Method for protecting linux operation system on loongson hardware platform
A hardware platform and operating system technology, applied in the field of information security, can solve problems such as piracy, copying, and file system encryption being cracked, and achieve the effect of protecting intellectual property rights
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0039] A method for protecting a Linux operating system on a Loongson hardware platform. The protection method adopts two methods of kernel encryption and file system encryption to comprehensively protect the data security of the operating system.
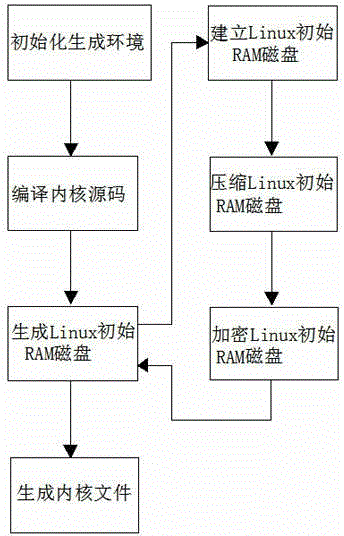
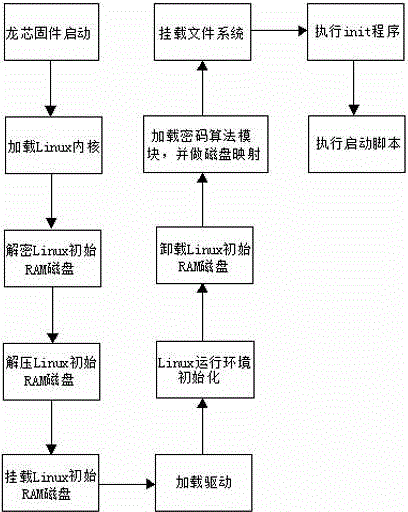
[0040] Among them, the kernel encryption is realized by encrypting the Linux initial RAM disk (initrd); during the kernel generation phase, the Linux initial RAM disk is encrypted, such as figure 1 As shown; at system startup, the Linux initial RAM disk is decrypted, such as figure 2 shown;
[0041] File system encryption is realized by Linux device mapping technology. Therefore, after the file system is encrypted, it cannot be mounted directly. It is necessary to map the encrypted file system and mount the mapped file system to read and write data on the file system.
[0042] The process of Linux initial RAM disk is a temporary file system mounted during the system boot process. The Linux boot process can be divided into two sta...
Embodiment 2
[0046] On the basis of embodiment 1, the implementation steps of kernel encryption described in this embodiment are as follows:
[0047] (1) Modify the kernel generation process, add the encryption process at the end of the Linux initial RAM disk generation script, and call the encryption program to encrypt the Linux initial RAM disk;
[0048] (2) Modify the initrd part of the Linux source code, embed the decryption function in it, modify the initrd processing code, and call the decryption function at the beginning to decrypt the Linux initial RAM disk;
[0049] (3) After the modification is completed, compile the Linux source code, and embed the generated kernel file into the Loongson hardware device.
Embodiment 3
[0051]On the basis of embodiment 1 or 2, the file system encryption implementation steps described in this embodiment are as follows:
[0052] (1) First add a new Linux device mapping driver, and embed the cryptographic algorithm in the driver;
[0053] (2) Compile the cryptographic algorithm driver module and load the driver module;
[0054] (3) Make a mapping for the disk of the Loongson hardware device, and specify the use of a cryptographic algorithm to drive the module when mapping;
[0055] (4) Mount the mapped virtual disk to a temporary directory, and copy the file system of the Loongson hardware device to this temporary directory to complete the encrypted storage of the file system;
[0056] (5) Modify the file system mounting process in the initial RAM disk of Linux, change the direct mounting to disk device mapping first, and then mount the mapped virtual disk device.
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com