention is characterized in that a secure area is constructed in an operation system; a set of processes is operated in the area by utilizing the three mechanisms including mandatory access control, resource isolation and trusted measurement; the set of processes is only capable of accessing resources in the area and is incapable of accessing resources outside the area; processes outside the area are also incapable of accessing resources in the area; and furthermore, the strategy of the area and application in the area need to be subjected to trusted measurement. Compared with the prior art, the secure container disclosed by the invention is capable of resisting various attacks in a network through the operation system level; therefore, the network information security problem is thoroughly solved; and the secure container and the design method thereof disclosed by the invention have good popularization and application value.
Owner:LANGCHAO ELECTRONIC INFORMATION IND CO LTD
Mandatory access control base
ActiveUS7593942B2Ease of administrationEnsure effective implementationComputer security arrangementsSpecial data processing applicationsData accessDatabase security
Owner:ORACLE INT CORP
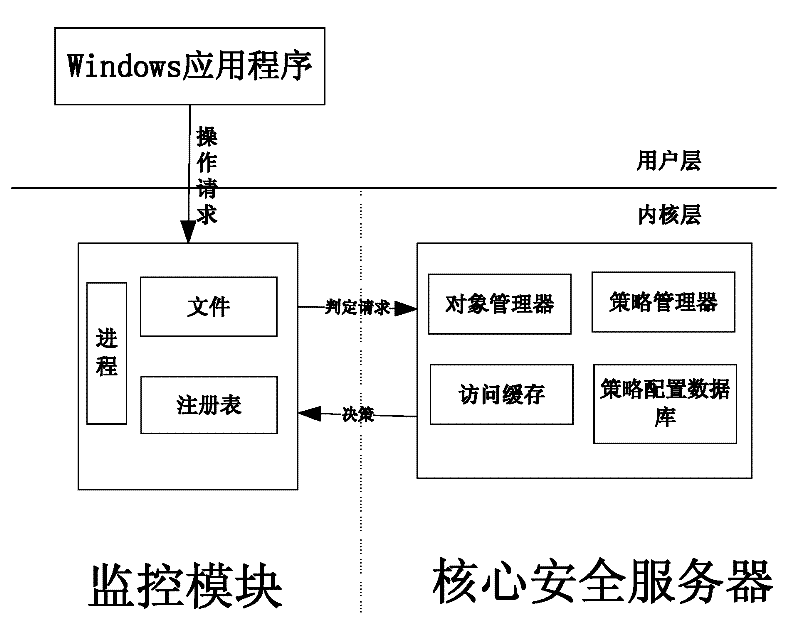
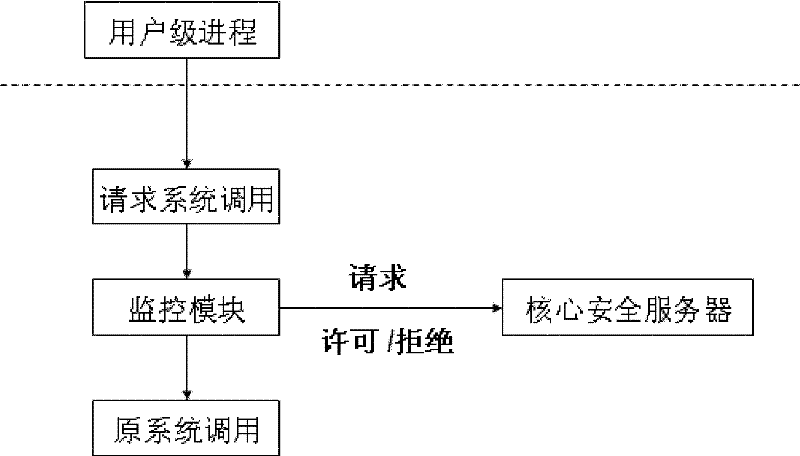
Device and method for controlling mandatory access based on Windows platform
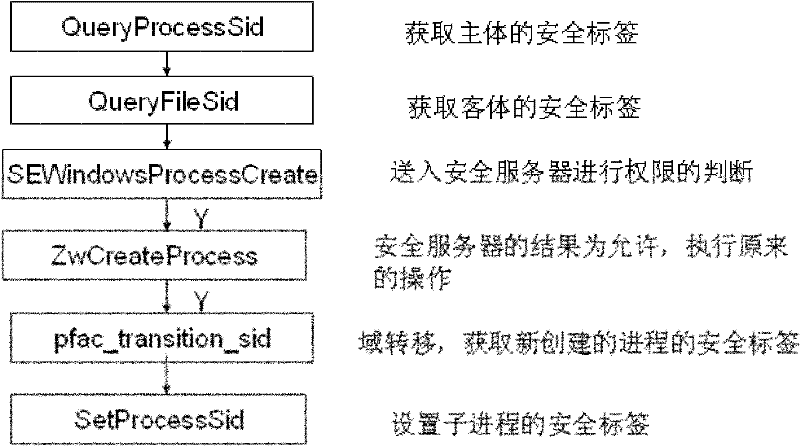
The invention discloses a device and method for controlling mandatory access based on a Windows platform. The device comprises a monitoring module and is characterized in that access control on progresses, files and register lists can be realized on the Windows platform, access requests of a subject of the access control on an object are intercepted and provided for a core safety server to be used for safety judgment; and the core safety server carries out authority judgment according to safety rules of mandatory access control and returns a result to the monitoring module so that the mandatory access control is realized. According to the device and method for controlling the mandatory access based on the Windows platform, disclosed by the invention, an access control decision of a windows system does not depend on the subject, and whether access is allowed or not is determined by comparing safety identifiers of the subject and the object through a safety policy; and the device for controlling the mandatory access based on the Windows platform, disclosed by the invention, is compatible with a windows-self-attached discretionary access control mechanism and also has higher safety grade compared with the original mechanism.
Owner:SUZHOU LINGXIAO TECH
Access control method of network storage equipment
ActiveCN101674334ASolve the bottleneck of centralized access controlReduce access control overheadTransmissionSpecial data processing applicationsExtensibilityData access control
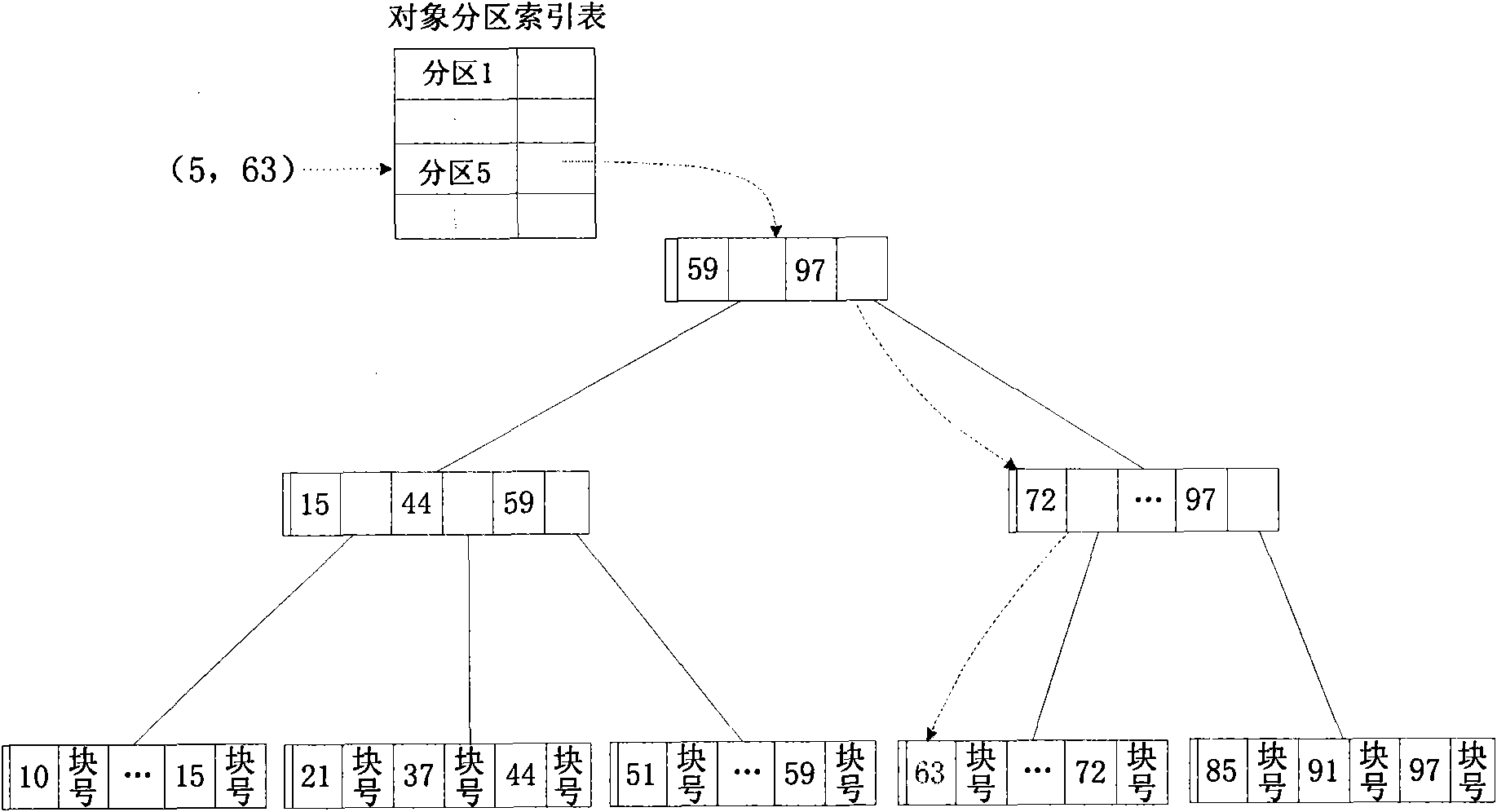
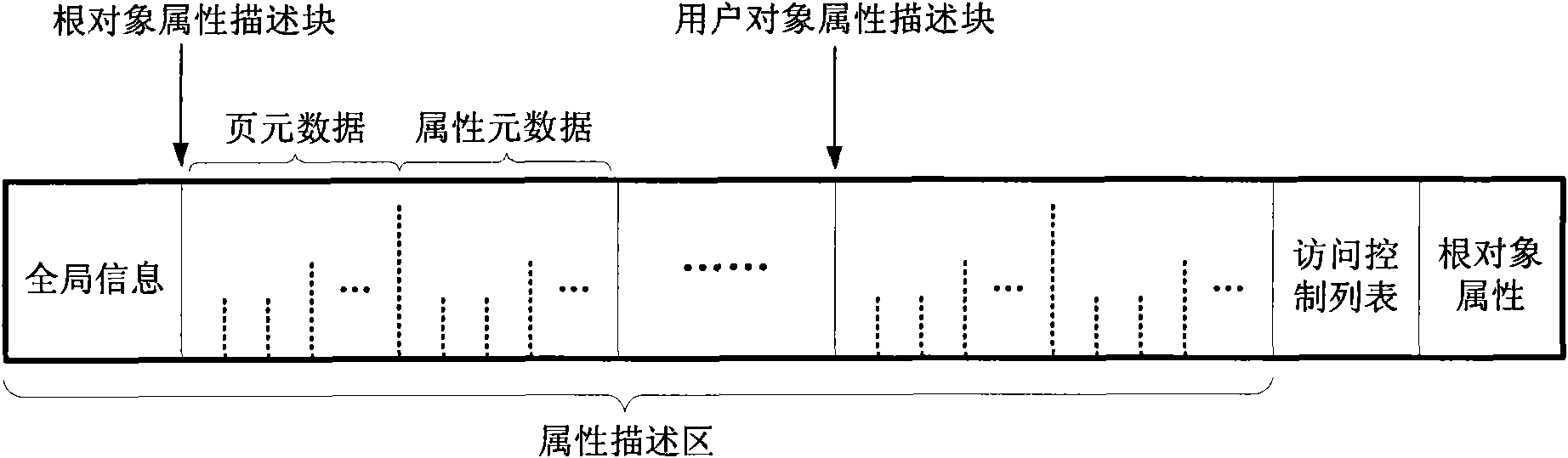
The invention relates to an access control method of network storage equipment, belonging to a computer network storage system. The invention solves the problem that the prior access control method maintains and manages one centralized access control list, thereby forming the performance bottleneck and influencing the performance and the expandability of the storage system. In the invention, the access control method comprises the steps of object establishment and object operation. The network storage equipment stores data objects and directory objects needed by users, each of the data objectsand the directory objects comprises an attribute part and a data part, and each attribute part comprises an access control list. The invention uses each access control list as a security attribute ofeach data object to be stored together with the data, defines the inherited rules of each access control list and the priority of each access control item, improves the flexibility of data access control, positions the corresponding access control list while reading the data to be operated by users, realizes the distributed access control, greatly reduces the access control cost of a distributedstorage system, and improves the expandability of the system.
Owner:HUAZHONG UNIV OF SCI & TECH
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com