Method for limiting authority of cloud computing privileged user by using mandatory access control
A technology for mandatory access control and privileged users, applied in computing, computer security devices, instruments, etc., to solve the problems of urgency, user loss, abuse, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
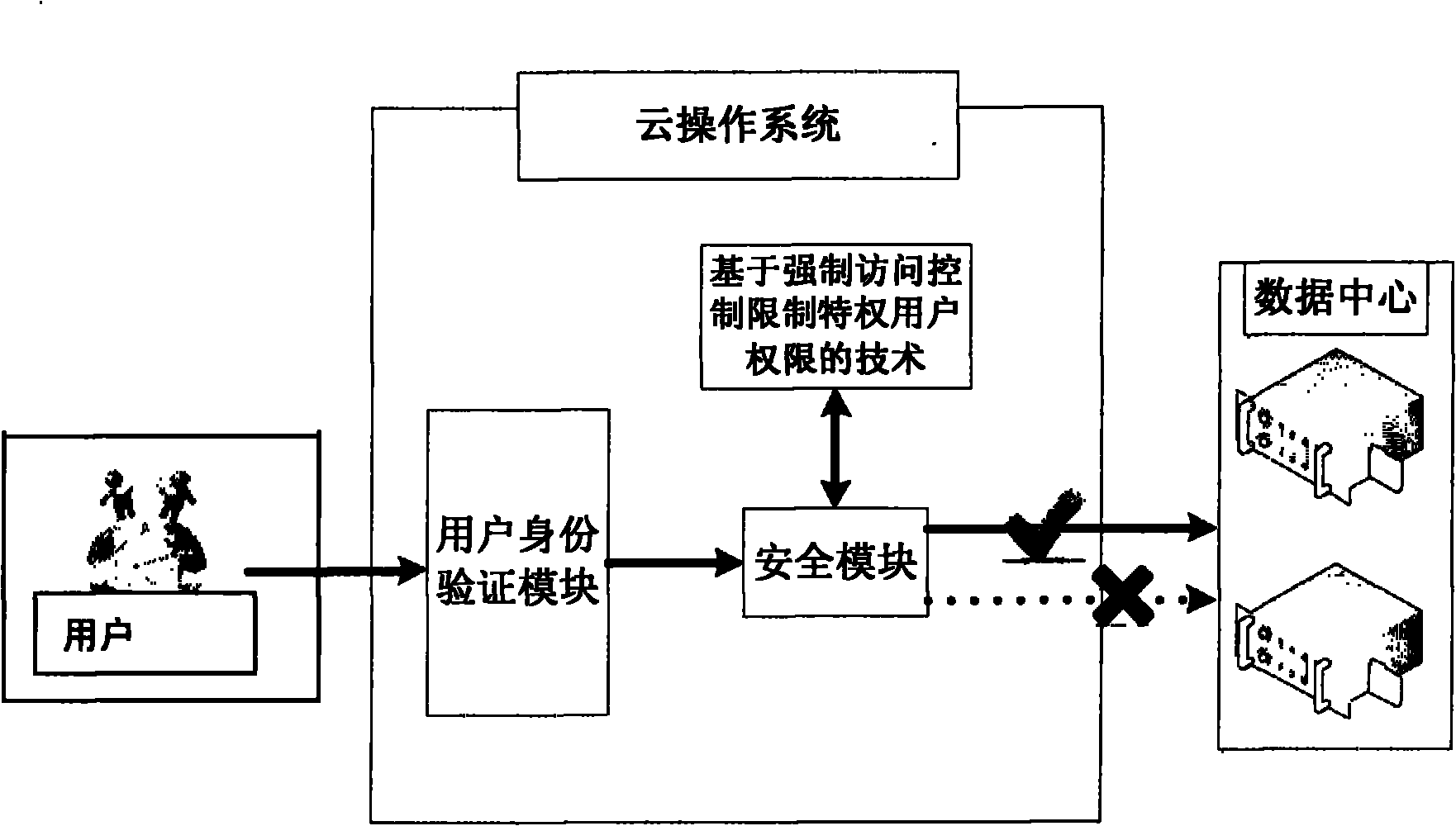
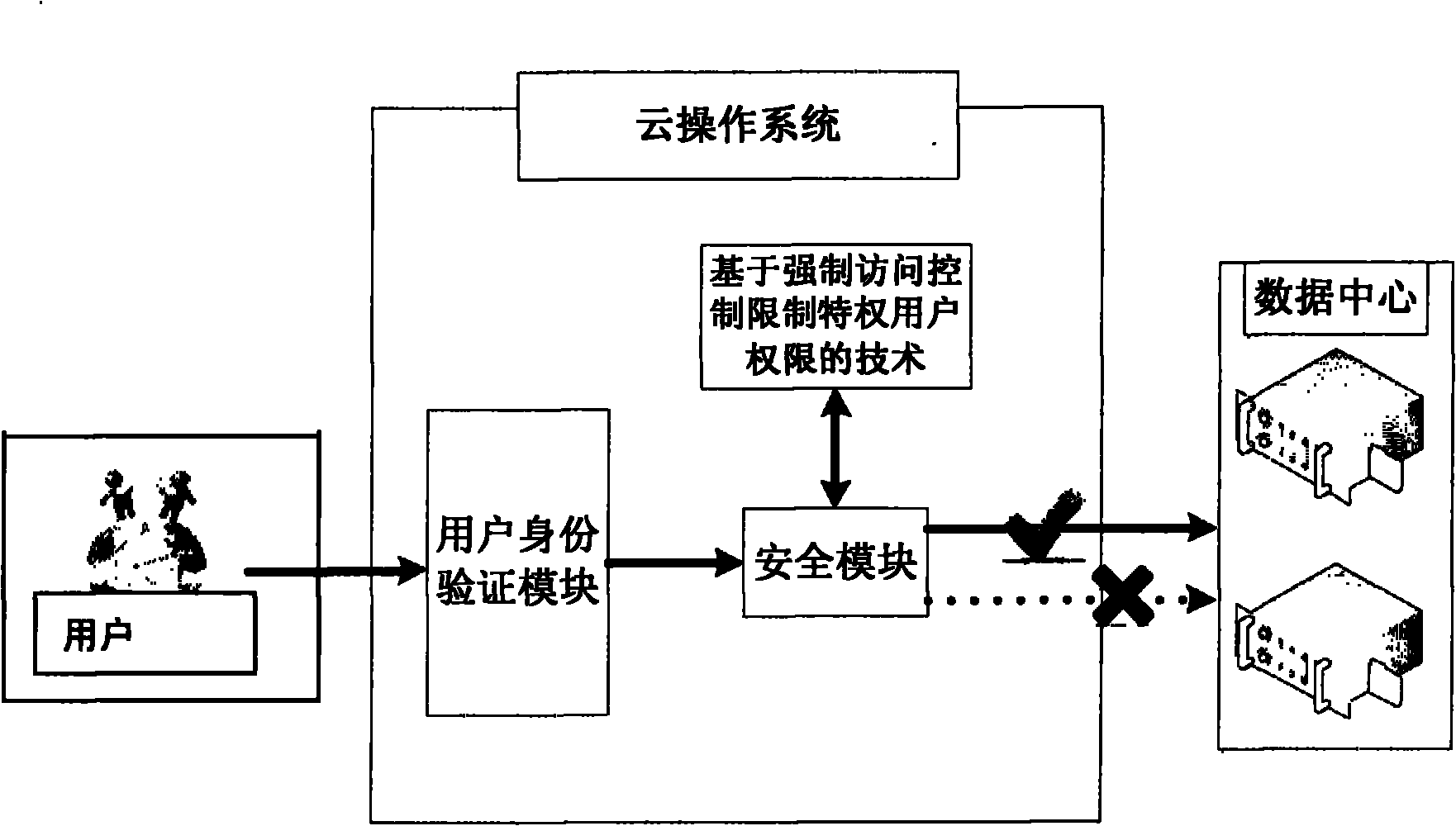
[0011] The method of the present invention is described in detail below with reference to the accompanying drawings.
[0012] A security module is added to the bottom layer of the cloud operating system to intercept and record all file access paths of privileged users, so as to meet the requirements of restricting privileged users from accessing the data center.
[0013] The main component of the security module is the Mandatory Access Control module.
[0014] The mandatory access control module is based on the user's access control to files, because all operations of privileged users can be converted into operations on files, so it is only necessary to control their operations on files.
[0015] The restriction steps are as follows:
[0016] The file system filter driver in the cloud security module inserts access rules one by one when it is initialized, and allows dynamic addition or deletion of specified nodes at any time, so as to intercept data I / O requests from privileg...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com