Method and system for identity authentication by finger print USBkey
A technology of identity verification and fingerprint verification, which is applied in the network field, can solve the problems of PIN code leakage security risks, etc., and achieve the effect of solving Trojan horse attacks, preventing being forgotten or leaked, and improving the safety factor
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0074] The present invention will be described in detail below in conjunction with the accompanying drawings.
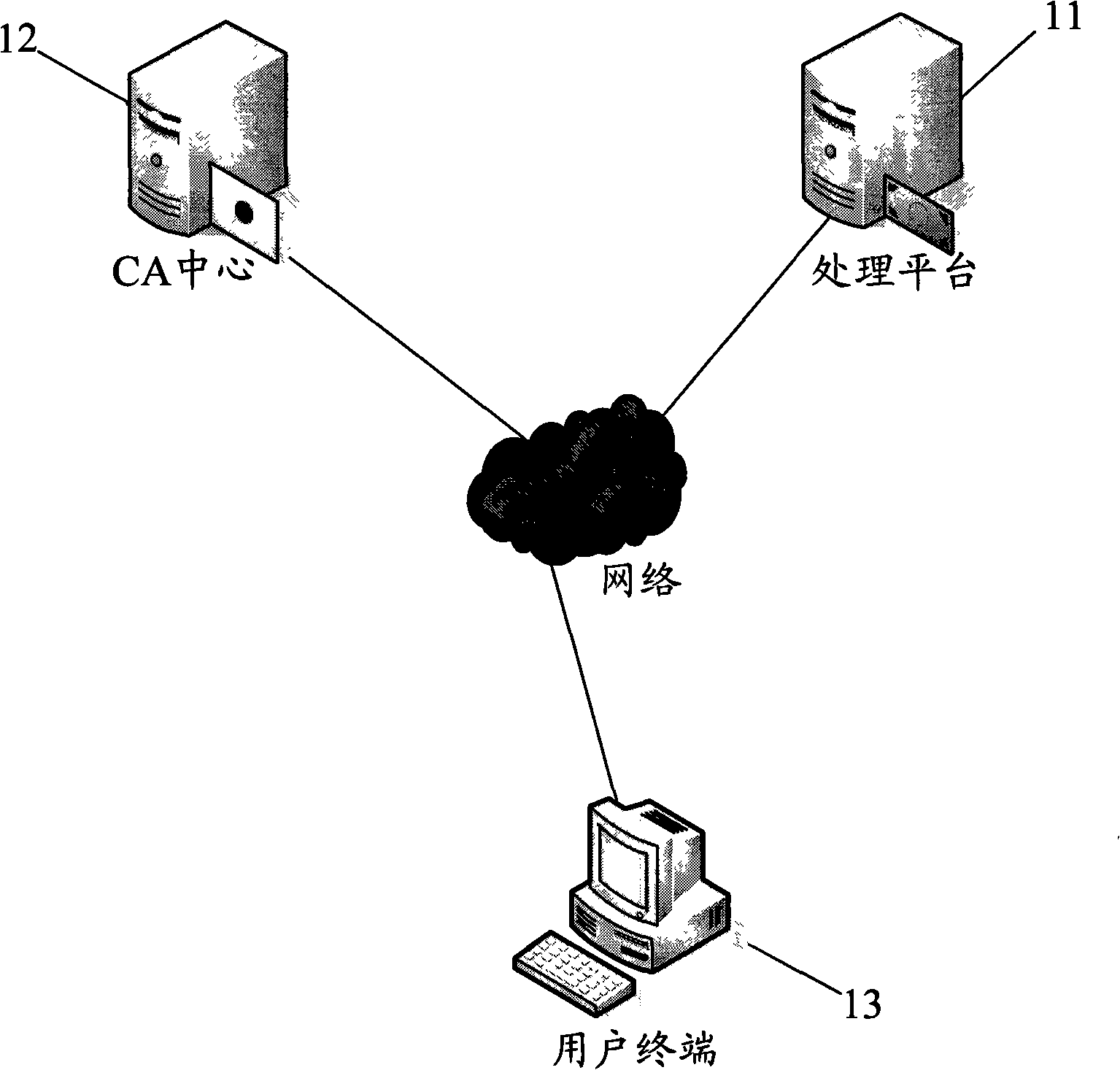
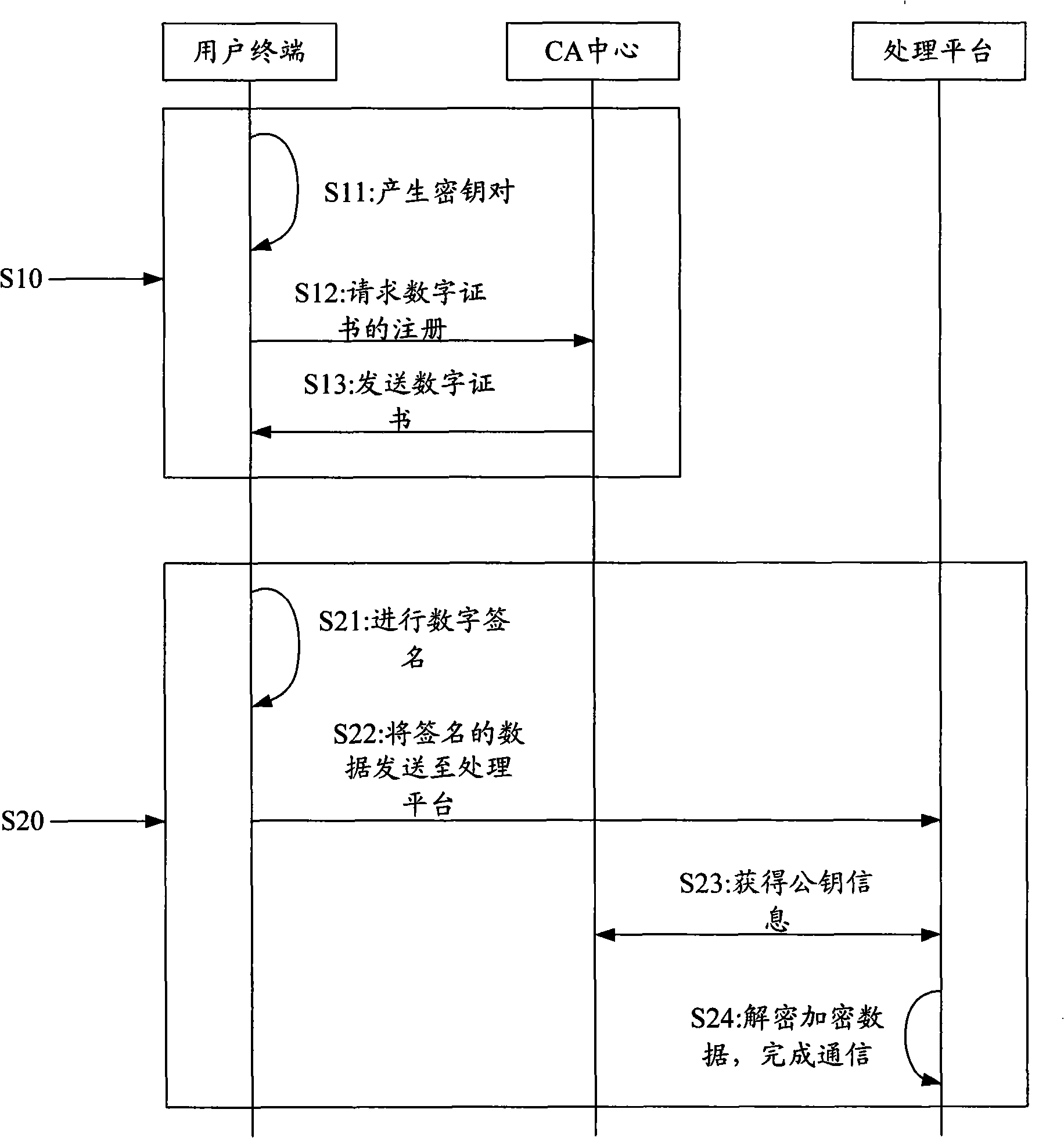
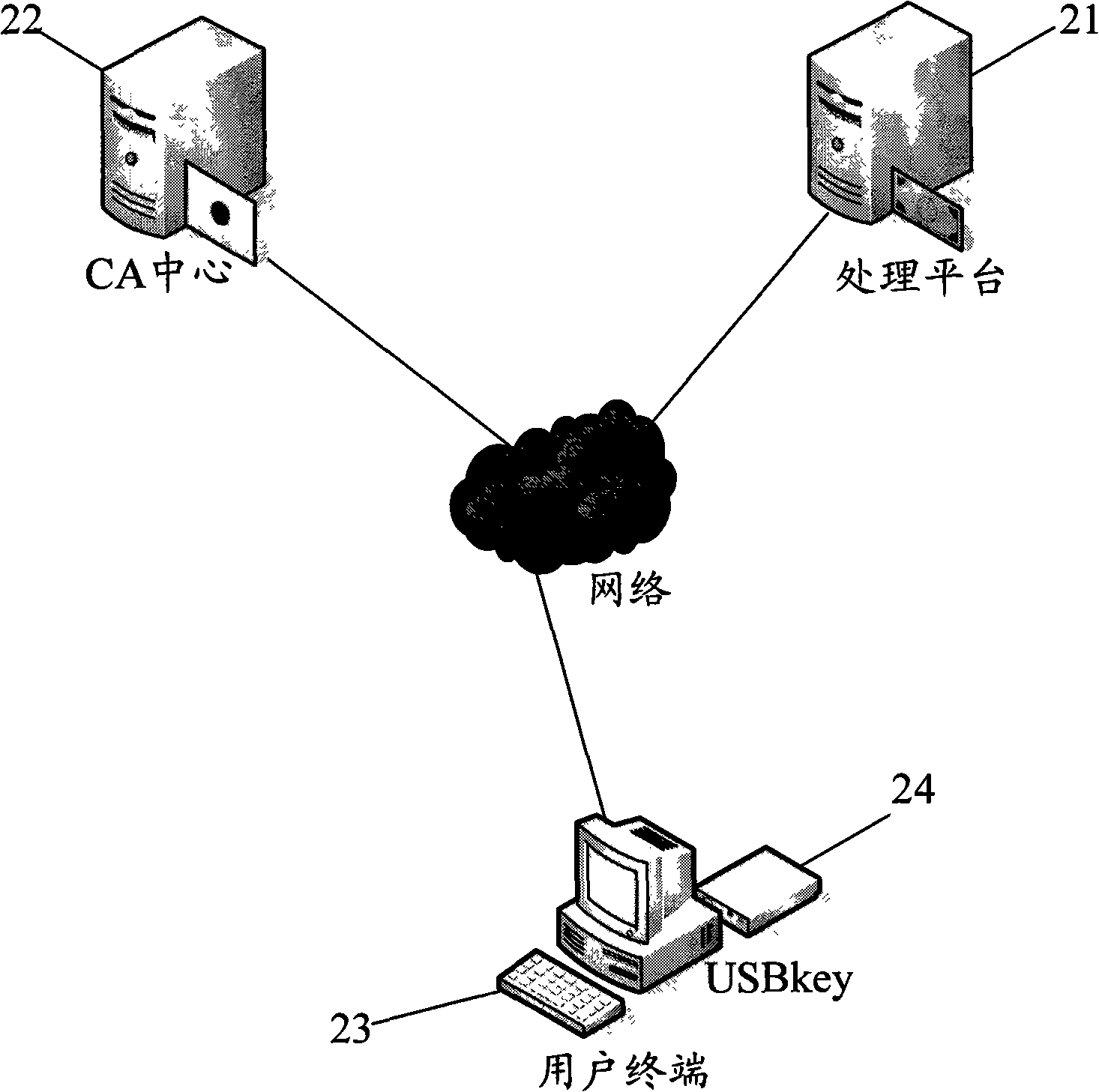
[0075] see Figure 5 , which is a schematic structural diagram of the system principle of using fingerprint USBkey for identity verification in the present invention. It includes client end, CA center 32 and processing platform 31 .
[0076] The user terminal further includes a personal terminal 33 and a fingerprint USBkey34. The personal terminal 33 may be a personal computer, or other devices with processing capability and provided with a USB interface, such as PDA and the like. The user terminal 33 is connected to the CA center 32 and the processing platform 31 through the network. The client can connect the CA center 32 and the processing platform 31 through a wireless network or the Internet. Connecting via a wired or wireless network is a well-known technology, and it is necessary to set up corresponding interface devices on both sides of the communication ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com