Patents
Literature
10132 results about "Web resource" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
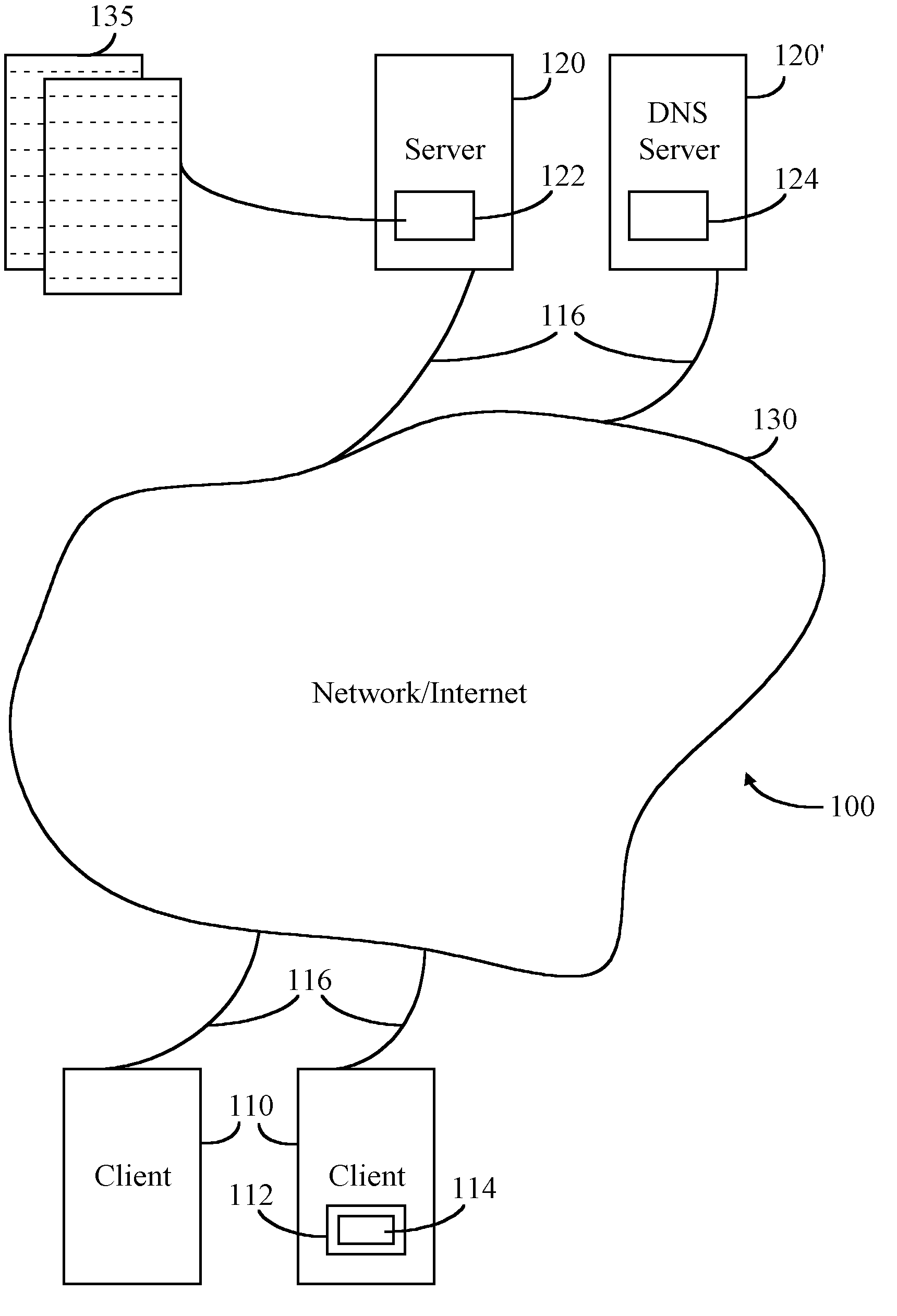
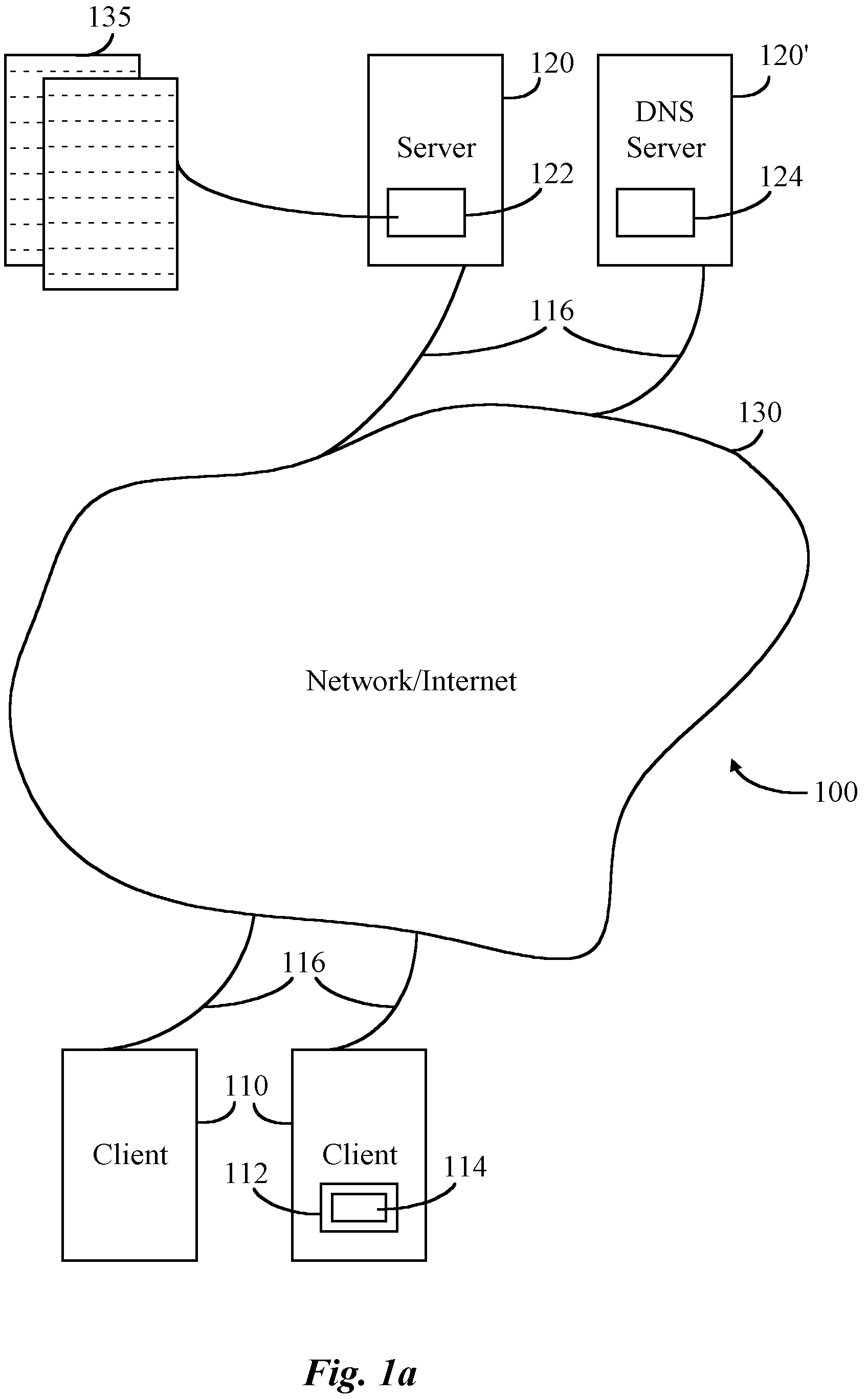
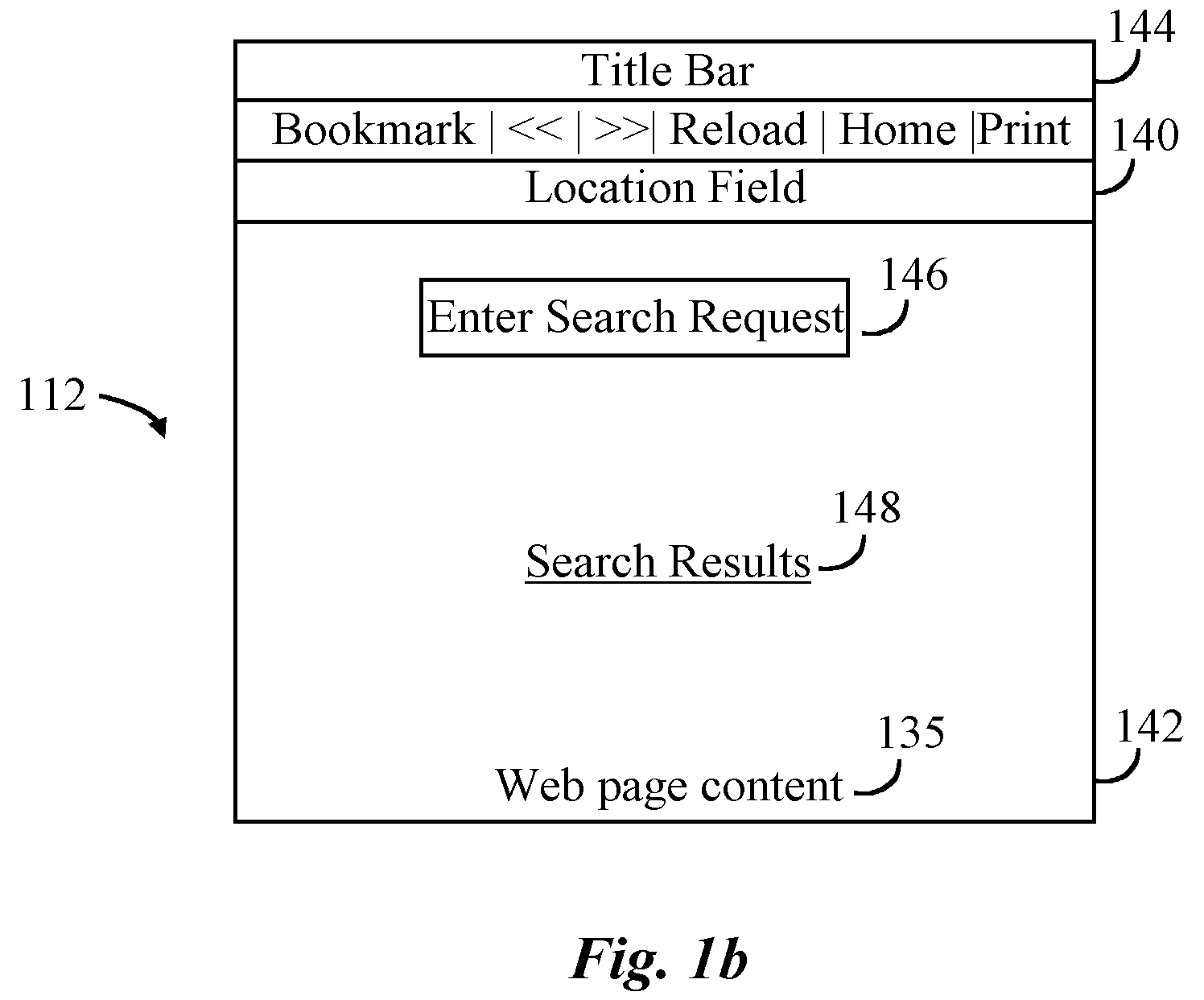
A web resource, or simply resource, is any identifiable thing, whether digital, physical, or abstract. Resources are identified using Uniform Resource Identifiers. In the Semantic Web, web resources and their semantic properties are described using the Resource Description Framework.
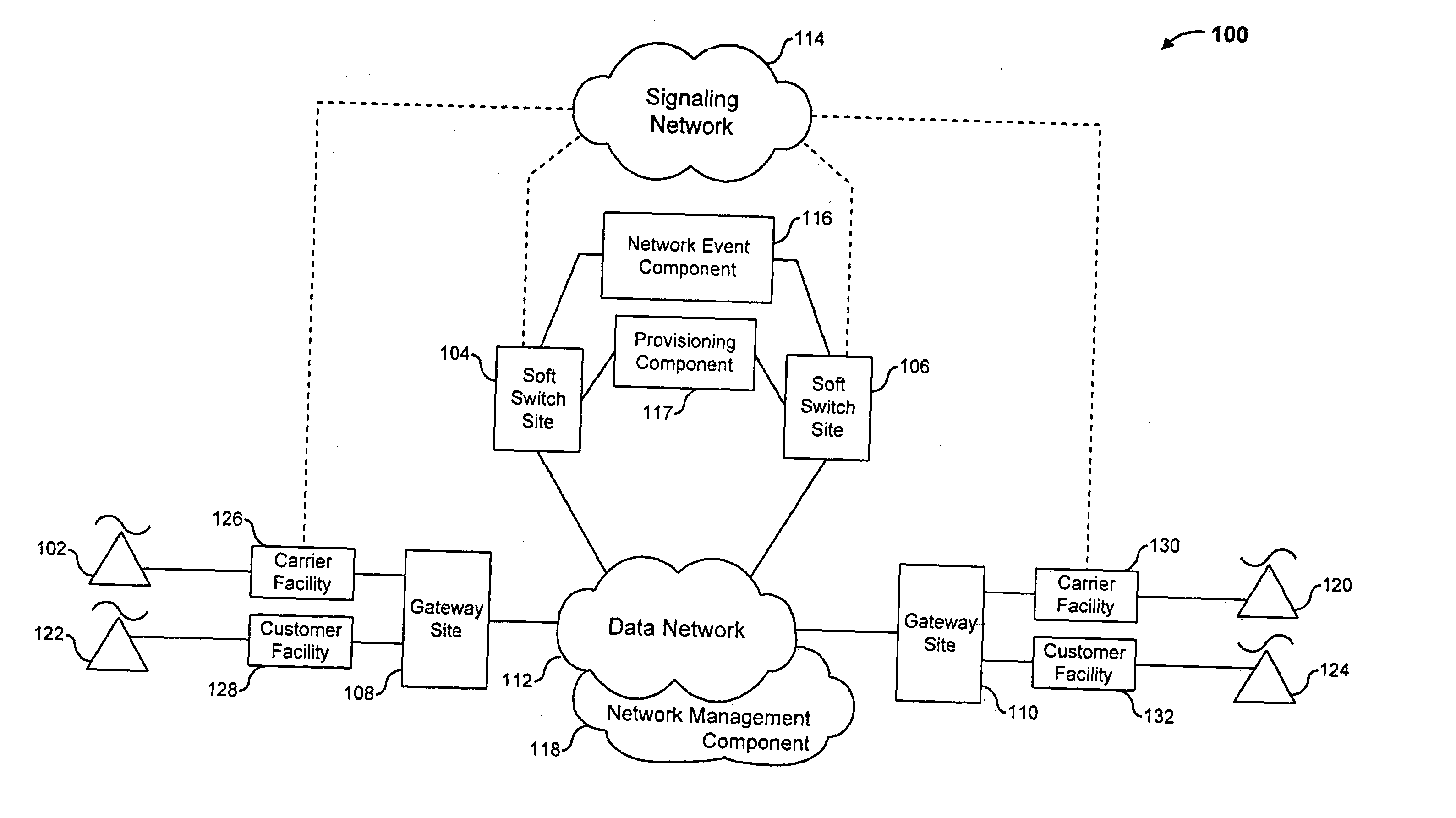
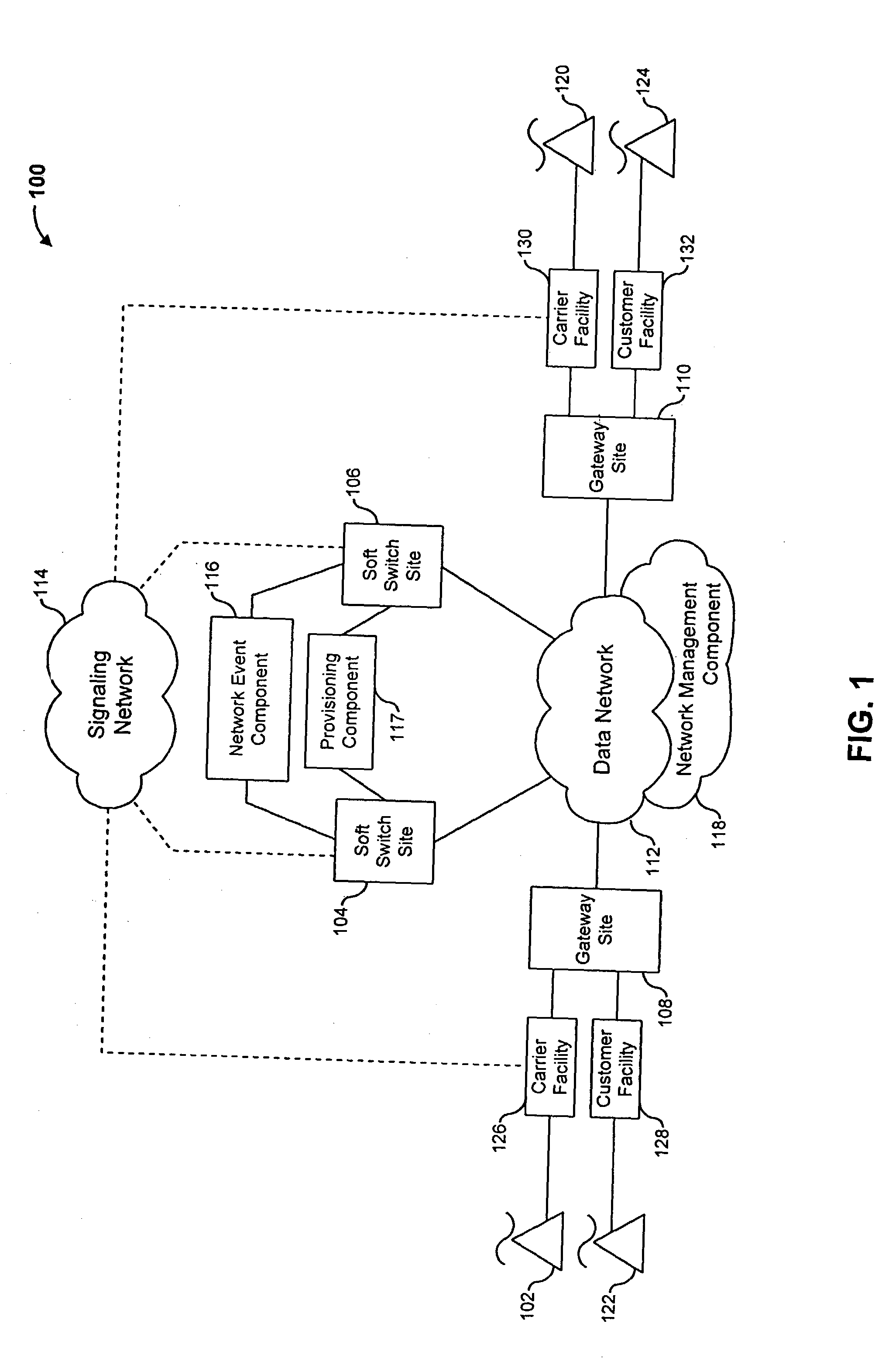
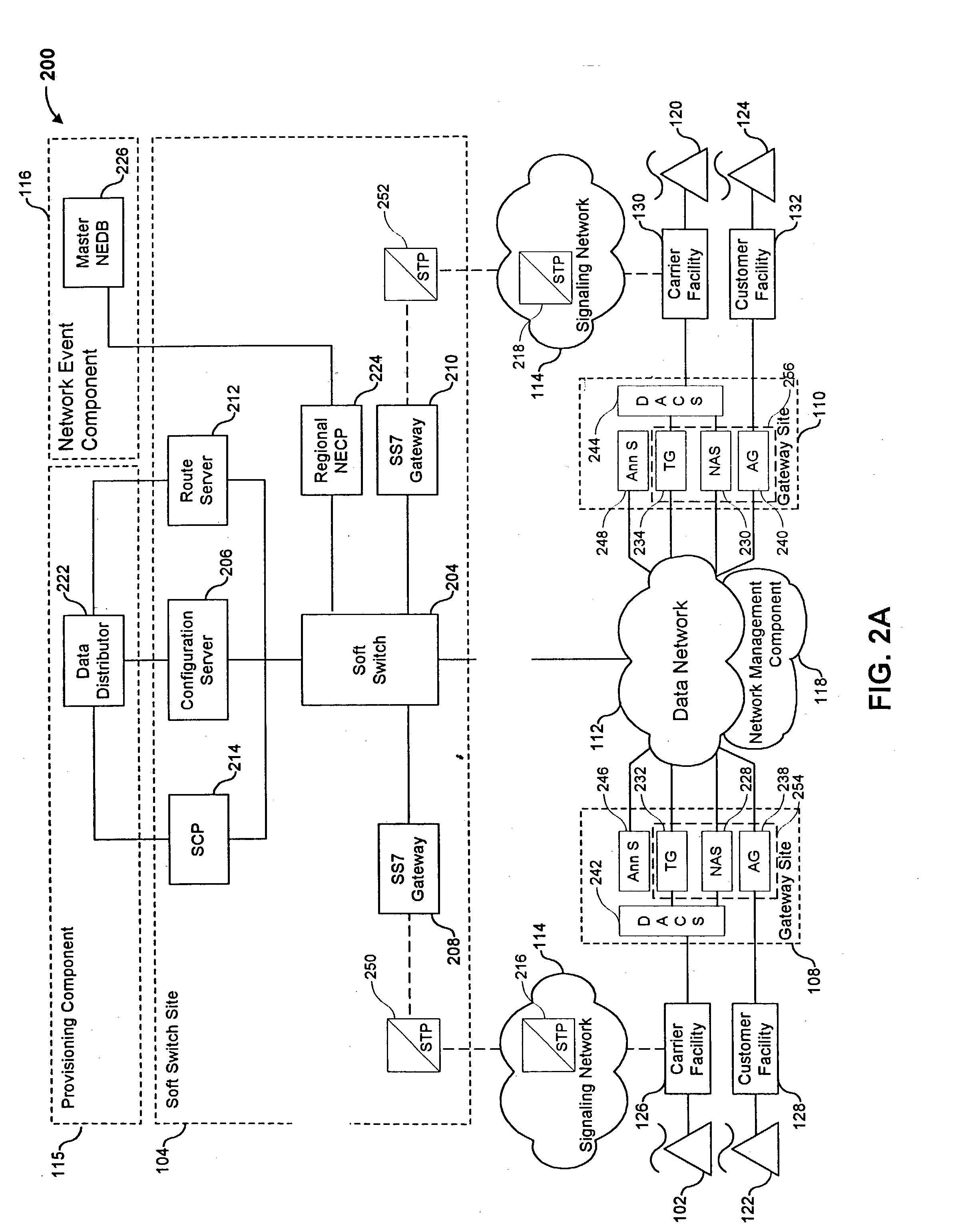
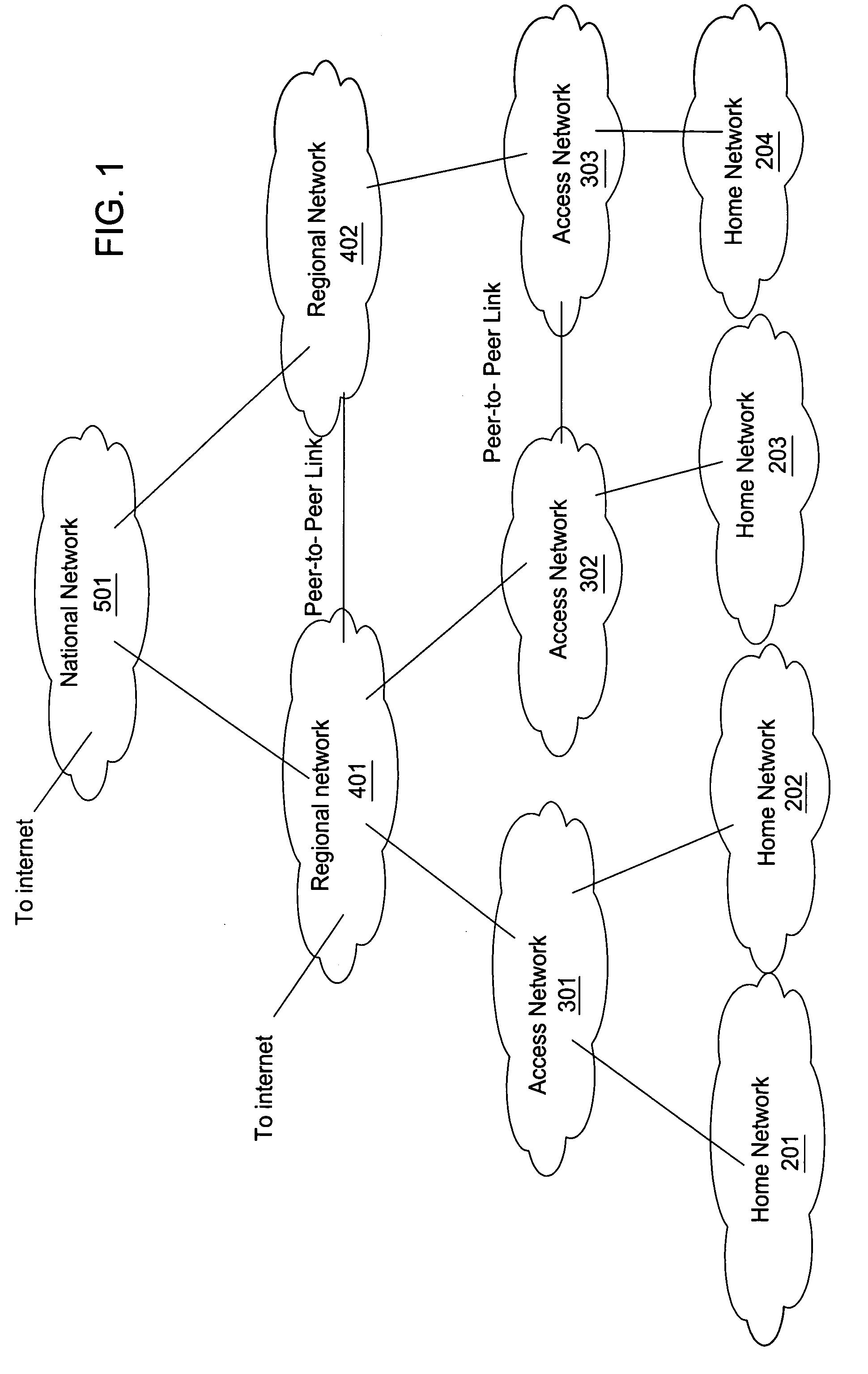
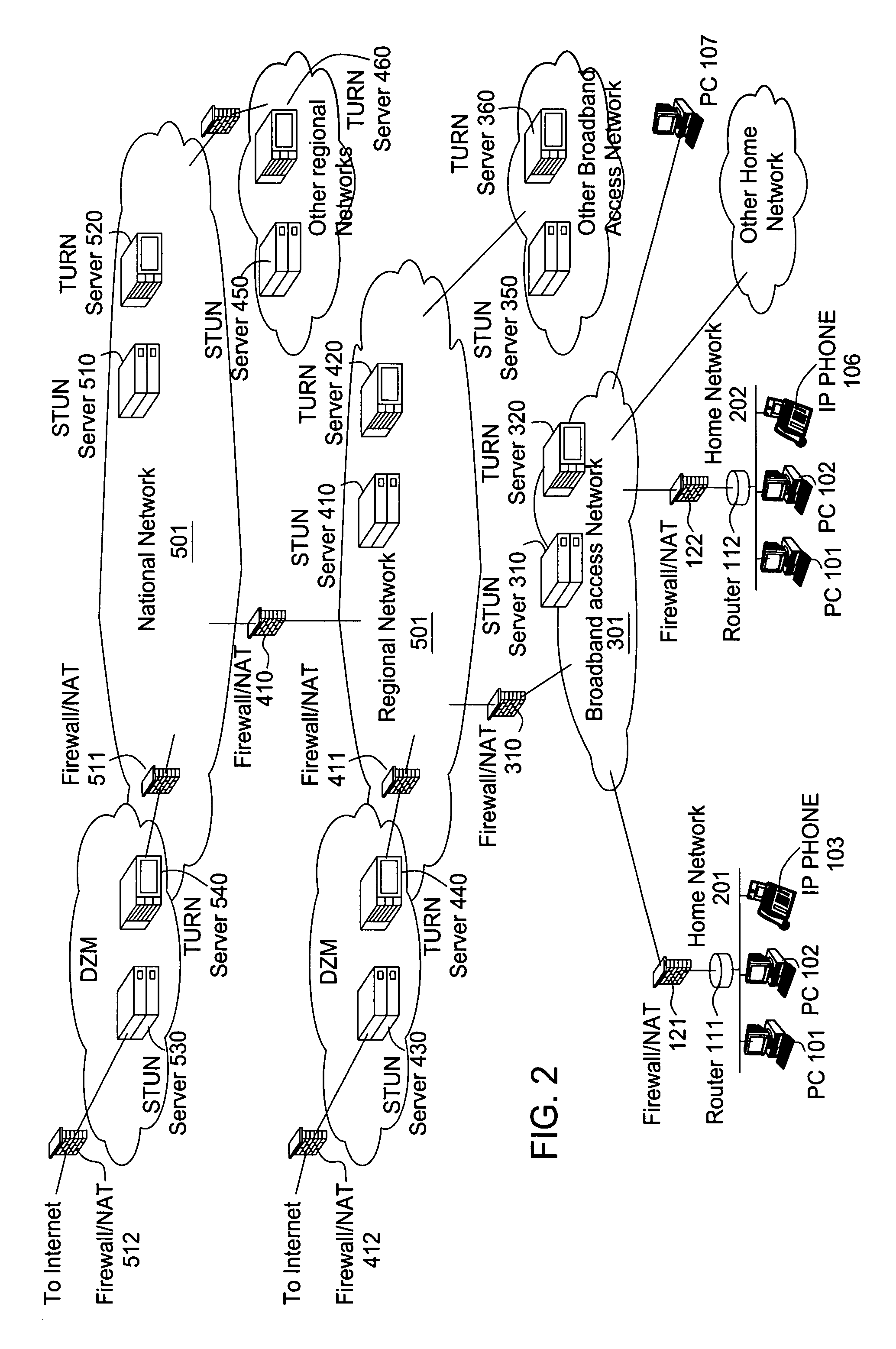
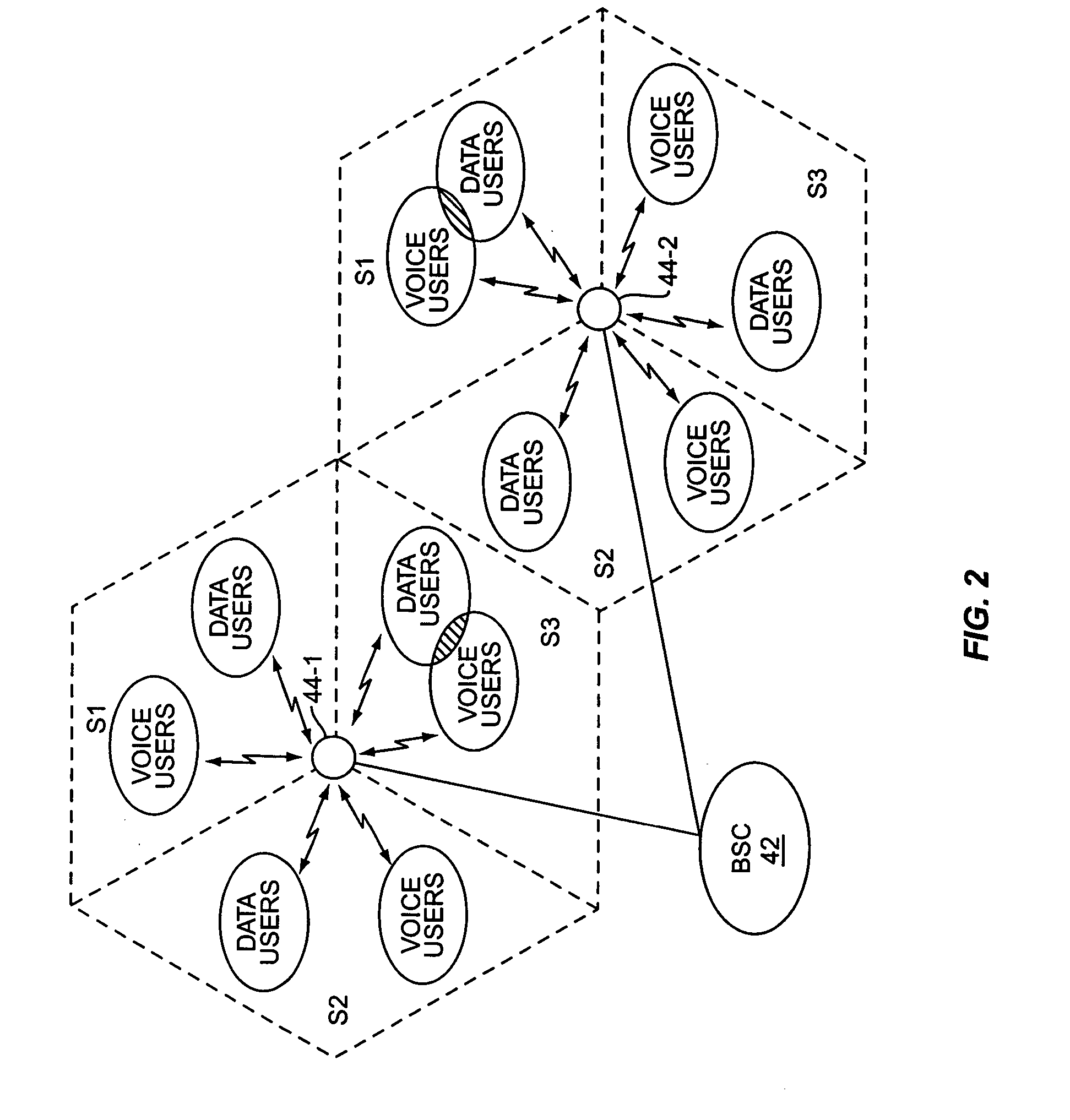
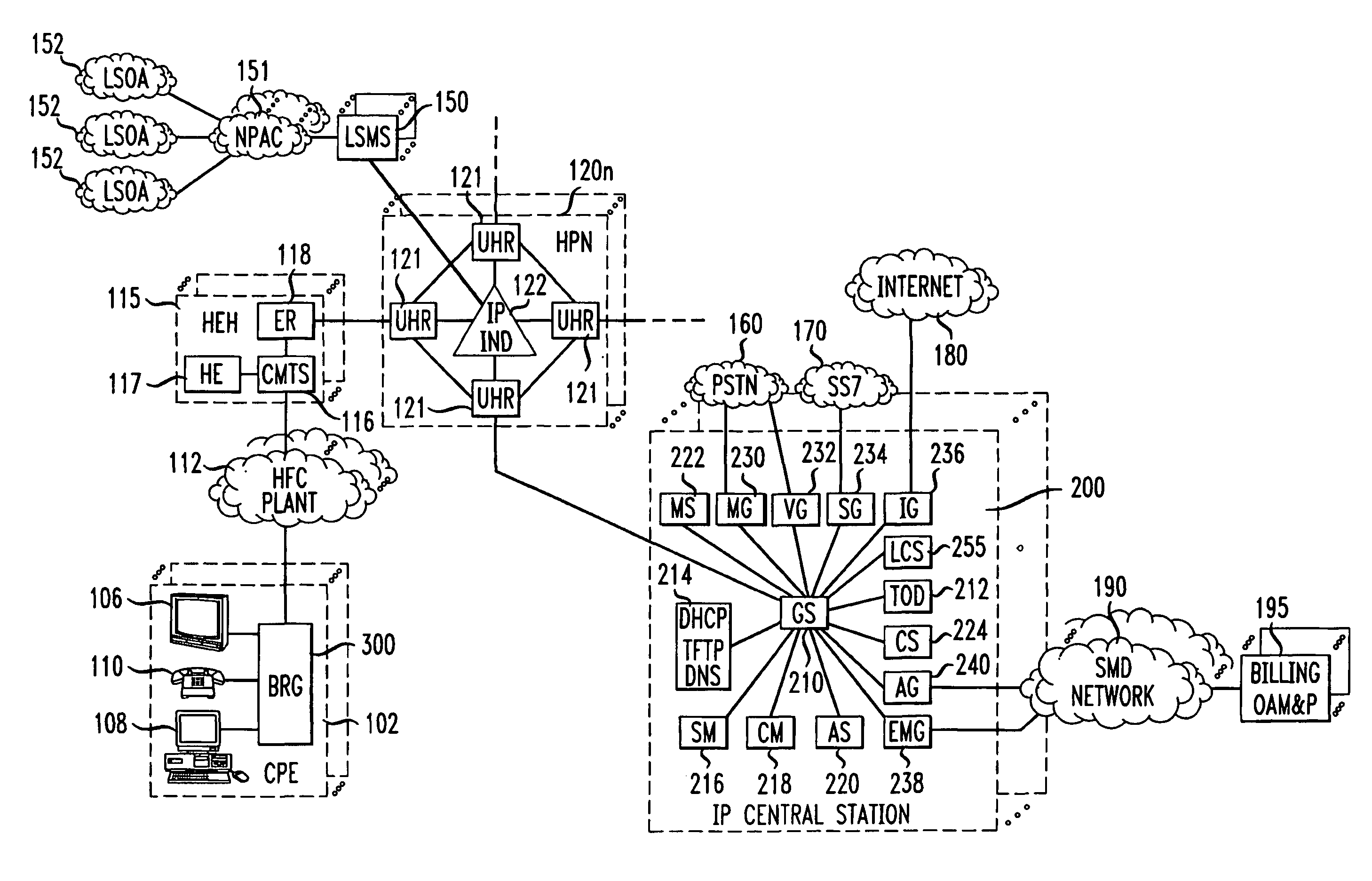
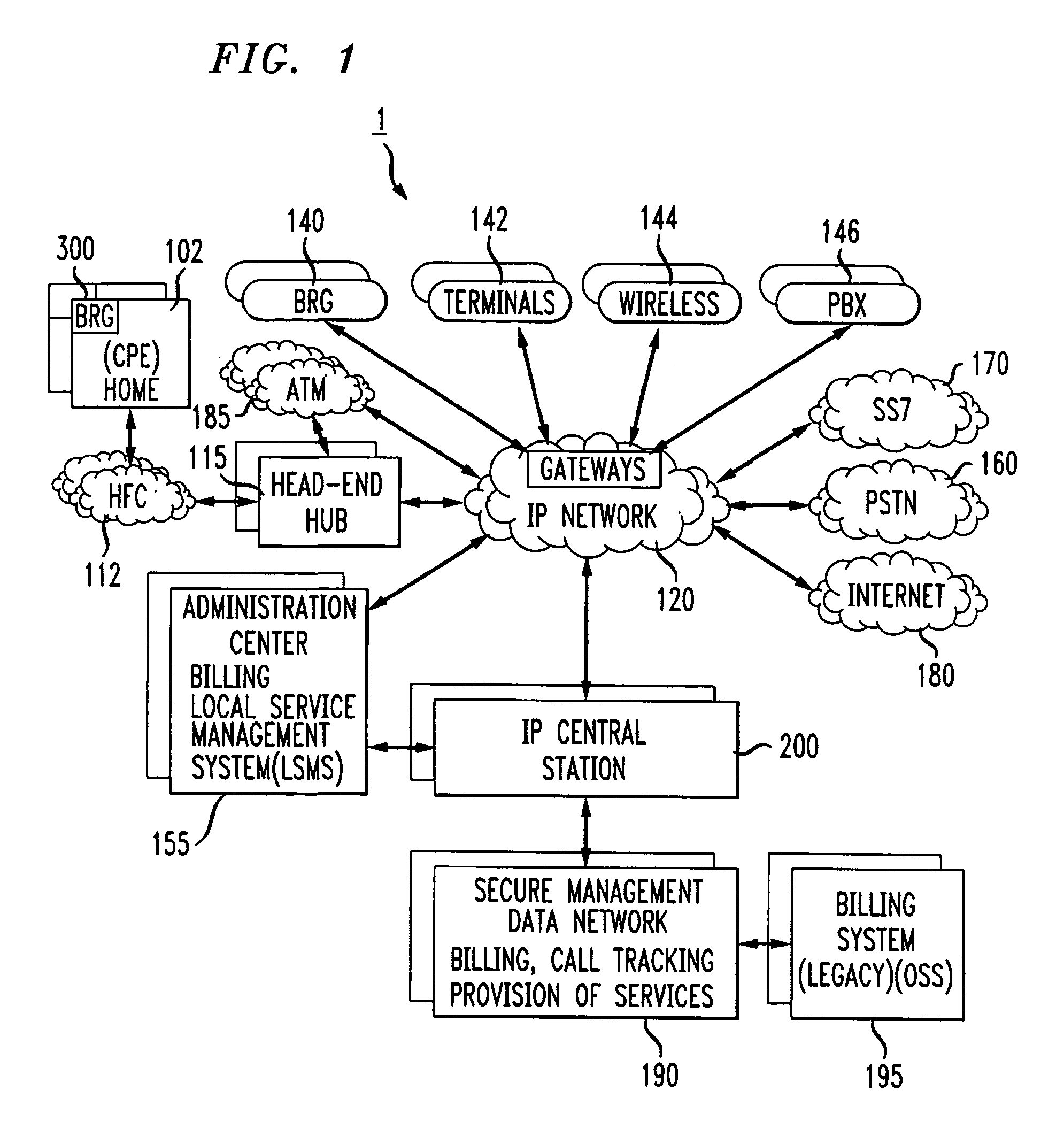
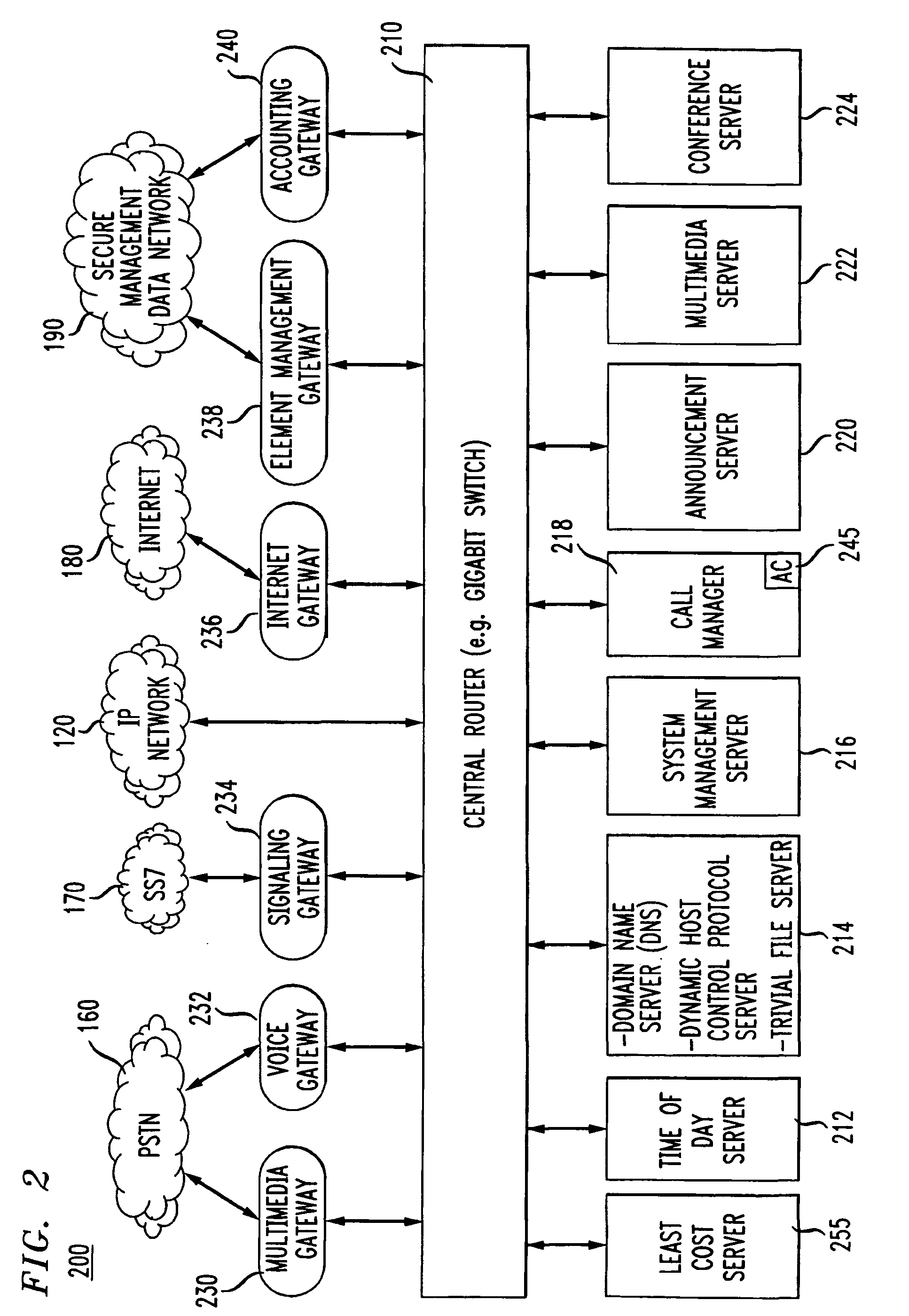
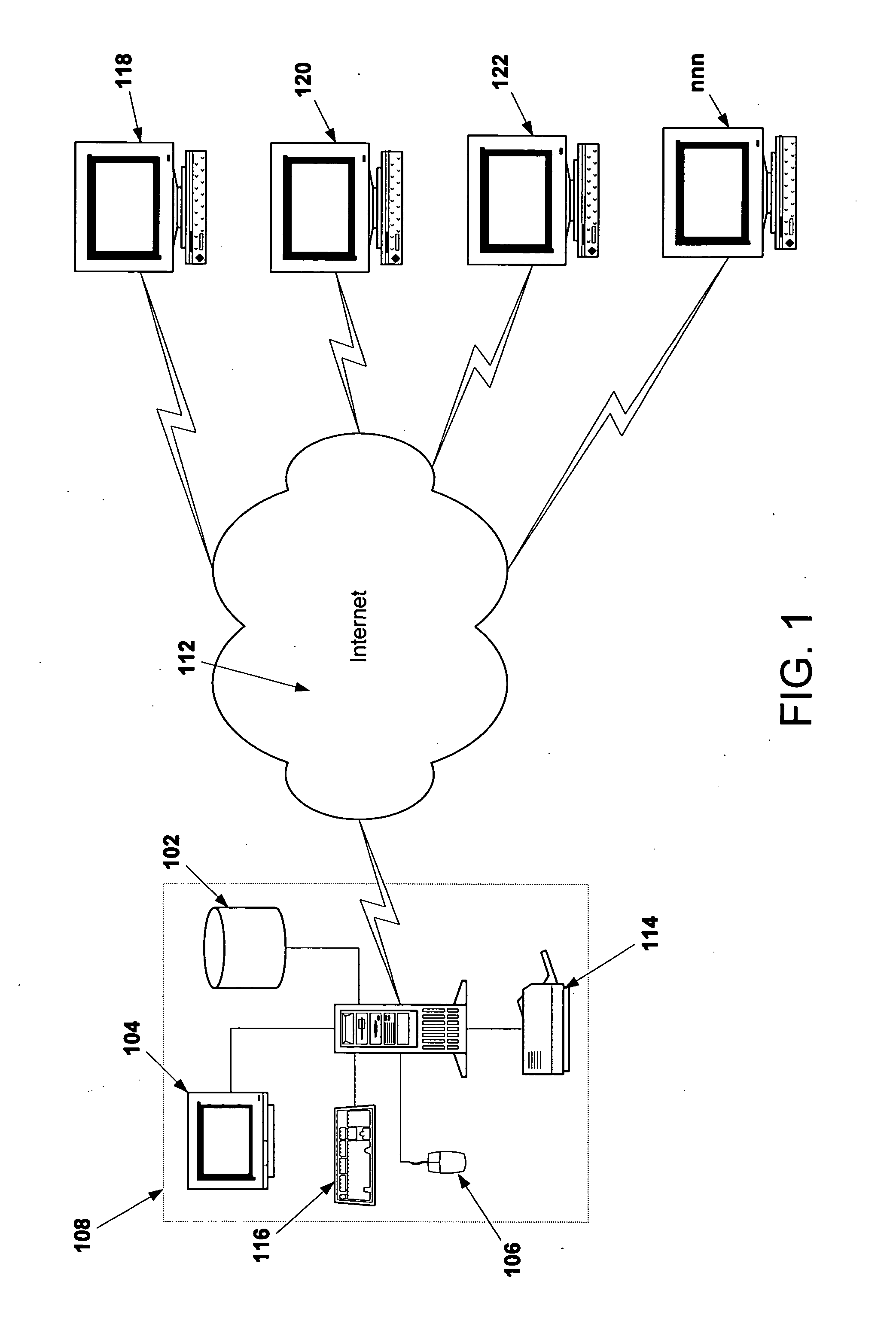
Voice over data telecommunications network architecture
InactiveUS6614781B1Interconnection arrangementsDc level restoring means or bias distort correctionNetwork operations centerNetwork architecture
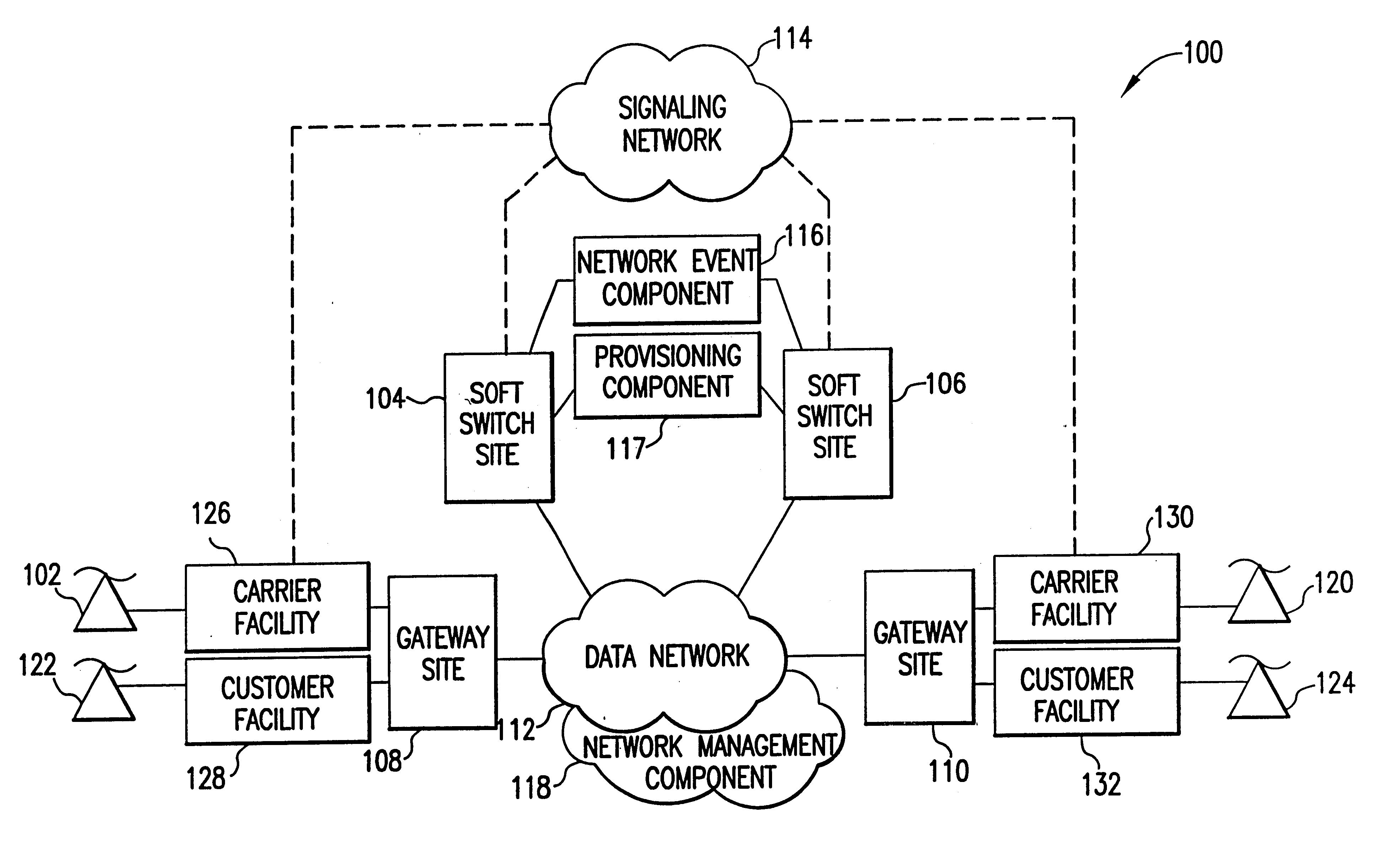
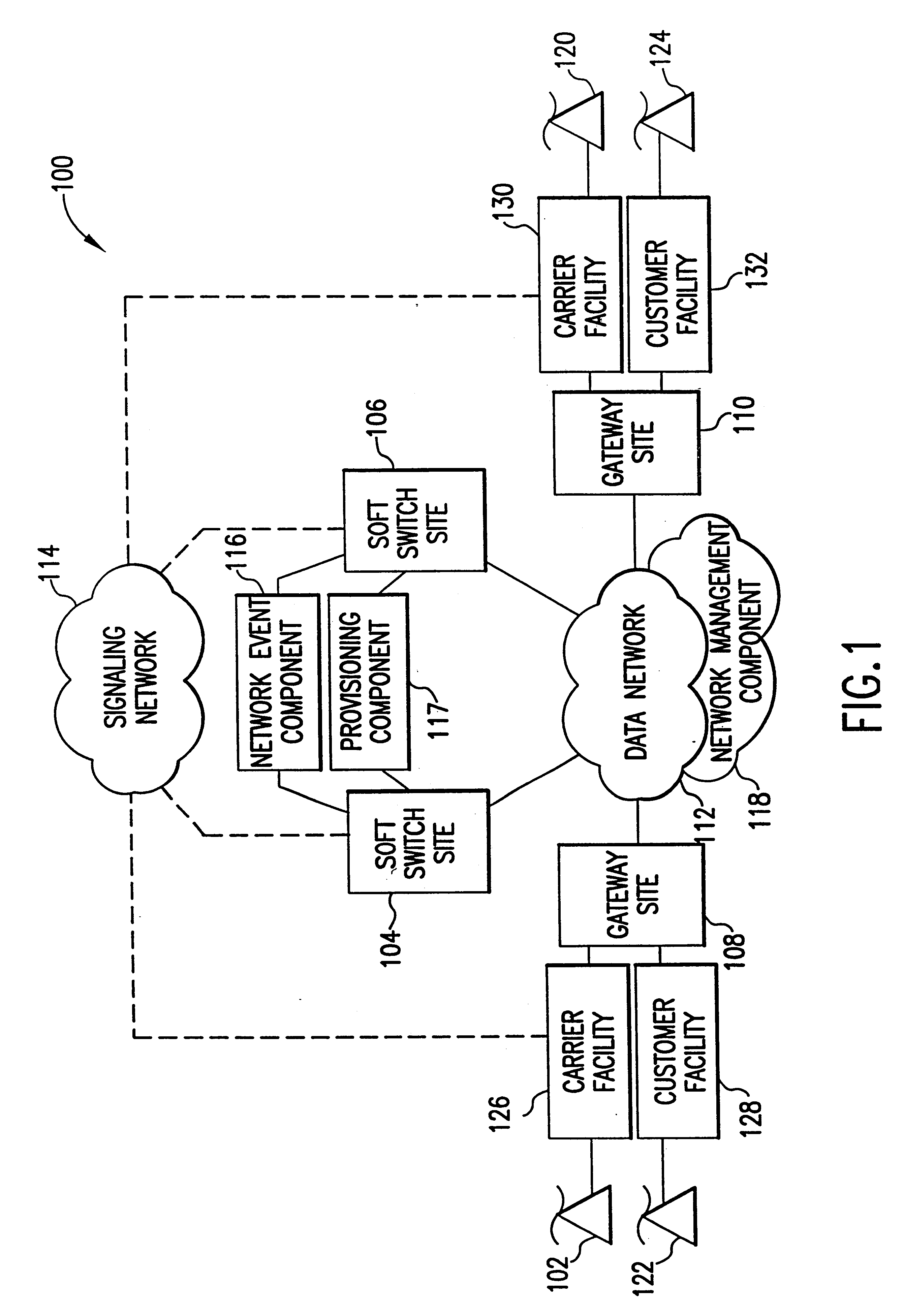
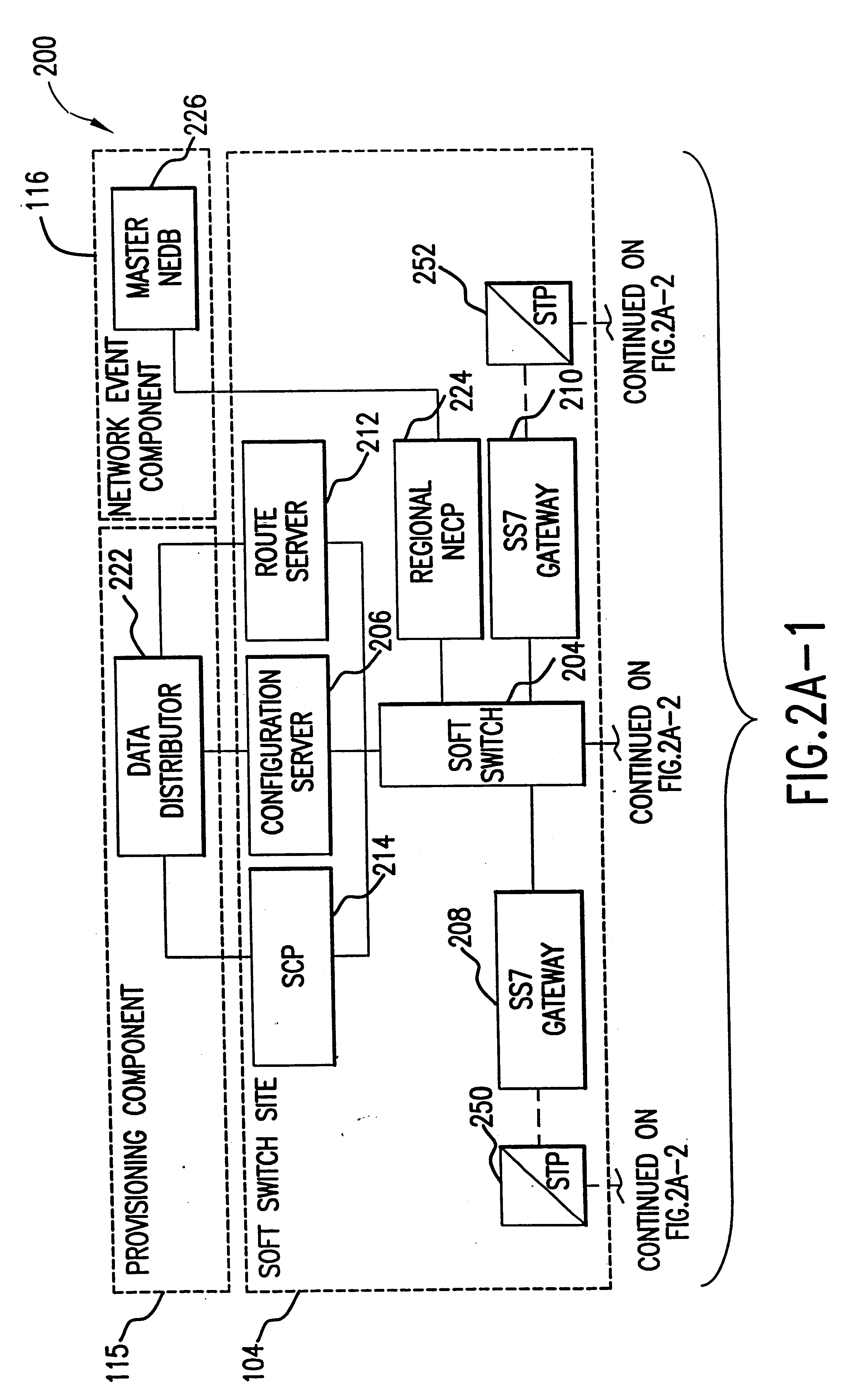
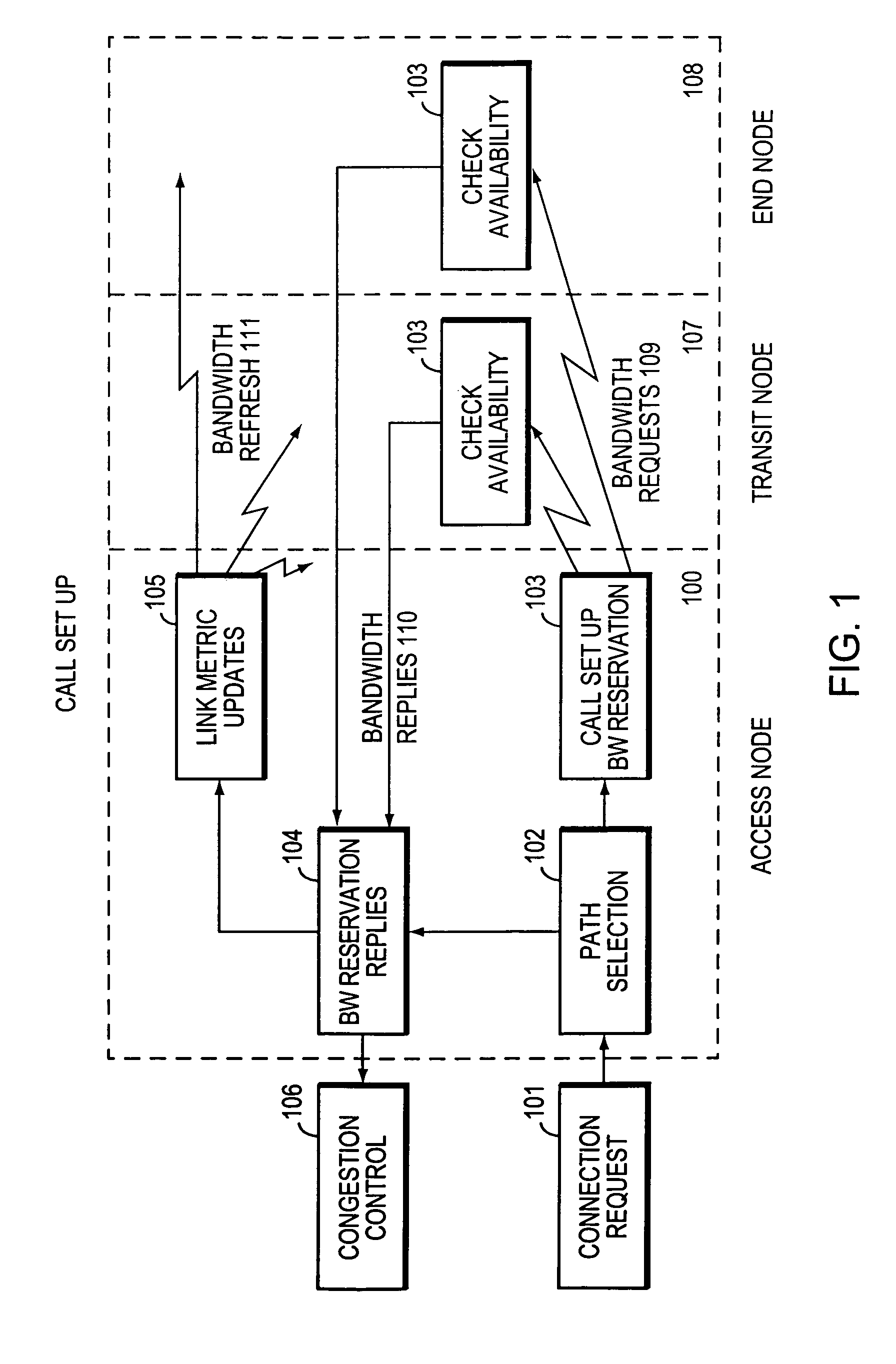
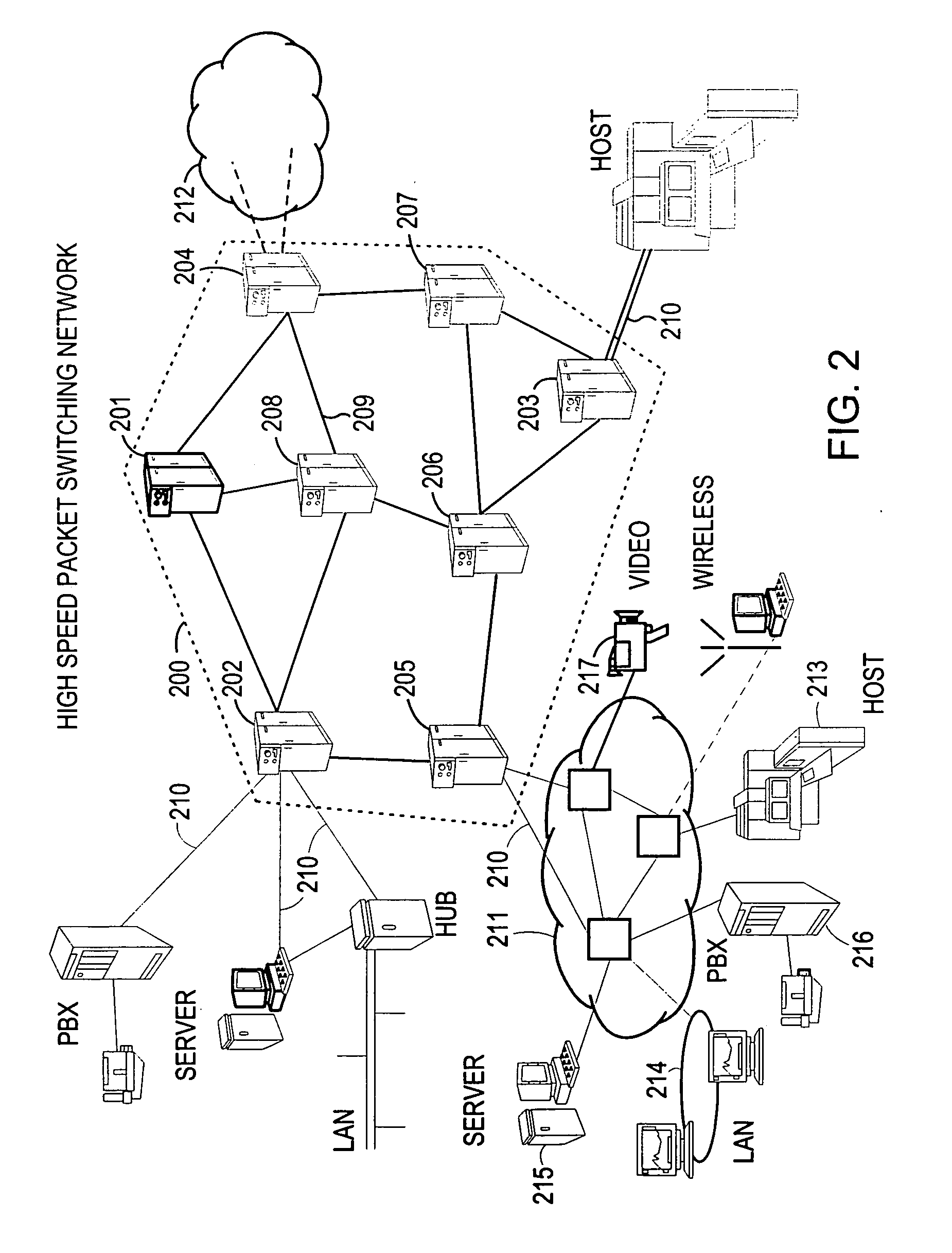
The present invention describes a system and method for communicating voice and data over a packet-switched network that is adapted to coexist and communicate with a legacy PSTN. The system permits packet switching of voice calls and data calls through a data network from and to any of a LEC, a customer facility or a direct IP connection on the data network. The system includes soft switch sites, gateway sites, a data network, a provisioning component, a network event component and a network management component. The system interfaces with customer facilities (e.g., a PBX), carrier facilities (e.g., a LEC) and legacy signaling networks (e.g., SS7) to handle calls between any combination of on-network and off-network callers.The soft switch sites provide the core call processing for the voice network architecture. The soft switch sites manage the gateway sites in a preferred embodiment, using a protocol such as the Internet Protocol Device Control (IPDC) protocol to request the set-up and tear-down of calls. The gateway sites originate and terminate calls between calling parties and called parties through the data network. The gateway sites include network access devices to provide access to network resources. The data network connects one or more of the soft switch sites to one or more of the gateway sites. The provisioning and network event component collects call events recorded at the soft switch sites. The network management component includes a network operations center (NOC) for centralized network management.
Owner:LEVEL 3 COMM LLC
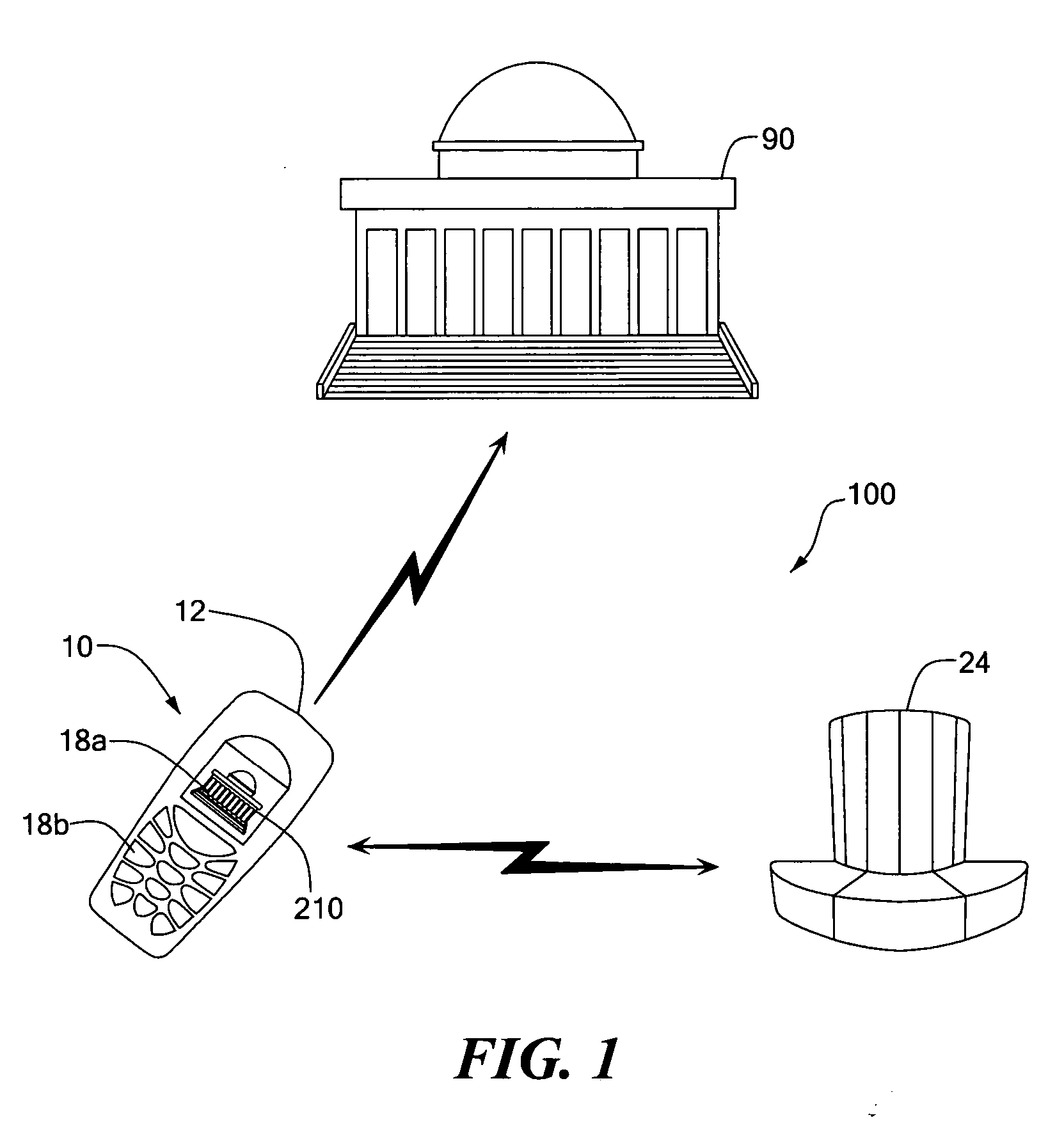
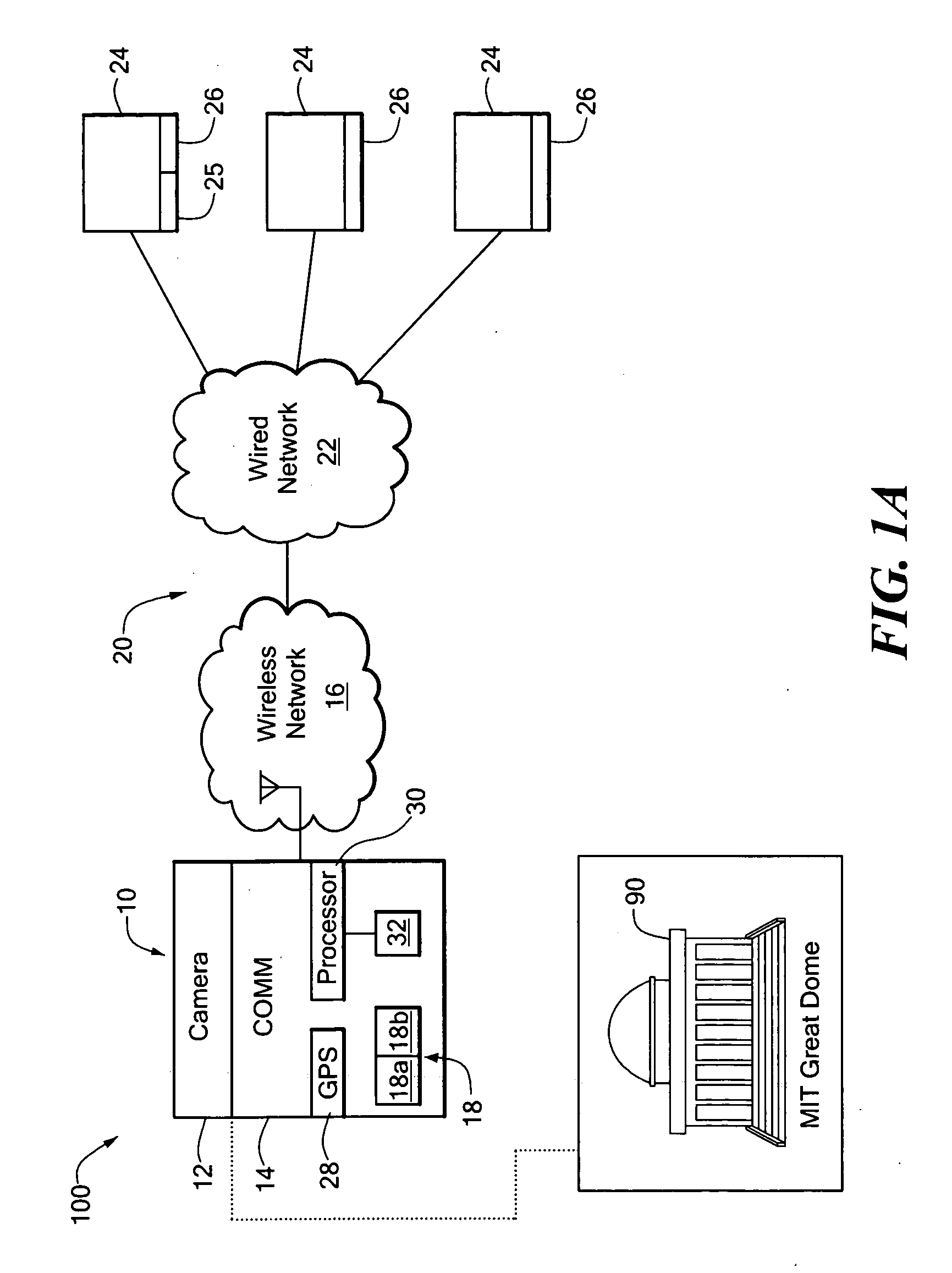
Photo-based mobile deixis system and related techniques
InactiveUS20050162523A1Quick identificationAvailable informationTelevision system detailsWeb data indexingWireless handheld devicesDisplay device
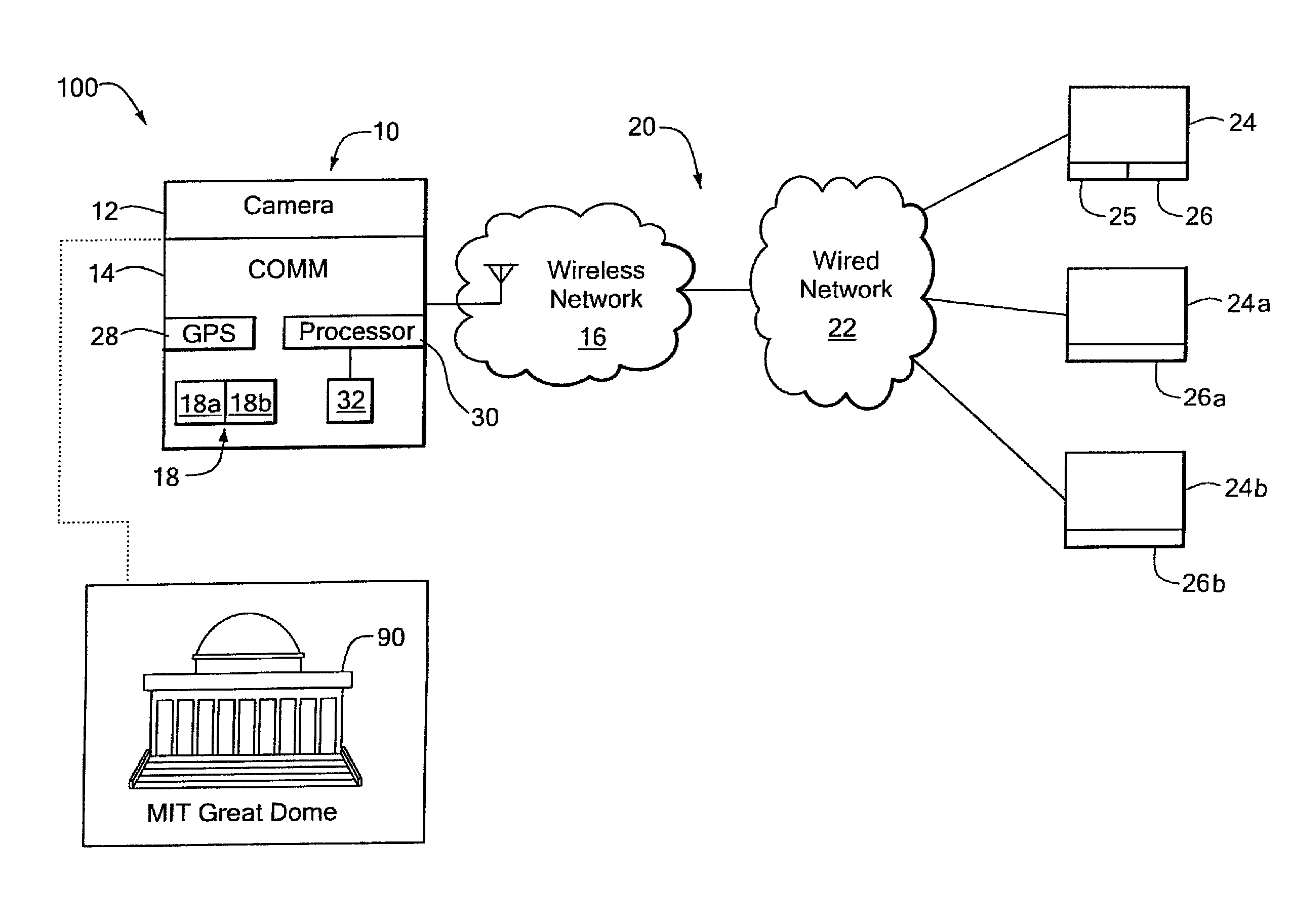
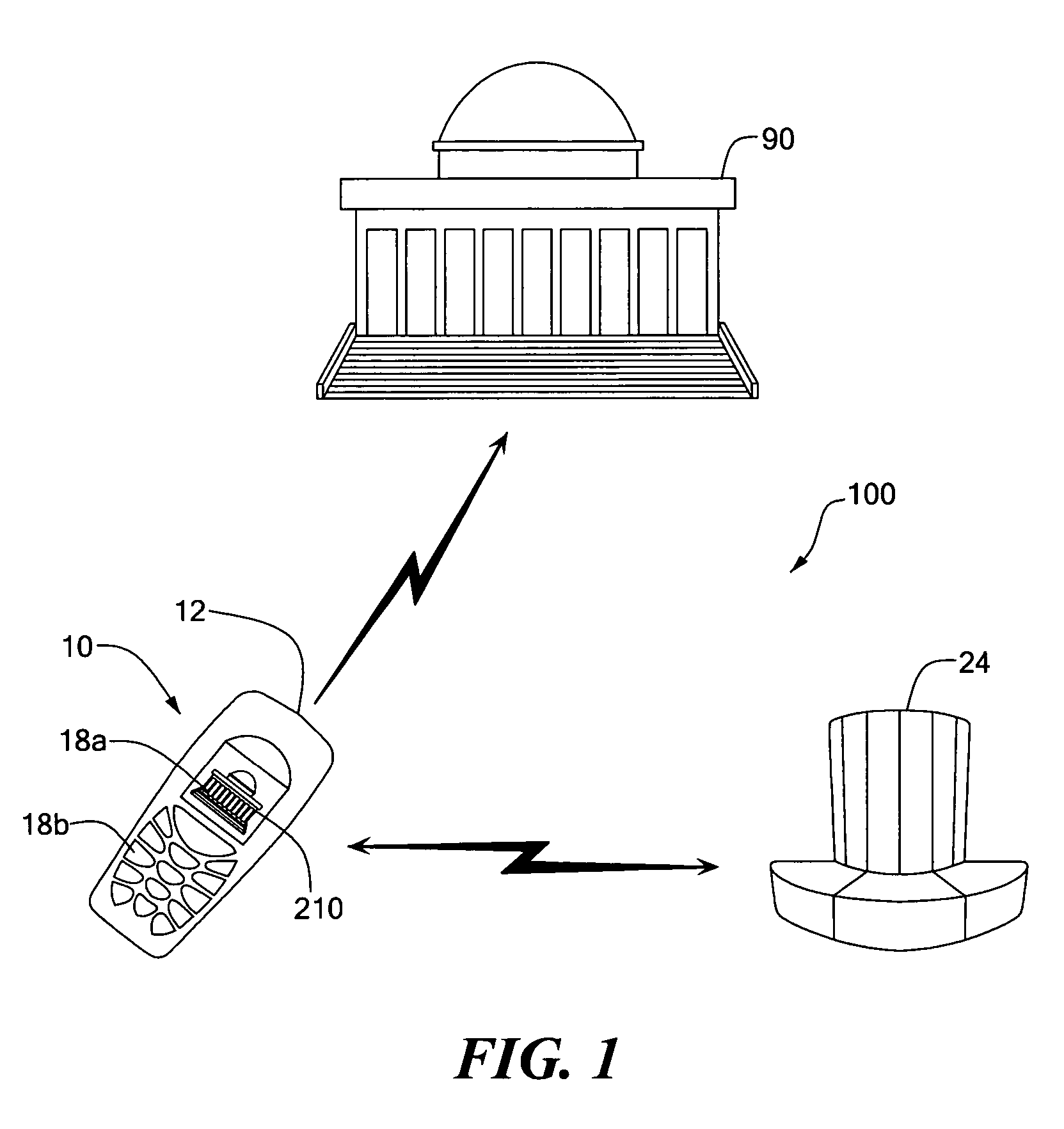
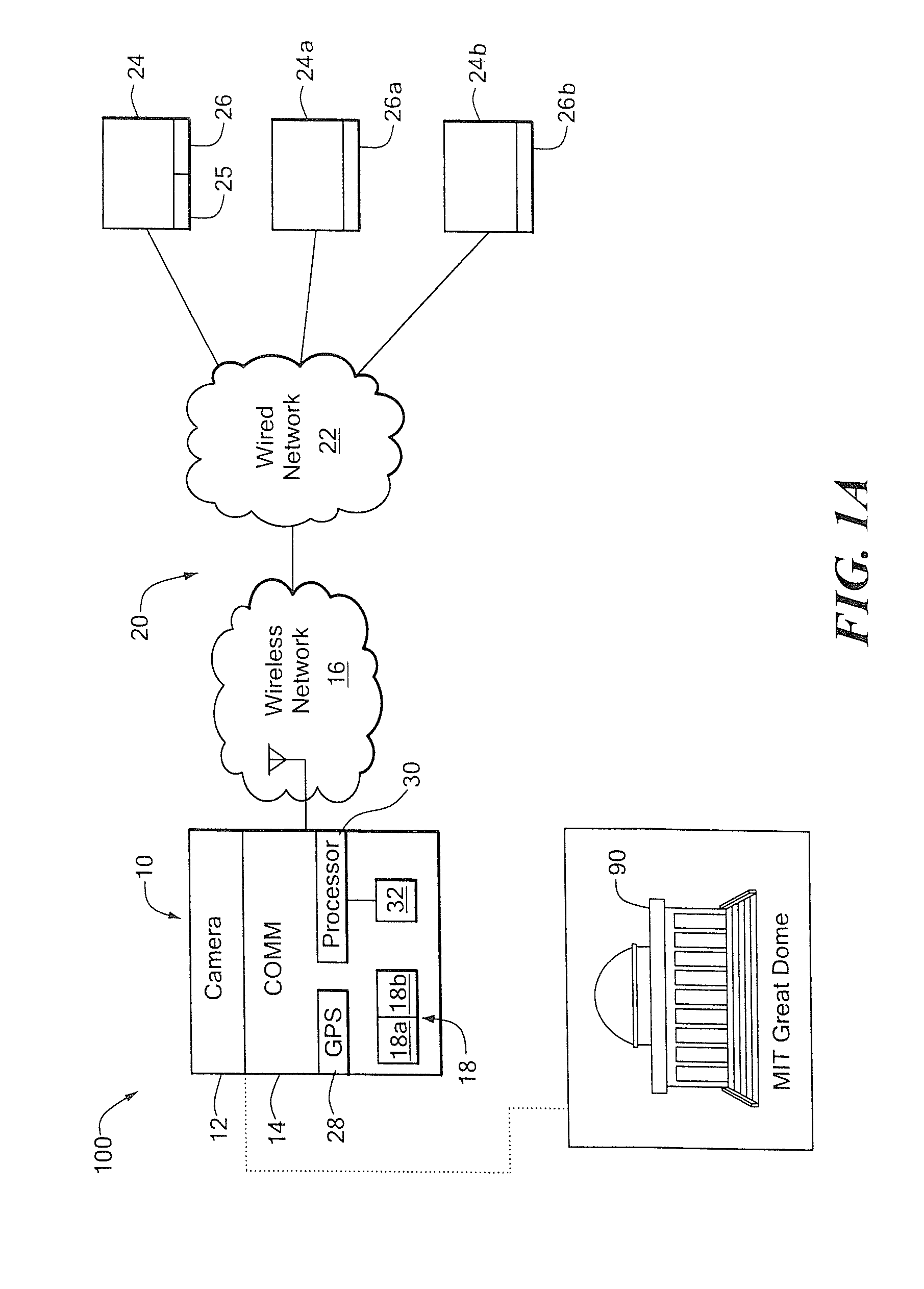
A mobile deixis device includes a camera to capture an image and a wireless handheld device, coupled to the camera and to a wireless network, to communicate the image with existing databases to find similar images. The mobile deixis device further includes a processor, coupled to the device, to process found database records related to similar images and a display to view found database records that include web pages including images. With such an arrangement, users can specify a location of interest by simply pointing a camera-equipped cellular phone at the object of interest and by searching an image database or relevant web resources, users can quickly identify good matches from several close ones to find an object of interest.
Owner:MASSACHUSETTS INST OF TECH
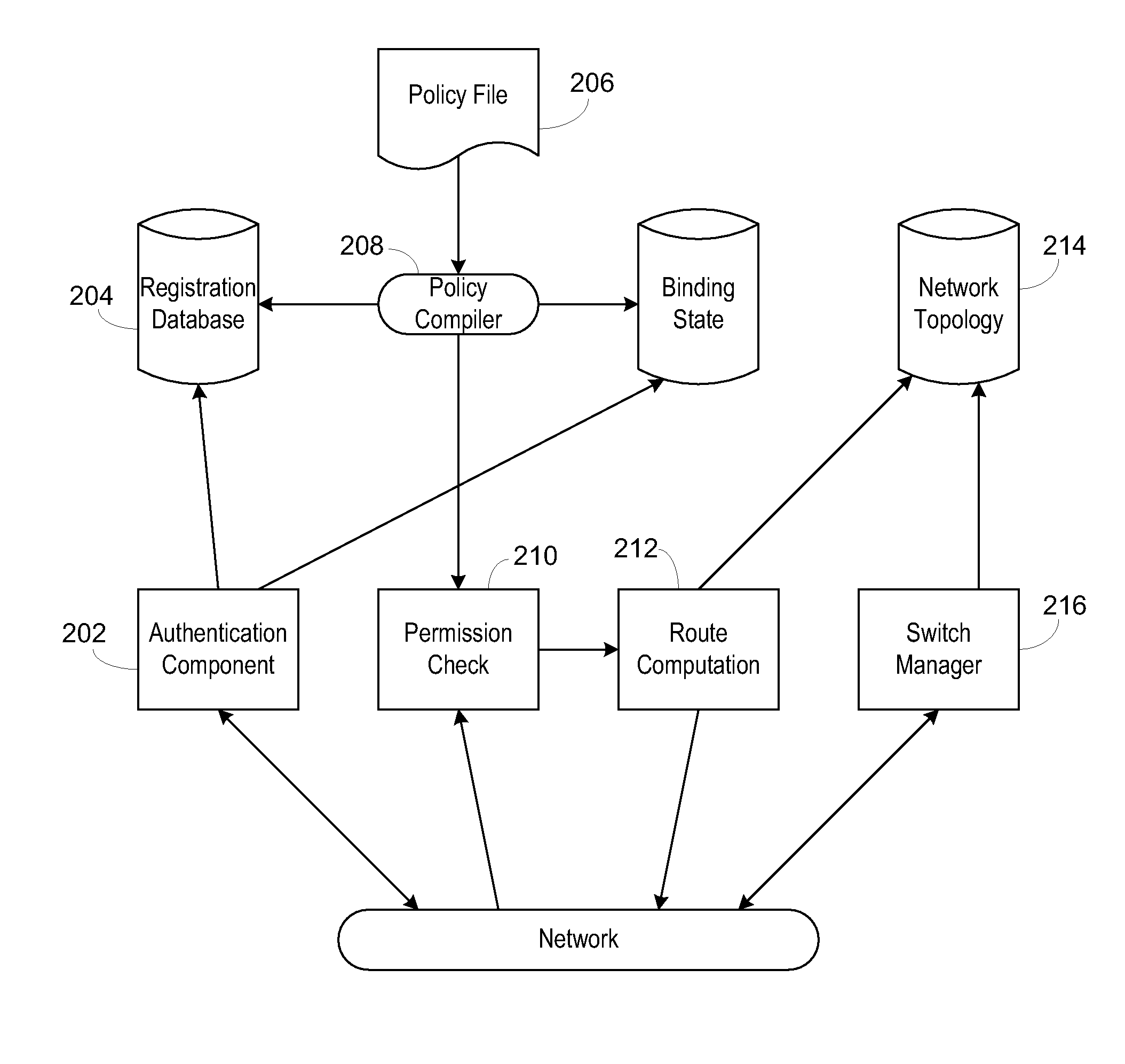
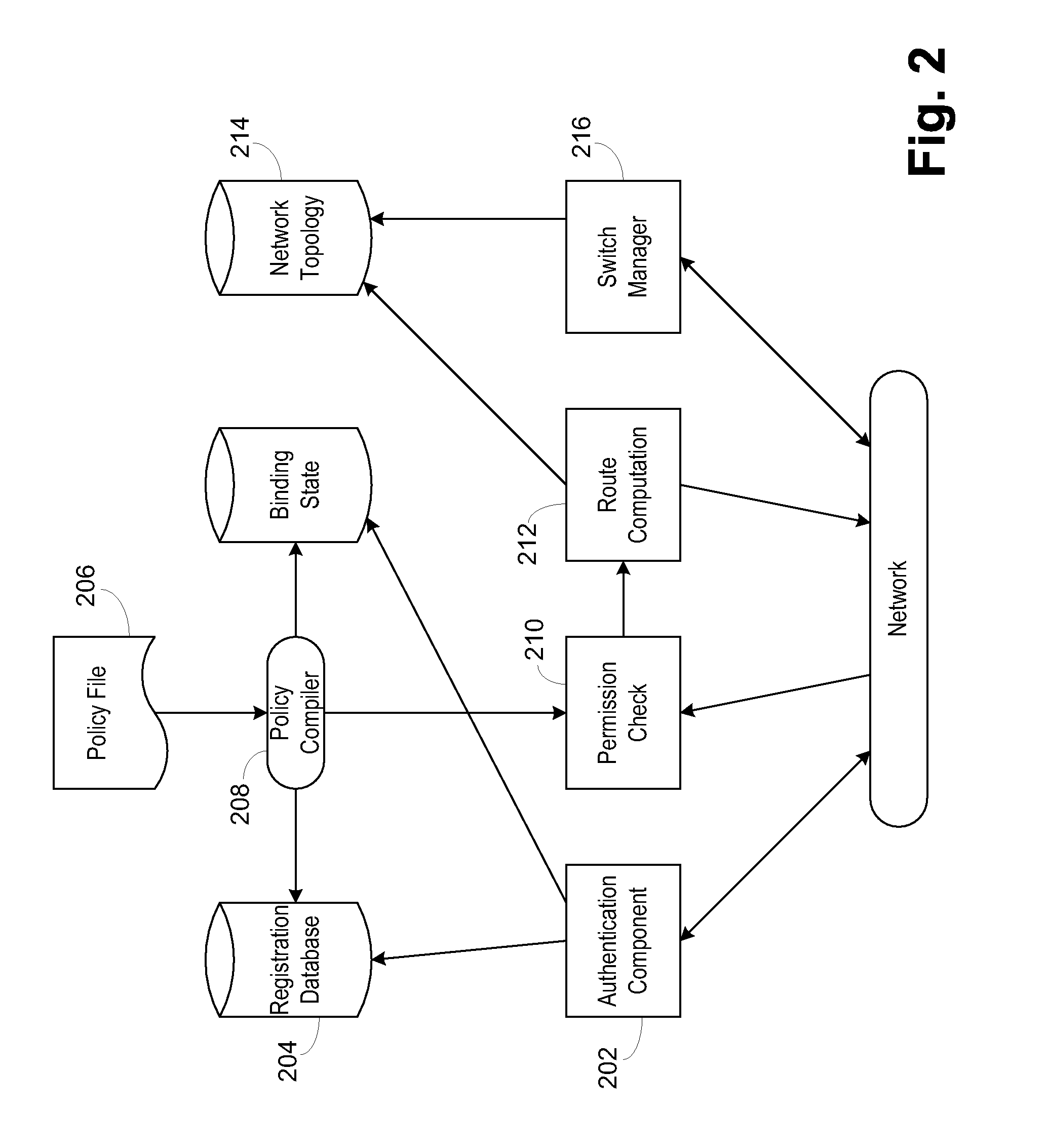
Secure network switching infrastructure
InactiveUS20080189769A1Reduces the trusted computing baseReduce overheadDigital data processing detailsUser identity/authority verificationNetwork packetNetwork control
Use of a centralized control architecture in a network. Policy declaration, routing computation, and permission checks are managed by a logically centralized controller. By default, hosts on the network can only route to the network controller. Hosts and users must first authenticate themselves with the controller before they can request access to the network resources. The controller uses the first packet of each flow for connection setup. When a packet arrives at the controller, the controller decides whether the flow represented by that packet should be allowed. The switches use a simple flow table to forward packets under the direction of the controller. When a packet arrives that is not in the flow table, it is forwarded to the controller, along with information about which port the packet arrived on. When a packet arrives that is in the flow table, it is forwarded according to the controller's directive.
Owner:THE BOARD OF TRUSTEES OF THE LELAND STANFORD JUNIOR UNIV
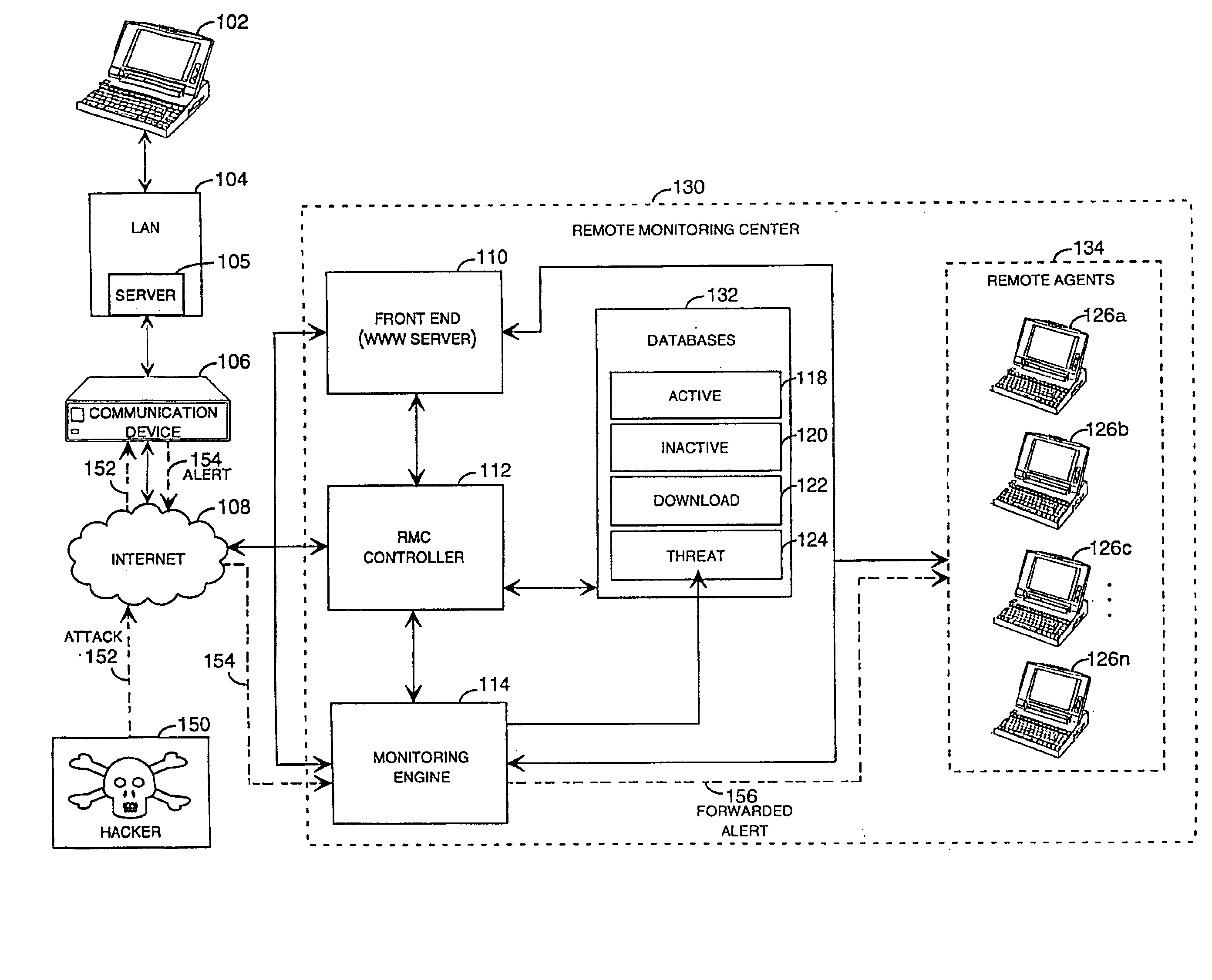
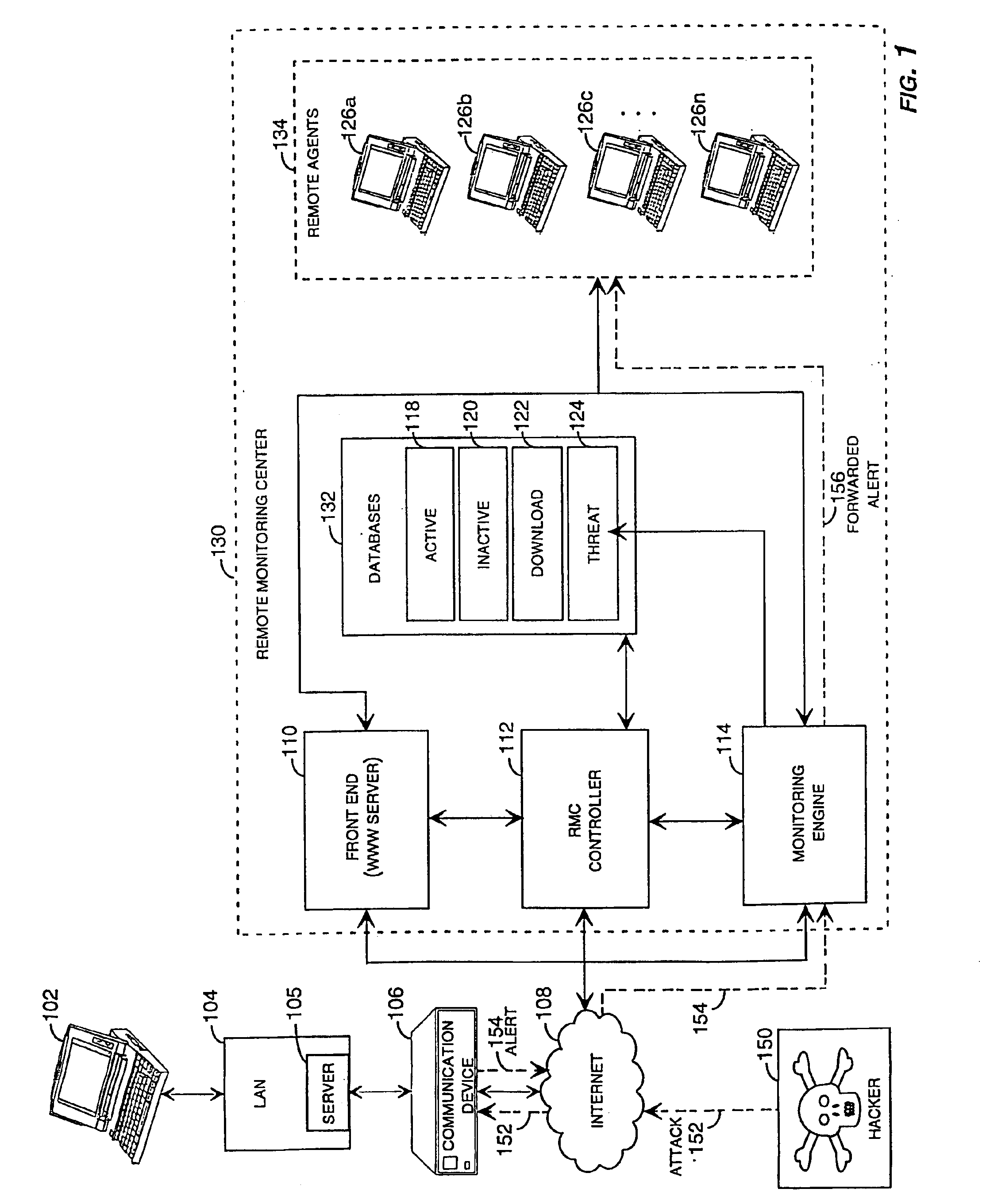
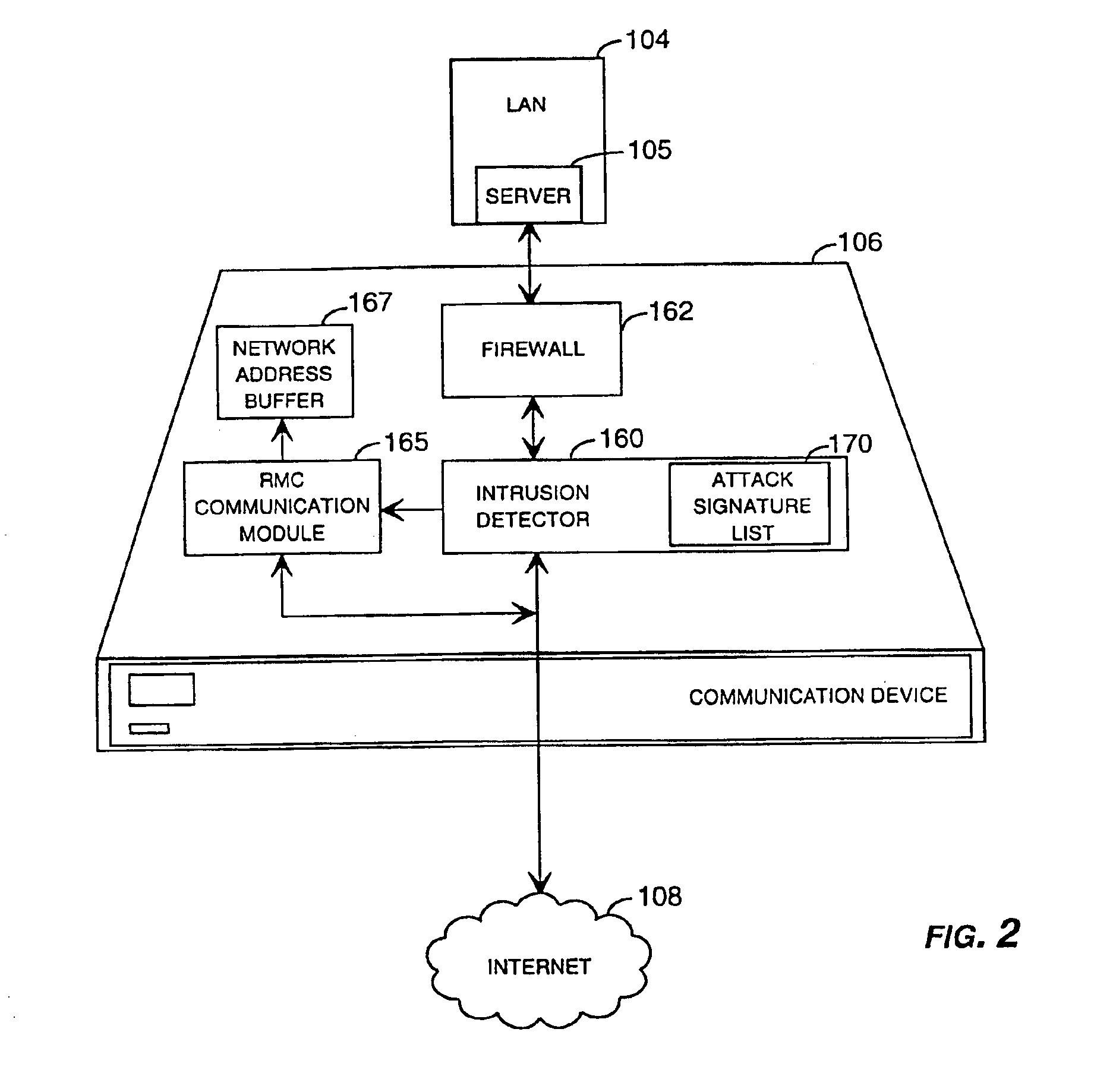
Method and system for remotely configuring and monitoring a communication device
InactiveUS6990591B1Rapid responseMemory loss protectionUnauthorized memory use protectionImage resolutionThe Internet
Owner:SECUREWORKS
Voice over data telecommunications network architecture
InactiveUS20040022237A1Interconnection arrangementsDc level restoring means or bias distort correctionNetwork operations centerNetwork architecture
Owner:LEVEL 3 COMM LLC
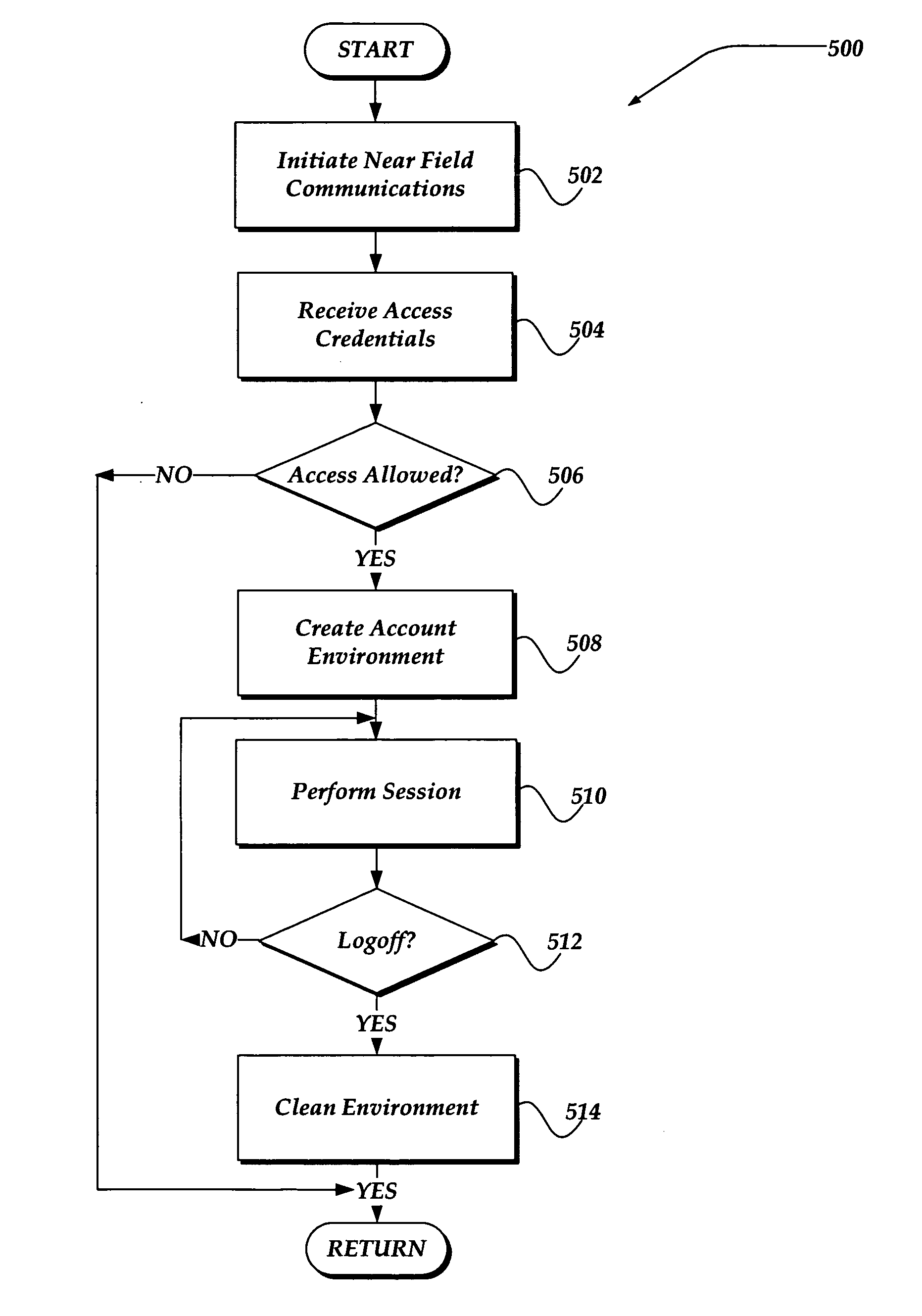
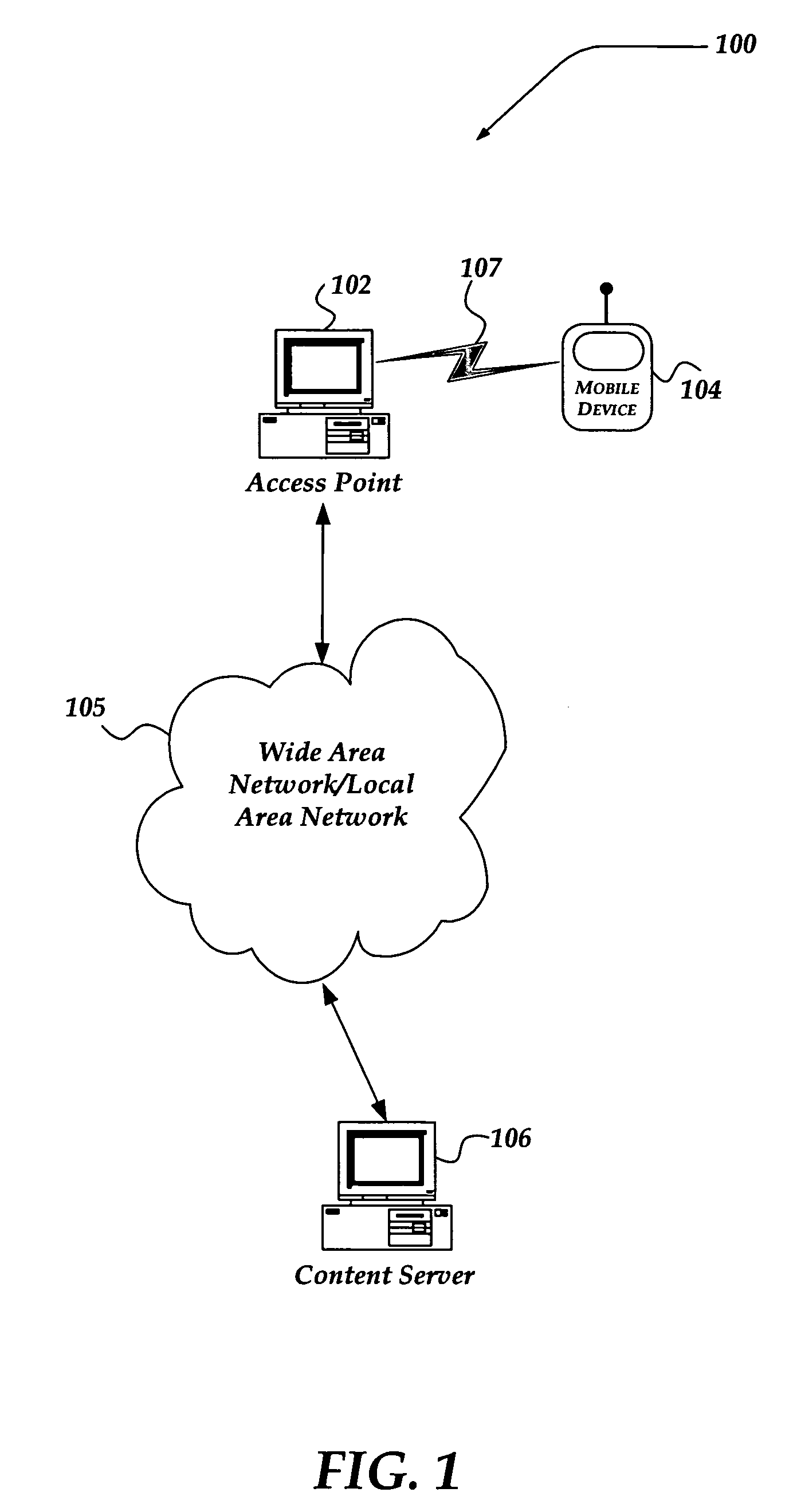
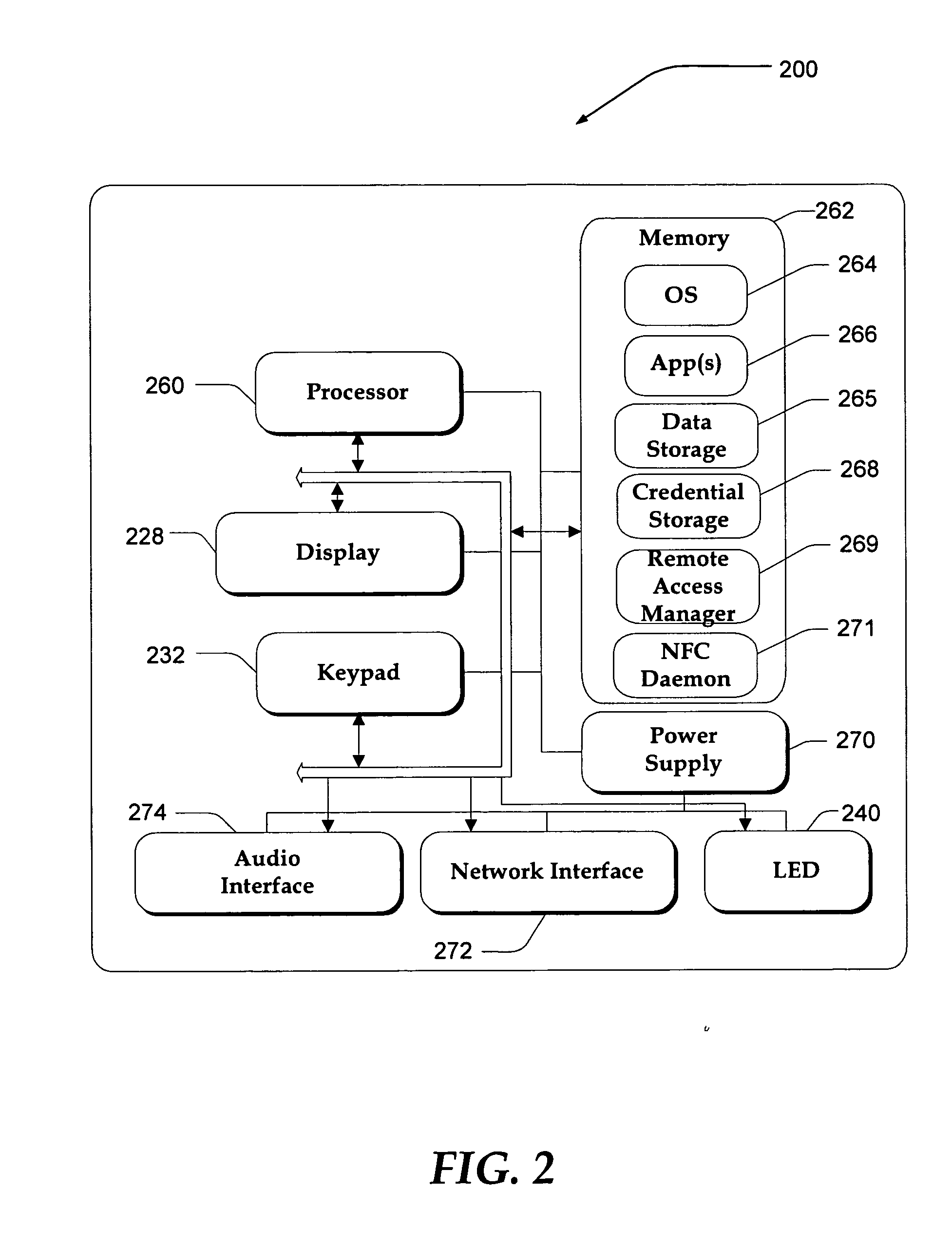
Managing an access account using personal area networks and credentials on a mobile device
InactiveUS20060183462A1Near-field transmissionUnauthorised/fraudulent call preventionAccess networkRelevant information
A system, apparatus, and method are directed towards automatically managing an access account at an access point using near field communications and credentials stored on a mobile device. The mobile device receives, out-of-band, information for use in creating an account for accessing network resources from the access point. As the mobile device is brought into proximity with the access point, a wireless network connection is established using a near field communication (NFC) protocol. The information, which may include a user credential, account information, and so forth, is communicated to the access point. The access point employs the information to establish an account and create an environment from which access to the network resources may be obtained. Upon termination, the access point removes from itself any user specific data. The access point may provide also session related information useable in billing the user of the mobile device.
Owner:NOKIA CORP
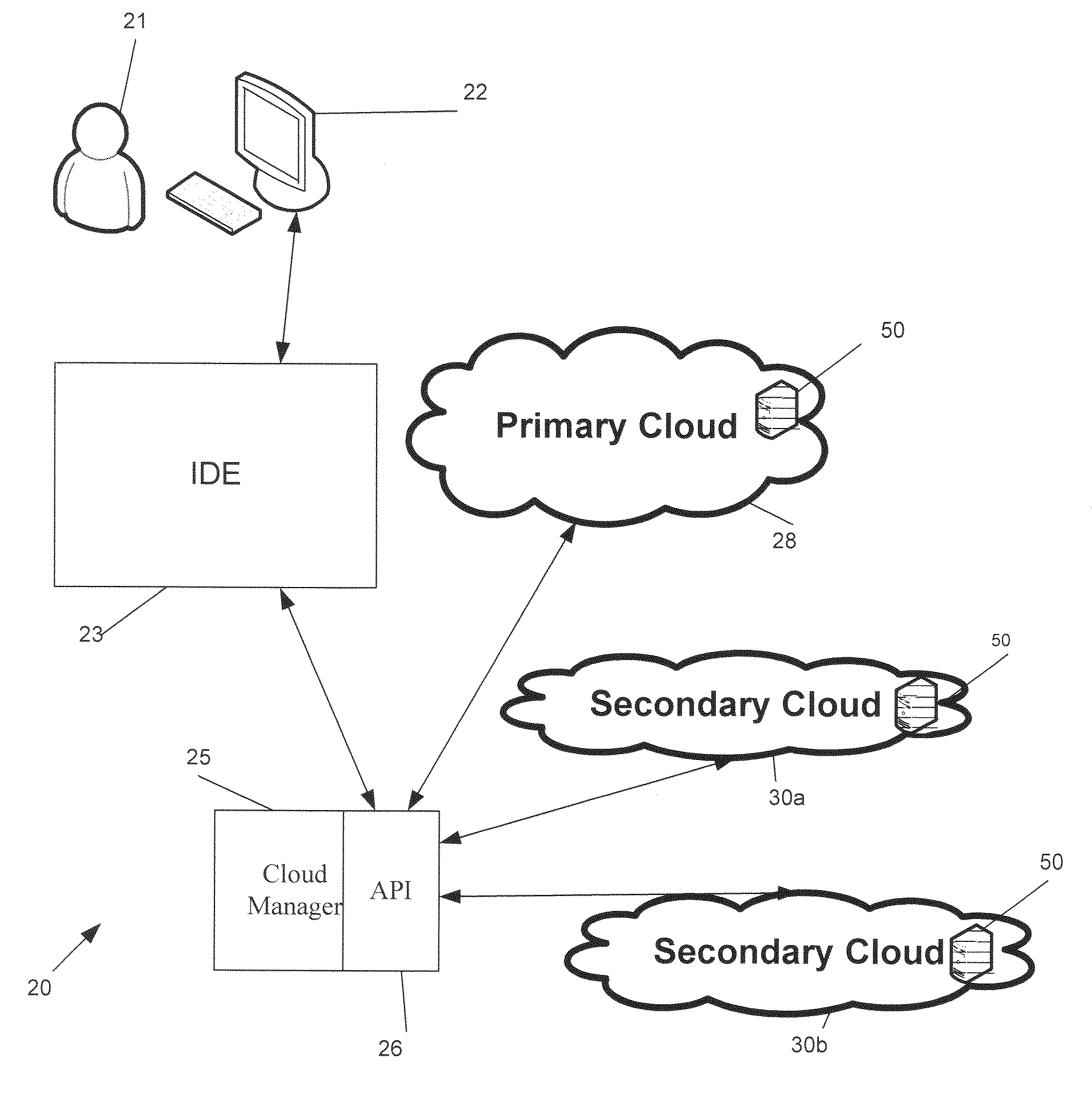
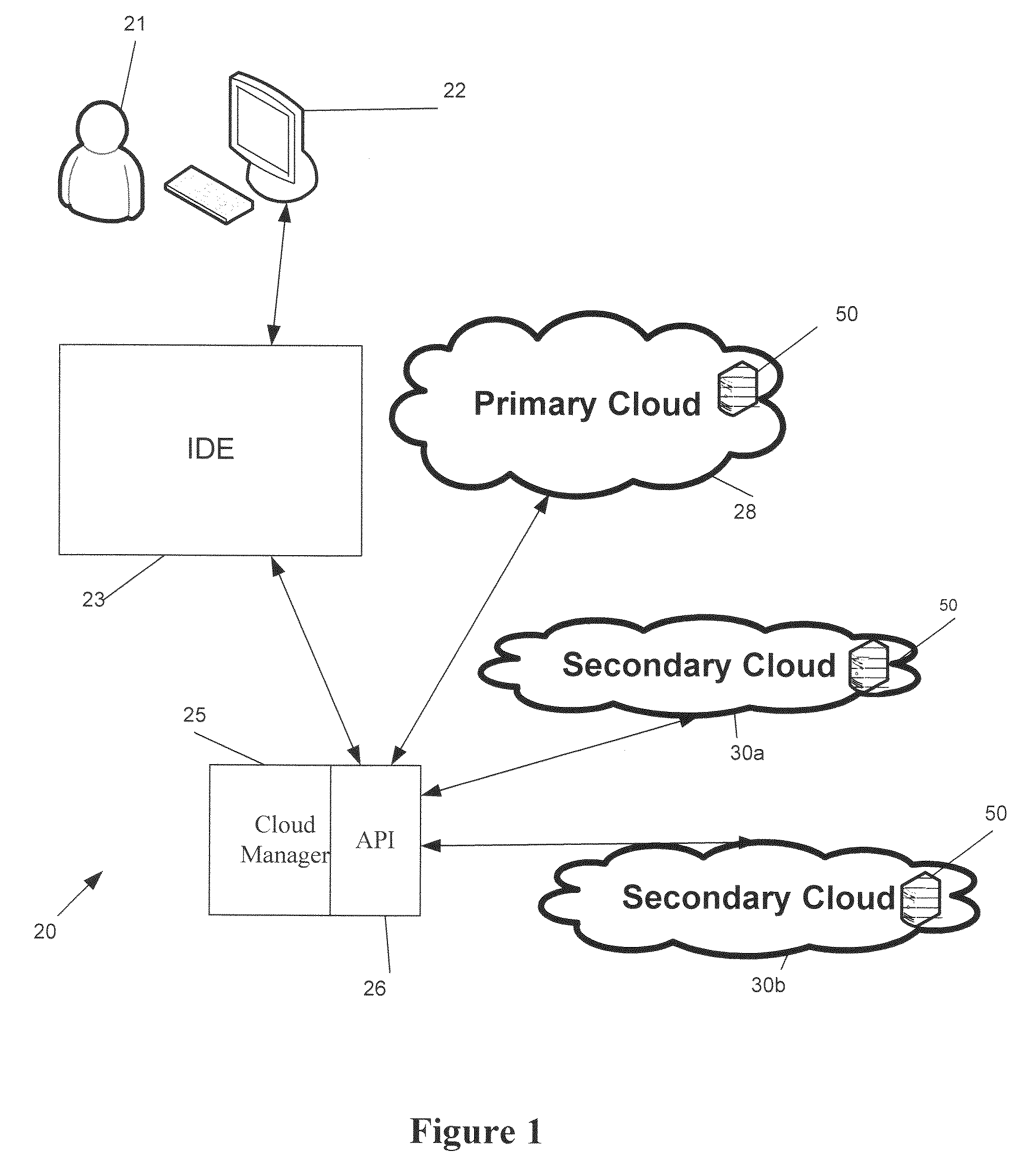
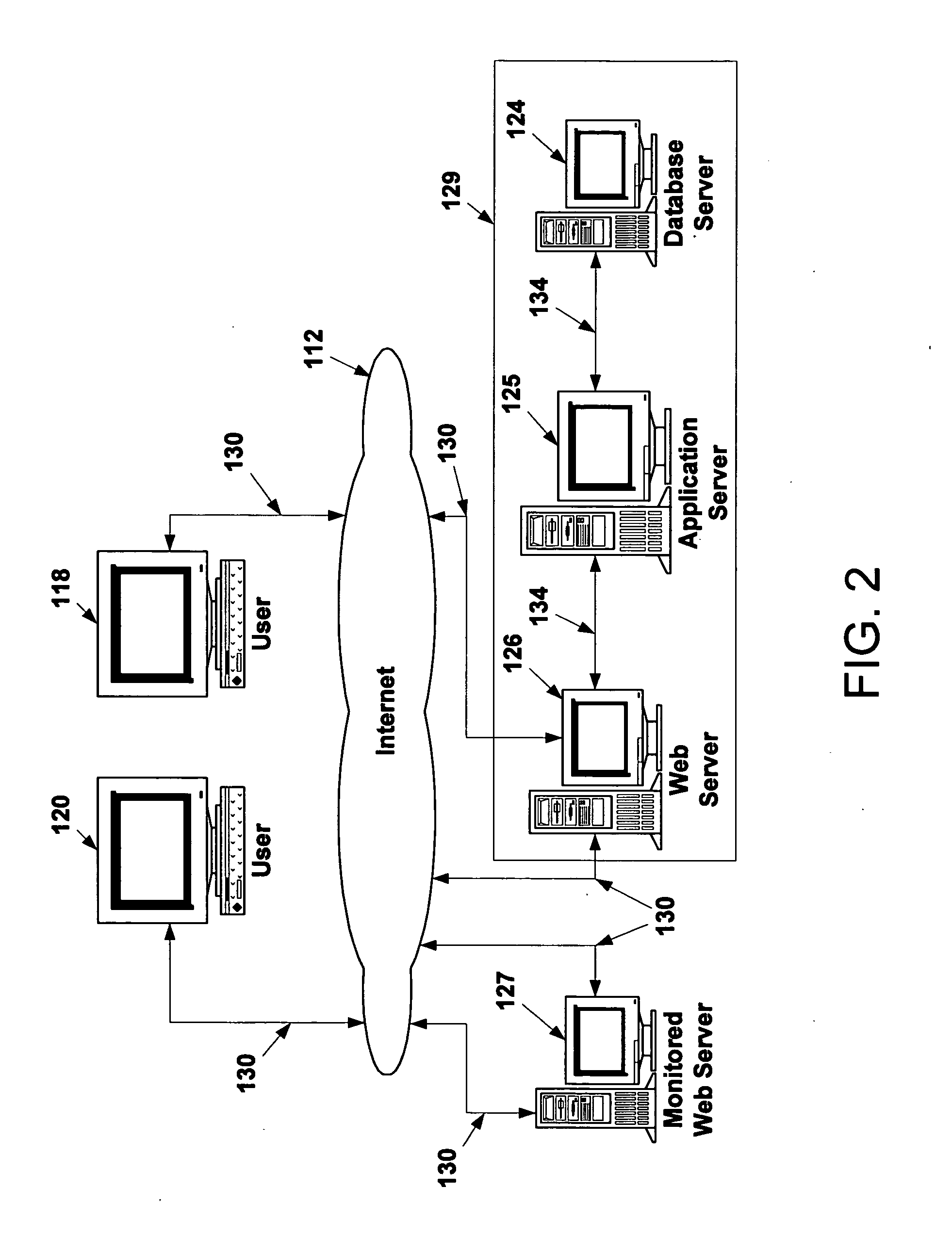
System and method for developing, deploying, managing and monitoring a web application in a single environment
InactiveUS7596620B1Guaranteed to workDigital computer detailsRequirement analysisWeb applicationThe Internet
A system and method for developing, deploying, managing and monitoring a web application in a single environment is disclosed herein. The single environment is preferably an integrated development environment (“IDE”). The system and method preferably allows for deployment to a cloud provider, and preferably allows for use of Web resources from multiple cloud providers. One preferred IDE is the APTANA® STUDIO IDE. An operator can use a user interface to access the integrated development environment and the cloud manager over the network, specifically the Internet.
Owner:APPCELERATOR
Method and system for minimizing the connection set up time in high speed packet switching networks
InactiveUS6934249B1Minimize delayMinimize in in to selectError preventionFrequency-division multiplex detailsTraffic capacityPacket switched
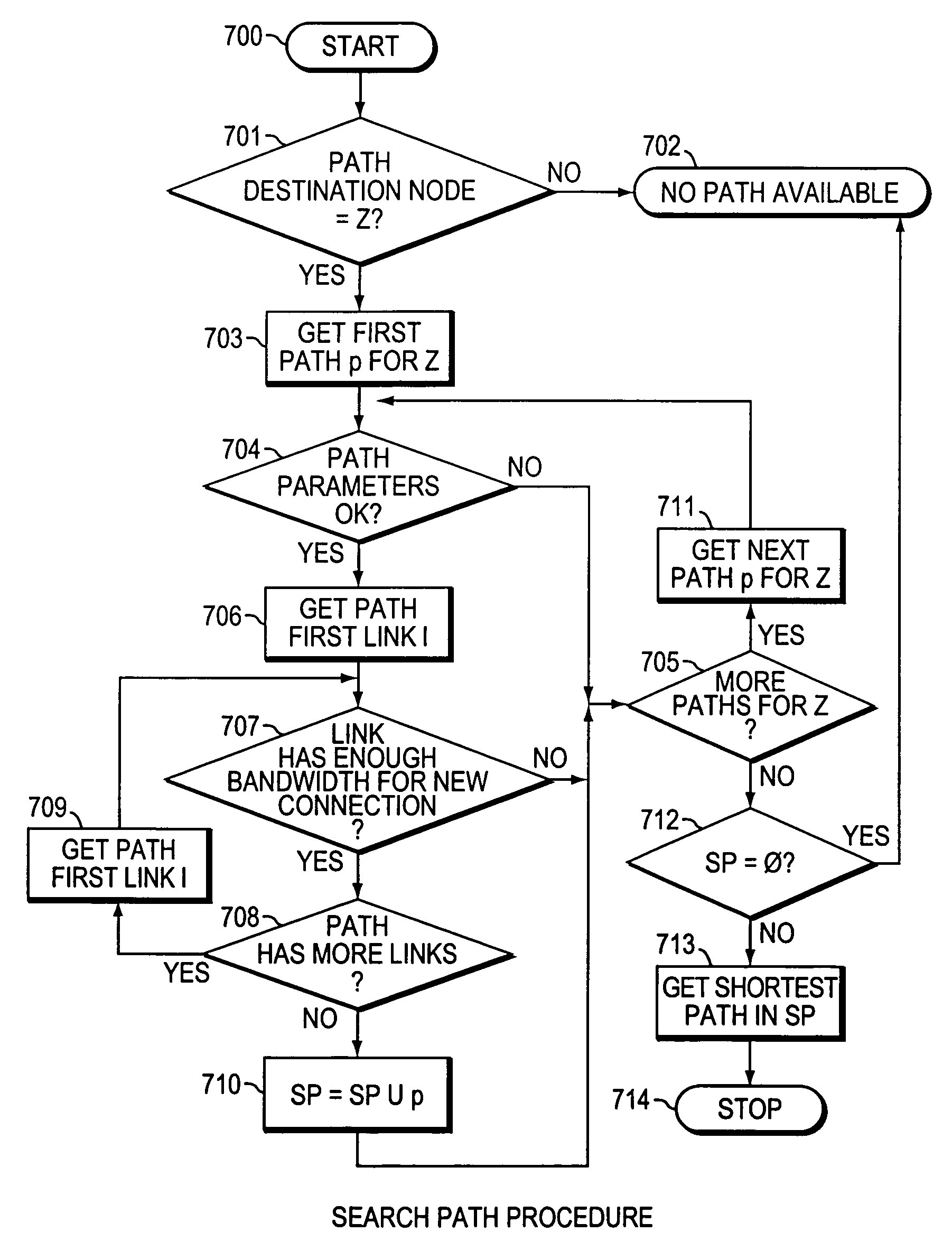
The present invention is directed to a high speed packet switching network and, in particular to a method and system for minimizing the time to establish a connection between an origin and a destination node. Due to high dynamicity of the traffic on transmission links, it is important to select a routing path according to a fully up-to-date information on all network resources. The simpler approach is to calculate a new path for each new connection request. This solution may be very time consuming because there are as many path selection operations as connection set up operations. On another hand, the calculation of paths based on an exhaustive exploration of the network topology, is a complex operation which may also take an inordinate amount of resources in large networks. Many of connections originated from a network node flow to the same destination network node. It is therefore possible to take a serious benefit in reusing the same already calculated paths for several connections towards the same node. The path calculated at the time the connection is requested is recorded in a Routing Database and updated each time a modification occurs in the network. Furthermore, alternate paths for supporting non-disruptive path switch on failure or preemption, and new paths towards potential destination nodes can be calculated and stored when the connection set up process is idle. These last operations are executed in background with a low processing priority and in absence of connection request.
Owner:CISCO TECH INC
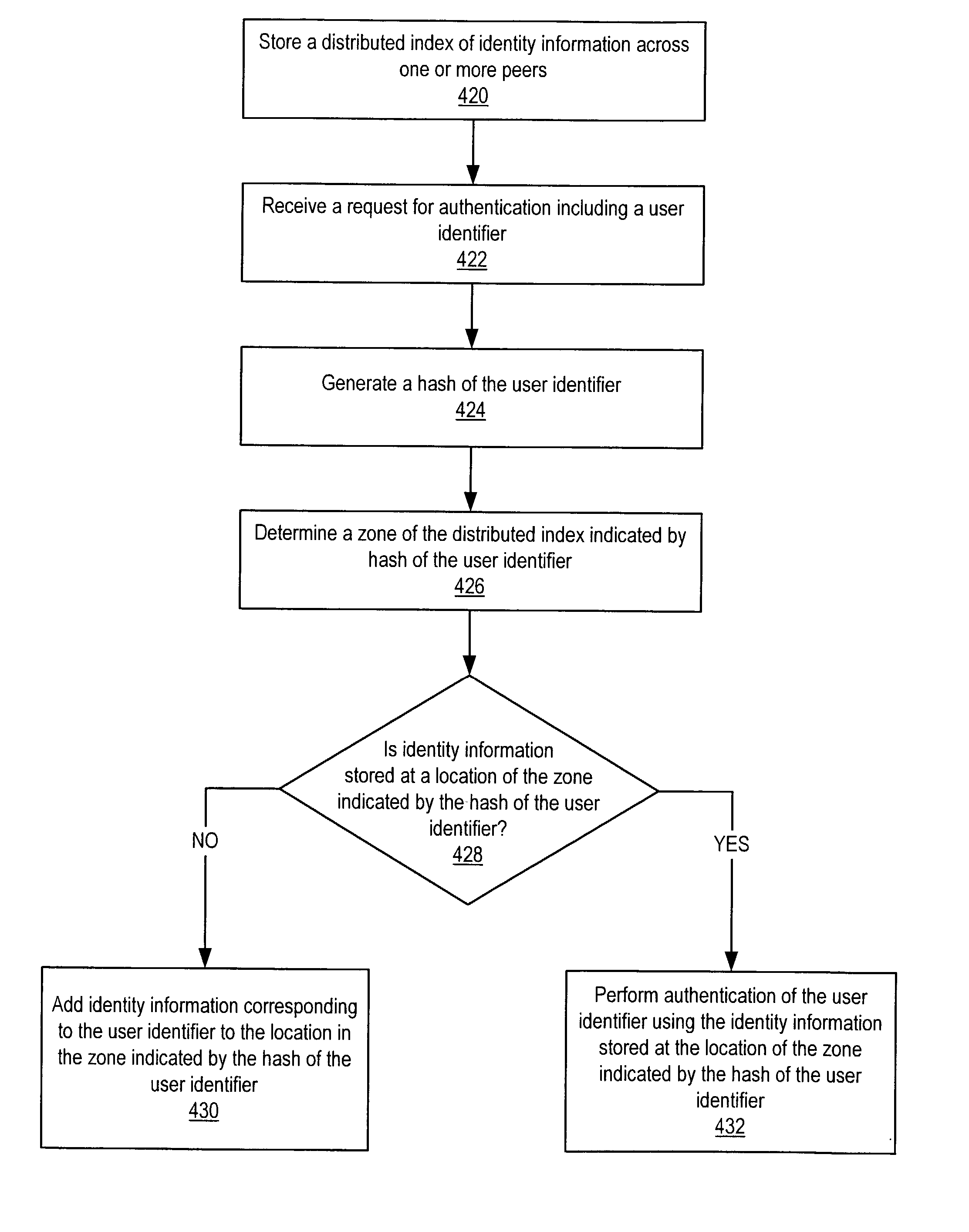
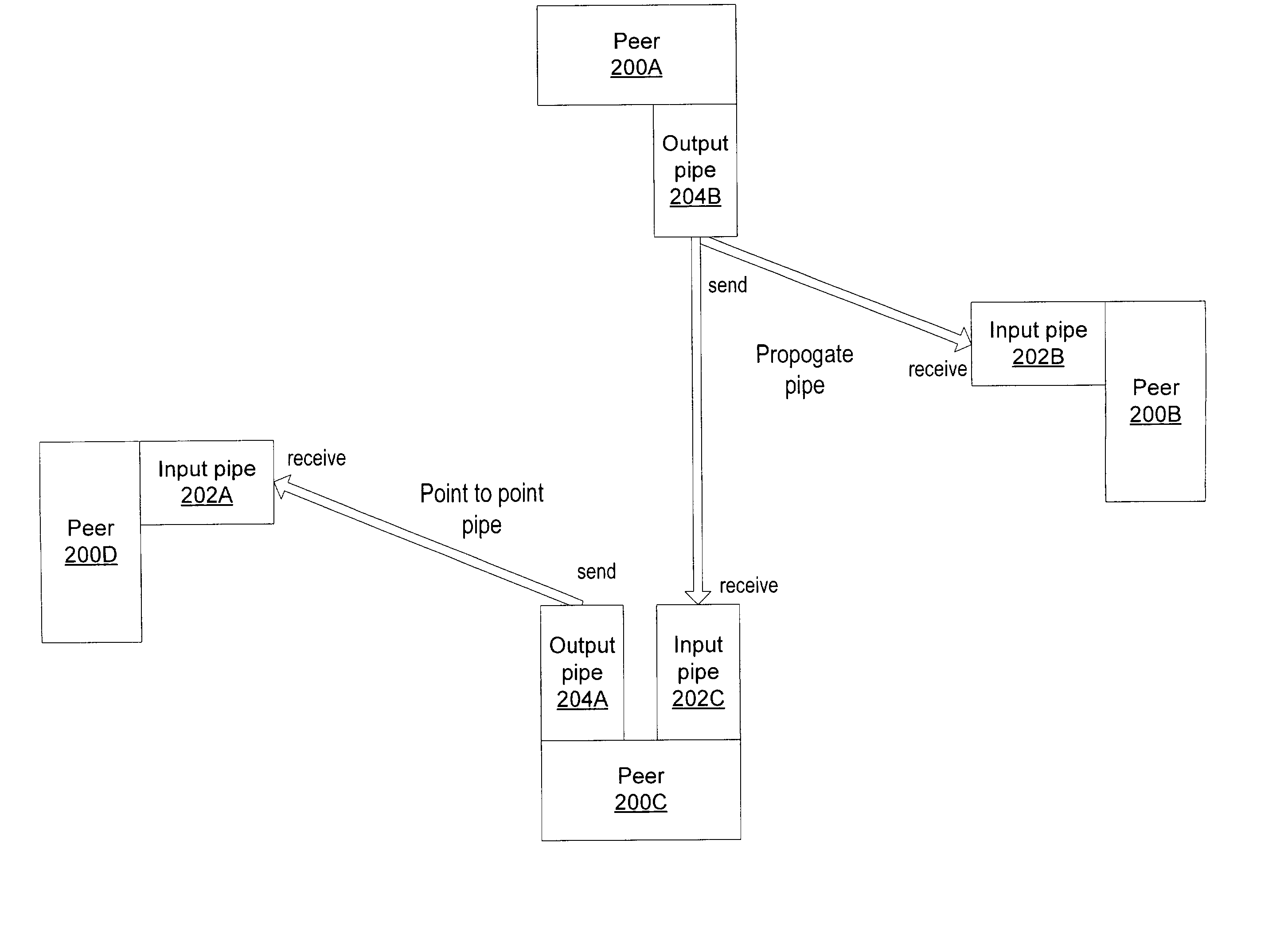
Distributed indexing of identity information in a peer-to-peer network
ActiveUS20040064693A1Digital data processing detailsUser identity/authority verificationDistributed indexDistributed hash table
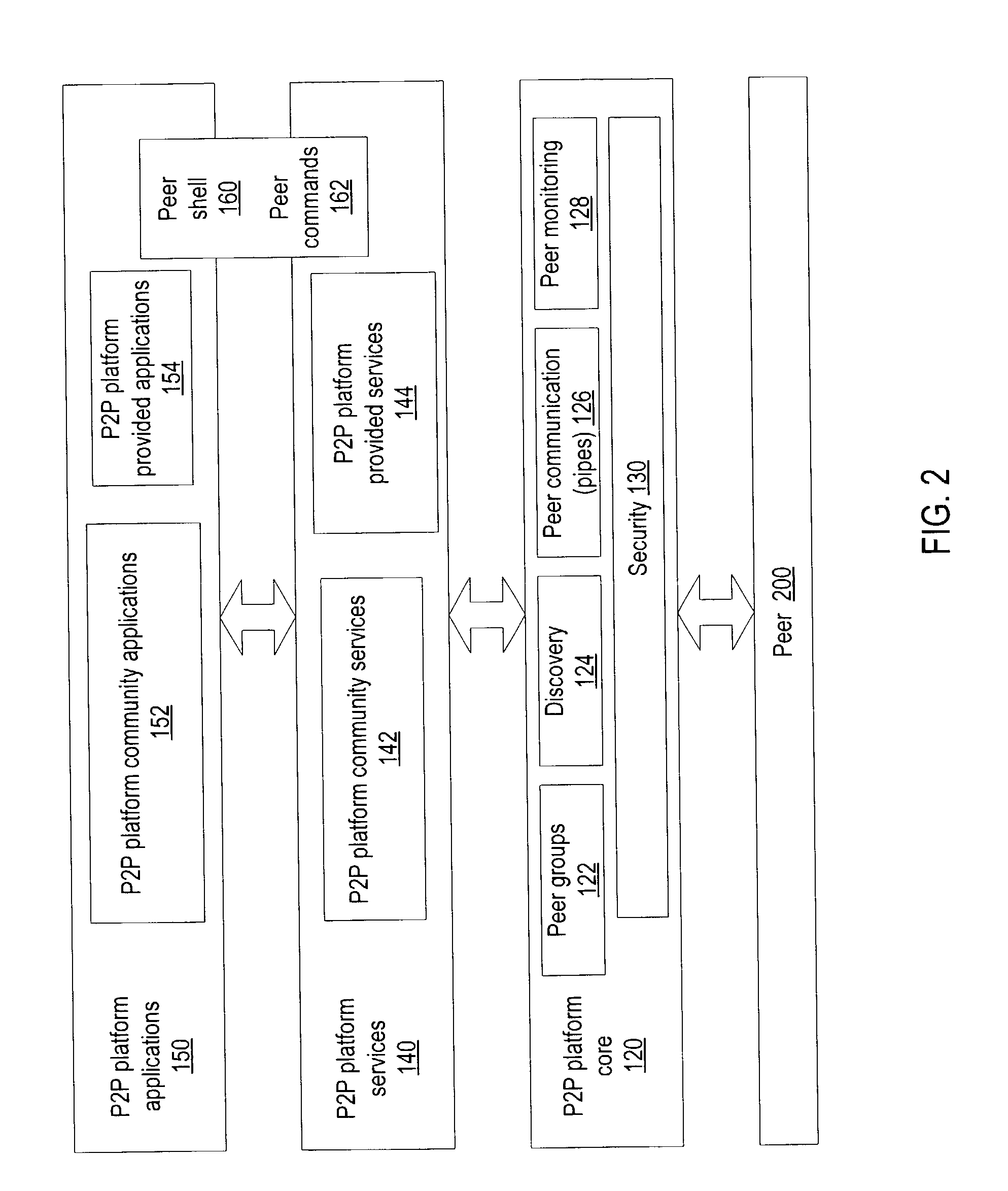
Embodiments of a distributed index mechanism for indexing and searching for identity information in peer-to-peer networks. In one embodiment, a distributed index may be used to store identity information in a decentralized manner on a plurality of peer nodes. The identity information may be used, for example, to authenticate users. Distributed indexes may allow identity information to be spread across multiple peer nodes so that the load is spread among the various peer nodes. In one embodiment, the distributed index may be a distributed hash table. One embodiment of a distributed index of identity information may be implemented in peer-to-peer networks implemented according to a peer-to-peer platform including one or more peer-to-peer platform protocols for enabling peer nodes to discover each other, communicate with each other, and cooperate with each other to form peer groups and share network resources.
Owner:ORACLE INT CORP
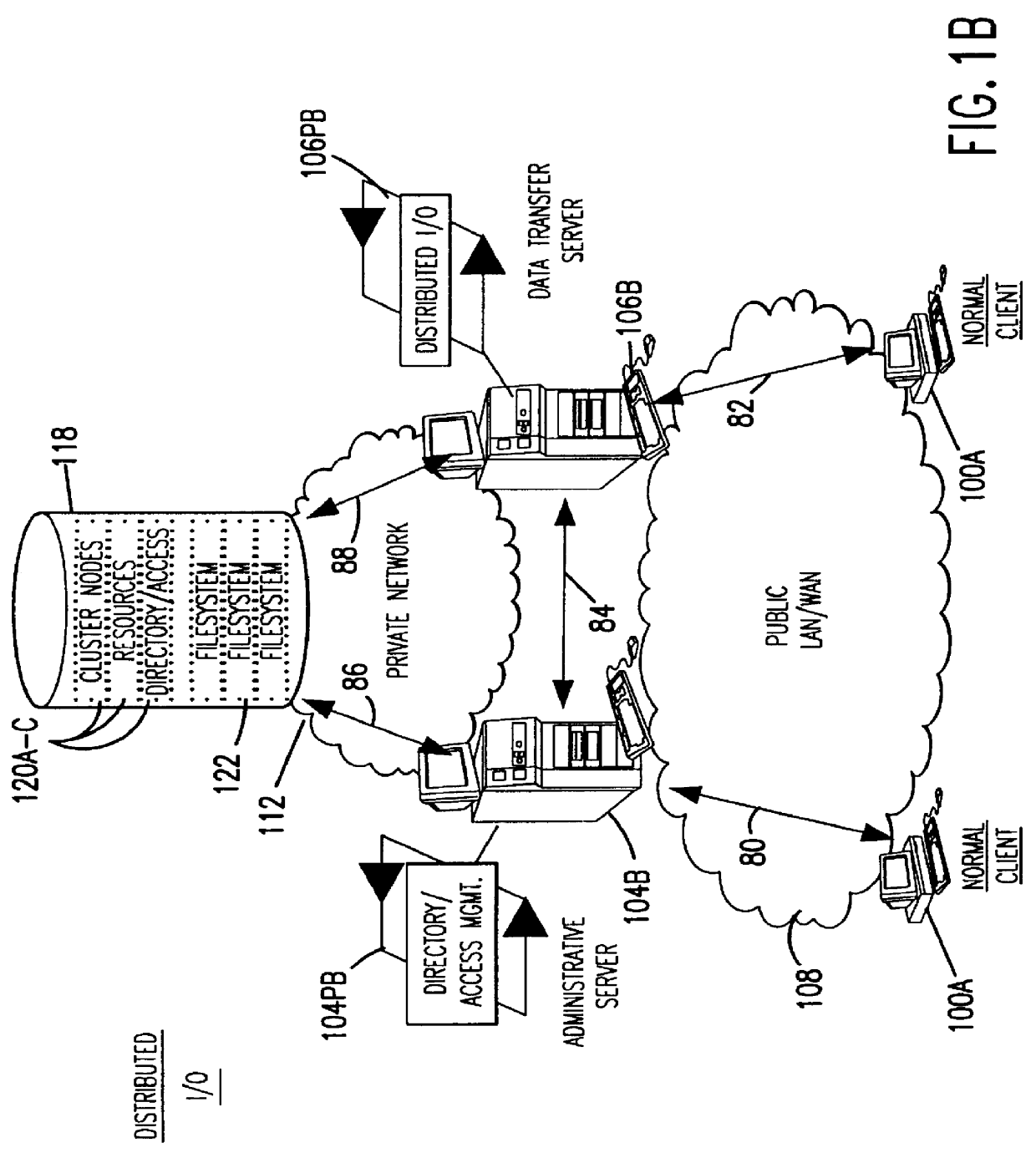
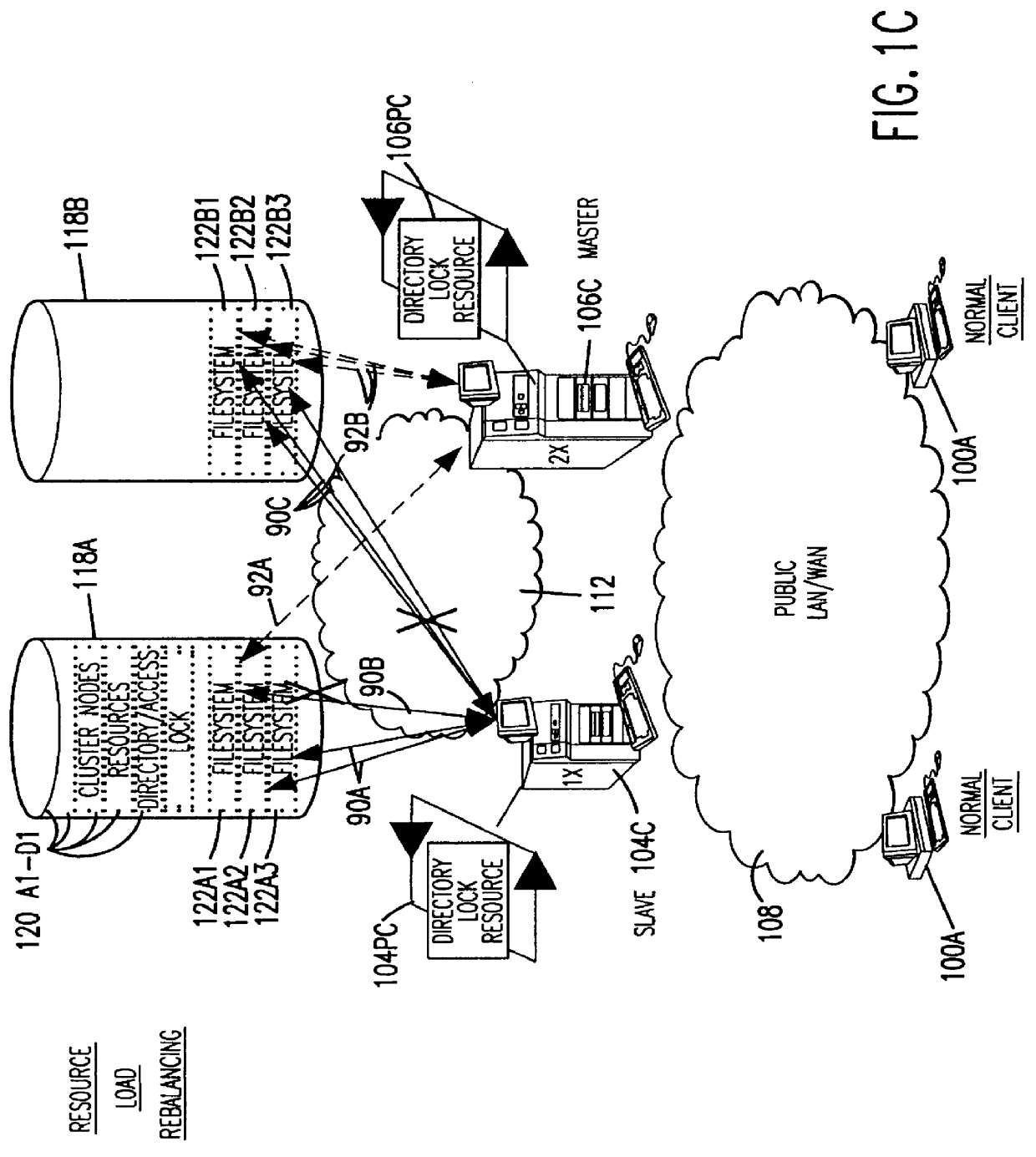
Clustered file management for network resources
InactiveUS6101508AData processing applicationsProgram synchronisationFile systemClustered file system
Methods for operating a network as a clustered file system is disclosed. The methods involve client load rebalancing, distributed Input and Output (I / O) and resource load rebalancing. Client load rebalancing refers to the ability of a client enabled with processes in accordance with the current invention to remap a path through a plurality of nodes to a resource. Distributed I / O refers to the methods on the network which provide concurrent input / output through a plurality of nodes to resources. Resource rebalancing includes remapping of pathways between nodes, e.g. servers, and resources, e.g. volumes / file systems. The network includes client nodes, server nodes and resources. Each of the resources couples to at least two of the server nodes. The method for operating comprising the acts of: redirecting an I / O request for a resource from a first server node coupled to the resource to a second server node coupled to the resource; and splitting the I / O request at the second server node into an access portion and a data transfer portion and passing the access portion to a corresponding administrative server node for the resource, and completing at the second server nodes subsequent to receipt of an access grant from the corresponding administrative server node a data transfer for the resource. In an alternate embodiment of the invention the methods may additionally include the acts of: detecting a change in an availability of the server nodes; and rebalancing the network by applying a load balancing function to the network to re-assign each of the available resources to a corresponding available administrative server node responsive to the detecting act.
Owner:HEWLETT-PACKARD ENTERPRISE DEV LP
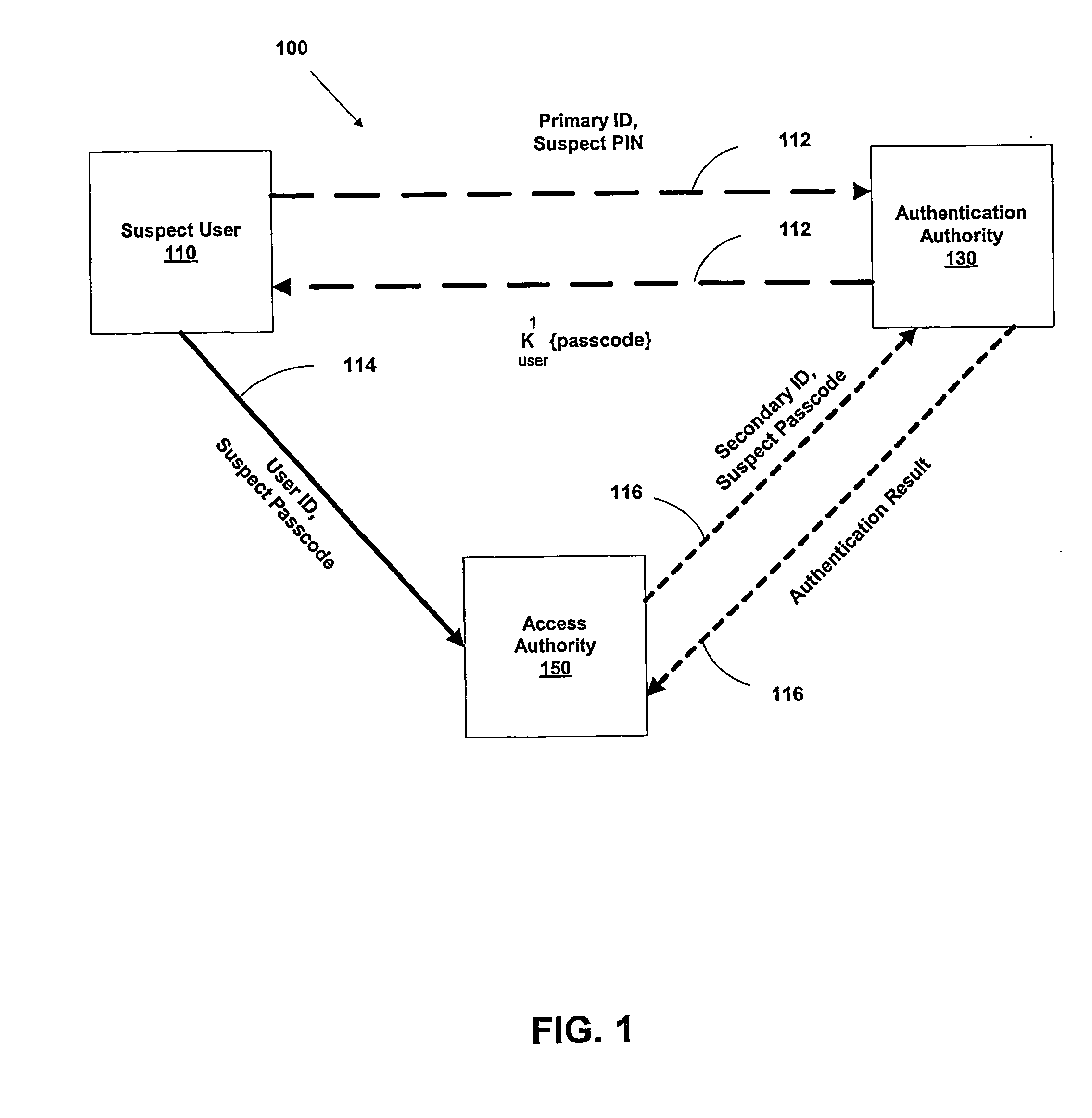
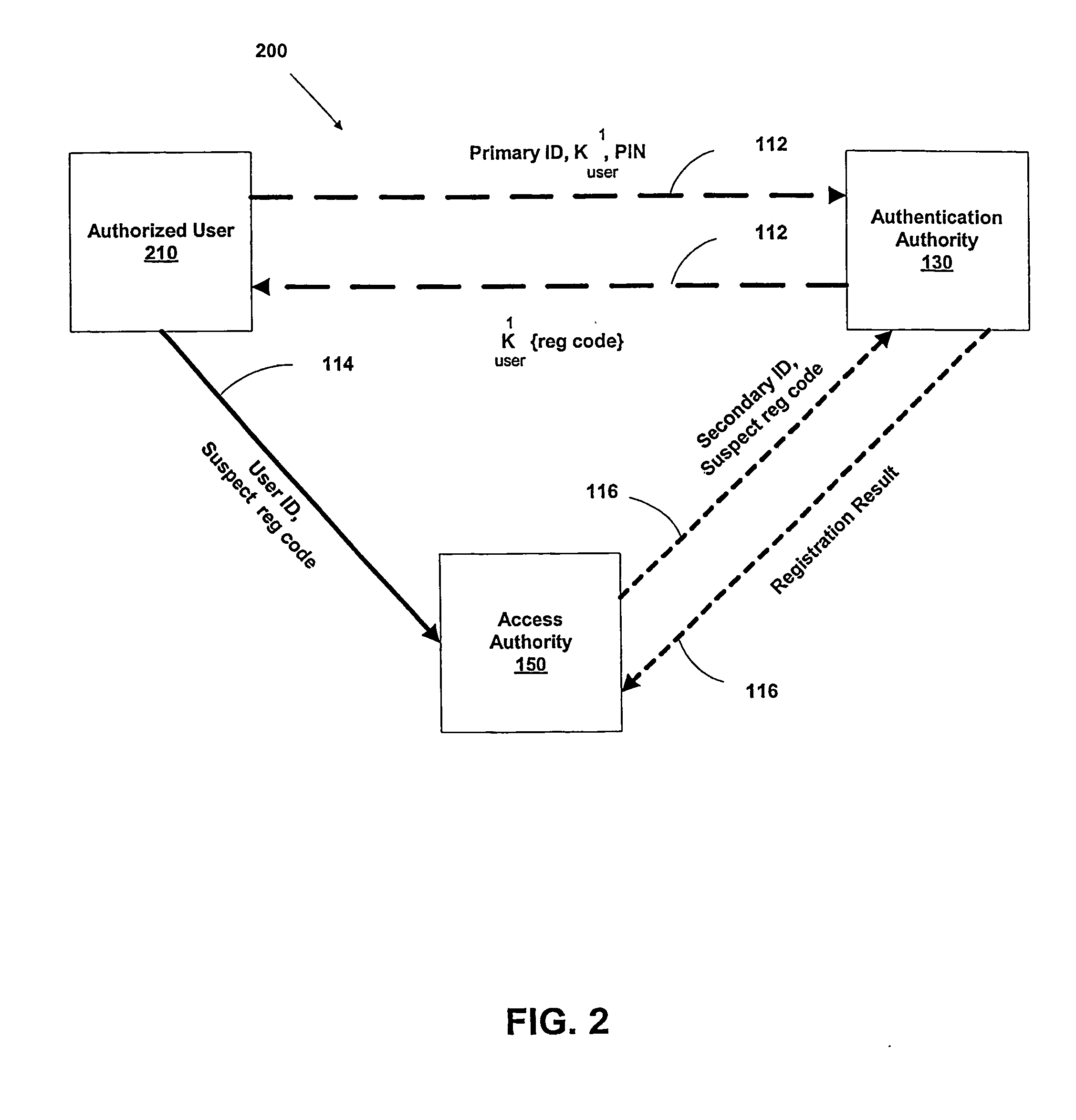
Multi-factor authentication system
InactiveUS20040187018A1Easy to understandUser identity/authority verificationUnauthorized memory use protectionPasswordUser identifier
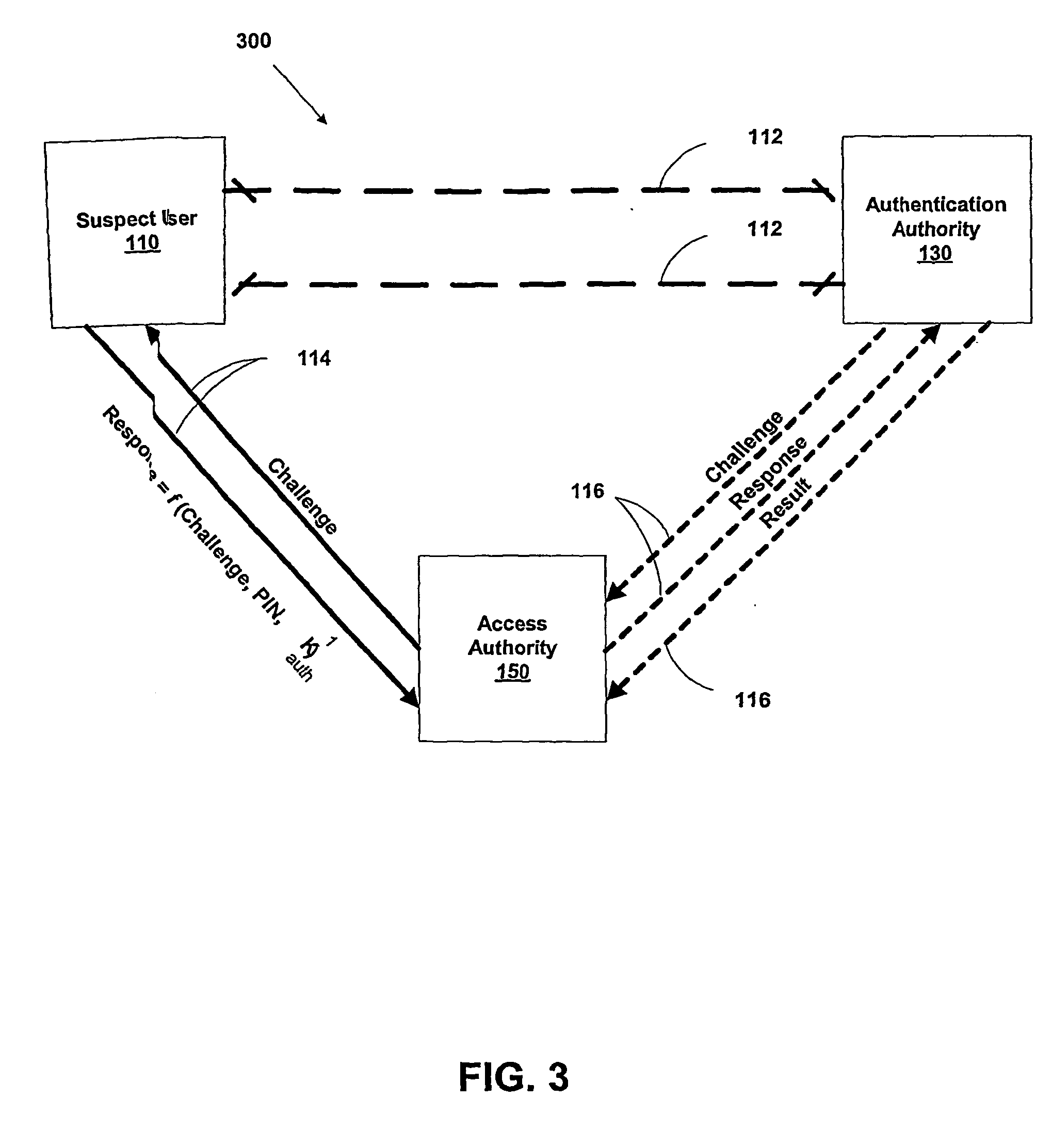
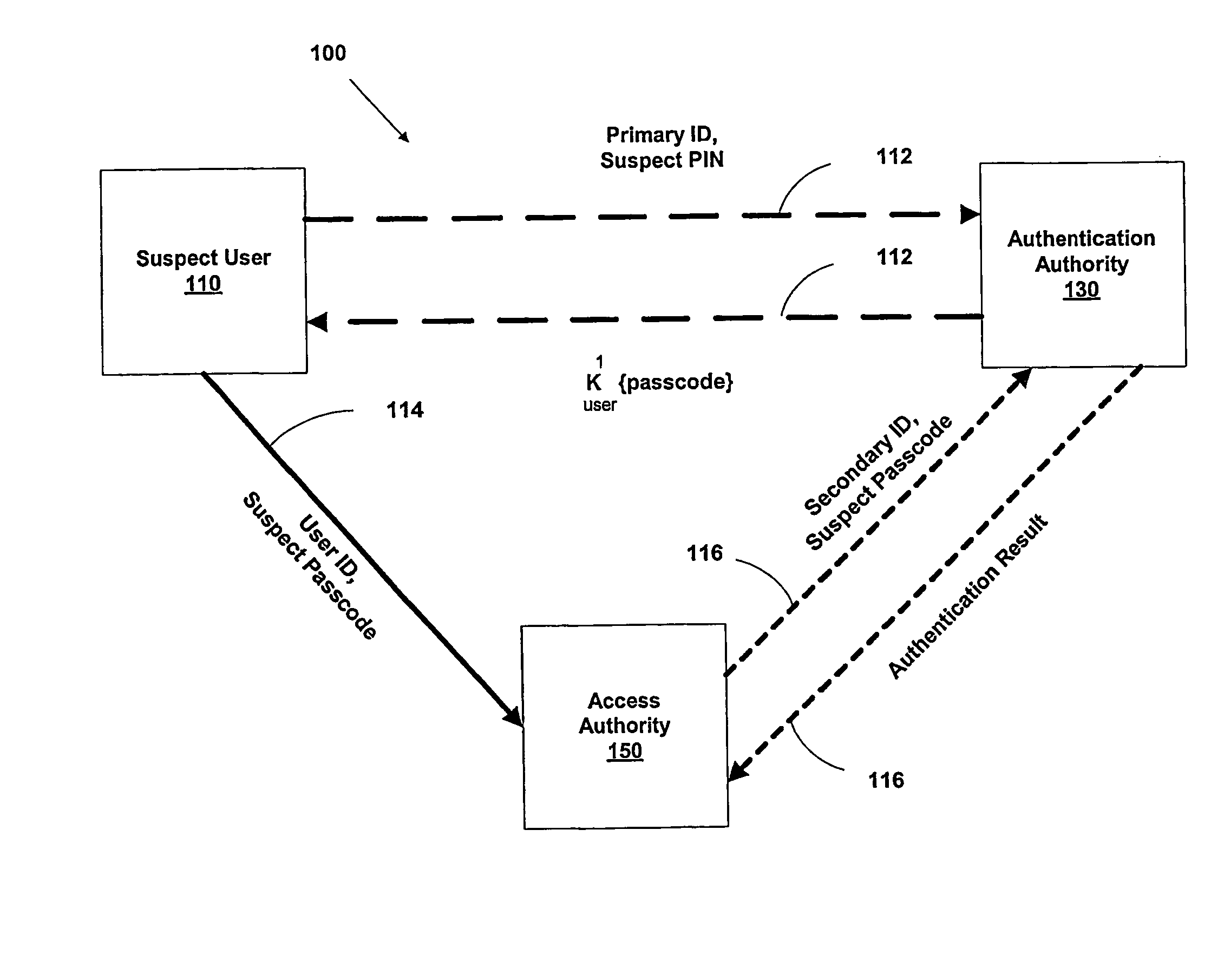
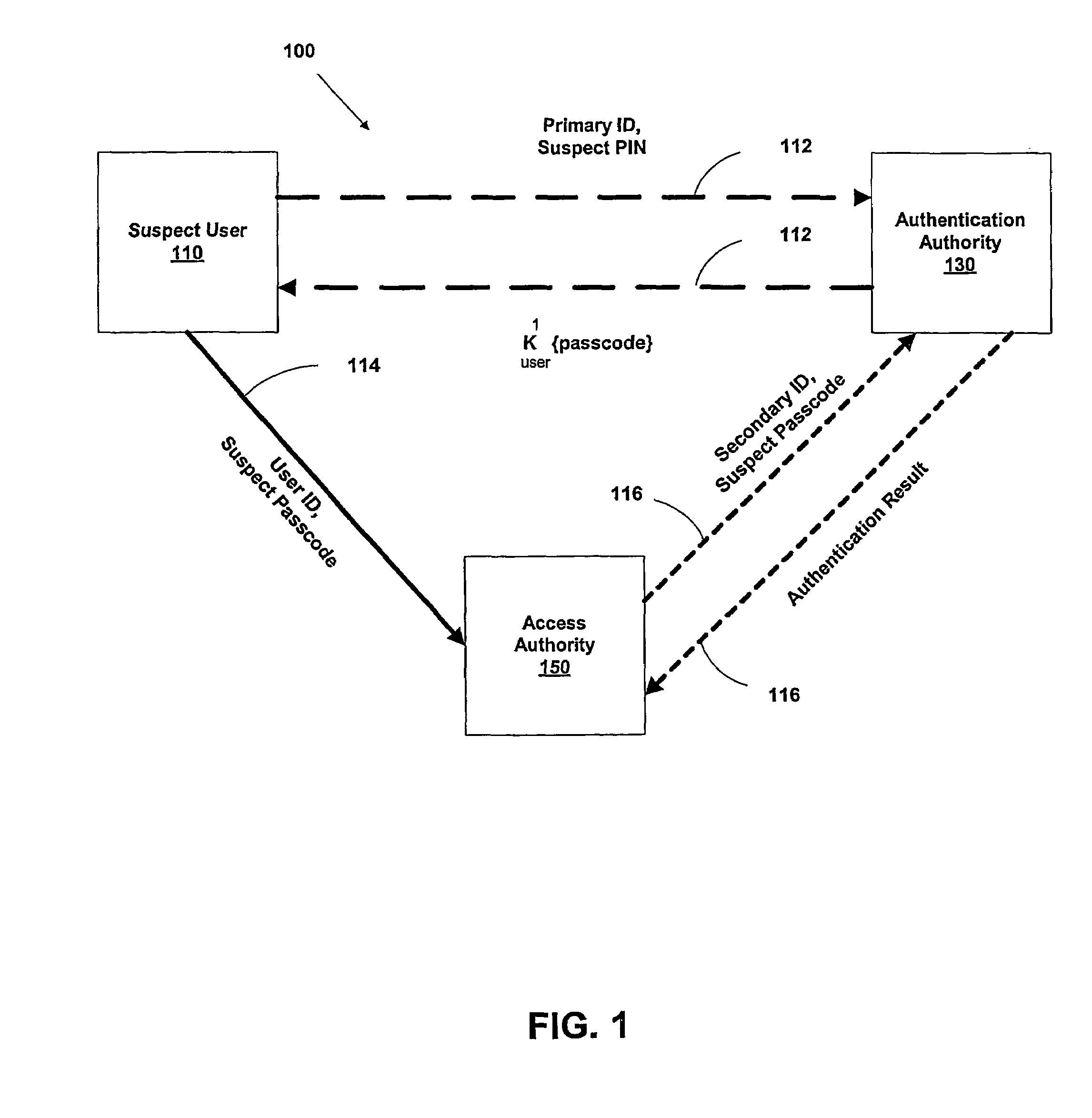
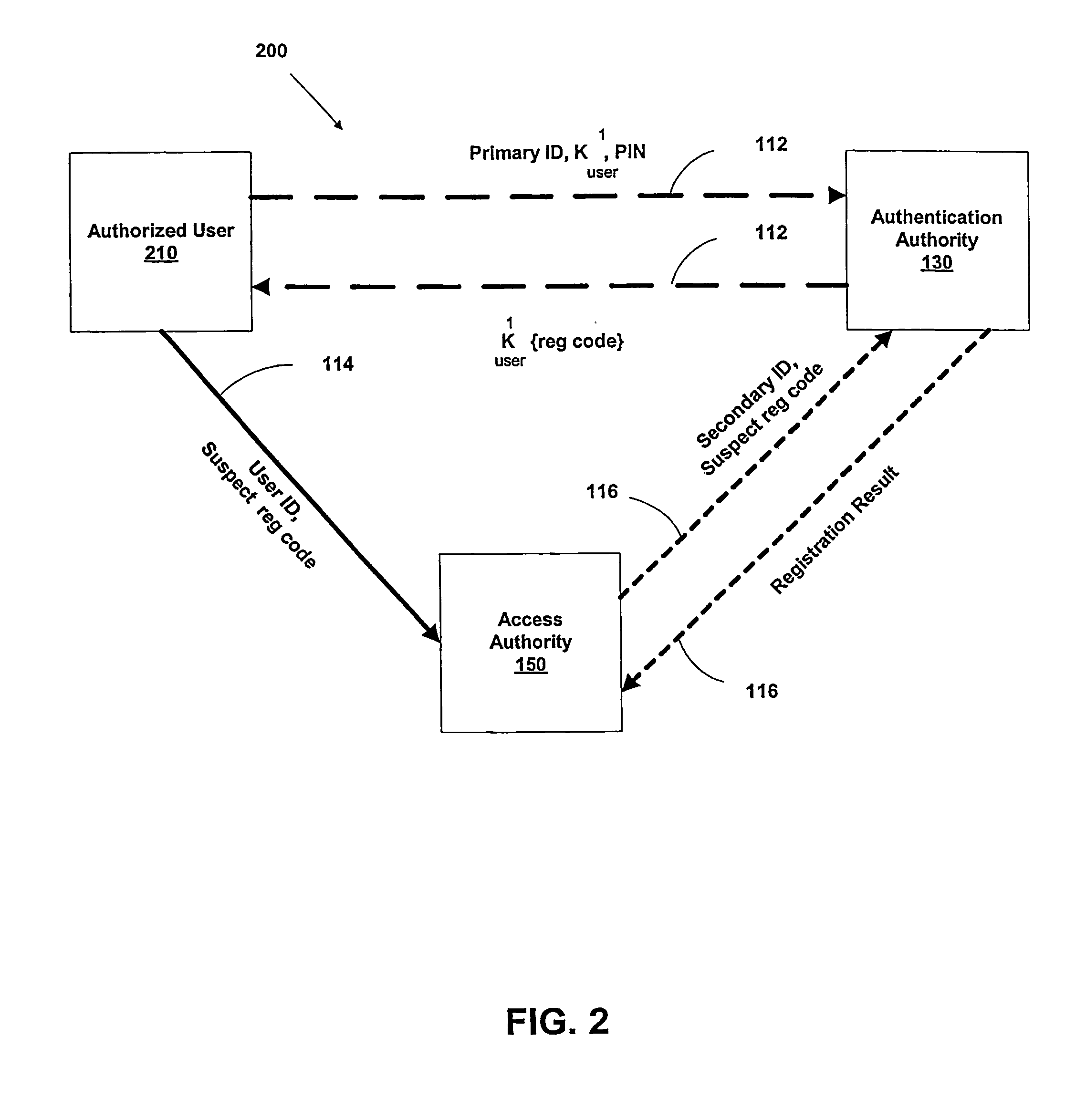
A suspect user (110) seeks access to a network resource from an access authority (150) utilizing a passcode received from an authentication authority (130). Initially, an ID of a device is bound with a PIN, the device ID is bound with a private key of the device, and the device ID is bound with a user ID that has been previously bound with a password of an authorized user. The device ID is bound with the user ID by authenticating the user ID using the password. Thereafter, the suspect user communicates the device ID and the PIN from the device over an ancillary communications network (112); the authentication authority responds back over the ancillary communications network with a passcode encrypted with the public key of the device; and the suspect user decrypts and communicates over a communications network (114) the passcode with the user ID to the access authority.
Owner:KARETEK HLDG LLC
Systems and methods for monitoring data and bandwidth usage
ActiveUS20100017506A1Assess restrictionMultiple digital computer combinationsResource consumptionResource utilization
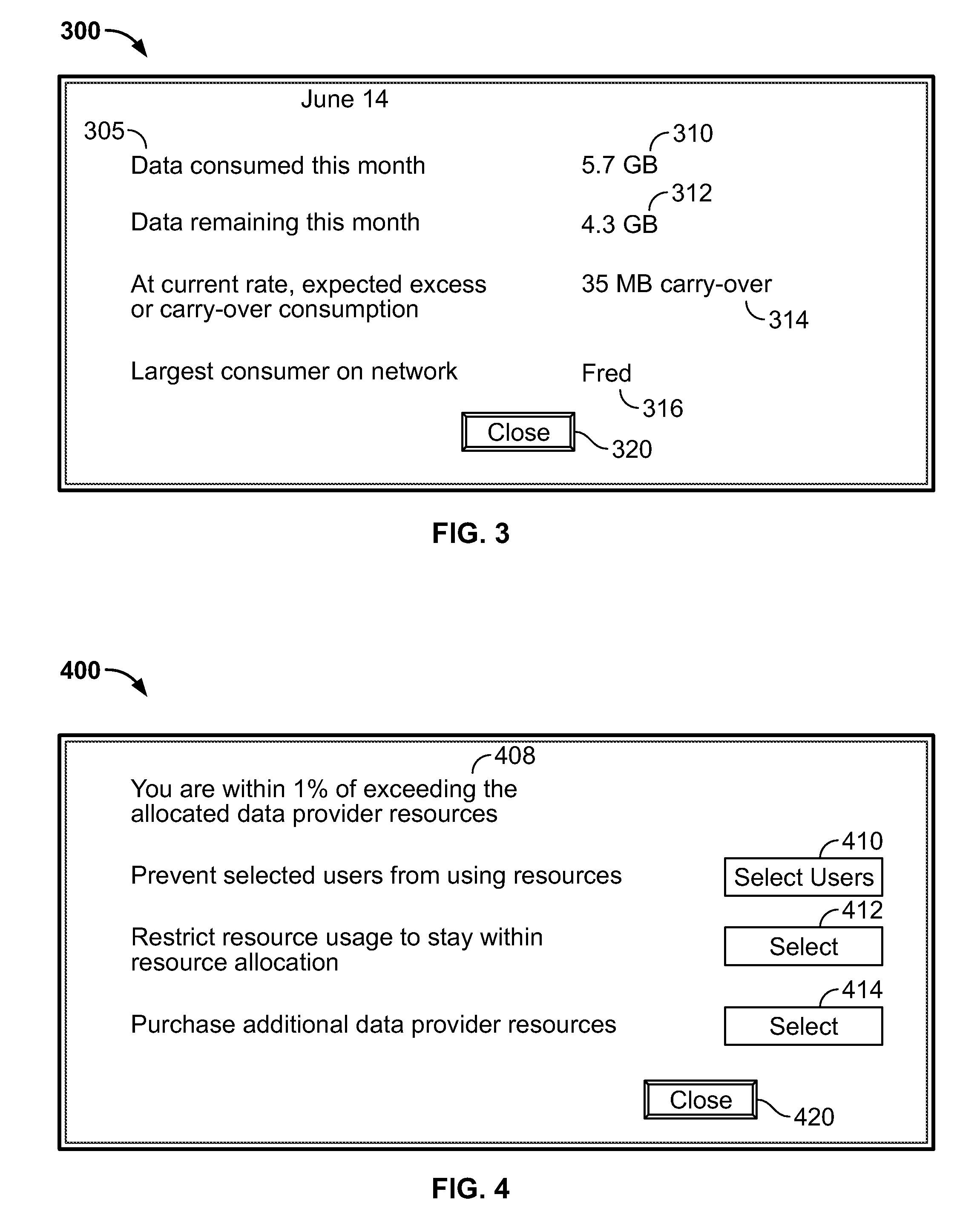
Access to a communications network may be provided via a data provider that may charge for access. In some cases, the access fee may be related to the amount of network resources consumed (e.g., amount of data downloaded or bandwidth used). In some cases, a user may have access to a particular amount of data provider resources and be required to pay an additional fee for using resources in excess of the particular amount. To assist the user in managing his data resource consumption, a resource utilization component may provide different alerts and notices informing the user of current consumption, expected future consumption, and recommendations for reducing data provider resources consumed (e.g., stopping particular processes or data provider requests, such as downloading media). If several electronic devices in a network are connected to the same data provider resources, a network component may manage the data provider resource use among the several electronic devices (e.g., allow only particular users or devices access).
Owner:APPLE INC
Presence detection using distributed indexes in peer-to-peer networks
ActiveUS20040064568A1User identity/authority verificationMultiple digital computer combinationsDistributed indexPeer-to-peer
Embodiments of a distributed index mechanism for indexing and searching for presence information in peer-to-peer networks. In one embodiment, a distributed index may be used to store presence information in a decentralized manner on a plurality of peer nodes. In one embodiment, a notification service may be implemented on top of the distributed index to notify peers of other peers joining a peer-to-peer session. Participating peers may query the distributed index to detect the presence of other participating peers registered in the distributed index. One embodiment of a distributed index of presence information may be implemented in peer-to-peer networks implemented according to a peer-to-peer platform including one or more peer-to-peer platform protocols for enabling peer nodes to discover each other, communicate with each other, and cooperate with each other to form peer groups and share network resources.
Owner:ORACLE INT CORP
Method and apparatus for performing data flow ingress/egress admission control in a provider network
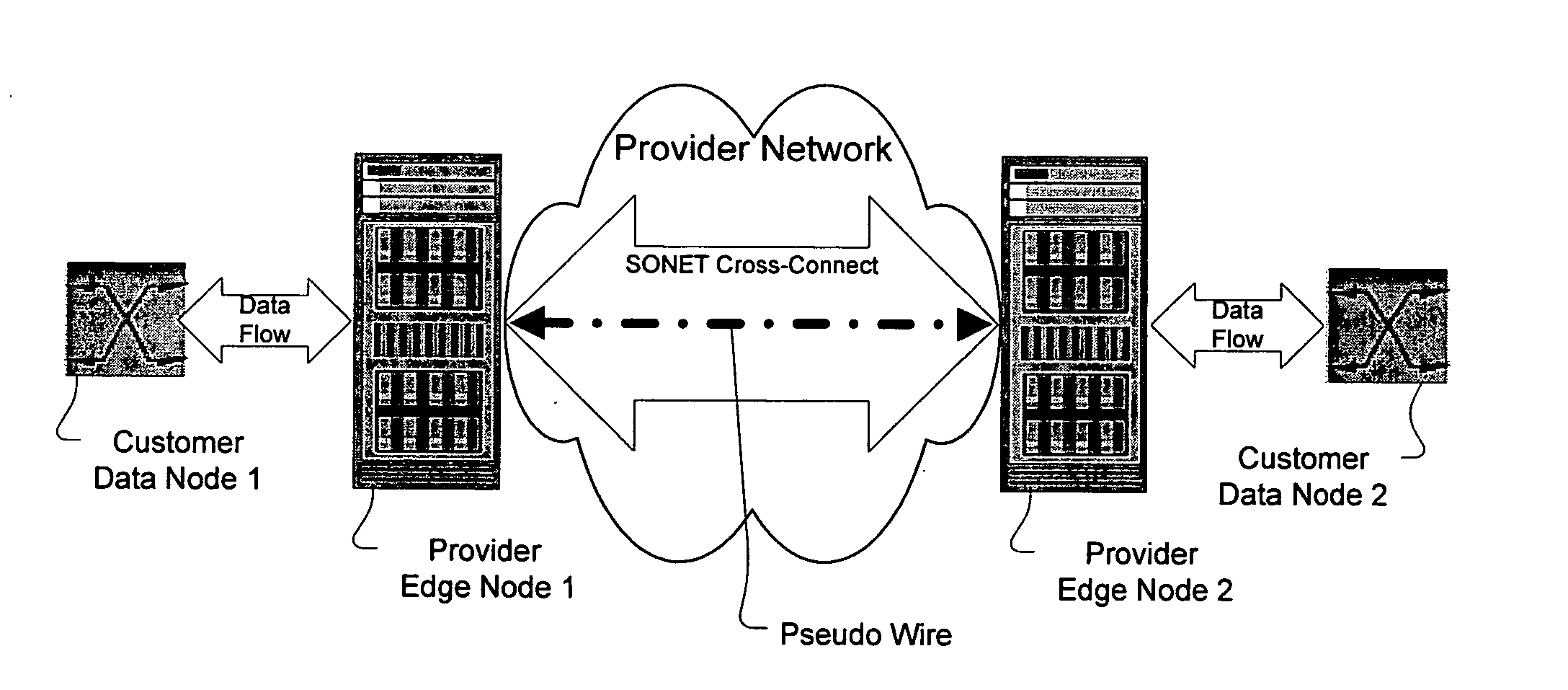
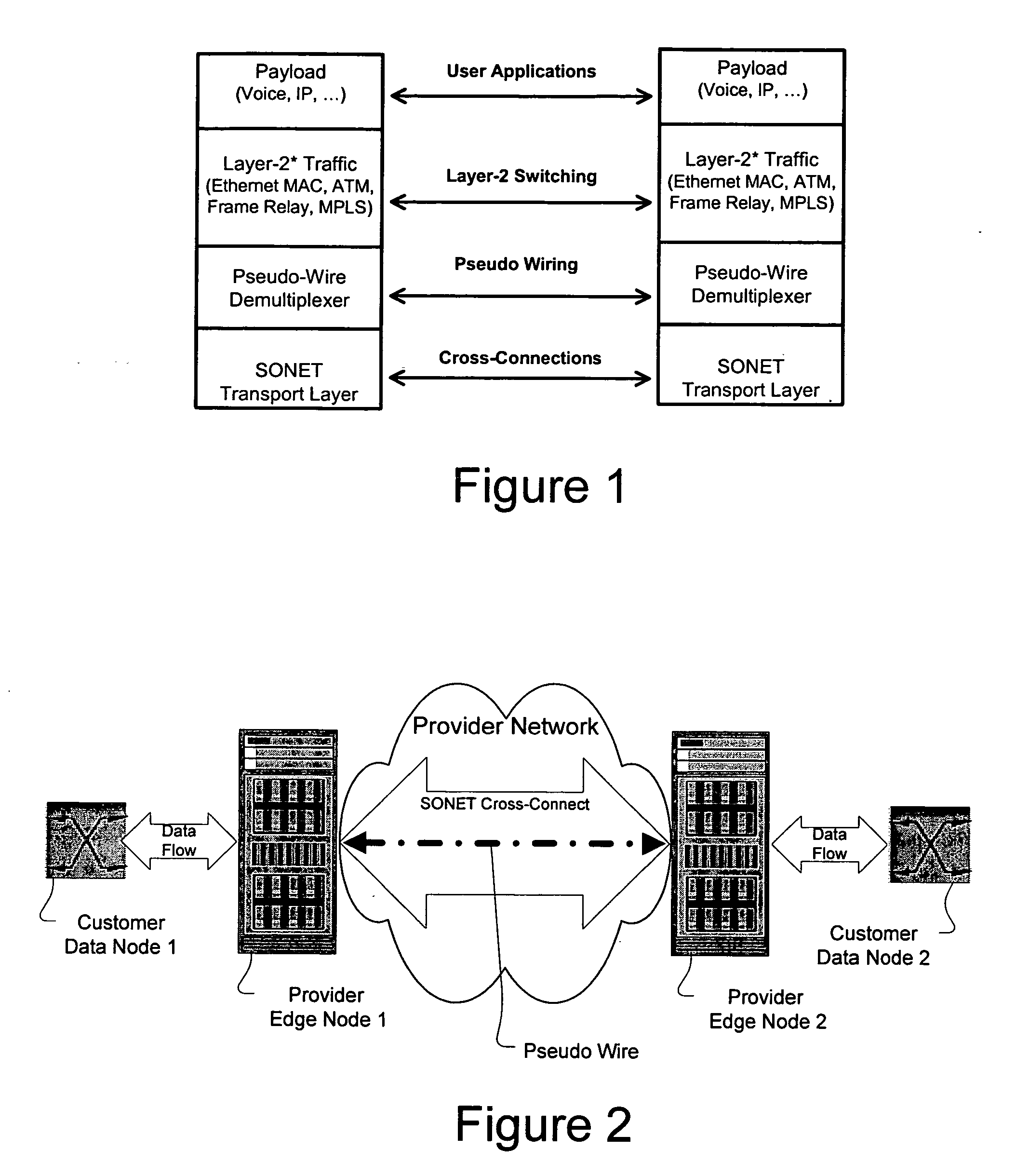
A method, apparatus and network for transporting layer-2 frames, such as Ethernet MAC, ATM AAL5, and Frame Relay, over MPLS, SONET / SDH, or OTN optical transport networks as well as electrical transport networks is disclosed. The method establishes "pseudo-wires" between, for example, routers, Layer-2 packet switches, or SONET / SDH switches. Inter-related ingress and egress resource tables may be used by provider edge nodes to negotiate consistently managed data tunnels across a provider network on behalf of data flowing from / to a diverse base of customer edge nodes. Detailed network resource information particular to each of the data flows is exchanged between provider edge nodes during the creation of pseudo-wires. Admission control algorithms are applied at the ingress and egress points in order to manage the data flows into a provider network and exiting from a provider network to customer equipment. By applying pseudo-wire shuffling and preemption techniques, the providers can make better use of their network resources by admitting more pseudo-wires.
Owner:CIENA
System and method for threat detection and response
InactiveUS20050018618A1Error preventionFrequency-division multiplex detailsNetwork packetDistributed computing
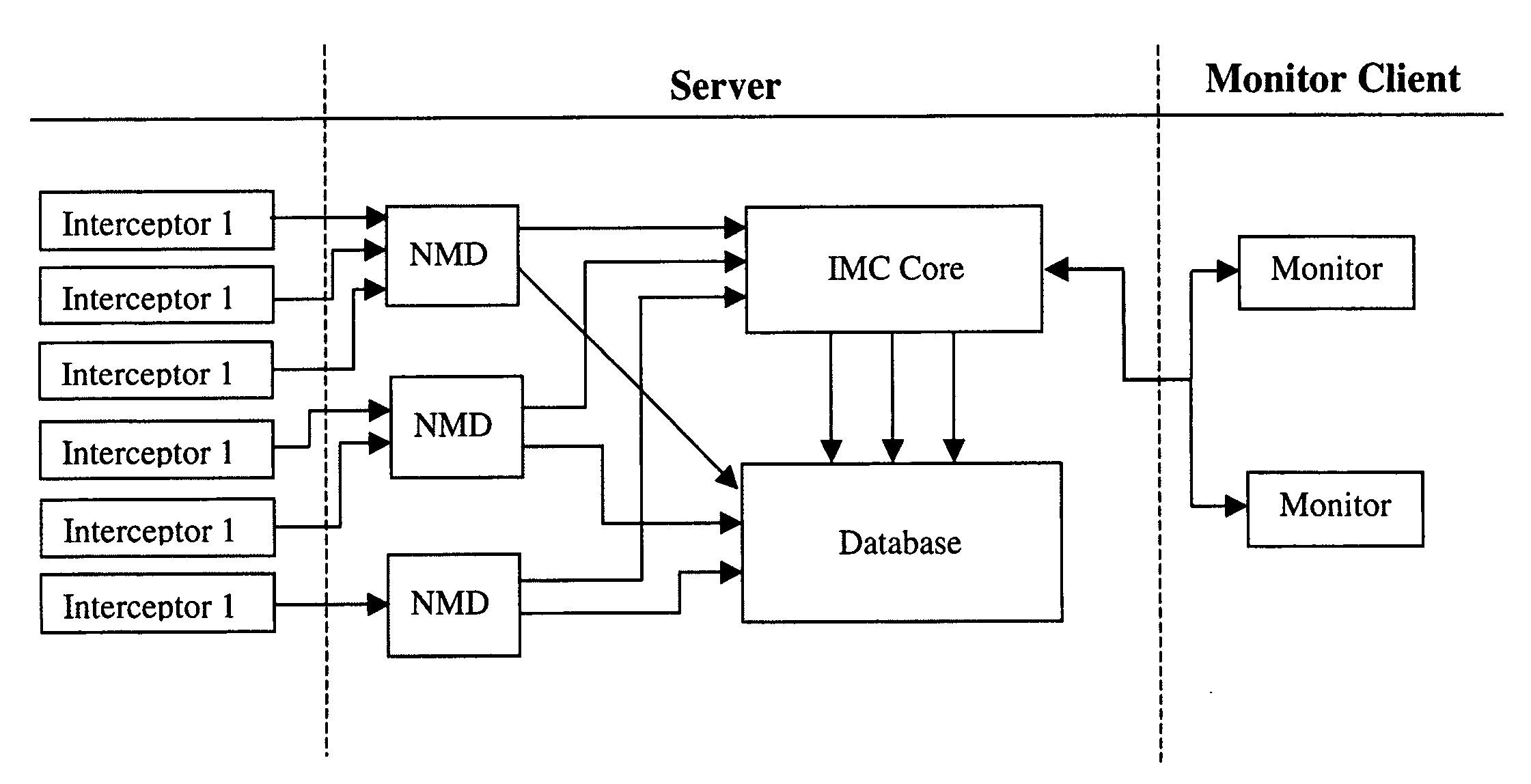
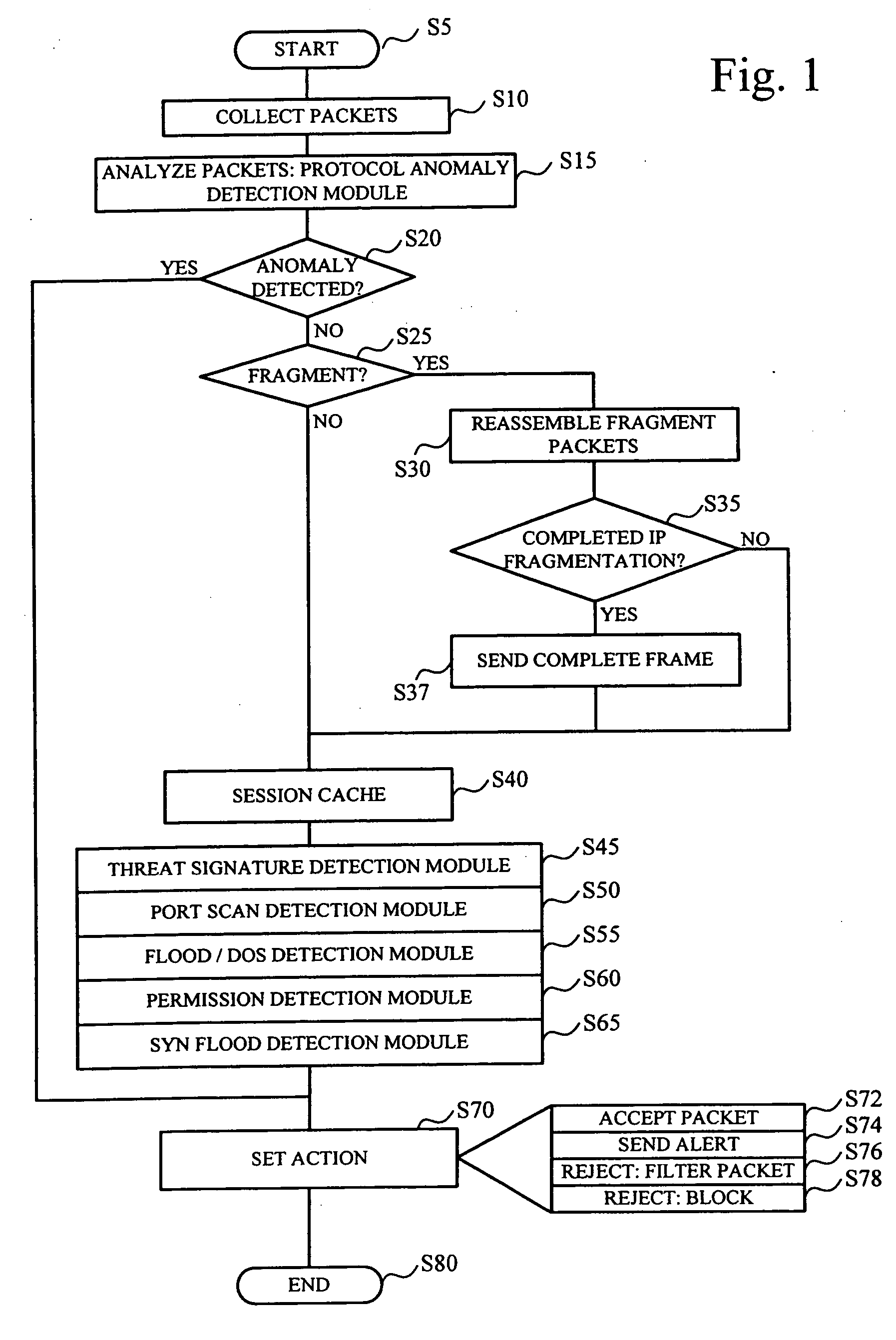
In accordance with varying embodiments of the invention, systems, devices and methods for analyzing a network packet received from a remote source and destined for a network resource, the network packet having associated packet data, and for identifying a plurality of network threats are disclosed.
Owner:STRATACLOUD
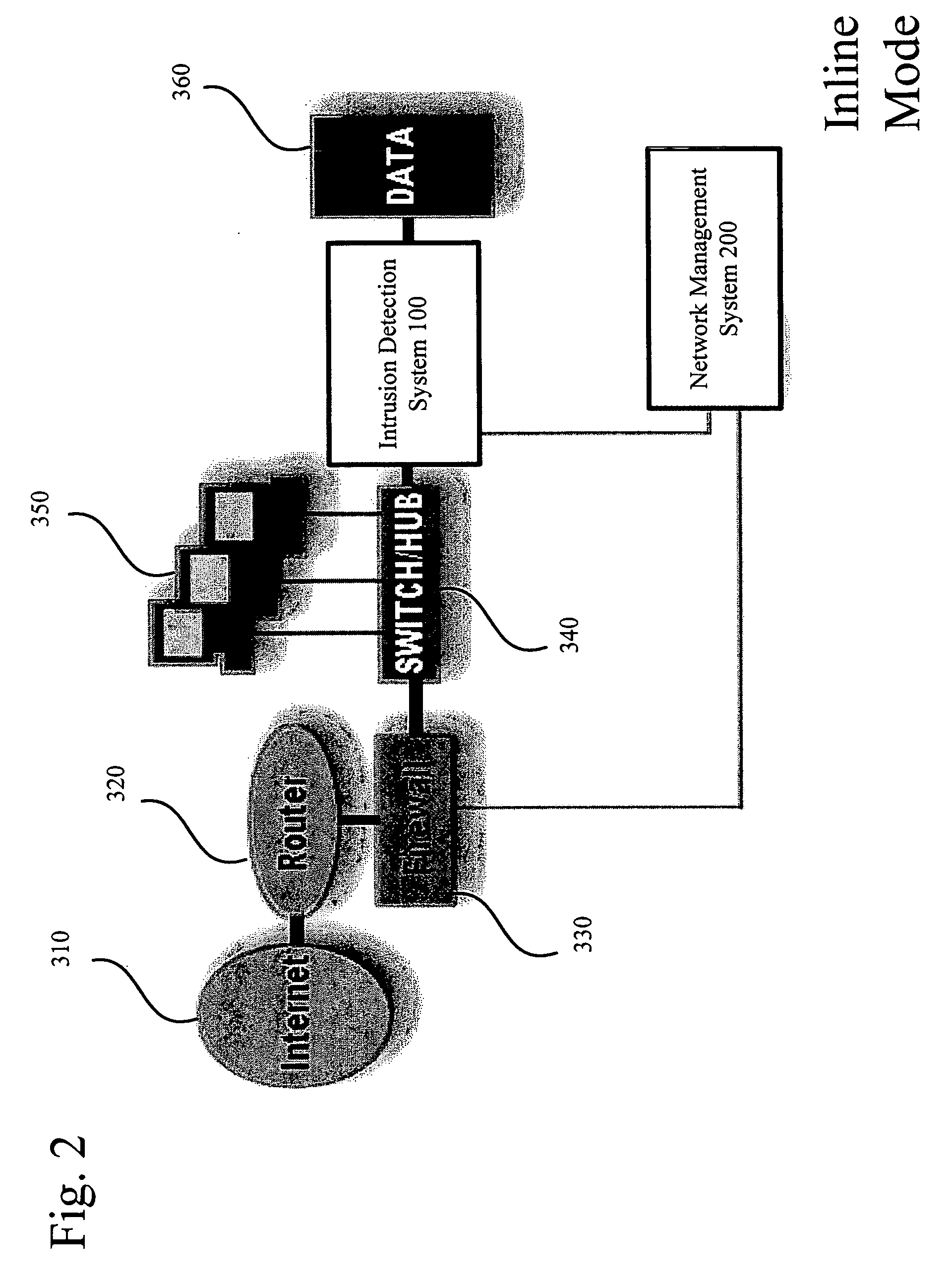
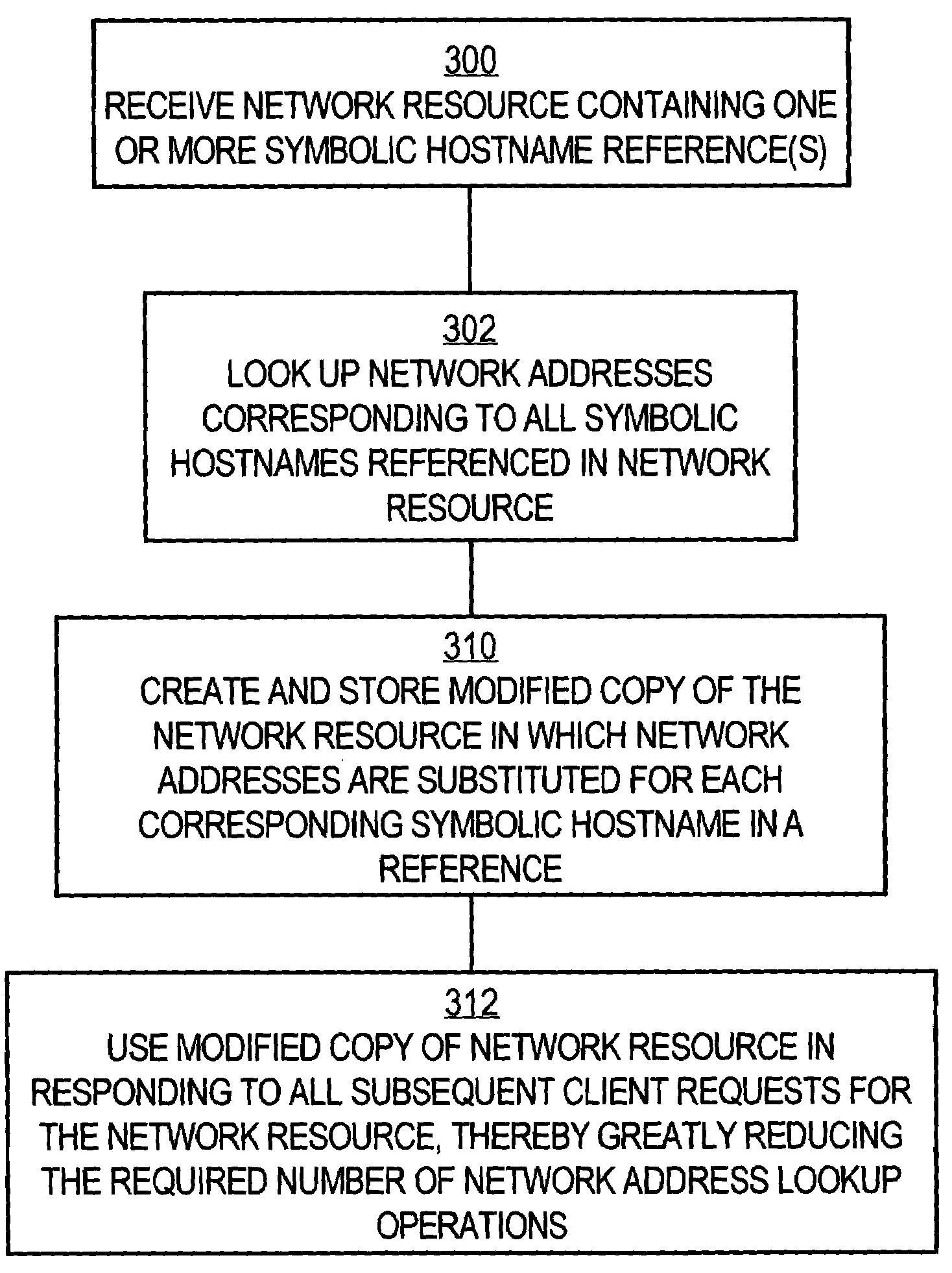
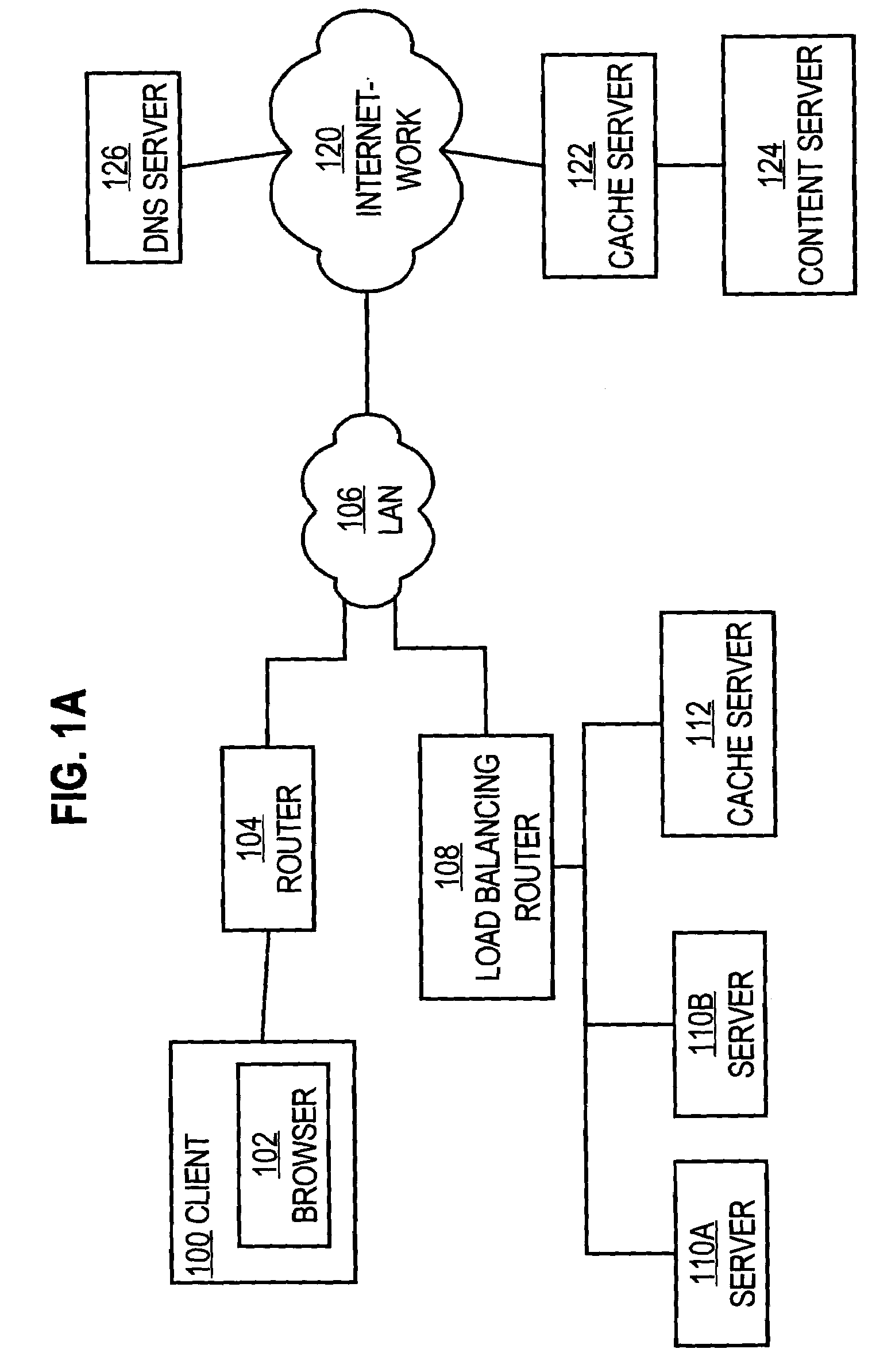
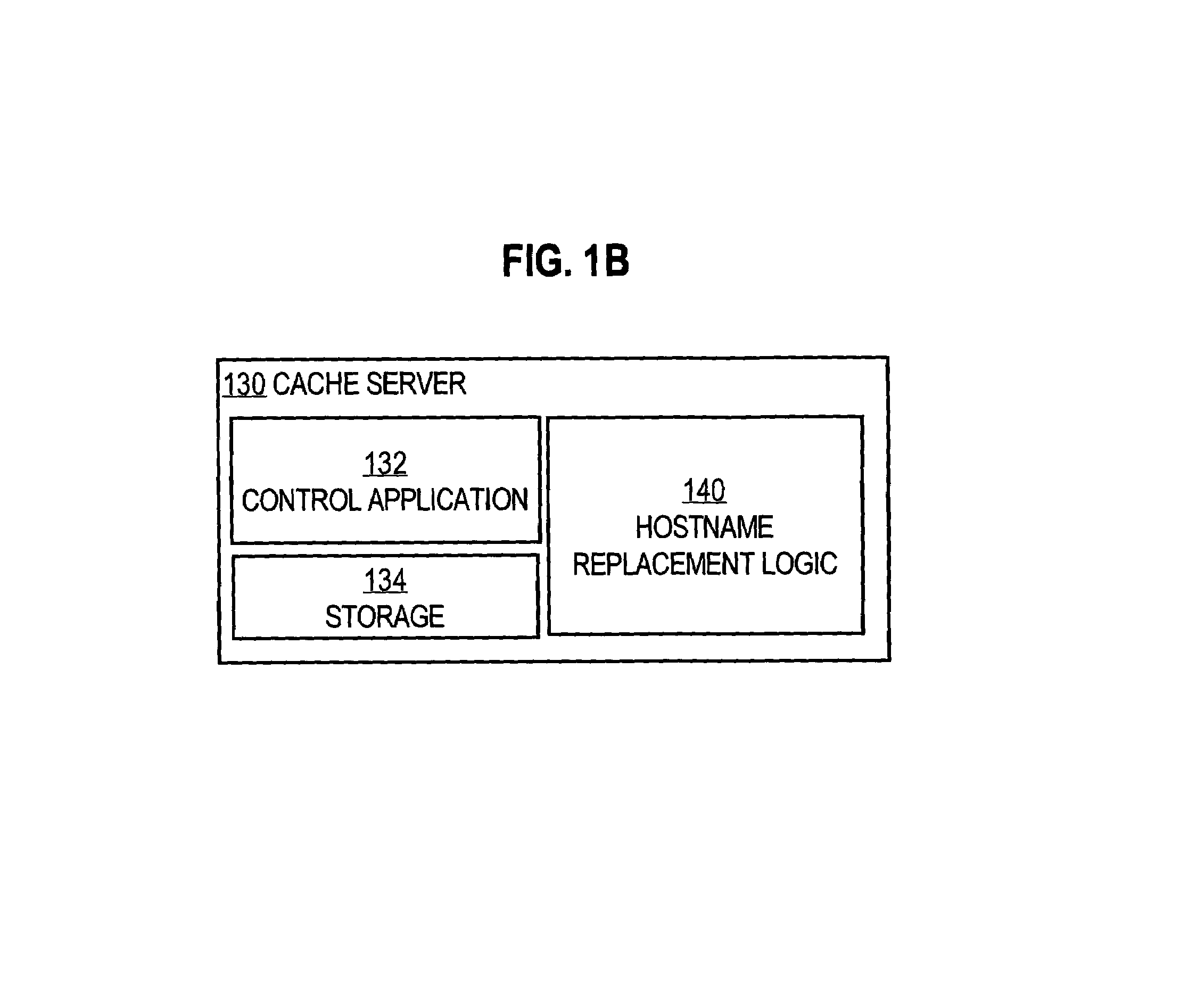
System and method of optimizing retrieval of network resources by identifying and substituting embedded symbolic host name references with network addresses in accordance with substitution policies
InactiveUS7082476B1Reduce in quantityEasy accessMultiple digital computer combinationsTransmissionCache serverNetwork addressing
A method and apparatus are provided for optimizing retrieval of network resources. In one embodiment, a method of optimizing access to a network resource is implemented in a computer program executed by a router, cache server, or proxy server. A network resource that contains one or more embedded symbolic host name references is received. A network address corresponding to each of the embedded symbolic host name references is determined. A modified copy of the network resource is created and stored; in the modified copy, a network address is substituted for each corresponding embedded symbolic host name reference. Thereafter, the modified copy of the network resource in responding to all subsequent client requests for the network resource, thereby greatly reducing the required number of network address lookup operations. In one specific embodiment, IP addresses are determined using DNS queries for the hostname portion of all URLs that are embedded in a Web page using image, applet, object, or embed tags. The IP addresses are stored in place of the hostname portions in a modified copy of the Web page, typically in a cache. As a result, when the modified page is subsequently served to clients, the clients need not carry out DNS resolution of all the embedded URLs, resulting in reduced network message traffic and more rapid page display.
Owner:CISCO TECH INC
Multi-factor authentication system
InactiveUS7373515B2User identity/authority verificationUnauthorized memory use protectionPasswordUser identifier
Owner:KARETEK HLDG LLC
Method for optimal path selection in traversal of packets through network address translators
InactiveUS20050259637A1Reduce administrative overheadFast convergenceMultiplex system selection arrangementsError preventionNetwork addressNetwork address translation
Reduction of administrative overhead in maintaining network information, rapid convergence on an optimal routing path through the data network, and utilization of only required network resources are realized by a novel method for establishing a call path between network users. The method is based upon deployment of a network information server that stores network topology information and that is addressable by each end user. In this method, the network information server receives a request to establish a call path. The request identifies at least the calling party. In response to the request, the network information server determines a network traversal between the calling party and a root network wherein the network traversal includes call path information about the sub-networks between the calling party and the root network. The request for establishing a call path can also identify the called party. Based on the calling and called party identification, the network information server also determines a second network traversal between the called party and the root network. The second network traversal is sent to either the calling party or the called party or to both the calling and called parties. The server can determine an intersection of the traversals and send the intersection information to the parties. The intersection information is known as a merge point and represents an optimal call path between the parties.
Owner:ALCATEL-LUCENT USA INC
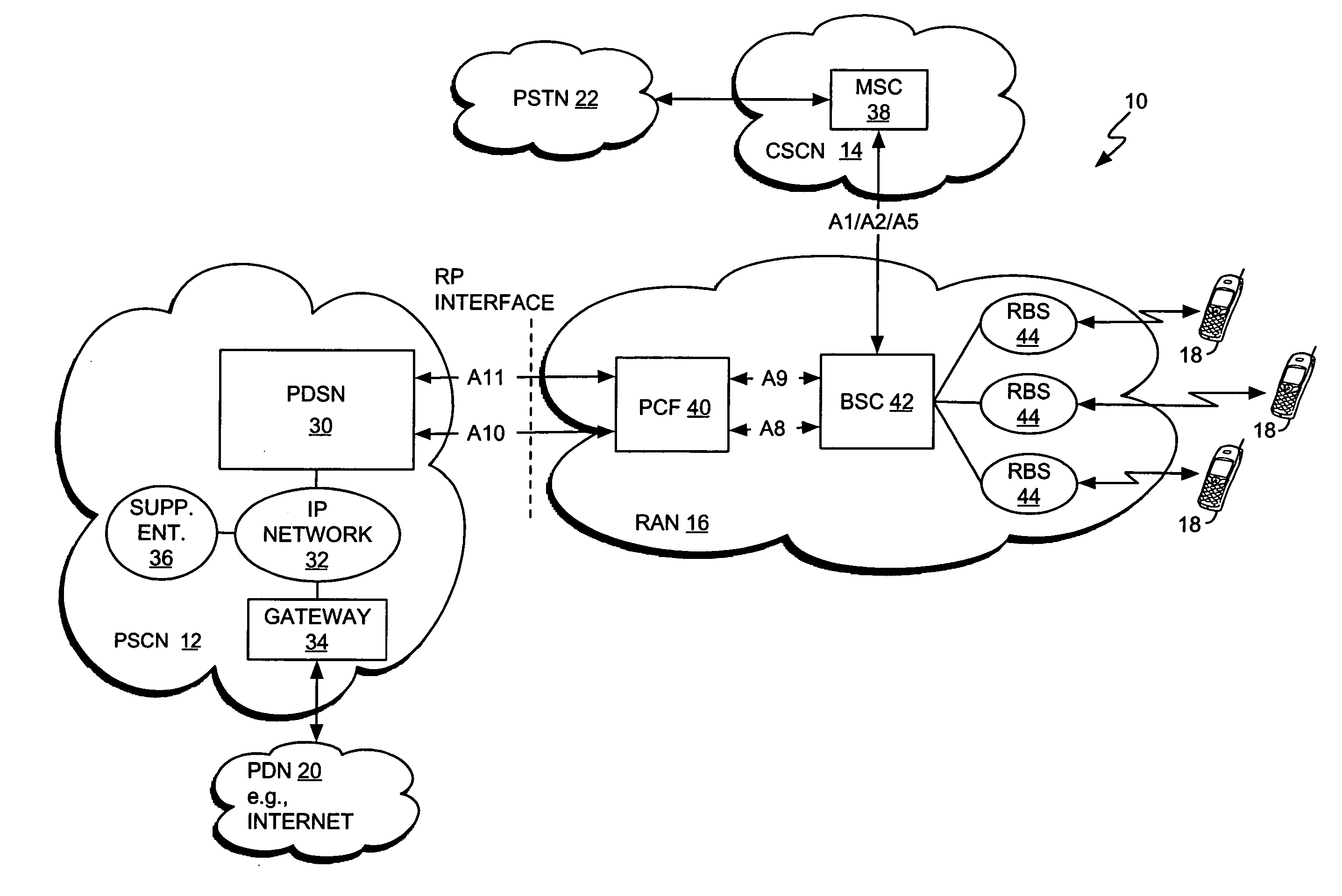
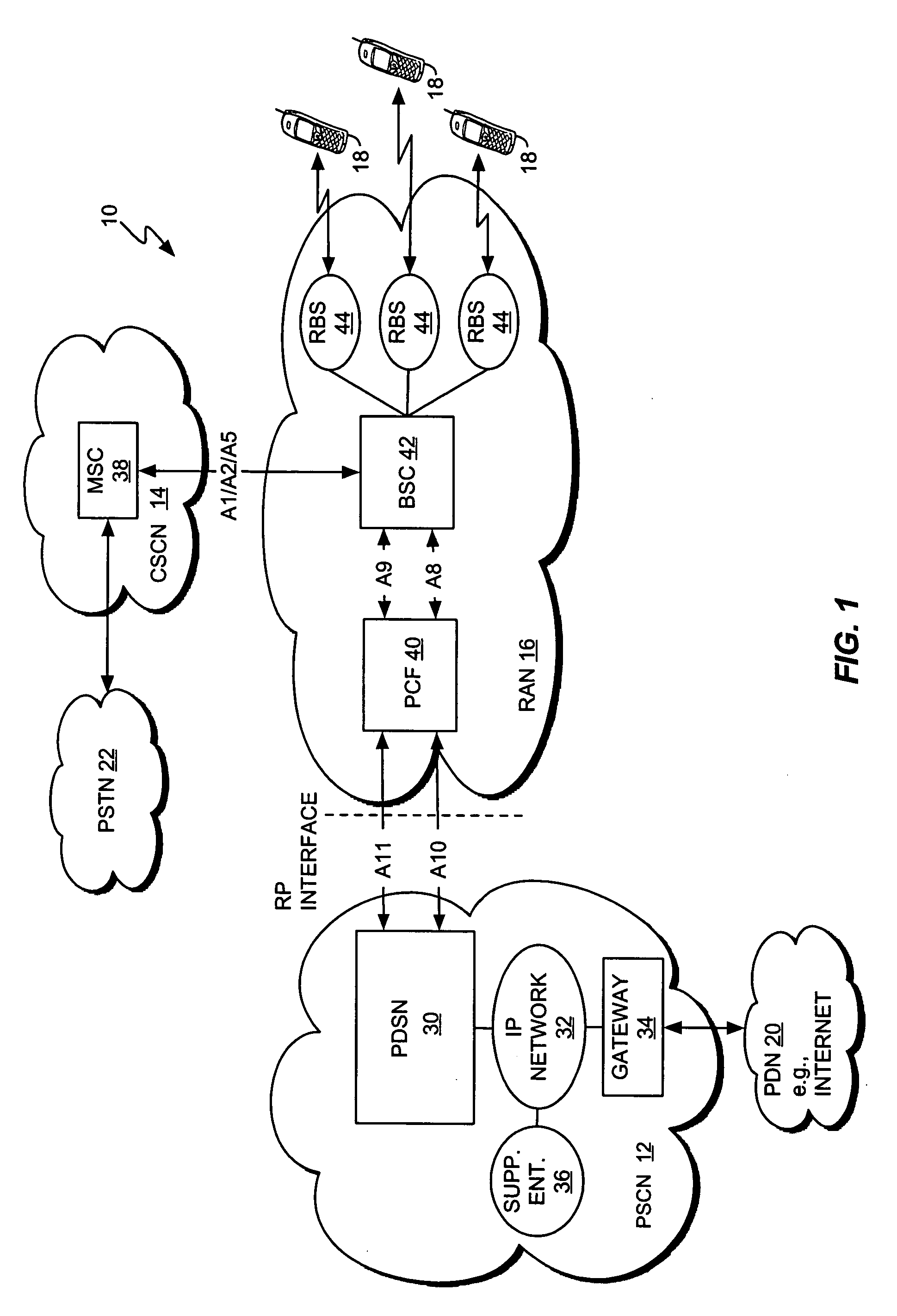
Dynamic voice over data prioritization for wireless communication networks
InactiveUS20050107091A1Reduce overheadIncrease network resource availableError preventionFrequency-division multiplex detailsData rateRate reduction
In a wireless communication network providing voice and data services, one or more entities in the network, such as a base station controller and / or radio base station, can be configured to reduce data services overhead responsive to detecting a congestion condition, thereby increasing the availability of one or more network resources for voice services. In one or more exemplary embodiments, one or more current data services users are targeted for modification of their ongoing data services to effect the reduction in data services overhead. Modifications can include, but are not limited to, any one or more of the following: forward or reverse link data rate reductions, and shifting of forward or reverse link traffic from dedicated user channels to shared user channels. Targeting of users for service modification can be based on reported channel quality information. For example, users reporting poor radio conditions can be targeted first for service modifications.
Owner:IDTP HLDG
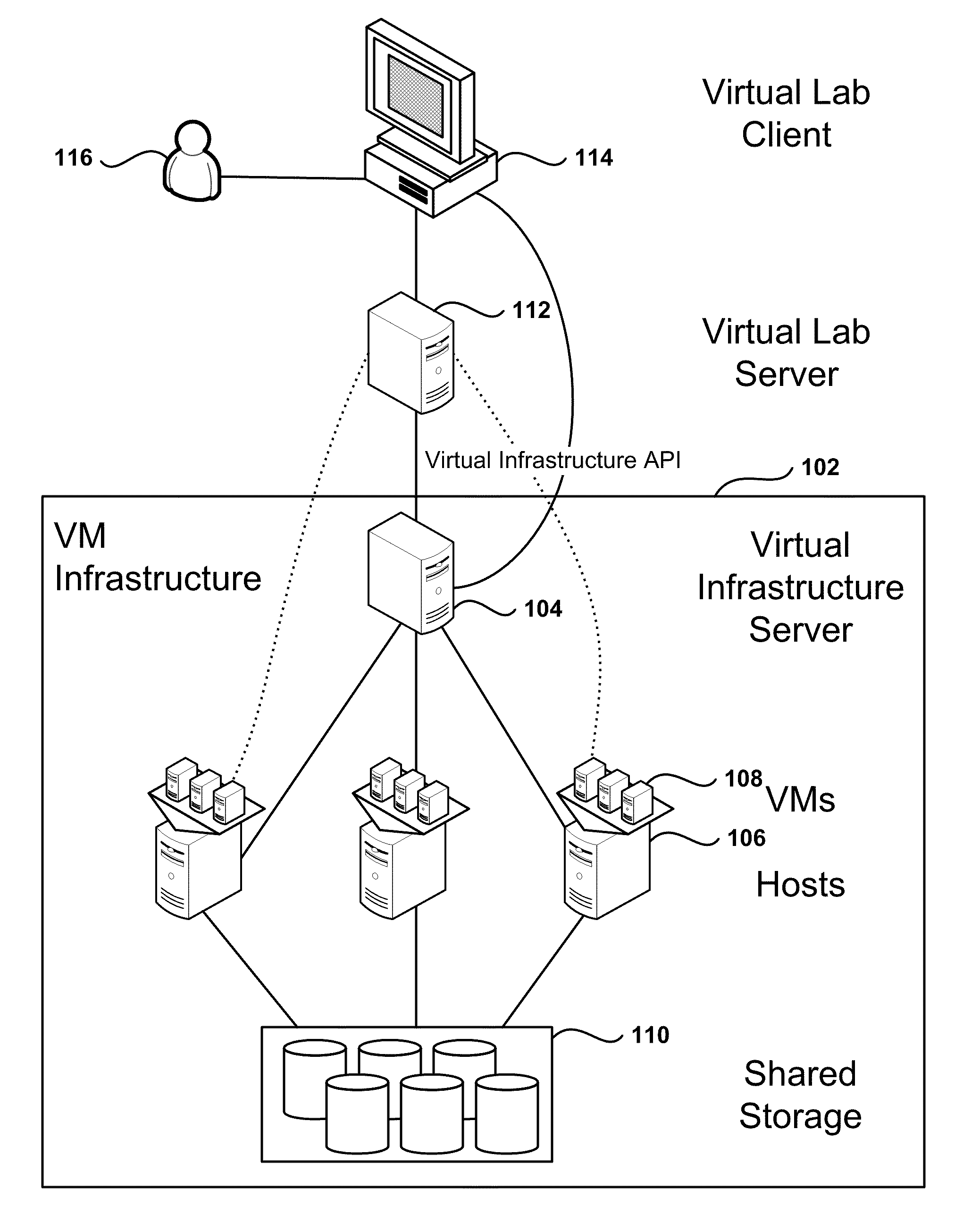
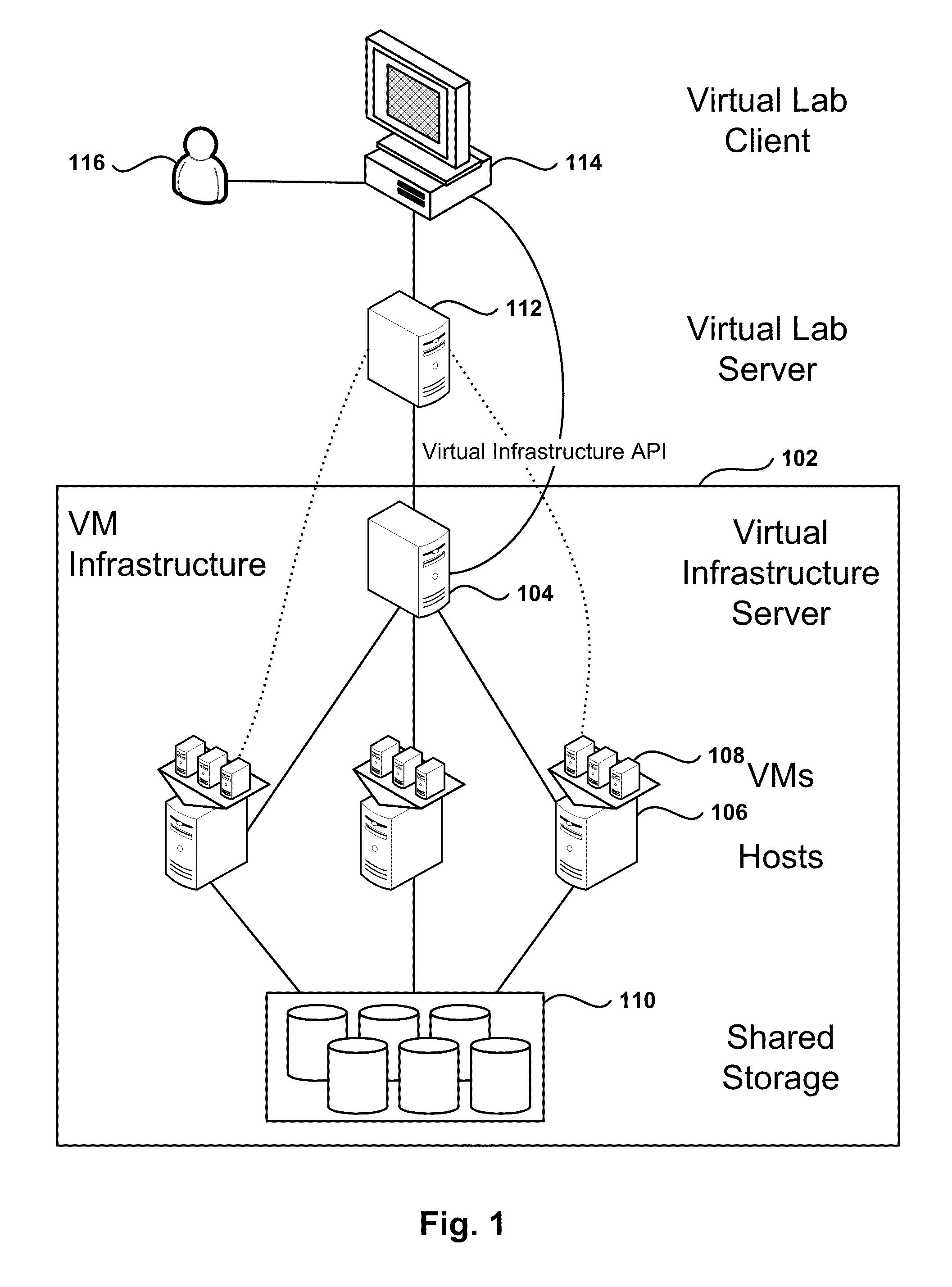
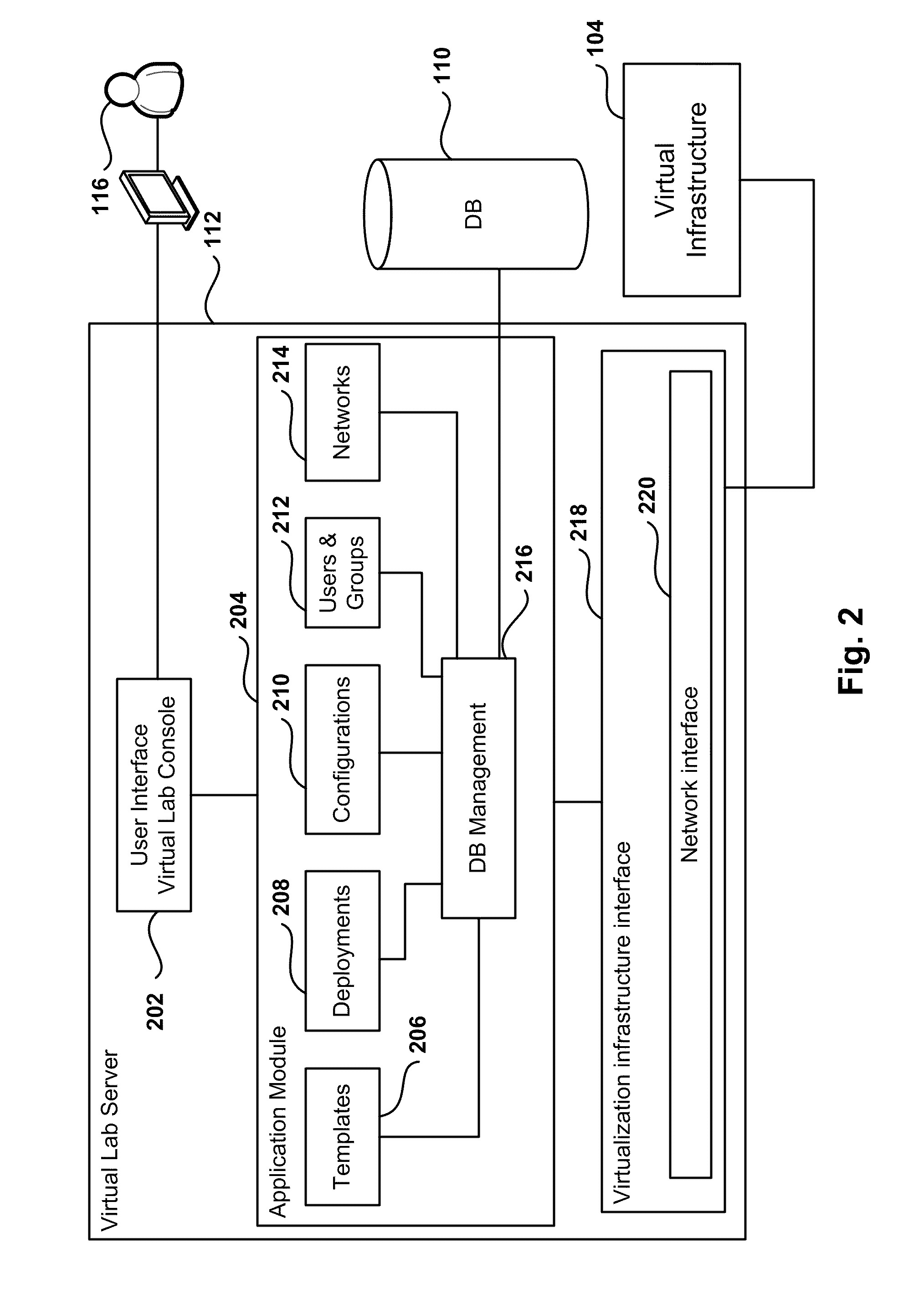
Automated Network Configuration of Virtual Machines in a Virtual Lab Environment
Methods, systems, and computer programs for creating virtual machines (VM) and associated networks in a virtual infrastructure are presented. The method defines virtual network templates in a database, where each virtual network template includes network specifications. A configuration of a virtual system is created, which includes VMs, virtual lab networks associated with virtual network templates, and connections from the VMs to the virtual lab networks. Further, the configuration is deployed in the virtual infrastructure resulting in a deployed configuration. The deployment of the configuration includes instantiating in the virtual infrastructure the VMs of the configuration, instantiating in the virtual infrastructure the virtual lab networks, retrieving information from the database, and creating and executing programming instructions for the VMs. The database information includes the network specifications from the virtual network templates associated with the virtual lab networks, and network resources for the virtual lab networks from a pool of available network resources. The programming instructions are created for the particular Guest Operating System (GOS) running in each VM based on the GOS and on the retrieved database information. When executed in the corresponding VM GOS, the programming instructions configure the VMs network interfaces with the corresponding network specifications.
Owner:NICIRA
Method for billing IP broadband subscribers
InactiveUS7289489B1Least costMetering/charging/biilling arrangementsTelephonic communicationQuality of serviceLeast cost
A method of billing a variable bit rate communication between a first terminal and a distant terminal to a broadband subscriber permits changing billing parameters during a call in real time in response to user inputs including user requested changes in quality of service, changes in data rate and changes in preferred service provider. A variable bit rate communication to be billed has a variable quality of service related to the degree of utilization of a plurality of different networks. The billing method comprises the steps of i.) receiving user identification data at a first terminal and data representing a required bit rate and a default quality of service selected by the user, ii.) verifying the user identification data to be associated with the broadband service subscriber, iii.) determining least cost alternative network resources available for achieving the communication at the user selected default quality of service and the required bit rate, iv.) determining cost data associated with the network resources, v.) outputting to the user a least cost for the communication according to their selected default quality of service and alternative least cost network resources, vi.) coupling the first terminal and the distant terminal via the least cost determined network resources at the default quality of service and the required bit rate responsive to user authorization and vii.) billing for the communication at the default quality of service and according to the required bit rate after the termination of the communication.
Owner:AMERICAN TELEPHONE & TELEGRAPH CO
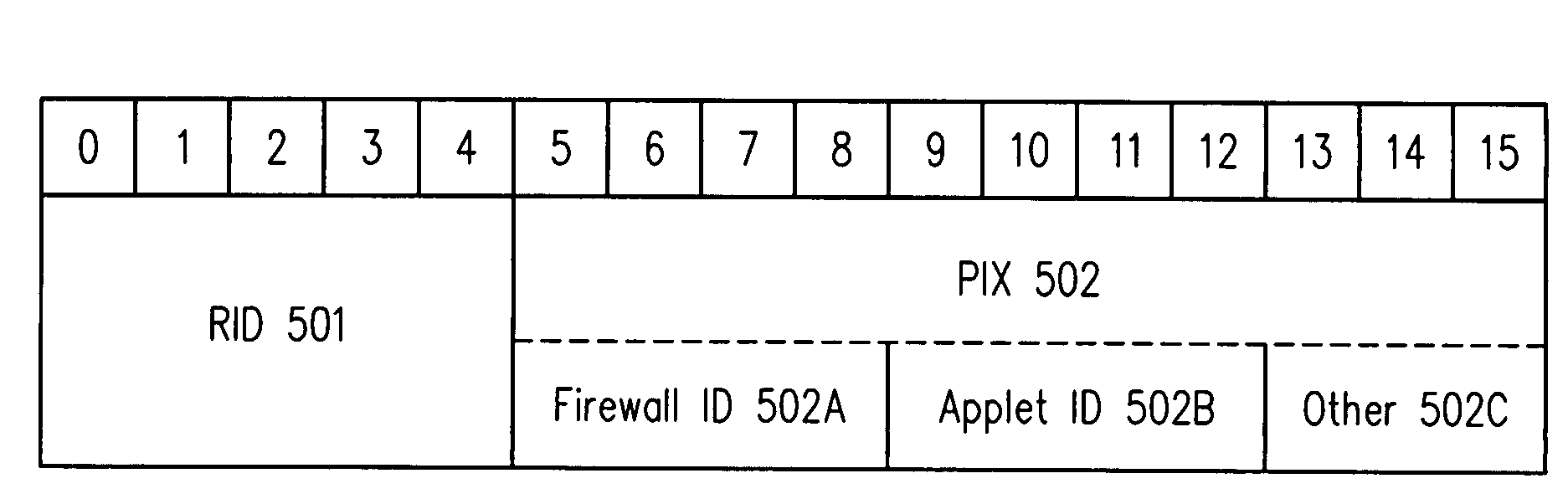
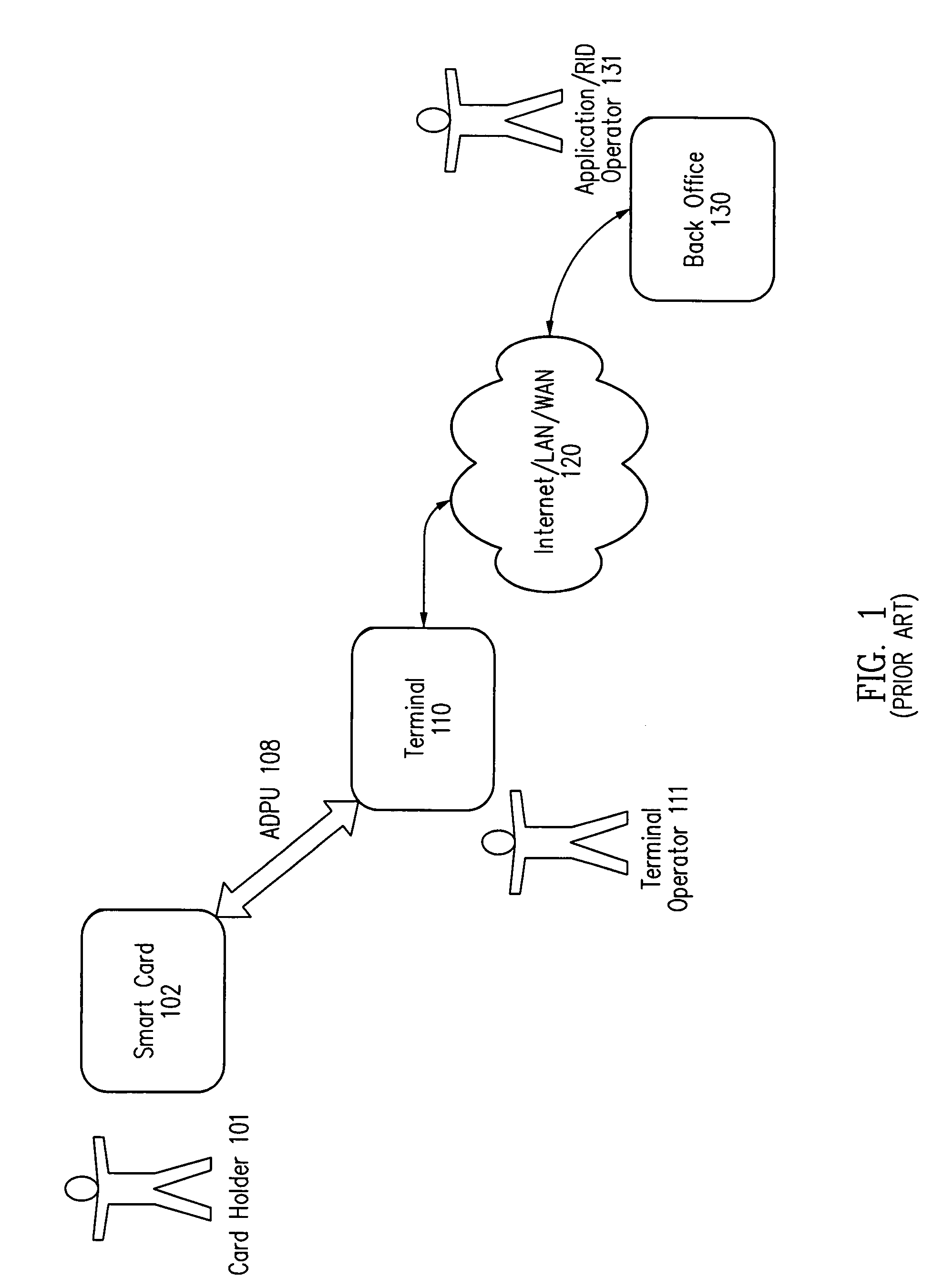
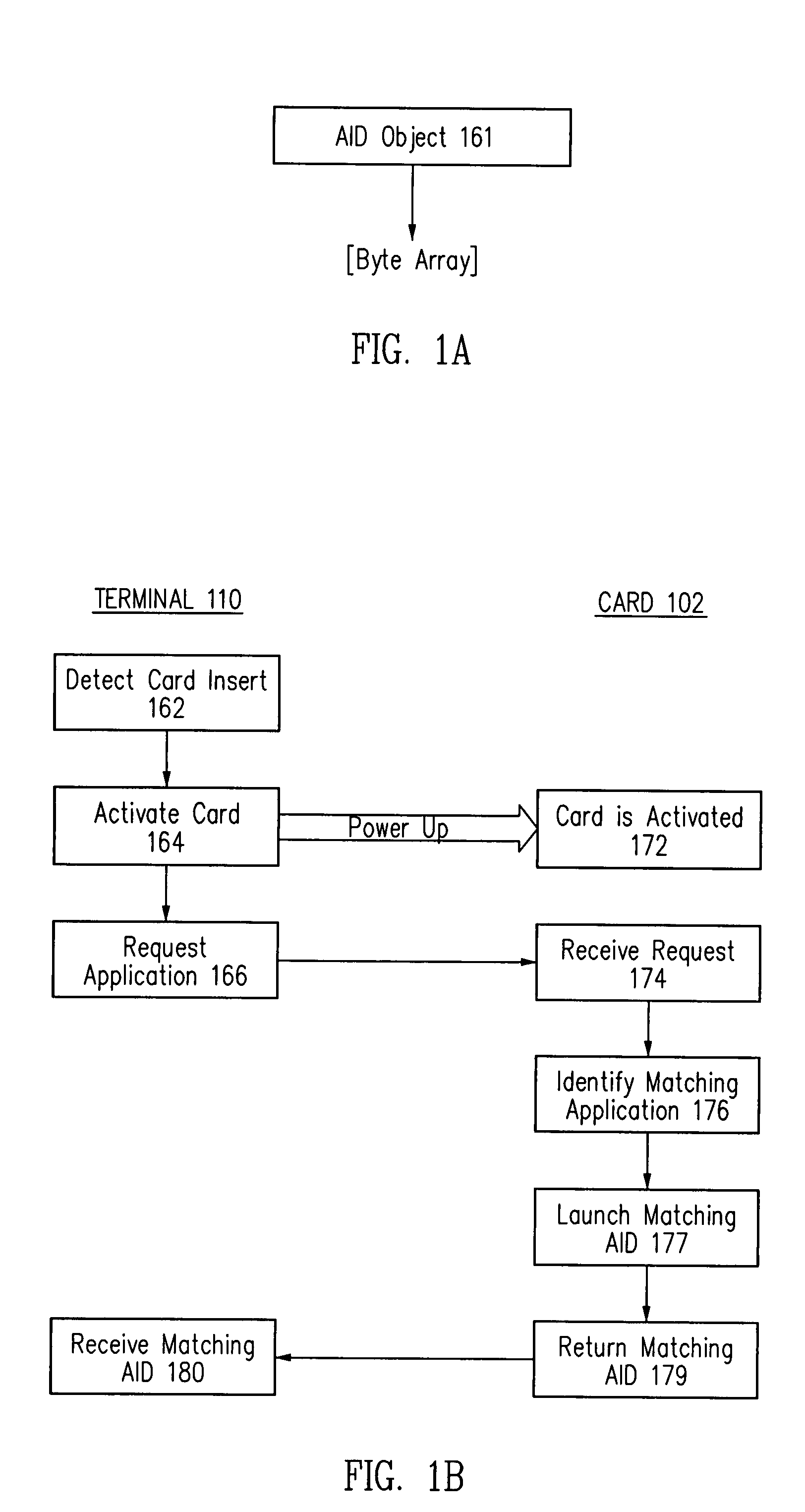
Method and apparatus for processing an application identifier from a smart card
An application identifier (AID) for an application installed on a smart card comprises a registered application provider identifier (RID). The AID may be processed by determining the RID for an application from the AID of the application, generating an identifier for a network resource from the RID, transmitting a request to the network resource using the identifier, and receiving a response to the request. The response comprises material for use in handling the application on the smart card.
Owner:ORACLE INT CORP
Instant messaging using distributed indexes
ActiveUS20040064512A1Special service provision for substationMultiple digital computer combinationsDistributed indexInstant messaging
Embodiments of a distributed instant messaging system that uses a distributed index in peer-to-peer networks. A distributed index may be used to implement an instant messaging system in a group of participating peers. The distributed index may be used, for example, to route messages between participating peers, in identifying and authenticating peers wishing to participate, in notifying peers of newly joined peers, and in notifying joining peers of participating peers. In one embodiment, zones of the distributed index may be moved to joining peers. In one embodiment, zones of the distributed index stored on departing peers may be moved to participating peers. One embodiment may be implemented in peer-to-peer networks implemented according to a peer-to-peer platform including one or more peer-to-peer platform protocols for enabling peer nodes to discover each other, communicate with each other, and cooperate with each other to form peer groups and share network resources.
Owner:ORACLE INT CORP
Techniques for user authentication
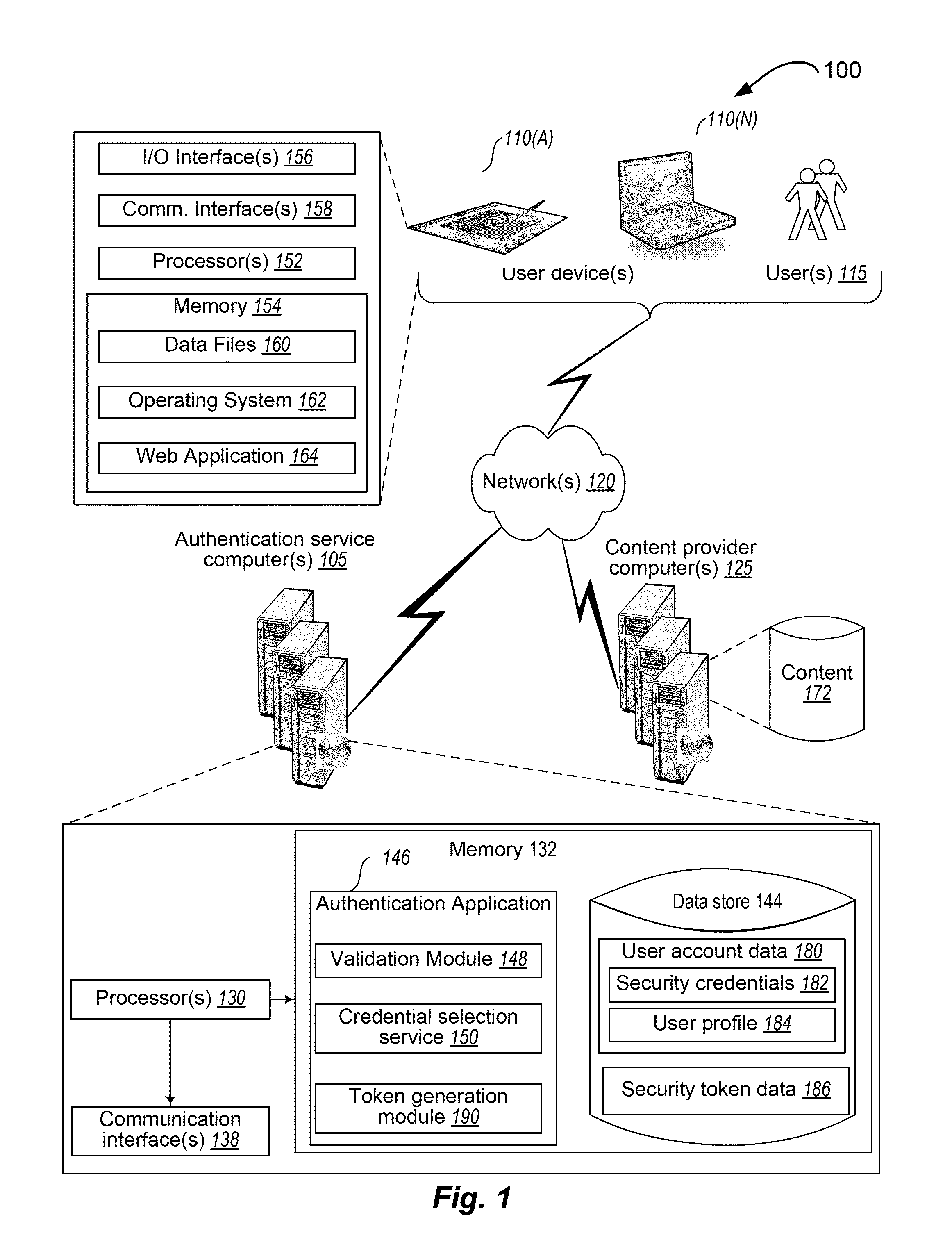
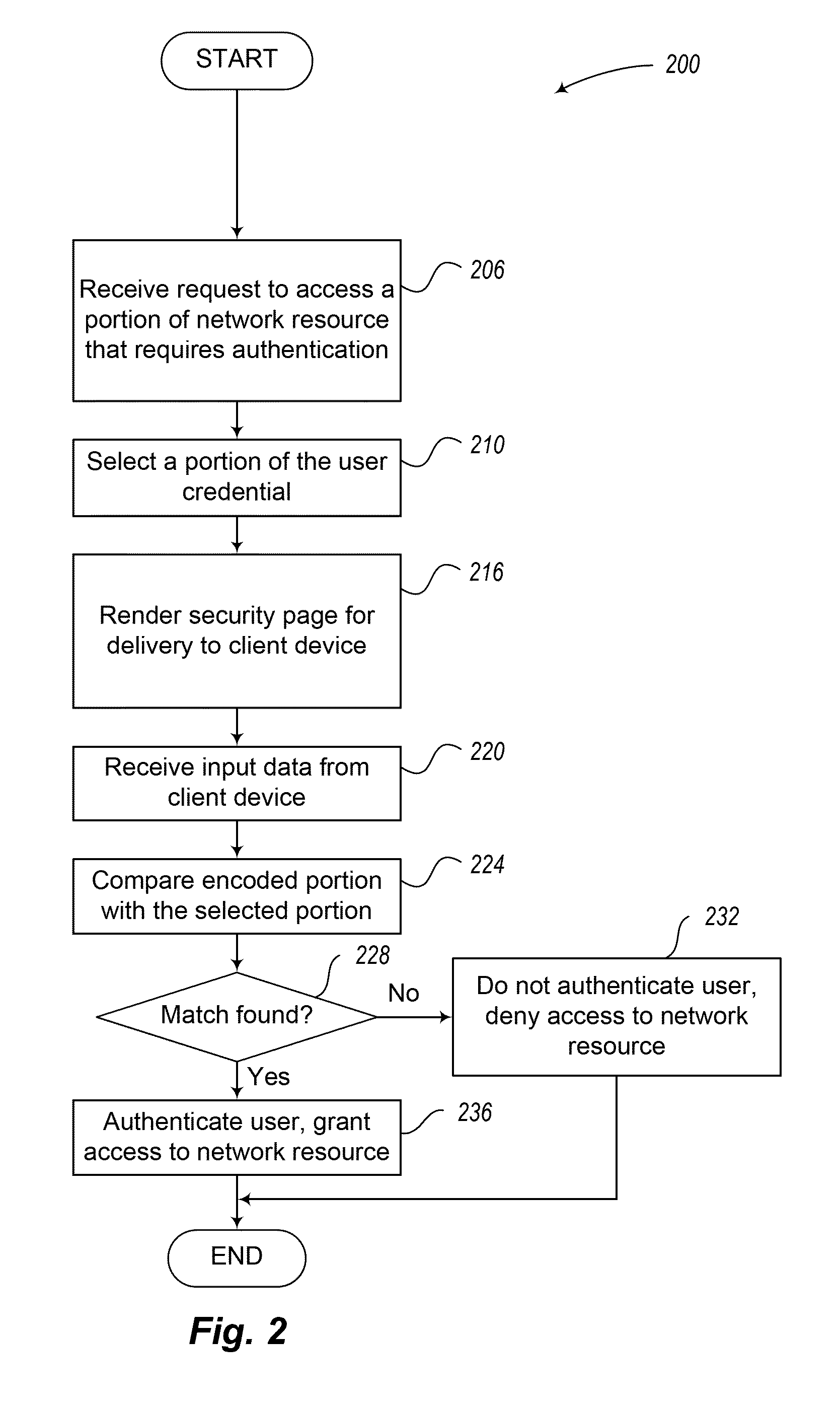
InactiveUS8613066B1Digital data processing detailsUser identity/authority verificationUser authenticationClient-side
Techniques for user authentication are disclosed. In some situations, the techniques include receiving, from a client device, an authentication request to access a network resource, the request including a user identifier, obtaining a security credential associated with the user identifier contained in the received request, generating an authorization code based on the obtained security credential, providing to the client device instructions to obtain first information corresponding to the generated authorization code, receiving, from the client device, the first information provided in response to the provided instructions, and, when the first information received from the client device corresponds to at least a portion of the generated authorization code, authorizing the client device to access the network resource.
Owner:AMAZON TECH INC
Method, product, and apparatus for resource identifier registration and aftermarket services
InactiveUS7188138B1Easy to understandReduce extra bandwidth requiredMultiple digital computer combinationsMarketingDomain nameWeb browser
When a network resource request having a domain name is received, it is determined whether the network resource can be accessed from the domain name. Rather than, or in addition to, displaying an error message or processing a search request in response to determining that a network resource can not be accessed, the domain name can instead be redirected to a registration service where the domain name can be automatically used to perform a registration request and determine domain name availability. When the domain name is not available for registration, domain name registrant information is provided. However, when the domain name is determined available, a registration form is provided. For example, such a domain name may be redirected from the autosearch feature of a web browser to a service, which determines that the domain name is available for registration enabling a potential registrant to register the available domain name by selecting a domain name registration provider from a list of domain name registration providers.
Owner:MEC MANAGEMENT LLC
Photo-based mobile deixis system and related techniques
InactiveUS7872669B2Quick identificationAvailable informationTelevision system detailsWeb data indexingWireless handheld devicesDisplay device
A mobile deixis device includes a camera to capture an image and a wireless handheld device, coupled to the camera and to a wireless network, to communicate the image with existing databases to find similar images. The mobile deixis device further includes a processor, coupled to the device, to process found database records related to similar images and a display to view found database records that include web pages including images. With such an arrangement, users can specify a location of interest by simply pointing a camera-equipped cellular phone at the object of interest and by searching an image database or relevant web resources, users can quickly identify good matches from several close ones to find an object of interest.
Owner:MASSACHUSETTS INST OF TECH
Computer interface method and apparatus with portable network organization system and targeted advertising
InactiveUS20050005242A1Permit targetingCathode-ray tube indicatorsProgram loading/initiatingPersonalizationSoftware distribution
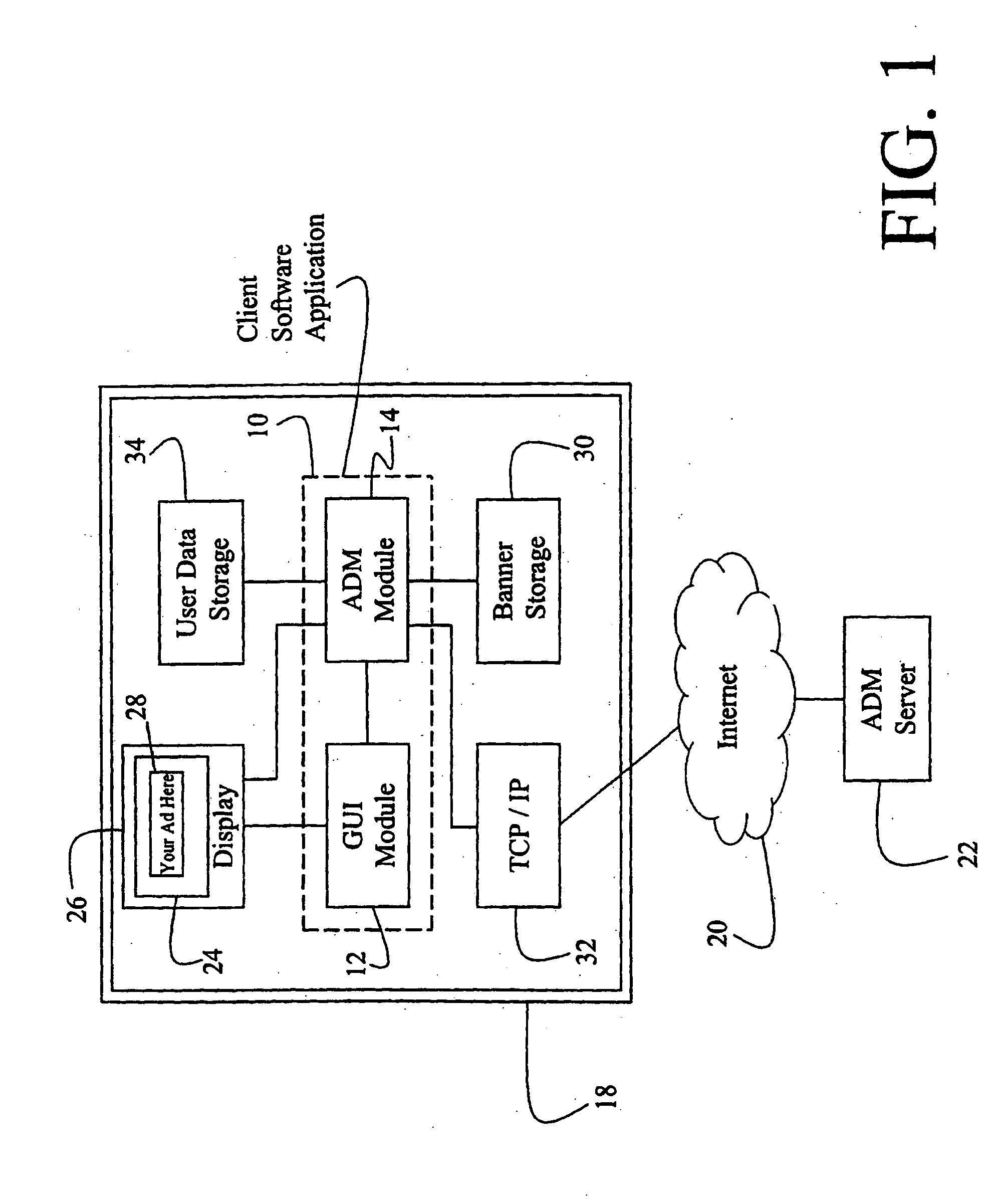
A method and apparatus for providing an automatically upgradeable software application includes targeted advertising based upon demographics and user interaction with the computer. The software application includes a display region used for banner advertising that is downloaded over a network such as the Internet. The software application is accessible from a server via the network and demographic information on the user is acquired by the server and used for determining what advertising will be sent to the user. The software application further targets the advertisements in response to normal user interaction with the computer. Data associated with each advertisement is used by the software application in determining when a particular advertisement is to be displayed. This includes the specification of certain programs that the user may have so that, when the user runs the program (e.g., a spreadsheet program), a relevant advertisement will be displayed (e.g., an advertisement for a stock brokerage). This provides two-tiered, real-time targeting of advertising—both demographically and reactively. The software application includes programming that accesses the server to determine if one or more components of the application need upgrading. If so, the components can be downloaded and installed without further action by the user. A distribution tool is provided for software distribution and upgrading over the network. Also provided is a user profile that is accessible to any computer on the network. Furthermore, multiple users of the same computer can possess Internet web resources and files that are personalized, maintained and organized.
Owner:BETECH
System and Method of Automatically Connecting A Mobile Communication Device to A Network using A Communications Resource Database
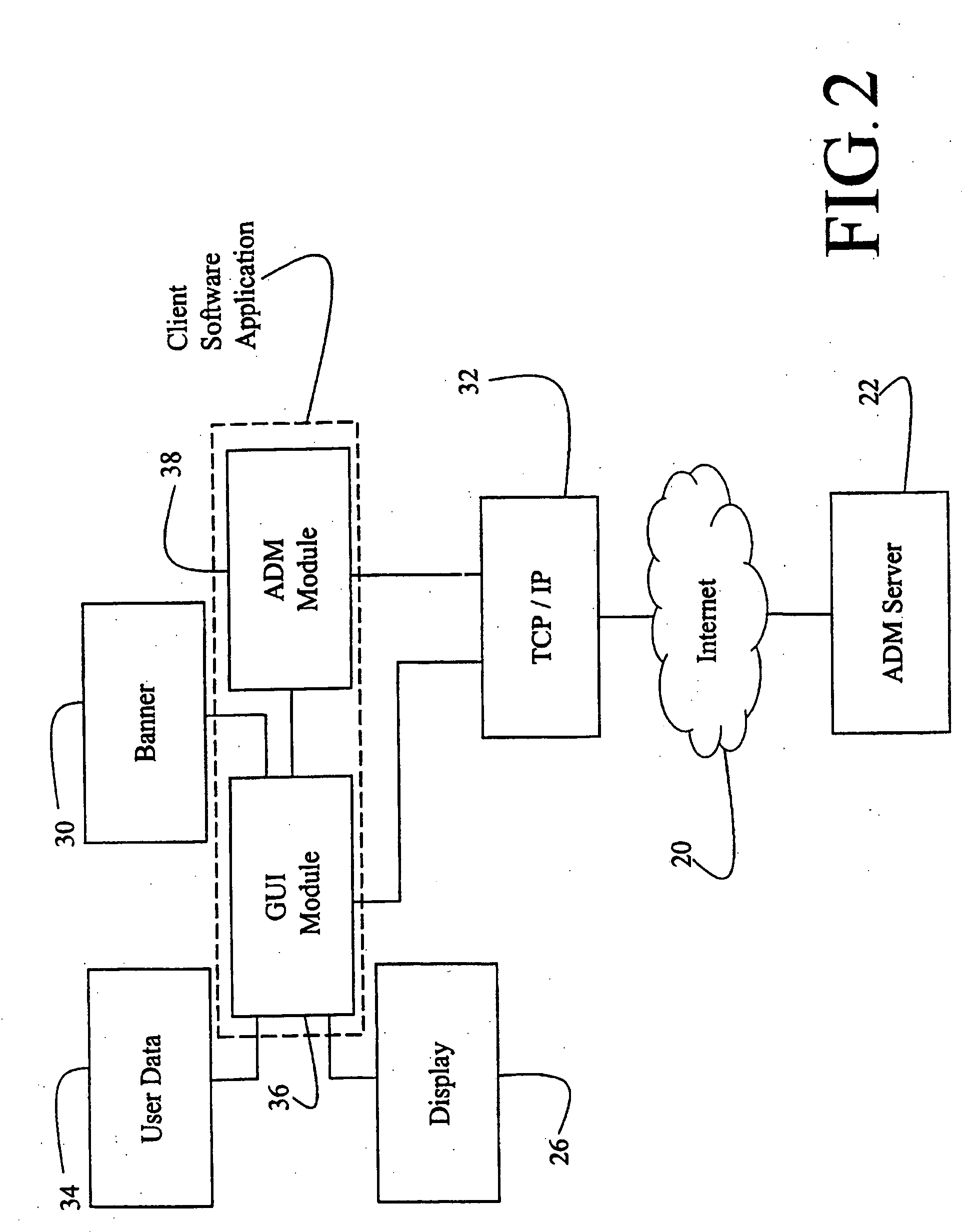
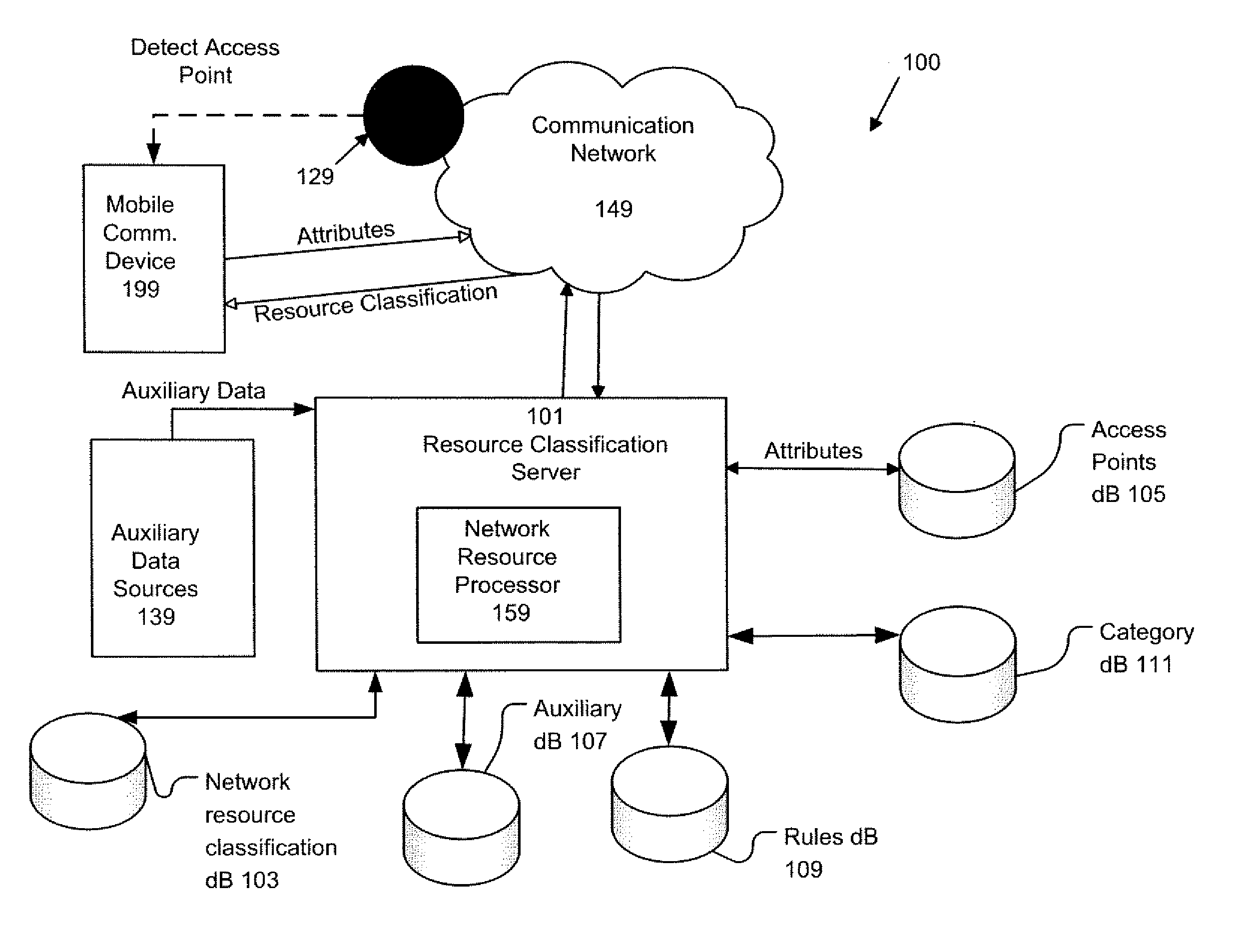
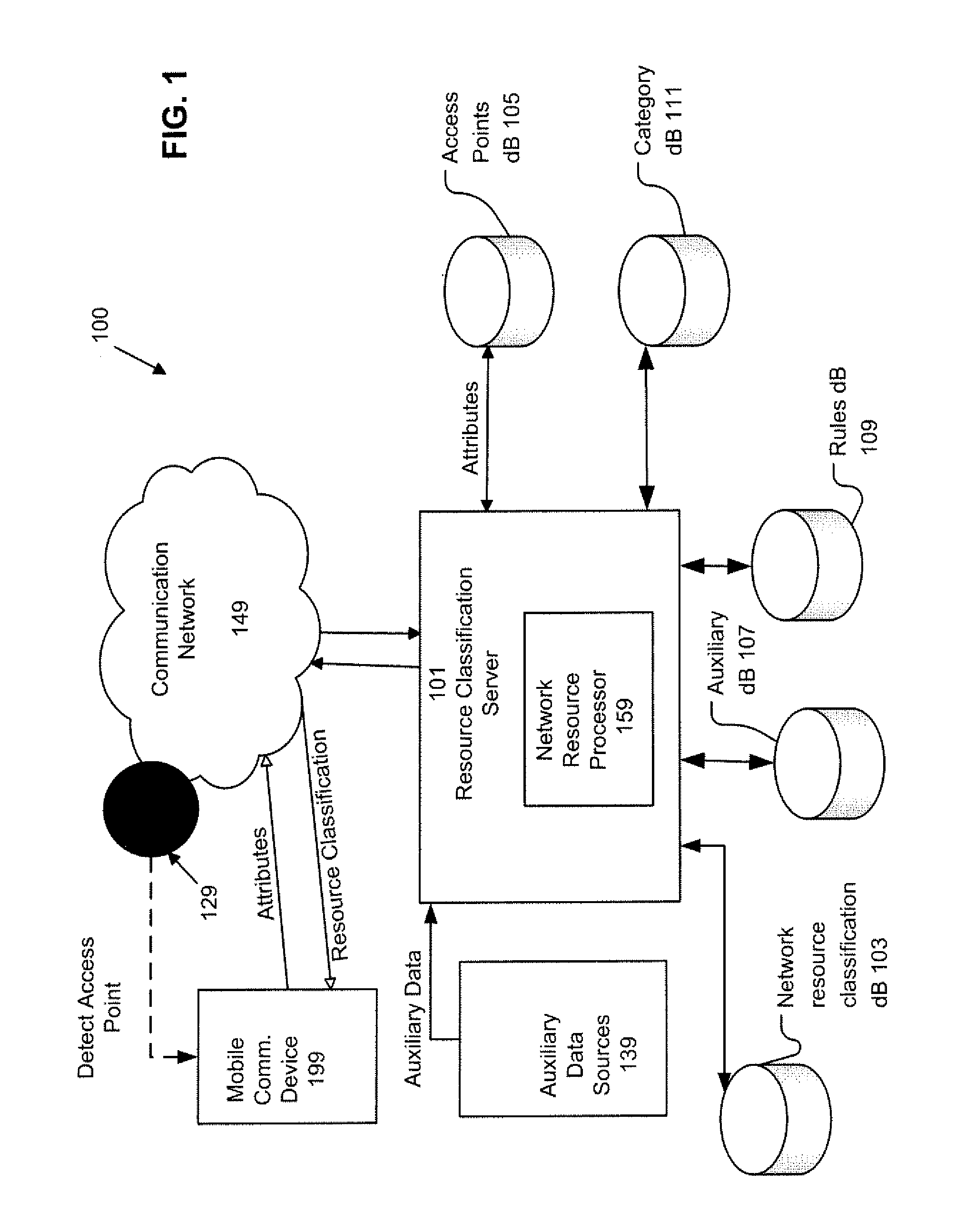
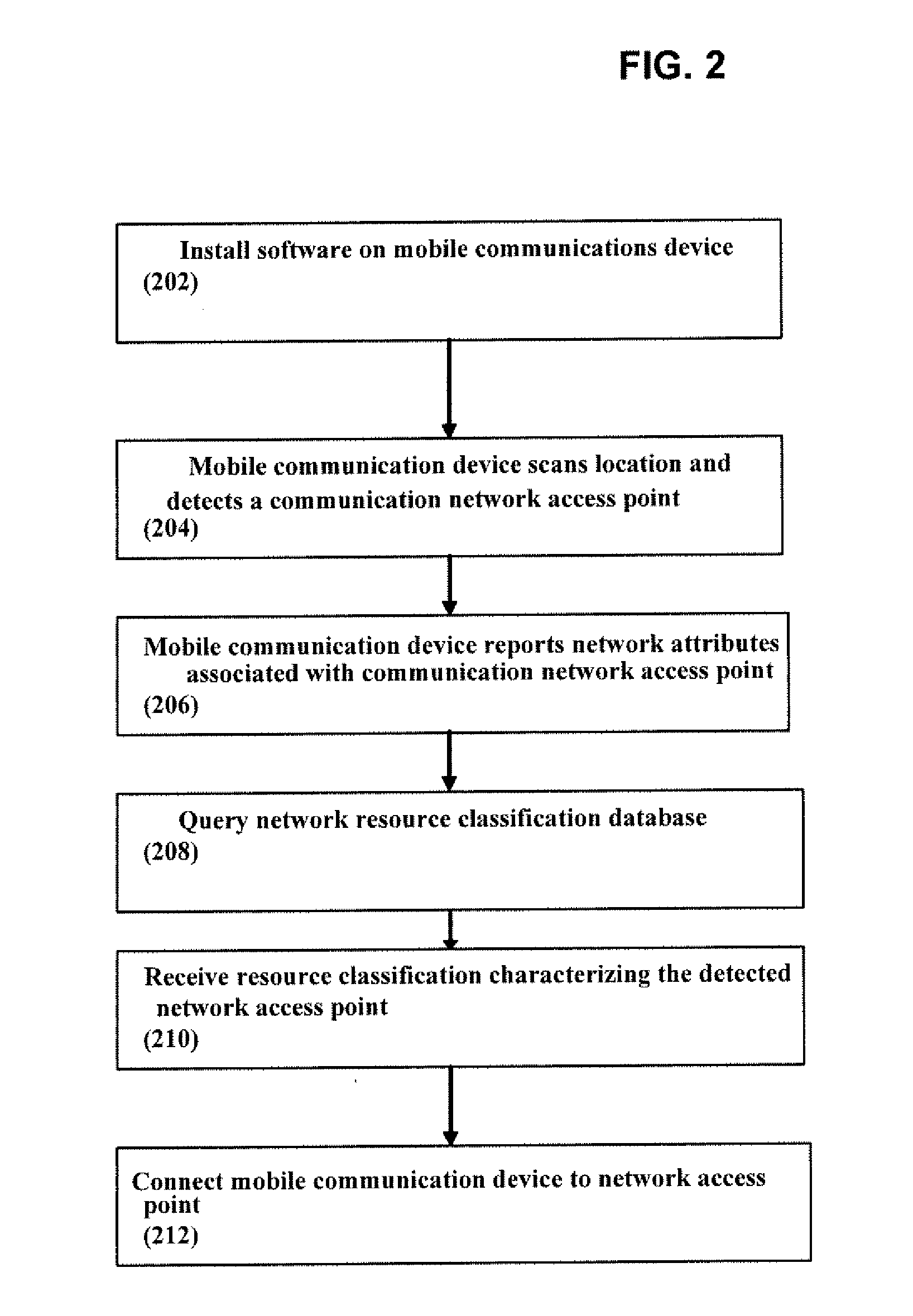
ActiveUS20110013569A1Bridging the gapEasy to useDigital data processing detailsAssess restrictionNetwork access pointCommunication device
A system, method, and computer program product of automatically connecting a mobile communication device to a communication network using a network resource classification database includes detecting a communication network access point using the mobile communication device and reporting network attributes associated with the access point to a resource classification server. The server analyzes and stores the network attributes, determines auxiliary data related to the access point, and uses a rules database to determine a category identifier associated with the access point. The server creates a resource classification characterizing the access point based upon the network attributes, auxiliary data, and category identifier. The mobile communication device queries the server, receives a resource classification, and connects to an access point based upon the received resource classification.
Owner:WEFI
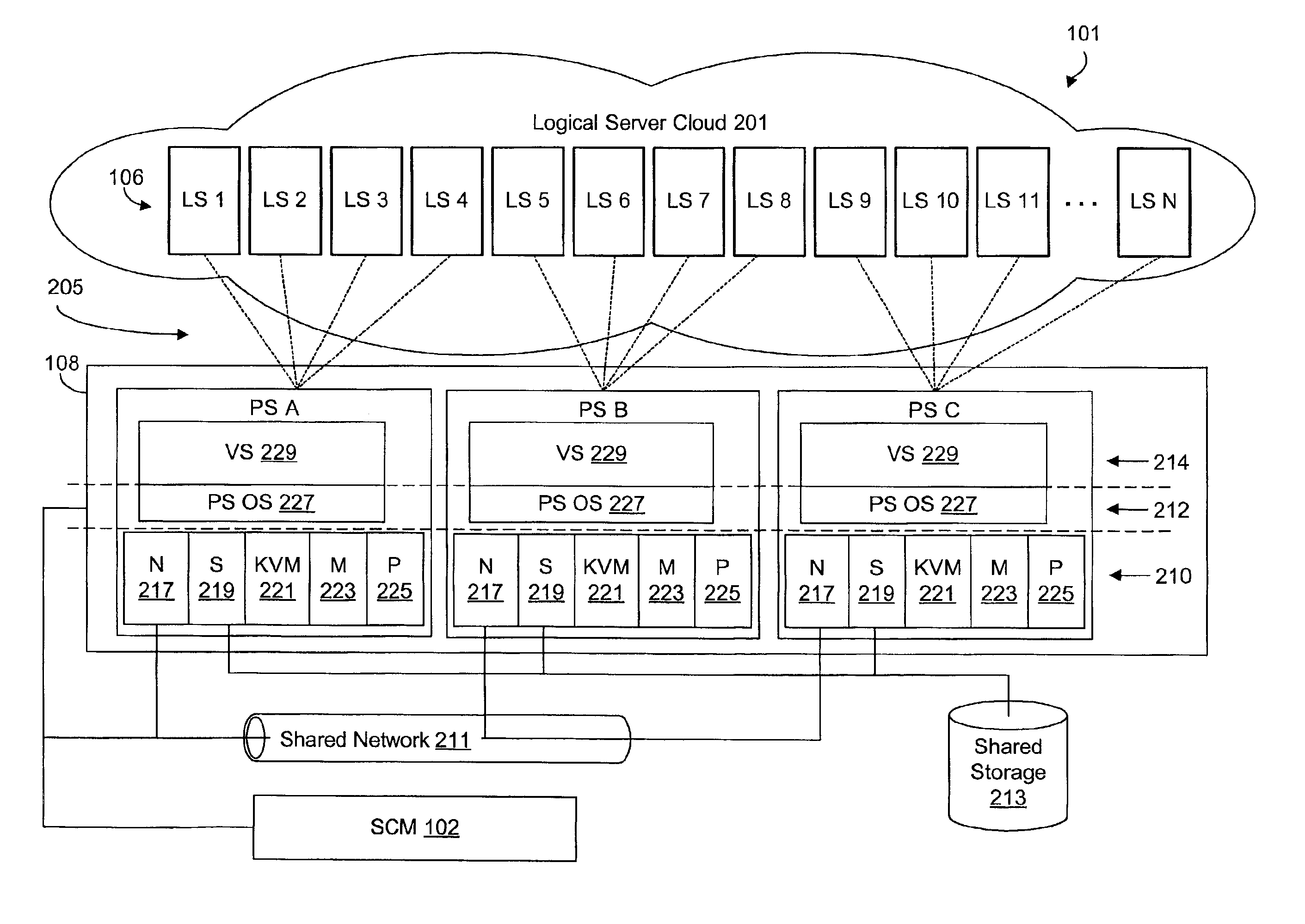
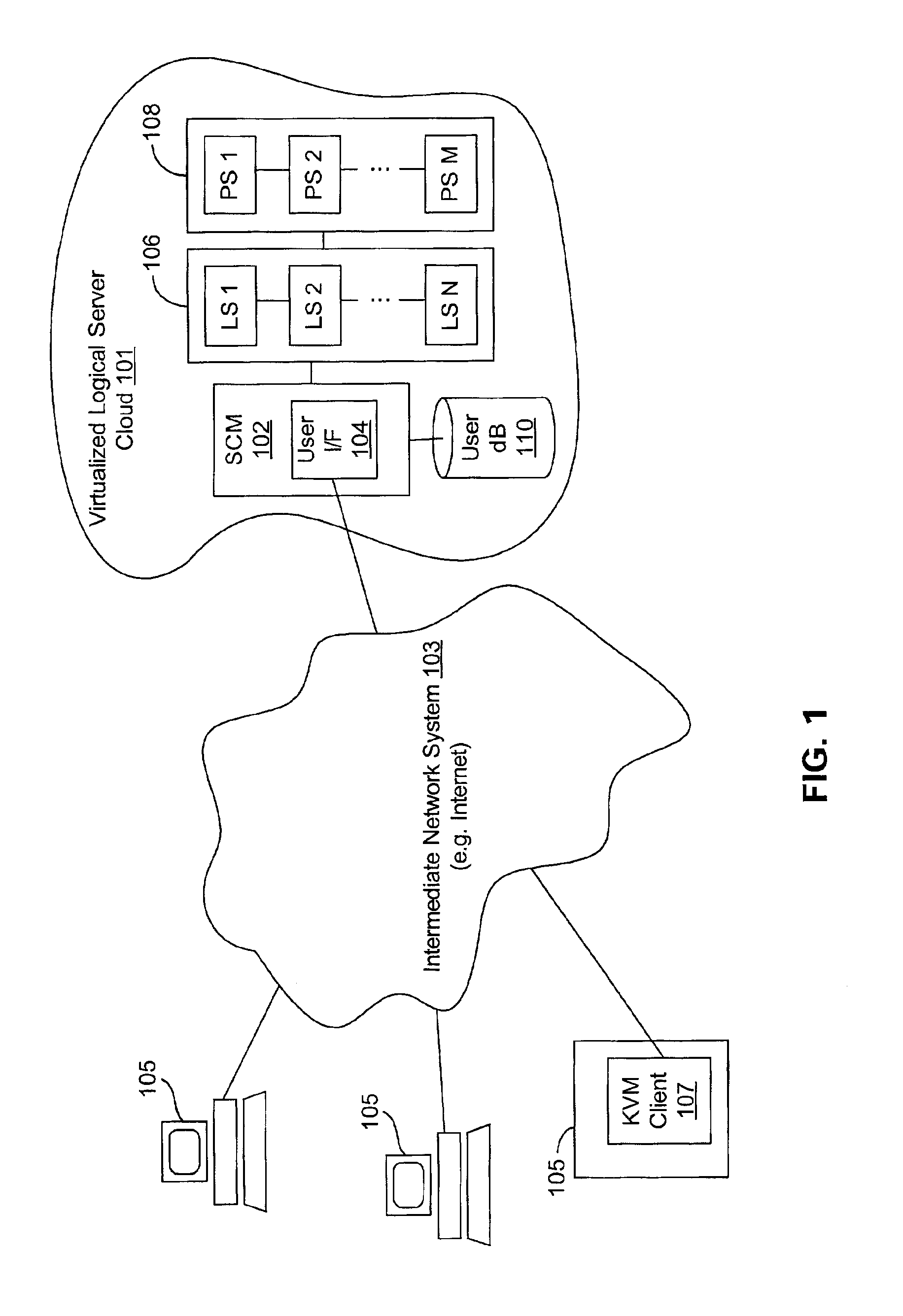
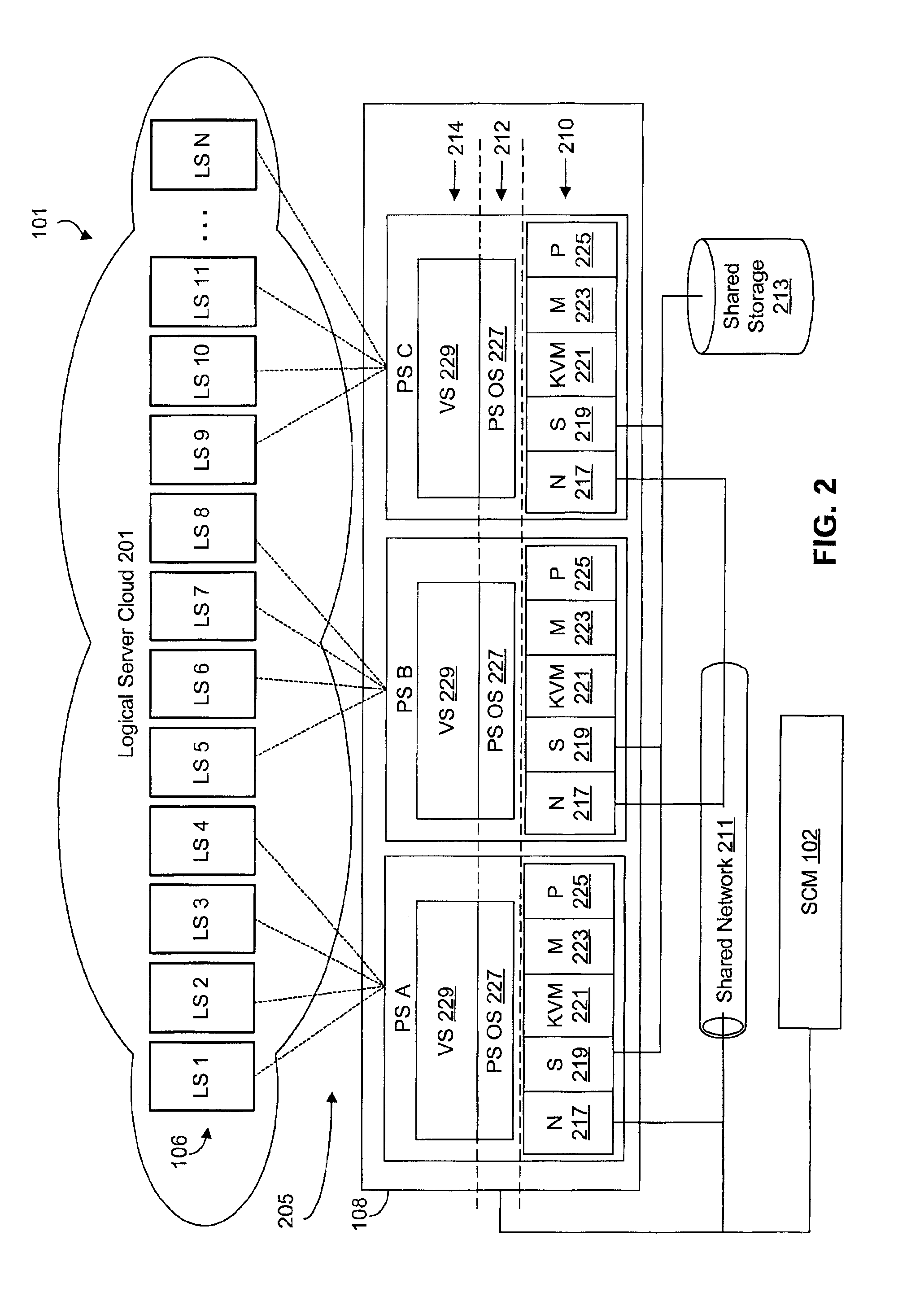
Virtualized logical server cloud providing non-deterministic allocation of logical attributes of logical servers to physical resources
InactiveUS6880002B2Resource allocationMultiple digital computer combinationsVirtualizationData store
A virtualized logical server cloud that enables logical servers to exist independent of physical servers that instantiate the logical servers. Servers are treated as logical resources in order to create a logical server cloud. The logical attributes of a logical server are non-deterministically allocated to physical resources creating a cloud of logical servers over the physical servers. Logical separation is facilitated by the addition of a server cloud manager, which is an automated multi-server management layer. Each logical server has persistent attributes that establish its identity. Each physical server includes or is coupled to physical resources including a network resource, a data storage resource and a processor resource. At least one physical server executes virtualization software that virtualizes physical resources for logical servers. The server cloud manager maintains status and instance information for the logical servers including persistent and non-persistent attributes that link each logical server with a physical server.
Owner:DELL PROD LP
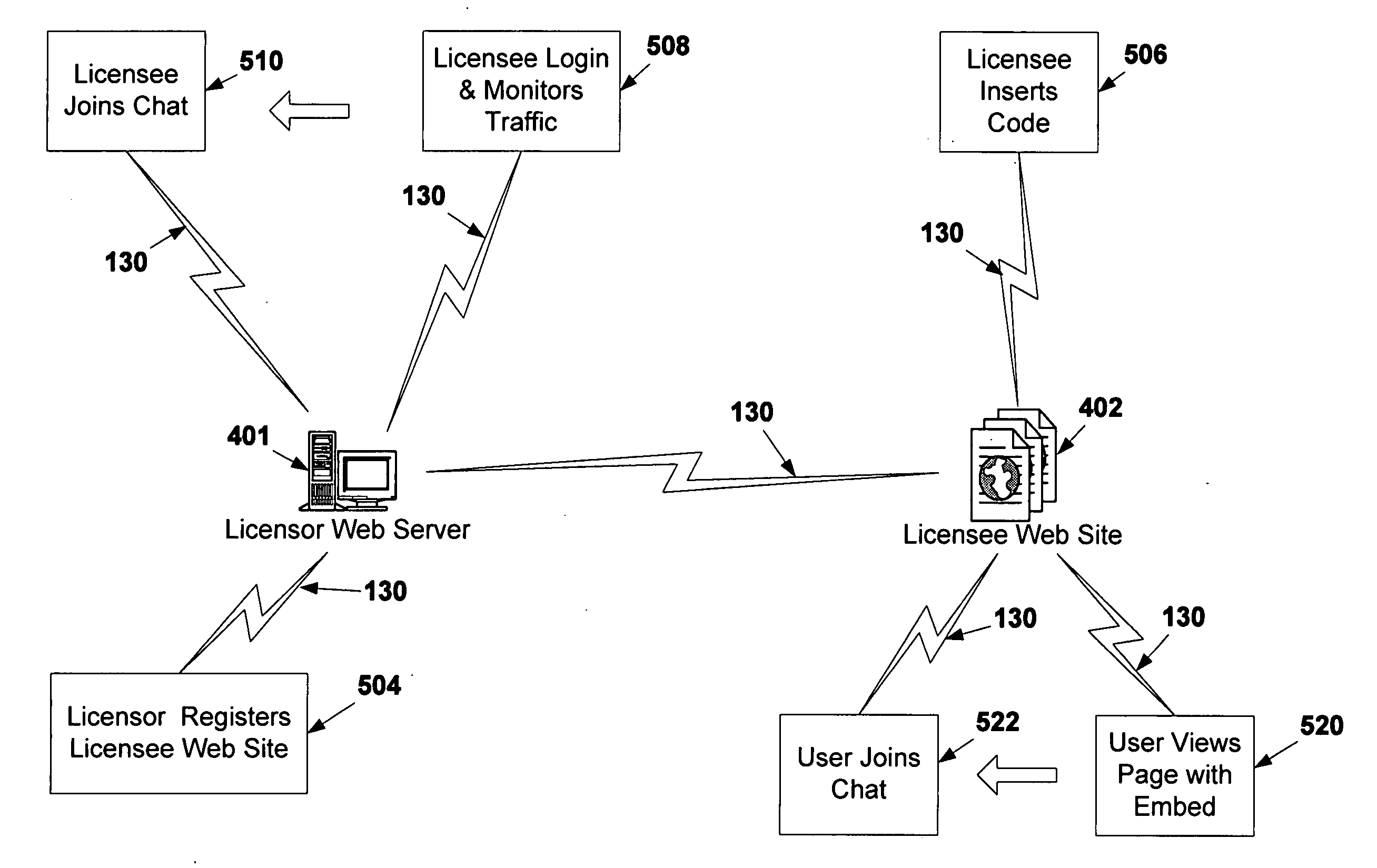
Web page monitoring and collaboration system
InactiveUS20050102358A1Facilitate conductionEasy to participateDigital data information retrievalMultiple digital computer combinationsInternet communicationWeb site
This invention relates to providing a system for improved methods of promoting, forming and managing Internet-based communities on the Internet through and within standard web pages without requiring the installation of additional software on a user's computer or on web sites where the system is implemented by using the latest software tools, presentation techniques and Internet communication methods. Additionally, this invention provides real time monitoring of user counts to all visitors and web page owners when a page with the embedded URL is accessed. In particular, this invention permits web page visitors to initiate and participate in anonymous ad hoc chat sessions initiated from a selected web page. Additionally, this invention provides a web-based location which permits Internet users to join and participate in Internet-based communities and the related activities such as messaging other members, participating in member chat sessions and web resource sharing without the need to install software.
Owner:GOLD STUART A +1
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com