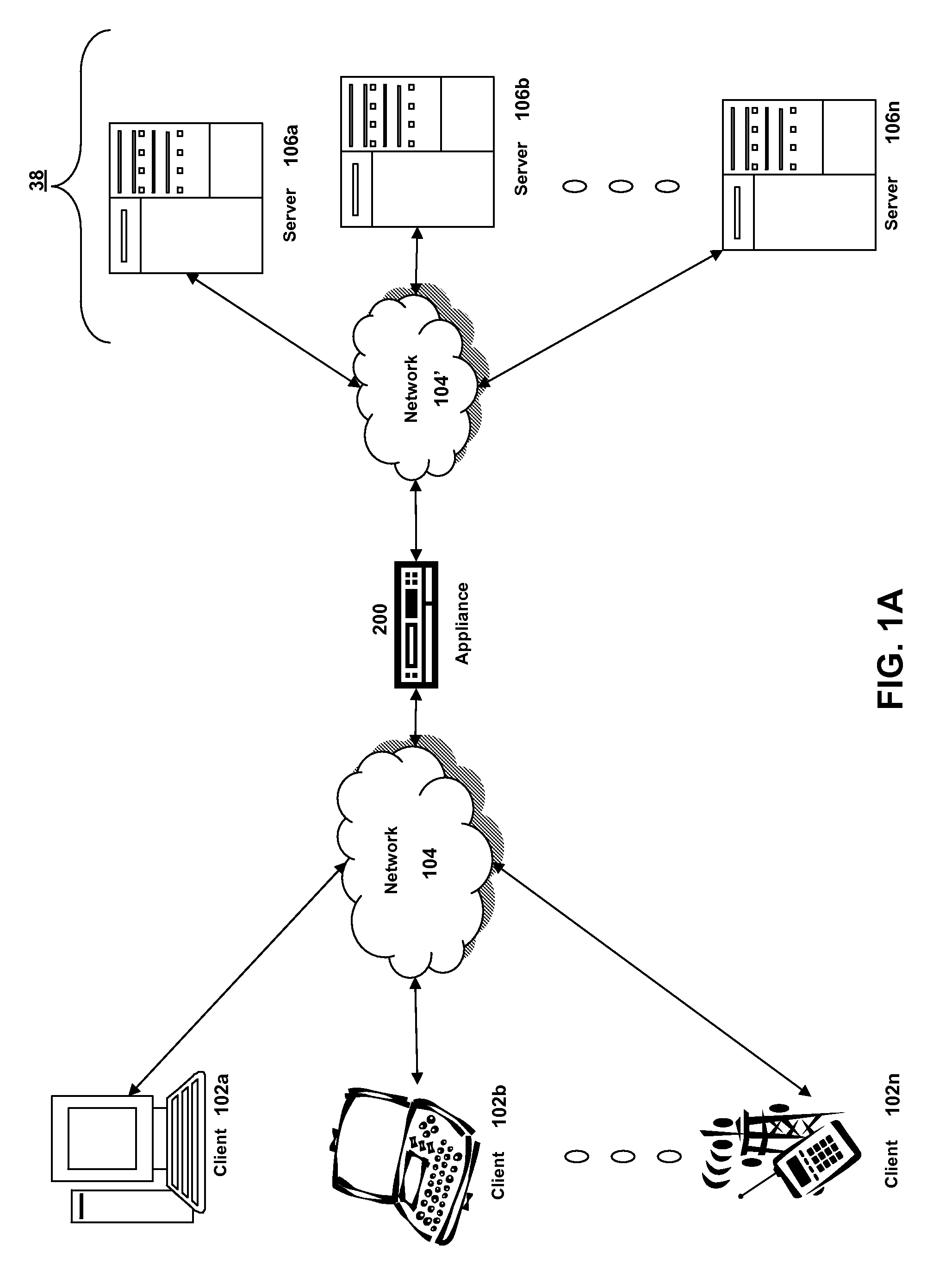
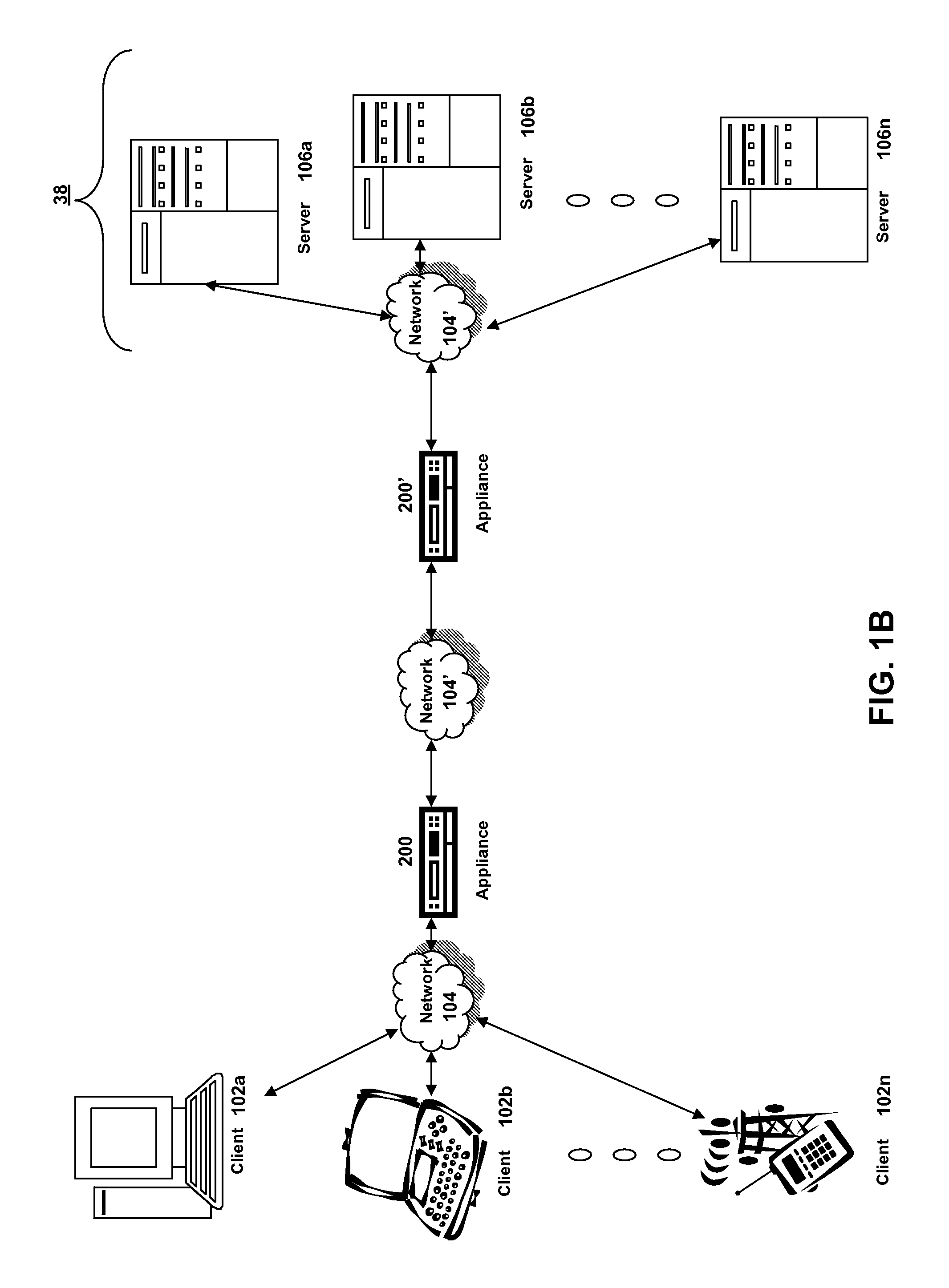
Patents
Literature
484 results about "Simple Network Management Protocol" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
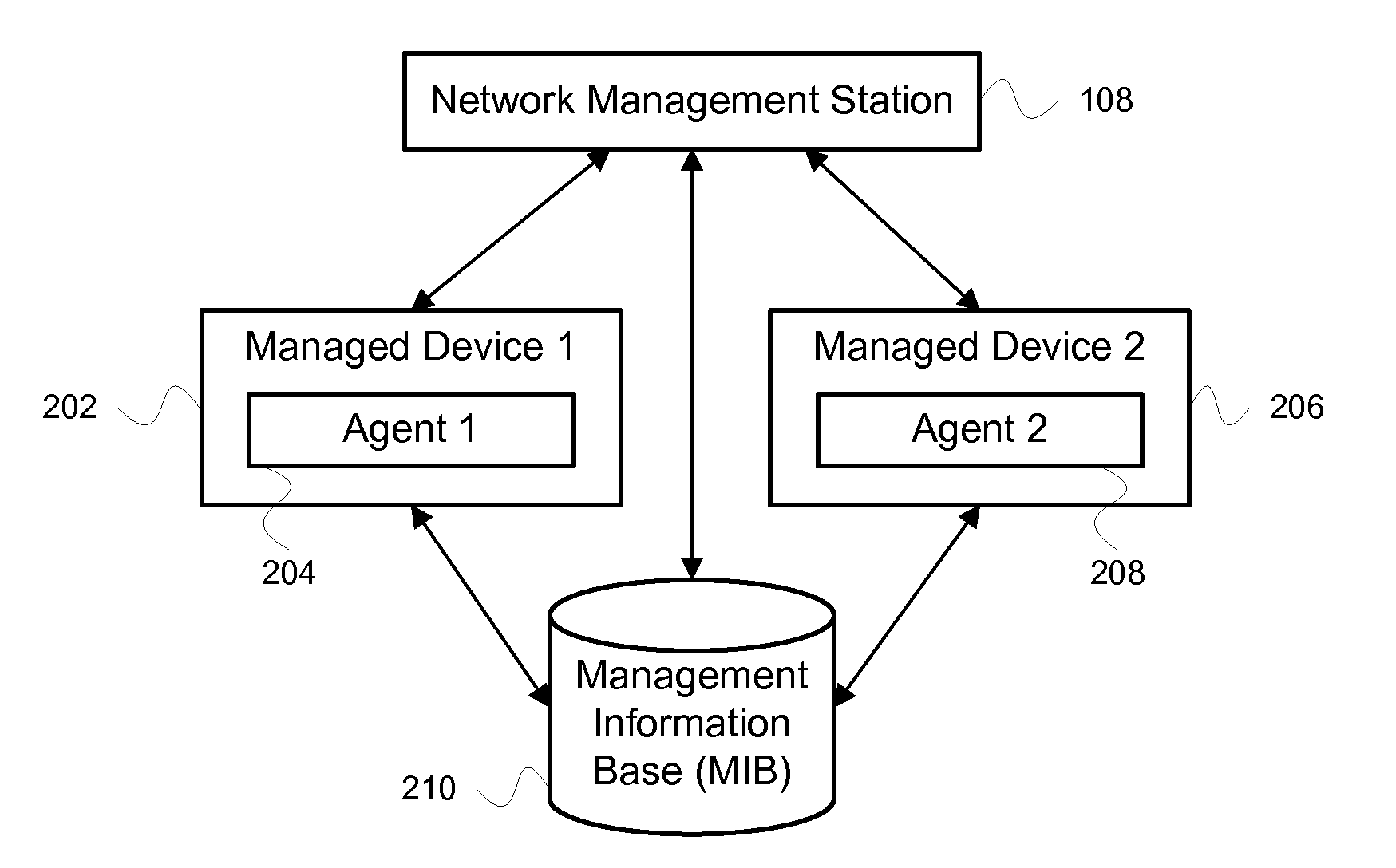
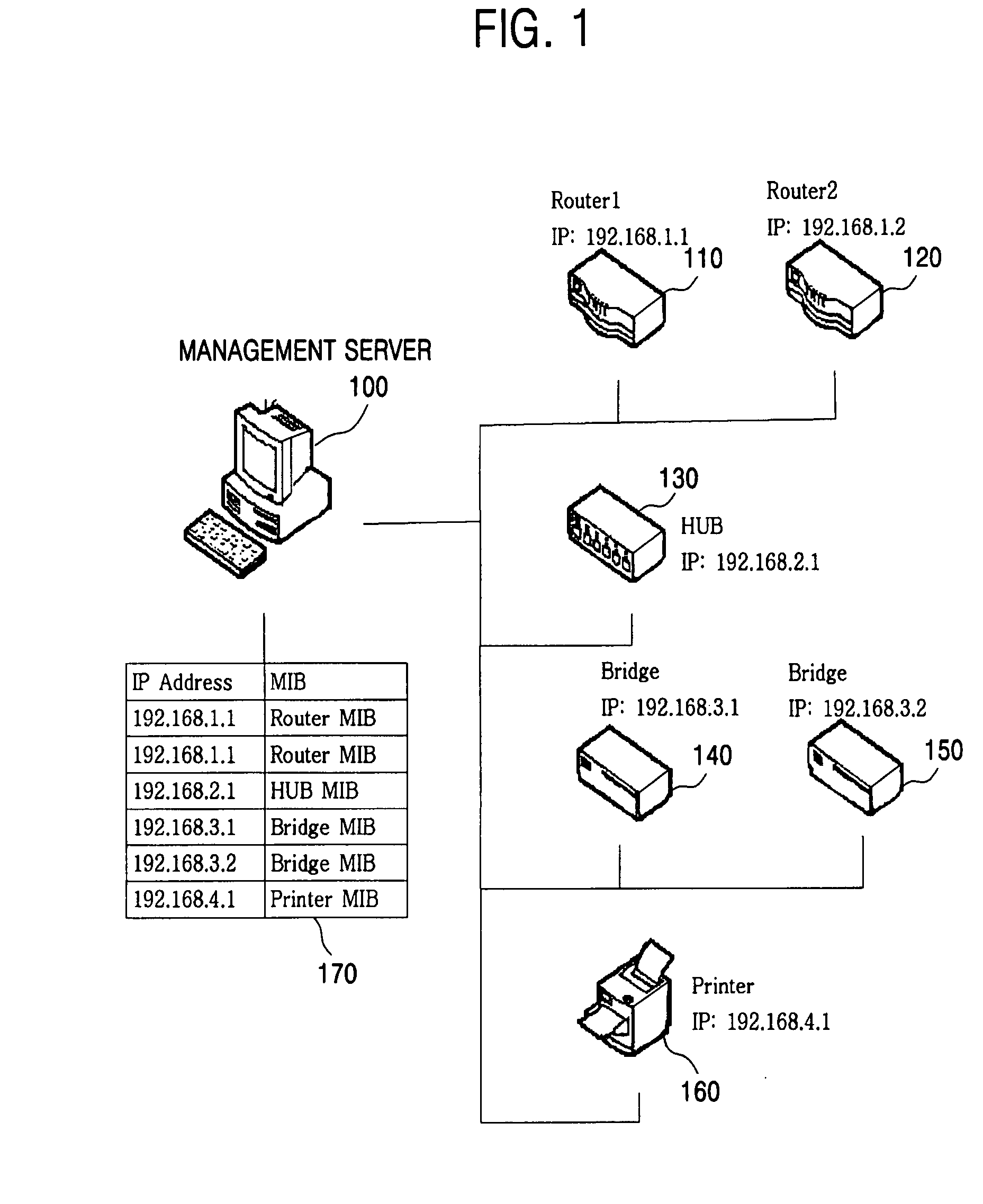
Simple Network Management Protocol (SNMP) is an Internet Standard protocol for collecting and organizing information about managed devices on IP networks and for modifying that information to change device behavior. Devices that typically support SNMP include cable modems, routers, switches, servers, workstations, printers, and more.
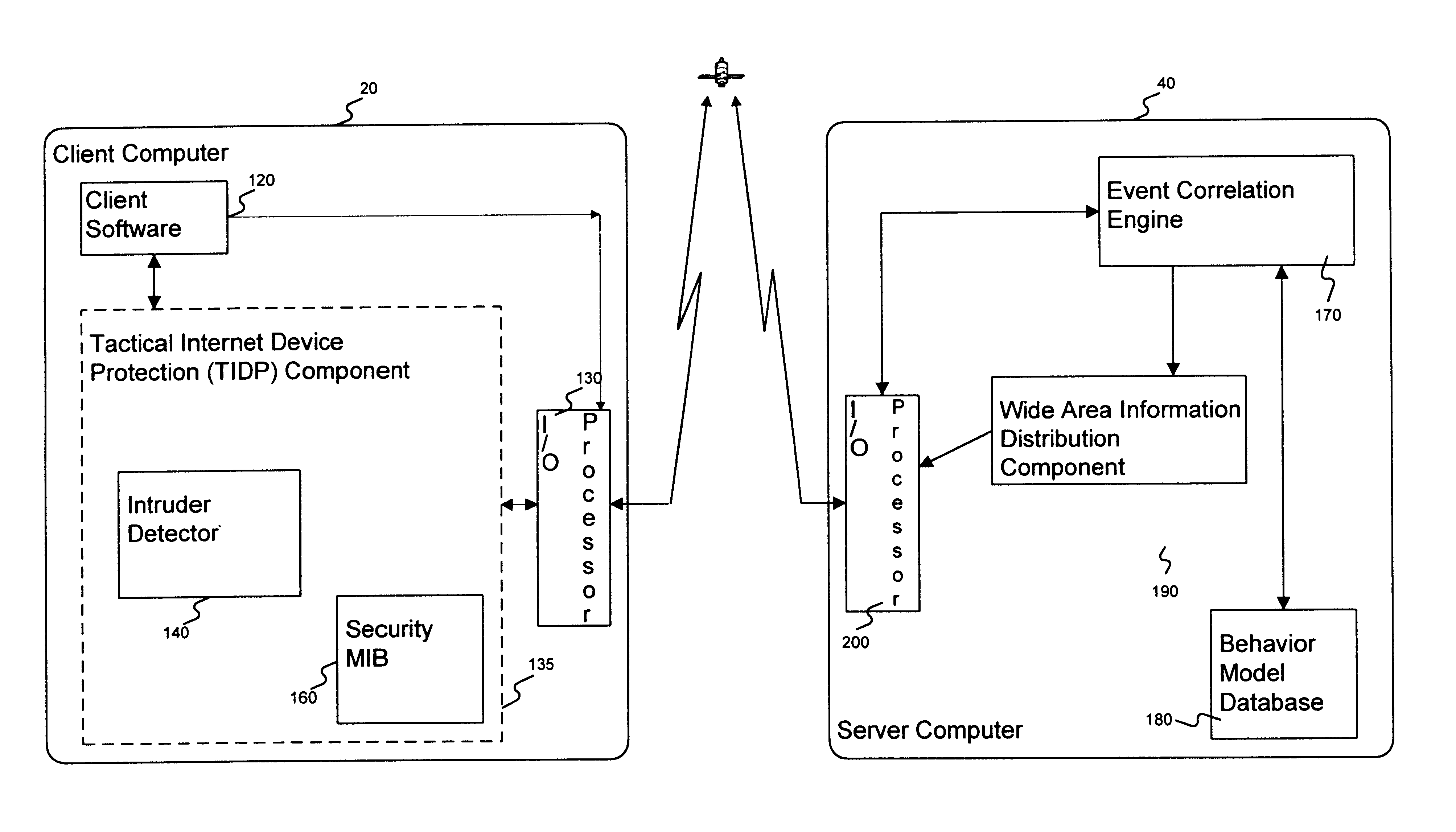
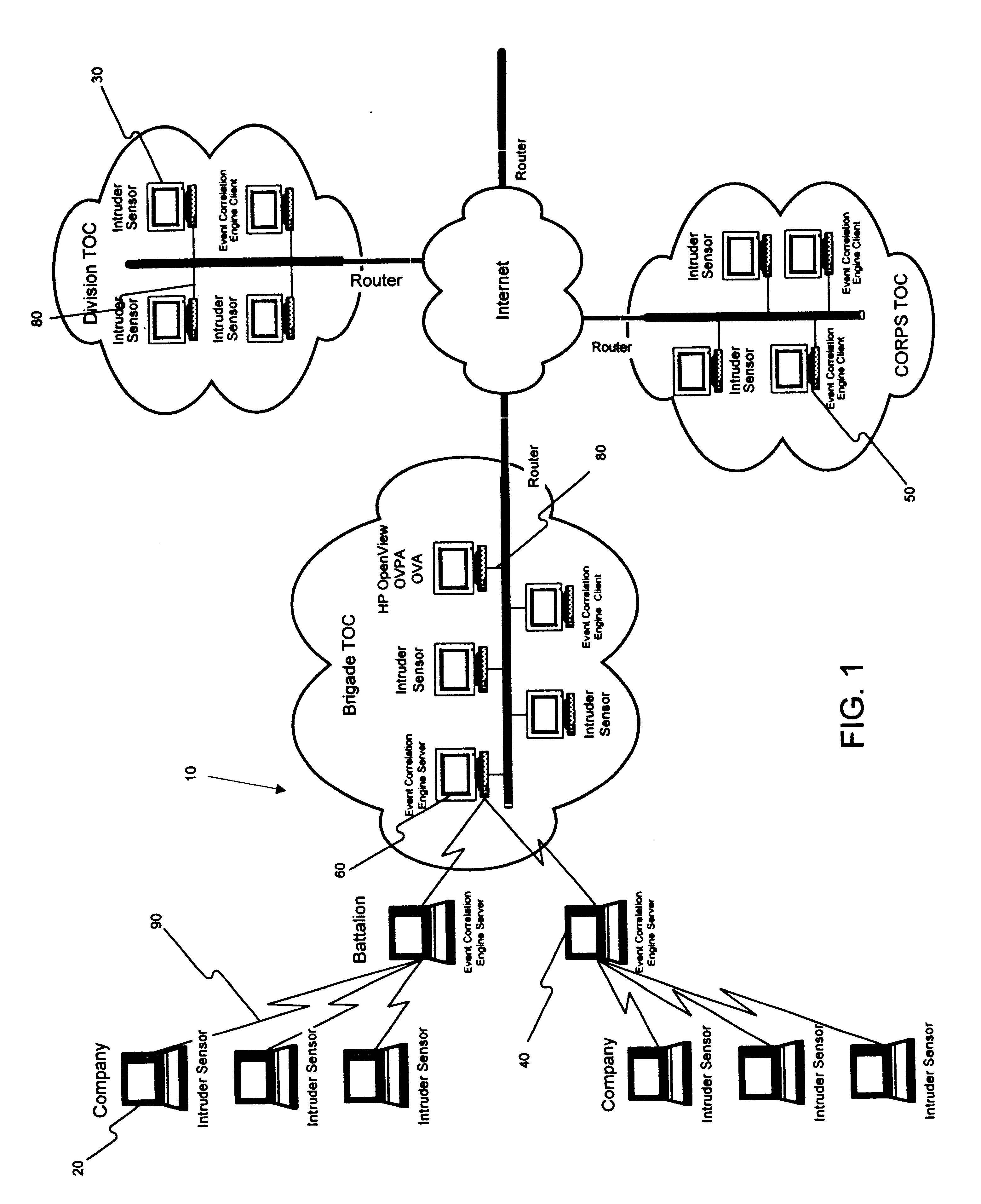
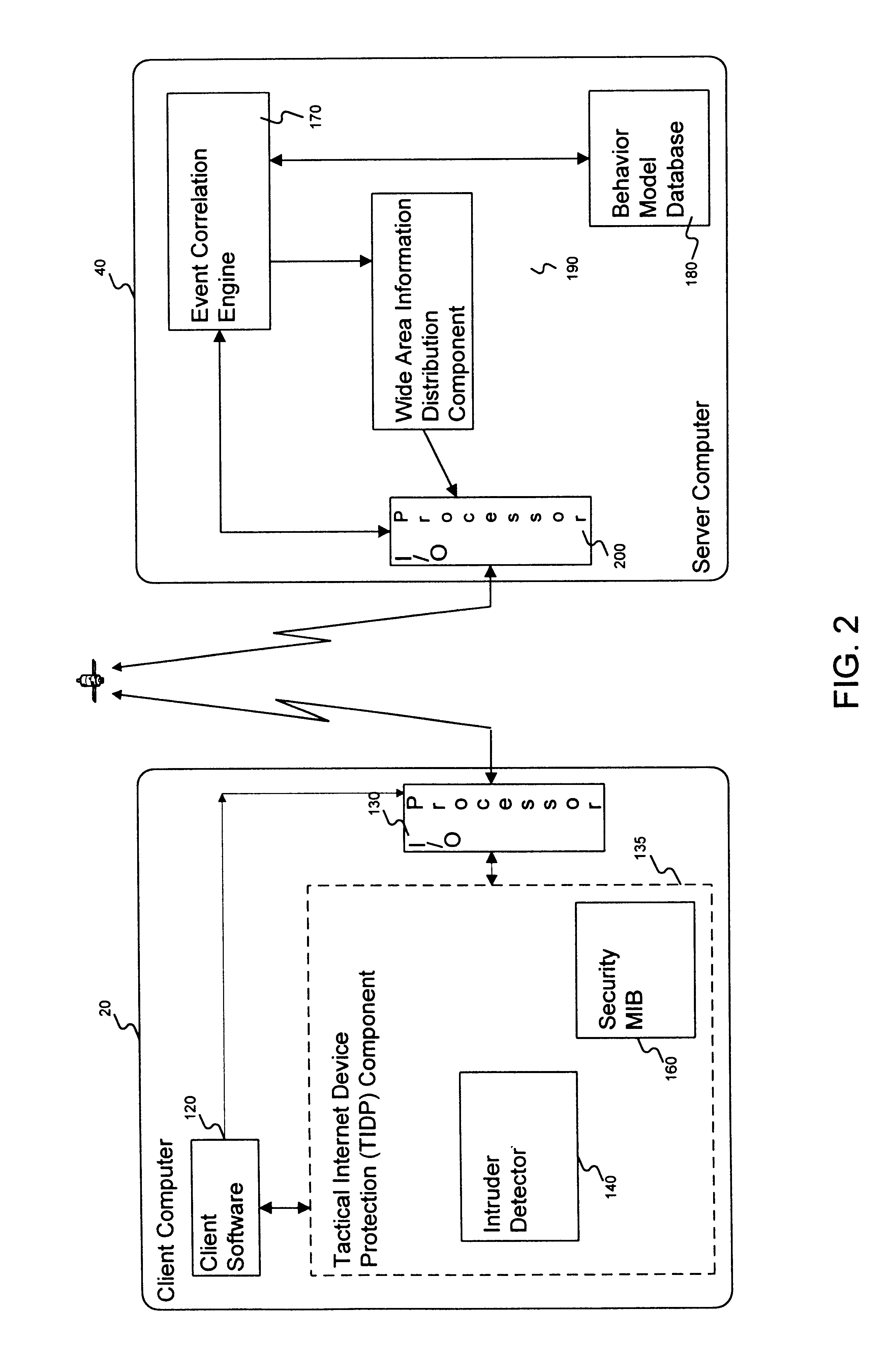
Method and apparatus for an intruder detection reporting and response system
InactiveUS6910135B1Improve securityWide rangeMemory loss protectionError detection/correctionThe InternetWorkstation
A method and apparatus is disclosed for improving the security of computer networks by providing a means operating passively on the network for detecting, reporting and responding to intruders. The system is comprised of a plurality of intruder sensor client computers and associated event correlation engines. Resident in the memory of the client computer and operating in the background is a Tactical Internet Device Protection (TIDP) component consisting of a passive intruder detector and a security Management Information Base (MIB). The passive intruder detector component of the TIDP passively monitors operations performed on the client computer and emits a Simple Network Management Protocol (SNMP) trap to an event correlation engine when it identifies a suspected intruder. The event correlation engine, through the use of a behavior model loaded in its memory, determines whether the user's activities are innocent or those of a perspective intruder. When the event correlation engine is unable to classify a user based on a single trap message, it can request historical information from the security MIB, a database of the operating history of the client computer including a chronology of the illegal operations performed on the client. Once the event correlation engine determines that an intruder is located at an associated client workstation, it generates a status message and transmits the message to all of its subscribers, informing them of the presence and location of a suspected intruder.
Owner:LEVEL 3 COMM LLC +2
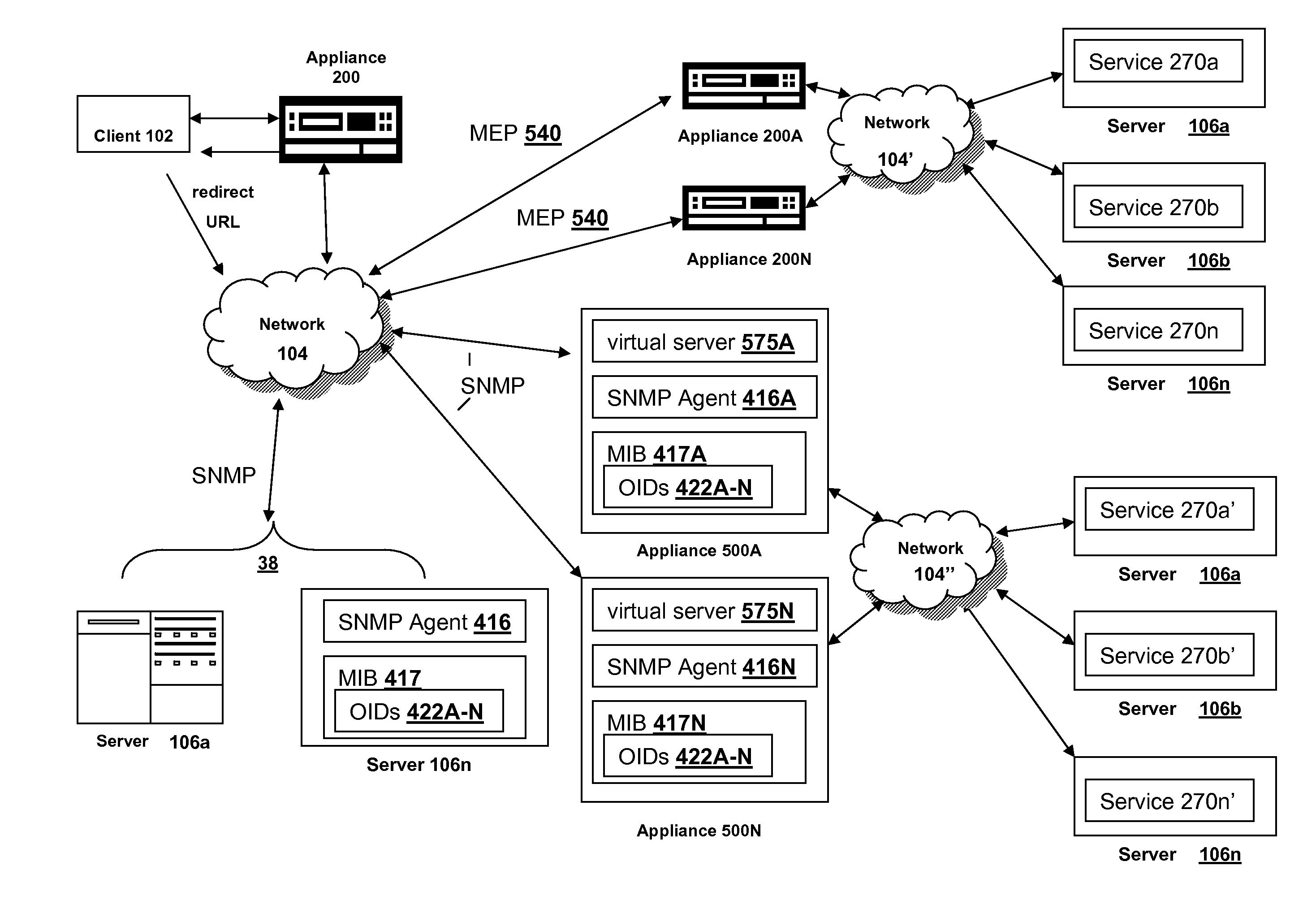
Systems and Methods for Load Balancing Based on User Selected Metrics
ActiveUS20080225710A1Good for load balancingGood flexibilityError preventionTransmission systemsDevice MonitorSimple Network Management Protocol
The present invention provides improvements to load balancing by providing a load balancing solution that allows a user to select metrics, weights and thresholds from metrics collected or determined by a load balancing appliance as well as metrics obtained from another device, such as a server running the service. The systems and methods described providing a load balancing technique in which load balancing decisions can be made based on metrics known by another device monitoring such metrics. The load balancing appliance uses a network management protocol and communication model, such as a Simple Network Management Protocol (SNMP), to identify and collect metrics from a server, service or other device. These metrics are available on the load balancing appliance with appliance determined metrics. Via a configuration interface of the appliance, a user can select one or more appliance determined metrics and / or the metrics obtained via the network management protocol to determine the load of a service.
Owner:CITRIX SYST INC
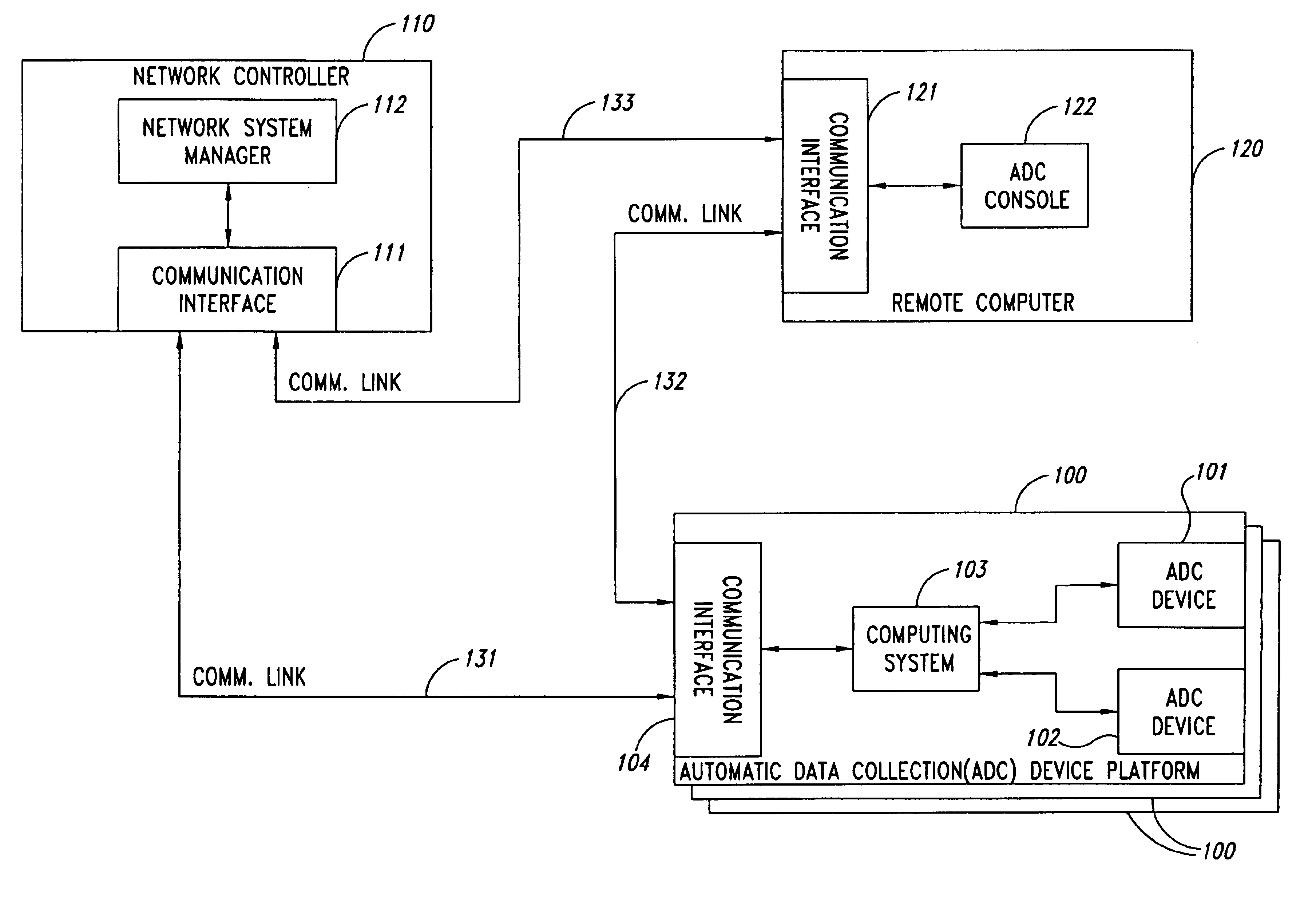
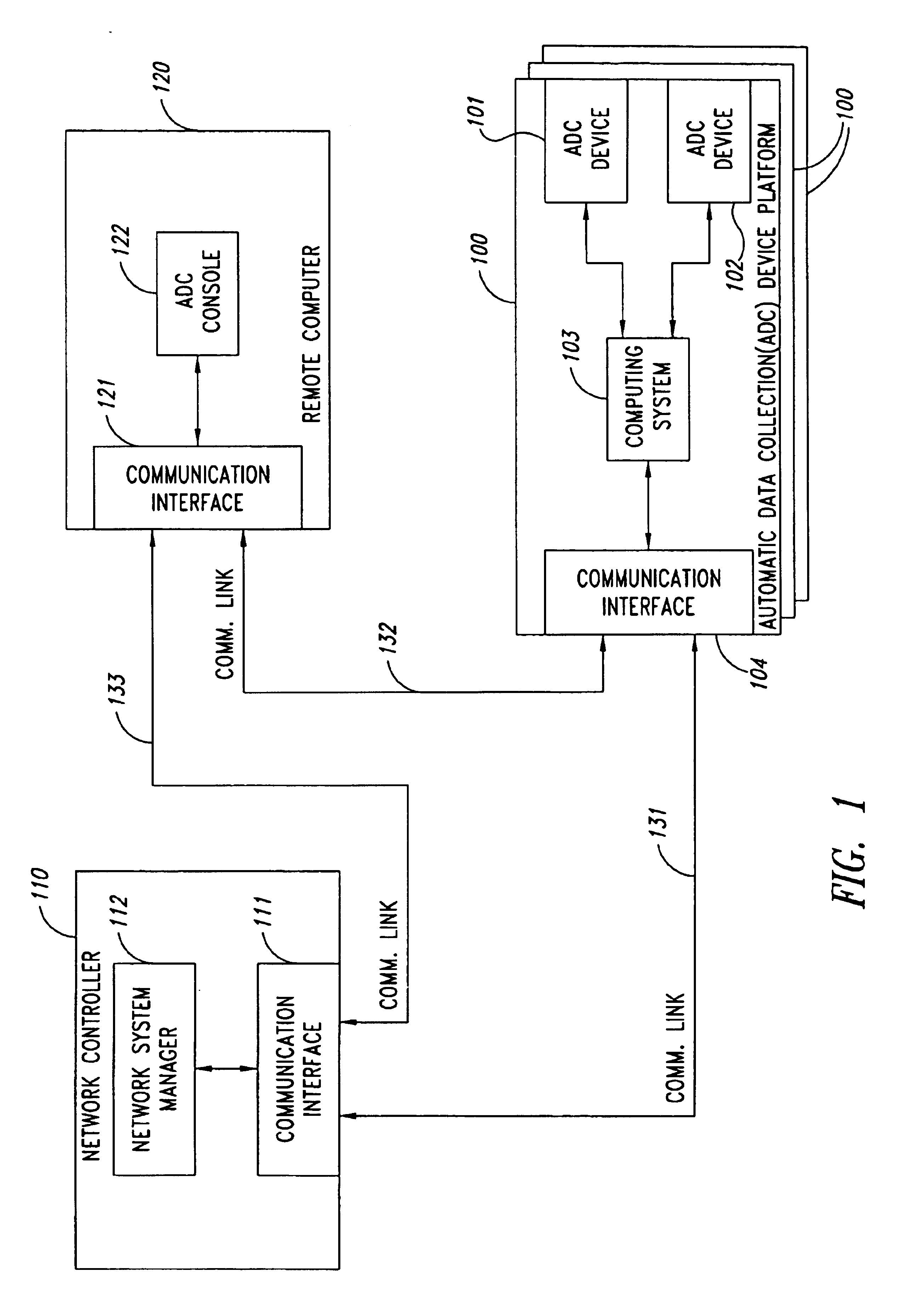
Remote anomaly diagnosis and reconfiguration of an automatic data collection device platform over a telecommunications network
InactiveUS6857013B2Detecting faulty hardware by remote testDigital computer detailsTelecommunications linkExtensible markup
Owner:INTERMEC IP CORP
System and method for proxying network management protocol commands to enable cluster wide management of data backups
Owner:NETWORK APPLIANCE INC
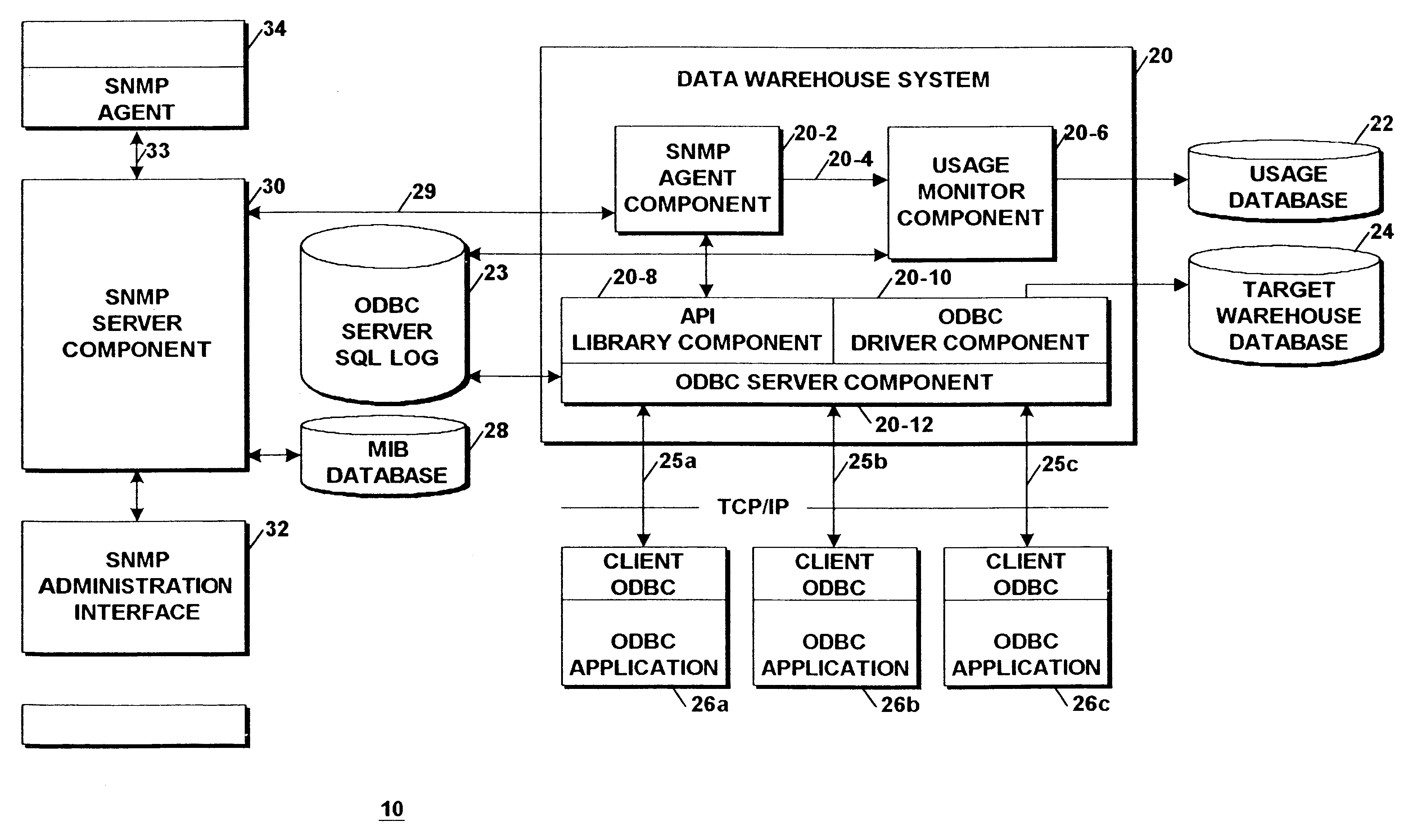
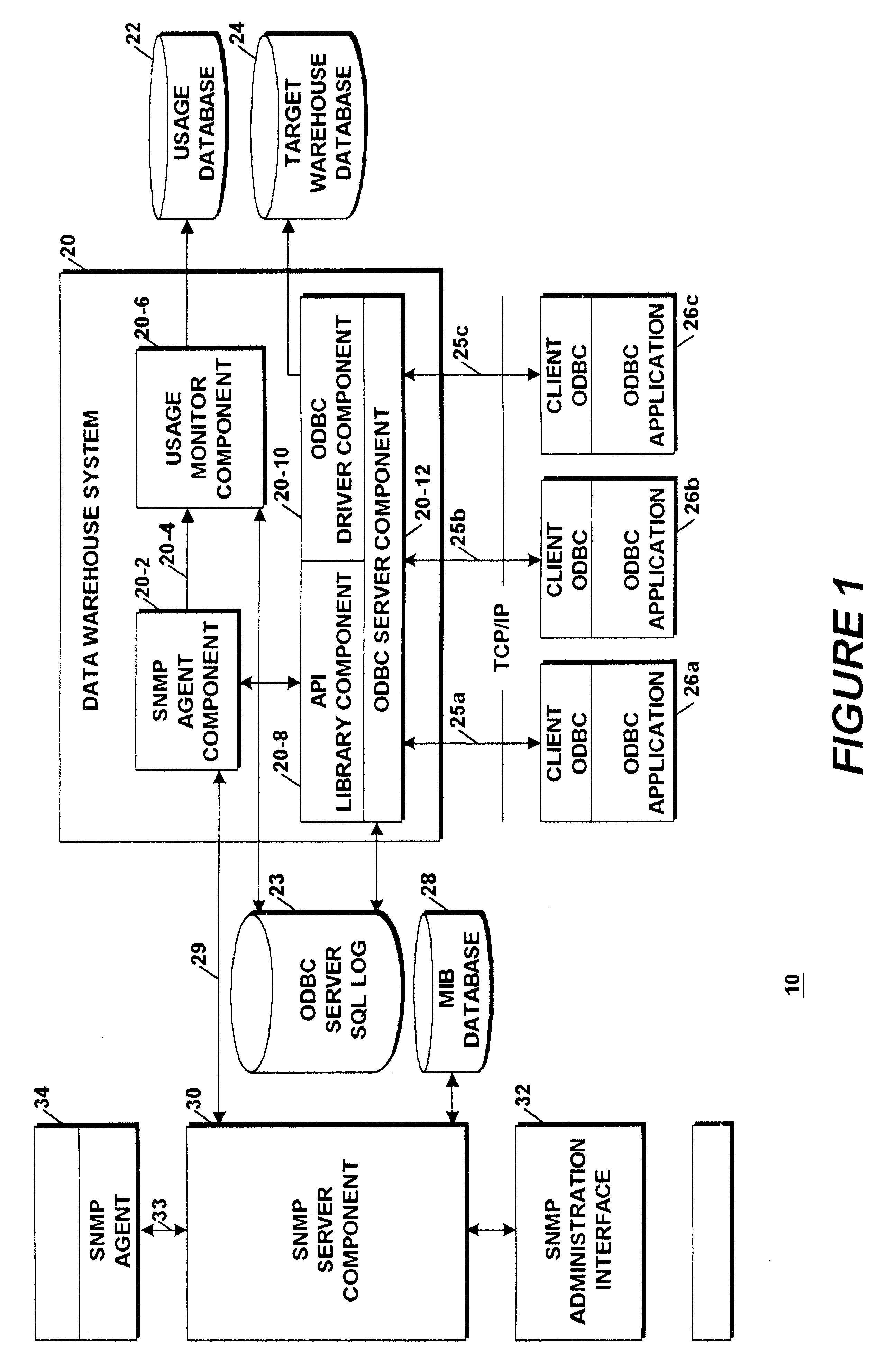
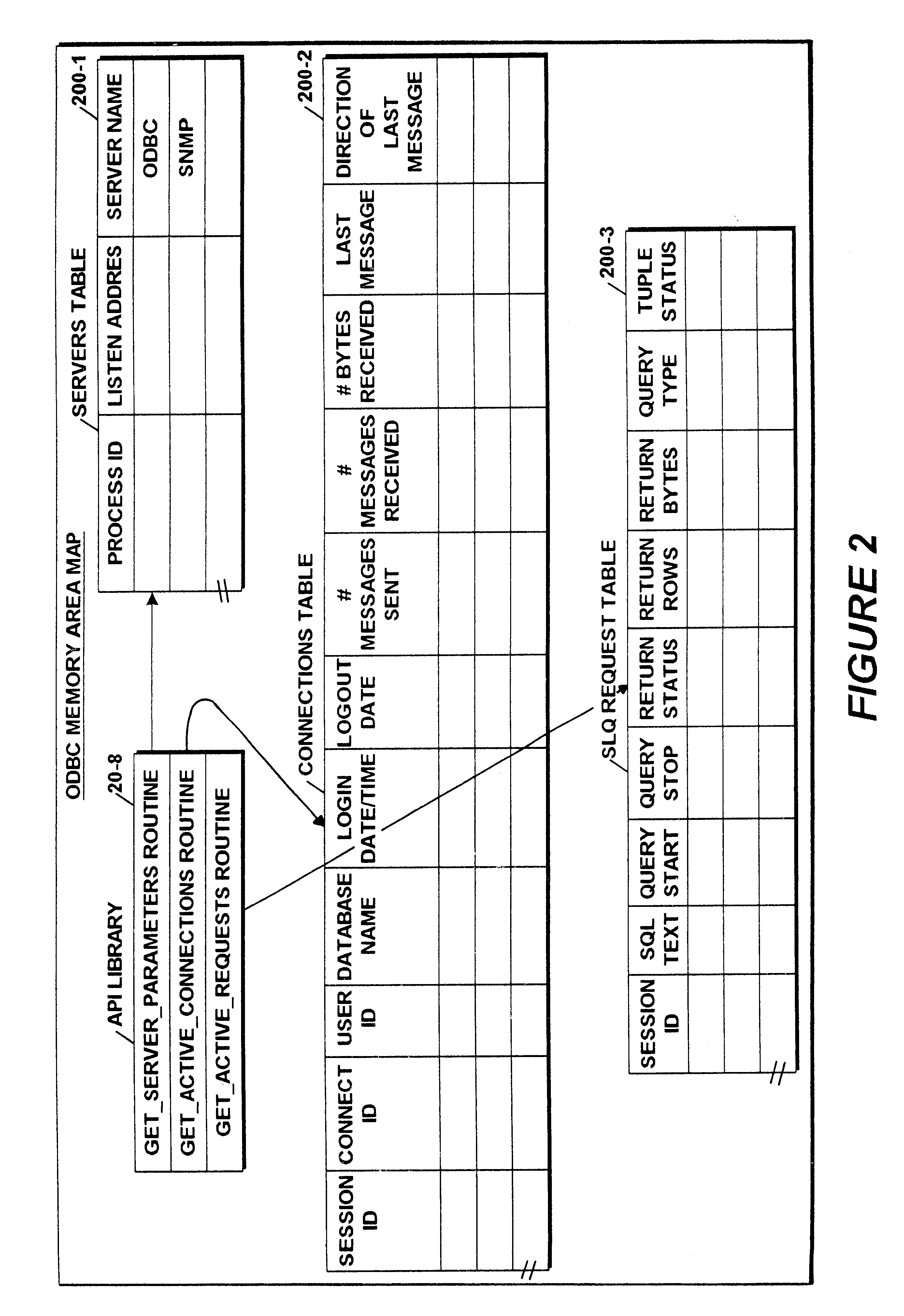
Application programming interface for monitoring data warehouse activity occurring through a client/server open database connectivity interface
InactiveUS6363391B1Simple processData processing applicationsDigital computer detailsData connectionData warehouse
An Application Programming Interface (API) provides interoperability between different monitoring and administrative components of a data warehouse system that utilizes different standard protocols. One of the protocols is the well known data connectivity protocol, Open Database Connectivity (ODBC) that defines a standard interface between applications and data sources. A second one of the protocols is the well known network management protocol, Simple Network Management Protocol (SNMP) that defines a standard interface between an agent component and a network management system. The API provides a facility that enables the different components to access user and connection information maintained by an ODBC server component derived from servicing client system application SQL queries made by system users.
Owner:BULL HN INFORMATION SYST INC
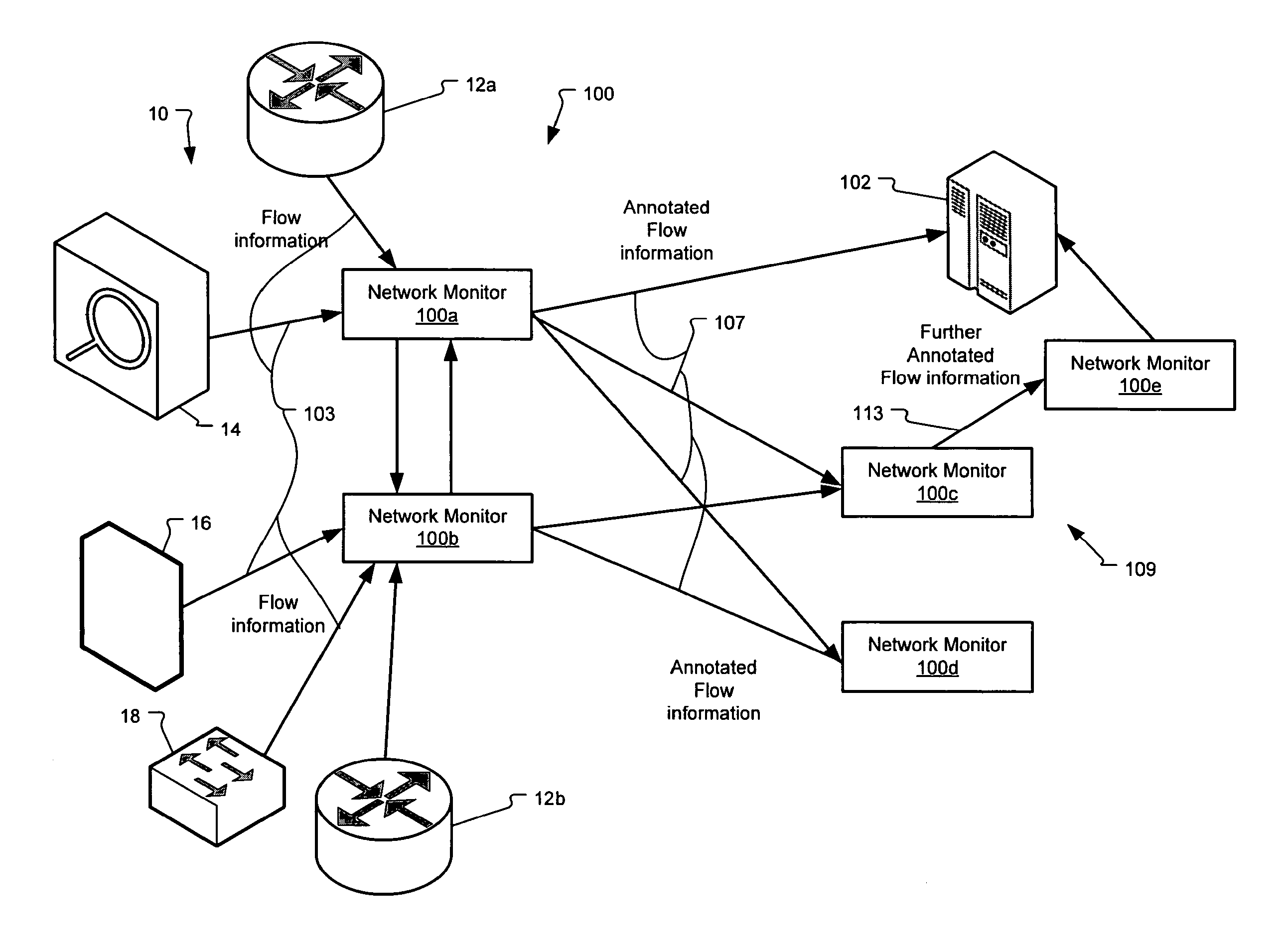
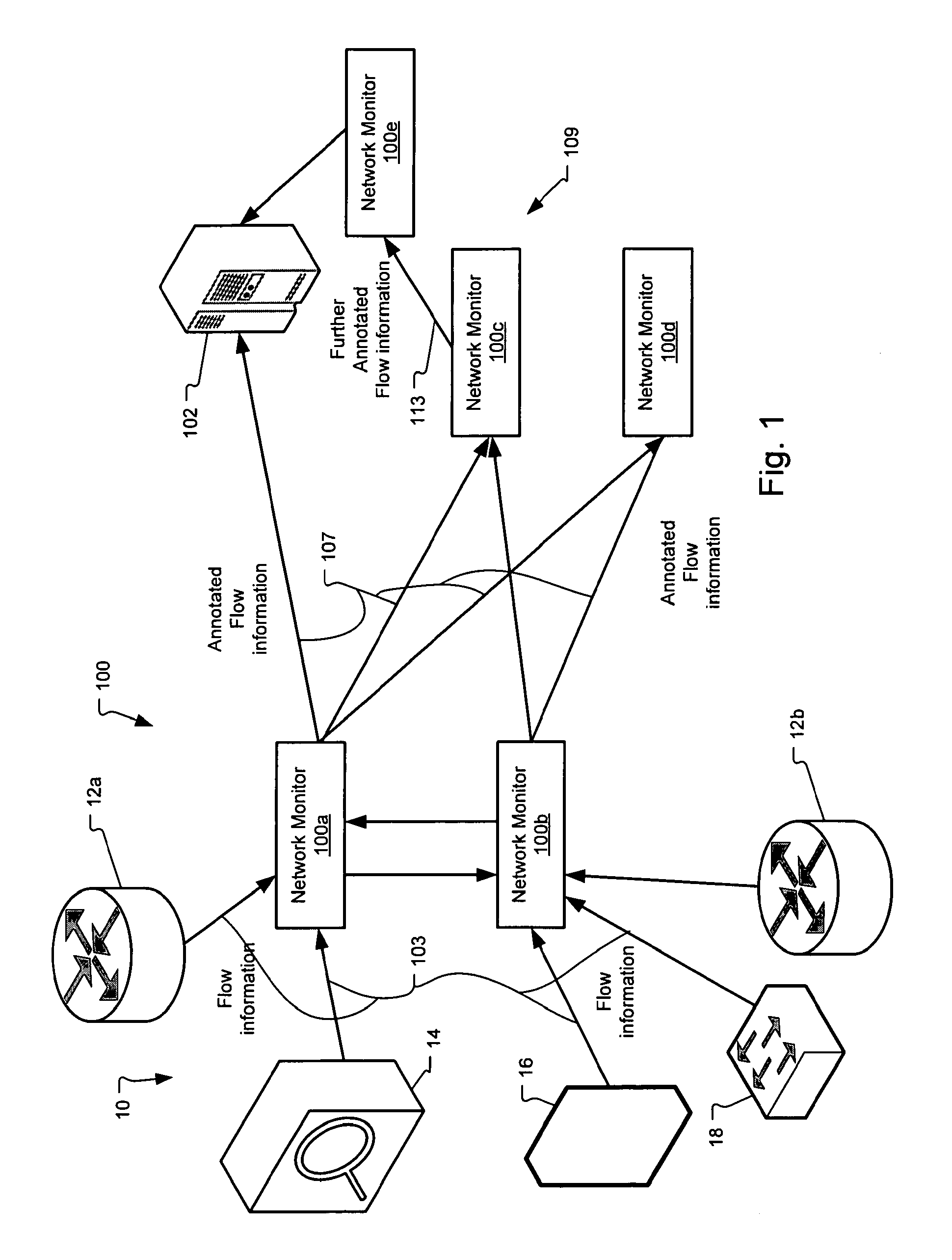
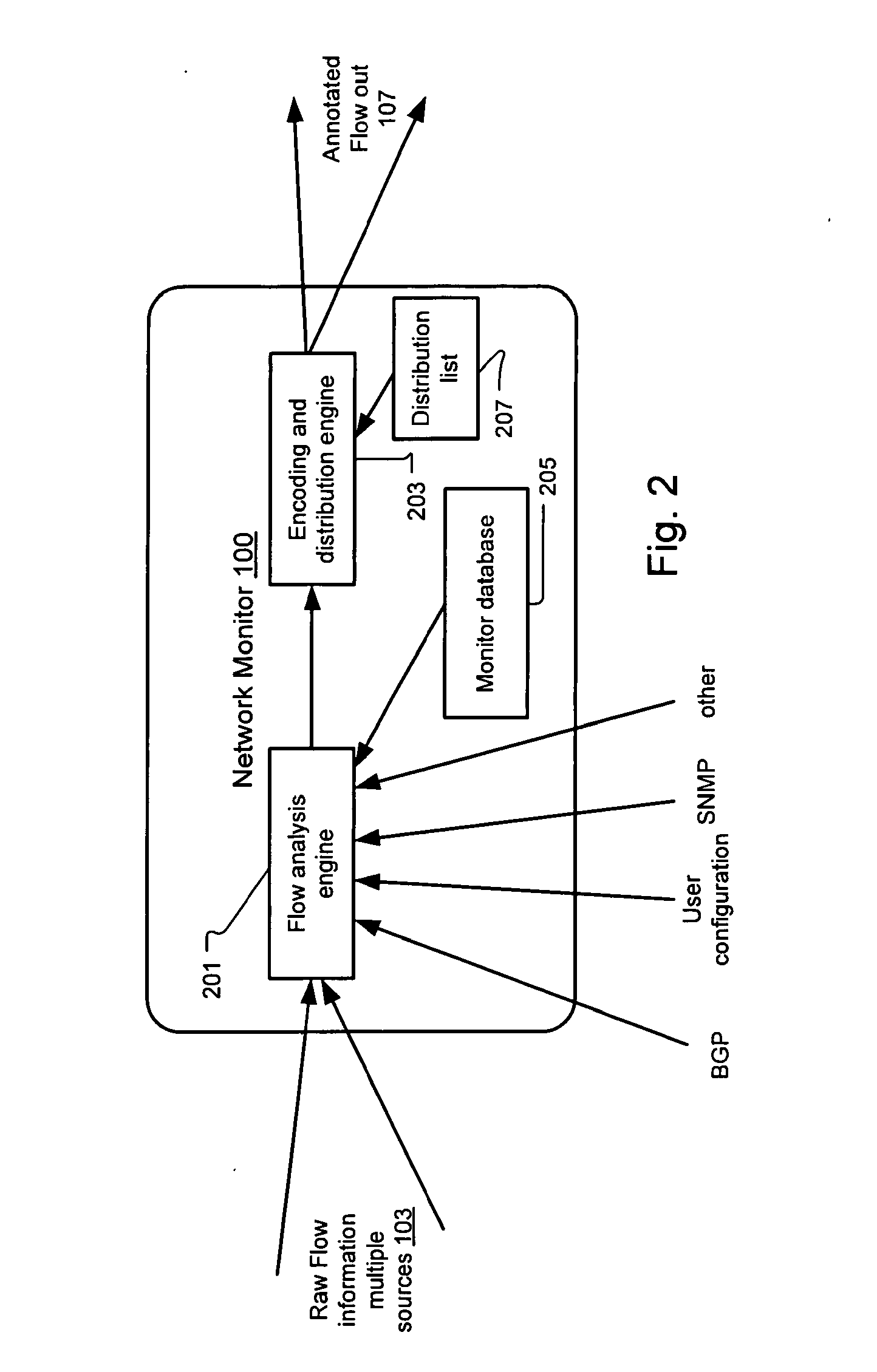
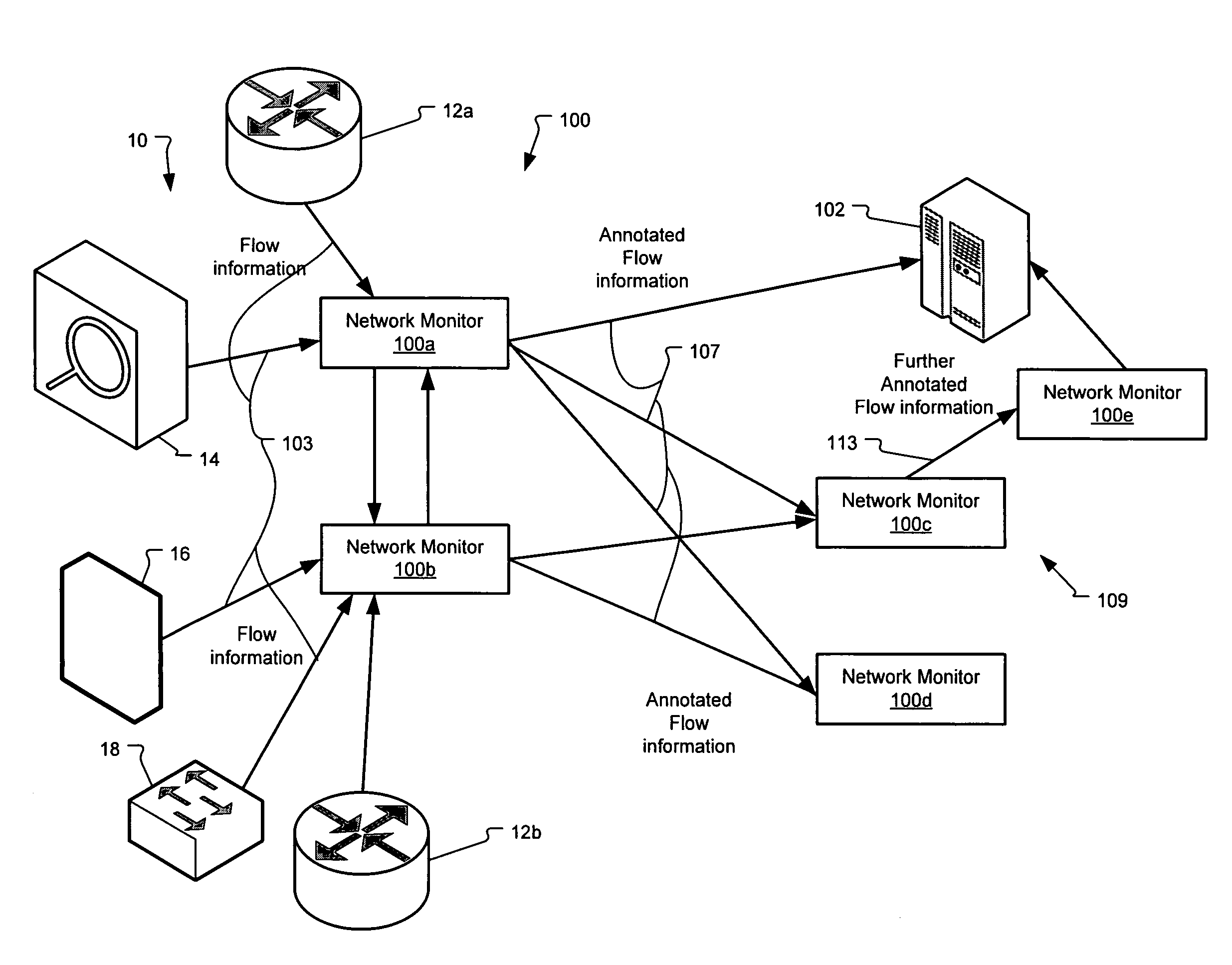
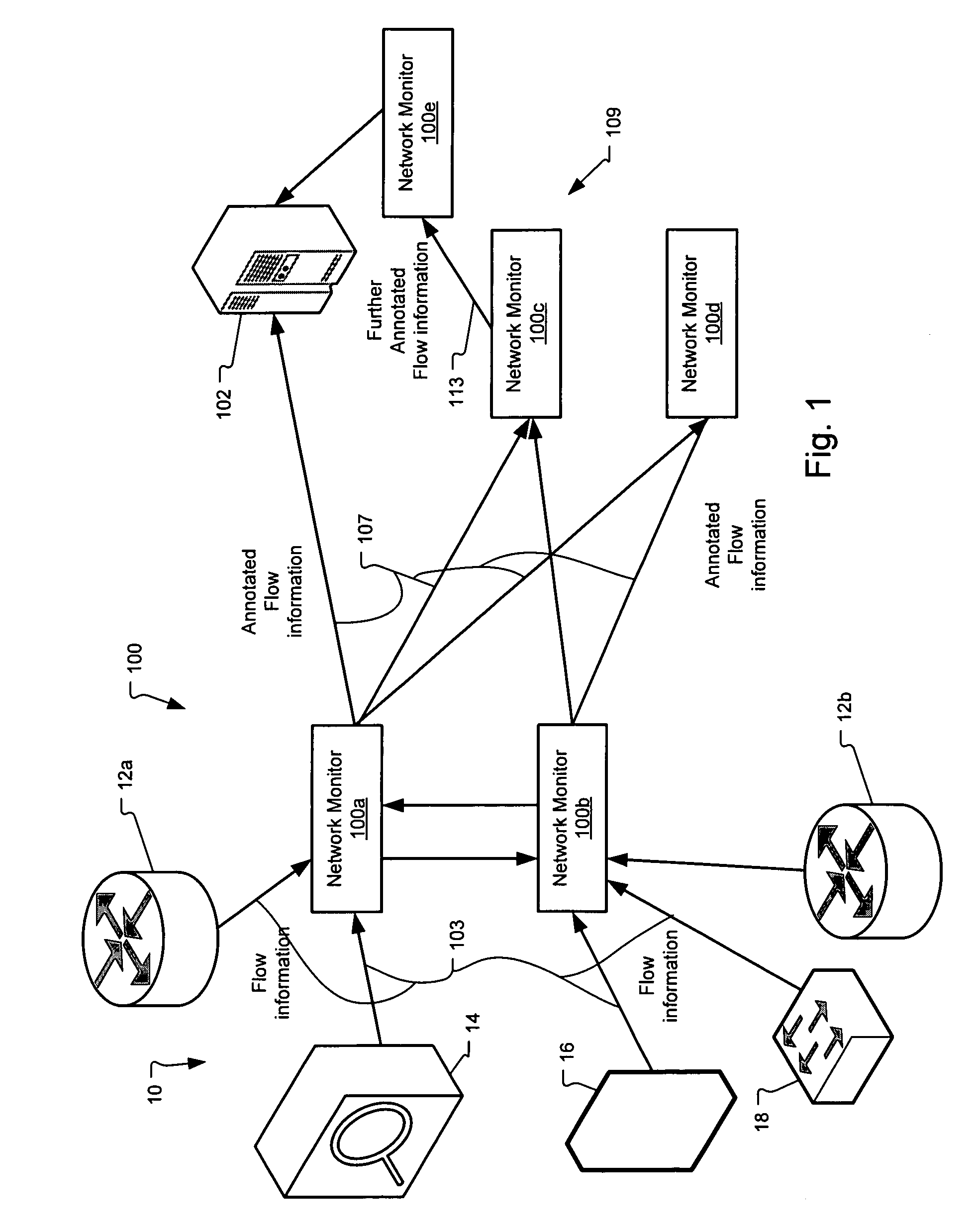
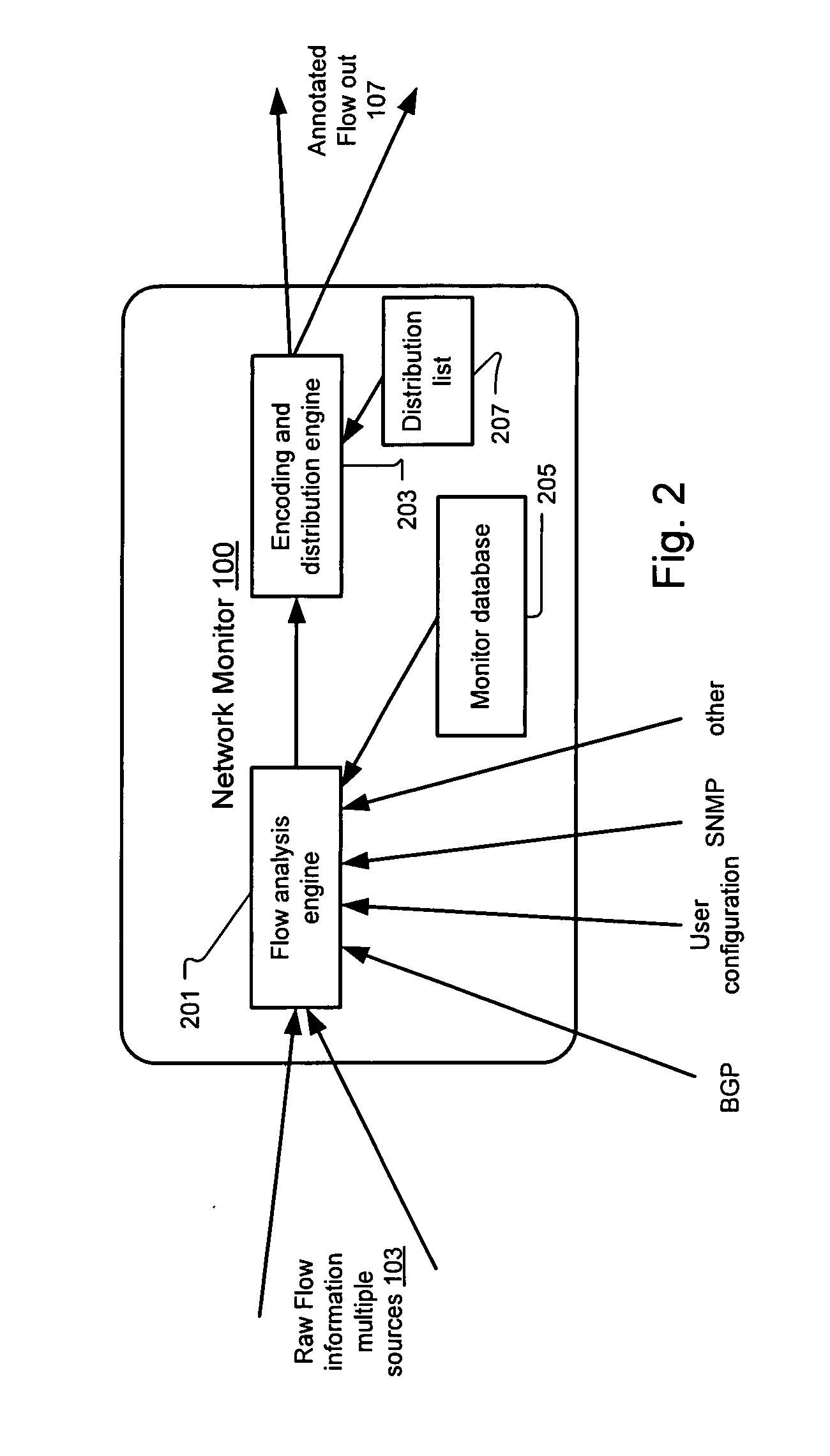
Method and system for annotating network flow information
ActiveUS20130290521A1Easy to createReduce overheadDigital computer detailsData switching networksBorder Gateway ProtocolStructure of Management Information
A scalable flow monitoring solution takes in standard flow records exported from network devices such as routers, switches, firewalls, hubs, etc., and annotates the flow with additional information. This information is derived from a number of sources, including Border Gateway Protocol (BGP), Simple Network Management Protocol (SNMP), user configuration, and other, intelligent flow analysis. These annotations add information to the flow data, and can be used to perform value-added flow analysis. The annotated flow is then resent to a configurable set of destinations using standard flow formatting, e.g., Cisco System Inc.'s NetFlow, in one implementation. This allows the annotated flow to be processed and the enhanced information to be used by other flow analysis tools and existing flow analysis infrastructure.
Owner:ARBOR NETWORKS
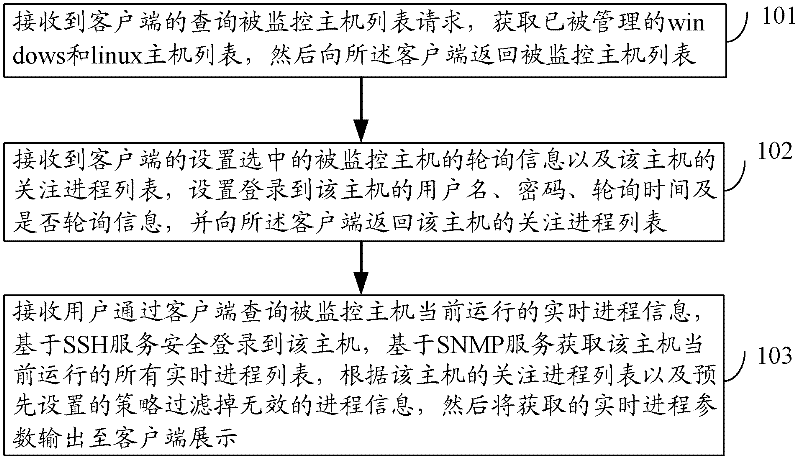
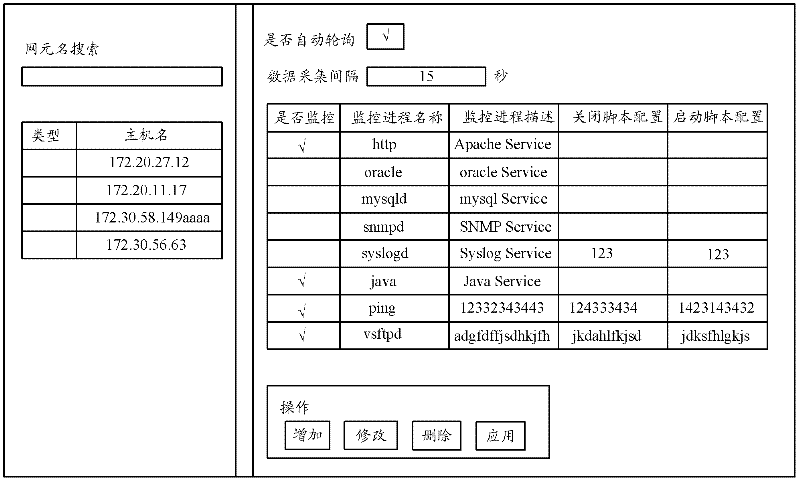
Process monitoring method and process monitoring system
InactiveCN102521099AReduce maintenance costsReduce development costsHardware monitoringTransmissionMonitoring systemSimple Network Management Protocol
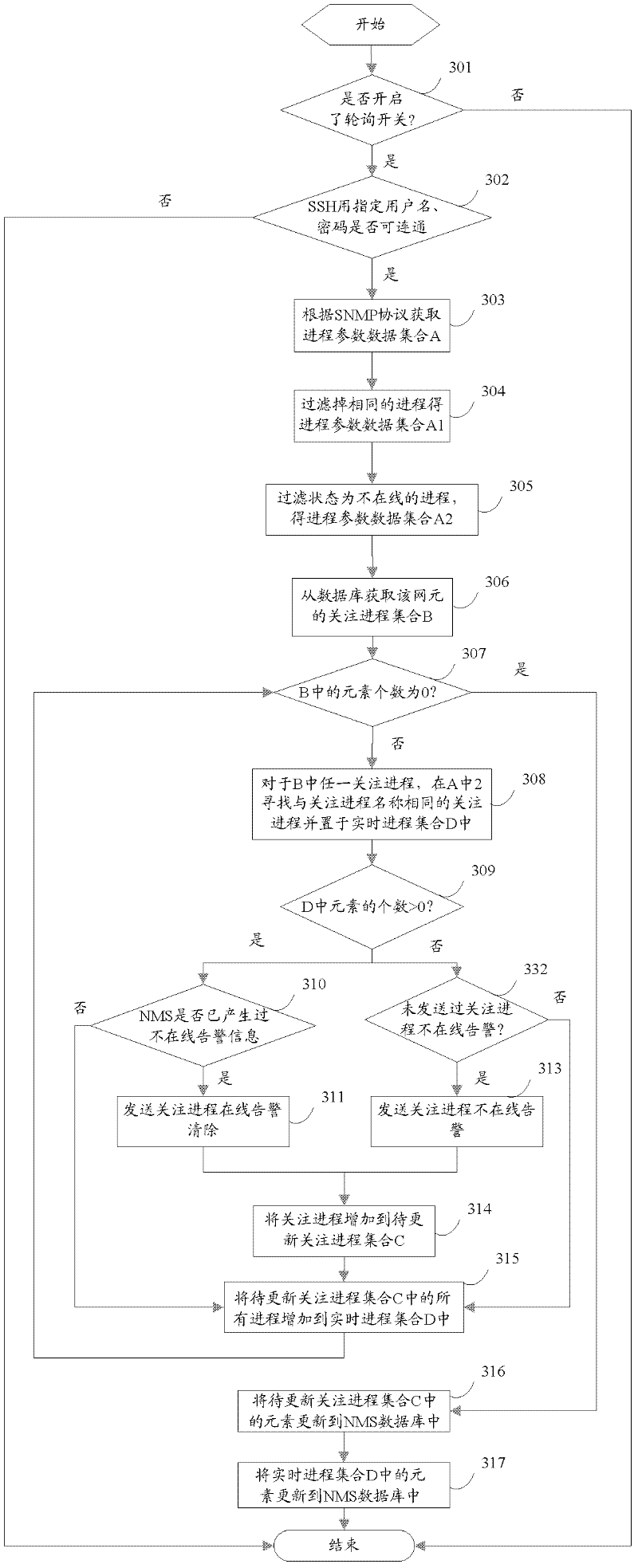
The invention discloses a process monitoring method and a process monitoring system. The method comprises the following steps of: receiving a request for querying the list of monitored hosts from a client, acquiring the list of managed Windows and Linux hosts, and returning the list of the monitored hosts to the client; receiving information for polling a monitored host and the concerned process list of the host from the client, setting login information for logging in the host, and returning the concerned process list of the host to the client; and receiving information for querying the currently-running real-time process of the monitored host from the client, securely logging in the host based on SSH (Secure Shell) service, acquiring the list of all currently-running real-time processes of the host based on SNMP (Simple Network Management Protocol) service, filtering invalid process information according to the concerned process list of the host and a preset strategy, and outputting the acquired real-time process parameters to the client for exhibition. With the adoption of the process monitoring method and the process monitoring system, the cross-platform process monitoring can be achieved, and the cost for maintenance and development can be lowered.
Owner:SHENZHEN COSHIP ELECTRONICS CO LTD
System And Server For Assigning Location-dependent Hostname To Client Device Over Network And Method Thereof
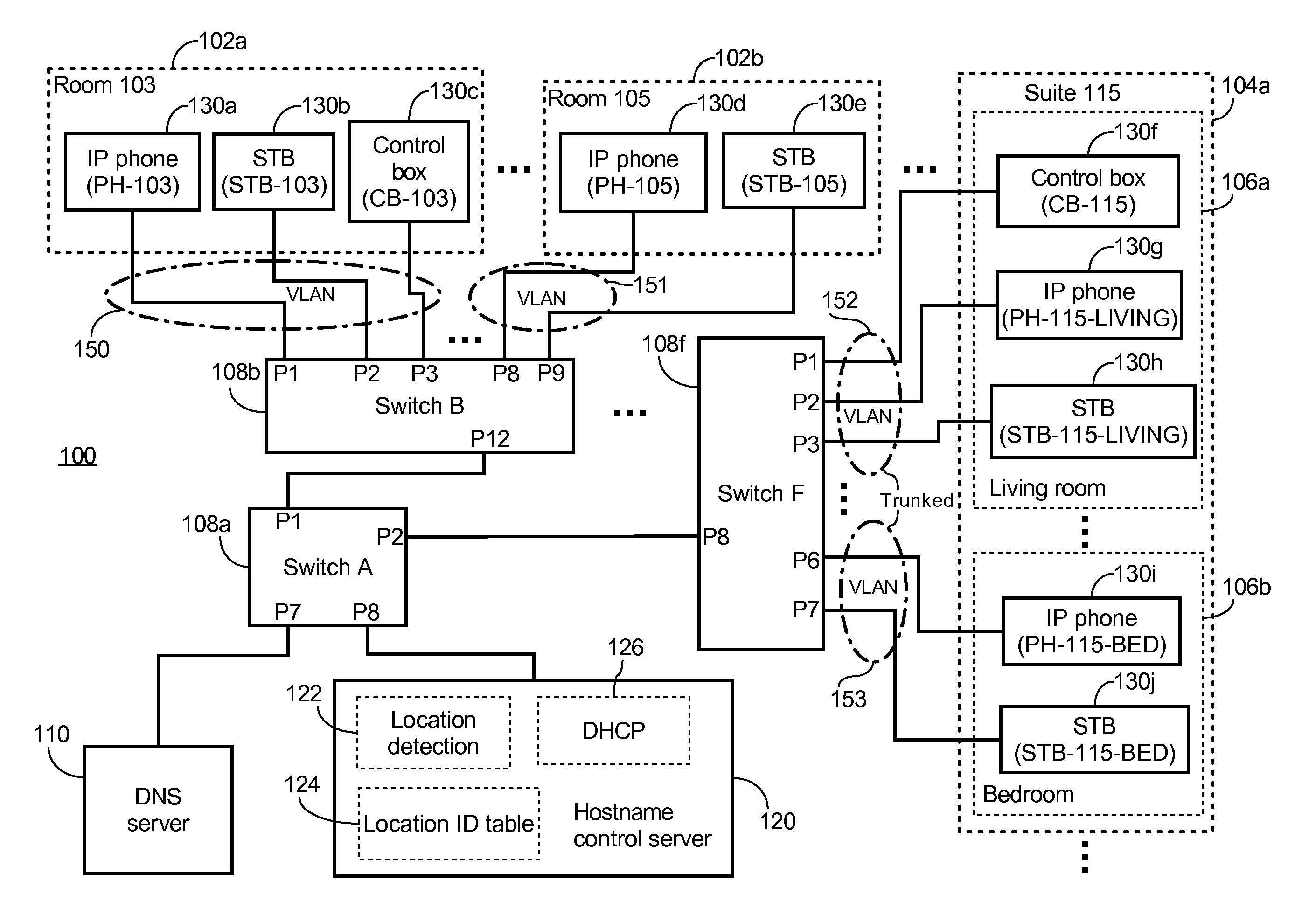
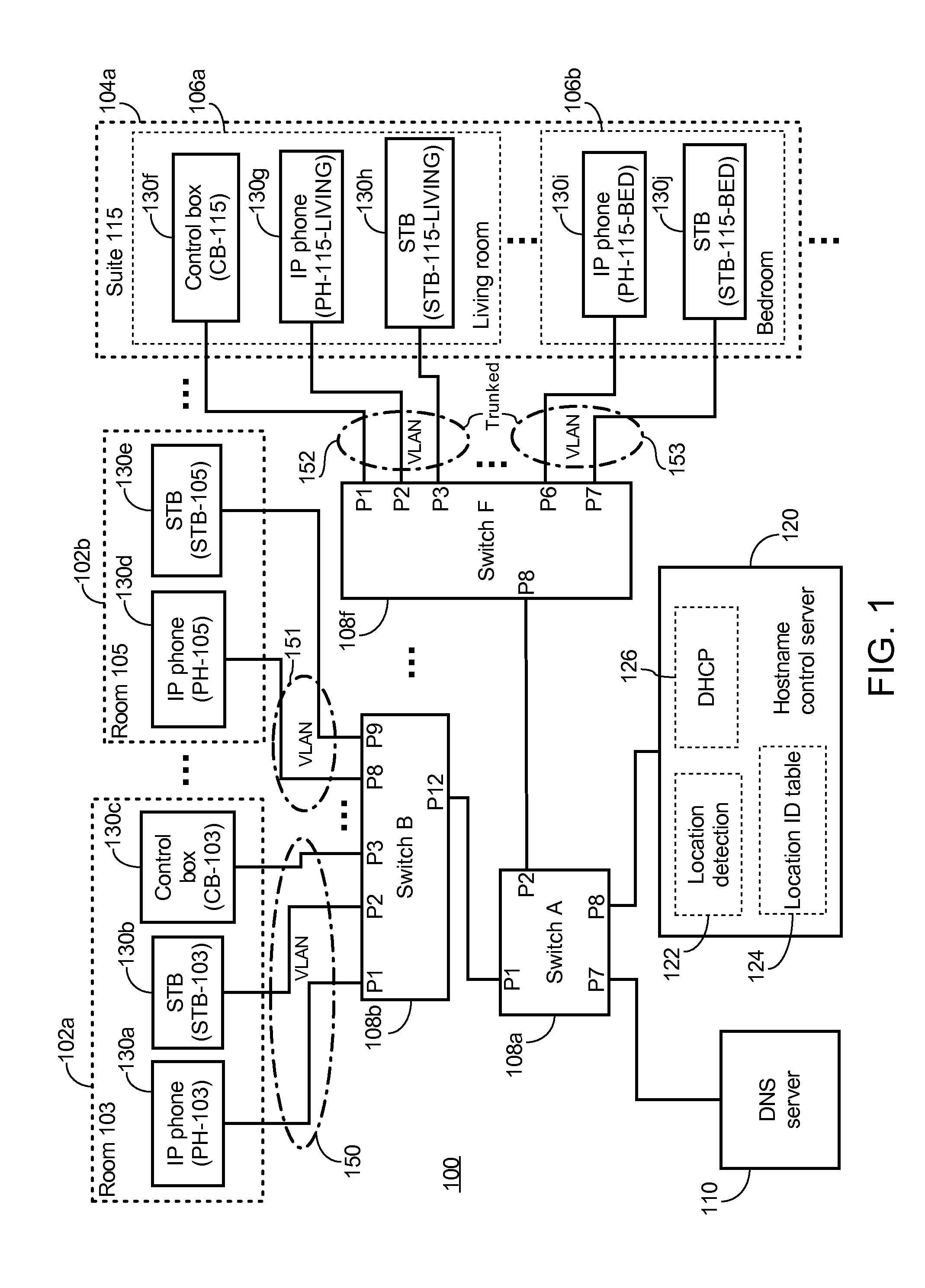
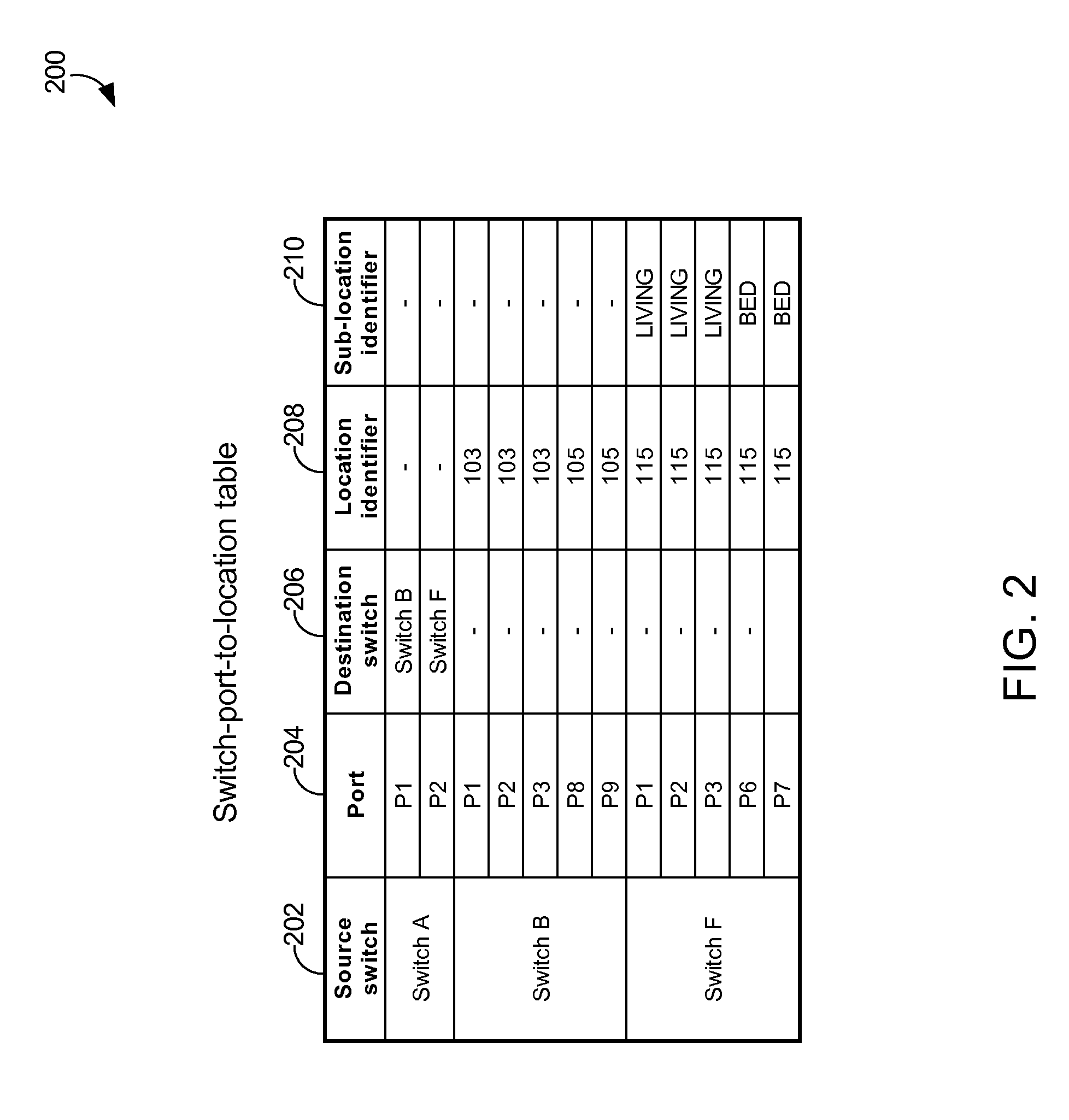
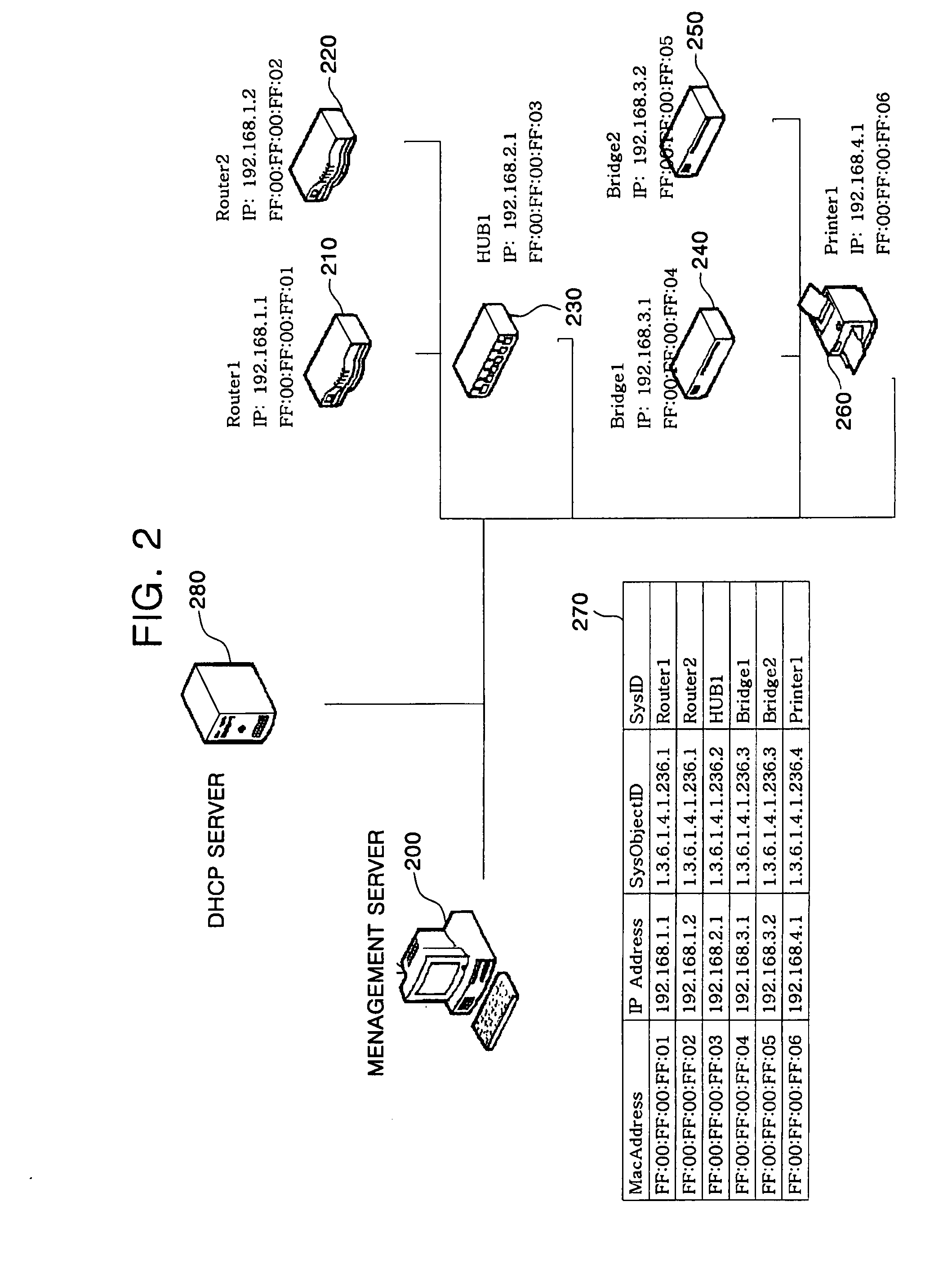
A method of automatic hostname configuration includes receiving a request from a client device. A location detection module may be utilized for determining a location identifier representing a location at which the client device is located. A hostname is formed including at least the location identifier, and a control server assigns the hostname to the client device by sending an acknowledgement including the hostname to the client device. The request and acknowledgement may be communicated using DHCP. Simple network management protocol messages may be sent to one or more switches to query for a MAC address of the client device to determine the source switch and port from which the request originated. The switch-port-to-location table may include several ports that map to a same location identifier. The hostname may further be formed by including a device type identifier associated with the client device.
Owner:GUEST TEK INTERACTIVE ENTERTAINMENT
Systems and Methods for Providing Global Server Load Balancing of Heterogeneous Devices
ActiveUS20080225718A1Good for load balancingGood flexibilityError preventionTransmission systemsVia deviceExchange protocol
The present invention provides improvements to load balancing by providing a load balancing solution that distributes a load among a plurality of heterogenous devices, such as different types of local load balancers, using metrics collected from the different devices. The load balancing appliance collects metrics from heterogenous devices using a network management protocol and communication model, such as a Simple Network Management Protocol (SNMP). These heterogenous device metrics are available on the load balancing appliance with appliance determined metrics and metrics obtained by the appliance from homogenous devices using a metric exchange protocol. Via a configuration interface of the appliance, a user can select one or more of these different metrics for global load balancing. As such, the load balancing appliance described herein obtains a multitude of metrics from the different devices under management. Additionally, the load balancing appliance described herein provides great flexibility in allowing the user to configure the global load balancer based on the user's understanding of these multitudes of metrics and to take into account the different characteristics and behaviors of the heterogenous devices.
Owner:CITRIX SYST INC
Network management providing network health information and lockdown security
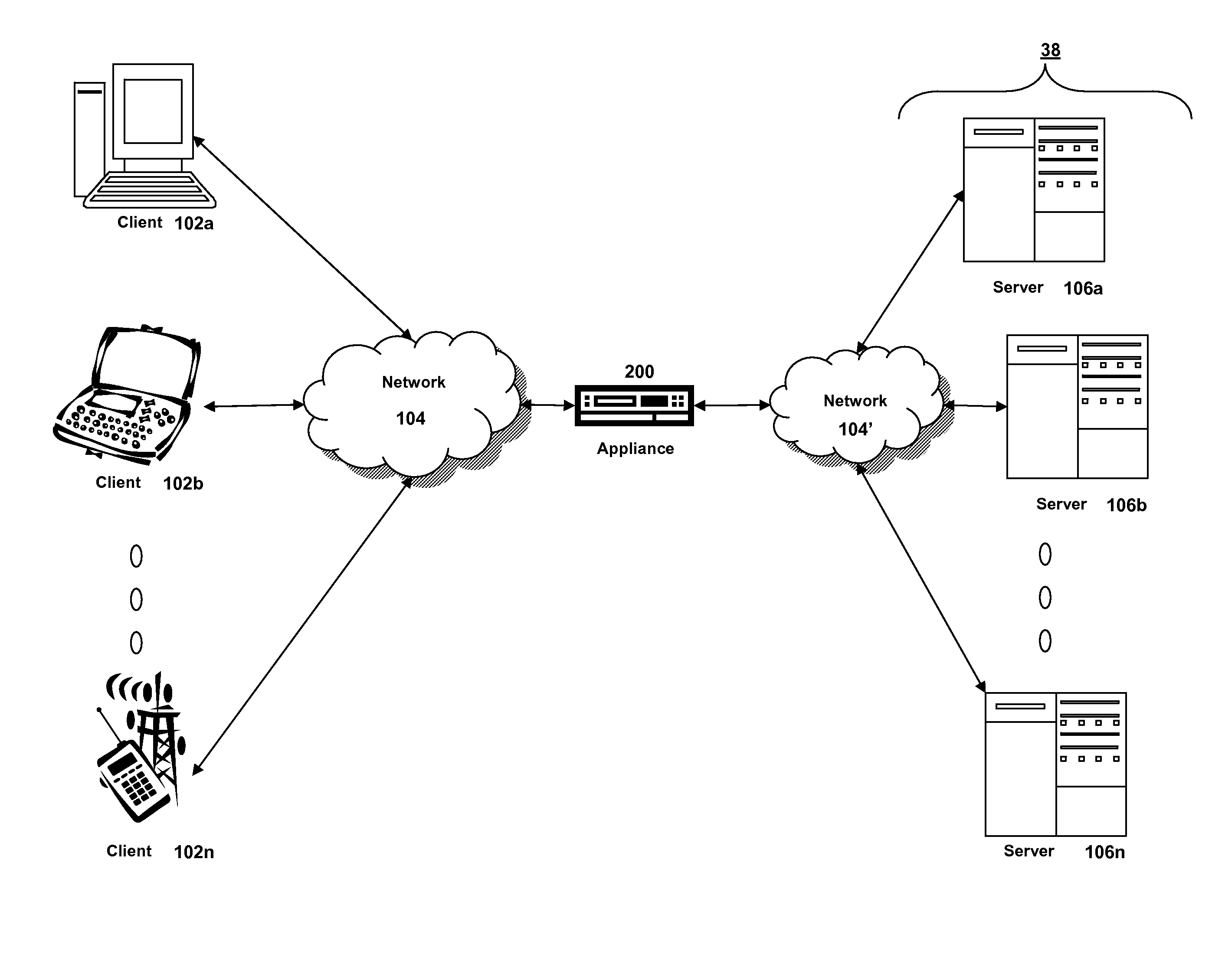
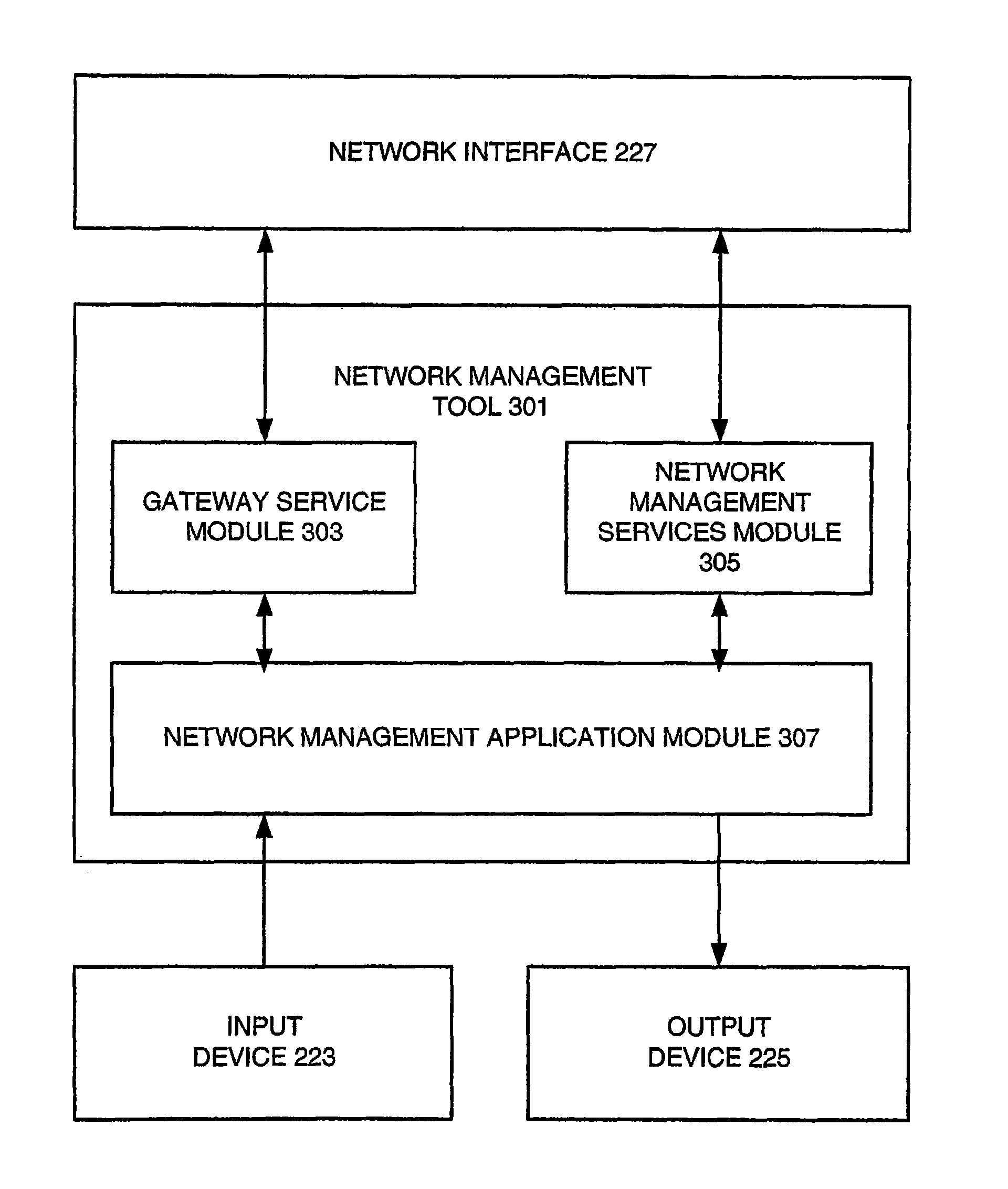
Network management to establish and maintain the health and security of a computing network, such as a home network. A network management tool may identify the media access control (MAC) address for each device in the network, and allow a user to identify which devices are authorized to be a member of the network. If the network gateway device supports MAC address filtering, a user can then employ the network management tool to configure the router to exclude non-authorized devices from joining or remaining in the network based upon their MAC addresses. Further, the network management tool may allow a user to configure a wireless gateway device to stop broadcasting its service set identifier (SSID), change the SSID, or both, identify to the user when a wireless gateway device is using encryption, and, if so, what type of encryption. Still further, the tool may monitor the status of various software applications on devices in the network, and then alert a user if the status of any of the devices in the network requires attention. Further, the network management tool may provide recommendations to a user for correcting or changing the status of the monitored software applications.
Owner:CISCO TECH INC
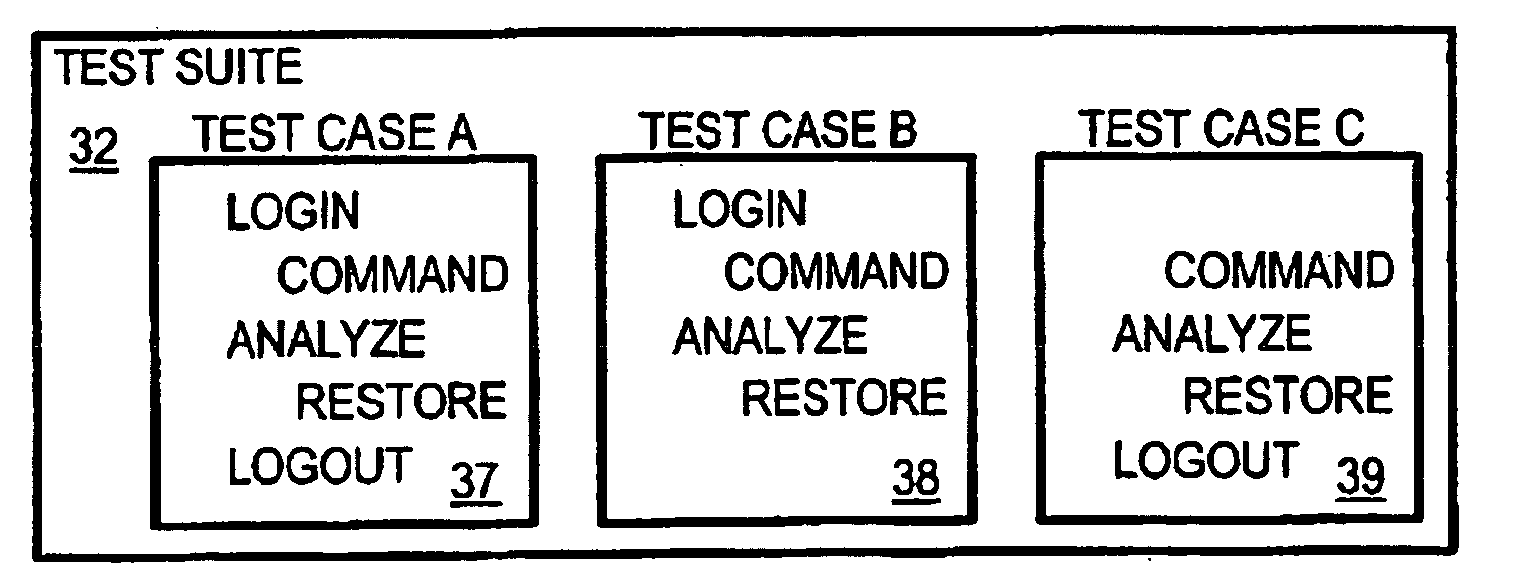
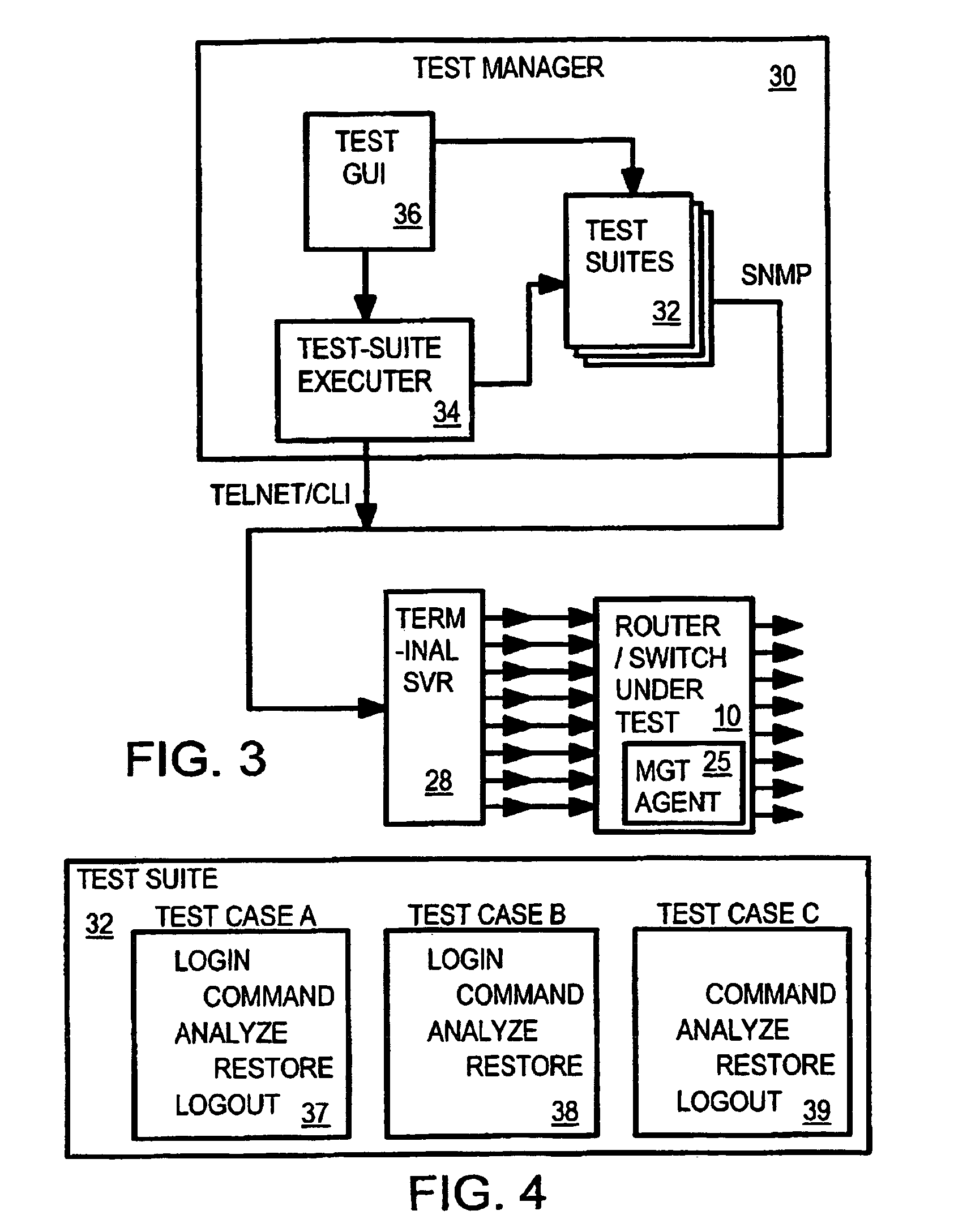
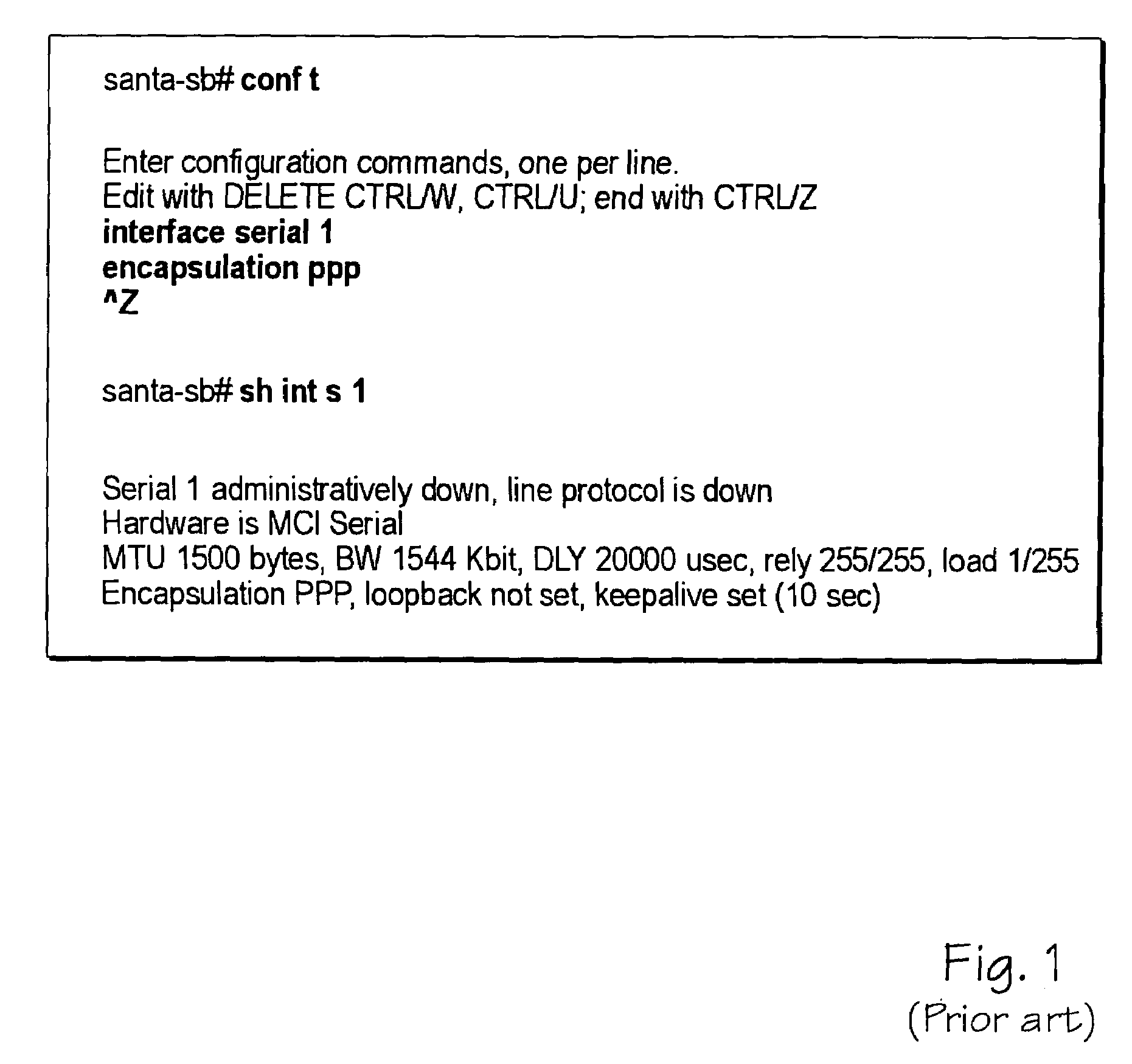
Interactive automatic-test GUI for testing devices and equipment using shell-level, CLI, and SNMP commands
ActiveUS7010782B2Digital variable displayResistance/reactance/impedenceComputer hardwareCommand-line interface
A test manager software program includes an interactive test graphical-user-interface (GUI) for testing network devices using high-level networking commands. The test GUI allows the test engineer user to enter high-level commands such as Simple Networking Management Protocol (SNMP) commands that read values in a management information database in a network device under test. The high-level commands can be sent from the test manager using a command-line interface (CLI) in a telnet session opened to the network device during testing. The user specifies high-level test, analyze, and restore commands in test cases that are collected into test suites. Rules for logging on to the network device under test are stored that include expected prompts from the network device and user responses such as passwords. Addresses of the network device under test can be re-mapped for testing other devices so the test suites can be reused.
Owner:SAPPHIRE INFOTECH
Method and System for Annotating Network Flow Information
InactiveUS20090168648A1Easy to createReduce overheadError preventionFrequency-division multiplex detailsTraffic capacityBorder Gateway Protocol
A scalable flow monitoring solution takes in standard flow records exported from network devices such as routers, switches, firewalls, hubs, etc., and annotates the flow with additional information. This information is derived from a number of sources, including Border Gateway Protocol (BGP), Simple Network Management Protocol (SNMP), user configuration, and other, intelligent flow analysis. These annotations add information to the flow data, and can be used to perform value-added flow analysis. The annotated flow is then resent to a configurable set of destinations using standard flow formatting, e.g., Cisco System Inc.'s NetFlow, in one implementation. This allows the annotated flow to be processed and the enhanced information to be used by other flow analysis tools and existing flow analysis infrastructure.
Owner:ARBOR NETWORKS
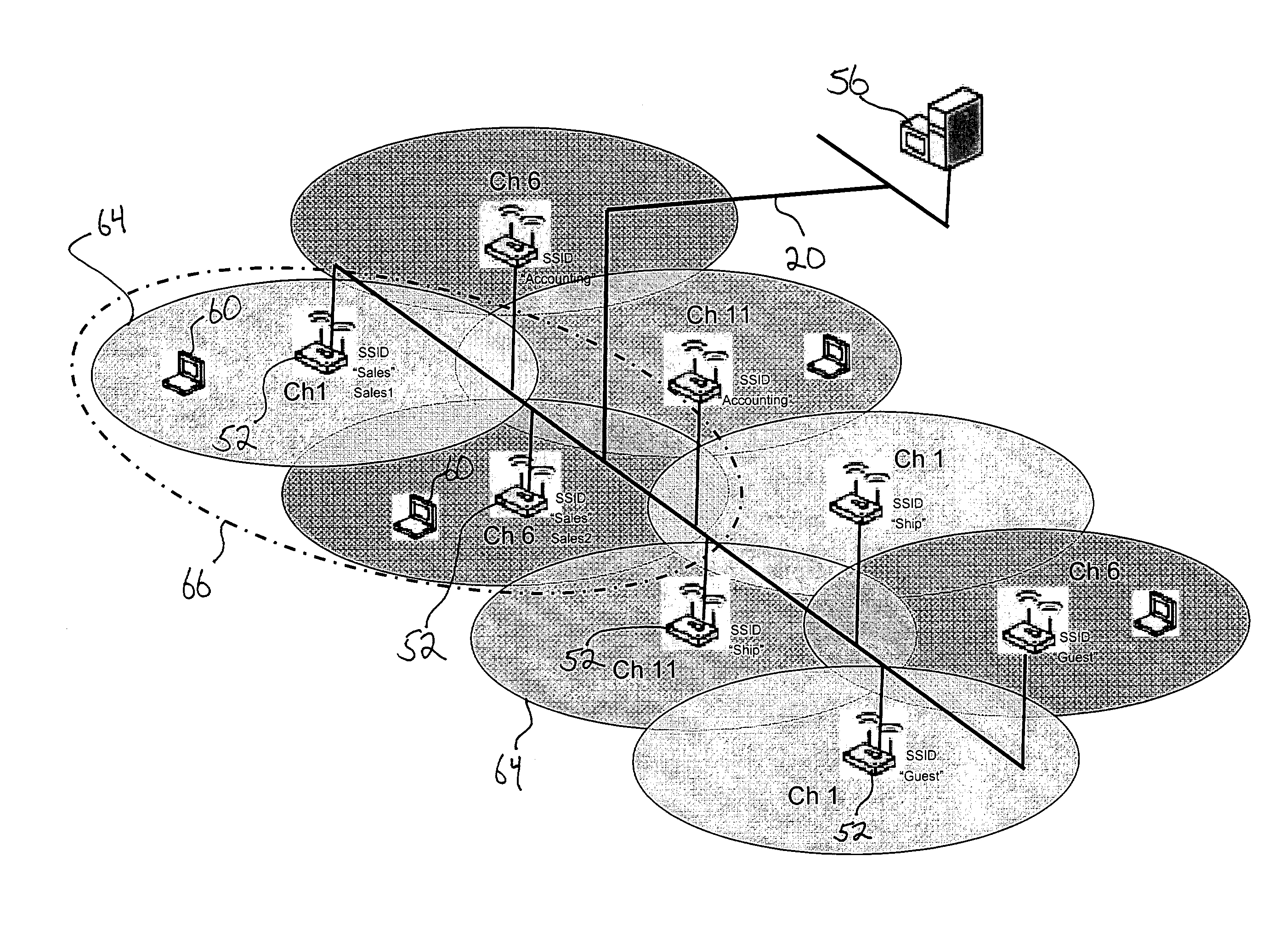
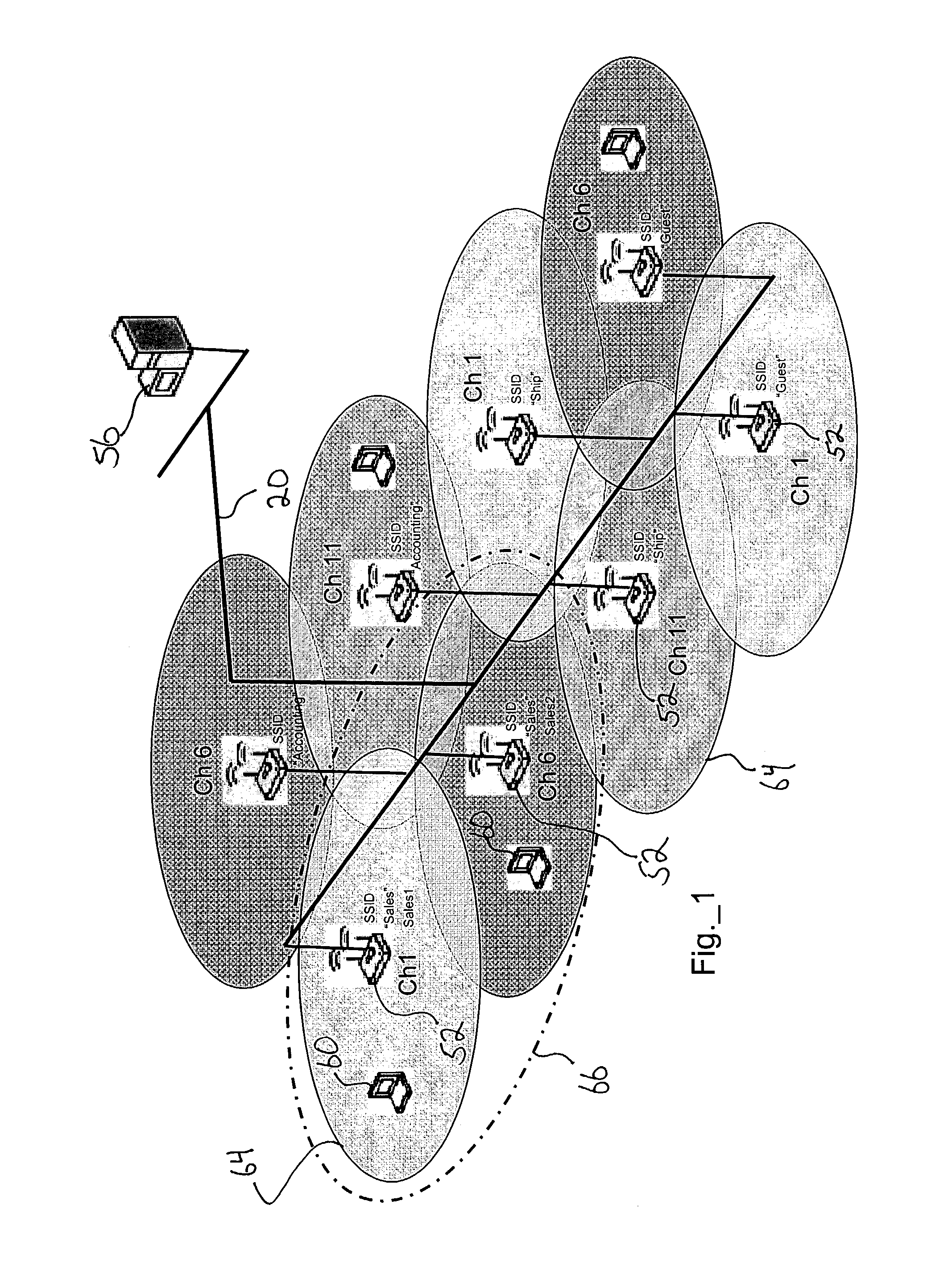
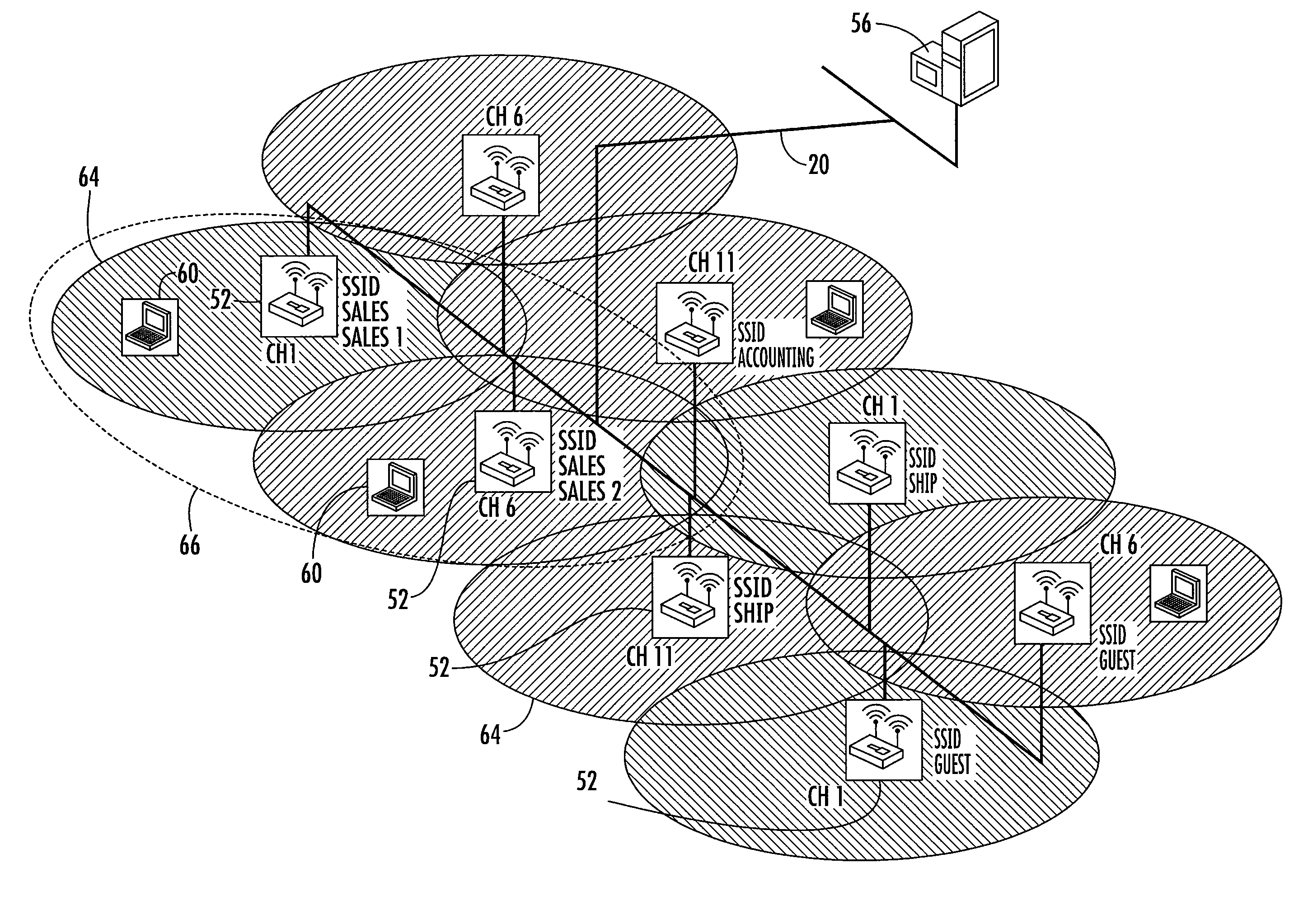
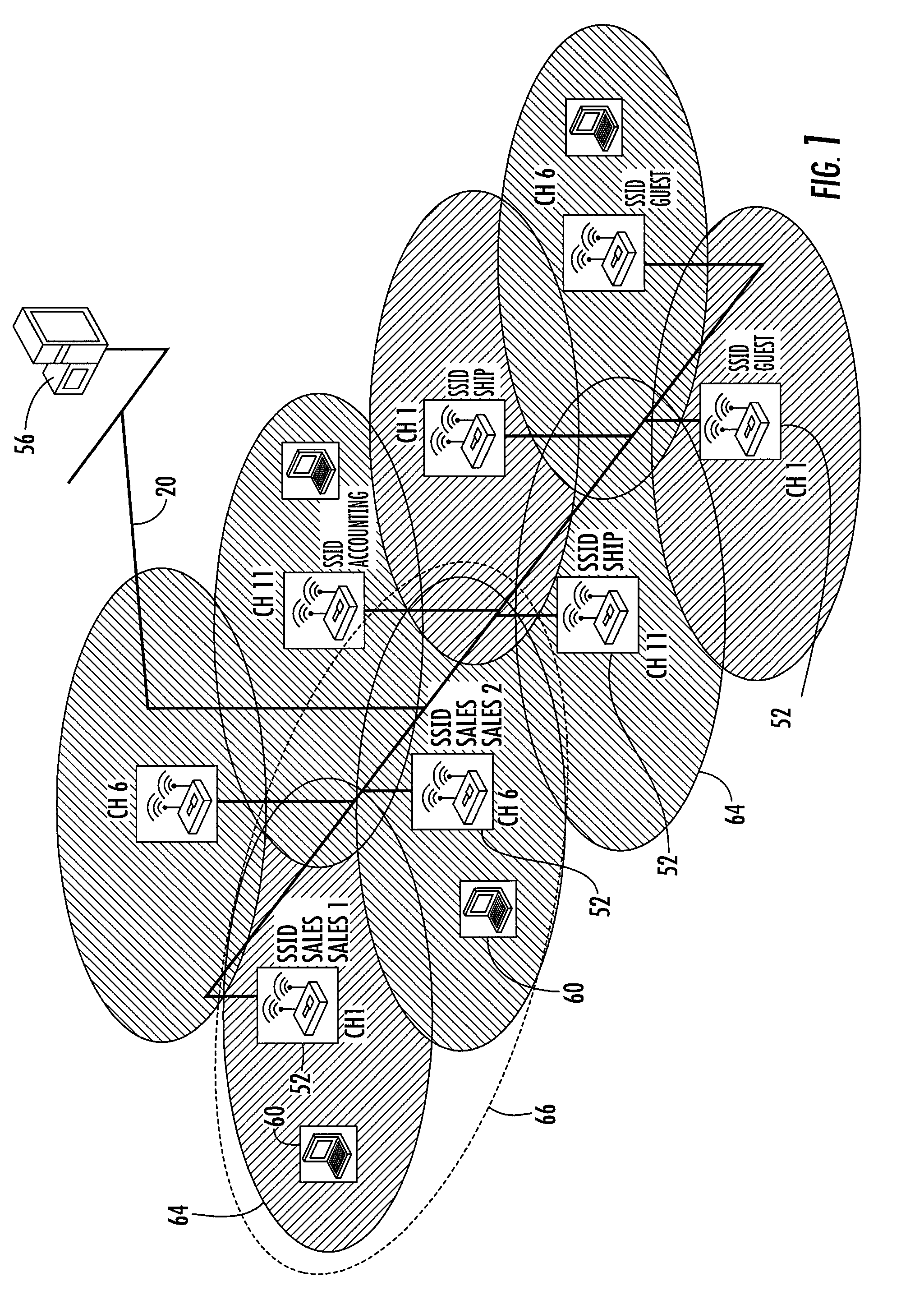
Methods, apparatuses and systems facilitating management of airspace in wireless computer network environments
ActiveUS7295524B1Improve isolationOptimizationCriteria allocationData switching by path configurationWireless trafficClient-side
Methods, apparatuses and systems facilitating the management of wireless computer network environments and the detection of rogue and other devices that may affect the performance and / or security of the wireless computer network. The present invention enables accurate and cost effective WLAN airspace mapping. In one embodiment, the present invention allows any conforming access point the ability to routinely scan its airspace, collect data on all operating frequencies and report this information back to a management platform. In one embodiment, the management and reporting functionality described herein uses a standards-based vehicle, such as Simple Network Management Protocol (SNMP). In one embodiment, the present invention allows for detection of all wireless traffic within or affecting an enterprise's computer network environment, picking up all active access points (Ad Hoc or Infrastructure) and all wireless clients data regardless of SSID, channel, or security settings. The management platform, according to an embodiment of the present invention, analyzes information received from the access points under management to detect and report the state of the computer network environment. In one embodiment, the present invention facilitates isolation of rogue wireless devices affecting the computer network environment and effective decision-making as to management of the detected device. The present invention also allows network administrators to optimize the configuration of the wireless network environment for performance and security.
Owner:HEWLETT-PACKARD ENTERPRISE DEV LP
Systems and methods for load balancing based on user selected metrics
ActiveUS8291108B2Good for load balancingGood flexibilityDigital computer detailsProgram controlDevice MonitorSimple Network Management Protocol
Owner:CITRIX SYST INC
Method and apparatus for large-scale automated distributed denial of service attack detection
ActiveUS20070283436A1Memory loss protectionUnauthorized memory use protectionService provisionIncident report
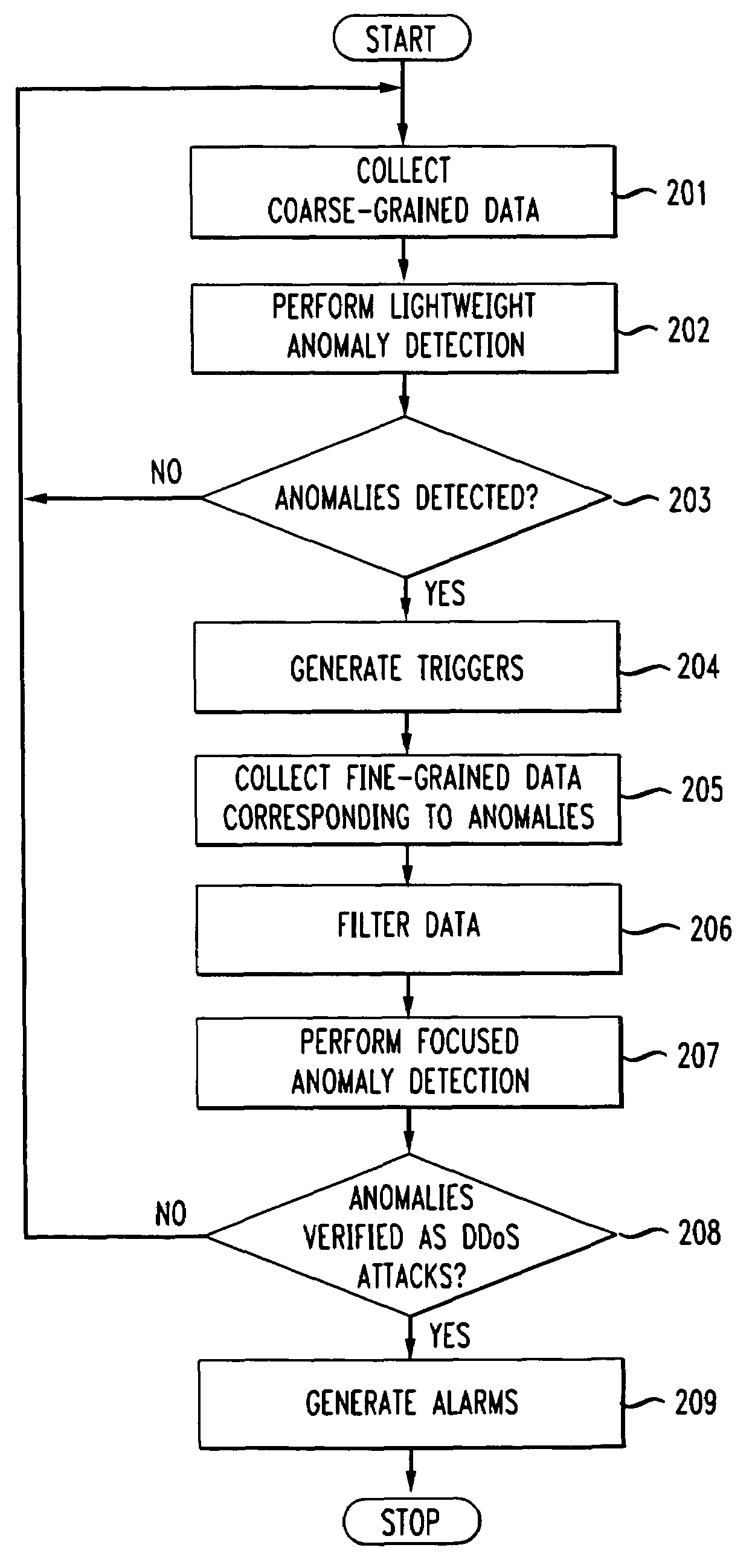
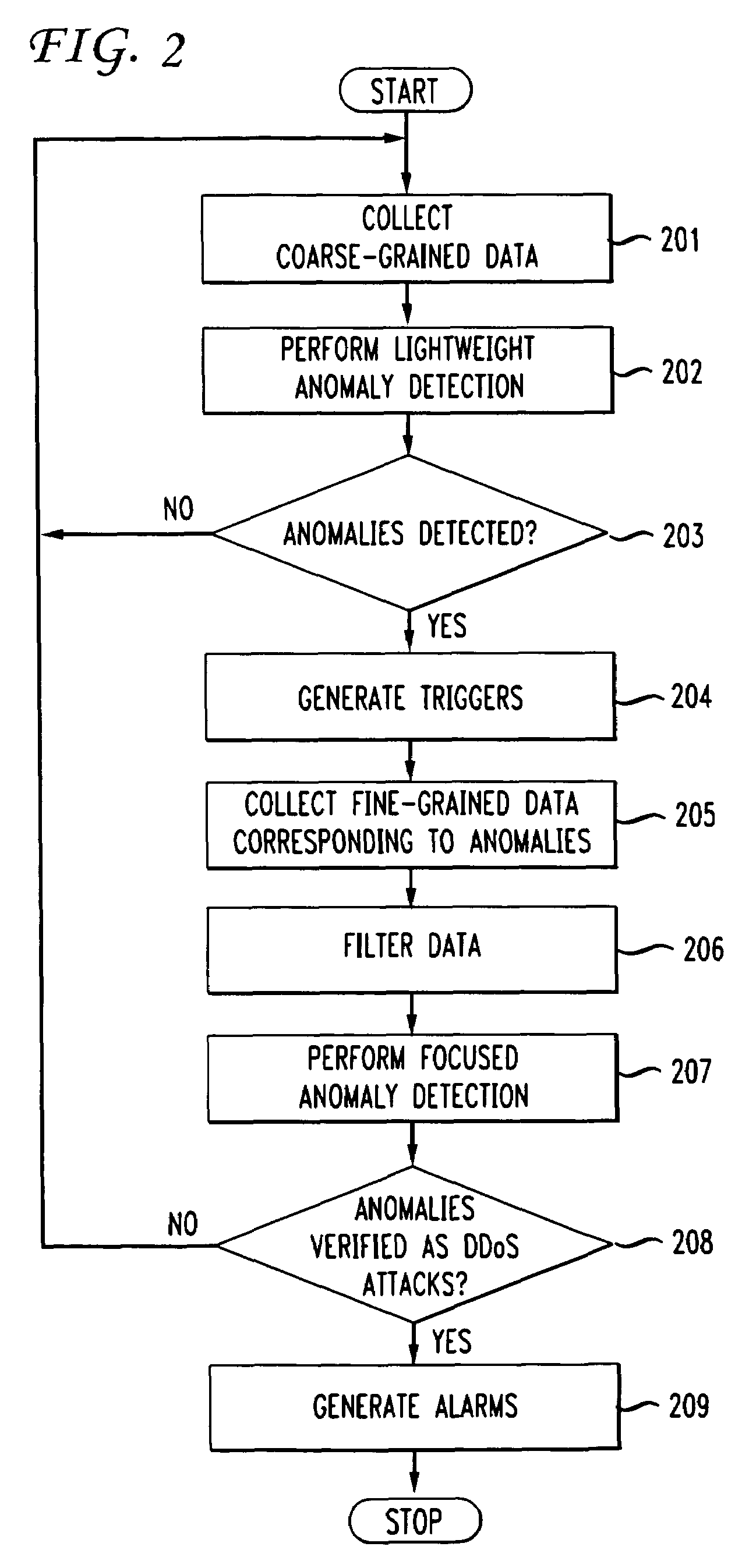
A multi-staged framework for detecting and diagnosing Denial of Service attacks is disclosed in which a low-cost anomaly detection mechanism is first used to collect coarse data, such as may be obtained from Simple Network Management Protocol (SNMP) data flows. Such data is analyzed to detect volume anomalies that could possibly be indicative of a DDoS attack. If such an anomaly is suspected, incident reports are then generated and used to trigger the collection and analysis of fine grained data, such as that available in Netflow data flows. Both types of collection and analysis are illustratively conducted at edge routers within the service provider network that interface customers and customer networks to the service provider. Once records of the more detailed information have been retrieved, they are examined to determine whether the anomaly represents a distributed denial of service attack, at which point an alarm is generated.
Owner:AT&T INTPROP II L P
Energy monitoring system using network management protocols
ActiveUS20090070447A1Digital computer detailsPower supply for data processingMonitoring systemSimple Network Management Protocol
A system and method are disclosed for integrating an intelligent electronic device (IED) in a network management system. The IED may be configured to communicate using the network management protocol of the network management system. IED variables may be mapped to associated network management protocol variables to allow the network management system to access the IED variables using the network management protocol.
Owner:SCHNEIDER ELECTRIC USA INC
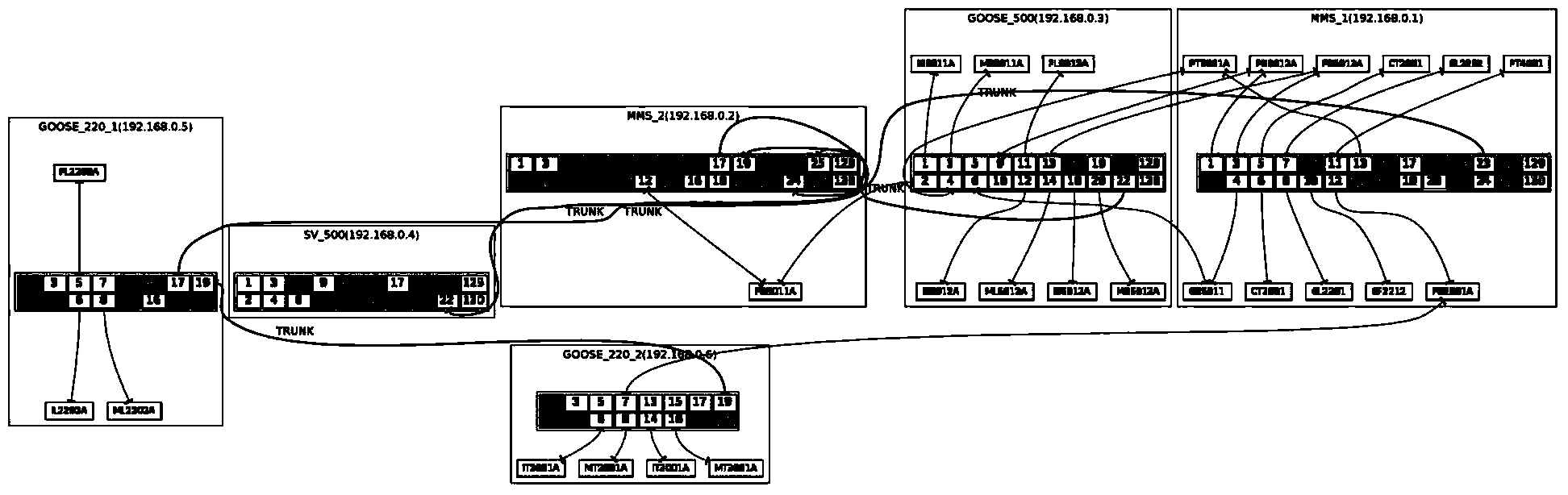
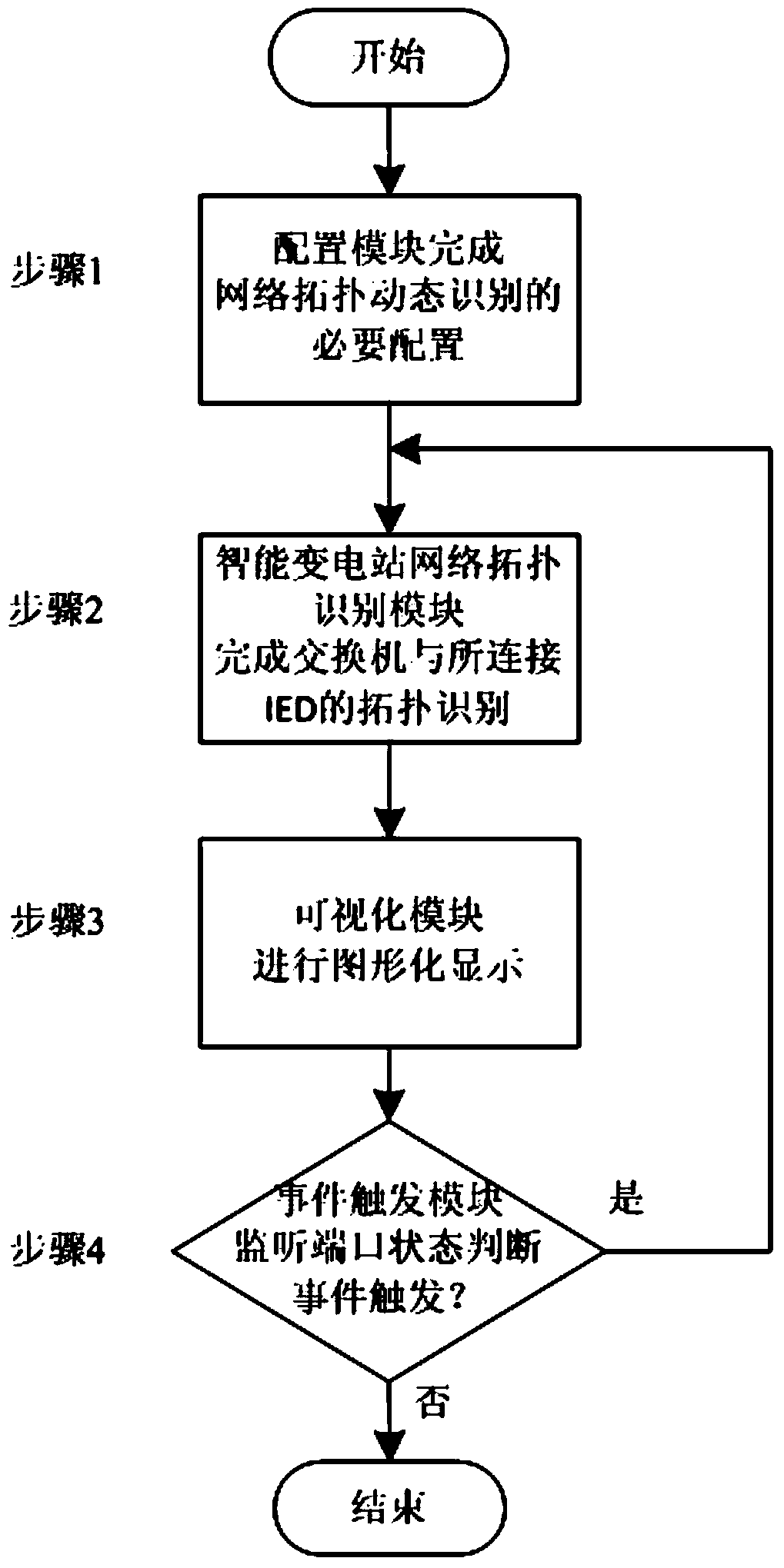
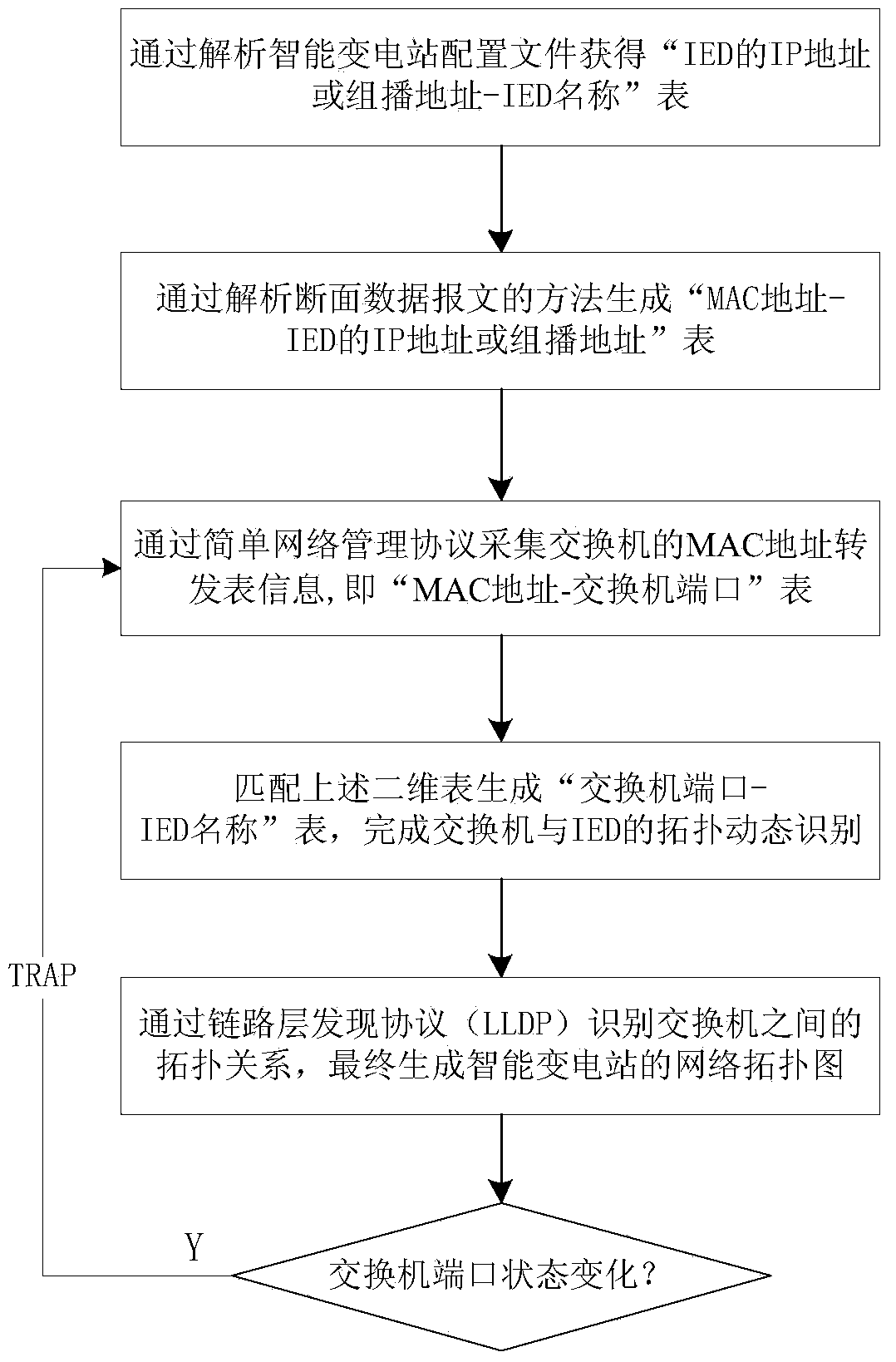
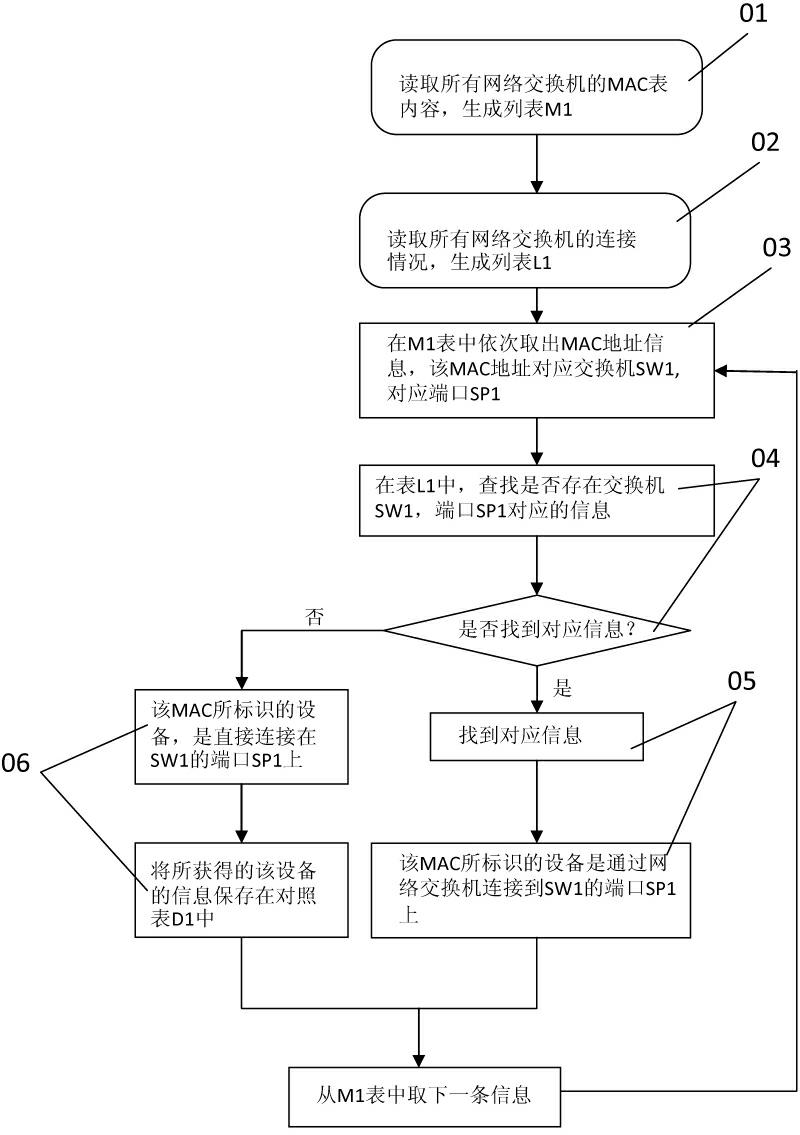
Dynamic recognition method for intelligent substation network device topology based on MAC address matching
ActiveCN103856579AEasy maintenanceMonitoring statusData switching networksHigh level techniquesTopology identificationSmart substation
The invention discloses a dynamic recognition method for intelligent substation network device topology based on MAC address matching. The method includes the steps that an corresponding relation table between the IP address / multicasting address of an intelligent electronic device (IED) and the name of the IED is obtained through analyzing an intelligent substation configuration file (SCD), and a corresponding relation table between the IP address / multicasting address of the IED and an MAC address is obtained through analyzing a section data message; an MAC address forwarding table of a switch is obtained through a simple network management protocol (SNMP); the MAC address serving as a foreign key is matched with the two-dimensional table to generate a switch port-IED name table, so that topology recognition of the switch and the connected IED is finished, and graphic displaying is performed. Based on a common topology search method of the switch, the method achieves dynamic recognition of IED topology in a network and helps the operation management level of the intelligent substation network to be improved.
Owner:STATE GRID CORP OF CHINA +2
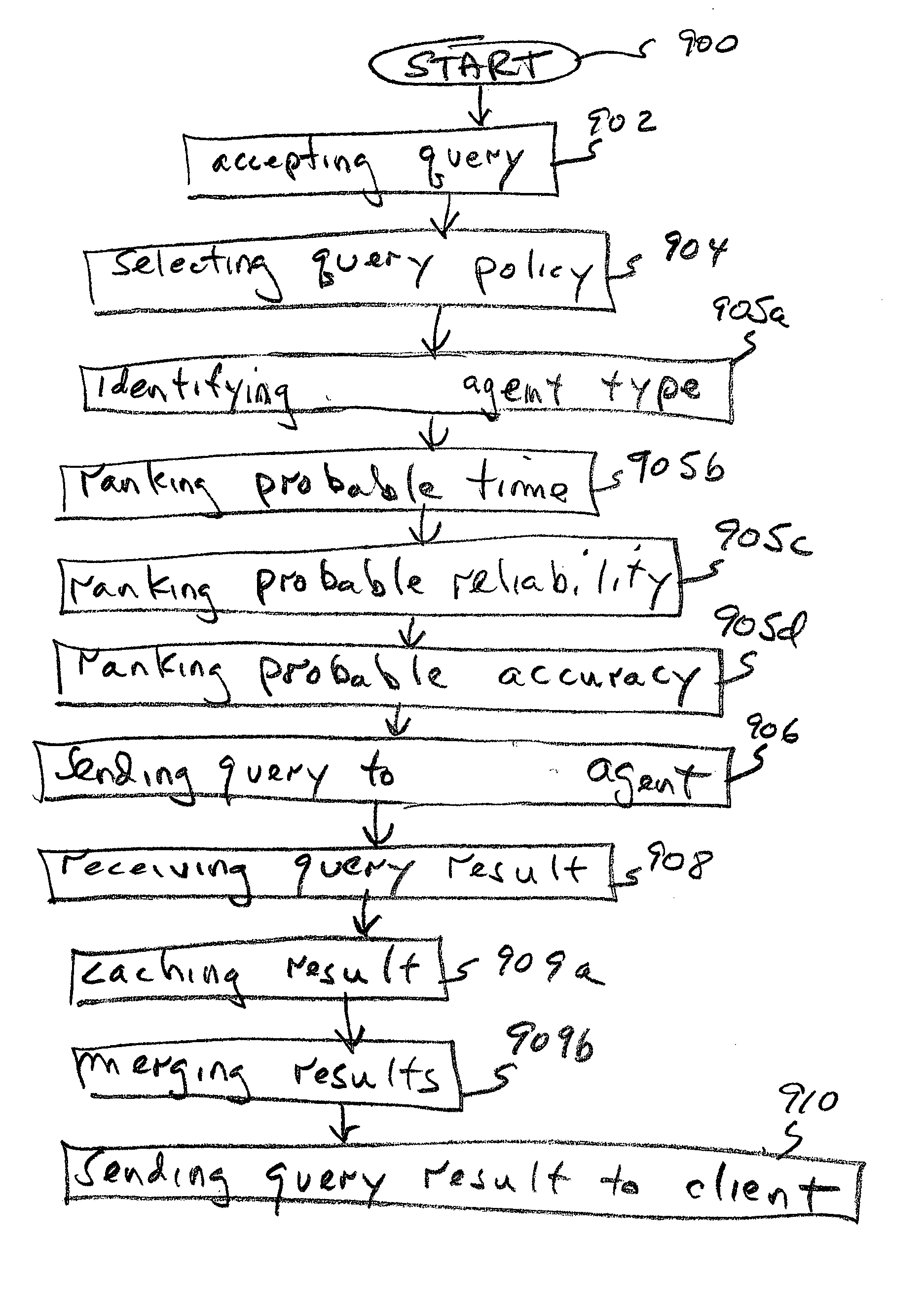
System and method for policy-driven device queries
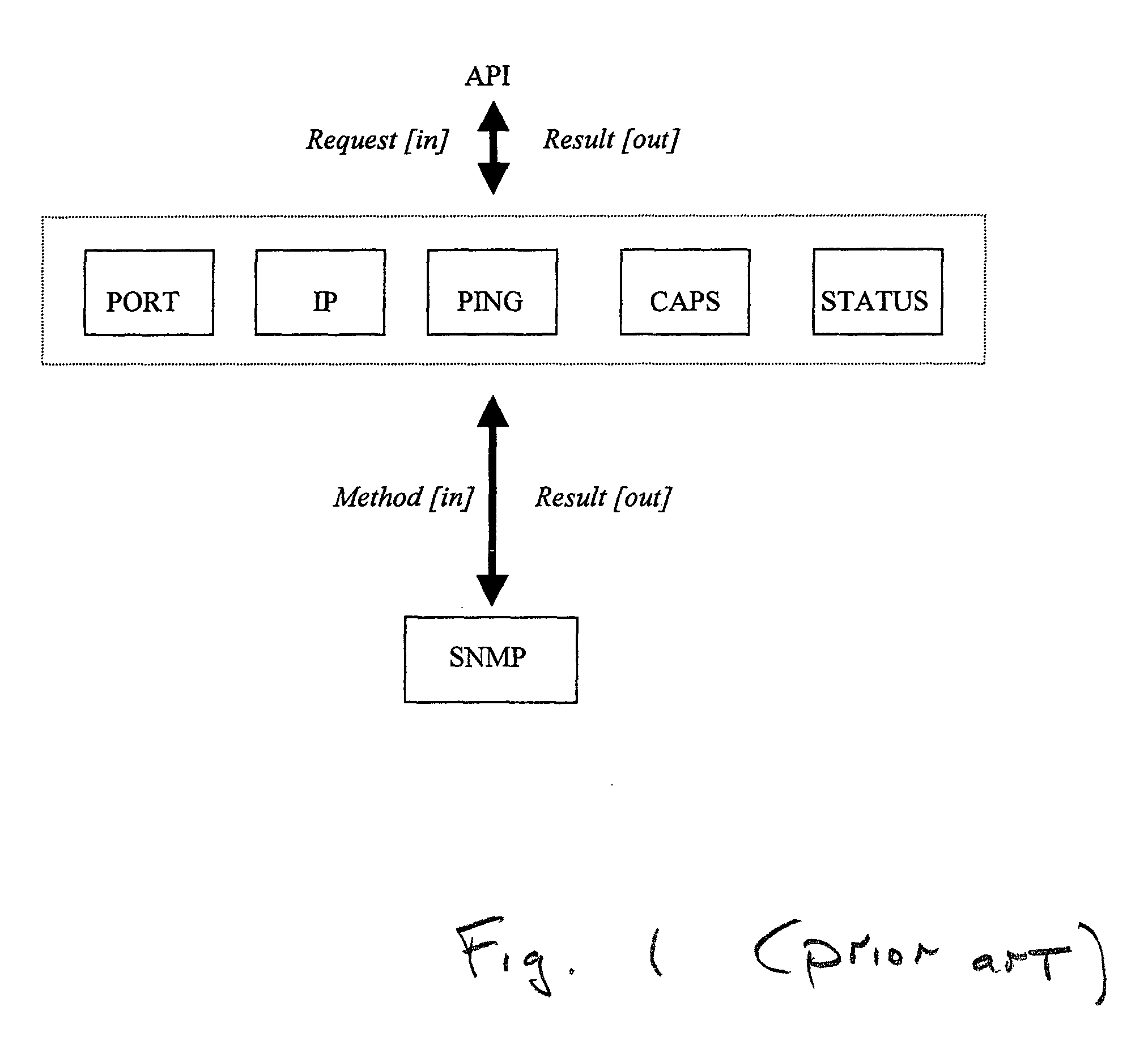
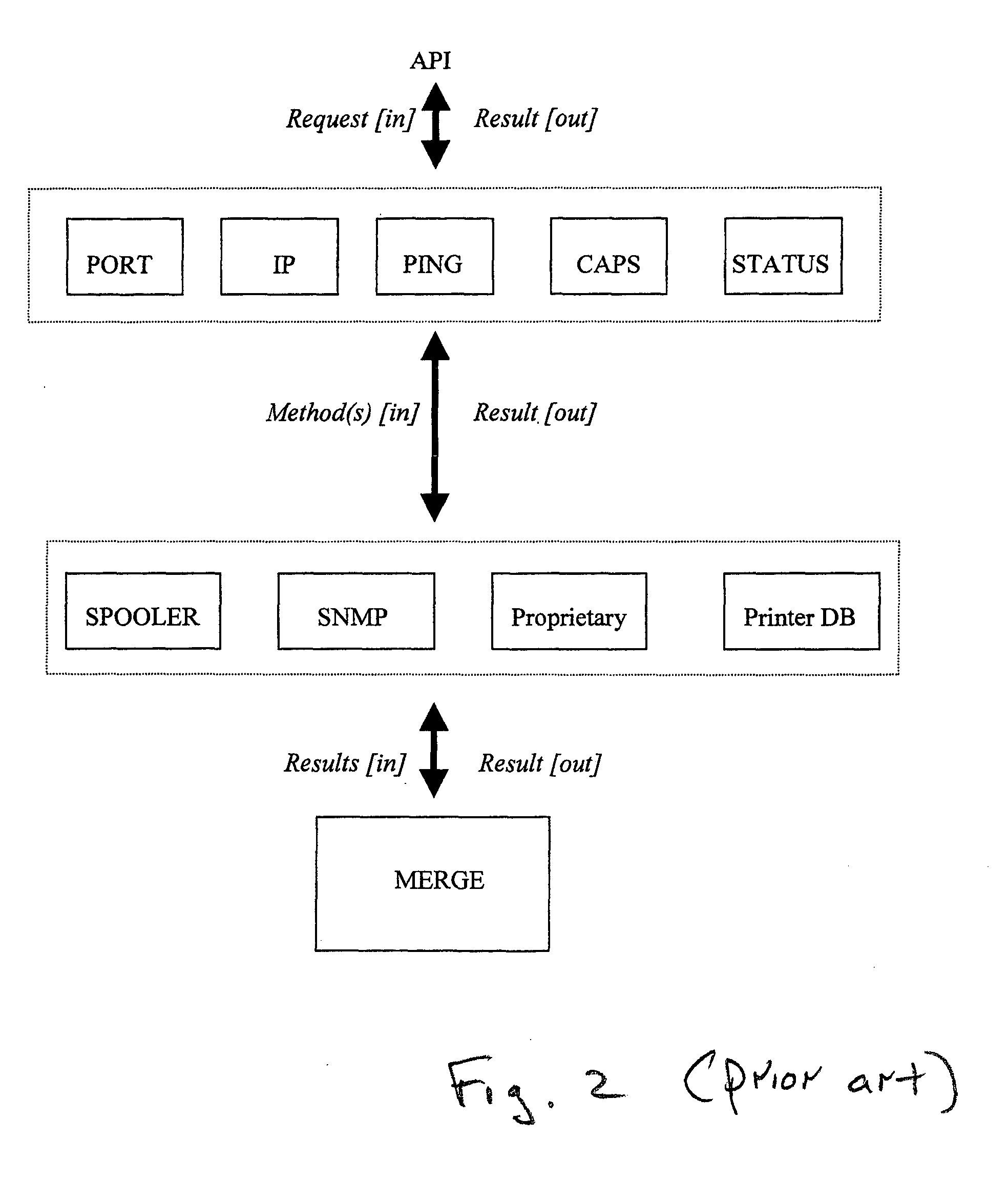
InactiveUS20050050013A1Digital data processing detailsOther printing apparatusComputer printingClient-side
A policy-driven system and method are provided for querying devices. The method comprises: accepting a query, from a client, directed to a device; selecting a query policy; and, sending the query to an agent using a method responsive to the selected query policy. The queries may concern a device communication port information, network information, communication checks (Ping), capability requests, or status updates. The methods may include spooler API, simple network management protocol (SNMP), printer database, proprietary protocol, Windows 2K directory service, service location protocol (SLP), and HTTP embedded device web page queries. The method further comprises: receiving a query result from the agent; and, sending the query result to the client using a method responsive to the selected query policy. In some aspects, an additional step merges a plurality of query results in response to the selected query policy. Then, the merged query result is sent to the client.
Owner:SHARP LAB OF AMERICA INC
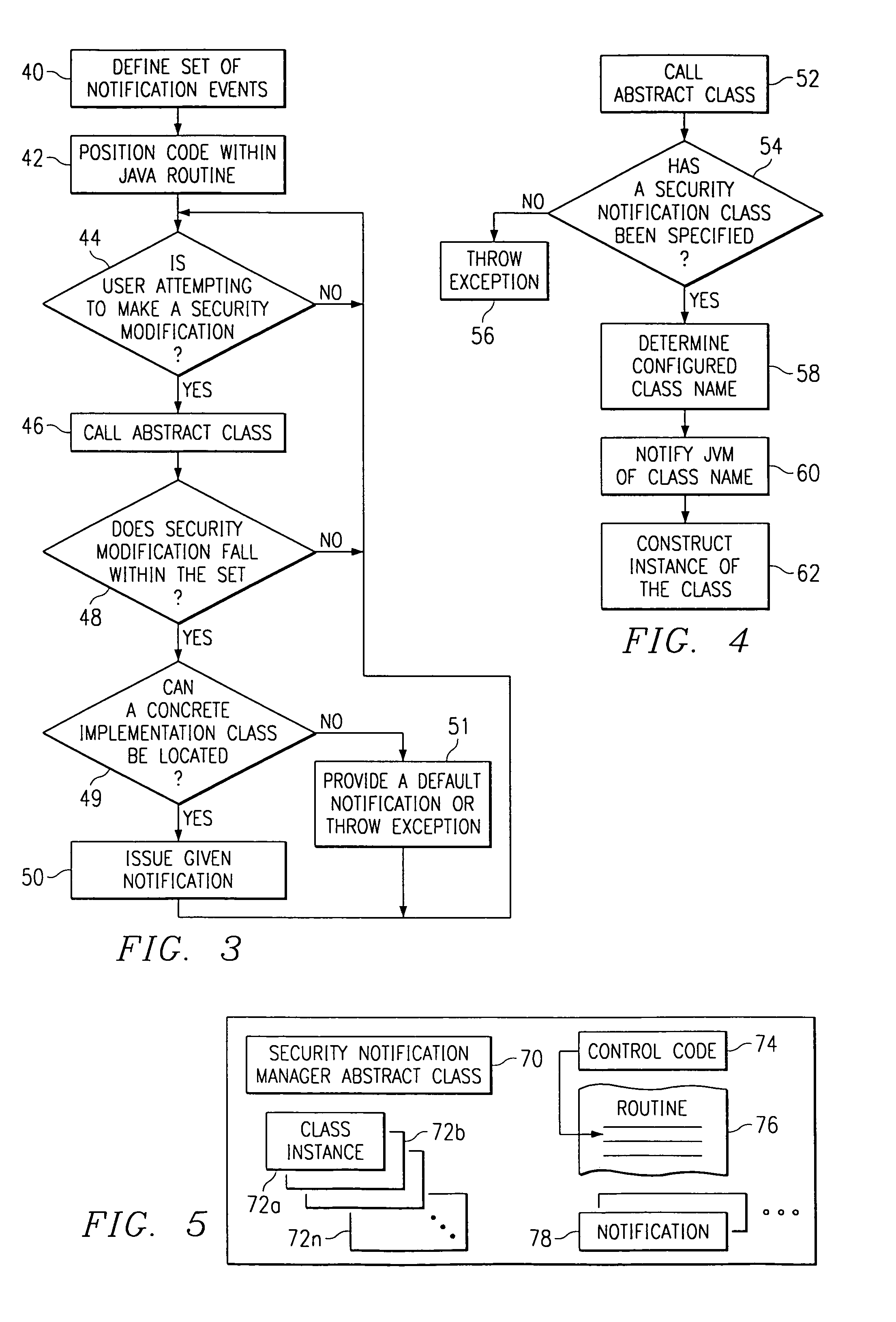
Notification of modifications to a trusted computing base
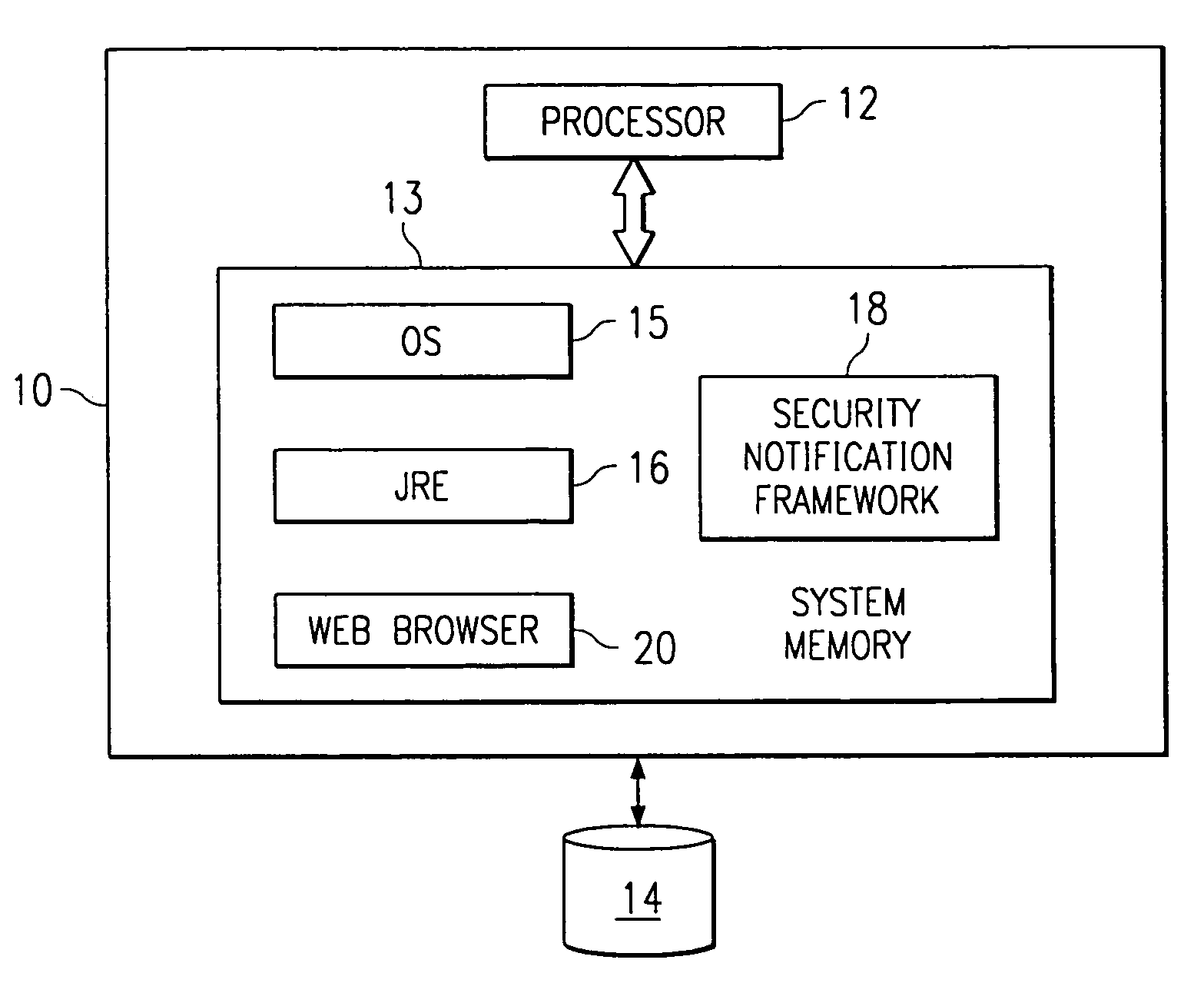
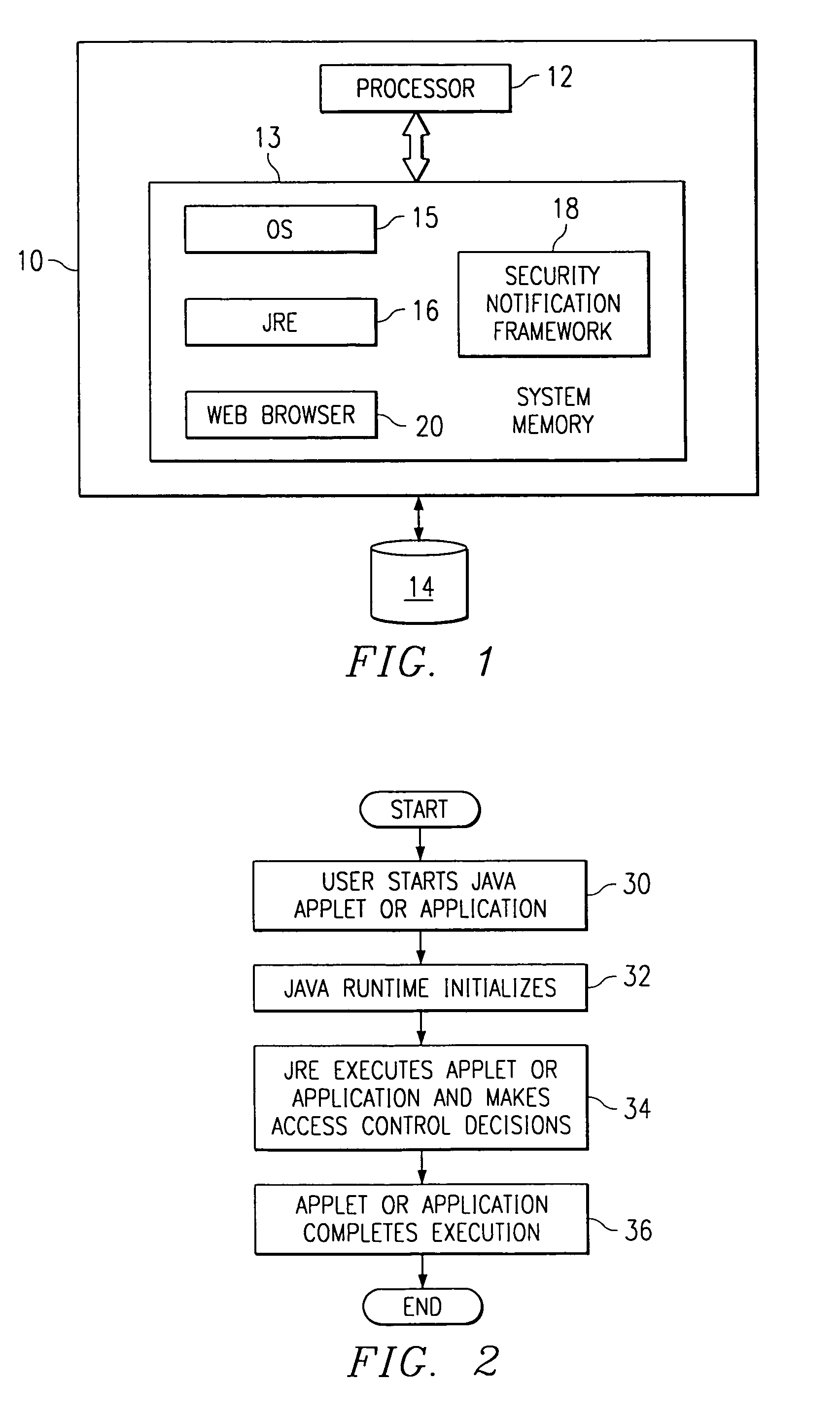
InactiveUS6961855B1Fully understandDigital data processing detailsUser identity/authority verificationTrusted ComputingDecision taking
A mechanism that allows enterprise authorities to be informed when security-sensitive decisions or actions have been or are attempting to be made by users of untrusted code executing in the trusted computing base. The mechanism may be implemented as an abstract class that is part of the trusted computing base. The class provides a framework abstract enough to permit multiple possible notifications (e.g., providing an e-mail to a system operator, sending an Simple Network Management Protocol (SNMP) alert, making an entry in an online database, or the like) in the event that a given action is taken by a user of untrusted code. The abstract class may provide a default notification, or the class may be extended to enable an authority to provide its own set of customized notifications.
Owner:CISCO TECH INC
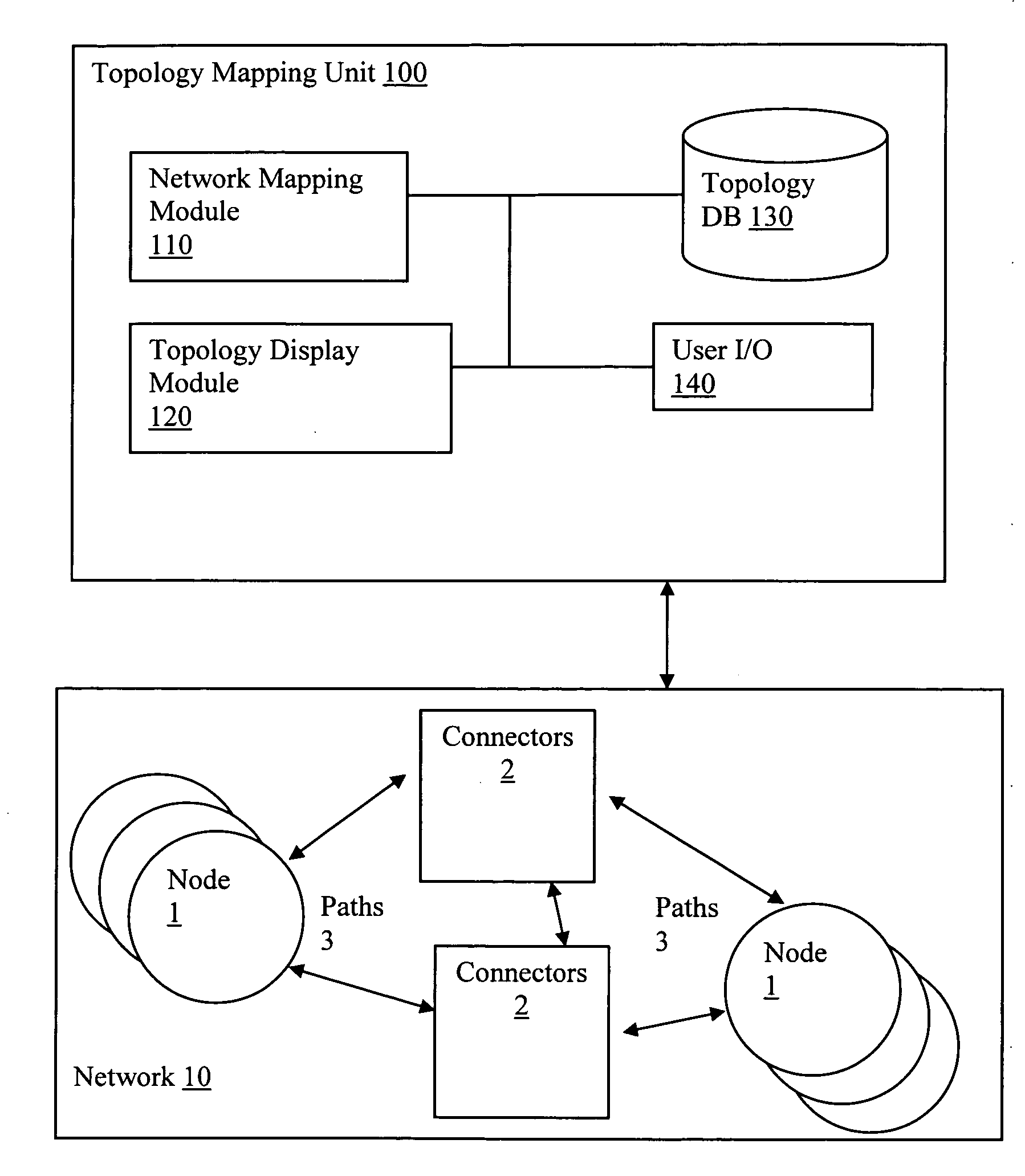
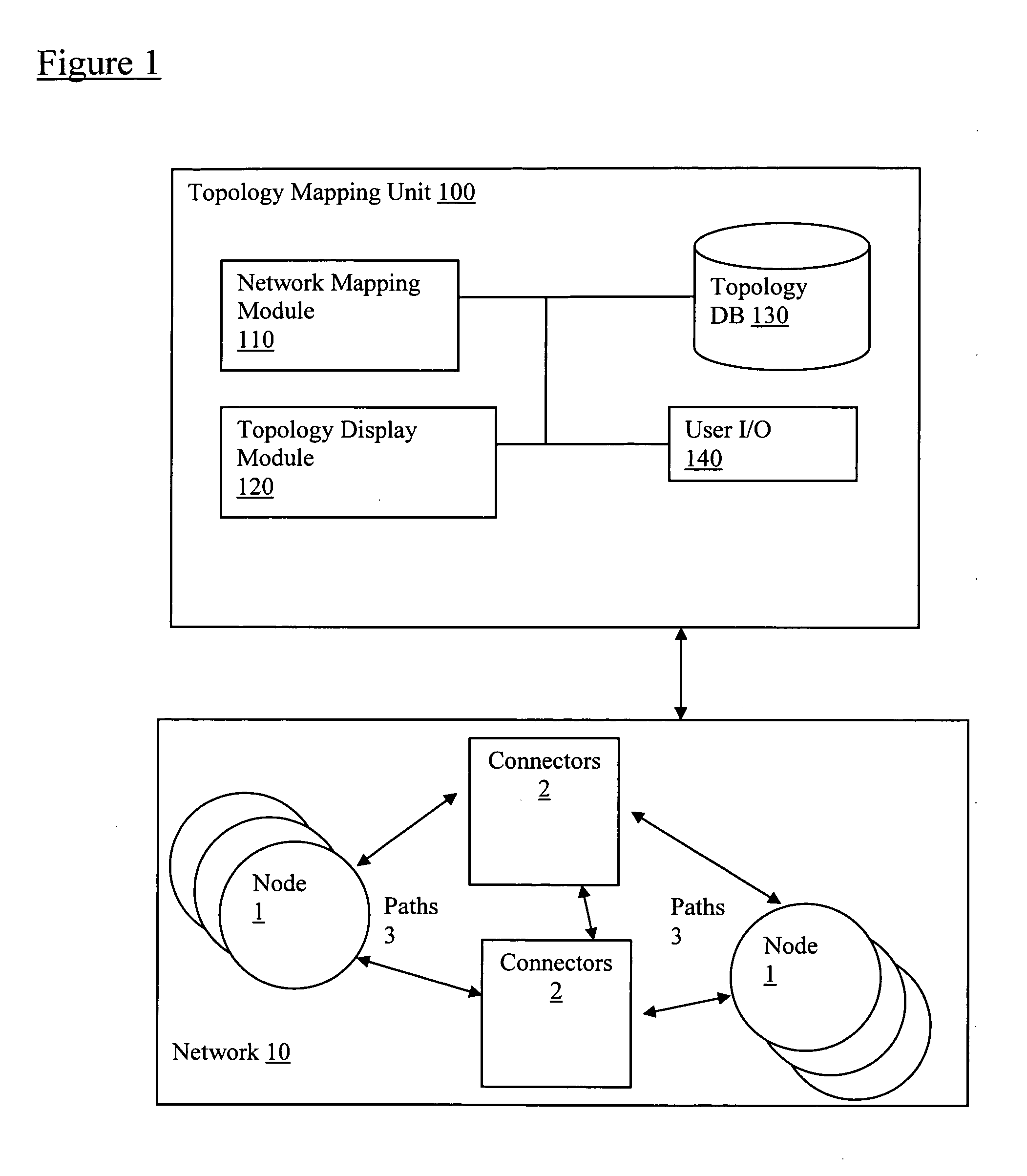
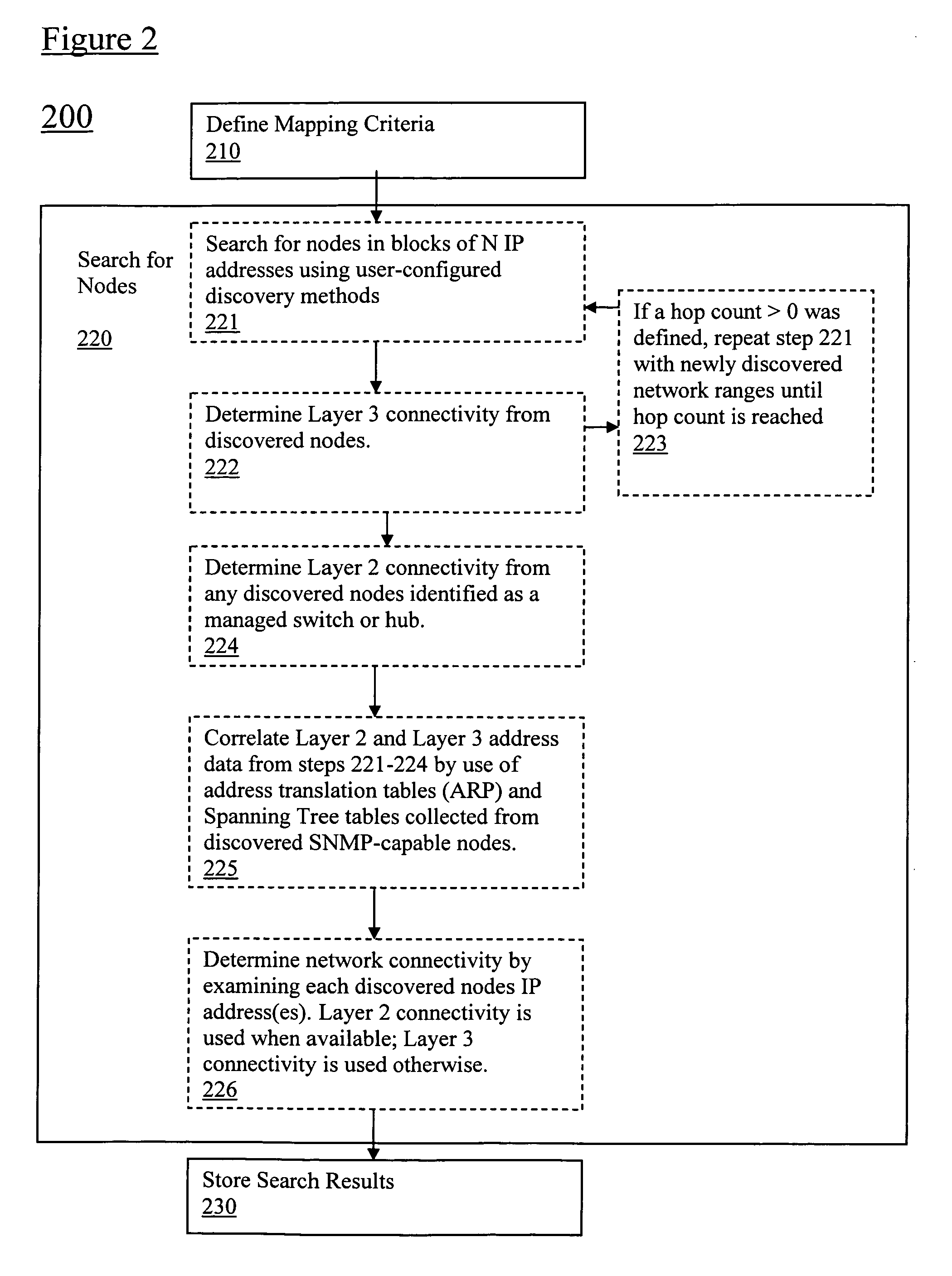
Filtering of map topology based on network discovery characteristics
Embodiments of the present application enable a user to map a network topology and to then dynamically filter the map display by hiding or showing nodes based on discovery characteristics, such as Simple Network Management Protocol (SNMP) status, Active Directory (AD) Domain Controllers (DC) status, group membership status, etc. to allow customization of maps views. In particular, a topology mapping is formed by collecting topology data of a network and storing this topology data. Filtering criteria are received from a user, and the stored topology data is filtered using this received filtering criteria. The filtered topology data is then displayed to the user.
Owner:SOLARWINDS WORLDWIDE
Methods, apparatuses and systems facilitating management of airspace in wireless computer network environments
ActiveUS20090028118A1Improve isolationOptimizationCriteria allocationWireless commuication servicesSimple Network Management ProtocolNetwork administrator
Owner:HEWLETT-PACKARD ENTERPRISE DEV LP
Real-time network analyzer
ActiveUS20070147271A1Data switching by path configurationClient-sideSimple Network Management Protocol
Owner:TAMIRAS PER PTE LTD LLC
Integrated gigabit ethernet PCI-X controller
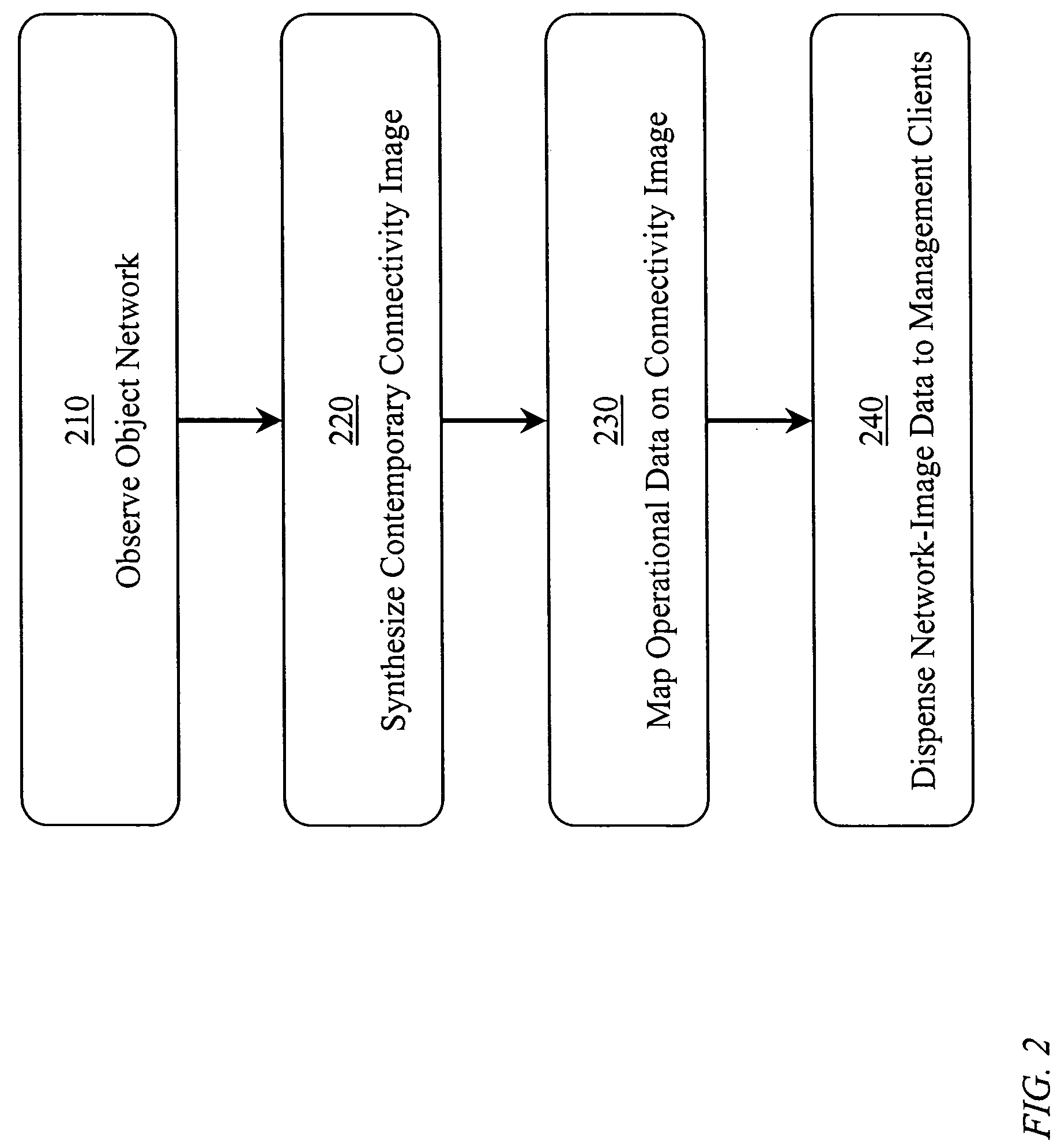
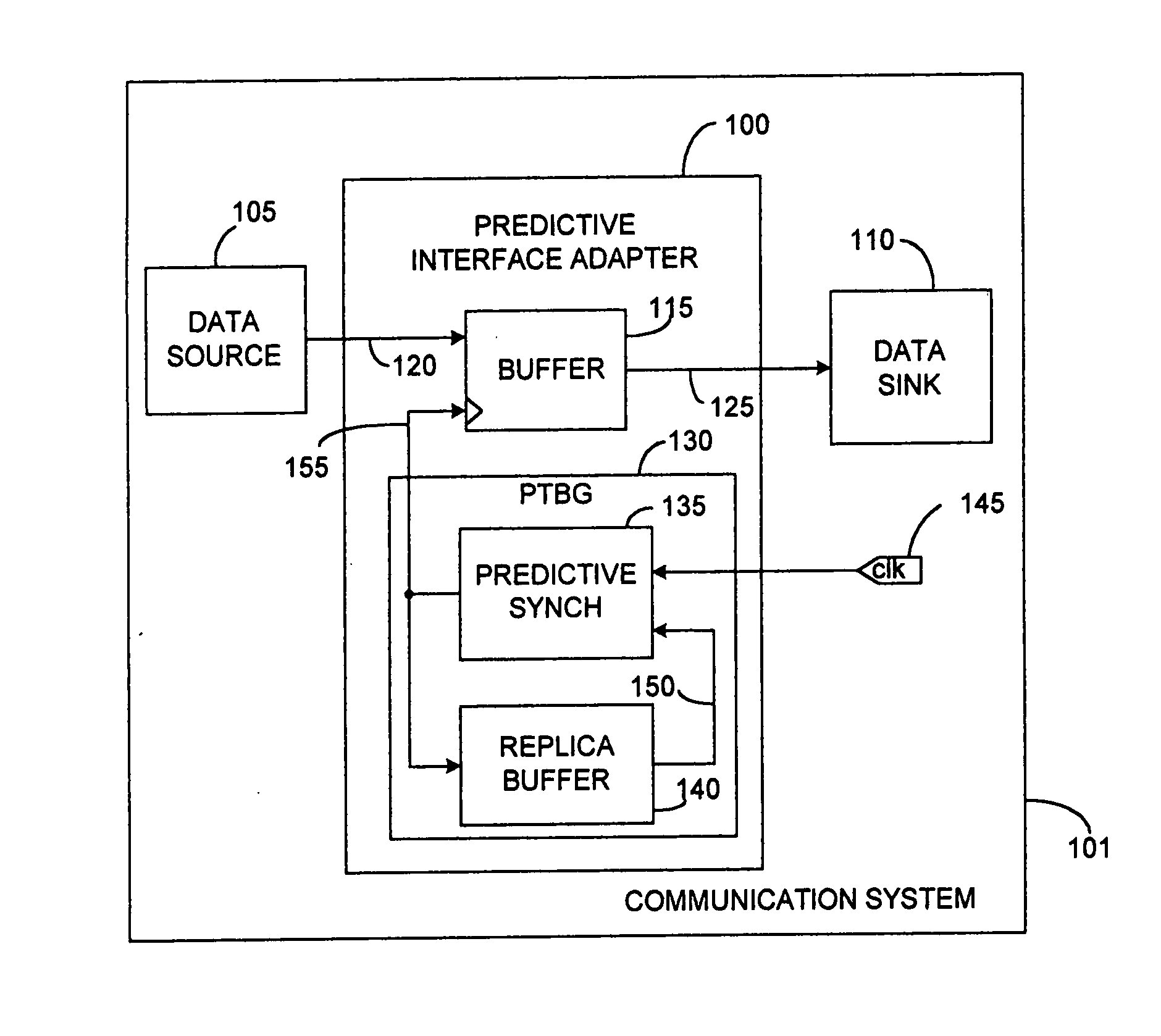
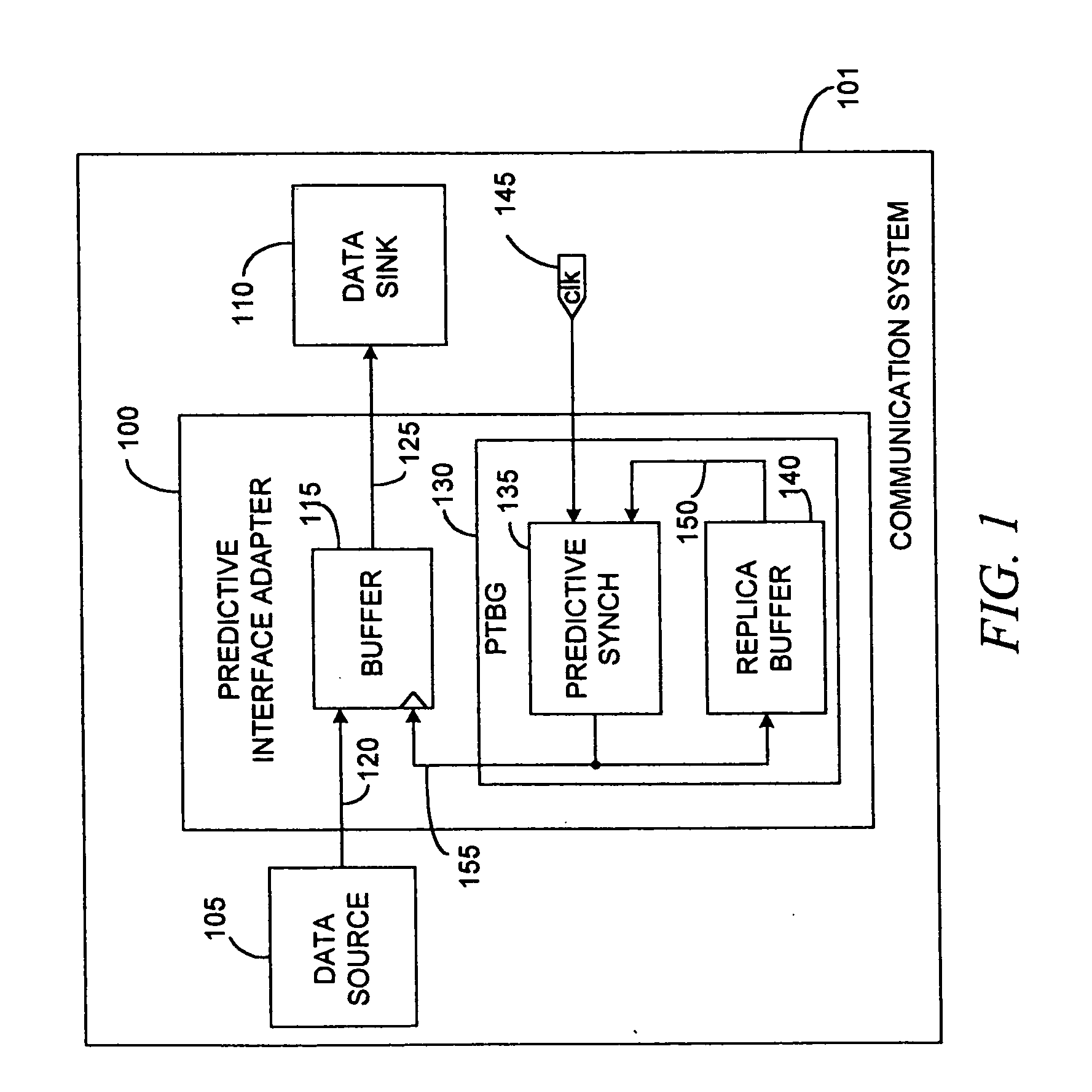
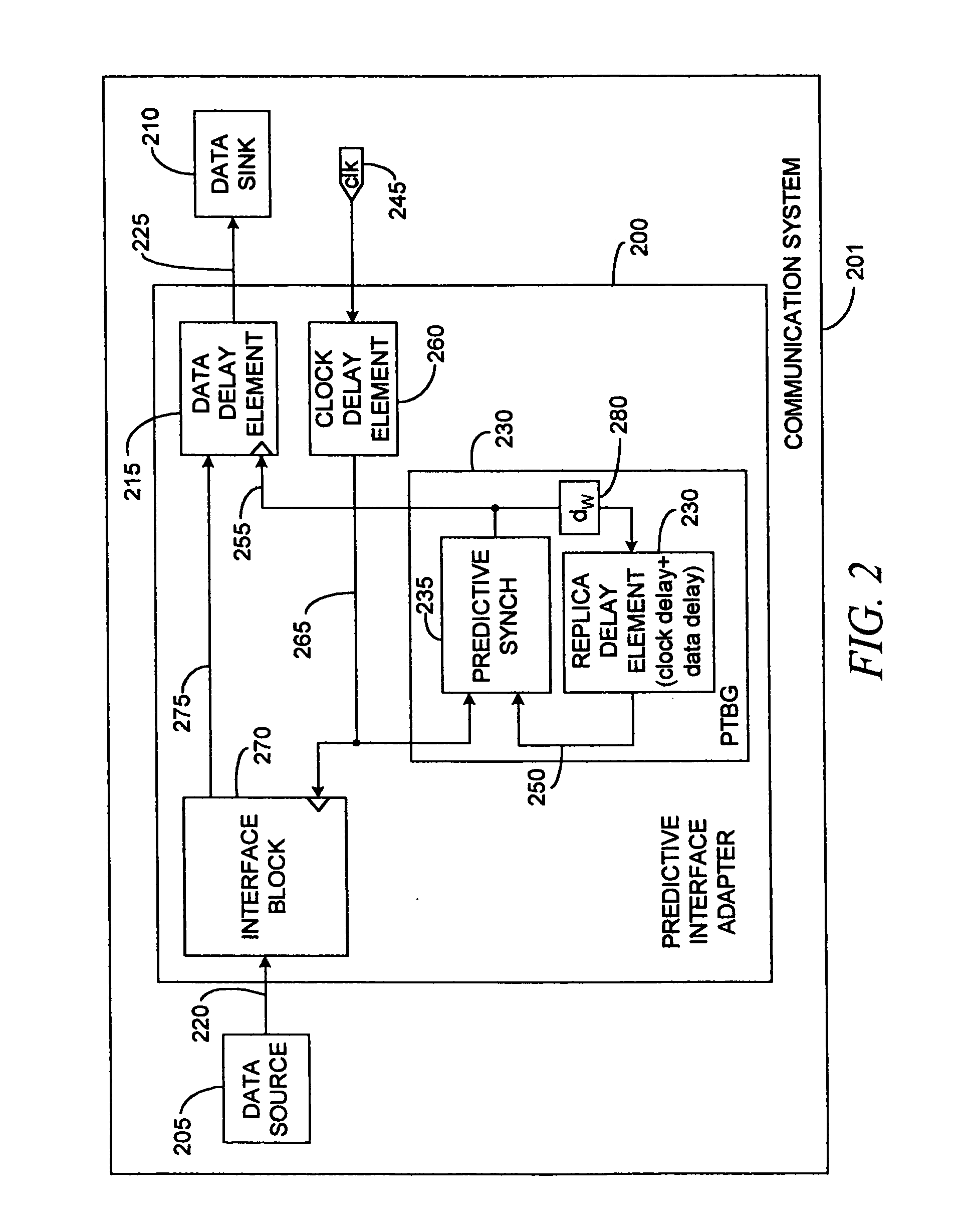
InactiveUS20060143344A1Reduce data latencyEnergy efficient ICTVolume/mass flow measurementTransceiverBus interface
A network controller having a multiprotocol bus interface adapter coupled between a communication network and a computer bus, the adapter including a predictive time base generator; and a management bus controller adapted to monitor and manage preselected components coupled with one of the communication network and the computer bus. The management bus controller is adapted to employ an Alert Standard Format (ASF) specification protocol, a System Management Bus (SMBus) specification protocol, an Intelligent Platform Management Interface (IPMI) specification protocol, a Simple Network Management Protocol (SNMP), or a combination thereof. The network controller also includes a 10 / 100 / 1000BASE-T IEEE Std. 802.3-compliant transceiver and media access controller coupled with the communication network; a buffer memory coupled with the MAC, wherein the buffer memory includes one of a packet buffer memory, a frame buffer memory, a queue memory, and a combination thereof; and a transmit CPU and a receive CPU coupled with the multiprotocol bus interface adapter and the management bus controller. The network controller can be a single-chip VLSI device in an 0.18 micron CMOS VLSI implementation.
Owner:AVAGO TECH INT SALES PTE LTD
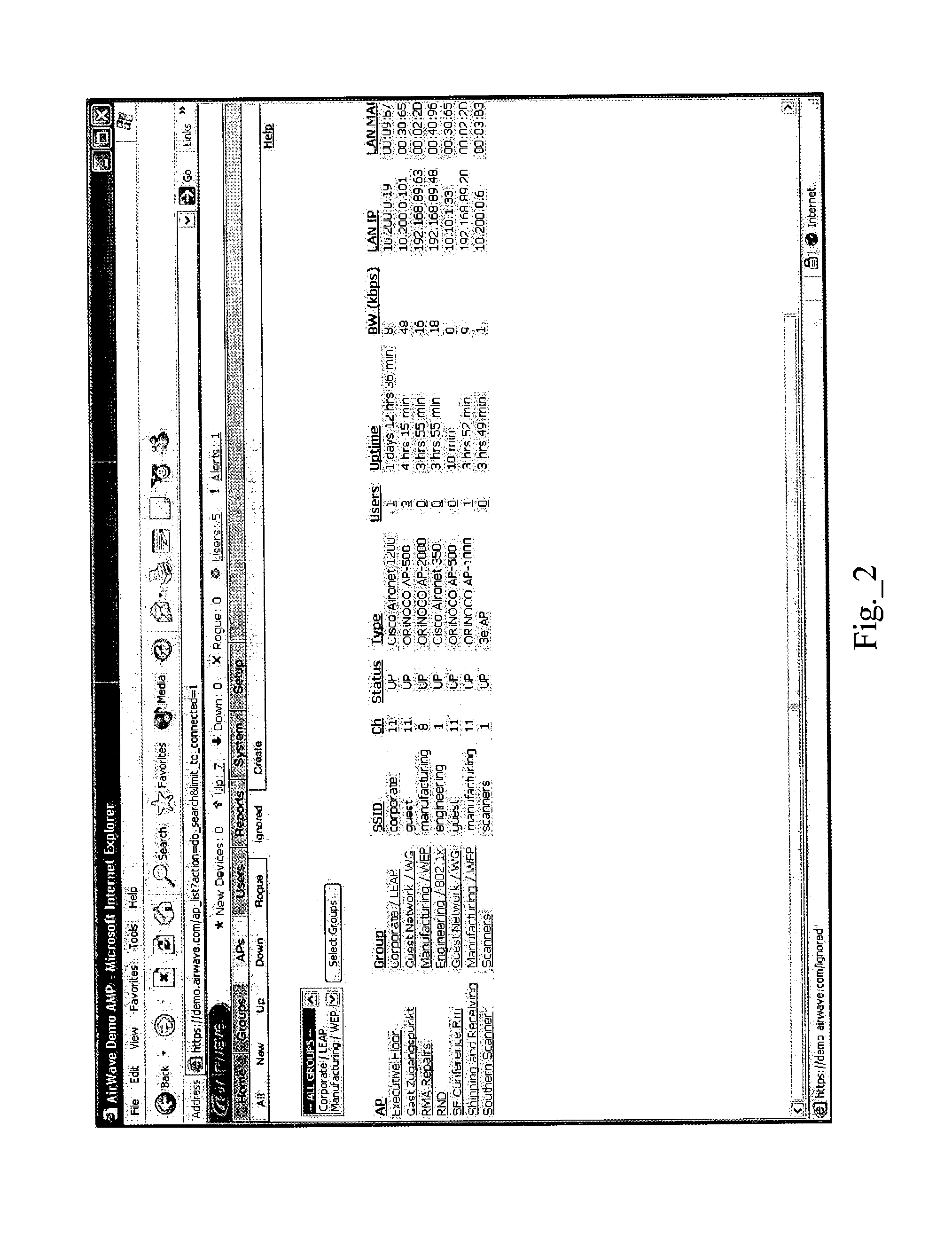
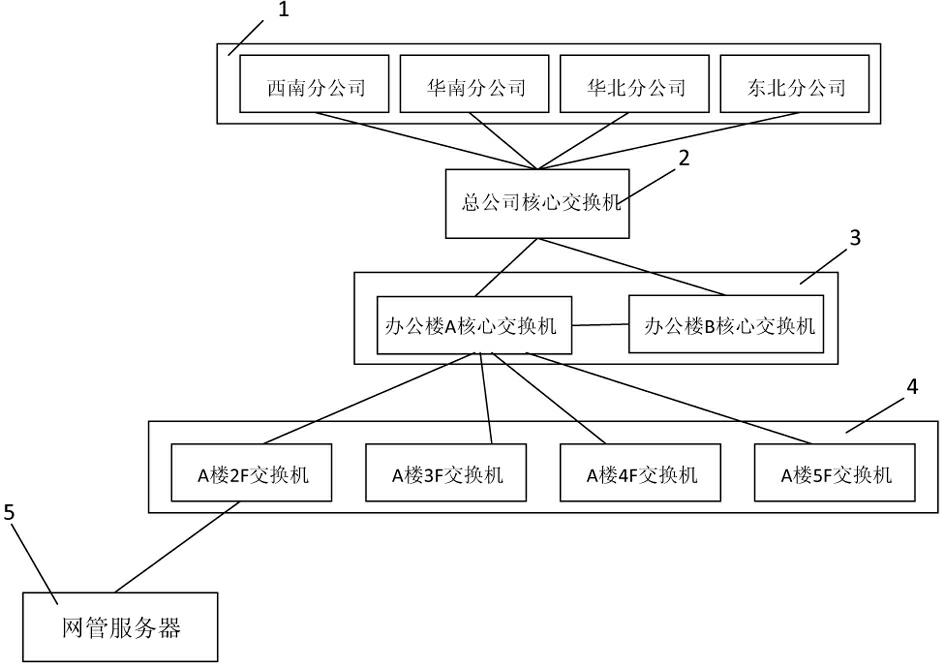
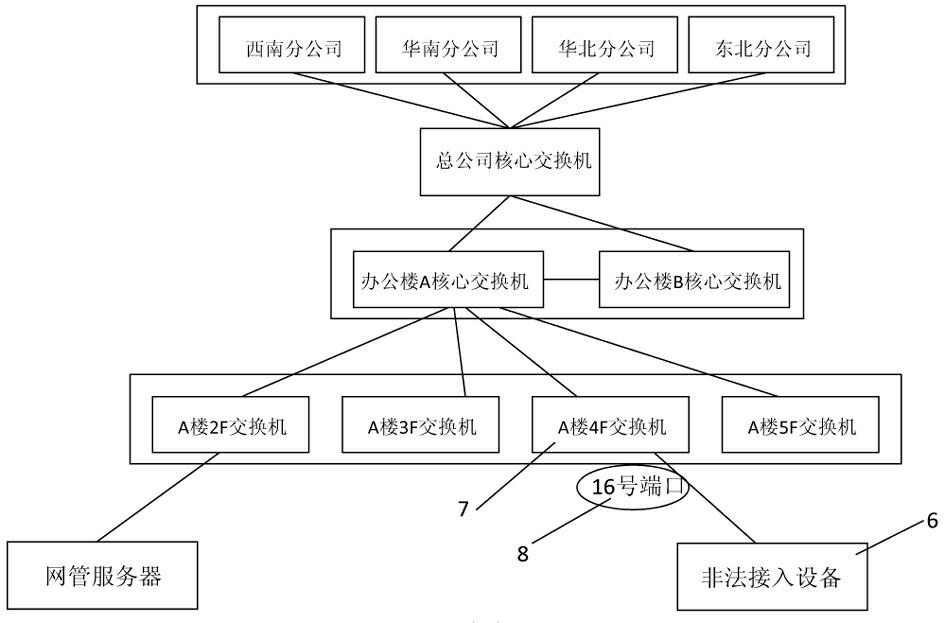
Method for discovering illegally-accessed equipment
ActiveCN102118271ALearn about real deploymentsNo manual operationData switching networksAddress Resolution ProtocolIp address
The invention discloses a method for discovering illegally-accessed equipment. According to the method, two defense lines are adopted. The first defense line comprises the following steps: utilizing a topological physical graph of network management software to display all equipment in a controlled local network onto the topological physical graph; obtaining all PC client side information connected with switches in the local network through an SNMP (Simple Network Management Protocol), an ARP (Address Resolution Protocol), and an Netbios (Network Basic Input / Output System Protocol); adopting an MAC address discrimination method to establish a standard comparison table containing the content of legal equipment in the local network; carrying out binding operations on IP addresses of PC client sides, MAC and port numbers of the switches according to the standard comparison table. The second defense line comprises the following steps: randomly adopting the MAC address discrimination method to obtain port information of the switches connected with the all PC client sides, comparing the port information with that of the comparison table, and determining the client sides which do not exist as new-emerging ones and as illegally-accessed equipment and blocking. The method provides double safety.
Owner:上海北塔软件股份有限公司
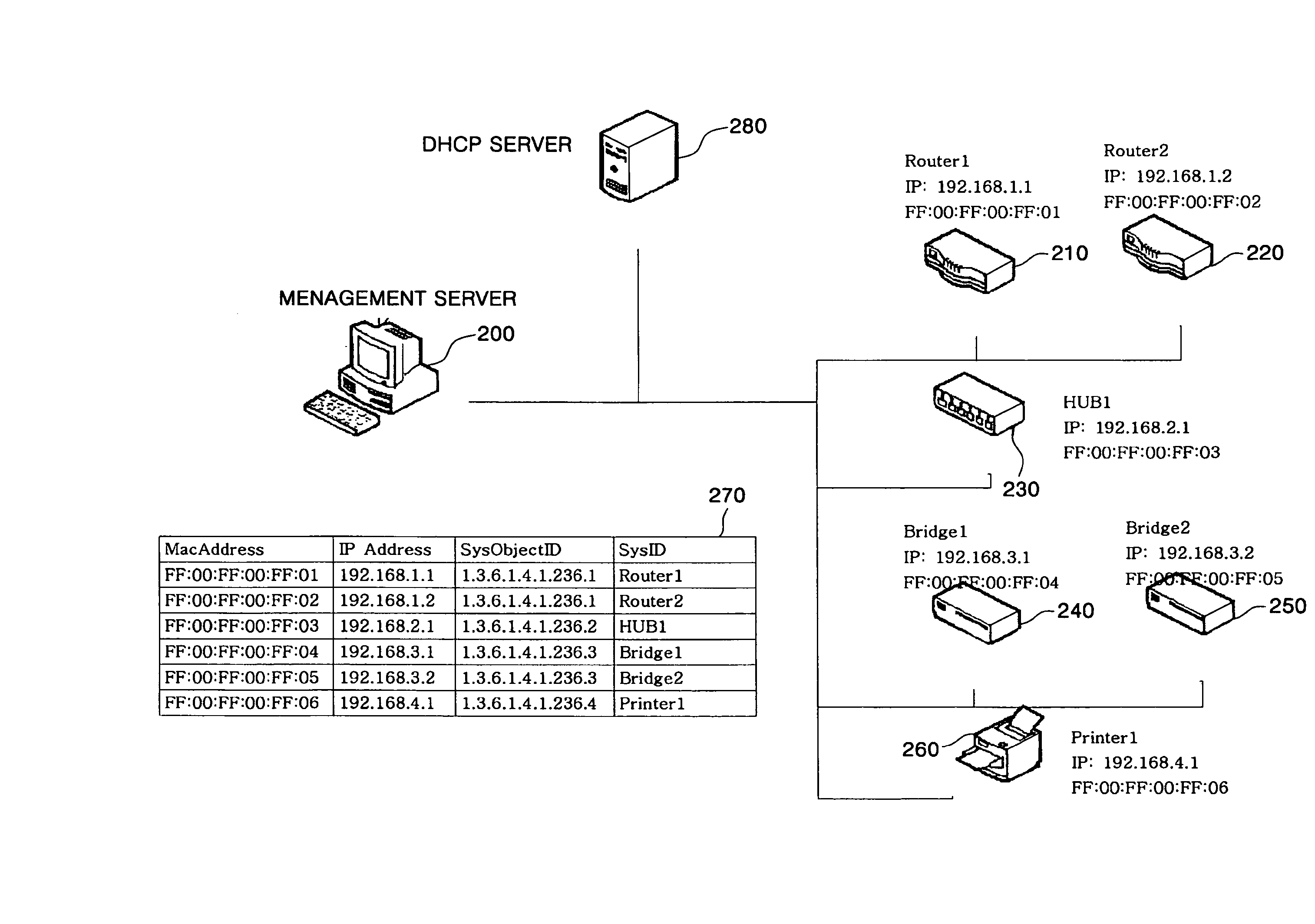
Management system and method of network elements using simple network management protocol
InactiveUS20080059623A1Digital computer detailsData switching by path configurationConfusionSimple Network Management Protocol
An NE management system and method using SNMP manages NEs and updates a management information list thereof without confusion even though NE settings are changed. The NE management system includes an NE and a management server. The NE generates NE settings in response to a setting change, transmits the NE settings to the management server, and receives a complete message from the management server. The management server receives the NE settings from the NE, acquires an element type of the NE based upon the received NE settings to determine an MIB to use, manages a registration list, and notifies the NE that a registration process is accomplished. The NE management method and system integrate registration and management of a plurality of NEs in a ubiquitous environment where various types and versions of the NEs exist together.
Owner:SAMSUNG ELECTRONICS CO LTD
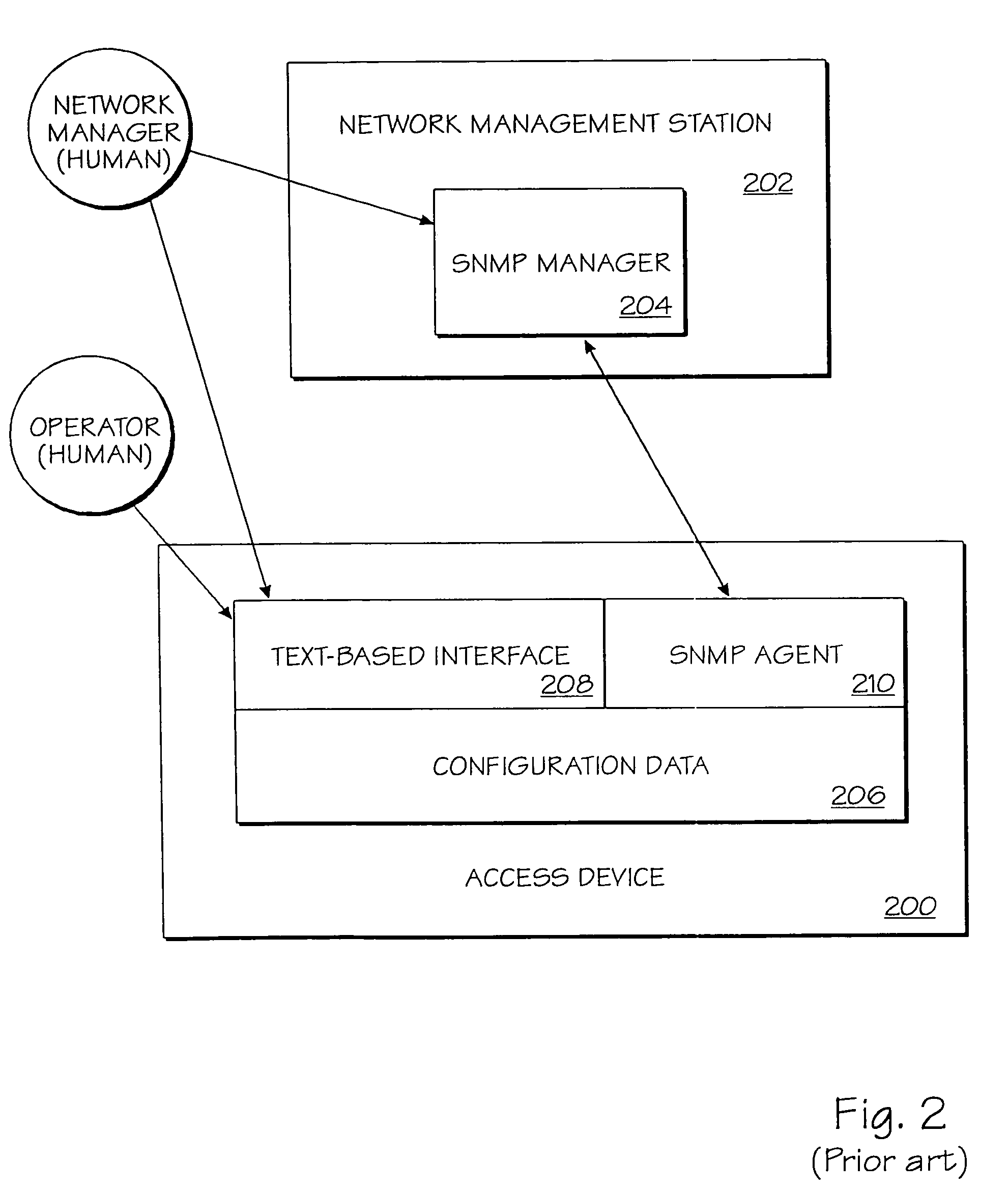
Method and apparatus for providing multiple management interfaces to a network device
InactiveUS7254781B1Avoid complexityAvoid problemsDigital data processing detailsSpecial data processing applicationsClient-sideSimple Network Management Protocol
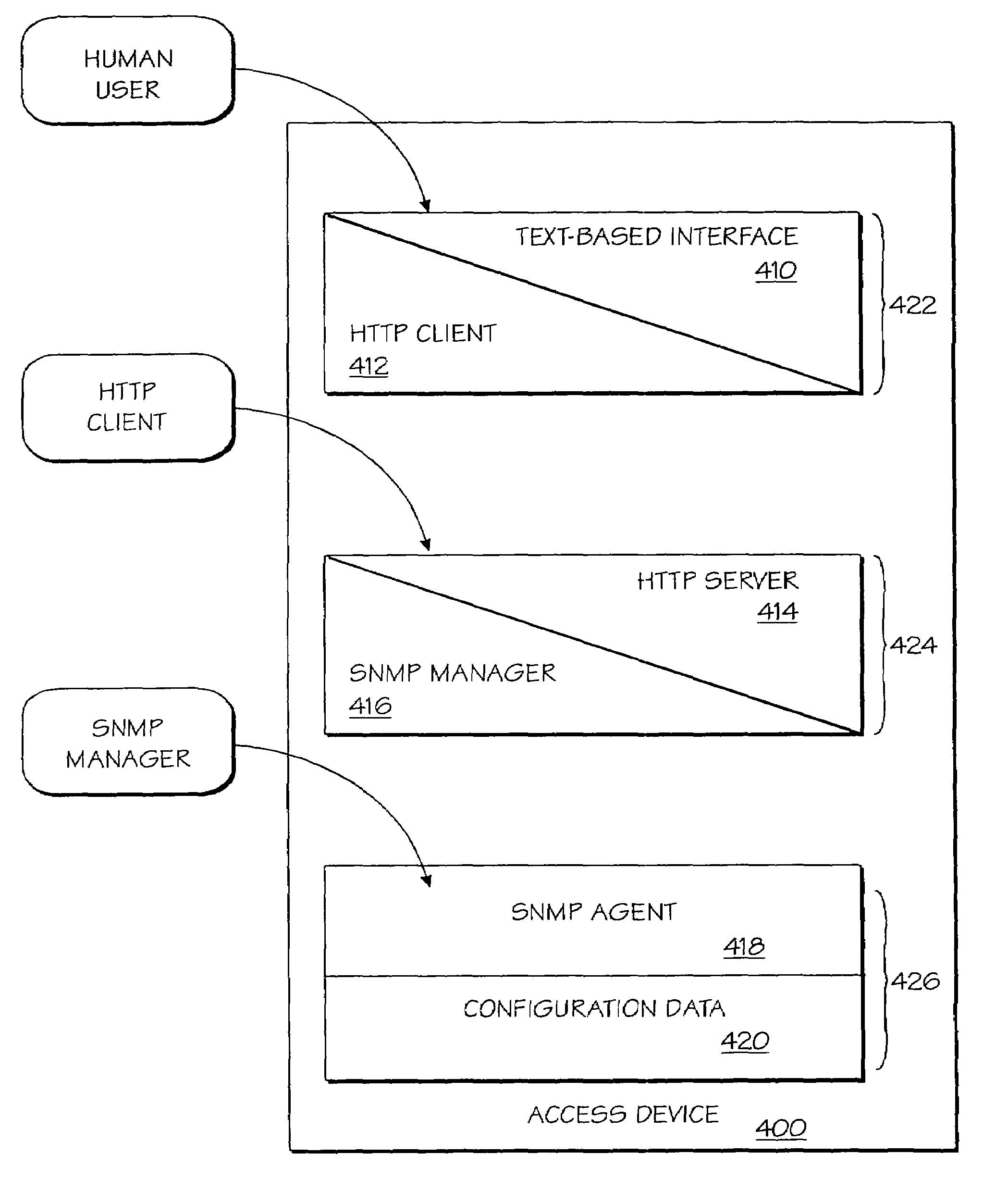
A method and apparatus for managing a network access device is provided. Embedded within the access device are three distinct software layers. The first layer is a combined text-interface generator and Hypertext Transport Protocol client. The second layer is a combined Hypertext Transport Protocol server and Simple Network Management Protocol manager. The third layer is a Simple Network Management Protocol agent that has direct access to the configuration data of the access device. A user can manage the device through the embedded text-interface generator, by using an external HTTP client to communicate with the embedded HTTP server, or by using an external SNMP manager to communicate with the embedded SNMP agent. Techniques are disclosed for embedding SNMP information in messages passed between HTTP clients and servers.
Owner:CISCO TECH INC
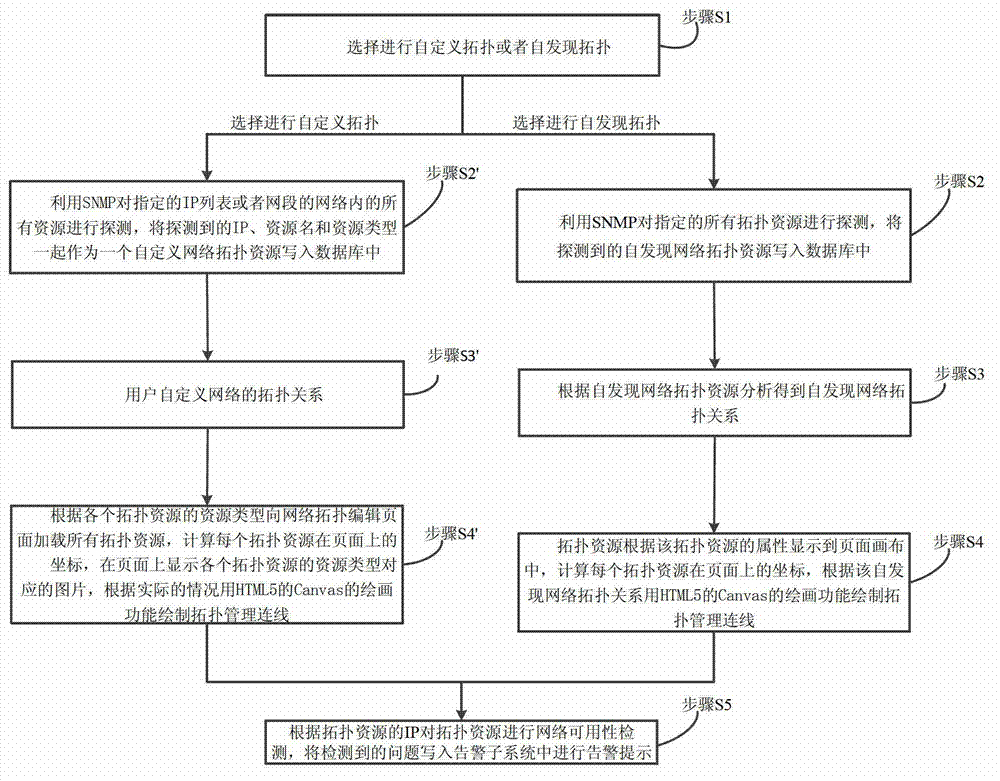
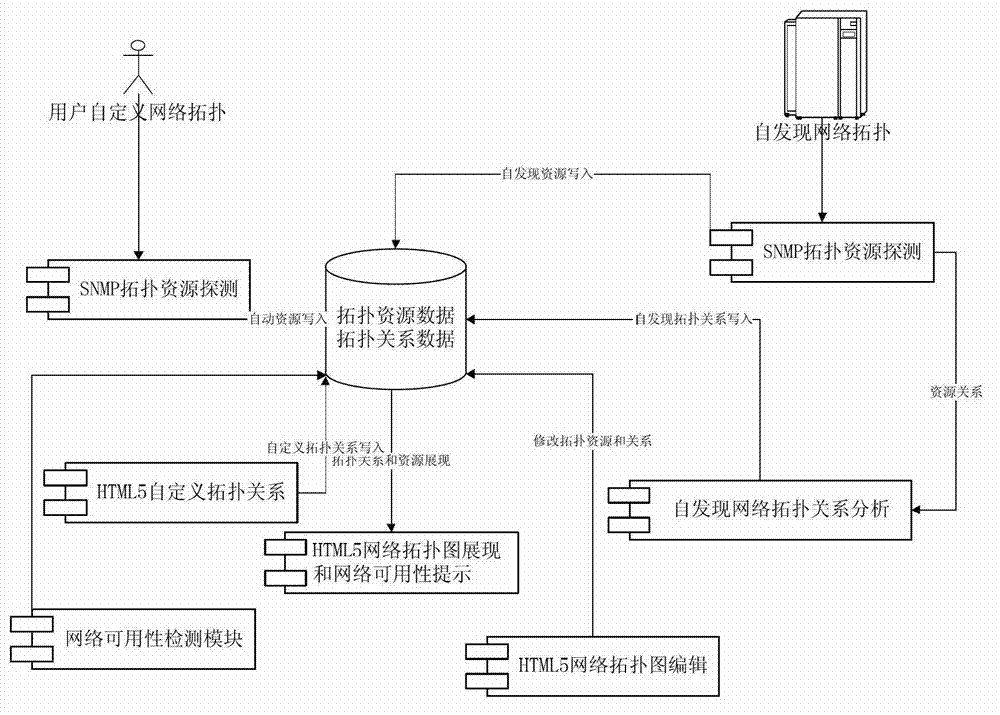
SNMP (Simple Network Management Protocol) and HTML5 (Hypertext Markup Language 5)-based method for realizing web network topology
The invention provides an SNMP (Simple Network Management Protocol) and HTML5 (Hypertext Markup Language 5)-based method for realizing web network topology. The method comprises the steps of: S1, selecting user-defined topology or self-discovered topology; S2, when selecting the self-discovered topology, detecting all resources by utilizing the SNMP, and writing the detected self-discovered network topology resources into a database; S3, according to the self-discovered network topology resources, analyzing to obtain a self-discovered network topological relationship; S4, according to the attributes of the topology resources, displaying the topology resources in a network topology editing page canvas, calculating coordinates of each topology resource in a network topology editing page, and drawing topology management connecting lines by utilizing the drawing function of the canvas of the HTML5 according to the self-discovered network topological relationship; and S5, conducting network usability detection to the topology resources according to the IP (Internet Protocol) of the topology resources, and writing the detected problems into an alarm subsystem for alarming and prompting. Through the method, the network topology presentation of the B / S (Browser / Server) structure can be done through the HTML5, and a user can select user-defined topology or self-discovered topology.
Owner:DAWNING CLOUD COMPUTING TECH CO LTD
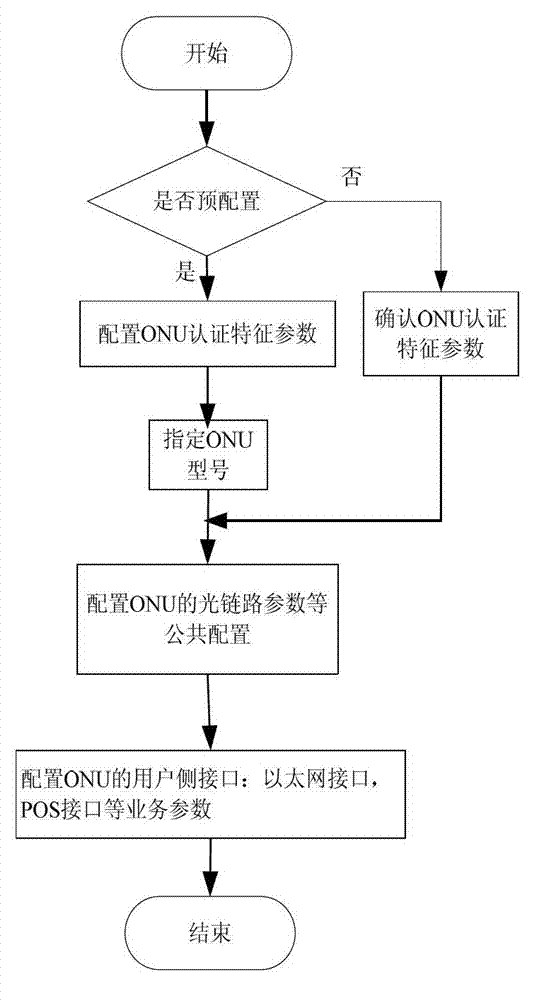
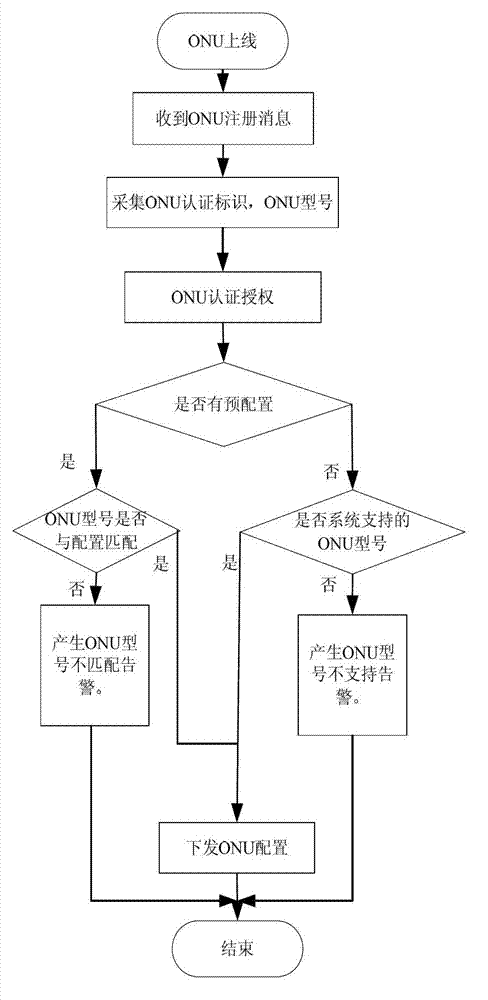
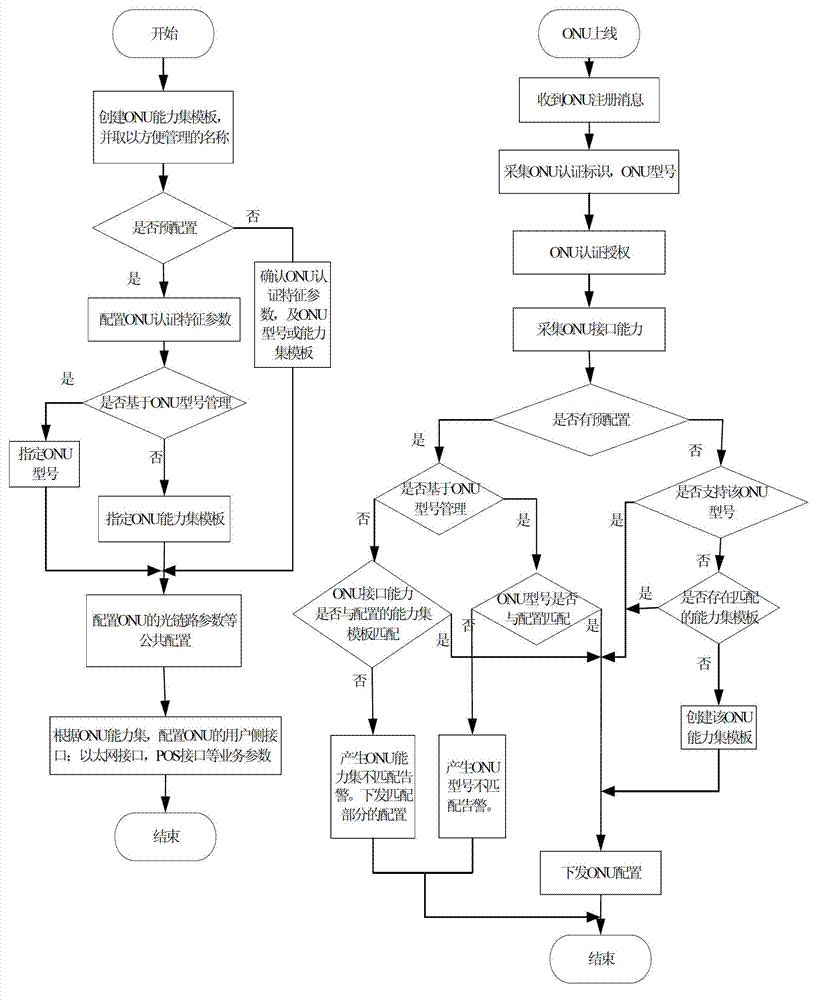
Method and system for managing optical network units (ONU) based on interface capability set
ActiveCN102833642AAdd supportEasy to manageMultiplex system selection arrangementsData switching networksSimple Network Management ProtocolOptical network unit
The invention relates to a method and a system for managing optical network units (ONU) based on an interface capability set. The method comprises the following steps of: dividing the ONU with the same interface capability to the same ONU interface capability set, and regarding the ONU as the same class of ONU for configuration management; establishing 'ONU interface capability set templates' of the ONU as ONU management models on an optical line terminal (OLT) and a network management system (NMS), and configuring the ONU management models by adopting standard administration and maintenance (OAM) or simple network management protocols (SNMP), so that the ONU can be accessed to a network and incorporated to management of an established passive optical network (PON) system. By the method and the system, on the premise that software of the OLT or the NMS is not required to be upgraded, the ONU type supported in the PON system can be flexibly expanded, the ONU based on ONU equipment type management can be compatible, the ONU based on the ONU interface capability set management is supported at the same time, the PON system can easily support and manage the 'newly developed or expanded' ONU, and the ONU produced by different factories can be plugged and played in the network.
Owner:FENGHUO COMM SCI & TECH CO LTD
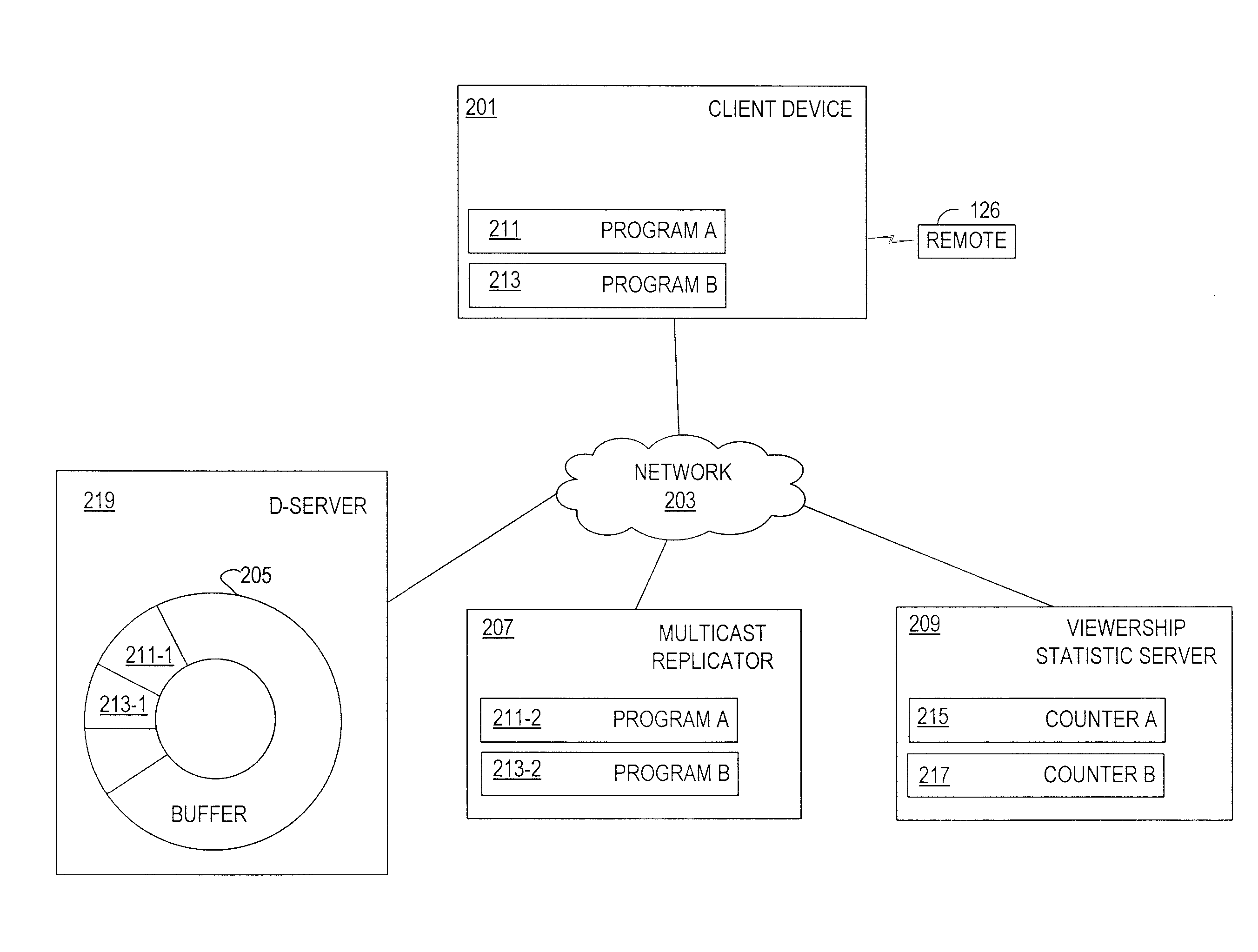
Digital television channel trending
ActiveUS8266644B2Analogue secracy/subscription systemsBroadcast information monitoringClient-sideSimple Network Management Protocol
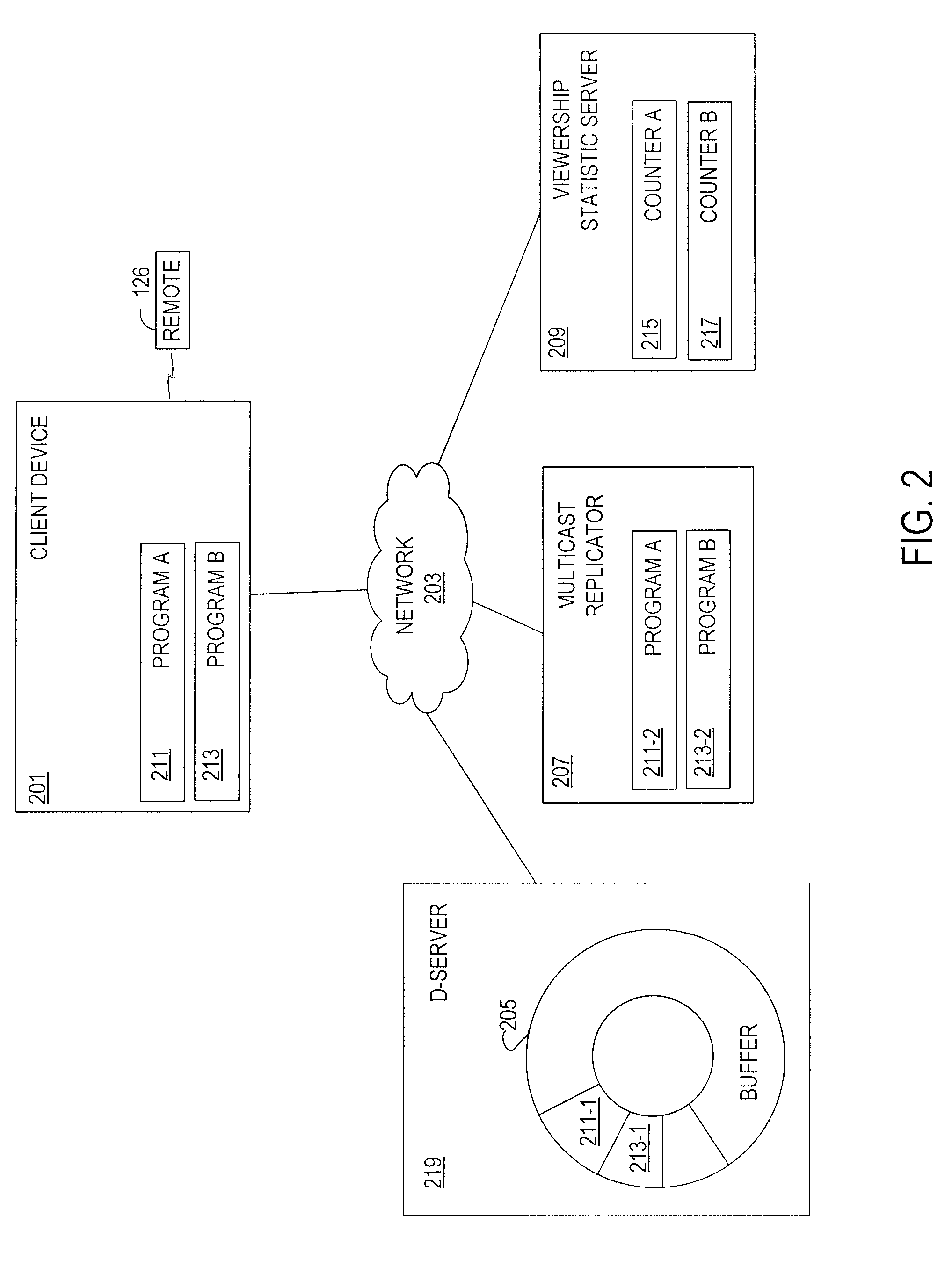
Channel trending, including determining a number of viewers watching a multimedia program, is achieved in a digital television network. Cached multimedia frames that correspond to portions of the multimedia program are maintained, for example, on a device located on an edge (i.e., in a network edge device) of the digital television network. In response to a request from a client device (e.g., a set-top box) to receive the multimedia program, cached multimedia frames are fed from the edge device to the client device. Upon a seamless transfer or handoff resulting in a simulcast replicator or multicast replicator providing further portions of the multimedia program, a signal (e.g., a simple network management protocol TRAP statement) is sent to a viewership statistic server for incrementing a counter.
Owner:AT&T INTPROP I LP
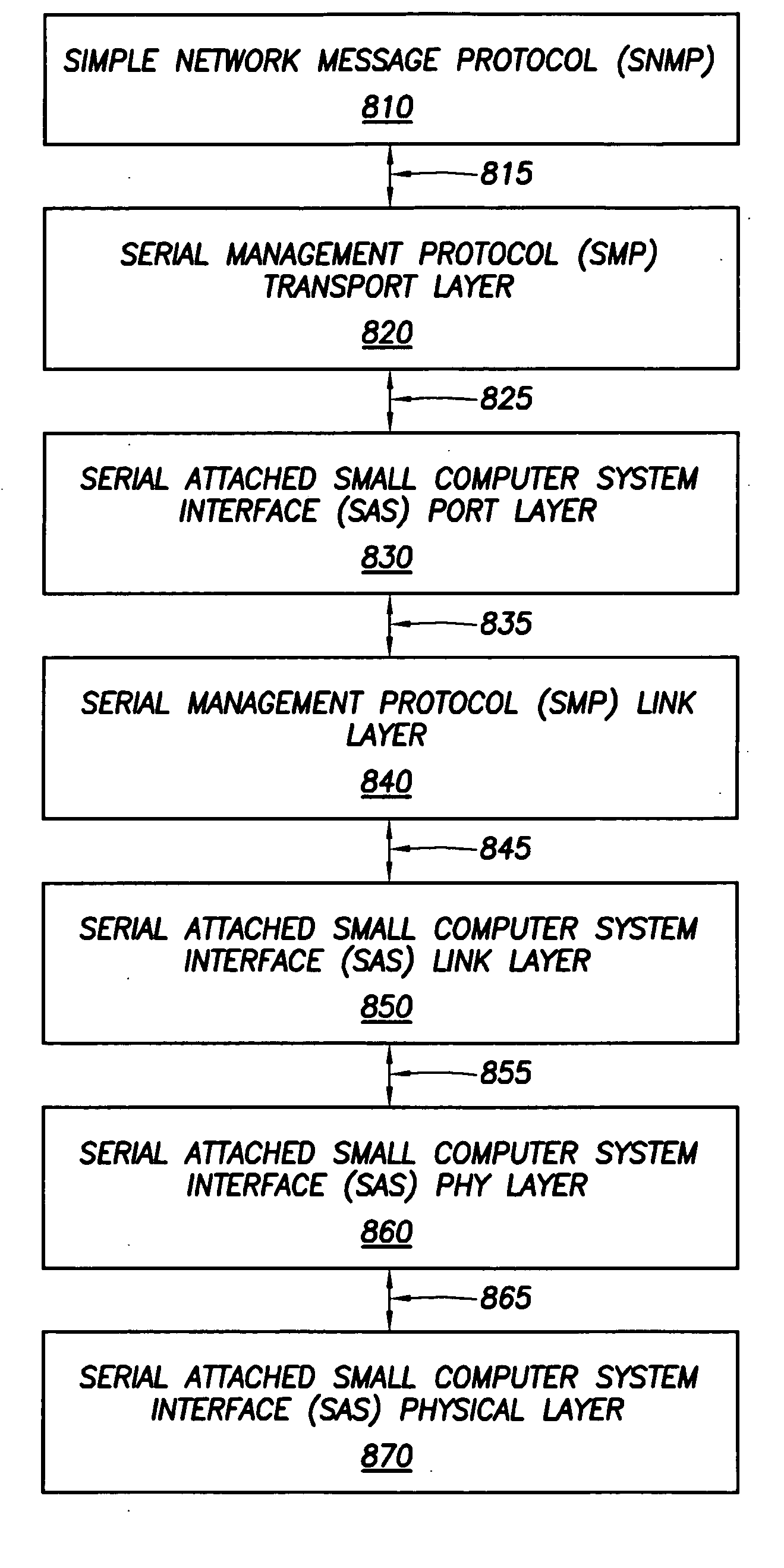
Method to encapsulate SNMP over serial attached SCSI for network management operations to manage external storage subsystems
InactiveUS20070064623A1Low costReduce complexityTime-division multiplexData switching by path configurationExternal storageSCSI
According to various illustrative embodiments of the present invention, a method to encapsulate a simple network management protocol (SNMP) over a serial attached small computer system interface (SCSI) system (SAS) for network management operations to manage external storage subsystems includes encapsulating a simple network management protocol (SNMP) message having a simple network management protocol (SNMP) header and a protocol data unit (PDU) in a serial management protocol (SMP) frame for the serial attached small computer system interface (SCSI) system (SAS). The method also includes facilitating the at least one network management operation to manage the at least one external storage subsystem in-band over the serial attached small computer system interface (SCSI) system (SAS) using the simple network management protocol (SNMP) message having the simple network management protocol (SNMP) header and the protocol data unit (PDU) encapsulated in the serial management protocol (SMP) frame for the serial attached small computer system interface (SCSI) system (SAS).
Owner:DELL PROD LP
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com