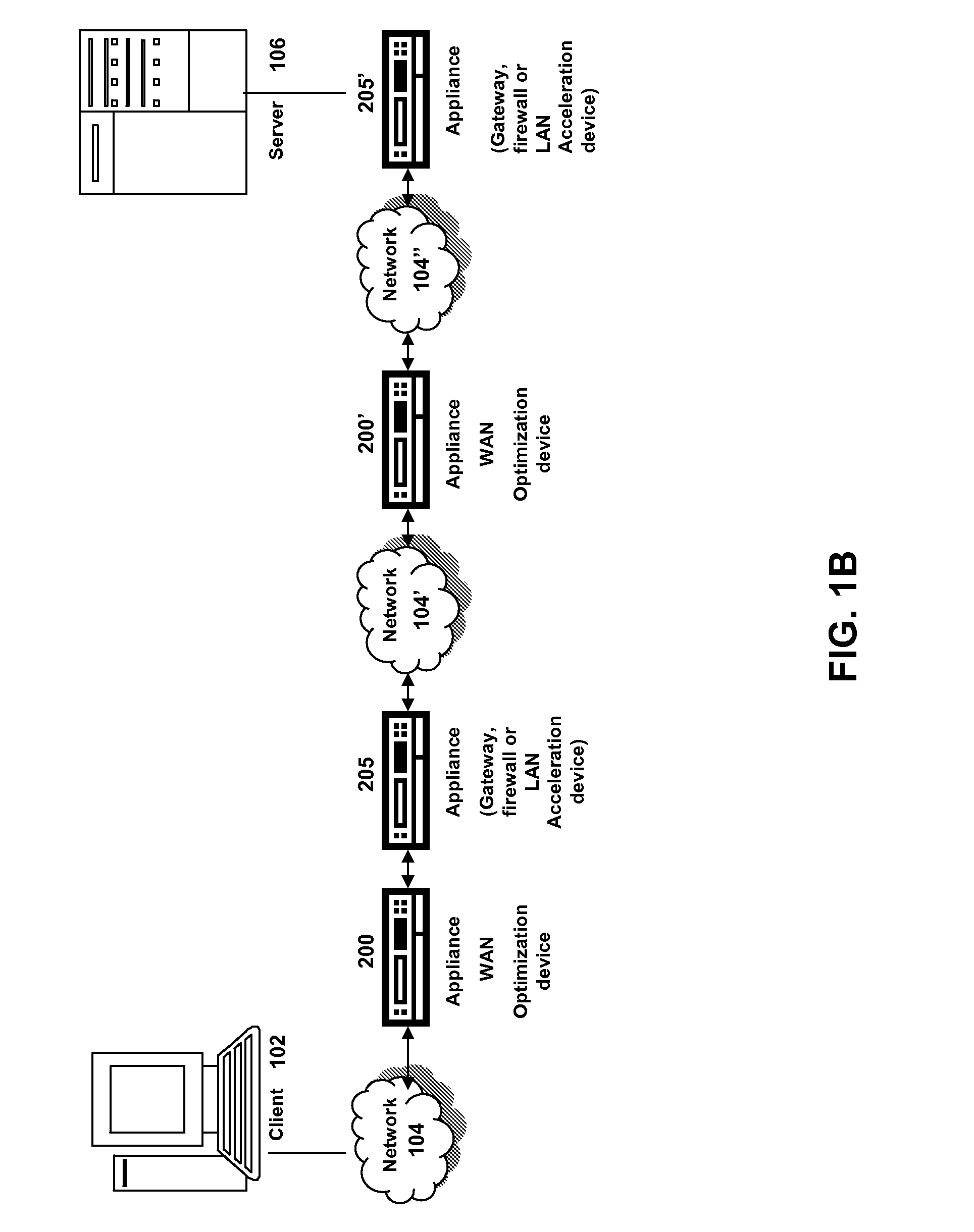
Patents
Literature
183 results about "Hostname" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
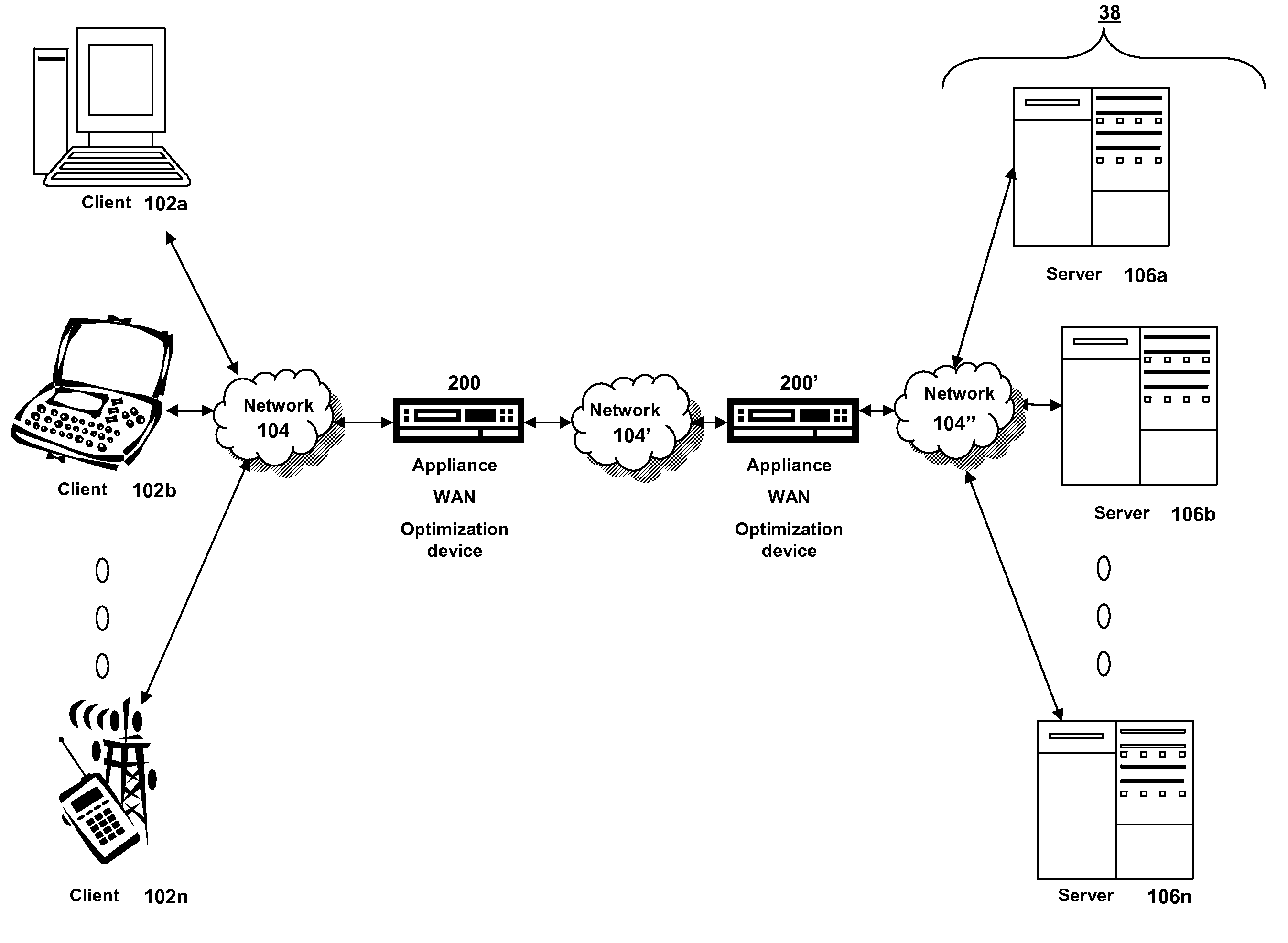
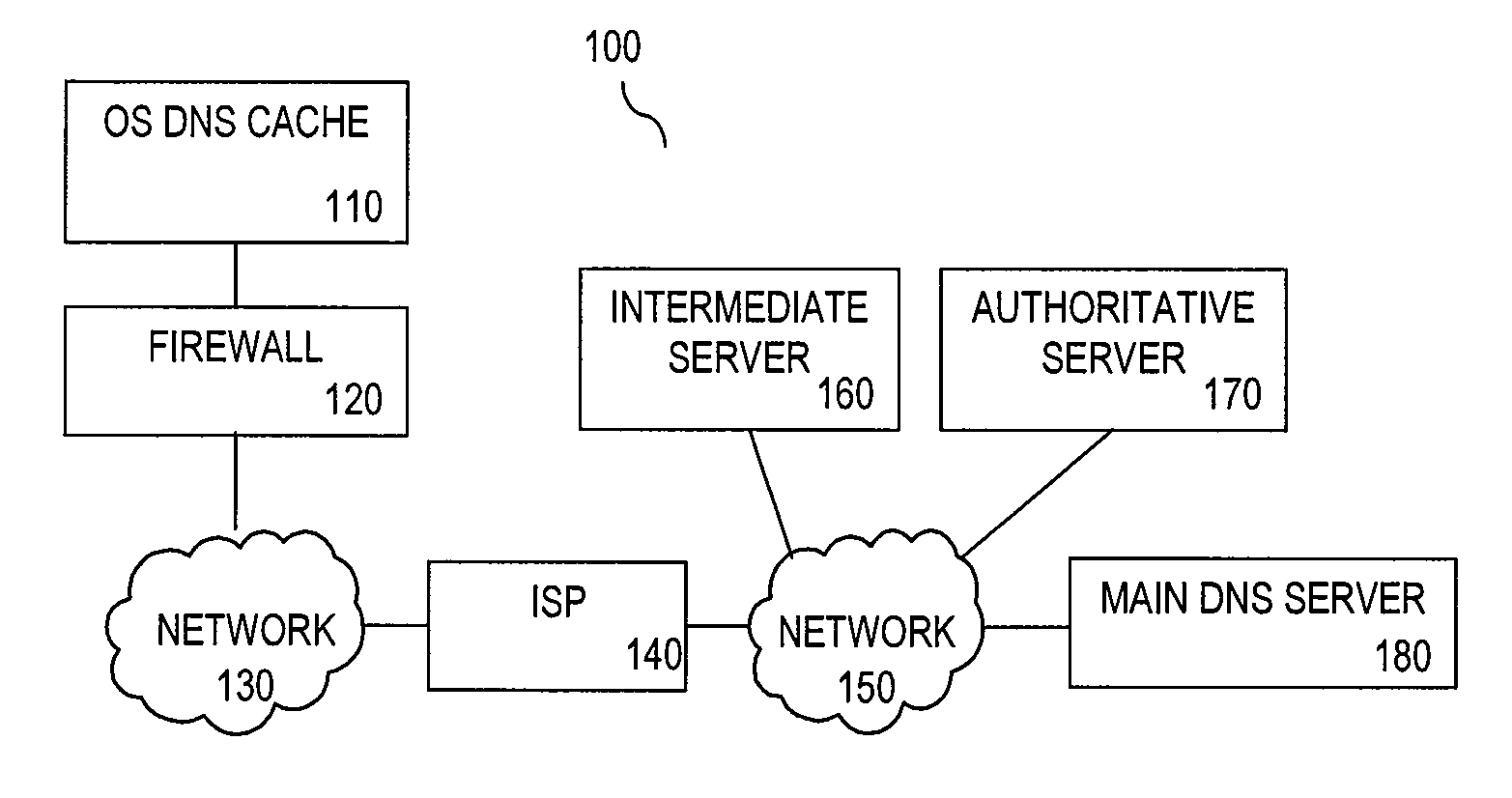
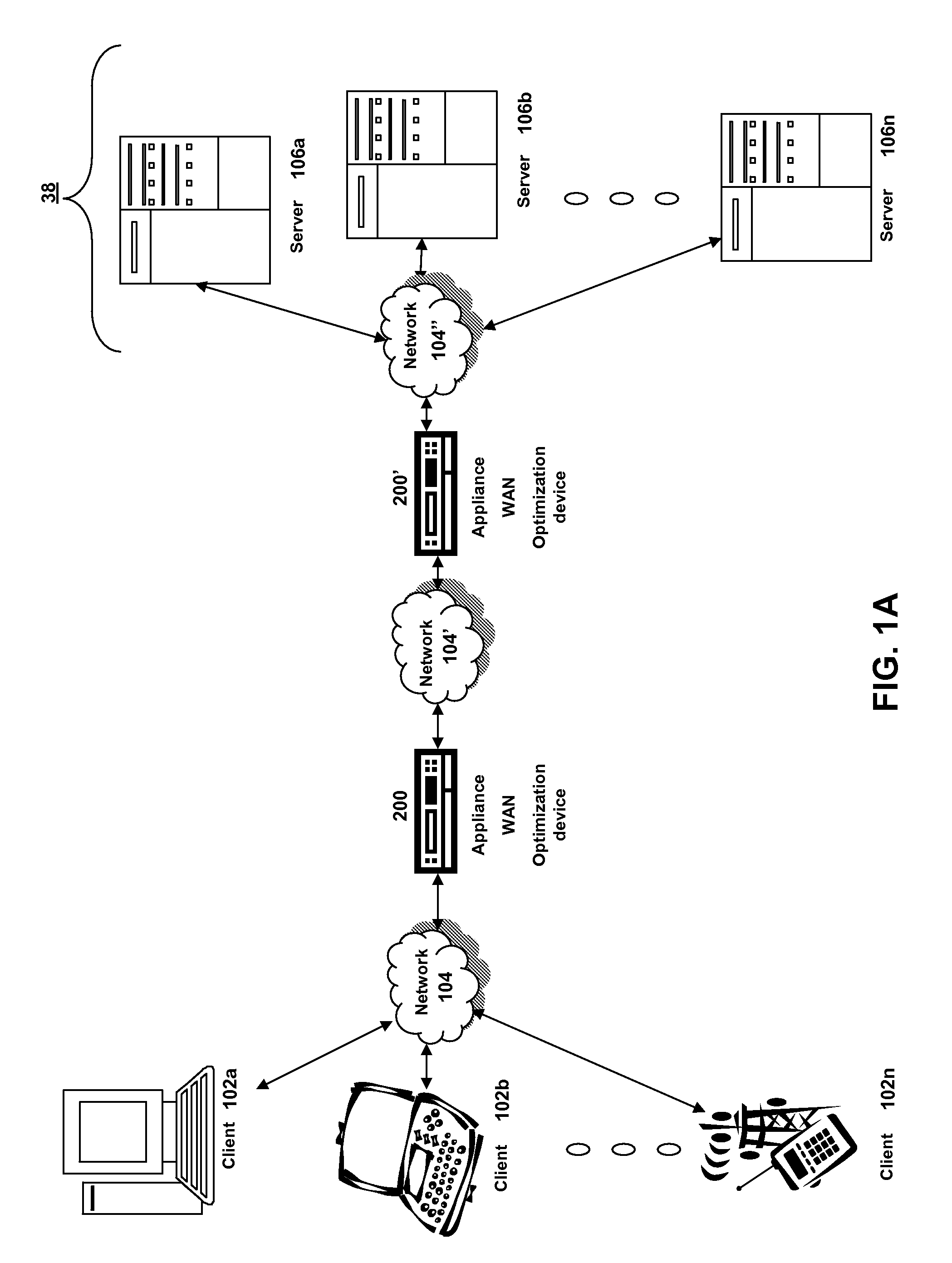
In computer networking, a hostname (archaically nodename) is a label that is assigned to a device connected to a computer network and that is used to identify the device in various forms of electronic communication, such as the World Wide Web. Hostnames may be simple names consisting of a single word or phrase, or they may be structured.
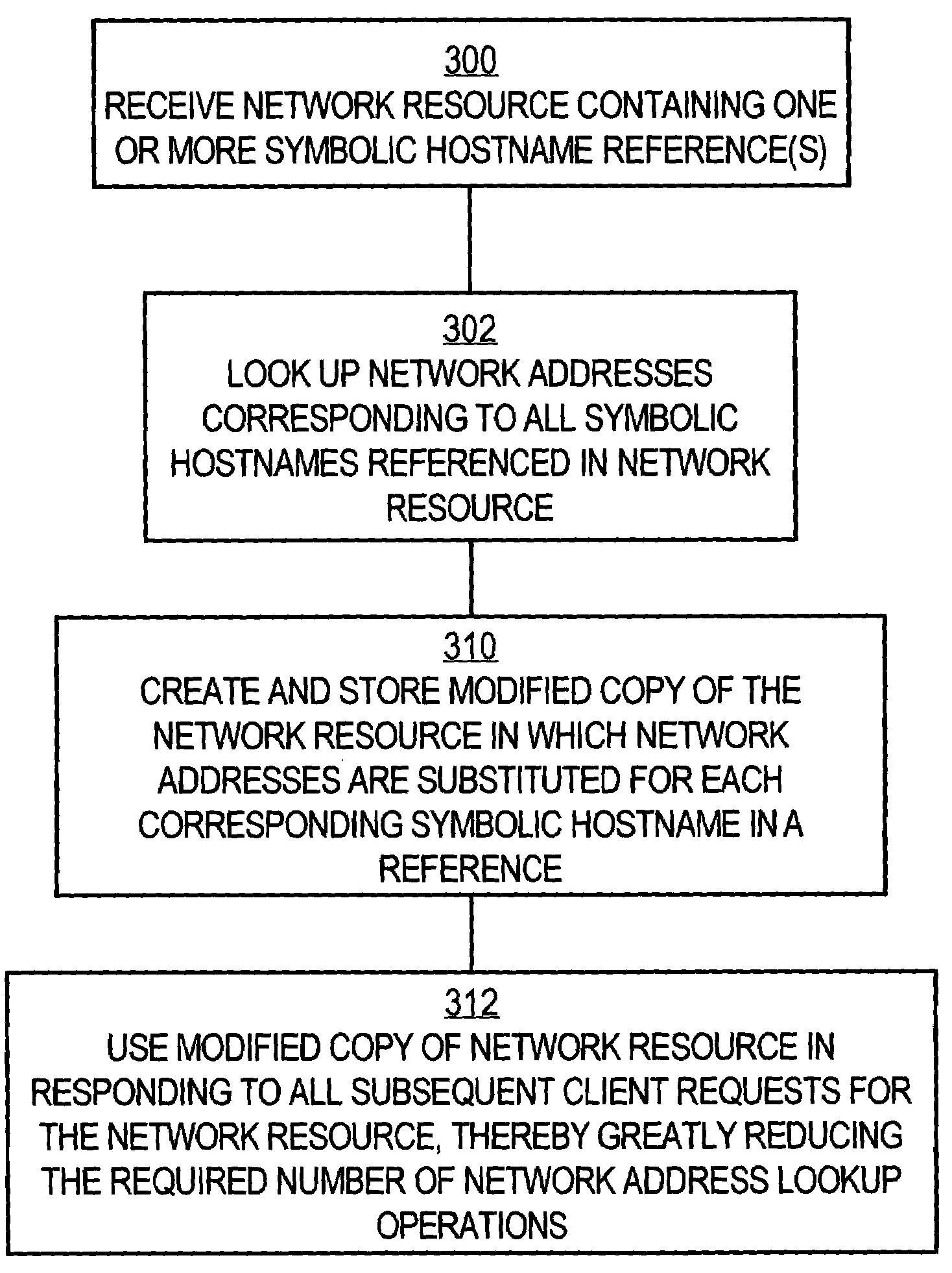
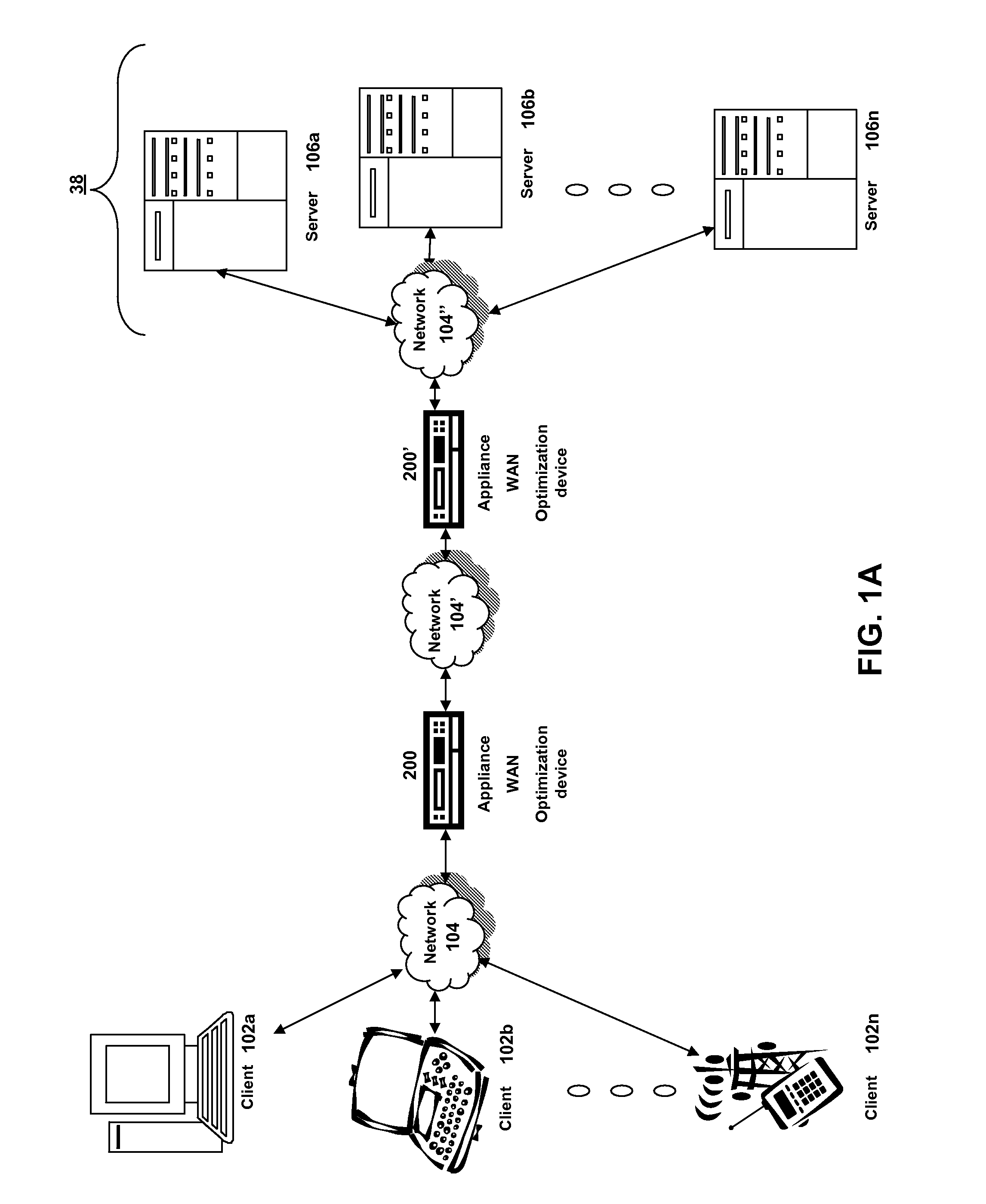
System and method of optimizing retrieval of network resources by identifying and substituting embedded symbolic host name references with network addresses in accordance with substitution policies
InactiveUS7082476B1Reduce in quantityEasy accessMultiple digital computer combinationsTransmissionCache serverNetwork addressing
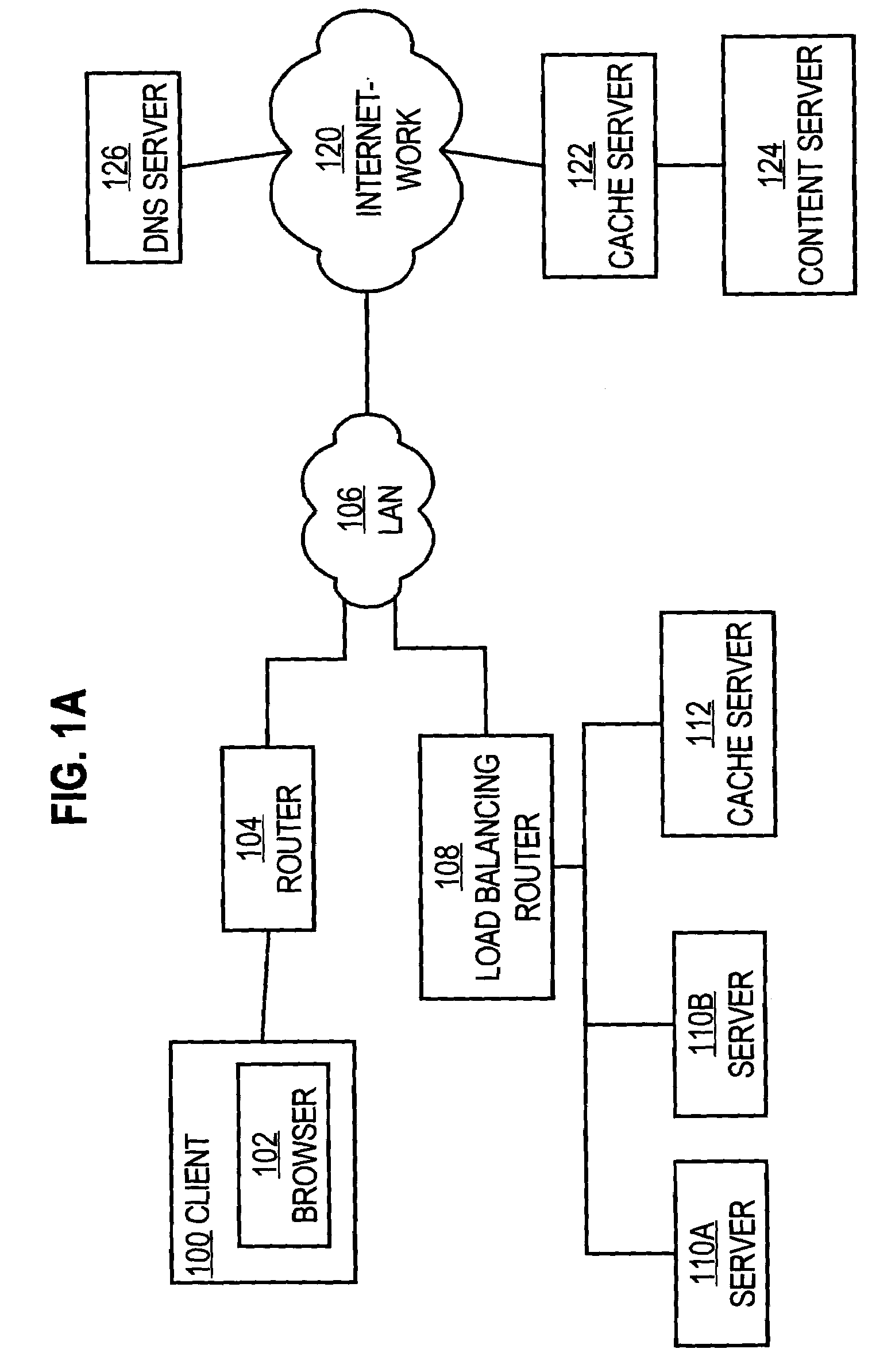
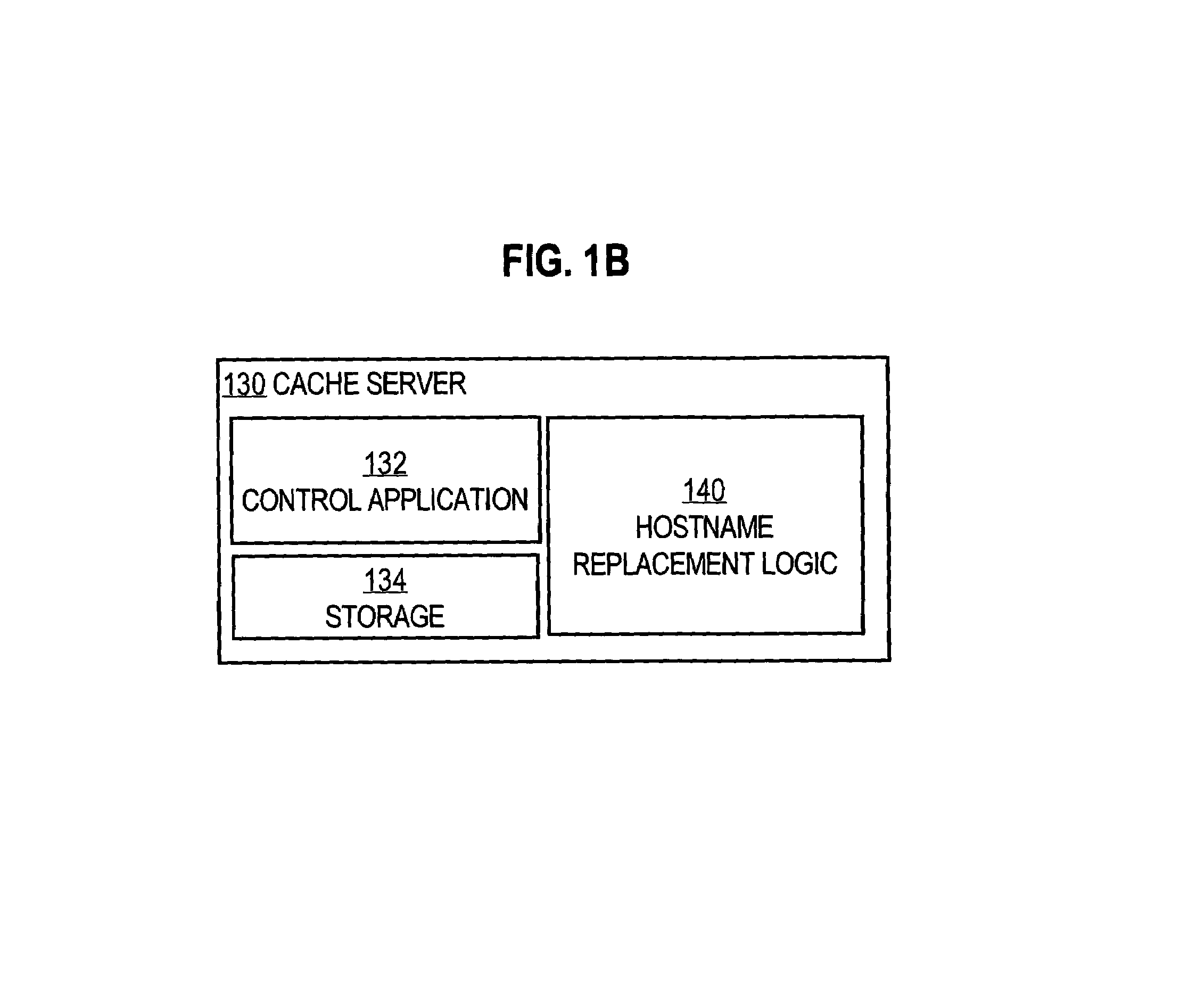
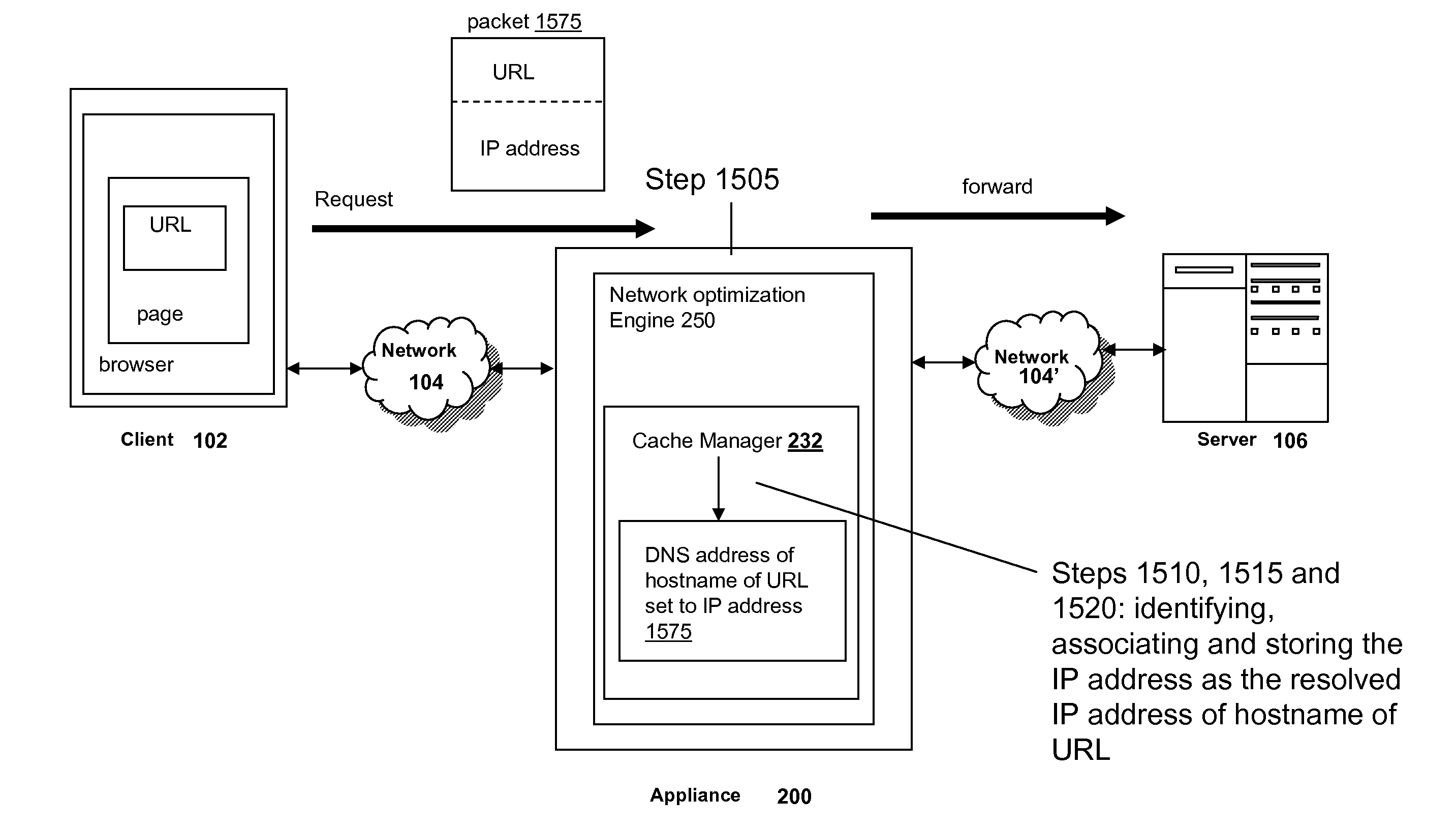
A method and apparatus are provided for optimizing retrieval of network resources. In one embodiment, a method of optimizing access to a network resource is implemented in a computer program executed by a router, cache server, or proxy server. A network resource that contains one or more embedded symbolic host name references is received. A network address corresponding to each of the embedded symbolic host name references is determined. A modified copy of the network resource is created and stored; in the modified copy, a network address is substituted for each corresponding embedded symbolic host name reference. Thereafter, the modified copy of the network resource in responding to all subsequent client requests for the network resource, thereby greatly reducing the required number of network address lookup operations. In one specific embodiment, IP addresses are determined using DNS queries for the hostname portion of all URLs that are embedded in a Web page using image, applet, object, or embed tags. The IP addresses are stored in place of the hostname portions in a modified copy of the Web page, typically in a cache. As a result, when the modified page is subsequently served to clients, the clients need not carry out DNS resolution of all the embedded URLs, resulting in reduced network message traffic and more rapid page display.
Owner:CISCO TECH INC
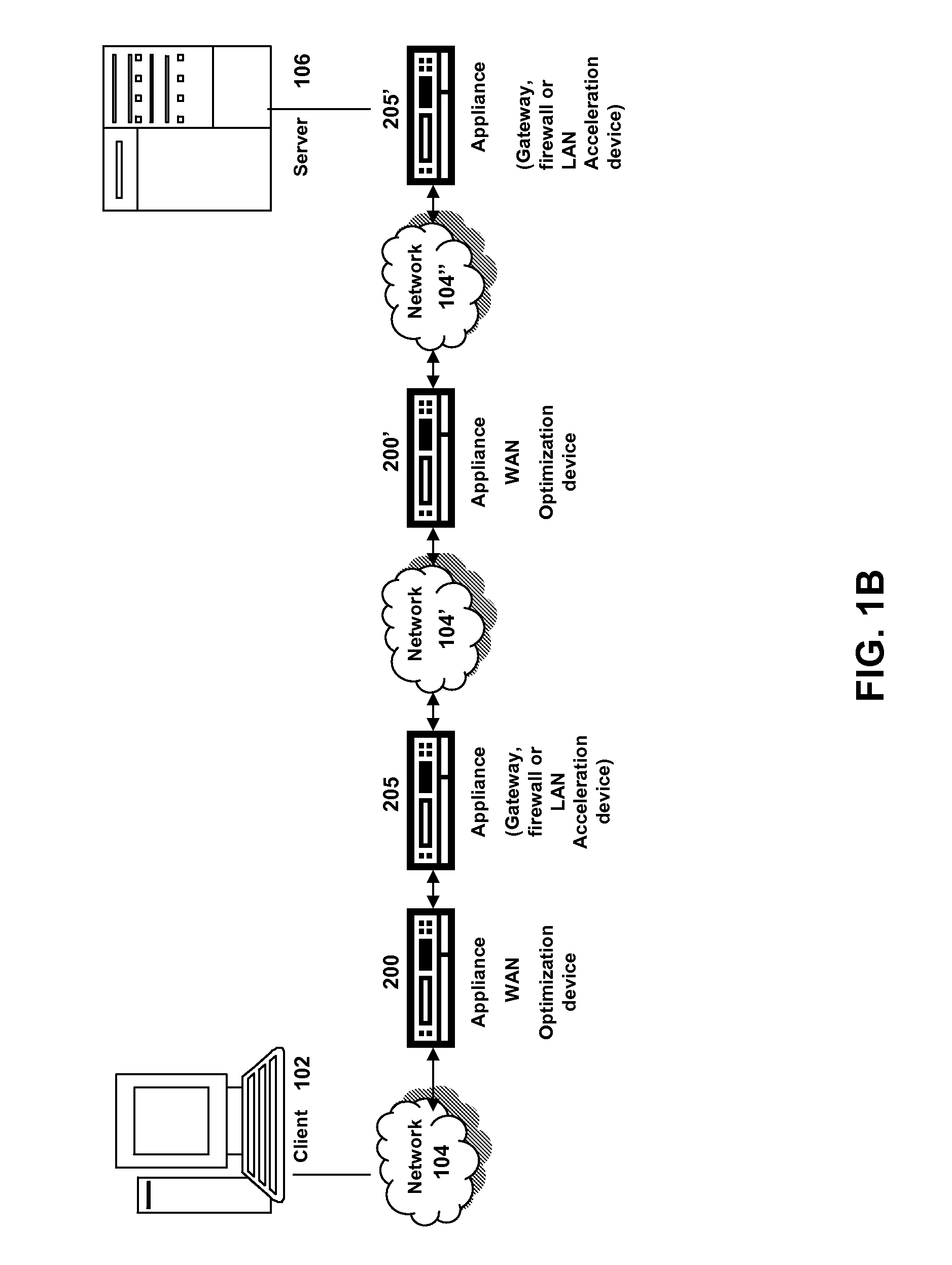
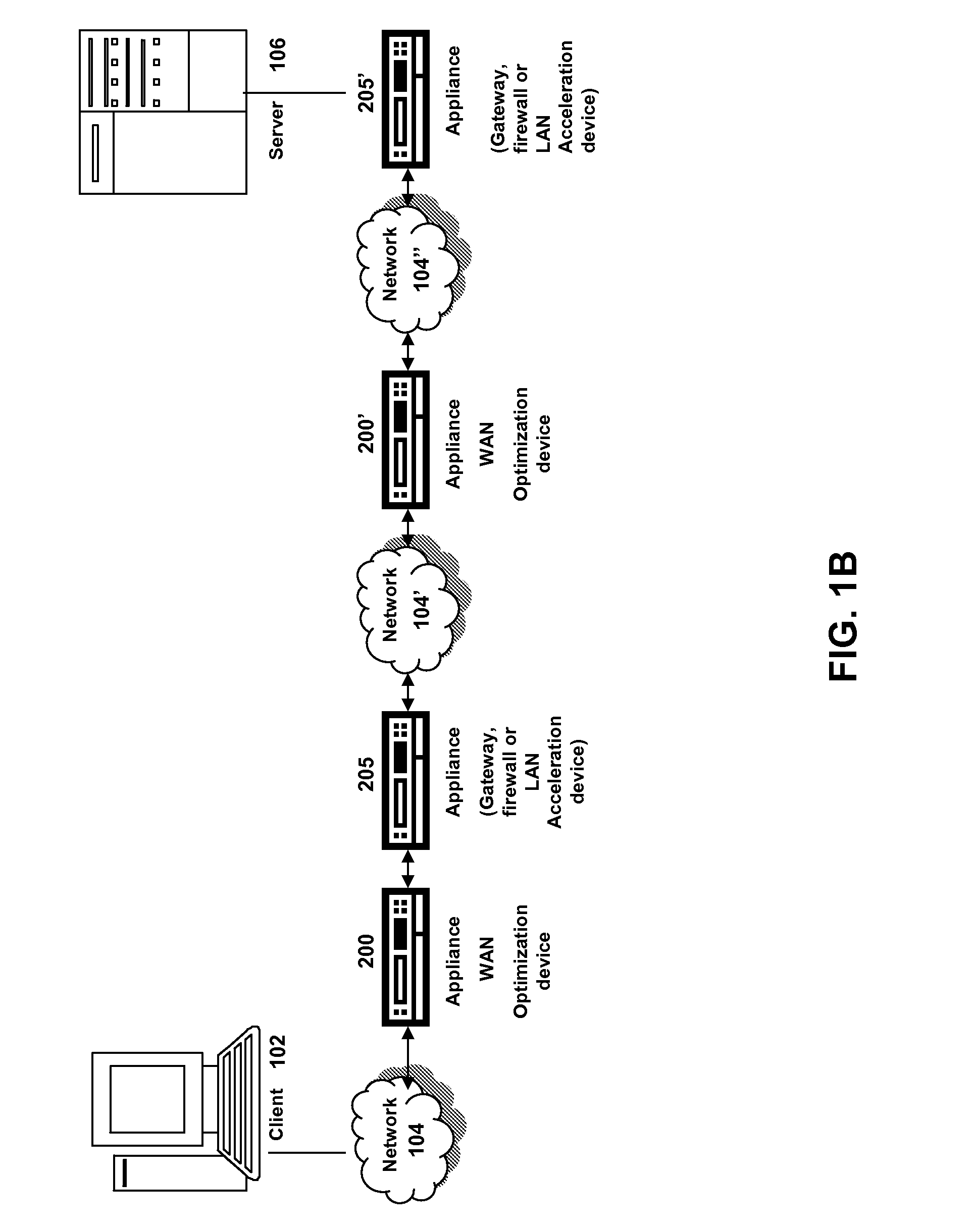
Systems and methods of using the refresh button to determine freshness policy
ActiveUS20080229025A1Improve efficiencyMore resolutionMemory architecture accessing/allocationMemory adressing/allocation/relocationClient agentDomain name
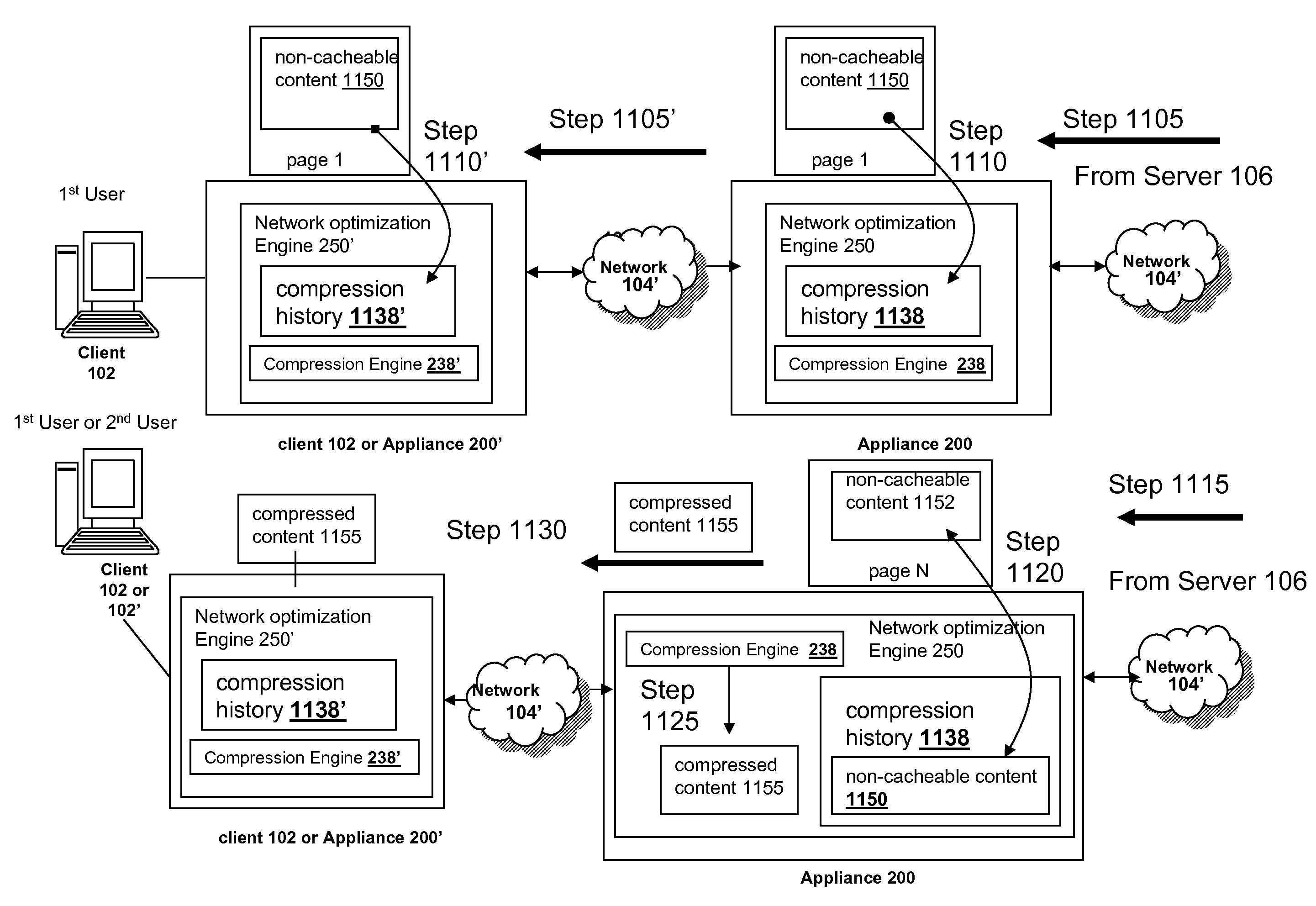
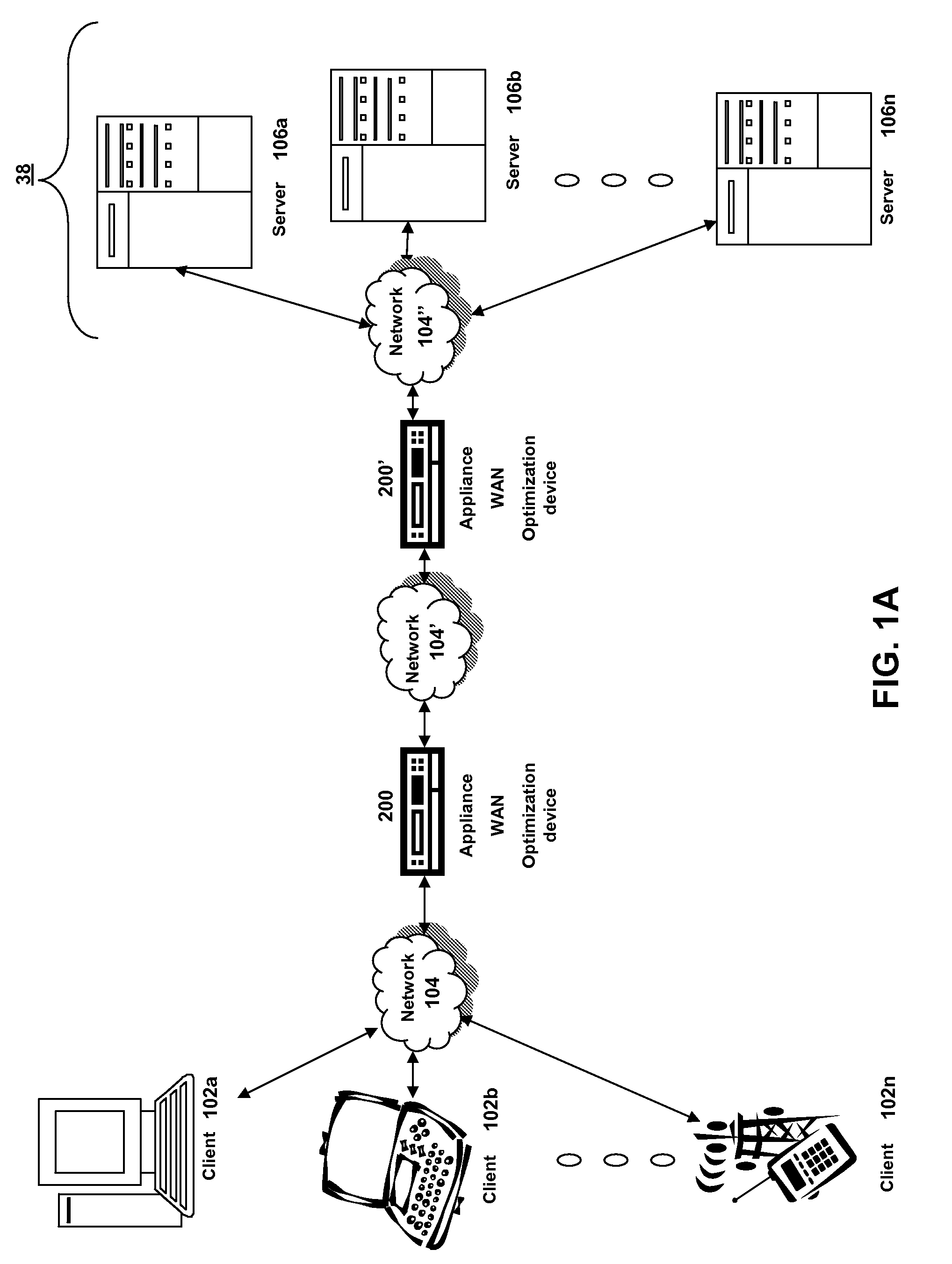
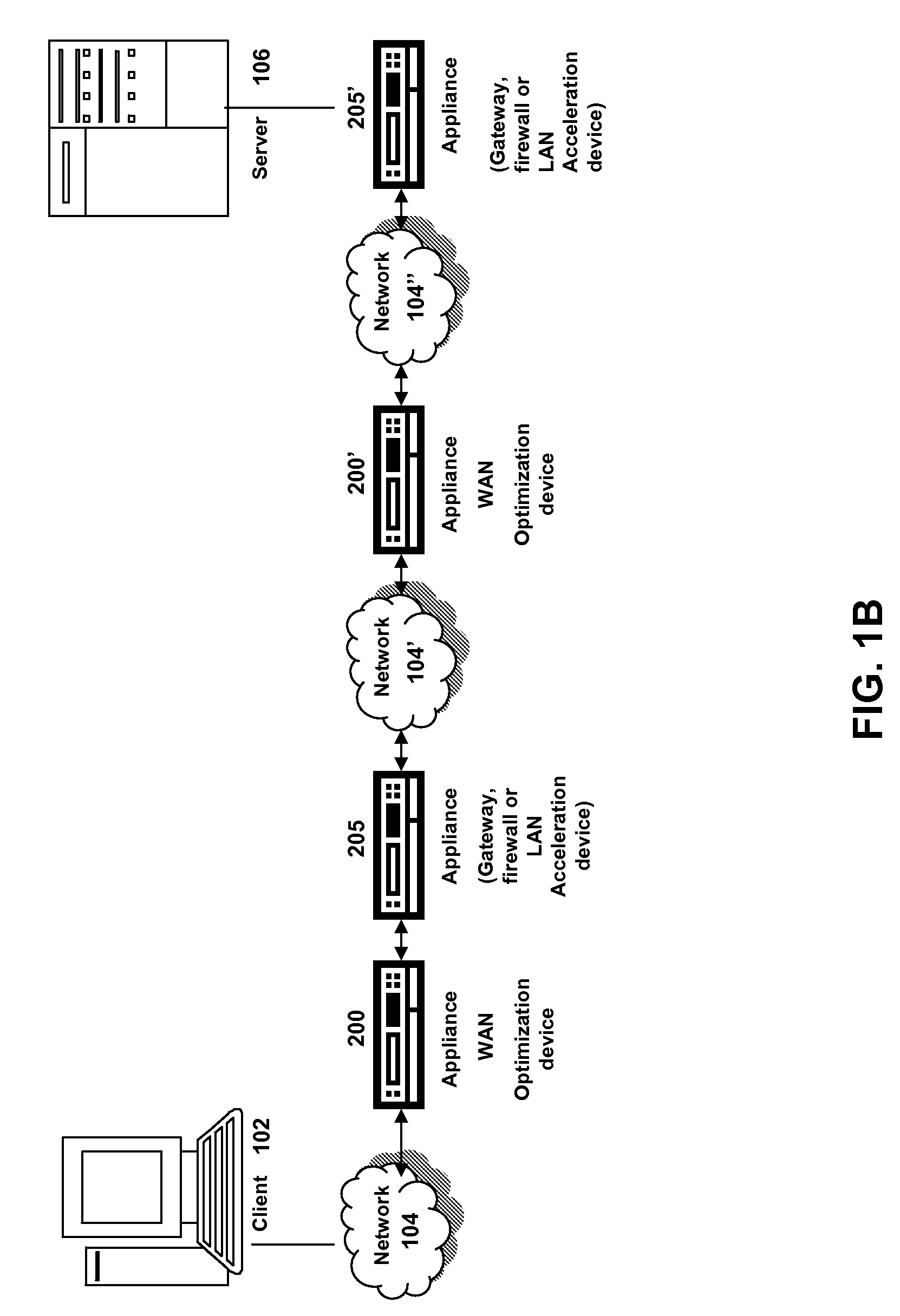
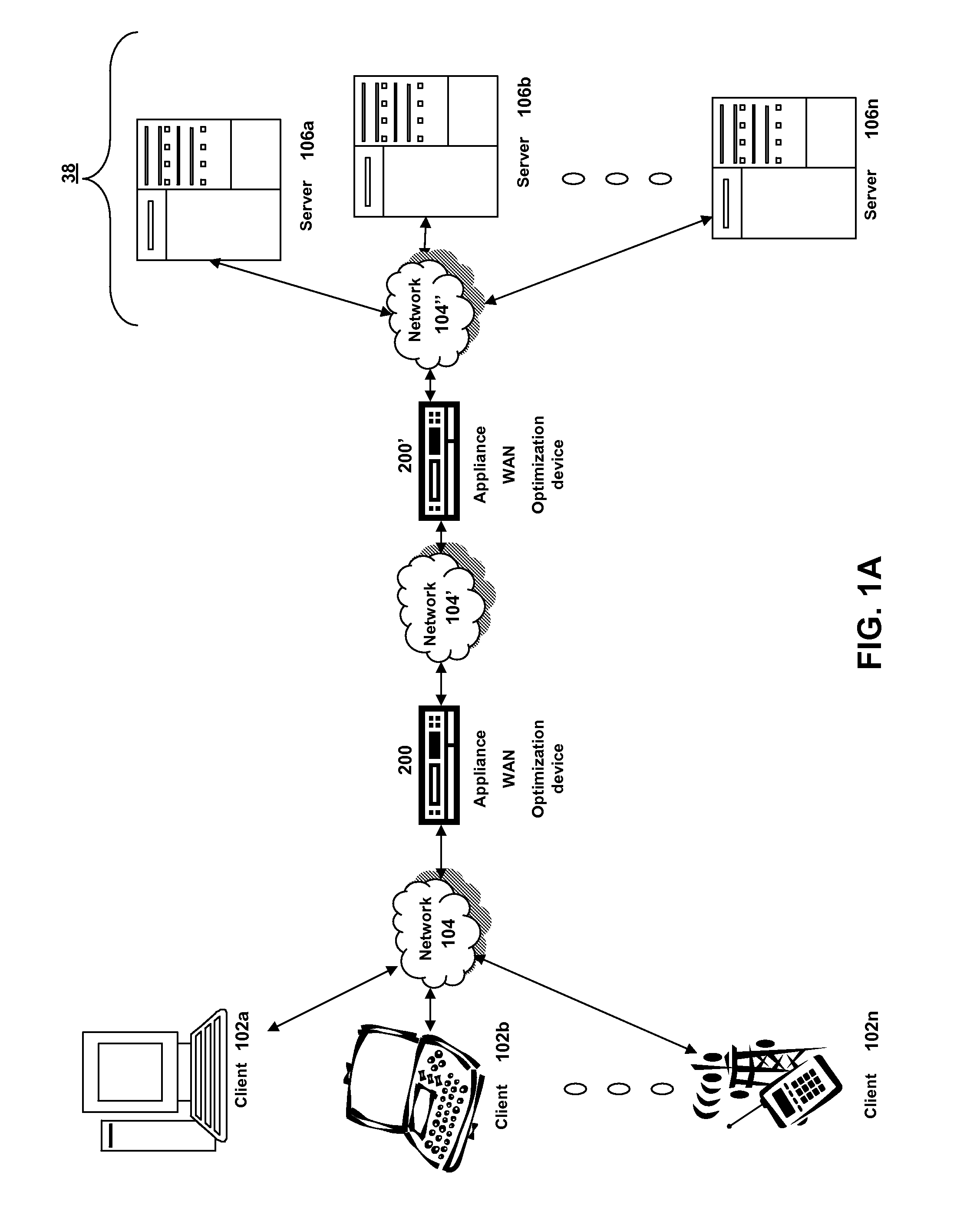
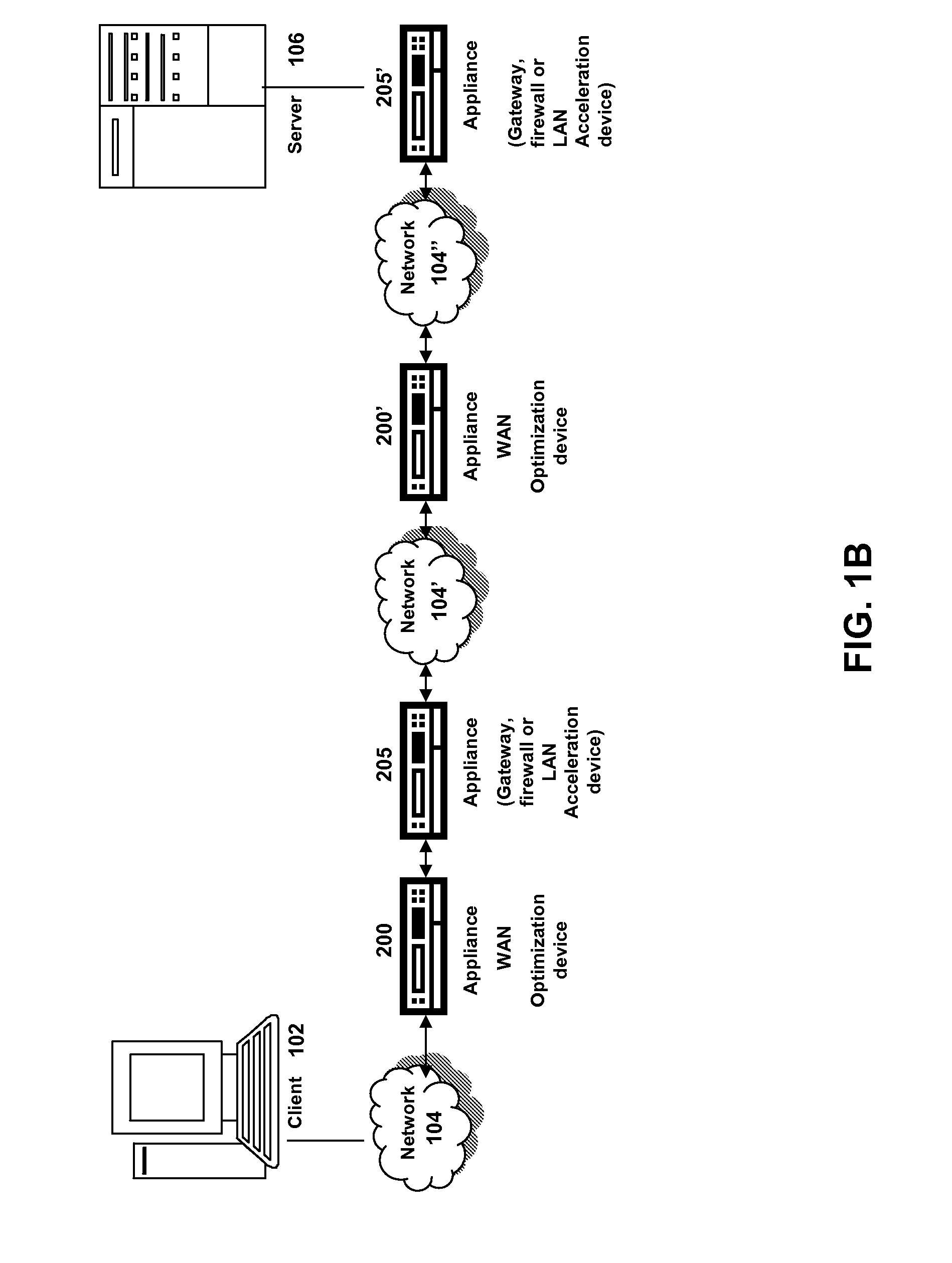
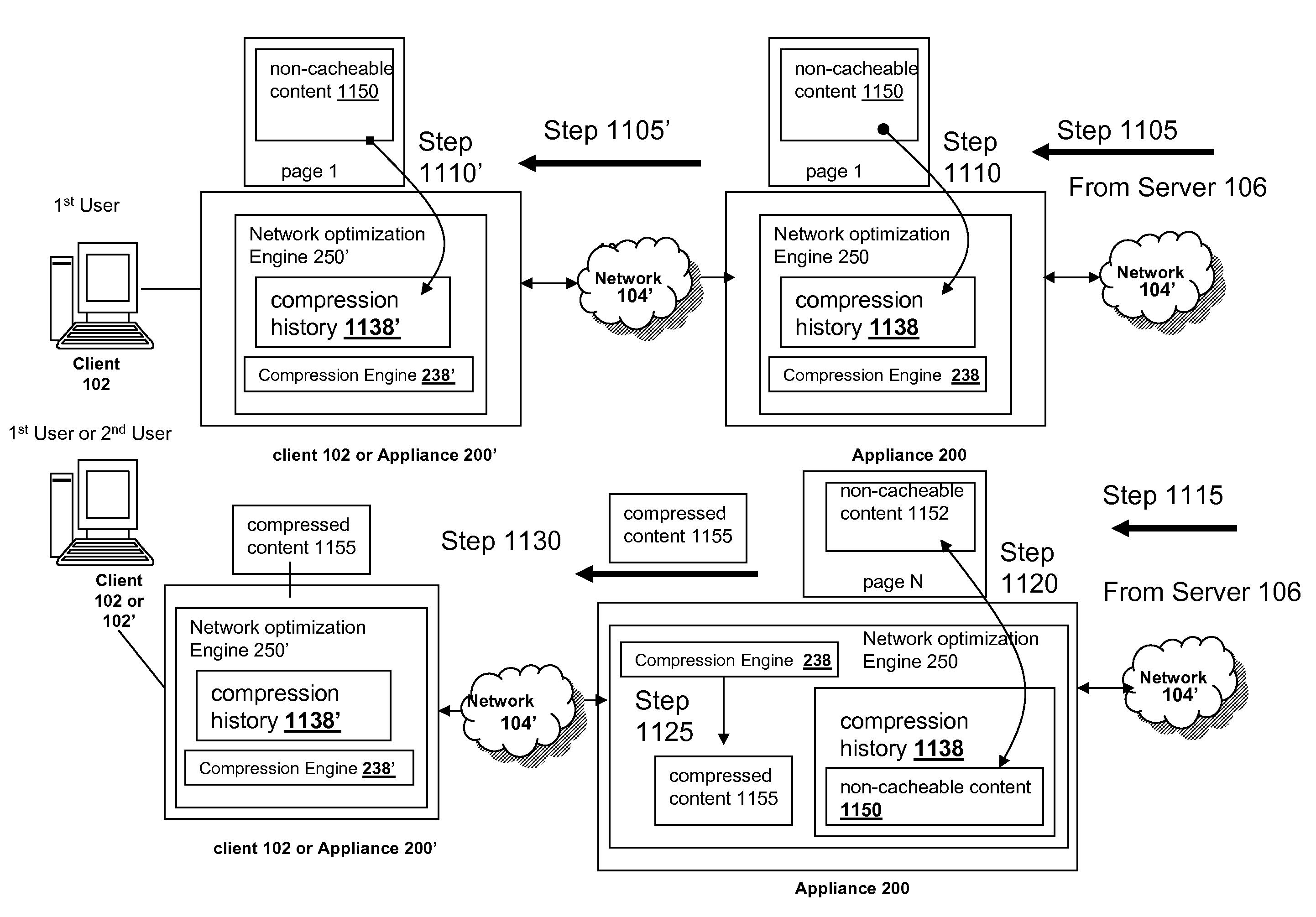
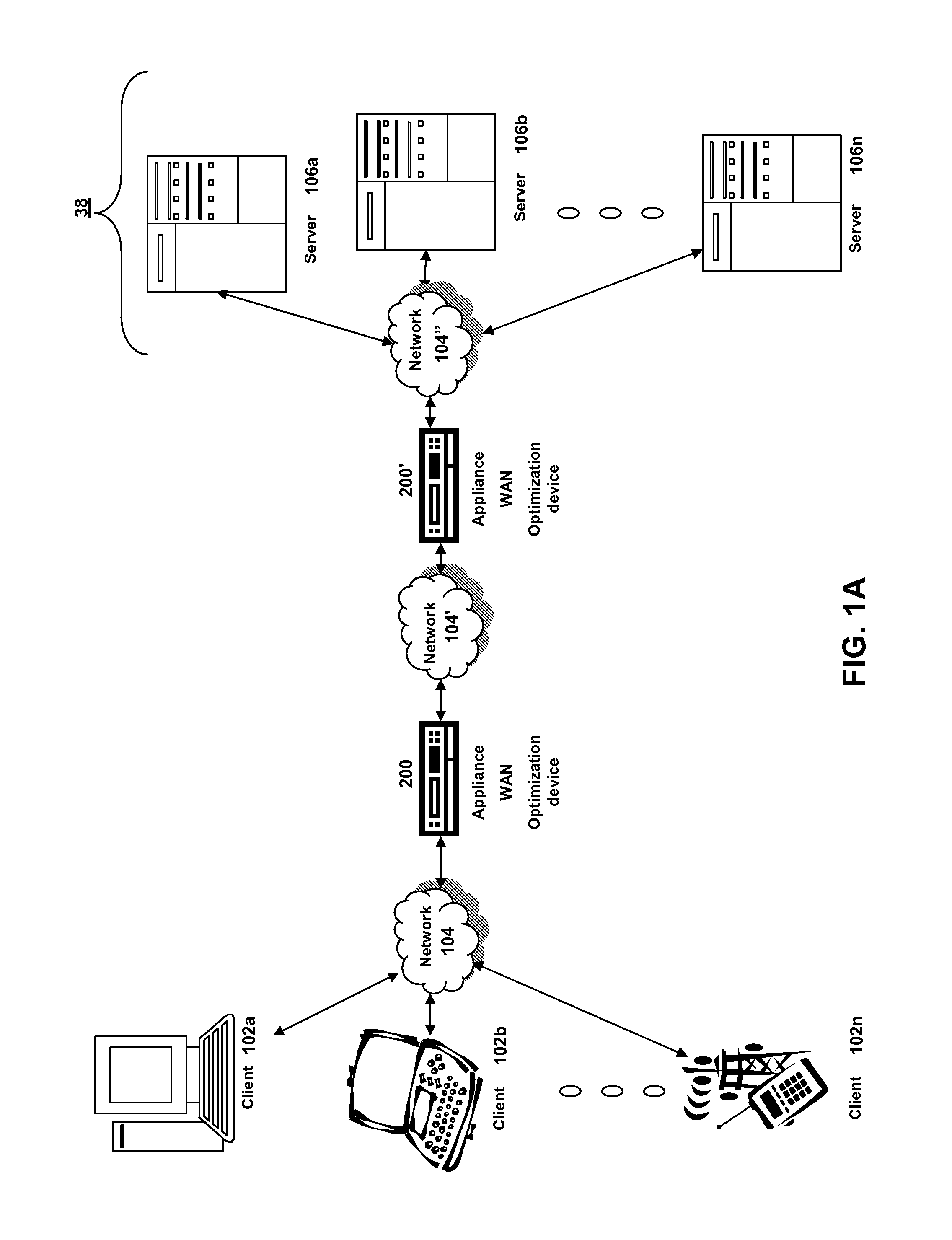
The present solution provides a variety of techniques for accelerating and optimizing network traffic, such as HTTP based network traffic. The solution described herein provides techniques in the areas of proxy caching, protocol acceleration, domain name resolution acceleration as well as compression improvements. In some cases, the present solution provides various prefetching and / or prefreshening techniques to improve intermediary or proxy caching, such as HTTP proxy caching. In other cases, the present solution provides techniques for accelerating a protocol by improving the efficiency of obtaining and servicing data from an originating server to server to clients. In another cases, the present solution accelerates domain name resolution more quickly. As every HTTP access starts with a URL that includes a hostname that must be resolved via domain name resolution into an IP address, the present solution helps accelerate HTTP access. In some cases, the present solution improves compression techniques by prefetching non-cacheable and cacheable content to use for compressing network traffic, such as HTTP. The acceleration and optimization techniques described herein may be deployed on the client as a client agent or as part of a browser, as well as on any type and form of intermediary device, such as an appliance, proxying device or any type of interception caching and / or proxying device.
Owner:CITRIX SYST INC
Discrete Mapping for Targeted Caching
Some embodiments provide systems and methods for implementing discrete mapping for targeted caching in a carrier network. In some embodiments, discrete mapping is implemented using a method that caches content from a content provider to a caching server. The method modifies a DNS entry at a particular DNS server to resolve a request that identifies either a hostname or a domain for the content provider to an address of the caching server so that the requested content is passed from the cached content of the caching server and not the source content provider. In some embodiments, the particular DNS server is a recursive DNS server, a local DNS server of the carrier network, or a DNS server that is not authoritative for the hostname or domain of the content provider.
Owner:EDGIO INC
Using virtual domain name service (DNS) zones for enterprise content delivery
InactiveUS20090119397A1Easy to integrateMinimal reconfigurationMultiple digital computer combinationsResourcesDomain nameThird party
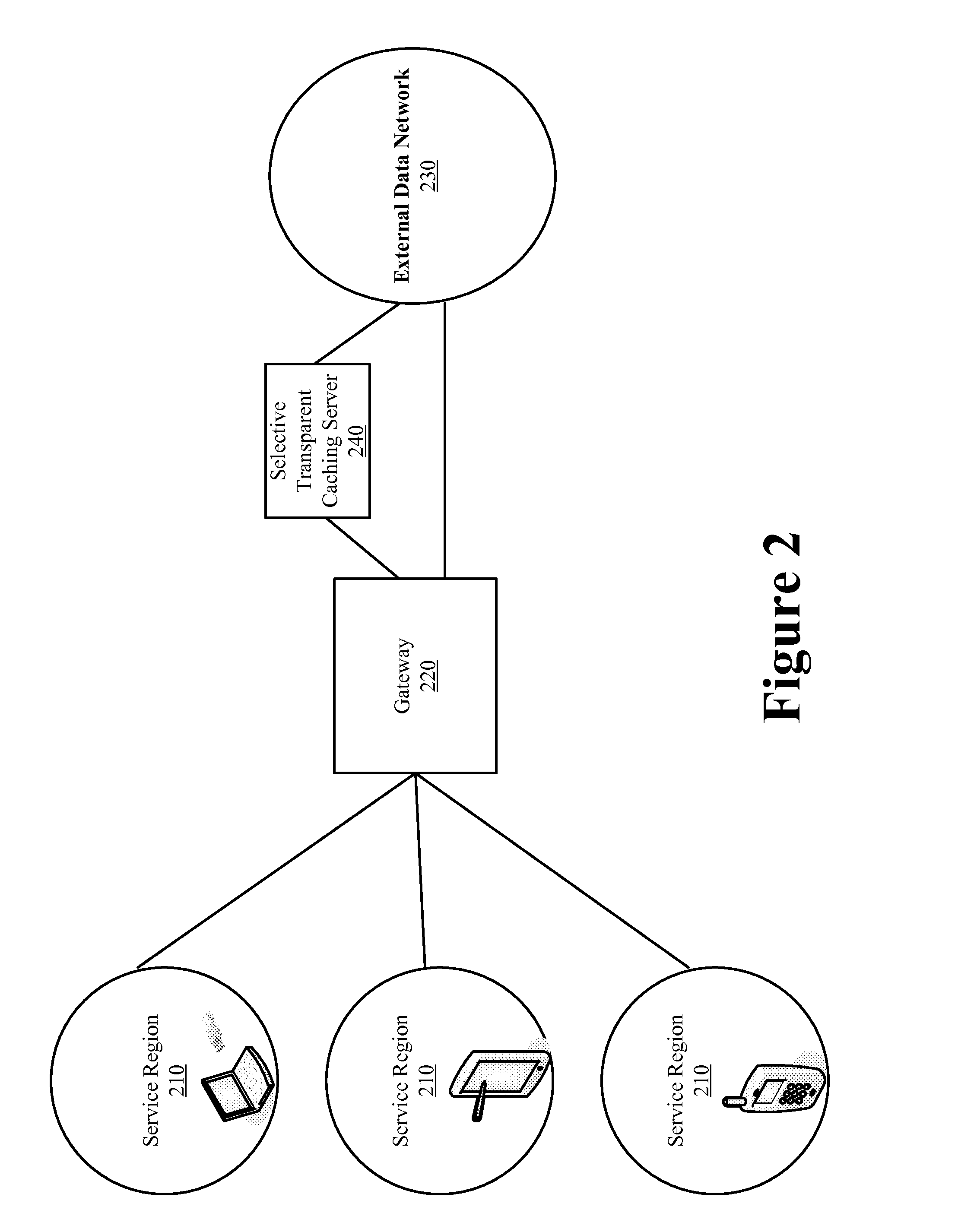
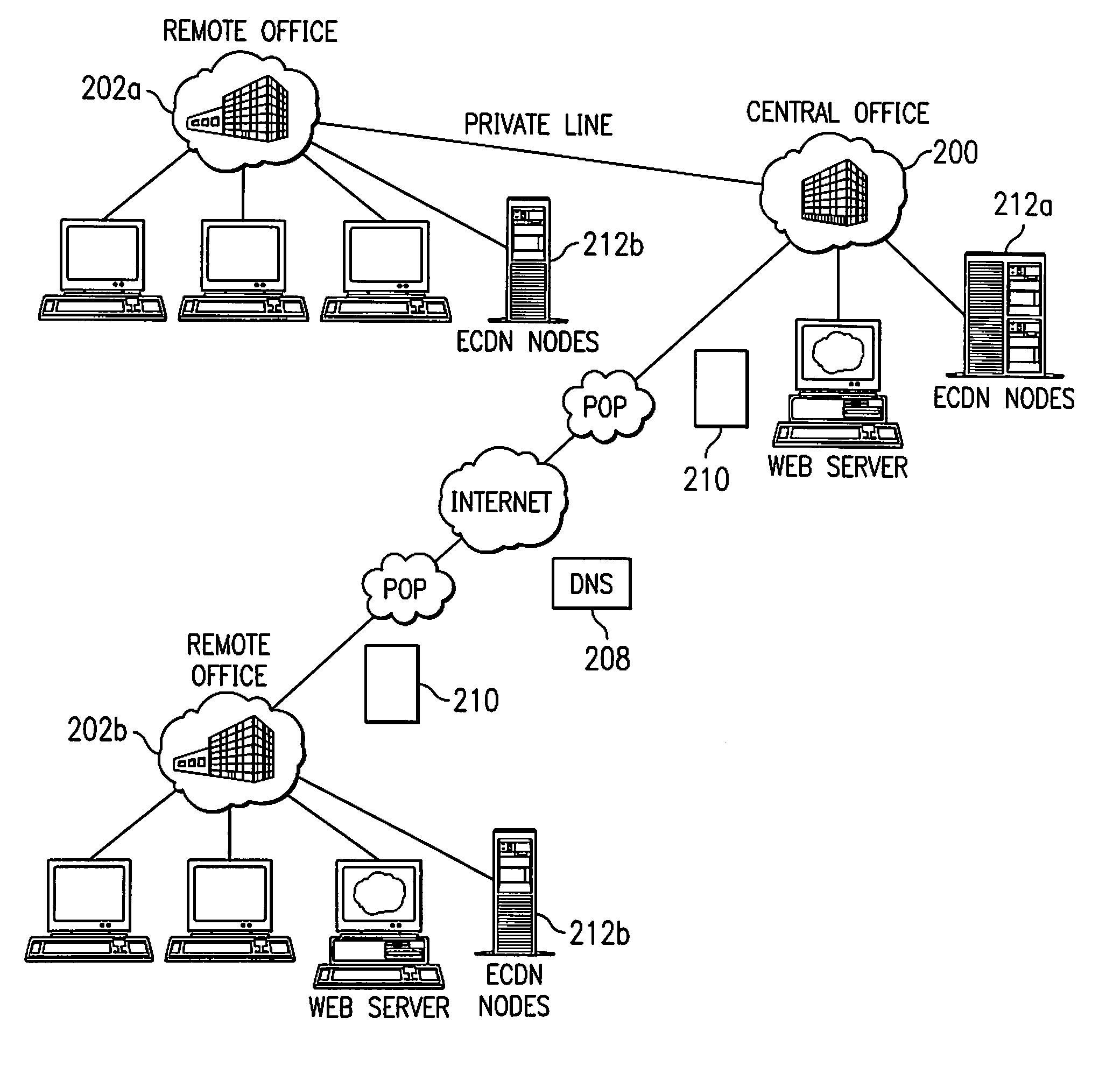
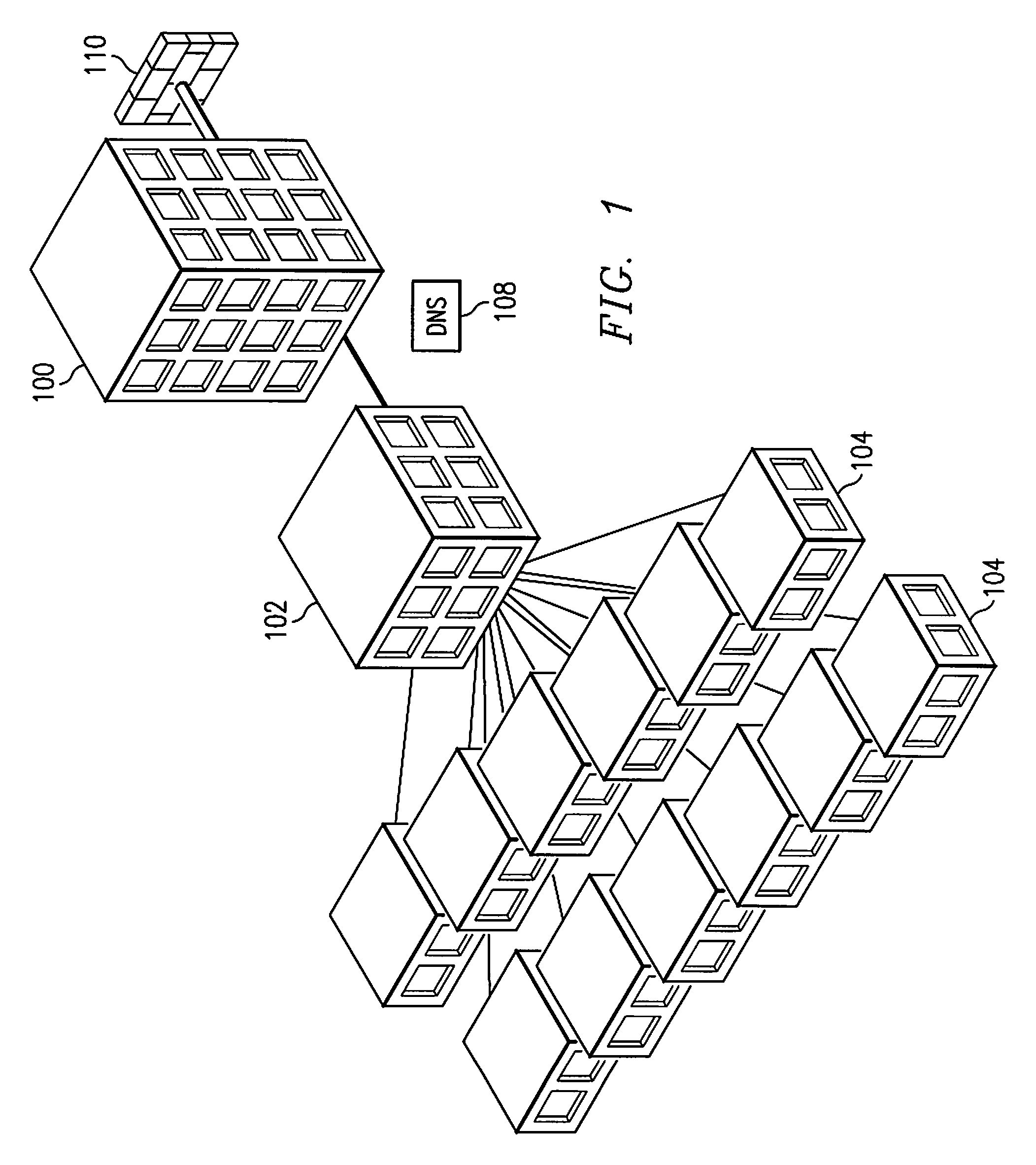
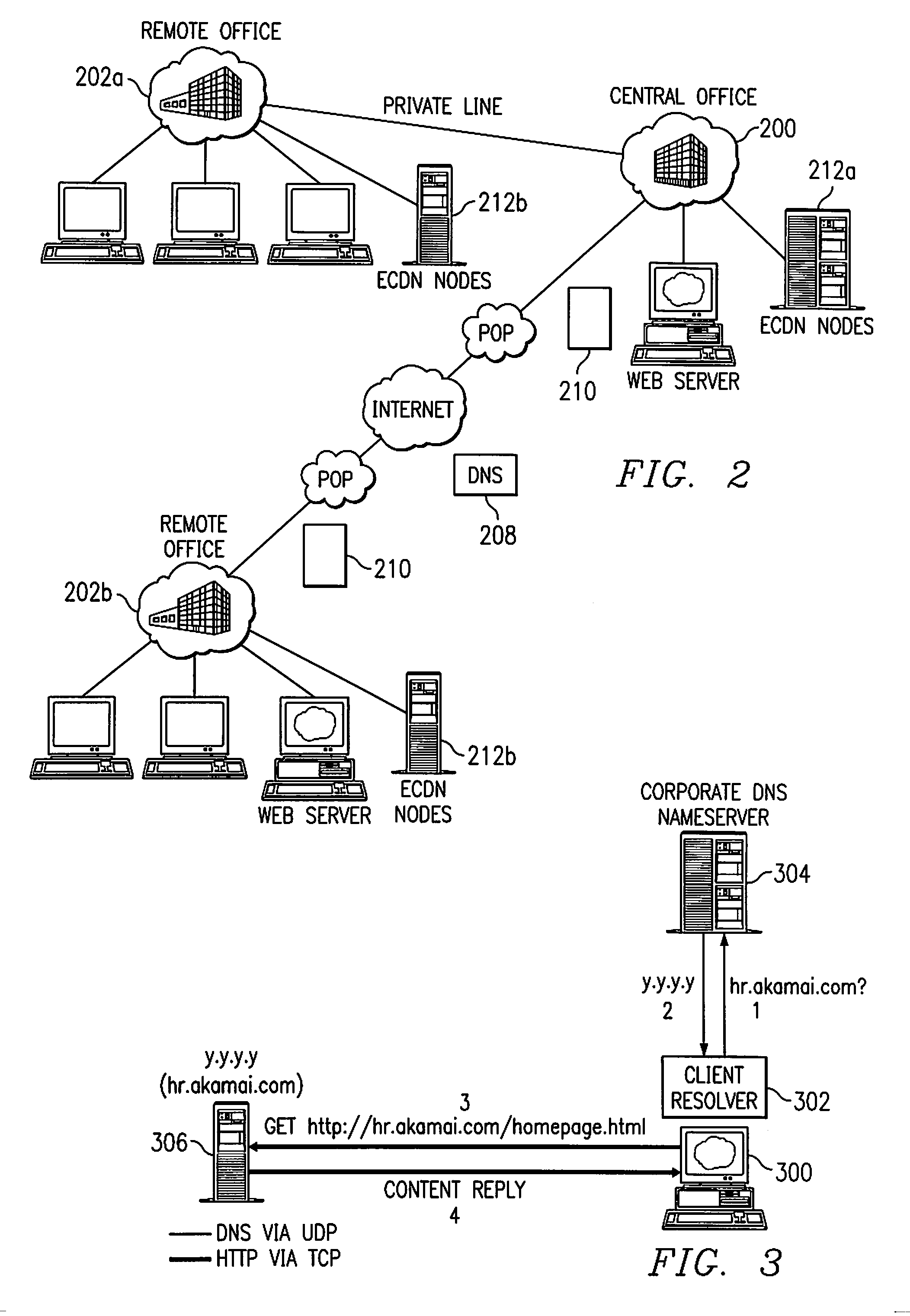
A domain to be published to an enterprise ECDN is associated (either by static configuration or dynamically) with a set of one or more enterprise zones configurable in a hierarchy. When a DNS query arrives for a hostname known to be associated with given content within the control of the ECDN, a DNS server preferably responds in one of three (3) ways: (a) handing back an IP address, e.g., for an ECDN intelligent node that knows how to obtain the requested content from a surrogate or origin server; (b) executing a zone referral to a next (lower) level name server in a zone hierarchy, or (c) CNAMing to another hostname, thereby essentially restarting the lookup procedure. In the latter case, this new CNAME causes the resolution process to start back at the root and resolve a new path, probably along a different path in the hierarchy. At any particular level in the zone hierarchy, preferably there is an associated zone server. That server preferably executes logic that applies the requested hostname against a map, which, using known techniques, may be generated from given (static, dynamic, internally-generated or third party-sourced) performance metrics. Thus, a given name query to ECDN-managed content may be serviced in coordination with various sources of distributed network intelligence. As a result, the invention provides for a distributed, dynamic globally load balanced name service.
Owner:AKAMAI TECH INC
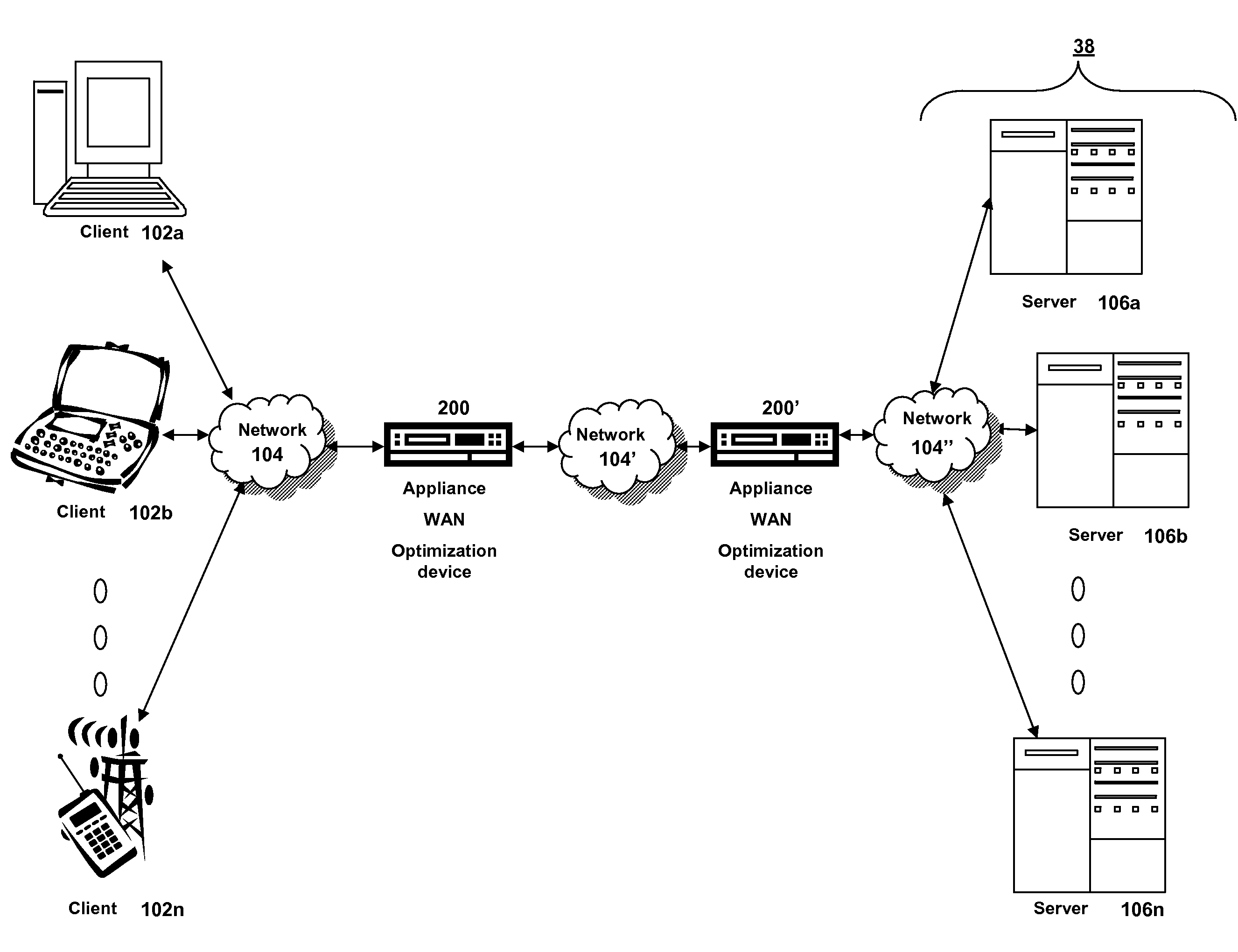
Systems and methods for prefetching objects for caching using QOS
ActiveUS7584294B2Improve efficiencyImprove intermediary or proxy cachingMultiple digital computer combinationsData switching networksClient agentTraffic capacity
The present solution provides a variety of techniques for accelerating and optimizing network traffic, such as HTTP based network traffic. The solution described herein provides techniques in the areas of proxy caching, protocol acceleration, domain name resolution acceleration as well as compression improvements. In some cases, the present solution provides various prefetching and / or prefreshening techniques to improve intermediary or proxy caching, such as HTTP proxy caching. In other cases, the present solution provides techniques for accelerating a protocol by improving the efficiency of obtaining and servicing data from an originating server to server to clients. In another cases, the present solution accelerates domain name resolution more quickly. As every HTTP access starts with a URL that includes a hostname that must be resolved via domain name resolution into an IP address, the present solution helps accelerate HTTP access. In some cases, the present solution improves compression techniques by prefetching non-cacheable and cacheable content to use for compressing network traffic, such as HTTP. The acceleration and optimization techniques described herein may be deployed on the client as a client agent or as part of a browser, as well as on any type and form of intermediary device, such as an appliance, proxying device or any type of interception caching and / or proxying device.
Owner:CITRIX SYST INC
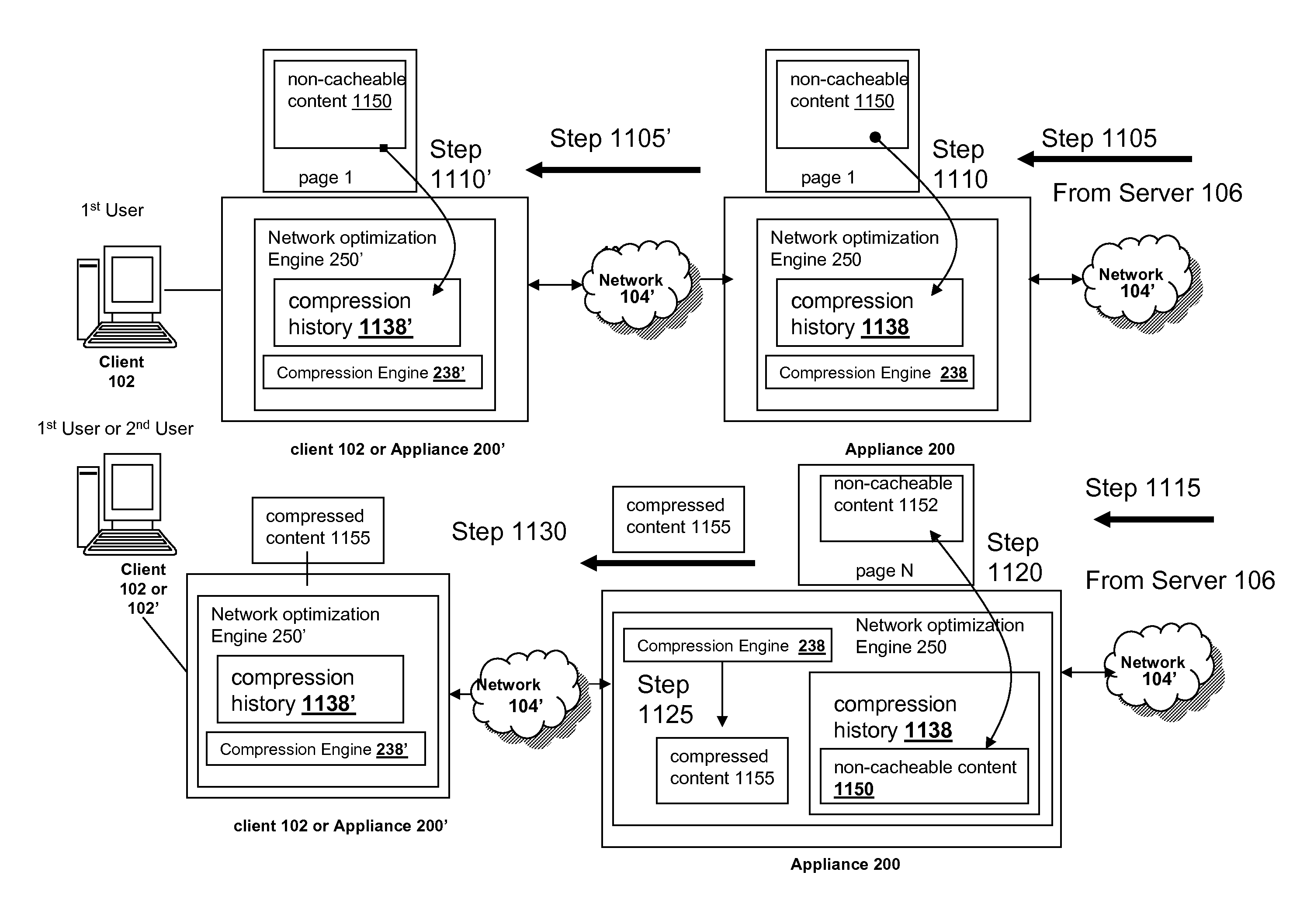
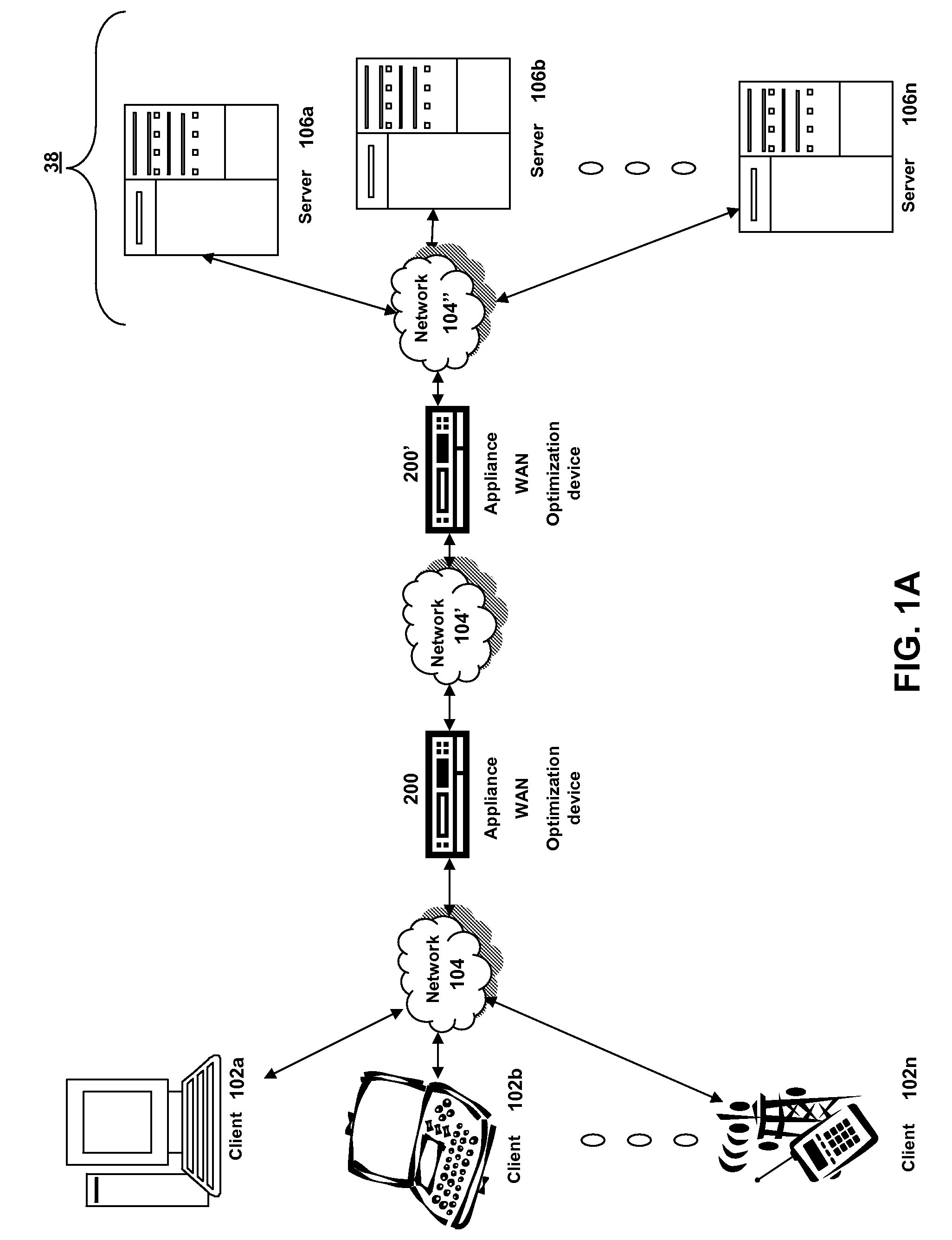
Systems and methods for prefetching non-cacheable content for compression history
InactiveUS20080228864A1Improve efficiencyMore resolutionDigital data information retrievalMultiple digital computer combinationsDomain nameClient agent
The present solution provides a variety of techniques for accelerating and optimizing network traffic, such as HTTP based network traffic. The solution described herein provides techniques in the areas of proxy caching, protocol acceleration, domain name resolution acceleration as well as compression improvements. In some cases, the present solution provides various prefetching and / or prefreshening techniques to improve intermediary or proxy caching, such as HTTP proxy caching. In other cases, the present solution provides techniques for accelerating a protocol by improving the efficiency of obtaining and servicing data from an originating server to server to clients. In another cases, the present solution accelerates domain name resolution more quickly. As every HTTP access starts with a URL that includes a hostname that must be resolved via domain name resolution into an IP address, the present solution helps accelerate HTTP access. In some cases, the present solution improves compression techniques by prefetching non-cacheable and cacheable content to use for compressing network traffic, such as HTTP. The acceleration and optimization techniques described herein may be deployed on the client as a client agent or as part of a browser, as well as on any type and form of intermediary device, such as an appliance, proxying device or any type of interception caching and / or proxying device.
Owner:CITRIX SYST INC
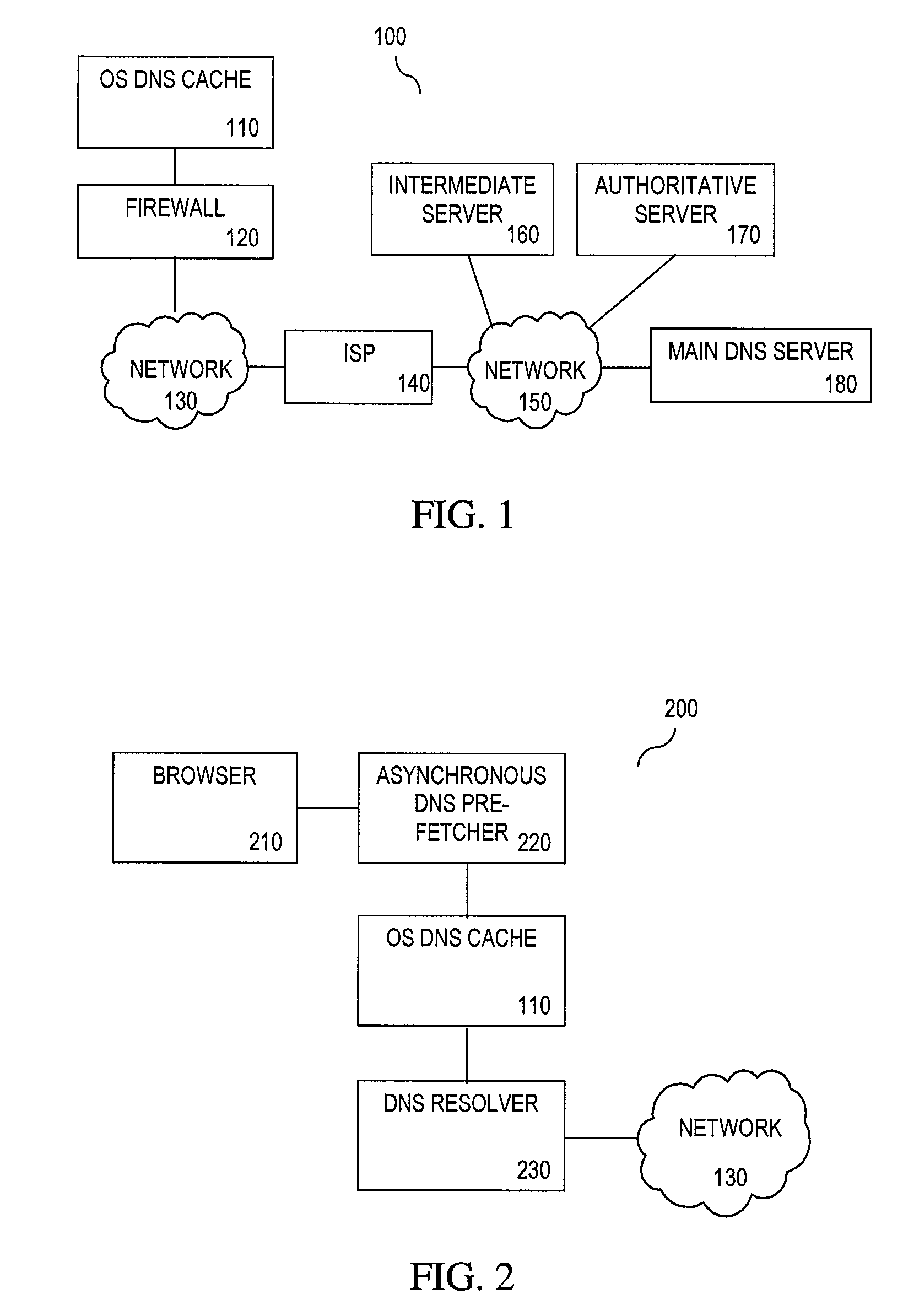
Parallel, Side-Effect Based DNS Pre-Caching
ActiveUS20100049872A1Digital data information retrievalMultiple digital computer combinationsDomain nameUniform resource locator
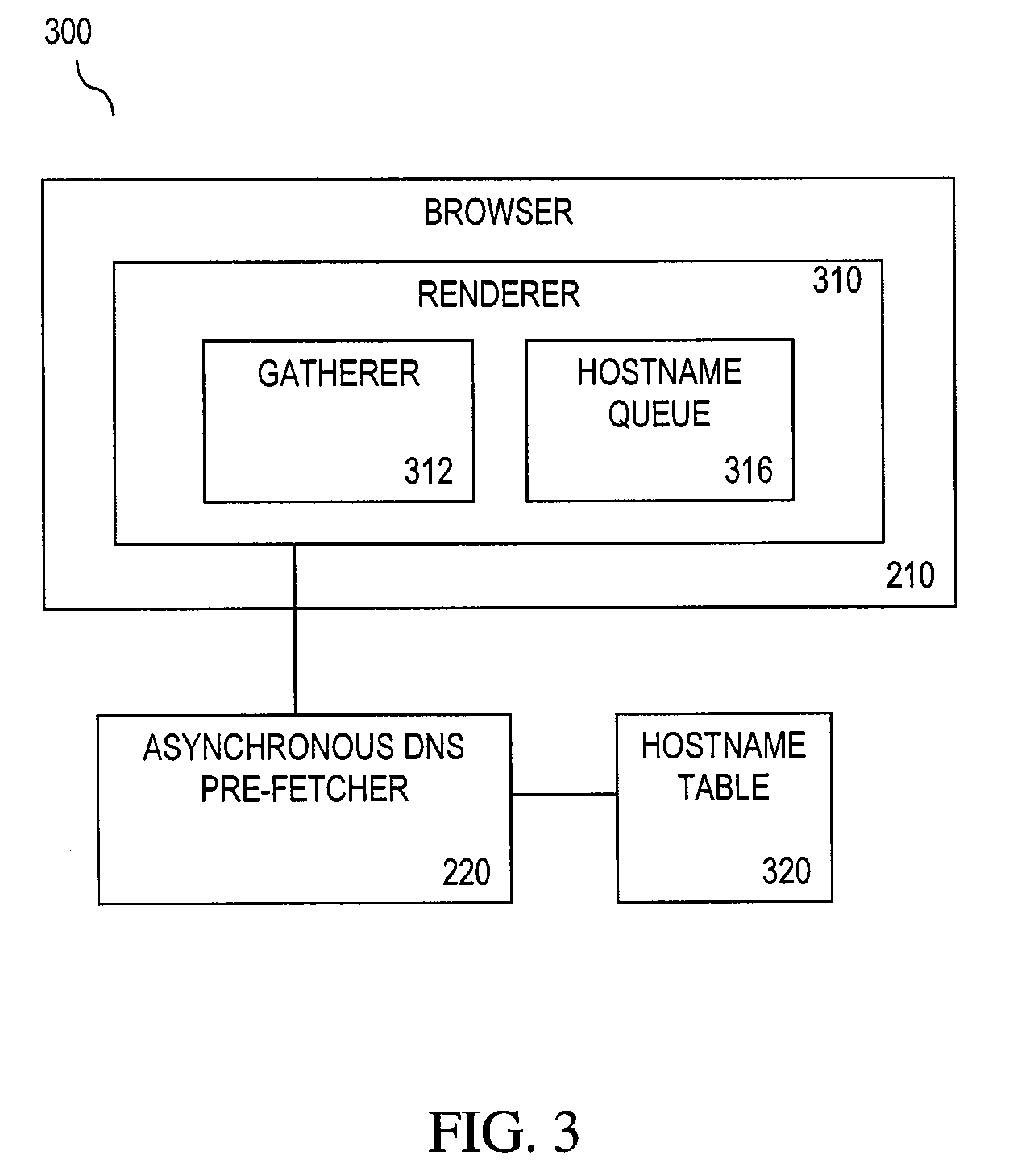
Embodiments of the present invention include methods and systems for domain name system (DNS) pre-caching. A method for DNS pre-caching is provided. The method includes receiving uniform resource locator (URL) hostnames for DNS pre-fetch resolution prior to a user hostname request for any of the URL hostnames. The method also includes making a DNS lookup call for at least one of the URL hostnames that are not cached by a DNS cache prior to the user hostname request. The method further includes discarding at least one IP address provided by a DNS resolver for the URL hostnames, wherein a resolution result for at least one of the URL hostnames is cached in the DNS cache in preparation for the user hostname request. A system for DNS pre-caching is provided. The system includes a renderer, an asynchronous DNS pre-fetcher and a hostname table.
Owner:GOOGLE LLC
Systems and methods for domain name resolution interception caching
ActiveUS20100088398A1Improve efficiencyImprove intermediary or proxy cachingMultiple digital computer combinationsTransmissionTraffic capacityDomain name
The present solution provides a variety of techniques for accelerating and optimizing network traffic, such as HTTP based network traffic. The solution described herein provides techniques in the areas of proxy caching, protocol acceleration, domain name resolution acceleration as well as compression improvements. In some cases, the present solution provides various prefetching and / or prefreshening techniques to improve intermediary or proxy caching, such as HTTP proxy caching. In other cases, the present solution provides techniques for accelerating a protocol by improving the efficiency of obtaining and servicing data from an originating server to server to clients. In another cases, the present solution accelerates domain name resolution more quickly. As every HTTP access starts with a URL that includes a hostname that must be resolved via domain name resolution into an IP address, the present solution helps accelerate HTTP access. In some cases, the present solution improves compression techniques by prefetching non-cacheable and cacheable content to use for compressing network traffic, such as HTTP. The acceleration and optimization techniques described herein may be deployed on the client as a client agent or as part of a browser, as well as on any type and form of intermediary device, such as an appliance, proxying device or any type of interception caching and / or proxying device.
Owner:CITRIX SYST INC
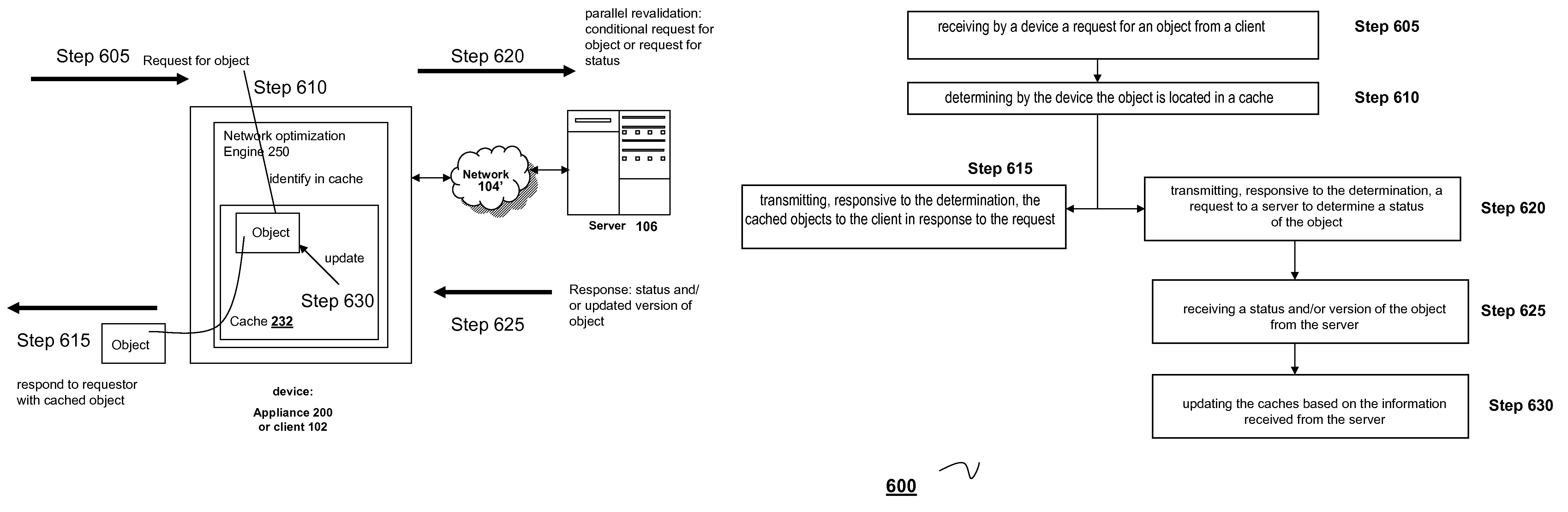
Systems and methods of revalidating cached objects in parallel with request for object
ActiveUS7783757B2Improve efficiencyImprove intermediary or proxy cachingMultiple digital computer combinationsTransmissionDomain nameClient agent
Owner:CITRIX SYST INC
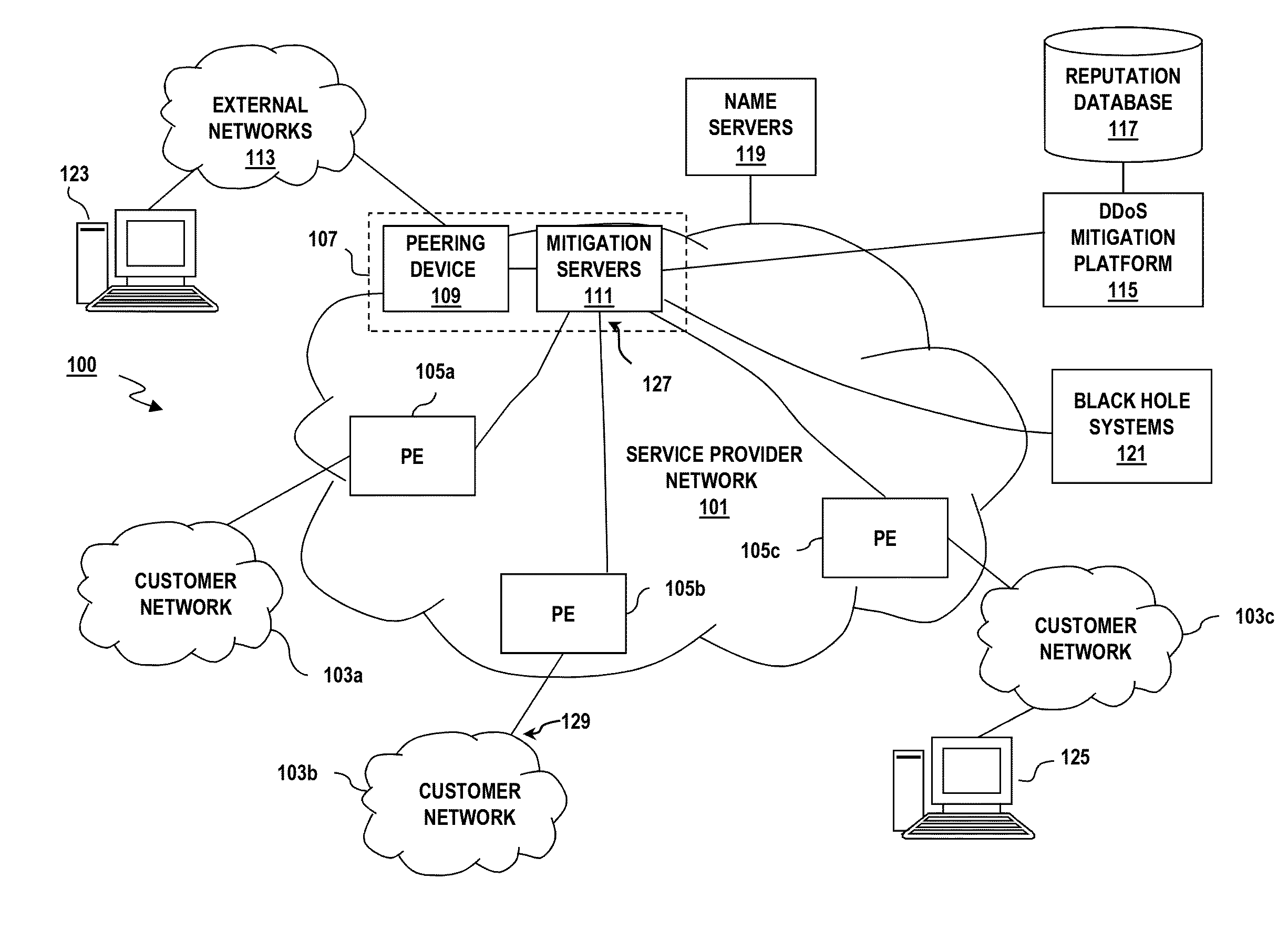
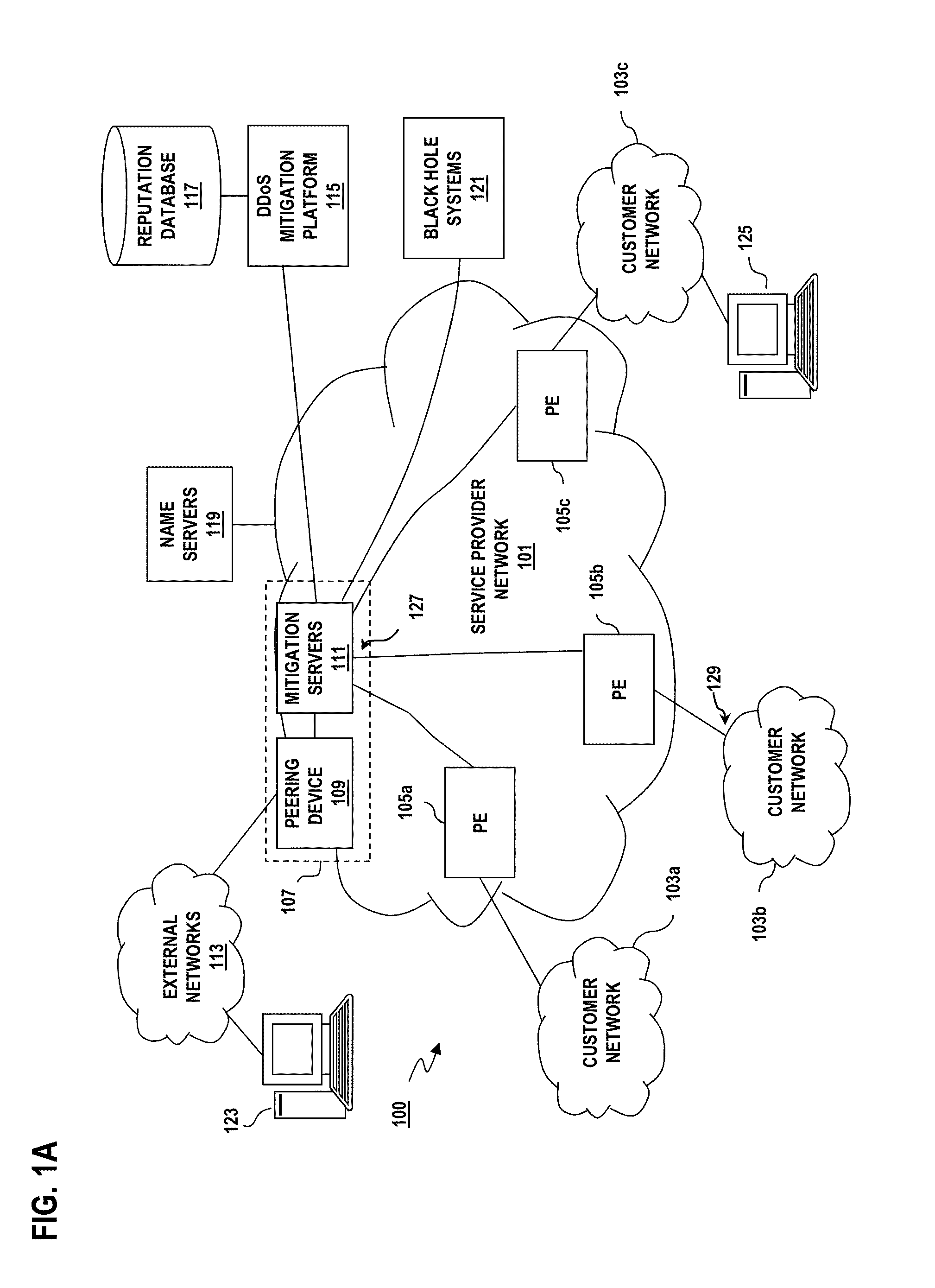
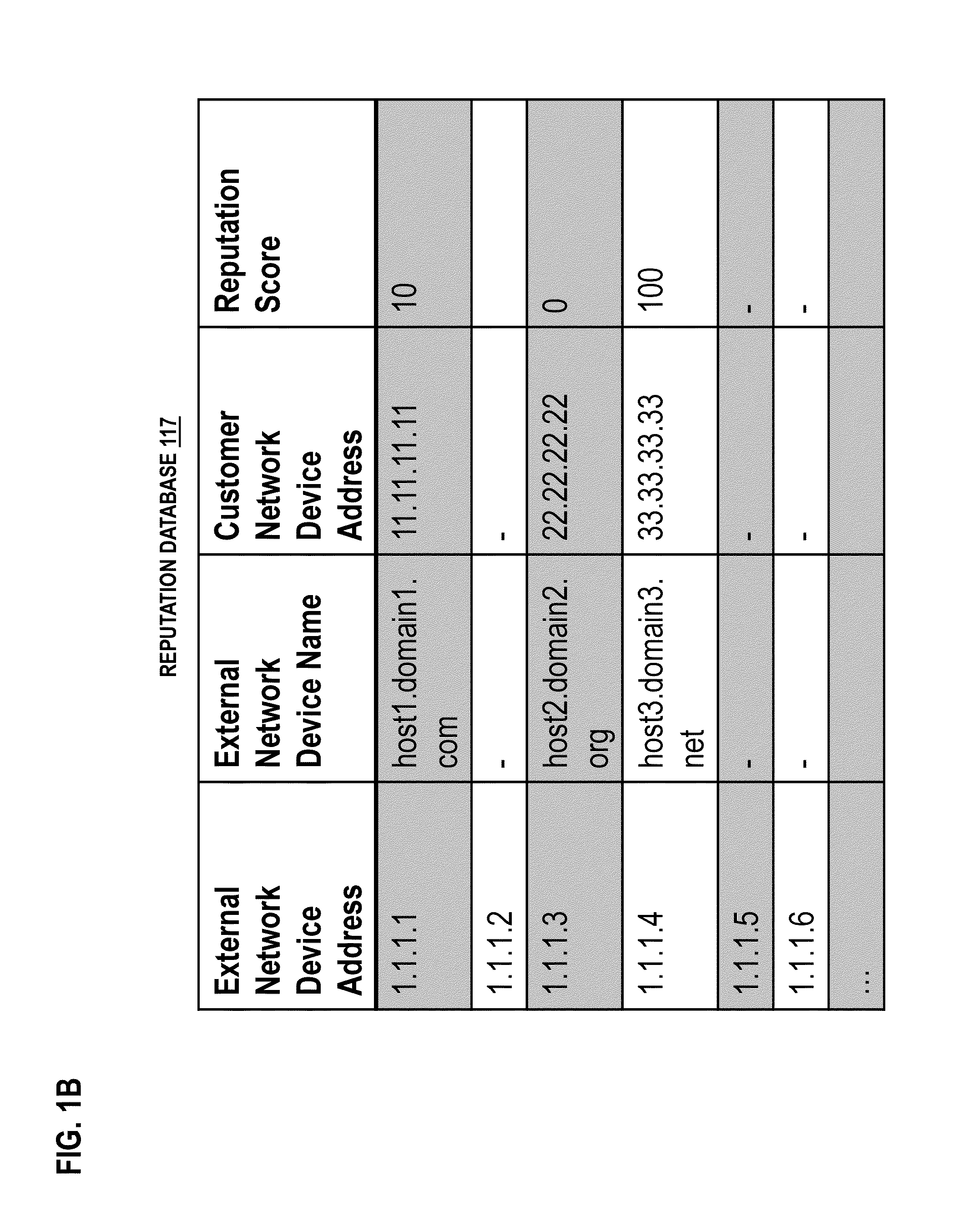
Method and apparatus for mitigating distributed denial of service attacks
ActiveUS20150058976A1Memory loss protectionError detection/correctionNetwork addressingDistributed computing
An approach for mitigating distributed denial of service (DDoS) attacks includes assigning a set of temporary network addresses to a hostname for a finite period and assigning one or more other sets of temporary network addresses to the hostname in one or more following finite periods, responding to a hostname lookup request based on the set of temporary network addresses, the one or more other sets of temporary network addresses, or a combination thereof that are active, responding to a network address lookup request based on at least one of the set of temporary network addresses and the one or more other sets of temporary network addresses that is associated with a current one of the finite period or the one or more following finite periods, and retiring the set of temporary network addresses, the one or more sets of temporary network addresses, or a combination thereof after a configurable number of finite periods, wherein no further network address or hostname lookup request is served based on the retired set of temporary network addresses, the retired one or more sets of temporary network addresses, or a combination thereof.
Owner:VERIZON PATENT & LICENSING INC
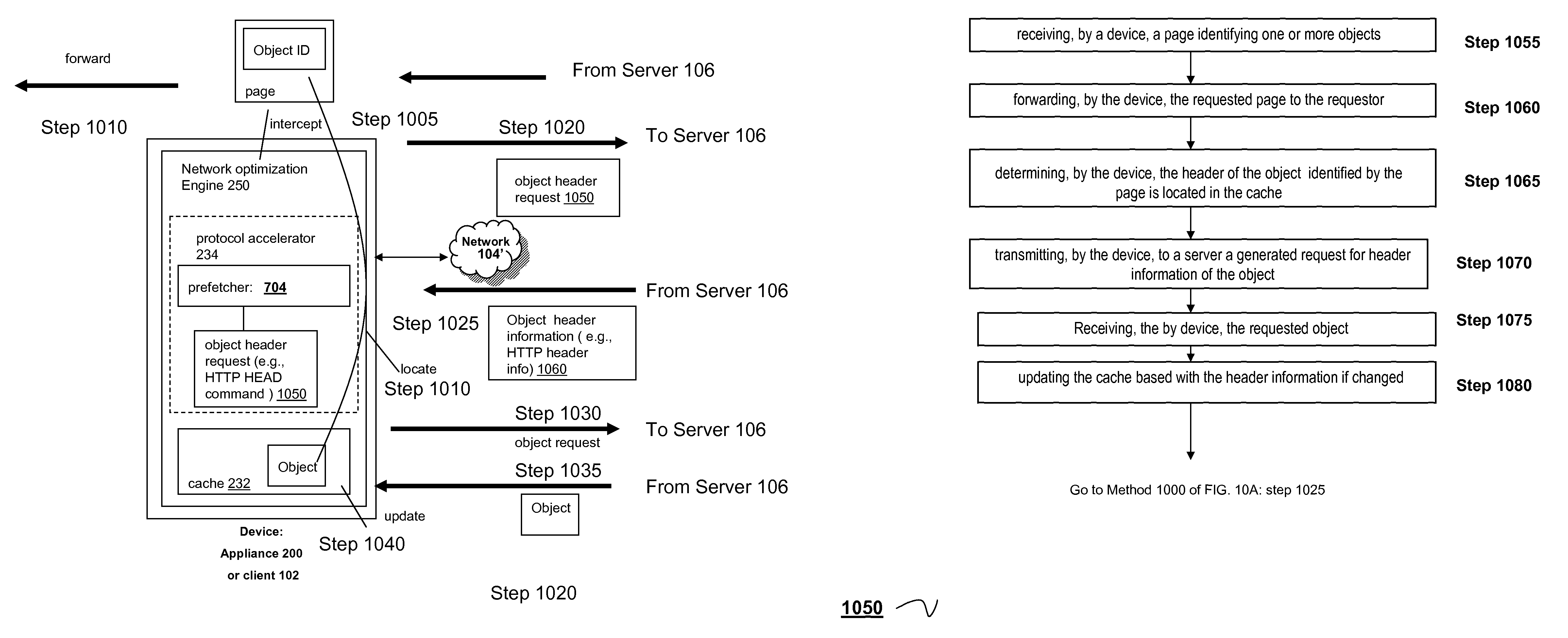
Systems and method of using HTTP head command for prefetching
ActiveUS7809818B2Improve efficiencyImprove intermediary or proxy cachingMultiple digital computer combinationsTransmissionClient agentDomain name
The present solution provides a variety of techniques for accelerating and optimizing network traffic, such as HTTP based network traffic. The solution described herein provides techniques in the areas of proxy caching, protocol acceleration, domain name resolution acceleration as well as compression improvements. In some cases, the present solution provides various prefetching and / or prefreshening techniques to improve intermediary or proxy caching, such as HTTP proxy caching. In other cases, the present solution provides techniques for accelerating a protocol by improving the efficiency of obtaining and servicing data from an originating server to server to clients. In another cases, the present solution accelerates domain name resolution more quickly. As every HTTP access starts with a URL that includes a hostname that must be resolved via domain name resolution into an IP address, the present solution helps accelerate HTTP access. In some cases, the present solution improves compression techniques by prefetching non-cacheable and cacheable content to use for compressing network traffic, such as HTTP. The acceleration and optimization techniques described herein may be deployed on the client as a client agent or as part of a browser, as well as on any type and form of intermediary device, such as an appliance, proxying device or any type of interception caching and / or proxying device.
Owner:CITRIX SYST INC
Numeric/voice name Internet access architecture and methodology
InactiveUS20050125723A1Easily access InternetMultiple digital computer combinationsSubstation equipmentDomain nameDisplay device
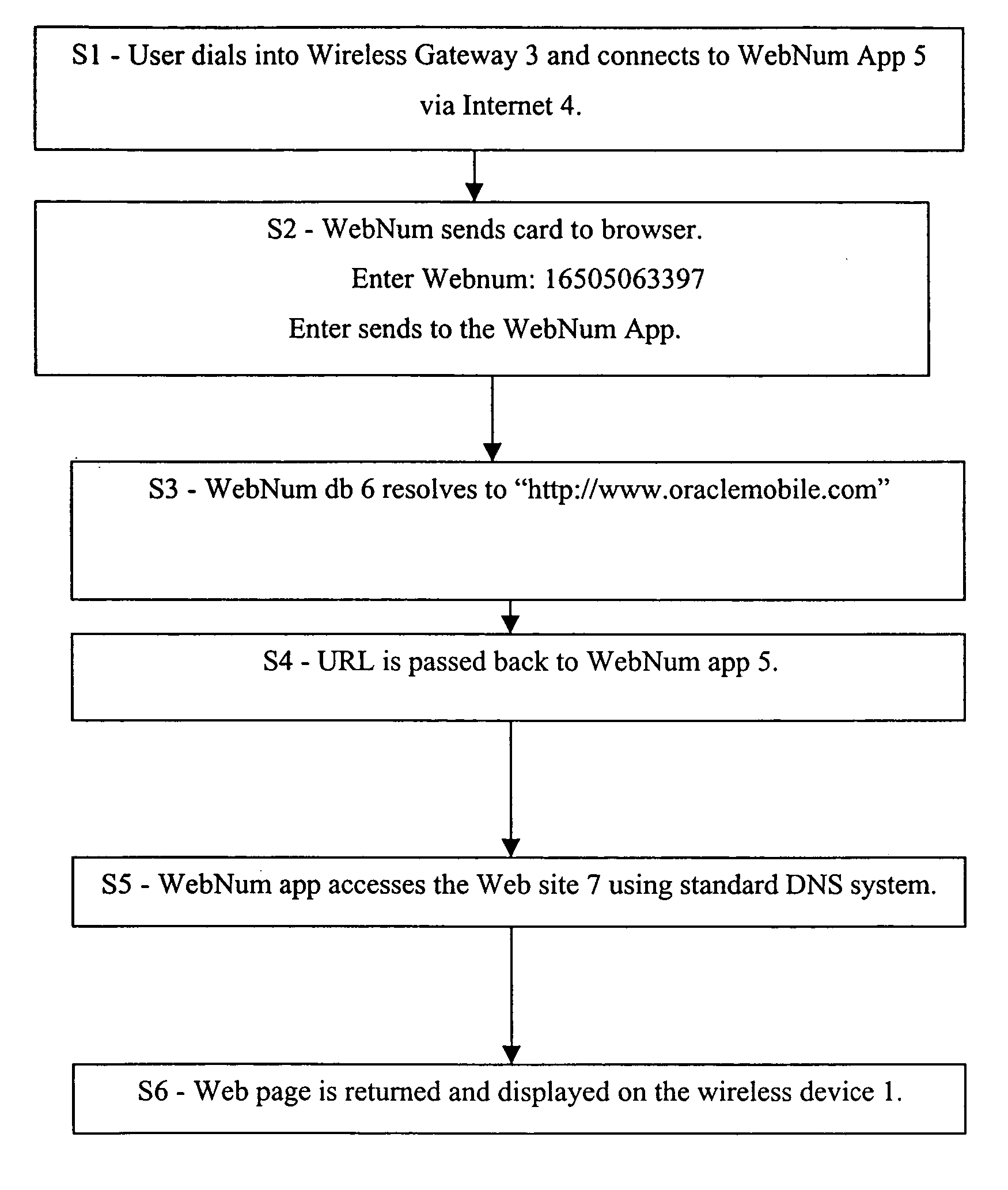
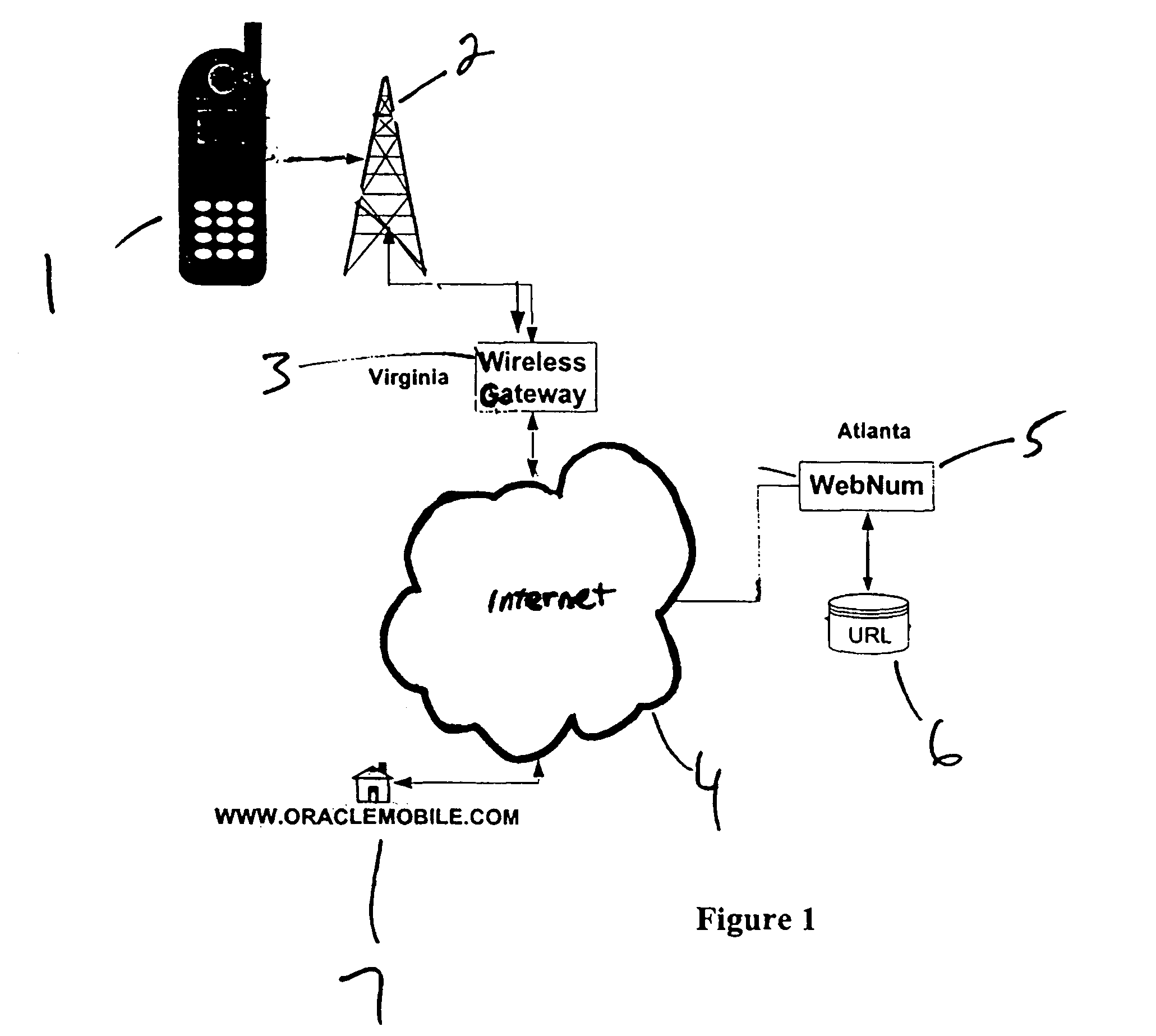
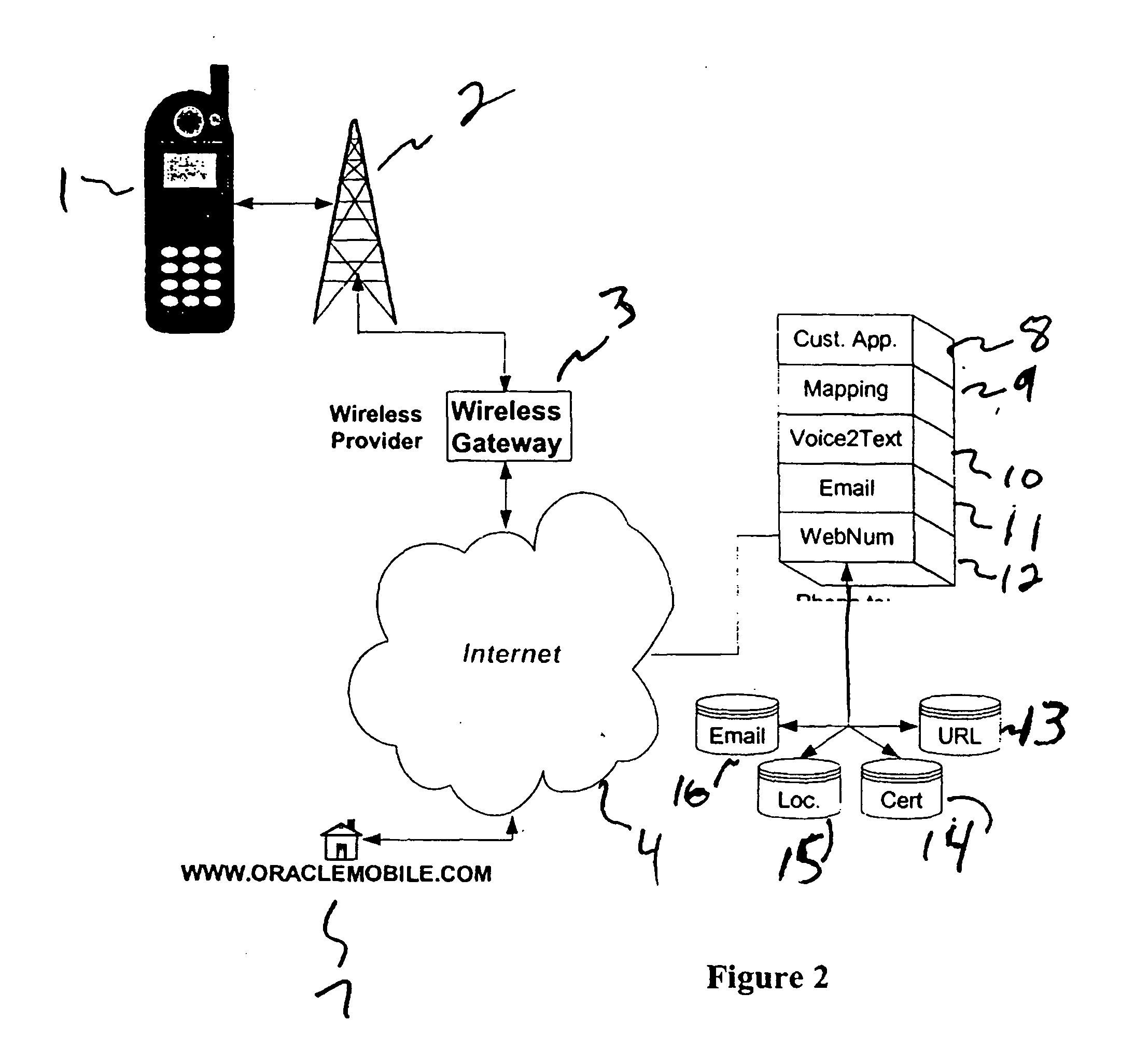
A system that provides users of both fixed and wireless Internet devices, a method of entering numbers instead of the text characters of Internet Uniform Resource Locators (URLs) and other Internet identifiers to access Internet resources and functions, such as Web sites, e-mail services, individual documents or files, location services, etc. When the user enters a WebNum, the digits of the WebNum are sent to a database on a system that is accessible over the Internet. The database maps the WebNum back to a Uniform Resource Locator (URL), which contains a hostname in the Internet domain name structure. This would subsequently be resolved through the Internet Domain Name System (DNS) to an IP address to identify the IP address of the Web site. The cell phone provider or WID network provider would then retrieve the home page of the Web site over the Internet, to return content to the cell phone or WID display.
Owner:DEPUY SPINE INC (US) +1
Systems and methods for securely and transparently proxying saas applications through a cloud-hosted or on-premise network gateway for enhanced security and visibility
Disclosed embodiments provide access to an application. An intermediary device may provide access to an application hosted by the server. The access may be provided to the client via a link that generates a first HTTP request for the application. The device may receive, from the client, the first HTTP request generated via the provided link. The device may rewrite an absolute URL of the application indicated in the first HTTP request, by replacing a first hostname of the server included in the absolute URL, with a URL segment generated by combining a unique string assigned to the first hostname with a second hostname of the device. The device may redirect the client to the rewritten absolute URL of the application.
Owner:CITRIX SYST INC
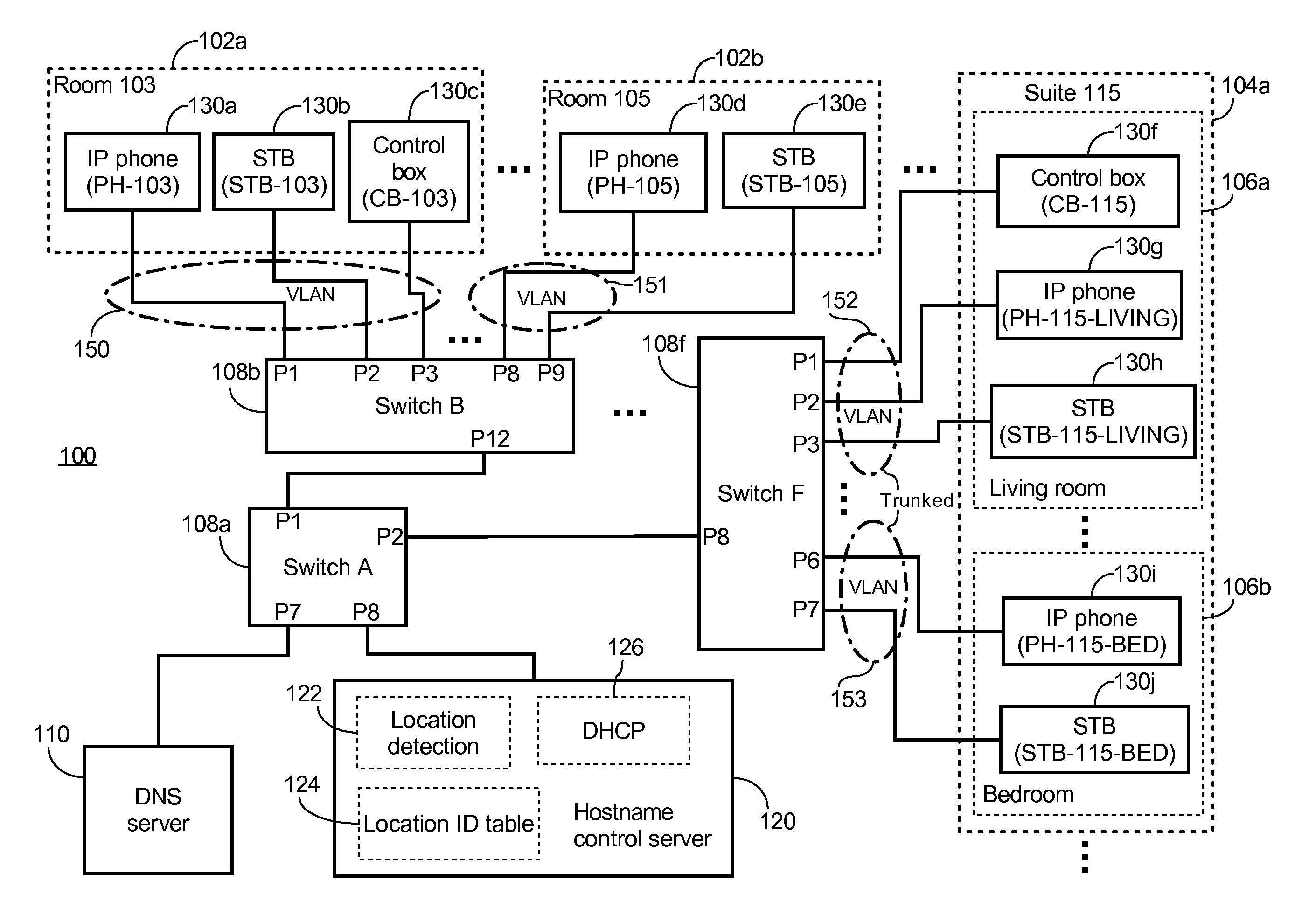
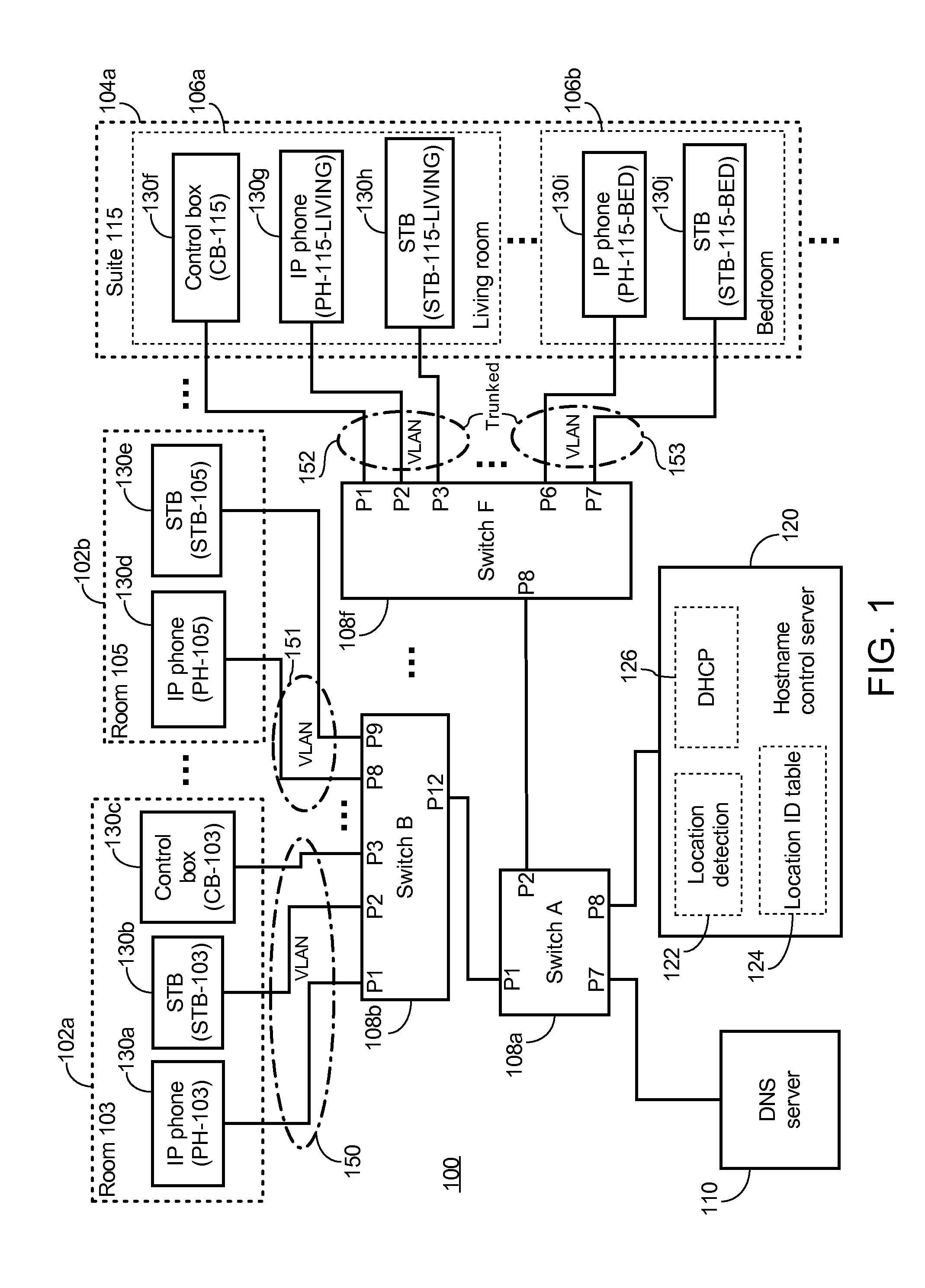
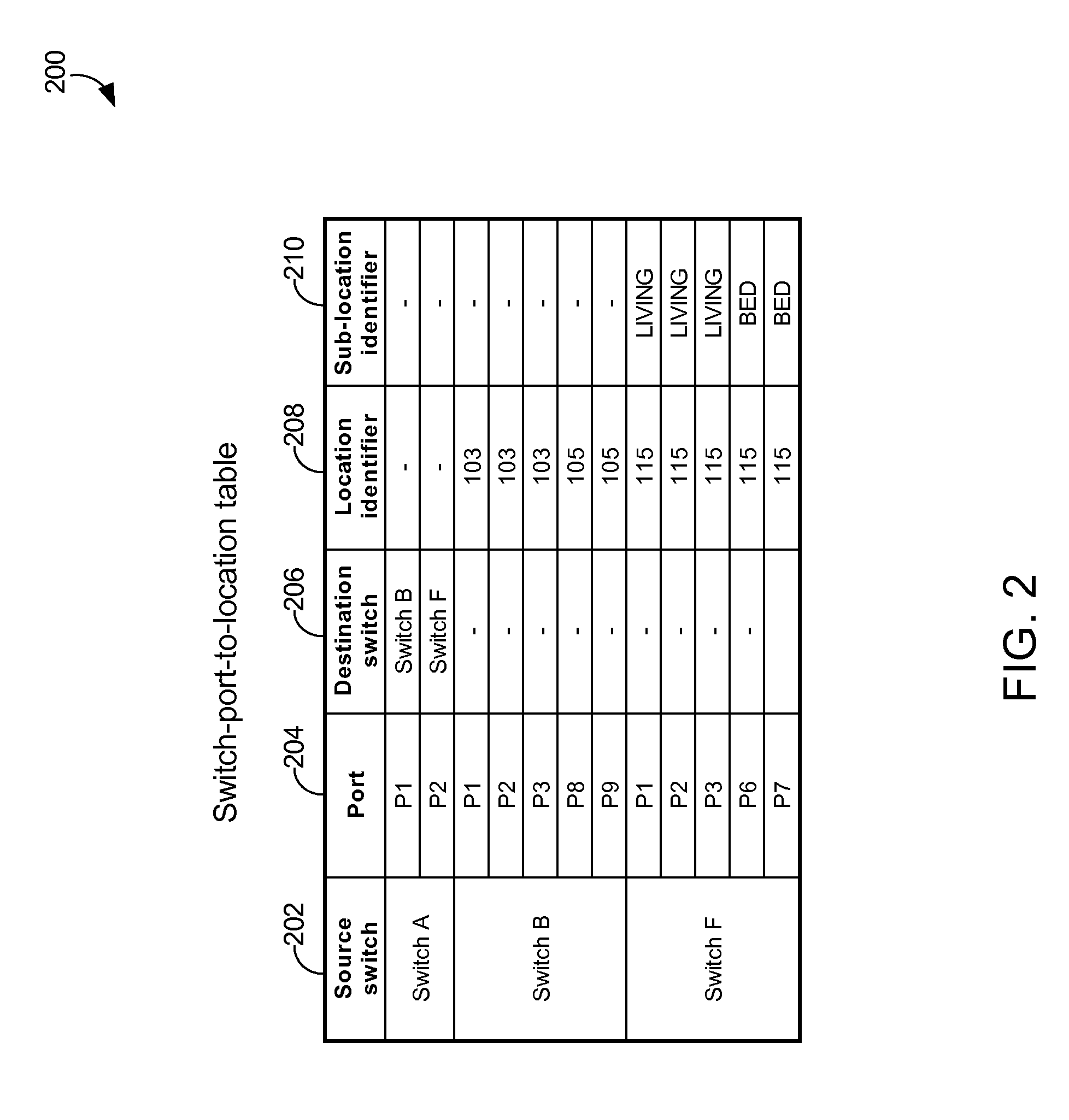
System And Server For Assigning Location-dependent Hostname To Client Device Over Network And Method Thereof
A method of automatic hostname configuration includes receiving a request from a client device. A location detection module may be utilized for determining a location identifier representing a location at which the client device is located. A hostname is formed including at least the location identifier, and a control server assigns the hostname to the client device by sending an acknowledgement including the hostname to the client device. The request and acknowledgement may be communicated using DHCP. Simple network management protocol messages may be sent to one or more switches to query for a MAC address of the client device to determine the source switch and port from which the request originated. The switch-port-to-location table may include several ports that map to a same location identifier. The hostname may further be formed by including a device type identifier associated with the client device.
Owner:GUEST TEK INTERACTIVE ENTERTAINMENT
Systems and methods of dynamically checking freshness of cached objects based on link status
ActiveUS20080229024A1Improve efficiencyMore resolutionMemory adressing/allocation/relocationMultiple digital computer combinationsDomain nameClient agent
The present solution provides a variety of techniques for accelerating and optimizing network traffic, such as HTTP based network traffic. The solution described herein provides techniques in the areas of proxy caching, protocol acceleration, domain name resolution acceleration as well as compression improvements. In some cases, the present solution provides various prefetching and / or prefreshening techniques to improve intermediary or proxy caching, such as HTTP proxy caching. In other cases, the present solution provides techniques for accelerating a protocol by improving the efficiency of obtaining and servicing data from an originating server to server to clients. In another cases, the present solution accelerates domain name resolution more quickly. As every HTTP access starts with a URL that includes a hostname that must be resolved via domain name resolution into an IP address, the present solution helps accelerate HTTP access. In some cases, the present solution improves compression techniques by prefetching non-cacheable and cacheable content to use for compressing network traffic, such as HTTP. The acceleration and optimization techniques described herein may be deployed on the client as a client agent or as part of a browser, as well as on any type and form of intermediary device, such as an appliance, proxying device or any type of interception caching and / or proxying device.
Owner:CITRIX SYST INC
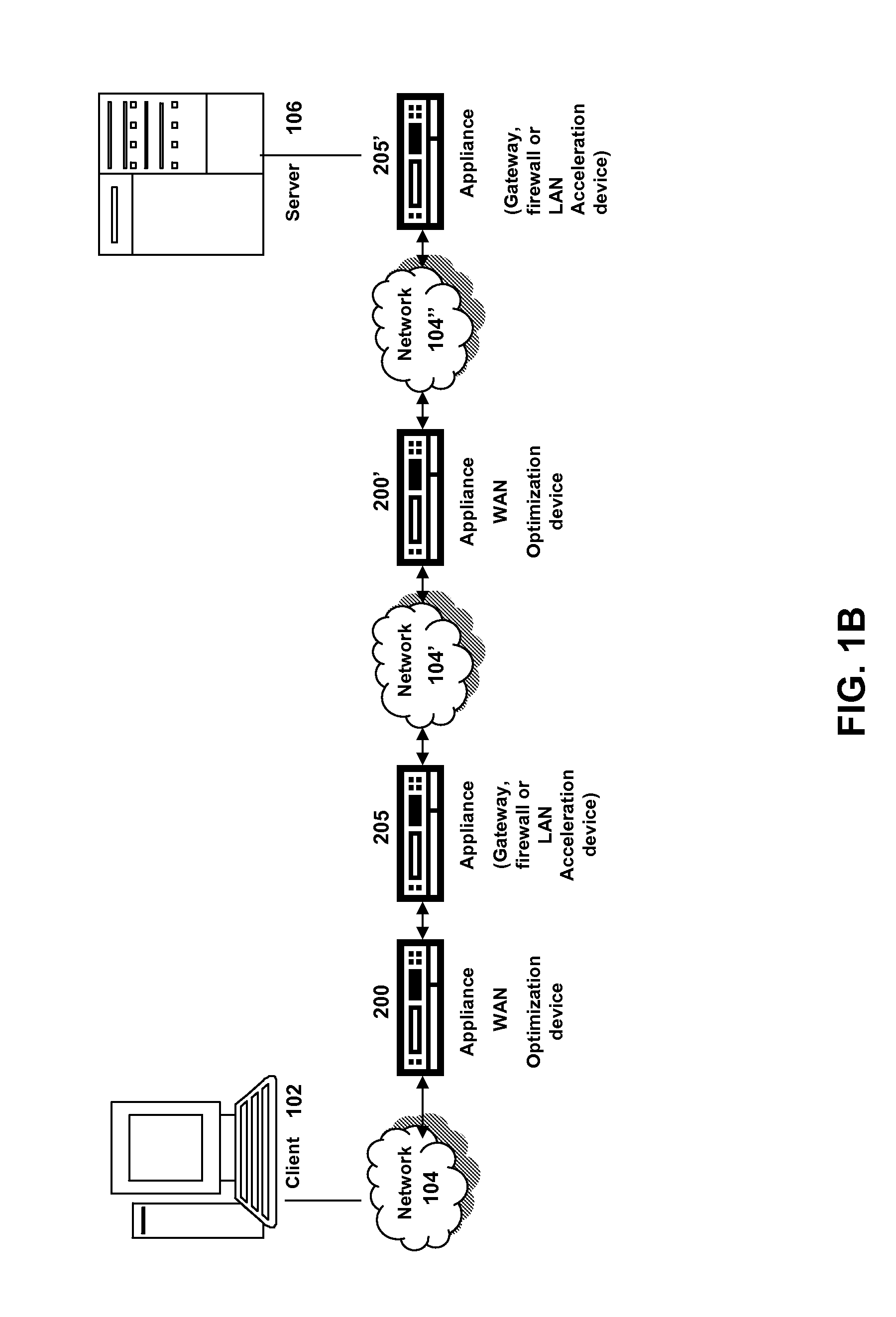
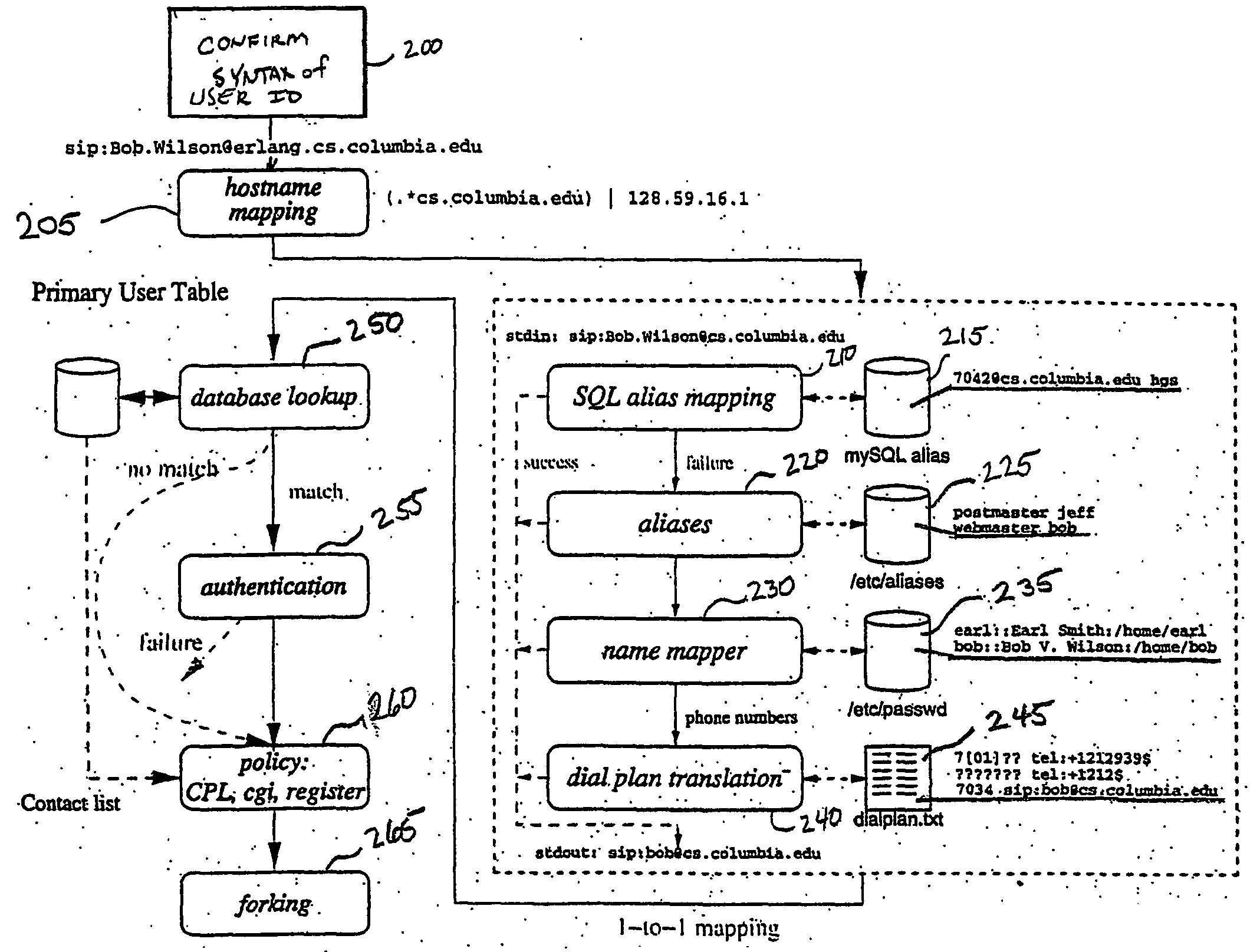
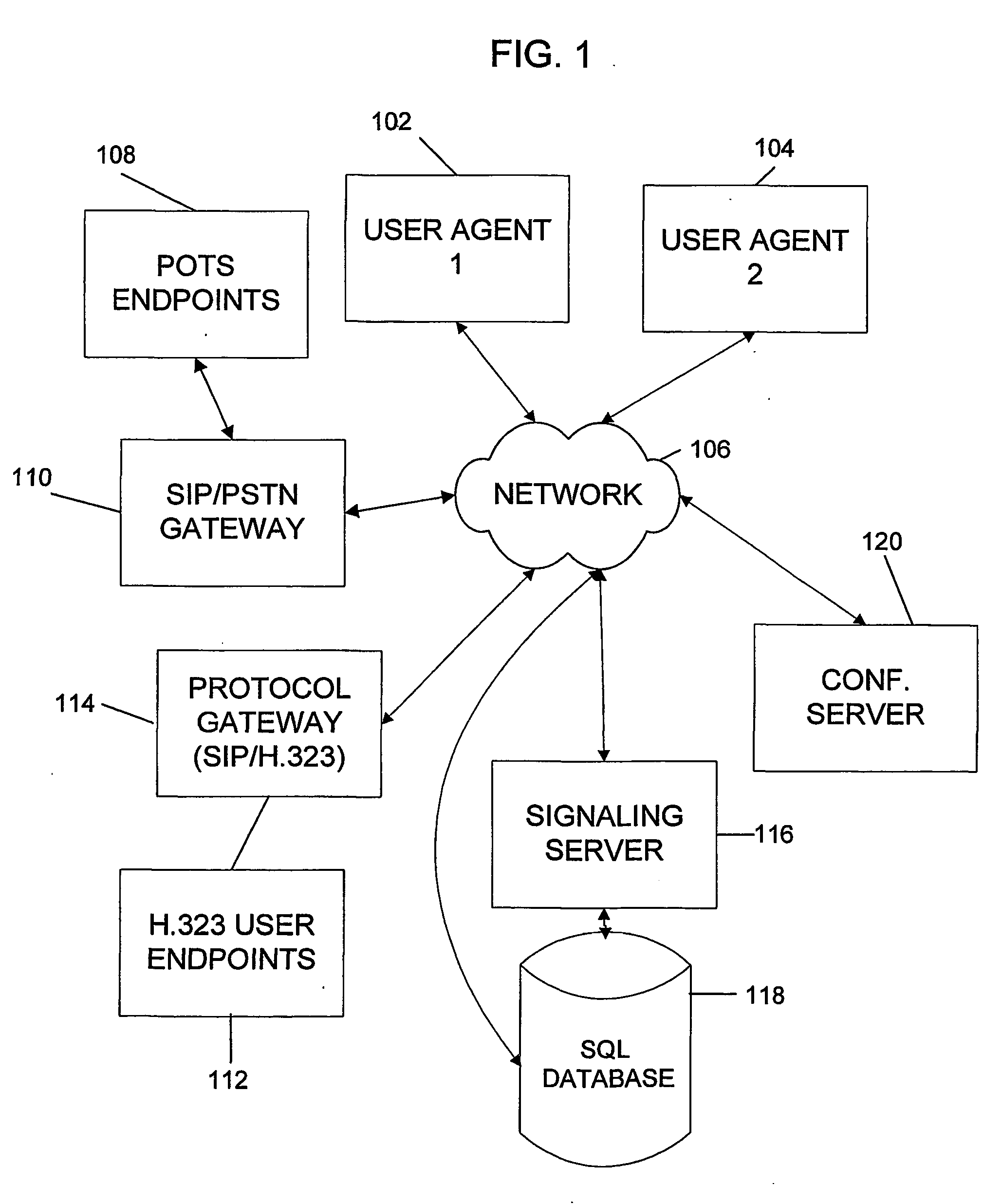
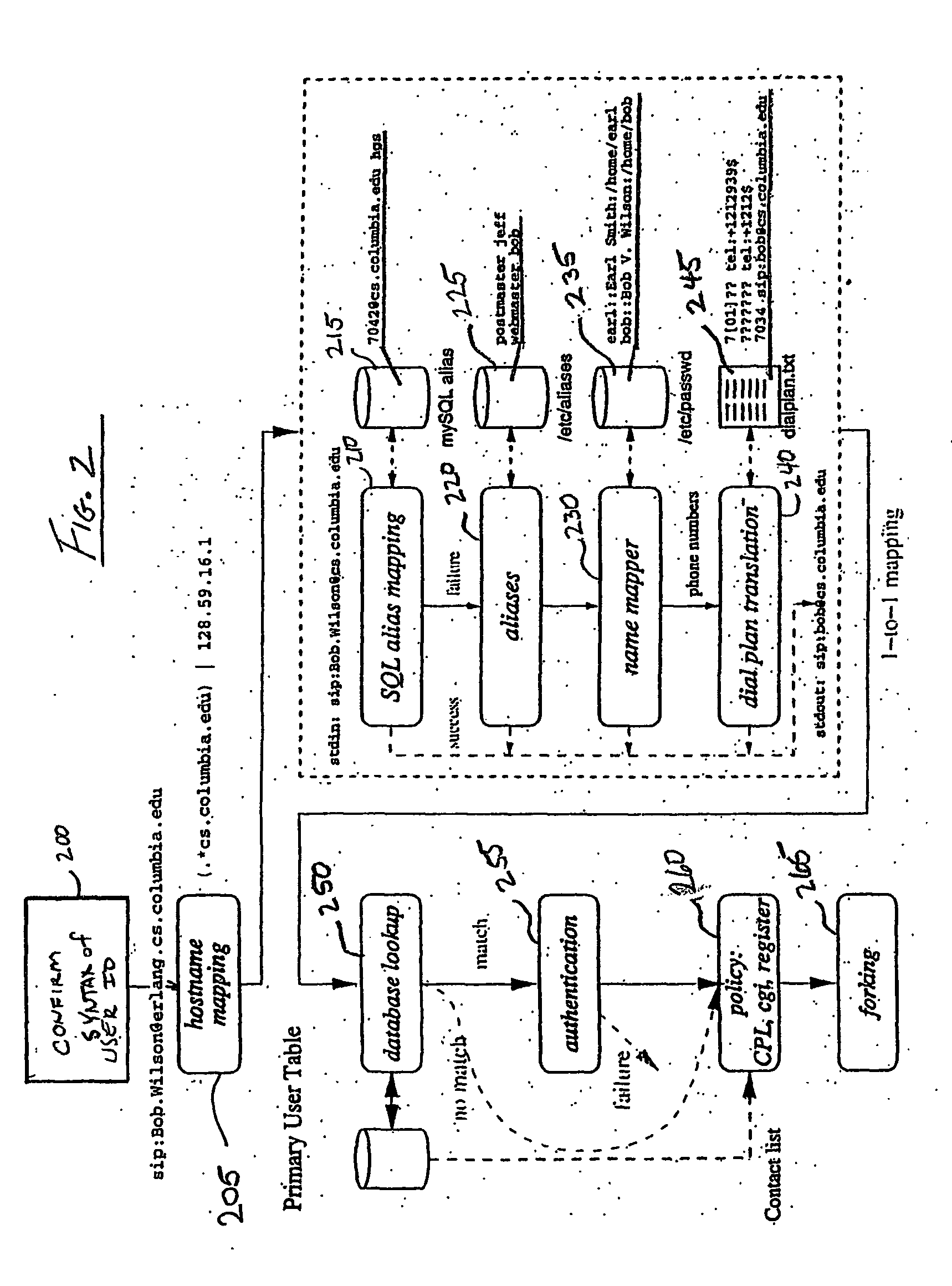
System and method for call routing in an ip telephony network
A method of processing a call request to a callee in a network telephony system is provided which includes mapping a hostname portion of a callee address to a canonical form of the hostname and determining a canonical form of a username portion of a callee address. The canonical form of the user identity of the callee is then used as an index to a user database to retrieve a callee database record. The callee database record is then used to determine call routing based on the retrieved callee database record, such as user location, preferences and policy data stored in the record. The method is generally performed by a signaling server in the network, such as a SIP proxy server. The signaling server can also provide security features such as caller authentication. A scalable signaling and routing architecture is also provided.
Owner:THE TRUSTEES OF COLUMBIA UNIV IN THE CITY OF NEW YORK
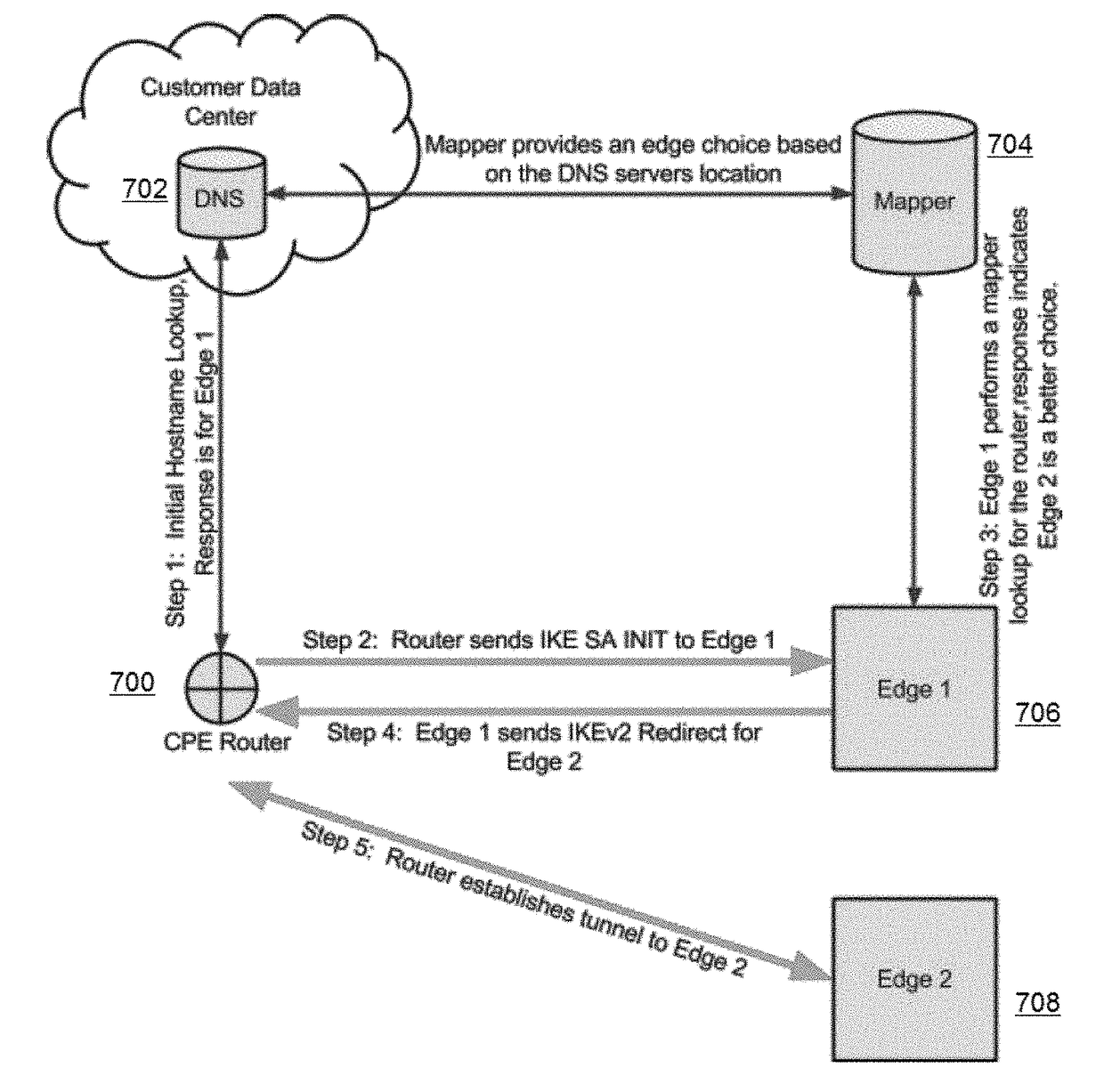
Overlay network ingress edge region selection
ActiveUS20170195161A1Enhanced overlay network-based transportResponse is deterioratedNetwork topologiesNetworks interconnectionBranch officeThe Internet
This disclosure relates to enhanced overlay network-based transport of traffic to and from customer branch office locations, facilitated through the use of the Internet-based overlay routing. A method of selecting an ingress edge region of the overlay network begins by mapping a service hostname to an IKEv2 destination of an outer IPsec tunnel associated with a first overlay network edge. An IKEv2 session is established from the first overlay network edge to the customer router. Upon tunnel establishment, a secondary lookup is performed to determine whether the first overlay network edge is an appropriate ingress region. Based on a response to the secondary lookup, a IKEv2 redirect is issued to a second overlay network edge. A new tunnel is then established from the second overlay network edge to the customer router. Thereafter, an additional lookup may also be performed to determine whether the second overlay network edge remains an appropriate ingress region.
Owner:AKAMAI TECH INC
Systems and methods of using HTTP head command for prefetching
ActiveUS20080229023A1Improve efficiencyMore resolutionMemory adressing/allocation/relocationMultiple digital computer combinationsClient agentDomain name
The present solution provides a variety of techniques for accelerating and optimizing network traffic, such as HTTP based network traffic. The solution described herein provides techniques in the areas of proxy caching, protocol acceleration, domain name resolution acceleration as well as compression improvements. In some cases, the present solution provides various prefetching and / or prefreshening techniques to improve intermediary or proxy caching, such as HTTP proxy caching. In other cases, the present solution provides techniques for accelerating a protocol by improving the efficiency of obtaining and servicing data from an originating server to server to clients. In another cases, the present solution accelerates domain name resolution more quickly. As every HTTP access starts with a URL that includes a hostname that must be resolved via domain name resolution into an IP address, the present solution helps accelerate HTTP access. In some cases, the present solution improves compression techniques by prefetching non-cacheable and cacheable content to use for compressing network traffic, such as HTTP. The acceleration and optimization techniques described herein may be deployed on the client as a client agent or as part of a browser, as well as on any type and form of intermediary device, such as an appliance, proxying device or any type of interception caching and / or proxying device.
Owner:CITRIX SYST INC
Systems and Methods of Providing A Multi-Tier Cache
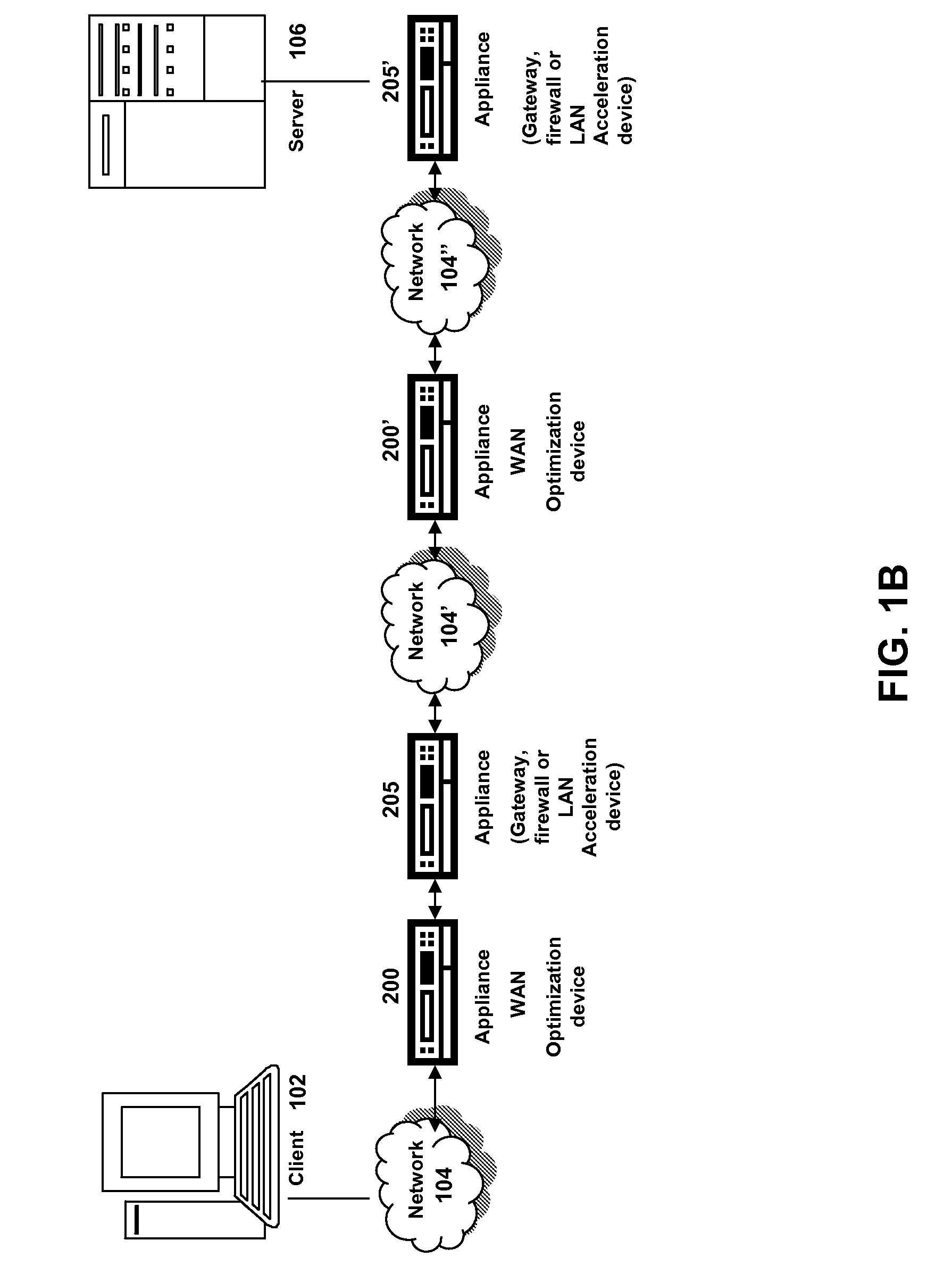
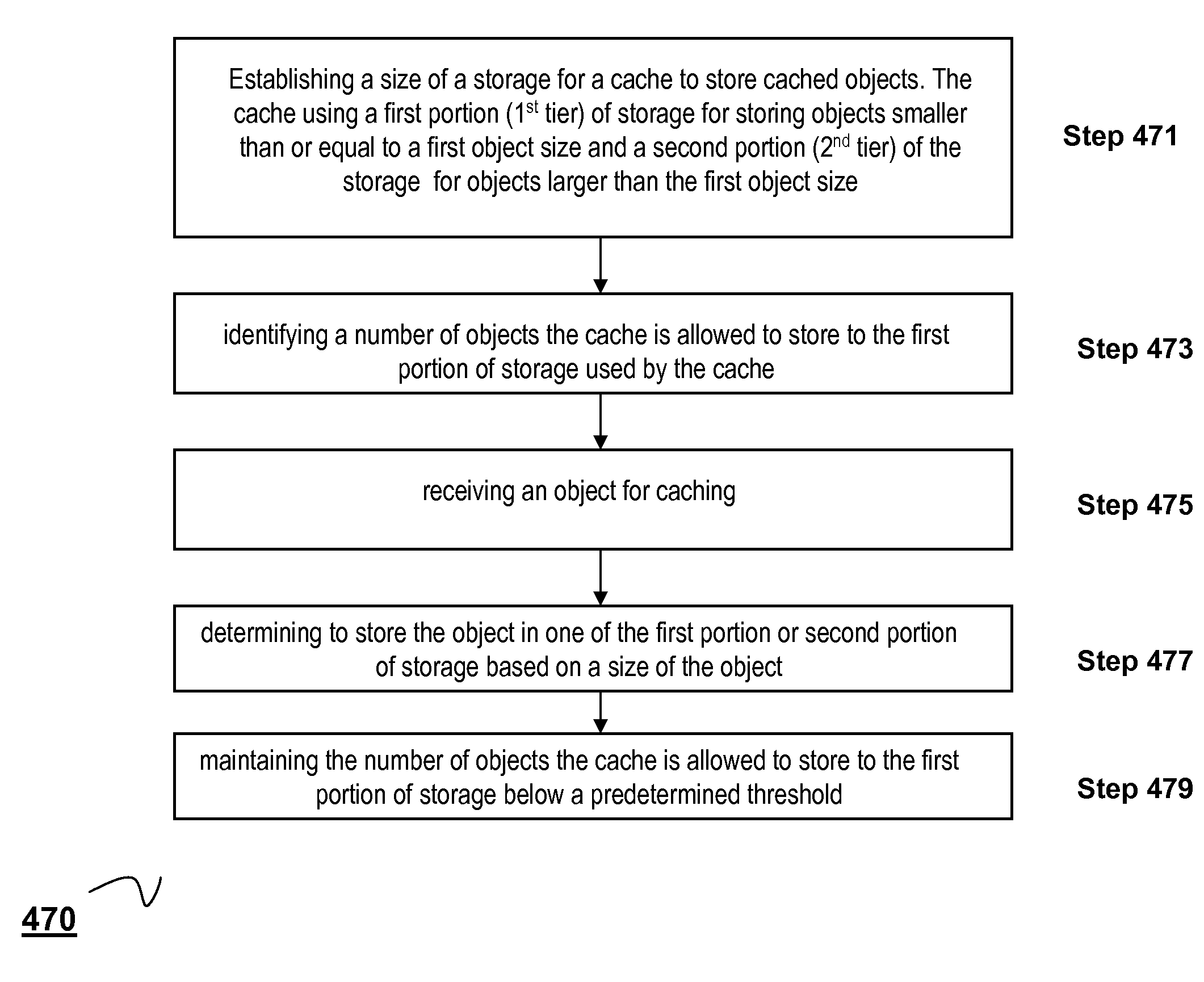
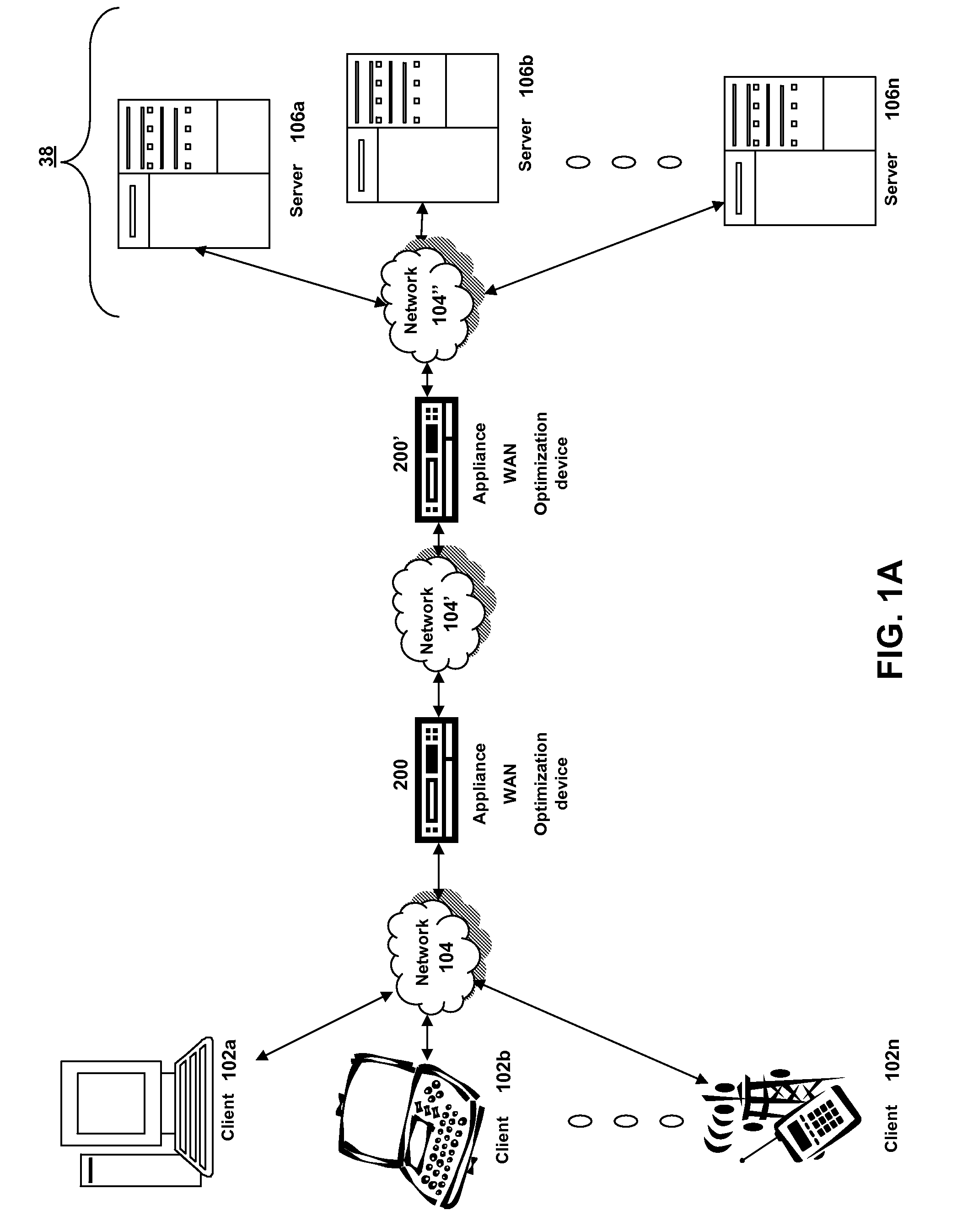
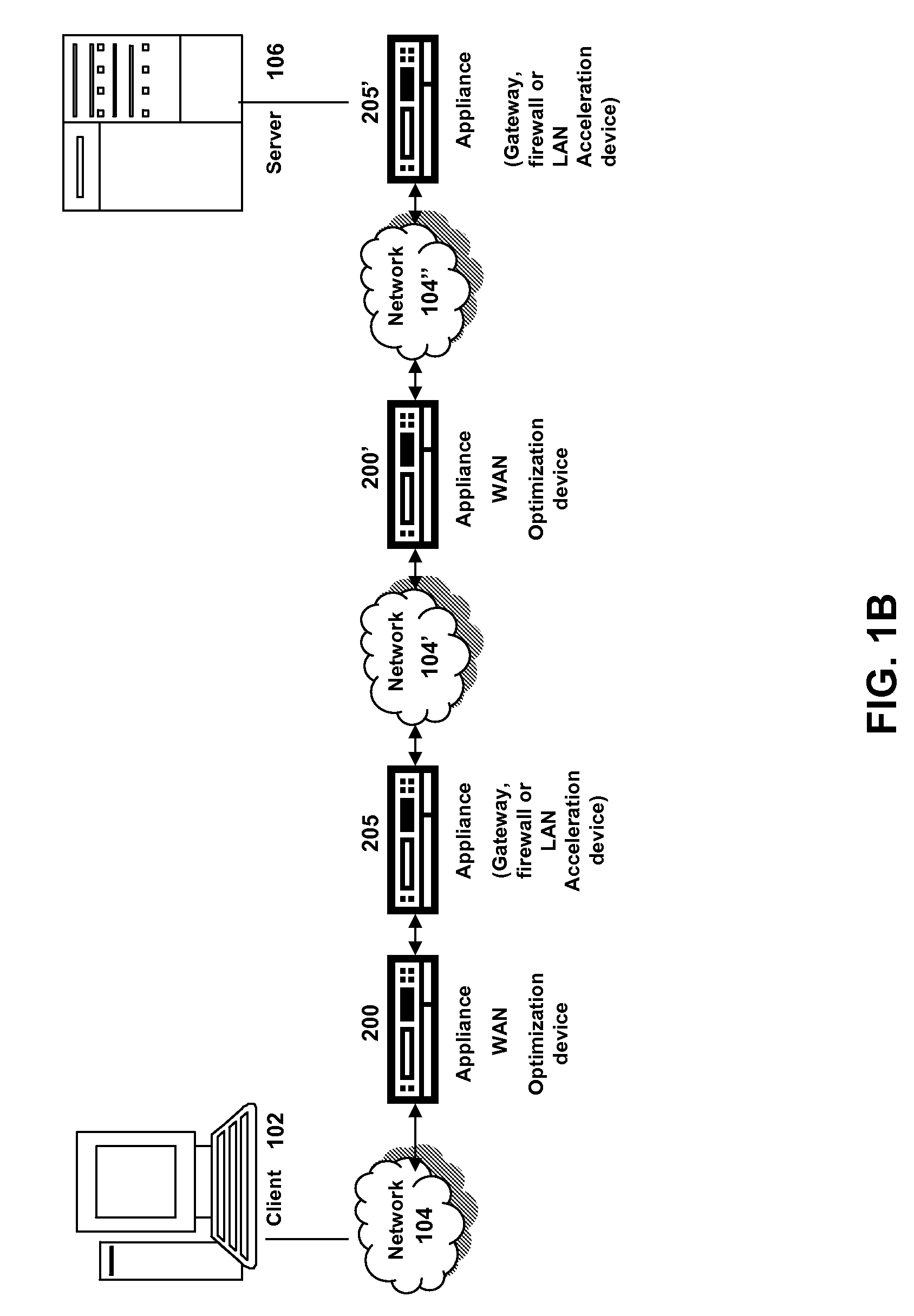
ActiveUS20080229020A1Improve efficiencyMore resolutionTransmissionMemory systemsDomain nameClient agent
The present solution provides a variety of techniques for accelerating and optimizing network traffic, such as HTTP based network traffic. The solution described herein provides techniques in the areas of proxy caching, protocol acceleration, domain name resolution acceleration as well as compression improvements. In some cases, the present solution provides various prefetching and / or prefreshening techniques to improve intermediary or proxy caching, such as HTTP proxy caching. In other cases, the present solution provides techniques for accelerating a protocol by improving the efficiency of obtaining and servicing data from an originating server to server to clients. In another cases, the present solution accelerates domain name resolution more quickly. As every HTTP access starts with a URL that includes a hostname that must be resolved via domain name resolution into an IP address, the present solution helps accelerate HTTP access. In some cases, the present solution improves compression techniques by prefetching non-cacheable and cacheable content to use for compressing network traffic, such as HTTP. The acceleration and optimization techniques described herein may be deployed on the client as a client agent or as part of a browser, as well as on any type and form of intermediary device, such as an appliance, proxying device or any type of interception caching and / or proxying device.
Owner:CITRIX SYST INC
Systems and Methods of Revalidating Cached Objects in Parallel with Request for Object
ActiveUS20080229021A1Improve efficiencyMore resolutionMemory adressing/allocation/relocationMultiple digital computer combinationsDomain nameClient agent
The present solution provides a variety of techniques for accelerating and optimizing network traffic, such as HTTP based network traffic. The solution described herein provides techniques in the areas of proxy caching, protocol acceleration, domain name resolution acceleration as well as compression improvements. In some cases, the present solution provides various prefetching and / or prefreshening techniques to improve intermediary or proxy caching, such as HTTP proxy caching. In other cases, the present solution provides techniques for accelerating a protocol by improving the efficiency of obtaining and servicing data from an originating server to server to clients. In another cases, the present solution accelerates domain name resolution more quickly. As every HTTP access starts with a URL that includes a hostname that must be resolved via domain name resolution into an IP address, the present solution helps accelerate HTTP access. In some cases, the present solution improves compression techniques by prefetching non-cacheable and cacheable content to use for compressing network traffic, such as HTTP. The acceleration and optimization techniques described herein may be deployed on the client as a client agent or as part of a browser, as well as on any type and form of intermediary device, such as an appliance, proxying device or any type of interception caching and / or proxying device.
Owner:CITRIX SYST INC
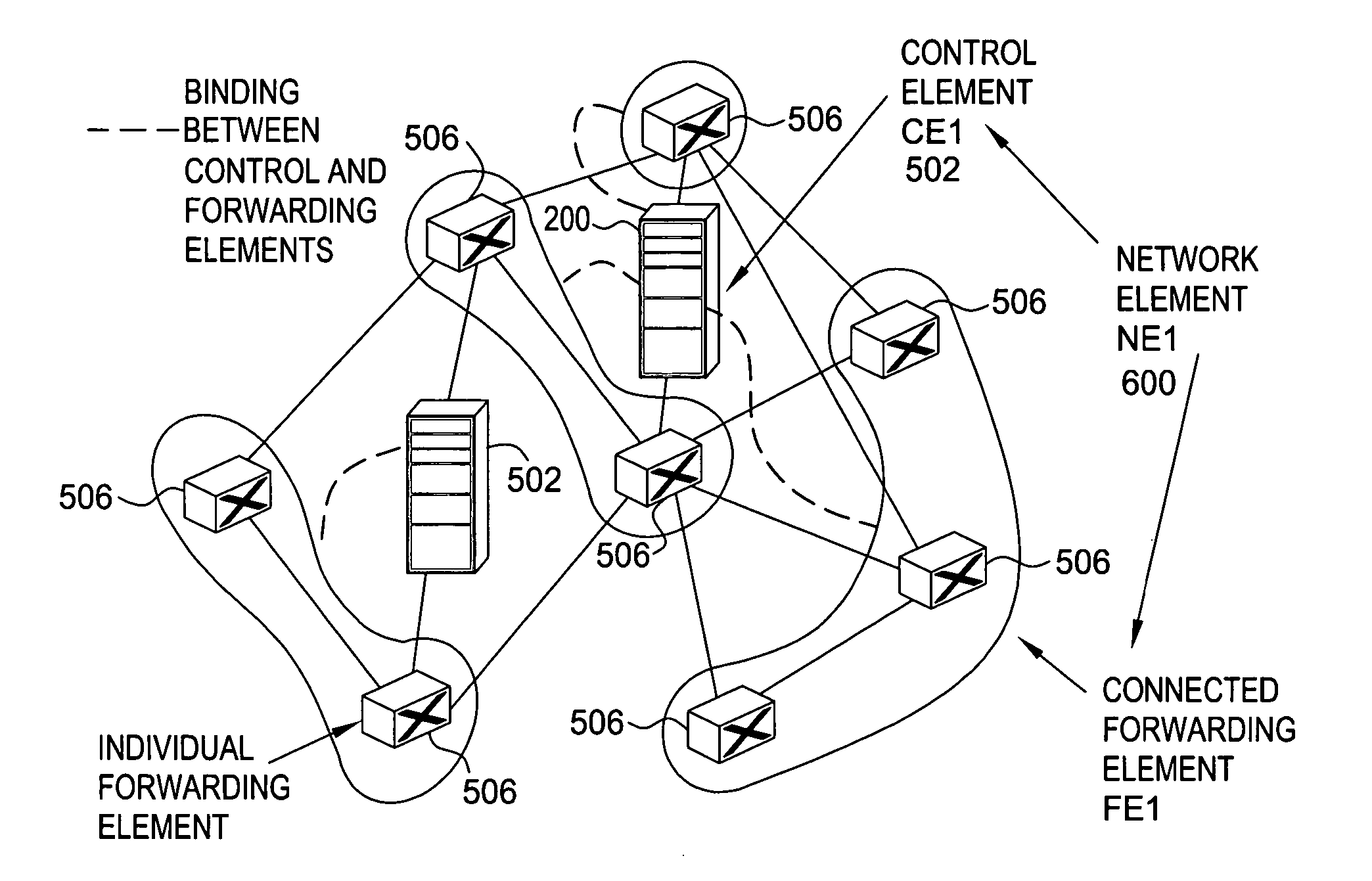
Softrouter dynamic binding protocol
ActiveUS20060092857A1Data switching by path configurationMultiple digital computer combinationsFailoverDistributed computing
A dynamic binding protocol has three tasks that run in parallel: discovery, association, and operation. During discovery, control elements (CEs) and forwarding elements (FEs) learn about immediate neighbors and CEs in a SoftRouter network that has separate control and data planes. During association, FEs associate with CEs and are configured with basic parameters, such as IP interface addresses, hostnames, and the like. During operation, failover and packet tunneling between CEs and FEs is handled.
Owner:NOKIA TECHNOLOGLES OY
Method, system and computer program product for generating and processing a disposable email address
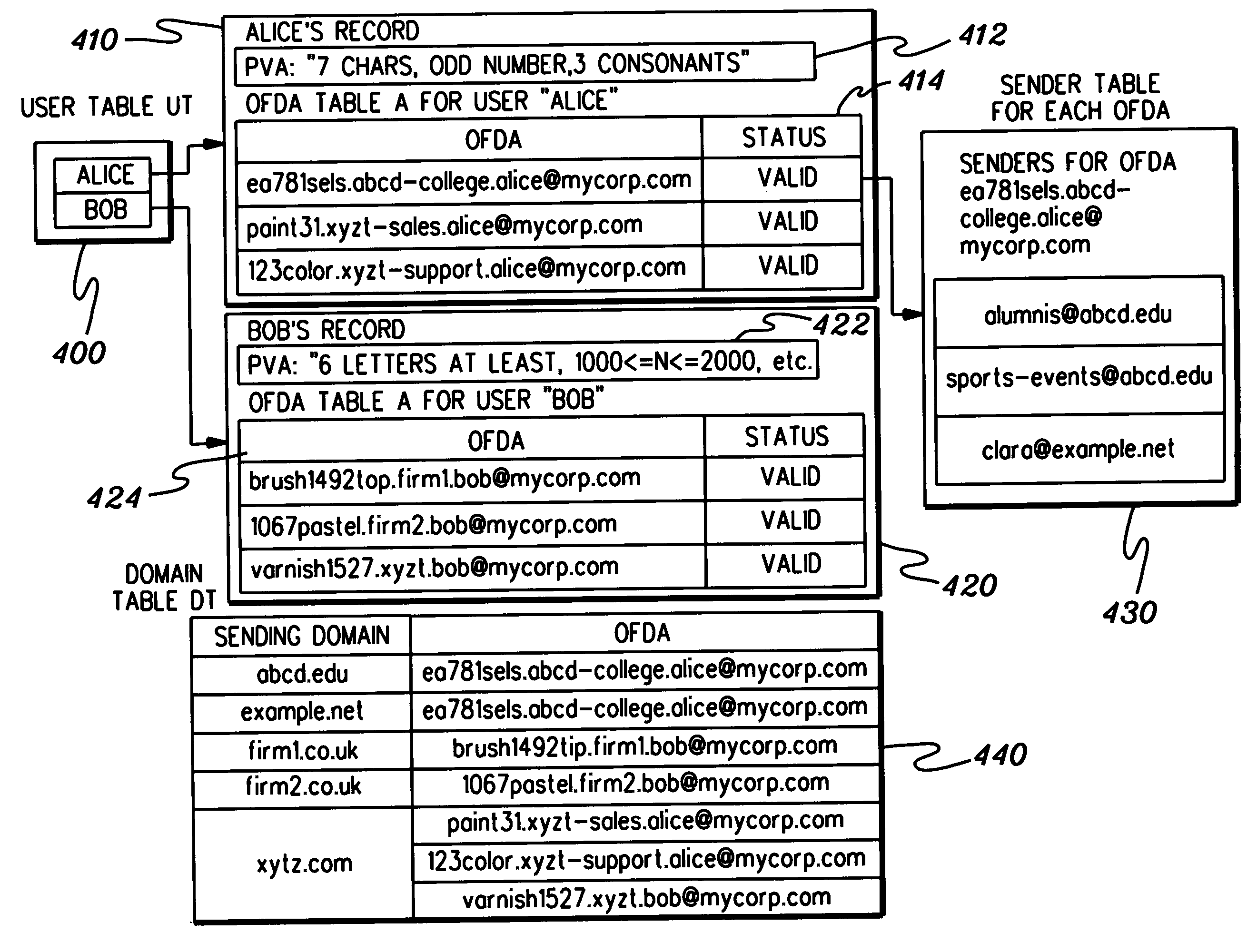
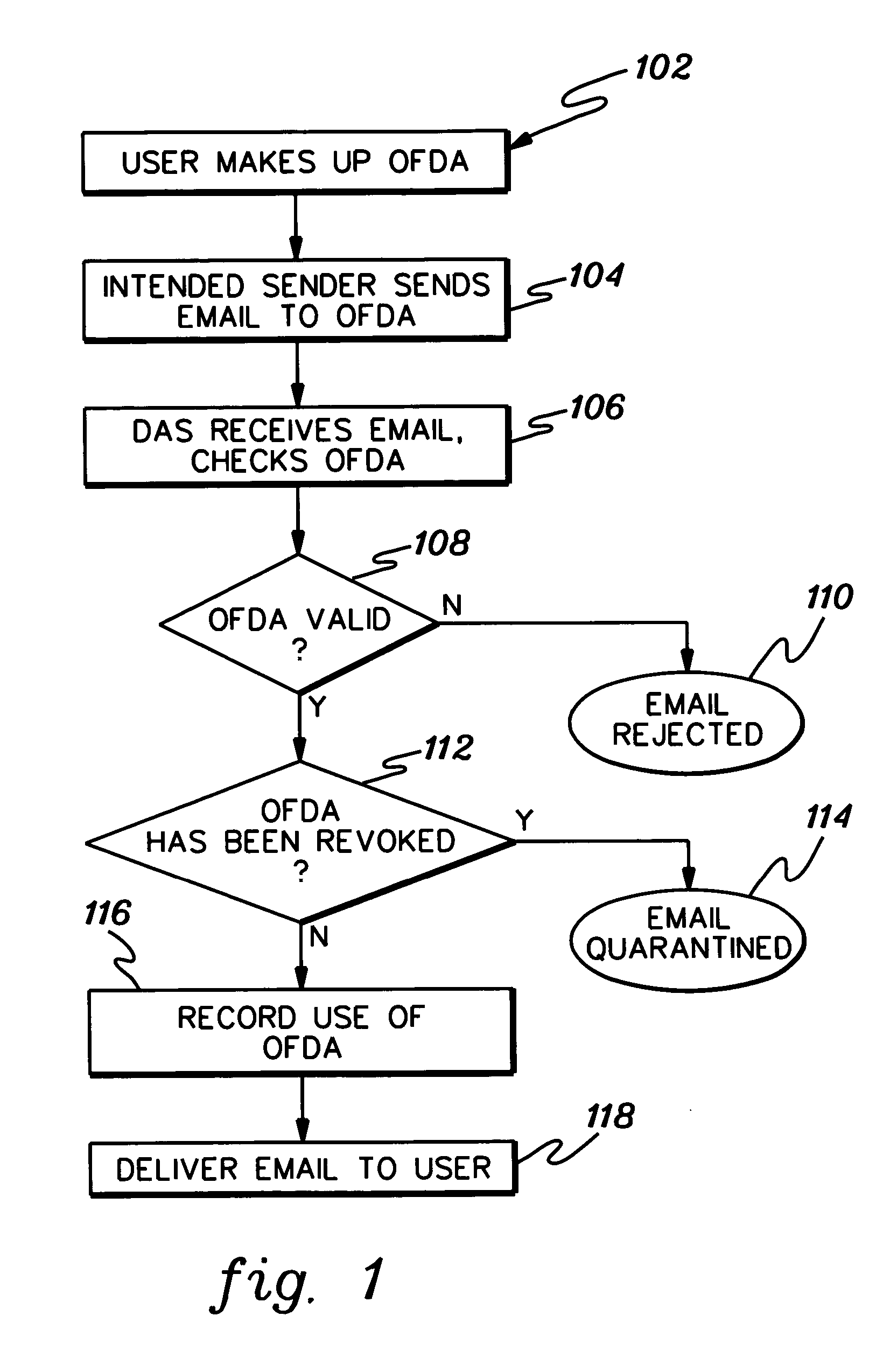
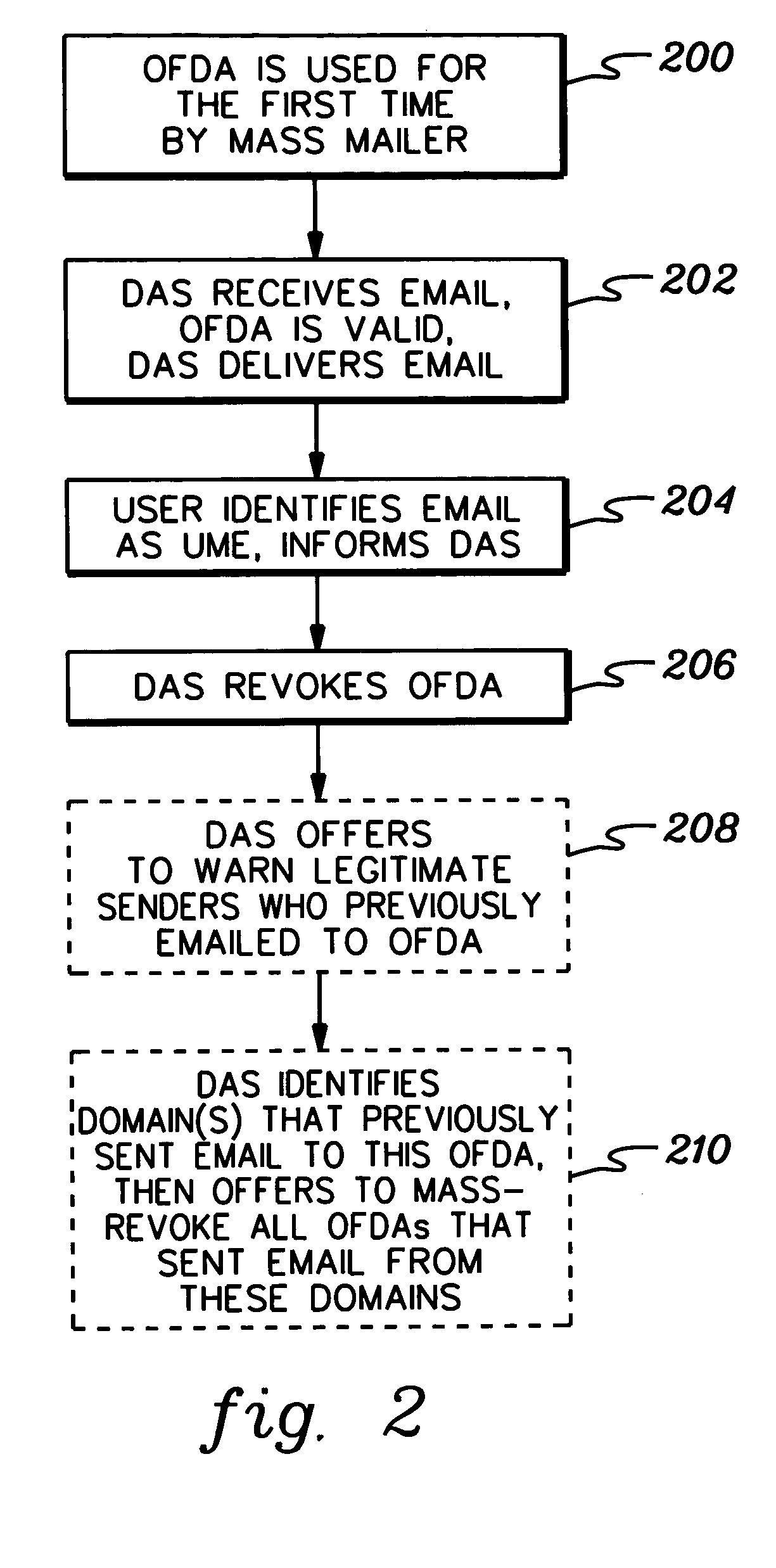
ActiveUS20050210107A1Data processing applicationsUnauthorized memory use protectionDisposable email addressDomain name
Disposable email address generation, and processing thereof at a disposable address system are provided. The generated disposable email address includes a hostname domain, a username, a domain tag, and a passcode, wherein the passcode is selected by a user employing a user chosen algorithm of a plurality of passcode validation algorithms provided to the user by the disposable address system. The user chosen algorithm for generating the passcode can be periodically changed for different disposable email addresses owned by the user. The disposable address system includes storage for holding an indication of revocation of a compromised disposable email address to prevent future emails with that destination email address from being forwarded to the user owning the email address.
Owner:TREND MICRO INC
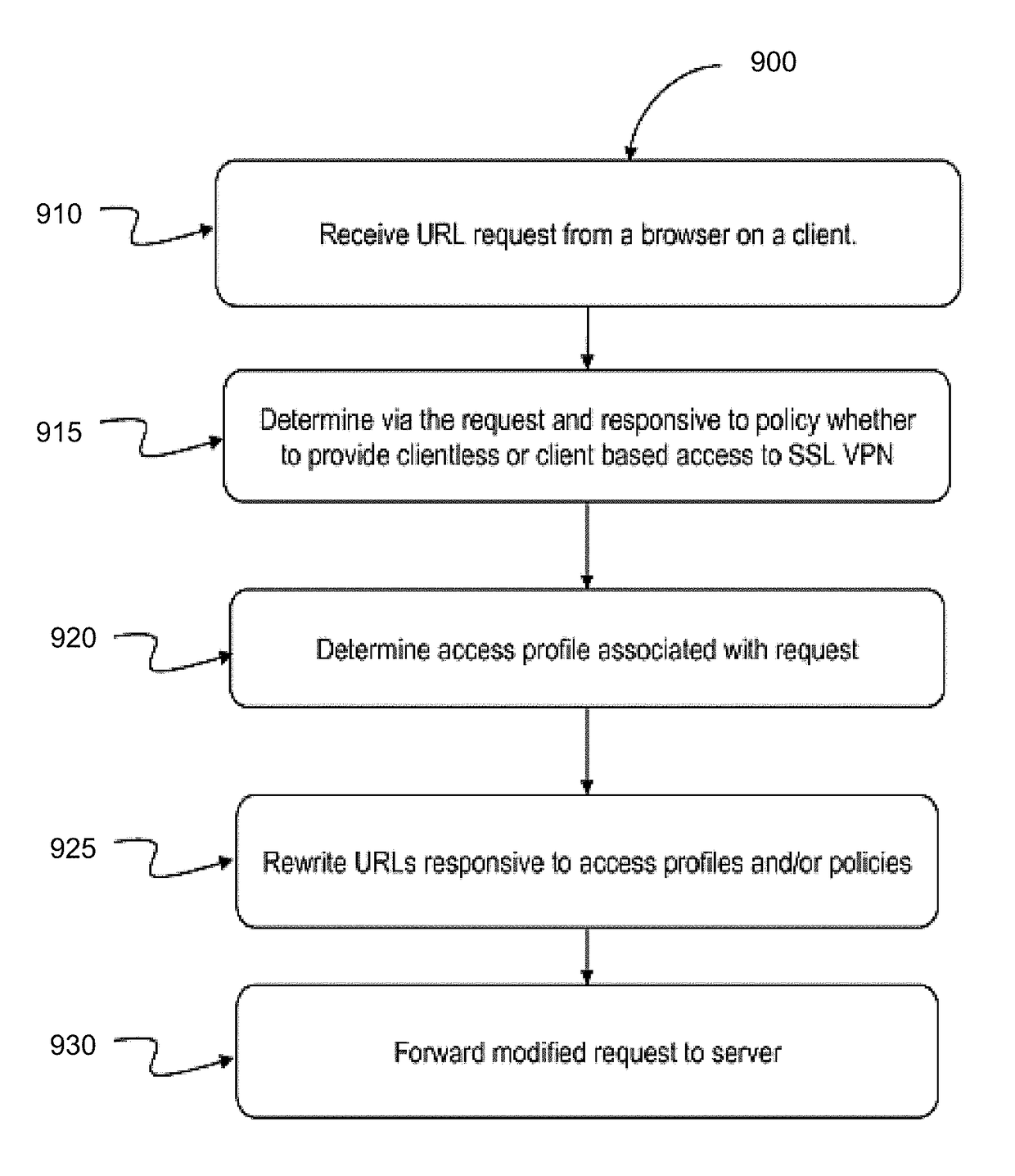
Systems and methods for a unique mechanism of providing 'clientless sslvpn' access to a variety of web-applications through a sslvpn gateway
The present disclosure is directed towards systems and methods for rewriting a HTTP response transmitted via a clientless SSL VPN session. An intermediary device may identify, in a HTTP response transmitted via a clientless SSL VPN session, an absolute URL that includes a first hostname of the server. The device may provide a unique string corresponding to the first hostname of the server. The device may generate a URL segment by combining the unique string with a second hostname of the device. The device may rewrite the absolute URL by replacing the first hostname in the absolute URL with the generated URL segment. A domain name system (DNS) server for the client may be configured with a DNS entry comprising a wildcard combined with the second hostname, to cause the DNS server to resolve the rewritten absolute URL to an IP address of the device.
Owner:CITRIX SYST INC
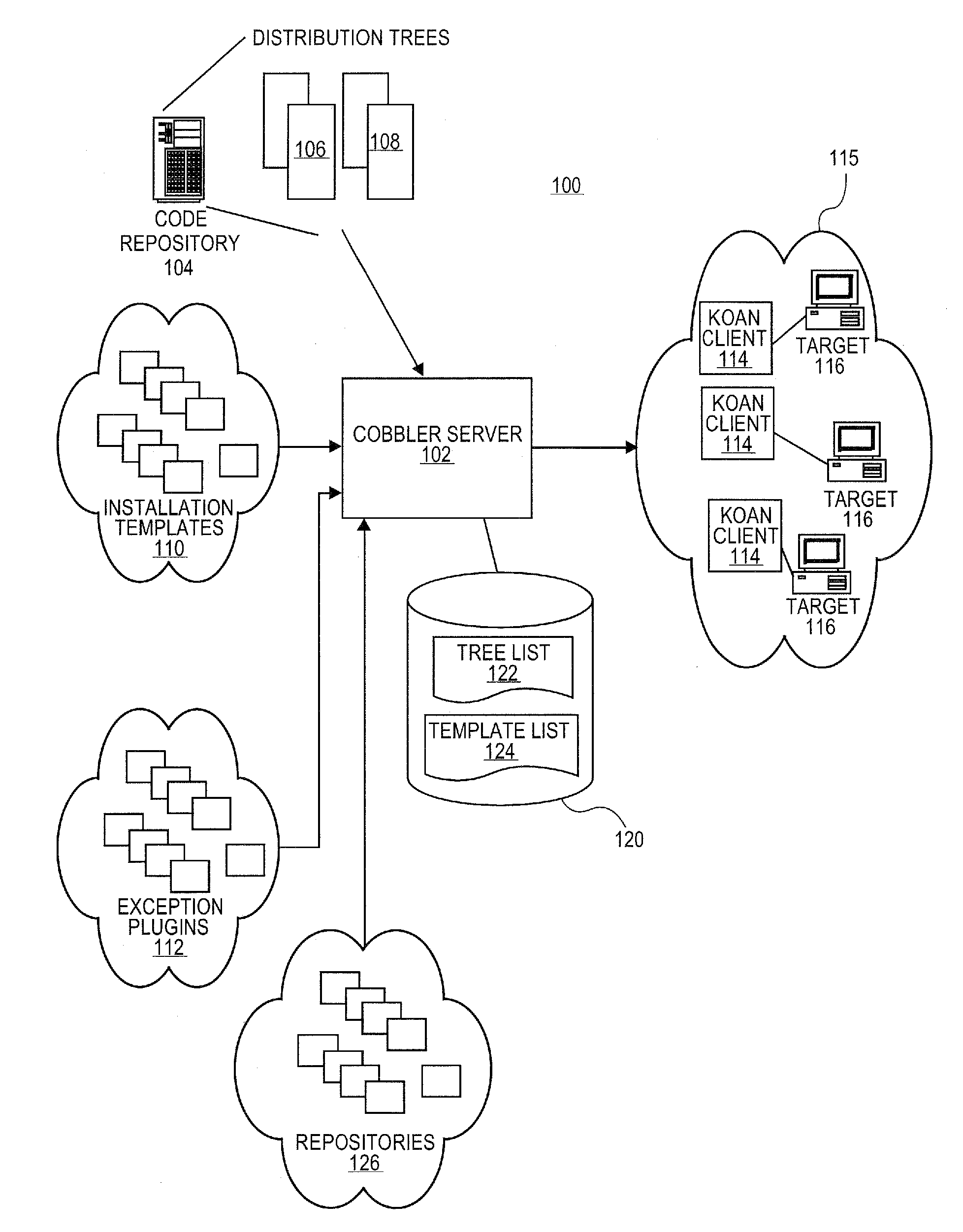
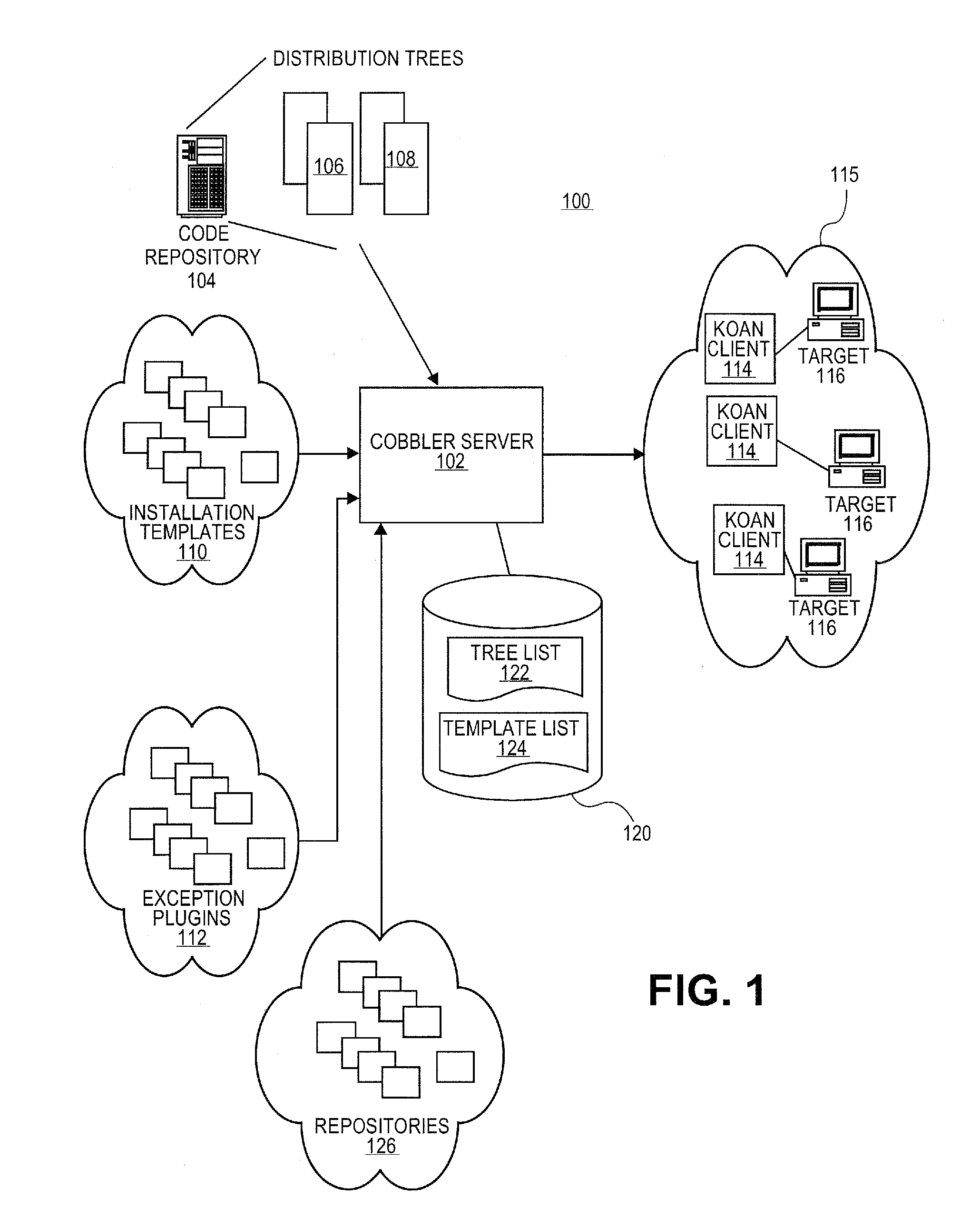
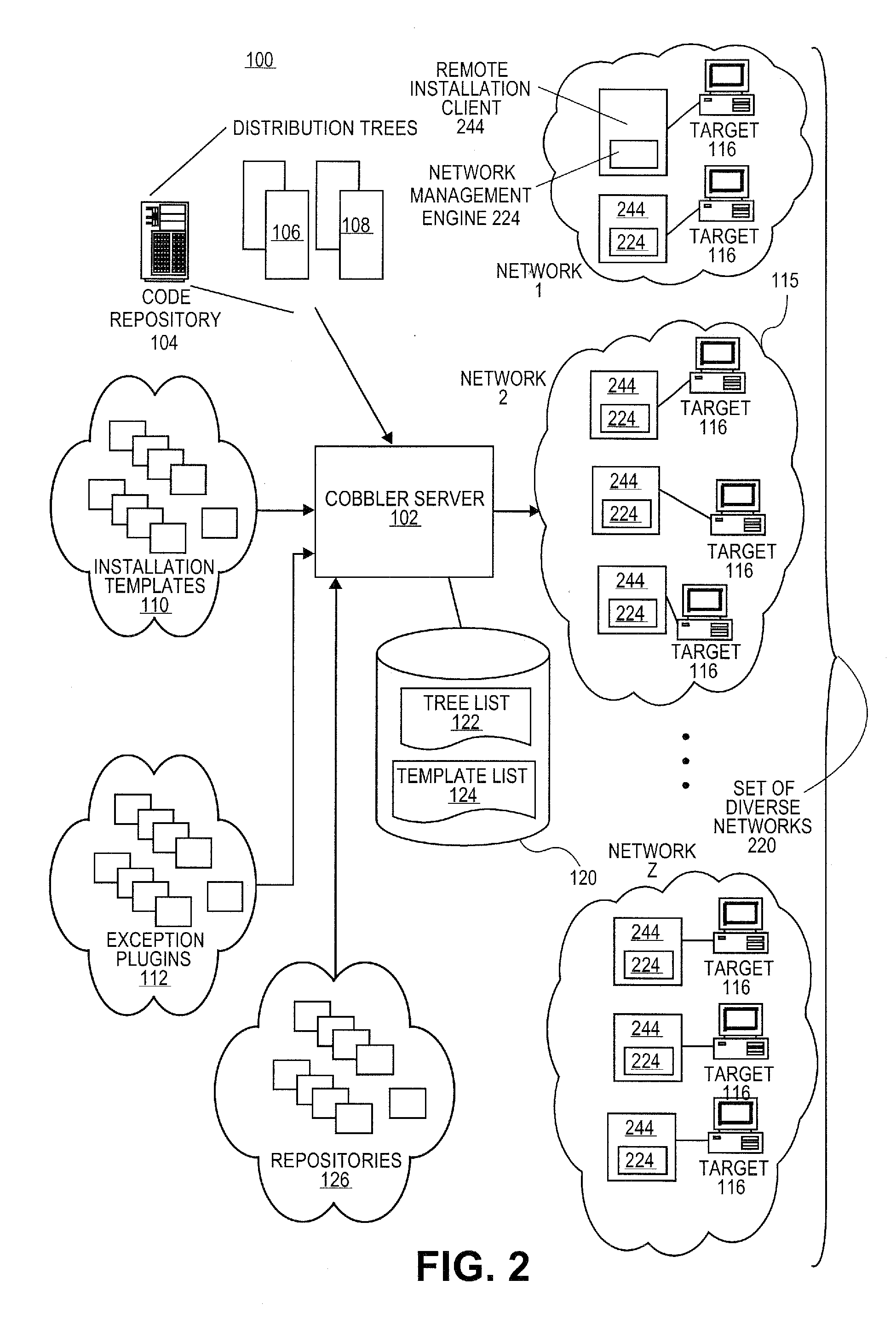
Systems and methods for software provisioning in multiple network configuration environment
Embodiments relate to systems and methods for provisioning software to machines in a set of diverse networks. A provisioning (or “cobbler”) server can interact with a remote installation client to initiate a software provisioning process to machines installed on two or more diverse networks, such as local area, wide area, virtual private, or other networks. The remote installation clients in different networks can report the network interface types and configurations of their networks to the cobbler server. During provisioning, the administrator can specify one software distribution to the entire set of diverse networks, and the cobbler server can generate different distribution versions tailored to the network configurations of the various different networks. In embodiments, the cobbler server can maintain a set of network configuration templates to automatically set network settings such as static IP addresses, gateway information, hostname information, network mask information, and other settings for the different network types.
Owner:RED HAT
Computer network with unique identification
InactiveUS8005981B2Function increaseMultiple digital computer combinationsData switching networksDomain nameComputer network server
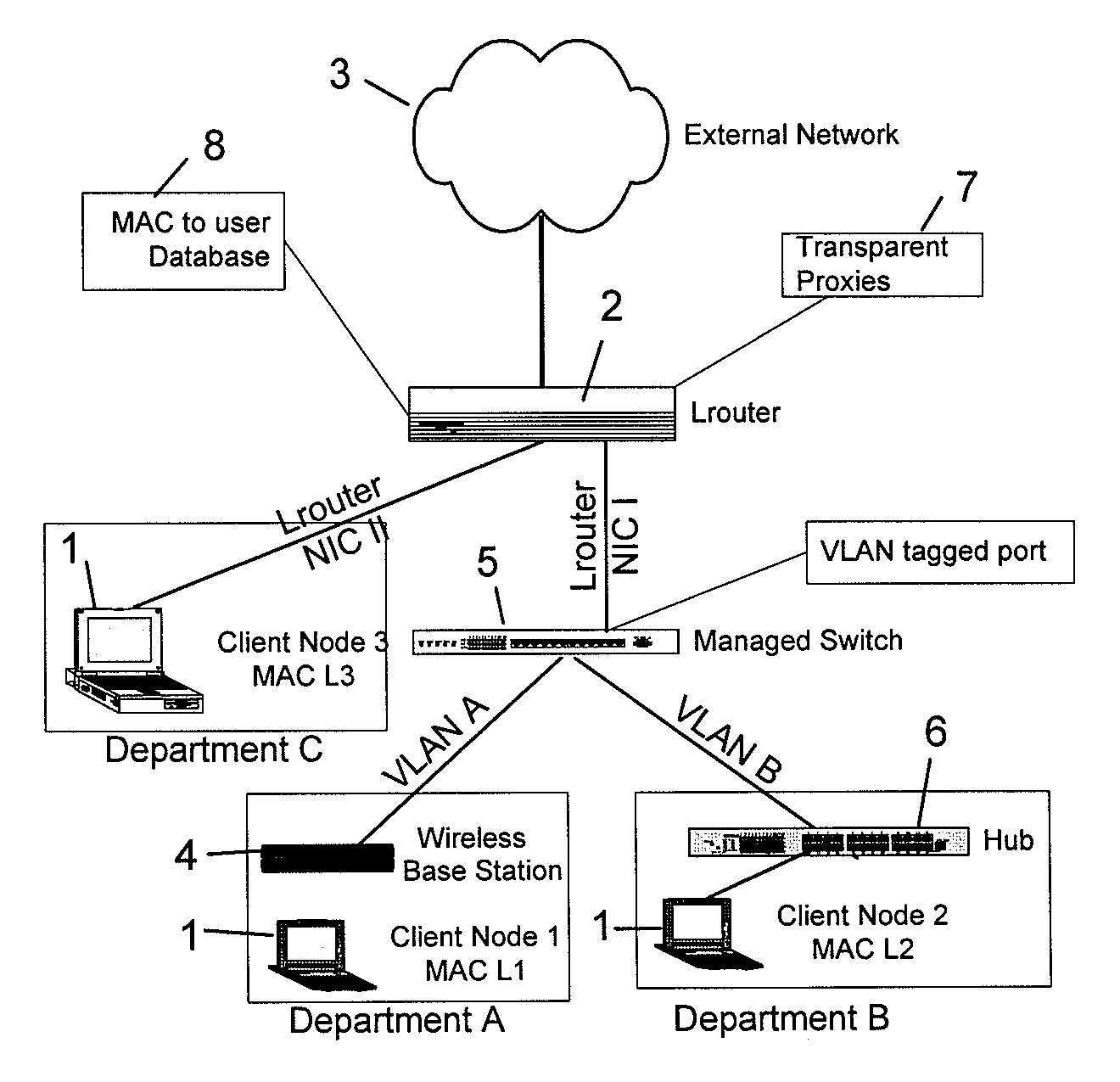
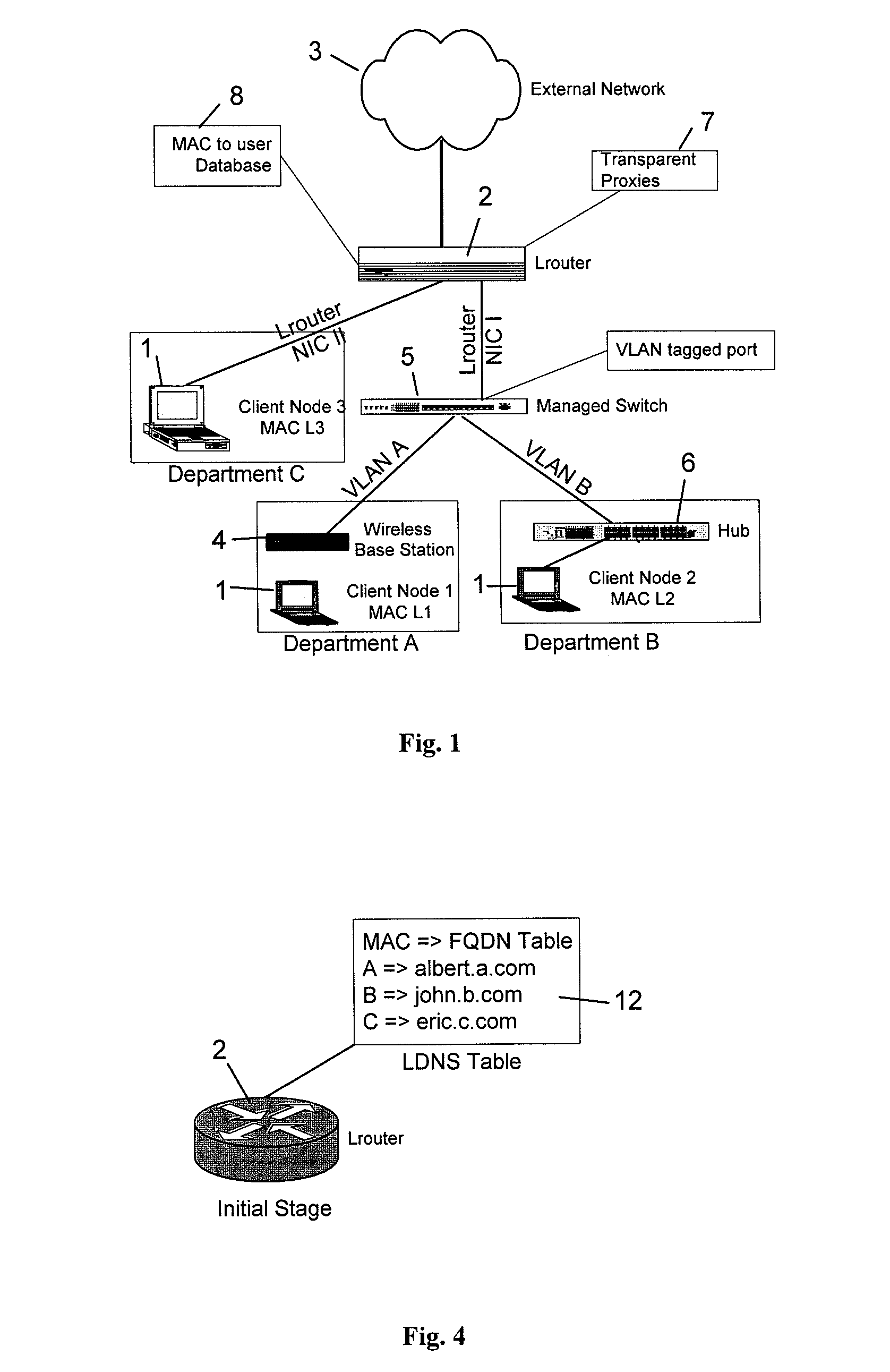
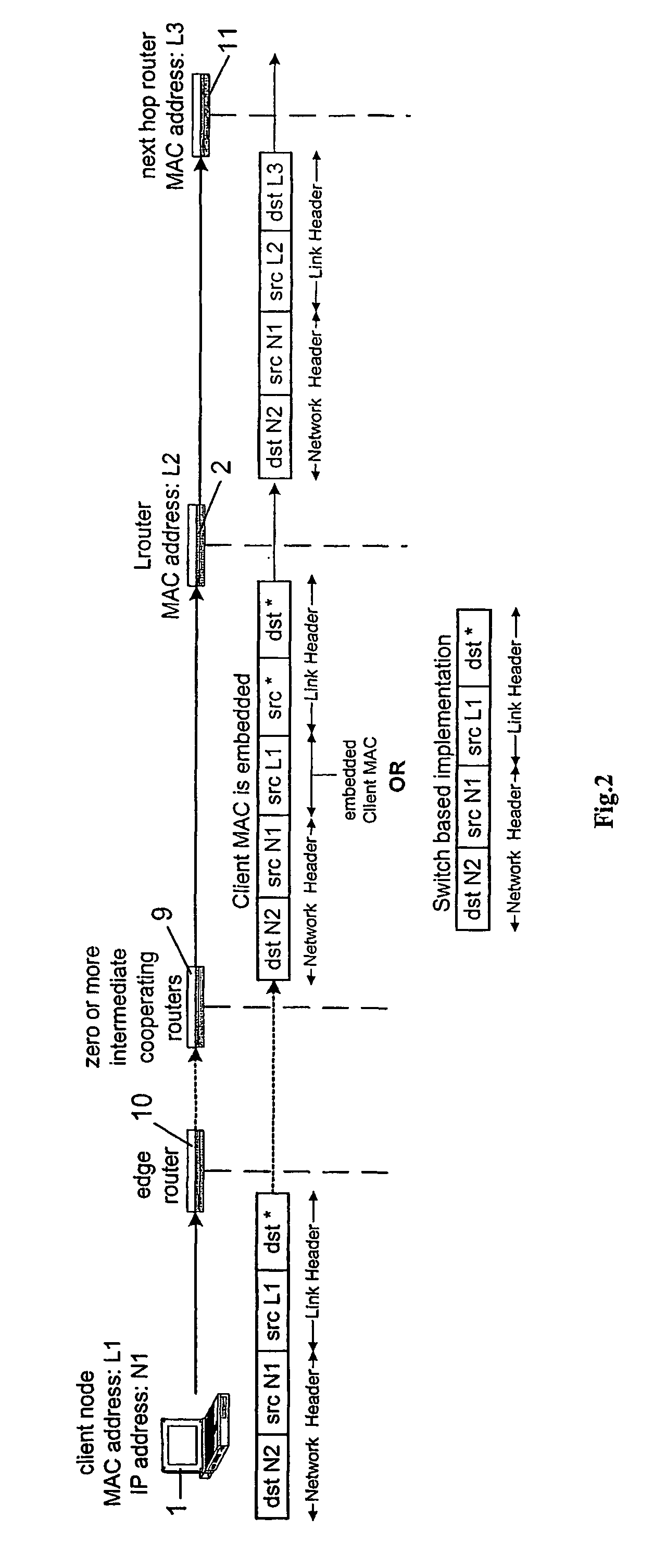
A computer network is described in which the data link layer address, e.g., MAC address, of the network cards of client nodes are used to uniquely identify the nodes in the provision of network to application layer services. A link layer aware router may determine the MAC address of a client node from a data packet transmitted by the client node, and determines the services to provide to the user, e.g., a proxy redirect of the packet, based on a database of client node MAC addresses to user attributes. By determining MAC addresses, the router can also identify unregistered MAC addresses, and can forward an HTTP request by an unregistered user to a remote configuration web page for registering the user, or to a security warning web page. The router may also support Network Address Translation and Domain Name System services using the MAC addresses, with a fully qualified domain name, hostname, or the like, being assigned to the MAC addresses.
Owner:ADVANCED NETWORK TECH LAB
System and method for controlling UNIX group access using LDAP
InactiveUS20030041154A1Computer security arrangementsMultiple digital computer combinationsUnixOperational system
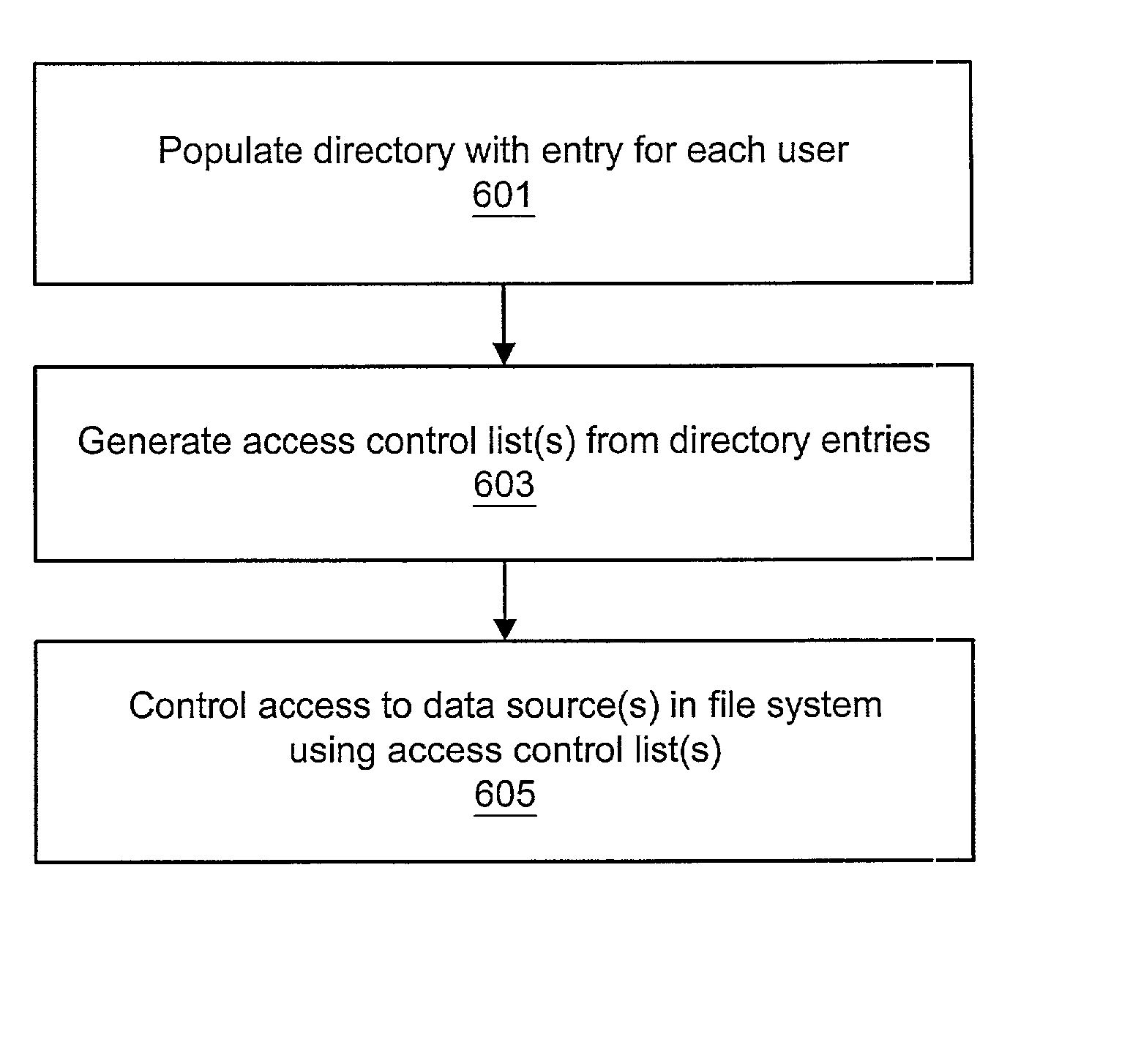
A system and method for controlling UNIX group access using an LDAP directory are disclosed. The system and method may be used to overcome a limitation on the size of groups that may be encountered in certain UNIX-based operating systems. A directory may be populated with entries for each of a plurality of users. Each entry in the directory may include information such as a user ID, user password, one or more group names, and optionally one or more hostnames. One or more access control lists may be generated from the directory entries. The operating system may check the access control list(s) to restrict access to the appropriate files or directories (i.e., data sources). For each data source which permits access by a particular group name, access may be granted to the data source to the users in the appropriate group access control list. Likewise, access may be denied to users who are not listed in the appropriate group access control list and who are not otherwise entitled to access (e.g., are not an owner of the data source). Access may include, for example, read, write, and / or execute access.
Owner:SUN MICROSYSTEMS INC
Techniques for dynamic updating and loading of custom application detectors
In various embodiments, a data-driven model is provided for an application detection engine for the detection and identification of network-based applications. In one embodiment, information can be input into an application detection database. The information may include a hostname, ports, transport protocol (TCP / UDP), higher layer protocol (SOCKS, HTTP, SMTP, FTP, etc), or the like. The information may be associated with a given application. The information may be used to create rule sets or custom program logic used by one or more various application detection engines for determining whether network traffic has been initiated by a given application. The information may be dynamically loaded and updated at the application detection engine.
Owner:ACTIANCE
Method to import/export or detach/attach a file to/from a remote mail server
InactiveUS7133897B1User identity/authority verificationMultiple digital computer combinationsPasswordUser input
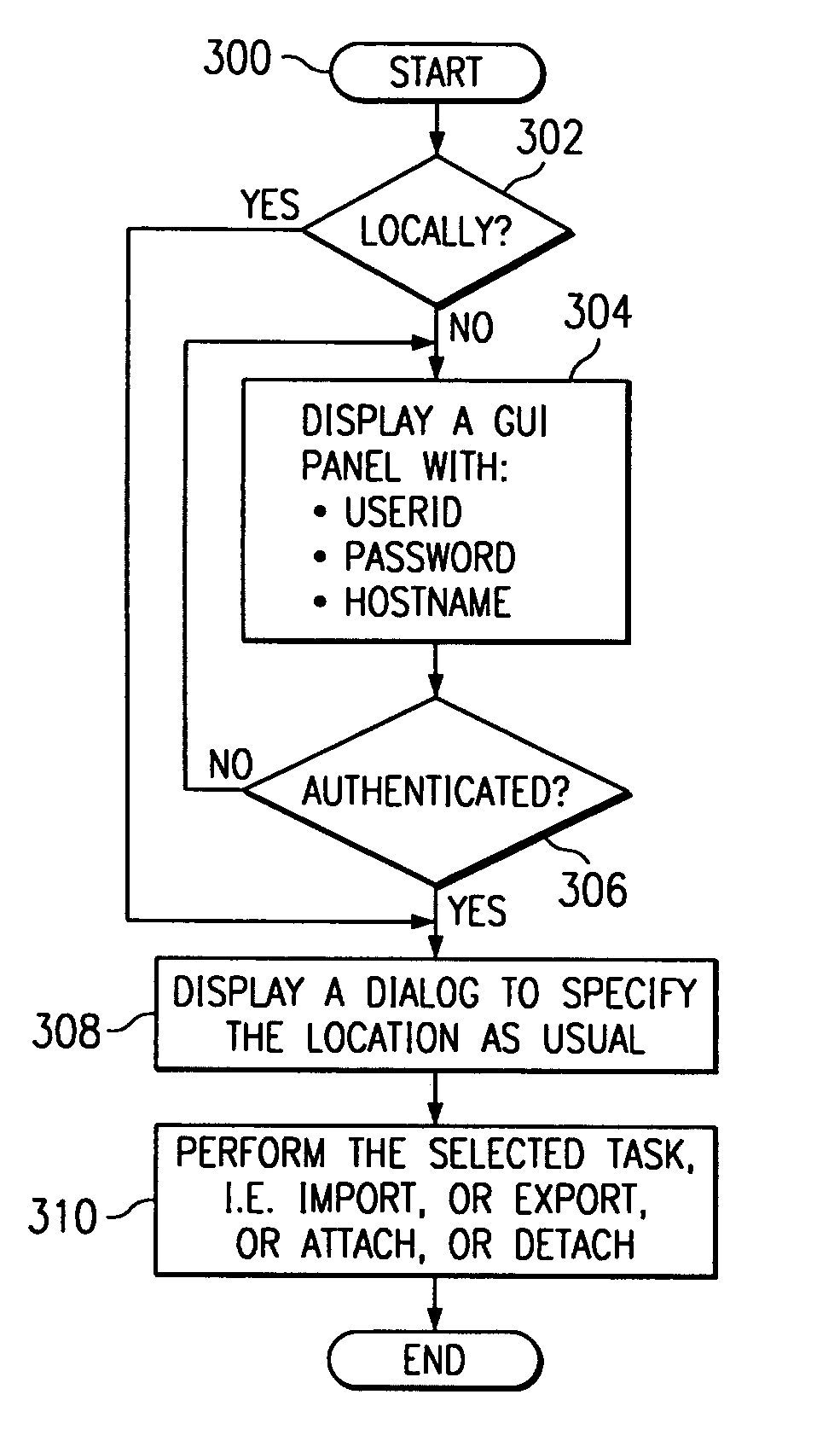
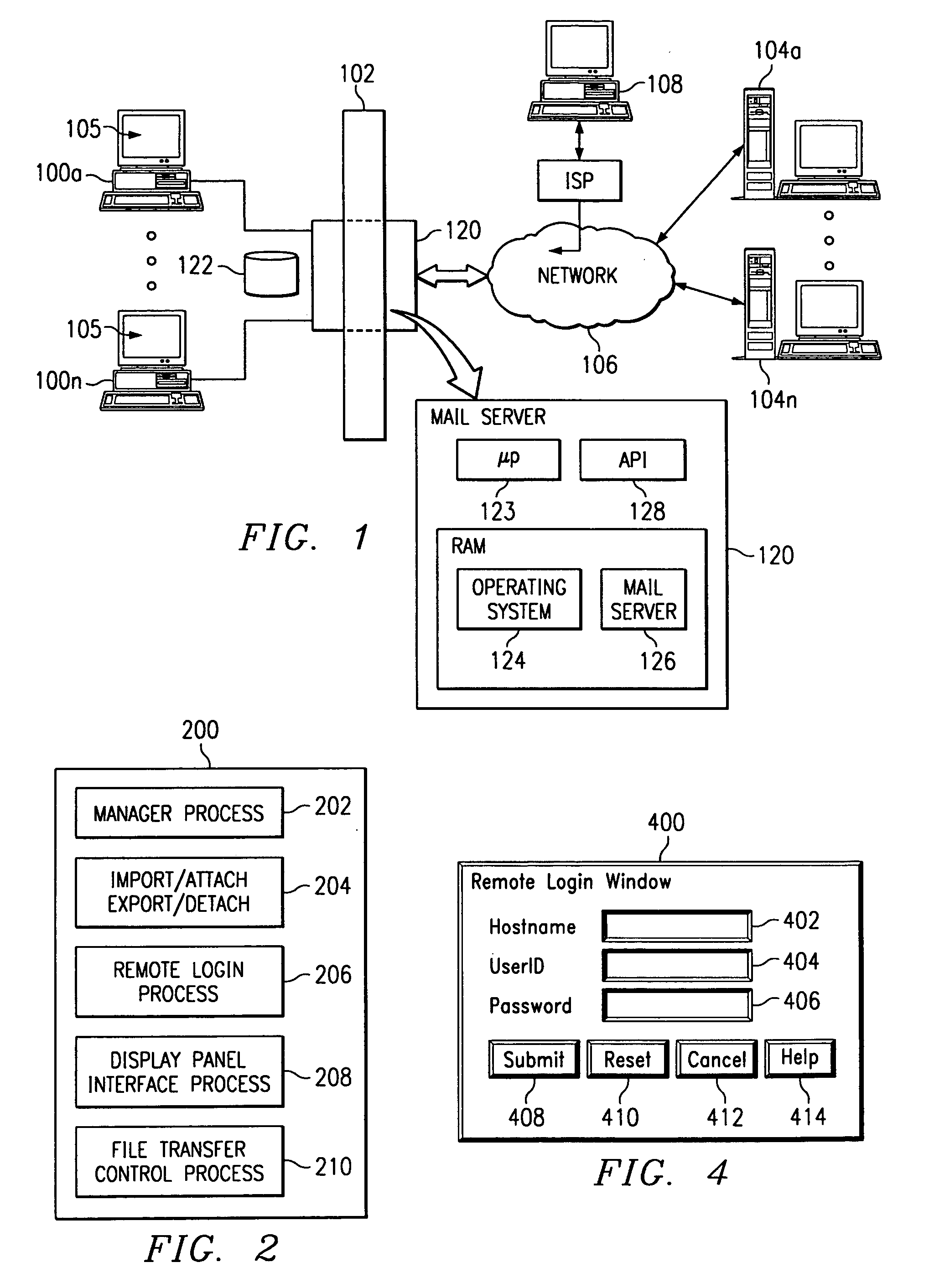
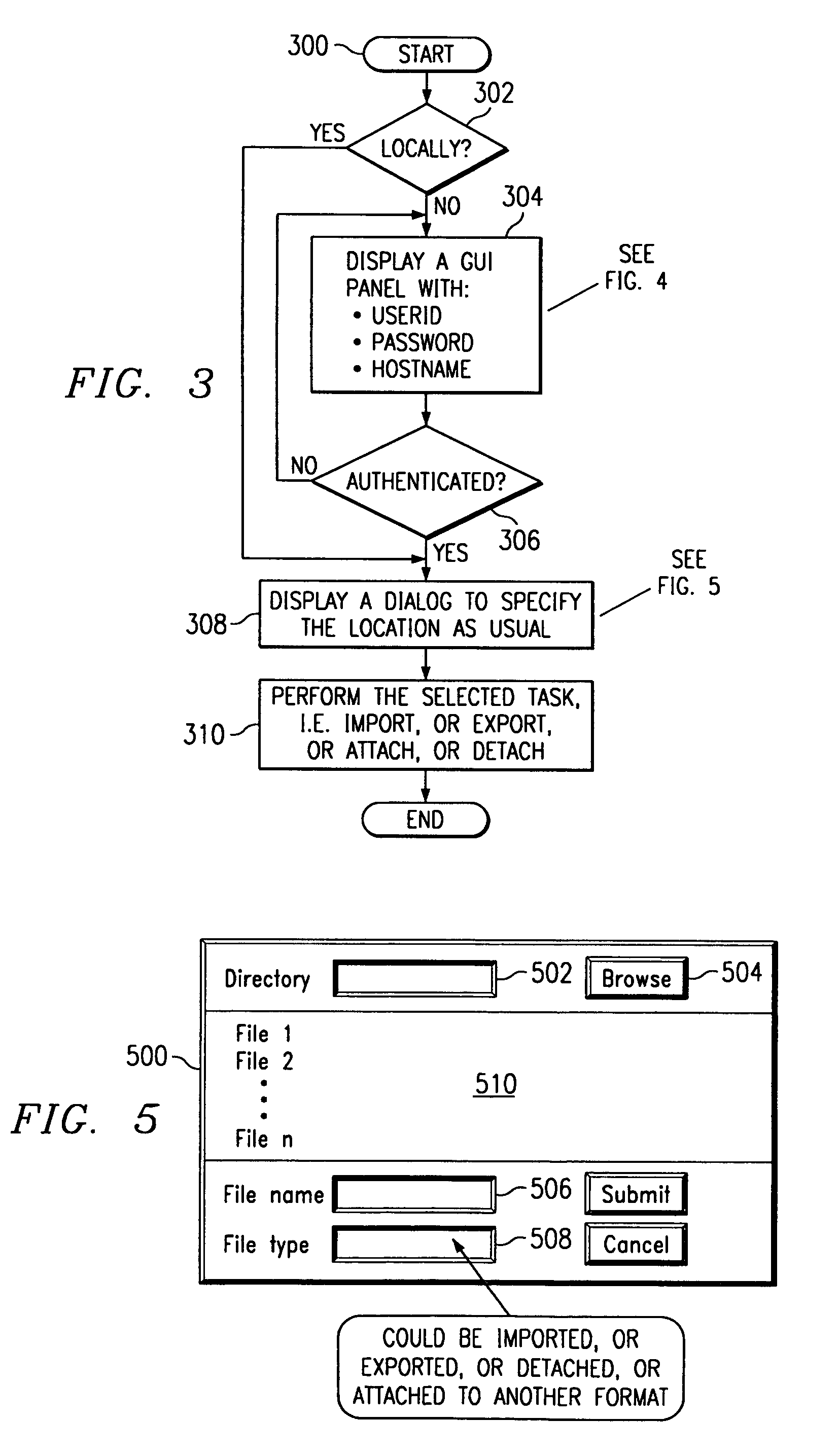
A computer-implemented method for importing / attaching or exporting / detaching a file during a given e-mail operation. From a user's perspective, the method begins when the user elects to perform the import / attach or export / detach function with respect to a given file. If the file resides locally, the operation proceeds as usual by carrying out the function as if the file is on the local system and resides in a known place. If, however, the file does not reside locally, a panel or other user interface is displayed. Using this panel, the user may then attempt to log into a remote system on which the file is supported. Thus, for example, the user interface may require the user to enter a userid, password, hostname, or some combination thereof. If the user login is successful, the routine gets or puts the file (e.g., using an FTP operation) as required, preferably as a background process. Upon completion of the file transfer, the routine then automatically completes the import / attach or export / detach function as if the file is on the local system and resides in the known location.
Owner:HCL TECH LTD
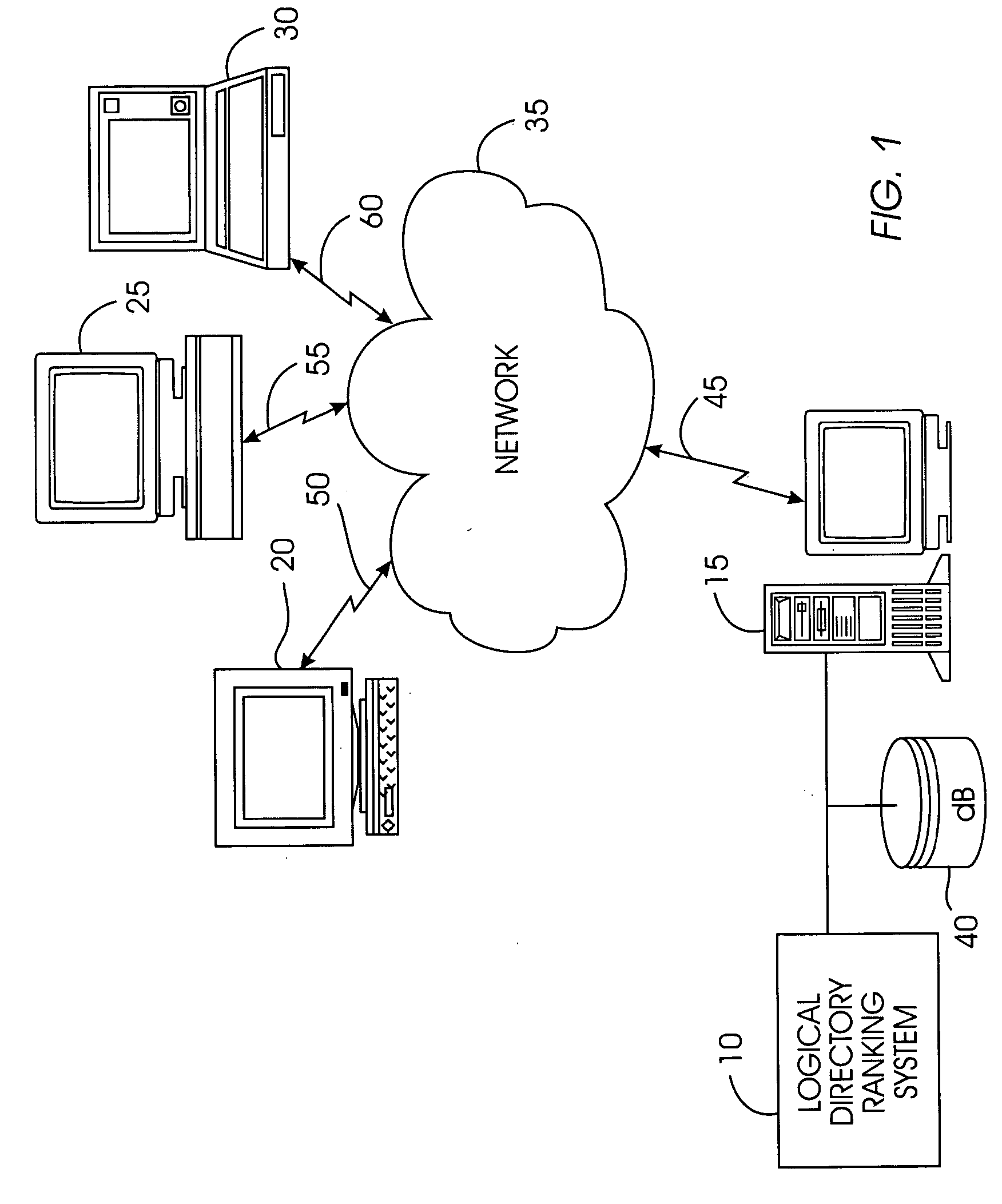
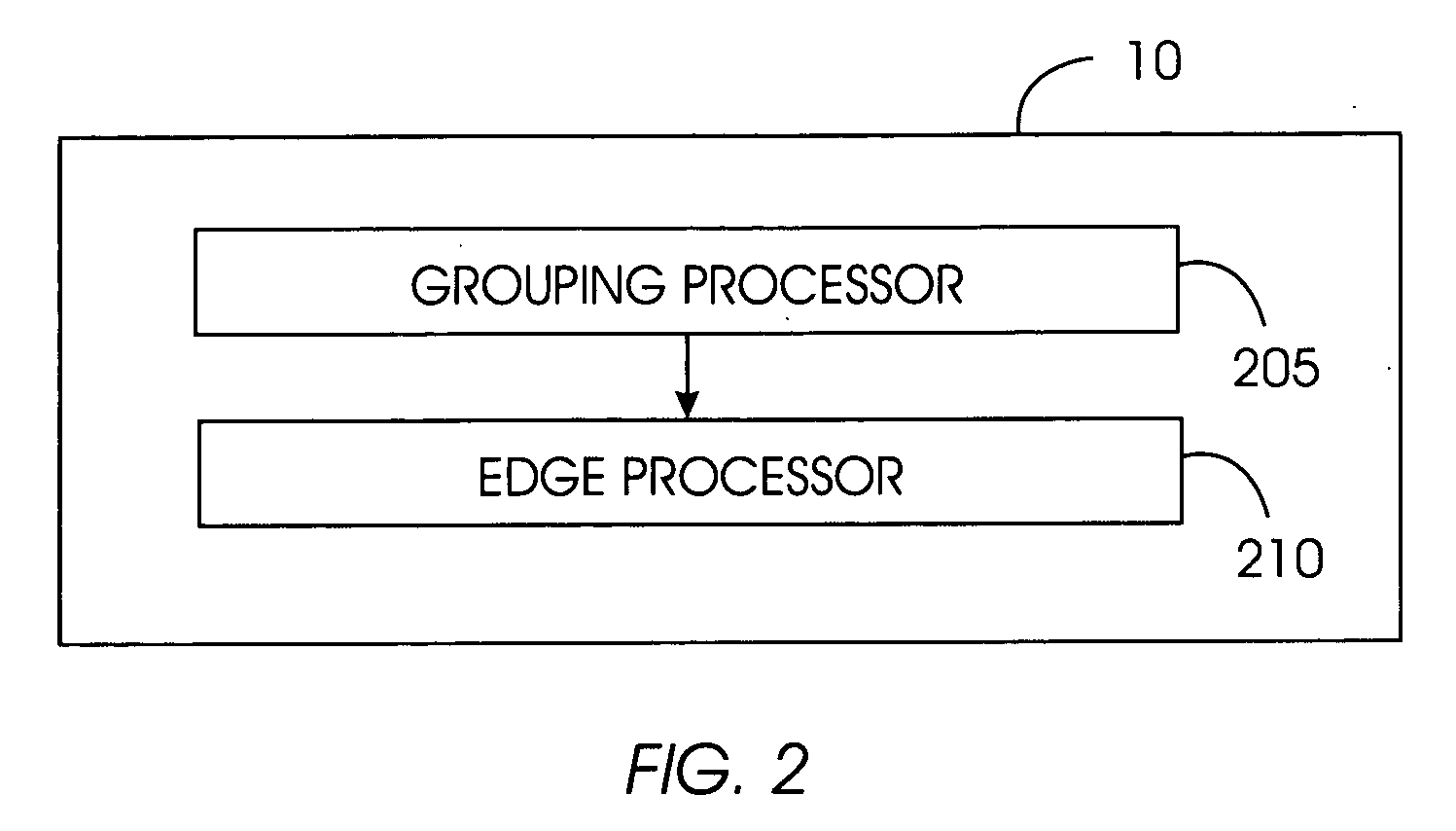
System and method for ranking logical directories
InactiveUS20050256887A1Reduce computationReduce the amount of dataData processing applicationsWeb data indexingGranularityPaper document
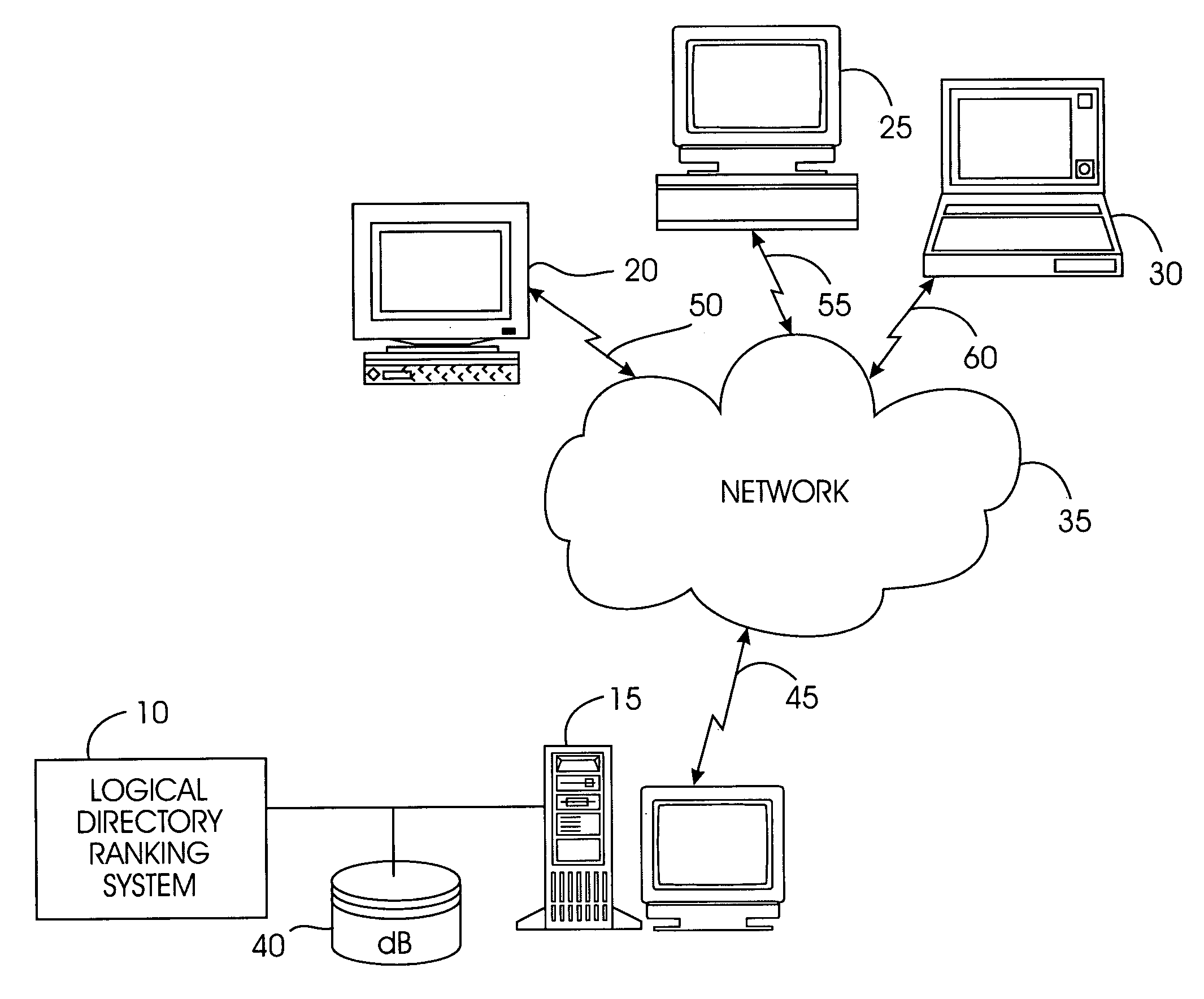
A logical directory ranking system ranks documents or web pages utilizing logical directories. From the hierarchical structure represented in a URL string, URLs can often be grouped into “compound documents” that represent a single unit of information. Such compound documents tend to comprise URLs that agree up to a last delimiter such as a forward slash ( / ). The present system groups together compound documents as a single information node with one or more leaves, constructing a logical directory graph. URLs can be grouped at a level of granularity below an individual directory. For example, the URLs may be grouped together on the basis of hostname, domain, or any level of the hierarchy of the URLs. Edges in the logical directory graph are formed by links between the logical directories. Edges have weights corresponding to the number of links between logical directories. Nodes have weights corresponding to the number of web pages or leaves represented by a node. A ranking level is determined for each node as a function of the node weight and the edge weight. The ranking level is then applied to each URL that the node represents.
Owner:IBM CORP
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com