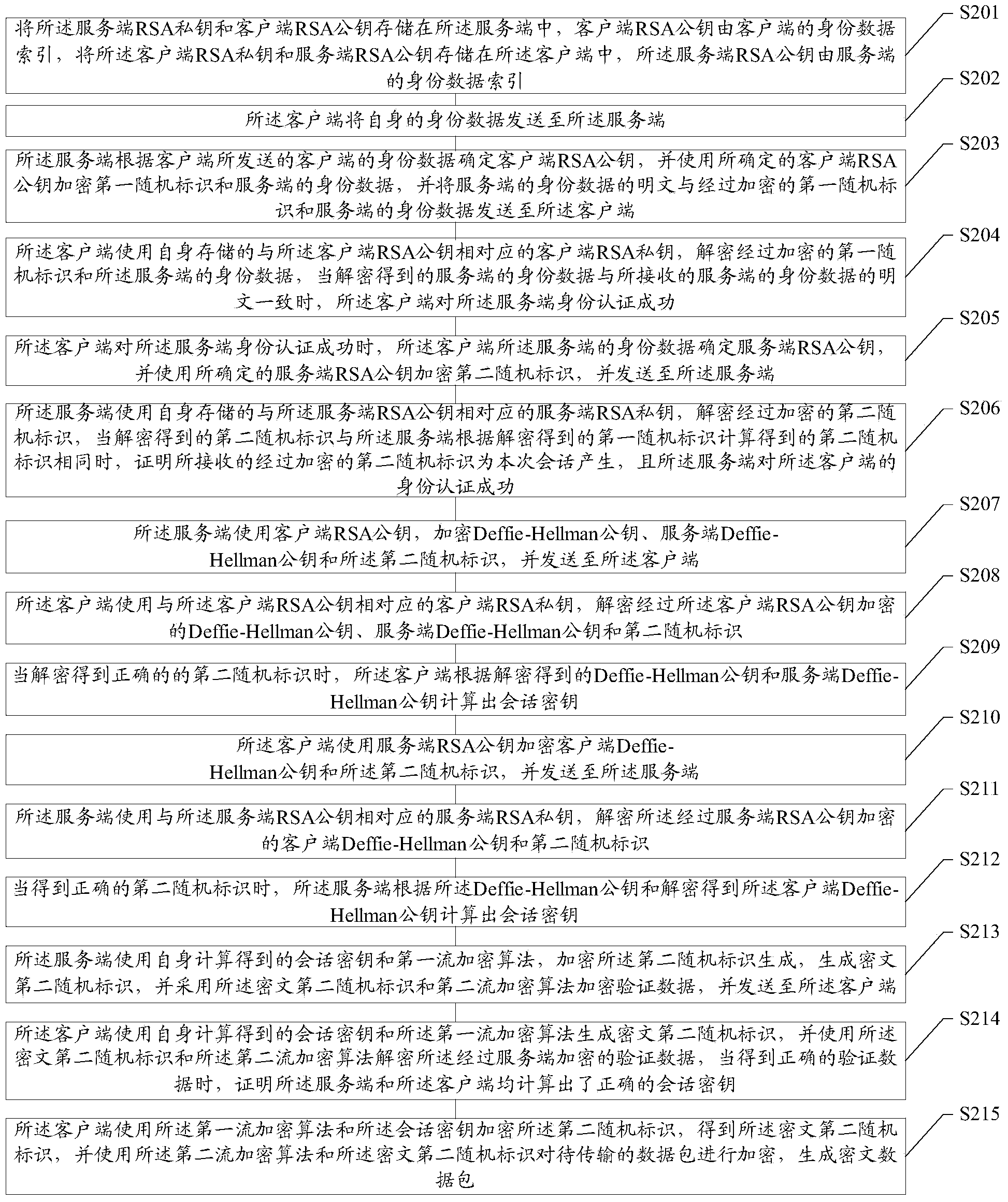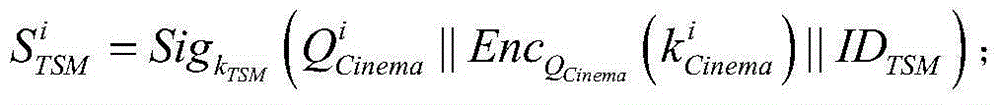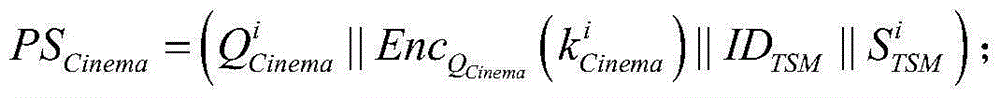Patents
Literature
433results about How to "Avoid interception" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
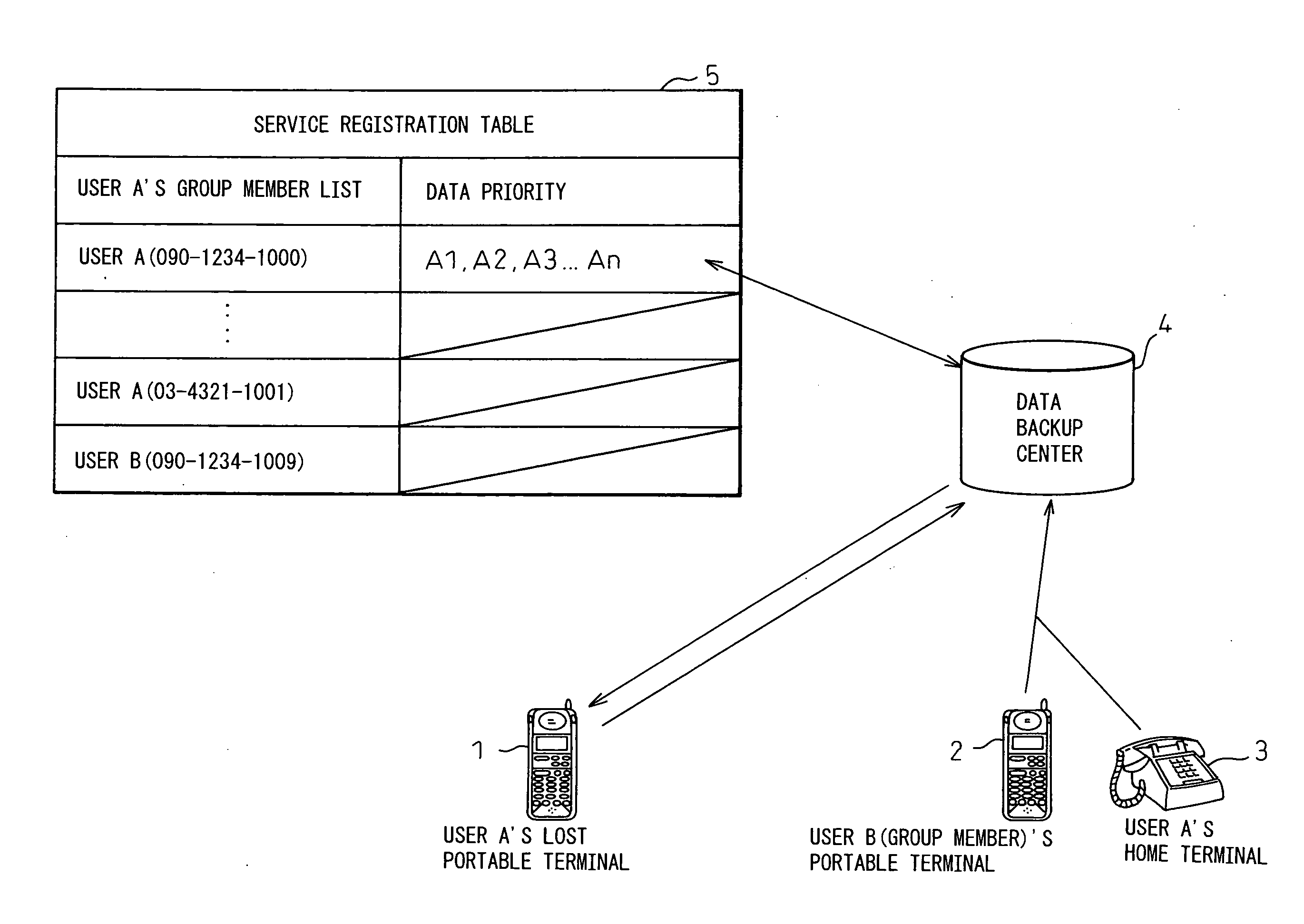
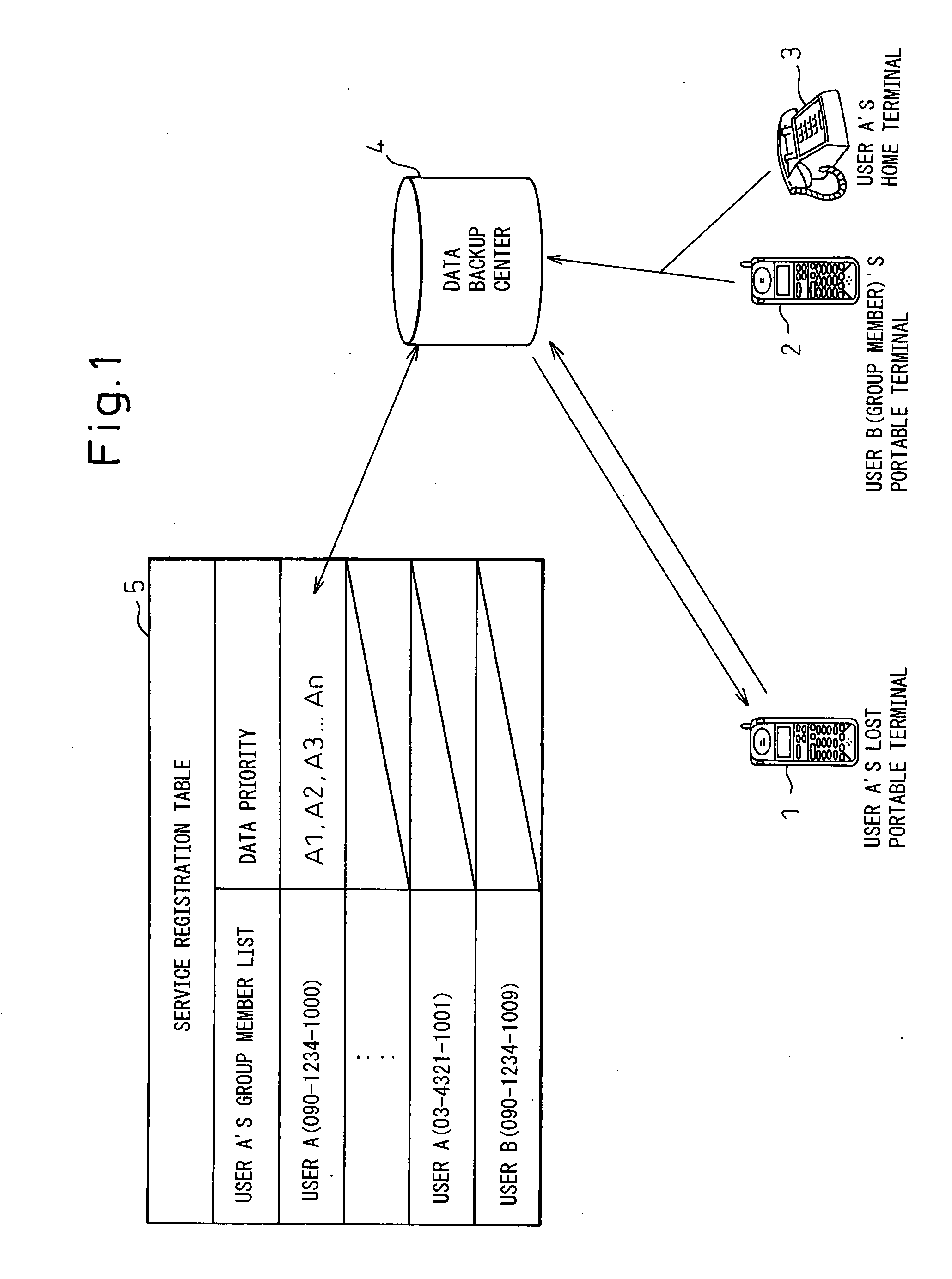
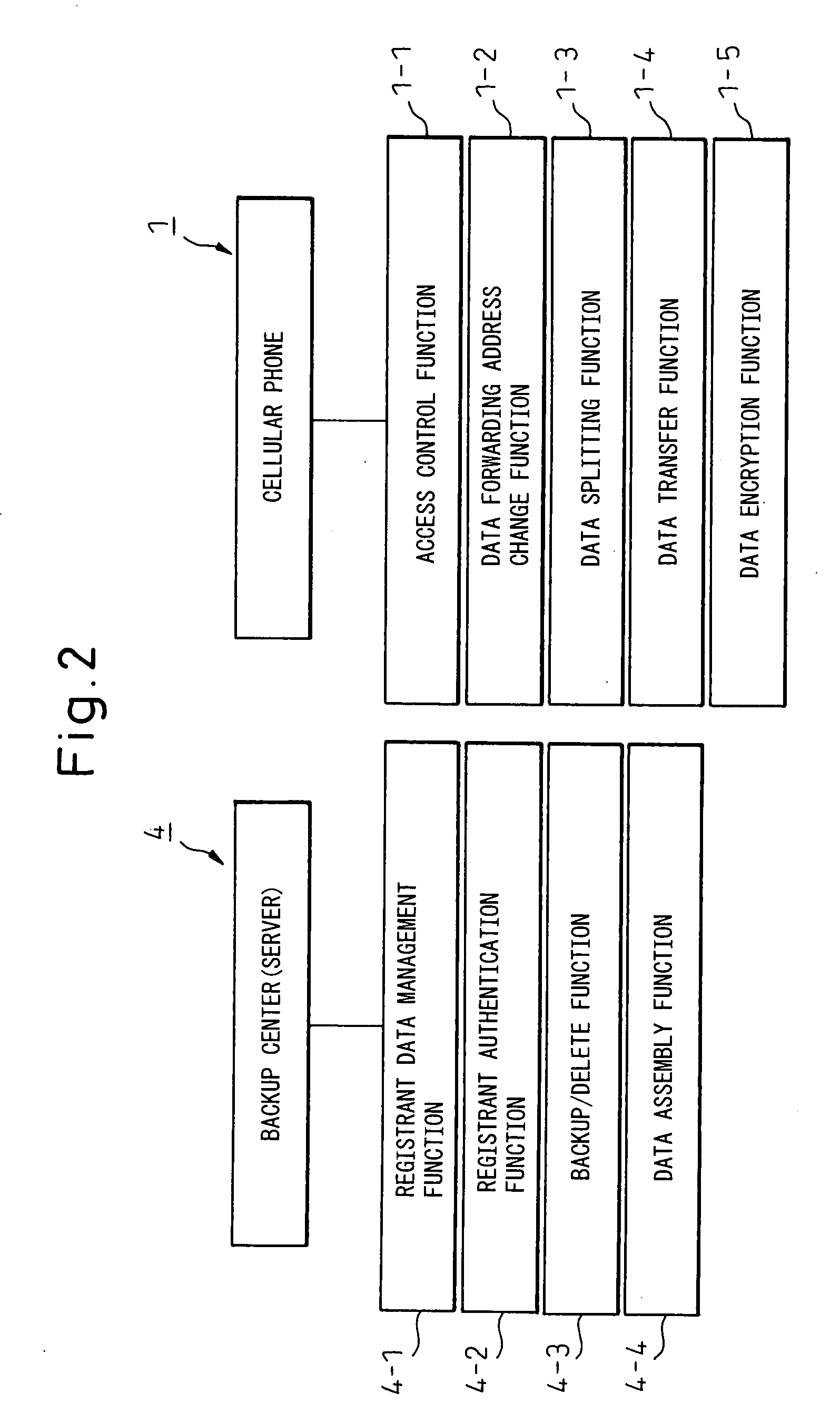
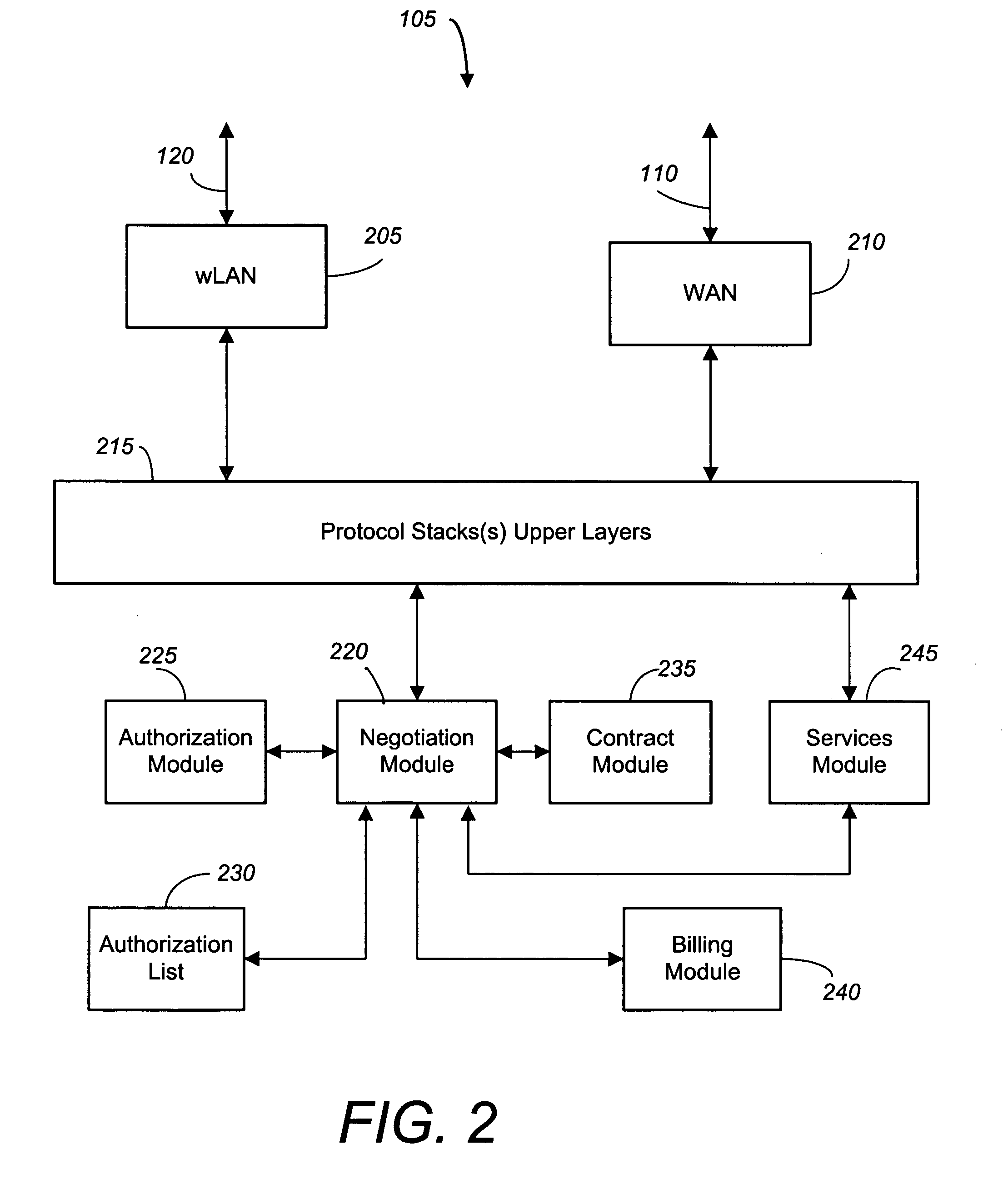
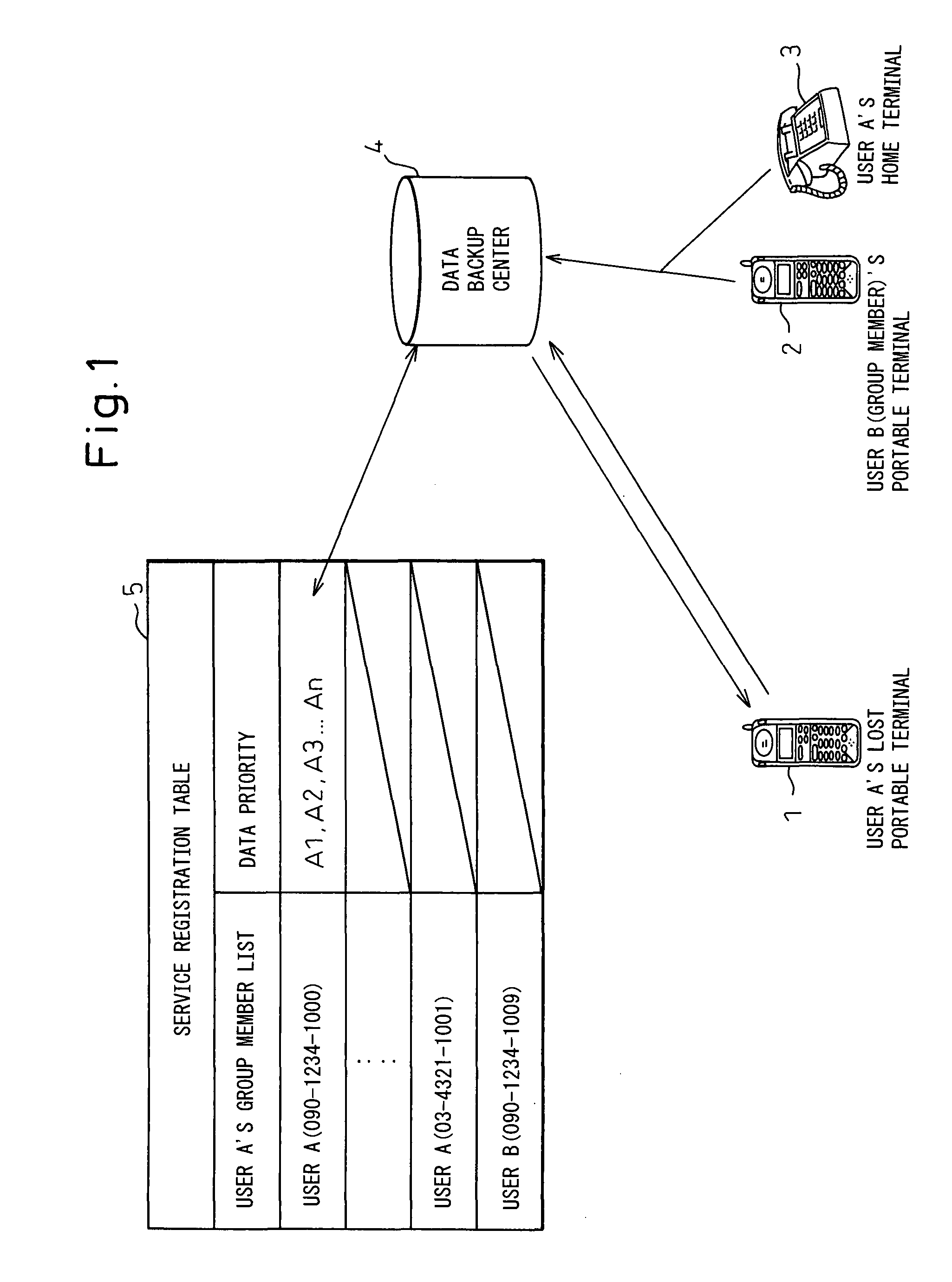
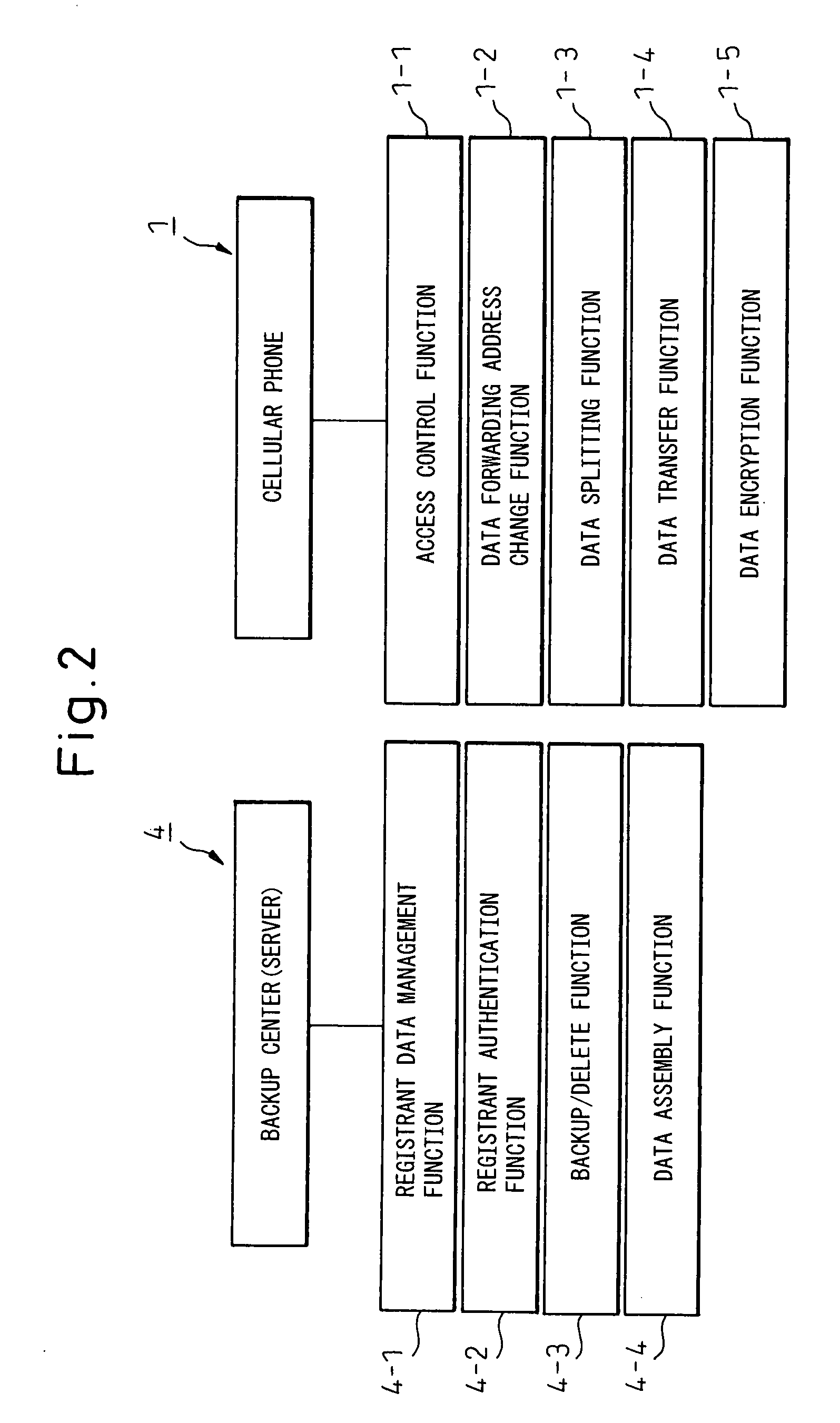
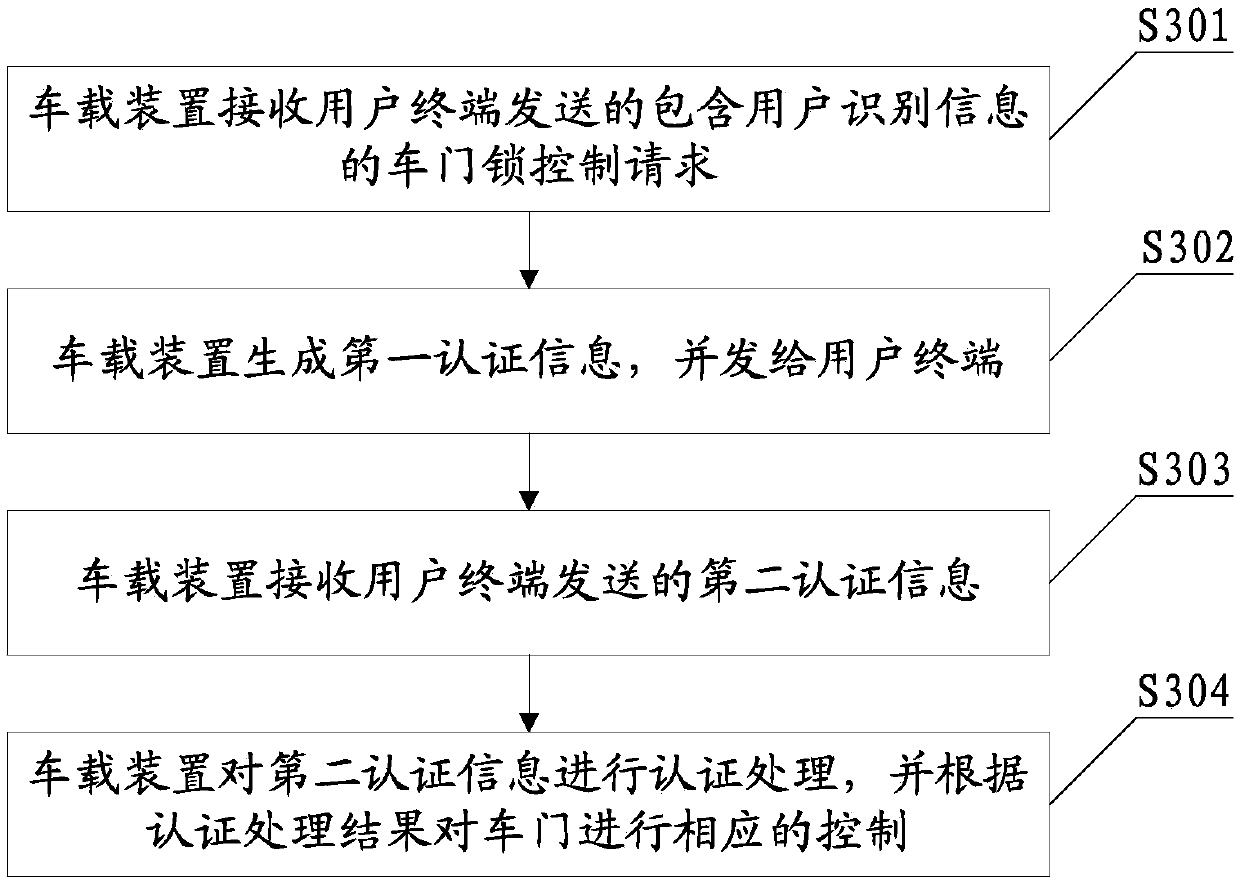
Portable wireless terminal and its security system
InactiveUS20070281664A1Avoid interceptionSafe removalUnauthorised/fraudulent call preventionEavesdropping prevention circuitsThird partyRemote control
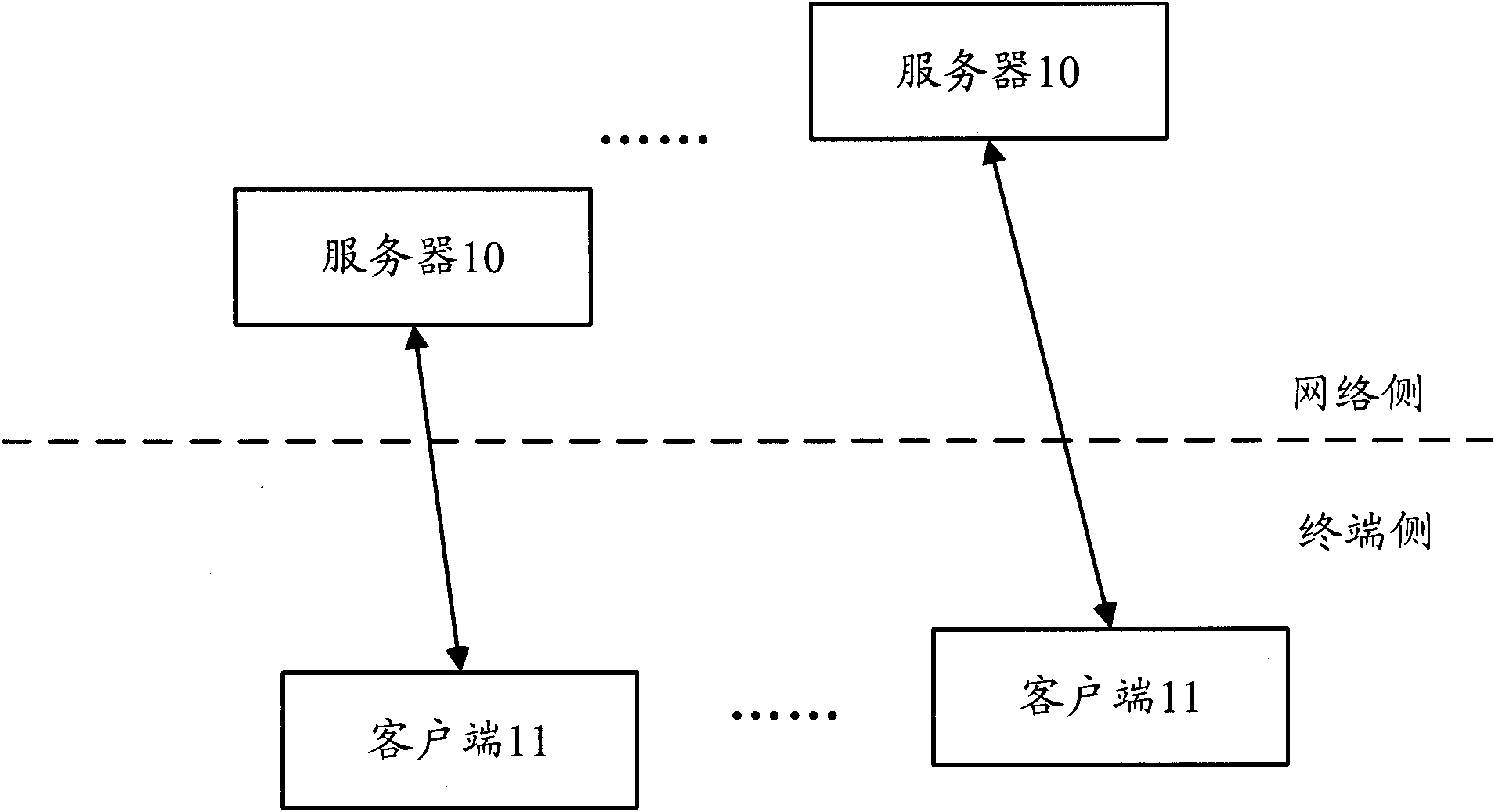
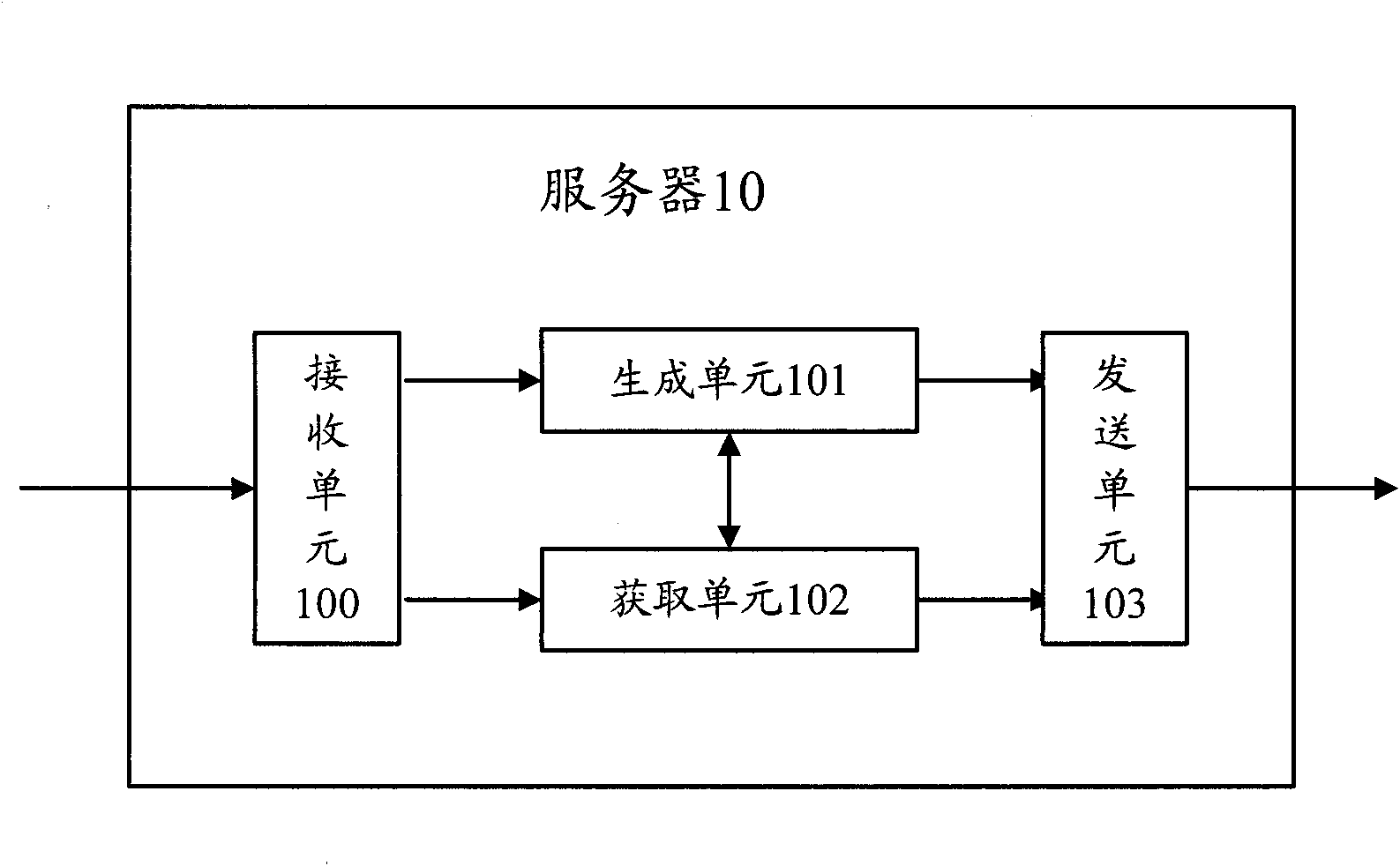
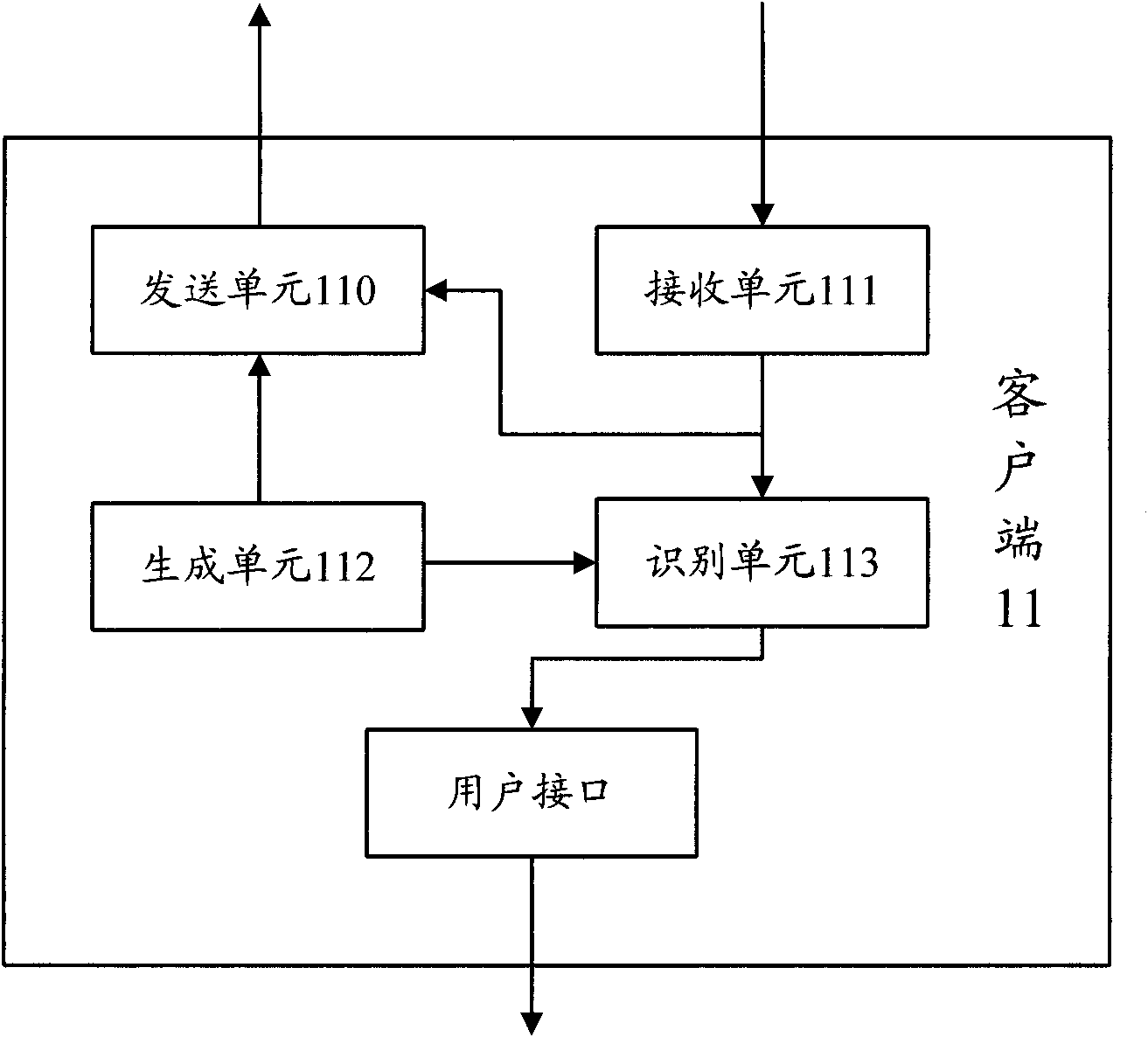
The present invention relates to a portable wireless terminal, and in particular, a portable wireless terminal such as a cellular phone, etc., and its security system that can reliably prevent, by remote control, improper use of the portable wireless terminal by a third party when it is lost or stolen. The portable wireless terminal that uploads backup data to a center by remote control from the center via a wireless network includes: a data access control section 1-1 that, in response to an instructions from the center, prohibits access to the backup data retained by a portable wireless terminal or deletes the backup data; an encryption section 1-5 that encrypts the backup data by using a public key notified from the center or a public key owned by the portable wireless terminal itself in response to instructions from the center; and a data transmission section 1-2 to 1-4 that transmits the backup data split into a plurality of data fragments on a plurality of communication paths to the center according to transmission priority of the backup data that is notified from the center or owned by the portable wireless terminal itself.
Owner:FUJITSU LTD
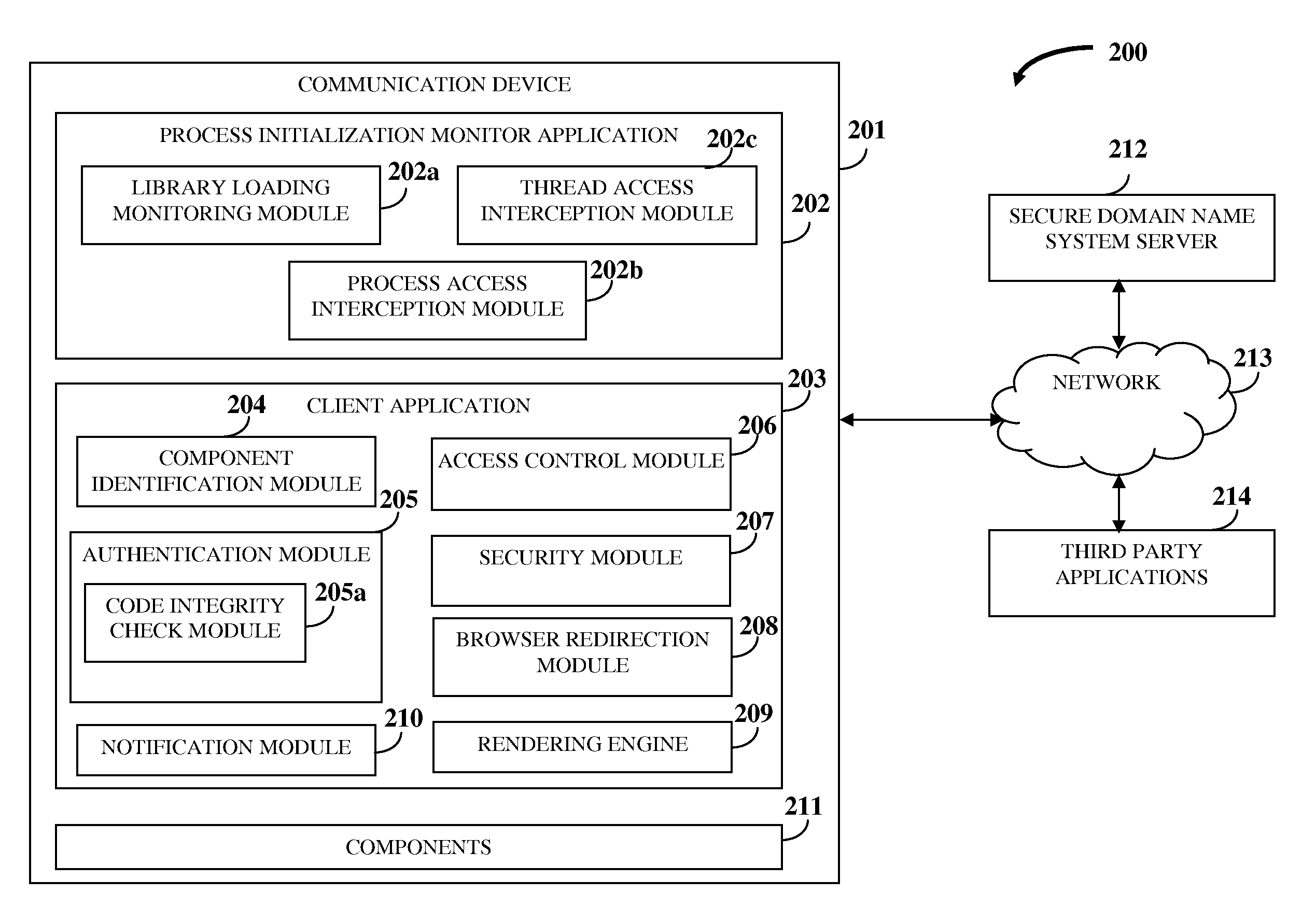
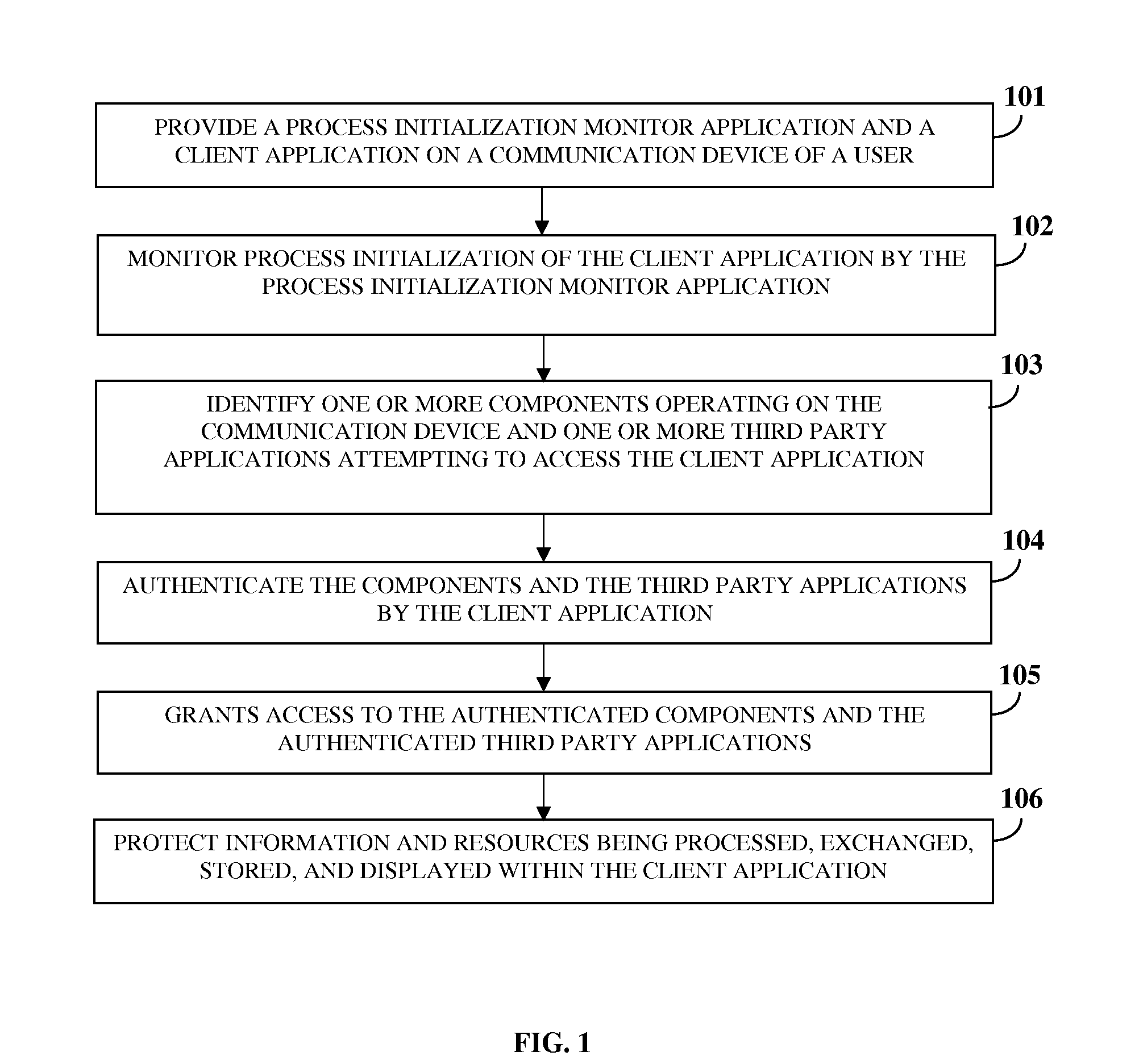
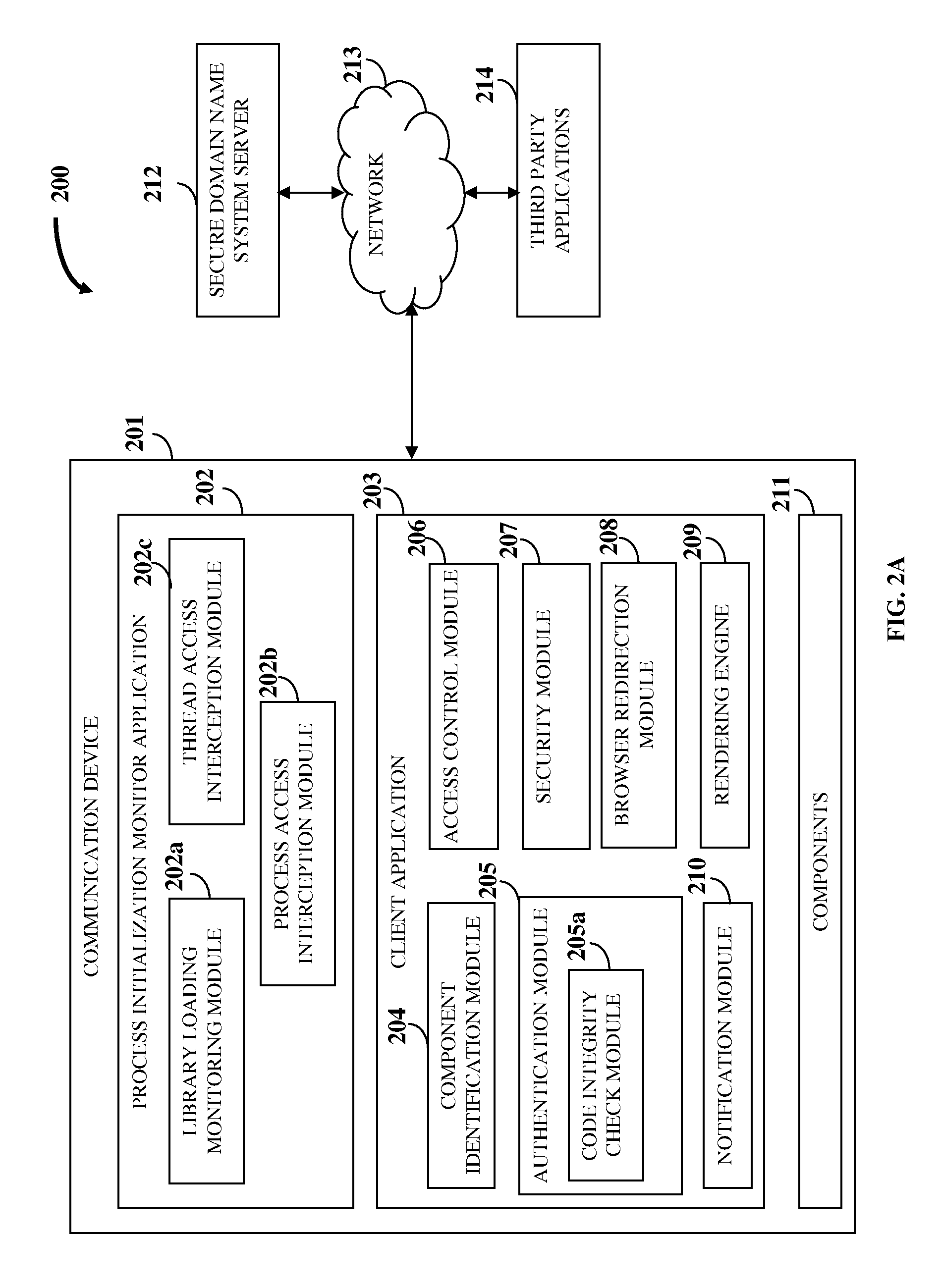
Online Protection Of Information And Resources
InactiveUS20110321139A1Avoid interceptionAvoid manipulationDigital data processing detailsMultiple digital computer combinationsThird partyApplication software
A computer implemented method and system for protecting information and resources in an online environment is provided. A process initialization monitor application monitors process initialization of a client application provided on a user's communication device. The client application identifies and authenticates one or more components operating on the communication device and one or more third party applications attempting to access the client application. The client application performs the authentication by performing a code integrity check integrated in the client application independent of the communication device, and grants access to the authenticated components and the authenticated third party applications. The client application protects information being processed, exchanged, stored, and displayed within the client application. The client application masks input information, encrypts a communication channel that transfers the input information, blocks attempts to monitor, intercept and manipulate information by unauthorized entities, and prevents access of certificates, resources, etc., by unauthorized entities.
Owner:K7 COMPUTING PRIVATE
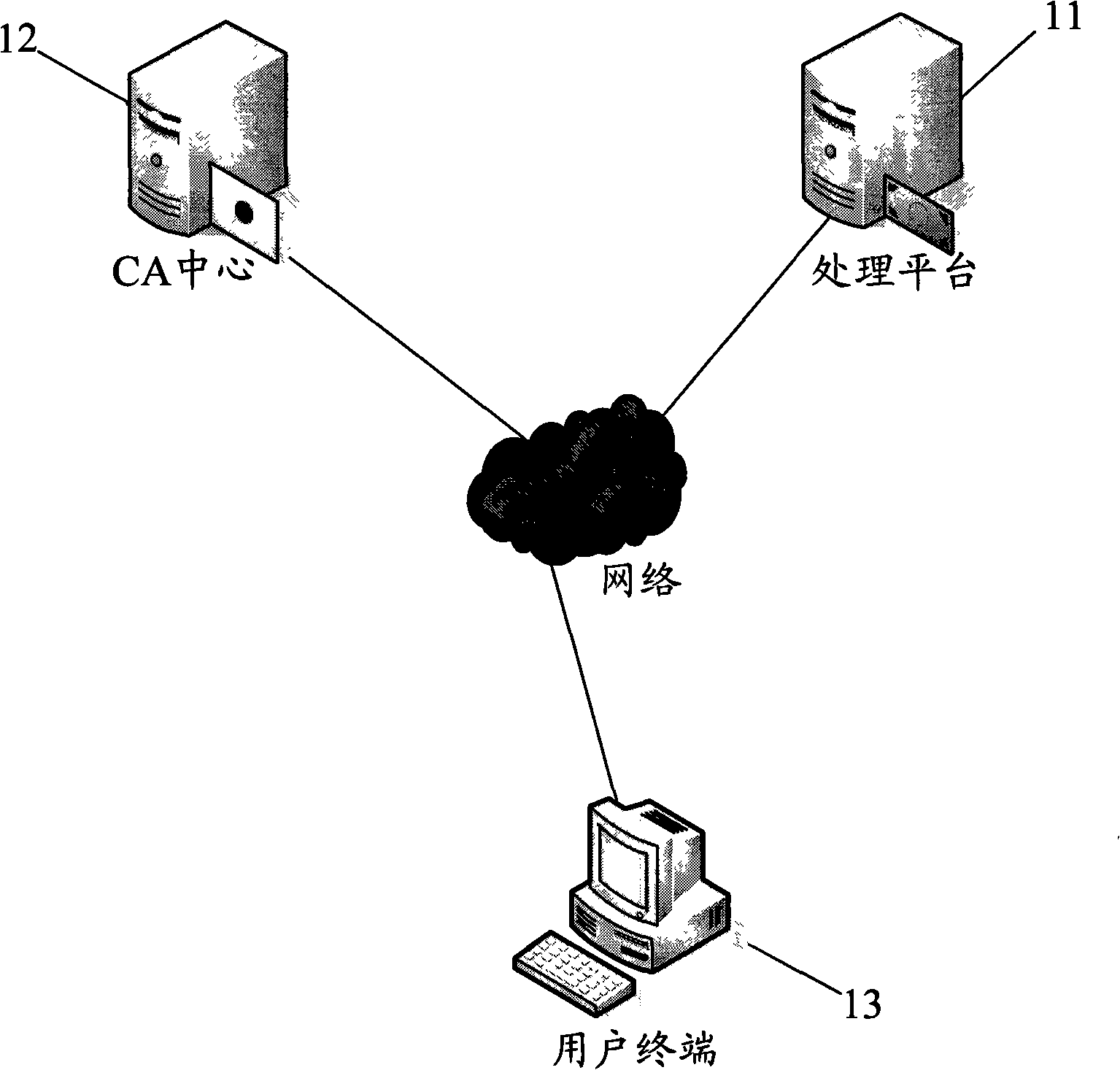
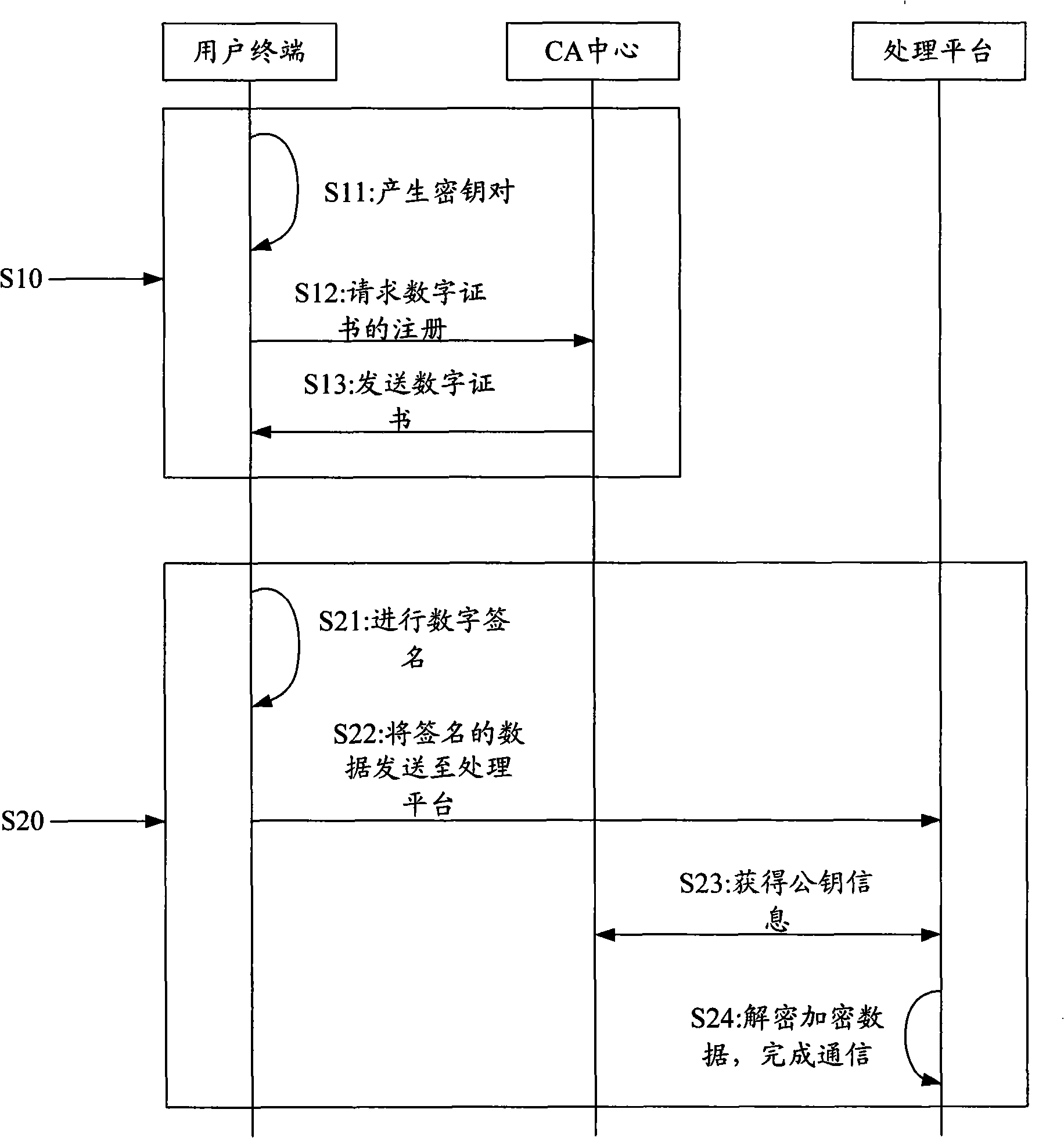
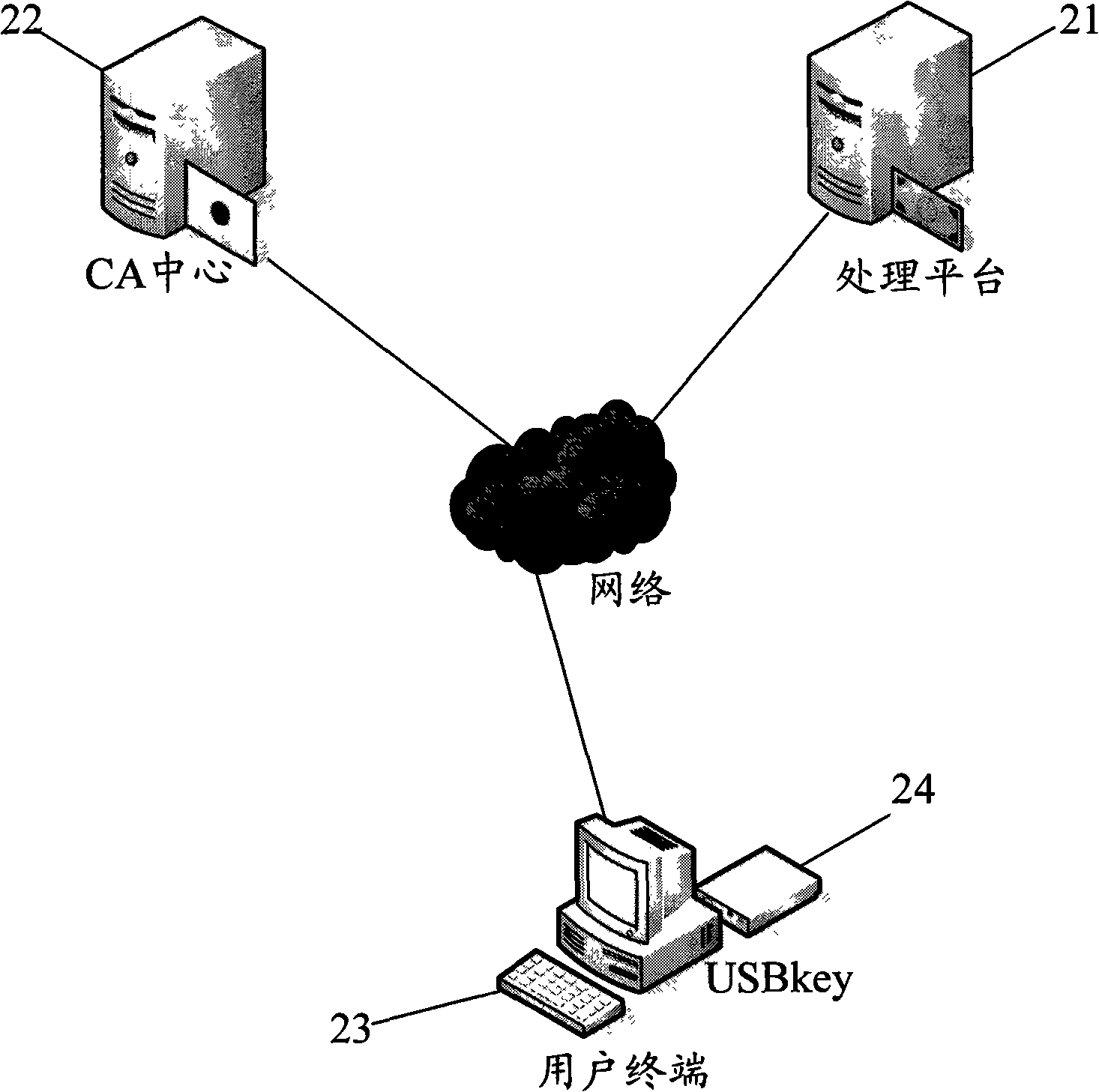
Method and system for identity authentication by finger print USBkey
InactiveCN101340285AEnsure safetyGuaranteed accuracyUser identity/authority verificationCommerceRelevant informationDigital signature
The invention discloses an identity authentication method by a fingerprint USBkey and includes the following steps: (1) the fingerprint information of users is recorded into the fingerprint USBkey and the information is saved in advance; (2) at least a digital certificate generated, which comprises the following steps: firstly, a pair of private and public keys are generated in the fingerprint USBkey; the relevant information of the public keys and the digital certificate is sent to a CA center and generating the digital certificate by the CA center; (3) each digital certificate and corresponding private keys stored and encrypted on the fingerprint USBkey; (4) when a user terminal communicates with a processing platform, the fingerprint USBkey at the user terminal firstly checks the fingerprints, digital signature is carried out on the data to be sent by the corresponding private keys and the data is transmitted to the processing platform for identity authentication. The method permits the digital signature after the fingerprints authentication succeeds; the loophole of PIN code input and transmission does not exist in the whole interactive process, which improves the transaction security to the utmost extent.
Owner:ZHEJIANG MIAXIS TECH CO LTD
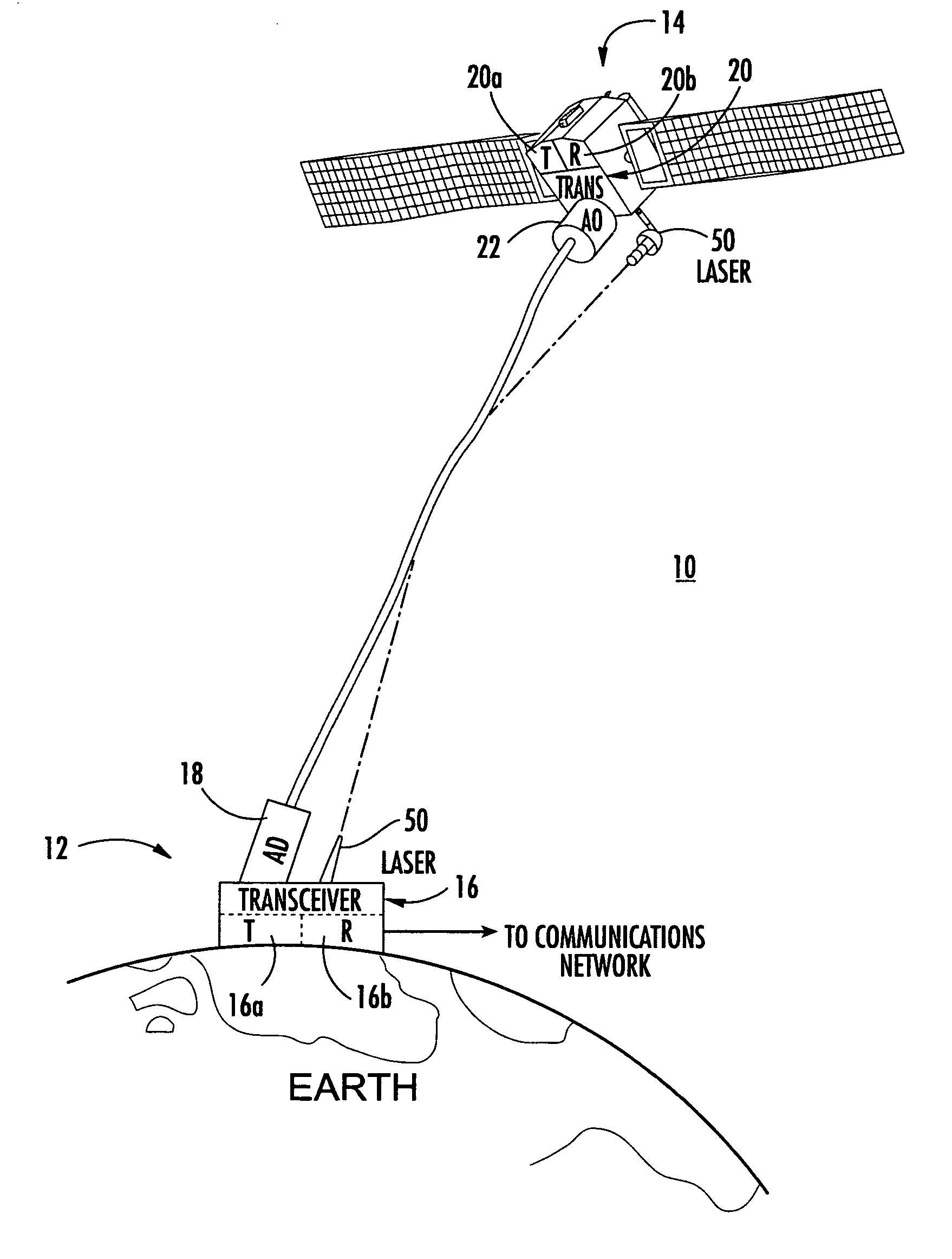
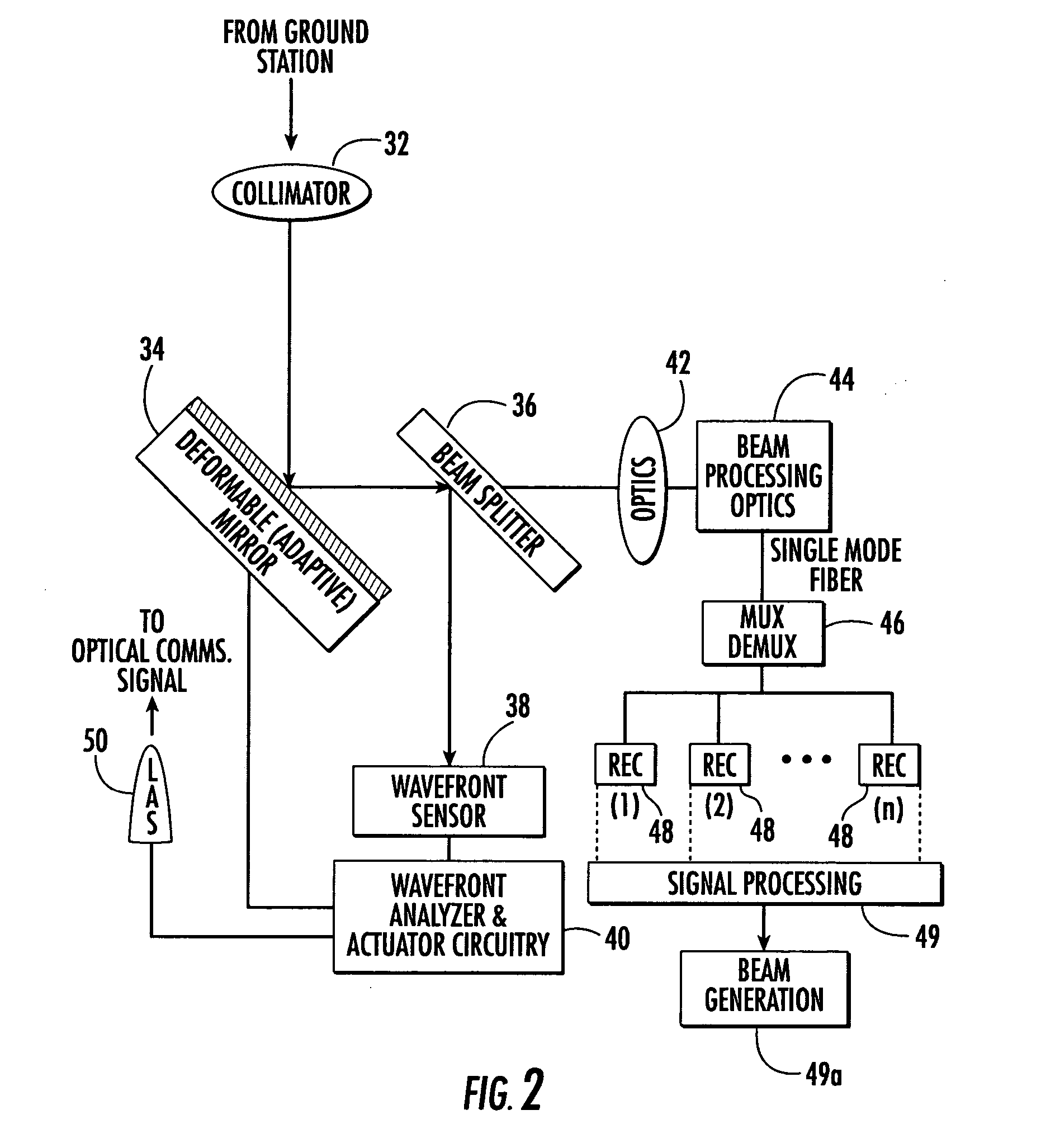
System and method of free-space optical satellite communications
InactiveUS20050100339A1Reduce and eliminate distortionIncrease volumeSatellite communication transmissionWavefrontTransceiver
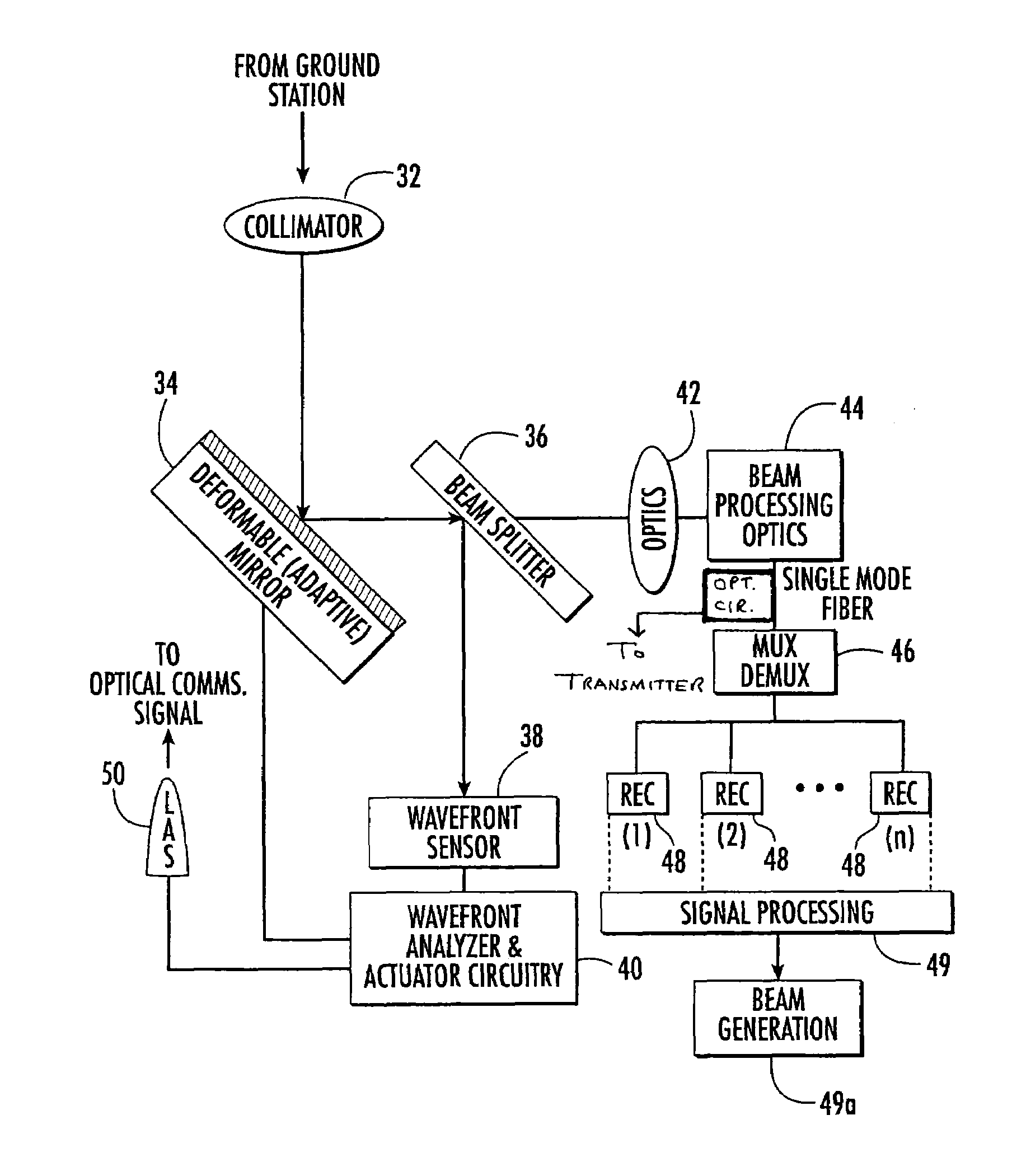
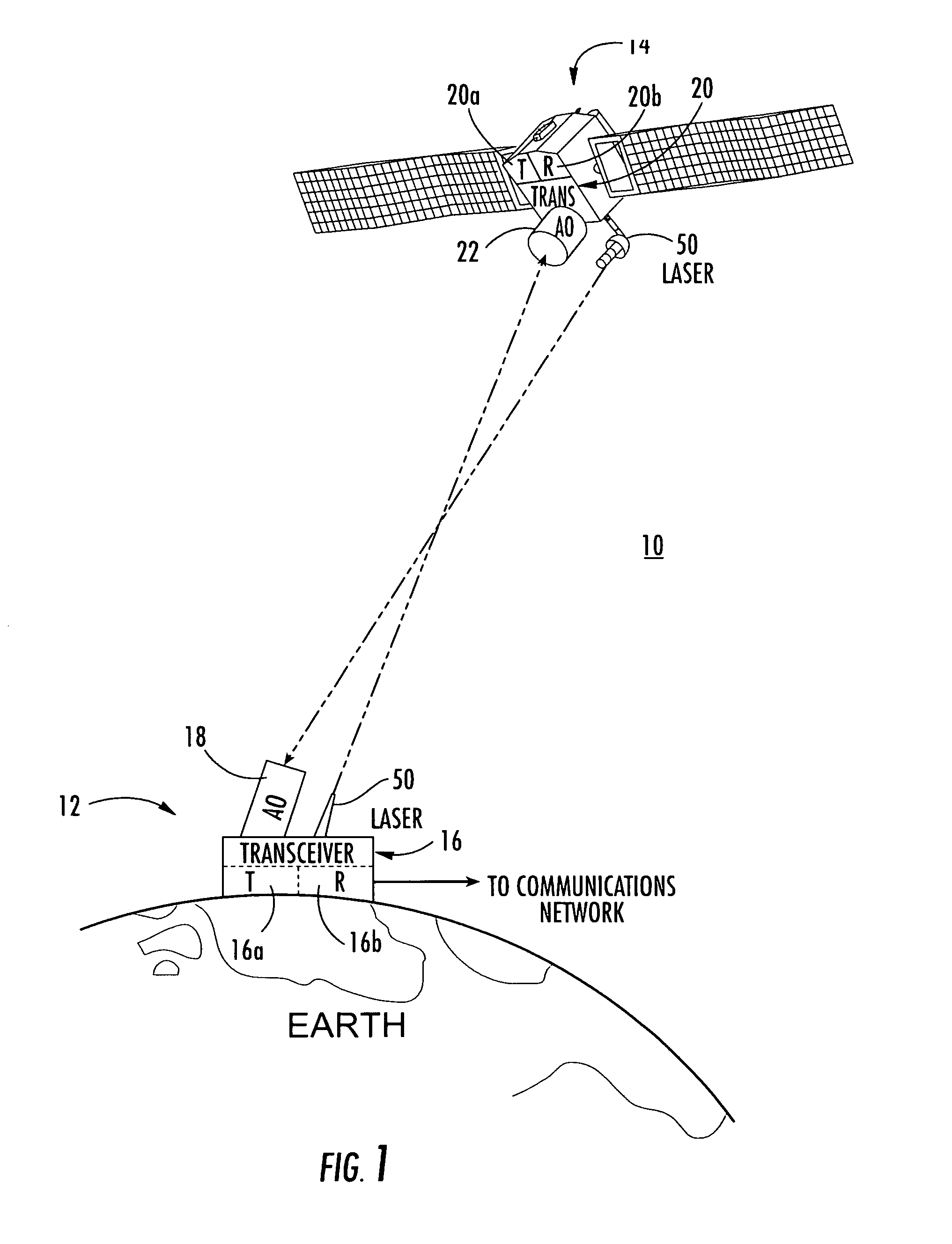
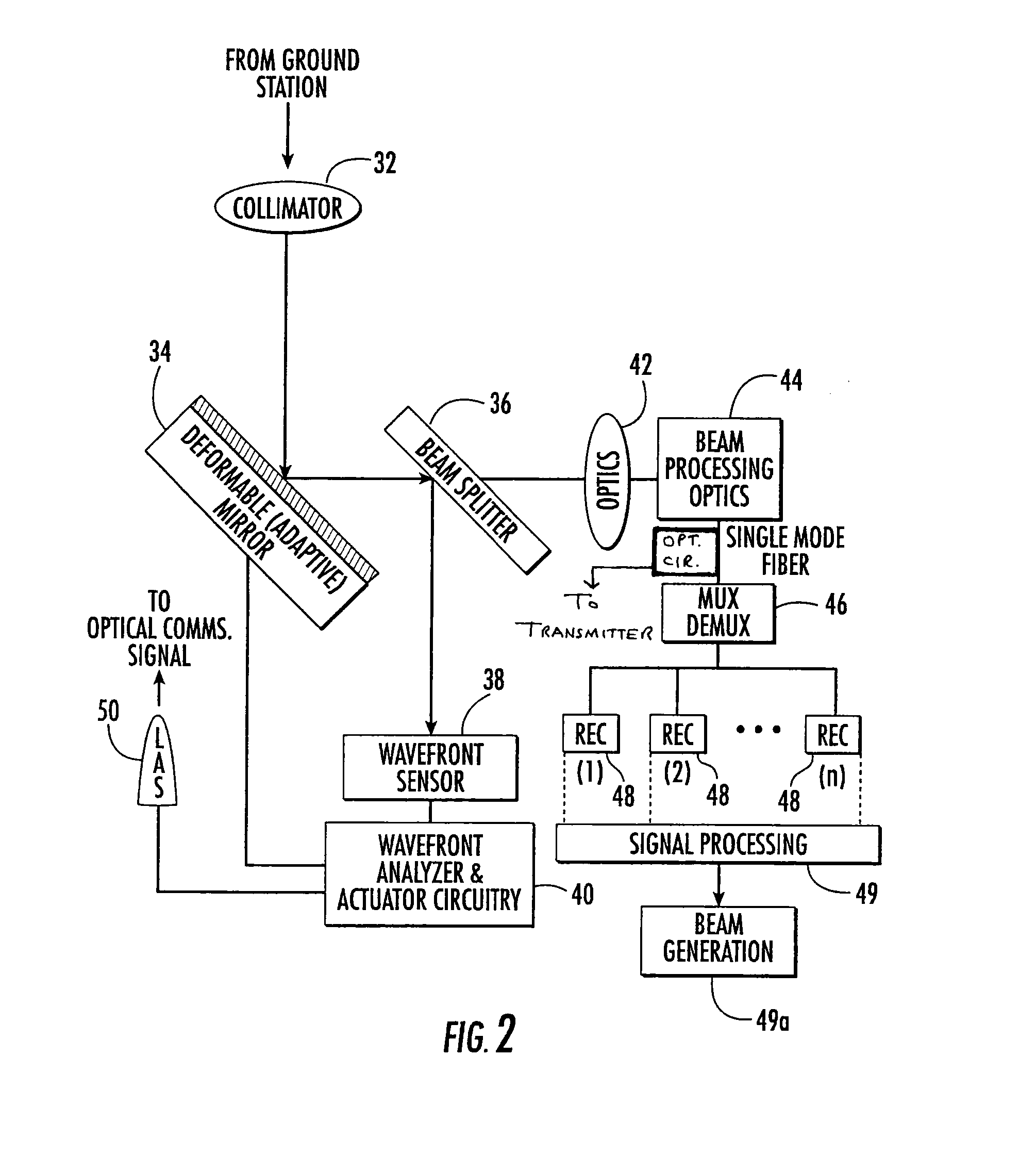
A system and method of free-space optical satellite communications includes a ground station and transceiver for transmitting and receiving an optical communications signal. Adaptive optics at the ground station are operative with the transceiver for determining the shape of any distortions in the wavefront of the optical communications signal and compensating at the ground station for the distortions. A satellite includes a transceiver for transmitting and receiving the optical communications signal and includes adaptive optics for determining the shape of any distortions in the waveform of the optical communications signal and compensating at the satellite for the distortions.
Owner:HARRIS CORP
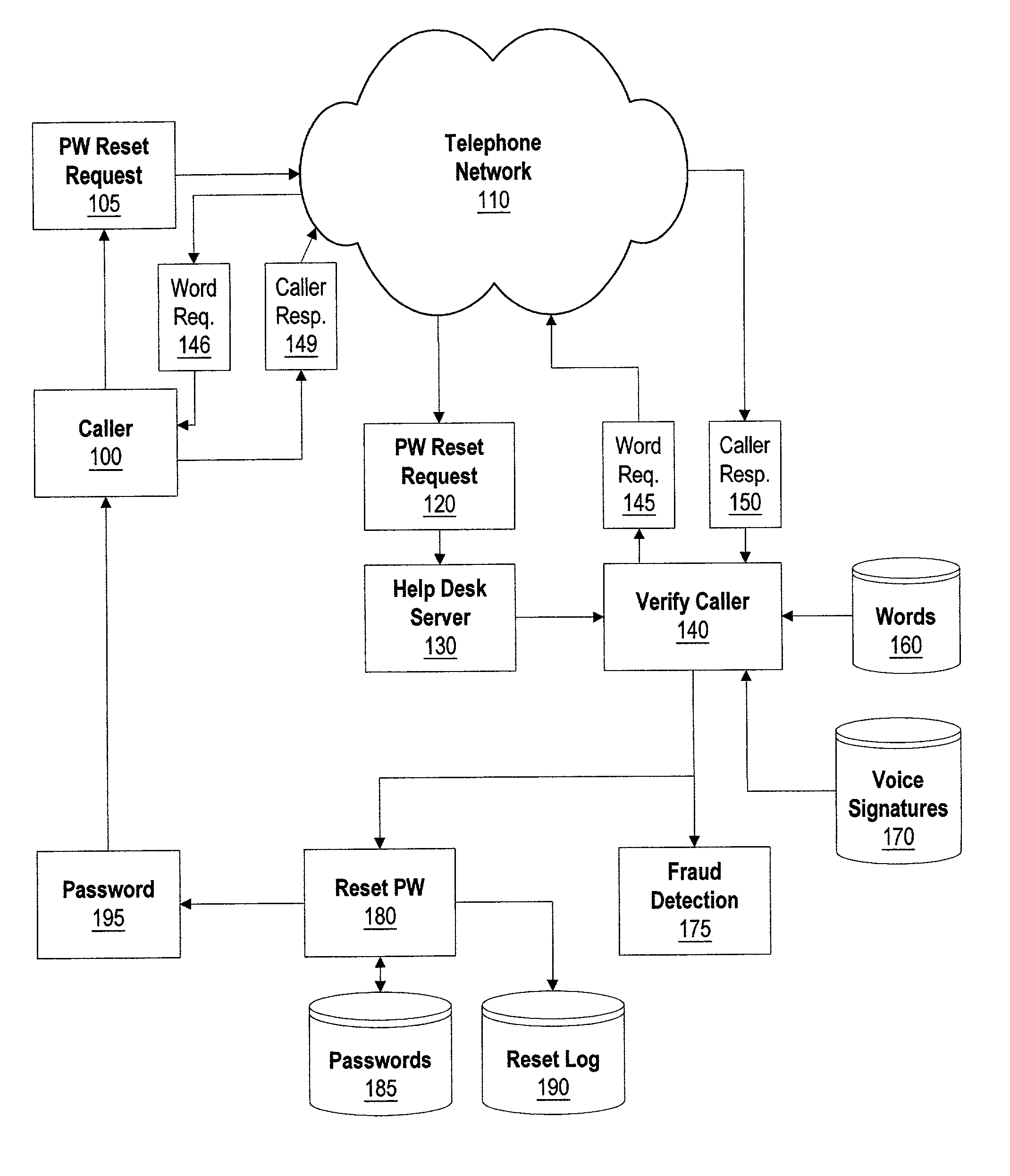
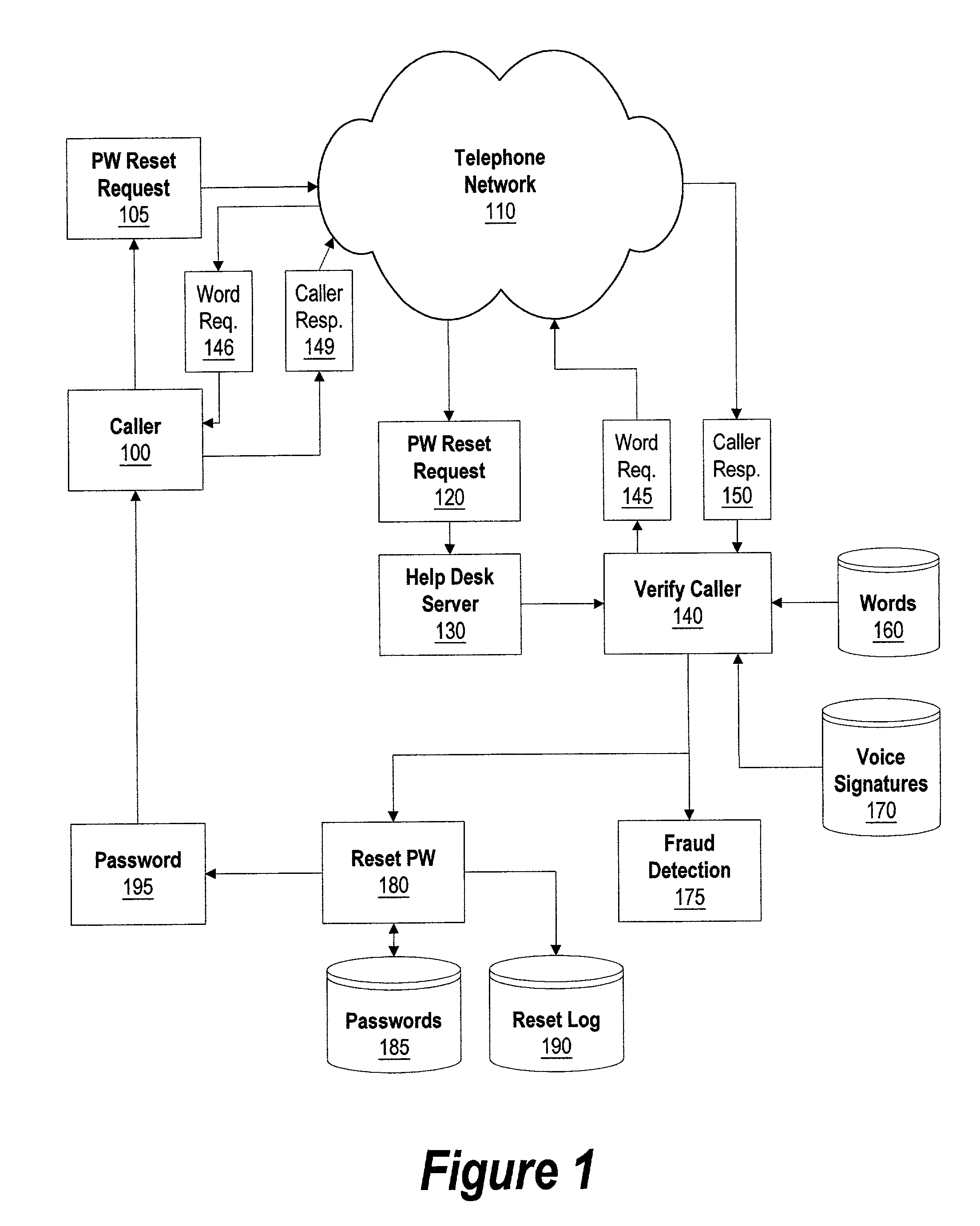
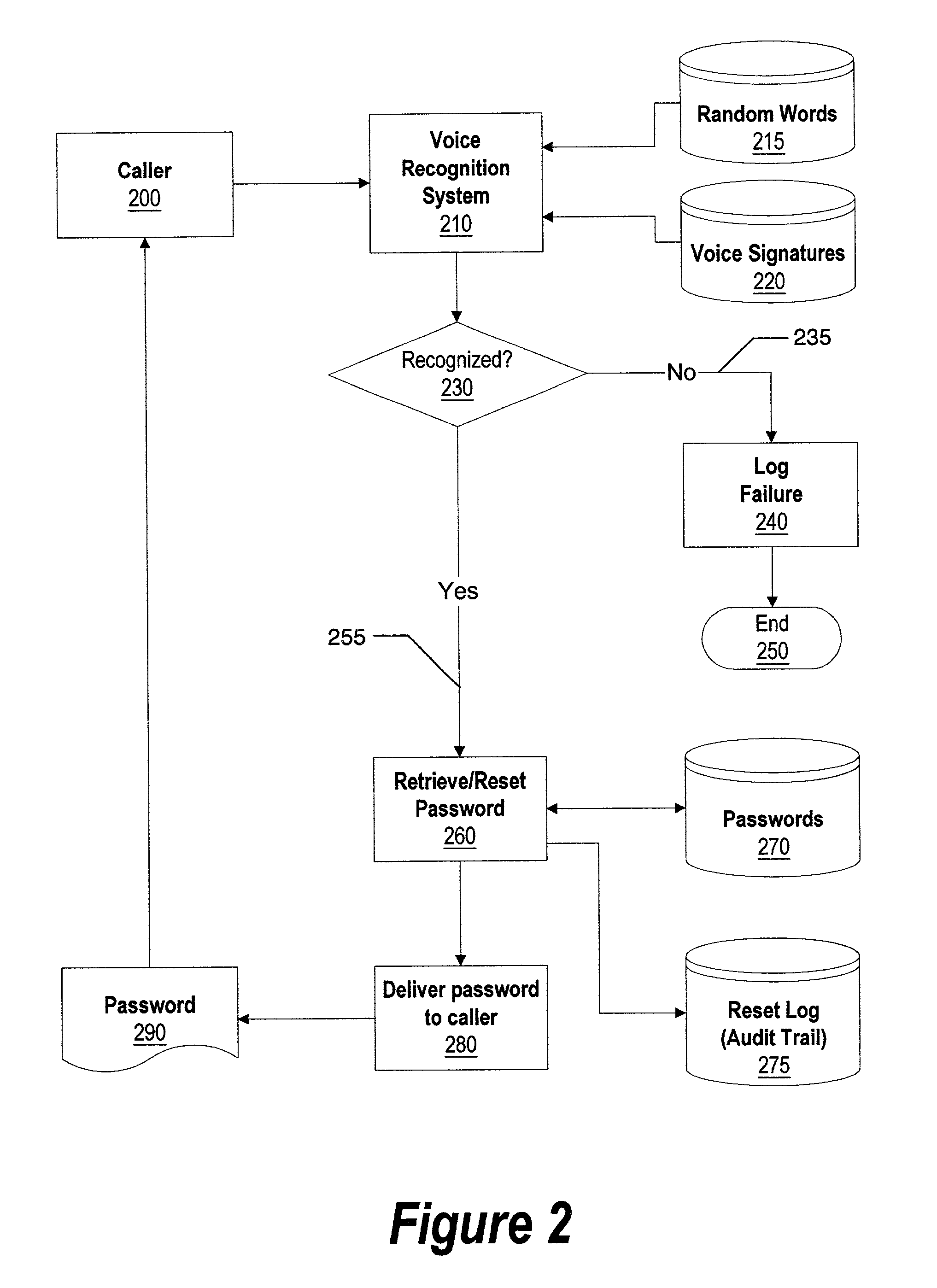
System and method for voice recognition password reset
InactiveUS6973575B2Improve securityReduce chanceDigital data processing detailsUser identity/authority verificationPasswordComputerized system
A system and method for providing a password to a user using voice recognition technology. The user's voice signature is captured and stored in order to identify the user. When the user forgets or otherwise loses a password needed to log into a computer system, he telephones a password reset system. An identifier corresponding to the user is provided by the user by using the telephone keypad or voice commands. One or more random words are requested by the password reset system. The user responds by repeating the words into the telephone receiver. The received words are matched against the user's stored voice signature to authenticate the user. If the user is authenticated, one or more desired passwords are provided to the user using a number of delivery mechanisms. If the user is not authenticated, the intrusion is logged to further maintain system security.
Owner:NUANCE COMM INC
Data communicating apparatus, data communicating method, and program
InactiveUS20050187966A1Avoid interceptionUser identity/authority verificationUnauthorized memory use protectionPublic key certificateEncryption
A data communicating method is disclosed for use with a user terminal, the method preventing both members of a given group including the terminal and nonmembers from intercepting, tampering with or falsifying data communicated between the members without recourse to a plurality of encryption keys. In a first step, validity verification data is generated by the terminal. In a second step, the validity verification data and an attestation identity public key certificate are sent from the terminal to a group management device. In a third step, the group management device determines whether the terminal is valid. If the terminal is found valid, then a group name, a member ID and a group-shared key are supplied to the terminal in a fourth step, and a member ID list is further supplied in a fifth step. Thereafter the terminal is allowed to communicate with other members of the same group. The disclosed method can be applied advantageously to video game machines for network-based games.
Owner:SONY CORP
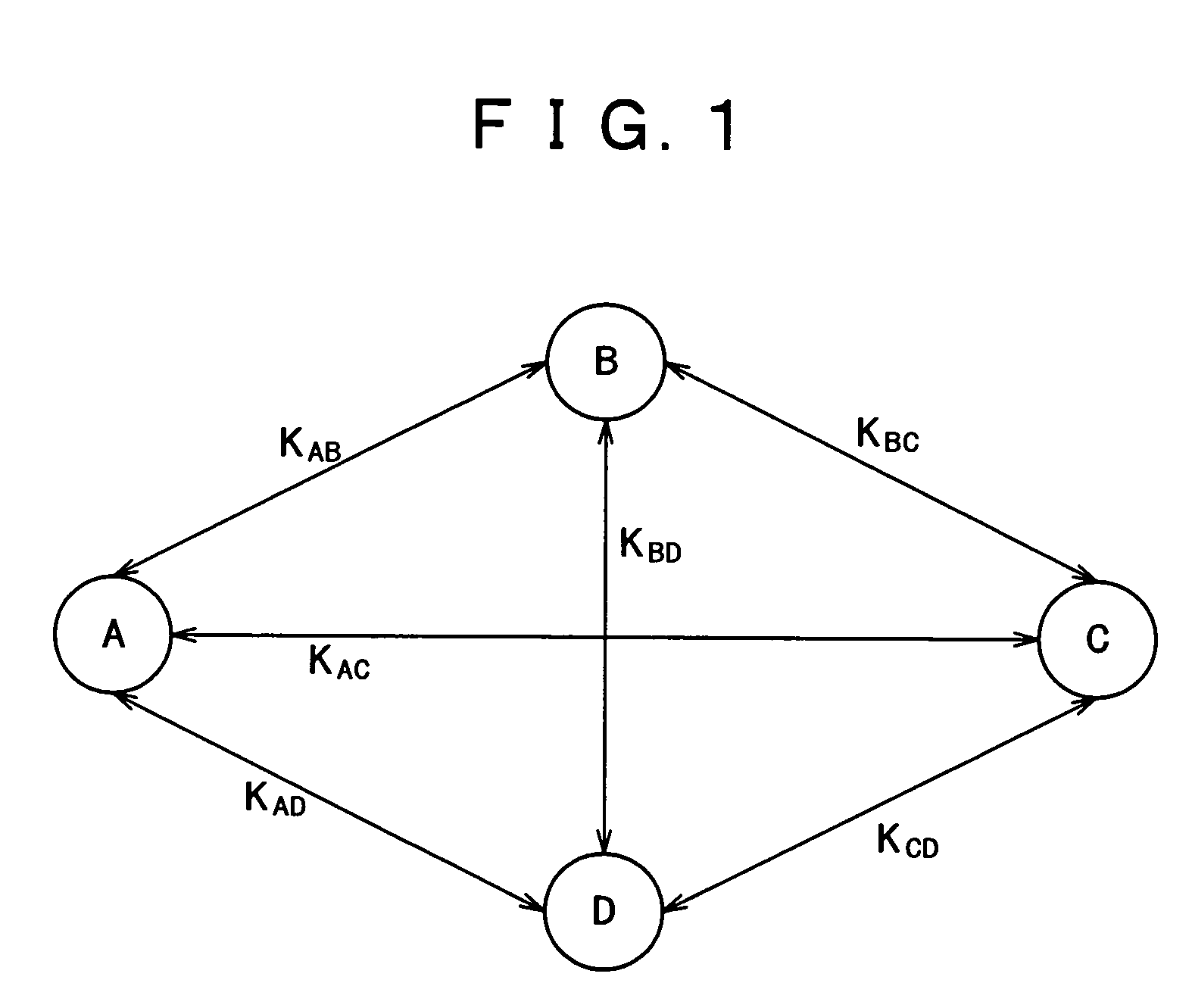
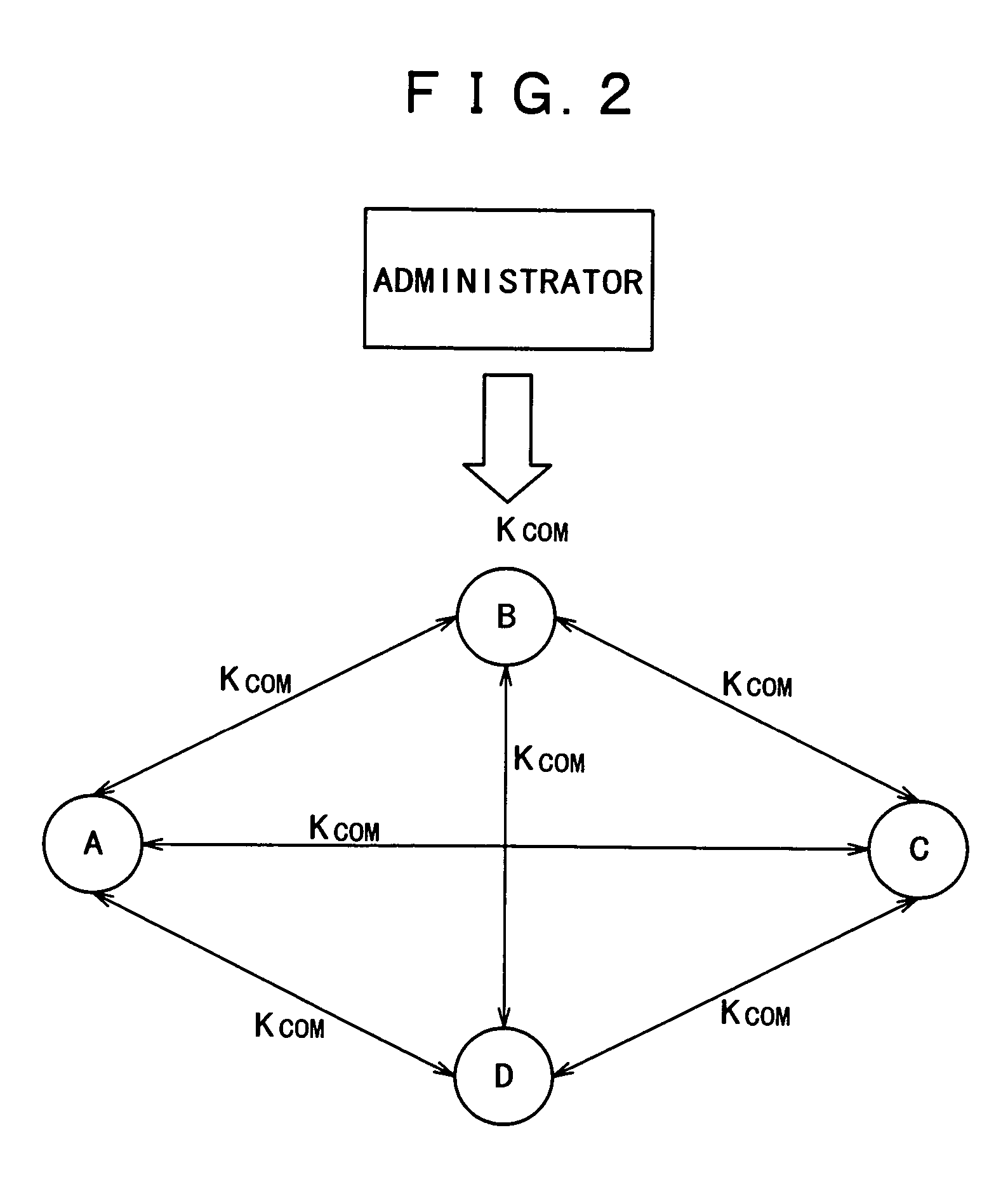
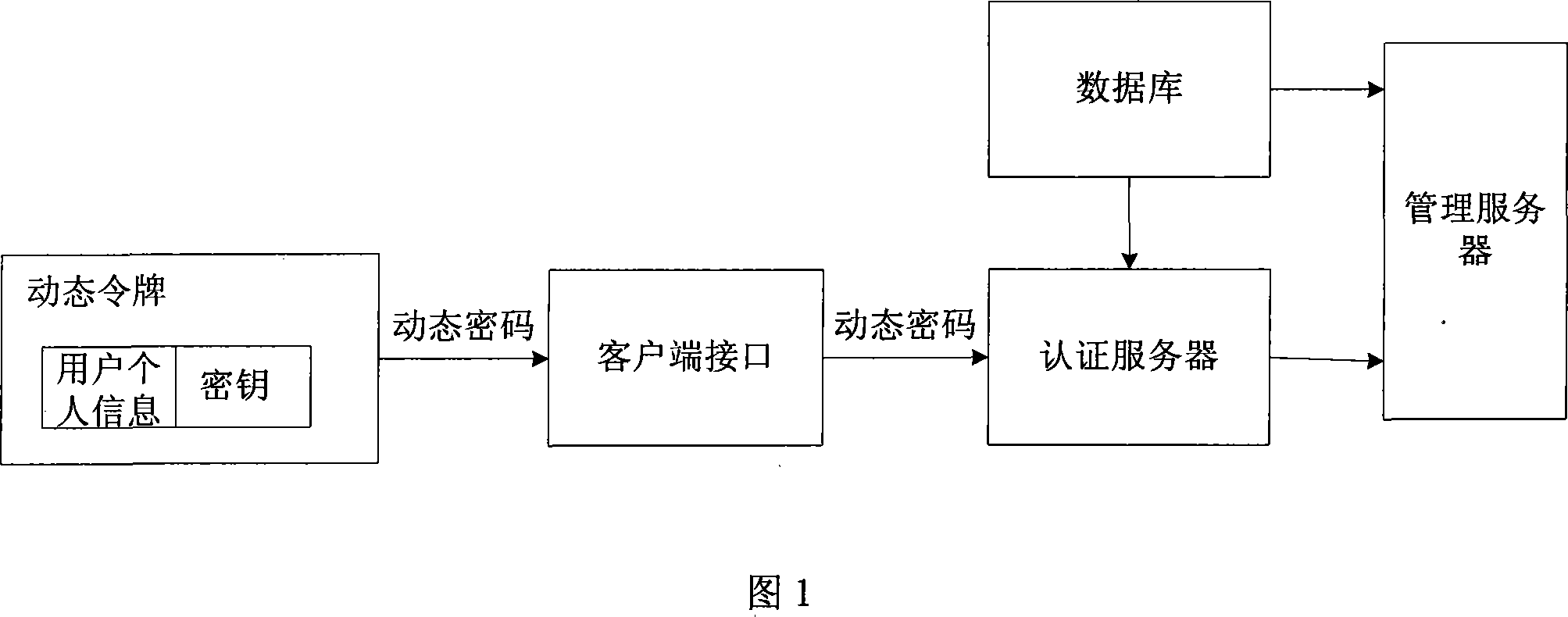
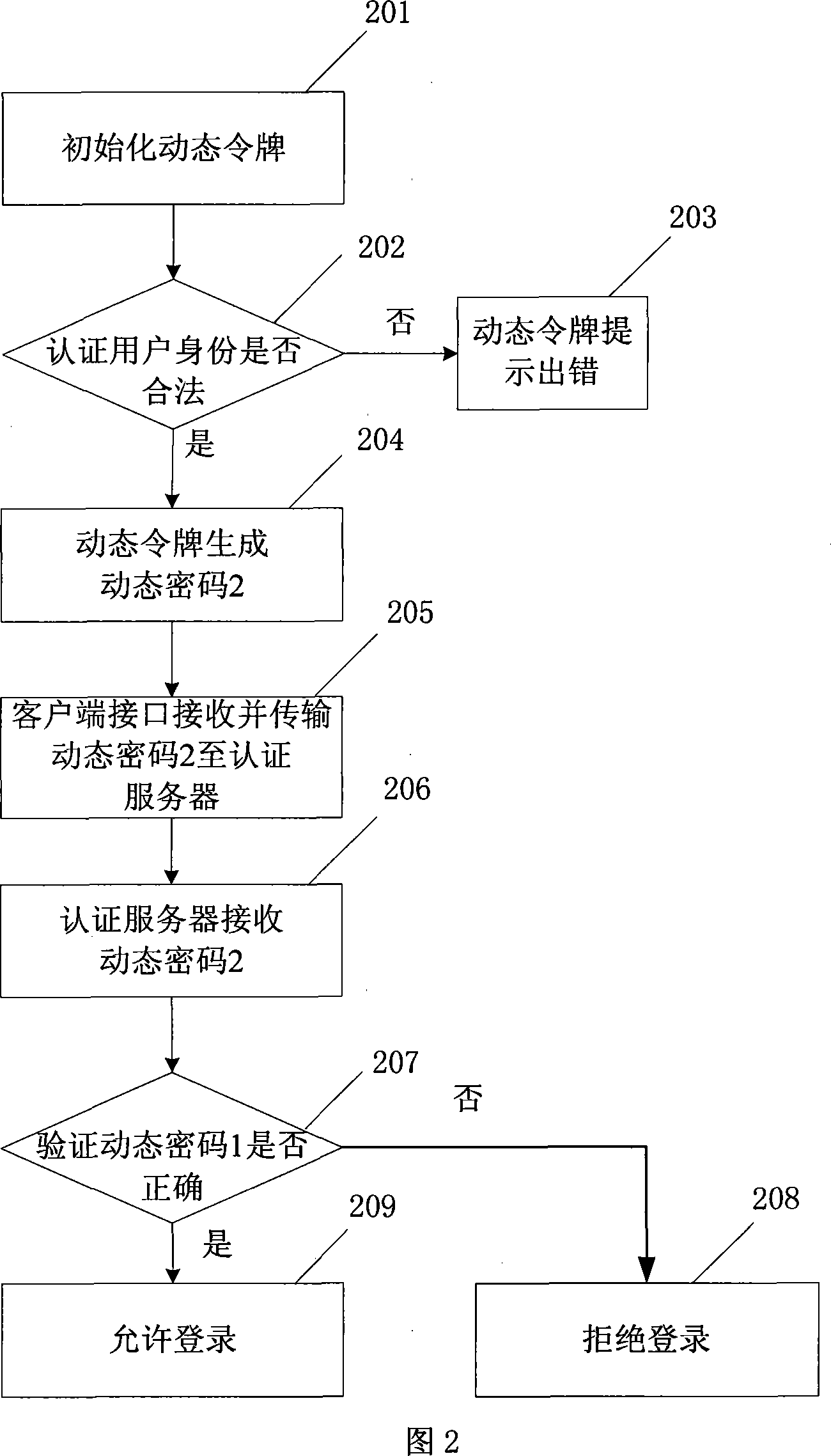
Dynamic cipher certifying system and method
ActiveCN101051908AAvoid interceptionPrivacy protectionMultiple keys/algorithms usageUser identity/authority verificationAuthentication serverClient-side
The system includes interface at client end, authentication server, database, management server, and dynamic token containing individual information of user. The method includes steps: dynamic token authenticates user ID; after authentication of user ID is passed, dynamic token generates dynamic cipher based on time / event factors and built-in individual information of user as well as combination with cipher key calculation; through interface at client end, user transfers dynamic cipher to authentication server; after receiving dynamic cipher, and obtaining individual information of user through calculation, the authentication server authenticates dynamic cipher. In the invention, user only needs to input current generated dynamic cipher to carry out log on authentication so as to raise performance of easy to use in dynamic cipher authentication mode. The invention also protects privacy of individual information of user.
Owner:FEITIAN TECHNOLOGIES
Data transmission method, server side and client
ActiveCN104023013ASecure transmissionSecure one-way transmissionUser identity/authority verificationKey exchangeClient-side
The invention discloses a data transmission method, a server side and a client. The data transmission method comprises the following steps that: the server side and the client carry out information interaction through an authentication protocol, and perform identity authentication with each other; a session key is generated by the server side and the client through a key exchange protocol; a data packet to be transmitted is encrypted by the client through adopting an encryption algorithm and the session key, and the encrypted data packet is transmitted to the server side; and the received encrypted data packet is decrypted by the server side through utilizing the session key and the encryption algorithm, and the corresponding operation is executed. According to the scheme, unidirectional transmission of the transmitted data packet from the client to the server side can be implemented, establishing process is simple, and the computing resource is effectively saved, so that the data transmission is safer and more reliable.
Owner:SHANGHAI DNION INFORMATION & TECH
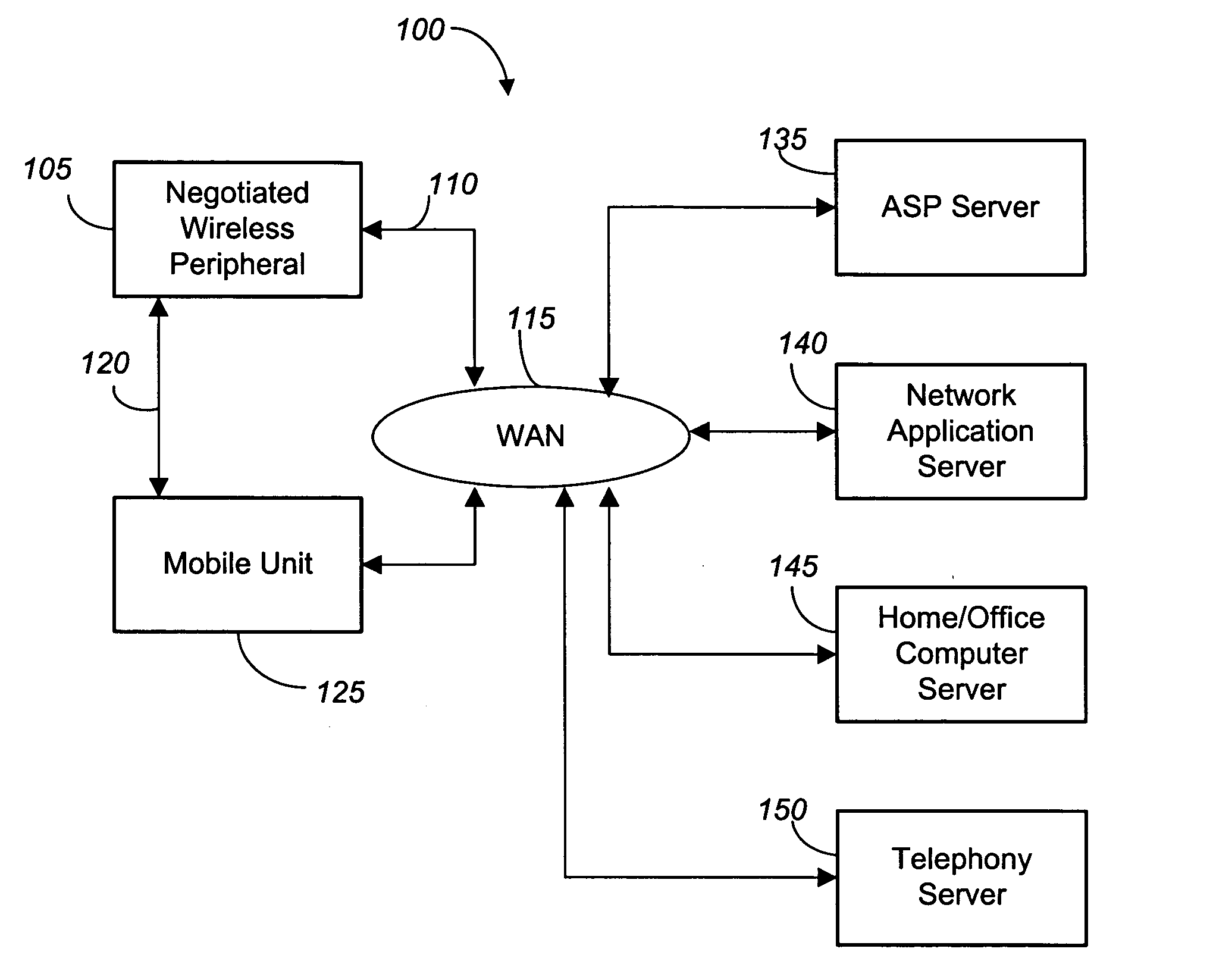
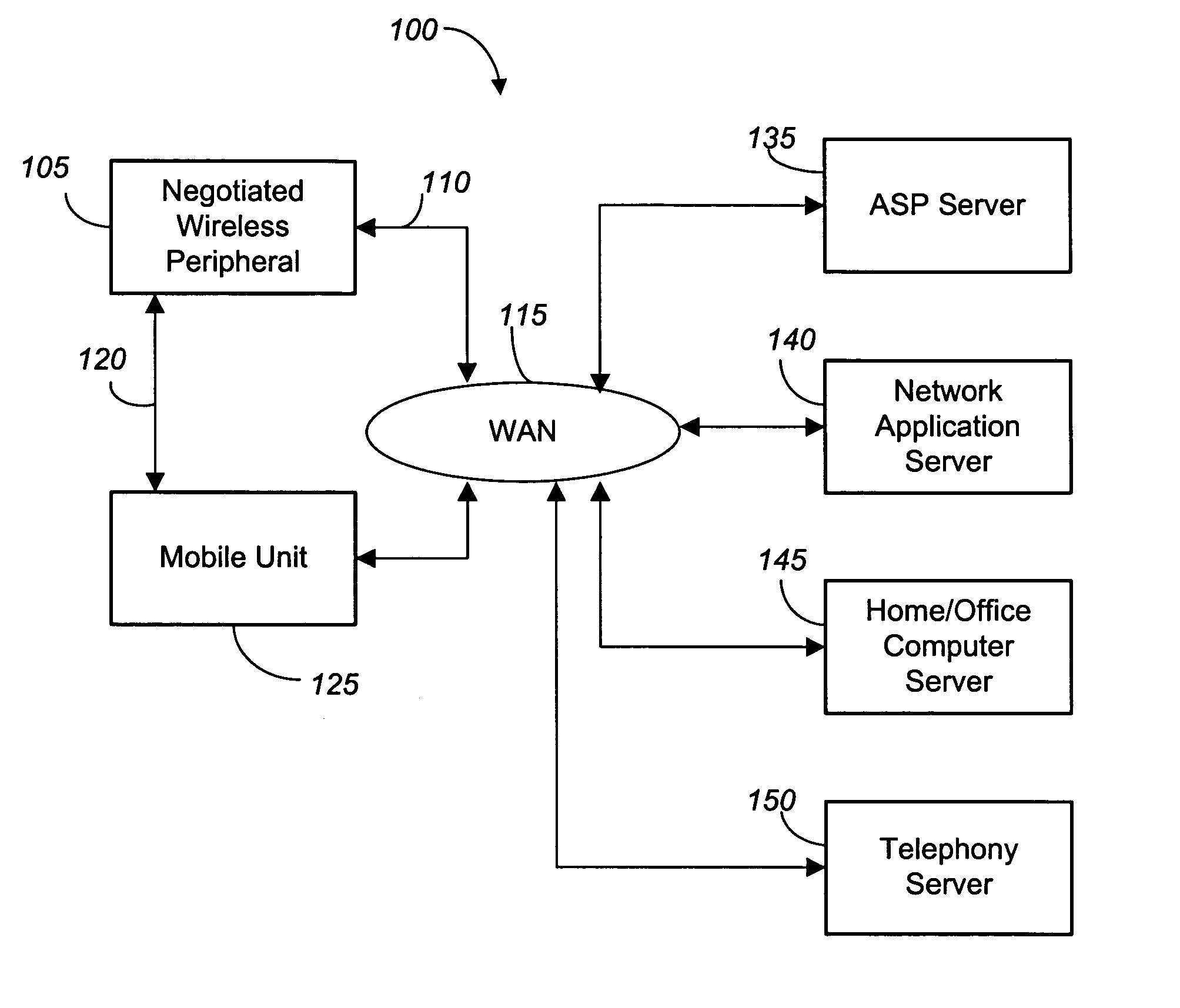
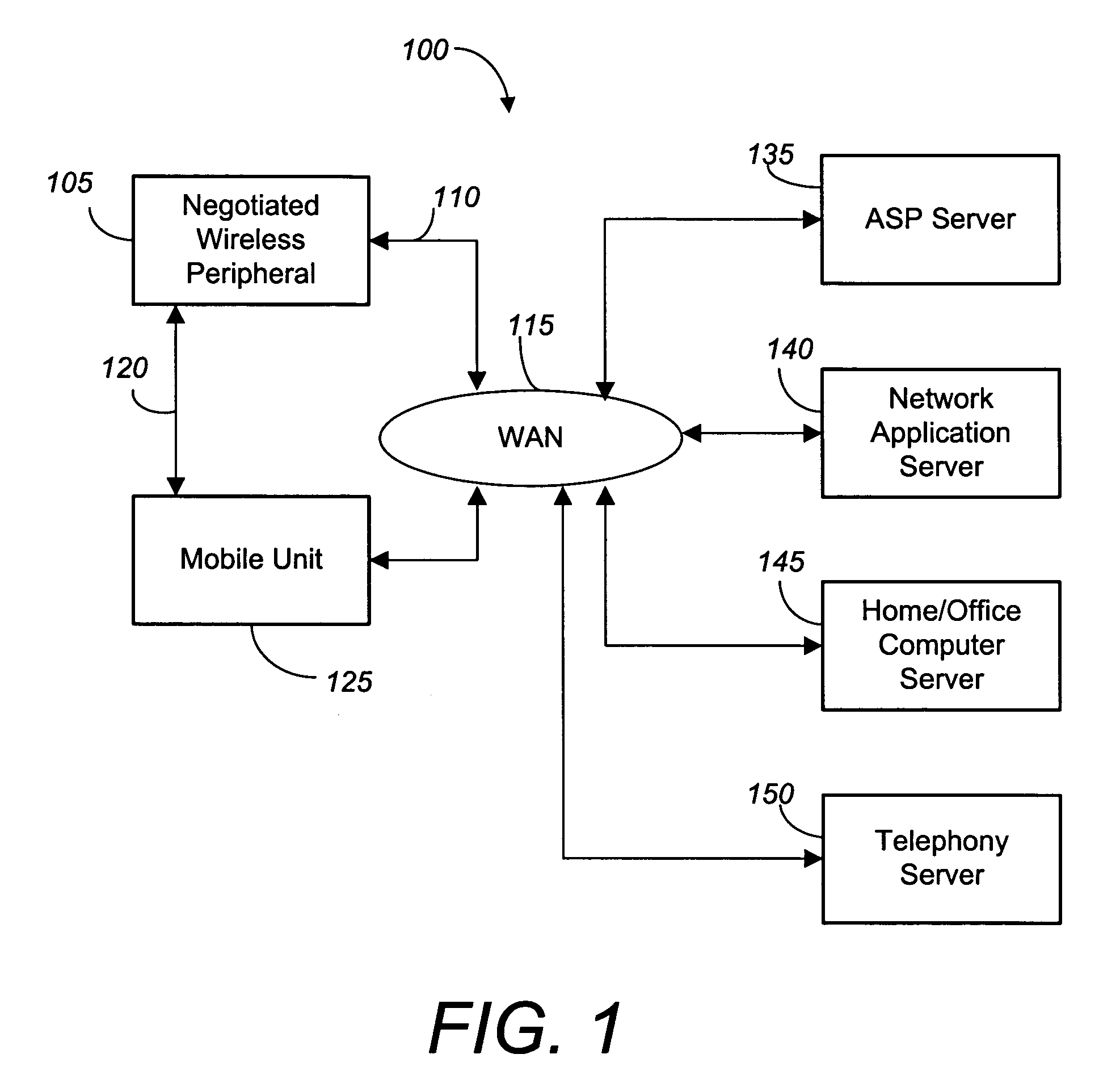
Negotiated wireless peripheral security systems
InactiveUS20050159173A1Consumes more powerAvoid interceptionData switching by path configurationMultiple digital computer combinationsNetwork connectionDisplay device
Methods, apparatus, and business techniques are disclosed for use in mobile network communication systems. A mobile unit such as a smart phone is preferably equipped with a wireless local area network connection and a wireless wide area network connection. The local area network connection is used to establish a position-dependent ecommerce network connection with a wireless peripheral supplied by a vendor. The mobile unit is then temporarily augmented with the added peripheral services supplied by the negotiated wireless peripheral. Systems and methods allow the mobile unit to communicate securely with a remote server, even when the negotiated wireless peripheral is not fully trusted. Also mobile units, wireless user peripherals, and negotiated wireless peripherals that project a non-area constrained user interface image on a display surface are taught.
Owner:RPX CORP
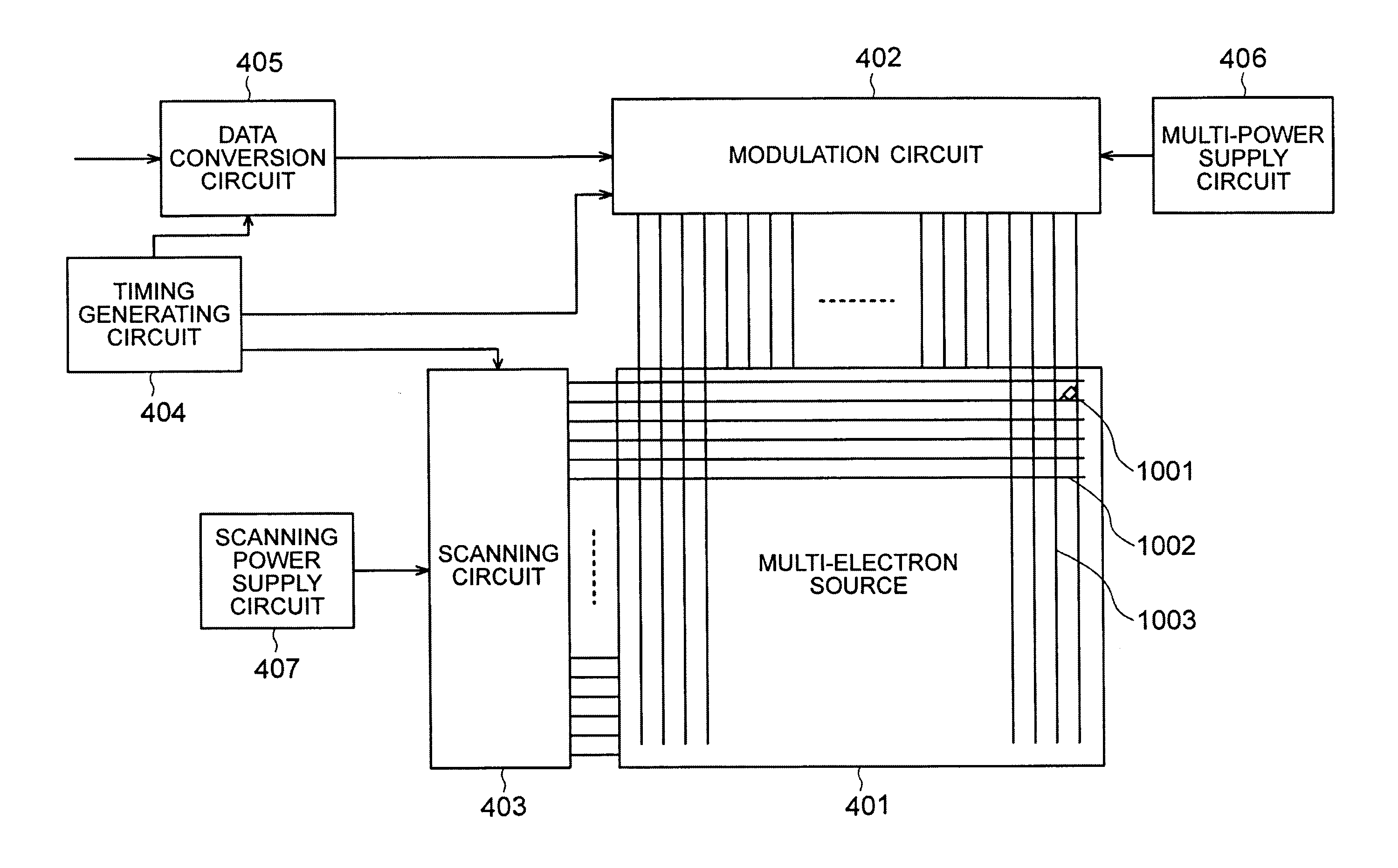
Signal processing method, image display apparatus, and television apparatus
InactiveUS20070052861A1Avoid interceptionReduce interceptionColor signal processing circuitsCathode-ray tube indicatorsSignal productionSignal processing
A signal processing method comprises the steps of: inputting three signals specifying a color of one pixel; and generating four signals from the input three signals, wherein each of said four signals represents intensities of four different colors to display a color of one pixel by mixing colors, wherein said generating step includes a first converting step of converting the input three signals to two signals representing intensities of two colors among the four colors and a signal representing intensity of a mixed color obtained by mixing (a) the four colors or (b) a plurality of colors among the four colors; and a second converting step of converting the signal representing intensity of the mixed color to a plurality of signals representing intensities of a plurality of colors including at least other two colors different from the two colors.
Owner:CANON KK
System and method of free-space optical satellite communications
InactiveUS7593641B2Reduce and eliminate distortionIncrease volumeSatellite communication transmissionTransceiverWavefront
A system and method of free-space optical satellite communications includes a ground station and transceiver for transmitting and receiving an optical communications signal. Adaptive optics at the ground station are operative with the transceiver for determining the shape of any distortions in the wavefront of the optical communications signal and compensating at the ground station for the distortions. A satellite includes a transceiver for transmitting and receiving the optical communications signal and includes adaptive optics for determining the shape of any distortions in the waveform of the optical communications signal and compensating at the satellite for the distortions.
Owner:HARRIS CORP
Access authentication method and system in mobile communication network
InactiveCN102036242AAvoid attackArrived without errorUser identity/authority verificationSecurity arrangementMan-in-the-middle attackDigest access authentication
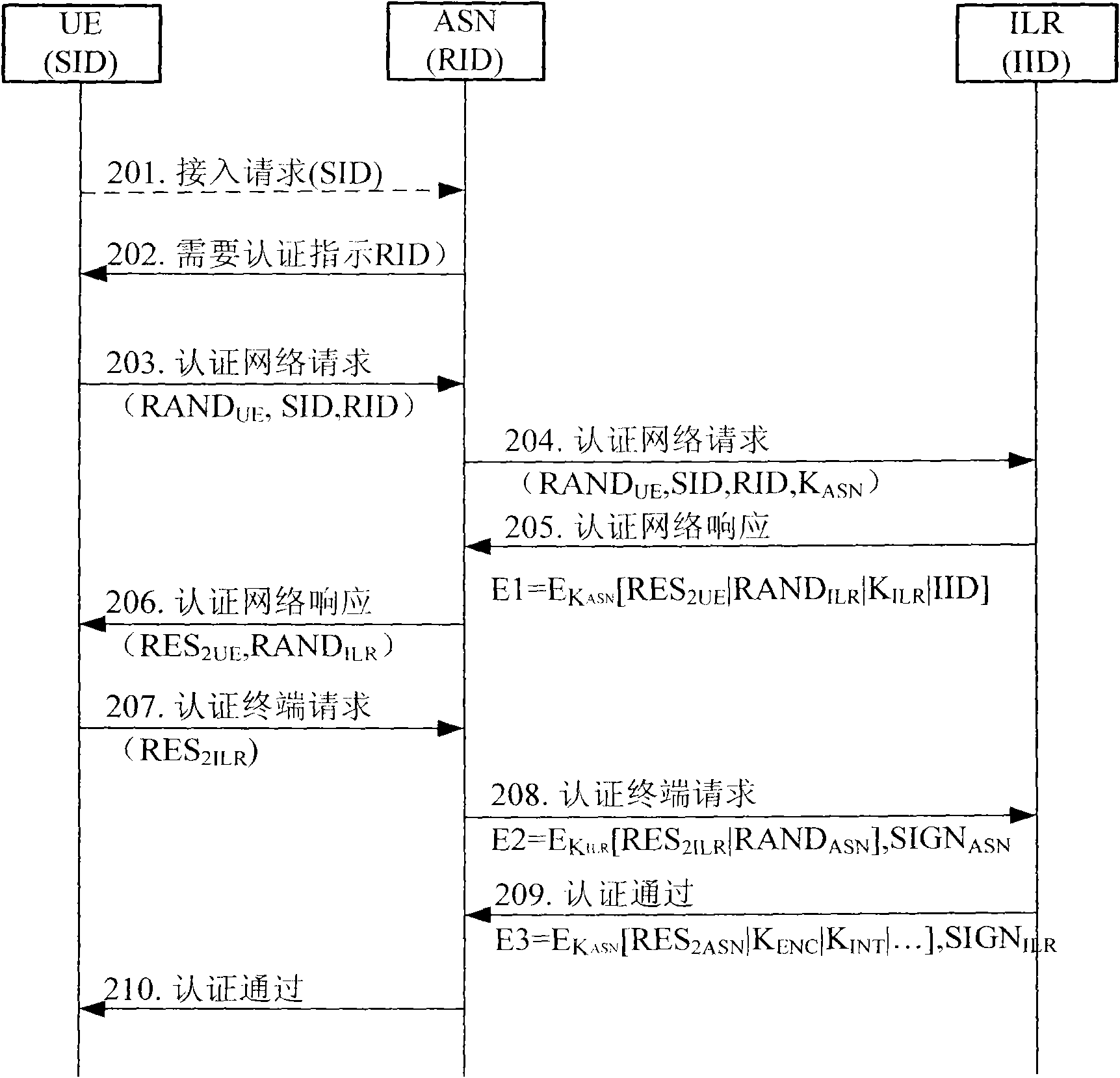
The invention discloses an access authentication method in a mobile communication network. The method comprises the following steps that: a user terminal generates a random number RANDUE, and acquires a random number RANDILR generated by route identification (RID) and an identity location register (ILR) of an access service node (ASN) in a network when needing to perform authentication; the user terminal calculates to obtain an authentication result RES2ILR by using a pre-shared key K1 and sends the RES2ILR to the ASN; the ASN generates a random number RANDASN and sends the RES2ILR and the random number RANDASN to the ILR; and the ILR calculates to obtain an authentication result XRES2ILR by using the pre-shared key K1 and compares the XRES2ILR with the received RES2ILR; and if the XRES2ILR is consistent with the RES2ILR, the access authentication is successful. Correspondingly, the invention also provides a system for implementing the method. Through the method and the system, Man-in-the-Middle attacks caused by an unreliable network can be effectively avoided.
Owner:ZTE CORP
Movie theatre mobile payment method based on near field communication (NFC)
ActiveCN105184553AAvoid interceptionEnsure mobile payment securityPayments involving neutral partyProtocol authorisationThird partyPayment transaction
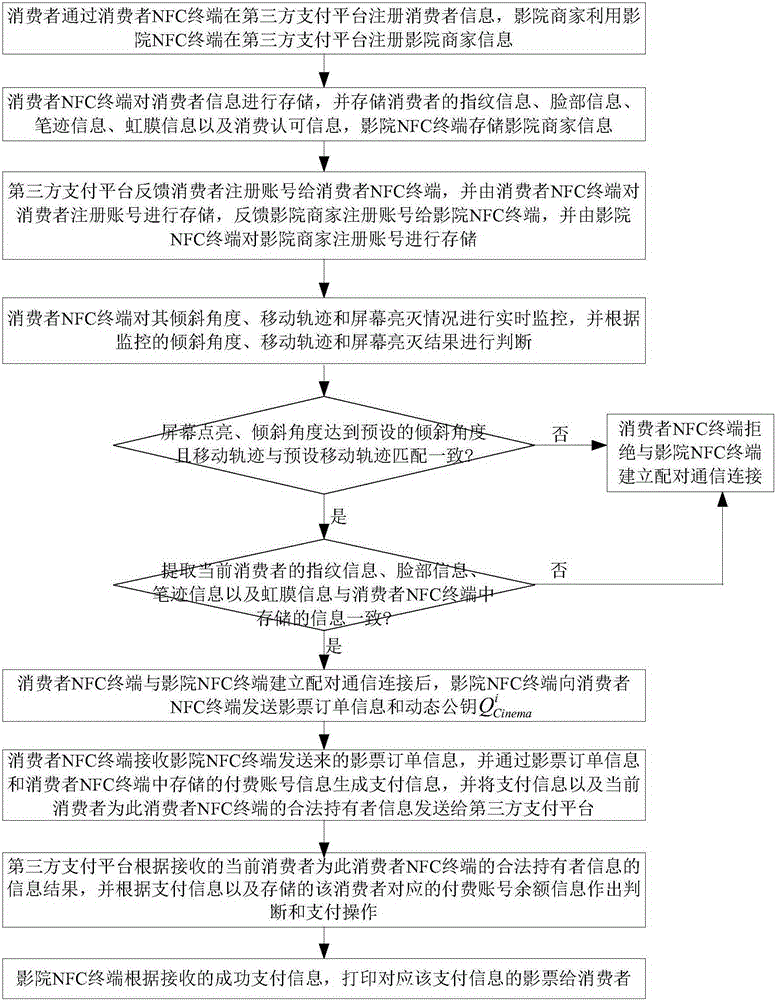
The invention relates to a movie theatre mobile payment method based on near field communication (NFC). A movie theatre NFC terminal sends movie ticket order information and a dynamic public key to a consumer NFC terminal; when the screen of the consumer NFC terminal is lighted and an inclination angle and a movement locus are consistent with a preset angles and a preset locus, if the consumer NFC terminal determines that biological characteristic information of a current consumer is consistent with information stored in the consumer NFC terminal, pairing communication is carried out with the movie theatre NFC terminal; and after dynamic public keys mutually sent by the consumer NFC terminal and the movie theatre NFC terminal are verified successfully by each other, a third-party payment platform finishes payment operation of a movie ticket order according to payment information, and the movie theatre NFC terminal prints a movie ticket for the consumer. According to the method provided by the invention, dynamic public key encryption is employed for protecting payment transaction data of the consumer NFC terminal and the movie theatre NFC terminal, the valid identity of the consumer is determined by use of the biological characteristic information, such that mobile payment of the movie ticket is conveniently finished, and the security of the mobile payment is also guaranteed.
Owner:NINGBO UNIV
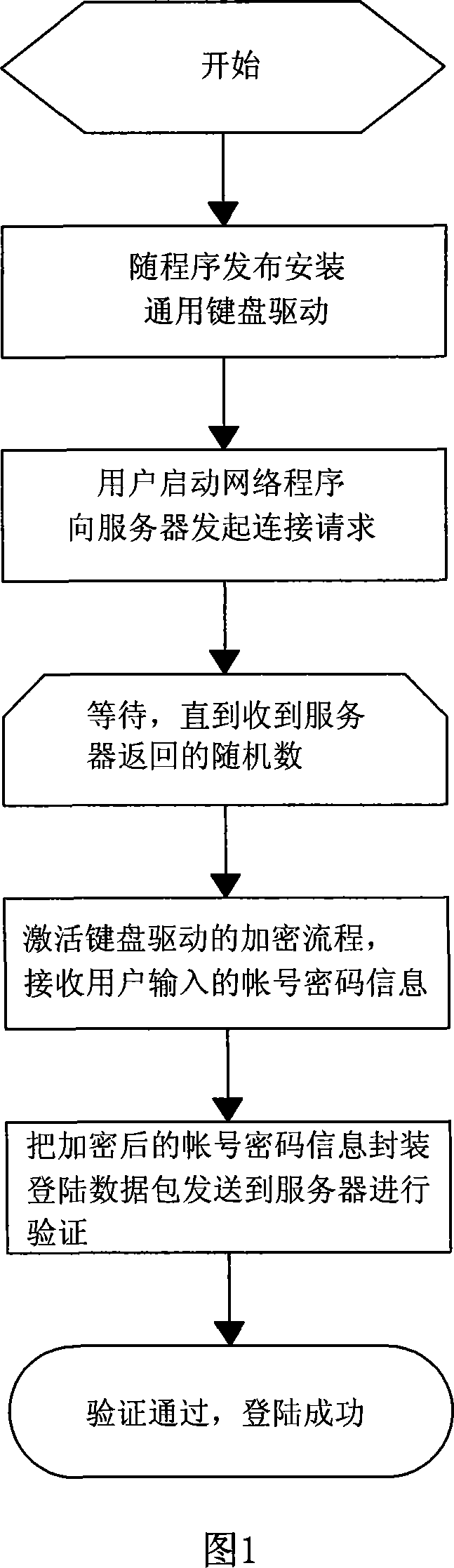
Method for landing by account number cipher for protecting network application sequence
ActiveCN101051904APrevent theftAvoid interceptionUser identity/authority verificationComputer hardwareOperational system
Through client end to input cipher, then the method carries out log on through authentication at server end. Characters are that universal keyboard drive program is setup at client end, encrypted private key and module for encrypting private key are preset inside the keyboard drive program; at same time, being identical to those setup at client end, the encrypted private key and module for encrypting private key are also setup at server end. The invention can prevent wooden horse virus process possessing function of recording keyboard and running at application layer on operation system from stealing account cipher input by user effectively as well as prevent network monitor tool (NMT) from intercepting log on data packet containing information of user account cipher etc, and prevent NMT implements chicaning log on through software method.
Owner:成都金山互动娱乐科技有限公司
Pornographic picture identification method based on joint detection of skin colors and featured body parts
ActiveCN101923652AReduce false detection rateAvoid interceptionImage analysisCharacter and pattern recognitionPattern recognitionImaging processing
The invention belongs to the technical field of image processing and provides a pornographyic picture identification method based on joint detection of skin colors and featured body parts, which comprises the following steps: (1) preparatory stage of sample training for acquiring needed parameters of the identification stage of an image to be detected, the preparatory stage of sample training comprises color skin sample training and featured body part sample training; (2) the stage of reading the image to be detected; (3) the identification stage of the image to be detected for judging whether the image to be detected is a pornographyic picture or not according to the parameters acquired at the preparatory stage of sample training: the skin color and the featured body parts are detected in sequence, and if the area of the skin color region accounts for more than a half of the whole image and at least one featured body part emerges, the picture is judged to be a pornographic picture. The method of the invention has the advantages of being capable of reducing false detection rate of pornographyic pictures, and having wide range of application and high accuracy rate.
Owner:HUAZHONG NORMAL UNIV
Method and device for identifying legality of website service
The invention discloses a method and a device for identifying the legality of a website service, which are used for improving access security when a user accesses the internet. The method comprises the steps of: when a client requires to use the website service, based on random numbers transmitted by the client, a server generates the corresponding temporary communication key by adopting a negotiated and appointed method, encrypts identification information by adopting the temporary communication key and transmits the encrypted identification information to the client; and the client decryptsthe received encrypted identification information by adopting a temporary communication key generated based on the same method and identifies the legality of the website service provided by the server based on the decrypted result and by adopting the preset mode. Therefore, the client can judge the legality of the website service according to the correctness of the identification information and effectively prevents information from being altered and intercepted midway, so that the security of using the website service by the user is effectively improved and the quality of the website serviceis improved. The invention also discloses the device for identifying the legality of the website service.
Owner:CHONGQING SHAHAI INFORMATION TECH
Portable wireless terminal and its security system
InactiveUS8208897B2Avoid interceptionSafe removalUnauthorised/fraudulent call preventionEavesdropping prevention circuitsThird partyData access control
Owner:FUJITSU LTD
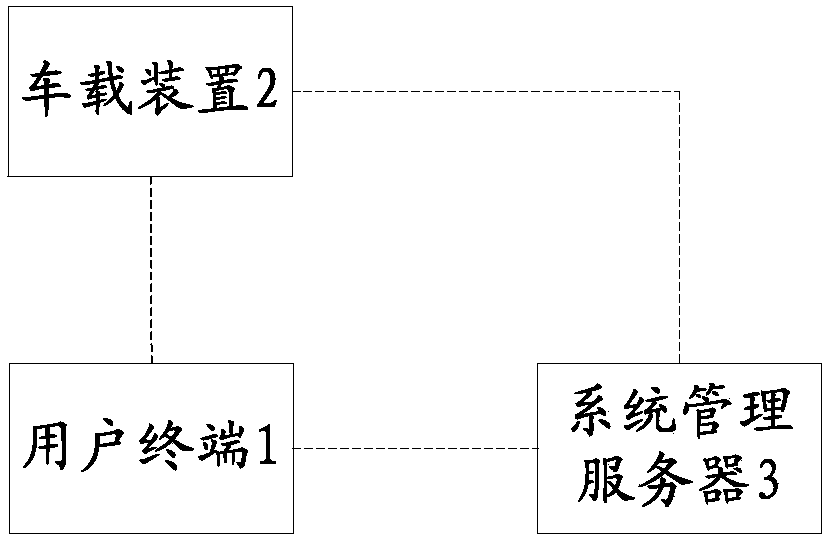
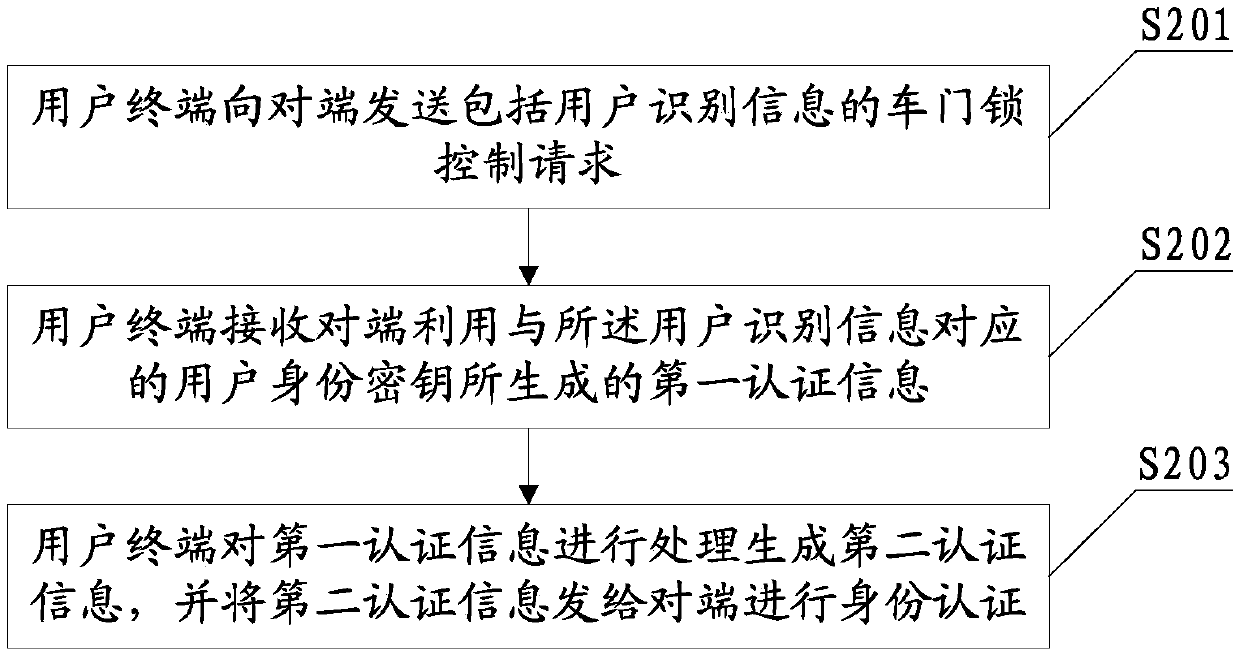
Automobile key-free control certification method, user terminal, vehicle-mounted device and server
PendingCN109586915AAvoid the problem of not being able to switch the door lock normallyImprove satisfactionKey distribution for secure communicationAnti-theft devicesSmart cardComputer terminal
The invention provides an automobile key-free control certification method, a user terminal, a vehicle-mounted device and a server. The user terminal sends a vehicle door lock control request including user identification information to the opposite side, first certification information generated by using user identity secret key corresponding to the user identification information by the oppositeside is received, the first certification information is processed by using the user identity secret key, corresponding to the user identification information, stored in a safety chip of an intelligent card to generate second certification information, and the second certification information is sent to the opposite side for identity certification, so that the opposite side controls a vehicle door correspondingly according to an identity certification result of the second certification information. The user terminal replaces an intelligent key specially used for the vehicle, the user identitysecurity key is stored in the safety chip of the intelligent card of the user terminal and is not transmitted between the user terminal and the opposite side in the certification process, and thus, the identity security key is avoided from being intercepted, and the safety and user experience are improved.
Owner:NATIONZ TECH INC
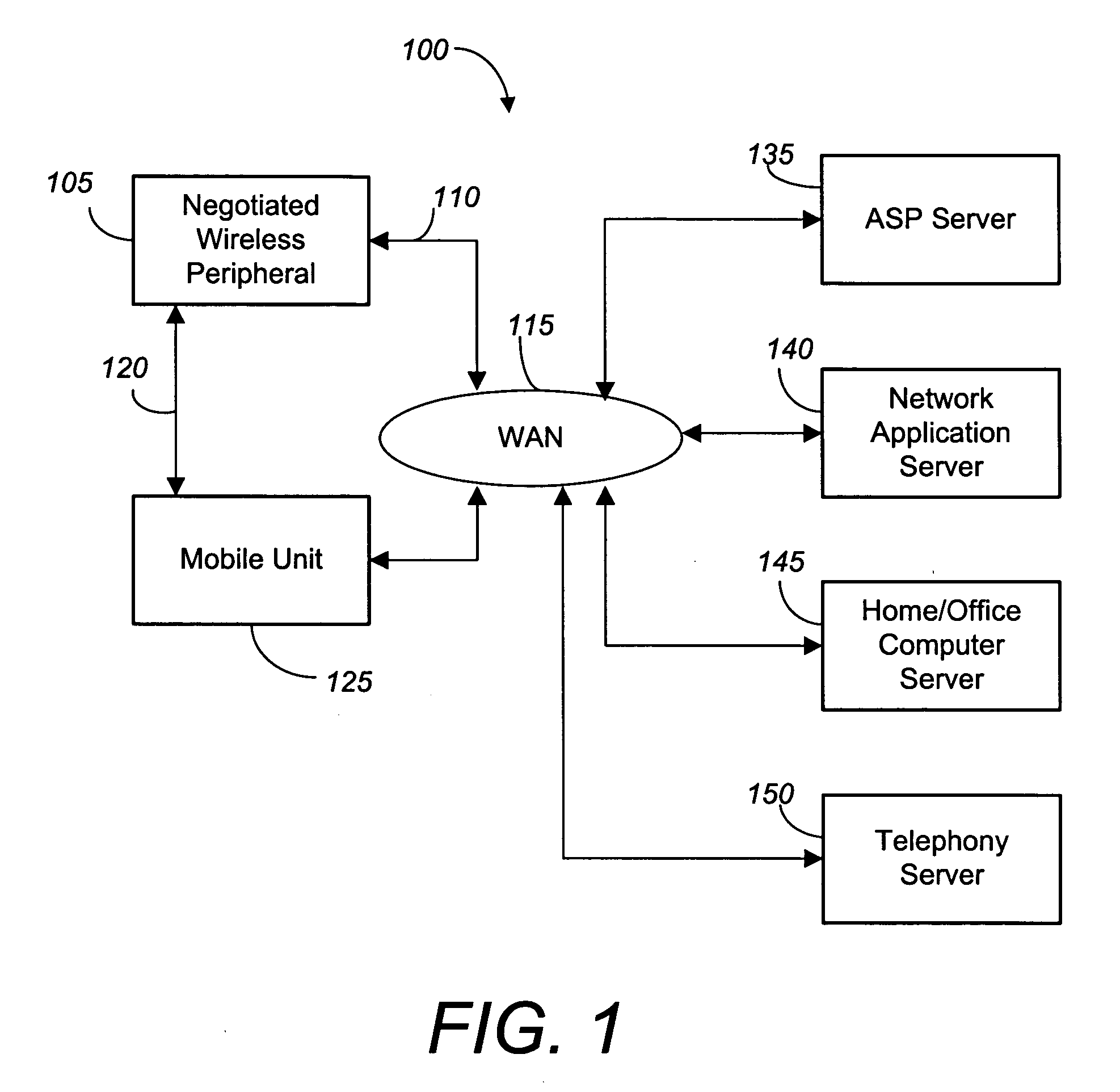
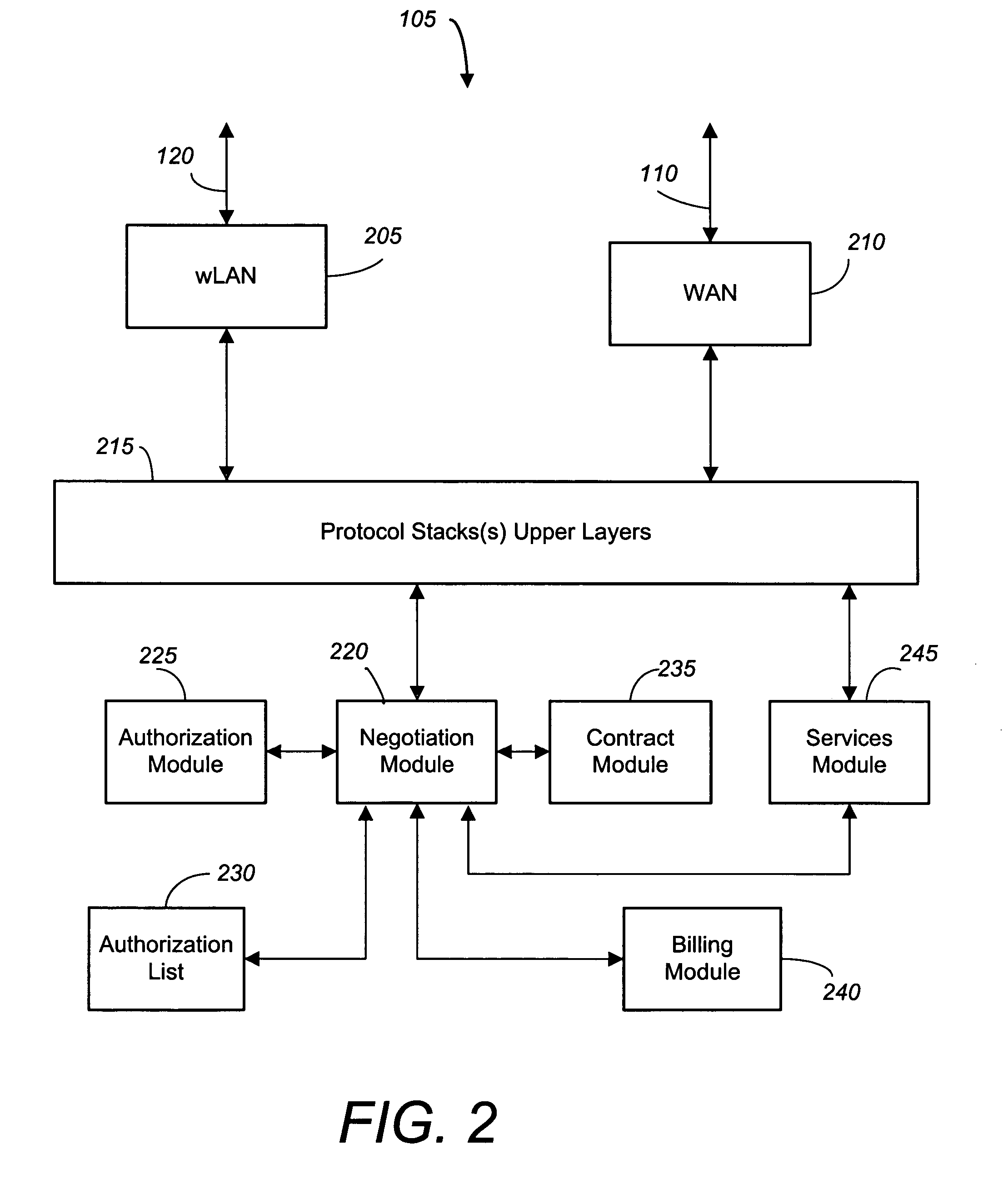
Negotiated wireless peripheral security systems
InactiveUS7209946B2Consumes more powerAvoid interceptionNetwork traffic/resource managementNetwork topologiesNetwork connectionDisplay device
Methods, apparatus, and business techniques are disclosed for use in mobile network communication systems. A mobile unit such as a smart phone is preferably equipped with a wireless local area network connection and a wireless wide area network connection. The local area network connection is used to establish a position-dependent ecommerce network connection with a wireless peripheral supplied by a vendor. The mobile unit is then temporarily augmented with the added peripheral services supplied by the negotiated wireless peripheral. Systems and methods allow the mobile unit to communicate securely with a remote server, even when the negotiated wireless peripheral is not fully trusted. Also mobile units, wireless user peripherals, and negotiated wireless peripherals that project a non-area constrained user interface image on a display surface are taught.
Owner:RPX CORP
Random number generator
ActiveUS7230971B1Avoid interceptionEfficient power consumptionMultiplex code generationTransmissionNumber generatorComputer science
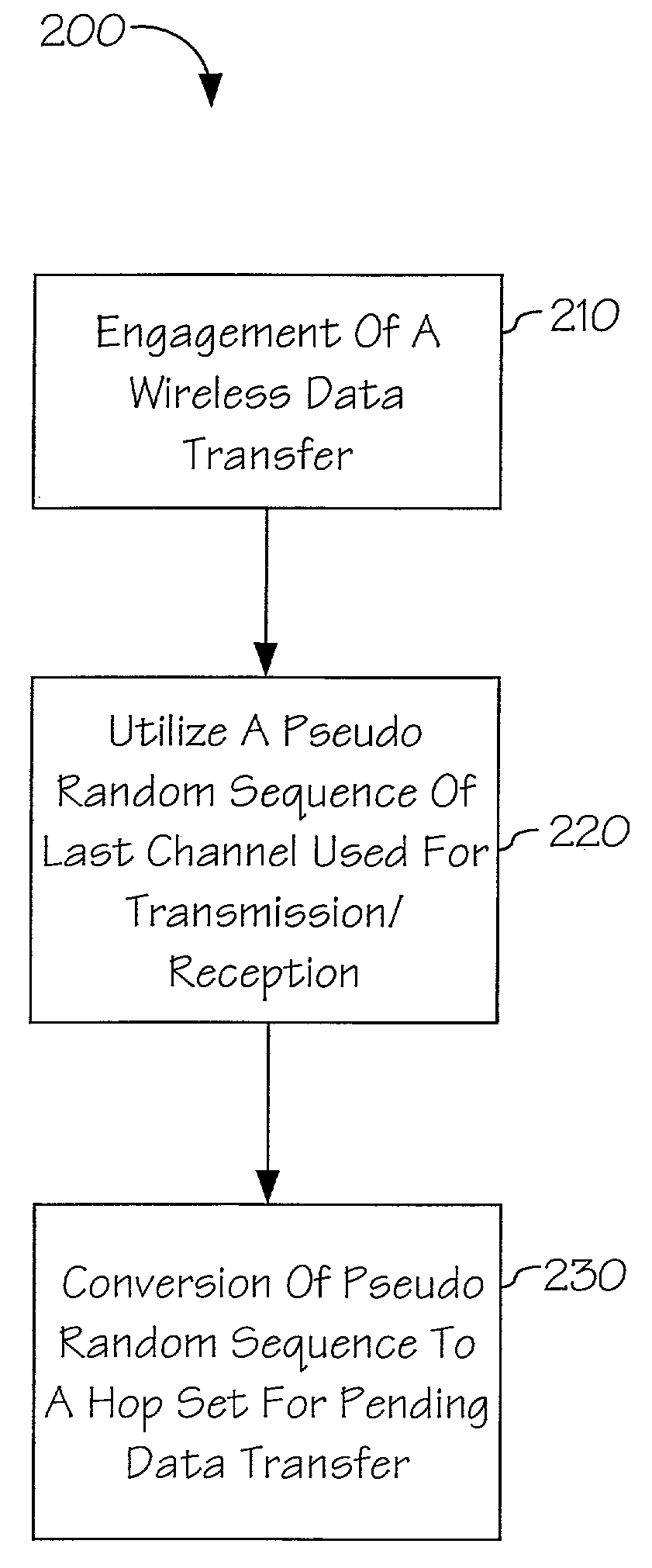
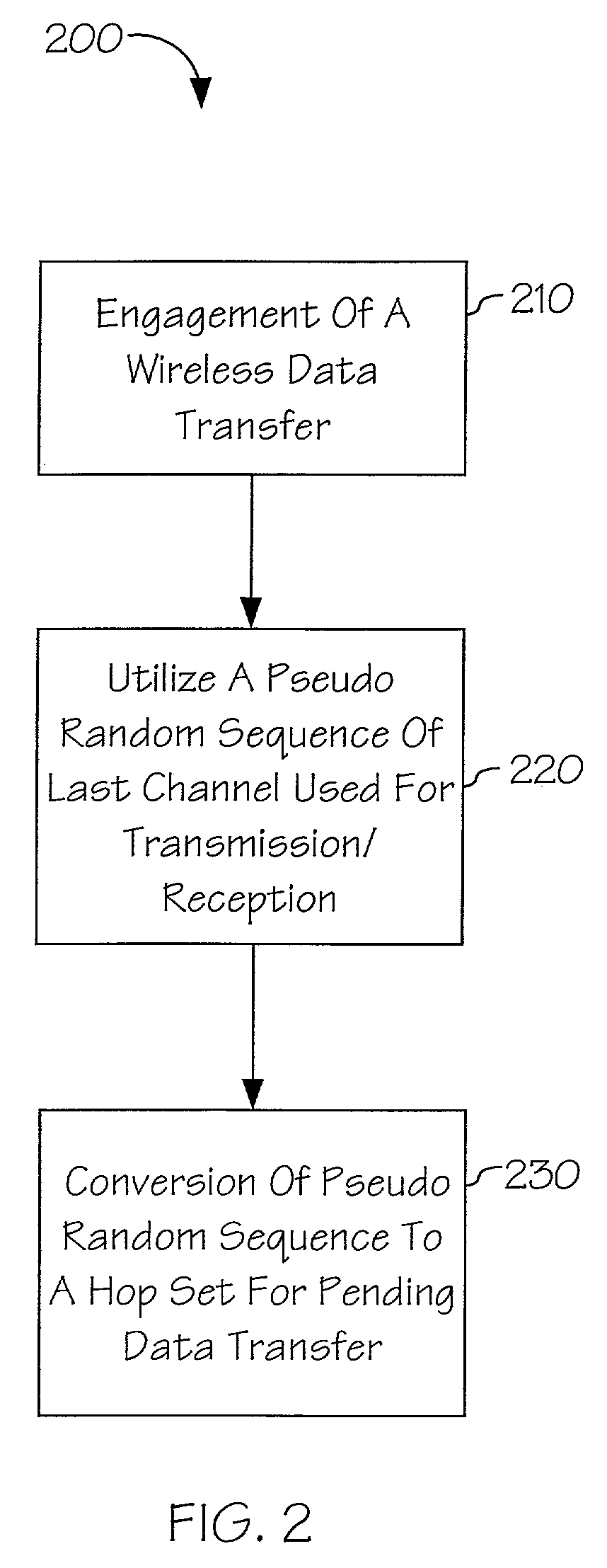
The present invention is a method and apparatus for providing a pseudo random sequence for a spread spectrum system that prevents interception and provides real estate and power consumption efficiency. A pseudo random sequence may be created in real-time by associating a pseudo random sequence of a channel location of the carrier frequency at an instant in time. For example, the entire band of the spread spectrum system may be scanned to detect a channel with a low received signal strength. The location of the channel, or the actual frequency of the channel, could be associated with a particular pseudo random sequence to create a hop set for frequency hopping. Additionally, the location of a characteristic of the spread spectrum system, such as a noise characteristic, could be utilized to determine a content of a pseudo random sequence.
Owner:MONTEREY RES LLC
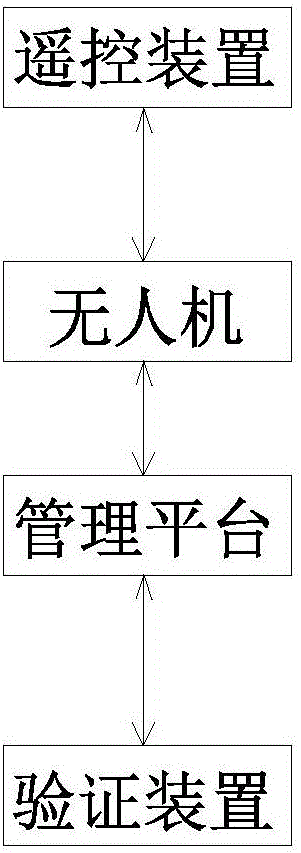
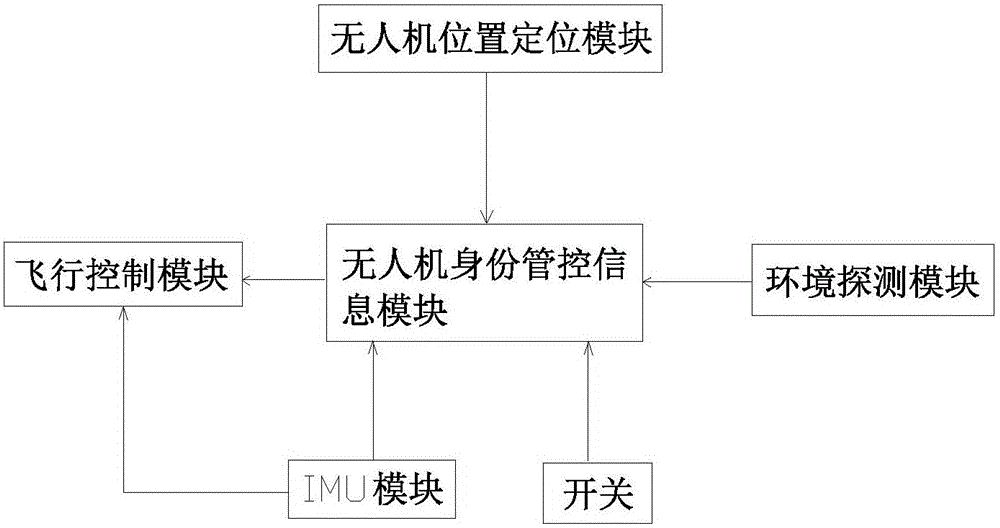
Unmanned aerial vehicle identification system
InactiveCN105827607AAvoid interceptionAvoid interferenceTransmission systemsTransmissionElectricityRemote control
The invention discloses a UAV identification system, which includes at least one UAV, a remote control device and a management platform. The UAV includes a flight control module, a UAV identity control information module and a UAV position positioning module. The flight control module and the UAV position positioning module are respectively electrically connected to the UAV identity management and control information module; the UAV identity management and control information module and the management platform perform signal transmission through waves. The UAV identity control information module is used as a transfer station between the flight control module and the remote control device. The UAV identity control information module records the identity information of the UAV. Once the UAV identity control information module is artificially destroyed, the remote control device It is impossible to control the flight of the drone.
Owner:赵文洁
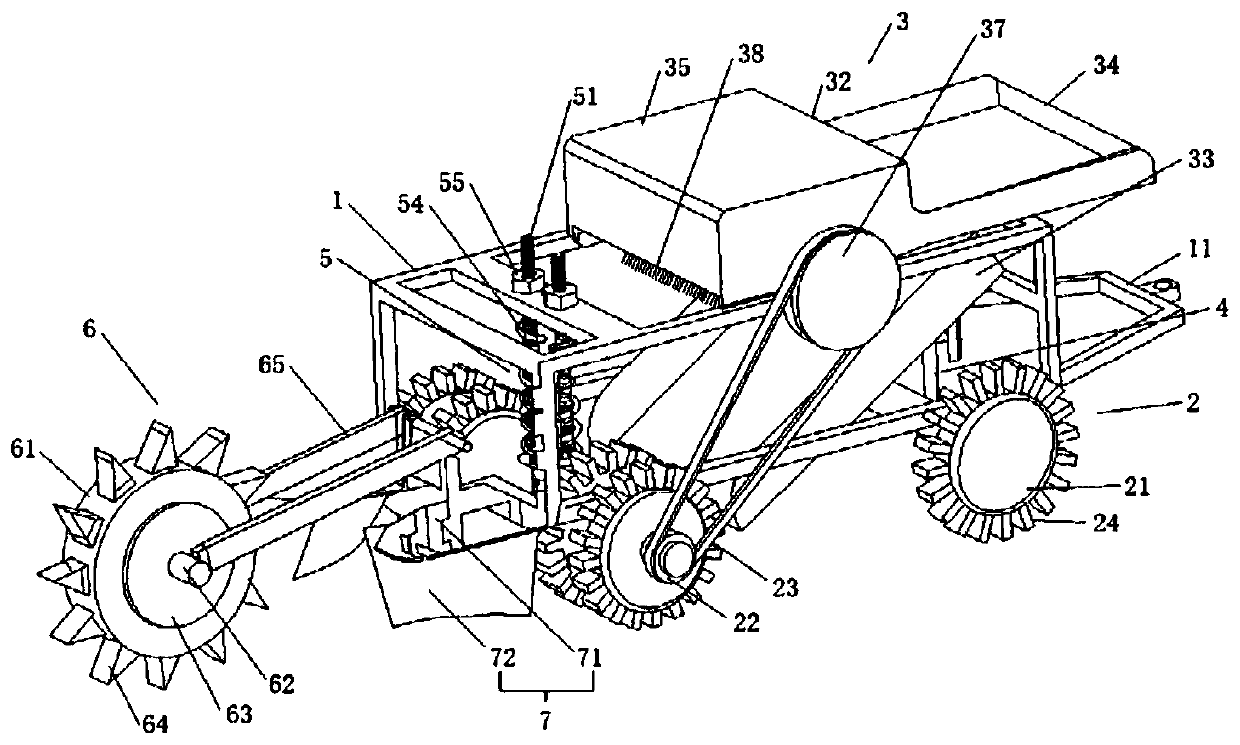
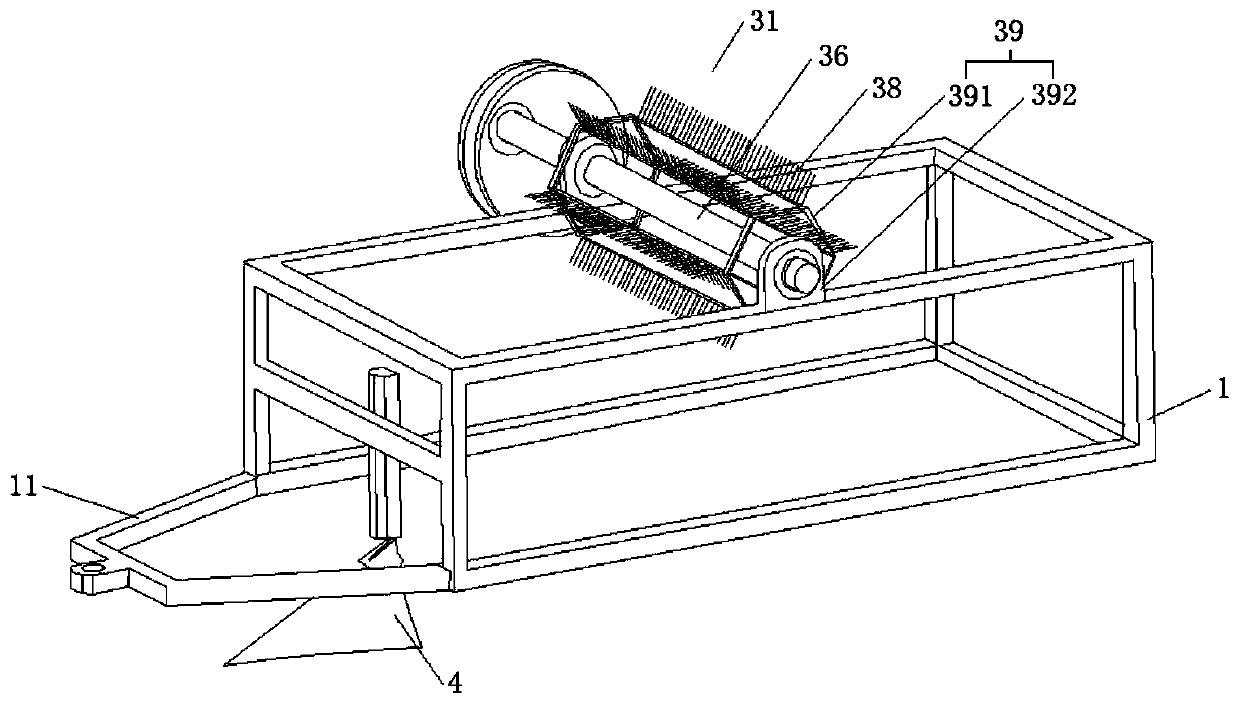
Multifunctional stereoscopic desert sand pressing grass growing machine
InactiveCN110100516AAvoid wastingIncrease roughnessSpadesSoil lifting machinesAgricultural engineeringEngineering
The invention discloses a multifunctional stereoscopic desert sand pressing grass growing machine, and belongs to the field of desert grass growing machines. The multifunctional stereoscopic desert sand pressing grass growing machine comprises a rack, a ground wheel train, a straw laying device, a ditching device, a straw pressing and earthing device and a sowing device; a toothed gear rotating shaft is installed on the upper surface of the rack and can rotate in the axis direction of the rack, four or more rows of straw laying rakes are uniformly distributed on the toothed gear rotating shaftin the circumferential direction, and a first transmission wheel is fixedly installed at one end of the toothed gear rotating shaft; the ground wheel train at least comprises two pairs of ground wheels, a second transmission wheel is fixedly installed at one end of one pair of the ground wheels, and the first transmission wheel and the second transmission wheel are in transmission connection through a belt. The multifunctional stereoscopic desert sand pressing grass growing machine has the advantages that the rack is provided with assemblies which have the dual functions of straw laying and grass growing, firstly, through ditching, straw laying and earthing, straw is buried in sand, then sowing is conducted nearby the embedded straw, thus the functions of automatic straw laying, straw burying and sowing are achieved, and then the purposes of laying of a straw checkerboard barrier and sowing are achieved.
Owner:LANZHOU PETROCHEM COLLEGE OF VOCATIONAL TECH
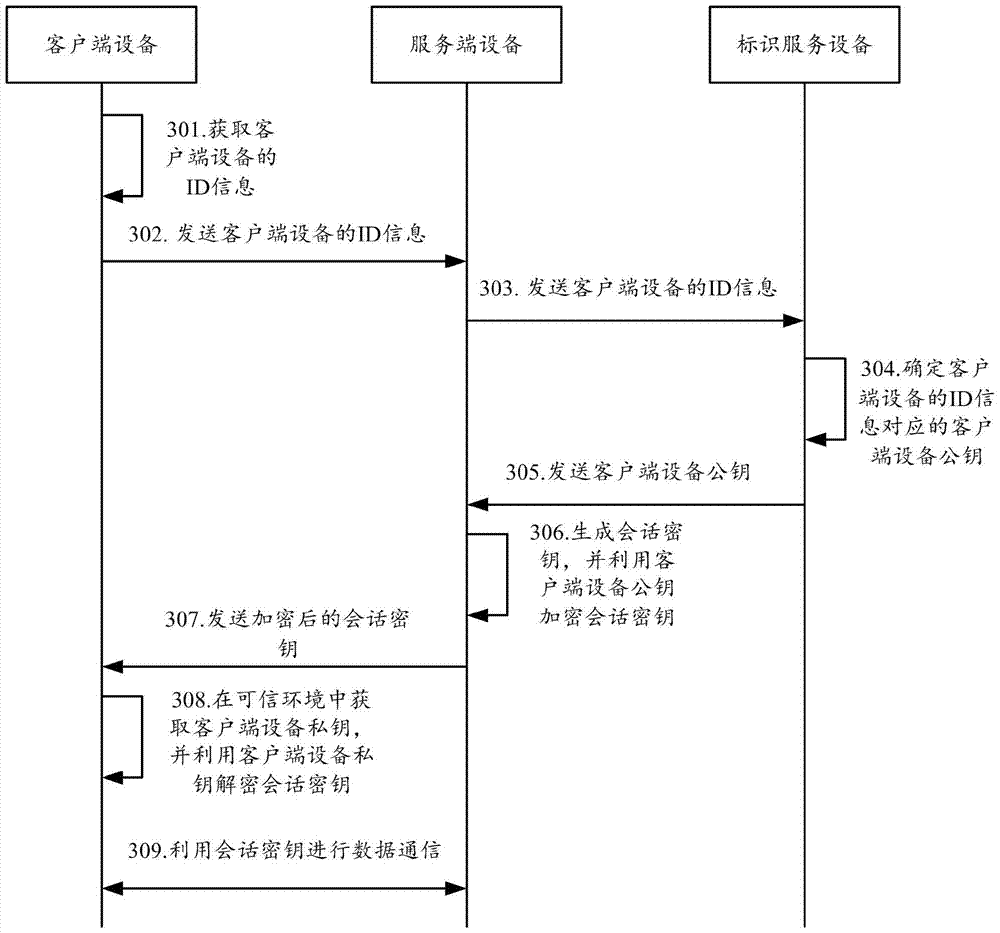
Identity information authentication method, server, client and system
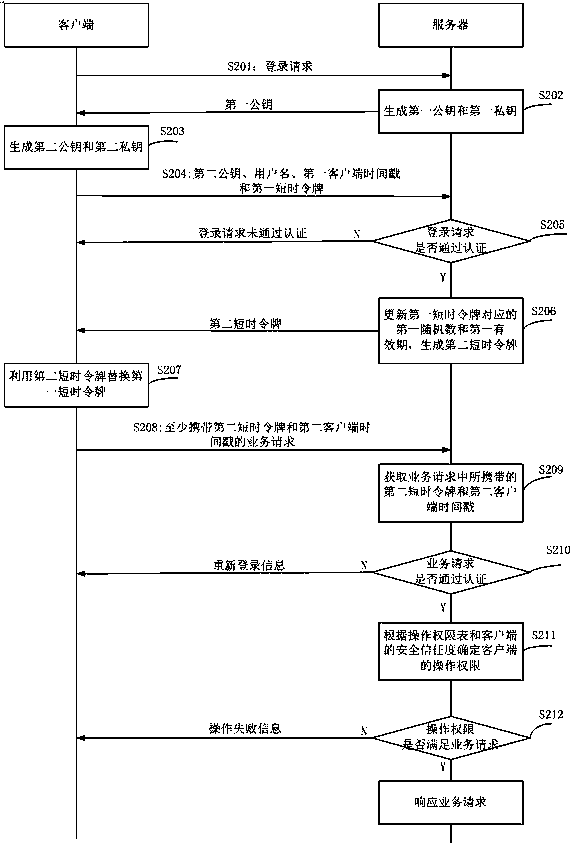
ActiveCN111212095AImprove securityAvoid interceptionKey distribution for secure communicationUser identity/authority verificationCommunications securityTimestamp
The invention provides an identity information authentication method, a server, a client and a system, and the method comprises the steps: enabling the server to determine whether a login request passes the authentication or not according to a second public key, a user name, a first client timestamp and a first short-time token of the client after receiving the login request of the client; if thelogin request passes the authentication, feeding back a newly generated second short-time token to the client, and generating the first short-time token and the second short-time token according to the user identity information, the equipment fingerprint information and the corresponding random number, wherein the client carries the second short-time token when the client sends the service request; if the server determines that the service request passes the authentication, determining the operation authority of the client according to the predetermined security trust degree of the client, andprocessing the service request according to the operation authority. In the scheme, the server generates the short-time token through the equipment fingerprint information, the short-time token is refreshed after login authentication is passed, and the operation authority of the client is determined through the security trust degree, so the communication security is improved.
Owner:STATE GRID E COMMERCE CO LTD +2
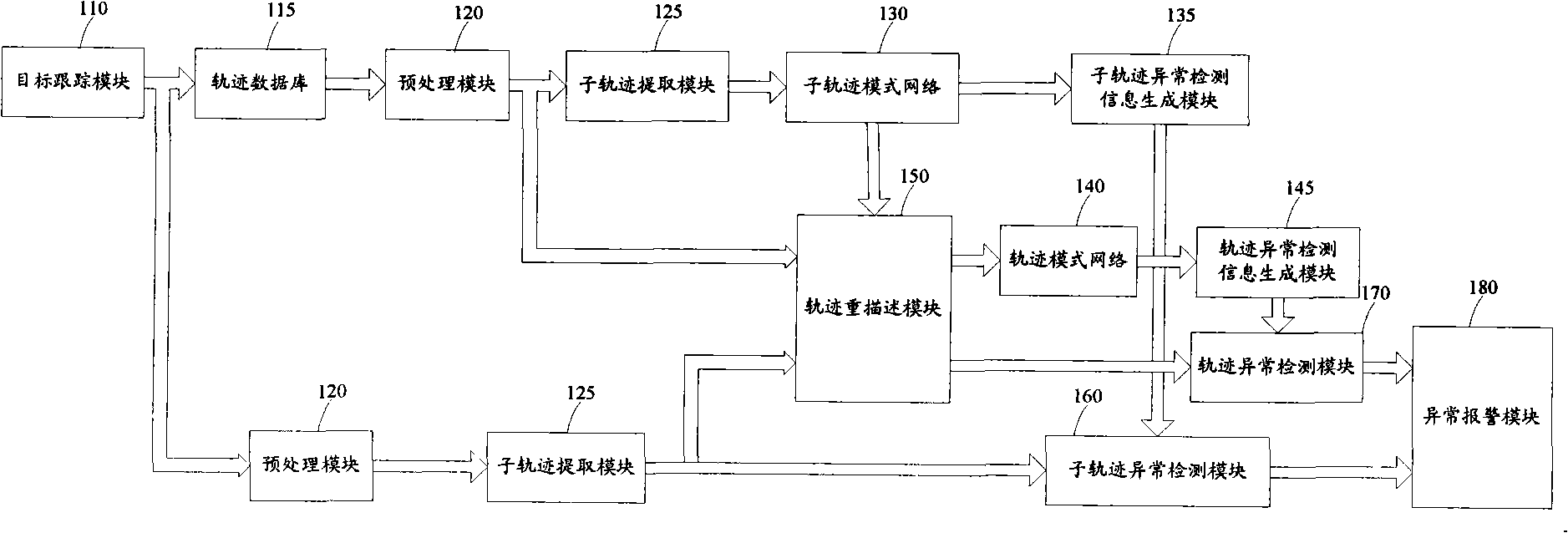
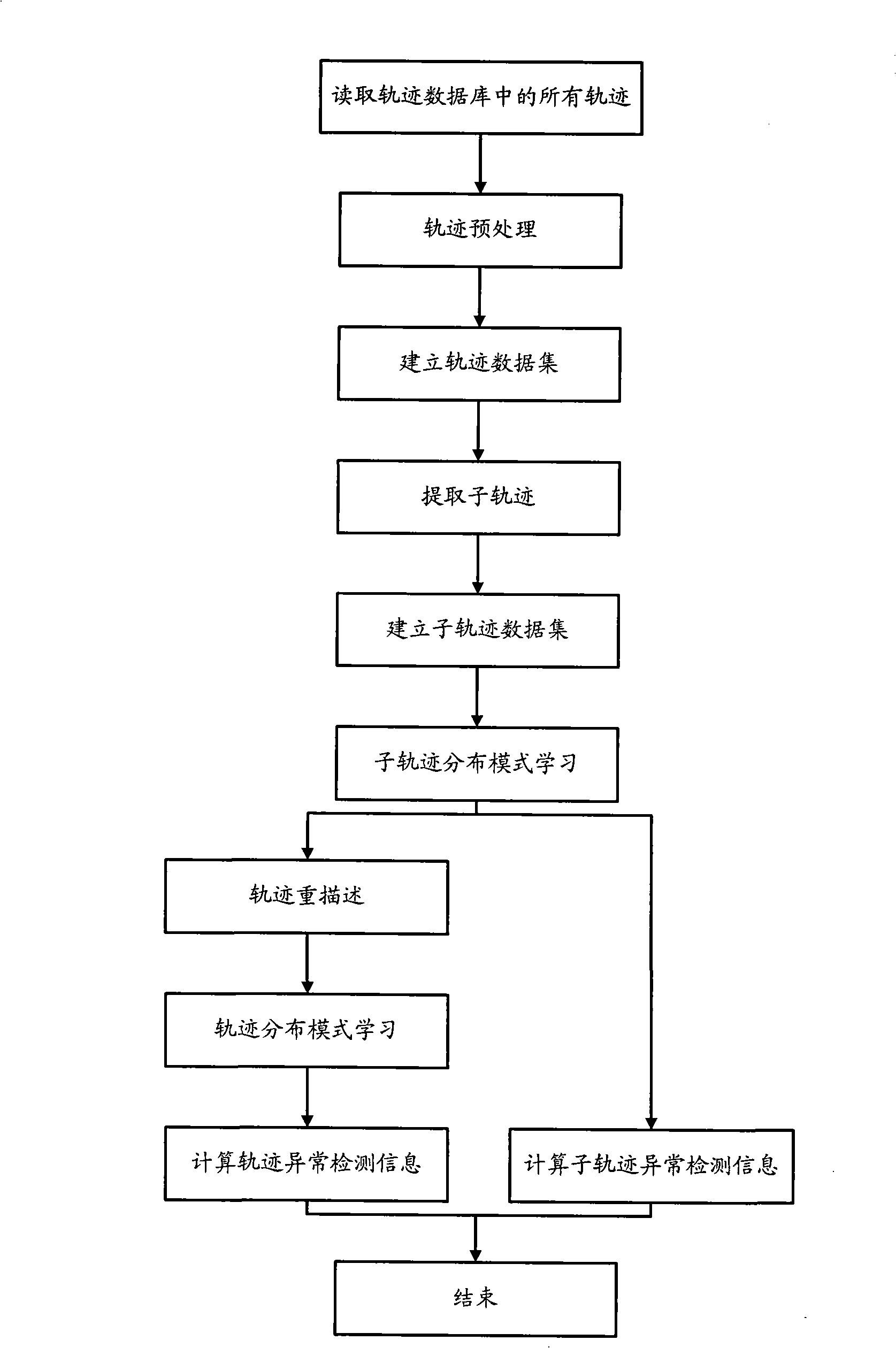
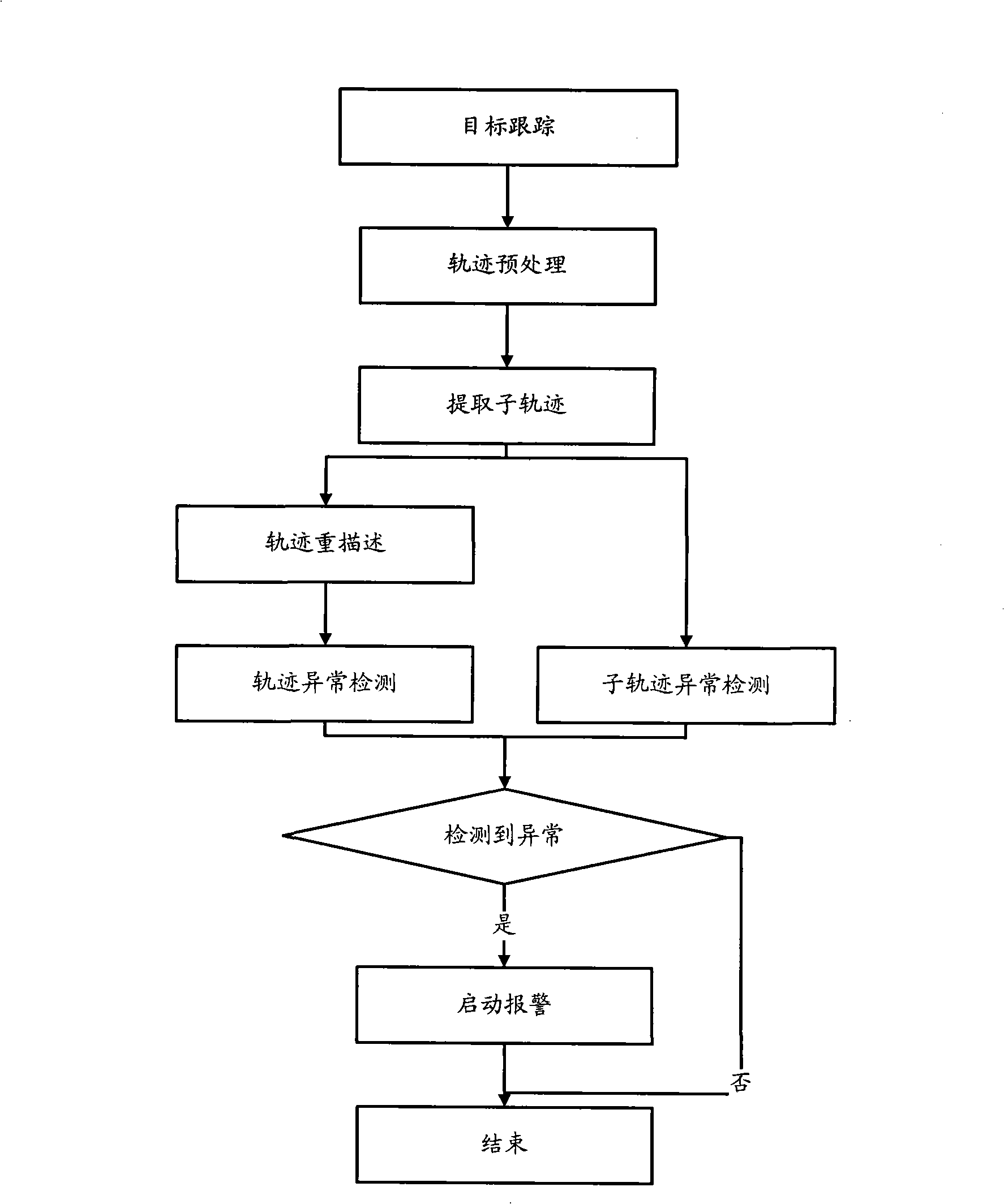
Method for detecting exception target behavior in intelligent vision monitoring
The invention discloses a method for detecting abnormal target behavior in intelligent visual surveillance. The method includes two processes, namely, target behavior learning and target behavior detection. The target behavior obtains the abnormal threshold value Epsilon of every sub-track distribution mode and the abnormal threshold value Epsilon of every track distribution mode of target trajectory which describes occurred target behavior; the target detecting processes calculate the distance from the target trajectory which describes the target behavior to be measured to every sub-track distribution mode and every track distribution mode so as to compare the distance with the abnormal threshold value and judge whether the target behavior is abnormal. The method uses the local and integral behavior modes of self-organizing map network acquisition target respectively, which can detect not only the integral abnormal behavior of a target, but also the local abnormal behavior of the target in moving process.
Owner:ZHEJIANG UNIV
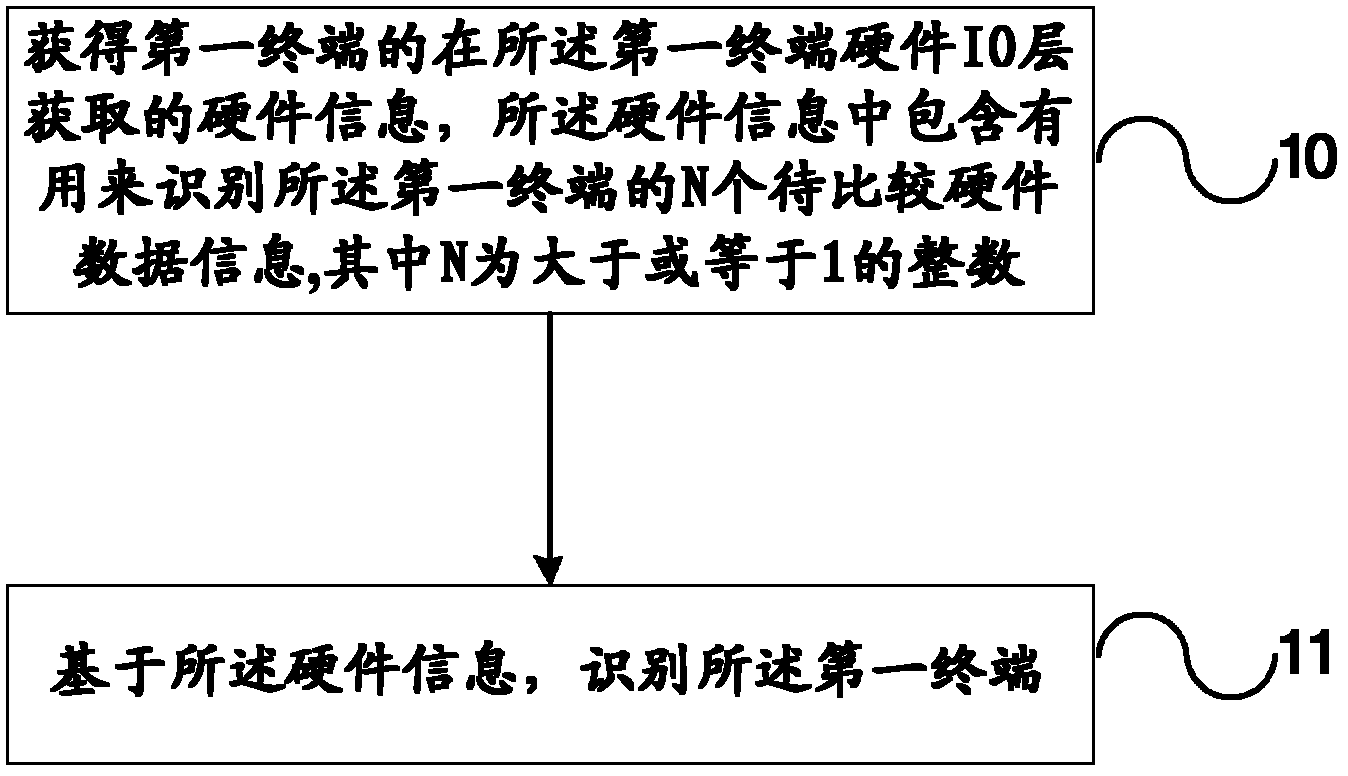
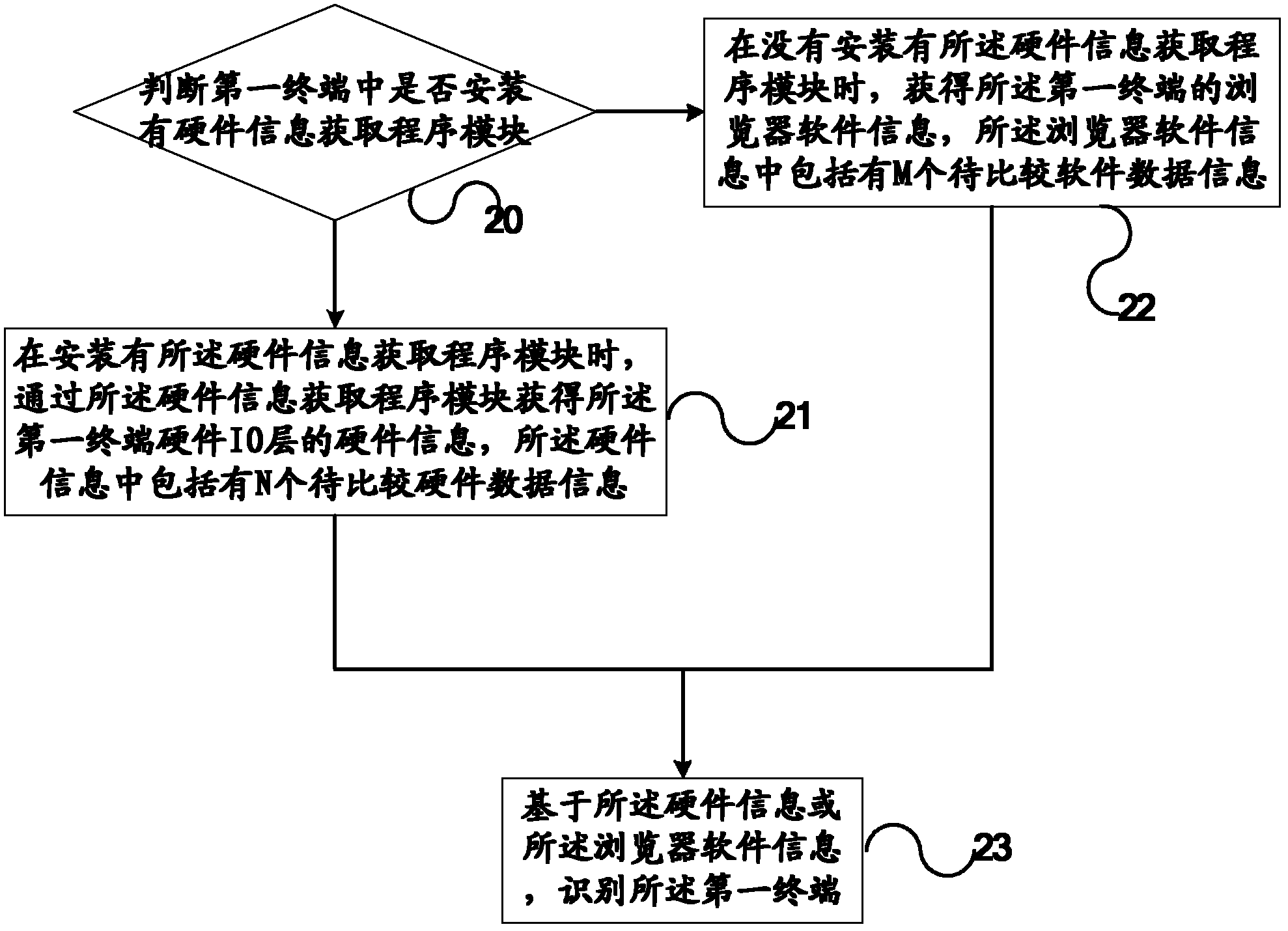
Method and system for identifying user terminal
The invention discloses a method and a system for identifying a user terminal. The method comprises the following steps of: judging whether a hardware information obtaining program module is installed in a first terminal; in the case that the hardware information obtaining program module is installed, obtaining hardware information of the first terminal via the hardware information obtaining program module, wherein the hardware information contains N pieces of to-be-compared hardware data information; in the case that the hardware information obtaining program module is not installed, obtaining browser software information of the first terminal, wherein the browser software information contains N pieces of to-be-compared software data information; and identifying the first terminal based on the hardware information or the browser software information. With the adoption of the method, the user terminal can be accurately identified regardless of whether a user control is installed or not.
Owner:ALIBABA GRP HLDG LTD
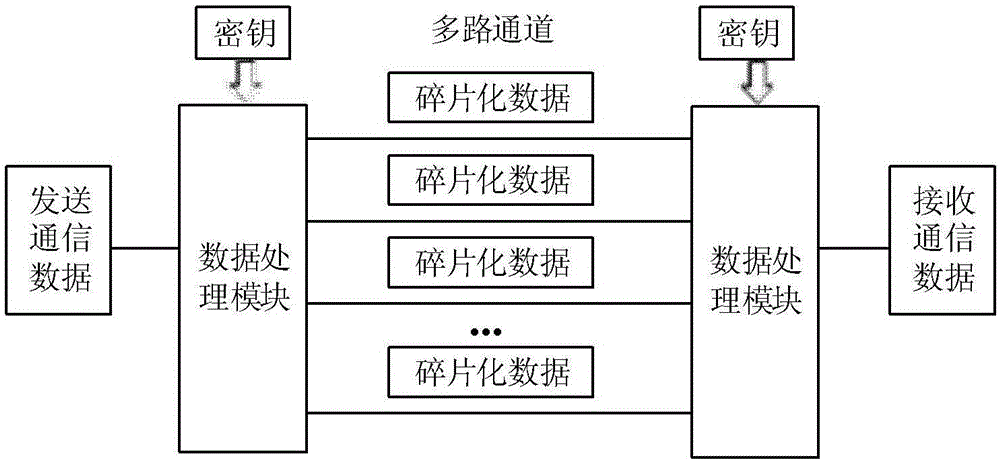
Secure communication method based on multichannel signal fragmentization transmission technology
The invention discloses a secure communication method based on multichannel signal fragmentization transmission technology. The secure communication method comprises the following steps: dispersing communication data into small fragments in an information transmitting terminal, and then transmitting the small fragments by multiple information channels according to a certain rule; and receiving fragmentization data transmitted by the multiple channels in an information receiving terminal, and integrating the fragmentization data according to the fragmentization rule when the information is sent to obtain complete data transmitted by the transmitting terminal. The dispersion and integration rules of the fragments are determined by keys in the transmission process. By adoption of the secure communication method provided by the invention, on one hand, the difficulty of a third party to intercept complete information from the communication data can be greatly increased, so that the third party is difficult to crack signals via ultrahigh performance calculation; and on the other hand, even if enough information is intercepted by the multiple channels, complete effective data is difficult to be extracted from the encrypted fragmentization information, and it is difficult to recombine and recover the original data, therefore the security is improved.
Owner:INST OF SEMICONDUCTORS - CHINESE ACAD OF SCI
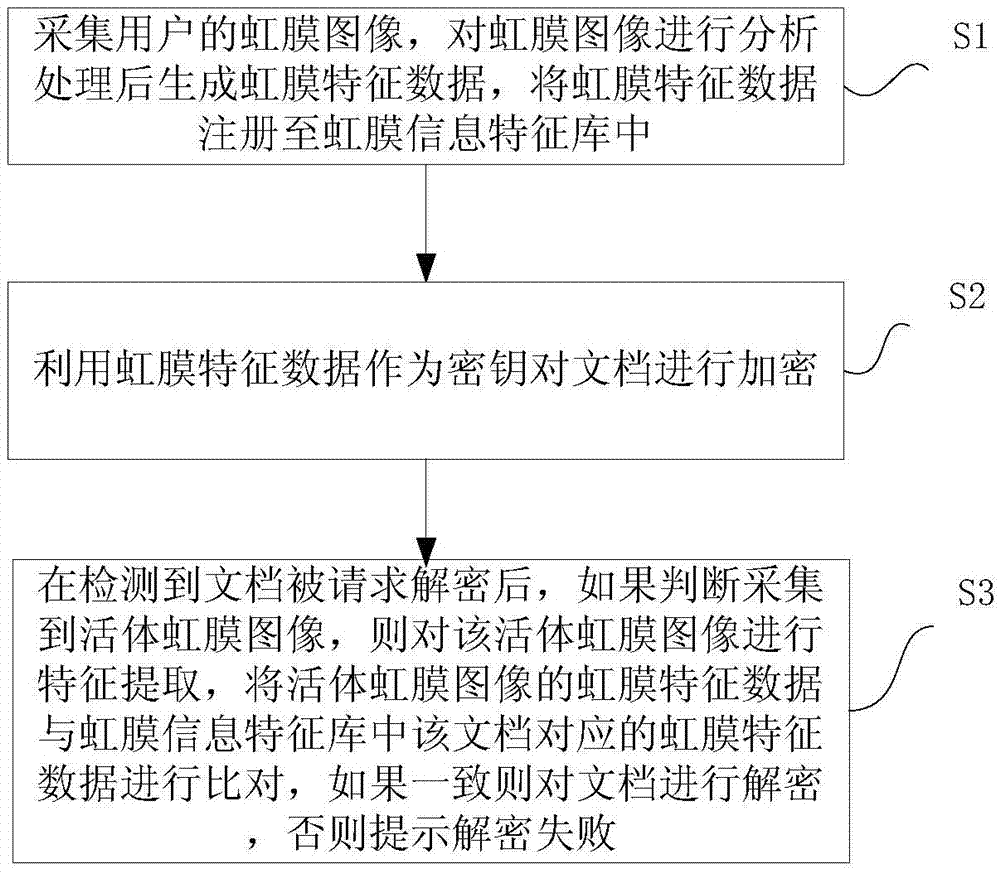
Document encryption/decryption method and apparatus based on iris recognition and authentication
InactiveCN105447405AAvoid interceptionSolve the problem of strong dependenceDigital data protectionDigital data authenticationFeature extractionIdentity recognition
The present invention proposes a document encryption / decryption method and apparatus based on iris recognition and authentication. The method comprises: collecting an iris image of a user, generating iris feature data after analyzing and processing the iris image, and registering the iris feature data into an iris information feature library; encrypting a document by using the iris feature data as a key; and after it is detected that the document is requested to be decrypted, determining whether a living body iris image is collected, if so, carrying out feature extraction on the living body iris image, acquiring iris feature data corresponding to the living body iris image, comparing the iris feature data of the living body iris image with the iris feature data corresponding to the document in the iris information feature library, and if iris feature data of the living body iris image are consistent with the iris feature data corresponding to the document, then decrypting the document, otherwise, prompting that the decryption fails. According to the document encryption / decryption method and apparatus based on iris recognition and authentication, the iris image with uniqueness can be used to carry out identity recognition, thereby triggering an encryption and decryption algorithm to realize security management for the document. The entire encryption / decryption process is simple, convenient and free of potential security hazards.
Owner:南京以太安全技术有限公司
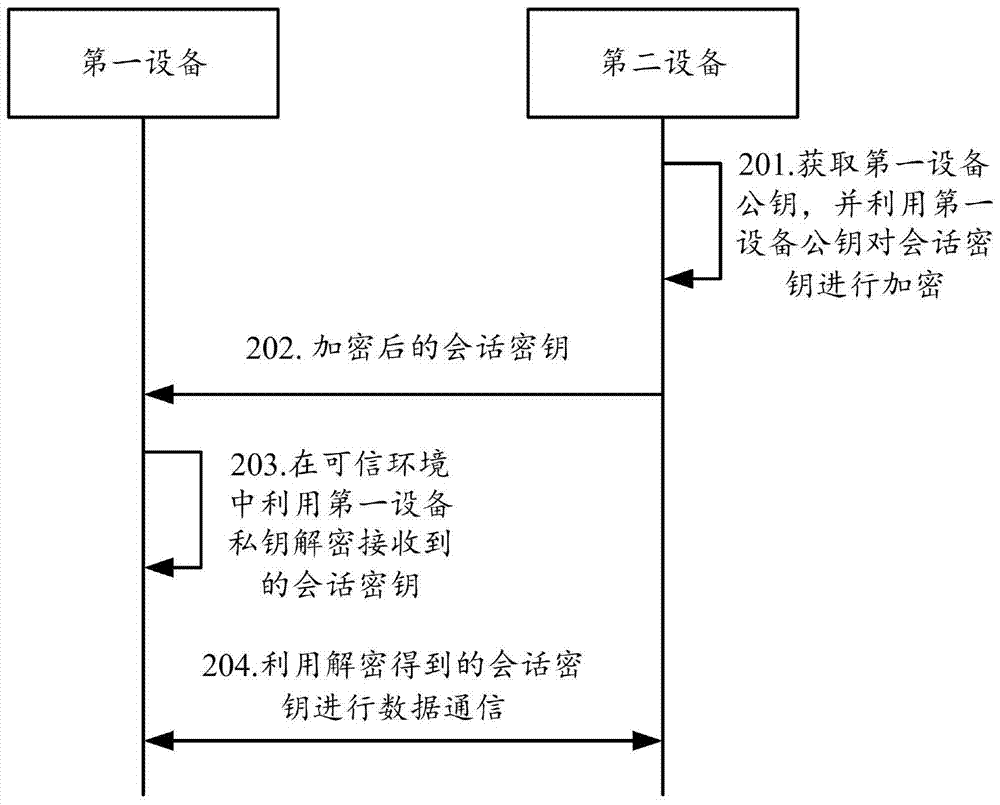
Method, device and system for establishing inter-equipment communication
ActiveCN107026727AImprove securityAvoid interceptionKey distribution for secure communicationInternal/peripheral component protectionComputer networkEngineering
The invention provides a method, a device and a system for establishing inter-equipment communication. The method comprises the following steps that: second equipment acquires a first equipment public key, and encrypts a session key with the first equipment public key; the second equipment transmits an encrypted session key to first equipment; the first equipment decrypts the received session key by using a first equipment private key in a trusted environment; and the first equipment performs data communication with the second equipment by using a decrypted session key. In the method, the device and the system for establishing the inter-equipment communication, decryption of the private key of the equipment and the session key is executed in the trusted environment, thereby preventing keys and session keys from being intercepted due to operating system (OS) bugs, and enhancing the security of the inter-equipment communication.
Owner:BANMA ZHIXING NETWORK HONGKONG CO LTD
Vehicle access control system for district
ActiveCN106097499AAvoid the defect of not distinguishing whether the owner is the ownerImprove securityCharacter and pattern recognitionIndividual entry/exit registersComputer moduleMedia access control
The invention discloses a vehicle access control system for a district. The vehicle access control system comprises: a data storage part; an entrance gate assembly, which comprises a first gate body, a first door leaf interfering in a passage path, a first camera and a second camera; and an image identification assembly, which comprises a first comparison module, a first output module, a second comparison module, a second output module and a control module. The control module is configured to sound an alarm when license plate information or face information falls into a blacklist set; and the second comparison module determines acquired face information and face information of an owner output by the first comparison module belong to the same owner, and the first door leaf is opened, or otherwise closed. According to the invention, the first camera and a third camera are used for long-distance identification of a license plate while the second camera and a fourth camera are used for long-distance identification of the image of the user, so the determination time of the access control system is shortened; and vehicles without authority are not allowed to pass through dual-identity authentication, so vehicles in the district are prevented from burglary, and the vehicle access control system is safer and more efficient, convenient and intelligent.
Owner:SHANGHAI XINGZHOU INFORMATION TECH
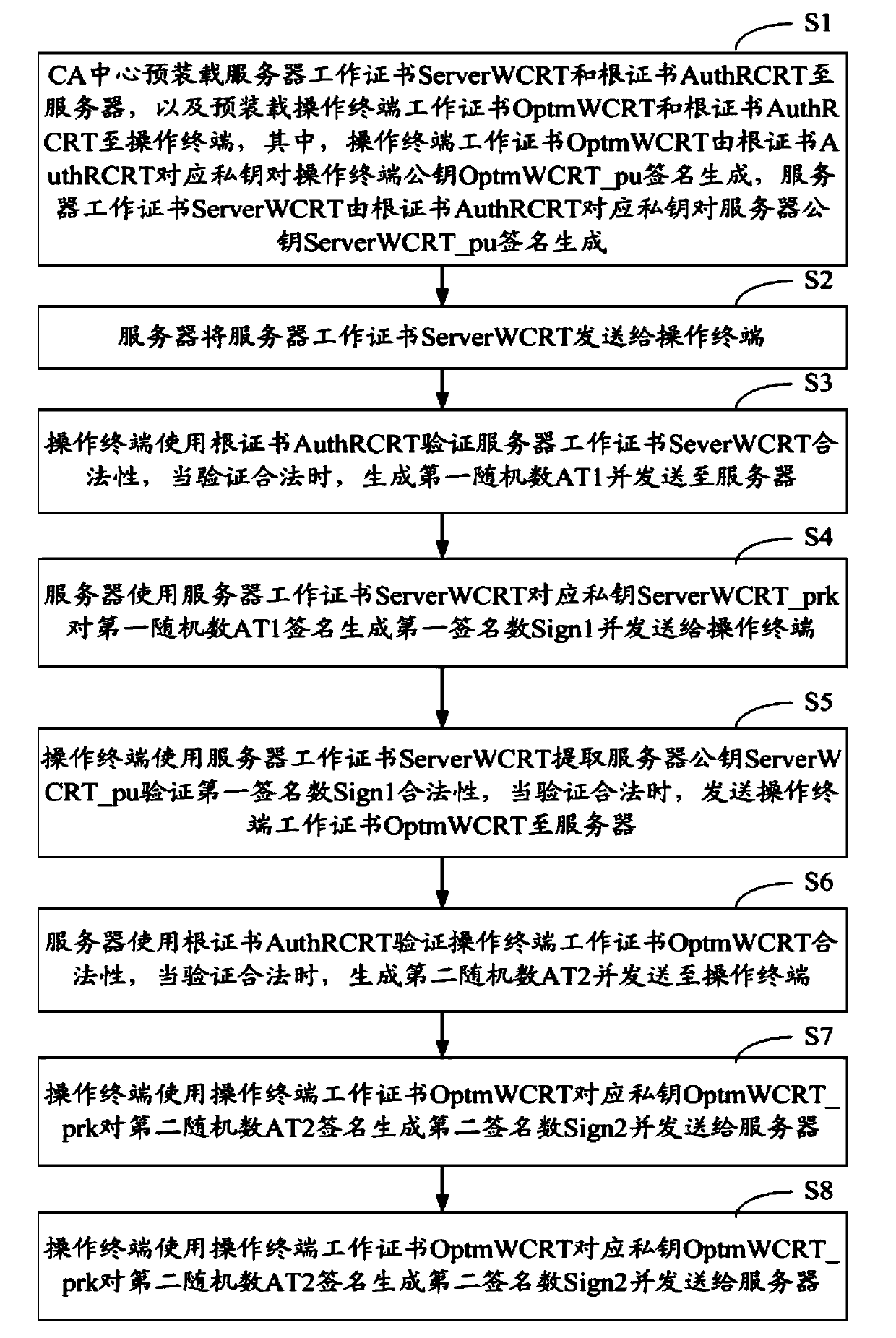
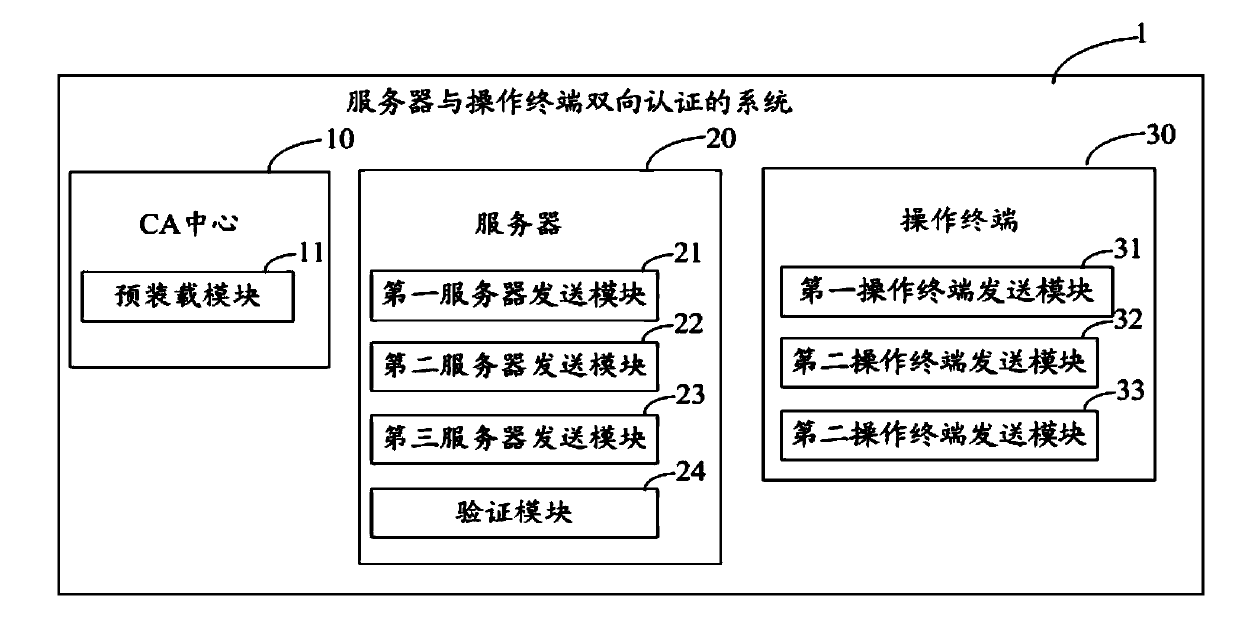
Bidirectional authentication method and system for server and operating terminal
ActiveCN103701609AImprove uploadImprove download securityKey distribution for secure communicationUser identity/authority verificationRoot certificateEncryption
The invention discloses a bidirectional authentication method and system for a server and an operating terminal. The bidirectional authentication method comprises the following steps that: the server sends a server public key to a CA (Certificate Authority) center, and the CA center signs the server public key by using a corresponding private key of a root certificate AuthRCRT to generate a server work certificate ServerWCRT; the CA center sends the work certificate ServerWCRT and the root certificate AuthRCRT to the server to store in a database; the operating terminal sends the public key to the CA center, the CA center signs the public key of the operating terminal by using the corresponding private key of the root certificate AuthRCRT to generate a work certificate OptmWCRT, and sends the OptmWCRT and the AuthRCRT to the operating terminal to store in an encryption module; bidirectional authentication is performed by using the generated certificates and the preset root certificate in a remote master private key download scheme, so that the system security is improved.
Owner:FUJIAN LANDI COMML EQUIP CO LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com