Patents
Literature
387 results about "Filter driver" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
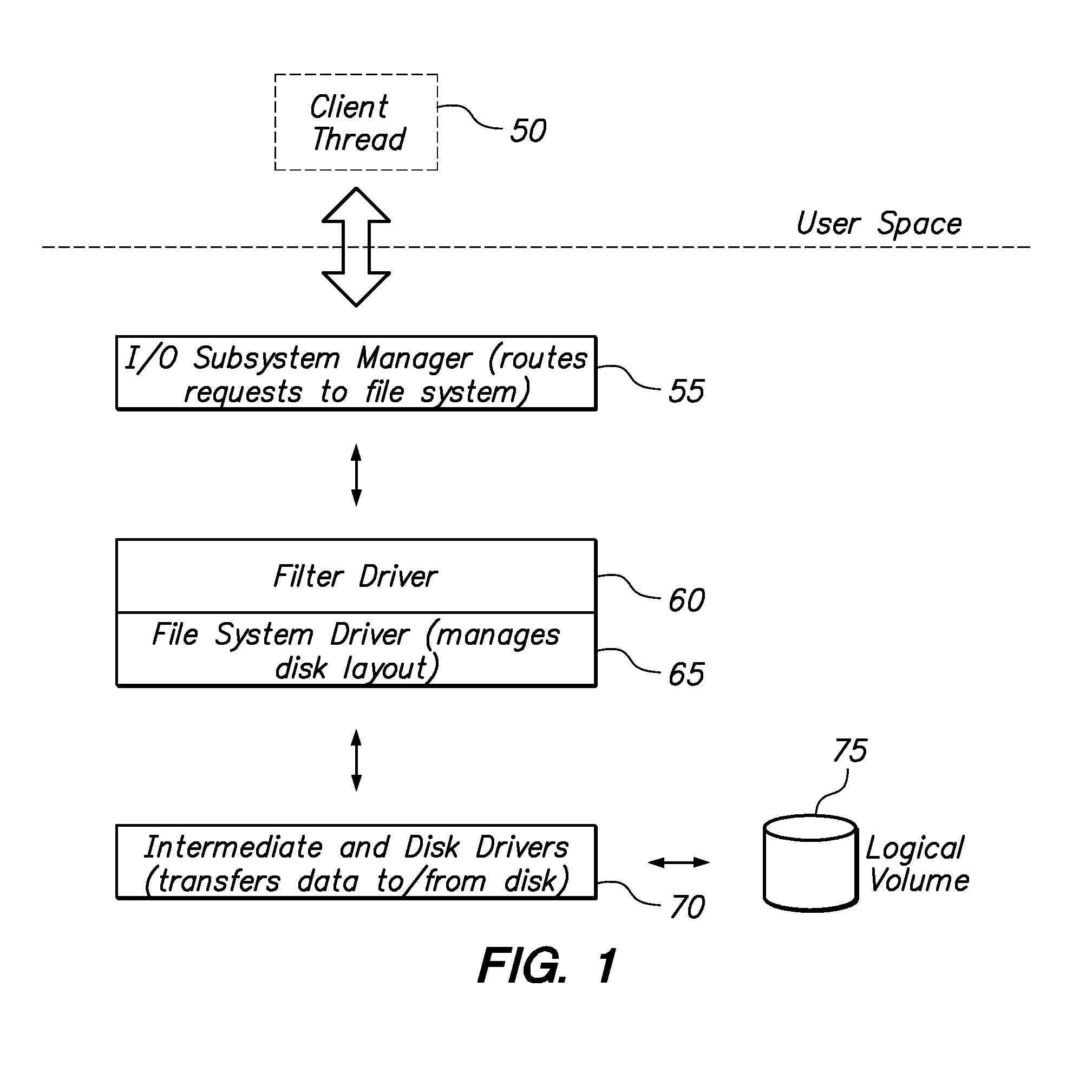
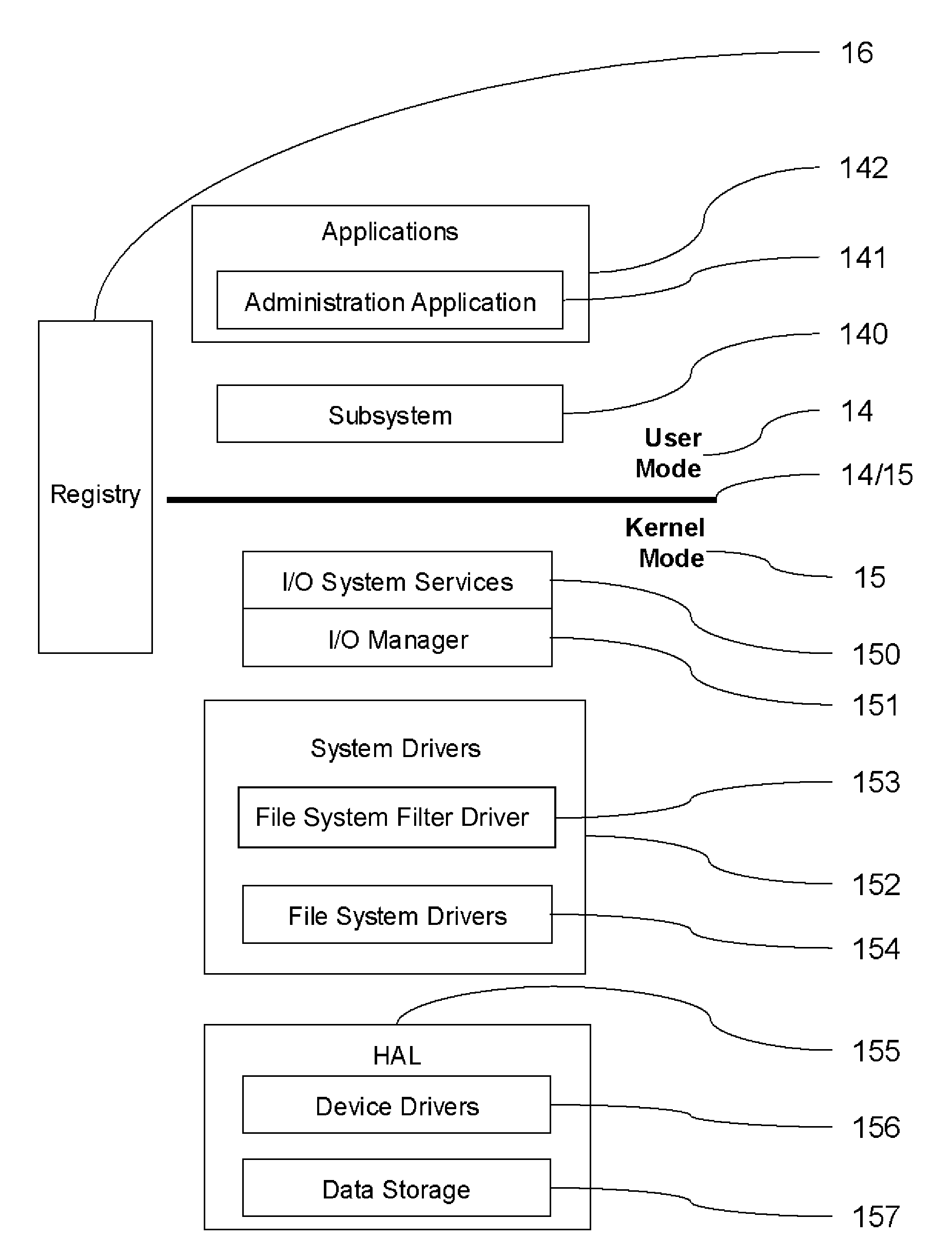
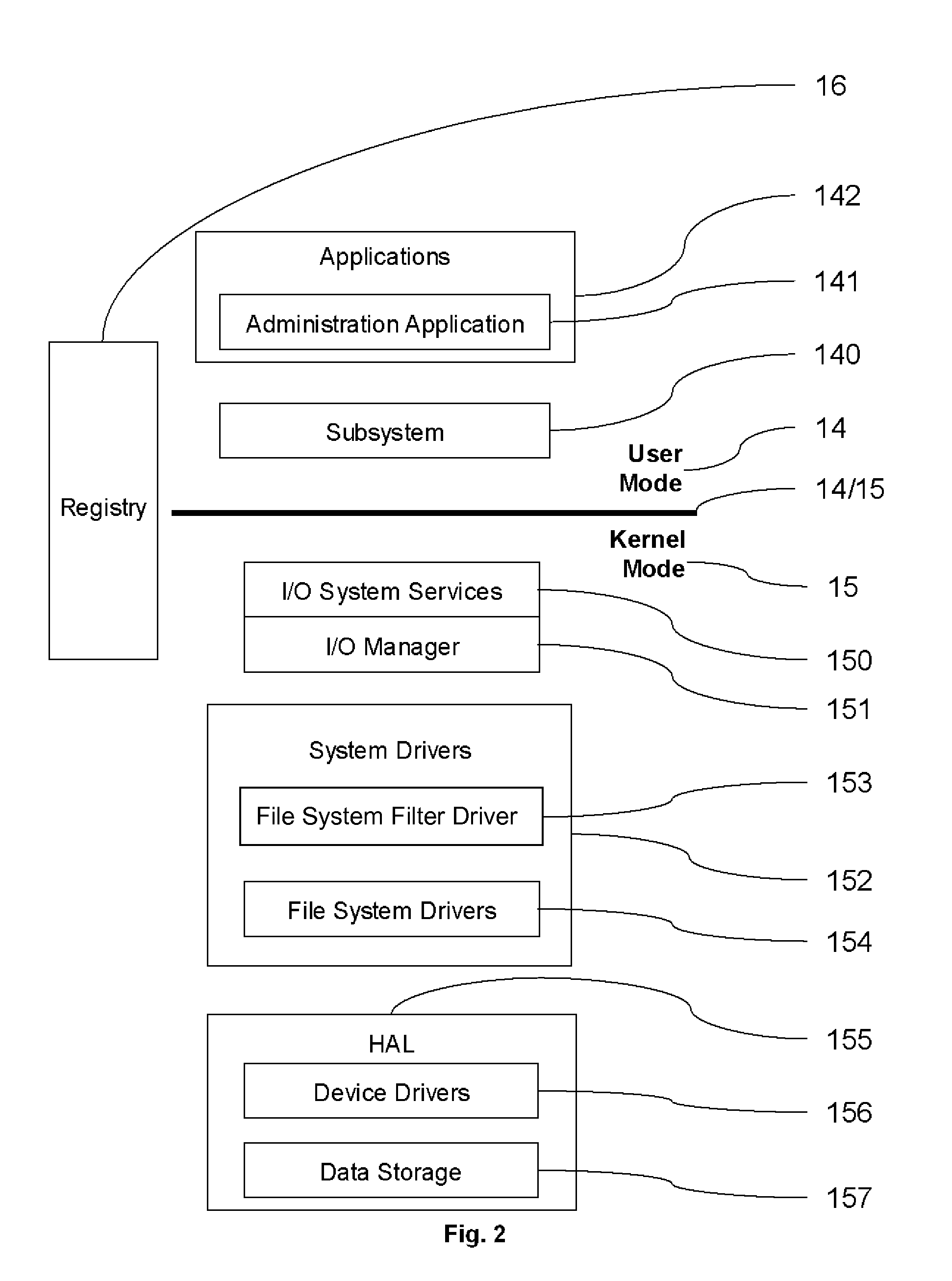
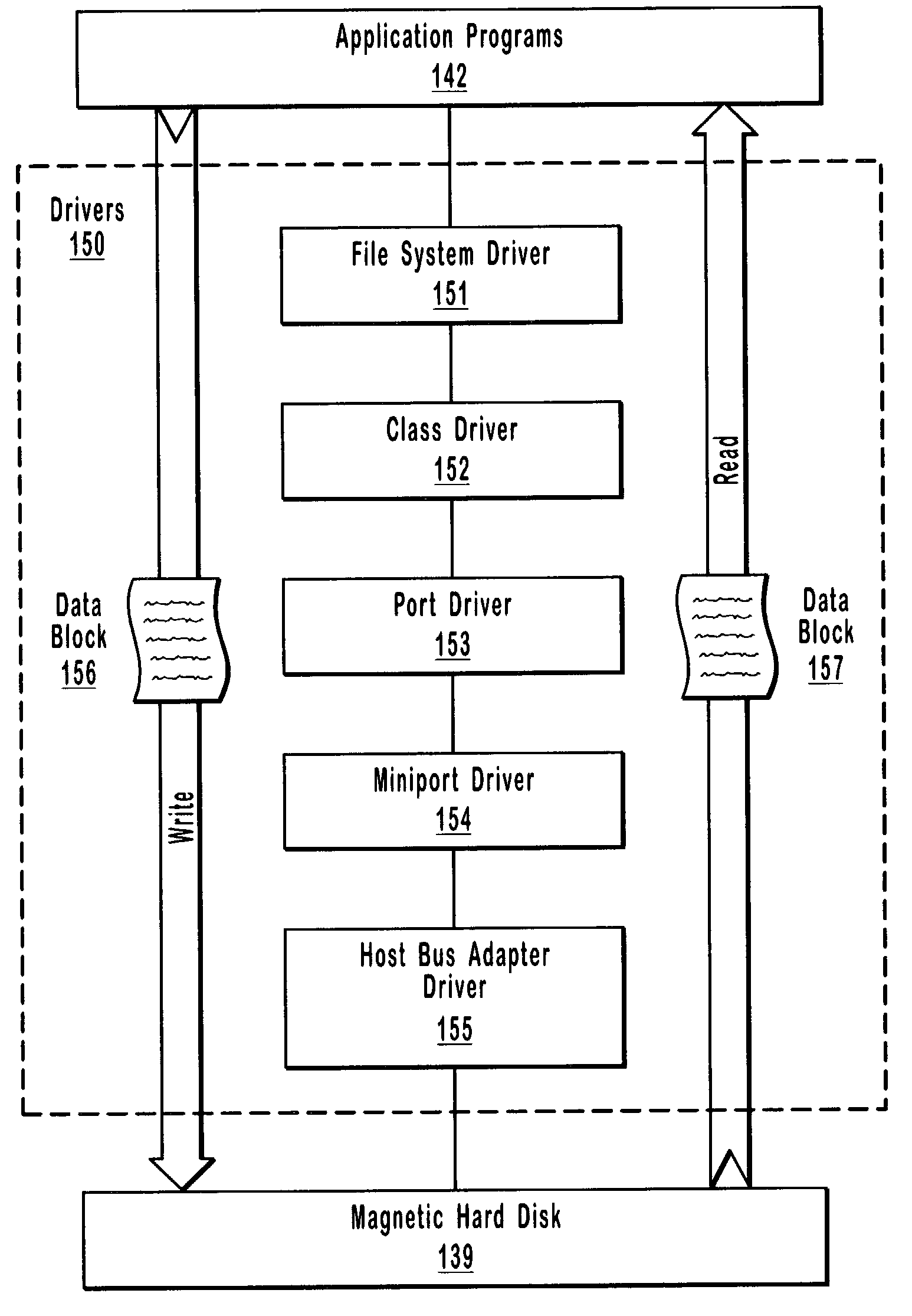
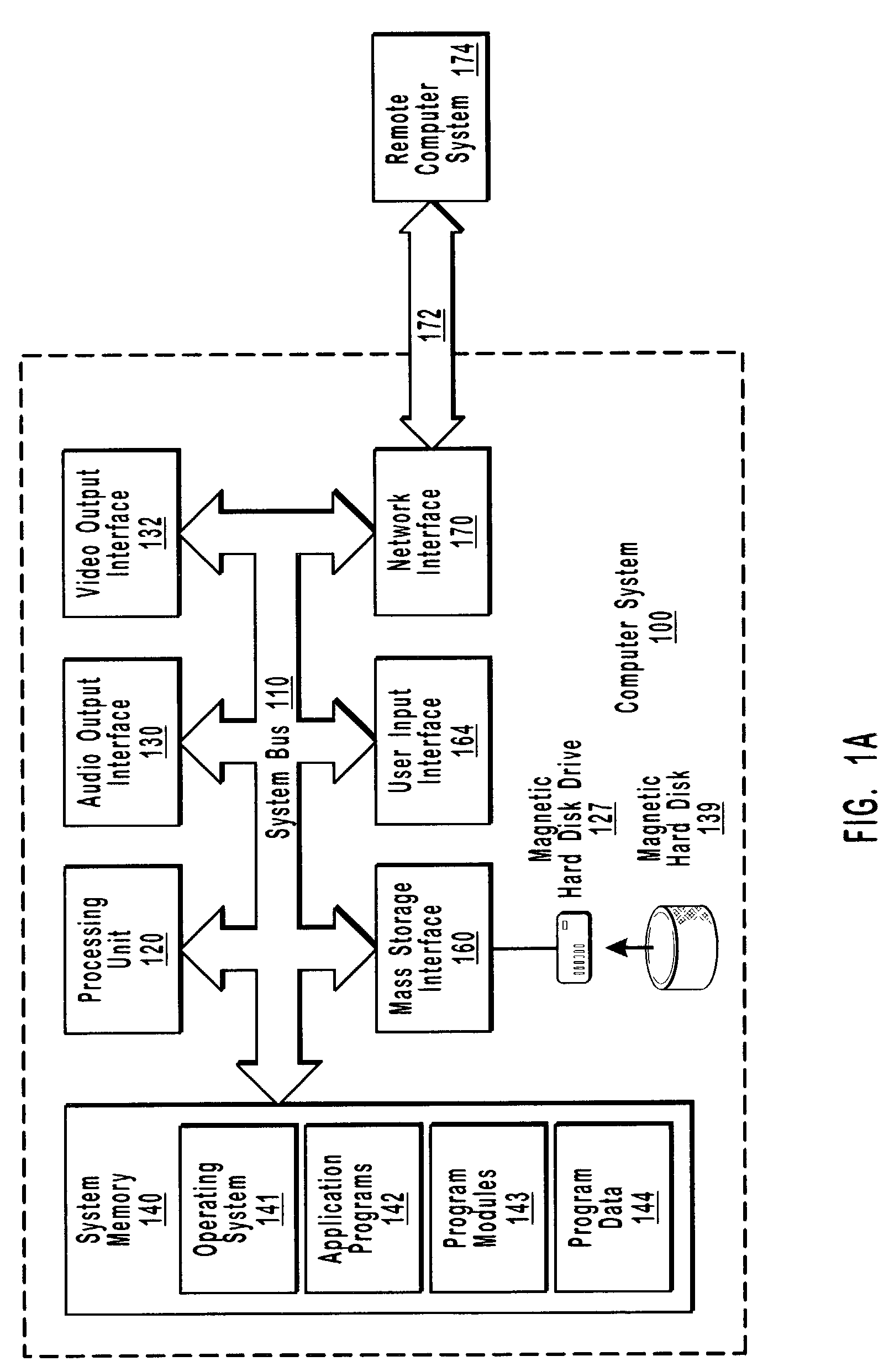
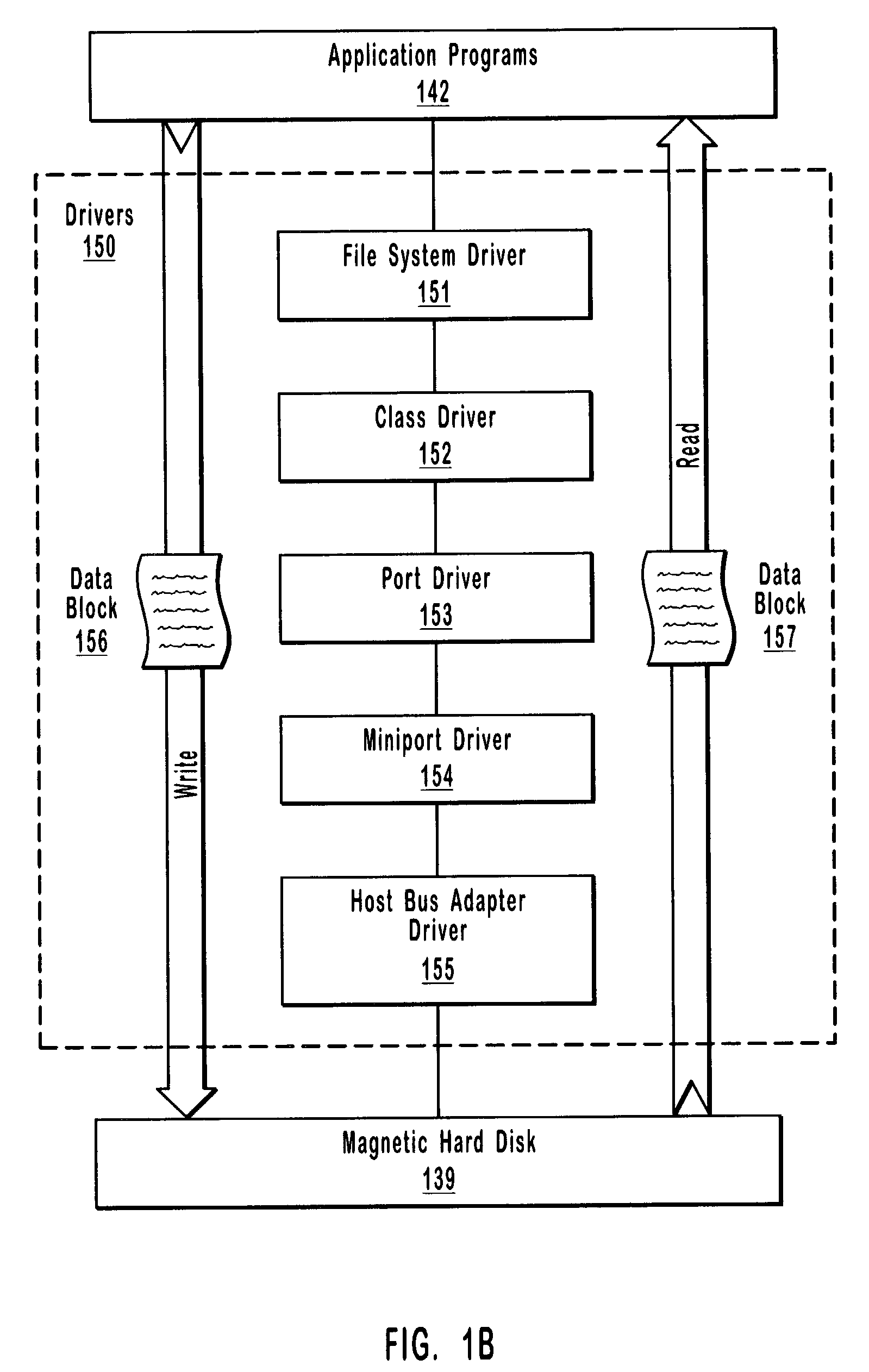
A filter driver is a Microsoft Windows driver that extends or modifies the function of peripheral devices or supports a specialized device in the personal computer. It is a driver or program or module that is inserted into the existing Driver Stack to perform some specific function. A filter driver should not affect the normal working of the existing driver stack in any major way. Written either by Microsoft or the vendor of the hardware, any number of filter drivers can be added to Windows. Upper level filter drivers sit above the primary driver for the device (the function driver), while lower level filter drivers sit below the function driver and above the bus driver.
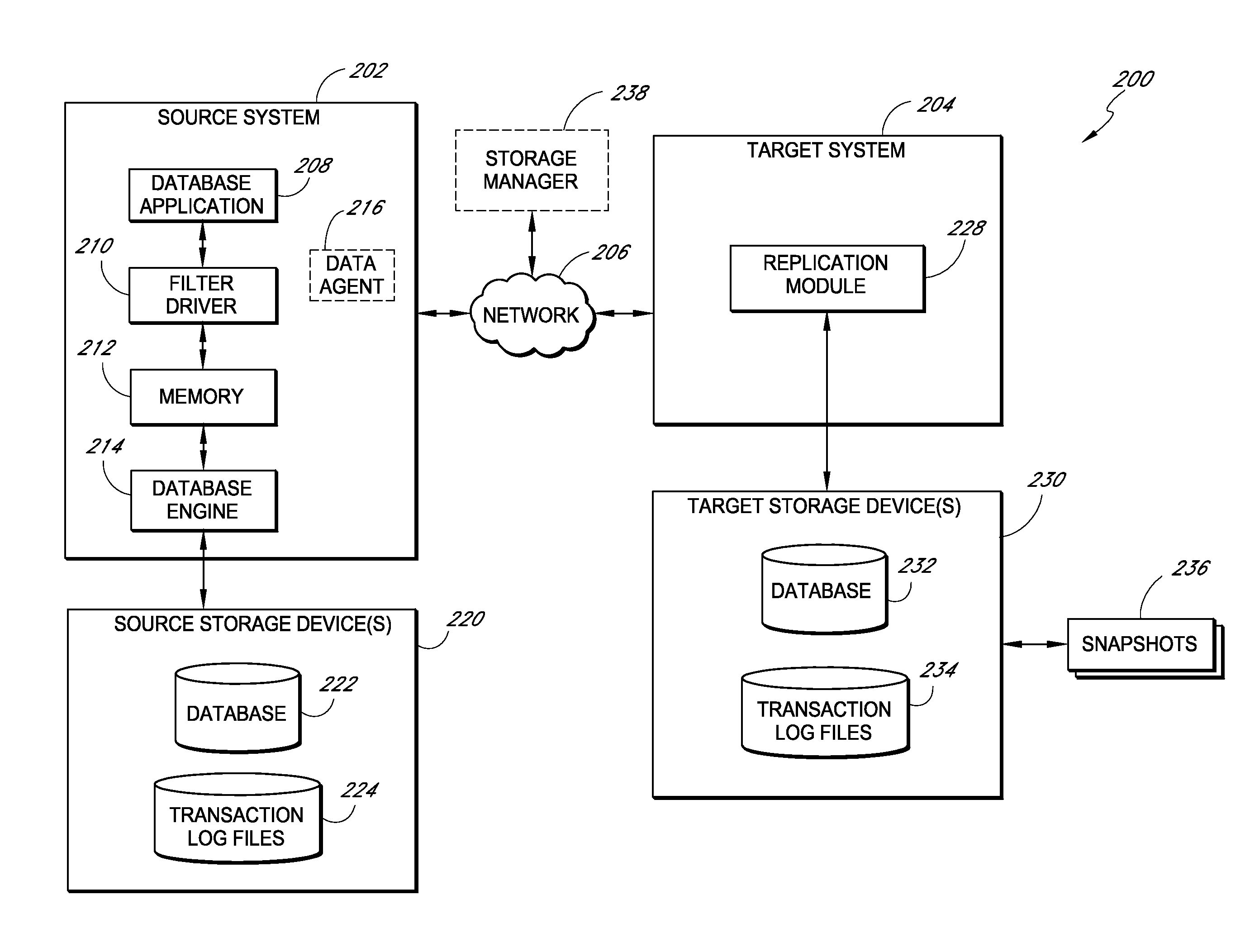
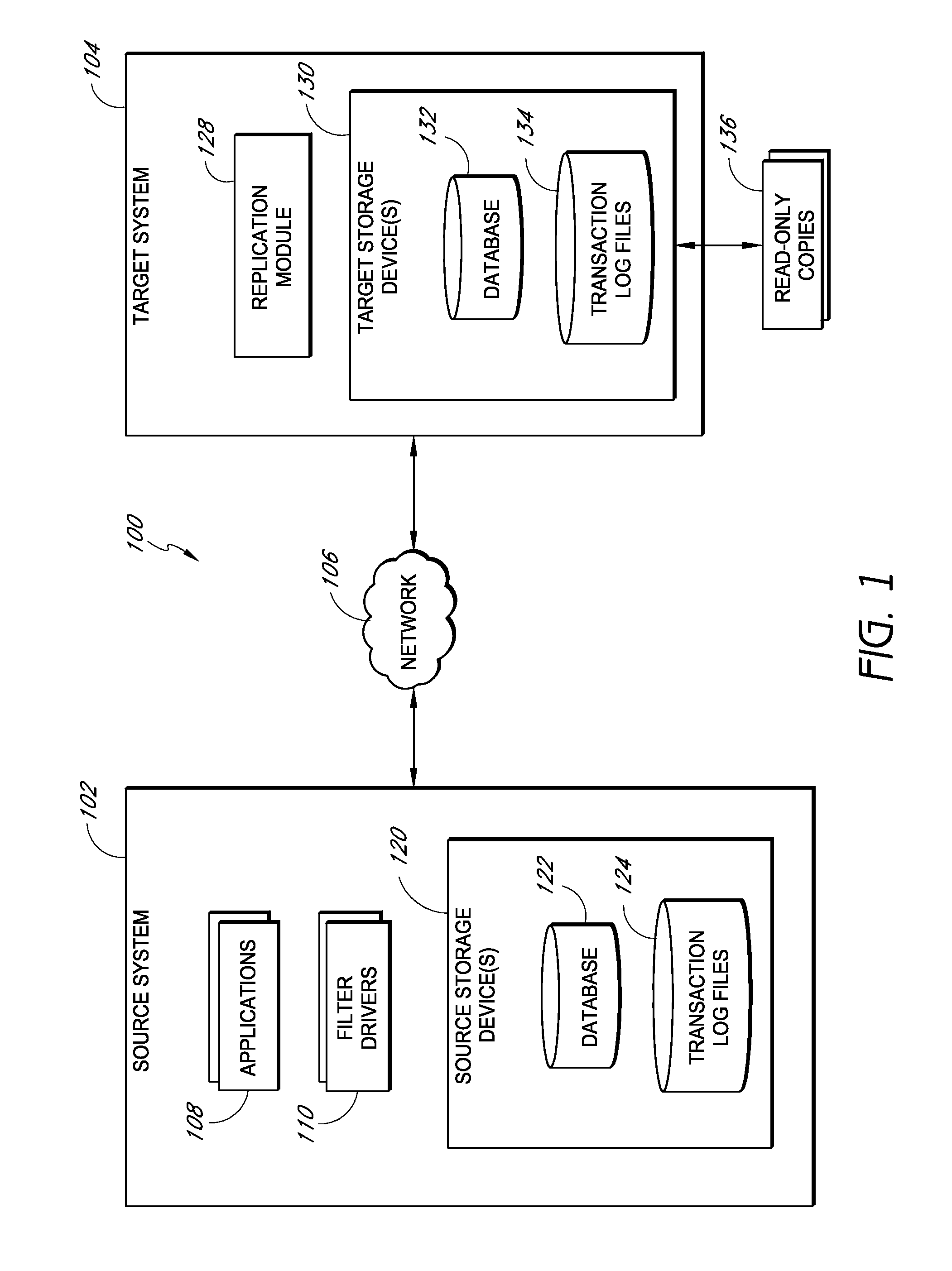
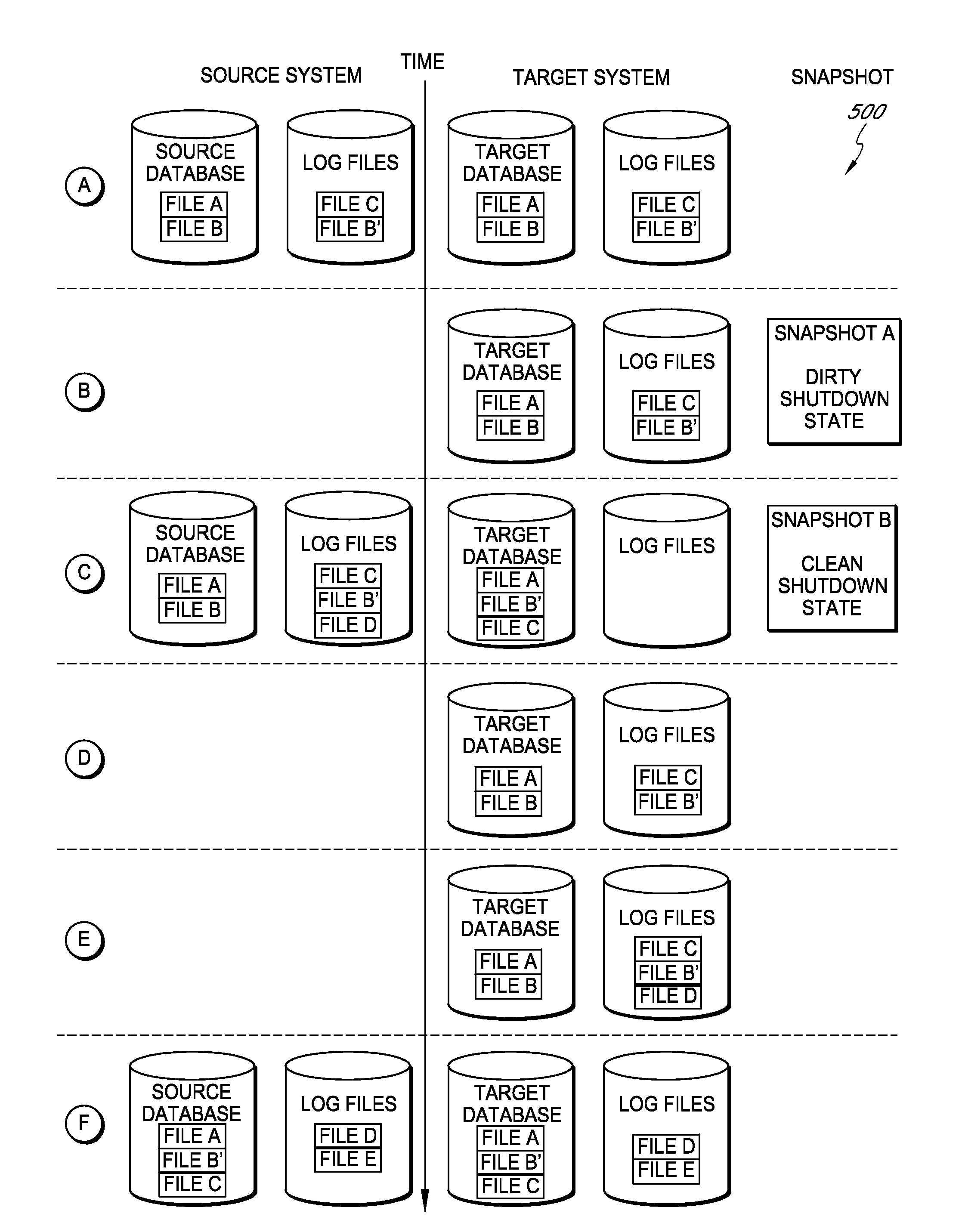
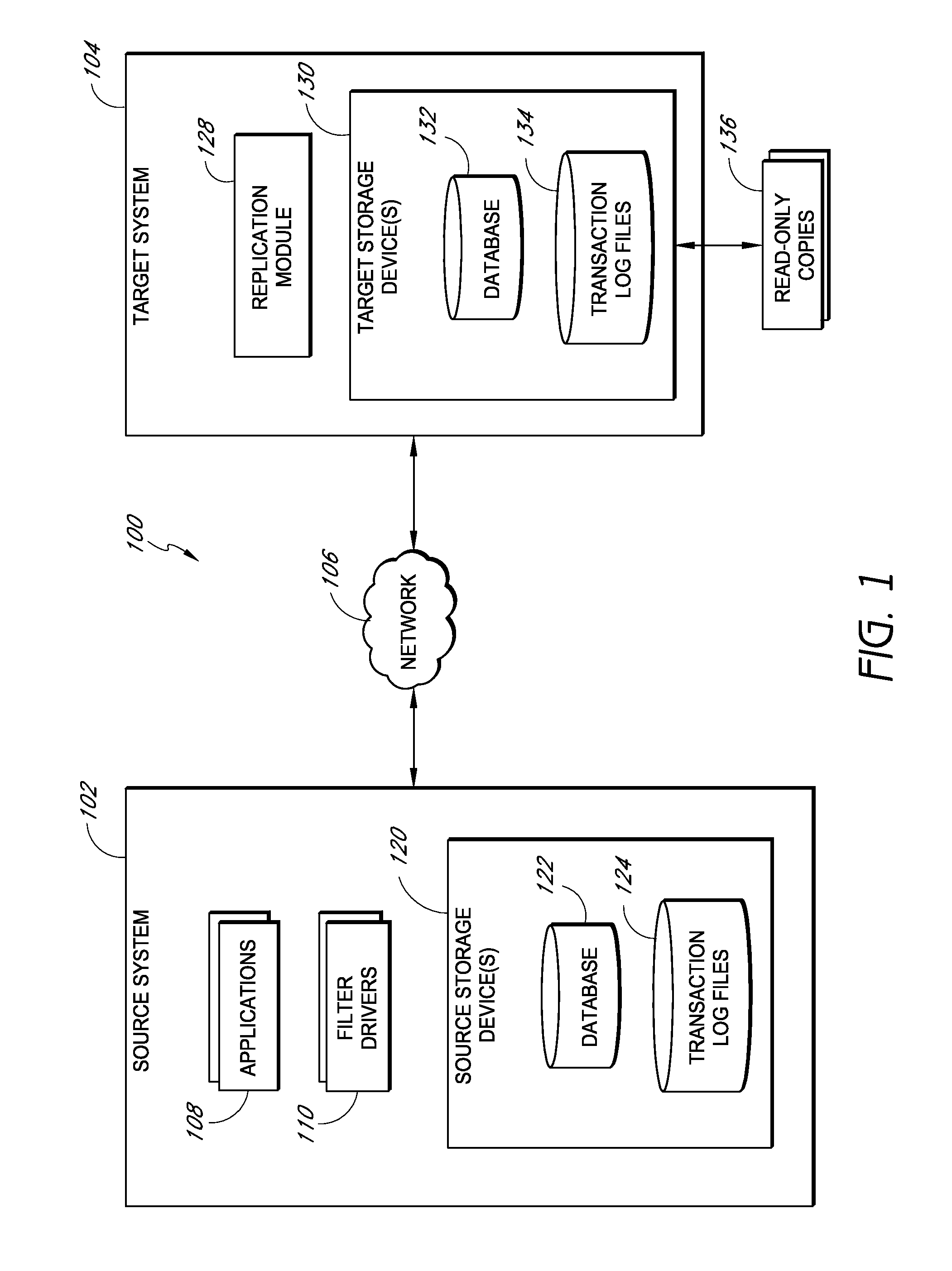
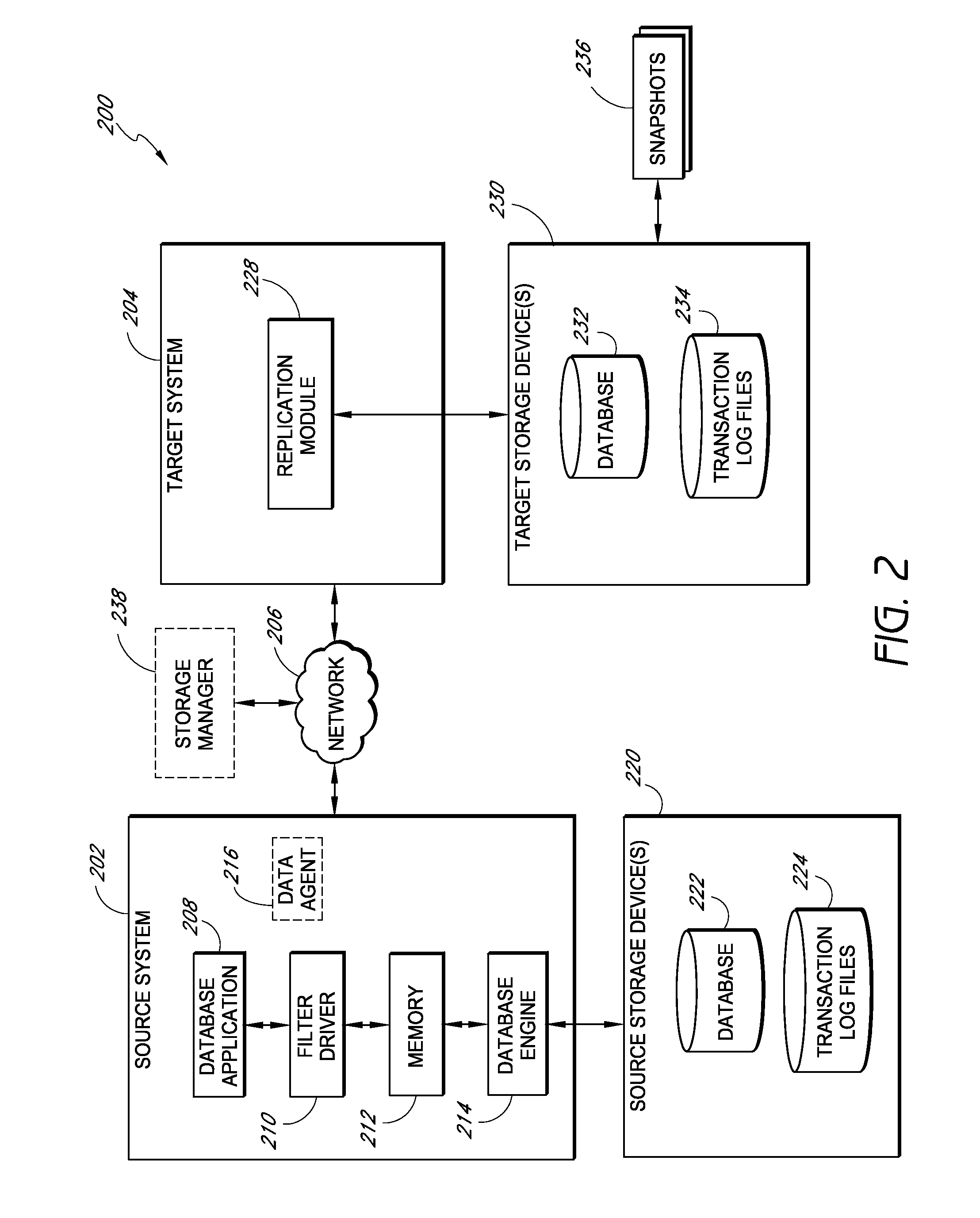
Systems and methods for managing replicated database data
ActiveUS20100145909A1Reduce memory requirementsImprove performanceError detection/correctionDigital data processing detailsDatabase applicationApplication software
Systems and methods for replicating database data and generating read-only copies of the replicated data in a clean shutdown state. For example, systems can include a tracking module (e.g., a filter driver) that monitors transactions from a database application to a source storage device to generate log entries having at least one marker indicating a known good state of the application. The systems further include a computer coupled to a target storage device comprising a database and log files. The computer processes the transactions, based on the log entries, to replicate data to the target storage device; performs a first snapshot on data stored in the database and log files; replays into the database data stored in the log files; performs another snapshot on the database; and reverts the database back to a state in which the database existed at the time of the first snapshot.
Owner:COMMVAULT SYST INC
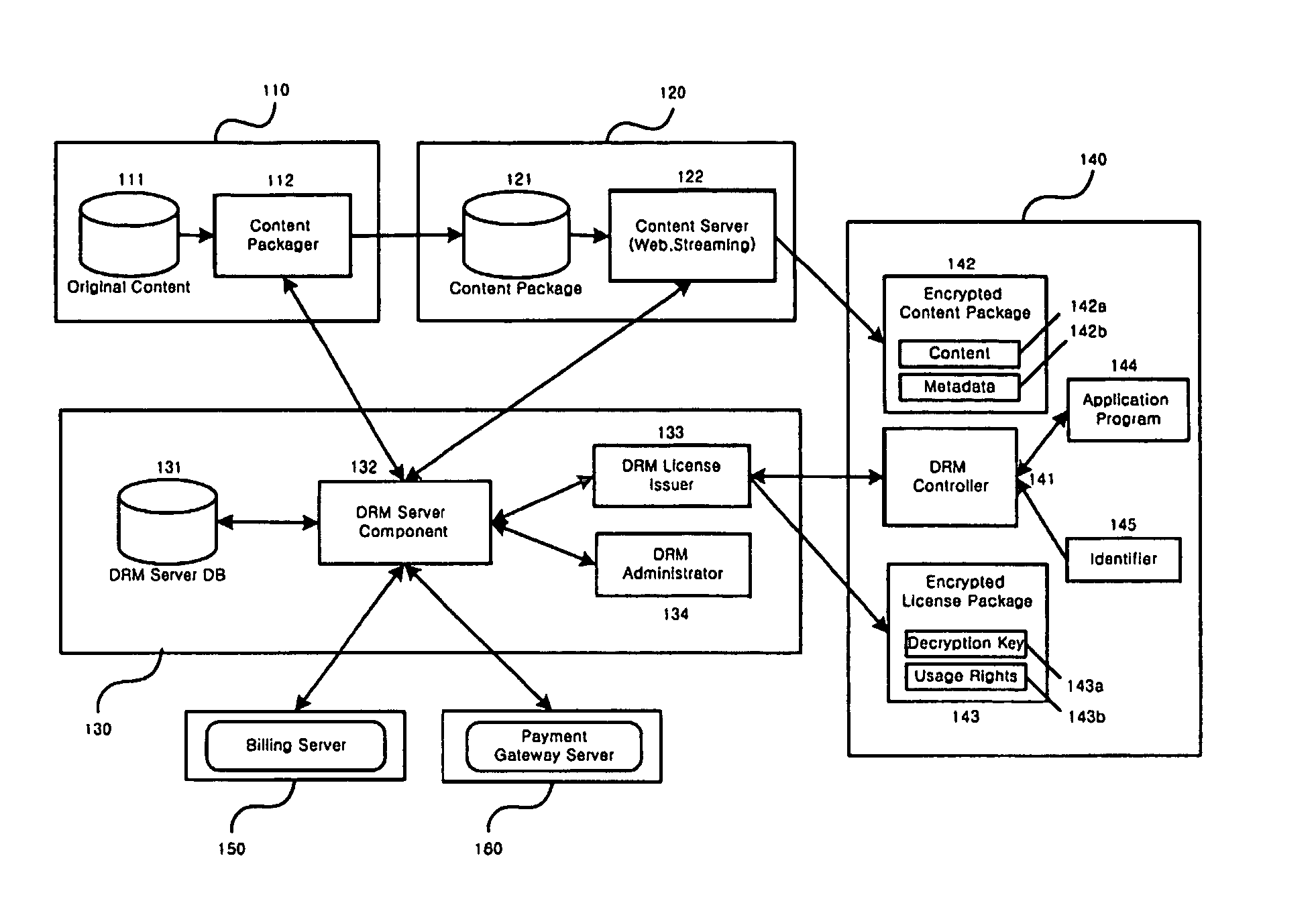
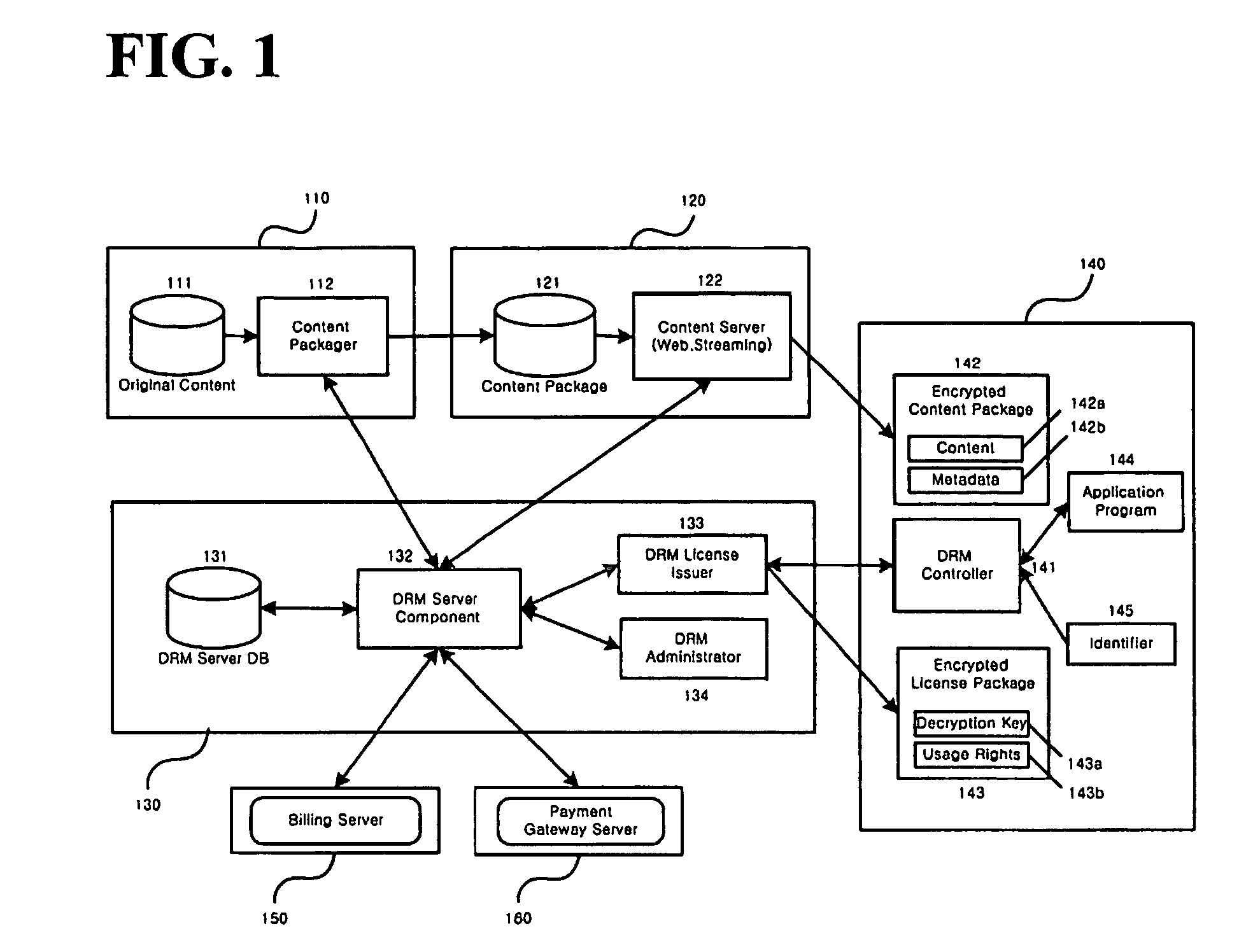
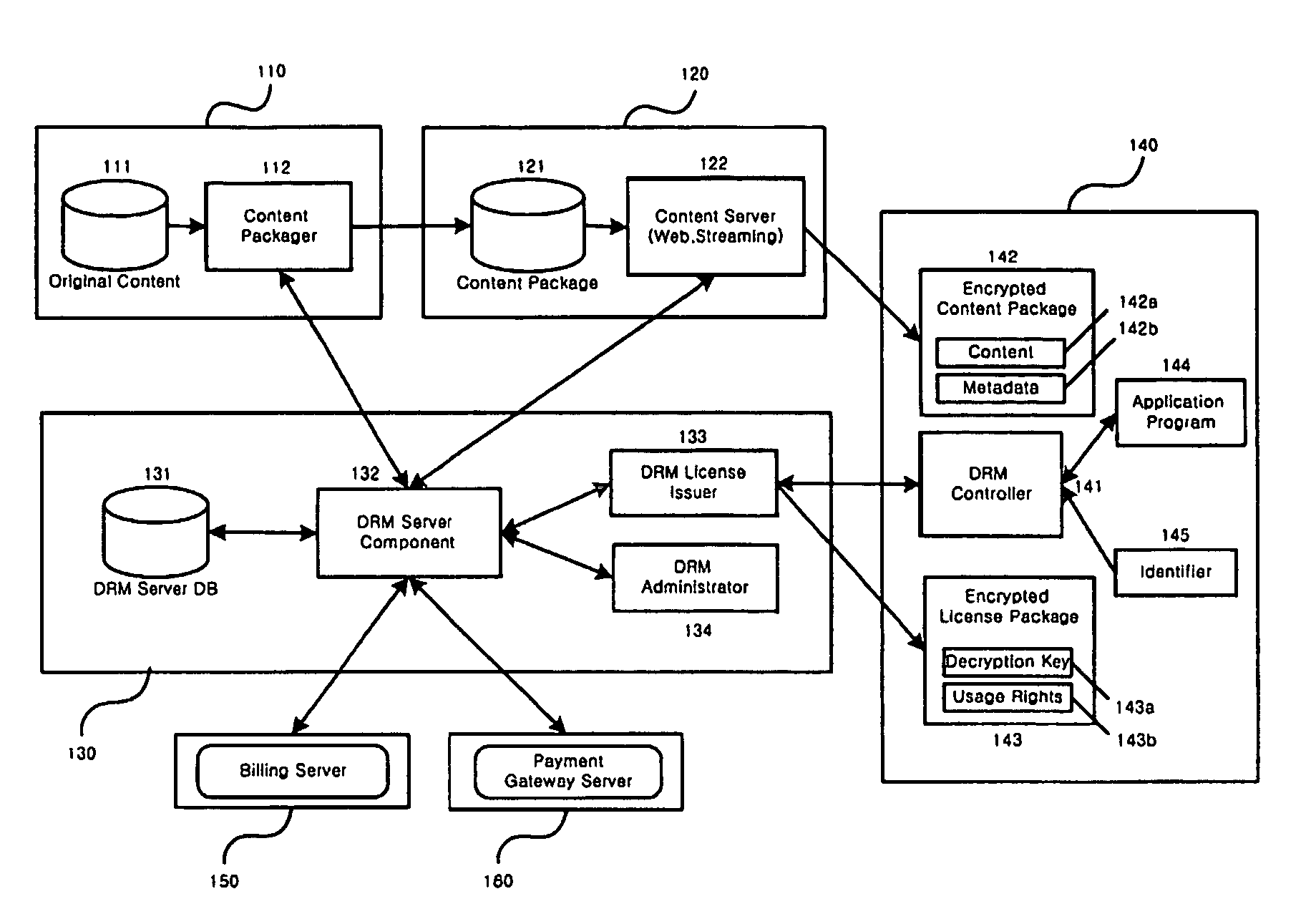
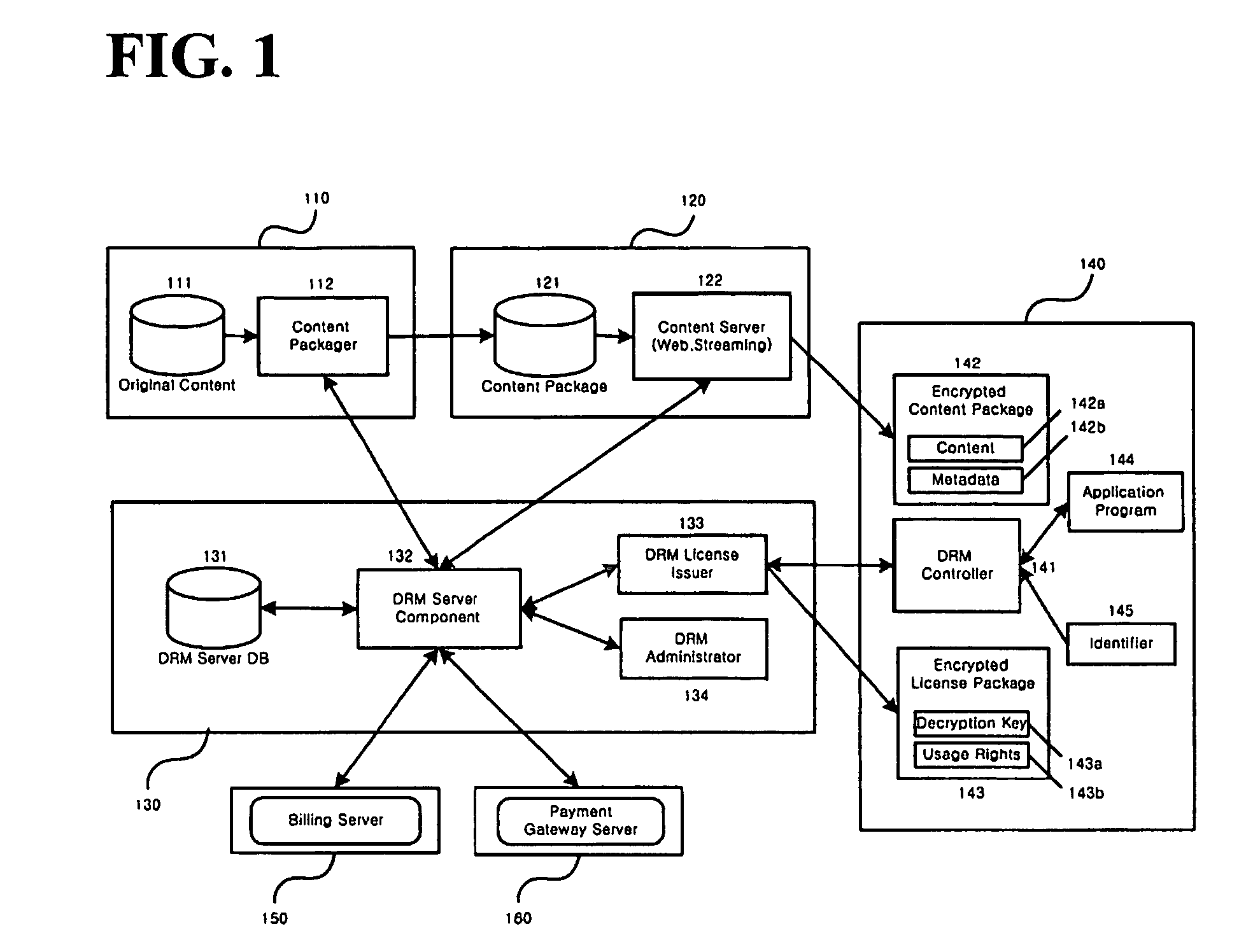
Method and system for the information protection of digital content
ActiveUS20050086501A1Add supportImprove securityDigital data processing detailsUser identity/authority verificationData packDigital content
The present invention relates to the information protection of digital content transferred by streaming and download service through wire or wireless Internet network. The information protection system in this invention suggests a drastic prevention method of copyrights infringement such as illegal copy and unauthorized distribution of digital content, by using of the encryption, decryption, distribution, and authentication technologies. This invention suggests the control technology of general viewer program, not the specific viewer program for information protection, using a network filter driver for streaming and file system filter driver for download service. The main function of network and file system filter driver is the filtering operation such as a hooking, changing, decrypting, and restoring of message and data packet, and transferring to the viewer program. The main idea and technology of this invention suggest higher secure and efficient digital information protection system for live / VOD / HTTP streaming and download service.
Owner:WOO JE HAK +6
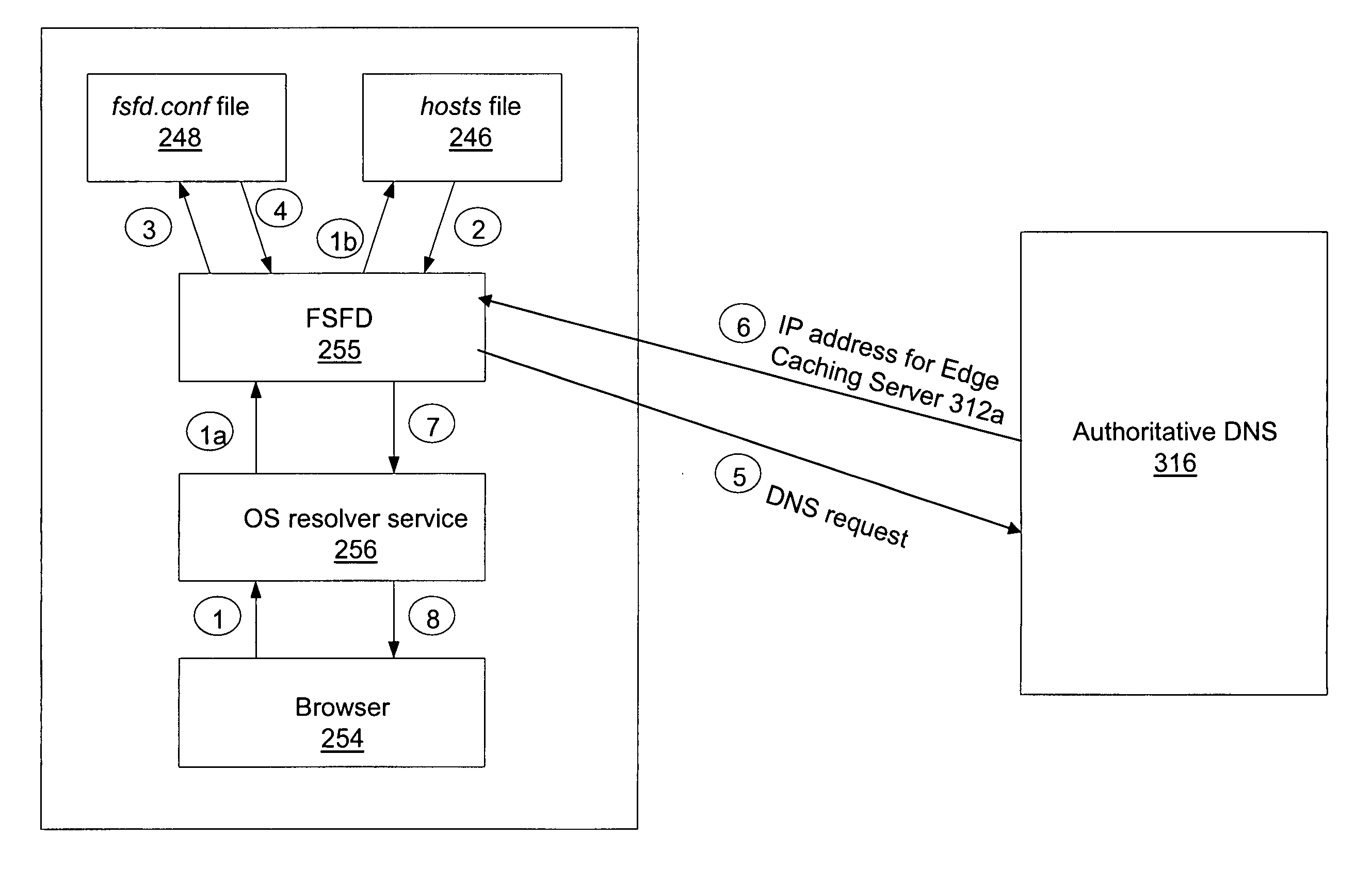
Determining address of closest edge server
A method and system is presented for bypassing a local Domain Name Server (DNS) when using edge caching servers. Domain names of frequently used business applications that are known to rely upon edge servers, together with the corresponding authoritative DNSs, are listed in both local hosts file and user defined FSFD local configuration file fsfd.conf. When the client computer's browser attempts to resolve a domain name, a File System Filtering Driver (FSFD) in the client computer intercepts the browser's request. If the domain name which is being resolved is found in a local FSFD configuration file fsfd.conf, then the FSFD initiates a DNS request directly to the appropriate authoritative DNS whose IP address gets extracted from the fsfd.conf record, thus bypassing the local DNS. The authoritative DNS returns the IP address for an edge caching server that is topographically proximate to the client computer's browser.
Owner:LINKEDIN
Method and system for the information protection of digital content
ActiveUS7484103B2Digital data processing detailsAnalogue secracy/subscription systemsDigital contentNetwork packet
The present invention relates to the information protection of digital content transferred by streaming and download service through wire or wireless Internet network. The information protection system in this invention suggests a drastic prevention method of copyrights infringement such as illegal copy and unauthorized distribution of digital content, by using of the encryption, decryption, distribution, and authentication technologies. This invention suggests the control technology of general viewer program, not the specific viewer program for information protection, using a network filter driver for streaming and file system filter driver for download service. The main function of network and file system filter driver is the filtering operation such as a hooking, changing, decrypting, and restoring of message and data packet, and transferring to the viewer program. The main idea and technology of this invention suggest higher secure and efficient digital information protection system for live / VOD / HTTP streaming and download service.
Owner:WOO JE HAK +6
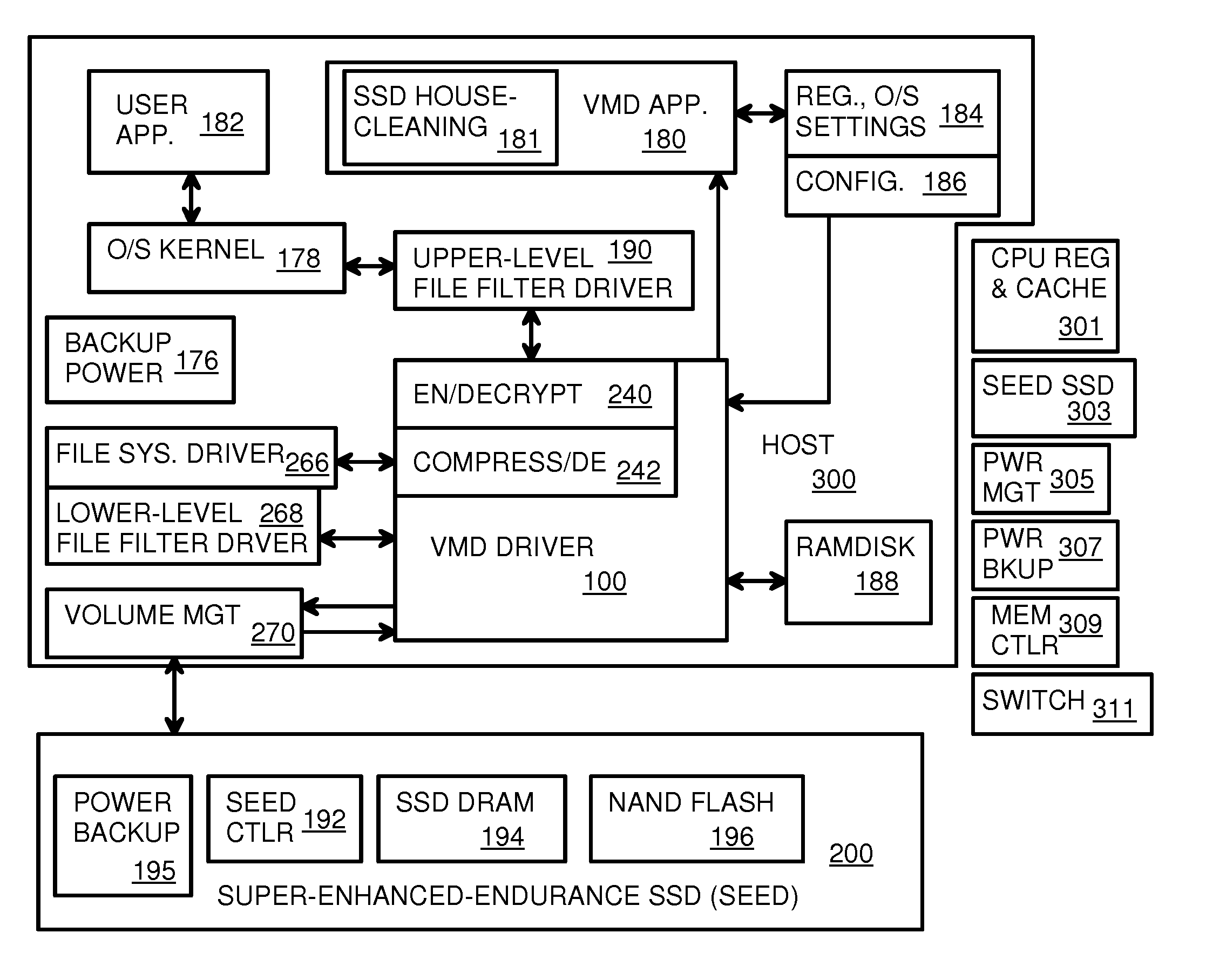
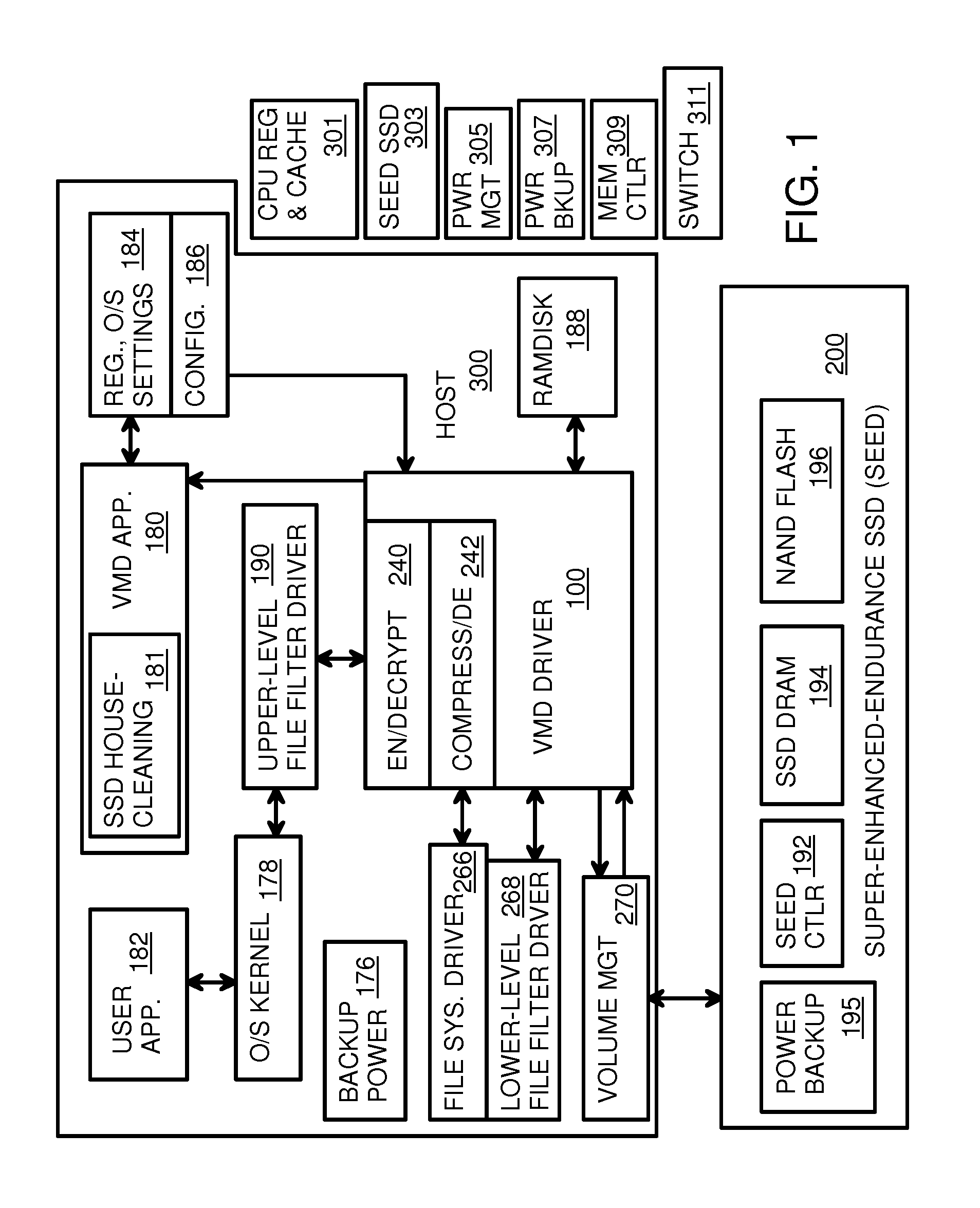
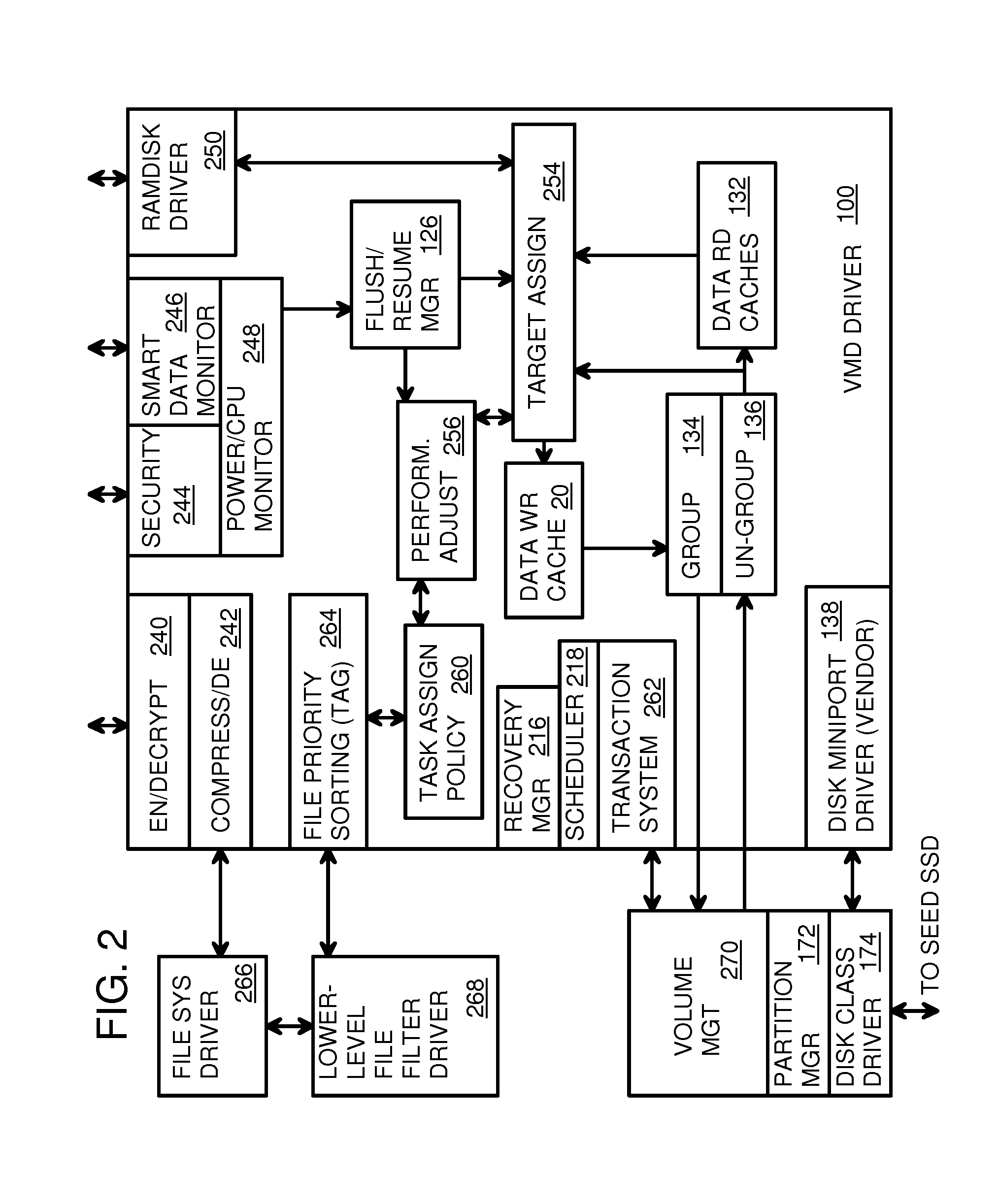
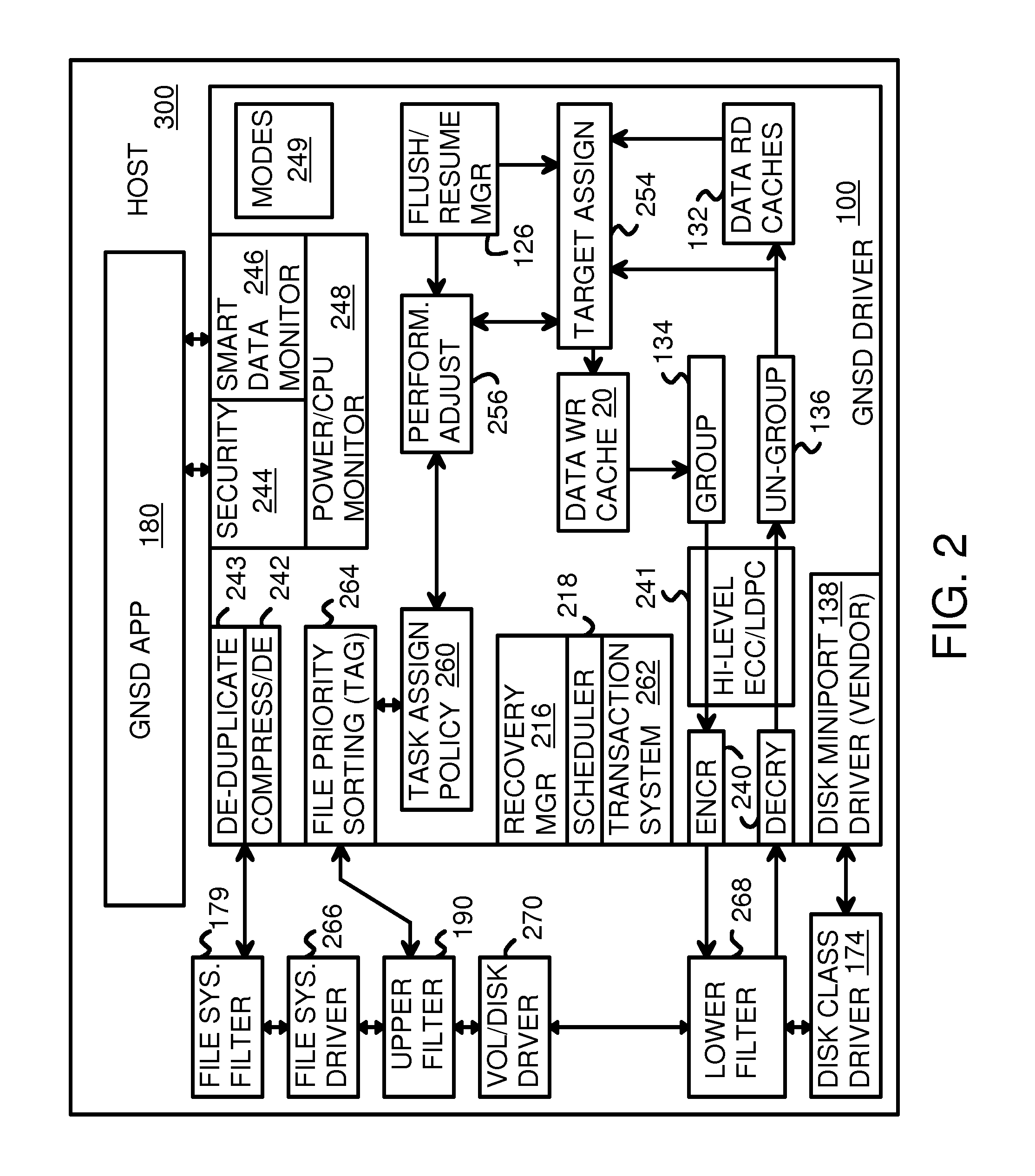
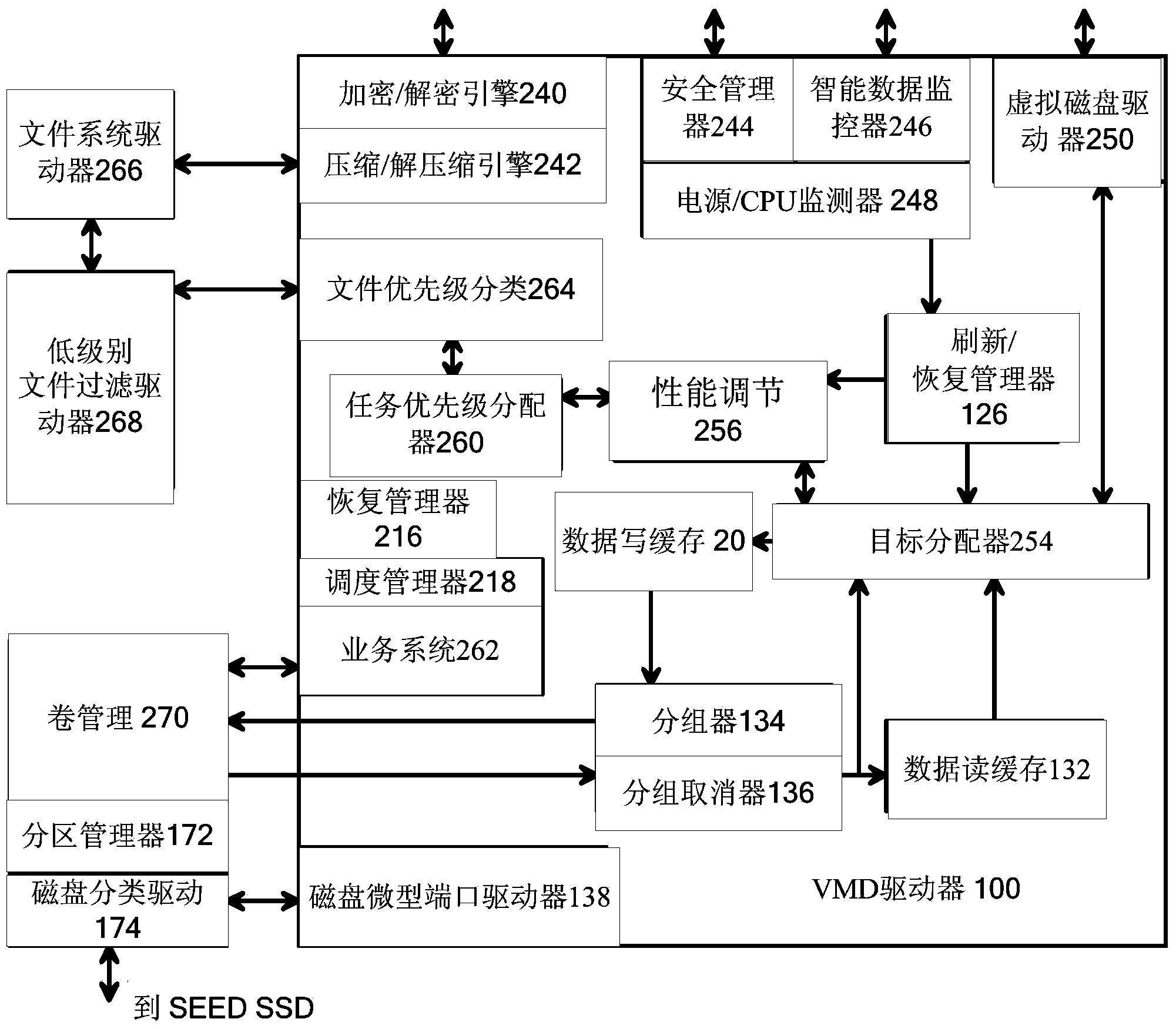
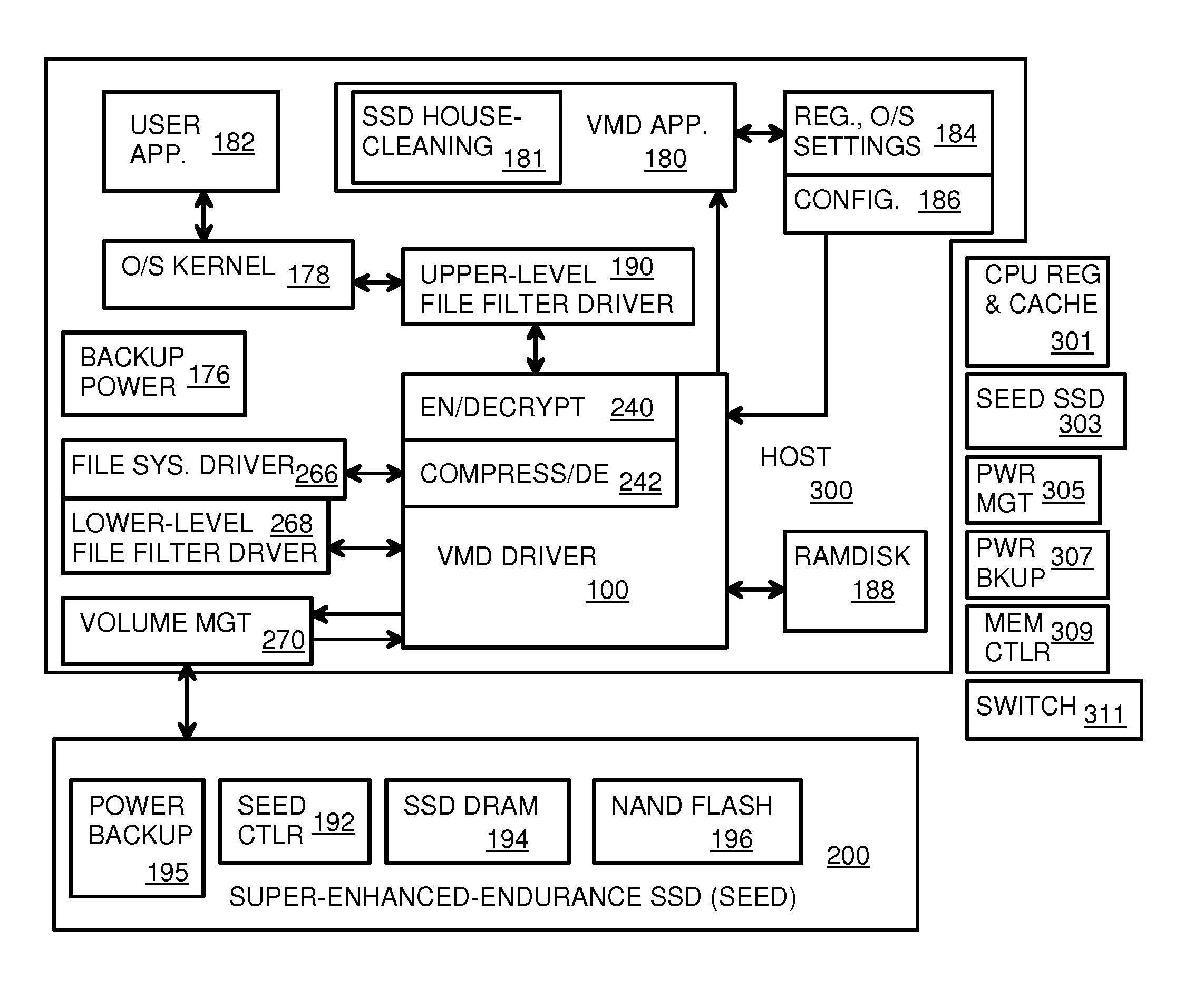
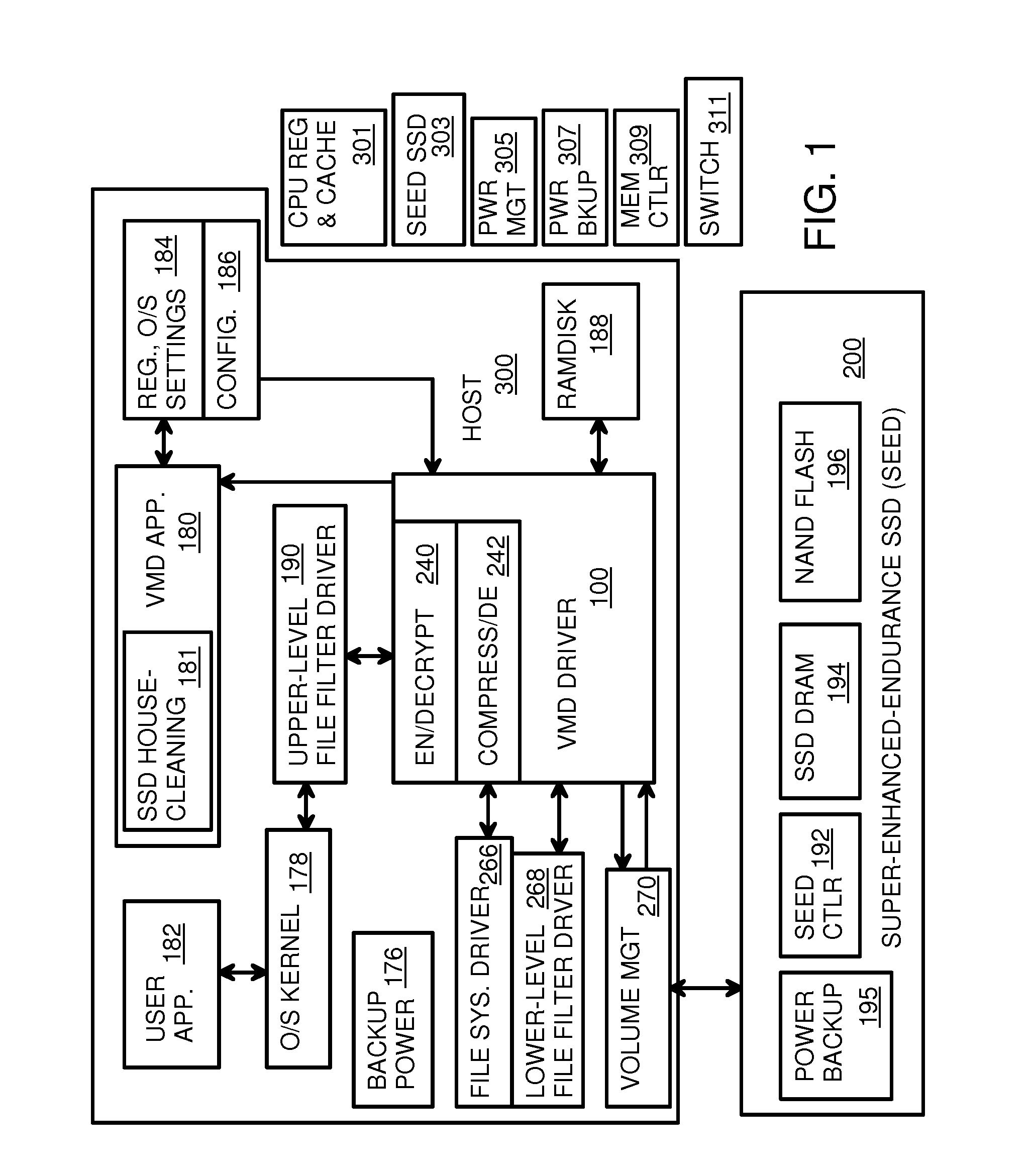
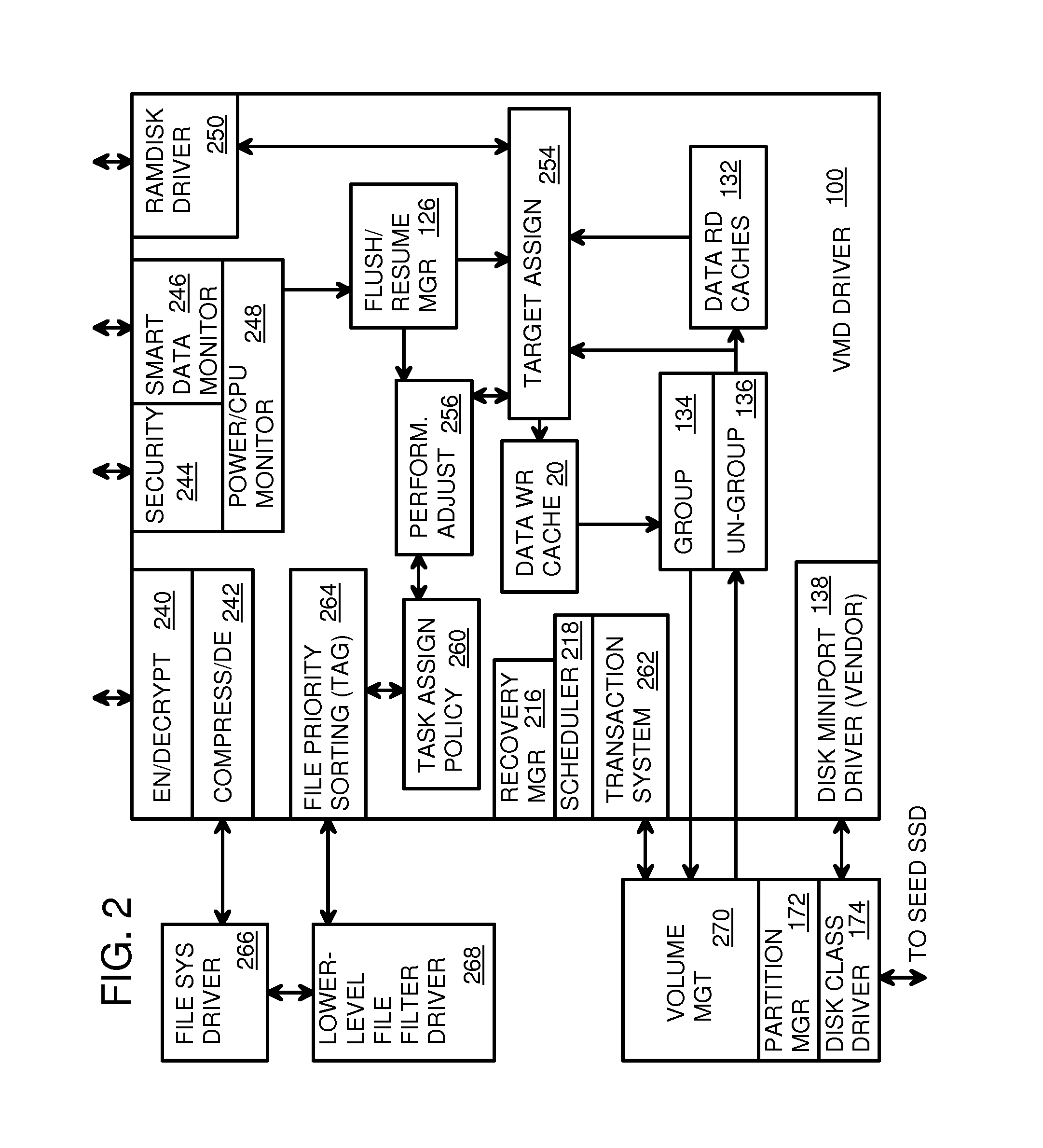
Virtual Memory Device (VMD) Application/Driver with Dual-Level Interception for Data-Type Splitting, Meta-Page Grouping, and Diversion of Temp Files to Ramdisks for Enhanced Flash Endurance
ActiveUS20130145085A1Memory architecture accessing/allocationMemory adressing/allocation/relocationFilename extensionData file
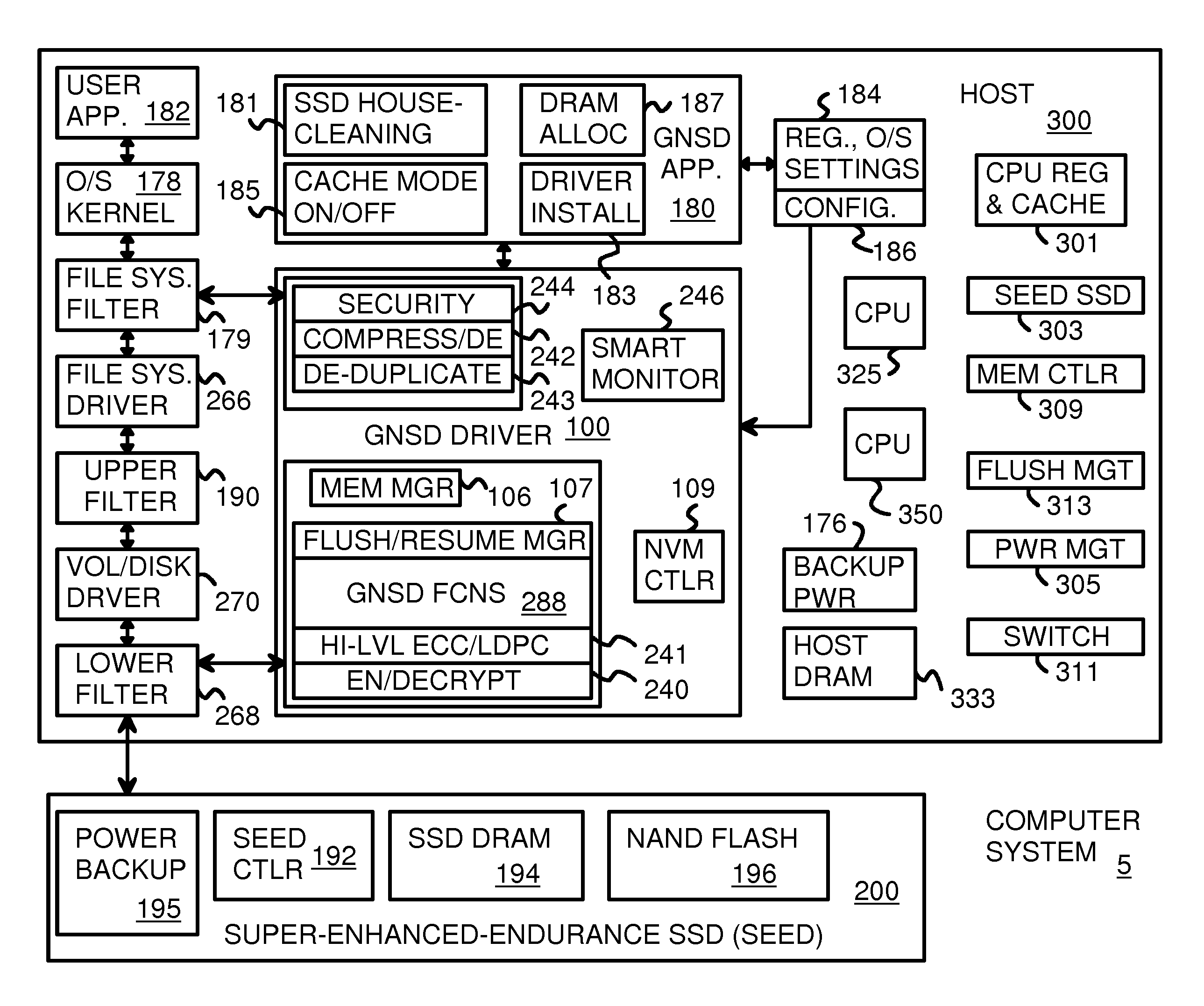
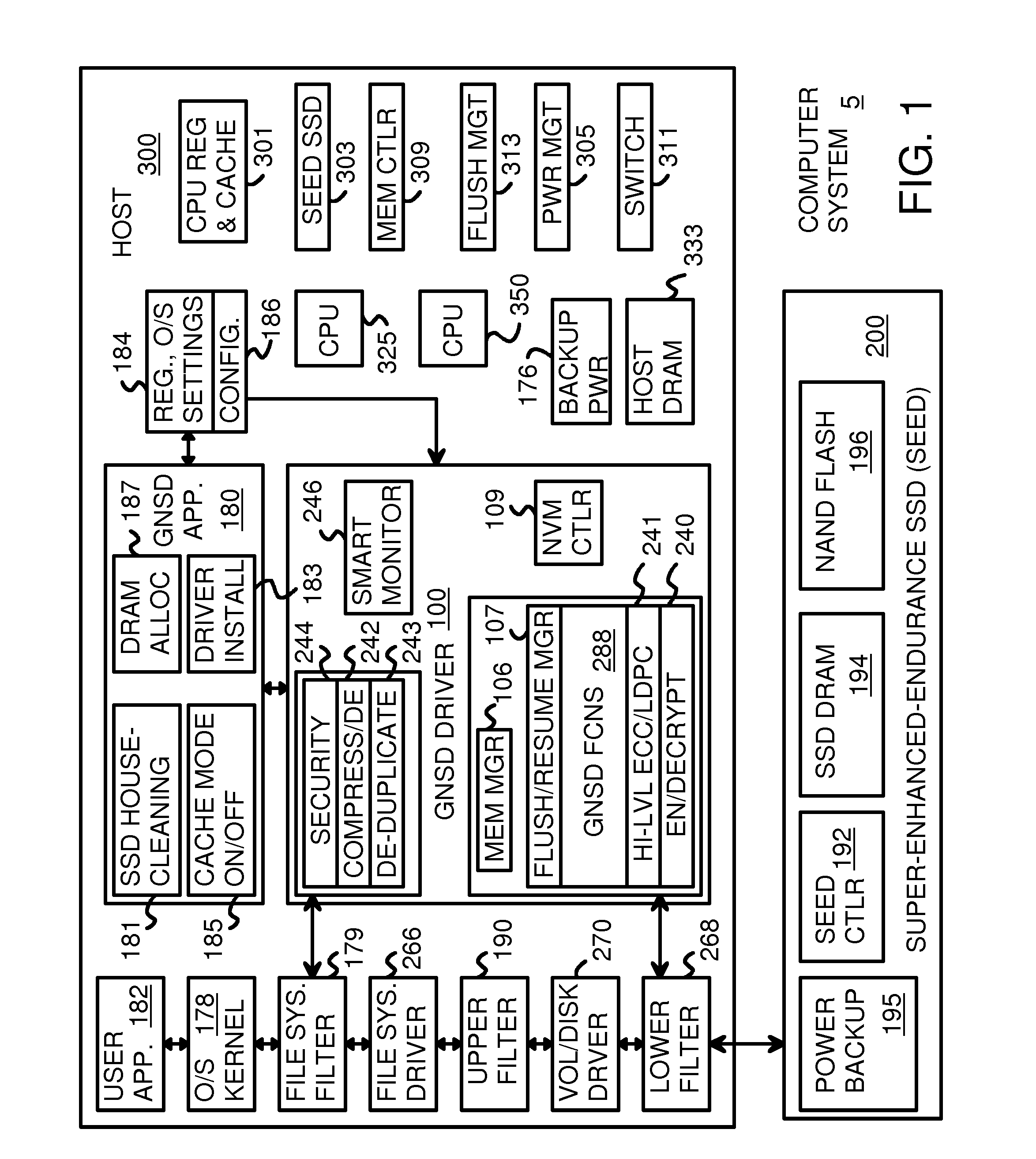
A Virtual-Memory Device (VMD) driver and application execute on a host to increase endurance of flash memory attached to a Super Enhanced Endurance Device (SEED) or Solid-State Drive (SSD). Host accesses to flash are intercepted by the VMD driver using upper and lower-level filter drivers and categorized as data types of paging files, temporary files, meta-data, and user data files, using address ranges and file extensions read from meta-data tables. Paging files and temporary files are optionally written to flash. Full-page and partial-page data are grouped into multi-page meta-pages by data type before storage by the SSD. ramdisks and caches for storing each data type in the host DRAM are managed and flushed to the SSD by the VMD driver. Write dates are stored for pages or blocks for management functions. A spare / swap area in DRAM reduces flash wear. Reference voltages are adjusted when error correction fails.
Owner:SUPER TALENT TECH CORP
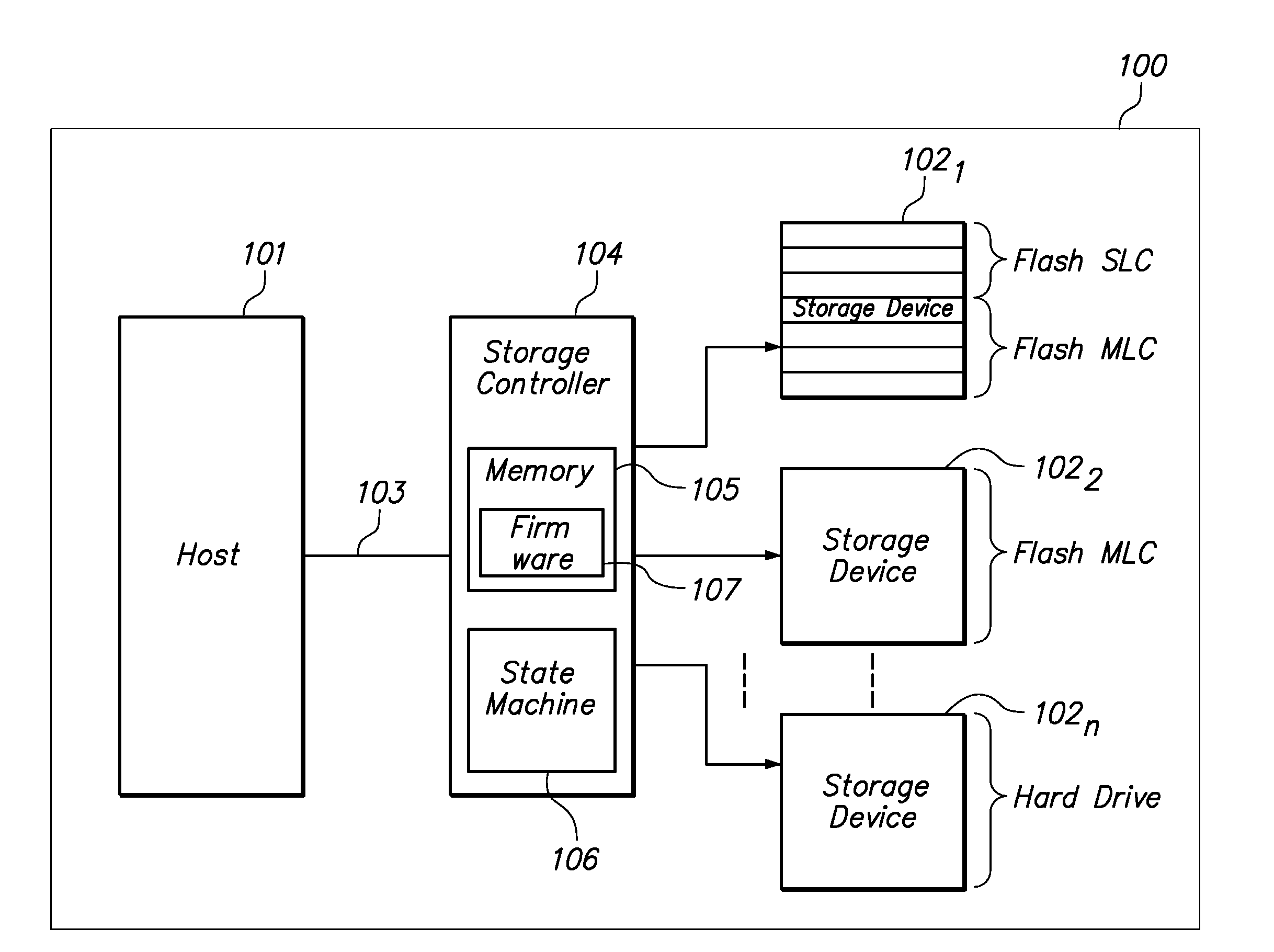
Smart Solid State Drive And Method For Handling Critical Files
InactiveUS20090043831A1Memory adressing/allocation/relocationInput/output processes for data processingControl storeComputerized system
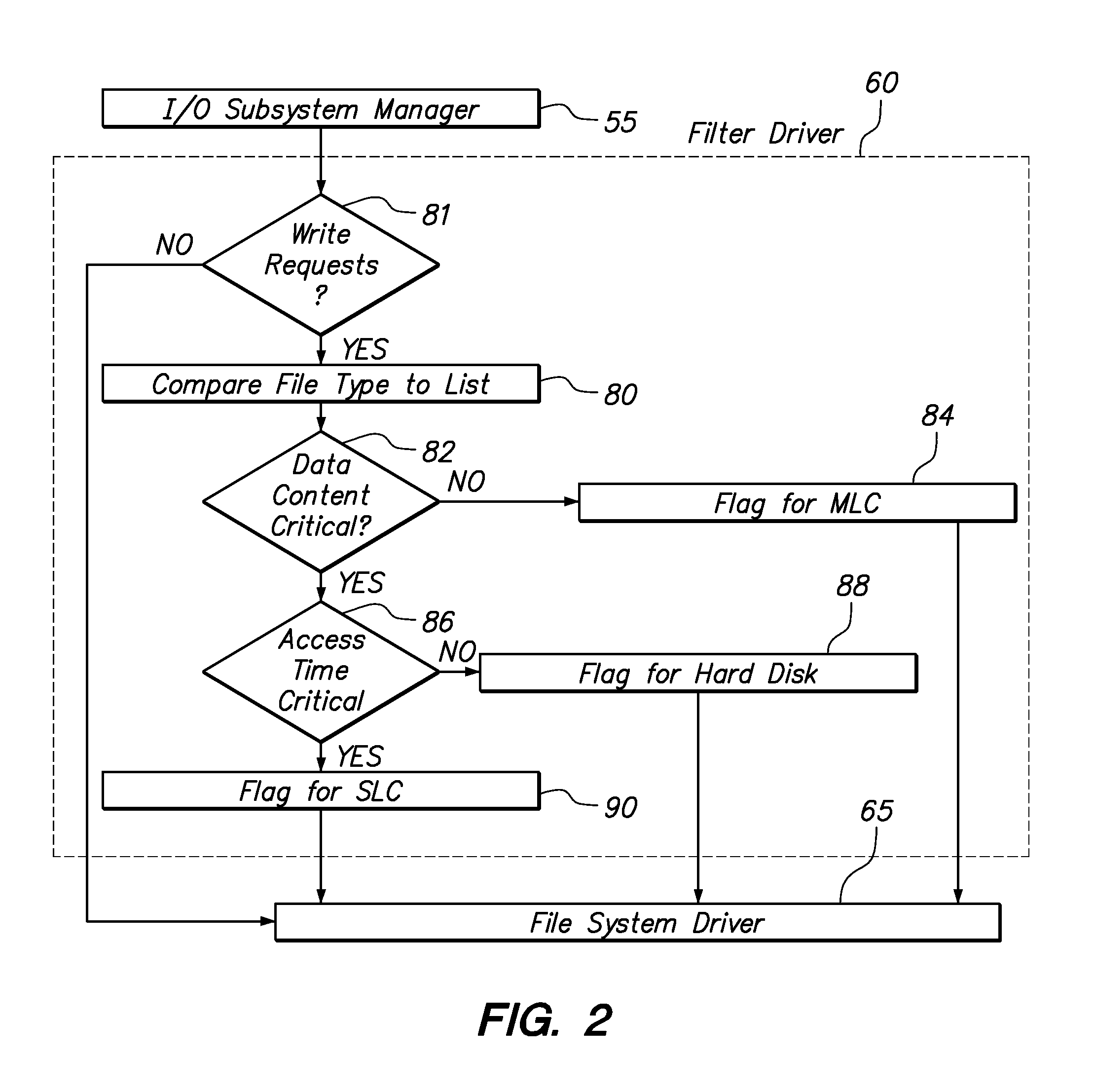
A method and apparatus for dynamically distributing data to an appropriate storage device based on the significance of the data. In one embodiment the method determines the significance of a data file using the format of the data file. The method also includes identifying a storage device and memory location of the storage device to write the data. In a software implementation, a computer system employs a filter driver and / or a device driver to identify and store data files. In another embodiment, a storage controller includes a state machine that initiates and executes firmware to determine the data file format and also the storage device location.
Owner:MCM PORTFOLIO LLC
Method and device for protecting digital data by double re-encryption
InactiveUS7093295B1Television system detailsKey distribution for secure communicationDigital videoDigital data
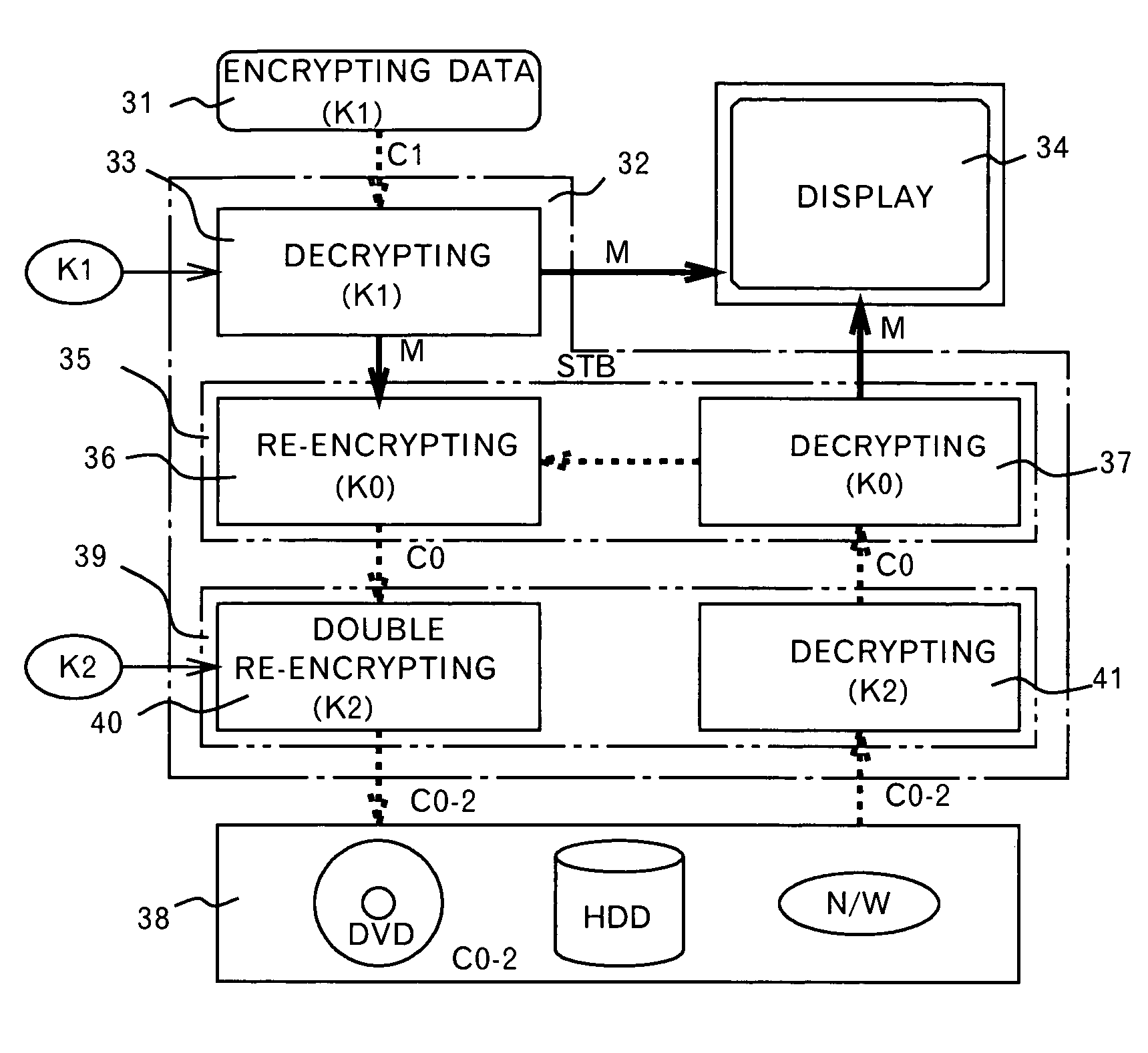
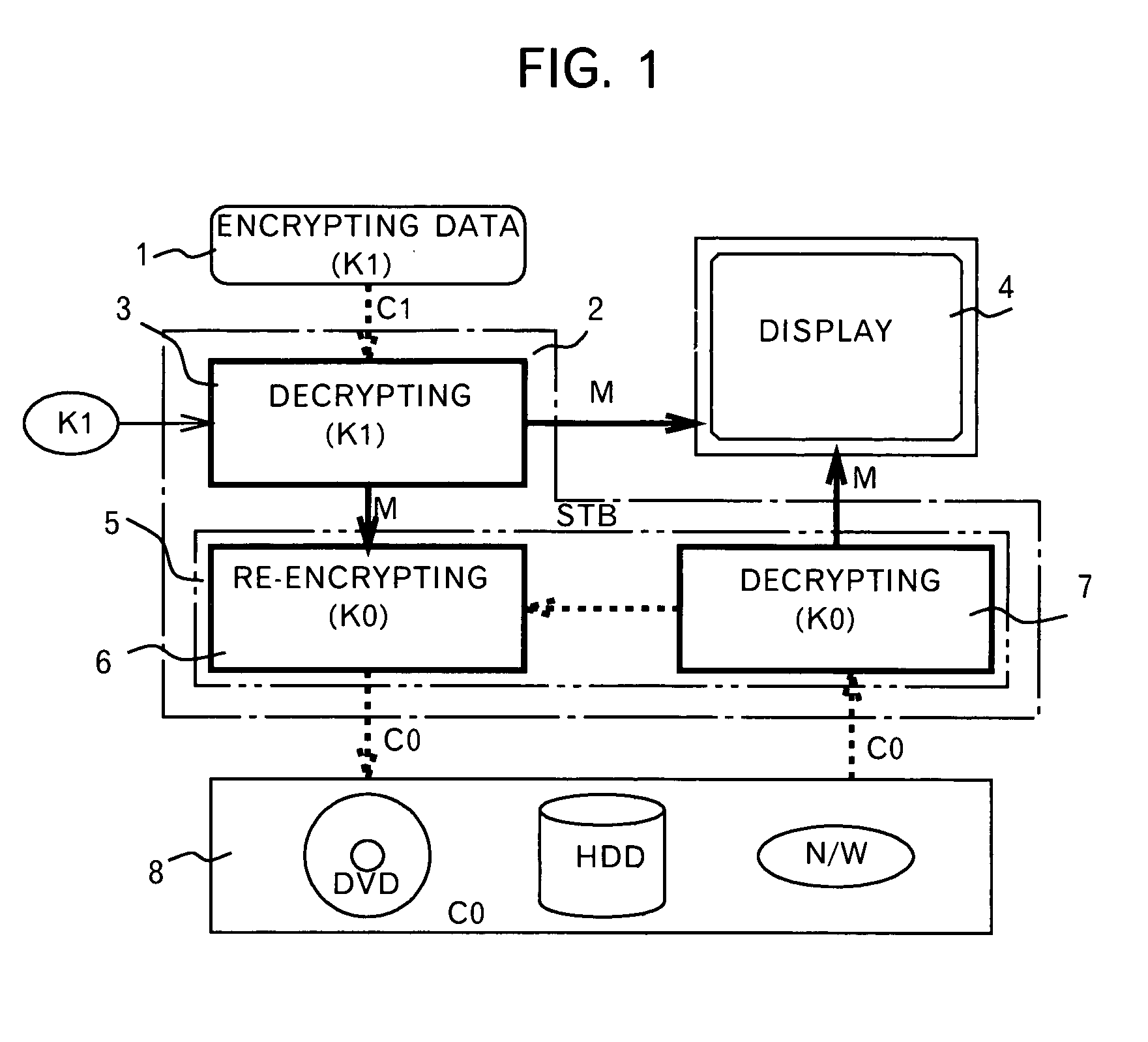
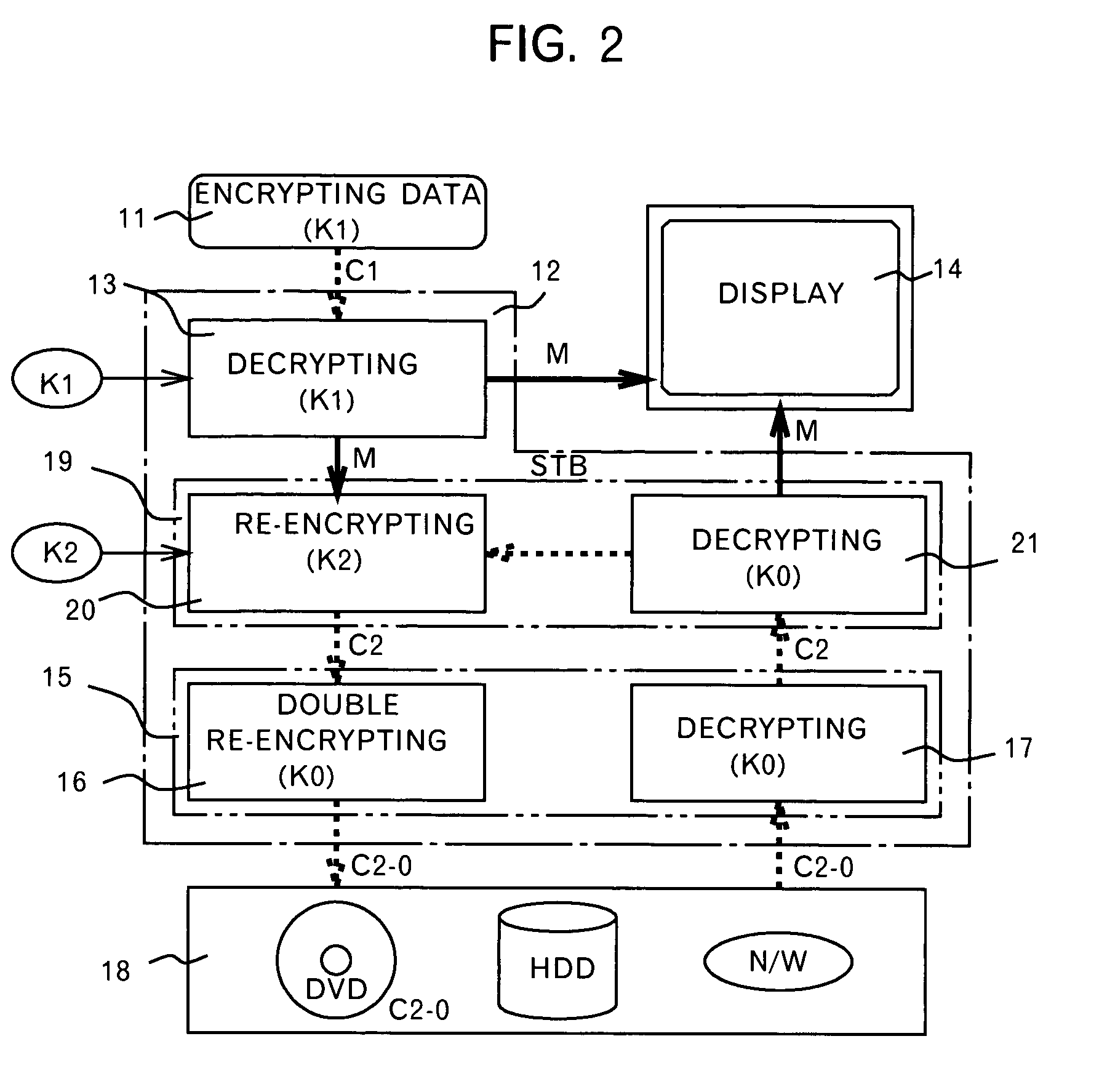
A method and an apparatus ensuring protection of digital data are provided. In addition to re-encrypting the data using an unchangeable key, the data is double re-encrypted using a changeable key. The changeable key is used first and the unchangeable key is then used, or in another case, the unchangeable key is used first, and the changeable key is then used. In the aspect of embodiments, there is a case adopting a software, a case adopting a hardware, or a case adopting the software and the hardware in combination. The hardware using the unchangeable key developed for digital video is available. In adopting the software, encryption / decryption is performed in a region below the kernel which cannot be handled by the user to ensure the security for the program and for the key used. More concretely, encryption / decryption is performed with RTOS using a HAL and a device driver, i.e., a filter driver, a disk driver and a network driver, in an I / O manager. Either one of two filter drivers, with a file system driver between them, may be used. Further, both filter drivers may be used.
Owner:KIOBA PROCESSING LLC
Creating frequent application-consistent backups efficiently
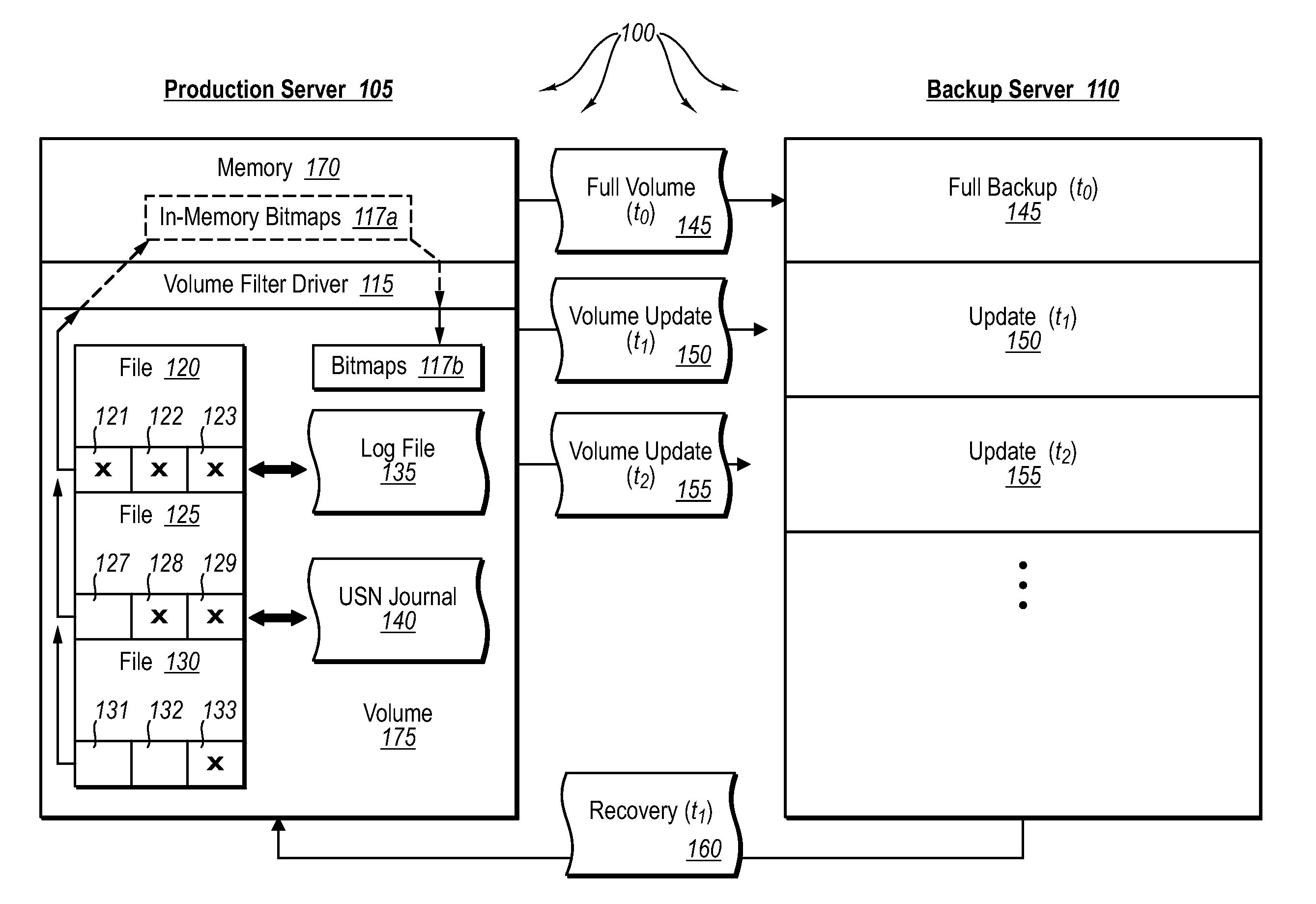
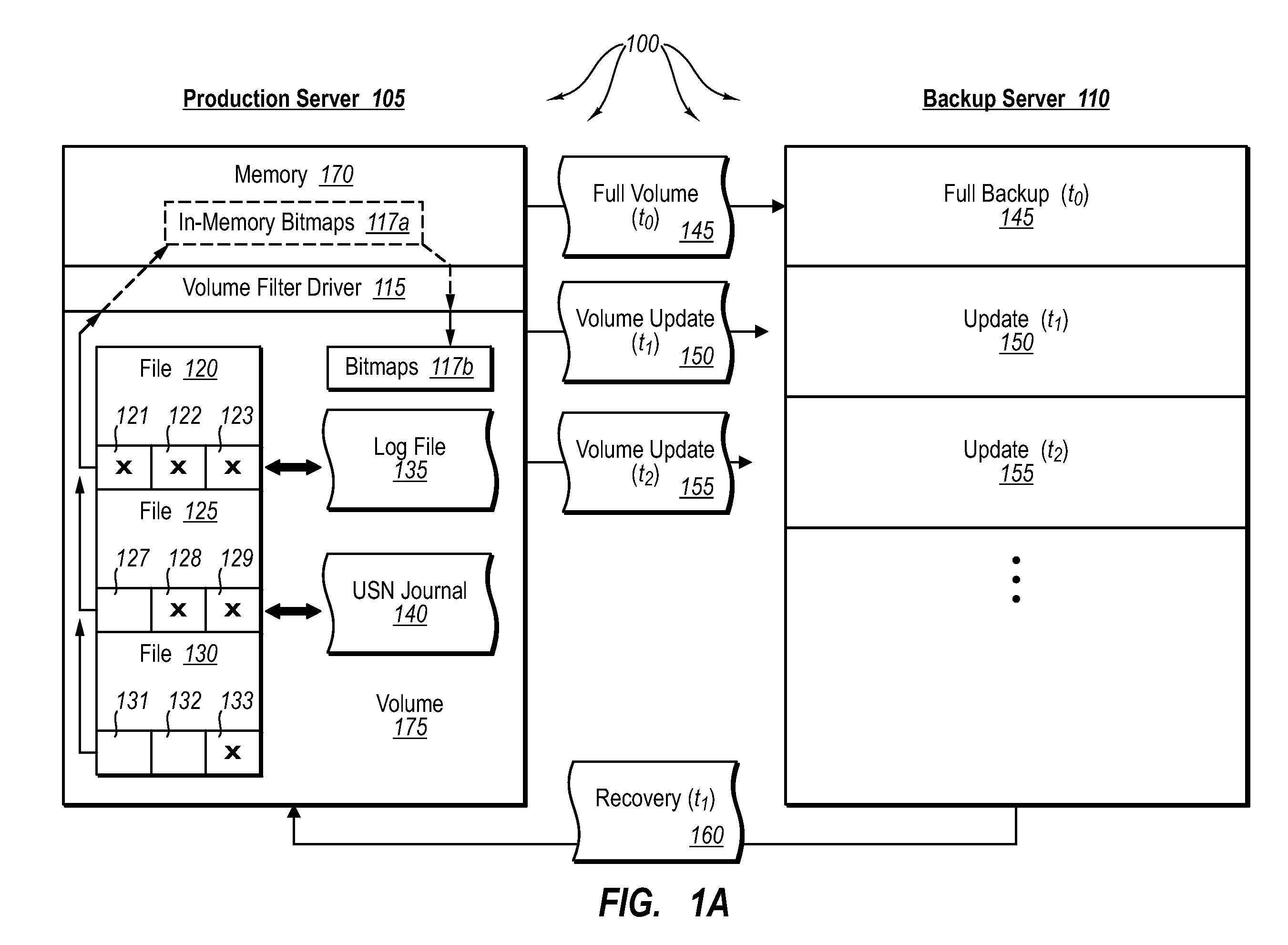
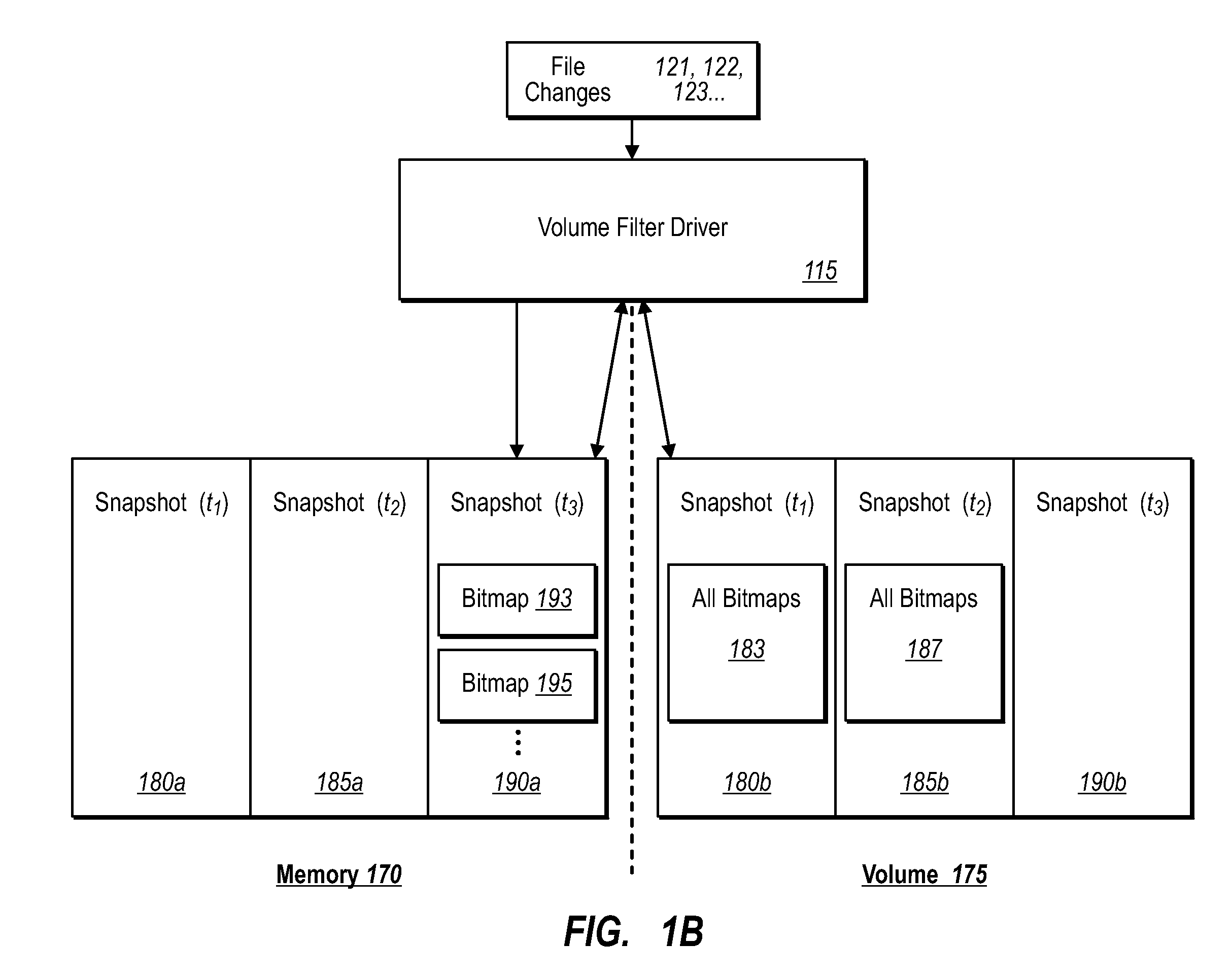
ActiveUS20070276885A1Save resourcesProduction serverData processing applicationsMemory loss protectionApplication softwareBitmap
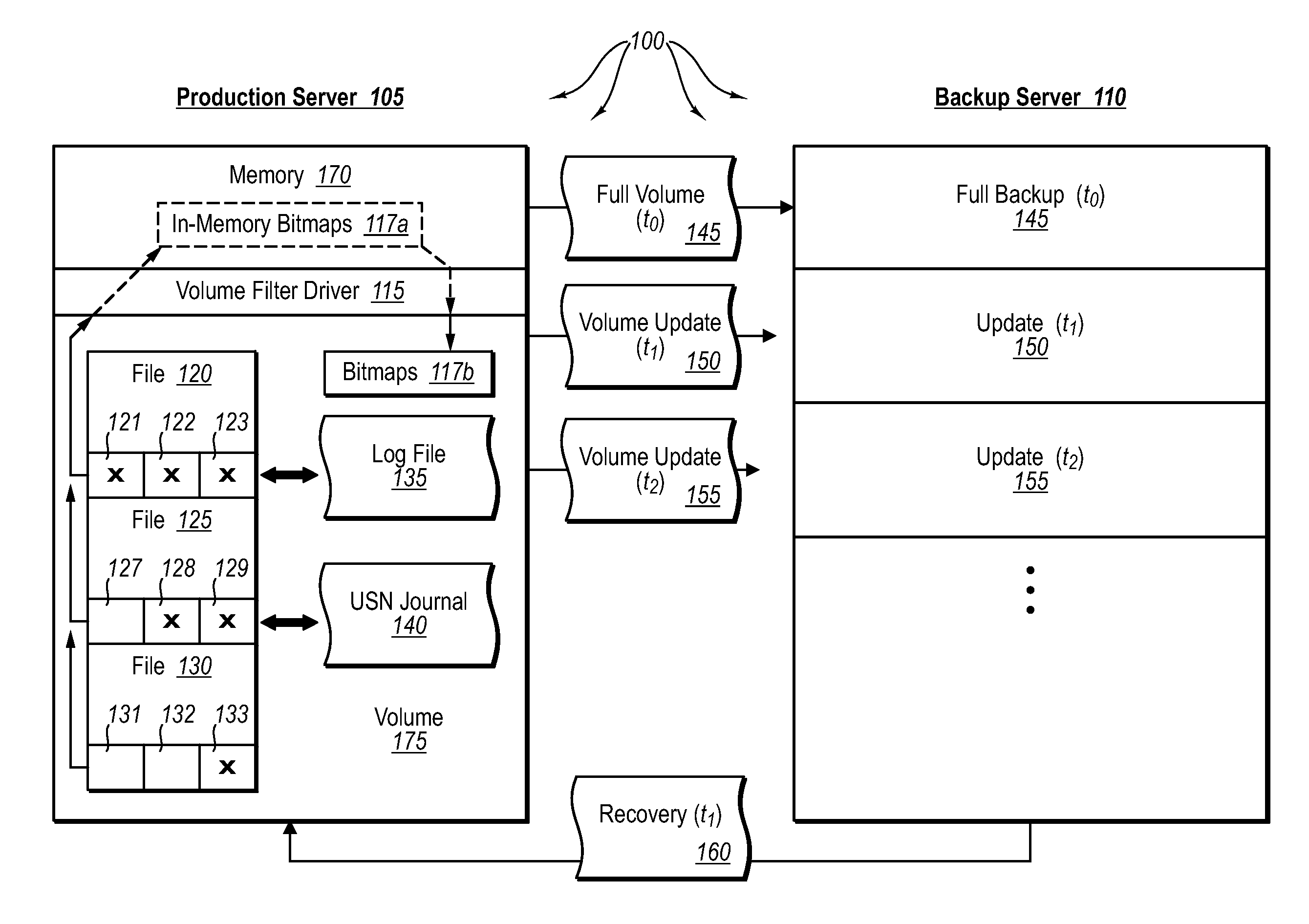
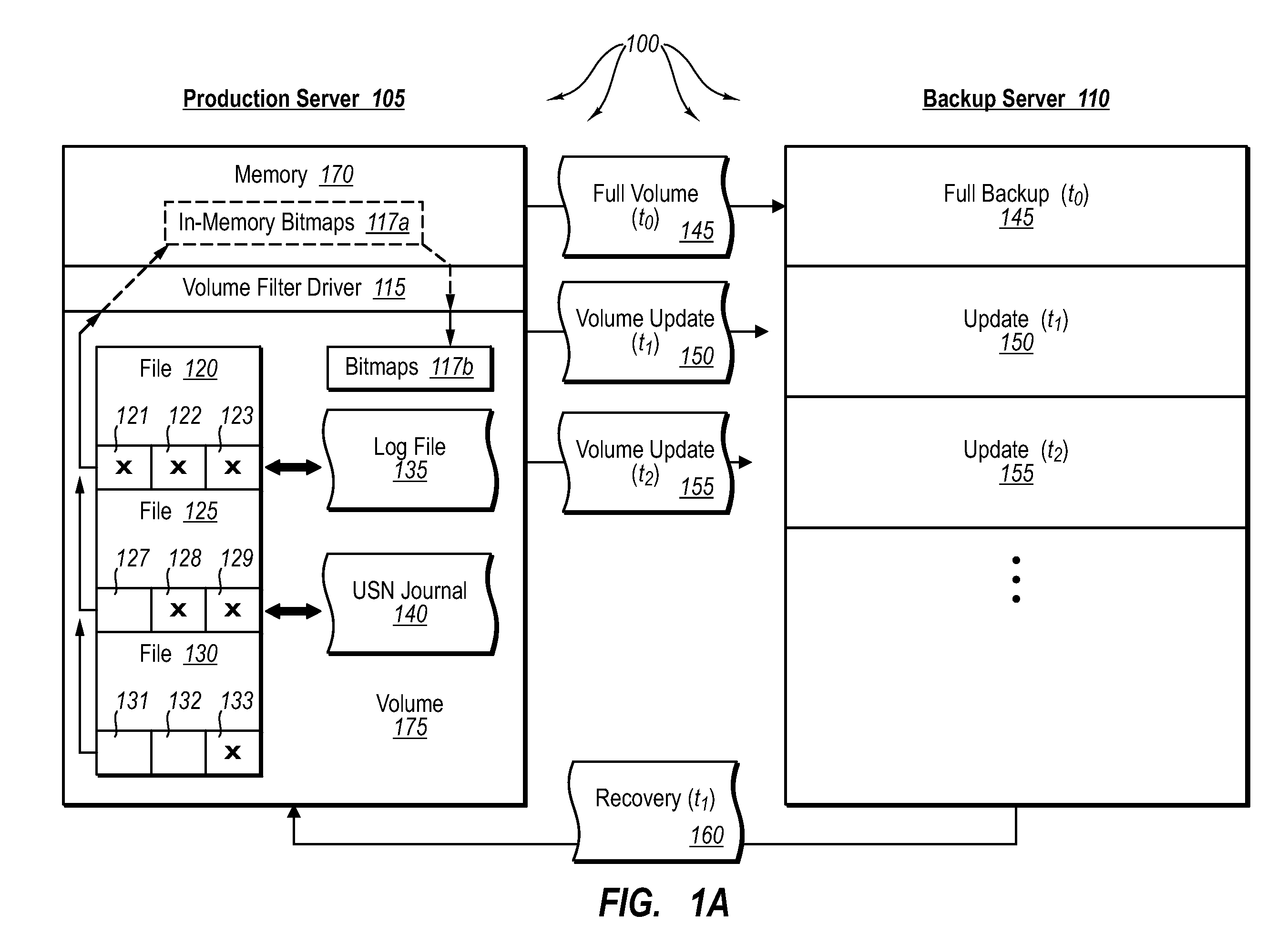
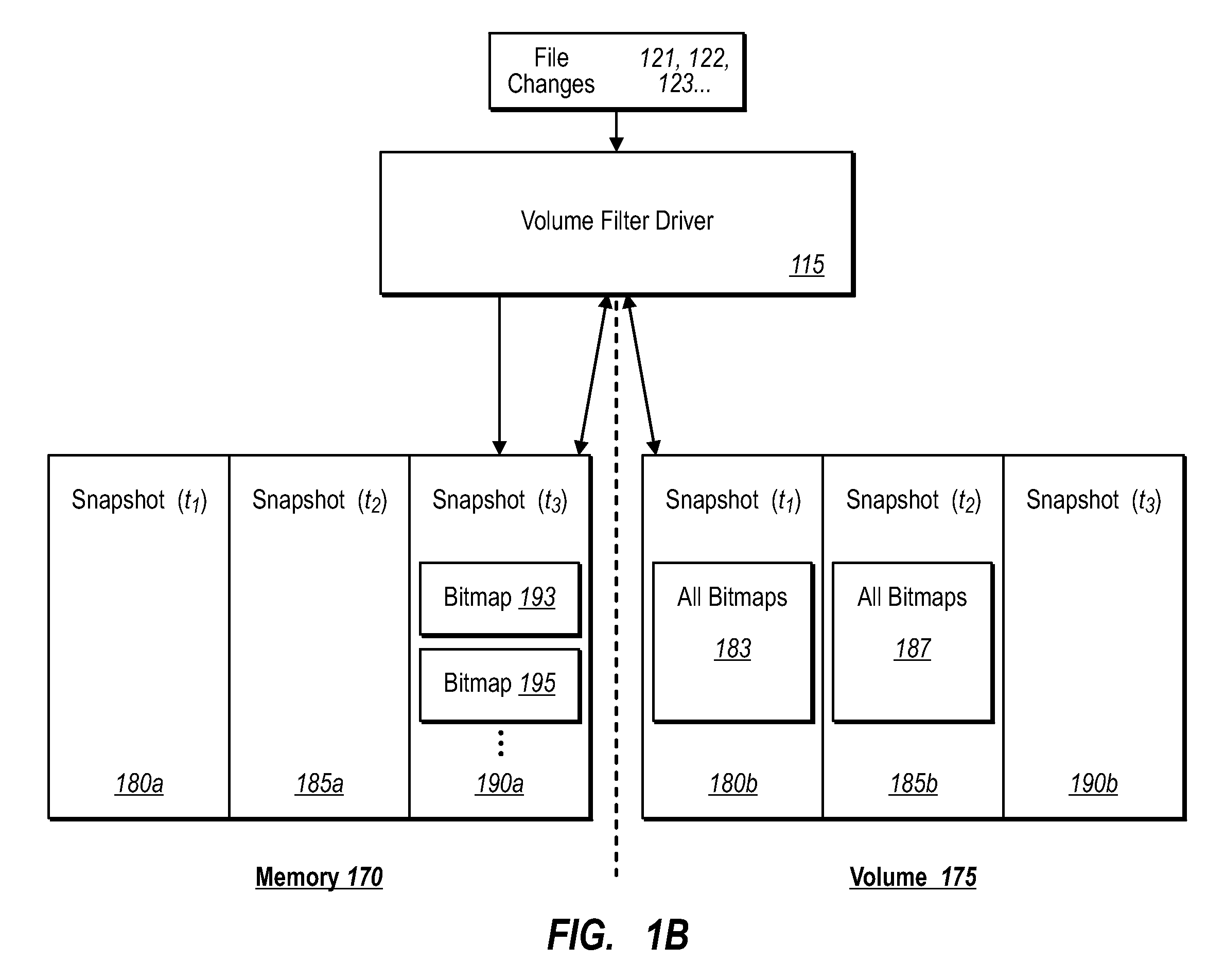
Data can be protected at a production server in a virtually continuous fashion, without necessarily imposing severe constraints on the source application(s). For example, a production server can create an application-consistent backup of one or more volumes, the backups corresponding to a first instance in time. A volume filter driver can monitor data changes in each volume using an in-memory bitmap, while a log file and / or update sequence number journal can keep track of which files have been added to or updated. The volume updates are also consistent for an instance (later) in time. At the next replication cycle, such as every few minutes (however configured), the volume filter driver passes each in-memory bitmap to the physical disk on the production server. The production server then sends the updates to the backup server, which thus stores application-consistent backups for the volume for multiple instances of time.
Owner:MICROSOFT TECH LICENSING LLC
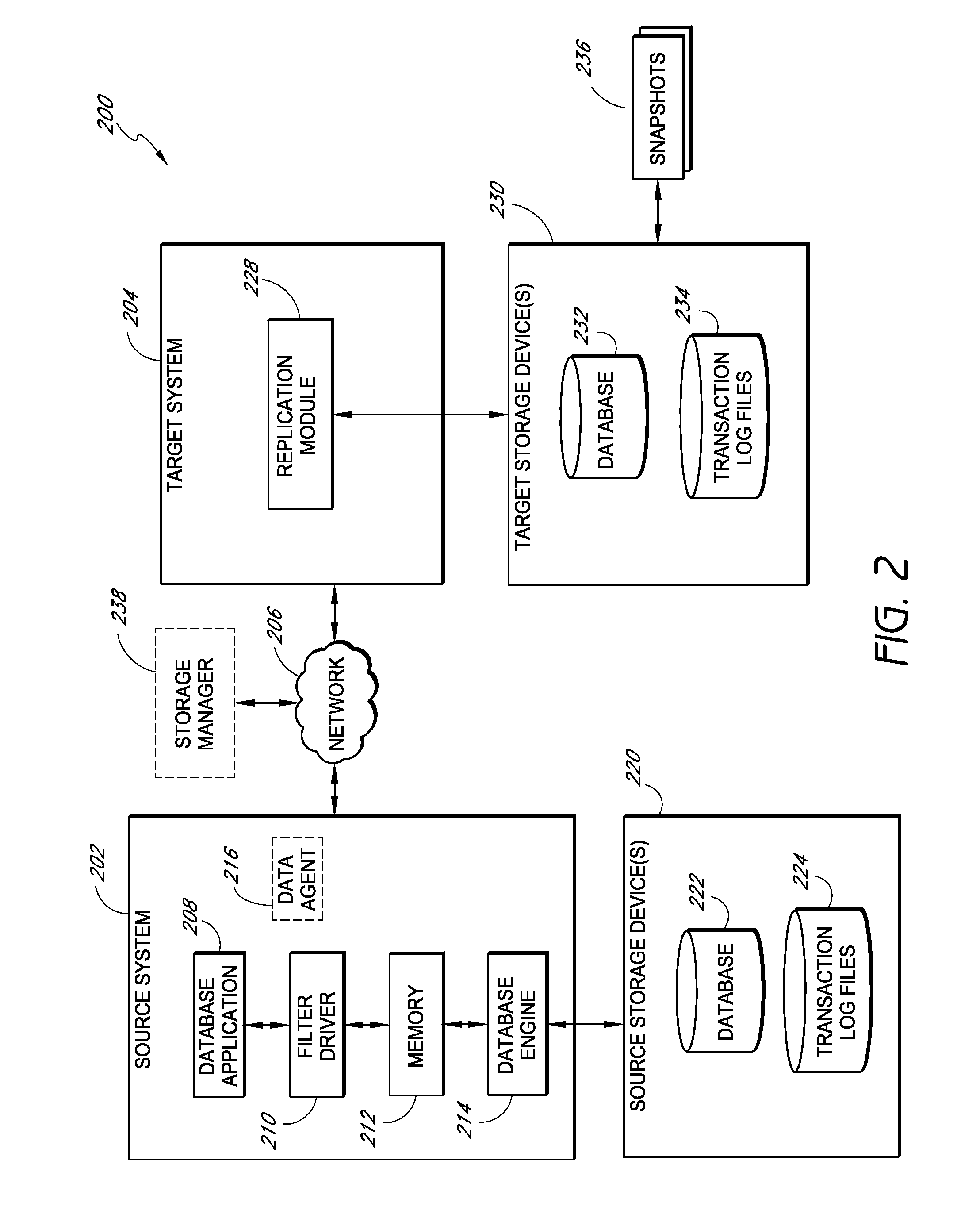
Systems and methods for managing replicated database data
ActiveUS8204859B2Reduce memory requirementsImprove performanceDigital data processing detailsError detection/correctionDatabase applicationApplication software
Systems and methods for replicating database data and generating read-only copies of the replicated data in a clean shutdown state. For example, systems can include a tracking module (e.g., a filter driver) that monitors transactions from a database application to a source storage device to generate log entries having at least one marker indicating a known good state of the application. The systems further include a computer coupled to a target storage device comprising a database and log files. The computer processes the transactions, based on the log entries, to replicate data to the target storage device; performs a first snapshot on data stored in the database and log files; replays into the database data stored in the log files; performs another snapshot on the database; and reverts the database back to a state in which the database existed at the time of the first snapshot.
Owner:COMMVAULT SYST INC
Computer protection against malware affection
ActiveUS20100043072A1Malware can be thwartedMemory loss protectionError detection/correctionOperational systemData memory
A method is provided of protecting a computer against malware affection. The computer has a data storage and an operating system for managing the data storage. The method comprises providing a filter module in the operating system which operates to detect an attempt to store data in the data storage, to determine a data format of the data to be stored in the data storage, and to prevent storage of the data if the data format is determined to relate to a predefined type. The filter module may be provided as a file system filter driver in a kernel of the operating system. The filter module may be arranged to operate between an input / output manager of the operating system and a driver associated with the data storage. The input / output manager and driver associated with the data storage may form part of the kernel of the operating system.
Owner:ROTHWELL WILLIAM GRANT
Systems and methods for maintaining data integrity during a migration
ActiveUS7770053B1Maintain integrityNon-redundant fault processingInput/output processes for data processingData integrityApplication software
Systems and methods are provided for maintaining data integrity in the event of device write failures during a non-disruptive migration. In one embodiment, a computer-implemented method is provided. According to the method, a filter driver in a kernel may clone an application write to both a source storage device and a target storage device. The method may detect whether the cloned application write to the source storage device or the cloned application write to target storage device failed. When the cloned application write to the source storage device or the cloned application write to target storage device failed, the method may allow application reads from only one of the source storage device and the target storage device thereafter.
Owner:EMC IP HLDG CO LLC
Creating frequent application-consistent backups efficiently
ActiveUS7613750B2Save resourcesProduction serverData processing applicationsMemory loss protectionApplication softwareBitmap
Data can be protected at a production server in a virtually continuous fashion, without necessarily imposing severe constraints on the source application(s). For example, a production server can create an application-consistent backup of one or more volumes, the backups corresponding to a first instance in time. A volume filter driver can monitor data changes in each volume using an in-memory bitmap, while a log file and / or update sequence number journal can keep track of which files have been added to or updated. The volume updates are also consistent for an instance (later) in time. At the next replication cycle, such as every few minutes (however configured), the volume filter driver passes each in-memory bitmap to the physical disk on the production server. The production server then sends the updates to the backup server, which thus stores application-consistent backups for the volume for multiple instances of time.
Owner:MICROSOFT TECH LICENSING LLC
Detecting low-level data corruption
ActiveUS7020798B2Low levelError preventionRedundant data error correctionMass storageOperational system
Checksum values are used to detect low-level data corruption. I / O operations, such as, for example, read operations and write operations, cause data blocks to pass through a number of low-level drivers when the data blocks are transferred between an operating system and mass storage location. A checksum filter driver intercepts a data block as the data block passes between low-level drivers as a result of the performance of an I / O operation. The checksum filter driver calculates a first checksum value for the data block. The checksum filter subsequently intercepts the data block as the data block passes between low-level drivers as a result of the performance of a subsequent I / O operation. The checksum filter driver calculates a second checksum value for the data block. The first checksum value and the second checksum value are compared. Data corruption is detected when a checksum mismatch occurs.
Owner:MICROSOFT TECH LICENSING LLC
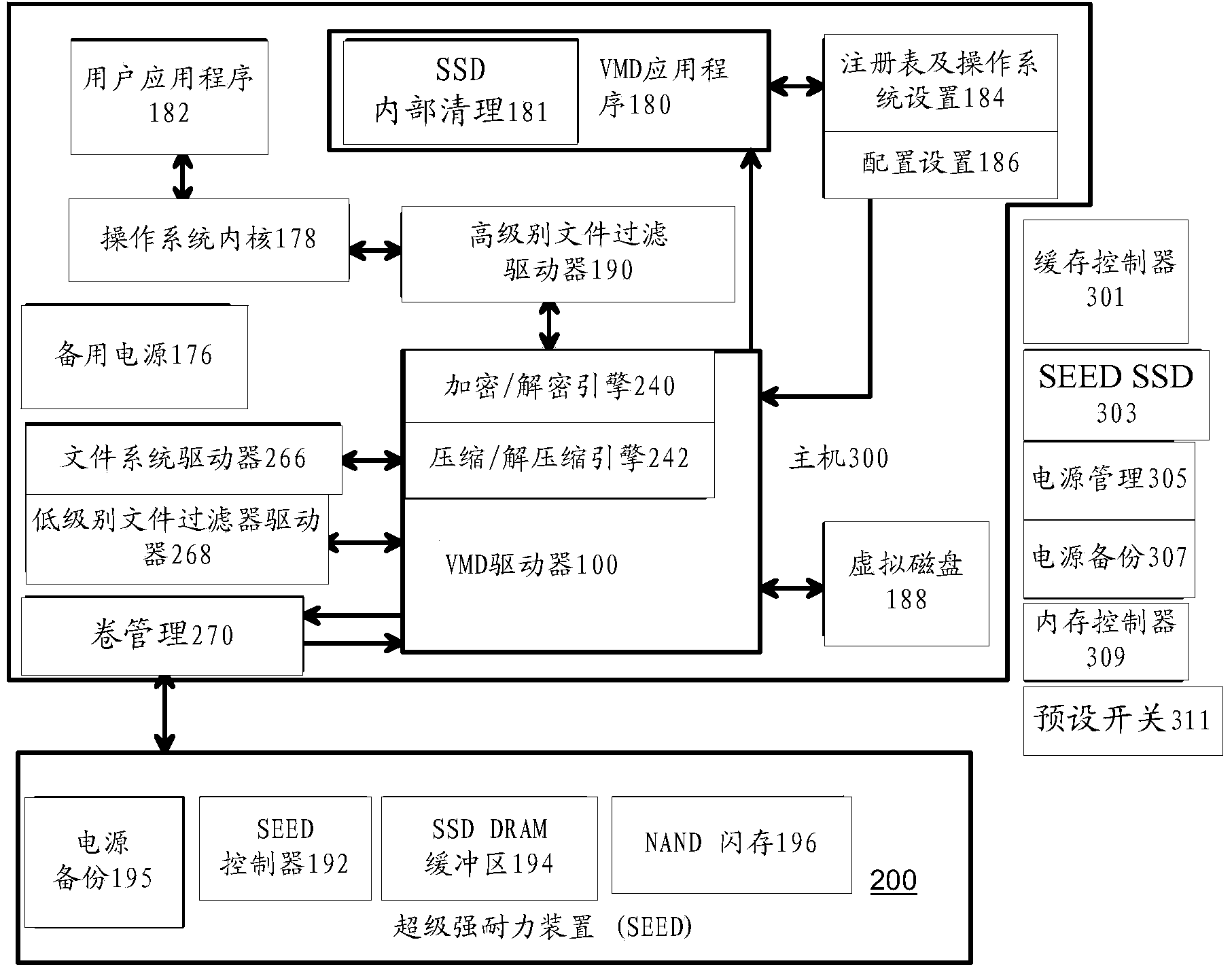
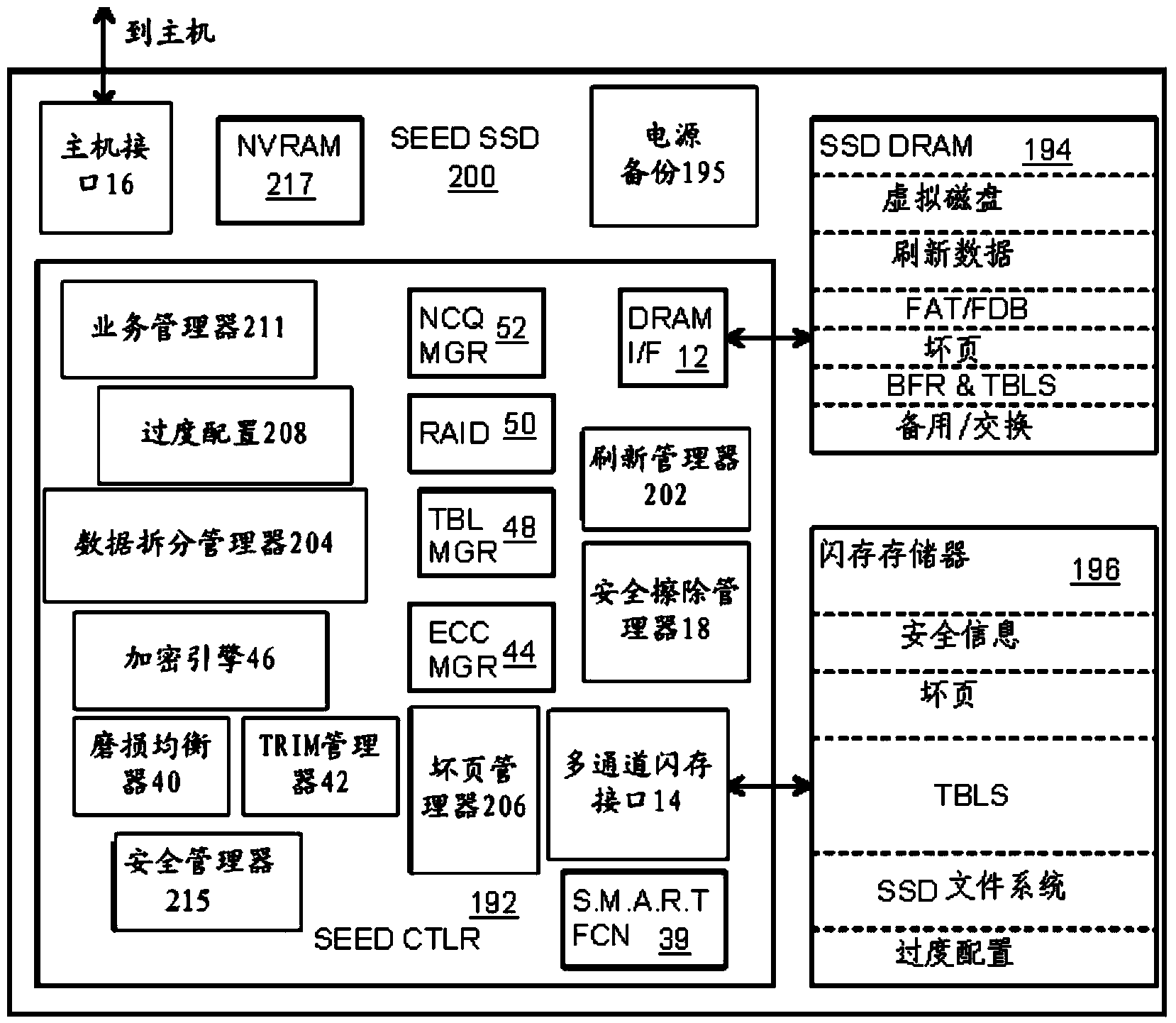
Data-Retention Controller/Driver for Stand-Alone or Hosted Card Reader, Solid-State-Drive (SSD), or Super-Enhanced-Endurance SSD (SEED)
ActiveUS20160070474A1Memory architecture accessing/allocationInput/output to record carriersSolid-state driveCard reader
A Green NAND SSD Driver (GNSD) driver executes on a host to increase data-retention of flash memory attached to a Super Enhanced Endurance Device (SEED) or Solid-State Drive (SSD). Host accesses to flash are intercepted by the GNSD driver using upper and lower-level filter drivers. A retention-check timer causes a retention routine to be periodically executed. The routine sends high-level commands to the SEED that causes the SEED to refresh either all data or just data blocks with older write dates. Data is refreshed by moving to a new physical block. The retention routine can track write dates of logical blocks and command a SSD to move logical blocks with older write dates. A retention card has a controller that performs the retention routine when not connected to a host, while a SEED power card allows the SEED to refresh data when no host is attached to the SEED.
Owner:SUPER TALENT TECH CORP
Vmd application/driver
The invention provides a VMD (Virtual-Memory Device) executed on a host and application thereof for enhancing flash memory endurance of an SEED (Super Enhanced Endurance Device) or an SSD (Solid-State Drive). The VMD driver utilizes a high-level or a low-level filtering driver to intercept and capture access to flash memory of the host and to sort access to the flash memory of the host into paging file data type, temporary files, meta data and user data files by using address range and file extensions read by the meta data. Optionally, the paging files and the temporary files are written in the flash memory. Full pages and local pages are grouped into multi-page metapage according to data type before SSD storage data passes. A virtual RAM disk and cache storing the data type in the host DRAM are managed and refreshed to SSD through the VMD driver. Write data is stored for blocks or pages managing functions. Flash memory abrasion is reduced in a backup / exchange area in the DRAM. The reference voltage is adjusted when error correction fails.
Owner:武汉网上网科技有限公司
Methods and systems for accessing remote user files associated with local resources
ActiveUS20080098006A1Digital data processing detailsDatabase distribution/replicationVirtualizationConfigfs
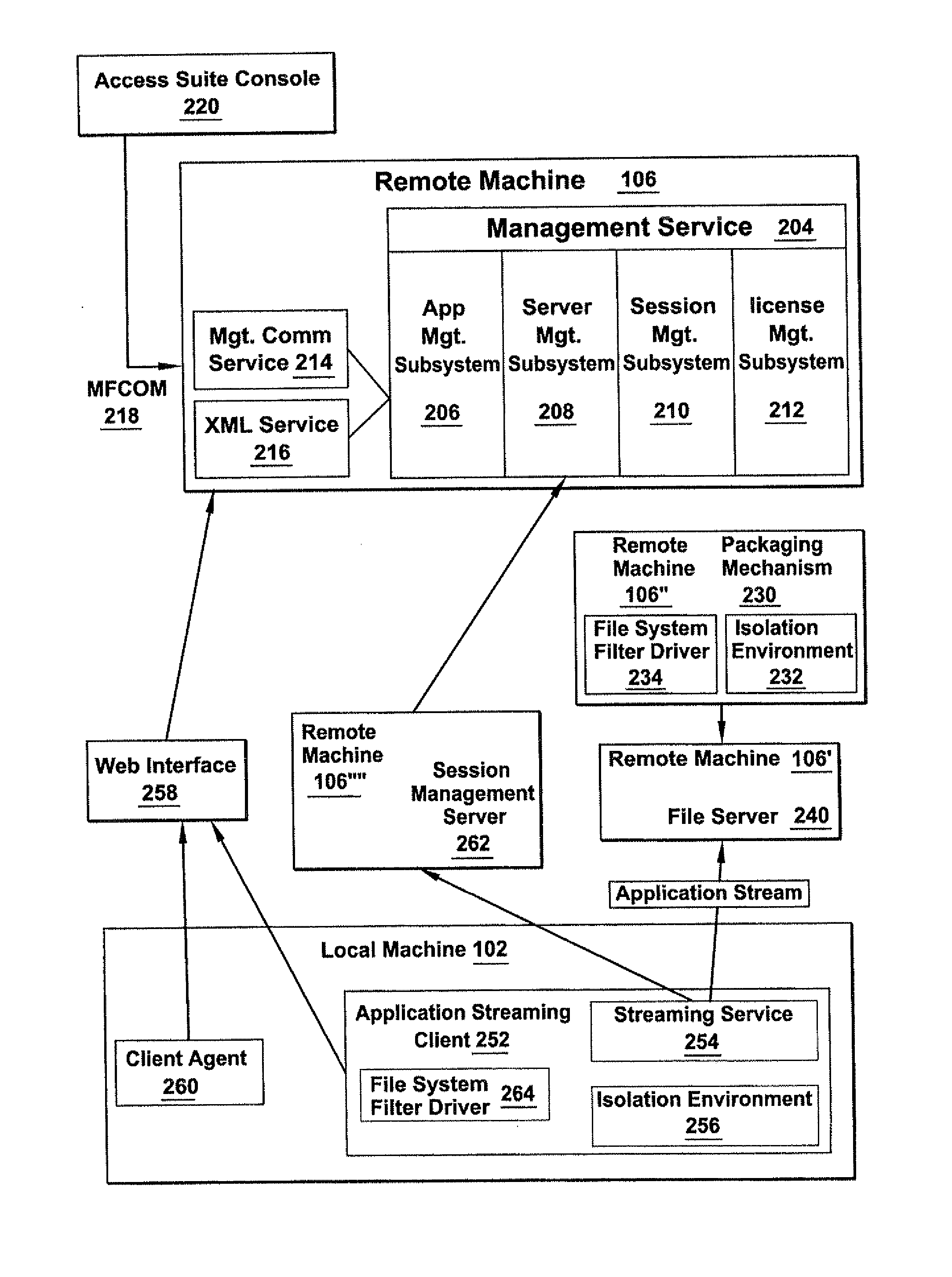
A system for accessing, by a resource, a setting in a virtualized user profile includes an isolation environment, a resource, and a filter driver. The resource executes outside an isolation environment on a local machine and requests access to a setting in a user profile. The filter driver intercepts the request for access and identifies one of the isolation environment and a remote machine, responsive to an application of a rule to the request. The filter driver redirects the request to the one of the isolation environment and the remote machine. A method includes intercepting an instruction from a resource to modify a setting on a local machine, the resource provided by a local machine and executing outside of an isolation environment. The method includes identifying the isolation environment, responsive to an application of a rule to the instruction. The method includes redirecting the instruction to the isolation environment.
Owner:CITRIX SYST INC
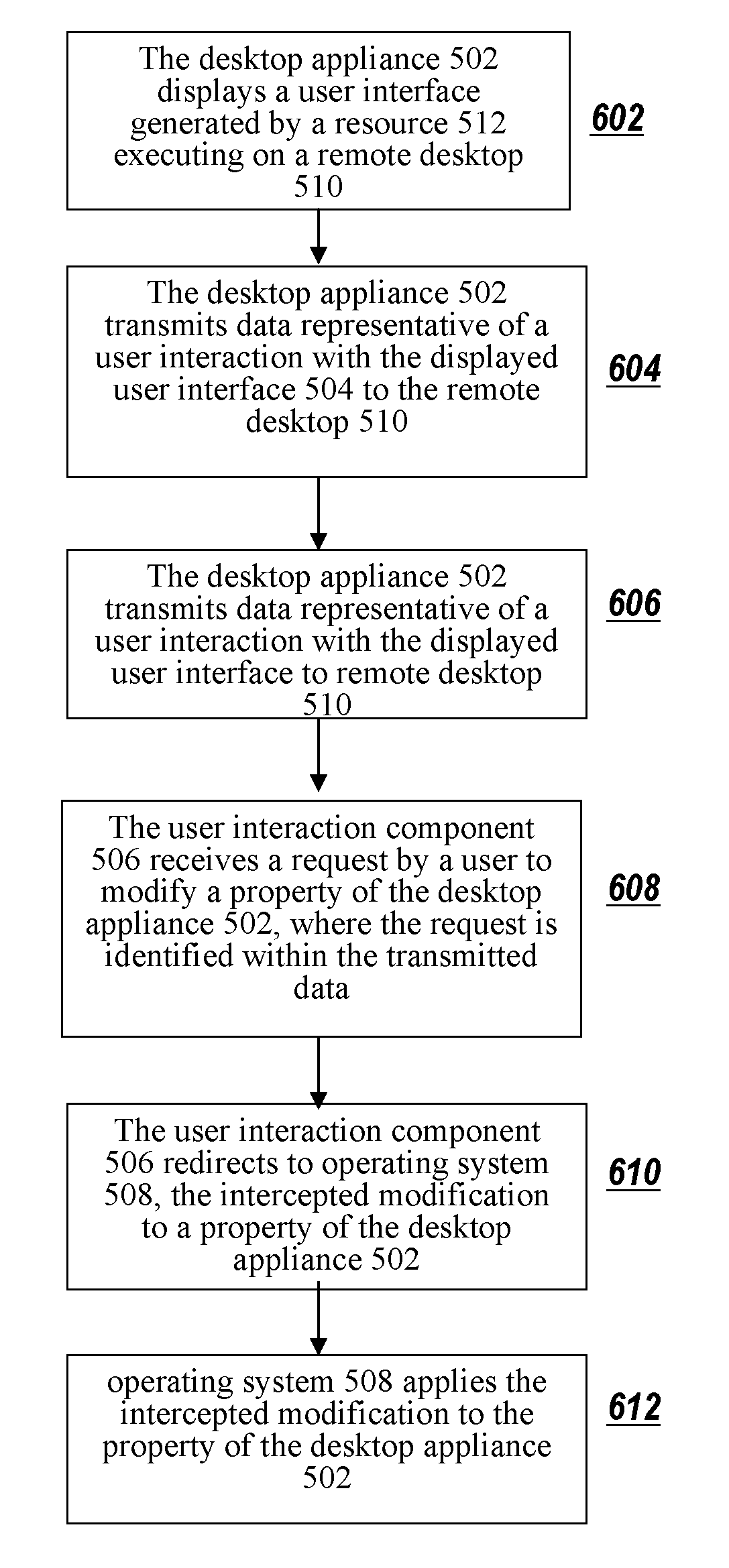
Methods and systems for providing a modifiable machine base image with a personalized desktop environment in a combined computing environment
A method and system for modifying, in a combined computing environment, a machine base image having a personalized desktop environment includes executing an operating system associated with a base disk; intercepting, by a filter driver, an instruction from at least one of a plurality of resources to modify a setting stored in at least one of a file system and a registry, the plurality of resources executing inside an isolation environment; storing, in a delta disk, a copy of the modified setting; restarting the operating system; replacing the setting stored in the at least one of the file system and the registry with the copy of the modified setting stored on the delta disk; and restarting at least one operating system process incorporating the modified setting.
Owner:CITRIX SYST INC
Data integrity for data storage devices shared by multiple hosts via a network
InactiveUS20090043971A1Digital data information retrievalMemory adressing/allocation/relocationData integrityNetworked system
Owner:LEE HEON SU
Methods and Systems for Forcing an Application to Store Data in a Secure Storage Location
ActiveUS20110277013A1User identity/authority verificationPlatform integrity maintainanceClient-sideClient machine
The present application is directed to methods and systems for redirecting write requests issued by trusted applications to a secure storage. Upon redirecting the write requests, the data included in those requests can be stored in the secure storage area of a client computer. In some embodiments, the methods and systems can include determining whether an application issuing the request is a trusted application that requires data to be stored in a secure storage repository. Upon making this determination, a filter driver can identify a secure storage area on a client computer and can redirect the write request to this secure storage. In other embodiments, the filter driver may deny requests of trusted applications to write to unsecure storage areas.
Owner:CITRIX SYST INC
System using a single host to receive and redirect all file access commands for shared data storage device from other hosts on a network
ActiveUS7457880B1Maintain data integrityDigital data information retrievalMultiple digital computer combinationsData integrityNetworked system
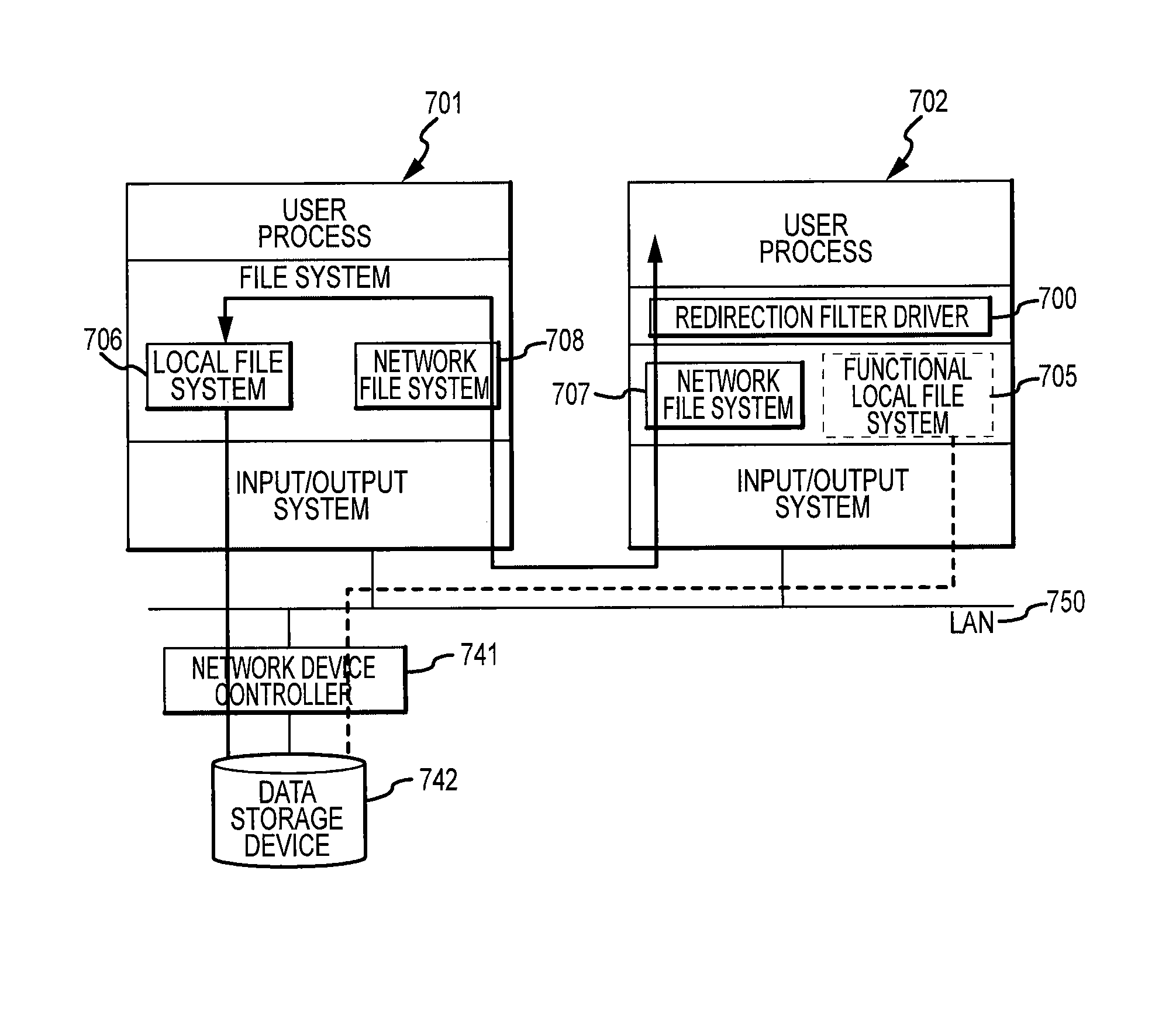
Access by multiple hosts, such as computers, to a data storage device by way of a network while maintaining data integrity. In one embodiment, a method for accessing the storage device includes acquiring a resource “lock” that provides exclusive access to one of the hosts at a time. In another embodiment, the file systems of a first and second host provide file system attributes stored in a storage device to provide mutually exclusive access for each host to free blocks of the device. In another embodiment, a networked system contains a first host having exclusive direct access to a storage device over a digital network. A second host requiring access to the storage device communicates with the first host by way of the digital network. File access requests generated by the second host are transferred by a redirection filter driver within the second host to the first host.
Owner:SYNKLOUD TECH LLC
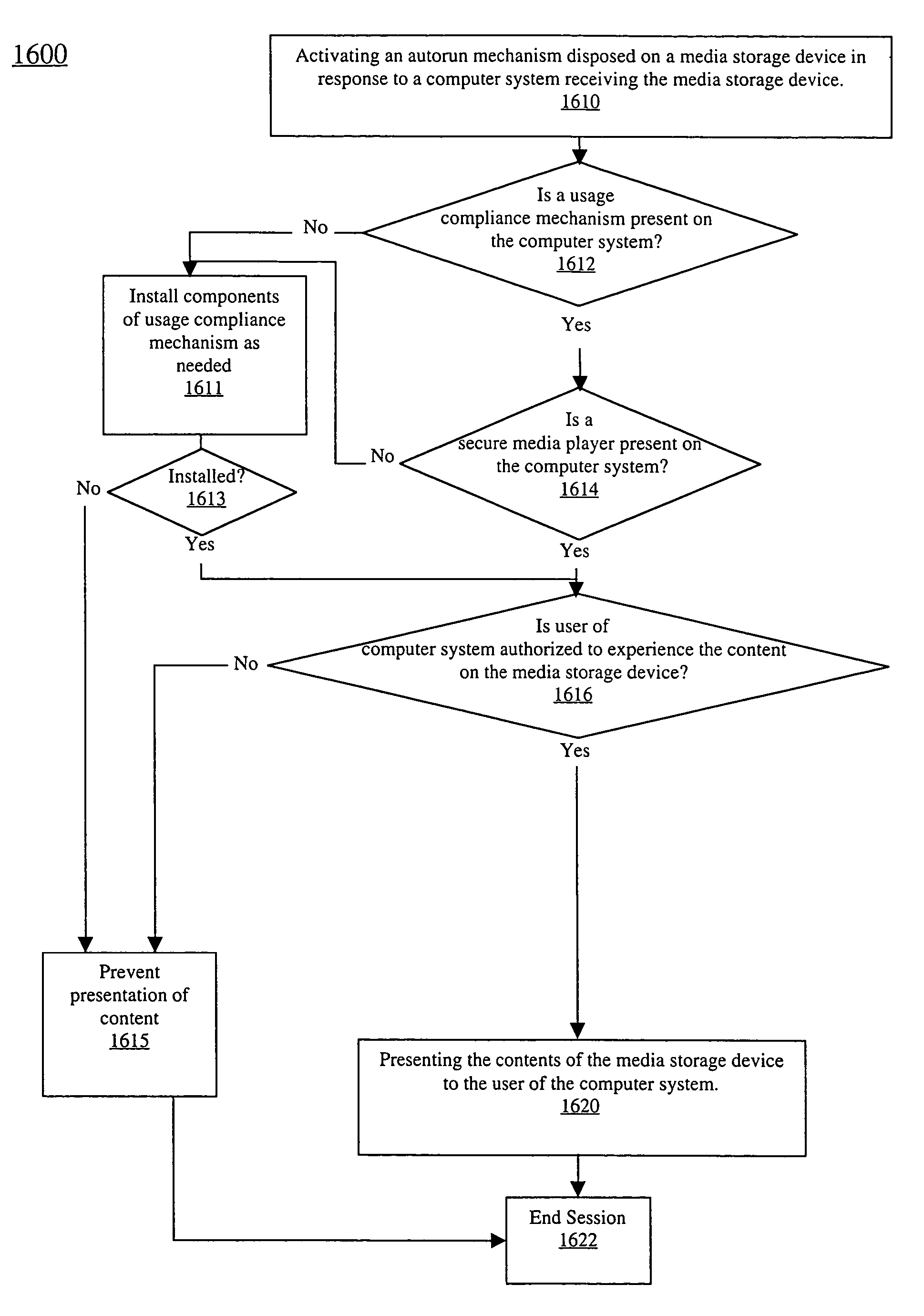
Method and system for controlling presentation of computer readable media on a media storage device
InactiveUS20050172122A1Digital data processing detailsUser identity/authority verificationPresent methodComputer science
A method of controlling presentation of content on a media storage device is described. The method is comprised of verifying the presence of a media presentation mechanism and a usage compliance mechanism on a computer system operated by a recipient to whom the media storage device is distributed. The usage compliance mechanism includes a file system filter driver for controlling data reads associated with the computer readable media. The media presentation mechanism is communicatively coupled with the usage compliance mechanism. The present method further includes the file system driver performing a first decryption of the computer readable media. The present method further includes the media presentation mechanism performing a second decrypting of the computer readable media concurrent with presenting the computer readable media to the recipient.
Owner:MUSIC PUBLIC BROADCASTING
Virtual Memory Device (VMD) Application/Driver for Enhanced Flash Endurance
ActiveUS20150106557A1Memory architecture accessing/allocationInput/output to record carriersVirtual memoryFilename extension
A Virtual-Memory Device (VMD) driver and application execute on a host to increase endurance of flash memory attached to a Super Enhanced Endurance Device (SEED) or Solid-State Drive (SSD). Host accesses to flash are intercepted by the VMD driver using upper and lower-level filter drivers and categorized as data types of paging files, temporary files, meta-data, and user data files, using address ranges and file extensions read from meta-data tables. Paging files and temporary files are optionally written to flash. Full-page and partial-page data are grouped into multi-page meta-pages by data type before storage by the SSD. Ramdisks and caches for storing each data type in the host DRAM are managed and flushed to the SSD by the VMD driver. Write dates are stored for pages or blocks for management functions. A spare / swap area in DRAM reduces flash wear. Reference voltages are adjusted when error correction fails.
Owner:SUPER TALENT TECH CORP
Electronic computer system secured from unauthorized access to and manipulation of data
ActiveUS20060069692A1Improve isolationFacilitate redirectionDigital data processing detailsDigital computer detailsSystem callAuthentication
A software security application for a Windows® OS based electronic computer system provides an isolated User environment which protects a User from unauthorized access to and manipulation of data on the system. The security software implements an isolated User file system and provides process / IPC isolation, Windows® registry isolation, network interface isolation, and isolated administrative control on the computer system. Interactive components of the system include an execution hook component that traps system calls, a job object component that creates / destructs, manages and manipulates job objects, a system call hook component for trapping and filtering all Windows registry I / O requests, a file system block device driver for mounting / unmounting the isolated User file system, a file system / filter driver, a network interface / NDIS hook component, and an environment handler. The environment handler provides the overall management interface for other system components, allowing definition of rules, managing authentication and other control / management functions.
Owner:VIIRII LLC
File aware block level deduplication
ActiveUS20110071989A1Digital data processing detailsError detection/correctionClient-sideBlock level
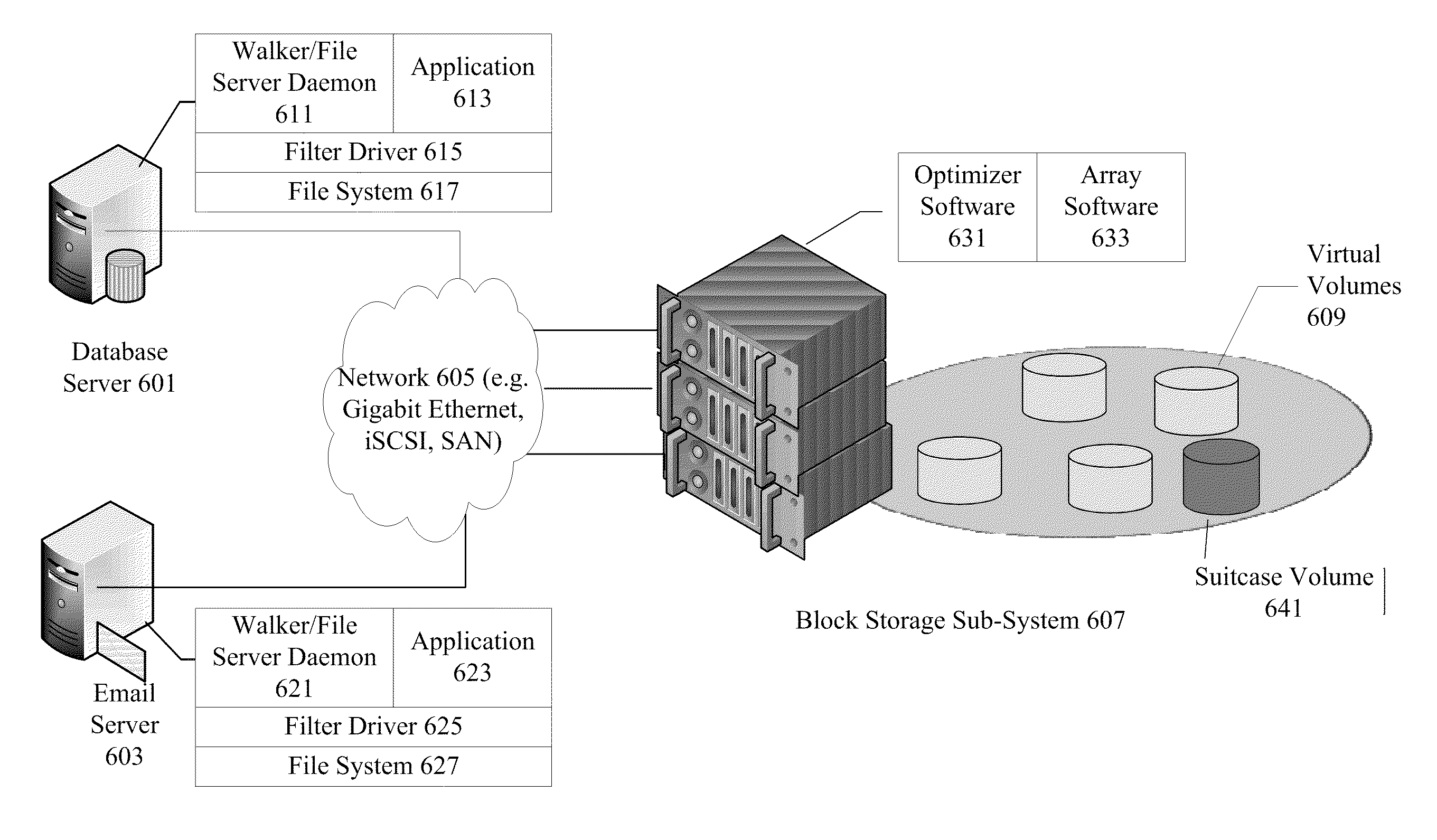
A system provides file aware block level deduplication in a system having multiple clients connected to a storage subsystem over a network such as an Internet Protocol (IP) network. The system includes client components and storage subsystem components. Client components include a walker that traverses the namespace looking for files that meet the criteria for optimization, a file system daemon that rehydrates the files, and a filter driver that watches all operations going to the file system. Storage subsystem components include an optimizer resident on the nodes of the storage subsystem. The optimizer can use idle processor cycles to perform optimization. Sub-file compression can be performed at the storage subsystem.
Owner:QUEST SOFTWARE INC
End-to-end checksumming for read operations
InactiveUS20030177435A1Error detection/correctionCode conversionData validationSource Data Verification
Described are techniques used in detection of a data corruption in a computer system in connection with read and write operations. For a write operation, a host issues a write request that includes a checksum value determined in accordance with data associated with the write request. The write request is received by a data storage system that performs data validation using the checksum. The host issues a vendor-defined write request operation that includes the checksum as a data field in the request packet sent to the data storage system. For a read operation, a host issues a read request and the data storage system determines a checksum value before servicing the read request. The checksum is validated at the top of the I / O stack on the host by the file system filter driver.
Owner:EMC IP HLDG CO LLC
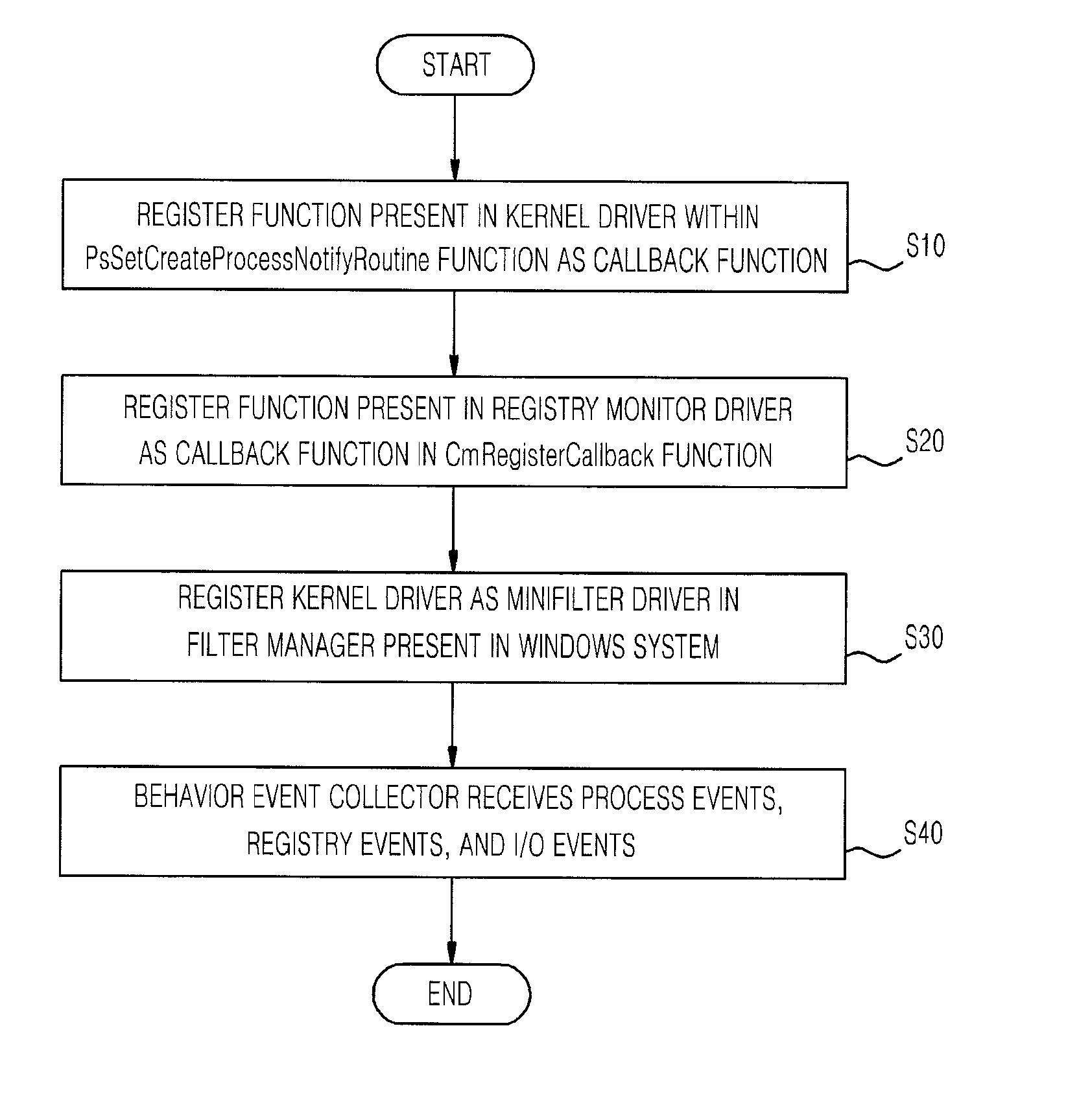
Malware auto-analysis system and method using kernel callback mechanism
InactiveUS20120079594A1Hamper efficiency of systemMalware may monitorMemory loss protectionError detection/correctionMalwareAnalysis method
In a malware auto-analysis method using a kernel callback mechanism, a function, present in a kernel driver within a PsSetCreateProcessNotifyRoutine function, is registered by a process monitor driver as a callback function when a computer boot. A function present in a registry monitor driver is registered by the registry monitor driver as a callback function in a CmRegisterCallback function when the driver is loaded. A kernel driver is registered by a file monitor driver as a mini-filter driver in a Filter Manager present in a Windows system. At least one of a process event, a registry event, or an Input / Output (I / O) event is received by a behavior event collector from the process monitor driver, the registry monitor driver, or the file monitor driver, respectively.
Owner:KOREA INTERNET & SECURITY AGENCY
Memory compression for computer systems
InactiveUS20030229761A1Memory architecture accessing/allocationData processing applicationsOperational systemComputerized system
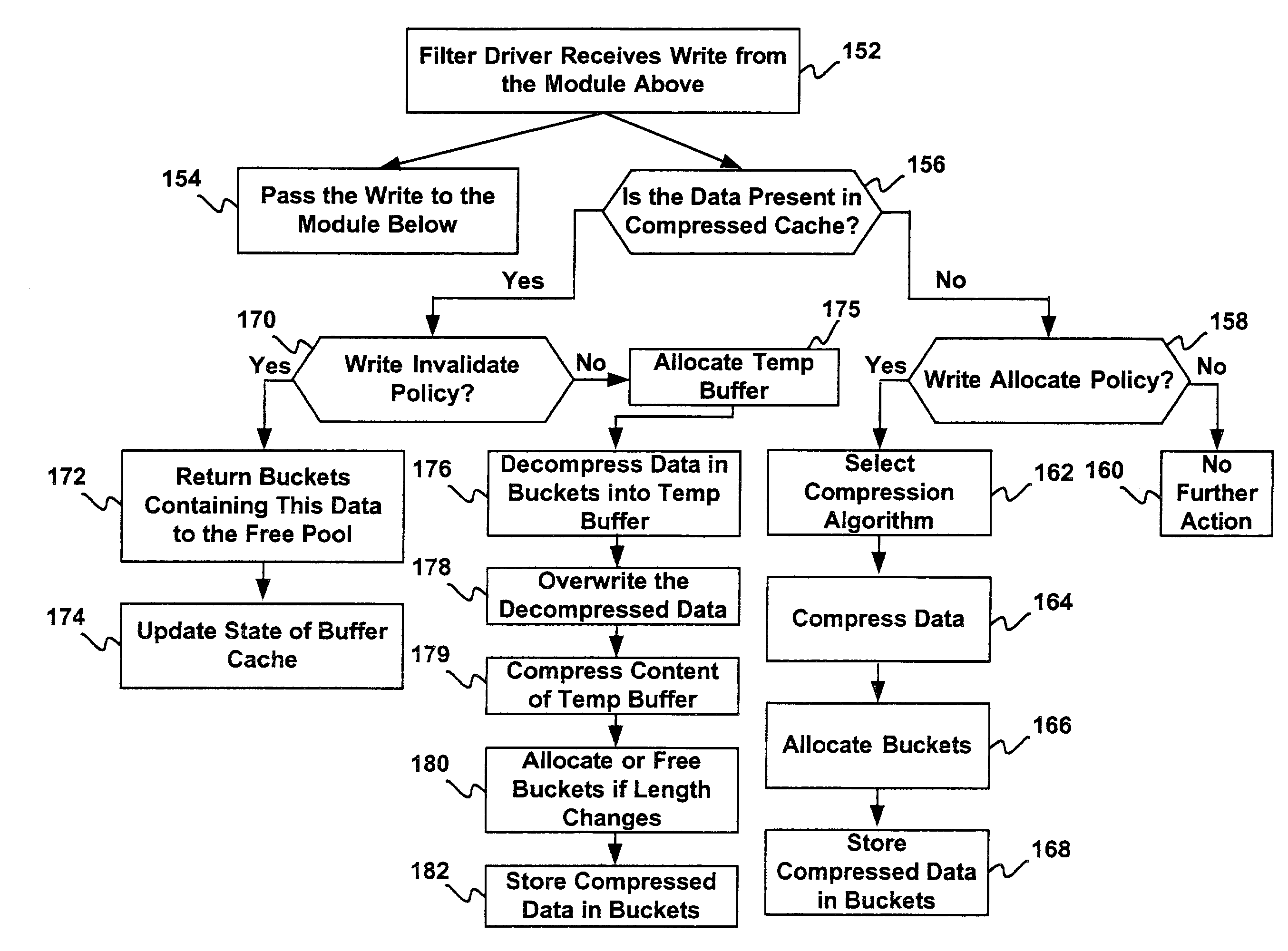
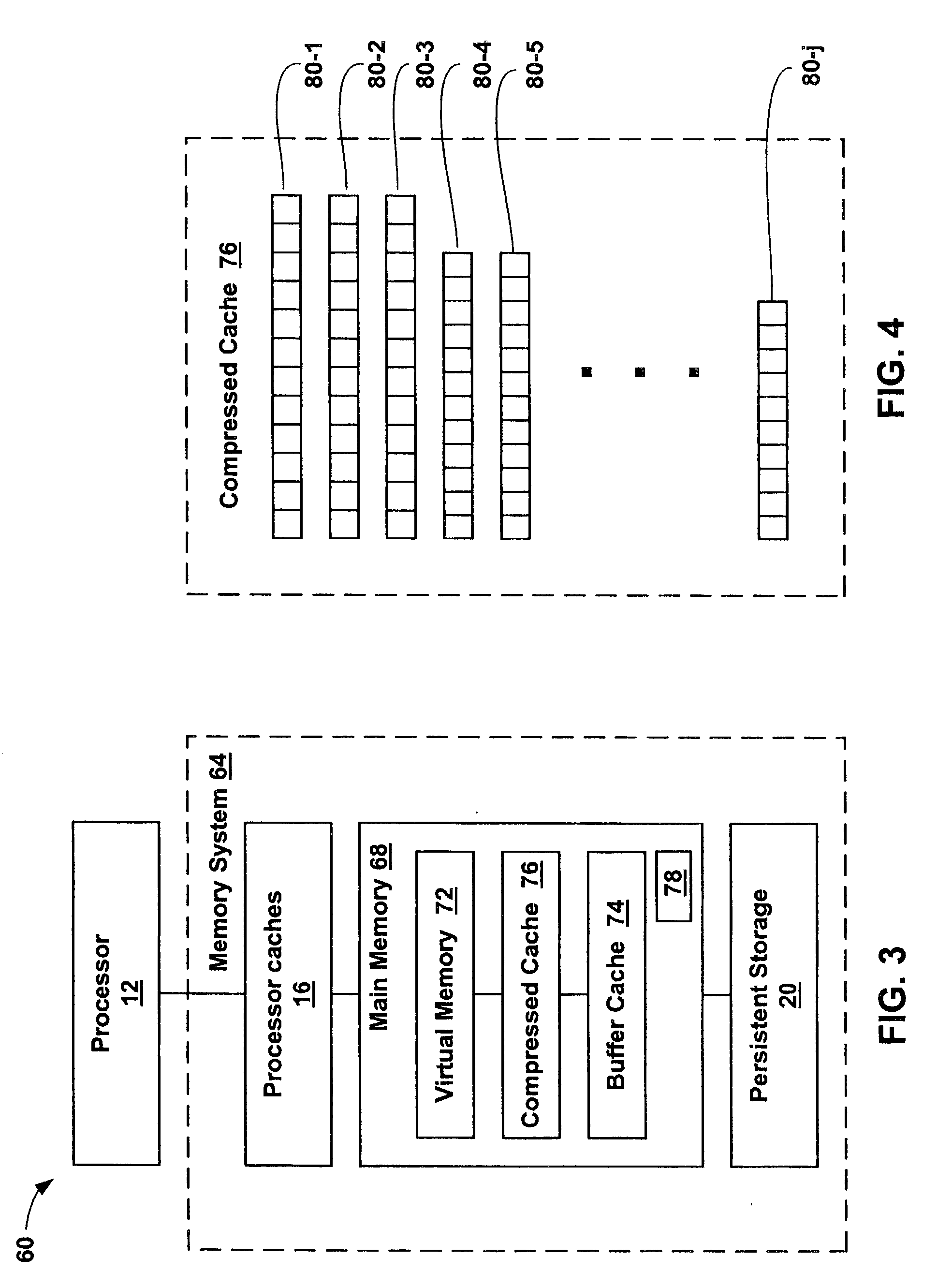
A computer system is provided including a processor, a persistent storage device, and a main memory connected to the processor and the persistent storage device. The main memory includes a compressed cache for storing data retrieved from the persistent storage device after compression and an operating system. The operating system includes a plurality of interconnected software modules for accessing the persistent storage device and a filter driver interconnected between two of the plurality of software modules for managing memory capacity of the compressed cache and the buffer cache.
Owner:VALTRUS INNOVATIONS LTD +1
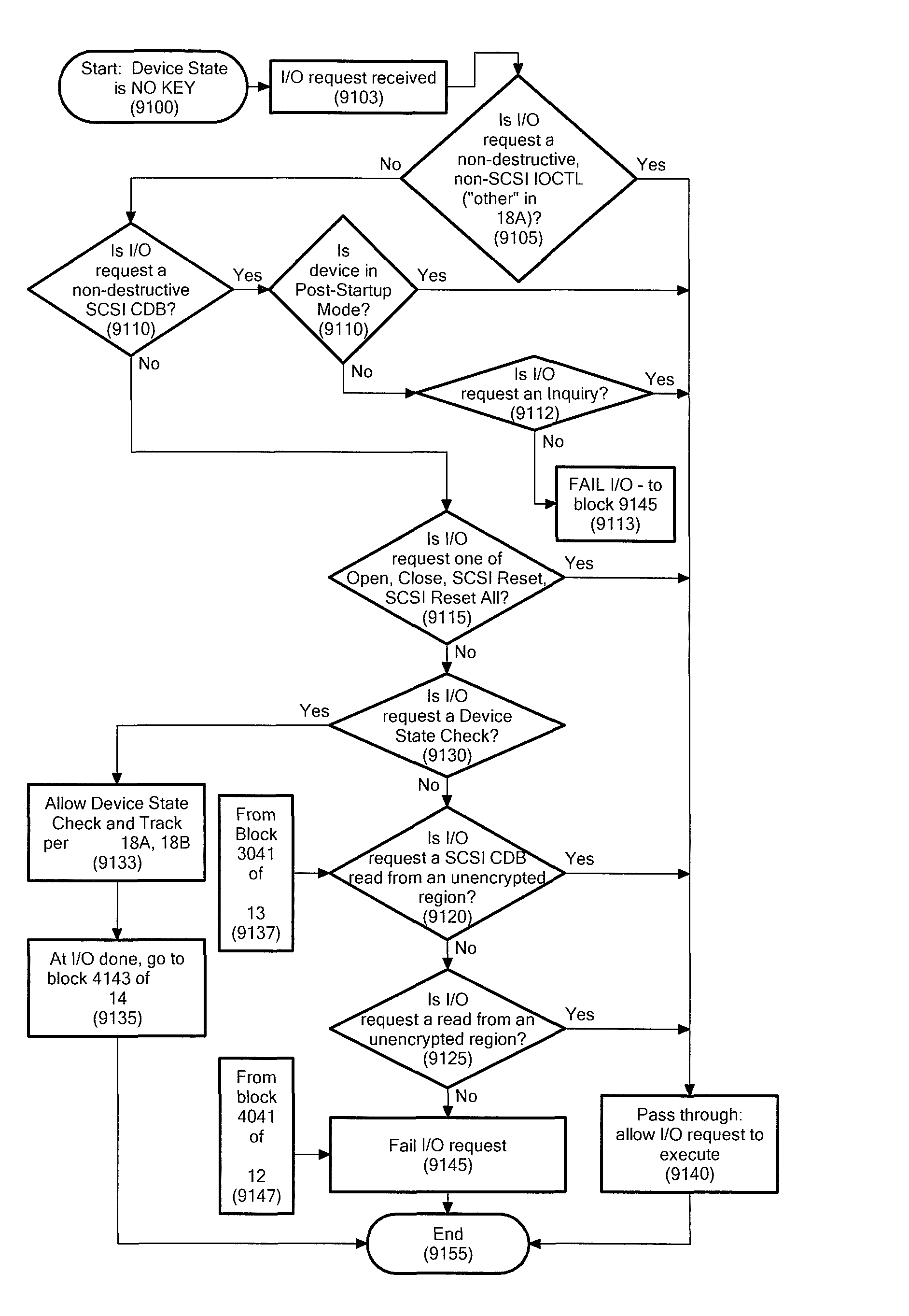
Selective I/O to logical unit when encrypted, but key is not available or when encryption status is unknown
ActiveUS8166314B1Improve interoperabilityVolume/mass flow measurementUnauthorized memory use protectionSCSILogic cell
A method is provided for controlling I / O request access to an encrypted storage device when the encryption key for the encrypted storage device is not available. The method comprises the unordered steps of: providing an I / O filter driver in operable communication with an encrypted storage device, such that all I / O requests to the encrypted storage device are processed first through the I / O filter driver; receiving at the I / O filter driver an I / O request to the encrypted storage device; determining, for each I / O request, the type of the I / O request and, if the I / O request comprises a read, SCSI read, write, or SCSI write, determining a location on the storage device to which the I / O request is directed; determining, in a processor, whether a time period for obtaining the encryption key is still running; and, based on at least one of the I / O request type, whether the time period for obtaining the encryption key is still running, and, if applicable, the location on the device to which the I / O is requested, determining, in a processor, whether the I / O request to the encrypted storage device will be allowed.
Owner:EMC IP HLDG CO LLC
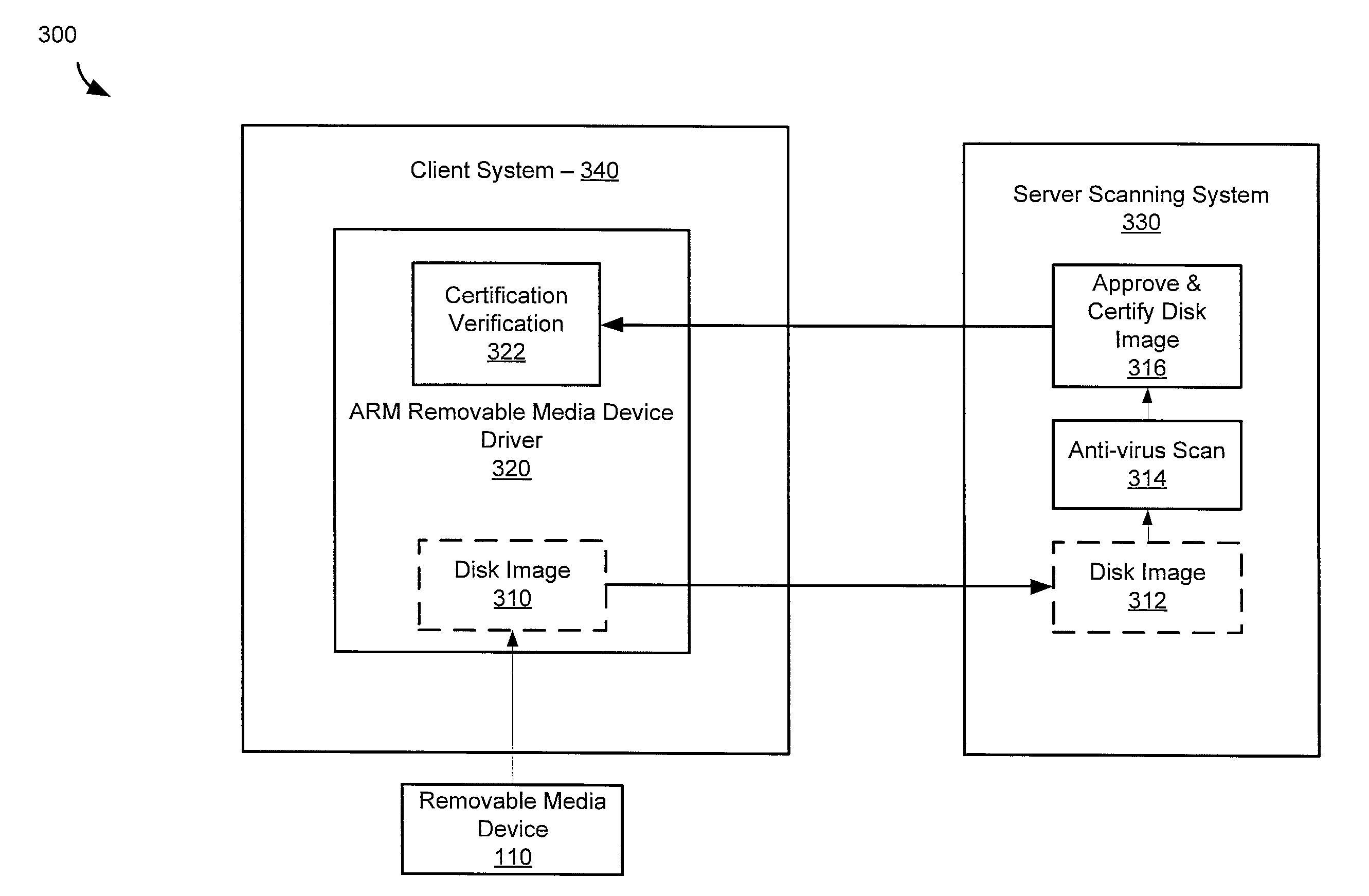
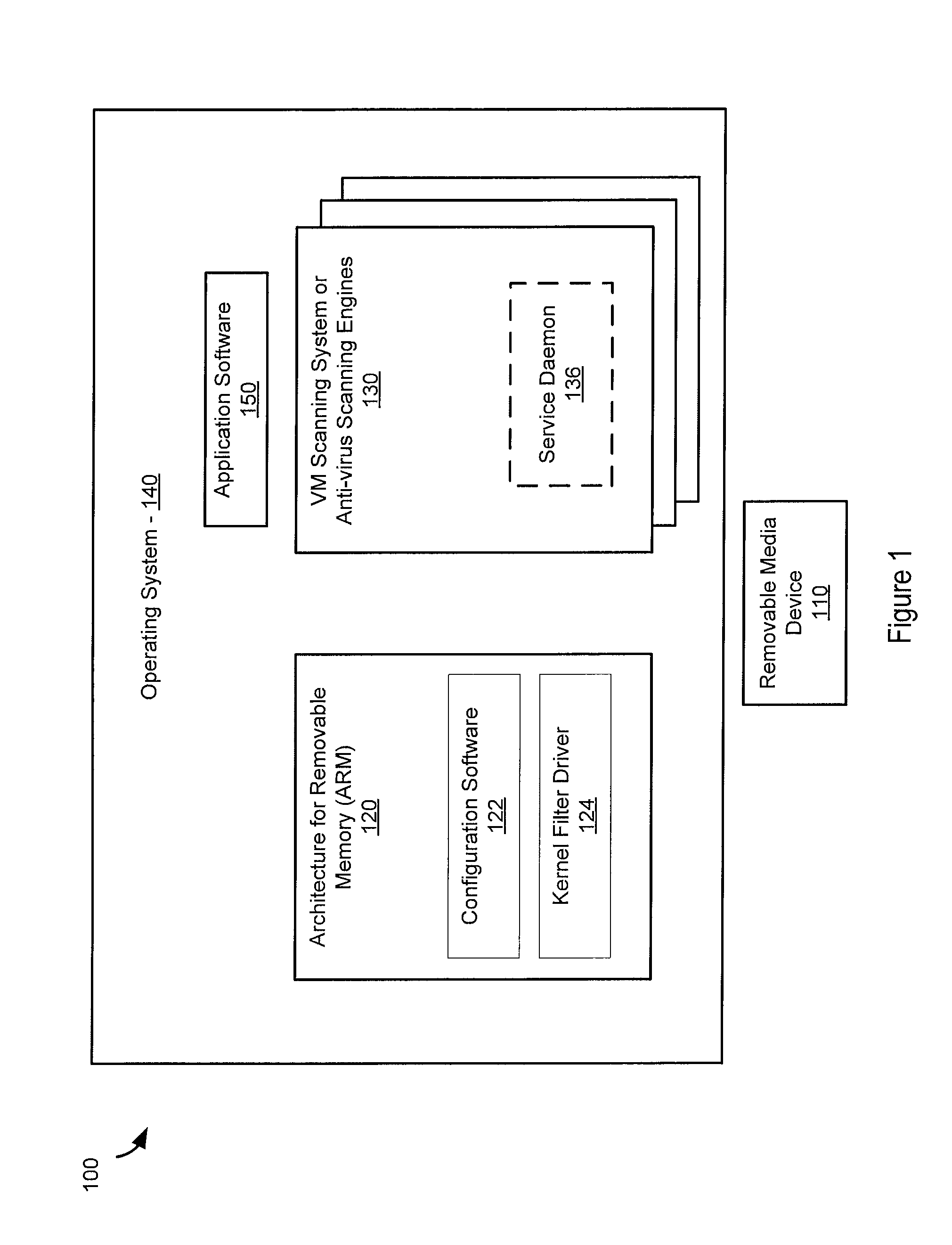
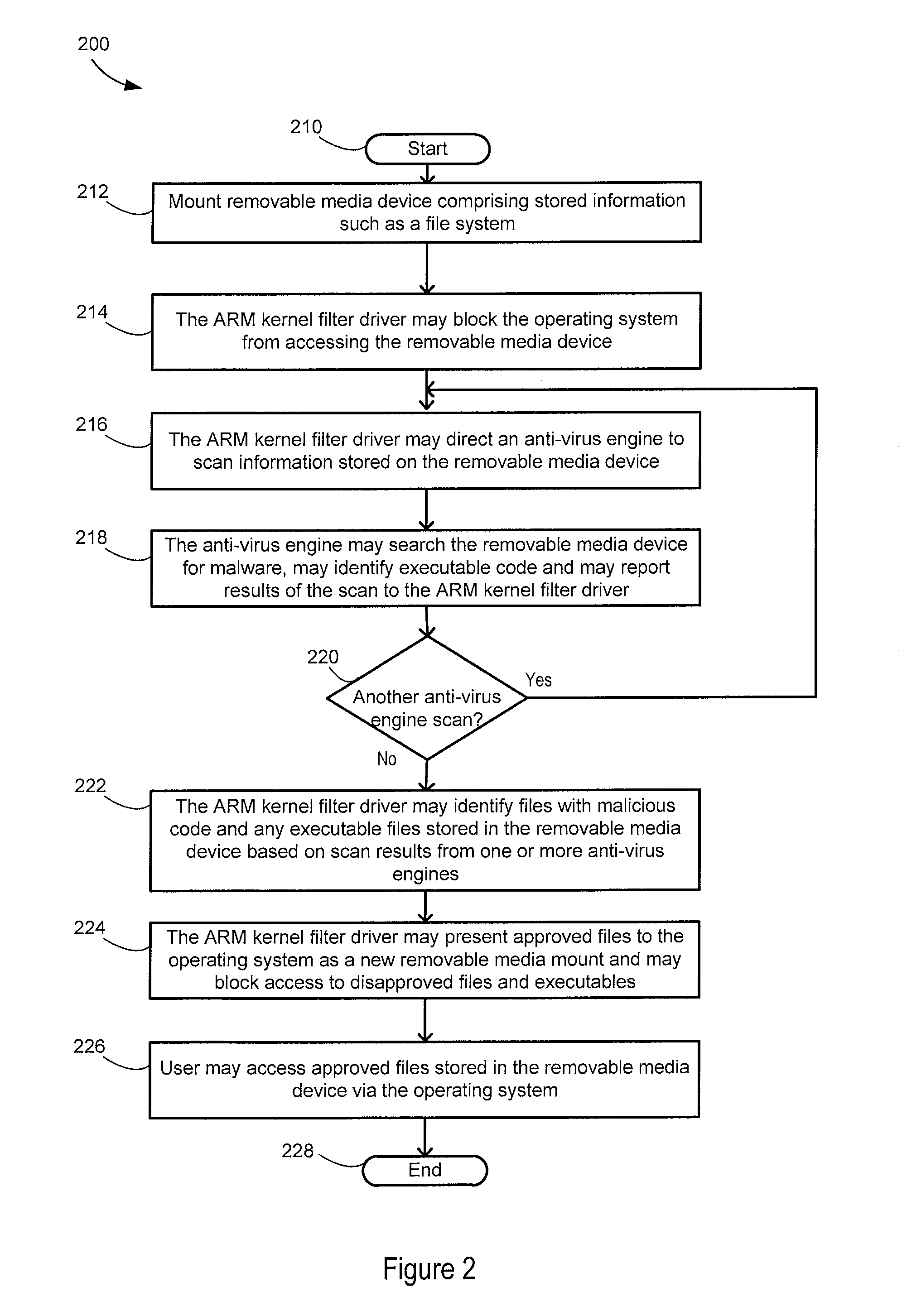
Architecture for removable media usb-arm
A storage device is coupled to a computing system comprising an operating system and application software. Access to the storage device is blocked by a kernel filter driver, except exclusive access is granted to a first anti-virus engine. The first anti-virus engine is directed to scan the storage device for malicious software and report results. Exclusive access may be granted to one or more other anti-virus engines and they may be directed to scan the storage device and report results. Approval of all or a portion of the information on the storage device is based on the results from the first anti-virus engine and the other anti-virus engines. The storage device is presented to the operating system and access is granted to the approved information. The operating system may be a Microsoft Windows operating system. The kernel filter driver and usage of anti-virus engines may be configurable by a user.
Owner:UT BATTELLE LLC
Method and System for Preventing Unauthorized Access and Distribution of Digital Data
InactiveUS20080295174A1Prevent tampering and unauthorized accessAvoid accessMemory loss protectionError detection/correctionDigital dataMonitoring system
A system and method for preventing tampering and unauthorized access to digital data stored on a device. The system can include 1) a data store for containing digital data to be protected and a listing of processes permitted to access the digital data, 2) a filter driver for intercepting a request issued from a process to access the digital data, 3) a central processor, in communication with the data store, upon receipt of a notification of the intercepted request from the filter driver, deciding to grant or deny the request by determining whether the process issuing the request is on the listing of processes permitted to access the digital data, and 4) a monitor process for monitoring one or more software components of the system including the central processor, filter driver, and data store, and for identifying and preventing any unauthorized processes from accessing and tampering with the software components of the system.
Owner:FAHMY ANDREA ROBINSON +2
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com