Patents
Literature
3053 results about "Secret code" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Multi-factor authentication system
InactiveUS20040187018A1Easy to understandUser identity/authority verificationUnauthorized memory use protectionPasswordUser identifier
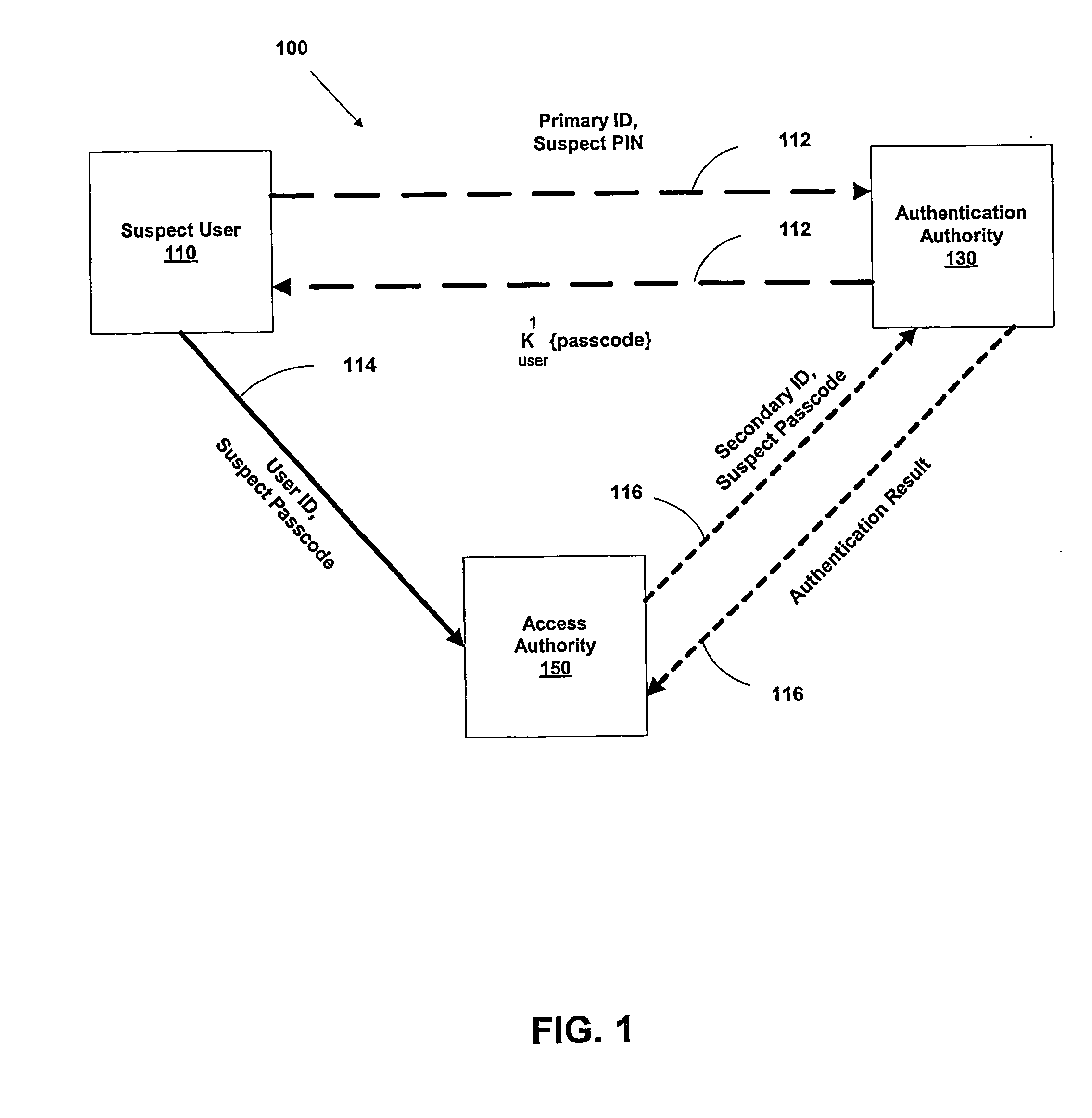
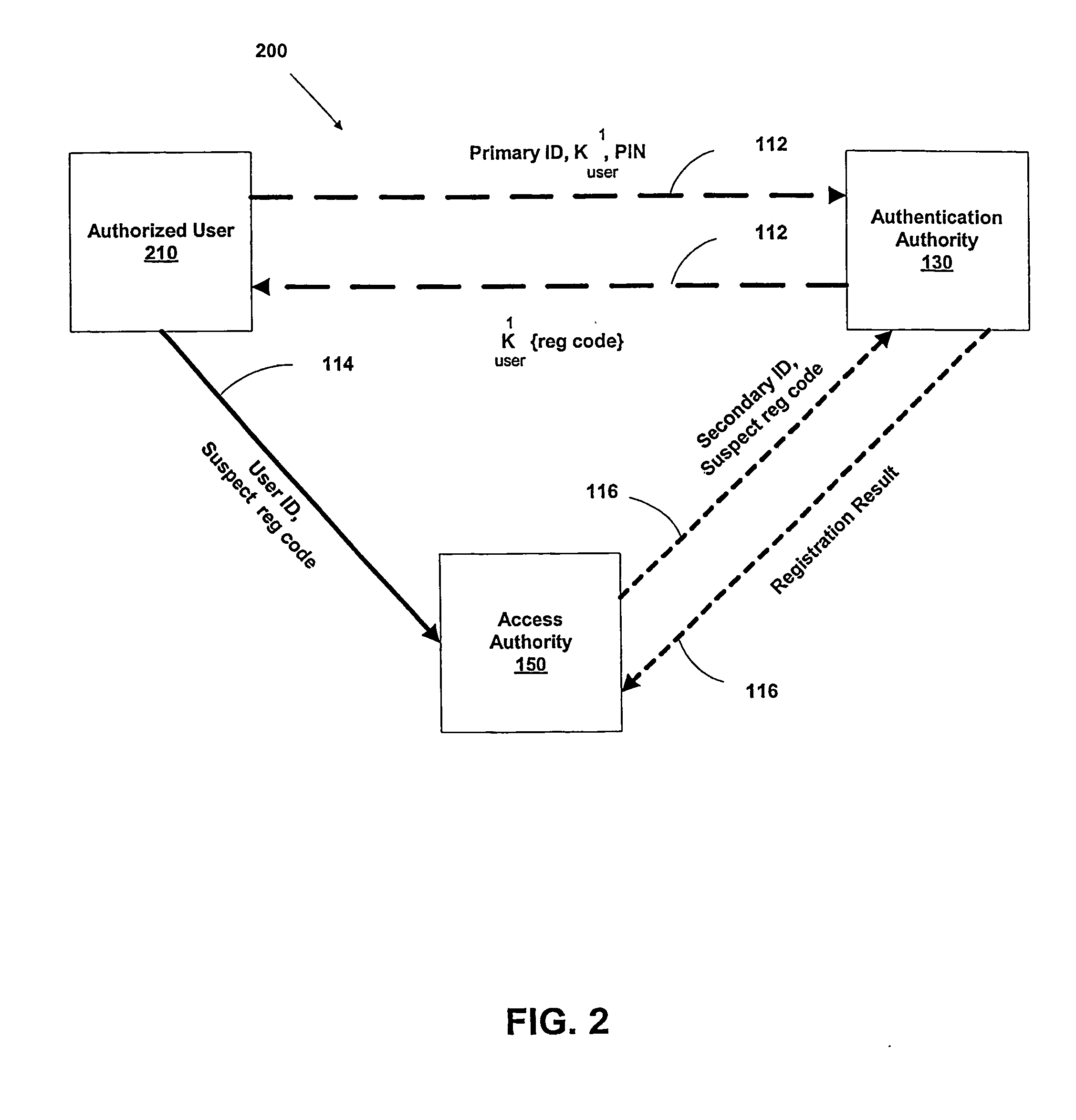
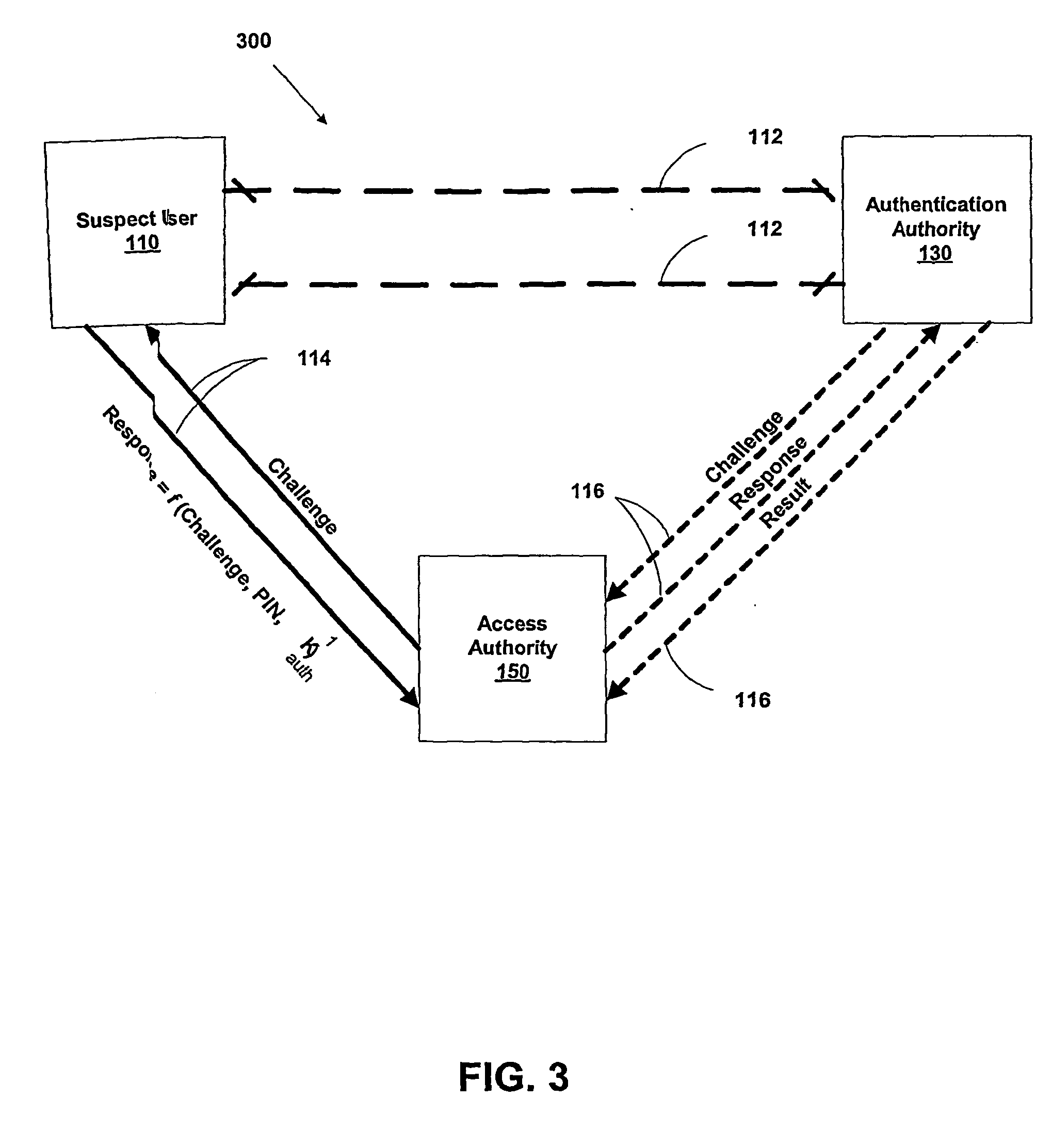
A suspect user (110) seeks access to a network resource from an access authority (150) utilizing a passcode received from an authentication authority (130). Initially, an ID of a device is bound with a PIN, the device ID is bound with a private key of the device, and the device ID is bound with a user ID that has been previously bound with a password of an authorized user. The device ID is bound with the user ID by authenticating the user ID using the password. Thereafter, the suspect user communicates the device ID and the PIN from the device over an ancillary communications network (112); the authentication authority responds back over the ancillary communications network with a passcode encrypted with the public key of the device; and the suspect user decrypts and communicates over a communications network (114) the passcode with the user ID to the access authority.
Owner:KARETEK HLDG LLC
Processing transactions with an extended application id and dynamic cryptograms
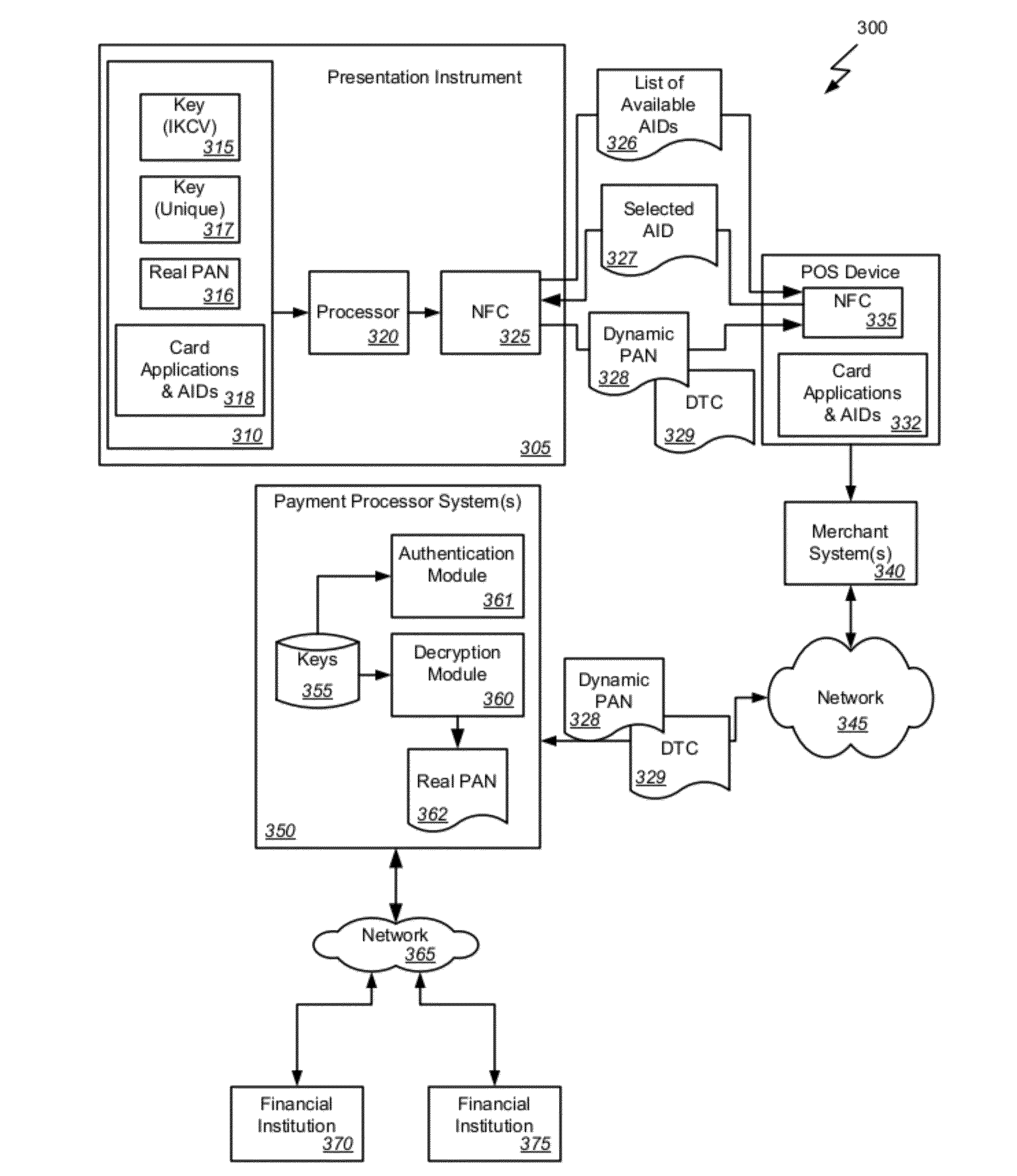
Methods, systems, and machine-readable media are disclosed for handling information related to a transaction conducted with a presentation instrument at a POS device. Extended application IDs and dynamic cryptograms are use for the transaction. According to one embodiment, a method of processing a financial transaction for an account having a primary account number (PAN) can comprise detecting initiation of the transaction with the presentation instrument, and providing from the presentation instrument to the POS device a list of one or more applications IDs. Each application ID identifies an application that can be used to communicate data concerning the transaction between the presentation instrument and the POS device. The POS device selects one of the application IDs and returns it to the presentation instrument. Under the control of the selected application, the presentation instrument generates a Dynamic Transaction Cryptogram (DTC) and a dynamic PAN that are each valid for only a single transaction.
Owner:FIRST DATA
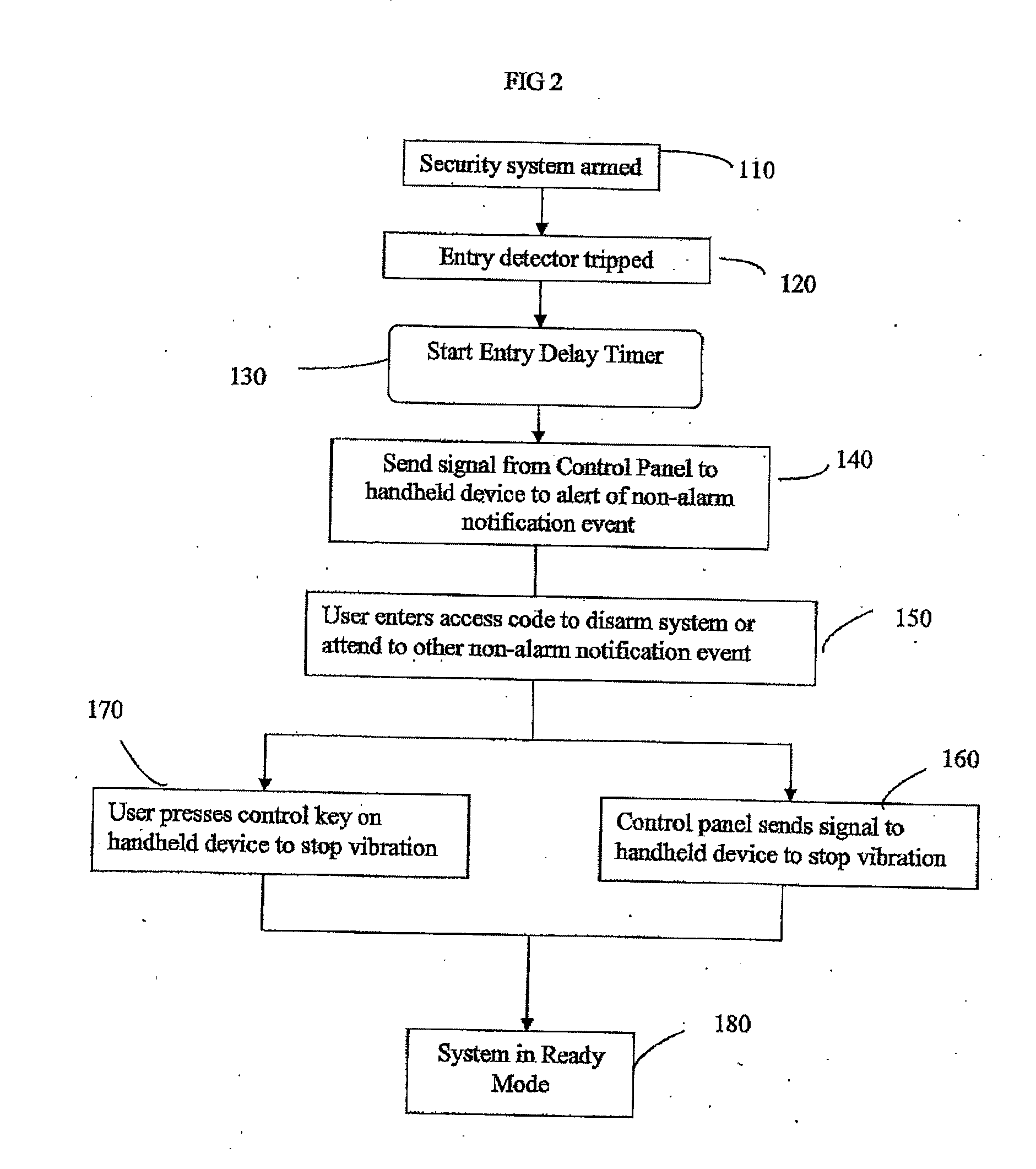
Security system with keyfob alert notification
A system and method are provided for notifying a hearing impaired user of one of a plurality of qualified events via a personal device rather than an audible alert to avoid unnecessary false alarms. The security system includes at least one detection device for monitoring a portion of the premises and a control panel configured to communicate with the at least one detection device. A personal device communicates with the control panel where the personal device is configured to mechanically vibrate upon receipt of a signal from the control panel representing a qualified event associated with the security system.
Owner:TYCO SAFETY PRODS CANADA
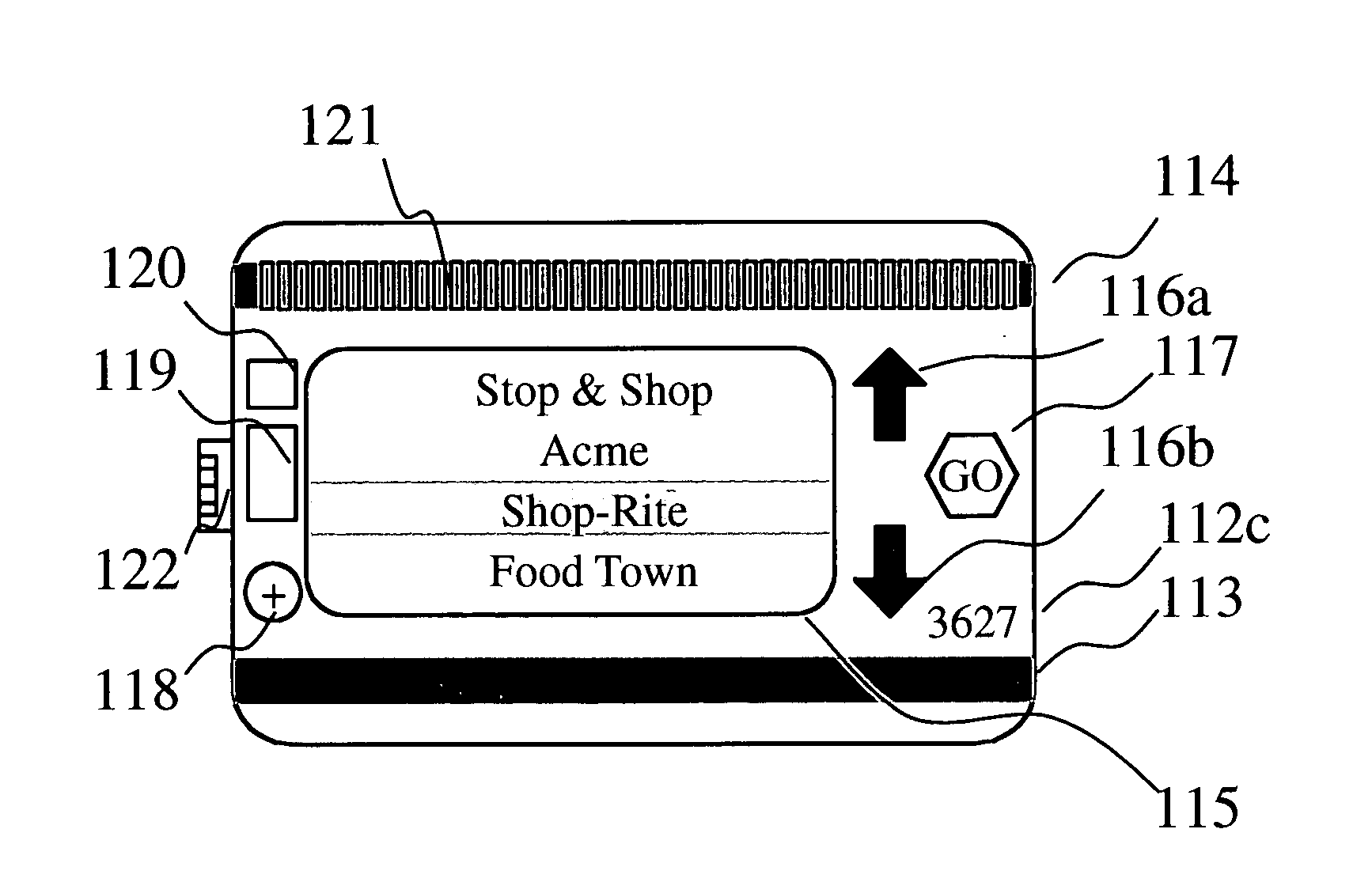
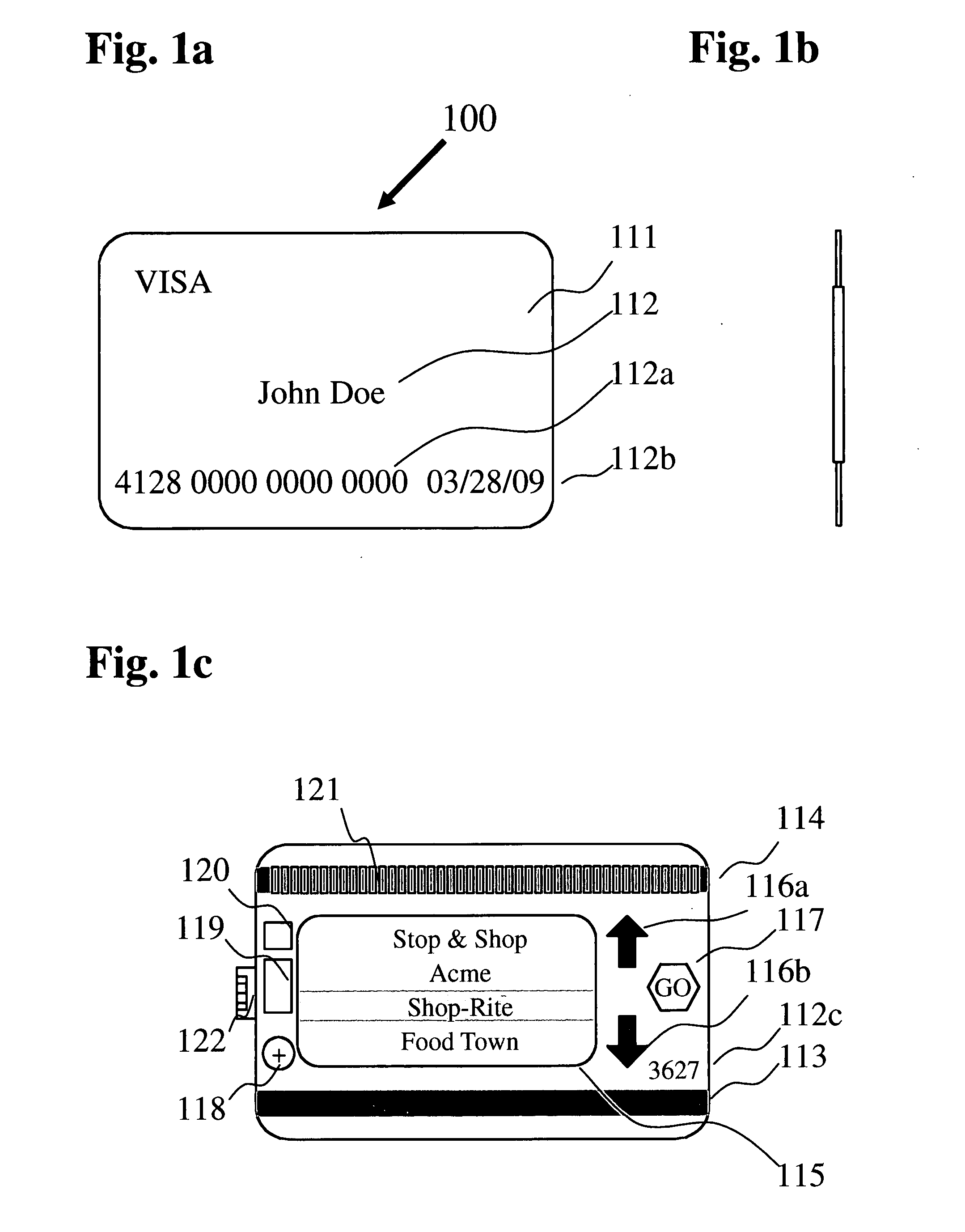
Consolidated membership/rewards card system
A bank or credit card issuing authority provided consolidated membership / rewards card has standard credit card features including cardholder's name, card number, expiration date, secret code and a permanently coded permanent magnetic strip. The card has a programmable second magnetic strip with inductors directly below the strip energized by a CPU in the card recording a merchant provided loyalty or discount number. The cardholder selects a merchant from a list displayed card screen by pressing up and down buttons and a ‘go’ button to program the second magnetic strip. A USB connector associated with the card is used for uploading merchant data from a personal computer and transmitting the card discount number to a USB enabled cash register. The cash register provides eligible discounts for purchases upon receipt of the card discount number by swiping the second magnetic strip or by establishing USB connectivity. Payment is made using the permanent magnetic strip of the card or by other payment means. Discounts and membership rewards are thereby provided to a cardholder without need for carrying a plurality of merchant issued membership / rewards cards. Credit card functionality facilitates immediate payment for the purchases made.
Owner:POLLIO MICHAEL J
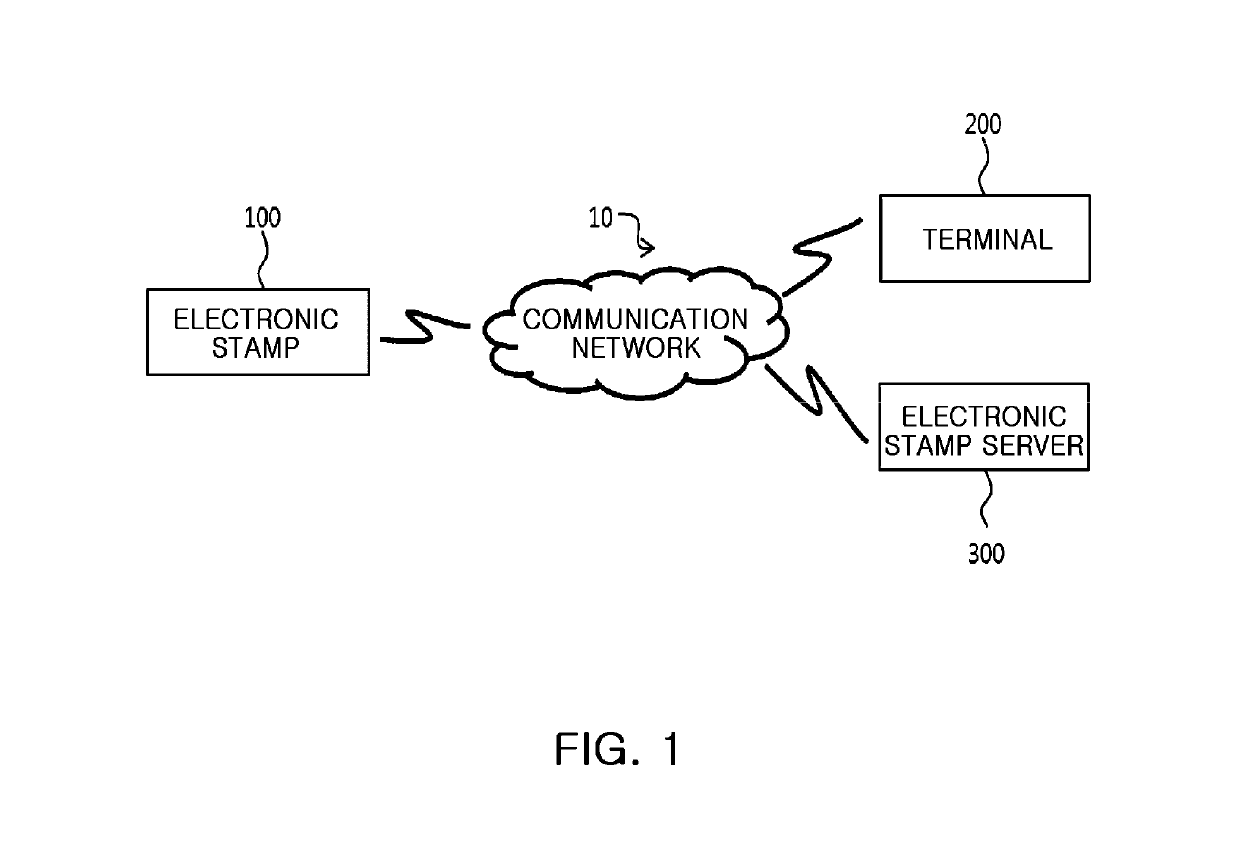
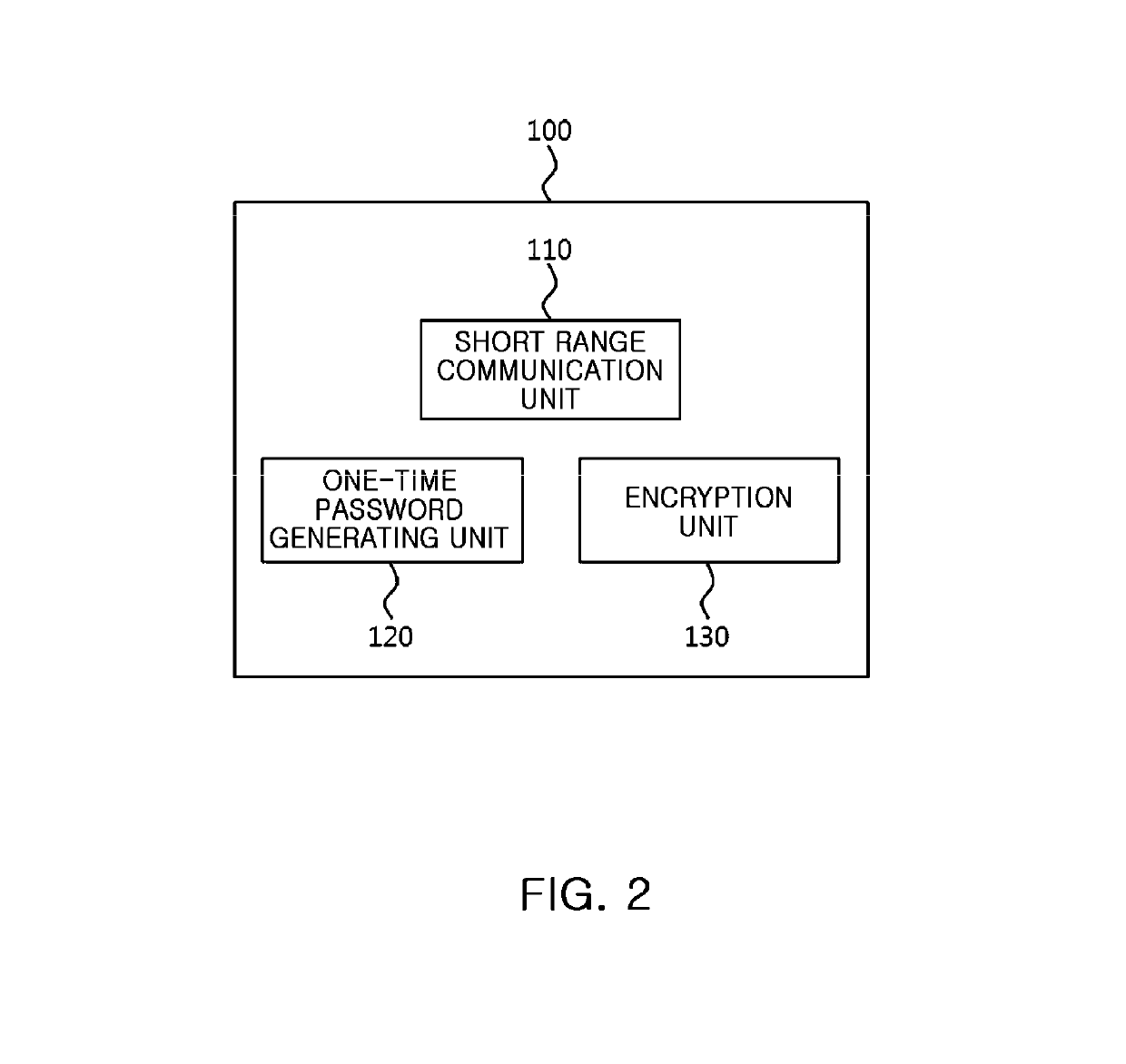
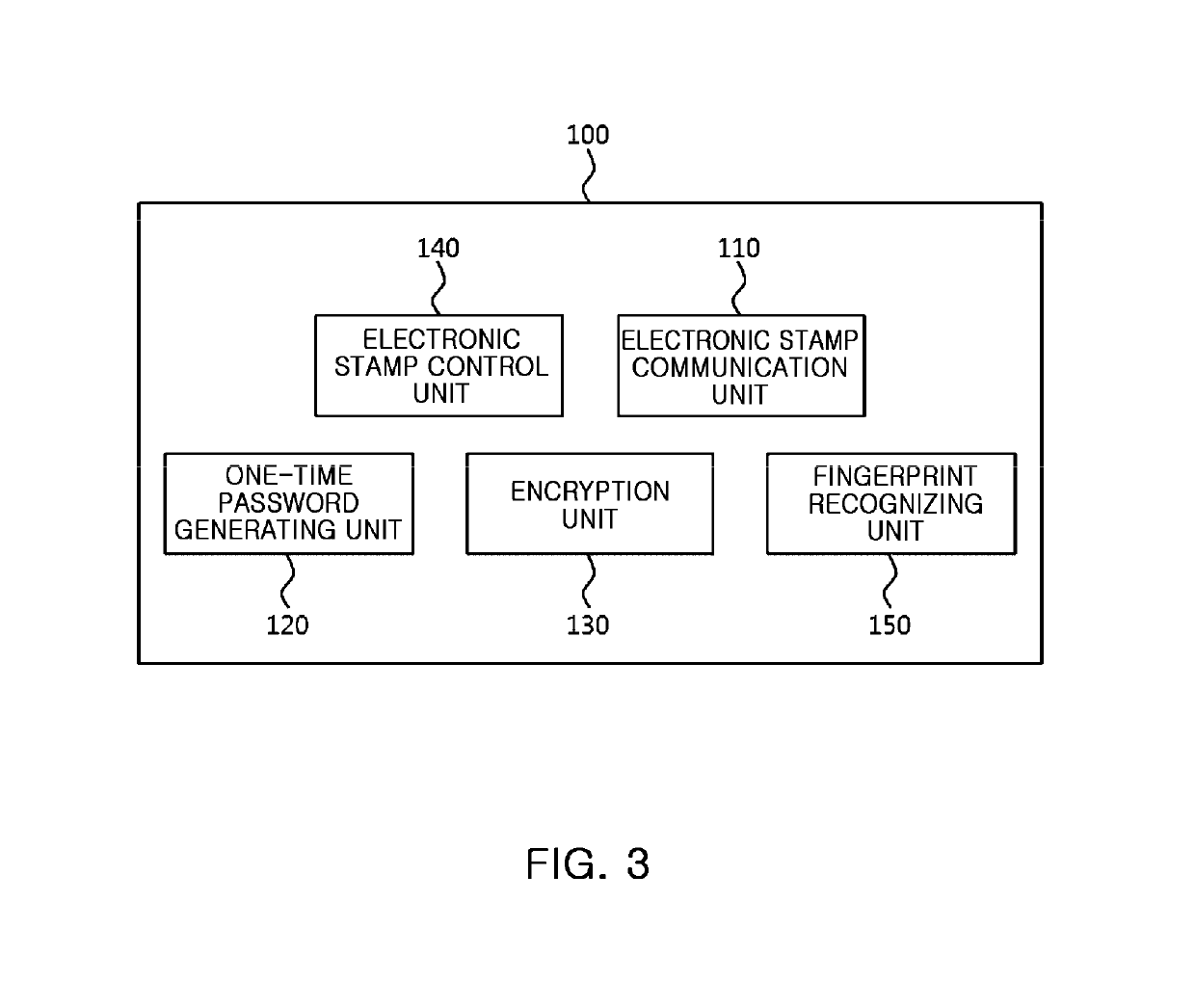
Electronic stamp system for security intensification, control method thereof, and non-transitory computer readable storage medium having computer program recorded thereon
ActiveUS10361857B2Key distribution for secure communicationDiscounts/incentivesComputer hardwareOne-time password
Provided are an electronic stamp system for security intensification, a control method thereof, and a non-transitory computer readable storage medium having a computer program recorded thereon. According to the invention, it is possible to generate an encrypted value based on a membership ID related to a user of a terminal provided from the terminal and an one-time password such as an OTP generated in the electronic stamp and provide the generated encrypted value to the terminal in the electronic stamp, provide the membership ID, electronic stamp information, and the encrypted value to an electronic stamp server from the terminal, and obtain a decryption key based on the electronic stamp ID extracted from the electronic stamp information and then decrypts the encrypted value based on the obtained decryption key, and verify authenticity of the electronic stamp by comparing the decrypted value and the membership ID in the electronic stamp server.
Owner:SK PLANET CO LTD
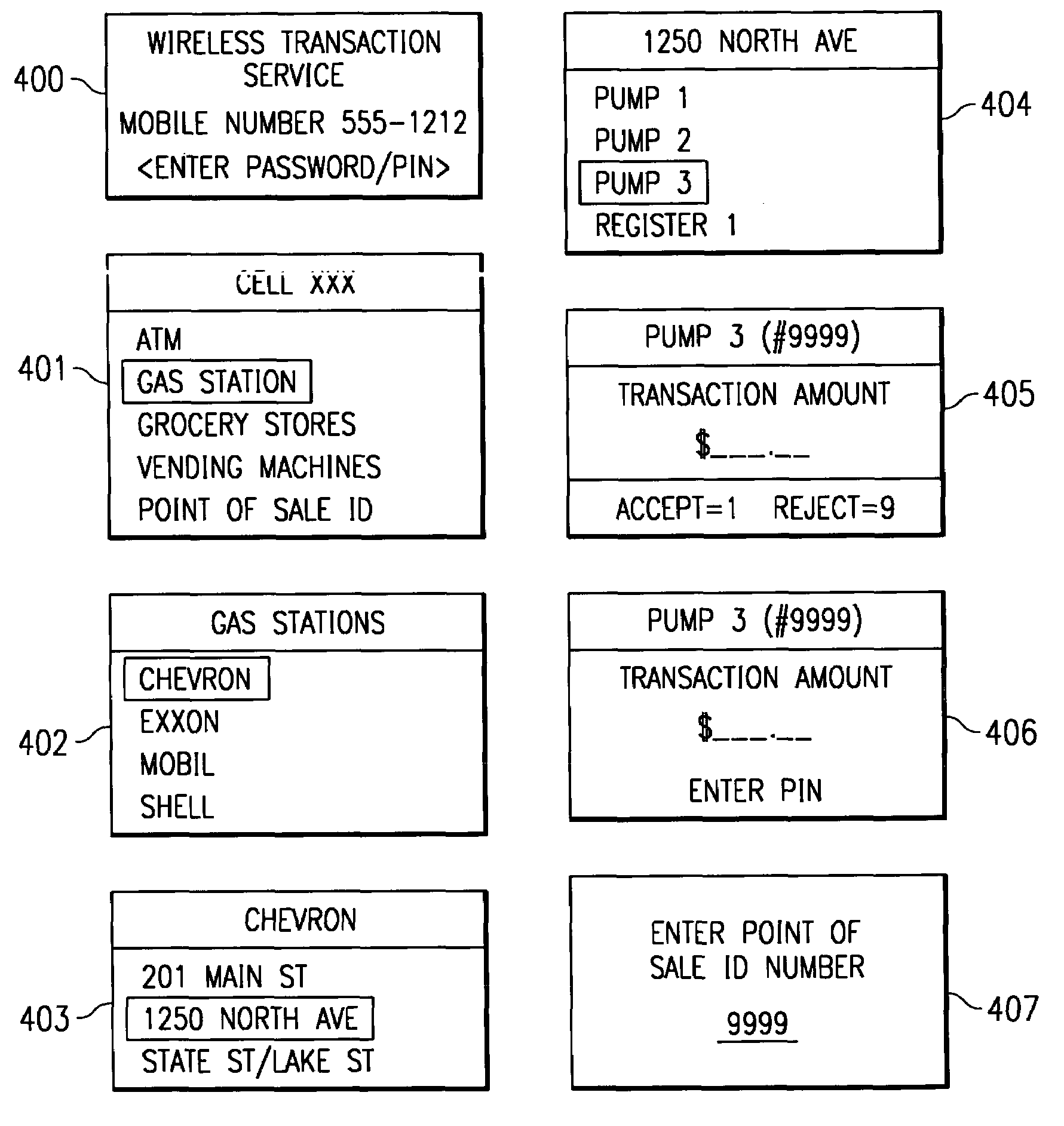
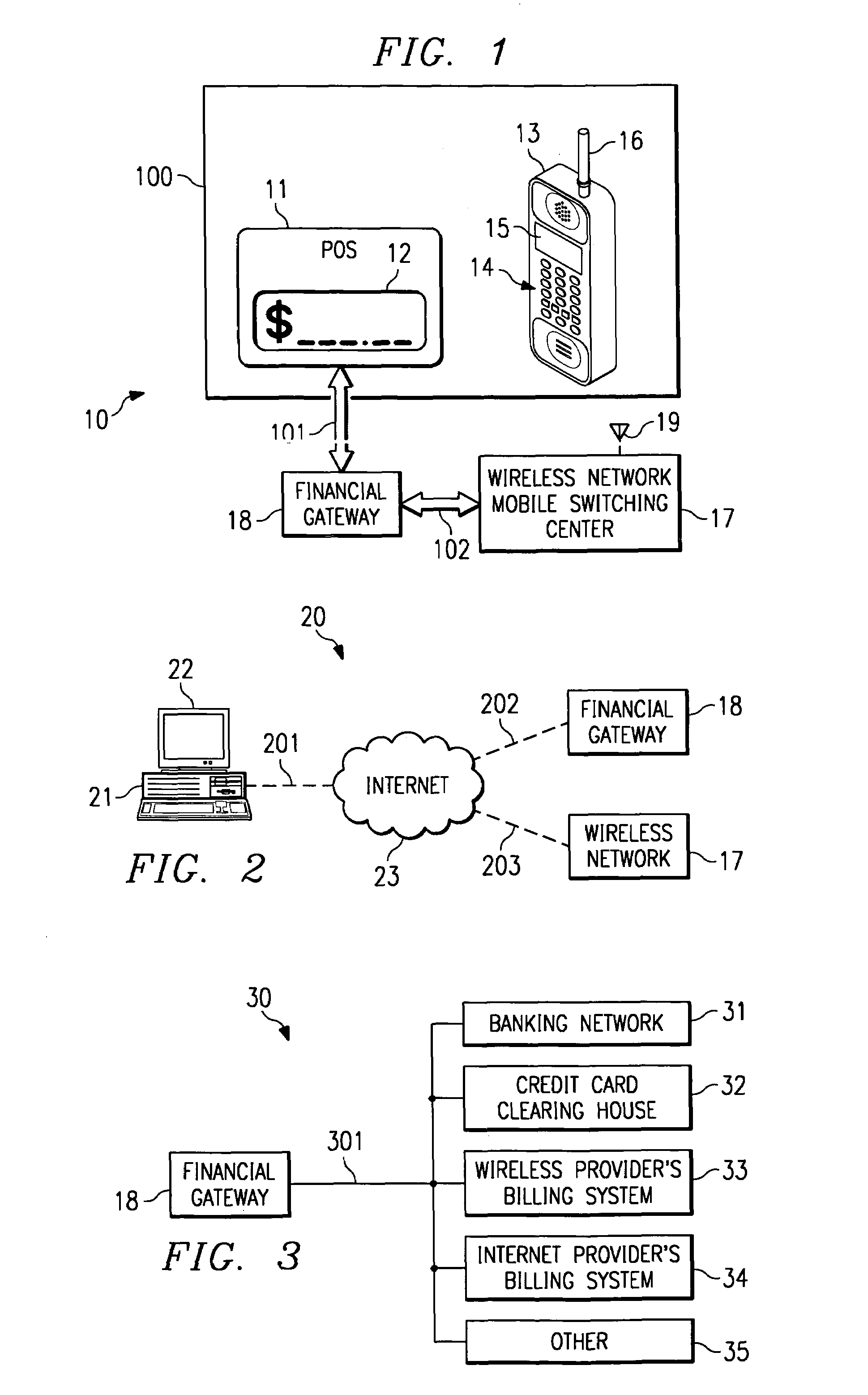
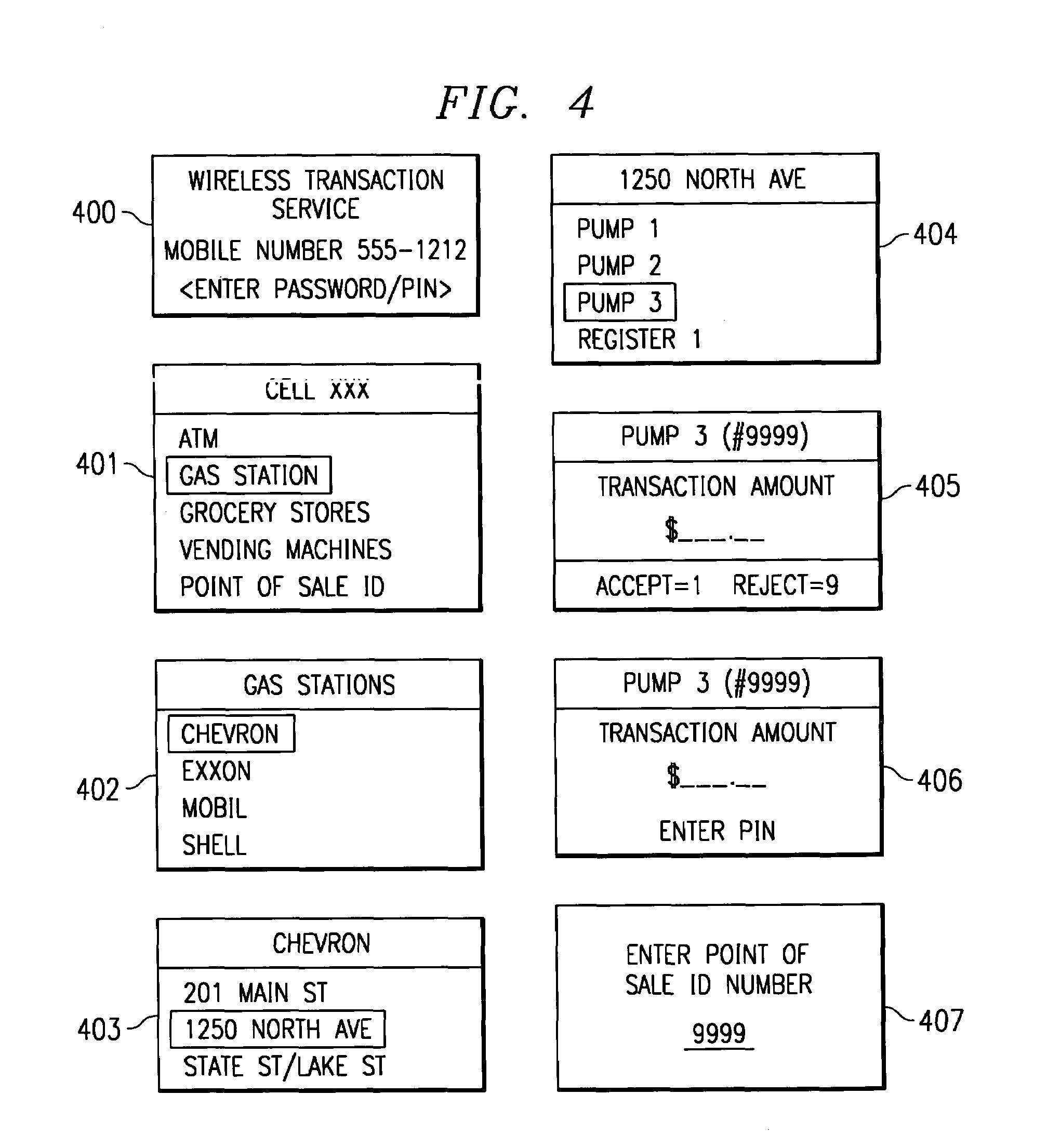
System and method for controlling financial transactions over a wireless network
InactiveUS7167711B1Hand manipulated computer devicesFrequency-division multiplex detailsCredit cardPersonal identification number
A system and method for controlling financial transactions is disclosed. A customer, using a wireless device, identifies a point of sale and the amount of a transaction at that point of sale is first communicated to a central service and then transmitted to the wireless device for display at the wireless device. The customer can either accept the transaction amount to complete the transaction or reject the amount to cancel the transaction. The customer may have to enter a password or personal identification number to verify the authorization to use the wireless financial system. The customer is billed for the transaction via credit, debit, ATM or other methods, such as the wireless carrier or an internet provider.
Owner:UNWIRED PLANET
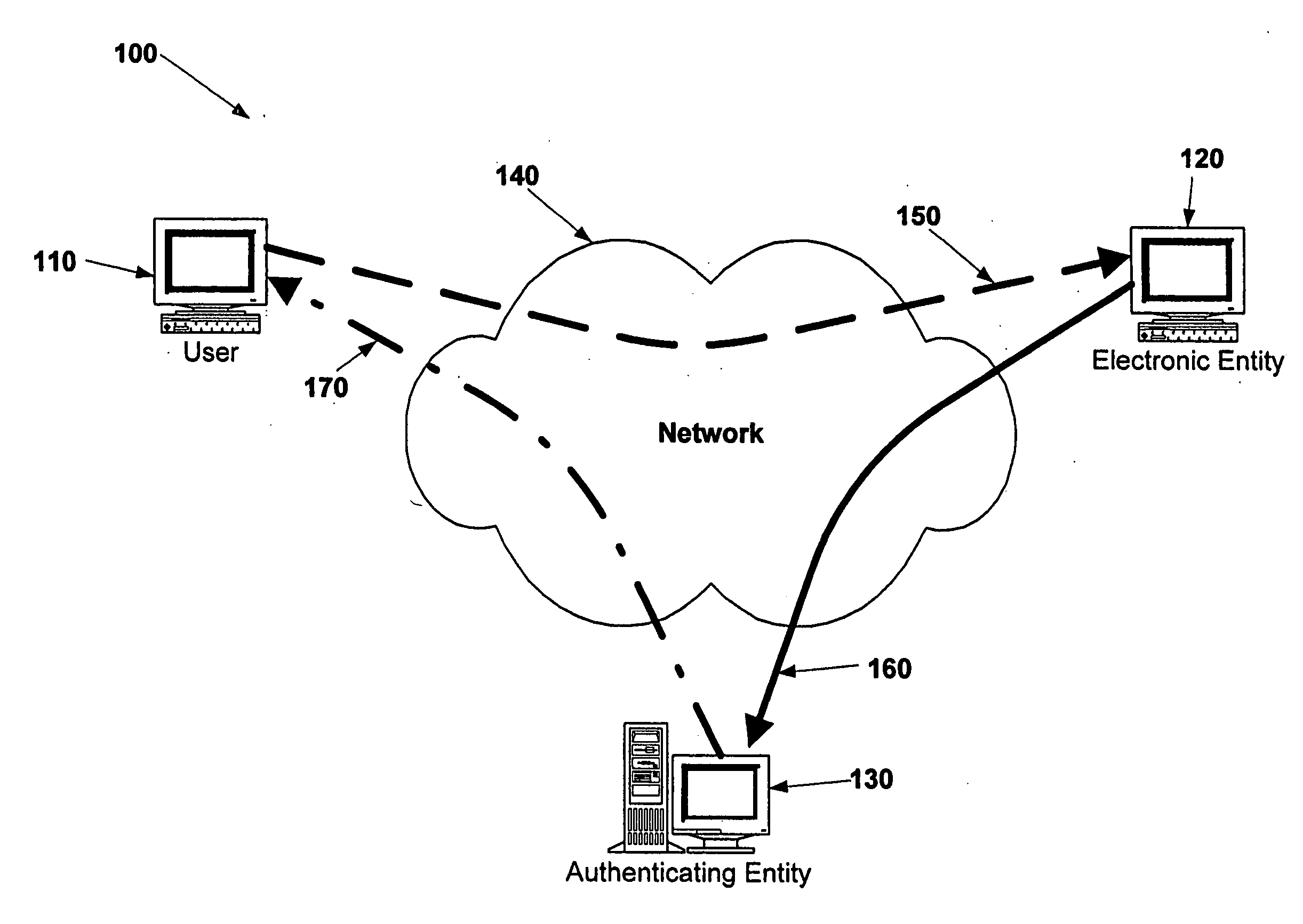
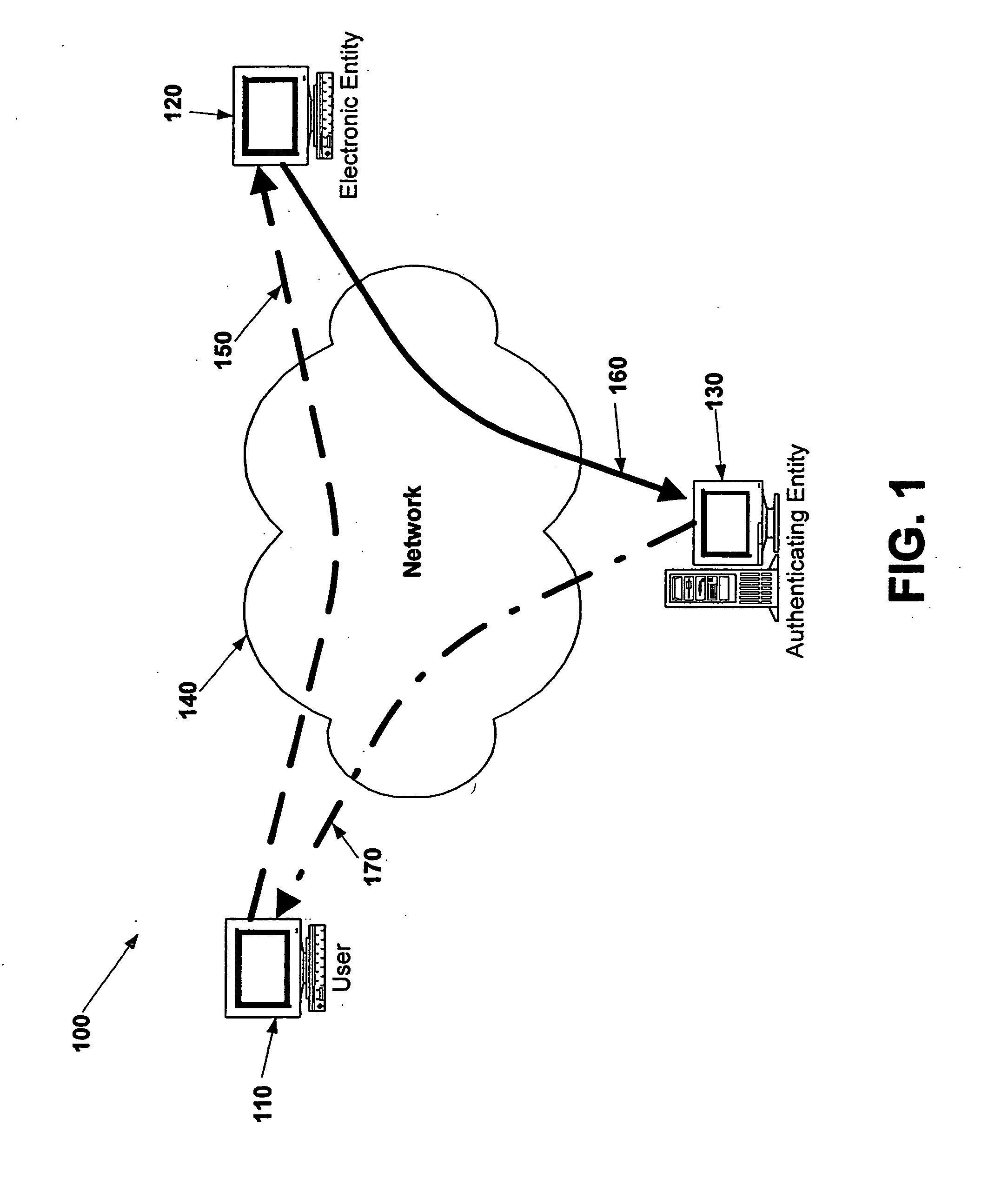
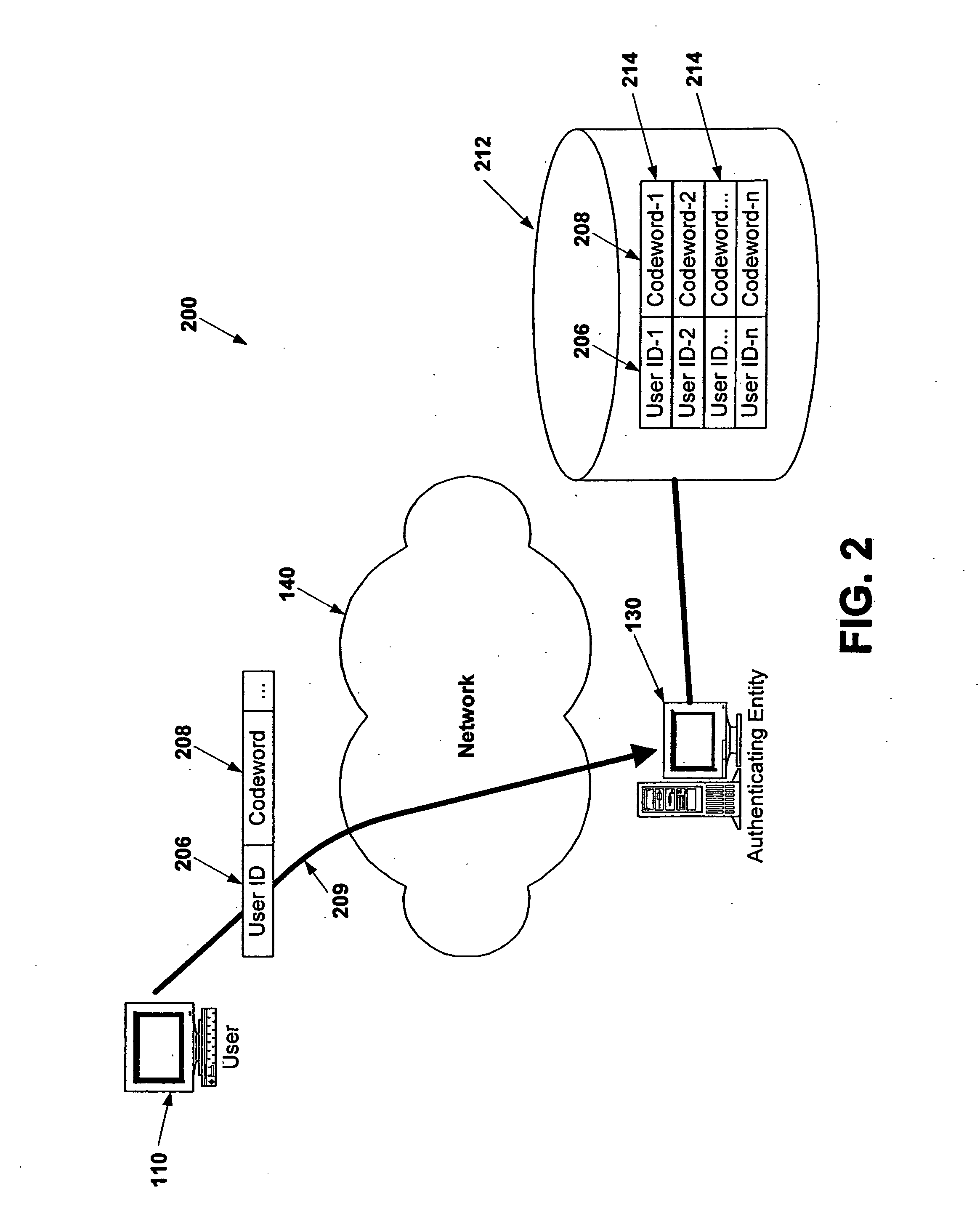
Electronic verification systems
ActiveUS20060200855A1Verify authenticityPrevent account hijacking and frustrate fraudulent electronic transactionsDigital data processing detailsUser identity/authority verificationObject basedThe Internet
A verification system which can be used over electronic networks, such as the Internet, to help prevent phishing, electronic identity theft, and similar illicit activities, by verifying the authenticity of electronic entities (for example, websites). Users and electronic entities register with an authenticating entity. The authenticating entity shares an encryption method with registered electronic entities and establishes a secret code for each registered electronic entity. The secret code is combined with other information and encrypted before being transmitted over the network to ensure that the secret code cannot be compromised. Also disclosed are systems for virtual token devices, which provided object-based authentication without a physical device. Also disclosed are dynamic media credentials, which display nearly-unique behavior, previously specified and known to a user, to assist in verifying the authenticity of the presenter.
Owner:SYCCURE INC
Single-use password authentication
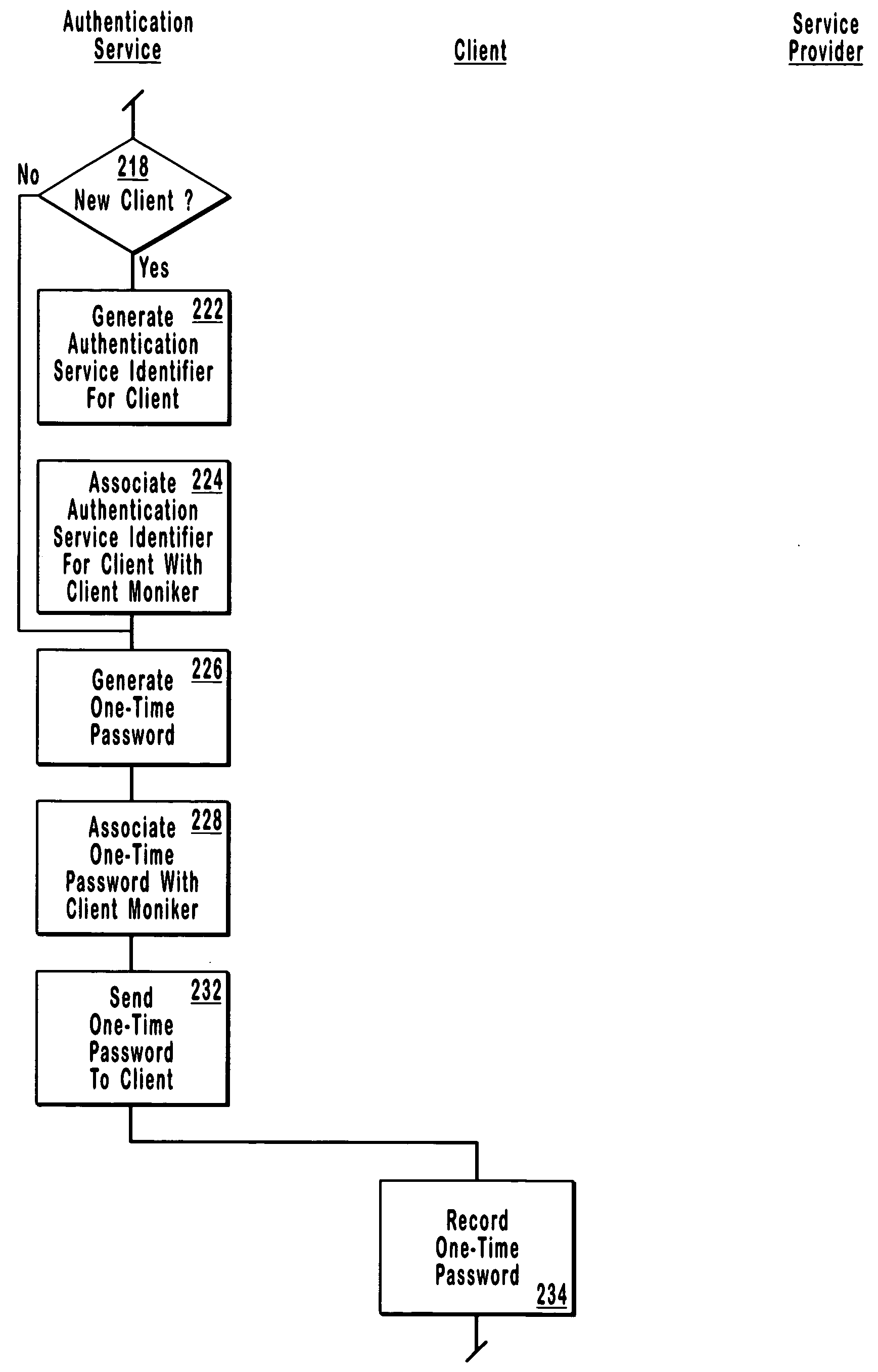
ActiveUS20060080545A1Reduce the possibilityLimited lifetimeDigital data processing detailsMultiple digital computer combinationsClient-sideOne-time password
Systems, computer program products and methods for authentication using a one-time password. In system that includes a client, a service provider, and an authentication service, the authentication service generates an authentication service identifier for the client. Any suitable identifier may be used for the authentication service identifier, which generally takes the form of an arbitrary number of characters. From the client, the authentication service receives a client moniker (e.g., a username) for the client to use when accessing the authentication service. The authentication service sends a one-time password to the client for the client to use in accessing the service provider. When the authentication service receives a one-time password from the service provider, the authentication service sends the authentication service identifier for the client to the service provider to authenticate the client if the one-time password received from the service provider matches the one-time password sent to the client.
Owner:TOKENYM
Multi-factor biometric authentication
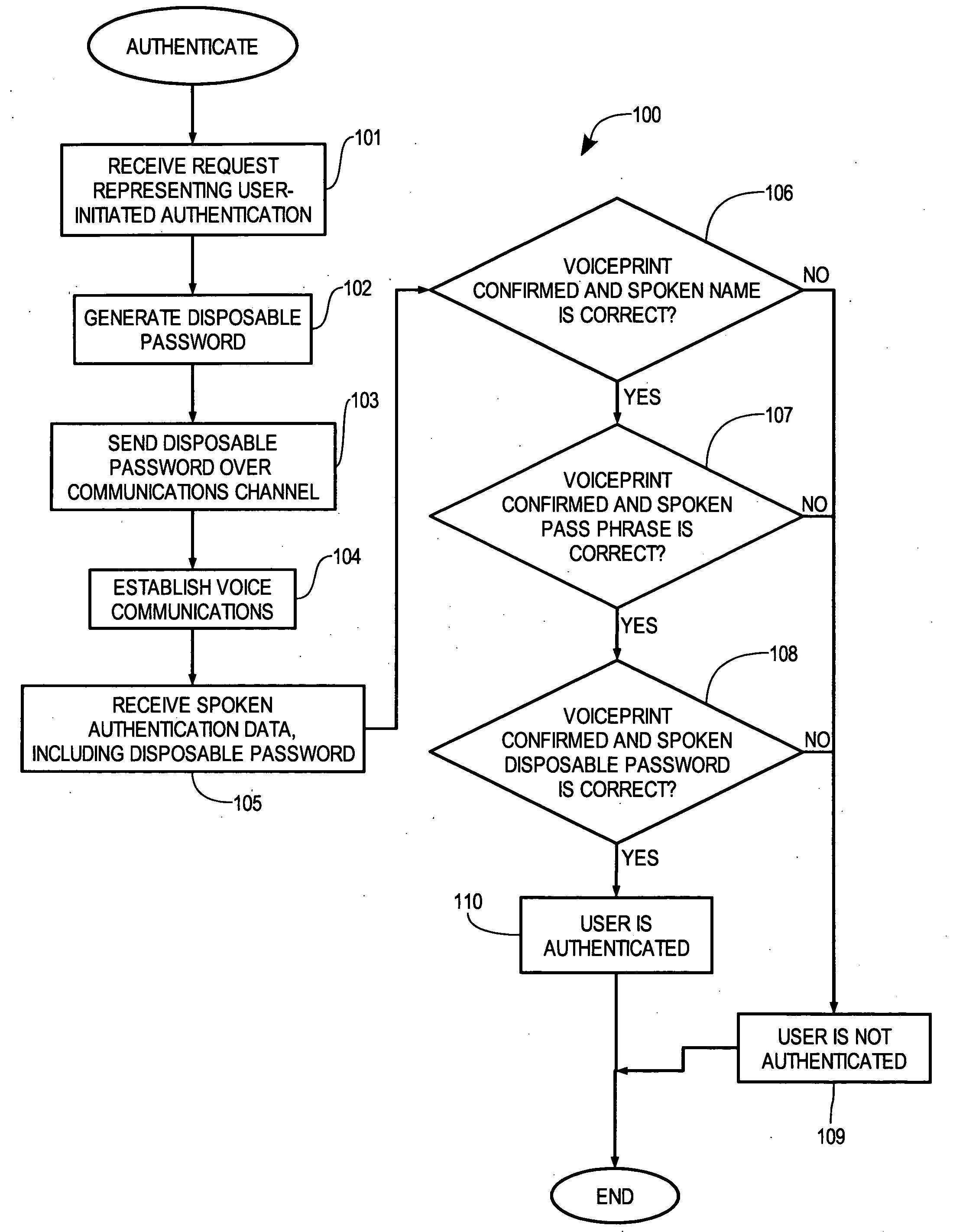
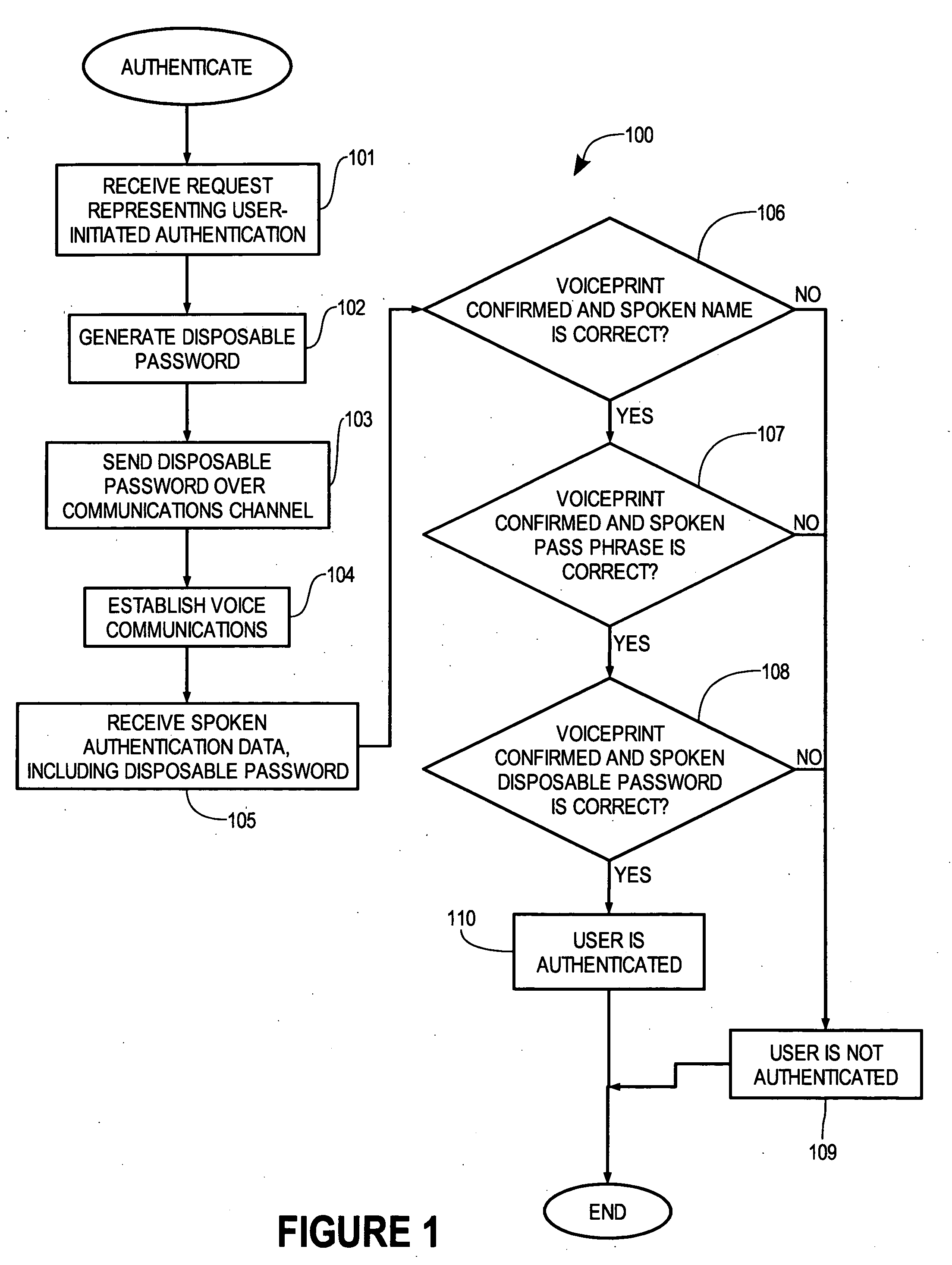
InactiveUS20070055517A1Digital data authenticationIndividual entry/exit registersSecret codeOne-time password
A method for verifying a person's identity in order to gain access to electronic data, a data network, a physical location, or enable a commercial transaction. A request for identity verification is processed over a data network and the system is initiated which (i) transmits a disposable pass phrase over a data network to the user, (ii) prompts the user to vocalize the disposable pass phrase, a pass phrase, and user id, (iii) compares the recited speech of the user to the stored voiceprint of the user, the stored pass phrase and id of the user, and the generated disposable pass phrase, then (iv) issues a token or signal that represents whether the user was verified or not.
Owner:AUTHENTIVOX
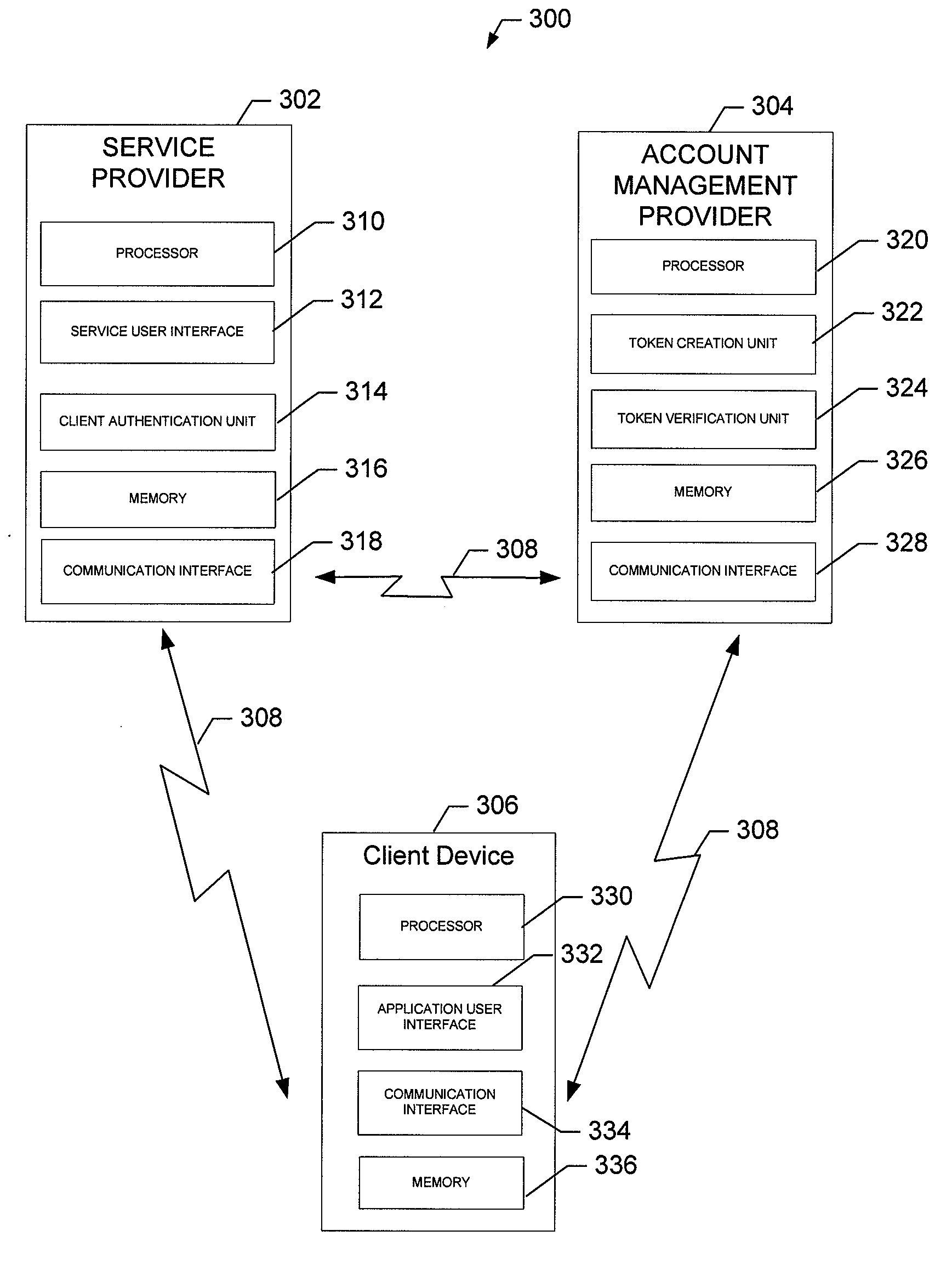
Methods, Apparatuses, and Computer Program Products for Providing a Single Service Sign-On
InactiveUS20090271847A1Enhanced interactionImprove securityDigital data processing detailsUser identity/authority verificationPasswordSecret code
An apparatus may include a processor configured to receive a request for an access token from a remote entity, wherein the request includes an indication of a requested service. The processor may be further configured to determine a request type, wherein the request type may be a user identification and password combination, a request token exchange, or an access token exchange. The processor may be additionally configured to extract one or more parameters included in the request based upon the determined request type and to perform one or more security checks based at least in part upon the one or more extracted parameters. The processor may be further configured to create an access token based at least in part upon the results of the one or more security checks and to provide the access token to the remote entity.
Owner:NOKIA TECHNOLOGLES OY
System and method for generating a strong multi factor personalized server key from a simple user password
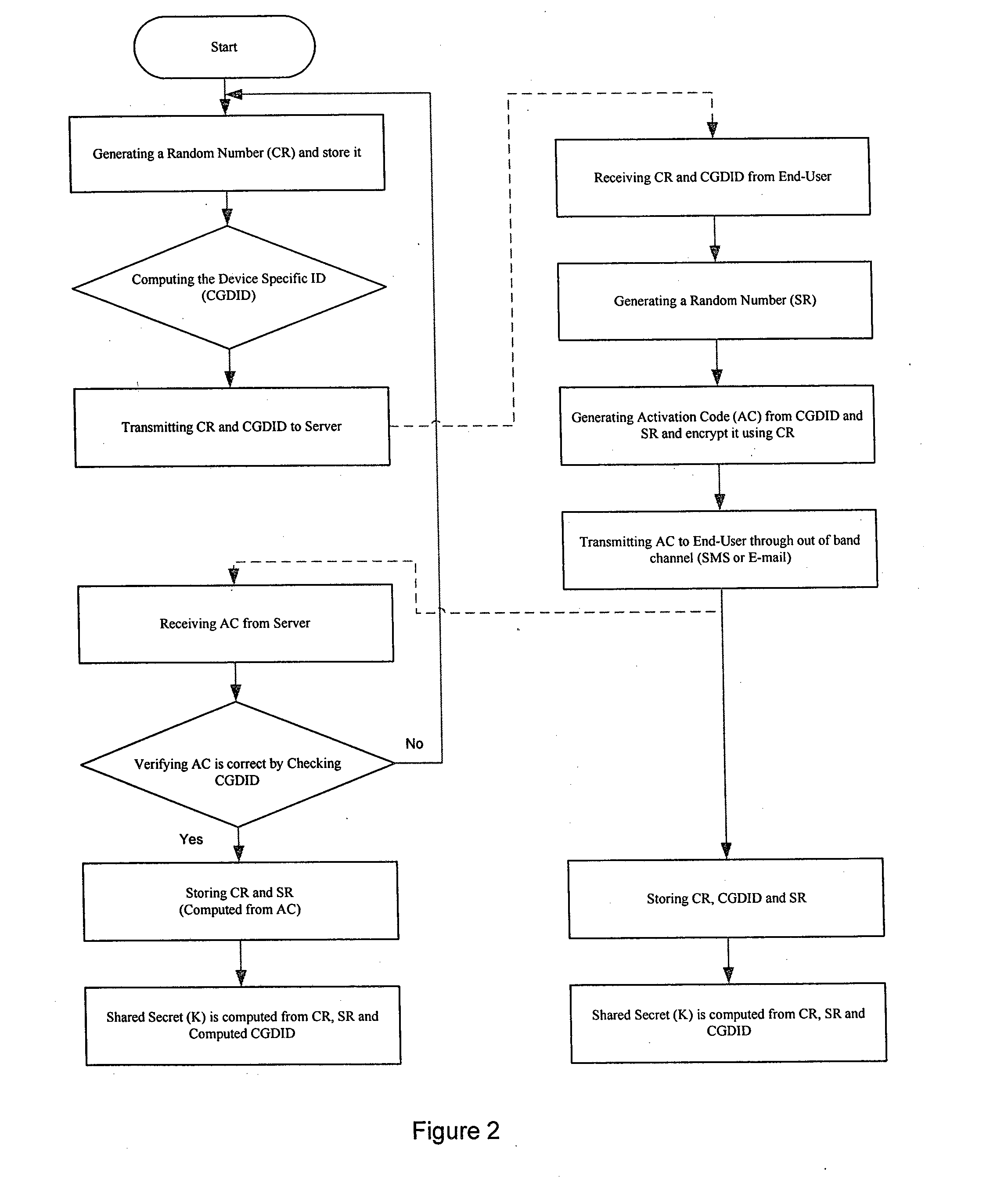
ActiveUS20130124292A1Method securityEfficient consumptionPayment architectureDigital data authenticationPersonalizationPersonal identification number
The present invention relates to a method of generating a multi-factor encryption key using a simple password in order to access control over information stored at a second entity from a first entity via at least one communication network. In one embodiment this is accomplished by, requesting to receive an application at the first entity from the second entity via the communication network, activating the first entity to generate a shared secret key, wherein the shared secret key is computed from a first entity specific ID and a random number generated at the first and second entity and allowing the user to register with the application of the second entity by the first entity, wherein the registration include entry of a personal PIN (personal identification number), a personal message etc.
Owner:JUTHANI NIRMAL
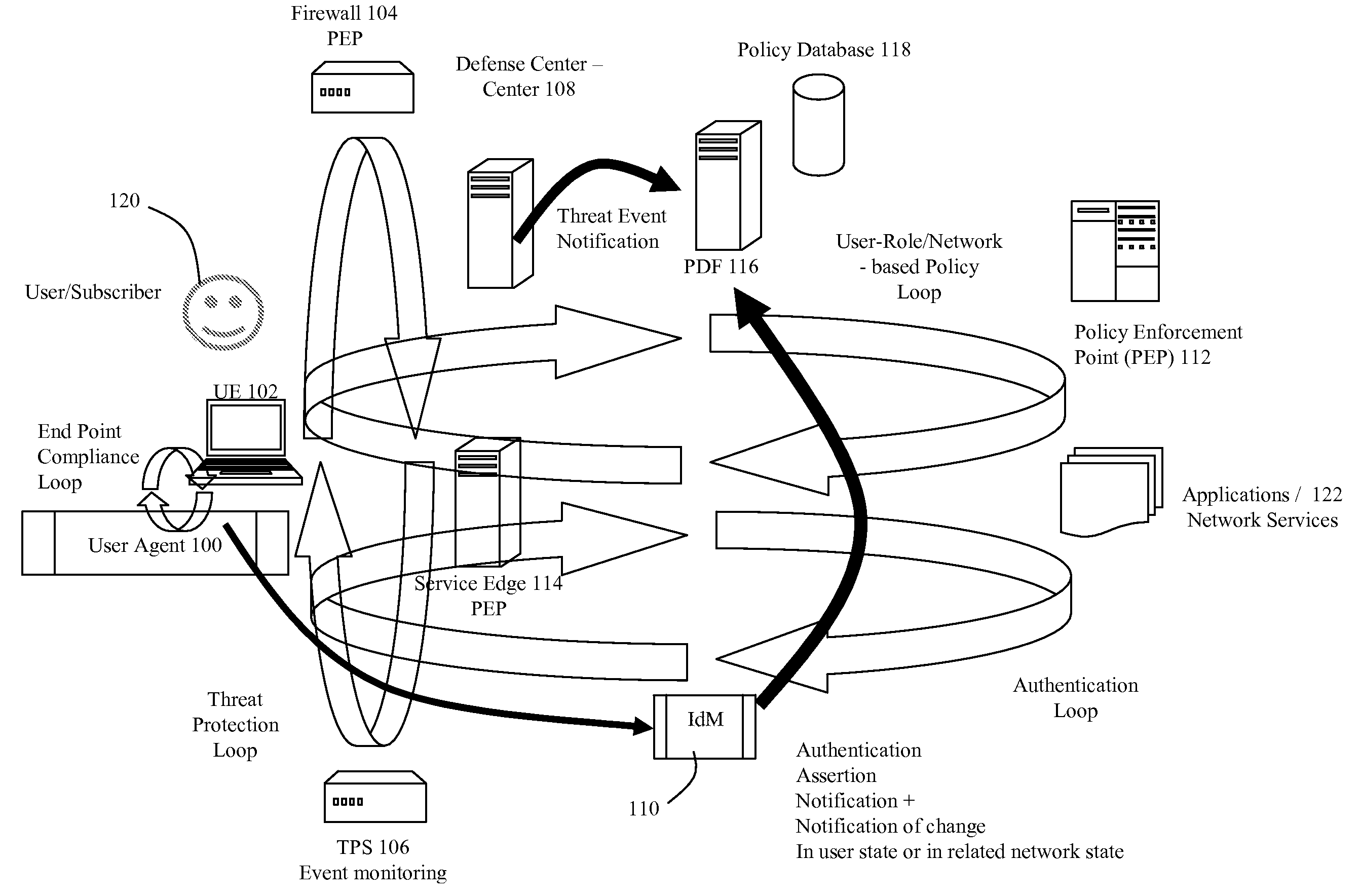
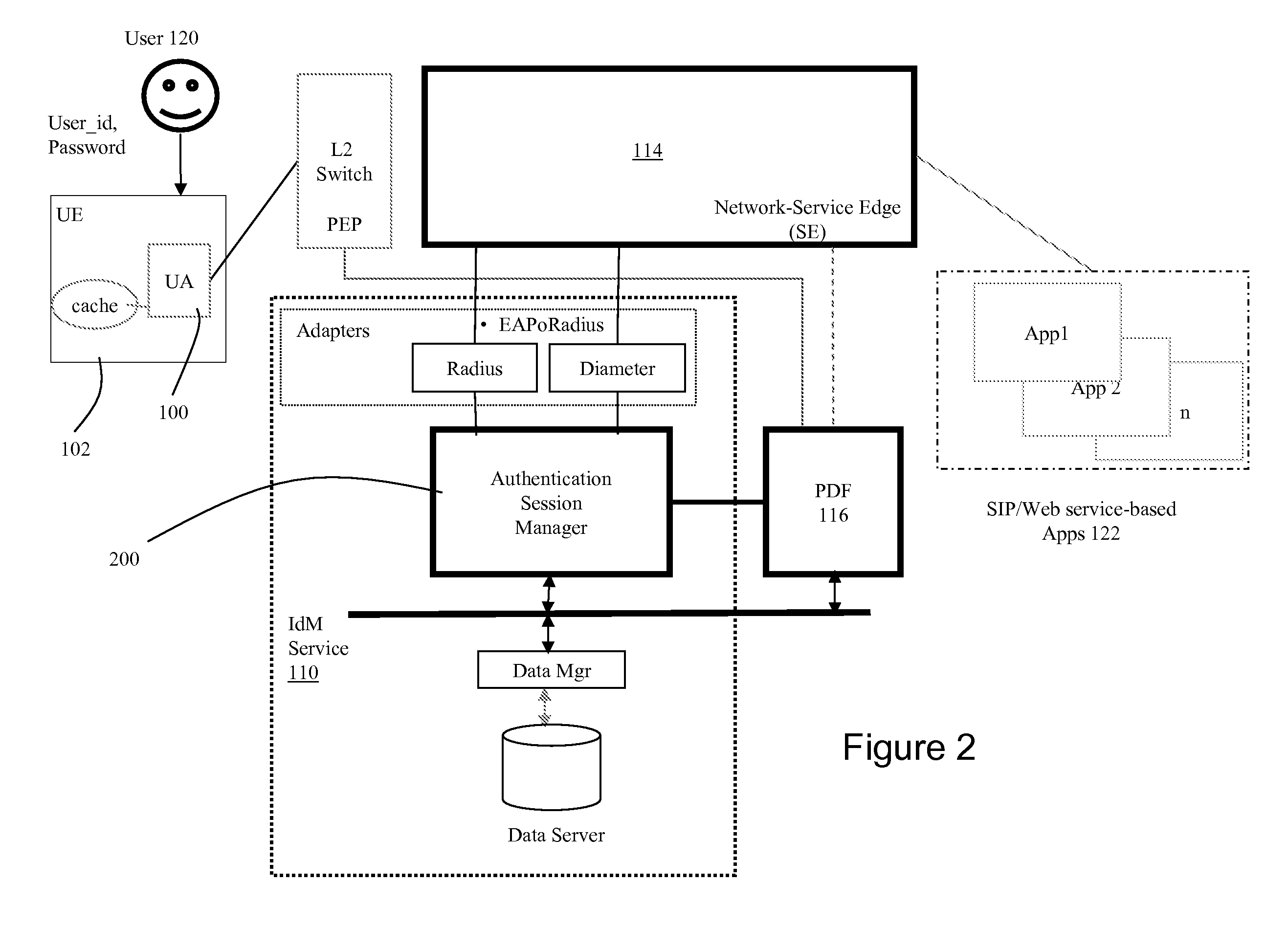
Dynamic Network Identity and Policy management
InactiveUS20070150934A1Network resource is limitedSpecial data processing applicationsSecurity arrangementTarget ResponsePassword
Network policies are managed based at least in-part on user / entity identity information with: a state monitor operable to monitor for state change events in user / entity state and related, network state or in traffic pattern and traffic flow state; an identity manager operable to obtain and validate user credentials; and a policy manager operable in response to a state change event detected by the state monitor (either the identity manager or a defense center) to select a policy based in-part on the user identity obtained by the identity manager or security context obtained by the defense center, and to prompt application of the selected policy. The policies are indicative of user / device authorization entitlements and restrictions to utilization of certain network resources, network services or applications. Dynamic policy selection and targeted responses can be used, for example, against a user who gains network access with stolen user ID and password, and subsequently attempts malicious behavior. In particular, the malicious behavior is detected and identified, and the malicious user can then be restricted from abusing network resources without adversely affecting other users, groups, network devices, and other network services.
Owner:NORTEL NETWORKS LTD
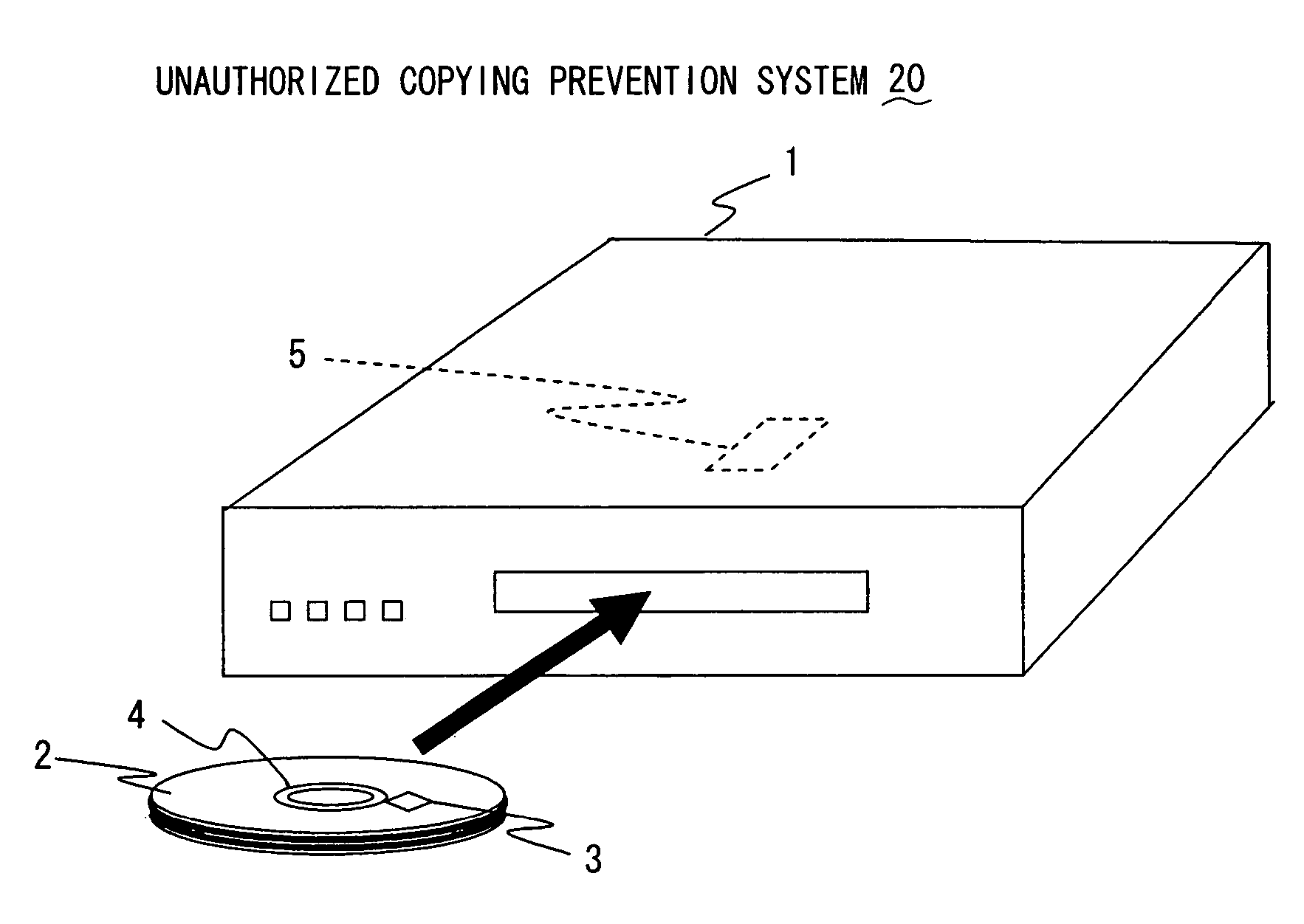
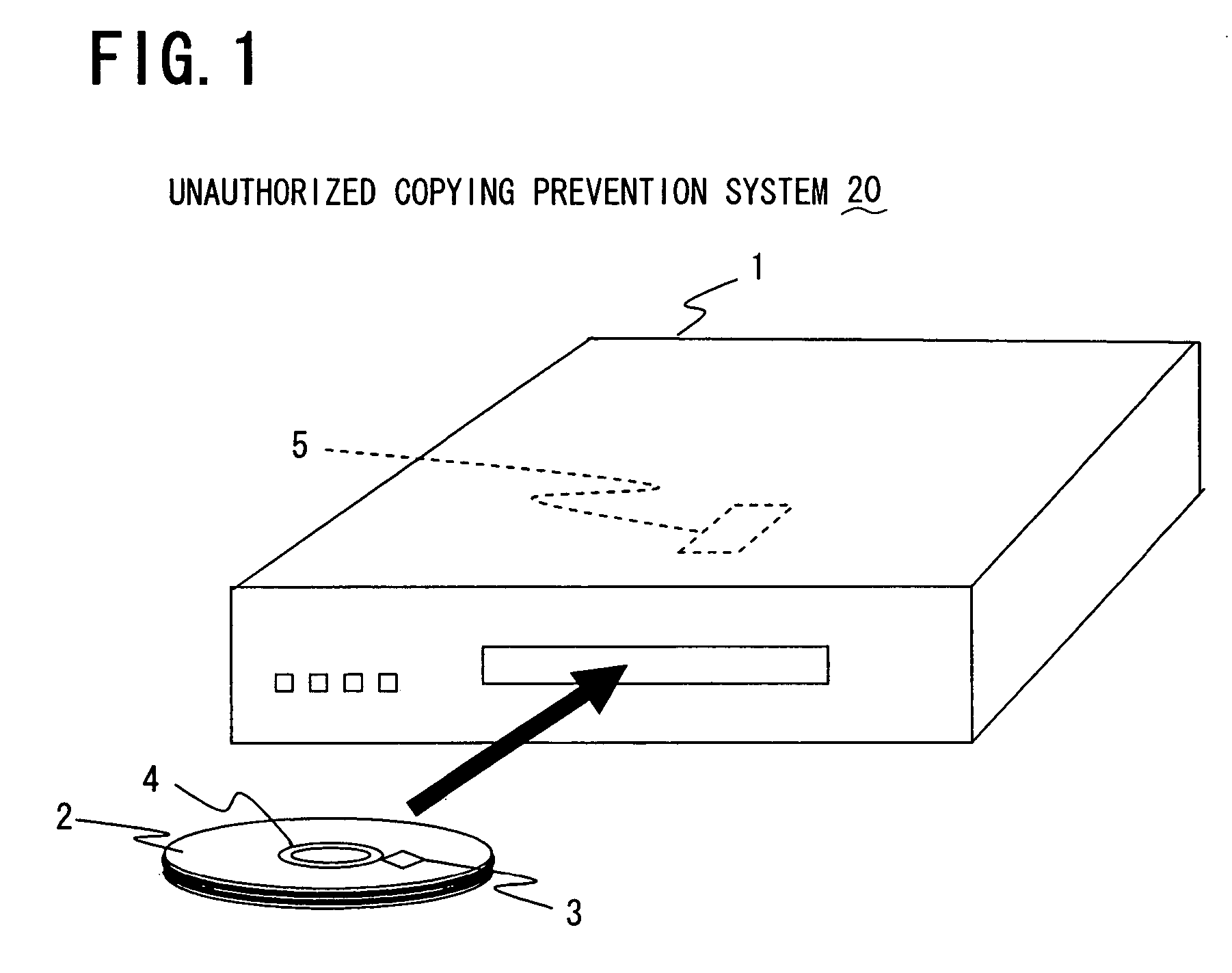
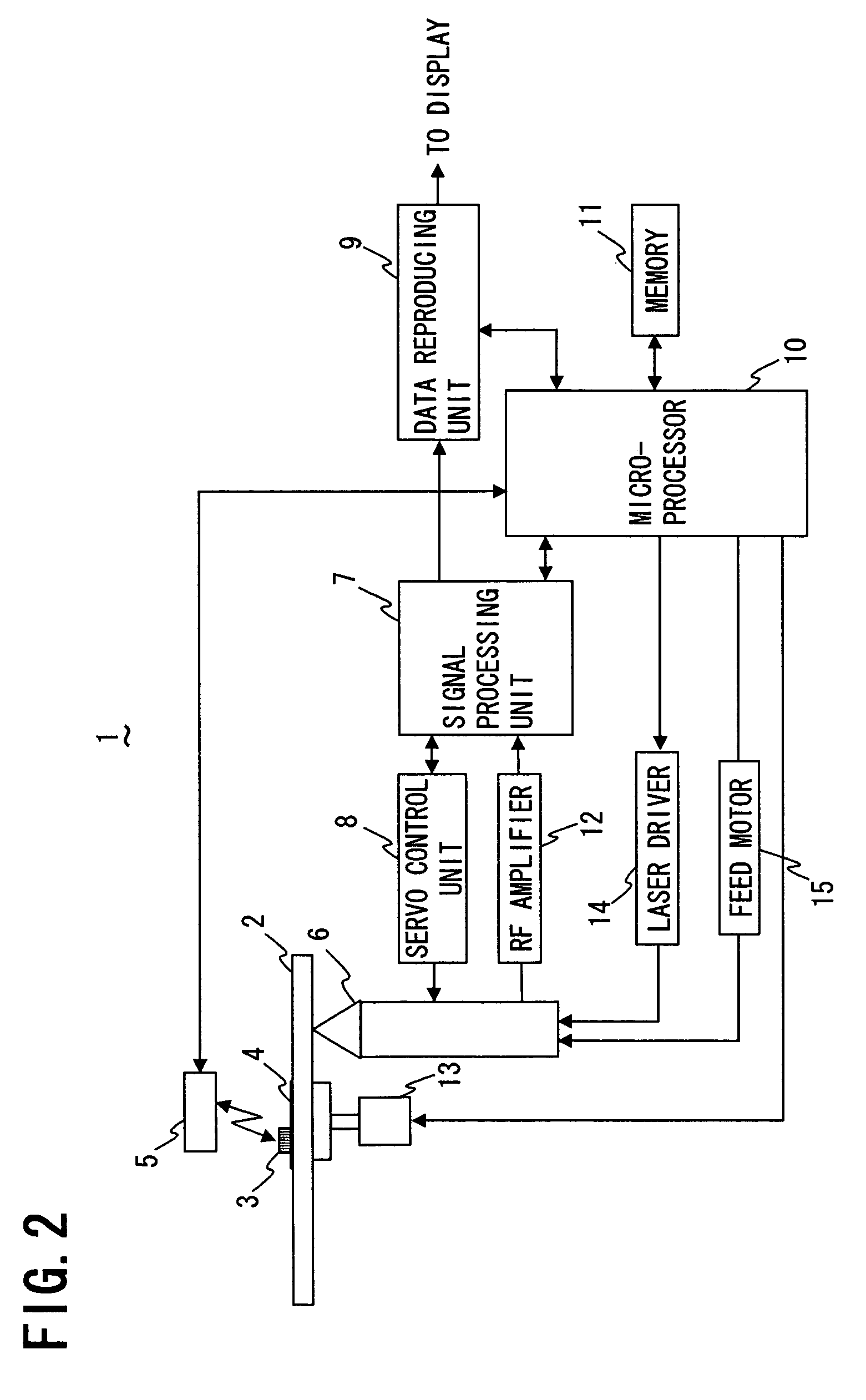
Optical disc having RFID tag, optical disc apparatus, and system for preventing unauthorized copying
InactiveUS7317396B2Reliable preventionInhibitory contentDigital data processing detailsMechanical recordingSecret codeInformation needs
In an optical disc having an RFID tag, disc control information needed for control of reproduction of the content recorded in the disc body of the optical disc is stored in the RFID tag. Thereby, even if the content recorded in the disc body is illegally copied in some way, common optical disc apparatus incapable of reading RFID tags cannot read and copy the disc control information stored in the RFID tag. Accordingly, unauthorized copying of the content recorded on the optical disc can be reliably prevented without the use of special cryptographic technology.
Owner:FUNAI ELECTRIC CO LTD
Method of and apparatus for sharing secret information between device in home network
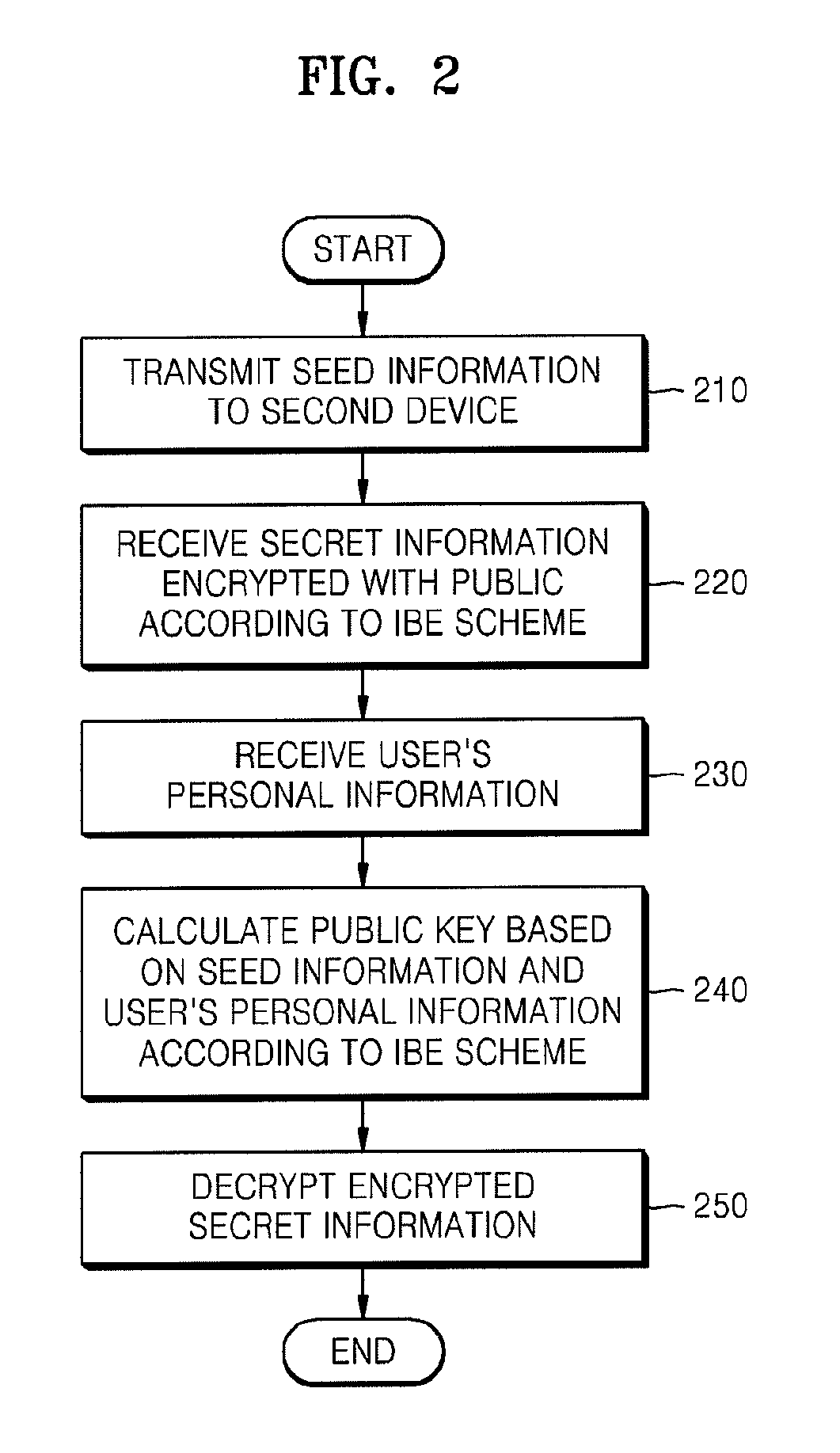
InactiveUS20090055648A1Reduce traffic problemsAvoid complex calculationsKey distribution for secure communicationPublic key for secure communicationID-based encryptionPassword
A method and apparatus for sharing secret information between devices in a home network are provided. In the method and apparatus, home network devices receive a password (credential) input by a user and encrypt secret information based on the credential by using keys generated according to a predetermined identity-based encryption (IBE) scheme. Accordingly, it is possible to securely share the secret information between home network devices without any certificate authority or certificate.
Owner:SAMSUNG ELECTRONICS CO LTD
Transaction verification system
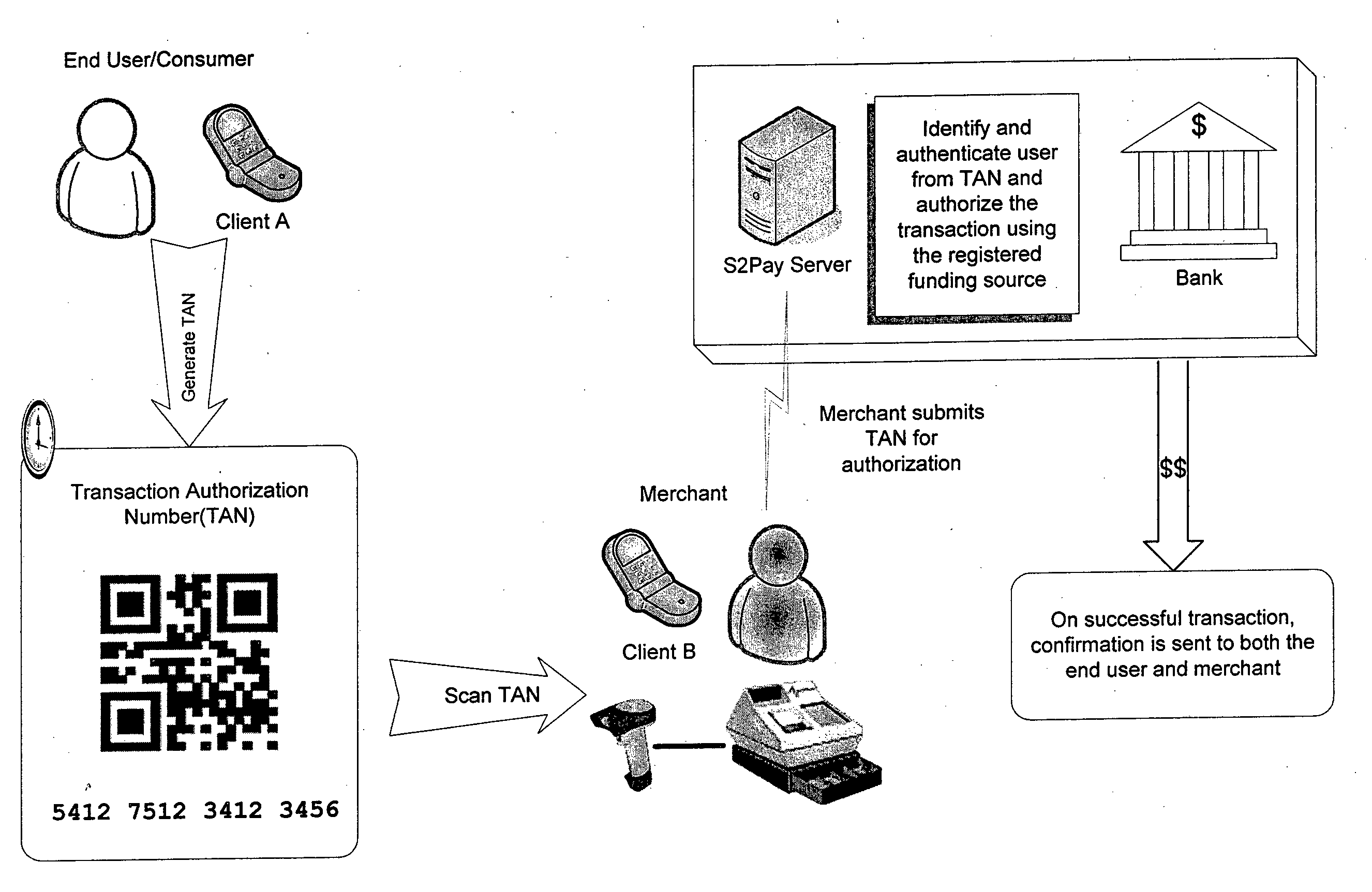
This invention uses separate, parallel communication channels to authorise and authenticate a transaction. A primary data channel (PSTN, radio or the like) is used to communicate between the merchant terminal and the bank, and a parallel data channel (a mobile phone network for instance) is used for the authentication process. In the example, the transaction is initiated (on a primary data channel), using a POS terminal as a transaction processing client. The transaction processing server and financial services provider fulfill their normal functions. At this point, the process loops into a transaction authorisation component using the parallel data channel, that requires authentication of the transaction initiator (the card holder). In the example, communications on the parallel data channel are by way of SMS. In the authorisation process, the card holder receives an SMS requesting authorisation of the transaction. If the card holder is not the transaction initiator, the card holder can cancel the transaction. If the transaction can be authorised, an authentication process is initiated in which the mobile phone is programmed to require the entry of a normally secret code (such as a personal identification number (PIN)) that serves to authenticate the card holder and to give final authorisation of the transaction.
Owner:NARAINSAMY SELVANATHAN
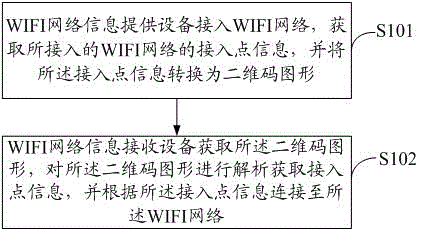
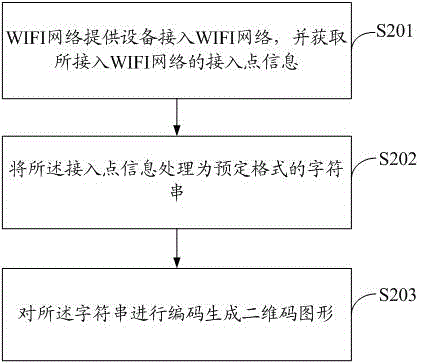
Method and system for sharing WIFI (wireless fidelity) network information on basis of two-dimensional code graphs
InactiveCN102724668AImprove sharing efficiencyImprove securityNetwork traffic/resource managementNetwork topologiesGraphicsPassword
The invention discloses a method and a system for sharing WIFI (wireless fidelity) network information on the basis of two-dimensional code graphs. The method includes that WIFI network information providing equipment accesses into the WIFI network, acquires access point information of the accessed WIFI network and converts the access point information into a two-dimensional code graph; WIFI network information receiving equipment acquires the two-dimensional code graph and analyzes the same to acquire the access point information and is connected to the WIFI network according to the access point information. By the method for sharing the WIFI network information on the basis of the two-dimensional code graphs, sharing efficiency of the WIFI network information is improved, and other users cannot acquire the network type, passwords and the like of the access point when seeing the two-dimensional code graph, and accordingly, access safety of the WIFI network is improved as well.
Owner:HUIZHOU TCL MOBILE COMM CO LTD
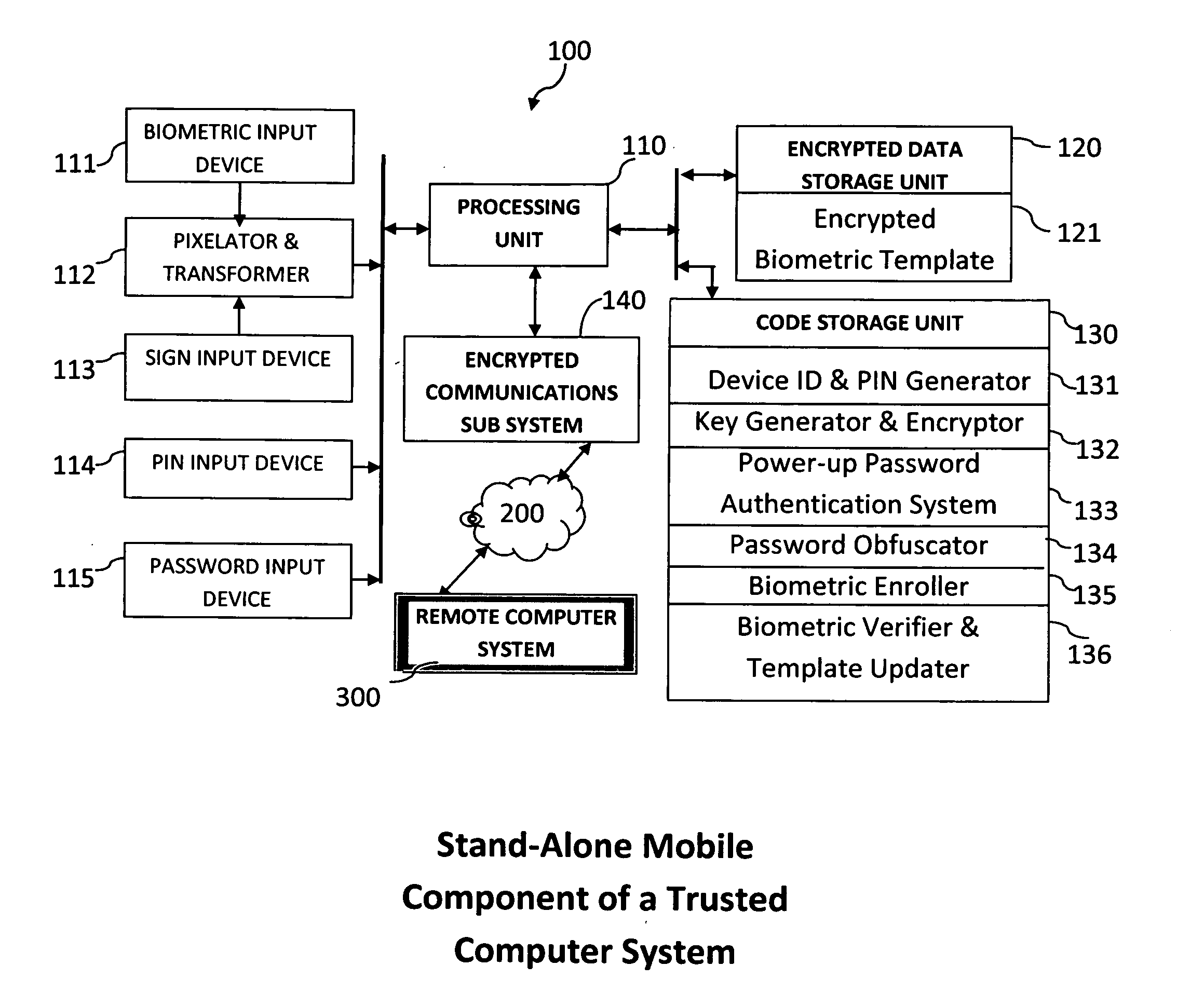
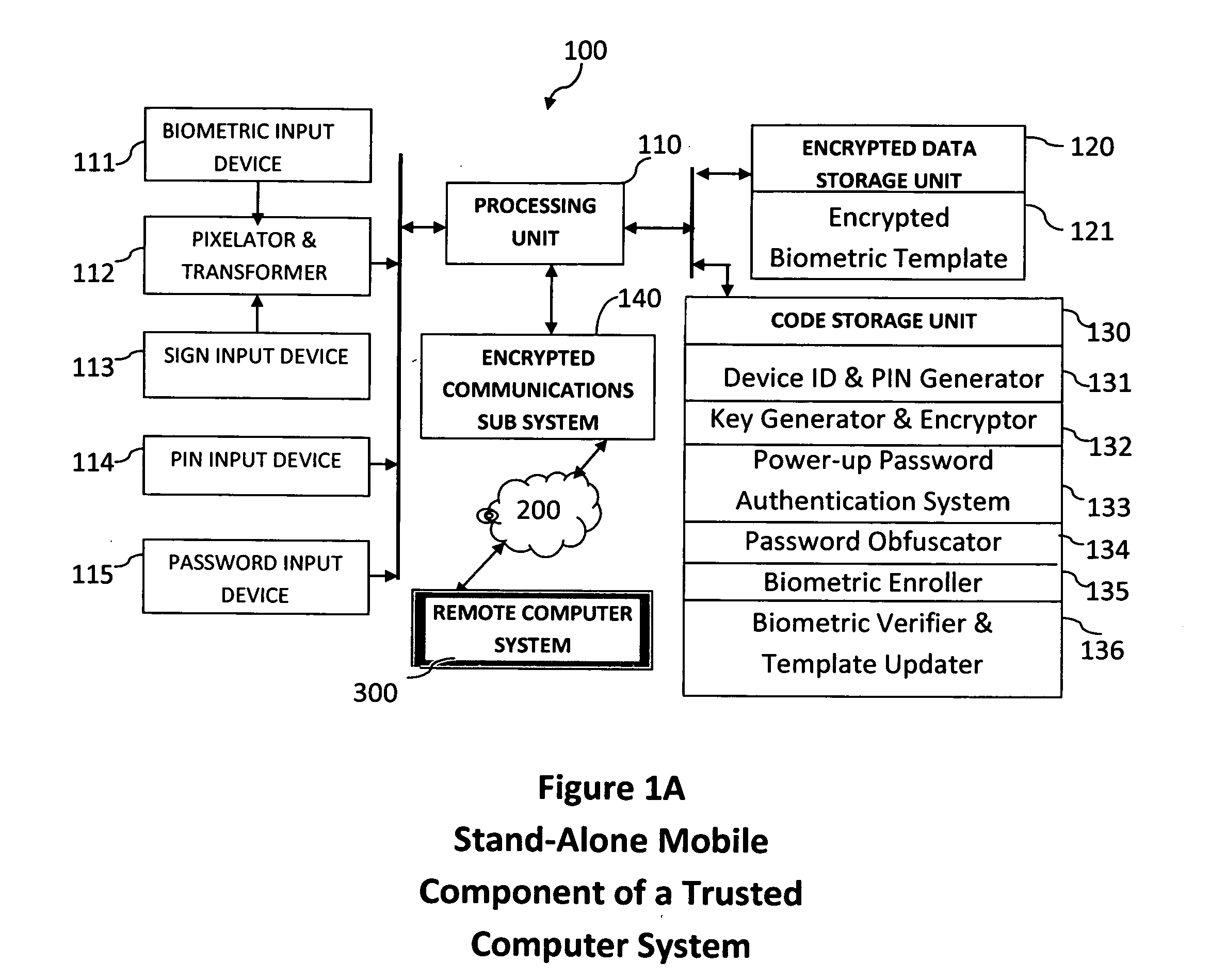
Method and system for combining a PIN and a biometric sample to provide template encryption and a trusted stand-alone computing device
ActiveUS20110126024A1Secure EncryptionEasy to useDigital data processing detailsUser identity/authority verificationBiometric dataTrust relationship
Biometric data, suitably transformed are obtained from a biometric input device contained within a stand-alone computing device and used in conjunction with a PIN to authenticate the user to the device. The biometric template and other data residing on the device are encrypted using hardware elements of the device, the PIN and Password hash. A stored obfuscated password is de-obfuscated and released to the device authentication mechanism in response to a successfully decrypted template and matching biometric sample and PIN. The de-obfuscated password is used to authenticate the user to device, the user to a remote computer, and to encrypt device data at rest on the device and in transit to and from the remote computer. This creates a trusted relationship between the stand-alone device and the remote computer. The system also eliminates the need for the user to remember and enter complex passwords on the device.
Owner:BIOCRYPT ACCESS LLC
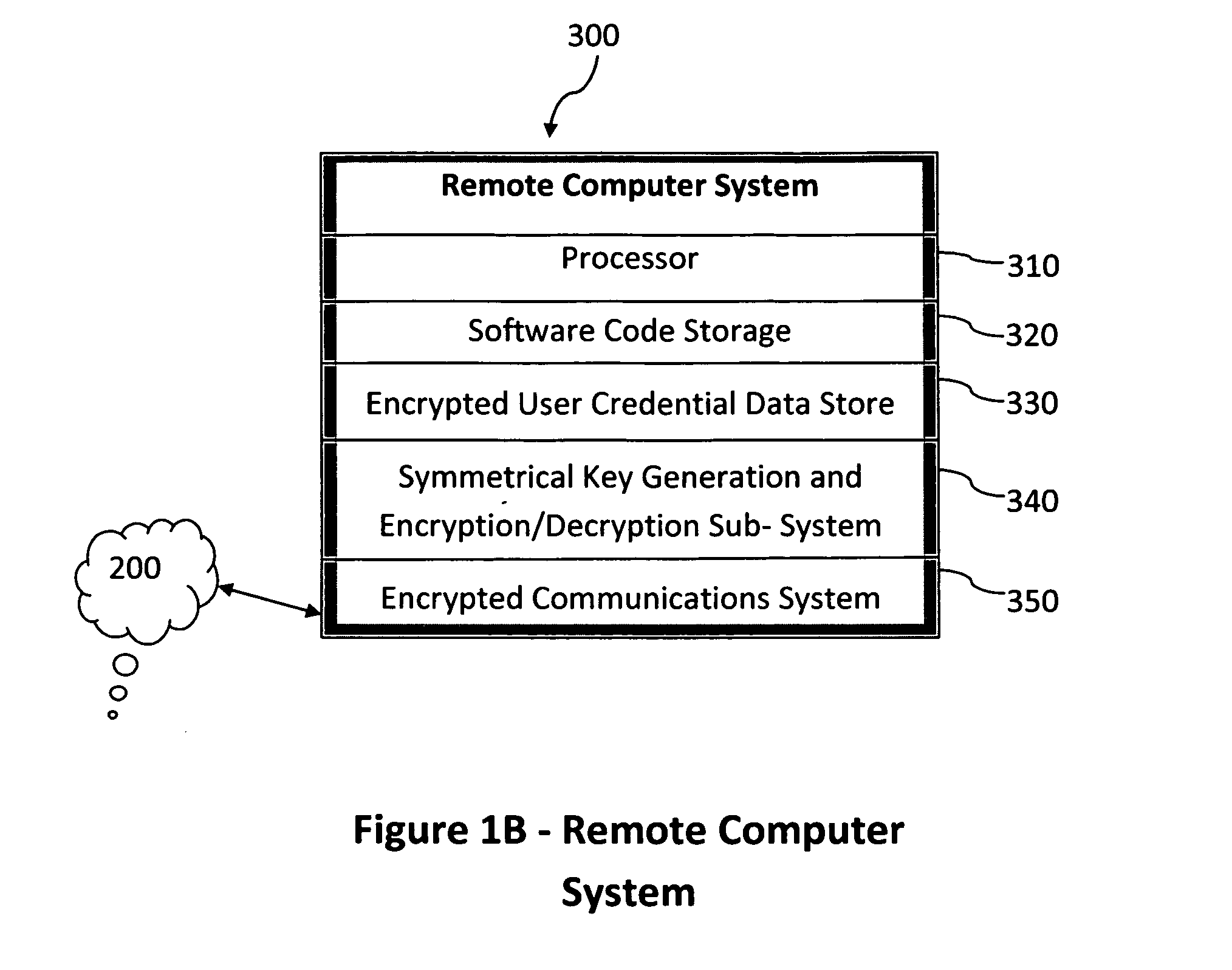
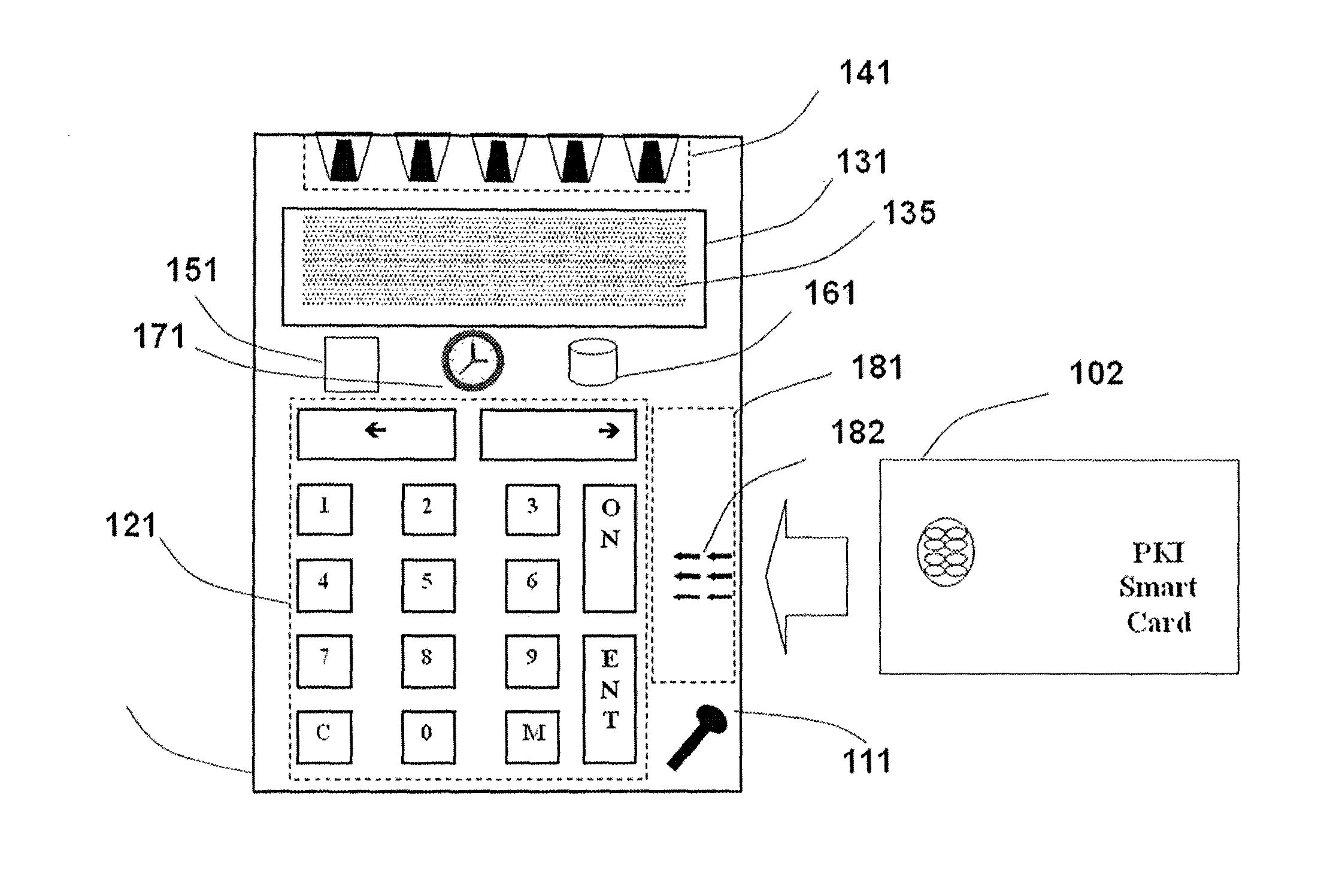
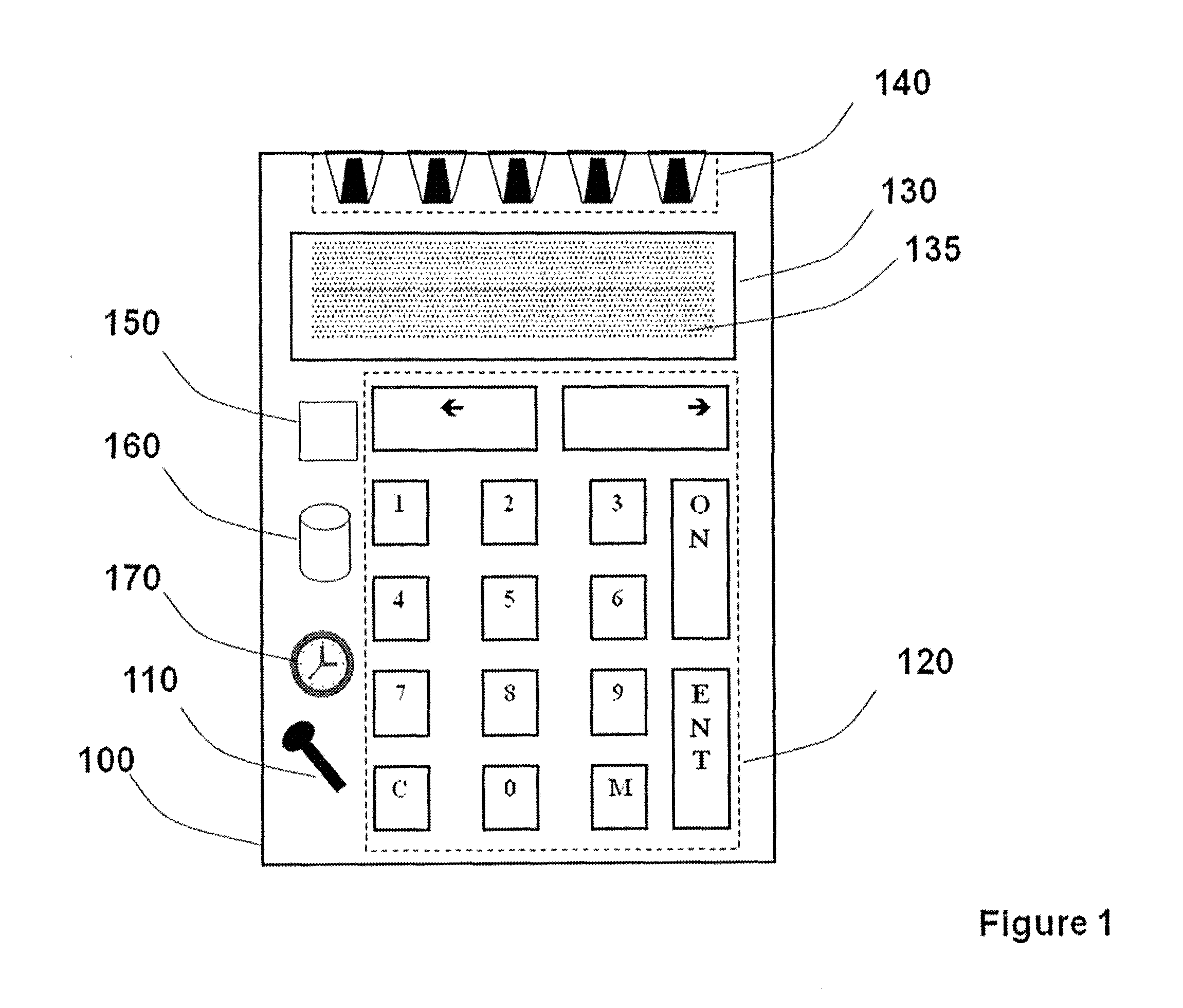
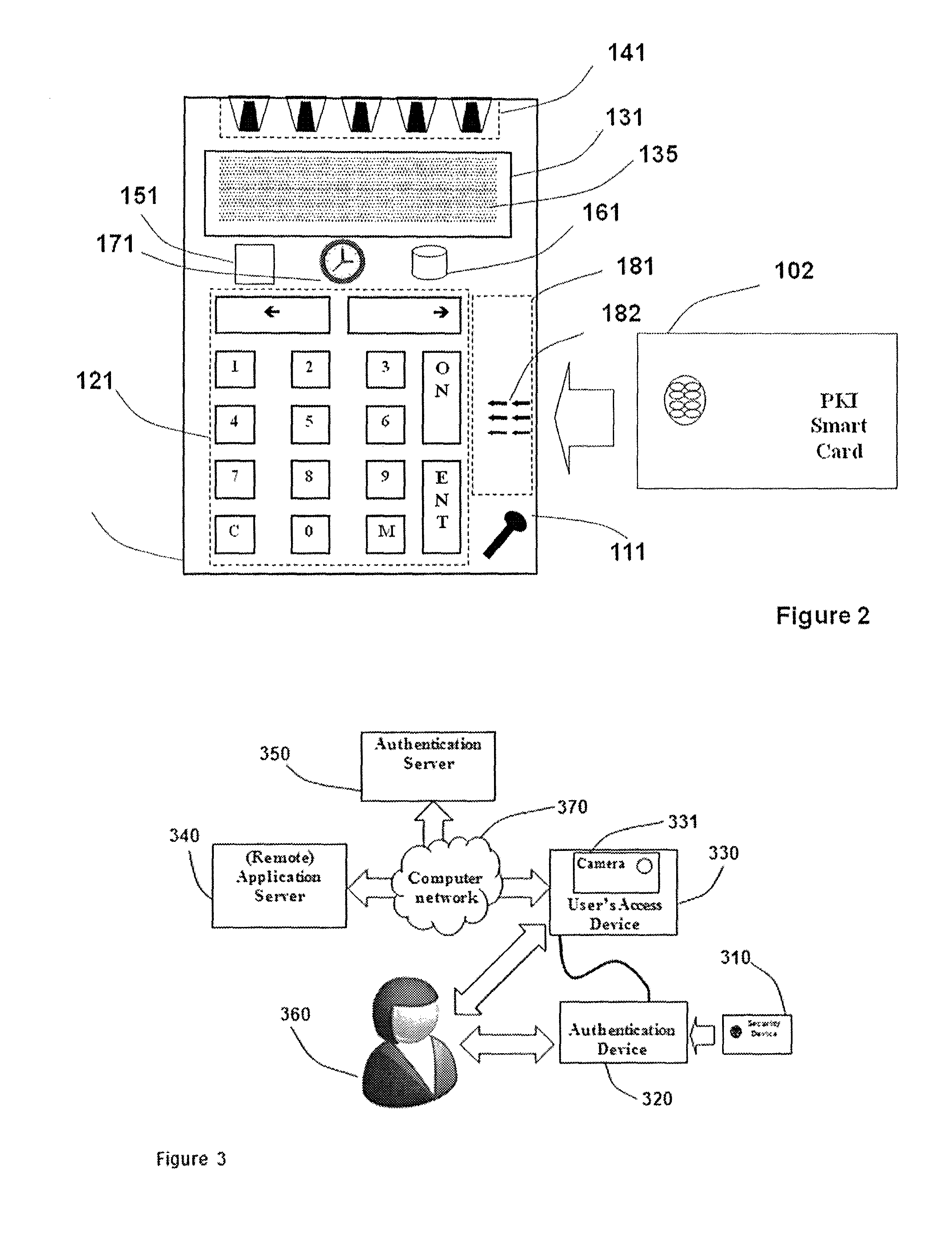
Strong authentication token with visual output of pki signatures
InactiveUS20130198519A1Improve securityUser identity/authority verificationDigital data authenticationDisplay deviceSecret code
A handheld authentication device comprising a data processor and a display is adapted to: generate an input value; submit the input value to an asymmetric cryptographic operation; obtain the result of said asymmetric cryptographic operation; generate an authentication message substantially comprising the result of the asymmetric cryptographic operation; encode the authentication message into one or more images; and display these images on the display. A method for securing computer-based applications remotely accessed by a user comprises capturing images displayed on the display of an authentication device of the user whereby these images have been encoded with an authentication message generated by the authentication device and whereby the authentication message comprises the result of an asymmetric cryptographic operation on an input value; decoding the images to retrieve the authentication message; retrieving the result of the asymmetric cryptographic operation from the authentication message; verifying the authentication message.
Owner:ONESPAN NORTH AMERICA INC
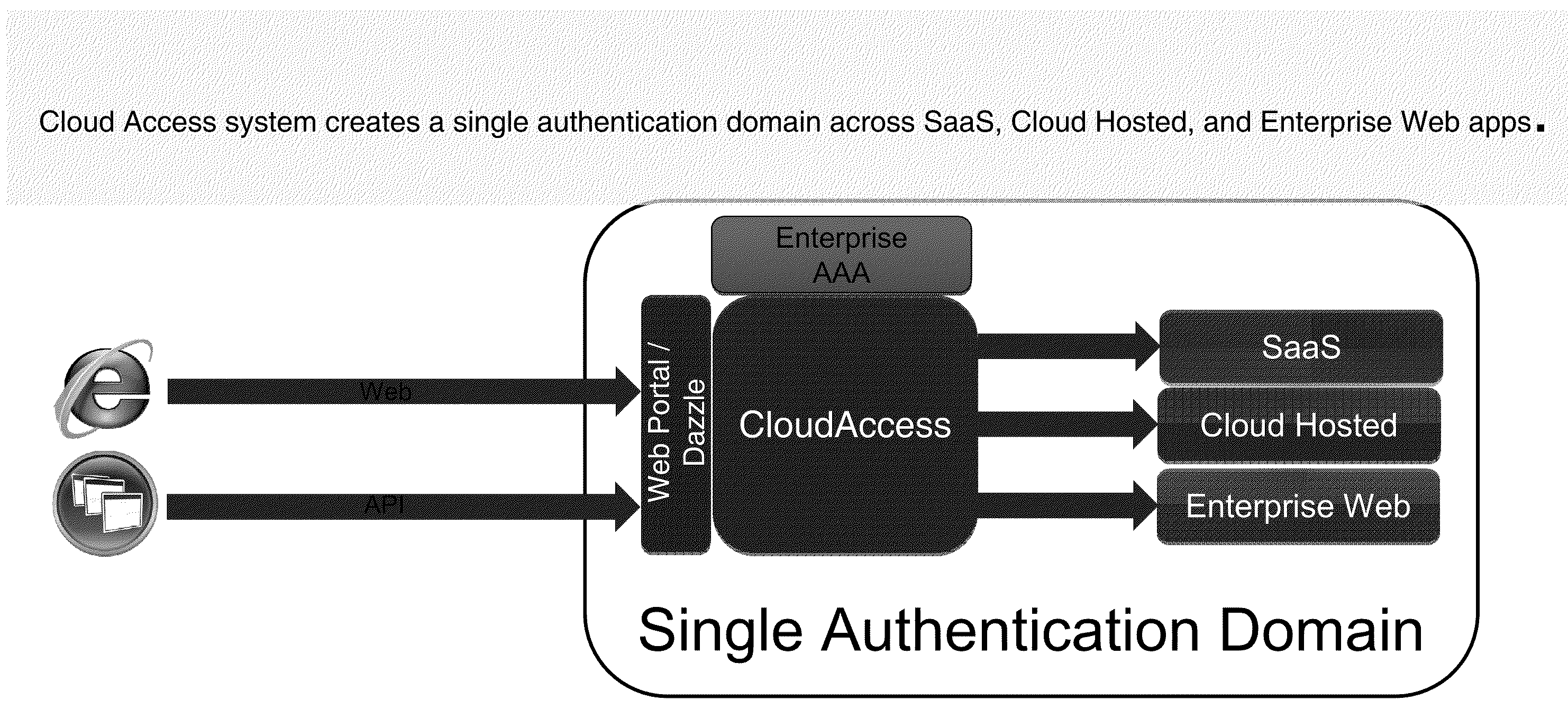
Systems and Methods for Providing Single Sign On Access to Enterprise SAAS and Cloud Hosted Applications
ActiveUS20110277026A1Digital data processing detailsUser identity/authority verificationPasswordSecret code
The solution of the present application addresses the problem of authentication across disparately hosted systems by providing a single authentication domain across SaaS and cloud hosted applications as well as traditional enterprise hosted applications. An application delivery controller intermediary to a plurality of clients and the disparately hosted applications providing single sign on management, integration and control. A user may log in via an interface provided, controlled or managed by the ADC, which in turns, authenticates the user to the application in accordance with policy and the host of the application. As such, the user may login once to gain access to a plurality of disparately hosted applications. From the user's perspective, the user seamlessly and transparently gains access to different hosted systems with different passwords and authentication via the remote access provided by the system of the present solution
Owner:CITRIX SYST INC
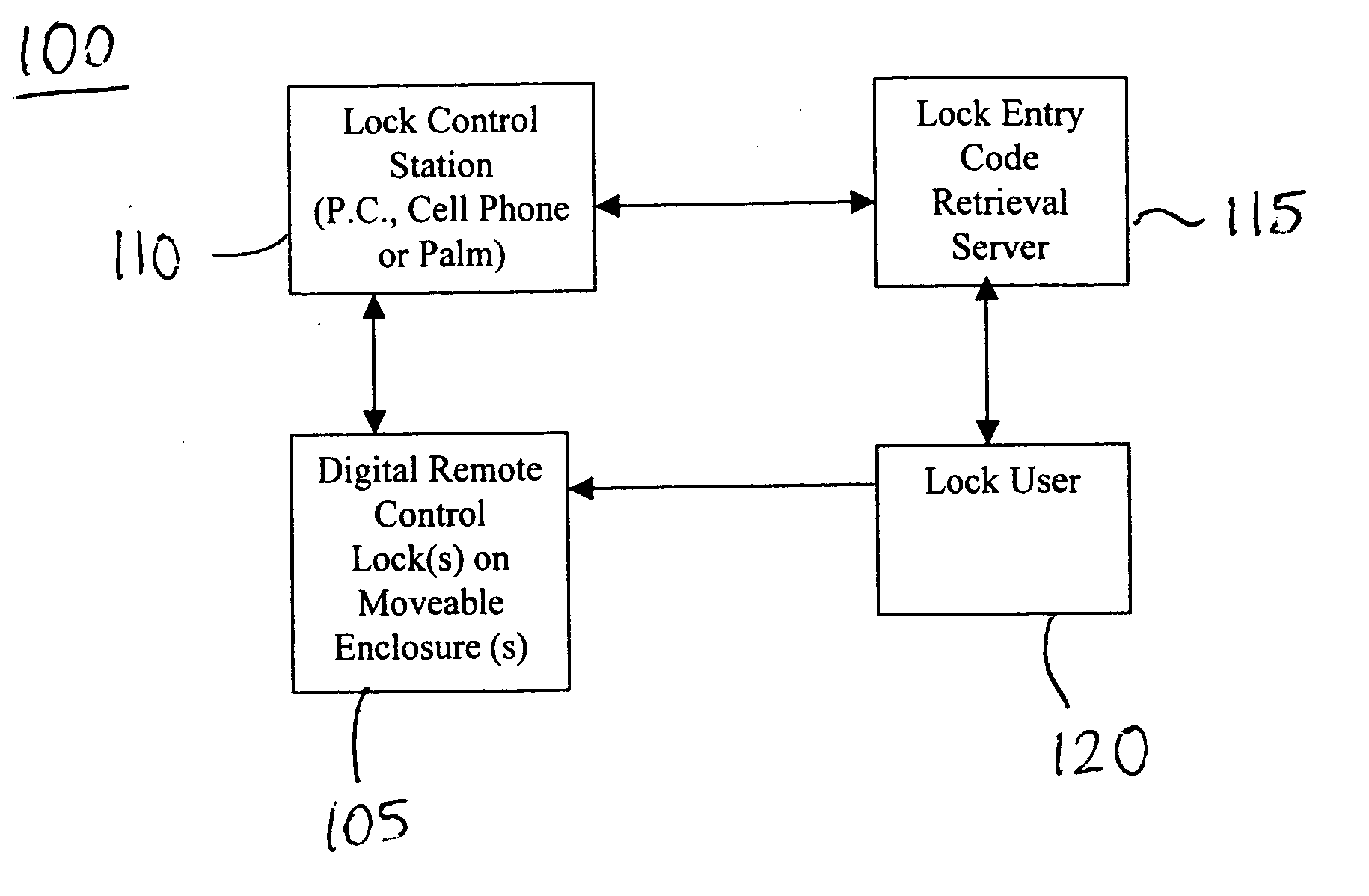
Method and system for setting entry codes via a communications network for access to moveable enclosures
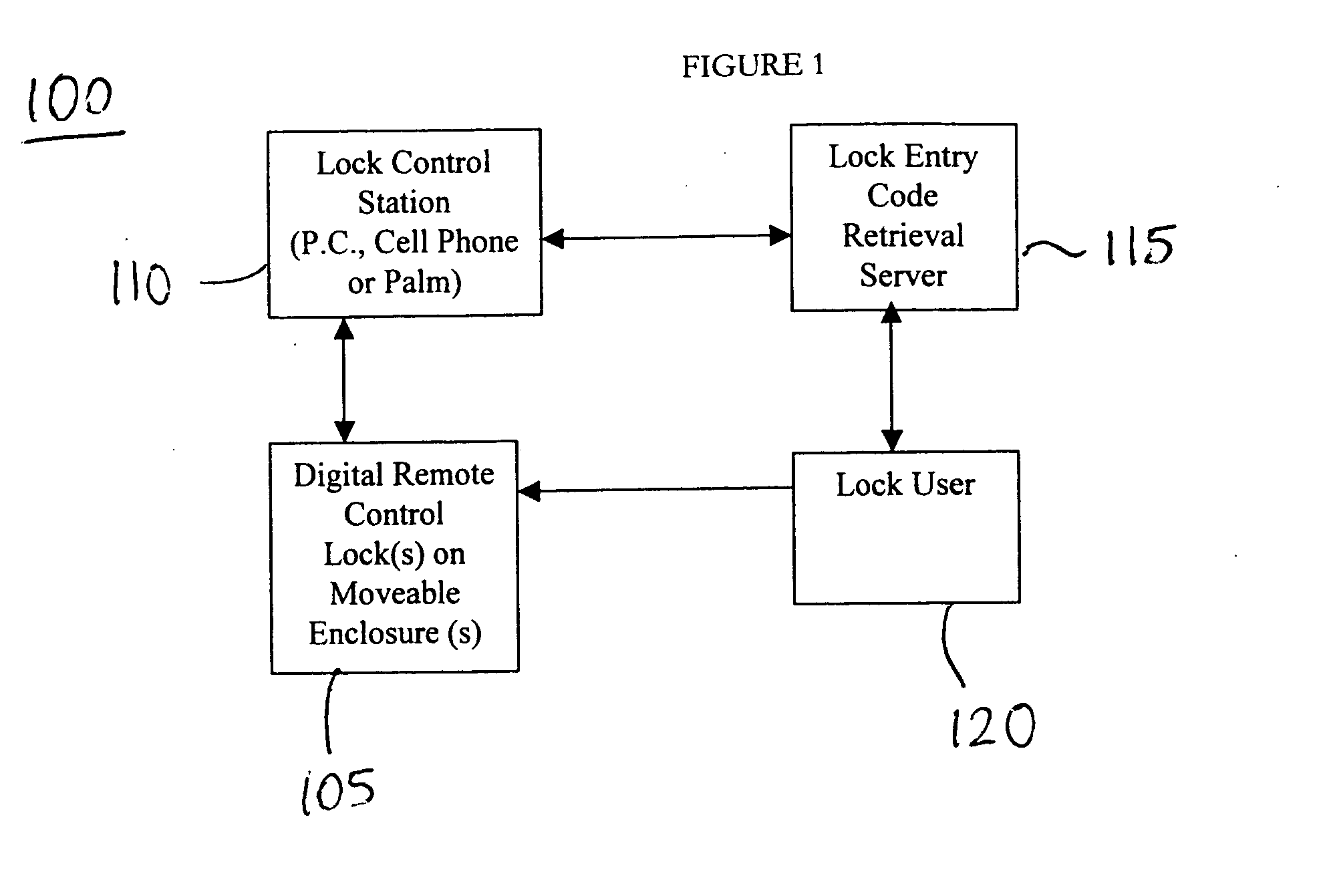
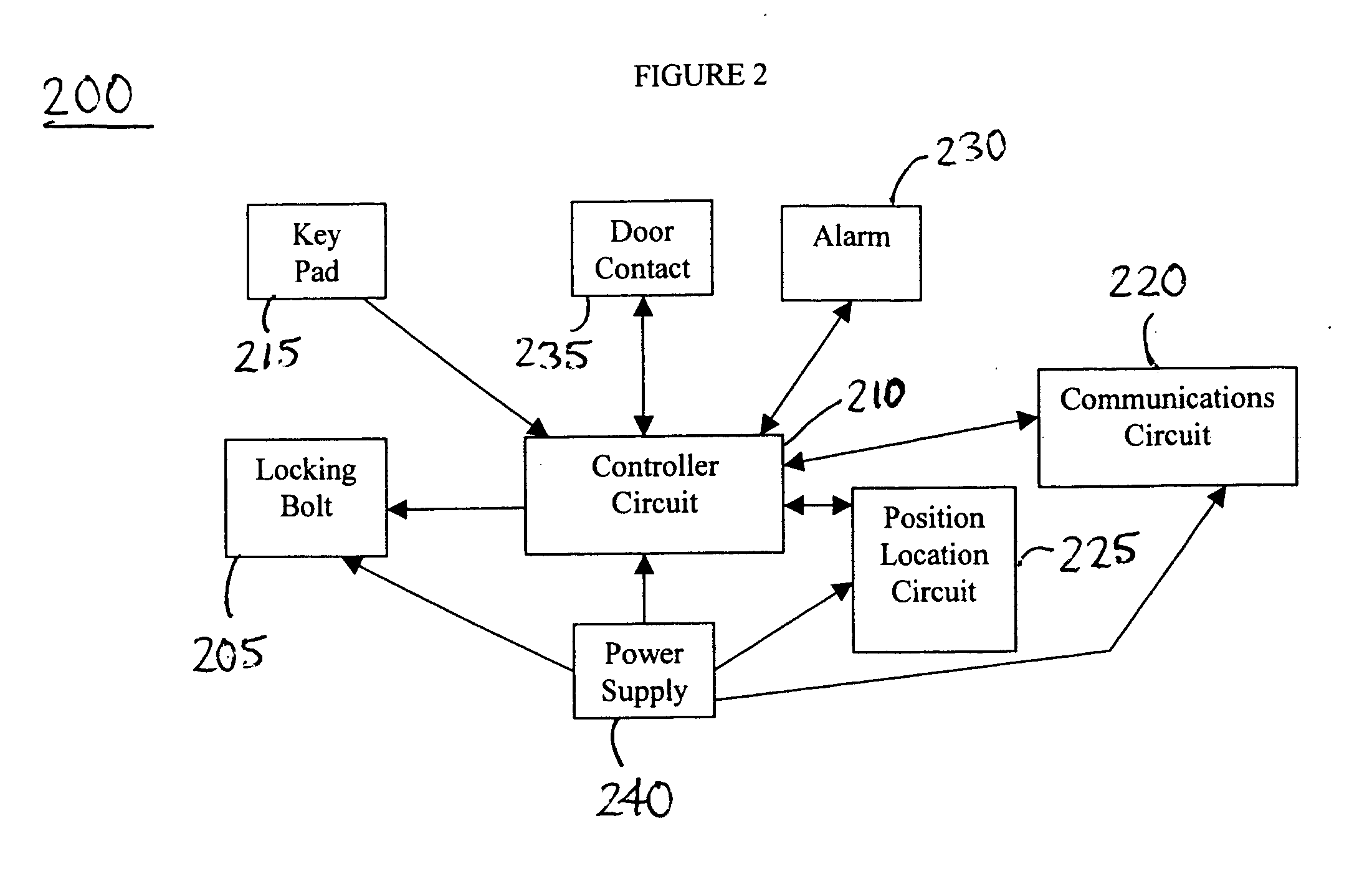
InactiveUS20050044906A1Electric signal transmission systemsDigital data processing detailsMeasurement deviceSecret code
A system and method for controlling access to a moveable enclosure are provided. The system includes a lock on the moveable enclosure, a control circuit coupled to the lock and configured to i) receive an entry code and ii) open the lock in response to receipt of the entry code, a time measurement device and / or Global Positioning System device coupled to the control circuit and configured to generate time and position data, such as latitude and longitude data, relating to the moveable enclosure; and a personal computing device wirelessly coupleable to the control circuit and configured to generate the entry code using the latitude and longitude data. The entry code may be erased after a single use. The validity of entry code may depend upon the time of its entry and the physical location of the moveable enclosure.
Owner:SPIELMAN TIMOTHY G
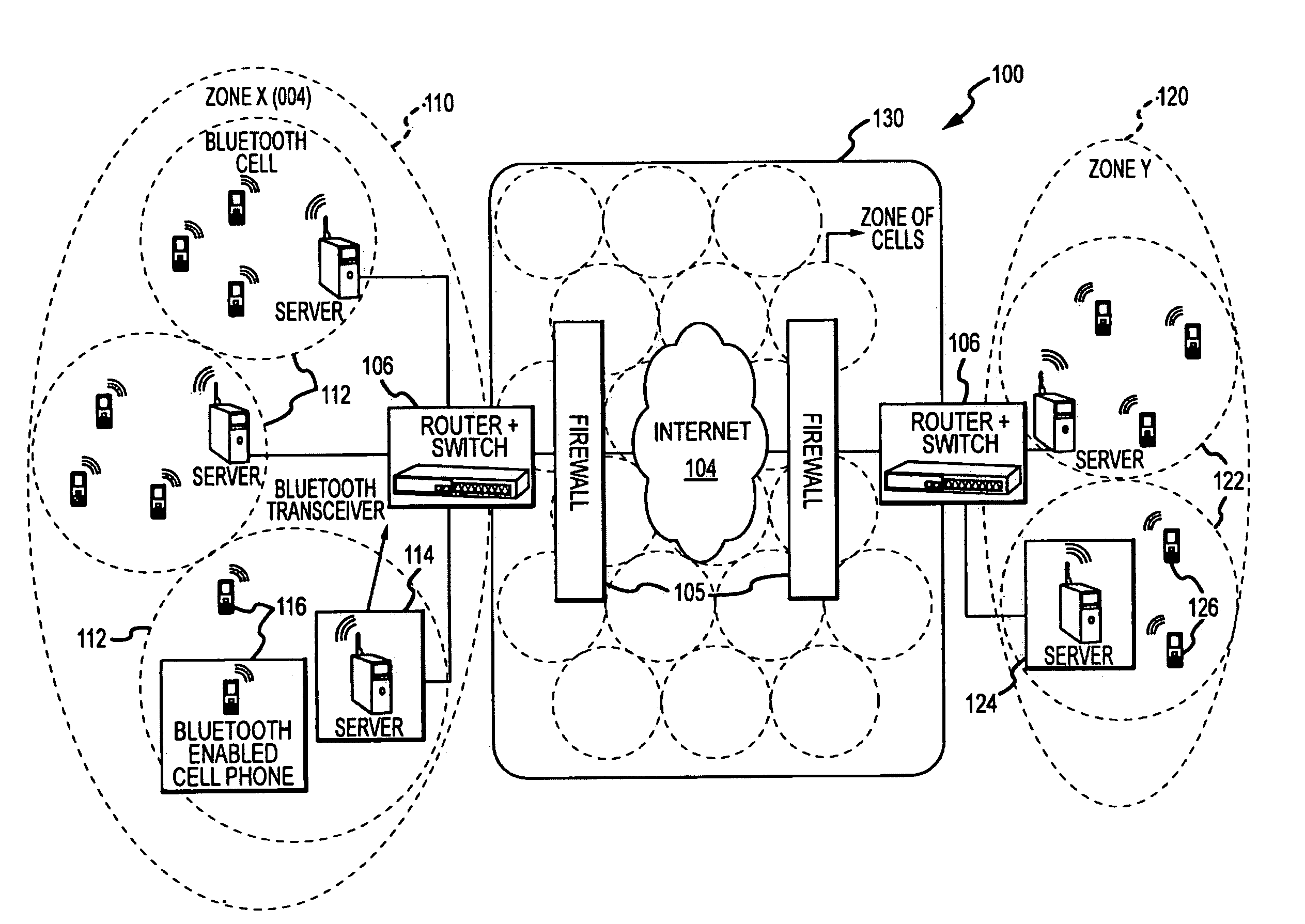
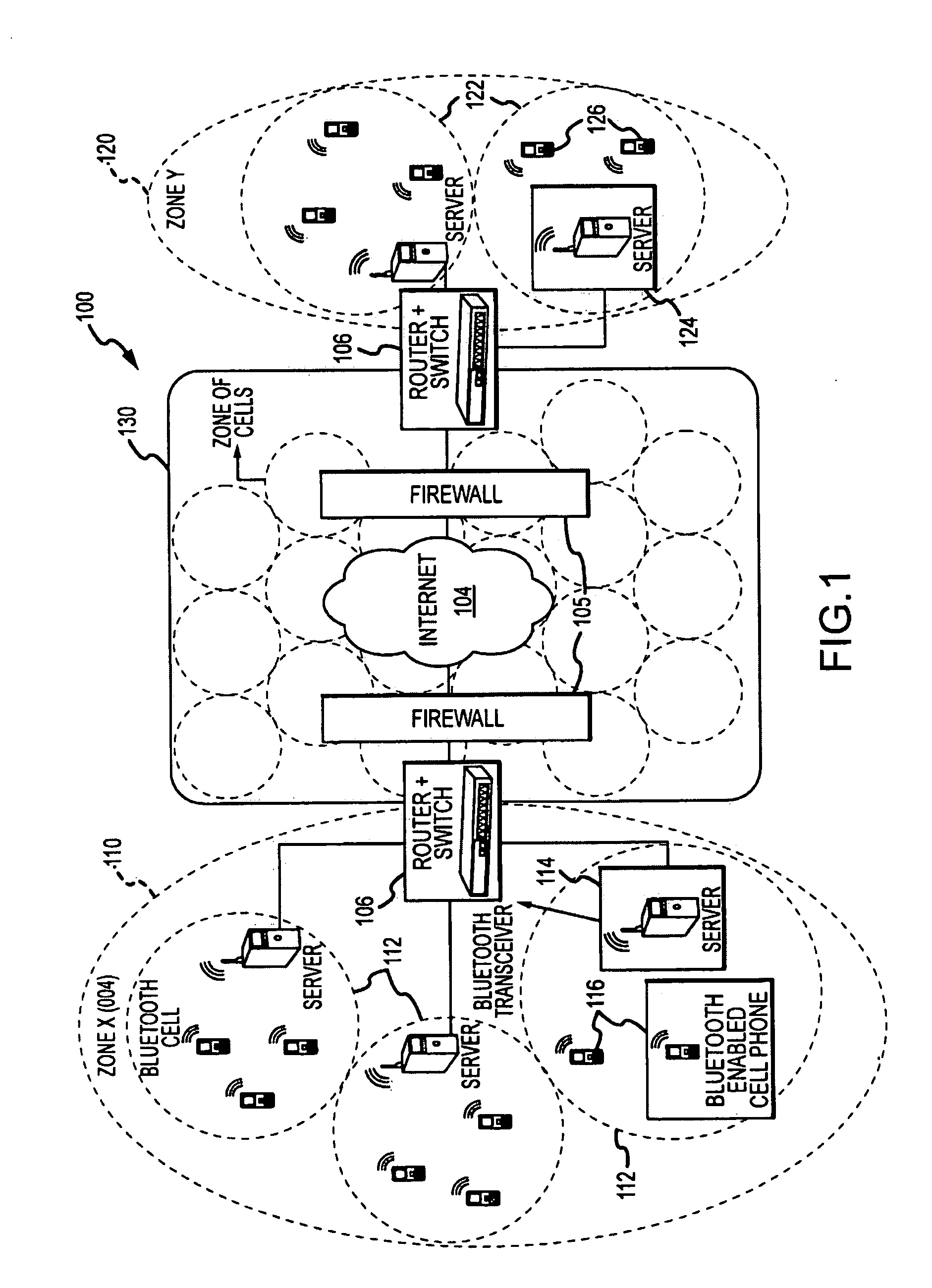
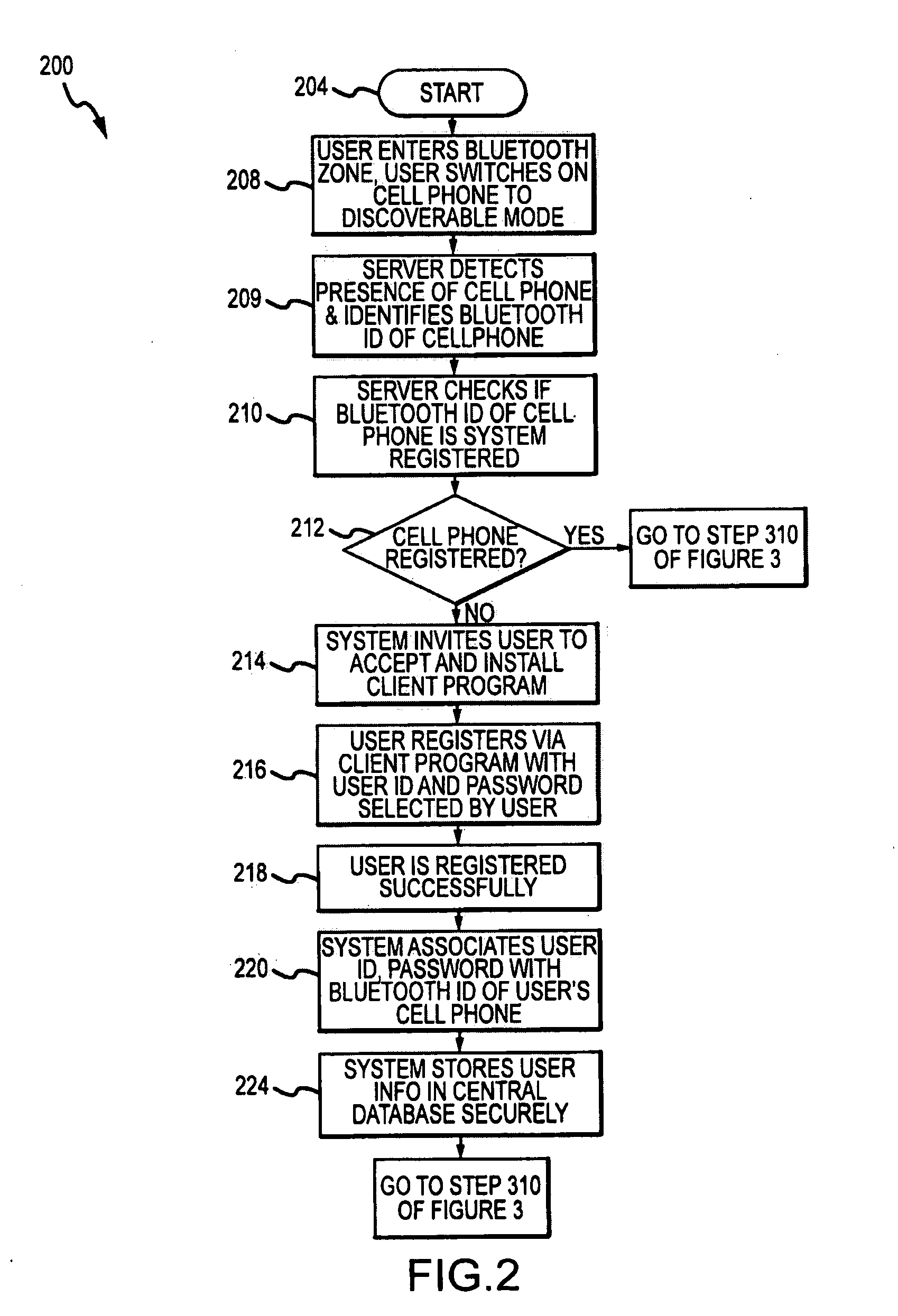
Data Communications Between Short-Range Enabled Wireless Devices Over Networks and Proximity Marketing to Such Devices
ActiveUS20090264070A1Increases duration of potential stayProlong duration of potential stayNetwork topologiesRadio transmissionDigital dataThe Internet
A method for allowing short-ranged communication devices to communicate with each other using the Internet. Cell servers are provided in a first and second zones linked to the Internet and adapted for transmitting voice and other digital data over the Internet such as using VoIP. The method includes registering users of short-range enabled devices, such as Bluetooth cell phones, with a communication system and storing a device identifier along with a user ID and password. A contact list is stored for each registered user. The method includes a registered user entering a cell serviced by a server, the server discovering the user's device, logging the user into the system based on the device identifier and an entered user ID and password, receiving a communication request to chat with one of the listed contacts, and establishing a communication session using time previously awarded to the user for receiving marketing content.
Owner:LIM SOON HOCK
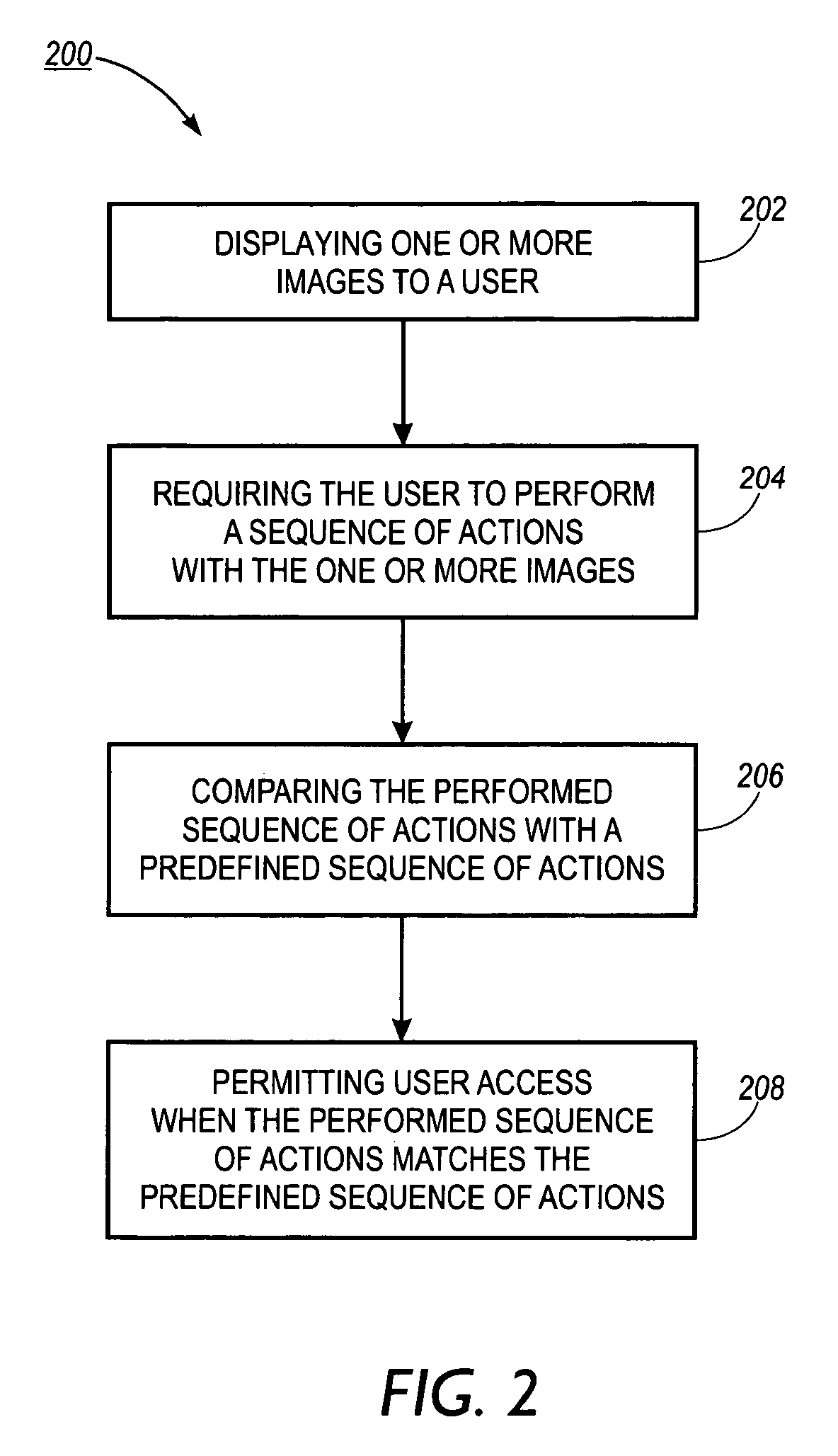
System, method and article of manufacture for knowledge-based password protection of computers and other systems
InactiveUS6934860B1User identity/authority verificationUnauthorized memory use protectionPasswordSoftware engineering
A system, method and article of manufacture are provided for password protecting user access to a computer system. One or more images are displayed to a user. The user is then required to perform a sequence of actions involving the images. The performed sequence of actions is compared with a predefined sequence of actions. If the performed sequence of actions matches the predefined sequence of actions, user access is permitted.
Owner:XEROX CORP
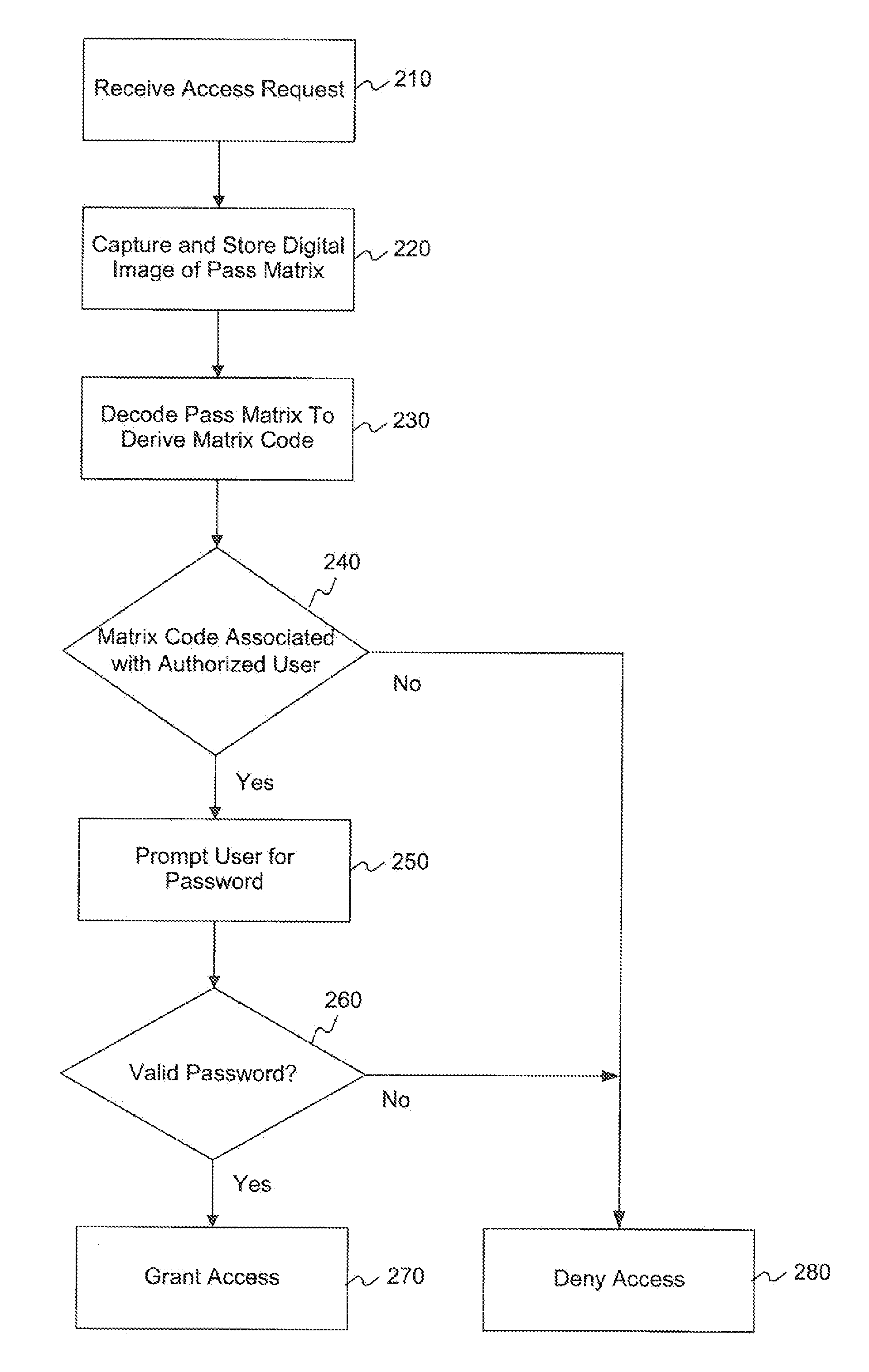
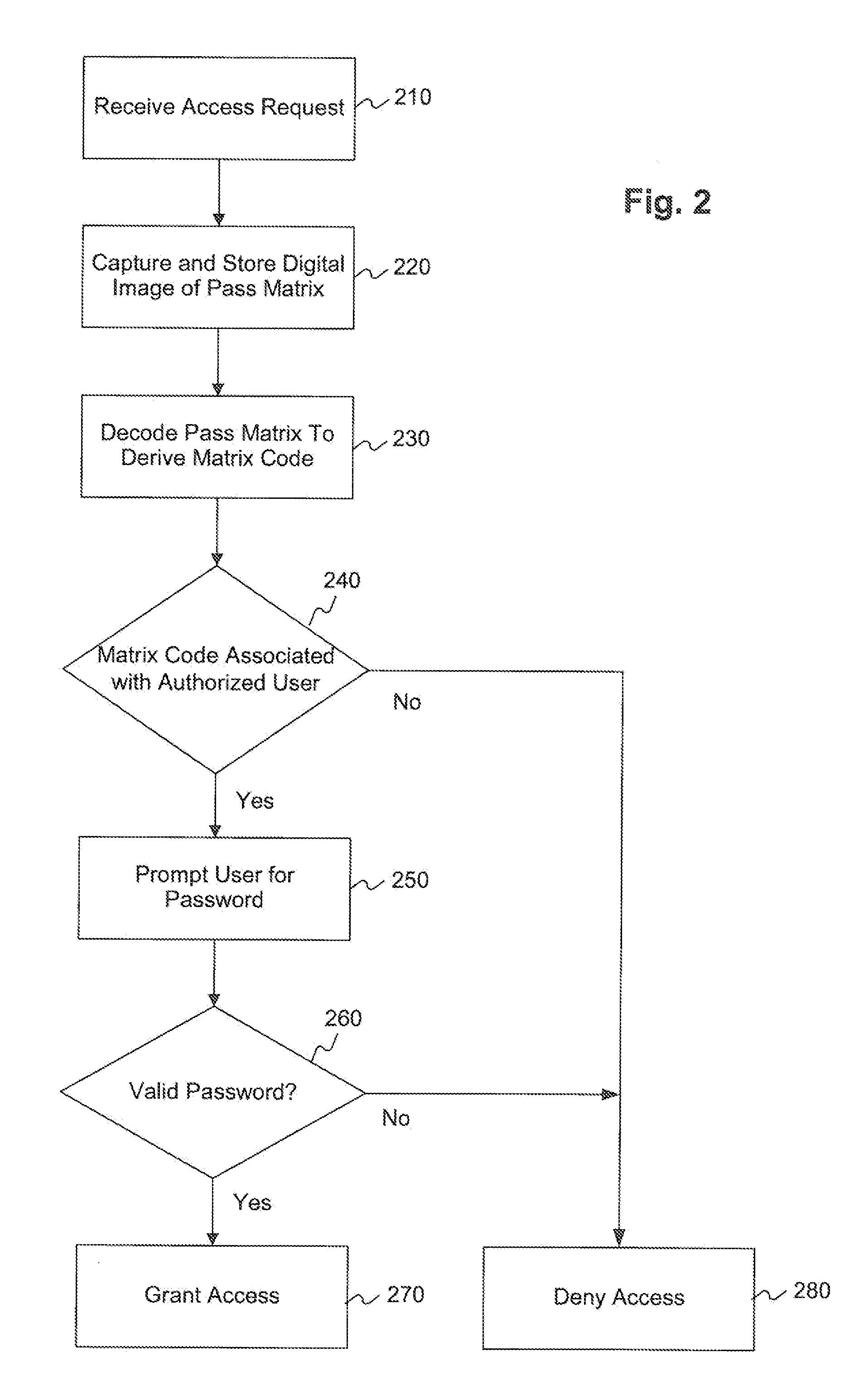
Multi-factor authentication using digital images of barcodes
ActiveUS20130031623A1Easy to operateReduce memory loadDigital data processing detailsUnauthorized memory use protectionComputer graphics (images)Password
Methods, systems, and computer-readable media for implementing a multi-factor authentication scheme utilizing barcode images in computing devices, such as standard mobile devices and smartphones having no native hardware support for reading barcodes other than standard digital camera componentry for capturing digital images of real-world phenomena. A mobile device may be configured by software to require a user, as a first authentication factor, to present a barcode, such as a Quick Response (QR) Code for image scanning using digital camera componentry built into the mobile device. The device analyzes the digital image of the barcode to decode the barcode into its encoded character data. If the device recognizes the character data as valid, then, as a second authentication factor, the device prompts the user to enter a valid password associated with the barcode. If the user-entered barcode is also valid, then the device may grant the user access.
Owner:XEROX CORP
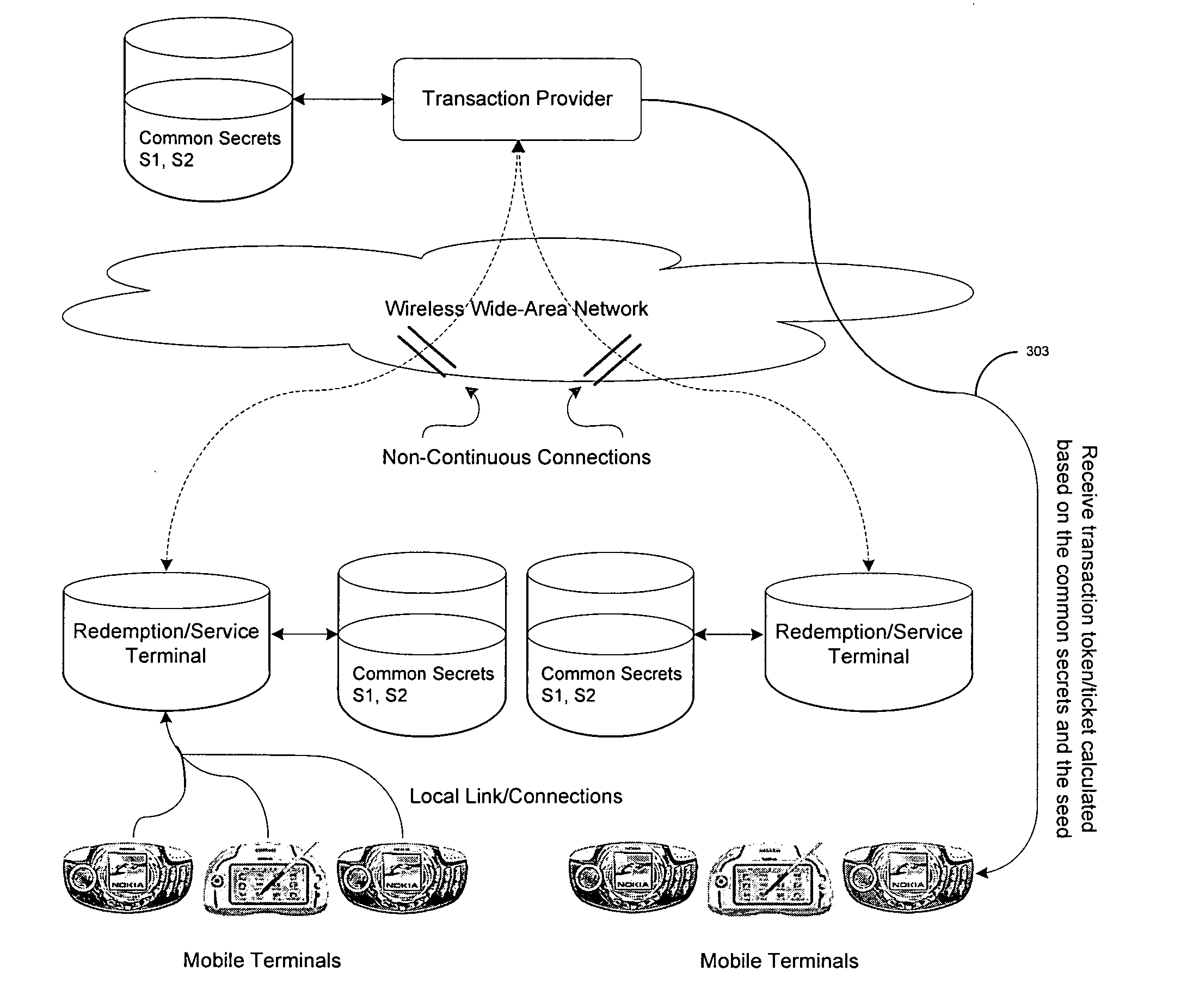
Transaction & payment system securing remote authentication/validation of transactions from a transaction provider
ActiveUS20050283444A1Ticket-issuing apparatusUser identity/authority verificationPasswordPayment system
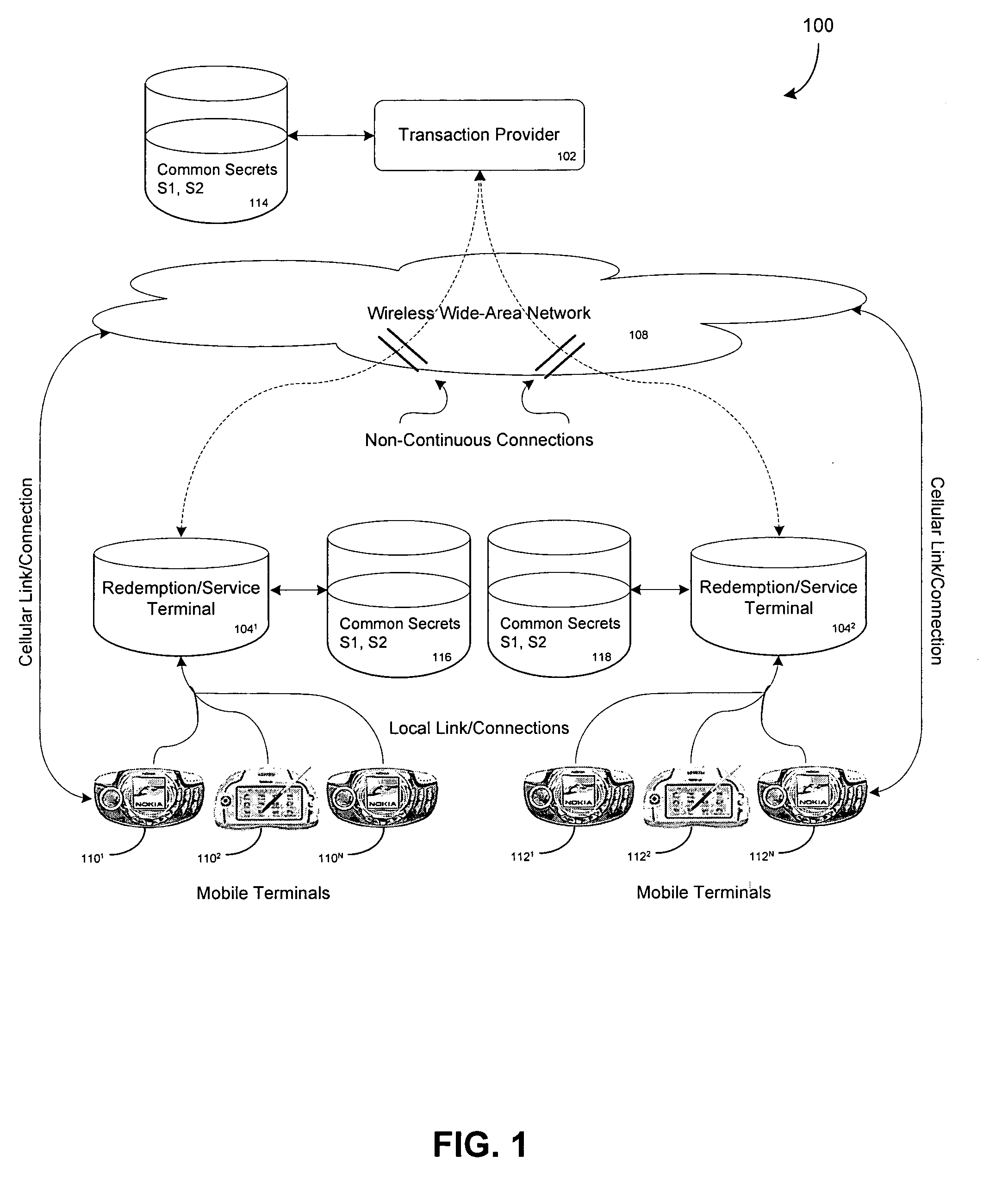
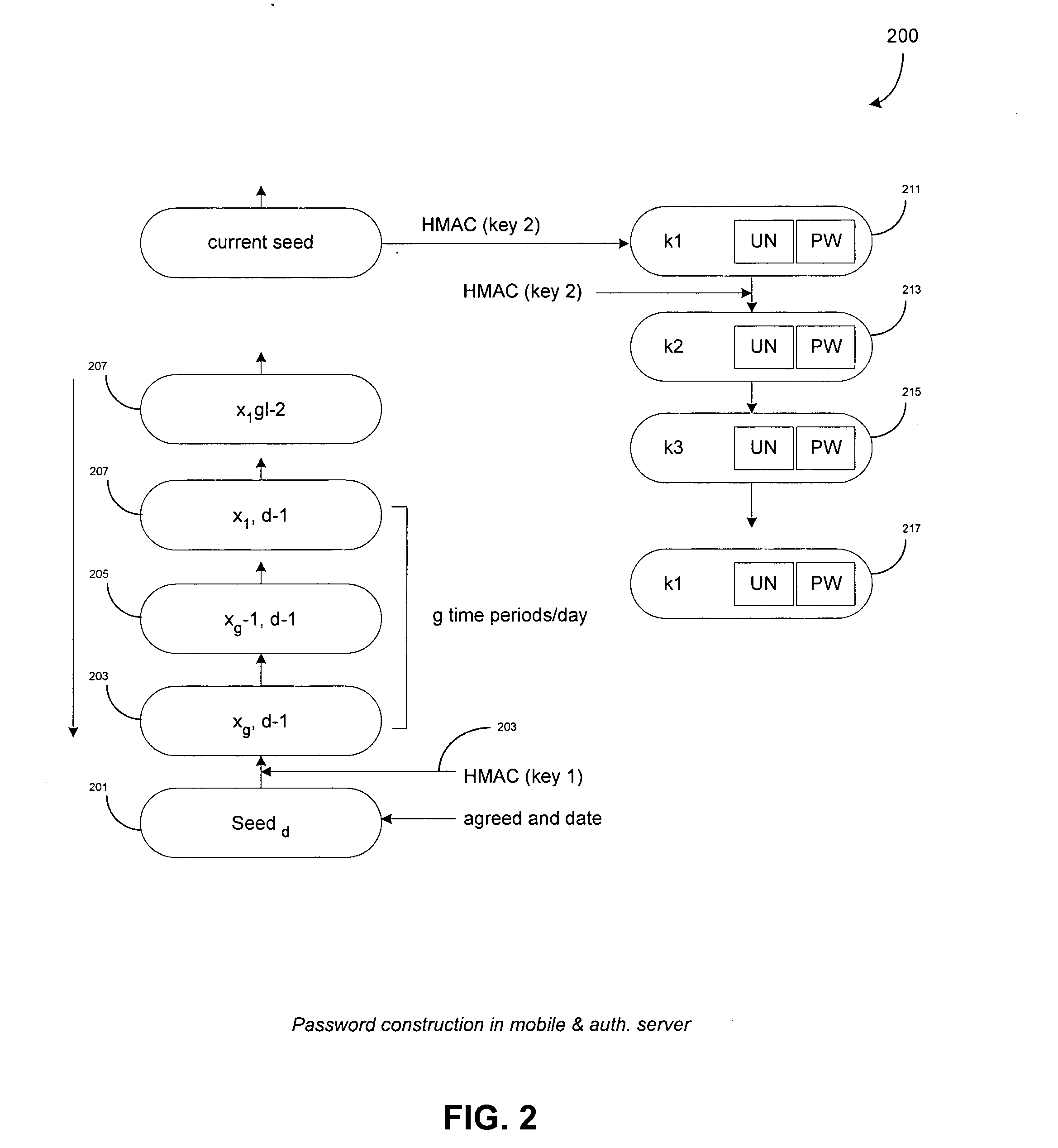
A mobile terminal is equipped for SMS payment and service authentication with a remote transaction provider. The remote provider uses common secrets & a seed in a keyed Hash Machine Address Code (HMAC) executing a Message Digest Algorithm to generate a list of authentication token (username-password) for the purchase of services an / or goods. The common secrets and seed are shared with local redemption devices which also generate the list of authentication token. A subscriber conducts payment with the remote transaction provider and receives an authentication token corresponding to the purchased service. The subscriber provides the authentication token to the redemption device which compares the authentication token with sets of valid authentication tokens generated by the redemption terminal. If the comparison indicates a match, the redemption device provides the service to the subscriber.
Owner:NOKIA TECHNOLOGLES OY
Method, apparatus, and system for determining whether a computer is within a particular location
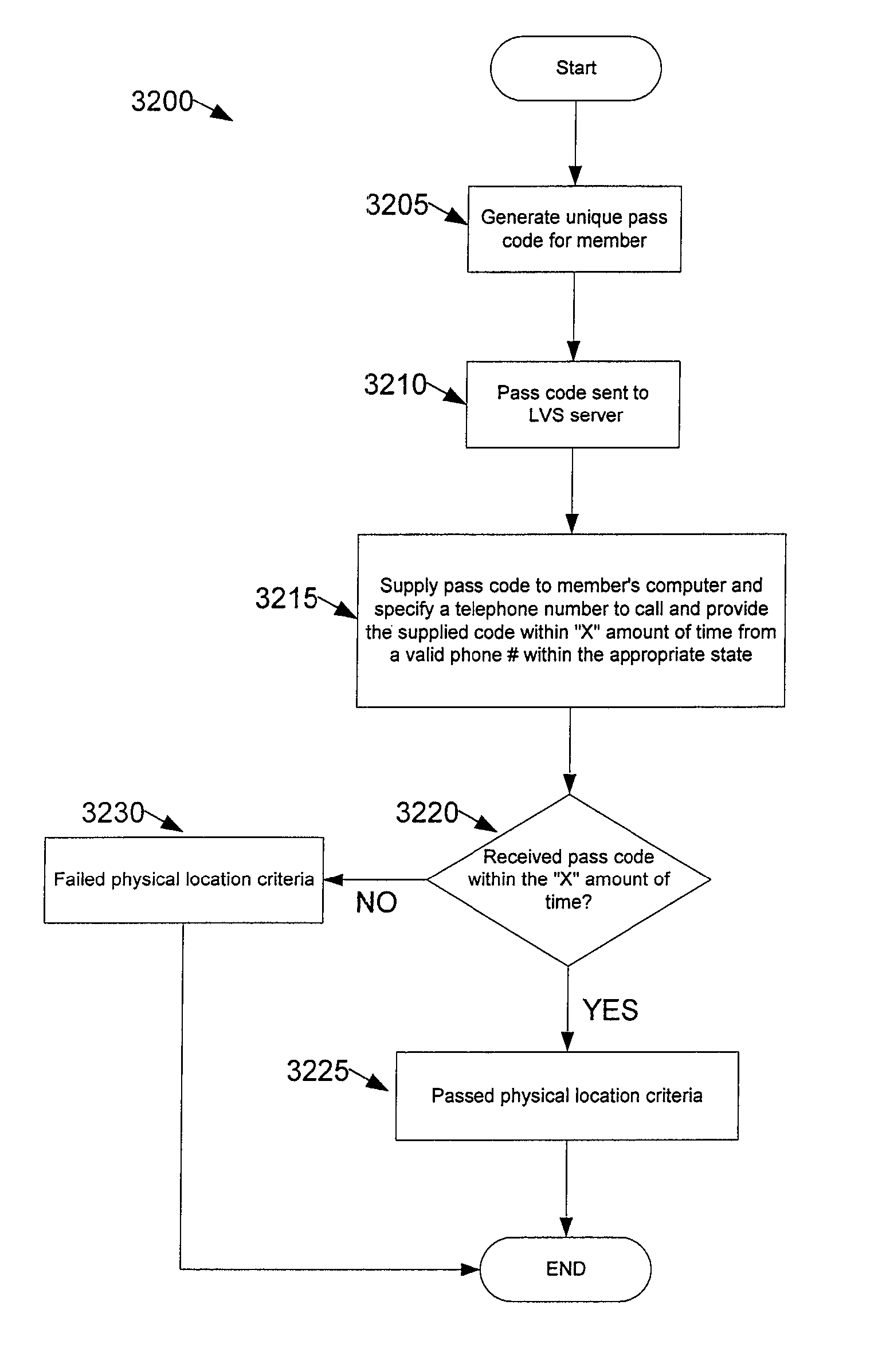
Some embodiments provide a method of determining whether a lottery player or the player's computer is within a particular location. The player's computer is connected to a computer network. The method transmits, through the computer network, a pass code and a telephone number to the lottery player's computer. The method requests the lottery player or the player's computer to call the number and provide the pass code within a pre-determined amount of time. The method determines whether the pass code is provided within a predetermined amount of time after the transmission of the pass code from a telephone specified to be within the particular location. The method verifies whether the lottery player or player's computer is within the particular location, based on the determination.
Owner:EC2 INC
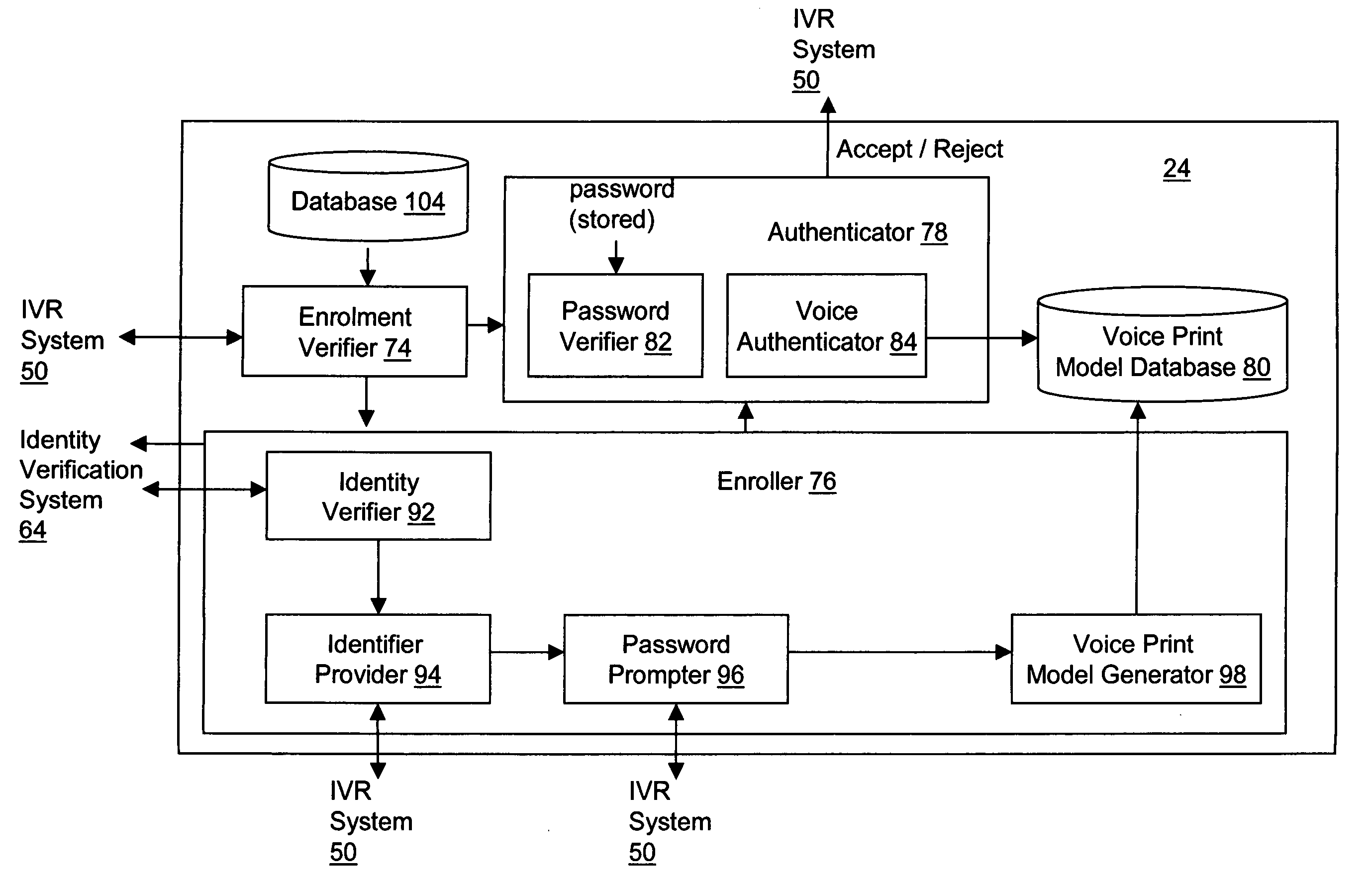
Voice authentication system and methods therefor
The present invention relates to methods and systems for enrolling a user for voice authentication and for performing voice authentication on a user of a network. The method of enrolling a user for voice authentication includes verifying the identity of the user and assigning an enrolment identifier to the user, if the identity of the user is verified. The enrolment identifier is then presented to the user. Subsequently, the user is prompted to utter a personal voice authentication password. The personal password uttered by the user is received and stored. A voice print model for the user is generated from the previously stored voice print. The method further includes storing the voice print model and associating the voice print model and the personal password with the enrolment identifier assigned to the user to facilitate retrieval thereof during voice authentication of the user. A method for performing voice authentication on a user of a network is also provided. The method includes determining whether the user is enrolled for voice authentication based on an available attribute of the logical address of the user on the network. Upon determining that the user is enrolled for voice authentication, a personal password and stored voice print model for the user is retrieved. The stored voice print model includes a voice print of a personal password previously uttered by the user. The method further includes prompting the user to utter the personal password and receiving a spoken response from the user. The spoken response is verified to determine whether it contains the personal password and whether it matches the stored voice print model. If the spoken response contains the personal password and matches the stored voice print model for the user, the identity of the user is authenticated.
Owner:TOMES EDWARD +1
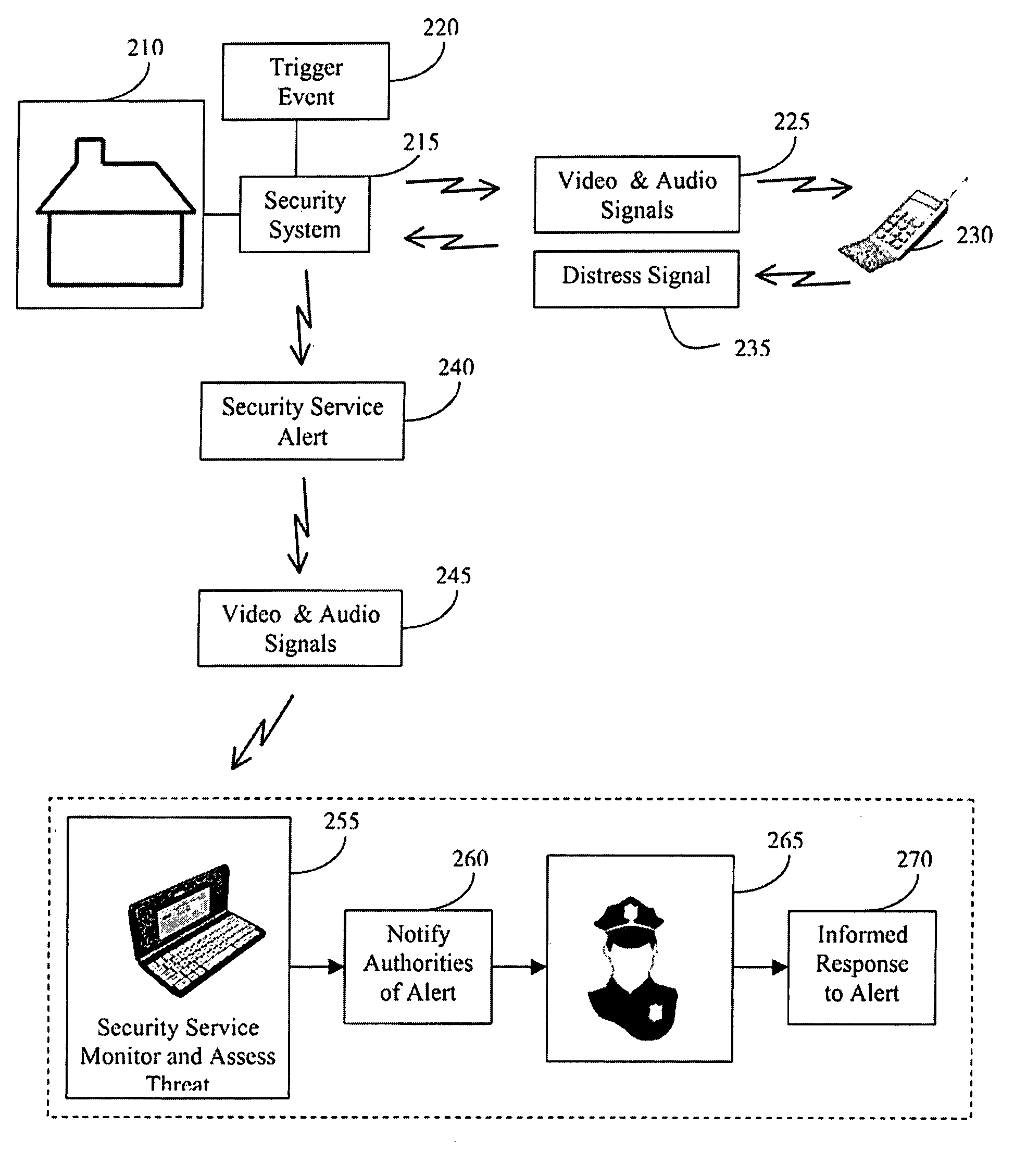
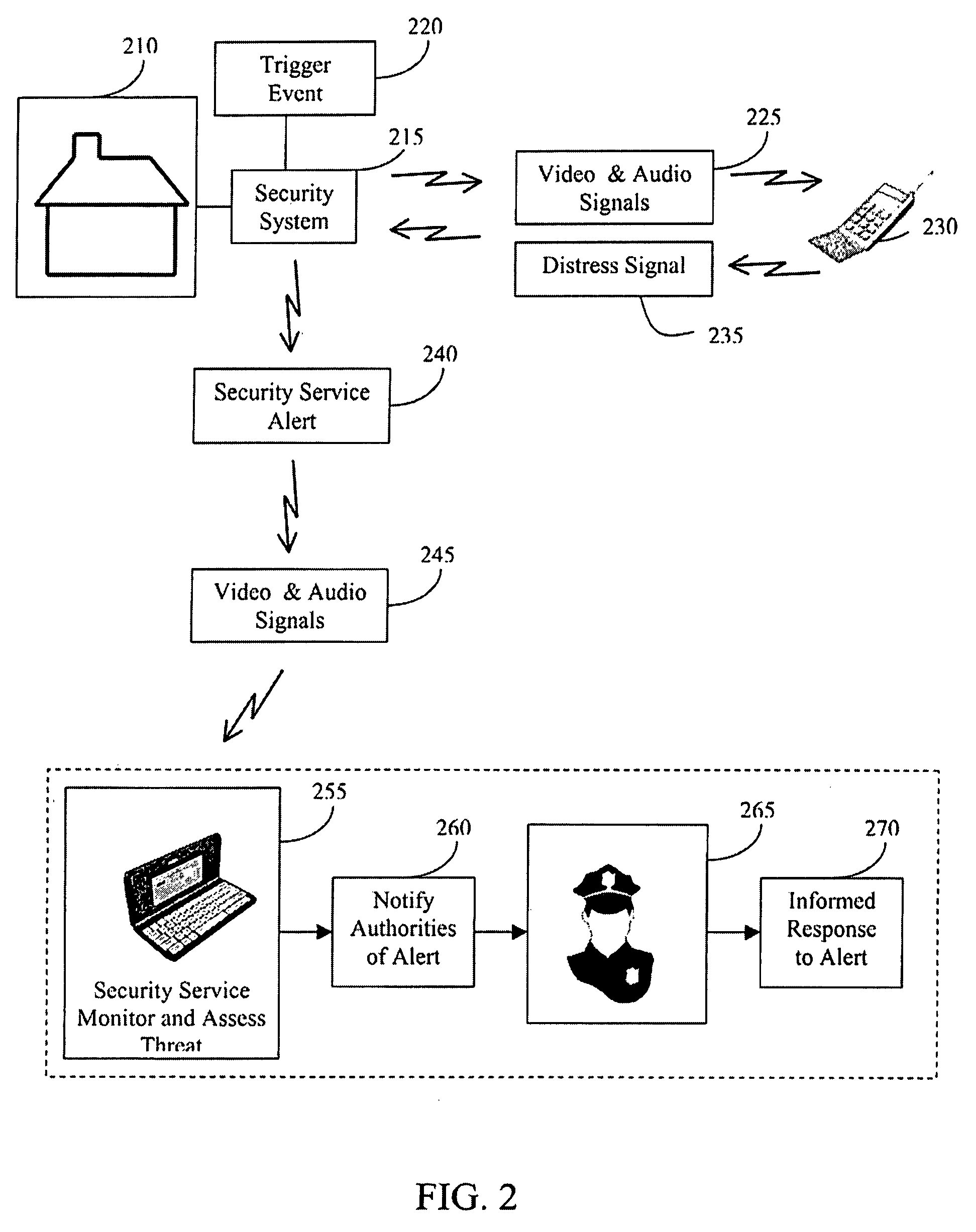
Cellular home security system
The invention provides an improved security system comprised of video cameras and microphones to remotely monitor a home using a cellular telephone. An activation button is mounted as a doorbell button and interconnected with the security system to trigger the audio and video transmissions. The security system will automatically call the homeowner and allow two-way conversation and video using a streaming transmission. In response to a wireless distress signal sent to the security system using the homeowner's cellular telephone establishes a wireless connection with the security system and a security service or local authorities allowing the third-party to monitor and assess the situation. The homeowner is contemporaneously receiving the audio and video signals from the home using his cellular telephone and is capable of communicating directly with the security service. The distress signal is a secret code consisting of an array of numbers.
Owner:GOOGLE LLC
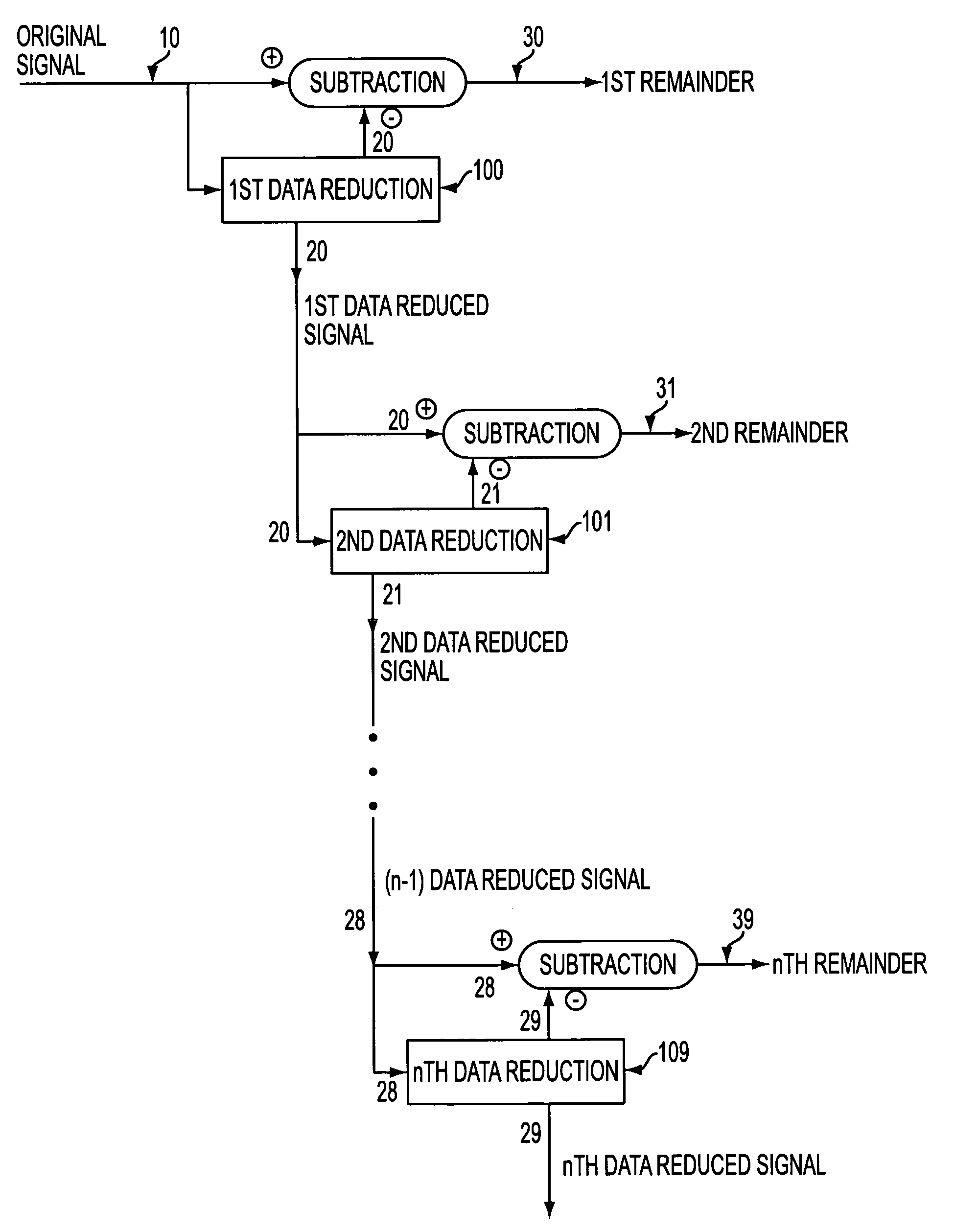
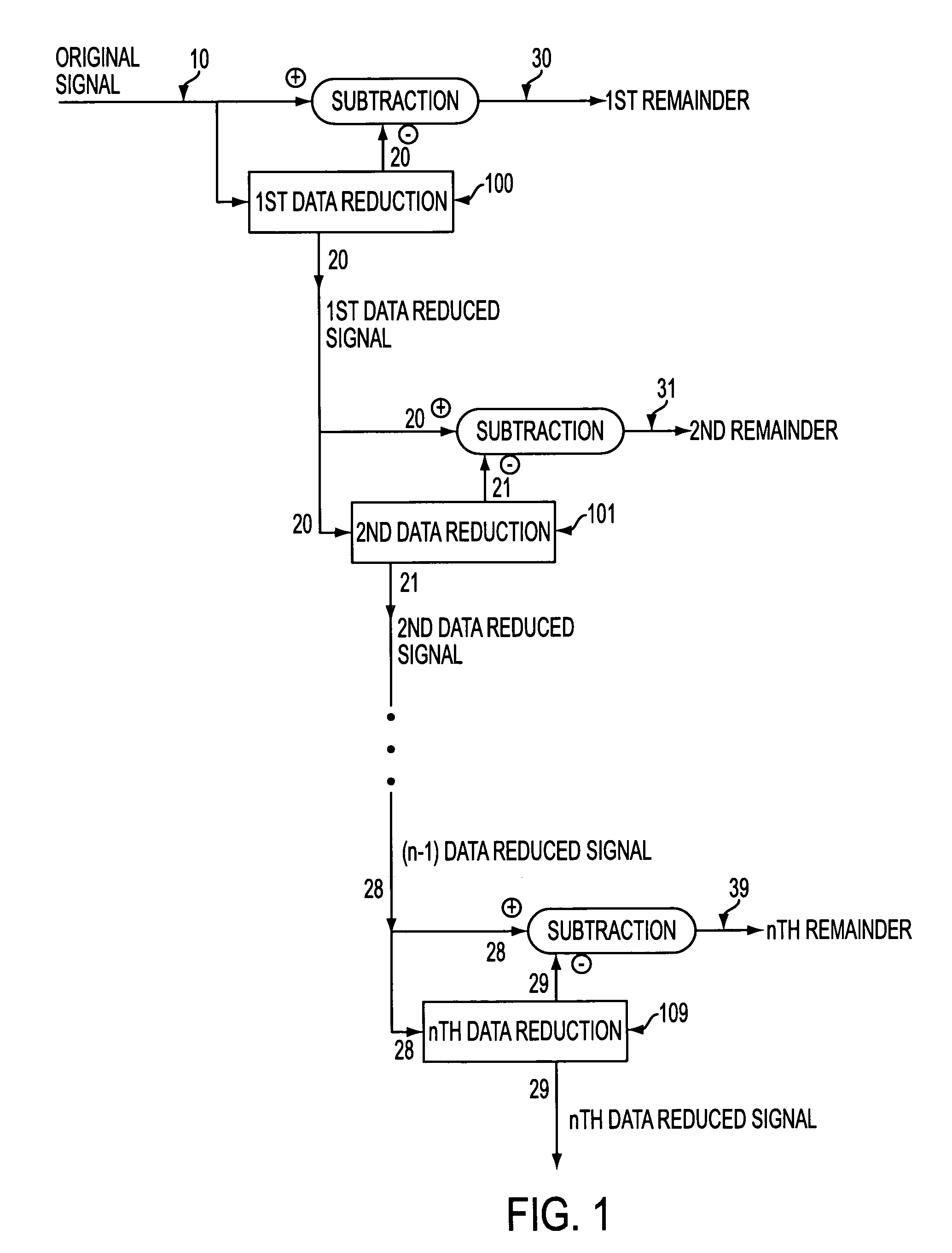
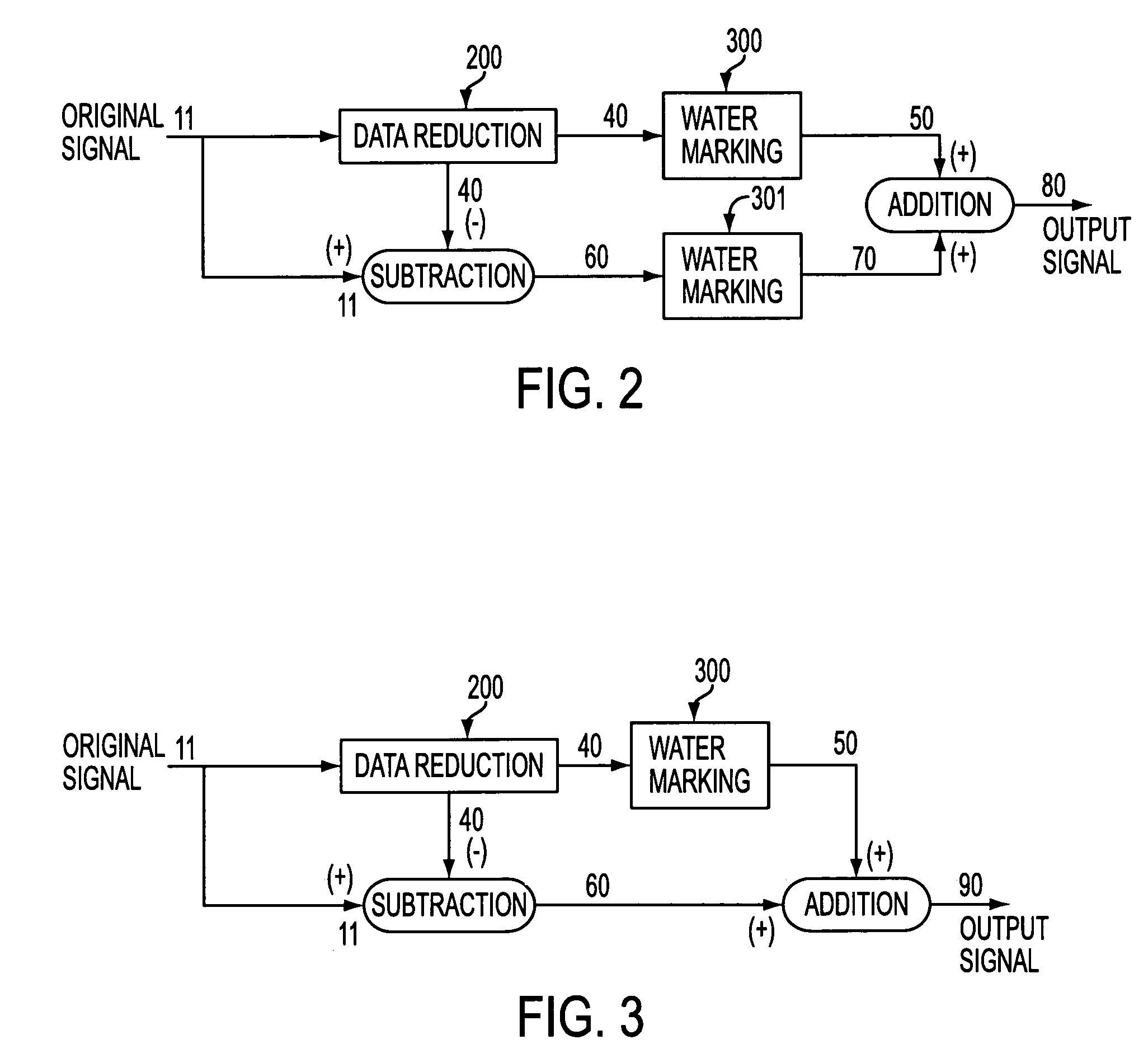
Utilizing data reduction in stegnographic and cryptographic systems
ActiveUS7123718B1Improve securitySafe formMultiple keys/algorithms usageUser identity/authority verificationSecret codeData signal
The present invention relates to methods for protecting a data signal using the following techniques: applying a data reduction technique to reduce the data signal into a reduced data signal; subtracting the reduced data signal from the data signal to produce a remainder signal; embedding a first watermark into the reduced data signal to produce a watermarked, reduced data signal; and adding the watermarked, reduced data signal to the remainder signal to produce an output signal. A second watermark may be embedded into the remainder signal before the final addition step. Further, cryptographic techniques may be used to encrypt the reduced data signals and to encrypt the remainder signals before the final addition step. The present invention also relates to systems for securing a data signal. Such systems may include computer devices for applying a data reduction technique to reduce the data signal into a reduced data signal and means to subtract the reduced data signal from the data signal to produce a remainder signal. Such systems may include means to apply a first cryptographic technique to encrypt the reduced data signal to produce an encrypted, reduced data signal and means to apply a second cryptographic technique to encrypt the remainder signal to produce an encrypted remainder signal; and means to add the encrypted, reduced data signal to the encrypted remainder signal to produce an output signal.
Owner:WISTARIA TRADING INC
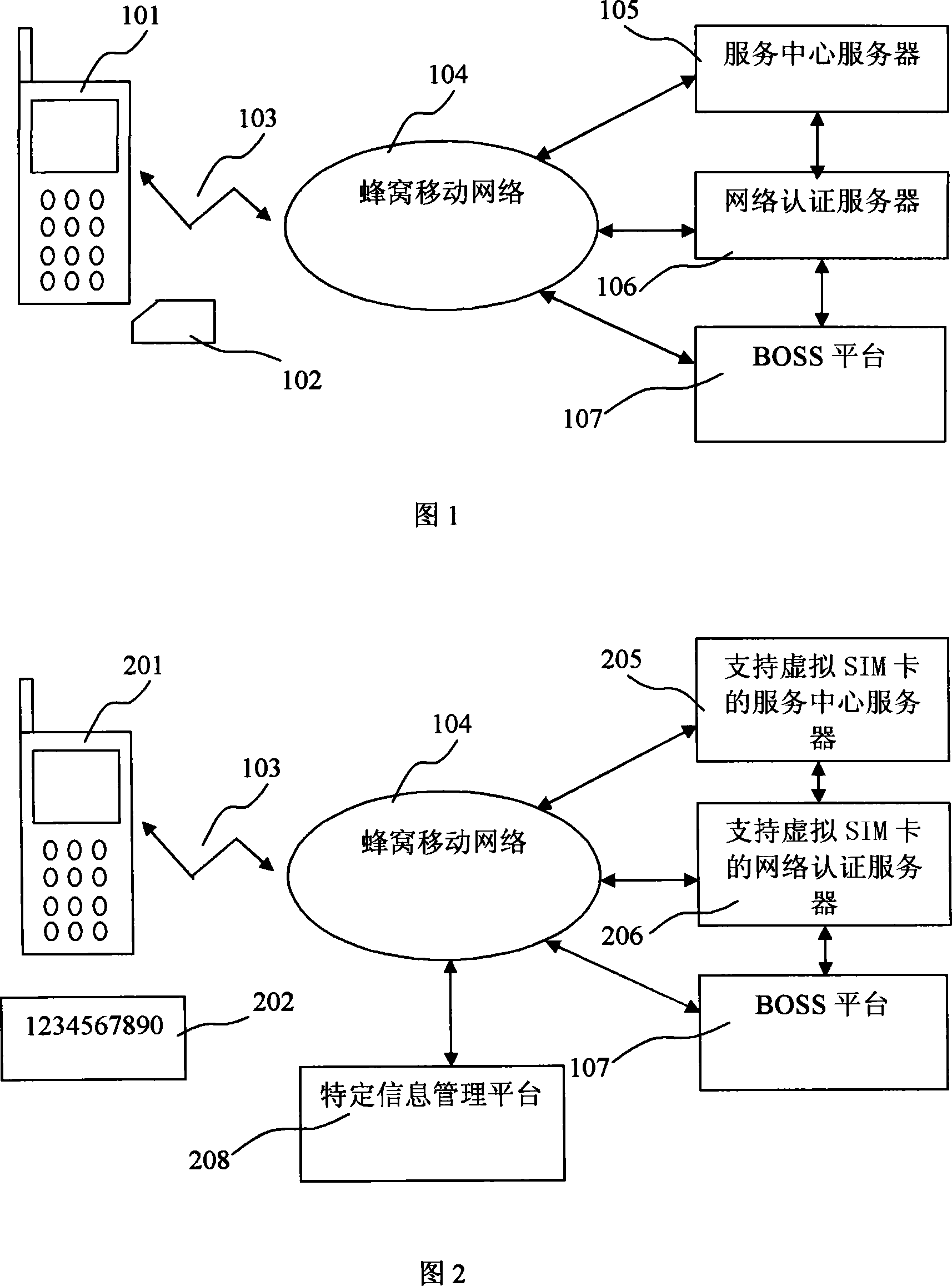
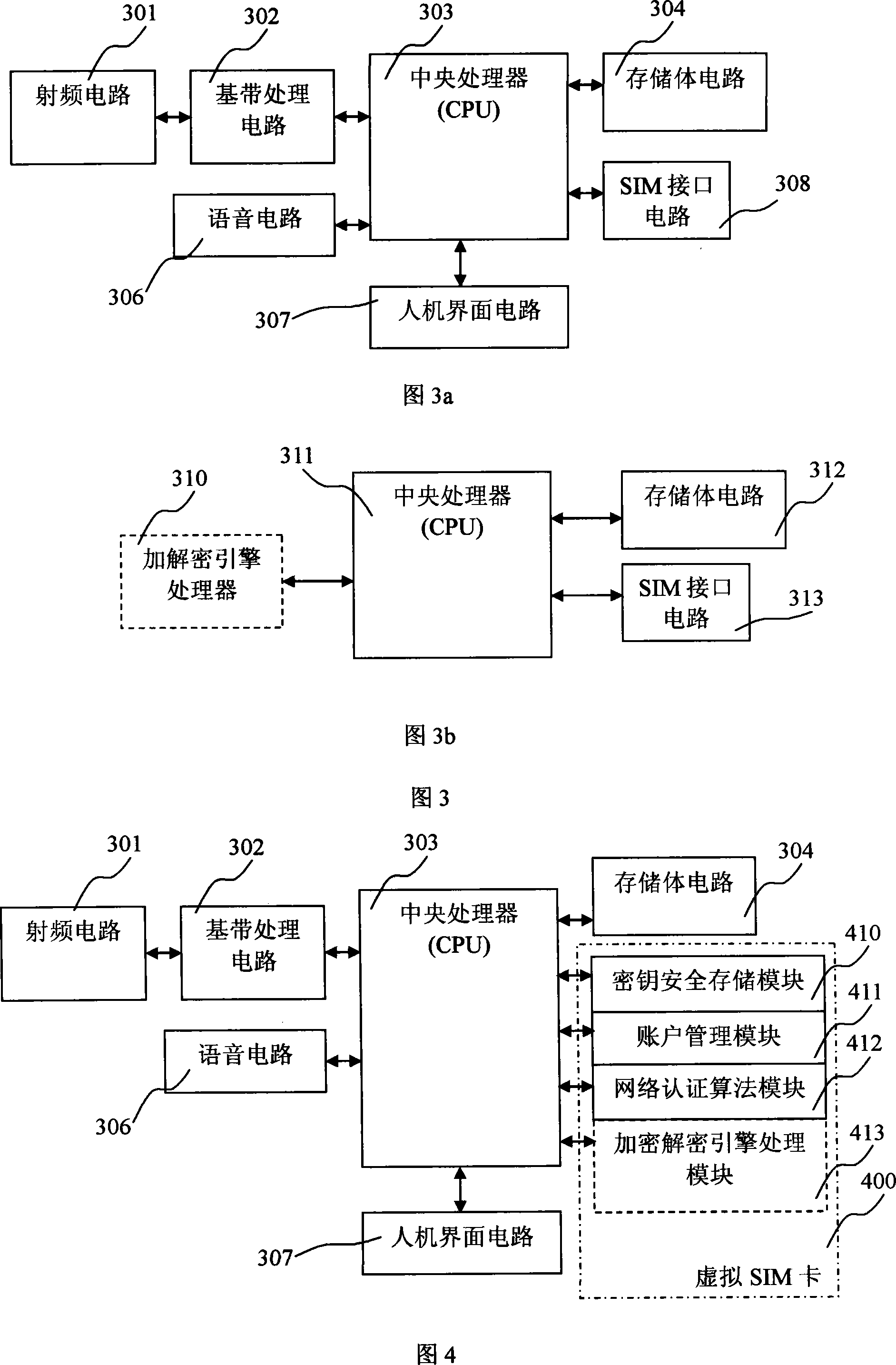
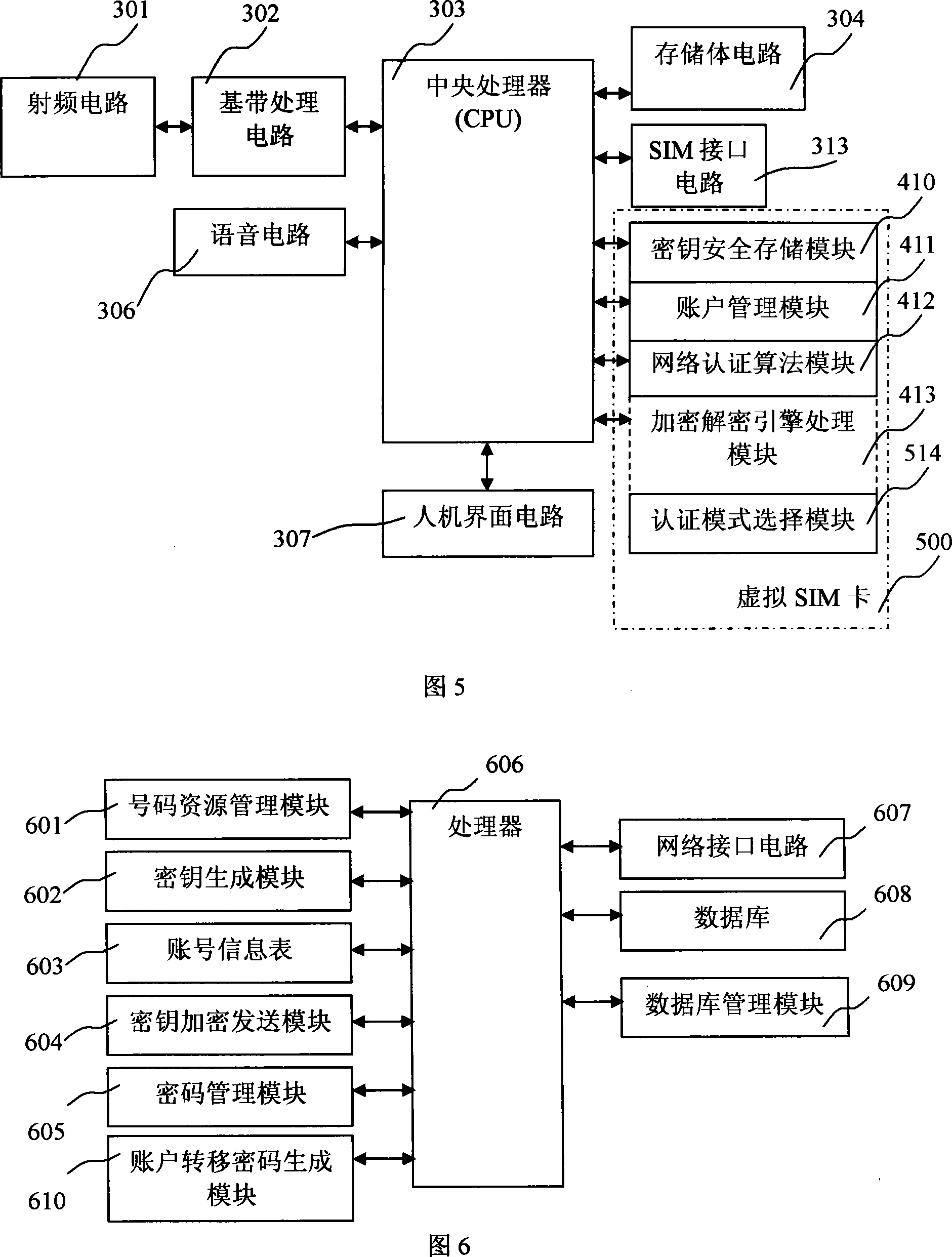
Mobile communication network system supporting virtual SIM card and authentication method thereof
InactiveCN101222711AEasy to integrateReduce consumptionRadio/inductive link selection arrangementsSecurity arrangementPasswordSecret code
The invention provides a mobile communication network system supporting a virtual SIM card and the authentication method thereof. Based on a current mobile communication network system, function modules are arranged on a mobile terminal, an authentication center and a call center service system; a password card is introduced to support the registration, the authentication, the network use and the expense computation of a virtual SMI card; programs and functions realized by the real SIM card are realized by the mobile terminal; account information is written into the mobile terminal through a mobile communication network by the local retrofit and the program updating to mobile network equipment, and an account is not activated by selling the real SIM card. The invention realizes the reduction of roaming fees and the reduction of the consumption of the SIM card in the transnational or trans-provincial or trans-municipal application, thereby reducing the waste of the resource. The invention provides a convenient, flexible, safe mode of using mobile phones in different places. To adopt the mobile communication network system supporting the virtual SIM card contributes to the realization of new functions of the mobile terminal and the decrease of the cost, and ensures that the popularization of the new functions gets easier.
Owner:江西代邦科技有限公司
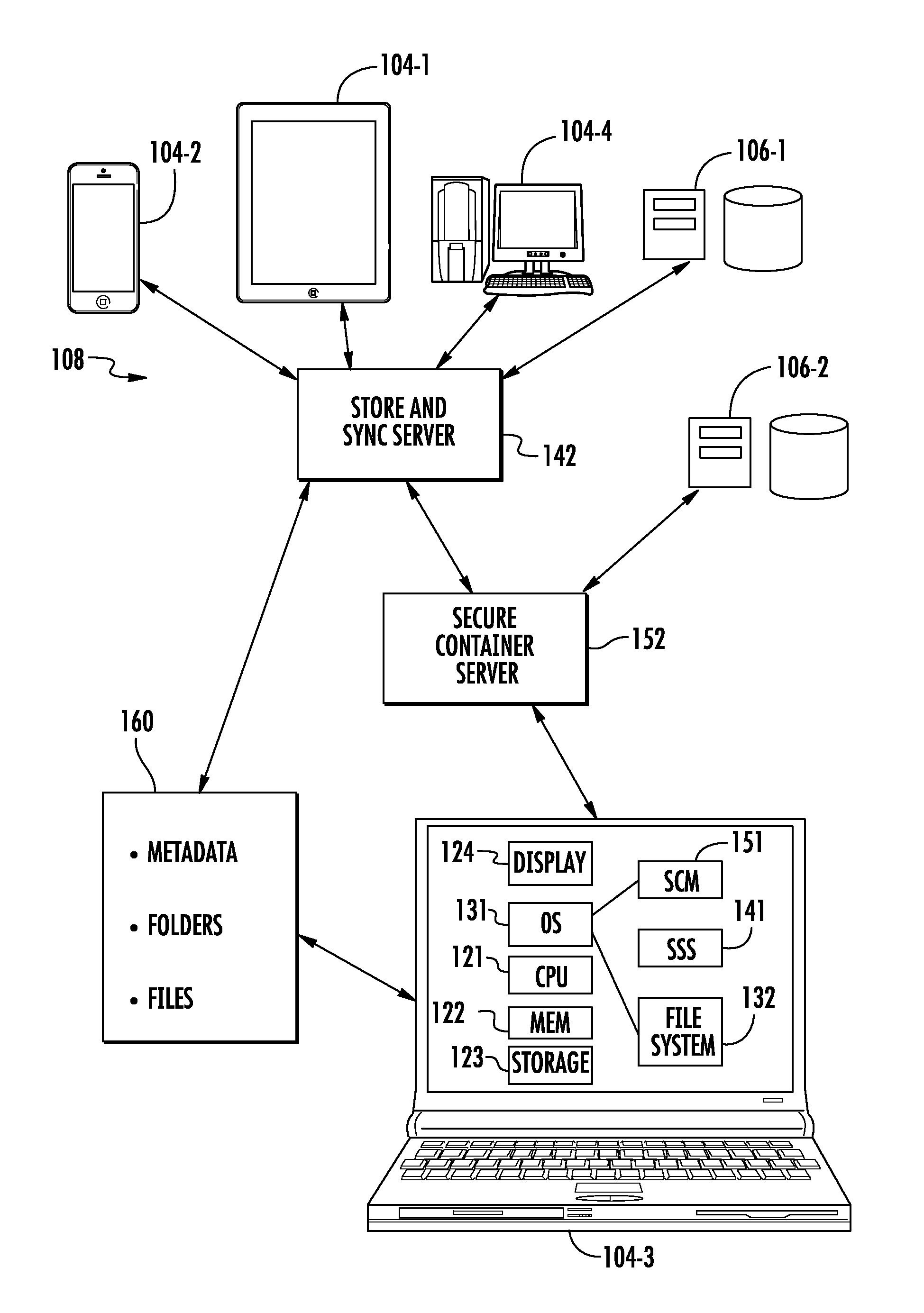
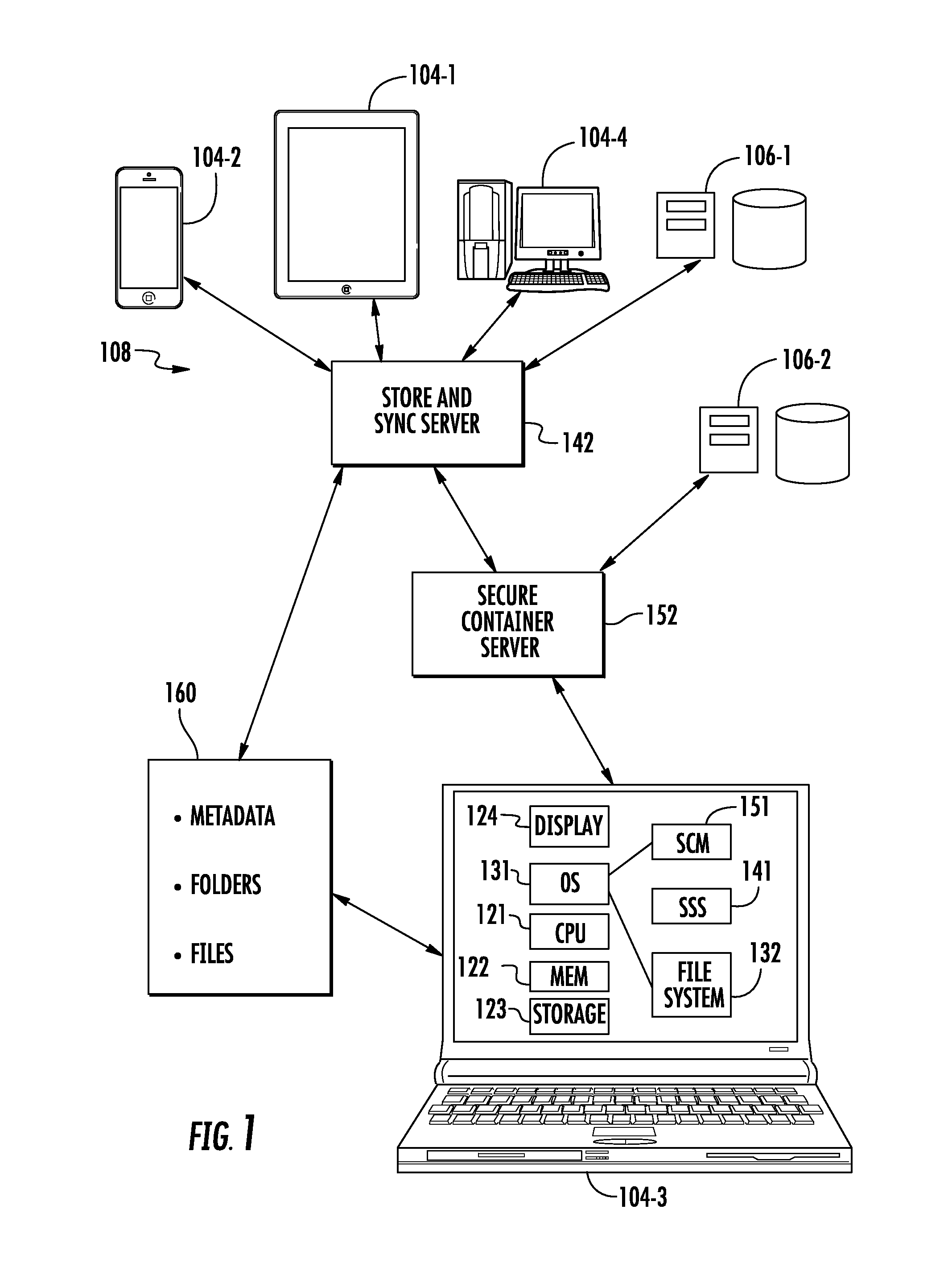
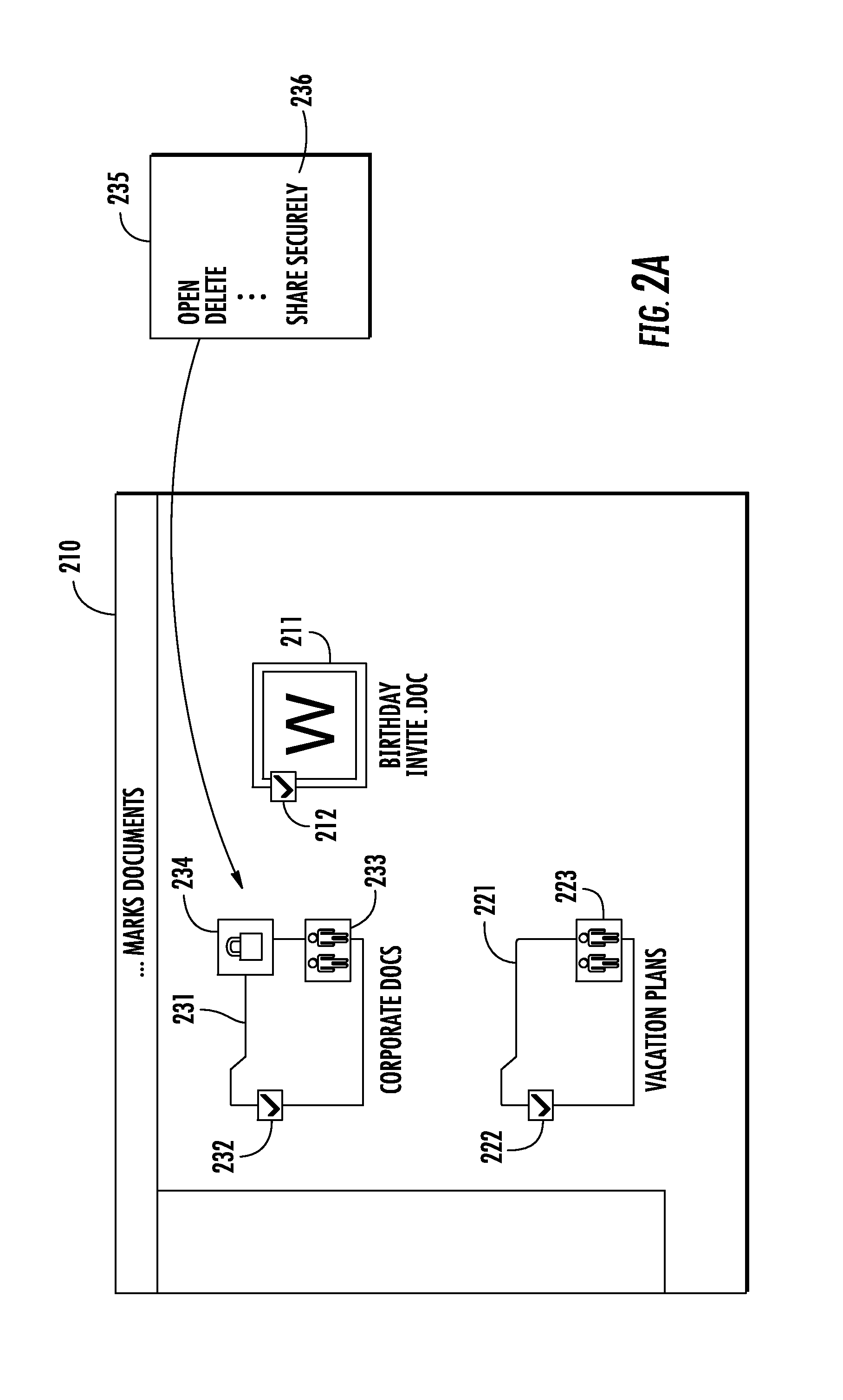
Seamless secure private collaboration across trust boundaries
ActiveUS8572757B1Key distribution for secure communicationDigital data processing detailsFile synchronizationTrust boundary
Seamless, secure, private, collaborative file synchronization across trust boundaries, typically as a companion to a store and sync file service. Information needed to recover a file is stored within the file itself, without giving away secret data. User specific personal keys are preferably only stored on the users' device(s). A unique ID is also created for each protected file; a password is generated that depends on (a) a key value that can either be (i) the user's personal key in the case of a file that is to be private or (ii) a shared key in the case of a file that is to be shared with other users, and (b) the unique file ID. The password is then encrypted using a recovery key and also stored in the file itself. The file is secured using a format that supports password-based content encryption.
Owner:NCRYPTED CLOUD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com