Patents
Literature
71 results about "Discretionary access control" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
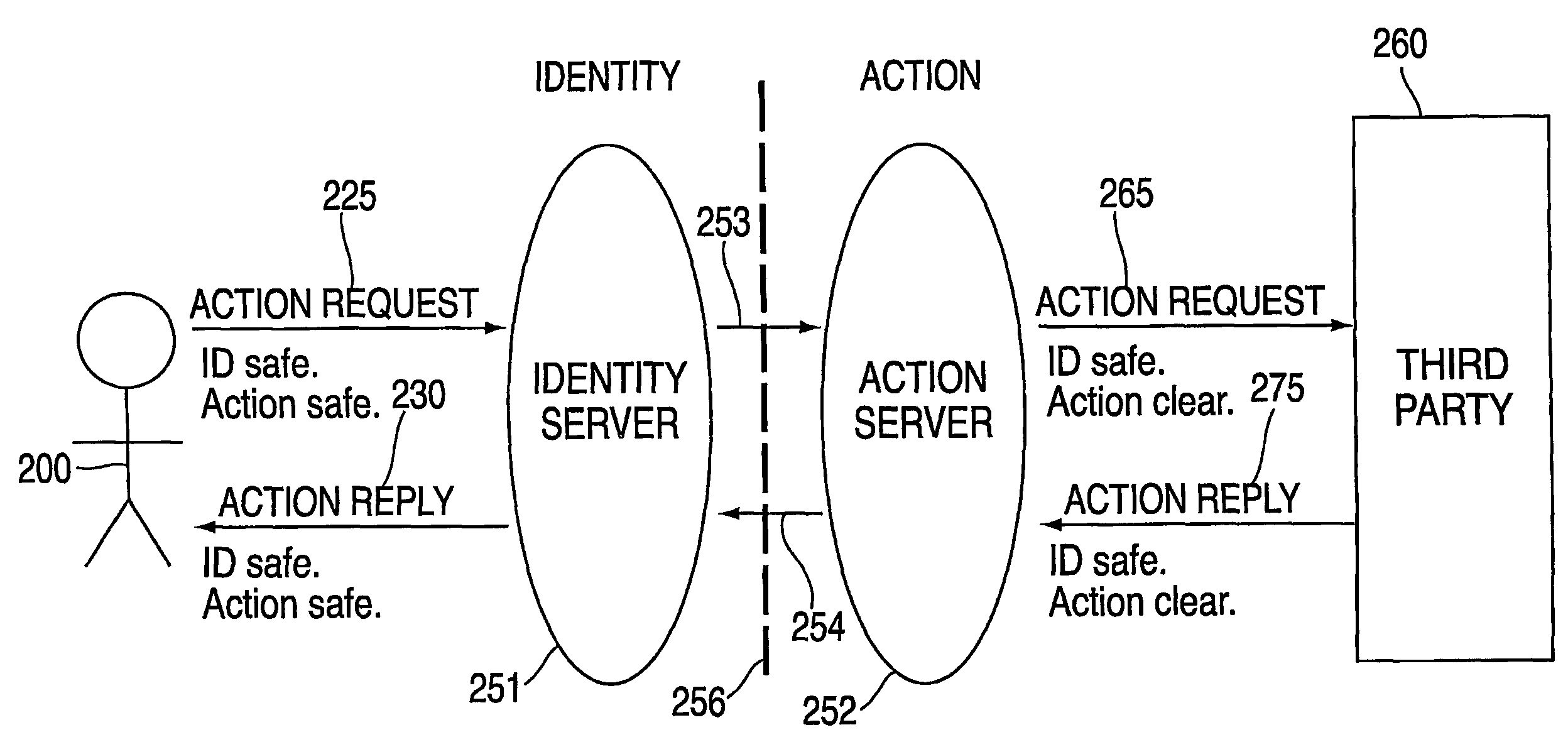
In computer security, discretionary access control (DAC) is a type of access control defined by the Trusted Computer System Evaluation Criteria "as a means of restricting access to objects based on the identity of subjects and/or groups to which they belong. The controls are discretionary in the sense that a subject with a certain access permission is capable of passing that permission (perhaps indirectly) on to any other subject (unless restrained by mandatory access control)".
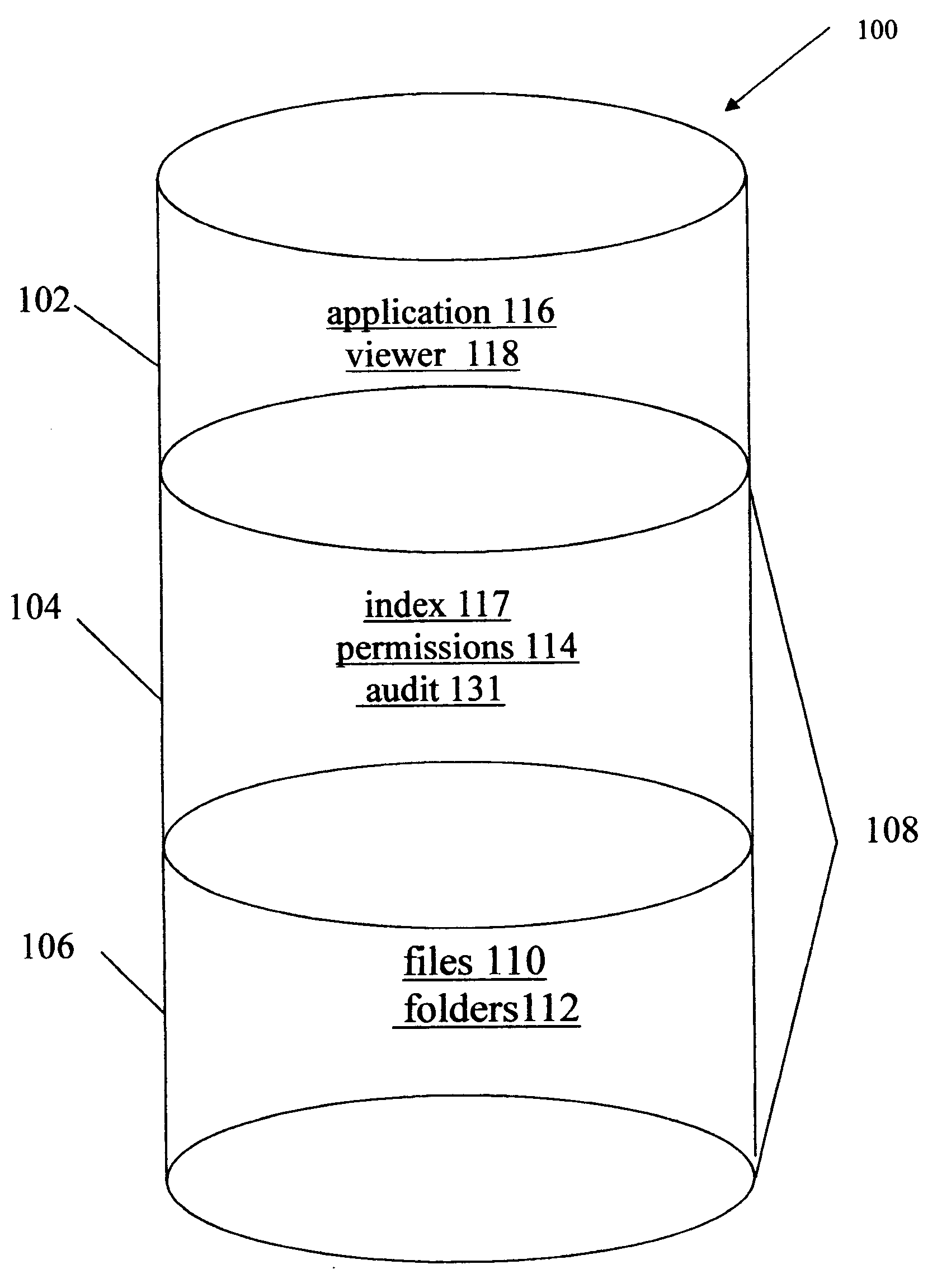
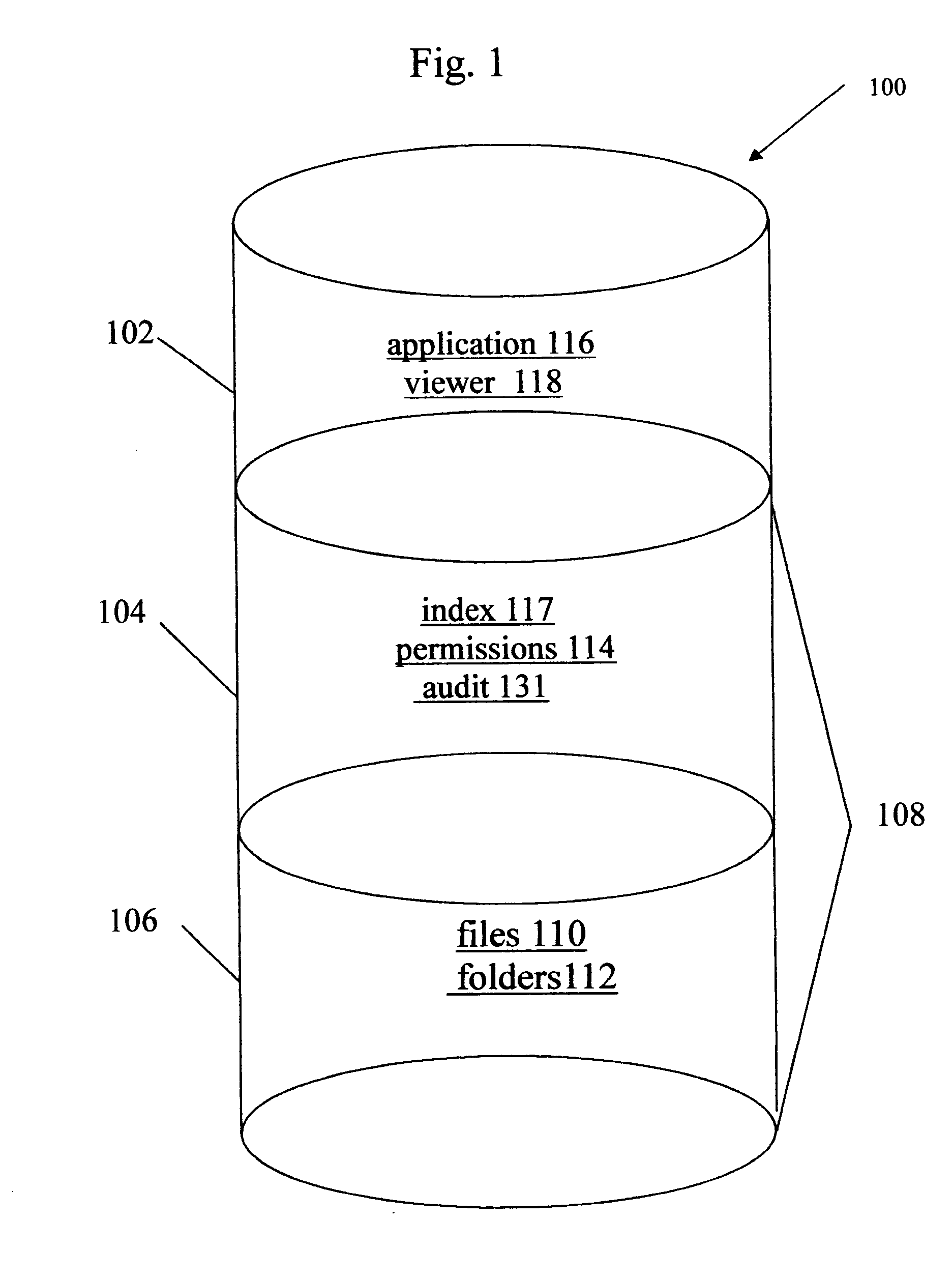
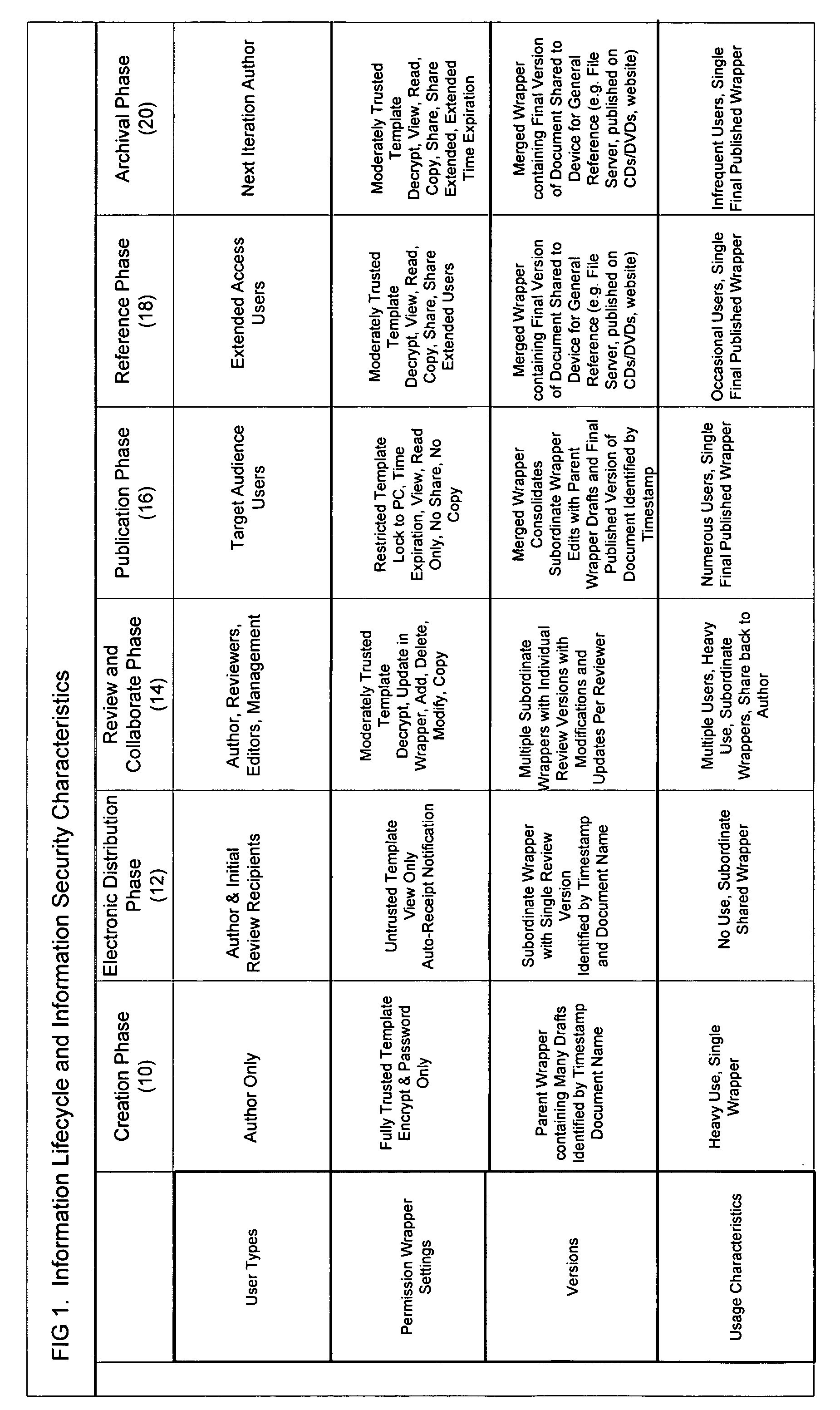
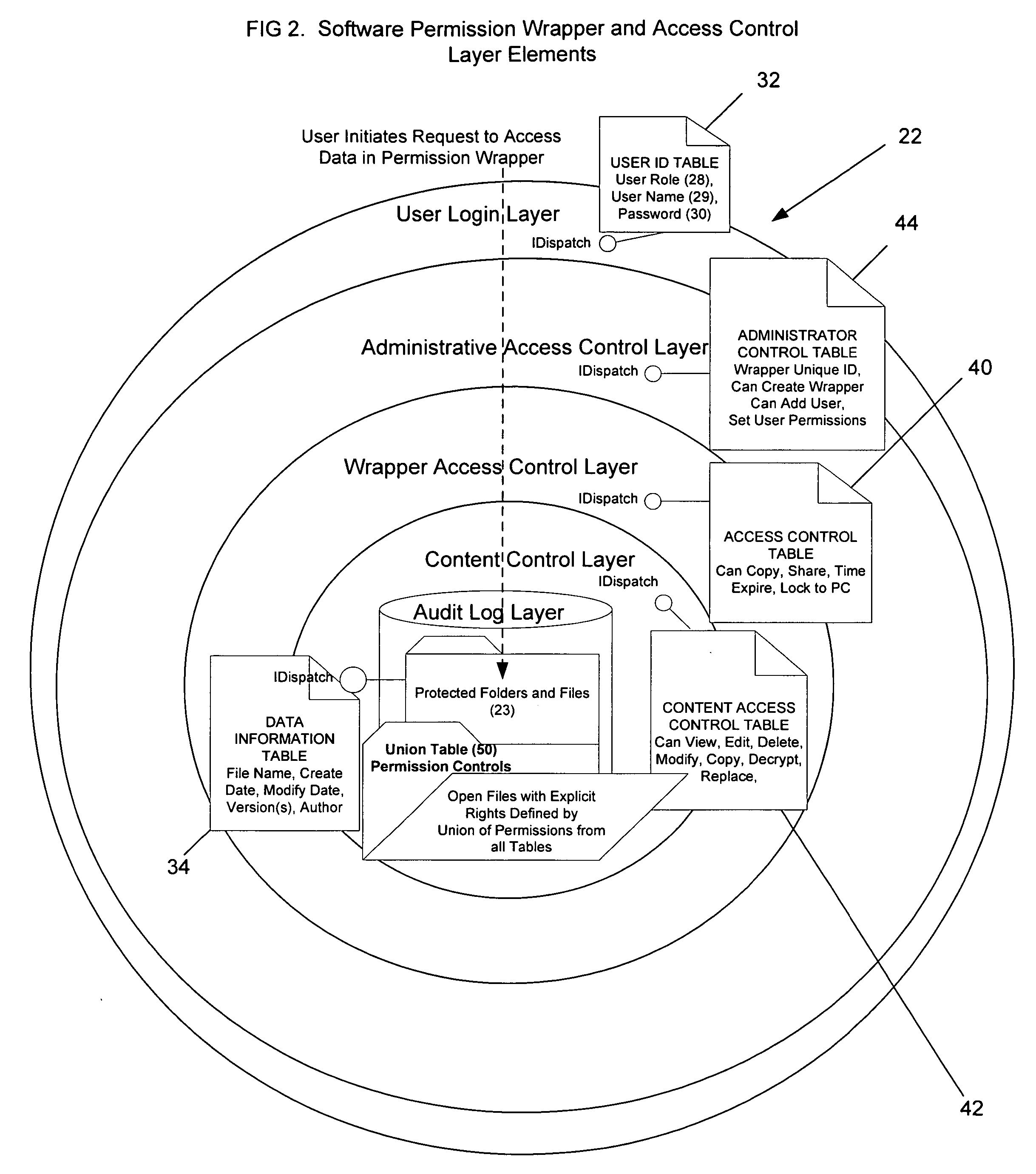
Data rights management of digital information in a portable software permission wrapper
InactiveUS20050114672A1Minimize impactImprove protectionSecret communicationProgram/content distribution protectionEmbedded securityTransaction management
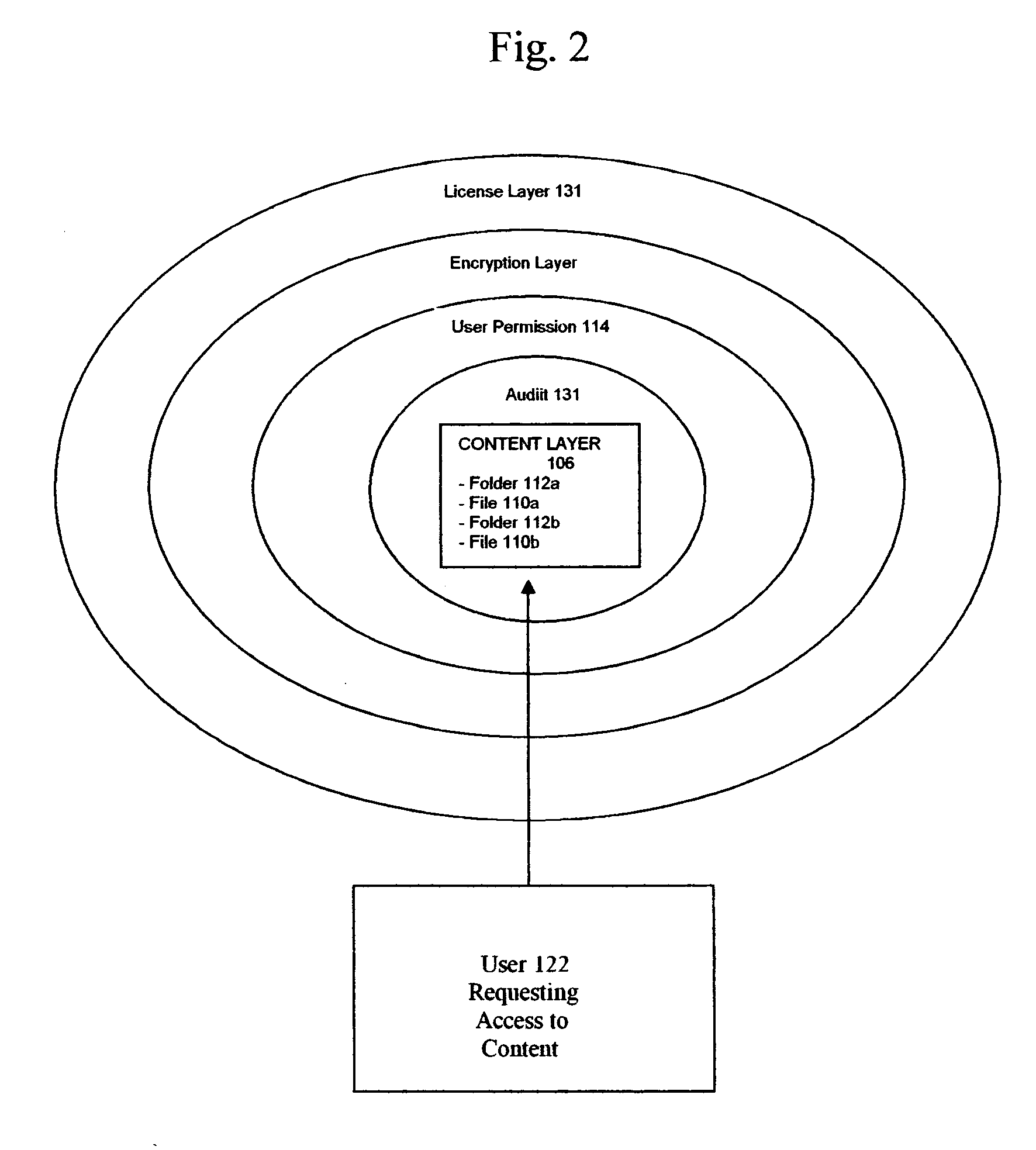
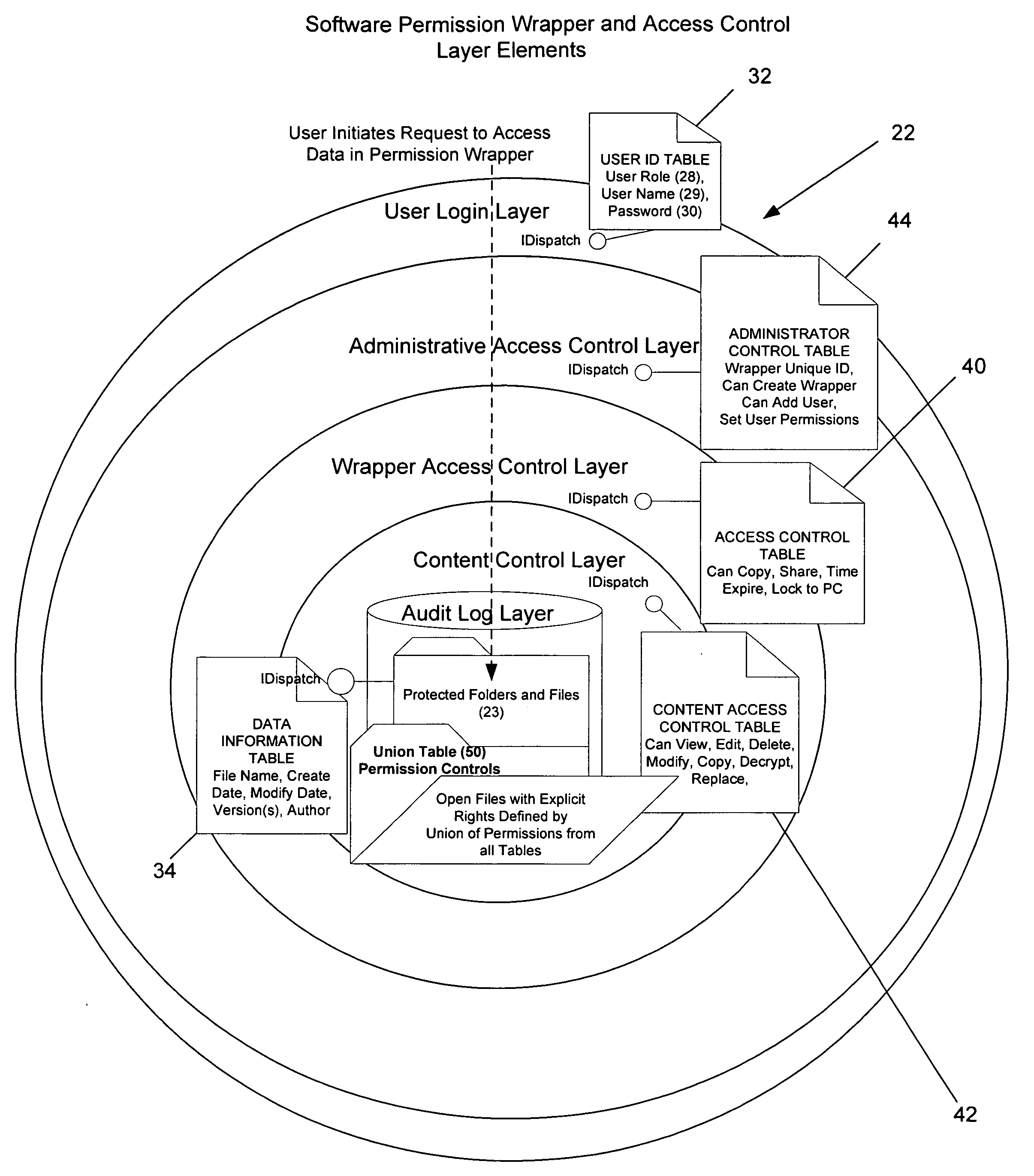
The present invention provides systems and methods for secure transaction management and electronic rights protection. The invention is a software permission control wrapper that is used to encrypt and encapsulate digital information for the purpose of enforcing discretionary access control rights to the data contained in the wrapper. The permission control wrapper enforces rules associated with users, and their rights to access the data. Those rights are based on deterministic security behavior of the permission wrapper based on embedded security policies and rules contained therein and that are based, in part, on the user type, network connectivity state, and the user environment in which the data is accessed.
Owner:ENCRYPTX CORP
Method and apparatus for automatically detecting sensitive information, applying policies based on a structured taxonomy and dynamically enforcing and reporting on the protection of sensitive data through a software permission wrapper
InactiveUS20060048224A1Reduce spreadMemory loss protectionError detection/correctionInformation controlAutomatic control
The present invention relates to the automatic detection of sensitive digital information, and the identification methods, application and enforcement of information security policies for digital information controlled through a software permission wrapper throughout the useful life of the information. This invention includes a unique taxonomy that defines the policies and rules regarding how the information is controlled automatically throughout its useful lifecycle based on the type of information, the stage of the information lifecycle, the user / group role accessing the information, the locality of the information, and the expected threats to the information. The taxonomy is maintained in a database that associates information security control policies and actions to sensitive data. These policies are enforced through a software permission wrapper that is used to encapsulate sensitive digital information. The software permission wrapper is used to control access and enforce digital rights to the information based on the taxonomy based policies for that information. The permission wrapper can automatically change the protection of the information based on pre-defined protection states that can automatically enforce discretionary access control rights to the sensitive information controlled in the permission wrapper. The changes to the level of protection occur dynamically based on changes in user locality, stage of information lifecycle, and user / group role and the detection of threats. In addition, there is provided an internal audit capability describing what actions the user has performed, where the data is located, with whom and how the data has been shared.
Owner:ENCRYPTX CORP
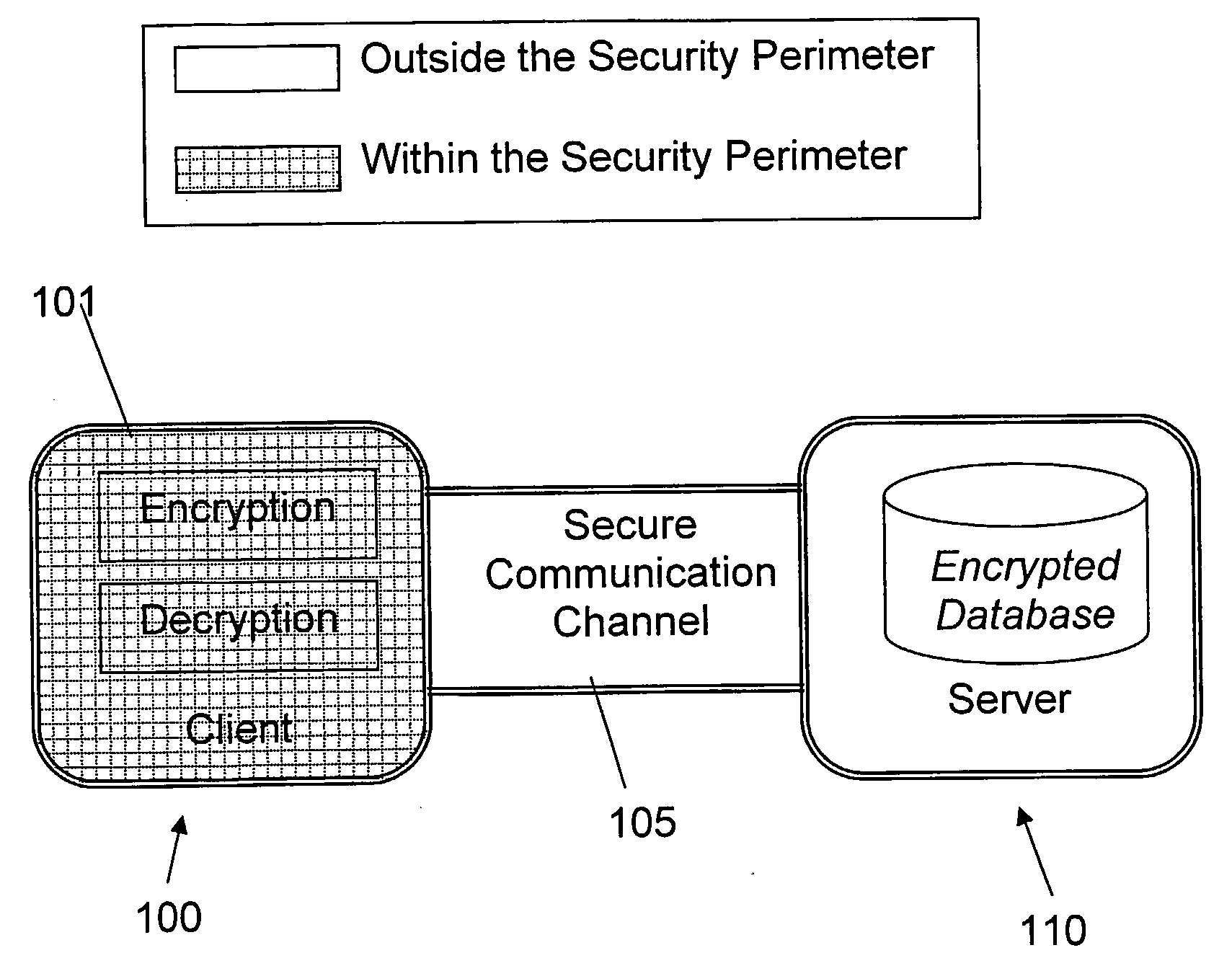
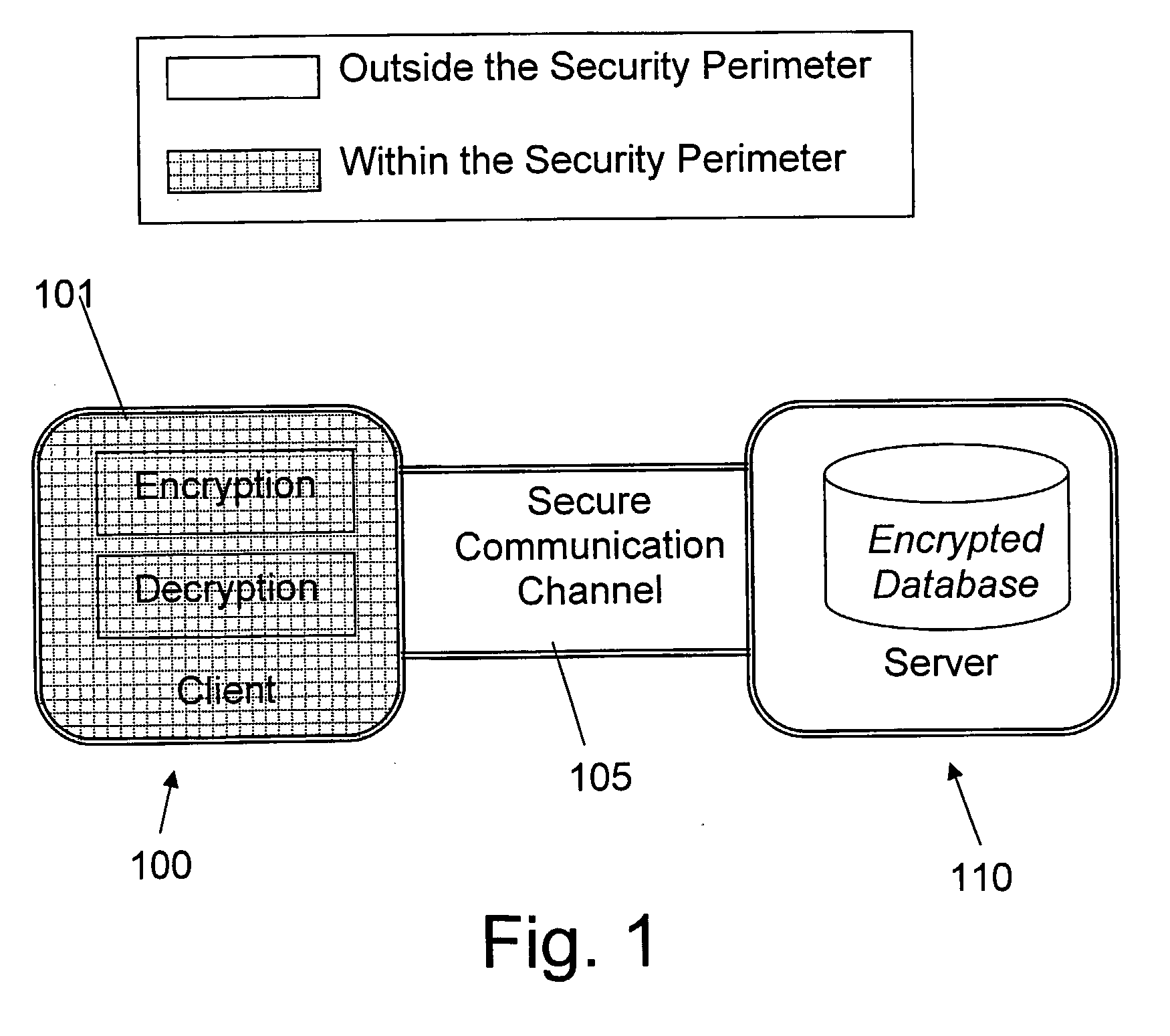
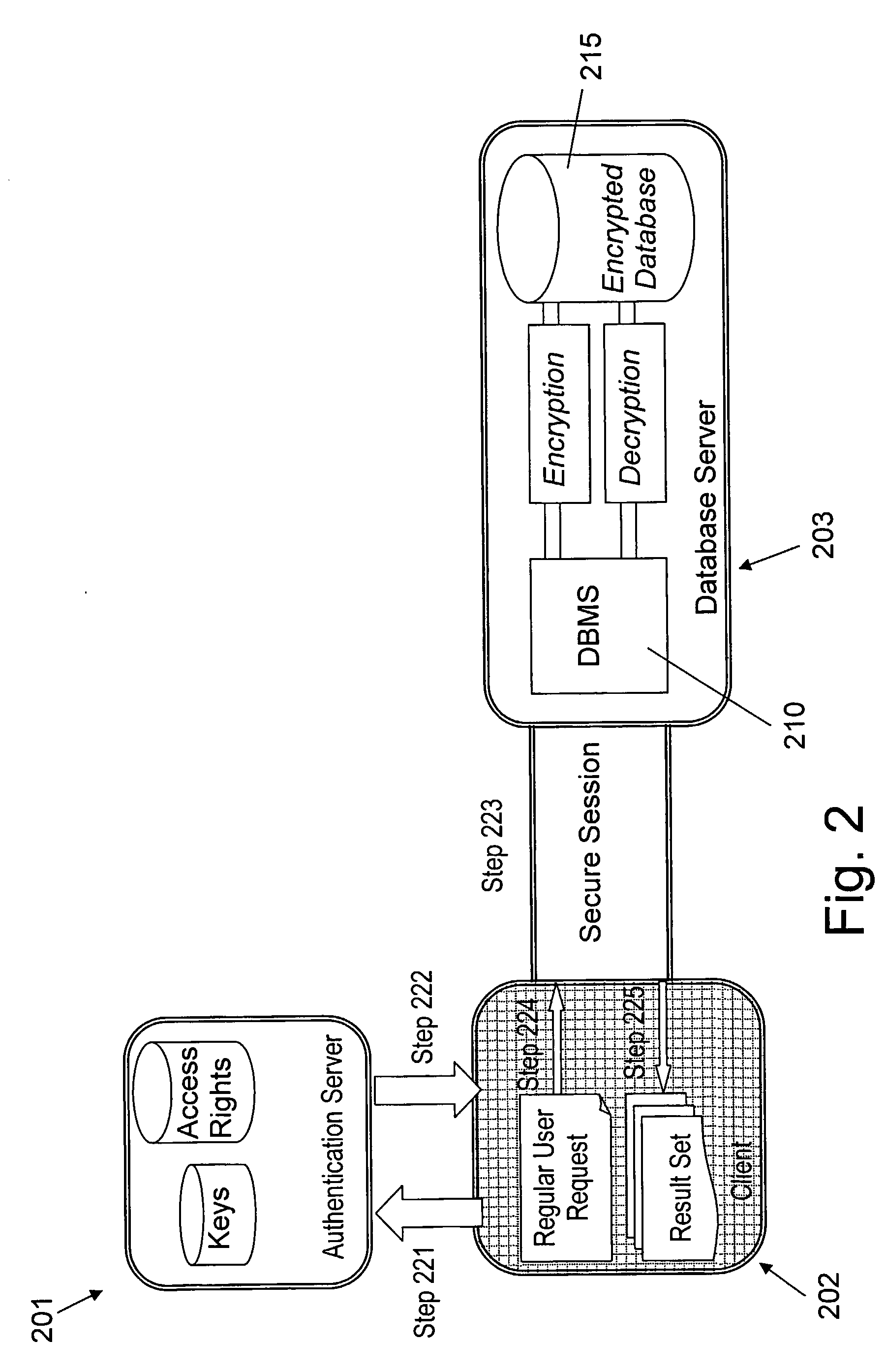
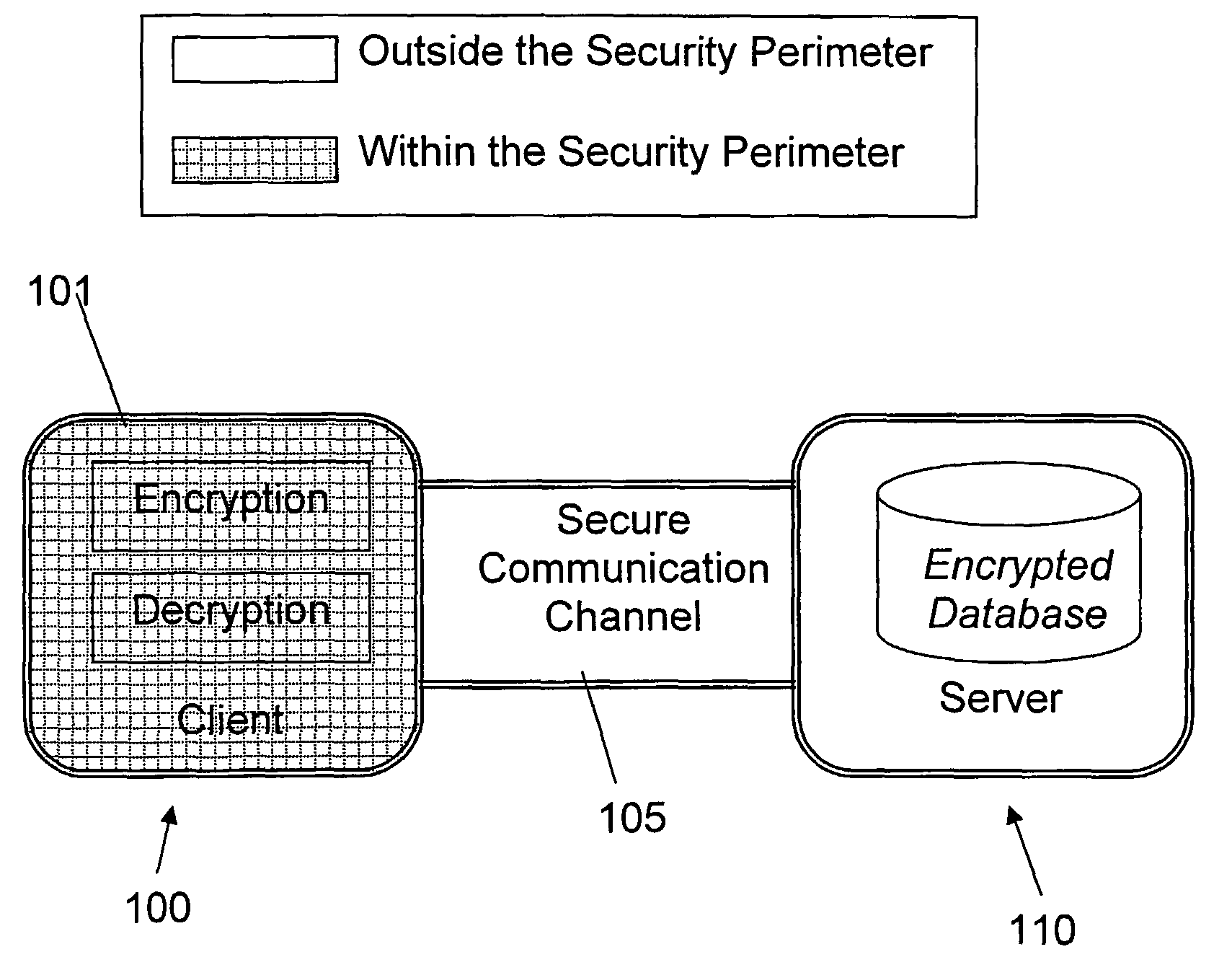
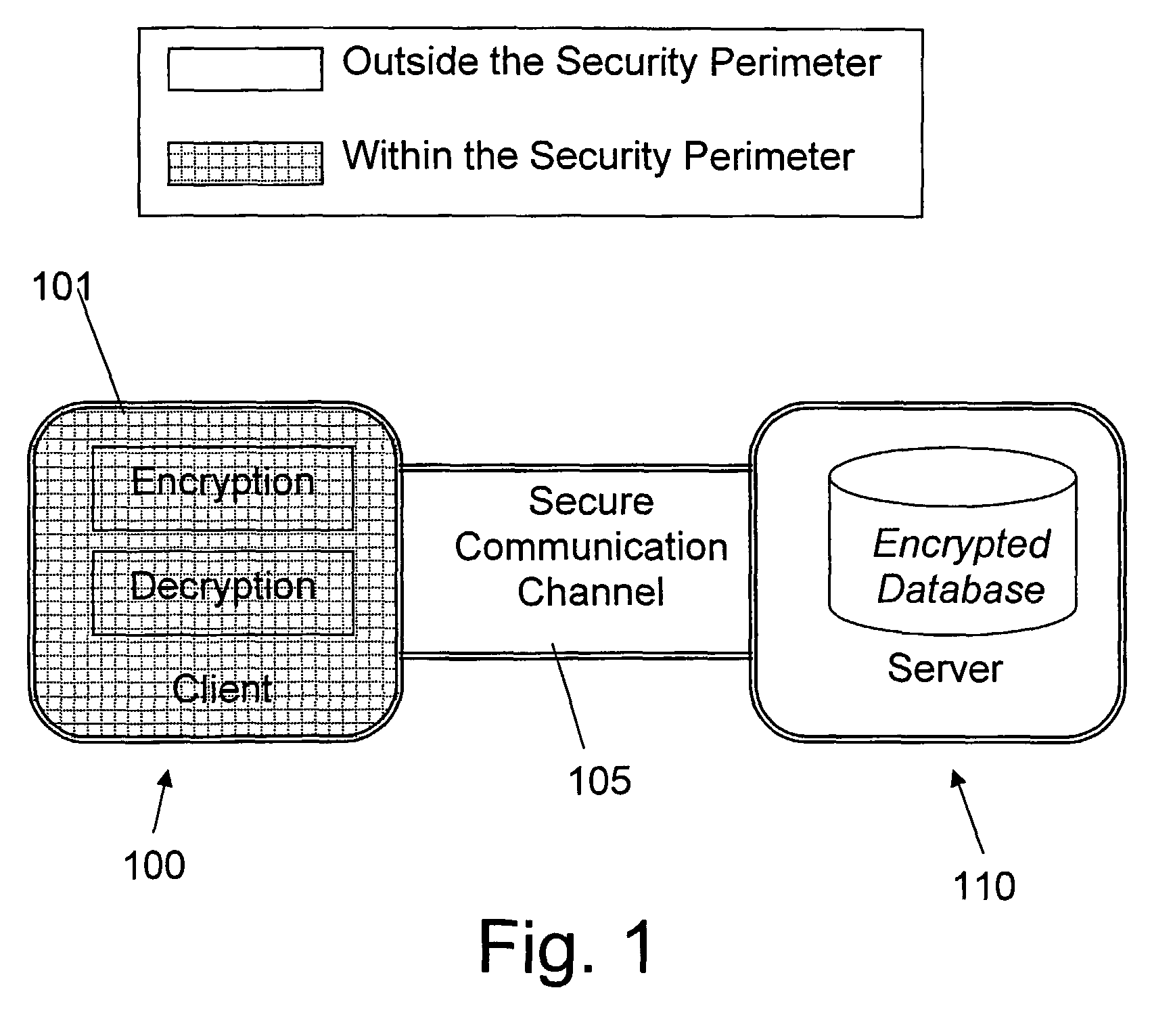
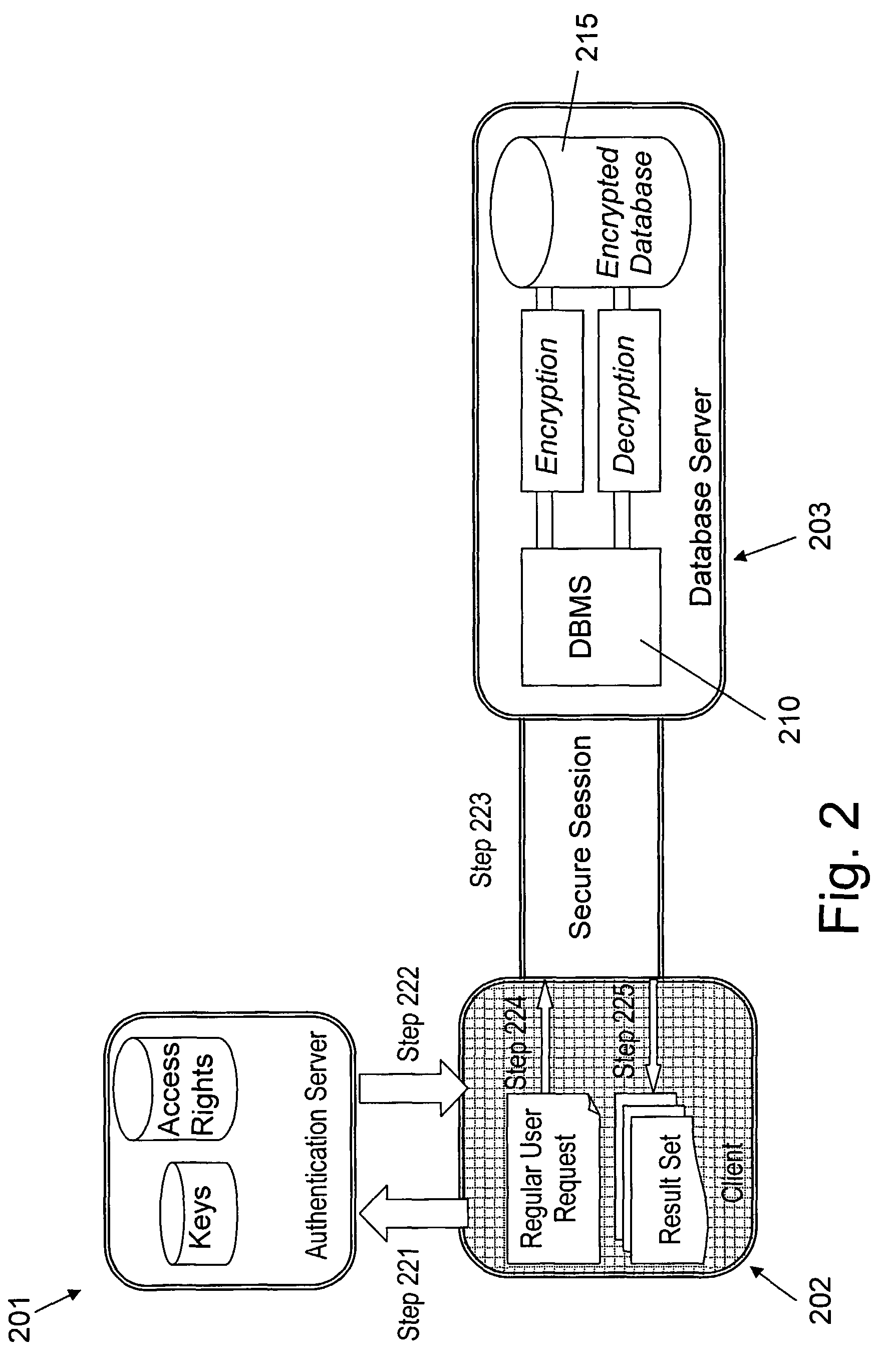
Structure Preserving Database Encryption Method and System
ActiveUS20080133935A1Easy accessAvoid contactKey distribution for secure communicationMultiple keys/algorithms usageDatabase indexMulti user environment
A database encryption system and method, the Structure Preserving Database Encryption (SPDE), is presented. In the SPDE method, each database cell is encrypted with its unique position. The SPDE method permits to convert a conventional database index into a secure one, so that the time complexity of all queries is maintained. No one with access to the encrypted database can learn anything about its content without the encryption key. Also a secure index for an encrypted database is provided. Furthermore, secure database indexing system and method are described, providing protection against information leakage and unauthorized modifications by using encryption, dummy values and pooling, and supporting discretionary access control in a multi-user environment.
Owner:BEN GURION UNIVERSITY OF THE NEGEV
System for providing session-based network privacy, private, persistent storage, and discretionary access control for sharing private data
InactiveUS20040143738A1Public key for secure communicationDigital data processing detailsPrivate communicationPrivate network
The invention provides secure and private communication over a network, as well as persistent private storage and private access control to the stored information, which is accomplished by imposing mechanisms that separate a user's actions from their identity. The system provides (i) anonymous network browsing, in which event the anonymity system is unaware of both the user's identity and browsing activities, (ii) private network storage and retrieval of data such as passwords, profiles and files in a manner such that the data can be stored into the system and later retrieved without the system knowing the contents or owners of the data, and (iii) the ability of the user to control and manage access to the remotely stored data without the system knowing the contents, owners, or accessors of the data.
Owner:PONOI CORP
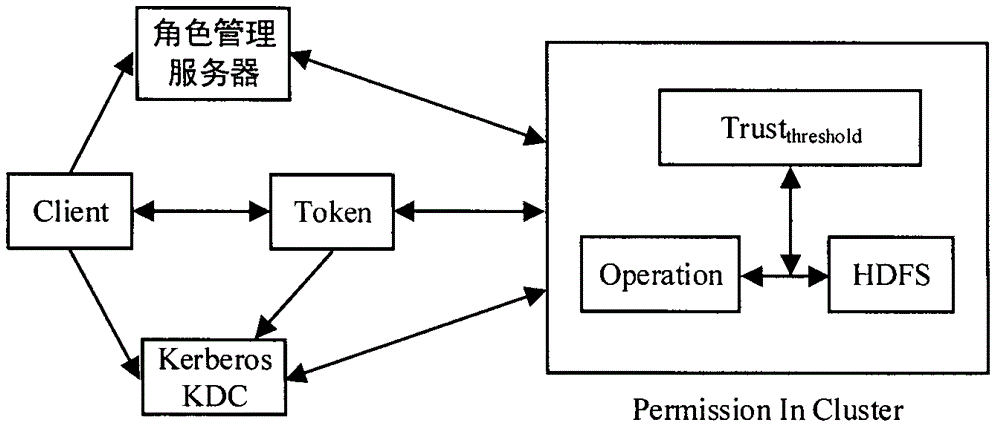
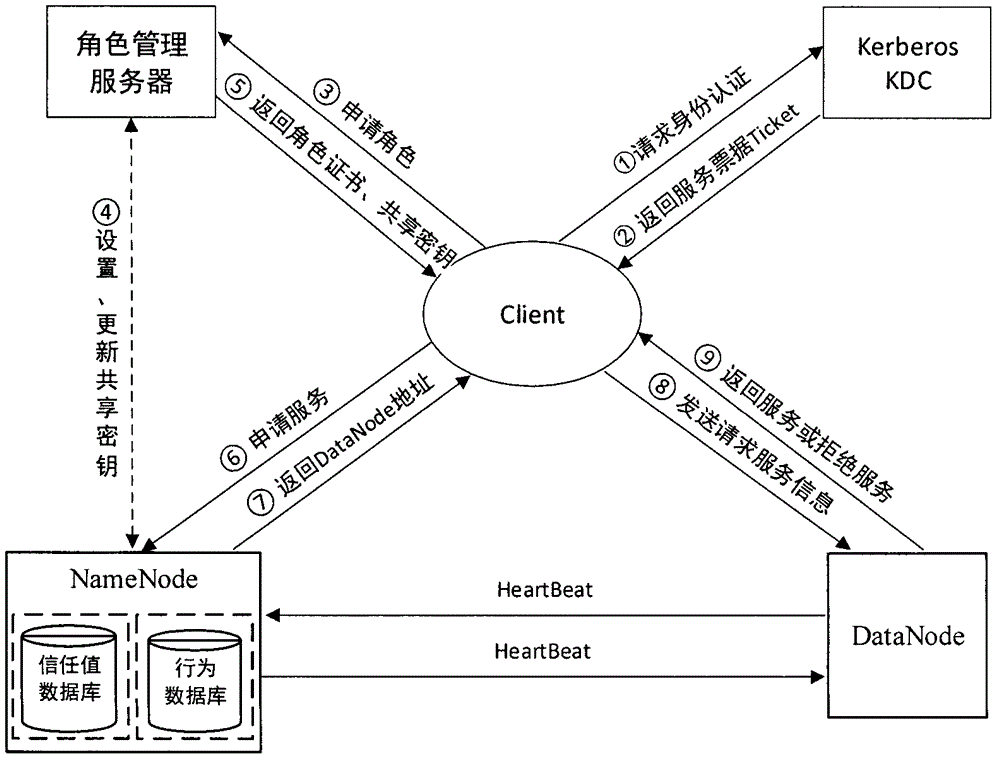
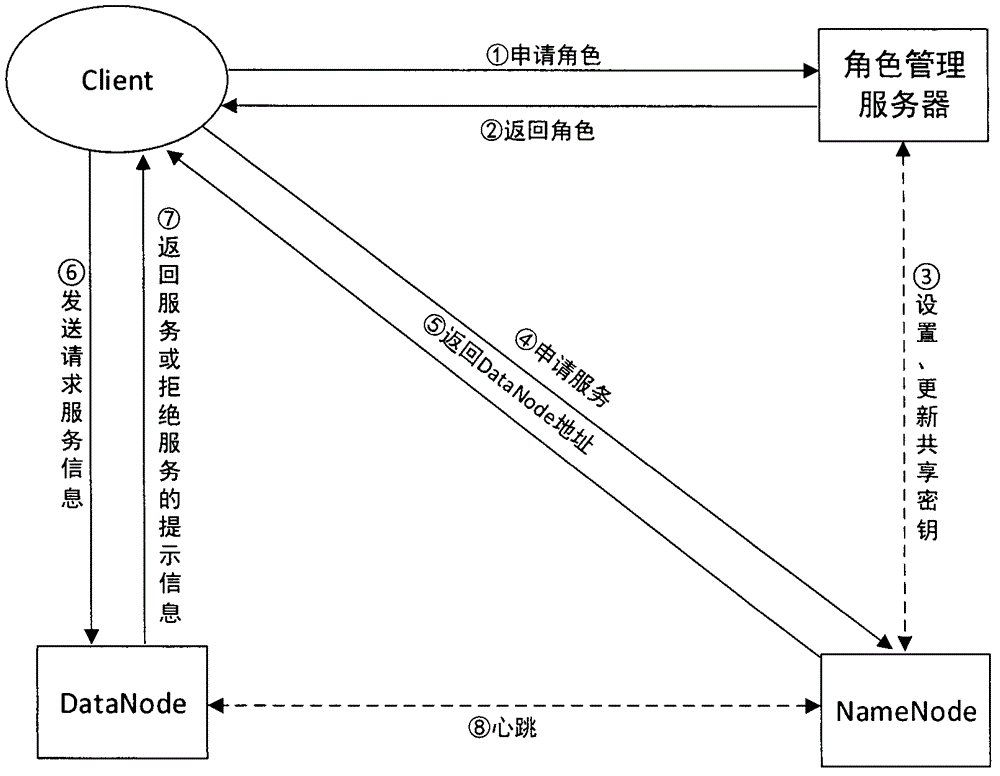
HDFS access control method based on role and user trust value
InactiveCN104935590AReduce complexityReduce administrative overheadUser identity/authority verificationCloud storageDiscretionary access control
The invention provides an HDFS access control method based on a role and a user trust value and belongs to the field of computer cloud storage access control. The HDFS access control method of the invention firstly combines with a role-based access control policy RBAC to replace a discretionary access control policy of an HDFS, thereby reducing complexity and management expenditure of HDFS authorization management and improving flexibility of the authorization management. When a user accesses the HDFS for the first time, a role is granted to the user, so that users are isolated from authorization through roles, and the management is facilitated. On this basis, the HDFS access control method of the invention further introduces a concept of the user trust value and sets one trust value for each user so that different users with the same role could obtain different access permissions because of their different trust values, and the trust value of the user is dynamically updated according to the later behavior of the user, thereby dynamically and effectively controlling the access of the user to a resource in the HDFS.
Owner:NANJING UNIV OF AERONAUTICS & ASTRONAUTICS
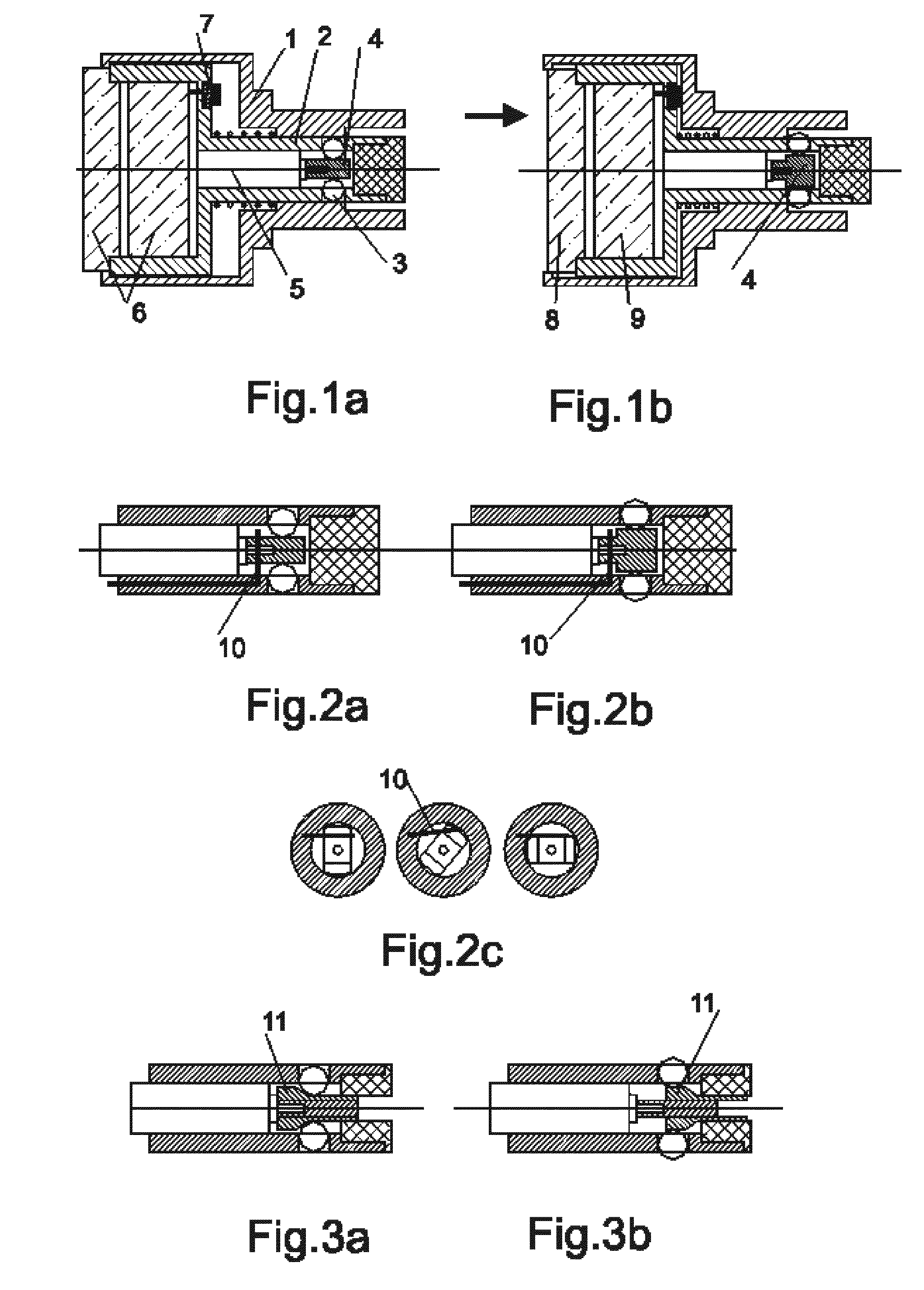
Electronic device for a mechanical blocking.
InactiveUS20110277520A1Reduce power consumptionSave energyNon-mechanical controlsControl powerElectrical battery
An electronic device for a mechanical blocking and power mechanisms on its basis, intended for use in electronic locks, hydraulic / pneumatic automation, electronically controlled valve(tap), electronically controlled power electrical switches and commutators, electro-mechanical clutches and couplings, etc. The devices based on invention are compact, have a simple design and are rather reliable in conditions of shocks and vibrations. Low electric power consumption and corresponding long battery life have been obtained at the prototypes of these devices. It will be effectively used in the systems of autonomous access control.
Owner:NUNUPAROV MARTYN SERGEEVICH
Structure preserving database encryption method and system
ActiveUS8639947B2Provide protectionKey distribution for secure communicationMultiple keys/algorithms usageDatabase indexMulti user environment
A database encryption system and method, the Structure Preserving Database Encryption (SPDE), is presented. In the SPDE method, each database cell is encrypted with its unique position. The SPDE method permits to convert a conventional database index into a secure one, so that the time complexity of all queries is maintained. No one with access to the encrypted database can learn anything about its content without the encryption key. Also a secure index for an encrypted database is provided. Furthermore, secure database indexing system and method are described, providing protection against information leakage and unauthorized modifications by using encryption, dummy values and pooling, and supporting discretionary access control in a multi-user environment.
Owner:BEN GURION UNIVERSITY OF THE NEGEV
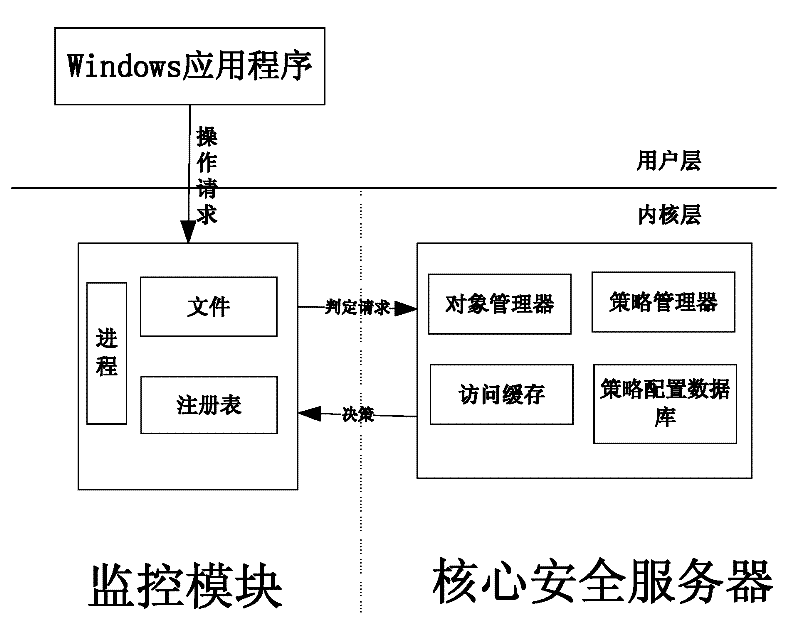
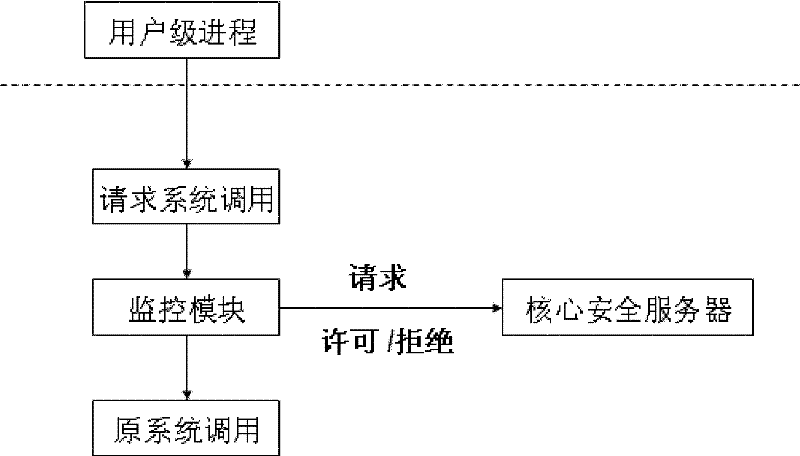
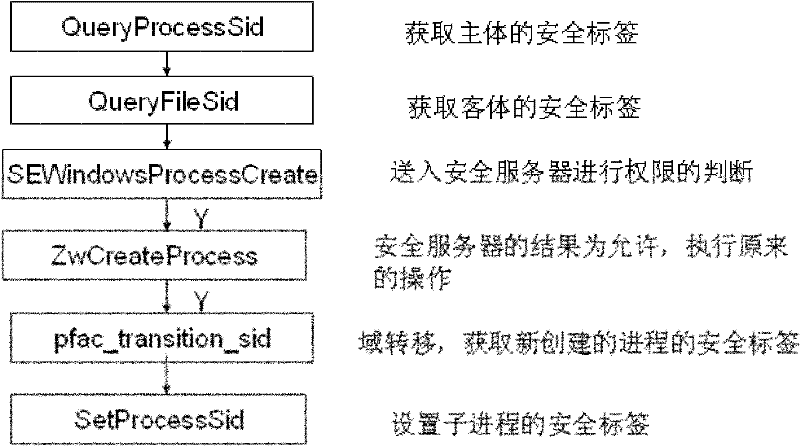
Device and method for controlling mandatory access based on Windows platform
The invention discloses a device and method for controlling mandatory access based on a Windows platform. The device comprises a monitoring module and is characterized in that access control on progresses, files and register lists can be realized on the Windows platform, access requests of a subject of the access control on an object are intercepted and provided for a core safety server to be used for safety judgment; and the core safety server carries out authority judgment according to safety rules of mandatory access control and returns a result to the monitoring module so that the mandatory access control is realized. According to the device and method for controlling the mandatory access based on the Windows platform, disclosed by the invention, an access control decision of a windows system does not depend on the subject, and whether access is allowed or not is determined by comparing safety identifiers of the subject and the object through a safety policy; and the device for controlling the mandatory access based on the Windows platform, disclosed by the invention, is compatible with a windows-self-attached discretionary access control mechanism and also has higher safety grade compared with the original mechanism.
Owner:SUZHOU LINGXIAO TECH
System for providing session-based network privacy, private, persistent storage, and discretionary access control for sharing private data
InactiveUS7437550B2Improve privacyReduce needDigital data processing detailsPublic key for secure communicationPrivate communicationPrivate network
Owner:PONOI CORP
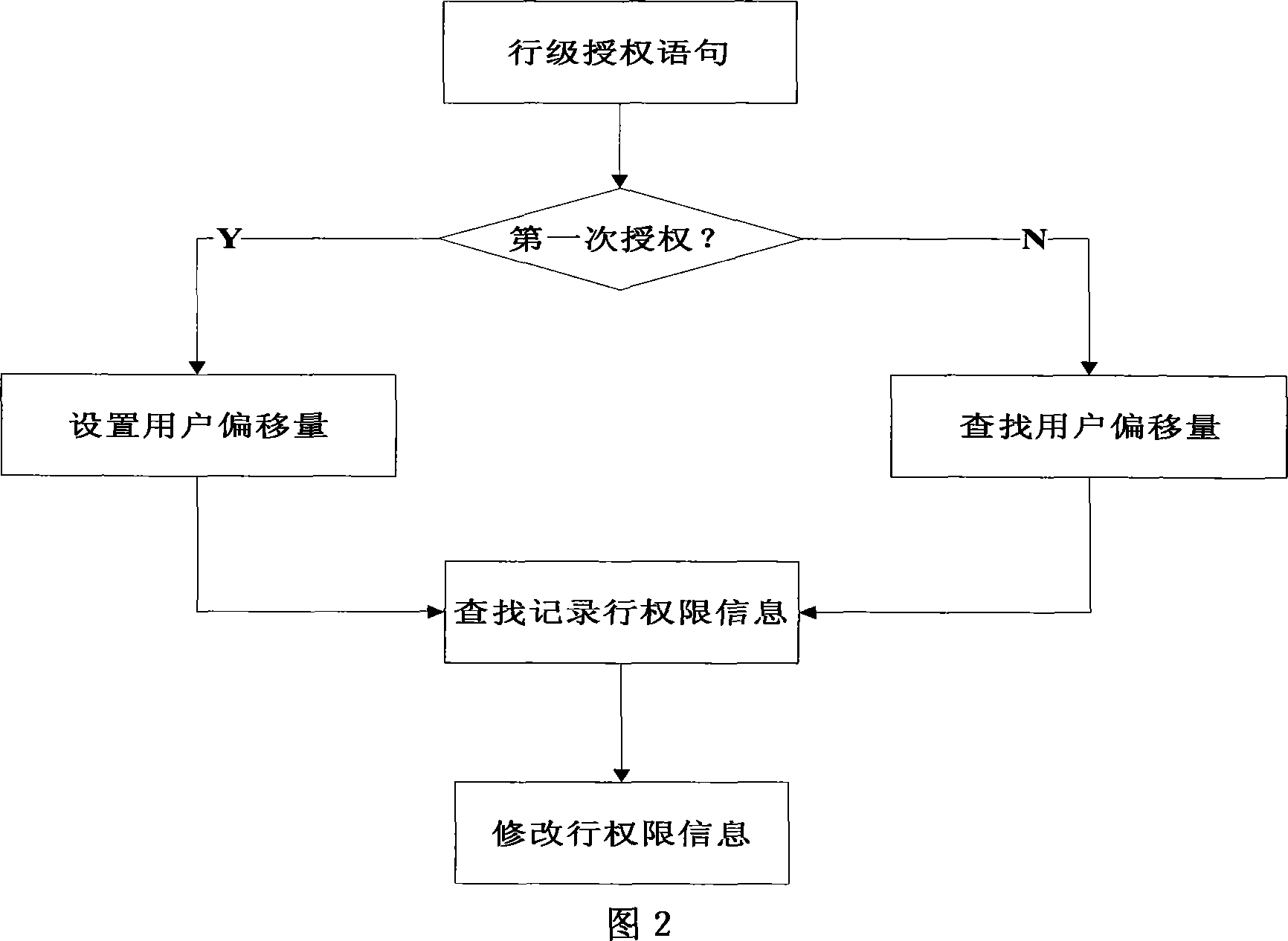
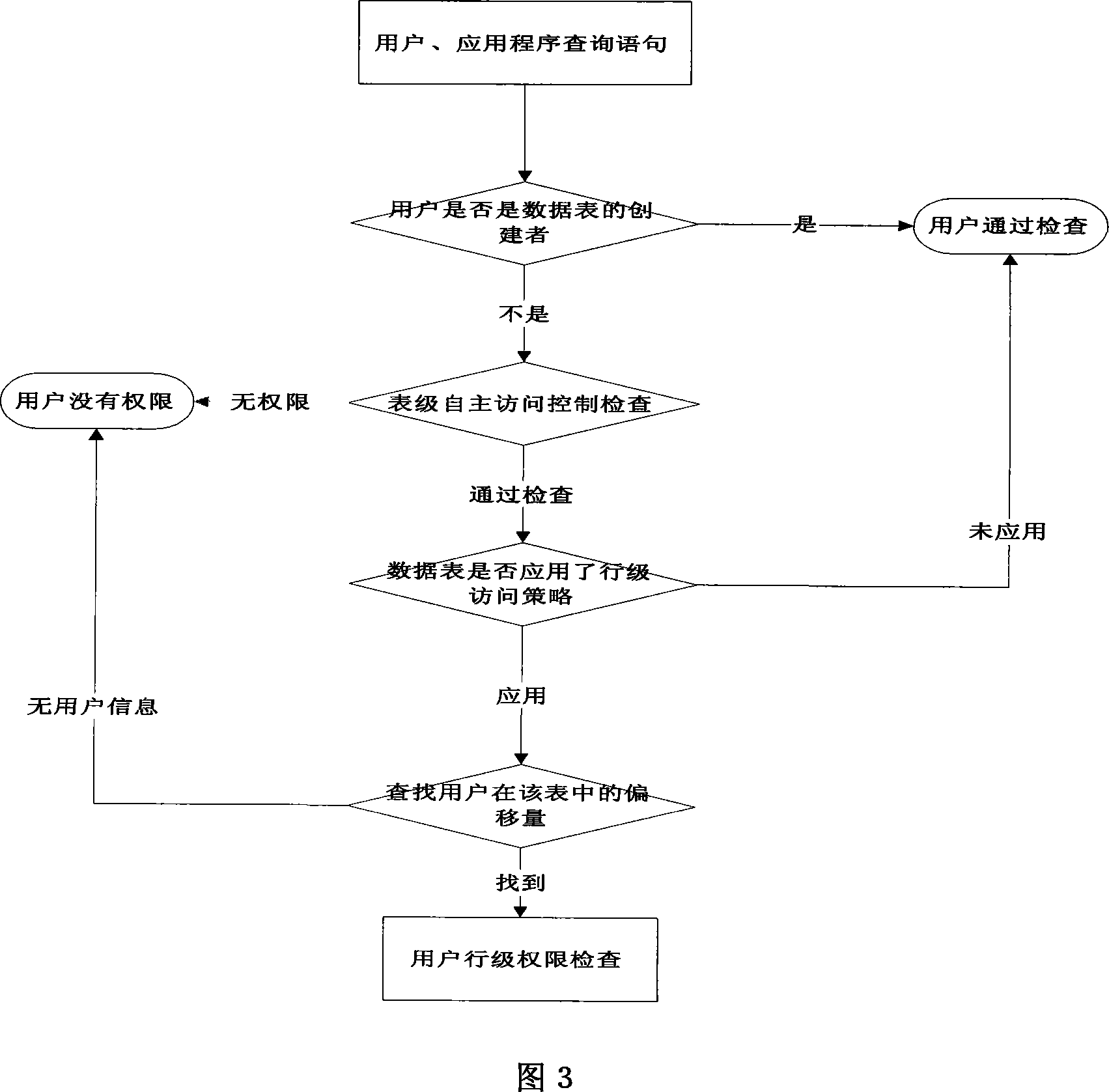
Method for self-contained access of database list row data
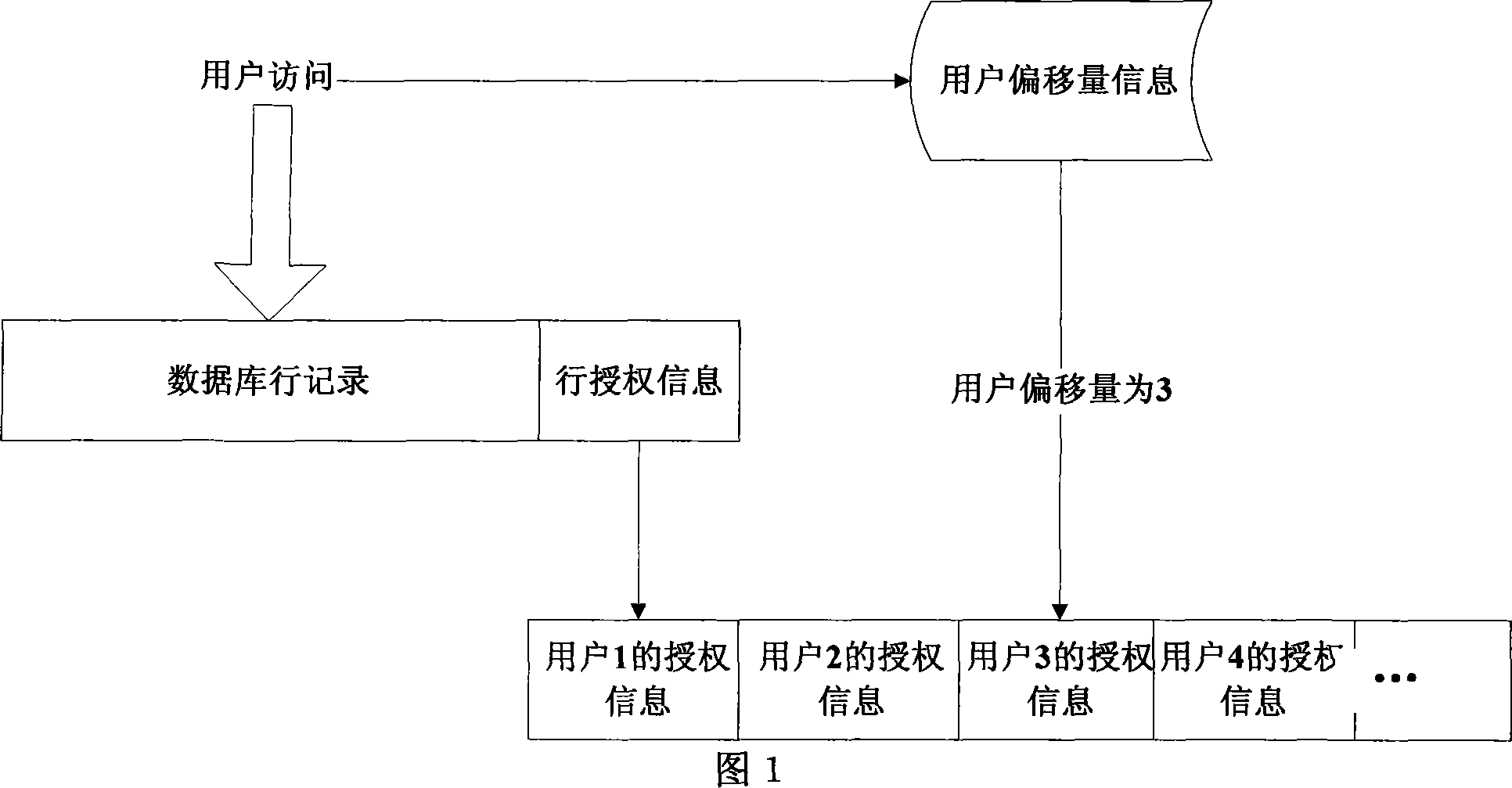
ActiveCN101075254AProtect row-level dataImprove securitySpecial data processing applicationsDatabase securityDiscretionary access control
A method for controlling active access of line grade data in databank table includes adding a control authority column of line grade access for enabling to use each databank table of line grade access control in order to record access control authority information of this line, granting relevant access authority and access type in databank table to user of databank, carrying out line grade access control on user according to line grade access authority granted to said user and control policy of said line grade access.
Owner:北京神舟航天软件技术股份有限公司
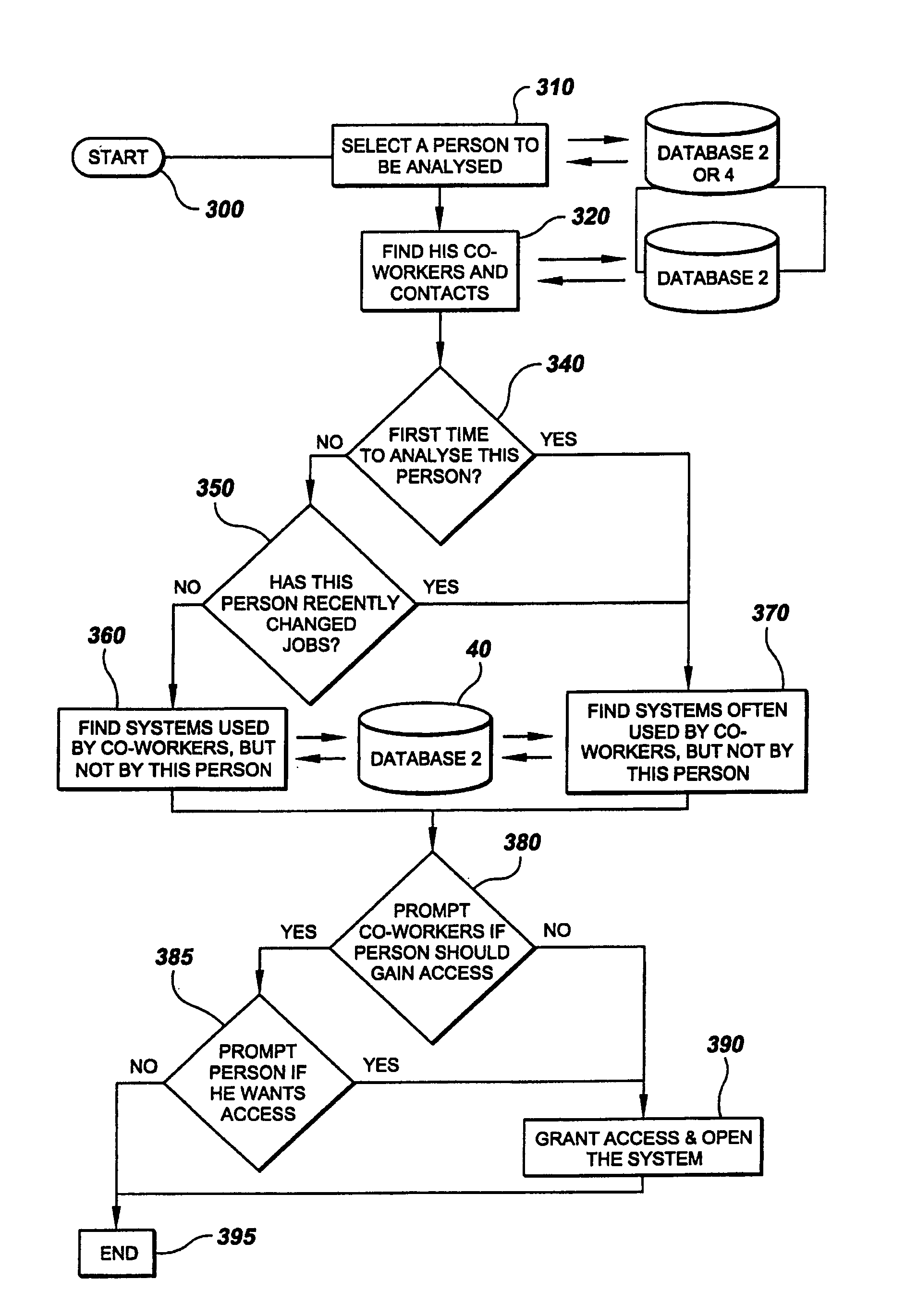
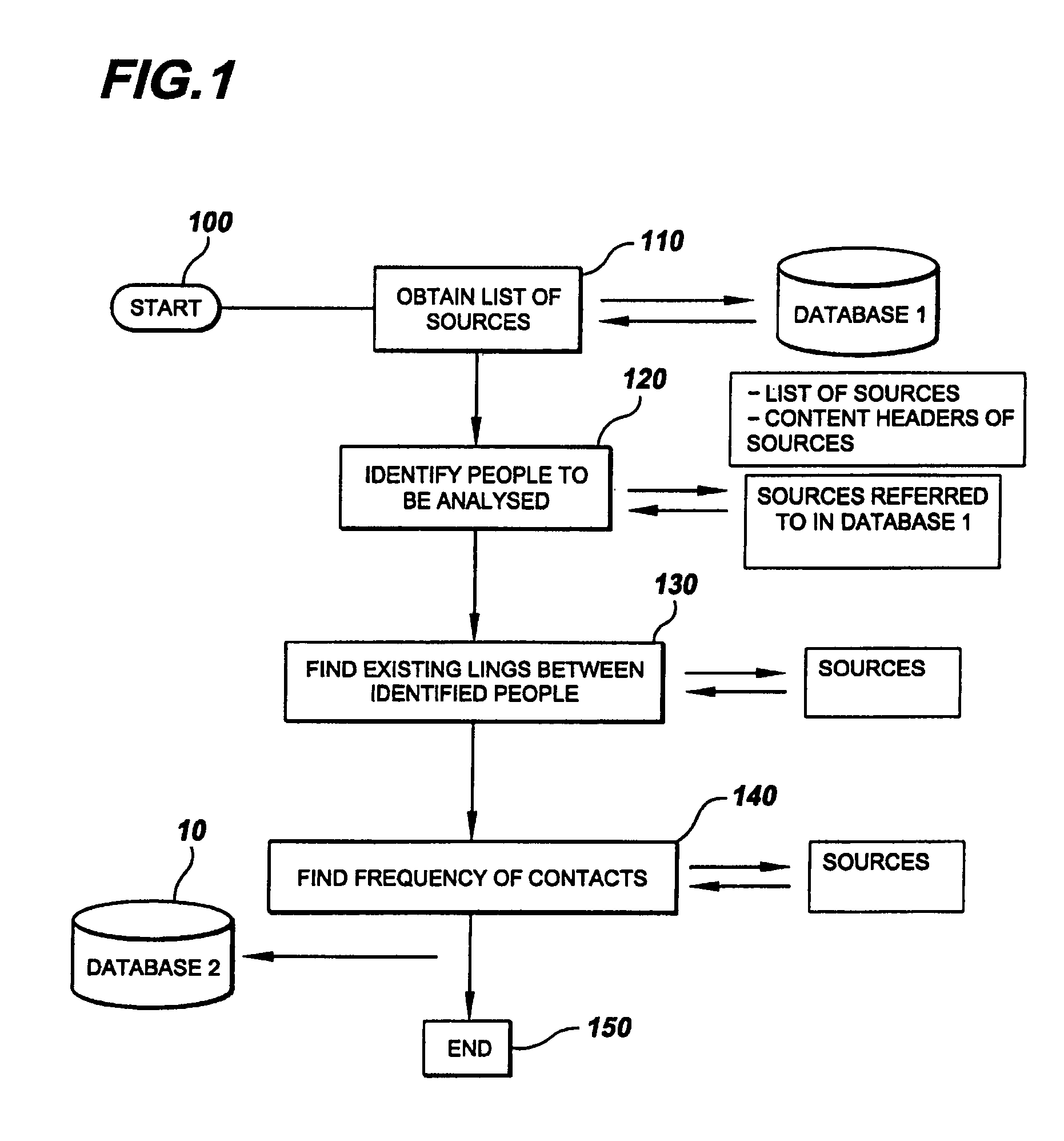
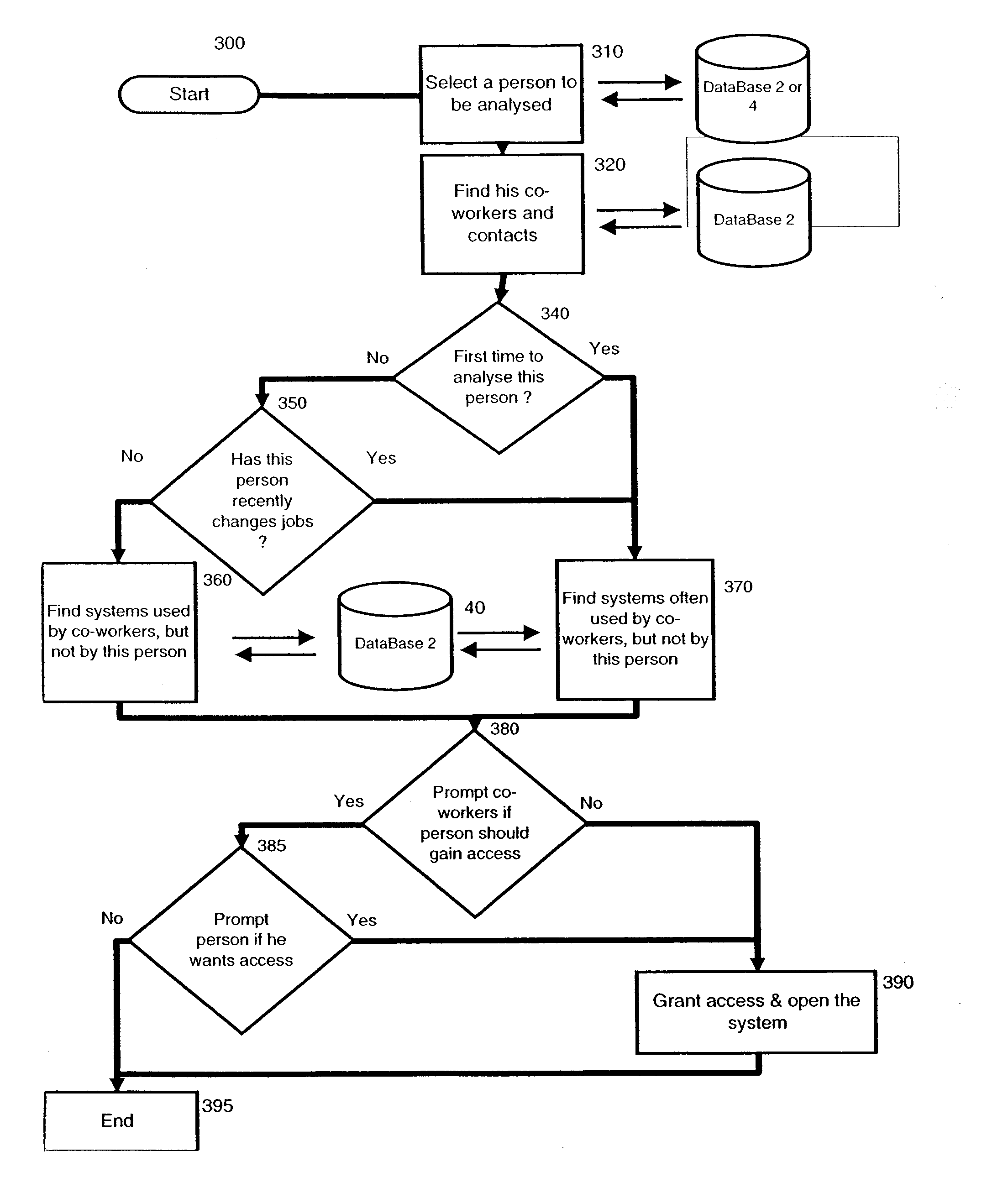
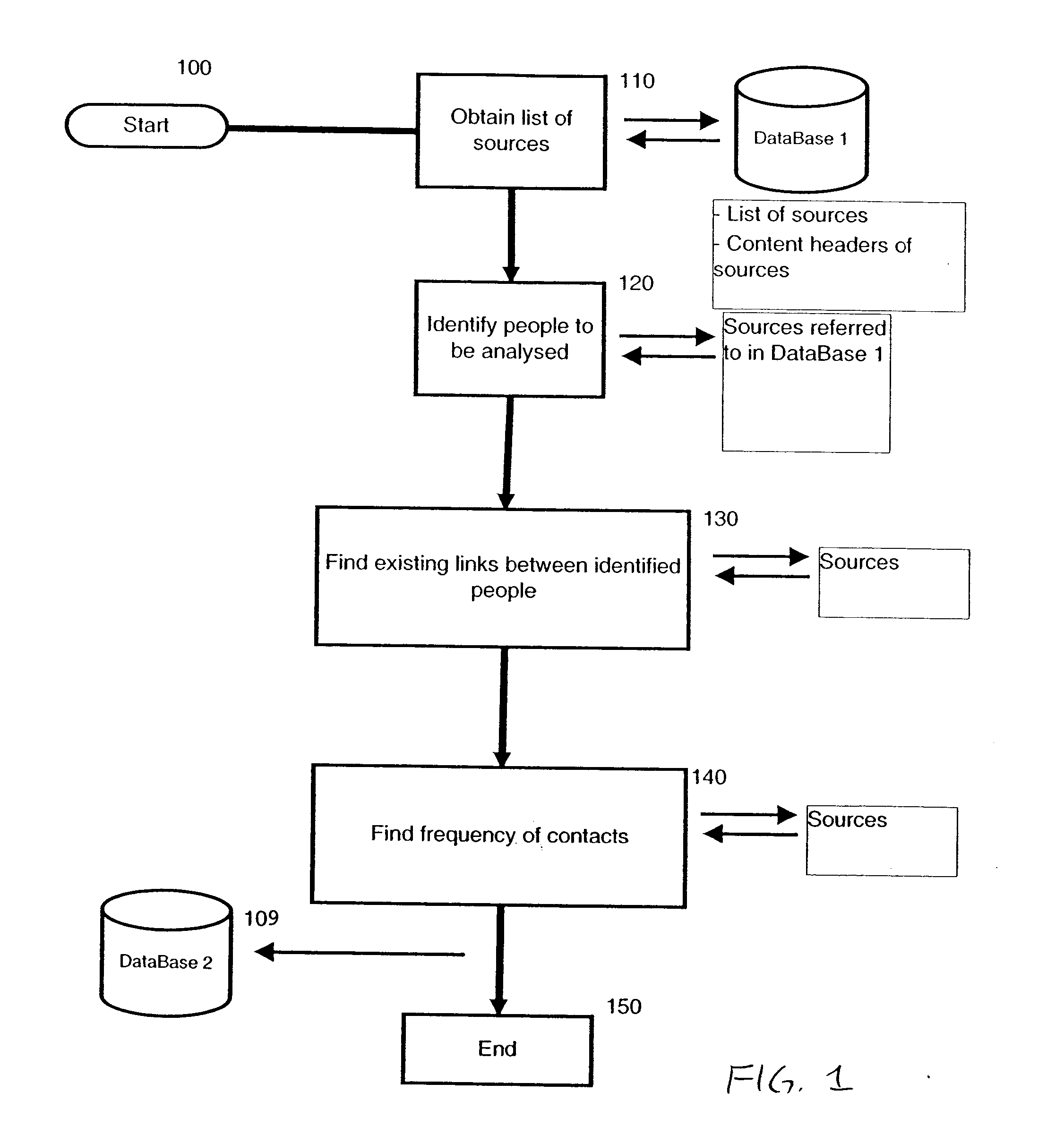
Apparatus and method for analysis of conversational patterns to position information and autonomic access control list management
ActiveUS7313827B2Data processing applicationsDigital data processing detailsComputer architectureApplication software
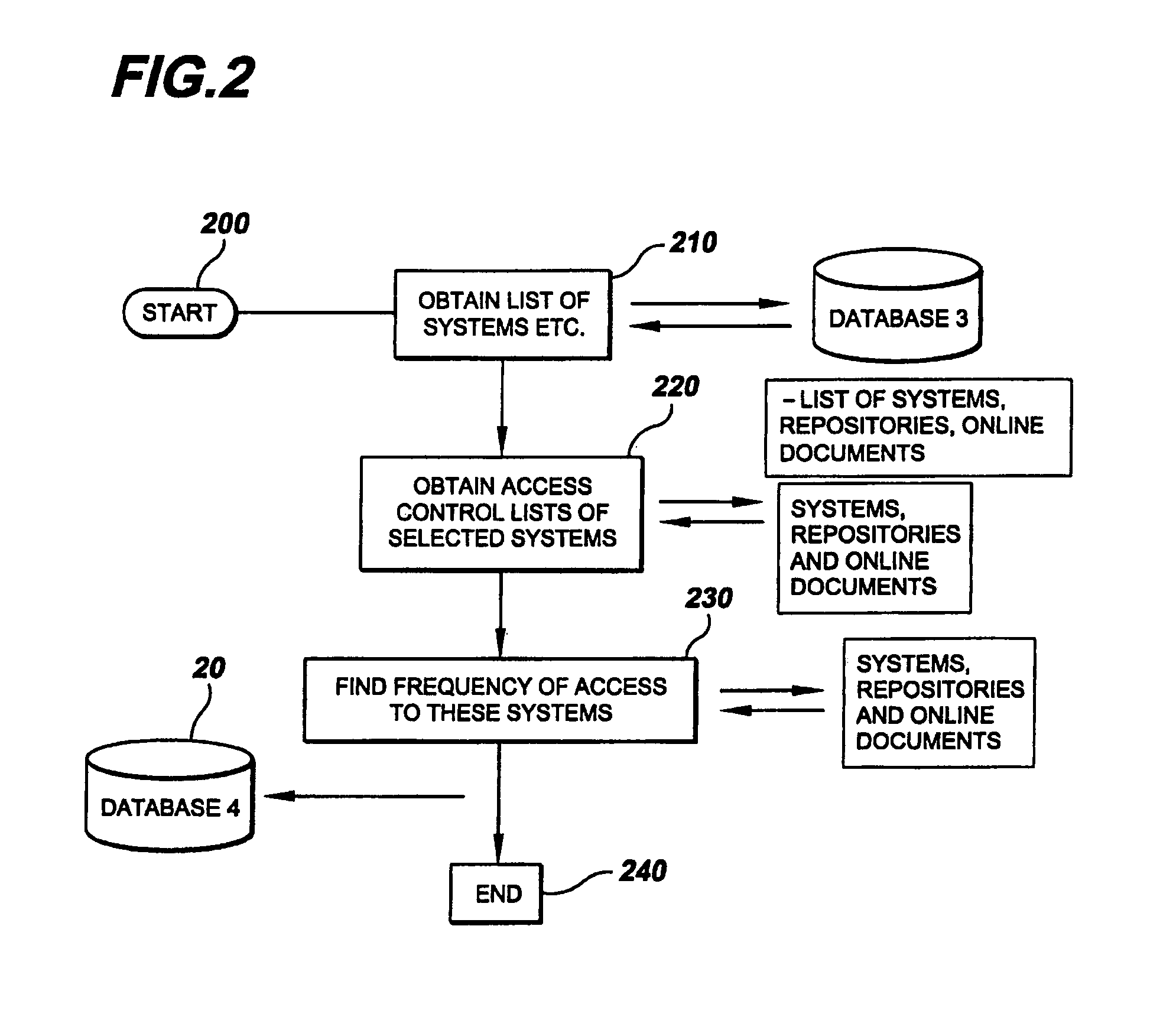
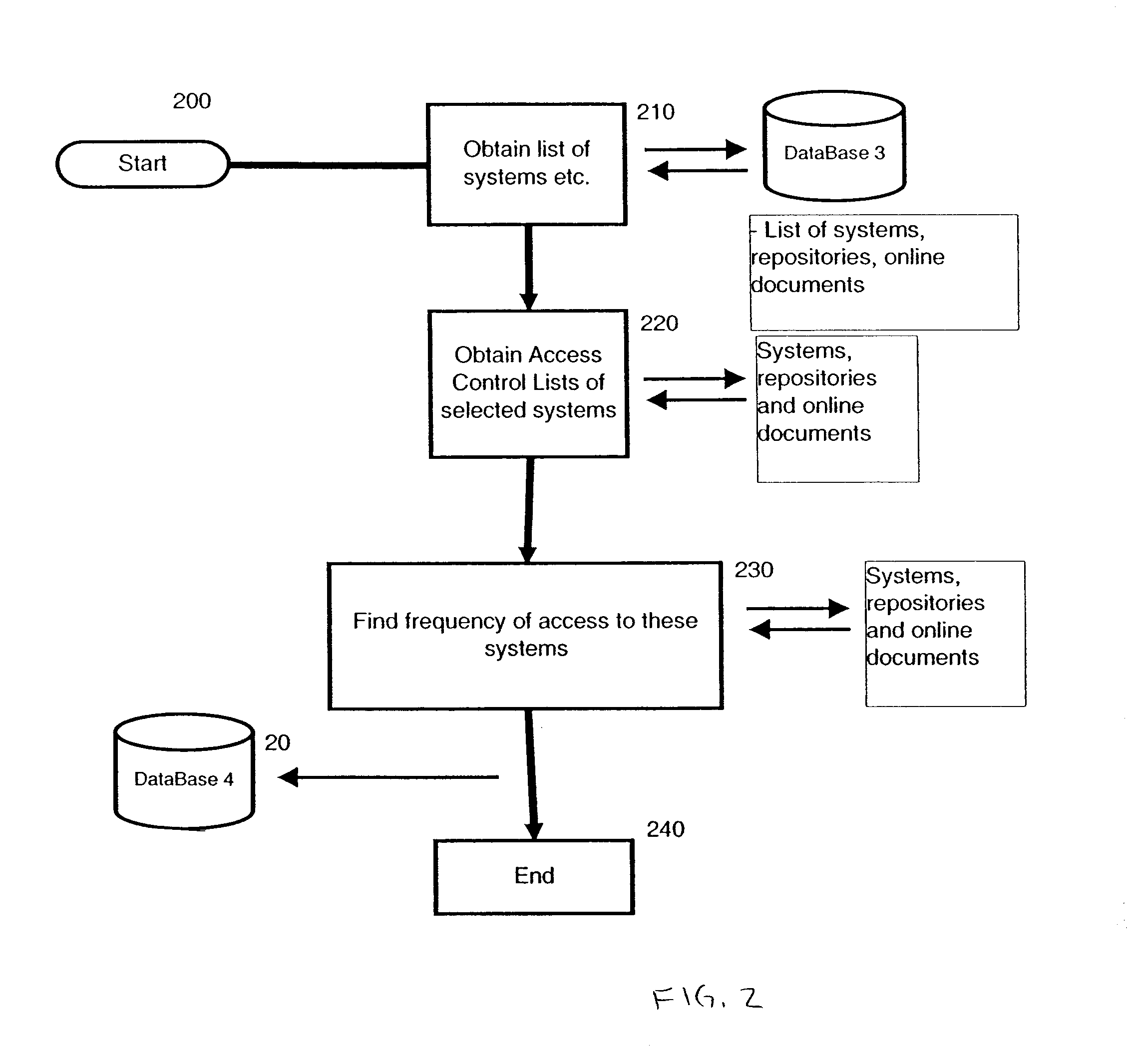
A method employing a software application for operation for analyzing conversational patterns between people and teams within an organization, locating inconsistencies in the required and actual access level to knowledge repositories, which ultimately results in dynamically updating access control lists of the knowledge repositories, and having the originator and anticipated users being prompted to further enable informed, fact-based manual control of the access control lists.
Owner:GOOGLE LLC
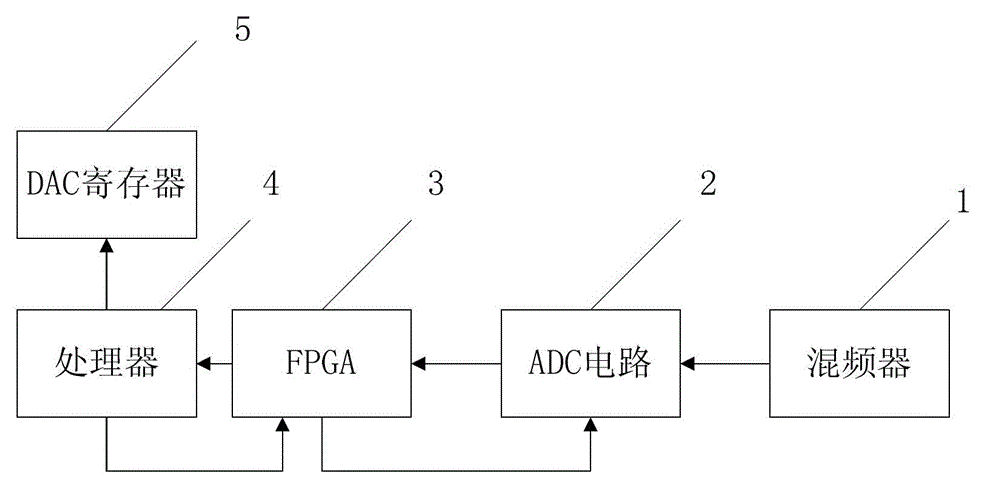
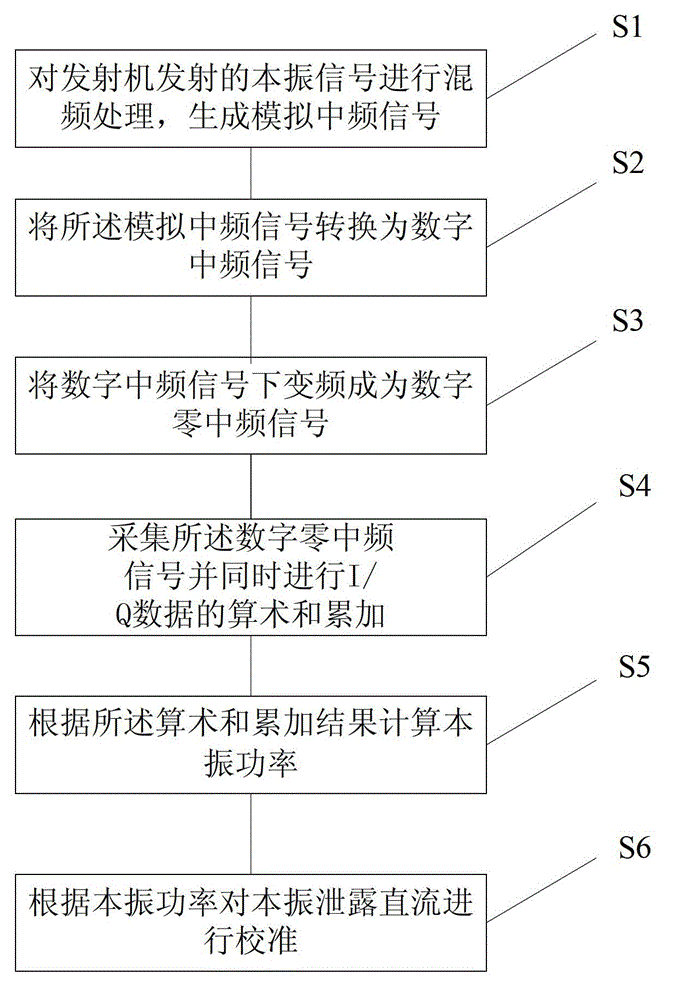
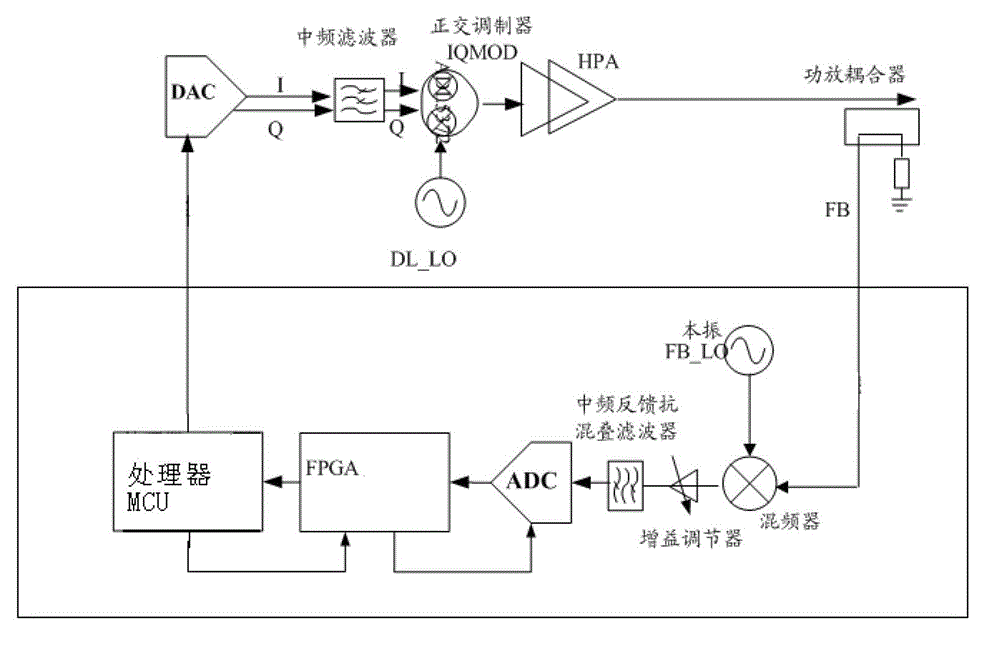
Device and method of local oscillator leakage fast calibration
ActiveCN103067321AAvoid interferenceAvoid misjudgmentDc level restoring means or bias distort correctionTransmitter/receiver shaping networksLocal oscillator signalIntermediate frequency
The invention provides a device and a method of local oscillator leakage fast calibration. The device and the method of local oscillator leakage fast calibration comprises a mixer, an analog to digital converter (ADC) circuit, field programmable gate array (FPGA), and a processor and a discretionary access control (DAC) register. The mixer is used for frequency conversion of a feedback signal formed by a local oscillator signal transmitted from a transmitter to generate an intermediate frequency signal. The ADC circuit is used for converting the intermediate frequency signal to a digital signal. The FPGA is used for collecting the digital signal and meanwhile calculating and accumulating in-phase / quadrature (I / Q) data. The processor is used for calculating local oscillator power according to results of calculating and accumulating. The DAC register is used for correcting local oscillator leakage direct current according to the local oscillator power. Through the device and the method of local oscillator leakage fast calibration, interference and miscalculation of feedback direct current leakage to transmitted direct current leakage can be avoided, and correction time of local oscillator leakage direct current can be shortened greatly.
Owner:DATANG MOBILE COMM EQUIP CO LTD
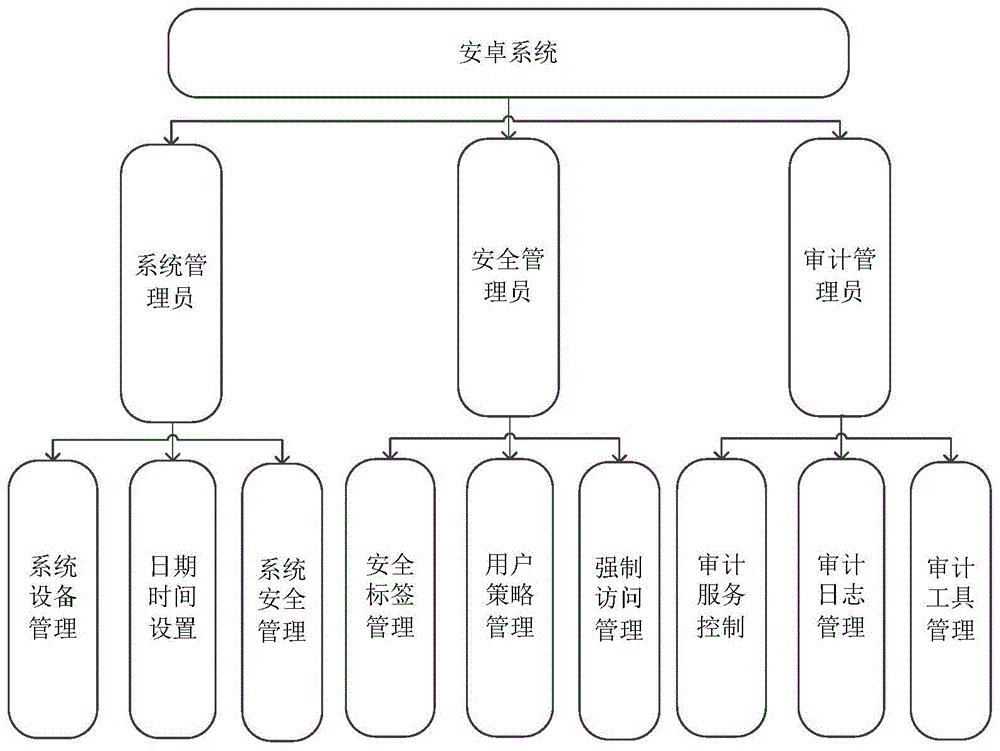
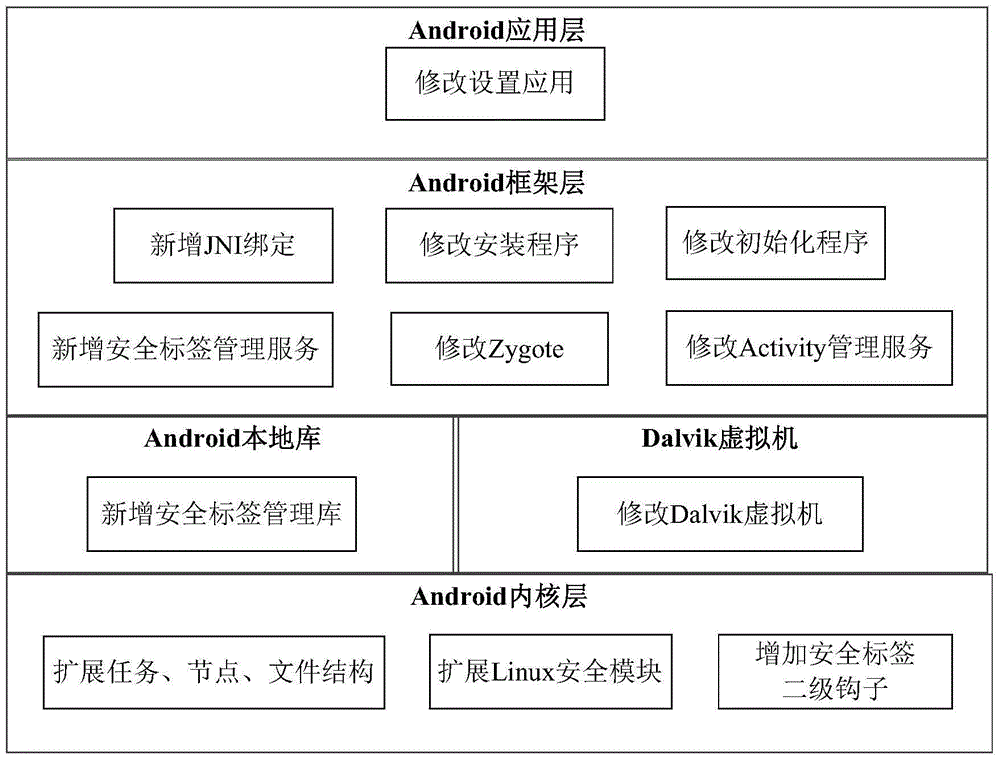
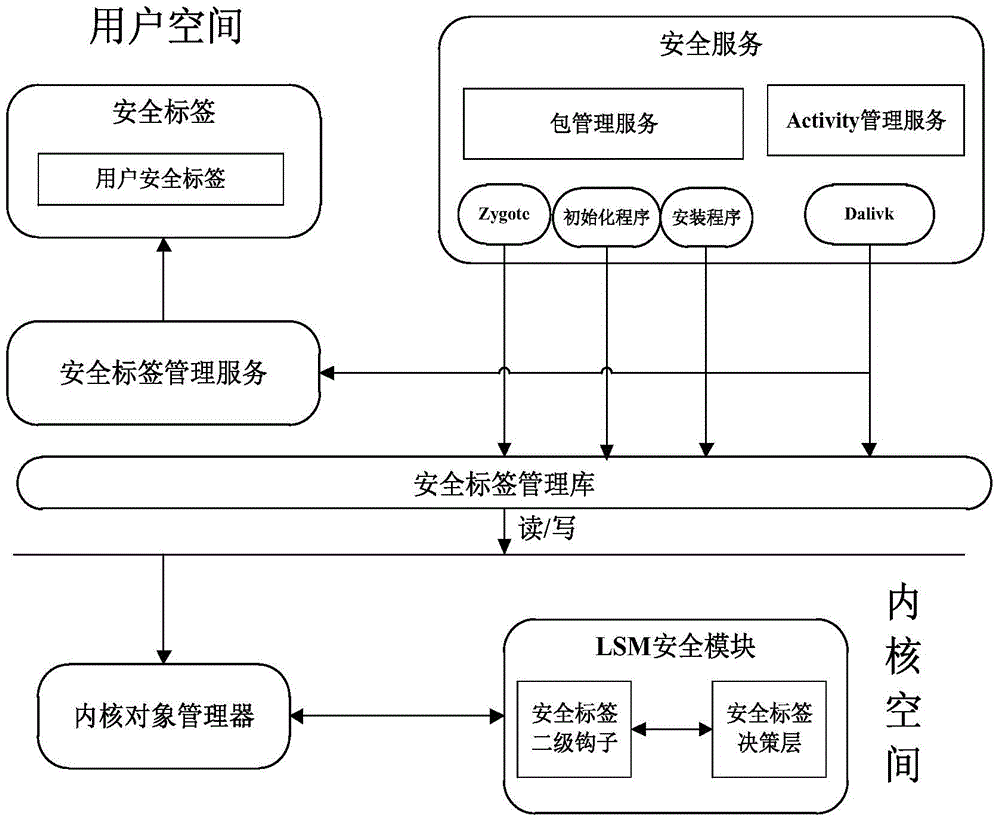
Resource access method of Android system
ActiveCN105046146AAvoid visitingImprove securityPlatform integrity maintainanceComputer securityDiscretionary access control
The invention discloses a resource access method of an Android system, and belongs to the technical field of a mobile system. The resource access method of the Android system aims at solving the technical problem that in the existing Android system, the security and the completeness of resources of a user can be threatened. The resource access method of the Android system comprises the following steps of: sequentially performing DAC (Discretionary Access Control) permission checking and MAC (Mandatory Access Control) permission checking on a resource accessing process; if the process passes the DAC permission checking and the MAC permission checking, obtaining a security label of the process and a security label of the resources; matching the security label of the process and the security label of the resources; and if the security label of the process and the security label of the resources are matched, allowing the process to access the resources.
Owner:CHINA STANDARD SOFTWARE
Trusted computer system
InactiveUS7210043B2Improve information securityDigital data processing detailsUnauthorized memory use protectionInformation processingComputerized system
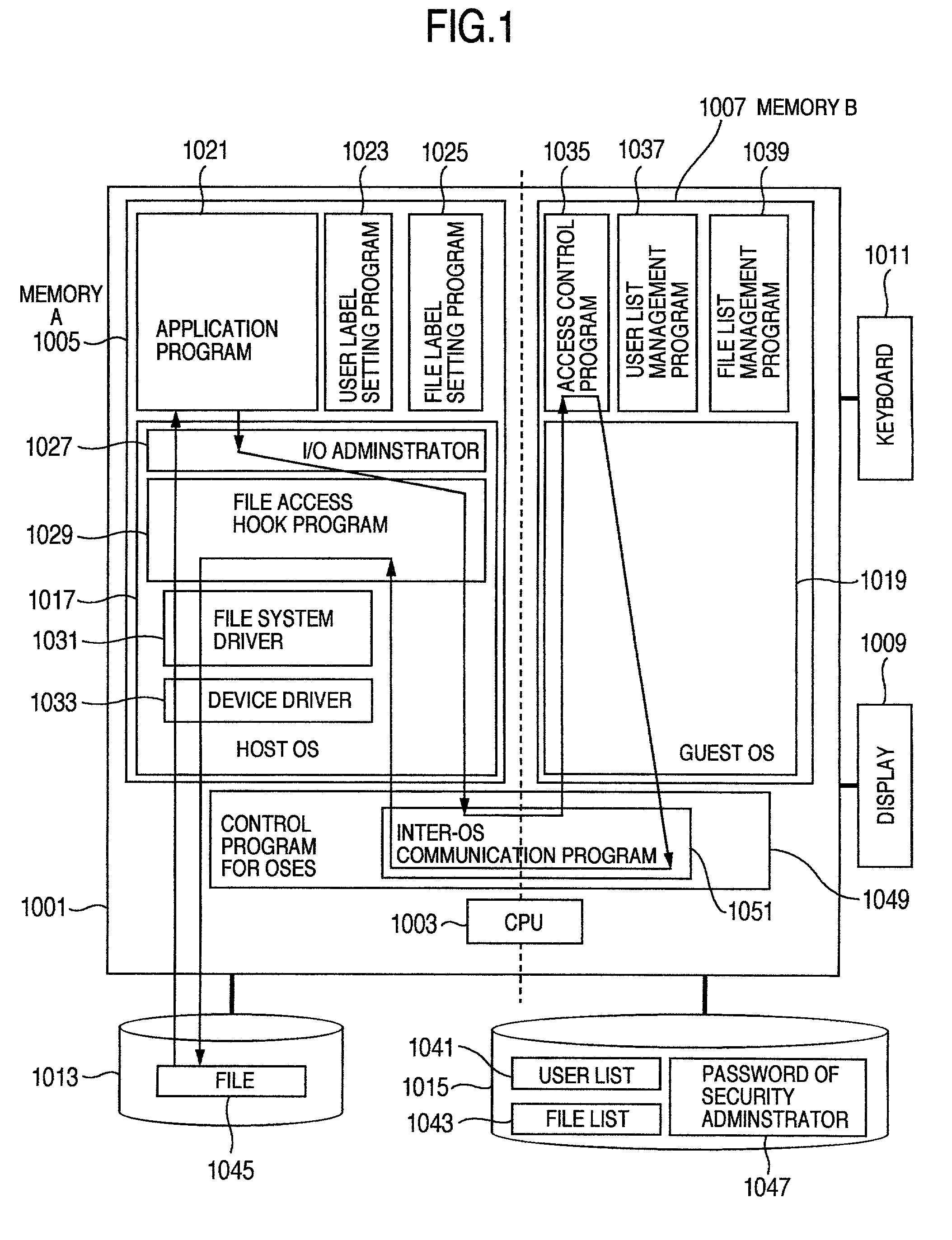
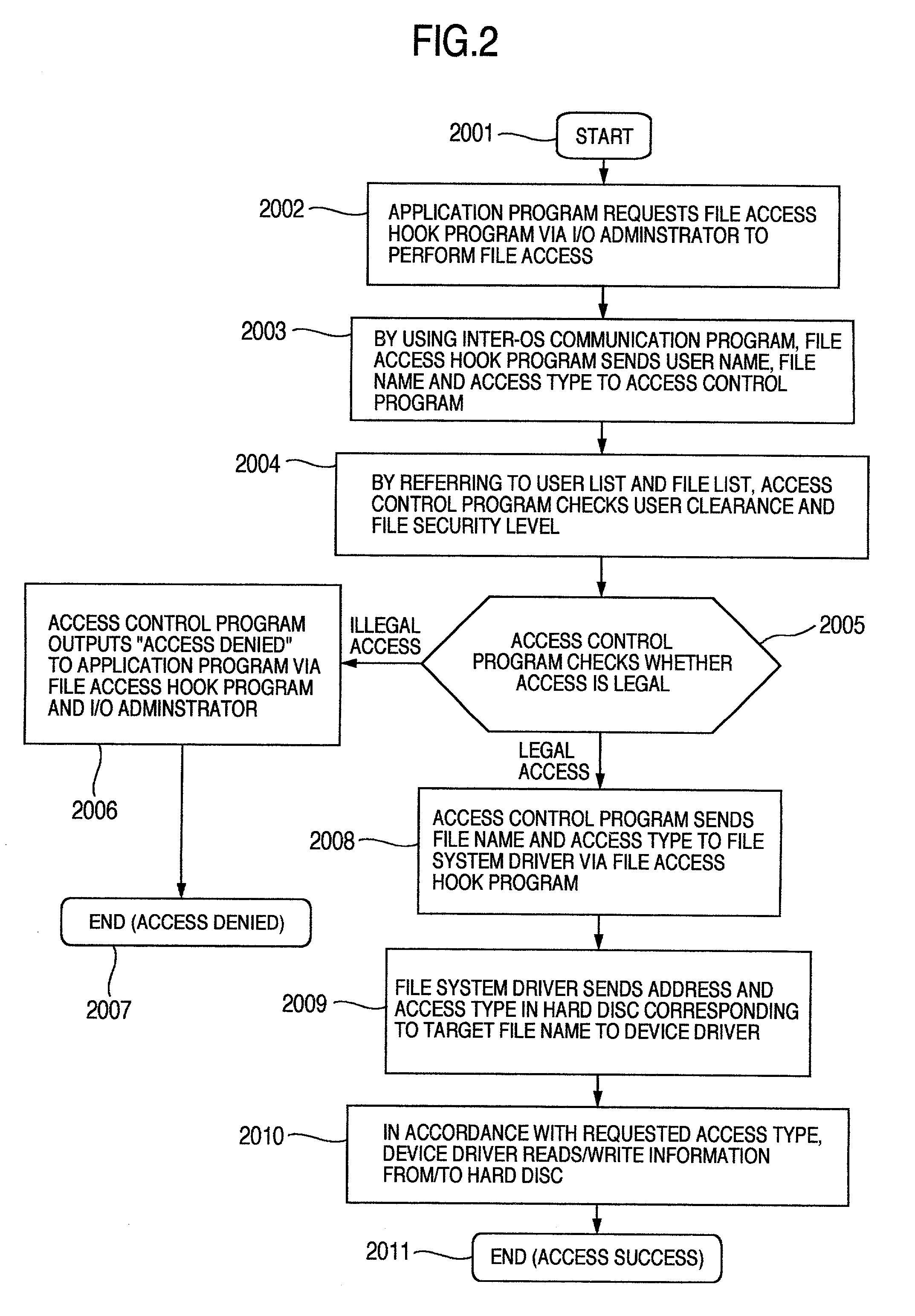
Techniques of improving the safety of an information processing system at low cost are provided, the information processing system having an OS provided with an access control function based upon discretionary access control for preventing illegal accesses to files. A method and apparatus for providing the information processing system with functions and areas usable only by a specific user different from a system administrator. The areas are provided with an access control function in order to prevent the access control function from being tampered.
Owner:HITACHI LTD
Apparatus and method for analysis of conversational patterns to position information and autonomic access control list management
ActiveUS20050010823A1Easy to controlData processing applicationsDigital data processing detailsEngineeringKnowledge management
A method employing a software application for operation for analyzing conversational patterns between people and teams within an organization, locating inconsistencies in the required and actual access level to knowledge repositories, which ultimately results in dynamically updating access control lists of the knowledge repositories, and having the originator and anticipated users being prompted to further enable informed, fact-based manual control of the access control lists.
Owner:GOOGLE LLC
Mobile phone Bluetooth-based auto-induction access control system and implementation method thereof
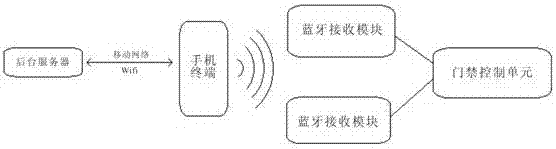
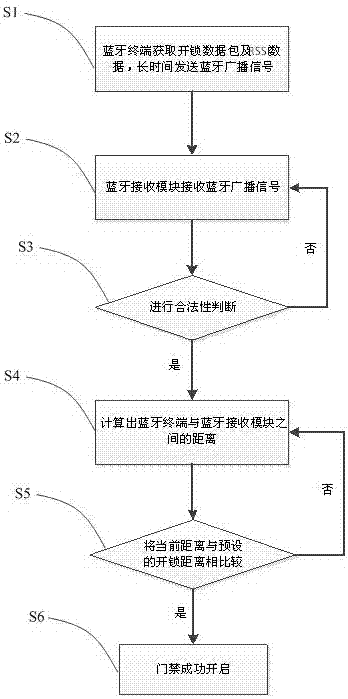
InactiveCN107103673AImprove experienceSimple structureIndividual entry/exit registersNetwork packetHand held
The invention discloses a mobile phone Bluetooth-based auto-induction access control system and an implementation method thereof and belongs to the field of access control systems. The system comprises a Bluetooth terminal and a Bluetooth receiving module. The Bluetooth receiving module is connected to an access control unit. The access control unit is connected to an unlocking executive device. The Bluetooth terminal is connected to a background server through a network. The Bluetooth terminal is used for acquiring an unlocking data packet from the background server and transmitting a Bluetooth broadcast signal with the unlocking data packet for long time in a holding state. The Bluetooth terminal transmits a Bluetooth broadcast signal with the unlocking data packet for long time so that when the Bluetooth terminal is close to the Bluetooth receiving module, the access control unit can automatically open the access control system without hand-held Bluetooth terminal operation, and a user carrying the Bluetooth terminal can smoothly open the access control system even if the user holds a heavy object or takes care of infants so that the system is free of both hands and improves user experience.
Owner:广州跨行网络科技有限公司
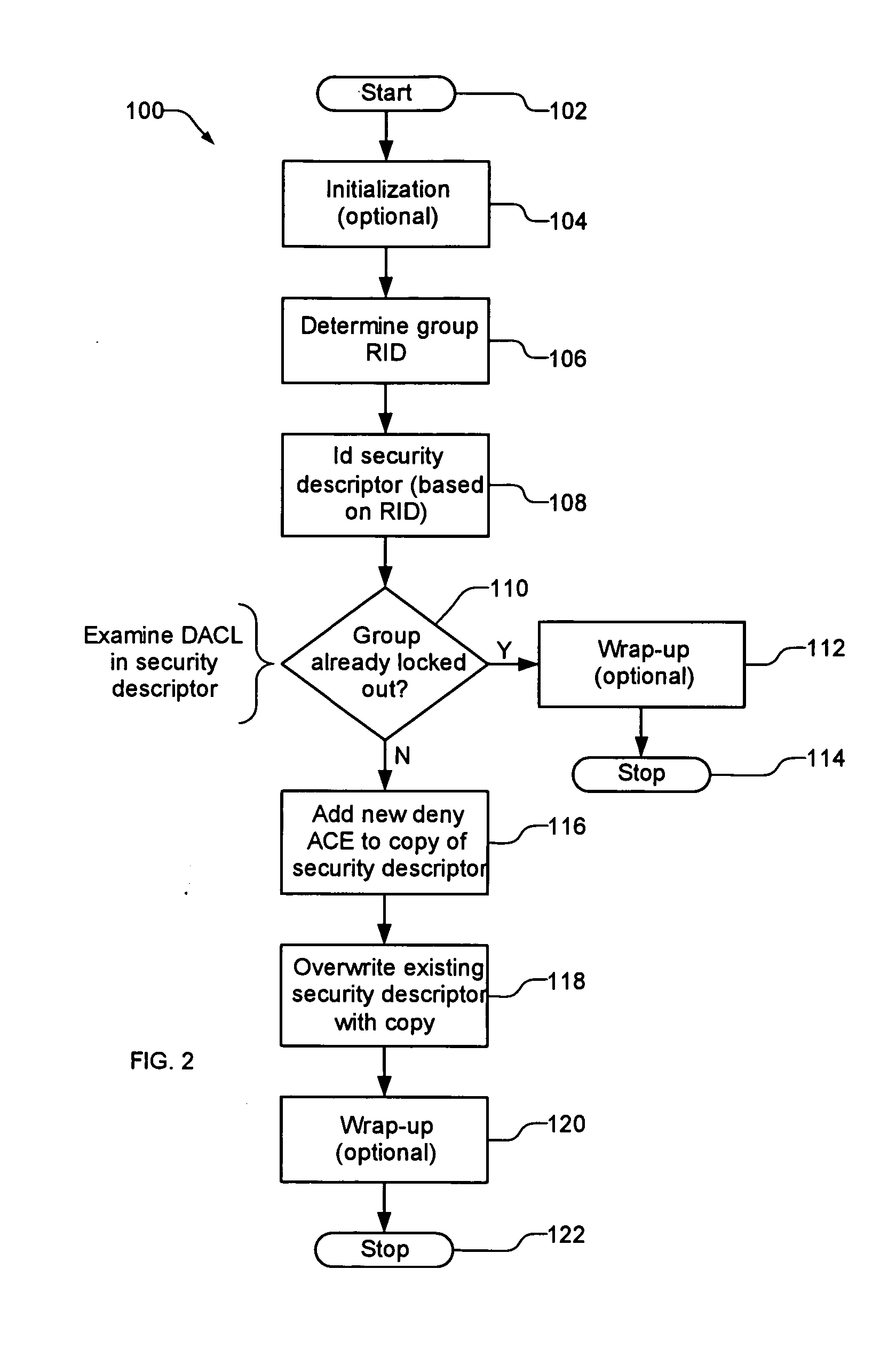
System for protecting domain system configurations from users with local privilege rights
ActiveUS20060015741A1High activityControl changesDigital data processing detailsAnalogue secracy/subscription systemsOperational systemSystem configuration
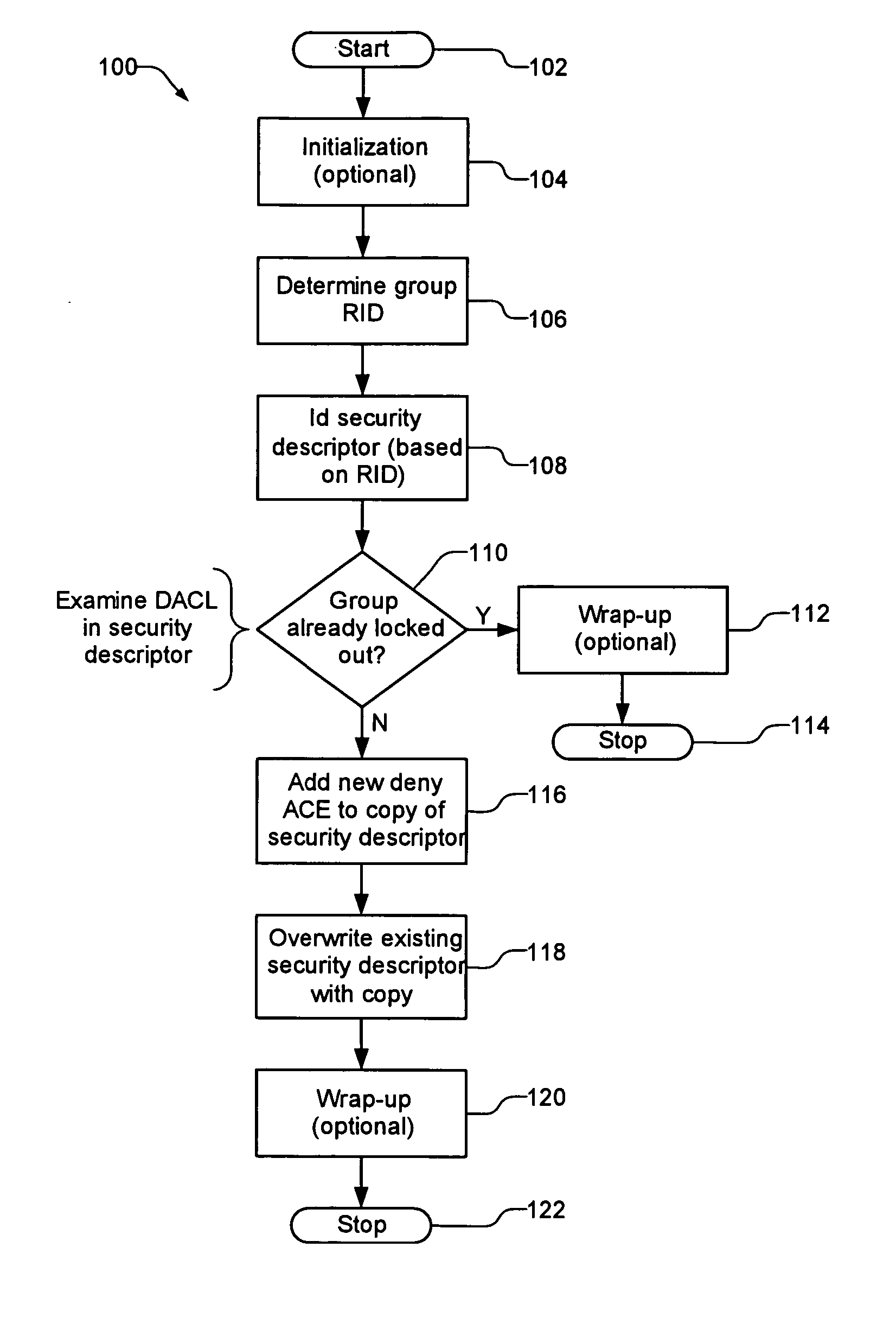
A group change lockout system for protecting the configuration of a securable object in an operating system from members of a locally privileged group, such as the local administrators group, when a security descriptor exists for the securable object that includes a discretionary access control list (DACL). A copy of the security descriptor is made. Then a new access control entry (ACE) is added to the DACL in the copy. This new ACE specifies denying the local administrators group an access right to the securable object. Then the security descriptor in the operating system is overwritten with the copy.
Owner:BEYONDTRUST SOFTWARE INC
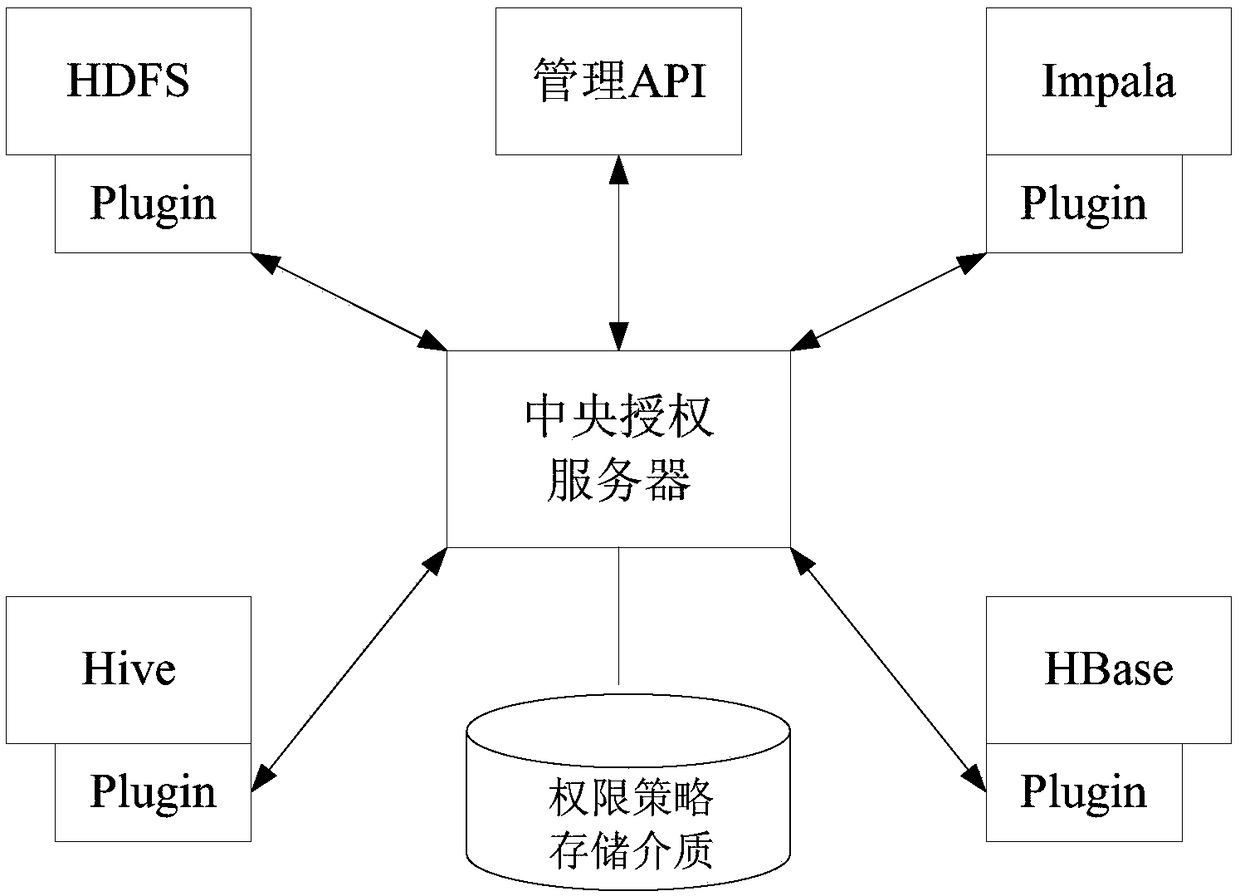
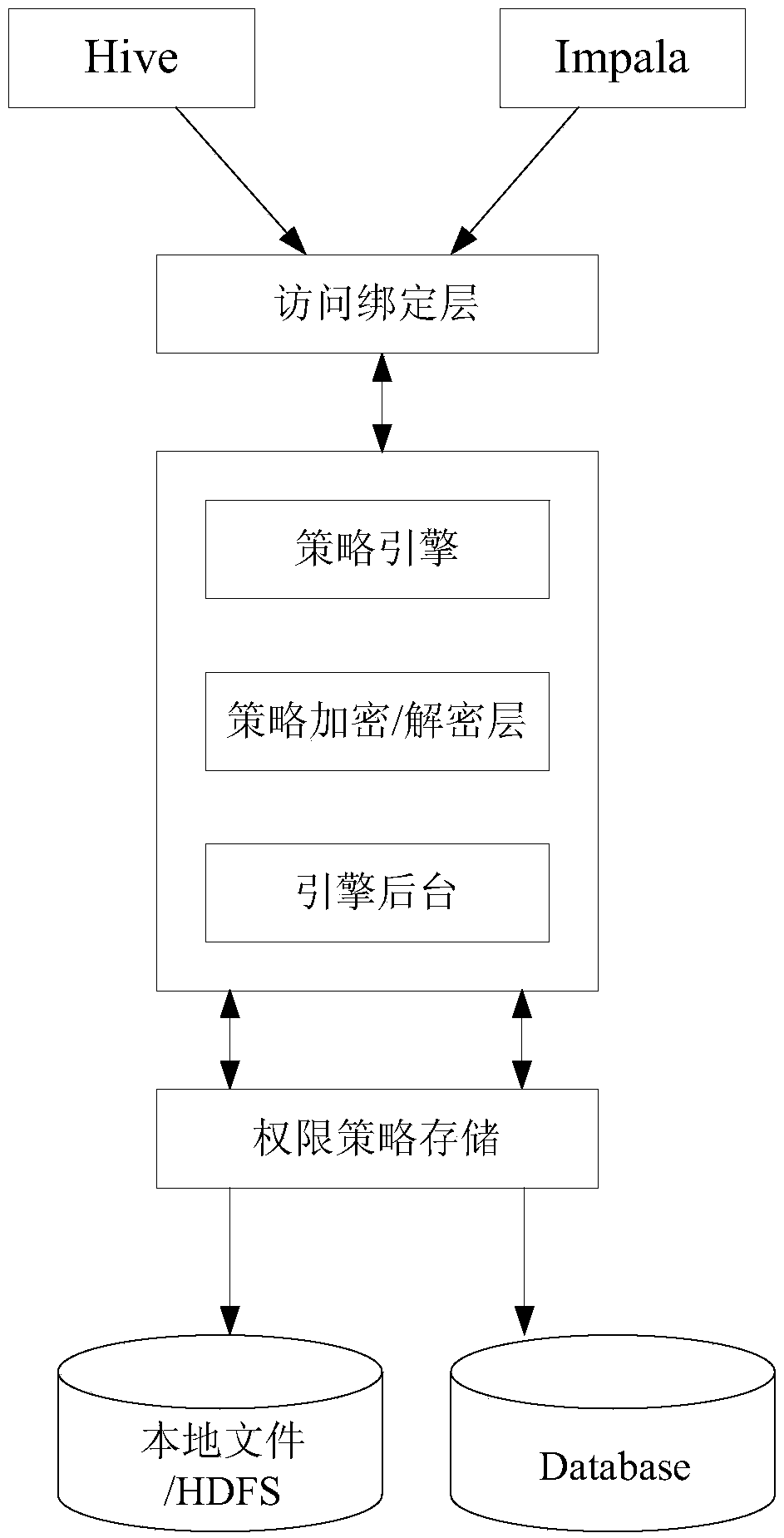
Cloud storage fine grit access control method and data uploading and data accessing method
ActiveCN108900483ATo achieve the purpose of fine-grained access controlGuaranteed safe storageTransmissionAttribute-based encryptionData access control
The invention provides a cloud storage fine grit access control method. The method is compatible to access control of a Hadoop assembly in a Plugin way and access control is performed through a central authorization server. Requests intercepted and sent to the central authorization server from the Plugins are accessed to a strategy engine by accessing a binding layer. Authority strategies are encrypted / decrypted through a strategy encryption / decryption layer, finally, through an engine background, storage and reading of the authority strategies are finished, and the storage form is authority encryption ciphers. The decrypted authority strategies are analyzed by the strategy engine, and authorities which can be identified by each Plugin are obtained through the analysis and returned to thecorresponding Plugins. Verification of the authorities is finished by the Plugins and whether user requests of this time are permitted is judged through the Plugins. According to the invention, by introducing autonomous access control, access control authorization of data by a data uploader is achieved; and by introducing a method based on attribute-based encryption, self-description of an accesscontrol structure is performed through attribute labels of data.
Owner:JIANGSU R & D CENTER FOR INTERNET OF THINGS
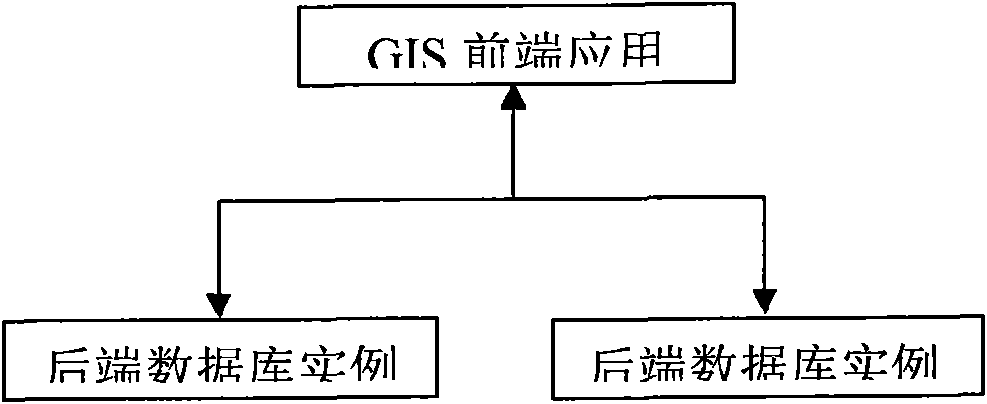
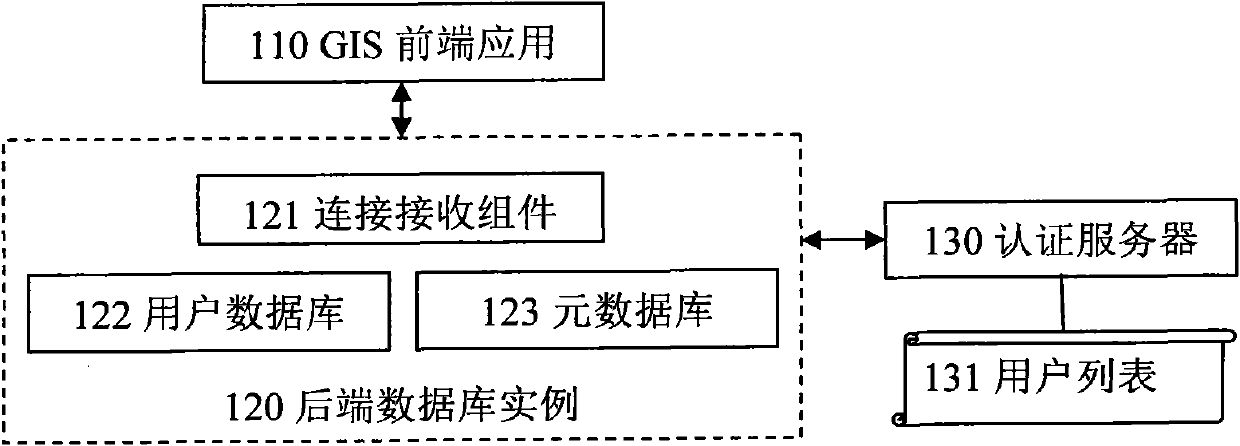
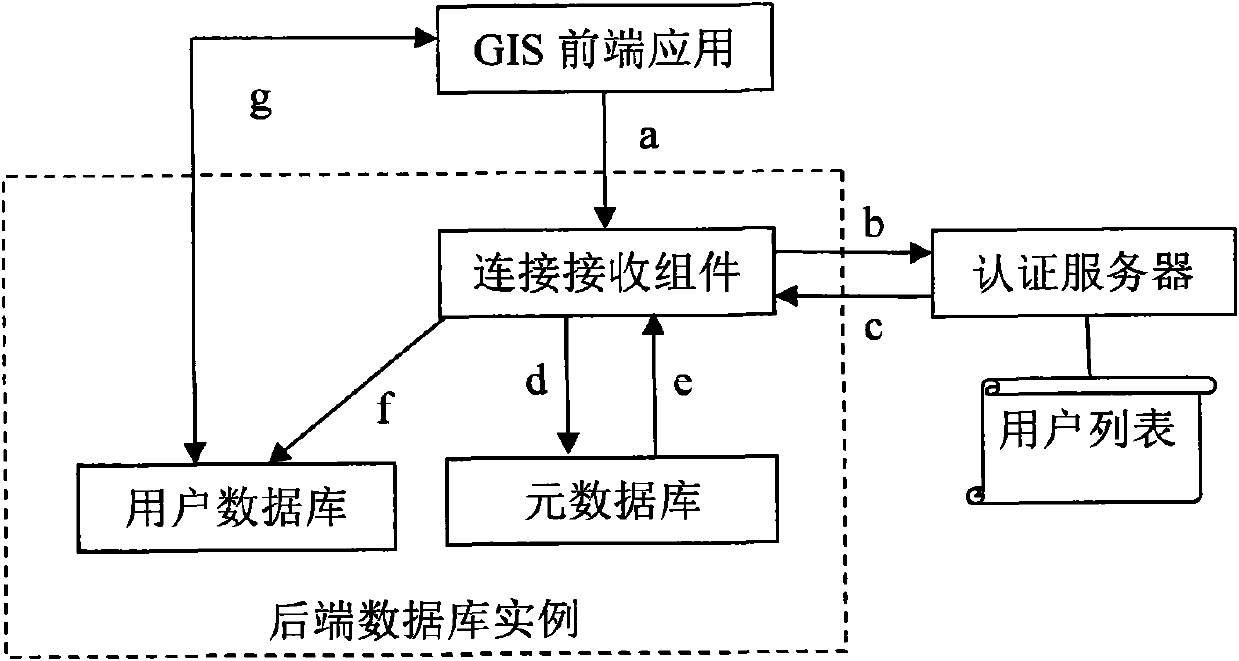
Multi-instance GIS platform unified user management method and system
InactiveCN102571380AImprove securityGuaranteed scalabilityData switching networksData synchronizationUser authentication
The invention discloses multi-instance GIS (Geographic Information System) platform unified user management system and method. By adopting the system and the method which are disclosed by the invention, technical personnel in the field can establish a unified user management view for a GIS including a plurality of rear-end database instances, and user one-to-one mapping between the application layer and the database rear end of the GIS is created to enable rich security functions (such as autonomous access control, enforced access control, security audit and the like) provided by the database rear end to be fully utilized and enhance the security of the GIS. Meanwhile, by adopting the system and the method, only one user identification and user authentication information duplicate is saved in an authentication server, so that synchronization problem of user data among the plurality of rear-end database instances is solved, and the expandability and the flexibility of the whole GIS are ensured.
Owner:北京博阳世通信息技术有限公司
Bi-directional access control system
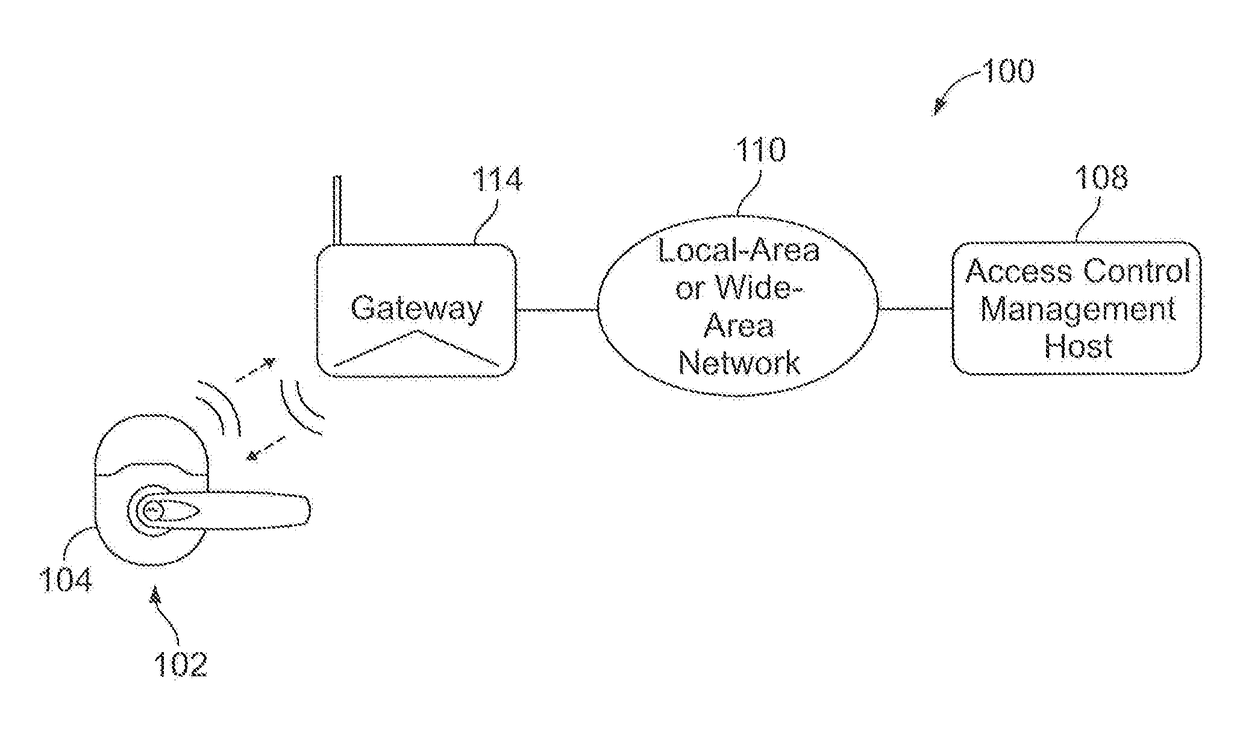
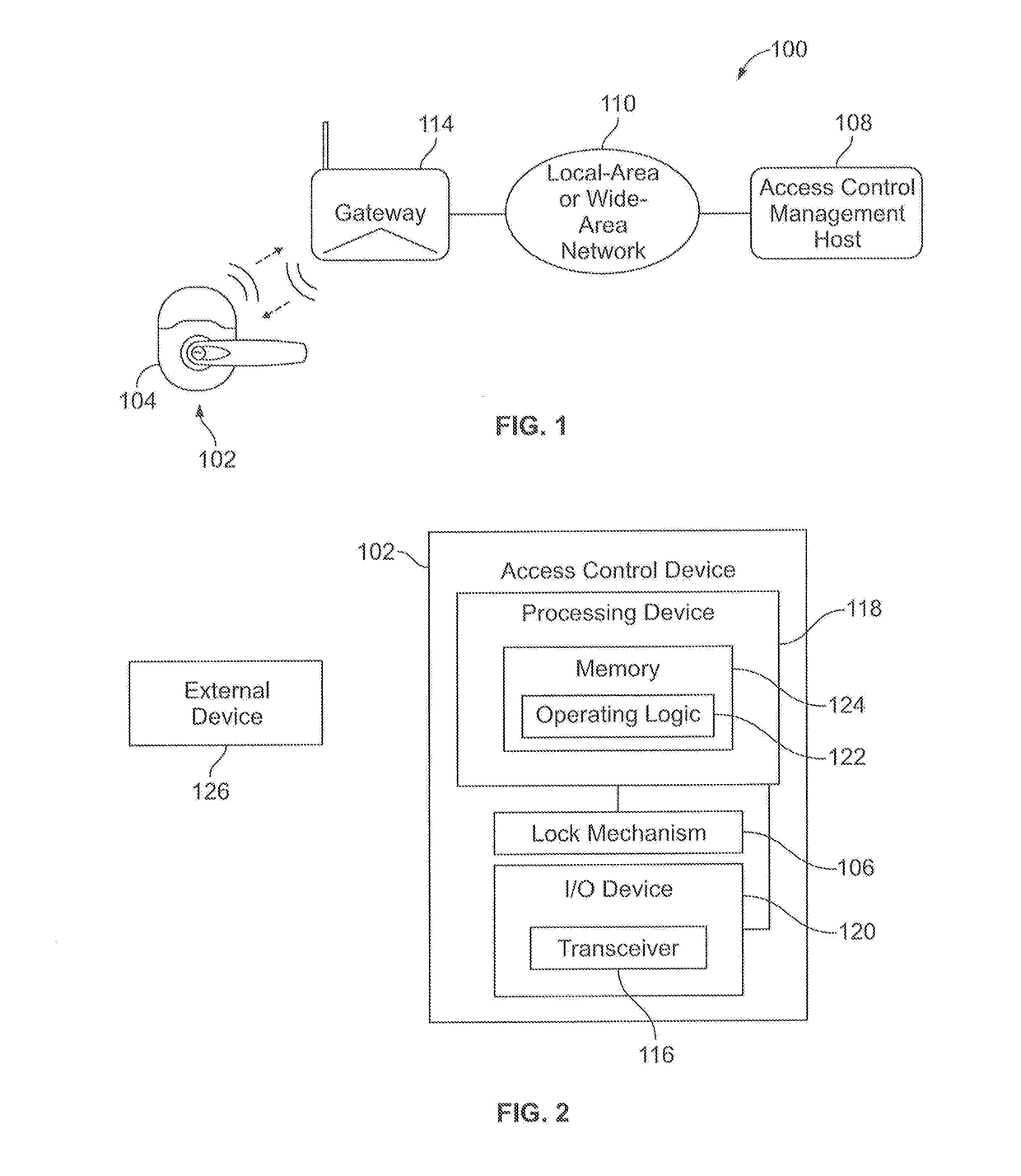
ActiveUS20170301165A1Individual entry/exit registersNetwork connectionsTime informationLatency (engineering)
Systems and apparatuses for real time, bi-directional communications between an access control management host and one or more access control devices. The access control devices can be structured to make certain decisions at the access control device and communicate, in real time, information to, as well as receive in real time information from, the access control management host via a networked gateway. The access control device and networked gateway can communicate via a first wireless protocol that at least assists in minimizing the energy of an electrical energy source, such as, for example, a battery, that is coupled to the access control device. Examples of the first wireless protocol can include low latency, low-power wireless technologies or protocols. The networked gateway can communicate with the access control management host using a second protocol via a wired or wireless connection.
Owner:SCHLAGE LOCK
System and methods for caching in connection with authorization in a computer system
InactiveUS7096367B2Easy to operateMore efficientData processing applicationsDigital data processing detailsComputer resourcesComputerized system
An authorization handle is supported for each access policy determination that is likely to be repeated. In particular, an authorization handle may be assigned to access check results associated with the same discretionary access control list and the same client context. This likelihood may be determined based upon pre-set criteria for the application or service, based on usage history and the like. Once an access policy determination is assigned an authorization handle, the static maximum allowed access is cached for that policy determination. From access check to access check, the set of permissions desired by the client may change, and dynamic factors that might affect the overall privilege grant may also change; however, generally there is still a set of policies that is unaffected by the changes and common across access requests. The cached static maximum allowed access data is thus used to provide efficient operations for the evaluation of common policy sets. In systems having access policy evaluations that are repeated, authorization policy evaluations are more efficient, computer resources are free for other tasks, and performance improvements are observed.
Owner:MICROSOFT TECH LICENSING LLC
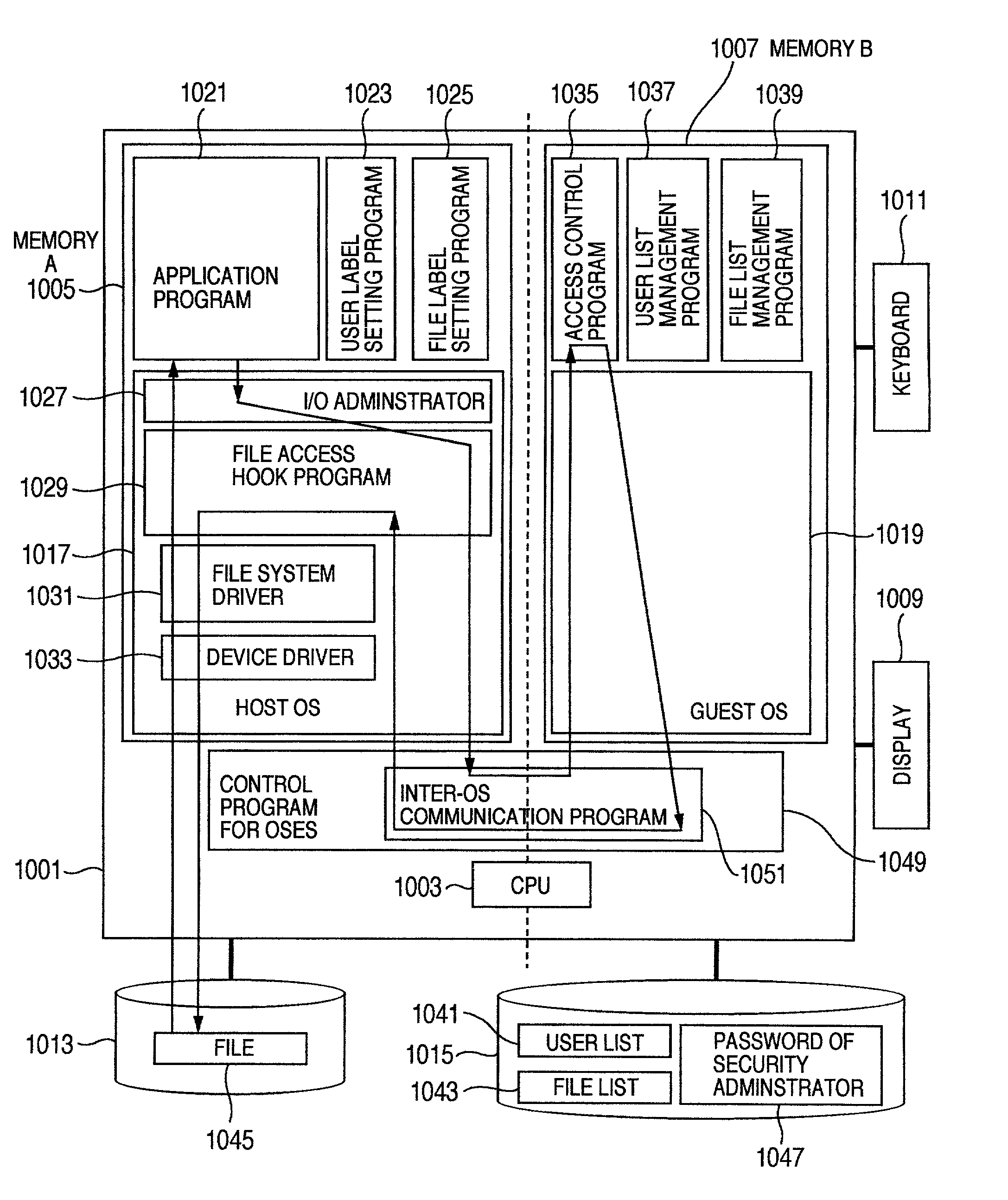
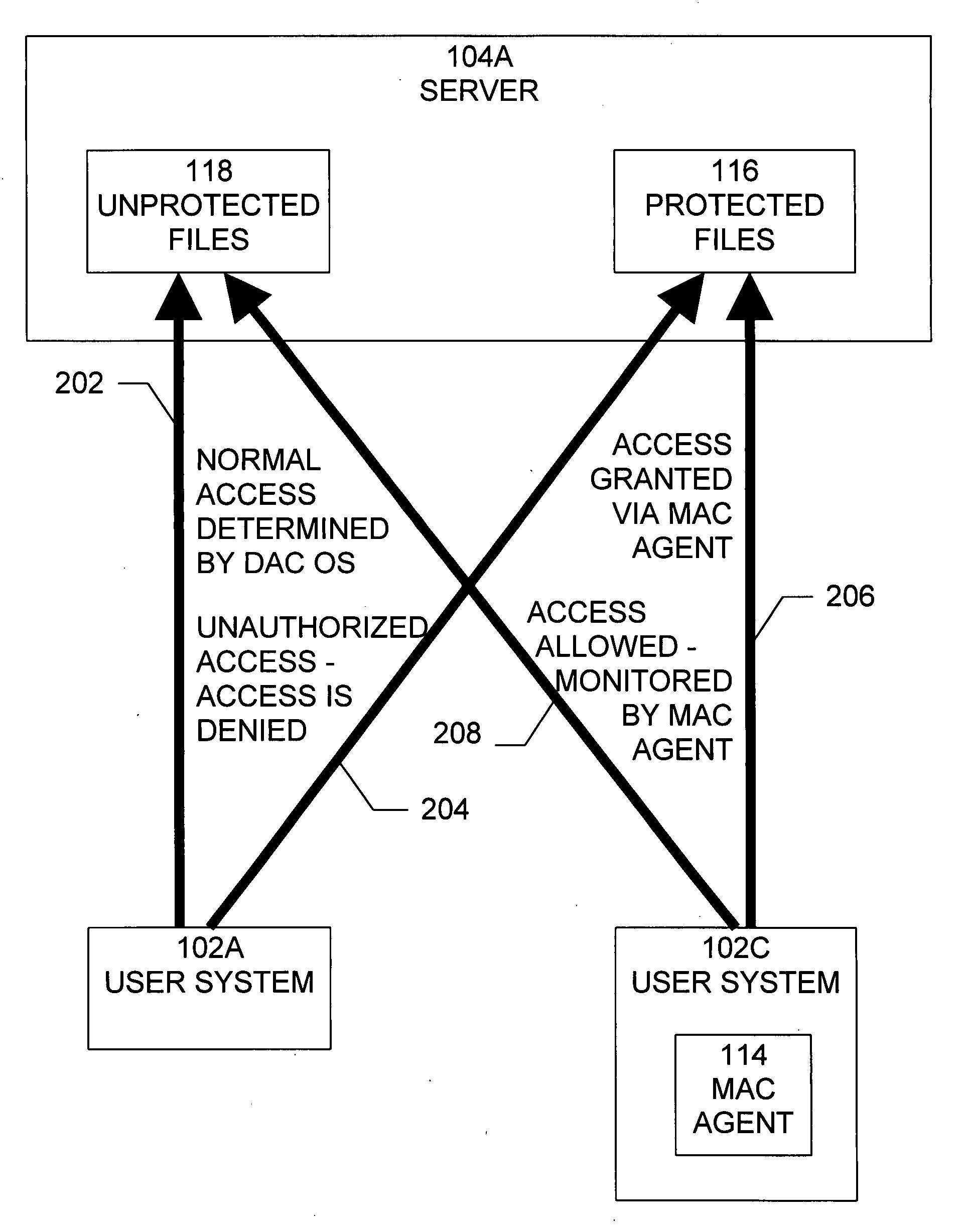
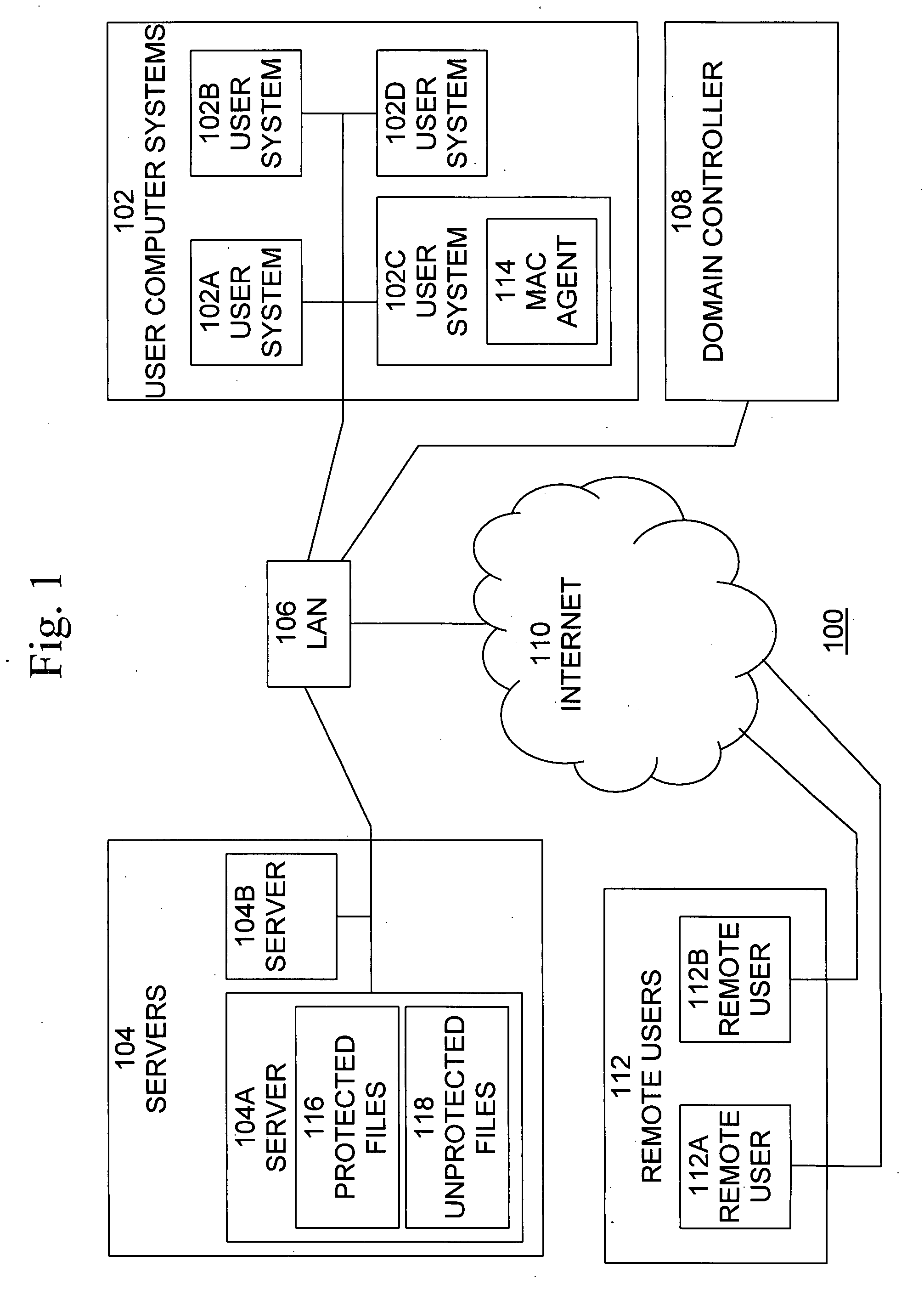
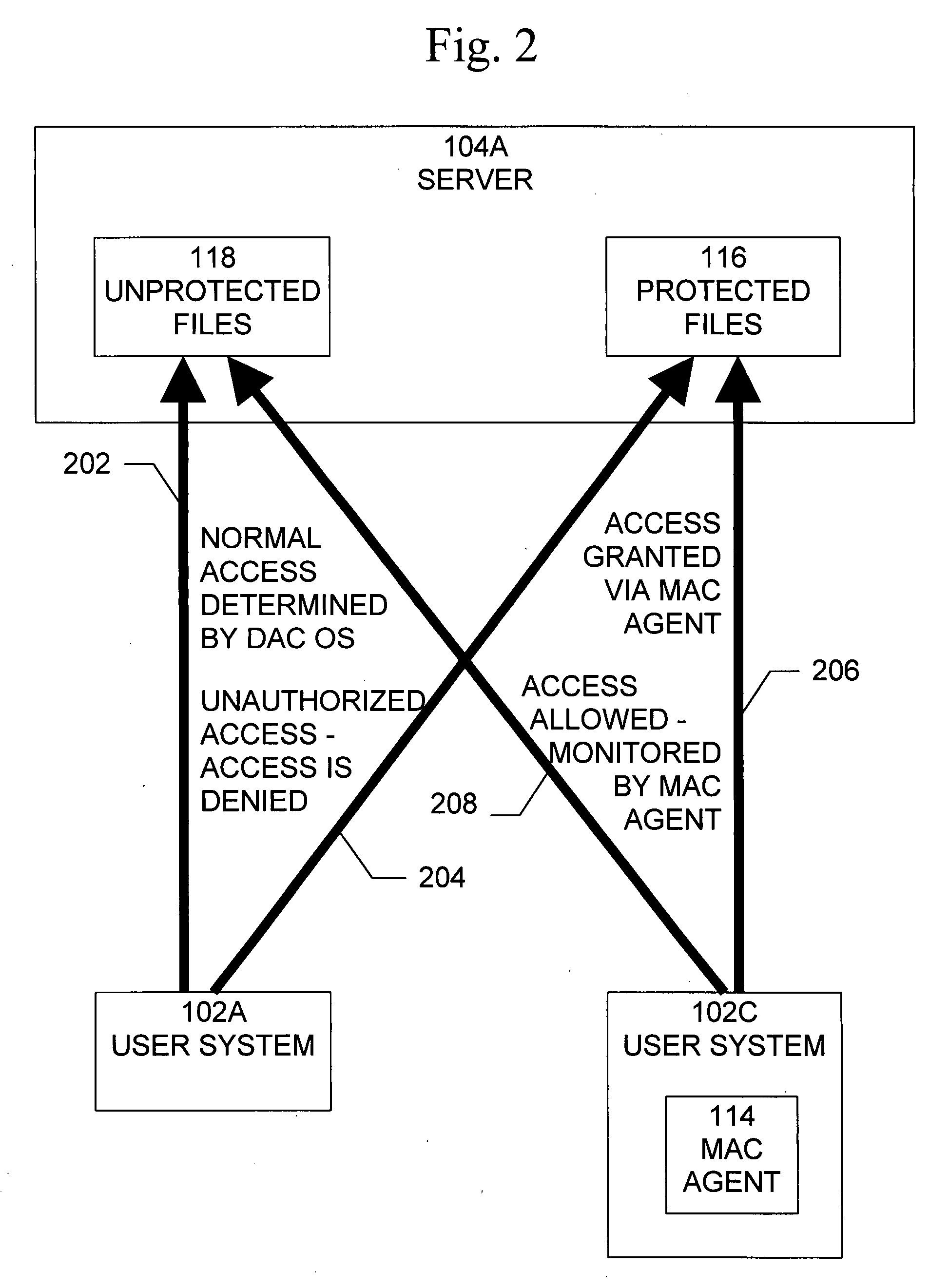
Method and system for implementing mandatory file access control in native discretionary access control environments
ActiveUS20080120695A1Security breachMaintain integrityDigital data processing detailsUser identity/authority verificationOperational systemSoftware agent
A method is provided for implementing a mandatory access control model in operating systems which natively use a discretionary access control scheme. A method for implementing mandatory access control in a system comprising a plurality of computers, the system comprising a plurality of information assets, stored as files on the plurality of computers, and a network communicatively connecting the plurality of computers, wherein each of the plurality of computers includes an operating system that uses a discretionary access control policy, and wherein each of a subset of the plurality of computers includes a software agent component operable to perform the steps of intercepting a request for a file operation on a file from a user of one of the plurality of computers including the software agent, determining whether the file is protected, if the file is protected, altering ownership of the file from the user to another owner, and providing access to the file based on a mandatory access control policy.
Owner:MUSARUBRA US LLC
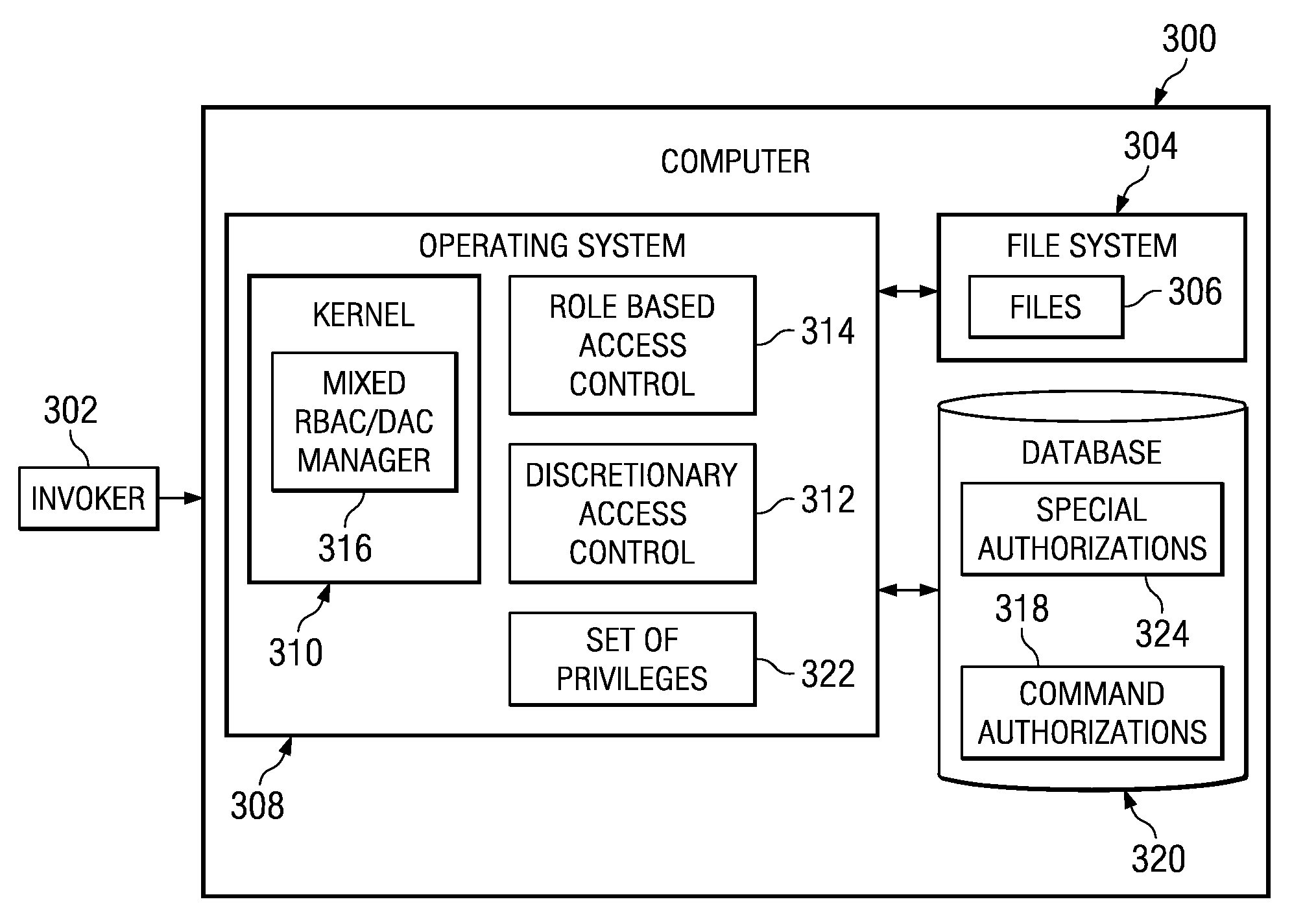
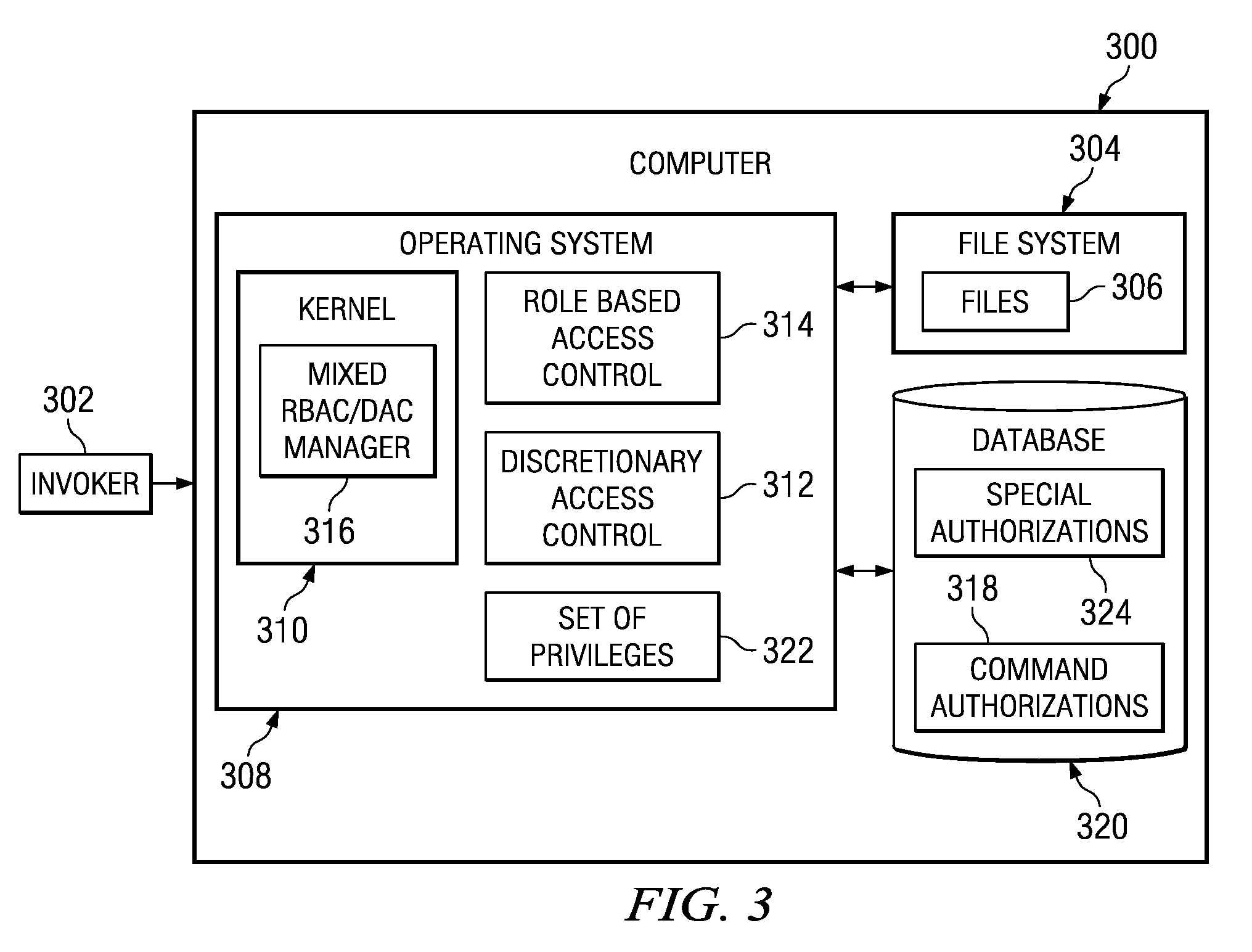
Determination of access checks in a mixed role based access control and discretionary access control environment
InactiveUS20080271139A1Digital data processing detailsUser identity/authority verificationDiscretionary access controlAuthorization
Owner:IBM CORP
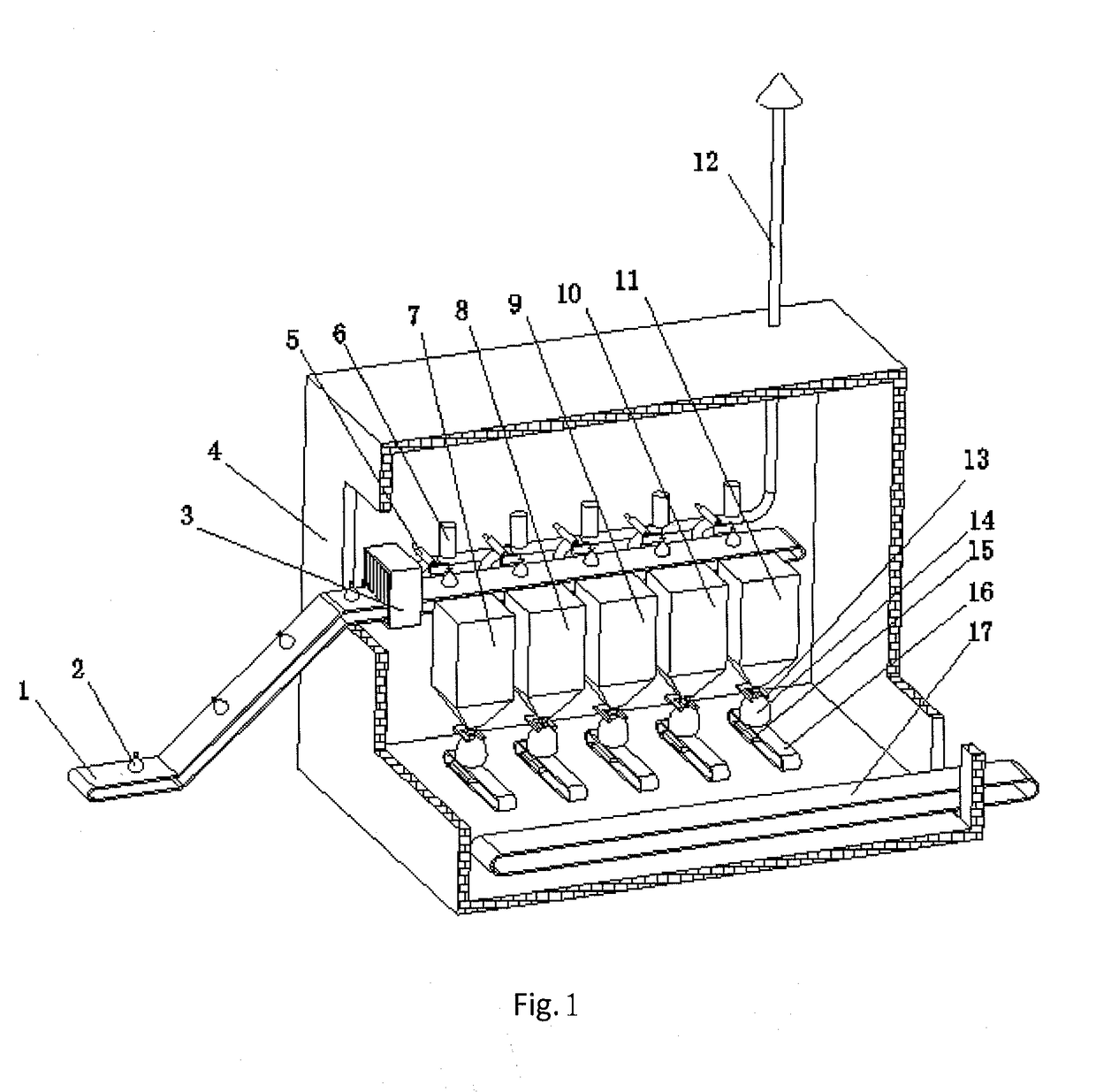
Environmentally-friendly medical waste treatment apparatus and method specific to medical institutions
ActiveUS20180311711A1Inhibit productionTransportation and packagingSolid waste disposalControl systemMedical waste
A medical waste treatment device for health-care facility includes a frame, a waste disposal device and a control system; wherein the waste disposal device comprises three or more waste disposal boxes which are arranged in a row; a feeding conveyor belt is disposed at one side of the waste disposal boxes and the feeding conveyor belt extends to positions above each of the waste disposal boxes; the feeding conveyor belt is driven by a motor; each of the waste disposal boxes is provided with a waste label identification component, a pushing component which is configured to push waste container into the waste disposal box, and a sealing component; a feeding access is opened on the top of each of the waste disposal boxes and a discharge access is opened on the bottom of each of the waste disposal boxes; a feeding access control system is provided at each of the feeding access and a discharge access control system is provided at each of the discharge access; a branch conveyor belt is disposed below the discharge access of the waste disposal boxes and a major conveyor belt is disposed adjacent to the branch conveyor belts; the control terminal of the motor, the waste label identification component, the pushing component, the sealing component, the feeding access control system and the discharge access control system are coupled with the central controller of the control system. The medical waste treatment device for health-care facility could avoid the collateral contamination caused by incineration, and further avoid the production of Dioxin. The medical waste treatment device could automatically identify and classify waste containers, and treat medical waste according to its category and then package and seal it.
Owner:QINGDAO BRIGHT MEDICAL MFG
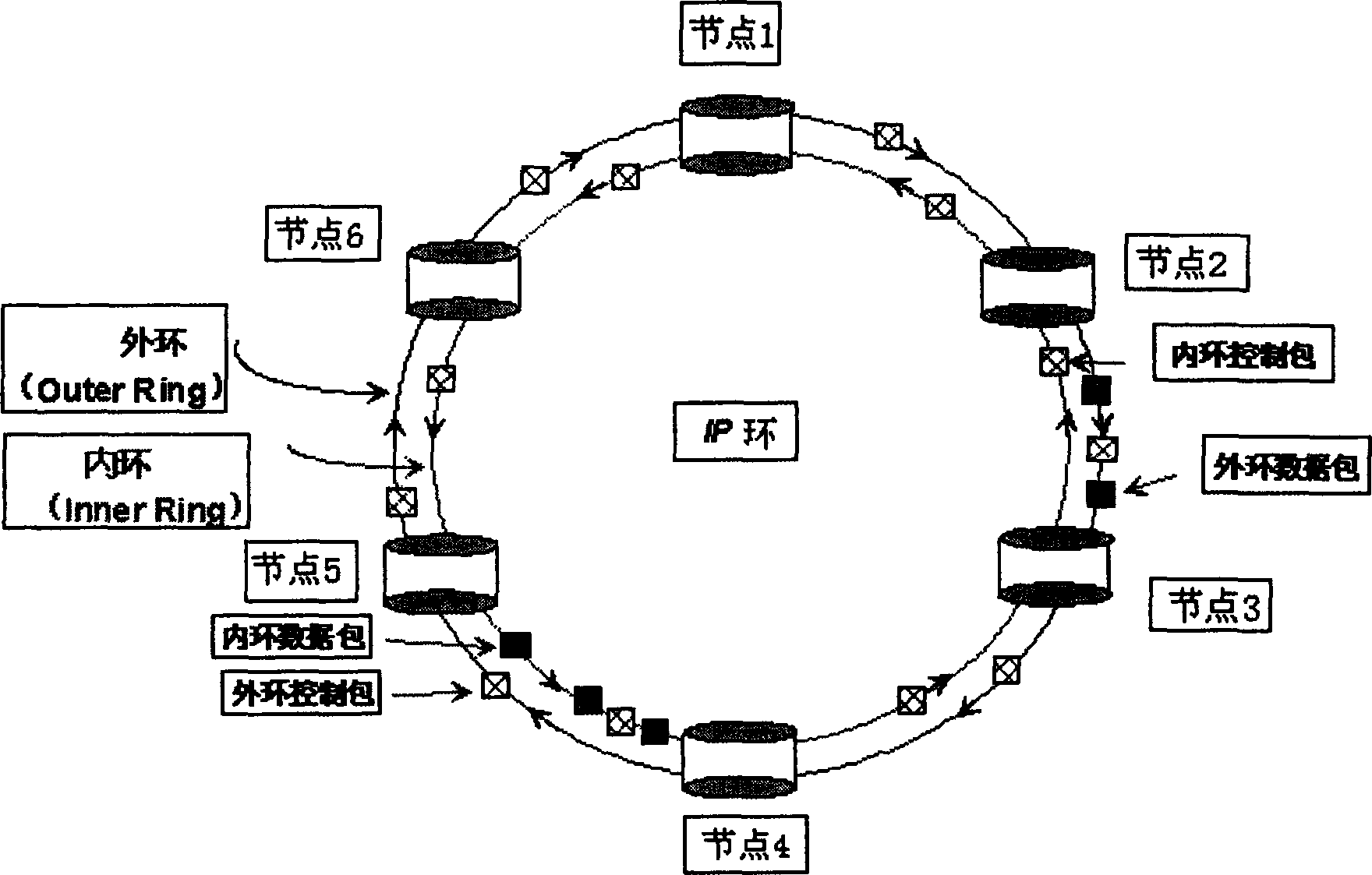
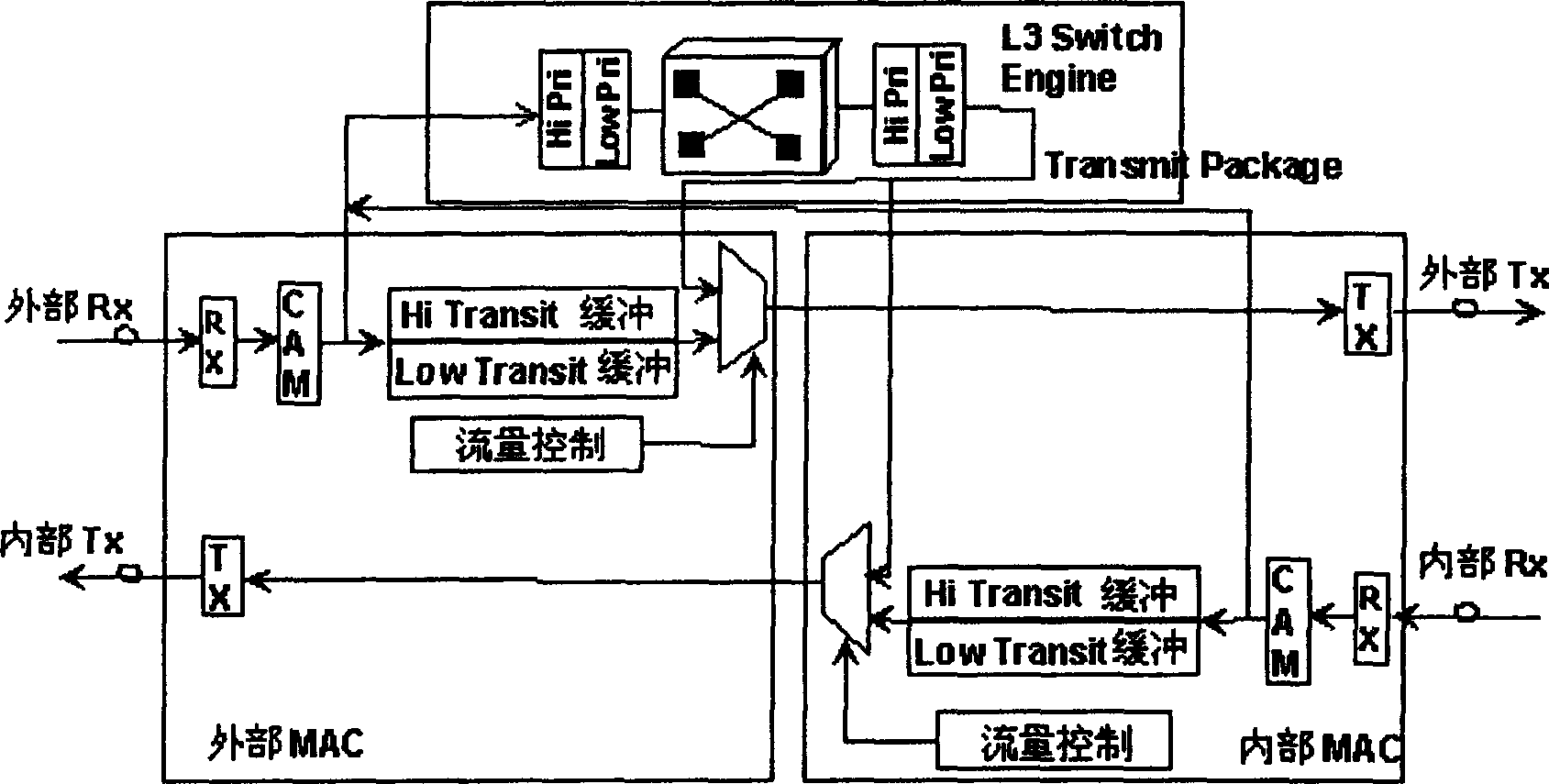
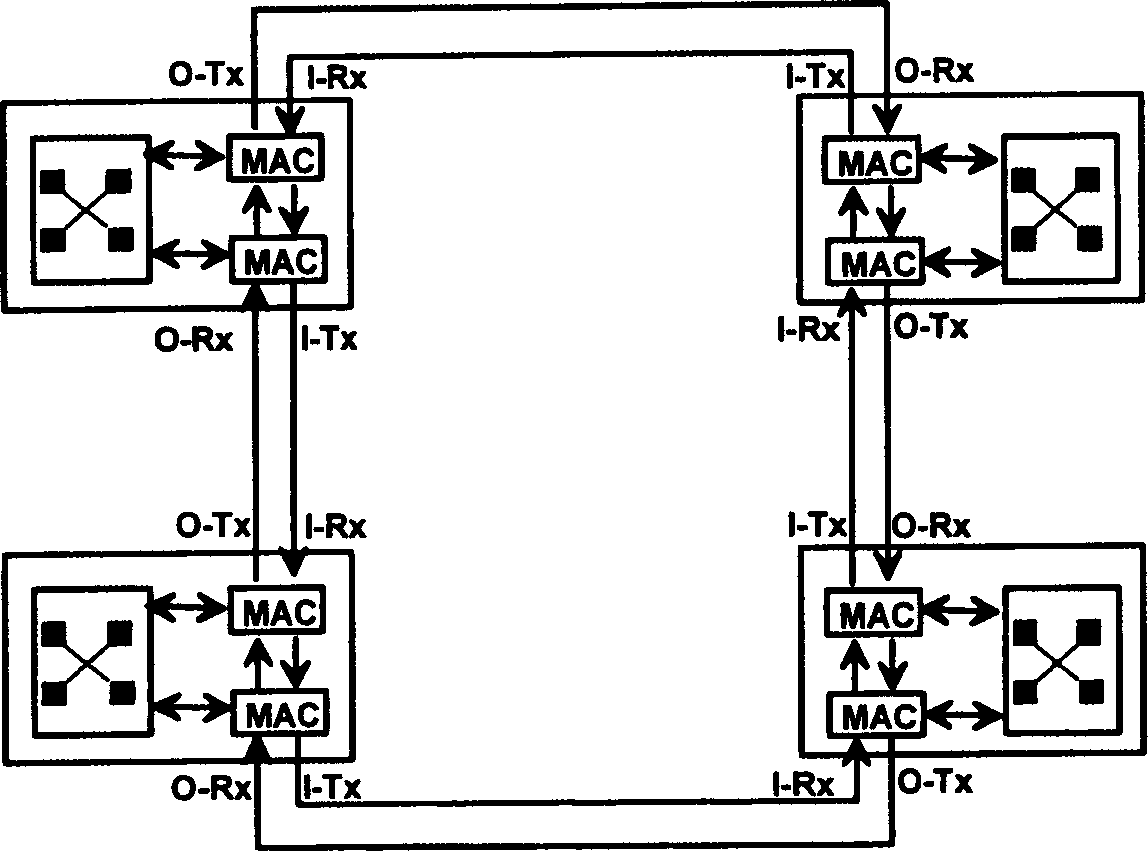
IP loop distribution type and width processing method
InactiveCN1466391AHigh bandwidthImprove self-healing abilityStore-and-forward switching systemsLoop networksTraffic capacityElectricity
An IP distributed bandwidth process method relating to electric communication technology is to carry out a certain access control to every nexus on the IP ring applying dual-ring topological structure, a flow control packet controls data transfer according to congestion nexus information on IP ring and its situated relative position to finish the flow control on each nexus by fair algorithm with weight to transfer flow information mutually, solving the problem of line head blocking
Owner:SHENZHEN HUAWEI TECHNOLOGIES SOFTWARE CO LTD
Database security reinforcing method and device
InactiveCN105512569AImprove securityAchieve accessDigital data protectionDatabase securityDatabase administrator
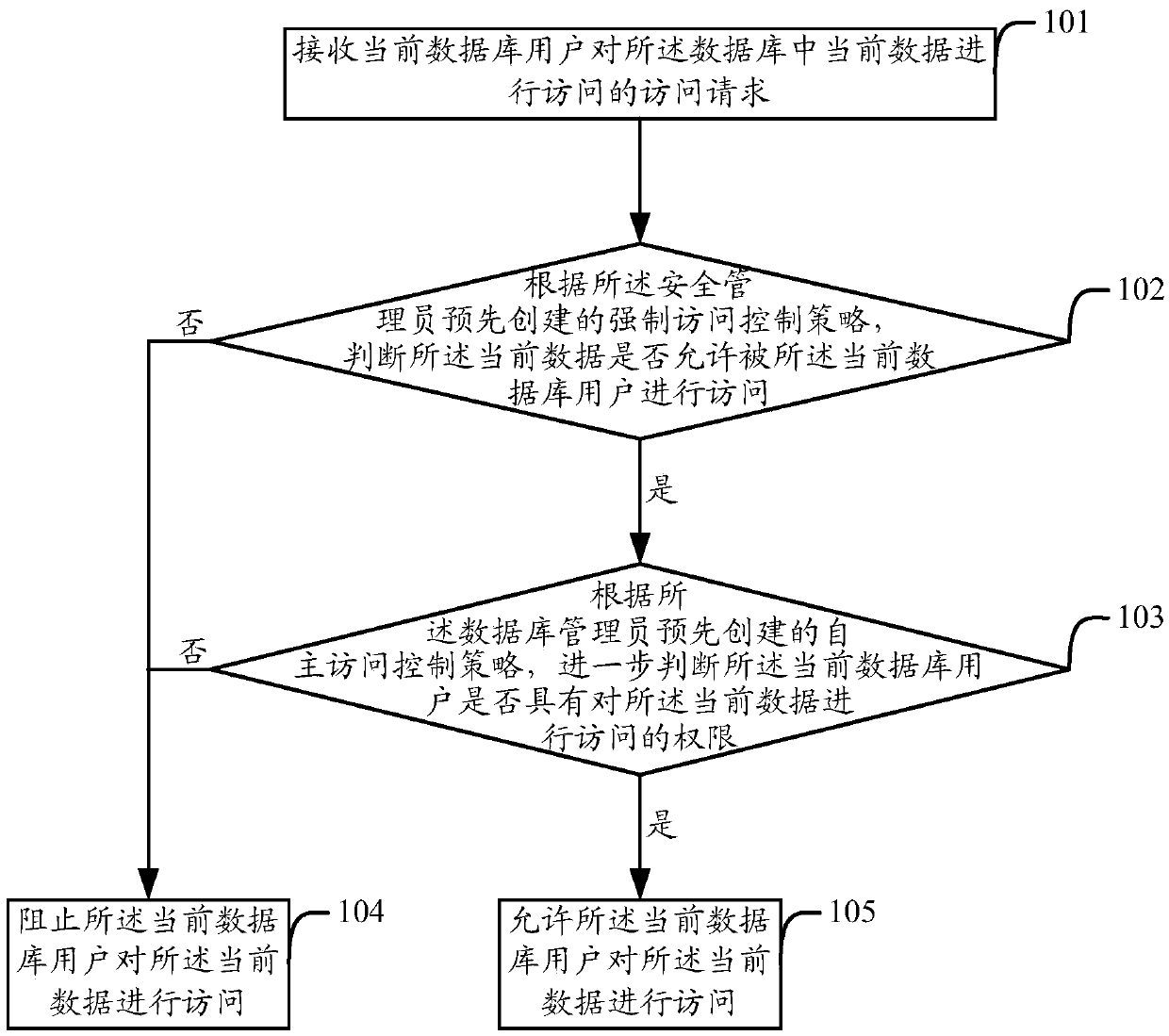
The invention provides a database security reinforcing method and device. The method and device are applied to a database of a pre-assigned database administrator and a pre-assigned security administrator. The method comprises the steps that an access request of a current database user for accessing current data from the database is received, and whether the current data is allowed to be accessed by the current database user or not is judged according to a mandatory access control strategy pre-established by the security administrator; if not, the current database user is prevented from accessing the current data, and if yes, whether the current database has the authority for accessing the current data or not is further judged according to a discretionary access control strategy pre-established by the database administrator; according to the further judgment result, if yes, the current database user is allowed to accessing the current data, and if not, the current database user is prevented from accessing the current data. According to the scheme, the database security can be improved.
Owner:LANGCHAO ELECTRONIC INFORMATION IND CO LTD
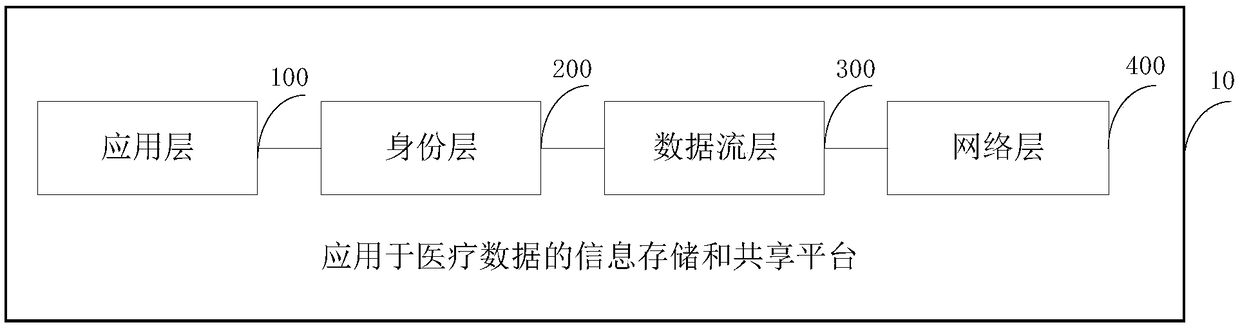
Information storage and sharing platform for medical data
ActiveCN109409100AMeet data source sensitivityEfficient storageDigital data protectionDigital data authenticationData streamConfidentiality
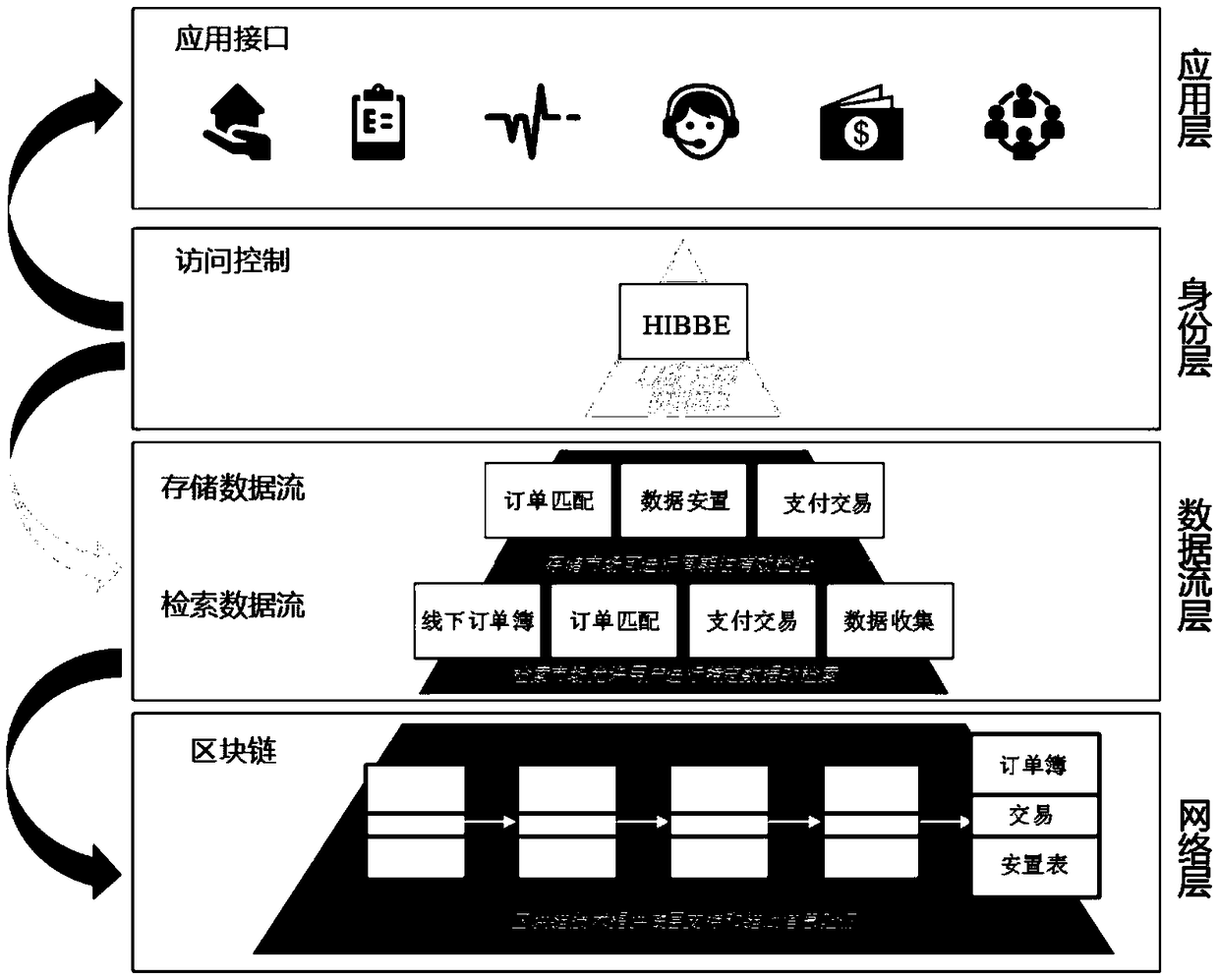
The invention discloses an information storage and sharing platform applied to medical data, which comprises an application layer, an identity layer, a data flow layer and a network layer. The application layer includes graphical interface and application layer interface, which provide information service to users in the form of application. The identity layer is used to achieve secure identity authentication and user management through HIBBE encryption scheme and discretionary access control. The data stream layer is used to control the flow of all user information data in the storage marketand the retrieval market. The network layer is used to store and share all data on the distributed cloud by recording and tracking all data storage and retrieval transactions on the decentralized block chain network. The device can not only solve the problem of isolated island of current medical data, but also effectively protect the security of sensitive data, ensure the integrity, recyclability,confidentiality and public verifiability of the data, so as to realize the safe and efficient storage and sharing of medical data.
Owner:BEIHANG UNIV
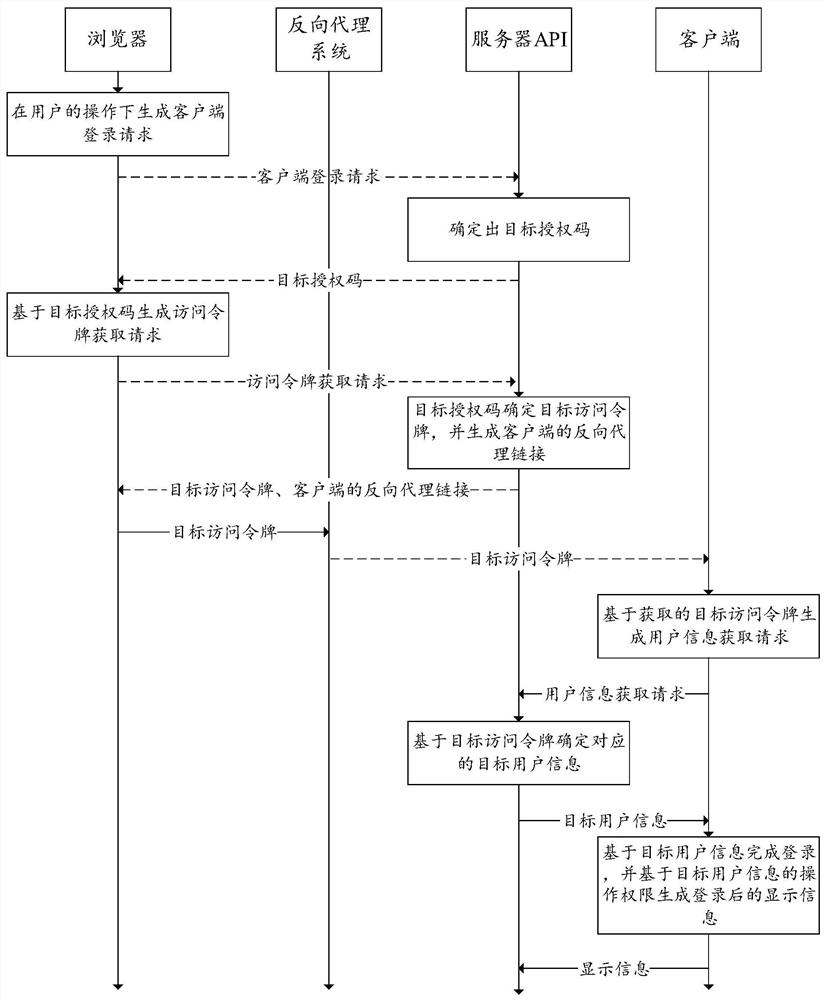
Single sign-on method, system and device and computer readable storage medium
PendingCN111832000AImplement Discretionary Access ControlImprove applicabilityDigital data authenticationIp addressEngineering
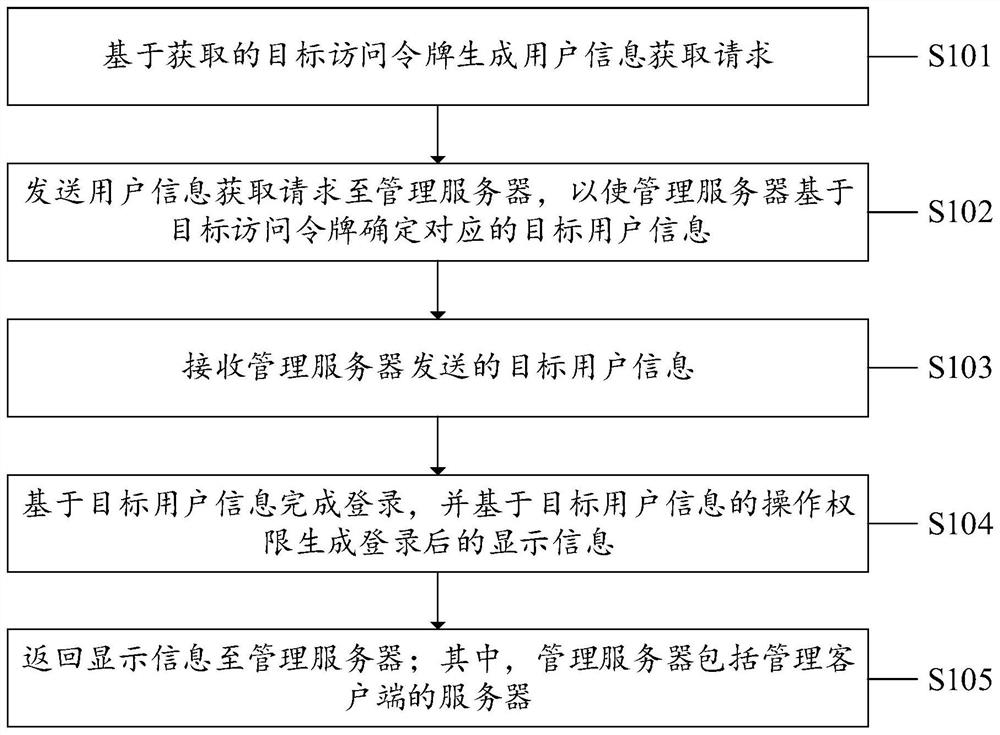
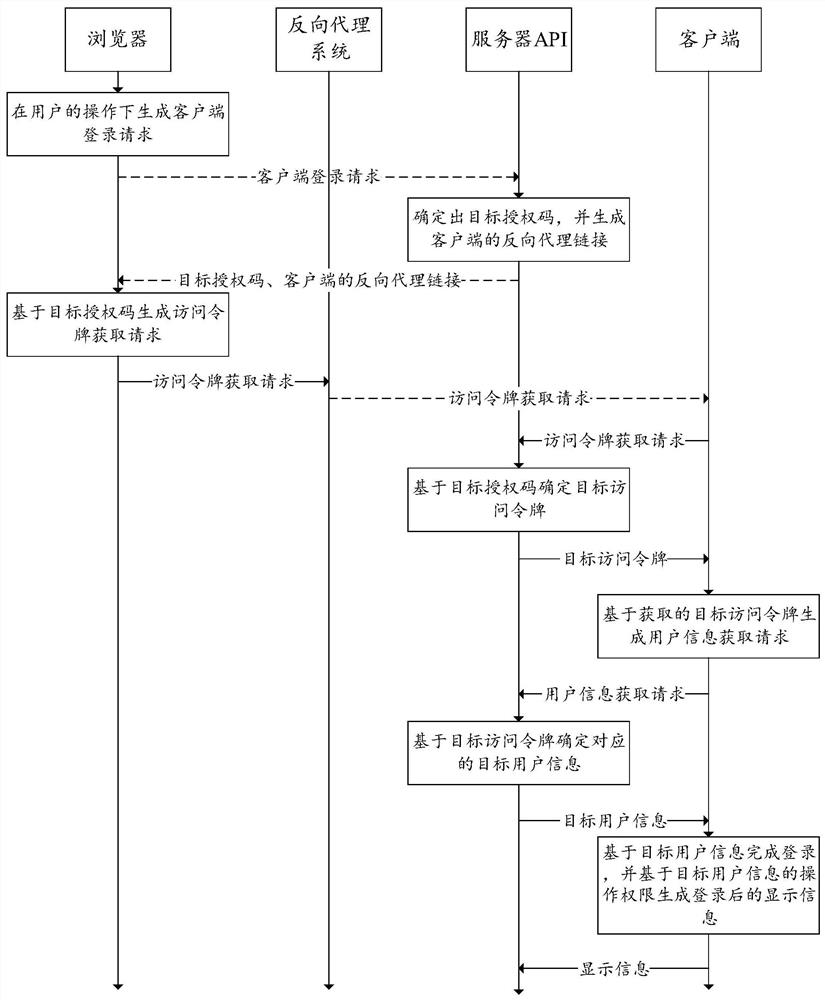
The invention discloses a single sign-on method, system and device and a computer readable storage medium; the method is applied to a client and includes generating a user information acquisition request based on a target access token; sending a user information acquisition request to a management server; receiving target user information sent by the management server; completing login based on the target user information, and generating display information after login based on the operation authority of the target user information; and returning the display information to the management server. In the present application, the client acquires corresponding target user information from the management server based on the target access token, completes login based on the target user information and generates display information after login based on the operation authority of the target user information, so the display information is enabled to correspond to the operation authority of thetarget user information; autonomous access control is also realized while single sign-on is realized, the login process is not influenced by the IP address of the management server, and the applicability is high.
Owner:SANGFOR TECH INC
Conditional access control
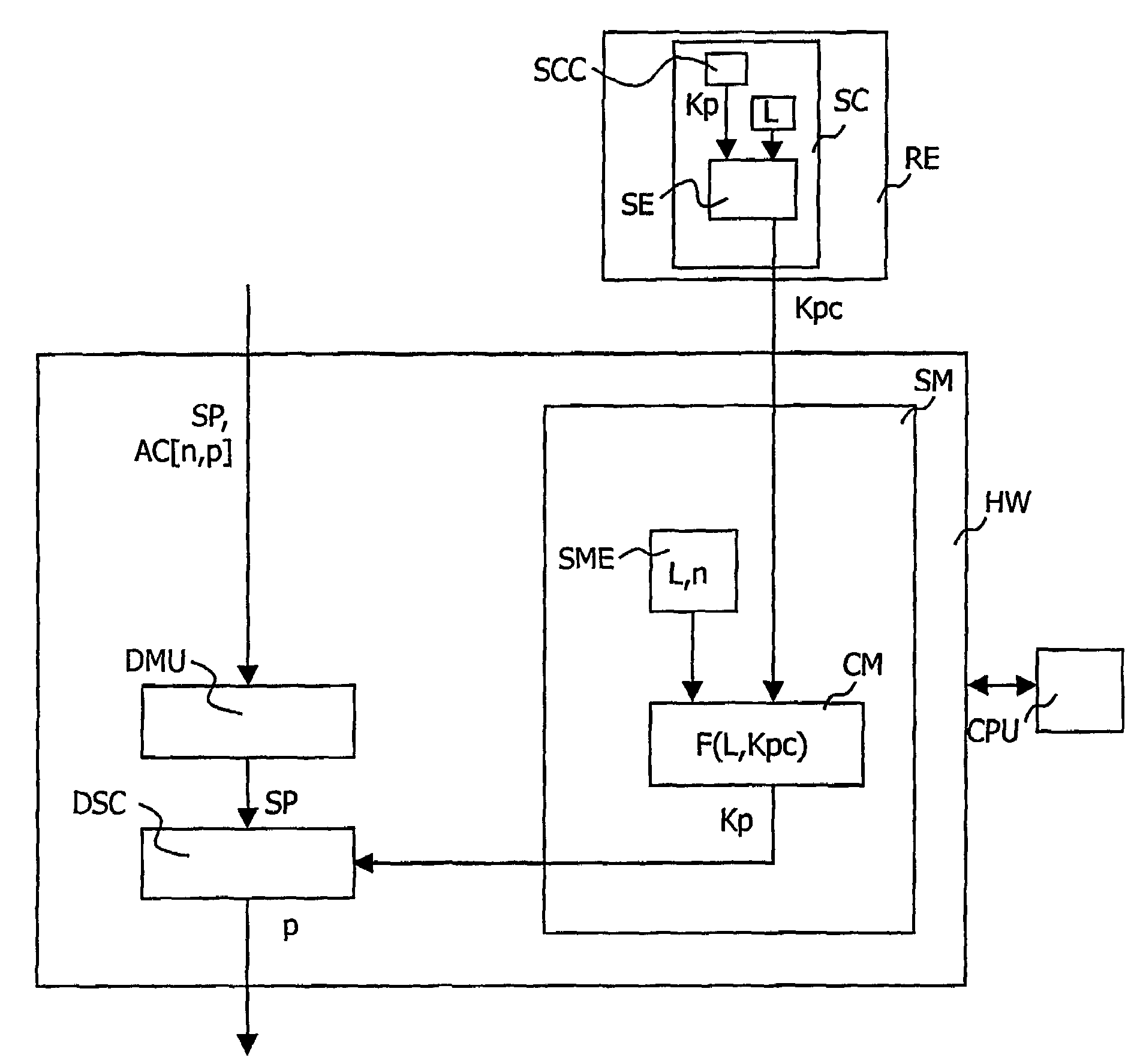
InactiveUS7552343B2Ensure safetyLow costKey distribution for secure communicationUnauthorized memory use protectionData processing systemConditional access
The invention relates to a secure data processing system including an unscrambling module [DSC] disposed on a dedicated hardware part [HW] of an integrated circuit and intended to unscramble a stream of data [SP] scrambled according to a scrambling key, a module [CM] for calculating an unscrambling key [Kp] disposed on said dedicated hardware part [HW] and intended to manipulate data under the control of a so-called calculation program stored on said dedicated hardware part [HW], a processor [CPU] for in particular controlling the functioning of the unscrambling [DSC] and calculation [CM] modules. Said system also includes a read only memory [SME] disposed on said dedicated hardware part [HW] for storing a secret key [Kp]. Said calculation program includes instructions for prompting said calculation module [CM] to use said secret key [L] and at least one data item [AC[n,p] or Kpc)] coming from outside the secure data processing system, in order to calculate an unscrambling key [Kp]. The unscrambling is enabled only if the unscrambling key [Kp] corresponds to the scrambling key.
Owner:ENTROPIC COMM INC
Method for limiting authority of cloud computing privileged user by using mandatory access control
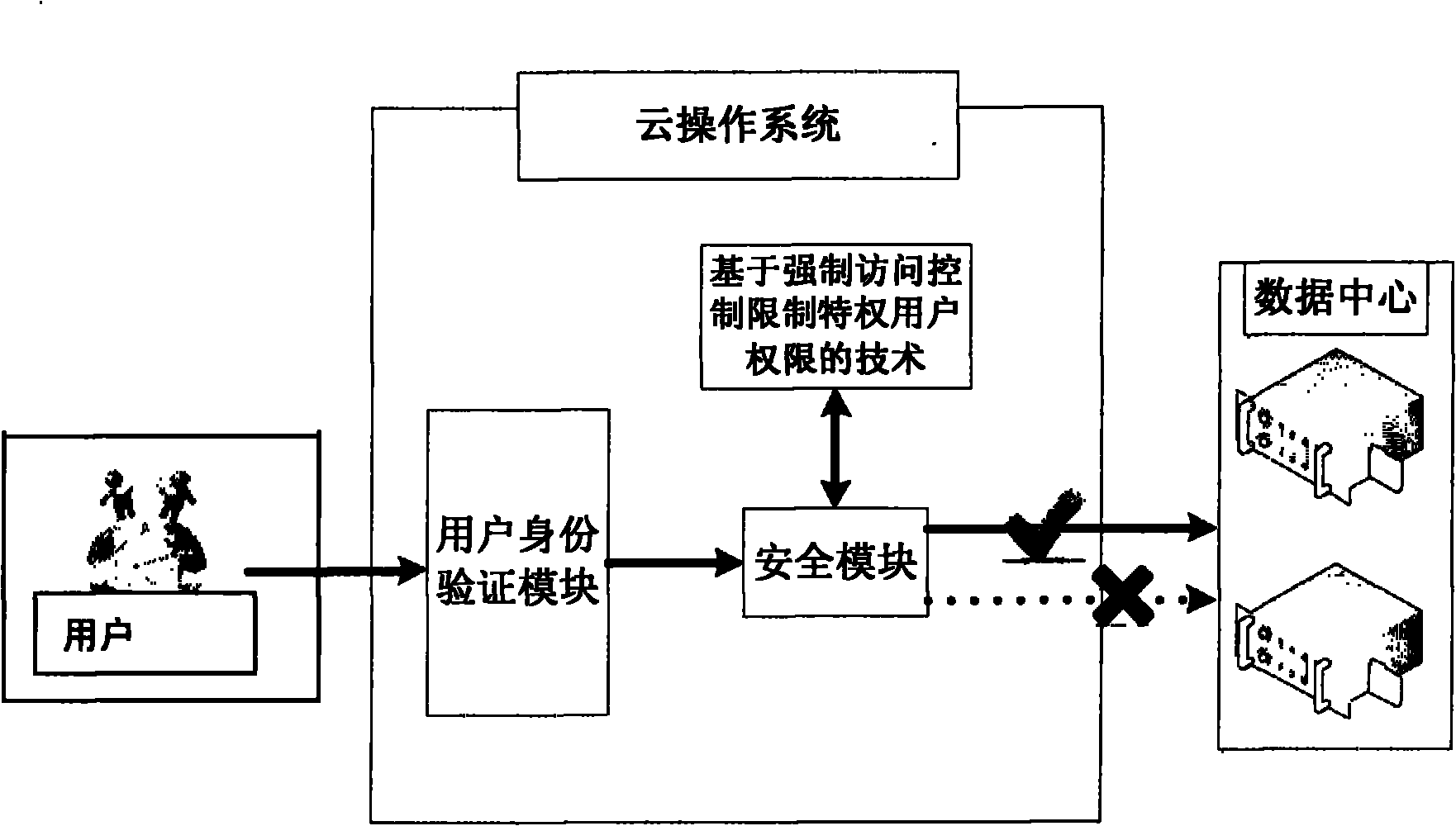
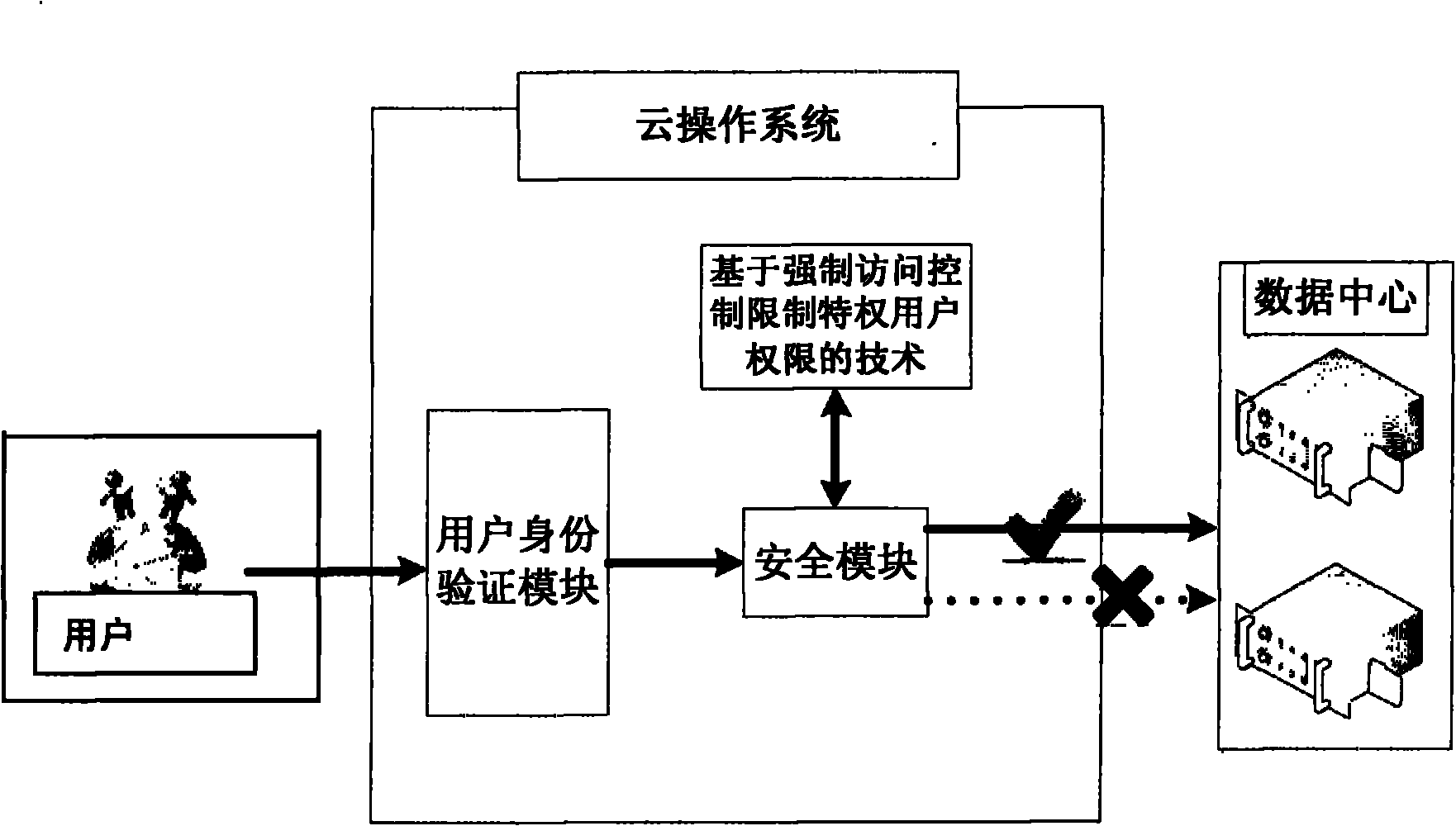
InactiveCN102156839ASolve the problem of mistrustDigital data authenticationTransmissionUser PrivilegeData access control
The invention provides a method for limiting authority of a cloud computing privileged user by using mandatory access control. In the method, whether the privileged user has the authority for operating resources of a cloud computing data center is checked by the mandatory access control, and the user access control authority is set by using the mandatory access control. Compared with the traditional discretionary access control, fine grit access control of the resources of the cloud computing data center can be realized, and job responsibility irrelevant operation of the privileged user is prevented.
Owner:LANGCHAO ELECTRONIC INFORMATION IND CO LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com