Patents
Literature
1420 results about "Data Web" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Data Web is a government open source project that was started in 1995 to develop open source framework that networks distributed statistical databases together into a seamless unified virtual data warehouse. Originally funded by the U.S. Census Bureau, with participation at various times by the Bureau of Labor Statistics, the Centers for Disease Control, Harvard University and other non-profits. The software provides an open source service-oriented architecture that pulls data from different data base structures and vendors that normalizes it into a standard stream of data. The normalized stream is intelligent and supports standard transformations, has the intelligence to understand how to geographically map itself correctly using the correct vintage of political geography, understands standard code-sets so that data can be combined in statistical appropriate ways, understands how weight survey data appropriately, understands variance and other appropriate statistical behaviors. The DataWeb network handles small data sets and very large datasets; including of course the Census.
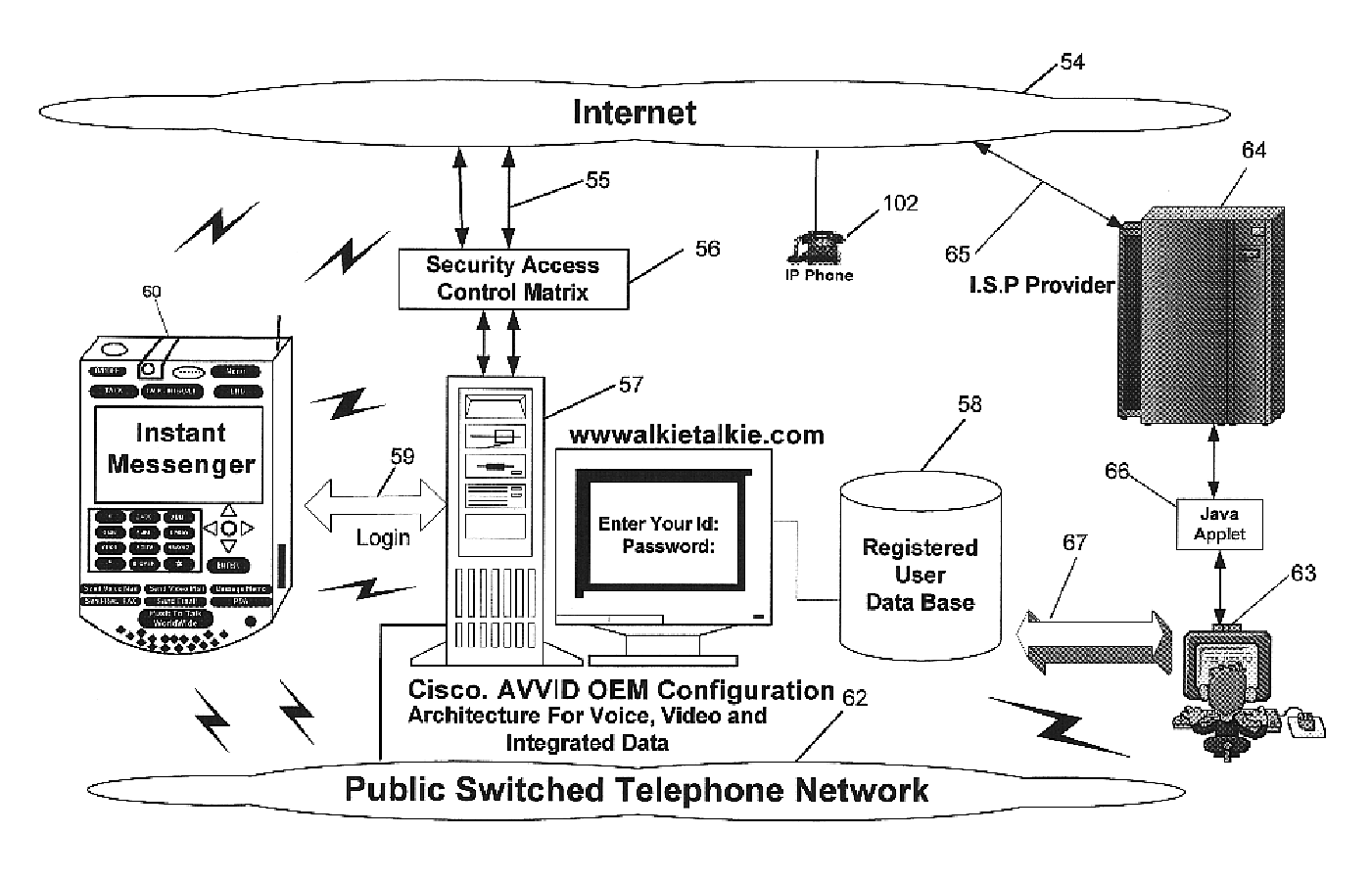
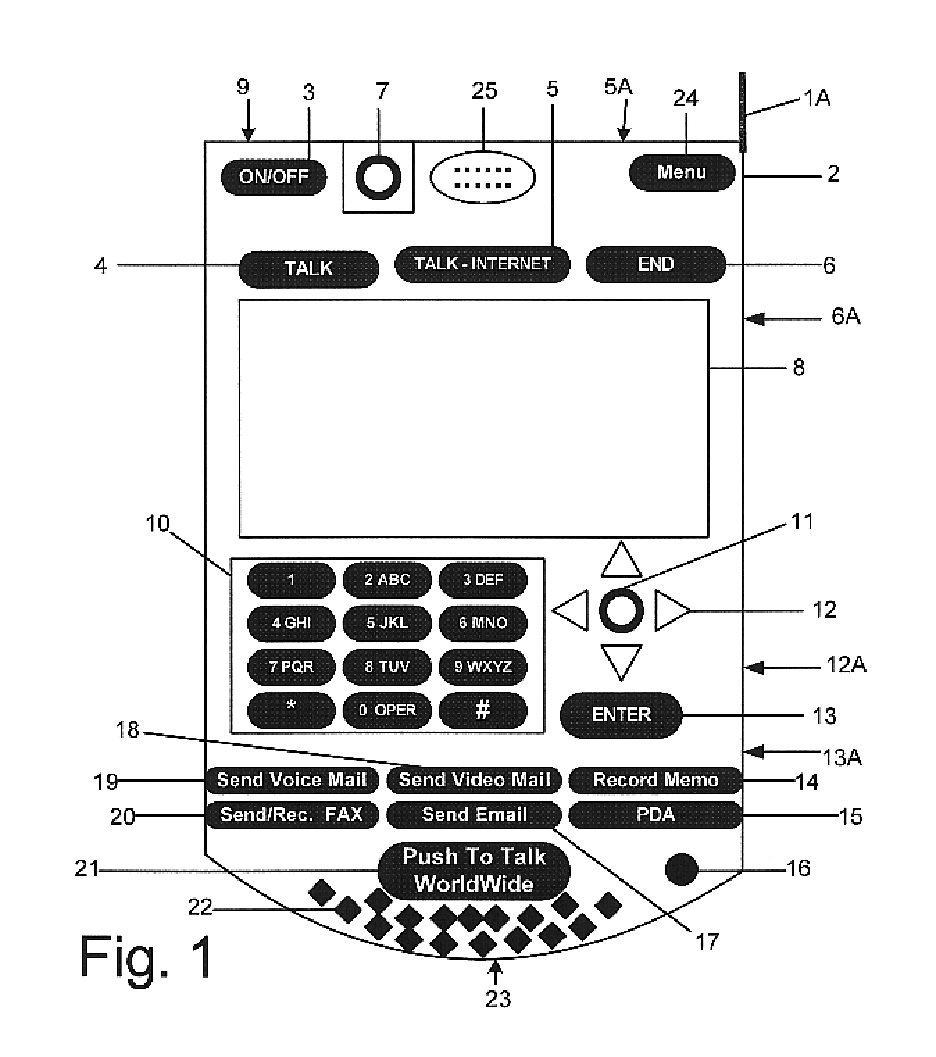
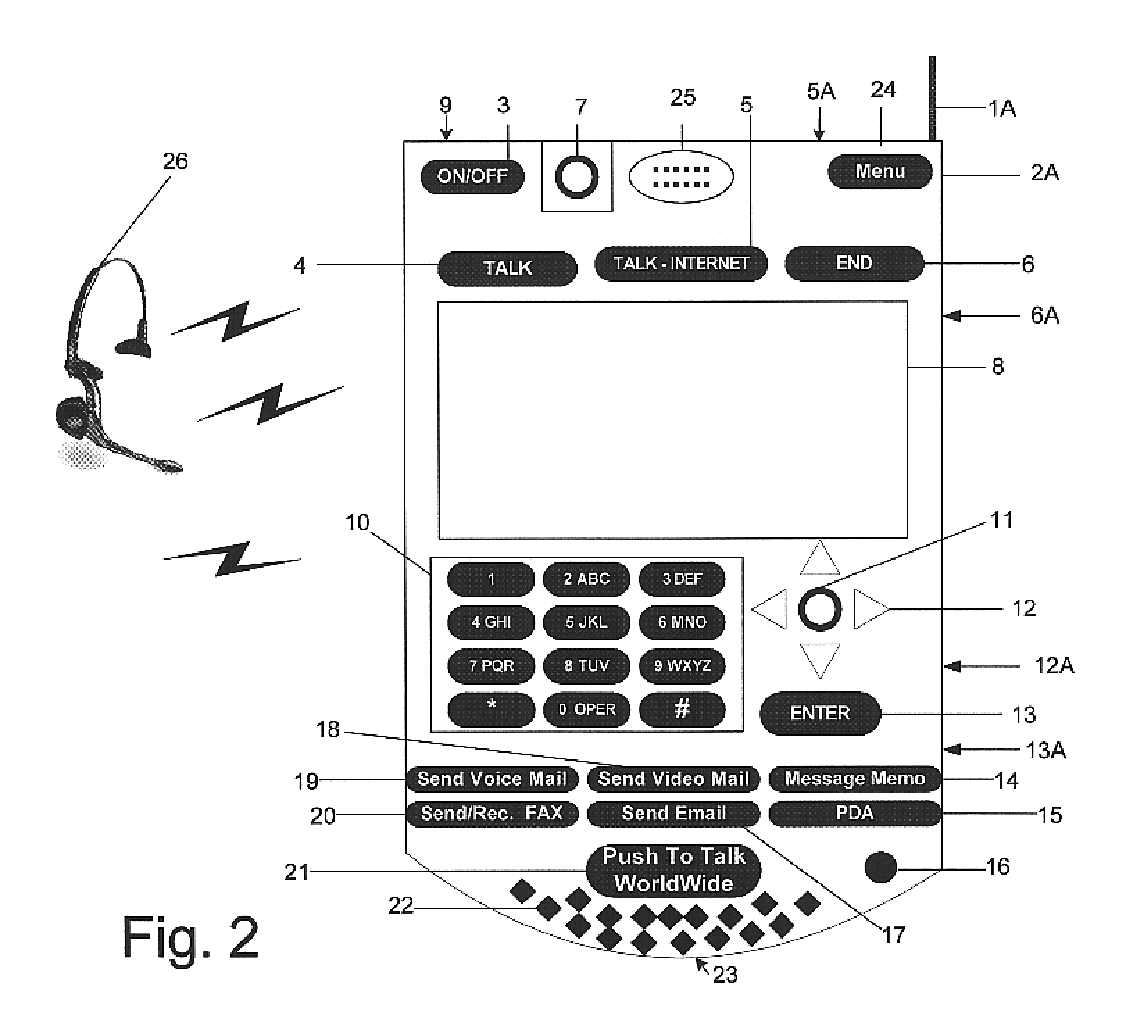
Multifunctional world wide walkie talkie, a tri-frequency cellular-satellite wireless instant messenger computer and network for establishing global wireless volp quality of service (QOS) communications, unified messaging, and video conferencing via the internet
InactiveUS6763226B1High quality voice and data communicationMinimal costCordless telephonesInterconnection arrangementsQuality of serviceMass storage
World-Wide-Walkie-Talkie, a high speed multifunction interstellar wireless computer / instant messenger communicator, Personal Digital Assistant (PDA), coupled with a resilient, robust, VoIP data network and internet server method, deploying multiple wireless networks and protocols such as Voice Over IP, GPRS, WAP, Bluetooth, PCS, I-Mode, comprising a high speed Intel Pentium 4 Mobile(TM) or compatible Processor, to formulate a internet gateway system (99) and network bridge (150) for establishing instant low cost, real time global communications to the Public Switched Telephone Network via the internet (54). A PUSH-TO-TALK-WORLDWIDE button (21) instantly initiates global bisynchronous communications, or videoconferencing sessions. Fax, VideoMail, and unified messaging services are immediately available. GPS and mass memory provides global navigational tracking and data storage. Internet users, telephones, and cellular / satellite phone users can intercommunicate with the invention via VoIP / IM services. The invention provides uniformed global wireless communications, eliminates traditional long distance costs, and operates anywhere on earth.
Owner:COMP SCI CENT
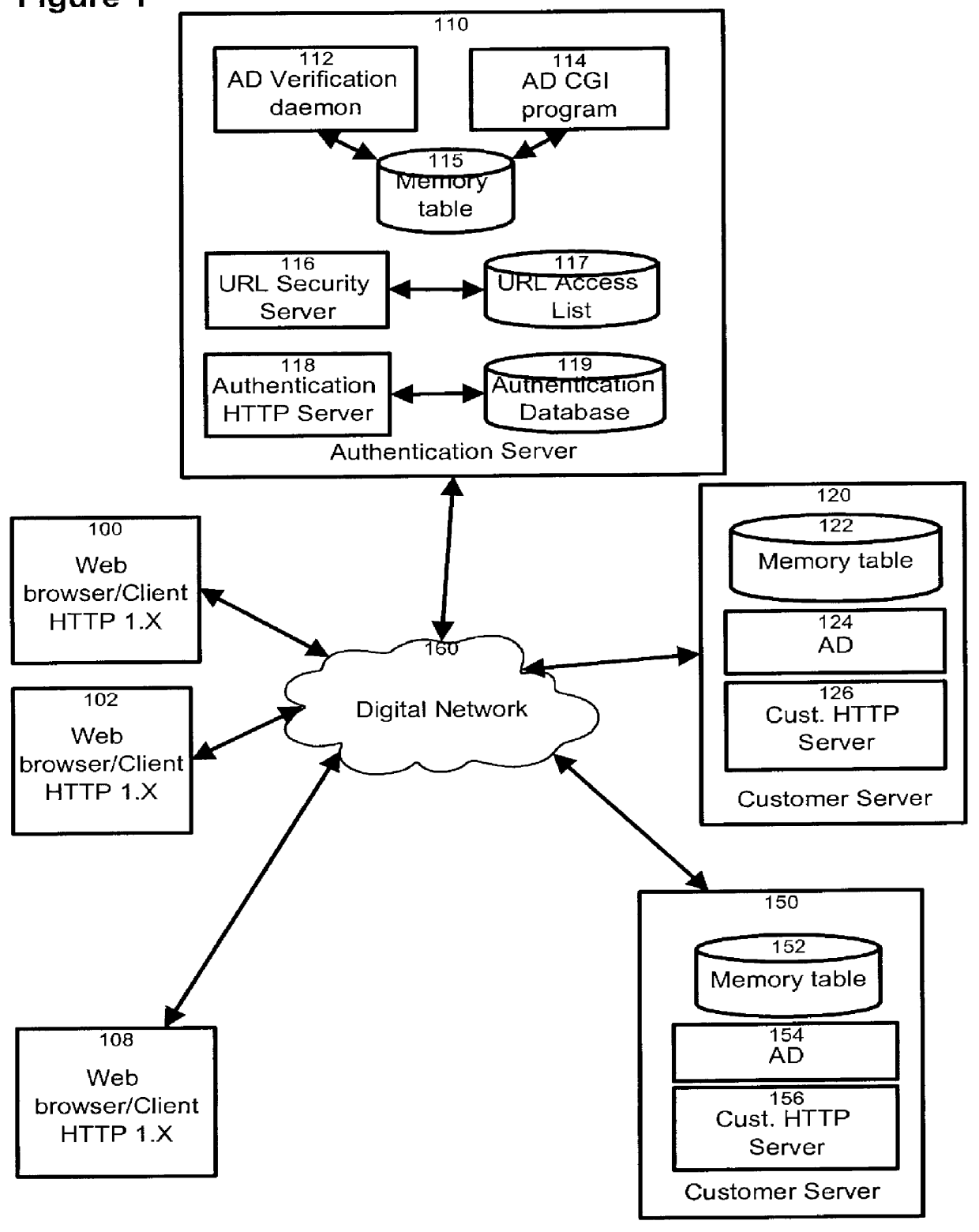
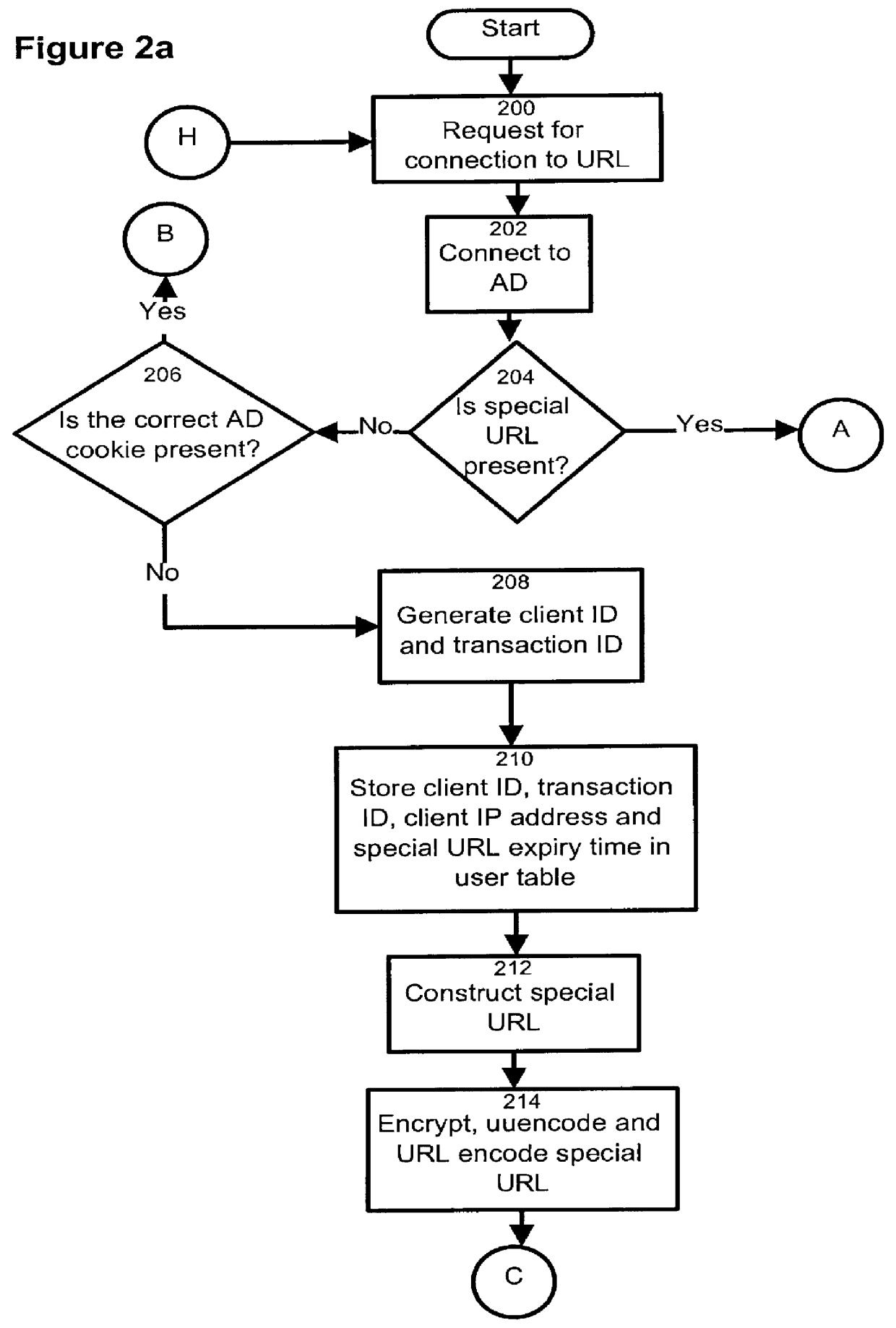
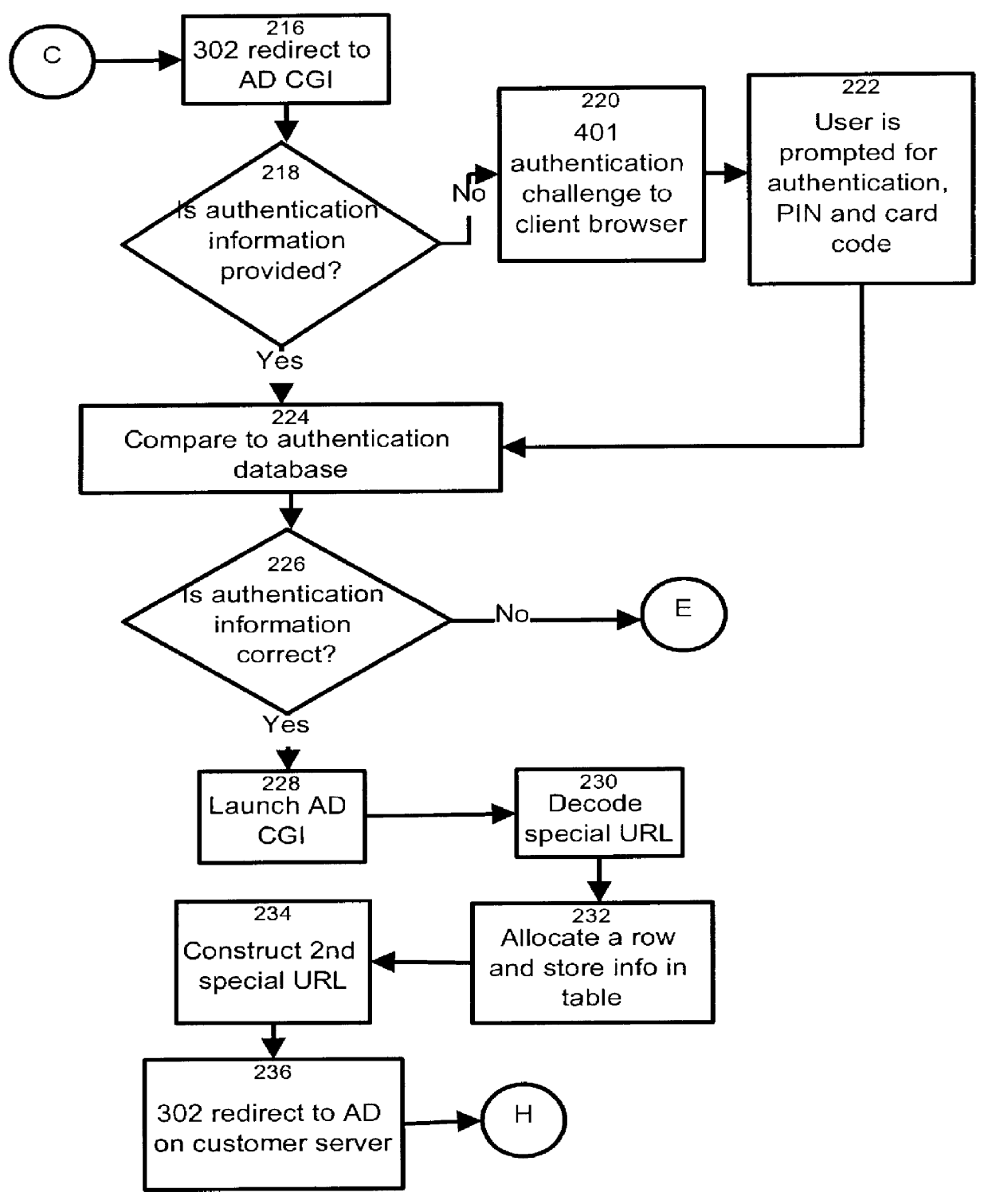
HTTP distributed remote user authentication system
InactiveUS6092196AExemption stepsAvoid necessityDigital data processing detailsUser identity/authority verificationUser authenticationUser identifier
The present invention relates to the field of data and computer network security. Data and computer network security is of the utmost importance to most organizations that possess such networks. One of the difficulties that users and managers of these networks face is that the users have to provide a user ID and password every time they wish to access one of the organization's secured HTTP servers or URLs. This creates a problem for users and managers since lists of numerous user IDs and passwords need to be maintained and therefore can easily be lost or their confidentiality compromised. This invention addresses these problems by providing a transparent, scalable, single point of authentication for remote users across any number of HTTP servers anywhere on a data network, such as an Intranet, using any user ID and password scheme implemented by a main authentication HTTP server.
Owner:RPX CLEARINGHOUSE
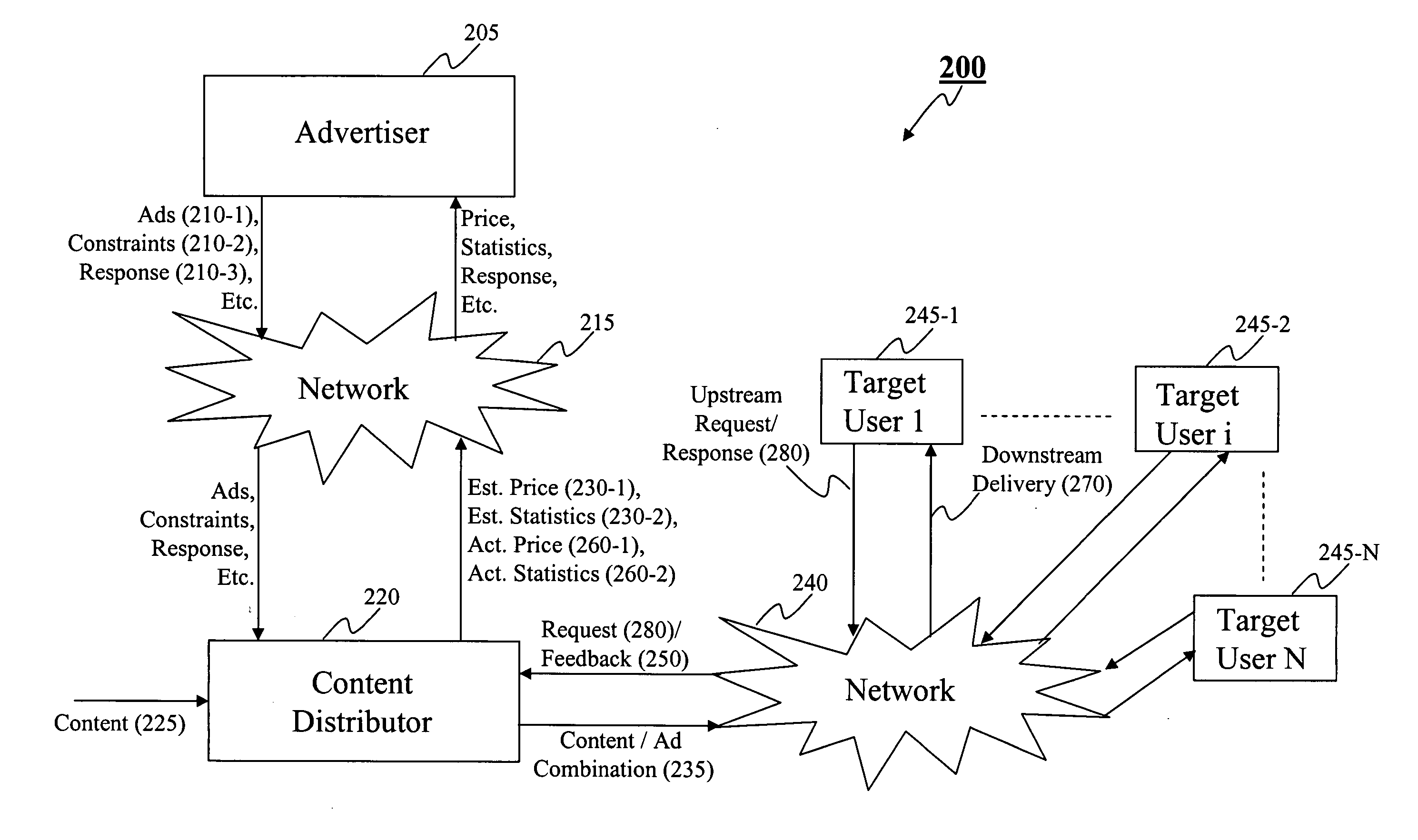
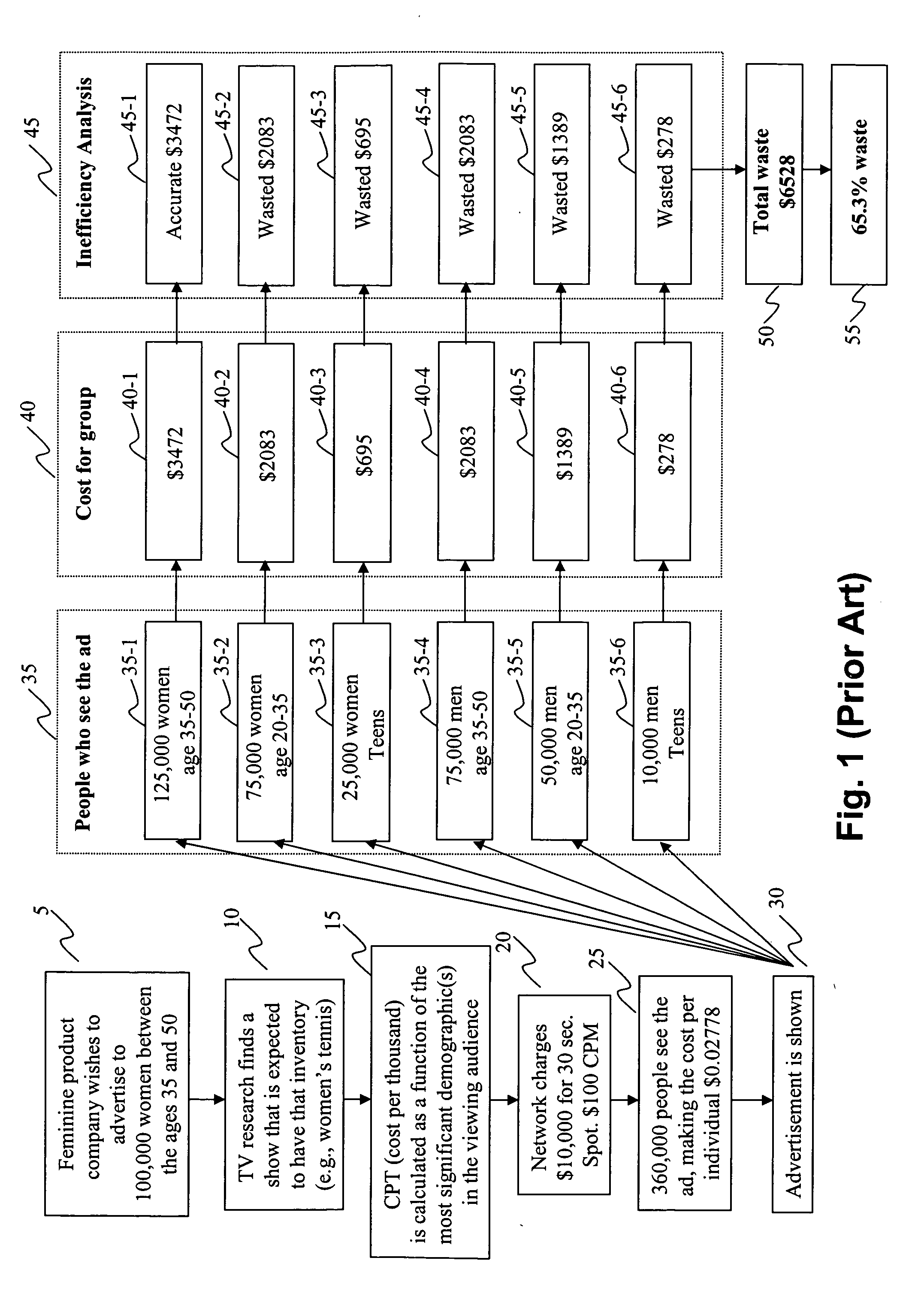
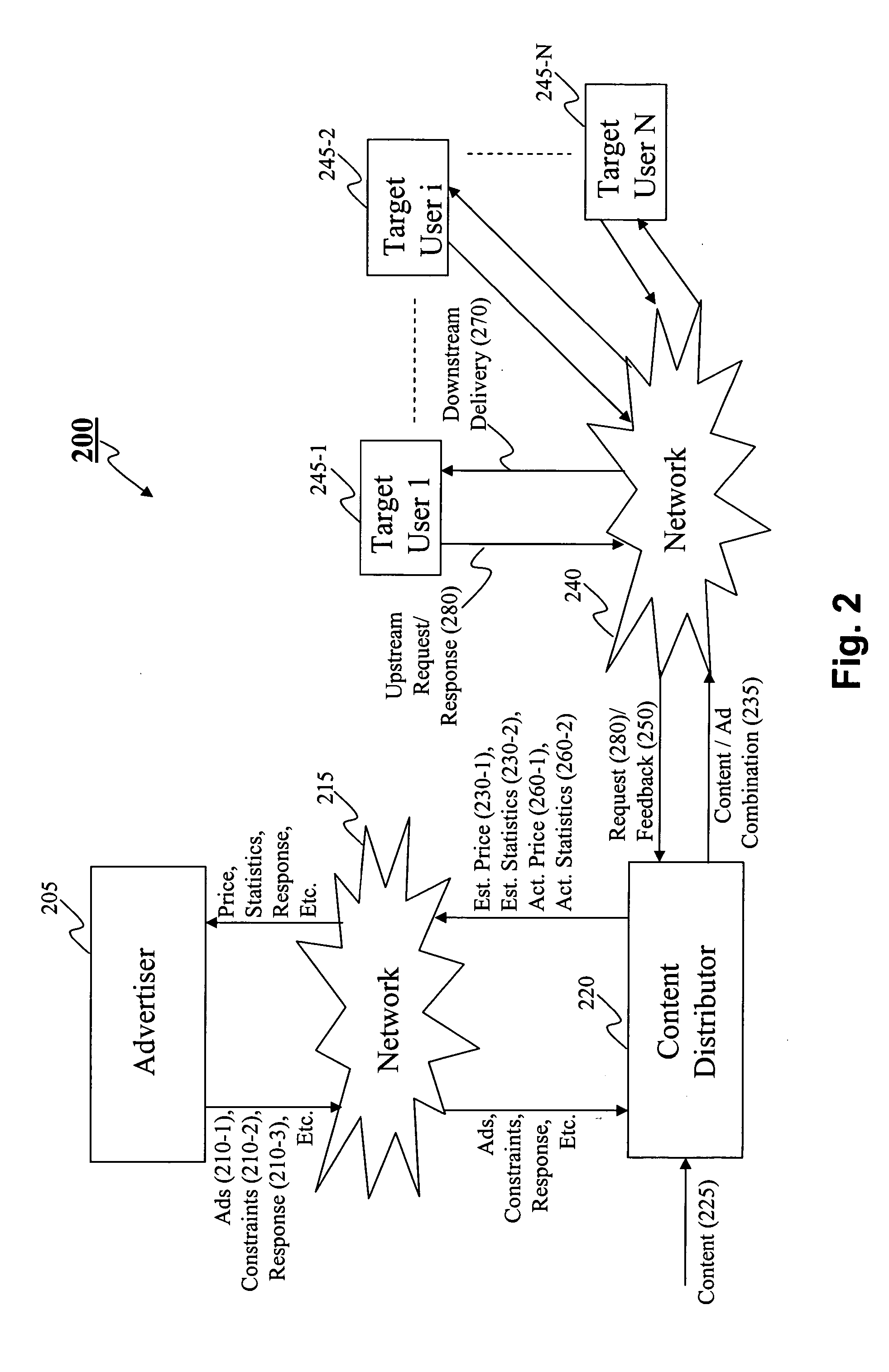
Method and system for advertising over a data network
A method and system for statistics-based individualized advertising over a network in which an advertiser provides to a content distributor one or more constraints defining the characteristics of desired target users and the manner by which the advertisement is to be delivered. The content distributor determines an estimated price based on statistics computed based on target users selected and the advertising periods allocated based on the constraints and individualized content delivery.
Owner:INDIVIDUAL NETWORK INC
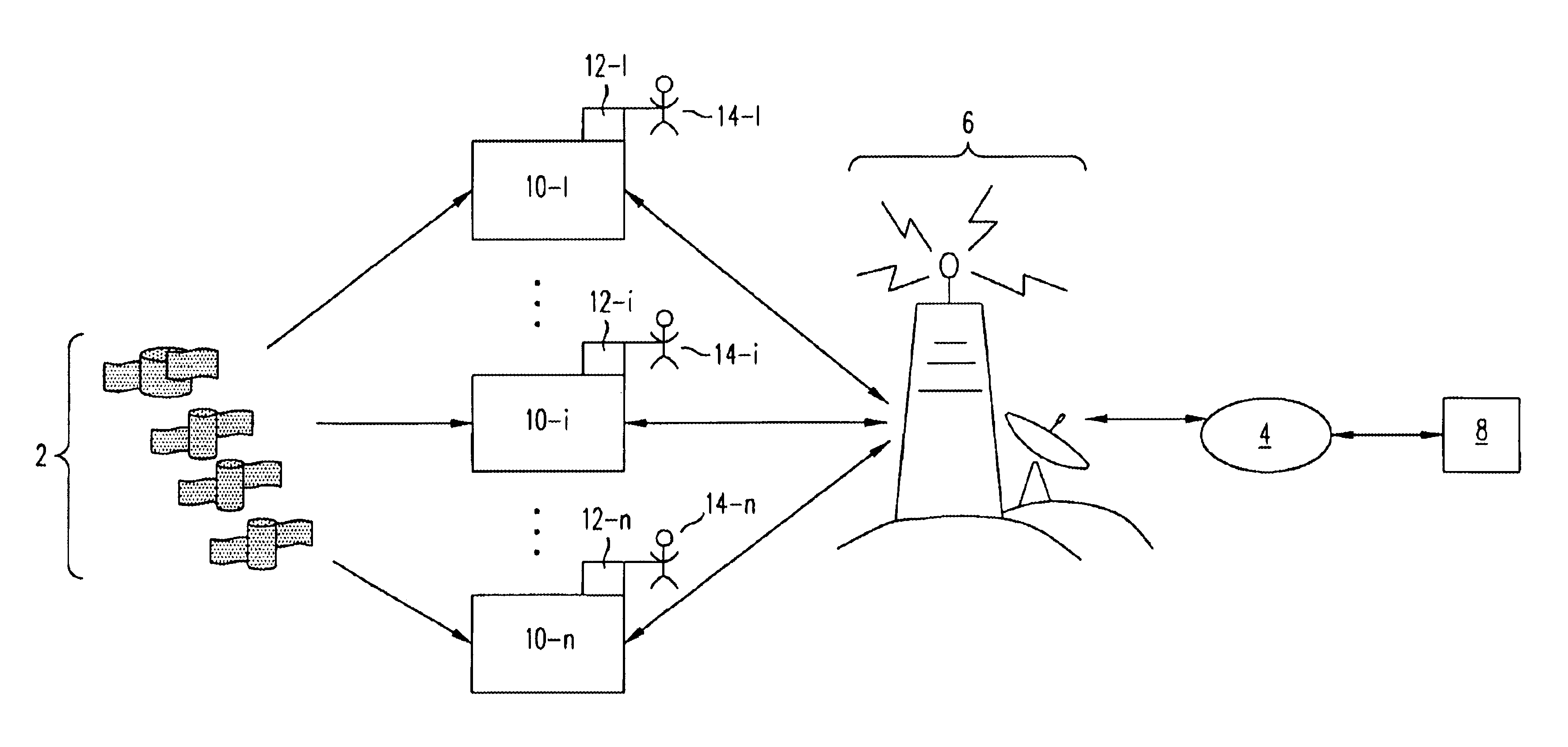
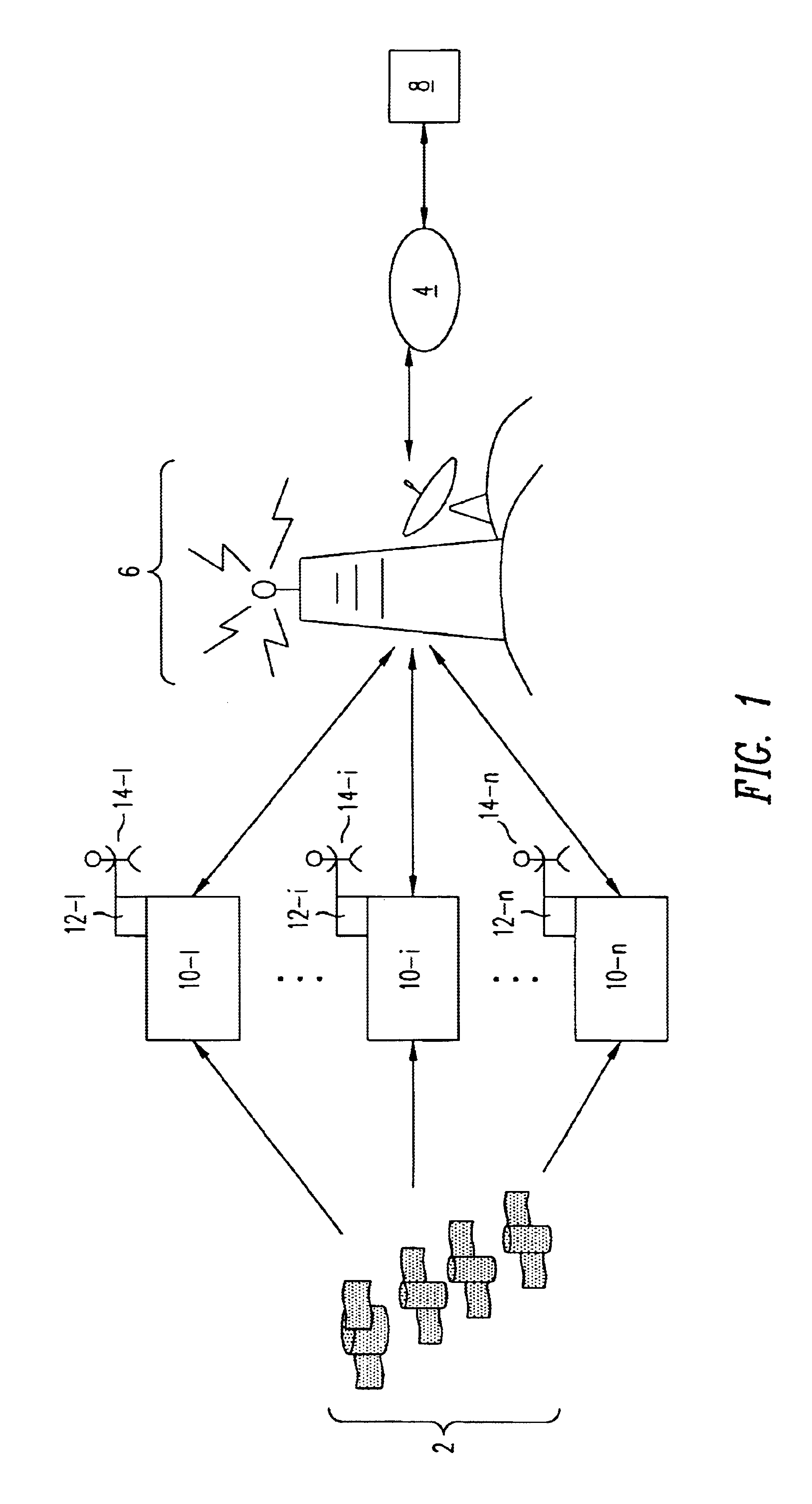
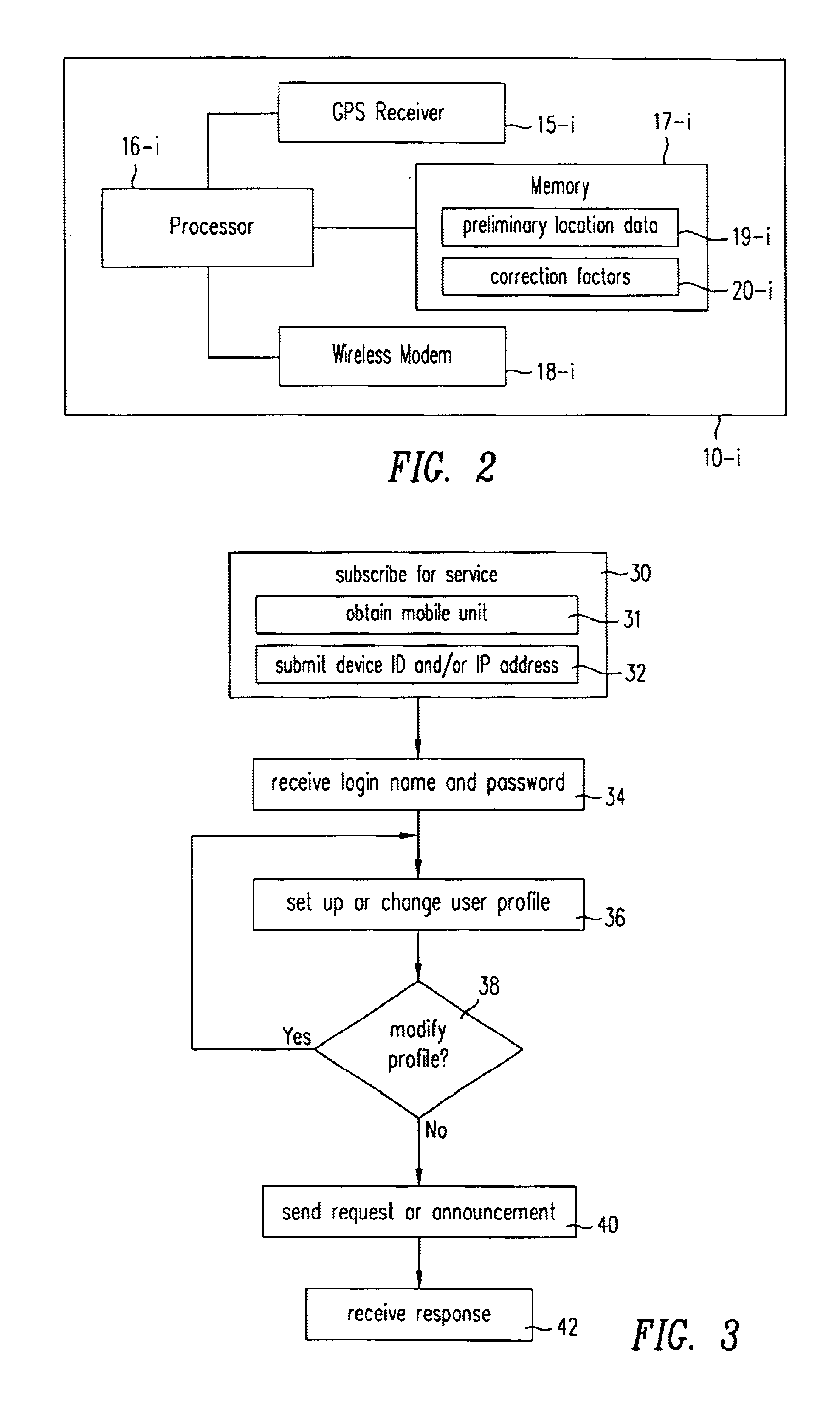
Method and system for a plurality of mobile units to locate one another
A method and system whereby two mobile units can locate each other is presented. A user connects an interface device, such as a personal digital assistance (PDA), a wireless phone, a laptop, or a pager, to a mobile unit. The mobile unit regularly obtains its location through a location-determining technology (e.g., GPS) and sends the location to a service provider computer. The service provider computer maintains a database of the current location of all the mobile units, and provides the location of mobile units to each of the mobile units. The mobile unit communicates with the service provider wirelessly through a communication network and a data network, for example the Internet.A user of the mobile unit can send messages to other users with a location stamp, which indicates the location of the message sender's mobile unit. In addition, a user can send a request to be notified when a target mobile unit reaches a reference point. The reference point may be defined relative to the location of the requester. Alternatively, the reference point may be an address or a landmark. Upon receiving the request, the service provider computer tracks the distance between the target mobile unit and the reference point, and sends a notification to the requester when the target mobile unit reaches the reference point.
Owner:TRIMBLE NAVIGATION LTD
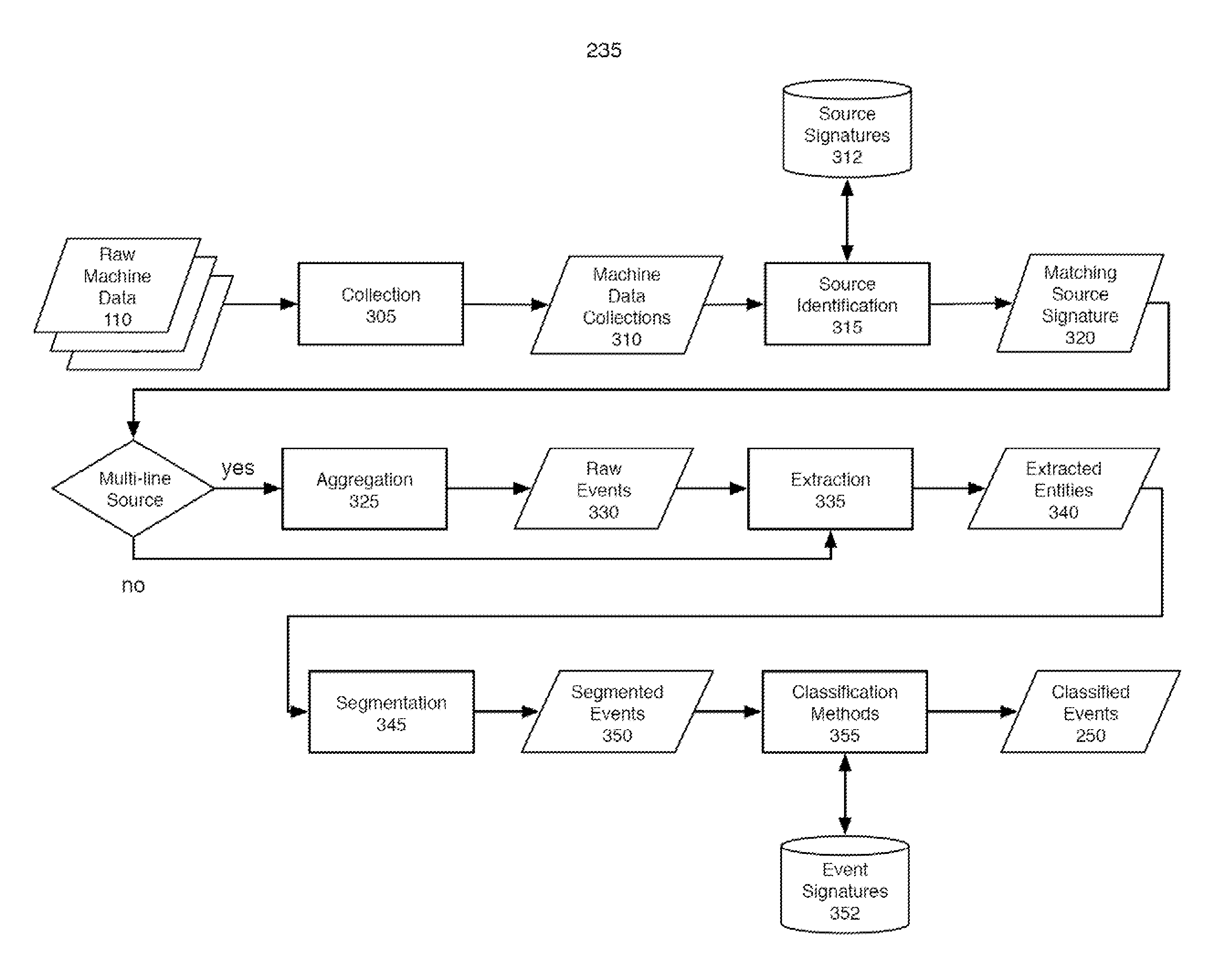
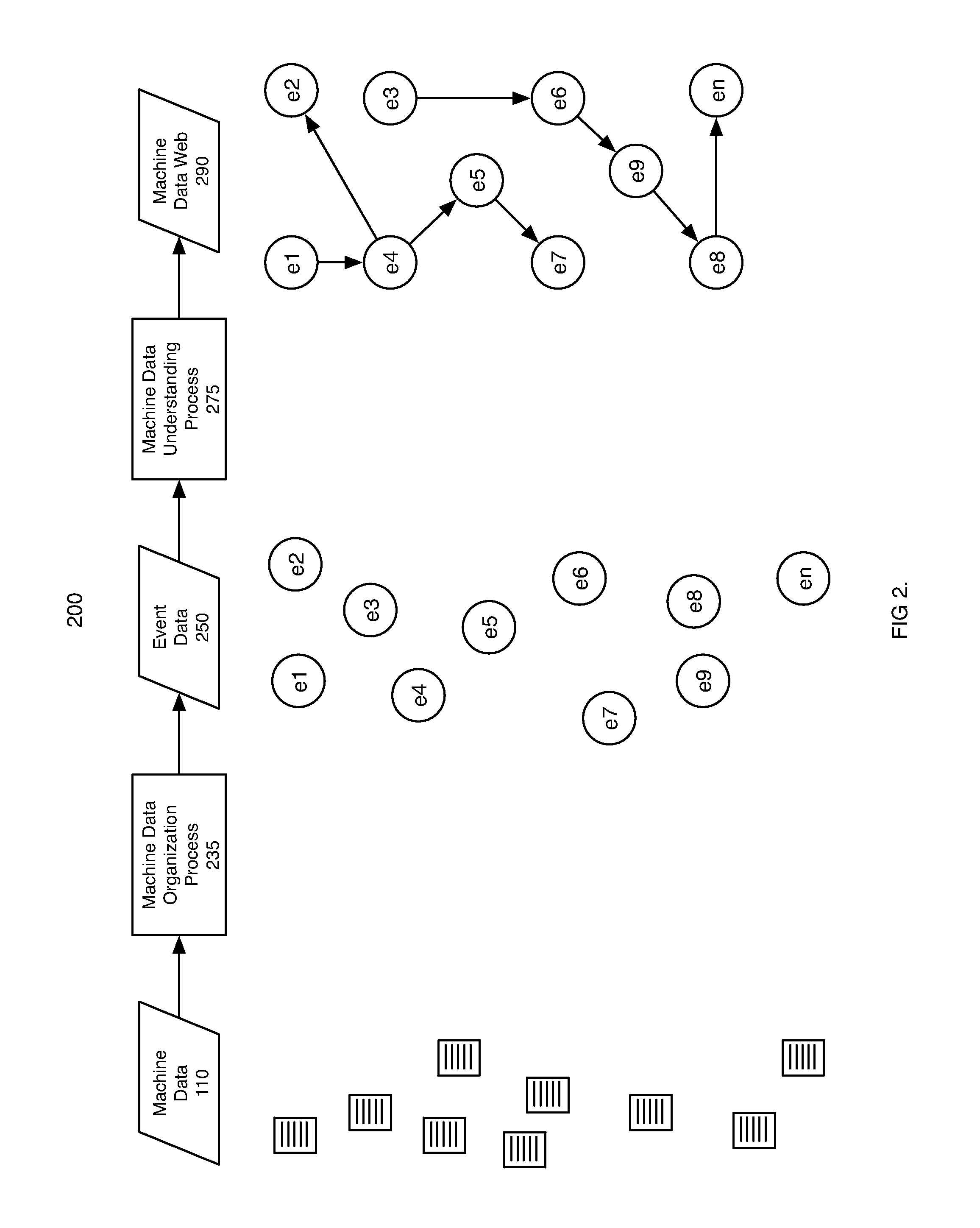
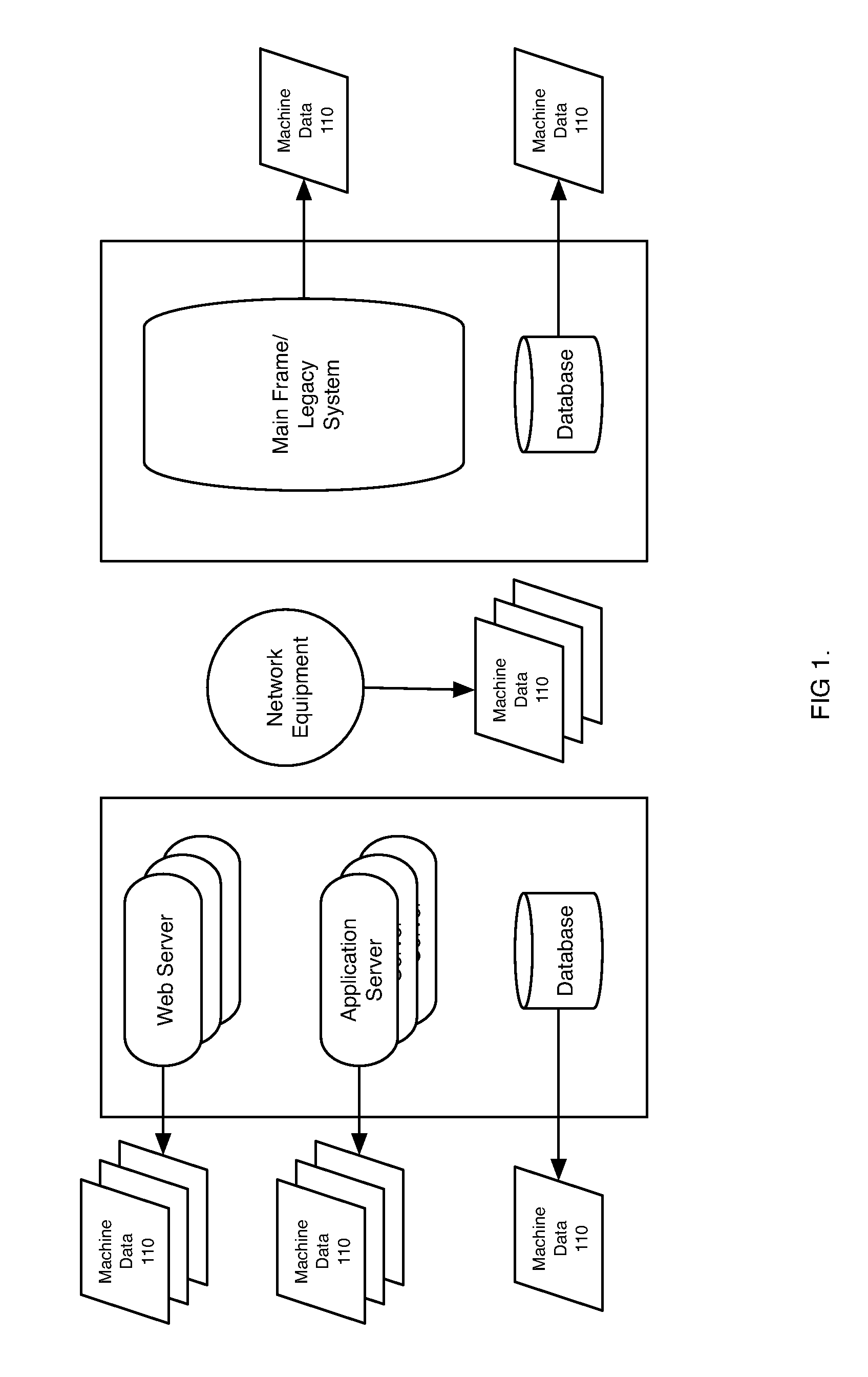
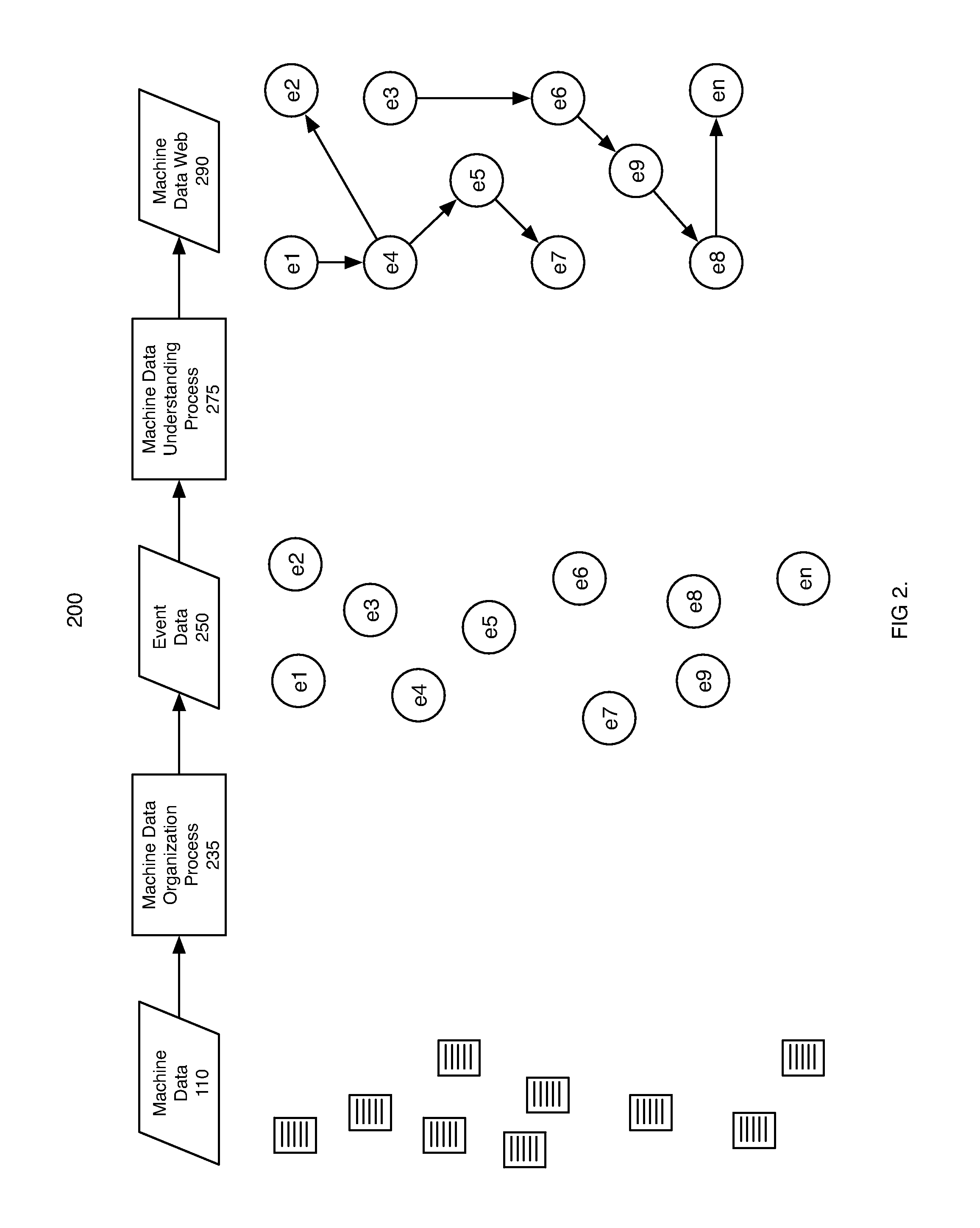
Machine data web
ActiveUS7937344B2Preserve integrityError detection/correctionInterprogram communicationInformation processingOriginal data
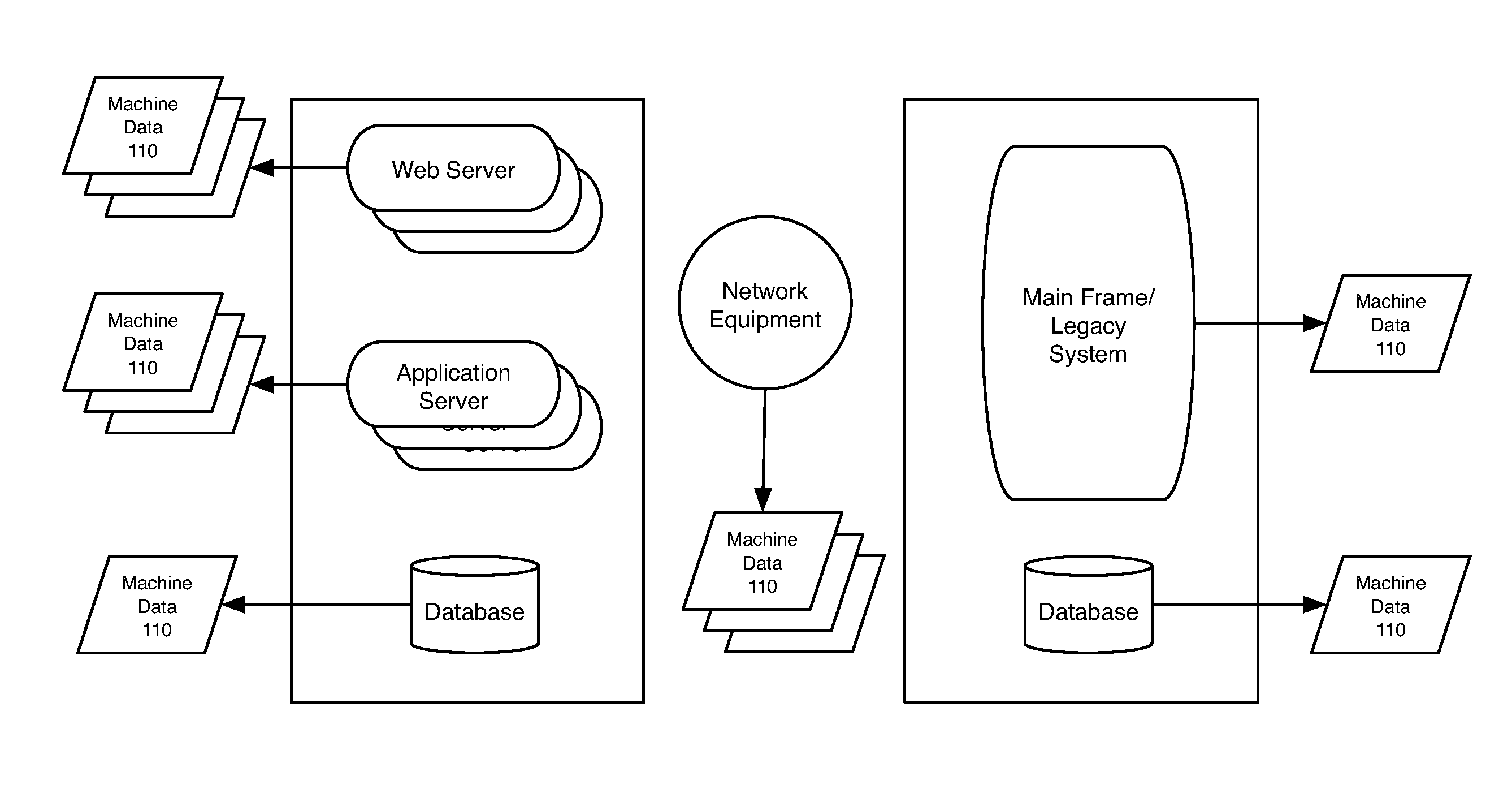
Methods and apparatus consistent with the invention provide the ability to organize and build understandings of machine data generated by a variety of information-processing environments. Machine data is a product of information-processing systems (e.g., activity logs, configuration files, messages, database records) and represents the evidence of particular events that have taken place and been recorded in raw data format. In one embodiment, machine data is turned into a machine data web by organizing machine data into events and then linking events together.
Owner:SPLUNK INC
Policy-based synchronization of per-class resources between routers in a data network
ActiveUS20020194369A1Multiple digital computer combinationsProgram controlCommunication interfaceData stream
A data network may include an upstream router having one or more data handling queues, a downstream router, and a policy server. In one embodiment, the policy server includes processing resources, a communication interface in communication with the processing resources, and data storage that stores a configuration manager executable by the processing resources. The configuration manager configures data handling queues of the upstream router to provide a selected bandwidth to one or more of a plurality of service classes of data flows. In addition, the configuration manager transmits to the downstream router one or more virtual pool capacities, each corresponding to a bandwidth at the upstream router for one or more associated service classes among the plurality of service classes. In one embodiment, the configuration manager configures the data handling queues on the upstream router only in response to acknowledgment that one or more virtual pool capacities transmitted to the downstream router were successfully installed.
Owner:VERIZON PATENT & LICENSING INC
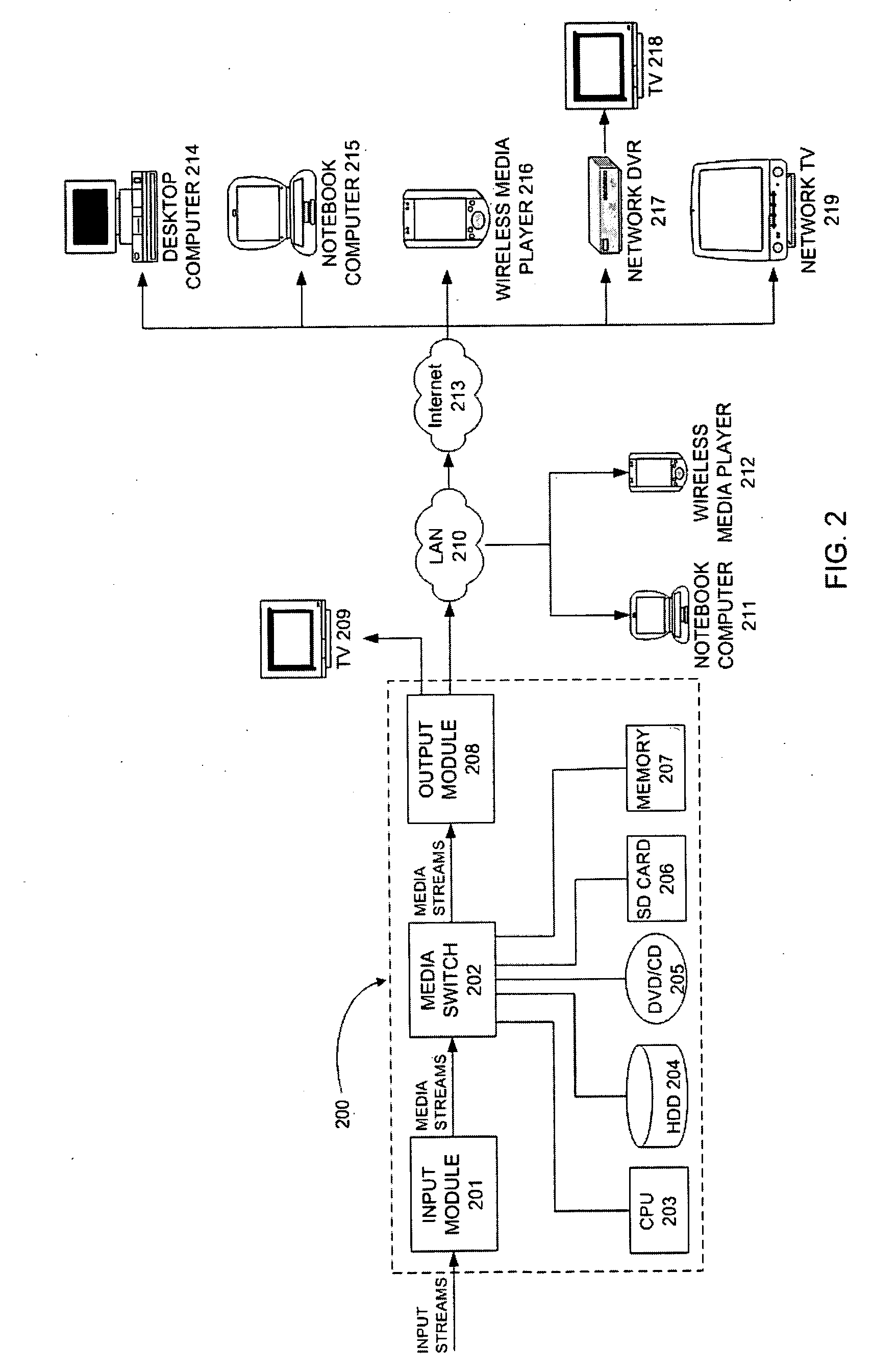
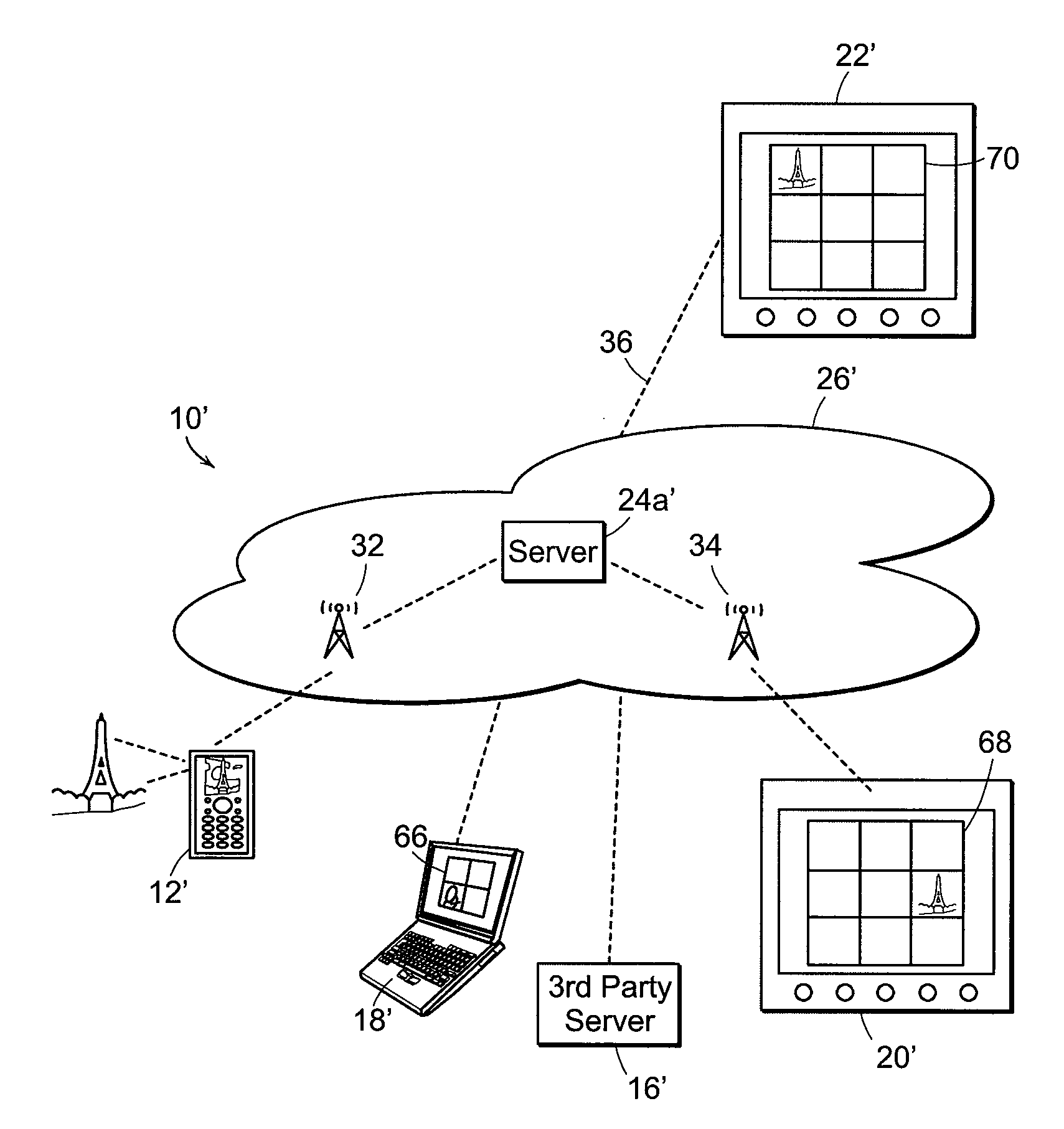
Method and system for accessing media content via the Internet
ActiveUS20070180485A1Rapidly initiate connectivityEasy to useTelevision system detailsAnalogue secracy/subscription systemsThe InternetDigital storage
A media storage and access system and methodology including a set-top box which receives and processes a plurality of signal sources and makes programming available locally through connected devices or via a data network such as a LAN, WAN, or the Internet. The system also integrates a multimedia storage system that allows programming content to be digitally stored. The system utilizes an integrated digital storage system and operating software to allow users to view a broadcast program (e.g., television, radio, etc.) with the option of instantly reviewing previous segments within the program. In addition, the system allows the user to store selected media programming while the user is simultaneously watching or reviewing another program. The system also allows stored media assets to be accessed locally via a media device connected to the unit or remotely via the Internet.
Owner:SYNDEFENSE
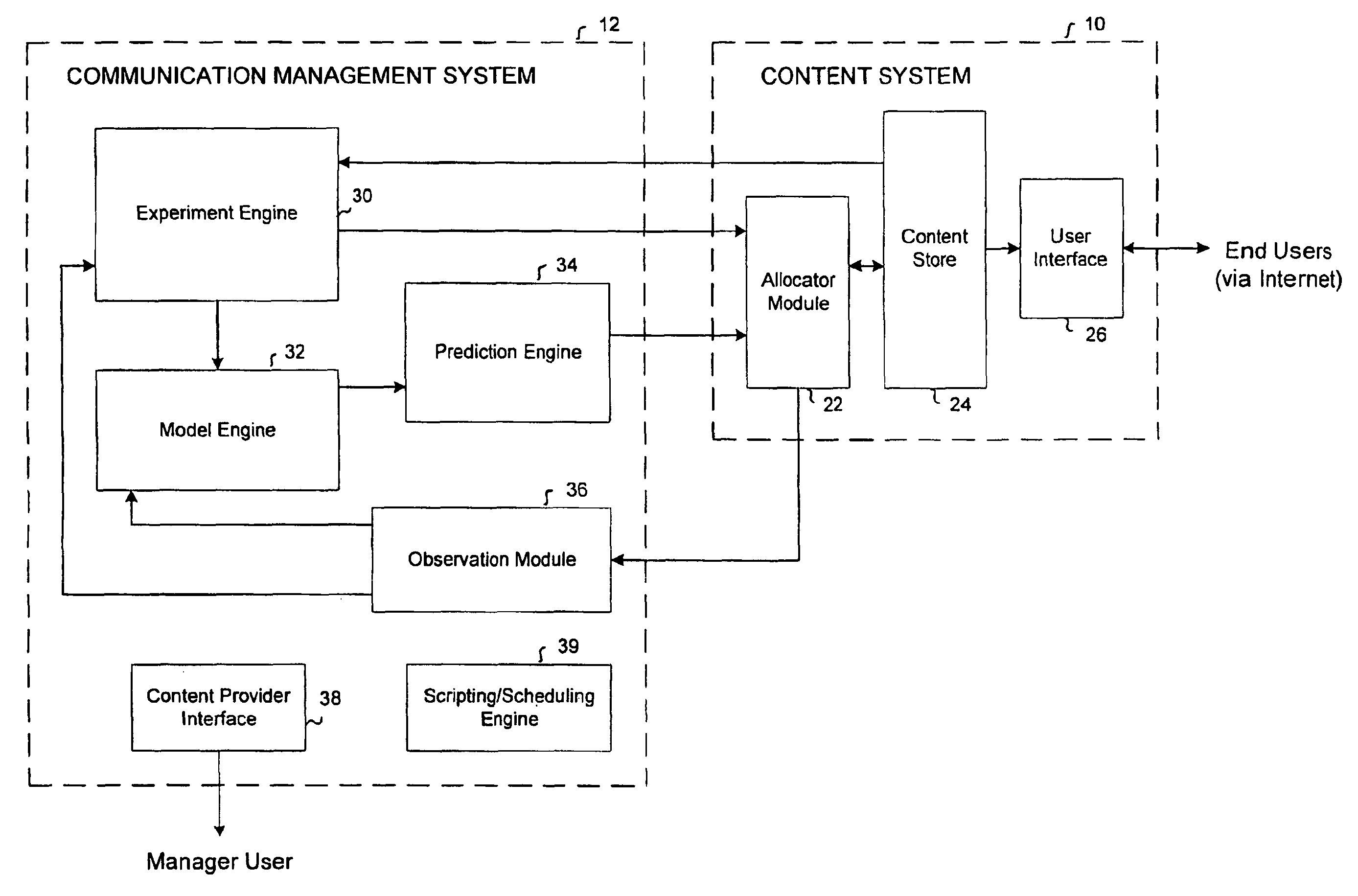
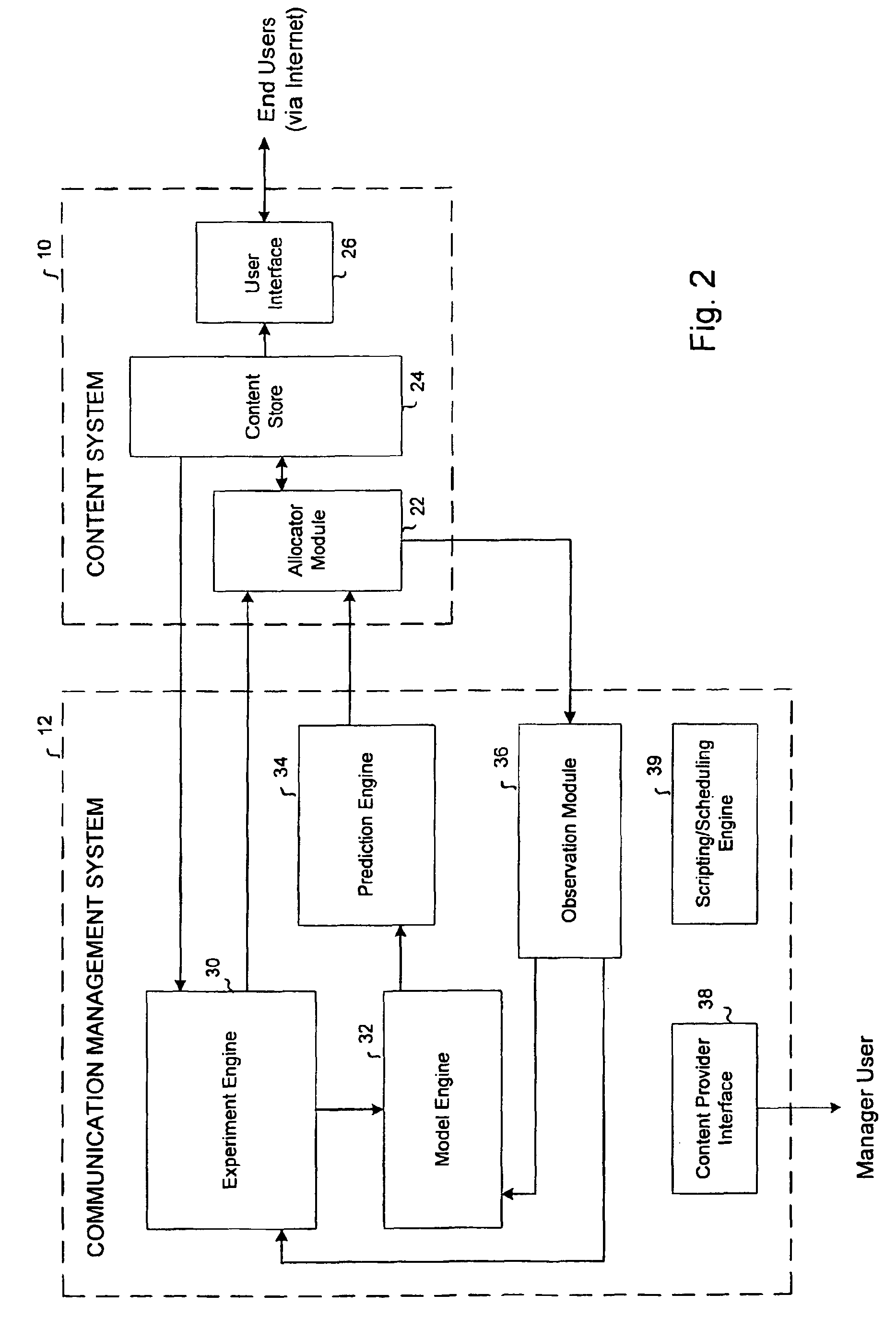
Automated on-line experimentation to measure users behavior to treatment for a set of content elements
An automated system for experimentation includes an experiment engine which can define an experiment relating to various treatments for a set of content elements. The experiment engine conducts the experiment over a data network. An observation module collects observation data relating to user behavior for each treatment. A scripting / scheduling engine coordinates the operation of the experiment engine and the observation module.
Owner:ACCENTURE GLOBAL SERVICES LTD
Method and apparatus for securing electronic data
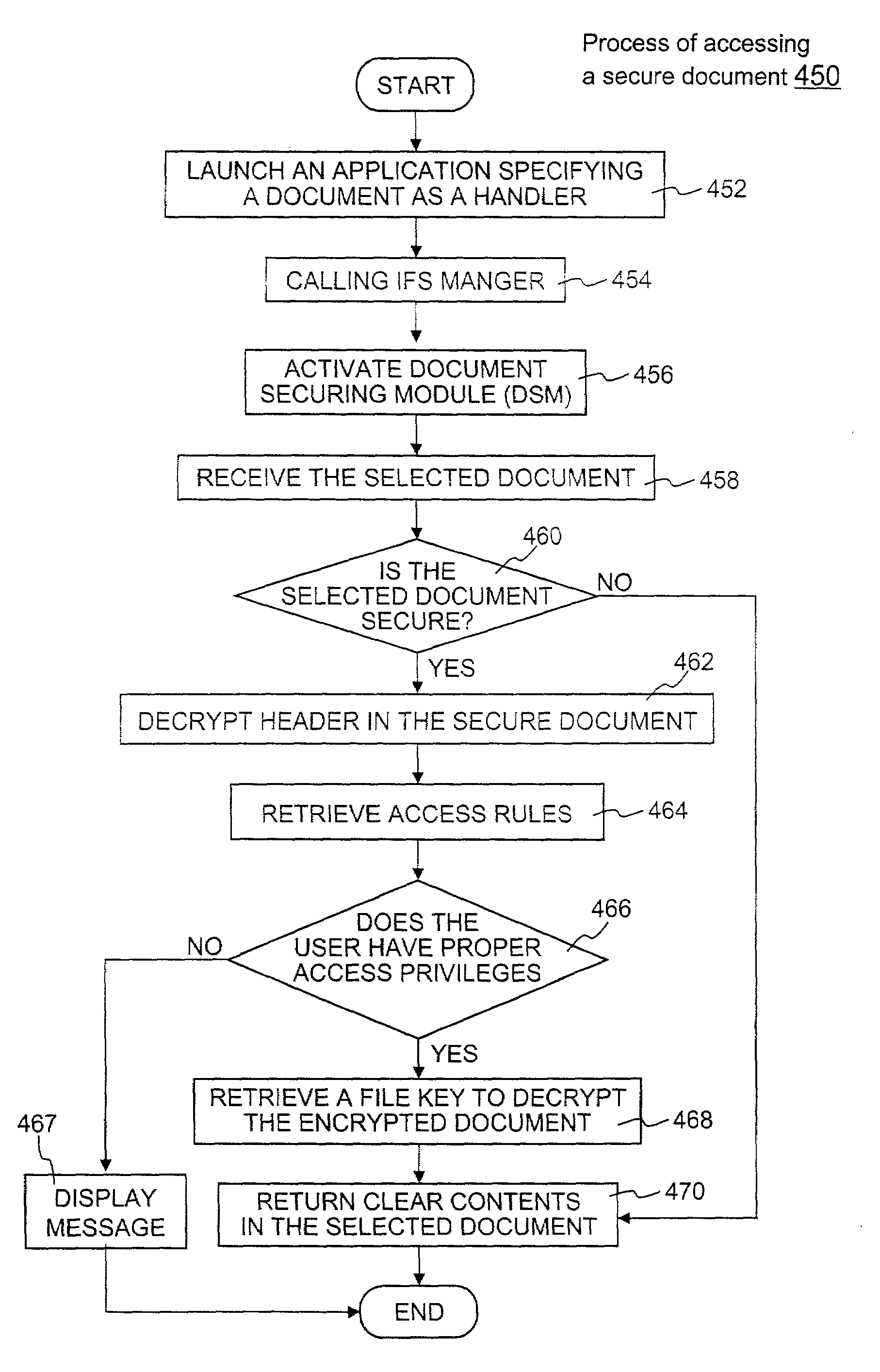
ActiveUS7681034B1Facilitate access control managementGood synchronizationDigital data processing detailsUnauthorized memory use protectionPathPingEngineering
Techniques for securing electronic data and keeping the electronic data secured at all times are disclosed. According to one embodiment, a client module in a client machine is configured to provide access control to secured documents that may be located in a local store, another computer machine or somewhere over a data network. The client module includes a document-securing module configured to operate in a path through which a document being accessed is caused to pass so that the document can be examined or detected for the security nature. If the document is secured, the document-securing module obtains a user or group key to decrypt security information in the secured document for access rules therein. If a user accessing the document is determined to have the access privilege to the secured document, a file key is retrieved from the security information and a cipher module is activated to decrypt the encrypted data portion with the file key. Likewise, if a document is to be secured, the cipher module encrypts clear data from the document to create the encrypted data portion. The document-securing module integrates proper or desired security information with the encrypted data portion to produce the secured document.
Owner:INTELLECTUAL VENTURES I LLC
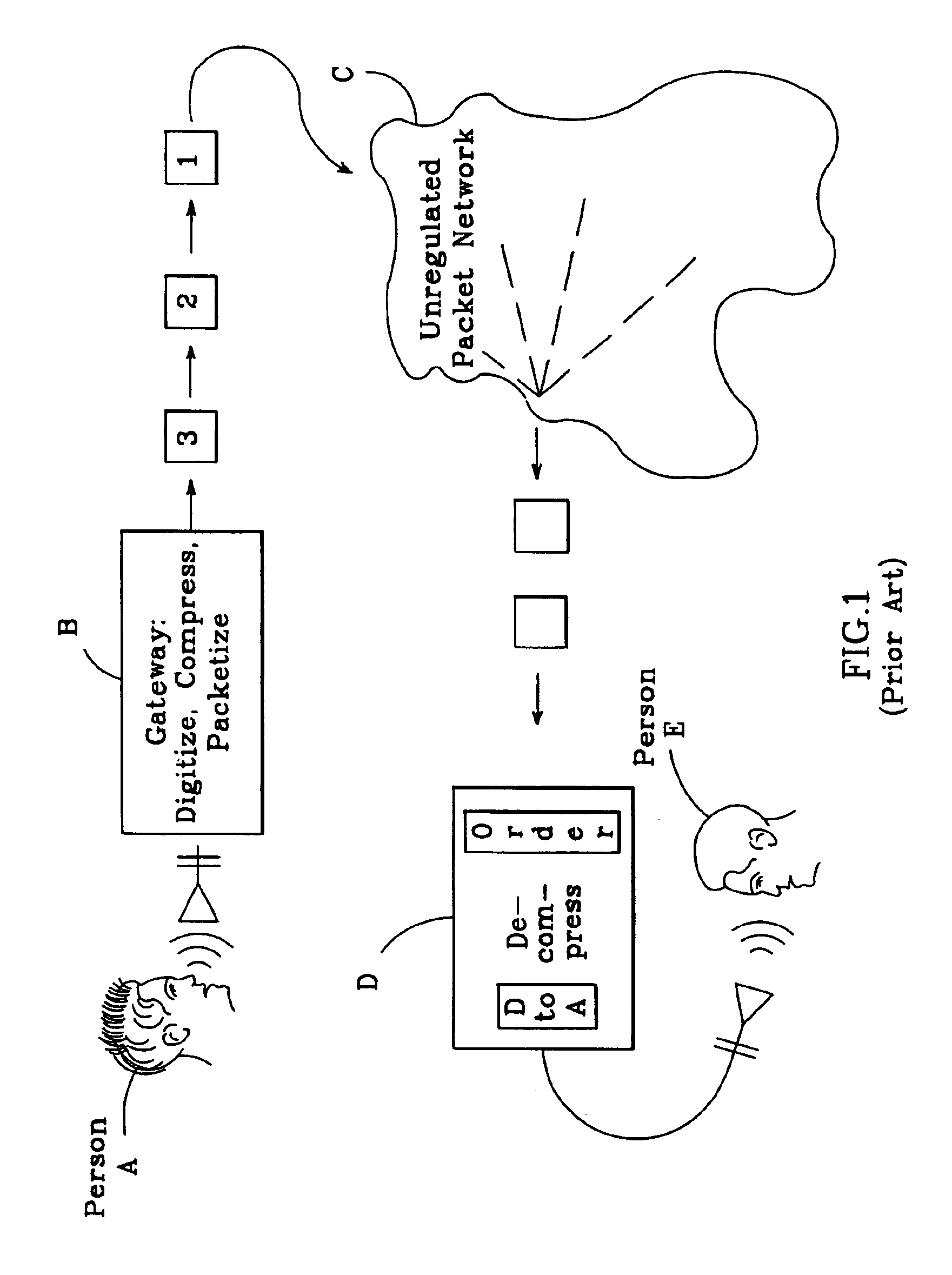
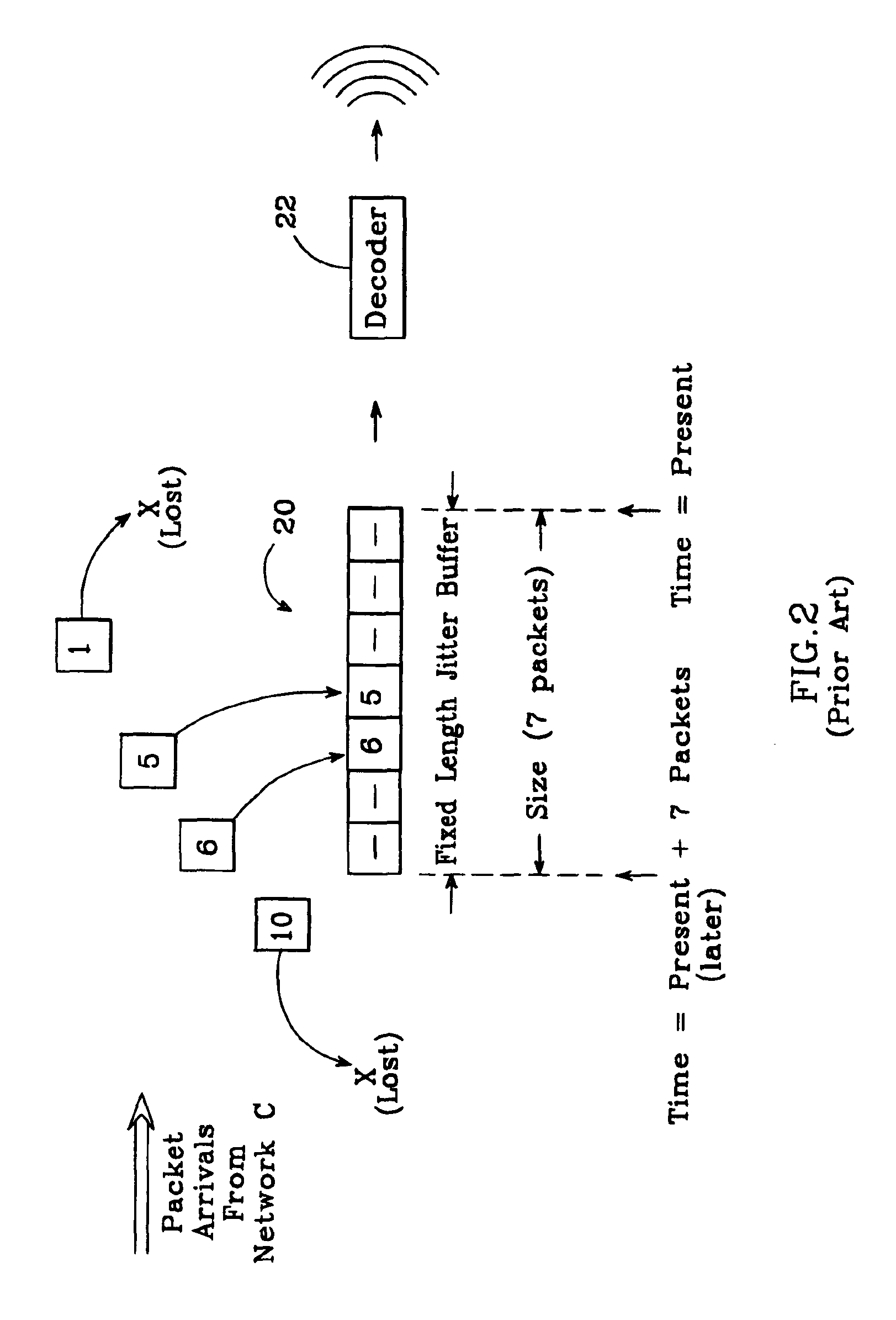
Adaptive jitter buffer for internet telephony
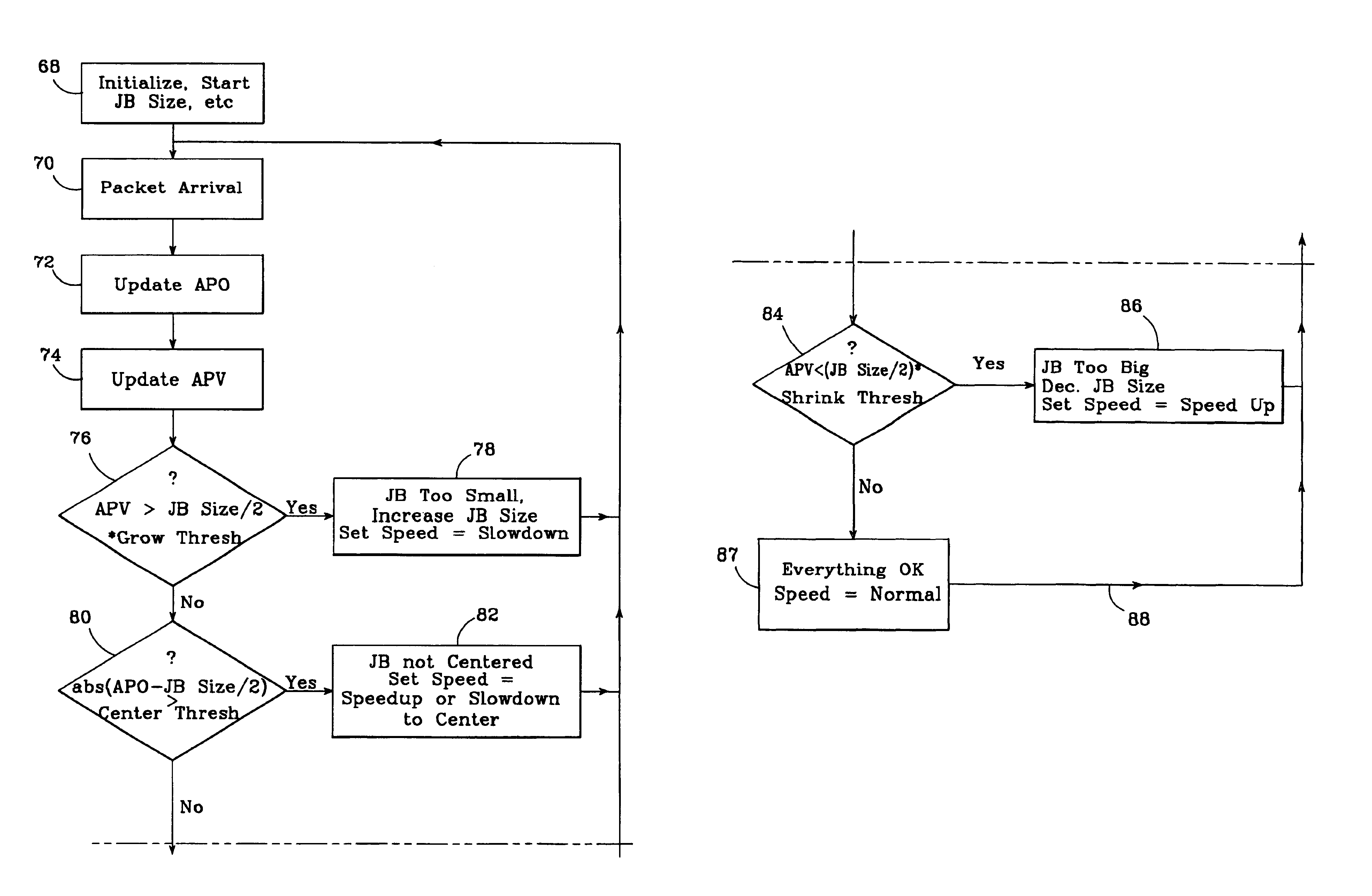
InactiveUS6862298B1Improve audio qualityTo overcome the large delayError preventionFrequency-division multiplex detailsPacket arrivalControl signal
In an improved system for receiving digital voice signals from a data network, a jitter buffer manager monitors packet arrival times, determines a time varying transit delay variation parameter and adaptively controls jitter buffer size in response to the variation parameter. A speed control module responds to a control signal from the jitter buffer manager by modifying the rate of data consumption from the jitter buffer, to compensate for changes in buffer size, preferably in a manner which maintains audio output with acceptable, natural human speech characteristics. Preferably, the manager also calculates average packet delay and controls the speed control module to adaptively align the jitter buffer's center with the average packet delay time.
Owner:GOOGLE LLC
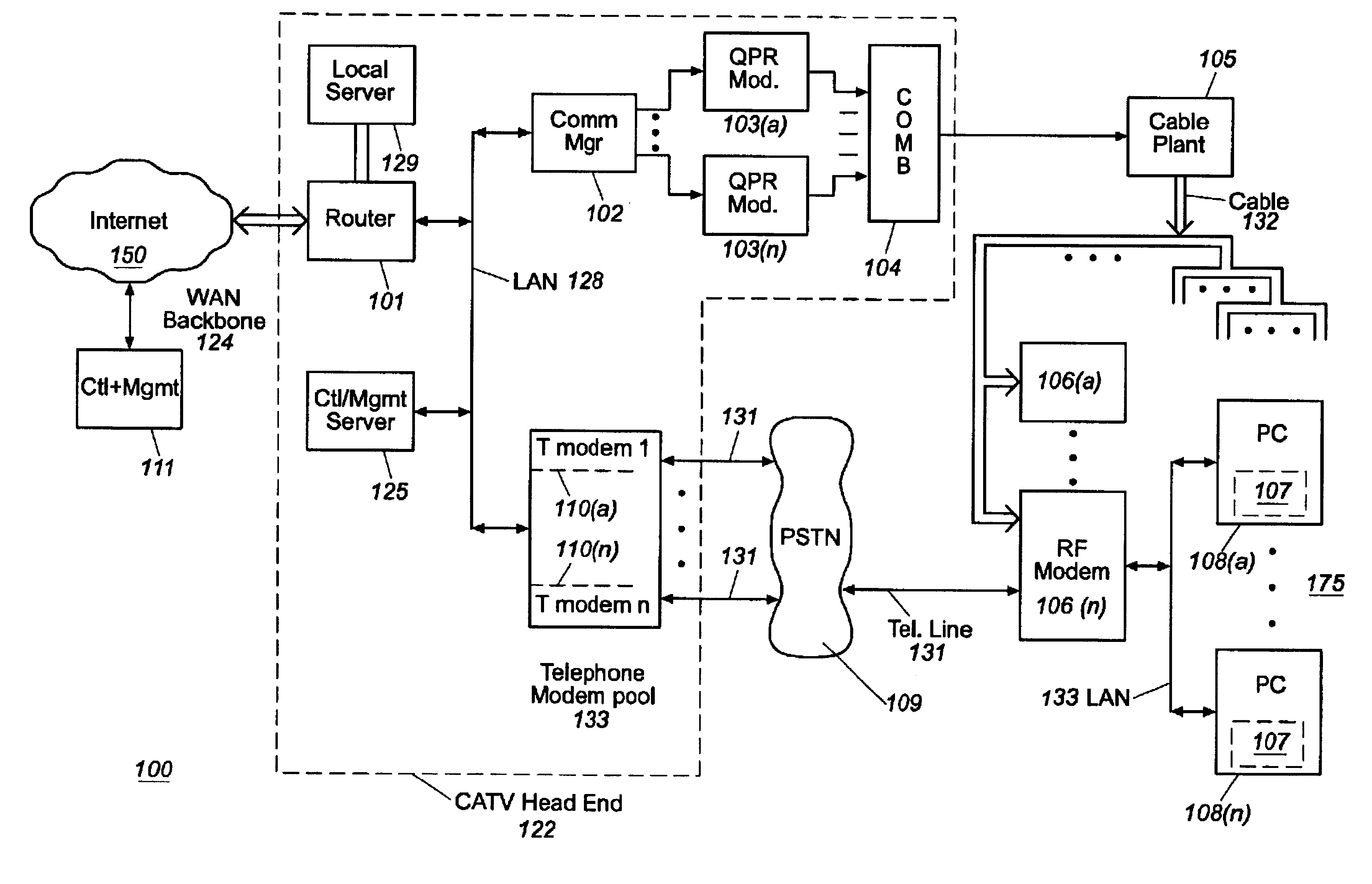
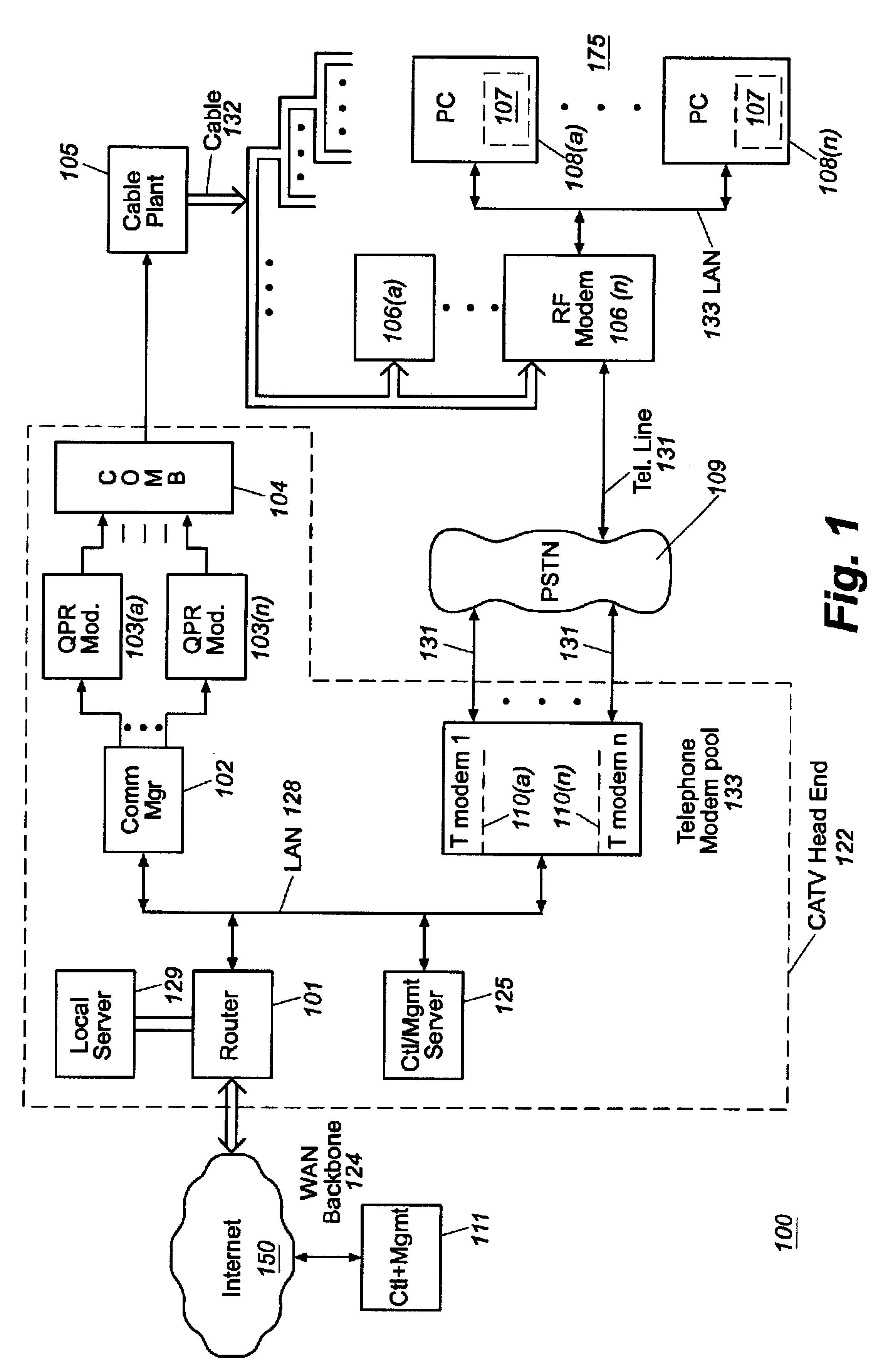
Usage statistics collection for a cable data delivery system
InactiveUS6308328B1Broadband local area networksBroadcast transmission systemsData connectionNetwork management
Apparatus for recording and collecting usage and other statistical data from components of a cable data network comprises a network manager for maintaining and collecting the statistics. Internet protocol addresses are associated with components of the network. The component maintains a software agent that manages a statistics database. Responsive to a manager request generated at a service provider defined time interval, the component software agent provides the usage statistics to the network manager in real-time during an Internet session with a host. When the host to Internet or other data connection is torn down due to failure, disconnect or inactivity time-out, remaining usage statistics data is collected and the session duration updated with the time of tear down. Usage statistics collected include the amount of data transferred to / from a host, the amount of data that is discarded due to insufficient resource capacity and amount of data that cannot be corrected despite forward error correction used in a downstream high capacity channel to the host. Data traps may be defined and downloaded to components of the network for implementation. As a result, billing of users of the cable data network can be usage sensitive and determined based on actual data transferred (including credit given for errored data) and / or time sensitive based on session duration.
Owner:CISCO TECH INC
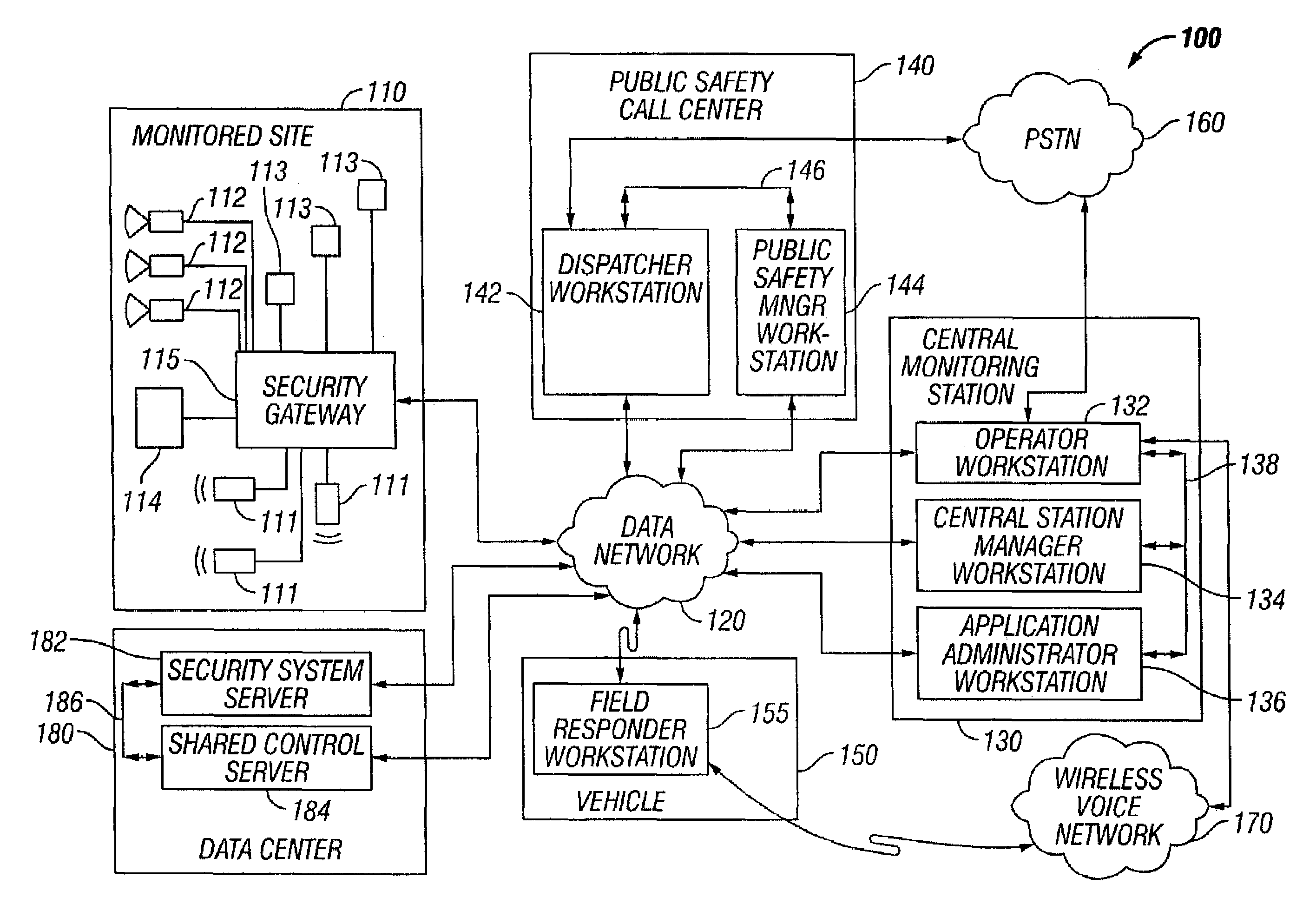
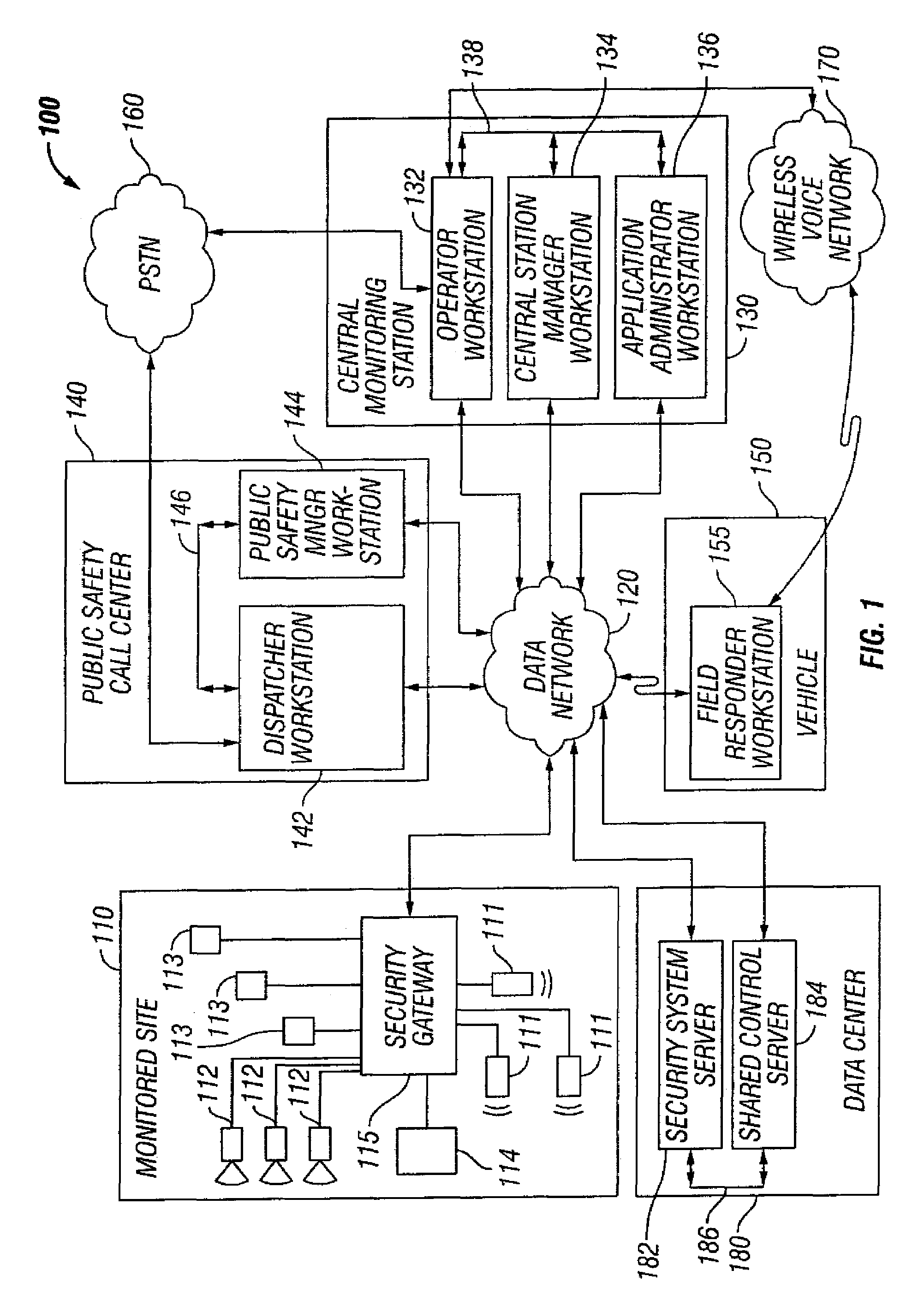
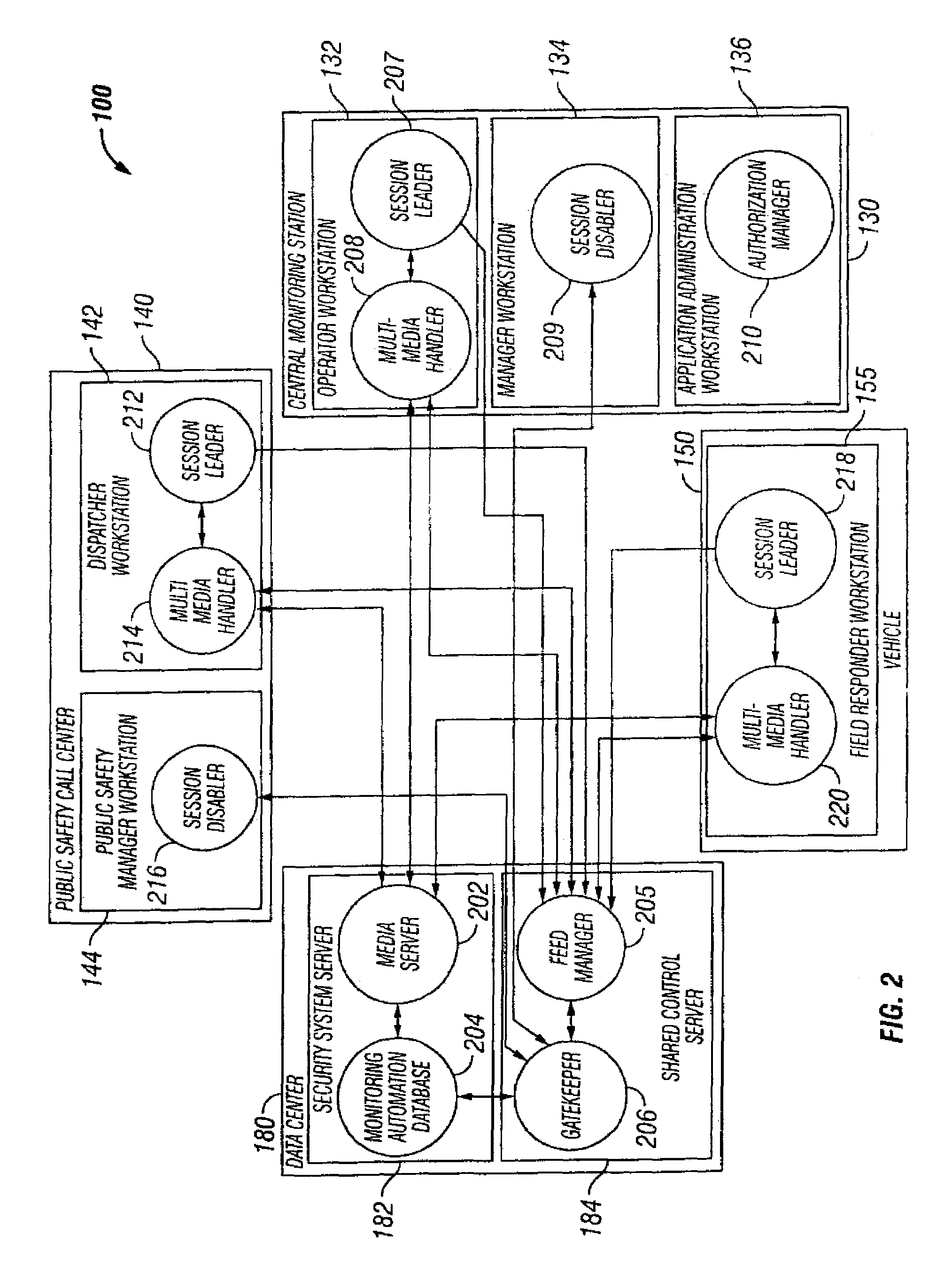
Security system configured to provide video and/or audio information to public or private safety personnel at a call center or other fixed or mobile emergency assistance unit
ActiveUS7158026B2Frequency-division multiplex detailsTelephonic communicationWorkstationAudio frequency
A security system for monitoring a premises. Alarm information, including a near real-time feed of video and / or audio data, is collected at the premises and retrieved by a remotely located monitoring computer workstation over a data network. If desired, a remotely located emergency response computer workstation coupled to the data network may be authorized, by the monitoring computer workstation, to retrieve the collected alarm information over the data network. The emergency response computer workstation may also be granted control of the alarm information collecting devices located at the monitored premises.
Owner:COMCAST CABLE COMM LLC
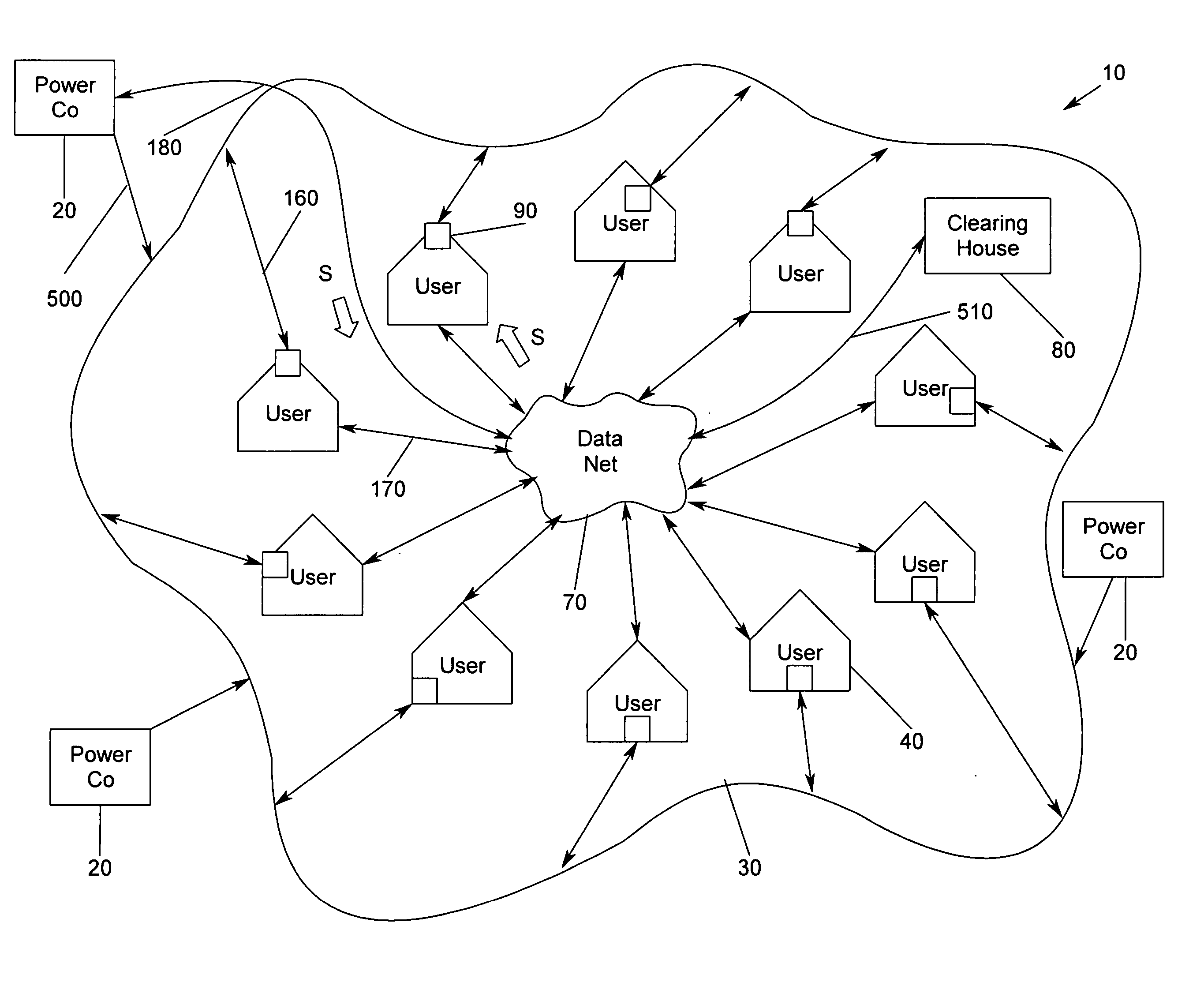
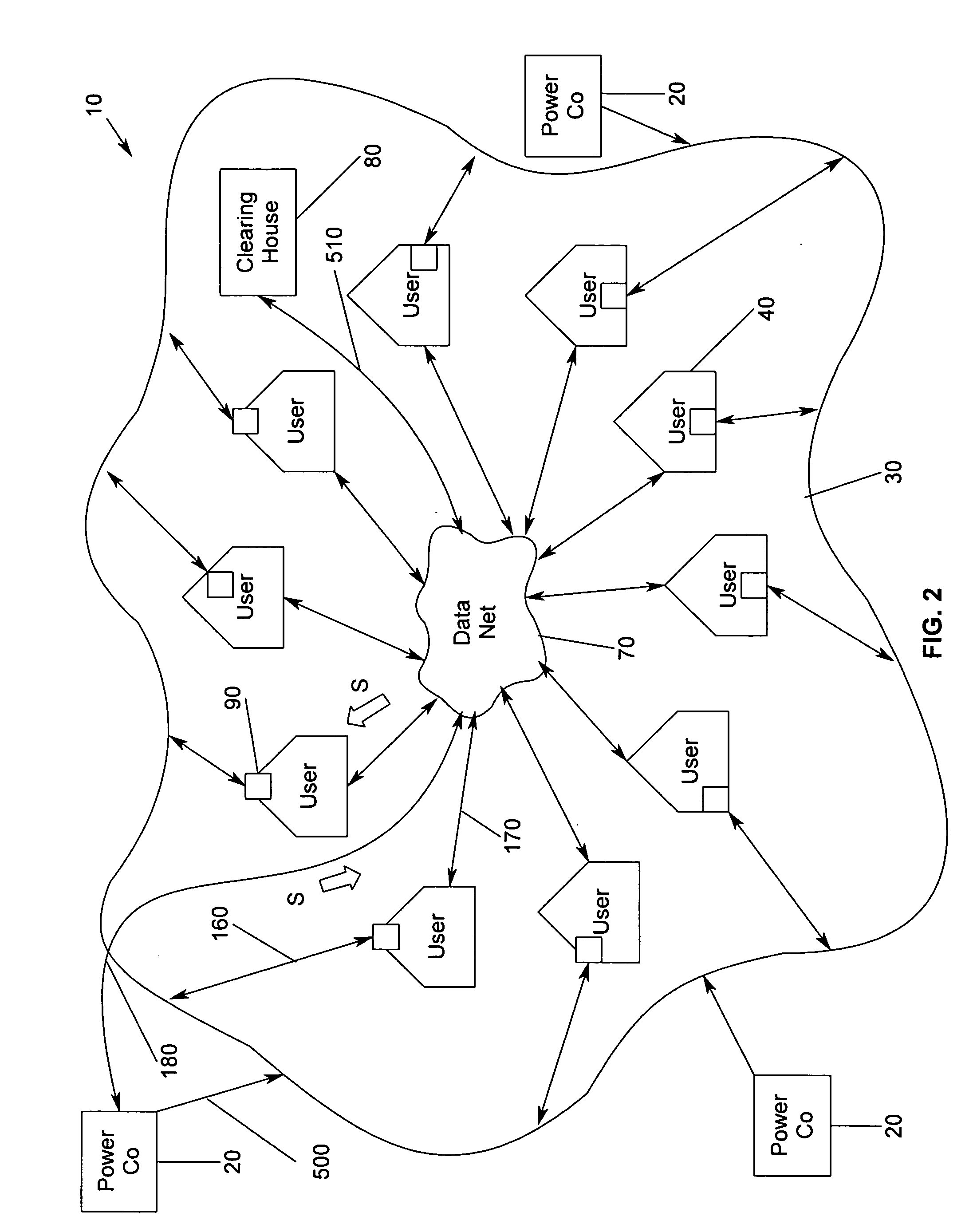
Electric power shuttling and management system, and method
InactiveUS20050125243A1Optimize energy costLow cost optionSubstation/switching arrangement detailsCommerceElectric power transmissionElectricity
A method and apparatus for shuttling, managing, and controlling energy flow between suppliers and users based on bid / ask pricing, wherein individual residential / commercial suppliers are aggregated for the purpose of supply and use, and wherein an electricity transmission utility controls the selection and flow of energy from suppliers to users via a controlling device, such as, for exemplary purposes only, a switch turned on by commands sent over a data net to multiple locations simultaneously.
Owner:VILLALOBOS VICTOR M
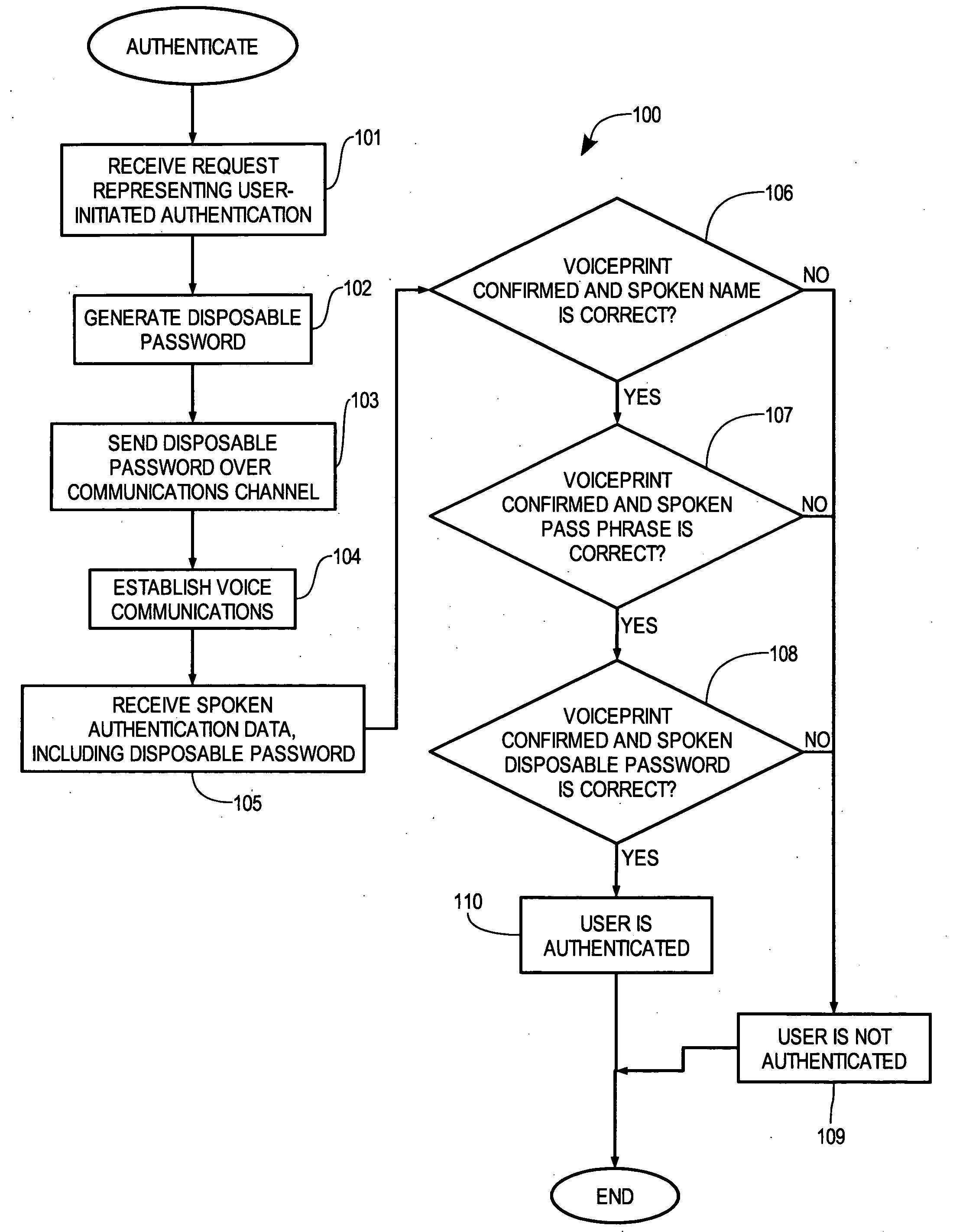
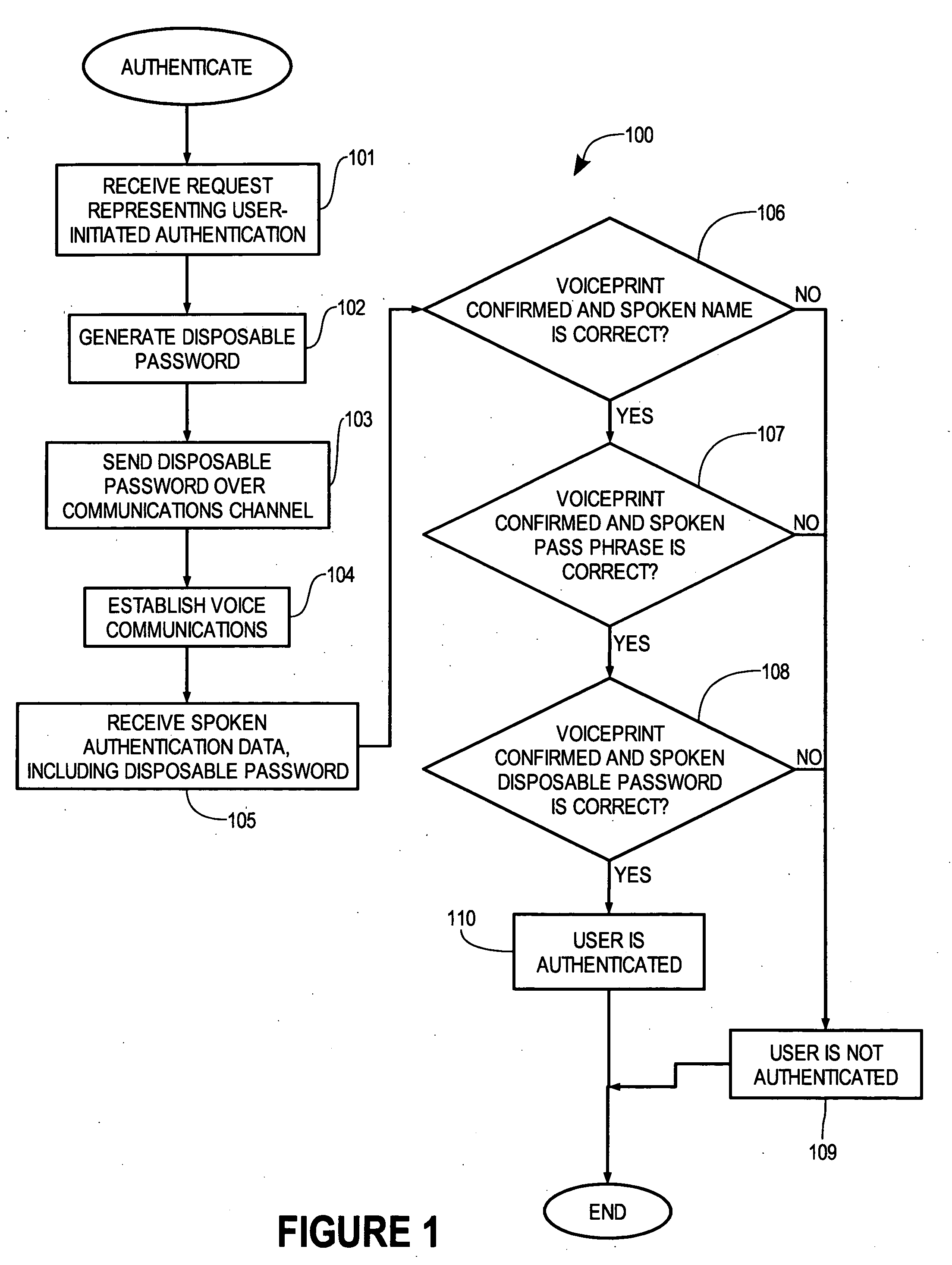
Multi-factor biometric authentication
InactiveUS20070055517A1Digital data authenticationIndividual entry/exit registersSecret codeOne-time password
A method for verifying a person's identity in order to gain access to electronic data, a data network, a physical location, or enable a commercial transaction. A request for identity verification is processed over a data network and the system is initiated which (i) transmits a disposable pass phrase over a data network to the user, (ii) prompts the user to vocalize the disposable pass phrase, a pass phrase, and user id, (iii) compares the recited speech of the user to the stored voiceprint of the user, the stored pass phrase and id of the user, and the generated disposable pass phrase, then (iv) issues a token or signal that represents whether the user was verified or not.
Owner:AUTHENTIVOX
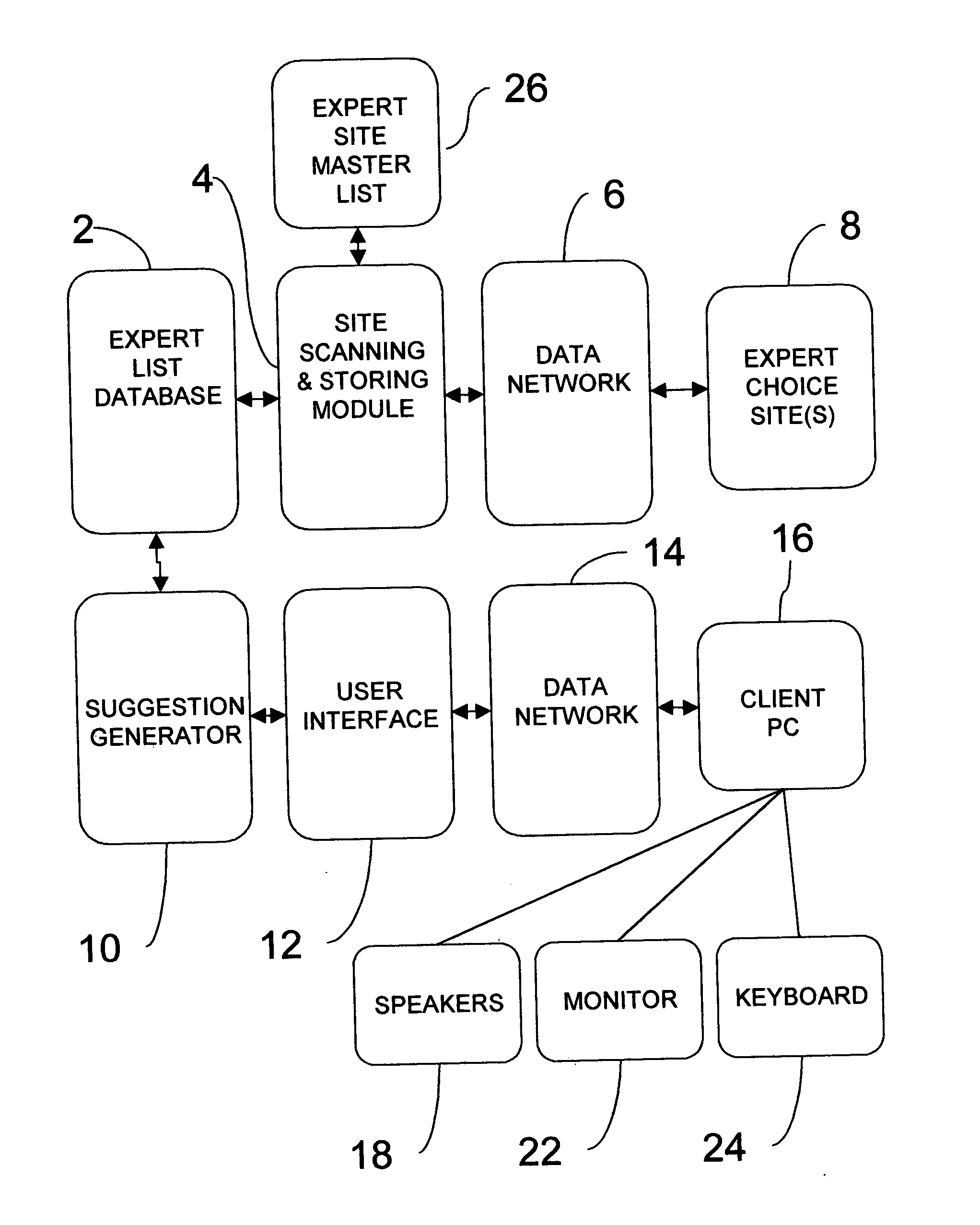
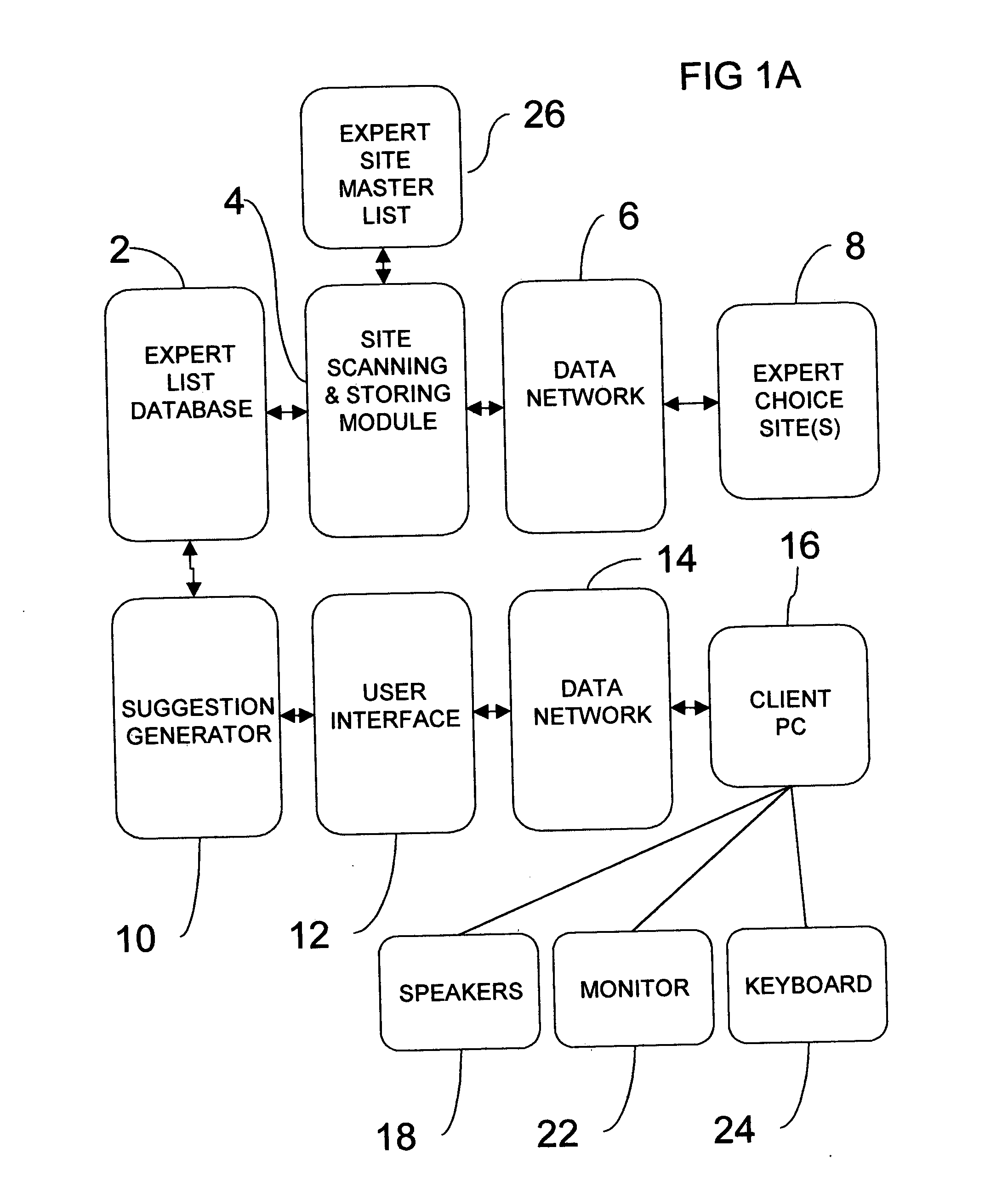
System and method for recommendation of media segments
InactiveUS20050060350A1Metadata audio data retrievalSpecial data processing applicationsWorld Wide WebText searching
A system and method of providing media recommendations and media segments based on expert choice lists is disclosed. Expert choice lists consisting of media segment references are retrieved through a data network and stored cumulatively in a database as records with text descriptor fields. Users of the suggestion system make requests in the form of text search descriptors and a desired output descriptor type. Descriptors of the output type in the expert choice list database are scored by the frequency with which they appear in expert choice lists possessing matches to the search descriptors. A list of the top-scoring descriptors is returned. In an alternate preferred embodiment, media segment references are scored by the frequency of their appearance in lists with matches to the search descriptors. The highest-scoring segment references are used to generate a playlist so that the recommended media segments can be presented to the user automatically.
Owner:BAUM ZACHARIAH JOURNEY +1
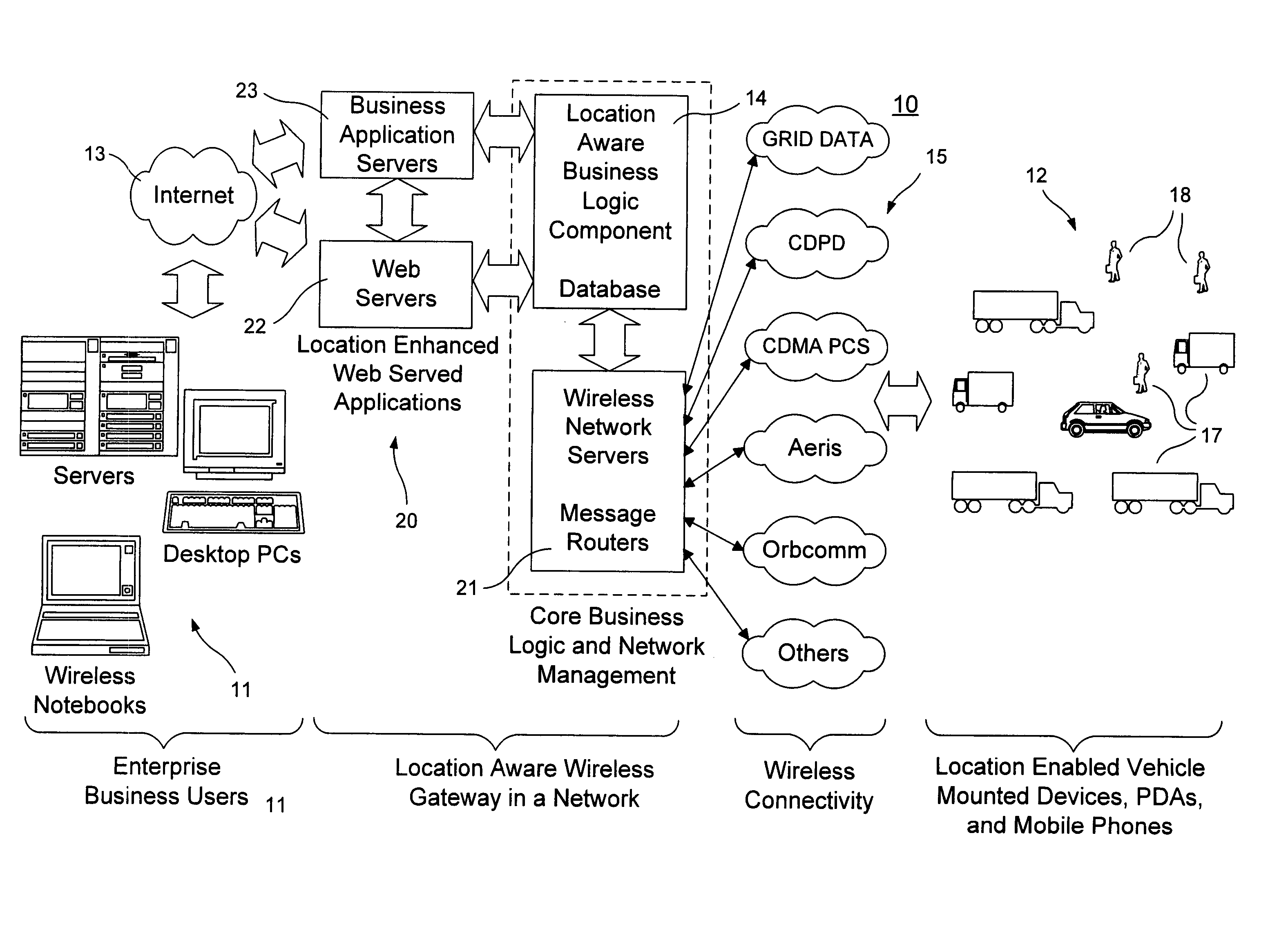
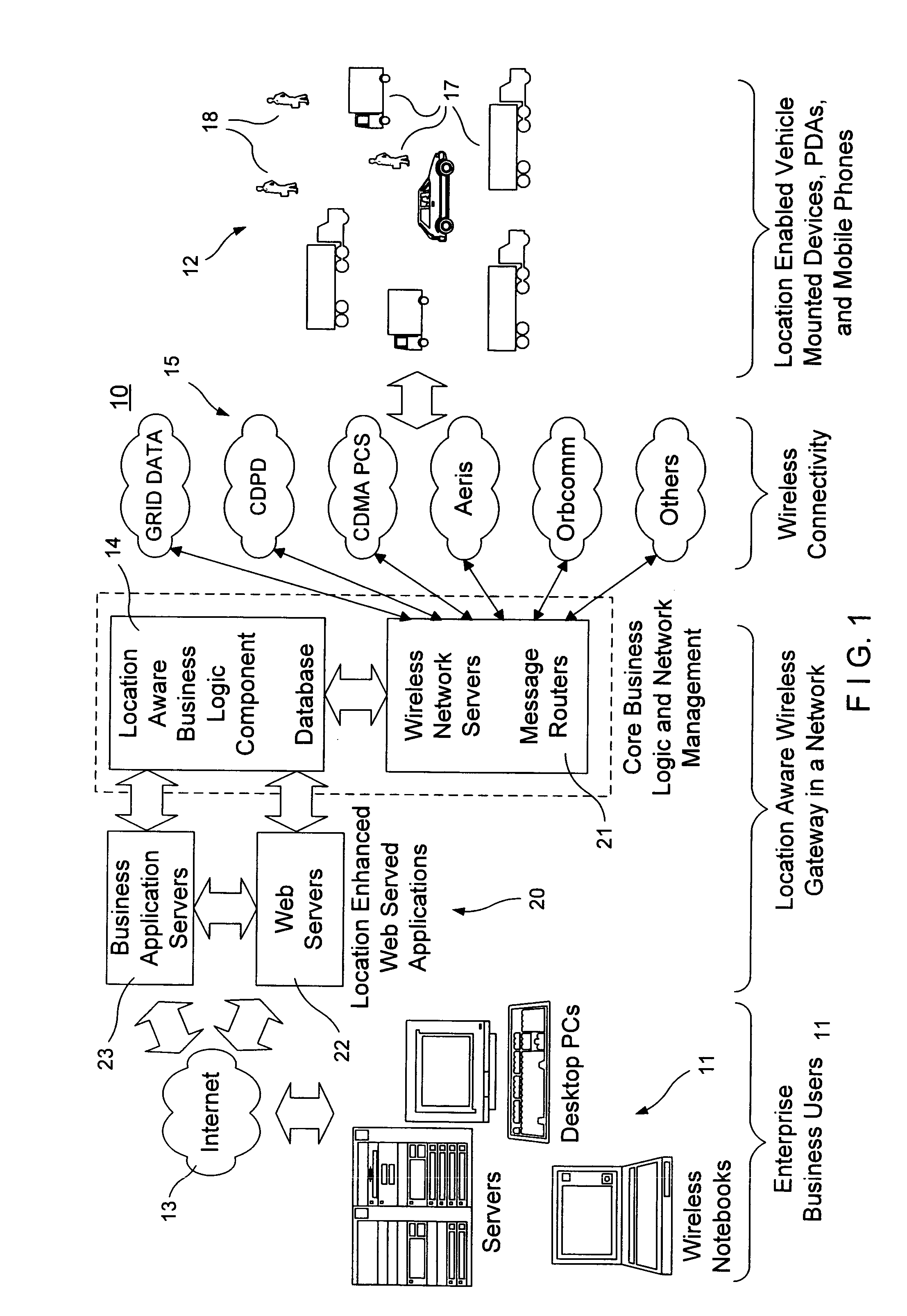
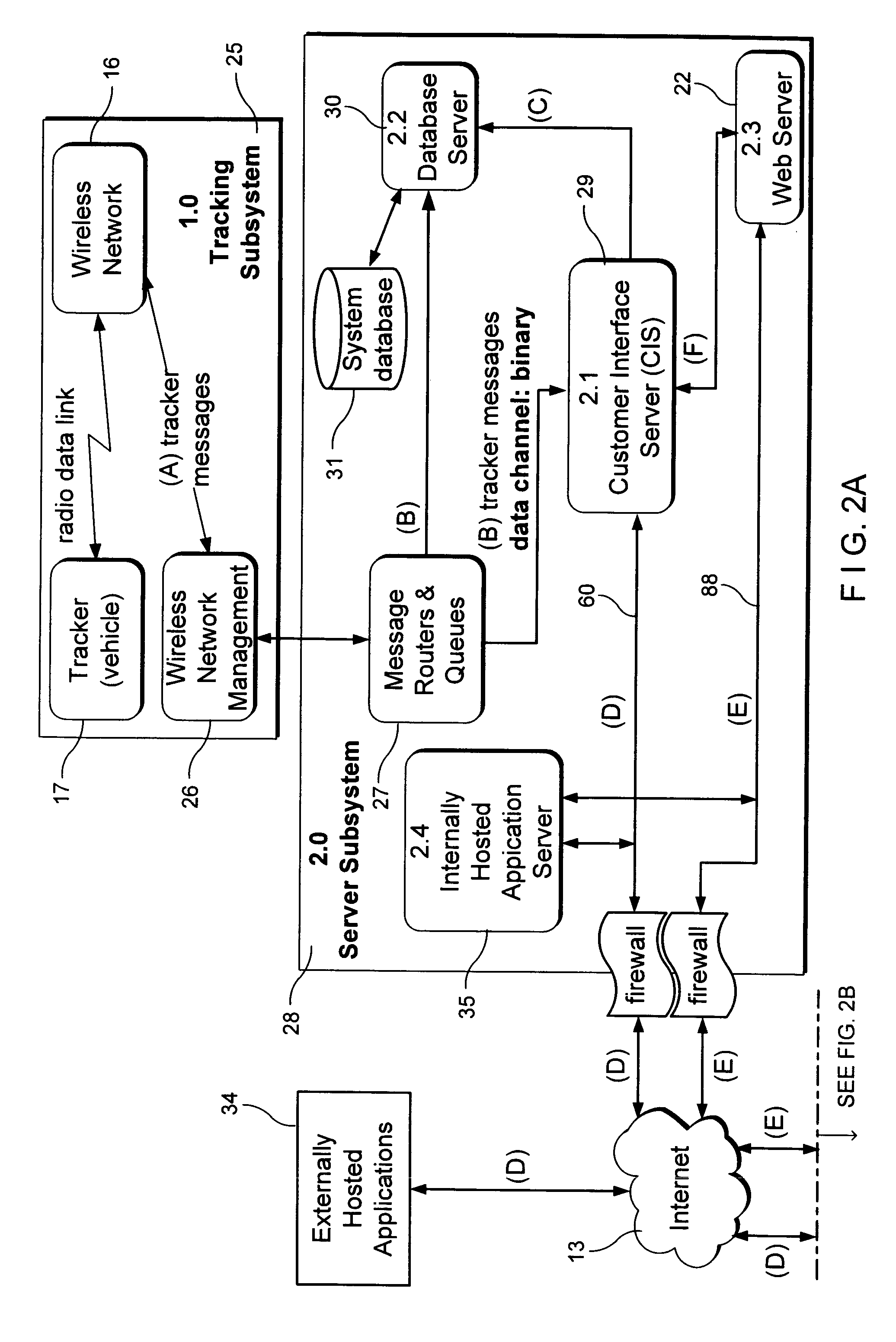
Location aware wireless data gateway
InactiveUS20060129691A1Fast and interactiveIntuitive imageMultiple digital computer combinationsTransmissionBusiness enterpriseThe Internet
A wireless gateway is provided that connects mobile and remote assets or employees to business enterprise users through multiple wireless networks and the Internet by using web served applications. The central core of the gateway is a location aware business component that sends and receives location based information to and from remote and mobile assets and applies business logic to the location data to enhance and automate business applications run by the enterprise user. This functionality considerably exceeds that of a traditional wireless gateway, which simply manages messages passed through multiple wireless networks but does nothing with the content of the messages. The business logic component provides a common interface and protocol for handling location information and allows applications that follow the protocol to interface with the gateway to take advantage of location information by using location data to trigger events or to tag events, messages, or other data.
Owner:GRID DATA
Routing in a data communication network
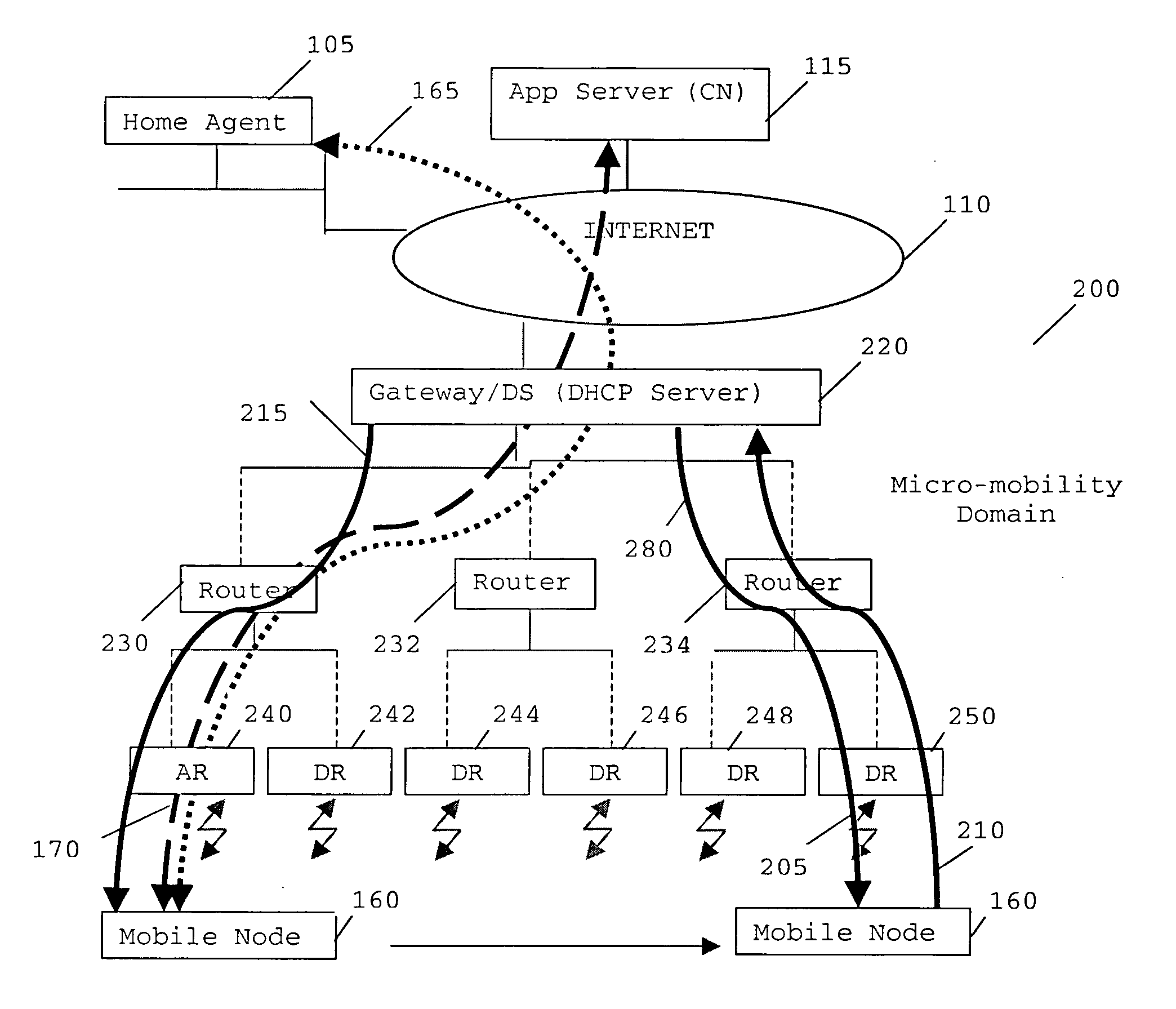
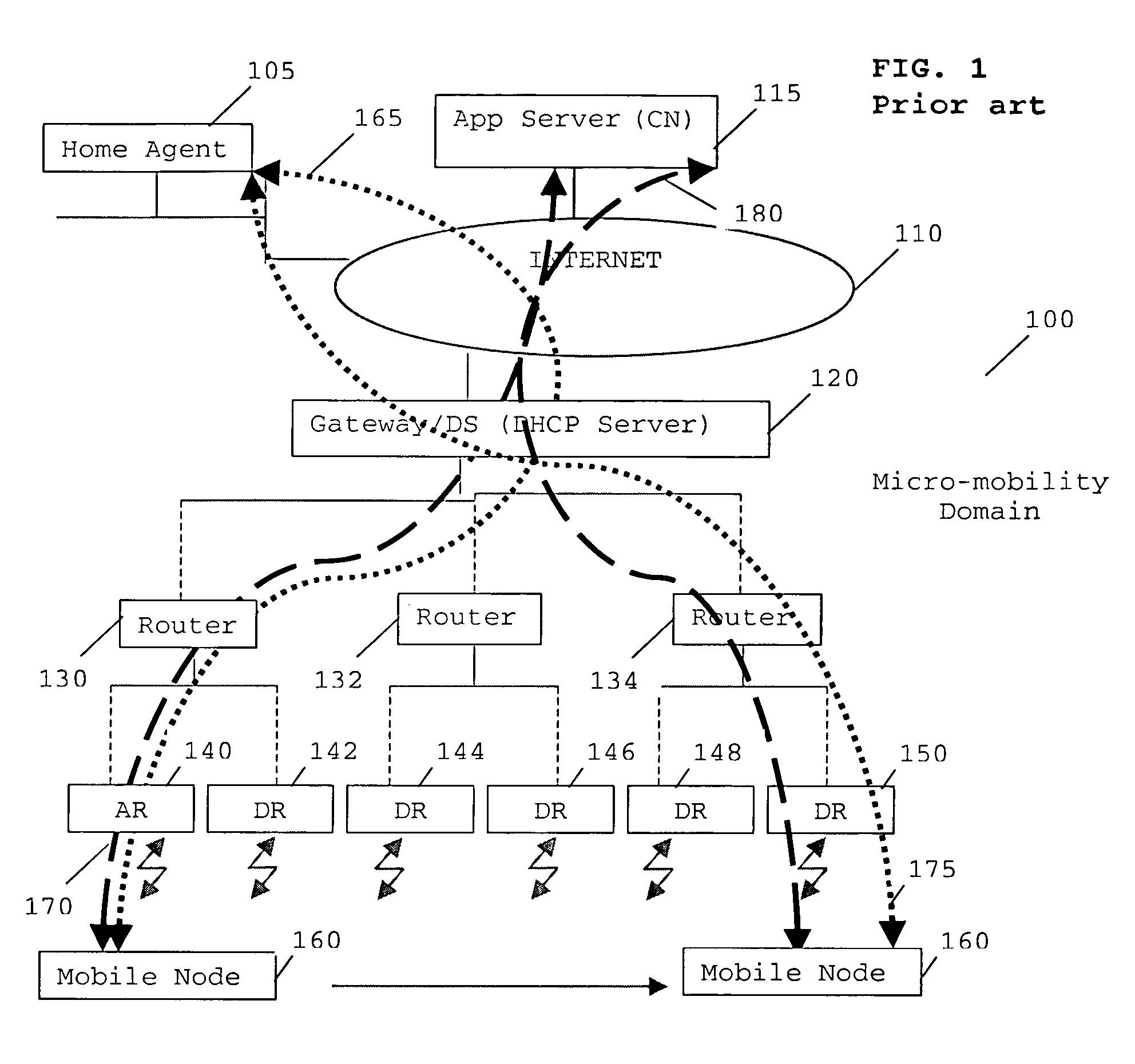
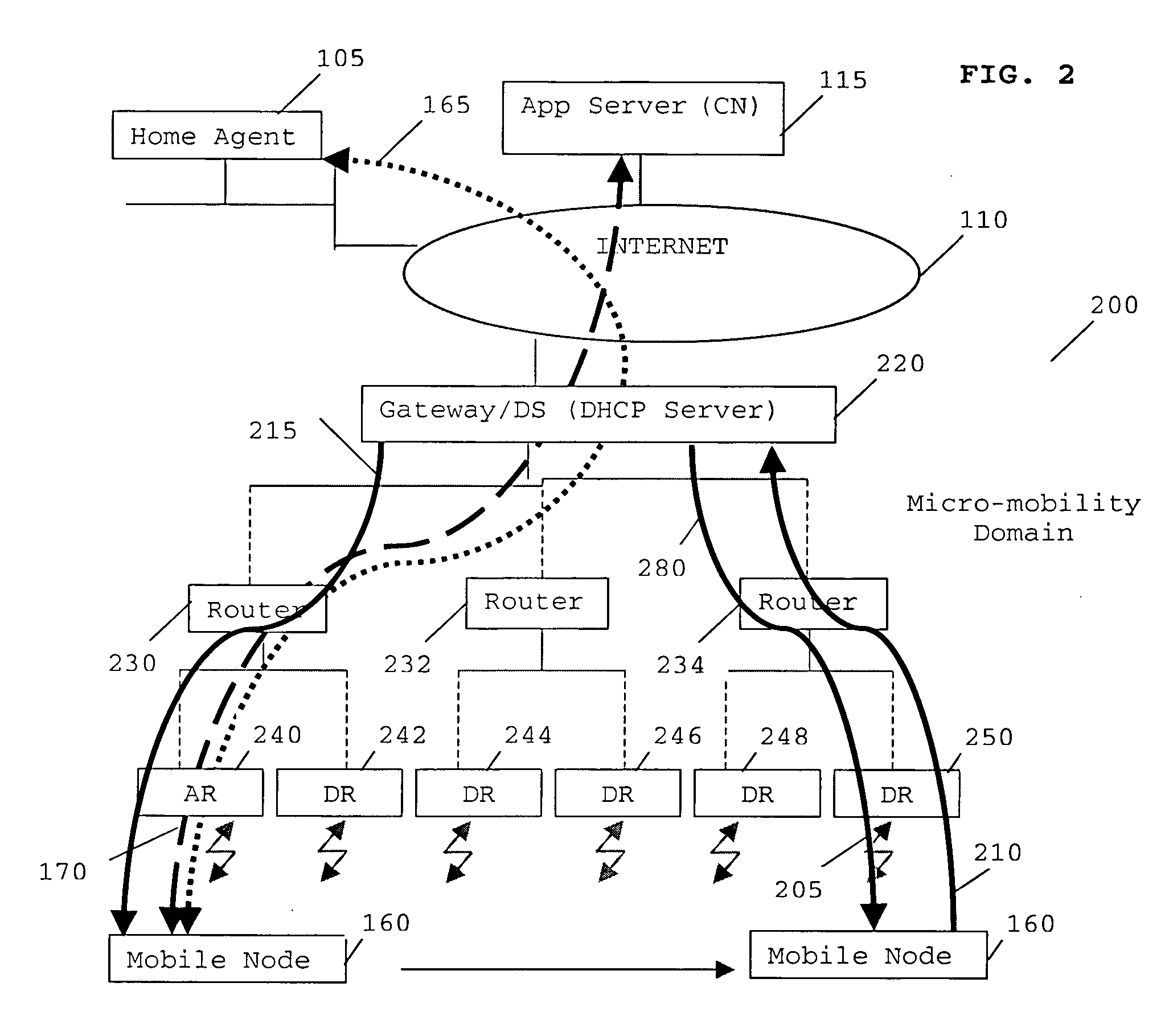
“A method of supporting mobility in an Internet Protocol (IP)-based data network. The method comprises the steps of generating a first stateful IP autoconfiguration message at a mobile node, whereby the message includes an address capable of use for routing maintenance. The mobile node transmits the generated message to a first access node, which incorporates its address and forwards the message to a dynamic host configuration protocol (DHCP) Server. The DHCP Server and access node analyse the message to determine a route to deliver data to and / or from the mobile node. One or more route update message are triggered from said access node and said DHCP server to a number of network elements between said access node and said DHCP server in the IP based data network to support mobility in an IP domain with minimum bandwidth use and minimum tunnelling required.”
Owner:GOOGLE TECH HLDG LLC
Machine Data Web
ActiveUS20070118491A1Preserve integrityError detection/correctionInterprogram communicationInformation processingConfigfs
Methods and apparatus consistent with the invention provide the ability to organize and build understandings of machine data generated by a variety of information-processing environments. Machine data is a product of information-processing systems (e.g., activity logs, configuration files, messages, database records) and represents the evidence of particular events that have taken place and been recorded in raw data format. In one embodiment, machine data is turned into a machine data web by organizing machine data into events and then linking events together.
Owner:SPLUNK INC
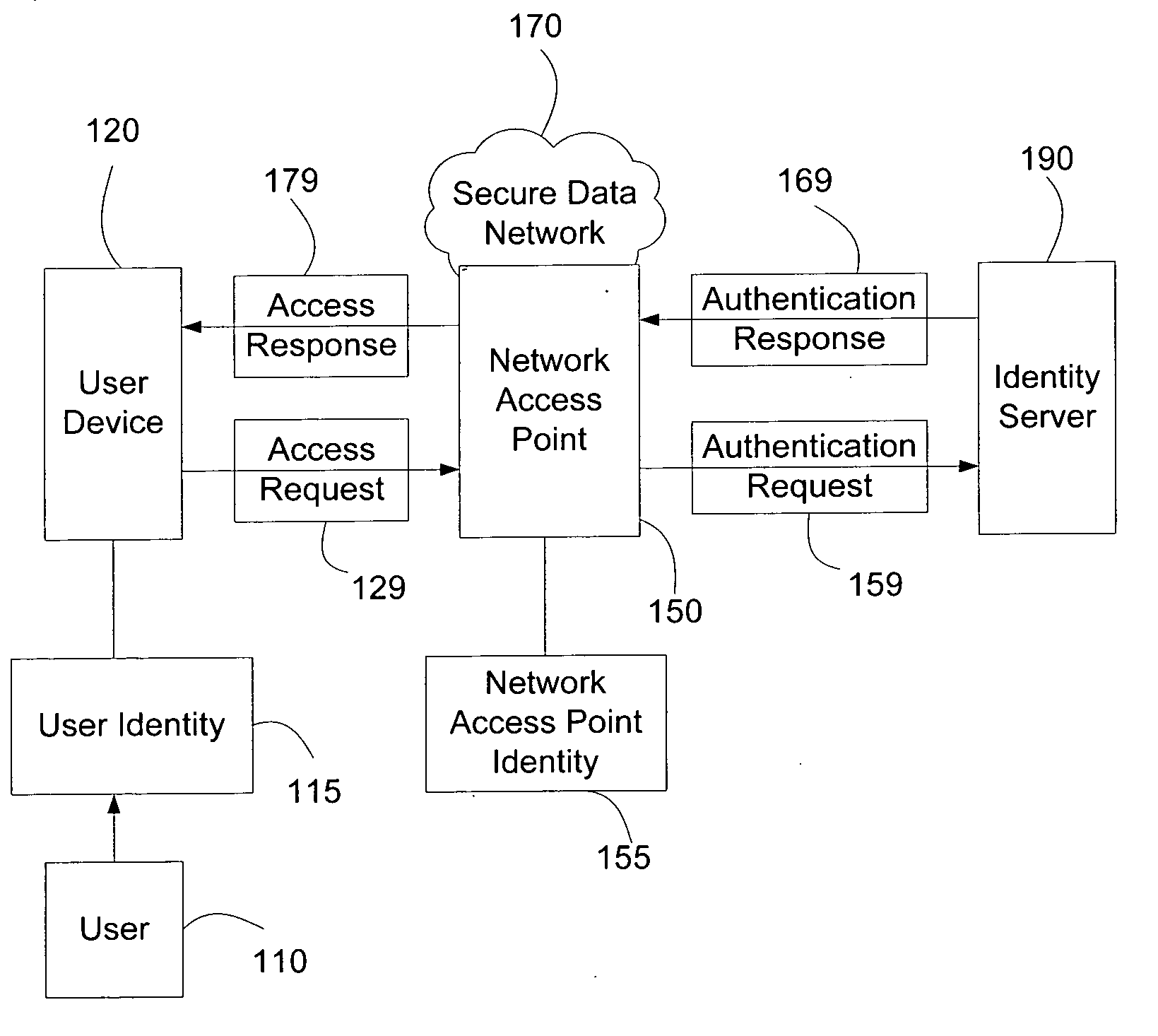
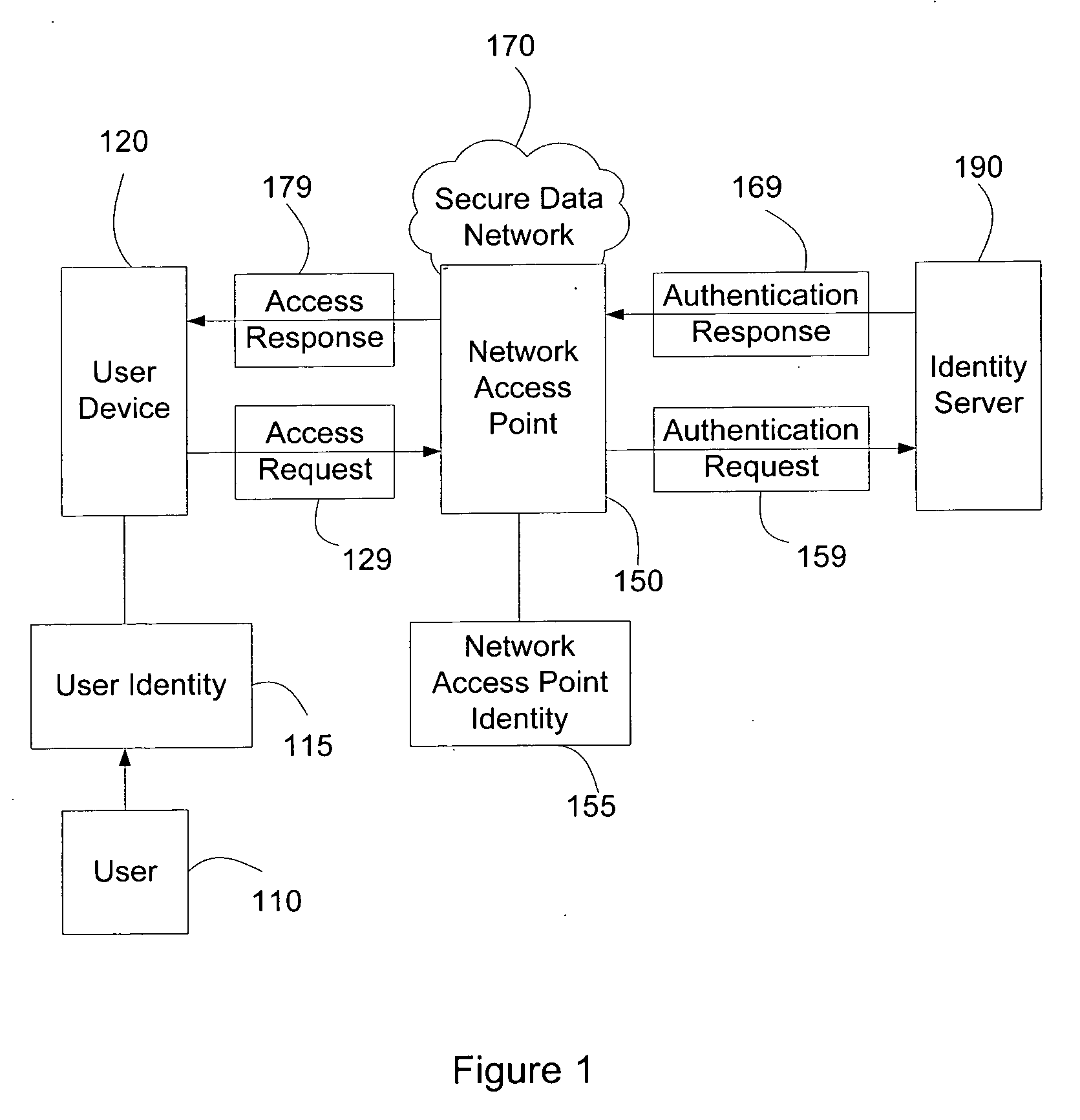
Systems and methods for user access authentication based on network access point
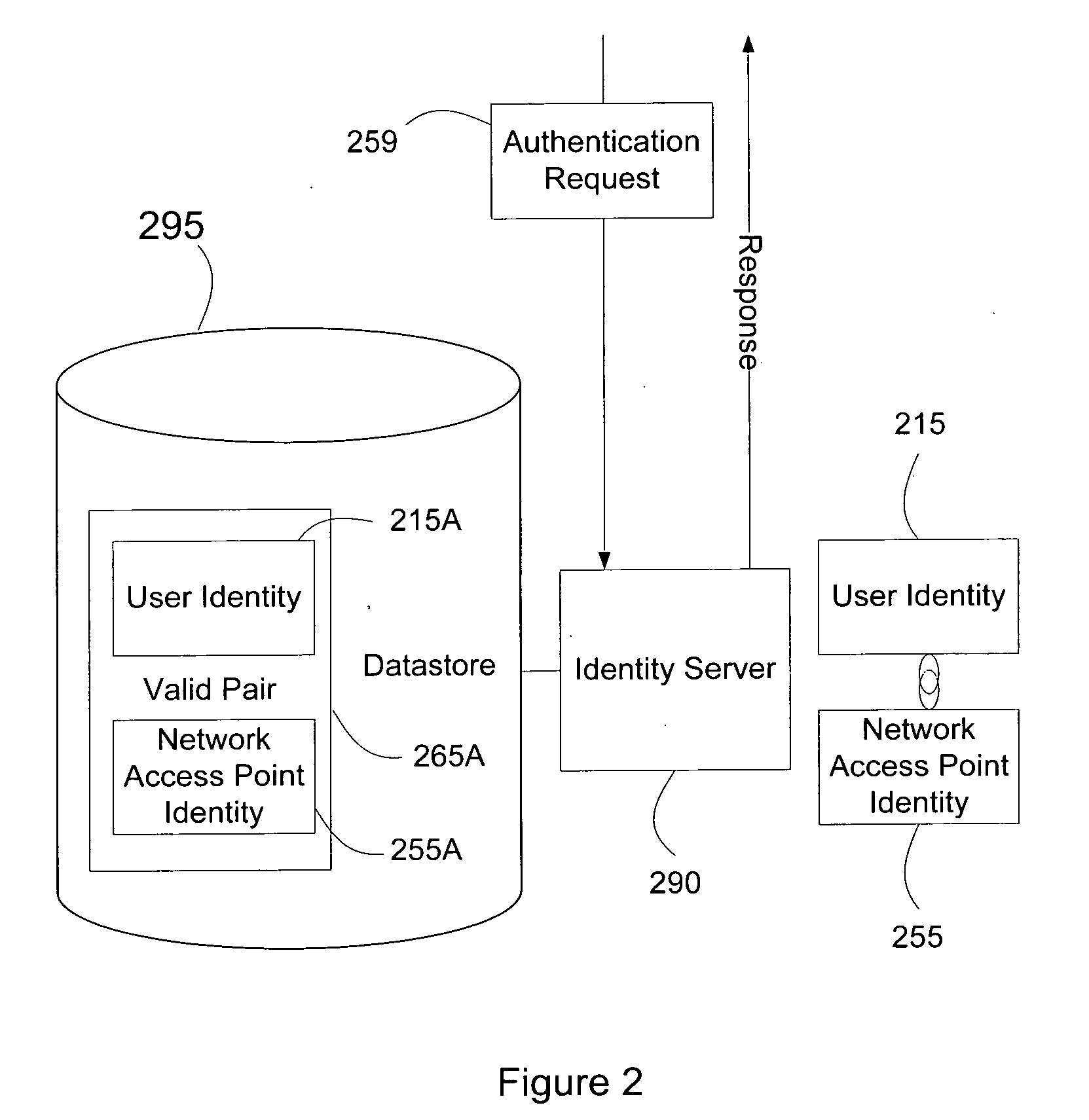
ActiveUS20070271598A1Random number generatorsUser identity/authority verificationTime informationAuthentication system
Systems and methods of authenticating user access based on an access point to a secure data network include a secure data network having a plurality of a network access points serving as entry points for a user to access the secure data network using a user device. The user is associated with a user identity, each network access point with a network access point identity. The user uses a user device to send an access request, requesting access to the secure data network, to the network access point, which then sends an authentication request to an identity server. The identity server processes the authentication request, by validating the combination of the user identity and the network access point identity, and responds with an authentication response, granting or denying access, as communicated to the user device via an access response. The secure data network may comprise an application level secure data network, in which the user uses the user device to request access to a network application. Furthermore, the identity server may validate the combined user identity and network access point identity data in conjunction with time information, access allowance data, and / or traffic volume data.
Owner:A10 NETWORKS
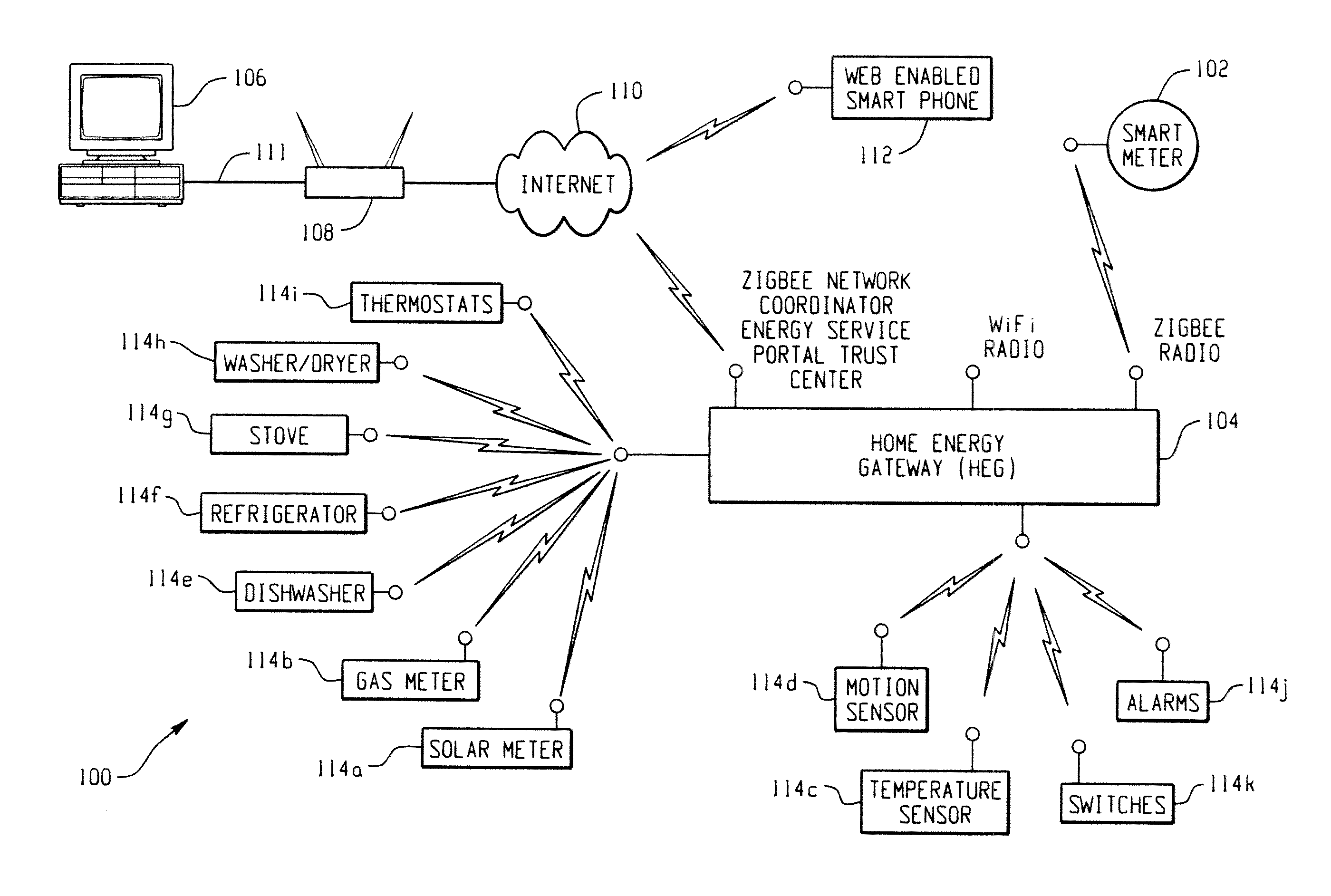
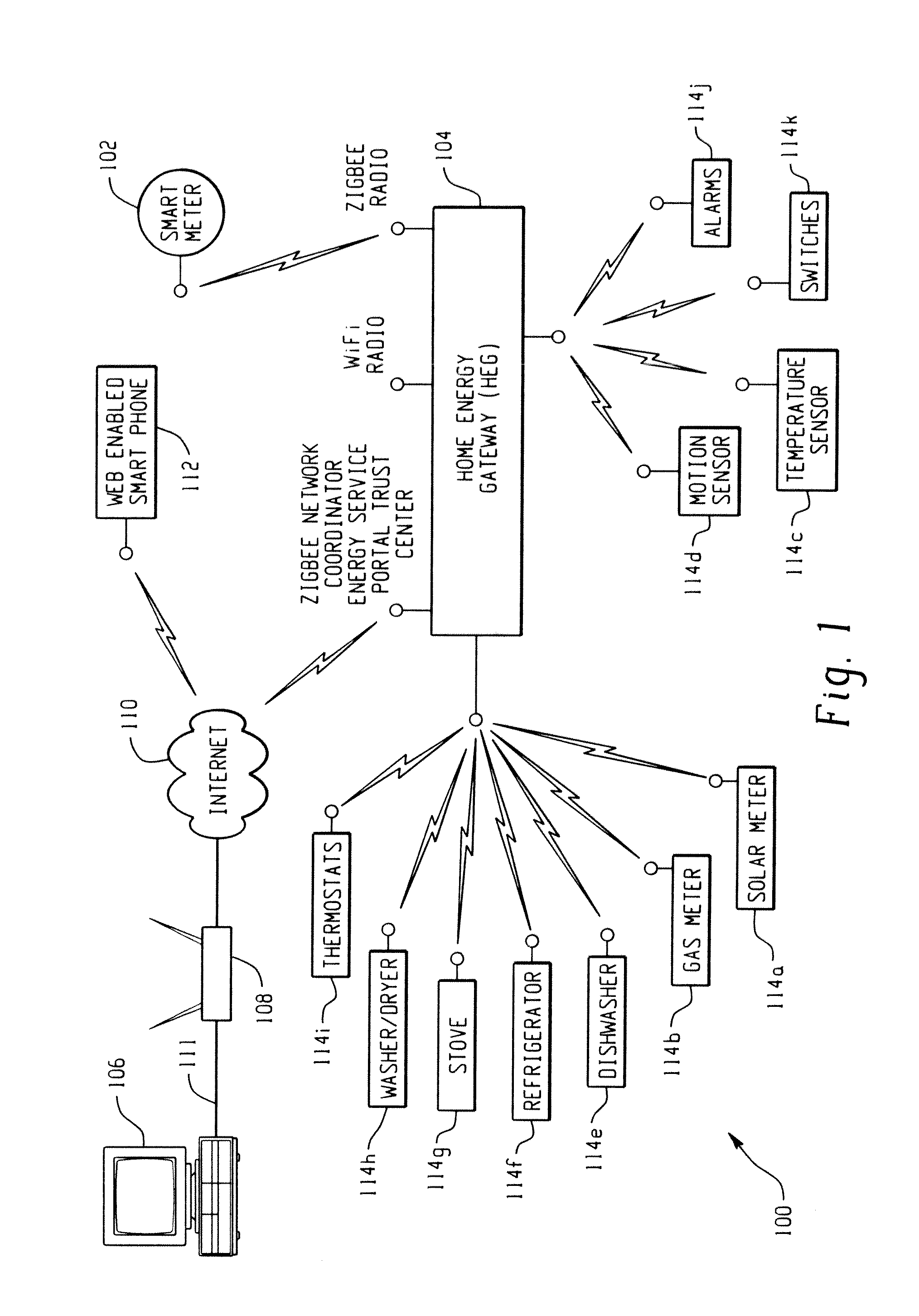
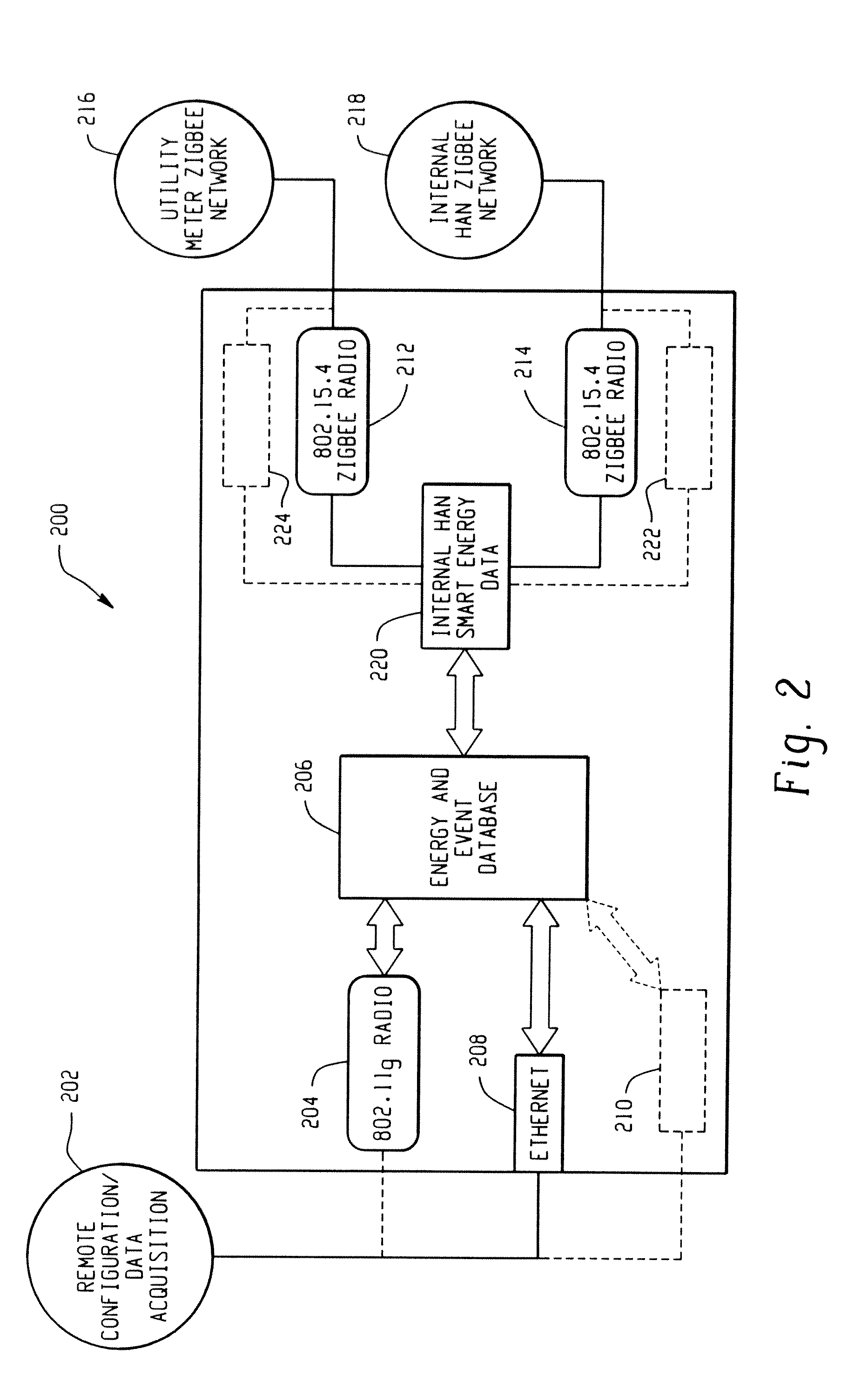
Low cost and flexible energy management system
ActiveUS20110202910A1Electrical apparatusMultiple digital computer combinationsData managementEnergy management system
A premises data management system includes a first communication network configured to transmit and receive data to and from a user interface. Another communication network is configured to access data from and provides data to accessories within the premises management system. A gateway of the system includes a first interface channel and another interface channel. The gateway receives the data from the first communication network, via the first interface channel. The gateway reformats the data from the first communication network for communication to the other communication network via the other interface channel. The gateway also requests data from the accessories via the other interface channel and replies to the user interface via the first interface channel.
Owner:HAIER US APPLIANCE SOLUTIONS INC
Systems and methods for multimedia content sharing
InactiveUS20100036967A1Easy to useFacilitates operator selectionMultiple digital computer combinationsTelevision systemsDisplay deviceContent sharing
The invention provides, in one aspect, a multimedia content sharing system that includes (i) a shared content server which stores items of content (such as still, moving images and audio) and (ii) a plurality of nodes, each of which is in communications with the shared content server via cellular telephone and / or other data networks. The shared content server transmits items of content to a first set of the nodes “automatically,” e.g., without requests by users of those nodes for the items. At least one node in that first set displays the content of received items (e.g., on an LCD screen) and accepts user feedback in regard to those items. That feedback—which may be, for example, a command to copy an item into an “album”, to rotate an item on the display, to block another node from displaying the items, and / or to block a sender (or creator) of the item from sending further items of content from presenting—is transmitted back to the shared content server for distribution to other nodes, which alter their own respective displays of the items accordingly.
Owner:ISABELLA PRODS
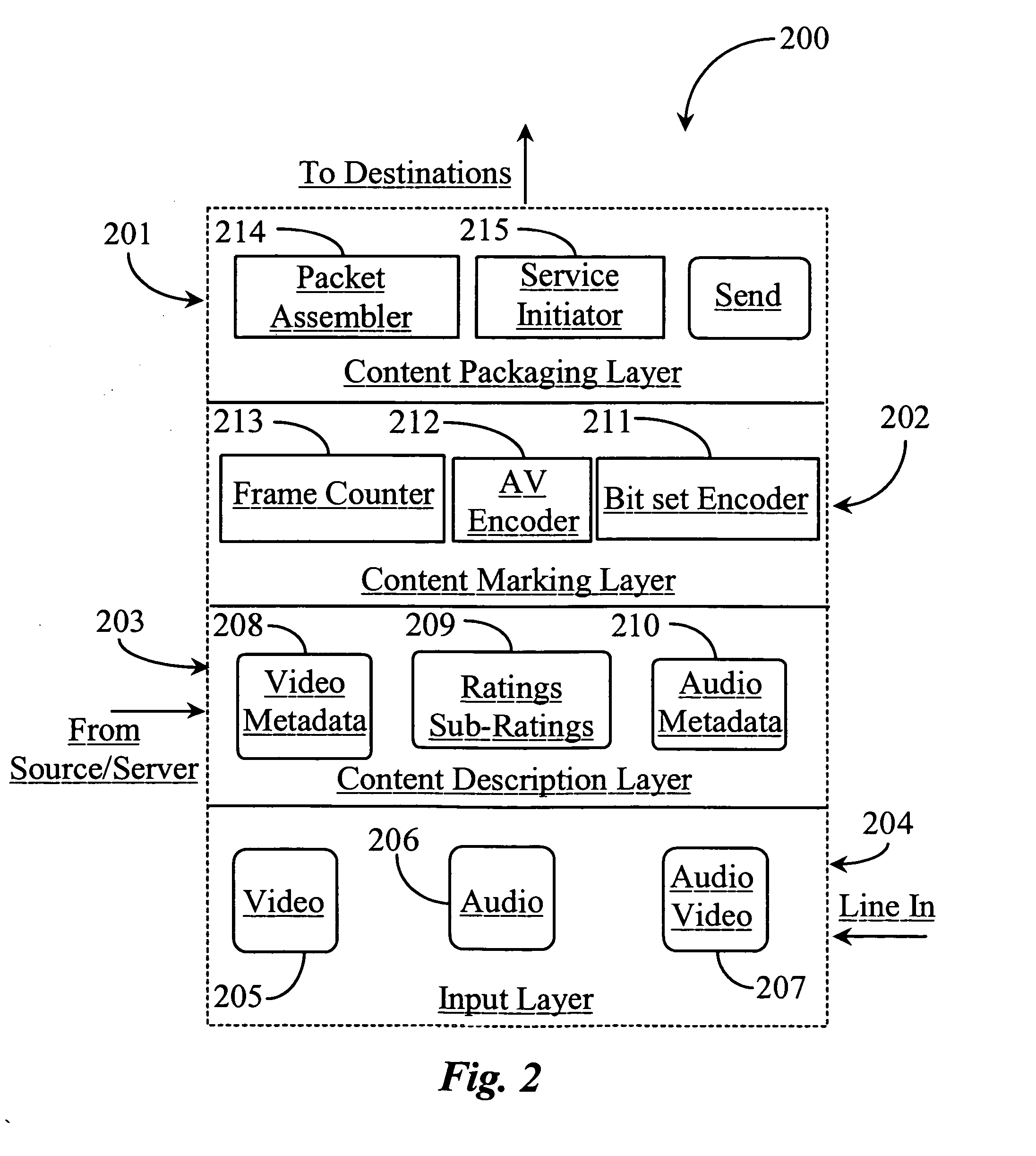
Distributive system for marking and blocking video and audio content related to video and audio programs
ActiveUS20060130118A1Television system detailsAnalogue secracy/subscription systemsRating systemSeries data
A system is provided for rating multimedia content streamed over a data network as a series of data frames, segments, or packets and for administering display of the rated content. The system includes at least one content source device for creating raw multimedia content; an intermediate content marking and delivery agent for marking and delivering the content created; and a content receiving device for displaying or rejecting delivered content according to detection of and comparison of content markings applied to at least one preset value. In one aspect, the content marking follows some existing or devised rating system and whereupon the marked content is identifiable at the receiving end for each received data frame, segment, or data packet carrying content in a payload.
Owner:ALCATEL LUCENT SAS
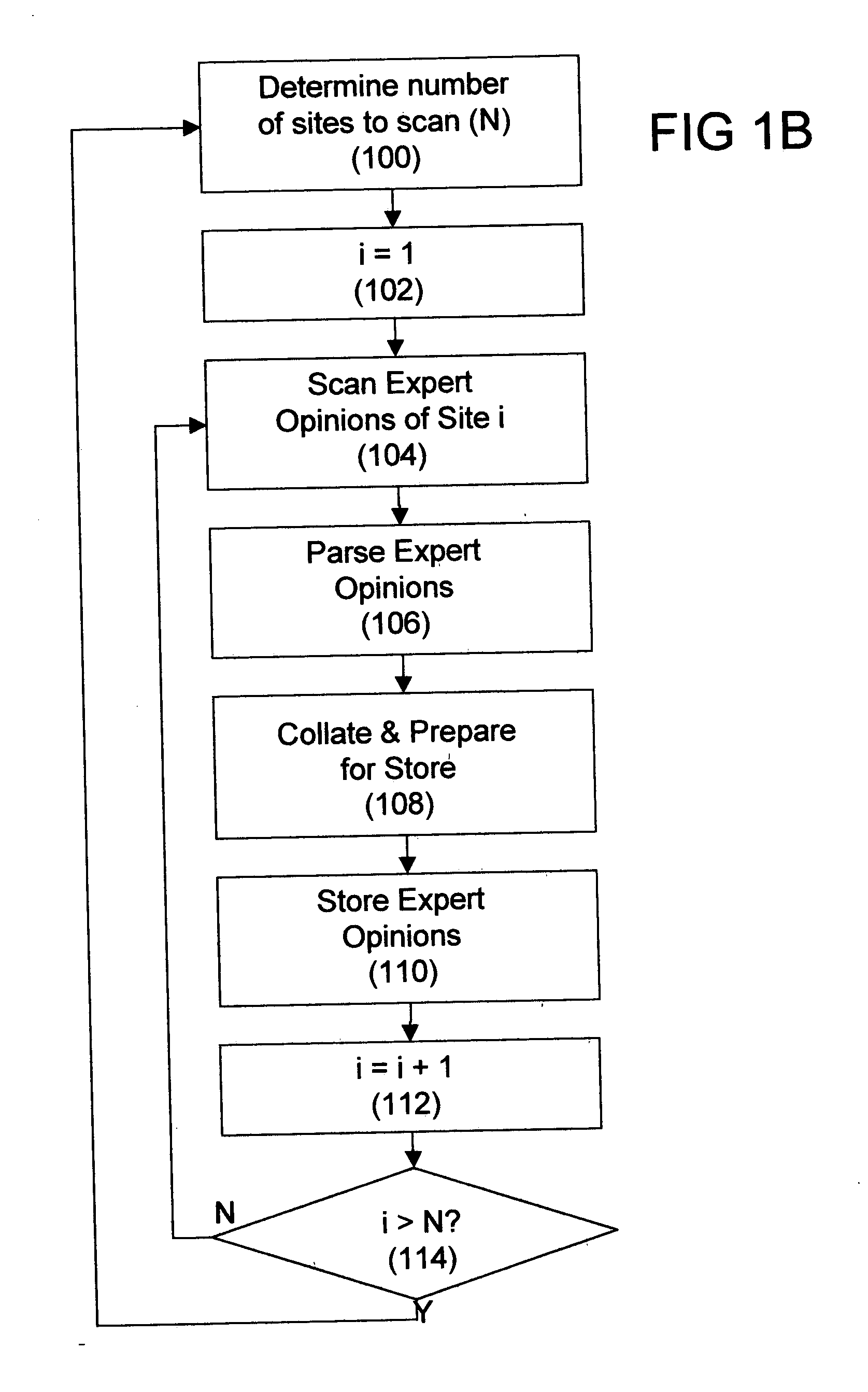
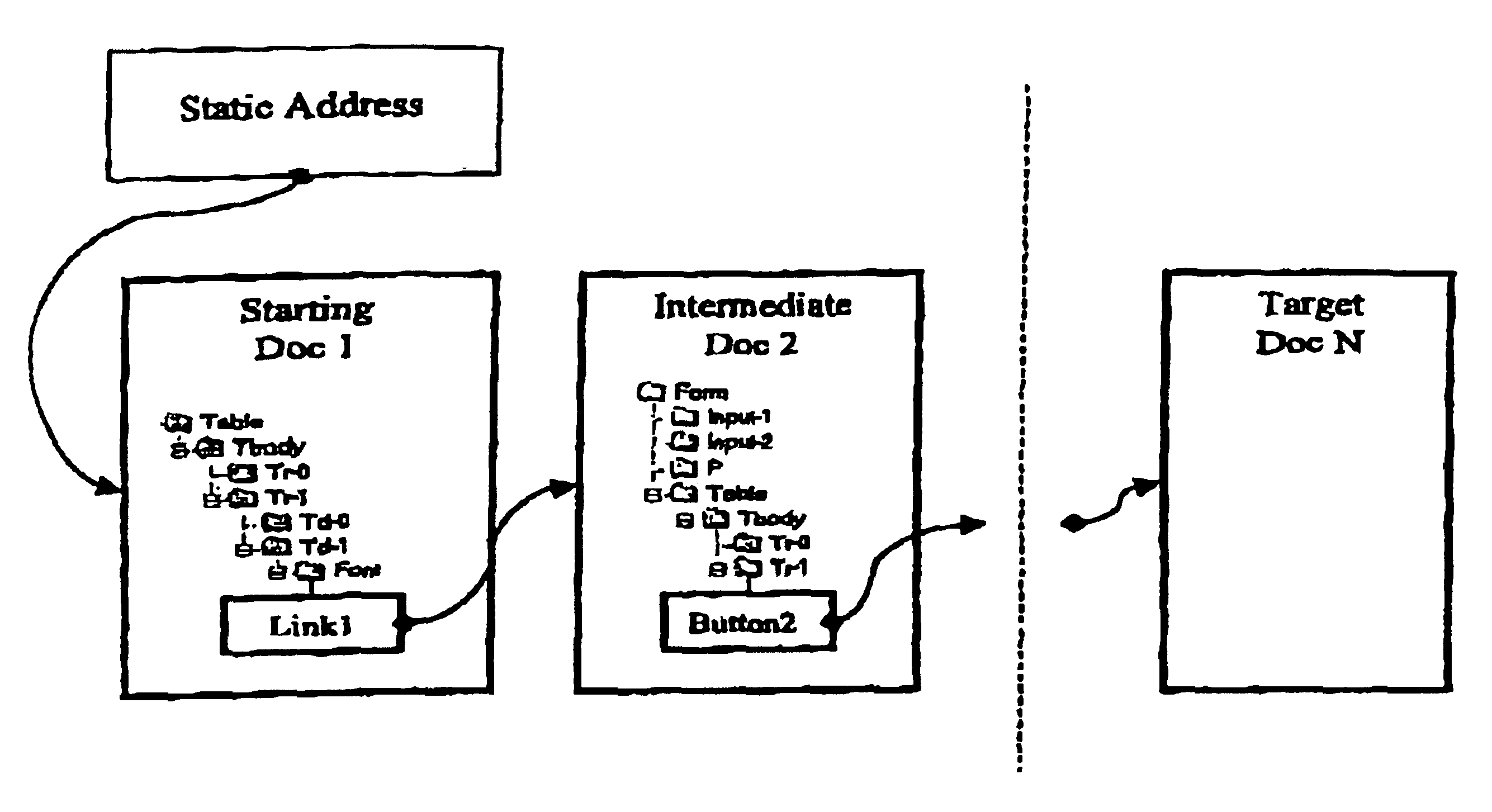
System and method for automatic retrieval of structured online documents
InactiveUS6842755B2Eliminate needData processing applicationsDigital data processing detailsComputerized systemDocumentation
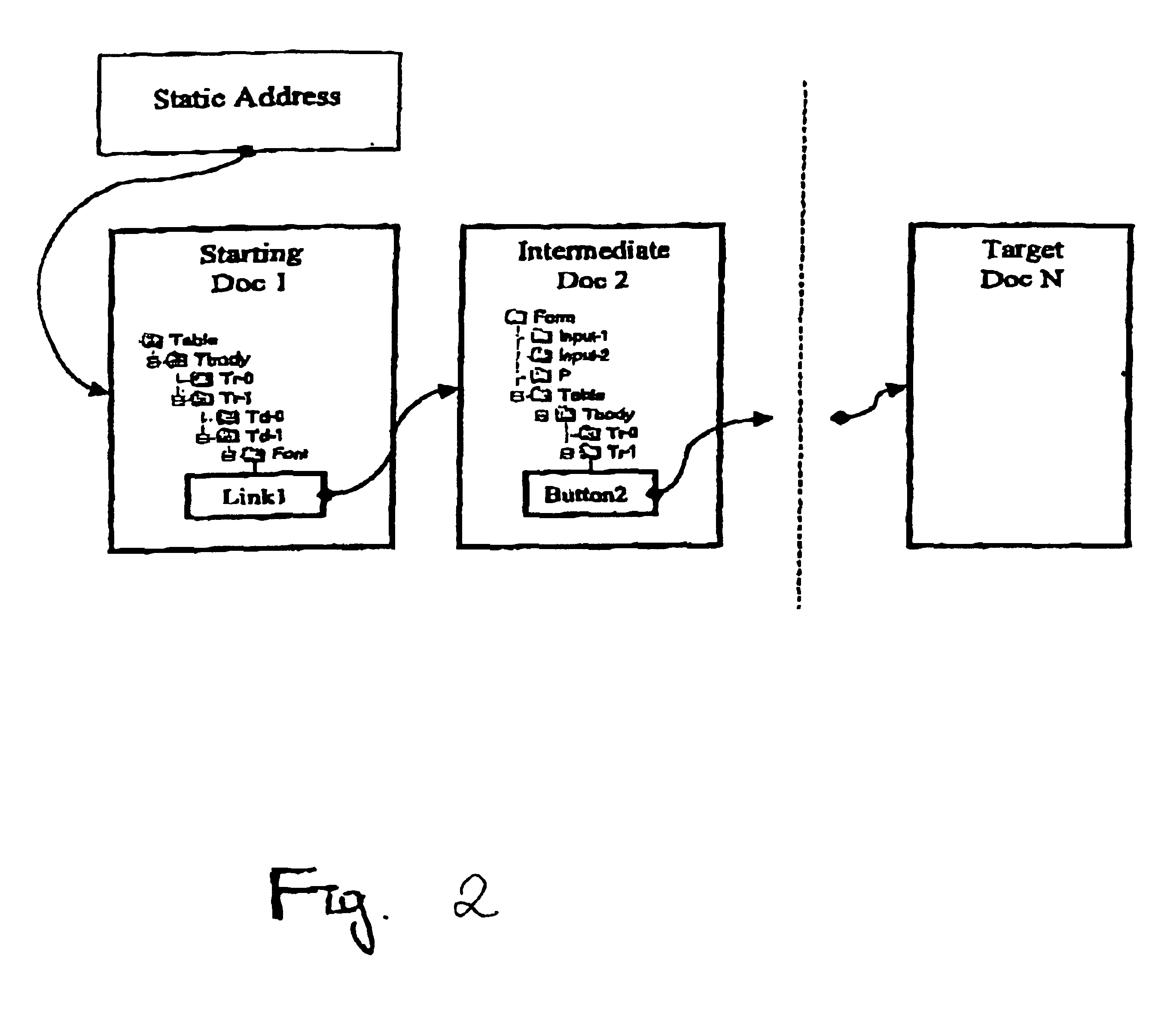
A method and system for automatic retrieval of a document linking to a starting document that has a static address on a data network. A sequence of commands that cause a browser in a computer system to navigate from a starting document to a target document on a data network is recorded. The recorded sequence of commands can be reproduced to cause the browser to navigate from the starting document through a sequence of intermediate documents to the refreshed version of the target document. More particularly, the invention allows retrieval of the target document even when the intermediate and the target documents are dynamically generated by a server computer and thus their online addresses change every time they are loaded.
Owner:DIVINE TECH VENTURES
Admission control for aggregate data flows based on a threshold adjusted according to the frequency of traffic congestion notification
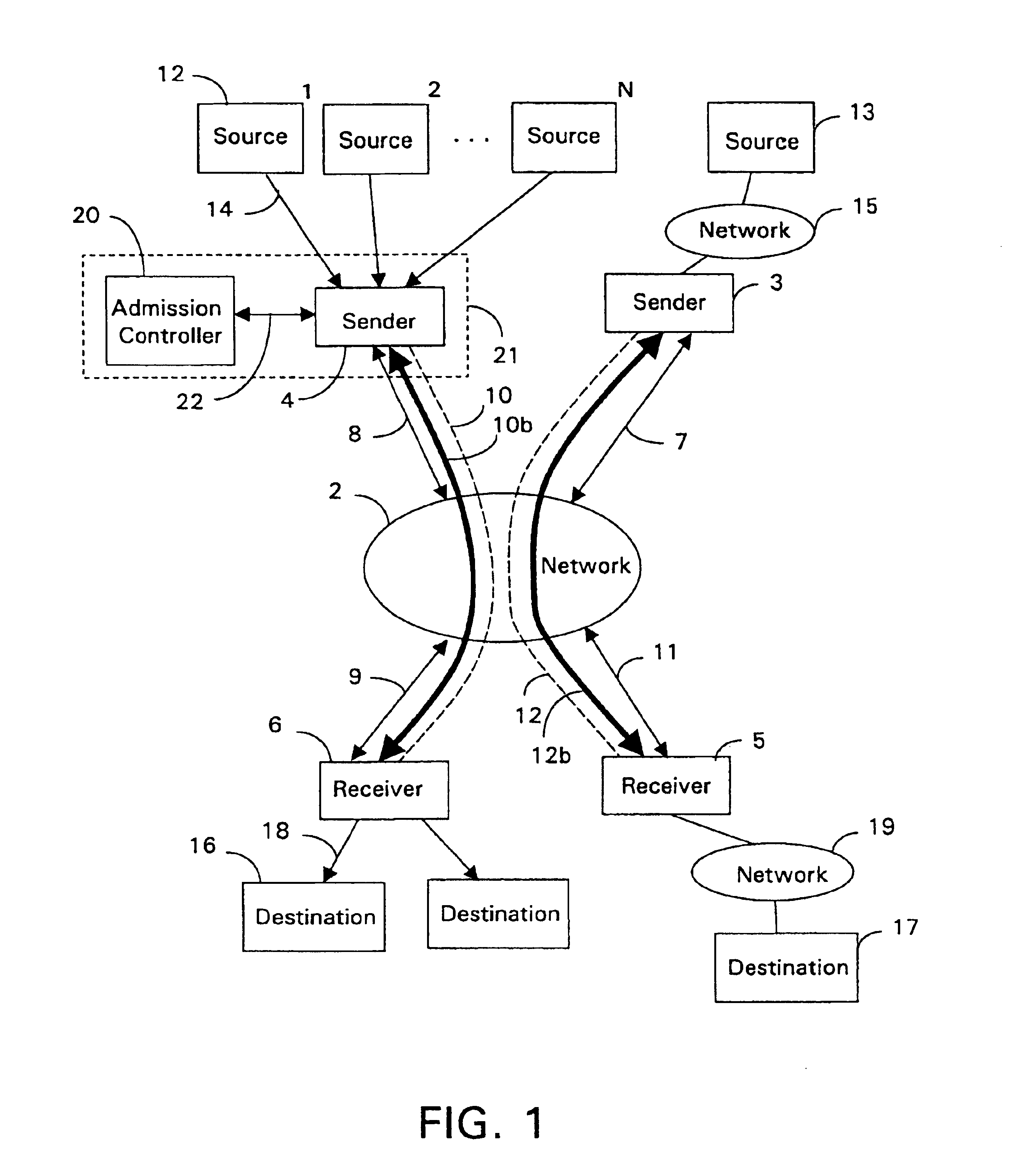
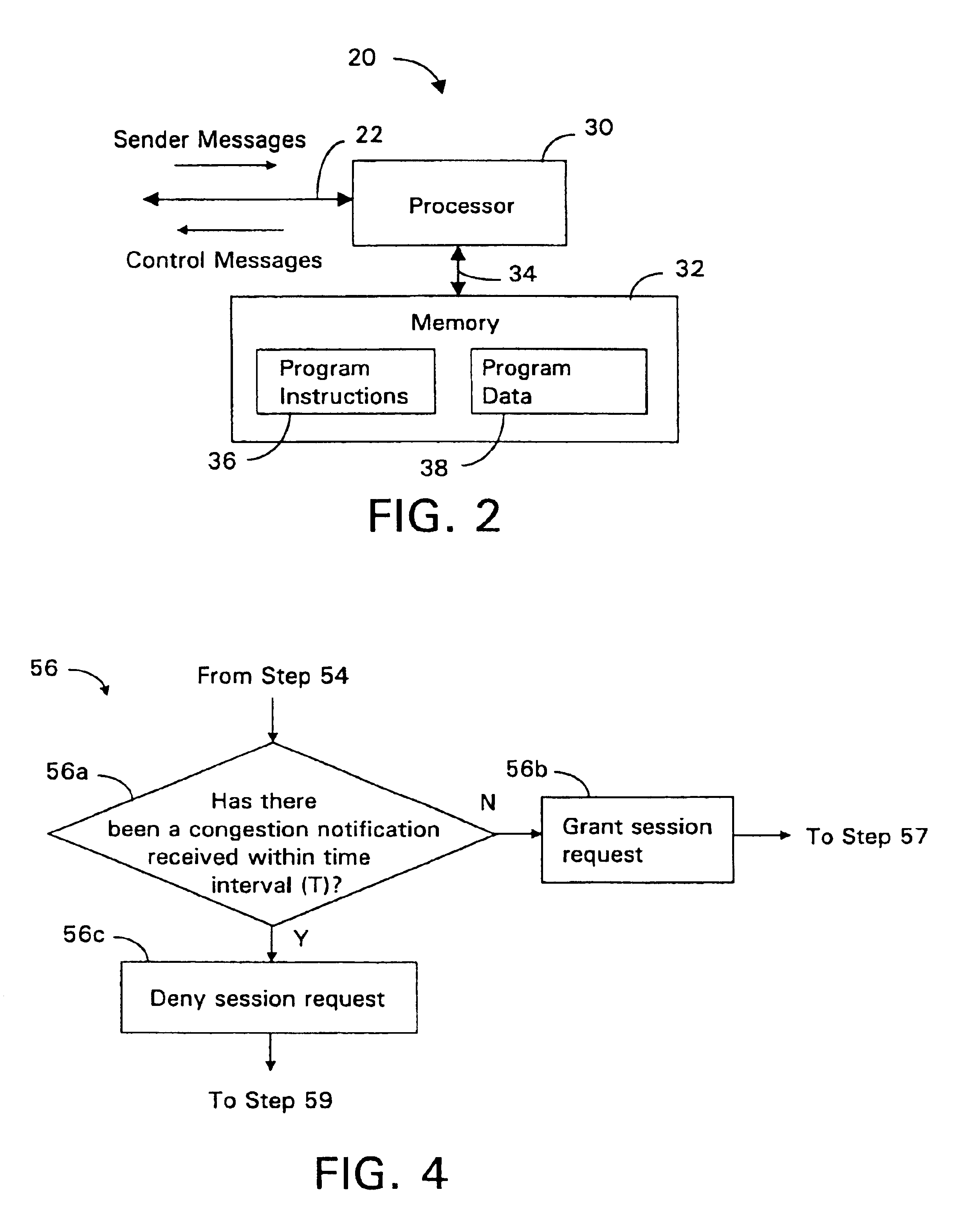
InactiveUS6839767B1Guaranteed bandwidthExacerbating congestion condition is avoidedError preventionTransmission systemsTraffic capacityData stream
An admission controller and its method of operation for controlling admission of data flows into an aggregate data flow are described. Admitted data flows are aggregated into an aggregate data flow for transmission by a router, for example, over a data network. The aggregate data flow typically follows a pre-established path through the network; for example a multi-protocol label switched (MPLS) path. The path has minimum and maximum bandwidth limits assigned to it. The admission controller controls admission of new data flows into the aggregate data flow by granting or denying new session requests for the new data flows. Congestion notifications received from the network and bandwidth limits of the path are considered in determining whether to grant or deny a new session request. In this way, the admission controller provides elastic sharing of network bandwidth among data flows without exacerbating network congestion and while remaining within the path's bandwidth limits. The data flows may include transaction oriented traffic.
Owner:RPX CLEARINGHOUSE
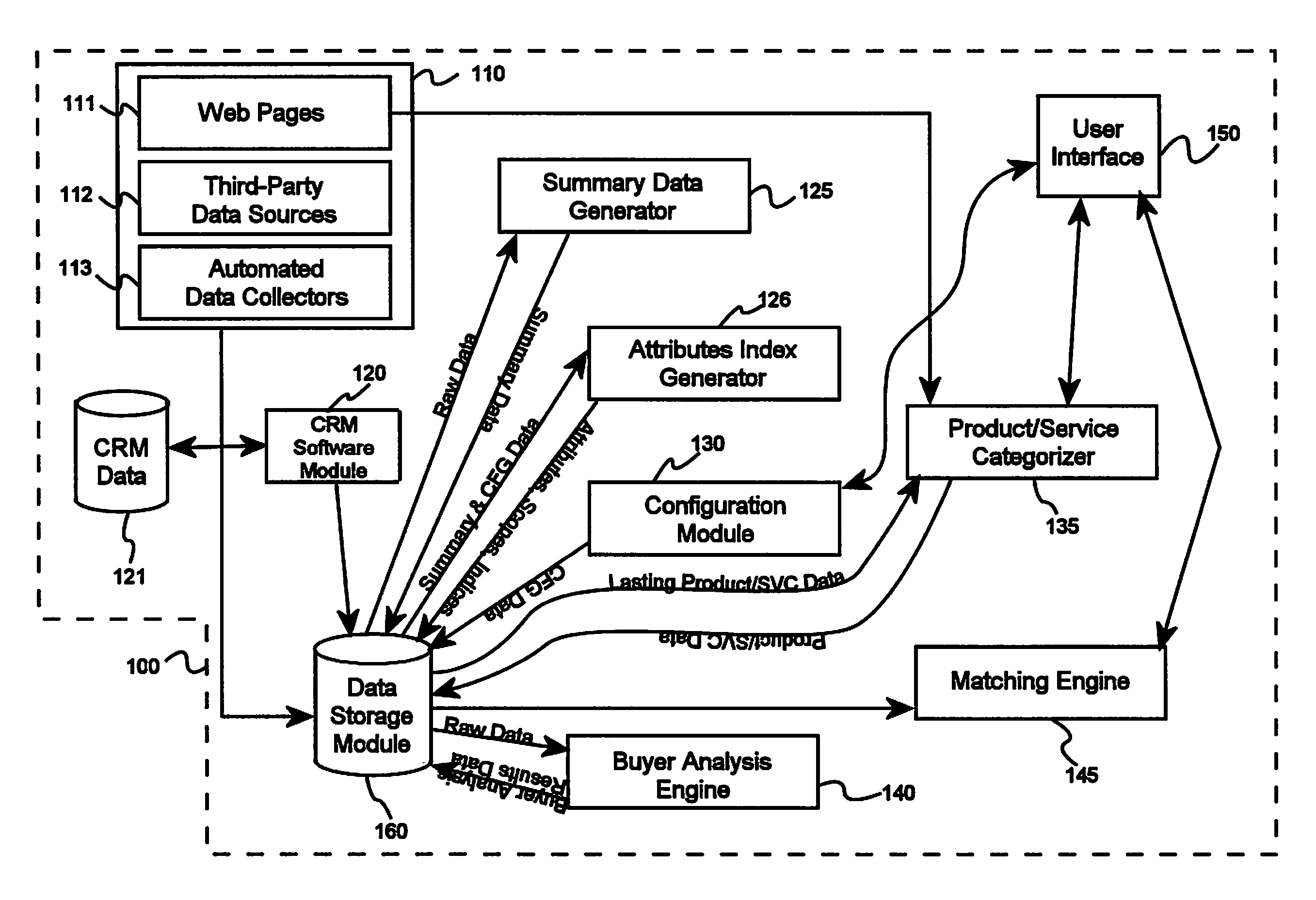
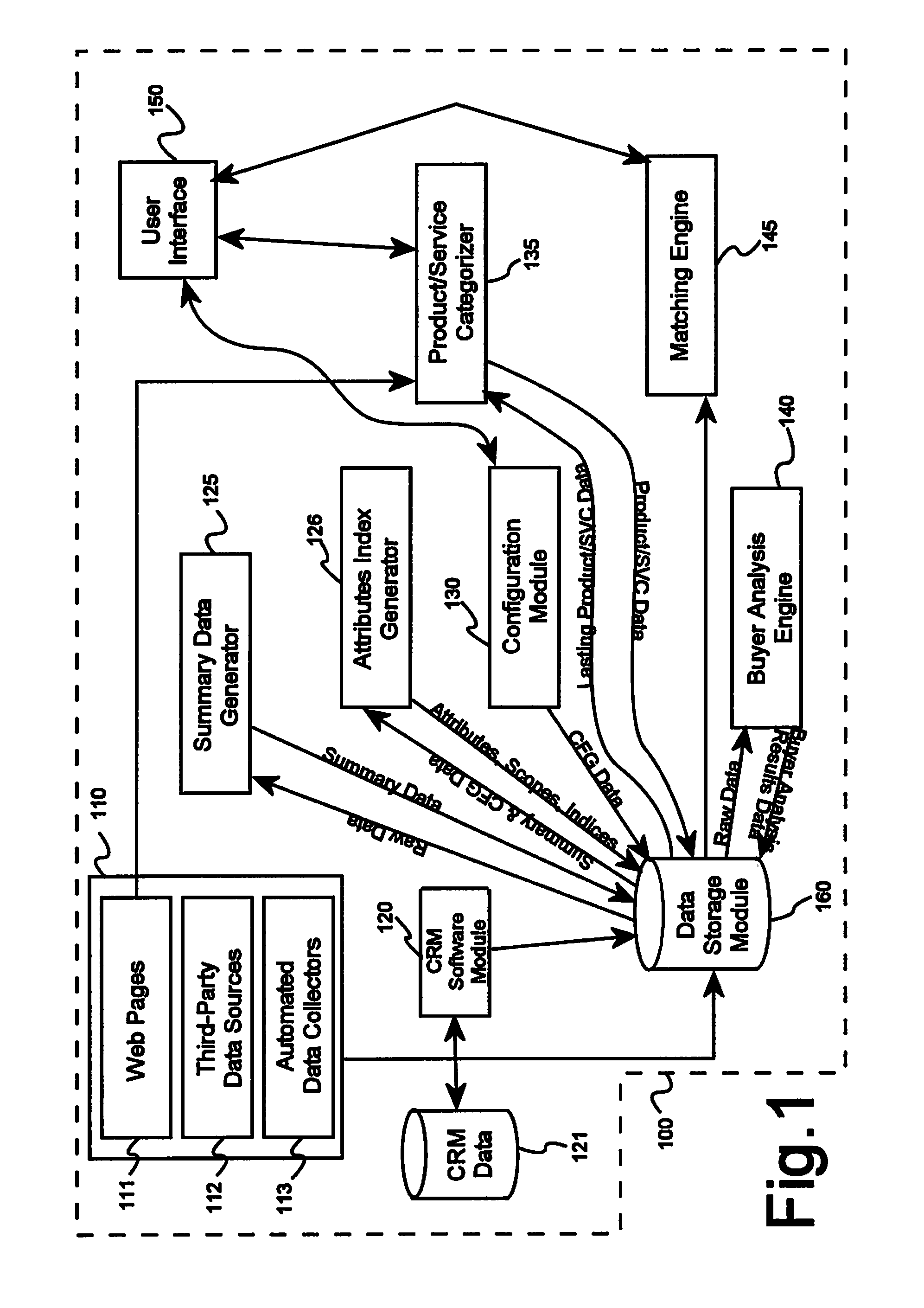
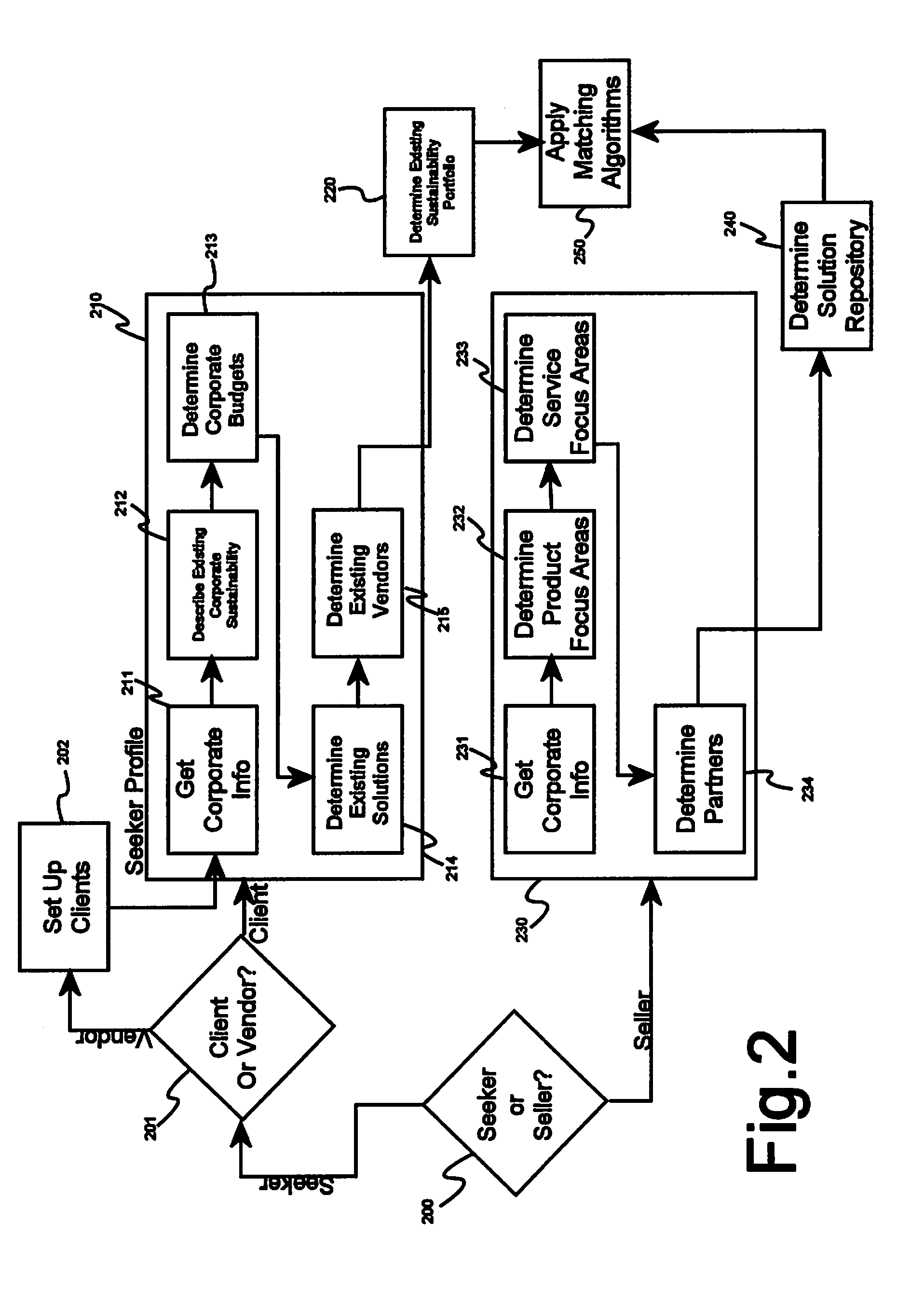
System and methods for matching potential buyers and sellers of complex offers
A system for matching potential buyers and sellers of complex offers, comprising a plurality of data collection devices, each connected to at least one packet-based data network and adapted to collect data pertaining to a plurality of potential buyers or sellers of complex offers, a summary data generator software module operating on a server computer and connected via a data network to a database, an attribute index generator software module operating on a server computer and connected via a data network to the database, a categorization software module operating on a server computer and connected via a data network to the database, a buyer analysis engine software module operating on a server computer and connected via a data network to the database, an analysis engine software module operating on a server computer and connected via a data network to the database, and a matching engine software module operating on a server computer and connected via a data network to the database. Data collected by the data collection devices is stored in the database and is used by the summary data generator software module to generate a plurality of summary data elements pertaining to a potential buyer of a complex offer, and the plurality of summary data elements is stored in the database and used by the attribute index generator software module to generate attribute indices each based on at least two summary data elements using a weighted relational algorithm, and at least some data collected by the data collection devices is used by the buyer analysis engine software module to determine at least a probability that a buyer will buy a specific complex offer, and the marching engine software module uses an optimization algorithm to determine an optimal matching of potential buyers and complex offers based at least in part on a plurality of attribute indices and a likelihood to buy for each potential pair of offers and potential buyers.
Owner:IVERIDIS
Method and system for detecting malicious behavioral patterns in a computer, using machine learning
InactiveUS20070294768A1Memory loss protectionUnauthorized memory use protectionComputer wormComputerized system
Method for detecting malicious behavioral patterns which are related to malicious software such as a computer worm in computerized systems that include data exchange channels with other systems over a data network. Accordingly, hardware and / or software parameters are determined in the computerized system that is can characterize known behavioral patterns thereof. Known malicious code samples are learned by a machine learning process, such as decision trees and artificial neural networks, and the results of the machine learning process are analyzed in respect to the behavioral patterns of the computerized system. Then known and unknown malicious code samples are identified according to the results of the machine learning process.
Owner:DEUTSCHE TELEKOM AG
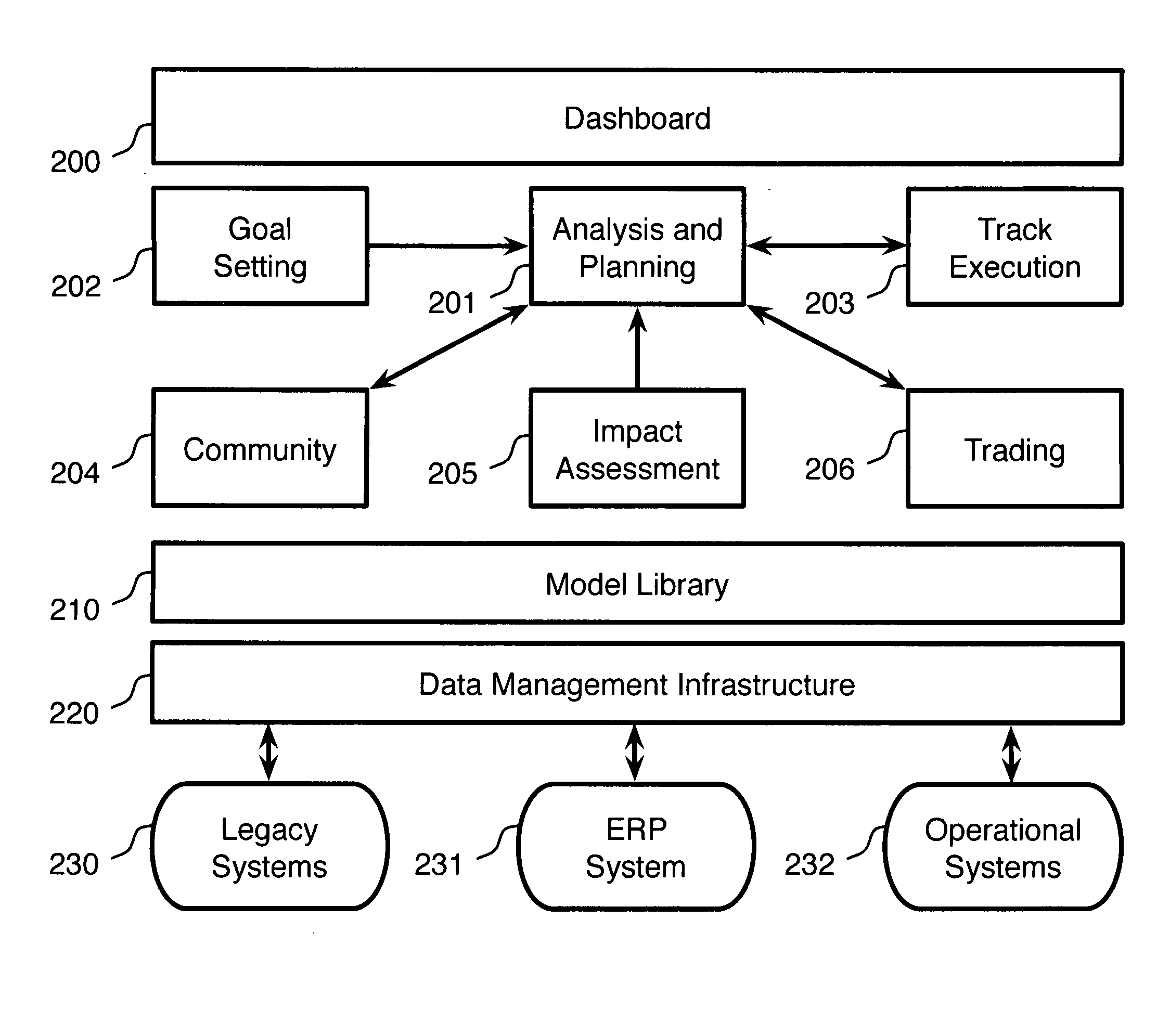
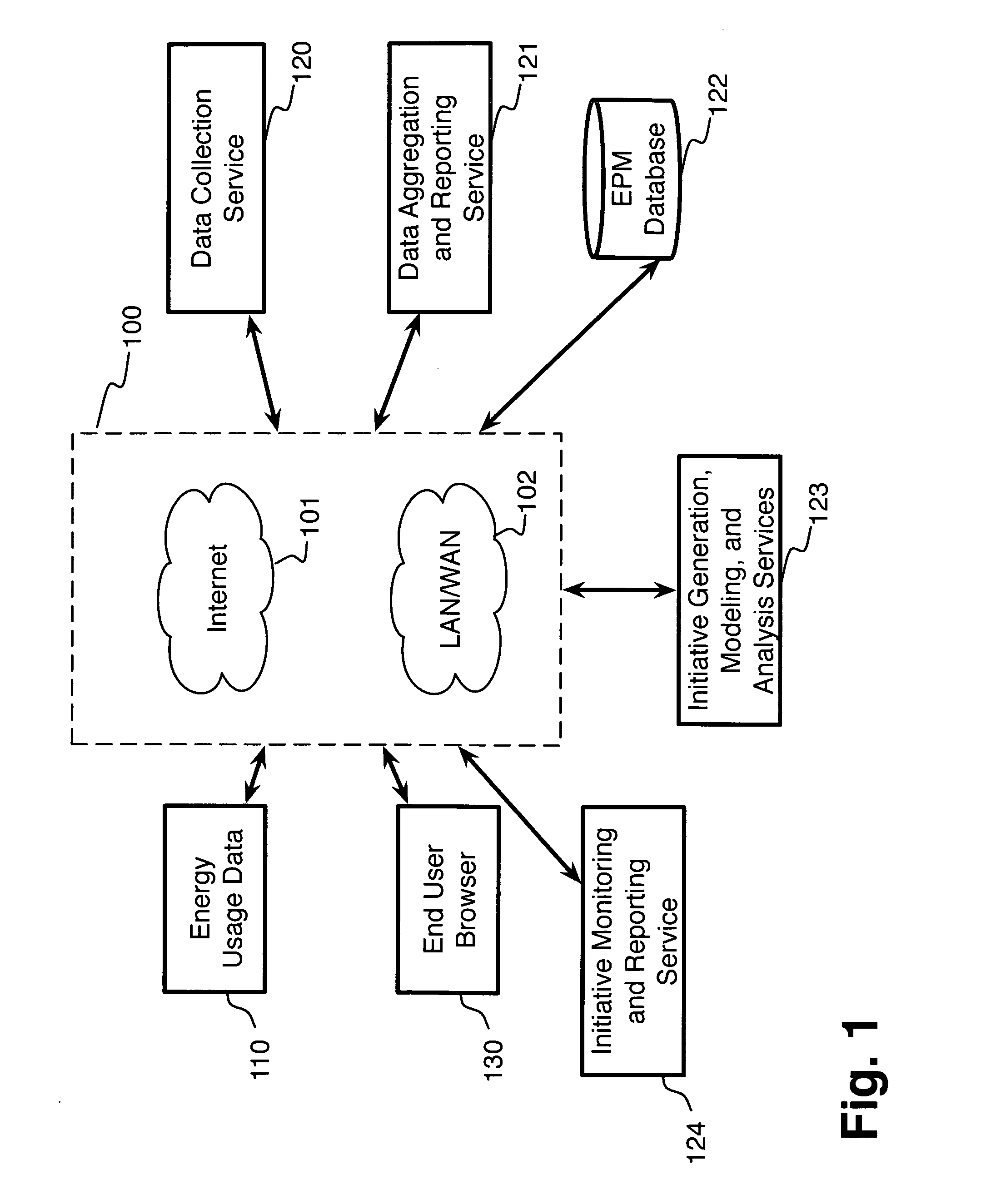
System and method for energy performance management
InactiveUS20120166616A1Data processing applicationsDigital computer detailsNetwork connectionProgram planning
A system for resource performance management, comprising a network-connected data collection service adapted to receive data from a plurality of resources, a network-connected data aggregation and reporting service adapted to aggregate resource-related data on at least temporal, organizational, geographic, and resource-specific dimensions, a network-connected initiative modeling service adapted to facilitate modeling by a user of a plurality of resource-related initiatives, and a network-connected initiative monitoring service adapted to receive data from one of the data collection service and the data aggregation and reporting service, and further adapted to measure performance of a plurality of resource-based initiatives, wherein a plurality of resource-based initiatives are assembled within the initiative modeling service into a plurality of initiative portfolios, and the plurality of initiative portfolios are modeled under a variety of forecast scenarios to determine an optimal initiative portfolio from among the plurality of portfolios, is disclosed.
Owner:LOGICBLOX
Method and apparatus for providing multi-cast transmissions using a distributed router
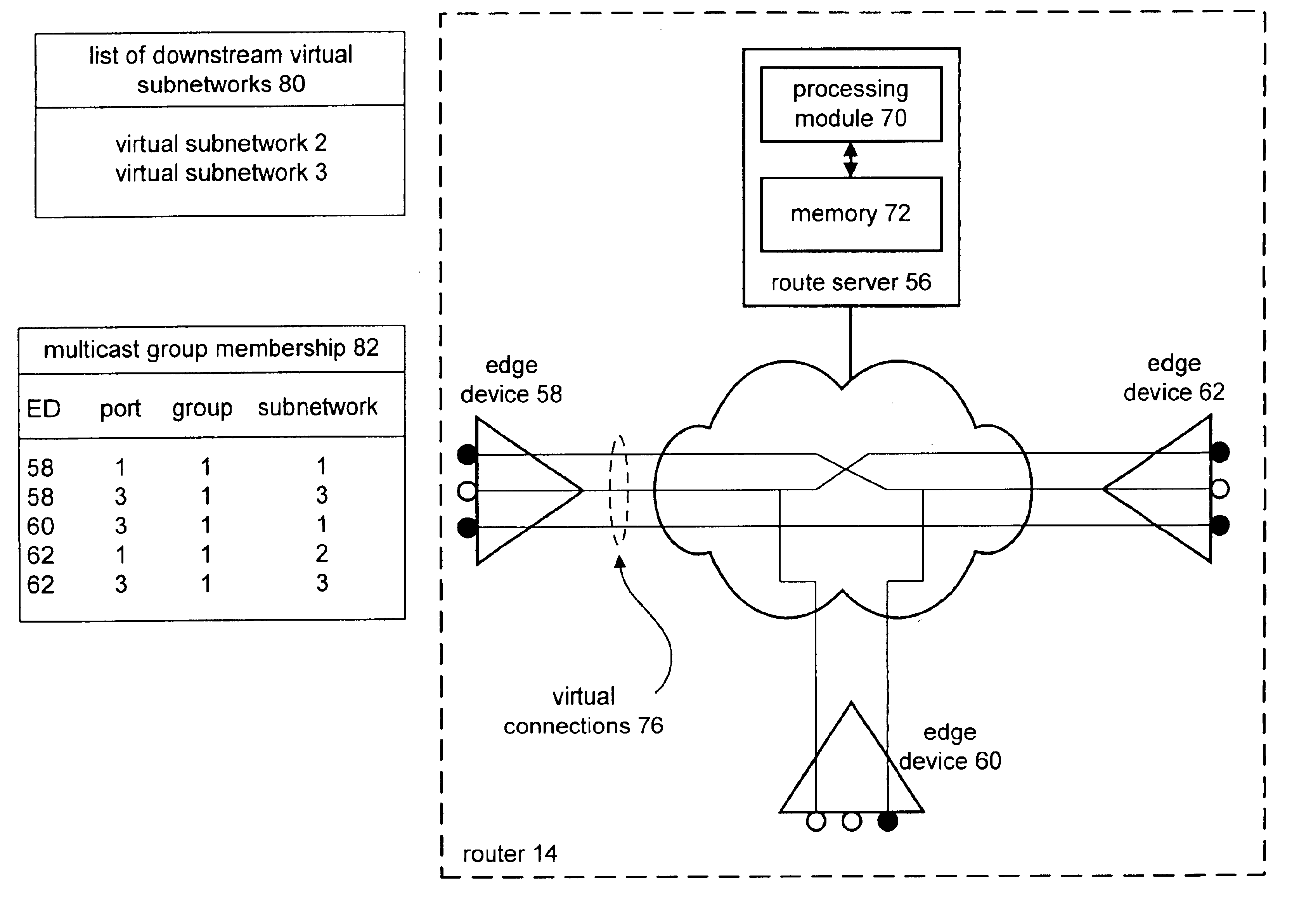
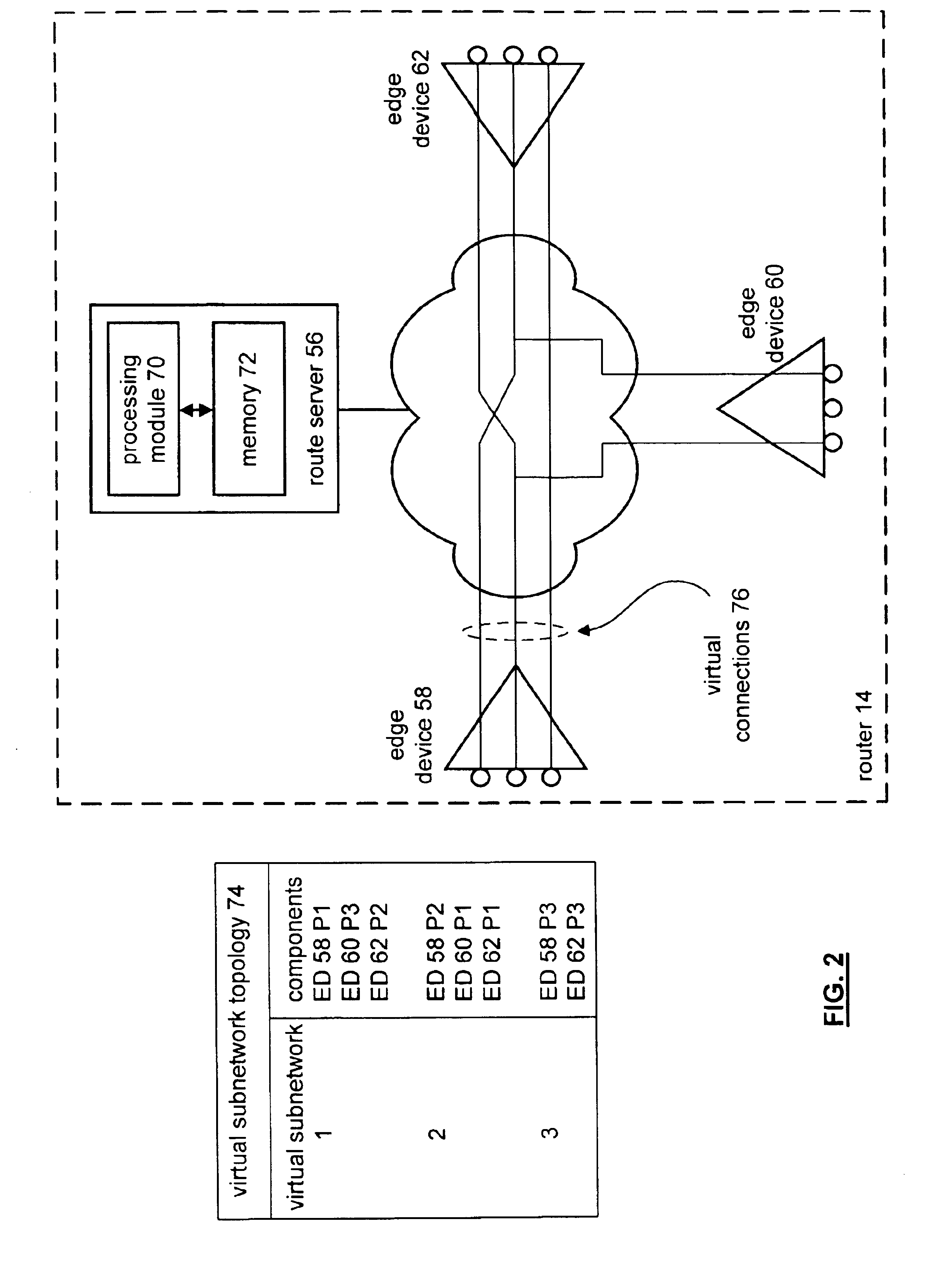
InactiveUS6914907B1Special service provision for substationTime-division multiplexTraffic volumeTraffic capacity
A method and apparatus that includes processing for providing multi-cast transmissions within a data network begins by determining, for a source virtual network, a list of downstream virtual sub-networks for multi-cast traffic based on a multi-cast routing protocol. The processing then continues by determining multi-cast group membership on as per downstream virtual sub-network, edge device, and port basis. The process continues when a data packet is received via the source virtual network. The processing then continues by generating a multi-cast session table entry based on the list of downstream virtual sub-networks and the multi-cast group membership. The process continues by establishing virtual connections between the source virtual network and edge devices coupled to virtual sub-networks identified in the list of downstream virtual sub-networks. Having generated the virtual connections, the processing continues by downloading the multi-cast session table to the edge devices. The edge devices utilize the multi-cast session table entry to determine where the received data packets are to be forwarded.
Owner:NEWBRIDGE NETWORKS
System for establishing secure access for users in a process data network
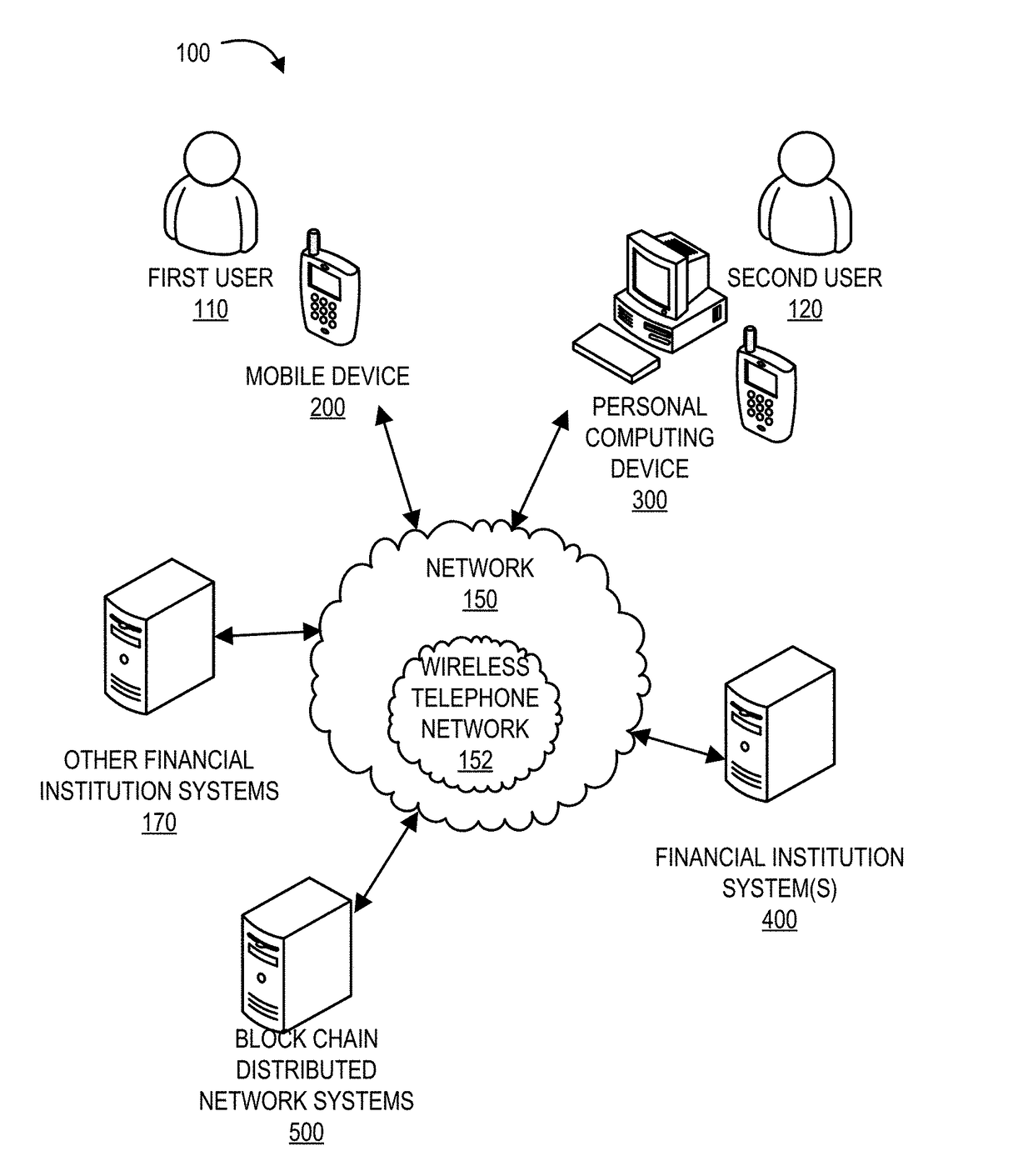
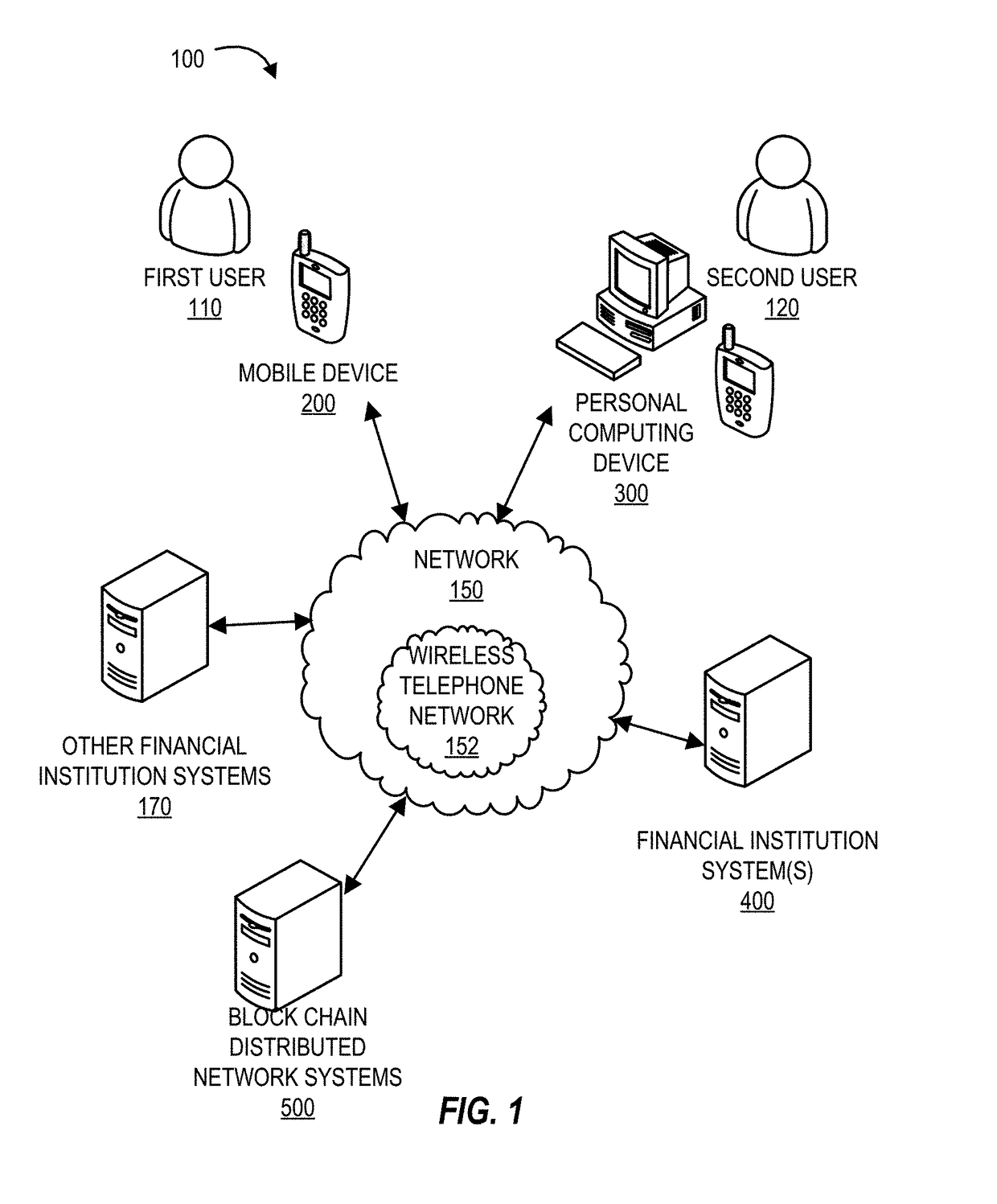
ActiveUS20170244707A1Cryptography processingSecuring communicationResource informationResource transfer
Systems, computer program products, and methods are described herein for a system for establishing secure access for users in a process data network. The present invention is configured to create a block chain of resource information based on at least aggregated information associated with past transfer of resources executed by an entity; analyze the block chain of resource information to determine a pattern associated with the past transfer of resources executed by the entity; receive an indication that the entity has executed a transfer of resources; receive information associated with the transfer of resources; compare the information associated with the transfer of resources with the pattern associated with the past transfer of resources executed by the entity to determine a match; and allow the execution of the transfer of resources.
Owner:BANK OF AMERICA CORP
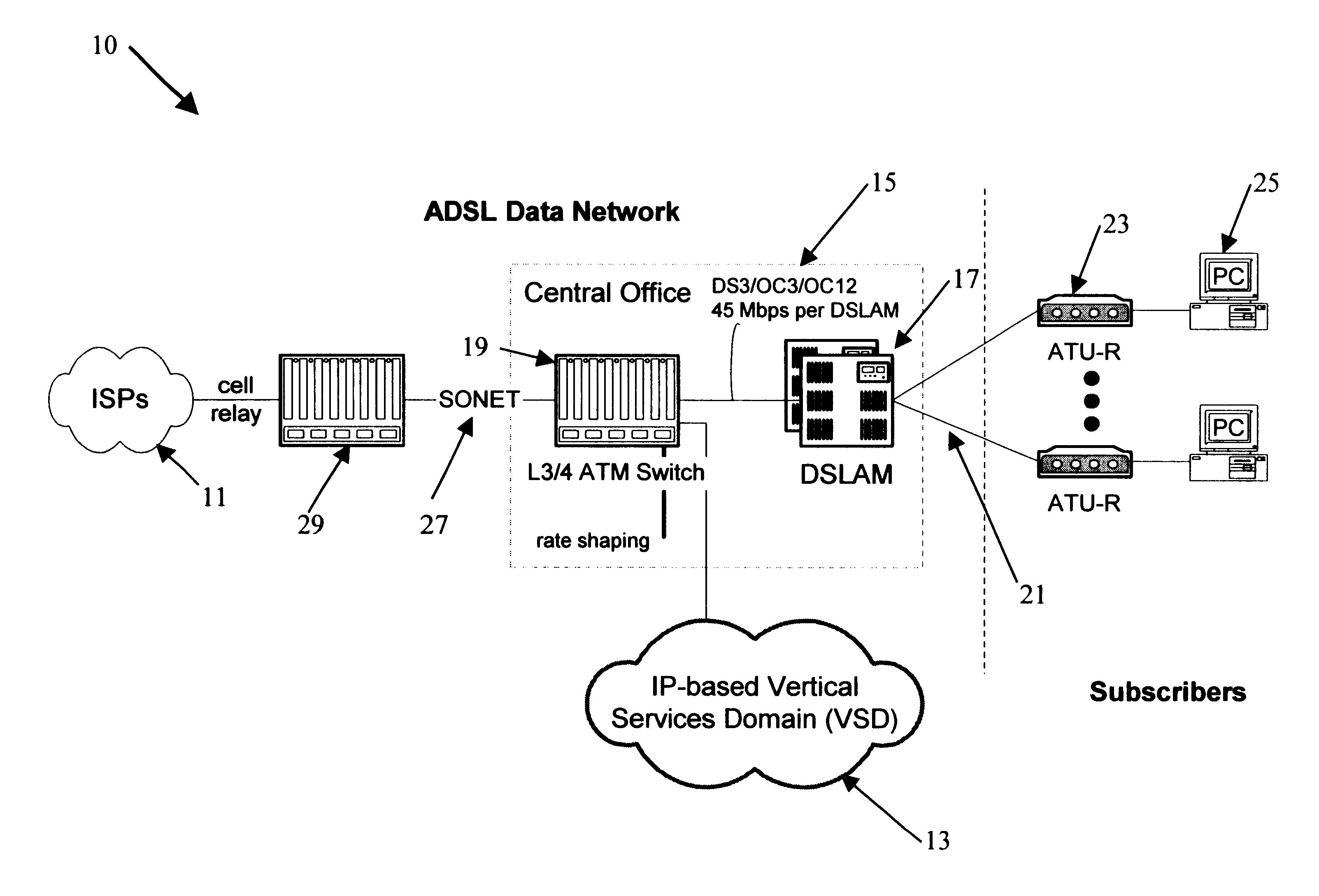
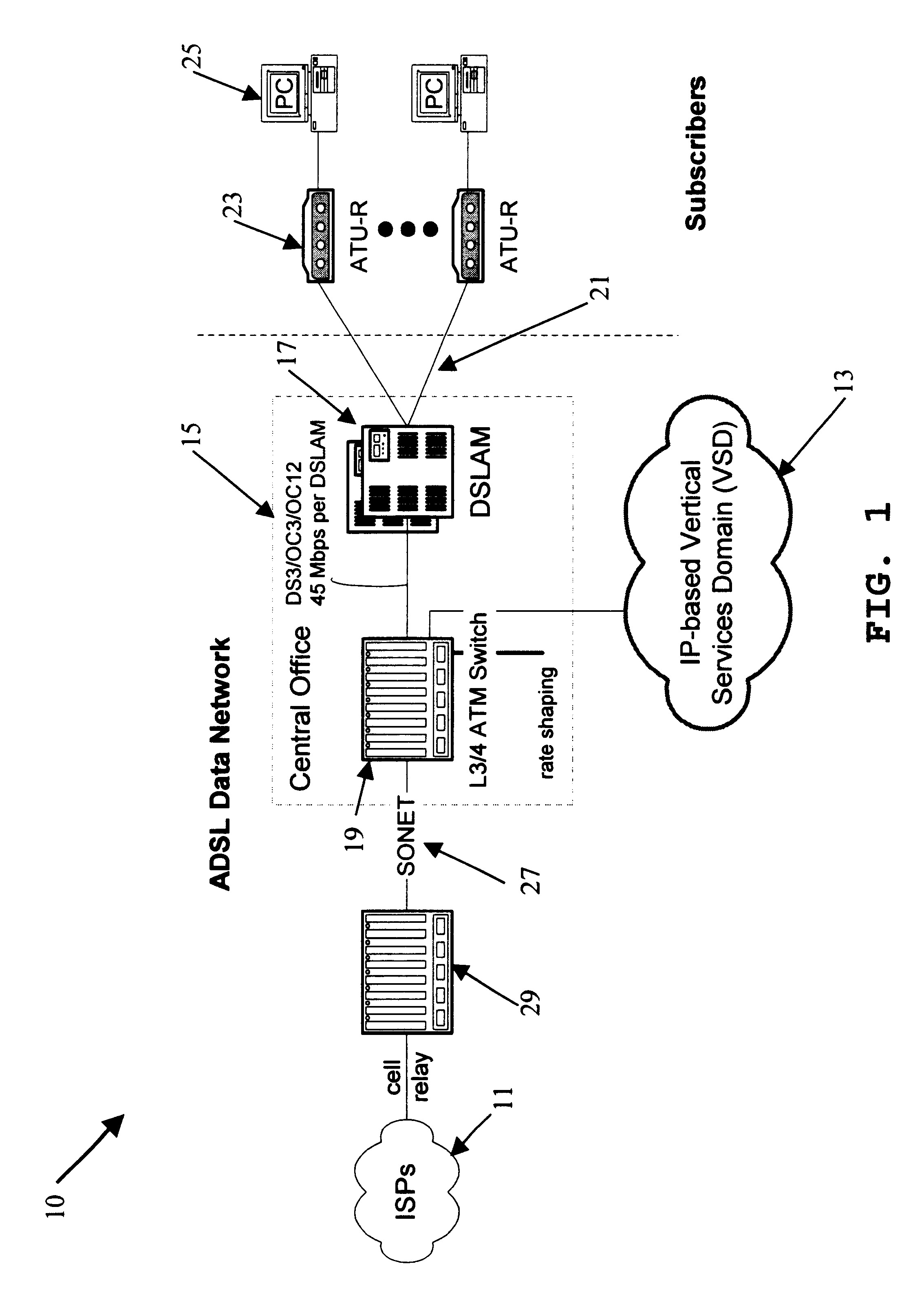
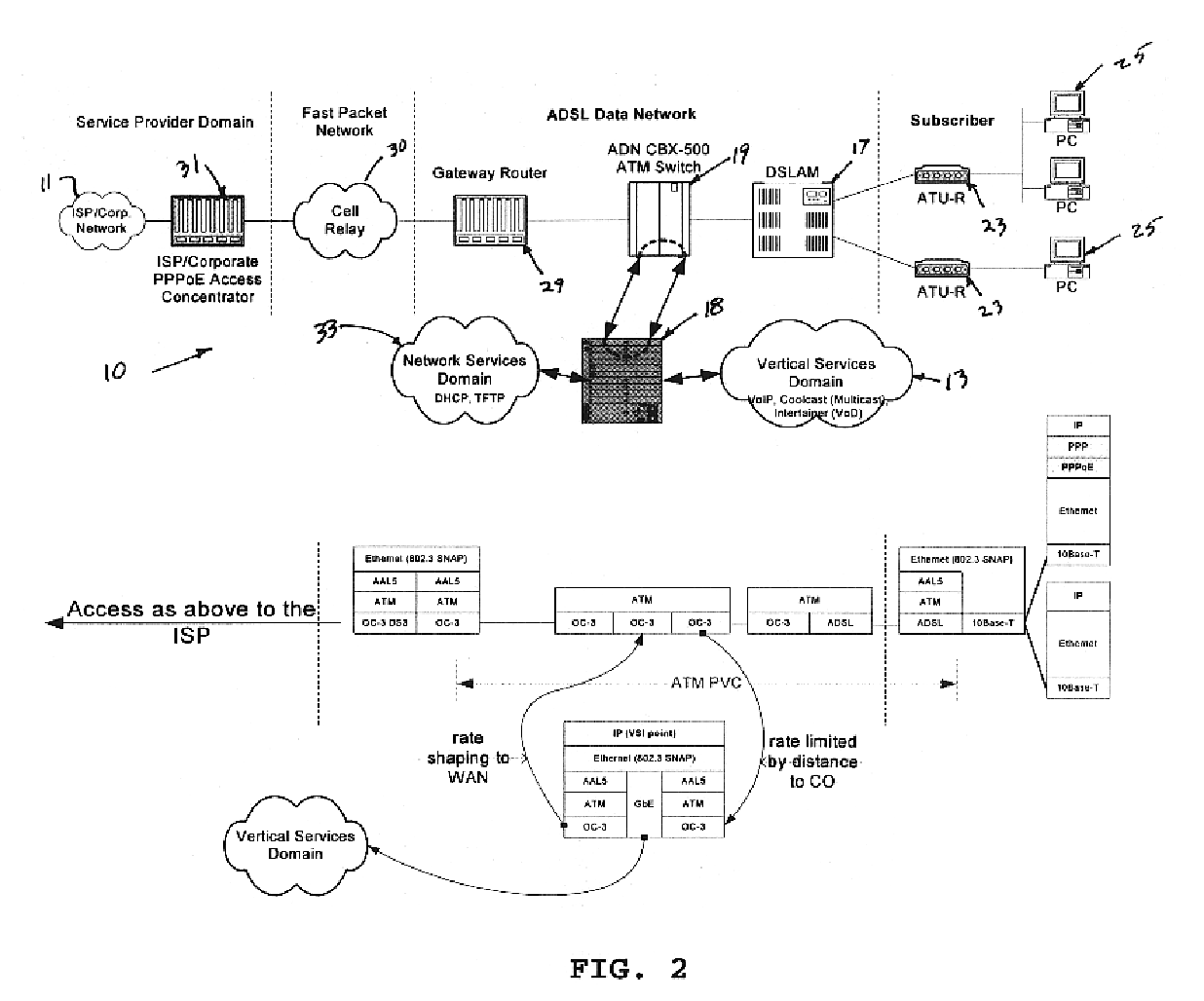
Support for quality of service and vertical services in digital subscriber line domain
InactiveUS6904054B1Increased cost-effectivenessReduce demandTime-division multiplexData switching by path configurationQuality of serviceFrame based
Offering vertical services to subscribers and service providers is an avenue to immediately improve the competitiveness of digital subscriber line access service, for example of the type offered by a local exchange carrier. To deliver high-quality vertical services, however, the underlying ADSL Data Network (ADN) or the like needs to establish Quality of Service (QoS) as a core characteristic and offer an efficient mechanism for insertion of the vertical services. The inventive network architecture introduces QoS into the ADN, in a manner that enables the delivery of sophisticated and demanding IP-based services to subscribers, does not affect existing Internet tiers of service, and is cost-effective in terms of initial costs, build-out, and ongoing operations. The architecture utilizes a switch capable of examining and selectively forwarding packets or frames based on higher layer information in the protocol stack, that is to say on information that is encapsulated in the layer-2 information utilized to define normal connectivity through the network. The switch enables segregation of upstream traffic by type and downstream aggregation of Internet traffic together with traffic from a local vertical services domain.
Owner:RAKUTEN INC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com