Patents
Literature
225results about How to "Bridging the gap" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
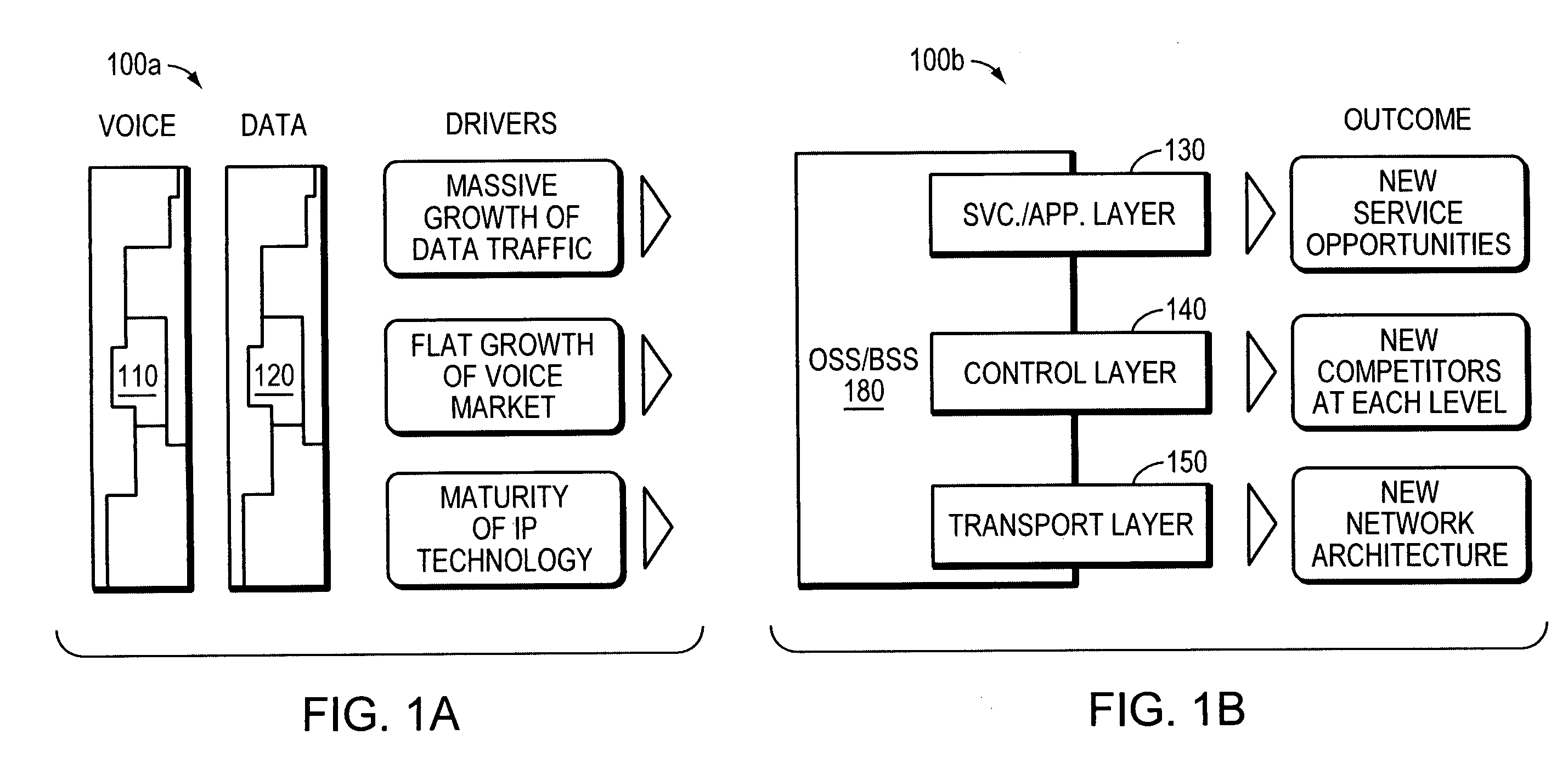
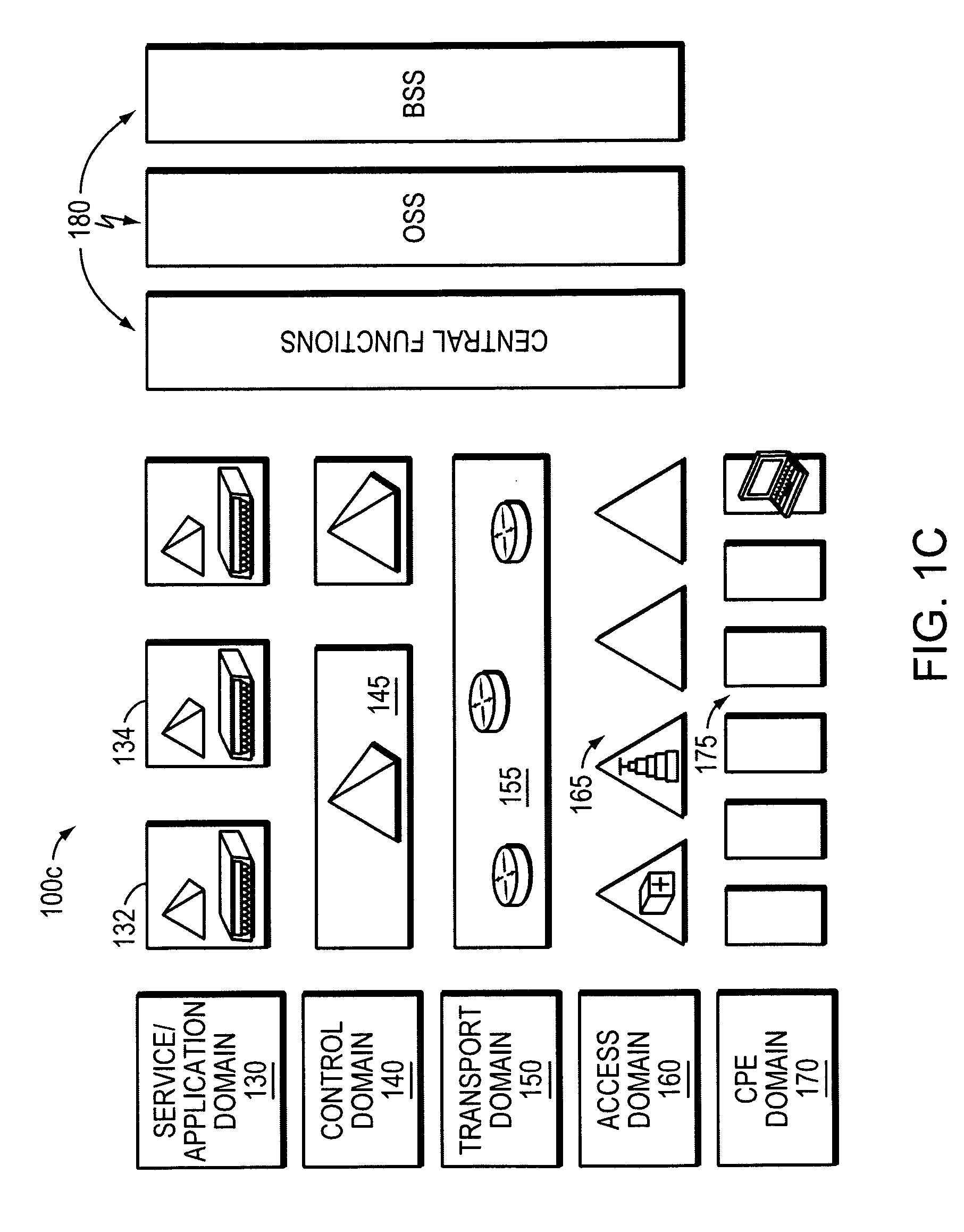
Demultiplexer for a molecular wire crossbar network (MWCN DEMUX)
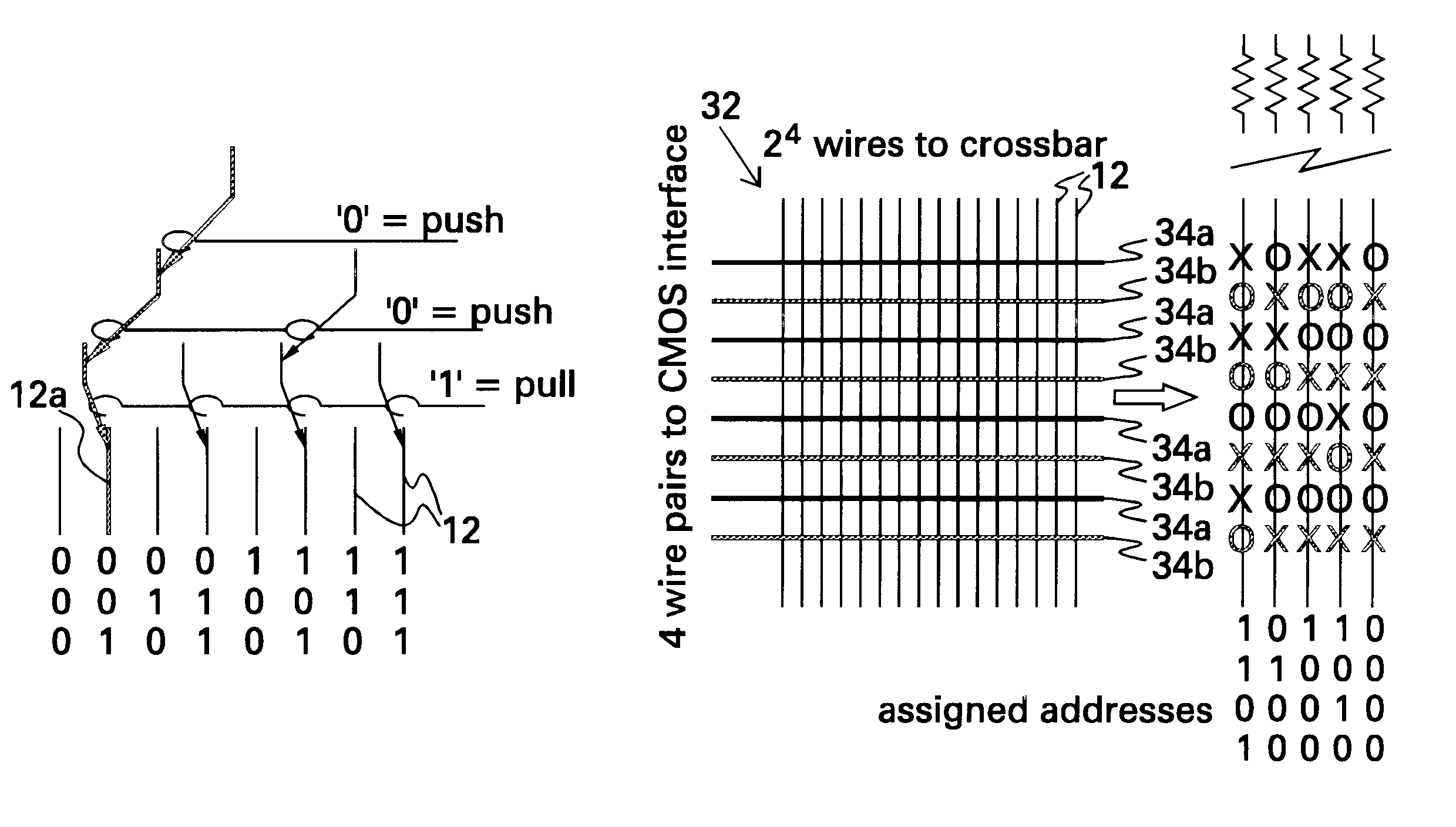
A demultiplexer for a two-dimensional array of a plurality of nanometer-scale switches (molecular wire crossbar network) is disclosed. Each switch comprises a pair of crossed wires which form a junction where one wire crosses another and at least one connector species connecting said pair of crossed wires in said junction. The connector species comprises a bi-stable molecule. The demultiplexer comprises a plurality of address lines accessed by a first set of wires in the two-dimensional array by randomly forming contacts between each wire in the first set of wires to at least one of the address lines. The first set of wires crosses a second set of wires to form the junctions. The demultiplexer solves both the problems of data input and output to a molecular electronic system and also bridges the size gap between CMOS and molecules with an architecture that can scale up to extraordinarily large numbers of molecular devices. Further, the demultiplexer is very defect tolerant, and can work despite a large number of defects in the system.
Owner:HEWLETT-PACKARD ENTERPRISE DEV LP
Software control plane for switches and routers
ActiveUS20080219268A1Bridging the gapImprove convenienceError preventionTransmission systemsQuality of serviceAbstraction layer
A Provider Network Controller (PNC) addresses the challenges in building services across Next Generation Network (NGN) architectures and creates an abstraction layer as a bridge, or glue, between the network transport and applications running over it. The PNC is a multi-layer, multi-vendor dynamic control plane that implements service activation and Layer 0-2 management tools for multiple transport technologies including Carrier Ethernet, Provider Backbone Transport (PBT), Multi-protocol Label Switching (MPLS), Transport MPLS (T-MPLS), optical and integrated networking platforms. Decoupling transport controls and services from the network equipment simplifies service creation and provides options for carriers to choose best-in-class equipment that leverages the PNC to enable rapid creation and management of transports and services. The PNC provides Service-Oriented Architecture (SOA) interfaces to abstract transport objects expressly designed to support both wholesale and retail services, and supports service offerings with varied bandwidth and Quality of Service (QoS) requirements, thus achieving enterprise Ethernet economics.
Owner:EXTREME NETWORKS INC
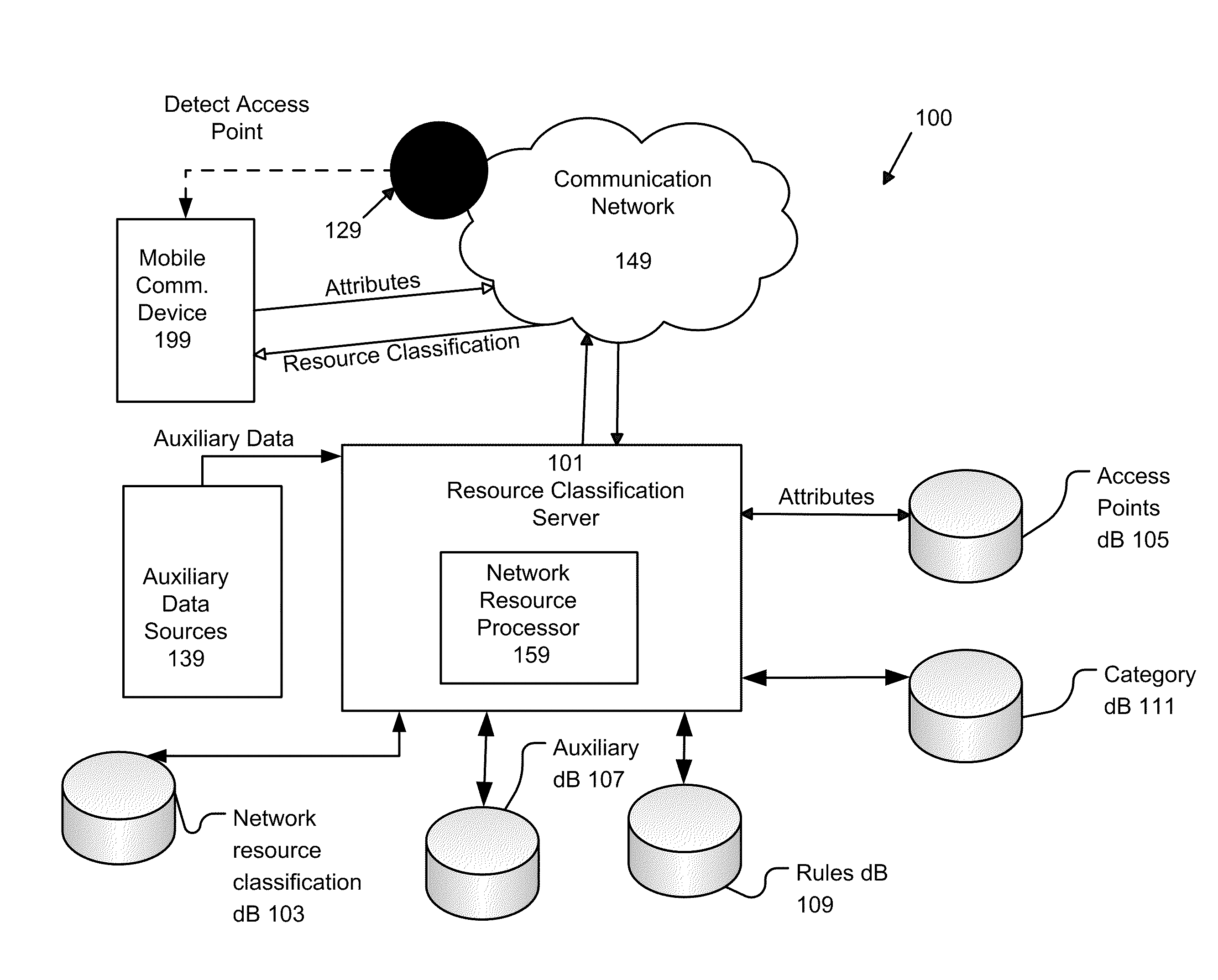
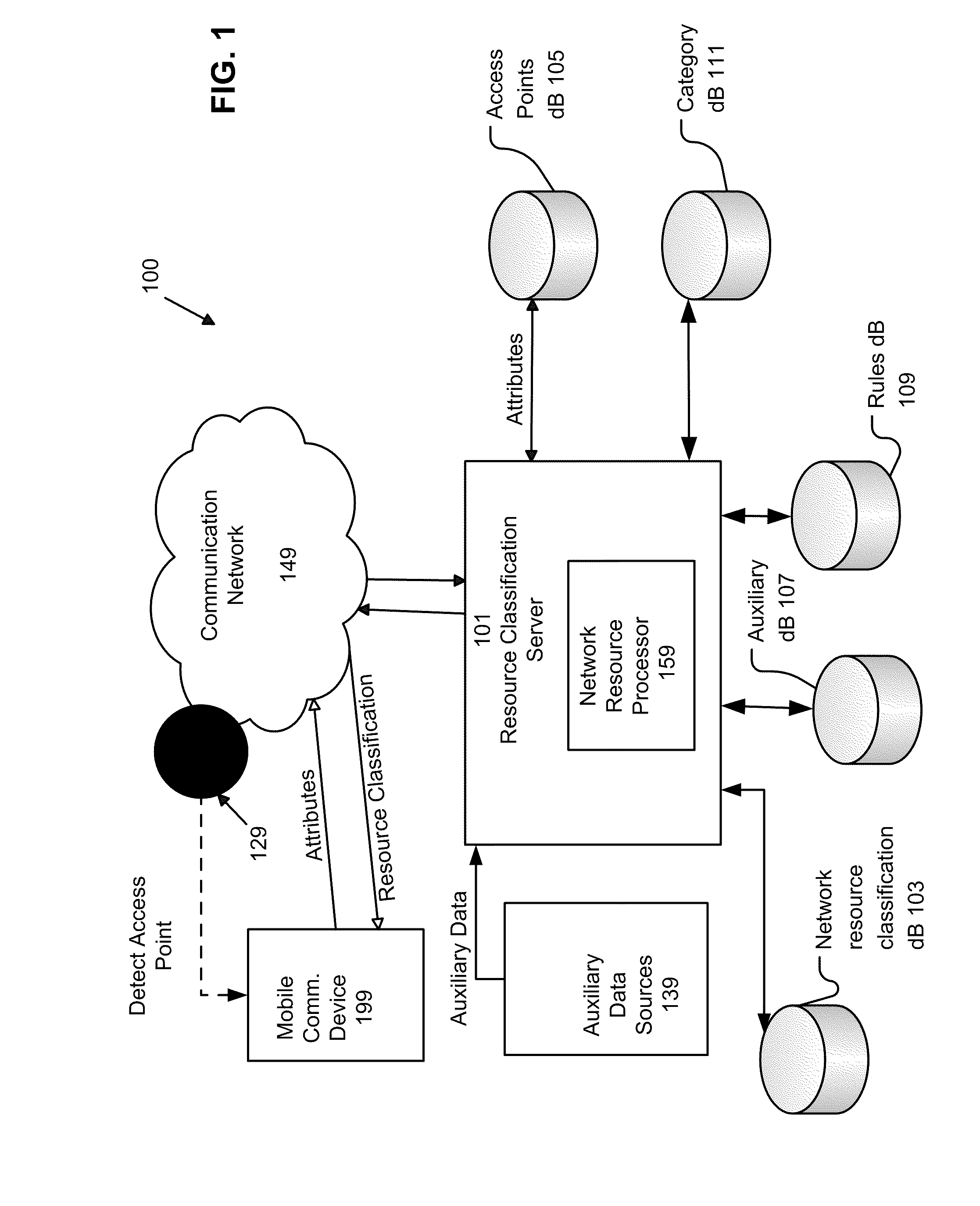
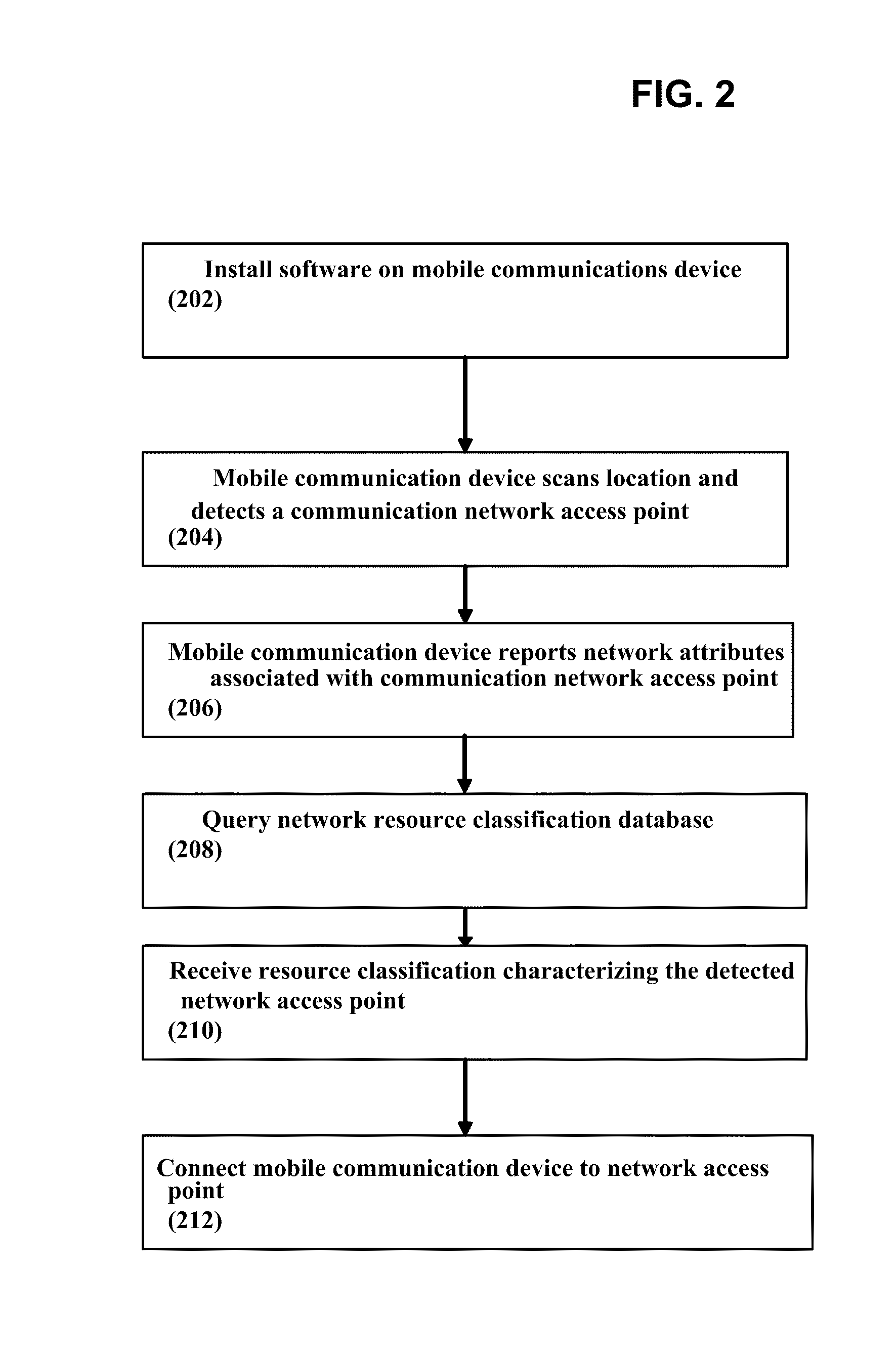
System and Method of Automatically Connecting a Mobile Communication Device to A Network Using a Communications Resource Database
ActiveUS20110159818A1Easy to useBridging the gapError preventionFrequency-division multiplex detailsNetwork access pointCommunication device
A system, method, and computer program product of automatically connecting a mobile communication device to a communication network using a network resource classification database includes detecting a communication network access point using the mobile communication device and reporting network attributes associated with the access point to a resource classification server. The server analyzes and stores the network attributes, determines auxiliary data related to the access point, and uses a rules database to determine a category identifier associated with the access point. The server creates a resource classification characterizing the access point based upon the network attributes, auxiliary data, and category identifier and the network attributes, auxiliary data, and / or category identifier data of other access points. The mobile communication device queries the server, receives a resource classification, and connects to an access point based upon the received resource classification.
Owner:WEFI
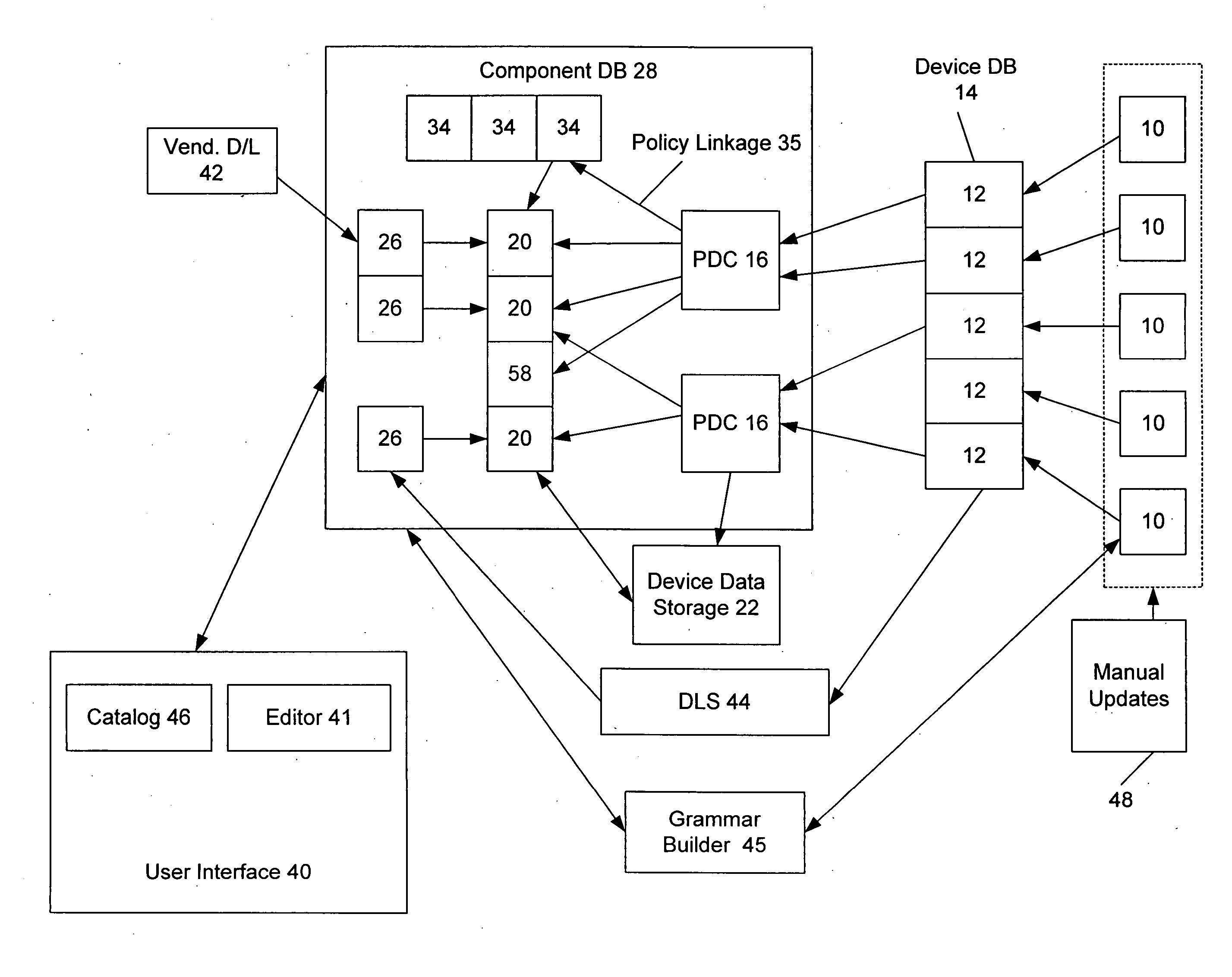
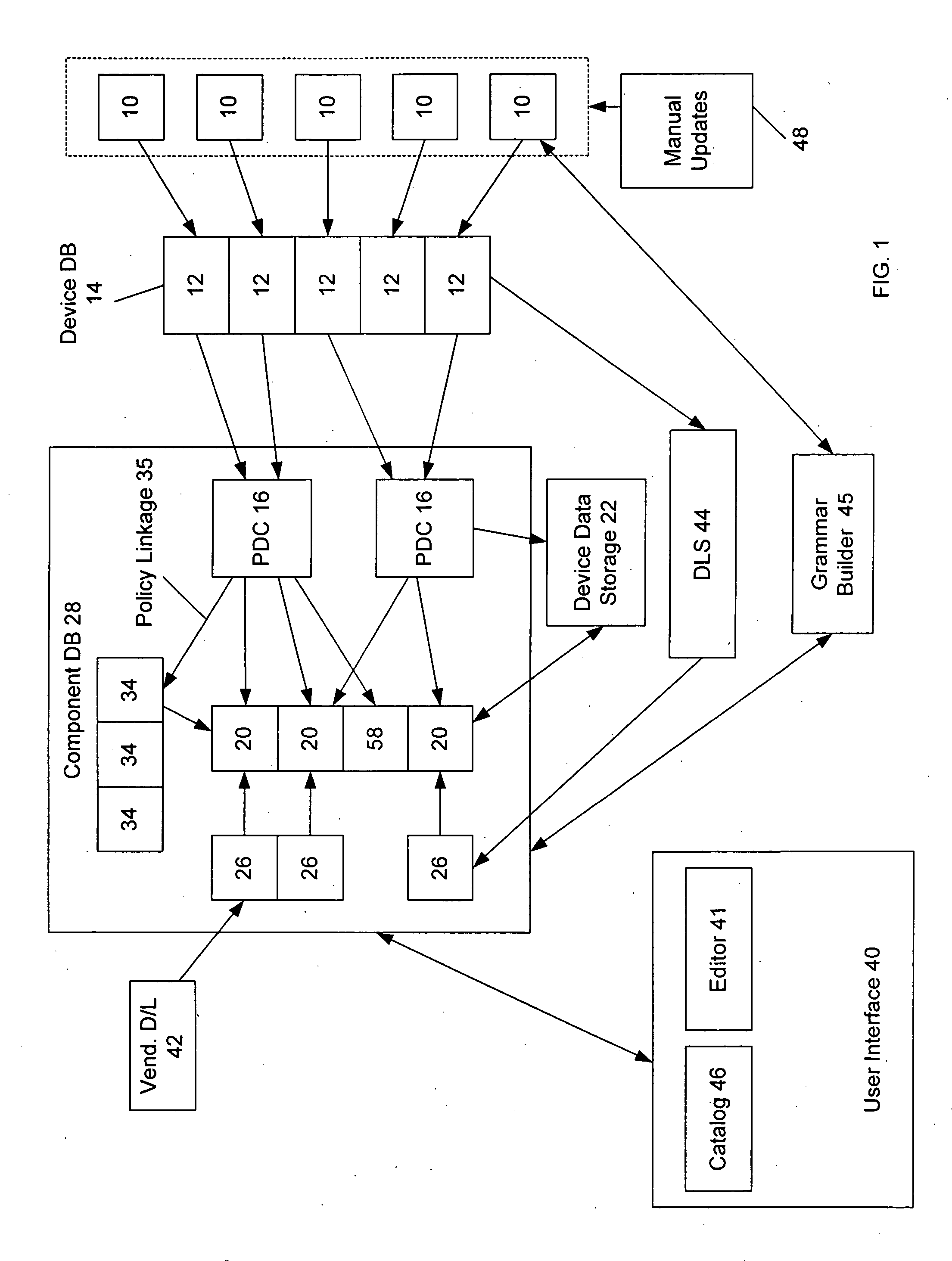
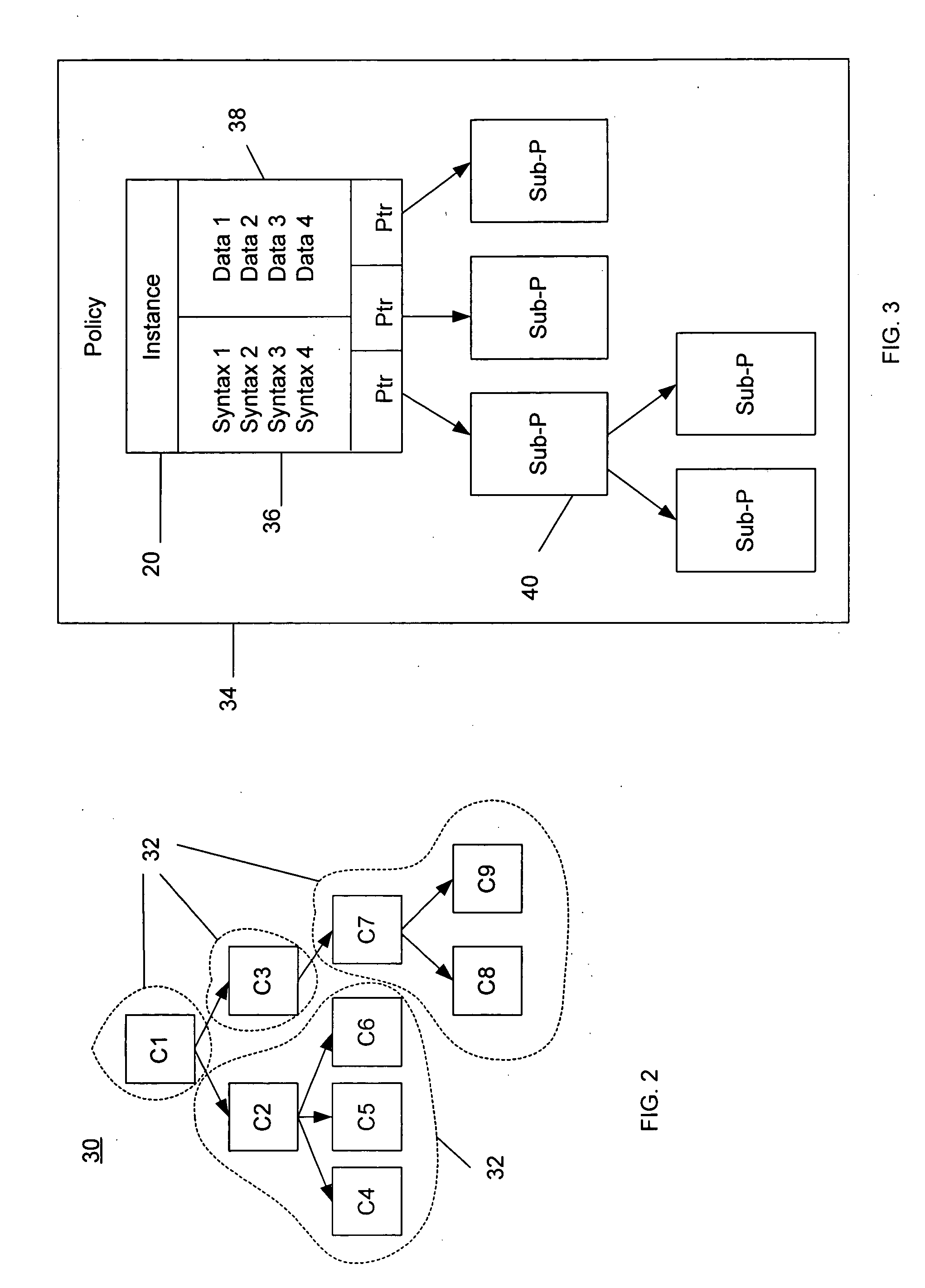
Methods and systems for controlling network infrastructure devices
InactiveUS20050004942A1Easy to createBridging the gapDigital data processing detailsData switching networksNetwork managementDistributed computing
A network management system is provided that allows a user to configure multiple devices according to a consistent set of policies. The system includes a device learning module that can read configuration data from a network device and automatically match that configuration data to existing policies and components of policies within the system. The device learning module also identifies unknown configuration data, which does not match any existing policy. The system further includes a grammar builder that can parse the unknown configuration data and construct a component or policy from the unknown data, by matching the unknown data to a grammar of configuration commands for the network device. The system also provided auditing capabilities, where policies are compared to running network configurations, and differences are identified.
Owner:NETWORK CLARITY
Quasi-plannar and FinFET-like transistors on bulk silicon
The types of quasi-planar CMOS and FinFET-like transistor devices on a bulk silicon substrate are disclosed. A first device has a doped and recessed channel formed in a shallow trench sidewall. A second device has a doped, recessed channel and has a plurality of edge-fins juxtaposed on an edge of an active region of the device. A third device has an undoped recessed channel formed in a sidewall of a shallow trench, wherein the undoped recessed channel further has a plurality of edge-fins disposed thereon. Additionally, an extra mask may be added to each device to allow for fabrication of both conventional transistors and FinFET-like transistors on bulk silicon. The extra mask may protect the source and drain areas from recess etching of the silicon substrate. Several methods of fabricating each device are also disclosed.
Owner:TAIWAN SEMICON MFG CO LTD
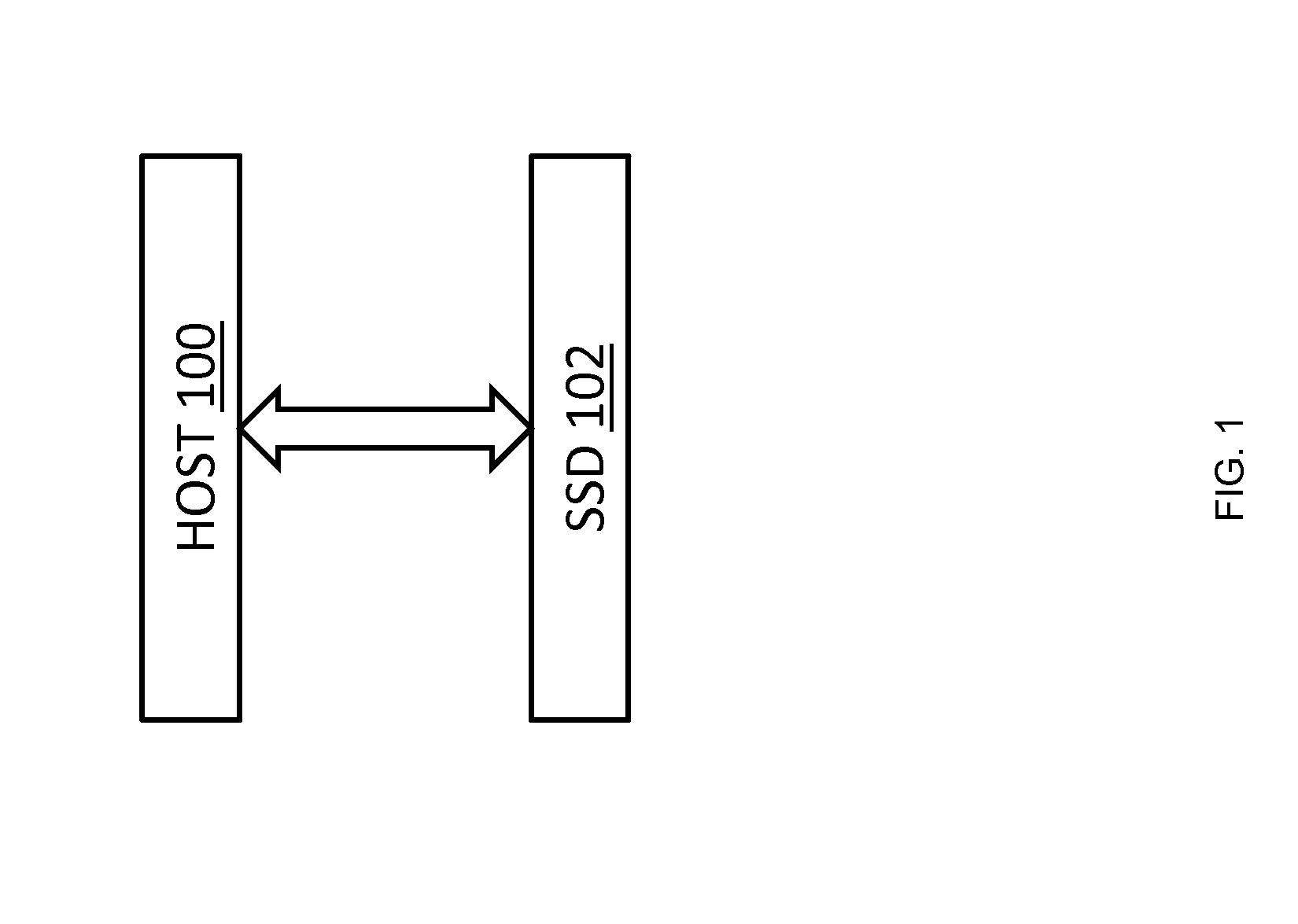
Content locality-based caching in a data storage system
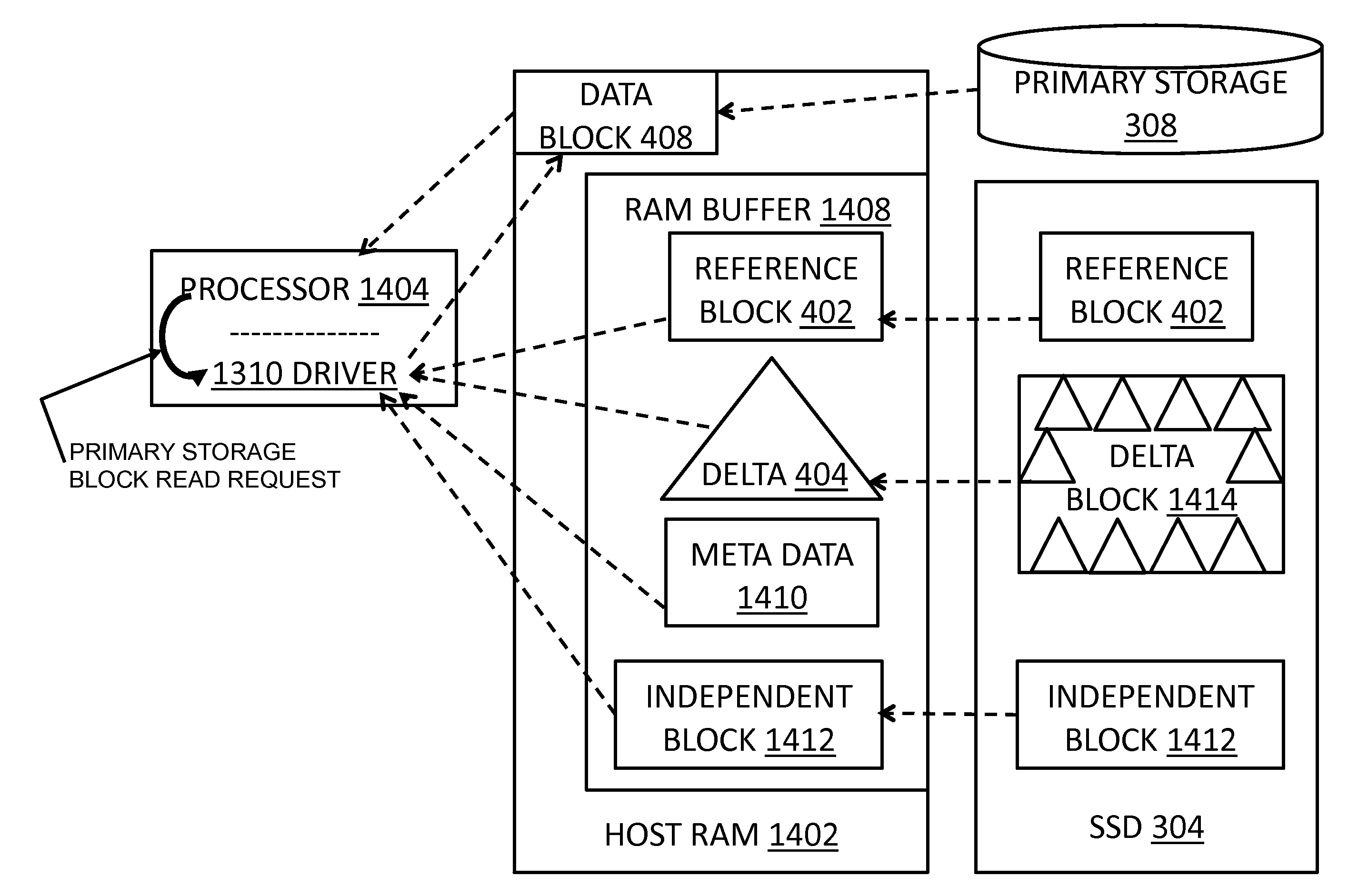
InactiveUS20120137059A1Quick upgradeLow costMemory architecture accessing/allocationEnergy efficient ICTData accessLeast frequently used
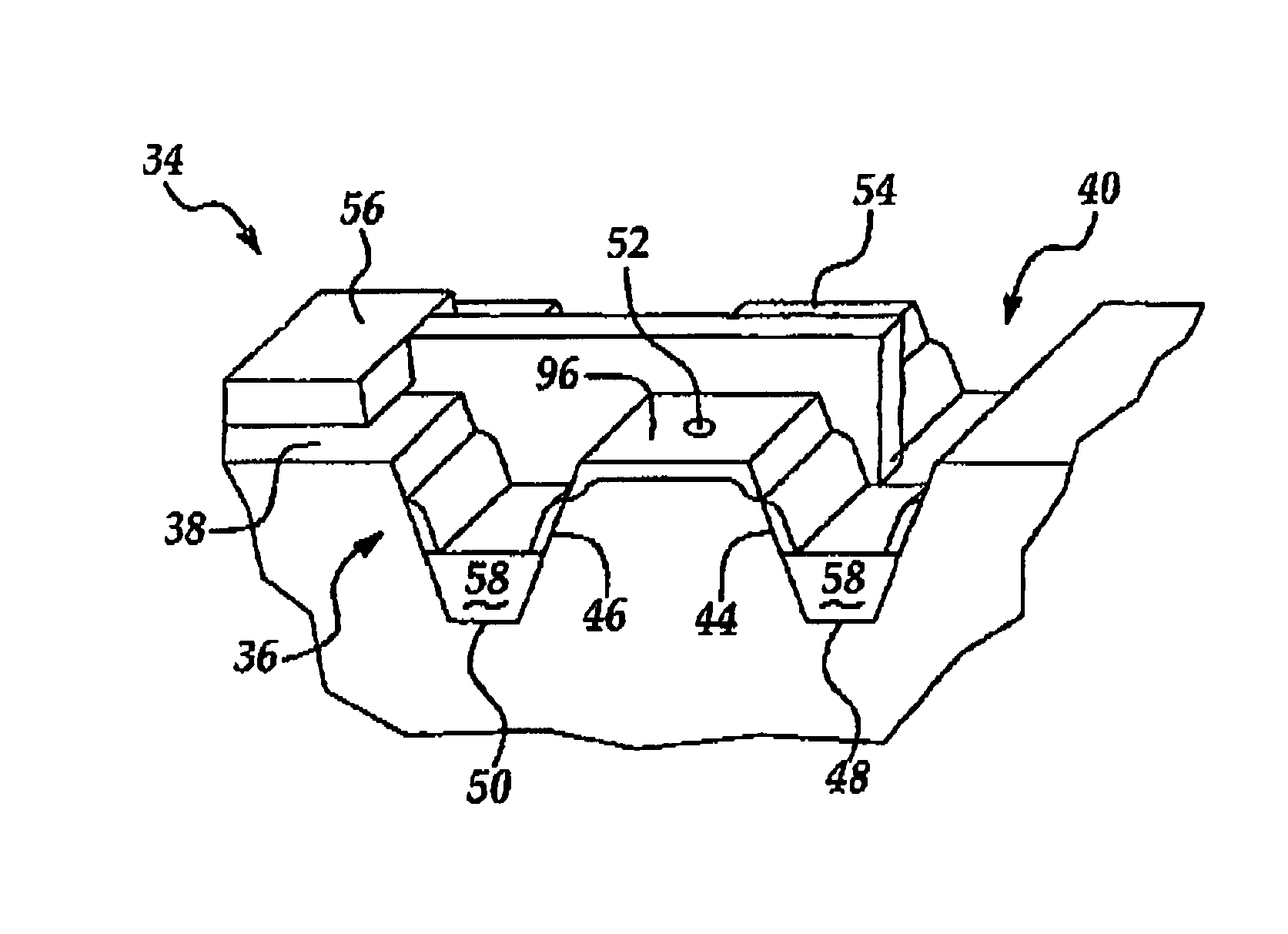
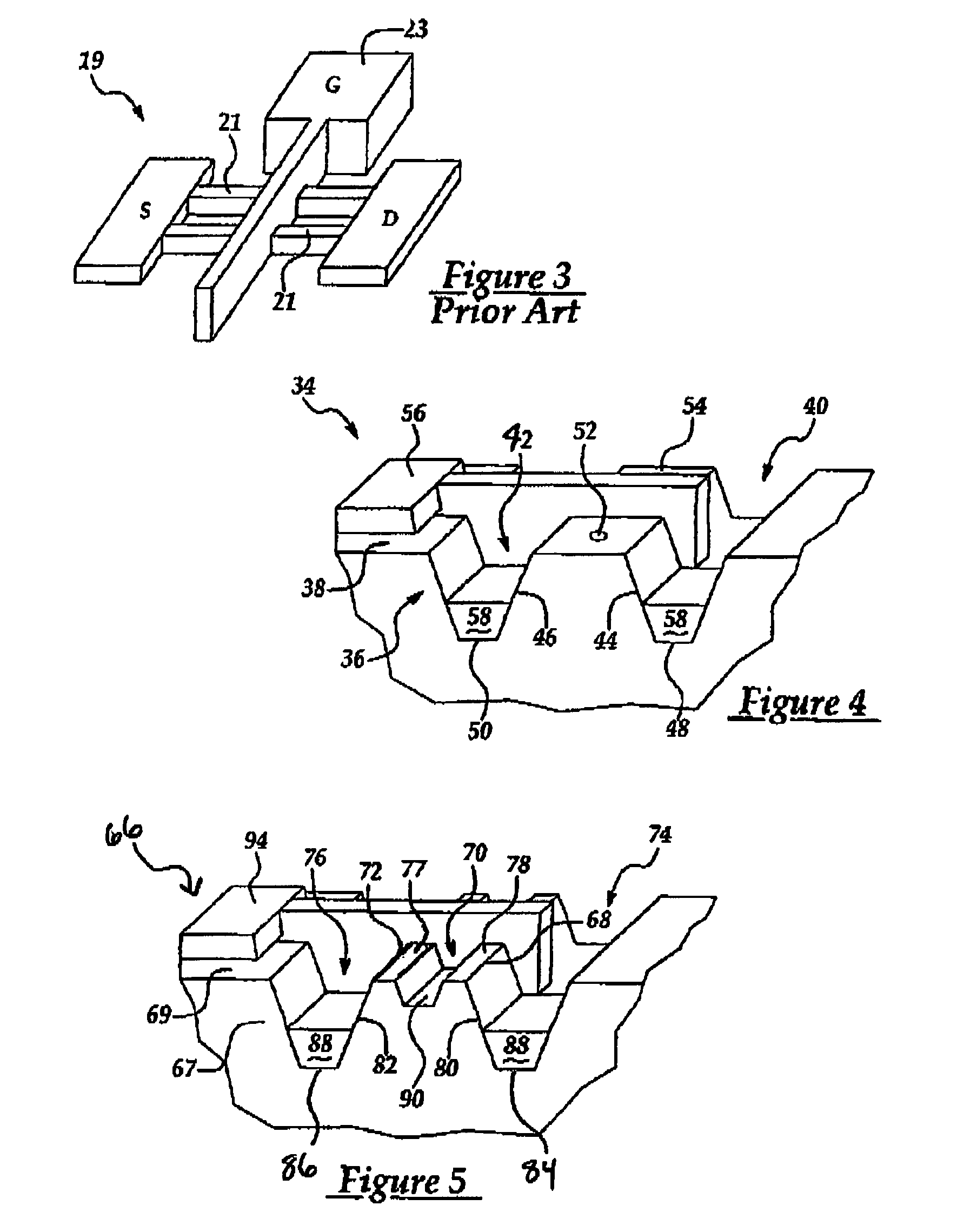
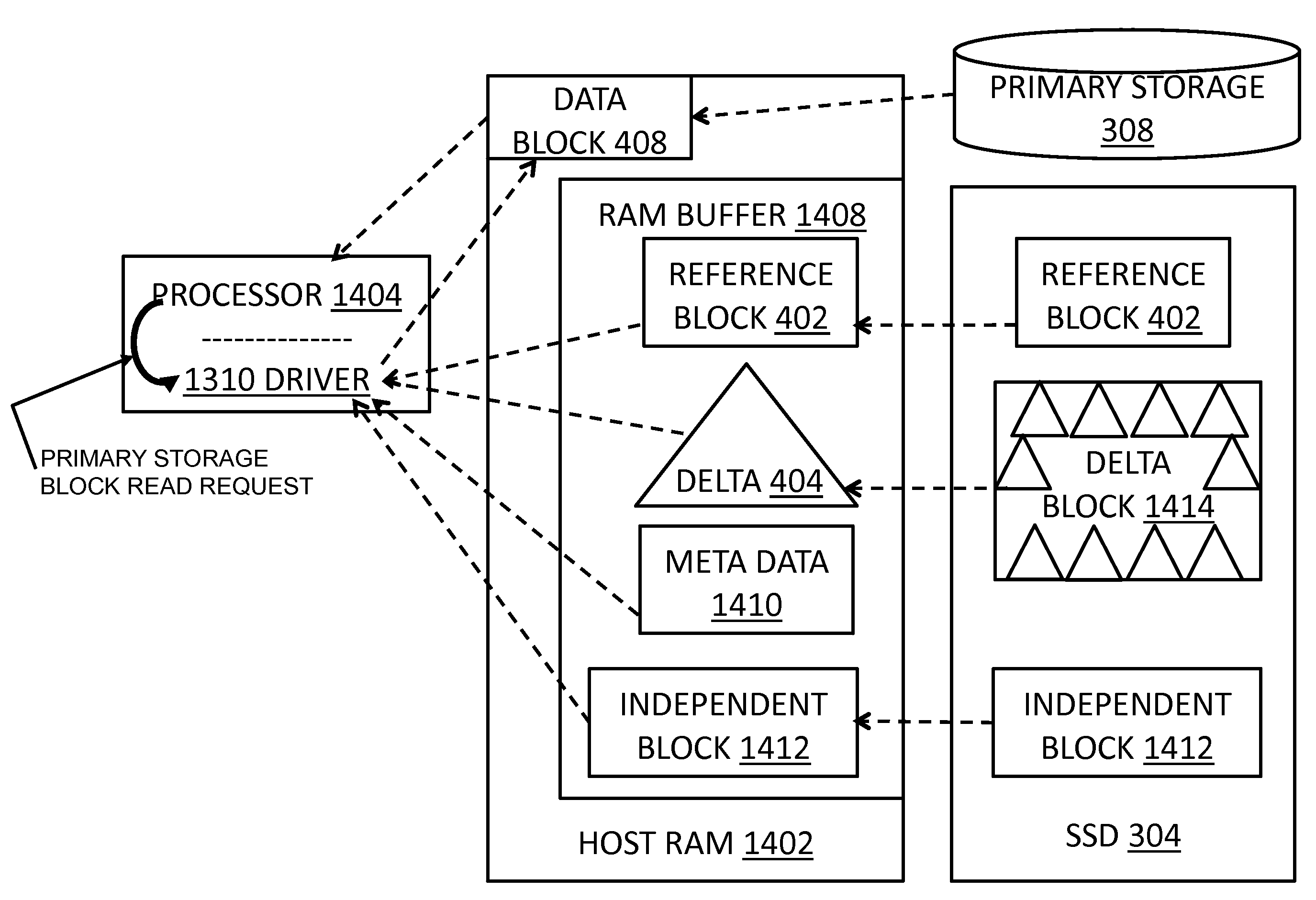
A data storage caching architecture supports using native local memory such as host-based RAM, and if available, Solid State Disk (SSD) memory for storing pre-cache delta-compression based delta, reference, and independent data by exploiting content locality, temporal locality, and spatial locality of data accesses to primary (e.g. disk-based) storage. The architecture makes excellent use of the physical properties of the different types of memory available (fast r / w RAM, low cost fast read SSD, etc) by applying algorithms to determine what types of data to store in each type of memory. Algorithms include similarity detection, delta compression, least popularly used cache management, conservative insertion and promotion cache replacement, and the like.
Owner:VELOBIT
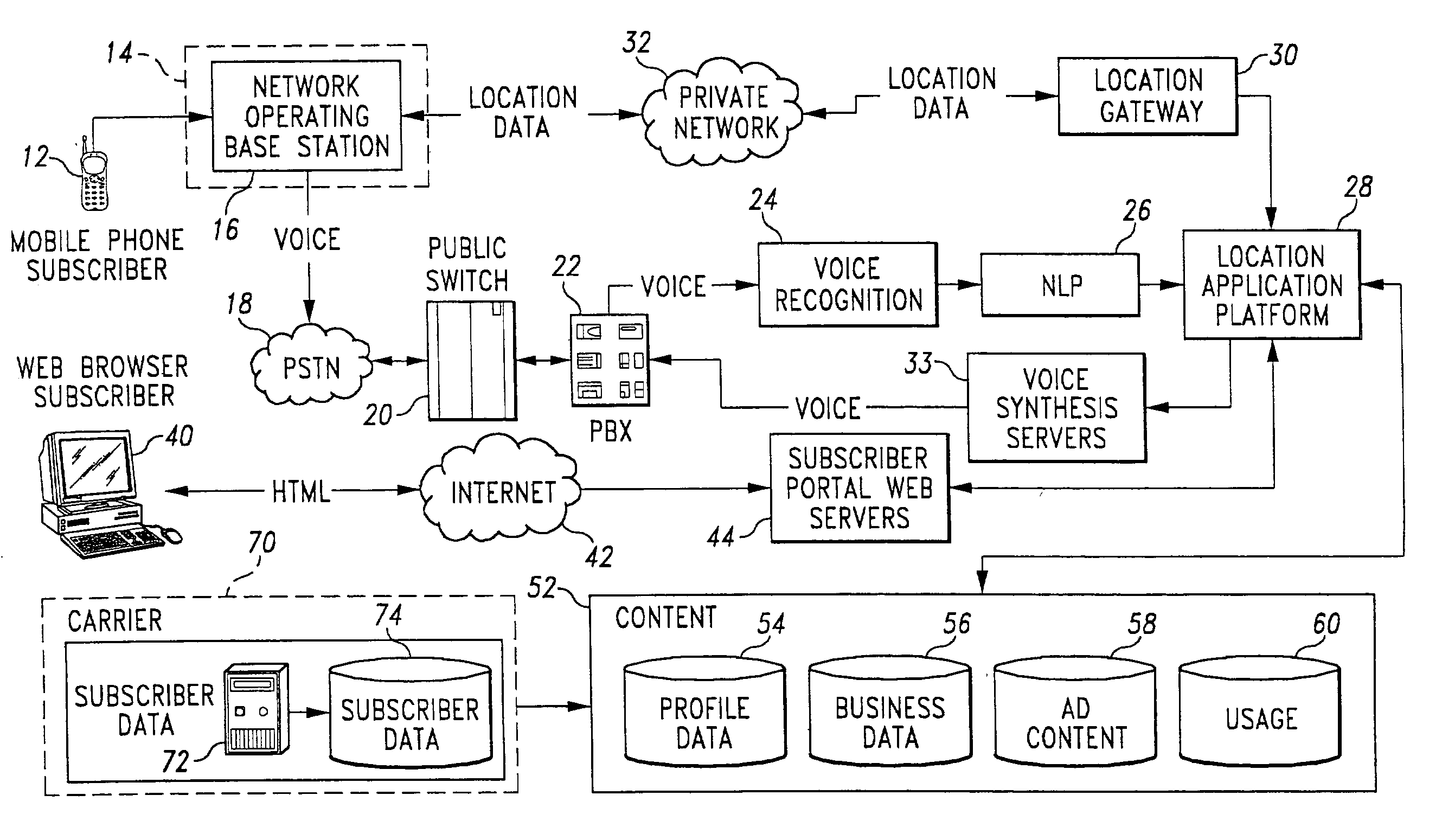
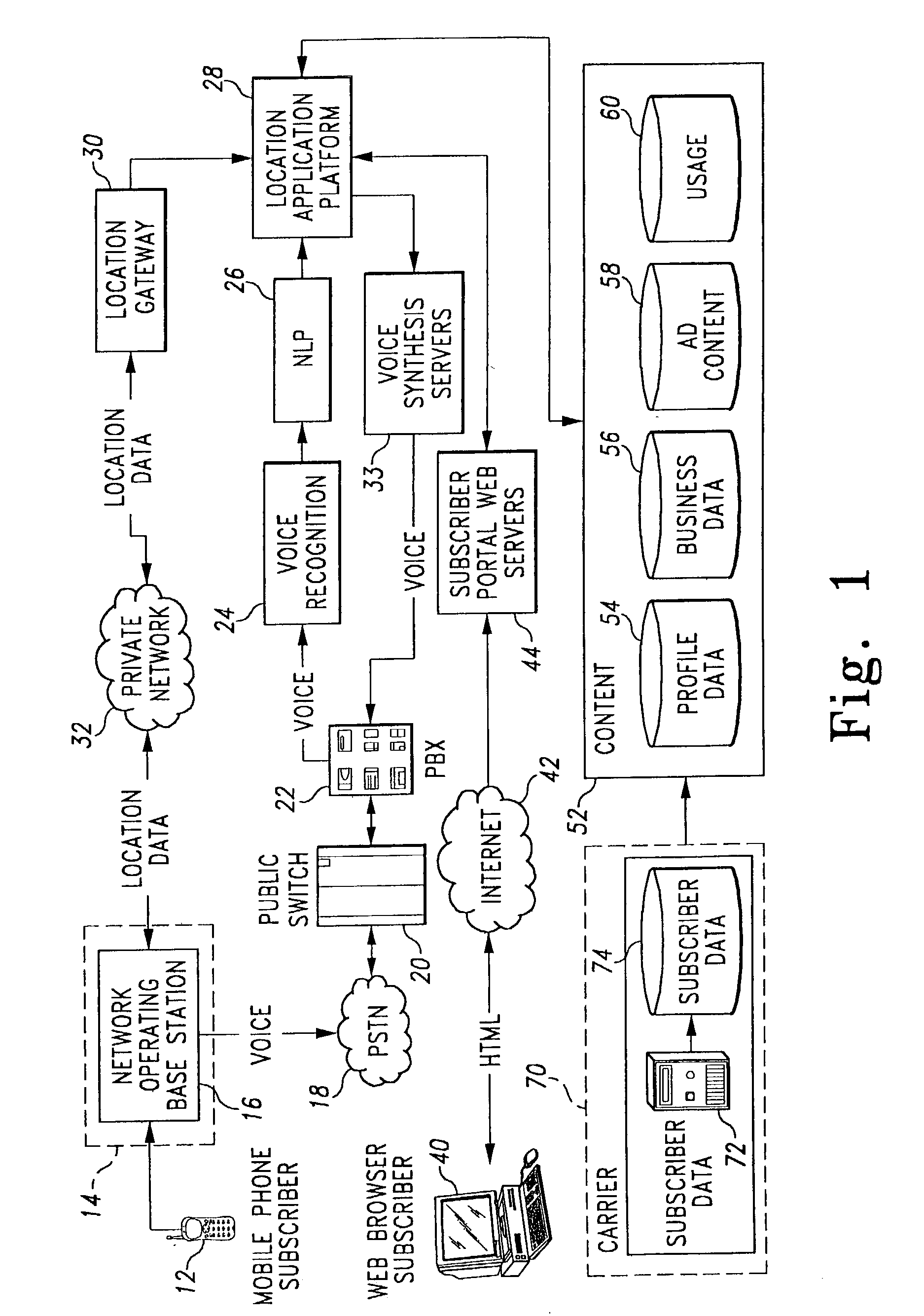
Natural language processing for a location-based services system
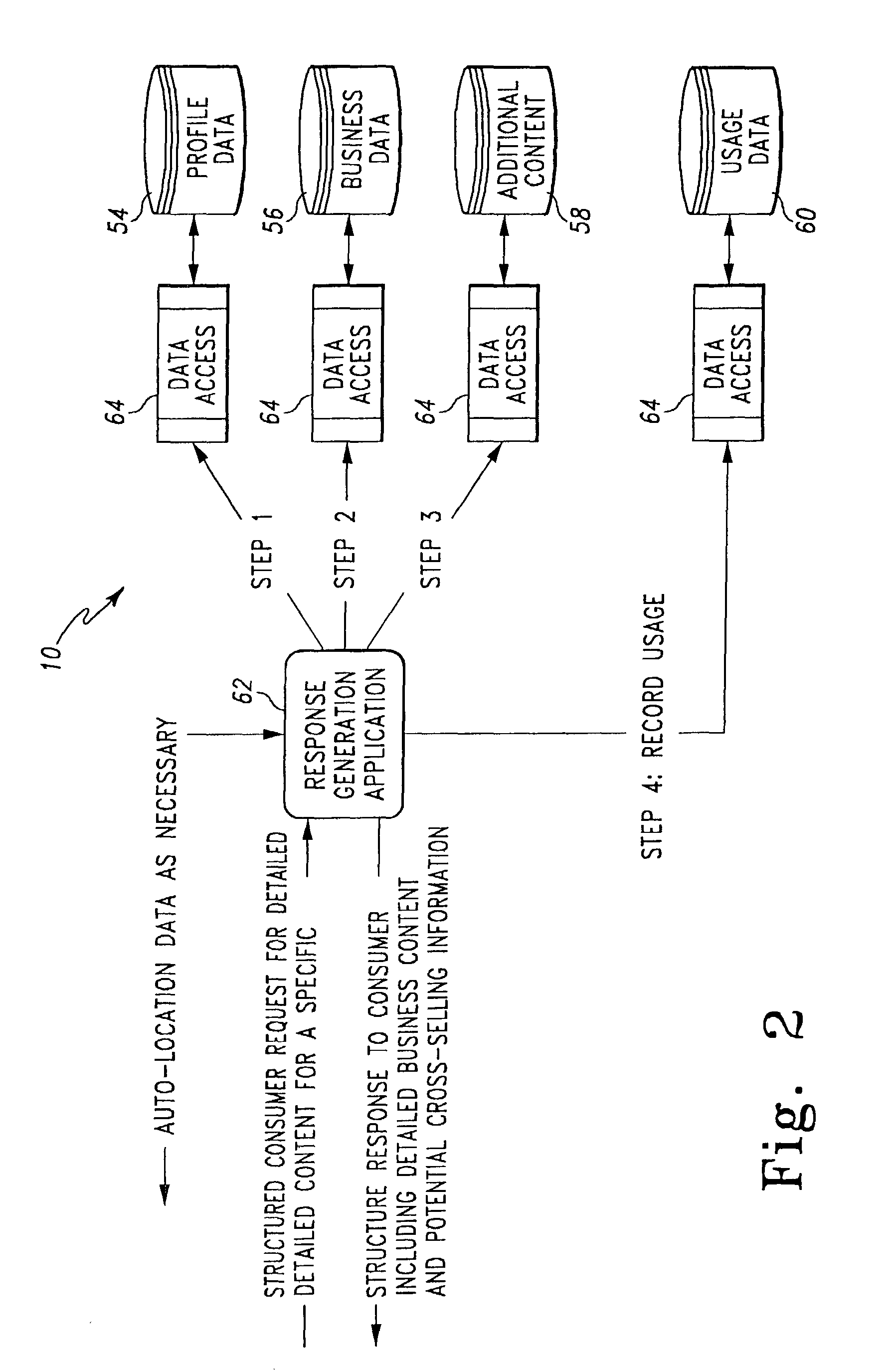
InactiveUS20040243417A9Improve speech recognition performanceImprove user experienceDigital data information retrievalSpecial service for subscribersResponse generationCommunications system
A method and system for providing natural language processing in a communication system is disclosed. A voice request is generated with a remote terminal that is transmitted to a base station. A voice recognition application is then used to identify a plurality of words that are contained in the voice request. After the words are identified, a grammar associated with each word is also identified. Once the grammars have been identified, each word is categorized into a respective grammar category. A structured response is then generated to the voice request with a response generation application.
Owner:ACCENTURE GLOBAL SERVICES LTD
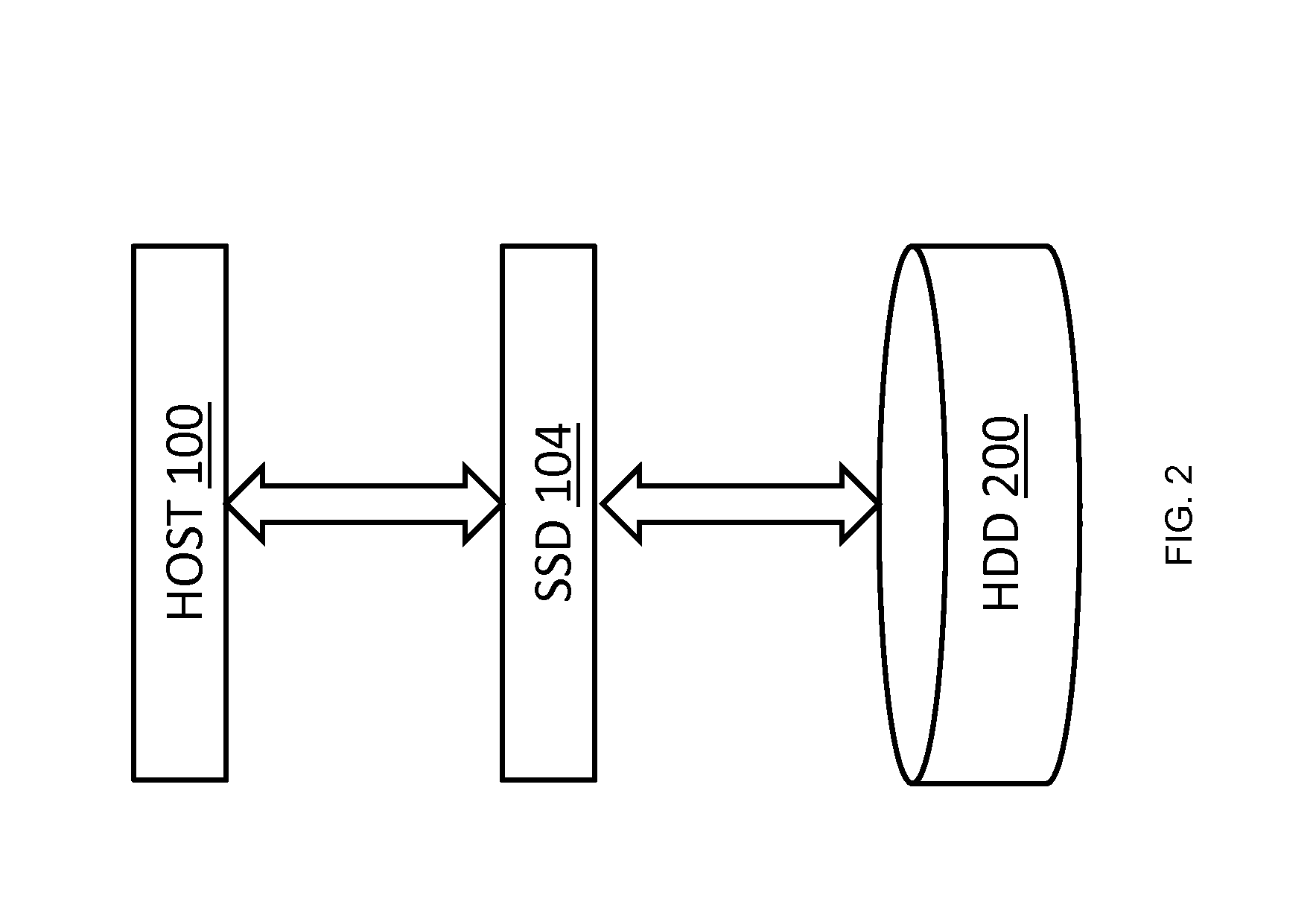
Pre-cache similarity-based delta compression for use in a data storage system
ActiveUS20120137061A1Quick upgradeHigh-speed random readMemory architecture accessing/allocationEnergy efficient ICTIndex compressionLeast frequently used
A data storage caching architecture supports using native local memory such as host-based RAM, and if available, Solid State Disk (SSD) memory for storing pre-cache delta-compression based delta, reference, and independent data by exploiting content locality, temporal locality, and spatial locality of data accesses to primary (e.g. disk-based) storage. The architecture makes excellent use of the physical properties of the different types of memory available (fast r / w RAM, low cost fast read SSD, etc) by applying algorithms to determine what types of data to store in each type of memory. Algorithms include similarity detection, delta compression, least popularly used cache management, conservative insertion and promotion cache replacement, and the like.
Owner:WESTERN DIGITAL TECH INC
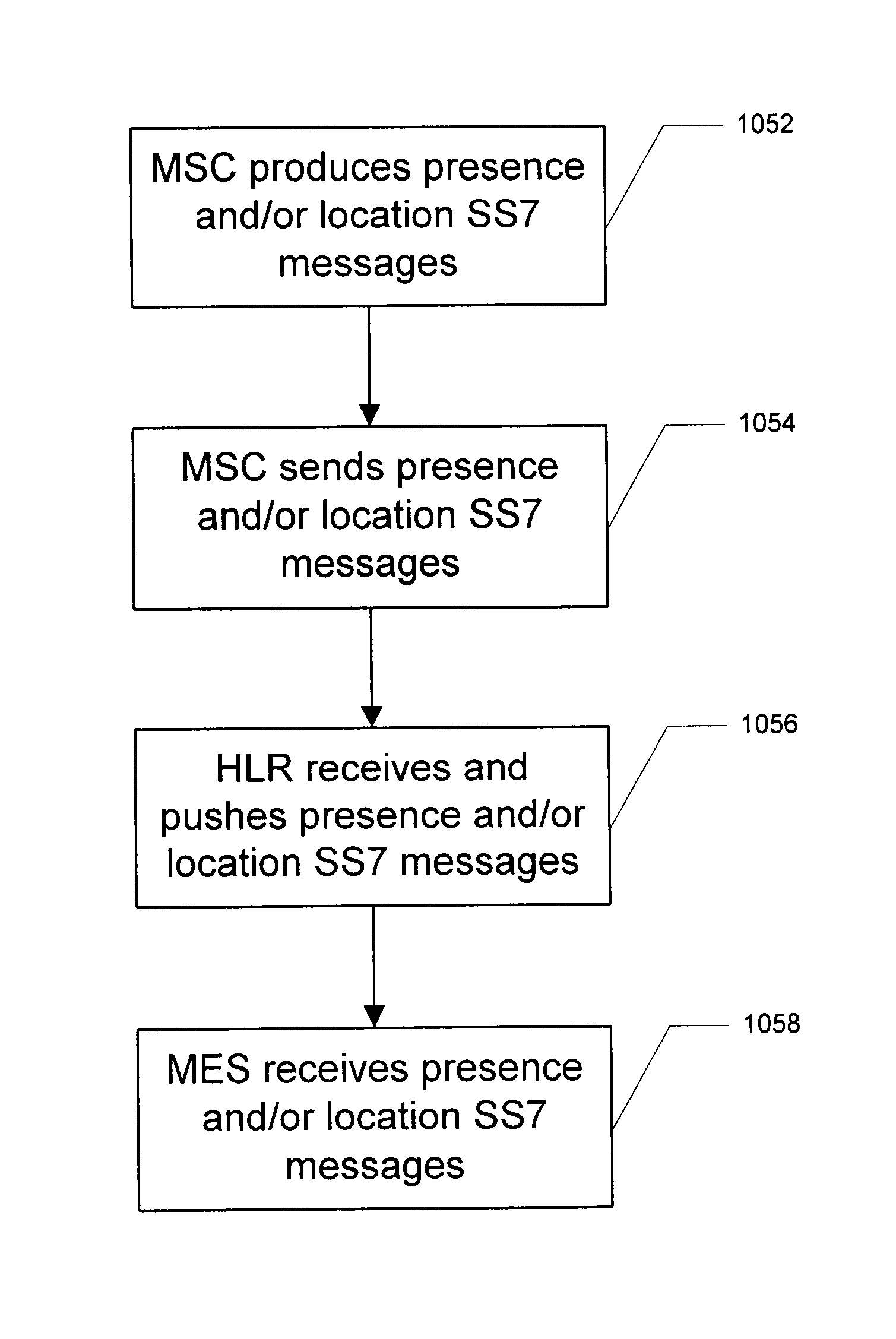
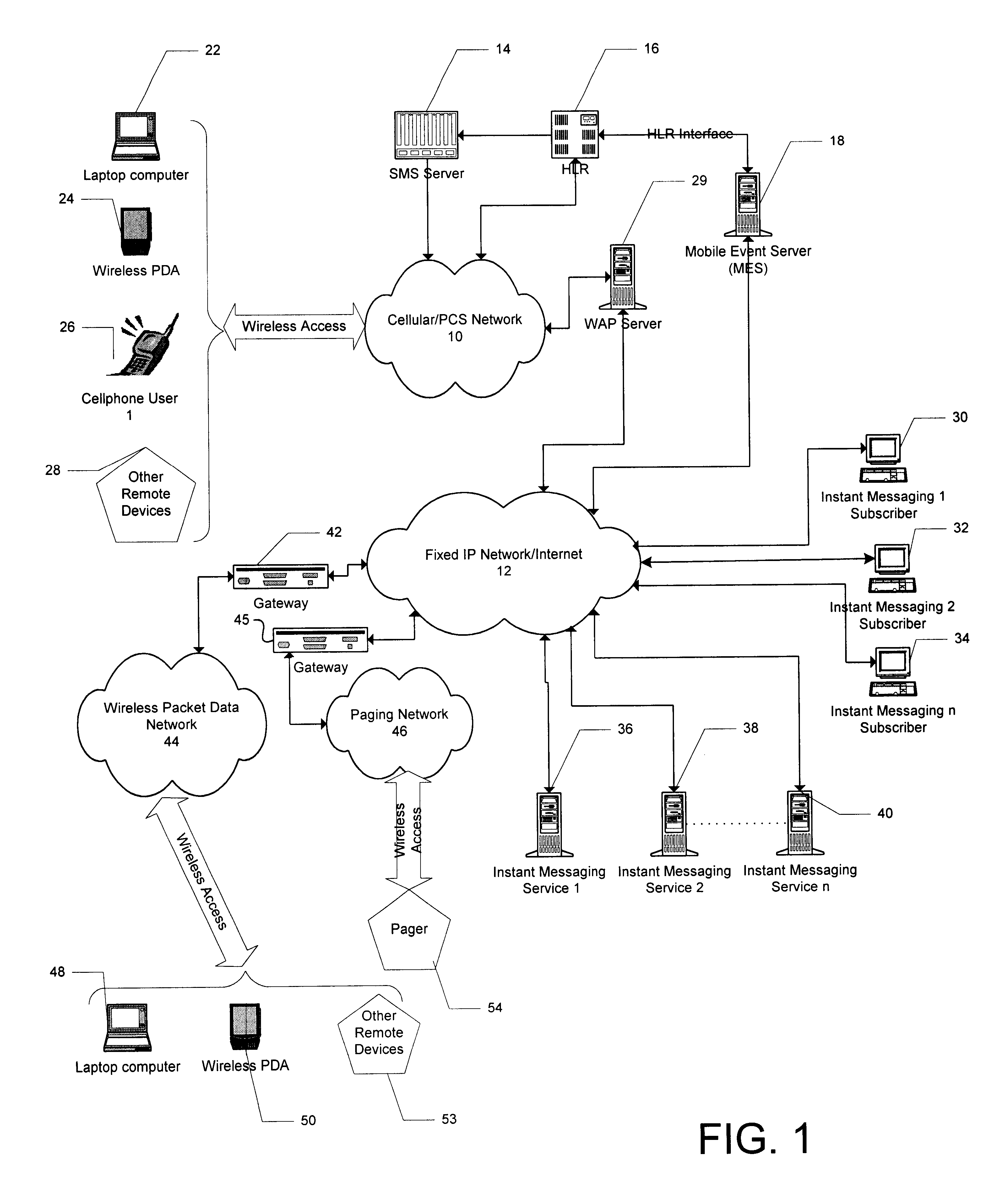
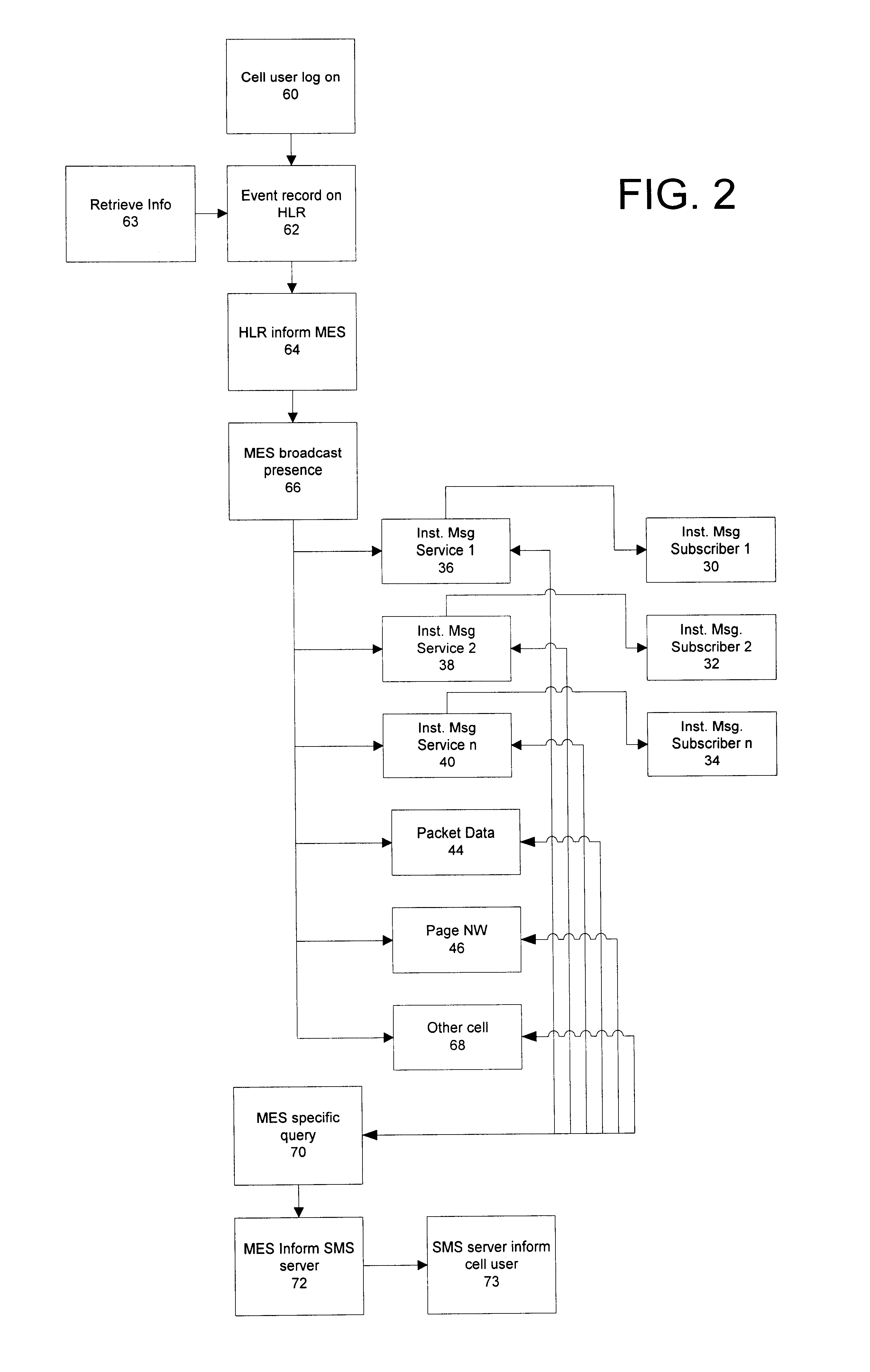
Method and apparatus for sharing mobile user event information between wireless networks and fixed IP networks
InactiveUS6839554B2Easy to shareBridging the gapData switching by path configurationRadio/inductive link selection arrangementsWireless mesh networkModem device
The present invention provides for a system and method for sharing user event information (such as, and without limitation, presence on a network) among mobile (wireless) devices and those connected to fixed IP networks such as the Internet. In accordance with embodiments of the invention, the system and method support instant messaging between wireless devices and fixed IP network devices and between wireless devices and other wireless devices. The term wireless device is used broadly to include cell phones, laptop computers with wireless modems, wireless PDAs, and any other remote wireless devices.
Owner:ALTAMIRA TECH
Operating system with haptic interface for minimally invasive, hand-held surgical instrument
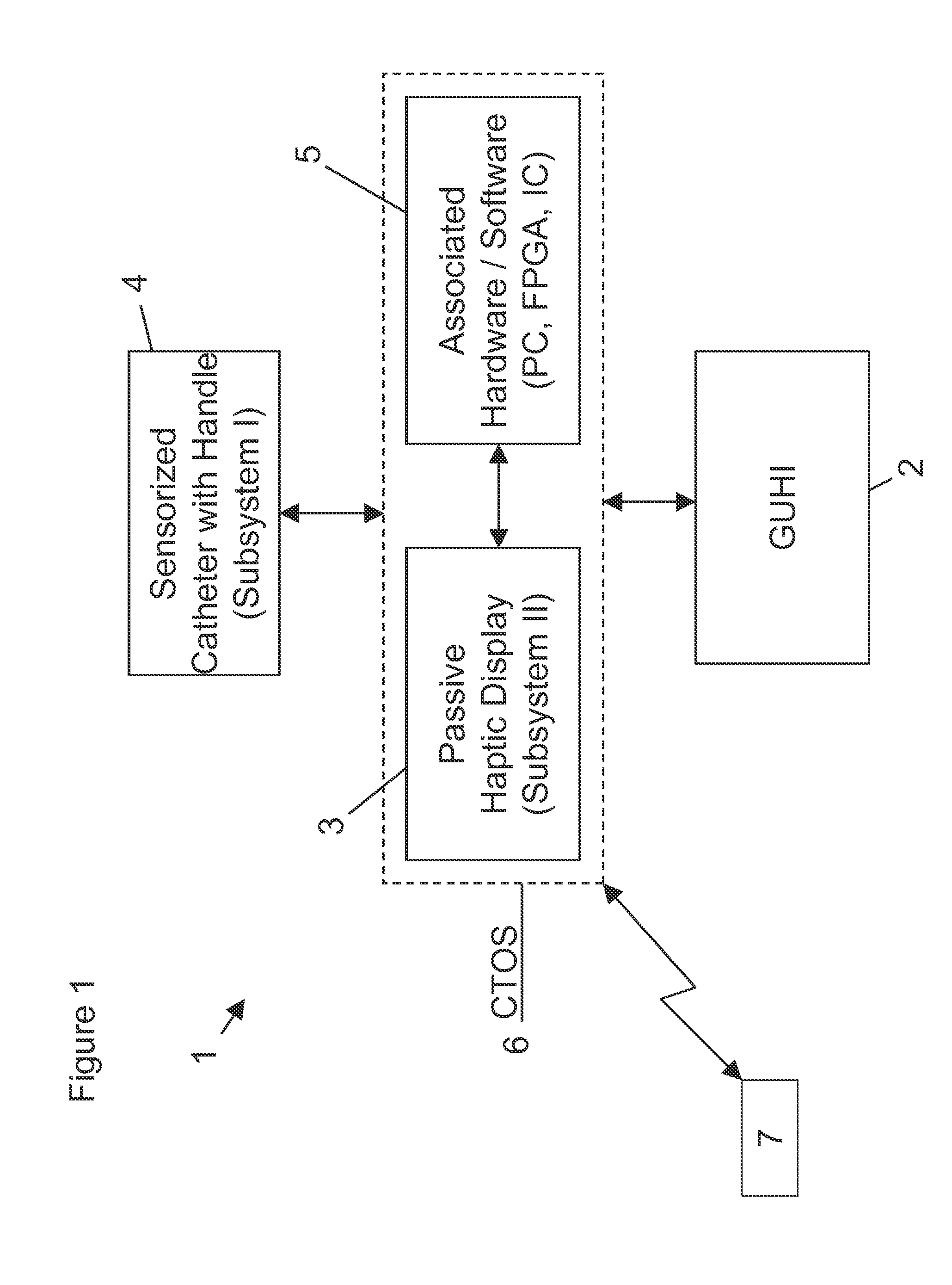
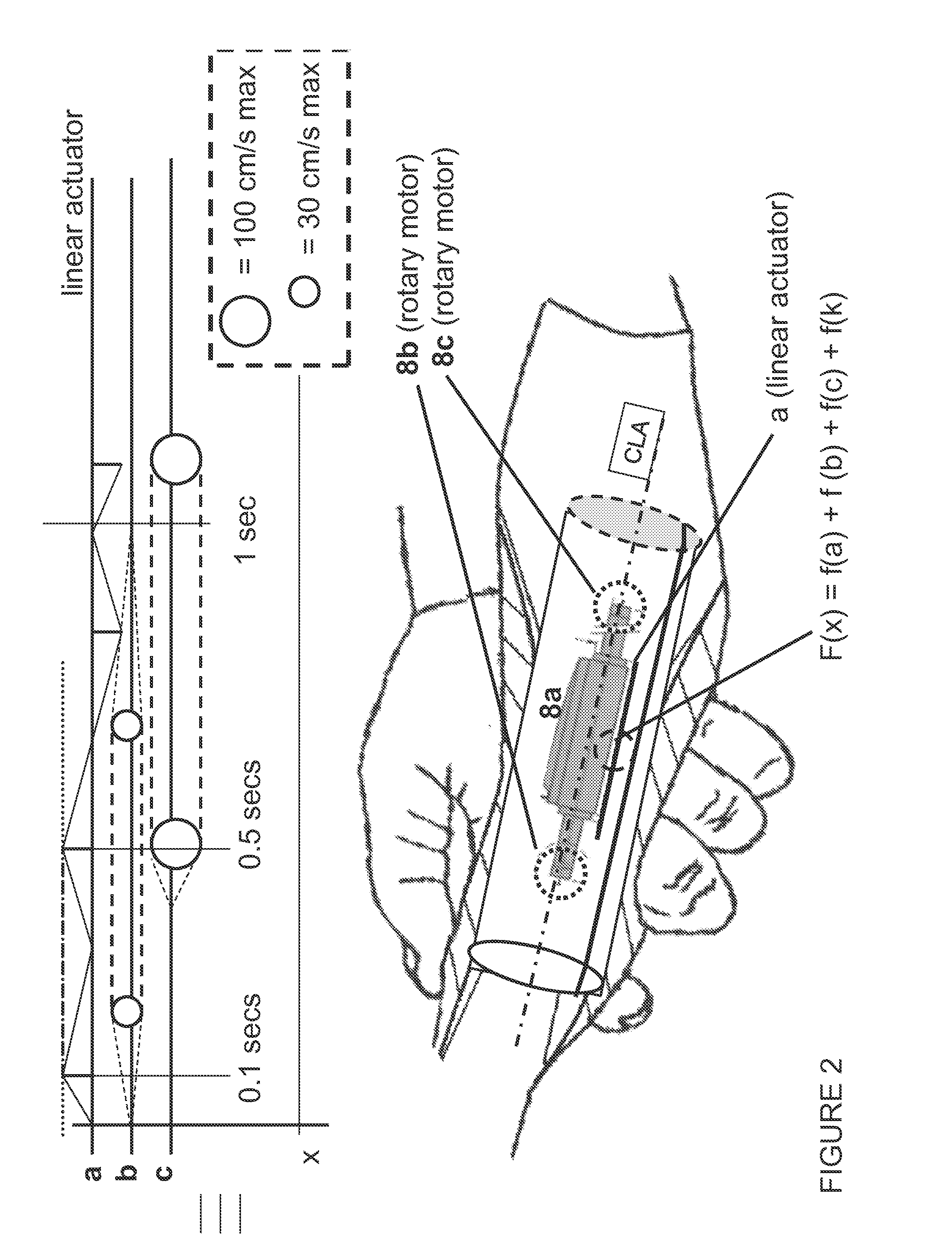
ActiveUS20130321262A1Bridging the gapMechanical/radiation/invasive therapiesSurgical navigation systemsGraphicsOperational system
A haptic system for a minimally invasive, hand-held surgical instrument and the system's various parts including a graphical user haptic interface, one or more haptic interfaces associated with a hand-held handle used to control a sensorized end-effector of the surgical instrument or inserted catheters, associated hardware, and an operating system. The system enables users to acquire, read, modify, store, write, and download sensor-acquired data in real time. The system can provide: an open, universally compatible platform capable of sensing or acquiring physiological signals / data in any format; processing of the sensor acquired data within an operating system; and outputting the processed signals to hardware which generates tangible sensations via one or more haptic interfaces. These tangible sensations can be modified by the user in real time as the system ensures the temporal relationship of sensed fiducial events are not altered or shifted relative to the generated and displayed haptic signals.
Owner:STUART SCHECTER LLC
Quasi-plannar and FinFET-like transistors on bulk silicon
The types of quasi-planar CMOS and FinFET-like transistor devices on a bulk silicon substrate are disclosed. A first device has a doped and recessed channel formed in a shallow trench sidewall. A second device has a doped, recessed channel and has a plurality of edge-fins juxtaposed on an edge of an active region of the device. A third device has an undoped recessed channel formed in a sidewall of a shallow trench, wherein the undoped recessed channel further has a plurality of edge-fins disposed thereon. Additionally, an extra mask may be added to each device to allow for fabrication of both conventional transistors and FinFET-like transistors on bulk silicon. The extra mask may protect the source and drain areas from recess etching of the silicon substrate. Several methods of fabricating each device are also disclosed.
Owner:TAIWAN SEMICON MFG CO LTD
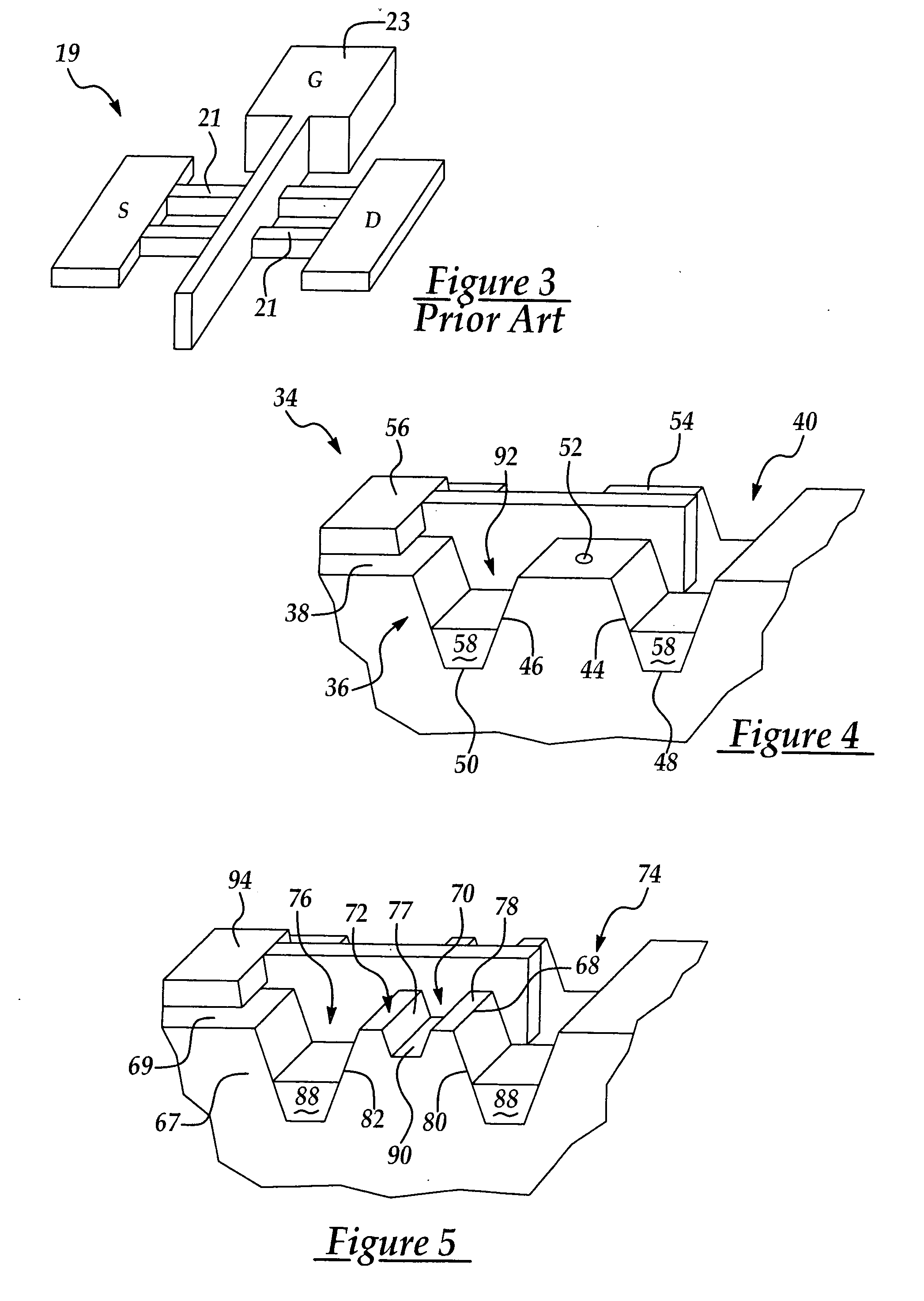
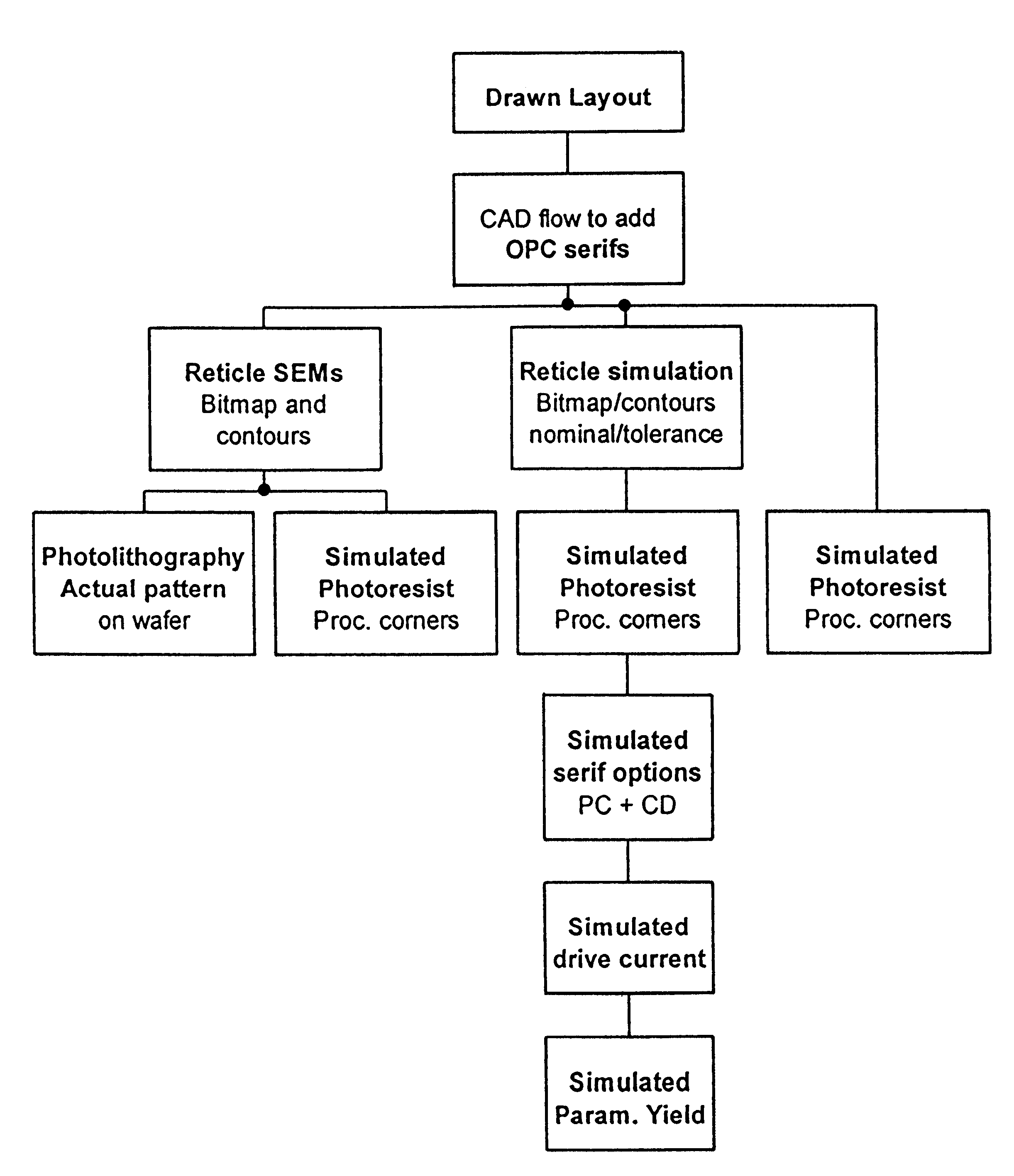
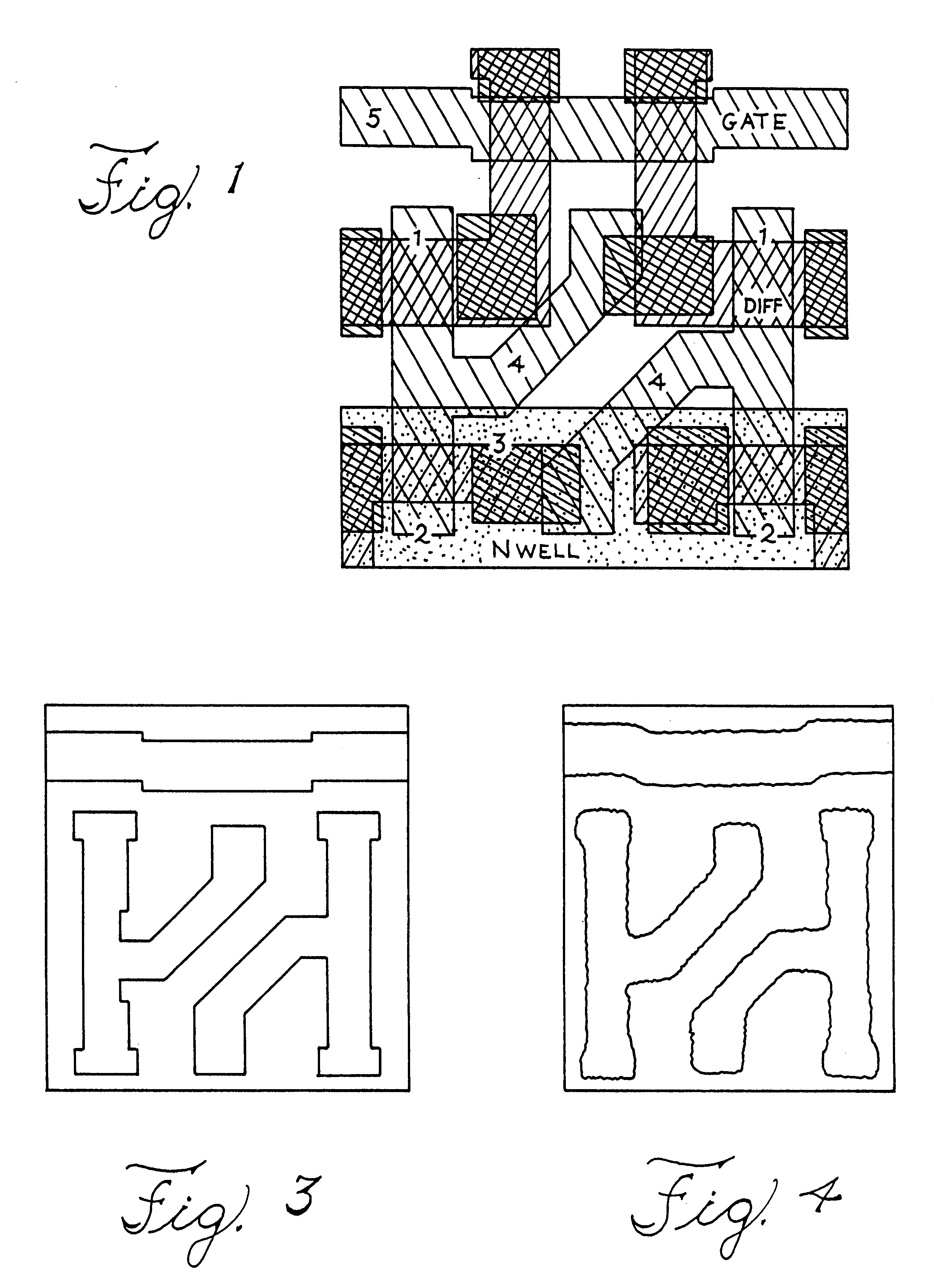
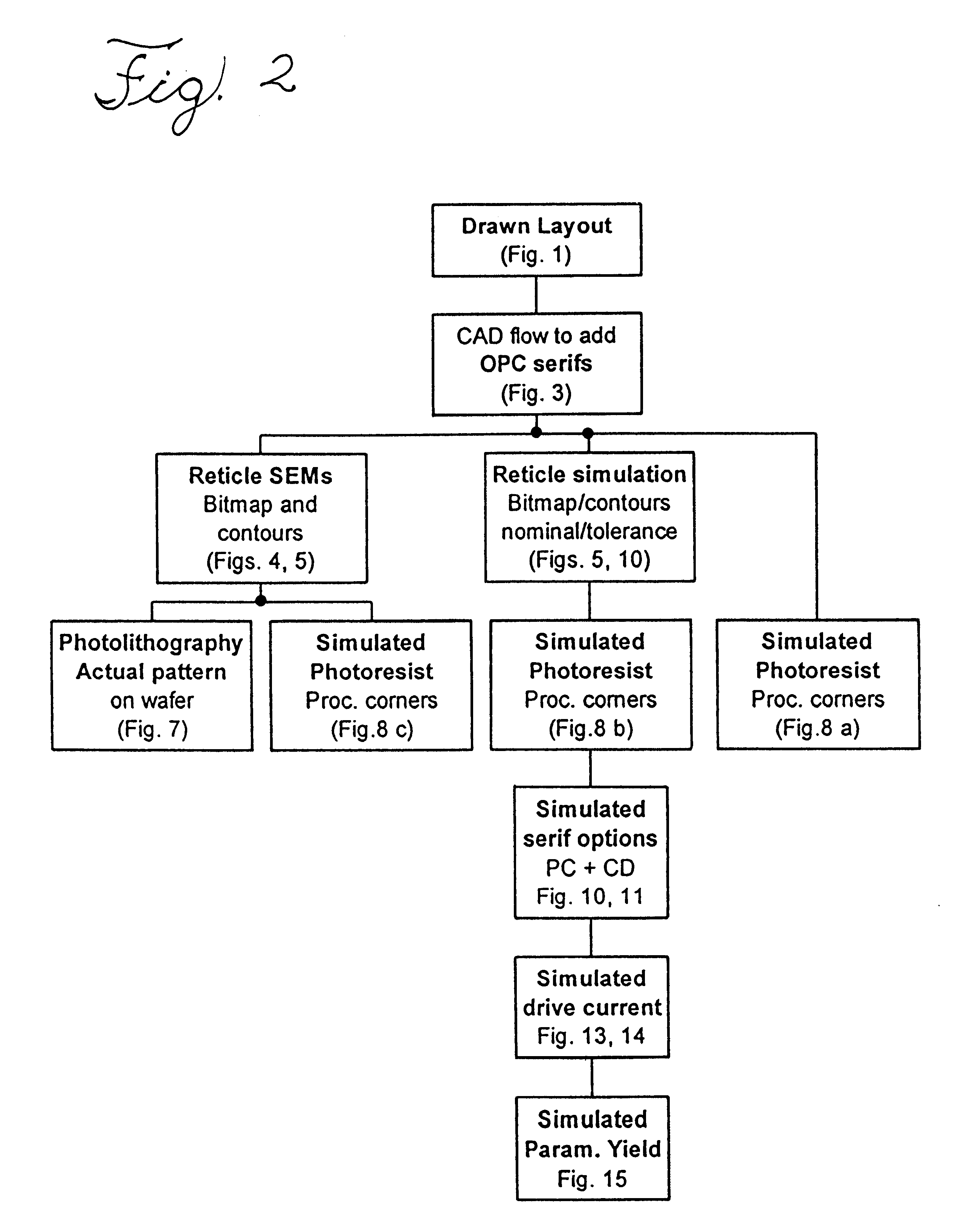
Integrated scheme for predicting yield of semiconductor (MOS) devices from designed layout
InactiveUS6562638B1Reduced device variabilityBridging the gapSemiconductor/solid-state device testing/measurementSemiconductor/solid-state device manufacturingMOSFETEngineering
A method for determining device yield of a semiconductor device design, includes determining statistics of at least one MOSFET parameter from a gate pattern, and calculating device yield from the at least one MOSFET parameter. The method provides a direct simulation link from device layout to device performance.
Owner:MONTEREY RES LLC +2
Probabilistic system for natural language processing
InactiveUS20020128816A1Free-text documents easierLess-expensive to produceSemantic analysisText processingProbit modelNatural language understanding
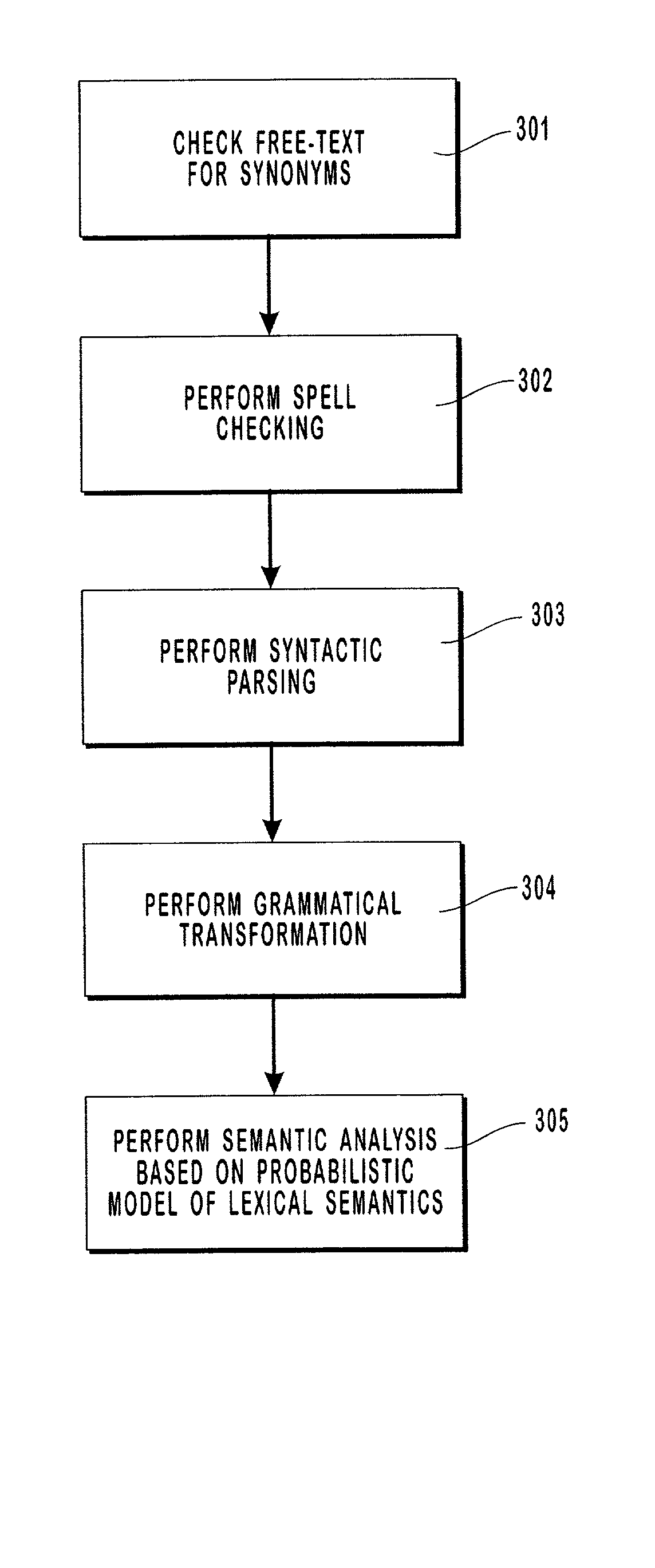
A natural language understanding system is described to provide generation of concept codes from free-text medical data. A probabilistic model of lexical semantics, is implemented by means of a Bayesian network, and is used to determine the most probable concept or meaning associated with a sentence or phrase. The inventive method and system includes the steps of checking for synonyms, checking spelling, performing syntactic parsing, transforming text to its "deep" or semantic form, and performing a semantic analysis based on a probabilistic model of lexical semantics.
Owner:INTERMOUNTAIN INTELLECTUAL ASSET MANAGEMENT LLC
Apparatus and method for converting an audiosignal into a parameterized representation, apparatus and method for modifying a parameterized representation, apparatus and method for synthesizing a parameterized representation of an audio signal
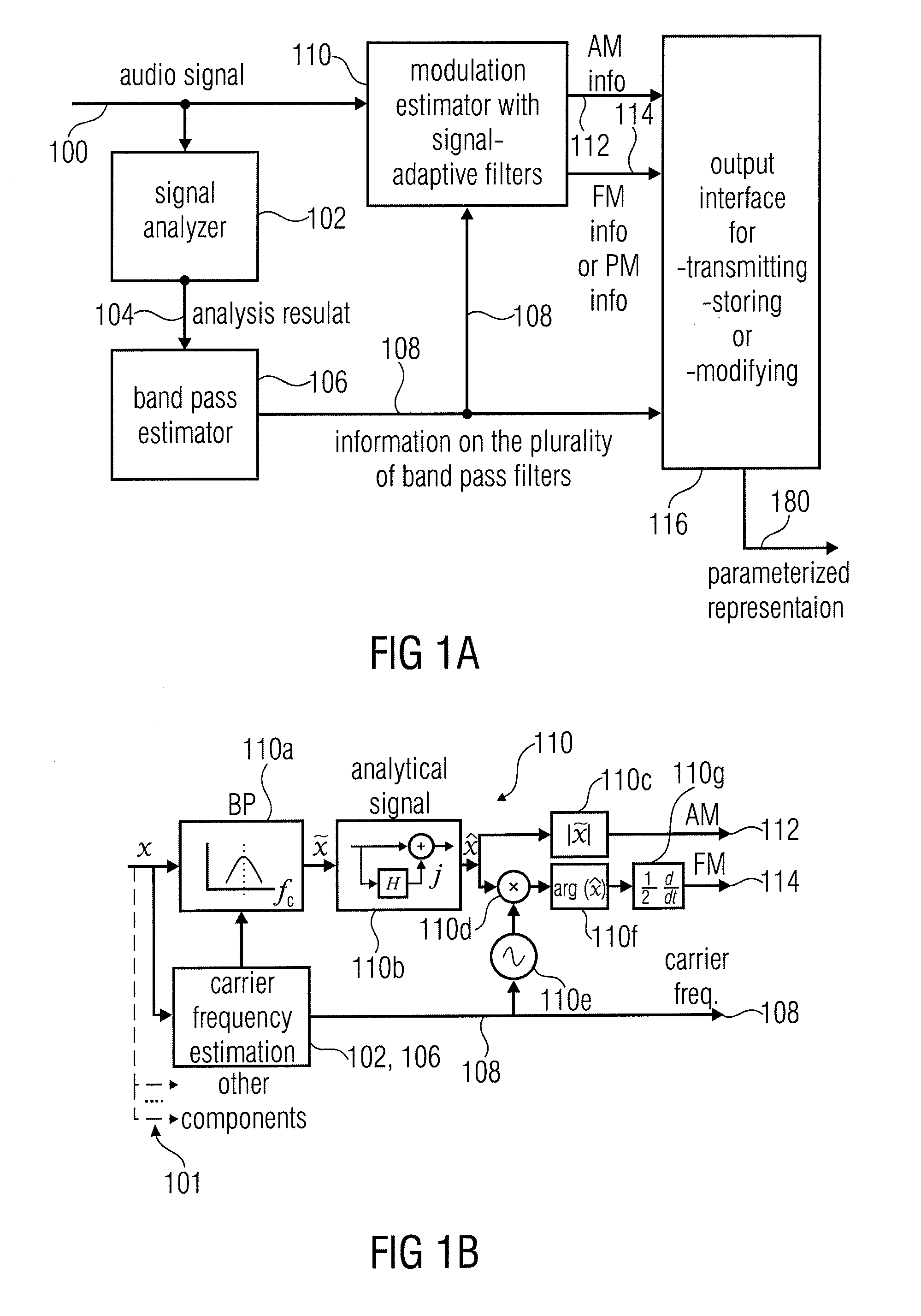
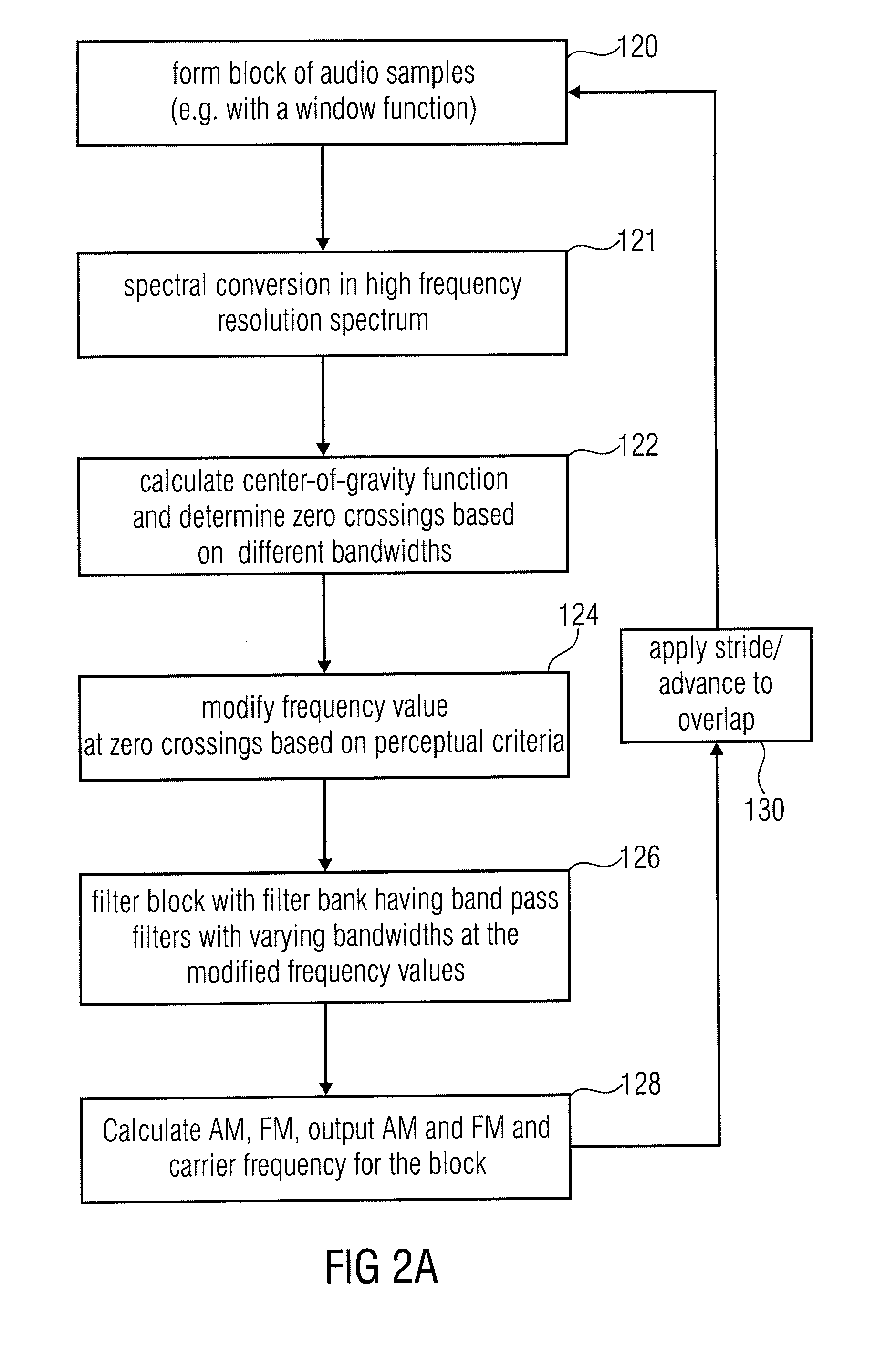
ActiveUS20110106529A1High resolutionImprove representationSpeech analysisFrequency spectrumSignal analyzer
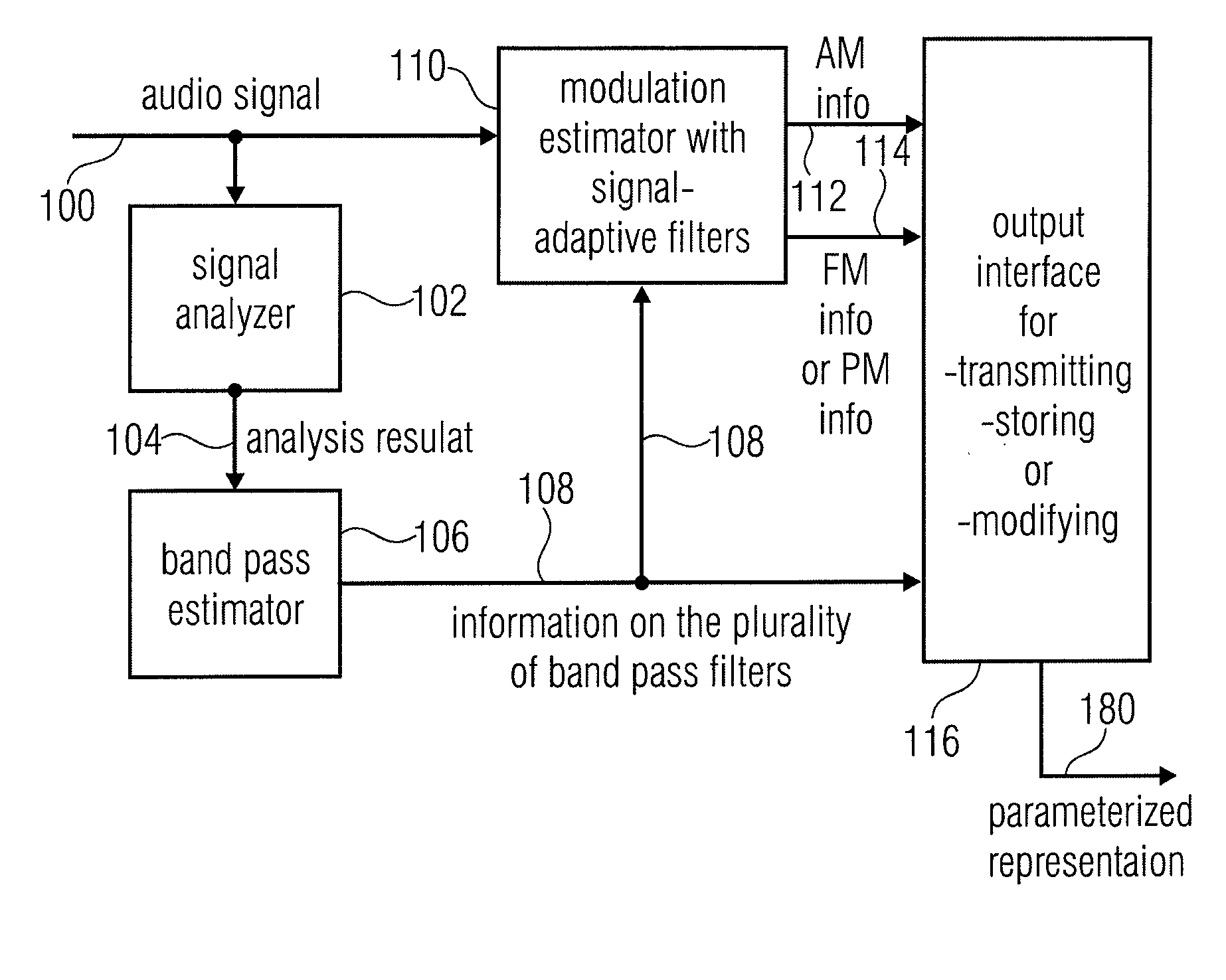
Apparatus for converting an audio signal into a parameterized representation, has a signal analyzer for analyzing a portion of the audio signal to obtain an analysis result; a band pass estimator for estimating information of a plurality of band pass filters based on the analysis result, wherein the information on the plurality of band pass filters has information on a filter shape for the portion of the audio signal, wherein the band width of a band pass filter is different over an audio spectrum and depends on the center frequency of the band pass filter; a modulation estimator for estimating an amplitude modulation or a frequency modulation or a phase modulation for each band of the plurality of band pass filters for the portion of the audio signal using the information on the plurality of band pass filters; and an output interface for transmitting, storing or modifying information on the amplitude modulation, information on the frequency modulation or phase modulation or the information on the plurality of band pass filters for the portion of the audio signal.
Owner:FRAUNHOFER GESELLSCHAFT ZUR FOERDERUNG DER ANGEWANDTEN FORSCHUNG EV
Method, system and apparatus for assessing vulnerability in Web services
InactiveUS20060090206A1Bridging the gapMemory loss protectionError detection/correctionWeb serviceOperating system
Disclosed is a computer implemented method for testing a Web service to determine whether the Web service is vulnerable to at least one known vulnerability. A test case is created and executed for the Web service to determine whether the Web service is vulnerable to the vulnerability. The test case is based on at least one vulnerability definition, at least one Web service operation or port, and at least one control request. The vulnerability definition includes information required to create a request and an expected result. Also disclosed is a computer implemented method of testing a Web service to determine whether the Web service complies with a policy, for example a security or vulnerability policy. A test case is created and executed for the Web service to determine if the Web service complies to the policy.
Owner:KENAI SYST
System and method for identifying network applications
InactiveUS7944822B1Way accurateLow evaluation overheadError preventionTransmission systemsBehavioral analyticsNetwork application
Embodiments of the invention provide a framework for traffic classification that bridges the gap between the packet content inspection and the flow-based behavioral analysis techniques. In particular, IP packets and / or IP flows are used as an input, network nodes are associated to specific network applications by leveraging information gathered from the web, and packet-level and / or flow-level signatures are extracted in an off-line fashion using clustering and signature extraction algorithms. The signatures learned are systematically exported to a traffic classifier that uses the newly available signatures to classify applications on-the-fly.
Owner:THE BOEING CO
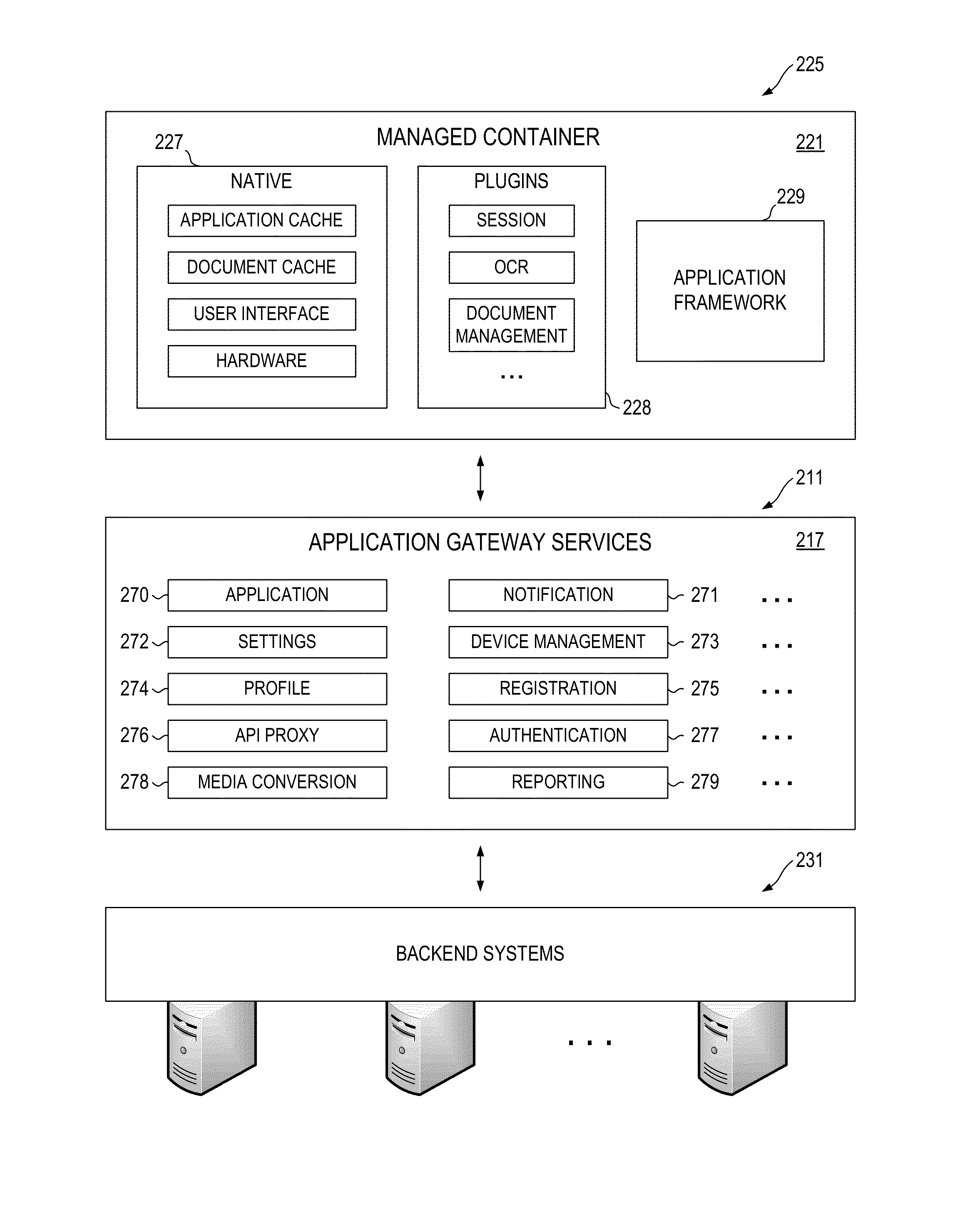
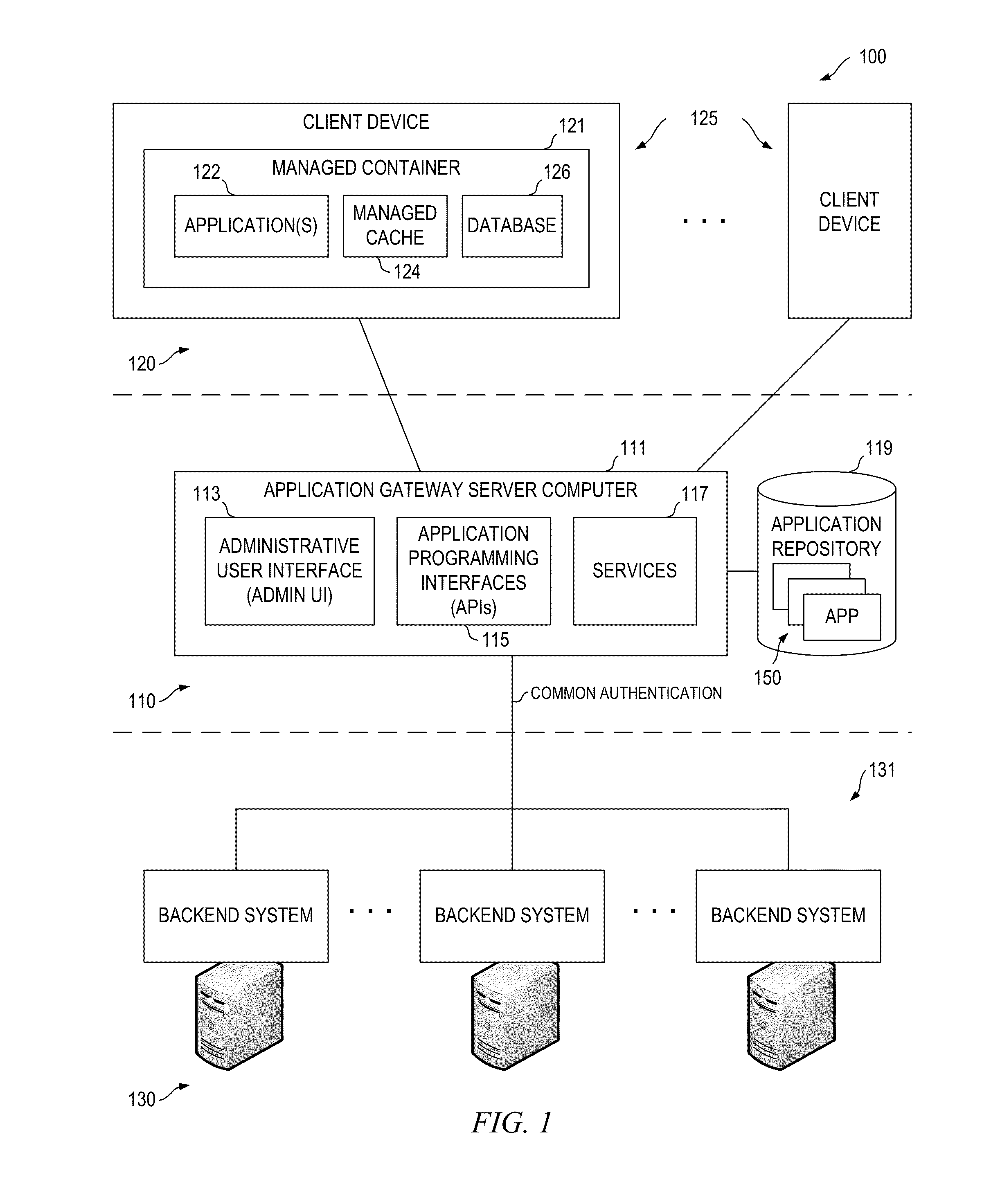
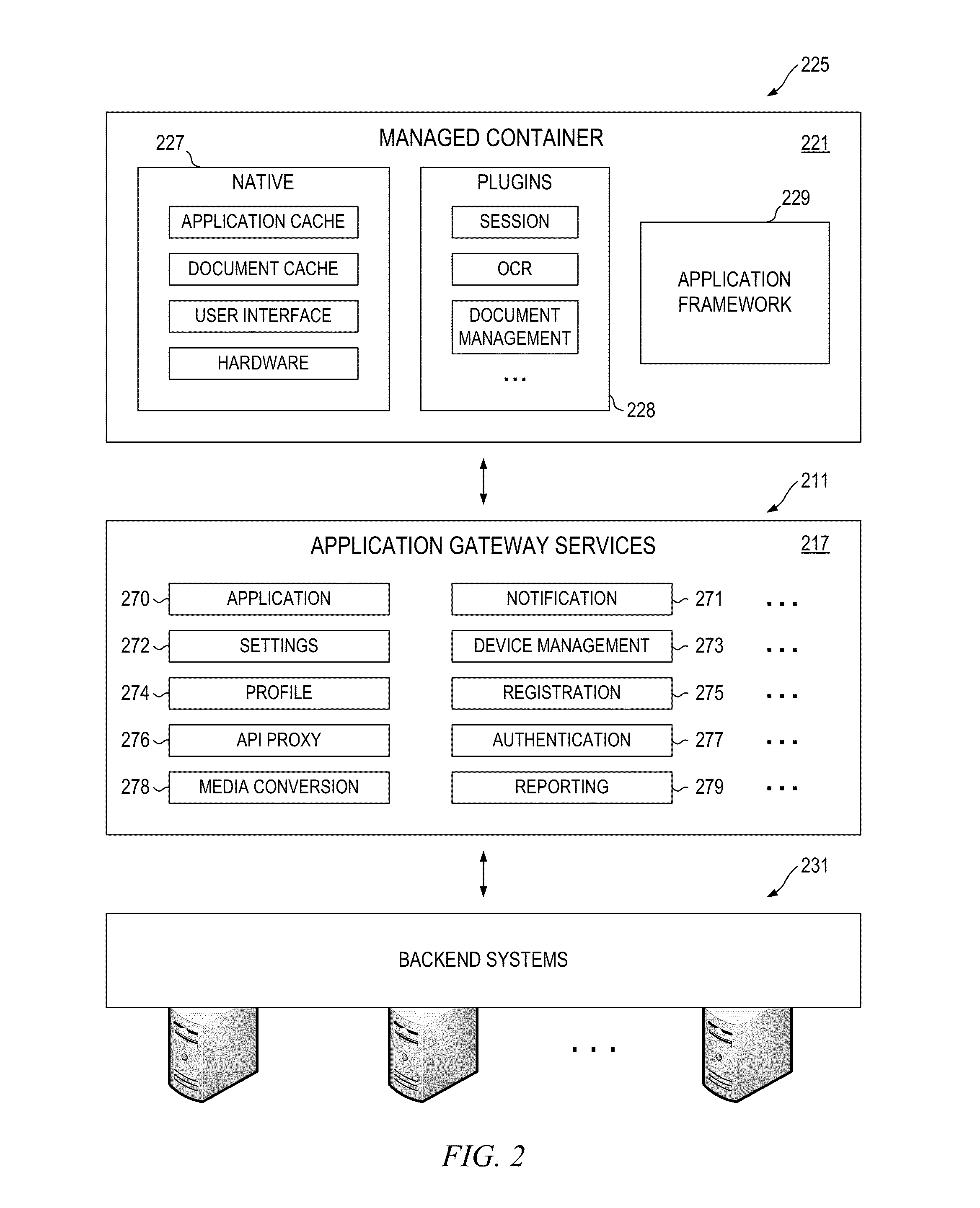
Application Gateway Architecture with Multi-Level Security Policy and Rule Promulgations
ActiveUS20150089224A1Retain controlSafe storageUser identity/authority verificationDigital computer detailsApplication programming interfaceCentralized management
Embodiments of an application gateway architecture may include an application gateway server computer communicatively connected to backend systems and client devices operating on different platforms. The application gateway server computer may include application programming interfaces and services configured for communicating with the backend systems and managed containers operating on the client devices. The application gateway server computer may provide applications that can be centrally managed and may extend the capabilities of the client devices, including the ability to authenticate across backend systems. A managed container may include a managed cache and may provide a secure shell for applications received from the application gateway server computer. The managed container may store the applications in the managed cache and control access to the managed cache according to rules propagated from at least one of the backend systems via the application gateway server computer.
Owner:OPEN TEXT SA ULC
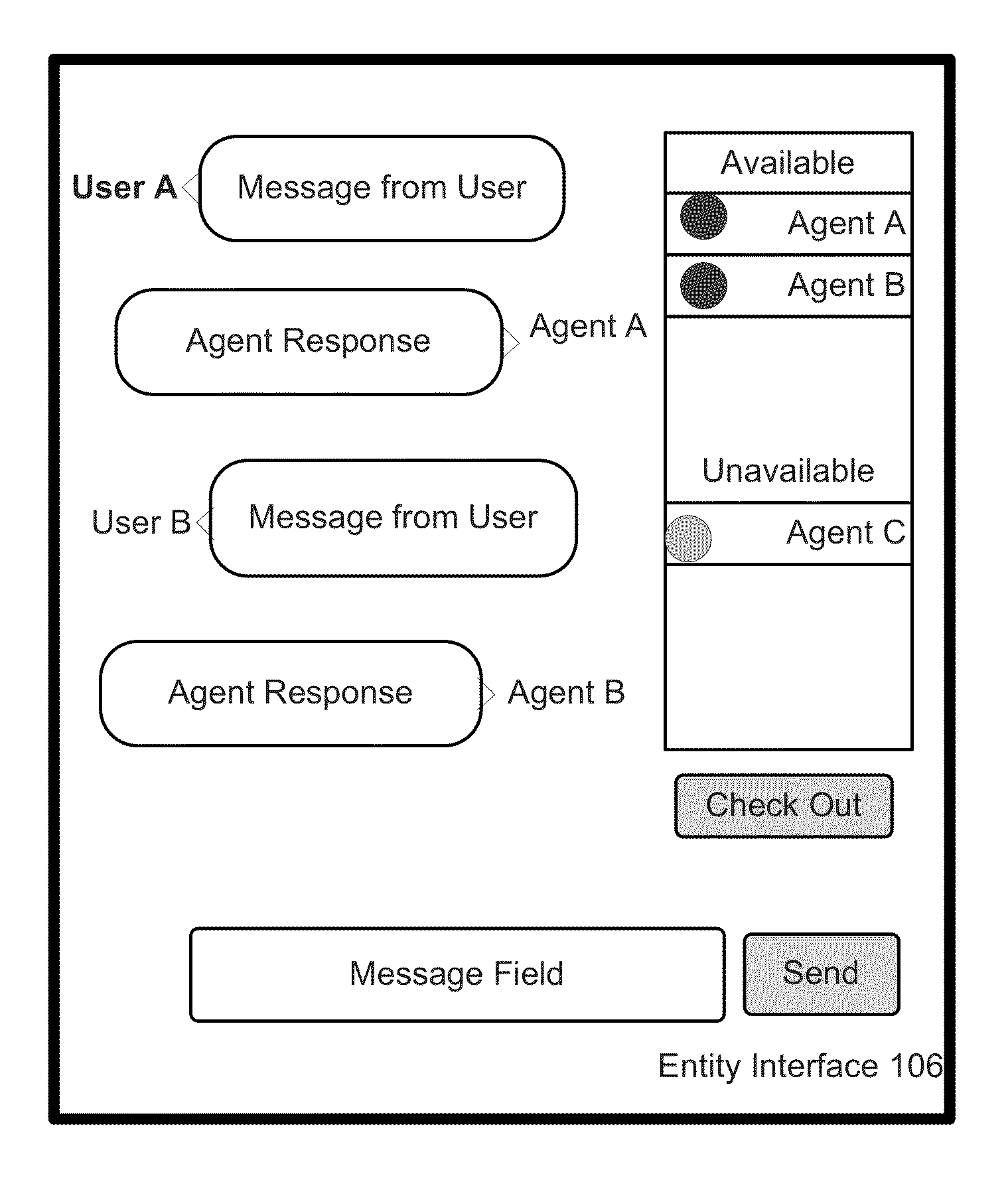
Multi-user communication system and method
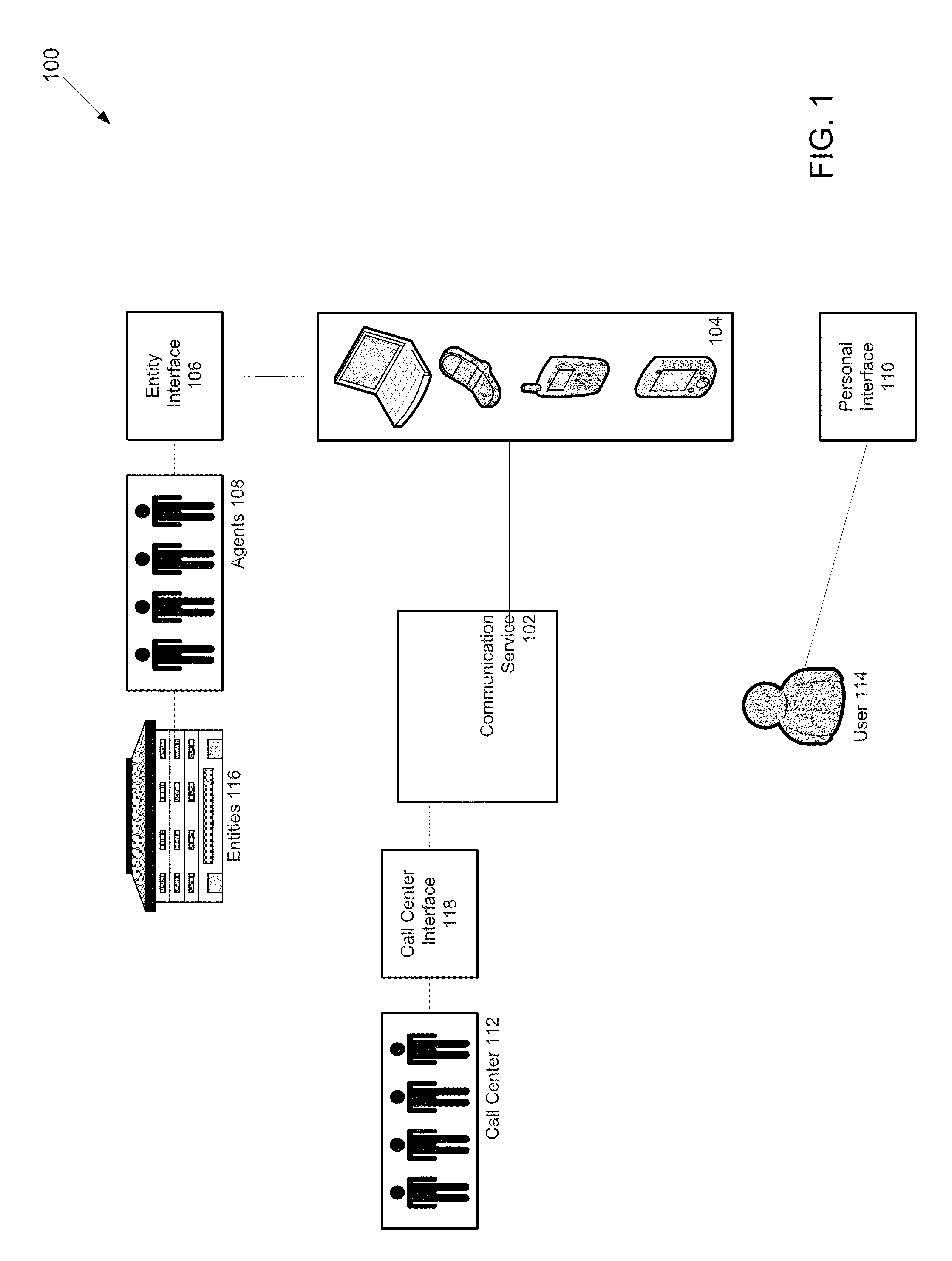
ActiveUS20130066987A1Conveniently madeBridging the gapMultiple digital computer combinationsOffice automationCommunications systemData mining
Systems and methods for enabling communication between a user and at least one entity by a communication service are disclosed. In one example, the method comprises acts of receiving a search for the at least one entity, analyzing the search, by a processor, to determine search results based on the search including the at least one entity, receiving a message from the user to the at least one entity, the message including inquiry information directed to the at least one entity, determining, by the processor, presence status associated with the at least one entity, establishing, by the processor, a communication channel between the user and the at least one entity based on the presence status, and transmitting a response to the message based on the inquiry information via the communication channel.
Owner:KAKAO CORP
Location based system utilizing geographical information from documents in natural language
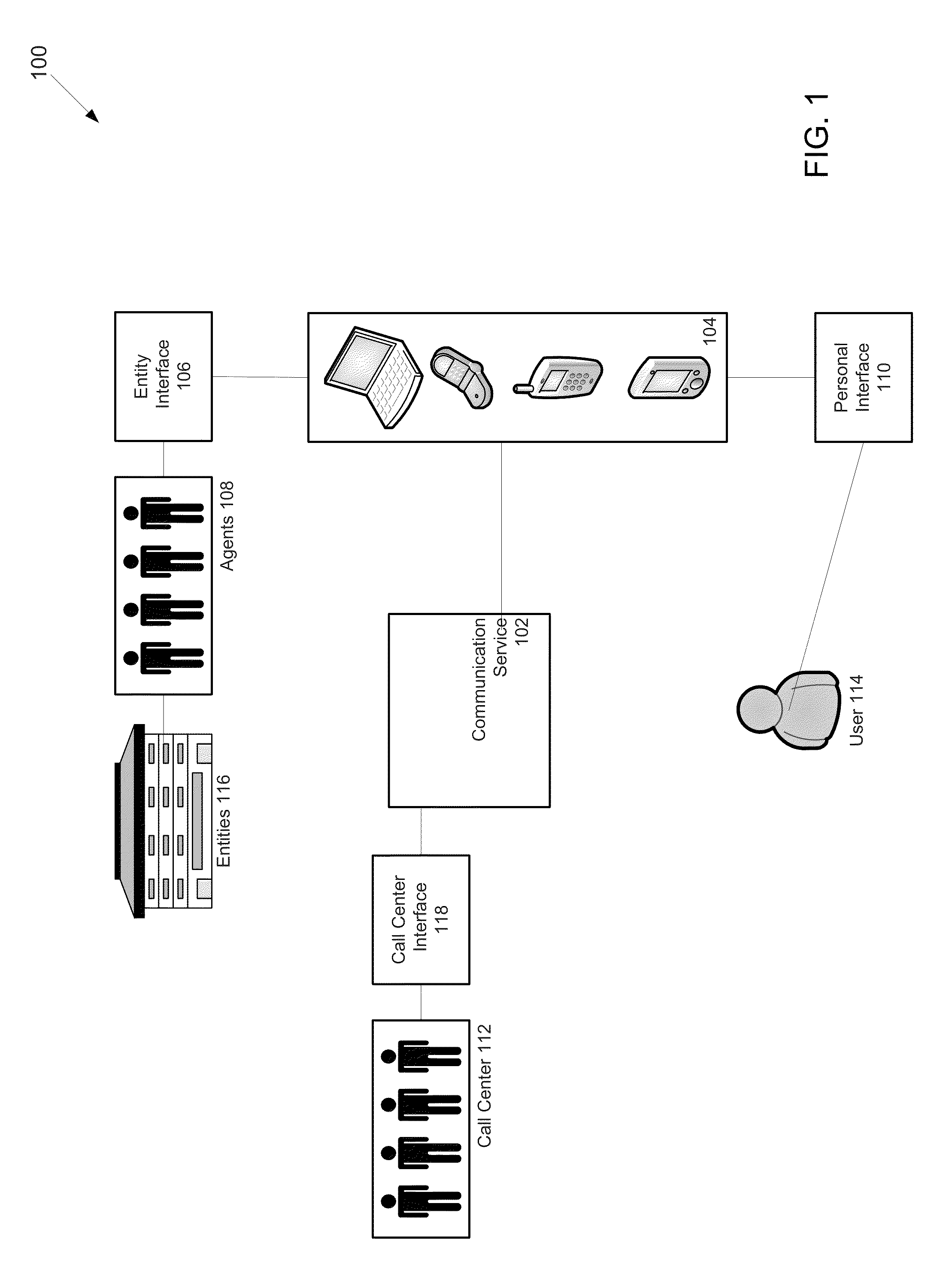
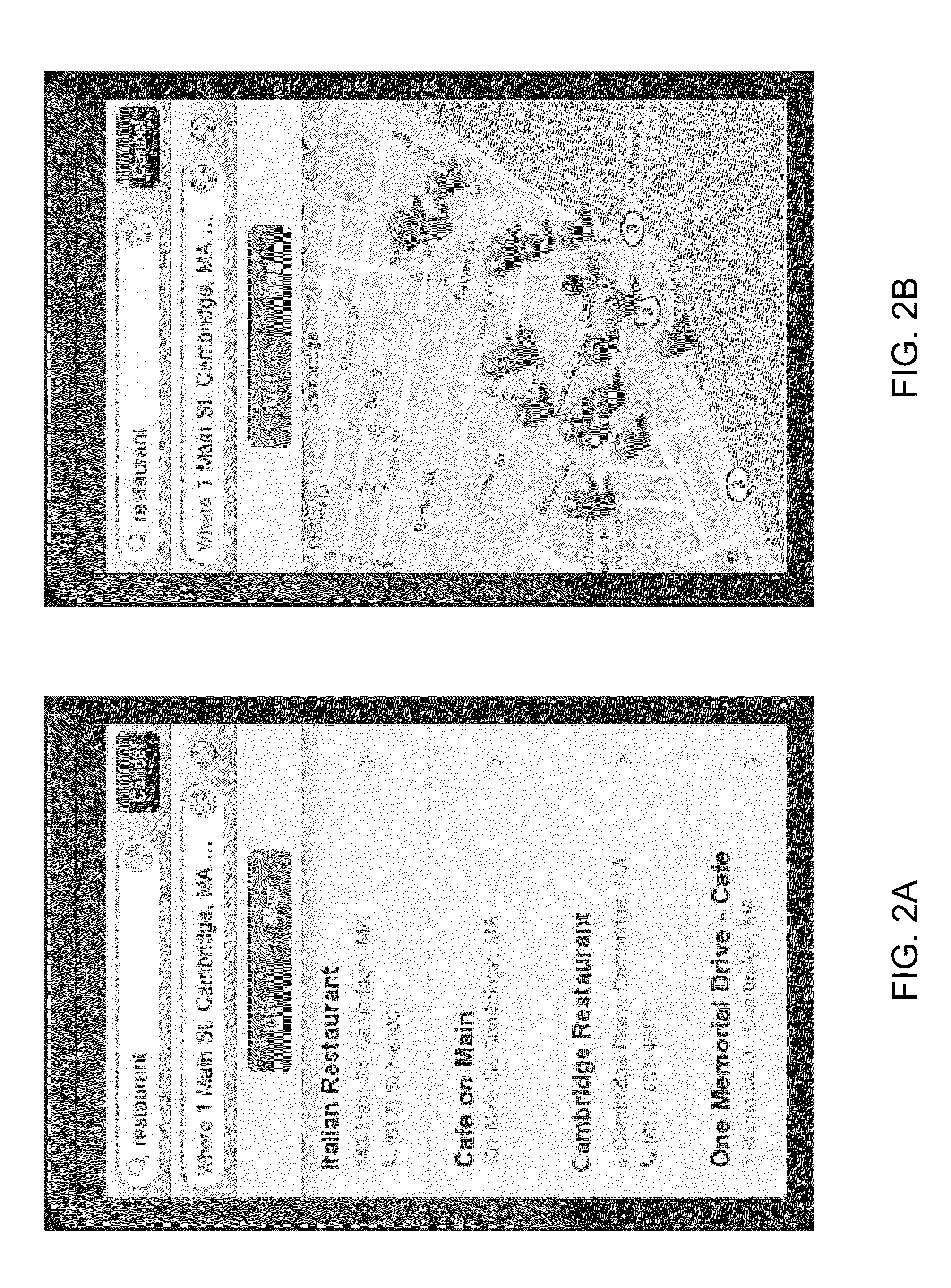
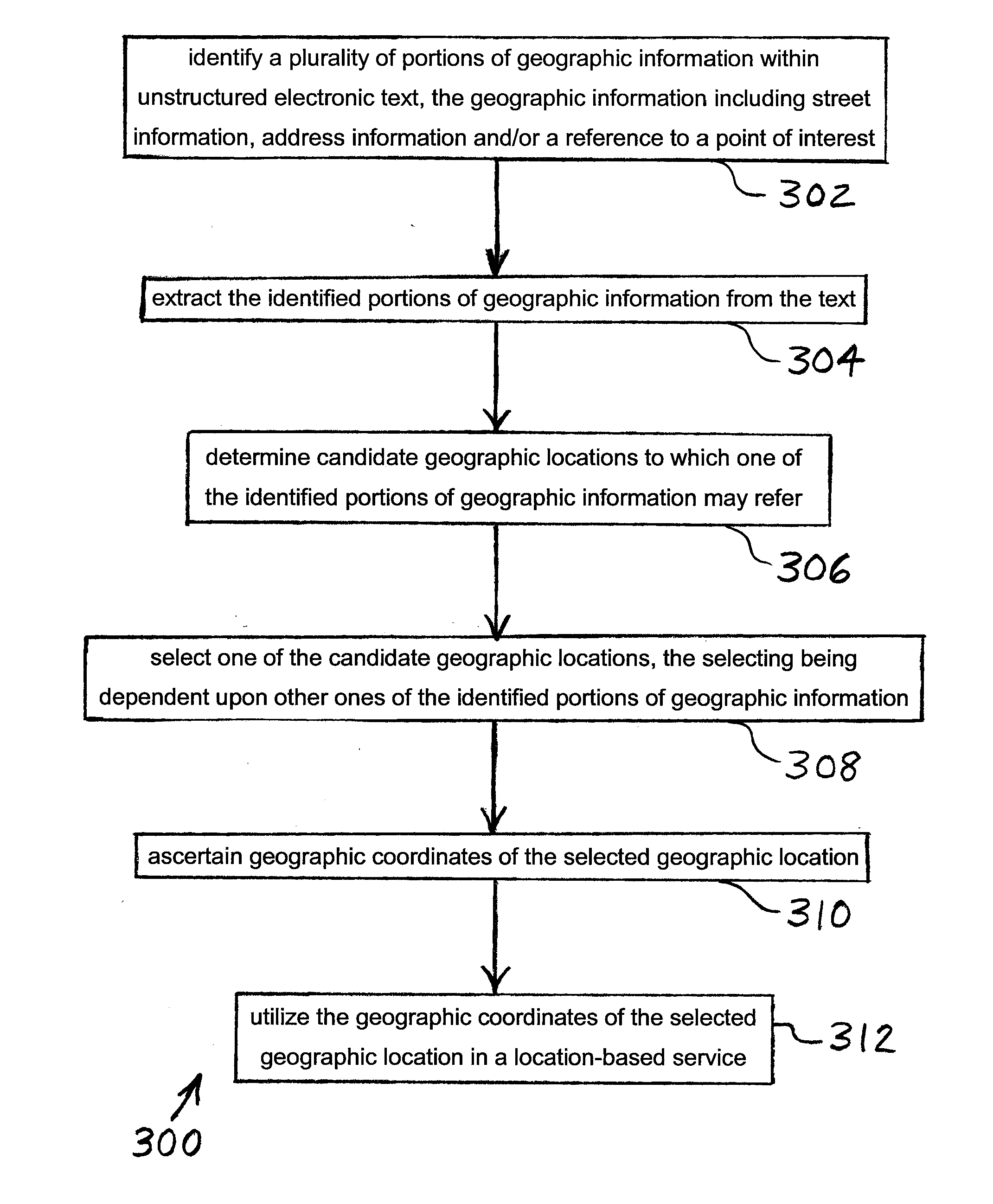
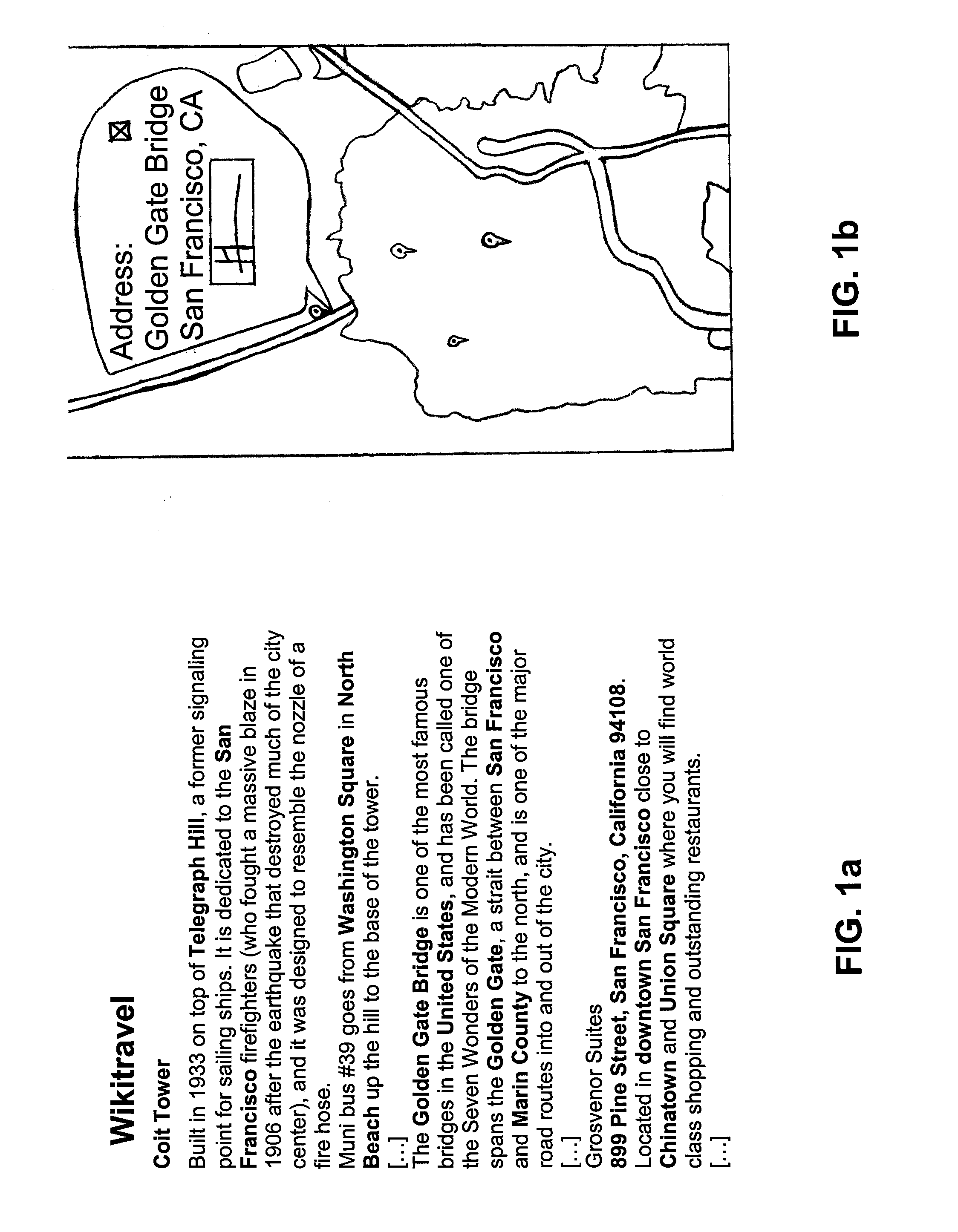
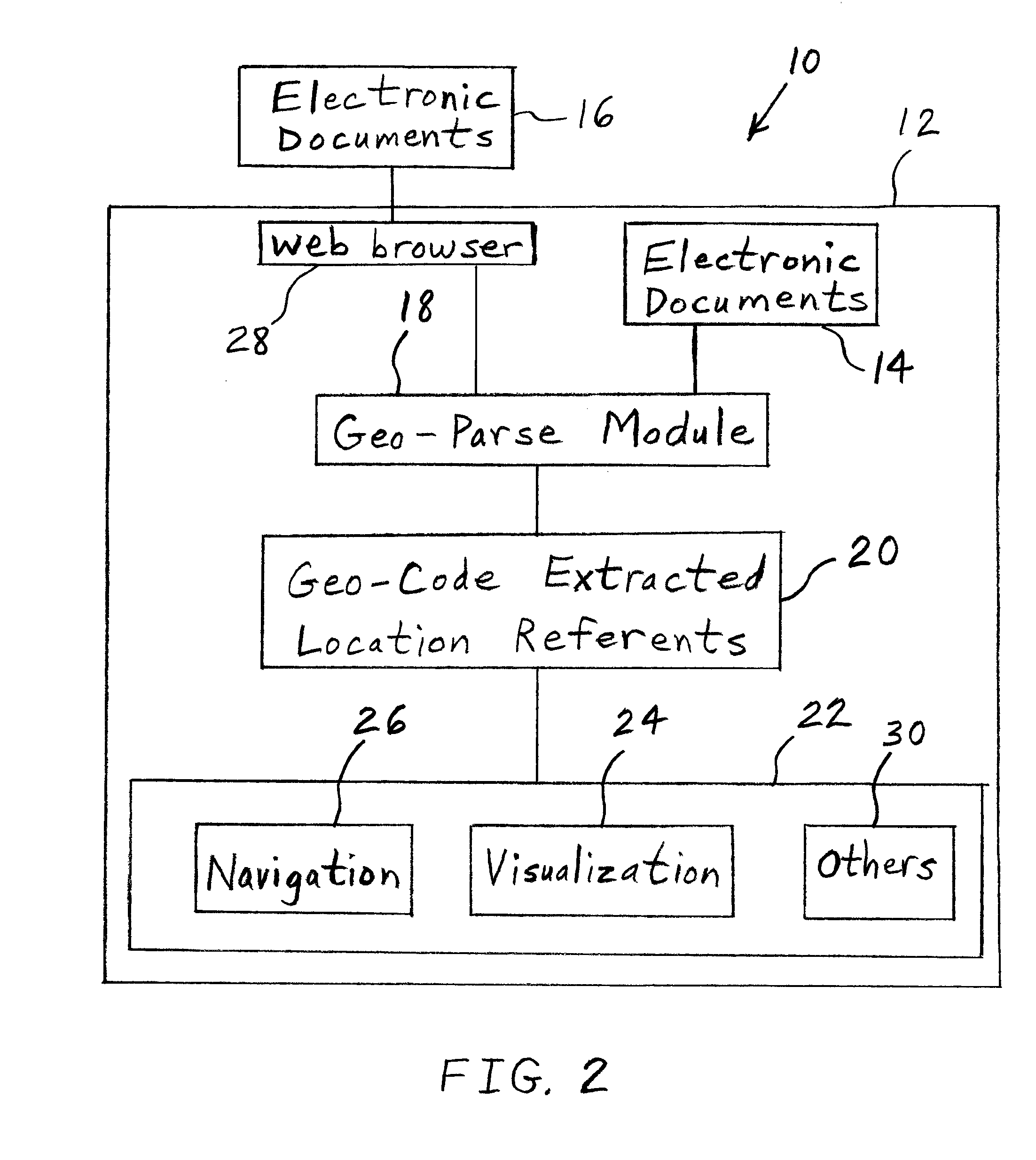
InactiveUS20100179754A1Bridging the gapDigital data information retrievalRoad vehicles traffic controlLocation based systemsGeolocation
A method of operating a location-based system includes identifying geographic information within unstructured electronic text. The identified geographic information, which includes street information, address information, or names of locations is extracted. Candidate geographic locations to which the identified geographic information may refer are determined. One of the candidate geographic locations is selected. An alphanumeric representation of the selected geographic location is utilized in a location-based service. The invented system performs each of the preceding steps. The system supports the extraction of all locations mentioned in the unstructured text, applying the steps mentioned above.
Owner:ROBERT BOSCH GMBH
System and method for establishing presence in a brokered chat system
ActiveUS20130066988A1Conveniently madeBridging the gapMultiple digital computer combinationsMultimediaUser state
Owner:KAKAO CORP
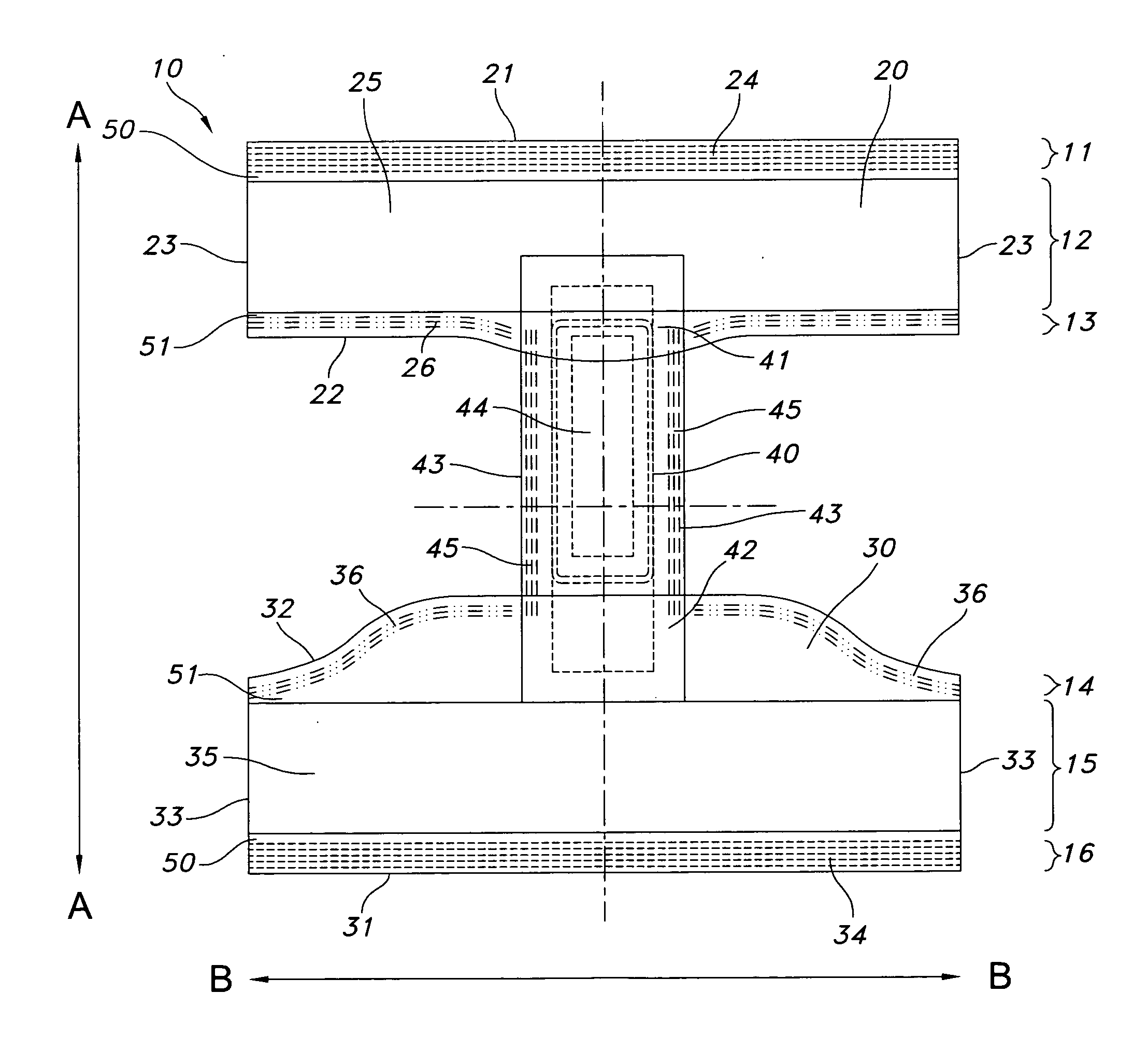
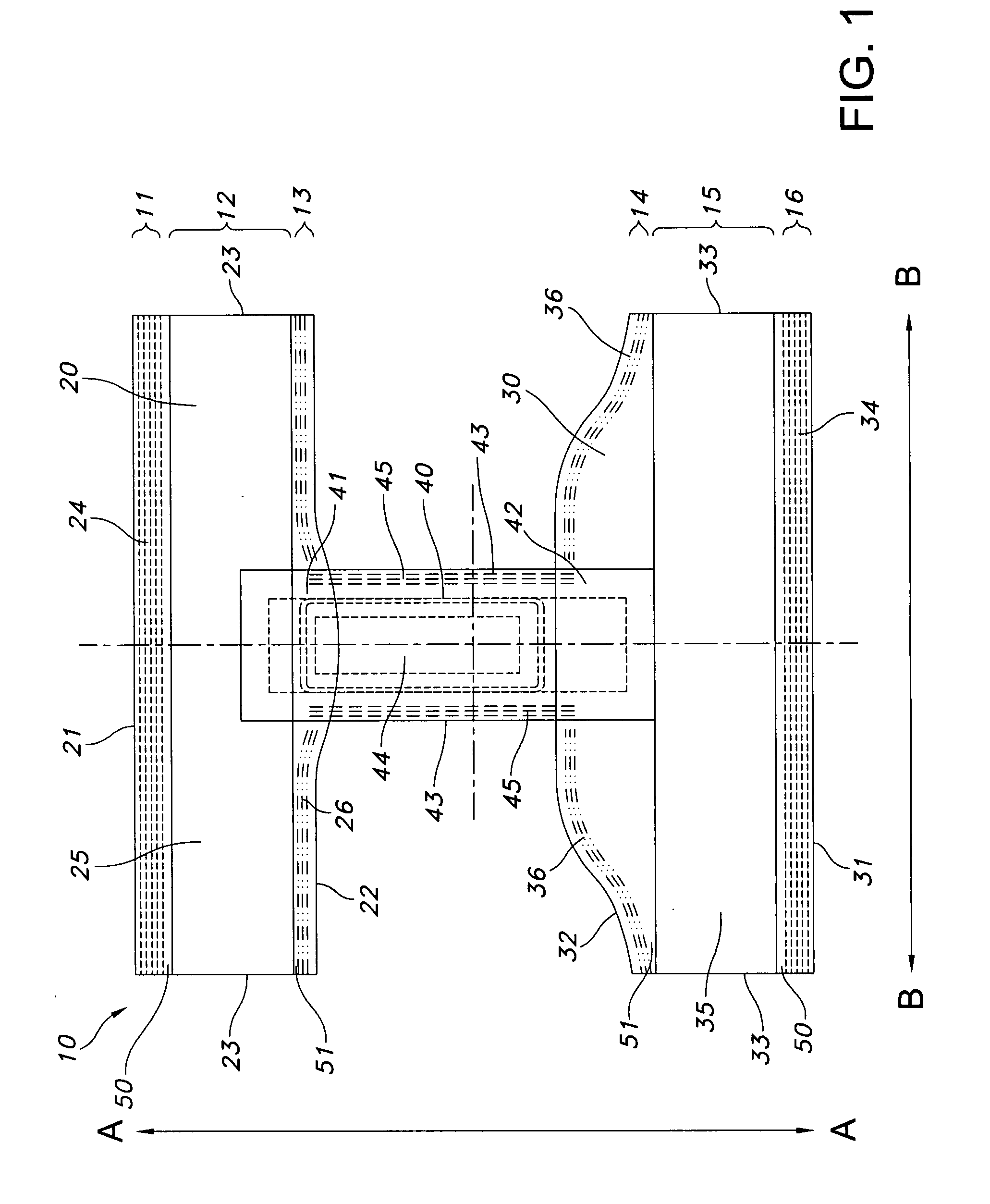
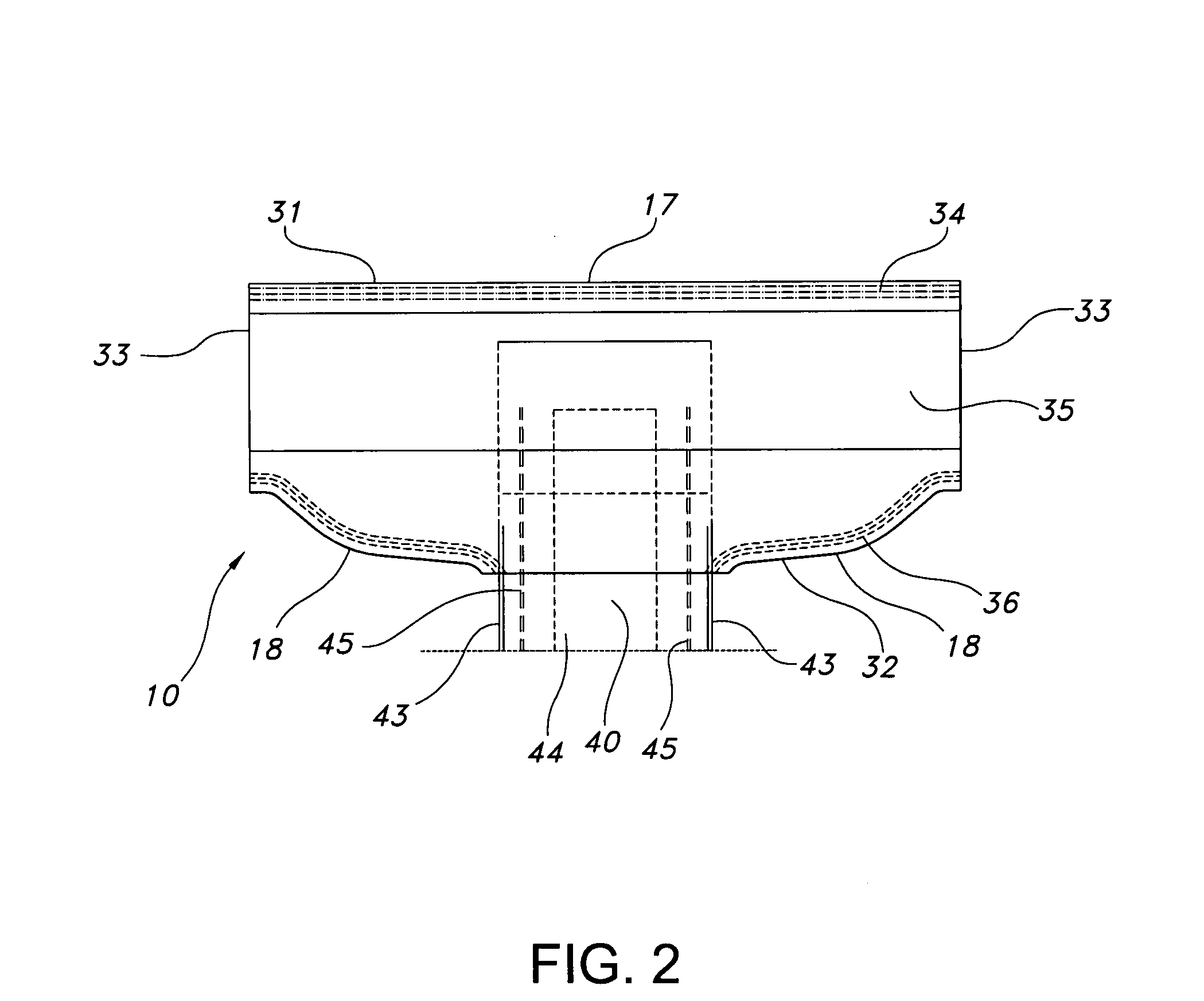
Absorbent article and method of making same
Disposable protective undergarments and methods for manufacturing the same, wherein a protective undergarment includes a front portion having a body-side and a garment side and including stretch material, a back portion longitudinally spaced from the front portion, and a crotch insert having a body-side and a garment-side, the body-side of the crotch insert has an front end fixed to the garment-side of the front portion and a back end fixed to the fixed to the body-side of the back portion and the crotch insert bridges a gap between the front and back portions. A disposable protective undergarment also includes a stretch material deactivated where the crotch insert is fixed to the front portion.
Owner:FIRST QUALITY RETAIL SERVICES
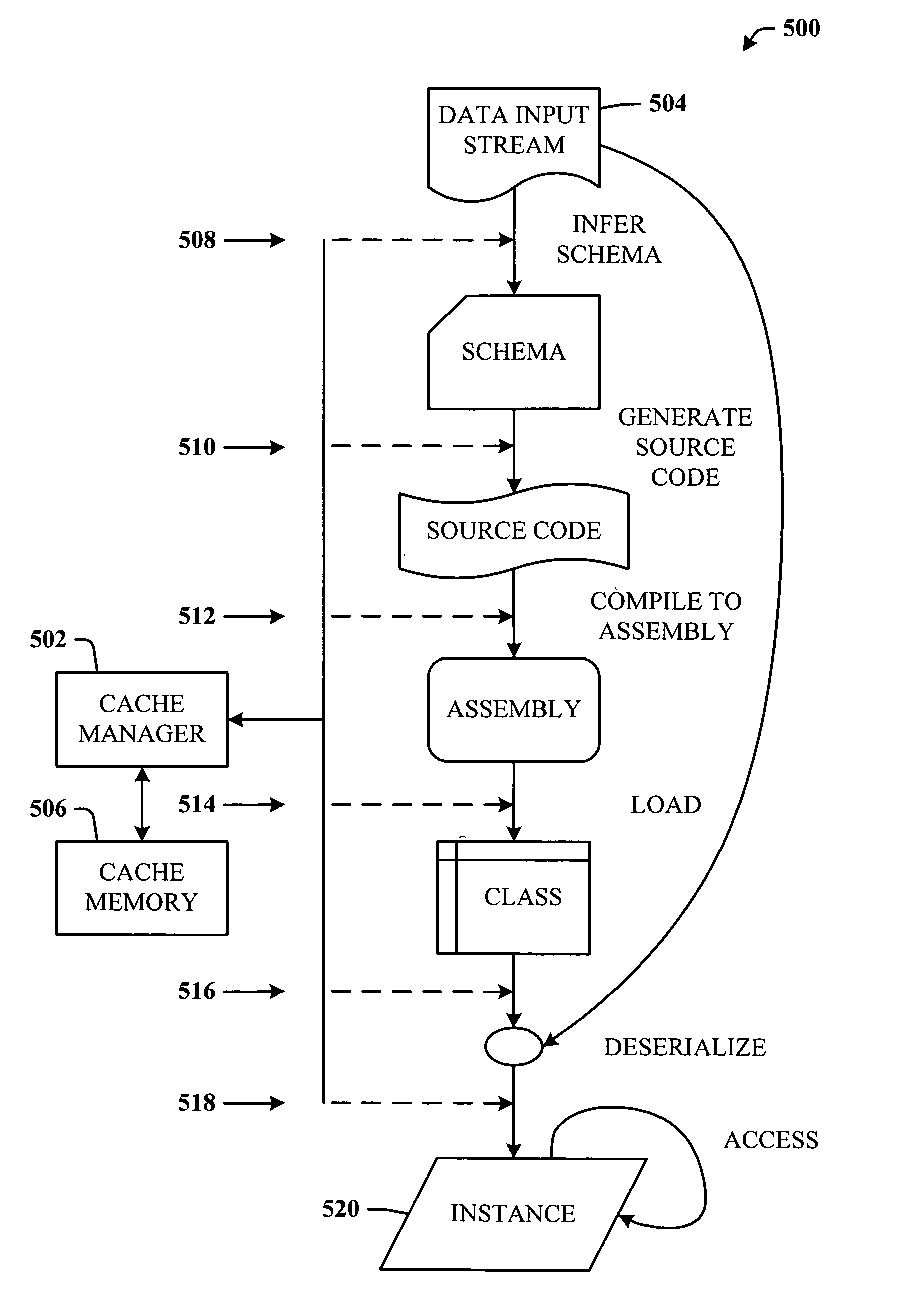
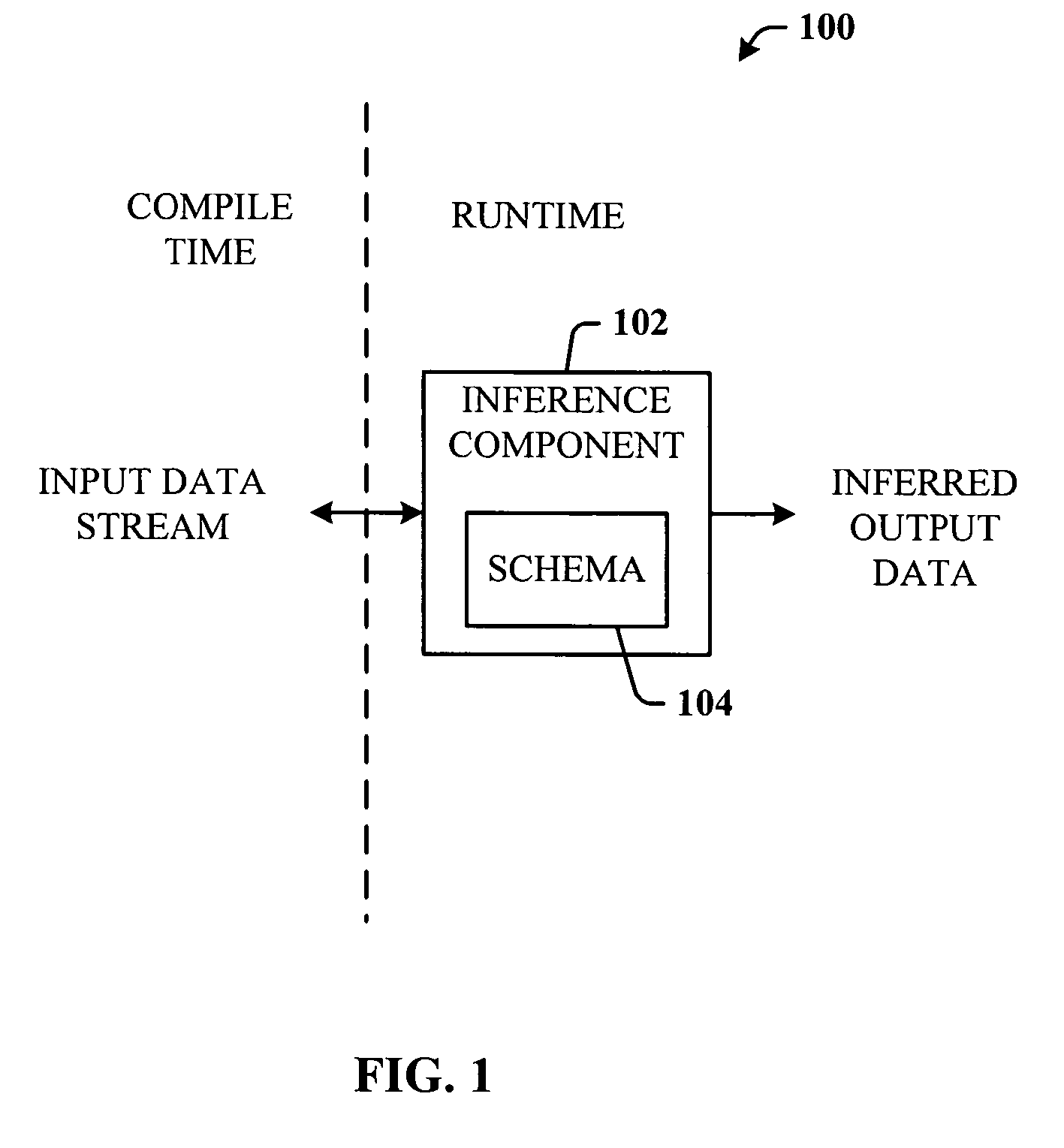
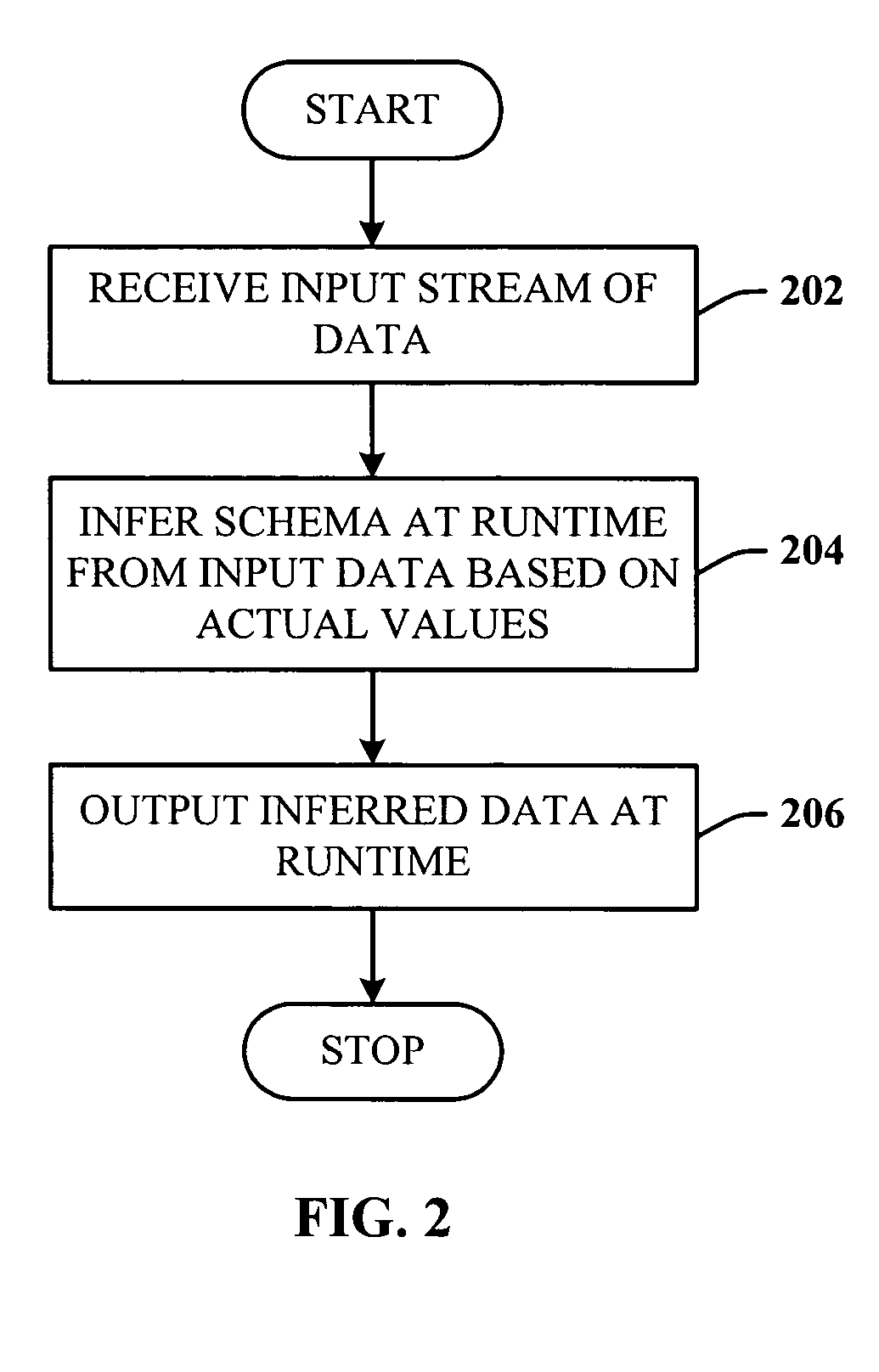
Efficient data access via runtime type inference
ActiveUS20060167880A1Accessed efficiently and convenientlyBridging the gapDigital data processing detailsSpecial data processing applicationsStreaming dataData stream
A system and methodology that provide schema inferencing at runtime. An inference component receives as an input an input data stream, and processes the input data stream at runtime to develop a schema based on actual values thereof. The inferred schema is then used to create an inferred output data that is a specialized representation of the input stream data, which can then be accessed efficiently and conveniently.
Owner:MICROSOFT TECH LICENSING LLC
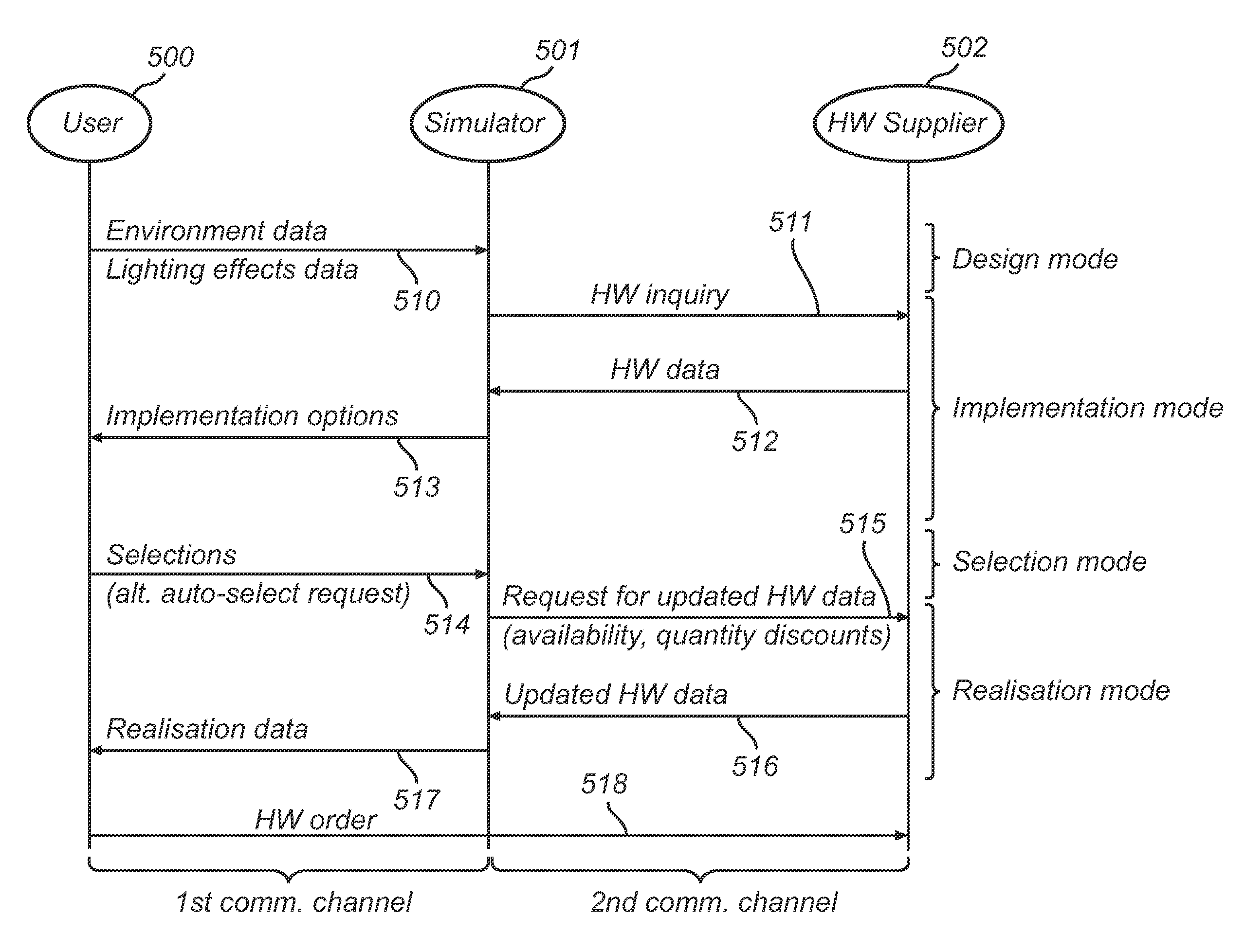
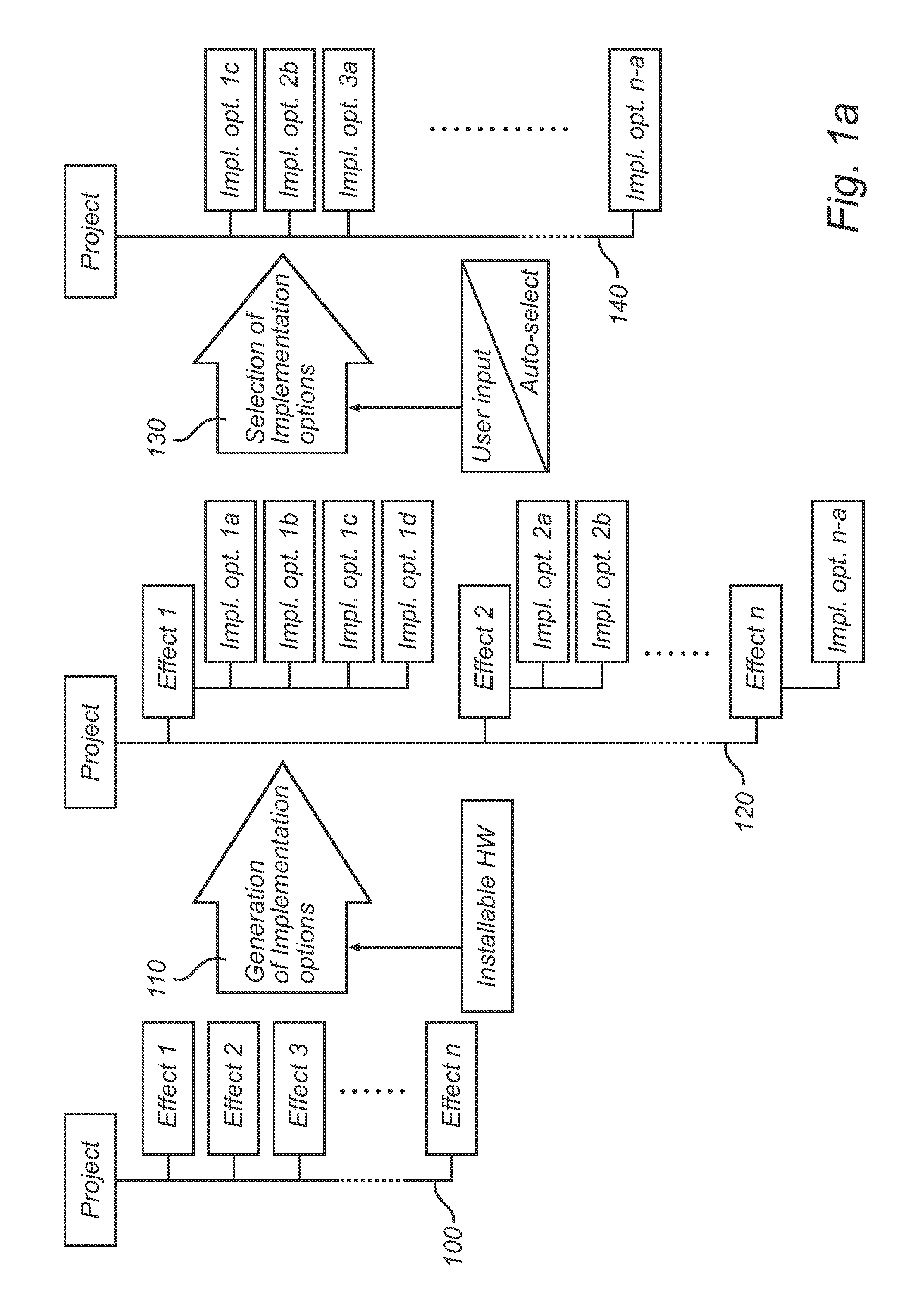
Effect-driven specification of dynamic lighting
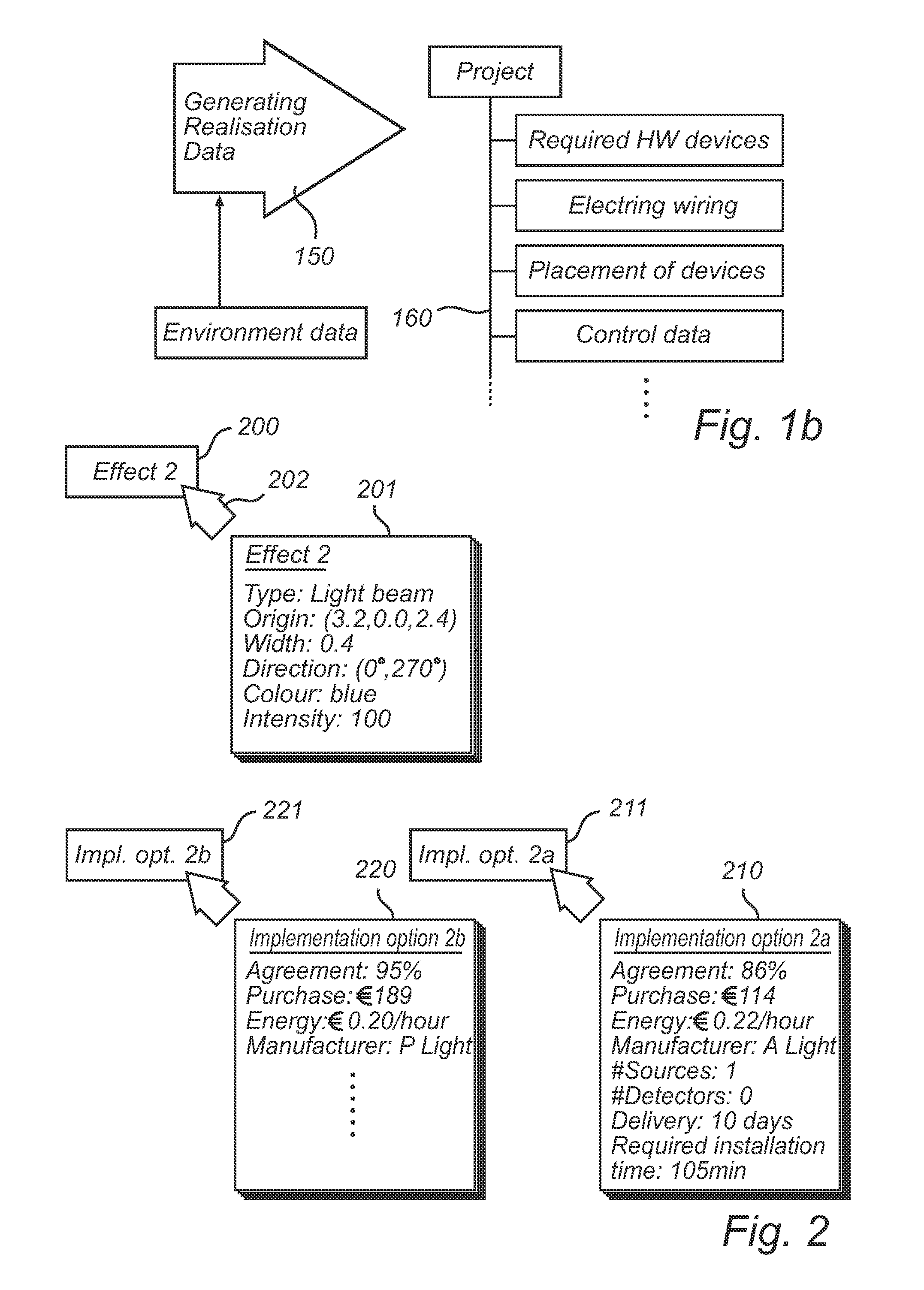
ActiveUS20120095745A1Bridging the gapEasy to addElectrical apparatusAnalogue computers for electric apparatusComputer graphics (images)Data provider
A method and a device for simulating the realization of lighting effects in an environment are disclosed. The method may receive environment data, user input indicative of lighting effects, and data indicative of what installable devices exist. Based thereon, the method may generate at least one implementation option for each lighting effect and select one implementation option for each lighting effect. As a result, realization data based on the environment data and selected implementation options options can be generated. A simulator for simulating realization of lighting effects is adapted to communicate, on the one hand, with a user or other provider of environment and lighting effect data, and, on the other, with a source of information on installable hardware device. The simulator can be operable in a design mode, an implementation mode, a selection mode and a realization mode.
Owner:SIGNIFY HLDG BV
Encryption Architecture
ActiveUS20150379277A1Avoid overheadBridging the gapMultiple keys/algorithms usageUnauthorized memory use protectionComputer hardwareNetwork structure
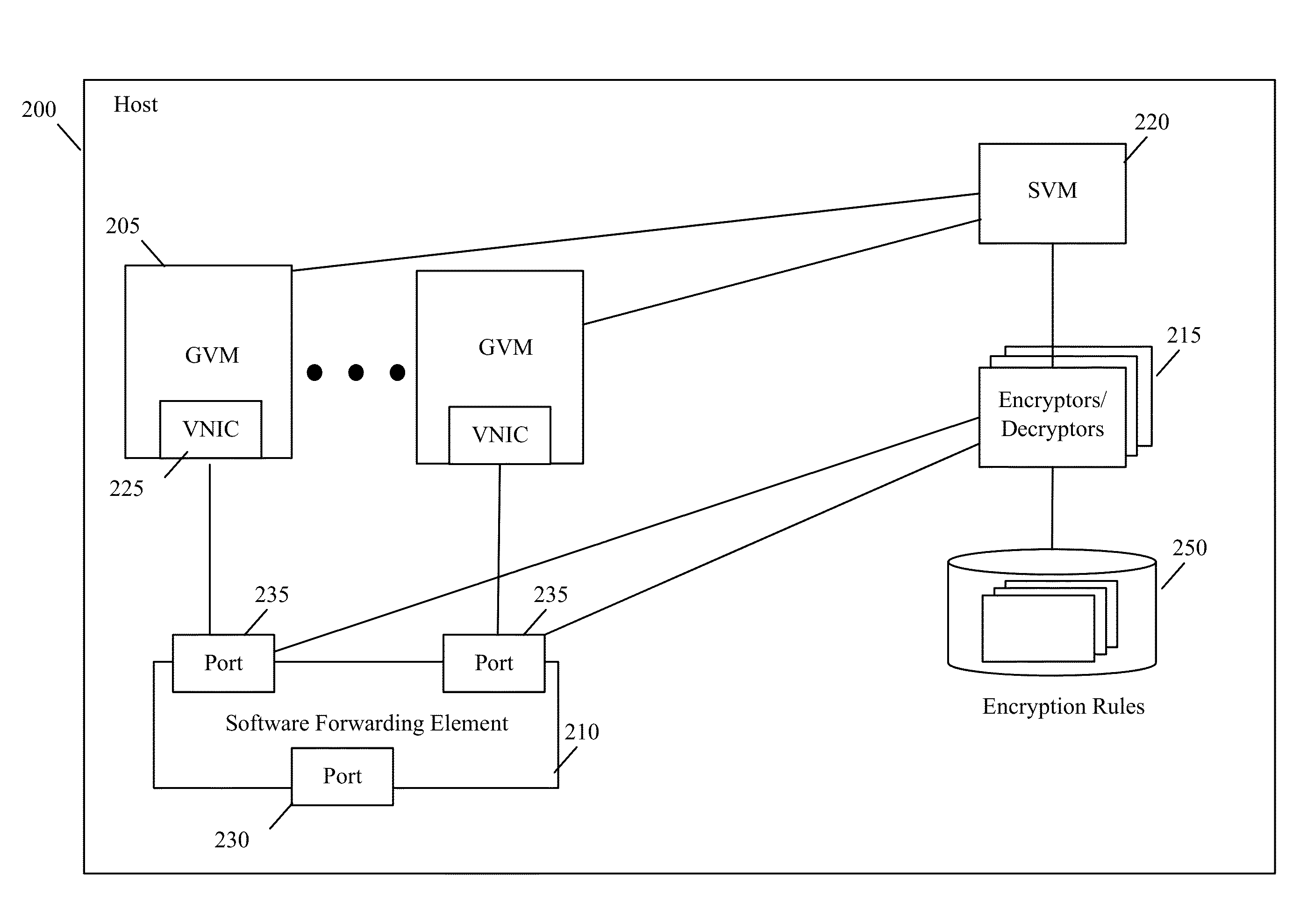
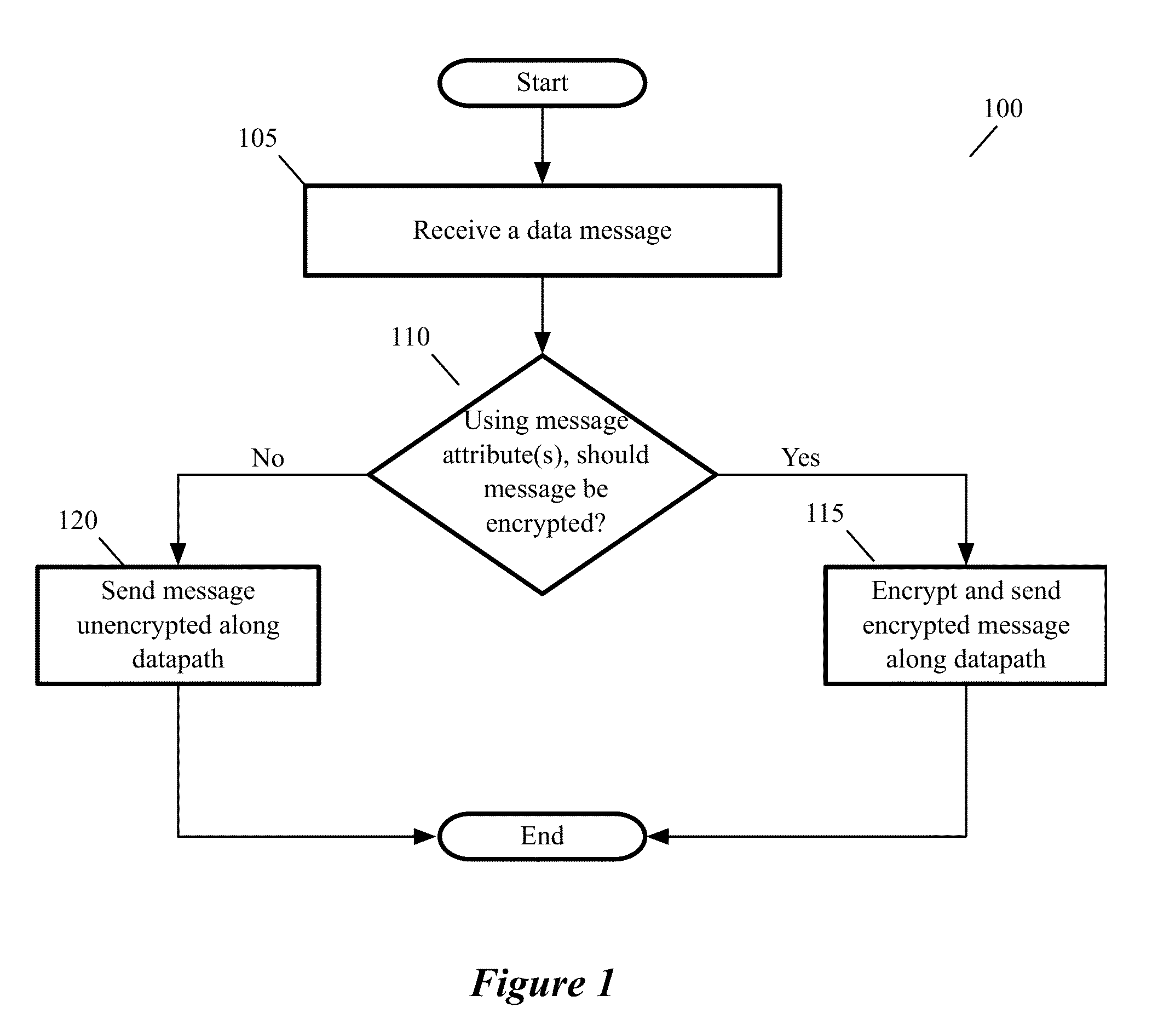
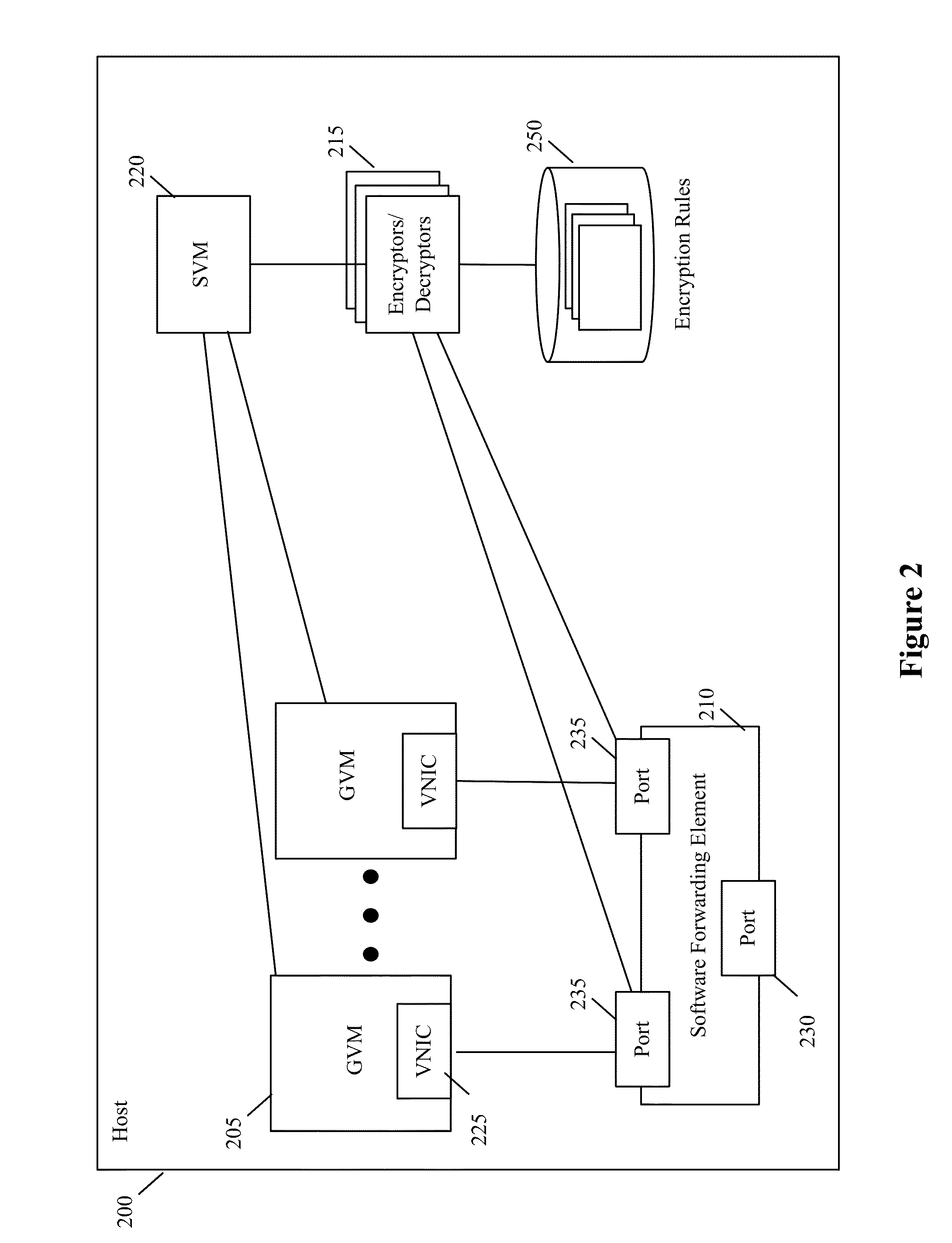
For a host that executes one or more guest virtual machines (GVMs), some embodiments provide a novel encryption method for encrypting the data messages sent by the GVMs. The method initially receives a data message to send for a GVM executing on the host. The method then determines whether it should encrypt the data message based on a set of one or more encryption rules. When the process determines that it should encrypt the received data message, it encrypts the data message and forwards the encrypted data message to its destination; otherwise, the method just forwards the received data message unencrypted to its destination. In some embodiments, the host encrypts differently the data messages for different GVMs that execute on the host. When two different GVMs are part of two different logical overlay networks that are implemented on common network fabric, the method in some embodiments encrypts the data messages exchanged between the GVMs of one logical network differently than the data messages exchanged between the GVMs of another logical network. In some embodiments, the method can also encrypt different types of data messages from the same GVM differently. Also, in some embodiments, the method can dynamically enforce encryption rules in response to dynamically detected events, such as malware infections.
Owner:NICIRA
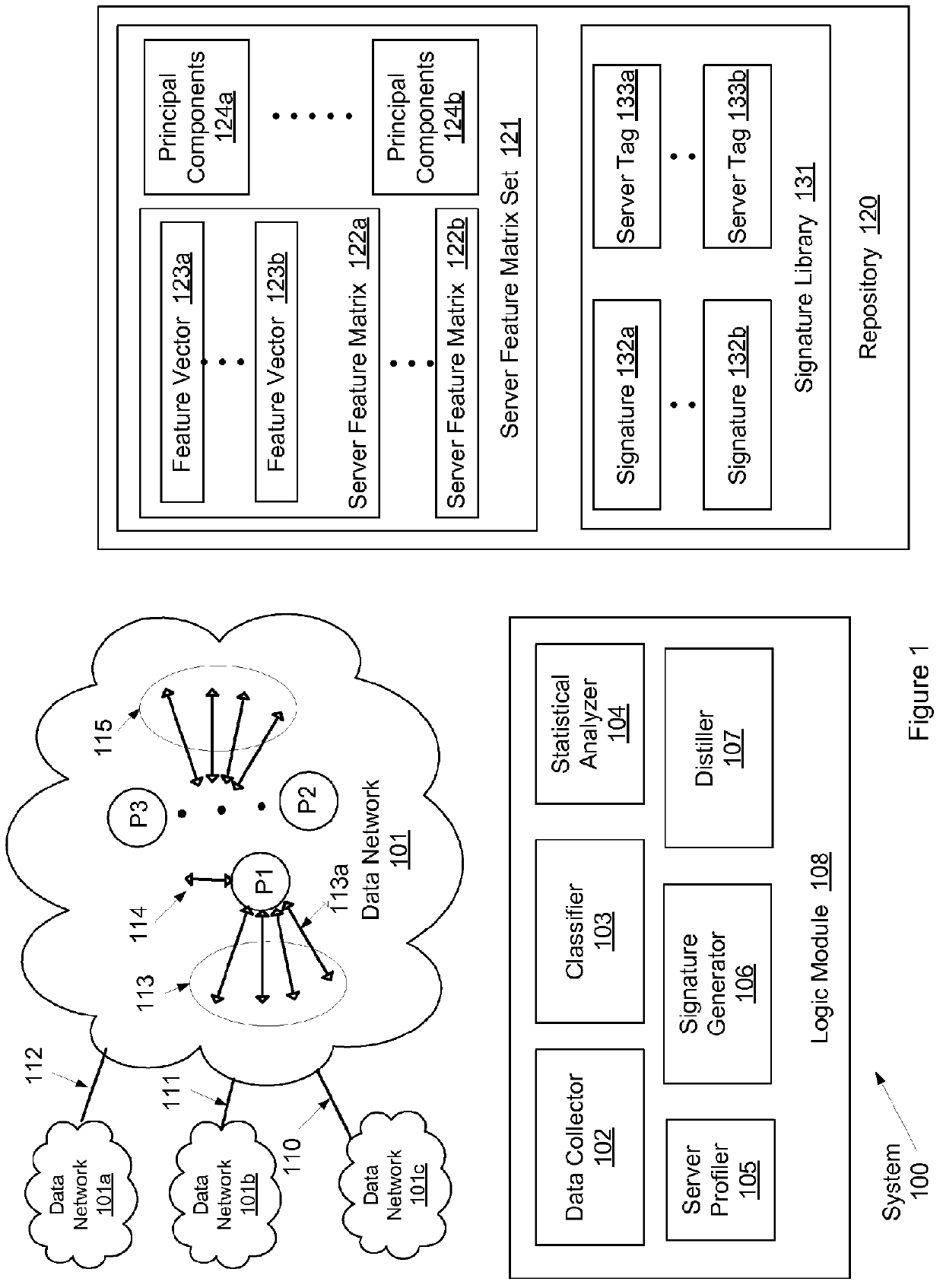
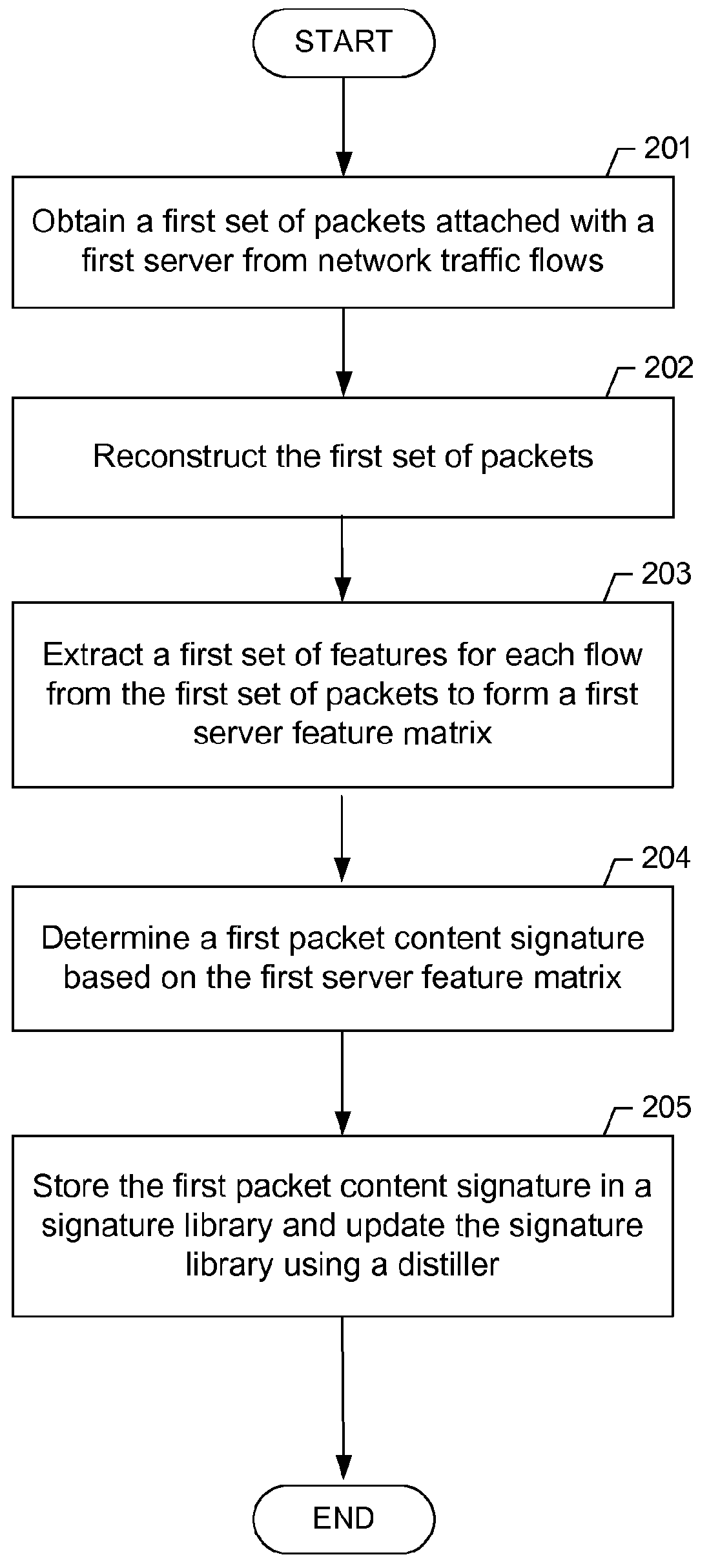
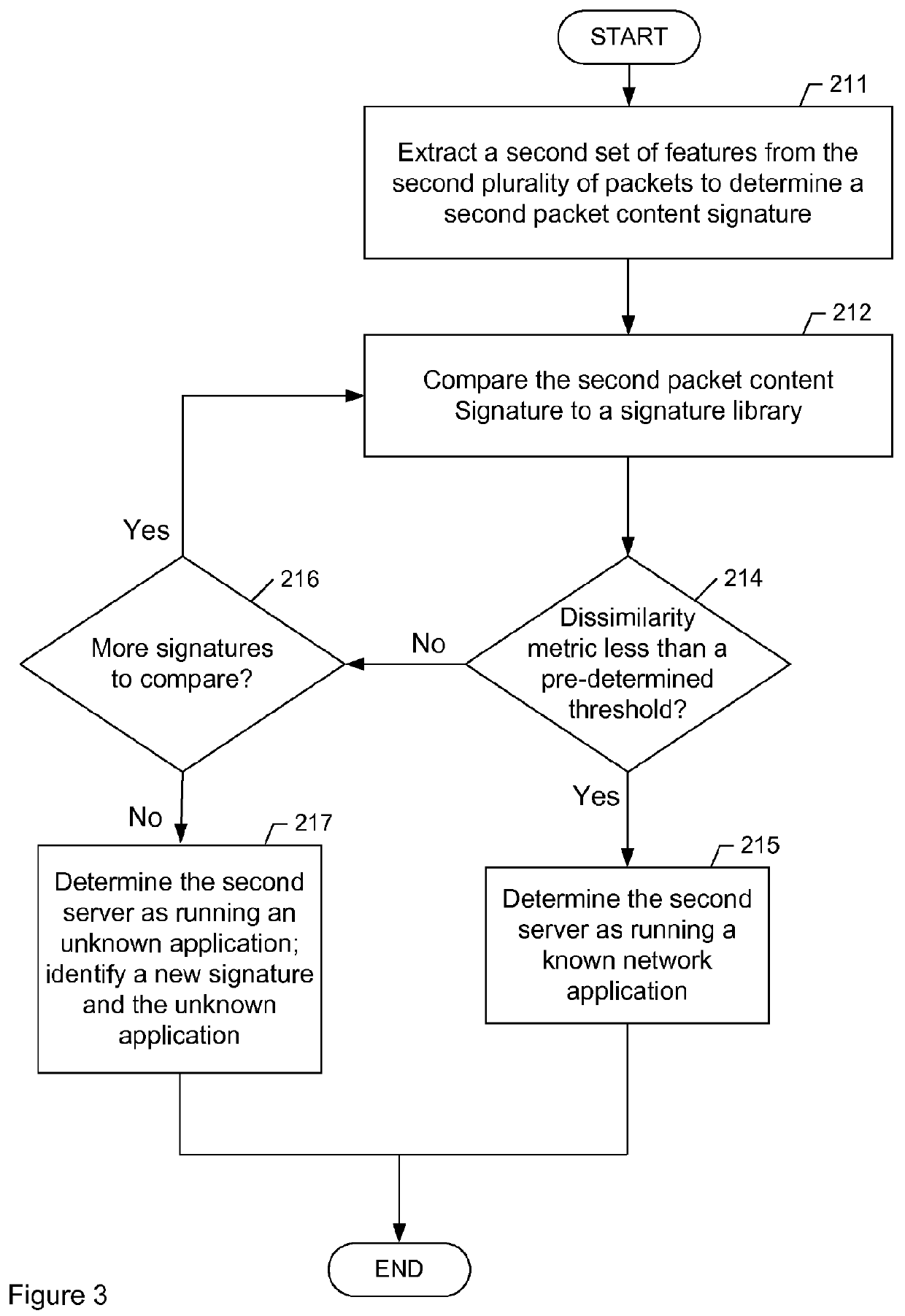
System and method for identifying network applications based on packet content signatures
ActiveUS8180916B1Bridging the gapWide applicabilityMultiple digital computer combinationsTransmissionData packBehavioral analytics
Embodiments of the invention provide a framework for traffic classification that bridges the gap between the packet content inspection and the flow-based behavioral analysis techniques. In particular, IP packets and / or IP flows are used as an input, network nodes are associated to specific network applications by leveraging information gathered from the web, and packet content signatures are extracted in an off-line fashion using clustering and signature extraction algorithms. The signatures learned are systematically exported to a traffic classifier that uses the newly available signatures to classify applications on-the-fly.
Owner:THE BOEING CO
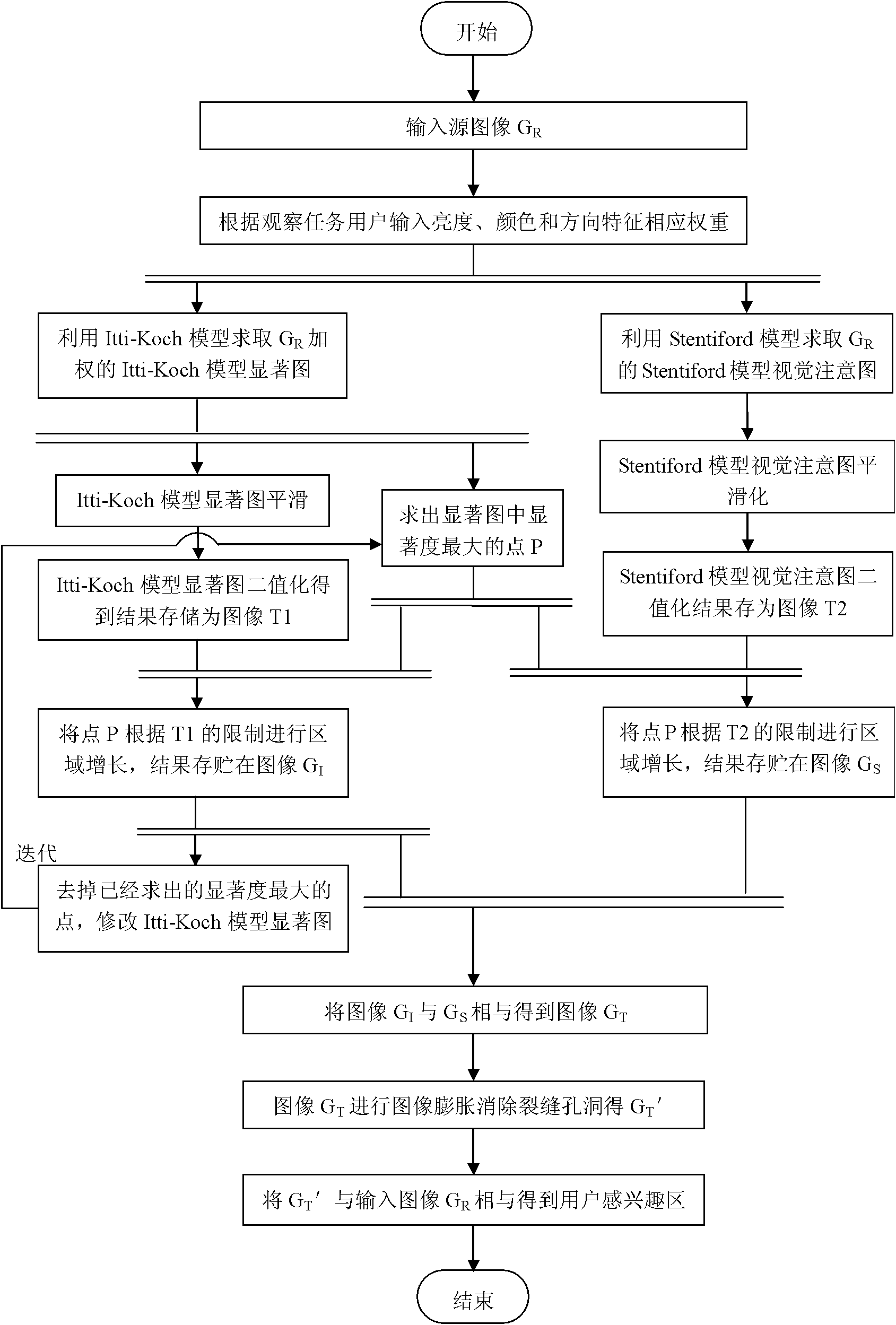
Method for extracting image region of interest by combining bottom-up and top-down ways
InactiveCN102063623AQuick extractionIncrease brightnessImage analysisCharacter and pattern recognitionPattern recognitionSaliency map
The invention provides a method for extracting an image region of interest by combining bottom-up and top-down ways. In the method, an interactive way is adopted, a user converts top-down information of observation tasks carried by the user into different weight values which are used for inputting the image bottom-layer features, an Itti-Koch model and a Stentiford model are combined, and the advantages of the two models are absorbed, thus the method for extracting region of interest combined with a user task and image visual stimulation is realized. Inquiry intention of the user and understanding on the image are converted into weights of a saliency map, namely the bottom-layer features are added corresponding weights to influence the solution of the saliency map, thus a gap between the inquiry intention of the user and the bottom-layer features of an image is reduced and the extracted region of interest is more consistent with the requirement of the user. The processing results of multiple images show that better result can be obtained by adopting the method to extract the region of interest for the user.
Owner:CENT SOUTH UNIV
Method and device for visually impaired assistance
ActiveUS9792501B1Replace and augment visionBridging the gapImage enhancementImage analysisVisually impairedTactile transducer
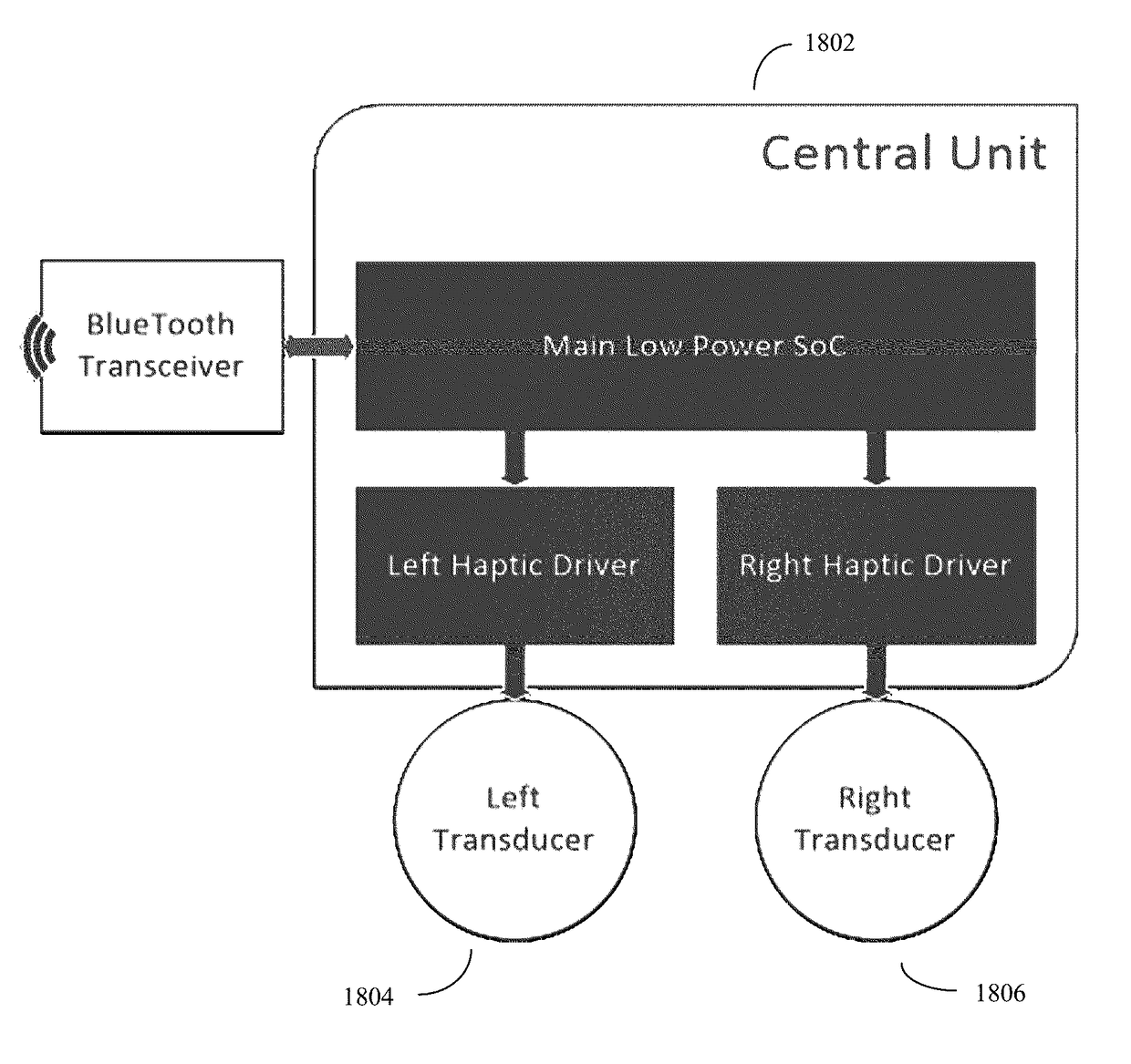
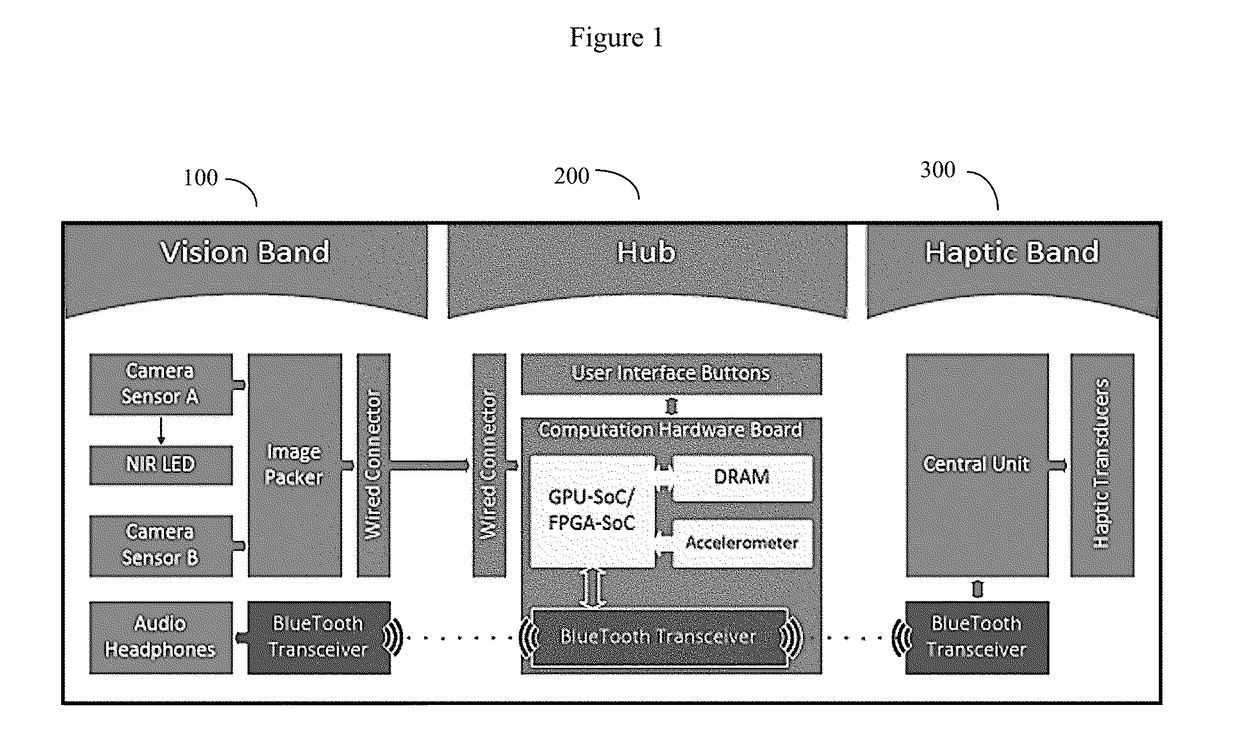
A device, system, and method of assistance for visually impaired users. The system comprises a plurality of video cameras, often head mounted, computer processors and associated support devices and algorithms configured for computer vision, and a user worn haptic band comprising a plurality (two or more) of distantly spaced haptic transducers. This haptic band is worn such that user's hands are free for other tasks. The system uses its video camera, depth processing algorithms, and object recognition algorithms (hardware and / or software based) to identify a limited number of navigationally important objects. The spatial locations of each object deemed important is output to the user by varying output to the haptic transducers accordingly. The system is configured to identify and report objects as generic objects, identified objects, and potential obstacle objects. The system can also optionally provide audio information pertaining to these objects as well.
Owner:MAHERIYA KIRAN K
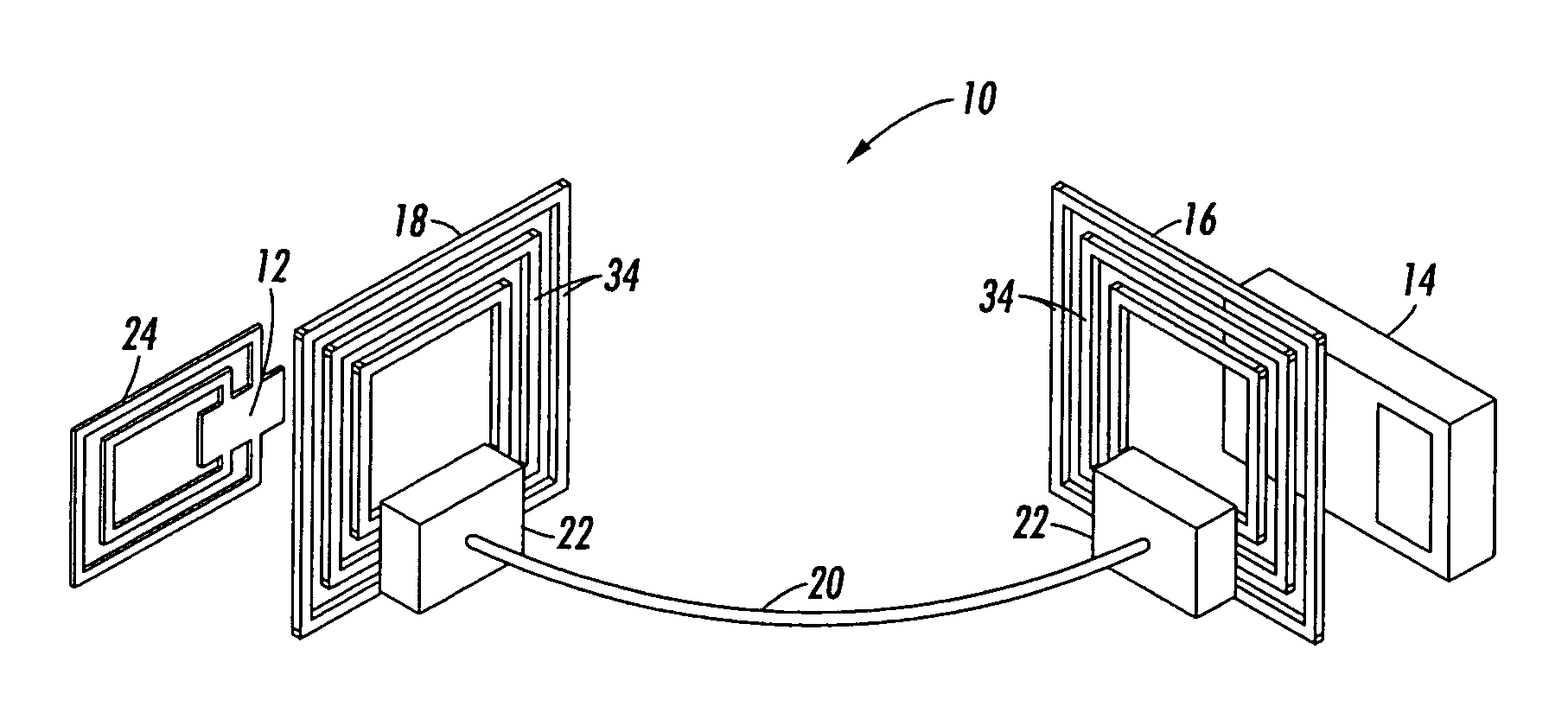
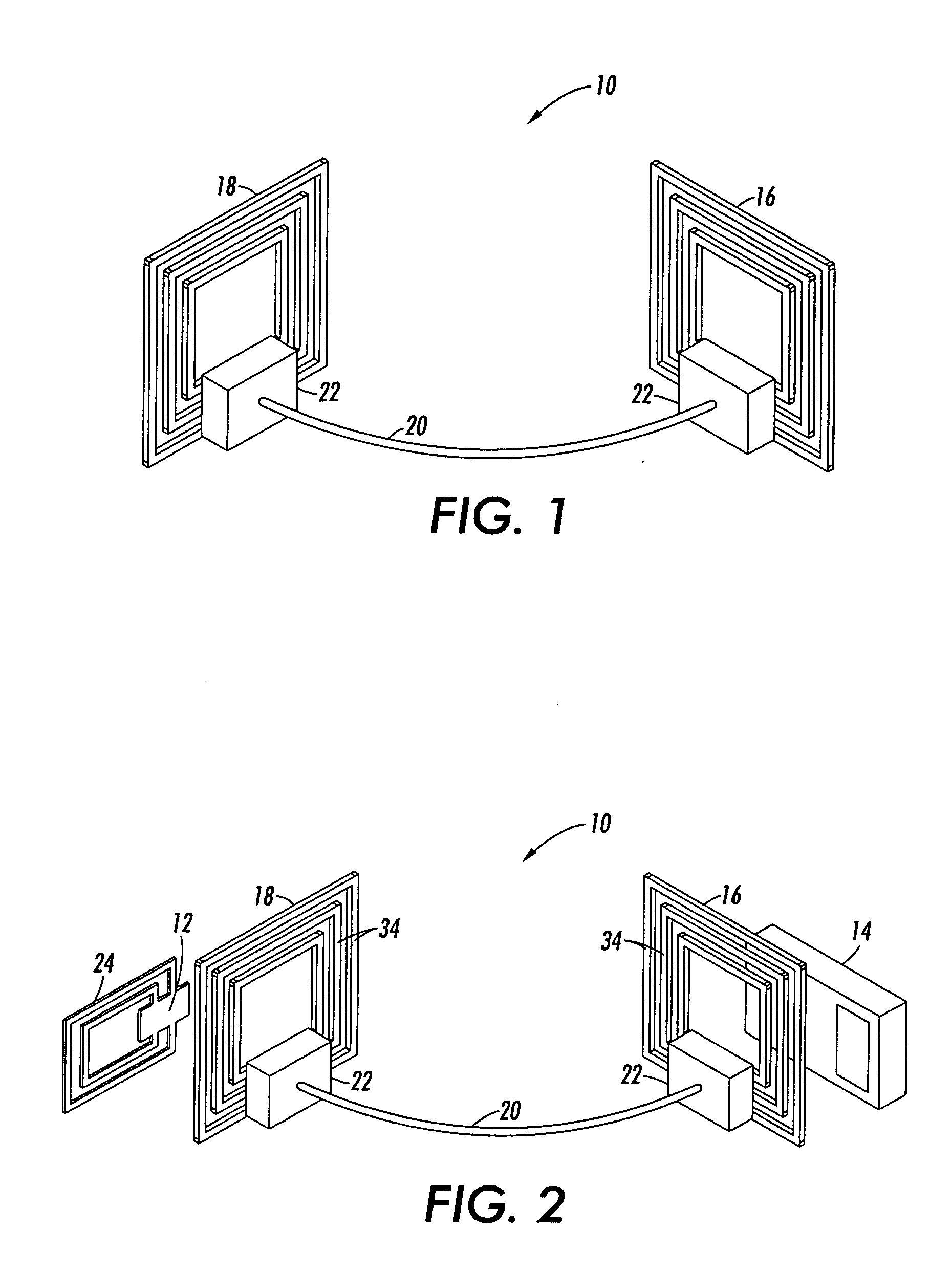
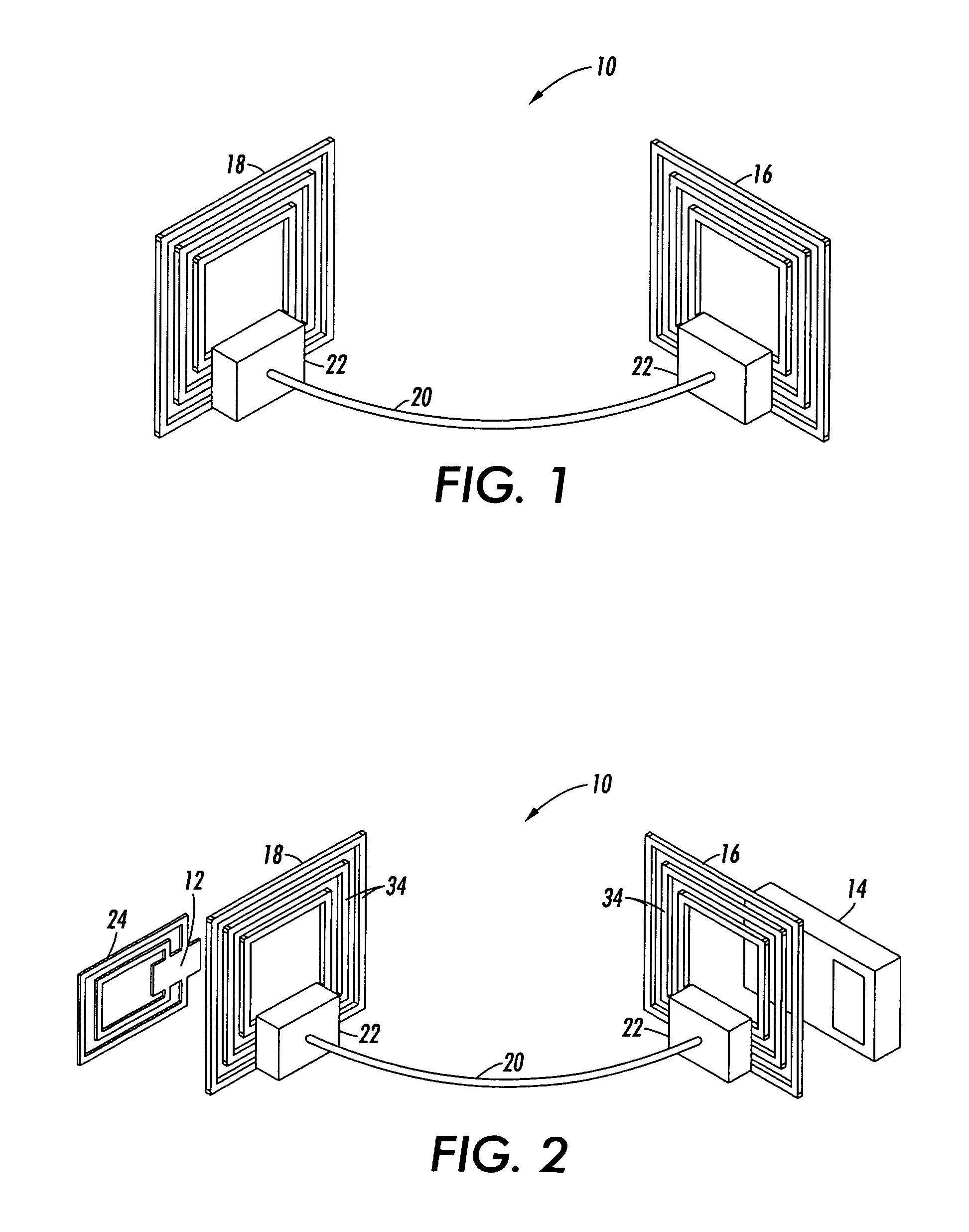
RFID bridge antenna
InactiveUS20070222604A1Increase distanceBridging the gapAntenna supports/mountingsMemory record carrier reading problemsElectrical conductorTag antenna
An RFID bridge antenna is positioned between a tag antenna associated with a tag and a reader antenna associated with a reader. The bridge includes at least two RF antenna elements spaced apart from one another and coupled together by an electrical conductor. The first RF antenna element is located proximate to the tag antenna and the second RF antenna element is located proximate to the reader antenna. An electromagnetic carrier signal transmitted by the reader antenna is received by one of the RF antenna element and retransmitted to the tag antenna by the other RF antenna element, increasing the distance over which the tag can communicate with the reader. Where the tag is attached to a packaged object, the RFID bridge antenna may be included in the package to allow wireless data communication between the tag and a reader. The reader may also be located external to the package. For example, one of the RF antenna elements may be attached to a label on the package, allowing data stored in the tag to be extracted by the external reader. The object may be a module, also known as a customer replaceable unit (CRU), and the tag may be configured as a customer replaceable unit monitor (CRUM).
Owner:XEROX CORP
Module with RFID tag and associated bridge antenna
ActiveUS7432817B2Increase distanceBridging the gapVoting apparatusAntenna supports/mountingsTag antennaElectrical conductor
Owner:XEROX CORP
Photonic wire bonds
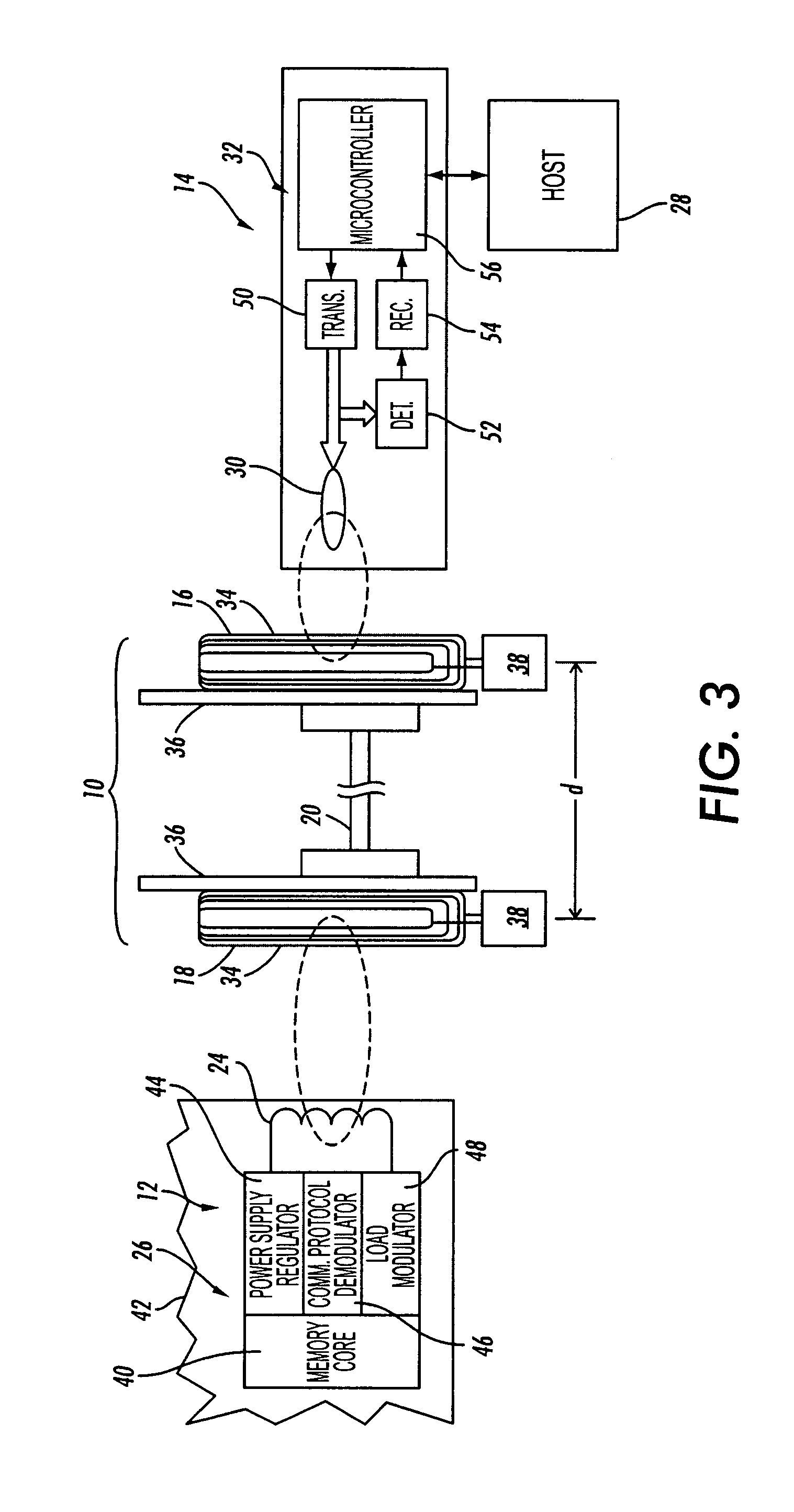
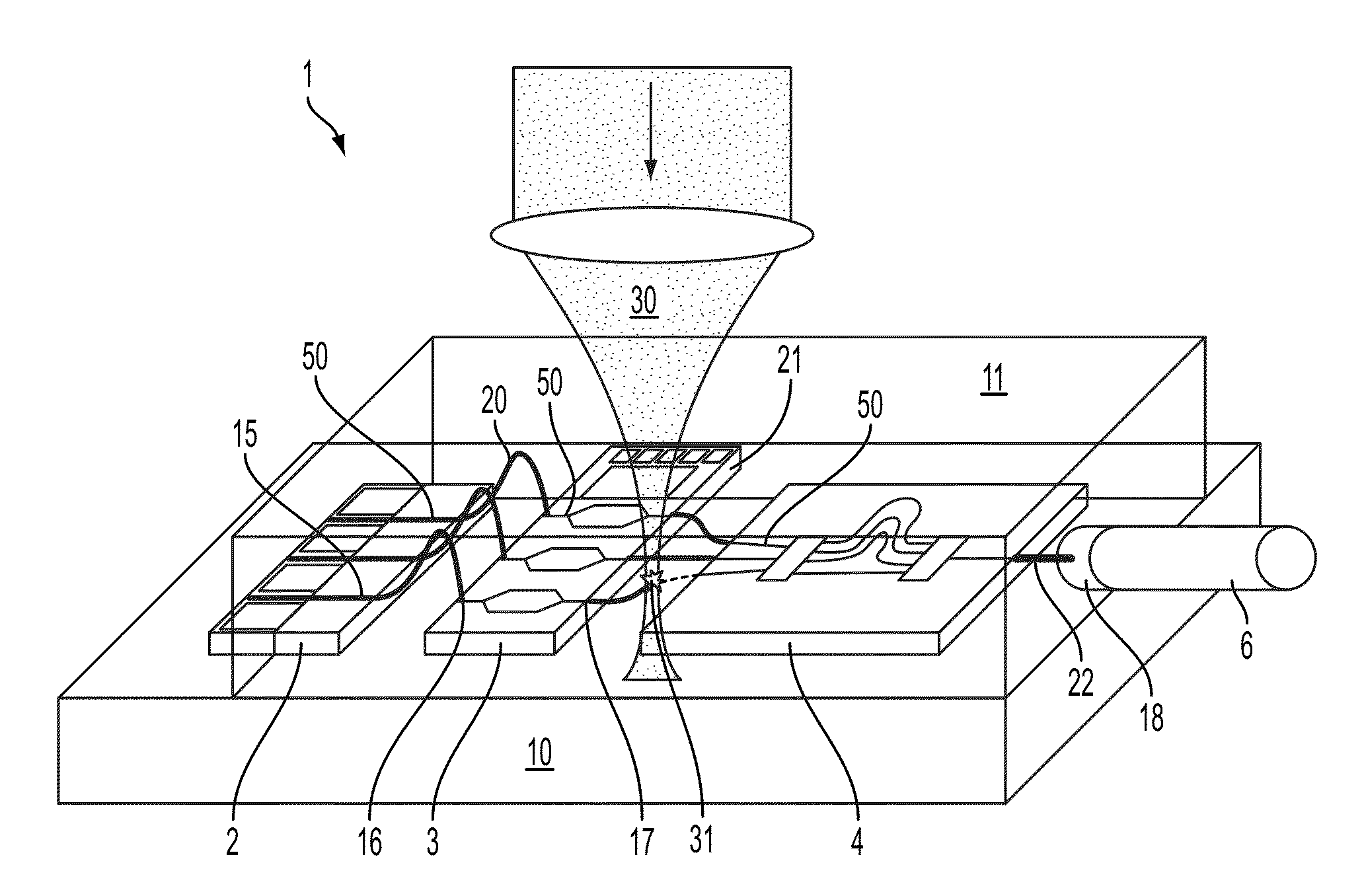
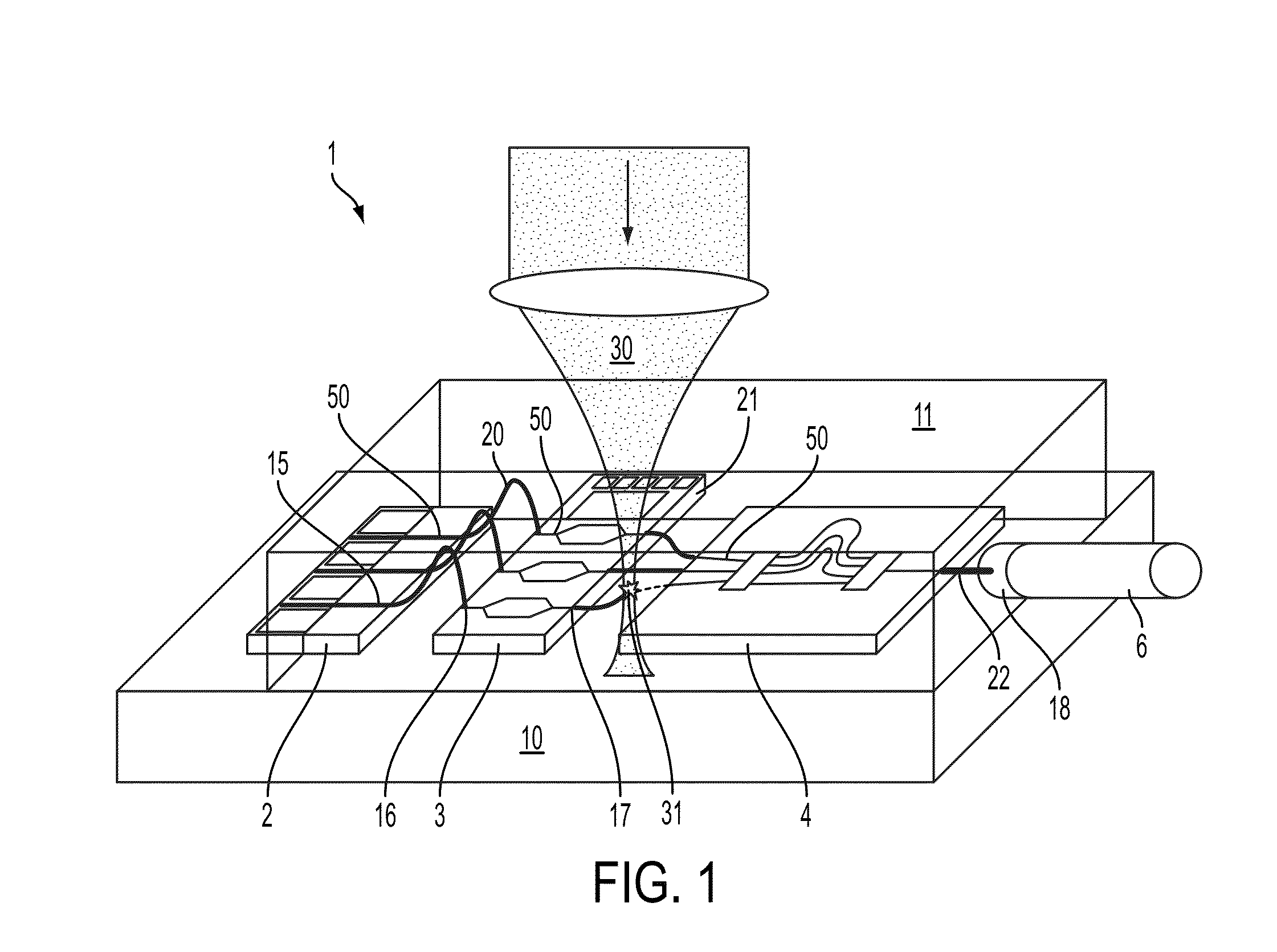
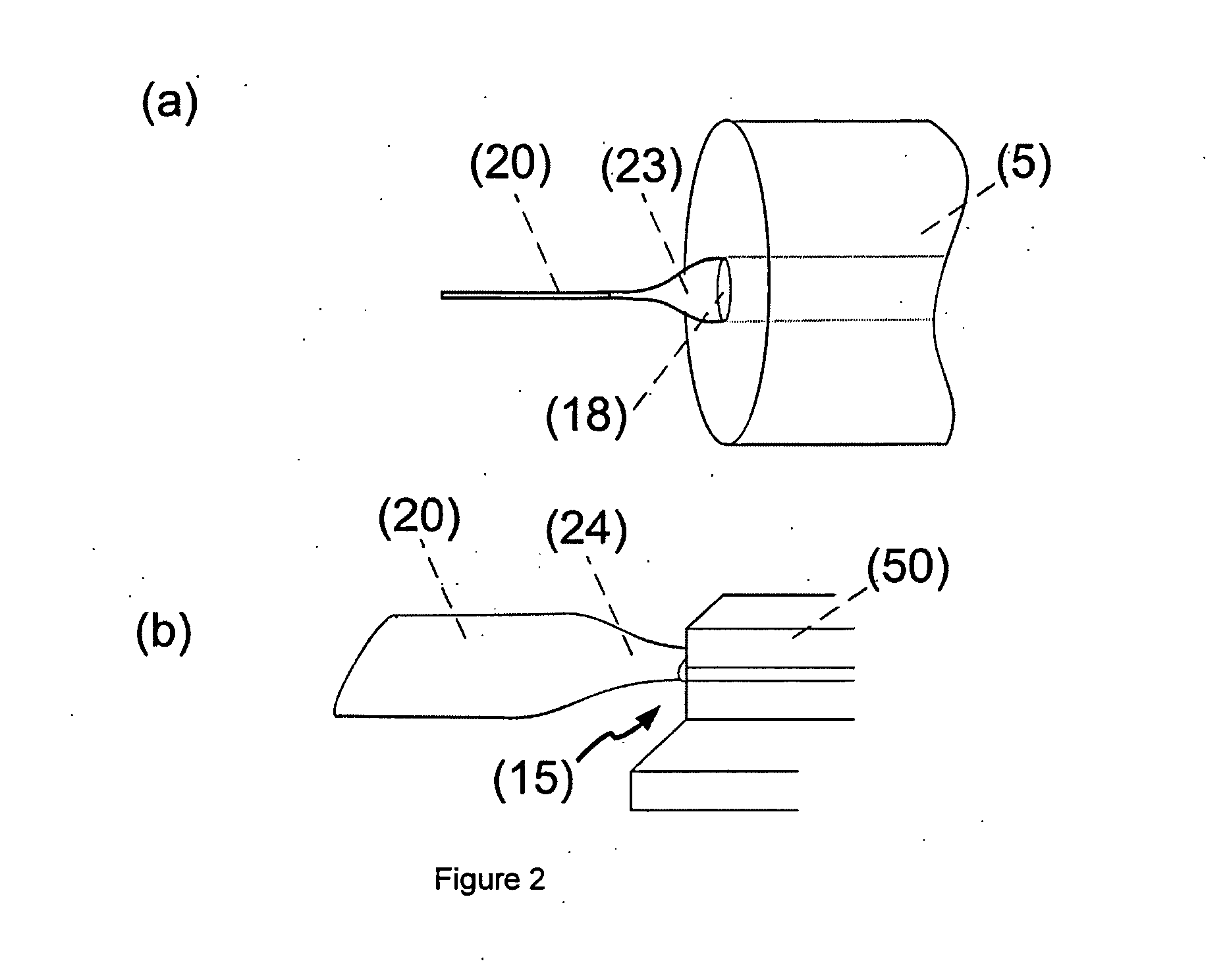
ActiveUS20130223788A1Bridging the gapHighly integratedCoupling light guidesOptical waveguide light guideRefractive index contrastPlanar substrate
An optical arrangement includes a plurality of planar substrates with at least one planar integrated optical waveguide on each planar substrate. At least one optical waveguide structure has at least one end connected via an optical connecting structure to one of the planar integrated optical waveguides. The optical waveguide structure is positioned at least partly outside the integration plane for the planar integrated optical waveguide and a refractive index contrast between a core region and a cladding region of the optical waveguide structure is at least 0.01.
Owner:KARLSRUHER INST FUR TECH
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com