Patents
Literature
133results about How to "Anti-counterfeiting" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
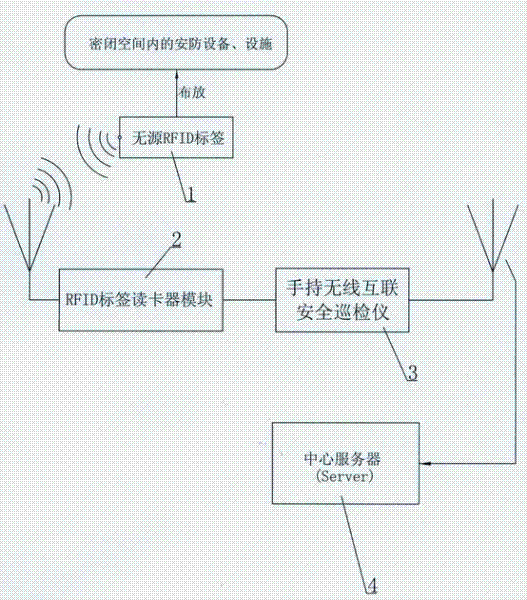
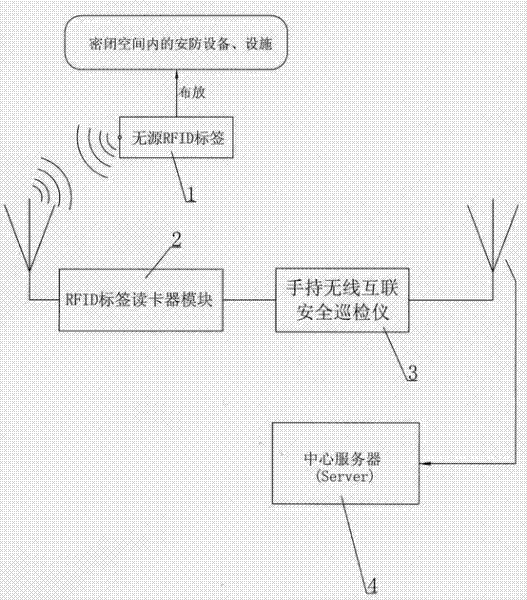
Equipment and facility safety inspection intelligent patrolling operation system and application method thereof
ActiveCN102176252AEffective maskingPrevent evasionChecking time patrolsTransmissionEmbedded systemCard reader
The invention discloses an equipment and facility safety inspection intelligent patrolling operation system and an application method thereof. The system consists of a handheld wireless interconnection security patrolling device, a radio frequency identification (RFID) label card reader module and a central server, wherein a passive RFID label is distributed on a security facility in a closed space; the label number and three-dimensional (3D) virtual digital modeling data of the closed space are input into a computer system and / or a server by utilizing a global information system (GIS); when an inspector enters the closed space to inspect by carrying the handheld wireless interconnection security patrolling device; and identification codes stored in the passive RFID label, use informationof related security facility and equipment and location information thereof, and to-be-collected data which are collected by the security equipment through manual and automatic wireless sensing and collected by manual artificial detection are uploaded to the central server or transmitted to the computer system by the handheld wireless interconnection security patrolling device automatically, and are determined by the central server or the computer system. The system prompts and monitors the inspectors to maintain the security facility and equipment in time, so that the safety, effectiveness and reliability of the security facility and equipment can be improved.
Owner:新疆中睿电子科技有限公司 +1
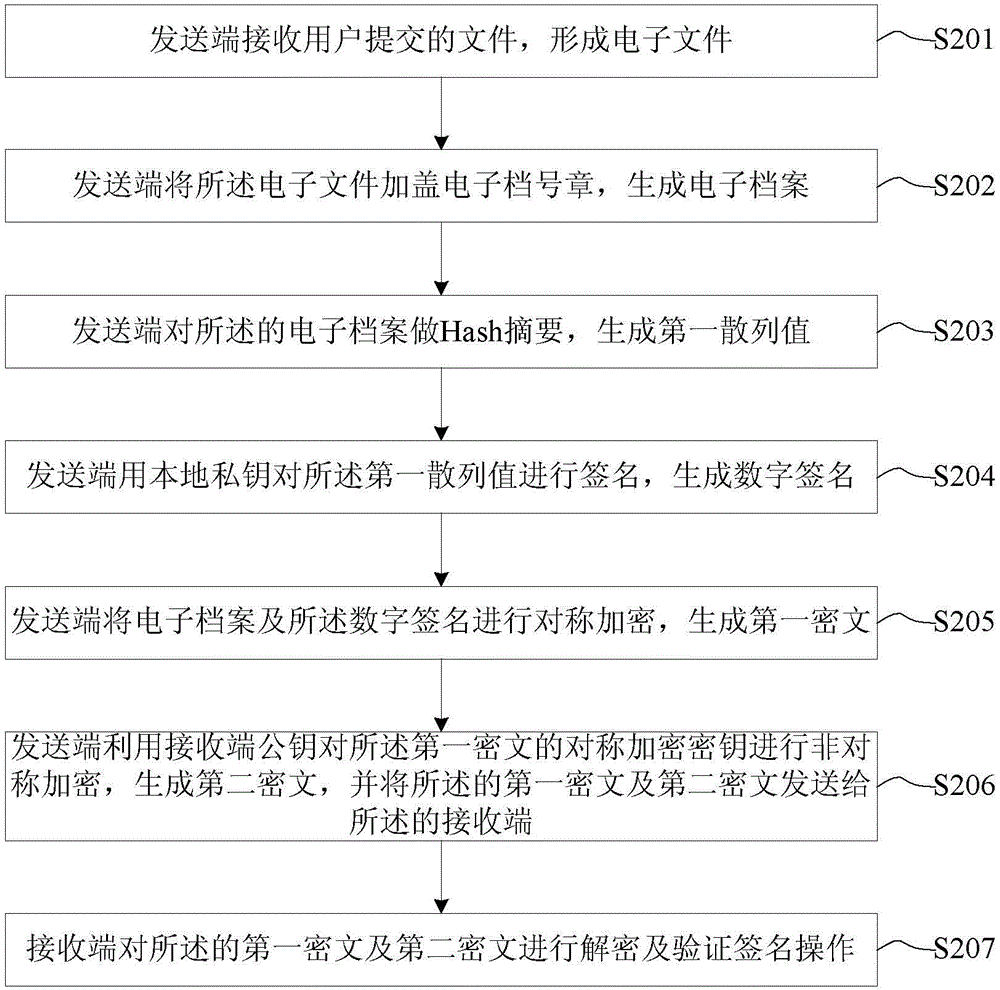
Electronic record validation method and device
ActiveCN104320257AAnti-counterfeitingAchieve tamper resistanceUser identity/authority verificationDigital signatureCiphertext
The invention provides an electronic record validation method and device. The electronic record validation method comprises the steps that a sending end receives files submitted by users and forms electronic files; the sending end seals electronic file number seals on the electronic files to generate electronic records; the sending end makes Hash abstracts for the electronic records to generate first hash values; the sending end uses local private keys to perform hash value signature so as to generate digital signatures; the sending end conducts symmetrical encryption on the electronic records and the digital signatures to generate first ciphertexts; the sending end utilizes a public key of a receiving end to perform asymmetrical encryption on symmetrical encryption keys of the first ciphertexts so as to generate second ciphertexts and sends the first ciphertexts and the second ciphertexts to the receiving end; the receiving end conducts decryption and signature operation verification on the first ciphertexts and the second ciphertexts. The electronic record validation method and device can prevent the electronic records from being counterfeited, tampered and disavowed.
Owner:李名选 +4
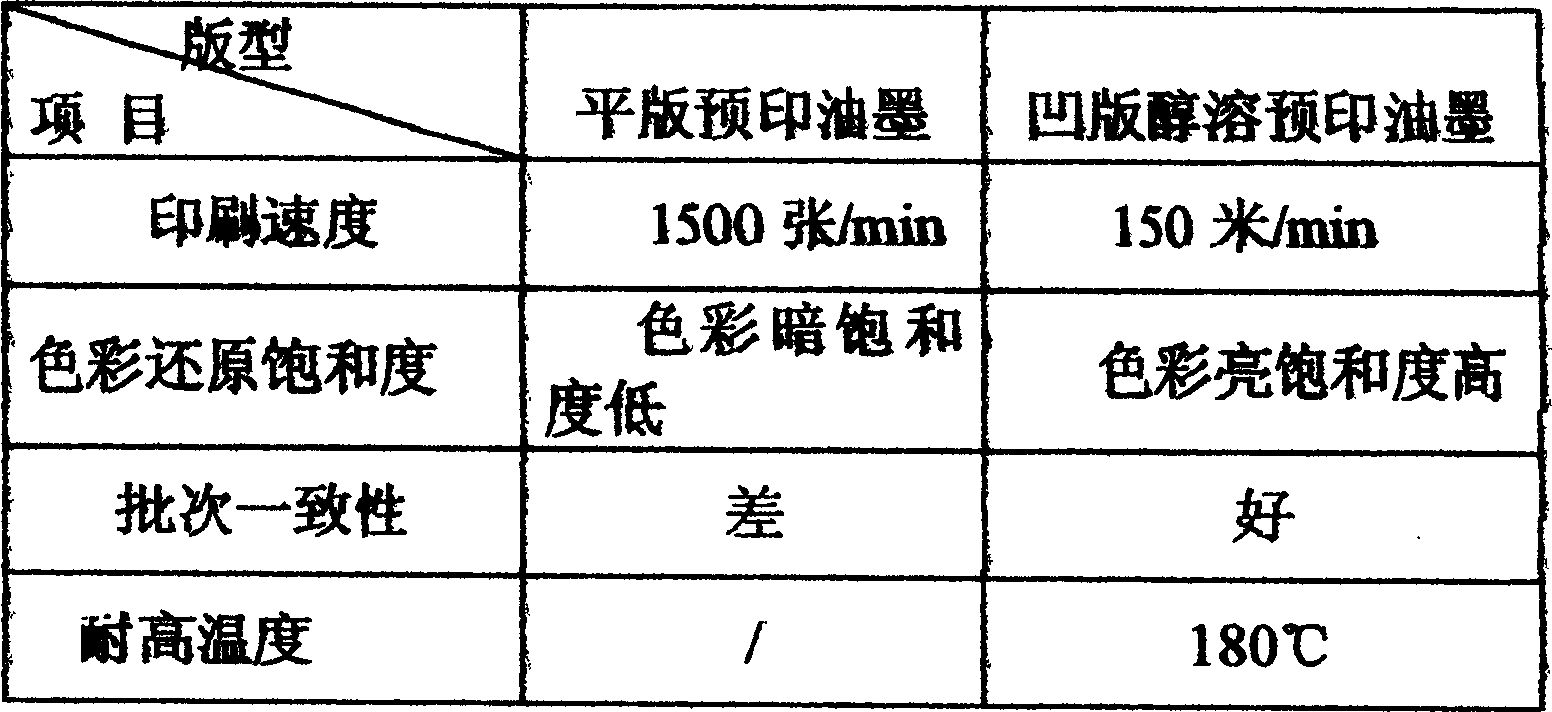
Alcohol soluble notch board paper box preprinting ink
An alcohol-soluble preprinting ink on gravure carton is composed of 6-10% nitrocellulose, methacrylate ester7-13%, propylene glycol methylether acetate 4-12%, dioctyl phthalate 2-6%, the dyestuff 15-25%, acetic ester 12-23%,absolute ethyl alcohol 32-43%. The ink has good glossiness, colour saturation degree and recurrence of halftone dot. It can defend the fake and resist to 180deg.C.
Owner:山西精华科工贸有限公司
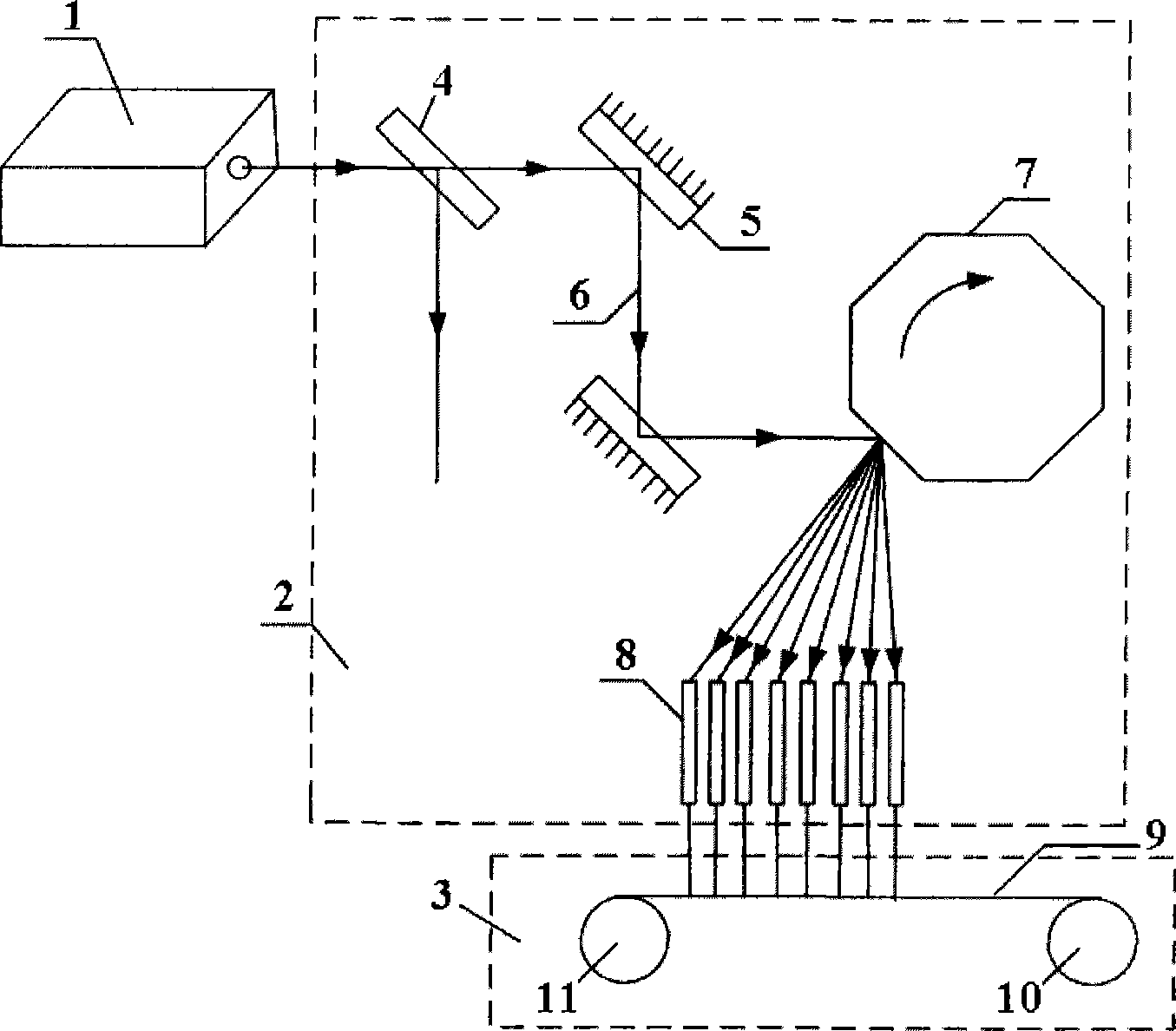
Cigarette tipping paper laser boring method and apparatus
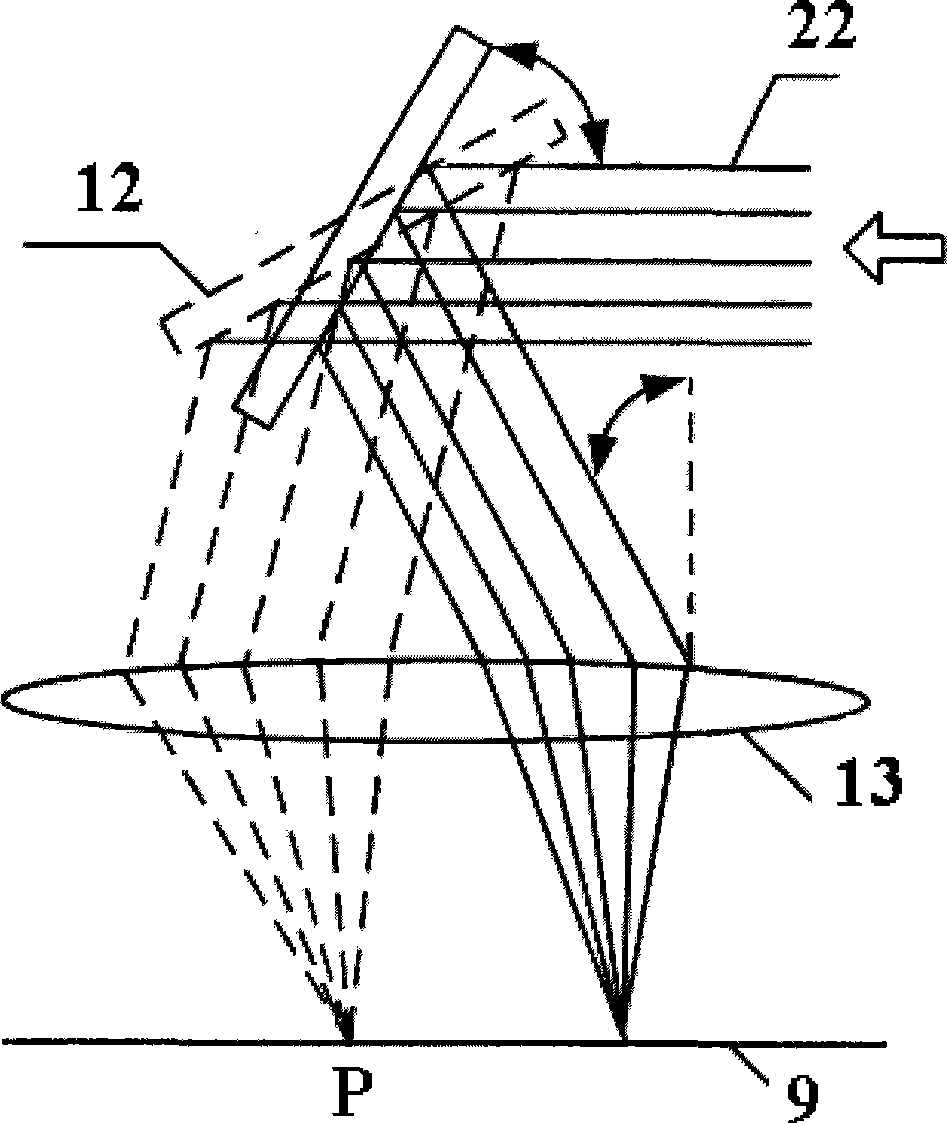
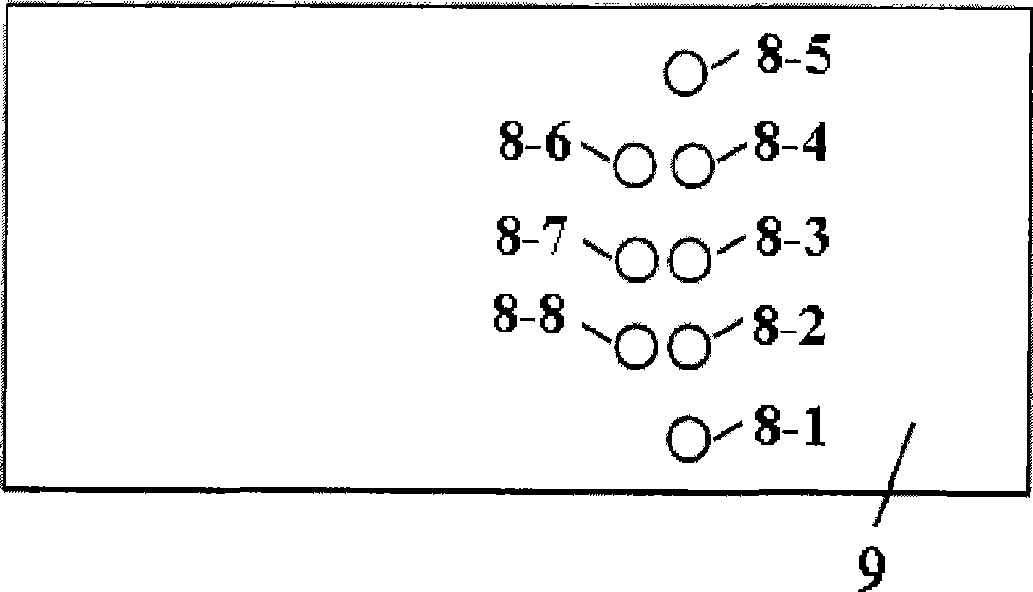
InactiveCN101462204AAnti-counterfeitingBeautiful and changeable appearanceMetal working apparatusLaser beam welding apparatusPunchingRepeat pattern
The invention provides two methods and equipment for laser punching of cigarette tipping paper. One is a rotary multi-prism punching method and equipment; and the other one is a vibrating mirror punching method and equipment. The methods and the equipment can utilize optical equipment to focus laser output by a laser; and punch pores (15) which are distributed in a single-row or multi-row curve or repeated pattern on the surface of continuously-moving tipping paper (9), such as pores (15) distributed in triangular, jagged, rhombic, trapezoidal, sine or cosine arrangement. The methods can carry out high-speed curve punching on the tipping paper, has the punching speed which is the same as linear punching speed and has good machining efficiency and good product quality; and the equipment has a simple structure, long service life, stable operation and high utilization efficiency of laser energy.
Owner:HUAZHONG UNIV OF SCI & TECH
Document encryption/decryption method and apparatus based on iris recognition and authentication
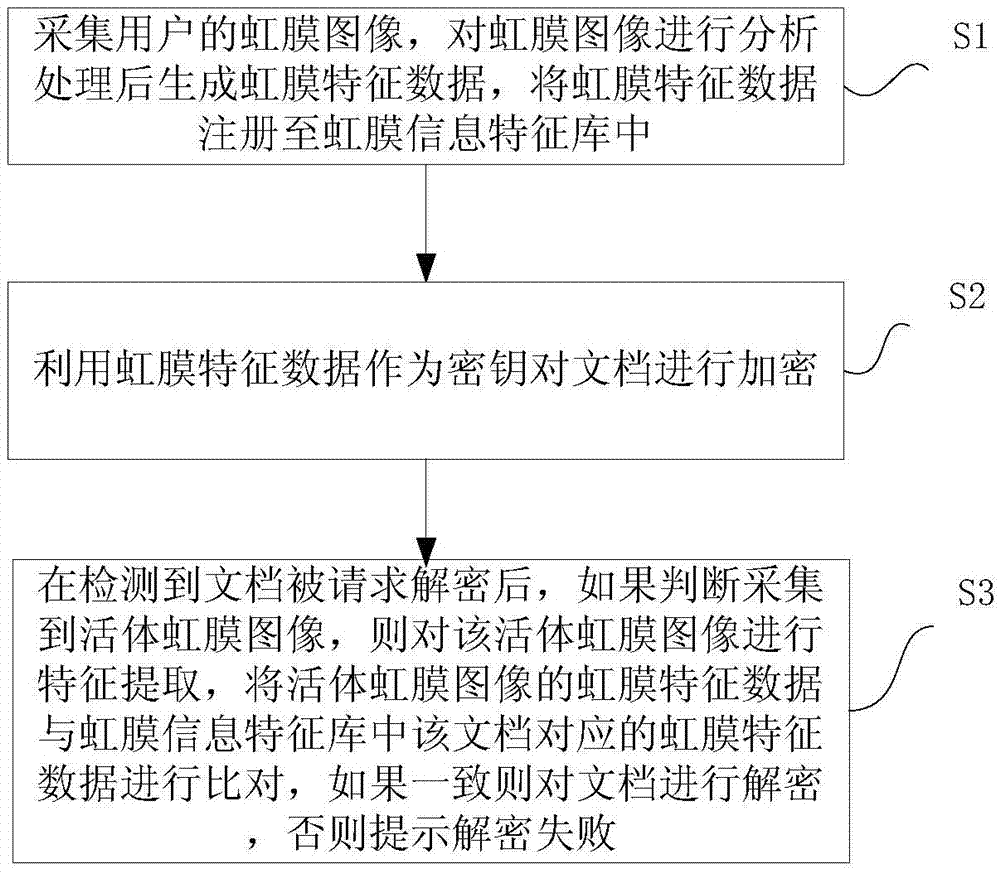
InactiveCN105447405AAvoid interceptionSolve the problem of strong dependenceDigital data protectionDigital data authenticationFeature extractionIdentity recognition
The present invention proposes a document encryption / decryption method and apparatus based on iris recognition and authentication. The method comprises: collecting an iris image of a user, generating iris feature data after analyzing and processing the iris image, and registering the iris feature data into an iris information feature library; encrypting a document by using the iris feature data as a key; and after it is detected that the document is requested to be decrypted, determining whether a living body iris image is collected, if so, carrying out feature extraction on the living body iris image, acquiring iris feature data corresponding to the living body iris image, comparing the iris feature data of the living body iris image with the iris feature data corresponding to the document in the iris information feature library, and if iris feature data of the living body iris image are consistent with the iris feature data corresponding to the document, then decrypting the document, otherwise, prompting that the decryption fails. According to the document encryption / decryption method and apparatus based on iris recognition and authentication, the iris image with uniqueness can be used to carry out identity recognition, thereby triggering an encryption and decryption algorithm to realize security management for the document. The entire encryption / decryption process is simple, convenient and free of potential security hazards.
Owner:南京以太安全技术有限公司
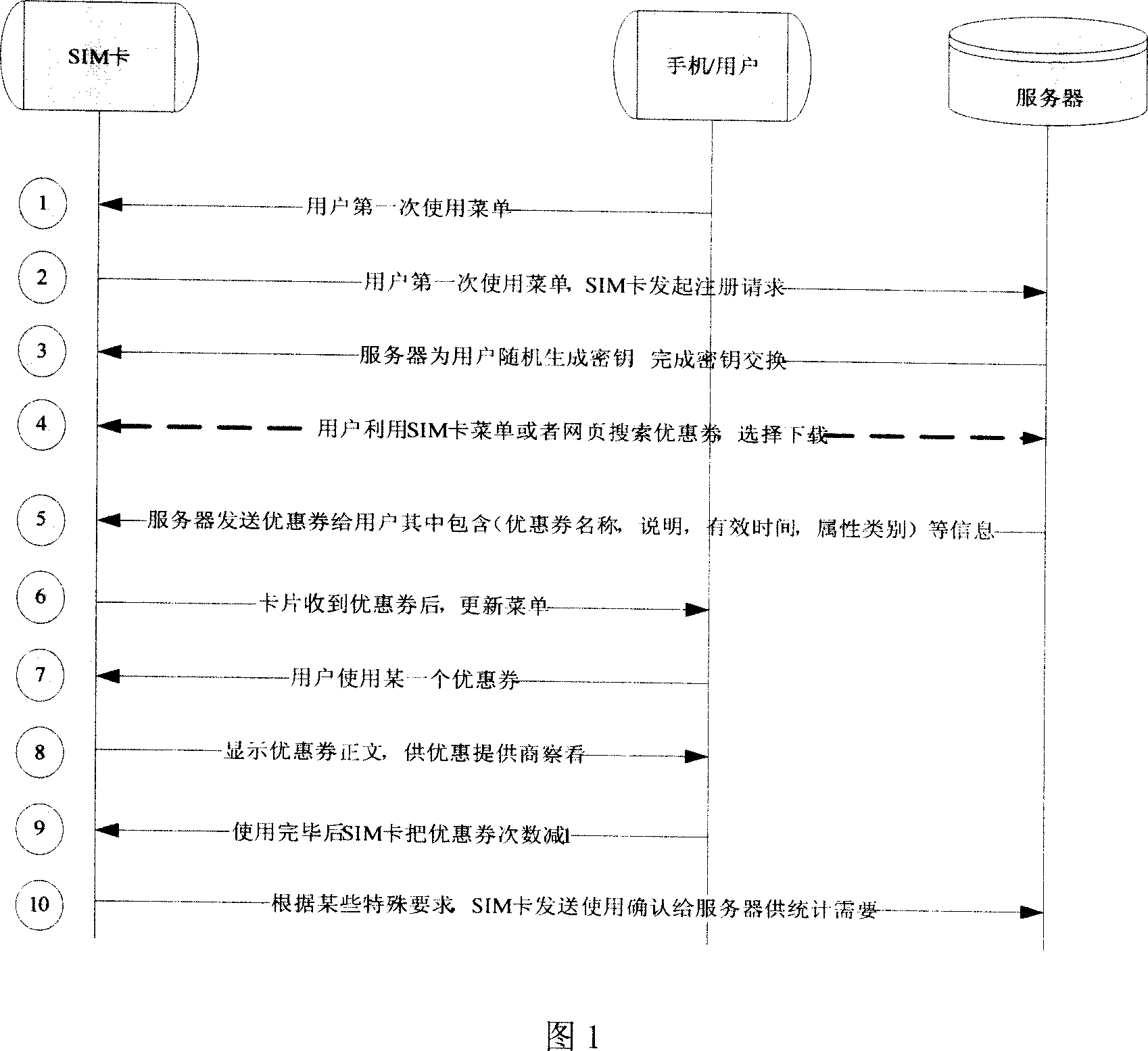
The method for utilizing the data SMS and STK menu to realize the SMS discount coupon
InactiveCN101009884AEnsure safetyAnti-counterfeitingKey distribution for secure communicationSpecial service for subscribersComputer hardwareTelegraphy
The related method in telegraphy field to send courtesy card by SMS comprises: 1. user initiates a register process to obtain a unique communication key; 2. user selects the courtesy card and sends download request; 3. the server receives the request to send the courtesy card by downloading the courtesy card as enciphered data SMS to a card; 4. the card stores received courtesy card into list of SIM card; 5. user selects courtesy card from the SIM menu; and 6. the server sends courtesy card according to set attribution. This invention has well anti-falsification feature to overcome the illegal utility in prior art, protects businessman safety, and is also benefit to consumer.
Owner:SHANGHAI COS SOFTWARE CO LTD
Encoding graph block and method and device for forming lattice graph through encoding graph block
ActiveCN103927572AAnti-counterfeitingGuaranteed difficultyRecord carriers used with machinesGraphicsCode point
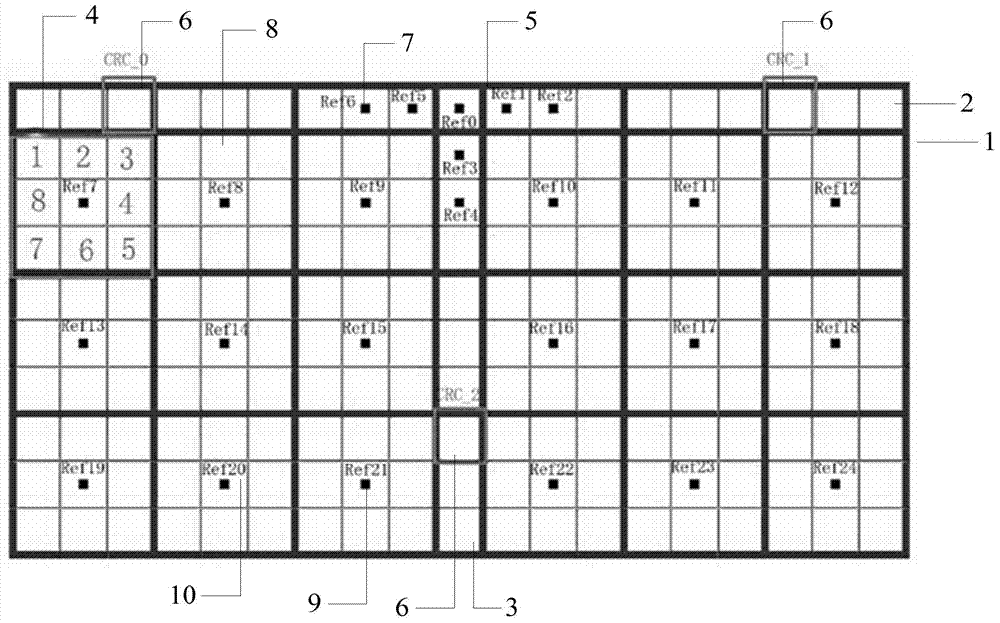
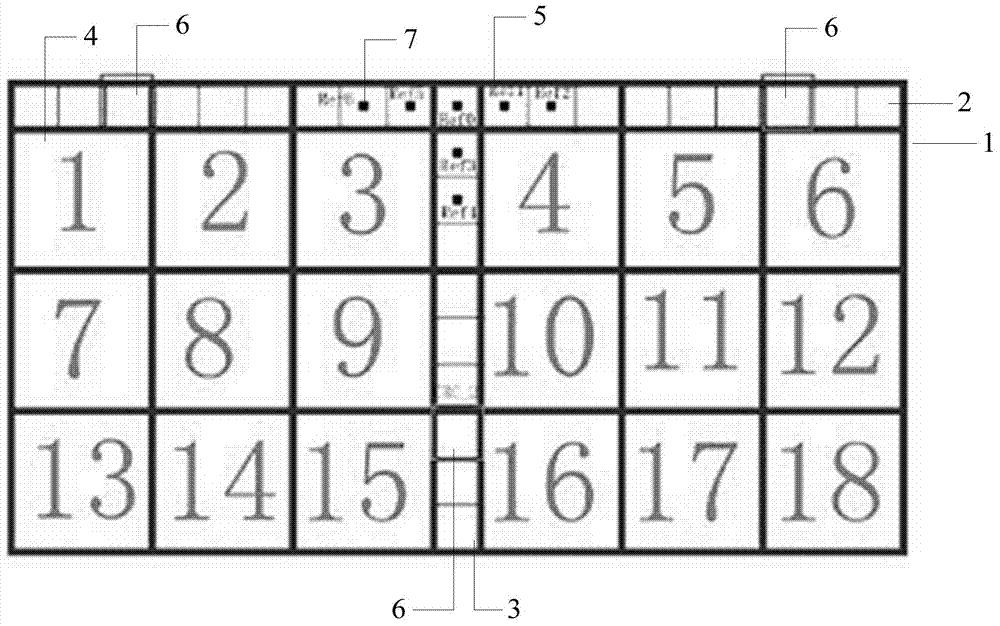
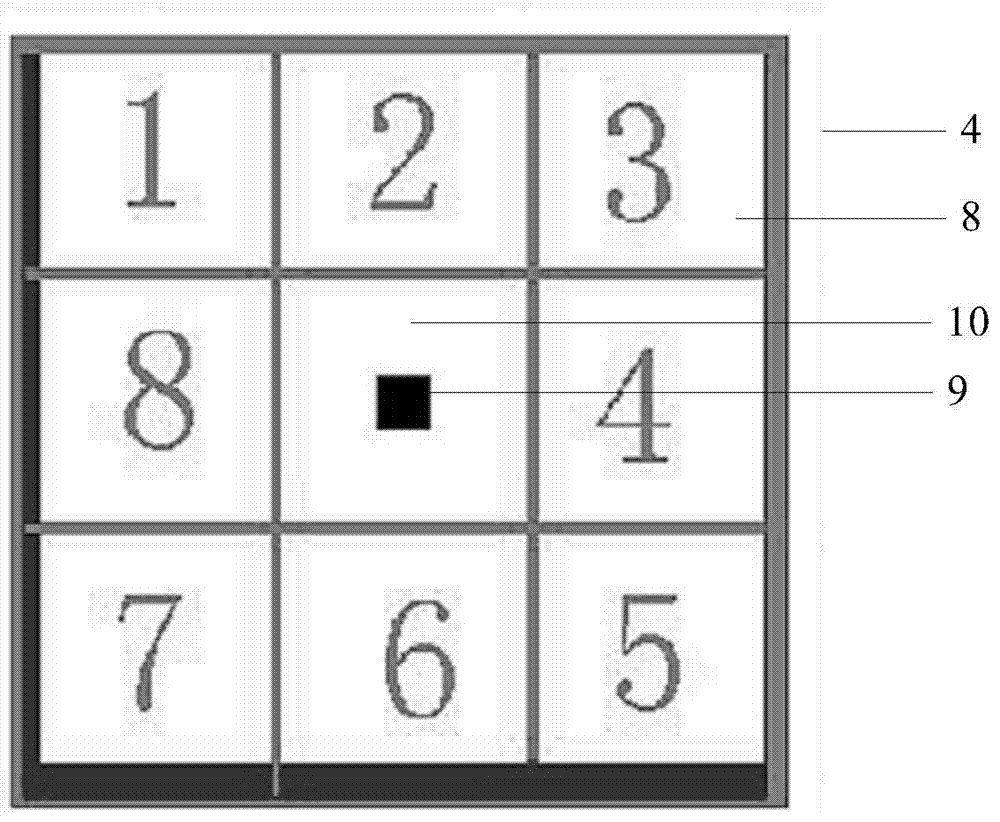
The invention provides an encoding graph block. The encoding graph block is composed of a direction sequence encoding unit block, CRC bits and a plurality of data encoding unit blocks. The direction sequence encoding unit block comprises a direction characteristic lattice sequence, and each data encoding unit block comprises data code points and data reference points. A method for forming a lattice graph through the encoding graph includes the steps that the style of the direction characteristic lattice sequence is defined; the number of the data encoding unit blocks and the distribution mode of the data reference points and the data code points are defined; the number of CRC blocks and the position relation between the CRC blocks are defined; decimal digits are converted into the data code points implanted into the code point bits; the encoding storage amount contained in the lattice graph is calculated. A device for implementing the method comprises a direction sequence definition module, a data encoding unit definition module, a CRC bit definition module, a data code point forming module and an encoding storage amount calculation module. The encoding graph block can store a large amount of data information and has the anti-fake function.
Owner:CHINA COMMERCE NETWORKS SHANGHAI
Multi-color overprinted tipping paper with metallic luster and preparation method thereof
ActiveCN109295806AStrong adhesionInhibit sheddingCoatings with pigmentsInksPulp and paper industrySolvent
The invention discloses multi-color overprinted tipping paper with metallic luster and a preparation method thereof, wherein an aluminized tipping base paper layer, an ink layer and a gloss oil layerare arranged sequentially from inside to outside. The tipping paper takes an aluminum layer of the aluminized tipping base paper as a printing face, and a bottom color adopts a transparent alcohol ester ink. Polar hydroxyl groups contained in the ink can be bonded with metal aluminum, and have excellent adhesion force to metal aluminum, so as to realize direct printing on a metal aluminum layer. At the same time, the ink is matched with tackifying resin, so that the bottom color ink layer adheres firmly to the metal aluminum layer and the multi-color overprinted ink layer without stripping. Inaddition, the adopted ink solvent has good release property, and the safety and hygiene indexes of the tipping paper product meet the standards. Under the mutual combination of metallic luster of thealuminum layer and the luster of the ink, the tipping paper has the advantages of obvious metallic luster visual effect, rich color, high-grade luxury, decoration with strong stereo texture and a certain anti-counterfeiting property.
Owner:玉溪接装纸制造有限公司
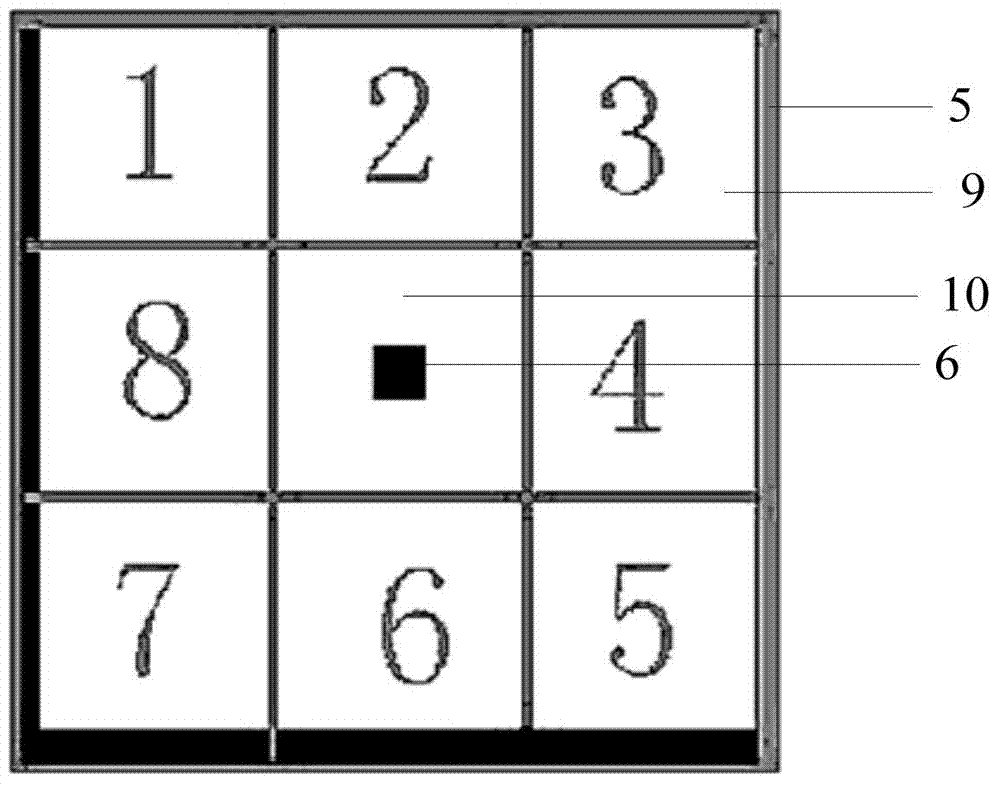
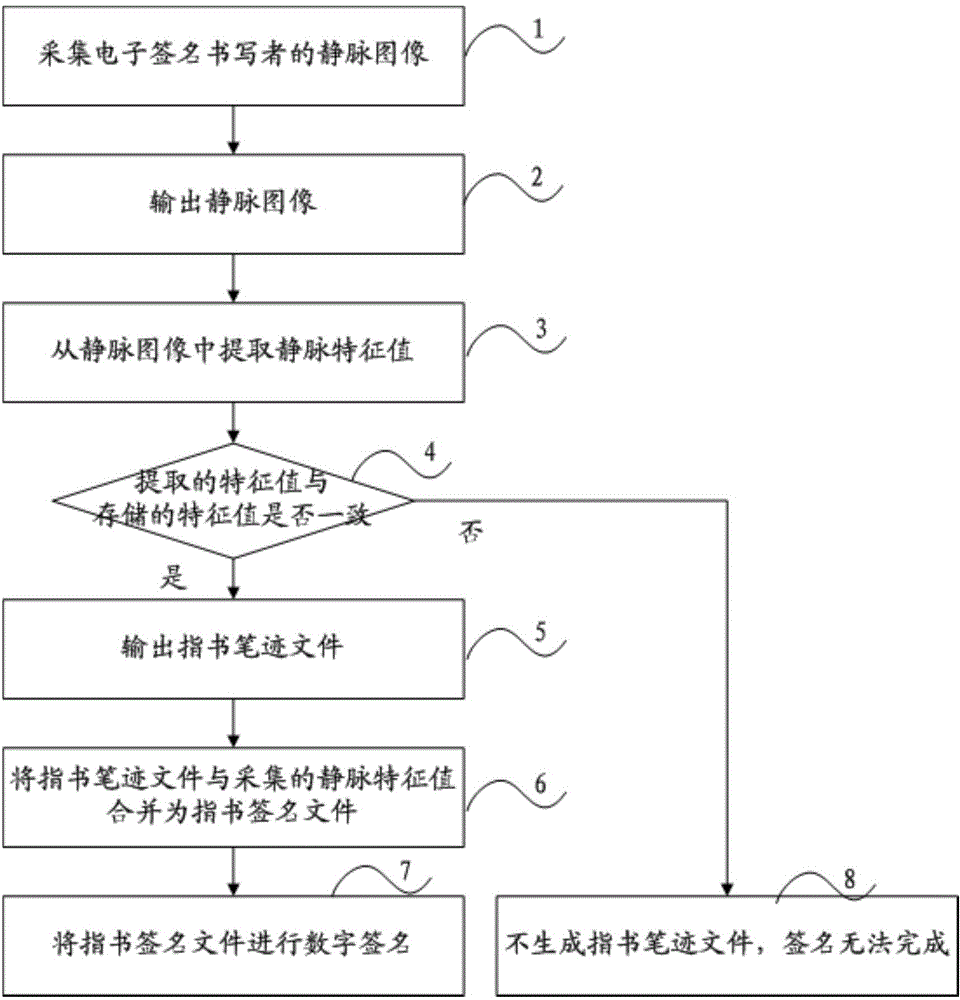
Method and system for finger-writing signatures on touch screen
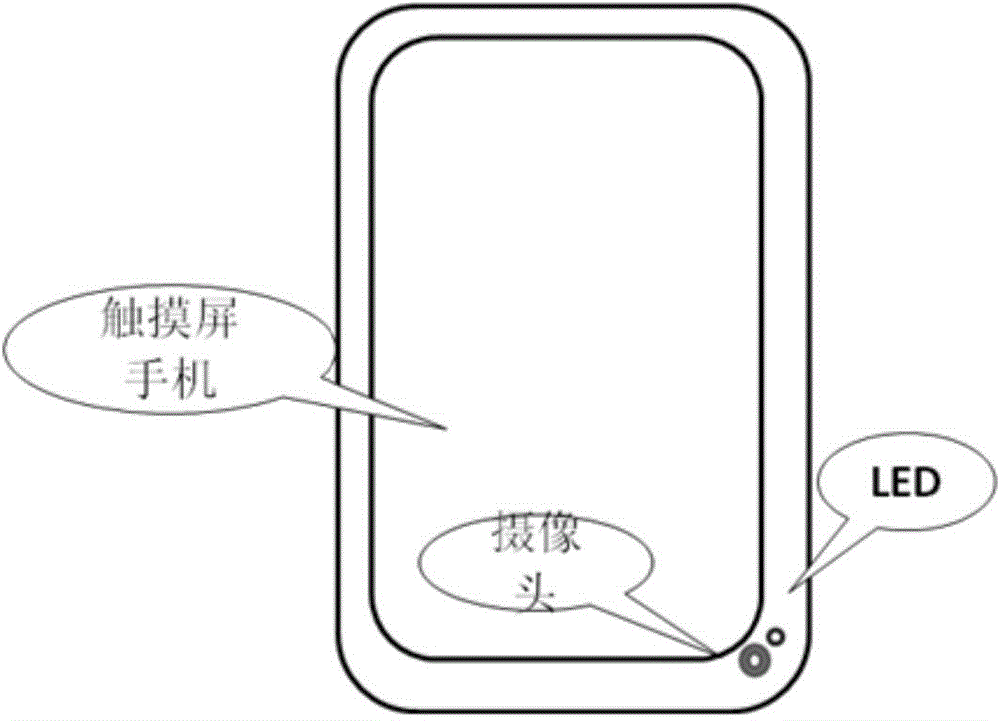
ActiveCN104462908AImprove accuracyAnti-counterfeitingDigital data authenticationHandwritingPattern recognition
The invention discloses a method and a system for finger-writing signatures on a touch screen. The method includes: a vein image of a writer of an electronic signature; outputting the vein image; extracting vein feature values from the vein image; comparing the extracted vein feature values to stored vein feature values; if consistence is confirmed, outputting finger writing files, and combing the finger writing files and the extracted vein feature values into a finger-written signature file. The method and the system have the advantages that authentication is more accurate and faking and tampering is prevented.
Owner:CHINA TELECOM CORP LTD
Internal network IP data packet management method and system, and devices
ActiveCN105959308AAnti-counterfeitingImplement security managementTransmissionNetwork packetComputer science
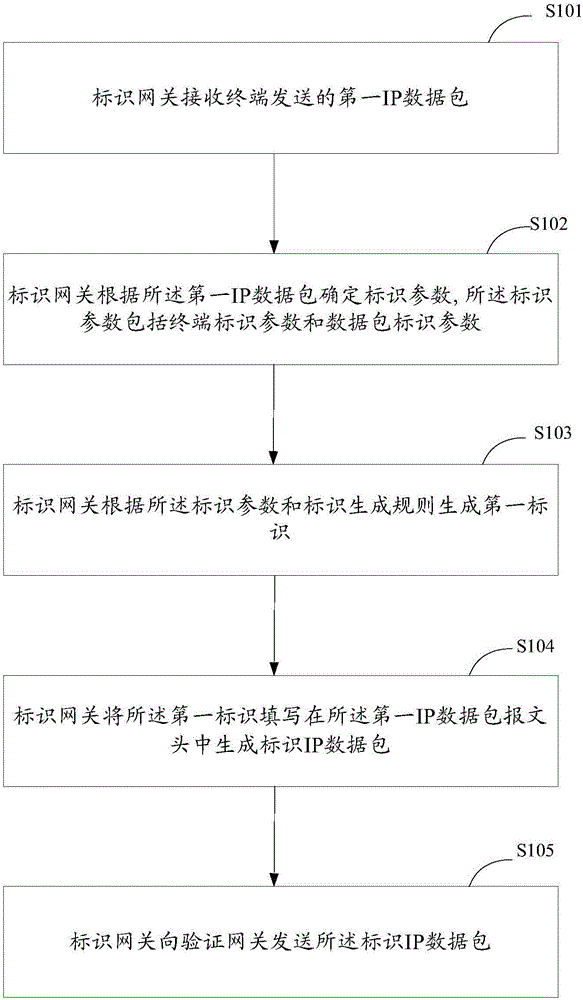
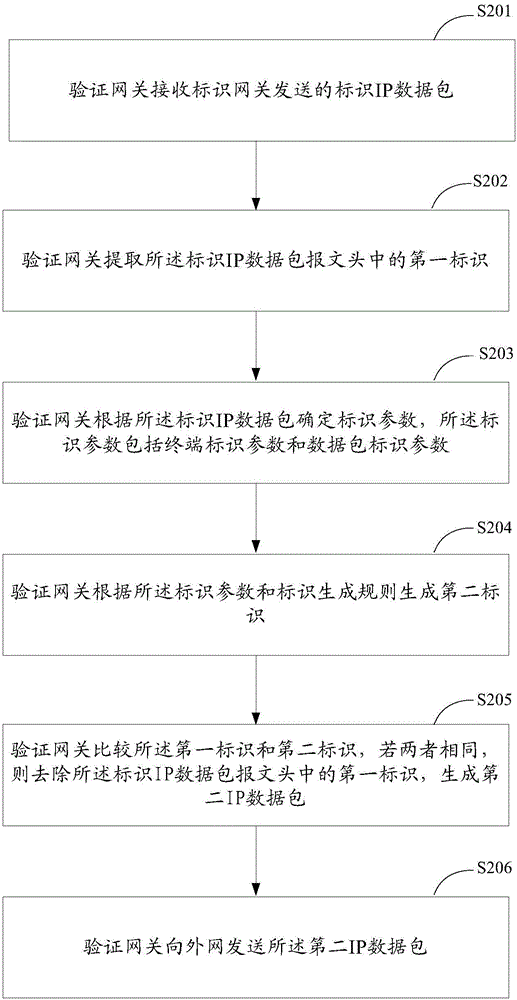
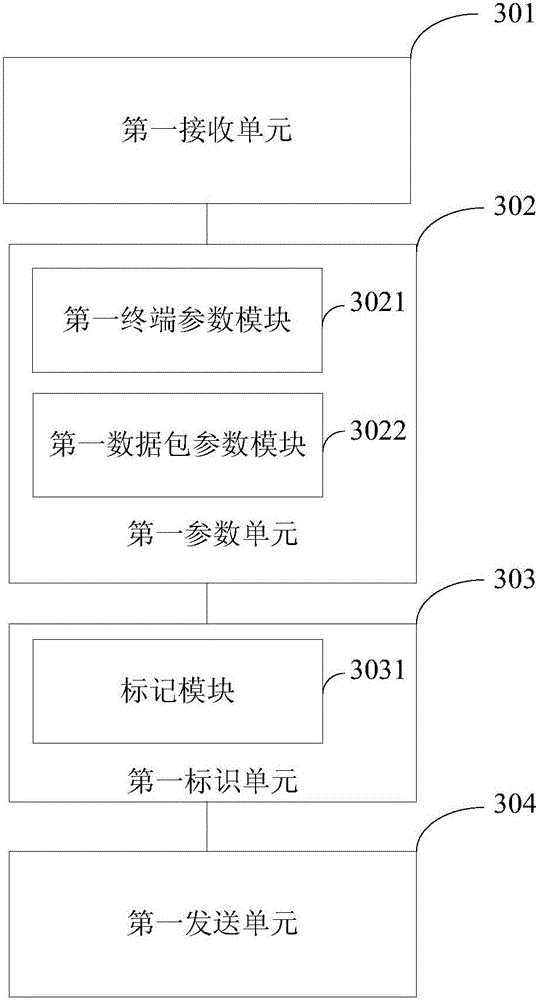
The invention provides an internal network IP data packet management method. An identification gateway receives a first IP data packet sent by a terminal; the identification gateway determines identification parameters according to the first IP data packet, wherein the identification parameters comprise terminal identification parameters and data packet identification parameters; the identification gateway generates a first identifier according to the identification parameters and an identifier generation rule, wherein the identifier generation rule is the rule for processing the identification parameters, thereby generating the identifier; the identification gateway fills the first identifier in the message header of the first IP data packet, thereby generating an identified IP data packet; and the identification gateway sends the identified IP data packet to a verification gateway. The method, the system and the devices are used for solving the safety management problem of all IP data packets sent by all terminals in the internal network of an enterprise in the prior art and satisfying the safety demands for forgery prevention and non-repudiation.
Owner:CEC CYBERSPACE GREAT WALL
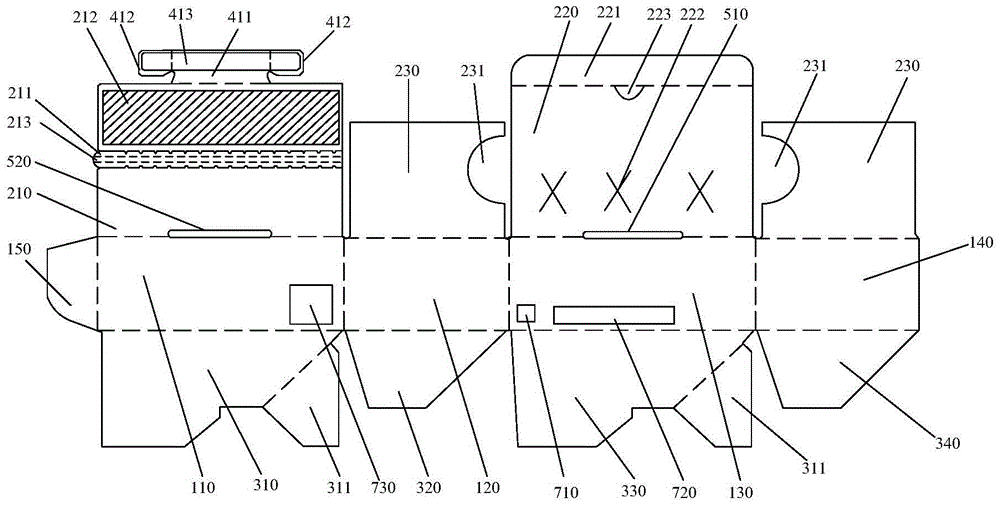
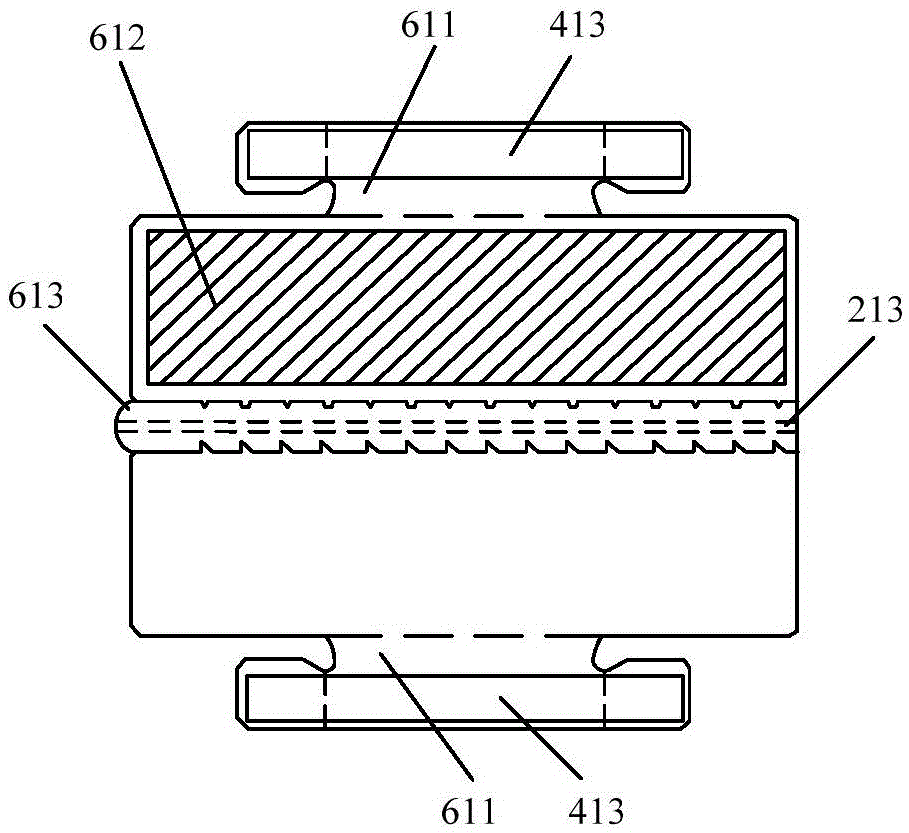
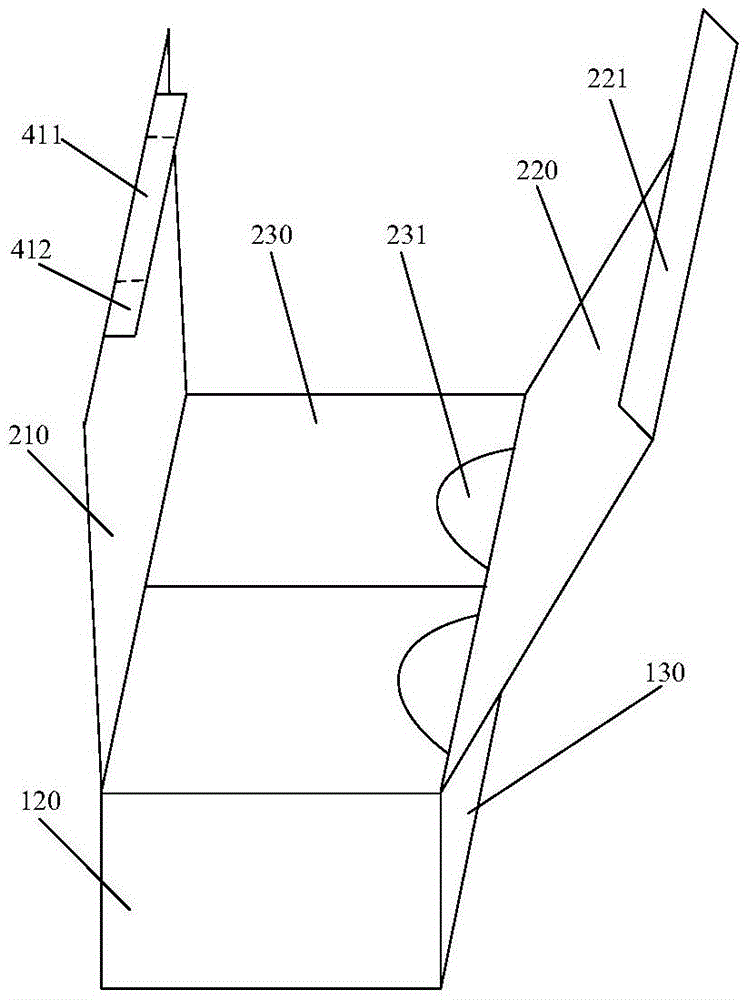
Digitalized antitheft compression-resistant reusable packaging box
ActiveCN105539978AHigh strengthIncrease the number of recyclingPackage recyclingRigid containersFirst insertionReusable packaging
The invention provides a digitalized antitheft compression-resistant reusable packaging box and relates to the technical field of packaging, aiming at solving the problems of the prior art that a packaging box cannot be reused, is relatively poor in safety and lacks digitalized application. The digitalized antitheft compression-resistant reusable packaging box comprises a box body, wherein the box body comprises a top cover part, a lateral side part, a bottom board part and a reinforcing board; the top cover part comprises an upper-layer top cover, a middle-layer top cover and a bottom-layer top cover; the upper-layer top cover is provided with a first double-wing insertion tongue and comprises a first tearing strip and a first adhesive area, a first insertion hole is formed at the connected part of the upper-layer top cover and a first side face; the reinforcing board is provided with two second double-wing insertion tongues; and the outer surface of the box body is provided with a two-dimension code, bar code and augmented reality recognition area. The digitalized antitheft compression-resistant reusable packaging box is high in safety performance, convenient to use, large in tensile strength, reusable and anti-counterfeiting, and is added with digitalized application, so that the user experience is higher.
Owner:SHENZHEN YUTO PACKAGING TECH
Holographic anti counterfeit polyurethane membrane
InactiveCN1709692AHigh strengthGood optical performanceSynthetic resin layered productsCalcium biphosphatePolyester
The present invention relates to one kind of counterfeit-resistant polyester-base film which contains two intrinsic surfaces and two exterior ones, and everyone of the intrinsic surface has a definitive proportional crystallizing polyester and polyester-based film trimming materials. One of the extrinsic surfaces is a holographic counterfeit-resistant film, the other is a holographic counterfeit-resistant film or a generic polyester-based film. The holographic counterfeit-resistant film contains 10-100 percent amorphous polyester and 0-90 percent additive carrier according to mass percent. The generic polyester-base film contains 50-90 percent crystal polyester and 10-50 percent additive carrier according to mass percent. The additive carrier talked about upward contains silicon dioxide, kaolin, calcium phosphate or barium sulfate, besides crystallizing polyester, and the content of the additive carrier is 3000pp which is counted according to mass percent. The holographic counterfeit-resistant polyester-based film, so that the holographic counterfeit-resistant design can be die stamped at first hand. It will increase of efficiency, reduce the cost of production.
Owner:WEIFANG FUWEI PLASTIC
Preparation process of anti-counterfeiting Xuan paper
InactiveCN102677524AEasy to identifyAnti-counterfeitingNon-fibrous pulp additionPaper-making machinesPulp and paper industry
The invention discloses a preparation process of anti-counterfeiting Xuan paper. The preparation process comprises pulp preparing for papermaking, paper fishing out and finished paper preparing, wherein flaky and silky identification materials convenient for identification are added in the step of pulp preparing for papermaking. The preparation process has the following beneficial effects: the identification materials are added to the pulp before the procedure of paper fishing out and will be flat pressed in the Xuan paper at last, so true or false of Xuan paper can be well identified via the flaky and silky identification materials; and besides, anti-counterfeiting image-text identifiers are arranged on the surface of a paper fishing out curtain for fishing out the Xuan paper and can be used for better anti-counterfeiting.
Owner:CHINA XUAN PAPER +1
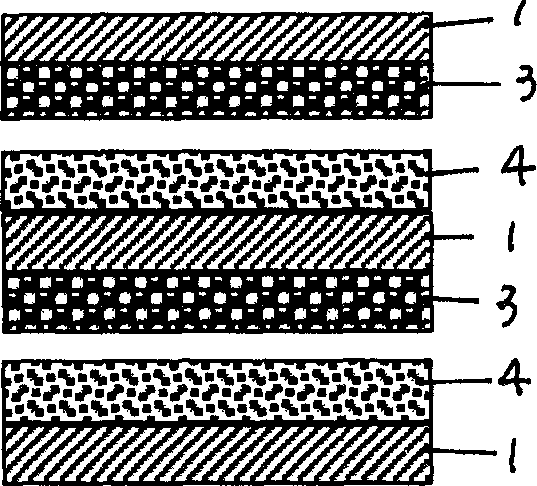
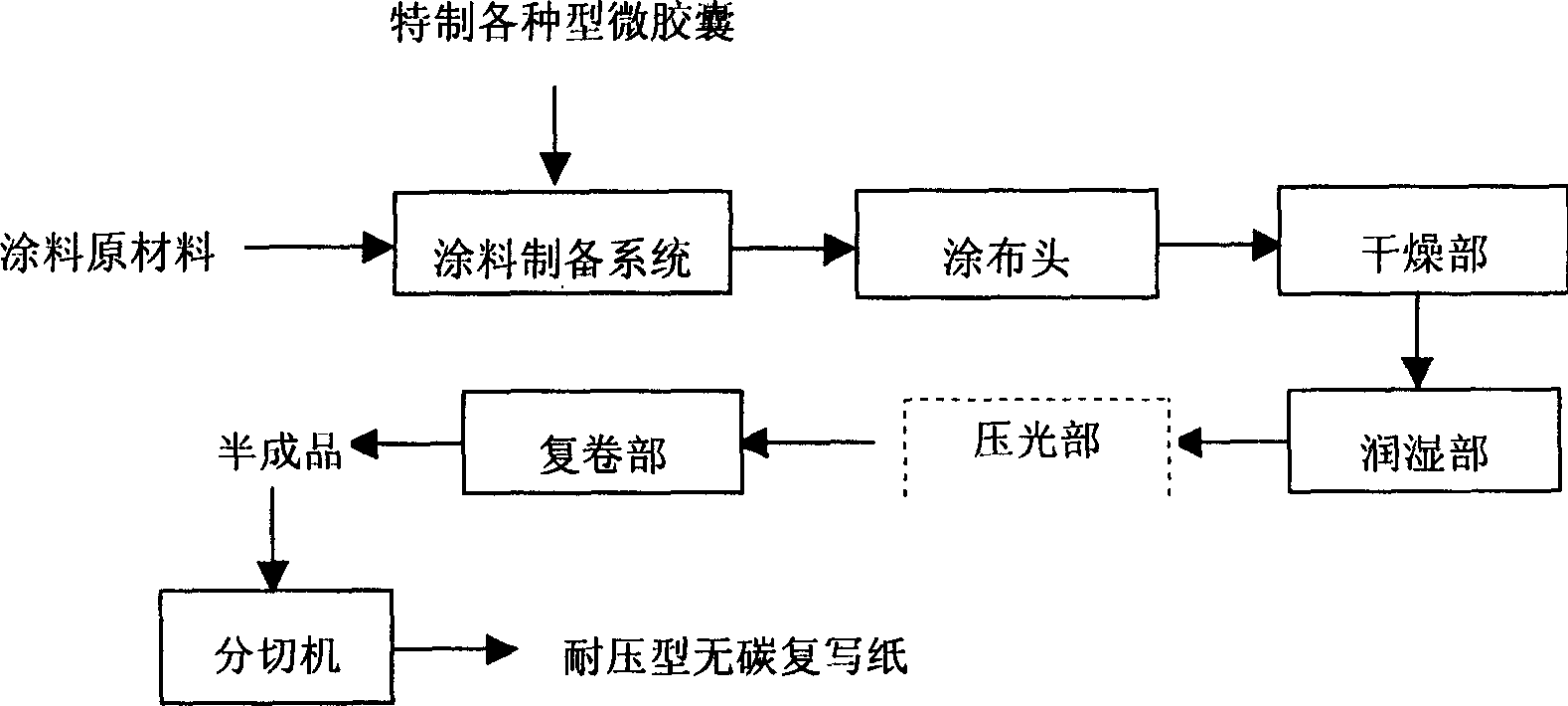
Pressure-resistant carbon-free duplicating paper and production thereof
InactiveCN1779071AImprove stress resistanceHigh opacityPaper/cardboardPaper/cardboard layered productsPulp and paper industryCarbonless copy paper
The invention is about a pressure carbon-free paper and its process. The aim of the invention is to solve the paper turning blue and skew ness in the roll-up printing process. The microcapsule is treated specially in the invention. The mean particle diameters about 3 microns and the opacity are about 75%. So it can be used for the double-sided printing and the word in the printing face is clear.
Owner:GUANGDONG GUANHAO HIGH TECH
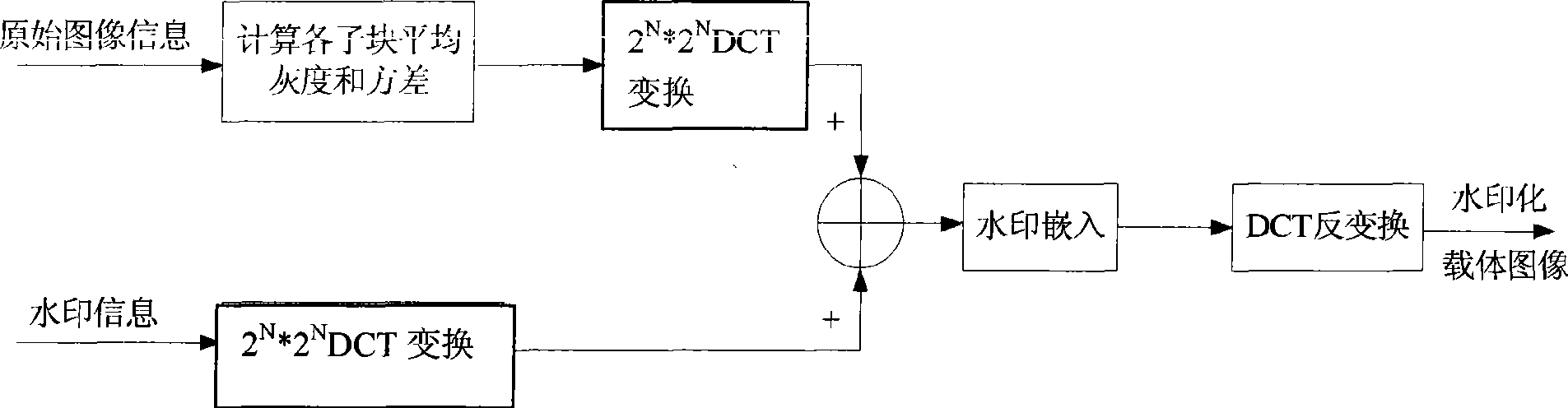
Digital image watermark imbedding method based on DCT algorithm
InactiveCN101504758AAnti-counterfeitingTamper proofImage codingImage data processing detailsComputer visionDigital image watermarking
The invention discloses a DCT algorithm-based method for digital image watermark embedment, which comprises: a first step of reading an original public image and a light and shade watermark image into two-dimensional arrays I and W respectively; a step two of dividing the original public image I and the watermark image W into 2*2 image blocks which do not cover each other respectively, computing the average gray m and a variance sigma of the sub blocks, and performing the DCT conversion of the sub blocks of the public image; a step three of embedding one element W(p,q) in the light and shade watermark in a sub block with a complex texture; a step four of performing the inverse DCT conversion of image blocks embedded with watermark information; and a step five of combining image the image blocks to obtain an image embedded with the light and shade watermark. The method is characterized by counterfeit prevention, falsification prevention, verification, and data security and integrity guarantee.
Owner:SHAANXI UNIV OF SCI & TECH
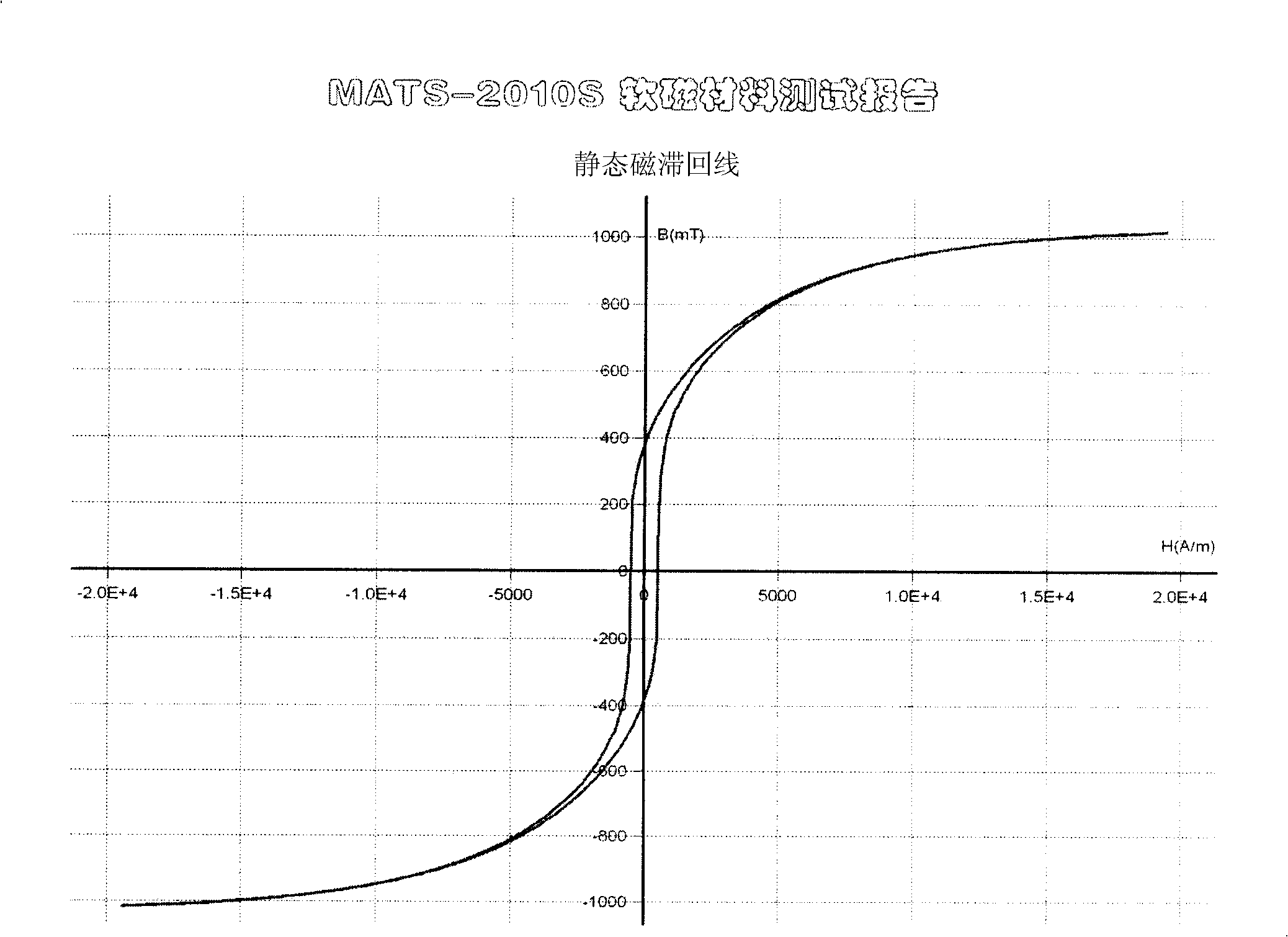
Diphasic stainless steel
The invention discloses a biphase stainless steel, which is especially suitable for the steel used for coinage. The biphase stainless steel comprises the chemical components by weight percentage (wt percent) as follows: C and N are less than or equal to 0.12 percent, Si is less than or equals to 1.0 percent, Mn is less than or equals to 6.0 percent, P is less than or equals to 0.04 percent, S is less than or equals to 0.01 percent, Ni is 3.0 to 7.0 percent, Cr is 20.0 to 28.0 percent, Mo is 0 to 2.0 percent, W is 0 to 2.0 percent, binary master alloy that is Ag-Cu is 0.10 to 1.0 percent, and the other weight percentage is composed of Fe and ineluctable impurities, wherein, the ratio (that is Creq / Nieq) between Cr valent weight and Ni valent weight ranges from 3.0 to 3.8. The volume percentage of the biphase stainless steel in a cold-rolling annealed ferrite is 65 to 85 percent, and the saturation magnetic induction thereof is 0.7 to 1.0T. The biphase stainless steel has good heat formability, low hardness and good plasticity; the erosion resistance is better than the existing coinage stainless steel, and the anti-fake performance and the bacteria resistance performance are realized.
Owner:CHINA BANKNOTE PRINTING & MINTING
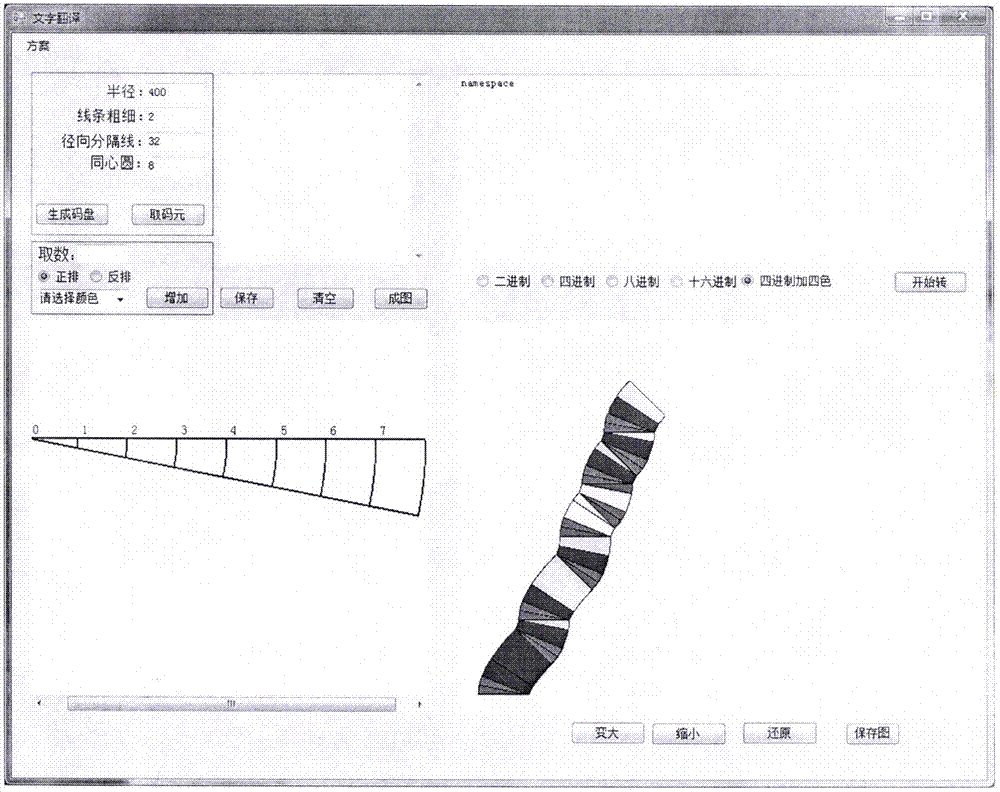
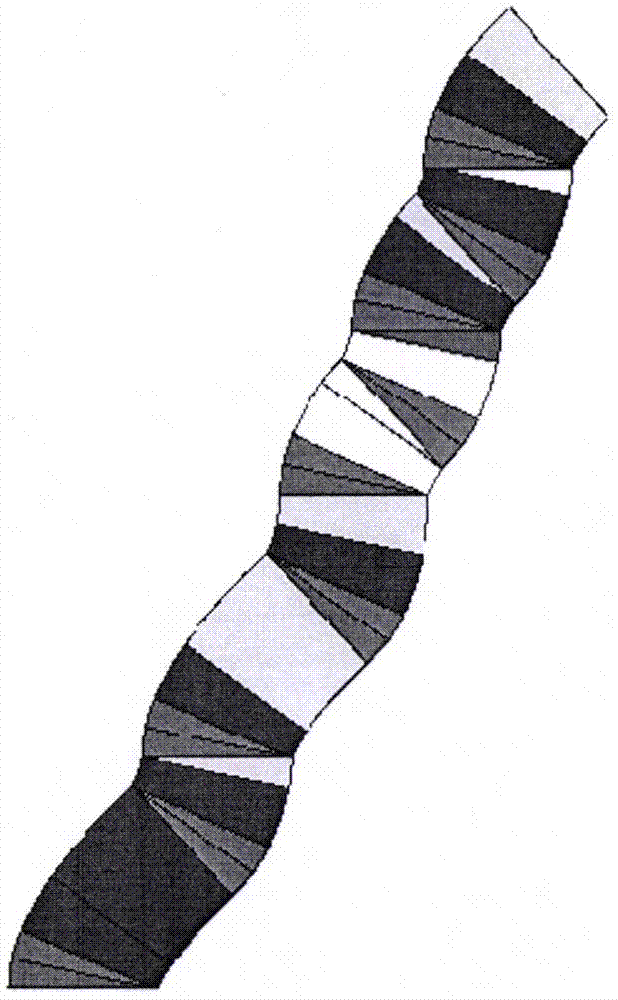
Visual three-dimensional code touch screen compiler and programming technique
ActiveCN105446747AReduce errorsImprove programming efficiencyVisual/graphical programmingCompiler constructionGeometric programmingProgram security
The invention discloses a visual three-dimensional code touch screen compiler product and its programming technique. According to the invention, visual geometric programming and three-dimensional code programming are realized; a programmer can finish programming work by one-hand or two-hand touch screen operation, therefore the workload of the programmer is greatly reduced; and the programming work is driven to humanized and intelligentized development. The built-in technologies of the new type geometric decoder and three-dimensional compiler of the invention comprise: generating a code plate and selecting a code element, coding a rule, information expression, hexadecimal number expression, conversion of digital and geometric codes, plane code to three-dimensional code, and so on; the functions of the compiler comprise: a touch screen function, program three-dimensional coding, a three-dimensional code paraphrasing function, an intelligent detection function, an automatic code storage function, an automatic connection function of three-dimensional code chains, and so on. According to the invention, the program code is converted into a shape code; a new pattern is provided for the security operation of the program; each code chain is not divided, so there is no leak for an external virus program to implant; the program is effectively prevented from being tampered and attached; and the program security is improved.
Owner:JIANGSU FIGURE CODE INFORMATION TECH LTD
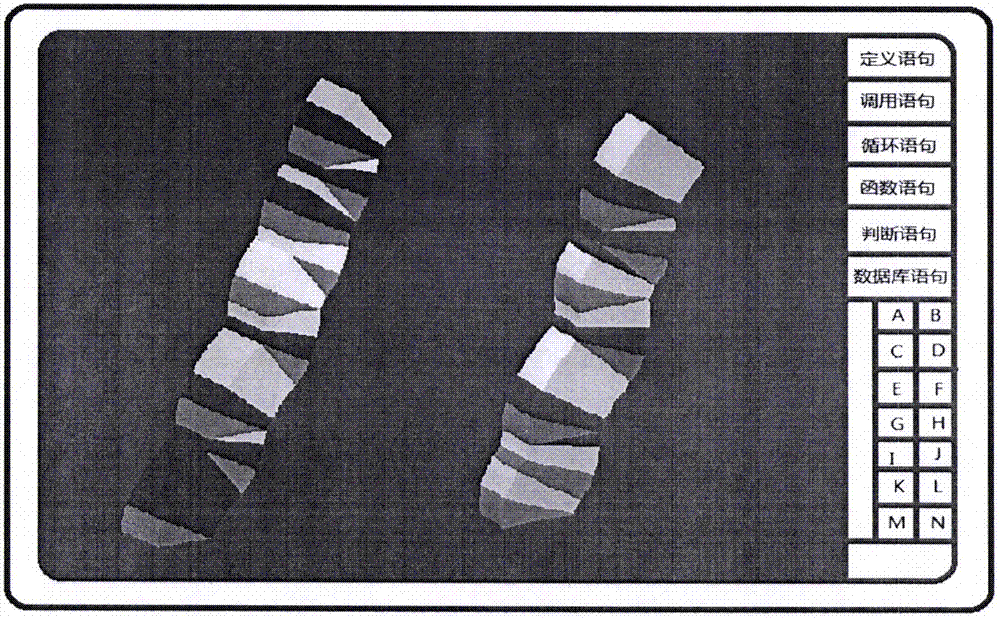
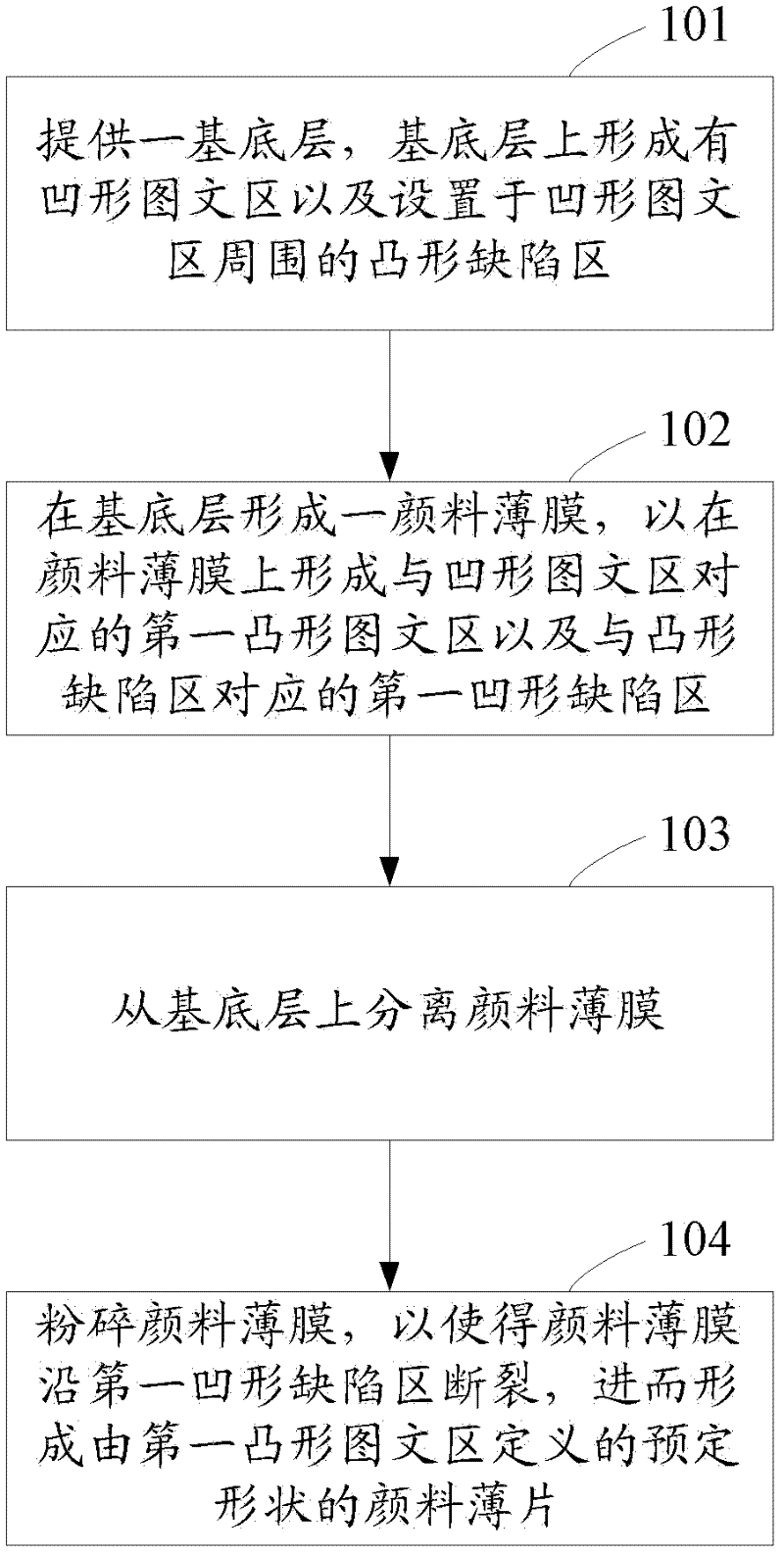
Pigment sheet and manufacturing method thereof
ActiveCN102504620AImprove completenessIncrease productivityInorganic pigment treatmentSynthetic resin layered productsEngineeringPigment
The invention discloses a manufacturing method for a pigment sheet. The method comprises the following steps of: providing a substrate layer, wherein a concave image-text area and convex defect areas formed on the periphery of the convex image-text area are formed on the substrate layer; forming a pigment film on the substrate layer to form a first convex image-text area which corresponds to the concave image-text area and a first concave defect area which corresponds to the convex defect area on the paint sheet; separating the pigment film from the substrate layer; and smashing the pigment film to fracture the pigment film along the first concave defect area and form a pre-shaped pigment sheet defined by the first convex image-text area. Moreover, the invention further discloses a pigment sheet of preset shape. Due to the adoption of the technical scheme, the pigment sheet of a preset shape can be formed at relatively high production efficiency, high integrality of information carried by the pigment sheet and a good representation effect, and can be applied to ink or other carriers for counterfeiting and decorating.
Owner:HUIZHOU FORYOU OPTICAL TECH
Duplex stainless steel with special magnetic property
InactiveCN101608286AExcellent thermoforming propertiesReduce hardnessChemical compositionVolume content
The invention provides a duplex stainless steel with special magnetic property, which comprises the following chemical compositions in percentage by weight: less than or equal to 0.12 percent of C+N, less than or equal to 1.0 percent of Si, 2.0 to 6.0 percent of Mn, less than or equal to 0.04 percent of P, less than or equal to 0.01 percent of S, 3.0 to 7.0 percent of Ni, 22.0 to 27.0 percent of Cr, less than or equal to 2.0 percent of Cu, less than or equal to 2.0 percent of Mo, less than or equal to 2.0 percent of W, less than 0.1 percent of Ce or less than 0.006 percent of B, and the balance of Fe and inevitable impurities, wherein the equivalent ratio of Cr to Ni (Creq / Nieq) is between 3.1 and 3.8. Under the control of the chemical compositions, ferrite volume content of materials in the state of cold rolling and anneal is between 68 and 85 percent, while the saturation magnetic induction density is between 0.72 and 1.0 T. The duplex stainless steel has good hot forming property, low hardness, good plasticity and anti-counterfeiting property, and is suitable for coining.
Owner:BAOSHAN IRON & STEEL CO LTD
Solvent-induced color change photonic crystal fabric and preparation and application thereof
ActiveCN109944073AAchieve color changeSimple methodPhysical treatmentFibre typesPolyesterExternal energy
The invention relates to a solvent-induced color change photonic crystal fabric and preparation and application thereof. The preparation method comprises the steps that P(St-BA-AA) colloidal microspheres of core-shell structures are dispersed in water and ultrasonically mixed with a trace amount of acetylene black uniformly, then a mixture is uniformly loaded on the surface of a fabric, and dryingis conducted to obtain the solvent-induced color change photonic crystal fabric. The solvent-induced color change photonic crystal fabric and the preparation and application thereof have the advantages that the polyester fabric self-assembled by the colloidal microspheres shows the original black color of the fabric, the color can change when the fabric meets water or other solvents, the color ofthe fabric is different if the solvents are different, and the fabric can achieve color change without consuming external energy and has application potentials in the fields of humidity detection, counterfeiting prevention and two-dimensional code hiding.
Owner:DONGHUA UNIV
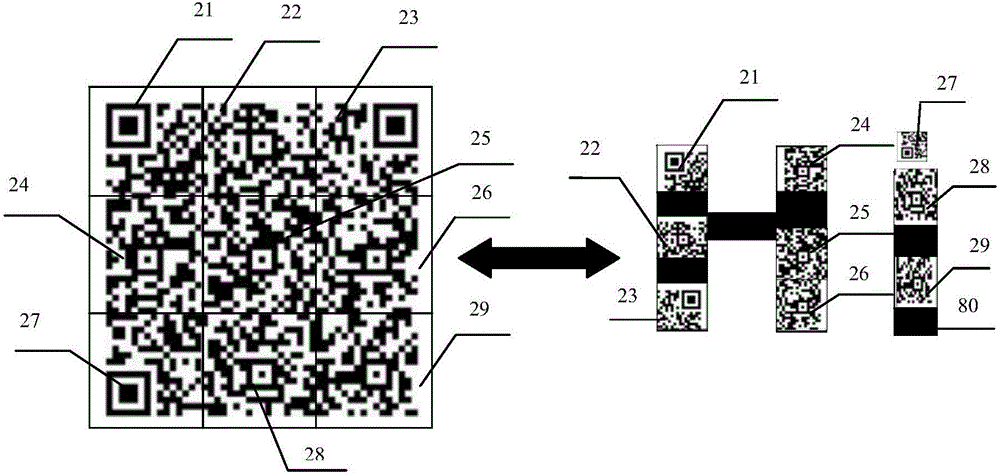
Anti-counterfeiting system and method realized in combination with two-dimensional code scanning technology
ActiveCN106779739ASmall footprintAnti-counterfeitingCo-operative working arrangementsCommerceComputer hardware
The invention relates to an anti-counterfeiting system and method realized in combination with a two-dimensional code scanning technology. The method is characterized by comprising the following steps of: splitting a two-dimensional code into at least two two-dimensional code fragments, and orderly distributing the two-dimensional code fragments in a mark pattern; converting at least one two-dimensional code fragment into a coloured two-dimensional code fragment, the colour of which is the same as the corresponding position of the mark pattern; scanning the at least one coloured two-dimensional code fragment in the mark pattern, and forming a recombined two-dimensional code; and verifying the recombined two-dimensional code. The coloured two-dimensional codes are combined into the mark pattern; and thus, appearance of a commodity cannot be influenced while anti-counterfeiting information is set. By means of the anti-counterfeiting system and method disclosed by the invention, the occupation space of the two-dimensional code on the commodity is saved; furthermore, the black and white two-dimensional code is eliminated; and thus, the commodity is relatively beautiful and practical.
Owner:联信摩贝软件(北京)有限公司
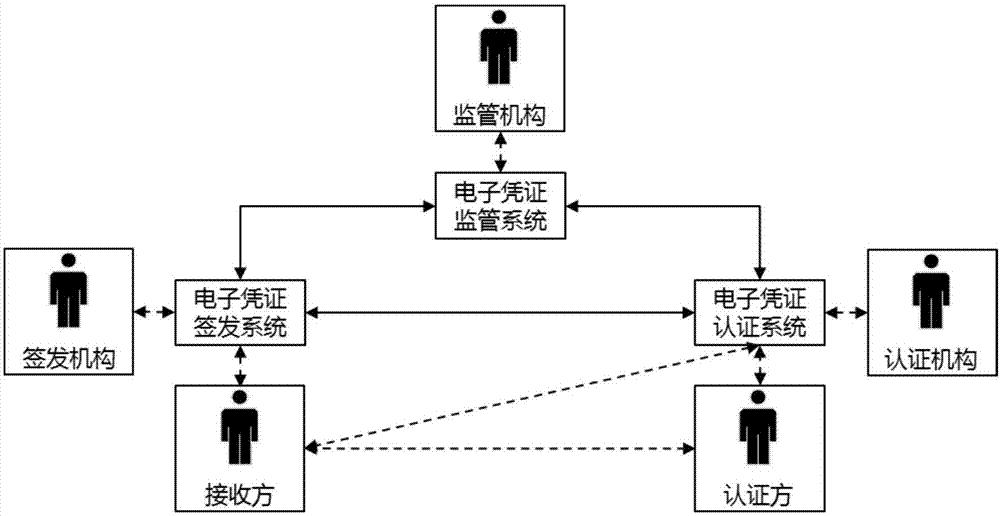
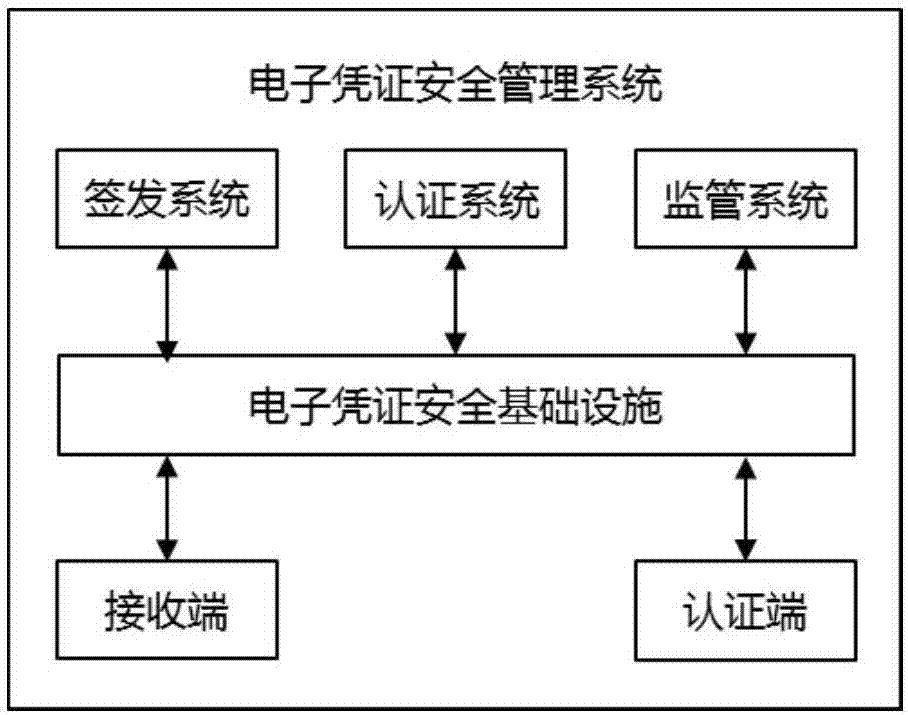
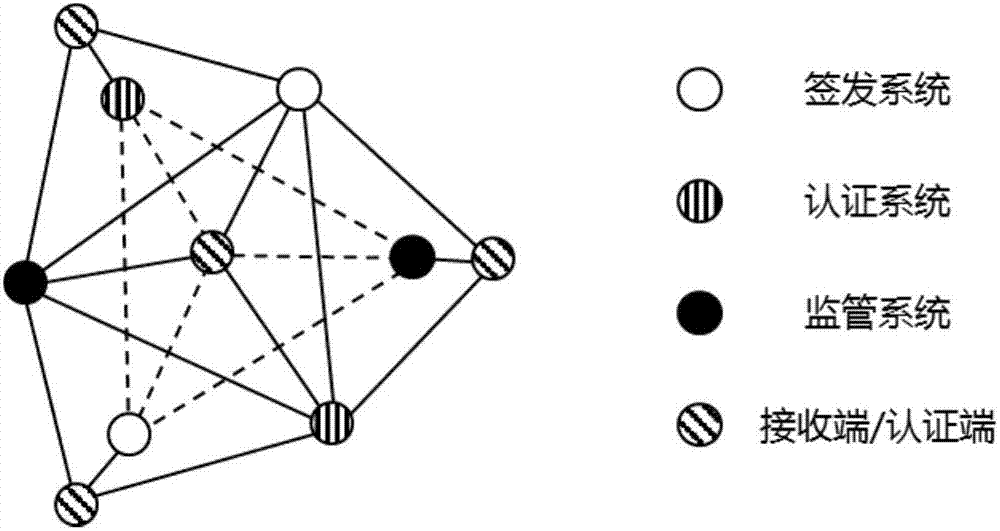
Electronic certificate security management method and system
ActiveCN107277000ASolve the costFix security issuesTransmissionMarketingSecurity managementAuthentication
The invention discloses an electronic certificate security management method and system. The electronic certificate security management method comprises the following steps: issuing electronic certificate signing and issuing application; authenticating the receiving end, generating the electronic certificate, and issuing the electronic certificate and the signing and issuing information to the security basic module of electronic certificate; obtaining the electronic certificate and the electronic certificate signing and issuing results from the electronic certificate security basic module; issuing the electronic certificate authentication application to the electronic certificate security basic module; authenticating the receiving end by means of the electronic certificate security basic module, issuing the authentication confirmation information to the electronic certificate security basic module, and waiting for the receiver to confirm; confirming the authentication confirmation information by the receiving end; and obtaining the authentication results of the electronic certificate from the electronic certificate security basic module. By means of the scheme disclosed by the invention, the defects of the electronic certificate issuing, authentication and supervision platform in the prior art in the aspects of cost, safety and convenience can be solved.
Owner:北京明朝万达科技股份有限公司
Packing container with curved surface and manufacturing method thereof
ActiveCN102431699ANew appearanceBeautiful appearanceTransfer printingPretreated surfacesTime transferEngineering
The invention relates to a packing container with a curved surface and a manufacturing method thereof. The packing container comprises a container with the curved surface and a laser image-text layer. The laser image-text layer is arranged on the curved surface of the container. According to the packing container provided by the invention, the laser image-text layer is adopted, so that compared with the existing packing container, the packing container has a novel and attractive appearance and anti-counterfeiting performance. In addition, since the laser image-text layer can be made in one-time transfer print, the automatic production is favored, and the production efficiency is improved.
Owner:SHENZHEN BEAUTY STAR
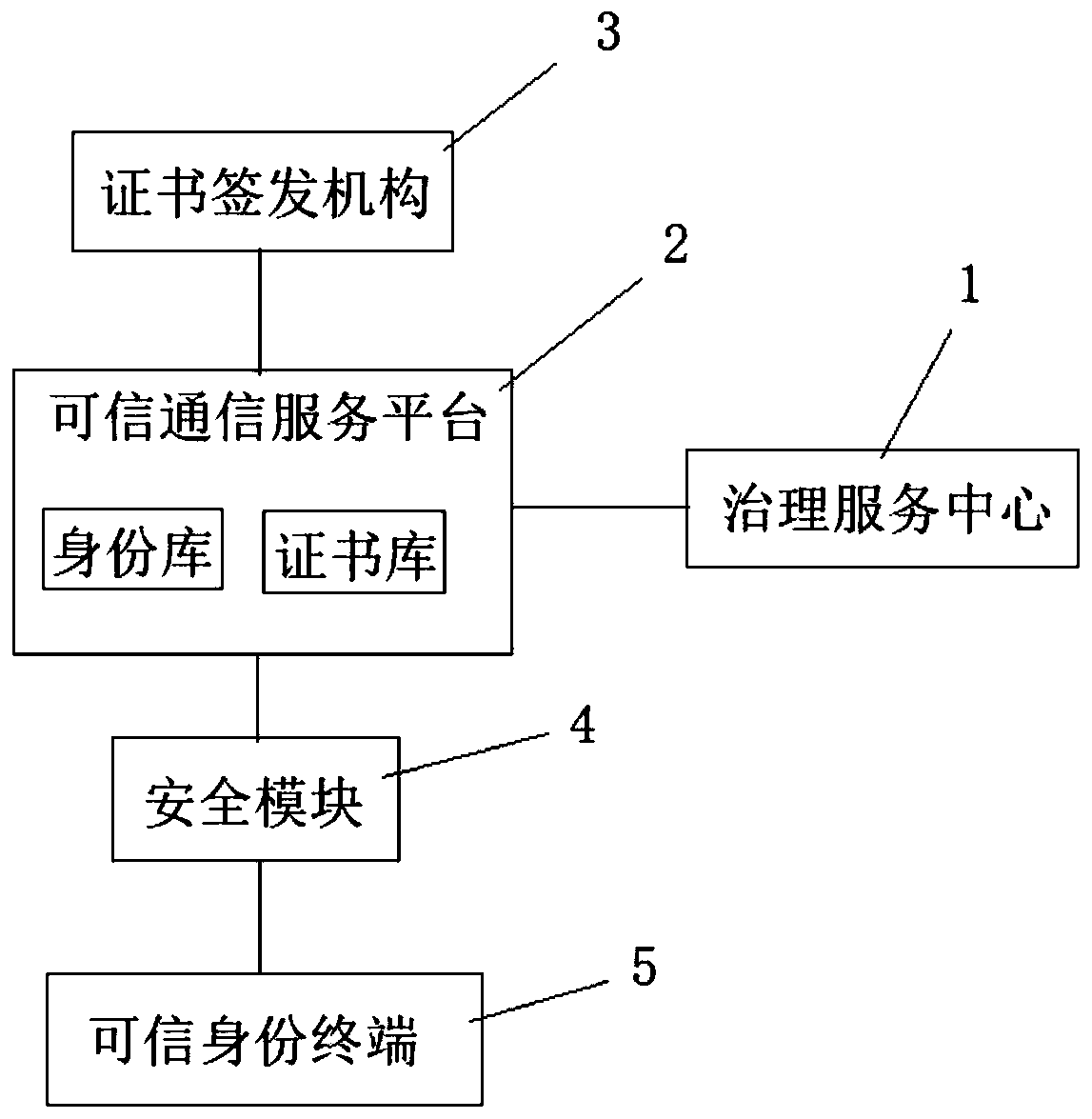
Trusted communication system and method
ActiveCN111556501AImprove protectionEnsure safetyTwo-way working systemsSecurity arrangementCommunications systemInternet privacy
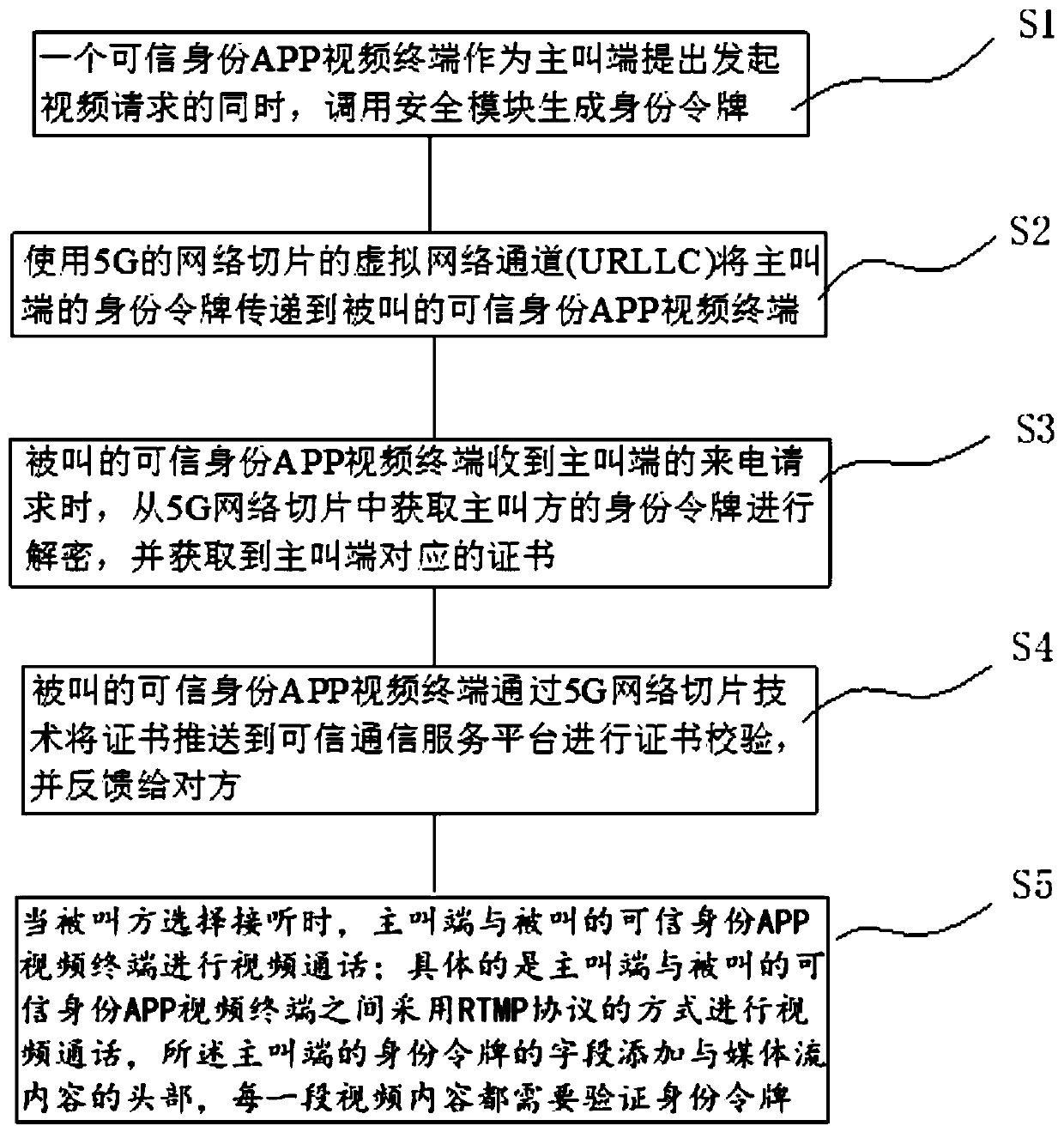
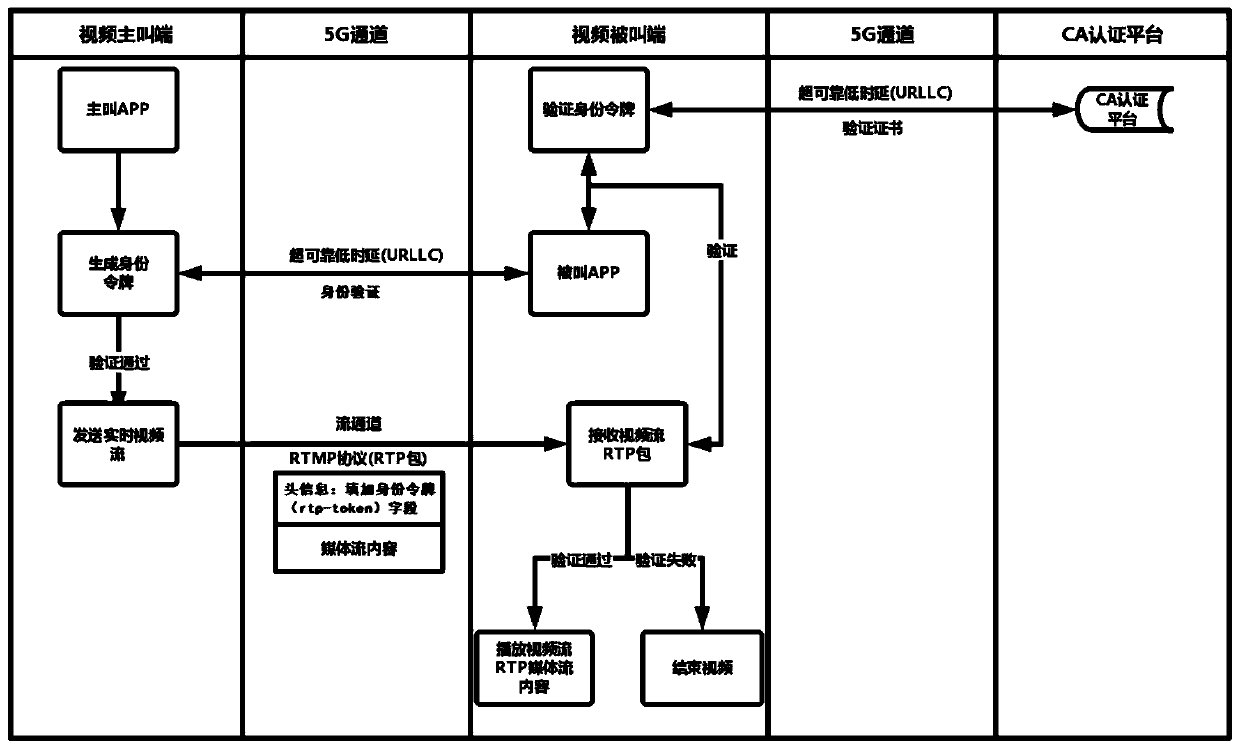
The invention discloses a trusted communication system and method. The system comprises a governance service center, a trusted communication service platform, a certificate issuing mechanism, the security module and a trusted identity terminal. The method comprises the following steps: S1, generating an identity token while a calling terminal makes a video initiating request; S2, transmitting theidentity token of the calling terminal to a called trusted identity APP video terminal; S3, the called terminal obtaining the identity token of the calling party from the 5G network slice for decryption, and obtaining a certificate; S4, the called terminal pushing the certificate to the trusted communication service platform for certificate verification through a 5G network slicing technology; andS5, selecting answering, and performing video call between the calling terminal and the called terminal. The trusted communication system and method provided by the invention comprise a certificate authentication mechanism, a reliable protection effect is provided for identity authentication, and a virtual network URLLC channel of a 5G network slicing technology is used, so that the low time delay of identity authentication can be ensured, and the security of a video call is also ensured.
Owner:WEIWEI SHANGHAI NETWORK TECH CO LTD
Anti-leakage sealing bottleneck structure for canned water
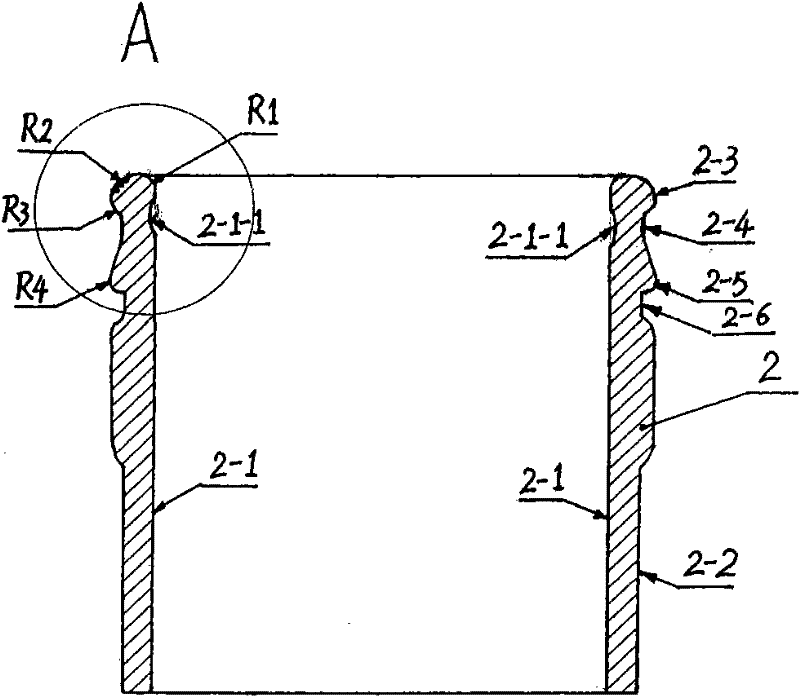
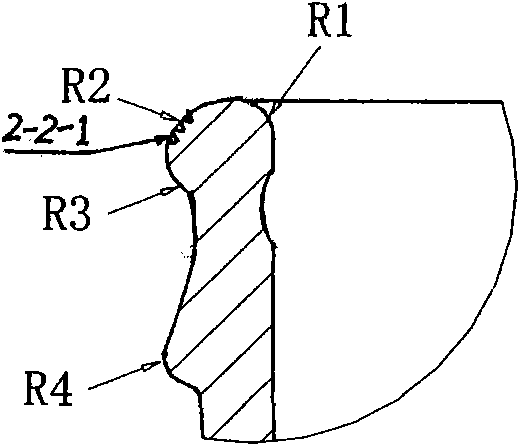
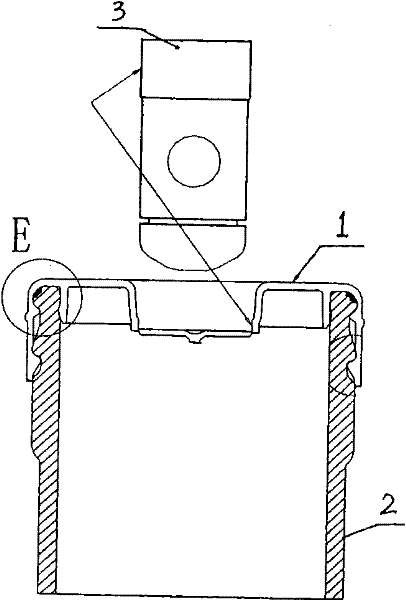
The invention relates to an anti-leakage sealing bottle structure for canned water, comprising a bottleneck (2). The anti-leakage sealing bottle structure is characterized in that the upper part or the middle part of the inner side wall (2-1) of the bottleneck (2) is provided with an arc-shaped concave ring (2-1-1); the joint part of the inner side wall (2-1) and the top part of the bottleneck (2) is shaped like an R arc-shaped ring (R1); the joint part of the outer side wall (2-2) and the top part of the bottleneck (2) is shaped like an R arc-shaped ring (R2); the upper part or the middle part of the outer side wall (2-2) of the bottleneck (2) is provided with an R arc-shaped ring (R3); an R arc-shaped convex ring (2-3) is formed between the R arc-shaped ring (R1) and the R arc-shaped ring (R3); and the lower part of the R arc-shaped ring (R3) is provided with a concave ring (2-4). The anti-leakage sealing bottle structure has the effects of double sealing, anti-leakage, anti-counterfeit and long shelf life, reduces the weight and volume of a bottle body, reduces the use amount and loss of raw materials, saves the energy and protects the environment. The anti-leakage sealing bottle structure for canned water is widely applicable to canned water with five-gallon specification and other various specifications.
Owner:DONG GUAN JIN FU IND CO LTD
Blended interweaved fabric made of mint fiber, soybean fiber and polyester fiber and manufacturing method thereof
ActiveCN108691063AGood hemostatic effectGood moisture absorption and moisturizingBiochemical fibre treatmentMulti-ply fabricsPolyesterYarn
The invention discloses a blended interweaved fabric made of mint fiber, soybean fiber and polyester fiber. A blended yarn is prepared from, by weight, 25-40% of mint fiber, 15-30% of soybean fiber, 25-40% of alginate fiber and 0-25% of polyester fiber with a saivia extracting solution. The blended interweaved fabric made of the mint fiber, the soybean fiber and the polyester fiber has good sweat-absorbing, antibacterial and deodorant effects and is especially applied in hot summer and regions with many mosquitoes.
Owner:如皋市志鹏纺织有限公司
Encoding pattern and method and device for forming lattice graph through encoding pattern
ActiveCN103927575AAnti-counterfeitingGuaranteed difficultyRecord carriers used with machinesGraphicsCode point
The invention provides an encoding pattern. The encoding pattern comprises a plurality of encoding unit blocks, a direction characteristic lattice sequence, CRC bits, data reference points and code points. A method for forming a lattice graph through the encoding pattern includes the steps that decimal digits are converted into multi-bit binary digits; the multi-bit binary digits are combined into a plurality of binary arrays in sequence; the binary arrays are converted into digits with the scale with the number same as the number of code point bits; code points are implanted into the code point bits corresponding to the digits of the scale; decimal digits corresponding to the CRC bits are acquired and converted into binary digits; the binary digits are split, and a value is given to each CRC bit; whether the code points can be implanted into the CRC bits or not is distinguished. A device for implementing the method comprises an encoding pattern definition module, a conversion module a, a binary array forming module, a conversion module b, a code point implanting module, an operation module, a splitting module and a code point definition module. The encoding pattern can store a large amount of data information and has the anti-fake function.
Owner:上海在赢端智能科技有限公司
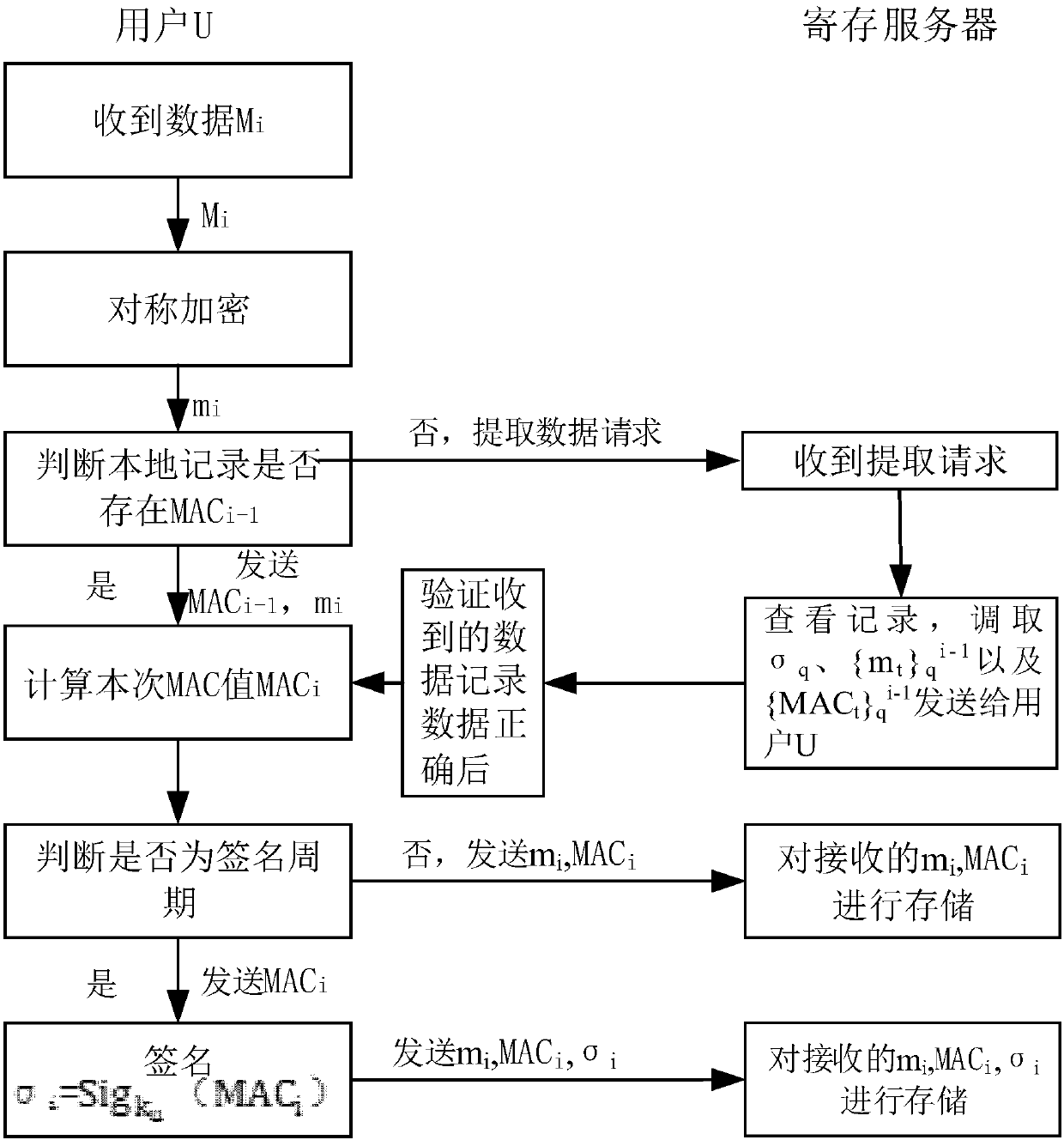
Generation method for data authentication code
ActiveCN107566360AReduce the risk of lossImprove reliabilityTransmissionComputer hardwareInitialization vector
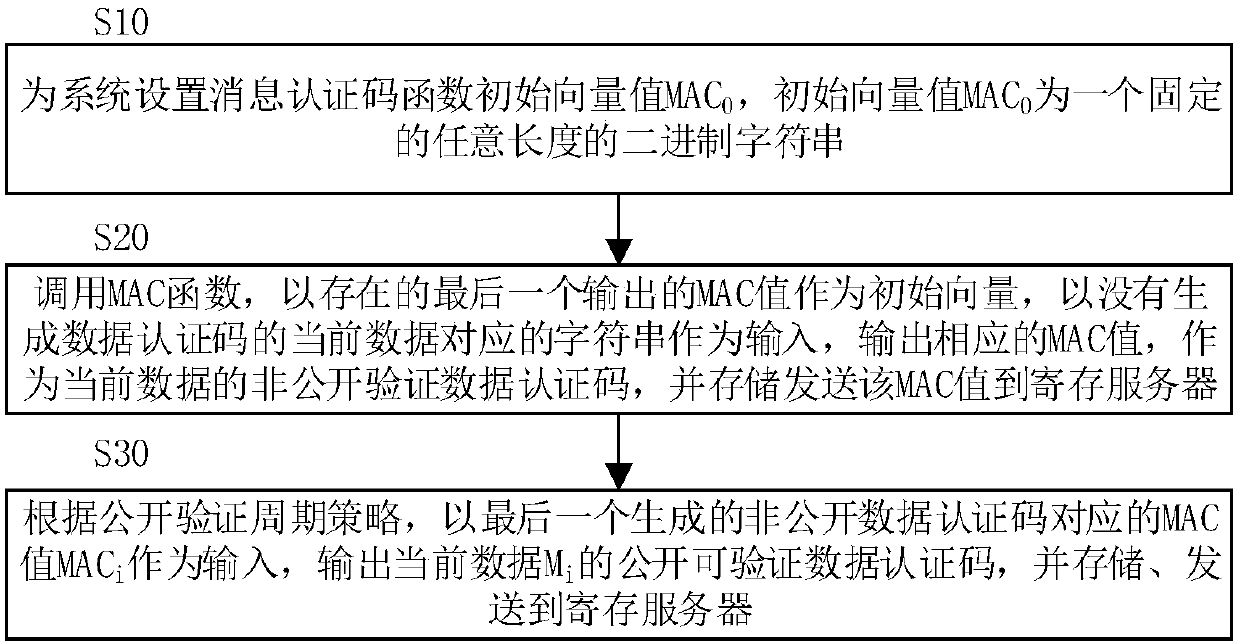
The invention discloses a generation method for a data authentication code. The method comprises the steps of setting a binary character string with a fixed random length as an initial vector value MAC0 of an MAC function; calling the MAC function, using a currently existing last output MAC value MACi-1 as an initial vector, using a character string corresponding to current data Mi of which the data authentication code is not generated as an input, outputting the corresponding MAC value MACi to serve as a non-public verification data authentication code of the current data Mi, and storing andsending the MAC value MACi to a register server; using the MAC value MACi corresponding to the last generated non-public verification data authentication code as the input according to a public verification period strategy, outputting a public verifiable data authentication code of the current data Mi, and storing and sending the code to the register server. According to the generation method provided by the invention, the generated data authentication code of the current data can authenticate all previous data, so that a data loss risk is reduced, reliability and security of data authentication are enhanced, and data authentication efficiency is improved.
Owner:北京中科锐链科技有限公司
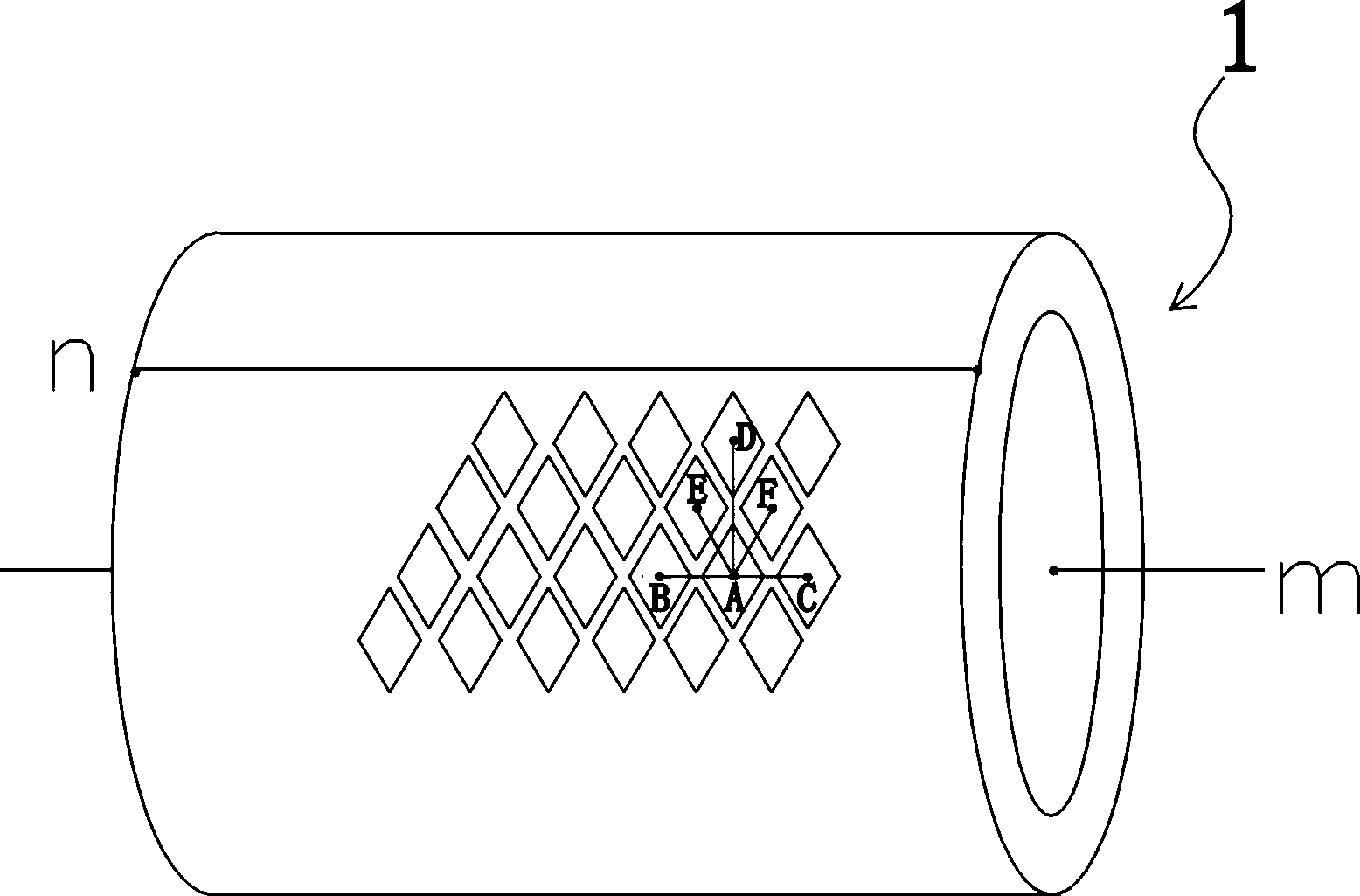
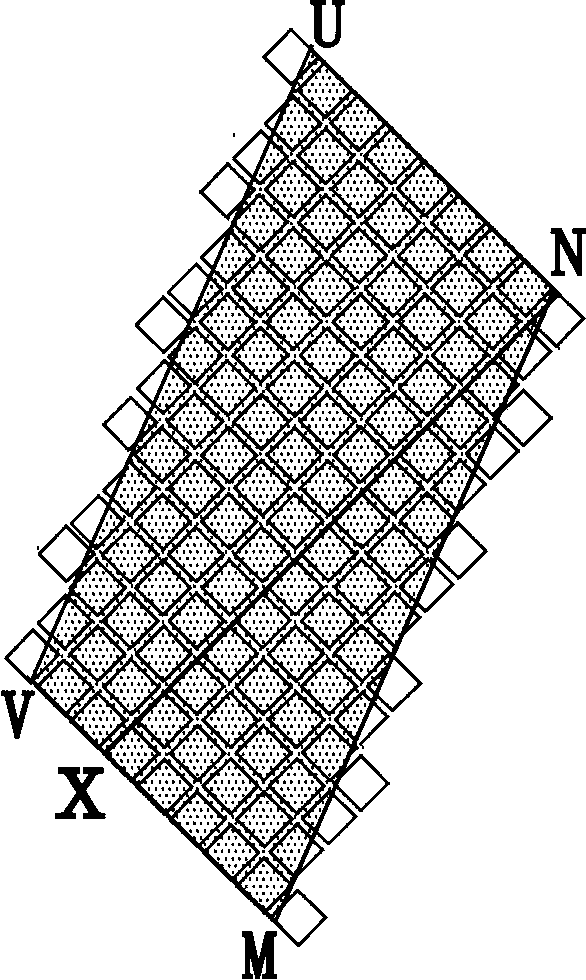
Gravure electronic mechanical carving method with anti-fake function
ActiveCN103862834AWith anti-counterfeiting functionEasy to identifyForme preparationEngineeringAngle alpha
The invention discloses a gravure electronic mechanical carving method with an anti-fake effect. The gravure electronic mechanical carving method comprises the following steps of (1) determining the size of a rhombus ink cell according to the required printed image, and determining an ink cell arrangement angle theta of the whole gravure; (2) selecting at least one straight line section as an anti-fake identification part, wherein the selected straight line section can meet the following conditions that the angular difference between an extending angle alpha of the straight line section and the ink cell arrangement angle theta of the whole gravure is 10 degrees-30 degrees; (3) revising the design value of the partial ink cell arrangement angle of the straight line section of the anti-fake identification part again, enabling the partial ink cell arrangement angle of the straight line section to be just be equal to the extending angle alpha of the straight line section, and recording the position of the straight line section; and (4) according to the design result, carrying out ink cell carving by adopting an electronic machine carving method to obtain a gravure with an anti-fake effect. The gravure electronic machine carving method provided by the invention has the advantages that the image printed by the carving gravure has the anti-fake effect, the identification is easy, the copy is hard, and the fabricating cost is also not increased.
Owner:SHANTOU KAIJIA MOLD
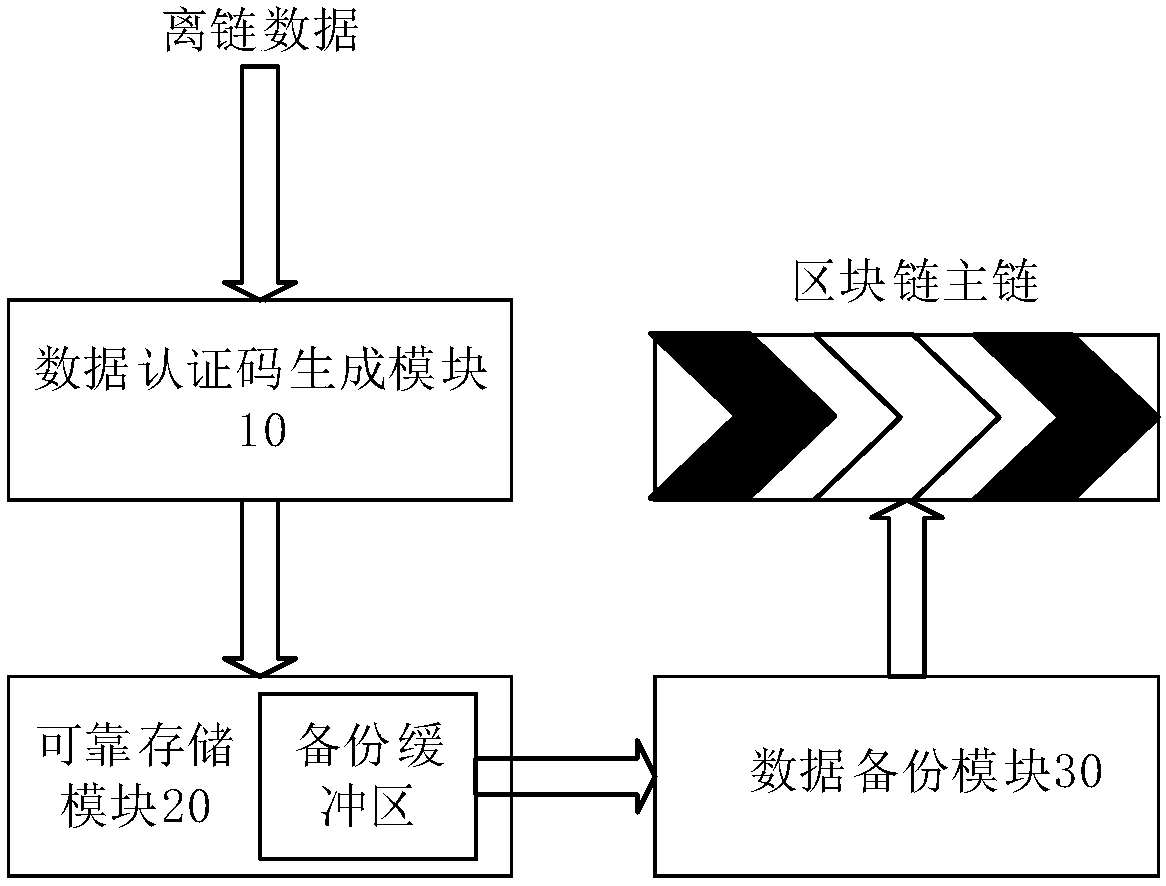
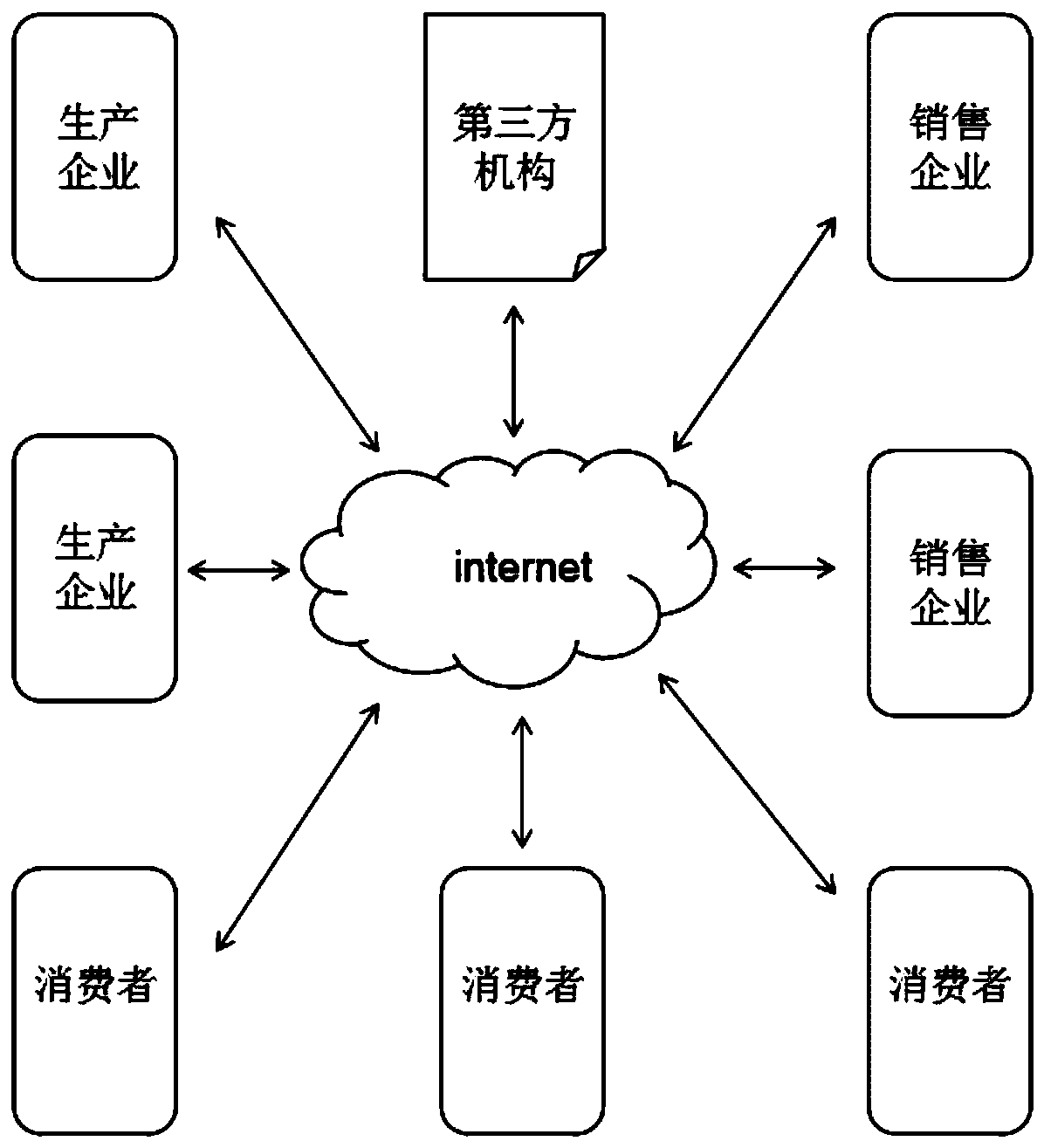
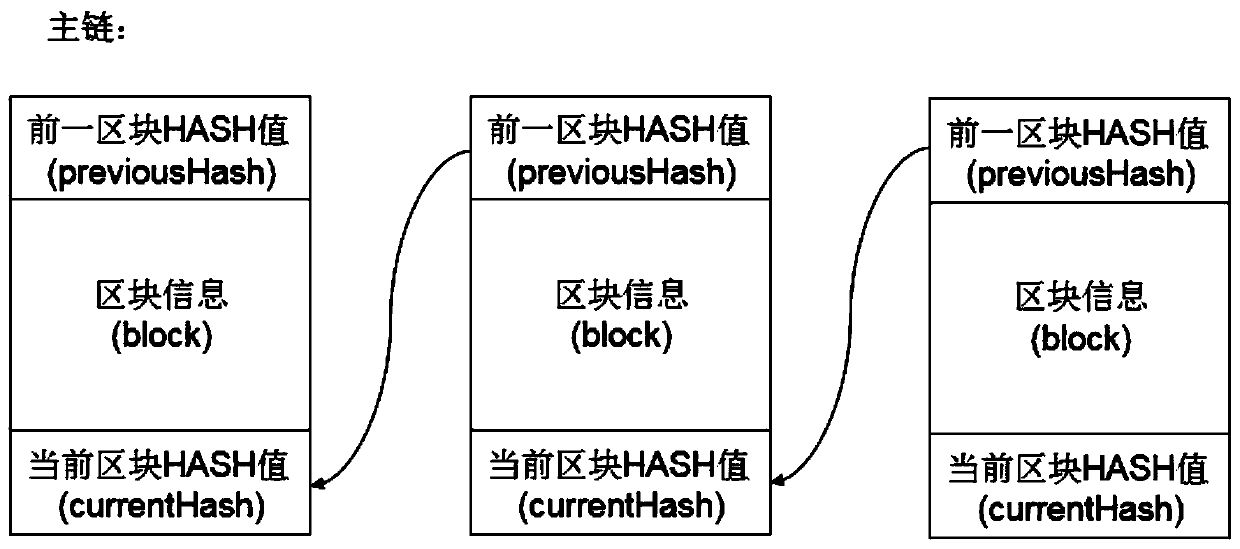
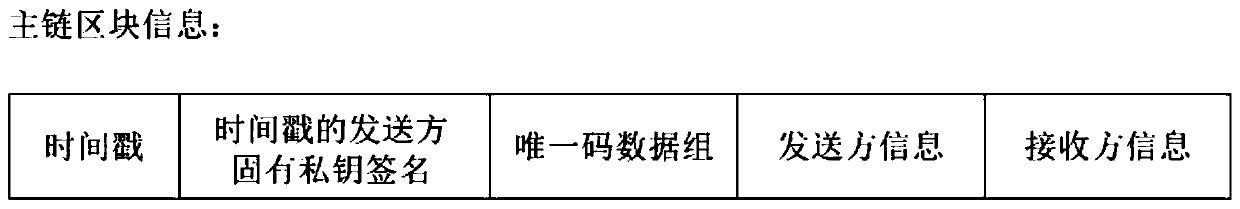
Food label unique code publishing and circulation traceability method based on block chain main and auxiliary chain technology
PendingCN110335051ASmall amount of calculationLighten the burden on hardwareCommerceBlockchainTimestamp
The invention discloses a food label unique code publishing and circulation traceability method based on a block chain main and auxiliary chain technology. The commodity label unique code informationblock chain technology based on public and private key pairing verification is adopted. Main chain and auxiliary chain information counterfeiting prevention, tampering prevention and replay preventionare achieved, food label unique code network propagation and independent chaining and rapid tracing of single piece of food information can be achieved, and a user comprises a third-party mechanism,manufacturers at all levels, a dealer and a consumer which are connected with the Internet. Server databases of the third-party mechanism, manufacturers and dealers at all levels store food label information block chain account books in server databases, new legal verification data issued by other parties is received in real time, local account books are updated in time, new data blocks are hookedaccording to food transfer conditions, and new block chain data are issued; and a consumer obtains the latest timestamp block chain from a plurality of enterprise servers during code scanning, and calculates and obtains the food traceability information chain by comparing the latest timestamp block chain.
Owner:烟台市同翔网络科技有限责任公司
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com