Patents
Literature
121results about How to "Retain control" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
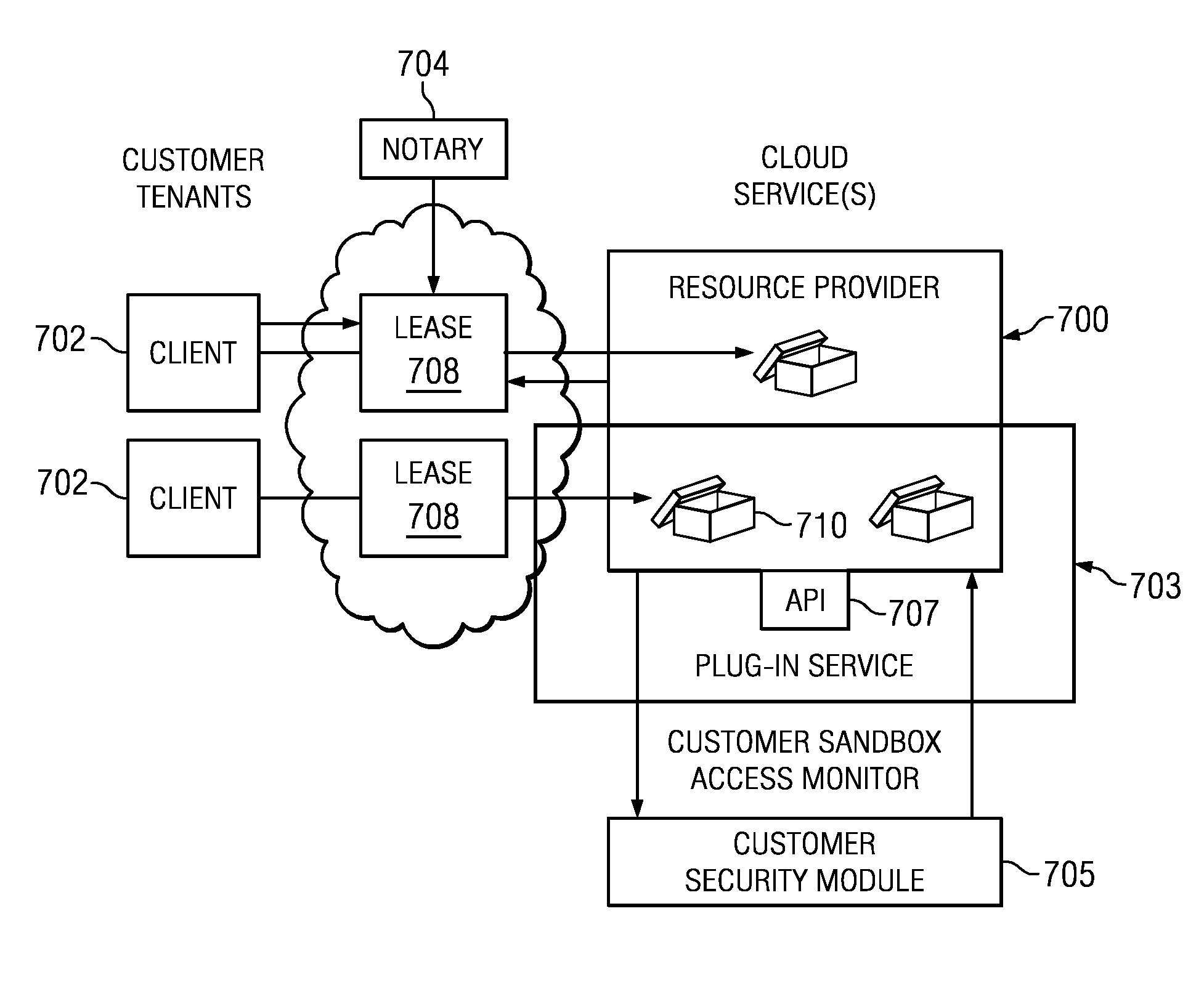
Authentication and authorization methods for cloud computing security
ActiveUS8769622B2Retain controlKey distribution for secure communicationDigital data processing detailsResource poolThird party
An authentication and authorization plug-in model for a cloud computing environment enables cloud customers to retain control over their enterprise information when their applications are deployed in the cloud. The cloud service provider provides a pluggable interface for customer security modules. When a customer deploys an application, the cloud environment administrator allocates a resource group (e.g., processors, storage, and memory) for the customer's application and data. The customer registers its own authentication and authorization security module with the cloud security service, and that security module is then used to control what persons or entities can access information associated with the deployed application. The cloud environment administrator, however, typically is not registered (as a permitted user) within the customer's security module; thus, the cloud environment administrator is not able to access (or release to others, or to the cloud's general resource pool) the resources assigned to the cloud customer (even though the administrator itself assigned those resources) or the associated business information. To further balance the rights of the various parties, a third party notary service protects the privacy and the access right of the customer when its application and information are deployed in the cloud.
Owner:IBM CORP
Authentication and authorization methods for cloud computing security platform
ActiveUS20130007845A1Retain controlDigital data processing detailsUser identity/authority verificationThird partyResource pool
An authentication and authorization plug-in model for a cloud computing environment enables cloud customers to retain control over their enterprise information when their applications are deployed in the cloud. The cloud service provider provides a pluggable interface for customer security modules. When a customer deploys an application, the cloud environment administrator allocates a resource group (e.g., processors, storage, and memory) for the customer's application and data. The customer registers its own authentication and authorization security module with the cloud security service, and that security module is then used to control what persons or entities can access information associated with the deployed application. The cloud environment administrator, however, typically is not registered (as a permitted user) within the customer's security module; thus, the cloud environment administrator is not able to access (or release to others, or to the cloud's general resource pool) the resources assigned to the cloud customer (even though the administrator itself assigned those resources) or the associated business information. To further balance the rights of the various parties, a third party notary service protects the privacy and the access right of the customer when its application and information are deployed in the cloud.
Owner:IBM CORP
System and Interface For Monitoring Information Technology Assets
ActiveUS20100229096A1Retain controlStandardize the interfaceInput/output for user-computer interactionError preventionApplication softwareApplication service provider
An application service provider (ASP)-based interface and system for analyzing performance and costs of respective enterprise information technology assets from the correlation of metrics data of enterprise SNMP-enabled devices.
Owner:DYNATRACE
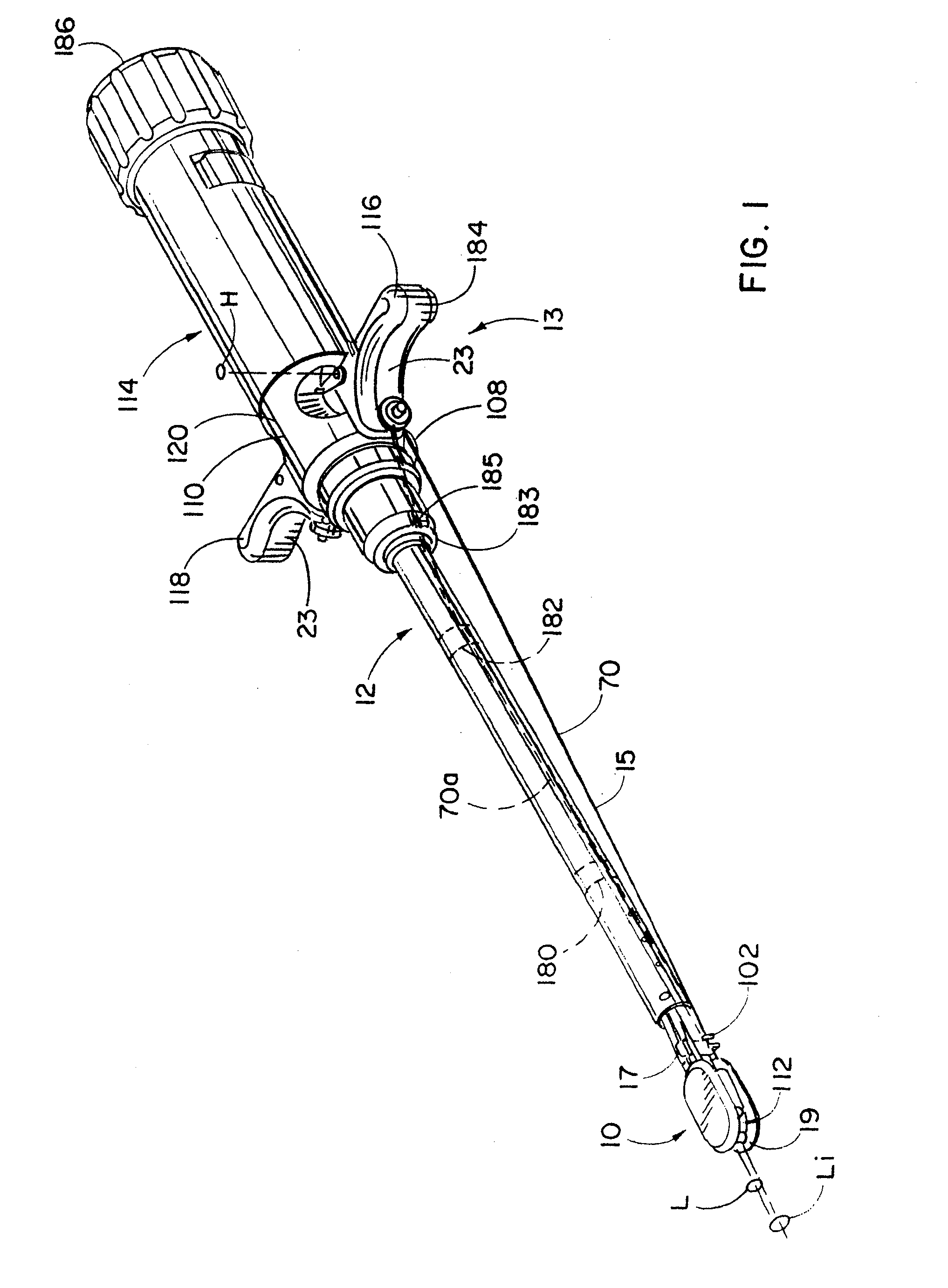
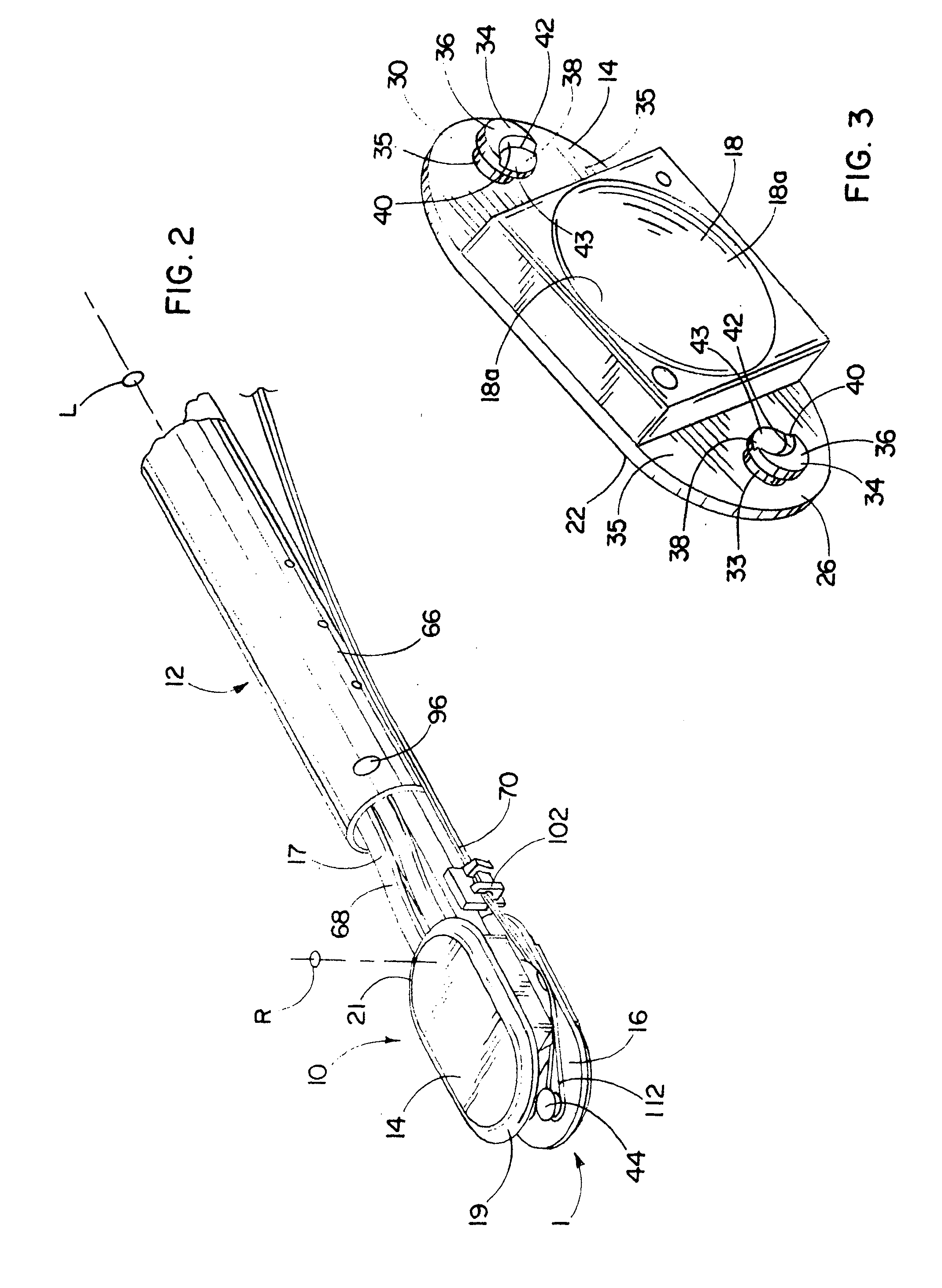
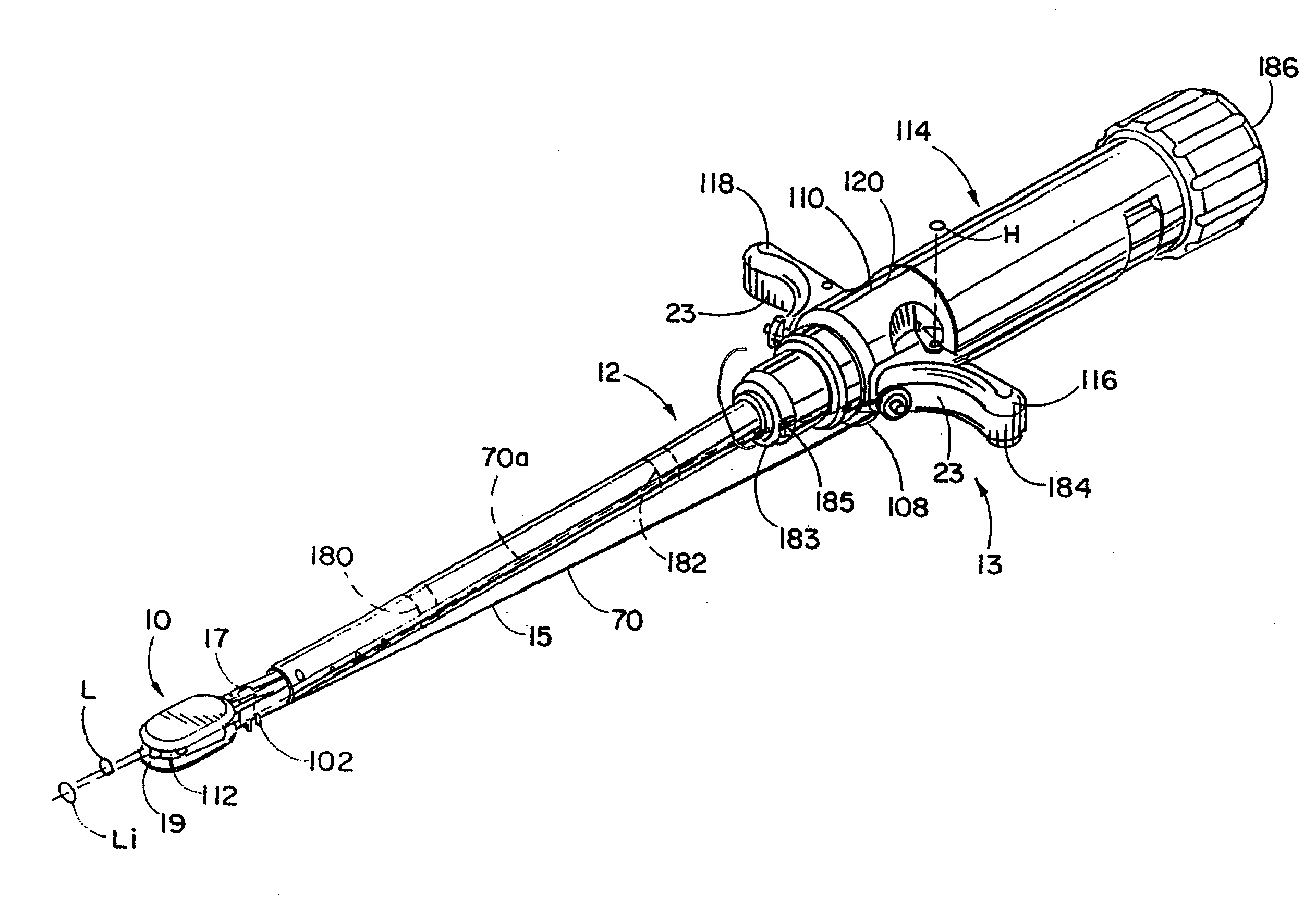
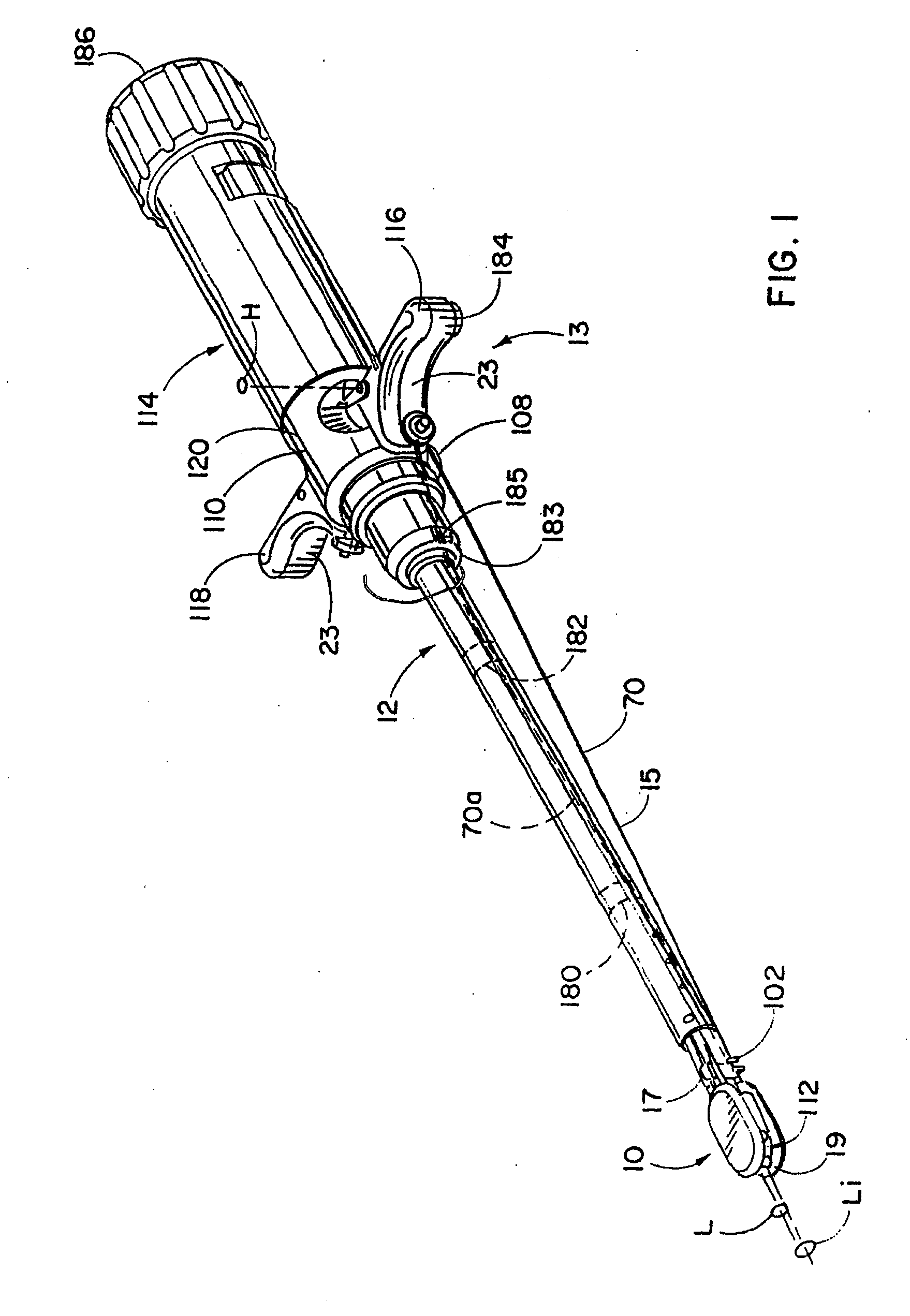
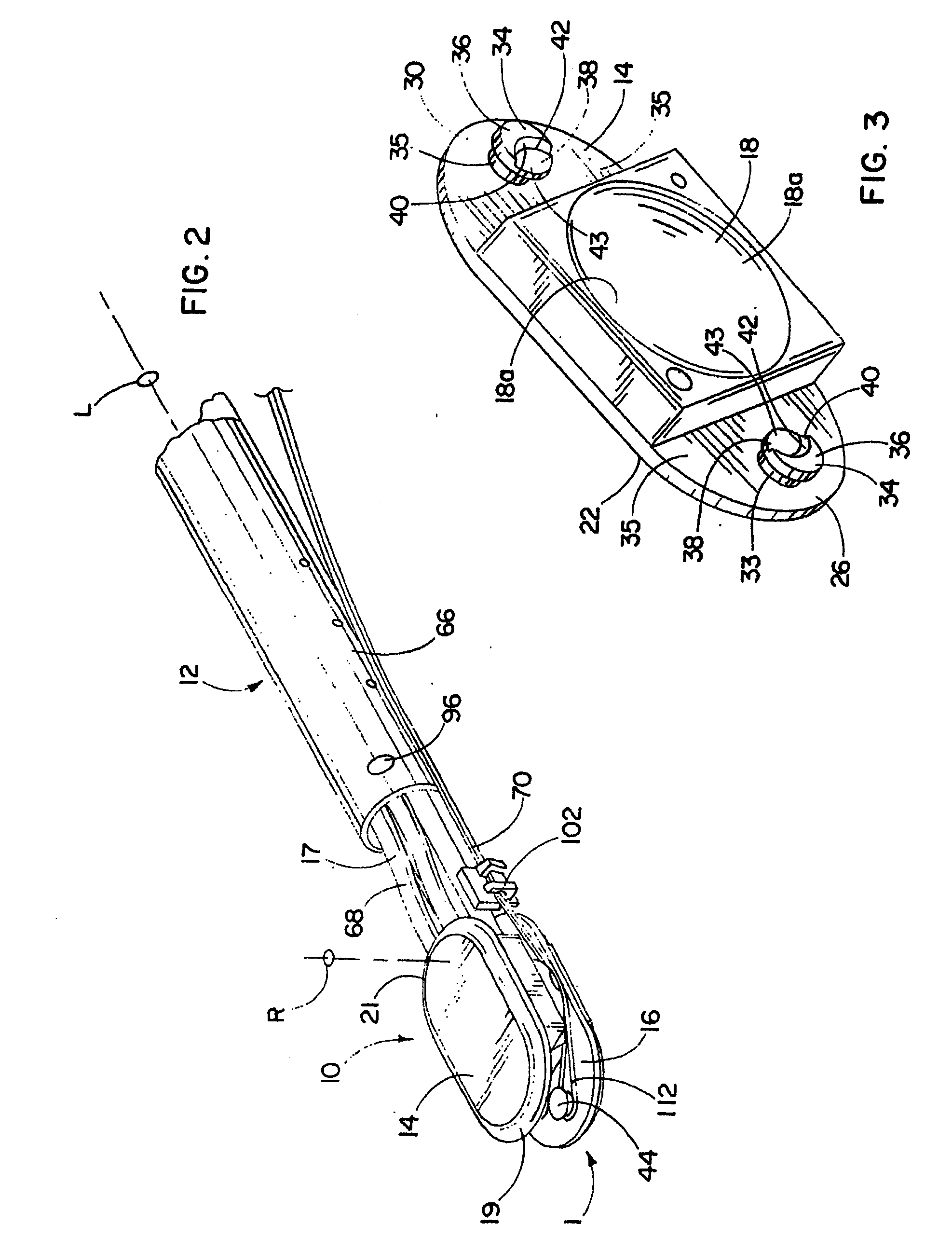
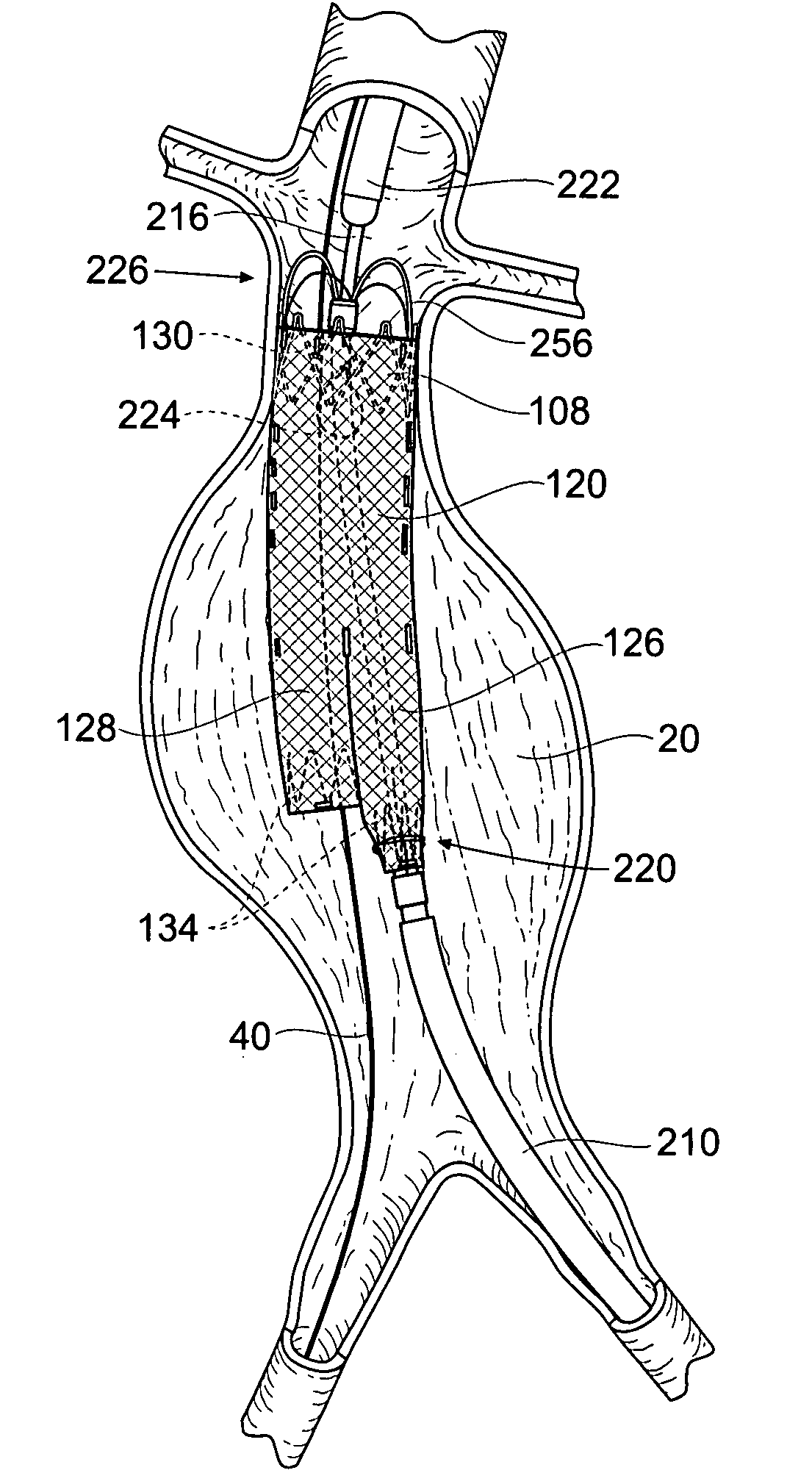
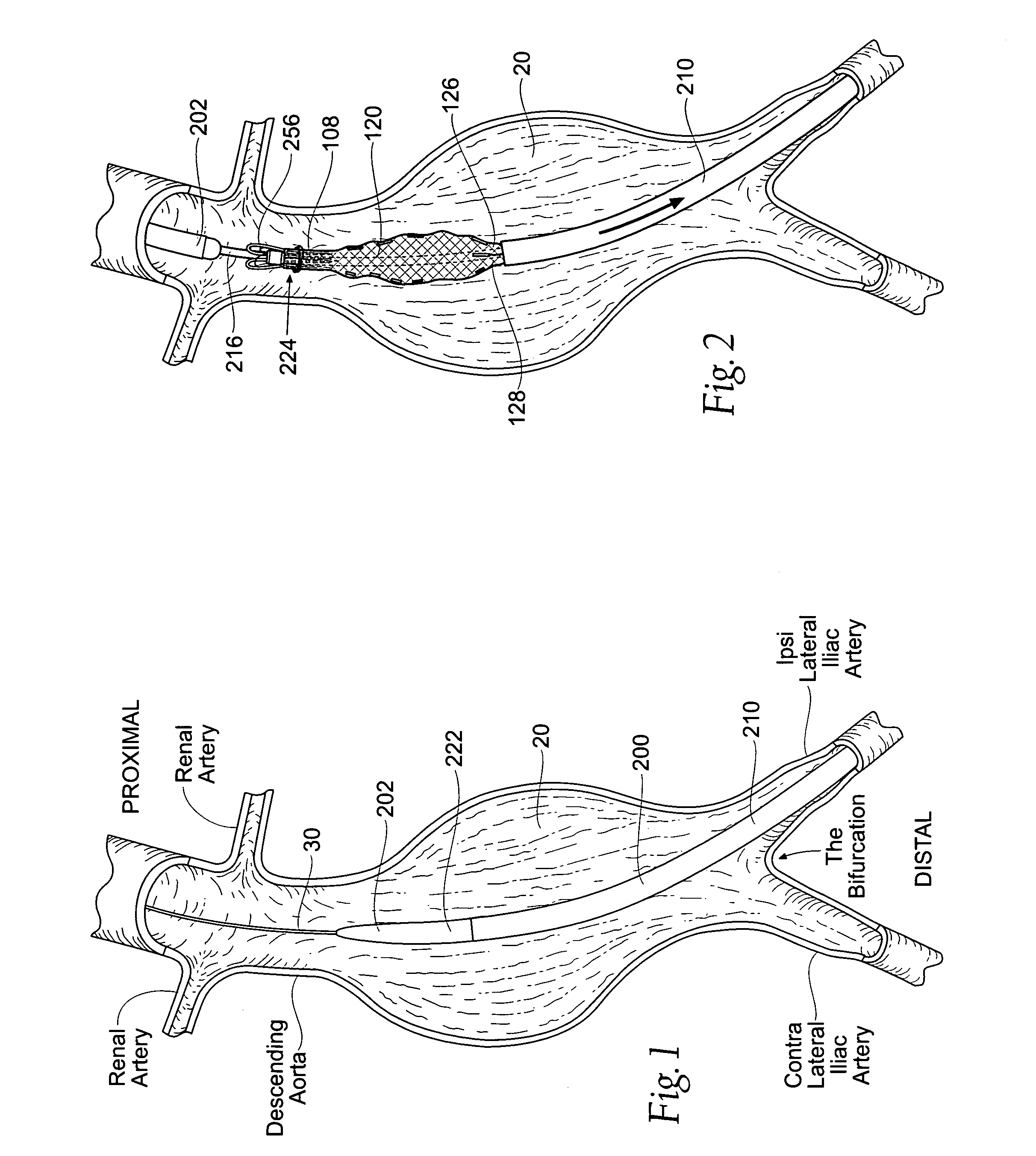
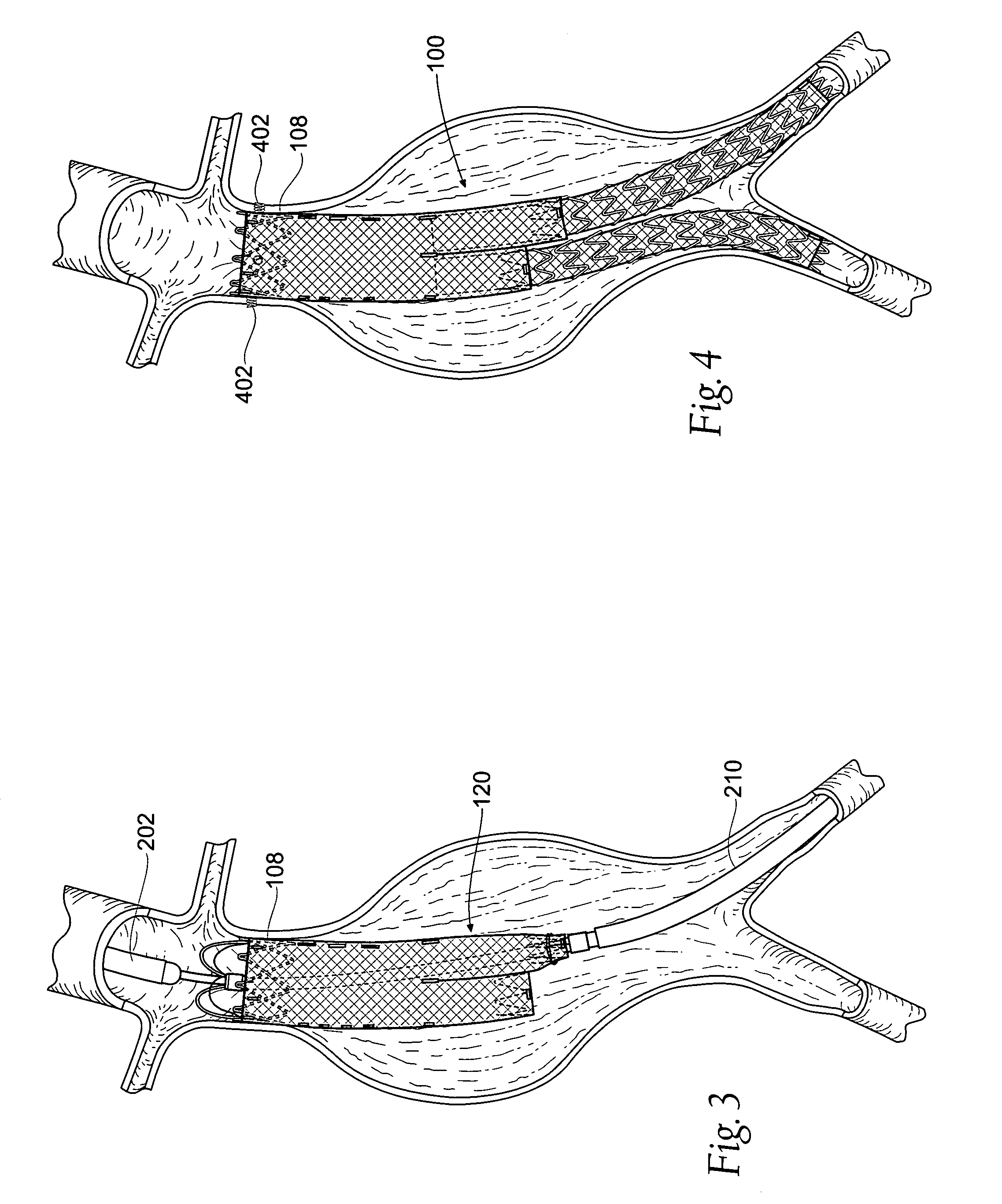
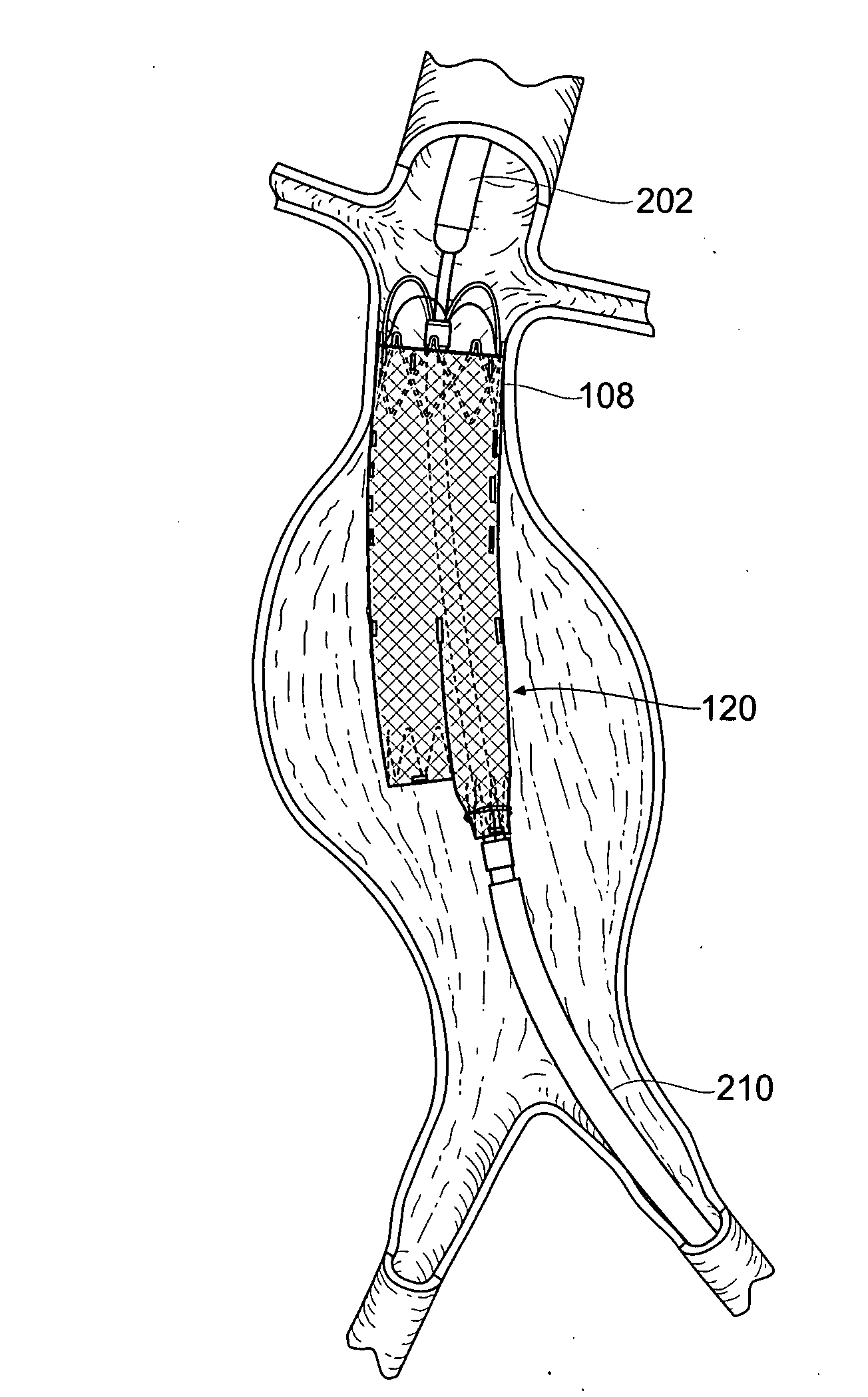
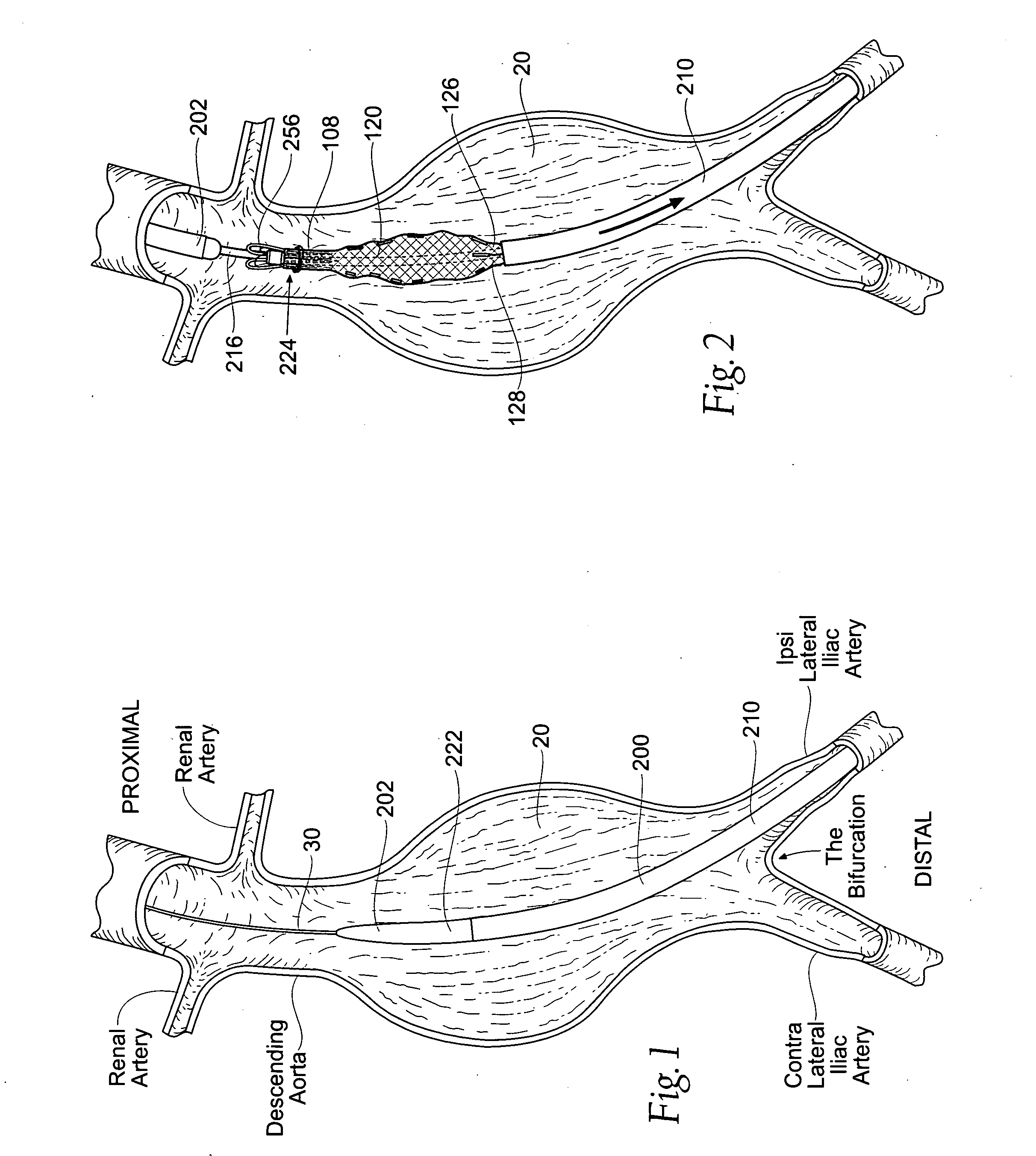
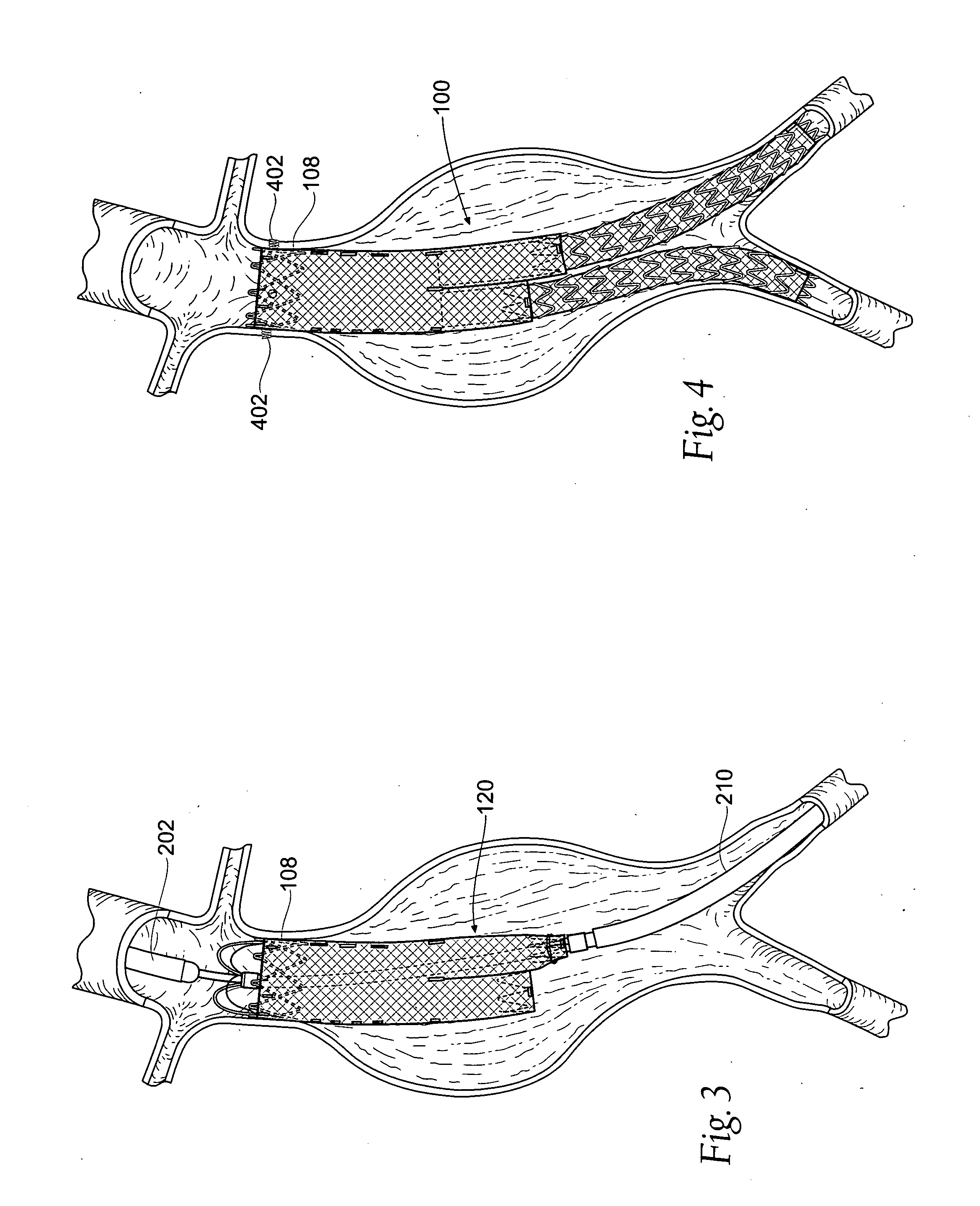
Devices, systems, and methods for prosthesis delivery and implantation
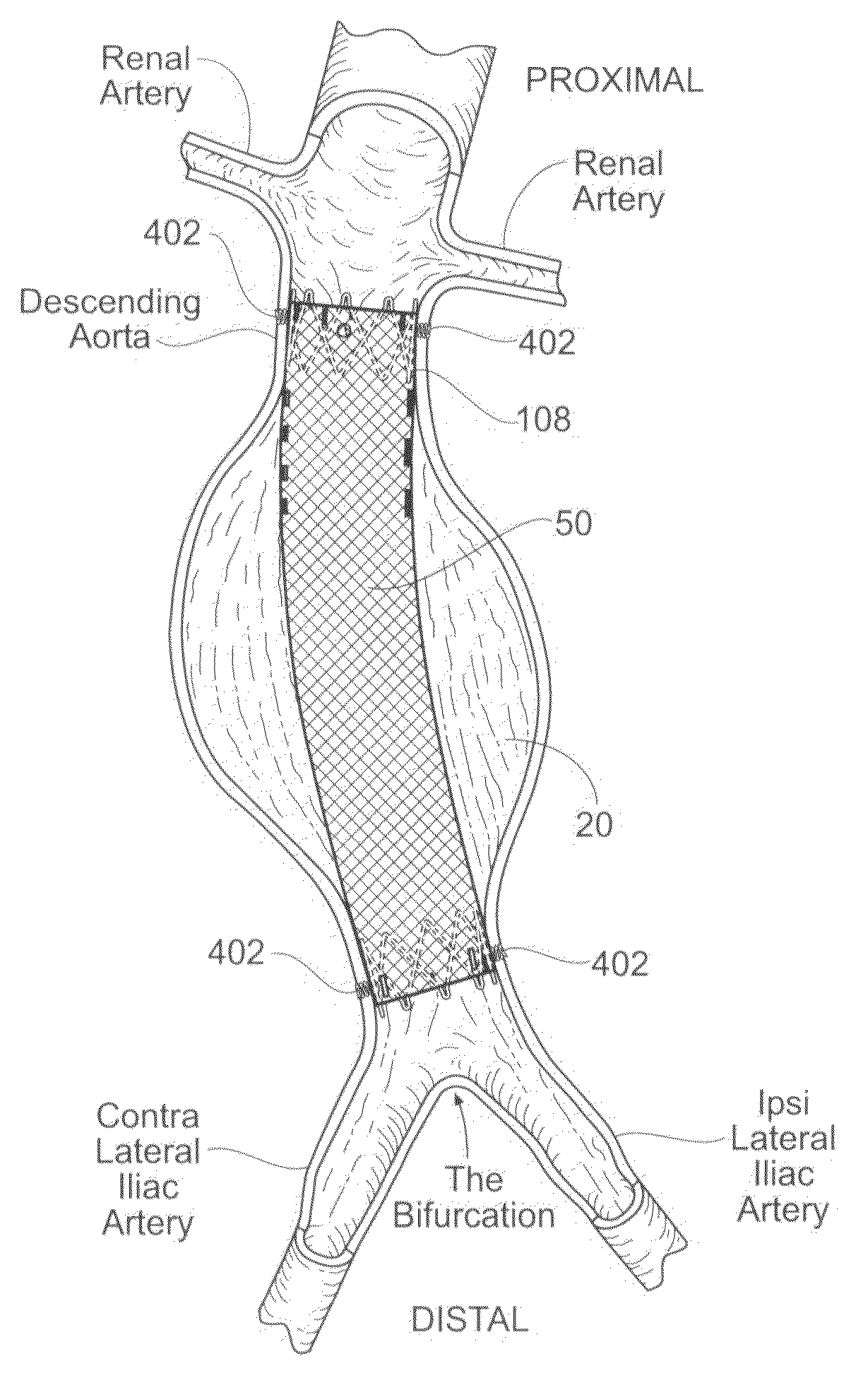
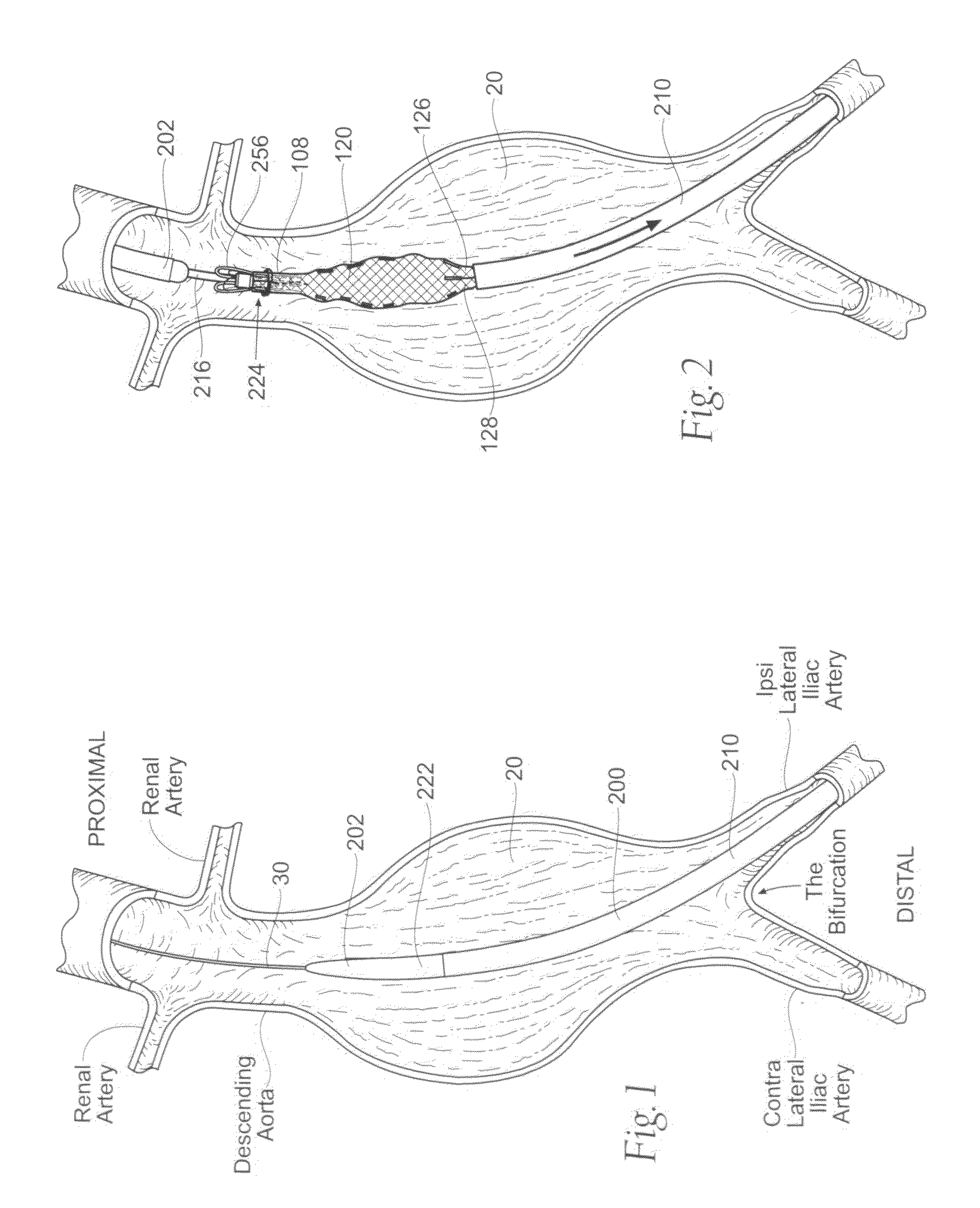
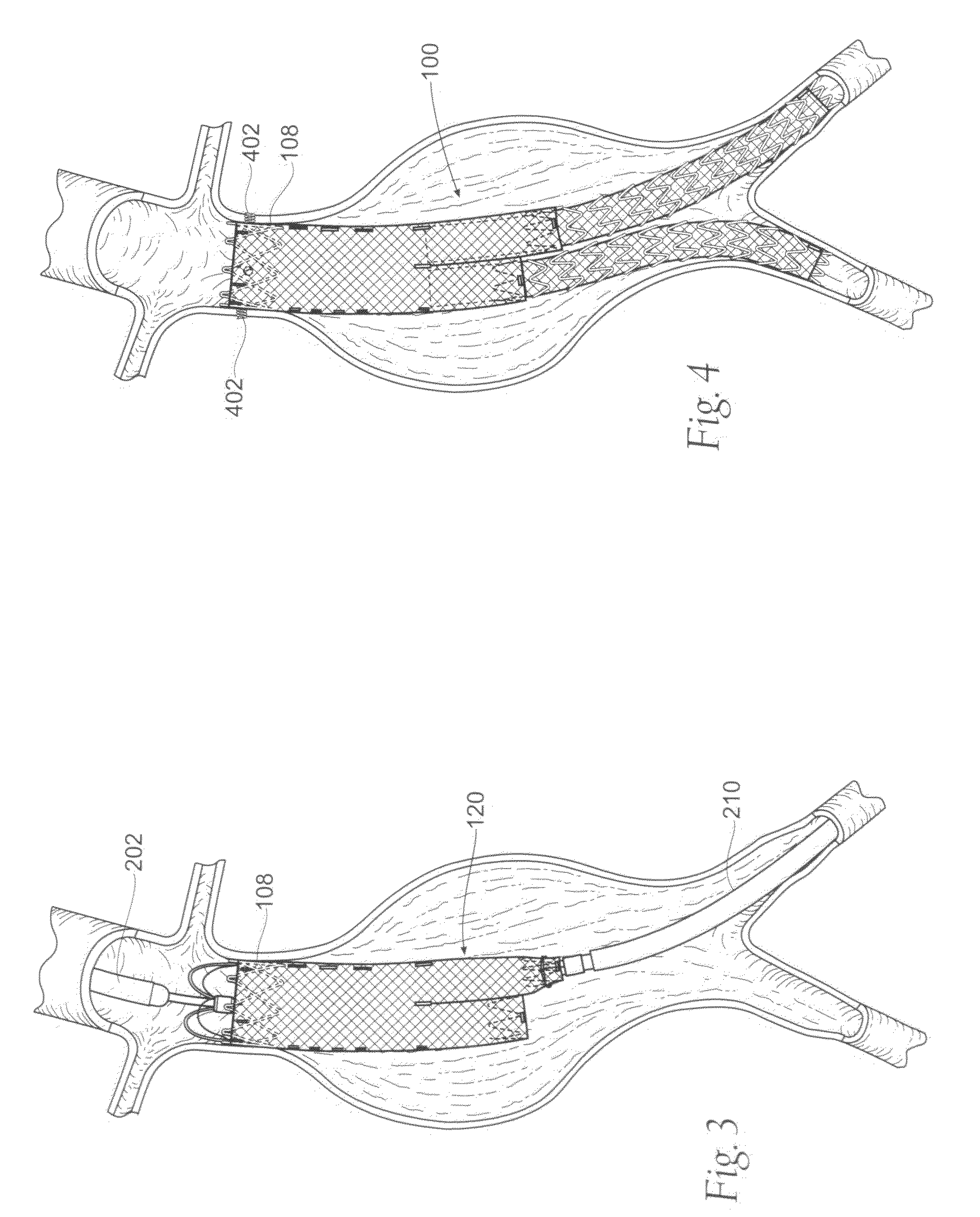
Devices, systems, and methods use a catheter device sized and configured for introduction to a targeted site in a hollow body organ or blood vessel. The catheter device includes a first release mechanisms coupled to the prosthesis to secure at least one region of the prosthesis to the catheter shaft, and a second release mechanism coupled to the prosthesis in cooperation with the first release mechanism to prevent full release of the at least one region of the at least one region of the prosthesis from the catheter shaft after actuation of the first release mechanism. A fastening device sized and configured for introduction to the targeted site in the hollow body organ or blood vessel occupied by the catheter device, includes an actuator to deploy a fastener in the at least one region of the prosthesis after actuation of the first release mechanism and before actuation of the second release mechanism.
Owner:APTUS ENDOSYST
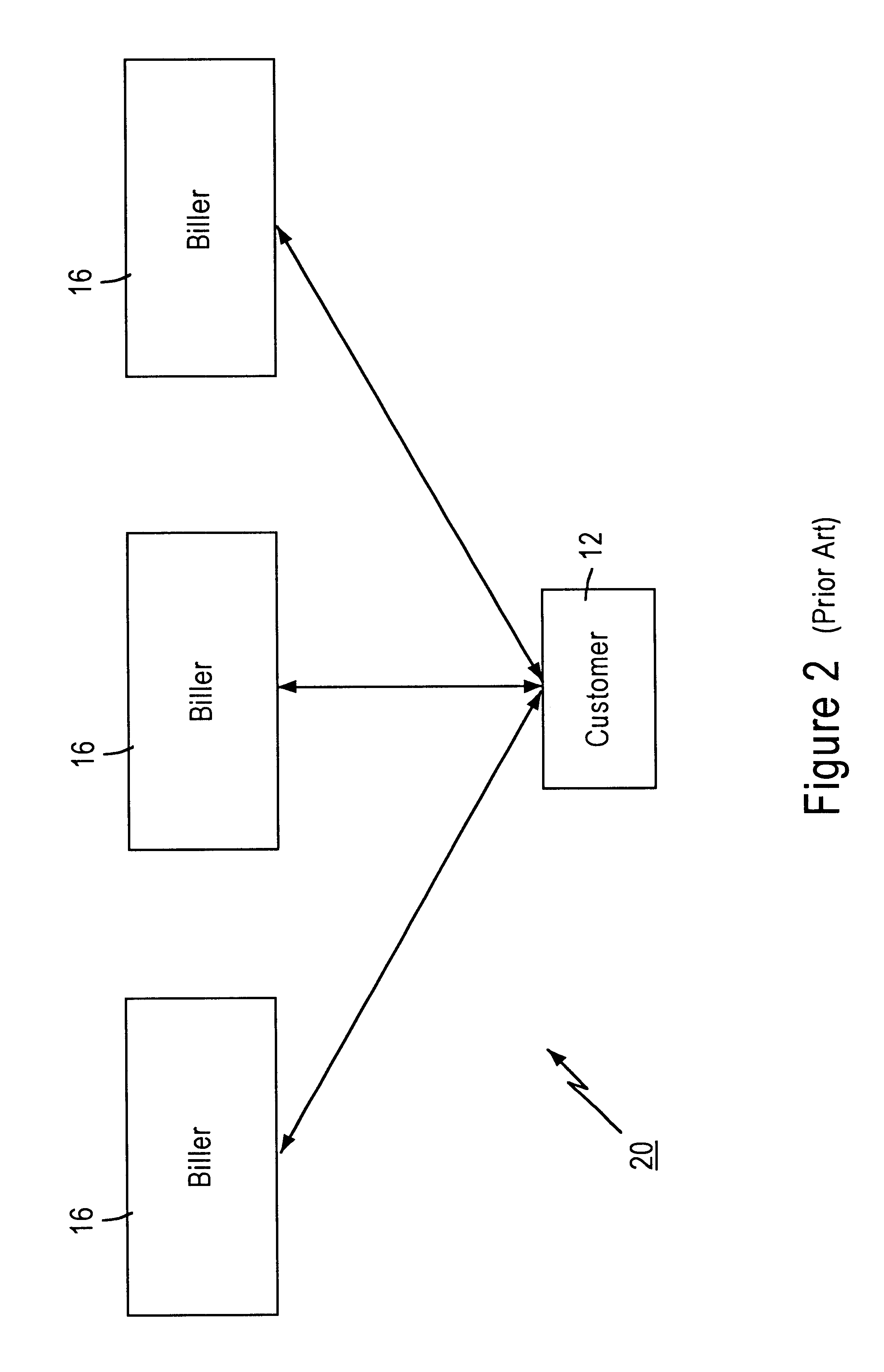
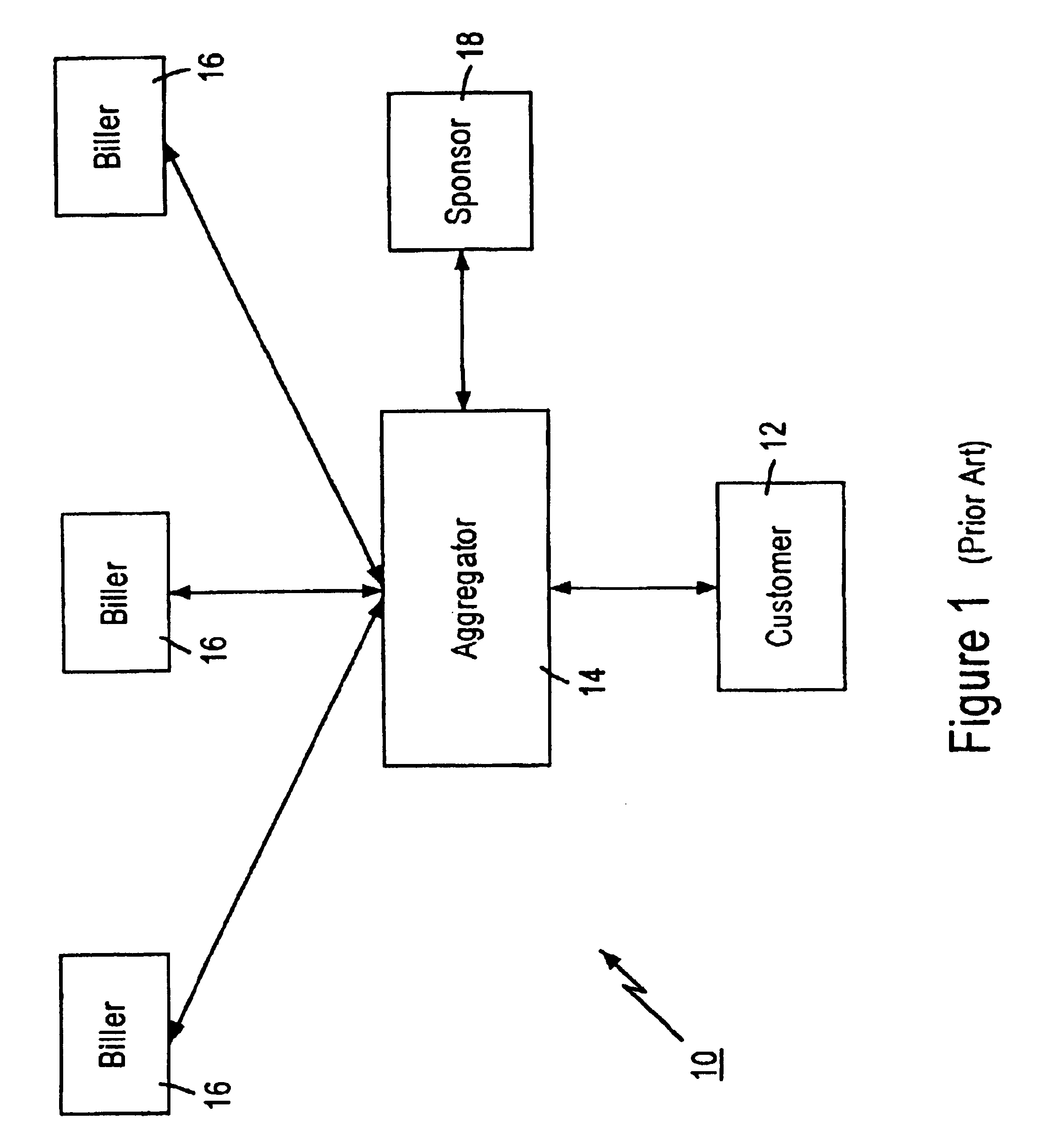
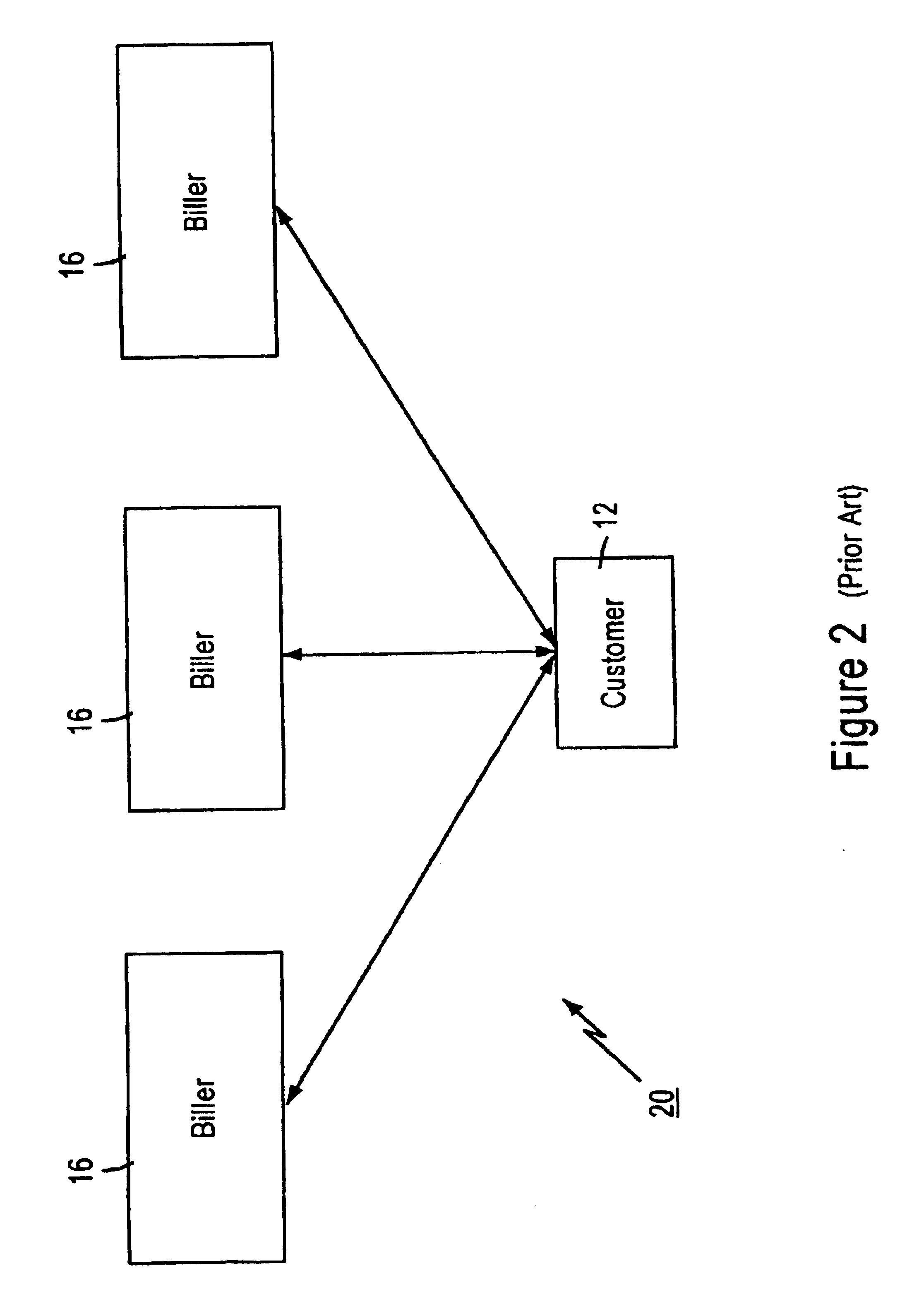
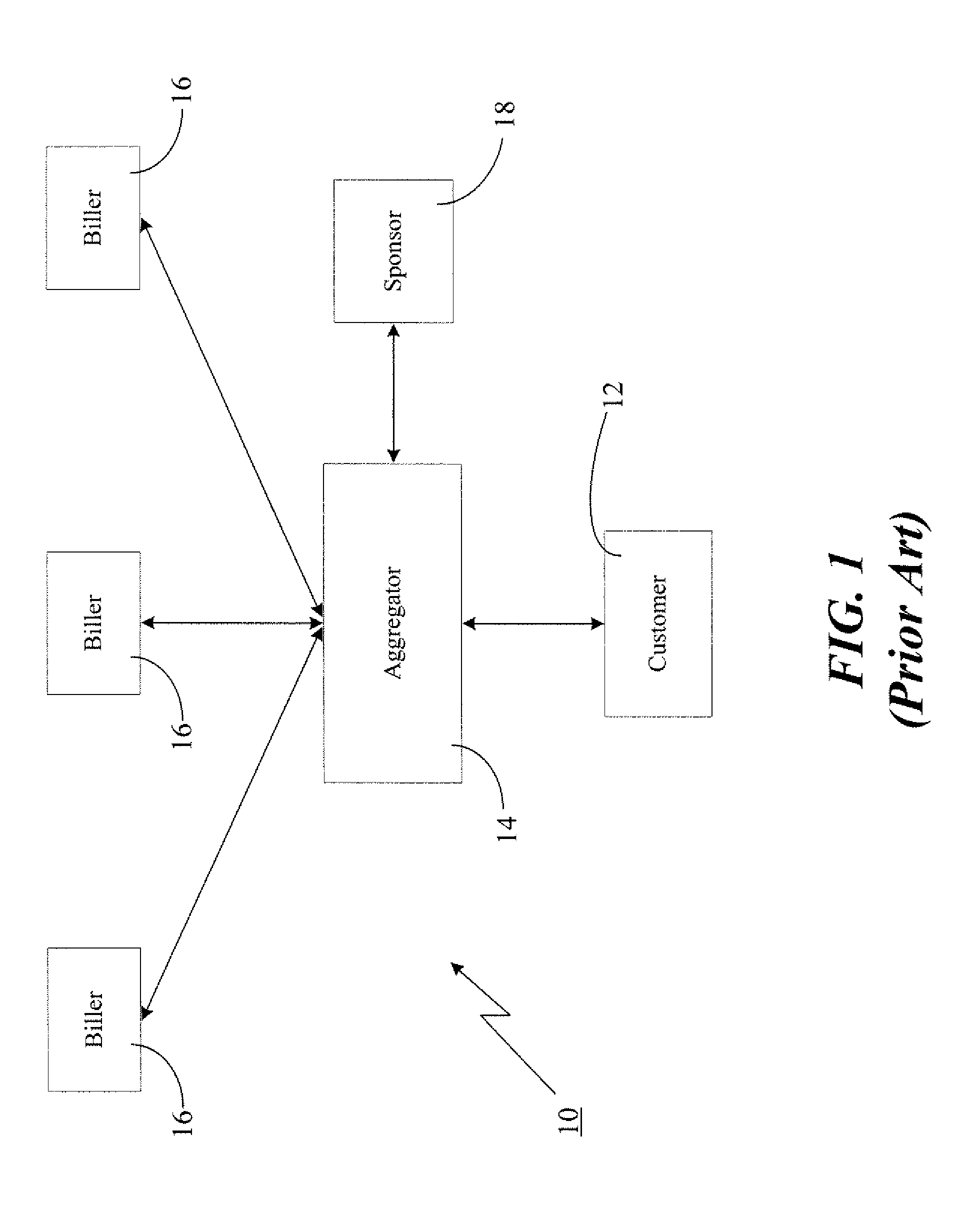
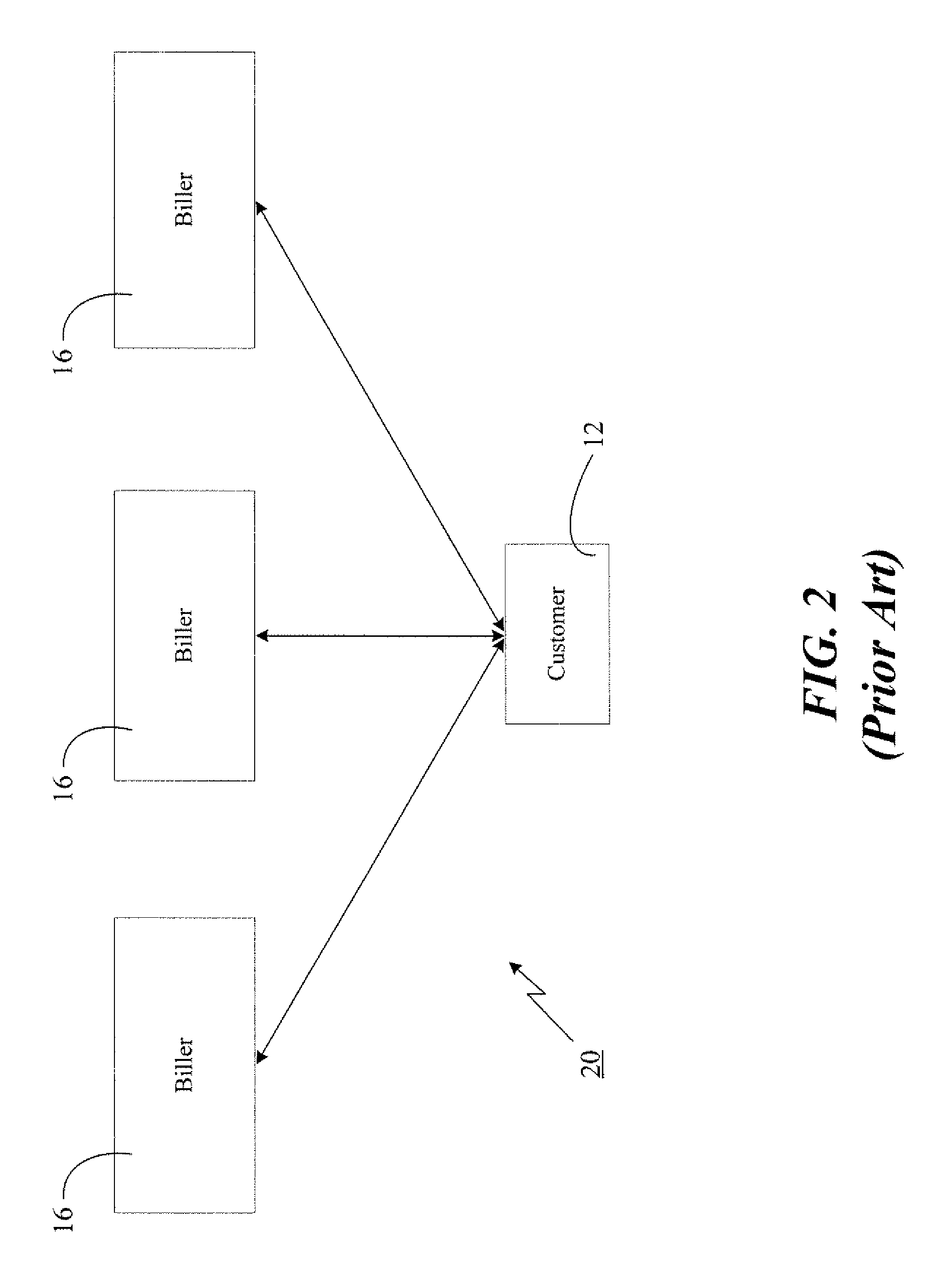
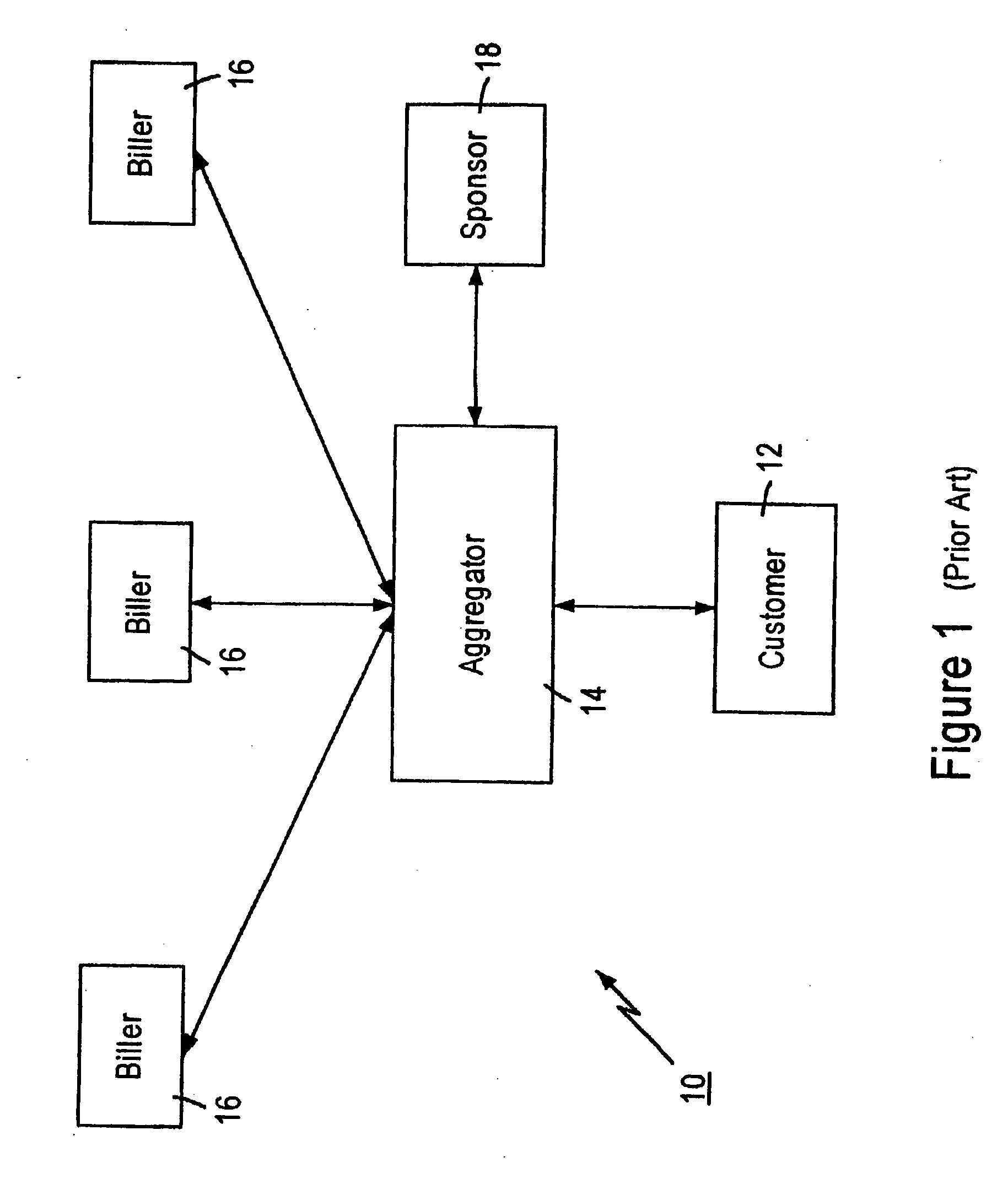
Distributed data accessing technique
InactiveUS6055567ADirect interactionRetain controlMultiple digital computer combinationsPayment architectureTelecommunicationsNetwork link
A distributed data accessing technique is disclosed. The technique is realized by storing, at a first network station, information identifying data which is available at a second network station, the second network station being different than the first network station. A signal is generated at the first network station representing the information identifying the available data and linking information to the second network station. The signal is transmitted to a third network station, the third network station being different than the first and the second network stations. The transmitted linking information is operable at the third network station to establish a network link over which the identified available data is transmittable from the second network station to the third network station.
Owner:CHECKFREE CORP
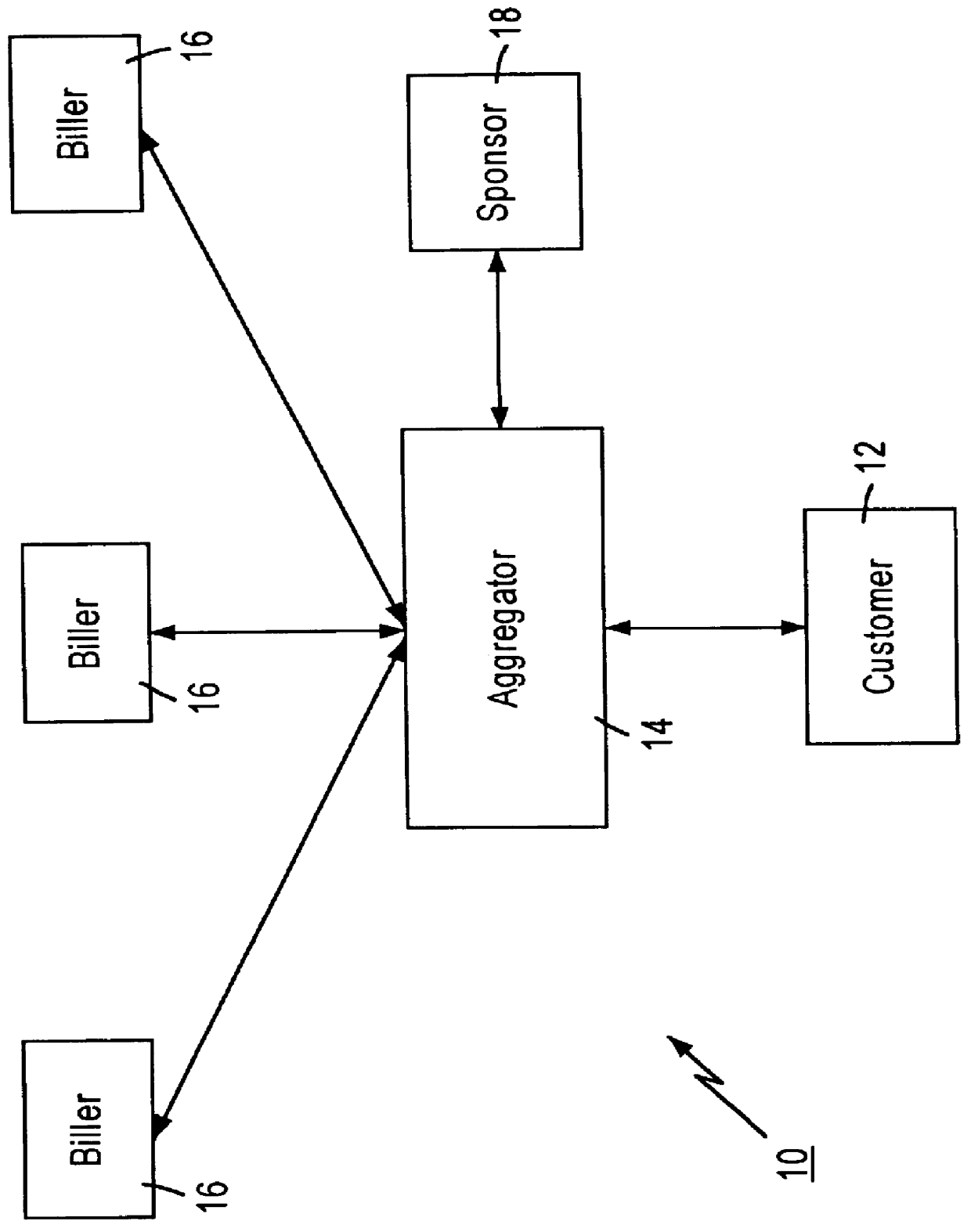
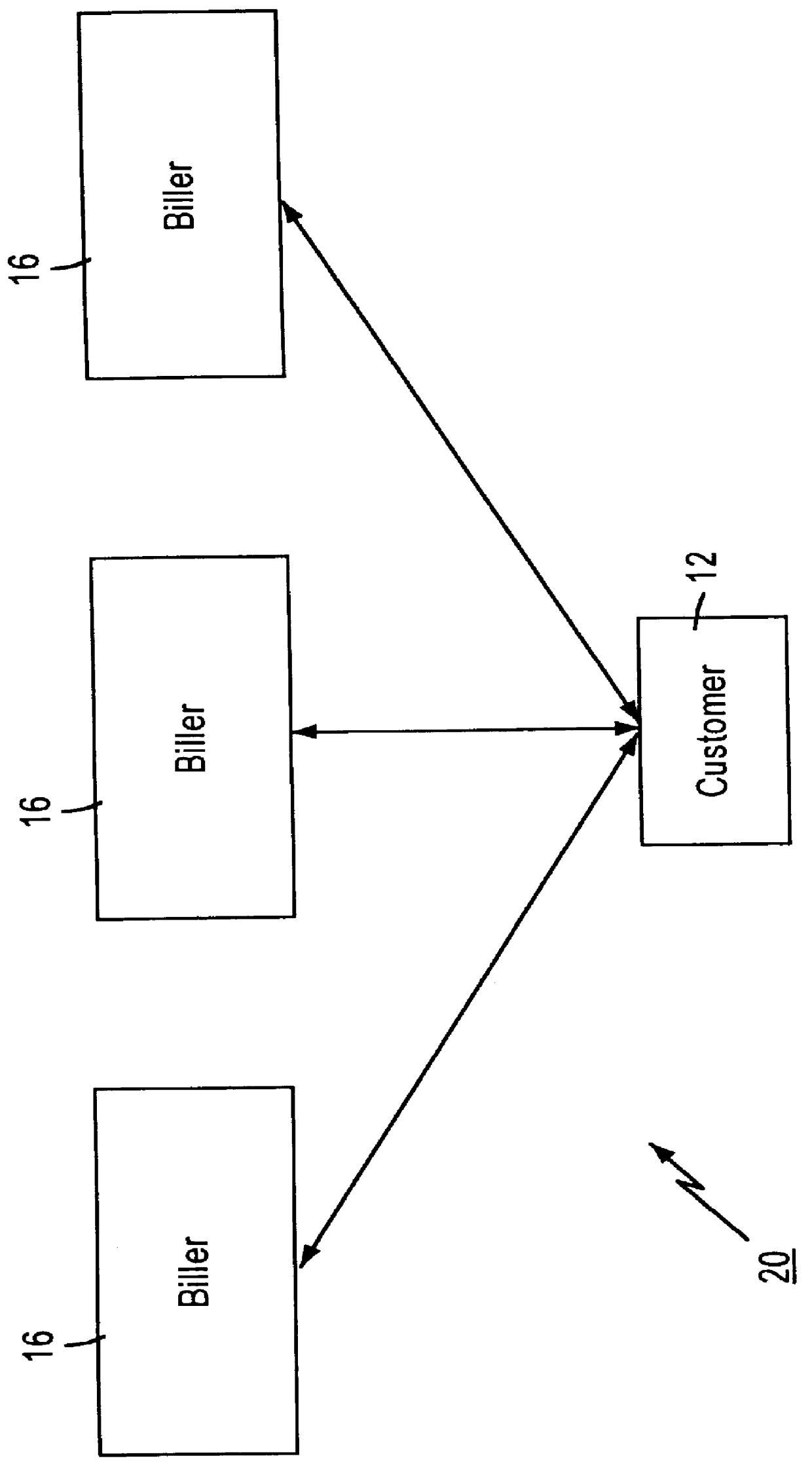
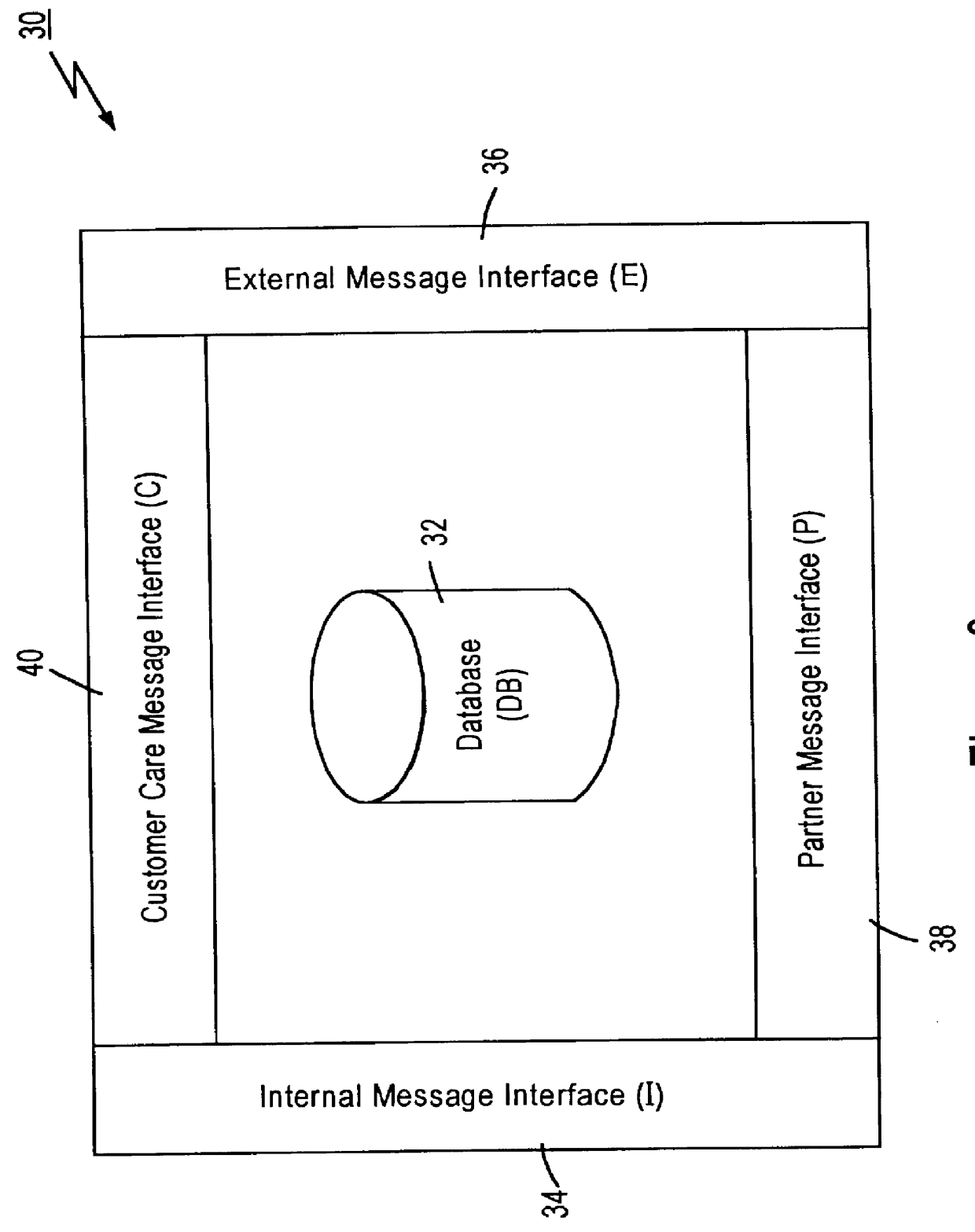
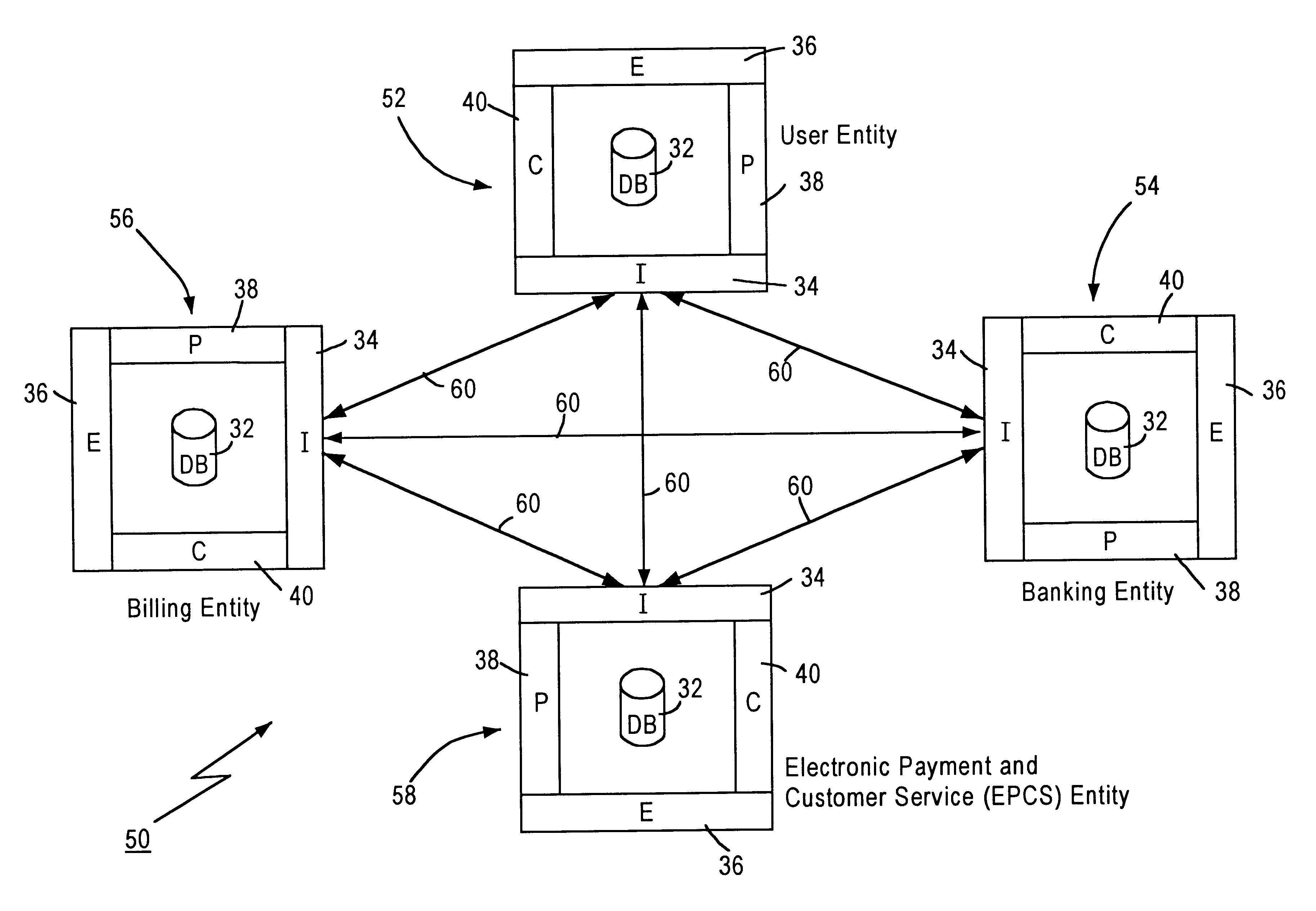
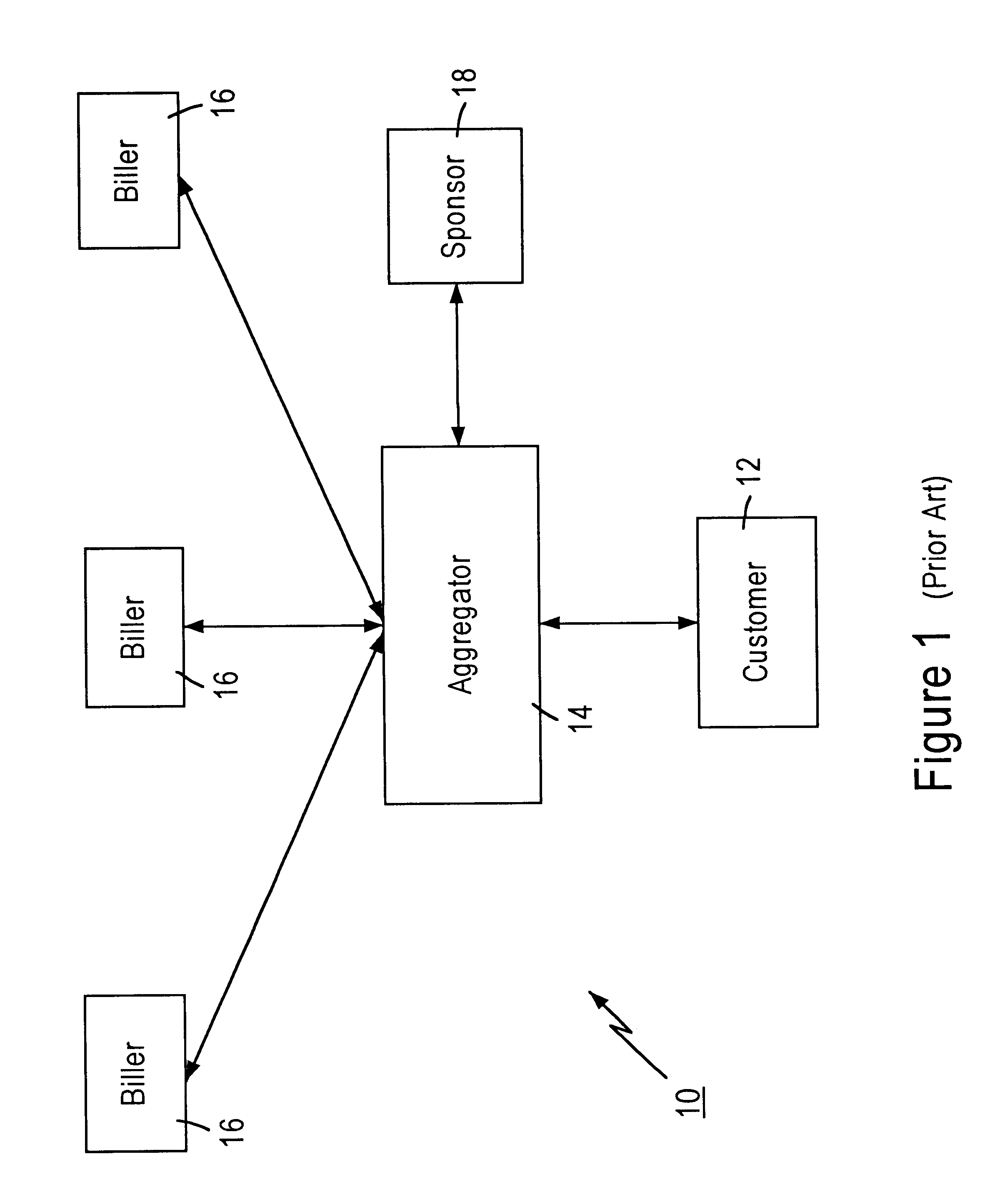
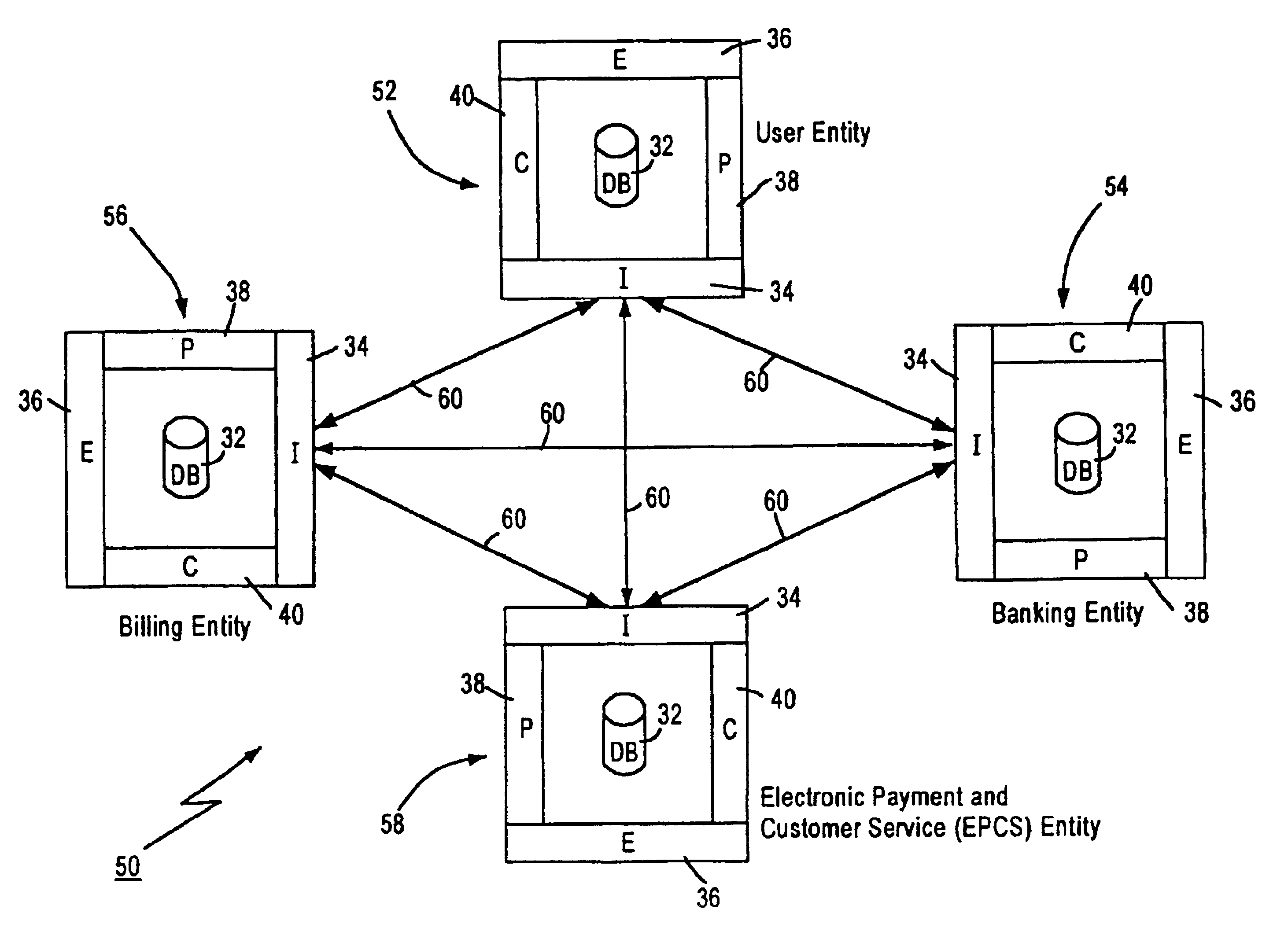
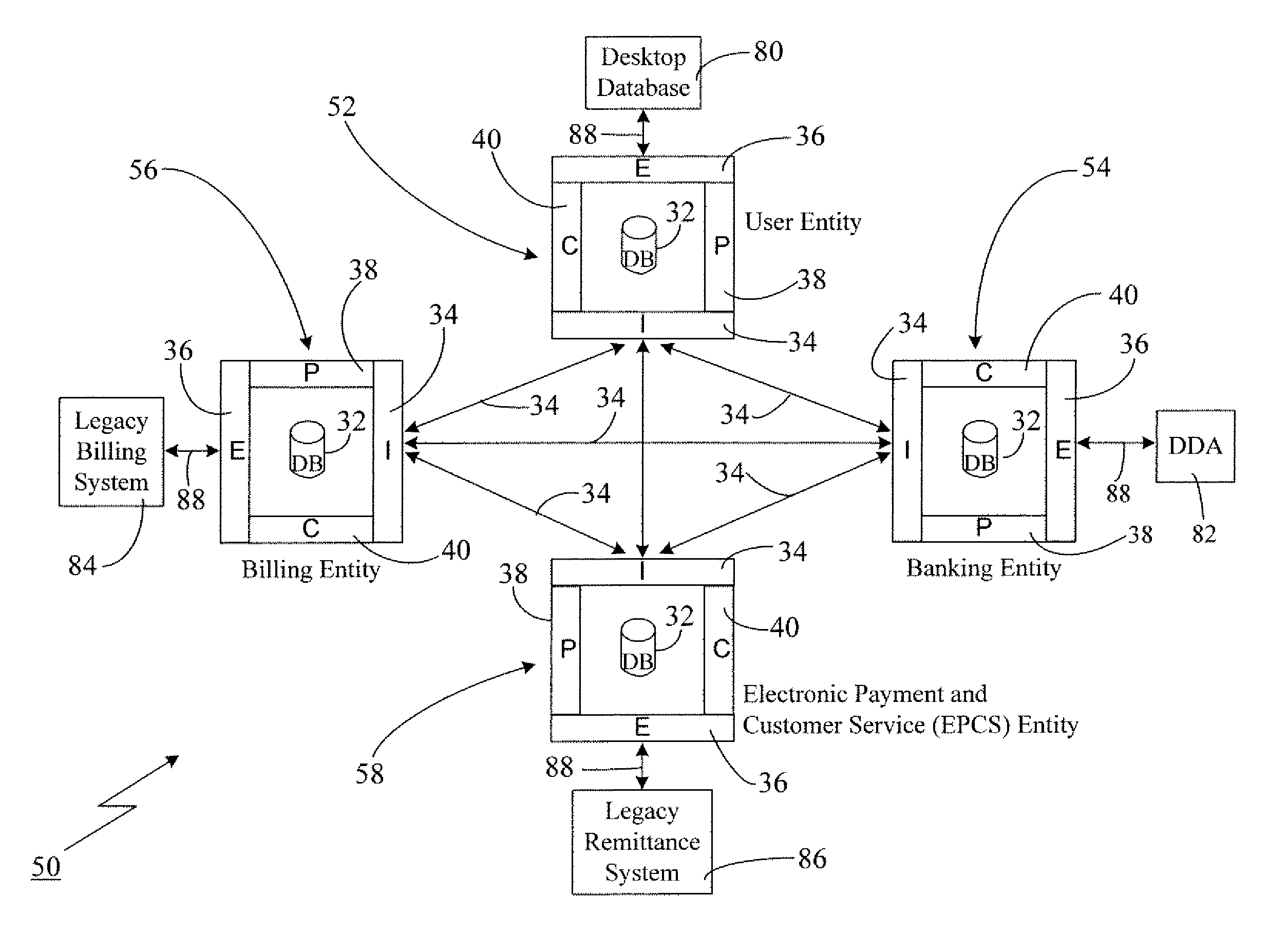
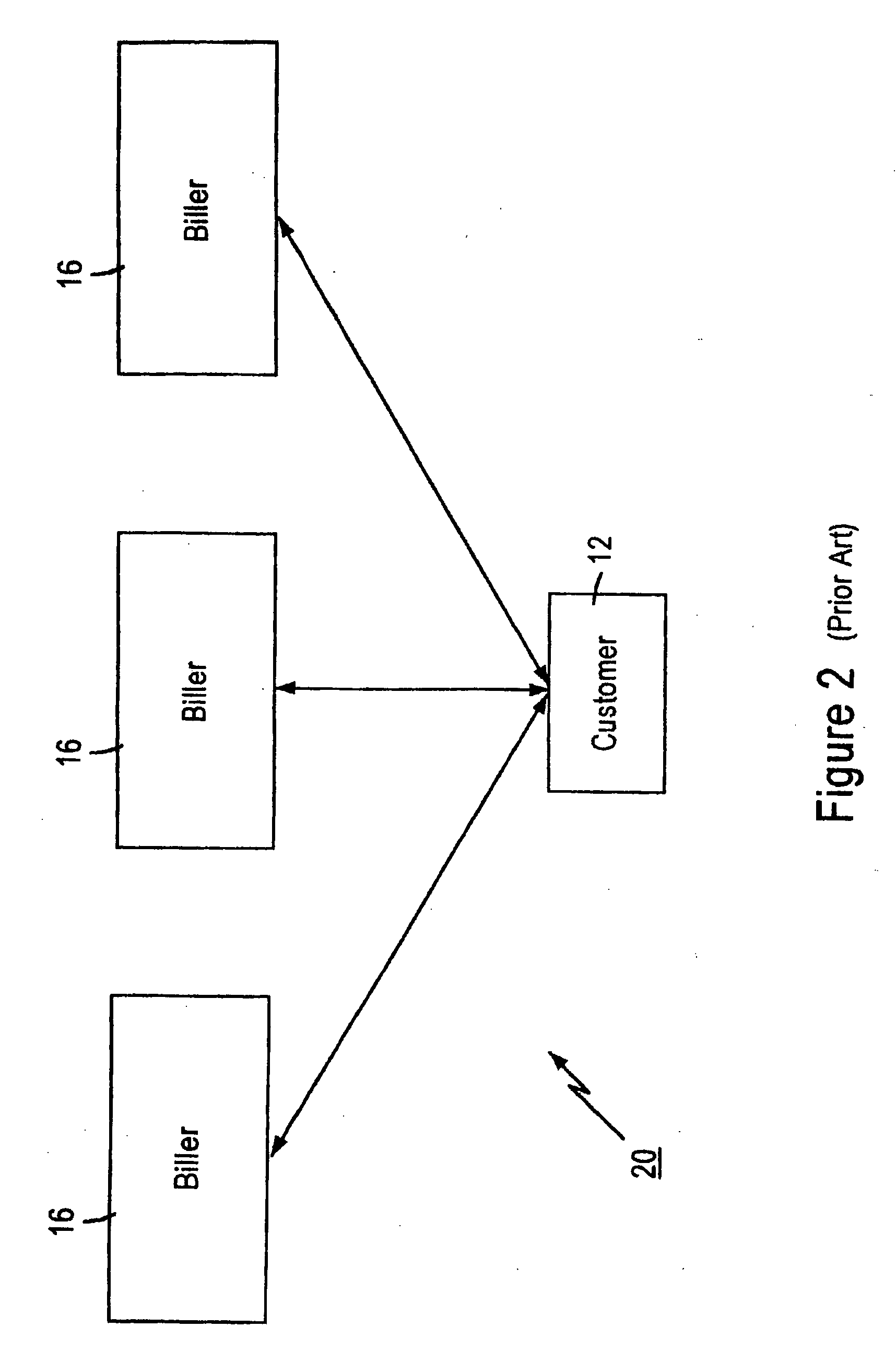
Technique for centrally tracking transactions in an electronic billing system
InactiveUS6334116B1Direct interactionRetain controlComplete banking machinesFinanceEngineeringFinancial transaction
A method is provided for centrally tracking transactions in an electronic billing system. The system includes multiple different billing entities, multiple different financial institute entities and multiple different user entities. Each of the multiple different billing entities is associated with a respective portion of the multiple different user entities and each of the multiple different financial institute entities is associated with a respective portion of the multiple different user entities. A message is received from any of the multiple different financial institute entities indicating a request from any of the multiple different user entities associated with the applicable financial institute entity to view billing information. The receipt of the request to view the billing information is logged in a database as first event information. A message indicative of the billing information of at least one of the multiple different billing entities associated with the applicable user entity which is available for viewing is transmitted to the applicable user entity. A message indicating a request from the applicable user entity to view the available billing information of that billing entity is received from any of the at least one of the billing entities. The receipt of the message indicating the applicable user entity request to view the billing information of the applicable billing entity is logged in the database as a second event information.
Owner:ORG WORLD INTPROP
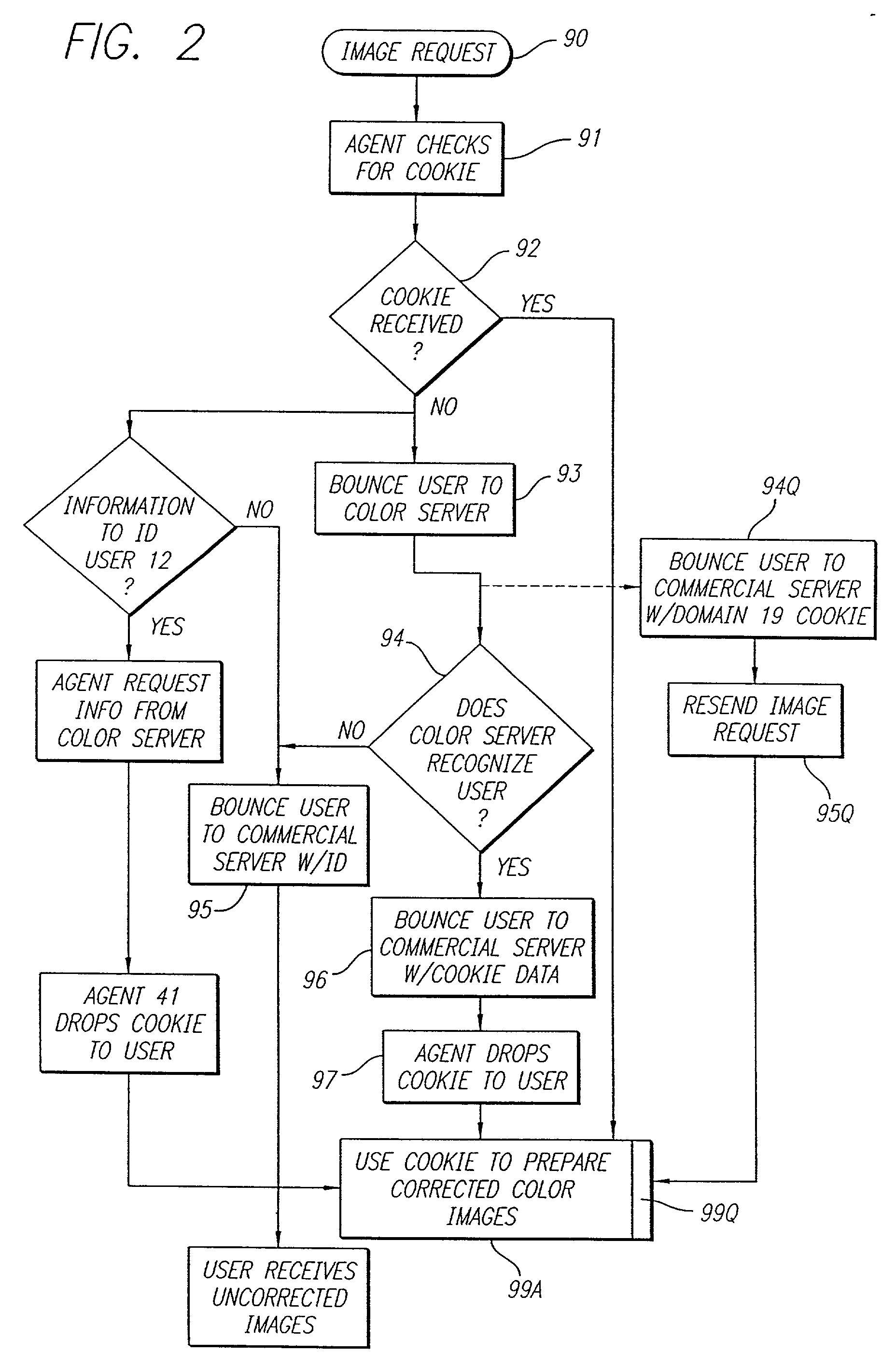
Image sharing for instant messaging
InactiveUS20020126135A1Retain controlImage enhancementCathode-ray tube indicatorsImage sharingFile sharing
Owner:RPX CORP +1
Desktop sharing method and system
ActiveUS20090292999A1Retain controlData switching networksInput/output processes for data processingClient-sideDistributed computing
In a distributed computer network where displayed information is shared between at least two computers, a method of enabling remote control of a host computer having a display region that is to be shared with at least one client computer. The method includes tracking time lapsed since a local user input event has occurred while the host computer is under local control and in the event that the time lapsed exceeds a threshold, enabling remote control of the host computer by a client computer.
Owner:SMART TECH INC (CA)
Electronic bill presentment technique with enhanced biller control
InactiveUS6856974B1Direct interactionRetain controlFinanceBilling/invoicingMobile stationReal-time computing
An electronic bill presentment system includes network, a central network station, and a plurality of user and biller network stations. Each of the user stations is associated with a respective one of a plurality of users and is operable to transmit first requests for bills via the network. The central network station receives the transmitted first requests and transmits, responsive thereto, bill availability information via the network. The user stations receive the transmitted bill availability information and are operable to transmit second requests for bills via the network. Each of the biller stations is associated with a respective one of the plurality of billers. The biller stations receive the transmitted second requests and transmit, responsive thereto, the requested bills via the network.
Owner:CHECKFREE CORP
System and Methods for Inserting a Spinal Disc Device Into an Intervertebral Space
InactiveUS20080109005A1Reduce unnecessaryReduces potentially awkward movementSpinal implantsOsteosynthesis devicesBiomedical engineeringIntervertebral space
A system for replacing a natural nuclear disc in an intervertebral space has a spinal device configured for placement in the intervertebral space. An insertion tool is configured for holding the spinal device while the spinal device is inserted into the intervertebral space. A gripping member of the insertion tool has an end for adjustably holding the spinal device within the intervertebral space. A steering actuator of the insertion tool is operably connected to the spinal device and configured for pivoting the adjustably held spinal device within the intervertebral space while the steering actuator is controlled remotely from the intervertebral space.
Owner:PIONEER SURGICAL TECH INC
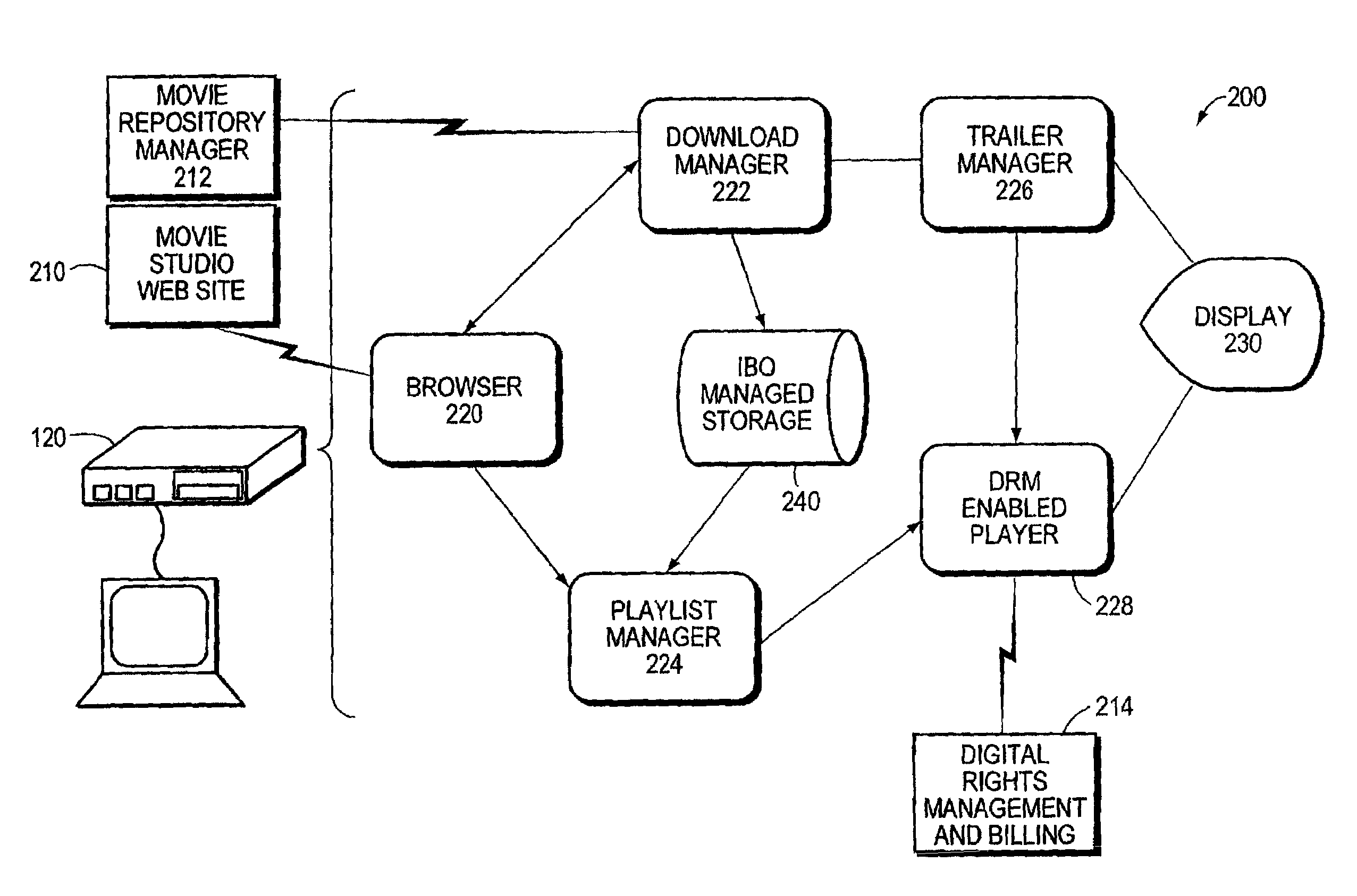
Method and mechanism for vending digital content
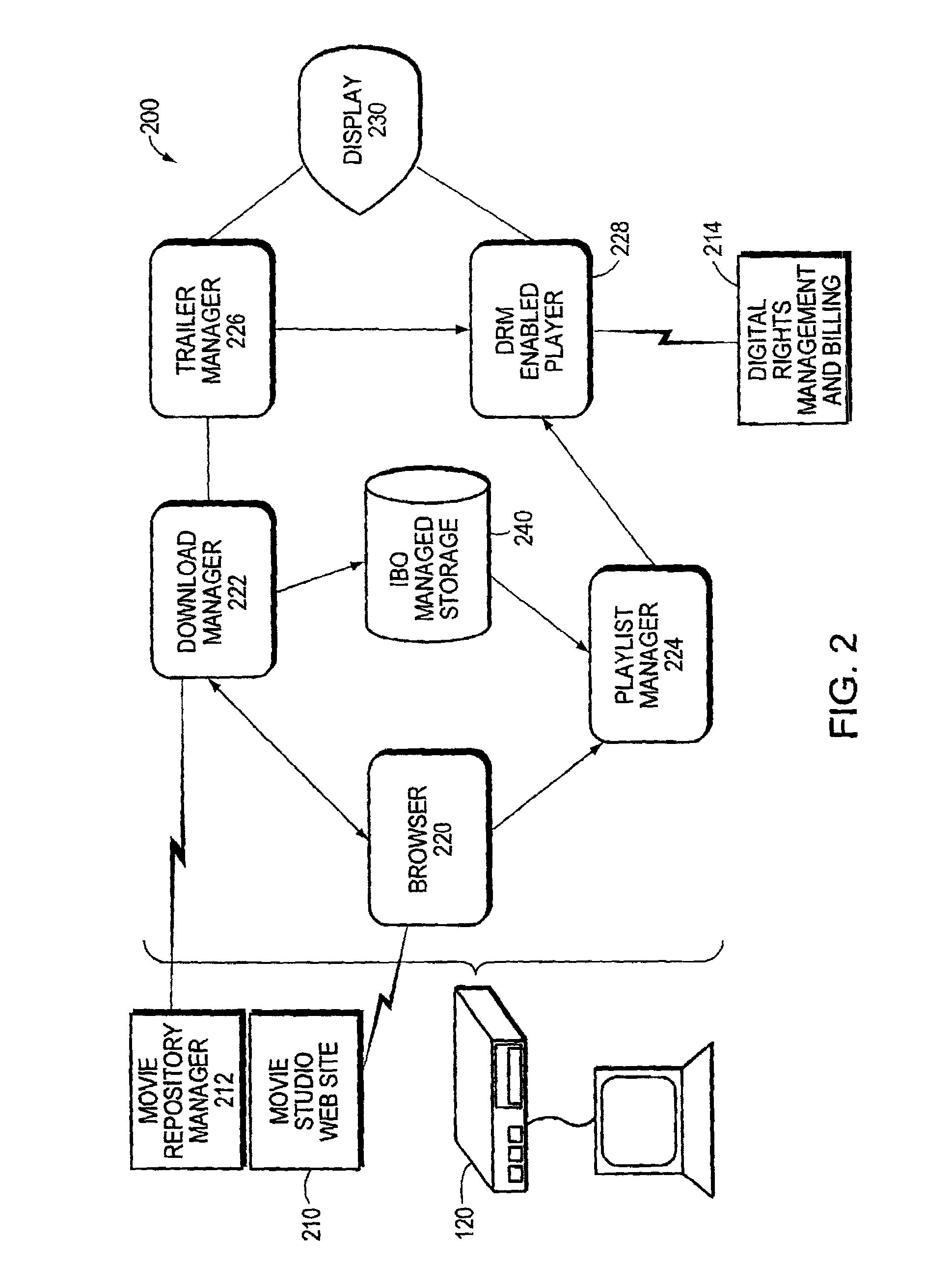
InactiveUS6993508B1Easy accessRetain controlAnalogue secracy/subscription systemsPayment architectureDigital rights management systemIntellectual property
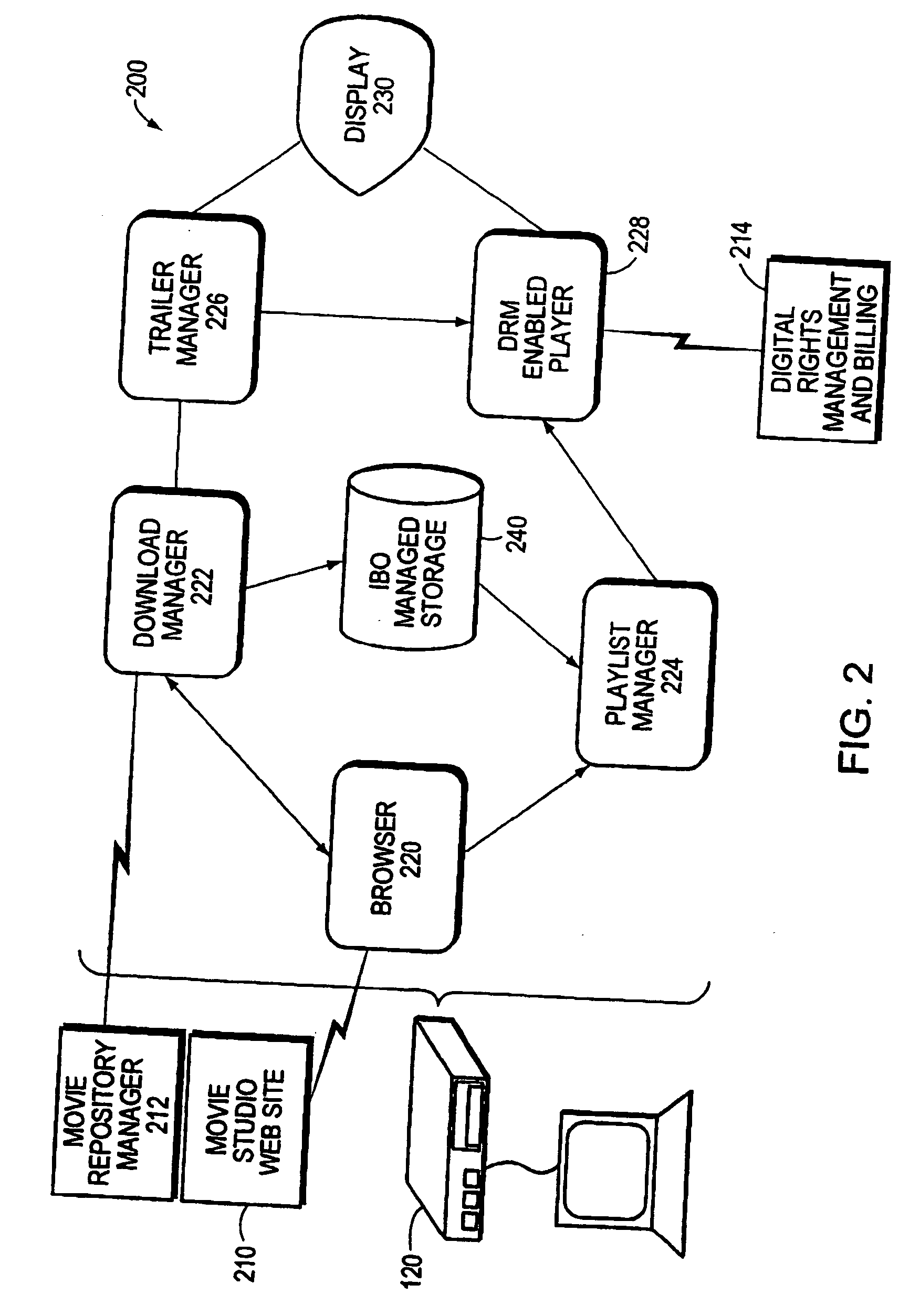
An Internet Box Office (IBO) system and technique vends digital content via a computer network, such as the Internet. The IBO system comprises a viewing system that cooperates with a Digital Rights Management system and various deployment enhancements within the Internet to provide an infrastructure that facilitates access to digital content in a manner that comports with copyright law and the control of intellectual property by the copyright owner. The IBO system enables a content copyright owner to retain control of its intellectual property while allowing a consumer to have transparent access to the copyright-protected content via the network. To that end, the IBO system operates to download and stage the copyrighted digital content on the viewing system of a consumer.
Owner:RPX CORP
System and methods for inserting a spinal disc device into an intervertebral space
InactiveUS20080077153A1Sure easyMinimizing damageSpinal implantsOsteosynthesis devicesLocking mechanismIntervertebral space
A system for replacing a natural nuclear disc in an intervertebral space has a spinal device configured for placement in the intervertebral space. An insertion tool is configured for holding the spinal device while the spinal device is inserted into the intervertebral space. A gripping member of the insertion tool has an end for adjustably holding the spinal device within the intervertebral space. A steering actuator of the insertion tool is operably connected to the spinal device and configured for pivoting the adjustably held spinal device within the intervertebral space while the steering actuator is controlled remotely from the intervertebral space. The steering actuator is rotatable about a longitudinal axis of the tool. A locking mechanism is provided to keep the spinal device from pivoting in an insertion position and to keep the disc device from being released unintentionally.
Owner:PIONEER SURGICAL TECH INC
Devices, systems, and methods for prosthesis delivery and implantation
Devices, systems, and methods use a catheter device sized and configured for introduction to a targeted site in a hollow body organ or blood vessel. The catheter device includes a first release mechanisms coupled to the prosthesis to secure at least one region of the prosthesis to the catheter shaft, and a second release mechanism coupled to the prosthesis in cooperation with the first release mechanism to prevent full release of the at least one region of the at least one region of the prosthesis from the catheter shaft after actuation of the first release mechanism. A fastening device sized and configured for introduction to the targeted site in the hollow body organ or blood vessel occupied by the catheter device, includes an actuator to deploy a fastener in the at least one region of the prosthesis after actuation of the first release mechanism and before actuation of the second release mechanism.
Owner:MEDTRONIC VASCULAR INC
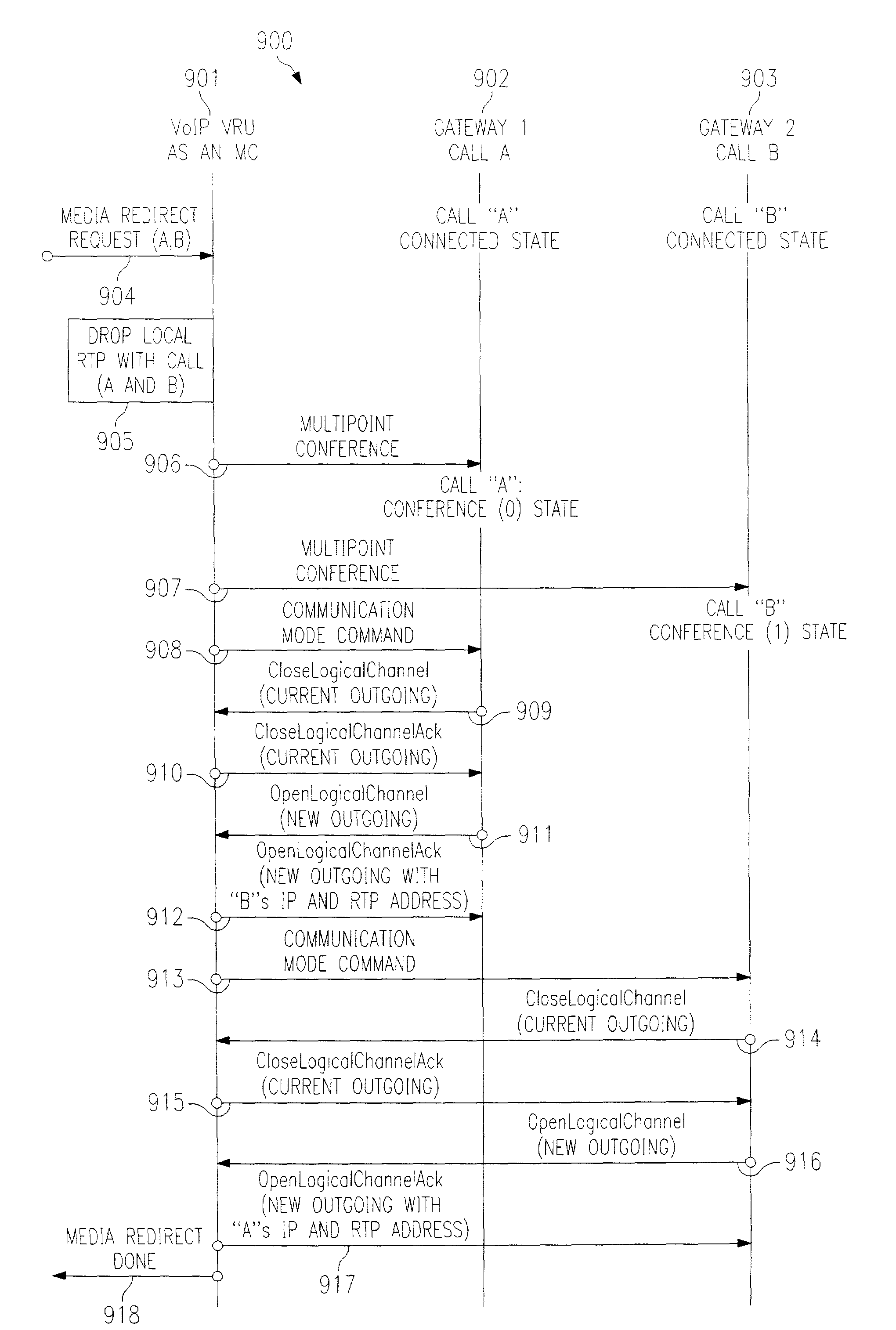
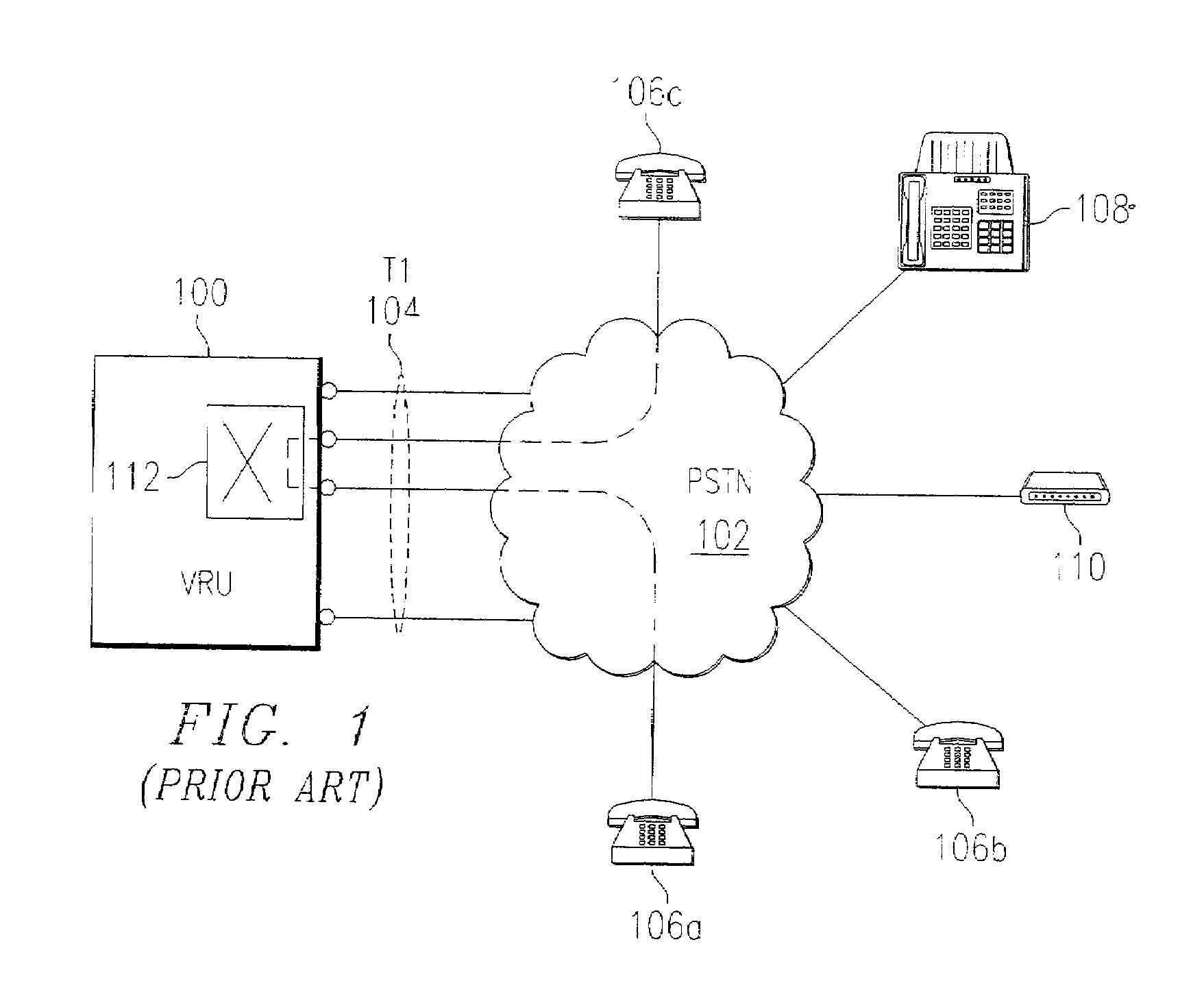
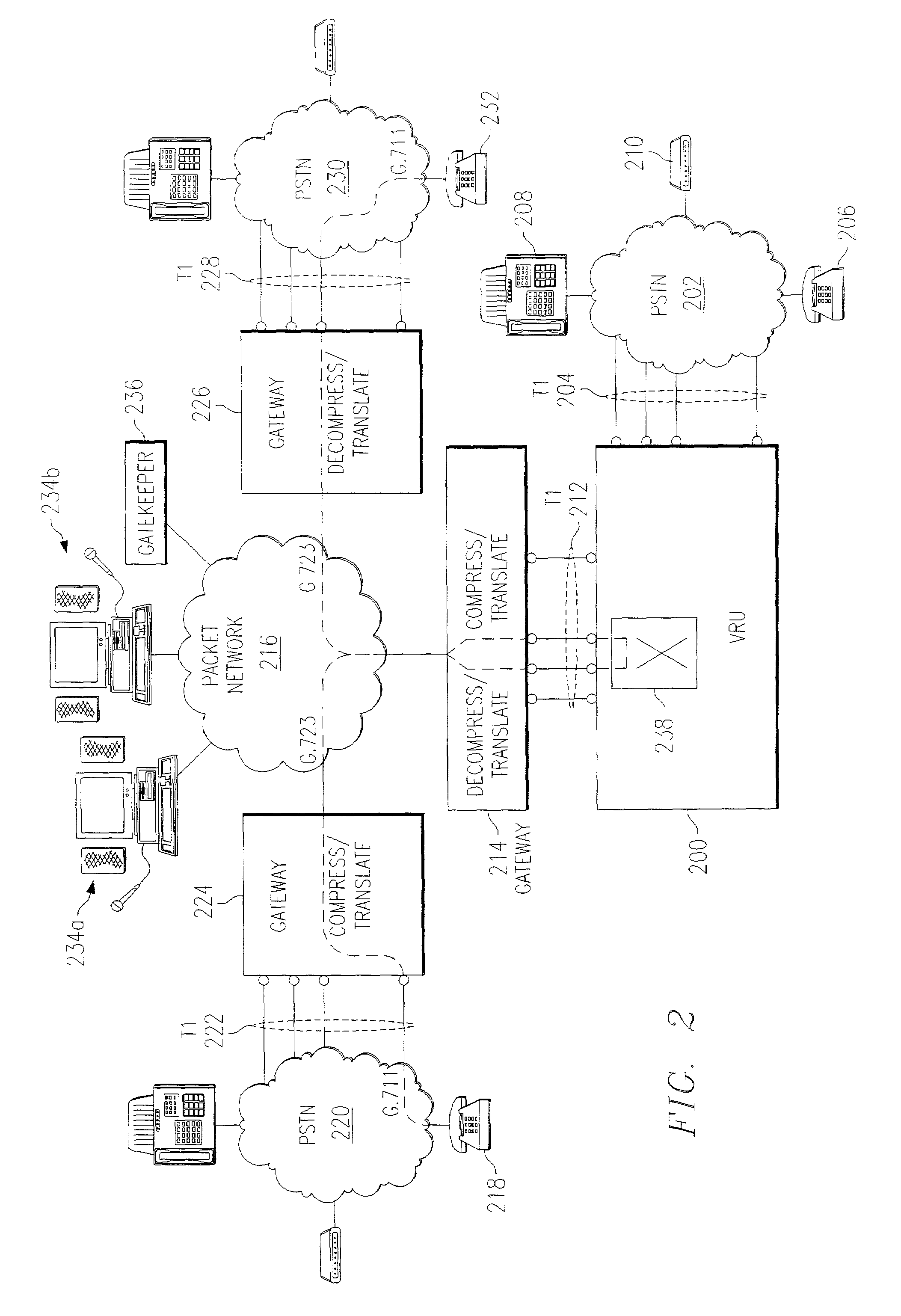
Cooperative media applications using packet network media redirection
InactiveUS7035252B2Good serviceAvoid conversionMultiplex system selection arrangementsSpecial service for subscribersNetworking protocolPacket generator
Owner:INTERVOICE PARTNERSHIP
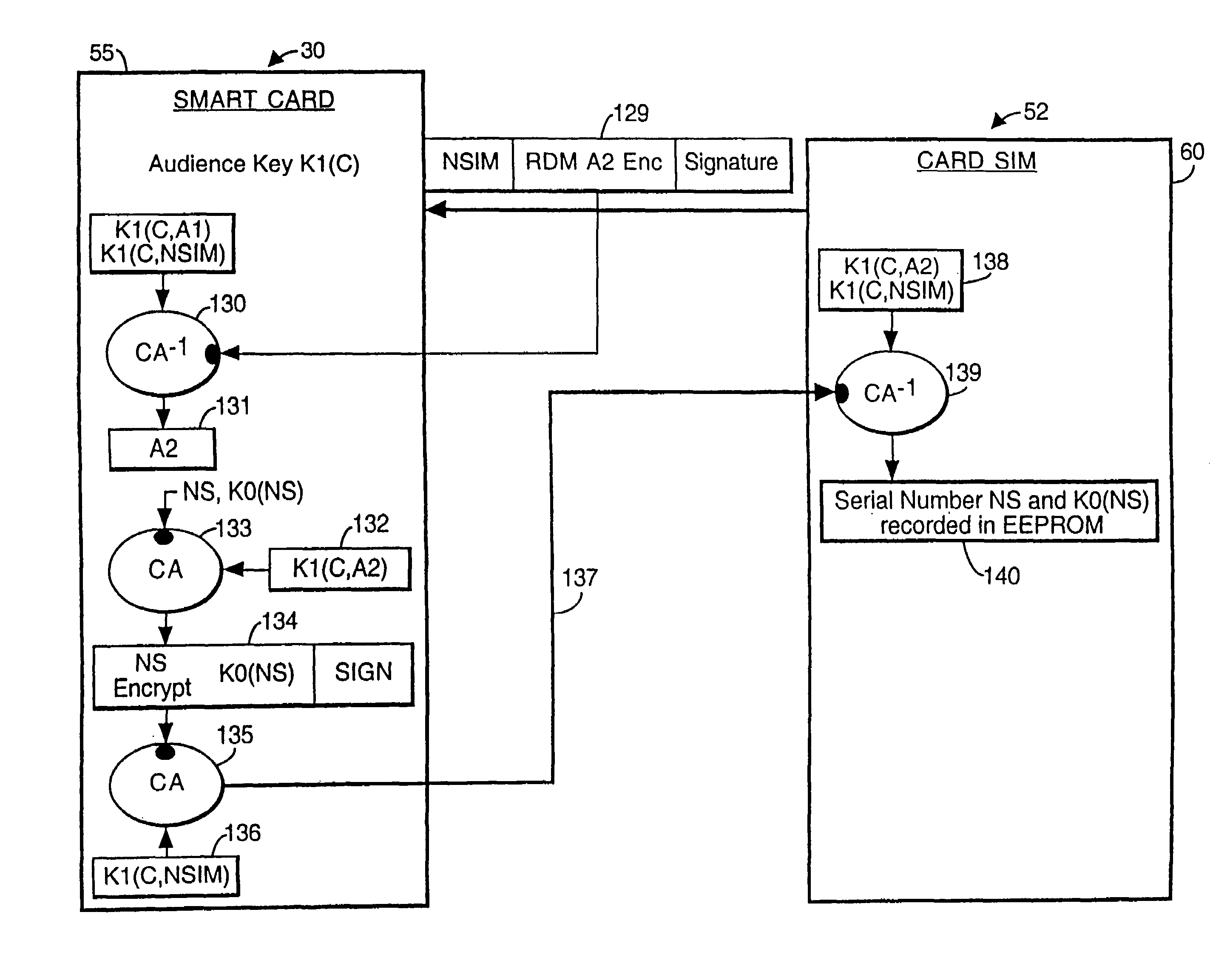
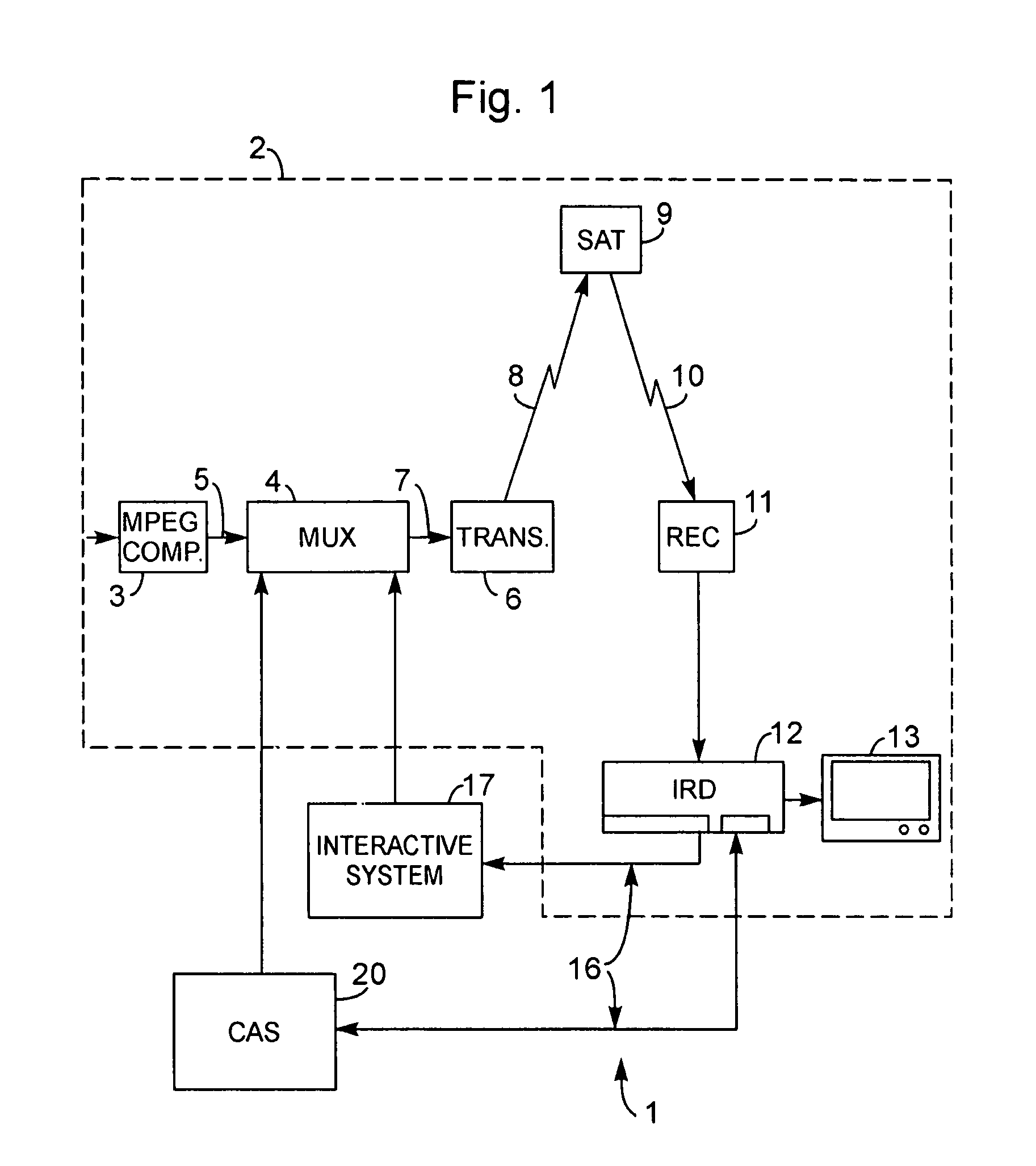
Method and apparatus for recording of encrypted digital data
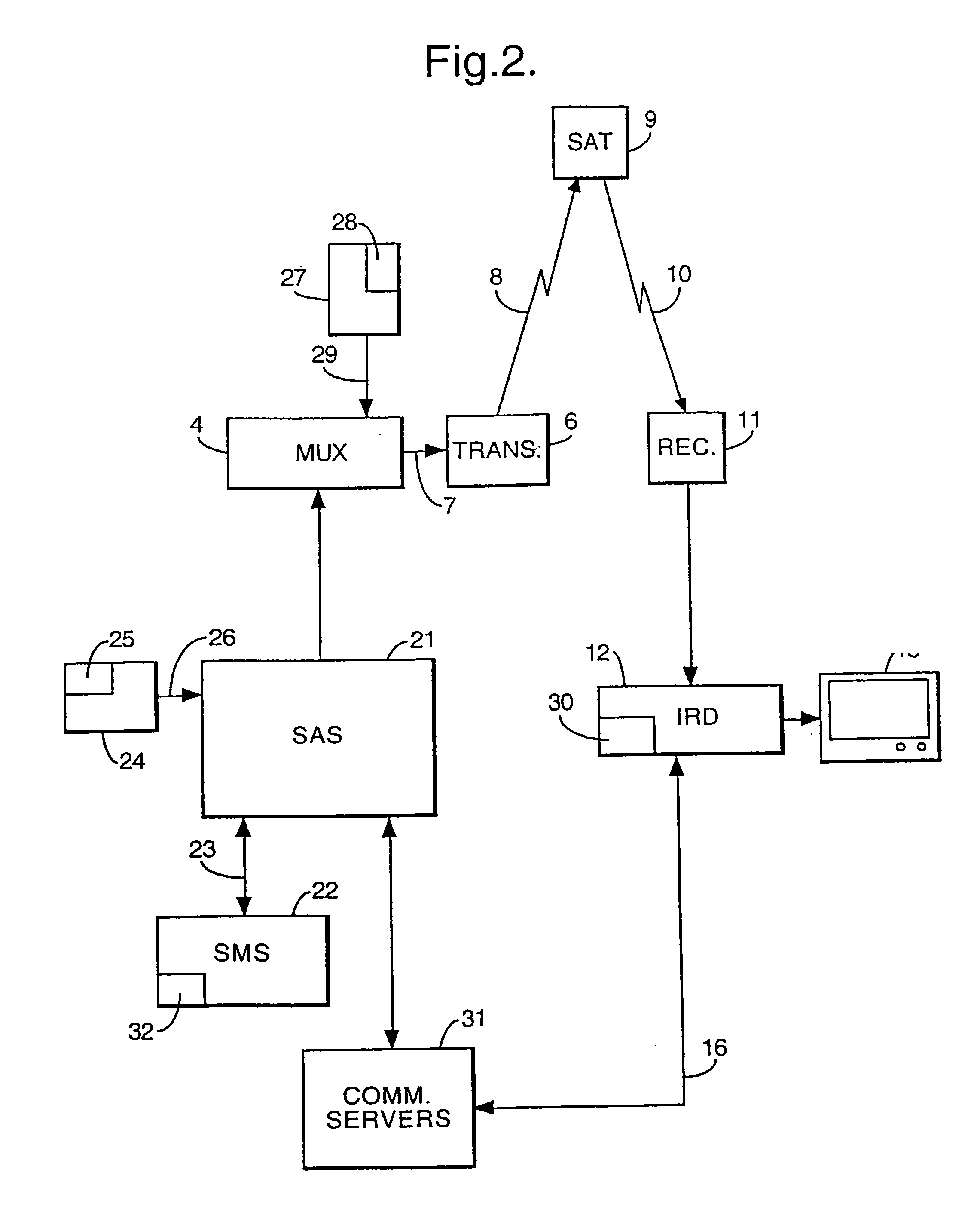
InactiveUS7239704B1Retain controlTelevision system detailsAnalogue secracy/subscription systemsDigital dataEncryption
A method relating to recording transmitted digital data in which transmitted digital information is encrypted by a recording encryption key. The recording encryption key is stored by a recording means on a recording support medium. Further, the recording encryption key is characterized in that an equivalent of the recording encryption key is encrypted by a recording transport key, which is also stored on the support medium with the encrypted information.
Owner:THOMSON LICENSING SA
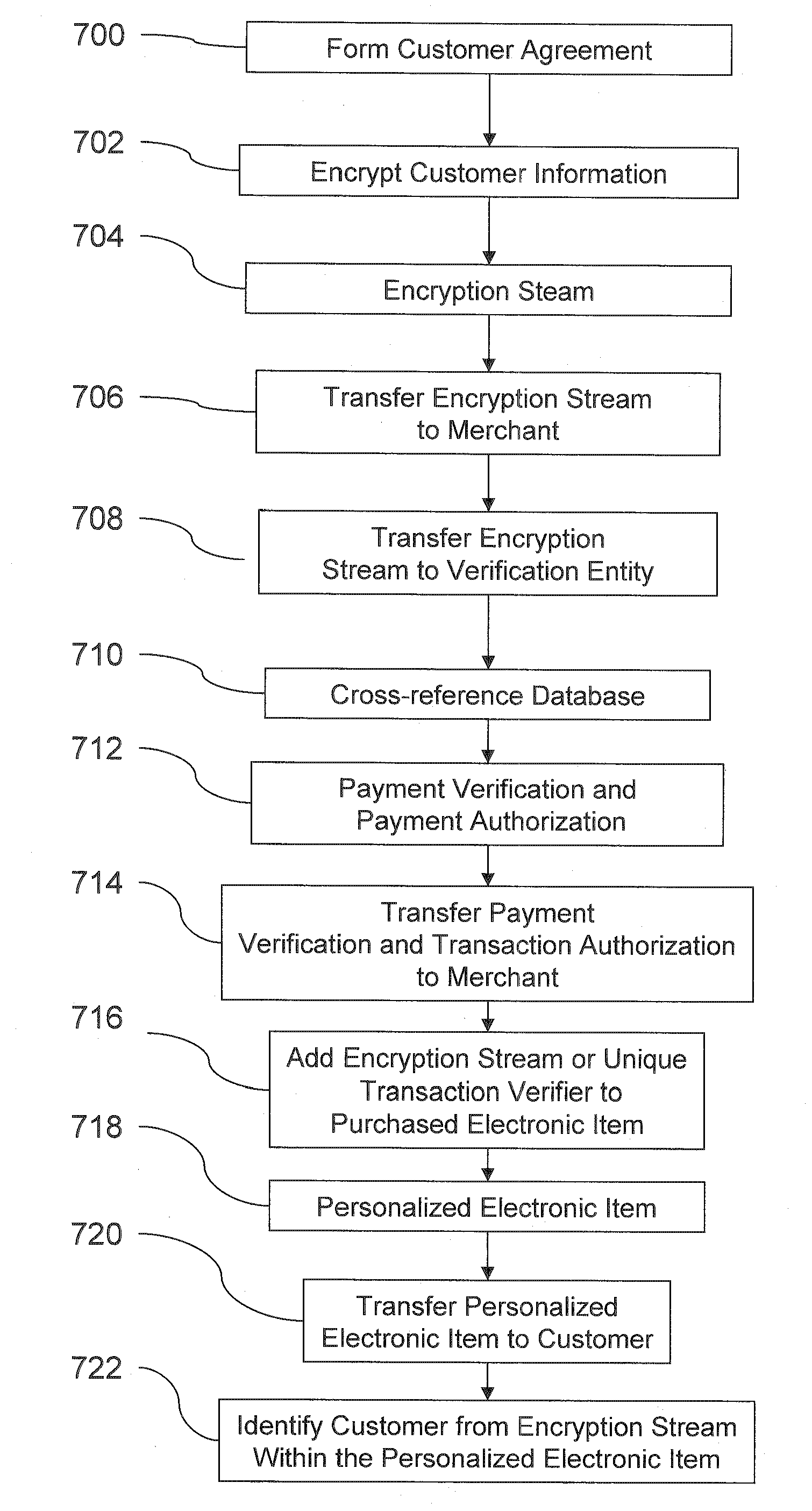
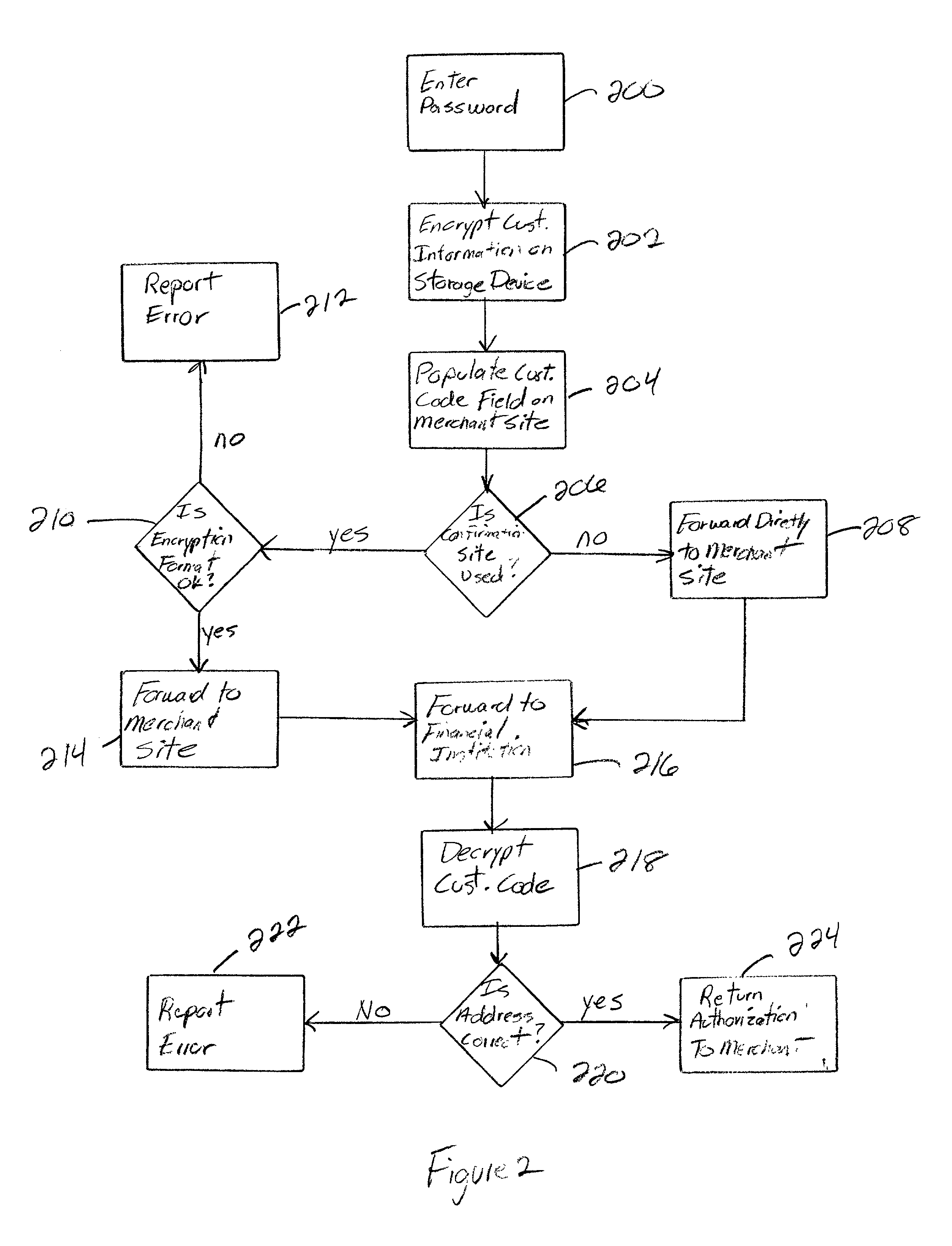
Transactional security over a network
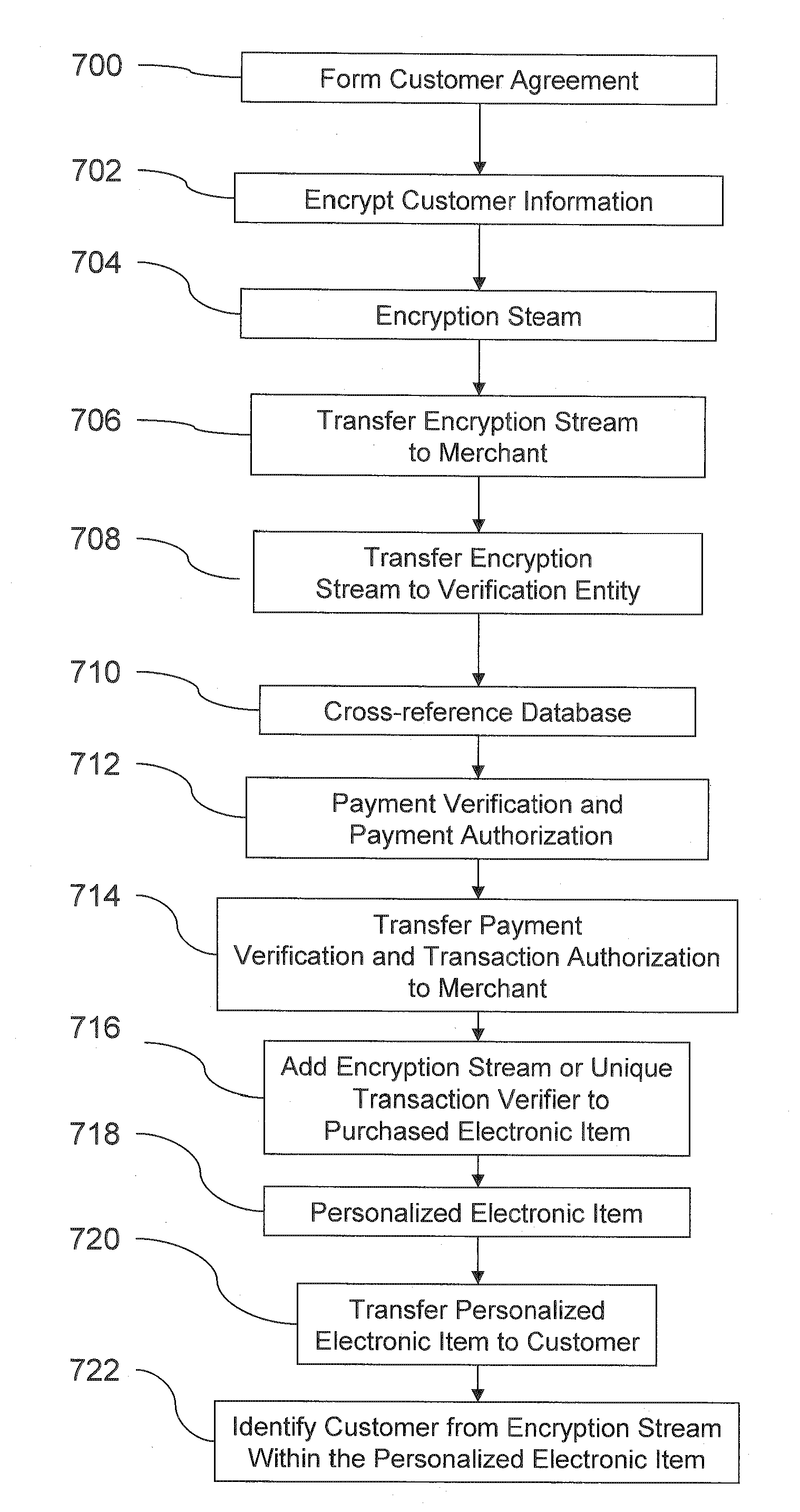
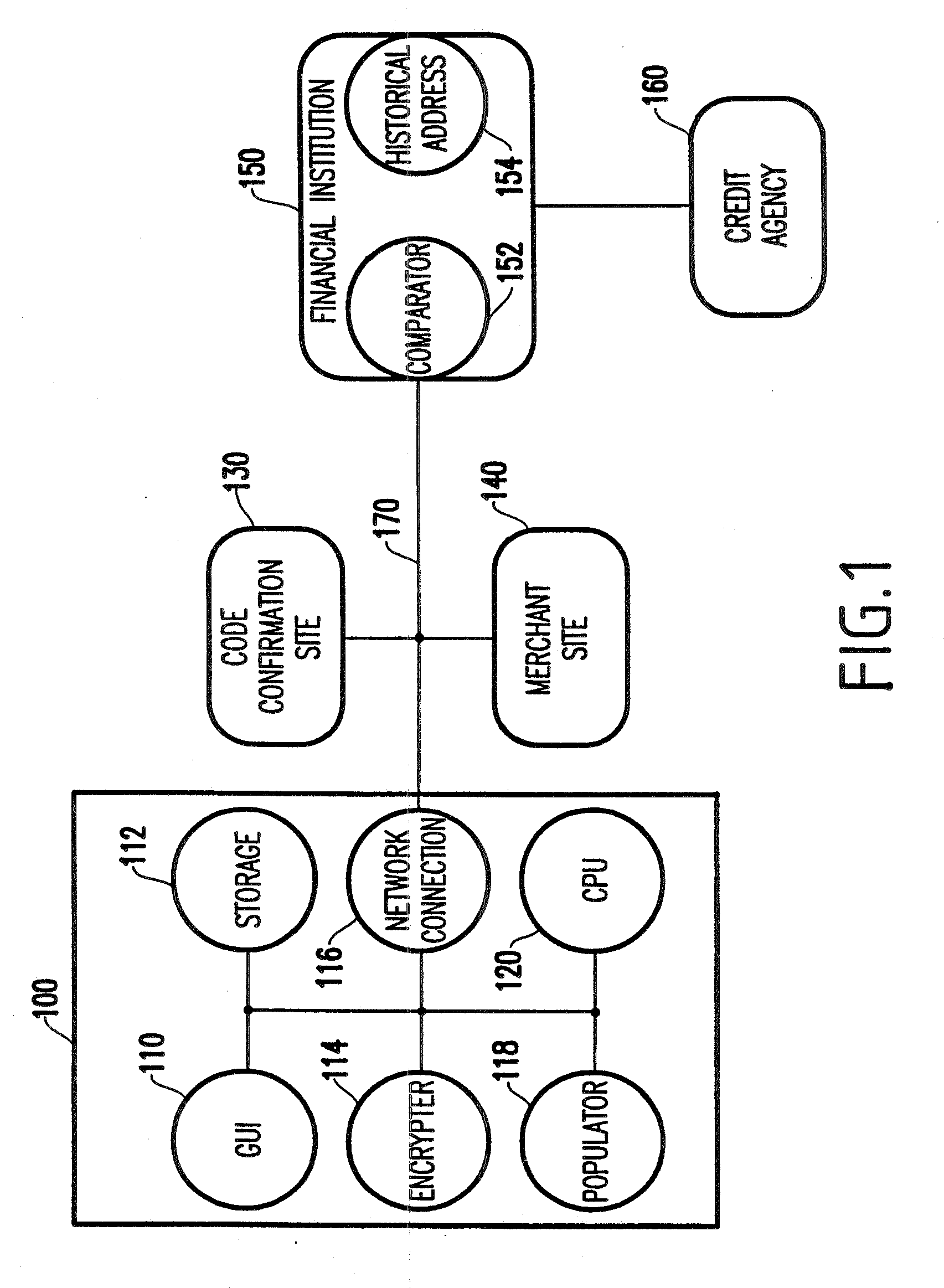
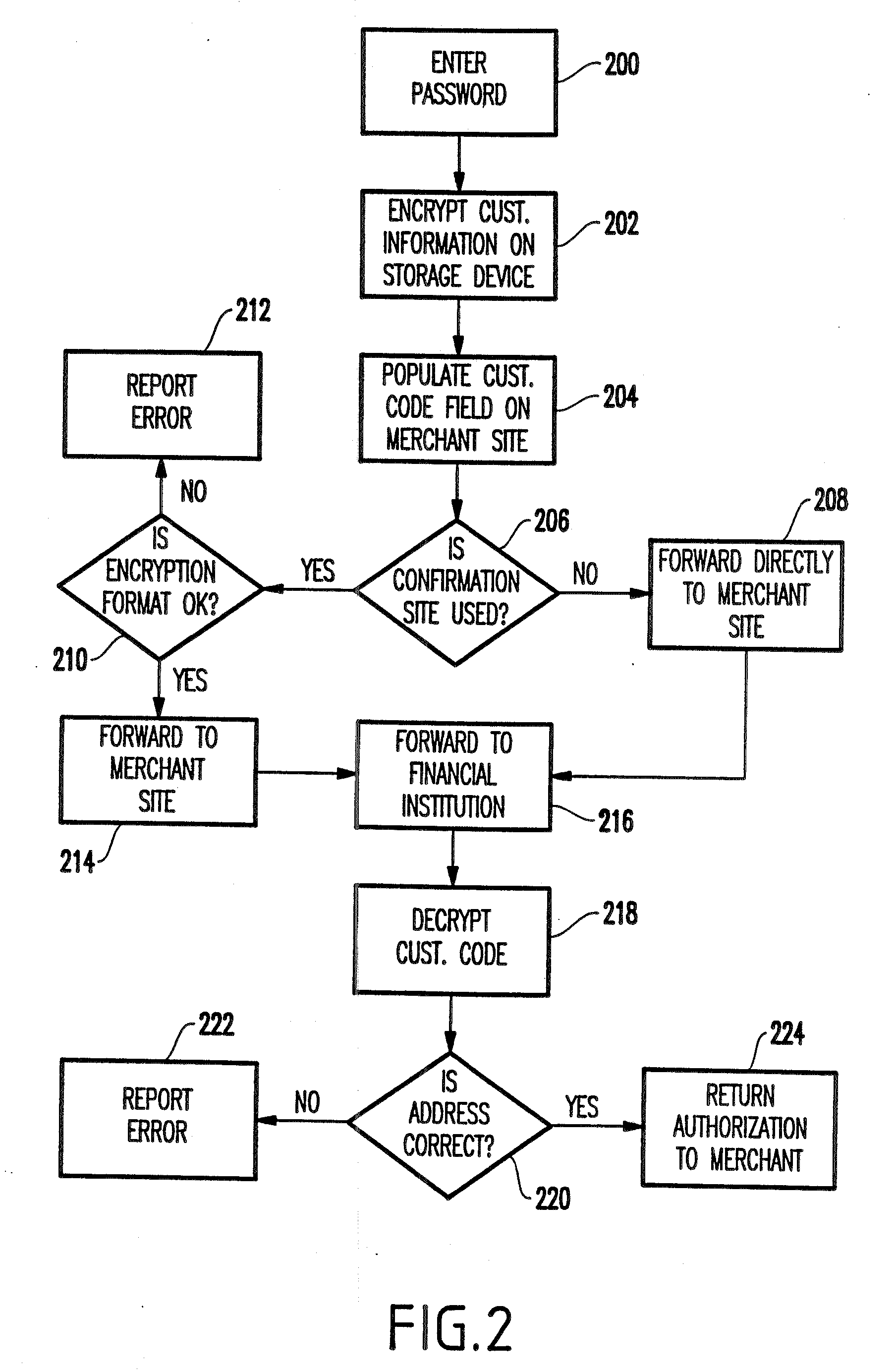
A system and method facilitating purchase transactions over a computer network, including the purchase of electronically storable items. The embodiments herein encrypt “customer identifier string” in an encryption stream and cause the encryption stream to be transferred from the customer to a merchant in the purchase transaction. A verification entity receives the encryption stream which is sent by the merchant for identity verification and payment authorization. Then, the verification entity verifies the identifiers contained in the encryption stream and transfers an identity verification and payment authorization from the verification entity to the merchant.
Owner:BENEDORTSE
Electronic billing with updateable electronic bill summary
InactiveUS7392223B1Easily implemented using computer softwareEasy programmingComplete banking machinesFinanceTelecommunicationsMobile station
An electronic bill payment network includes a plurality of user network stations associated with different users, a plurality of biller network stations associated with different billers, and a central network station. A first user station operates, in real time, to transmit information relevant to an amount of an available bill and an instruction to pay the available bill. A first biller station operates, in real time, to receive the transmitted information and to compute the amount of the available bill based upon the received information. The central network station operates to receive the computed amount of the available bill and the transmitted pay instruction, and to direct payment of the computed amount of the available bill based upon the transmitted instruction to pay that bill.
Owner:CHECKFREE CORP
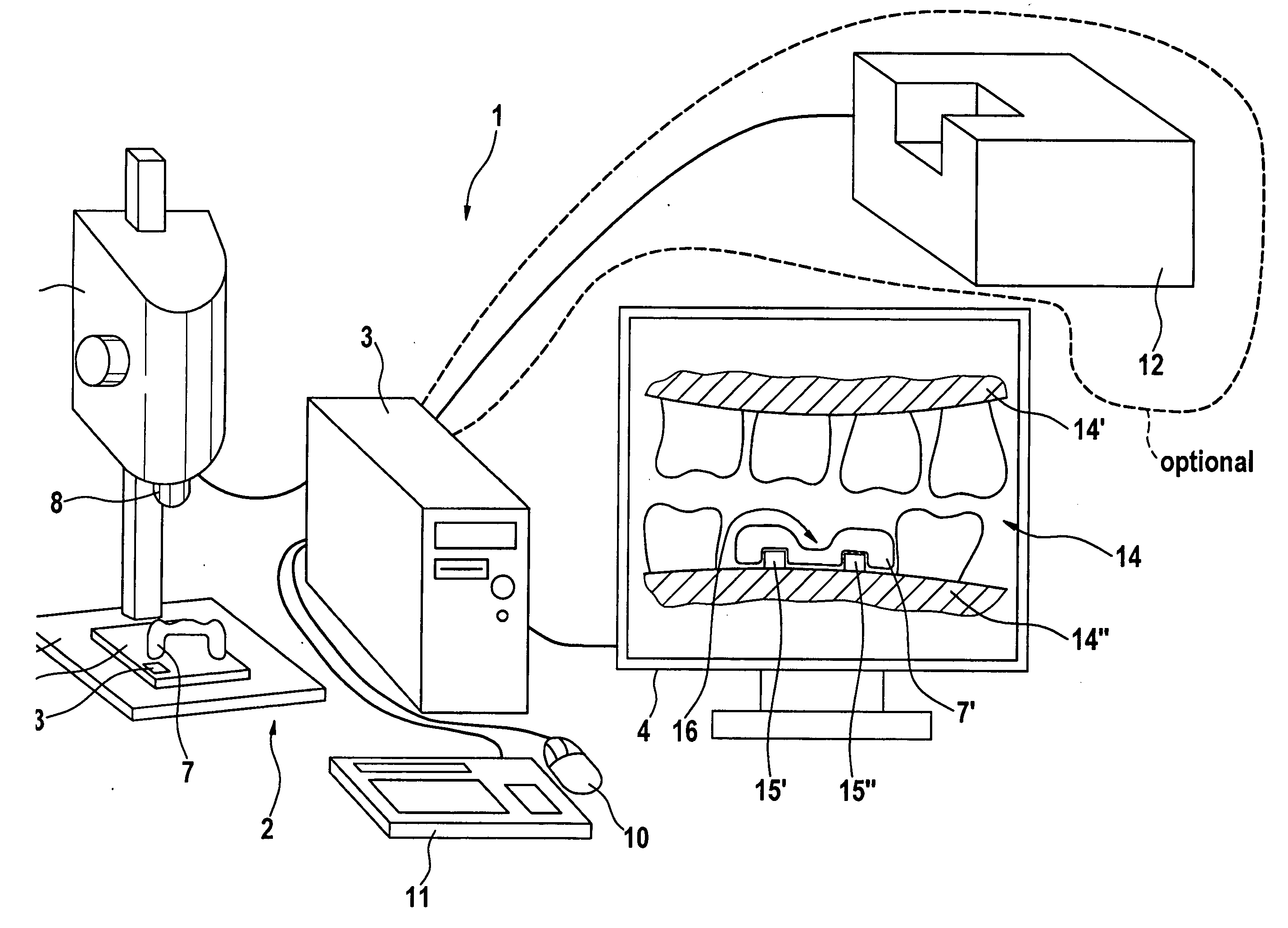
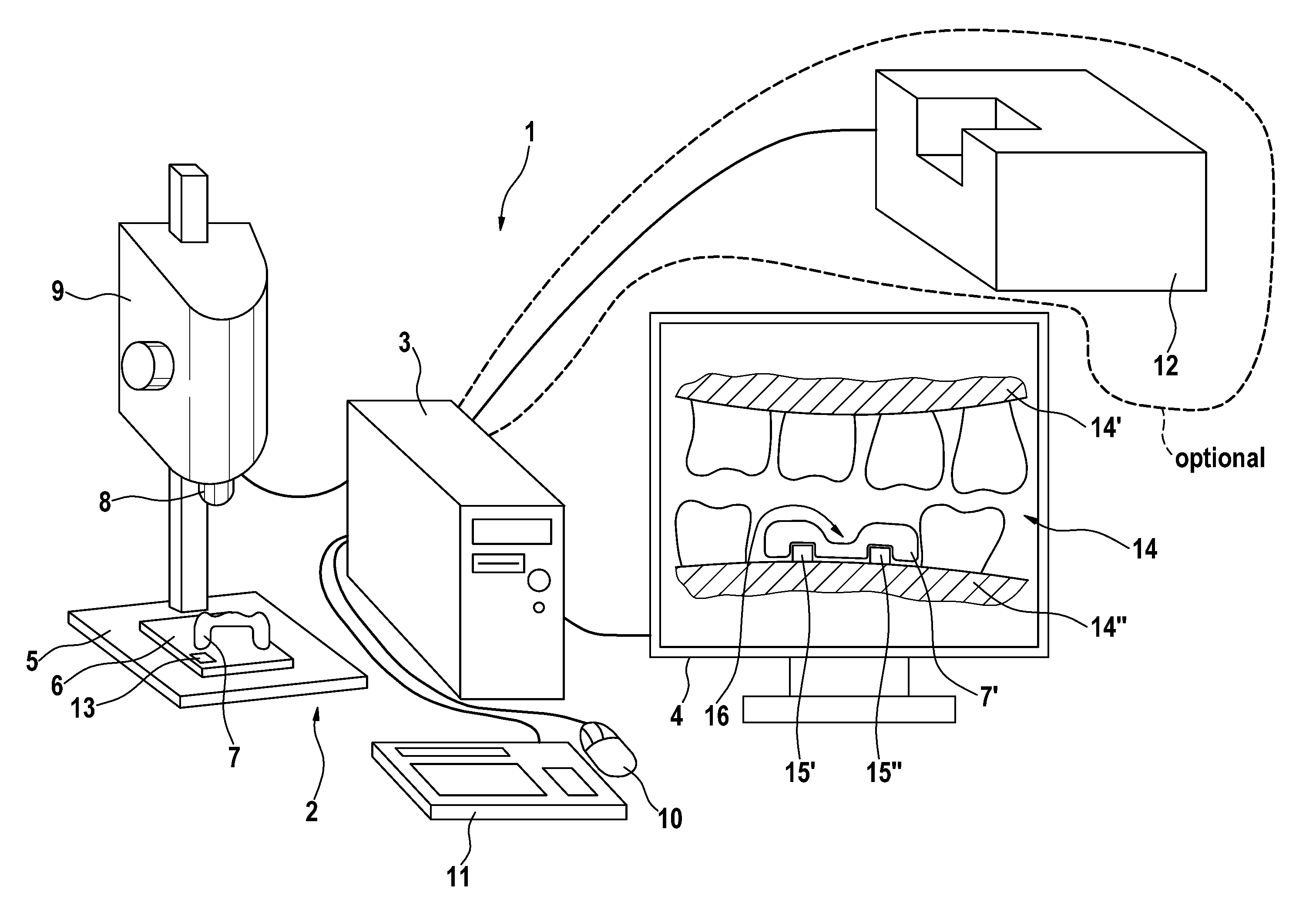
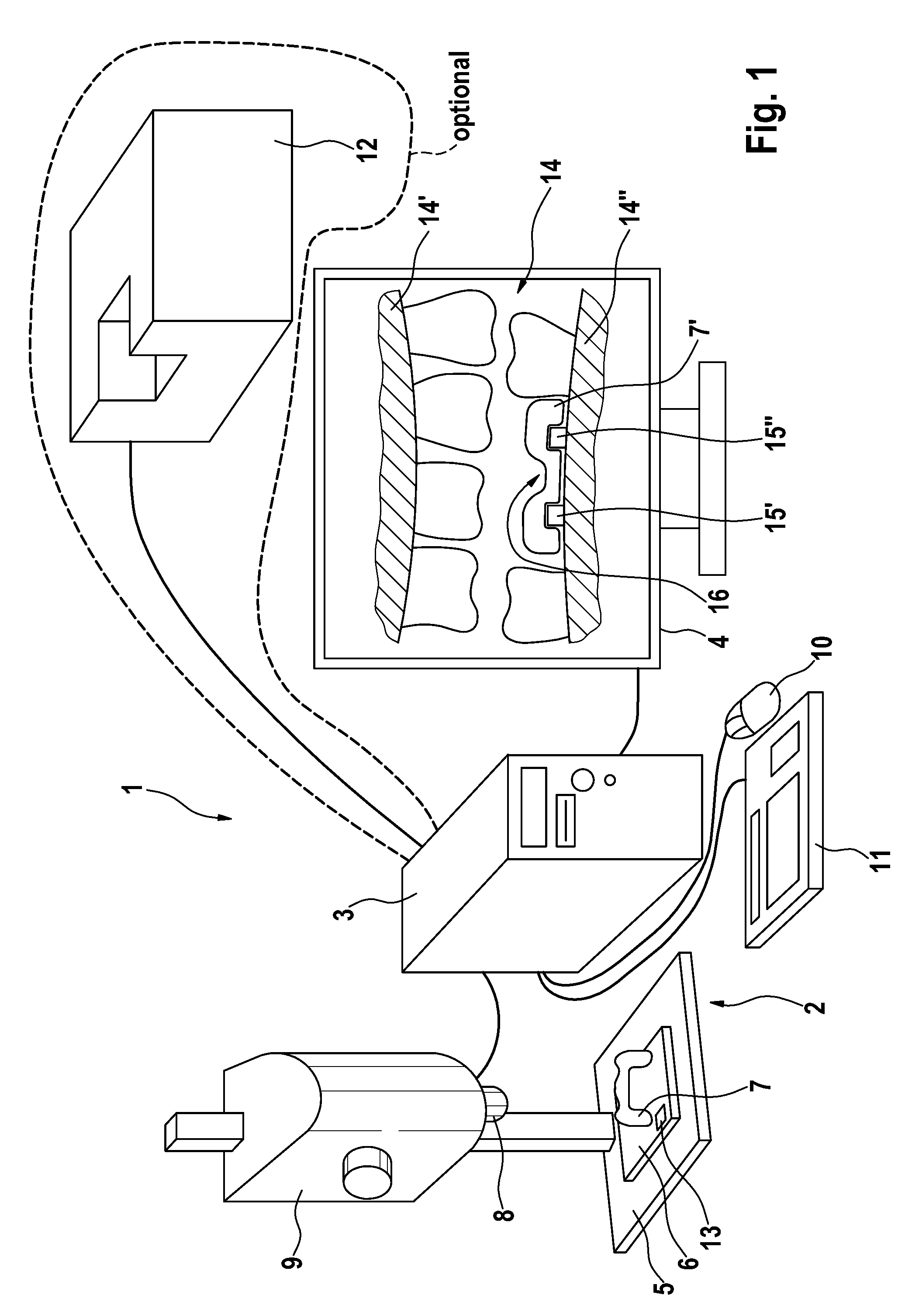
Method and Device for Producing Dental Prosthesis Elements
InactiveUS20090081616A1Easy to monitorAccurate fitDental implantsAdditive manufacturing apparatusDenturesProsthesis
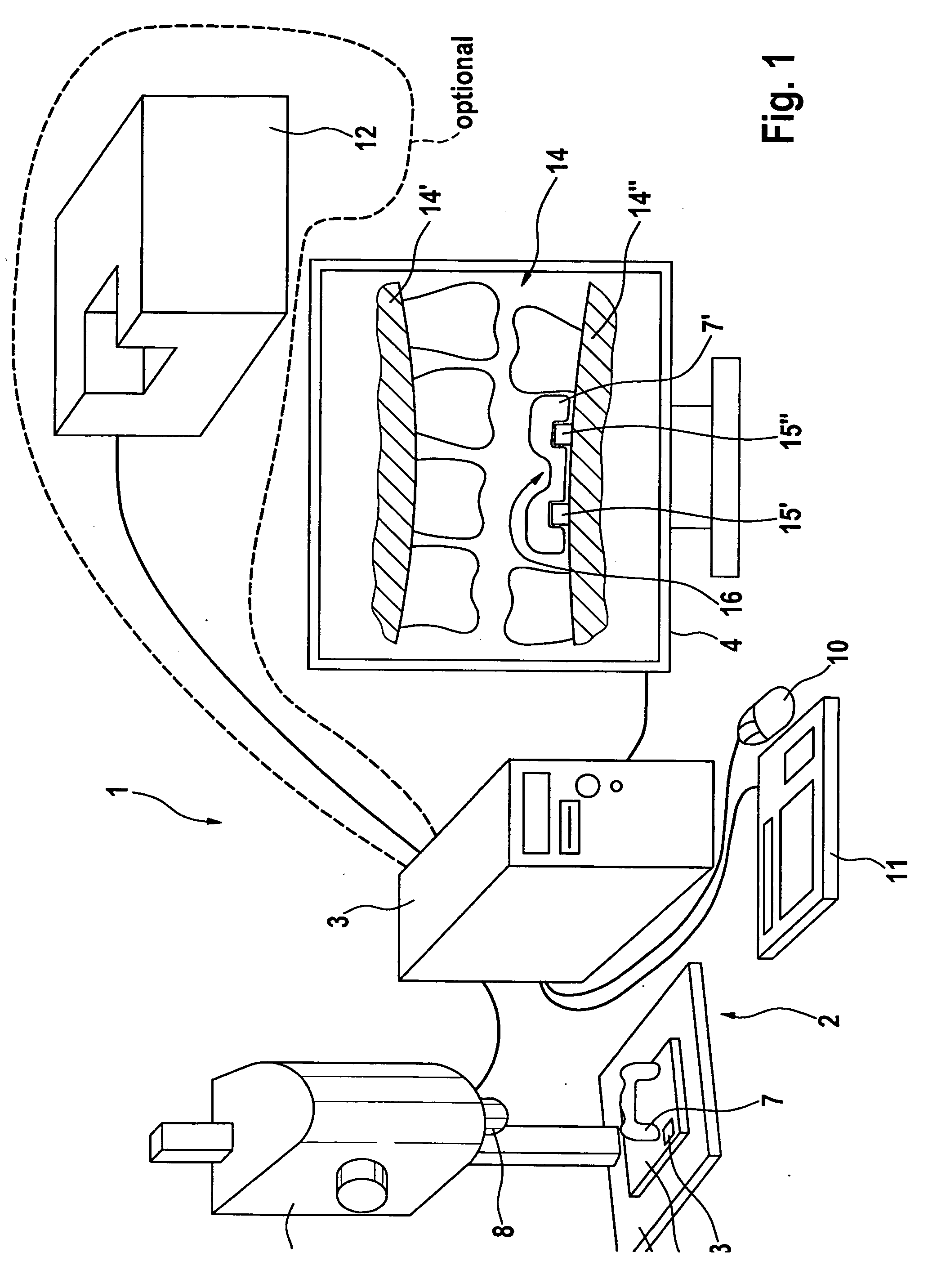
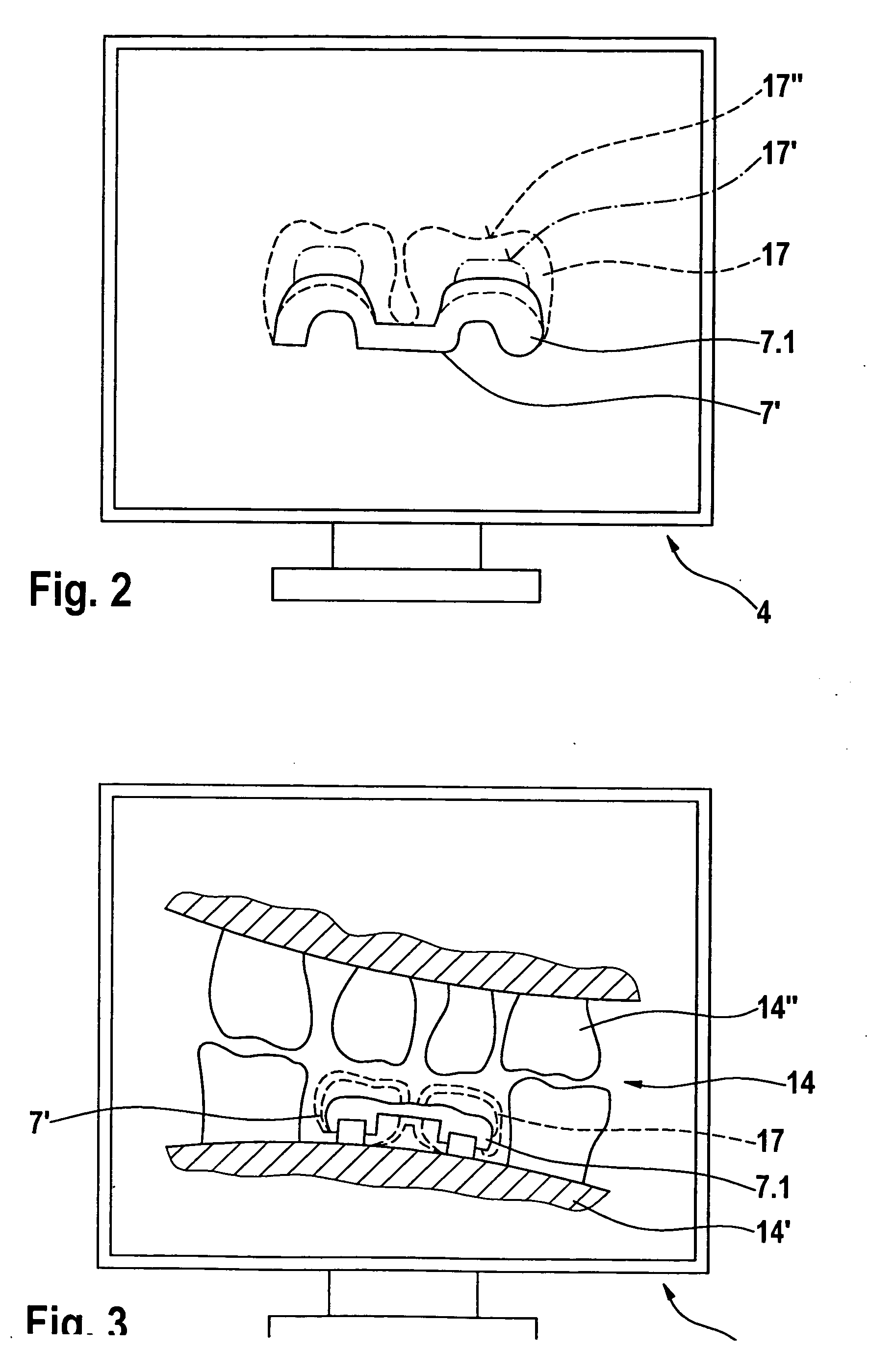
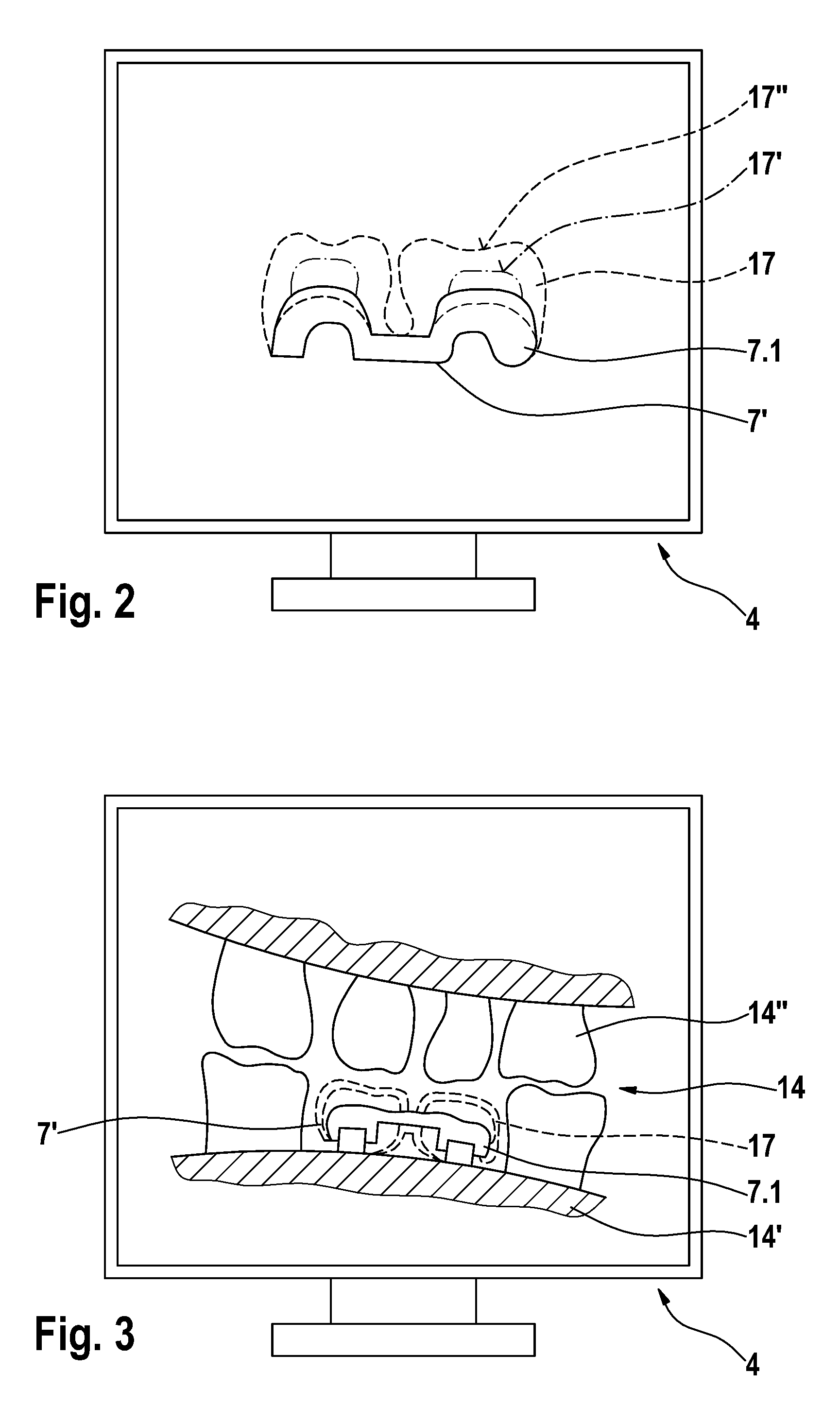
The invention relates to a method for producing a dental prosthesis element (7), according to which the dental prosthesis element (7) is manually reworked. Construction data (17, 17′, 17″) relating to the dental prosthesis element to be produced is recorded together with measurement data (7′) relating to the dental prosthesis element (7) to be produced and is reproduced on a display (4), the measurement data having been recorded by means of a three-dimensional measurement device (2). The invention also relates to one such method whereby a 3D data record of the tooth situation (14) is reproduced on the display (4) instead of the construction data. The invention further relates to a device for the partial manual treatment of the dental prosthesis element. Said device comprises a three-dimensional measurement device (2), a display (4), and a computer unit (3) comprising means for the correlation and comparison of two data records and for graphically presenting the data generated by the comparison.
Owner:SIRONA DENTAL SYSTEMS
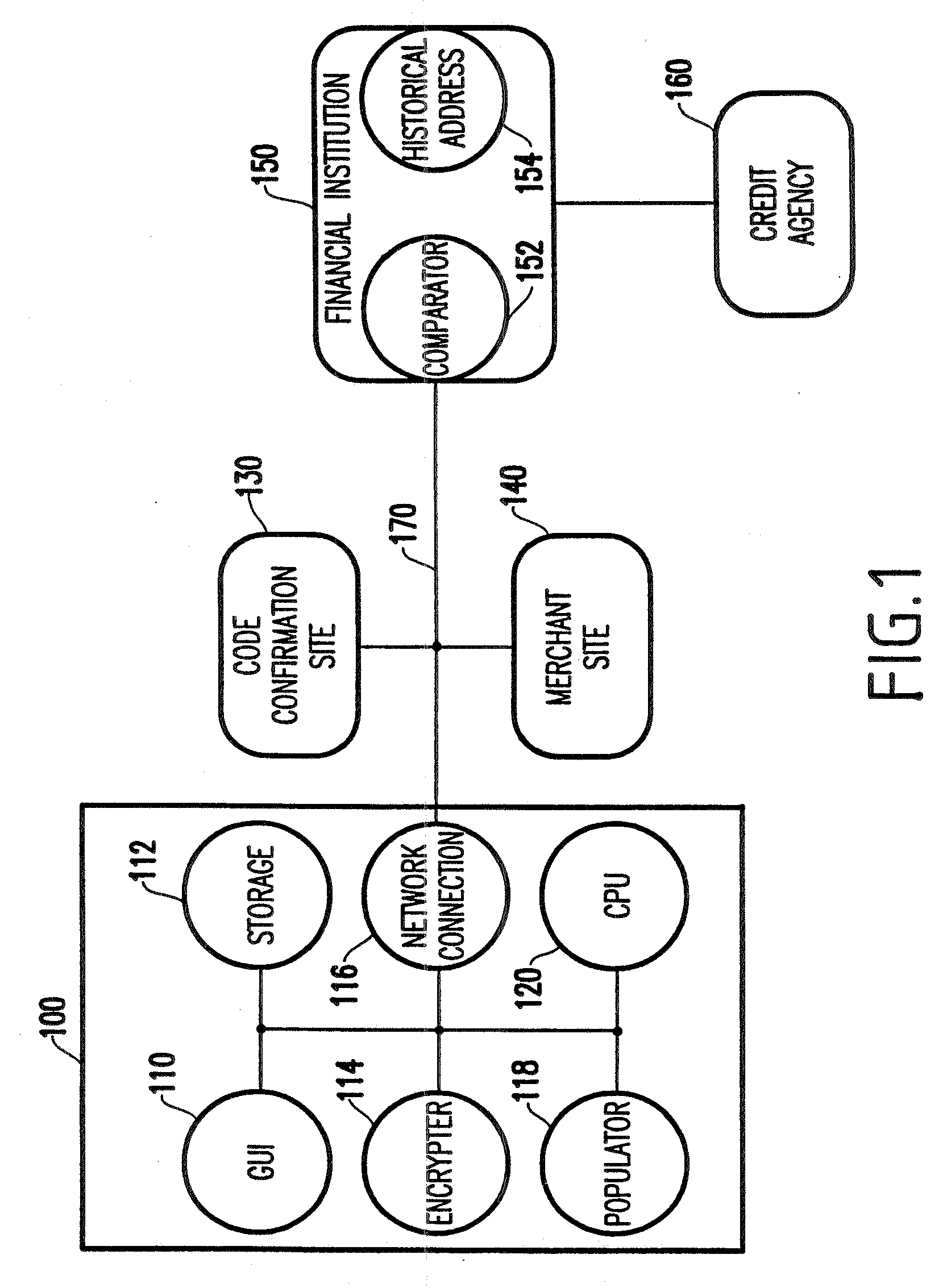
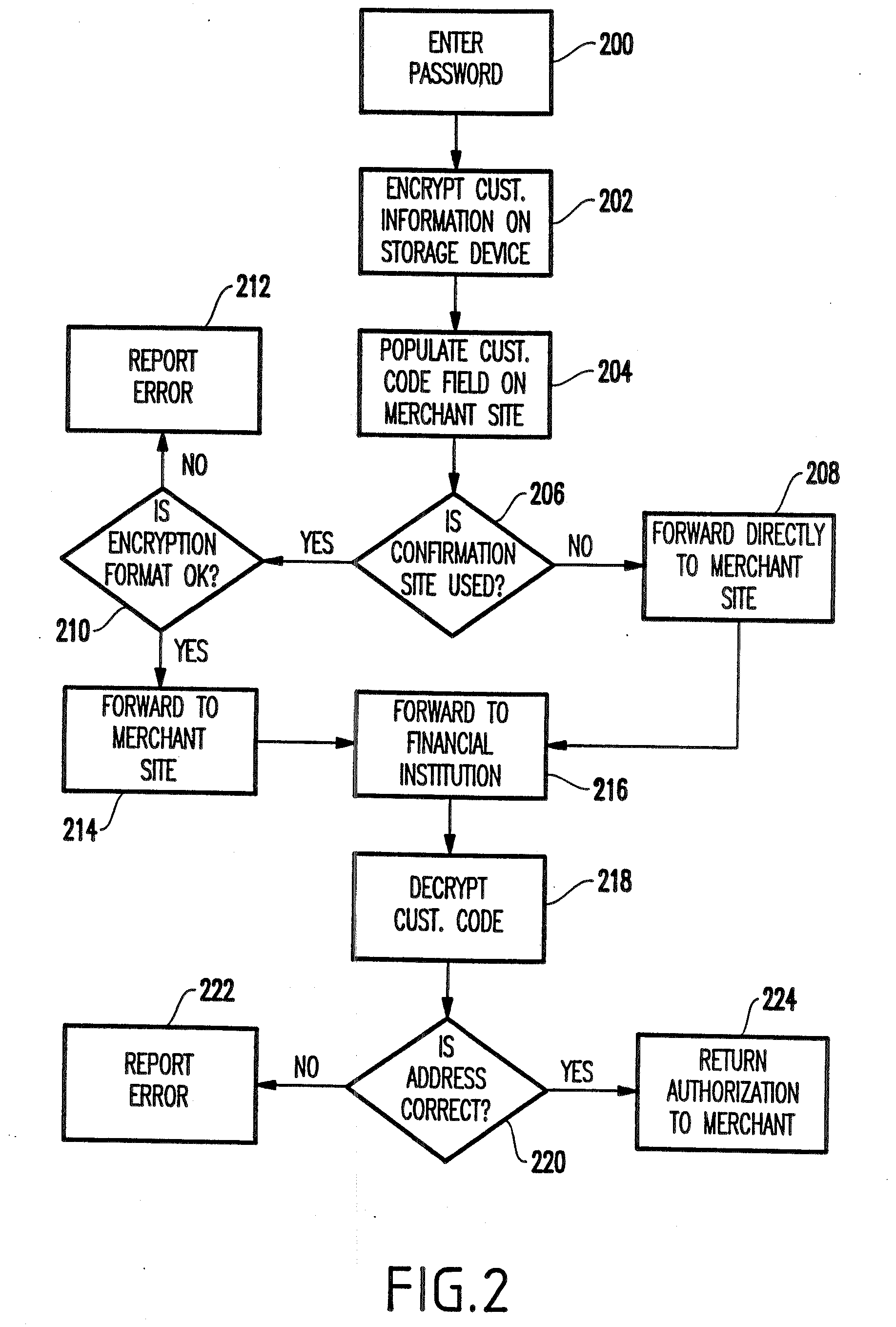
Method and apparatus to provide secure purchase transactions over a computer network
InactiveUS20020069177A1Easy to useRetain controlFinanceSecret communicationCredit cardHard disc drive
A method and structure for providing secure credit facility transactions for purchasing goods and services over a computer network such as the Internet that stores user's privileged information and other transactional data on the user's own computer. The method includes encryption of all information before or during its storage to the user's hard drive. The method and system includes the ability for the user to complete electronic commerce (e-commerce) transactions without revealing certain of the encrypted information, such as credit card numbers, to the merchant. The method and system creates and controls sub-accounts on a single credit facility, such as a credit card, with unique user reporting and corresponding password identifiers. The method and system sets and control sub-accounts spending amounts and replenishment periods. The method enables the user to create and control recurring debit accounts on a single credit facility, such as a credit card, over varying transactional periods.
Owner:BENEDORTSE
Devices, systems, and methods for prosthesis delivery and implantation
Devices, systems, and methods use a catheter device sized and configured for introduction to a targeted site in a hollow body organ or blood vessel. The catheter device includes a first release mechanisms coupled to the prosthesis to secure at least one region of the prosthesis to the catheter shaft, and a second release mechanism coupled to the prosthesis in cooperation with the first release mechanism to prevent full release of the at least one region of the at least one region of the prosthesis from the catheter shaft after actuation of the first release mechanism. A fastening device sized and configured for introduction to the targeted site in the hollow body organ or blood vessel occupied by the catheter device, includes an actuator to deploy a fastener in the at least one region of the prosthesis after actuation of the first release mechanism and before actuation of the second release mechanism.
Owner:MEDTRONIC VASCULAR INC
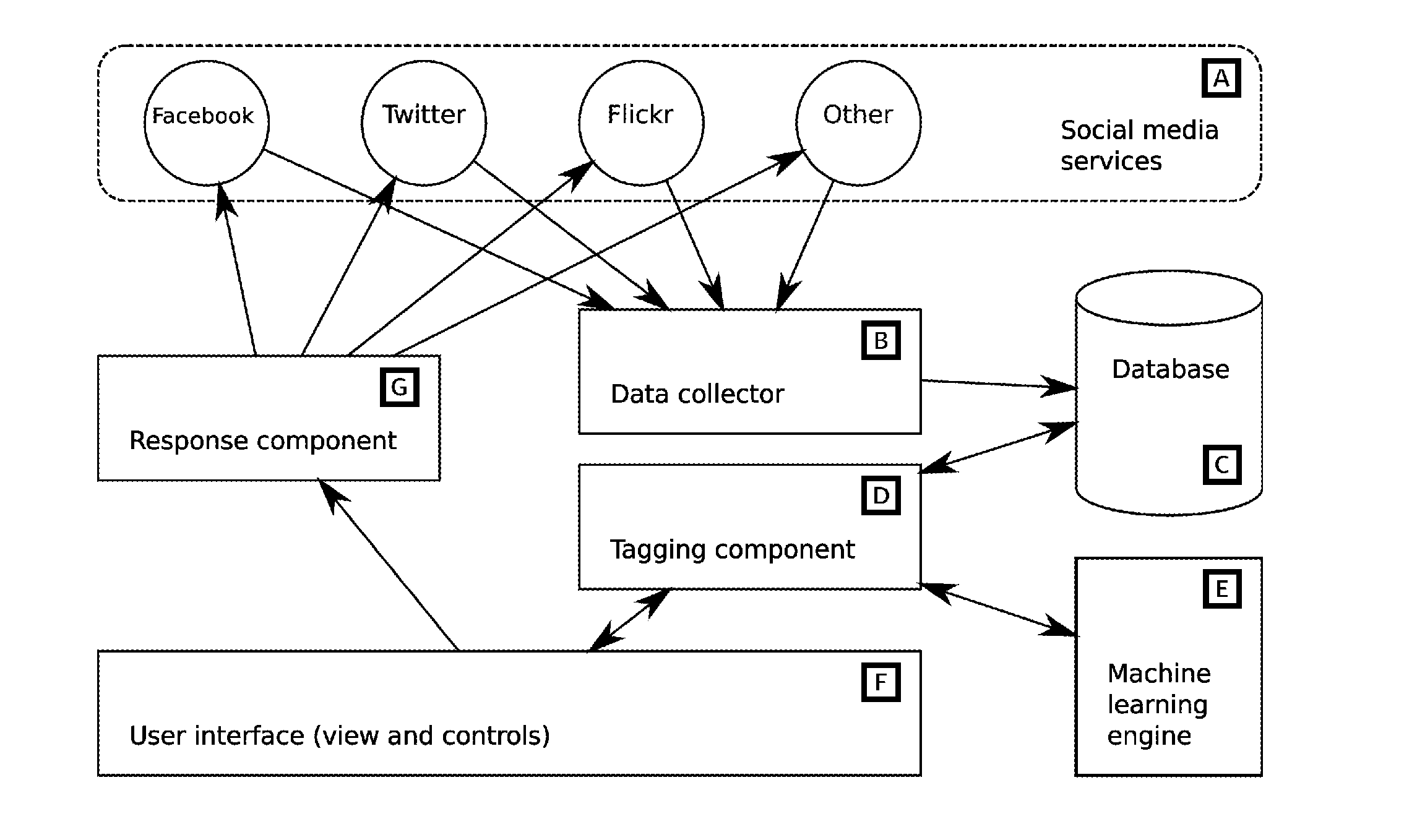
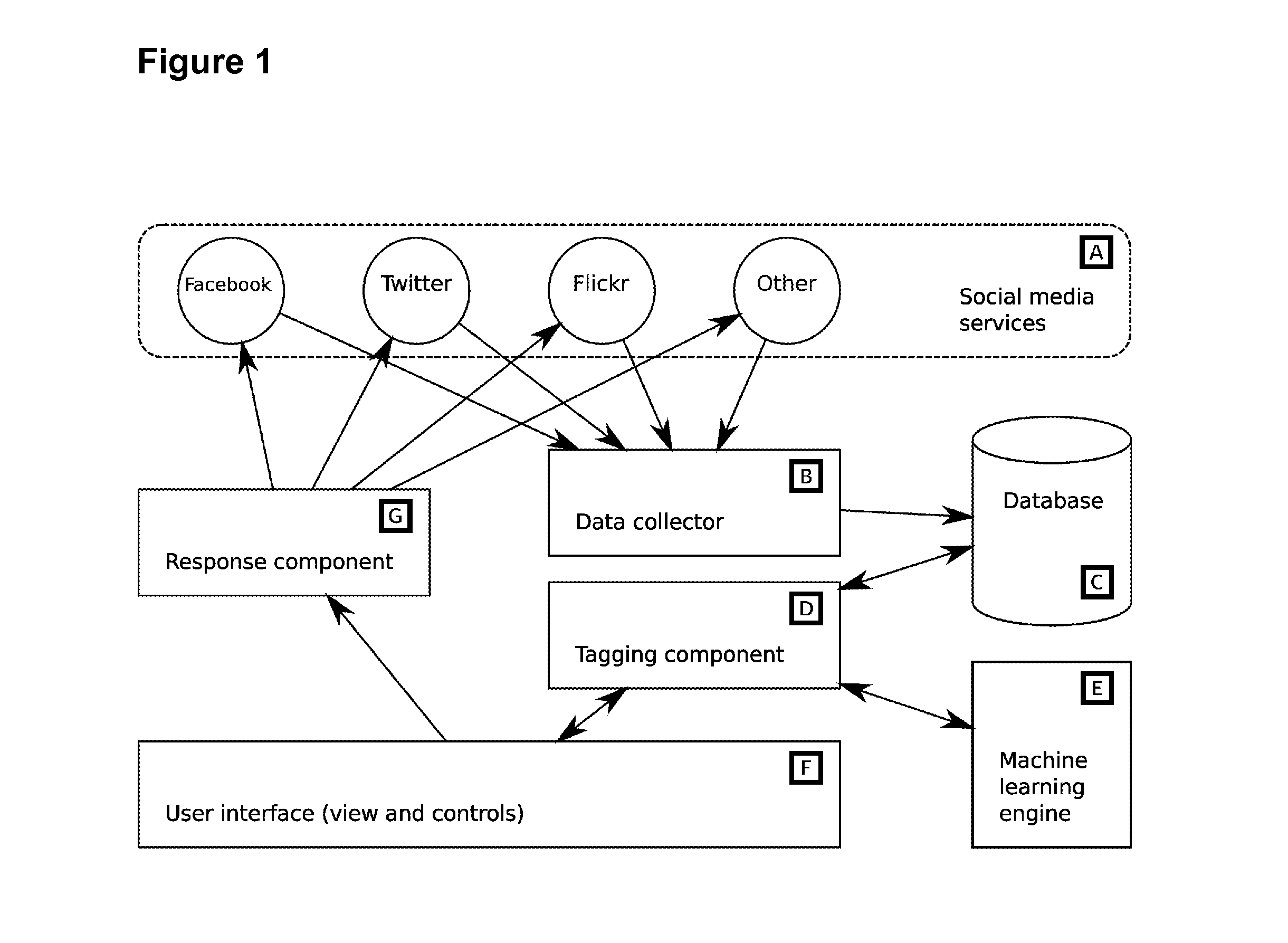
System for organising social media content to support analysis, workflow and automation
InactiveUS20110078584A1Optimize volumeEasy to handleInput/output for user-computer interactionDigital computer detailsSocial mediaApplication software
A social media workflow application includes a social media search component executable by a computing system, a tagging system for annotating search results with textual tags, and a user interface enabling the display of filtered results based on tag, and potentially other, criteria. The new invention is a system to automate tagging and other actions, and the use of such automation to provide a flexible semi-automated workflow tool for the improved use of social media, with particular relevance for marketing and public communications business functions.
Owner:WINTERWELL ASSOCS
Method and device for producing dental prosthesis elements
InactiveUS7865261B2Accurate fitRetain controlDental implantsAdditive manufacturing apparatusGraphicsDentures
Owner:SIRONA DENTAL SYSTEMS
Method of administering call handover between cells in a communications system
InactiveUS20080070575A1Avoid uncertaintyIncrease in the call tariffAssess restrictionNetwork topologiesCommunications systemHandover
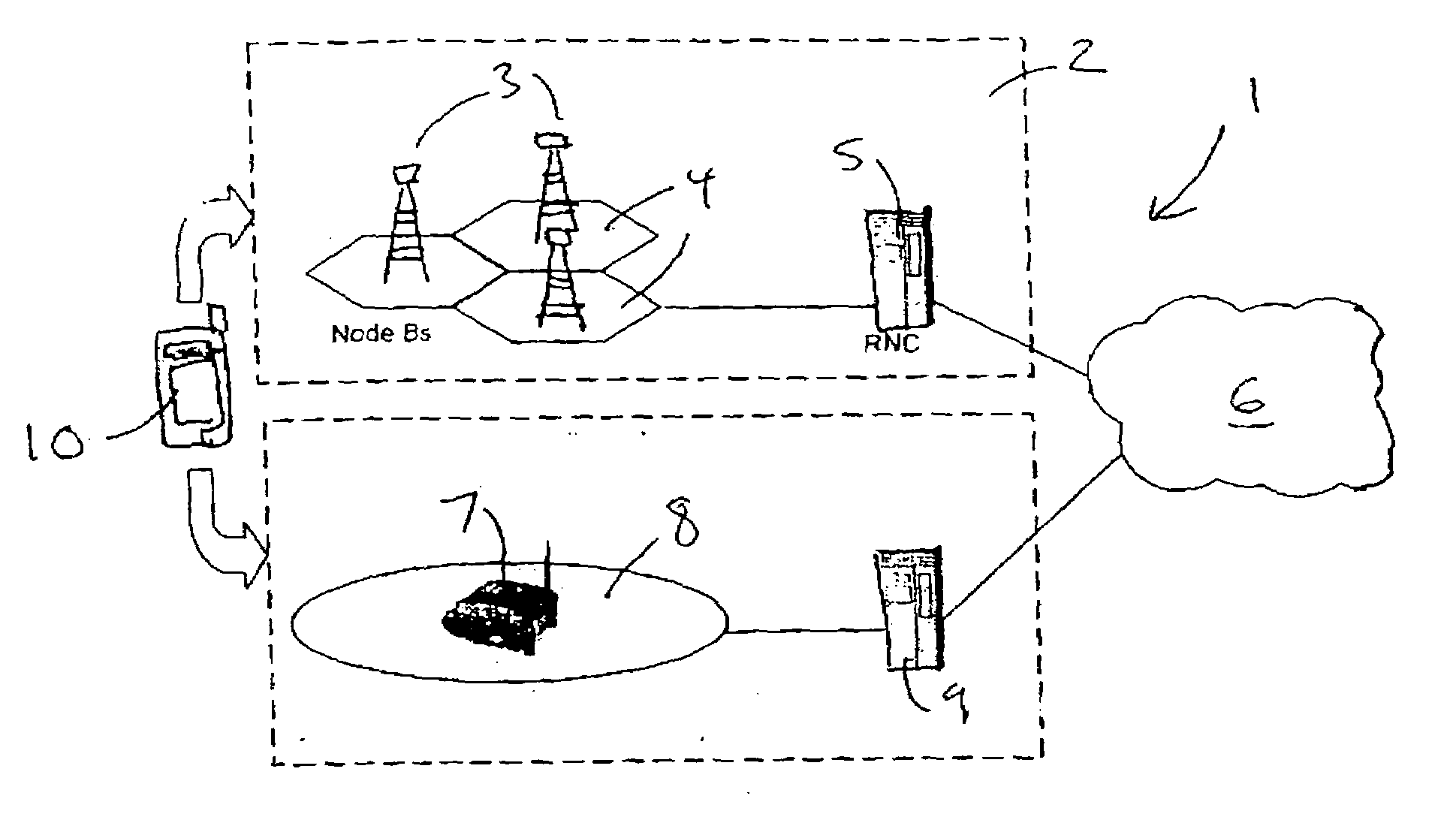
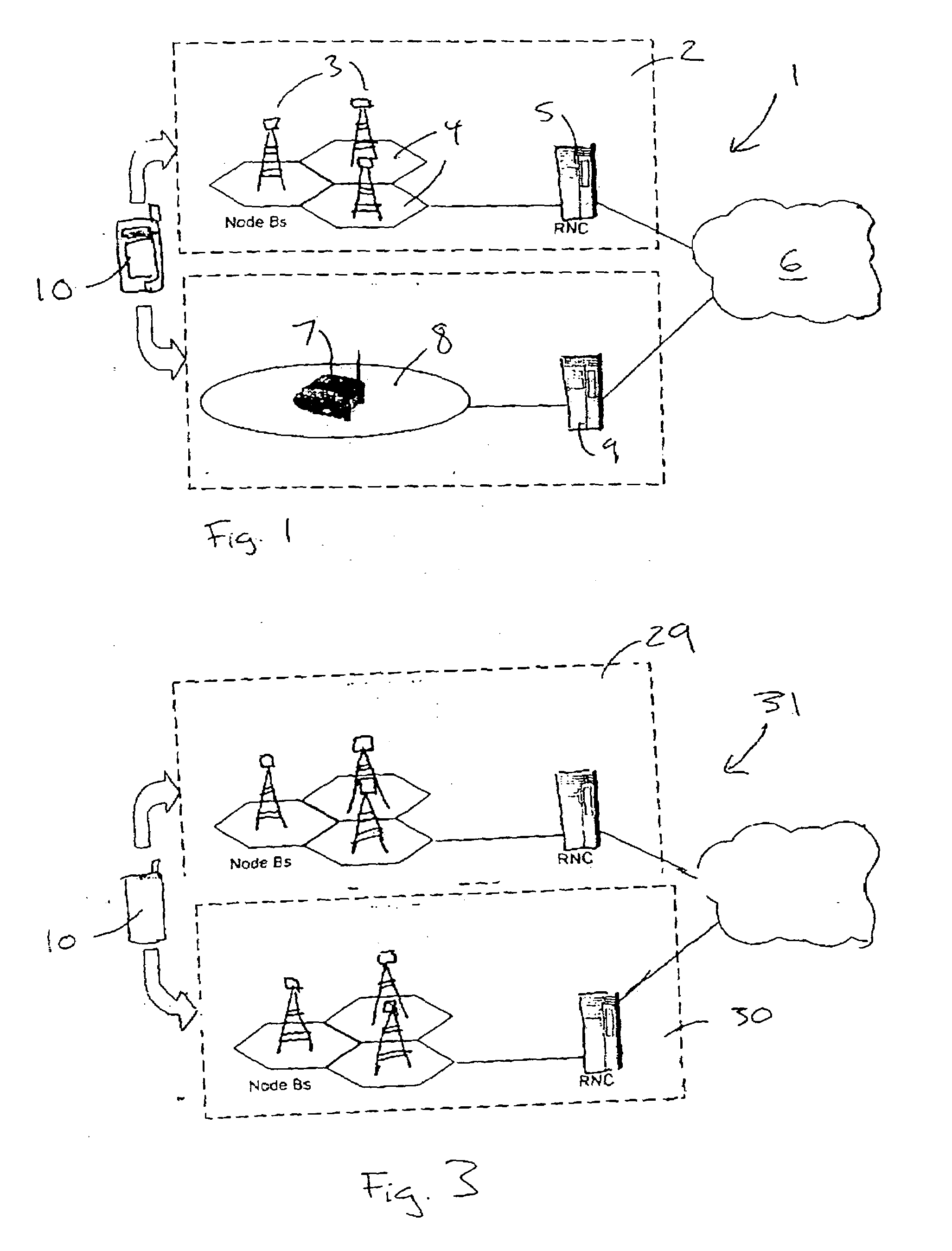
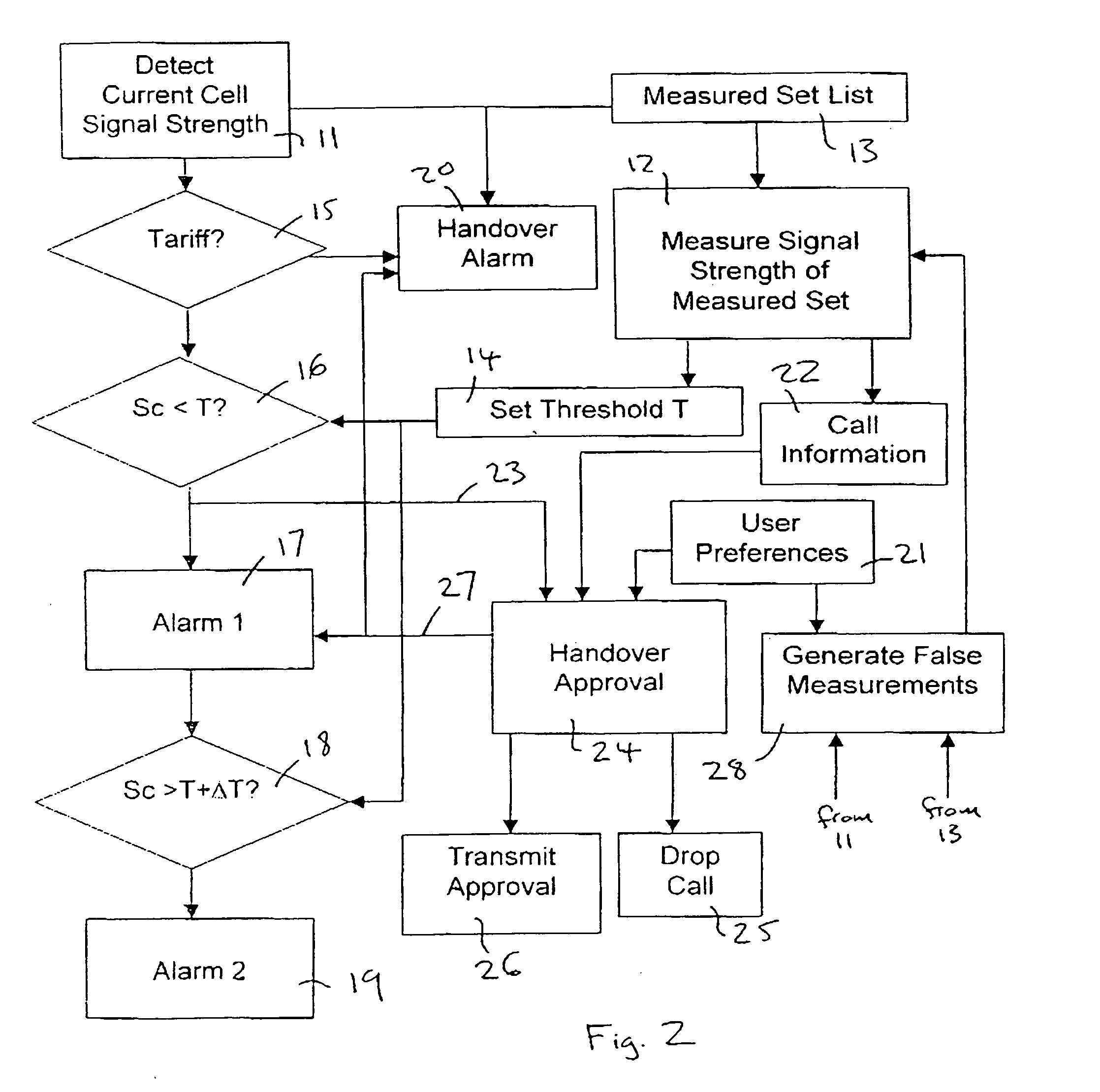
A communications system 1 includes an underlay network 2, which a cellular communications network implemented using UMTS technology, and an overlay home cell 8 set up by a user using a base station router 7, or other similar access device. A call may be transferred from the home cell 8 to a cell of the underlay network 2 and vice versa. If these operate at different tariffs, the user may find that handover between them results in extra charges for an on-going call.The user terminal 10 is enabled so as to allow the user to determine if handover should be performed, and thus retain control of costs incurred in making a call. The user terminal 10 may give an alert if there is a risk of imminent handover, allowing the user to take avoiding action if desired, or the user may configure preferences to control under what conditions handover may be performed.
Owner:LUCENT TECH INC
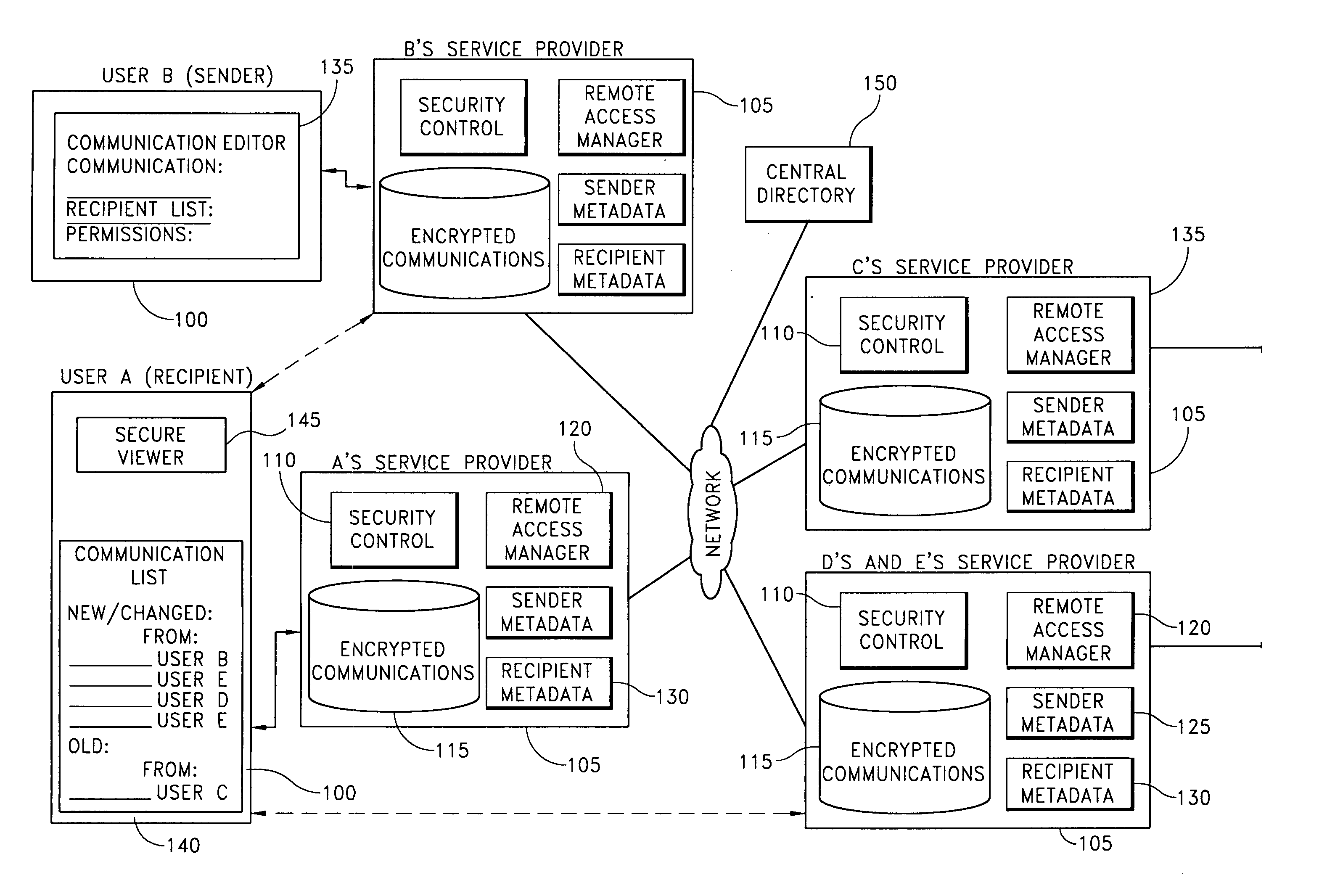
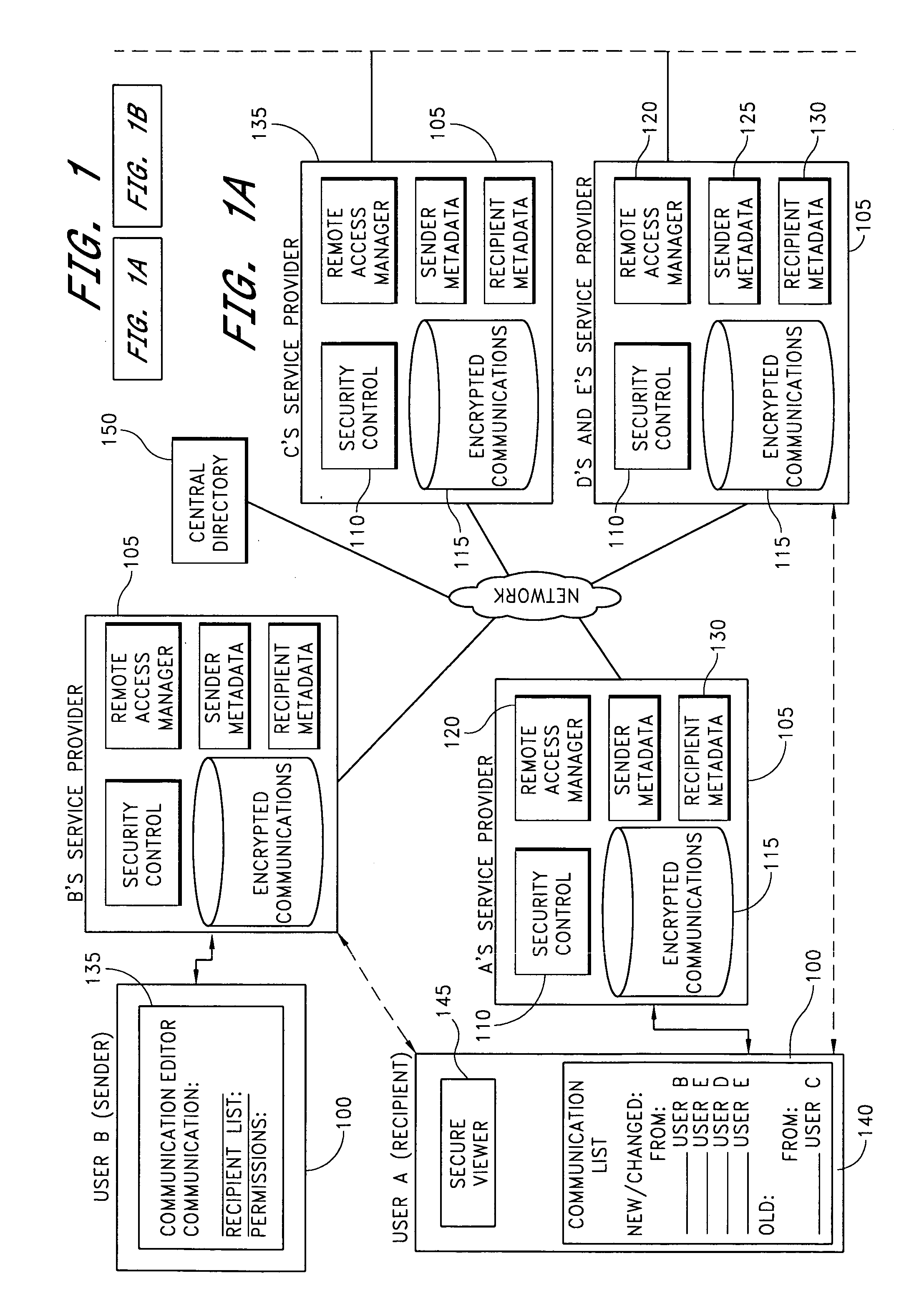
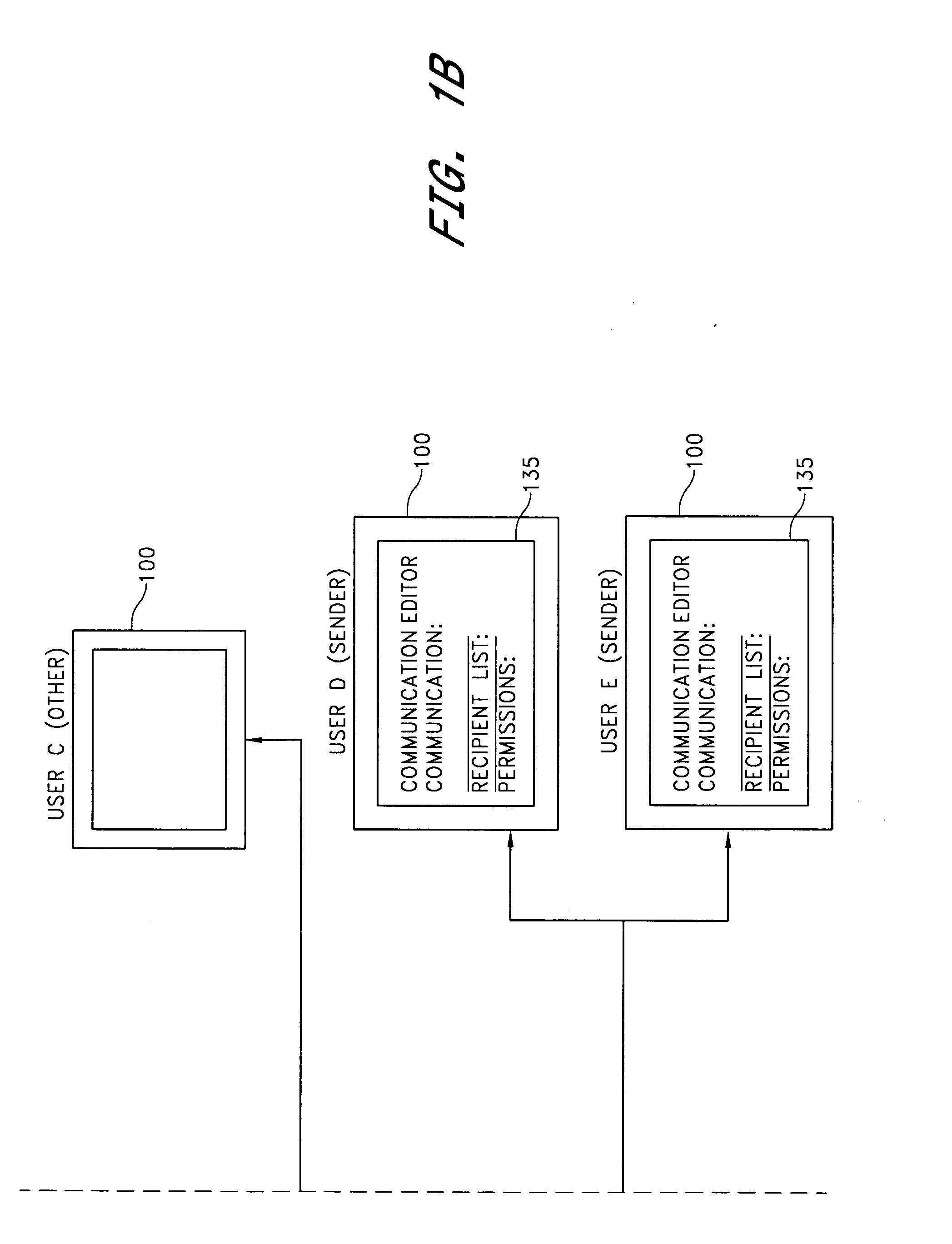
Distributed secure repository
InactiveUS20060059544A1Reduce memory spaceRetain controlDigital data processing detailsUser identity/authority verificationInternet privacyMetadata
A distributed secure repository and related methods allow users of a communications management system to securely store and share communications with other users. A user shares a communication by securely storing the communication, identifying the recipient, and specifying permissions that limit actions that the recipient is permitted to take with respect to the communication. Mechanisms are provided for limiting a recipient's ability to view, copy, store, forward, print, and modify the communication. Metadata associated with the communication is transmitted to the recipient, notifying the recipient of the securely stored communication. The recipient uses the metadata to request an encrypted copy of the communication, to view the communication, or to otherwise interact with the communication in accordance with the sender's permissions. The sender retains control of the communication and can modify the communication and associated permissions.
Owner:H-E-B
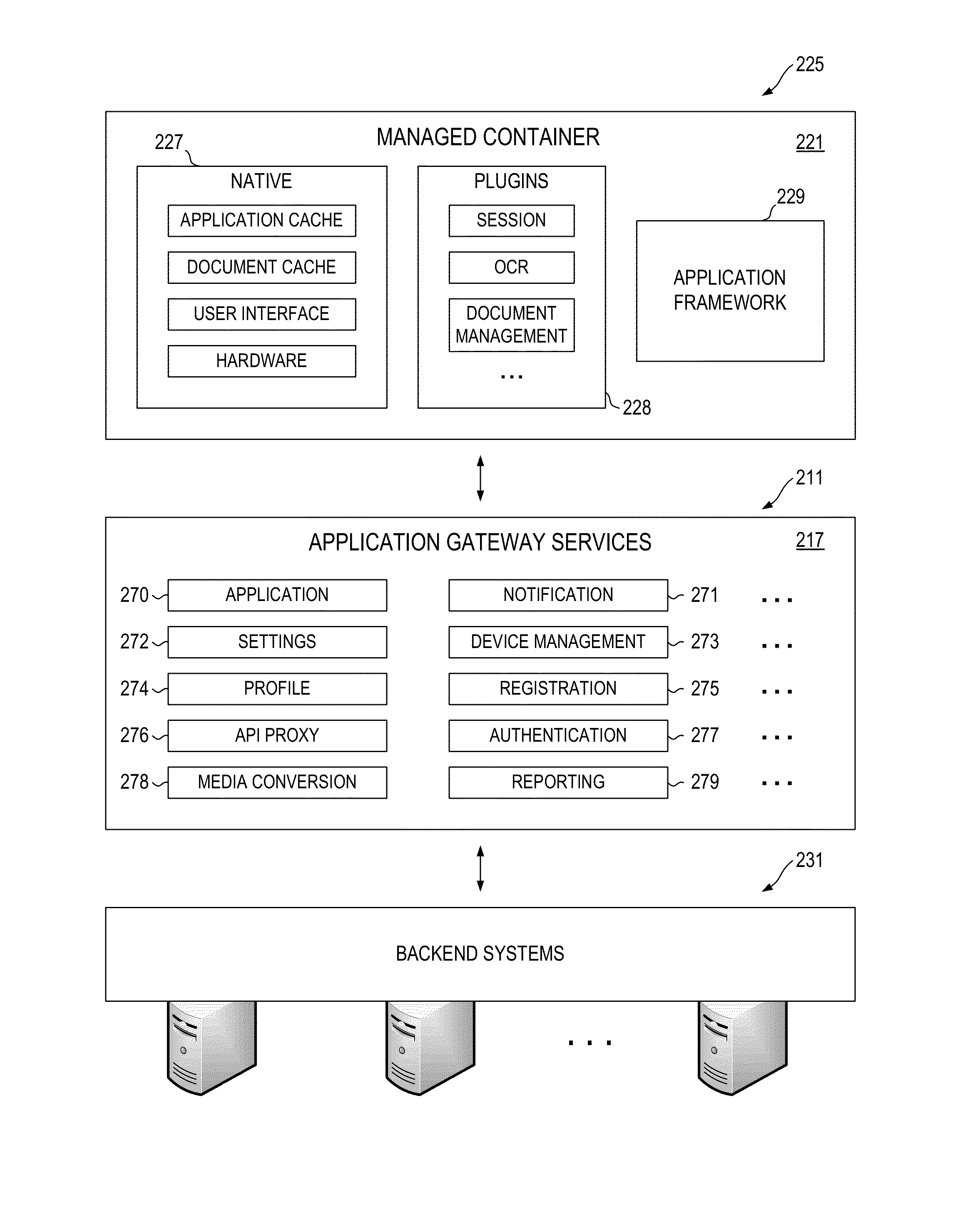
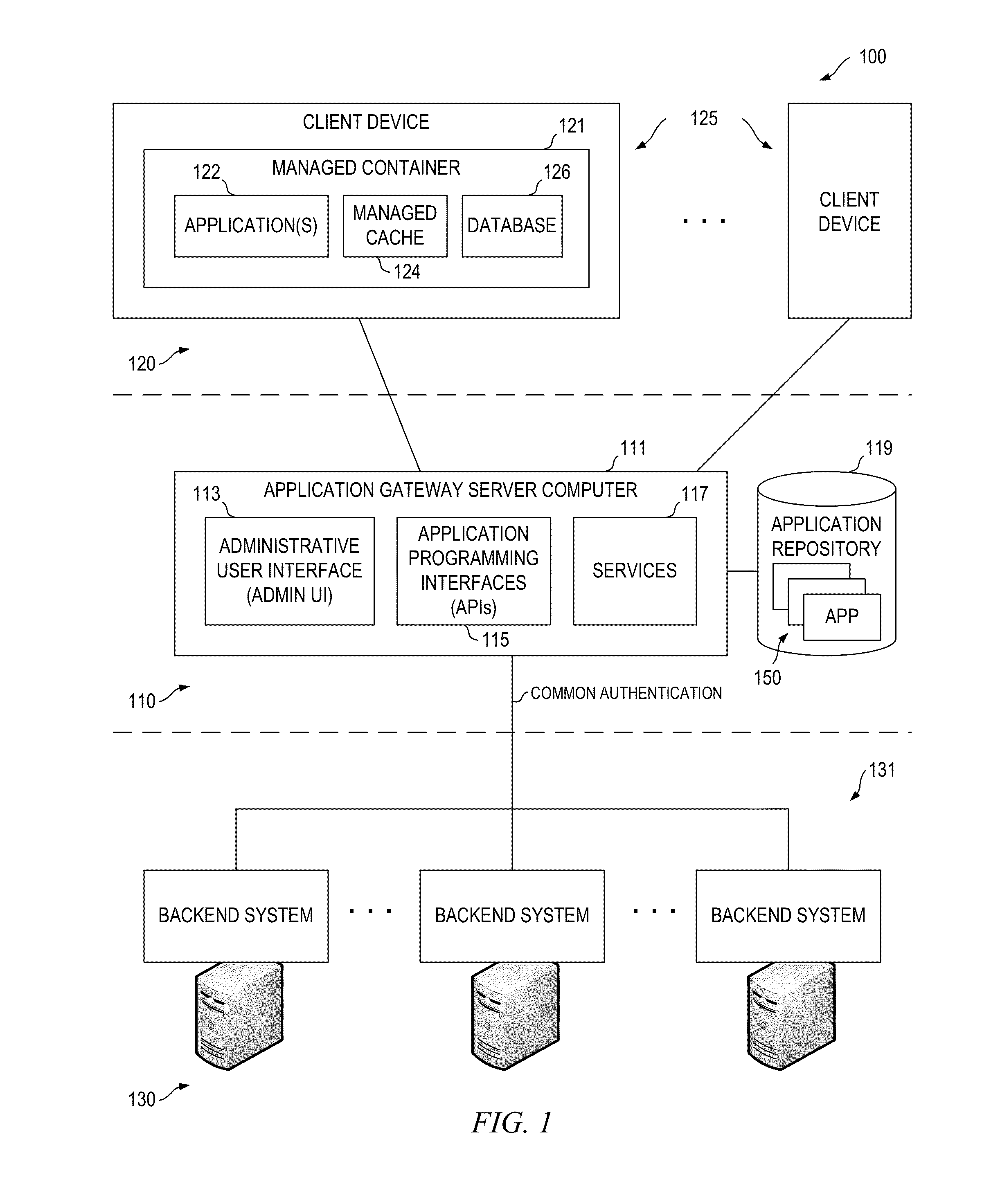
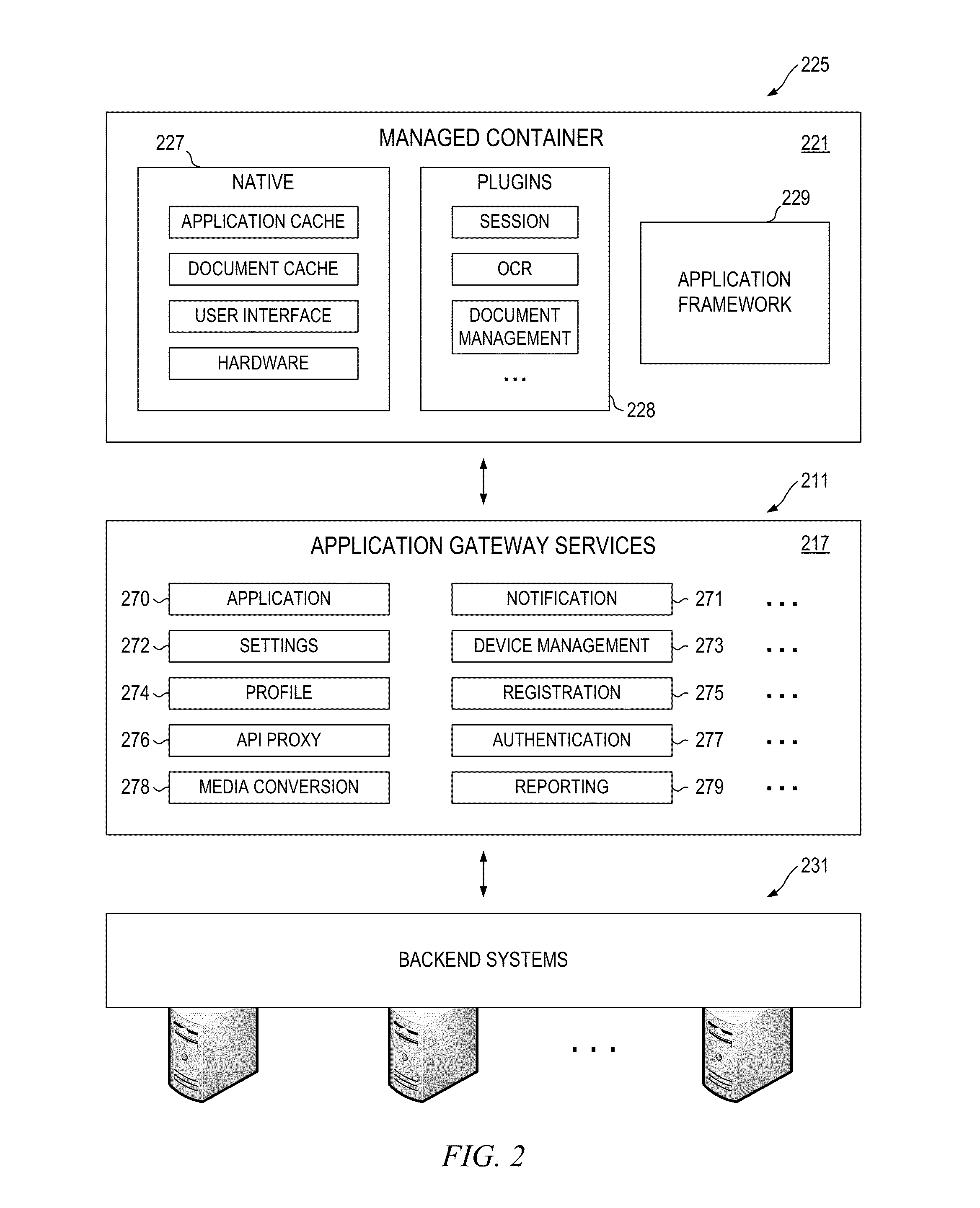
Application Gateway Architecture with Multi-Level Security Policy and Rule Promulgations
ActiveUS20150089224A1Retain controlSafe storageUser identity/authority verificationDigital computer detailsApplication programming interfaceCentralized management
Embodiments of an application gateway architecture may include an application gateway server computer communicatively connected to backend systems and client devices operating on different platforms. The application gateway server computer may include application programming interfaces and services configured for communicating with the backend systems and managed containers operating on the client devices. The application gateway server computer may provide applications that can be centrally managed and may extend the capabilities of the client devices, including the ability to authenticate across backend systems. A managed container may include a managed cache and may provide a secure shell for applications received from the application gateway server computer. The managed container may store the applications in the managed cache and control access to the managed cache according to rules propagated from at least one of the backend systems via the application gateway server computer.
Owner:OPEN TEXT SA ULC
Presentation and payment of bills over a wide area communications network
InactiveUS20050137978A1Direct interactionRetain controlComplete banking machinesFinancePaymentUser input
A bill is presented and payment of the presented bill is requested over a communications network having a first network site associated with a bill payment entity, a second network site, which is different than the first network site, associated with a user, and a third network site, which is different than the first and the second network sites, associated with a bill presentment entity, which is different than the bill payment entity. A first signal, representing a request of the user for billing information, is transmitted from the second network site to the first network site. Responsive to the transmitted first signal, a second signal representing a bill availability identifier for a bill of a biller for the user, is transmitted from the first network site to the second network site. The bill availability identifier represented by the transmitted second signal is displayed and a first user input representing a selection of the displayed bill availability identifier is received, at the second network site. A third signal, representing a request of the user for the identified bill, is transmitted from the second network site to a third network site responsive to the first user input. Responsive to the transmitted third signal, a fourth signal representing the requested bill and an associated pay bill indicator, is transmitted from the third network site to the second network site. The bill and associated pay bill indicator represented by the transmitted fourth signal are displayed and a second user input representing a selection of the displayed pay bill indicator is received at the second network site. Responsive to the second user input, a fifth signal representing a request of the user that the bill payment entity pay the displayed bill on behalf of the user, is transmitted from the second network site to the first network site.
Owner:CHECKFREE CORP
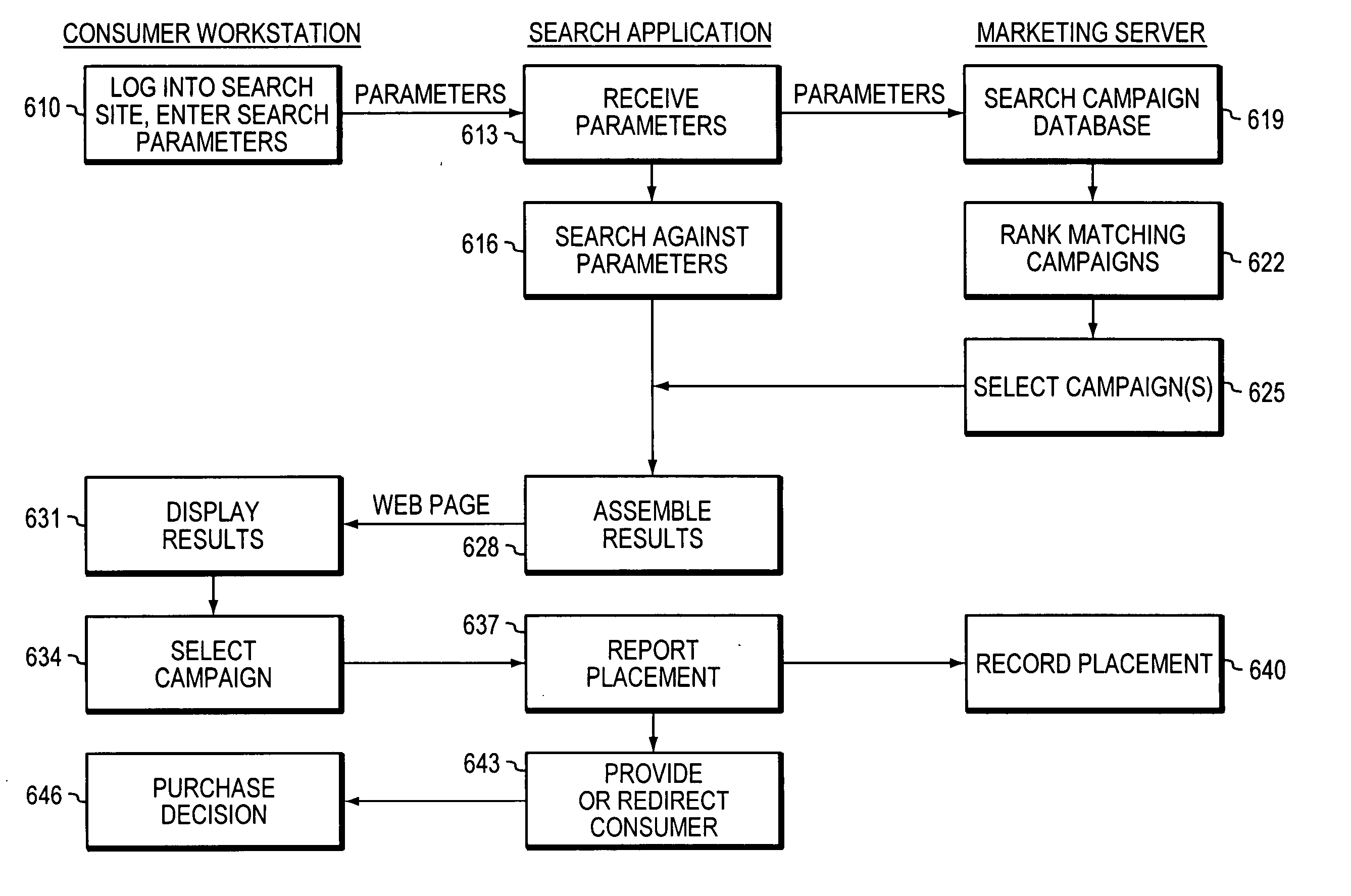
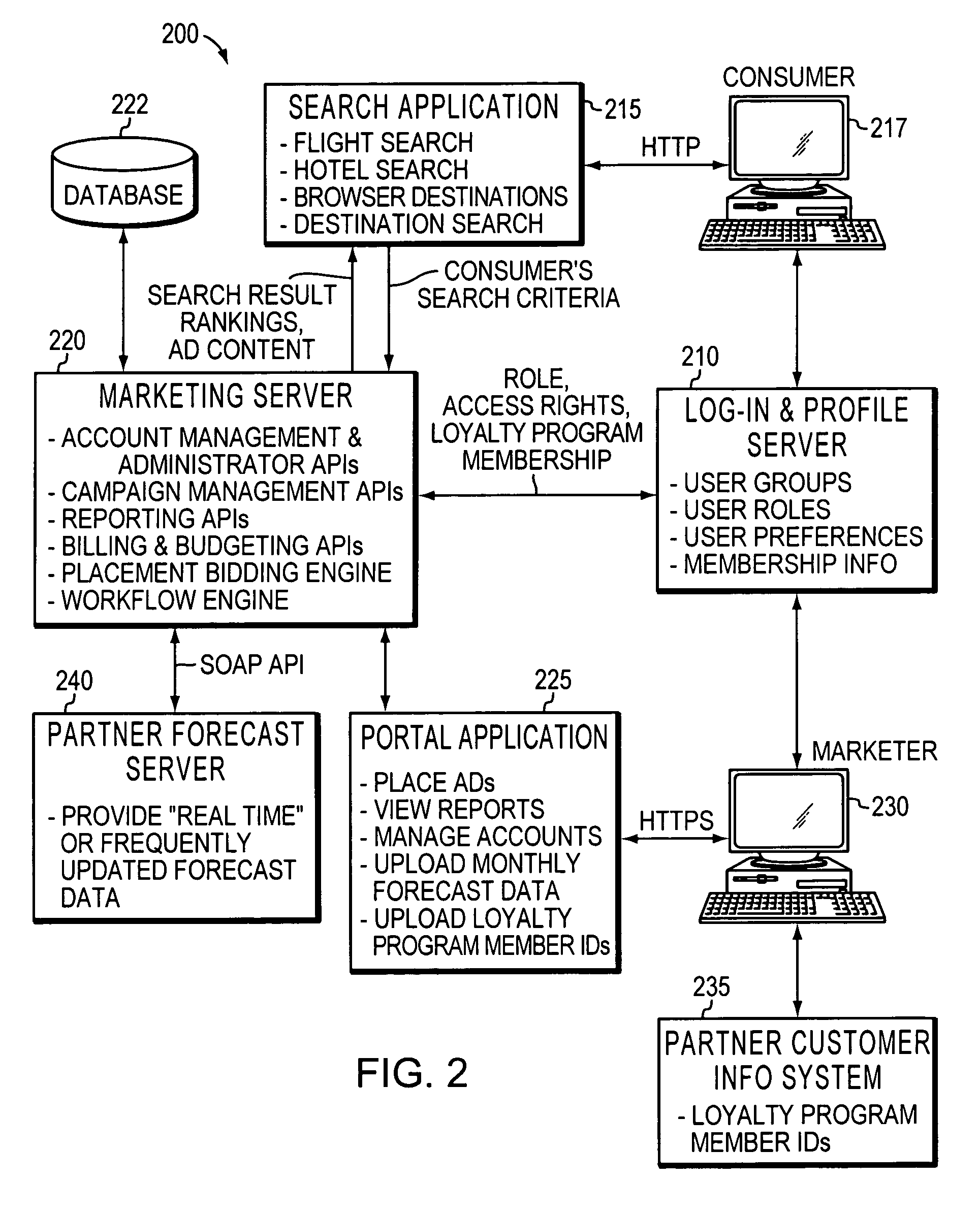
Individualized marketing to improve capacity utilization
Suppliers of goods and / or services subject to shifts in capacity utilization design and implement marketing campaigns around utilization forecasts, targeting marketing expenditures on periods of excess capacity rather than periods without excess capacity, and in some embodiments also to alter variables such as pricing, consumer targeting, or even the intensity of the campaign itself on a dynamic basis in response to changing market conditions.
Owner:KAYAK SOFTWARE CORP
Transactional security over a network
InactiveUS20070288394A1Facilitates purchase transactionEasy to useDigital data authenticationCommercePaymentPersonalization
A system and method facilitates purchase transactions over a computer network, including the purchase of electronically storable items. The embodiments herein encrypt “customer information” in an encryption stream and cause the encryption stream to be transferred from the customer to a merchant in the purchase transaction. A verification entity receives the encryption stream which is sent by the merchant for identity verification and payment authorization. Then, the verification entity verifies the identifiers contained in the encryption stream and transfers an identity verification and payment authorization from the verification entity to the merchant. The encryption stream or unique transaction identifier can be added, by the merchant, to a purchased electronic item to create a personalized electronic item.
Owner:BENEDOR CORP
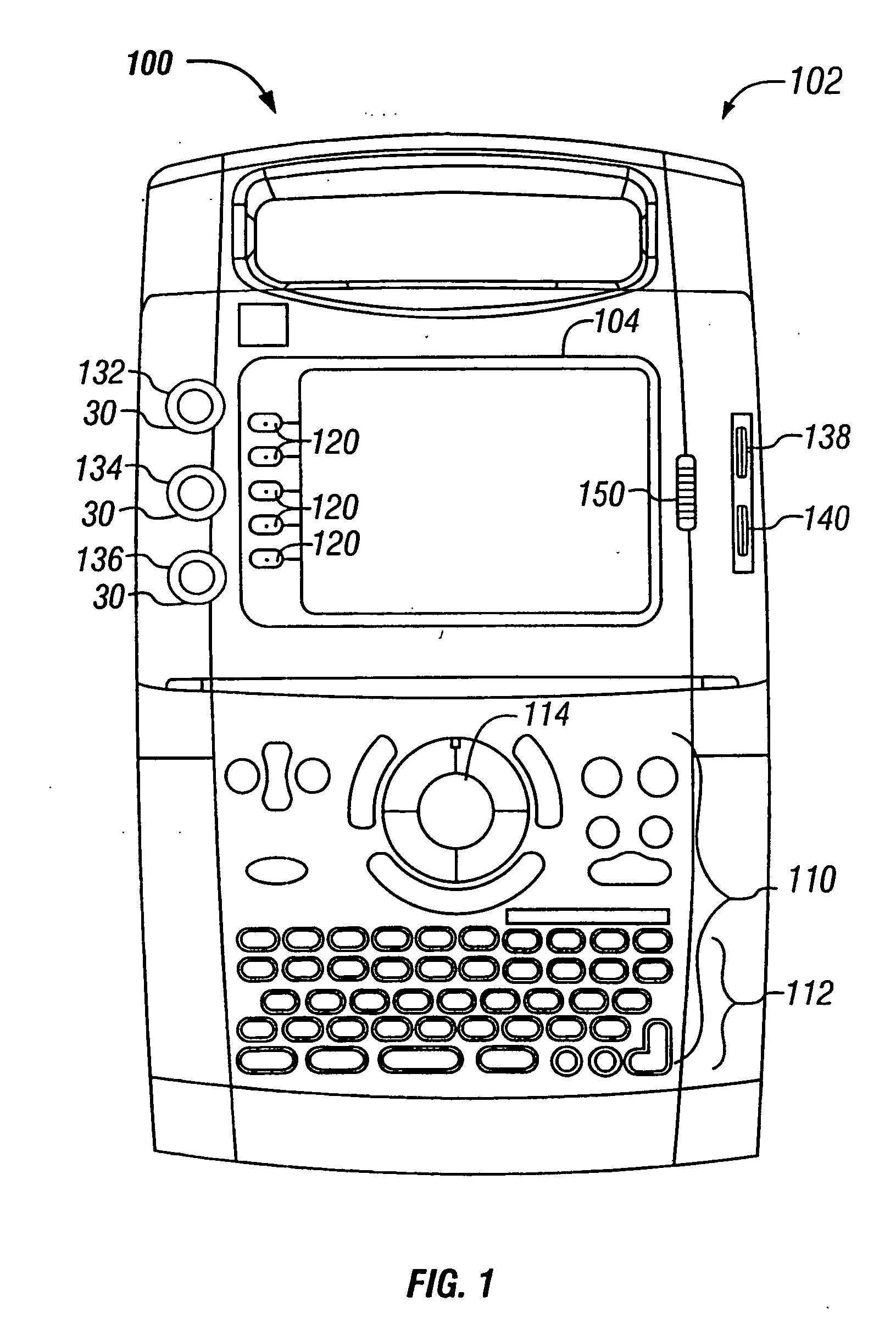
Medical diagnostic ultrasound instrument with ECG module, authorization mechanism and methods of use
InactiveUS20060025684A1Restricts modificationRestricts replacementElectrocardiographyBlood flow measurement devicesDiagnostic modalitiesColor doppler
Owner:FUJIFILM SONOSITE
Method and mechanism for vending digital content
InactiveUS20060059098A1Easy accessRetain controlPayment architectureBuying/selling/leasing transactionsDigital rights management systemDigital content
An Internet Box Office (IBO) system and technique vends digital content via a computer network, such as the Internet. The IBO system comprises a viewing system that cooperates with a Digital Rights Management system and various deployment enhancements within the Internet to provide an infrastructure that facilitates access to digital content in a manner that comports with copyright law and the control of intellectual property by the copyright owner. The IBO system enables a content copyright owner to retain control of its intellectual property while allowing a consumer to have transparent access to the copyright-protected content via the network. To that end, the IBO system operates to download and stage the copyrighted digital content on the viewing system of a consumer.
Owner:RPX CORP
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com