Patents
Literature
6448 results about "Authentication system" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Authentication Systems aid the process of verifying the legitimacy of data, most often data used by people attempting to access a system.
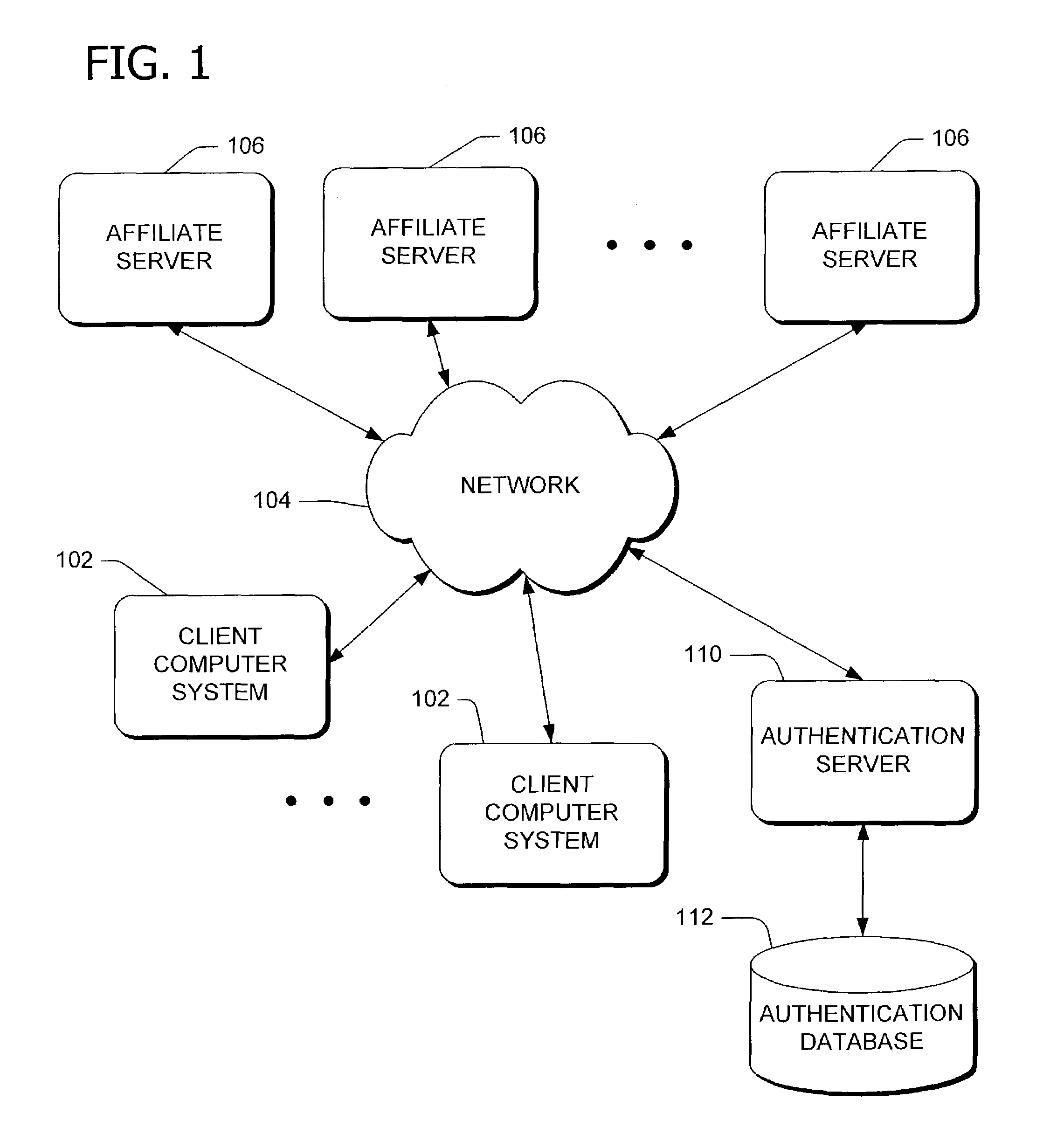
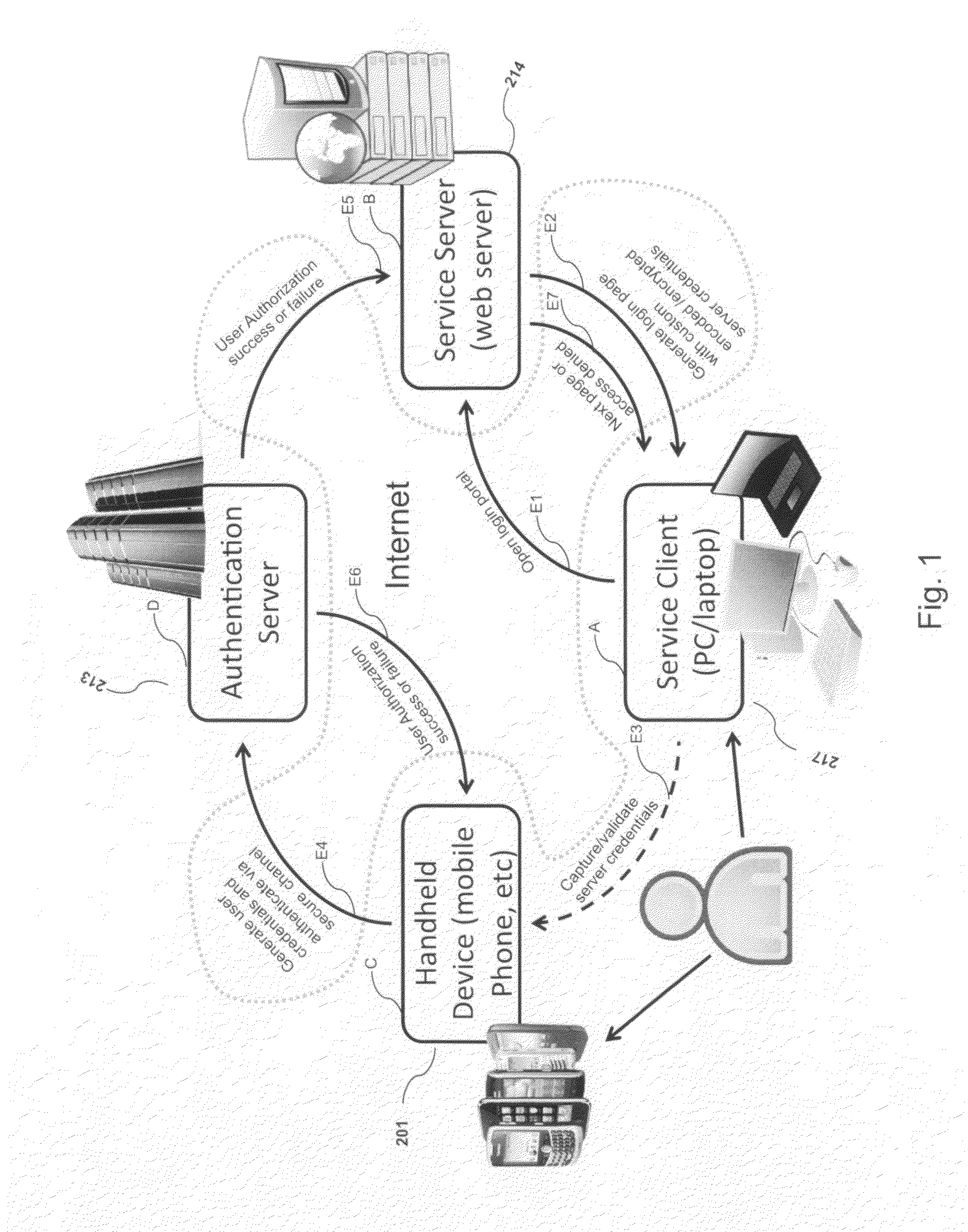
HTTP distributed remote user authentication system
InactiveUS6092196AExemption stepsAvoid necessityDigital data processing detailsUser identity/authority verificationUser authenticationUser identifier
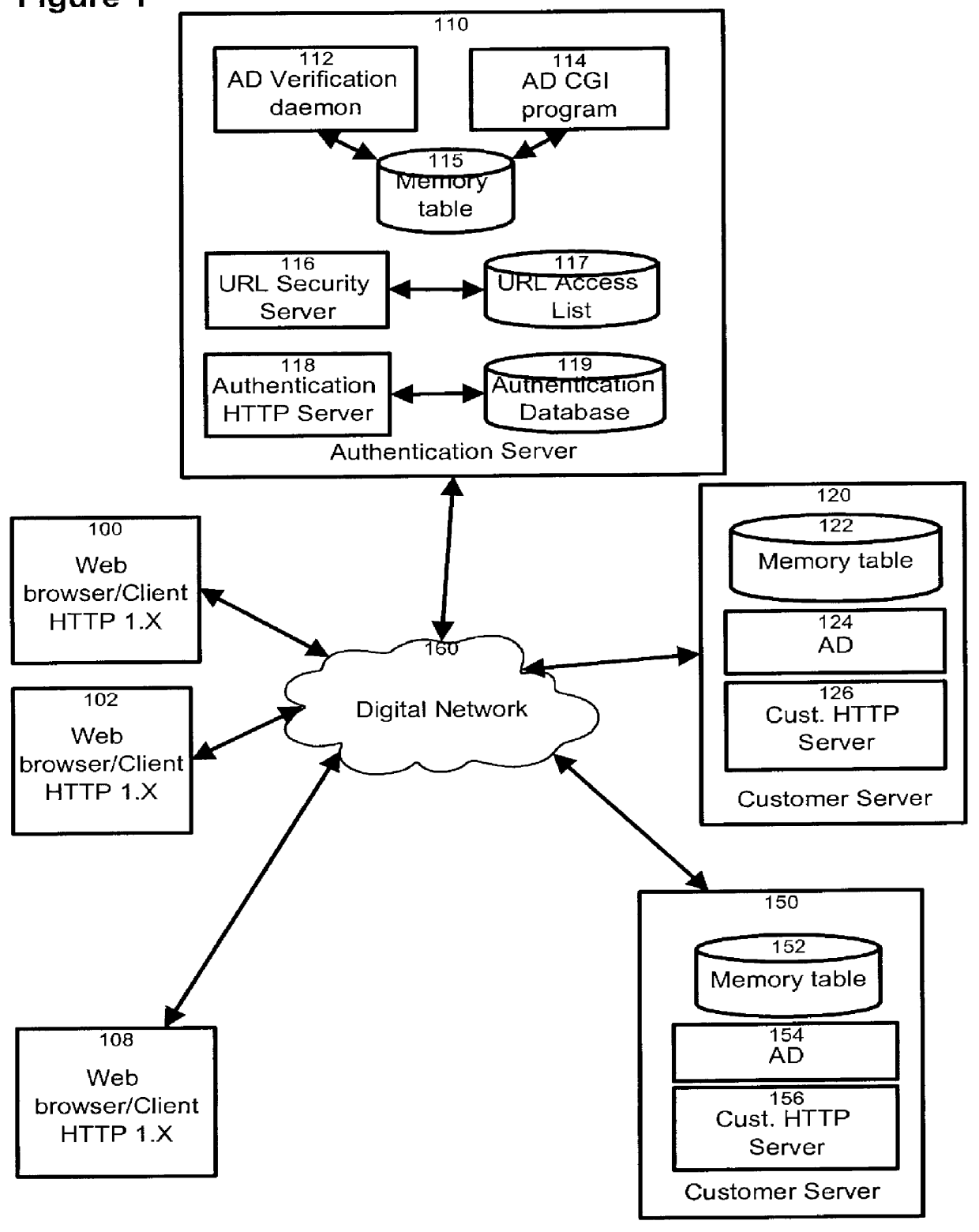
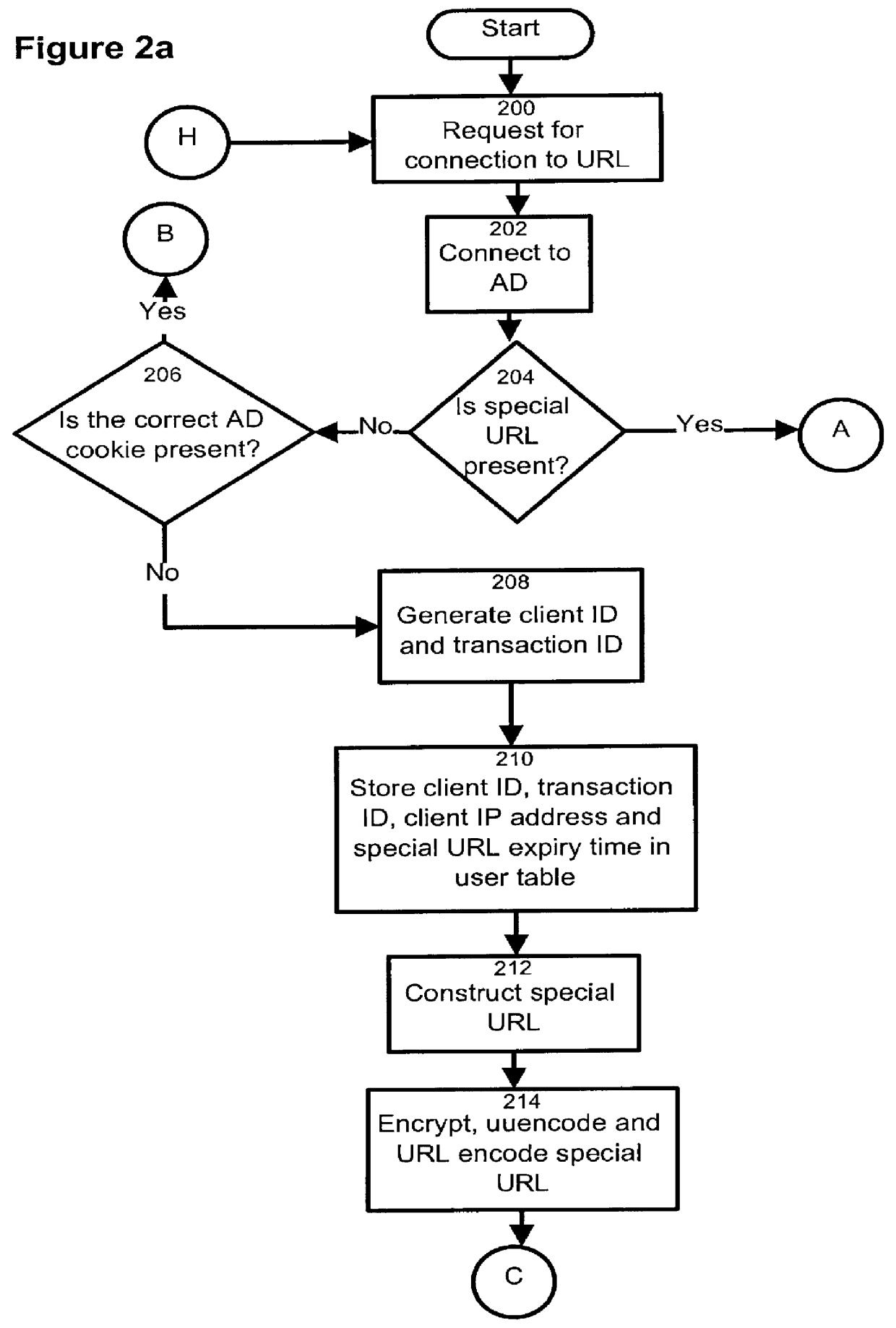
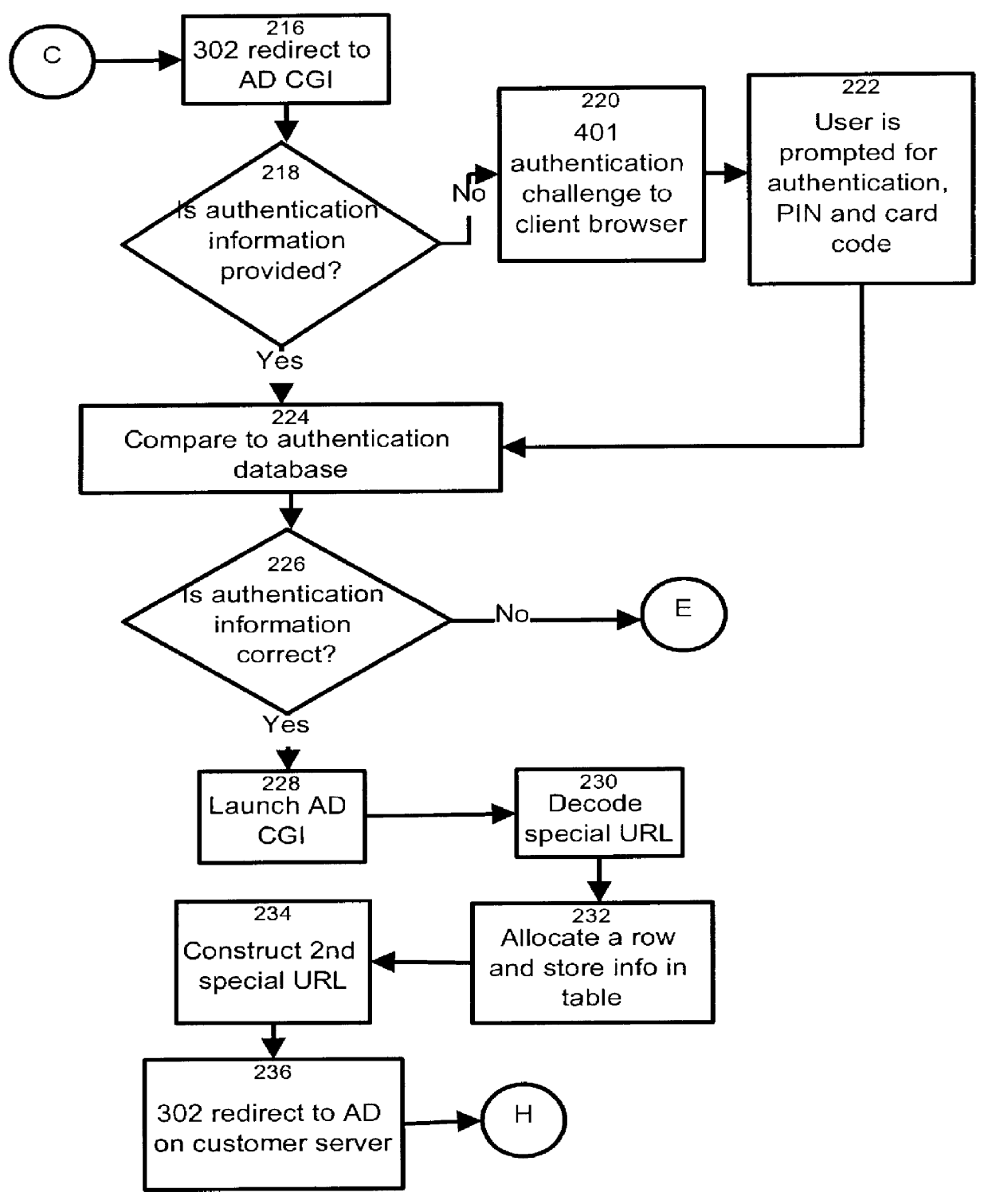
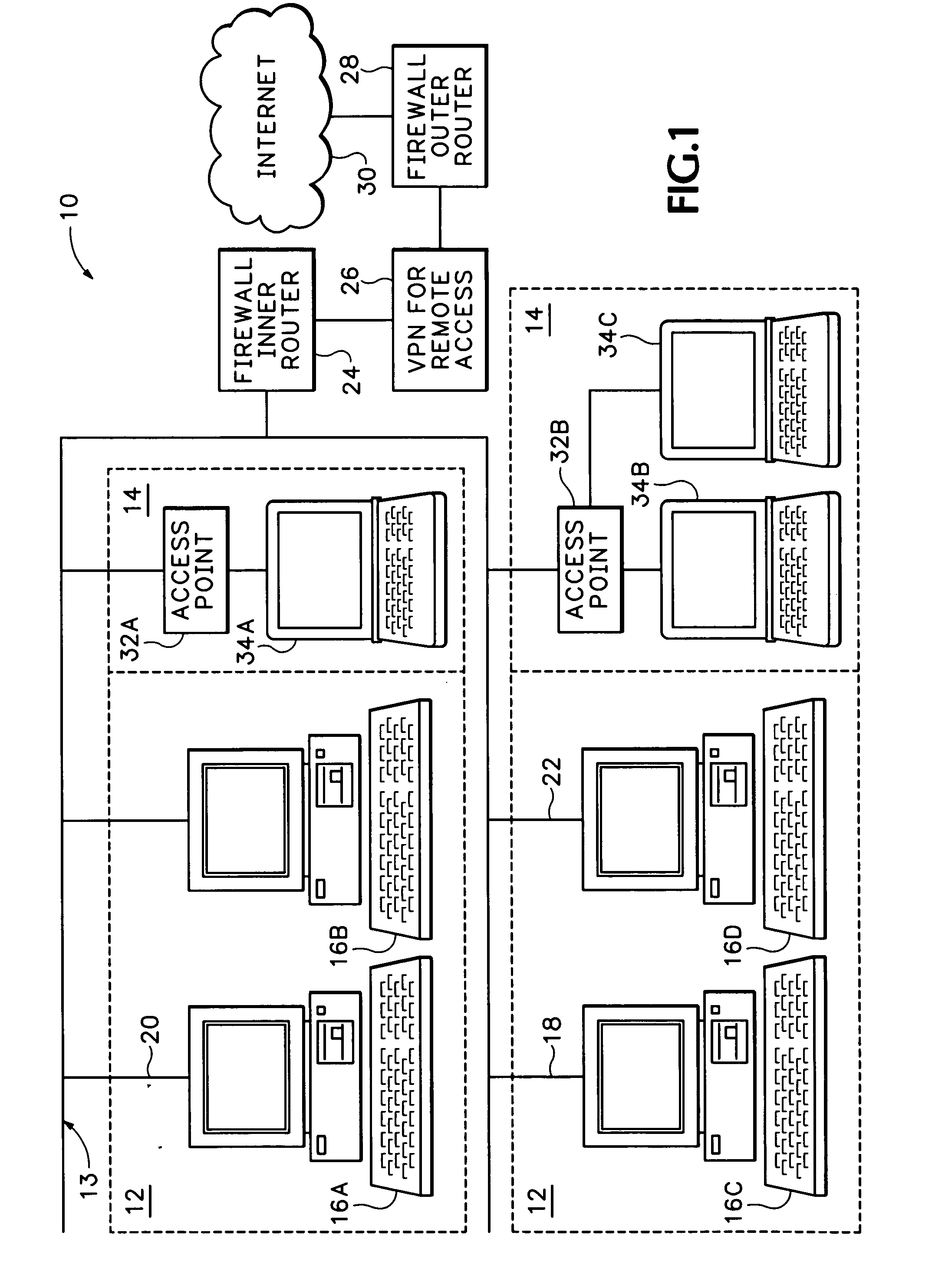
The present invention relates to the field of data and computer network security. Data and computer network security is of the utmost importance to most organizations that possess such networks. One of the difficulties that users and managers of these networks face is that the users have to provide a user ID and password every time they wish to access one of the organization's secured HTTP servers or URLs. This creates a problem for users and managers since lists of numerous user IDs and passwords need to be maintained and therefore can easily be lost or their confidentiality compromised. This invention addresses these problems by providing a transparent, scalable, single point of authentication for remote users across any number of HTTP servers anywhere on a data network, such as an Intranet, using any user ID and password scheme implemented by a main authentication HTTP server.
Owner:RPX CLEARINGHOUSE
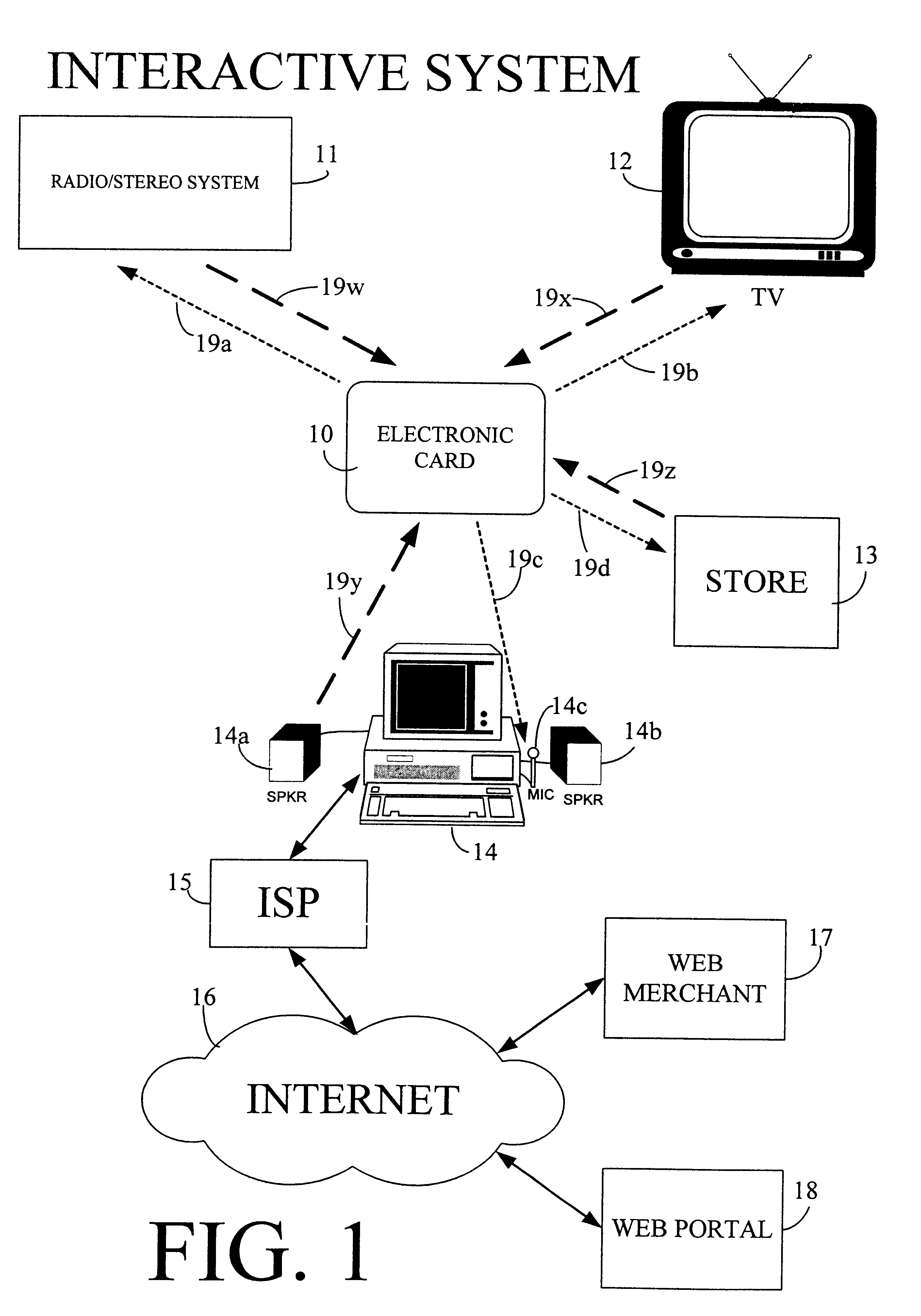
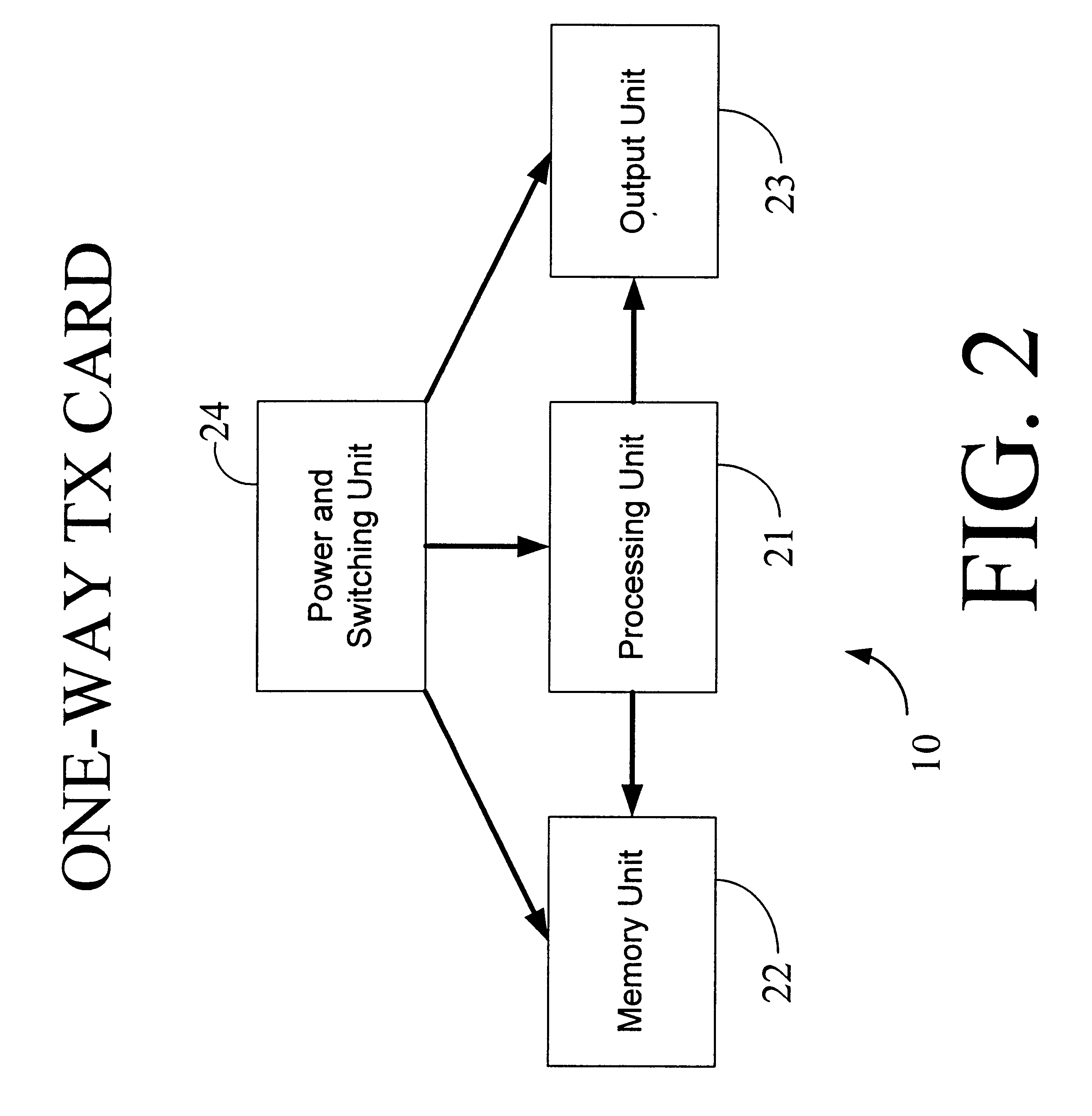
Physical presence digital authentication system
InactiveUS6607136B1Enhanced interactionMass scalableCredit registering devices actuationDiscounts/incentivesCrowdsAcoustic wave
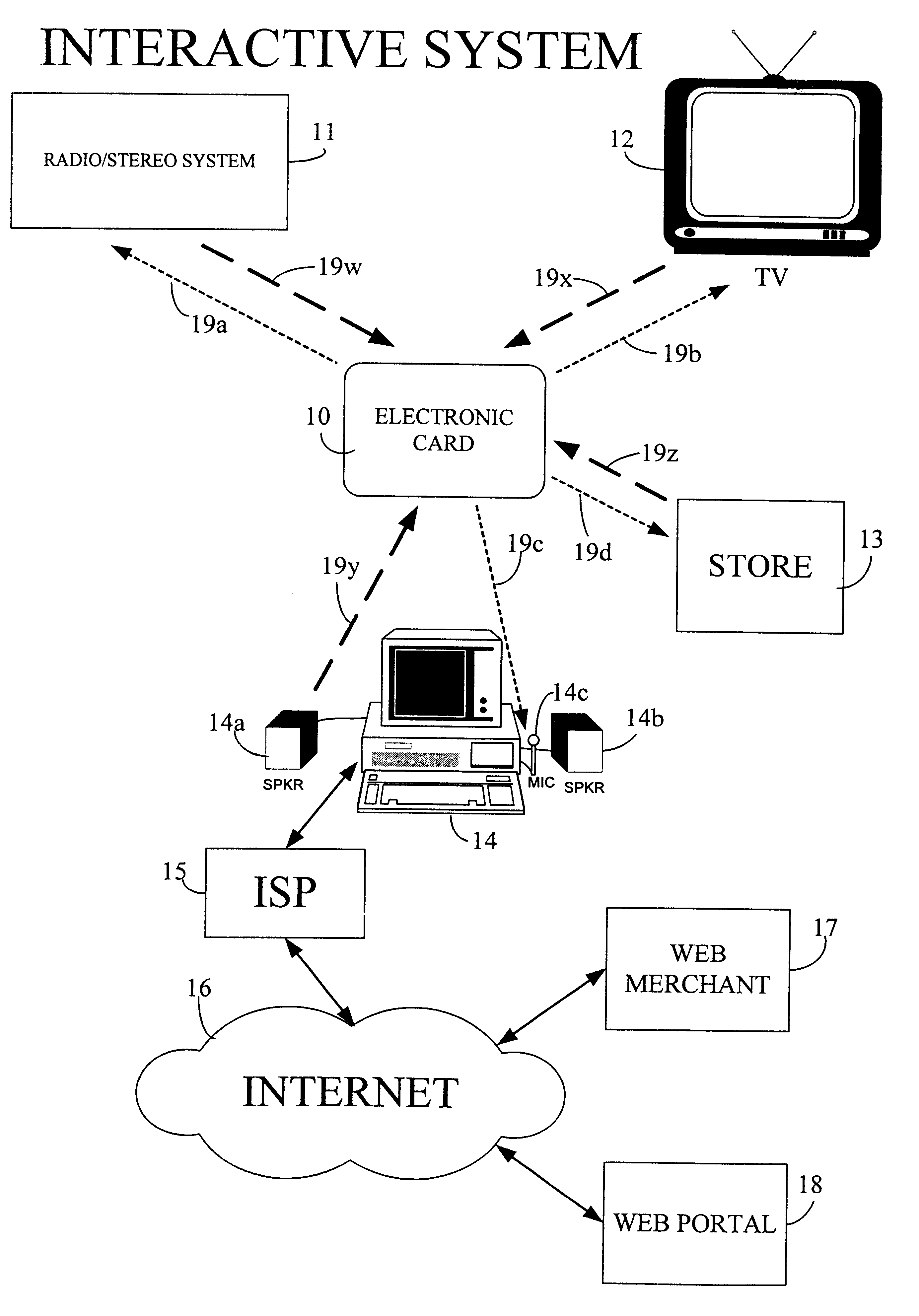
The interactive authentication system allows a consumer to interact with a base station, such as broadcast media (e.g., television and radio) or PC, to receive coupons, special sales offers, and other information with an electronic card. The electronic card can also be used to transmit a signal that can be received by the base station to perform a wide variety of tasks. These tasks can include launching an application, authenticating a user at a website, and completing a sales transaction at a website (e.g., by filling out a form automatically). The interaction between the base station and the electronic card is accomplished by using the conventional sound system in the base station so that a special reader hardware need not be installed to interact with the electronic card. The user is equipped with an electronic card that can receive and transmit data via sound waves. In the various embodiments, the sound waves can be audible or ultrasonic (which can be slightly audible to some groups of people).
Owner:SONIXIO INC
Authentication system for reusable surgical instruments
ActiveUS9706674B2DiagnosticsCircuit arrangements on insulating boardsEngineeringAuthentication system
An authentication system for use in a surgical stapling device includes an authentication board assembly disposed at a proximal end of a loading unit and having a contact assembly, and an adapter board assembly disposed at a distal end of an adapter assembly. When the loading unit is engaged with the adapter assembly, the authentication board engages the adapter board assembly.
Owner:COVIDIEN LP
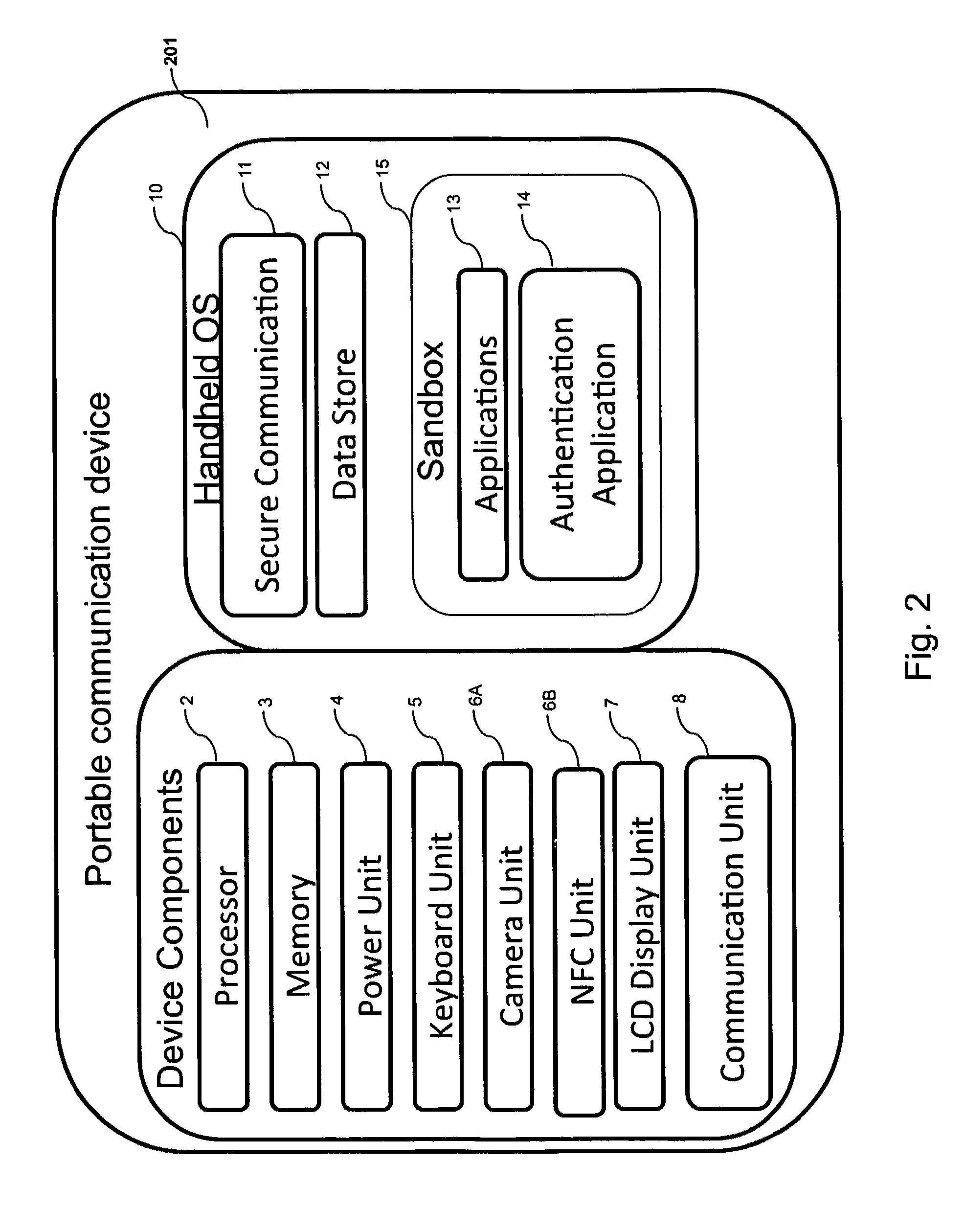
Embedded authentication systems in an electronic device
ActiveUS20090083847A1Digital data processing detailsUser identity/authority verificationAuthentication systemVisual perception
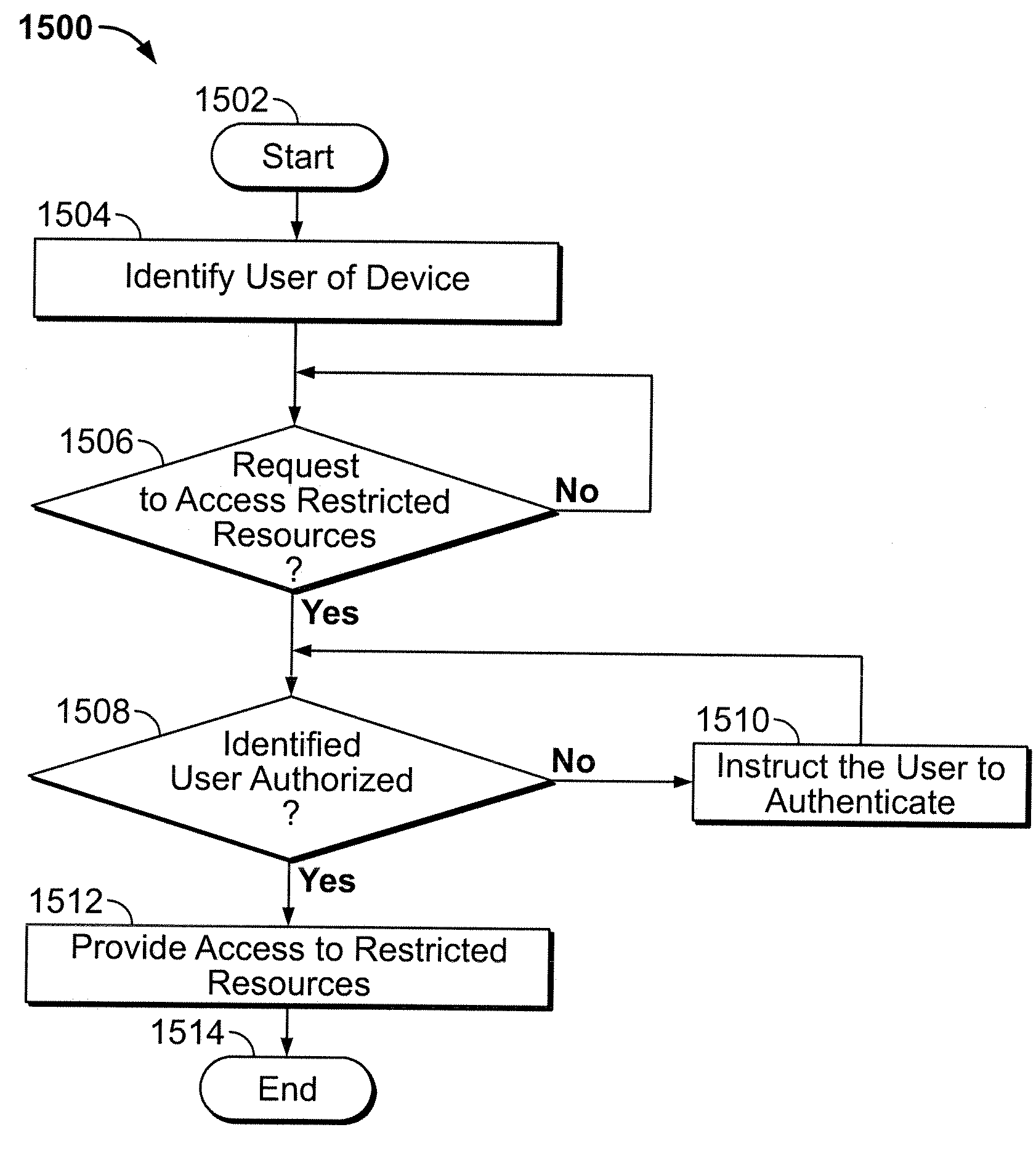
This invention is directed to an electronic device with an embedded authentication system for restricting access to device resources. The authentication system may include one or more sensors operative to detect biometric information of a user. The sensors may be positioned in the device such that the sensors may detect appropriate biometric information as the user operates the device, without requiring the user to perform a step for providing the biometric information (e.g., embedding a fingerprint sensor in an input mechanism instead of providing a fingerprint sensor in a separate part of the device housing). In some embodiments, the authentication system may be operative to detect a visual or temporal pattern of inputs to authenticate a user. In response to authenticating, a user may access restricted files, applications (e.g., applications purchased by the user), or settings (e.g., application settings such as contacts or saved game profile).
Owner:APPLE INC
Multi-factor authentication system
InactiveUS20040187018A1Easy to understandUser identity/authority verificationUnauthorized memory use protectionPasswordUser identifier
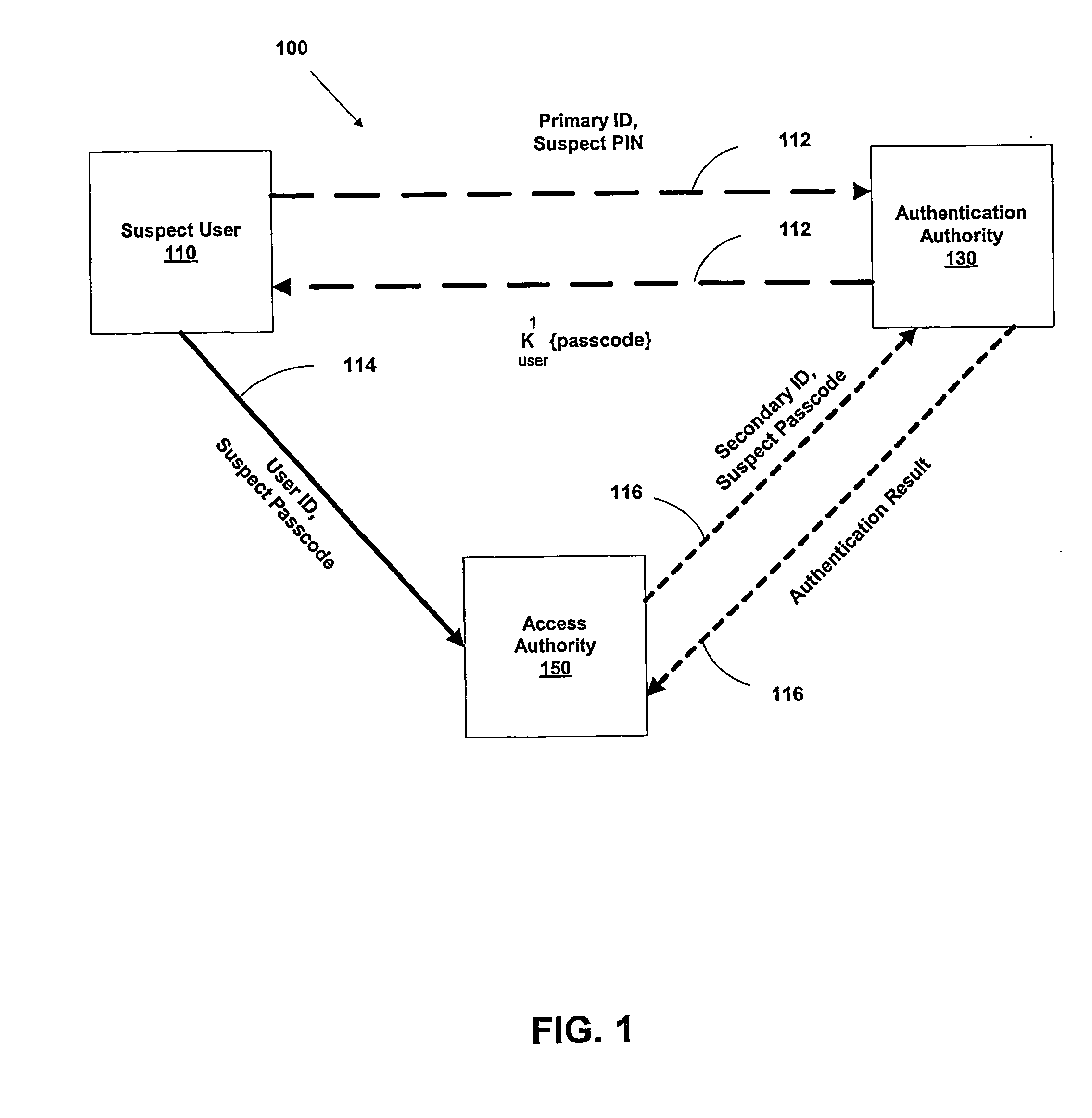
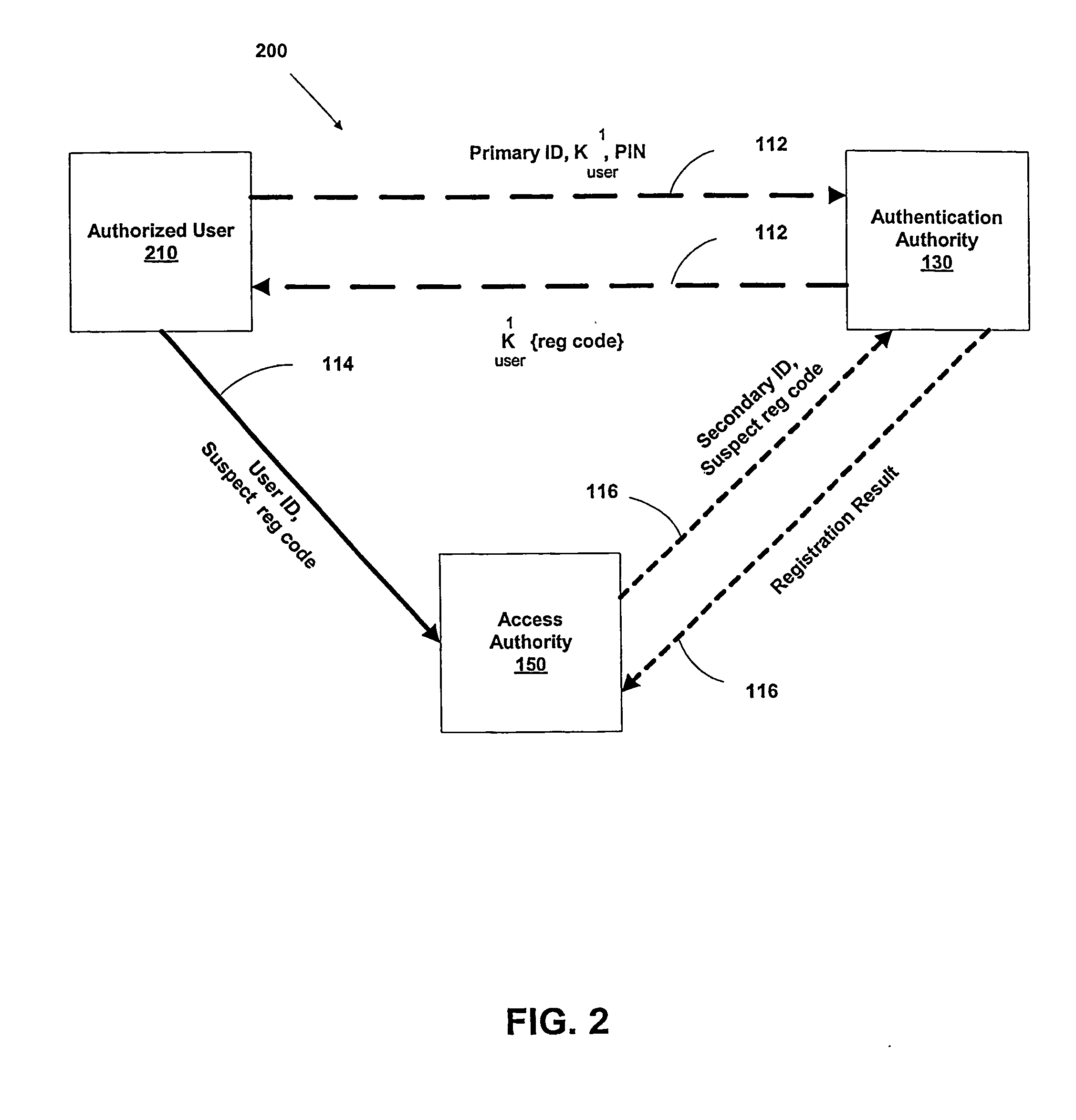
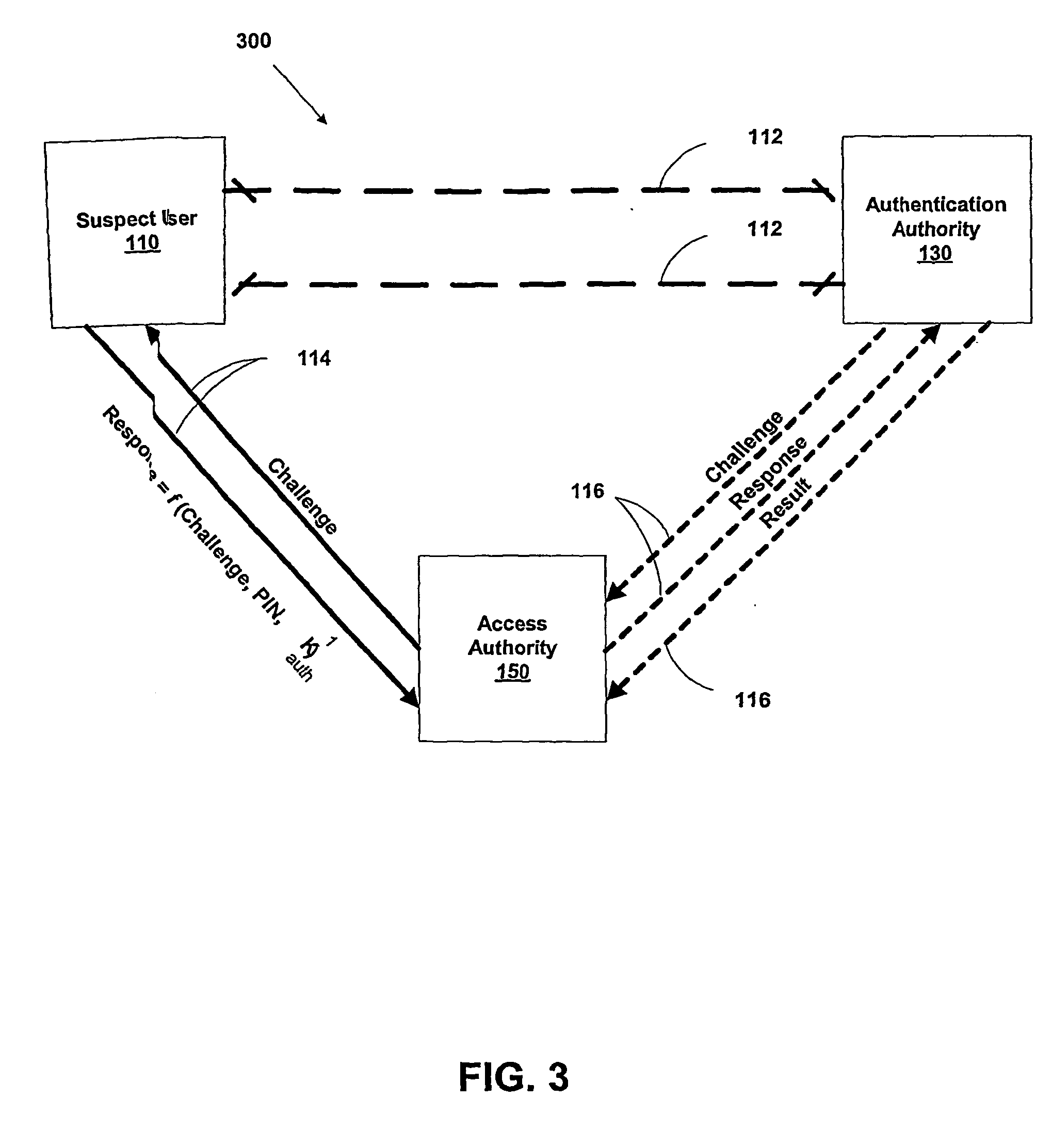
A suspect user (110) seeks access to a network resource from an access authority (150) utilizing a passcode received from an authentication authority (130). Initially, an ID of a device is bound with a PIN, the device ID is bound with a private key of the device, and the device ID is bound with a user ID that has been previously bound with a password of an authorized user. The device ID is bound with the user ID by authenticating the user ID using the password. Thereafter, the suspect user communicates the device ID and the PIN from the device over an ancillary communications network (112); the authentication authority responds back over the ancillary communications network with a passcode encrypted with the public key of the device; and the suspect user decrypts and communicates over a communications network (114) the passcode with the user ID to the access authority.
Owner:KARETEK HLDG LLC
System and method for authorizing access to access-controlled environments
ActiveUS20140337930A1Digital data processing detailsMultiple digital computer combinationsMobile deviceSecure authentication
Systems and methods are provided for authorizing a user to access an access-controlled environment. The system includes a system server platform that communicates with fixed PC's, servers and mobile devices (e.g., smartphones) operated by users. The systems and methods described herein enable a series of operations whereby a user attempting to access an access-controlled environment is prompted to biometrically authenticate using the user's preregistered mobile device. Biometric authentication can include capturing images of the user's biometric features, encoding the features as a biometric identifier, comparing the biometric identifier to a previously generated biometric identifier and determining liveness. In addition, the authentication system can further authorize the user and electronically grant access to the access-controlled environment. In this manner the secure authentication system can, based on biometric authentication, authorize a user's access to devices, online services, physical locations or any networked environment that require user authorization.
Owner:VERIDIUM IP LTD
Method, system and service for conducting authenticated business transactions
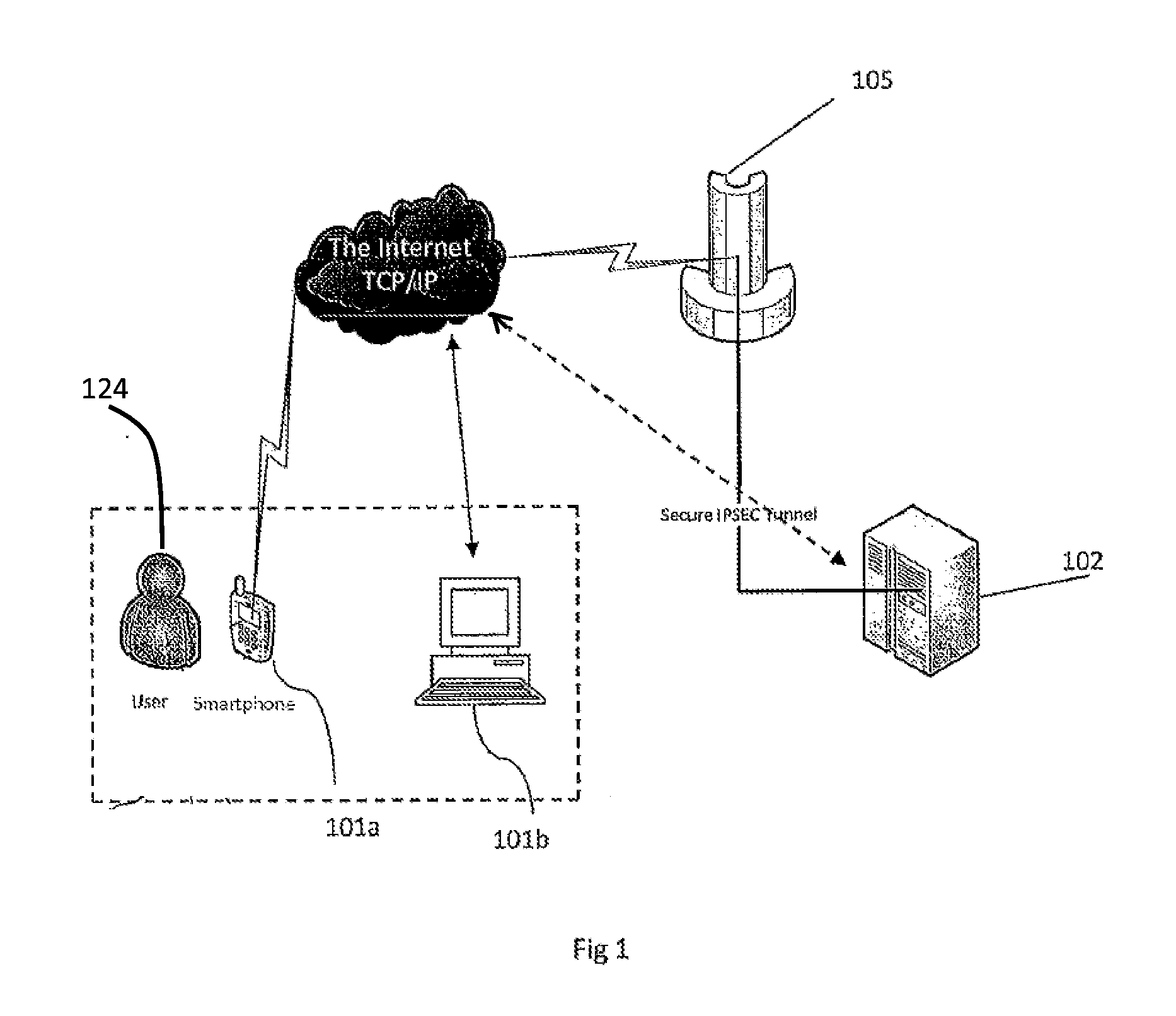
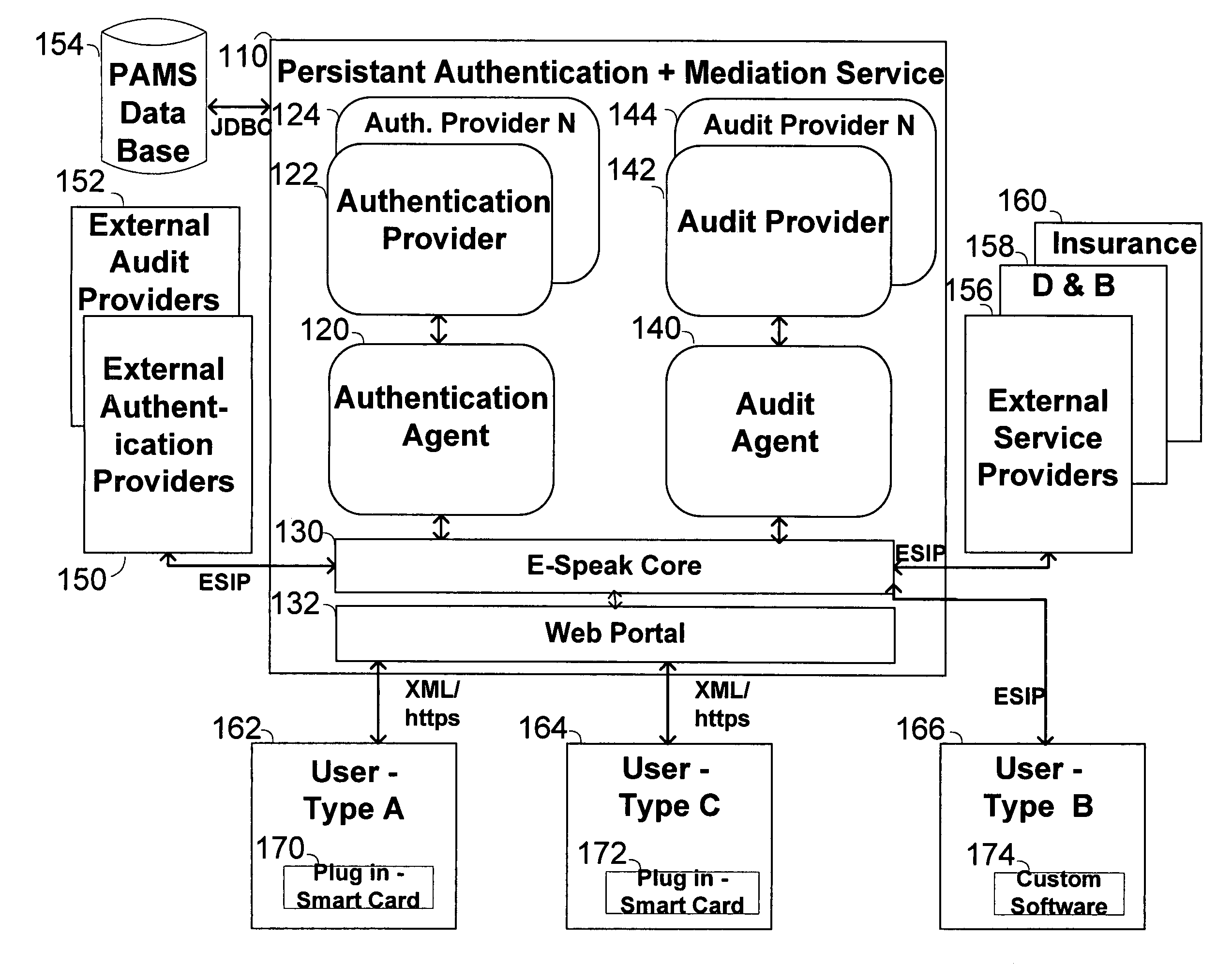
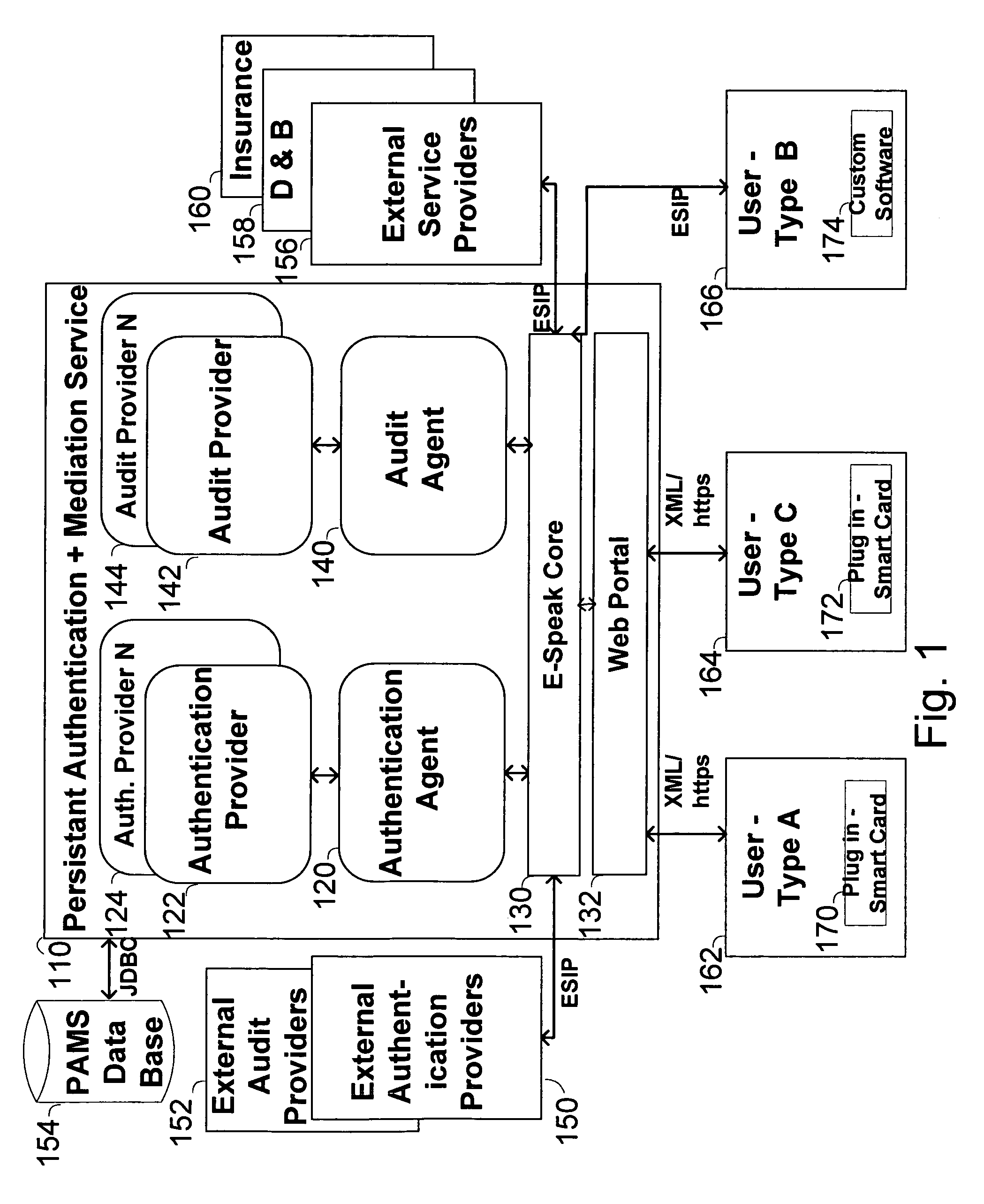
InactiveUS6957199B1Fast authenticationImprove securityComputer security arrangementsCommerceService provisionThe Internet
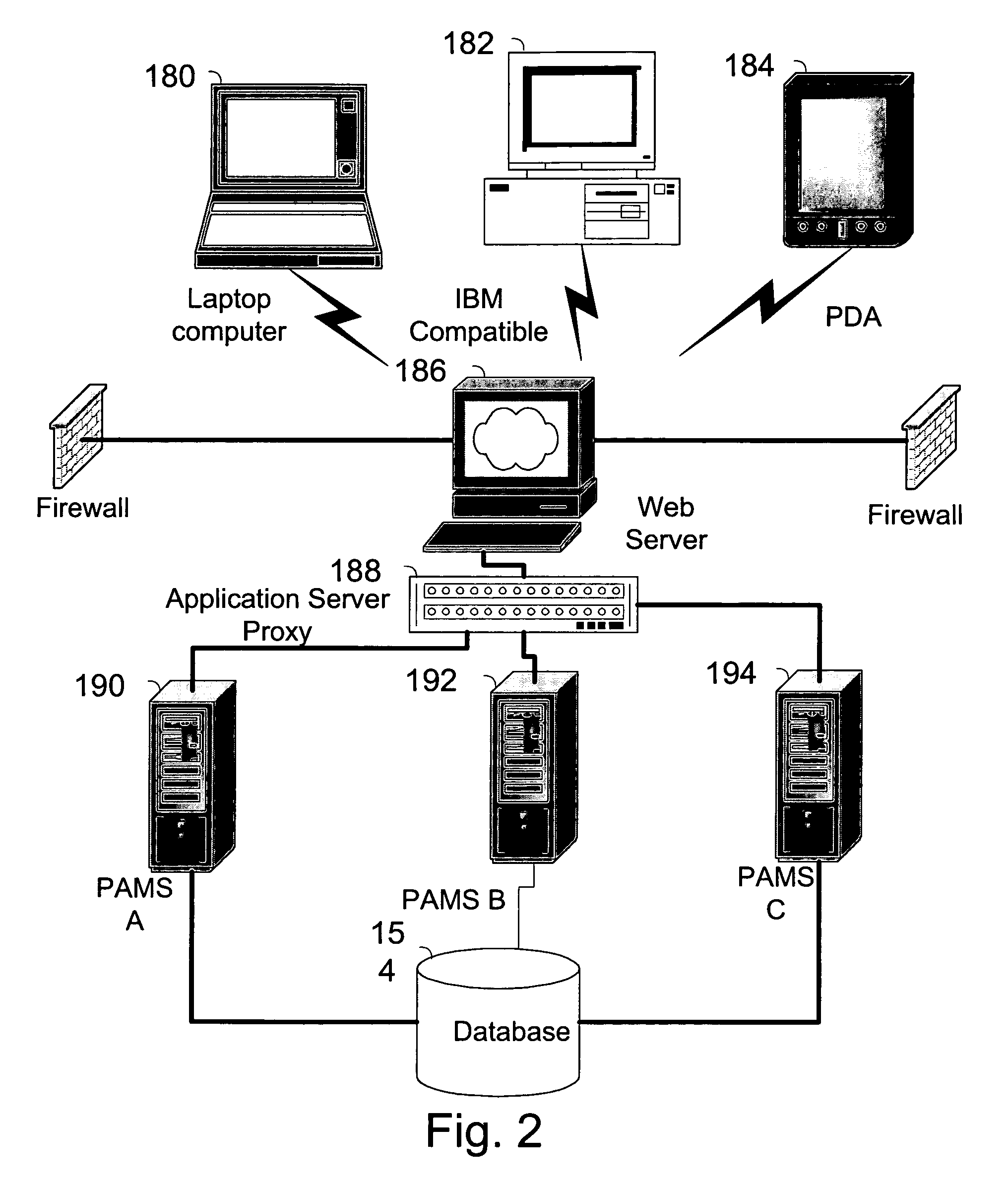
The invention pertains to a method, online service, and system, for creating partnerships based on trust relationships over a public network, authenticating trade partners, infrastructure providers and collaborators to each other, and providing users with an environment suitable for conducting transactions requiring a high level of trust. A service according to the invention is a persistent authentication and mediation service (PAMS) which is provided as an on-line service. One embodiment is a method for conducting authenticated business transactions involving microprocessor equipped devices over the Internet comprising:A. providing an on-line authentication service available on the distributed network;B. authenticating a plurality of users to said on-line authentication service using a closed authentication system to produce a plurality of authenticated users; andC. connecting a group of at least two of said plurality of authenticated users under persistent mediation of said on-line authentication service, producing a connected group of authenticated users.
Owner:FISHER DOUGLAS
Embedded authentication systems in an electronic device
ActiveUS20090083850A1Digital data processing detailsUser identity/authority verificationAuthentication systemVisual perception
This invention is directed to an electronic device with an embedded authentication system for restricting access to device resources. The authentication system may include one or more sensors operative to detect biometric information of a user. The sensors may be positioned in the device such that the sensors may detect appropriate biometric information as the user operates the device, without requiring the user to perform a step for providing the biometric information (e.g., embedding a fingerprint sensor in an input mechanism instead of providing a fingerprint sensor in a separate part of the device housing). In some embodiments, the authentication system may be operative to detect a visual or temporal pattern of inputs to authenticate a user. In response to authenticating, a user may access restricted files, applications (e.g., applications purchased by the user), or settings (e.g., application settings such as contacts or saved game profile).
Owner:APPLE INC
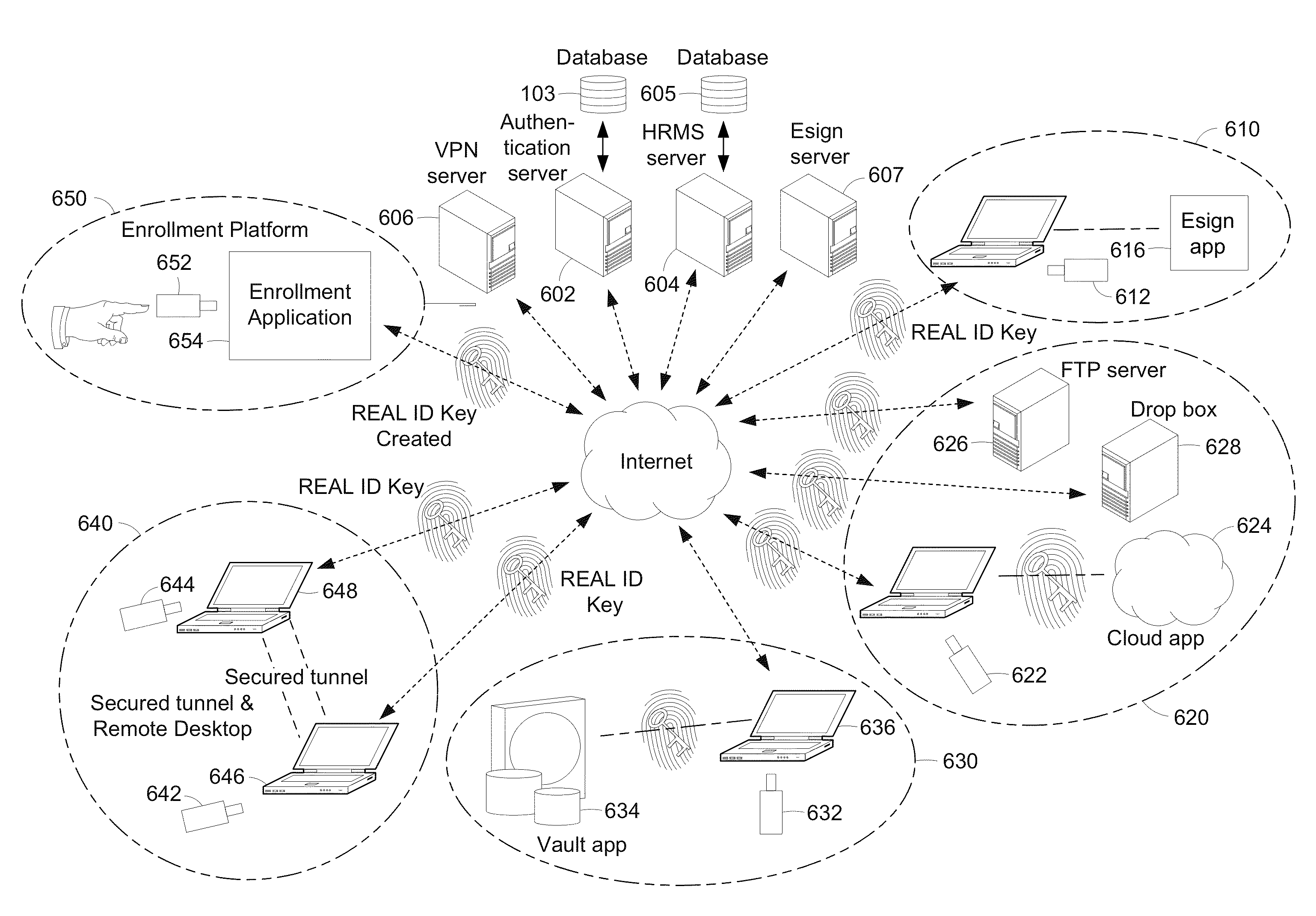
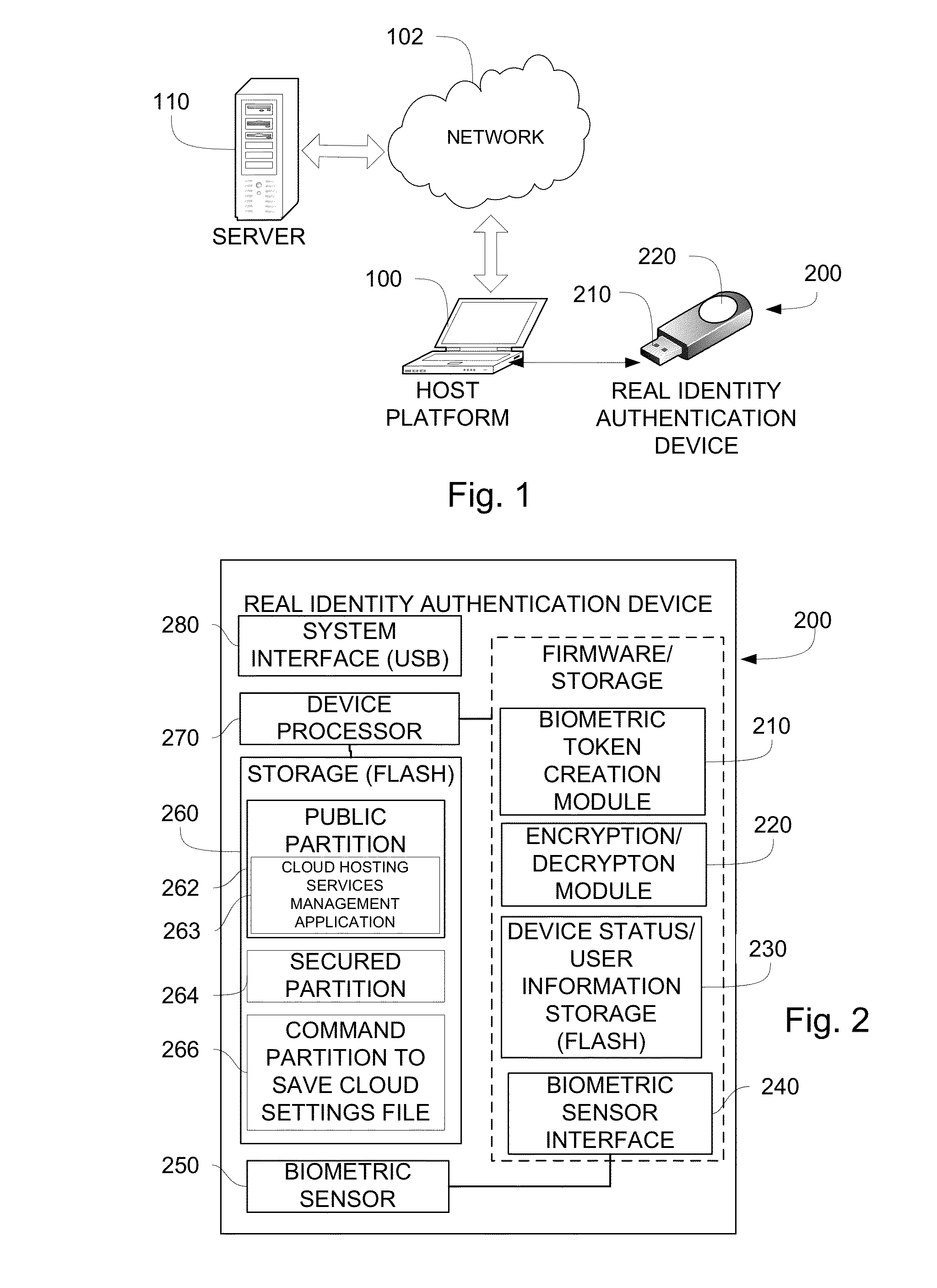
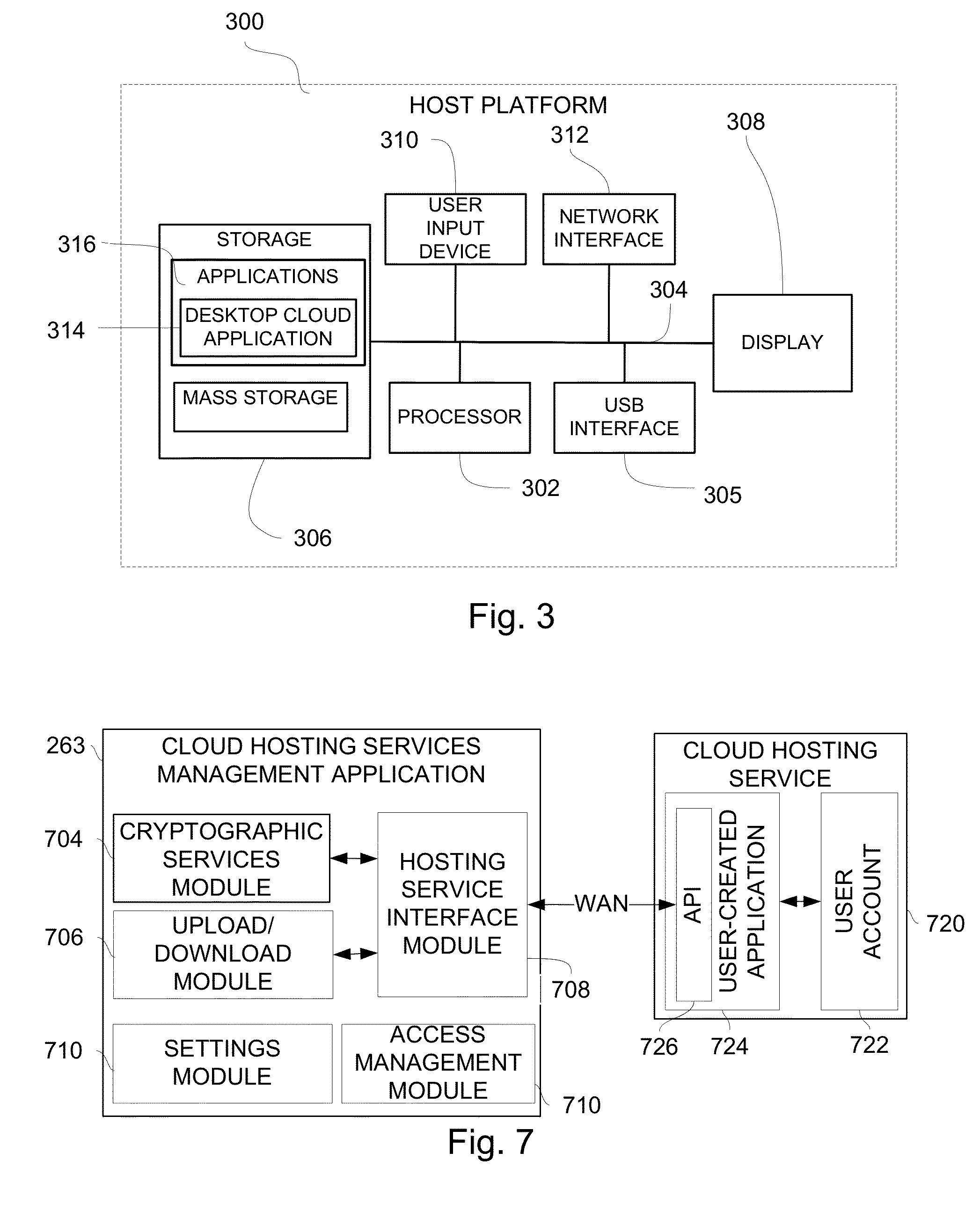
Cloud-based file distribution and management using real identity authentication
InactiveUS20140101434A1Unauthorized memory use protectionDigital data authenticationAuthentication systemInternet privacy
Owner:MSI SECURITY
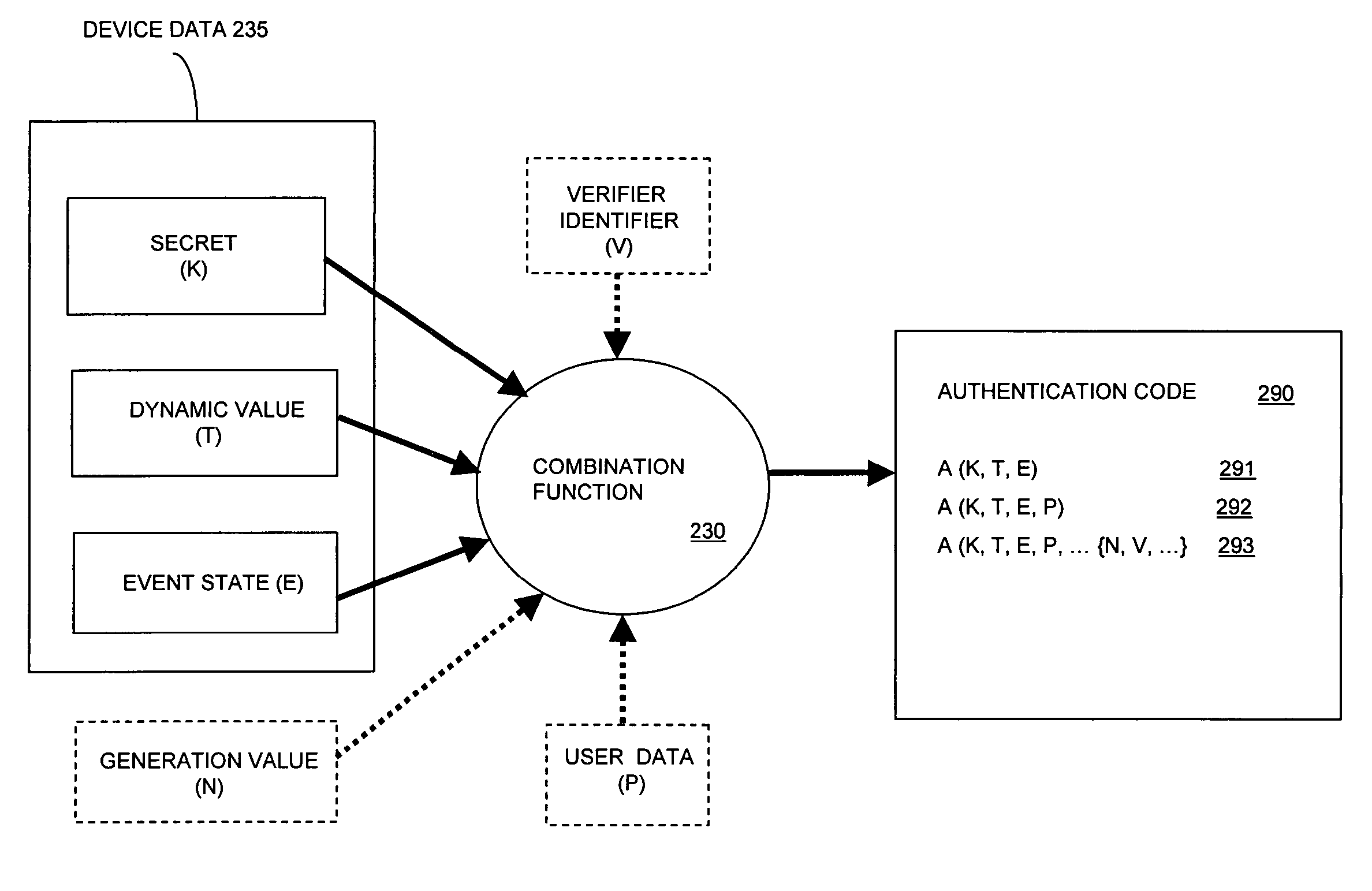
Identity authentication system and method
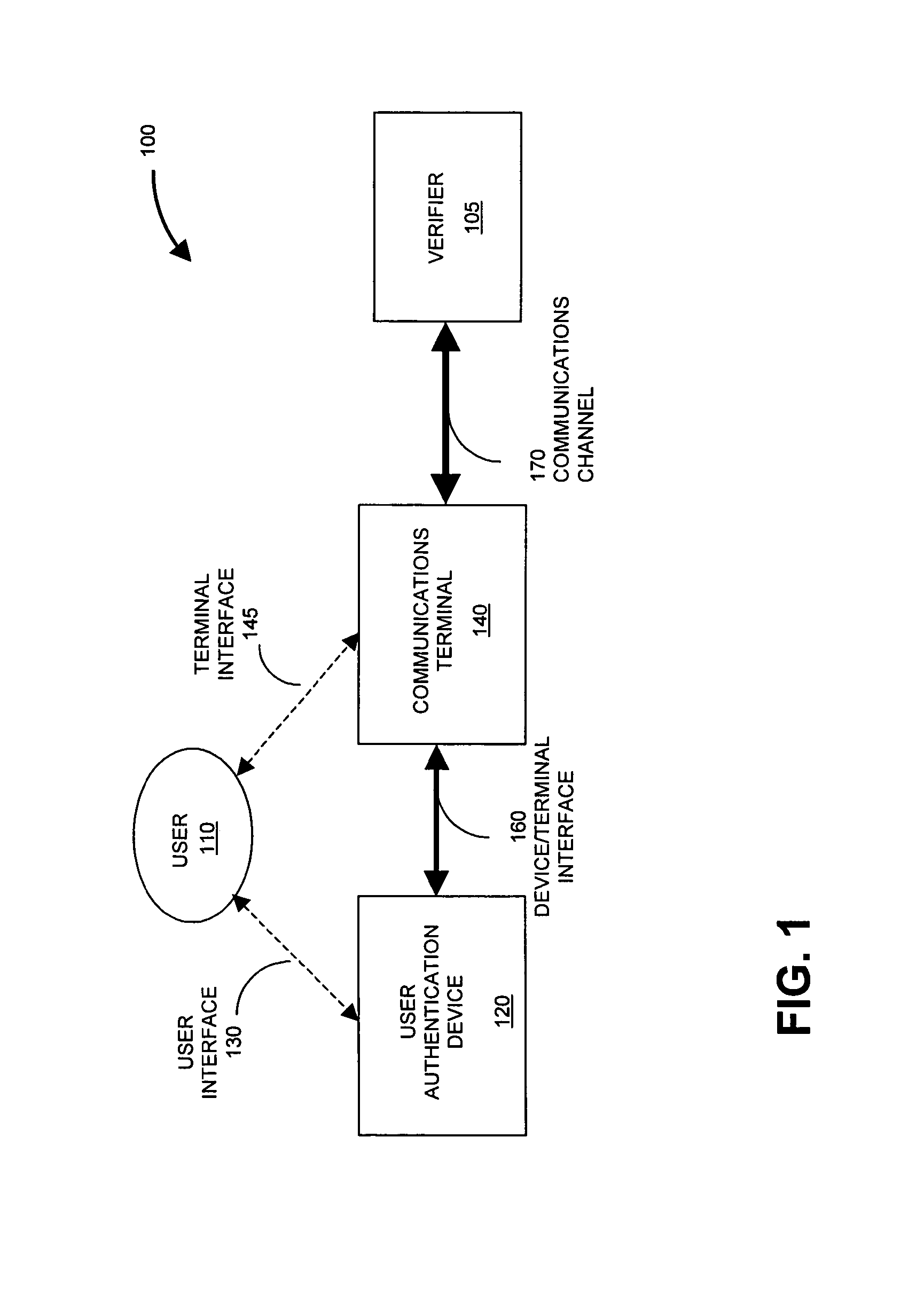
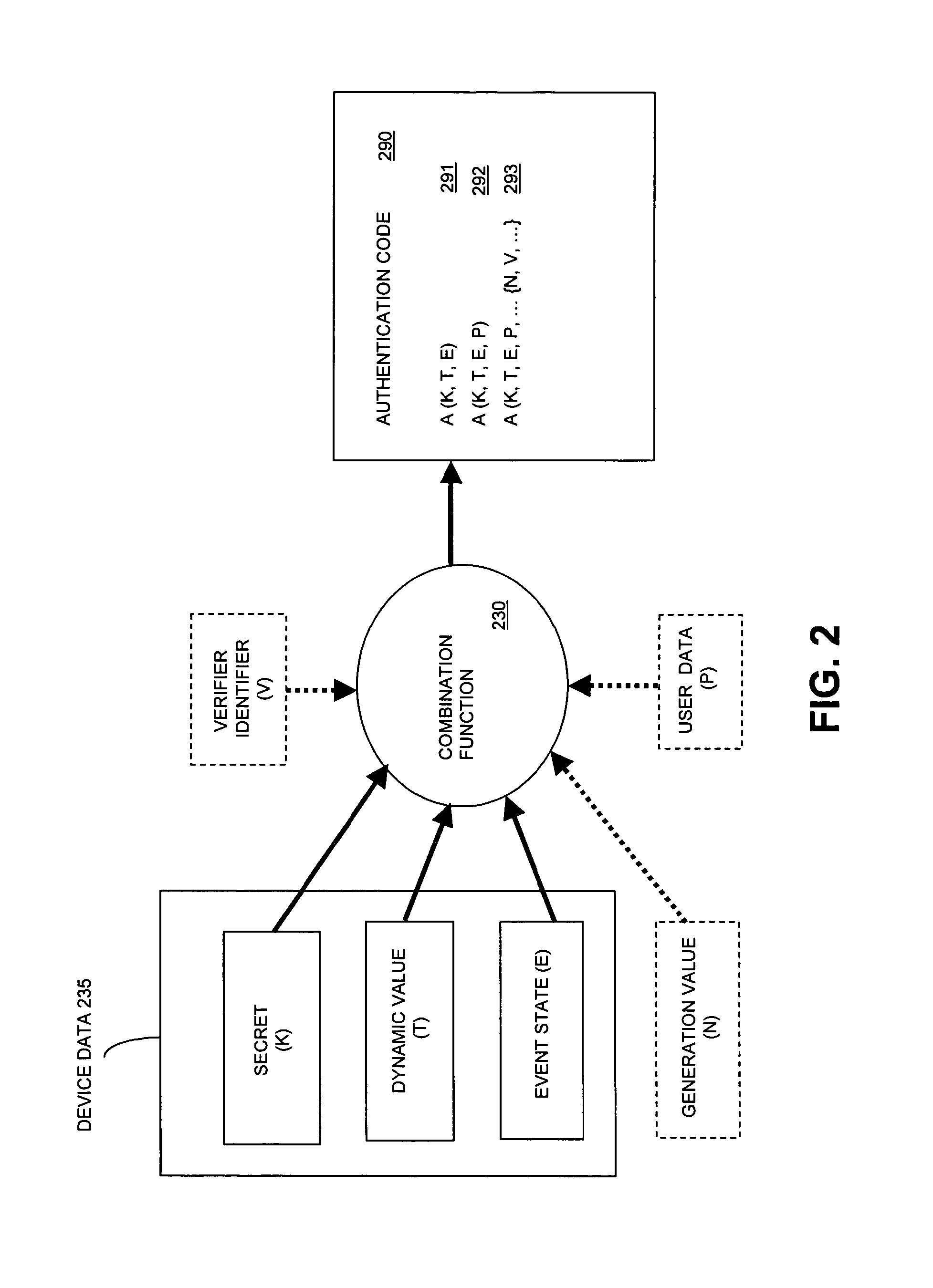
ActiveUS7502933B2Efficient verificationEfficiently authenticatingDigital data processing detailsUser identity/authority verificationInternet privacyEngineering
A method and system for generating an authentication code that depends at least in part on a dynamic value that changes over time, an event state associated with the occurrence of an event, and a secret associated with an authentication device. By generating the authentication code responsive to an event state, an identity authentication code can be used to verify identity and to communicate event state information, and to do so in a secure manner.
Owner:EMC IP HLDG CO LLC
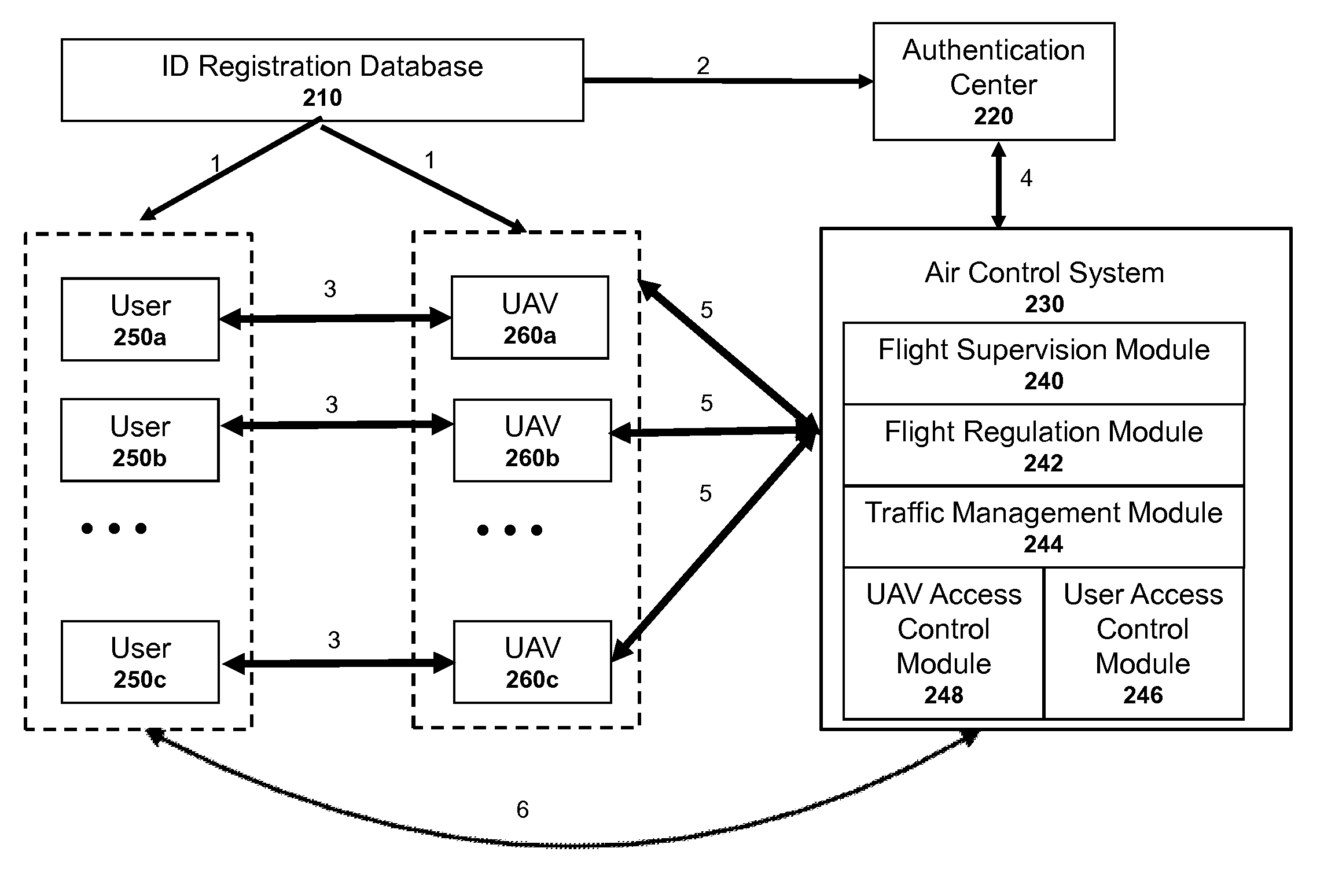
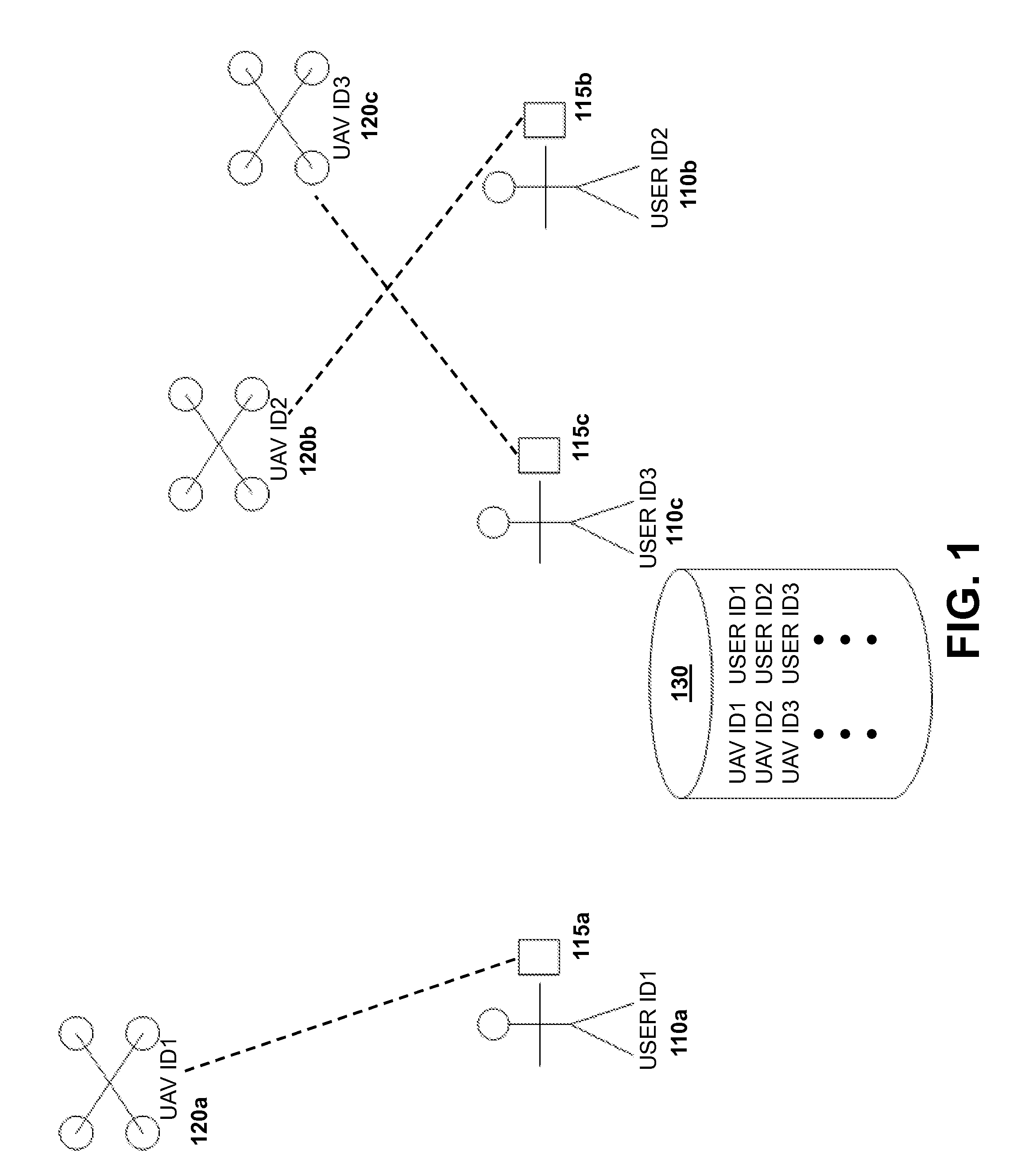
Authentication systems and methods for generating flight regulations
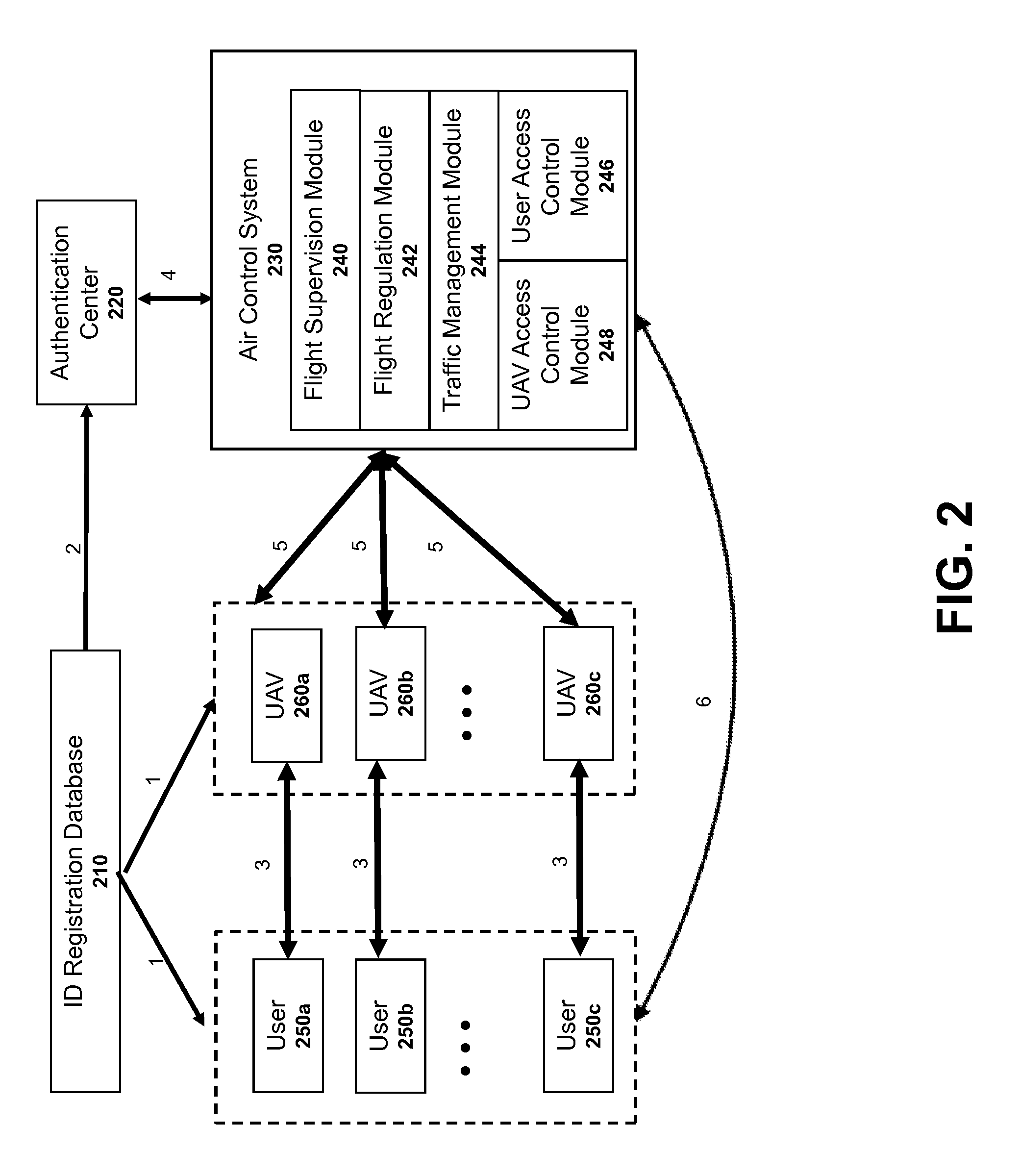
ActiveUS9412278B1Improve flight safetyRemote controlled aircraftDigital data authenticationAuthentication systemComputer science
Systems and methods for UAV safety are provided. An authentication system may be used to confirm UAV and / or user identity and provide secured communications between users and UAVs. The UAVs may operate in accordance with a set of flight regulations. The set of flight regulations may be associated with a geo-fencing device in the vicinity of the UAV.
Owner:SZ DJI TECH CO LTD
System and method for authentication of network users
InactiveUS6857073B2Avoiding terminationReducing cost and unnecessary useDigital data processing detailsUser identity/authority verificationInternet privacyInformation design
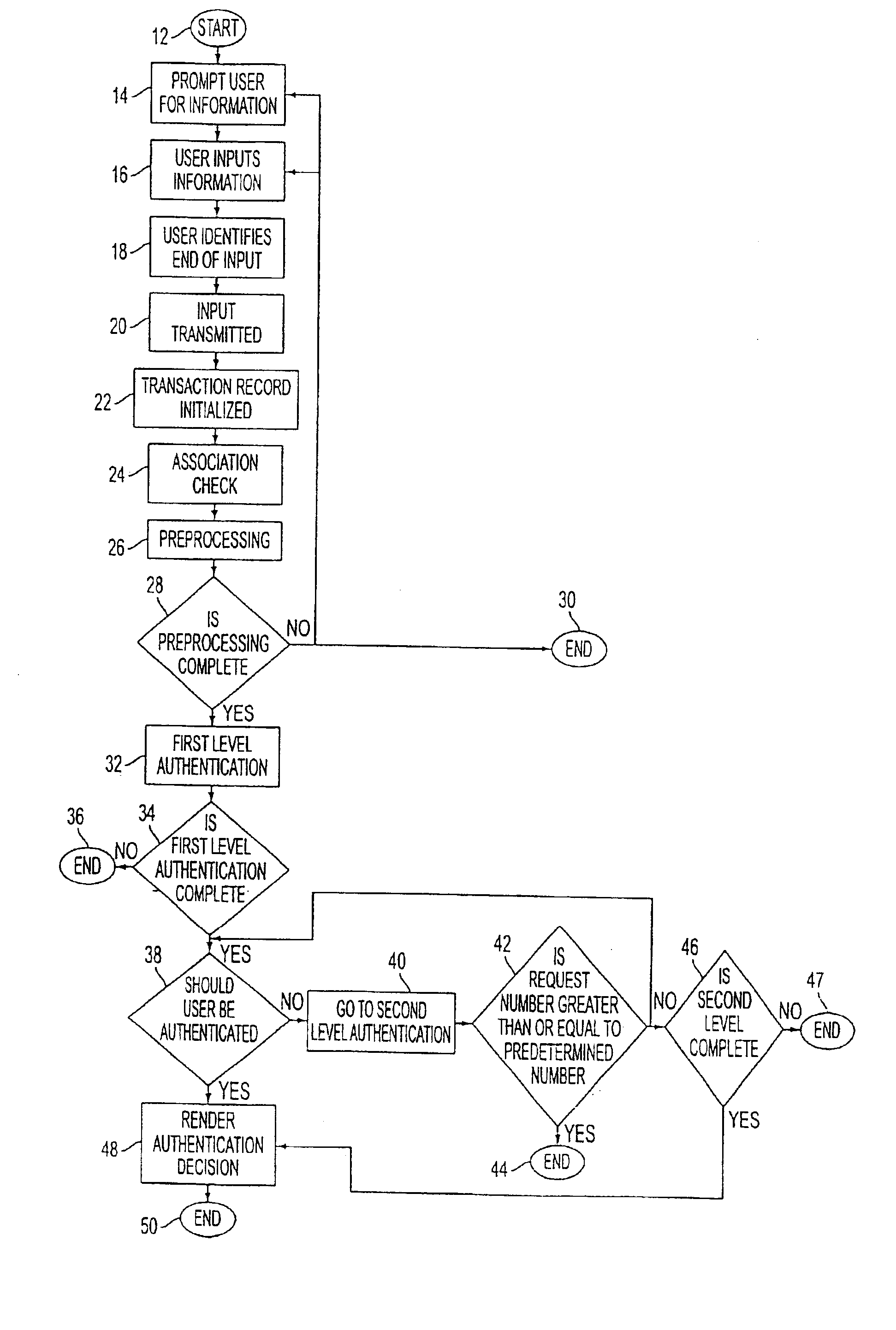
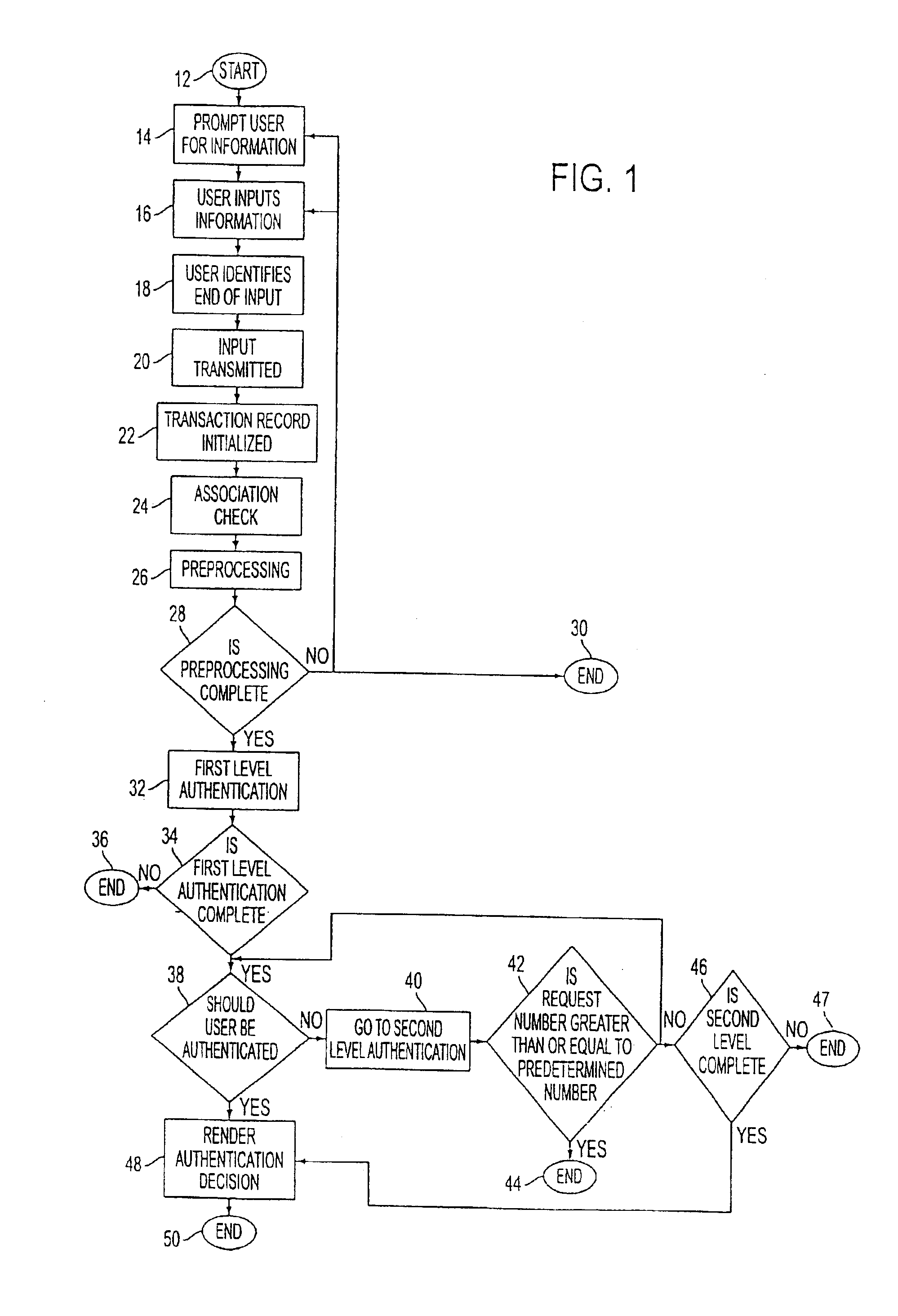
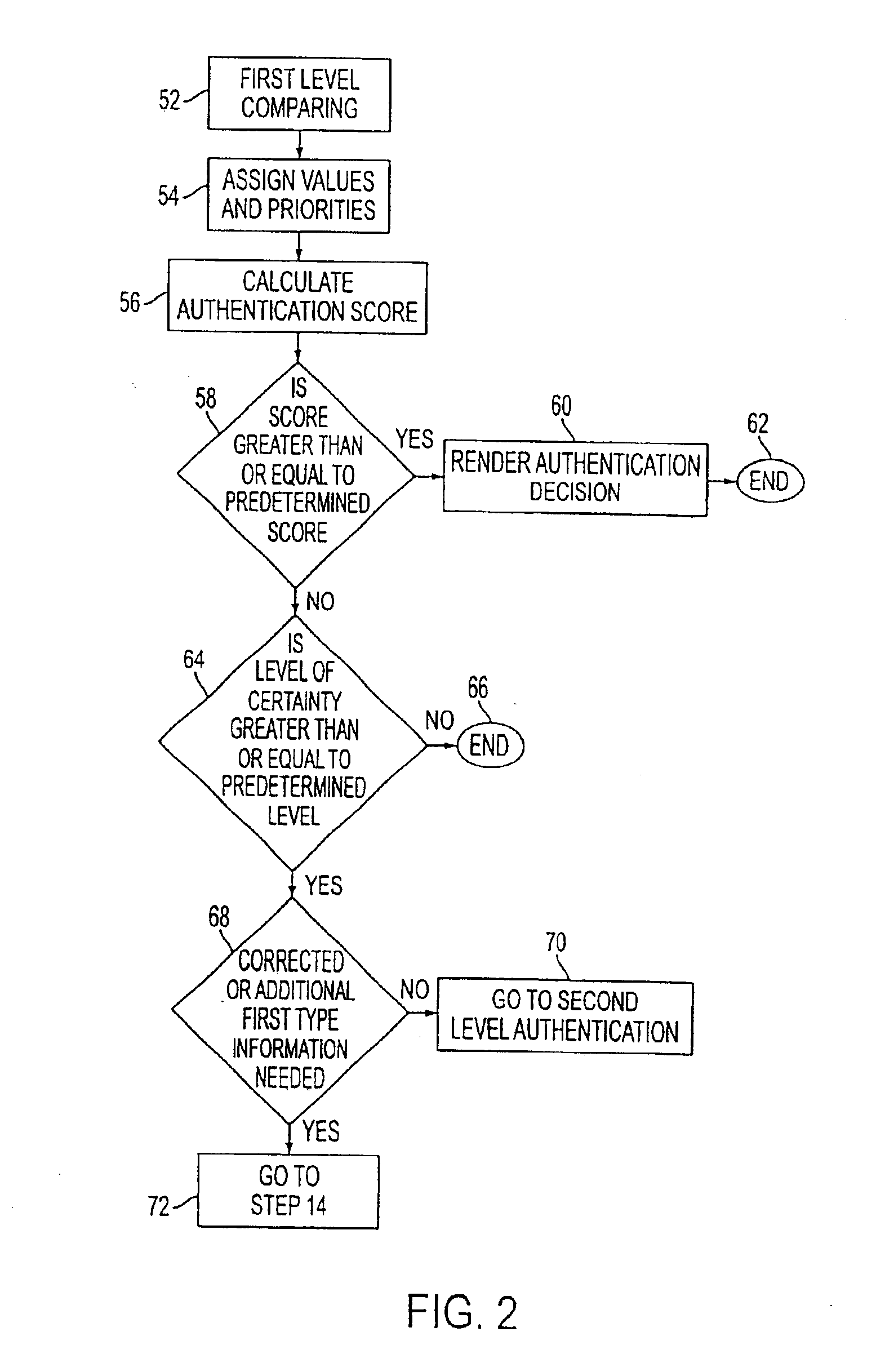
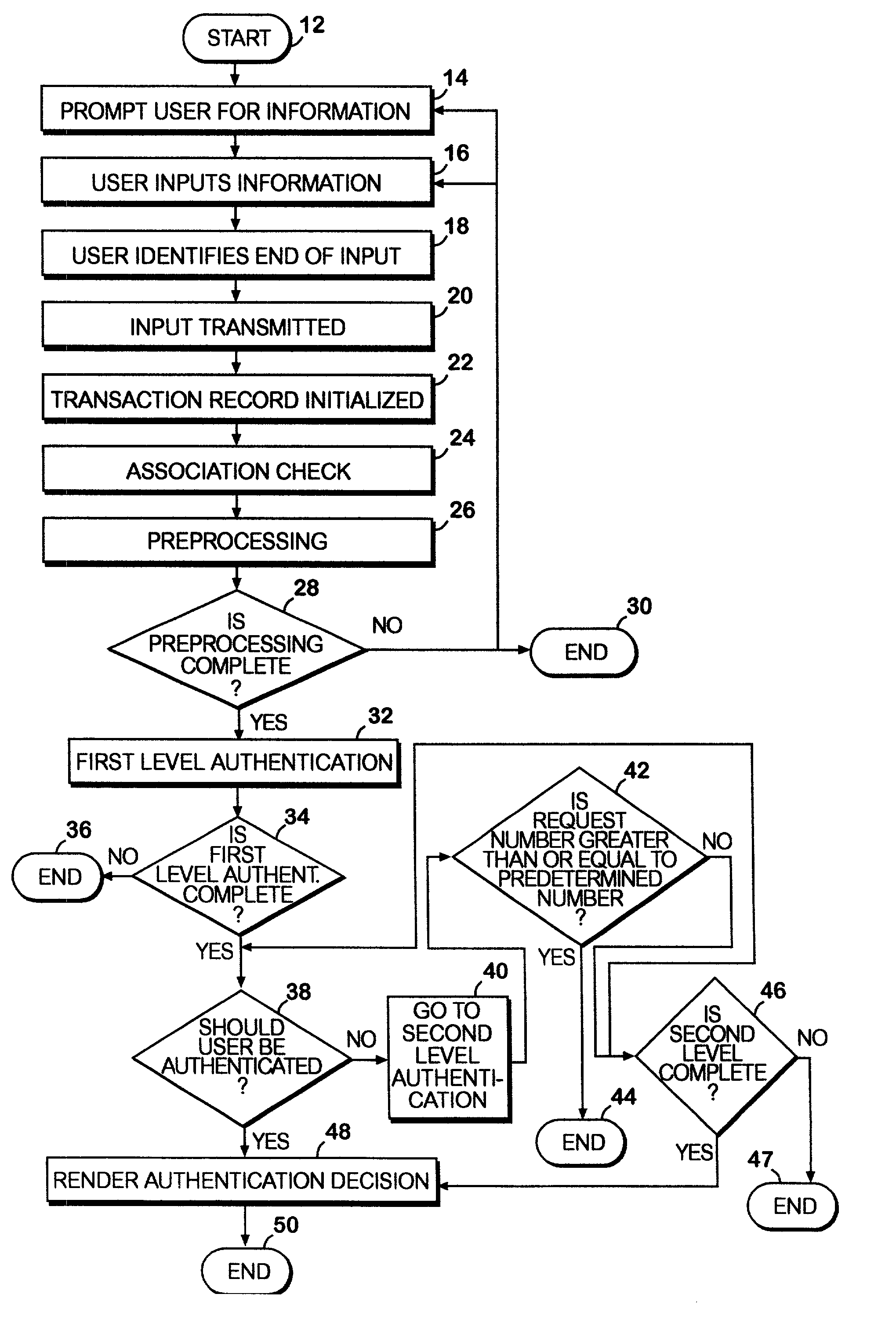
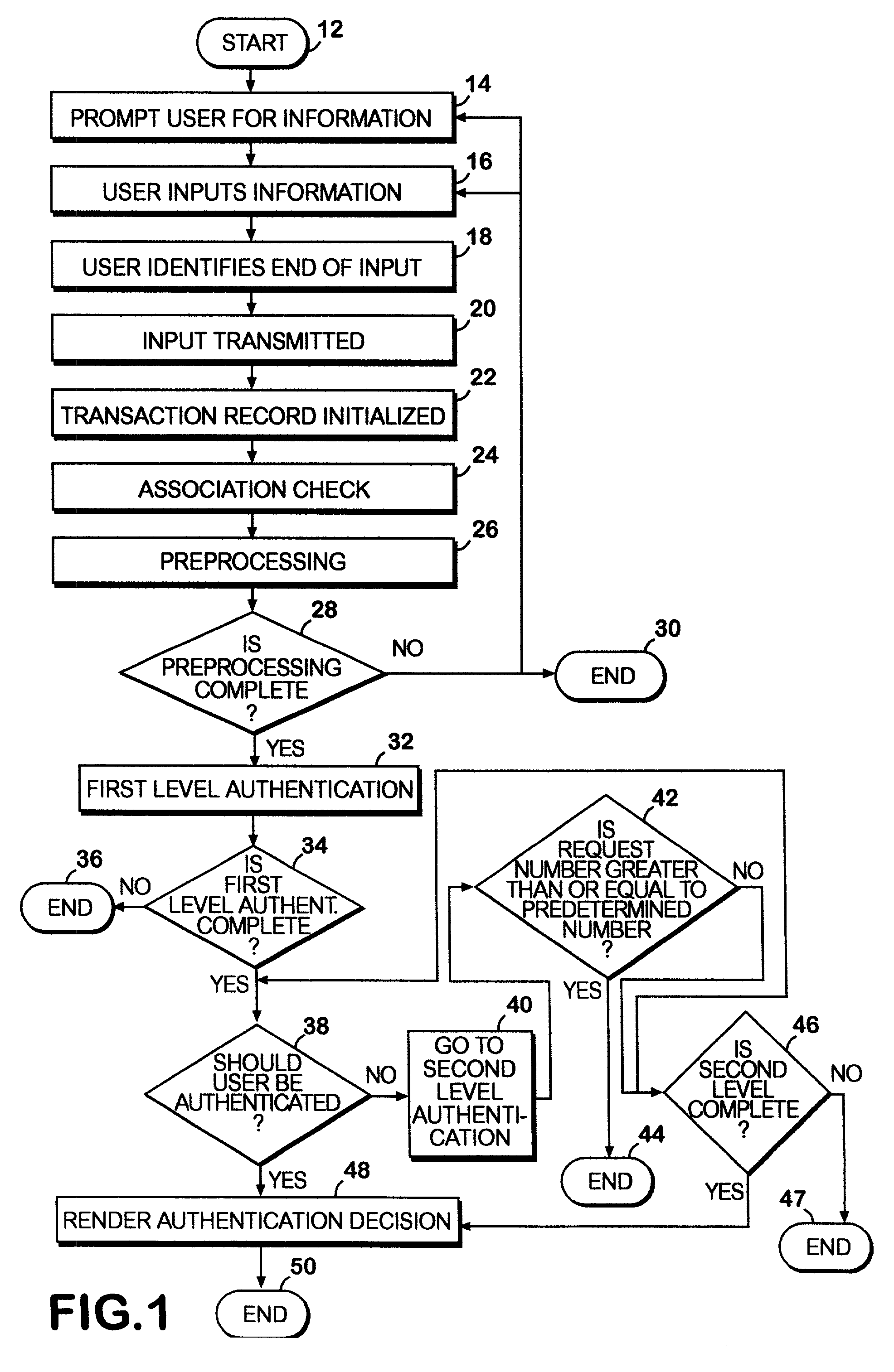
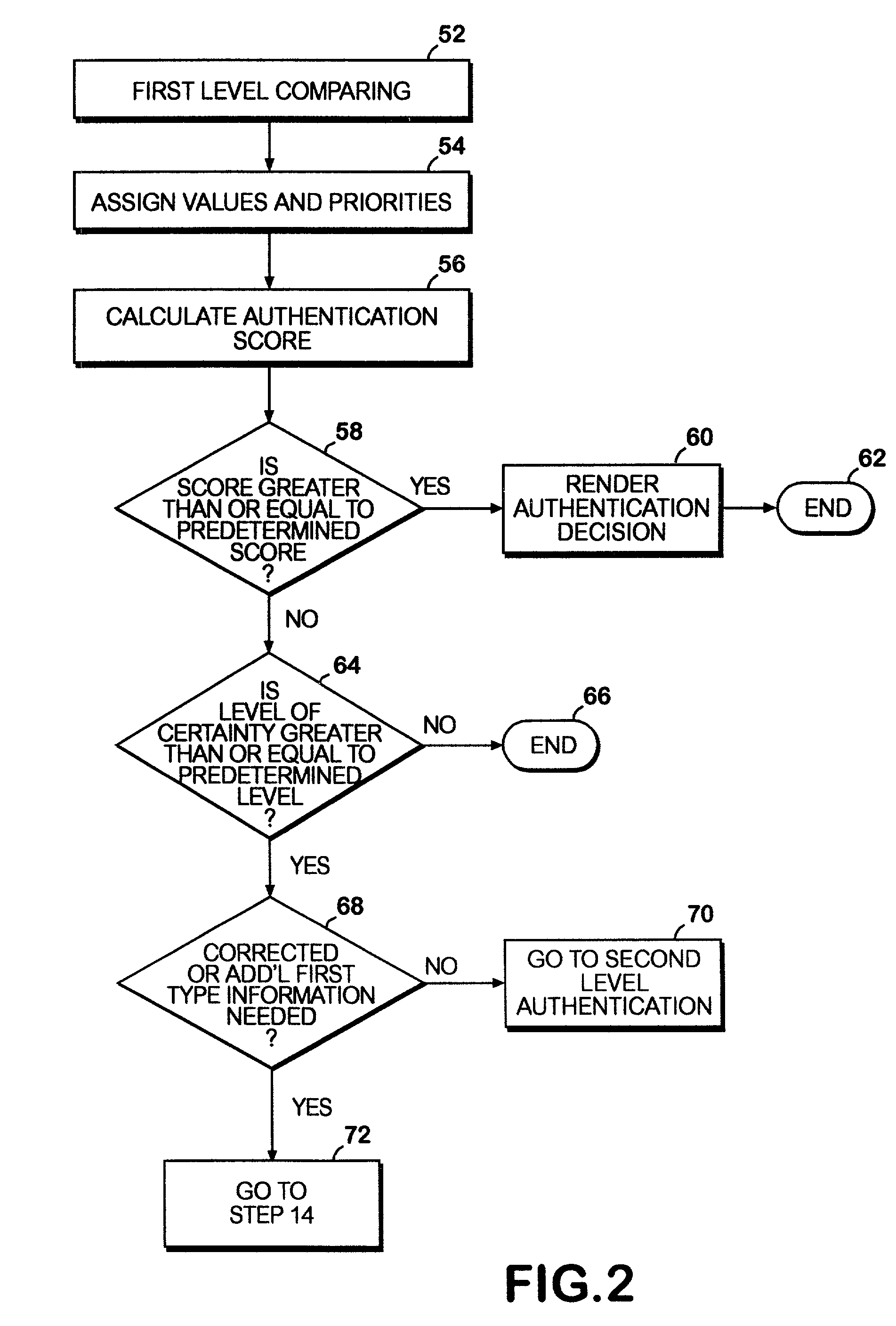
A network authentication system provides verification of the identity or other attributes of a network user to conduct a transaction, access data or avail themselves of other resources. The user is presented with a hierarchy of queries based on wallet-type (basic identification) and non-wallet type (more private) information designed to ensure the identity of the user and prevent fraud, false negatives and other undesirable results. A preprocessing stage may be employed to ensure correct formatting of the input information and clean up routine mistakes (such as missing digits, typos, etc.) that might otherwise halt the transaction. Queries can be presented in interactive, batch processed or other format. The authenticator can be configured to require differing levels of input or award differing levels of authentication according to security criteria.
Owner:EQUIFAX INC
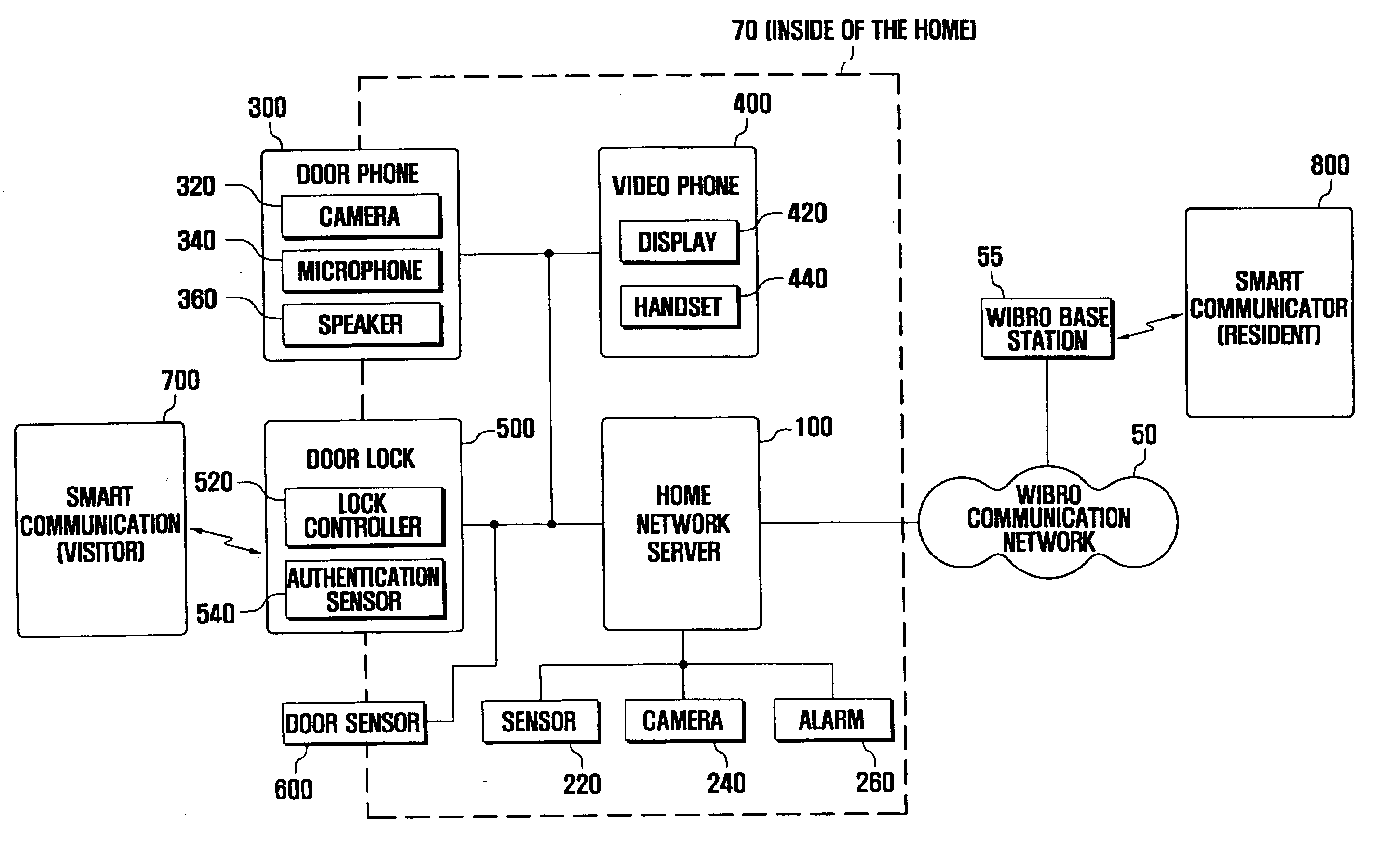
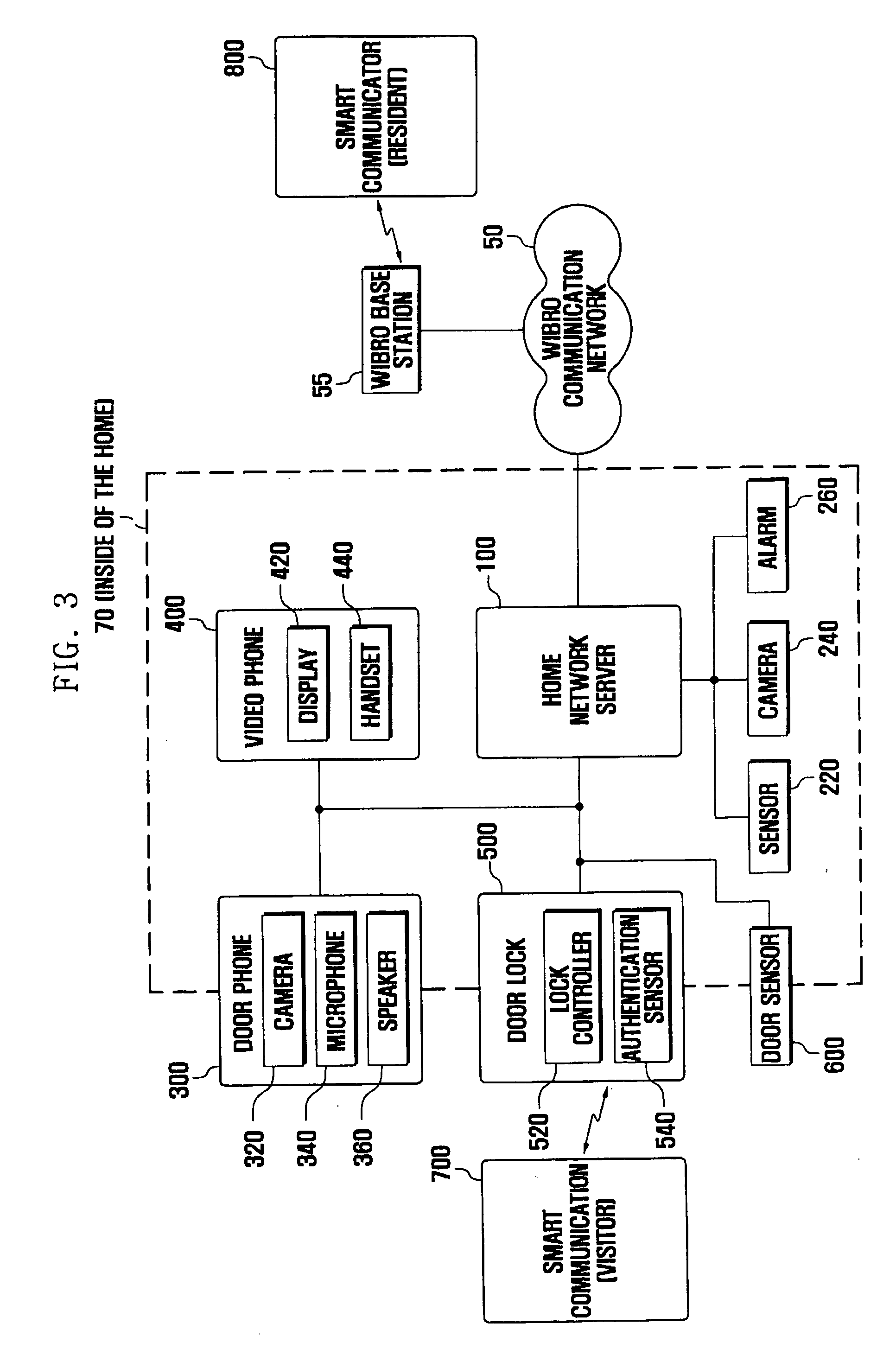
Access authentication system and method using smart communicator
ActiveUS20070216764A1Electric signal transmission systemsMultiple keys/algorithms usageCommunication controlAuthentication system
Disclosed is an intelligent access authentication system and method. The intelligent access authentication system includes a door lock that can be locked and released in a predetermined manner, a door phone for communicating with the visitor; a smart communicator which configures access approval levels of expected visitors and access authentication information for each access approval level, communicates with the visitor, and controls the door lock, and a home network server which stores the access approval levels of expected visitors and access authentication information for each access approval level received from the smart communicator, checks the access approval level of the visitor attempting to release the door lock by referring to previously stored information, and transmits a door lock operating command to the door lock according to the access approval level of the visitor. In the present invention, the resident can check the visitor and control the door lock to be released according to the access approval level of the visitor, even at a remote location.
Owner:HUAWEI TECH CO LTD
Facial Recognition Authentication System Including Path Parameters
ActiveUS20160063235A1Improve securityAuthorization may be expandedDigital data processing detailsMultiple digital computer combinationsInternet privacyAuthentication system
Systems and methods for enrolling and authenticating a user in an authentication system via a user's camera of camera equipped mobile device include capturing and storing enrollment biometric information from at least one first image of the user taken via the camera of the mobile device, capturing authentication biometric information from at least one second image of the user, capturing, during imaging of the at least one second image, path parameters via at least one movement detecting sensor indicating an authentication movement of the mobile device, comparing the authentication biometric information to the stored enrollment biometric information, and comparing the authentication movement of the mobile device to an expected movement of the mobile device to determine whether the authentication movement sufficiently corresponds to the expected movement.
Owner:FACETEC INC
System and method for production and authentication of original documents
InactiveUS20050038756A1Improve shielding effectImprove accuracyOther printing matterUser identity/authority verificationDocument IdentifierPaper document
A system and method for authenticating documents and content thereof. A counterfeit resistant document recording medium is provided, having thereon a predefined unique document identifier and at least one security feature. The recording medium is thereafter imprinted with document content, which typically varies between documents. The document content is stored in a database, indexed by an associated document identifier. The document may then be authenticated by checking the security feature and comparing the stored document content with a perceived document content. The system provides a number of opportunities for commercial exploitation, including sales of identified recording media, recording of information in a database, on-line authentication transactions, differential accounting for document validations and counterfeit identifications, imprinting devices, authentication devices, and the like. The system prevents counterfeiting of valuable documents through casual means by providing both physical and logical security.
Owner:ESECUREDOCS
Communication device, communication system and authentication method
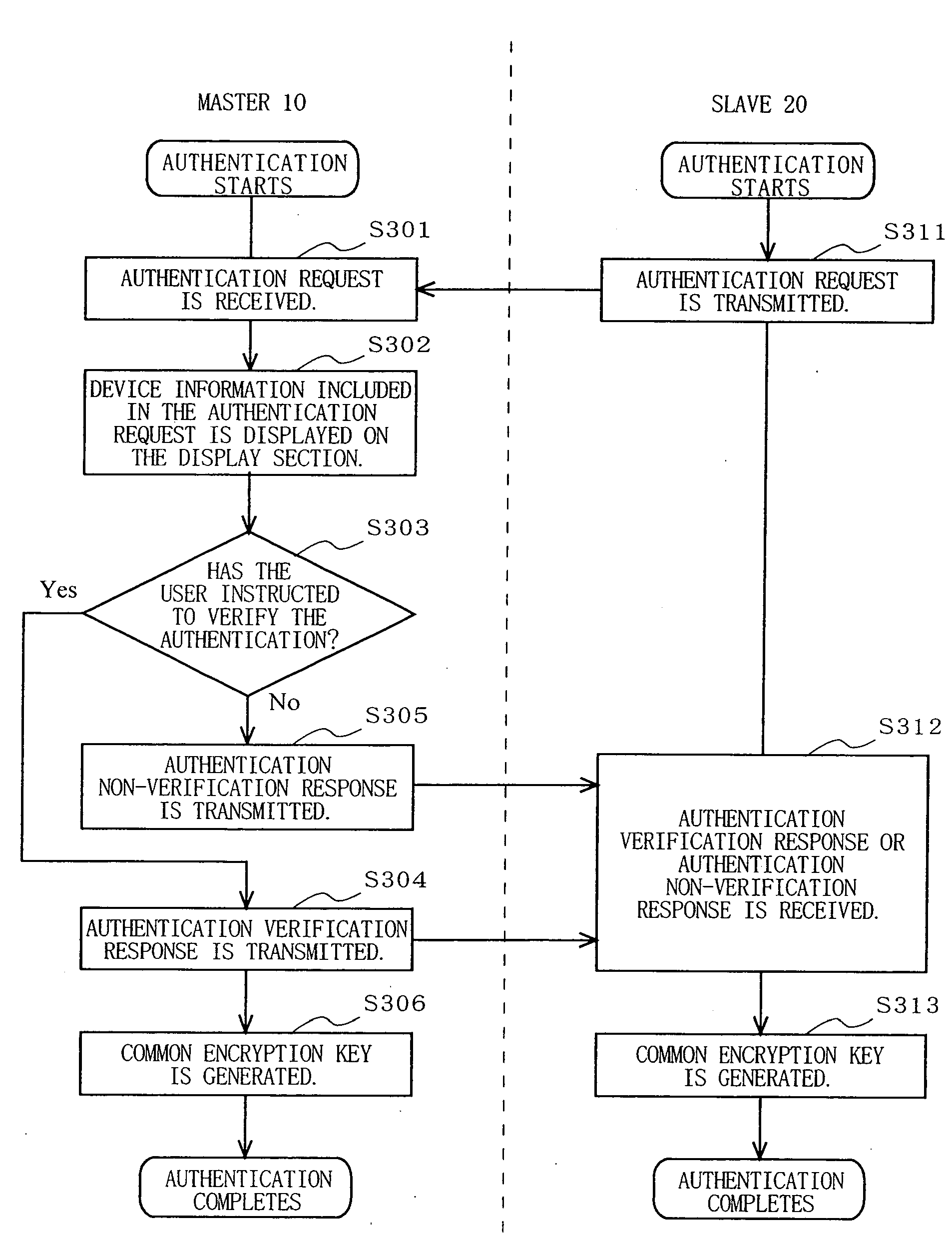
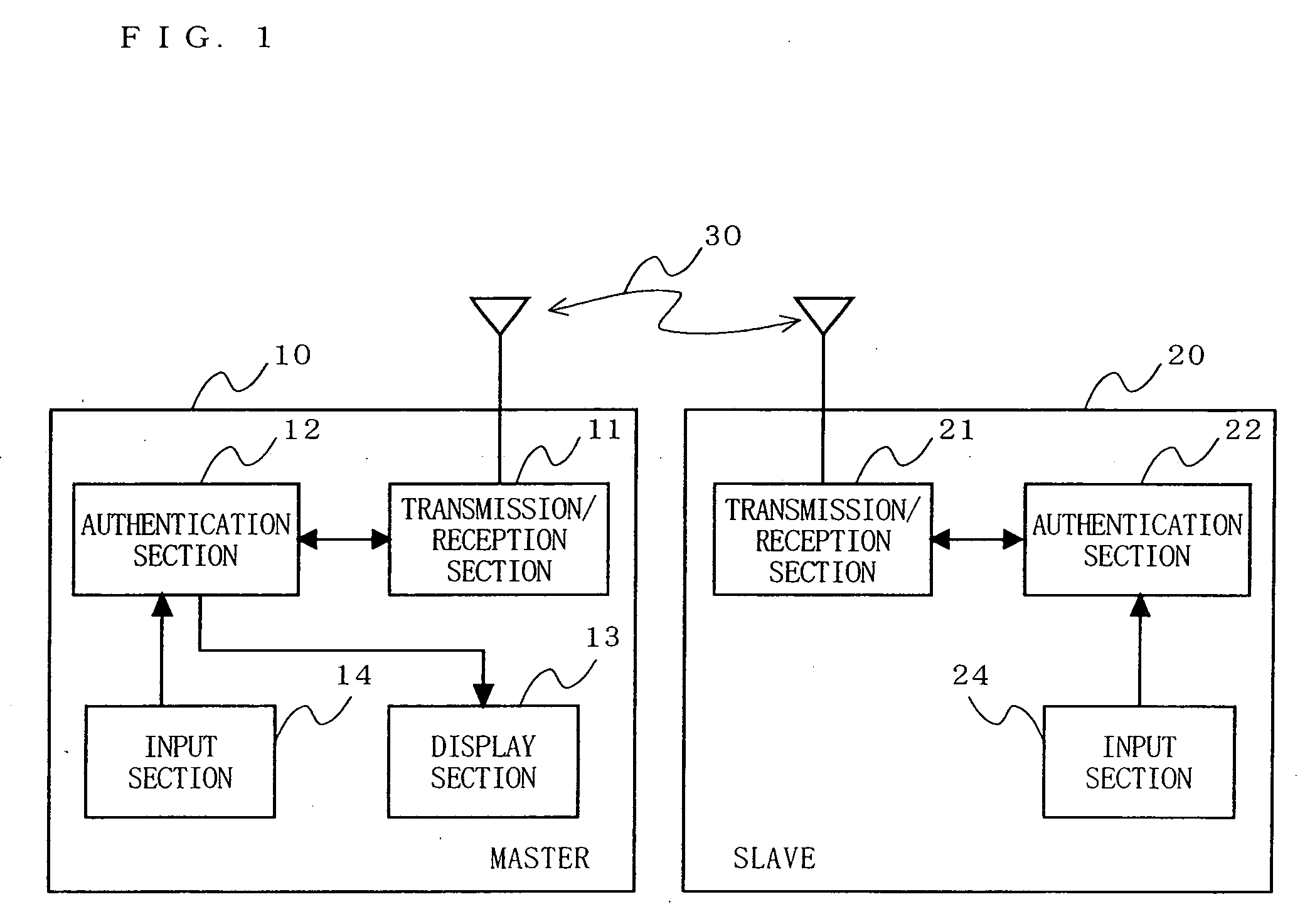
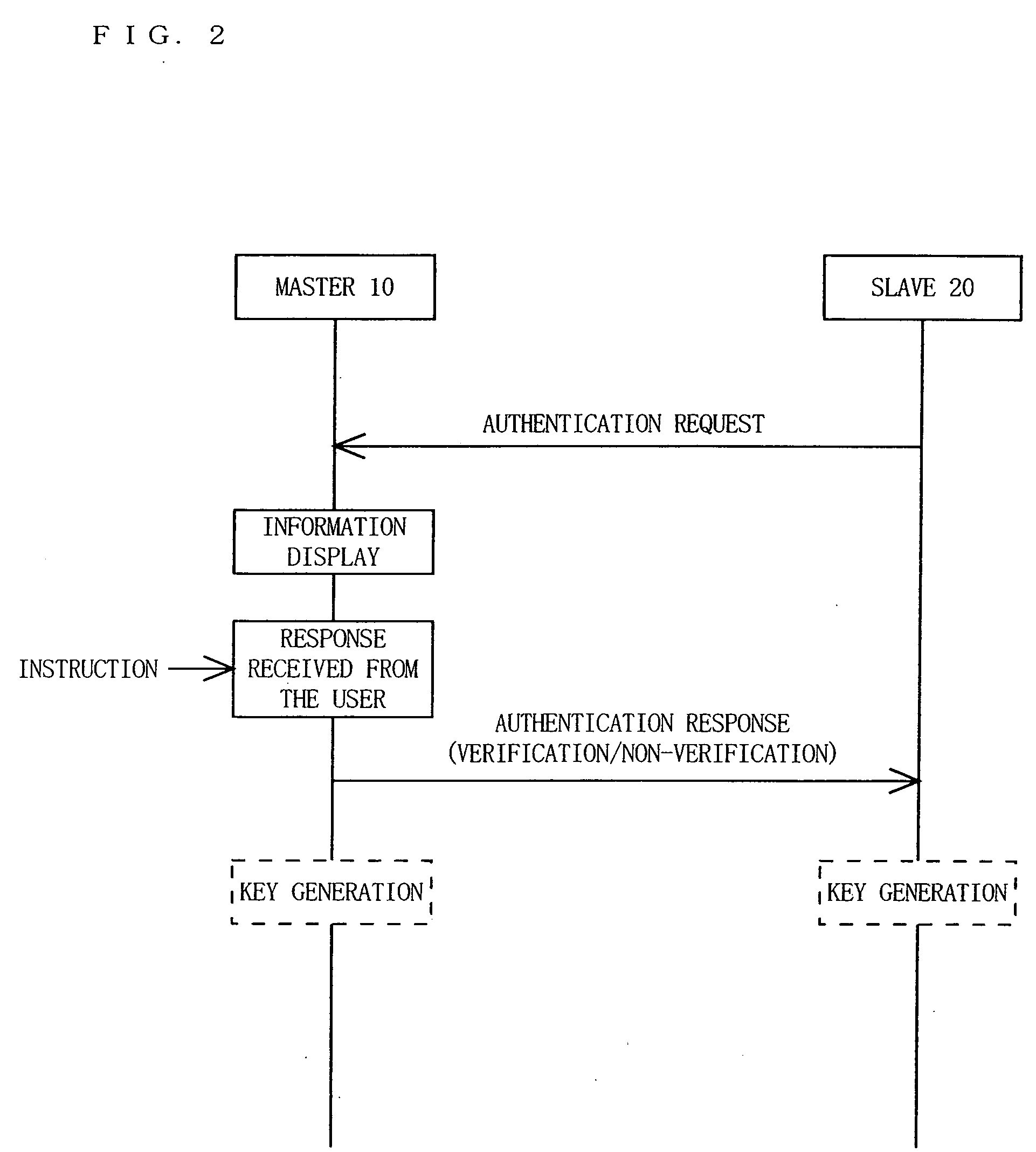
InactiveUS20070106894A1Sure easyEnhanced authenticationKey distribution for secure communicationDigital data processing detailsCommunications systemAuthentication system
A communication device, a communication system and an authentication system for preventing a disguising act by an illegal man-in-the-middle and improving the safety and certainty of authentication processing are provided. A slave (20) transmits an authentication request including device information to a master (10). The master (10) receives the authentication request and displays the device information included in the authentication request on a screen of a display section (13). The user visually checks the device information displayed on the screen of the display section 13 (13), determines whether or not to verify the authentication, and instructs the master (10) of the determination result via an input section (14). The master (10), instructed to verify or not to verify the authentication, transmits a response in accordance with the instruction to the slave (20).
Owner:SOVEREIGN PEAK VENTURES LLC
Data authentication system
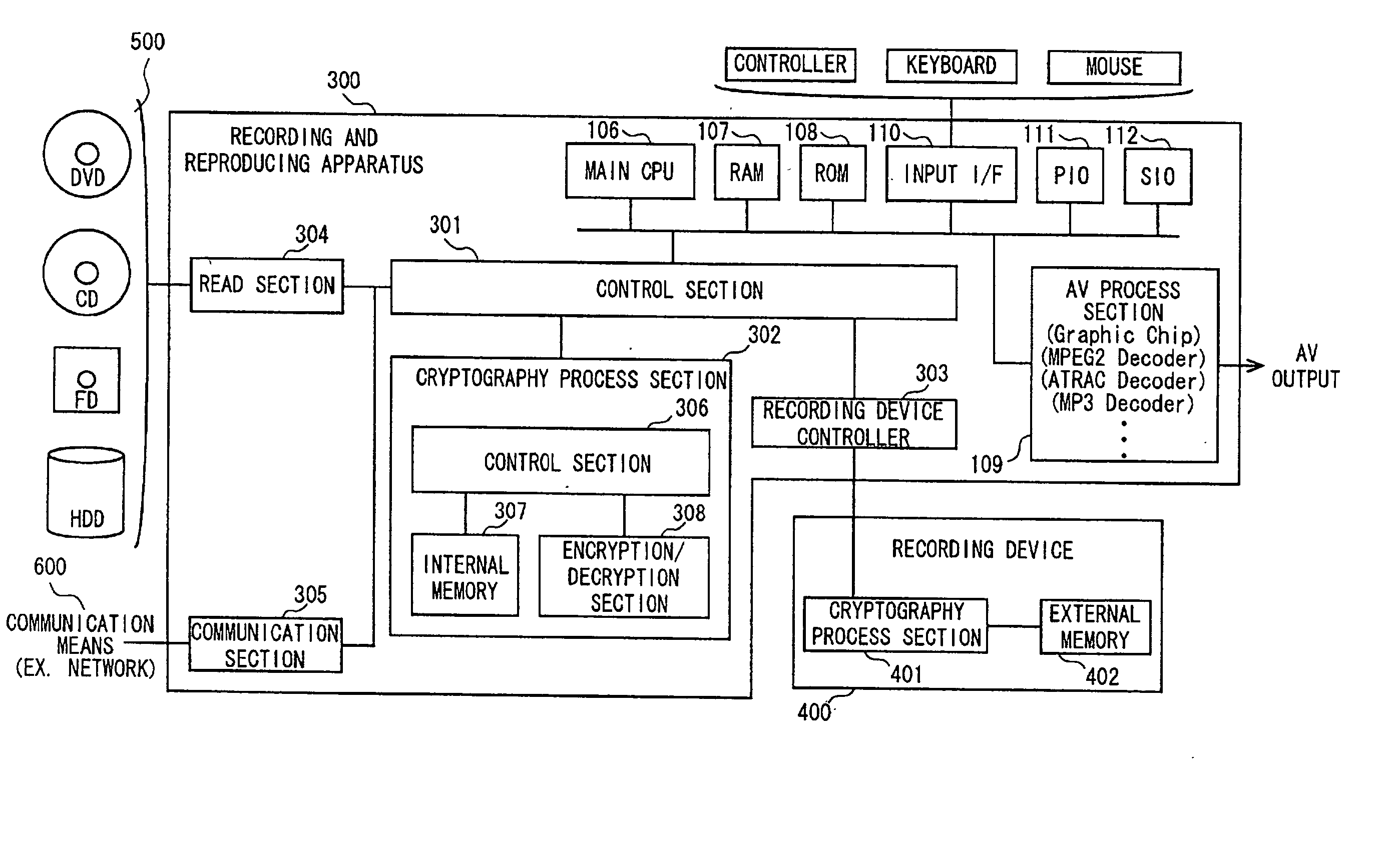
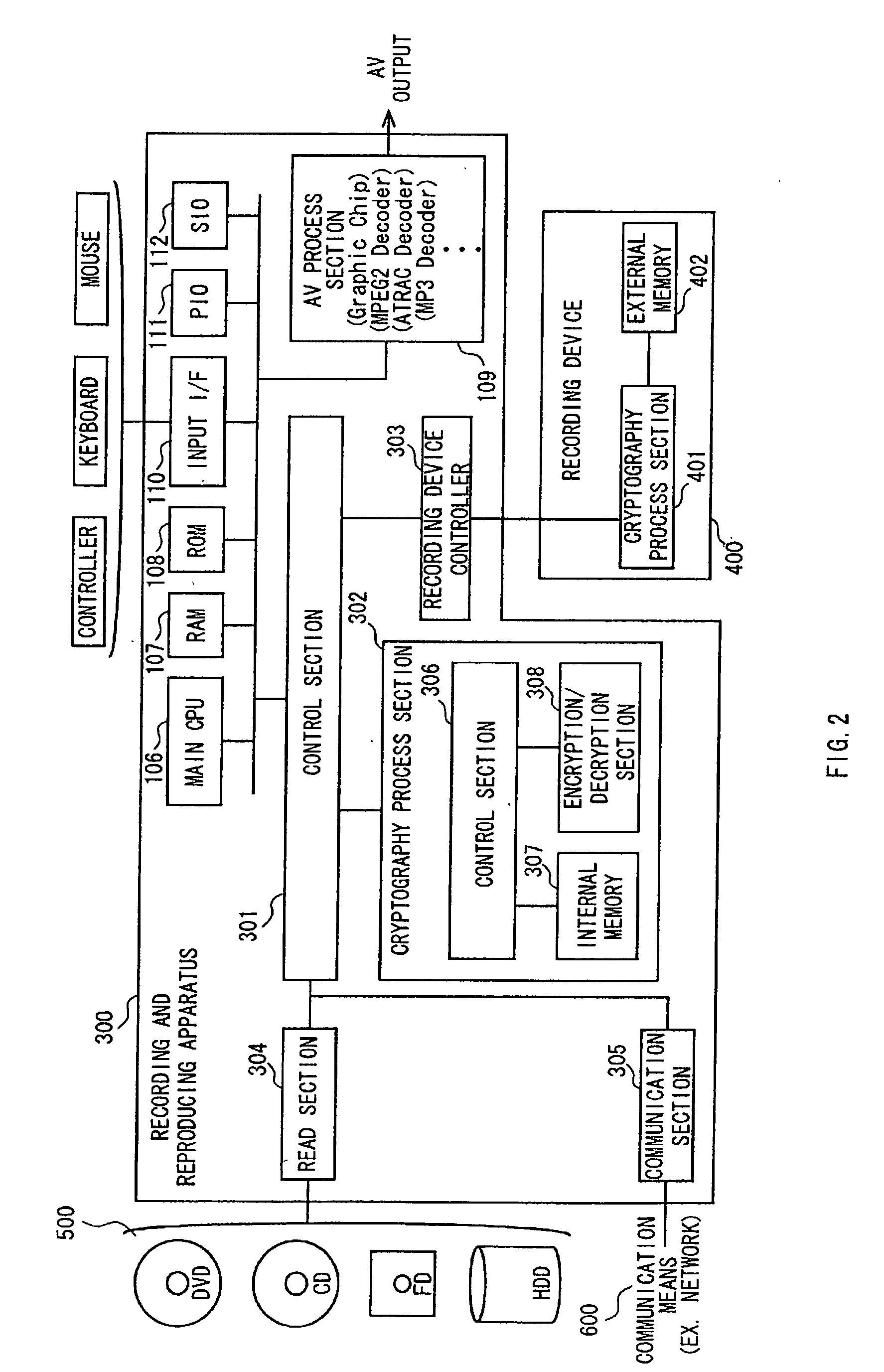
InactiveUS20020169971A1Efficient verificationPossibility of leakageTelevision system detailsMultiple keys/algorithms usageKey storageMaster key
A data processing apparatus a data processing method efficiently ascertain that data are valid, prevent encryption processing key data from leaking, eliminate illegal use of contents data, restrict contents utilization, apply a different plurality of data formats to contents and efficiently execute reproduction processing of compressed data. The verification process of partial data is executed by collating the integrity partial data as check values for a combination of partial data of a content, and the verification process of the entirety of the combination of partial data is executed by collating partial-integrity-check-value-verifying integrity check values that verify the combination of the partial integrity check values. Master keys to generate individual keys necessary for a process of such as data encryption are stored in the storage section and keys are generated as required. An illegal device list is stored in the header information of a content and referred to when data is used. Keys specific to a data processing apparatus and common keys are stored and the keys are selectively used according to the content use restriction. Plural content blocks are coupled, and at least a part of the content blocks is applied to an encryption process by an encryption key Kcon, then encryption key data that is the encryption key Kcon encrypted by an encryption key Kdis is stored in the header section. A content data is made of compression data and an expansion processing program or a combination of types of compression programs and the reproducing apparatus can determine an expansion program applicable to a compressed content.
Owner:SONY CORP
System and method for authentication of network users
InactiveUS7234156B2Reducing cost and unnecessary useChanceDigital data processing detailsUser identity/authority verificationBatch processingInformation design
A network authentication system provides verification of the identity or other attributes of a network user to conduct a transaction, access data or avail themselves of other resources. The user is presented with a hierarchy of queries based on wallet-type (basic identification) and non-wallet type (more private) information designed to ensure the identity of the user and prevent fraud, false negatives and other undesirable results. A preprocessing stage may be employed to ensure correct formatting of the input information and clean up routine mistakes (such as missing digits, typos, etc.) that might otherwise halt the transaction. Queries can be presented in interactive, batch processed or other format. The authenticator can be configured to require differing levels of input or award differing levels of authentication according to security criteria.
Owner:EQUIFAX INC
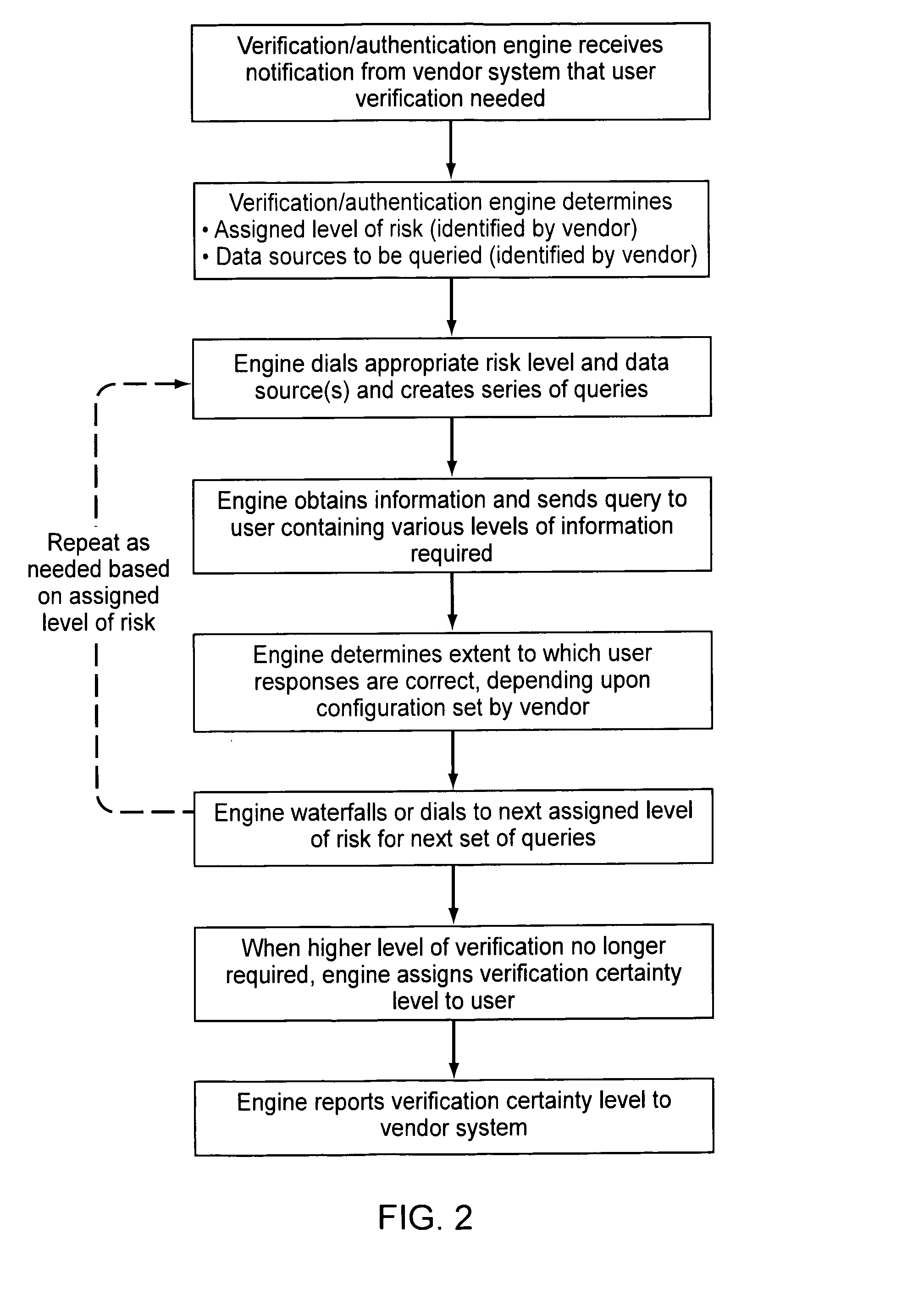
Verification and authentication systems and methods
ActiveUS20080086759A1Improve securityMinimal amountDigital data processing detailsUser identity/authority verificationRisk levelExternal data
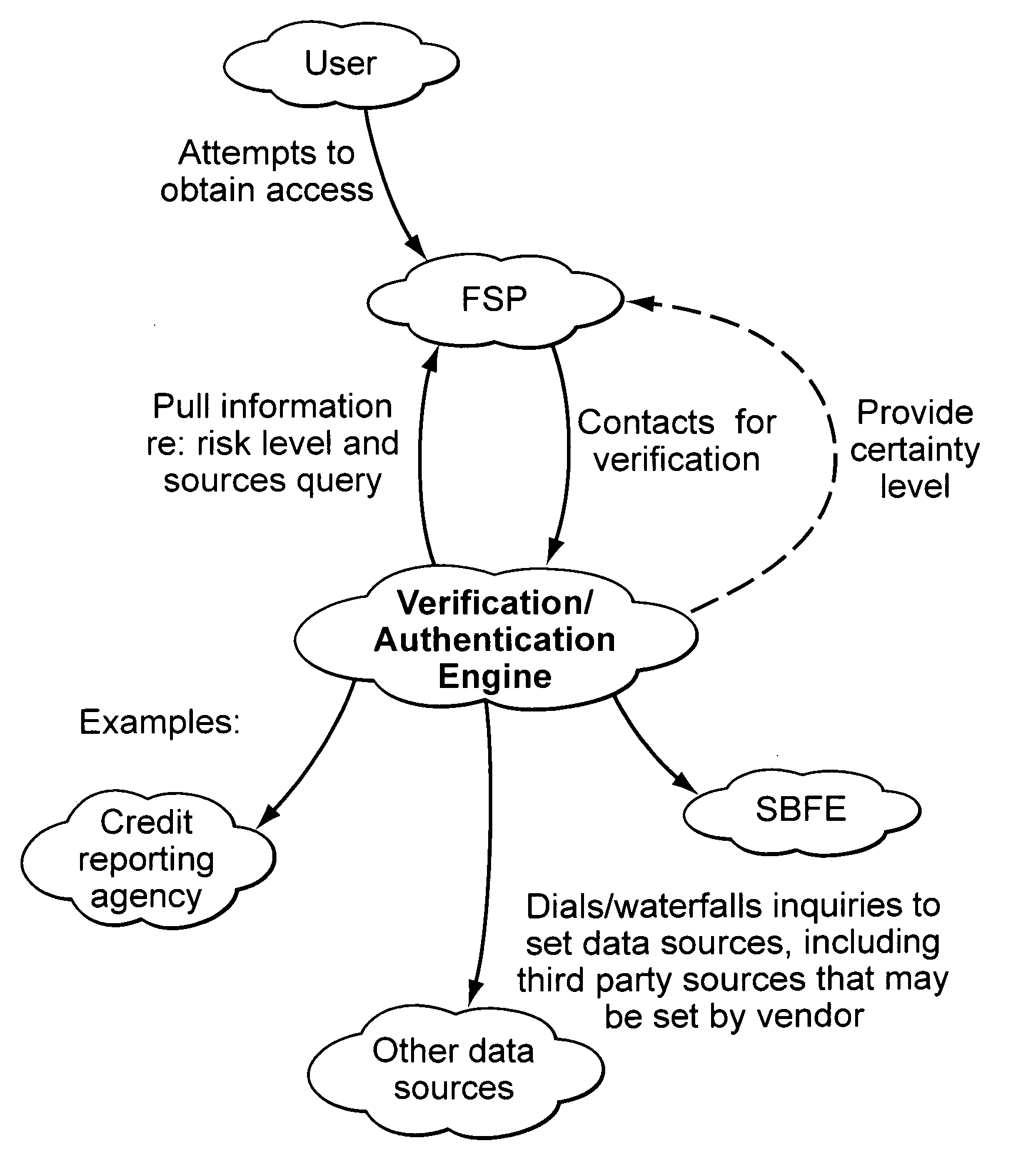
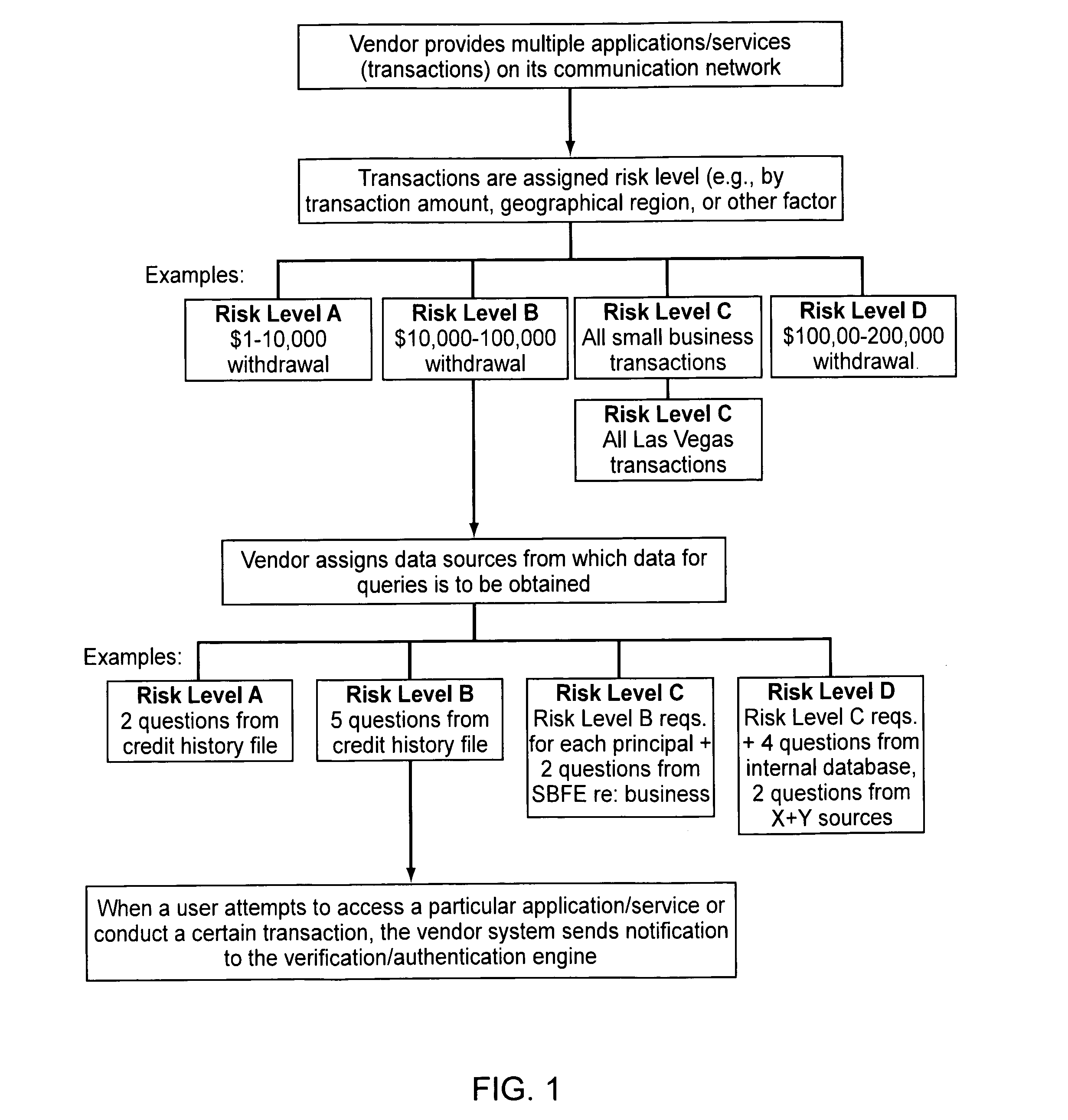
Embodiments of the present invention provide verification and / or authentication service engines that provide a customizable solution that can be “dialed” based on the risk level assigned to individual or grouped applications. The systems can also incorporate internal and external sources of data used to verify information provided by the user. It is dynamic and can pull information from a myriad of sources during the verification process, enabling credit reporting agencies (e.g., Equifax and others), FSPs, and other service providers to facilitate real-time approval and access to products and services.
Owner:EQUIFAX INC
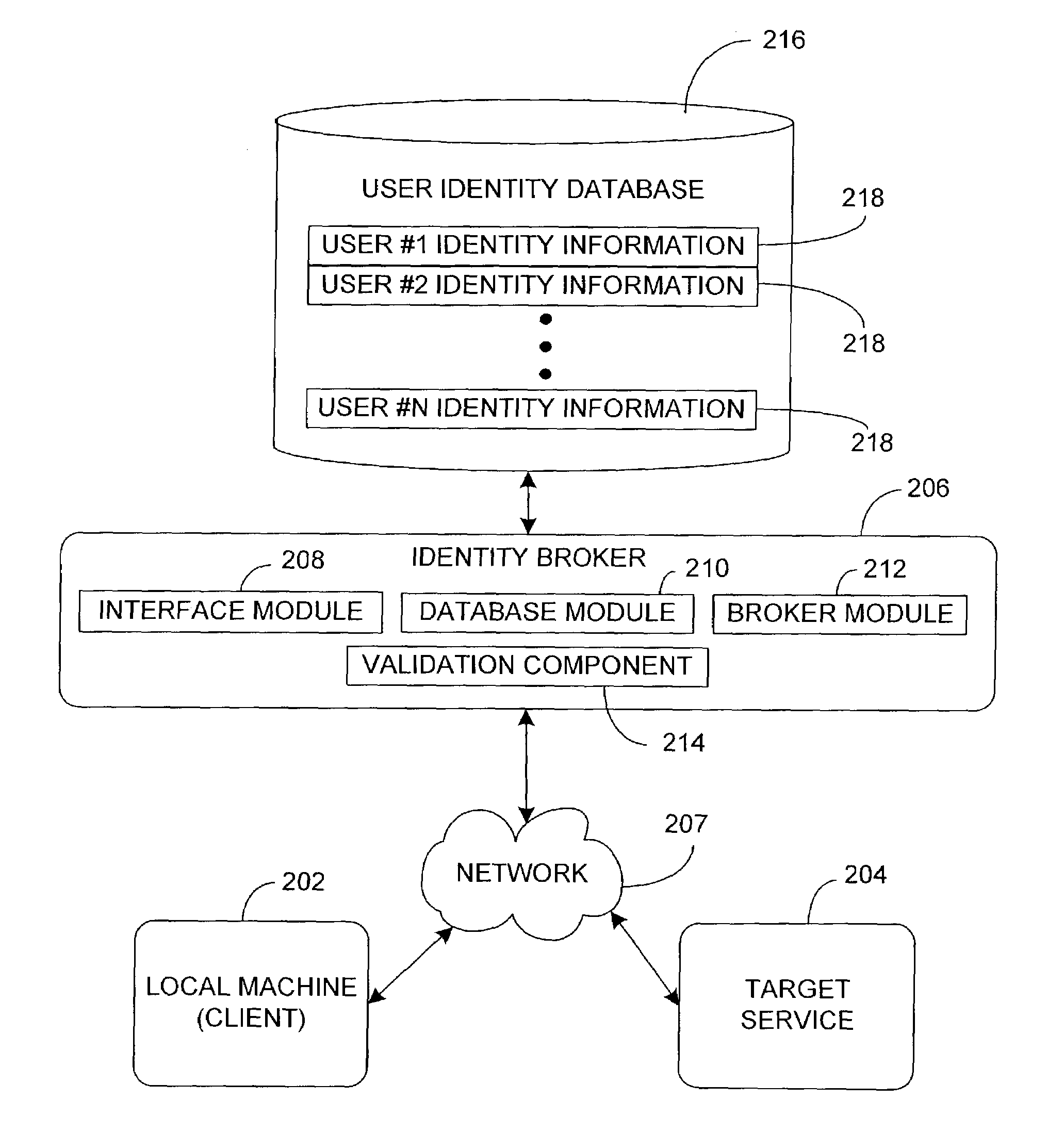
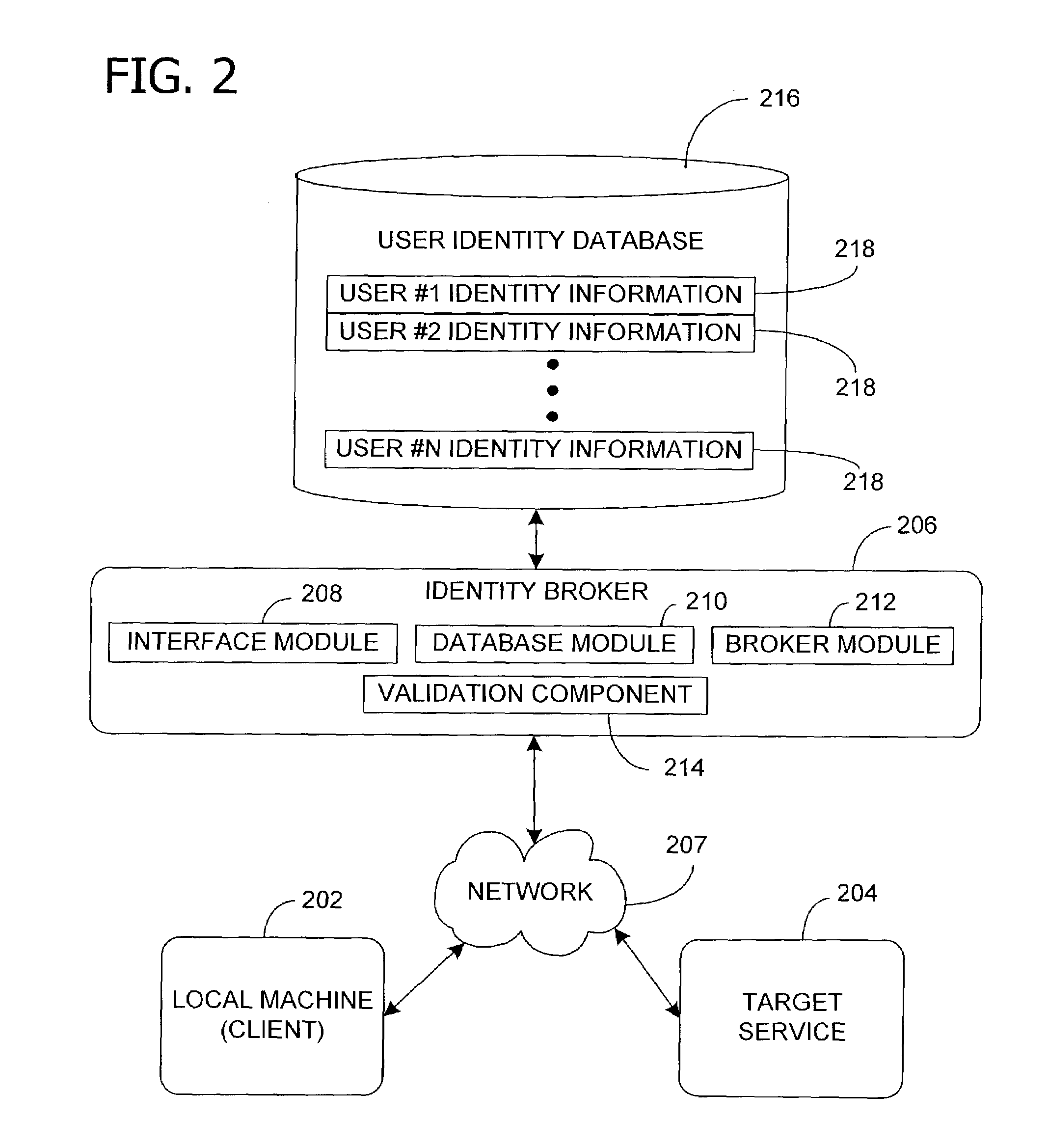
Managing multiple user identities in authentication environments
InactiveUS7428750B1Easy to useDigital data processing detailsMultiple digital computer combinationsAuthentication systemInternet privacy
Managing a plurality of identities associated with a user. The invention includes a system for managing multiple credentials within the same authentication system and across federated authentication systems in such a manner that signing in with one credential allows access to content, information or services that may be associated with another credential.
Owner:MICROSOFT TECH LICENSING LLC
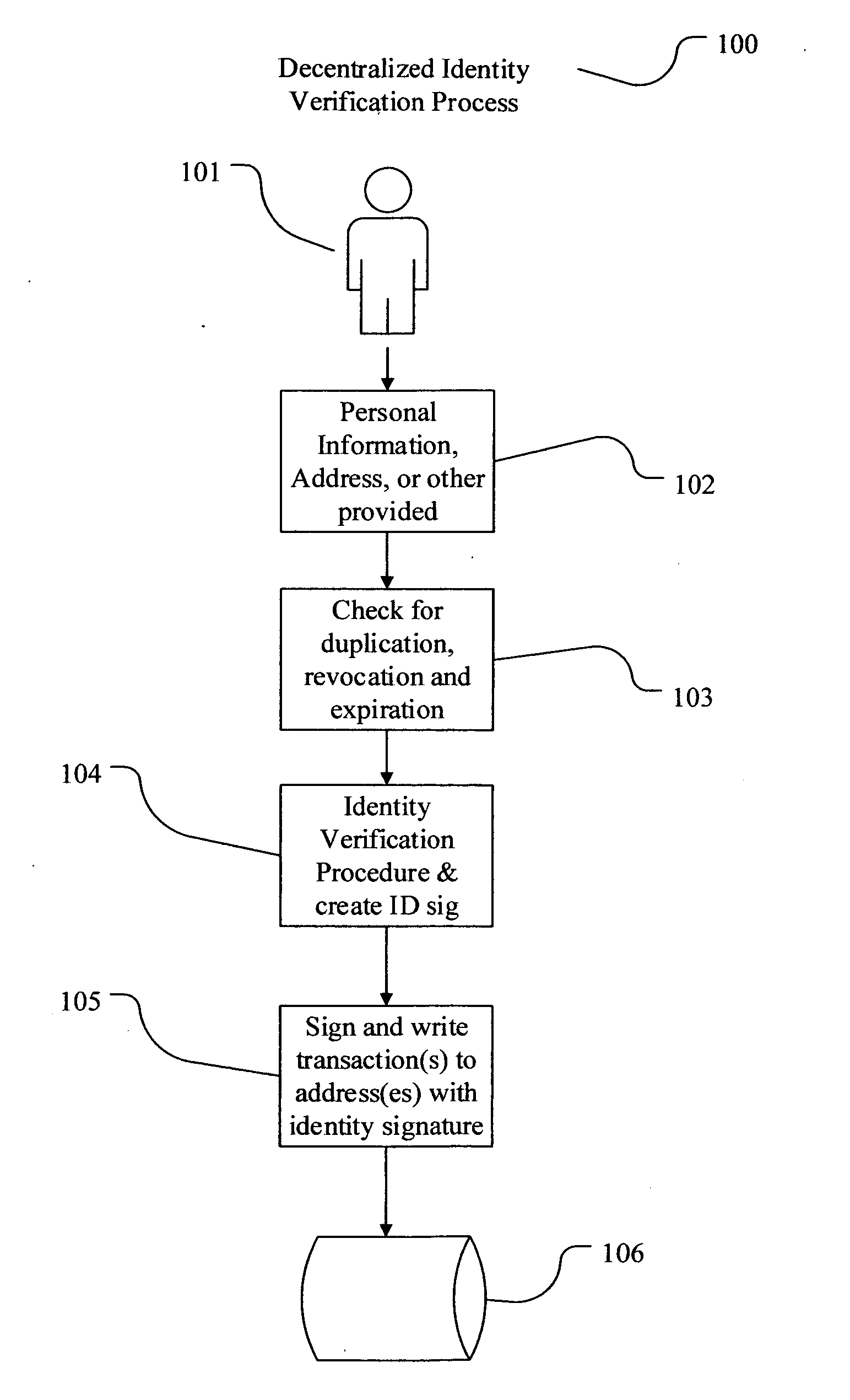
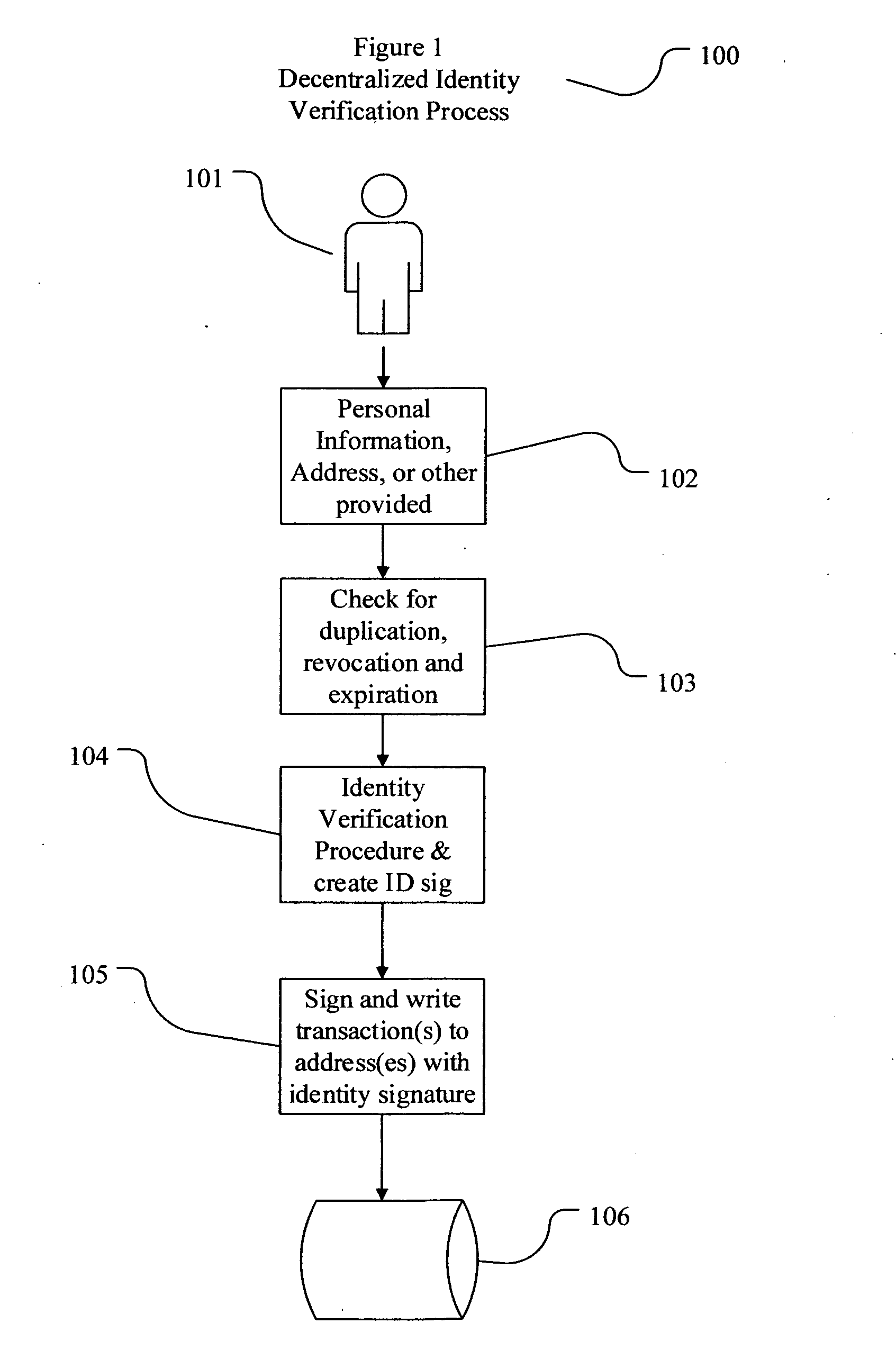
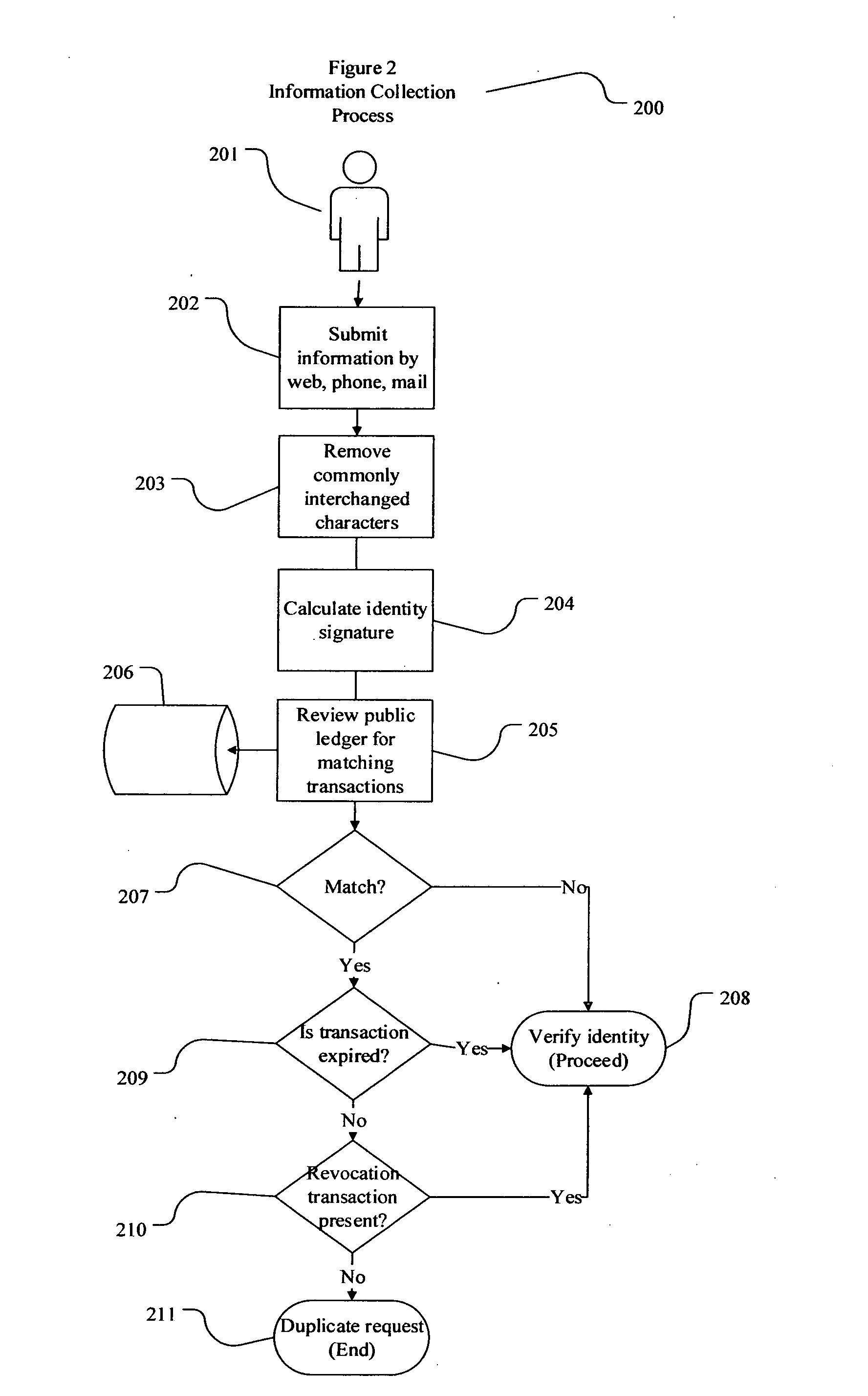
Decentralized identity verification systems and methods
InactiveUS20150356523A1Cryptography processingUser identity/authority verificationRegulatory authorityFinancial transaction
The present invention involves systems and methods that allow participants in cryptocurrency networks to exchange cryptocurrency for traditional currency legally and safely without requiring the use of a traditional exchange or online brokerage as a fiduciary. The invention accomplishes this through the use of a decentralized identity verification protocol that allows a service provider to verify the identity of a participant and then publish an identity signature on the participant's cryptocurrency address or addresses. The invention enables full compliance with Country specific customer identification program and anti-money laundering requirements, and maintains the ability to independently satisfy requests for information or data retention requirements if requested by legally authorized parties, but does not require that the participant store the private keys or access controls to their cryptocurrency on an exchange or brokerage service.The invention serves to verify a participant's identity in full compliance with US Bank Secrecy and Patriot Act provisions or similar regulations where identification may be achieved through non-documentary or documentary identity verification procedures. After passing the applicable verification procedure, the service provider stamps the participant's cryptocurrency address with a transaction containing an identity signature. This identity signature within the transaction consists of a public indicator of the participant's Country and subdivision, a compliance level code, an ID type indicator, and an identity hash. The identity hash is created from the digests of cryptographic hash functions where the participant's personal information is used as an input. The service provider signs the transaction with their authorized private key that corresponds to their publicly accessible public key. This serves as a publicly verifiable confirmation that the identity associated with the address in question was validated by the service provider authorized to act on behalf of the regulatory authority.The participant may then purchase and sell cryptographic currency from and to a third party exchange or brokerage service legally and safely when using their verified cryptocurrency address. This is because the third party is able to confirm compliance by openly referencing and verifying the identity verification transaction present on the address. Subsequent transactions where the third party sells or purchases cryptocurrency for the verified participant are similarly stamped with a transaction conforming to the identity verification protocol. This allows the third party interacting with the verified participant's address to observe any regulations limiting the amount or frequency of transactions over a variable period of time. It follows that this address could be used with any third party or participant in the cryptocurrency network that observes the decentralized identity verification protocol, all without requiring the third party or participant to collect and verify personal information redundantly. The ability to verify an identity remotely also eliminates the need for the third party to act as a fiduciary holding the private keys or access controls to the verified address. Lawful requests for information by authorized authorities are served to the service provider as digitally signed transactions that may then be linked to the participant's identity and transactions, allowing the protocol to observe subpoenas or similar lawful requests for information. The encrypted personal information may be held in escrow by the service provider indexed to the verified cryptocurrency address for such purposes. An alternate embodiment would store the encrypted personal information in a decentralized network of other participants, with the information accessible for retrieval using the public key of the verified cryptocurrency address and decryption using the corresponding private key, decentralizing the process entirely except for the identity verification step.
Owner:CHAINID
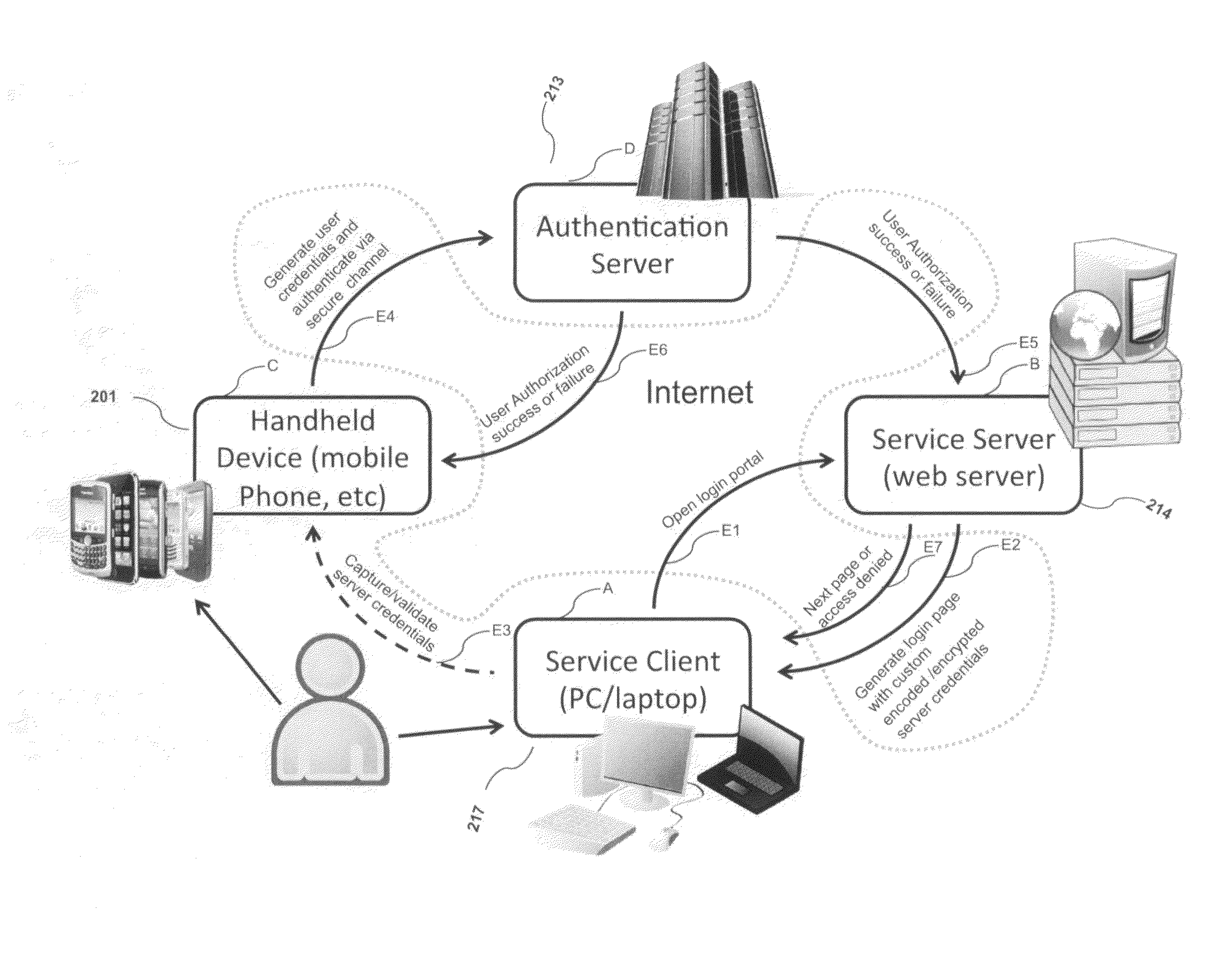
System, design and process for strong authentication using bidirectional OTP and out-of-band multichannel authentication
ActiveUS8763097B2Digital data information retrievalDigital data processing detailsOutbound communicationBarcode
Owner:GCOM IP LLC
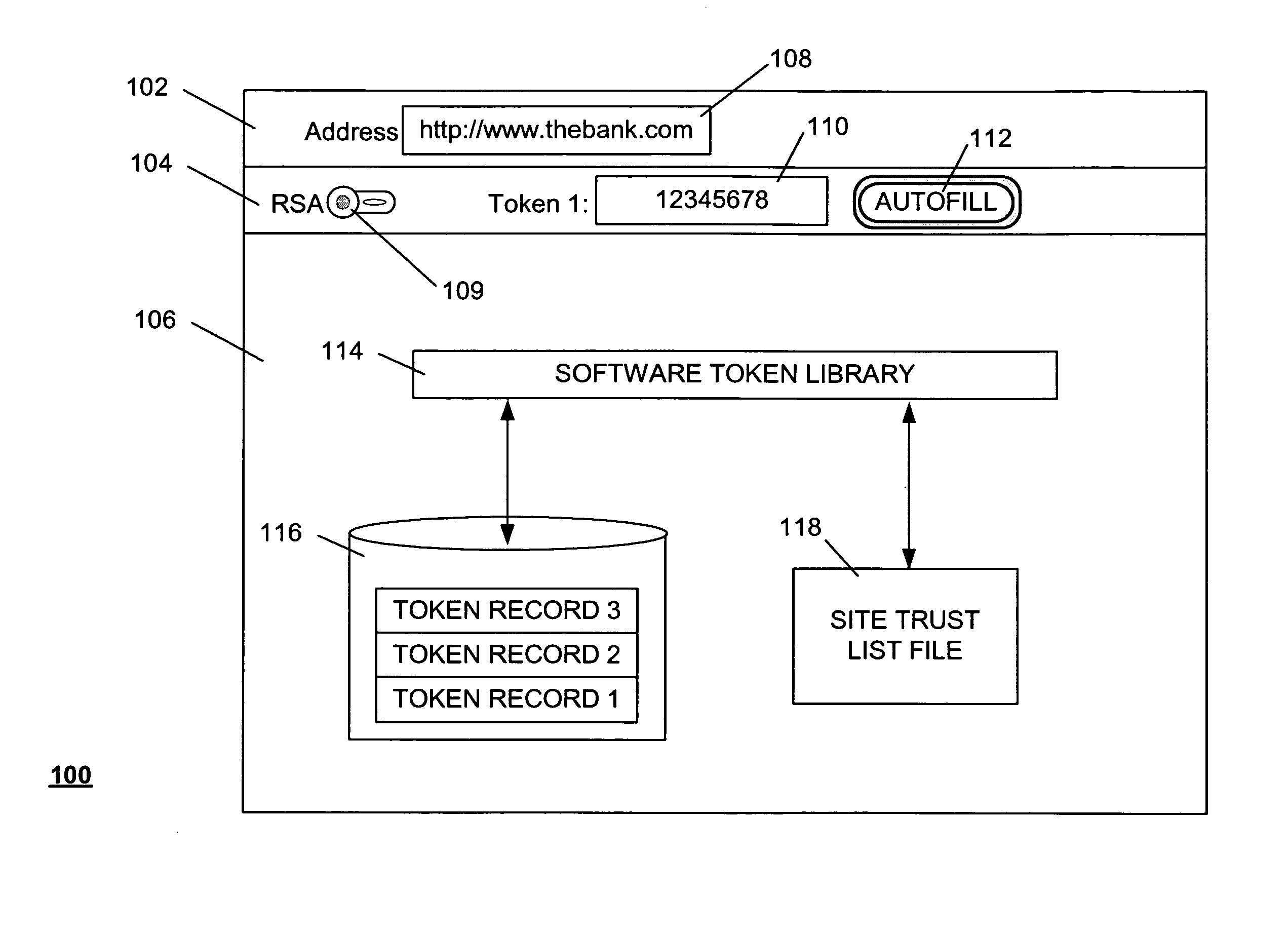
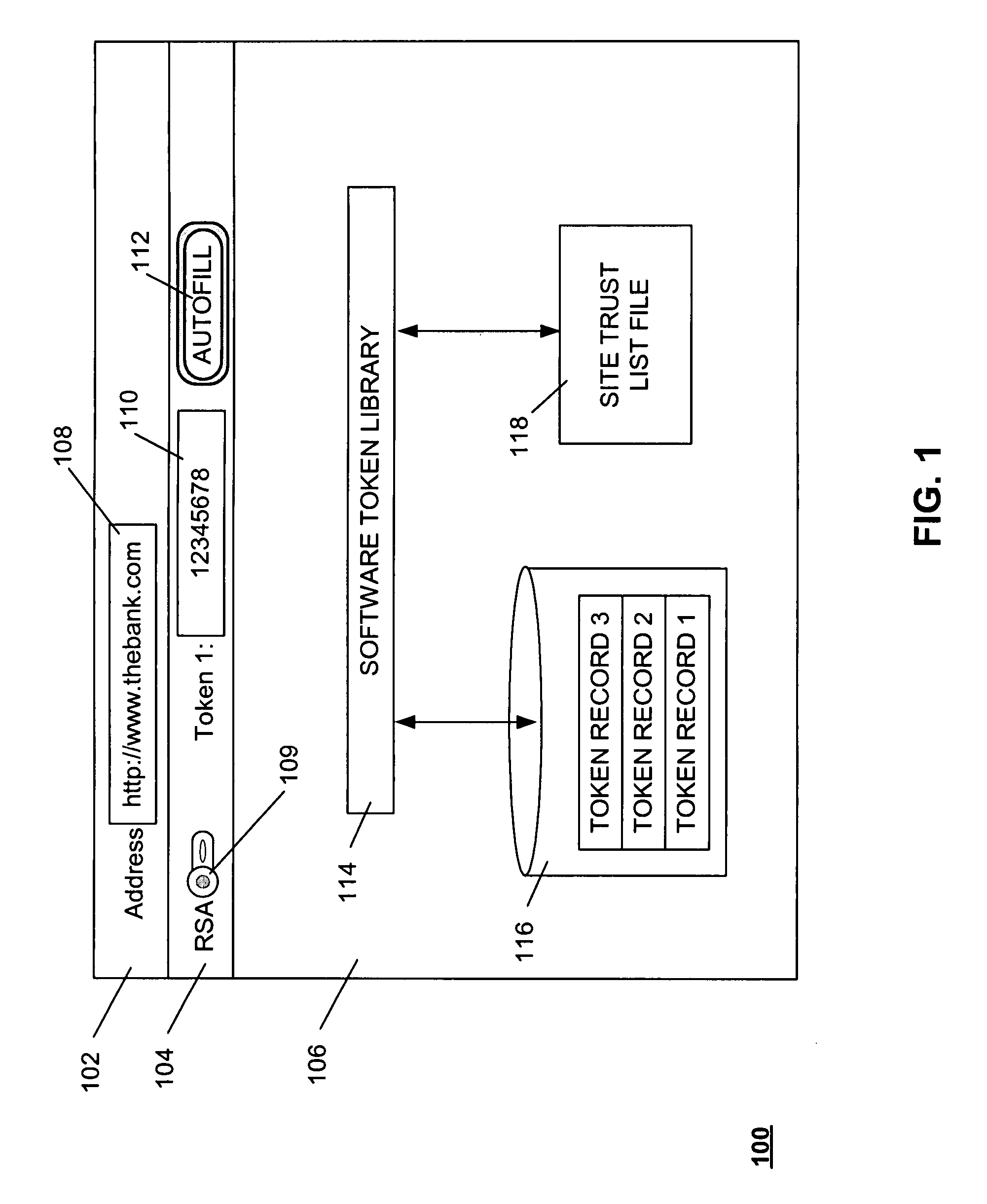
Method and system for providing a one time password to work in conjunction with a browser
ActiveUS20080028447A1Digital data processing detailsUser identity/authority verificationOne-time passwordAuthentication system
A method of submitting information as part of an authentication operation includes generating a one time password that is intended for use in an authentication operation. The method further includes providing the one time password in a display field, wherein the display field is adapted to work in conjunction with a browser to submit the one time password in response to a request for the one time password. A method of controlling submission of identity information within an authentication system includes receiving a trust list from the authentication system. The trust list identifies entities that are authorized to receive the identity information. The method further includes receiving a request to submit the identity information to a candidate entity for an authentication operation, and providing the identity information to the candidate entity if the trust list indicates that the candidate entity is authorized to receive the identity information.
Owner:EMC IP HLDG CO LLC
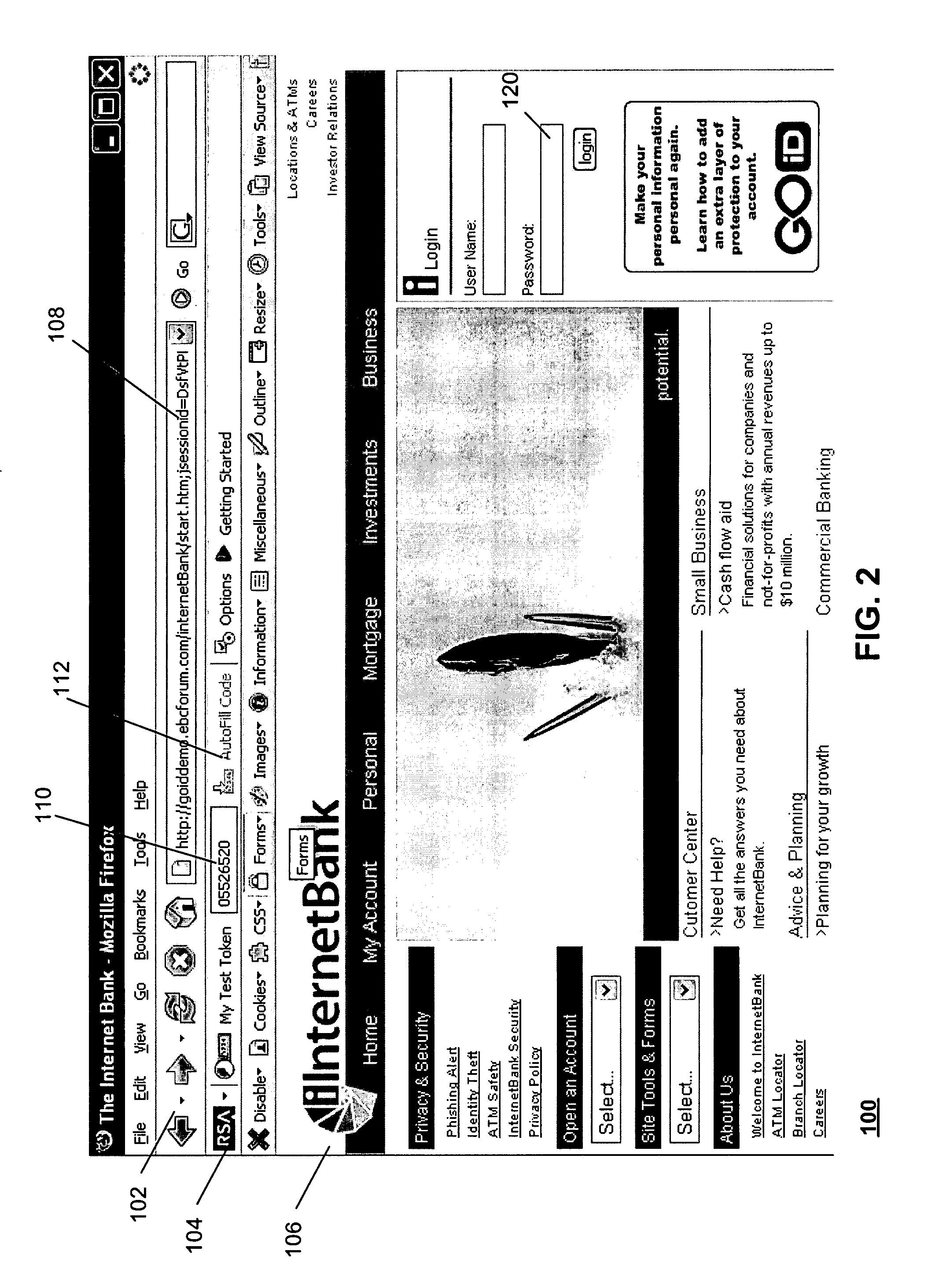
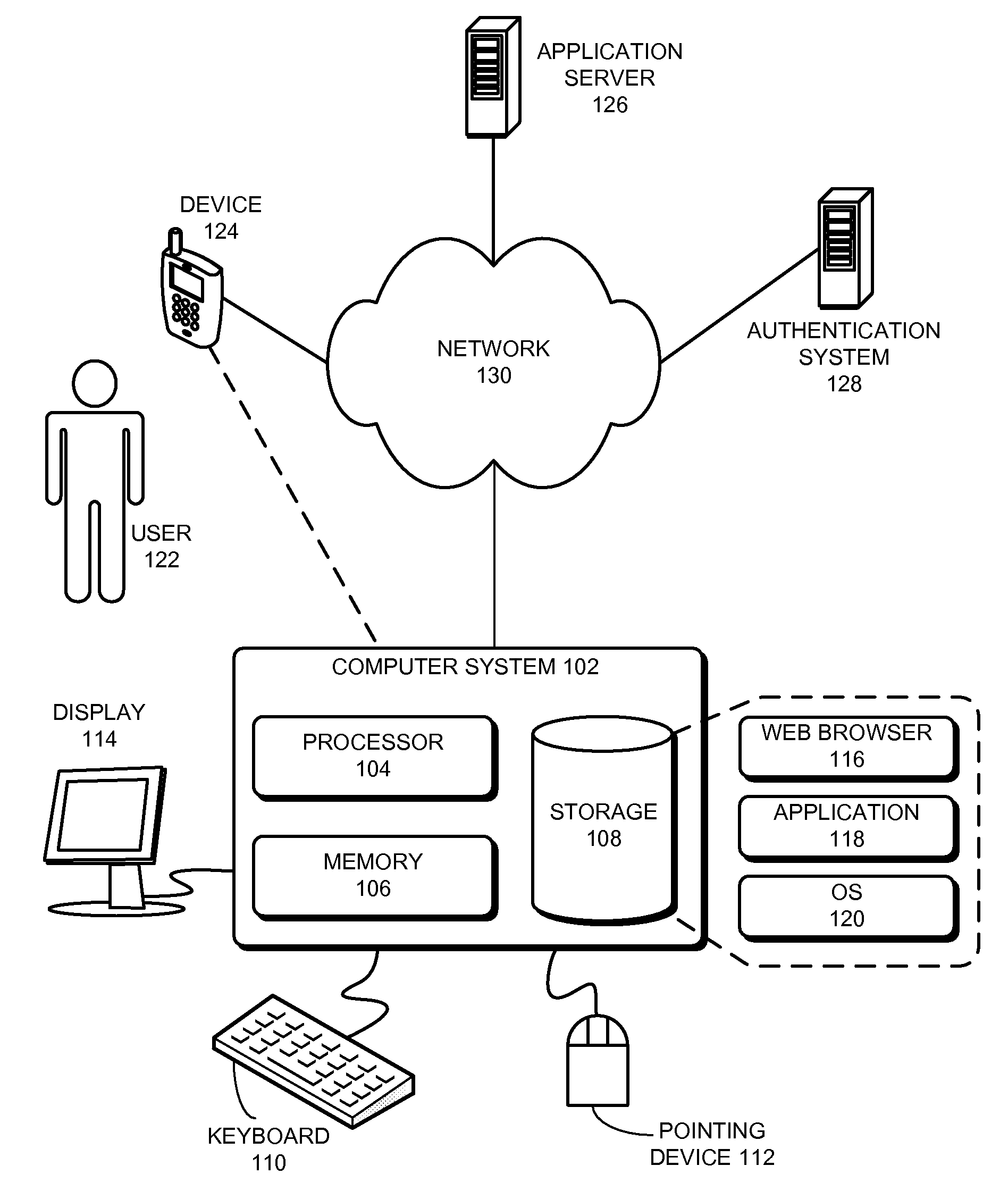
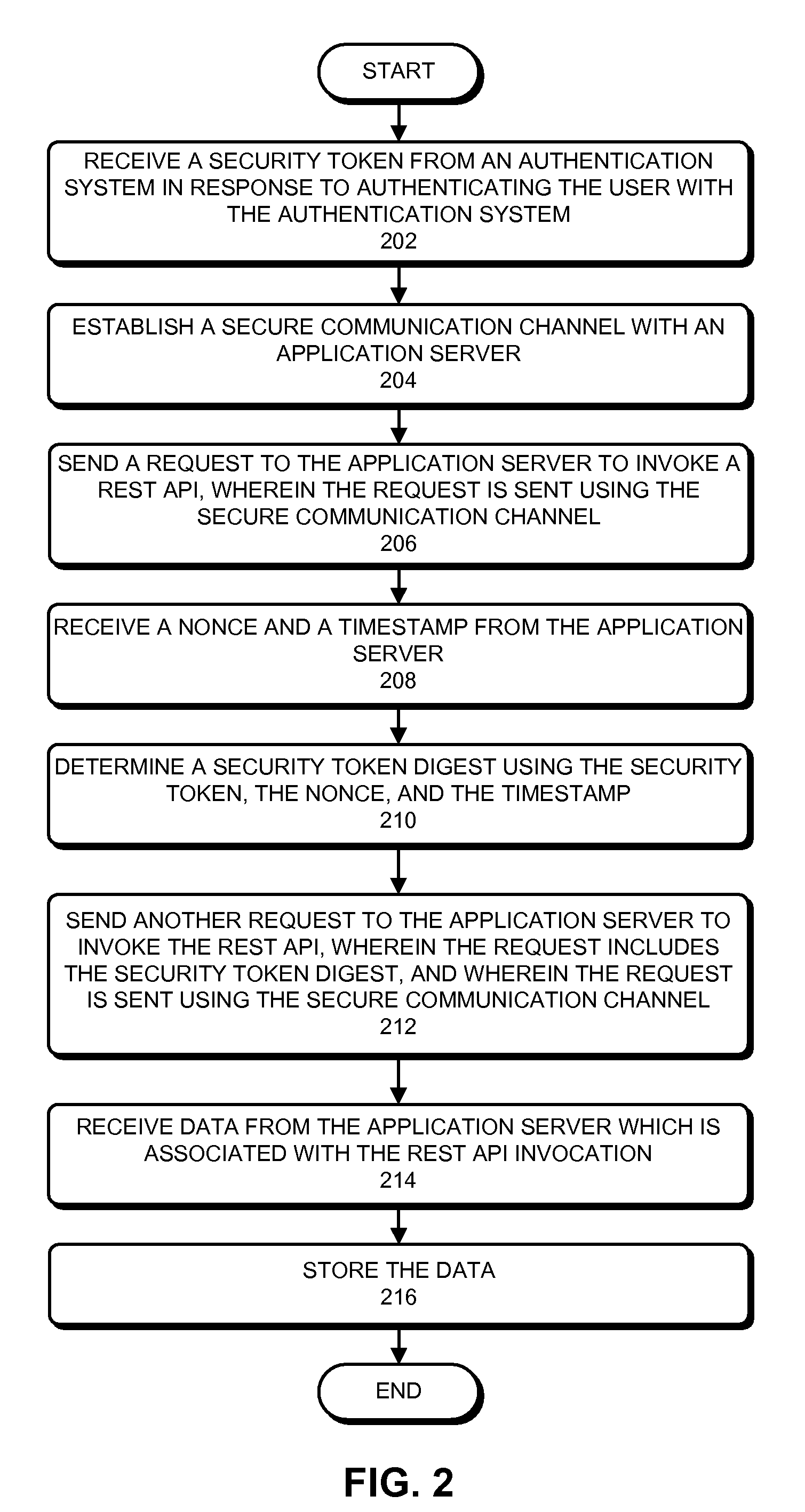
Method and apparatus for securely invoking a rest api
ActiveUS20090235349A1Web data retrievalDigital data processing detailsAuthentication systemClient-side
Owner:INTUIT INC
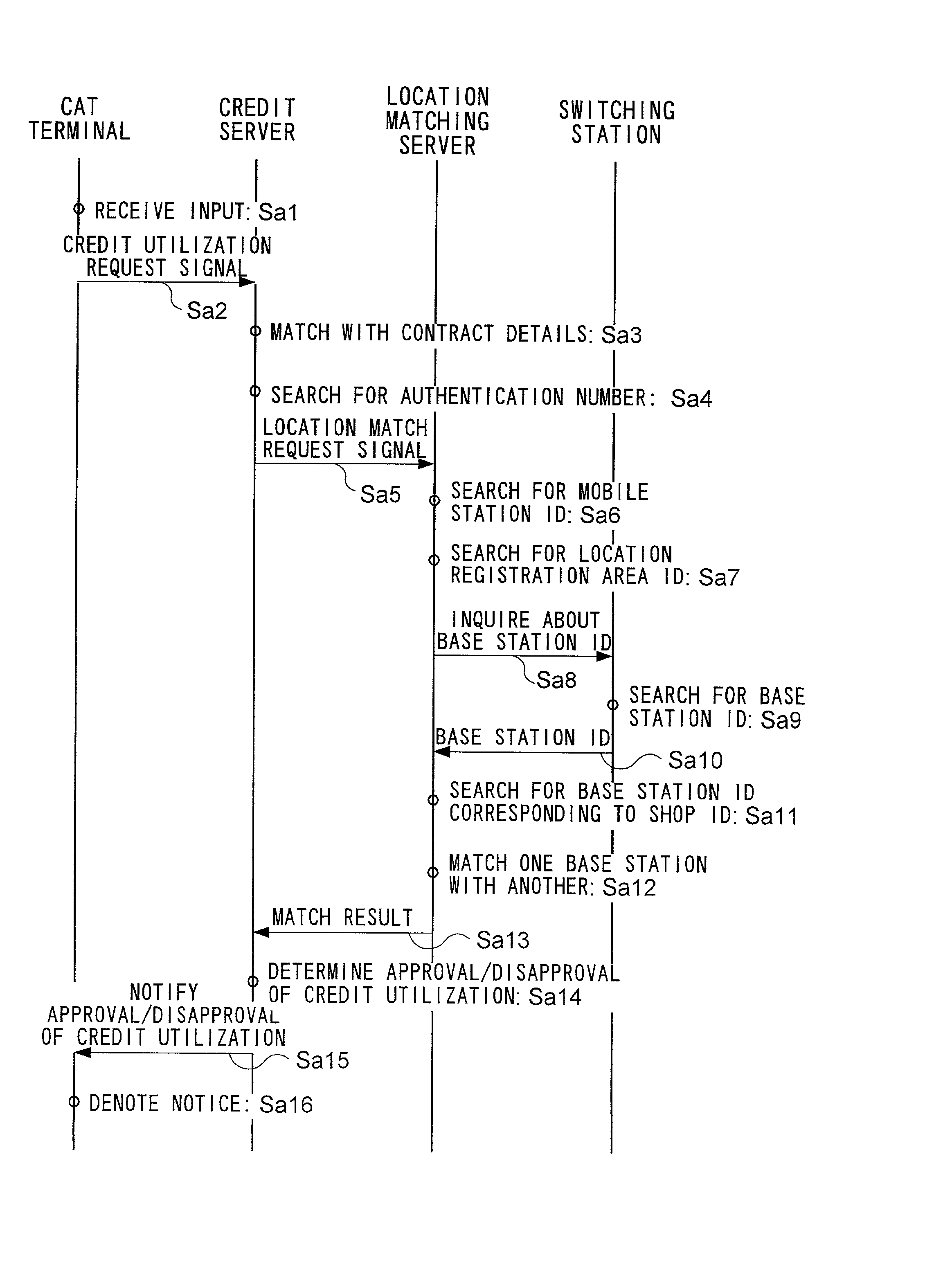
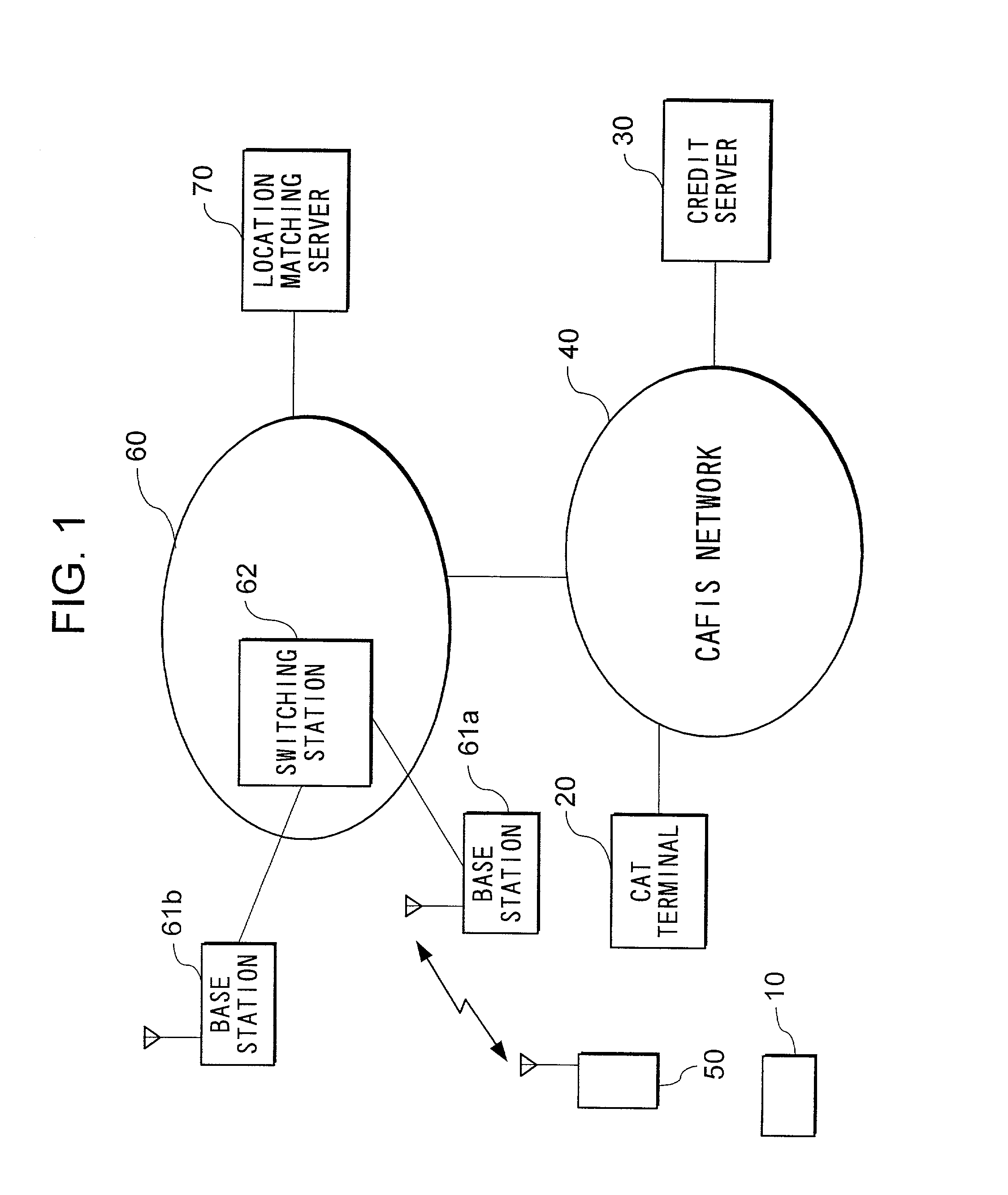
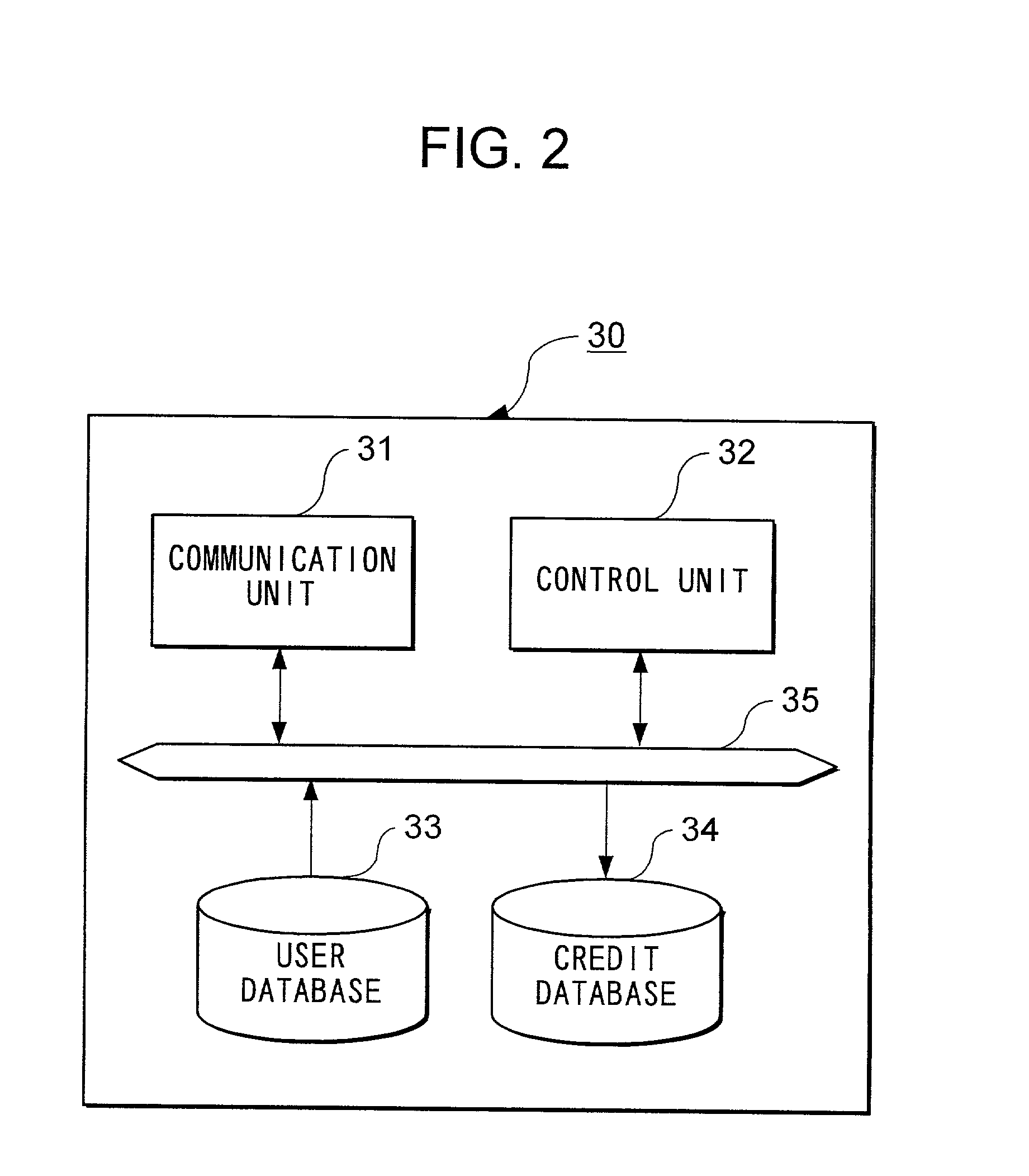
Authentication system and method
InactiveUS20020108062A1Reduce inconvenienceMaximize efficiencyDigital data processing detailsUser identity/authority verificationCredit cardMobile station
To utilize credit, a user possesses credit card 10 and mobile station 50. Location matching server 70 detects a location of mobile station 50 which a user possesses, and a shop which accepts credit utilized by the user. If these locations do not accord, it is judged that a user at a shop possesses credit card 10 but does not possess mobile station 50, and so is not the proper owner of credit card 10.
Owner:NTT DOCOMO INC
Secure wireless local area network
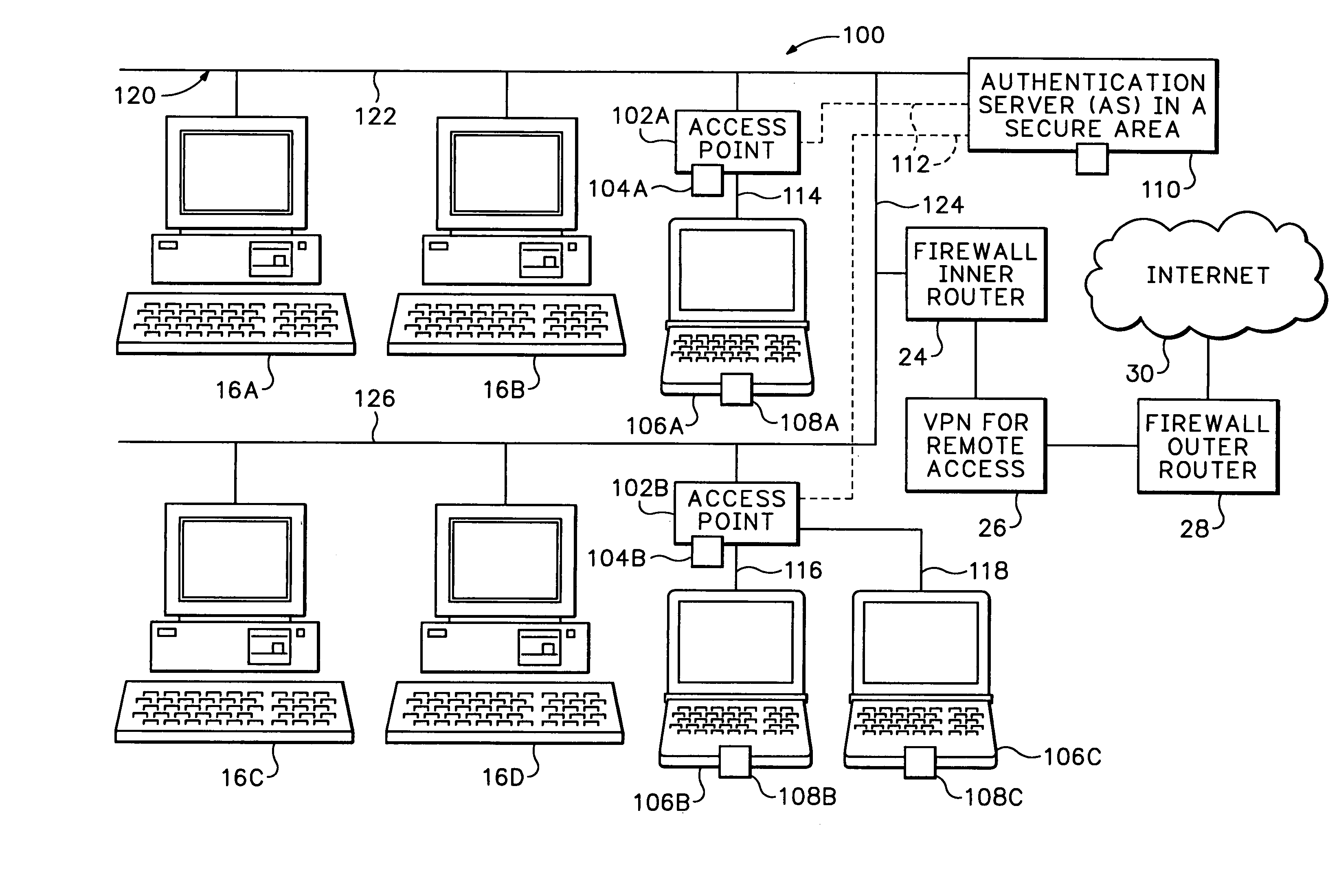
InactiveUS7174564B1Digital data processing detailsUser identity/authority verificationPasswordNetwork addressing
The secure wireless local area network of the present invention includes a single wired network that supports both wired and wireless devices. The network addresses security concerns by including an authentication server that services a plurality of access points. Each access point includes a first authentication device that generates and transmits a first authentication message to the corresponding wireless device over an air channel. The first authentication message includes encrypted validating information about the access point including an access point key that uniquely identifies the access point. Each wireless device includes a second authentication device. The wireless device receives the first authentication message and determines whether the access point is authorized to connect to the wired network. If the access point is valid, the second authentication device responds to the first authentication message by generating and transmitting a second authentication message to the access point. The second authentication message includes encrypted validating information about the wireless device and operator, e.g., a device key and the operator's logon name and password. The access point determines the authenticity of the wireless device by decrypting the portion of the second authentication message that includes the device key. If the wireless device is valid, the AP opens a control channel with the authentication server. The AP transmits the first and second authentication messages to the authentication server. If the authentication server validates the access point and the operator's logon name and password, it will authorize access to the wired network.
Owner:INTEL CORP
System, Method, and Apparatus for Preventing Identity Fraud Associated With Payment and Identity Cards
InactiveUS20070291995A1Easy and efficient to manufactureDurable and reliable constructionCharacter and pattern recognitionInternal/peripheral component protectionIdentity fraudDriver's license
The system, method, and apparatus of the present invention, address the problem of identity theft associated with the use of payment cards such as credit and debit cards, as well as identity theft associated with the use of identity cards such as driver's licenses and social security cards. An apparatus including a biometric input component that authenticates a system user is disclosed herein. Upon authentication, a proxy account number and a time varying security code are generated and displayed on the apparatus. The dynamically generated number and security code are then used to validate the user's identity within the system. Furthermore, the system, method, and apparatus of the present invention can be used to consolidate into one instrument, several payment and identity instruments.
Owner:RIVERA PAUL G
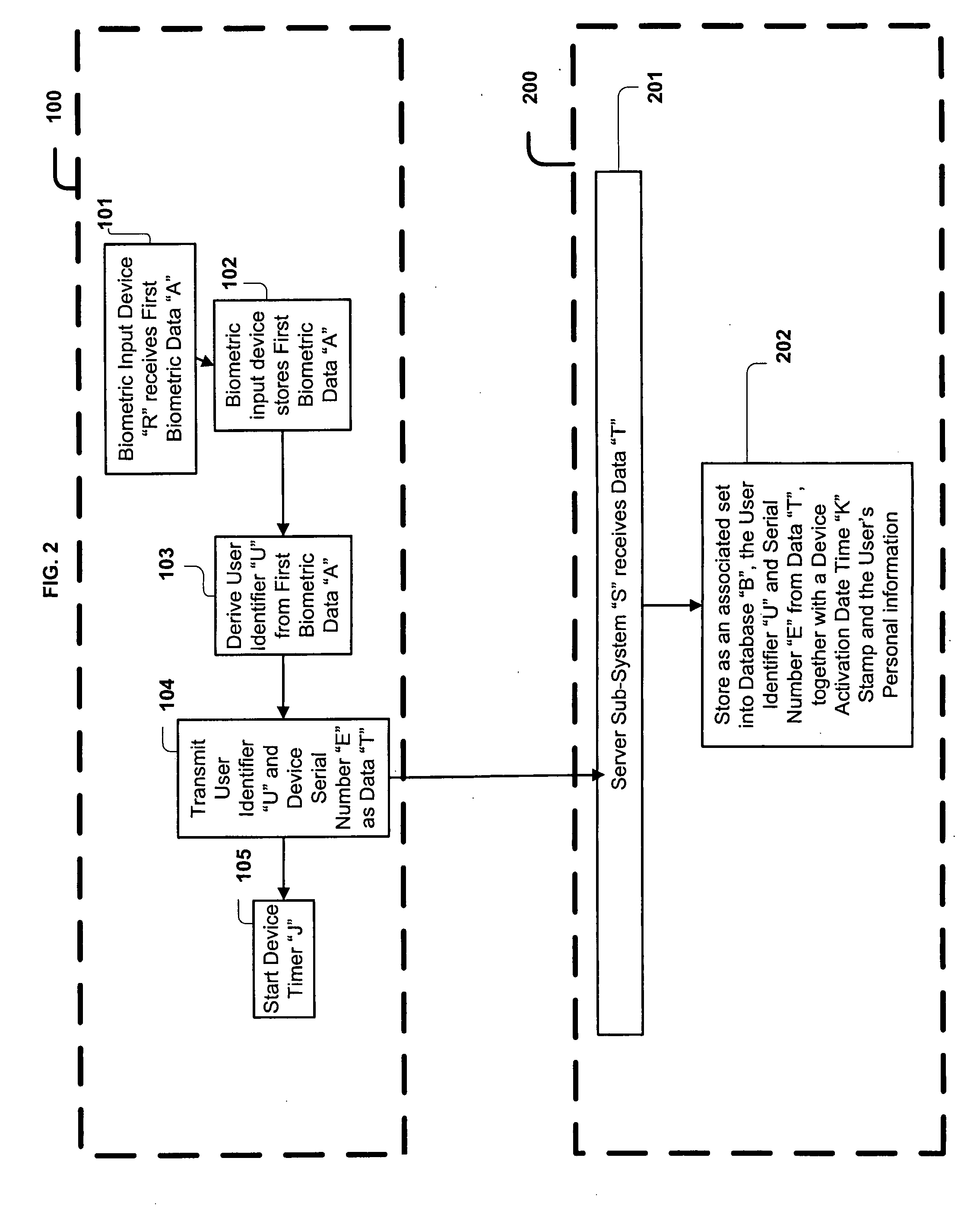
Automated banking machine component authentication system and method
ActiveUS7121460B1Increased resistenceAvoid modificationComplete banking machinesAcutation objectsComputer hardwareAuthentication system
An automated banking machine is provided which includes a first component and a second component. The first component is operative generate a first hash of a first identity data and a public key associated with the second component. The first component is operative to encrypt a randomly generated secret key using the public key associated with the second component. The second component is operative to receive at least one message from the first component which includes the encrypted secret key and the first hash. The second component is operative to decrypt the secret key with a private key that corresponds to the public key. The second component is operative to permit information associated with a transaction function to be communicated between the first and second components which is encrypted with the secret key when the first hash is determined by the second component to correspond to the first component.
Owner:DIEBOLD SELF SERVICE SYST DIV OF DIEBOLD NIXDORF INC
Biometric Identity Verification System and Method
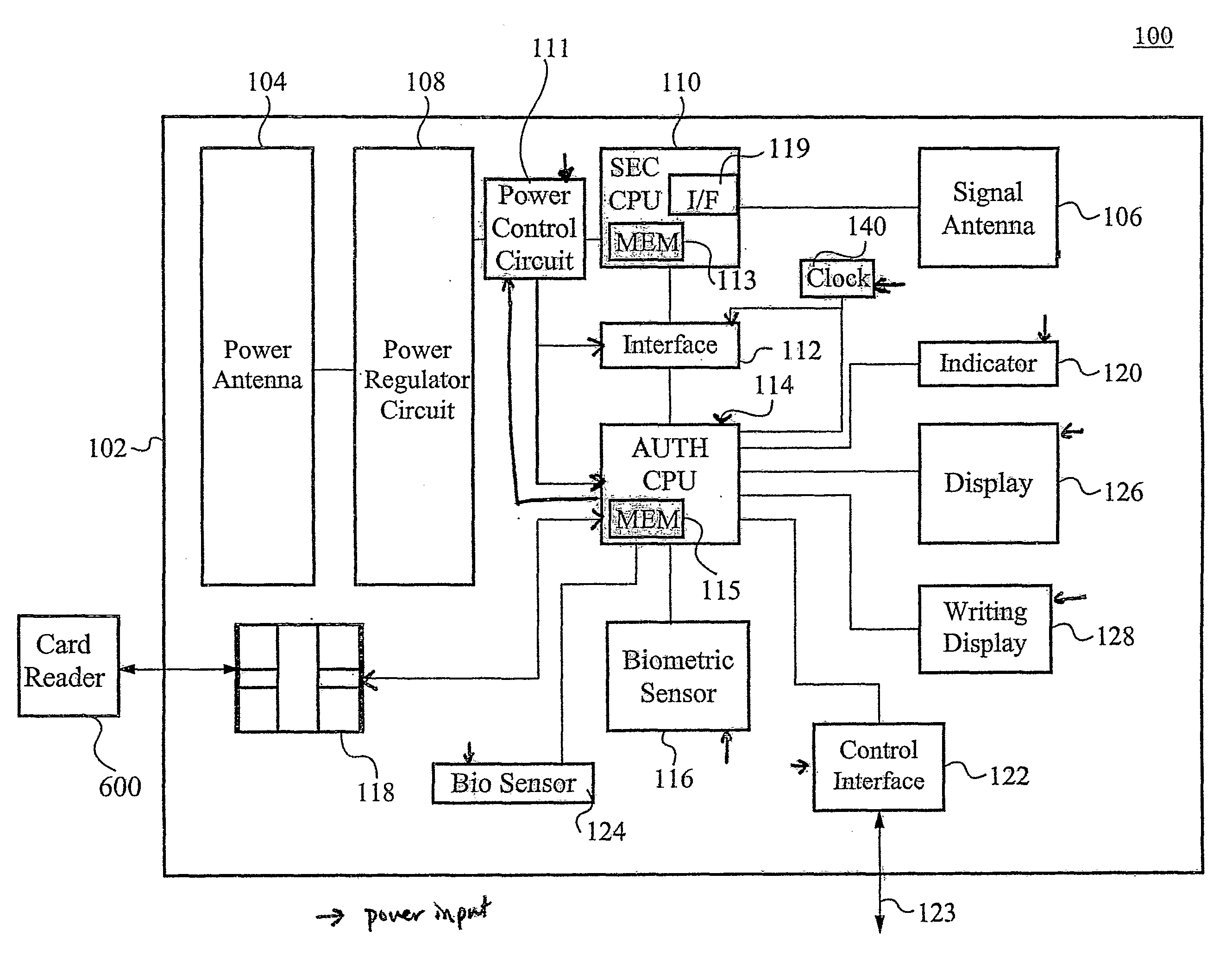
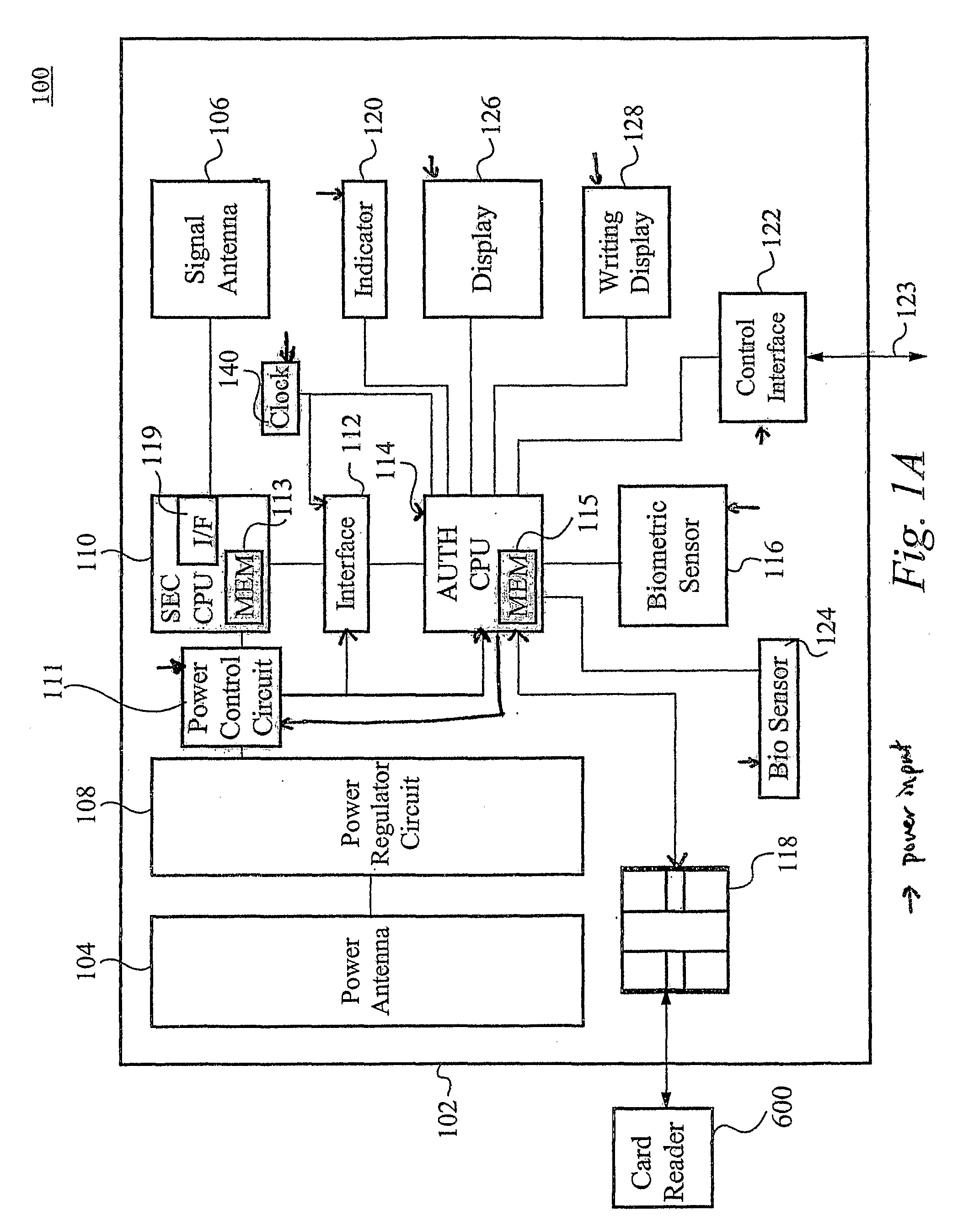
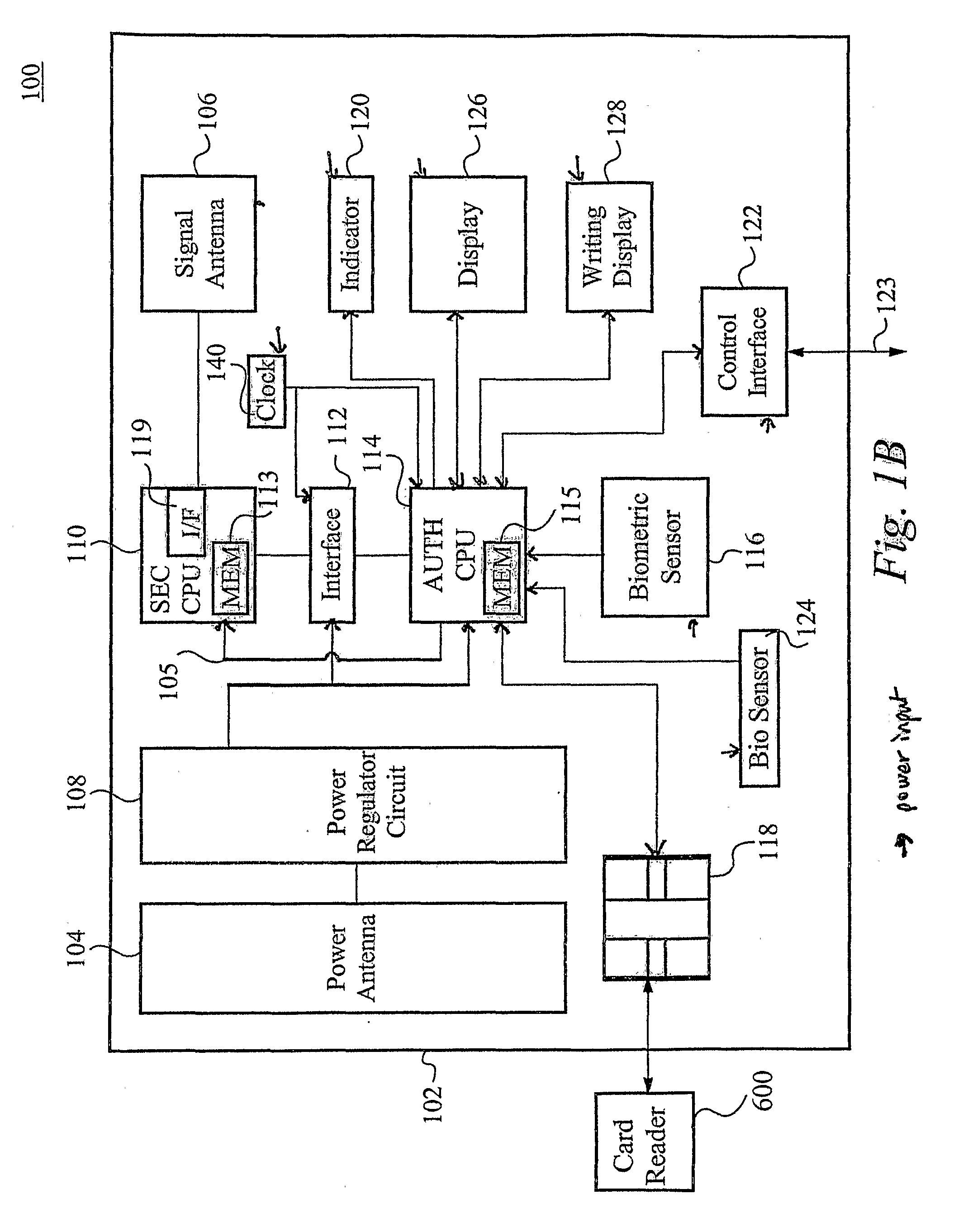
A card authenticates a cardholder. The card includes a substrate, a sensor module, a wireless transceiver module, and a power circuit. The sensor module includes (a) a biometric sensor adapted to detect biometric information from a person's body, (b) a processor unit adapted to authenticate the person in response to the detected biometric information and generate an authentication signal representing an authentication result, and (c) a memory adapted to store biometric information of a specific individual associated with the card. The wireless transceiver module transmits signals received from the processor unit and receives a wirelessly-transmitted power signal. The power circuit generates at least one supply voltage from the received power signal and provides the supply voltage to the sensor module. An electronic passport is embedded with the card, and a terminal module is used for wirelessly transmitting power to and receiving signals from the electronic passport.
Owner:IVI HLDG
Authentication card system
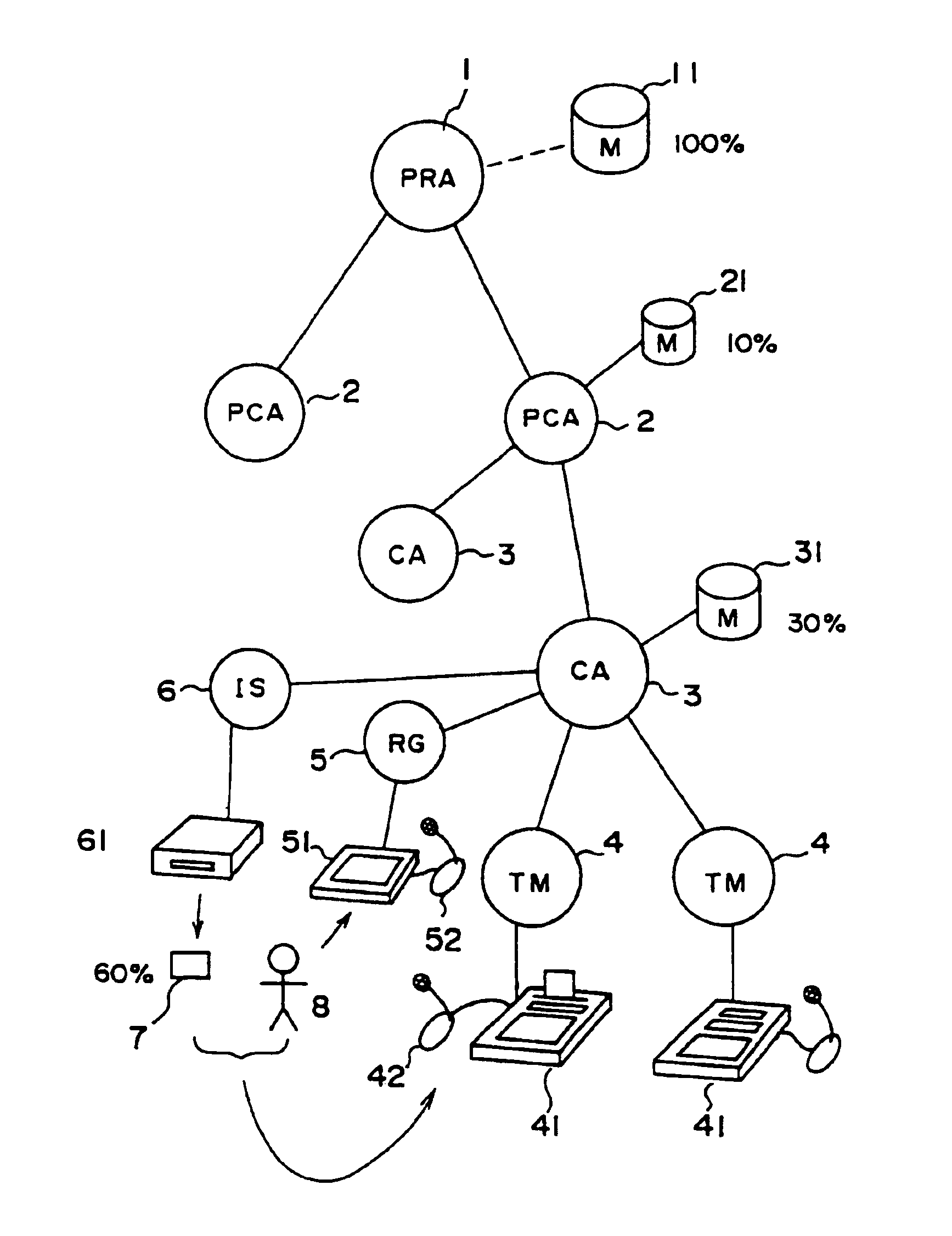
InactiveUS6990588B1Recognizable more easily and securelyUser identity/authority verificationCo-operative working arrangementsComputer terminalUser authentication
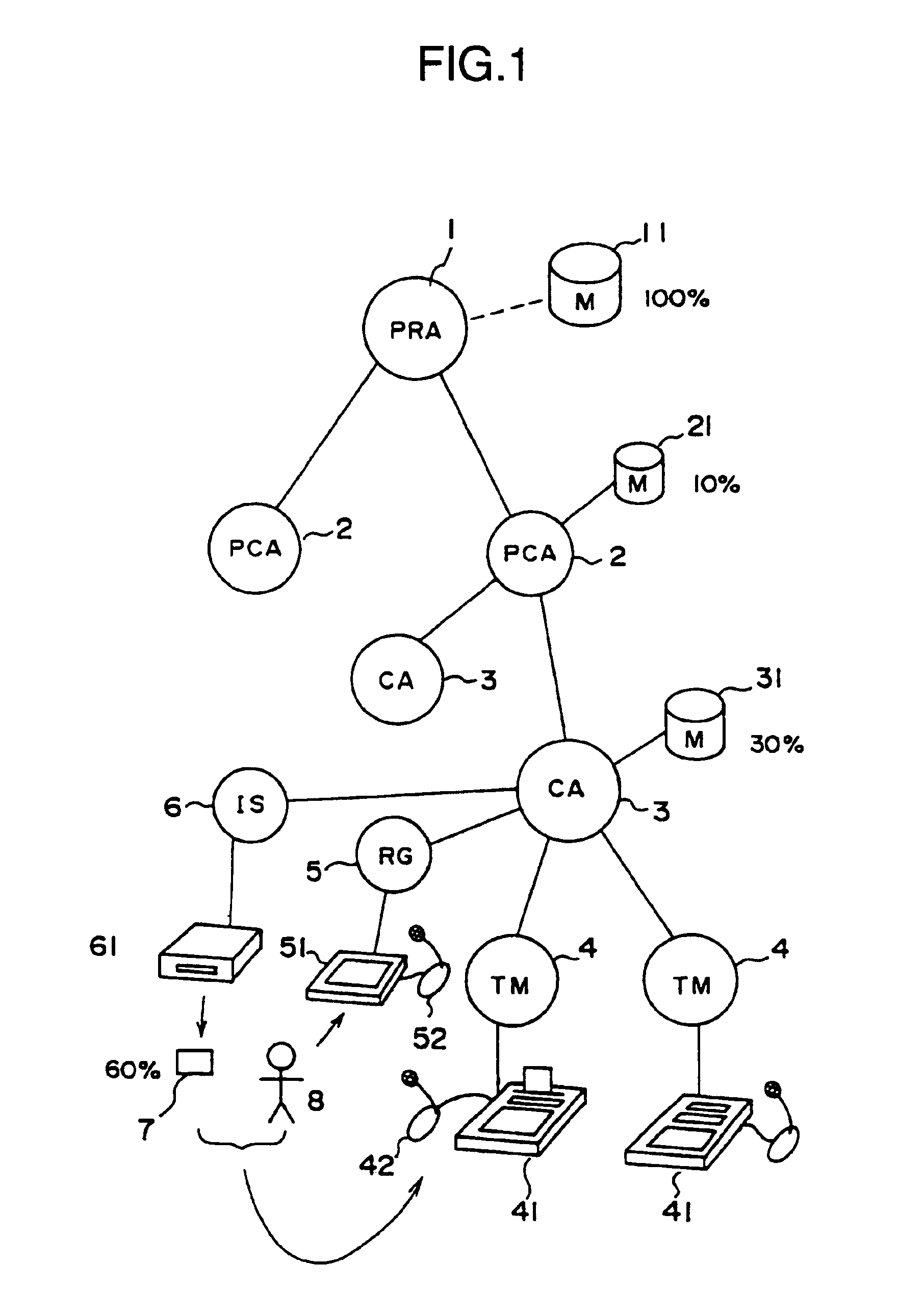
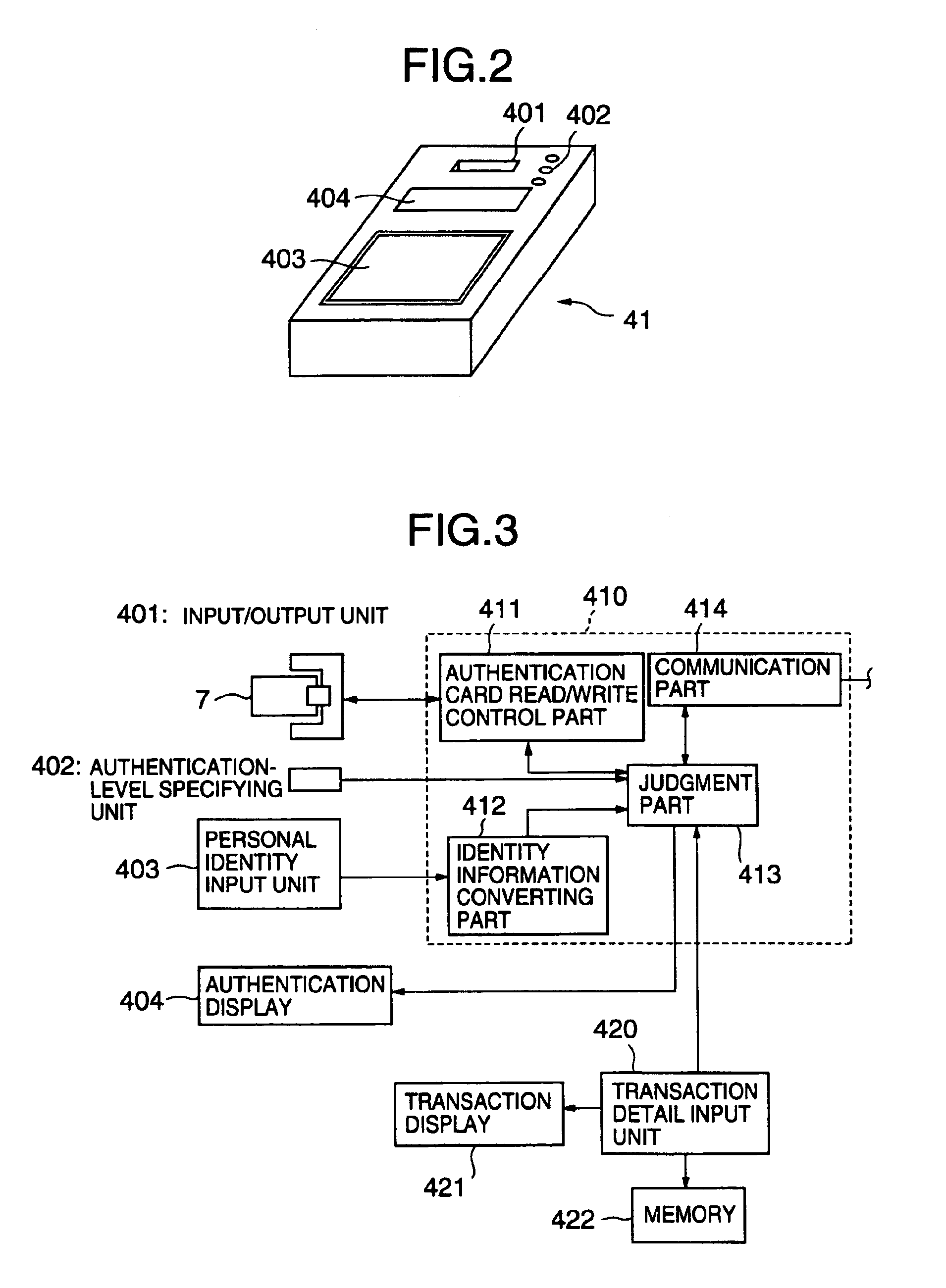
Biological individuality data for use in distinguishing the individuality of a user (8) are picked up, and a user authentication card (7) with at least part of the biological individuality data recorded thereon is issued. The contents of the record in the user authentication card (7) are read out by an authentication-card reader (41), and compared with biological individuality data input by the user through an identity acquisition device. Such personal authentication is directly executed at an authentication access terminal (4). The system also includes certification authorities (2), (3), each of which records part of the biological individuality data so that the certification authorities can additionally authenticate personal identification in response to inquiry from the authentication access terminal (4), thus improving the reliability. The authentication IC card used in the system is provided with a CPU, an authentication file storing identity information, and an application file classified into files according to the depth of authentication.
Owner:YASUKURA YUTAKA
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com