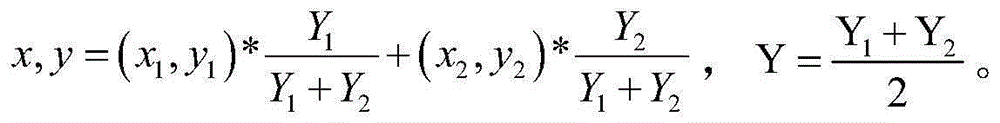Patents
Literature
61 results about "Copyright infringement" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Copyright infringement (colloquially referred to as piracy) is the use of works protected by copyright law without permission for a usage where such permission is required, thereby infringing certain exclusive rights granted to the copyright holder, such as the right to reproduce, distribute, display or perform the protected work, or to make derivative works. The copyright holder is typically the work's creator, or a publisher or other business to whom copyright has been assigned. Copyright holders routinely invoke legal and technological measures to prevent and penalize copyright infringement.
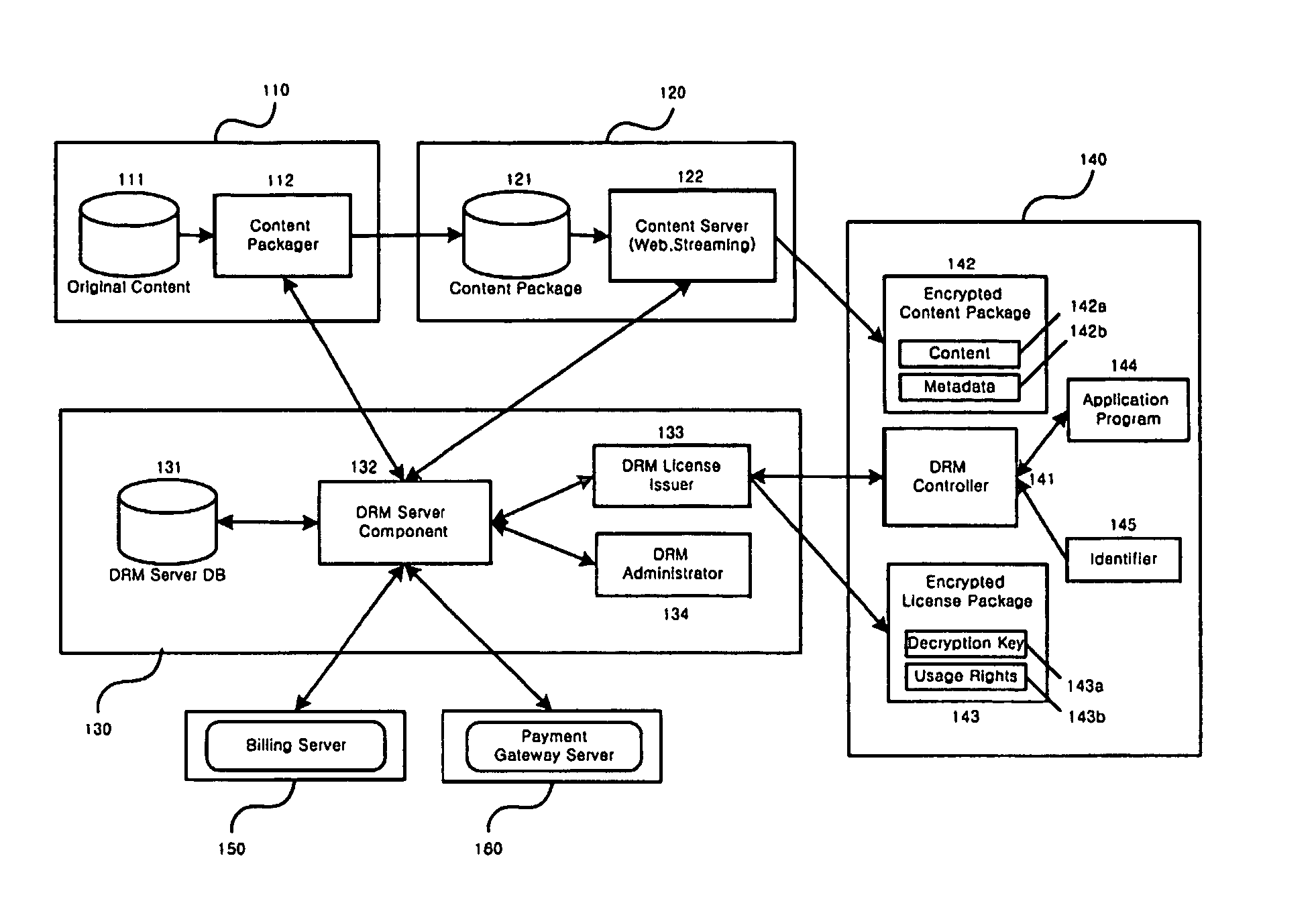
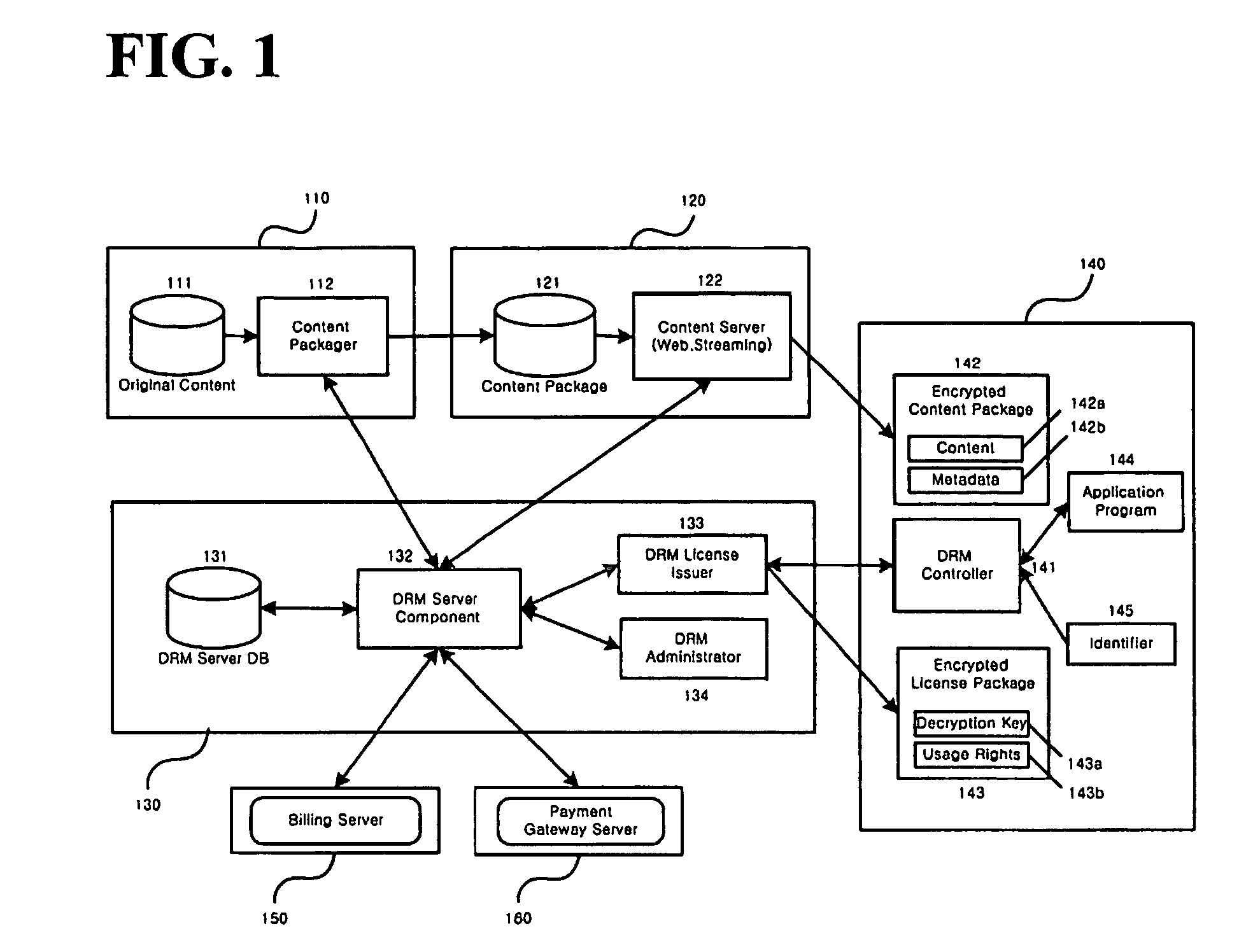
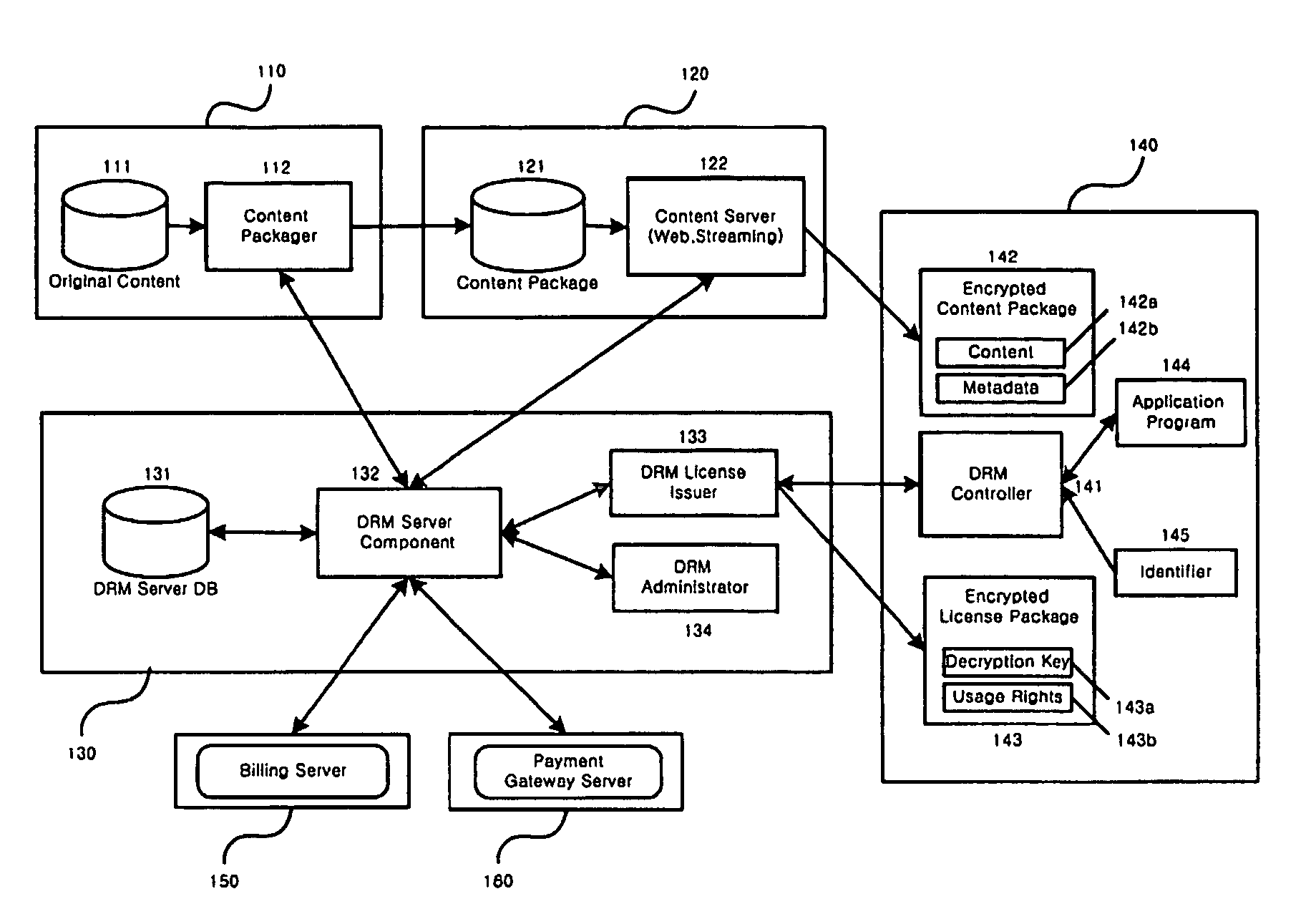
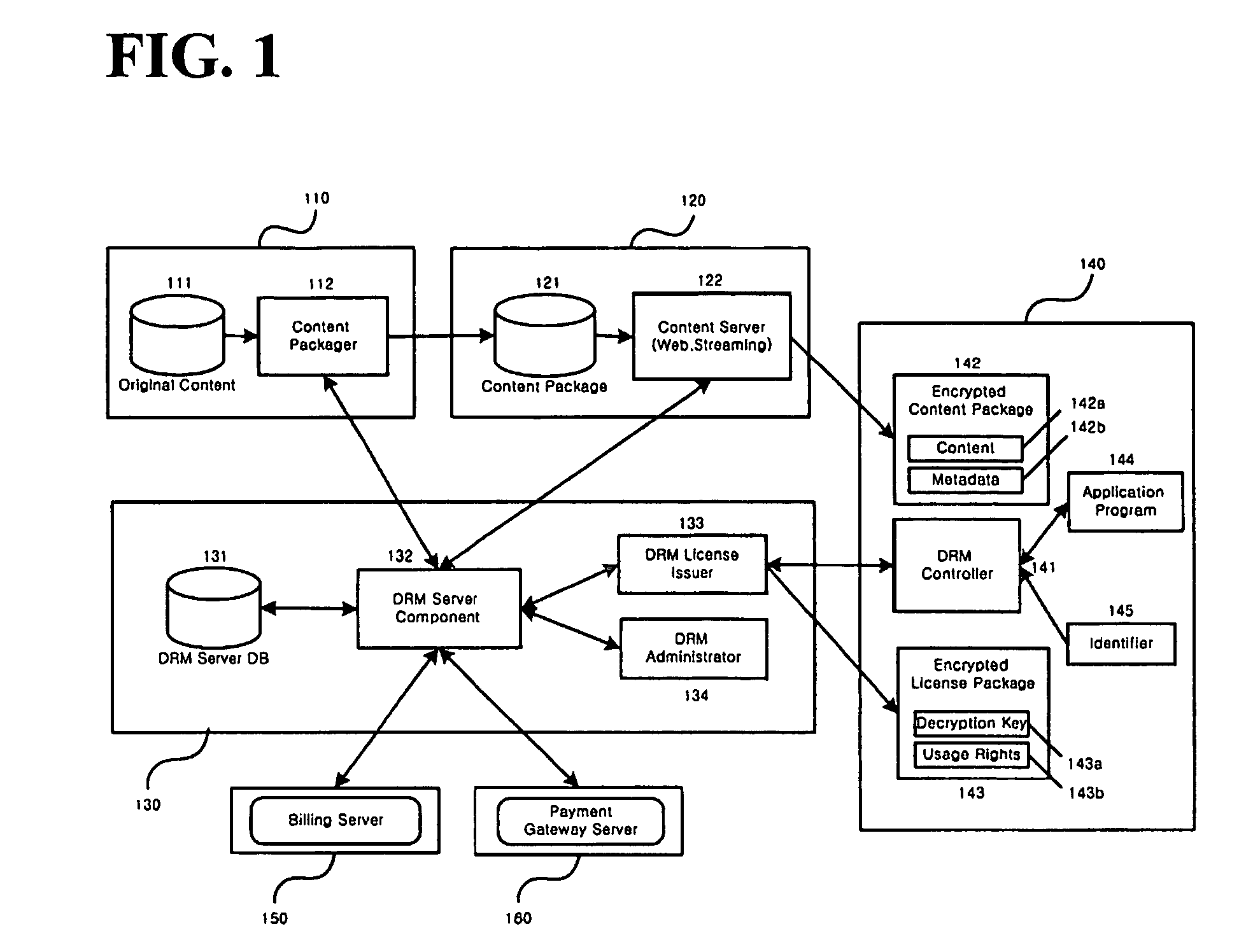
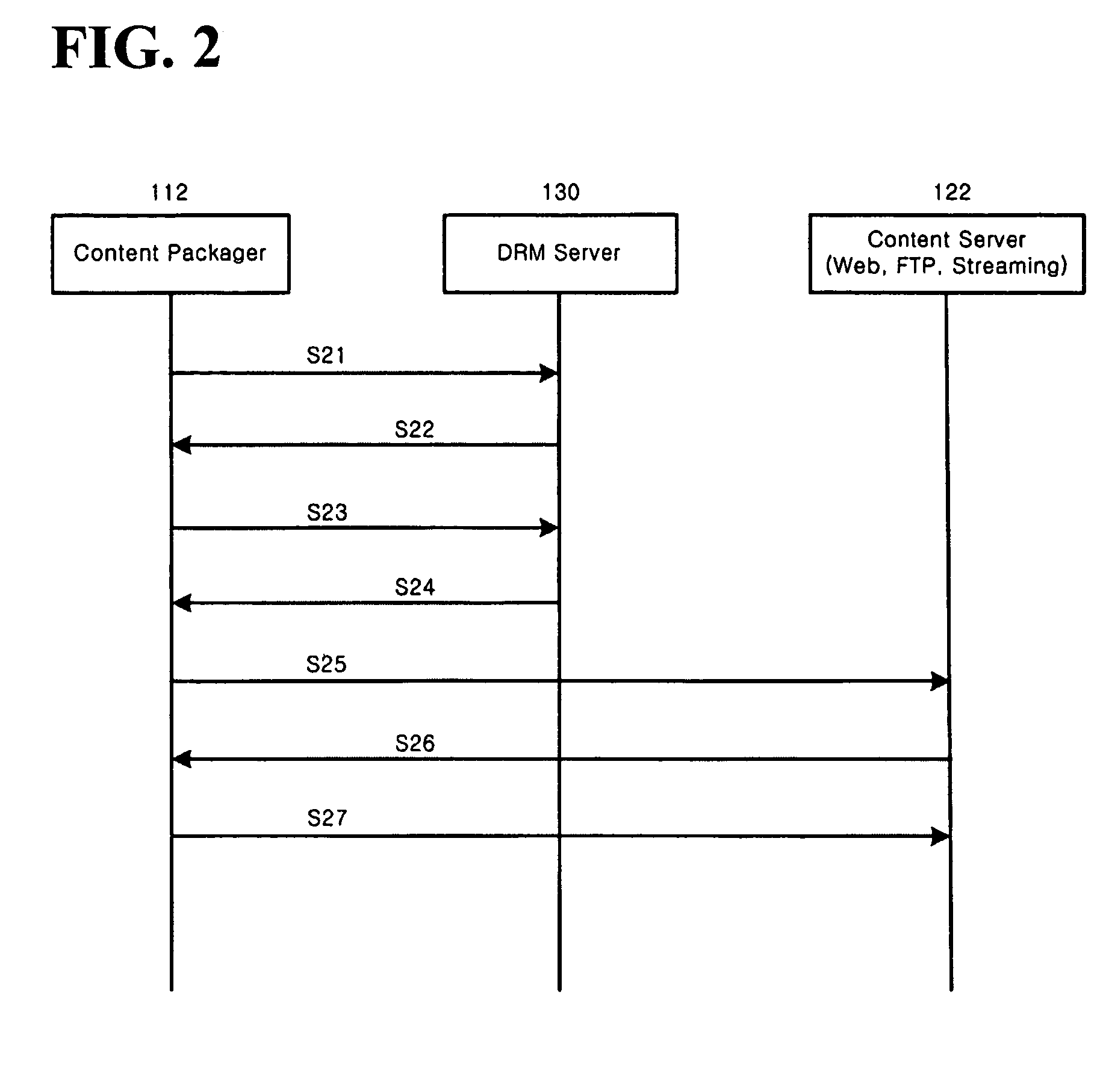
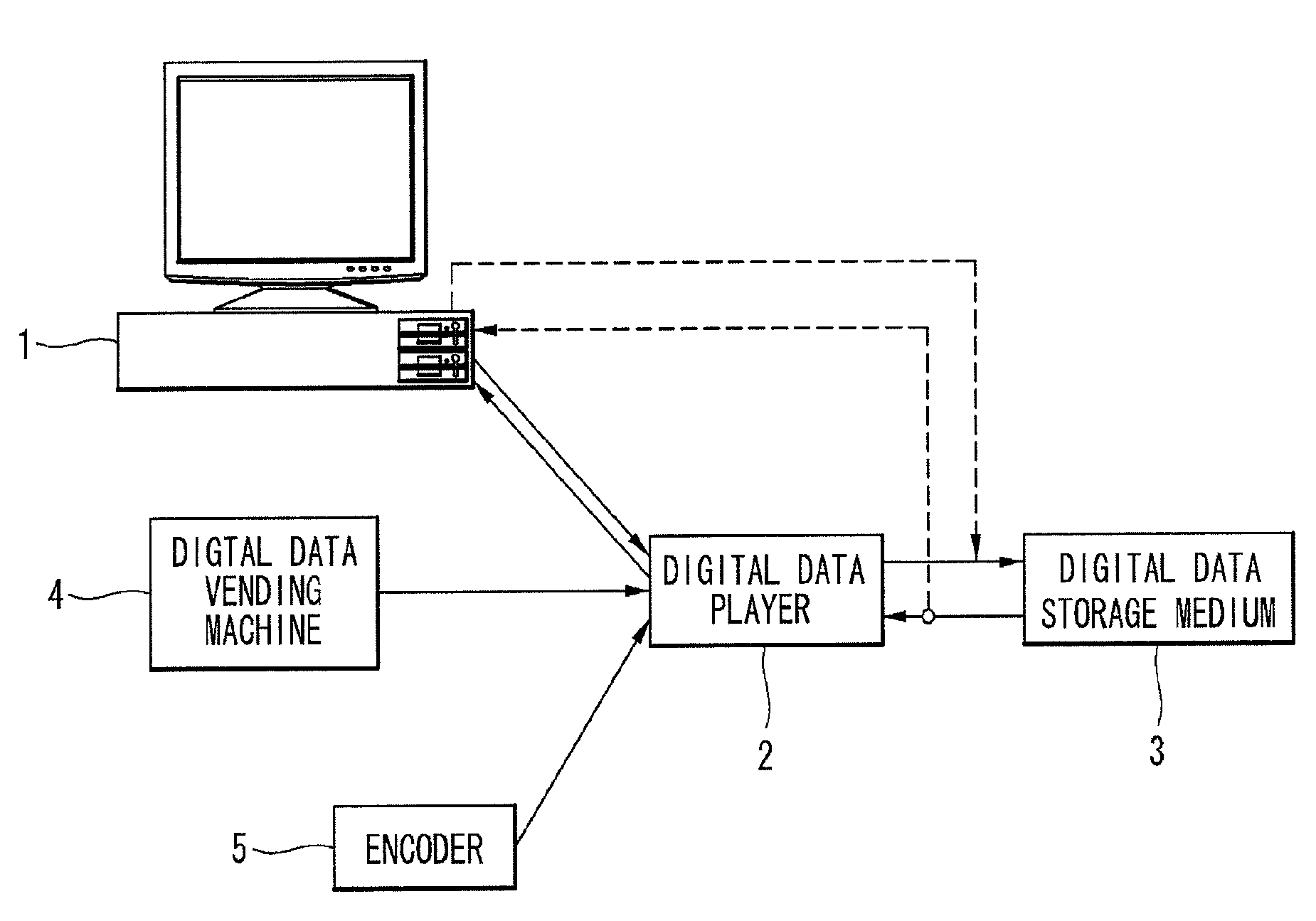
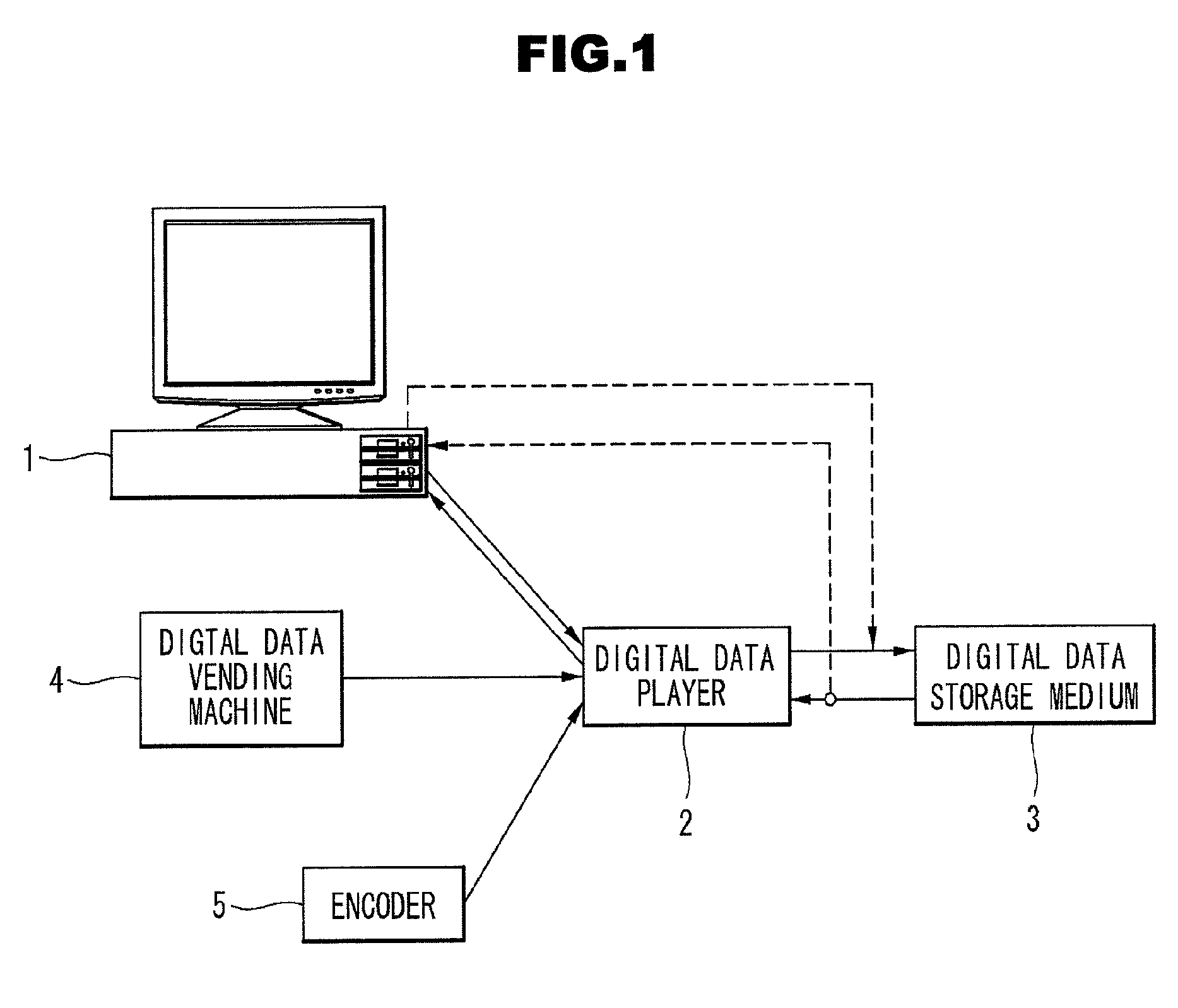
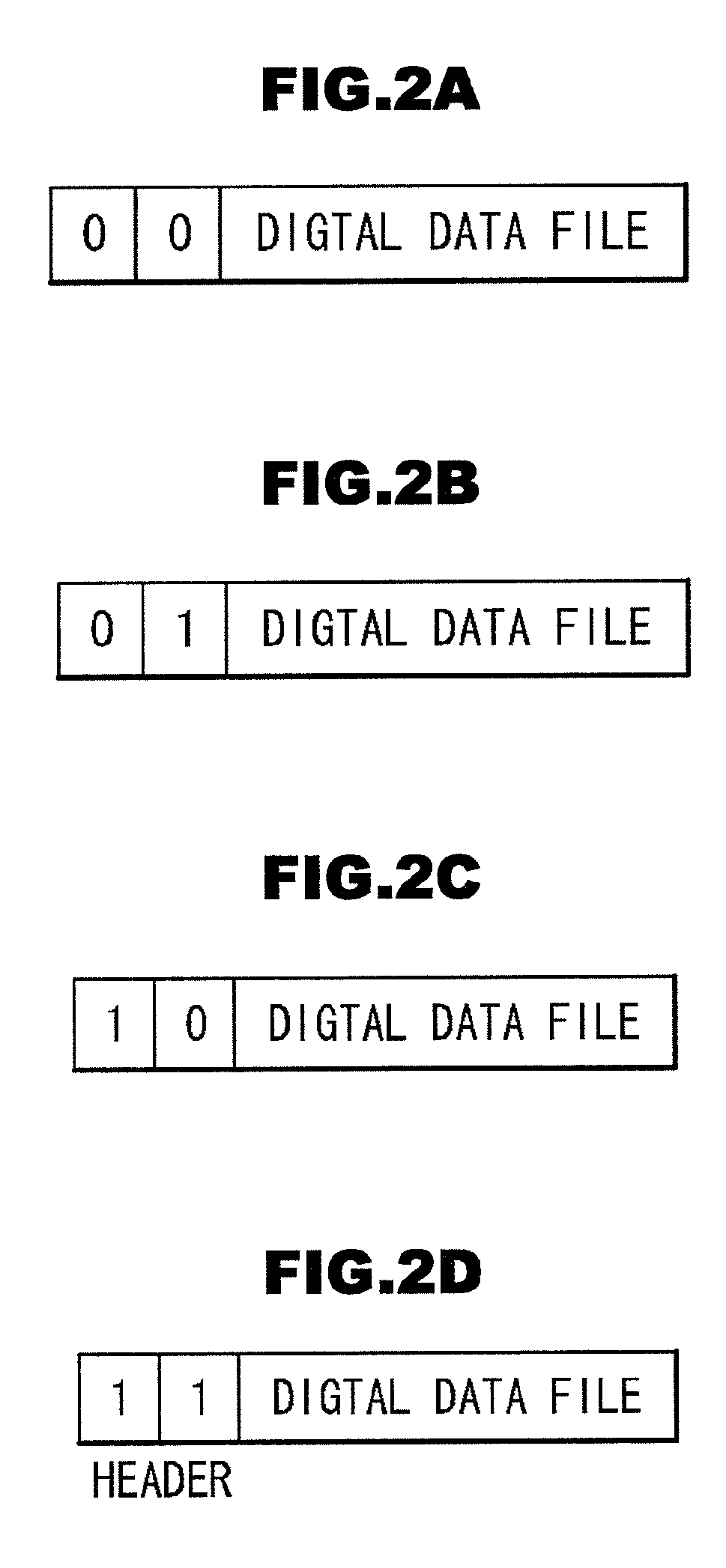
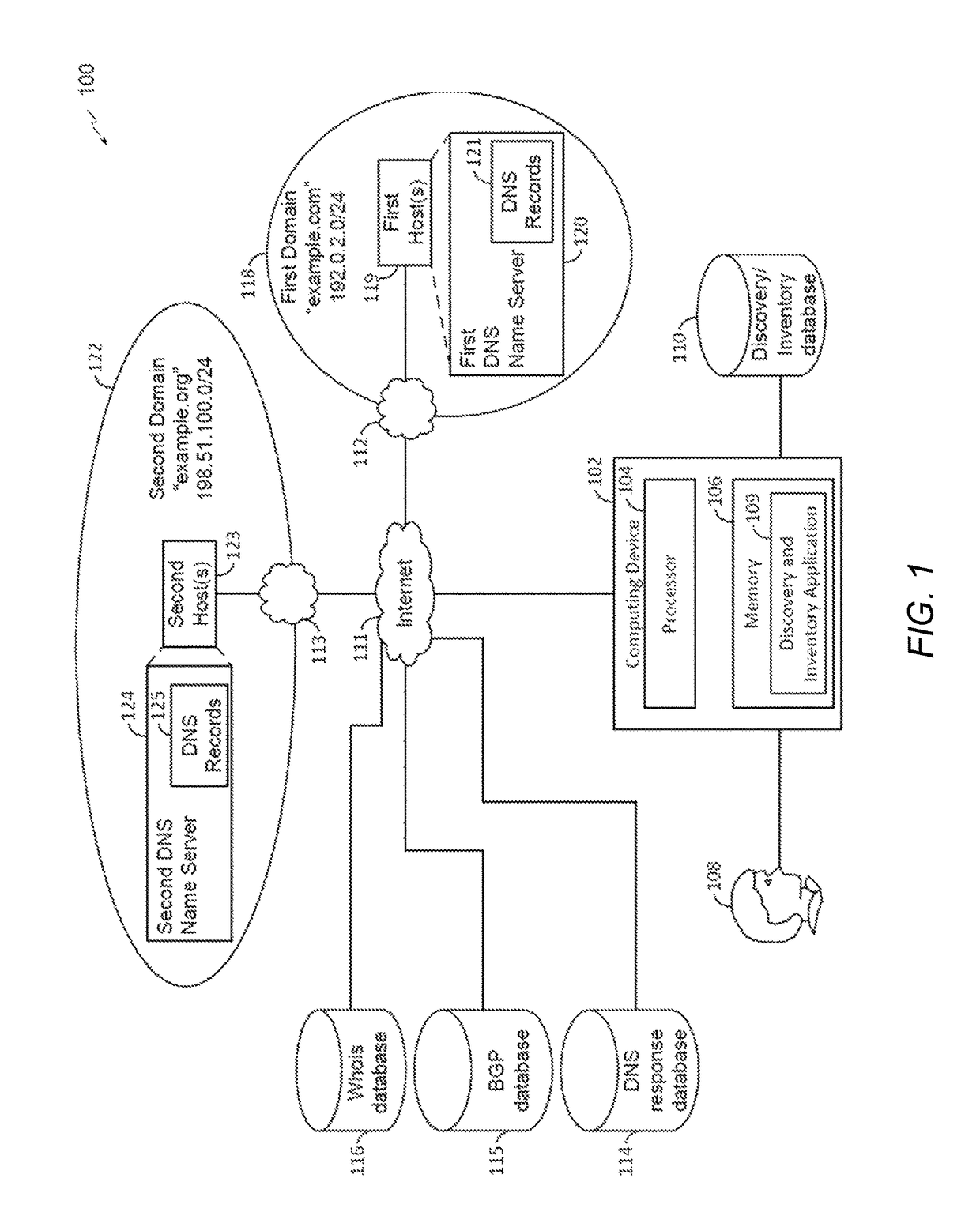
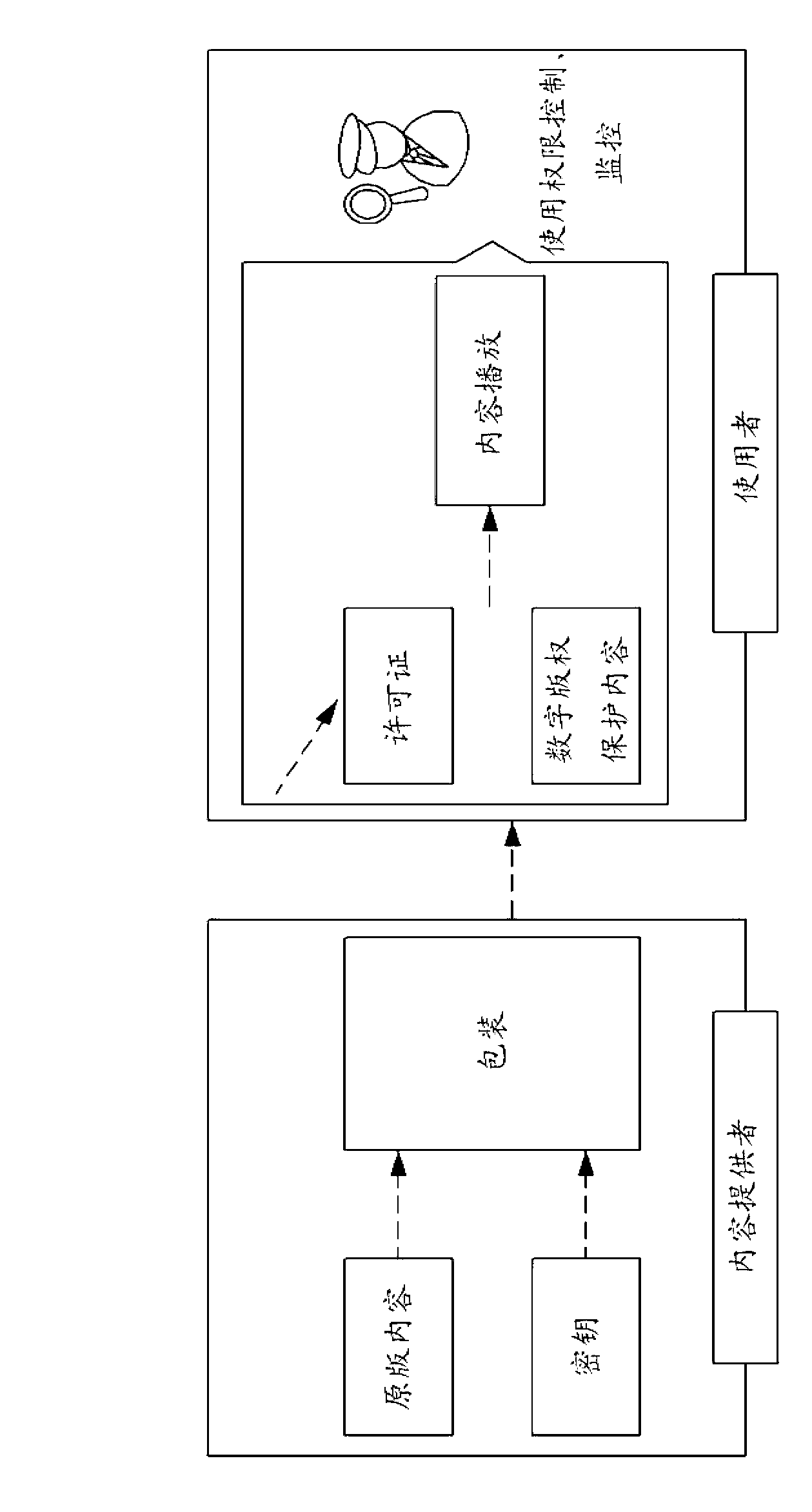
Method and system for the information protection of digital content
ActiveUS20050086501A1Add supportImprove securityDigital data processing detailsUser identity/authority verificationData packDigital content
The present invention relates to the information protection of digital content transferred by streaming and download service through wire or wireless Internet network. The information protection system in this invention suggests a drastic prevention method of copyrights infringement such as illegal copy and unauthorized distribution of digital content, by using of the encryption, decryption, distribution, and authentication technologies. This invention suggests the control technology of general viewer program, not the specific viewer program for information protection, using a network filter driver for streaming and file system filter driver for download service. The main function of network and file system filter driver is the filtering operation such as a hooking, changing, decrypting, and restoring of message and data packet, and transferring to the viewer program. The main idea and technology of this invention suggest higher secure and efficient digital information protection system for live / VOD / HTTP streaming and download service.
Owner:WOO JE HAK +6
Method and system for the information protection of digital content
ActiveUS7484103B2Digital data processing detailsAnalogue secracy/subscription systemsDigital contentNetwork packet
The present invention relates to the information protection of digital content transferred by streaming and download service through wire or wireless Internet network. The information protection system in this invention suggests a drastic prevention method of copyrights infringement such as illegal copy and unauthorized distribution of digital content, by using of the encryption, decryption, distribution, and authentication technologies. This invention suggests the control technology of general viewer program, not the specific viewer program for information protection, using a network filter driver for streaming and file system filter driver for download service. The main function of network and file system filter driver is the filtering operation such as a hooking, changing, decrypting, and restoring of message and data packet, and transferring to the viewer program. The main idea and technology of this invention suggest higher secure and efficient digital information protection system for live / VOD / HTTP streaming and download service.
Owner:WOO JE HAK +6
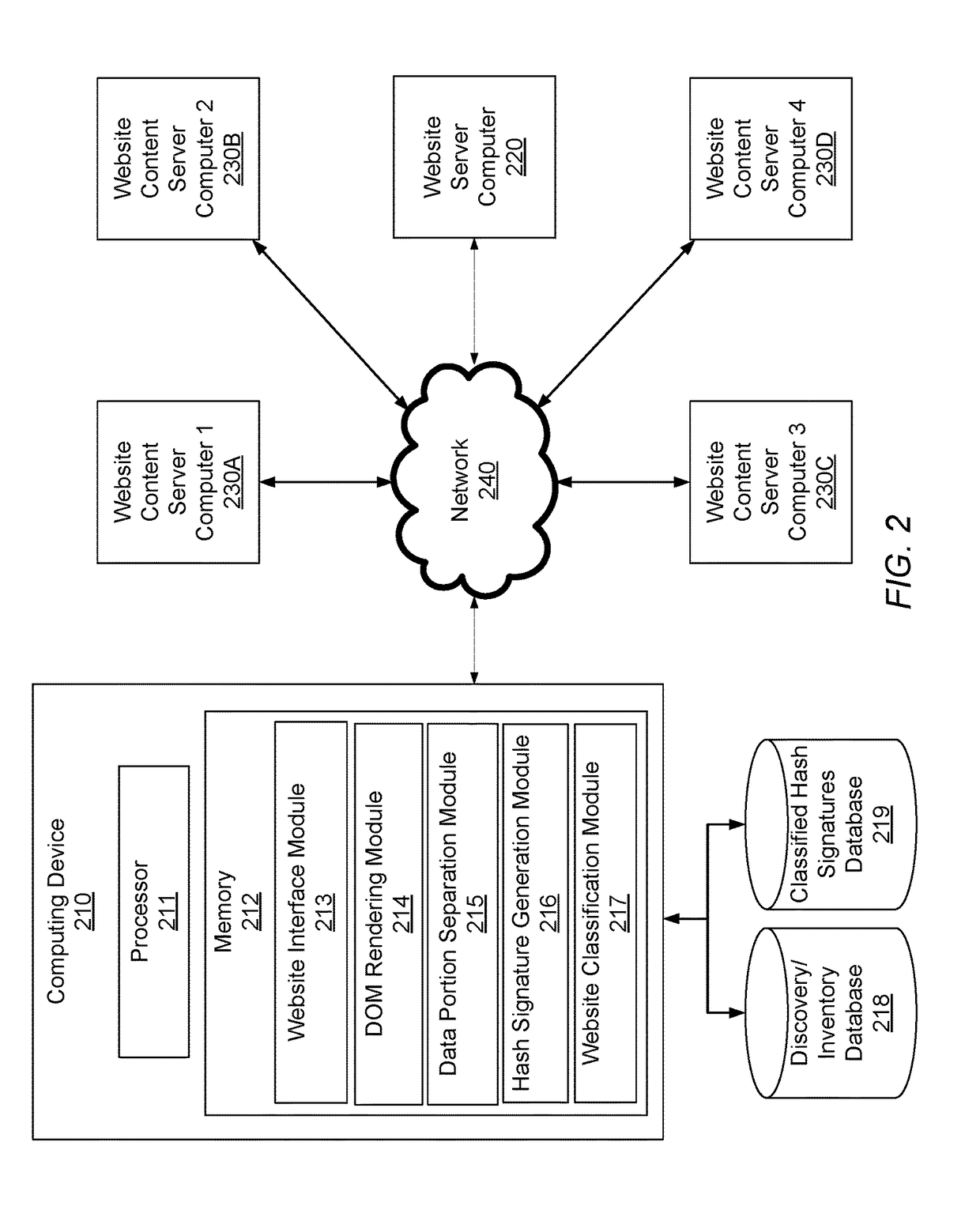
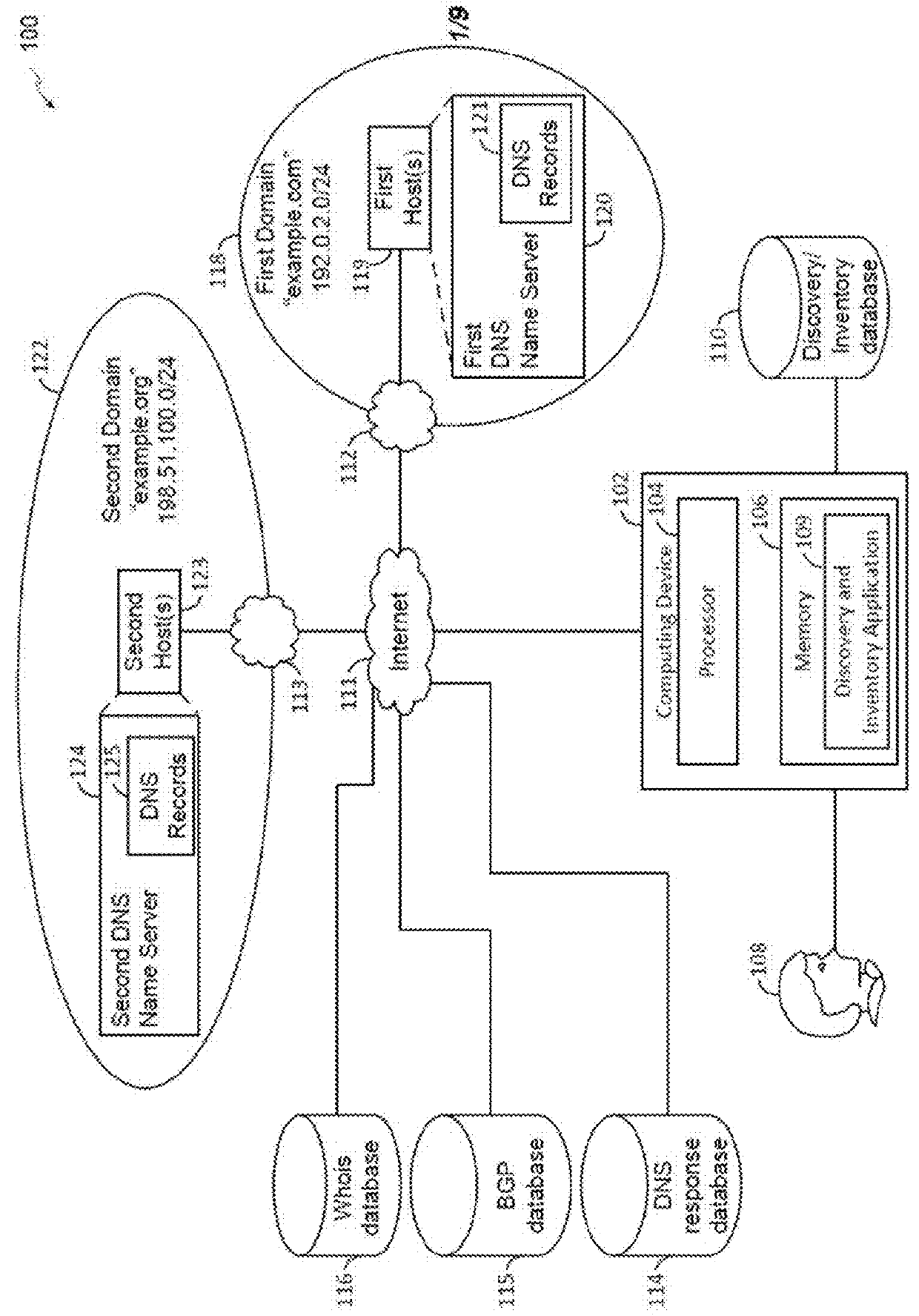
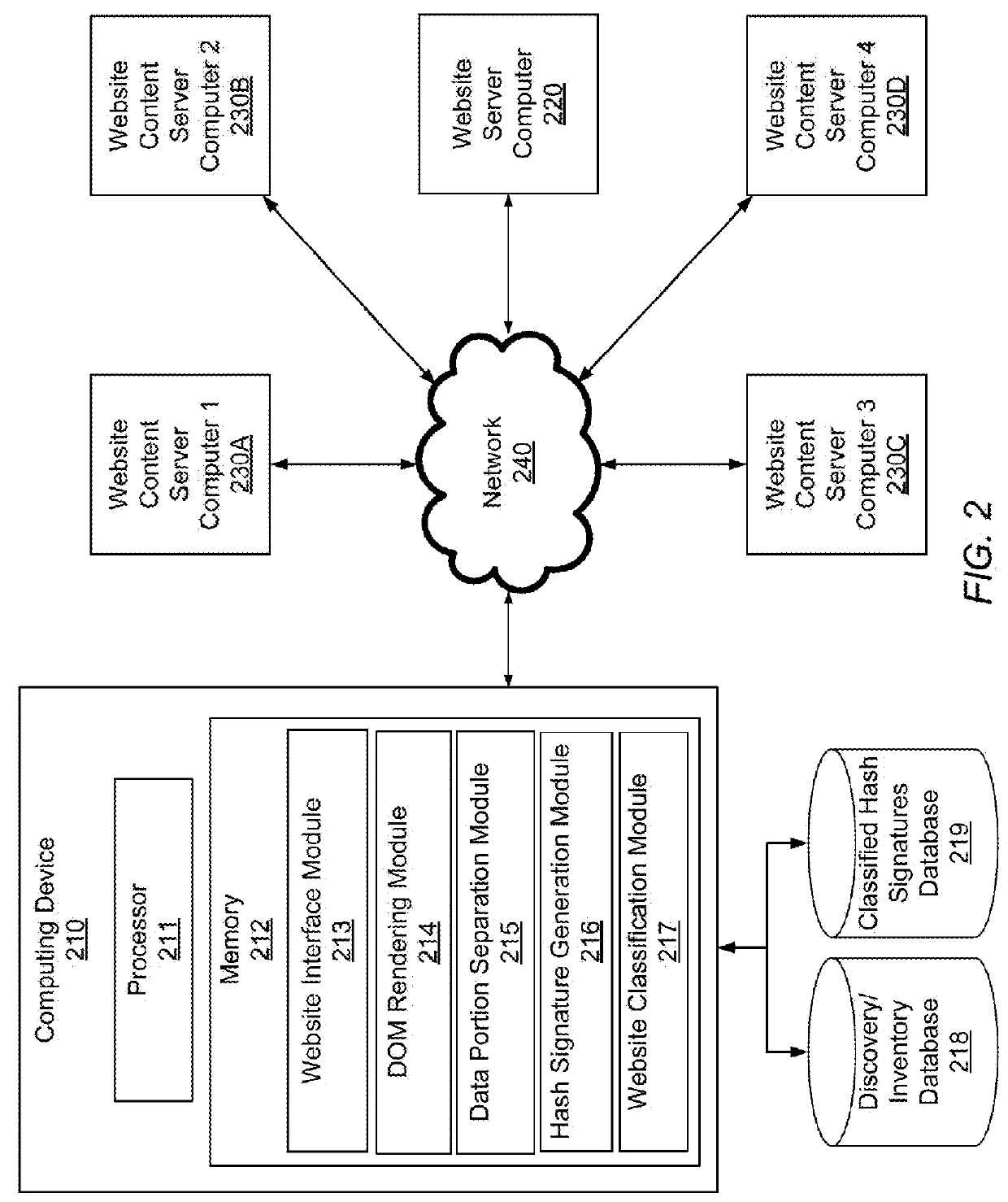
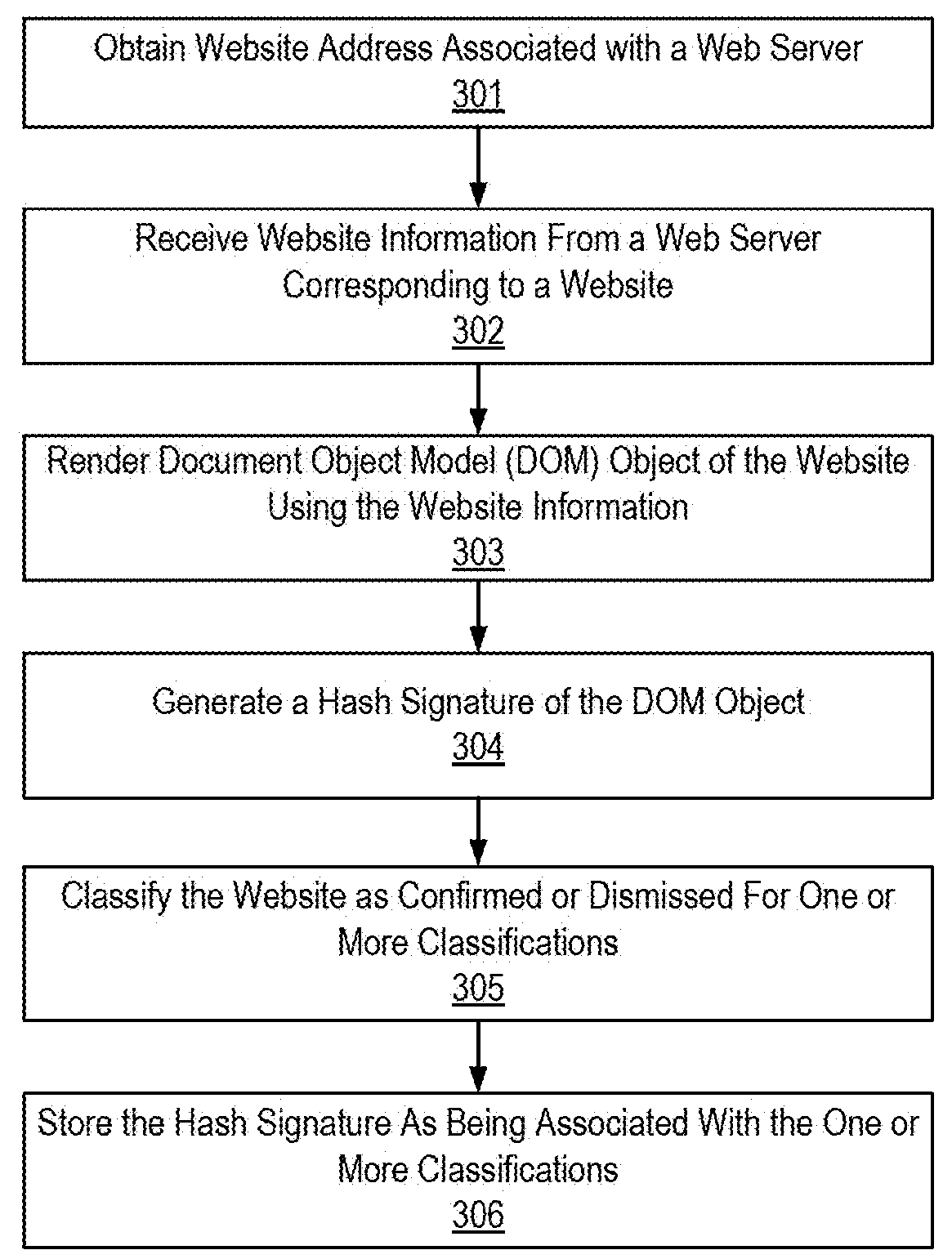
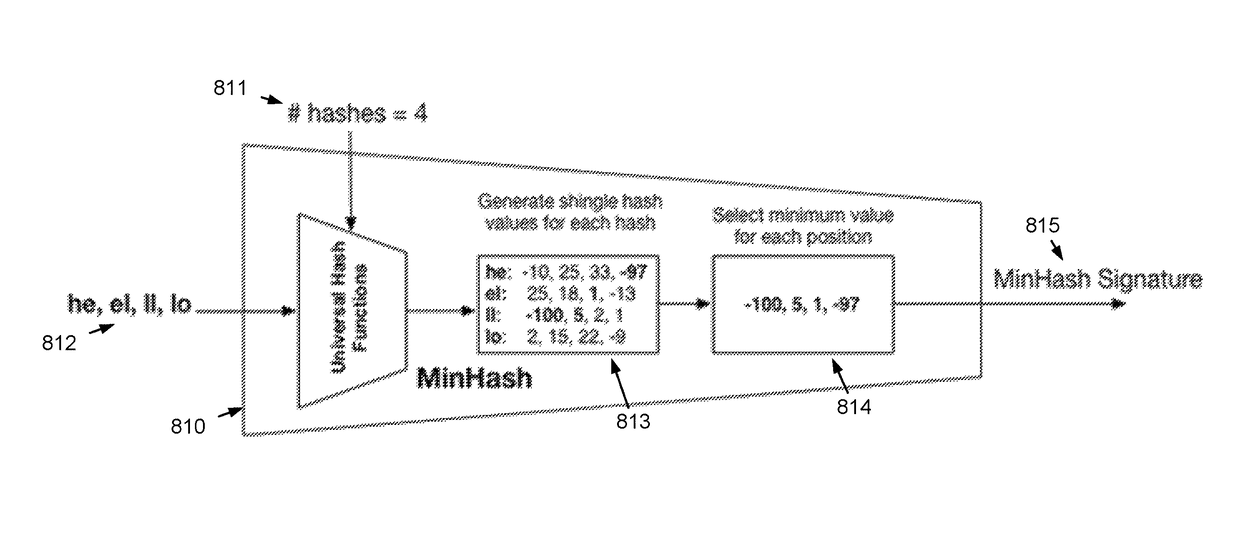
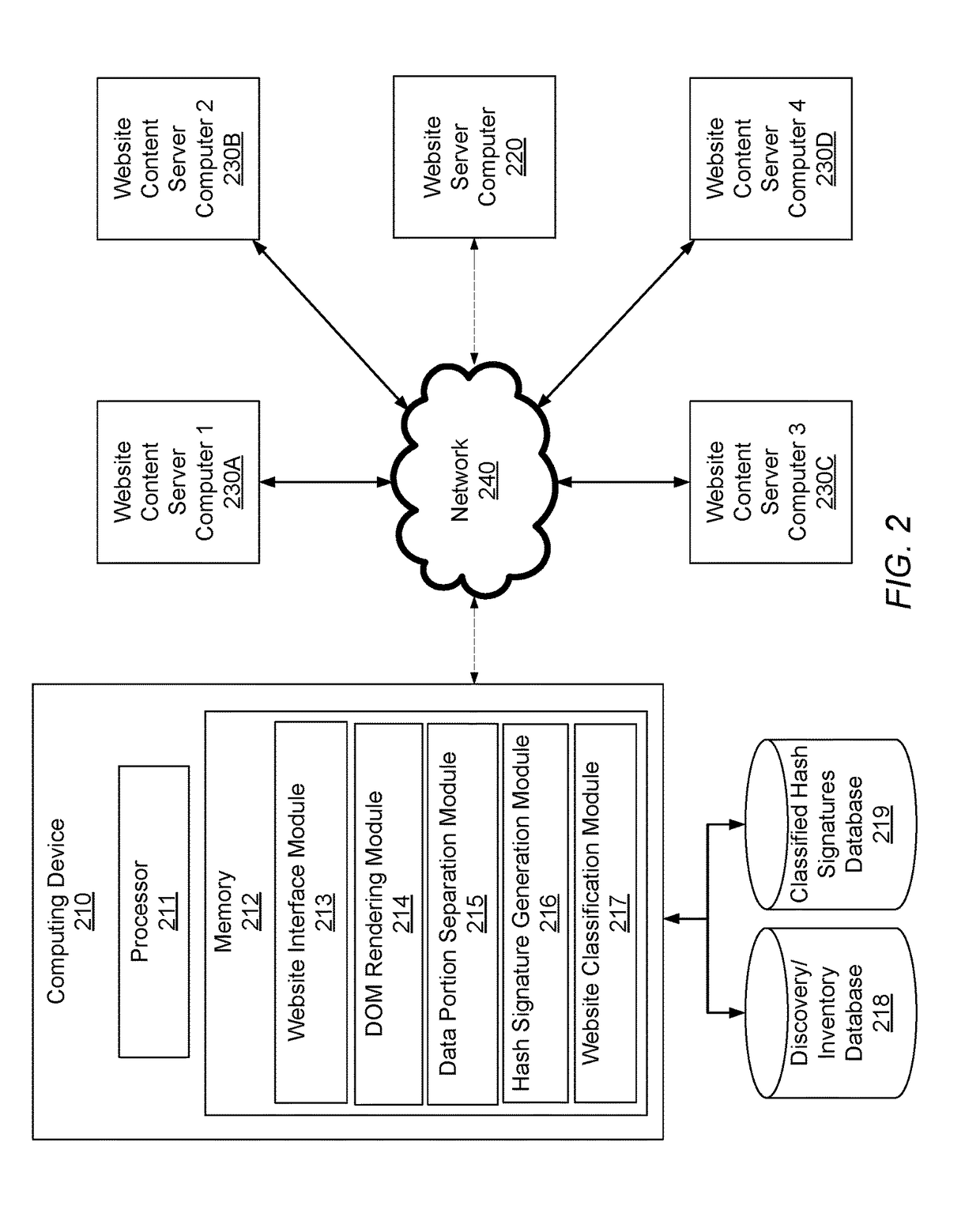
Using hash signatures of dom objects to identify website similarity
ActiveUS20170286544A1Web data indexingUser identity/authority verificationPattern recognitionSelection criterion
Embodiments are directed to using a hash signature of a rendered DOM object of a website to find similar content and behavior on other websites. Embodiments break a DOM into a large number of data portions (i.e., “shingles”), apply a hashing algorithm to the shingles, select a predetermined number of hashes from the hashed shingles according to a selection criteria to create a hash signature, and compare the hash signature to that of a reference page to determine similarity of website DOM object content. Embodiments can be used to identify phishing websites, defaced websites, spam websites, significant changes in the content of a webpage, copyright infringement, and any other suitable purposes related to the similarity between website DOM object content.
Owner:MICROSOFT TECH LICENSING LLC
Using hash signatures of DOM objects to identify website similarity
ActiveUS9386037B1Web data indexingUser identity/authority verificationSelection criterionCopyright infringement
Embodiments are directed to using a hash signature of a rendered DOM object of a website to find similar content and behavior on other websites. Embodiments break a DOM into a large number of data portions (i.e., “shingles”), apply a hashing algorithm to the shingles, select a predetermined number of hashes from the hashed shingles according to a selection criteria to create a hash signature, and compare the hash signature to that of a reference page to determine similarity of website DOM object content. Embodiments can be used to identify phishing websites, defaced websites, spam websites, significant changes in the content of a webpage, copyright infringement, and any other suitable purposes related to the similarity between website DOM object content.
Owner:MICROSOFT TECH LICENSING LLC
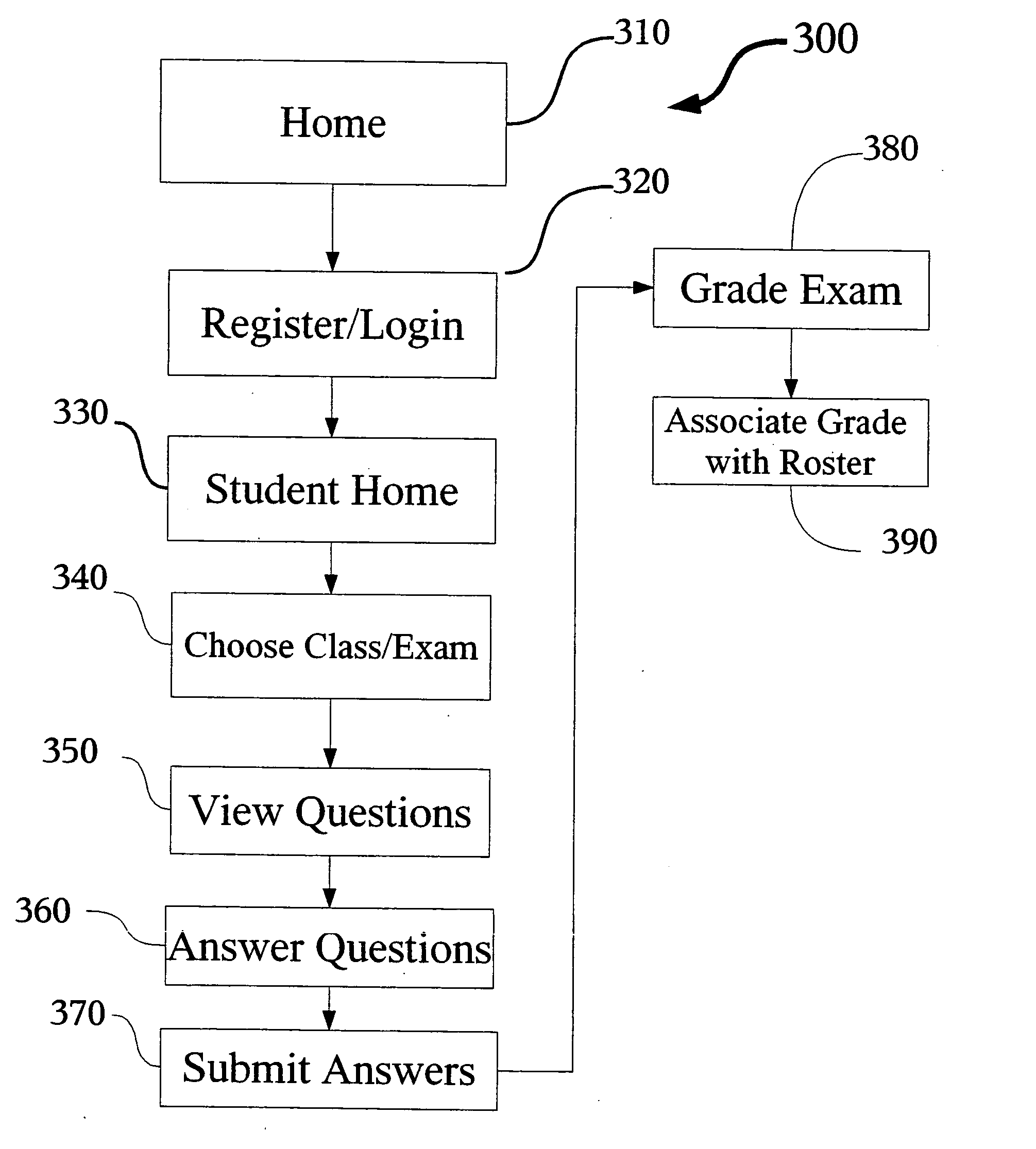
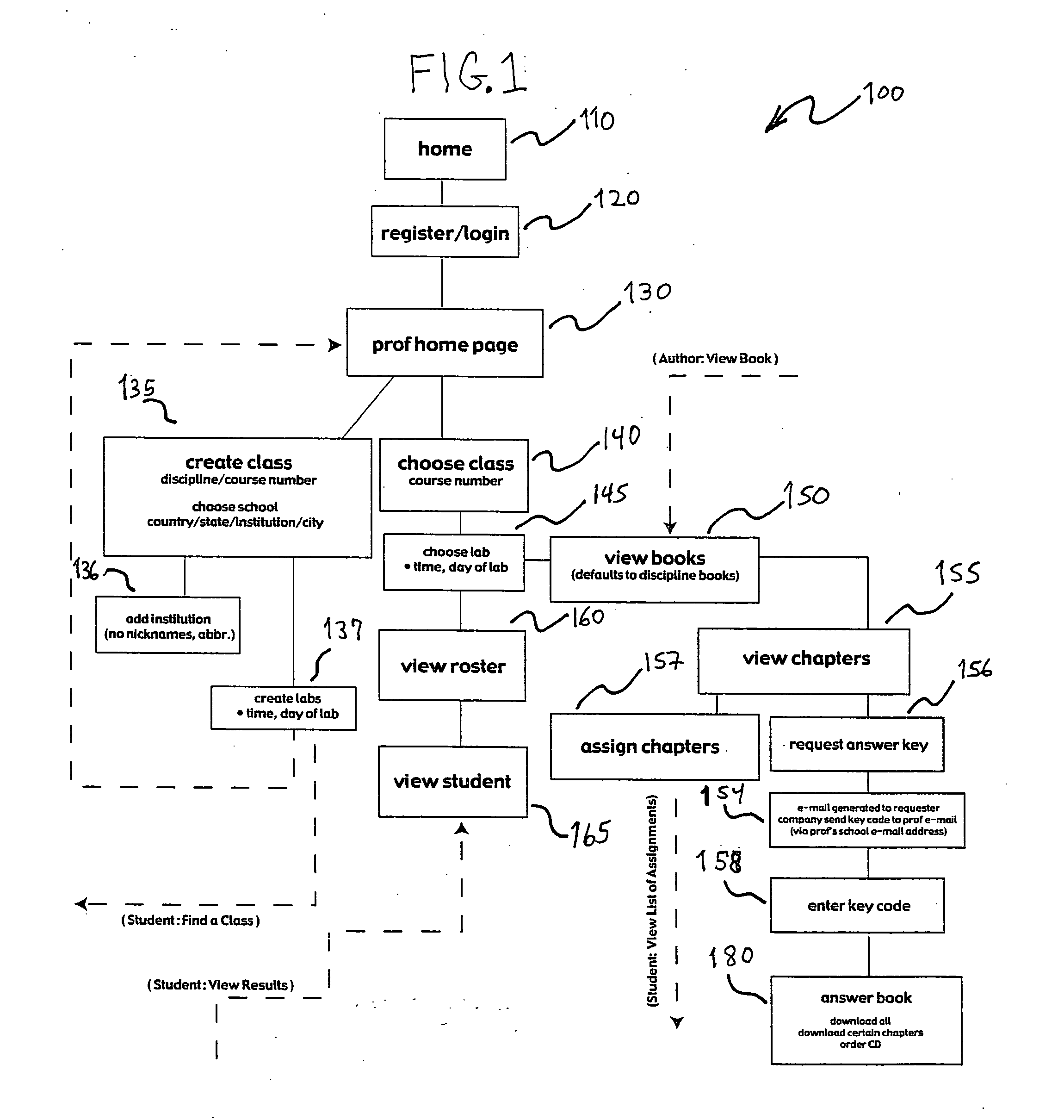
Method of publication and distribution of instructional materials
A method has been developed for the electronic creation and distribution of customized educational materials. An educator compiles a customized text from a catalog of available materials. The customized text is then indexed in an electronic database where it is available for purchase in an electronic format by students. Copyright infringement is discouraged by providing the educator the option of electronic testing and grading such that only students that actually purchase the educational materials are eligible to receive a grade in the class. The custom textbook is easily changed or updated to correct errors without the publisher incurring traditional printing and distribution costs, while simultaneously reducing the time to market for new editions of materials.
Owner:STUDENTS CHOICE LLC
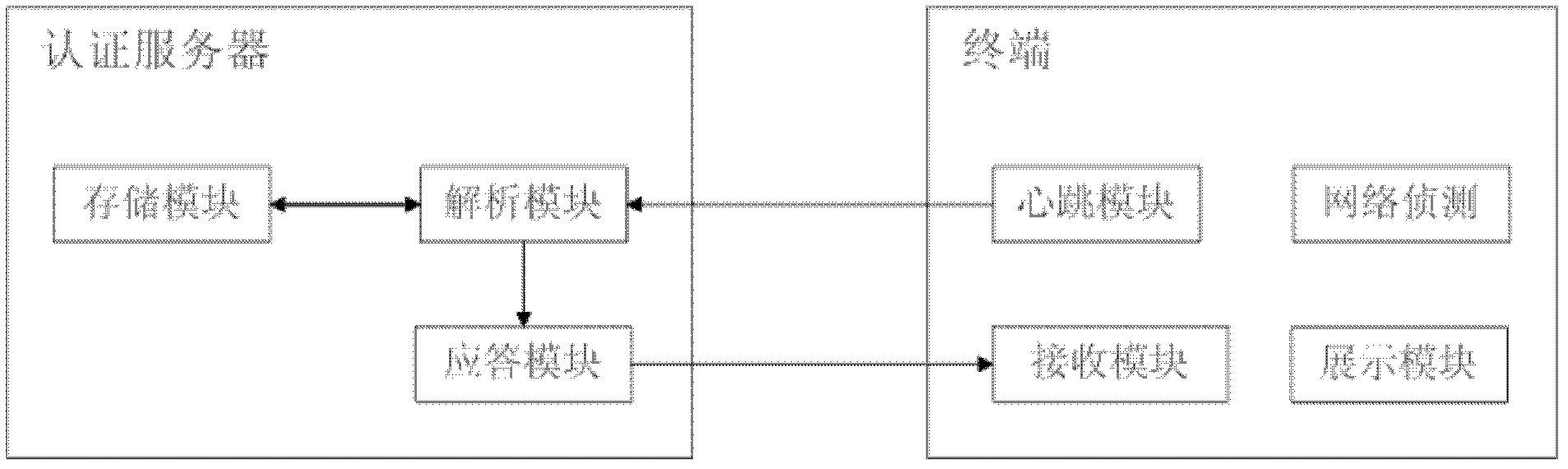
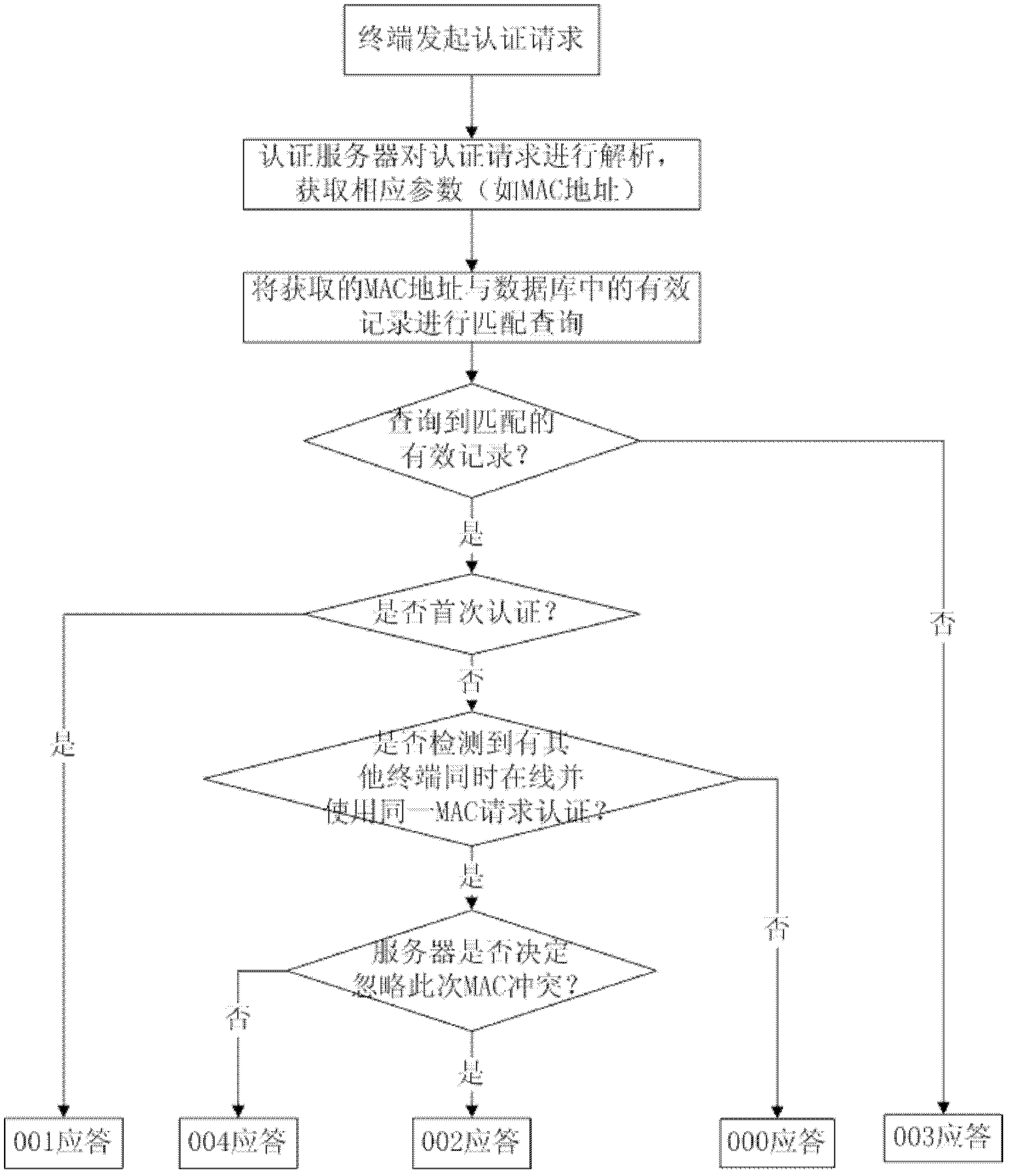
A method and a server for software backend authentication
ActiveCN102983968AAvoid confictZero troubleshooting costUser identity/authority verificationPhysical addressSoftware fault
The present invention discloses a method and a server for software backend authentication, and a terminal. The method for software backend authentication comprises: MAC filing, an authentication server establishes a filing database of the built-in network card physical address MAC of the terminal in a storage module in advance; MAC resolution and determination, when an authentication request from the terminal is received, a resolution module of the authentication server resolves the physical address of the built-in network card physical address MAC of the terminal, a match query with information in the filing database is performed, and based on the obtained matching result, a response module of the authentication server is instructed to give the terminal a corresponding response instruction; and response instruction, based on the decision of the resolution module, the response module sends the corresponding response instruction to the terminal. By adopting the technical solution of the present invention, conflicts of network card physical addresses MAC of terminals are prevented at the application level, possible software troubleshooting cost is directly reduced to zero, and at the same time, software copyright infringement acts damaging the interests of software vendors are completely eradicated.
Owner:HAIMEN BIWEI INTPROP SERVICE CO LTD
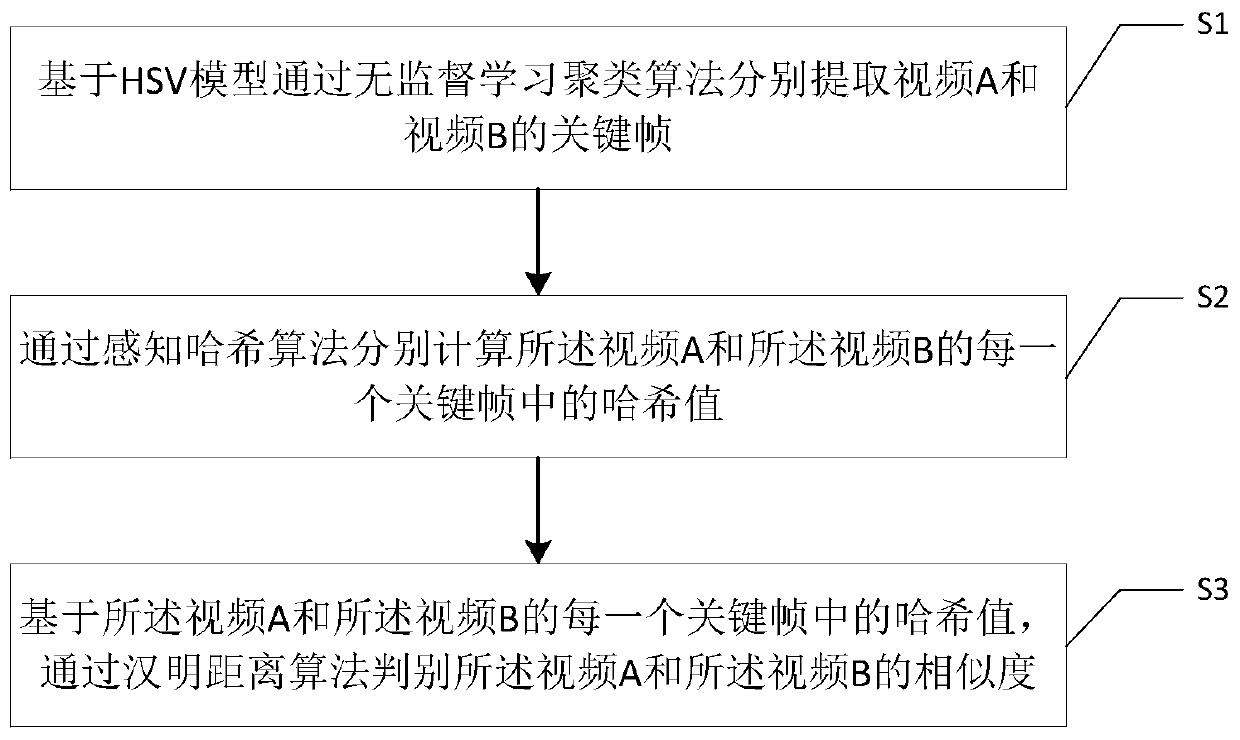
Video content similarity discrimination method and system based on computer vision
InactiveCN110427895ATo achieve the purpose of determining copyright infringementPoor resolutionVideo data indexingCharacter and pattern recognitionCluster algorithmCopyright infringement
The embodiment of the invention discloses a video content similarity discrimination method and a system based on computer vision, and relates to the technical field of video image processing, and themethod comprises the following steps: respectively extracting key frames of a video A and a video B through an unsupervised learning clustering algorithm based on an HSV model; respectively calculating a hash value in each key frame of the video A and the video B through a perceptual hash algorithm; and based on the hash value in each key frame of the video A and the video B, judging the similarity of the video A and the video B through a Hamming distance algorithm. According to the method and the system, the problems that the representativeness of key frames is not enough, the accuracy can begreatly reduced under the condition that the content change amplitude between the frames is relatively small, and the effect of the existing picture local feature value processing technology is poorunder the condition of image brightness change are effectively solved; hash value comparison is carried out through the Hamming distance, similarity judgment is carried out on videos of different channels, and therefore the purpose of video copyright infringement judgment is achieved.
Owner:李震
Data management method
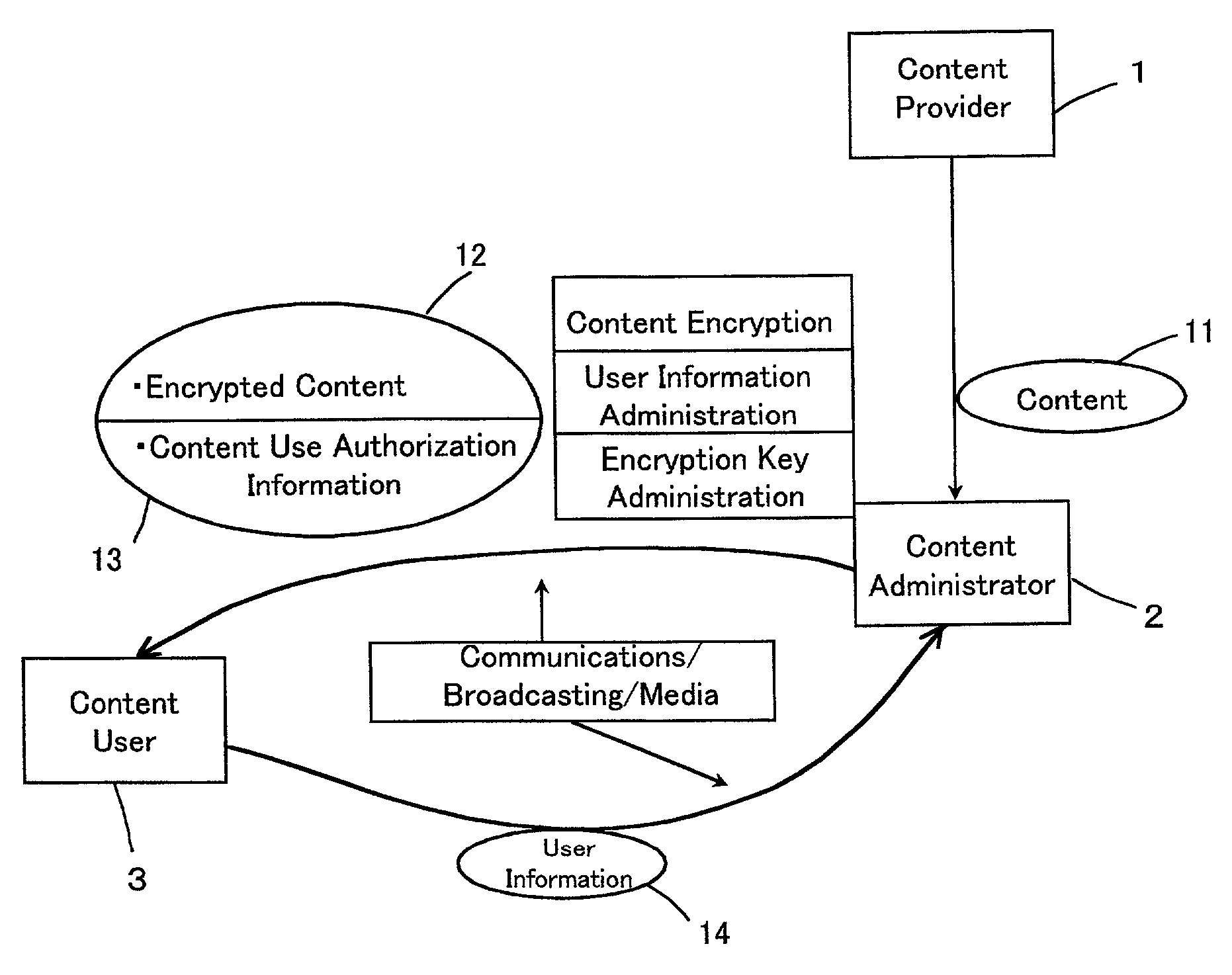
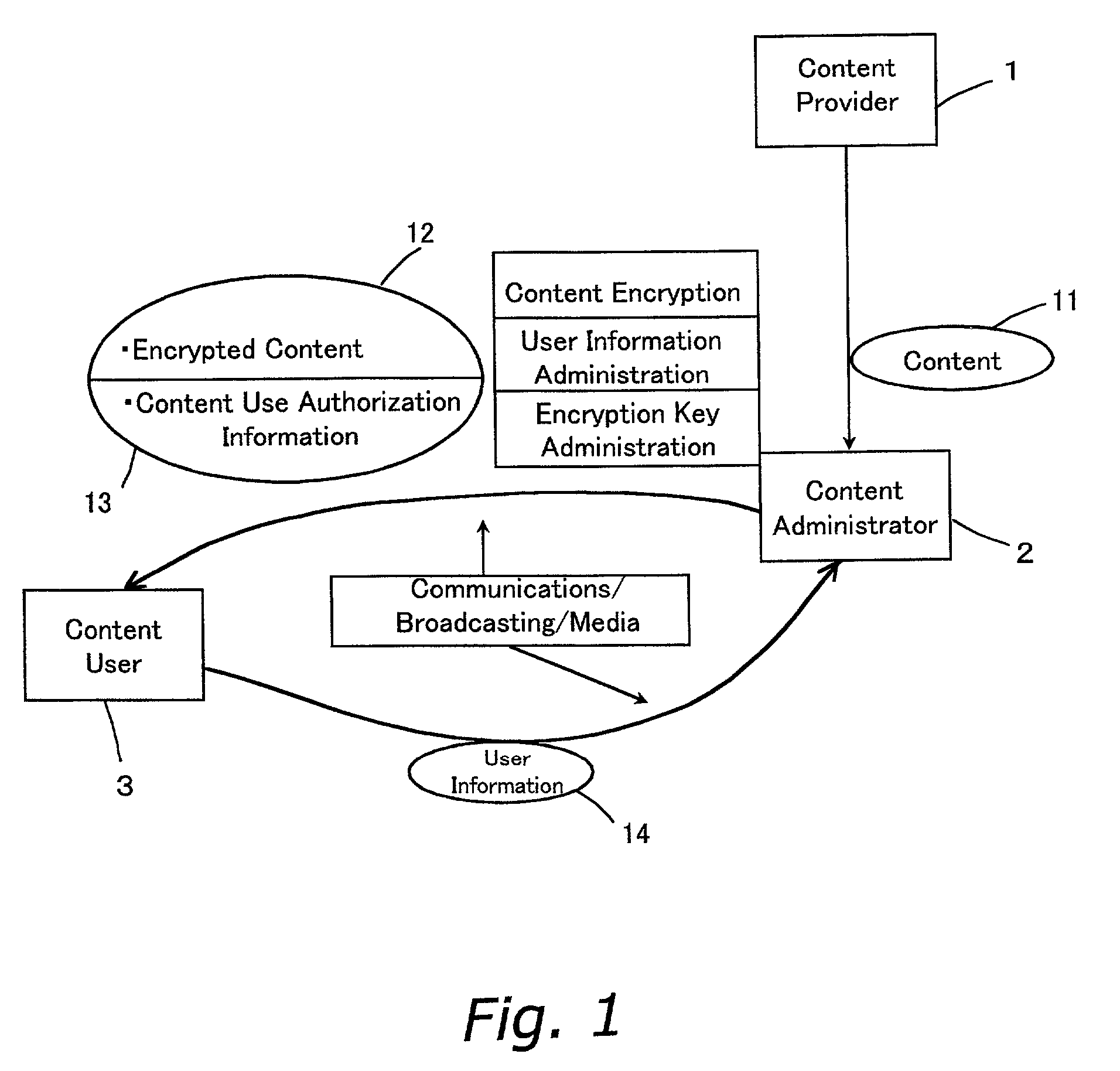
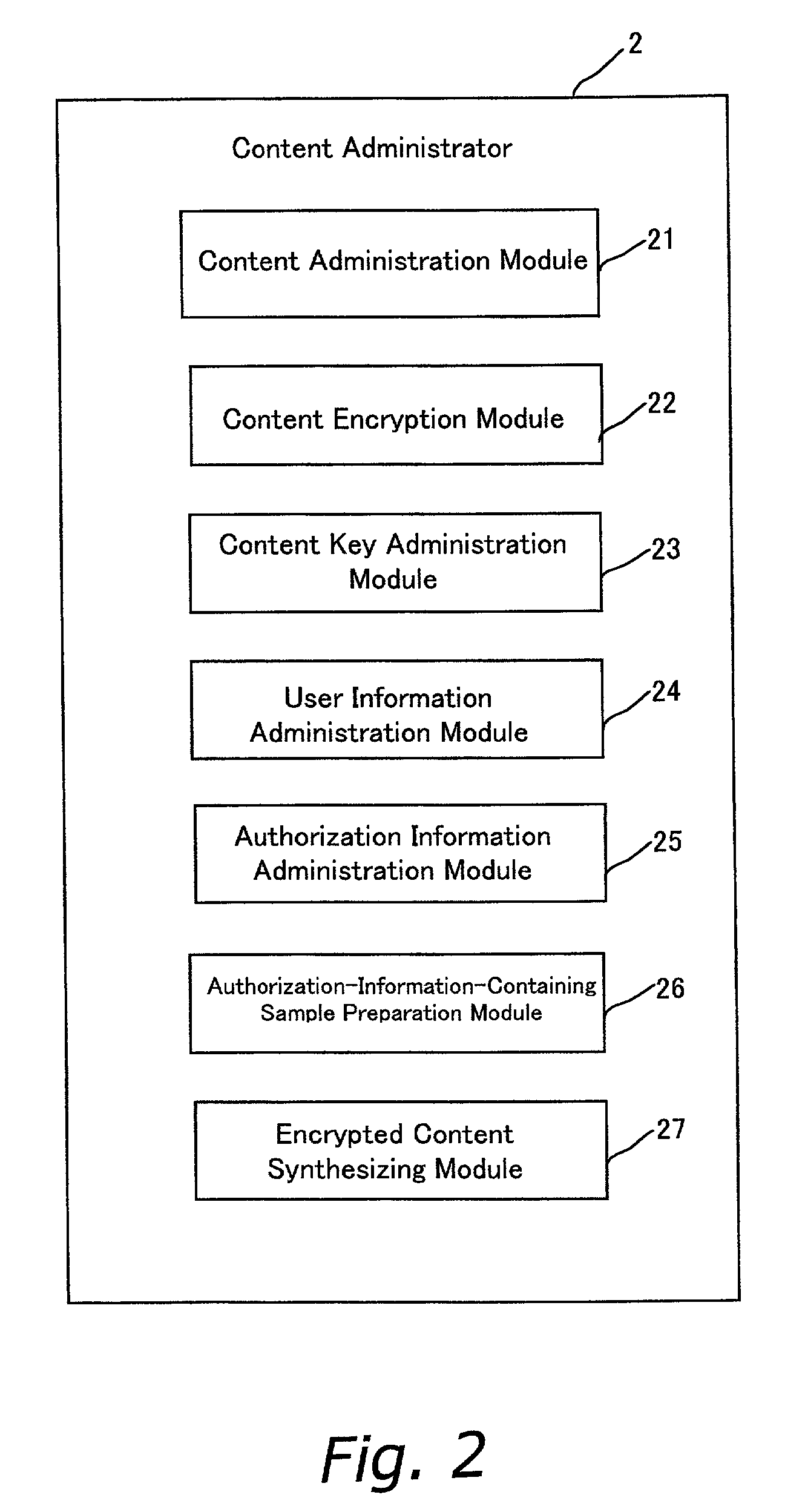
InactiveUS7145492B2Prevents copyright infringementPreventing breakage and lossElectric signal transmission systemsAnalogue conversionDigital contentData management
A data management method that by encrypting and distributing digital content prevents copyright infringement, and that prevents authorization information for decrypting the encrypted digital content from being damaged or otherwise lost. Encrypted content 45 is prepared by encrypting digital content 11 with a content key 44. A portion of the digital content 11 is extracted as sample data 41. A secret key 46, by which the content key 44 is encrypted with user information 14, is embedded as invisible information into the sample data 41, thus preparing watermarked sample data 47. The watermarked sample data 47 is synthesized with the encrypted content 45 to form synthesized data 48. The synthesized data 48 is distributed.
Owner:FUJITSU LTD
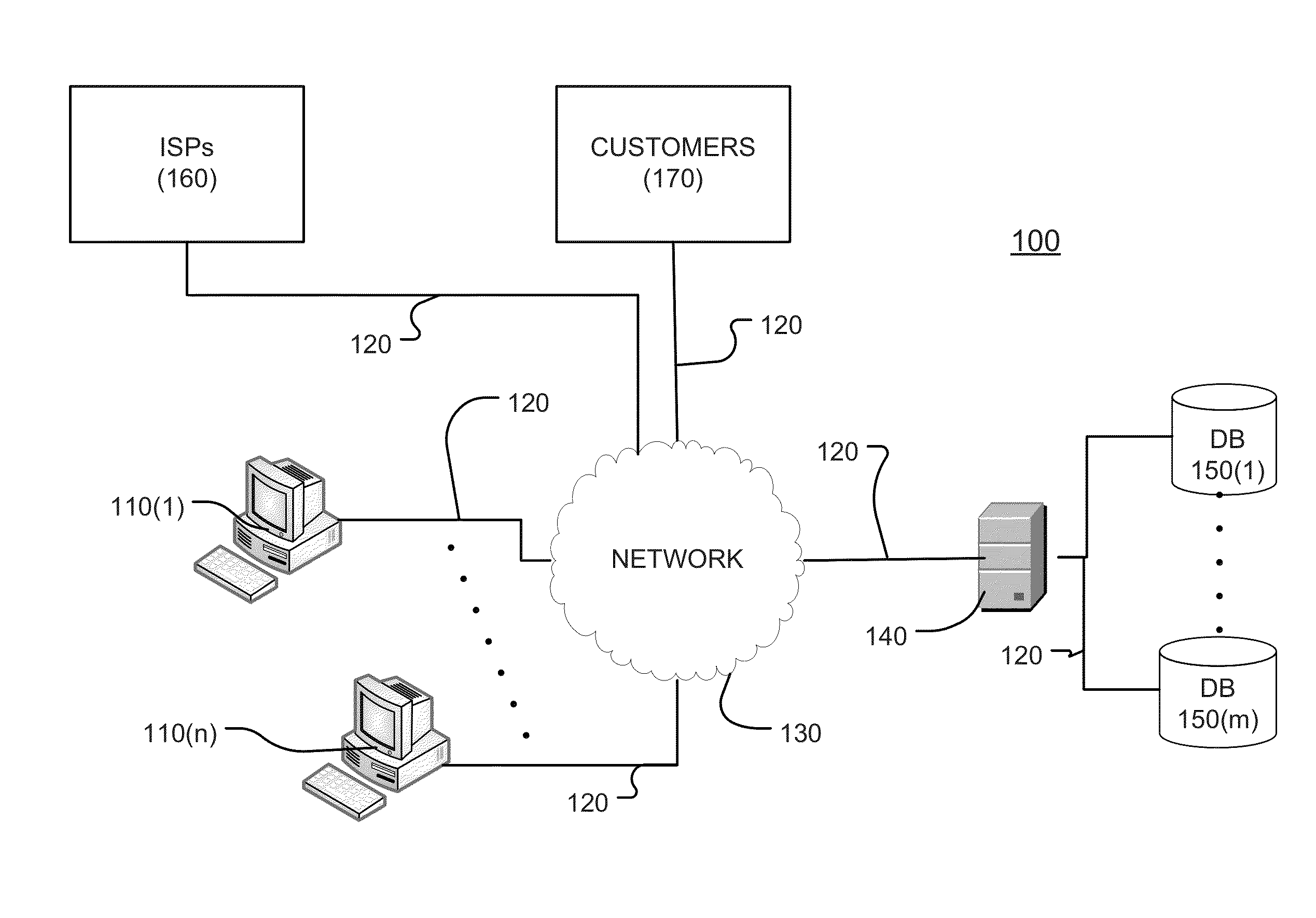
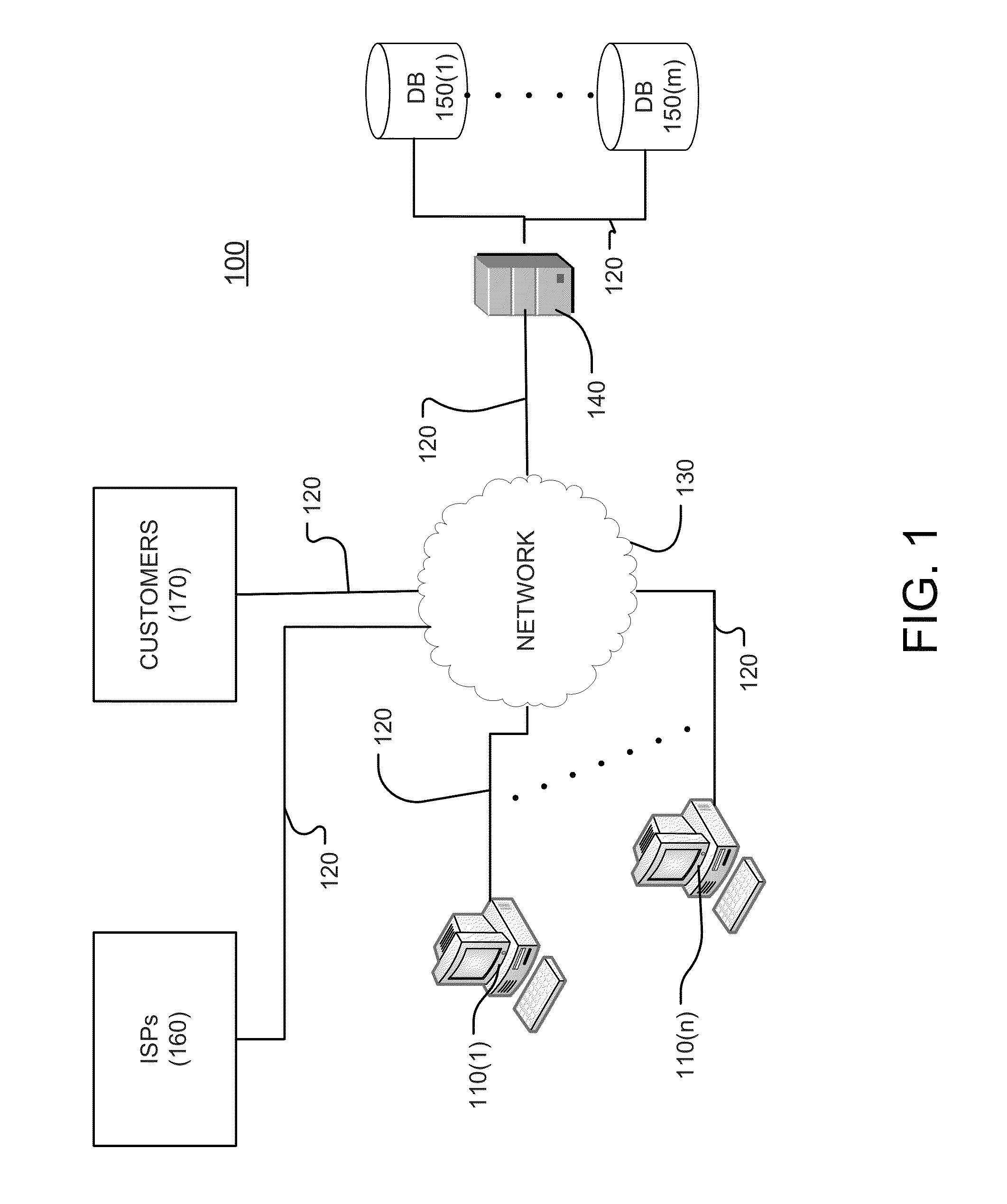
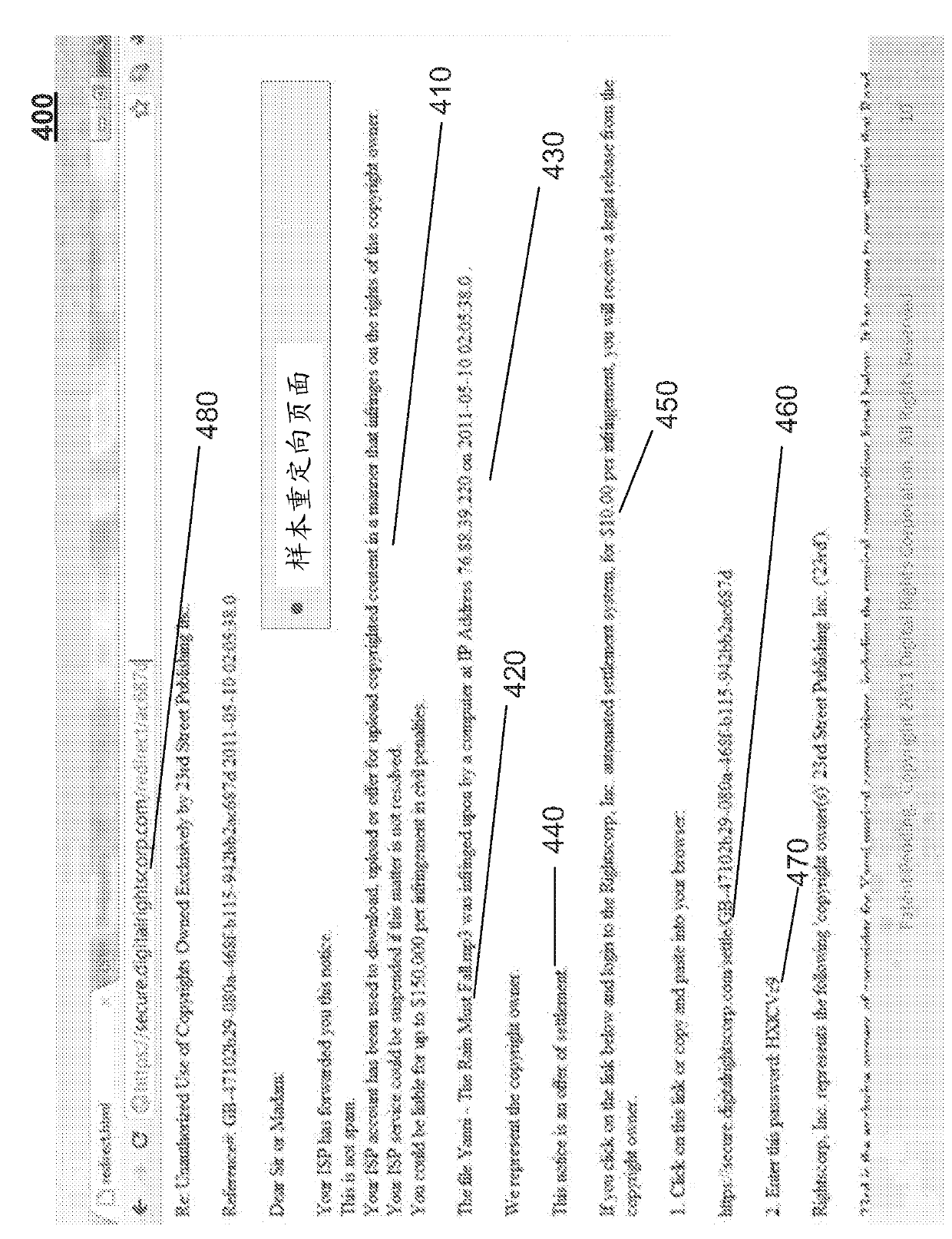
System and Method for Determining Copyright Infringement and Collecting Royalties
InactiveUS20110276449A1RelievingPrevents from maliciously modifyingComplete banking machinesTelephonic communicationPaymentData validation
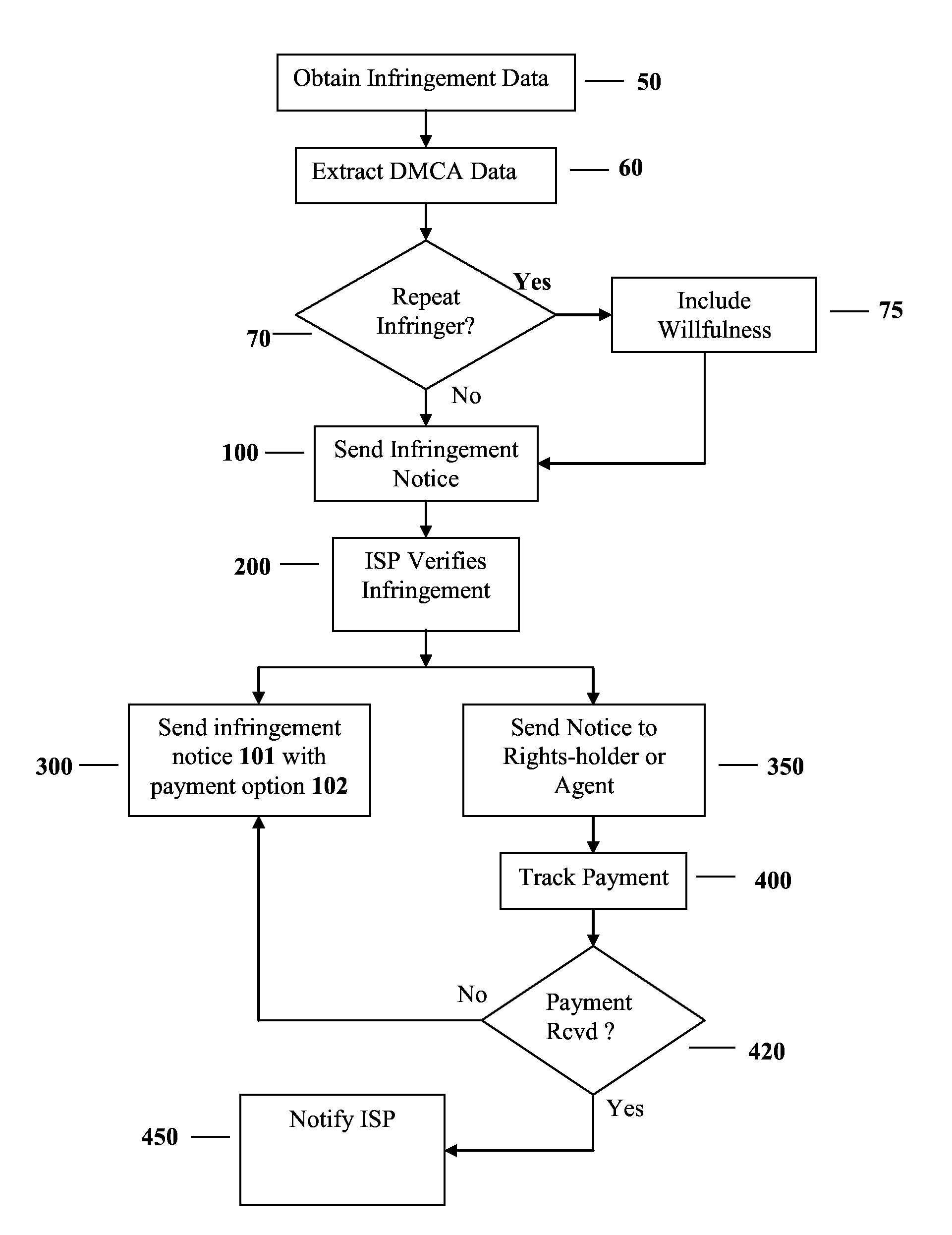
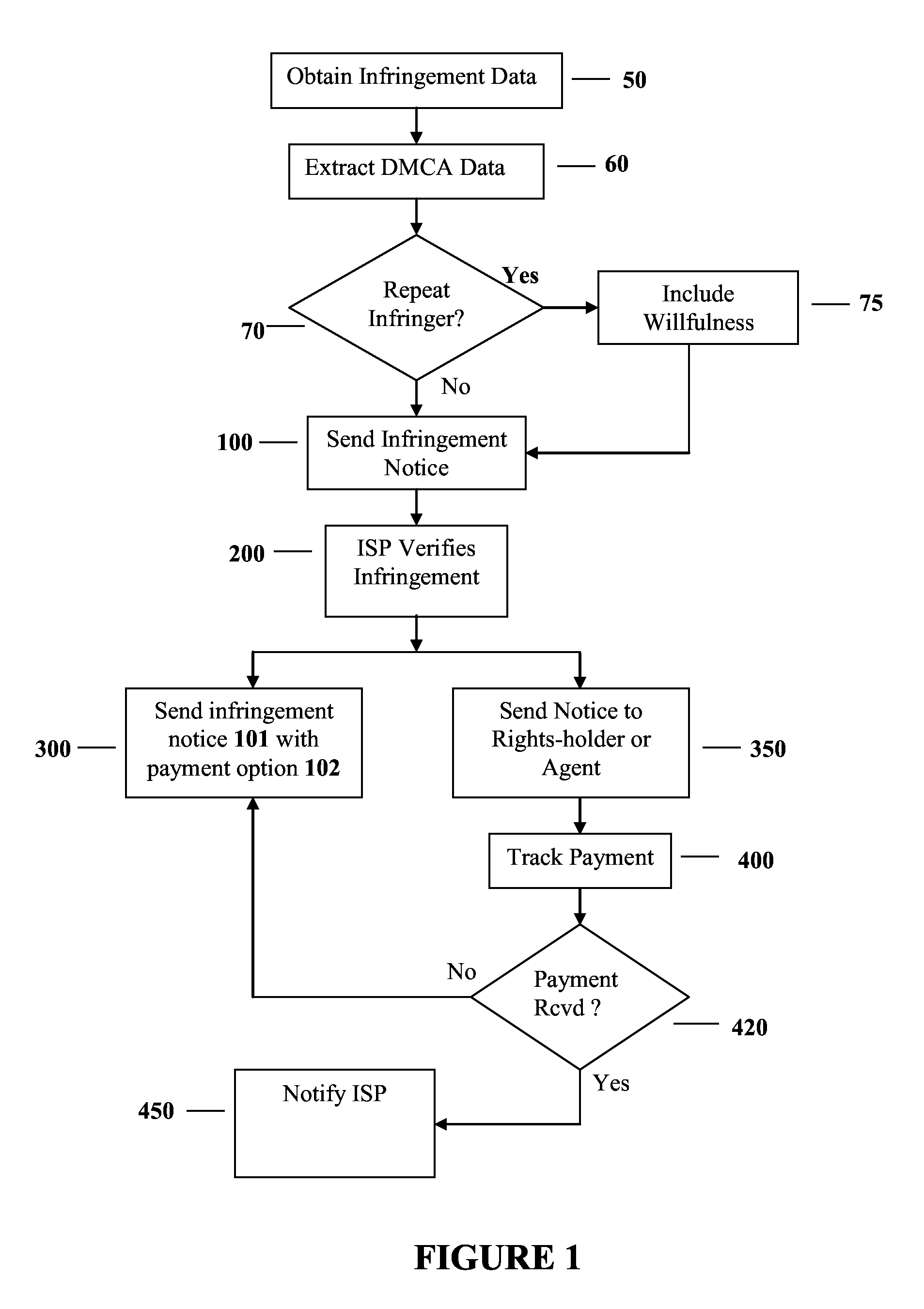
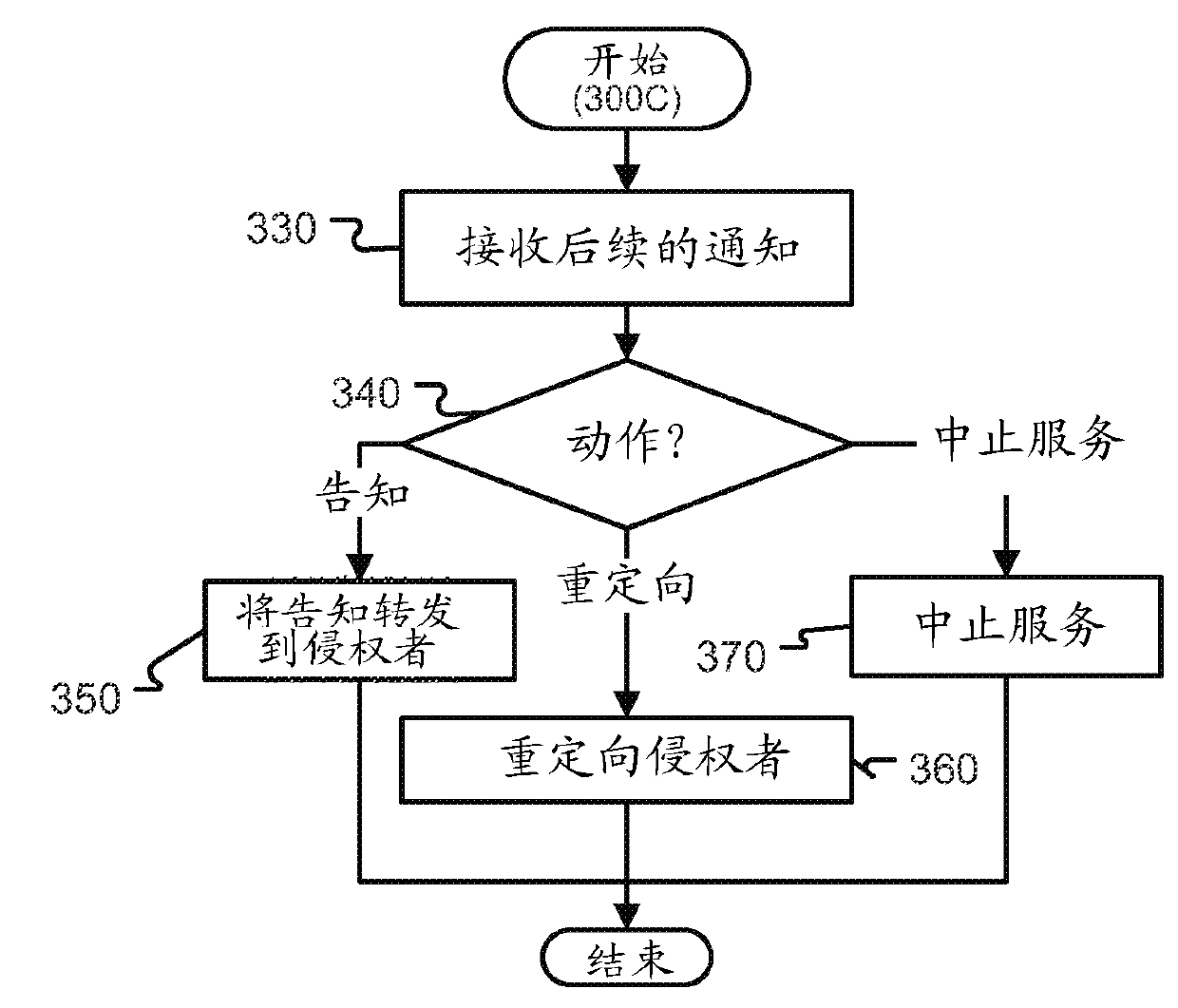
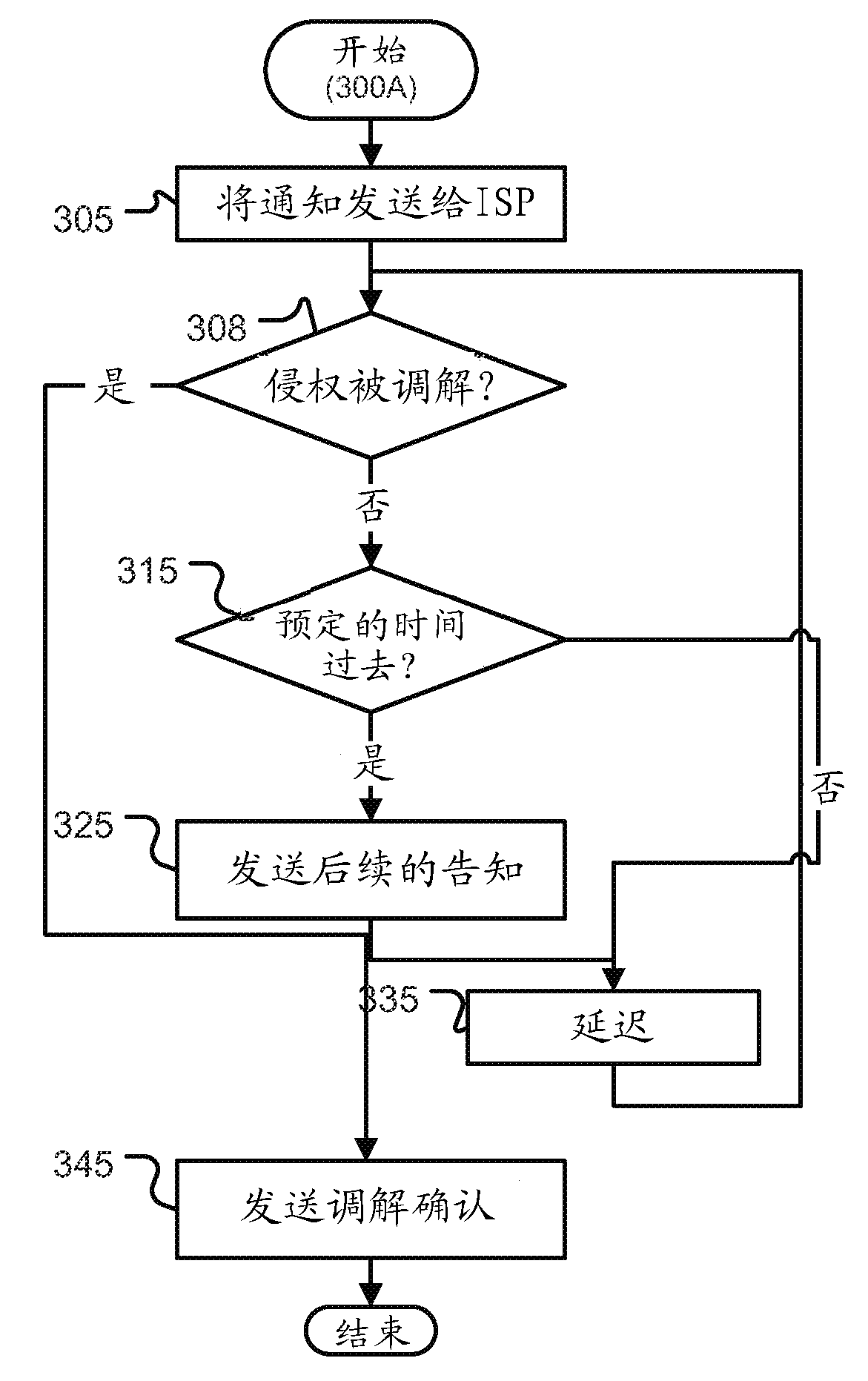
The present invention describes methods for obtaining compensation for copyright infringement wherein in one embodiment the invention comprises the steps of obtaining infringement data related to a copyright infringement; extracting infringement information from the infringement data; sending an infringement notice to an Internet Service Provider, wherein the Internet Service Provider verifies that an infringer has committed copyright infringement based upon the infringement data that was provided to the Internet Service Provider; and sending a notice to the infringer regarding the infringement information, wherein the notice includes a payment option for reconciling the copyright infringement. Additionally, the present invention discloses a computer-readable storage medium containing a set of instructions for a general purpose computer comprising the set of instructions including: obtaining infringement data; extracting infringement information from the infringement data; sending an infringement notice to an Internet Service Provider, wherein the Internet Service Provider verifies that an infringer has committed copyright infringement based upon the infringement data that was provided to the Internet Service Provider; and sending a notice to the infringer regarding the infringement information, wherein the notice includes a payment option for reconciling the copyright infringement.
Owner:PAYARTISTS
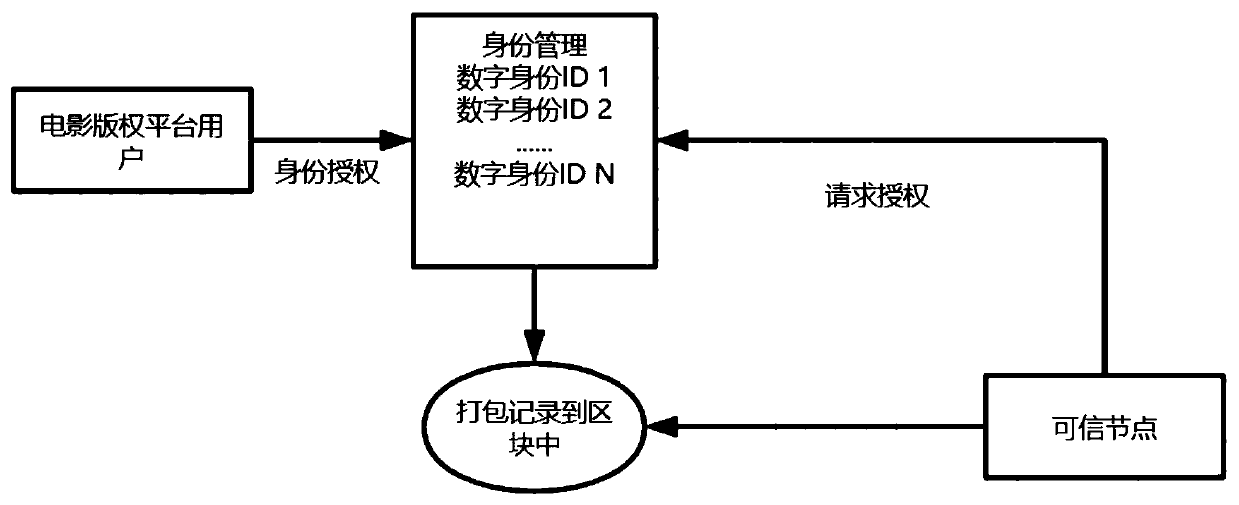
Movie copyright protection method based on block chain
InactiveCN110855428ASecure collaborationTrusted collaborationEncryption apparatus with shift registers/memoriesUser identity/authority verificationInternet privacyEngineering
The invention provides a movie copyright protection method based on a blockchain, and belongs to the technical field of blockchain smart contracts, symmetric encryption and decryption, and asymmetricencryption and decryption, the movie copyright protection method based on the blockchain comprises the following steps: 1) movie copyright evidence storage is performed by using the blockchain; the method comprises the steps of (1) movie copyright detection and tracking, (2) movie copyright verification, (3) movie copyright infringement evidence storage and (4) movie copyright asset sharing through an intelligent contract, it is guaranteed that all parties carry out safe and credible cooperation on the block chain, and convenient management and fair and transparent content consumption income division are facilitated.
Owner:山东爱城市网信息技术有限公司
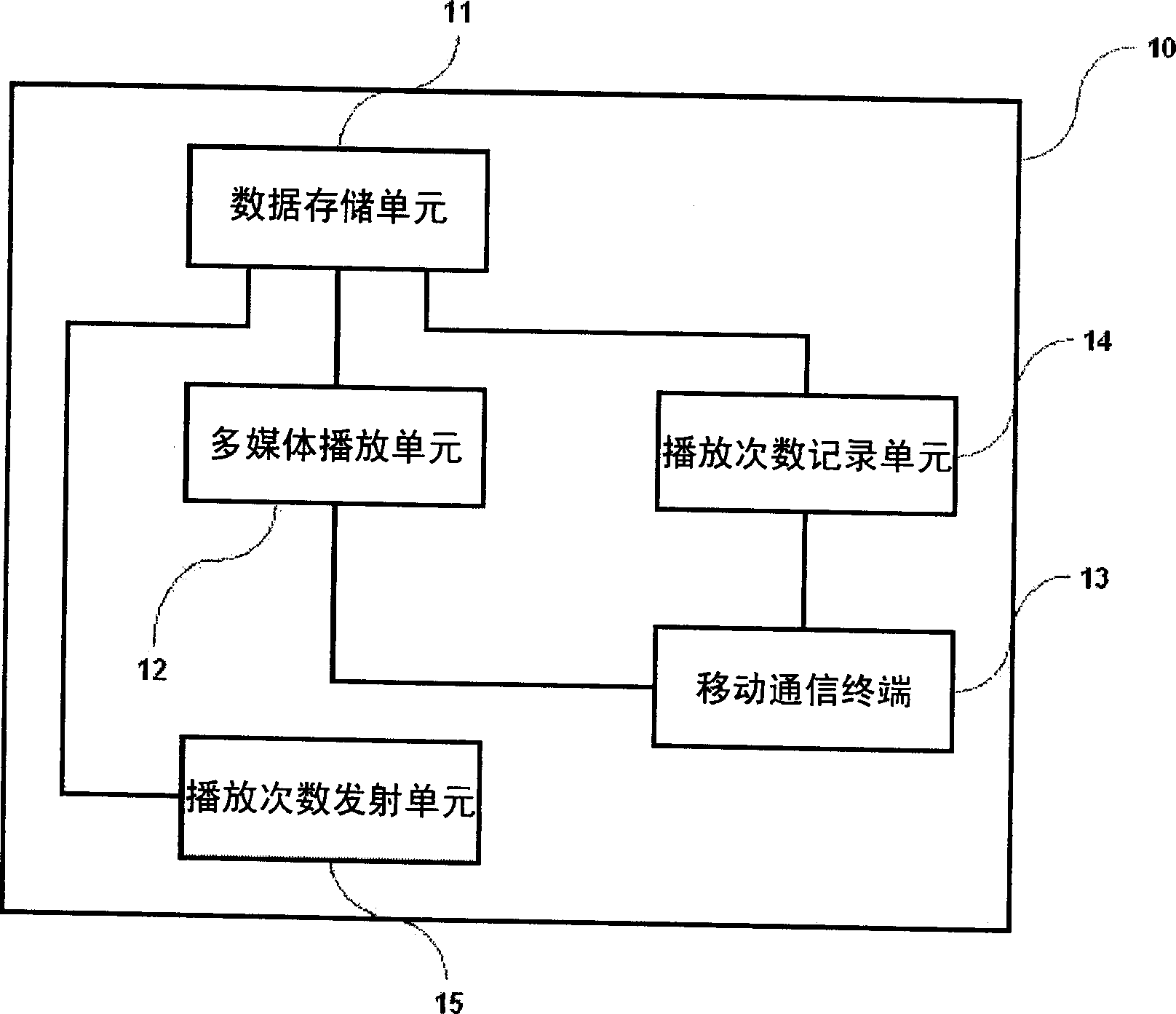
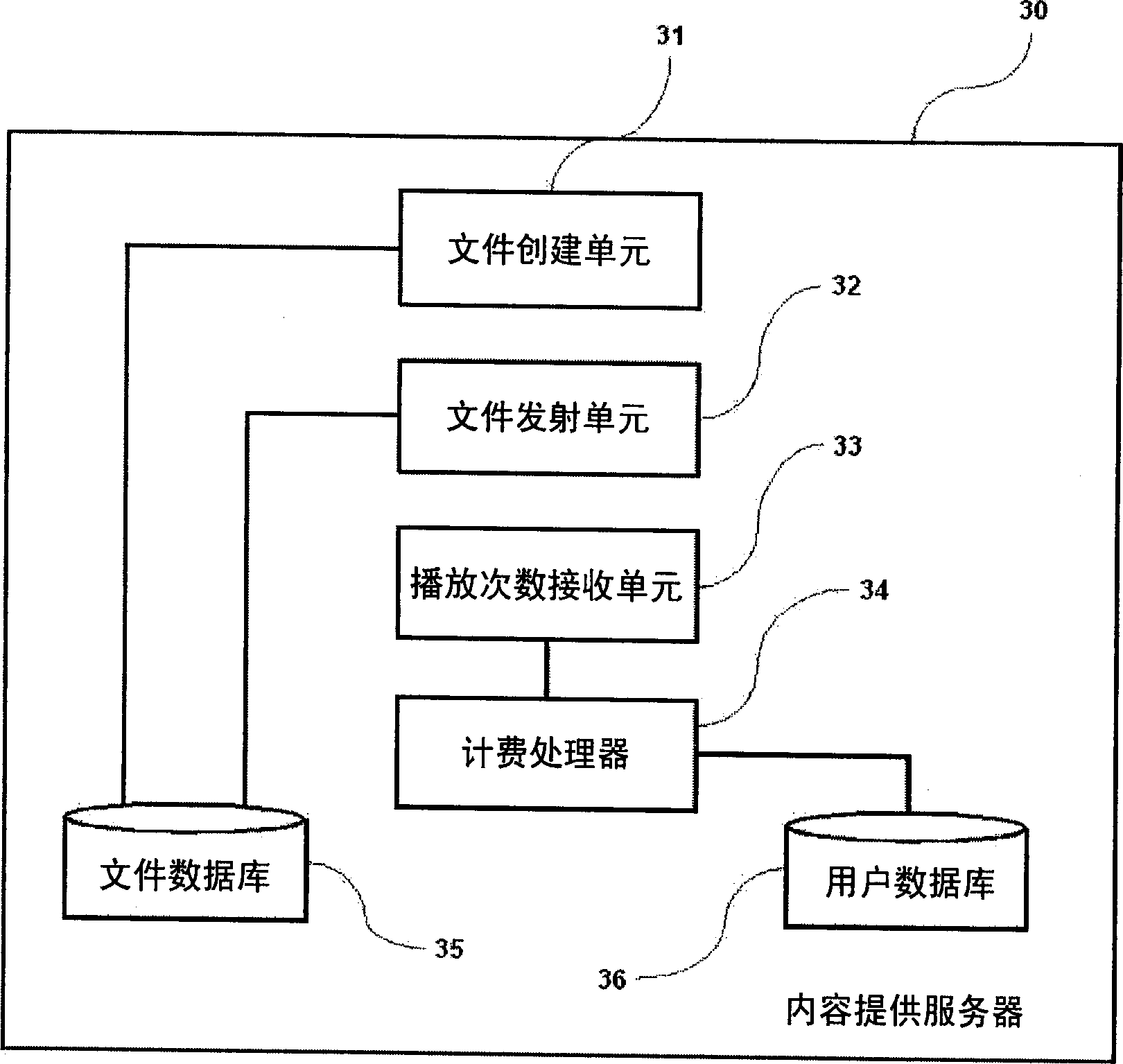
Post-paid billing system and method for multimedia files
InactiveCN1791211AAvoid Copyright InfringementLarge containersAnalogue secracy/subscription systemsPaymentCopyright infringement
The present invention relates to a system and method for determining whether playback has occurred after music has been provided from an online audio source server and played in a user's player, such as an MP3 player, determining the number of times playback has occurred, and based on These determinations are charged, whereby the user is charged for the multimedia file on a post-paid basis, overcoming the problems of the traditional method of charging when the user accesses an online source server and downloads or plays the music. More particularly, a post-pay billing system and method wherein, first, a multimedia file is provided to a user, and then charges are made based on the number of times the user has played the provided multimedia file. According to the present invention, users can play and enjoy multimedia files at a lower price. Copyright owners are able to earn royalties as a result of clear and accurate fees. Since multimedia files can be freely copied / distributed, copyright infringement due to unauthorized copying can be substantially avoided.
Owner:朴琇民
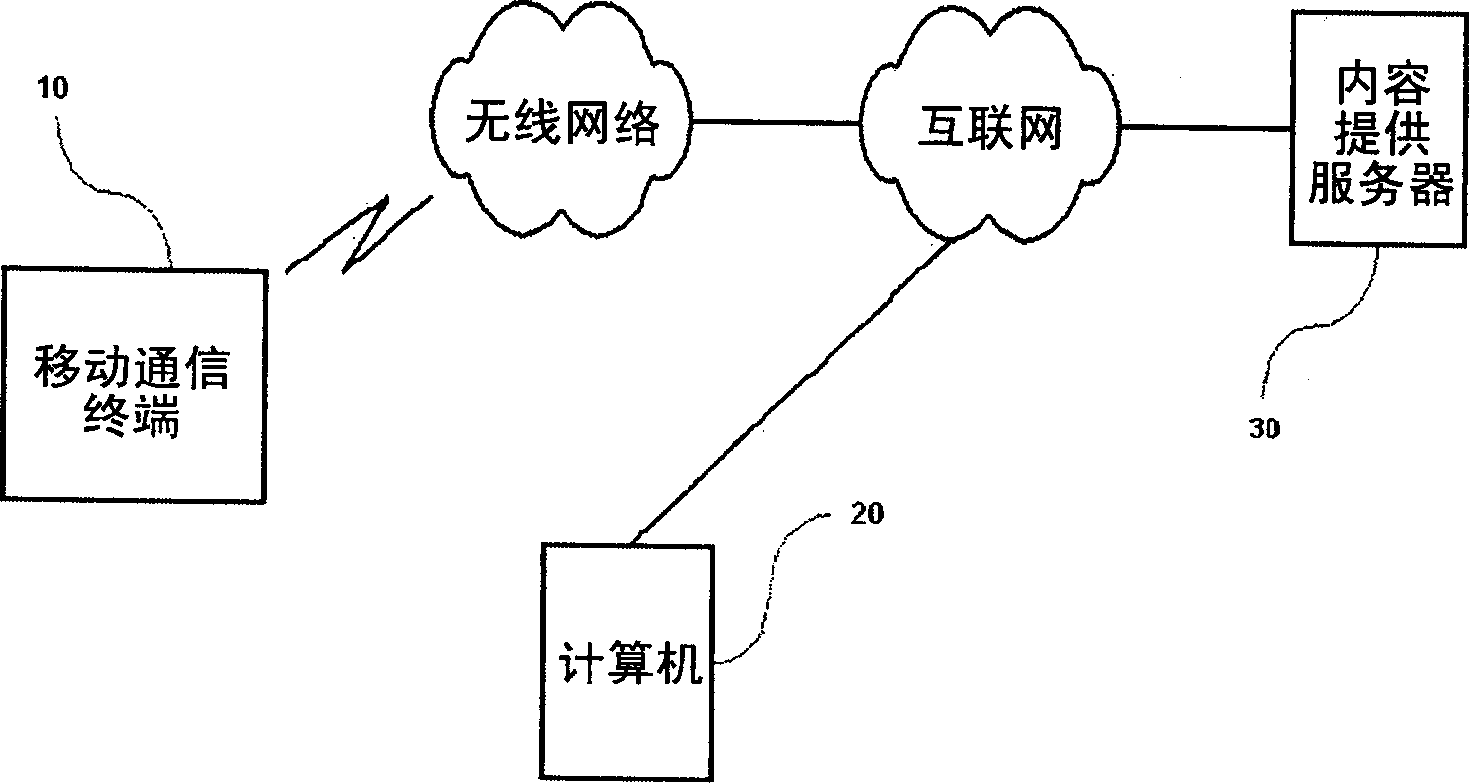
Mobile device for preventing illegal distribution of digital data contents and operating method thereof
InactiveUS7640596B1Digital data processing detailsDigital computer detailsDigital dataDigital content
A method, apparatus and computer programs for preventing illegal distribution of digital content data, are discussed. In an embodiment, the apparatus includes a controller configured to control the apparatus to: store at least first and second program code segments; receive the digital content data from a first device, the digital content data including a copyright code segment for managing copyright infringement; check the copyright code segment by using the first program code segment for selectively reproducing the digital data contents at a second device; and control an output operation of the digital content data by using the second program code segment based on the copyright code segment, wherein the digital content data is downloaded from a digital data server to the first device through a communication network, wherein decrypting and reproduction operations of the digital content data are executed by a software program provided by the digital data server.
Owner:LG ELECTRONICS INC
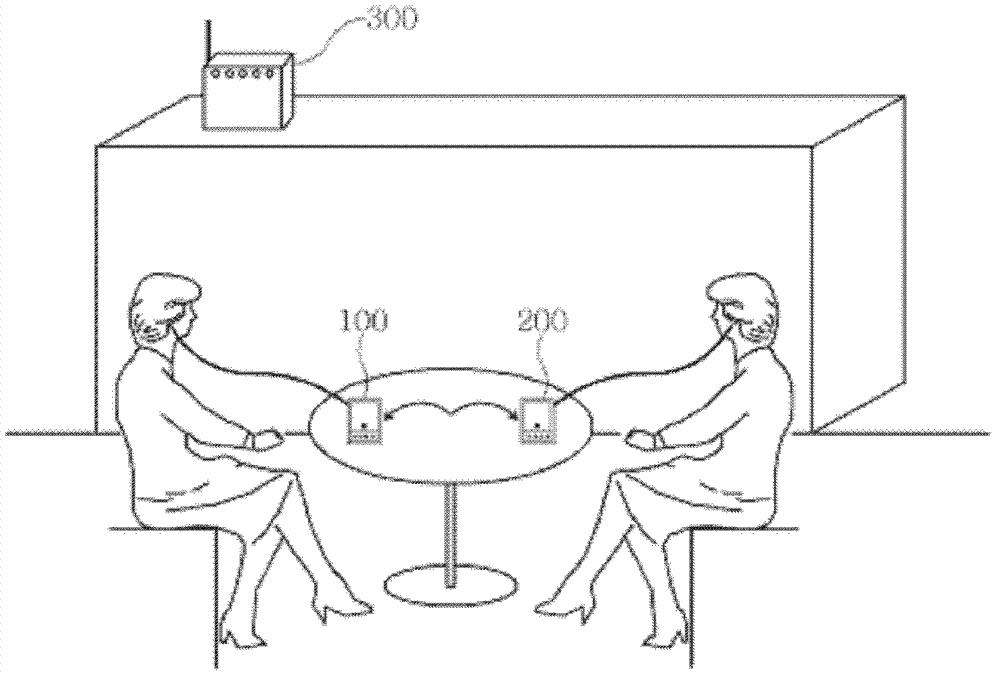
Content simulcast terminal, system thereof and simulcast method
InactiveCN103096249ASimultaneous playback is convenientImprove playbackAssess restrictionBroadcast service distributionShared environmentCopyright infringement
The invention relates to a content simulcast terminal, a system thereof and a simulcast method. Terminal information which is in a single wireless access point network environment and spreads in a broadcast mode is adopted for identifying an adjacent terminal, a share environment which simulcasts content for setting and permitting with any adjacent terminal needs is stipulated, so that one-to-one content sharing and simulcasting can be achieved among terminals, simultaneous watching the same content can just be achieved without the need for a complex share process between every two adjacent terminals, and meanwhile, a simple share process of network environment identifying, searching and adjacent terminal choosing is used for achieving simulcast content. Therefore, an individual management server which is needed by content share and terminal confirmation is of no need, share and simulcast content between the adjacent terminals are convenient. When content needs to be shared on two terminals which are in one-to-one connection, a terminal on one side transmits in an information stream mode, a terminal on the other side receives transmitted content and simulcasts between the adjacent terminals, so that the content can disappear after broadcasting of the adjacent terminals, and thereby copyright infringement legal disputes can be prevented.
Owner:M SERVICE
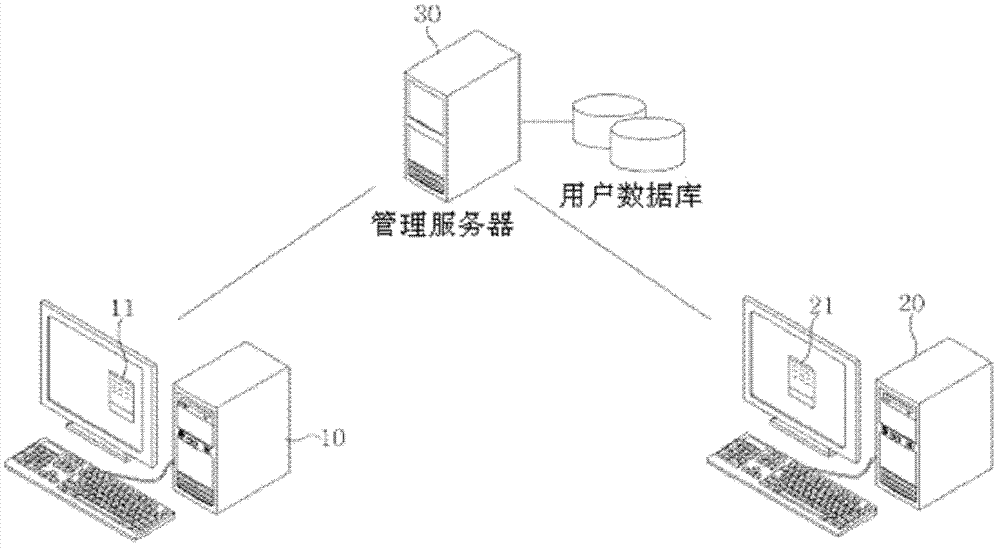
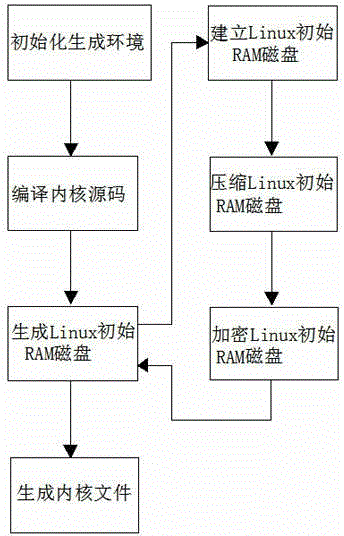
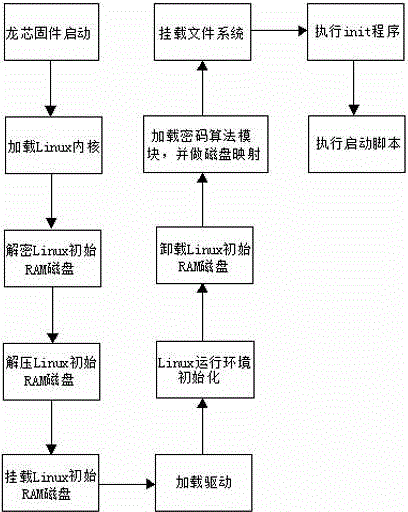
Method for protecting linux operation system on loongson hardware platform
InactiveCN104636685AAnti-piracyProtect intellectual propertyInternal/peripheral component protectionOperational systemRandom access memory
The invention discloses a method for protecting a linux operation system on a loongson hardware platform. According to the method for protecting linux operation system on the loongson hardware platform, a core encryption method and a file system encryption method are used. Core encryption is implemented by encrypting a Linux initial RAM (random-access memory) magnetic disk. The core encryption method comprises the following steps of encrypting the Linux initial RAM magnetic disk at a core generation stage; and decoding the Linux initial RAM magnetic disk when the system is started. File system encryption is implemented by using a linux equipment mapping technology, after file system encryption is implemented, file system mounting cannot be carried out directly, an encrypted file system requires to be mapped, and data of the file system can be read or written after mounting the mapped file system. By the method for protecting the linux operation system on the loongson hardware platform, a Linux core process is improved, and the inner operation mechanism, the procedure principle and key data of the Linux core process are protected fundamentally. The method not only can be used for preventing software copyright infringement and protecting intellectual property rights in a business environment, but also can be used for an environment requiring encryption such as defense and military, and has an anti-cracking function and an information leakage preventing function.
Owner:SHANDONG CHAOYUE DATA CONTROL ELECTRONICS CO LTD
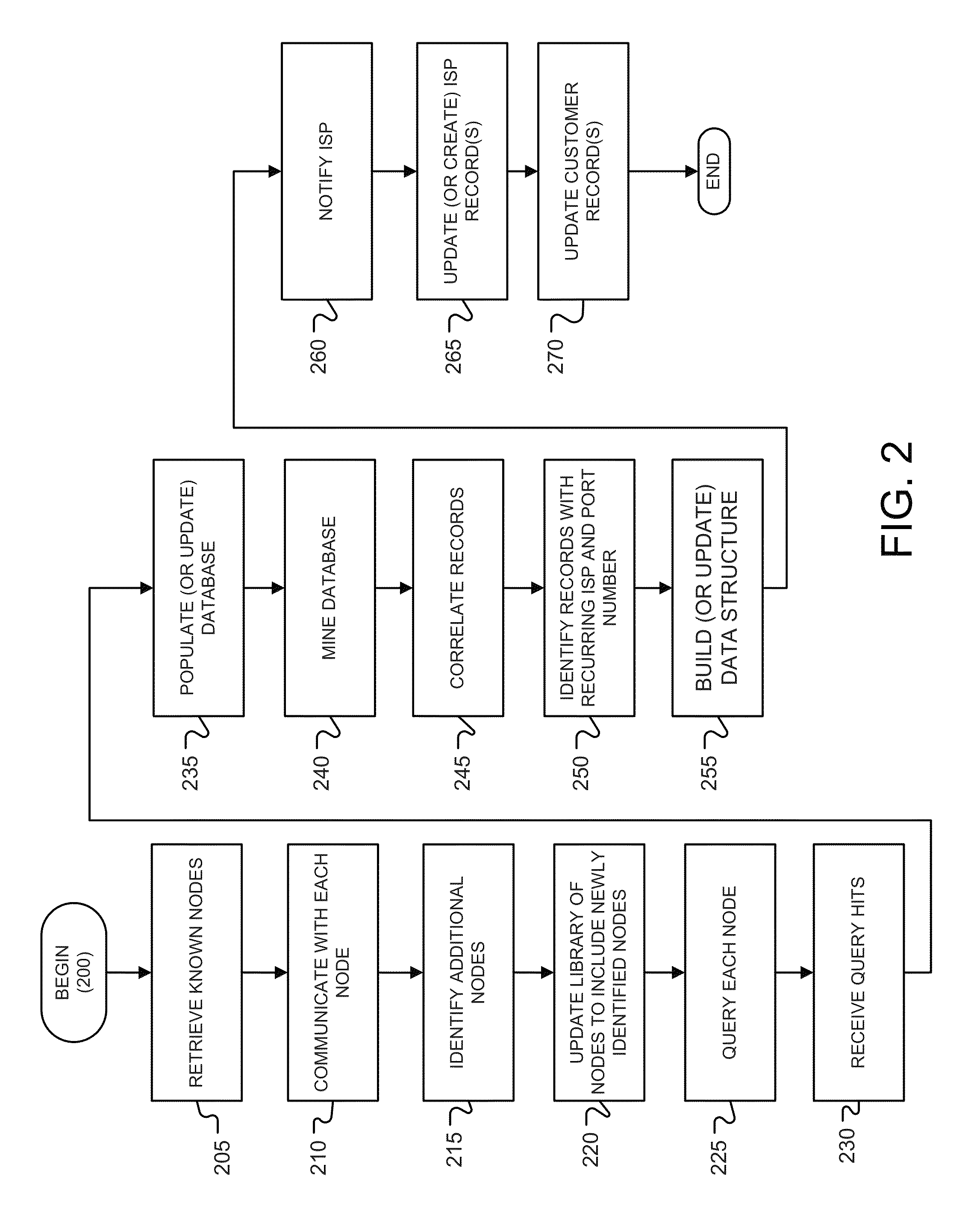
System to identify multiple copyright infringements
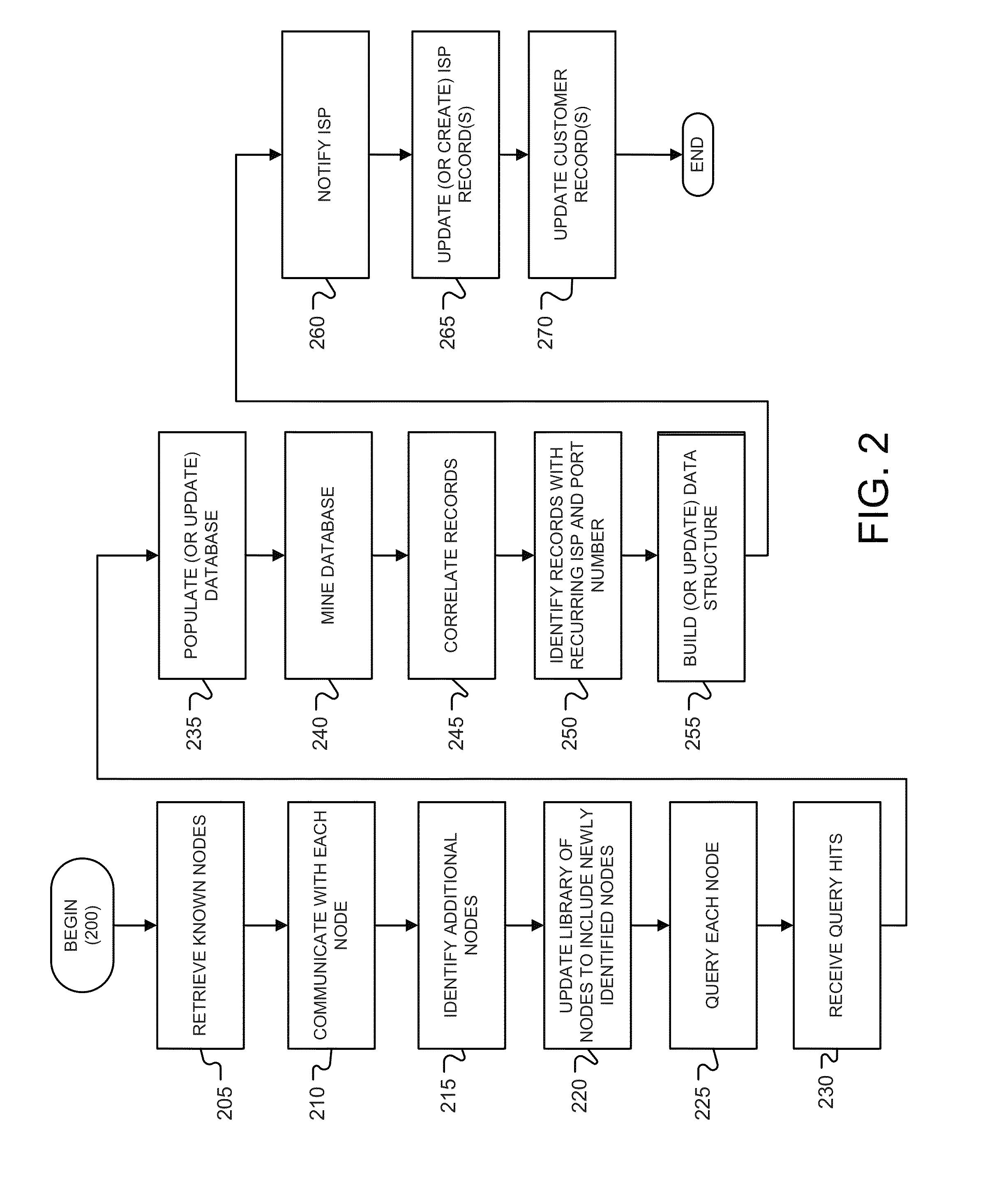
A system, a method, and a computer program for determining multiple copyright infringement events, identifying a stopped reporting repeat infringer, identifying a started reporting repeat infringer, and determining if the stopped reporting repeat infringer and the started reporting repeat infringer are using the same computer.
Owner:RIGHTSCORP
Using hash signatures of DOM objects to identify website similarity
Embodiments are directed to using a hash signature of a rendered DOM object of a website to find similar content and behavior on other websites. Embodiments break a DOM into a large number of data portions (i.e., “shingles”), apply a hashing algorithm to the shingles, select a predetermined number of hashes from the hashed shingles according to a selection criteria to create a hash signature, and compare the hash signature to that of a reference page to determine similarity of website DOM object content. Embodiments can be used to identify phishing websites, defaced websites, spam websites, significant changes in the content of a webpage, copyright infringement, and any other suitable purposes related to the similarity between website DOM object content.
Owner:MICROSOFT TECH LICENSING LLC
Internet system for monitoring progress of a music student
A method of utilizing the Internet to permit music teachers to measure and document the progress of their music students without infringing the copyright of the owners of the music the students are learning. In order to avoid copyright infringement the method assures that all performances of the copyrighted works be made in private and not displayed publicly. In a preferred embodiment the method includes the creation of a number of secure private Internet systems, one for each student, with each system limited to a studio administrator, the student, his teacher, and a limited number (preferably less than 25) of designated third parties such as family members and friends of the student. In other preferred embodiment student performances are made available to the general public through the Internet for a fee which is shared with the owner, if any, of the copyright.
Owner:LIFE EMPOWERMENT
A system of publication and distribution of instructional materials and method therefor
Owner:SOLDAVINI MICHAEL ANTHONY
Network audio-visual management supporting copyright service sub-system
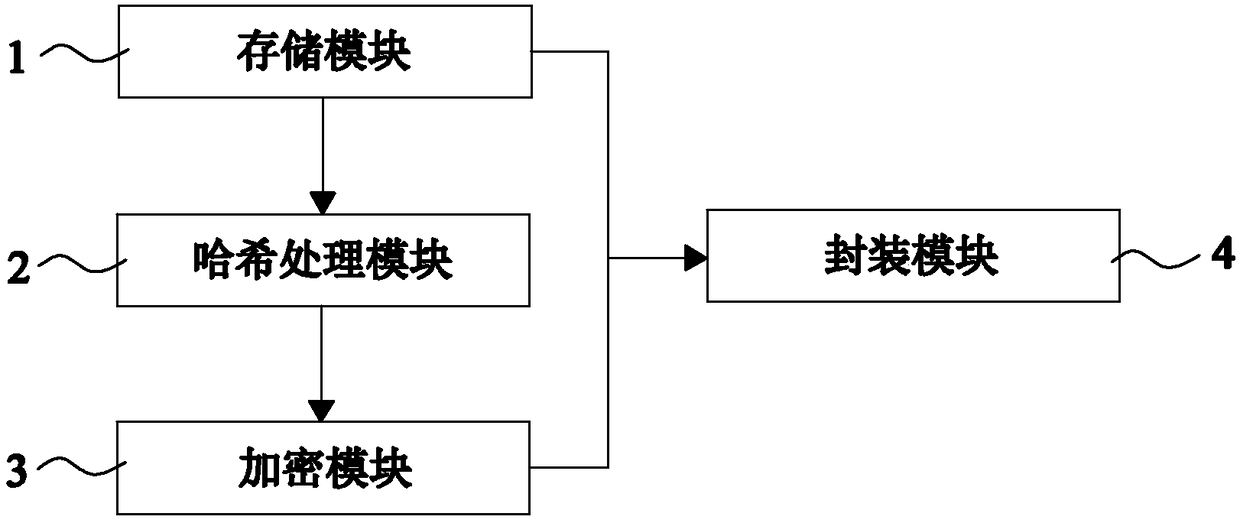
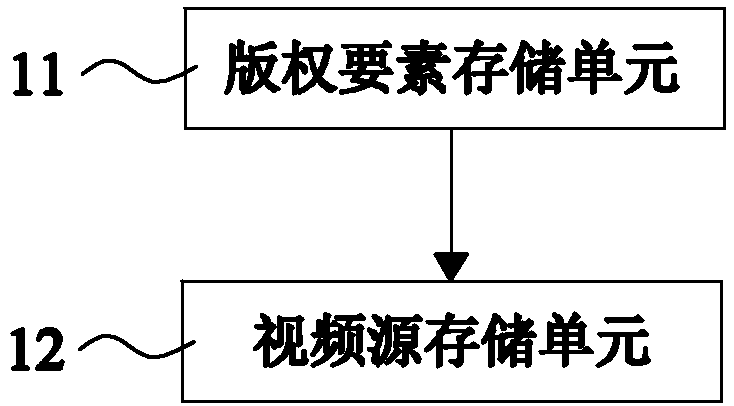
ActiveCN108595920AImprove securityImprove stabilityProgram/content distribution protectionUnique identifierCopyright infringement
The invention provides a network audio-visual management supporting copyright service sub-system. According to the sub-system, real-name registration is performed on a copyright owner, a video sourceis uploaded and is automatically confirmed as a legal copy according to an automatic acquisition principle of Berne Convention; the uploaded video source needs to be hashed and encrypted to obtain a hash value as a unique identifier ID of the video and simultaneously obtain an encrypted video source; the unique identifier and the encrypted video source are finally packaged to complete the step ofcopyright confirmation. After completion of the copyright confirmation, the copyright owner and an authorized party can obtain online services such as viewership checking and suspected copyright infringement checking and offline legal services such as copyright protection and copyright infringement protection by virtue of the sub-system. Through the abovementioned sub-system, the safety and stability of copyright video encryption package can be effectively improved, and the copyright registration record service, the copyright checking service and the management service of supervision departments are organically combined so as to provide a supervision service for the network video copyright efficiently and accurately.
Owner:ZHONGGUANG REDIANYUN TECH CO LTD +1
Multi-party digital content copyright management system based on blockchain
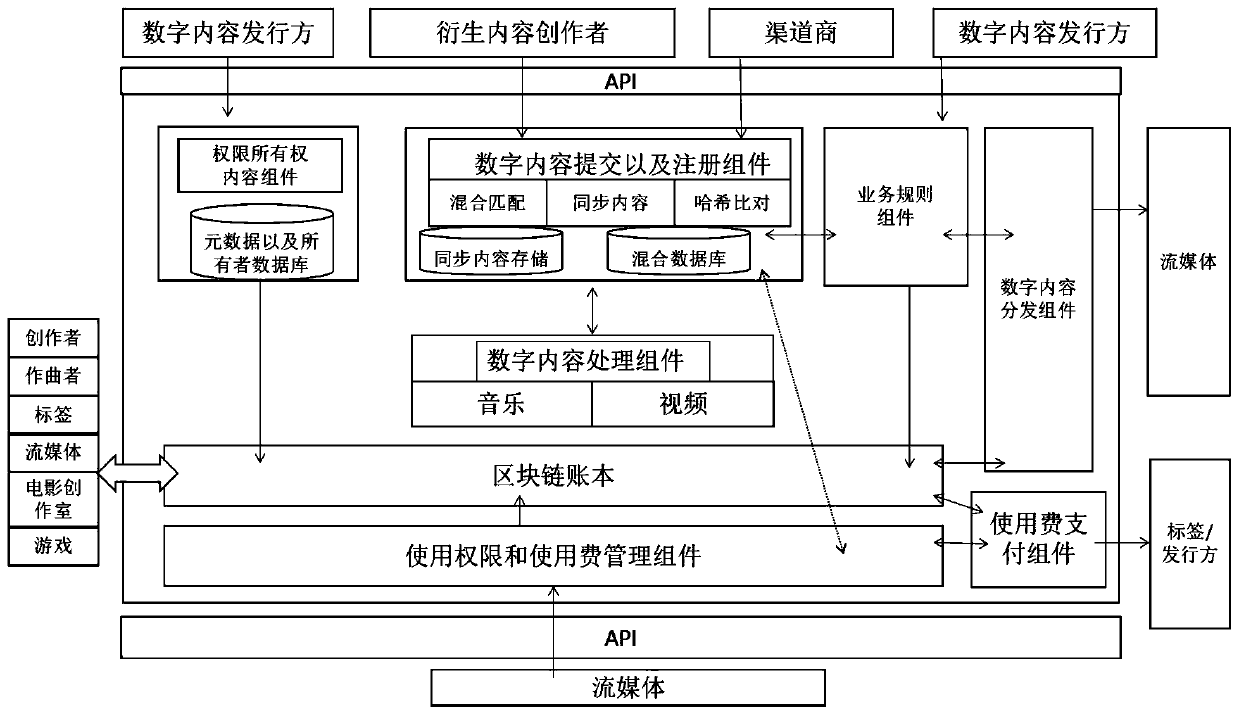
PendingCN111241495AImprove distributionEasy to importDigital data protectionProgram/content distribution protectionInternet privacyDigital content
The invention provides a multi-party digital content copyright management system based on a blockchain. The system comprises a plurality of metadata and an owner database, wherein the plurality of metadata and the owner database comprise an authority ownership content component, a digital content submitting and registering component, a service rule component, a digital content processing component, a digital content distribution component, a use authority and use fee management component and a use fee payment component; the digital content submitting and registering assembly comprises a mixedmatching assembly, a synchronous content assembly and a hash comparison assembly. According to the invention, the problems of digital copyright infringement evidence collection and difficulty in evidence collection in the prior art are solved.
Owner:无锡井通网络科技有限公司
Porcelain product body copyright protection method with embedded invisible identification image
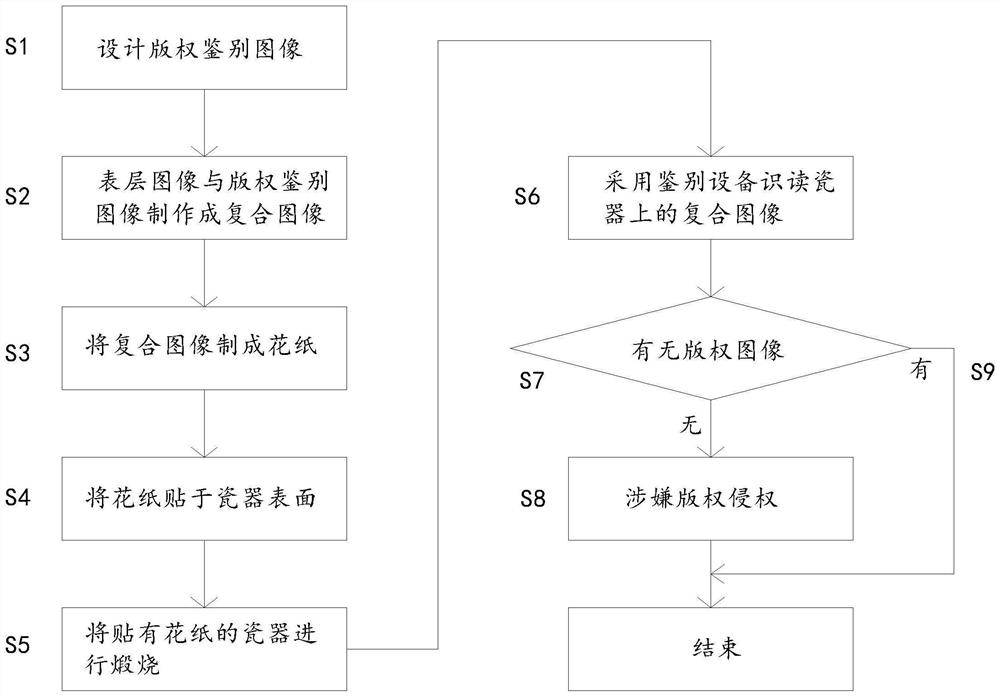
PendingCN111882746ADoes not affect normal readingReduced color contrastPaper-money testing devicesEngineeringComputer vision
The invention relates to a porcelain product body copyright protection method with an embedded invisible identification image, which comprises the following steps of: embedding the copyright identification image into a porcelain product body with copyright to form an invisible image, hiding the invisible image on the surface of porcelain, observing the embedded position through auxiliary equipment, and judging whether a product or a product has copyright information according to whether the invisible image can be obtained or not; judging whether copyright exists or not according to whether copyright identification image information exists or not. The copyright identification image used in the method is a portrait or LOGO of a copyright owner, information transmission is clear and visual, and an observation method is simple and clear at a glance; the invisible image is attached to the porcelain body and cannot be separated; and the invisible image is invisible, so that the method has copy resistance and high identification conclusion credibility. The method can effectively solve the problem of copyright infringement identification of porcelain and other crafts, is suitable for porcelain works or products with different processes, different categories, different shapes, different curved surfaces and different sizes, and does not influence the effect due to different shapes, curved surfaces and sizes.
Owner:周晓明
Digital movie playing server and movie playing control method
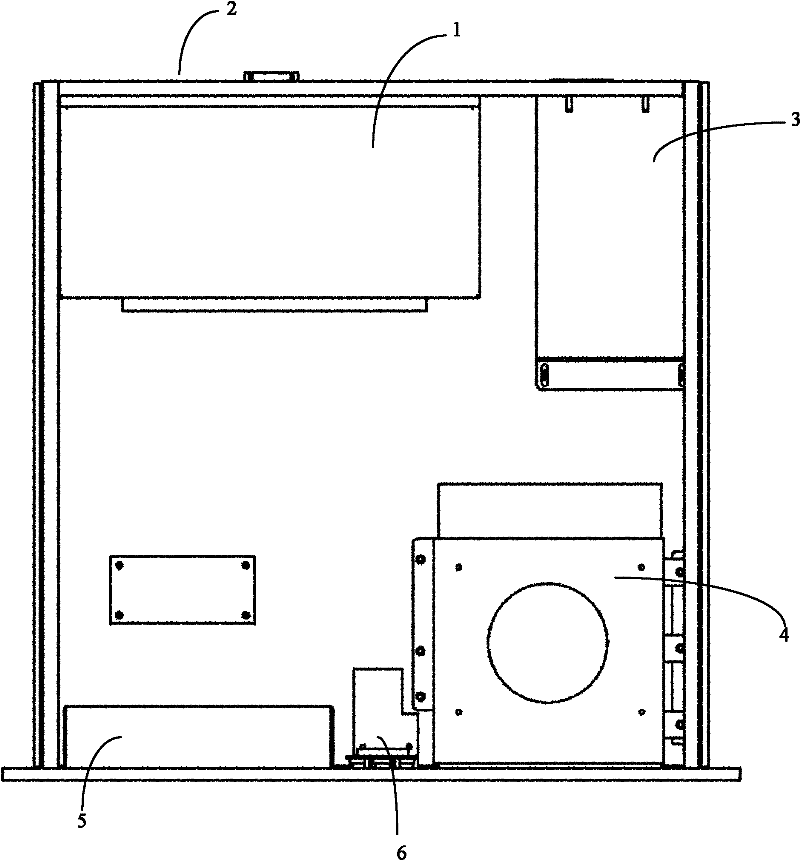
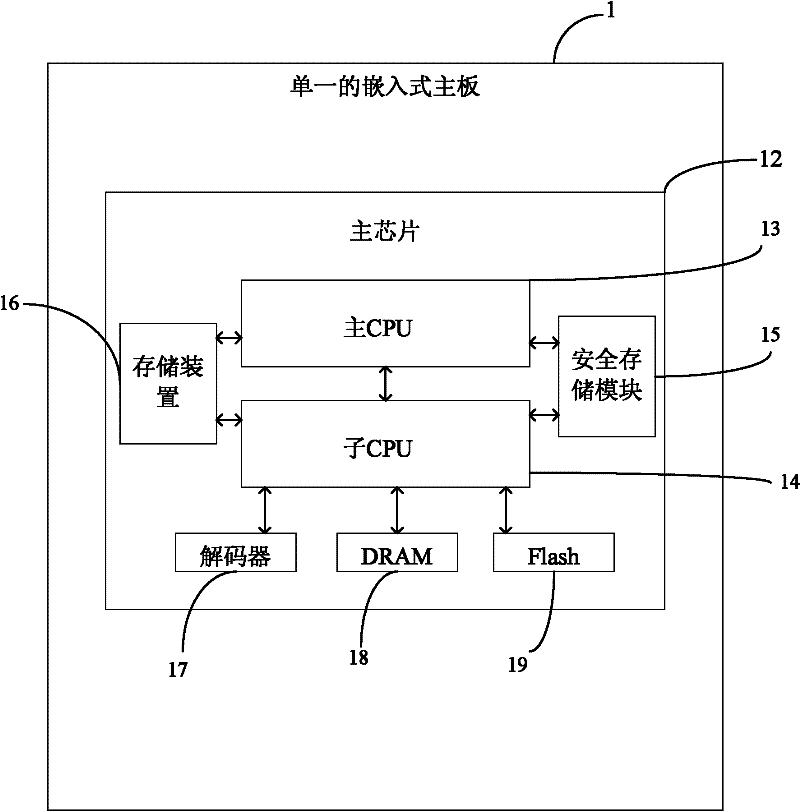
ActiveCN102682809APrevent interception and piracySimple internal structureRecord information storageRecording on magnetic disksSecurity Accounts ManagerMarket place
The invention relates to a digital movie playing server and a movie playing control method. The digital movie playing server comprises a casing. A single embedded main board is arranged in the casing, is used for unpacking of release-edition movie program sources to led movie program sources, de-encapsulation of media exchange format, decryption of video streaming, decoding of video and audio and movie playing and can adopt a universal serial bus (USB) electronic key decryption mode or a secret key transmission message decryption mode at any time. Therefore, intercepting copyright infringement of signal flows of release-edition movie program sources is prevented effectively, an inside structure of a complete machine product is simplified, the physical connection is reduced, and the digital movie playing server is strong in stability and high in safety, simultaneously is compatible with a USB electronic key and a security account manager (SAM) chip, accords with two key delivery message (KDM) digital movie secret key issue management modes of digital movie plan organization norms, and has strong flexibility in market application and a multi-channel mode for issuing mid-range digital movie programs.
Owner:DINGJUSNG TECH
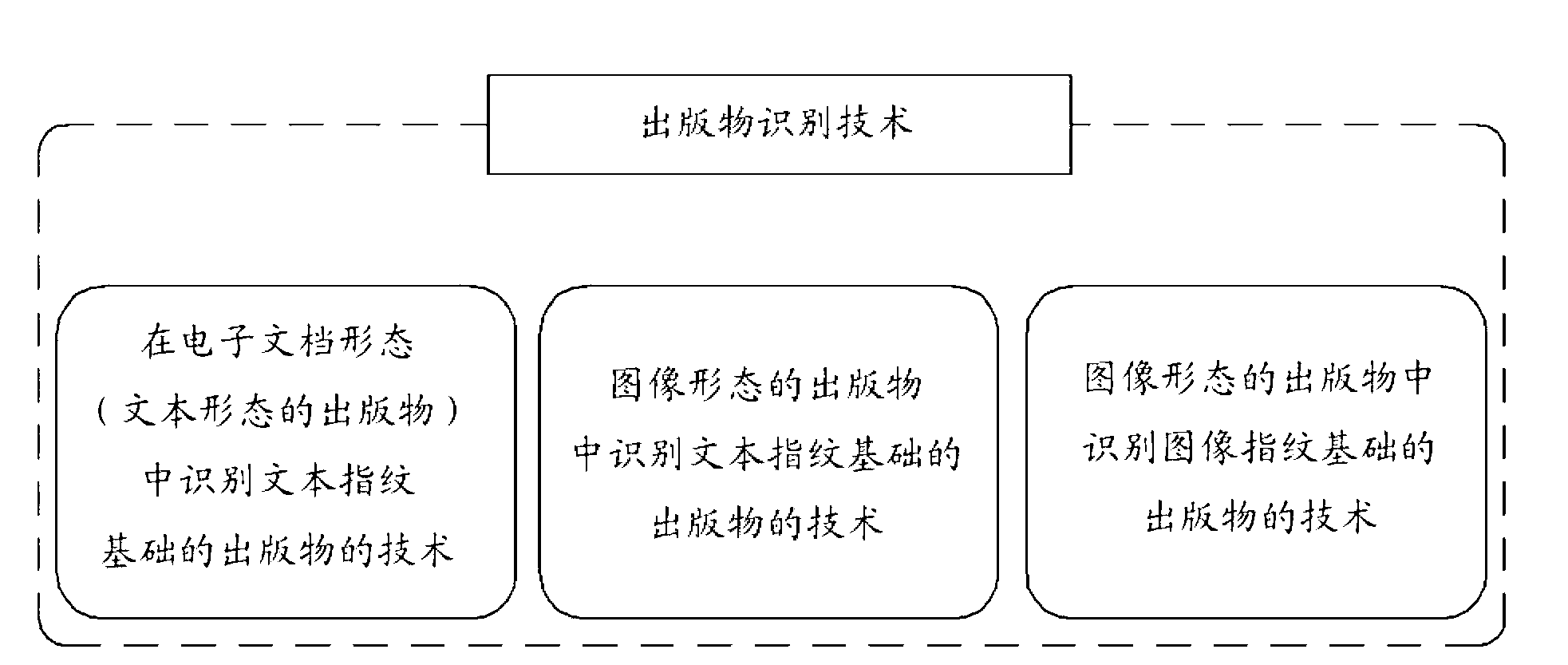
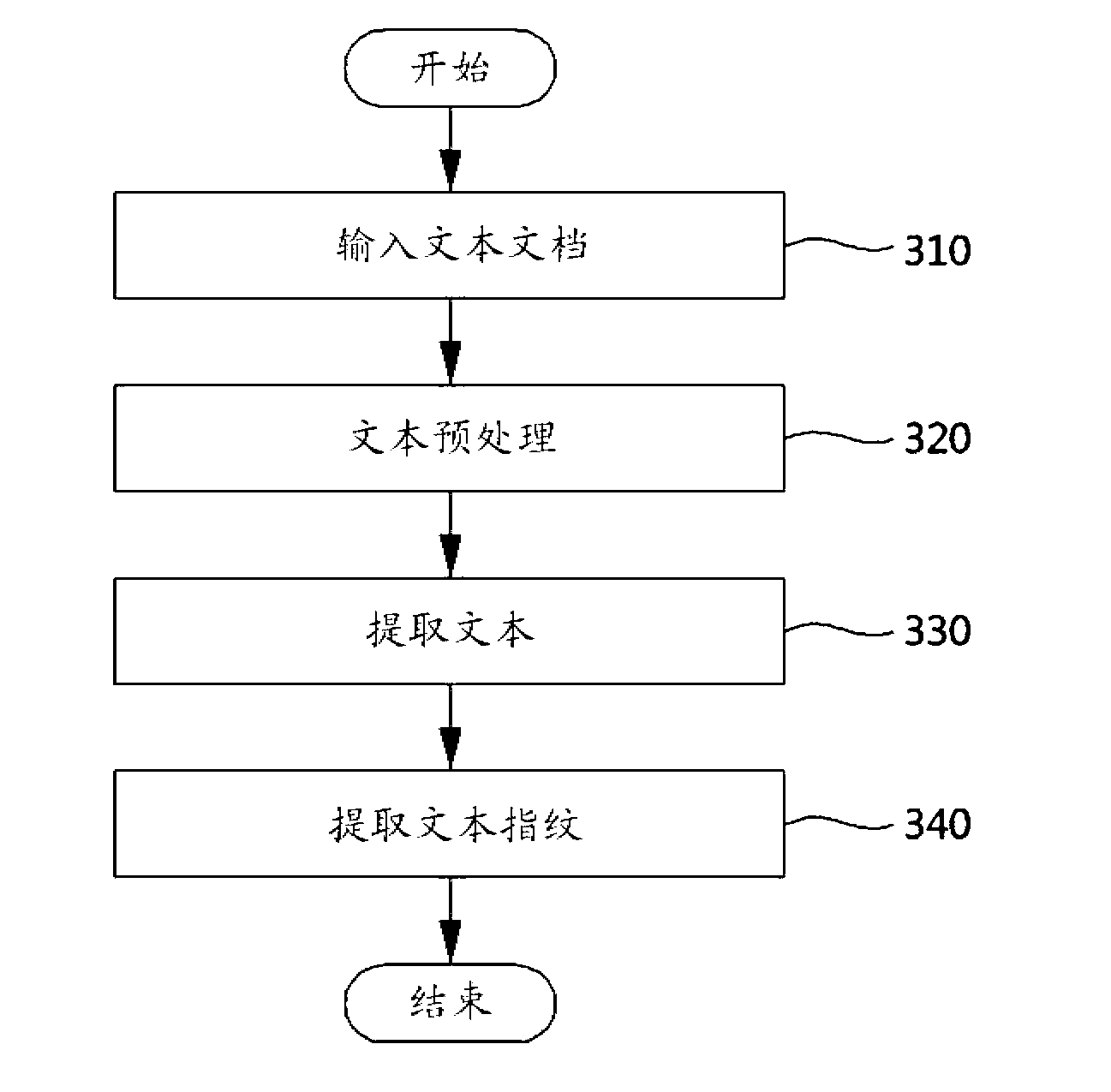
Method for extracting fingerprint of publication, apparatus for extracting fingerprint of publication, system for identifying publication using fingerprint, and method for identifying publication using fingerprint
InactiveCN103154957AReduce transmissionEasy to identifyDigital data authenticationProgram/content distribution protectionCopyright infringementData mining
Disclosed are a method for extracting a fingerprint of a publication, an apparatus for extracting a fingerprint of a publication, a system for identifying a publication using a fingerprint, and a method for identifying a publication using a fingerprint which can easily identify copyright infringement and can effectively protect copyrights. The system for identifying the publication using the fingerprint includes: a fingerprint extraction unit for extracting fingerprints for collected query publications to identify the copyright infringement; a fingerprint query unit for querying fingerprints of original publications corresponding to the fingerprints for the query publications provided from the fingerprint extraction unit; a DBMS for storing the fingerprints extracted from the original publications and additional information from the original publications, and providing a search result candidate group which is composed of fingerprints of at least one of the original publications corresponding to the queries of the fingerprint query unit; and a candidate group verification unit for determining copyright infringement for the query publications by verifying the search result candidate group provided from the DBMS. Consequently, the present invention can easily identify copyright infringement for the publications and can thereby prevent copyright infringement.
Owner:ELECTRONICS & TELECOMM RES INST
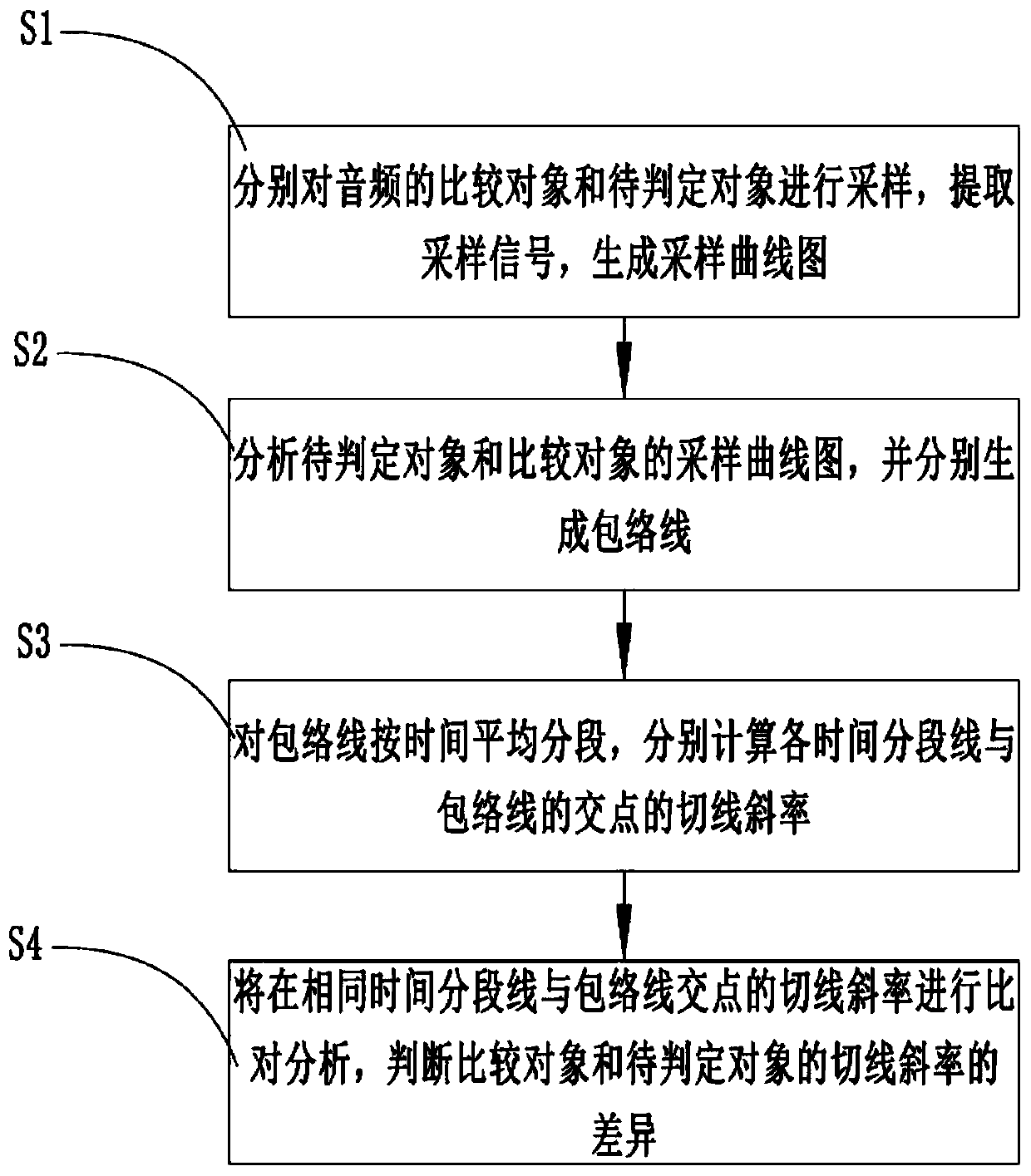
Infringement evidence obtaining method and system for audio works
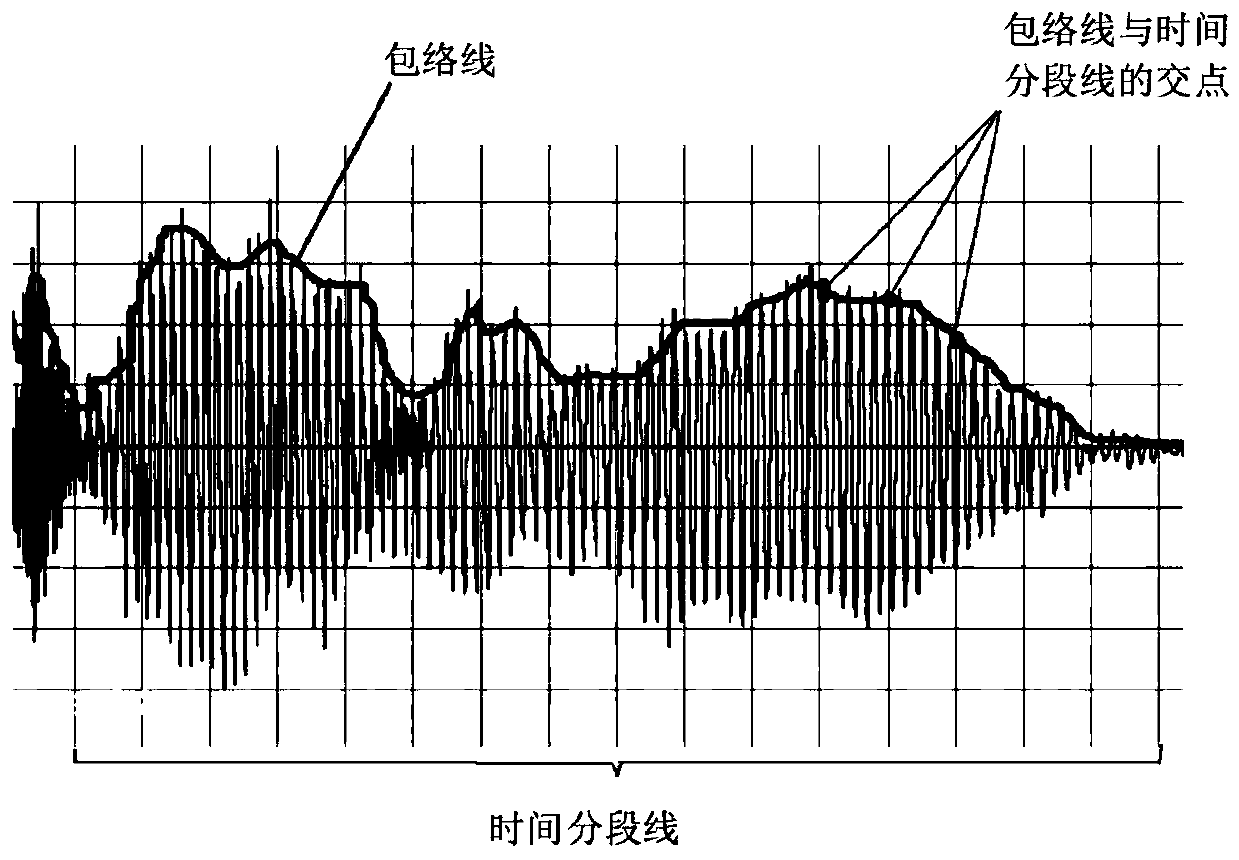
ActiveCN109829265AProtection of legal rightsData processing applicationsProgram/content distribution protectionAlgorithmTime segment
The invention discloses an infringement evidence obtaining method and system for audio works. The method comprises the following steps: respectively sampling a comparison object and a to-be-judged object of an audio work; extraction of sampled signals, generating a sampling curve chart, analyzing the sampling curve charts of the comparison object and the object to be judged, generating envelope lines respectively, averagely segmenting the envelope lines according to time, calculating the tangent slope of the intersection point of each time segment line and the envelope lines respectively, andjudging the similarity of the comparison object and the object to be judged by utilizing the slope analysis of the comparison object and the object to be judged. Whether the audio frequency of the comparison object and the audio frequency of the object to be judged have similar characteristics or not can be calculated through calculation of the slope of the sampling curve graph and comparison of the error approximation rate, and in the actual rights protection process, the characteristic can be used as music copyright infringement evidence.
Owner:杭州拾贝知识产权服务有限公司
System to identify multiple copyright infringements and collecting royalties
InactiveCN103875002ATransmissionProgram/content distribution protectionIp addressCopyright infringement
Owner:罗伯特·斯蒂尔
Method and device for theme authorization
ActiveCN103150496AAddress plagiarismSolve the problem of piracyDigital data authenticationProgram/content distribution protectionCopyright infringementAuthorization
The invention discloses a method and a device for theme authorization and belongs to the technical field of computers. The method comprises the following steps: an authorization request message for a default theme is sent by a receiving terminal, wherein the authorization request message is sent along with a user identification of a user and digital summary information of each module that is included in the default theme; according to the digital summary information of each module that is included in the default theme, the digital summary information of each module is checked to determine whether all the modules of the default theme are used by the user; and when all the modules of the default theme are used by the user, the receiving terminal is authorized to use the default theme. According to the invention, the digital summary information of each module is checked to determine whether the user is allowed to use each module, and when all the modules are allowed to be used by the user, the whole theme is authorized, so that the problem of theme plagiarism and copyright infringement is effectively solved.
Owner:XIAOMI INC
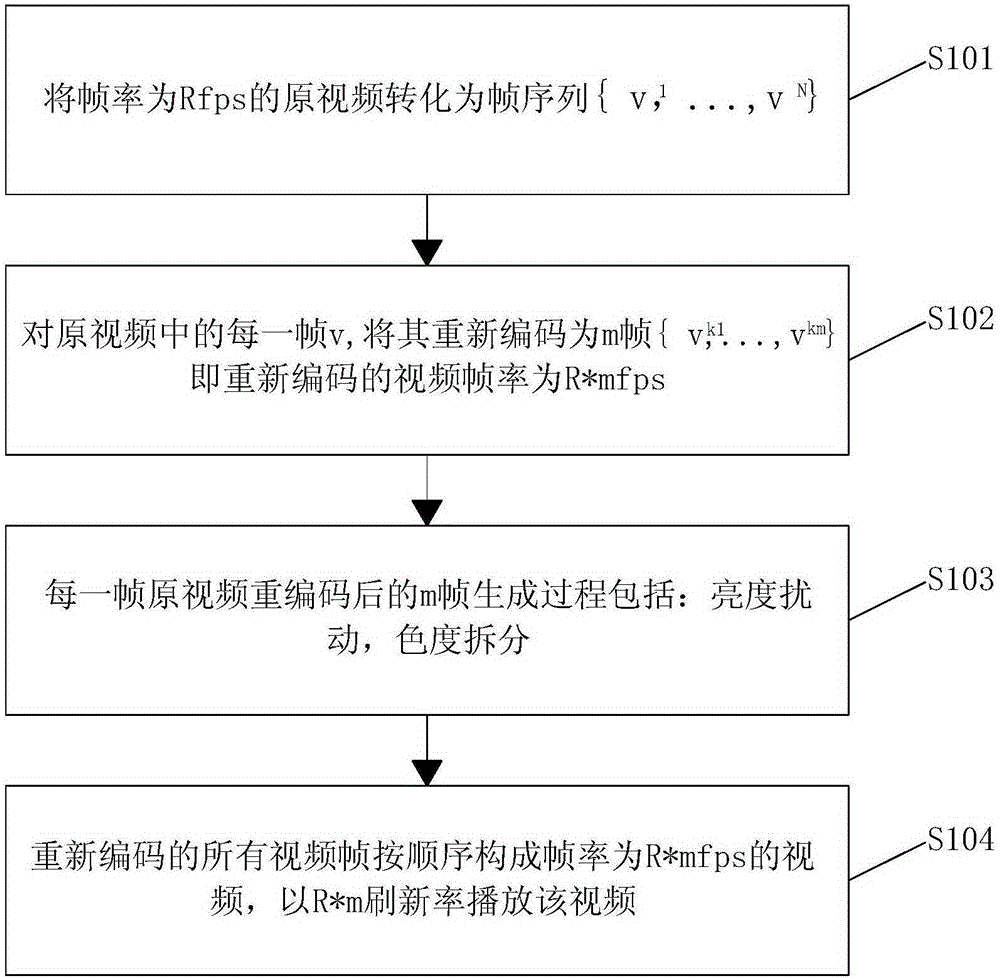
Video playing method capable of preventing pirating and copying
ActiveCN105187756ARemake preventionBroad application of copyright protectionTelevision system detailsColor signal processing circuitsComputer graphics (images)Copyright infringement
The invention discloses a video playing method capable of preventing pirating and copying. According to the method, original video frames are decomposed and recoded to obtain a new video format. During playing of recoded videos, visual effects presented to field audience are not influenced, but the quality of videos pirated or copied through a commercial camera or mobile equipment is lowered greatly, so that TS videos cannot be watched, and video copyright infringement behaviors due to pirating are prevented effectively. Any existing film and video can be recoded and played with the video playing method; only an existing commercial display or projector needs to be taken as imaging equipment; and a commercial computer can be used for playing videos without any special projection equipment. Through adoption of the video playing method, various video recorders and mobile equipment can be effectively prevented from copying. The video playing method has the advantages of high universality, good effect and low cost, and can be widely applied to copyright protection of played content in playing scenes of various videos / films.
Owner:无锡赛睿科技有限公司
System to identify multiple copyright infringements
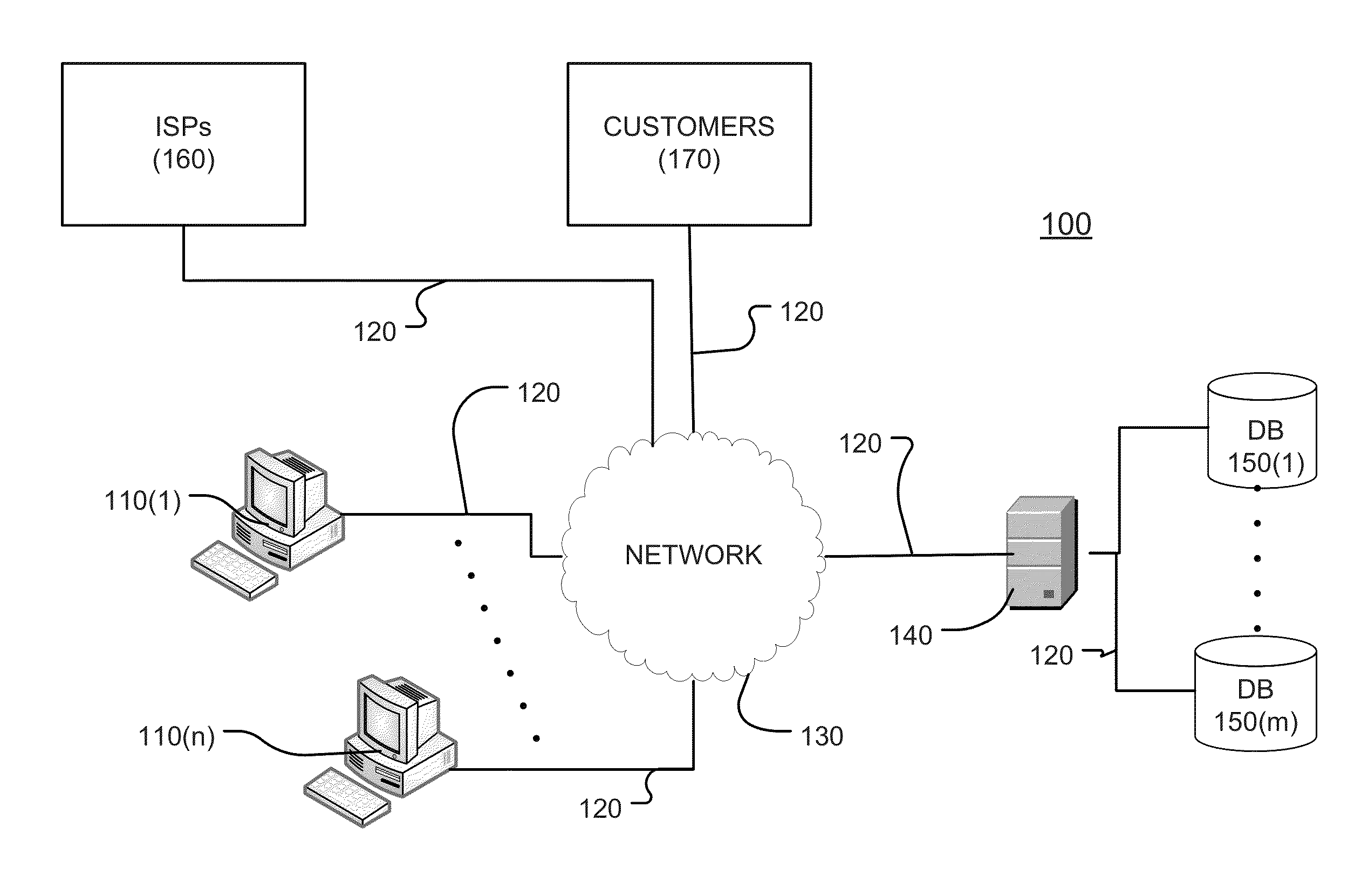
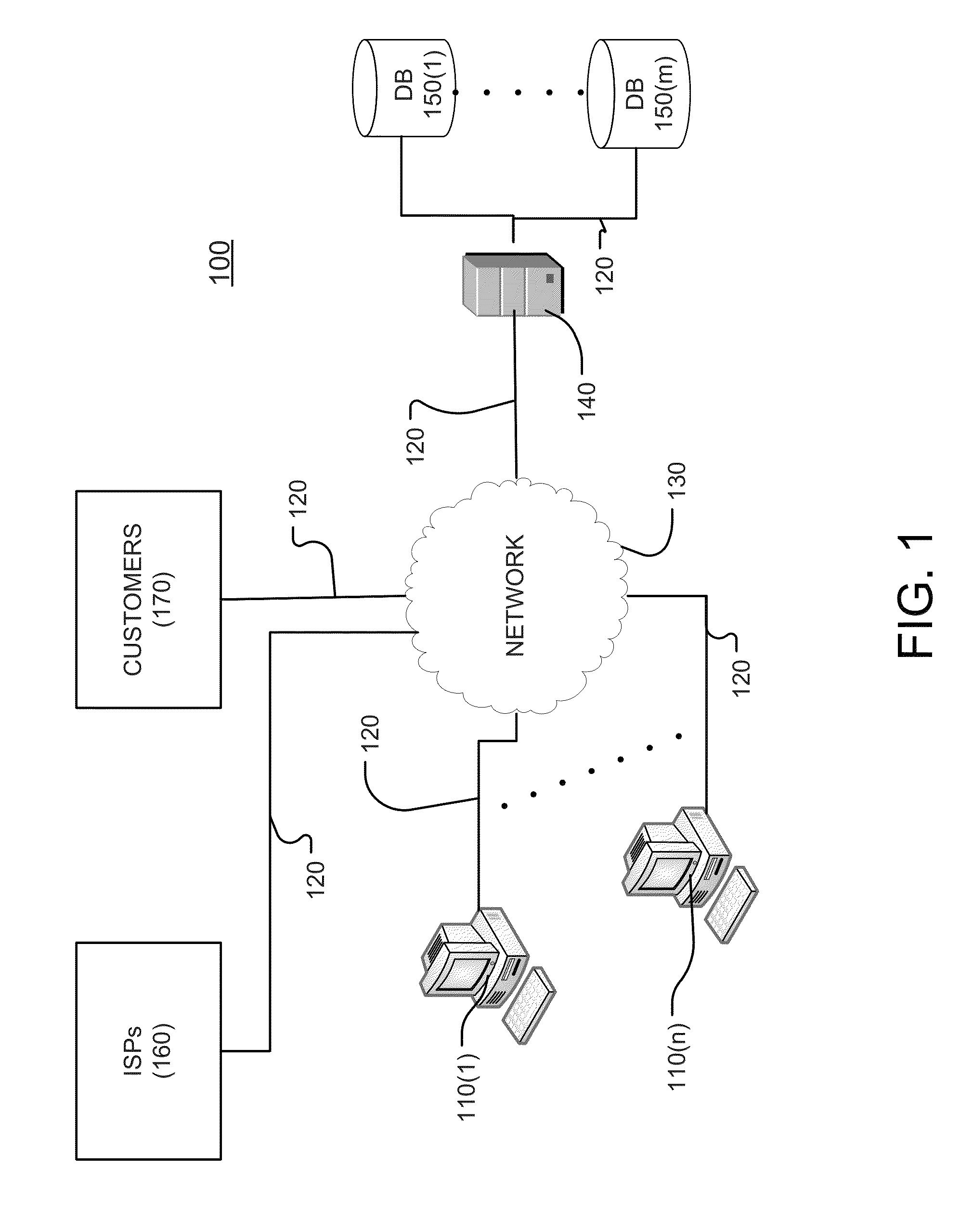
A system, a method and a computer program for determining multiple copyright infringement events, identifying a particular IP address-port number combination associated with the multiple infringement events, and notifying an ISP and / or a customer regarding the multiple copyright infringement events.
Owner:RIGHTSCORP
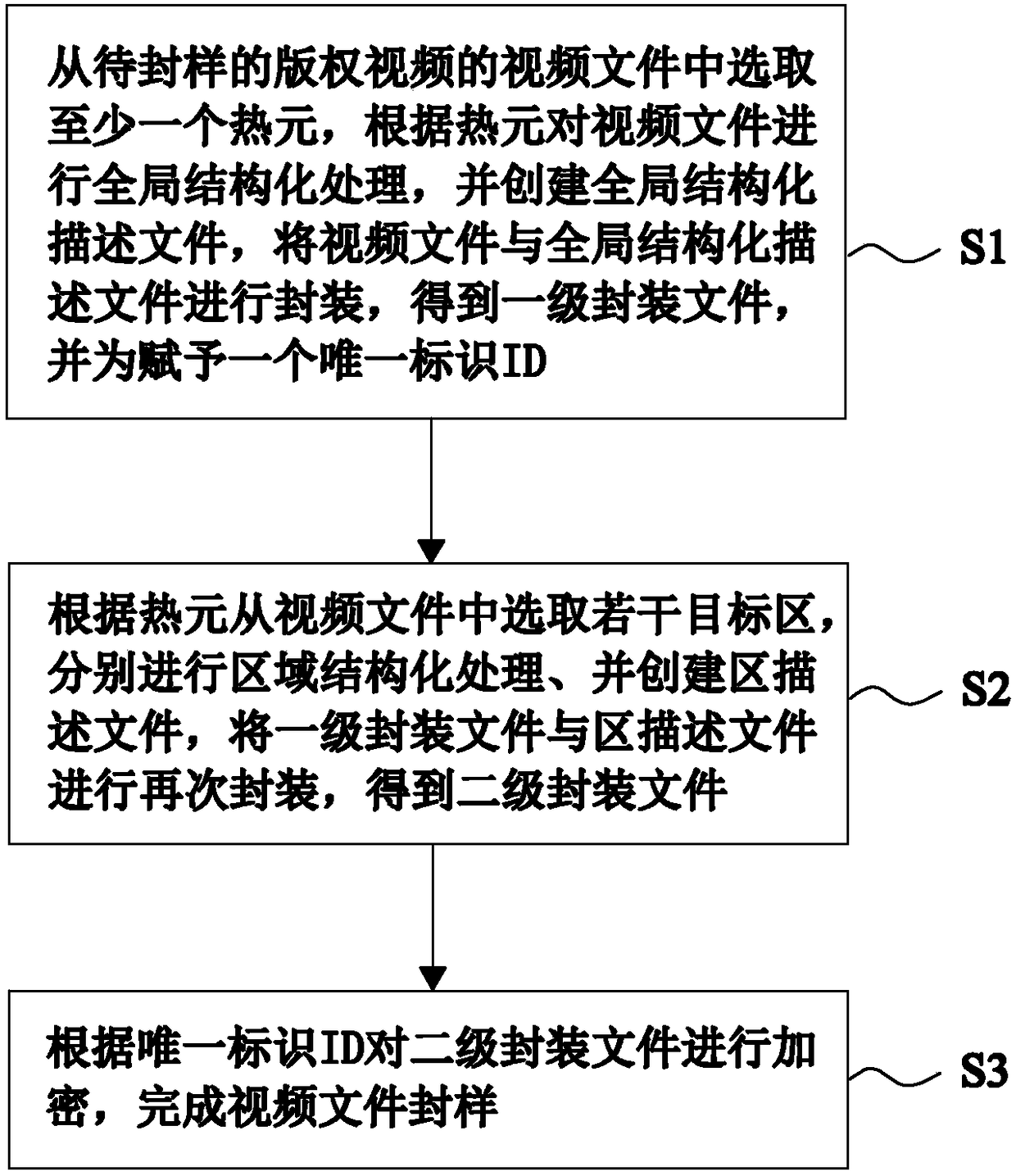
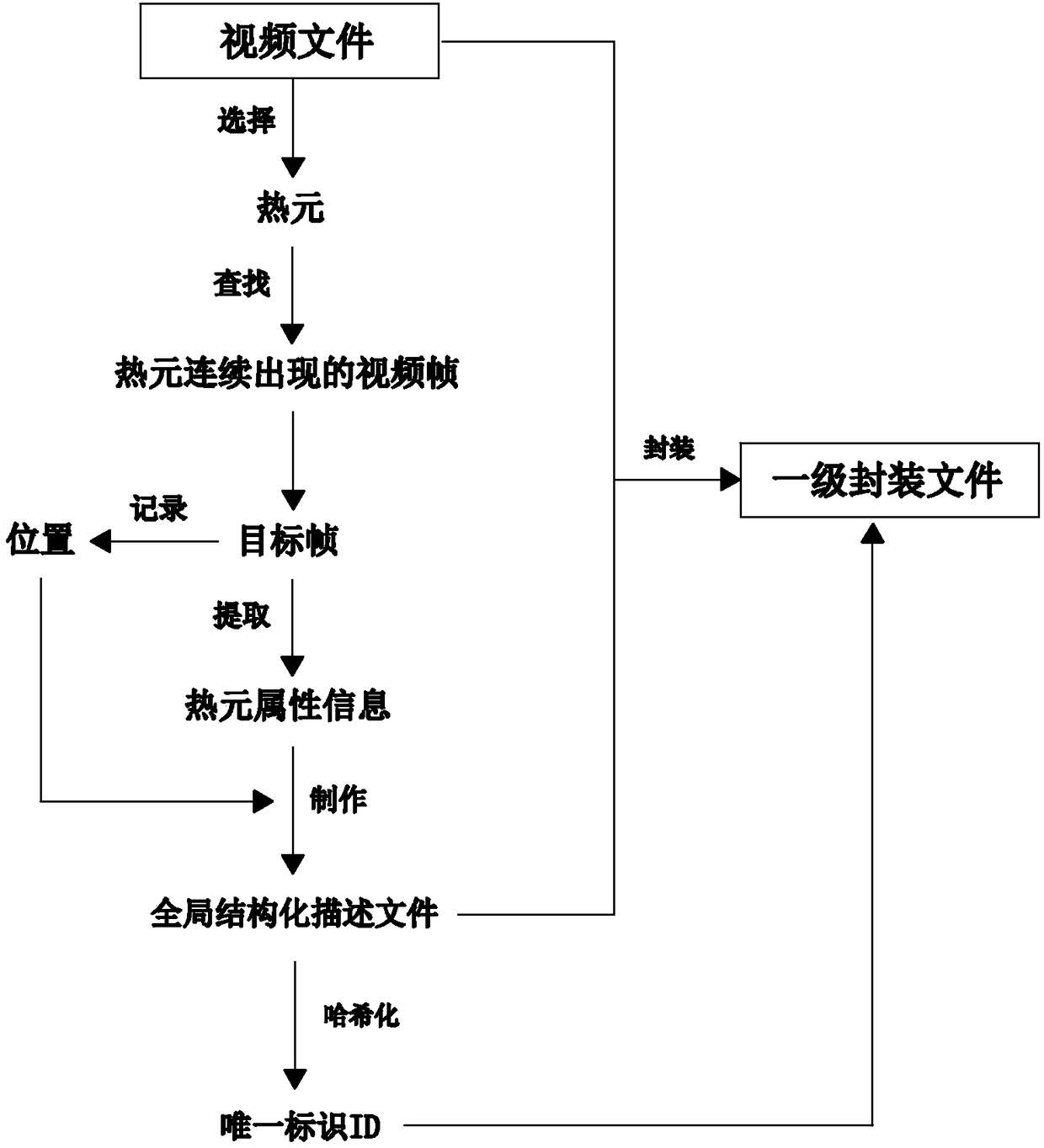
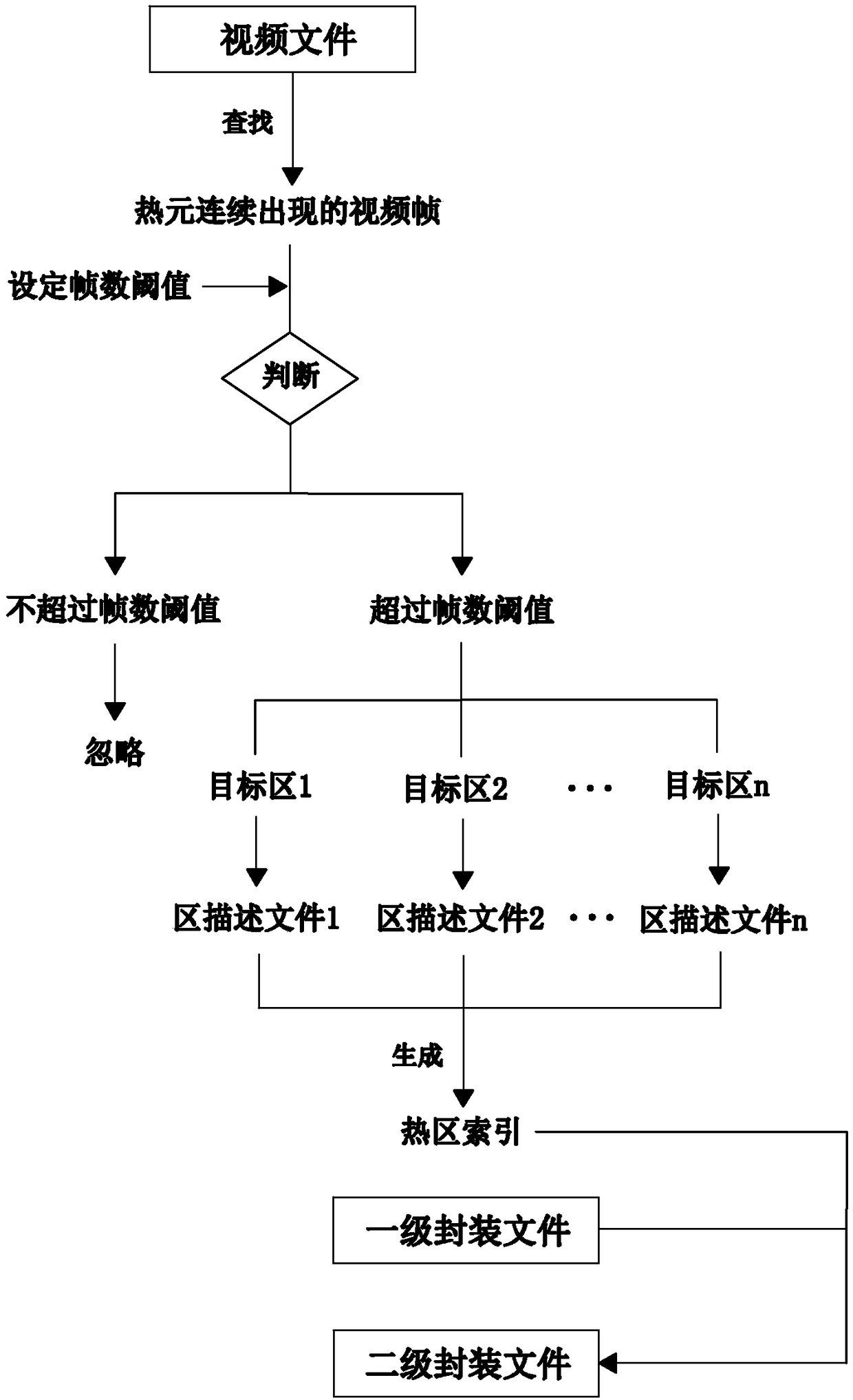
Method for structured arrangement on copyright video information to complete sample sealing
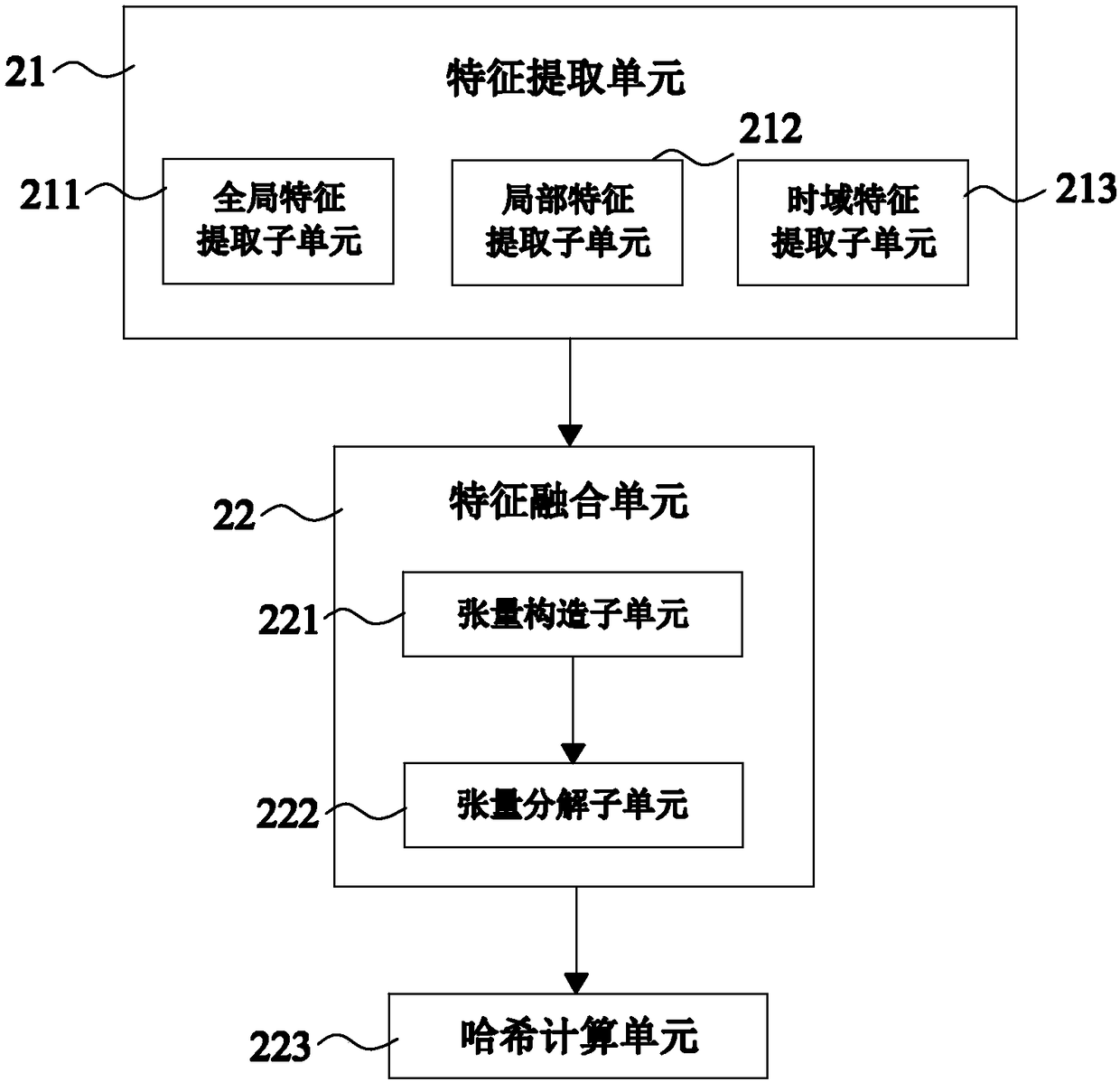
ActiveCN108566562ASafety communicationLegal disseminationSelective content distributionData informationComputer graphics (images)
The invention provides a method for structured arrangement on copyright video information to complete sample sealing, comprising the steps of performing structured description on a video file at a global level to reflect overall features of the video file through quantifiable features, and then performing structured description on a selected target region at a regional level to reflect regional characteristics through the position and attribute of the target region. The features of the video can be quantified and characterized globally and locally by double structured description on the videofile, and the video file is converted into intuitive and brief data information, so that the features of the video file are expressed more comprehensively and specifically, and the workload of copyright infringement check is greatly reduced. Meanwhile, the security and integrity of information preservation and the complexity and stability of encryption can also be improved by double packaging on the video file after the double structured description, so that the copyright video is propagated securely and legally and the data is prevented from being lost or embezzled.
Owner:ZHONGGUANG REDIANYUN TECH CO LTD +1
Method and terminal for encrypting and decrypting forwarding prohibition and mixed transmission mode DRM files
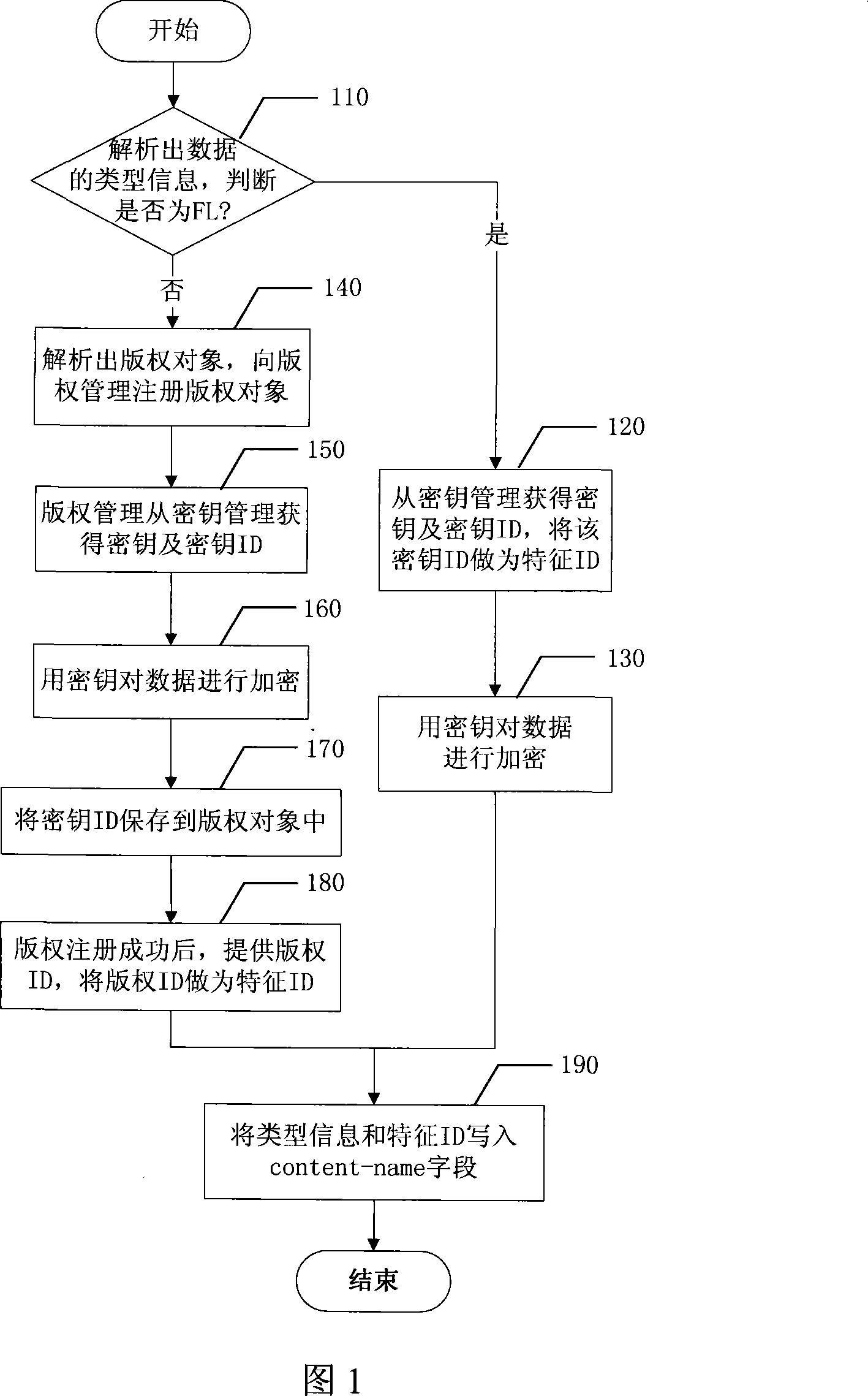
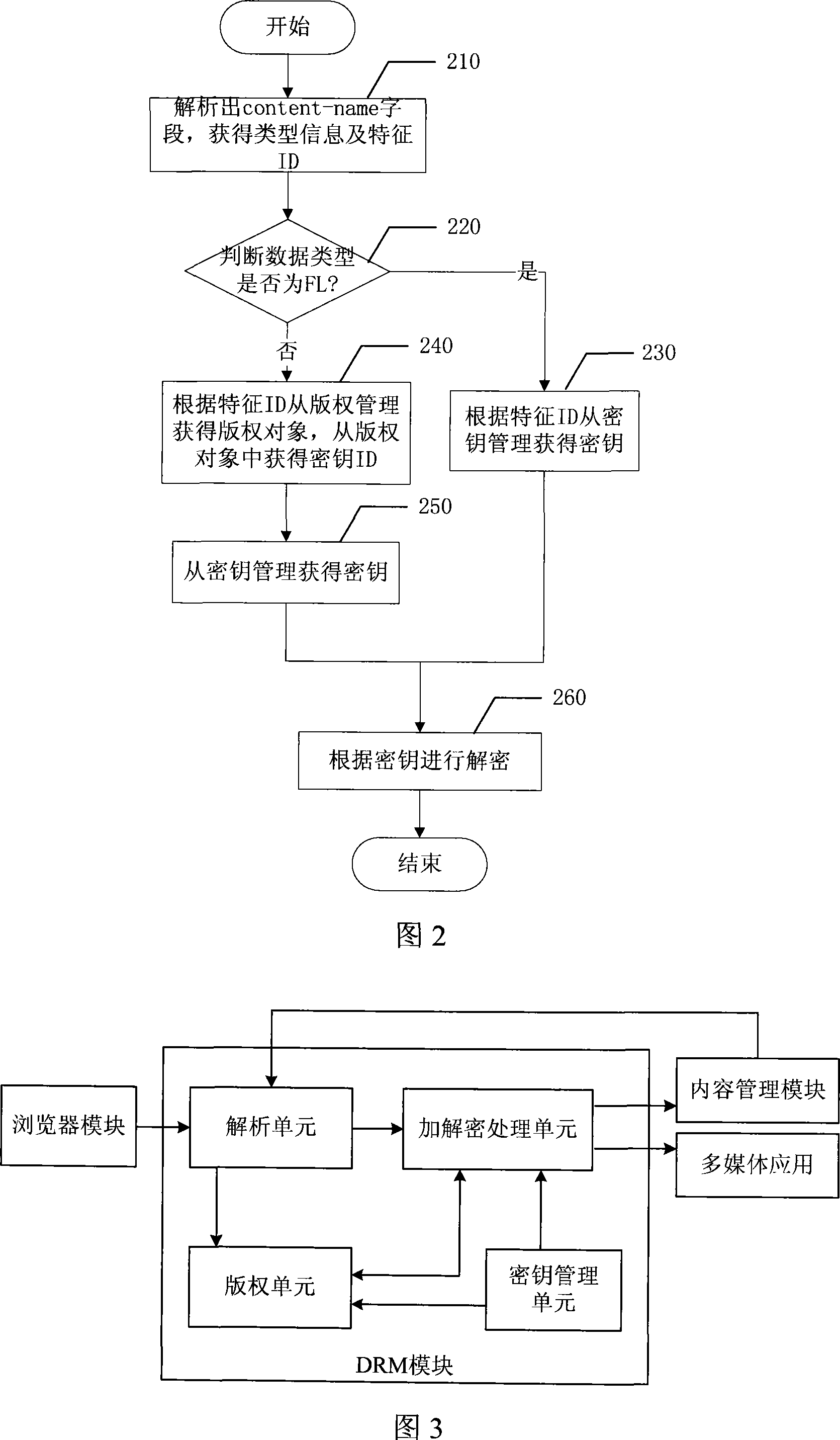
InactiveCN101183937AEnsure safetyImprove the efficiency of obtaining keysData switching networksSecuring communicationCiphertextDigital rights management
The invention discloses an encryption and decryption method of a forward limited and mixed transmission digital copyright management file, and the terminal for realizing the method. The encryption method comprises the following two situations: first, when the data type is forward limited (FL), obtain the key and the ID of the key from the key management, encrypt the data by utilizing the key, usethe ID of the key as the feature ID which is written-in the DCF file together with the type message; second, when the data type is mixed transmission, the CD pattern, register the analyzed copyright object to the copyright management, the copyright management asks the key and the ID of the key from the key management and encrypt the data by utilizing the key, and store the ID of the key in the copyright object. When the copyright object is registered successfully, take the copyright ID as the feature ID which is written-in the DCF file together with the type message. The invention has the advantages that the cipher text object sent by FL and CD can be encrypted and decrypted rapidly and efficiently.
Owner:ZTE CORP
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com