Patents
Literature
4728results about How to "Improve confidentiality" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
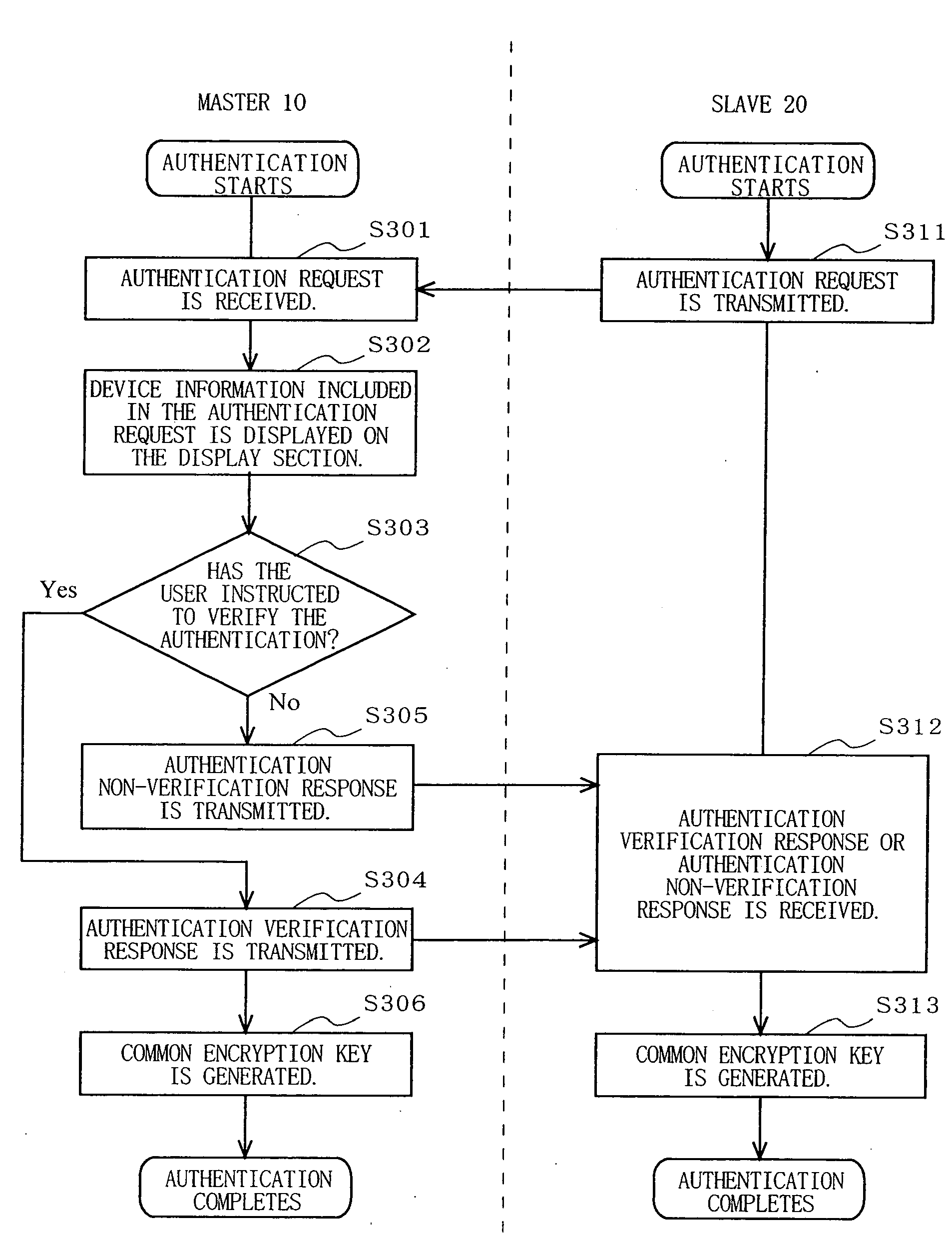
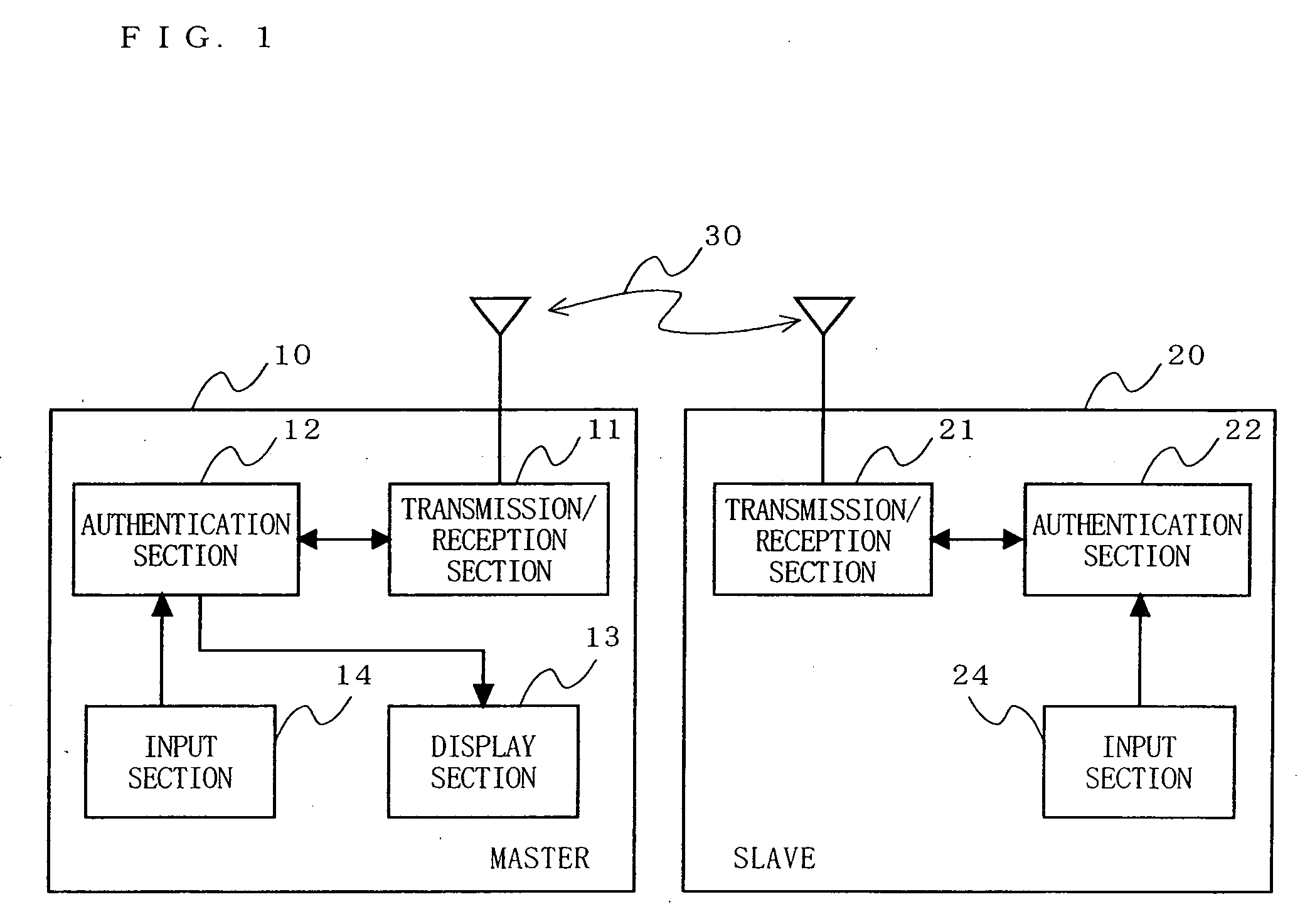
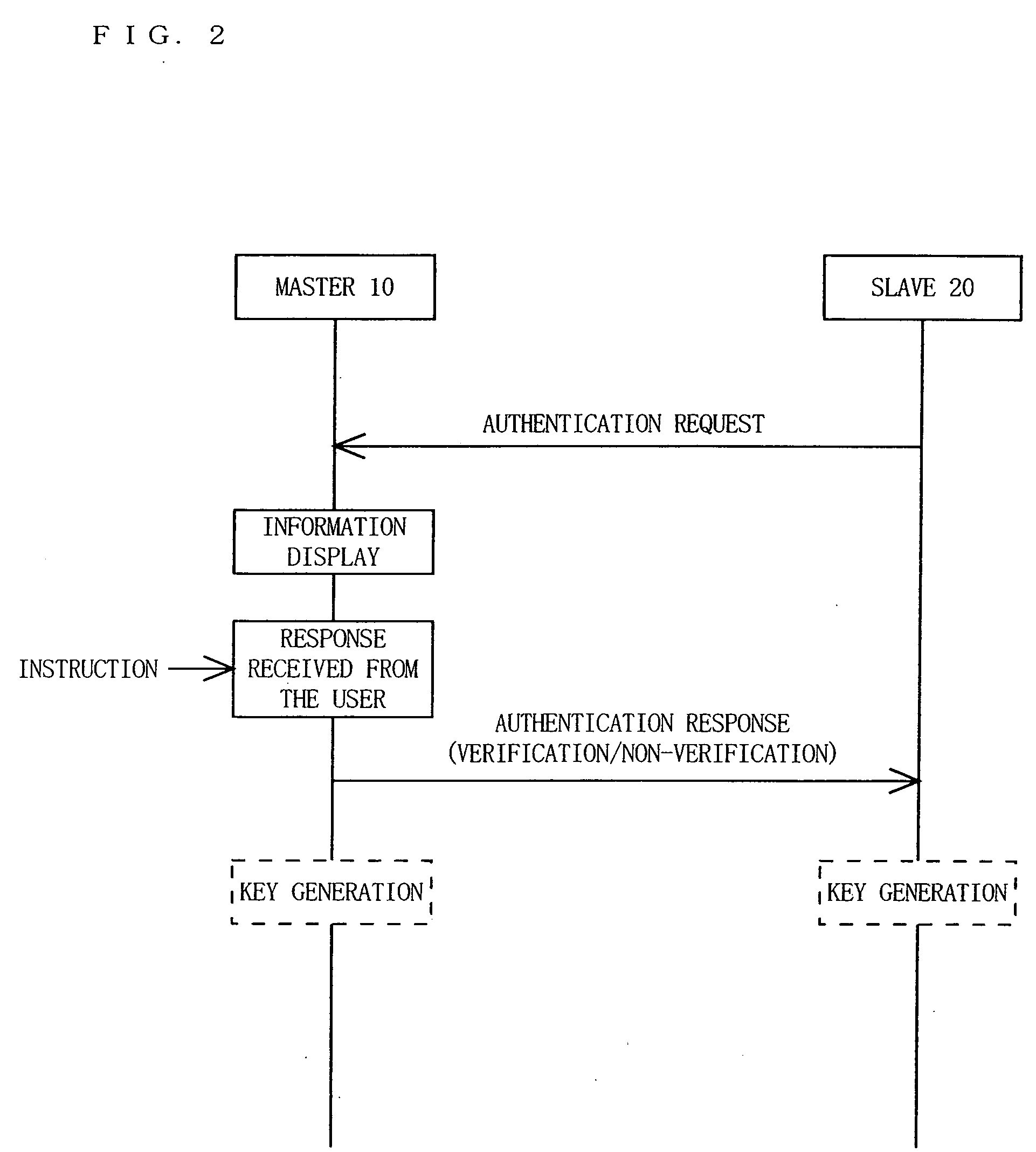
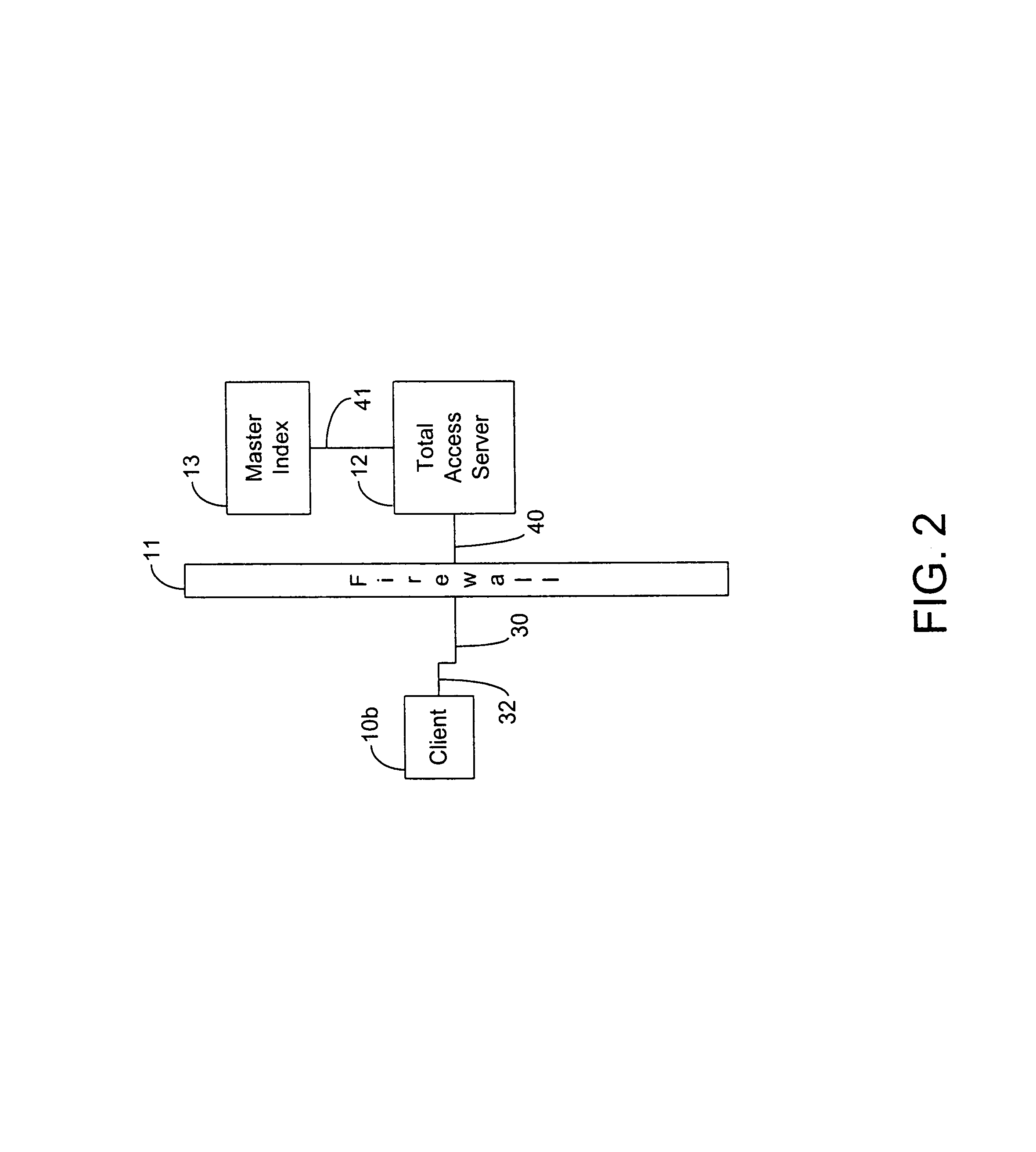
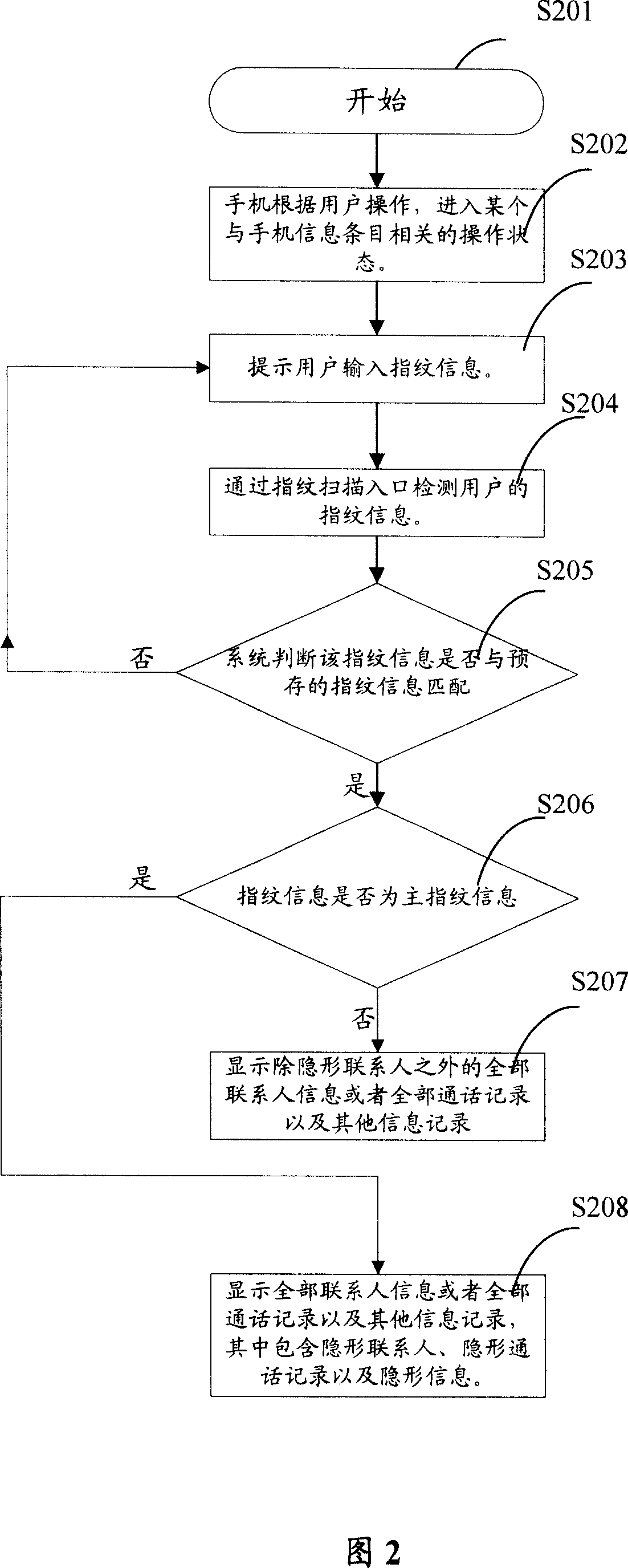
Communication device, communication system and authentication method
InactiveUS20070106894A1Sure easyEnhanced authenticationKey distribution for secure communicationDigital data processing detailsCommunications systemAuthentication system
A communication device, a communication system and an authentication system for preventing a disguising act by an illegal man-in-the-middle and improving the safety and certainty of authentication processing are provided. A slave (20) transmits an authentication request including device information to a master (10). The master (10) receives the authentication request and displays the device information included in the authentication request on a screen of a display section (13). The user visually checks the device information displayed on the screen of the display section 13 (13), determines whether or not to verify the authentication, and instructs the master (10) of the determination result via an input section (14). The master (10), instructed to verify or not to verify the authentication, transmits a response in accordance with the instruction to the slave (20).
Owner:SOVEREIGN PEAK VENTURES LLC
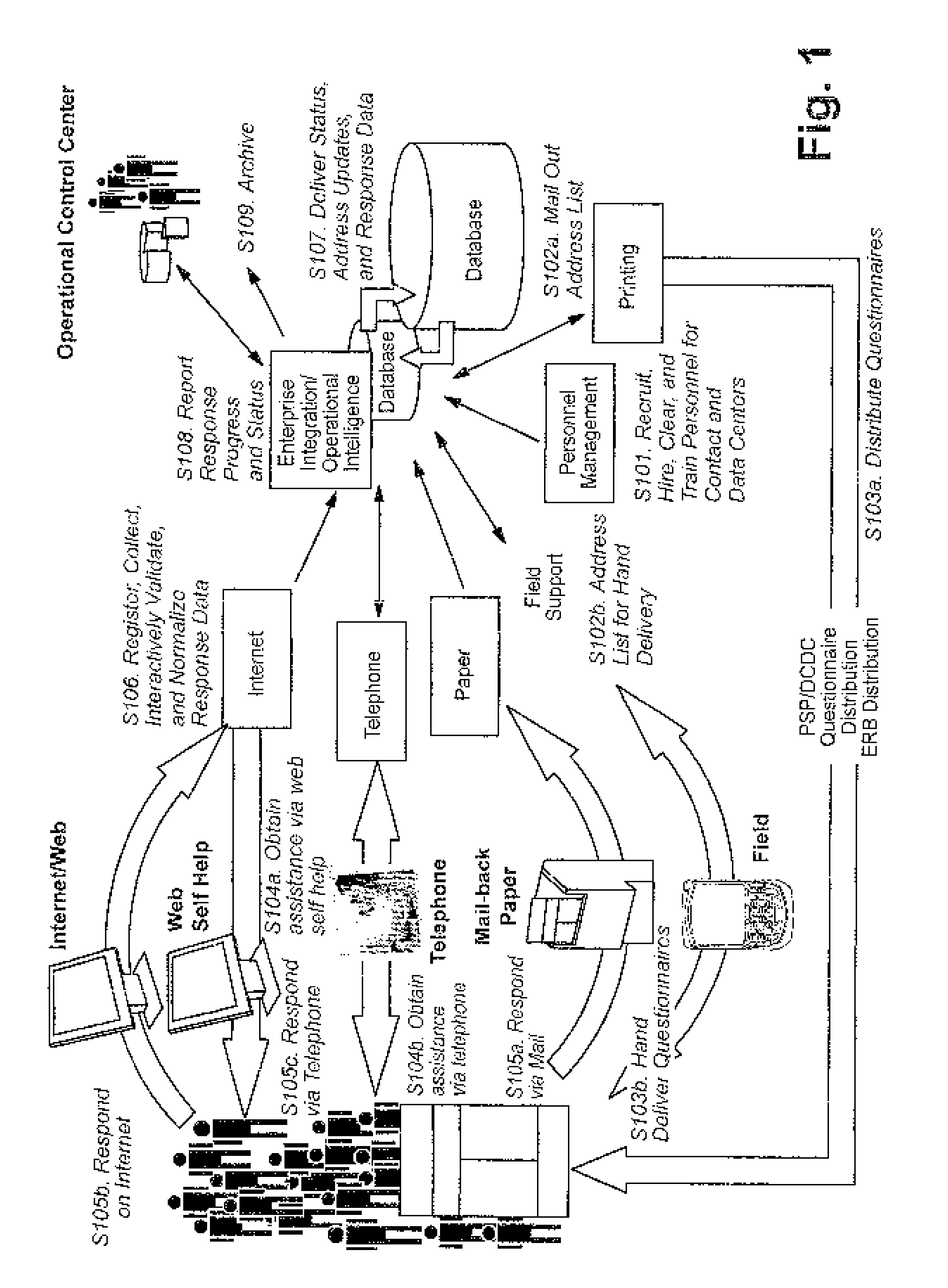
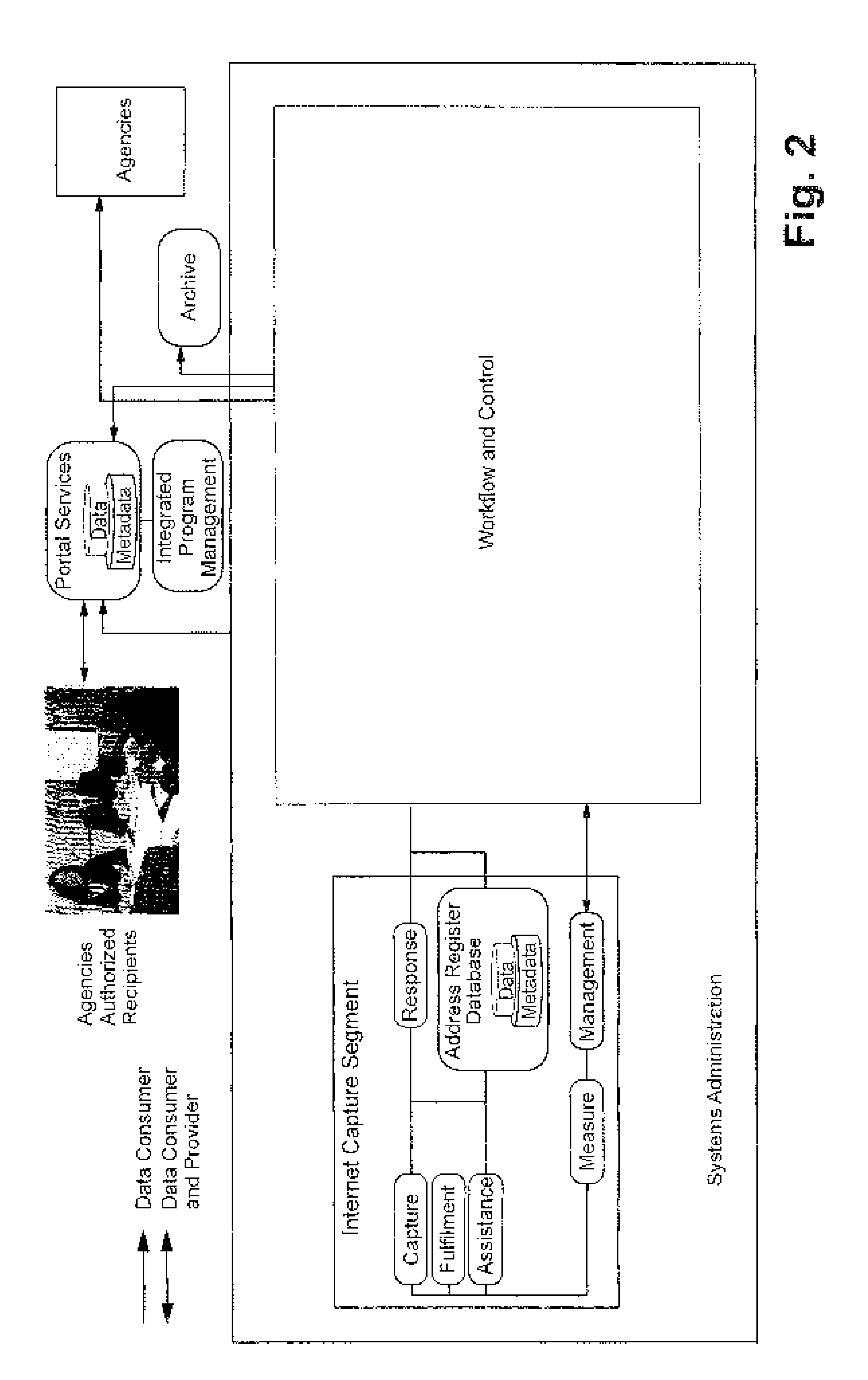
Dynamically generated web surveys for use with census activities, and assocated methods
InactiveUS20100281313A1Improve economyFoster just societyInput/output for user-computer interactionFault responseLook and feelApplication software
Certain example embodiments disclosed herein relate to online survey systems and / or methods. In certain example embodiments, the questions to be asked are substantially insulated from an application that asks the questions. This abstraction may be accomplished in certain example embodiments by dynamically generating a computer-accessible (e.g., web-based) survey from one or more definition files. For example, a survey may be defined via a response definition file and a user interface definition file, thereby enabling the definition files to be read and the survey to be presented with the appropriate questions, validations, and transformations being specified by the response definition file, and with the look and feel being specified by the user interface definition file. Answers to questions may be persisted for a respondent in a storage location remote from the respondent. Such online surveys systems and / or methods may be suitable for census-related activities.
Owner:LOCKHEED MARTIN CORP
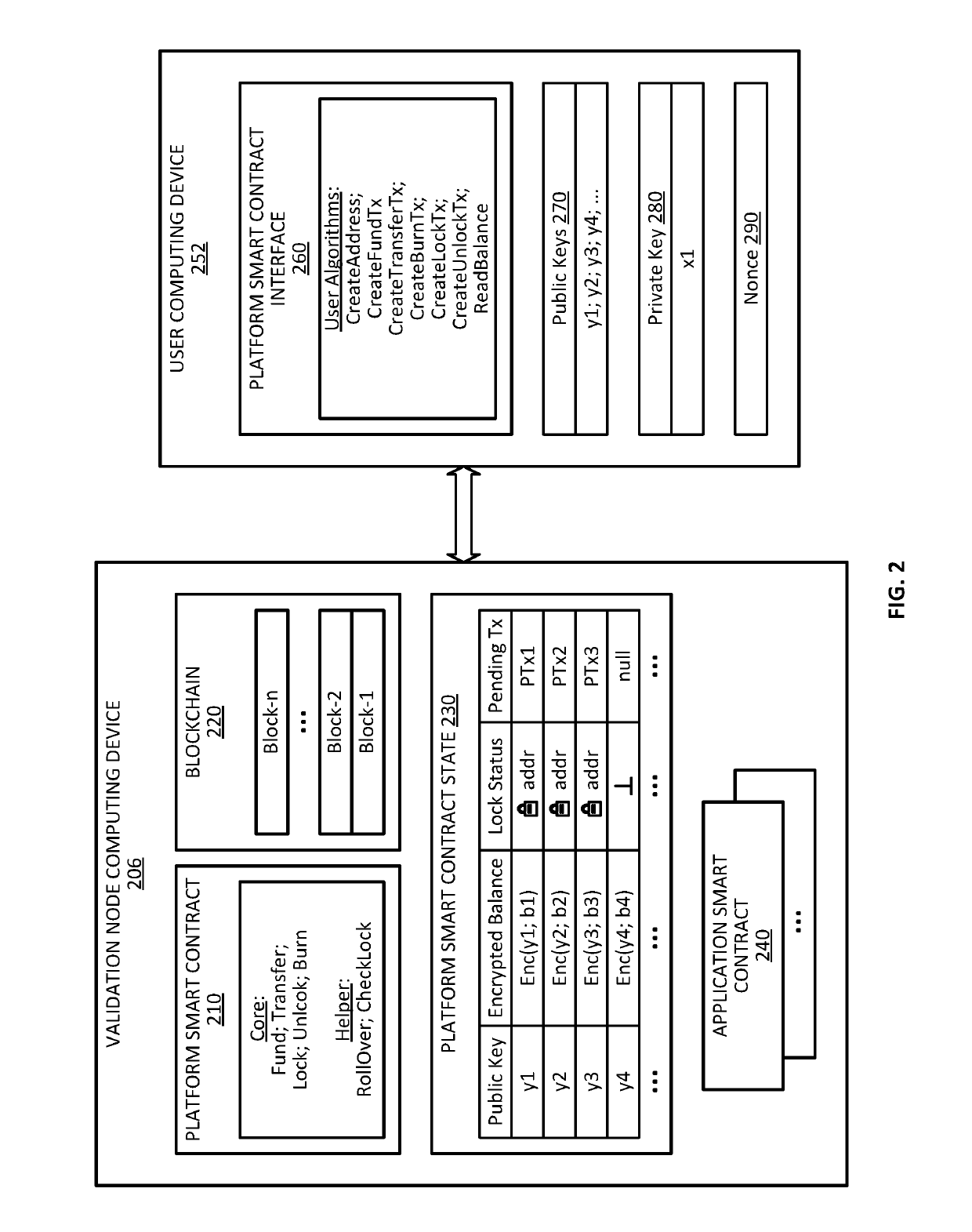
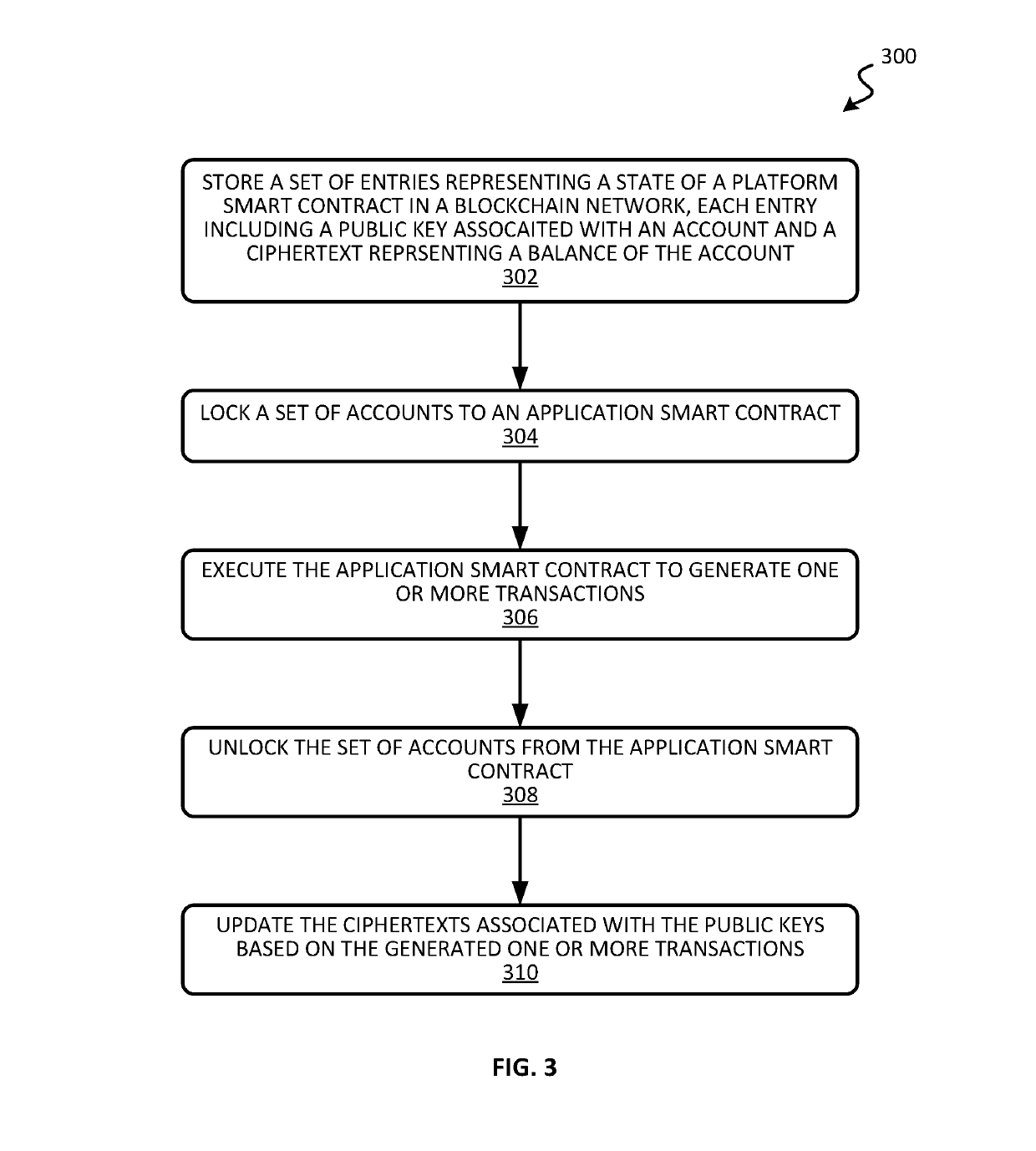
Blockchain system for confidential and anonymous smart contracts
ActiveUS20190164153A1Improve confidentialityEnhanced anonymityEncryption apparatus with shift registers/memoriesCryptography processingInternet privacyPrivacy preserving
Blockchain-based, smart contract platforms have great promise to remove trust and add transparency to distributed applications. However, this benefit often comes at the cost of greatly reduced privacy. Techniques for implementing a privacy-preserving smart contract is described. The system can keep accounts private while not losing functionality and with only a limited performance overhead. This is achieved by building a confidential and anonymous token on top of a cryptocurrency. Multiple complex applications can also be built using the smart contract system.
Owner:VISA INT SERVICE ASSOC +1
Information security management and control method under cloud manufacturing environment
InactiveCN102710605ASolve the problem of update and maintenanceAvoid complex proceduresPublic key for secure communicationUser identity/authority verificationConfidentialityPrivate network
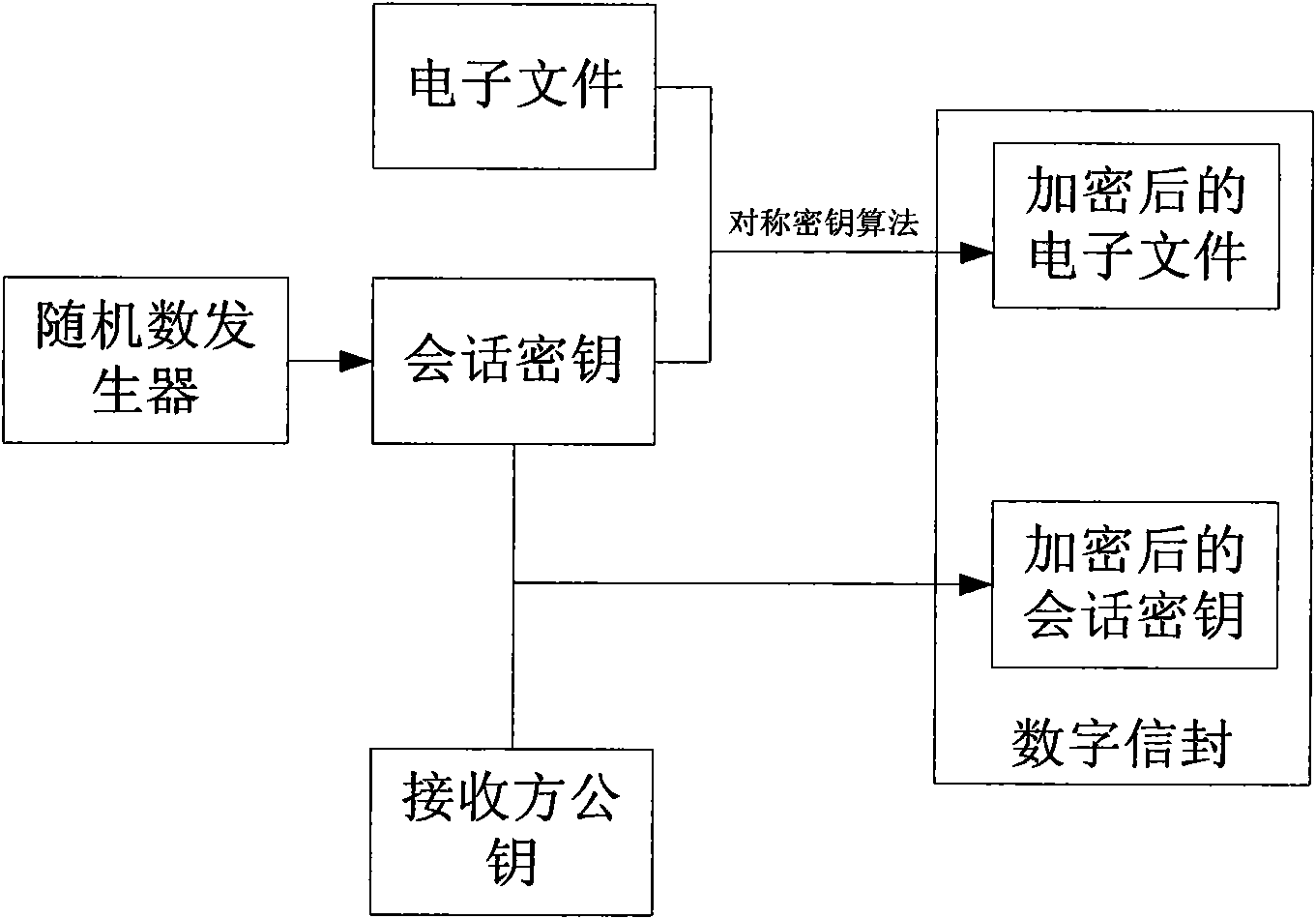
The invention discloses an information security management and control method under a cloud manufacturing environment. On the basis of a network security protocol, a password technology and a public key infrastructure (PKI), comprehensive security guarantee is supplied to information interaction among cloud internal networks, between one cloud and another cloud, and between a user and each cloud by using implementation technologies and methods, such as a virtual private network (VPN) based on multiple layers of protocols, a digital envelope and a password algorithm; Intranet, Extranet and Internet of a cloud manufacturing system are covered; comprehensive management and control technical information files are stored and transmitted to each used loop; a session key (SK) which is randomly produced by using a key production protocol is used for symmetrically encrypting the technical information files; and a receiver public key obtained according to a PKI digital certificate asymmetrically encrypts the SK to form the digital envelope for protecting the technical information files and the SK. The information security management and control method has the characteristics of being high in confidentiality, high inefficiency, flexible in arrangement and the like and can be widely applied to the cloud manufacturing system and other network manufacturing systems.
Owner:CHONGQING UNIV
Electronic document safe sharing system and method thereof
InactiveCN101989984AGuarantee authenticitySafe storagePublic key for secure communicationUser identity/authority verificationClient-sideSafe storage
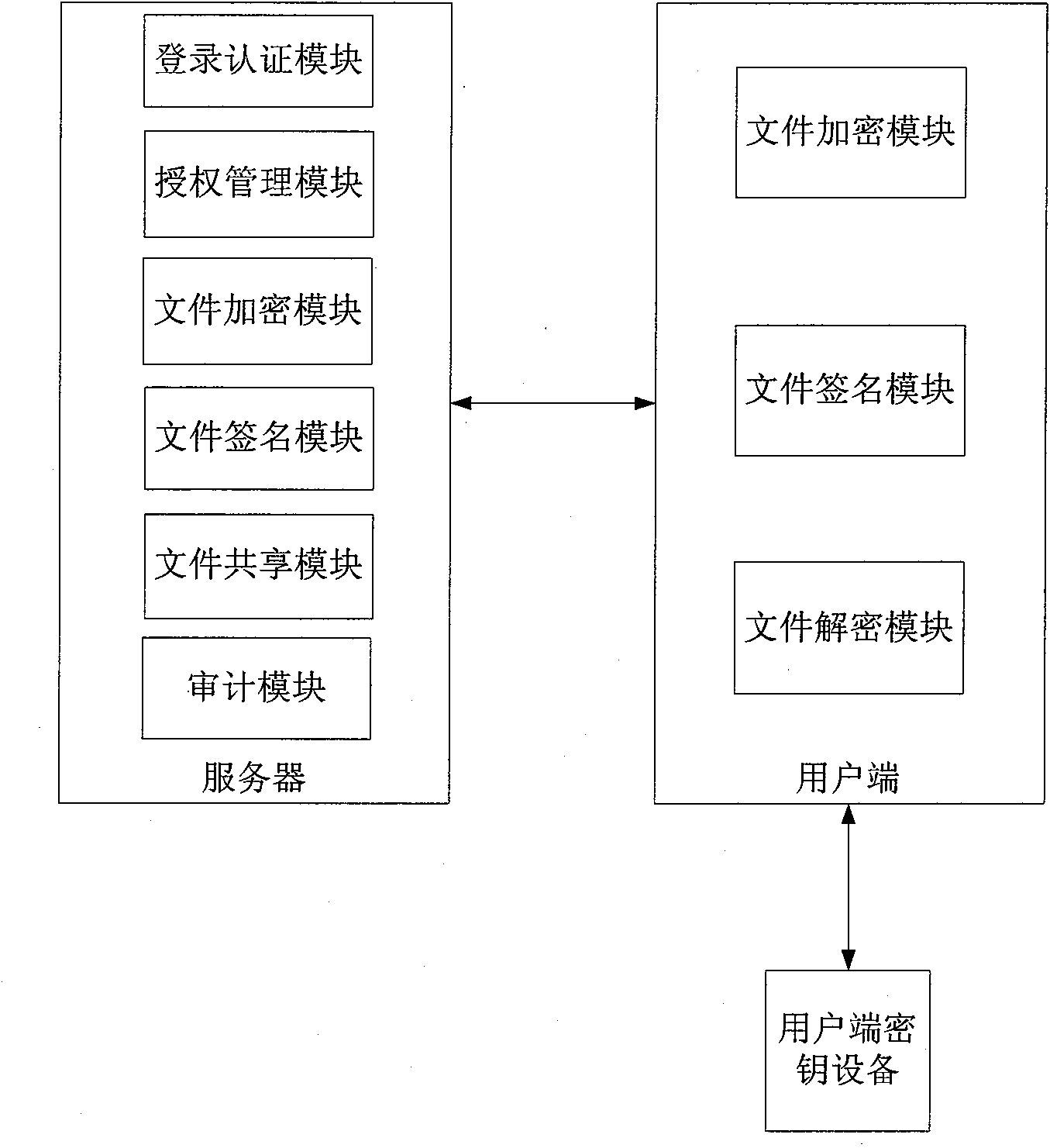
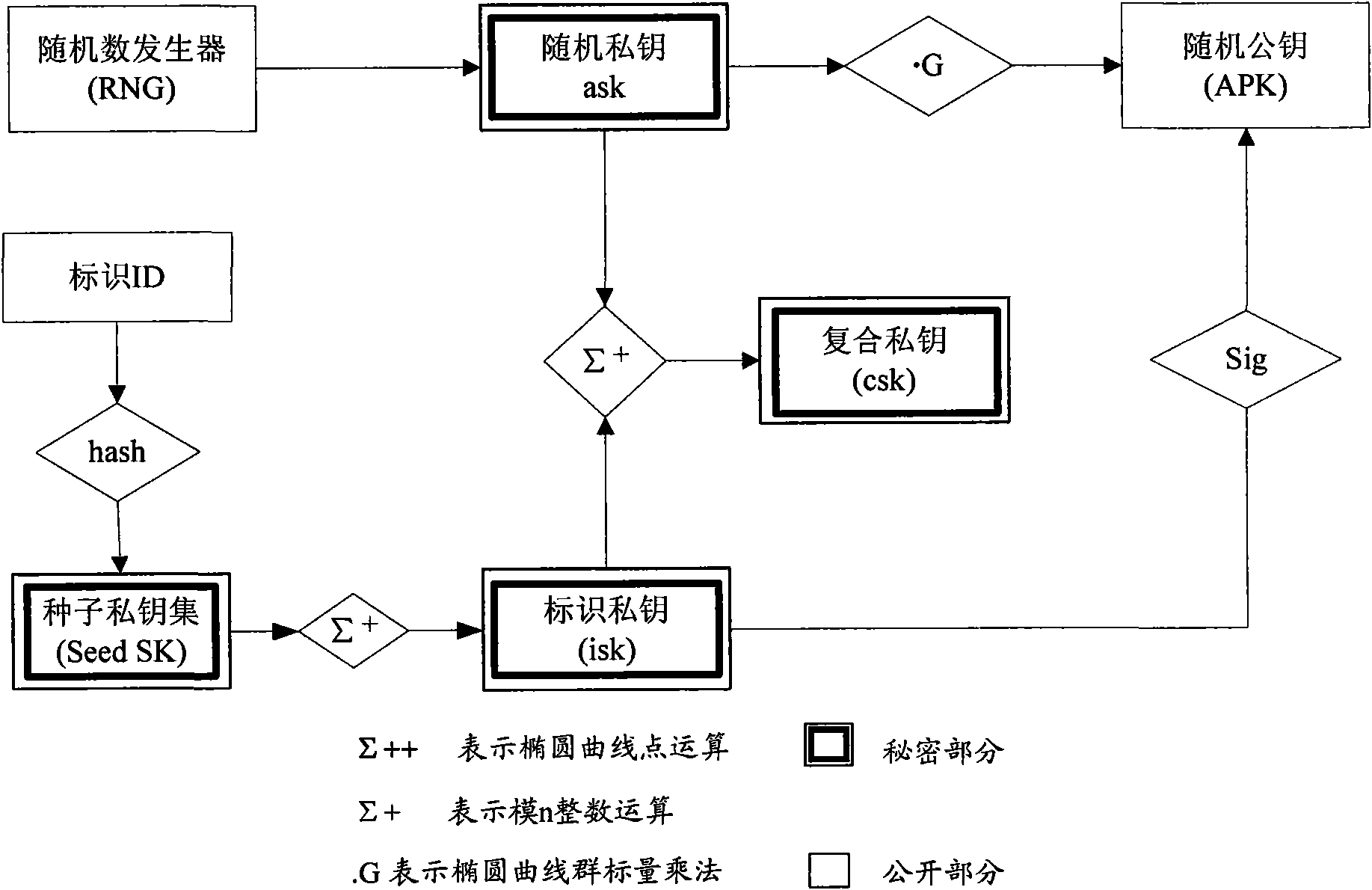
The invention discloses an electronic document safe sharing system which can realize safe storage and fully sharing of secret document. The electronic document safe sharing system comprises a document encrypting module and a document decrypting module; wherein the document encrypting module utilizes a session key to symmetrically encrypt electronic document data, receiver identification (public key) is utilized to asymmetrically encrypt the session key, and finally the encrypted symmetric key and encrypted electronic document data are packed into a digital envelop; and the document decrypting module utilizes an own private key to decrypt the digital envelop. The electronic document safe sharing method of the invention takes CPK combined public key or CPK compound public key technology as the basis, flexible digital signature and secret key exchange capacity thereof are utilized, and a confidential document management system which is from a server to a client, contains information storage and transmission to each use link and is integrated with document data encryption, access control, authorization management, dynamic key exchange and process audit trail into a whole is constructed.
Owner:BEIJING E HENXEN AUTHENTICATION TECH +1
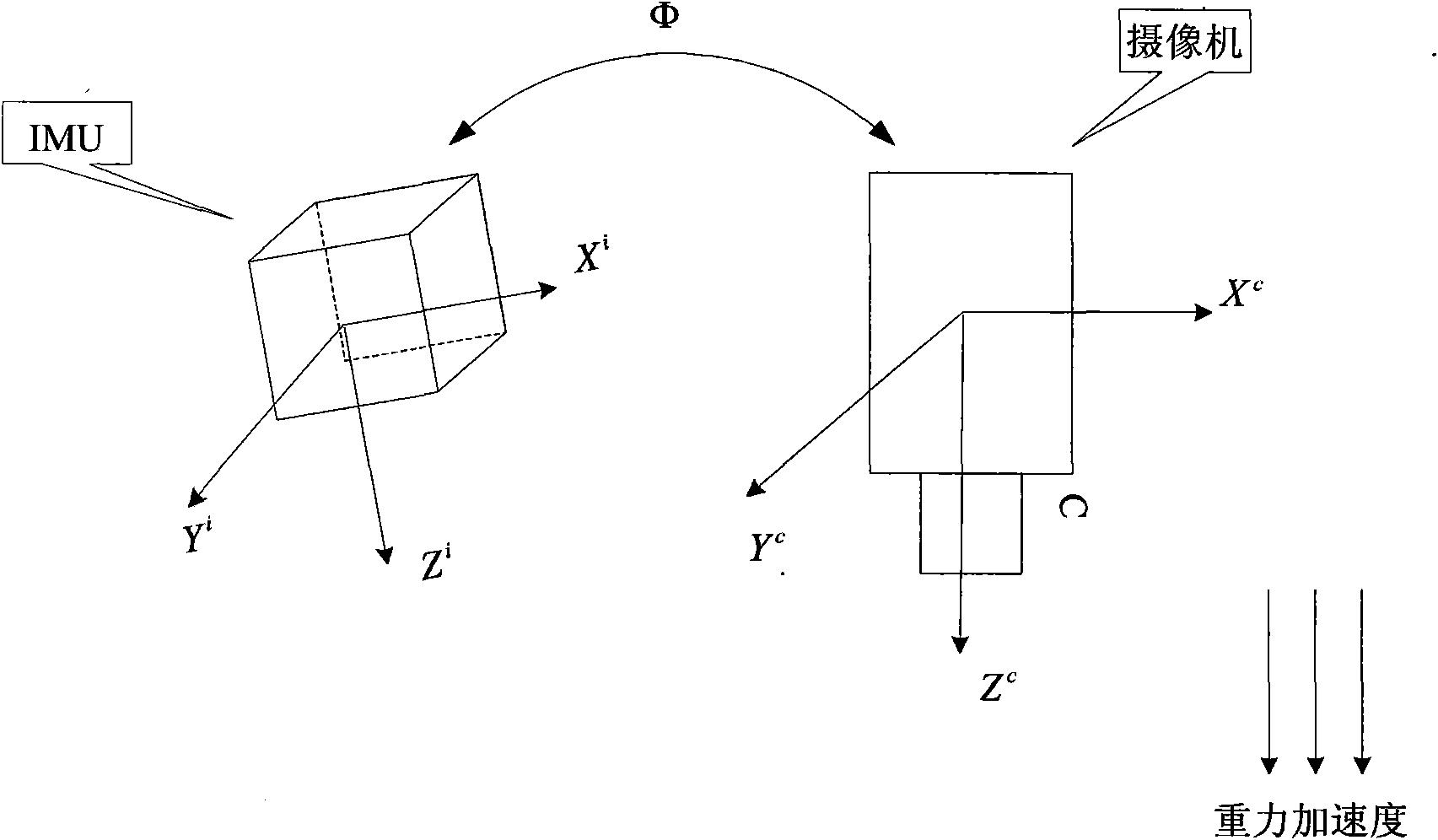
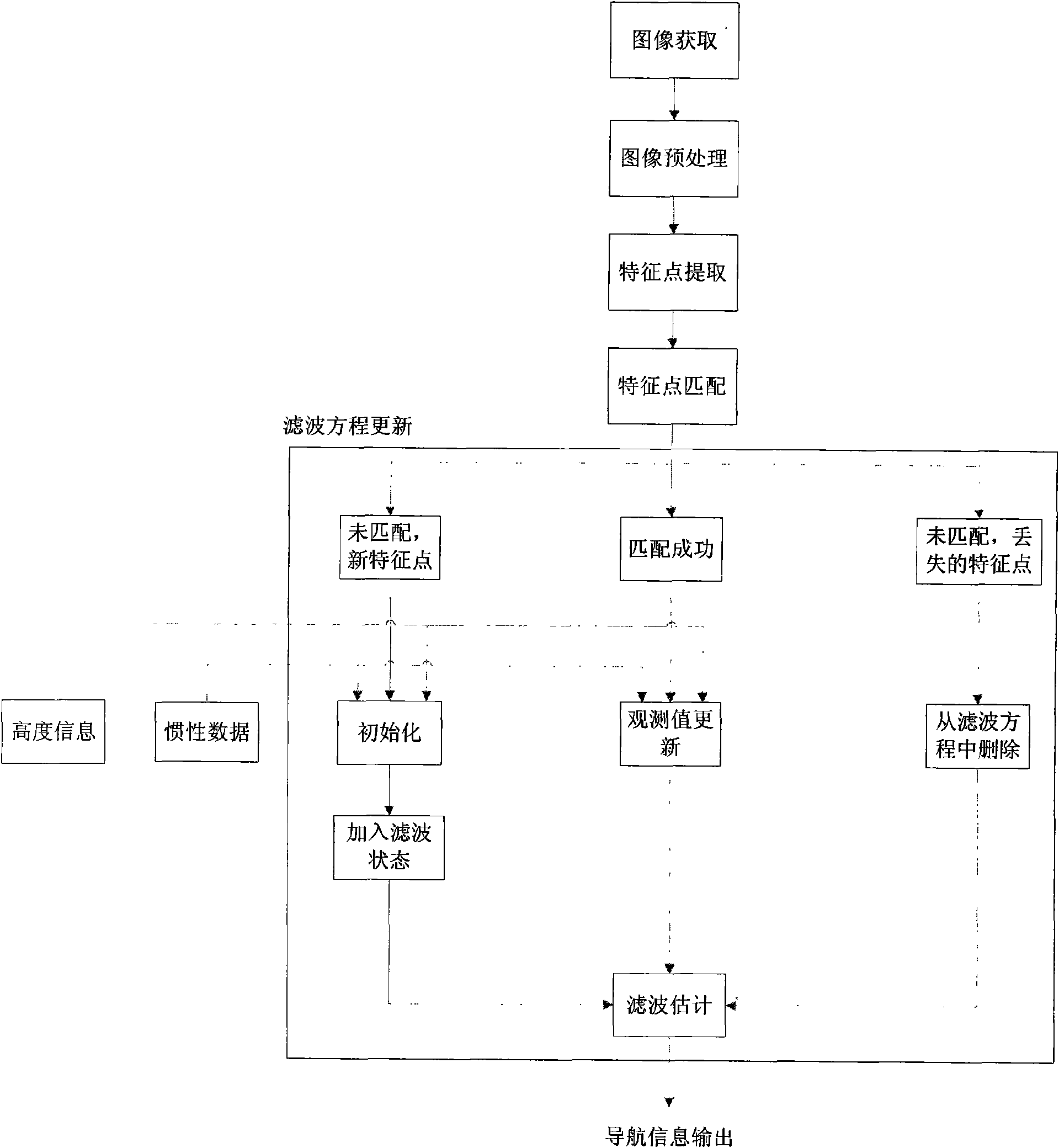
Unmanned aerial vehicle vision/inertia integrated navigation method in unknown environment
InactiveCN101598556AWide adaptabilityImprove concealmentInstruments for comonautical navigationImaging processingCanyon
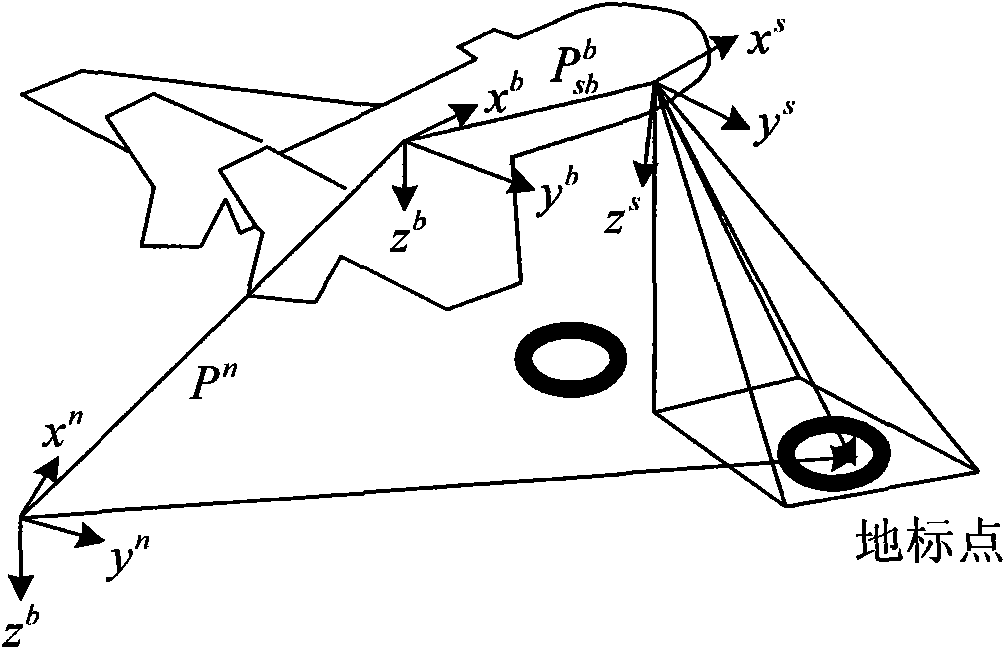
The invention relates to an unmanned aerial vehicle vision / inertia integrated navigation method in the unknown environment. The method relates to image processing, inertial navigation calculation and filtering estimation, so that the steps of defining coordinate system, aligning the coordinate system, setting up filter equation and the like are firstly carried out before the main navigation method is implemented. The navigation process of the method comprises five steps: acquiring and pretreating image; extracting feature points by a SIFT method; matching the feature points; updating the filter equation; and carrying out the filtering estimation on the updated filter equation. The method only needs the current ground image instead of specific external information for matching, so as to be used in any environment (including underwater, shelter, canyon, underground and the like) in theory; furthermore, the method has the advantages of good sheltered property and high accuracy.
Owner:BEIHANG UNIV
Standing order database search system and method for internet and internet application
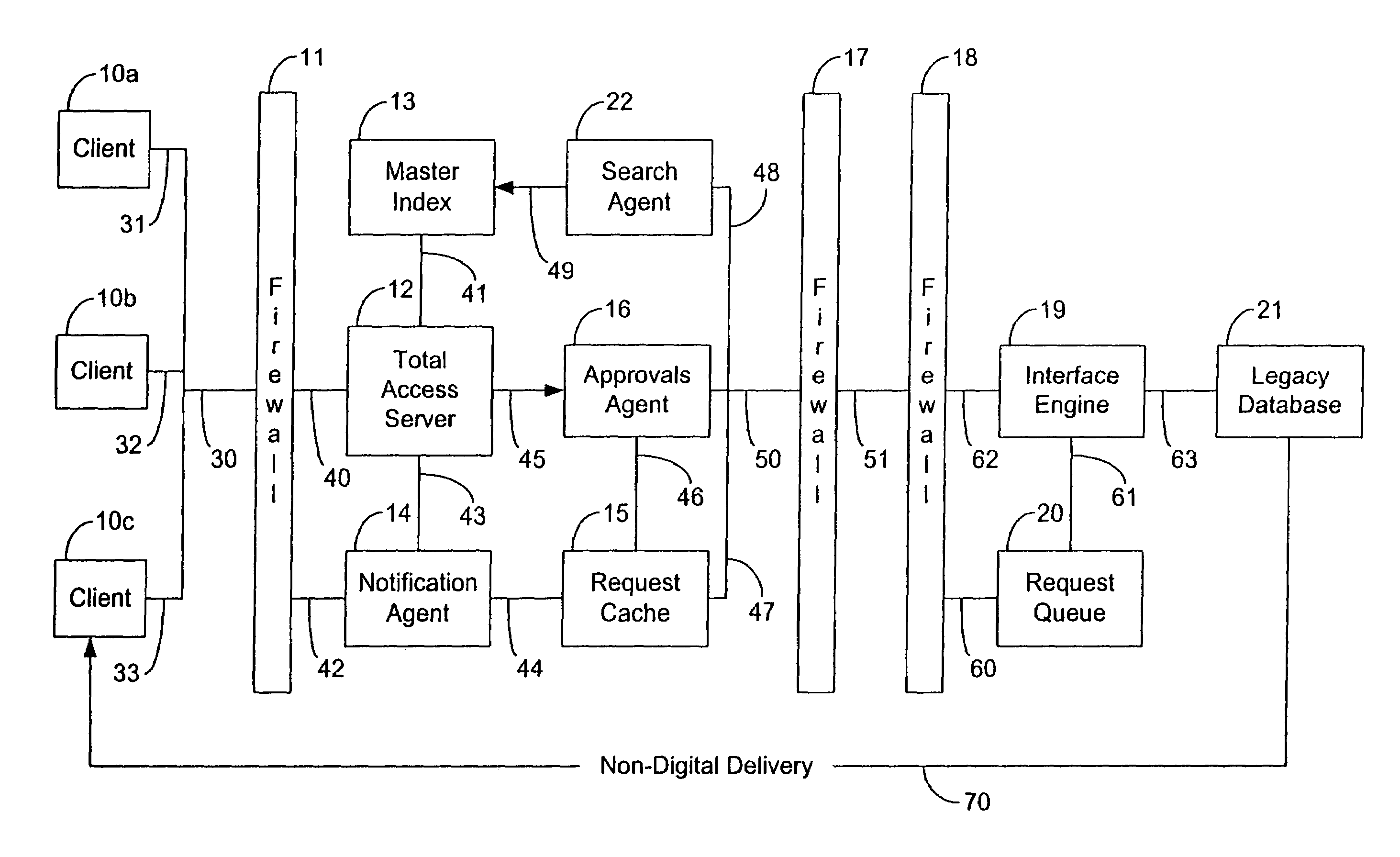
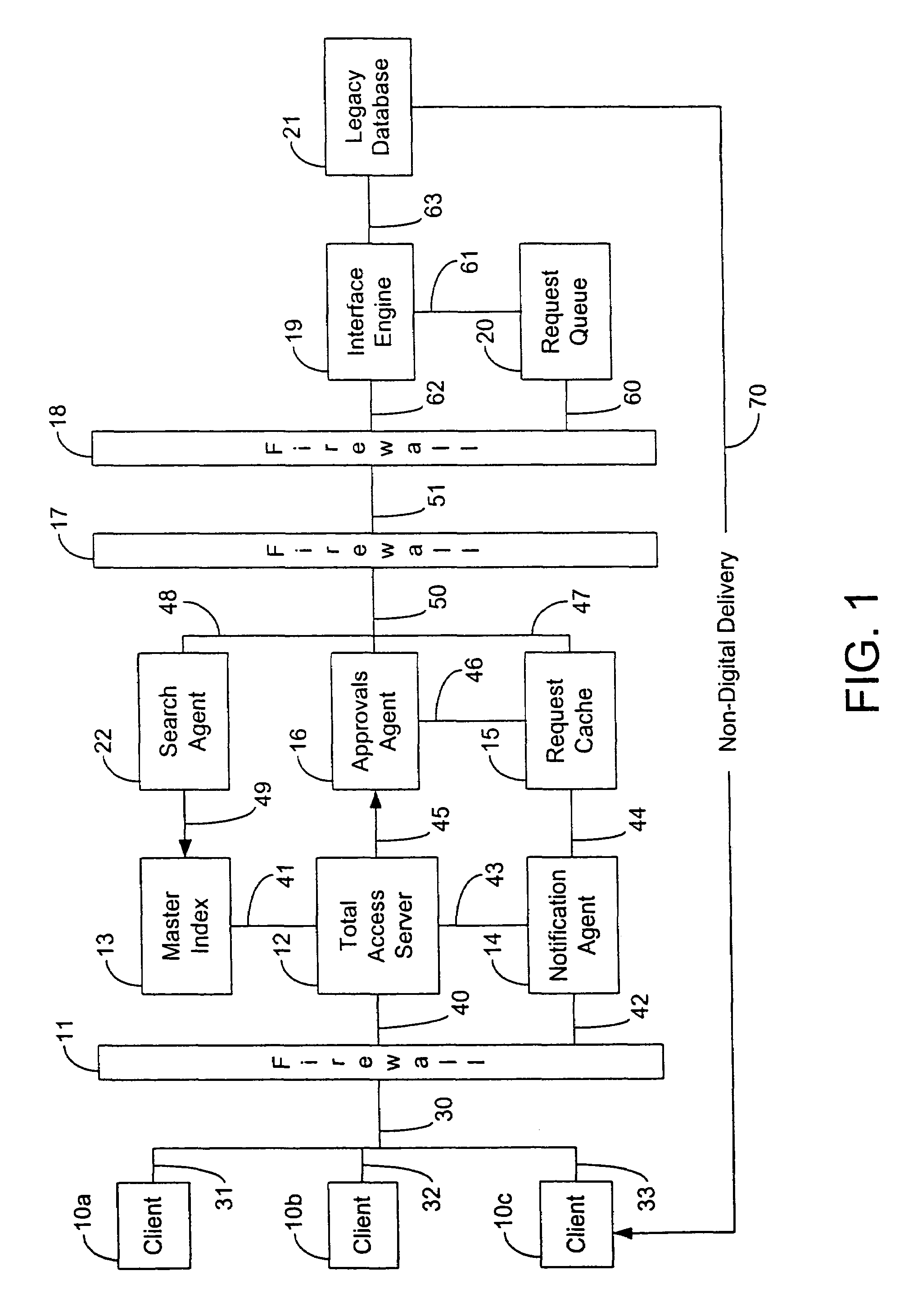
InactiveUS7028049B1Improve confidentialityData processing applicationsWeb data indexingMedical recordCost effectiveness
An internet and / or intranet based database search system and method for conducting searches of highly confidential records such as individual patient medical records and to automate the process of securing required approvals to make such records available to a properly authorized and authenticated requesting party. The system's central premise is that the patient has a fundamental right to the confidentiality of their personal medical records and should control that right through specific, informed consent each time that a party requests to receive them. It reinforces the widely held conception of privacy in general as well as of the sanctity of the doctor / patient relationship by granting the doctor the right, subject to the patient's express permission, to initiate a search request. At the same time, it provides an expedited and cost-efficient means for transfer of such records as demanded by many healthcare reform proposals and gives the repositories where these records are held the right to stipulate the specific terms and conditions that must be fulfilled before they will release documents entrusted to their care, thereby substantially reducing the risk of litigation alleging breaches of patient confidentiality. And it carries out all of these legitimate interests in a way that is fast, simple to use and easy to audit. The system optionally includes a billing mechanism to pay for any added cost associated with providing this additional protection; and in its preferred embodiment, is applicable to both digital as well as non-digital records.
Owner:PRIVATE ACCESS +1
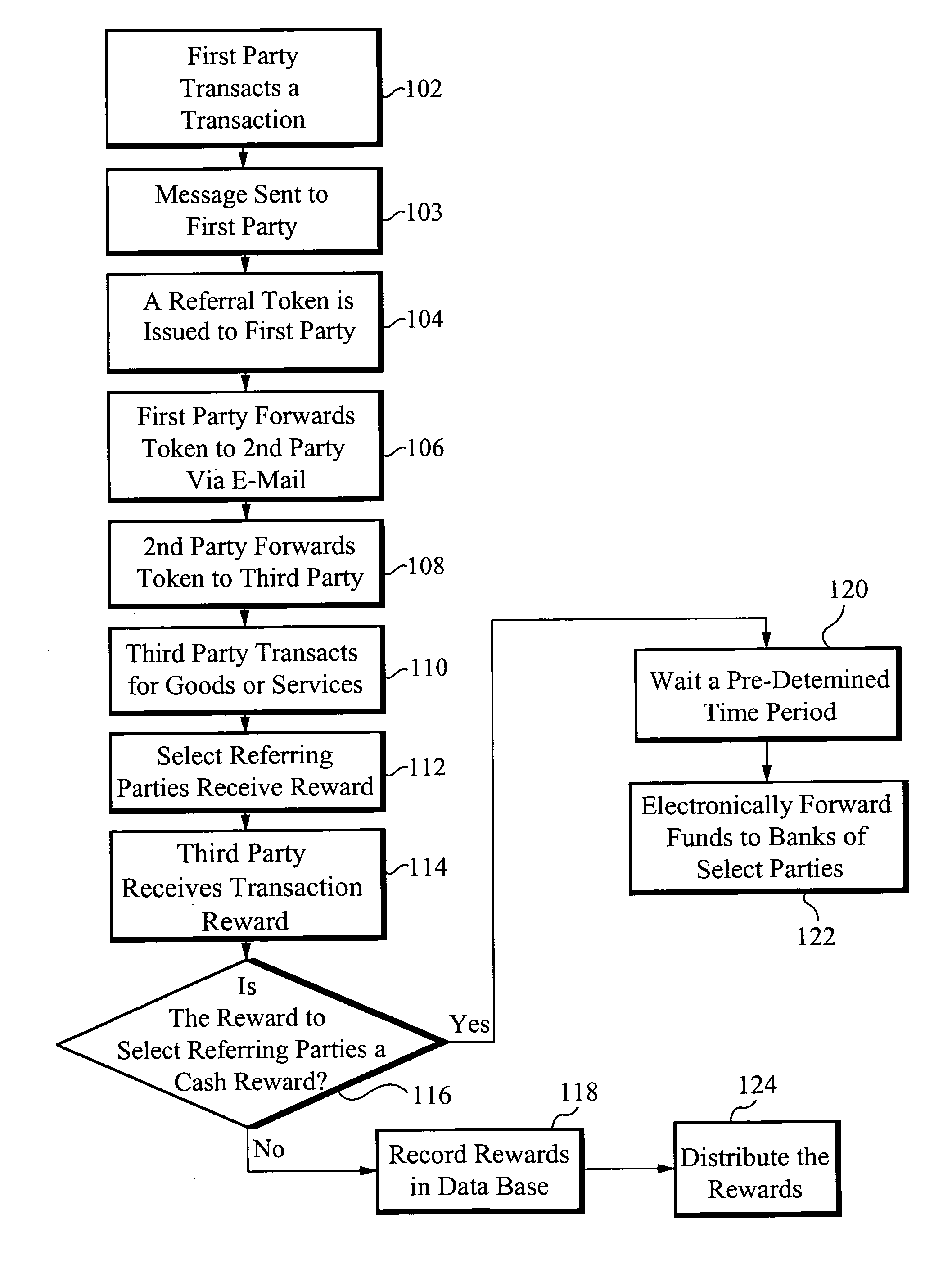
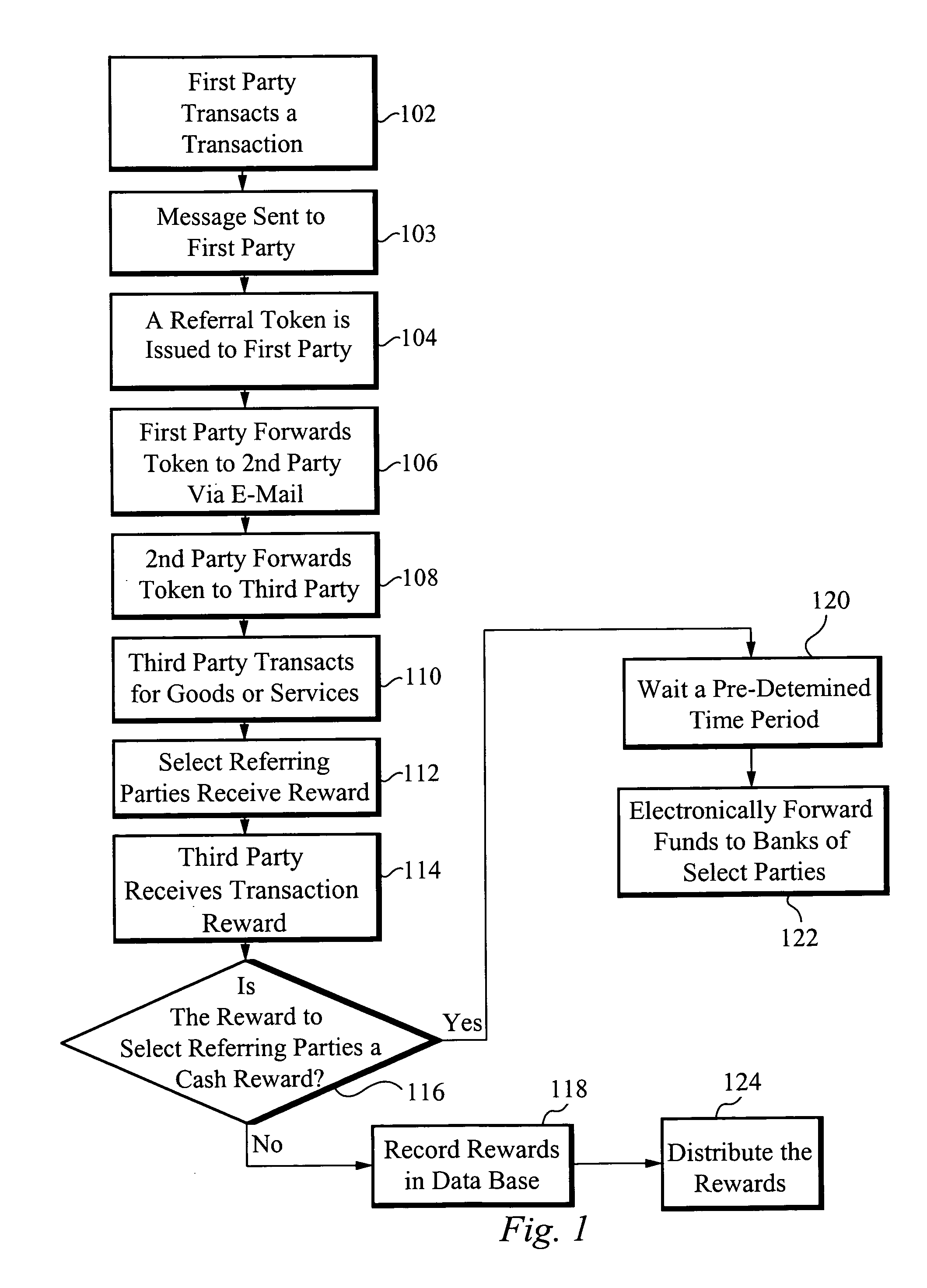
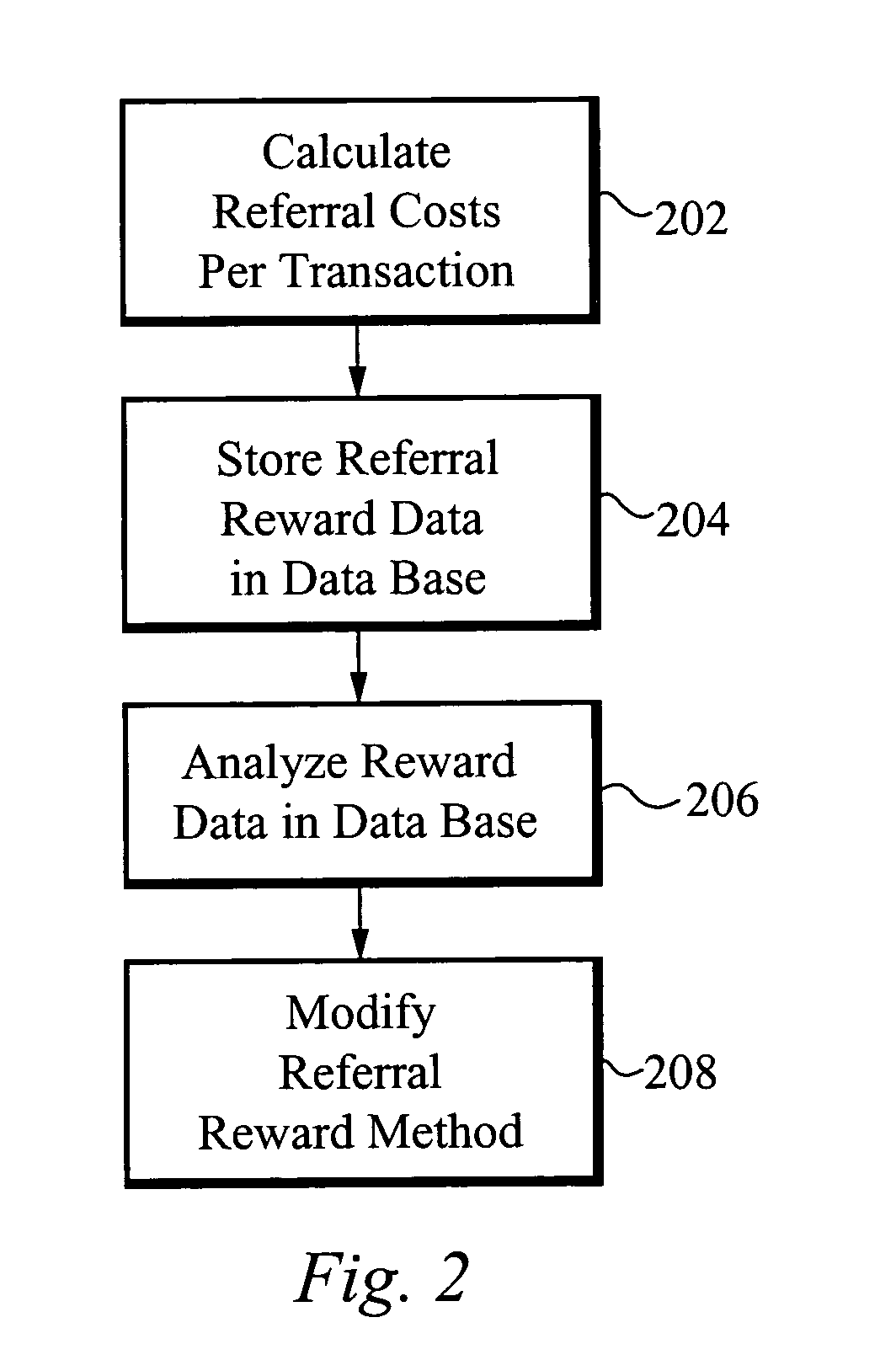
Methods of anti-spam marketing through personalized referrals and rewards
ActiveUS7774229B1Protect privacy and confidentialityConfidenceDiscounts/incentivesAdvertisementsDigital dataPersonalization
A marketing method comprising a Provider offering a potential reward to a first party in exchange for promotional assistance of forwarding a first e-mail message to a second party comprising a personalized referral for the marketable entity, a first set of data comprising a first serial number and a first URL link. A first Web site corresponding to the first URL link is created which provides information on the referenced marketable entity and an offer to transact. The first set of data in the first e-mail message is correlated to a first set of database data within a digital database controlled by the Provider. The first e-mail message is forwarded from the Provider to the first party. The first e-mail message is forwarded from the first party directly to the second party without giving any identifying information about the second party to the Provider.
Owner:STRIPE INC
Method and system for identity authentication by finger print USBkey
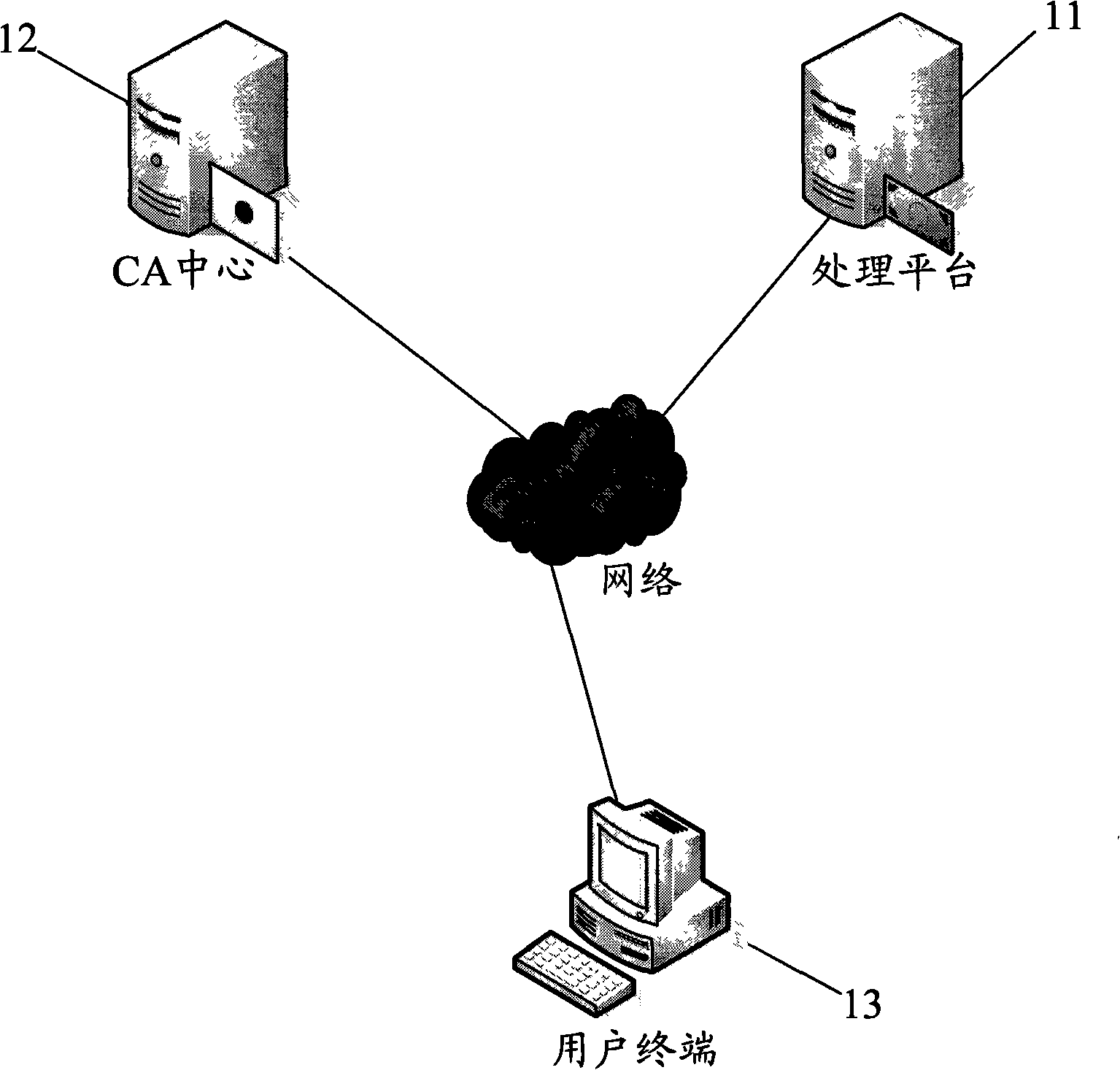
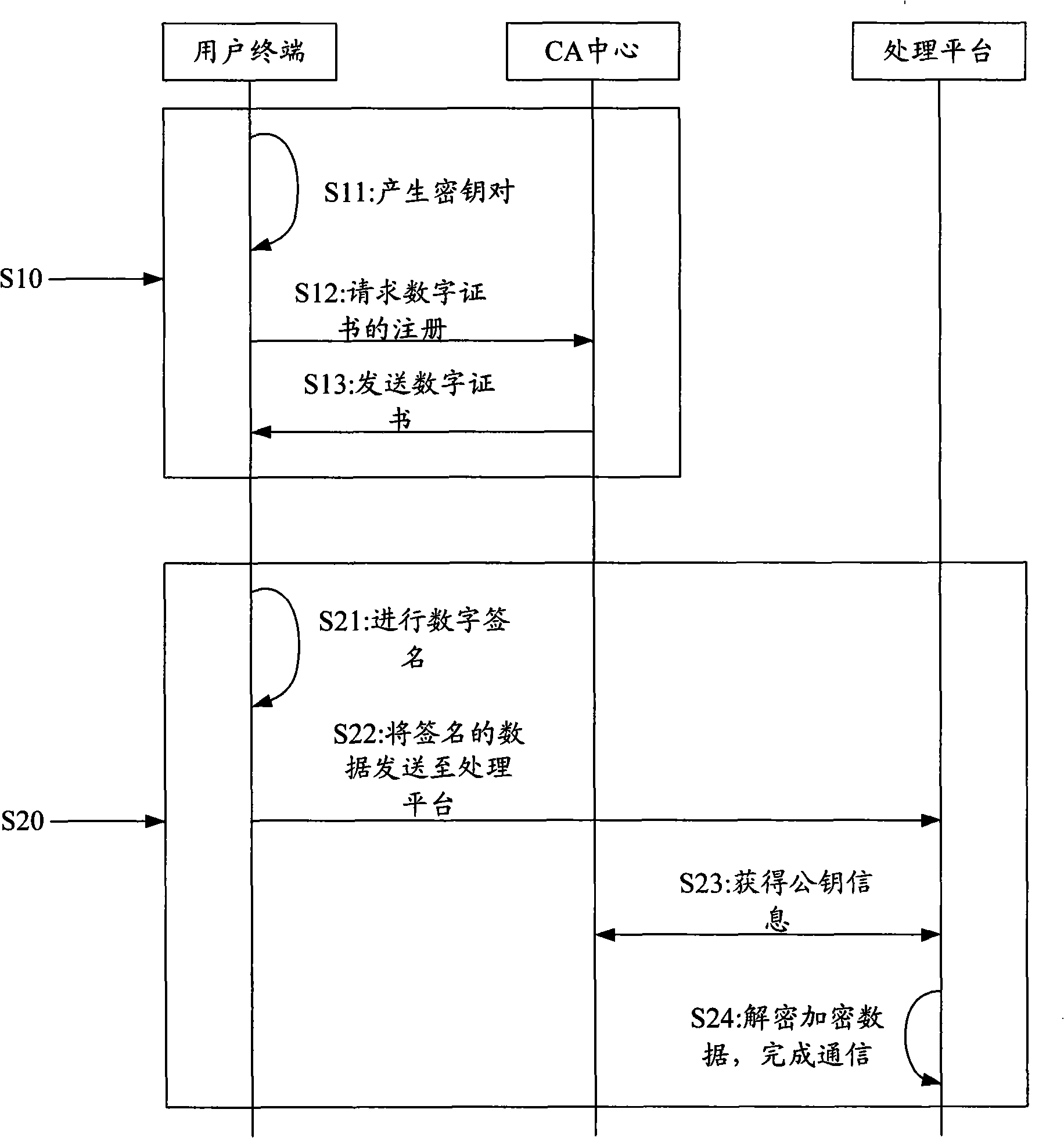
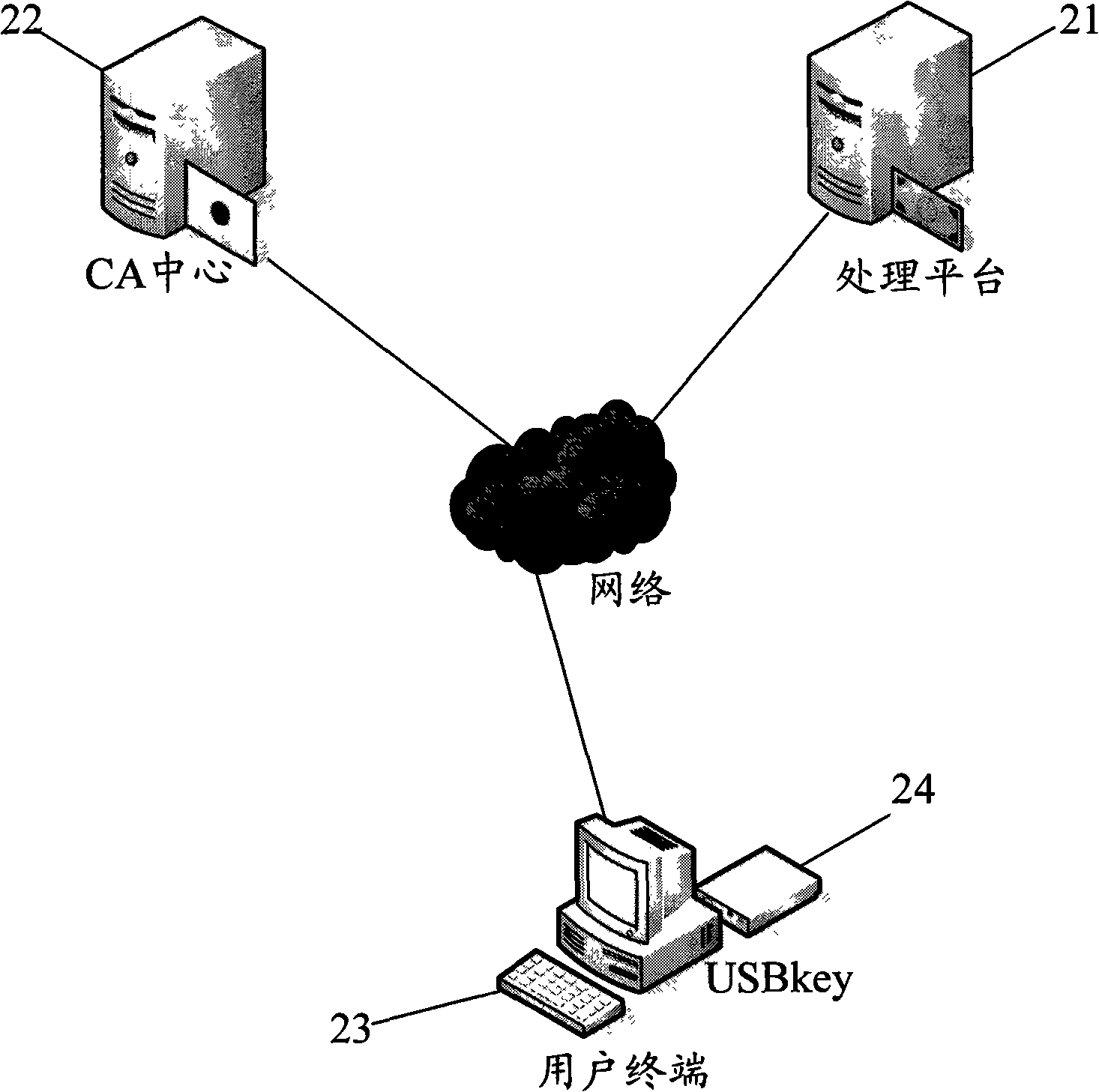
InactiveCN101340285AEnsure safetyGuaranteed accuracyUser identity/authority verificationCommerceRelevant informationDigital signature
The invention discloses an identity authentication method by a fingerprint USBkey and includes the following steps: (1) the fingerprint information of users is recorded into the fingerprint USBkey and the information is saved in advance; (2) at least a digital certificate generated, which comprises the following steps: firstly, a pair of private and public keys are generated in the fingerprint USBkey; the relevant information of the public keys and the digital certificate is sent to a CA center and generating the digital certificate by the CA center; (3) each digital certificate and corresponding private keys stored and encrypted on the fingerprint USBkey; (4) when a user terminal communicates with a processing platform, the fingerprint USBkey at the user terminal firstly checks the fingerprints, digital signature is carried out on the data to be sent by the corresponding private keys and the data is transmitted to the processing platform for identity authentication. The method permits the digital signature after the fingerprints authentication succeeds; the loophole of PIN code input and transmission does not exist in the whole interactive process, which improves the transaction security to the utmost extent.
Owner:ZHEJIANG MIAXIS TECH CO LTD
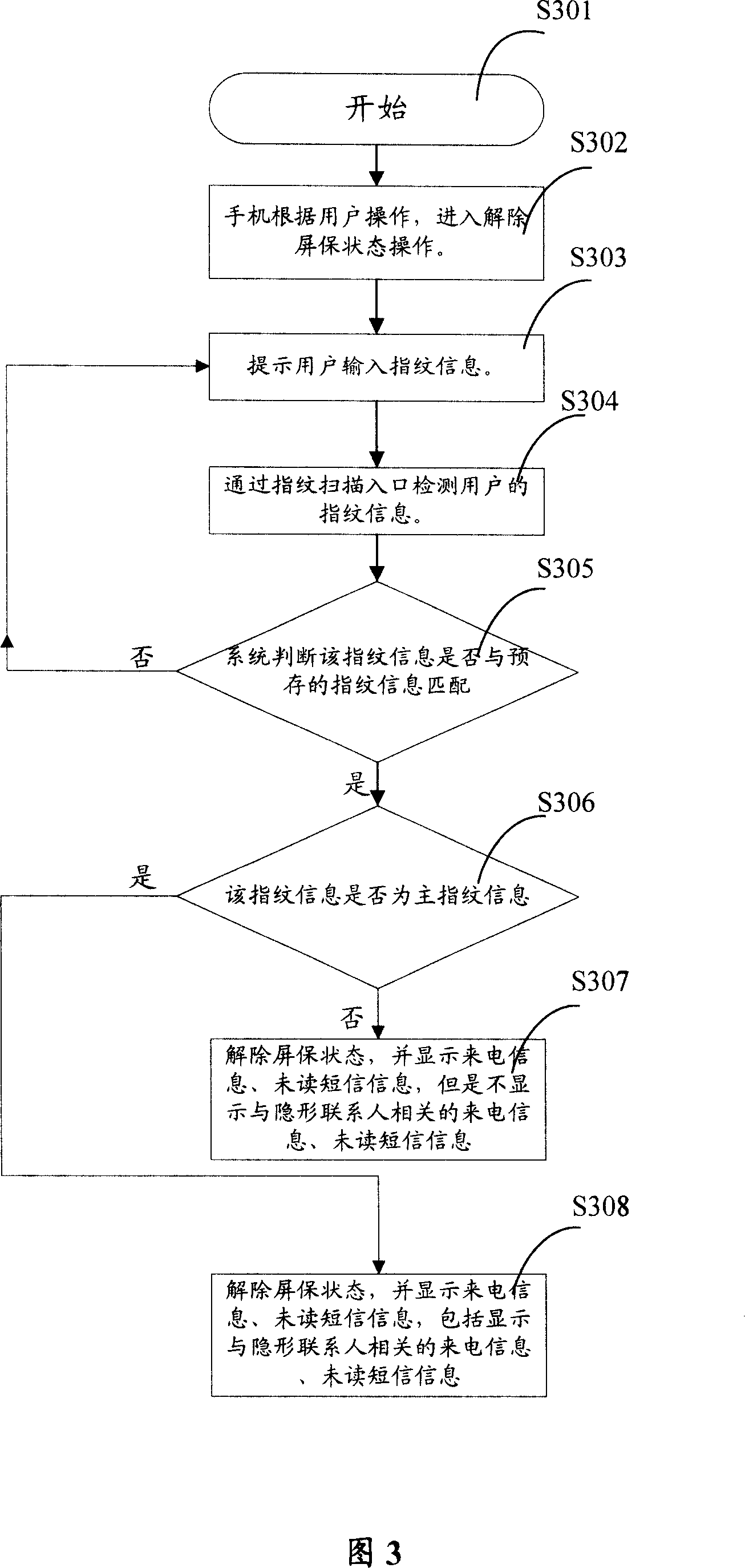
Mobile phone privacy protection method
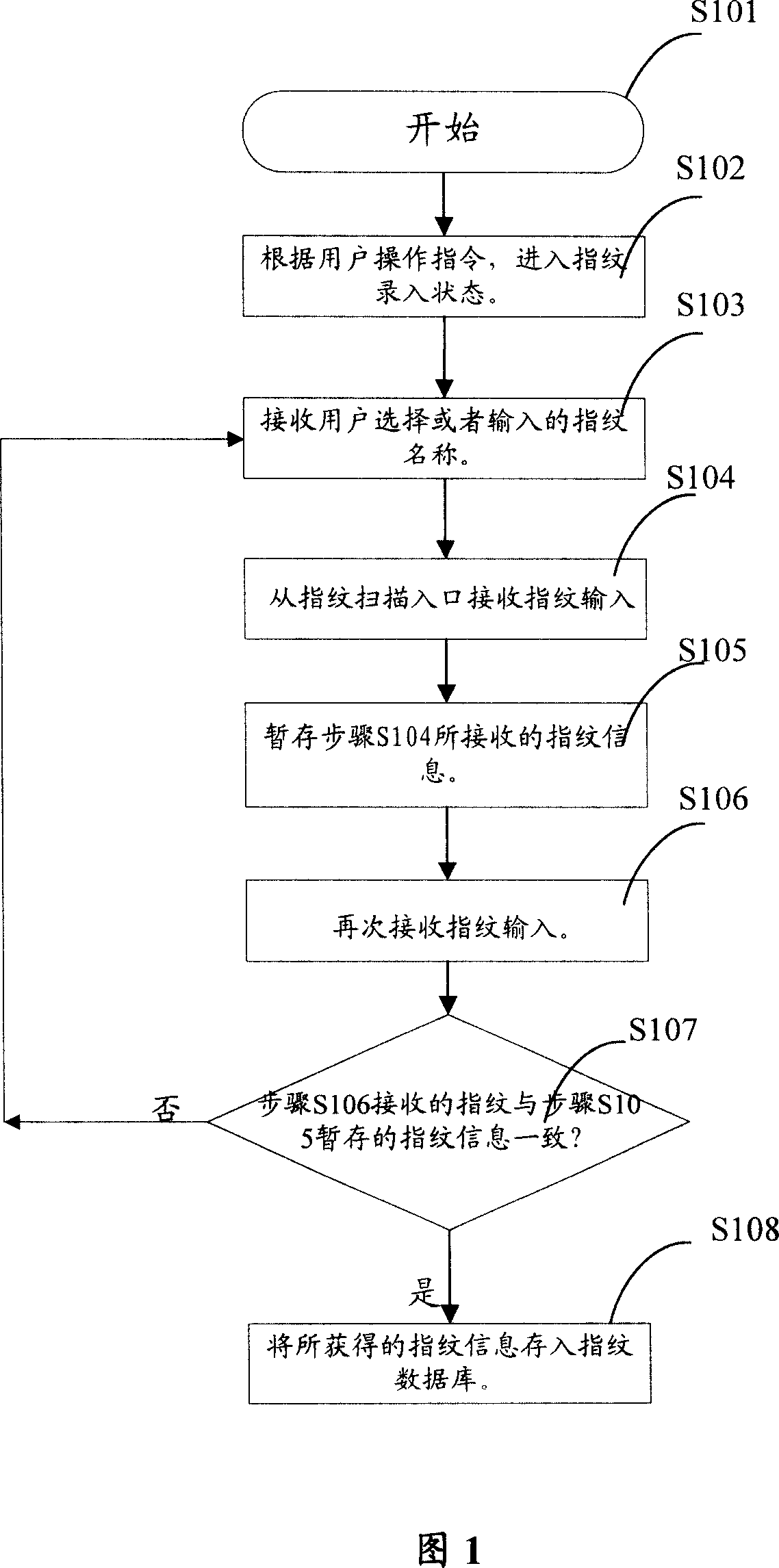
InactiveCN101035335AImprove confidentialityCharacter and pattern recognitionDigital data authenticationRelevant informationPrivacy protection
The present invention relates to a method of private and secret information protection on the mobile telephone. It includes: 11) checking consumer's fingerprint information; 12) checking if the information judging the given fingerprint are authorized; If it come into existence, then going to step 13); If it does not , then the telephone comes into private and private protection state; 13) unlock the private and secret protection state. The fingerprint information can be saved as following steps: 21) The telephone turns into fingerprint record state according to consumer operation; 22) Receiving a fingerprint from the fingerprint scanning entrance; 23)The fingerprint information is saved into the fingerprint data base. Compared with present available technology, the invention has provided the physiology characteristics distinguishing the human body. It has realized that private and secret information protecting in the mobile telephone.
Owner:CECT
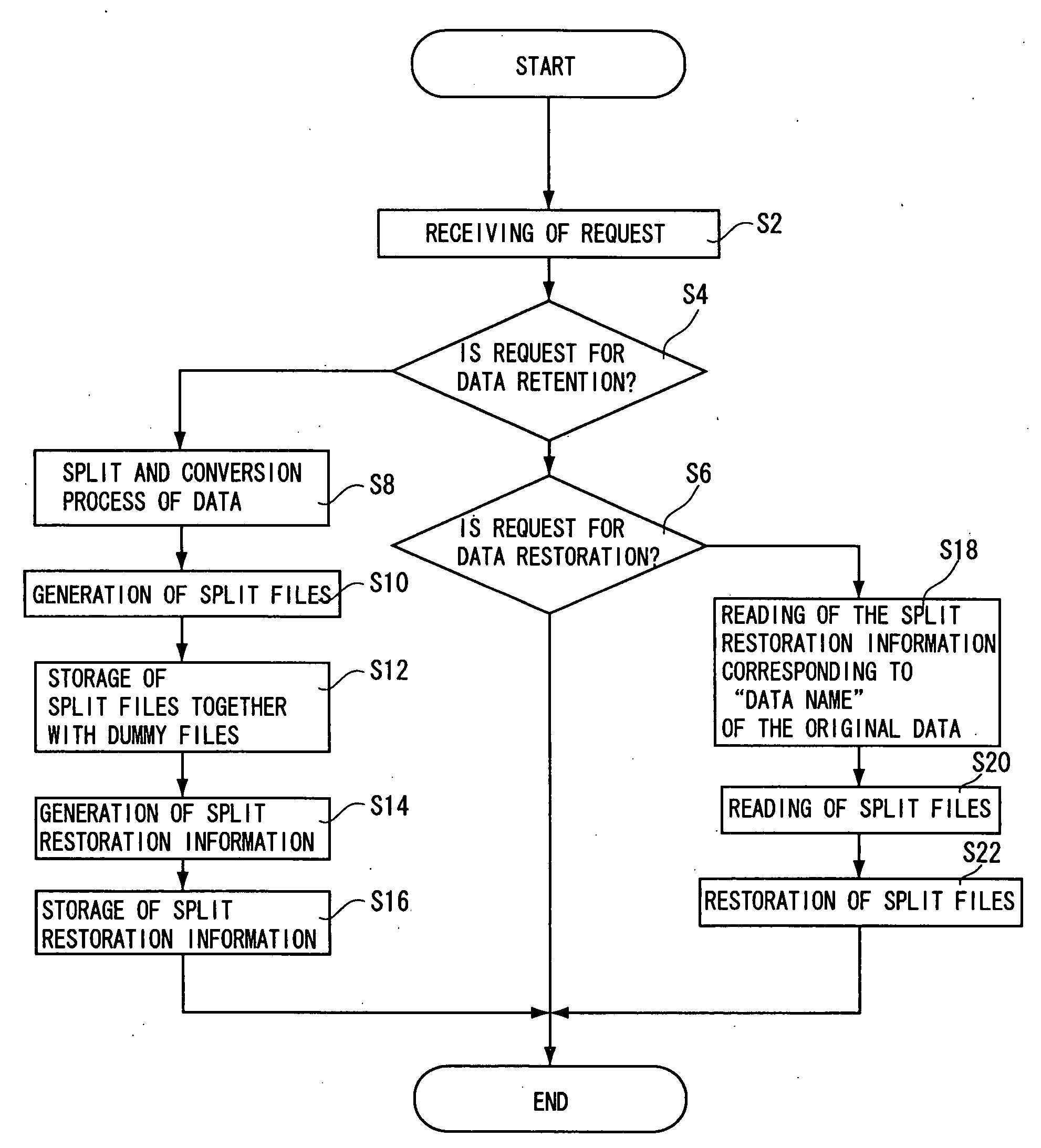
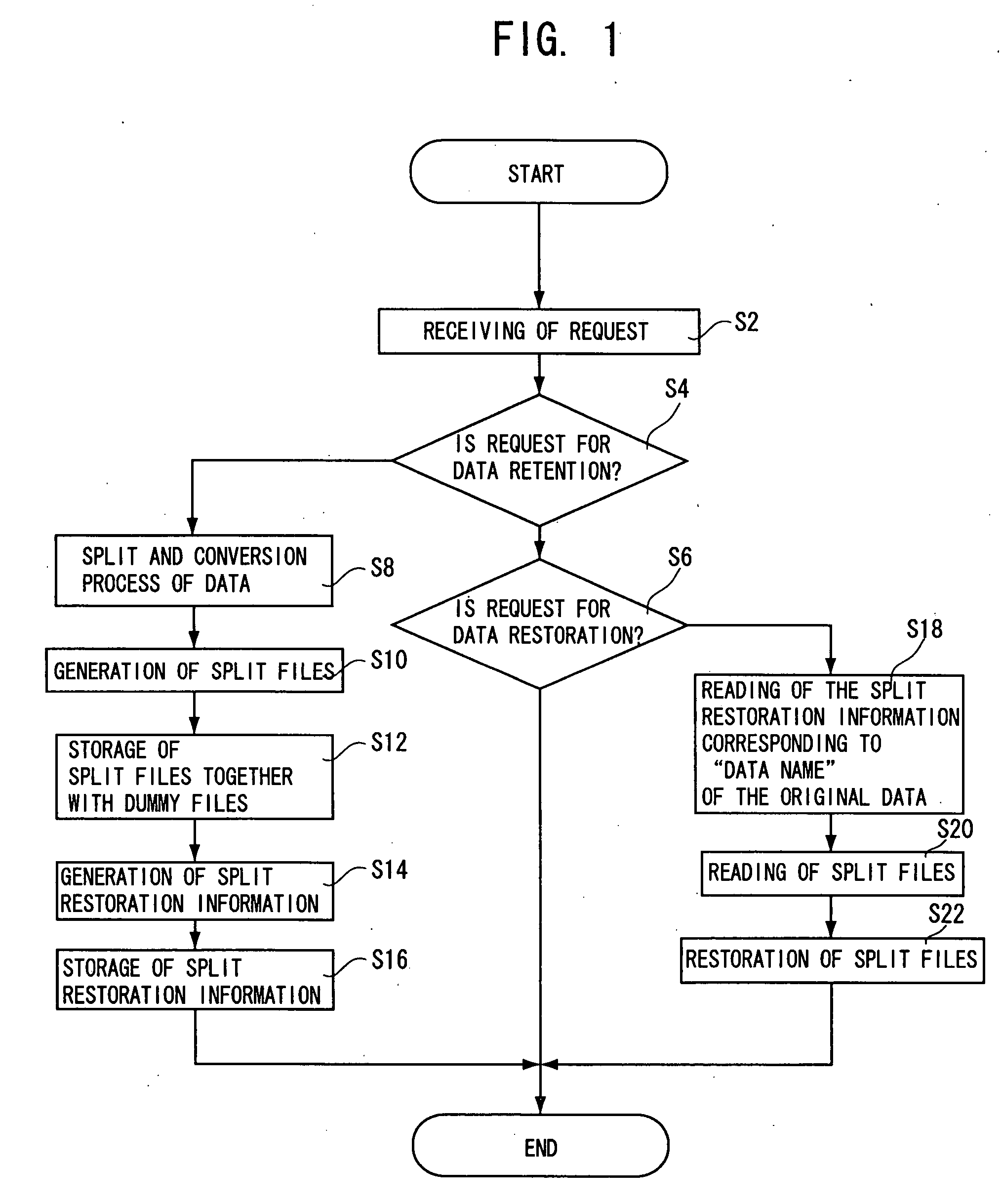
Electronic information retention method/system, electronic information split retention method/system, electronic information split restoration processing method/system, and programs for the same
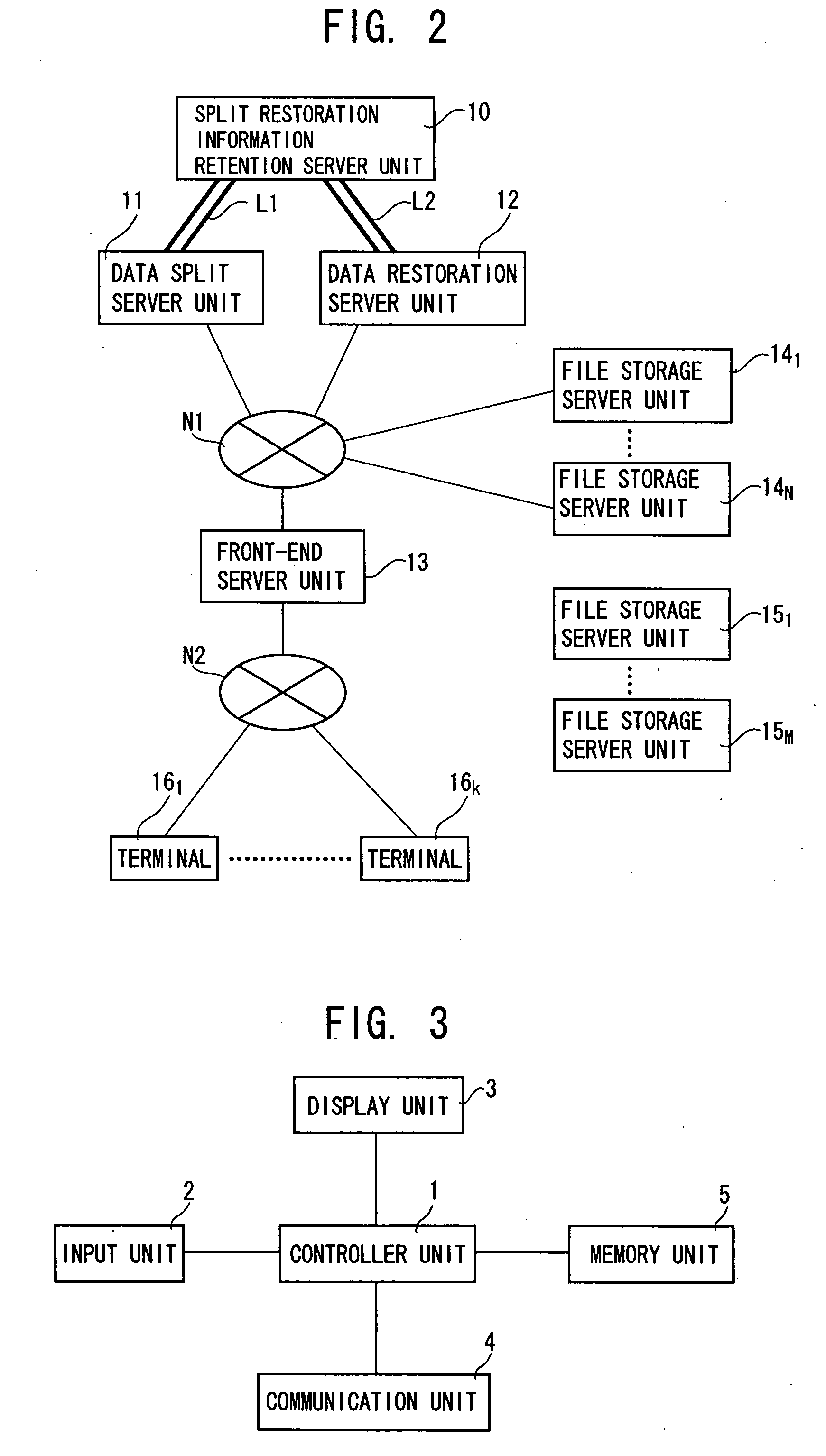
InactiveUS20100058476A1Reduce riskIncrease costDigital data processing detailsAnalogue secracy/subscription systemsInformation processingElectronic information
The invention aims to provide an electronic information split restoration processing method / system capable of processing massive electronic information at high speed while preventing leakage of the electronic information with reliability, and without causing deterioration in immediacy, centrally controlling electronic information to be processed by information processing units that are distributed geographically in a wide area, and connected via network. When electronic information is to be retained, a reversible split process and a reversible conversion process are applied to the electronic information (step S8), to thereby generate a plurality of split files (step S10), and store the split files together with dummy files (step S12). Split restoration information is generated (step S14) to be stored by relating processing information concerning the split and conversion process together with file names of the split files and information on storage destinations thereof, to data name of the original electronic information. When electronic information is to be read, split files are collected on the basis of the split restoration information (step S20) and the electronic information is restored by reversely applying the split and conversion process (step S22).
Owner:SB SYST CORP
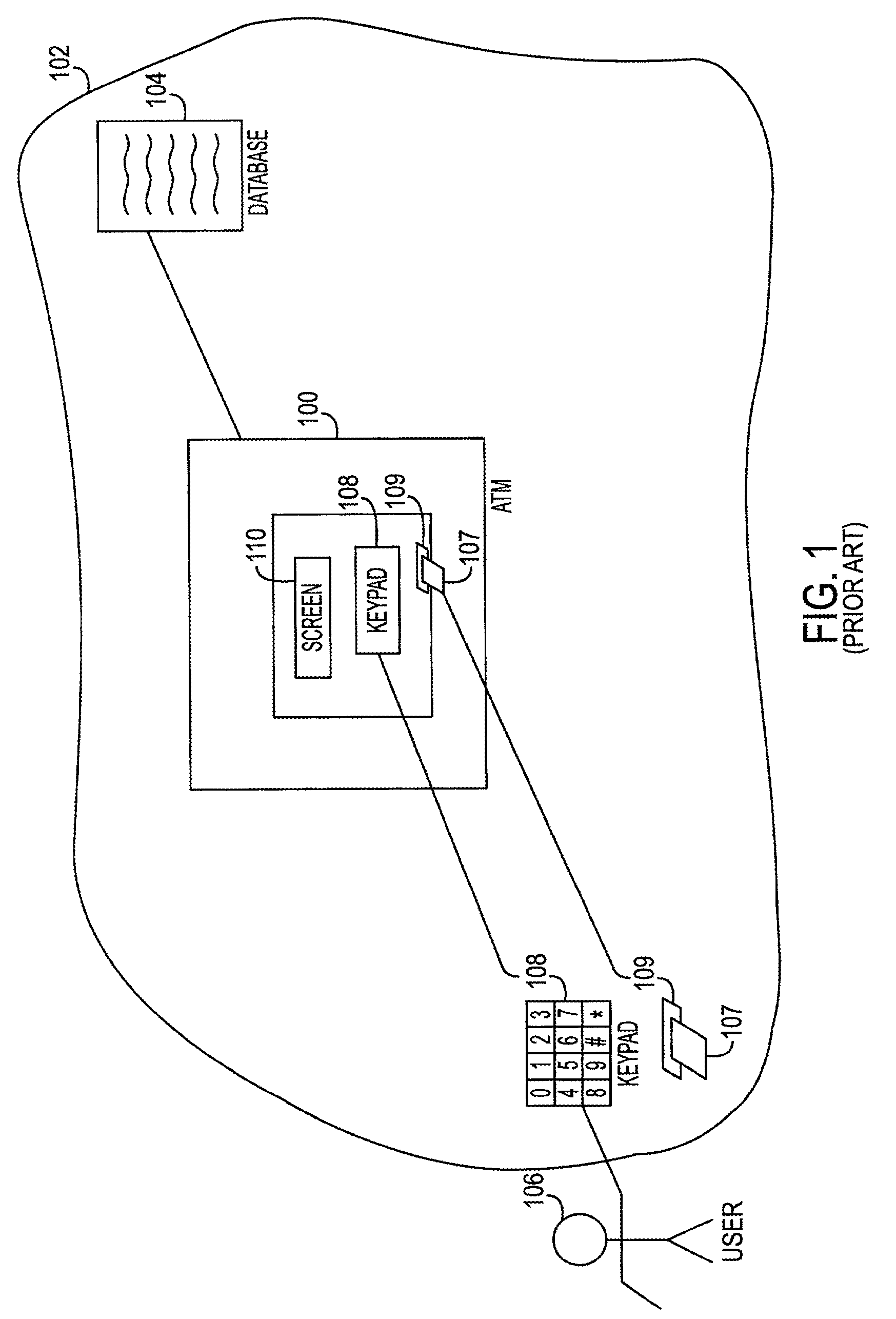
Automated transaction machine digital signature system and method
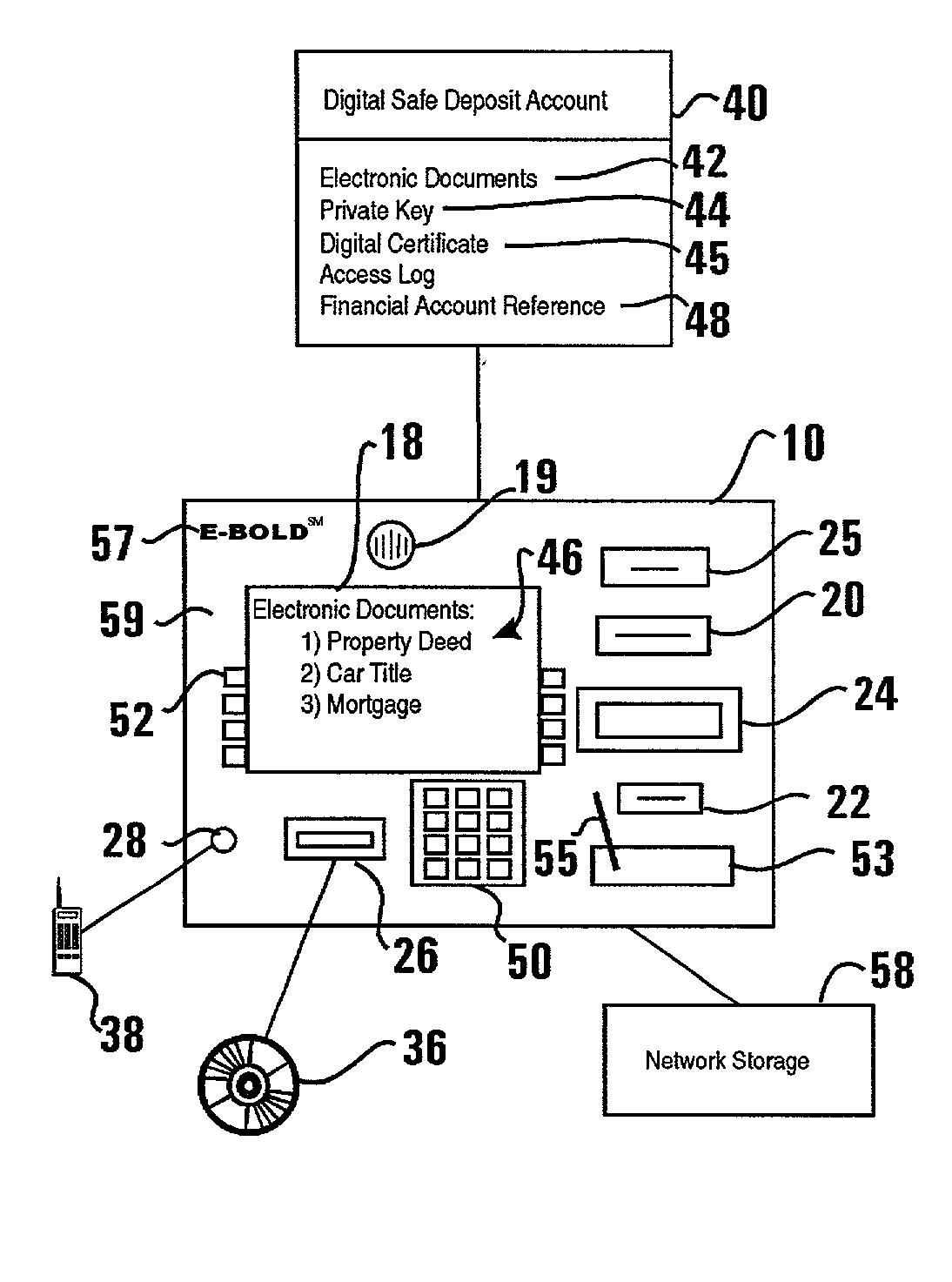
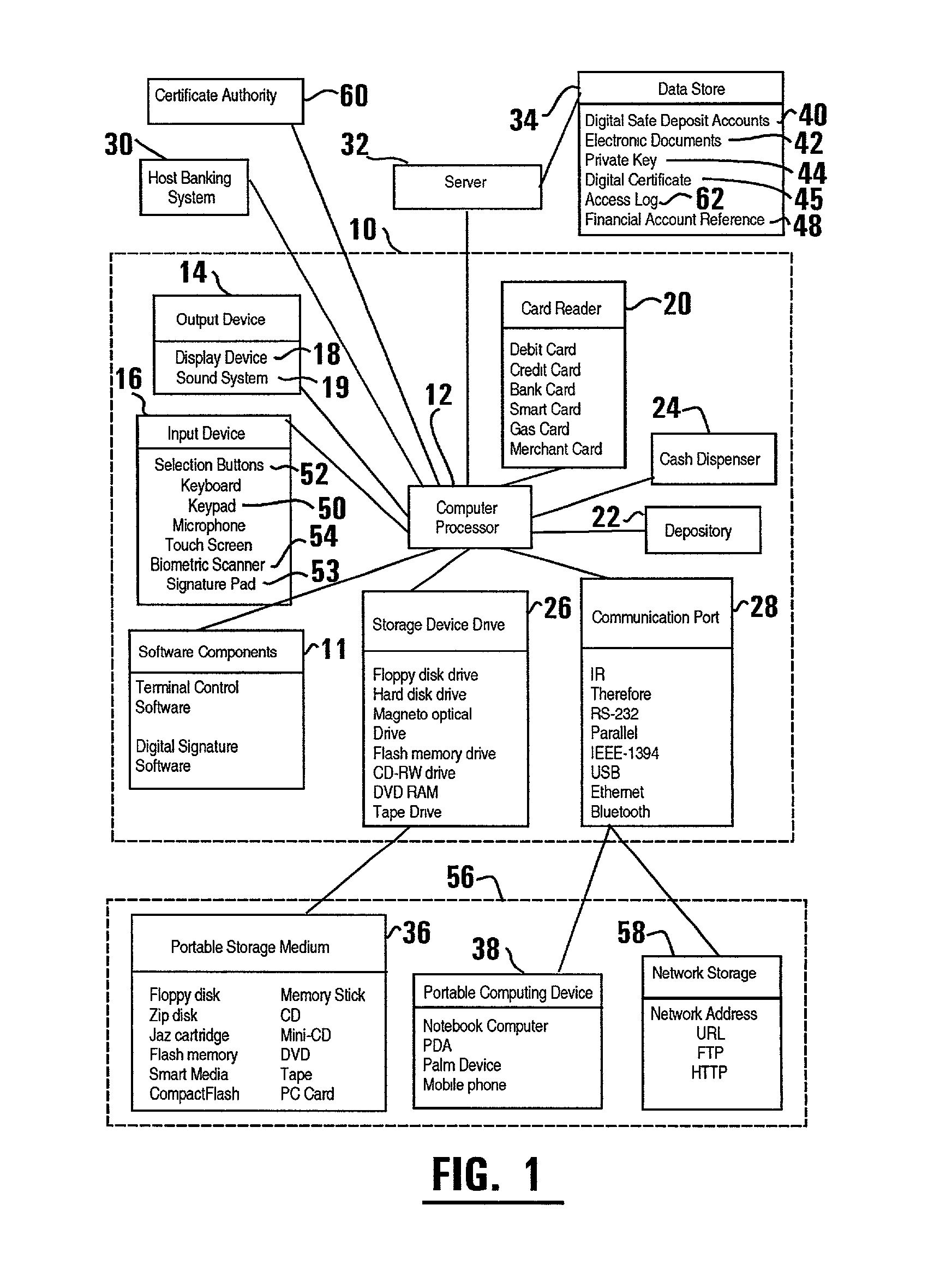
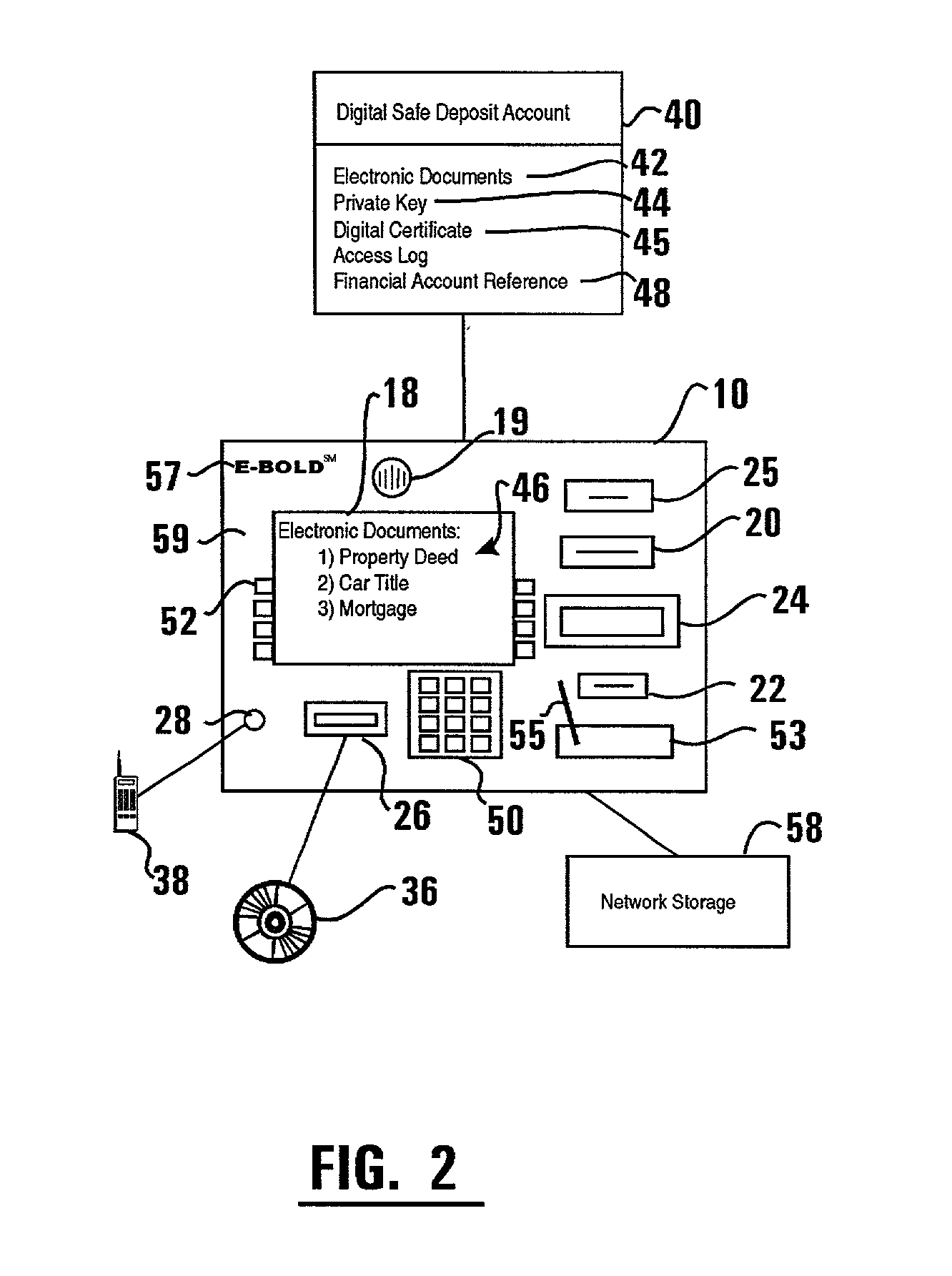
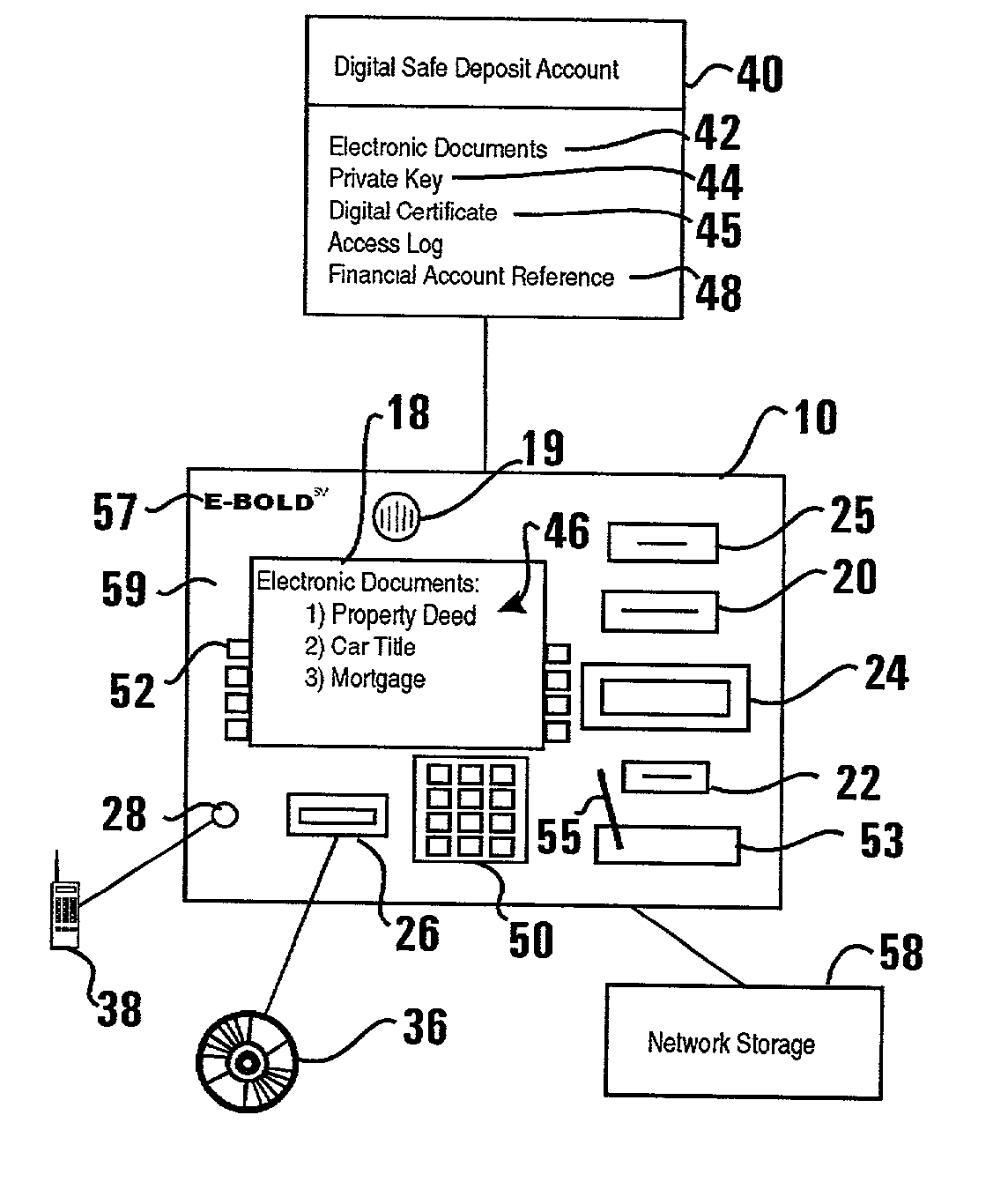
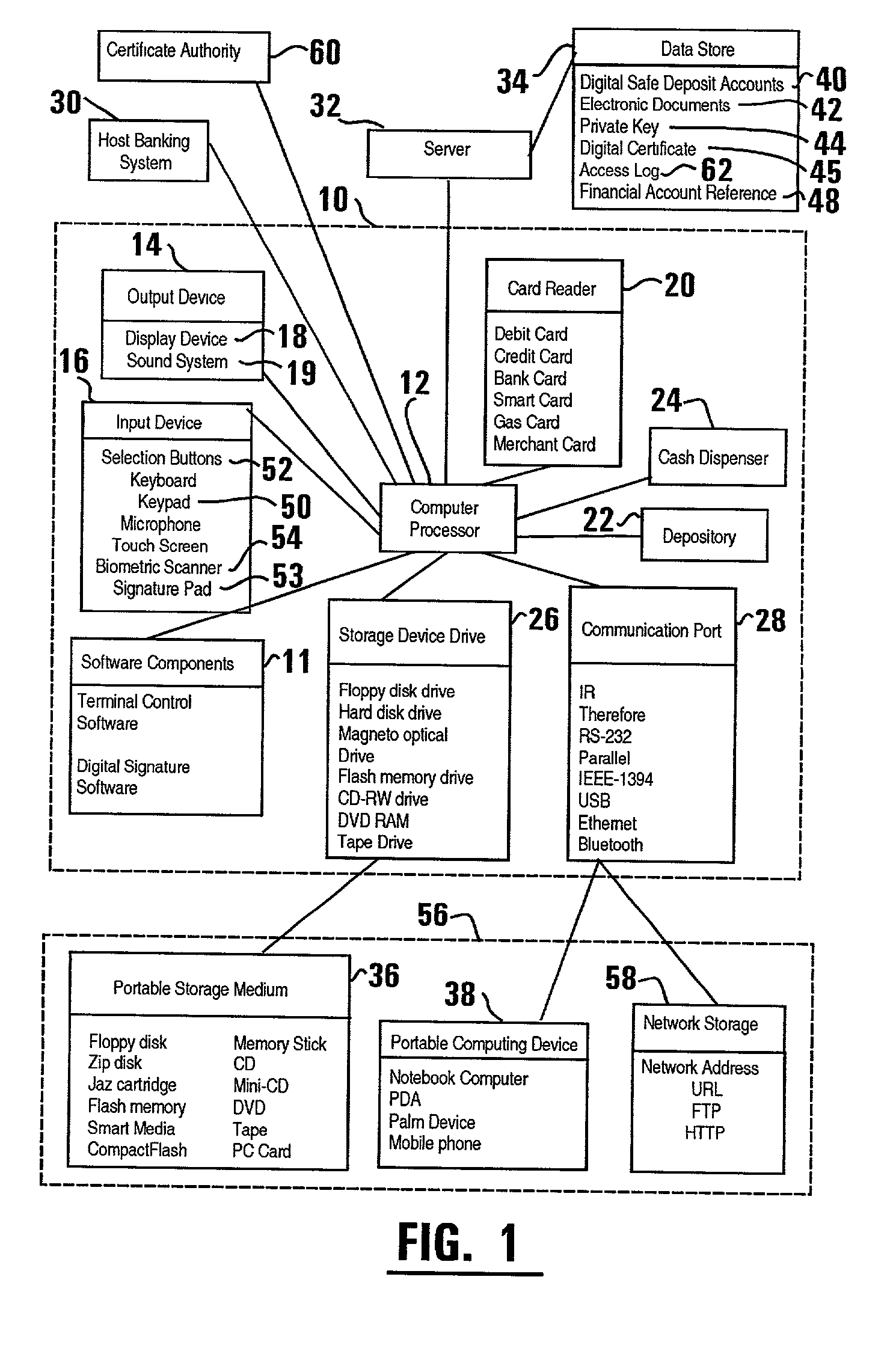
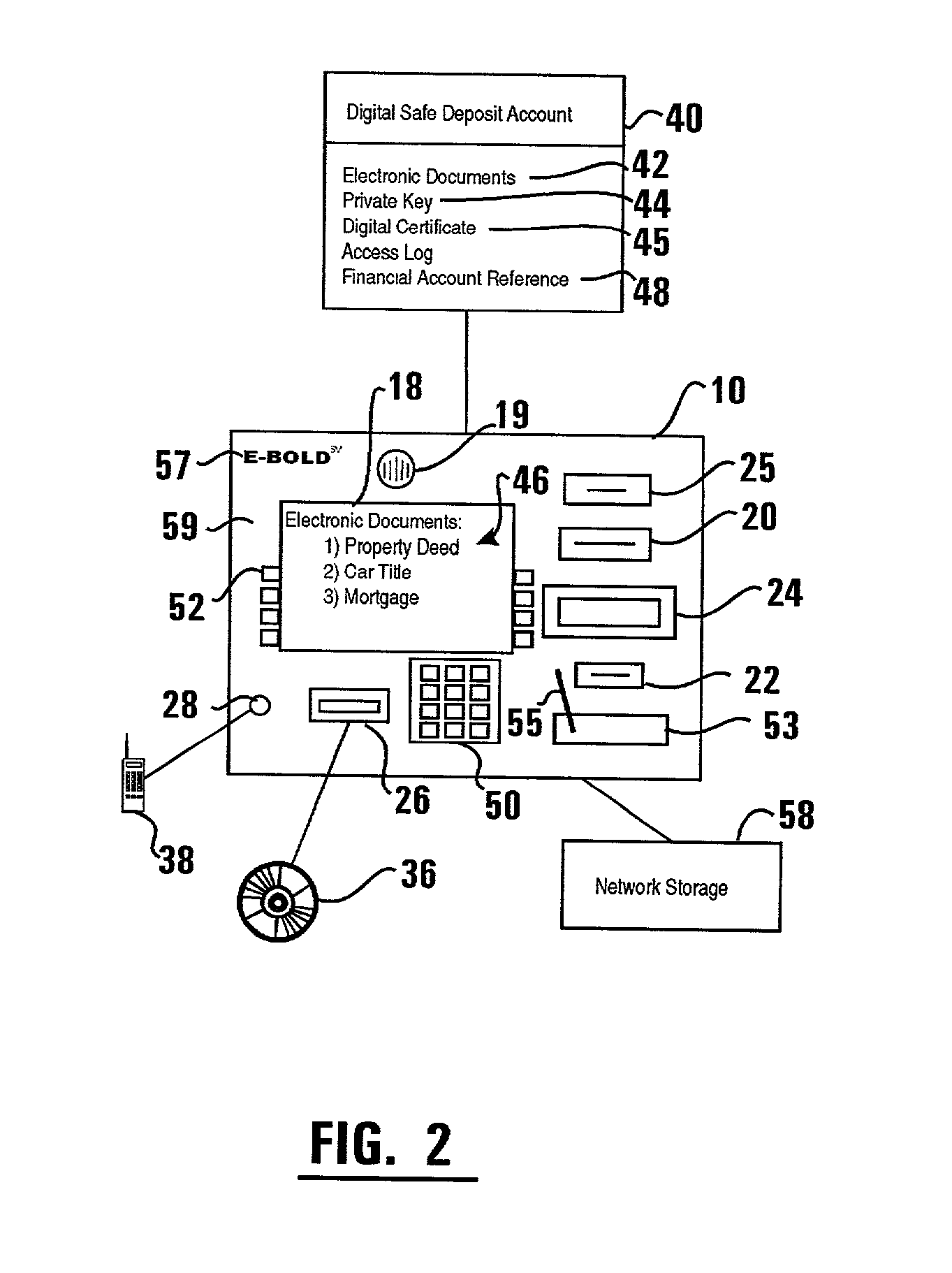
ActiveUS20020129257A1Easily employEasily employedComplete banking machinesFinanceElectronic documentDocumentation procedure
An automated transaction machine such as an ATM (10) is provided. The ATM is operative to digitally sign electronic documents (42). The ATM may be in operative connection with a storage server (32). The storage server is operative responsive to the ATM to maintain electronic documents (42) in a data store (34) in association with the user's digital safe deposit account (40) and / or a financial account (48) such as checking, savings, debit, or credit account. The storage server is further operative to store a private key (44) of a user in association with the user's digital safe deposit account and / or financial account. The ATM is operative to cause electronic documents to be signed using the private key associated with the user. The ATM is further operative to output the electronic document on a display device (18) of the ATM where the user may view and edit the electronic document.
Owner:DIEBOLD NIXDORF
Cross-physical isolation data transparent transmission system and method between intranet and extranet
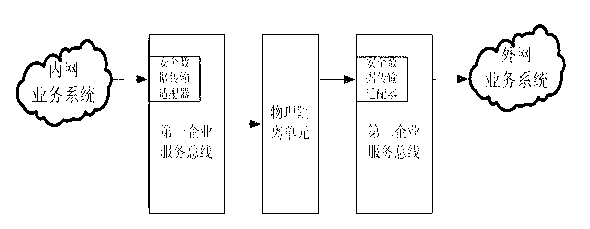
ActiveCN102843352ARetrofit smallEasy to deployUser identity/authority verificationBus networksEnterprise servicesWorkload
The invention relates to a cross-physical isolation data transparent transmission system between an intranet and an extranet. The system comprises a first enterprise service bus and a second enterprise service bus which are respectively arranged on the two sides of physical isolation, wherein a first safety data transmission adapter and a second safety data transmission adapter are respectively deployed on the first and second enterprise service buses, the physical isolation is arranged between gateways of the intranet and the extranet for performing network safety area isolation, the first and second enterprise service buses are used for respectively providing calling interfaces and simultaneously communicating with the physical isolation, and the first and second safety data transmission adapters are respectively responsible for safety certification and calibration of integrity and effectiveness of data of the intranet and the extranet. The invention further relates to a cross-physical isolation data transparent transmission method of the system. Improvement of data transmission can be performed under a physical isolation environment through the system and the method, the difficulty in transformation and the workload of the service system can be simplified, and the safety in data transmission can be further enhanced through the safety data transmission adapters.
Owner:MAOMING POWER SUPPLY BUREAU GUANGDONG POWER GRID CORP
Method and device for vehicle passive keyless entering, starting and locking based on ultra-wide band
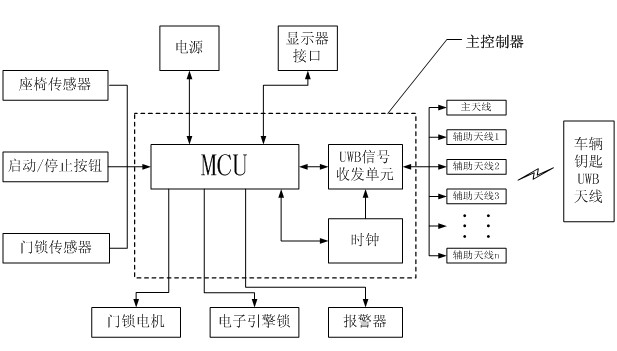
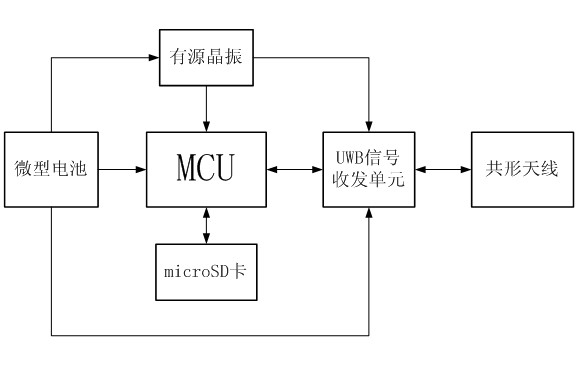
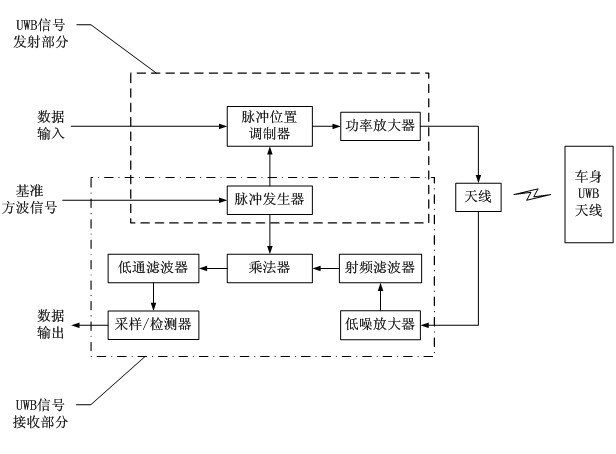
InactiveCN102602363AHigh range resolutionLess prone to misjudgmentAnti-theft devicesIndividual entry/exit registersDriver/operatorMaster controller
The invention discloses a method and a device for vehicle passive keyless entering, starting and locking based on ultra-wide band. The device comprises a vehicular key, a master controller, a door lock sensor, a starting / stopping button, a seat sensor and a vehicular body antenna array, wherein the door lock sensor, the starting / stopping button, the seat sensor and the vehicular body antenna array are all connected with the master controller through a vehicular body circuit. The method includes: using UWB (ultra-wide band) signals to precisely position the vehicular key, detecting the position of the vehicular key and the position information of personnel in the vehicle according to each trigger action of a driver, and using a joint judgment method to control operation of a vehicular door lock, a starting system and an alarming system. In addition, the vehicular key is capable of recording and storing information interested by the driver and vehicular dynamic information. Using the method and the device can better avoid accidents caused by misjudgment of the master controller or misoperation of personnel.
Owner:SOUTH CHINA UNIV OF TECH
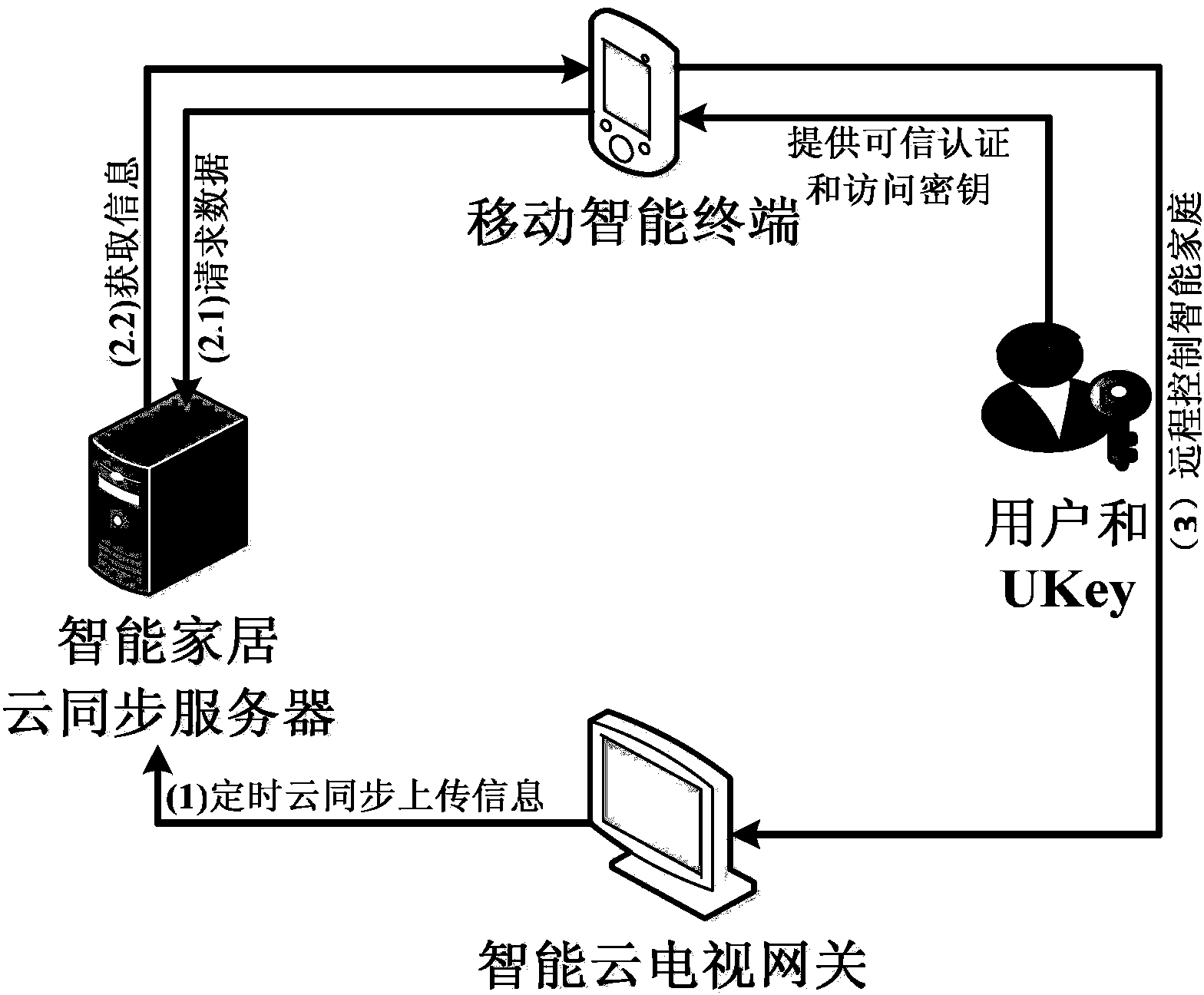
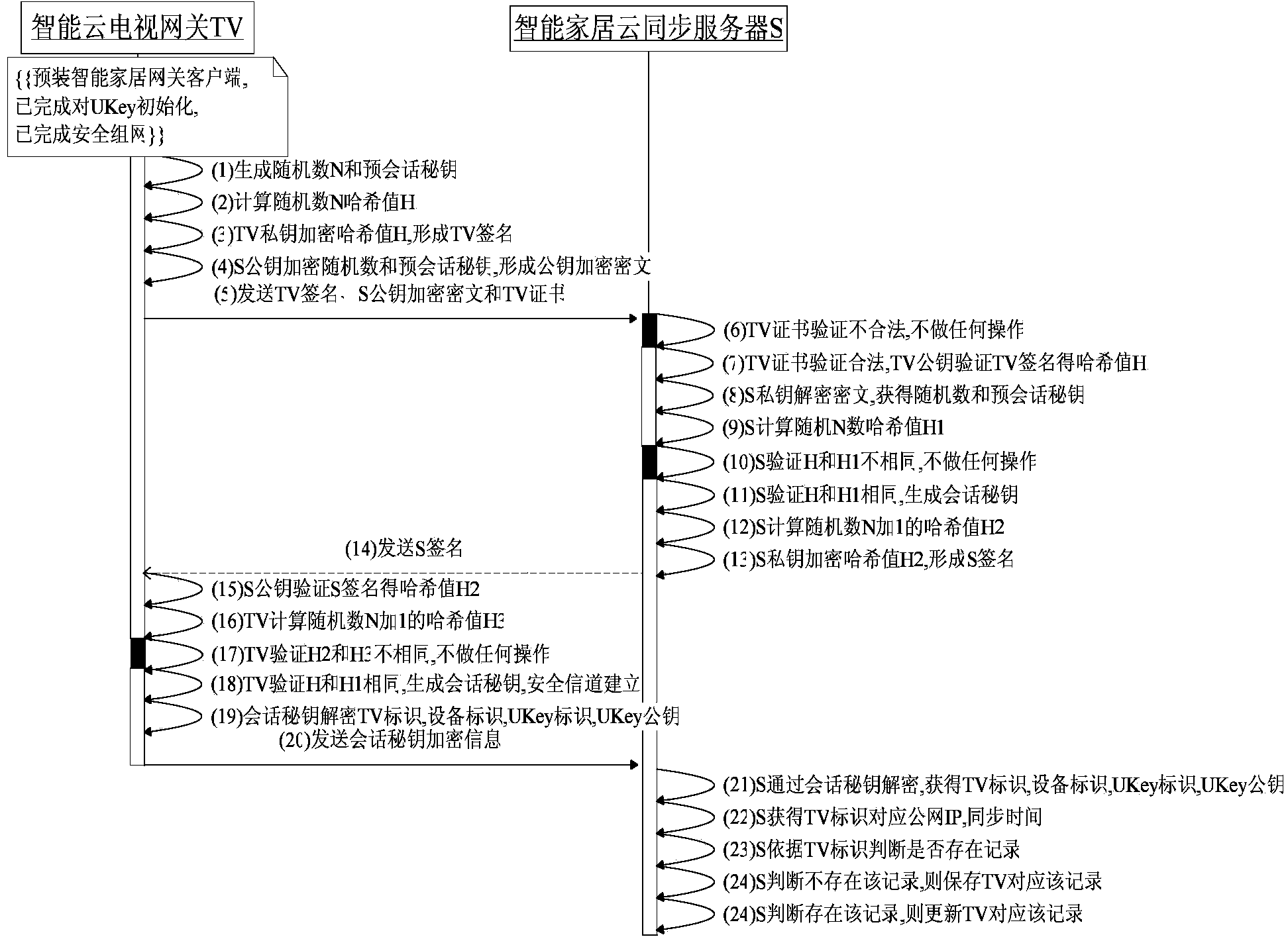
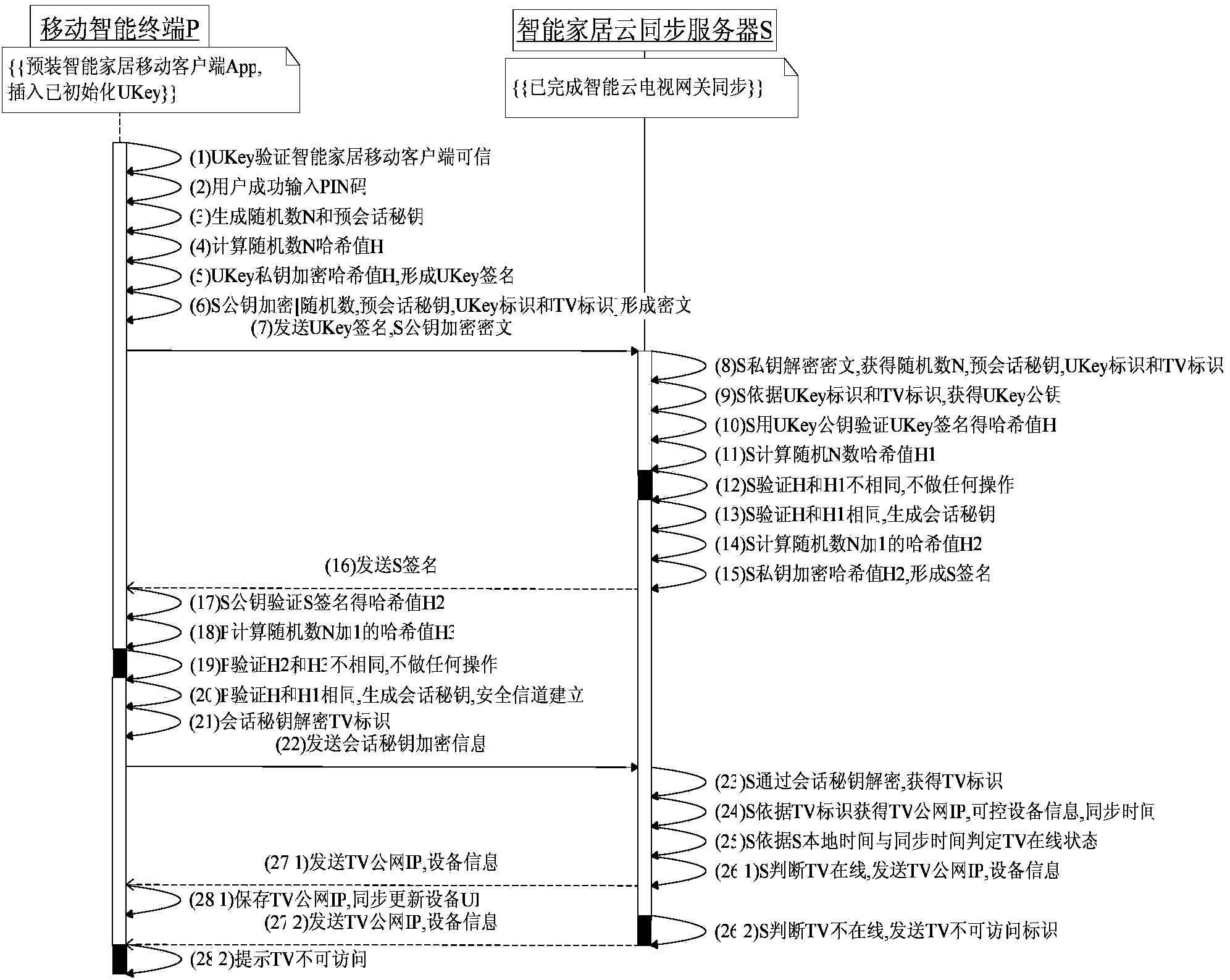
Smart home remote security access control implementation method based on smart cloud television gateway
InactiveCN103731756AImprove experienceImprove versatilityTransmissionSelective content distributionConfidentialityComputer terminal
The invention relates to a smart home remote security access control implementation method based on a smart cloud television gateway. A smart home external network refers to a network environment which is also known as a smart home outer network and is formed by the way that a smart cloud television is used as a user smart home gateway, and in the household ADSL environment, the smart cloud television is in interaction with public network environment equipment (such as a mobile intelligent terminal and a smart home cloud synchronization server of the user). The smart cloud television has already obtained a terminal certificate based on a PKI digital certificate system and can provide a secure storage area for secure reading and writing, and the smart cloud television is also called the smart cloud television gateway. A portable UKey refers to the equipment which is provided with an equipment mutual communication module and a secure calculation module (like a secure chip). The smart home cloud synchronization server can regularly record the mapping binding relation between the smart cloud television gateway and the IP of a public network which is accessed by the smart cloud television gateway and synchronize the identification of controllable home equipment of the smart cloud television gateway. The smart home remote security access control implementation method based on the smart cloud television gateway has the advantages of being high in security, high in confidentiality and good in universality and user experience performance.
Owner:INST OF INFORMATION ENG CHINESE ACAD OF SCI
Device and method for proceeding encryption and identification of network bank data
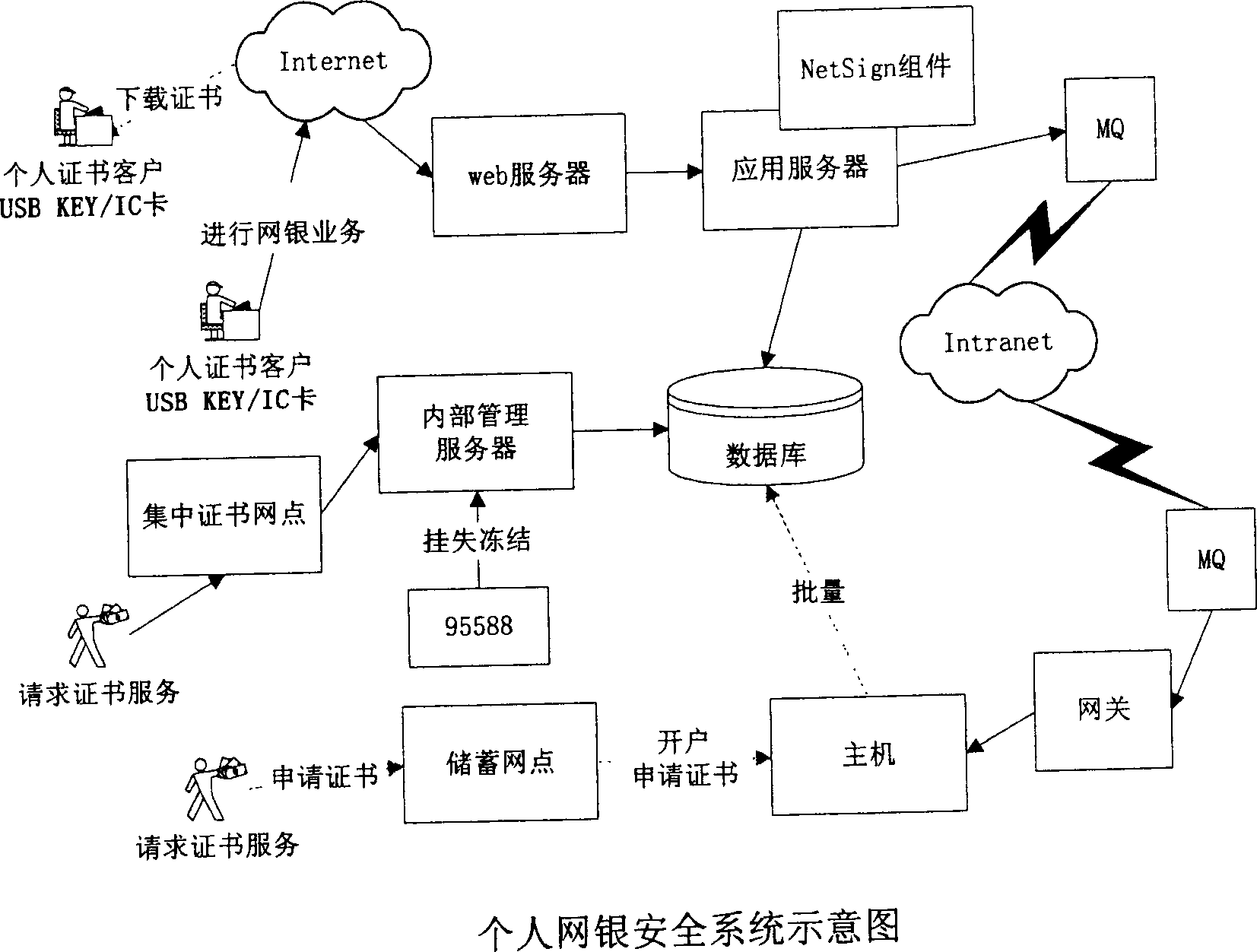
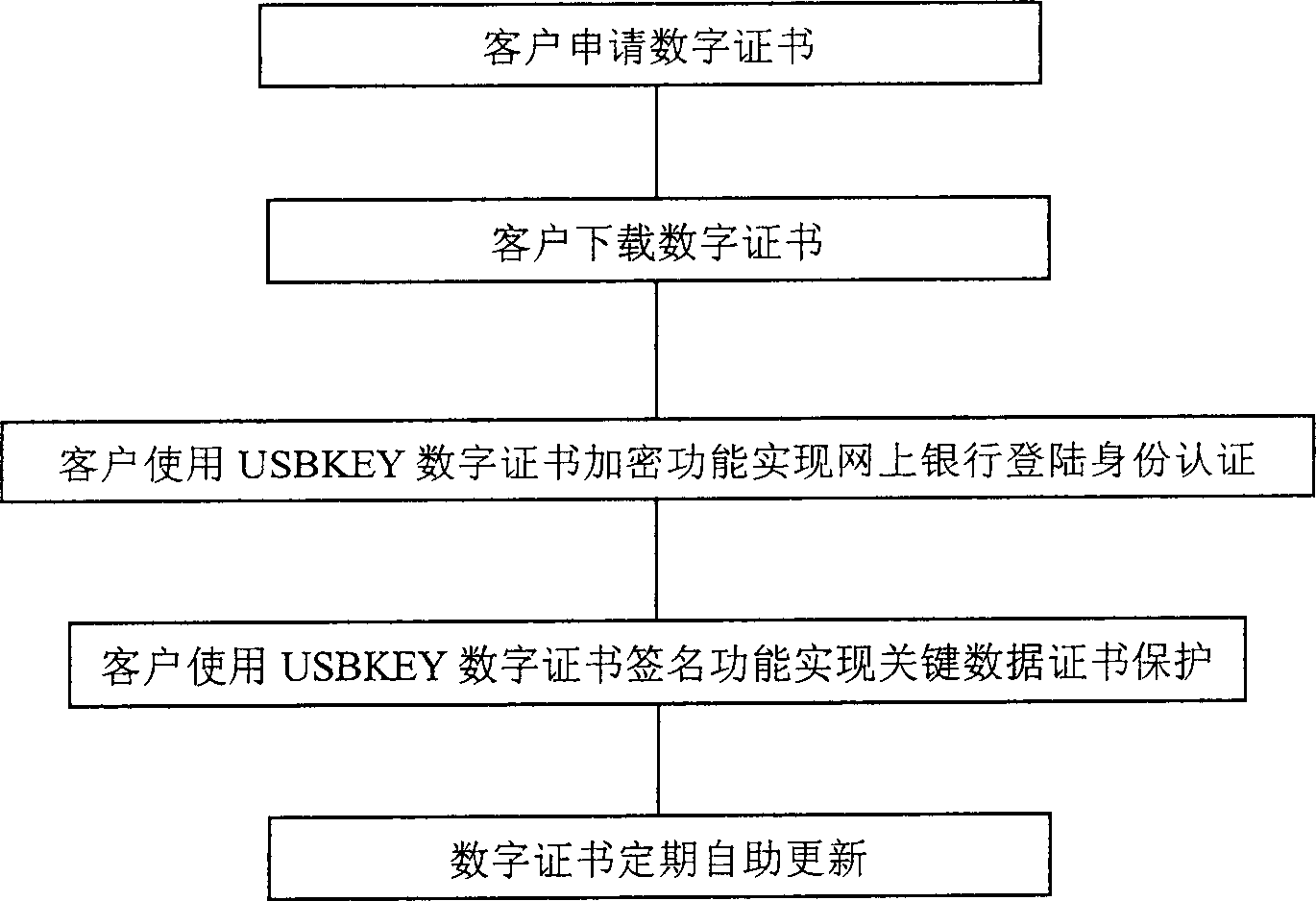
ActiveCN1556449AGuarantee the security of transactionsRealize self-service downloadDigital data processing detailsSpecial data processing applicationsInternal memoryDigital signature
The invention discloses a method of encrypting and certificating network bank data by using a USB KEY, and its characteristics: it includes the steps: a), according to the user information, generating a digital certificate corresponding to the use; b), storing the digital certificate in a USB to be allocated to the user; c), when the user makes a login with the network bank for processing data, it confirms the user ID or digital signature by the USB KEY. It also discloses an implementing device of encrypting and certificating network bank data by using the USB KEY and because every USB KEY has an only serial number and the private key can not leave the internal memory, and it can not make network transaction until the user ID is confirmed, it has high secrecy and safety.
Owner:INDUSTRIAL AND COMMERCIAL BANK OF CHINA
Automated transaction machine digital signature system and method
ActiveUS20020128969A1Easily employedPreserve integrityDigital data processing detailsUser identity/authority verificationElectronic documentCredit card
An automated transaction machine such as an ATM (10) is provided. The ATM is operative to digitally sign electronic documents (42). The ATM may be in operative connection with a storage server (32). The storage server is operative responsive to the ATM to maintain electronic documents (42) in a data store (34) in association with the user's digital safe deposit account (40) and / or a financial account (48) such as checking, savings, debit, or credit account. The storage server is further operative to store a private key (44) of a user in association with the user's digital safe deposit account and / or financial account. The ATM is operative to cause electronic documents to be signed using the private key associated with the user. The ATM is further operative to output the electronic document on a display device (18) of the ATM where the user may view and edit the electronic document.
Owner:DIEBOLD NIXDORF
User-computer interaction method for use by a population of flexible connectable computer systems
InactiveUS7249266B2Improve confidentialityUnauthorized memory use protectionHardware monitoringComputerized systemSystem usage
A user-computer interaction method for use by a population of flexibly connectible computer systems and a population of mobile users, the method comprising storing information characterizing each mobile user on an FCCS plug to be borne by that mobile user; and accepting the FCCS plug from the mobile user for connection to one of the flexibly connectible computer systems and employing the information characterizing the mobile user to perform at least one computer operation.
Owner:SAFENET DATA SECURITY ISRAEL
Method and system for secure packet communication
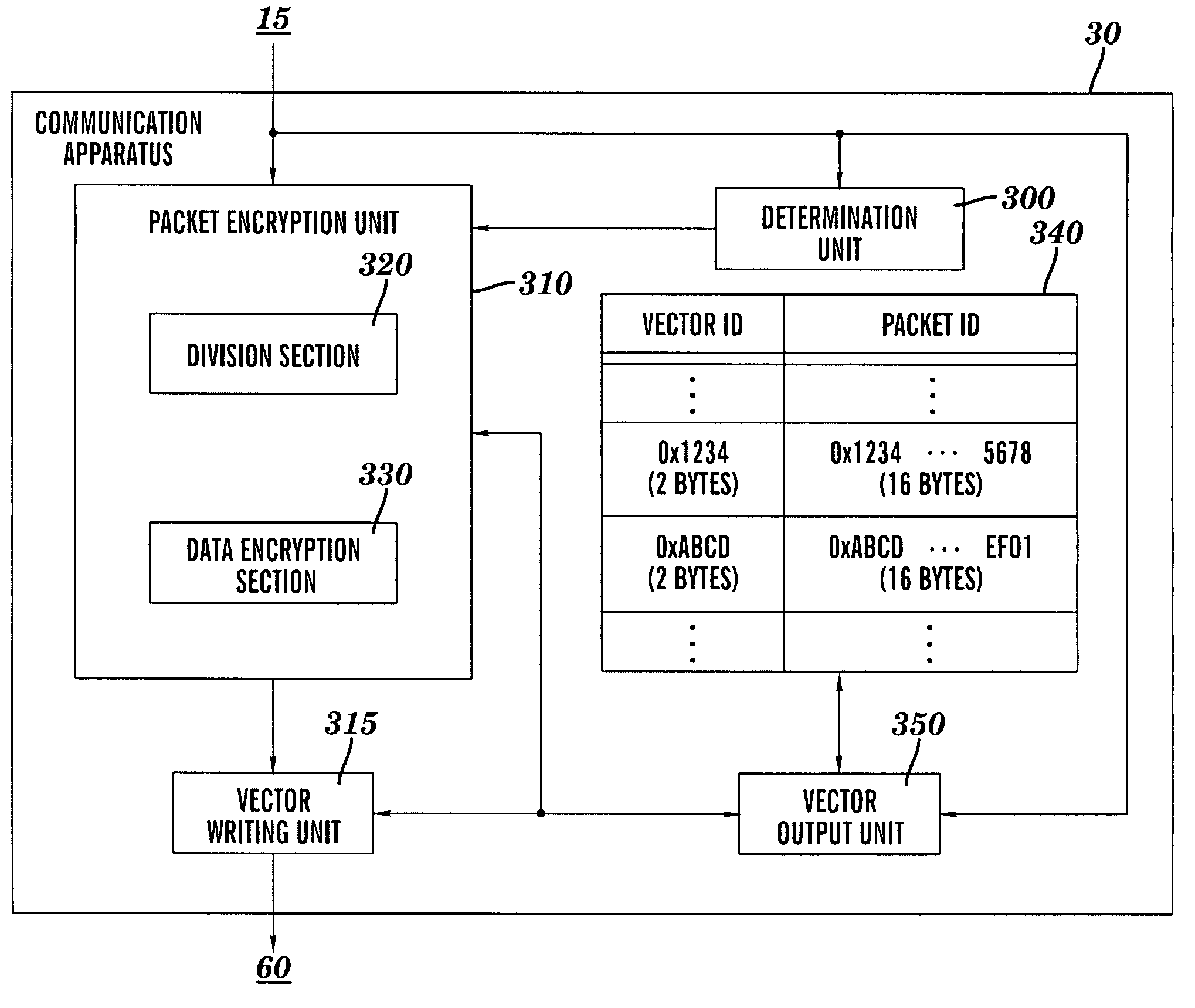
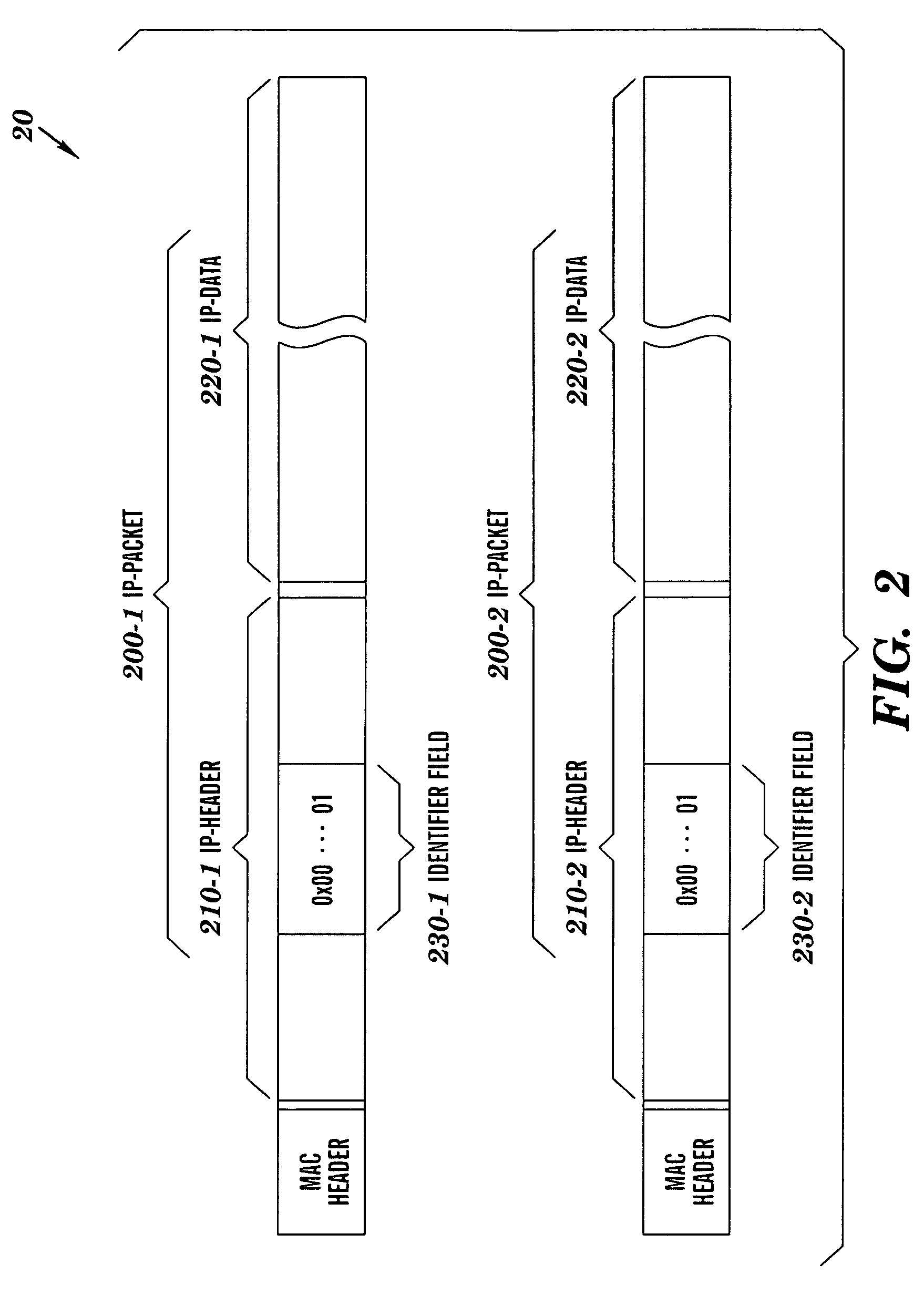
InactiveUS7869597B2Improve confidentialityIncreasing communication frame size and processing timeSecret communicationSecuring communicationPacket communicationPlaintext
A method for processing a communication data item. The communication data item is divided into at least two unencrypted packets to be encrypted. Each encrypted packet is generated from a corresponding unencrypted packet. Each unencrypted packet has a packet header and plaintext data. The packet header has an identifier field that includes a packet identifier. The packet identifier is identical for all unencrypted packets. Generating an encrypted packet for each unencrypted packet includes: determining a vector identifier from the identical packet identifier, wherein the vector identifier is associated with the identical packet identifier; ascertaining an initial vector from the vector identifier; and forming an encrypted packet header by inserting the vector identifier into a first portion of the packet header and encrypting a second portion of the packet header through use of the initial vector. The encrypted packets are subsequently decrypted and combined to reconstruct the communication data item.
Owner:HULU
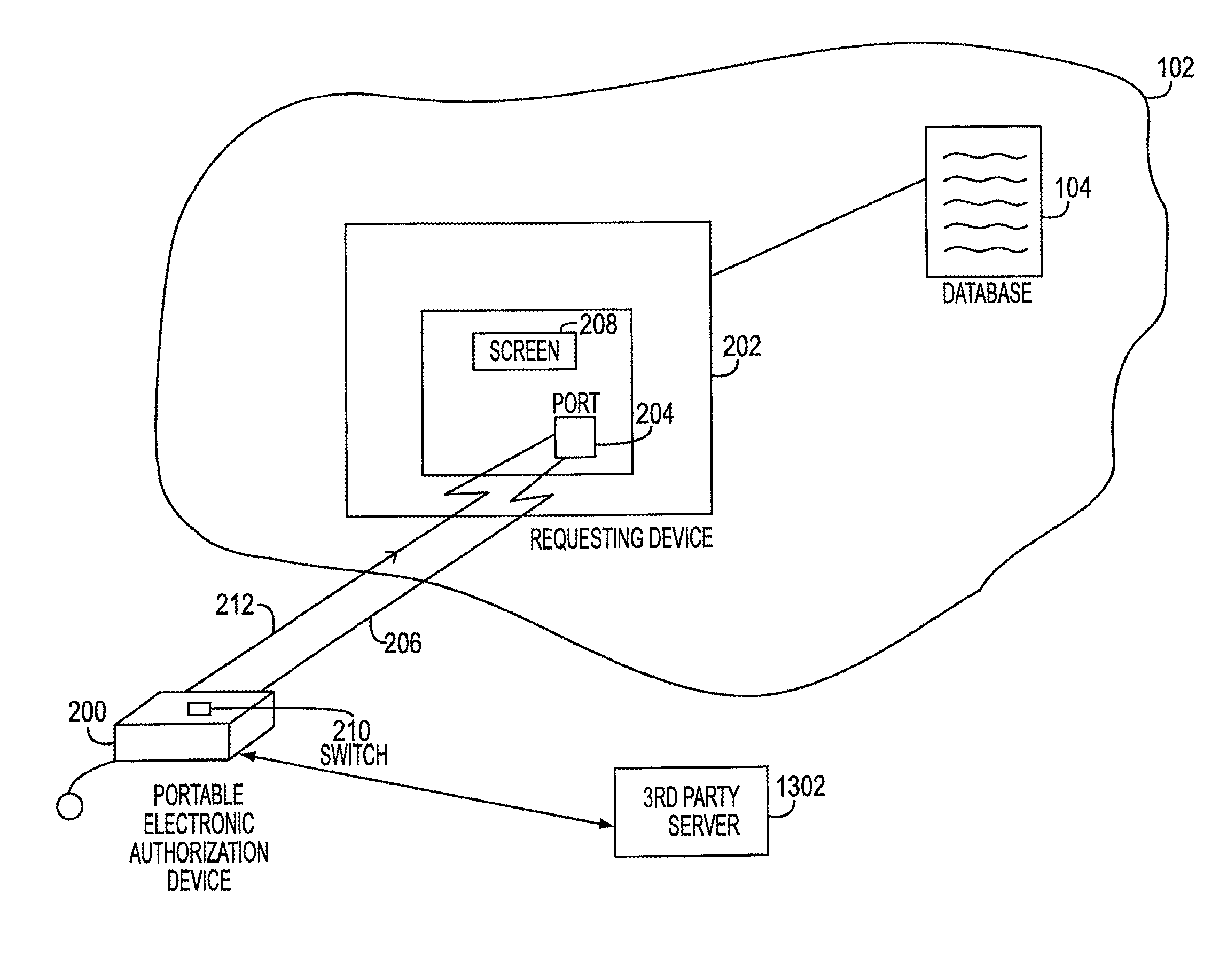
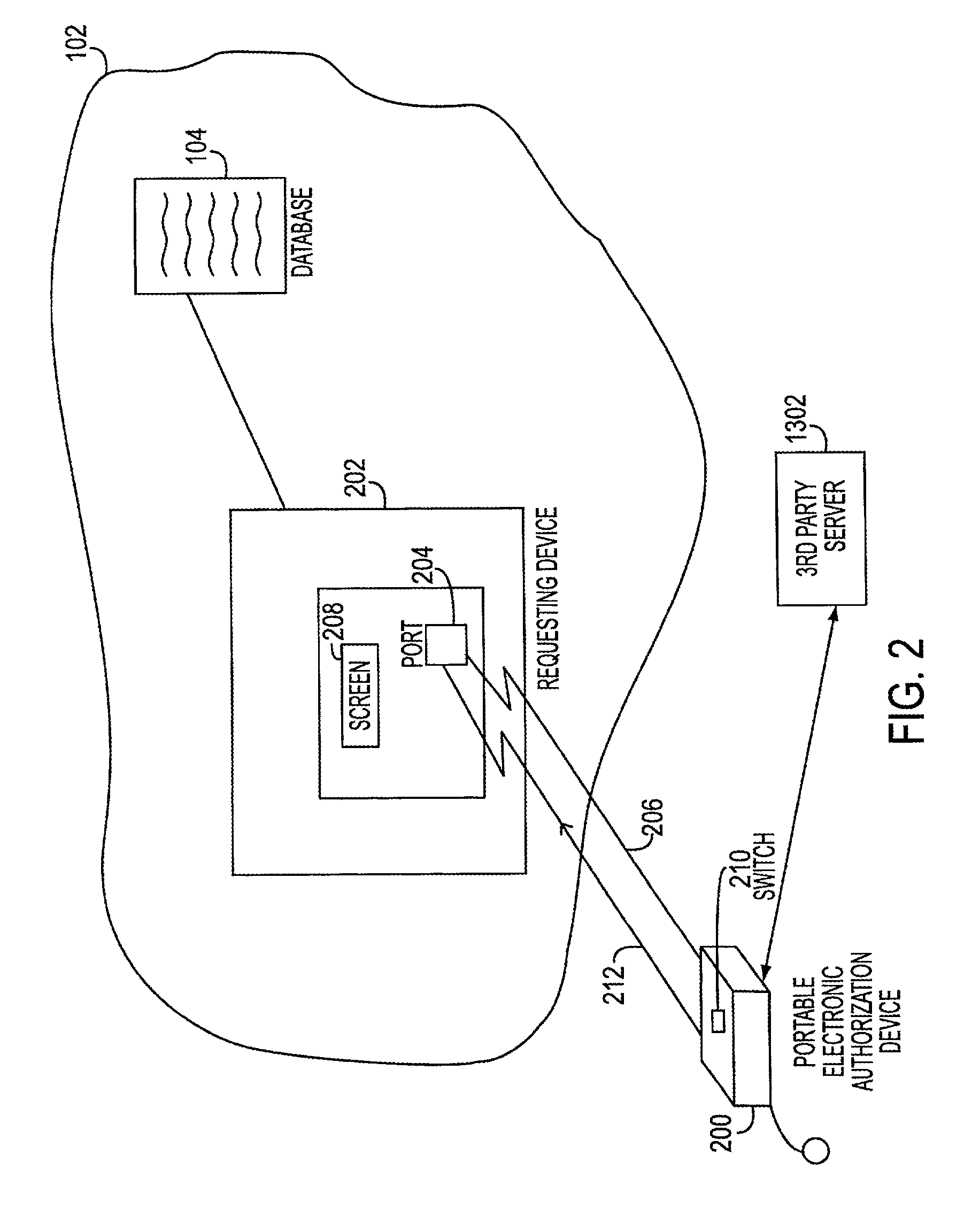
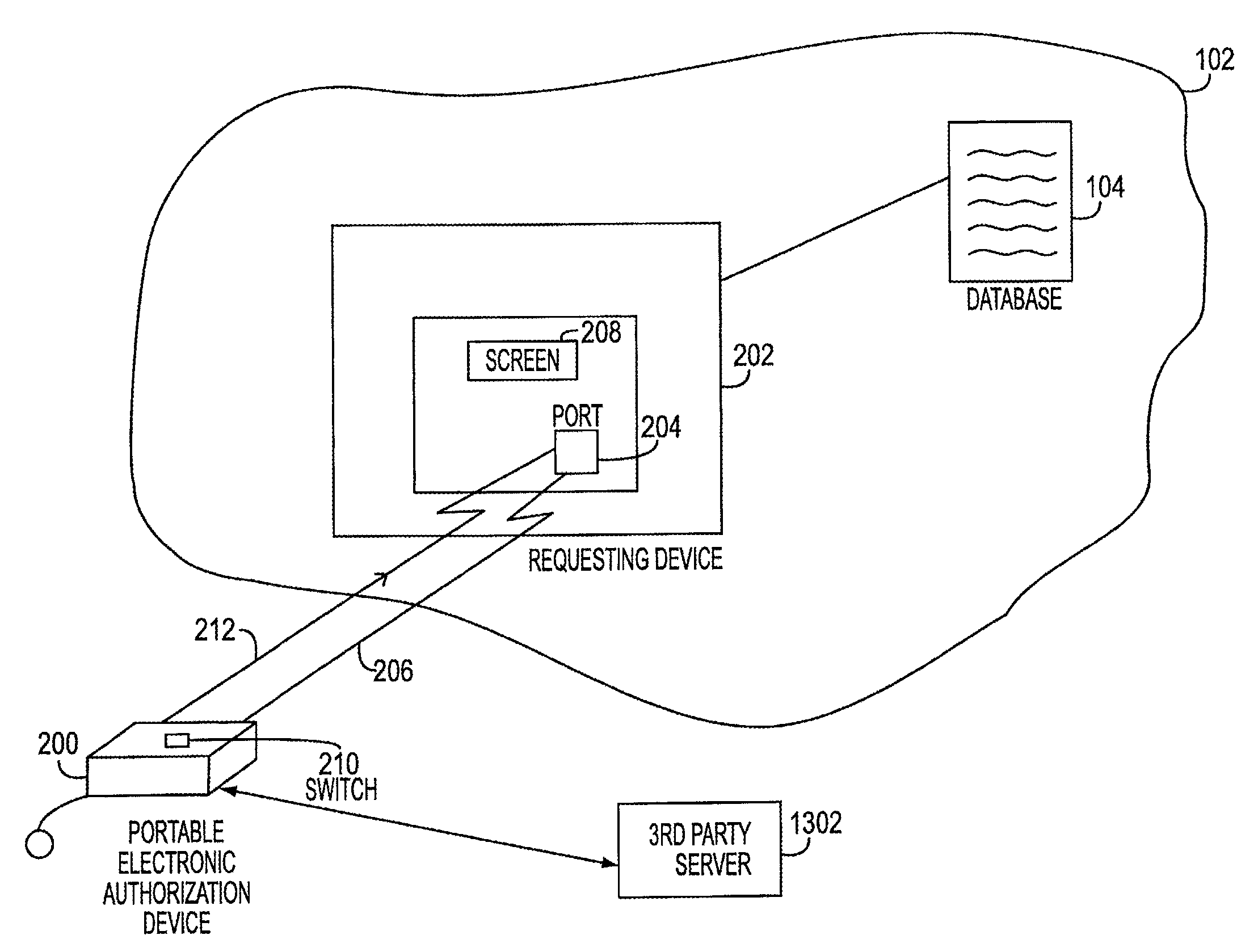
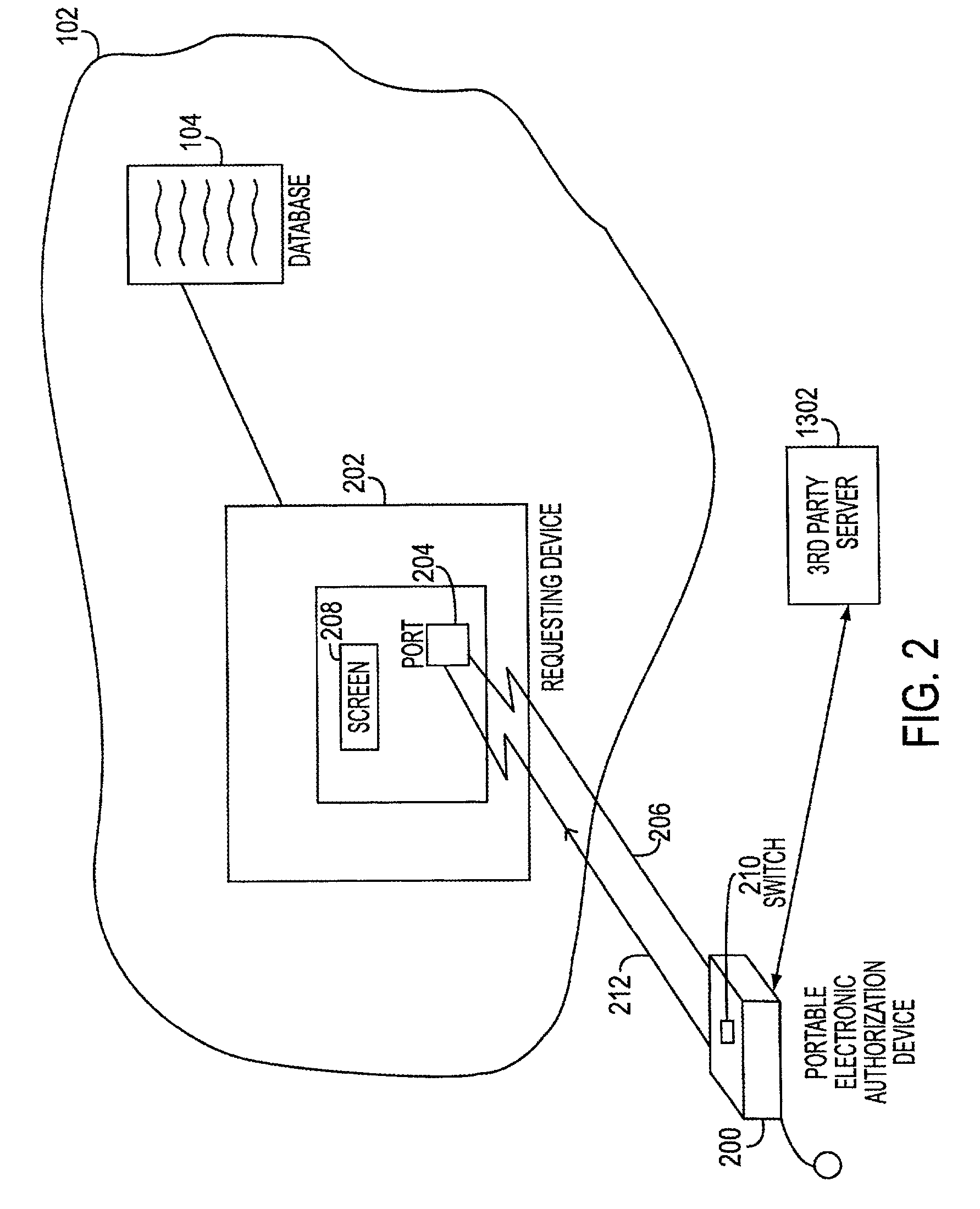
Electronic transaction systems and methods therfeor
InactiveUS20070089168A1Facilitates nonrepudiationImprove identityComplete banking machinesFinanceAuthorizationDigital data
The method includes the steps of receiving at the PEAD first digital data representing the transaction request. The PEAD provides information to the user regarding an ability to approve the transaction request. When the transaction request is approved by the user, the PEAD receives second digital data representing the electronic service authorization token. A remote agent server may provide a bridge between the electronic transaction system and the PEAD. In another embodiment, the private key is stored on the portable device, encrypted. The decryption key is stored outside of the device, at a trusted 3rd party location. When the user attempts to make a signature the software sends a request for the decryption key, along with the user's password or pass phrase keyed in at the keyboard of the PDA, smart phone, or cell phone, to a server belonging to the trusted 3rd party.
Owner:SERVSTOR TECHNOLOGIES LLC +1
Electronic transaction systems and methods therefor
InactiveUS7635084B2Improve confidentialityIntegrity of the transaction approval processComplete banking machinesFinanceDigital dataThird party
The method includes the steps of receiving at the PEAD first digital data representing the transaction request. The PEAD provides information to the user regarding an ability to approve the transaction request. When the transaction request is approved by the user, the PEAD receives second digital data representing the electronic service authorization token. A remote agent server may provide a bridge between the electronic transaction system and the PEAD. In another embodiment, the private key is stored on the portable device, encrypted. The decryption key is stored outside of the device, at a trusted 3rd party location. When the user attempts to make a signature the software sends a request for the decryption key, along with the user's password or pass phrase keyed in at the keyboard of the PDA, smart phone, or cell phone, to a server belonging to the trusted 3rd party.
Owner:SERVSTOR TECHNOLOGIES LLC +1
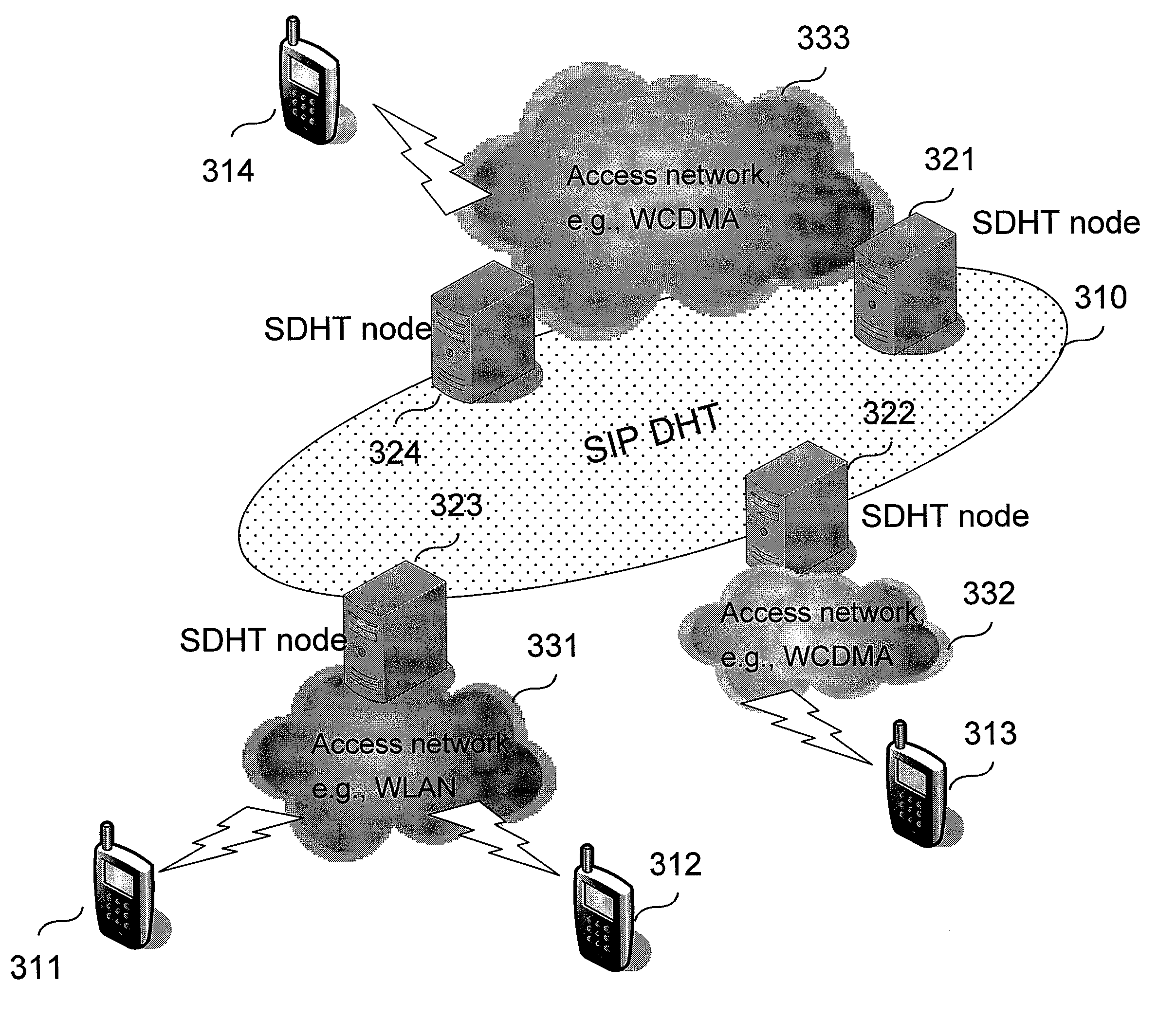
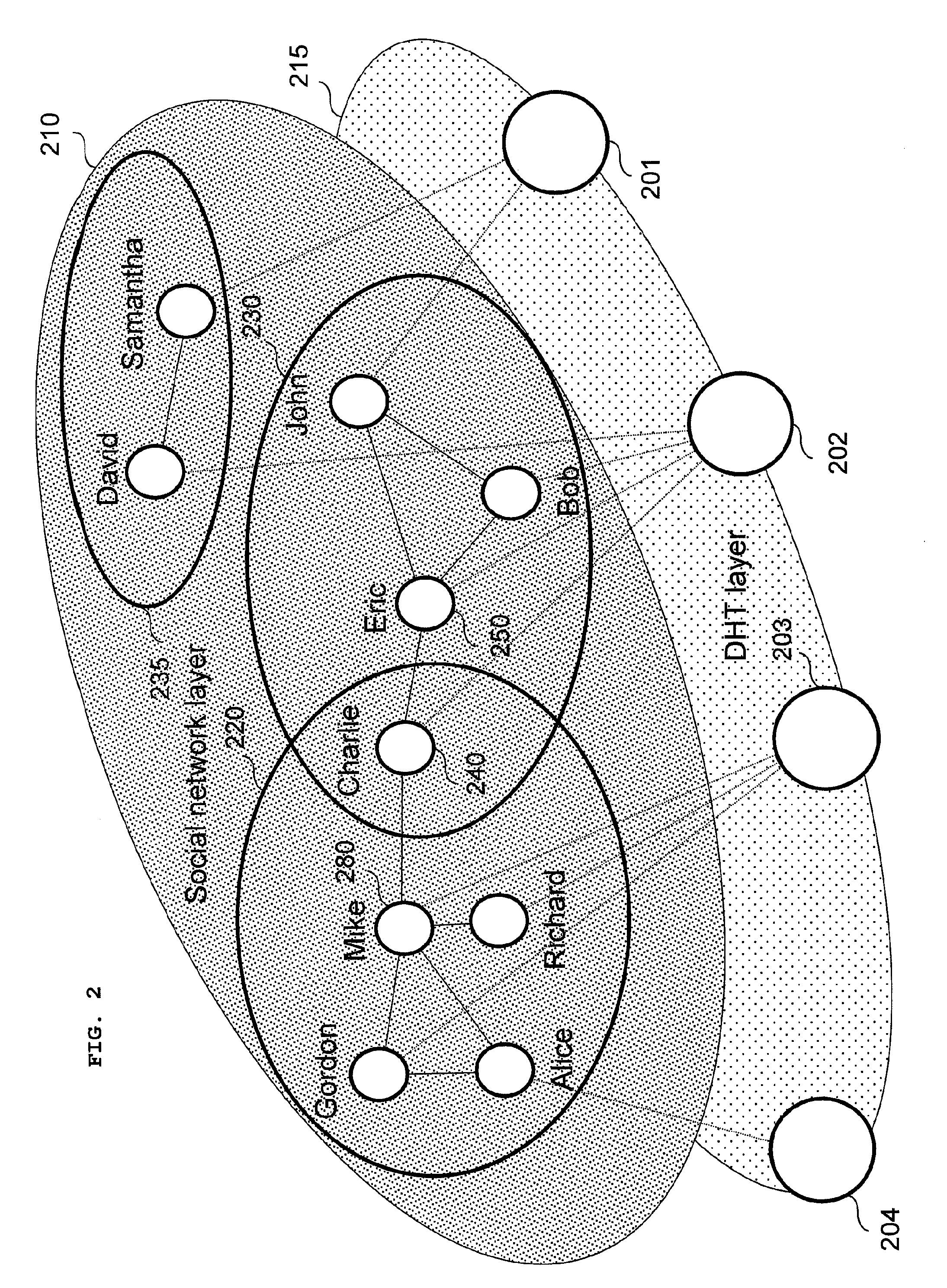
Method, System, and Devices for Network Sharing or Searching Of Resources
InactiveUS20100095009A1Improve and provide certain serviceResource searchingMultiple digital computer combinationsTransmissionCommunications systemContent sharing
The invention presents an architecture of a distributed communication system that combines strengths of Distributed Hash Table (DHT) algorithms and social networks. The system forms a cost efficient platform for providing innovative mobile Services. Possible implementations of the proposed system in the IP Multimedia Subsystem and as a standalone SIP based system are presented. The architecture may also be deployed in other systems. Further, a content sharing inside community service is provided.
Owner:NOKIA CORP
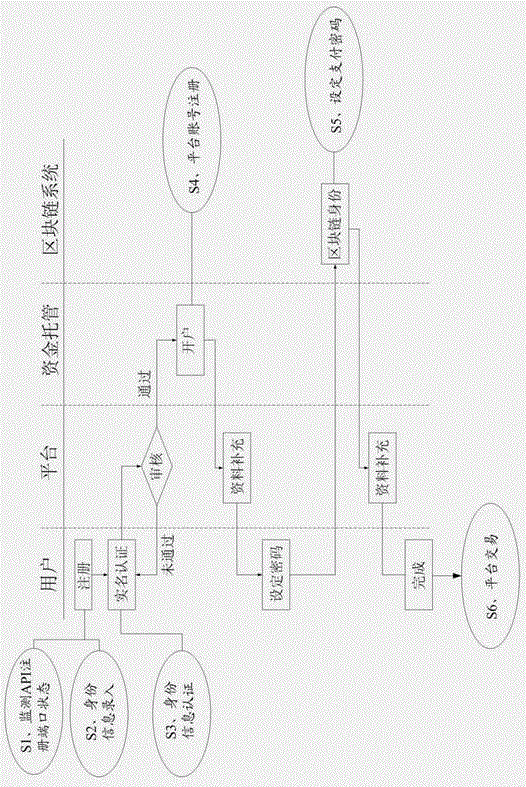
Method for realizing user identity digitalization based on block chain
InactiveCN106529946AImprove data stabilityHigh data reliabilityPayment protocolsPayments involving neutral partyTechnical supportAuthentication system
The invention discloses a method for realizing user identity digitalization based on a block chain. The method comprises the following steps: S1, monitoring a state of an API registration port; S2, inputting identity information; S3, performing identity information authentication, i.e., checking user identities through a police real name authentication system and bankcard binding mode according to information input by users in a registrant name input window, a registrant identity card number input window and a bank card number input window; S4, registering a platform account, and distributing block chain identities to the users; S5, setting a payment password; and S6, performing platform transaction. The method is a digital transaction method under the support of a block chain technology. According to the invention, under the technical support of a third-party service platform, the block chain identities can be provided for the users, it is ensured that the users can carry out digital economic transaction under the block chain technology, the security and the confidentiality are quite high, the transaction content cannot be tampered, traceability can also be performed in case of a transaction problem, and the transaction reliability is improved.
Owner:北京金股链科技有限公司
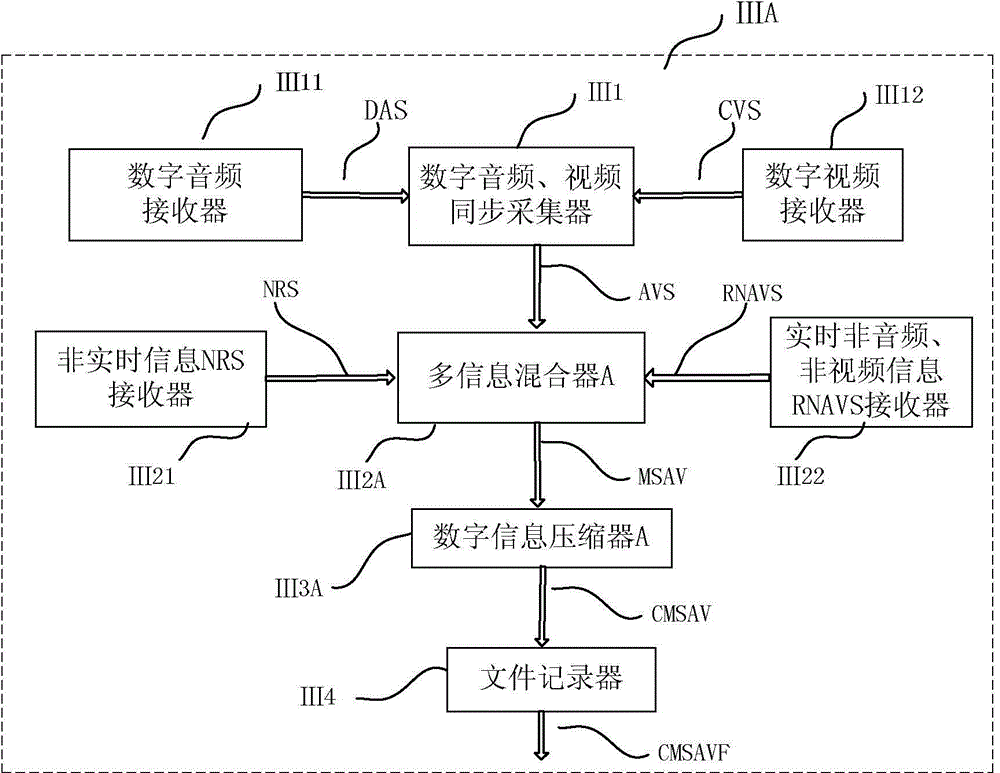
Method for synchronously reproducing multimedia multi-information and application thereof
InactiveCN104869342AAvoid non-real-time problems that cannot reproduce playback at the same timeOptimize storage methodTelevision system detailsColor television detailsComputer hardwareEngineering
A method for synchronously reproducing multimedia multi-information is to combine a plurality of relevant documents and a plurality of information flows, which have associated information relation via a multi-information modulation unit, and to synchronously reproduce with a player which can be used for synchronously reproducing multi-information. The step of synchronously recording multi-information of the method is to insert non-audio and video information in audio flow, video flow or file before condensing or after condensing with the multi-information modulation unit, that is to say to embed needed video frame or audio frame in an additional information block carried with the non-audio and video information and / or creating or inserting an additional information frame carried with the non-audio and video information among the needed video frame and the needed audio frame. The method can be used for simultaneously storing a multimedia multi-information file in same file in real time and ensure highly synchronization when inquiring and playing back.
Owner:LIUZHOU GUITONG TECH
Data sharing method based on blockchain and related to private data
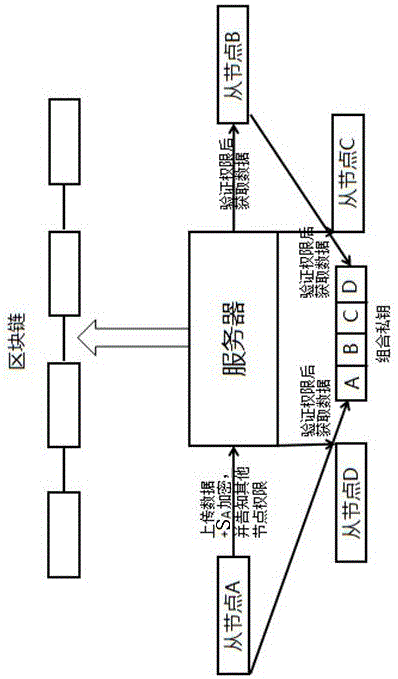
InactiveCN106778343AEnsure safetyImprove confidentialityDigital data protectionTransmissionData nodeData exchange
The invention relates to the technical field of information security and provides a data sharing method based on blockchain and related to private data. The method includes the steps that a private key S is allocated by the blockchain and held by four slave nodes A, B, C and D, when the private key S is generated, a piece of verification information is written into each part in the private key, and through comparison of the verification information, one certain node in the blockchain judges the identity of another node on the basis; the private data of each slave node uses the corresponding part of private key in an encrypted mode, and a network needs to be informed of which node can obtain what data during encryption; when one certain slave node intends to have access to the private data uploaded by other nodes, the network makes the verification information compared with verification information carried by part of the private key of an upload data node, and when the verification result is one of the nodes informed by the upload data node, the node applying at the moment can have access to the private data uploaded by another node. The method is capable of guaranteeing safety of exchange and obtaining of the private data in the blockchain.
Owner:苏州展识科技有限公司
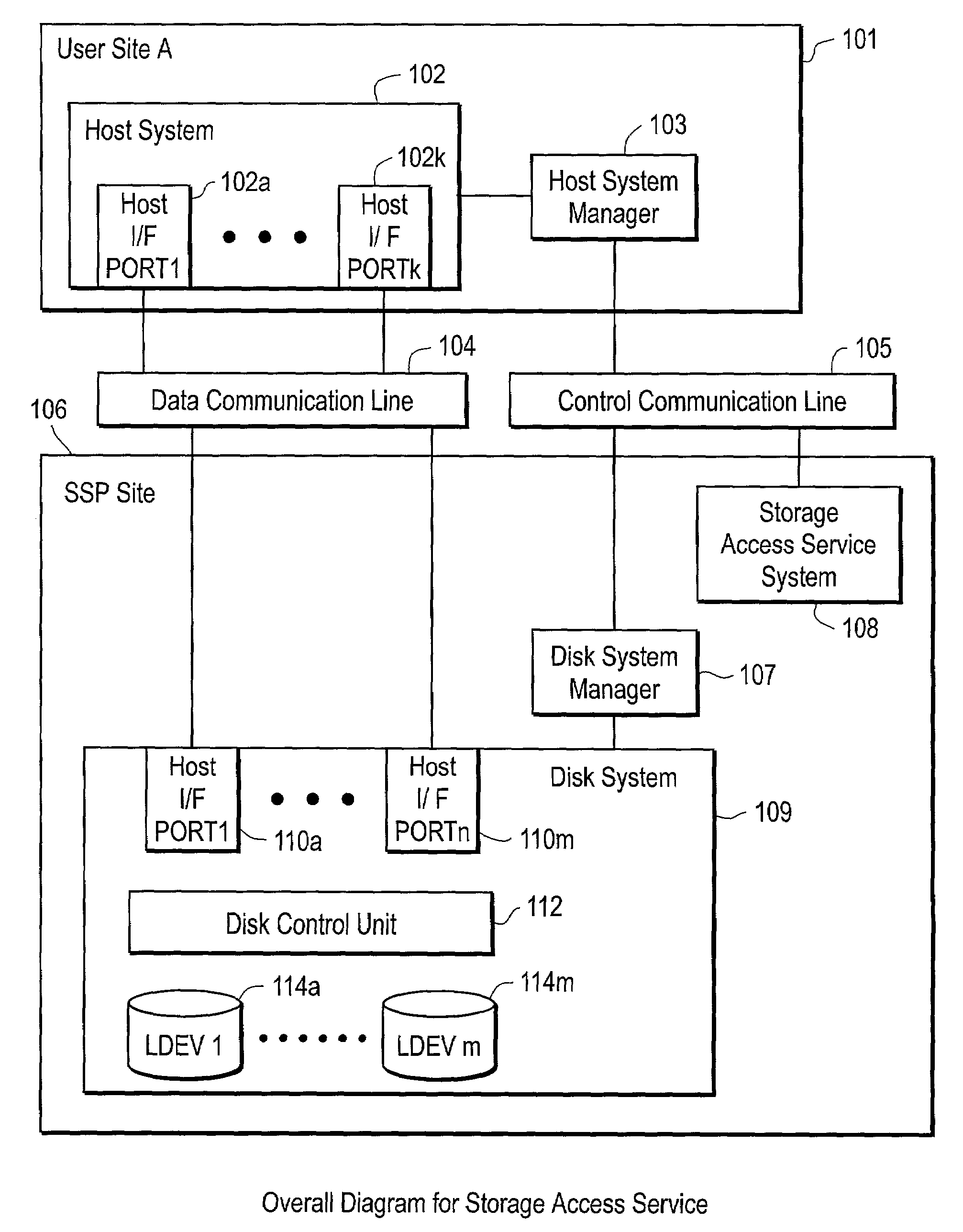
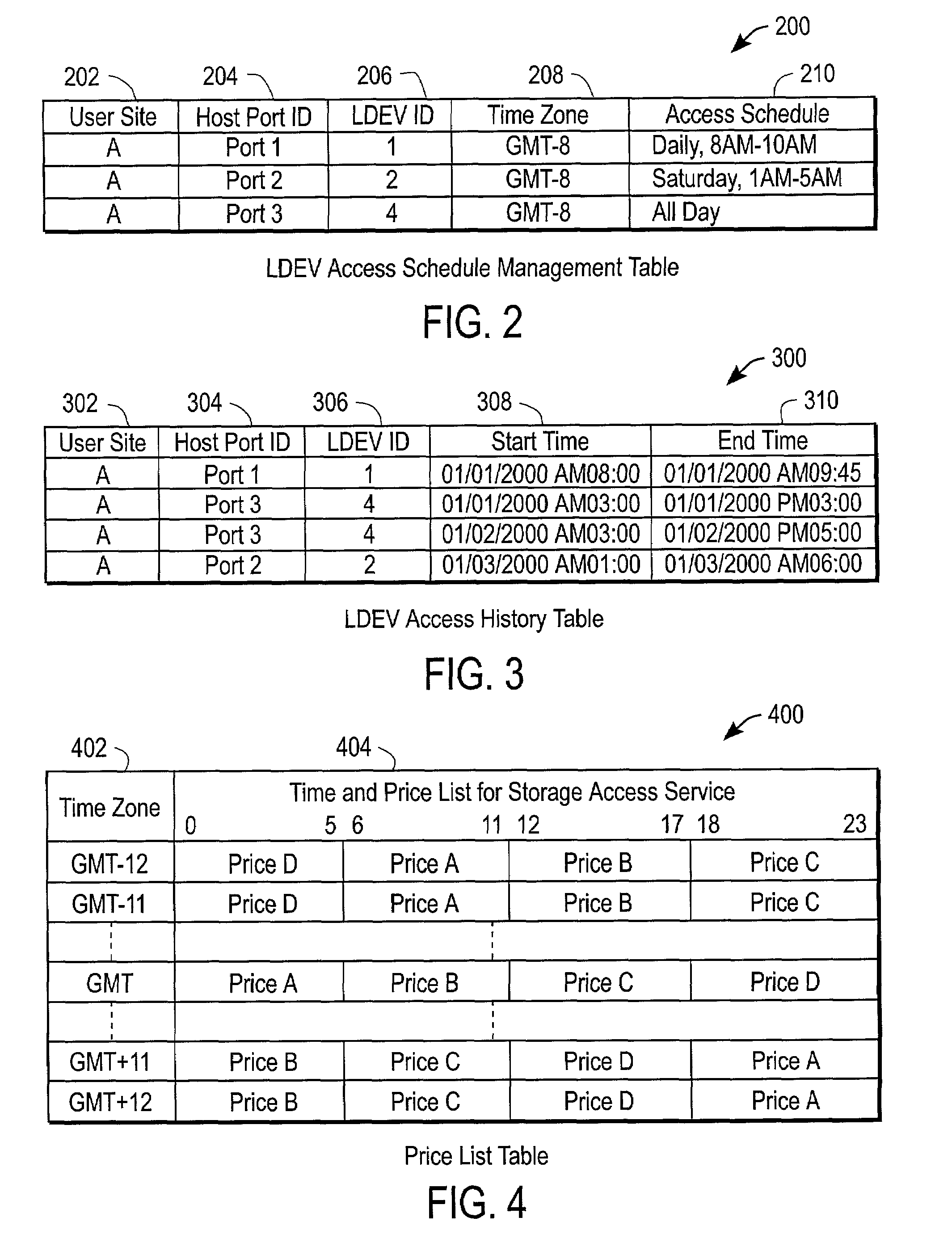
Method and system for time-based storage access services
InactiveUS7010493B2Improve confidentialityLow costMetering/charging/biilling arrangementsInput/output to record carriersAccess timeService mode
The present invention provides techniques for managing access to storage resources according to an access time. Specific embodiments provide a variety of different kinds of time based access billing. For example, in specific embodiments, one or more of a time time-card storage access service mode, a time-lock storage access service mode, and a semi-timecard storage access service mode are provided.
Owner:HITACHI LTD
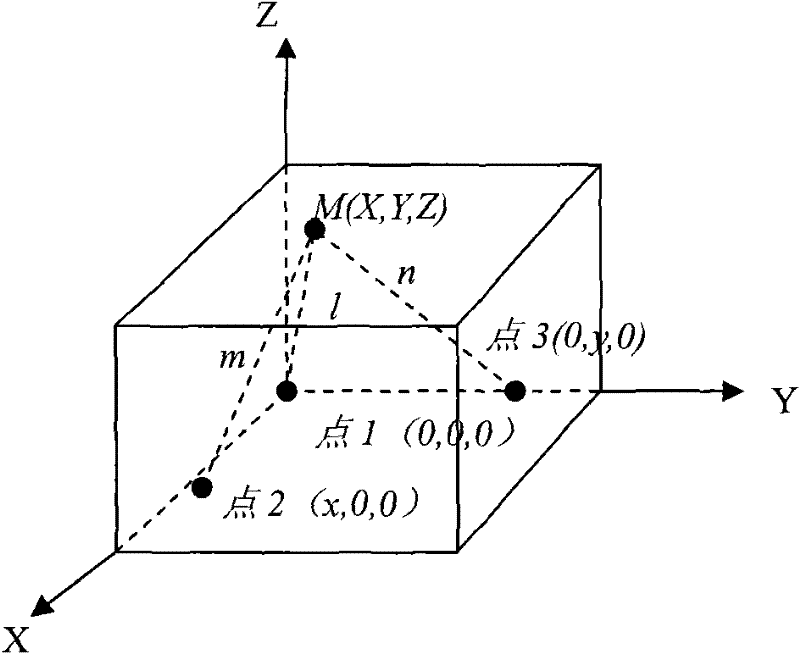
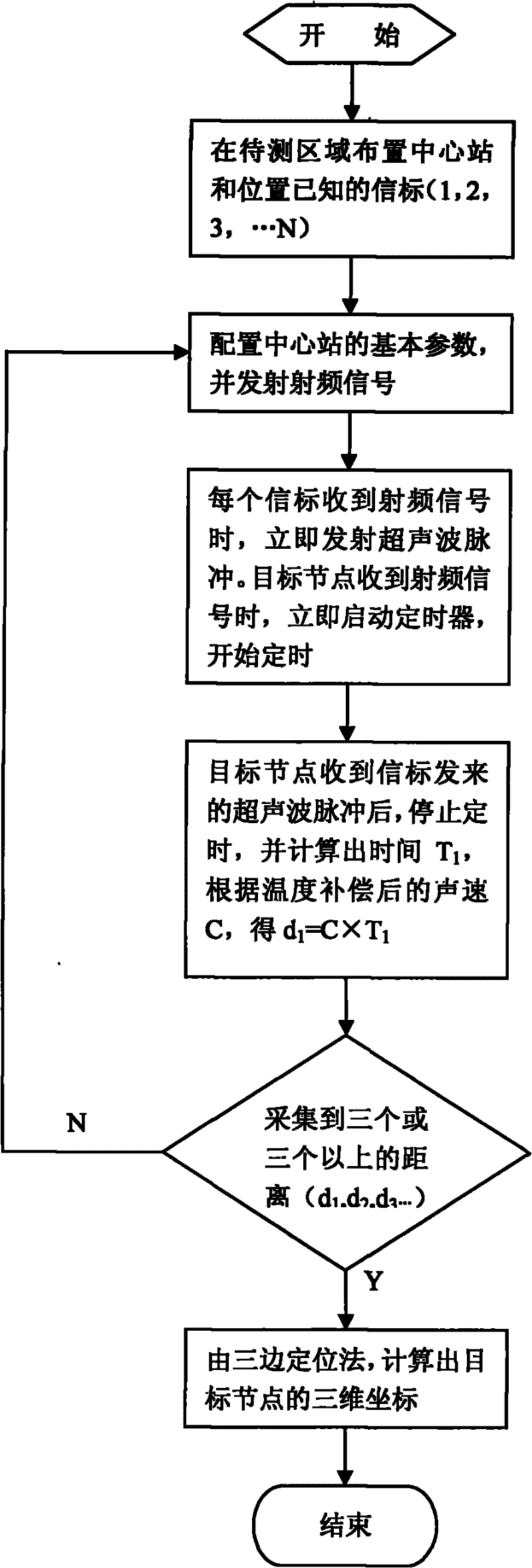
Ultrasonic wave based indoor three-dimensional positioning system and method
InactiveCN102253367ARealize real-time positioningImprove indoor positioning accuracyPosition fixationConfidentialityWireless sensor networking
The invention provides an ultrasonic wave based indoor three-dimensional positioning system and method, which belong to the technical field of positioning and navigation. The system is a wireless sensor network system, and through combining with the radio frequency technology and the ultrasonic technology, the system can implement accurate positioning by using a TDOA (time difference of arrival) algorithm and a trilateral location algorithm. By using the system provided by the invention, the centimeter-level positioning accuracy can be achieved, and the real-time positioning of a plurality of target nodes in a passive positioning mode can be realized, so that the application of the system in positioning or navigating a plurality of targets becomes possible. The system also has the advantages of good confidentiality, low cost and low power consumption.
Owner:CHANGCHUN UNIV OF SCI & TECH
Image printing apparatus and display device and job processing method therefor
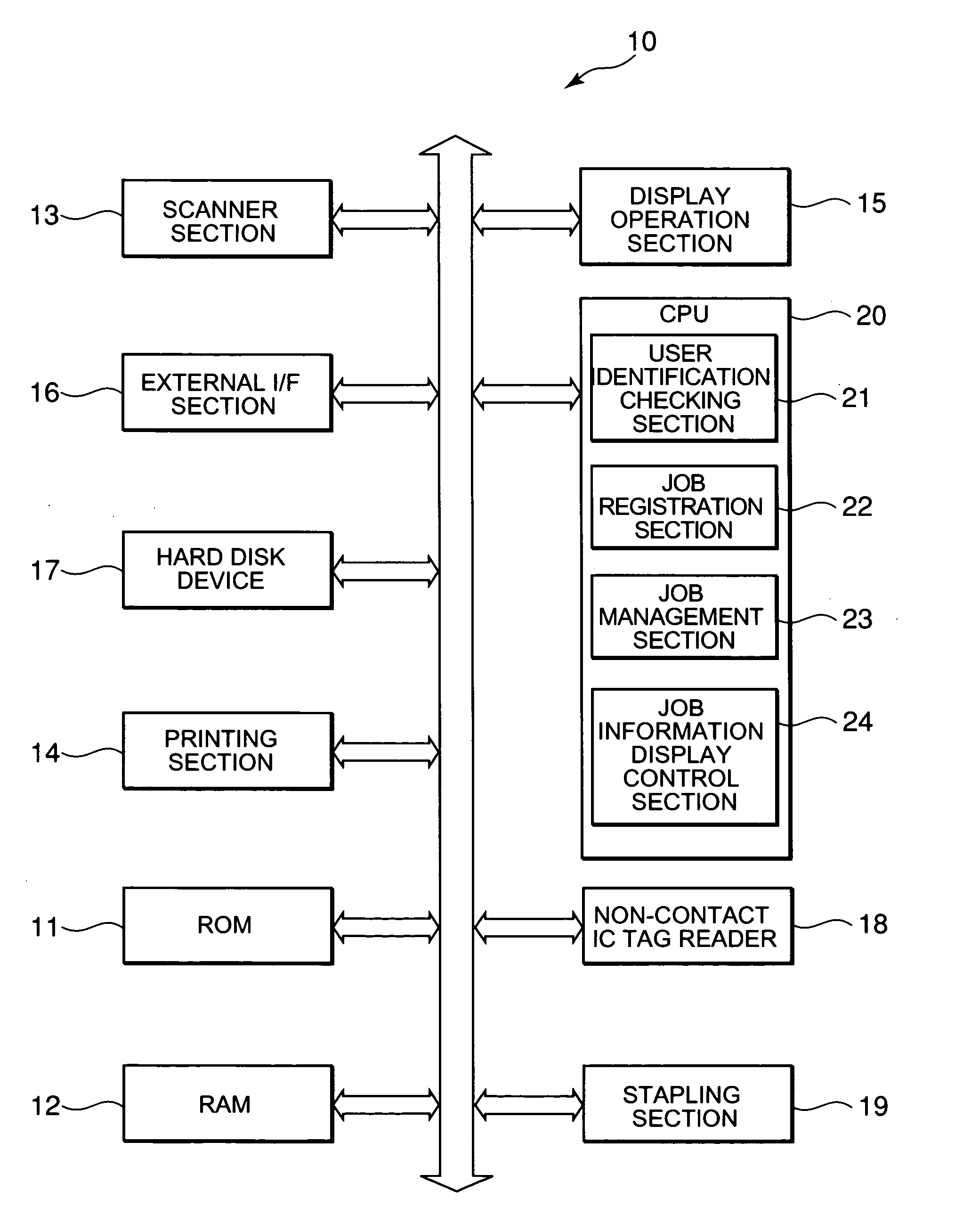
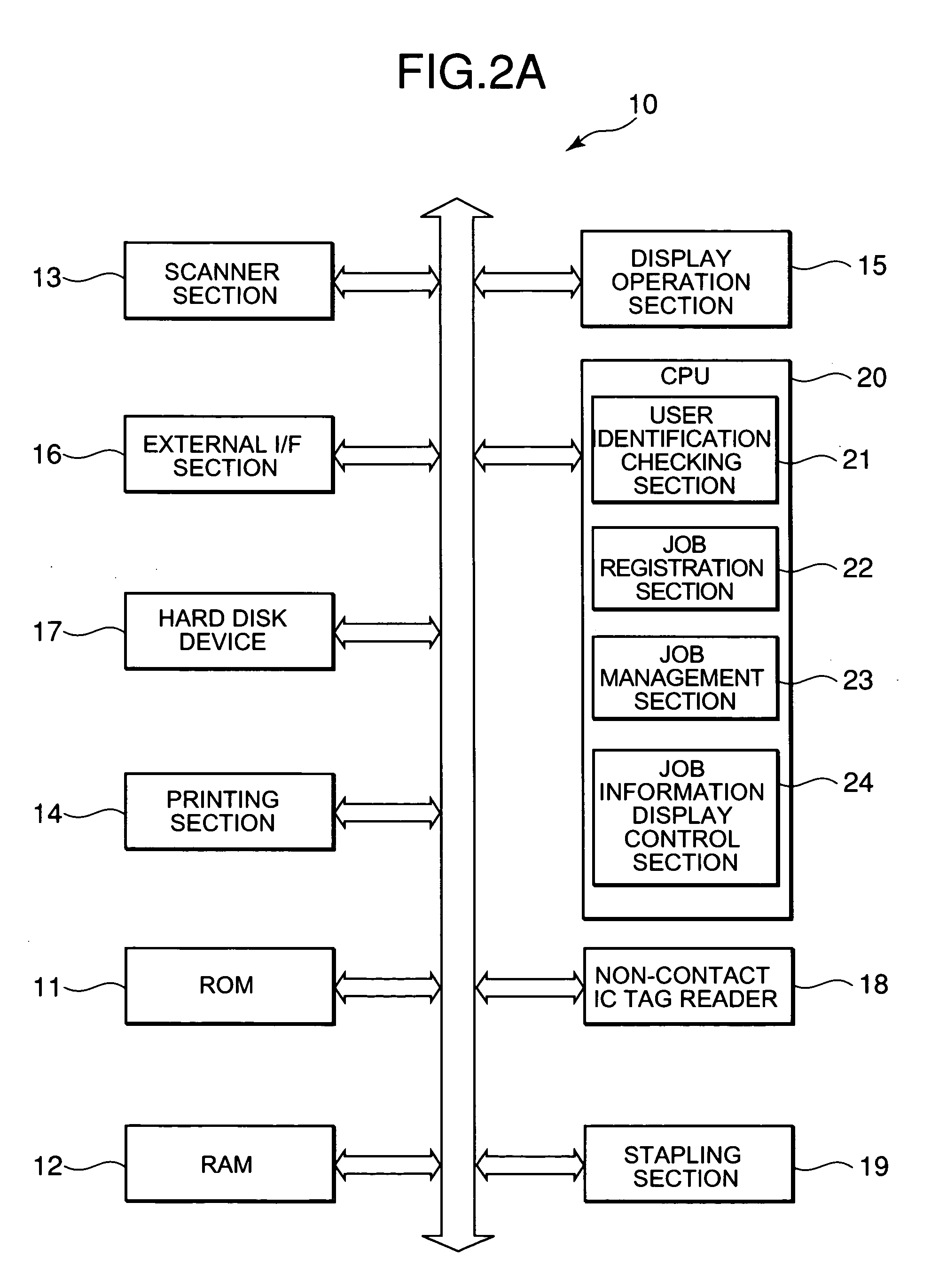
InactiveUS20060001898A1Ensure confidentialityImprove confidentialityDigital computer detailsVisual presentationConfidentialityDisplay device
There is provided an image printing apparatus which can ensure confidentiality by including an identification section which identifies whether or not a user who requests a job is present in a predetermined range from the image printing apparatus, a queue which stores the job and manages an execution of the job in stored order, a job registration section which registers the job at the end of the queue, and a job management section which suspends the start of execution of the job registered in the queue when the identification section does not recognize the presence of the user who requests the job, and permits the start of execution of the job registered in the queue when the identification section recognizes the presence of the user who manages the job. A display device and a job processing method are also provided.
Owner:KONICA MINOLTA BUSINESS TECH INC
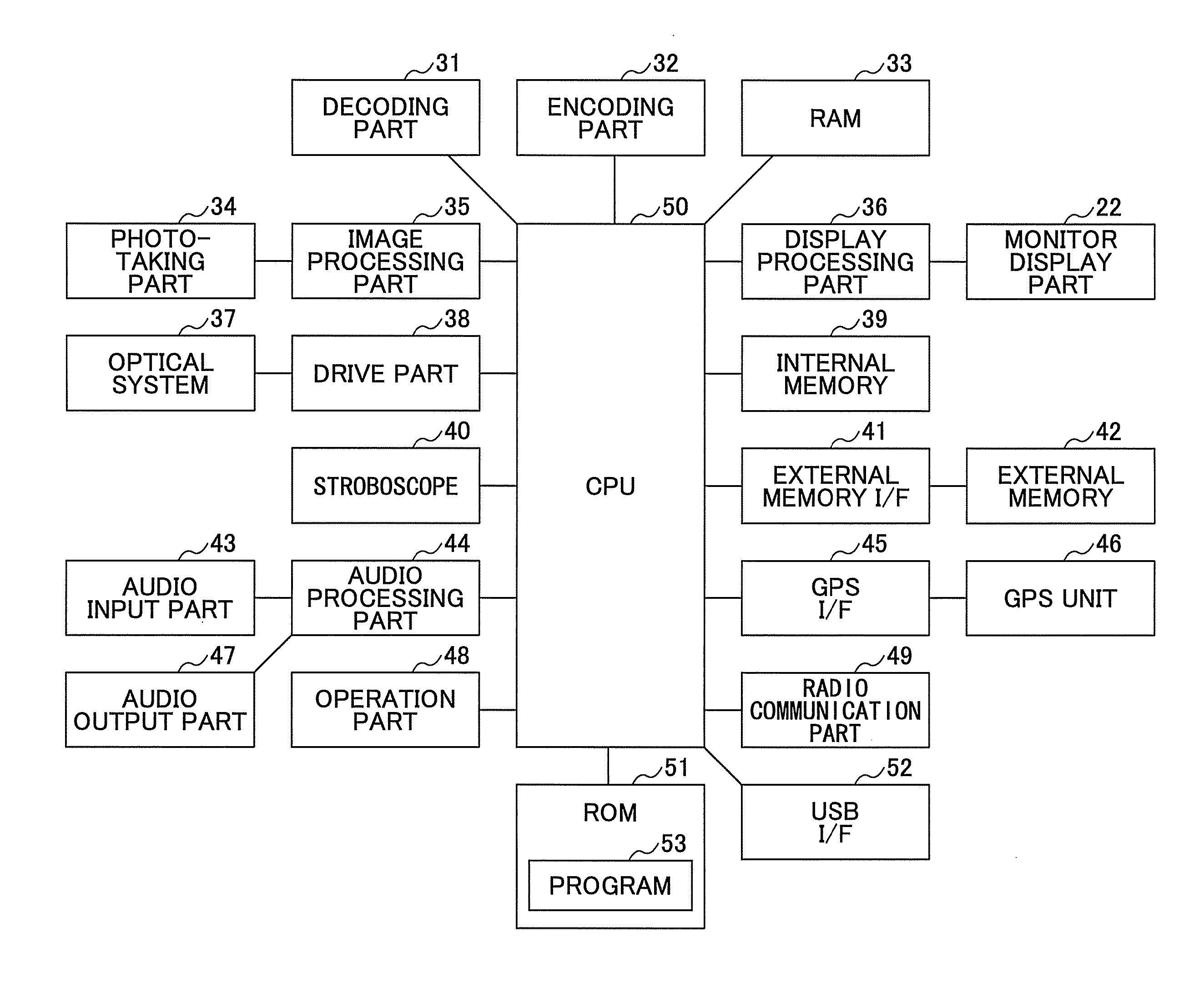
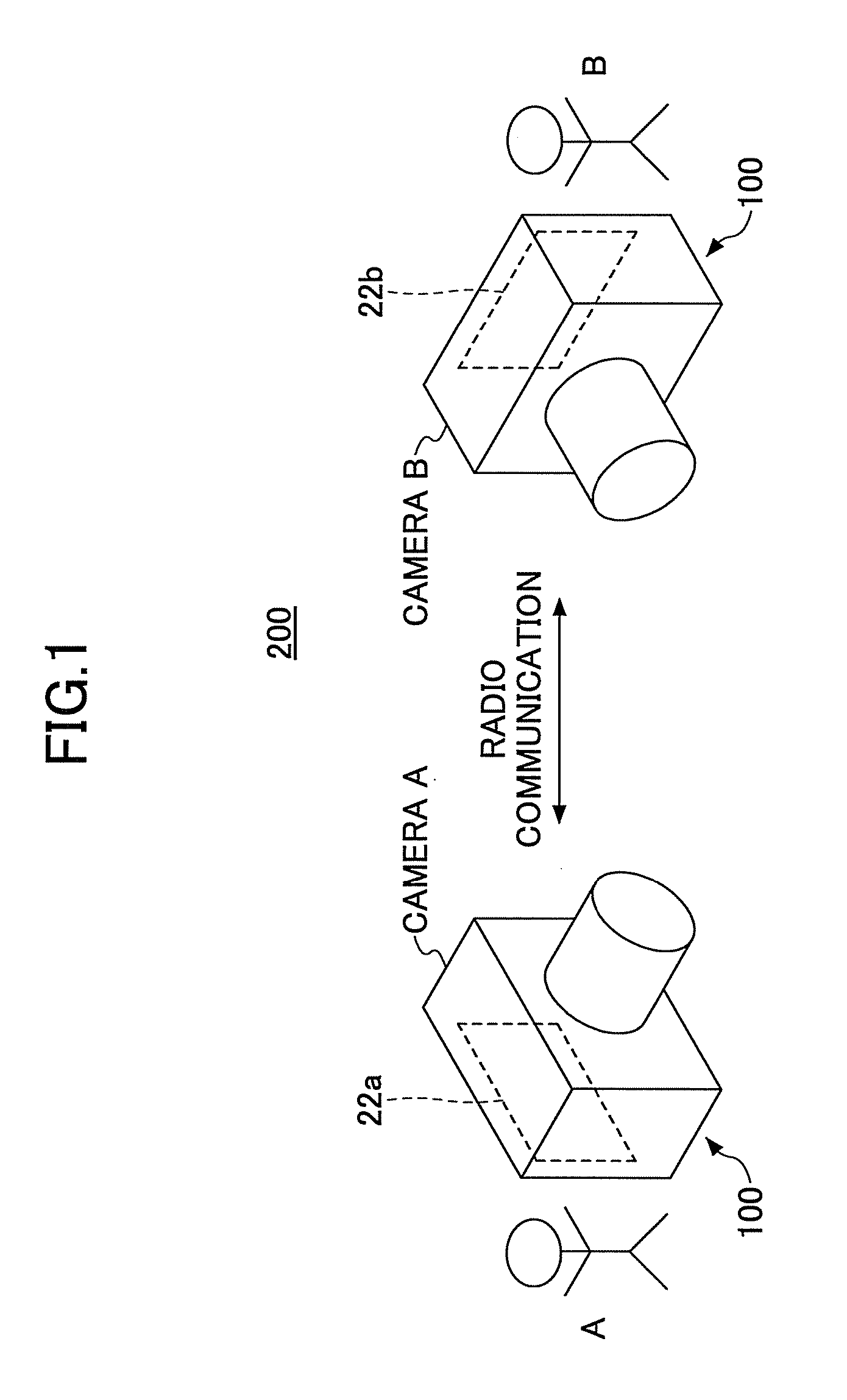
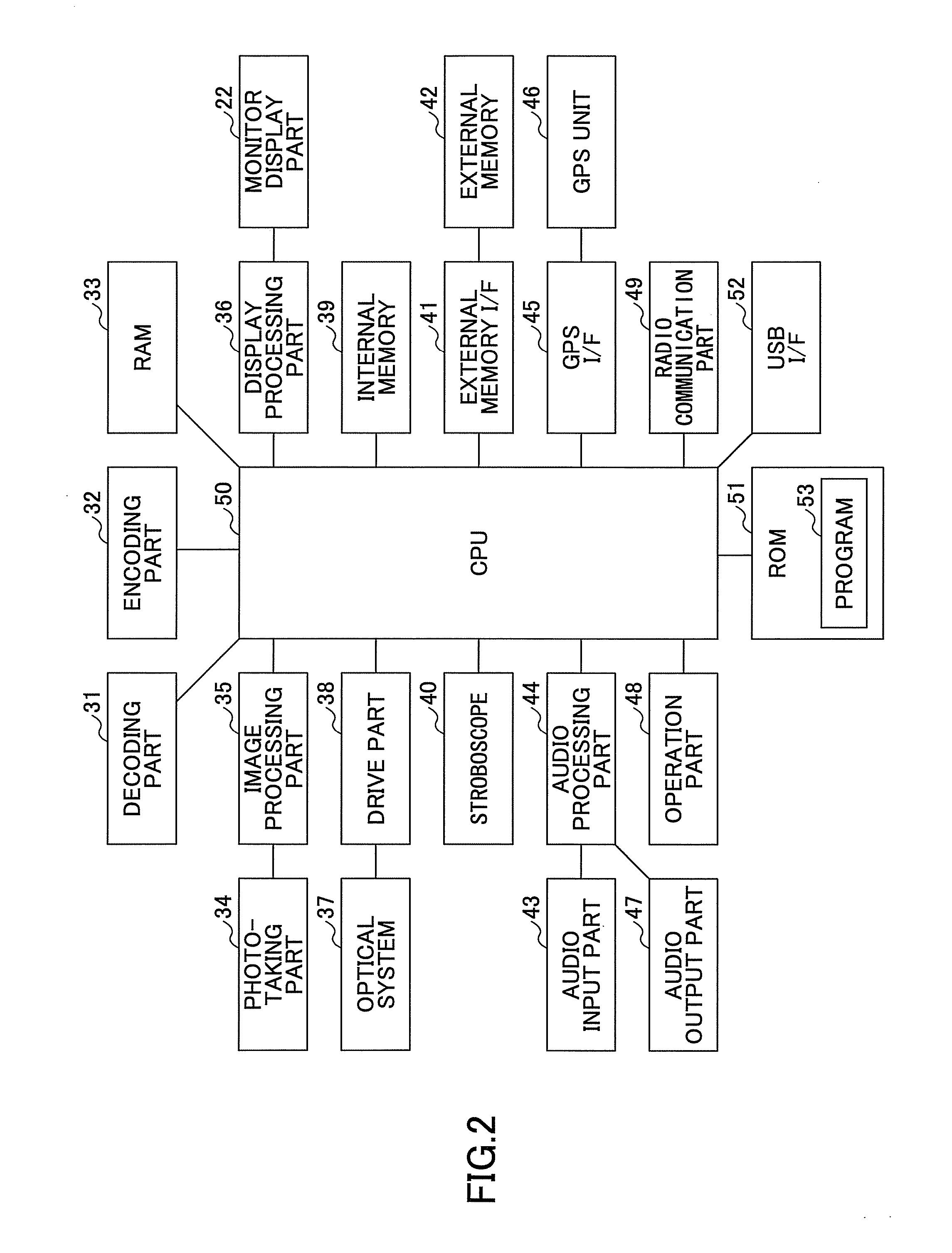
Photographing apparatus and communication establishing method and program
InactiveUS20110050926A1Eliminate the problemEasy maintenanceTelevision system detailsColor television detailsComputer hardwareAuthentication information
In a photographing apparatus, an encoding part creates a code image from authentication information of the photographing apparatus. A photographing part takes a photograph of a connection code image displayed on a display part of another apparatus. A decoding part decodes the connection code image contained in the photograph taken by the photographing part to decode encoded connection information containing communication setup information, which has been encoded according to the authentication information of the photographing apparatus. A restoration part restores the communication setup information from the encoded connection information by using the authentication information of the photographing apparatus. A radio communication part communicates with the another apparatus by using the communication setup information restored by the restoration part.
Owner:RICOH KK
Method and system for using phone to generate authentication pattern to perform POS payment as well as mobile phone
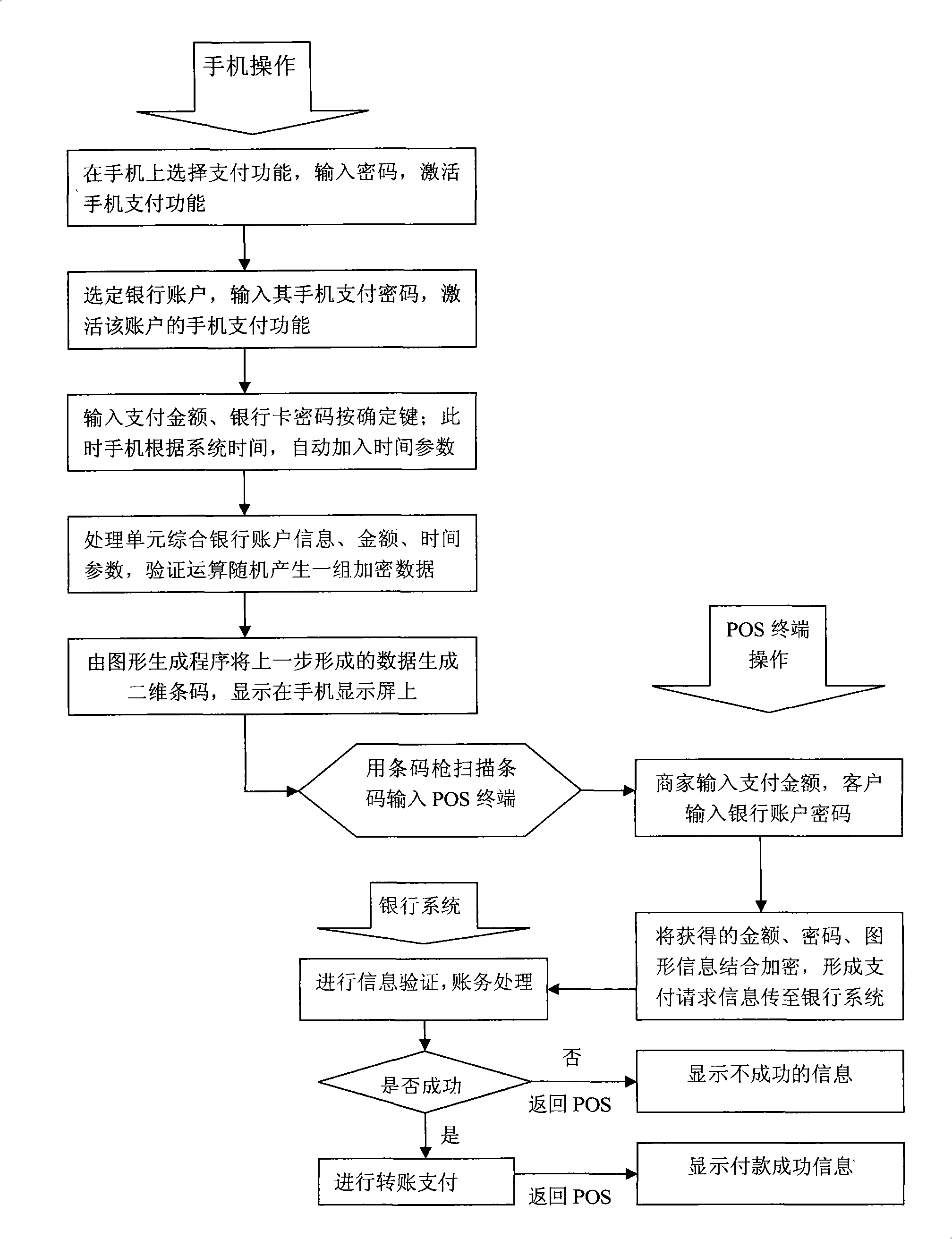
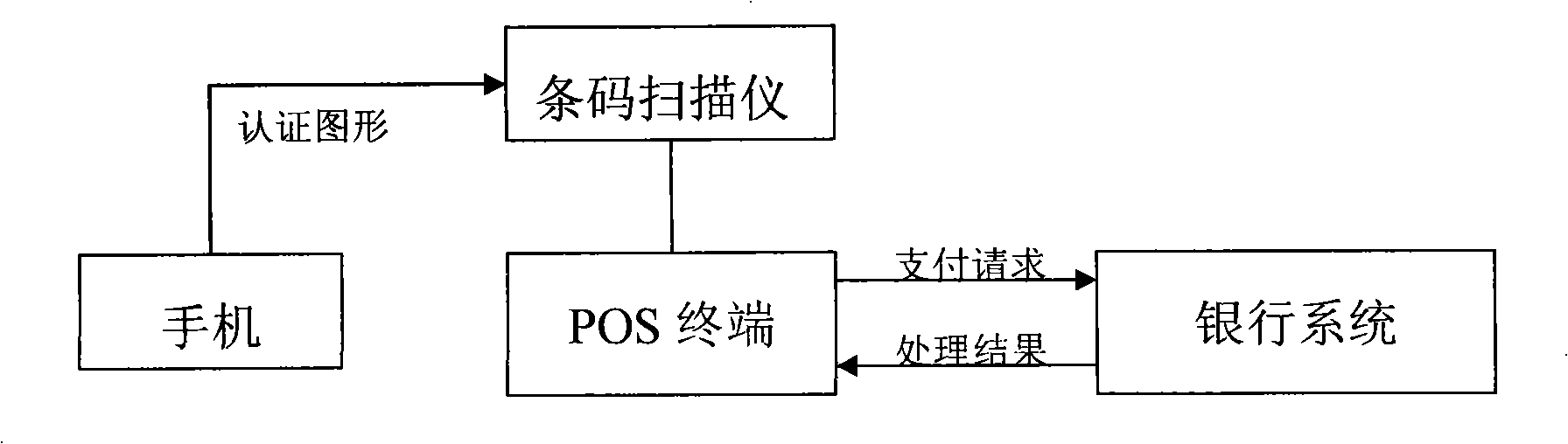
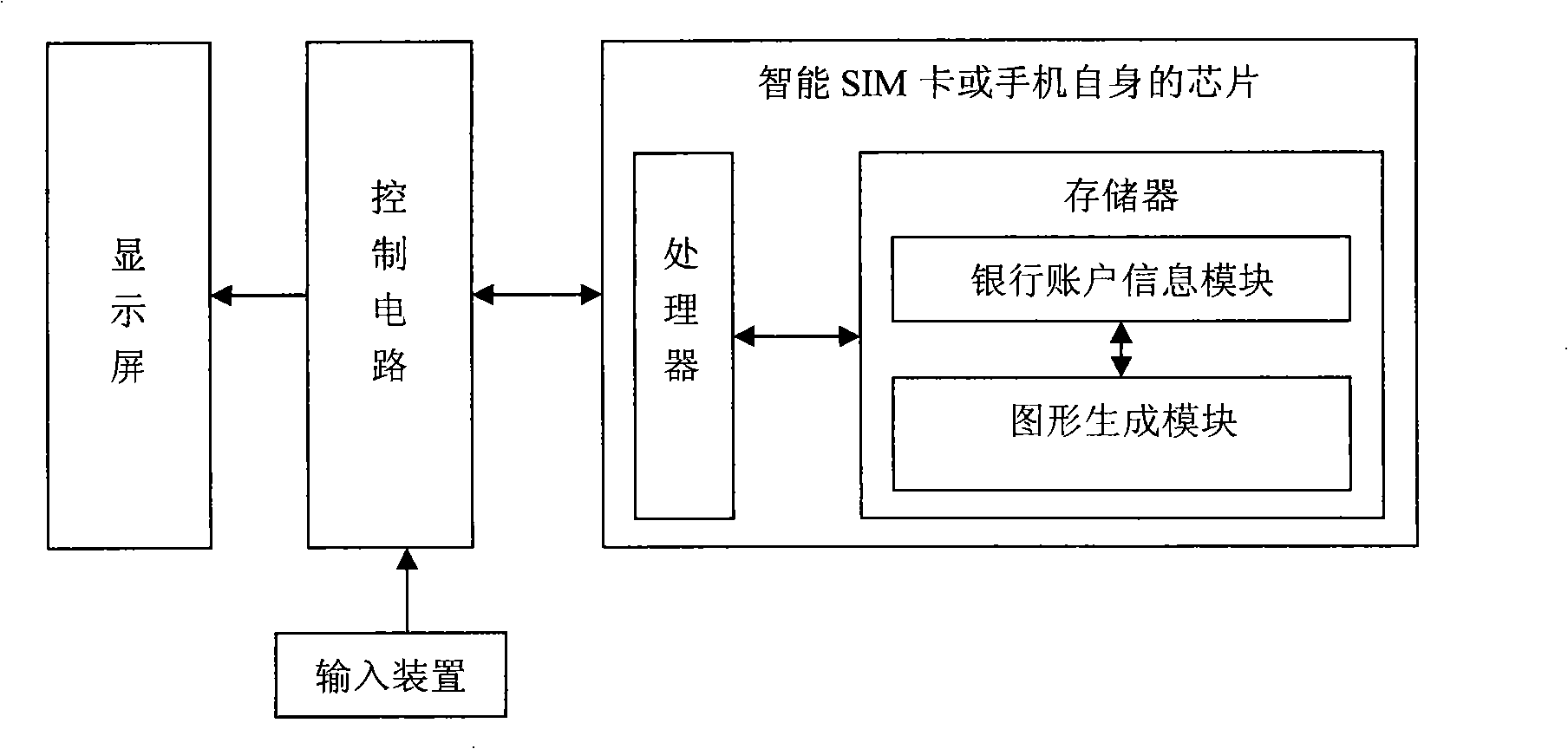
InactiveCN101299286AEliminate the inconvenience of carrying a cardImprove confidentialityCash registersPoint-of-sale network systemsGraphicsBank account
A method using the mobile phone generated authentication pattern to execute POS payment, writes one or a plurality of bank account information in the mobile phone chip, so that the mobile phone is associated with the corresponding bank account. The POS payment includes: recording the amount paid in the POS terminal; selecting the corresponding bank account on the mobile phone, executing verification arithmetic to the mobile phone chip and accidentally producing a set of enciphered data and generating authentication pattern on the mobile phone display screen to display; recording the authentication pattern in the POS terminal by the pattern recording apparatus; combining and ciphering the authentication pattern and the available information as the payment solicited message to transmit to the bank system; the bank system executing information verification, account process; and feeding back the process result onto the POS. The method can replace the card brushing, avoids the inconvenience of users for carrying a plurality of cards; the method can conveniently and safely use by slightly modifying the terminal reading data mode of the prior POS payment system terminals. At the same time, the present inventions provides a system and mobile phone for implementing the payment method.
Owner:胡红雨 +1
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com