Patents
Literature
121 results about "Proprietary protocol" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
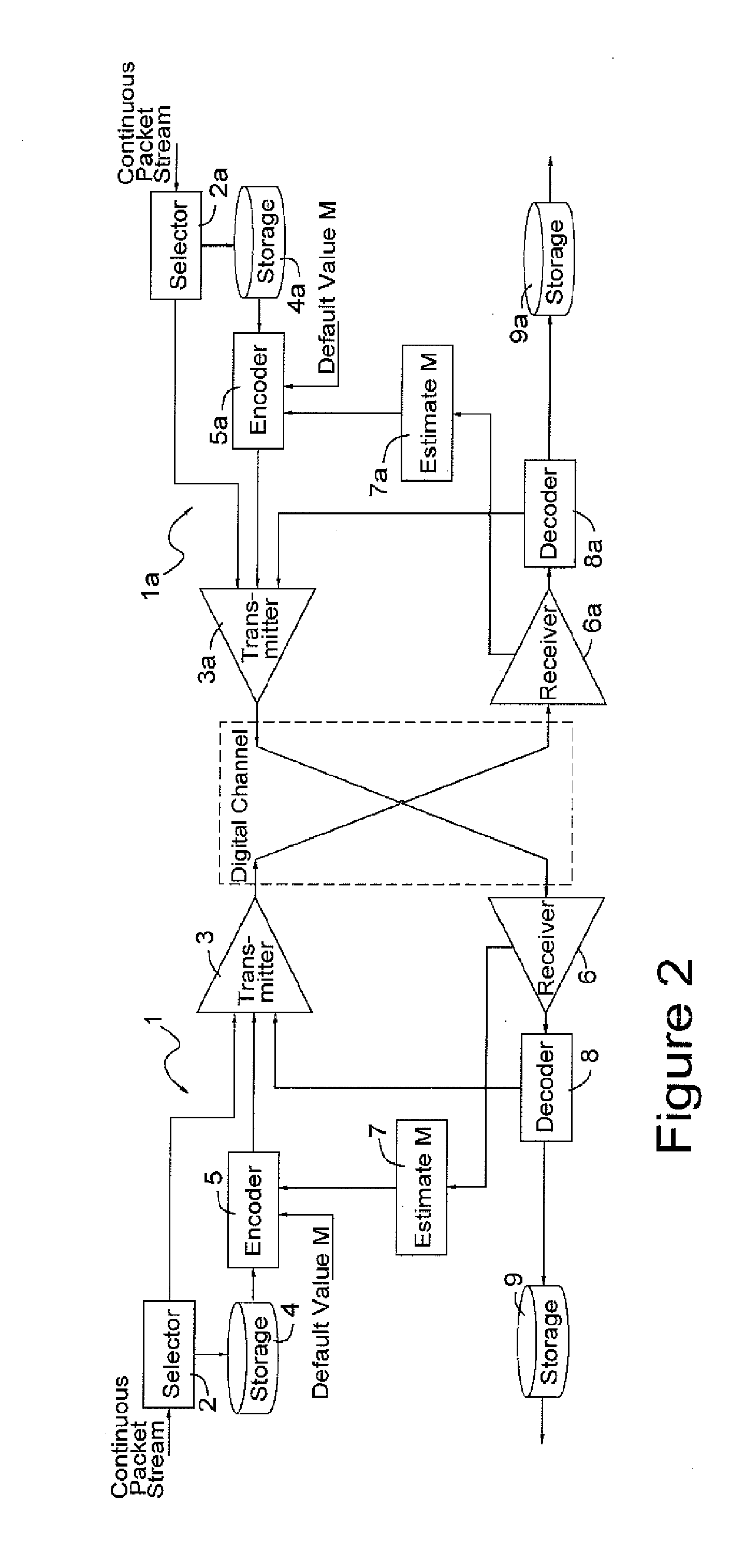
In telecommunications, a proprietary protocol is a communications protocol owned by a single organization or individual.
Heuristic behavior pattern matching of data flows in enhanced network traffic classification
ActiveUS7664048B1Easy to classifyOptimize networkError preventionTransmission systemsAnalysis dataData stream
Methods, apparatuses and systems facilitating enhanced classification of network traffic that extends beyond analysis of explicitly presented packet attributes and holistically analyzes data flows, and in some implementations, related data flows against known application behavior patterns to classify the data flows. Implementations of the present invention facilitate the classification of encrypted or compressed network traffic, or where the higher layer information in the data flows are formatted according to a non-public or proprietary protocol.
Owner:CA TECH INC
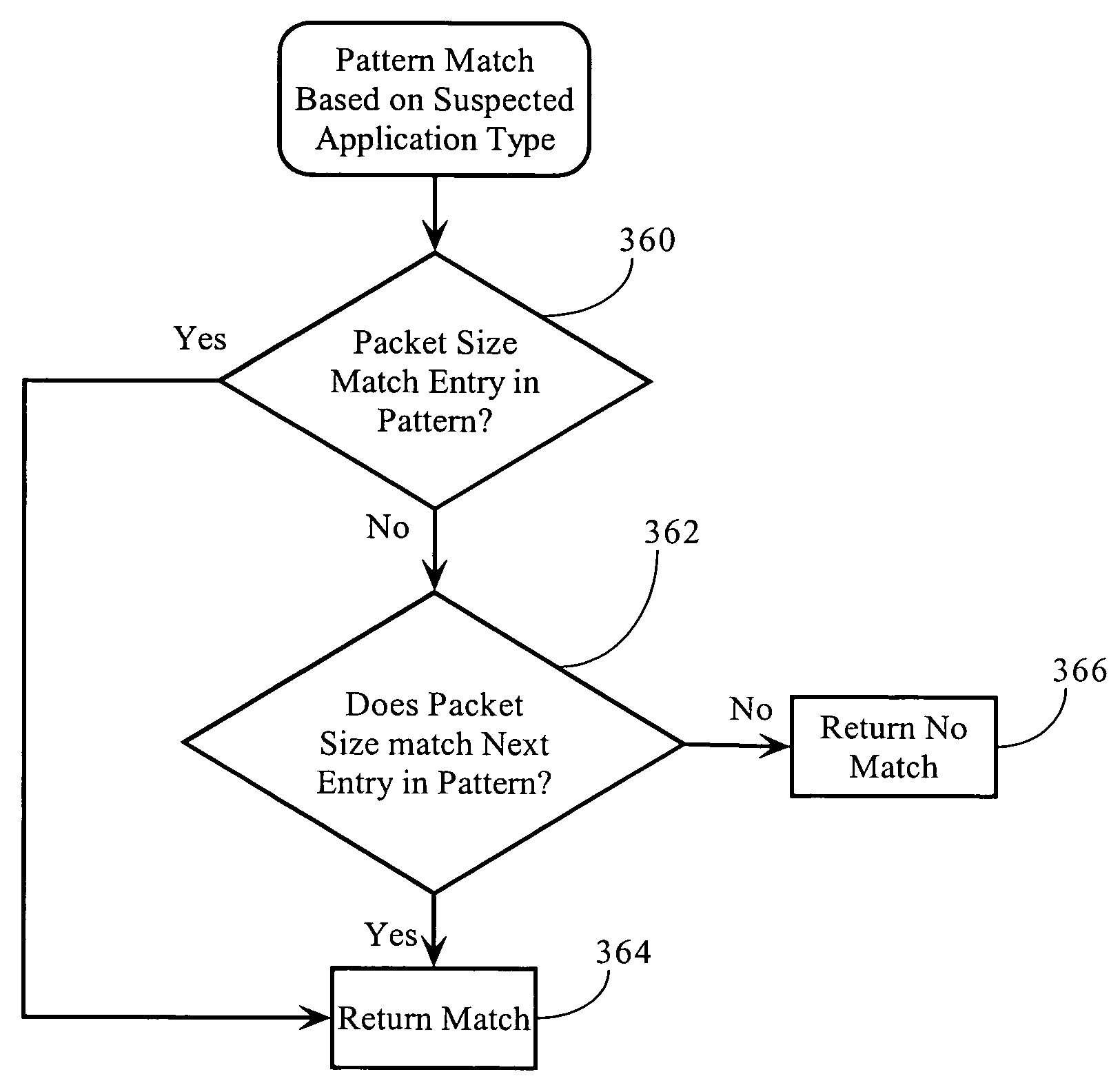
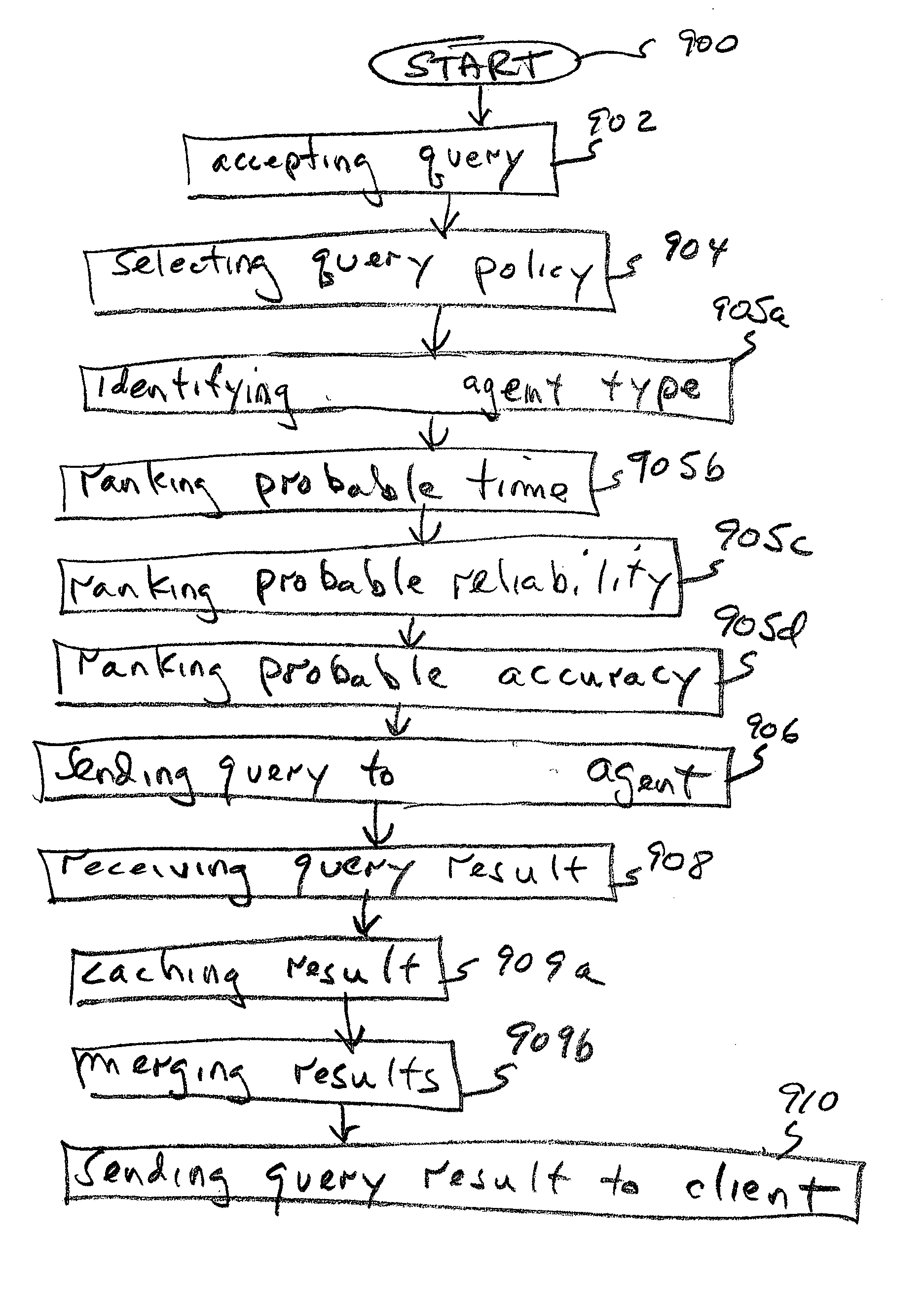
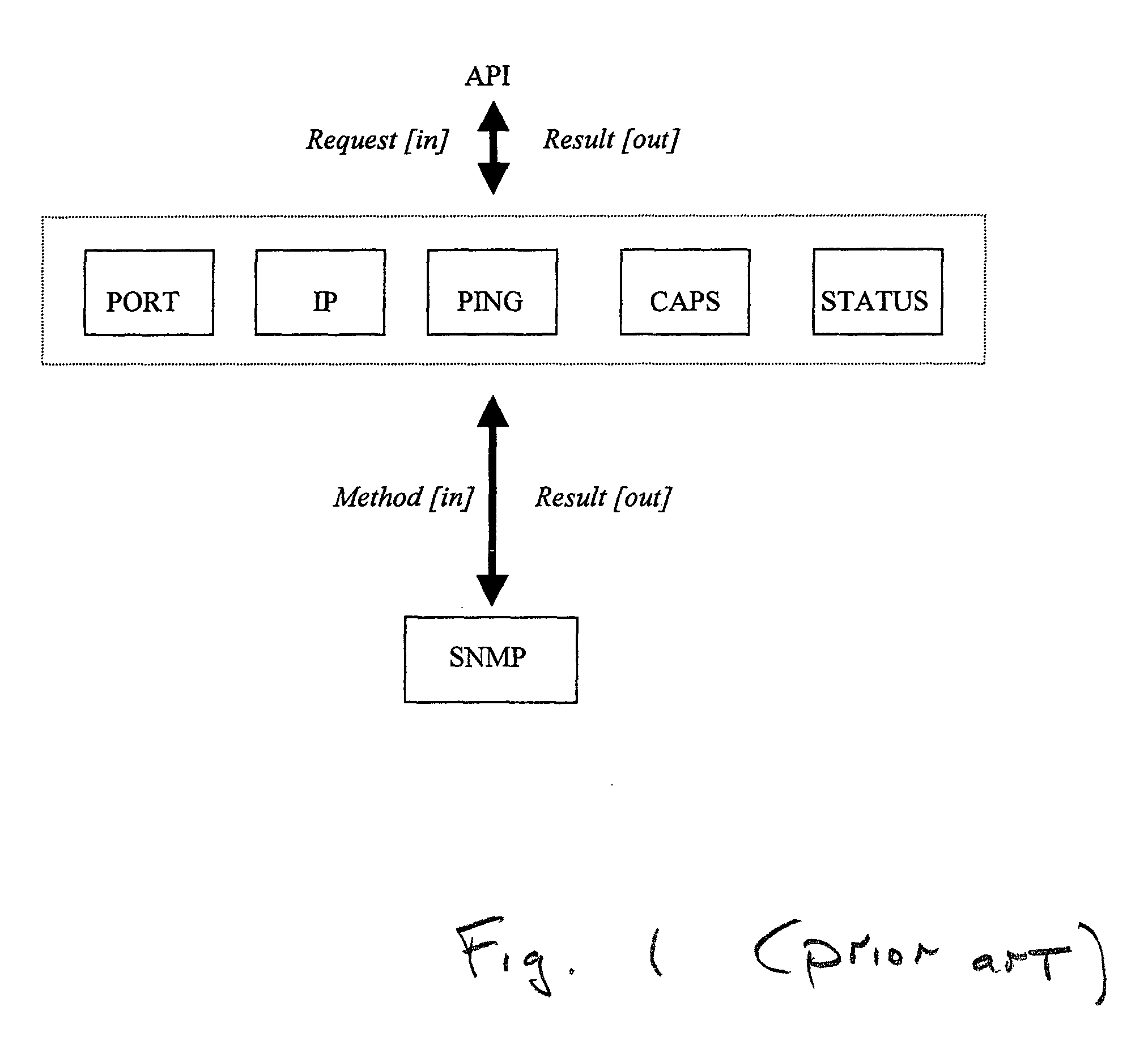
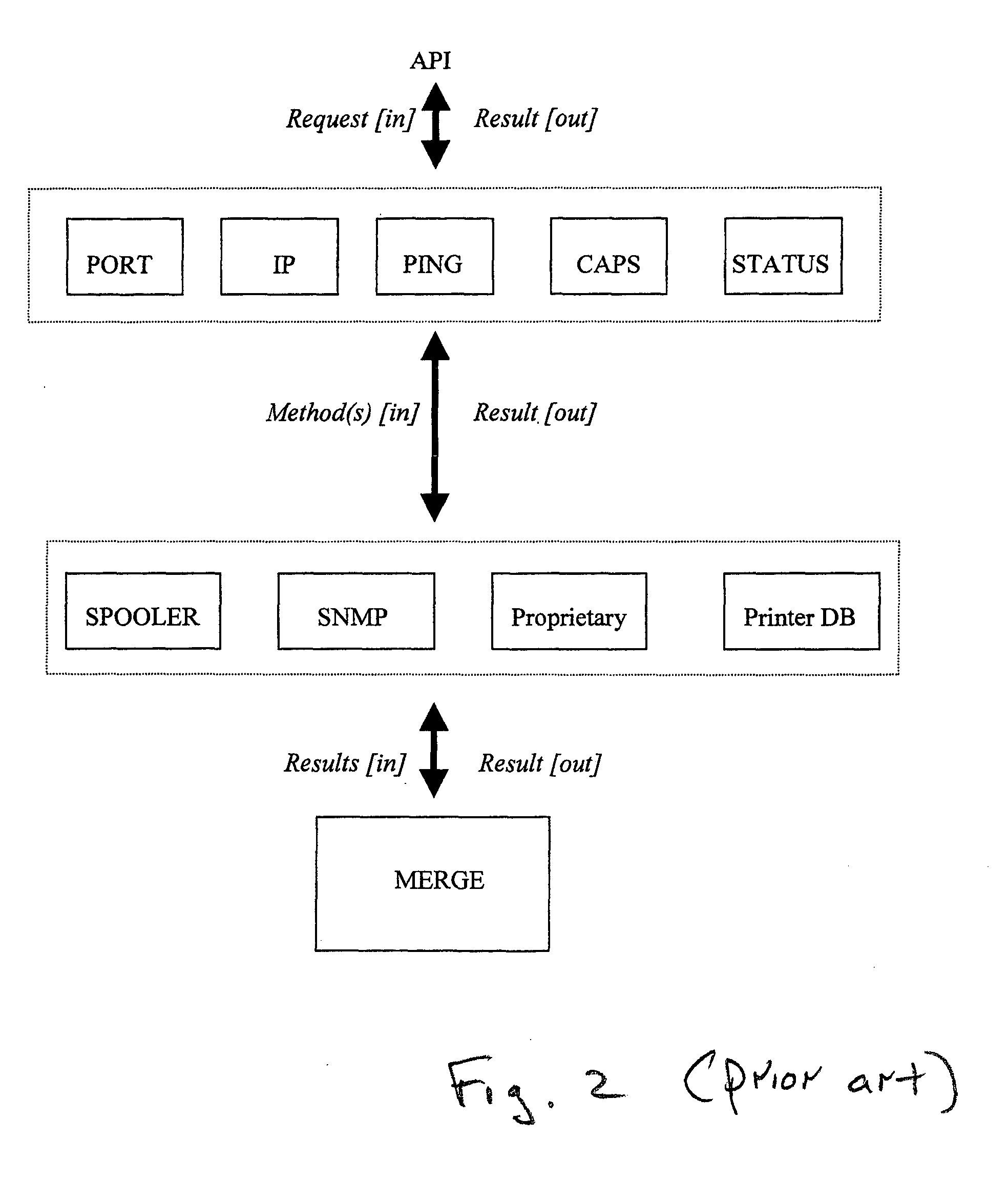
System and method for policy-driven device queries
InactiveUS20050050013A1Digital data processing detailsOther printing apparatusComputer printingClient-side
A policy-driven system and method are provided for querying devices. The method comprises: accepting a query, from a client, directed to a device; selecting a query policy; and, sending the query to an agent using a method responsive to the selected query policy. The queries may concern a device communication port information, network information, communication checks (Ping), capability requests, or status updates. The methods may include spooler API, simple network management protocol (SNMP), printer database, proprietary protocol, Windows 2K directory service, service location protocol (SLP), and HTTP embedded device web page queries. The method further comprises: receiving a query result from the agent; and, sending the query result to the client using a method responsive to the selected query policy. In some aspects, an additional step merges a plurality of query results in response to the selected query policy. Then, the merged query result is sent to the client.
Owner:SHARP LAB OF AMERICA INC
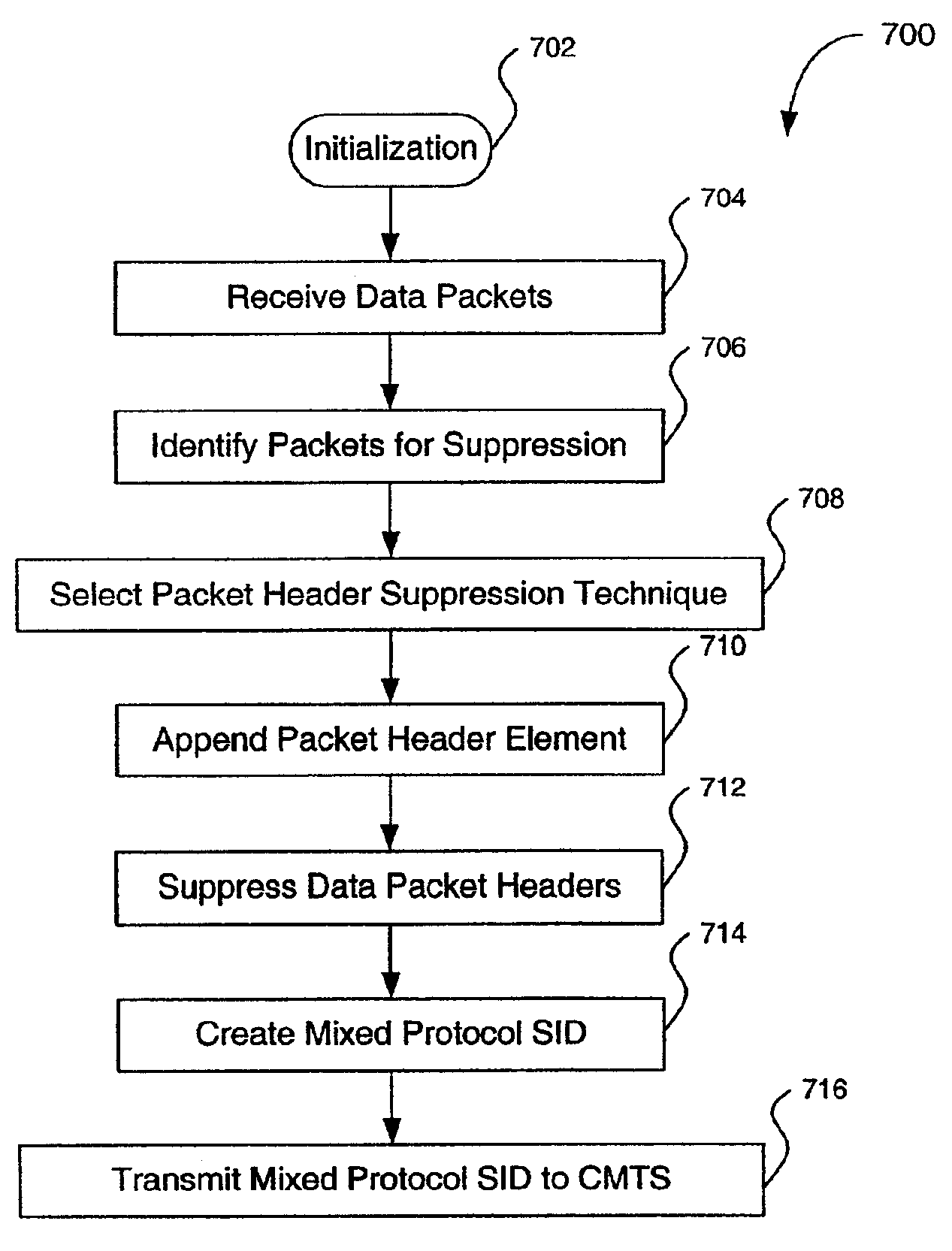
Cable modem system and method for dynamically mixing protocol specific header suppression techniques
InactiveUS6963931B2Network traffic/resource managementBroadband local area networksEngineeringData transmission
A cable modem system and method is provided for the transfer and processing of data in accordance with specialized data transfer protocols while utilizing conventional cable modem termination system (CMTS) equipment. A cable modem system in accordance with the invention includes a cable modem that provides for the modification of data packets in accordance with one or more proprietary protocols and the addressing of the modified data packets to a CMTS. The CMTS is adapted to reconstruct the data packets.
Owner:AVAGO TECH INT SALES PTE LTD
Proprietary protocol analysis and identification method
ActiveCN104506484AEfficient analysisEasy to implementTransmissionStructure of Management InformationClient-side
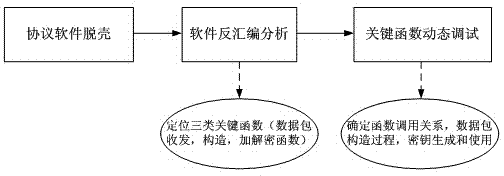
The invention relates to the technical field of protocol communication, and discloses a proprietary protocol analysis and identification method. The method comprises the following specific steps: I, performing shelling processing on communication client software by adopting a proprietary protocol; disassembling an original program; and dynamically debugging a key function in an assembly code; II, fetching the network flow data of the proprietary protocol, performing message data packet classification according to different stages of protocol interaction, and resolving the field structure of each type of message data packet respectively; III, extracting and inducing protocol characteristics in an interaction process, wherein the protocol characteristics comprise interaction process information and the field structure characteristics of the message data packets; and IV, setting a matching expression of protocol identification by using the protocol characteristics obtained in the step III, and identifying flow acquired in a network. Through the method, the analysis and identification of the proprietary protocol are realized.
Owner:NO 30 INST OF CHINA ELECTRONIC TECH GRP CORP
Method for transferring data in internet of things, internet of things system and corresponding device
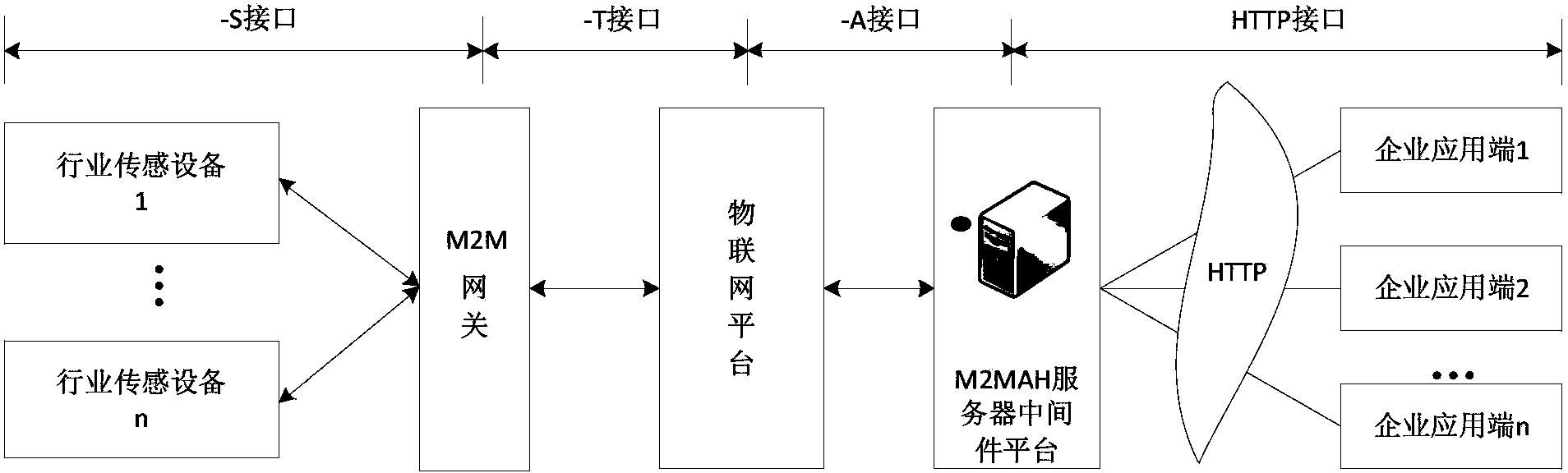
ActiveCN103428627AOvercome technical issues with high development costsSolve the difficulty of developmentWireless network protocolsWireless commuication servicesThe InternetWorkload
The invention discloses a method for transferring data in internet of things, an internet of things system and a corresponding device, and relates to the technical field of internet of things. The technical problem that in the prior art, development workload is large on a network side because a proprietary protocol of industry sensing equipment is not standard is solved. The system comprises an M2M gateway and a middleware platform. The M2M gateway is used for receiving data sent by the industry sensing equipment, finding slave protocol configuration information of the industry sensing equipment according to identification of the industry sensing equipment in the data, converting protocol formats and interpretation meaning of the data into protocols which can be recognized by the gateway according to the protocol configuration information, and sending the protocols to an internet of things platform. The middleware platform is used for analyzing key information from the data transferred from the internet of things platform, determining the protocol category of the key information according to message body type of the key information, adding corresponding identification to the certain protocol category, and converting the key information into data of which the protocol formats can be recognized by enterprise application terminals according to the identification and a preset state machine.
Owner:CHINA MOBILE GROUP JIANGSU
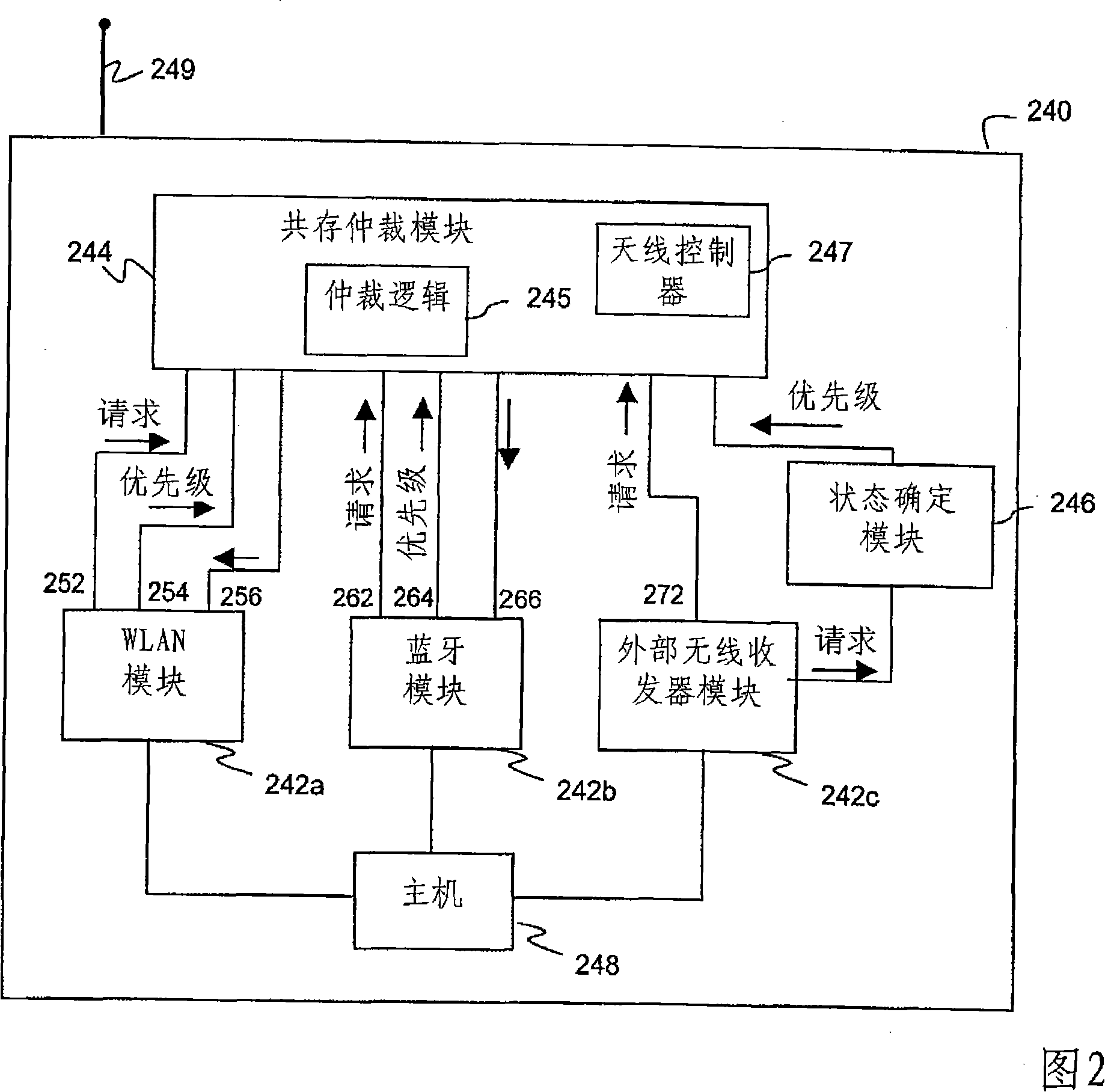
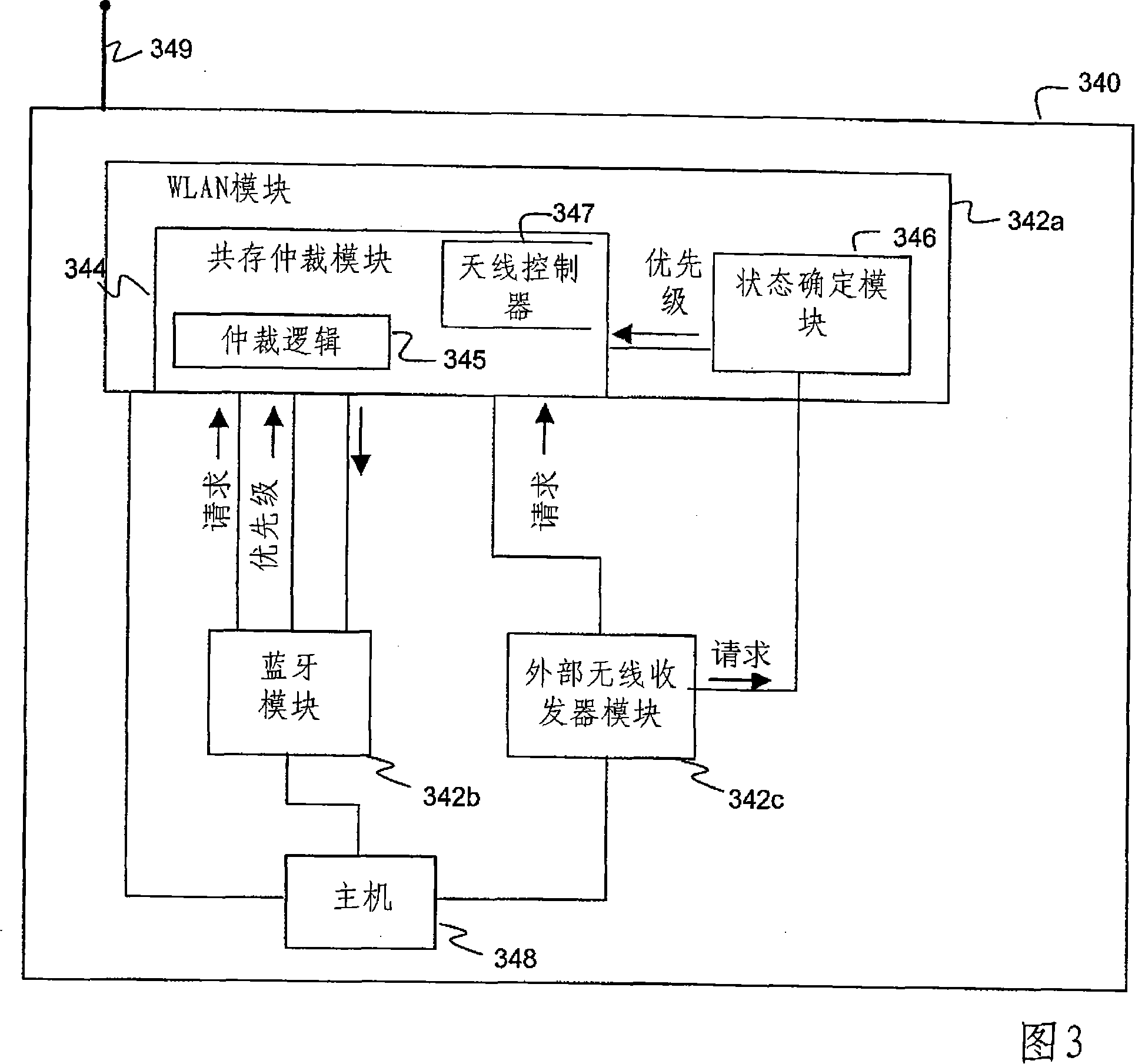
Systems and methods for enabling coexistence of multiple wireless components operating in the same frequency band
Methods and systems for enabling coexistence of multiple potentially interfering wireless components in a device are provided. A device may include a wireless module using a proprietary protocol and one or more modules using standardized protocols. The device further includes a coexistence arbitration module configured to arbitrate access to a shared communication medium among the wireless modules based on assertion of medium access requests by the modules and the associated priority of the asserted medium access requests. When multiple medium access requests have the same priority, precedence for access to the shared medium is determined based on additional criteria. The coexistence arbitration module may be a separate module or may be integrated into another module or distributed among the modules. The device may include a host processor for altering transmission characteristics of a module to increase the likelihood that another module can receive data within a reasonable time period.
Owner:AVAGO TECH INT SALES PTE LTD
Method & apparatus for improving the performance of TCP and other network protocols in a communication network
ActiveUS20150100858A1Reduce overheadCode conversionWireless network protocolsMultiplexingTraffic capacity
Owner:AKAMAI TECH INC
Systems and/or methods for streaming reverse HTTP gateway, and network including the same
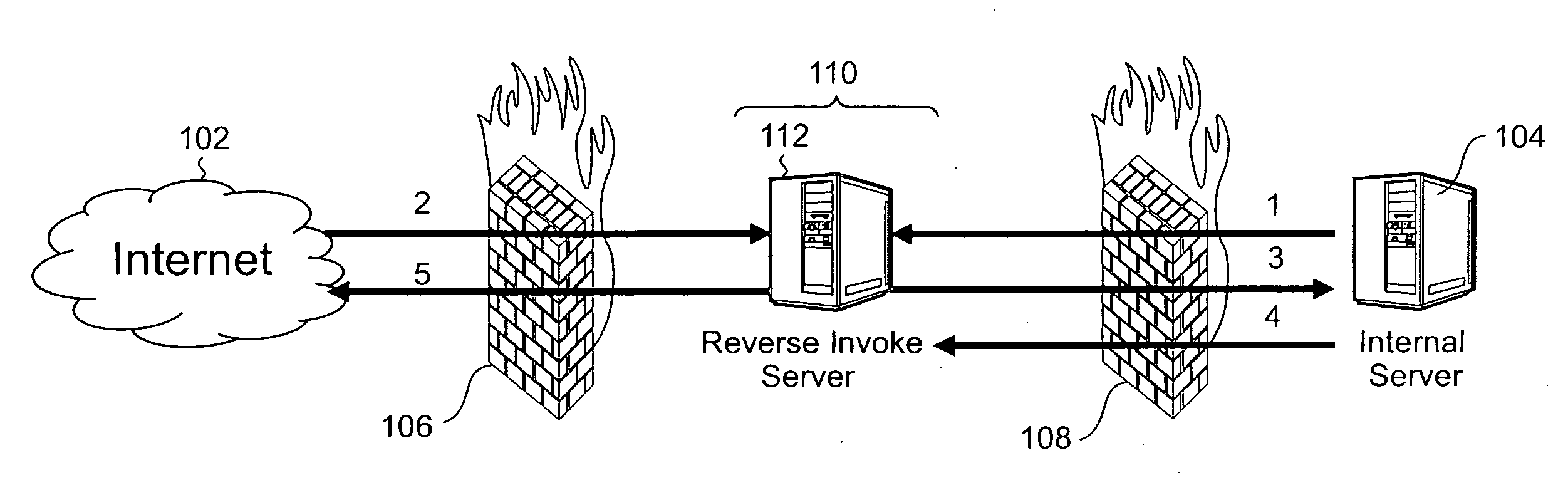
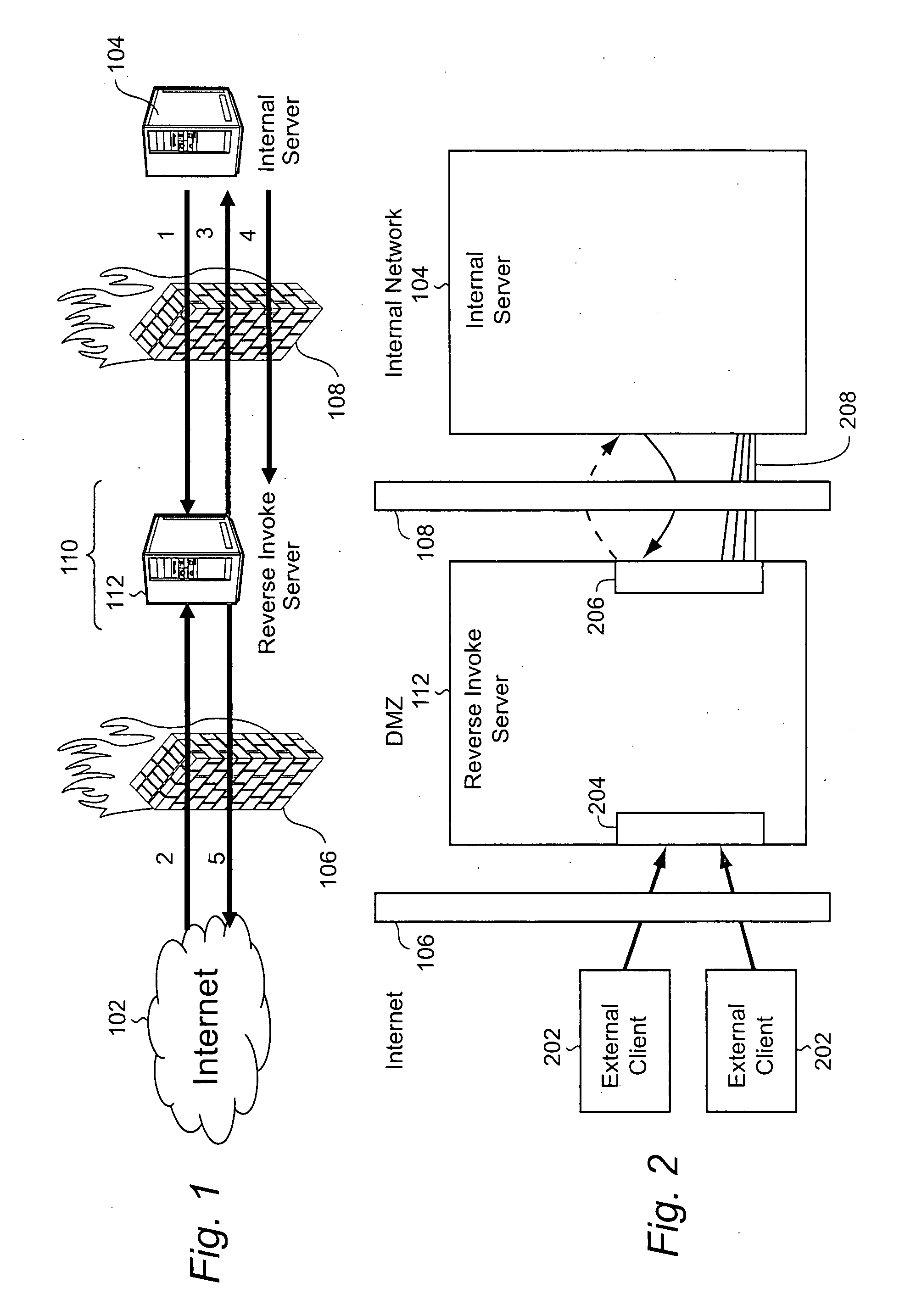
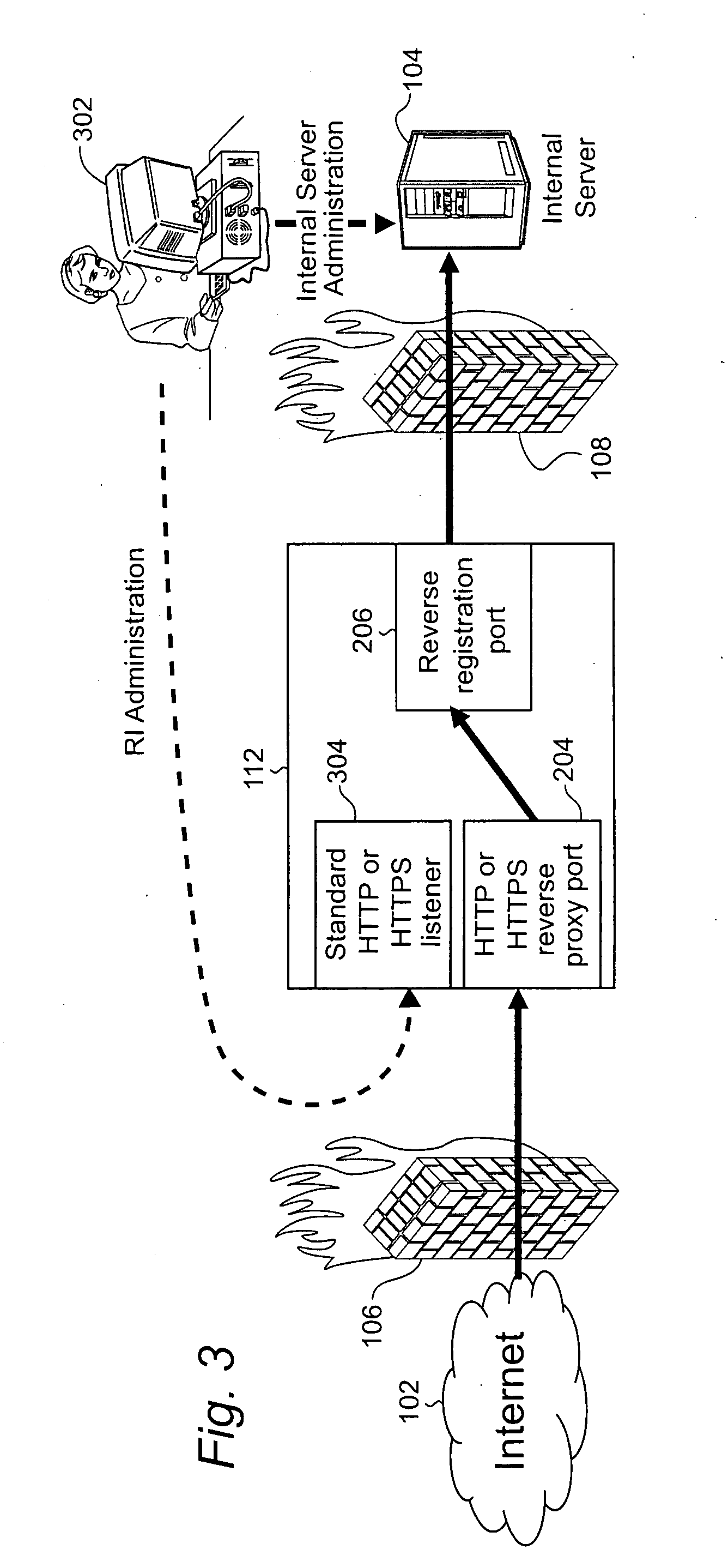
ActiveUS20090064307A1Provide securityDigital data processing detailsUser identity/authority verificationClient-sideReverse connection
In certain example embodiments of this invention, there is provided systems and / or methods for a streaming reverse HTTP gateway, and / or networks including the same. In such a network, a reverse HTTP gateway is located within a demilitarized zone (DMZ) disposed between public (or external) and private (or internal) networks for providing security therebetween. Requests from external clients may be streamed from the external network to the internal network over various connections and ports, including a substantially persistent reverse connection between an internal server and a reverse HTTP gateway. The reverse HTTP gateway architecture of certain example embodiments removes the need for proprietary protocols implemented between the reverse HTTP gateway located in the DMZ and the internal server located in the internal network. In certain example embodiments, the reverse HTTP gateway architecture is configured to leverage the capabilities of HTTP 1.1.
Owner:SOFTWARE AG USA
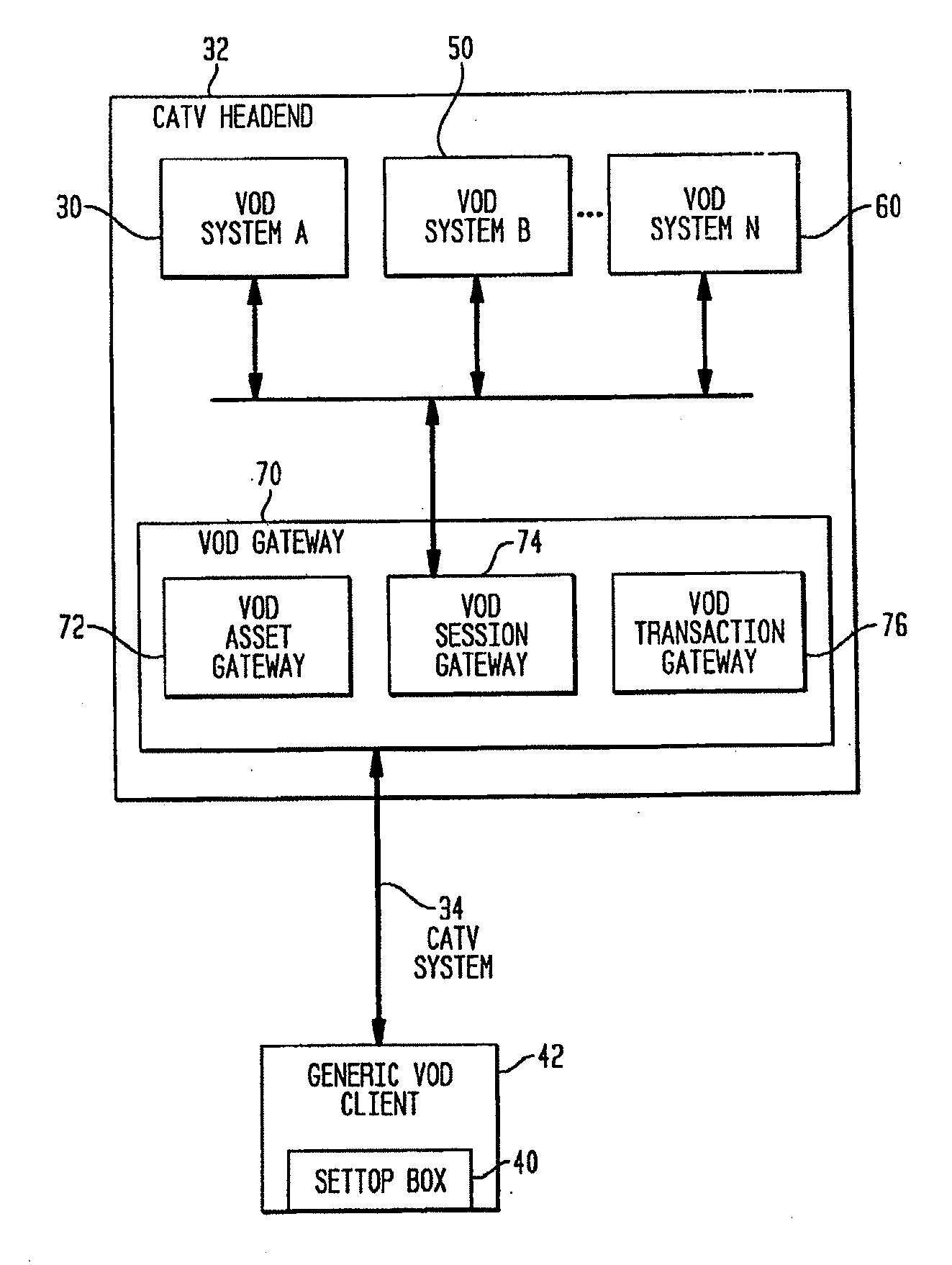
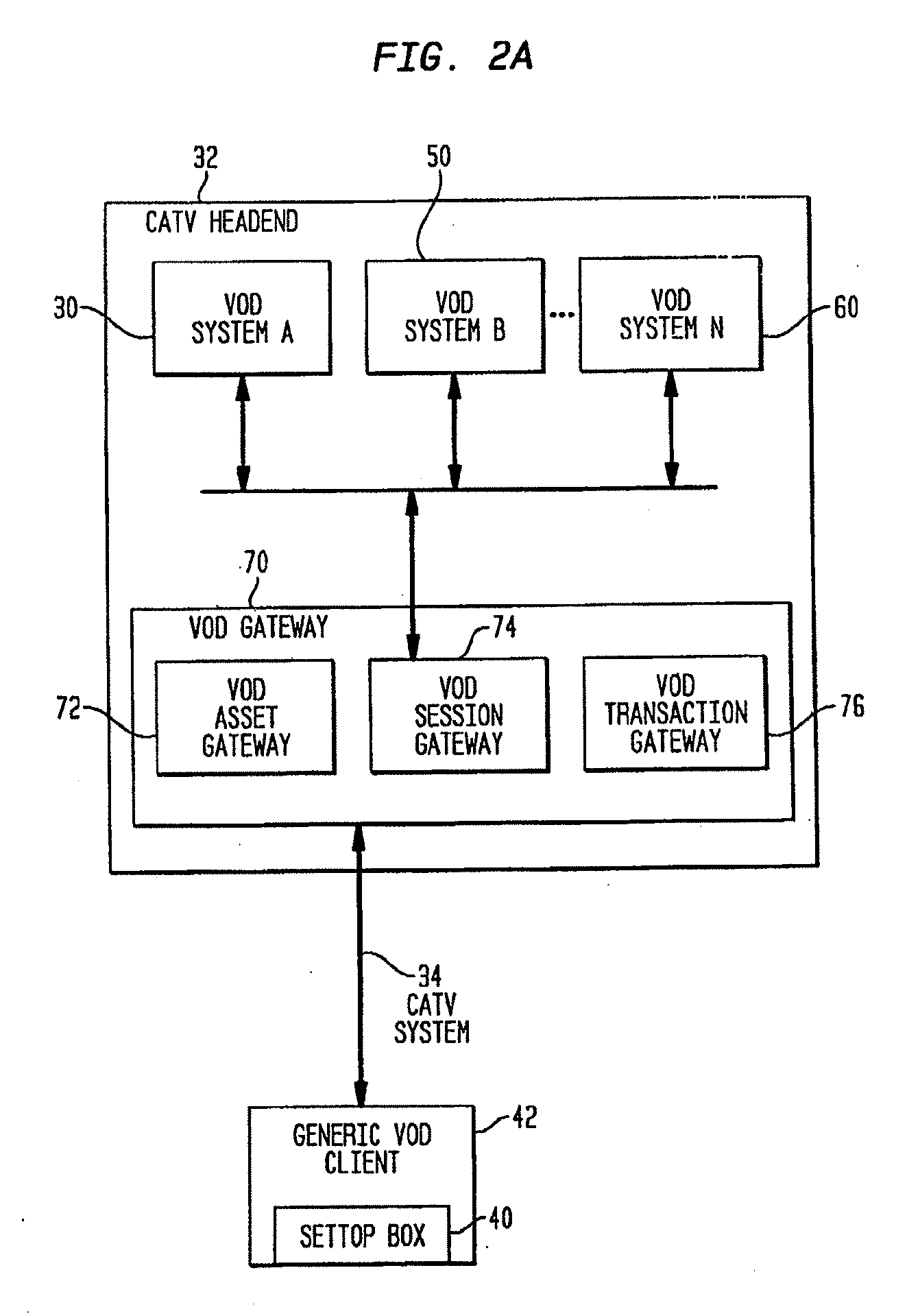
Video on Demand Gateway
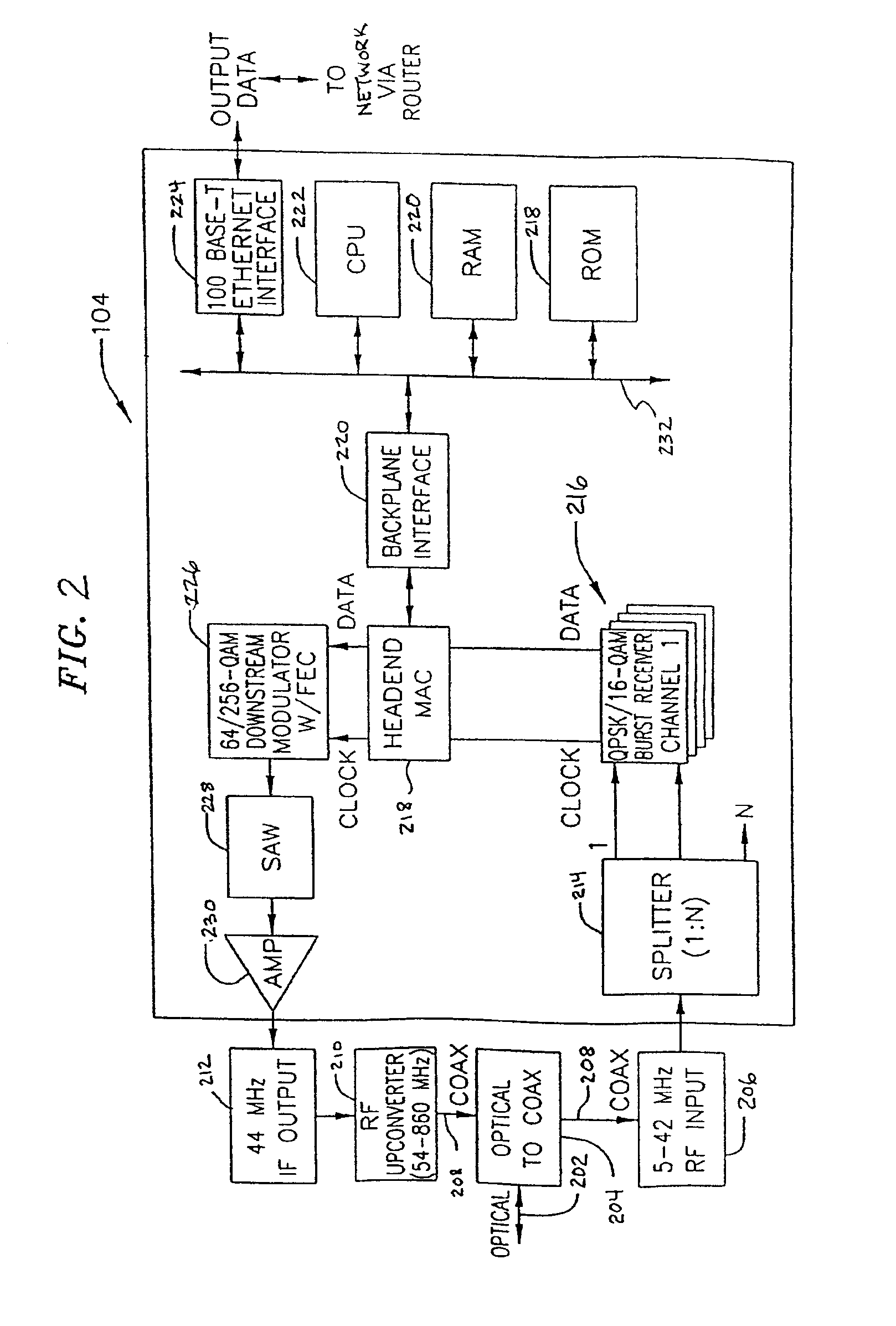
InactiveUS20090235319A1Increase capacityLow costTwo-way working systemsSelective content distributionClient-sideProprietary protocol
A video on demand (VOD) gateway allows multiple incompatible and non-interoperable VOD systems to function as a single unified VOD system. A VOD gateway system includes a VOD asset gateway, a VOD session gateway, a VOD transaction gateway and a generic VOD client software program. The generic VOD client software resides in a CATV set-top box. The VOD asset gateway at the headend aggregates video inventory from multiple VOD vendor's equipment. The VOD session gateway at the headend translates a subscriber request in a generic protocol for VOD program into the proprietary protocol for a specific VOD system. The VOD transaction gateway at the headend aggregates embodiment, a VOD gateway permits operators of multiple CATV systems to use multiple incompatible and non-interoperable VOD systems in each plurality of separate CATV systems.
Owner:TVWORKS
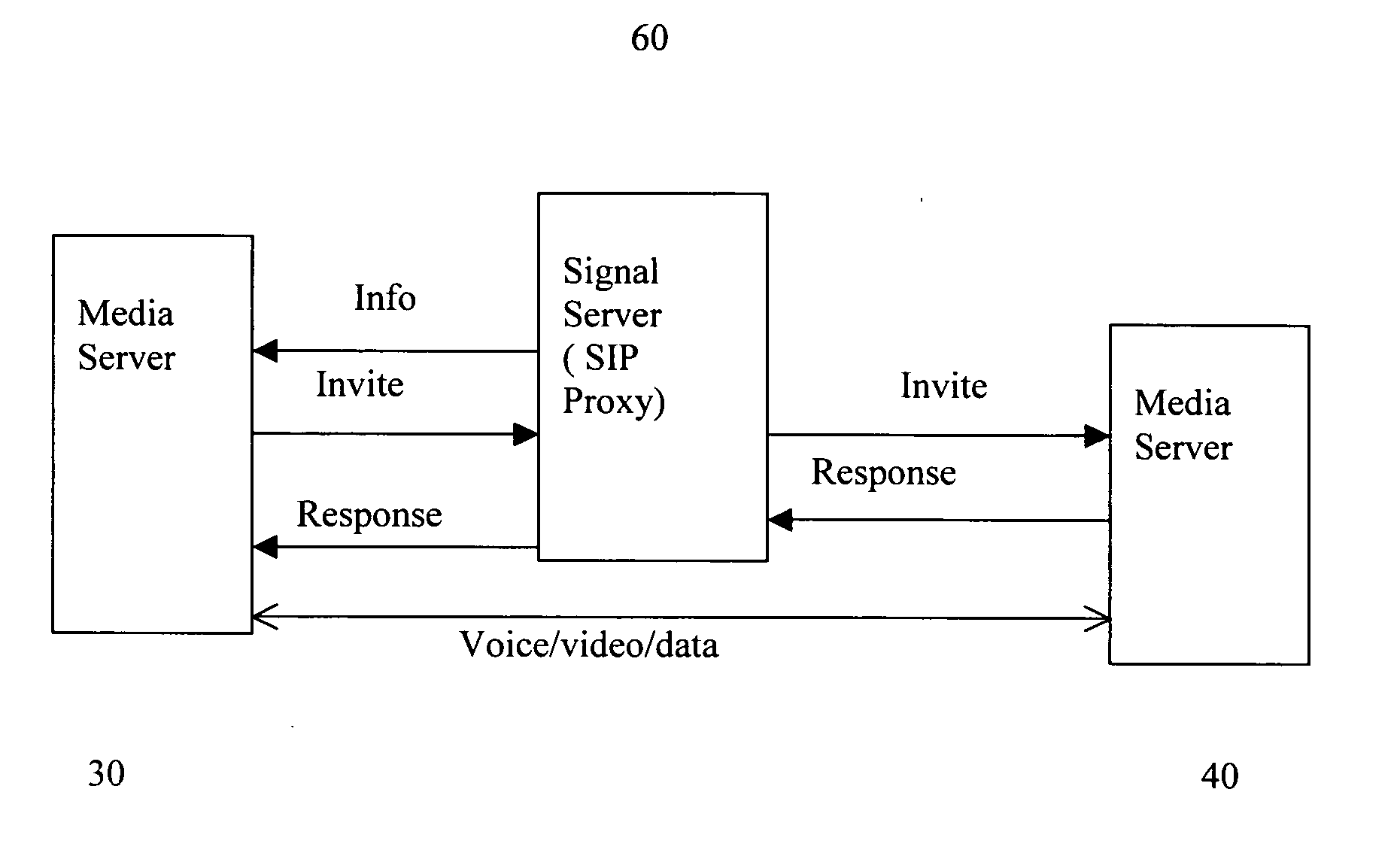
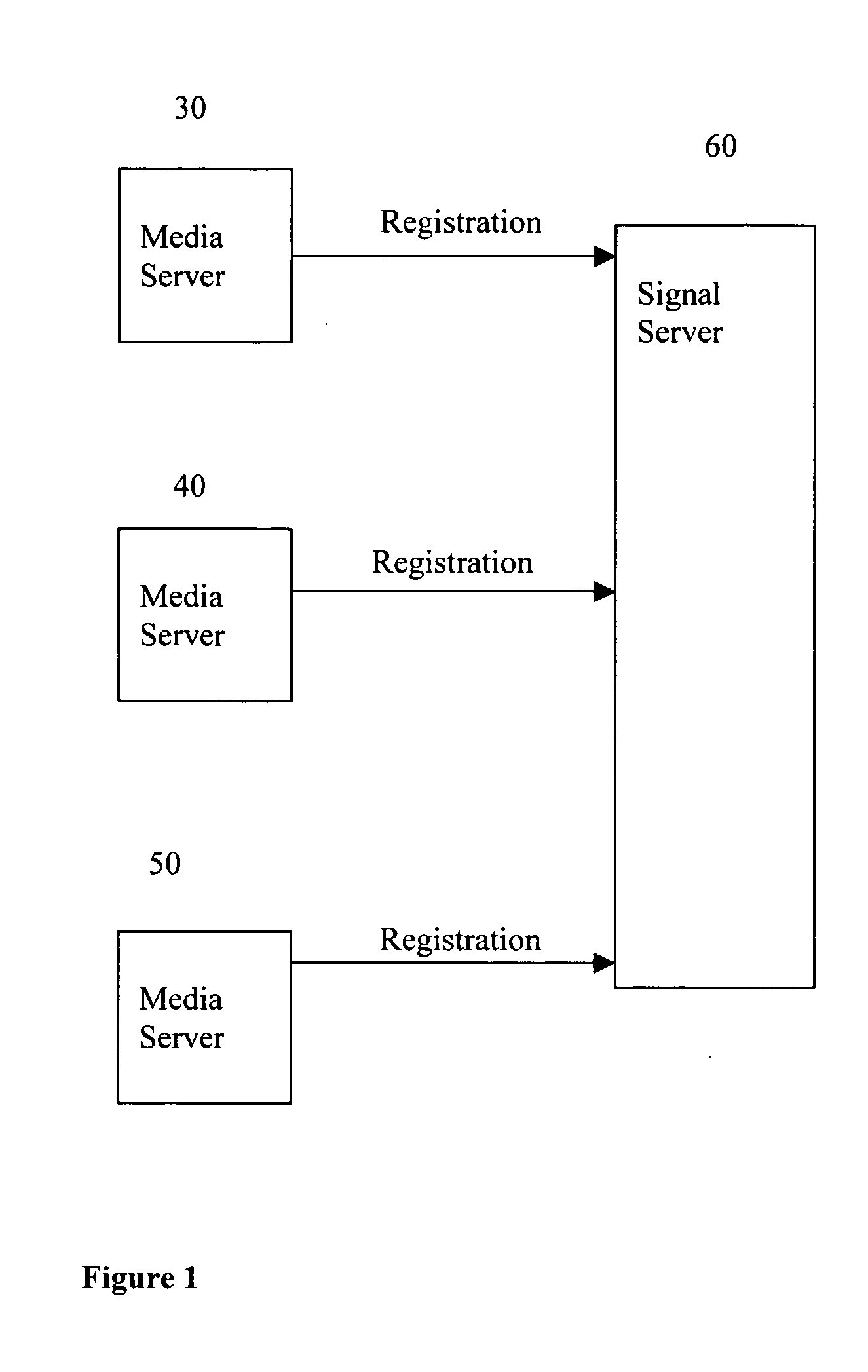
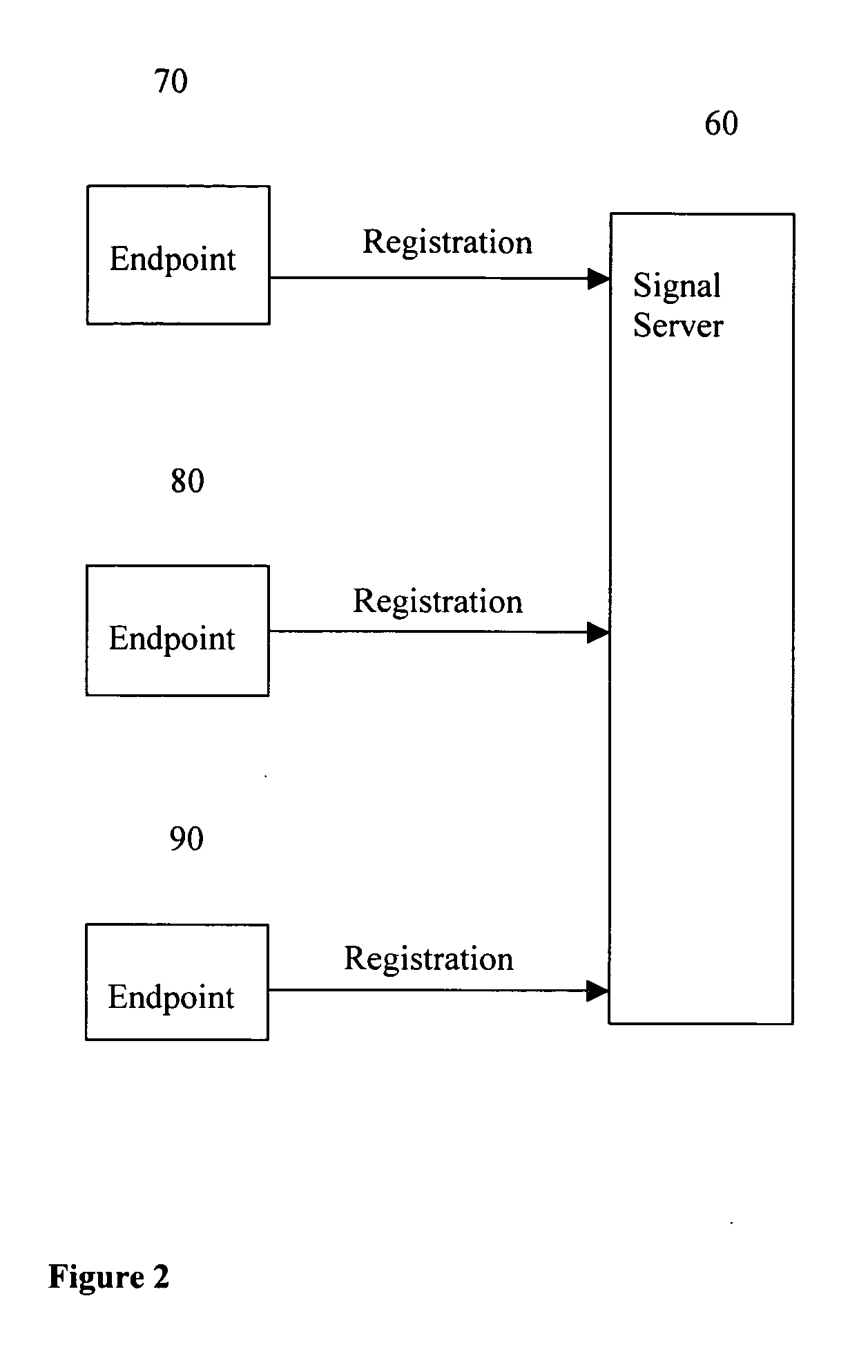
Method to allow voice, video and data conference with minimum bandwidth consumption between two or more geological locations and achieve quality of service (QoS) and scalability
InactiveUS20050076128A1Reduce bandwidth consumptionSpecial service for subscribersMultiple digital computer combinationsQuality of serviceData stream
A system and method to allow voice, video and data conference with minimum bandwidth consumption with endpoints in two or more geological locations. The system includes signal server to manage one or multiple media servers. The method supports transmission of only one data stream between two media servers while each media server can support multiple endpoints. The method can achieve voice / video / data quality of service (QoS) and scalability. The servers and endpoints send / receive commands and data using TCP, UDP or any proprietary protocol, depending on server's configuration and protocol requirements. This method is compatible with existing communication standards, such as H.323, SIP, MGCP, MEGACO, and T.120.
Owner:TSAI MINGTAR
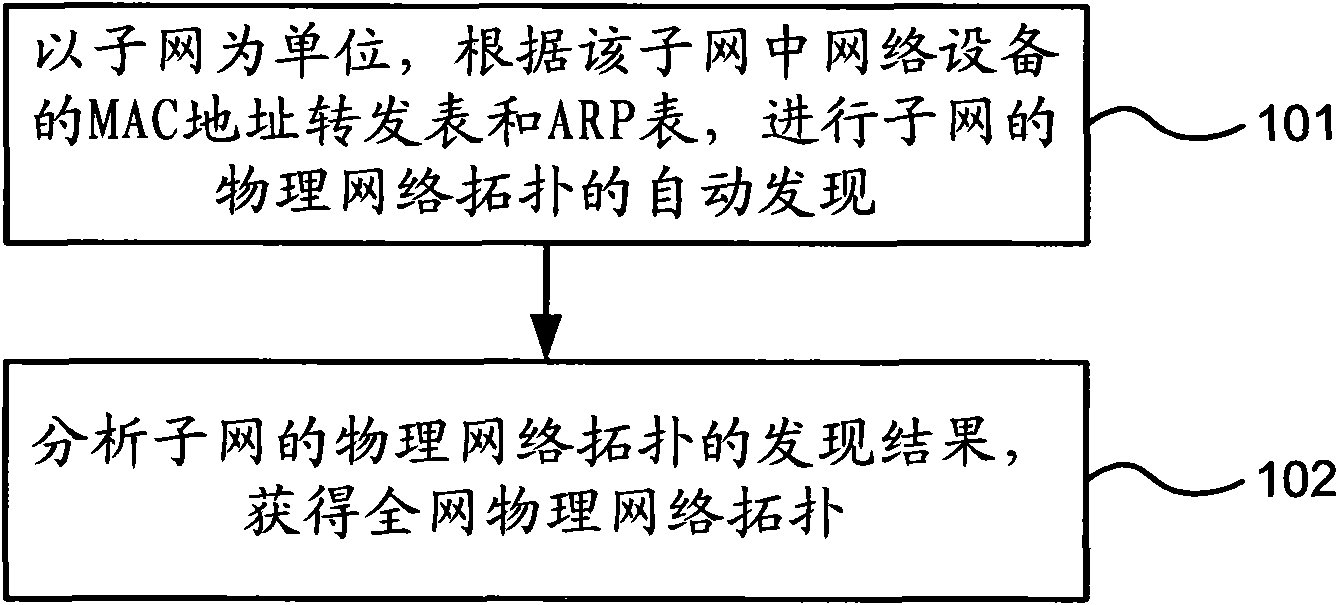
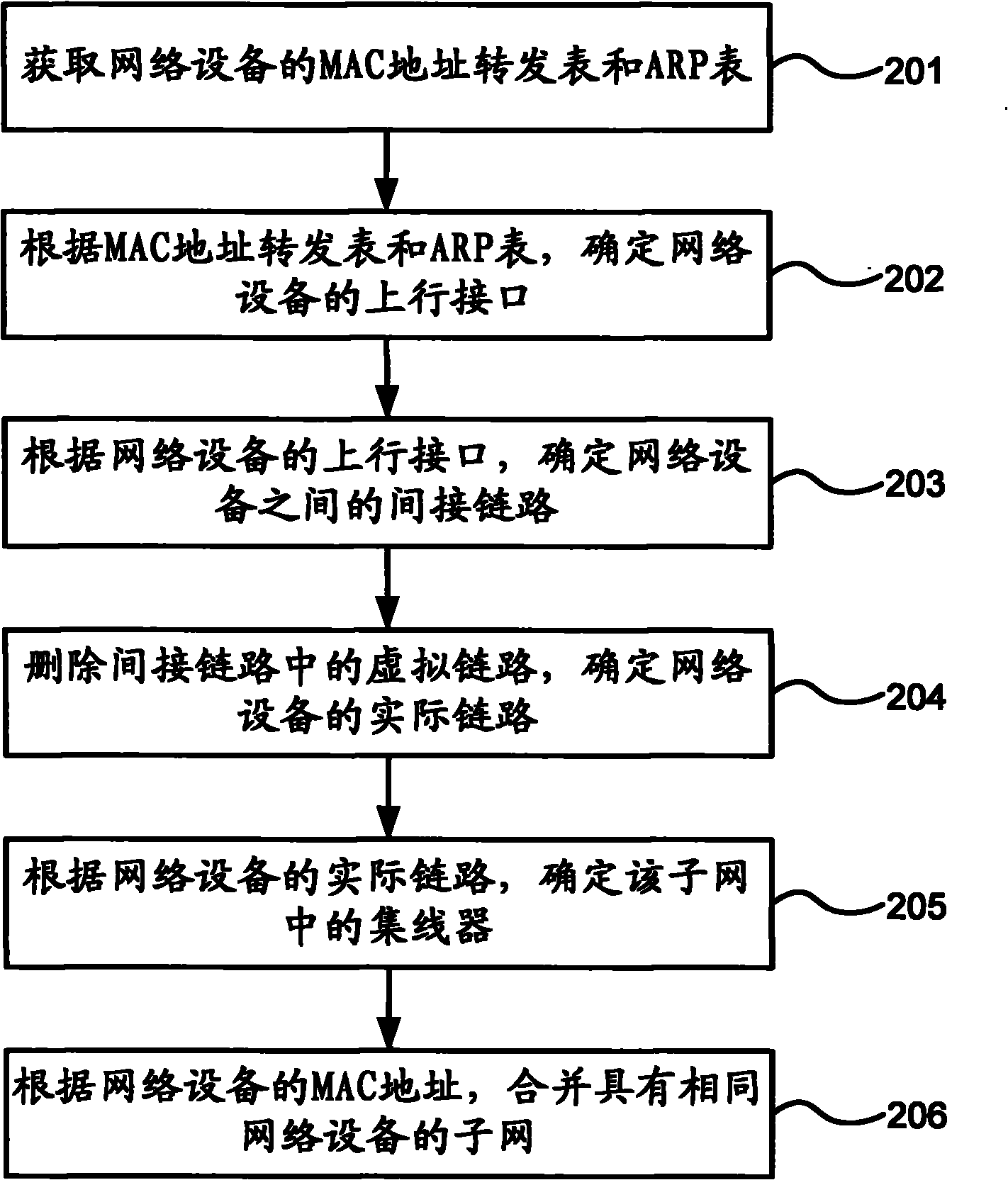
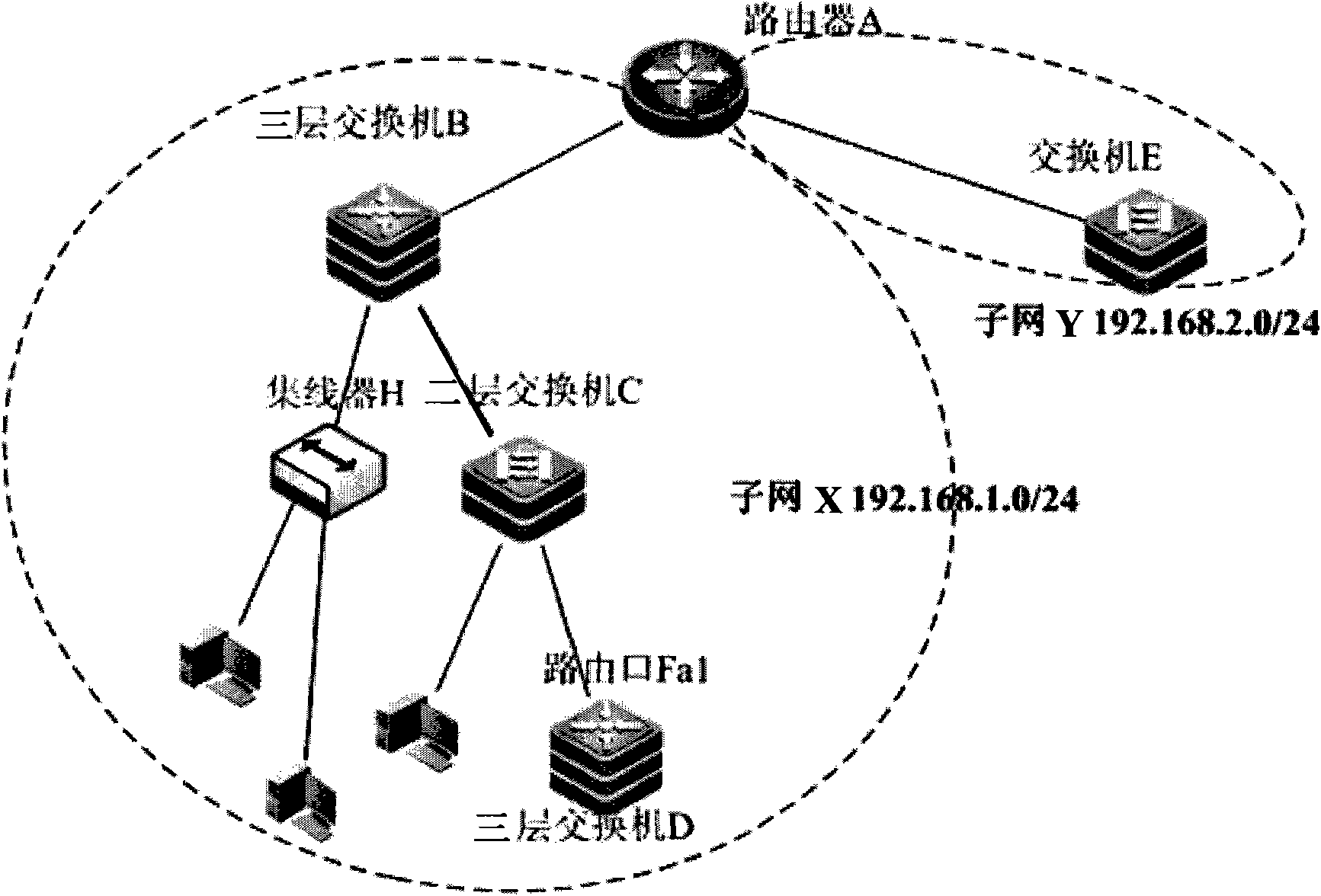
Method and device for discovering physical network topology
ActiveCN101873230ASolve the shortcomings of private agreementsRealize discoveryData switching networksAddress Resolution ProtocolMedia access control
The invention provides a method and device for discovering physical network topology. The method comprises the following steps: with a subnet as a unit, carrying out automatic discovery of physical network topology of the subnet according to a media access control address forwarding table and an address resolution protocol table of network equipment in the subnet; and analyzing the discovery result of physical network topology of the subnet and obtaining total physical network topology. The device comprises a subnet physical network topology discovery module and a total physical network topology obtaining module. The embodiment of the invention carries out automatic discovery of physical network topology in the subnet by utilizing the media access control address forwarding table and the address resolution protocol table in network equipment, thus overcoming the defect that discovery of physical network topology in the prior art depends on the proprietary protocols of the network equipment manufacturers, and meanwhile, discovery of total physical network topology is realized according to the discovery result of subnet physical network topology.
Owner:BEIJING XINWANG RUIJIE NETWORK TECH CO LTD
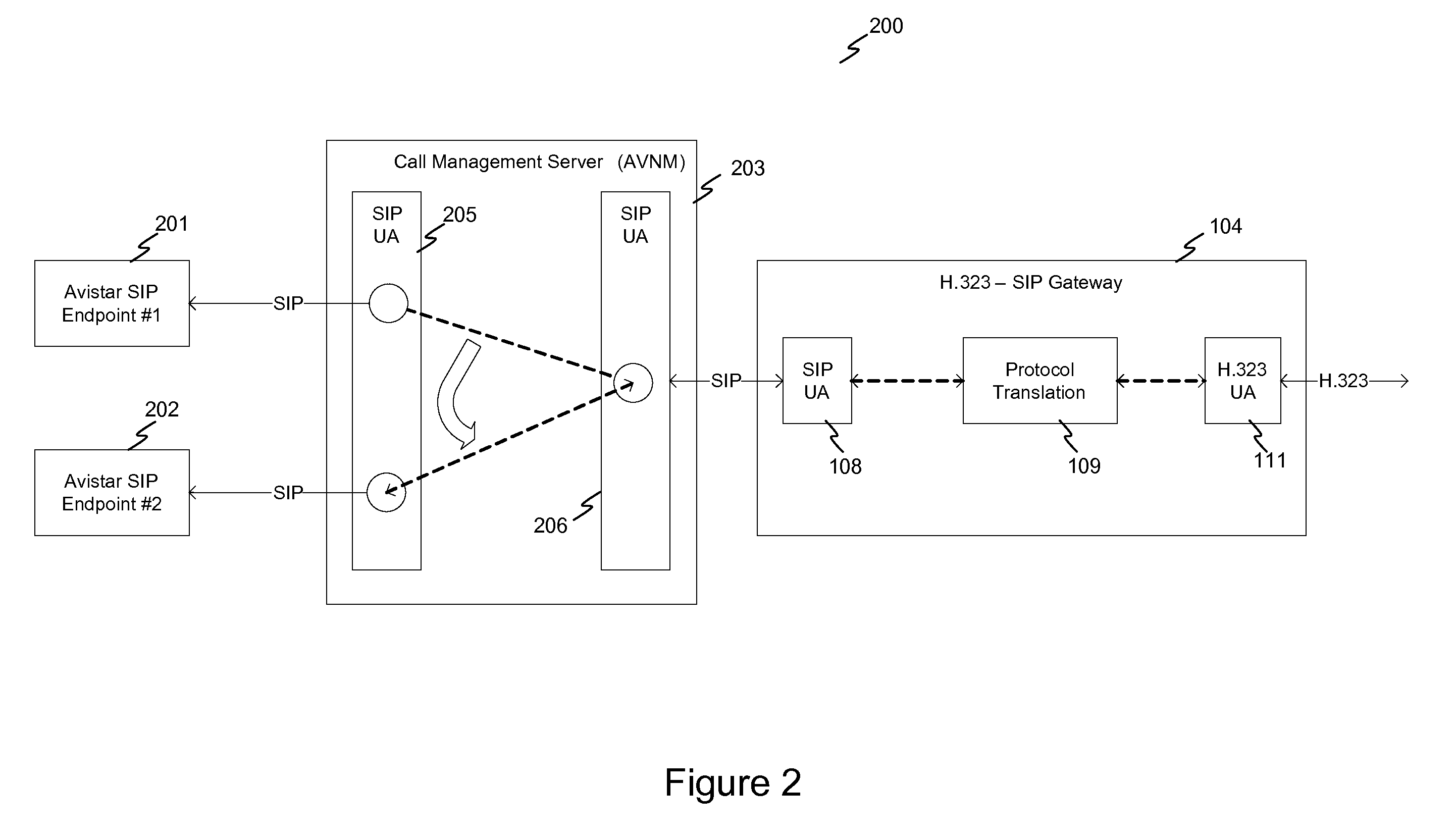
System and method for achieving interoperability between endpoints operating under different protocols
InactiveUS20100085959A1Multiple digital computer combinationsNetwork connectionsTeleconferencePolicy-based management
A teleconferencing system for achieving interoperability between a multiple endpoints including a first endpoint following SIP protocol, a second endpoint following H.323 protocol and a third endpoint following a proprietary protocol. The teleconferencing system incorporates a signaling gateway and a call control server. In the teleconferencing system, the signaling gateway and a call control server are configured to perform policy-based management of calls between the first endpoint, the second endpoint and the third endpoint.
Owner:AVISTAR COMM
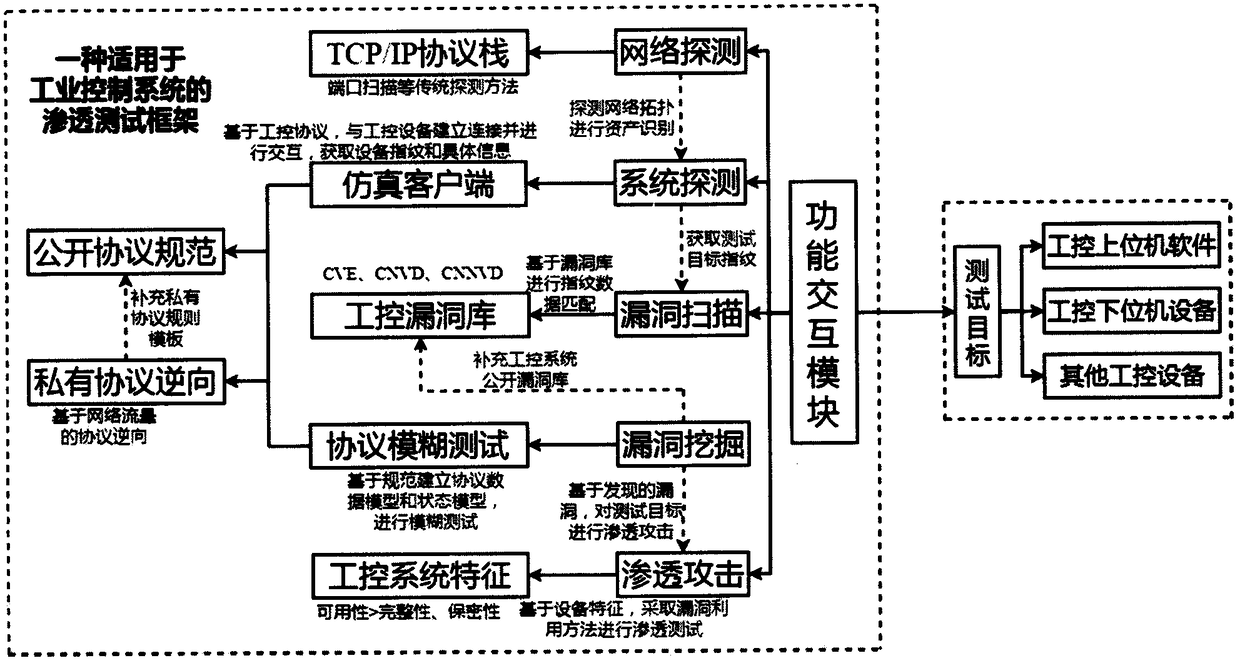
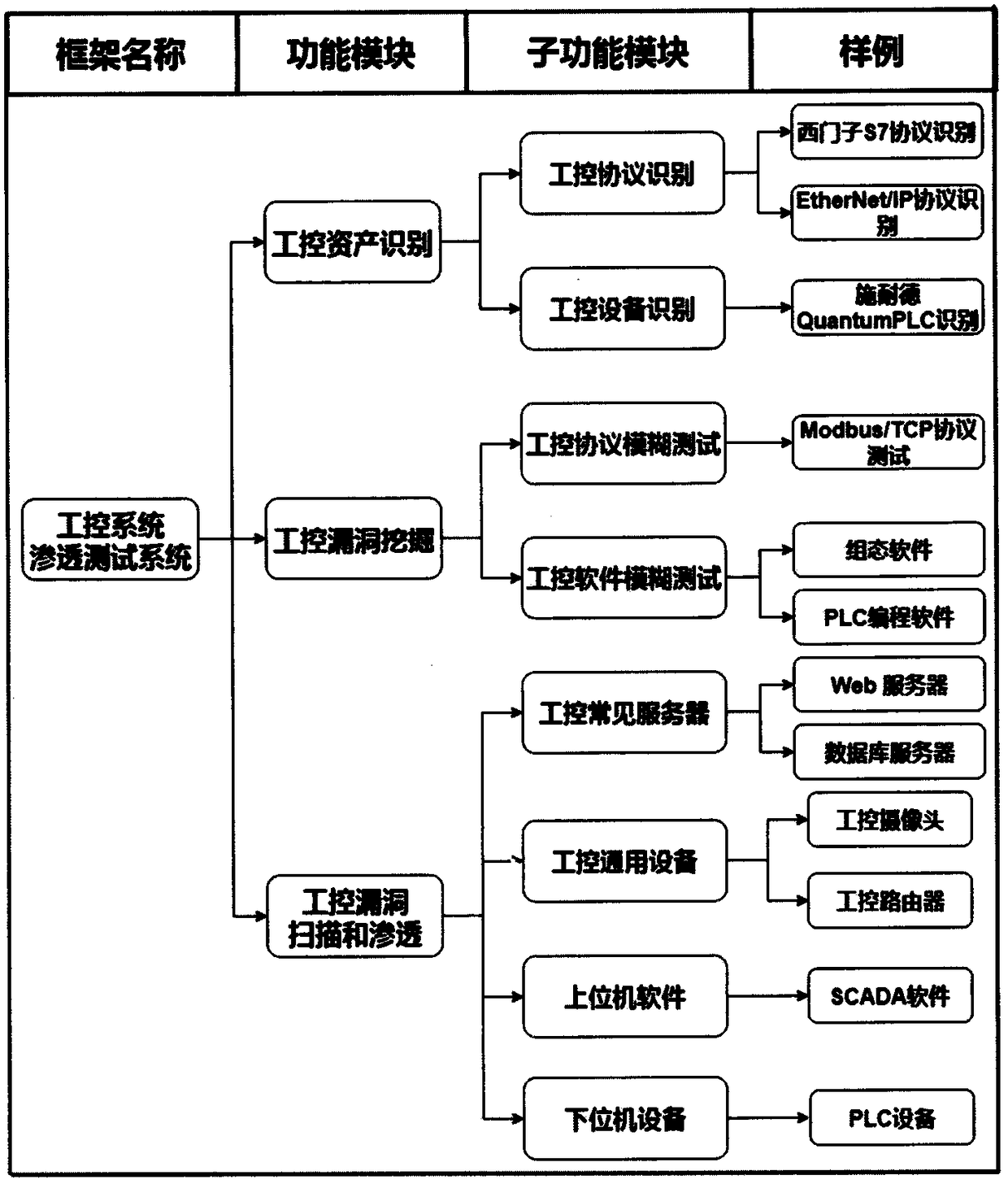
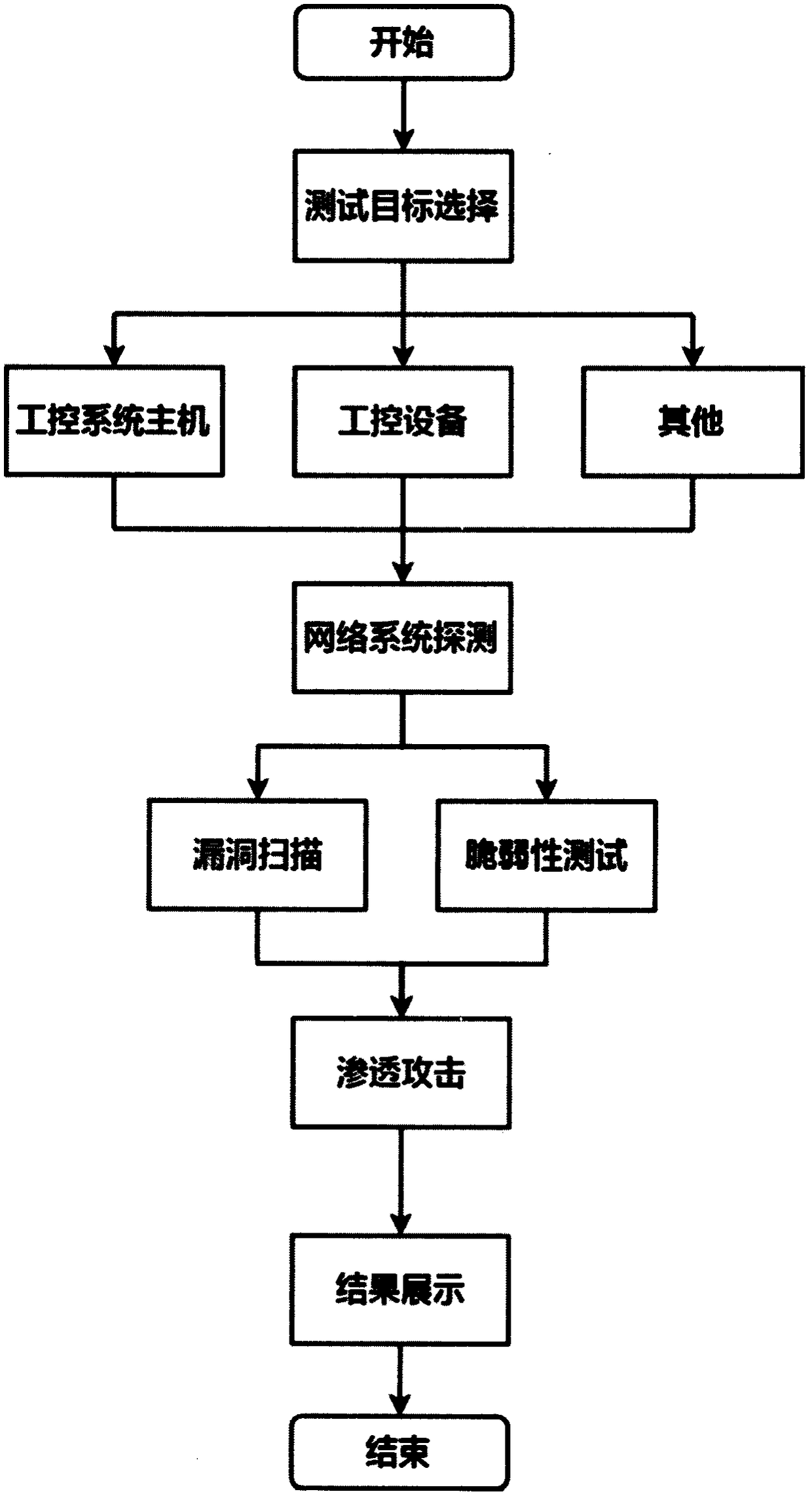
Penetration test framework suitable for industrial control system
InactiveCN108809951AStrong targetingValid device version informationTransmissionNetwork topologyVulnerability scanning
The invention discloses a penetration test framework suitable for an industrial control system. The penetration test framework comprises the following modules: (1) a functional interaction module based on a test target; (2) asset identification and network topology detection on a target network based on a TCP / IP protocol stack; (3) system detection based on an industrial control simulation client,and acquisition of target fingerprint information through a feature data packet; (4) vulnerability scanning based on an industrial control vulnerability library; (5) vulnerability mining based on anindustrial control proprietary protocol, and a blurring test of an industrial Ethernet protocol test; and (6) penetration attack based on features of the industrial control system, and an effective simulation attack on the test target. The framework can perform an effective penetration test on the industrial control system, and solve the problems of of low detection efficiency of the industrial control system, low coverage of industrial control vulnerabilities, difficult detection of industrial control environment vulnerability and single use of vulnerabilities of the existing penetration testtools.
Owner:NANJING UNIV +3
No-feedback one-way data transmission method based on single fiber structure
The invention discloses a no-feedback one-way data transmission method based on a single fiber structure; equipment comprises two one-way fiber data transmission cards which belong to a transmitting end and a receiving end respectively, and the two one-way fiber data transmission cards are connected by a single fiber through a fiber receiver, data communication between the transmitting end and the receiving end adopts a proprietary protocol to carry out data encapsulation, and the reliability of the one-way data transmission is ensued by correcting and deleting codes; as the connection between the transmitting end and the receiving end does not adopt an Ethernet protocol, a data packet is not treated by a TCP / IP protocol stack, so as to eliminate the possibility that a malicious user or a hacker uses the data packet sniffing tool to detect the proprietary protocol format and greatly enhance the transmission safety.
Owner:INST OF NAT SECURITY SCI & TECH +1
Method for analyzing network data package
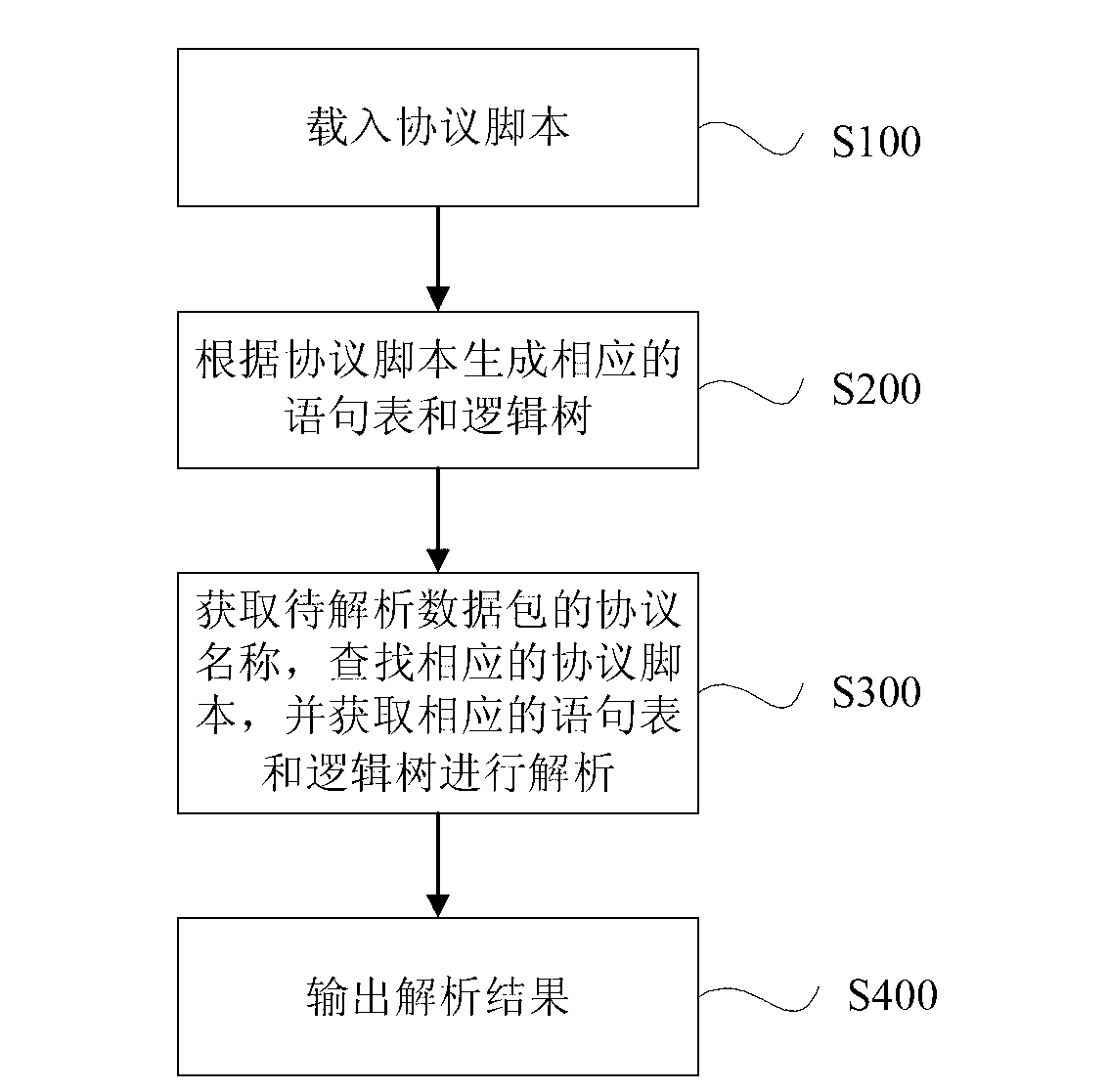
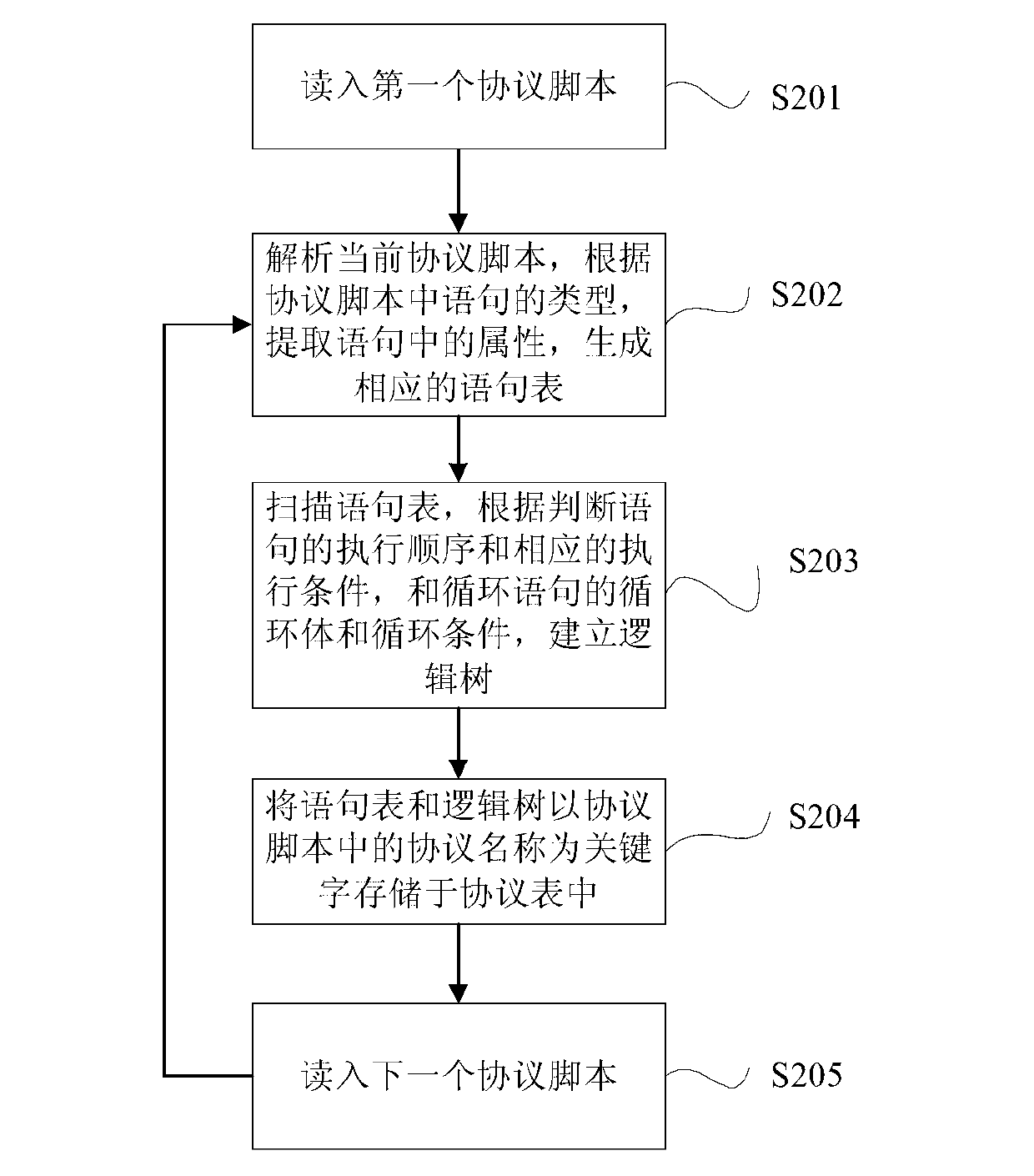
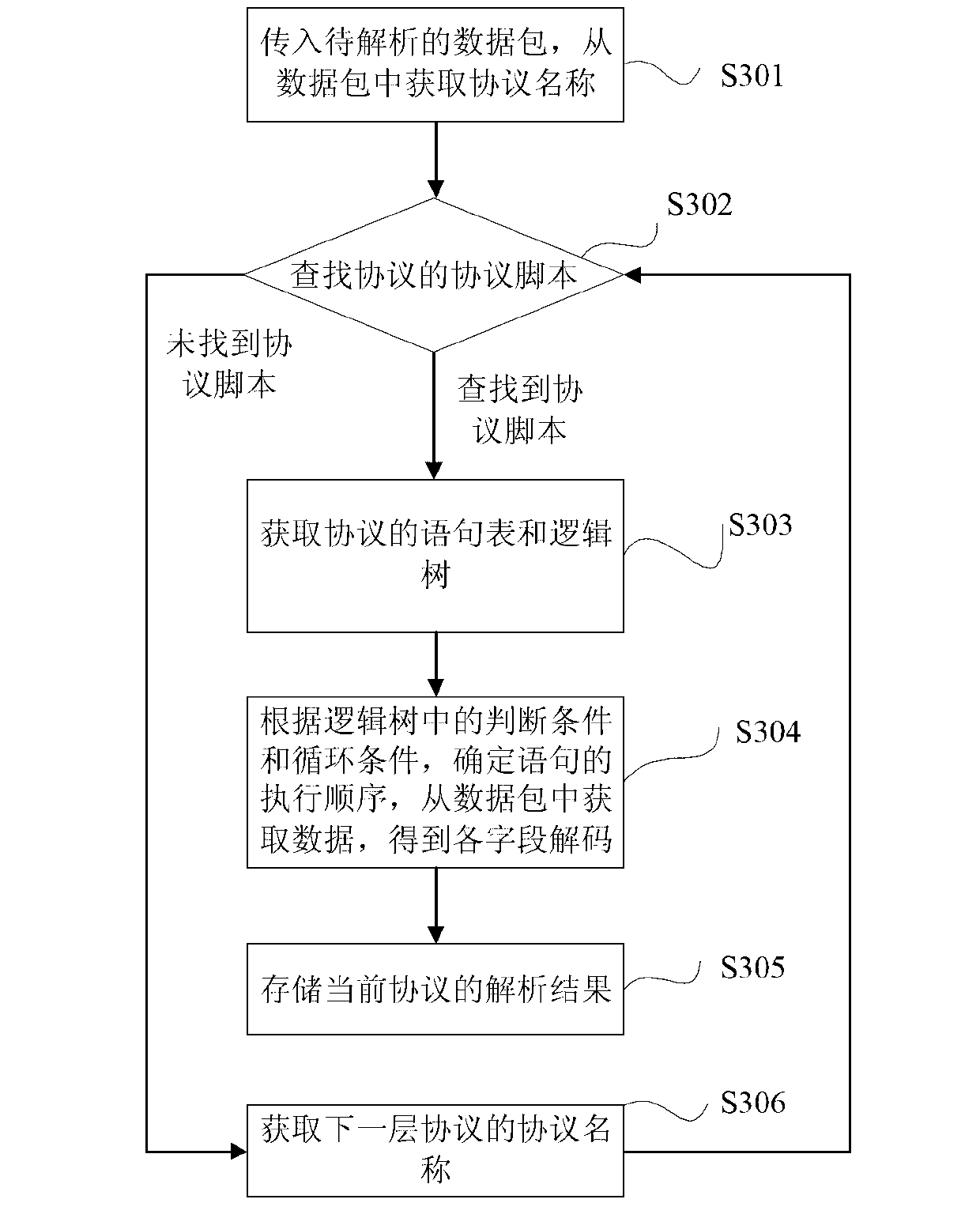
ActiveCN103001971AEasy to addImprove scalabilityTransmissionNetwork packetStructure of Management Information
The invention discloses a method for analyzing a network data package. The method comprises the steps of (1), generating a protocol script of a protocol according to a protocol structure of the protocol and storing the protocol script; (2) generating a statement list and a logic tree according to the protocol script; and (3) loading the data package to be analyzed to obtain a protocol name of the data package to be analyzed, searching for the corresponding protocol script according to the protocol name, obtaining the corresponding statement list and logic tree, analyzing the data package to be analyzed, and outputting analyzing results. The method for analyzing the network data package is strong in expansibility and low in cost, and facilitates addition of new protocols. The method can further analyze data packages with proprietary protocols.
Owner:科来网络技术股份有限公司
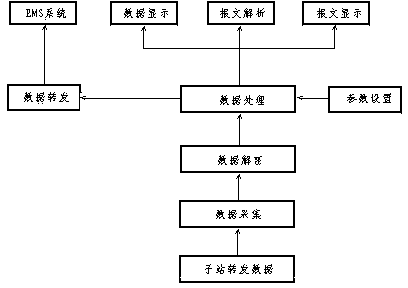
Method and system for acquiring monitoring videos
InactiveCN106162062AClosed circuit television systemsSelective content distributionWeb browserMonitor equipment
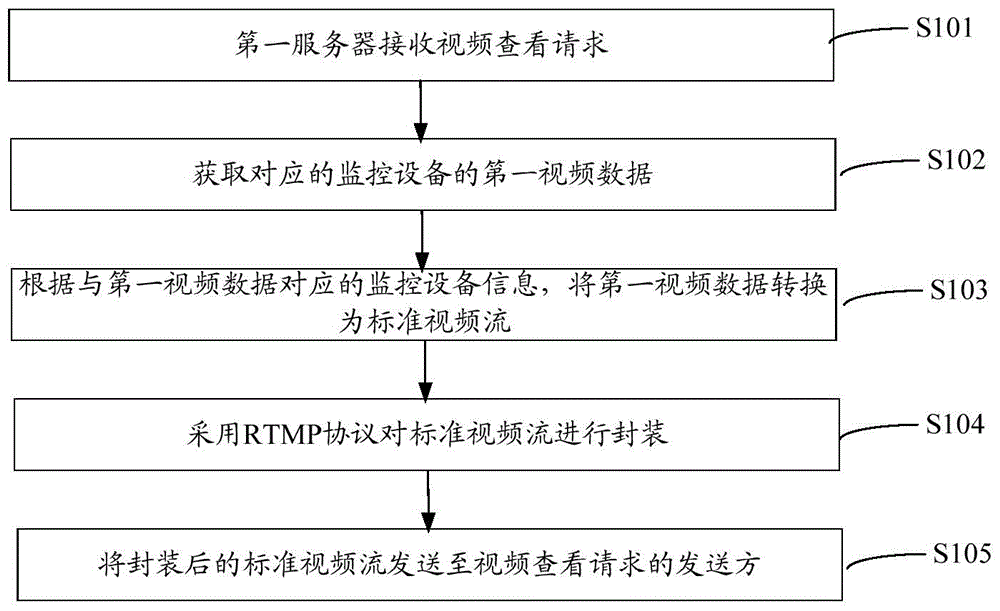
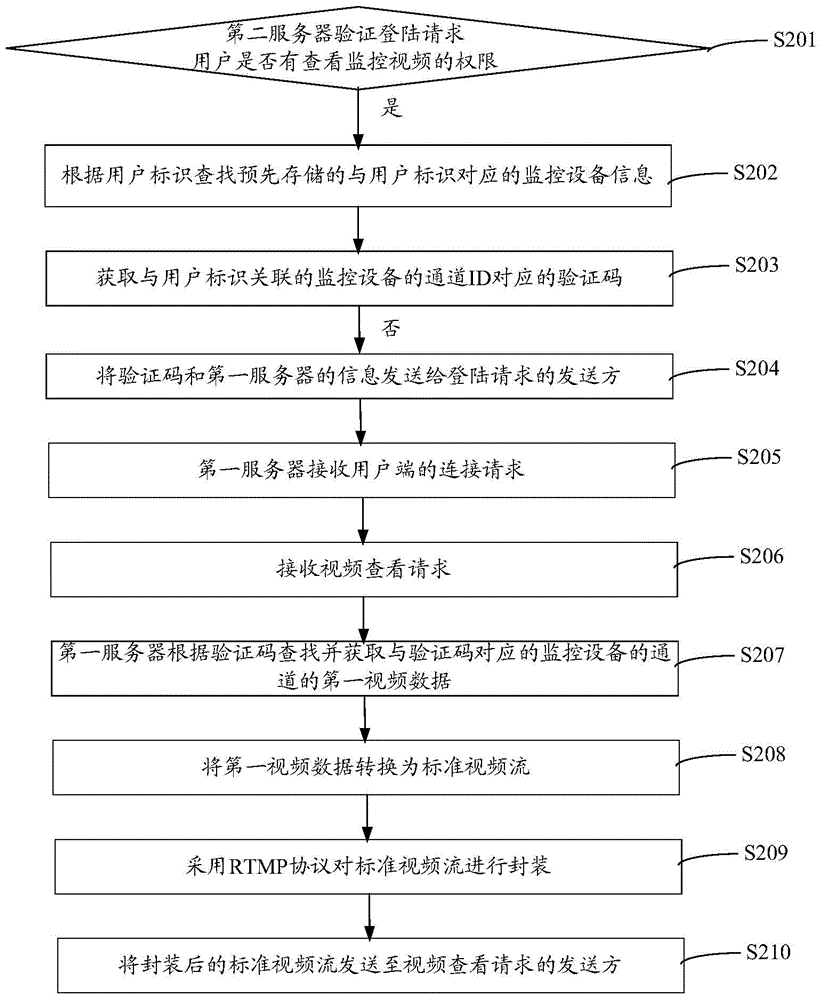
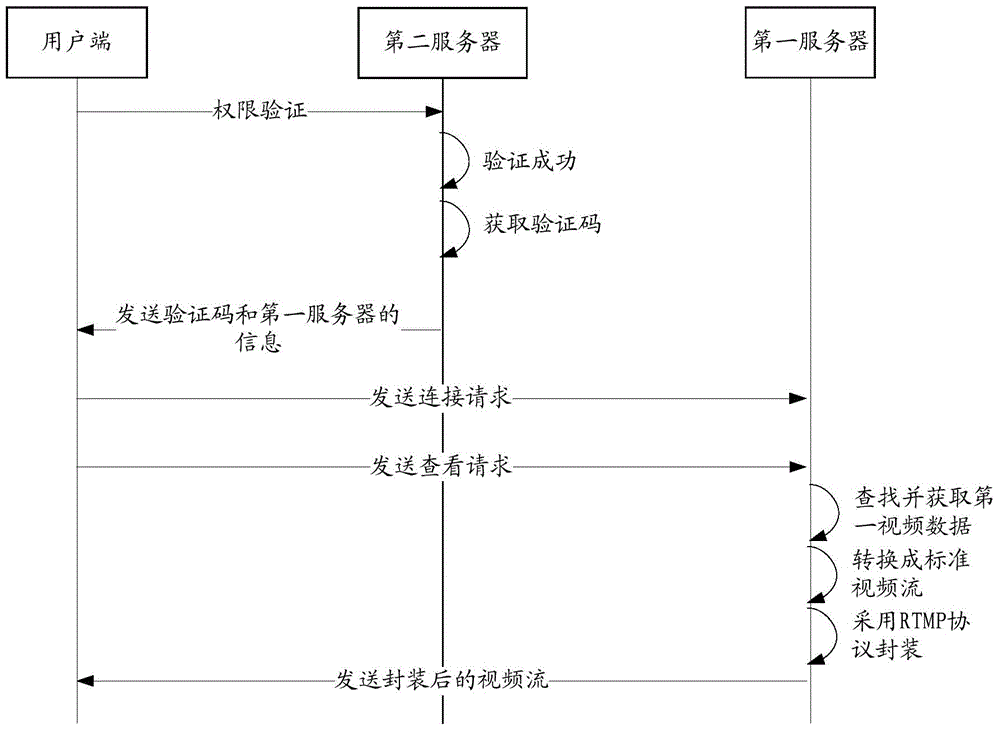
The invention relates to a method and a system for acquiring monitoring videos. The method comprises the following steps: receiving a video check request and acquires first video data of a corresponding monitoring device by a first server; converting the first video data into standard video stream according to monitoring device information corresponding to the first video data; packaging the standard video stream by using a RTMP; and sending the packaged standard video stream to a sender of the video check request. According to the method for acquiring the monitoring videos, the first video data formed by encoding according to a proprietary protocol of the monitoring device manufacturer is converted into the standard video stream, and the standard video stream is packaged by using the RTMP. FLASH streaming media is currently the most widely used streaming media, web browsers directly support the playback of FLASH video stream, and when users check corresponding monitoring videos on web pages, the users can directly play the monitoring videos on the web pages by using FLASH players without downloading the control of the manufacture, thereby bringing great convenience for the users.
Owner:深圳市视高电子技术有限公司
System and method for implementing automatic configuration of equipment
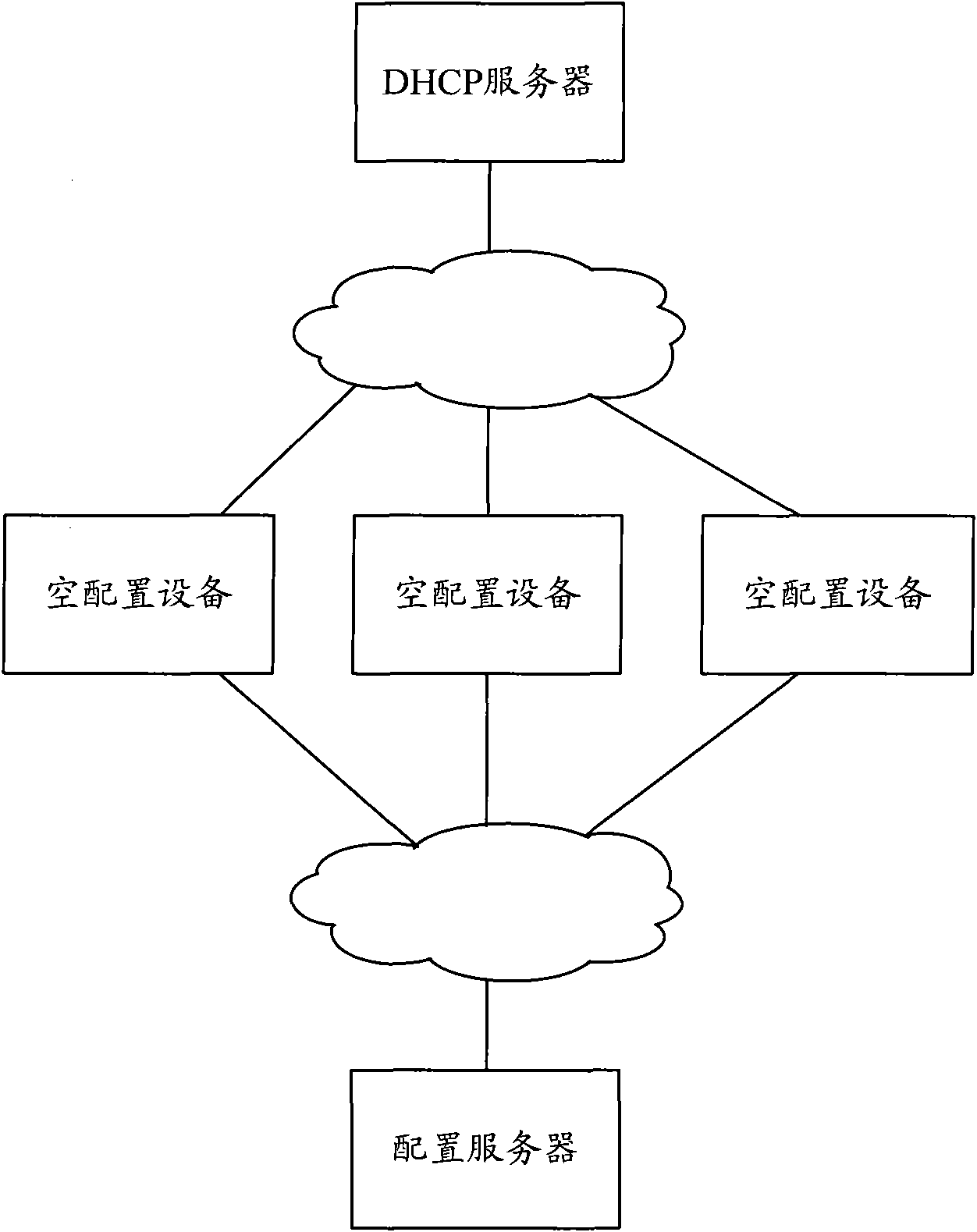
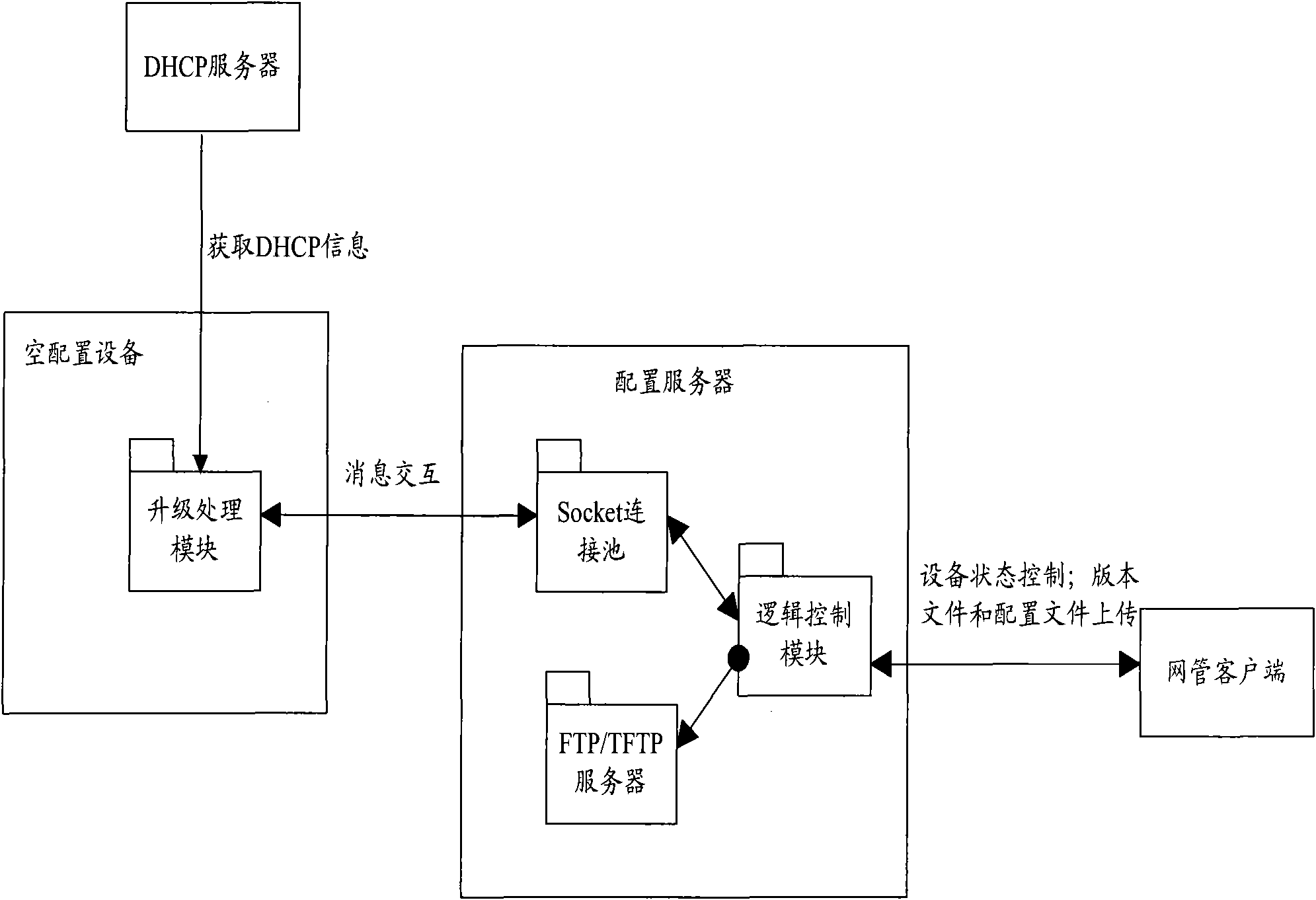
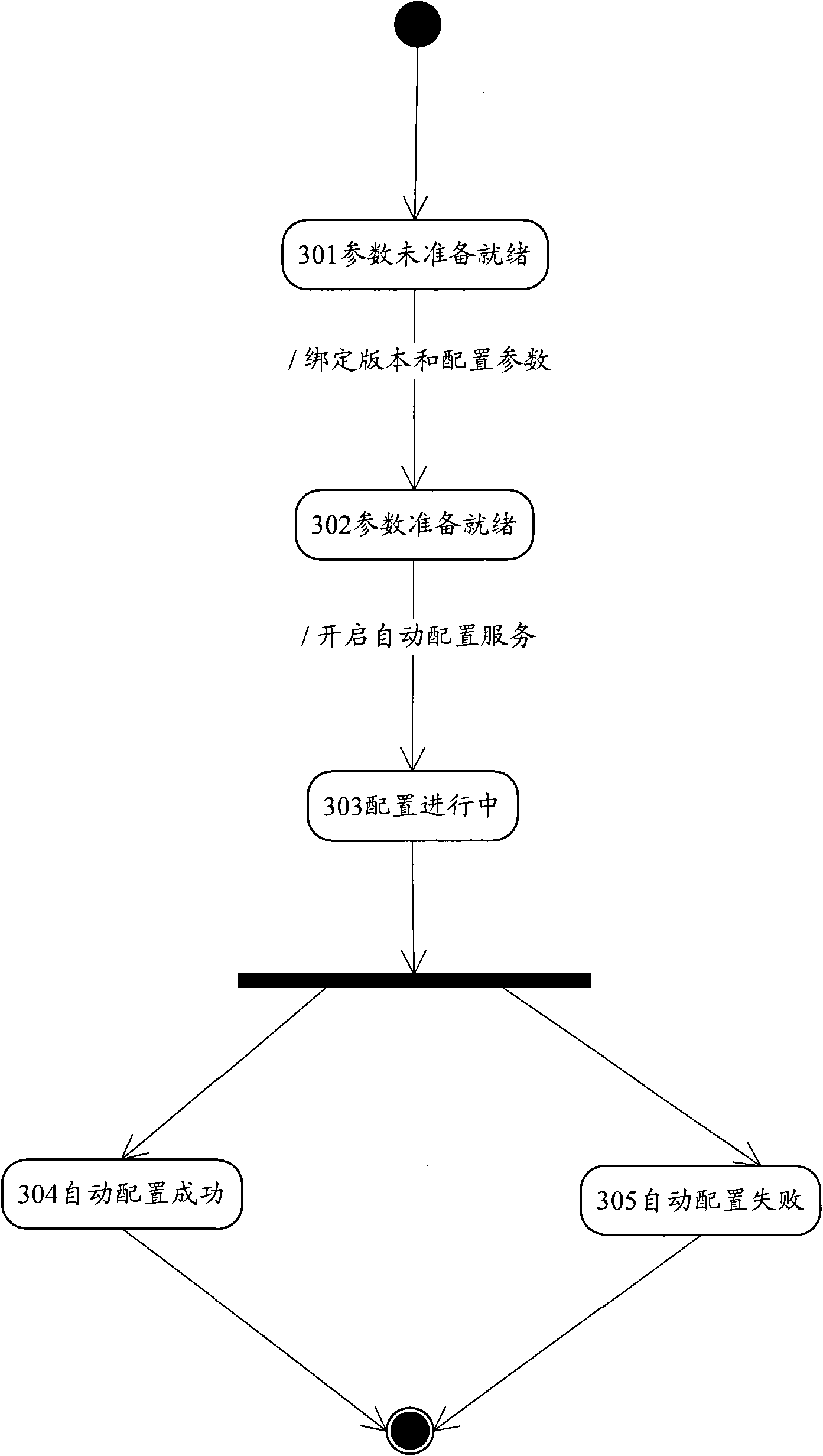
InactiveCN101860545AReduce labor costsReduce error rateData switching networksAuto-configurationIp address
The invention discloses a system for implementing automatic configuration of equipment. The system comprises a dynamic host configuration protocol (DHCP) server, empty configuration equipment and a configuration server, wherein the configuration server is used for continually interacting with the empty configuration equipment based on a proprietary protocol till the upgrade of to-be-updated version files and configuration files of the empty configuration equipment is finished. The invention also discloses a method for implementing the automatic configuration of the equipment. The method comprises that: any one of empty configuration equipment in a network interacts with the DHCP server based on a DHCP protocol to acquire an IP address required by the empty configuration equipment and related parameters of the configuration server, and the empty configuration equipment continually interacts with the configuration server based on the proprietary protocol till the upgrade of the to-be-updated version files and configuration files of the empty configuration equipment is finished. The system and the method of the invention can support the empty configuration equipment and realize batch automatic configuration of the equipment.
Owner:ZTE CORP
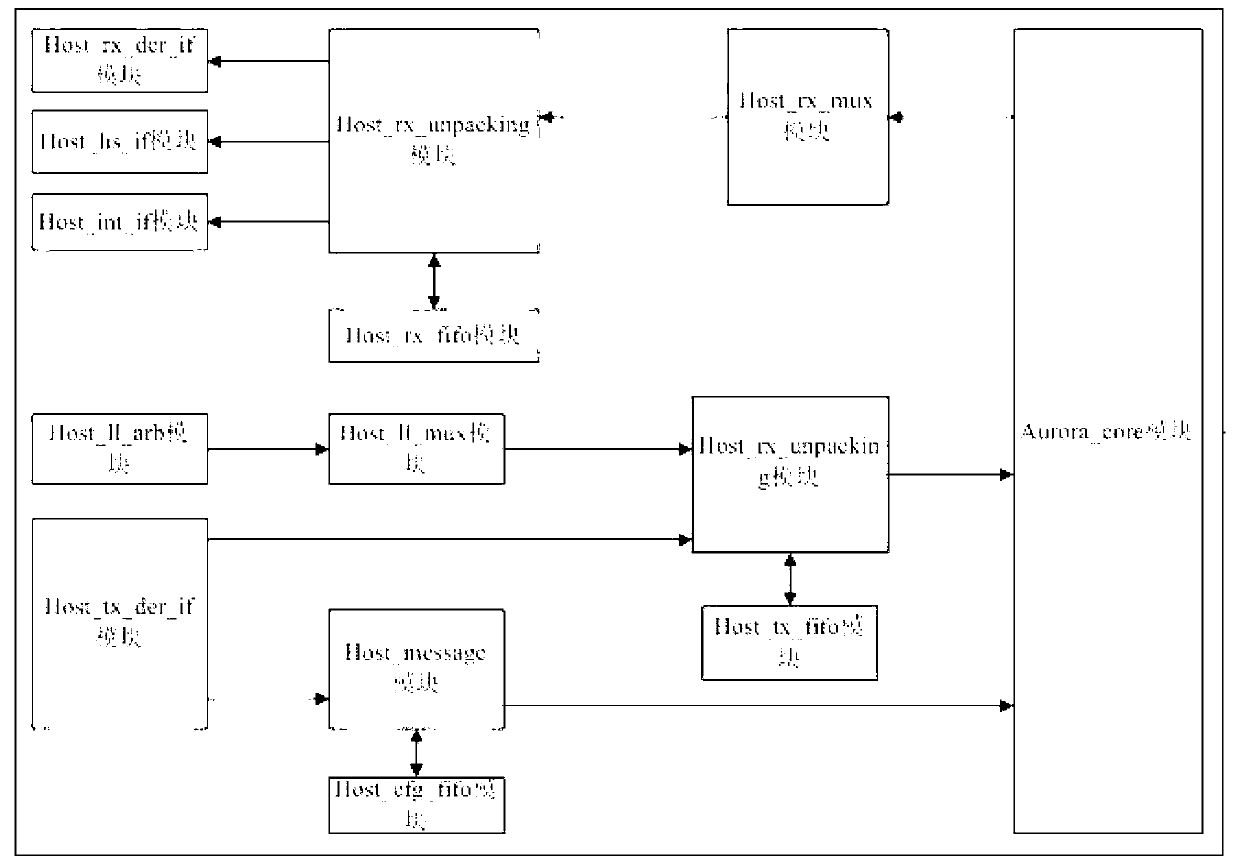
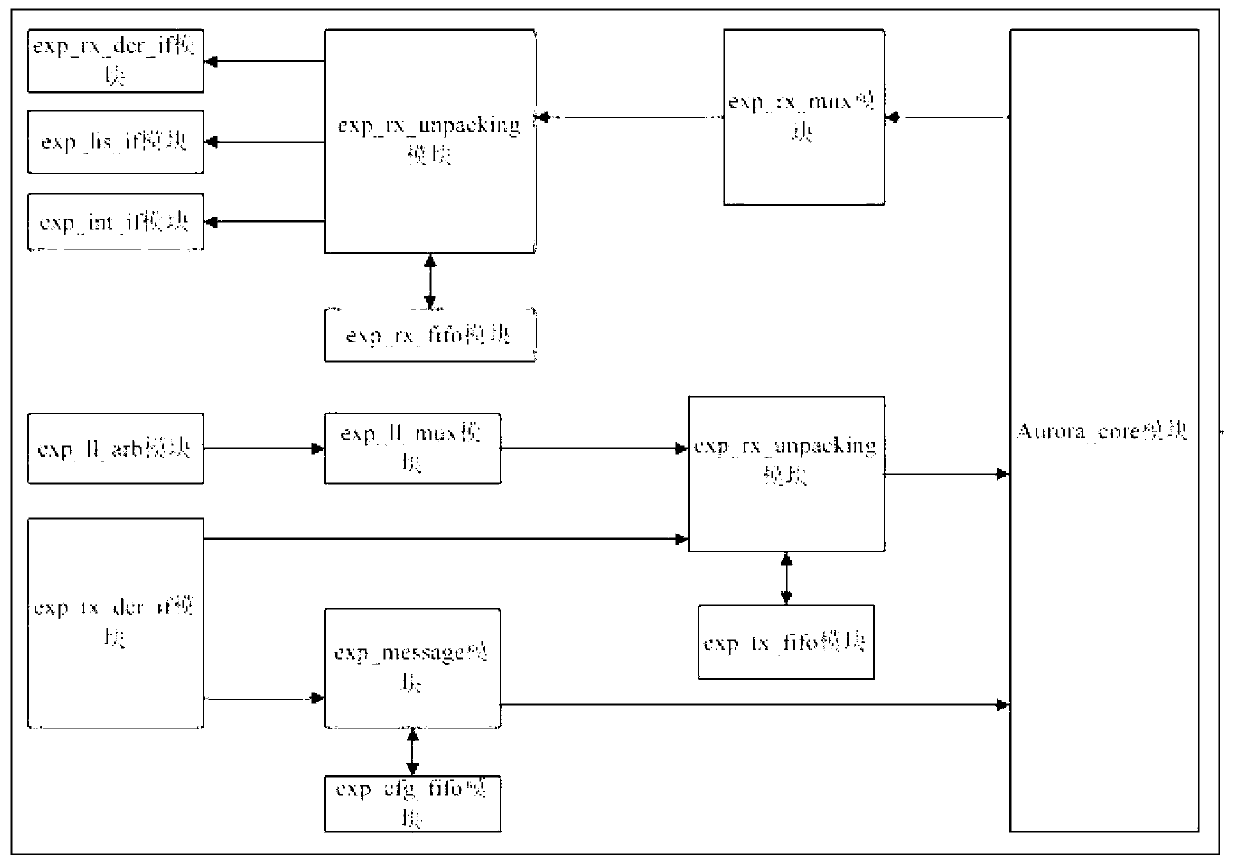
High speed bus interface expansion structure based on aurora protocol
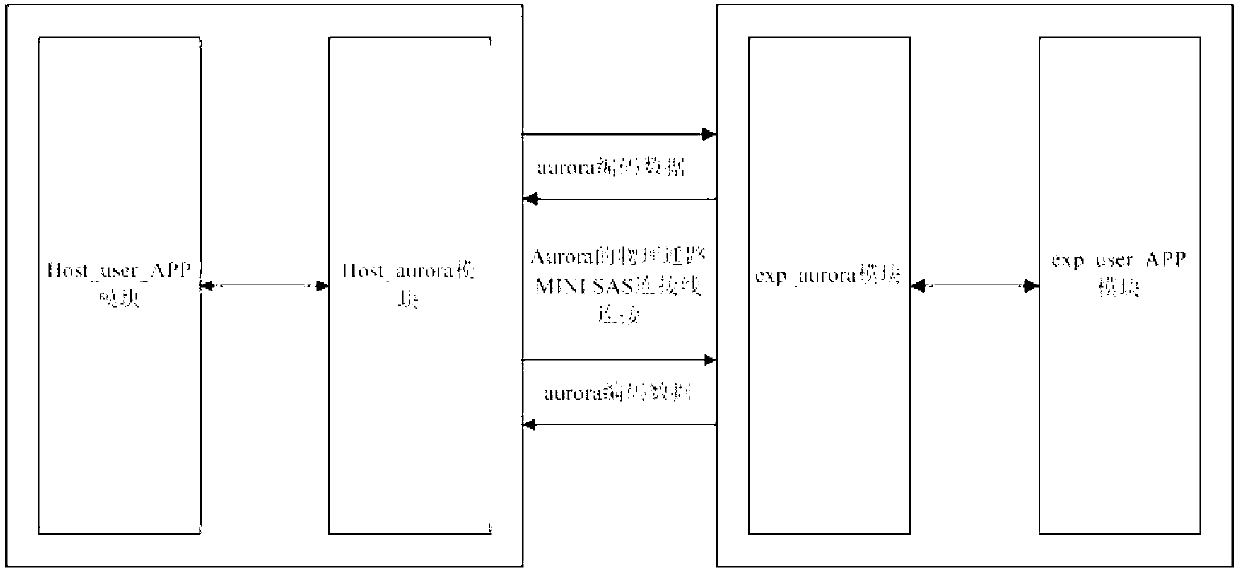
InactiveCN103106169AImplement extensionsSmooth transmissionElectric digital data processingMemory interfaceEngineering
The invention discloses a high speed bus interface expansion structure based on the aurora protocol. The high speed bus interface expansion structure based on the aurora protocol comprises a host_aurora (host computer terminal aurora interface) module, a host_user_app (host computer terminal user application interface) module, an exp_aurora (expansion board terminal aurora interface) module and an exp_user_app ( expansion board terminal user application terminal) module.The high speed bus interface expansion structure based on the aurora protocol ensures stable transmission of high speed data and achieves highly-efficient, flexible and convenient expansion of the storage interface through customization of a proprietary protocol which achieves expansion of a storage interface through a high-speed bus light weight interface function of the aurora protocol.
Owner:无锡北方数据计算股份有限公司
Communication safety protection method for by means of wireless public network
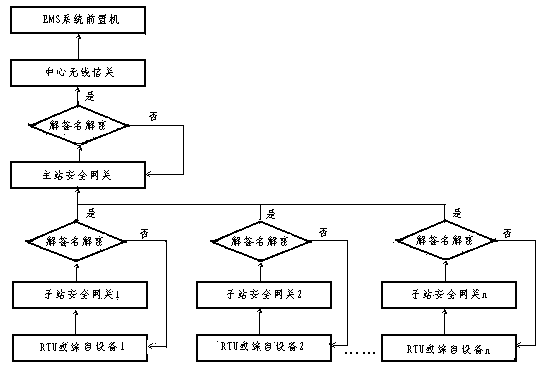
InactiveCN104243437AImprove the strength of security protectionGuaranteed safe operationCircuit arrangementsTransmissionReliable transmissionElectric power system
The invention discloses a communication safety protection method by means of a wireless public network. The method comprises the steps that a master station is isolated from a public network through a serial port power proprietary protocol; dispatch digital certificate authentication and transmission encryption are achieved on the master station and a substation; a safety gateway is additionally arranged; data received by the wireless public network are transmitted to an SCADA system through a communication interface. Meanwhile, a safety policy is adopted to limit the access range and resources. The TCP / IP network communication technology, the IPSEC safety tunnel technology and the USBKET encryption authentication technology are integrated, emergency recovery, temporary debugging and safety access with no power communication conditions are achieved on the condition that power system communication is abnormal, and a safe and reliable transmission channel is provided for power grid dispatch automation real-time data transmission. Safe running of a power system is ensured on the condition that existing application environment and software do not need to be changed. The communication safety protection method has the advantages that the step design is reasonable, safety protection measures are competent, working performance is stable and reliable, and the method is suitable for being popularized for industries.
Owner:STATE GRID CORP OF CHINA +1
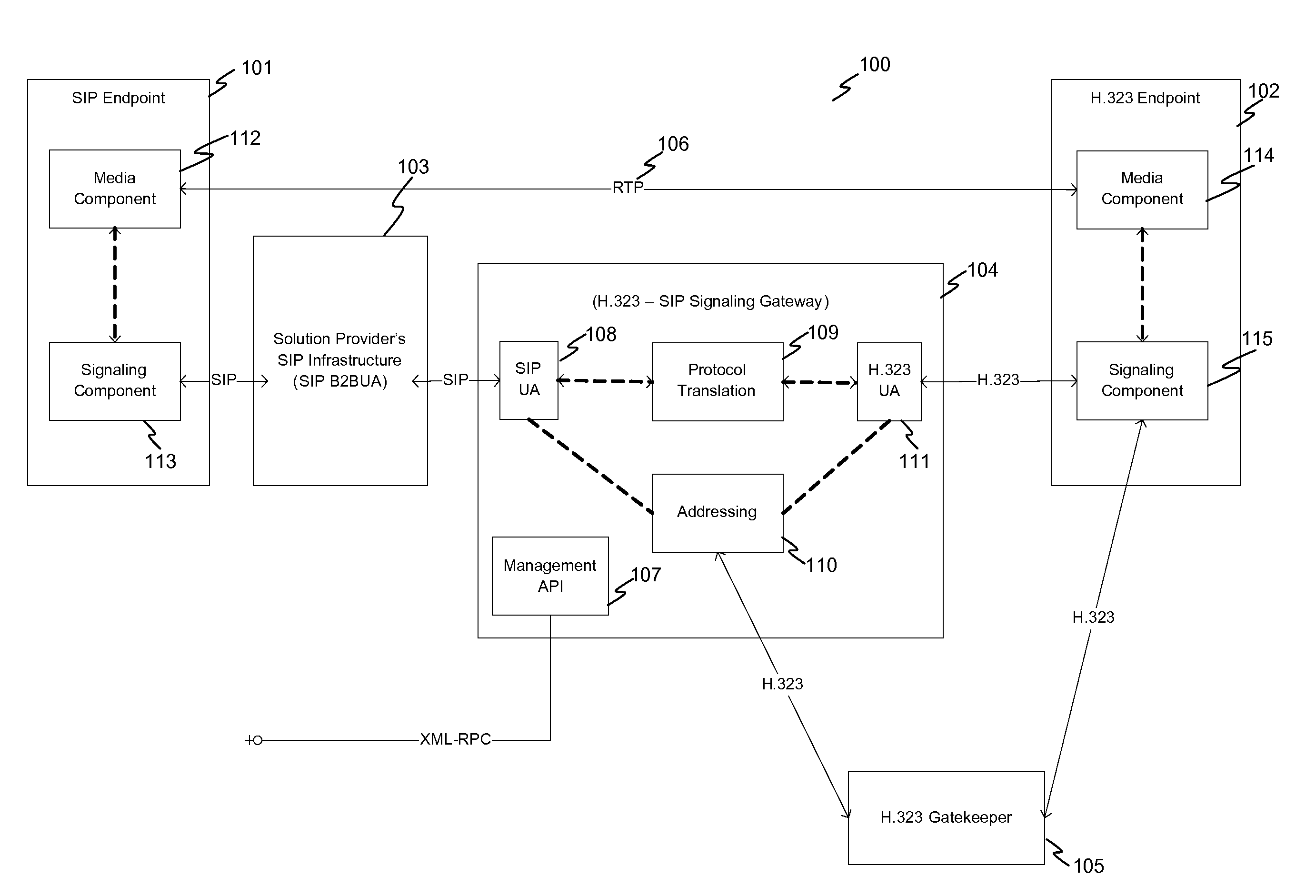
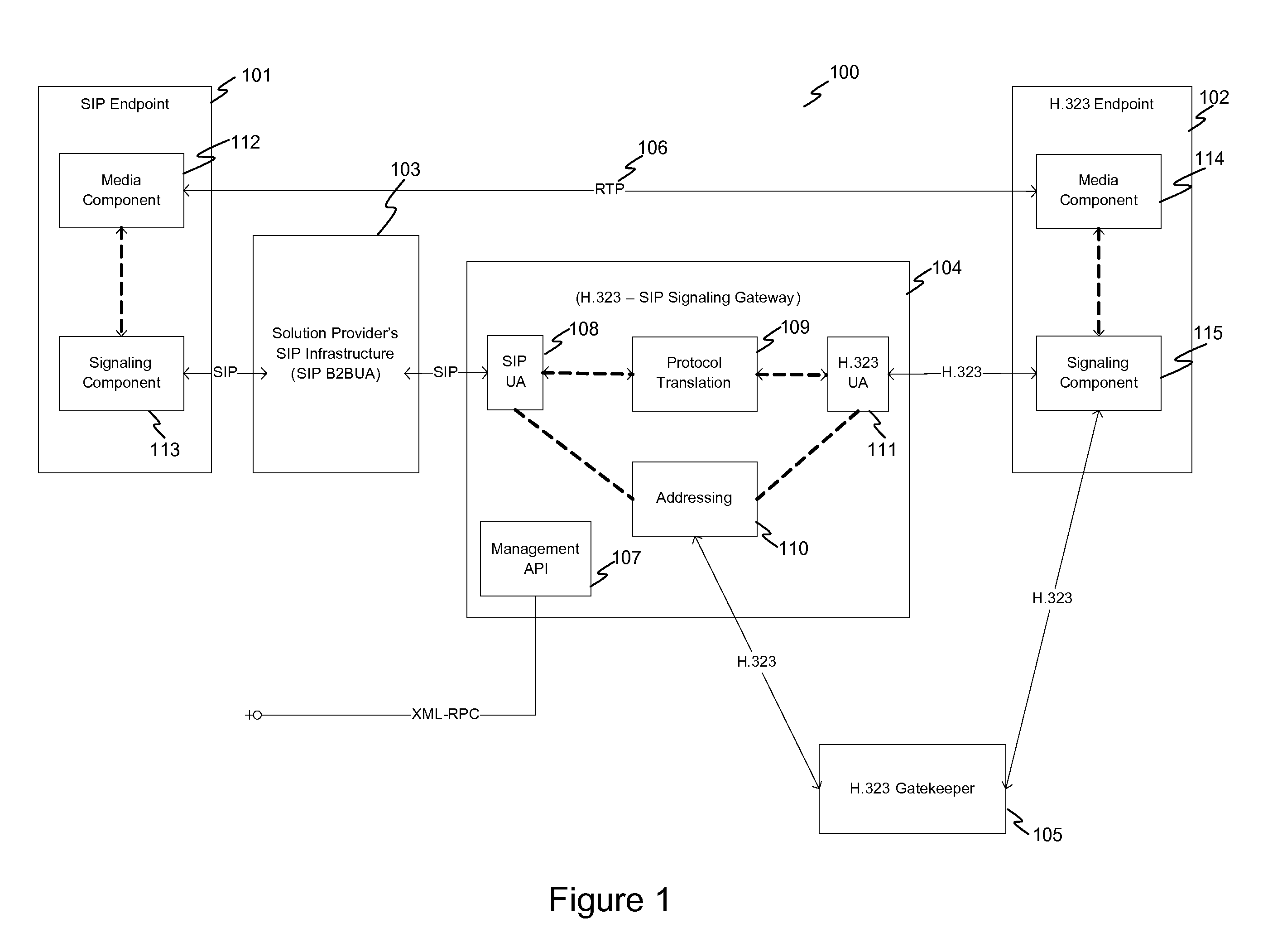
System and method for multimedia communication across disparate networks
ActiveUS20100177786A1Reduce riskEffectively actTime-division multiplexMultiple digital computer combinationsProprietary protocol
A method of communication between endpoint devices that includes converting data packets from a multiport protocol to a proprietary port protocol so that the data packets can traverse firewalls protecting the endpoint devices. A system that includes networks protected by firewall wherein the communication between the networks is in a proprietary protocol and the system further including a device for managing the communication between the protected networks.
Owner:DIRECTPACKET RES
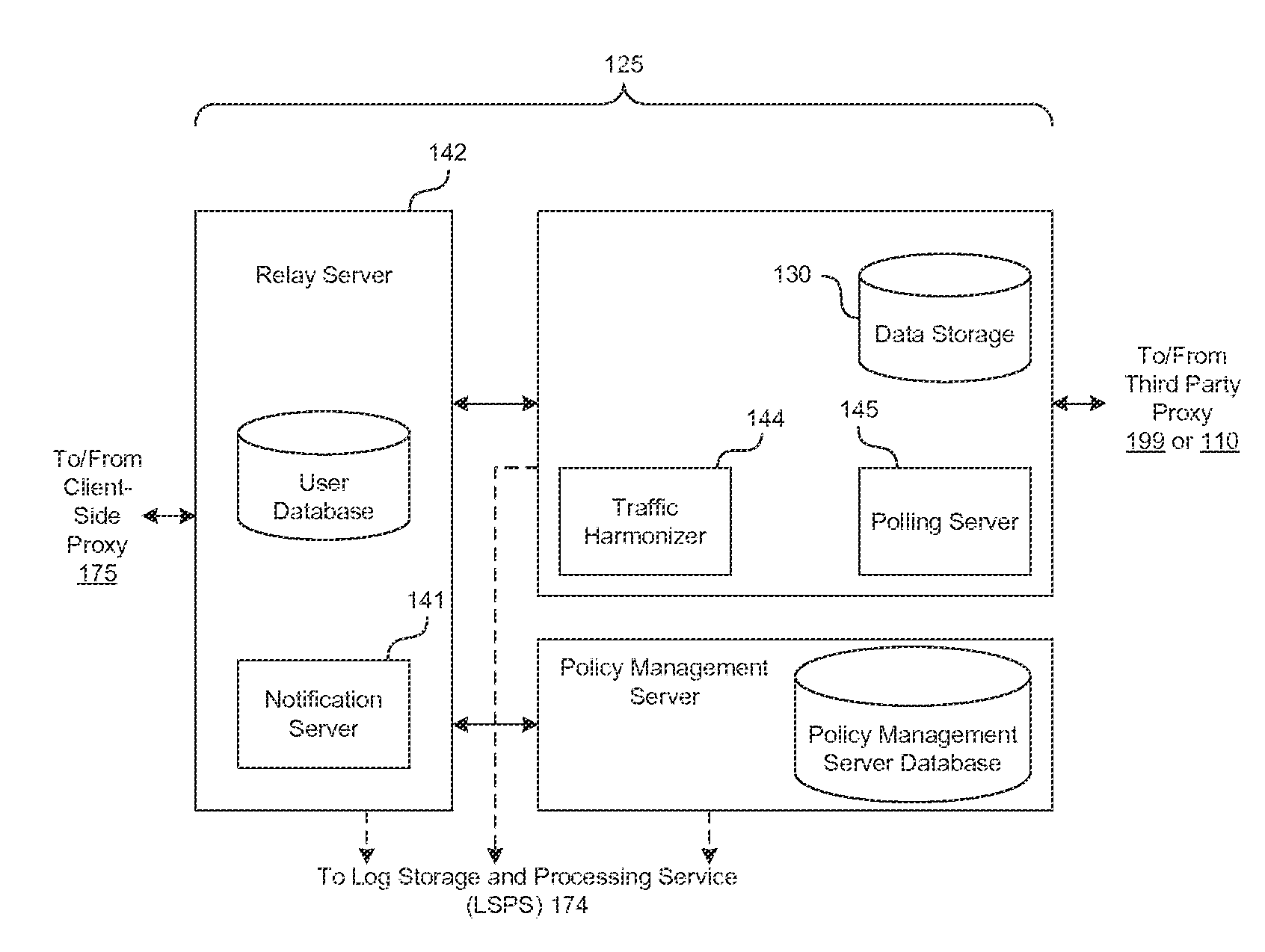
Policy management for signaling optimization in a wireless network for traffic utilizing proprietary and non-proprietary protocols
InactiveUS20150312102A1Digital data information retrievalNetwork traffic/resource managementSubject matterClient-side
The subject matter described herein includes methods, systems, and computer program products for policy management for signaling optimization in a wireless network. According to one system, a policy control function (PCF) is configured to provide policy management in a communications network. The PCF includes a client services node (CSN) that provides front-end interfaces to a client device. An update target calculation engine (UTCE) is configured to asynchronously calculate updates to the client device without waiting for the client device to request the configuration updates. A generic update delivery system (GUDS) receives the updates from the UTCE and delivers the updates to client devices.
Owner:SEVEN NETWORKS INC
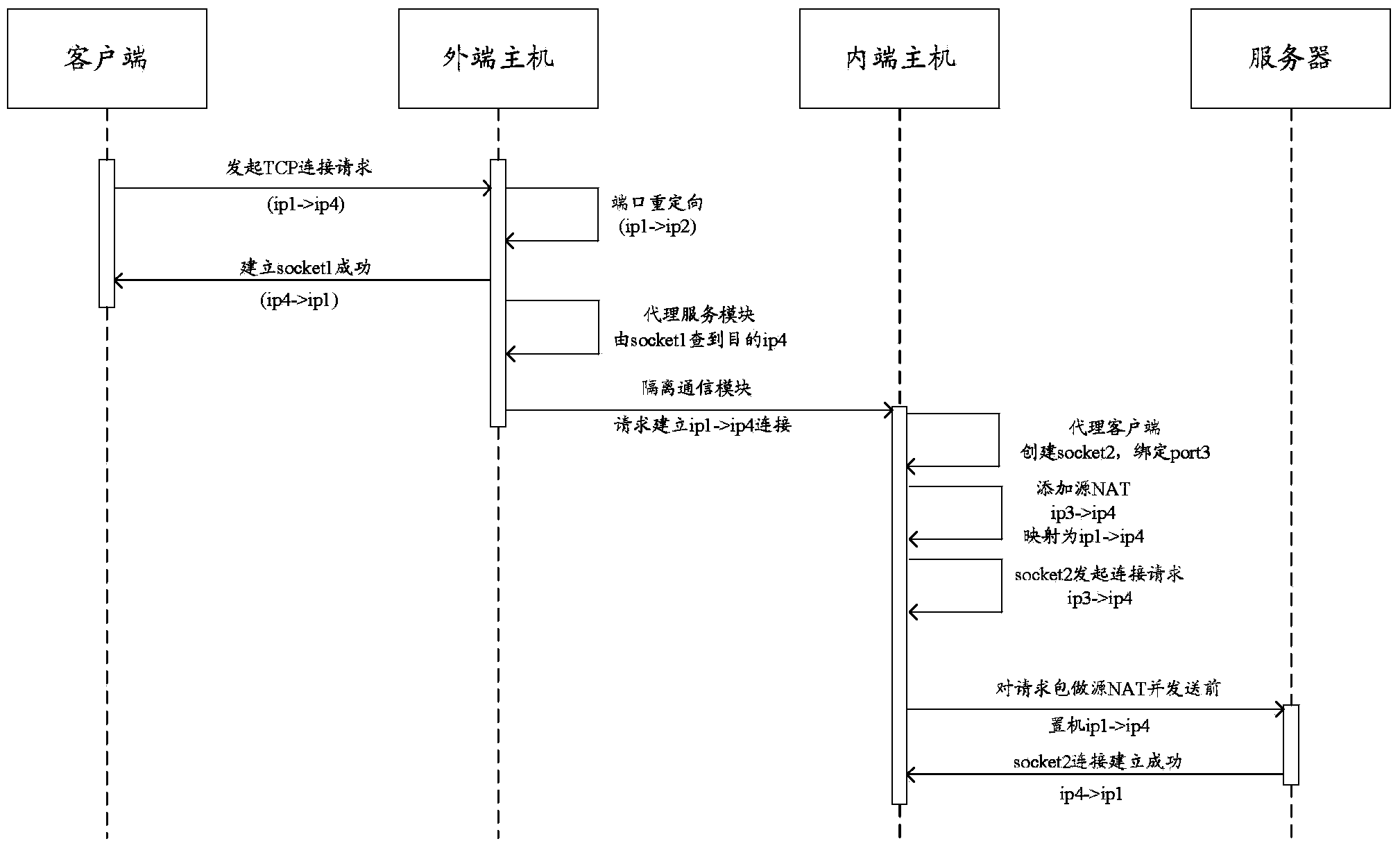
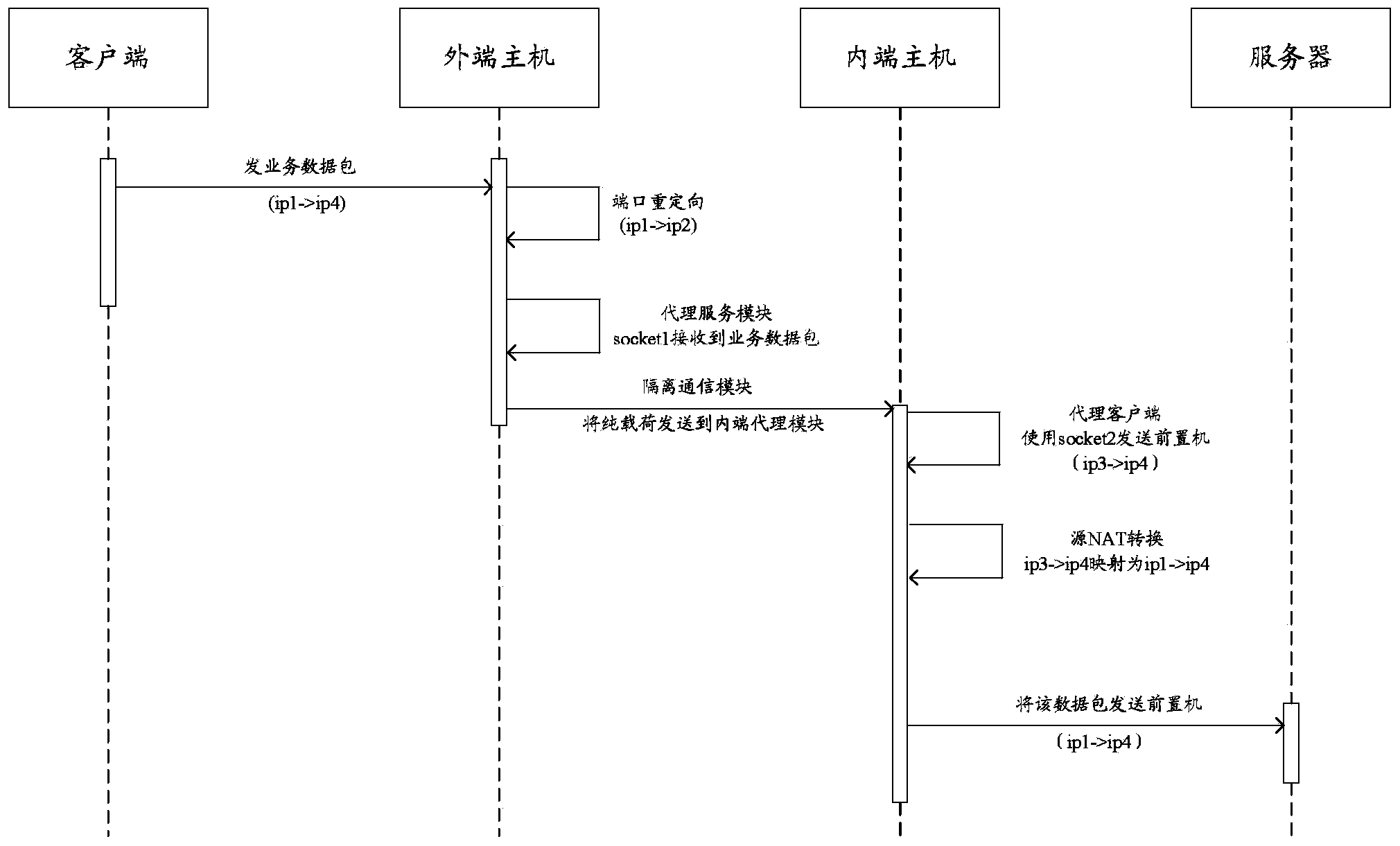
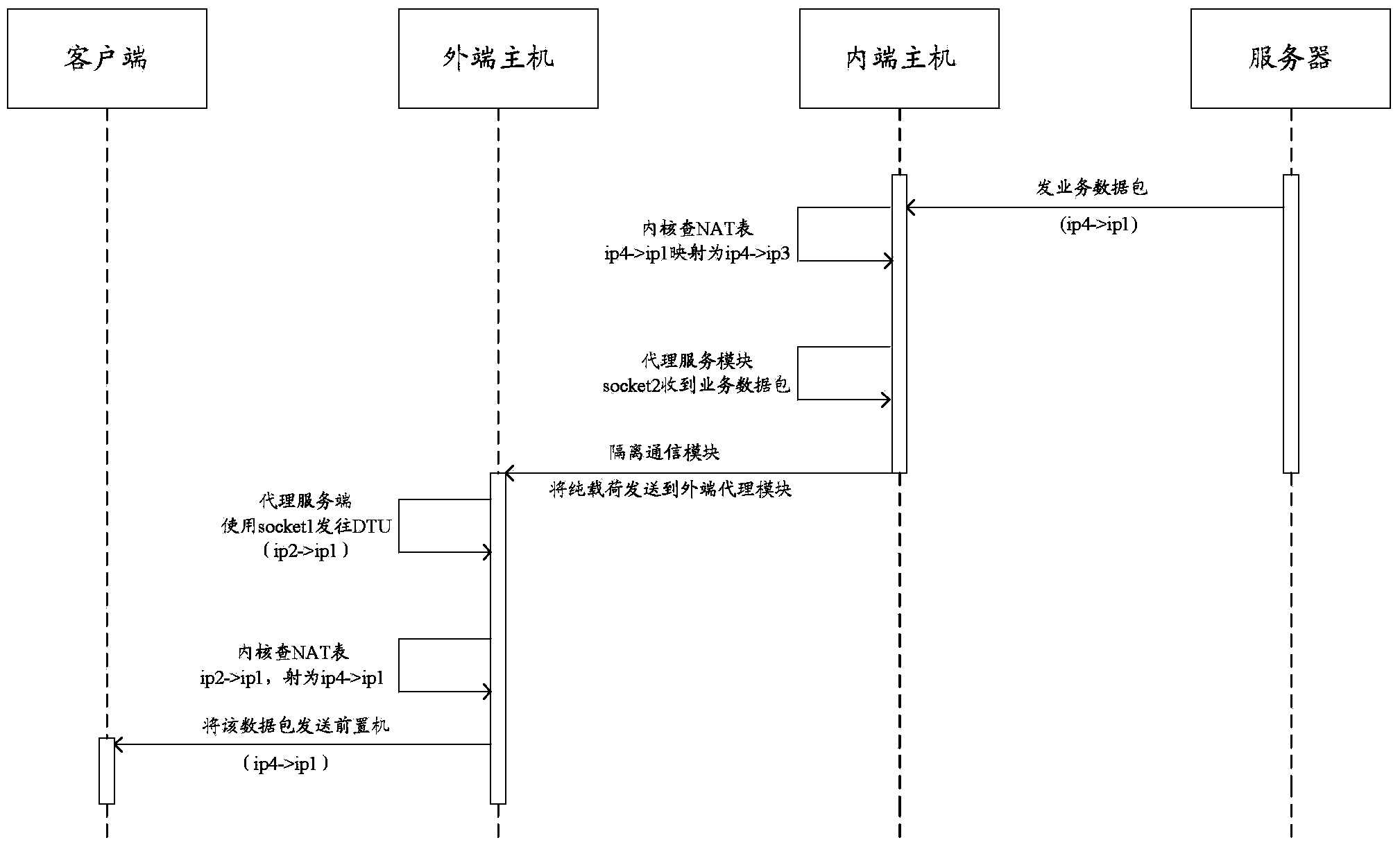
Data isolation device based on non-network mode, and method and system thereof
The invention provides a data isolation device based on a non-network mode, and an isolation method and an isolation system thereof. The data isolation device comprises an intranet host, an extranet host, and an isolated communication module. The intranet host and the extranet host are loaded with a network protocol stack, and respectively maintain a TCP proxy client module and a TCP proxy server module. A TCP connection socket1 is established and data forwarding is carried out between the TCP proxy server module and a service data packet client. A TCP connection socket2 is established and data forwarding is carried out between the TCP proxy client module and a service data packet server. The isolated communication module uses a proprietary protocol. The TCP header and following message headers of a service data packet are removed. Only pure service data load forwarding is carried out. Four-layer isolated subsystem communication between inner-end and outer-end hosts is realized on the whole, all network attacks except proprietary-protocol-based internal attacks are effectively prevented, and high network data exchange efficiency is ensured on the premise of physical isolation between the internal network and the external network.
Owner:ELECTRIC POWER RES INST OF GUANGDONG POWER GRID
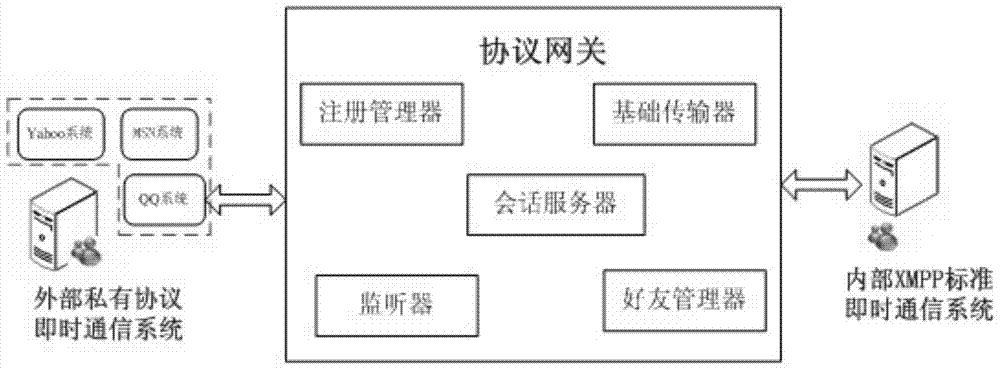
Protocol gateway and method supporting interconnection and interworking of enterprise-class instant messaging systems
InactiveCN103685004AMeet the needs of mutual communicationEasy to manage centrallyNetwork connectionsCommunications systemInterconnection
The invention discloses a protocol gateway supporting interconnection and interworking of enterprise-class instant messaging systems. The protocol gateway comprises a register manager, a friend manager, a sound monitor, a basic transmitter and a conversation server, wherein the register manager manages and configures the register binding between internal users and external users, the friend manager calls a friend list API of an external proprietary protocol instant messaging system, reads the friend list, displays the friend list to an internal enterprise-class instant messaging system and marks the external instant messaging system, the sound monitor monitors the messaging requests between the internal users and the external users, the basic transmitter connects an internal server address and an external server address in a bi-directional mode, an identifier is removed when the internal users connect the external users, the identifier is added when the external users connect the internal users, the conversation server finishes messaging between the users of the internal enterprise-class instant messaging system and the users of the external instant messaging system. The protocol gateway and method achieve interconnection and interworking of the different instant messaging platforms, and are high in safety.
Owner:SOUTH CHINA UNIV OF TECH +2
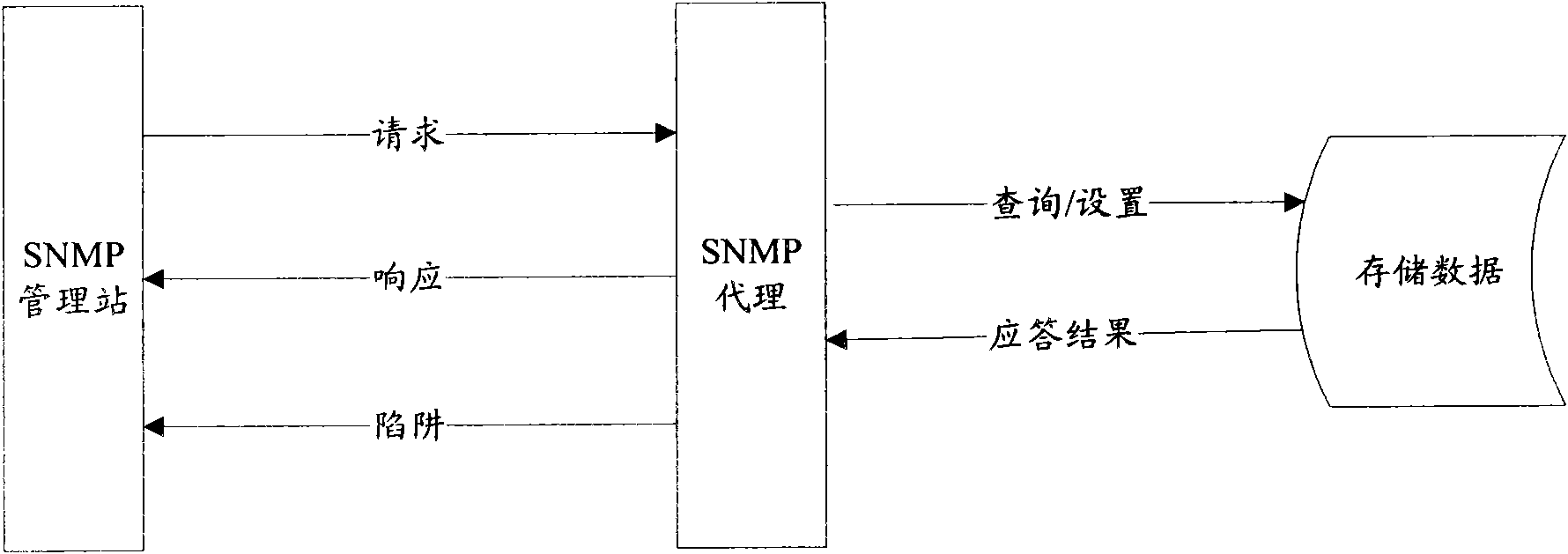
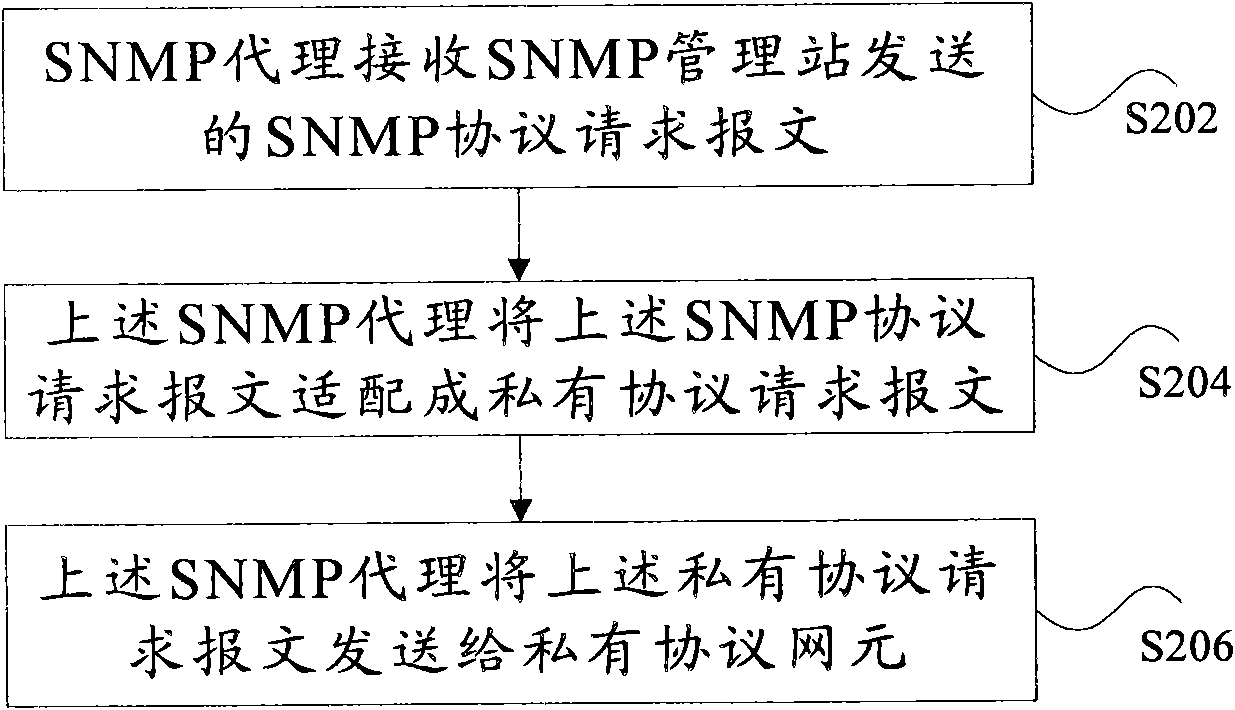
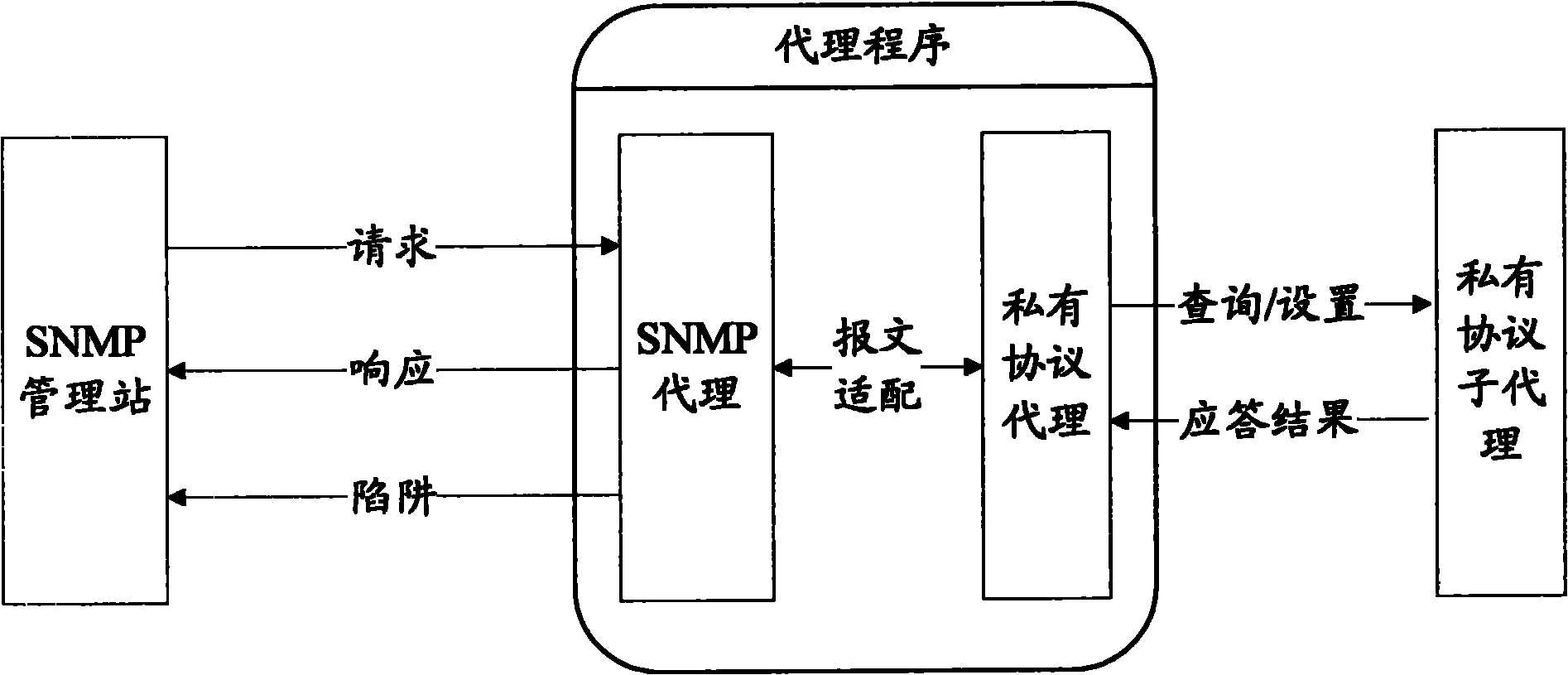
SNMP (Simple Network Management Protocol) network element and communication method of SNMP network element and proprietary protocol network element
InactiveCN101848107AImprove development efficiencyAvoid the defect that the communication message cannot be obtained correctlyData switching networksDirect communicationSimple Network Management Protocol
The invention discloses an SNMP (Simple Network Management Protocol) network element and a communication method of the SNMP network element and a proprietary protocol network element, wherein the communication method of the SNMP network element and the proprietary protocol network element comprises the following steps that an SNMP proxy receives an SNMP protocol request message sent by an SNMP management station; the SNMP protocol request message is adapted to a proprietary protocol request message by the SNMP proxy; and the SNMP proxy sends the proprietary protocol request message to the proprietary protocol network element. The invention carries out adaptation on the SNMP protocol message and the proprietary protocol message through the SNMP proxy and solves the problem that the SNMP network element can not be in direct communication with the proprietary protocol network element in the prior art, therefore, communication can be carried out between the SNMP network element and the proprietary protocol network element.
Owner:ZTE CORP
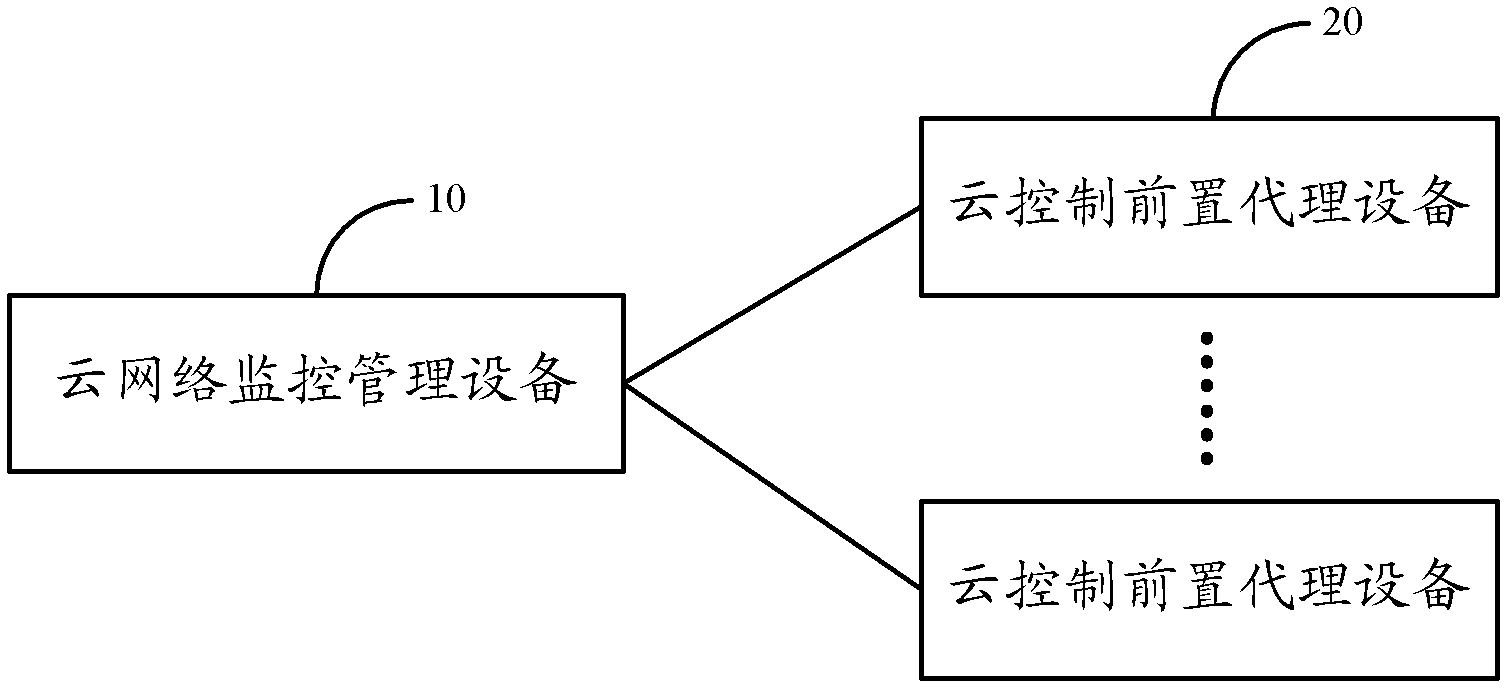
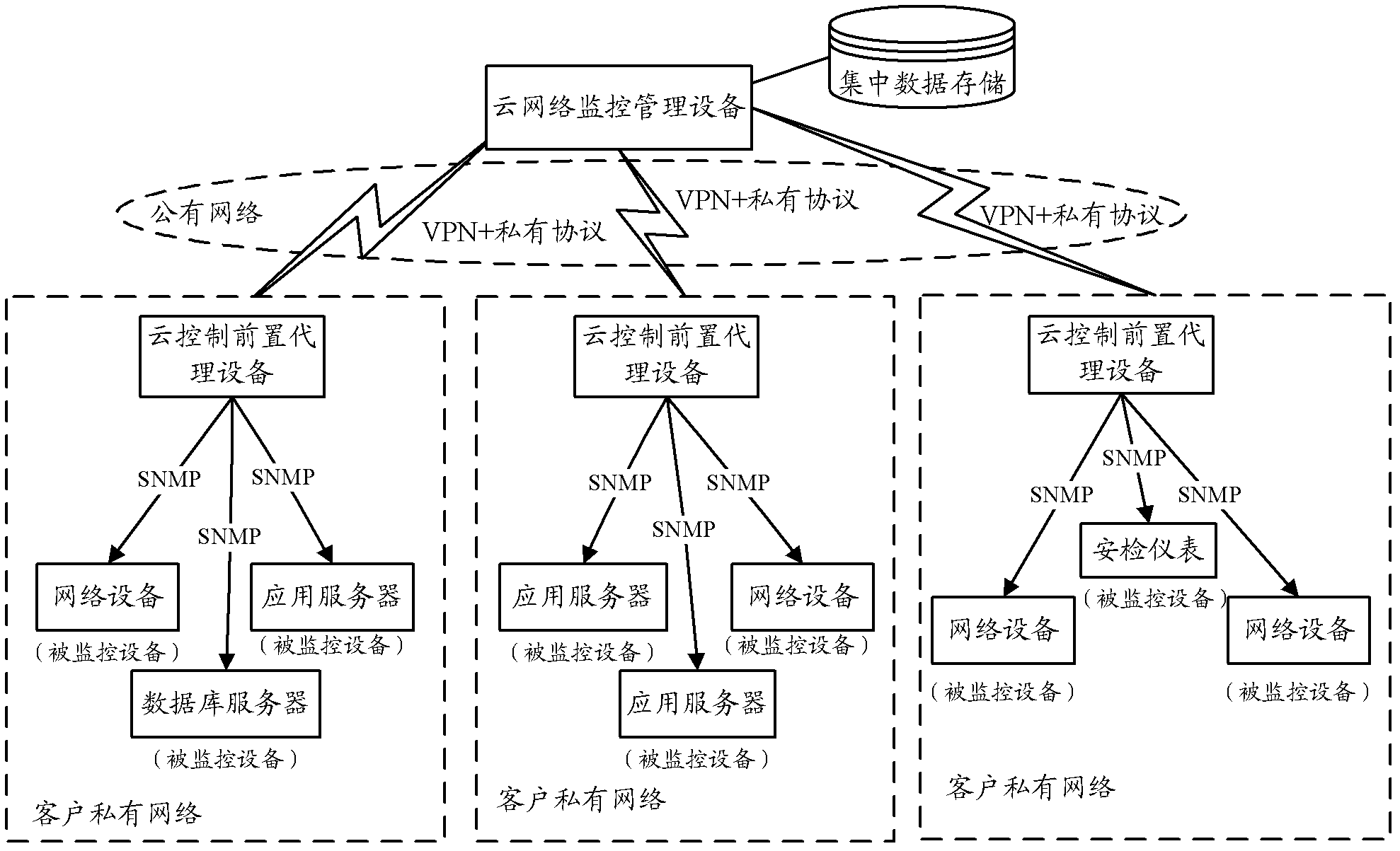
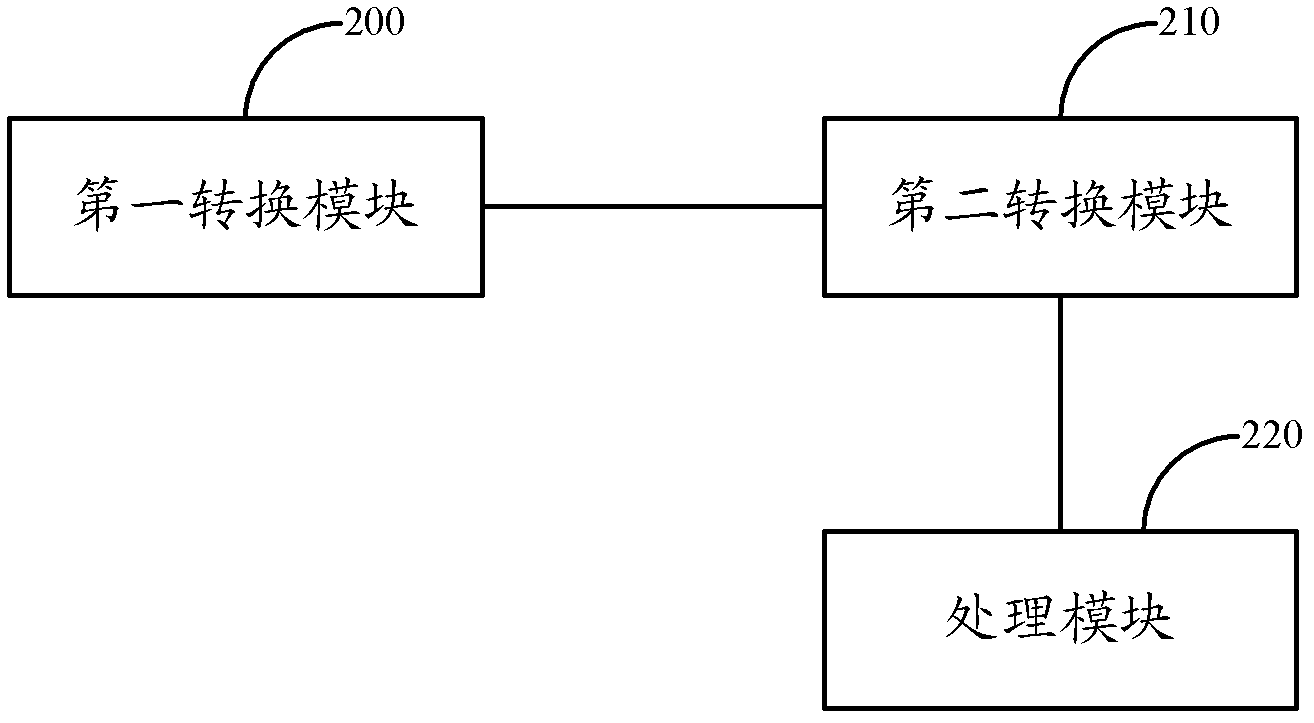
Method, system and device for network monitoring process
The invention relates to the field of network security management, in particular to a method, a system and a device for network monitoring process. The problems that in the prior art, an existing monitoring method can not cross a wide area network, and in a public network, the security is low can be solved. The method for the network monitoring process comprises the following steps that cloud control pre-positioned proxy equipment converts a received data message based on a proprietary protocol from a cloud network monitoring management device to a data message based on a simple network management protocol (SNMP), and sends the data message to a corresponding monitored device; the cloud control pre-positioned proxy equipment converts a received data message based on the SNMP from the monitored device to a data message based on the proprietary protocol and sends the data message to the cloud network monitoring management device. Due to the fact that the data message is converted between the proprietary protocol and the SNMP, monitoring can be achieved in the proprietary protocol, the monitoring method can cross the wide area network, and the safety in the public network is improved.
Owner:FOUNDER BROADBAND NETWORK SERVICE
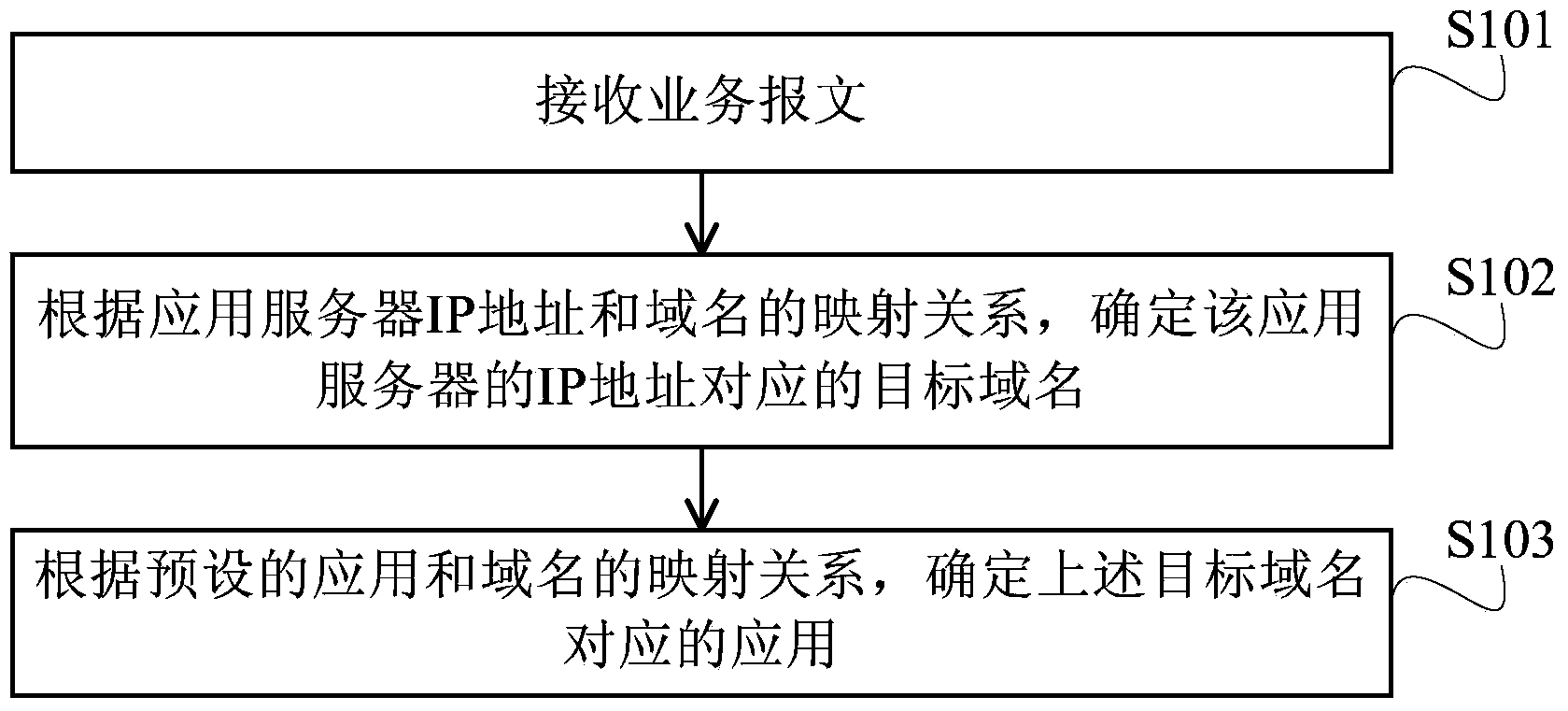
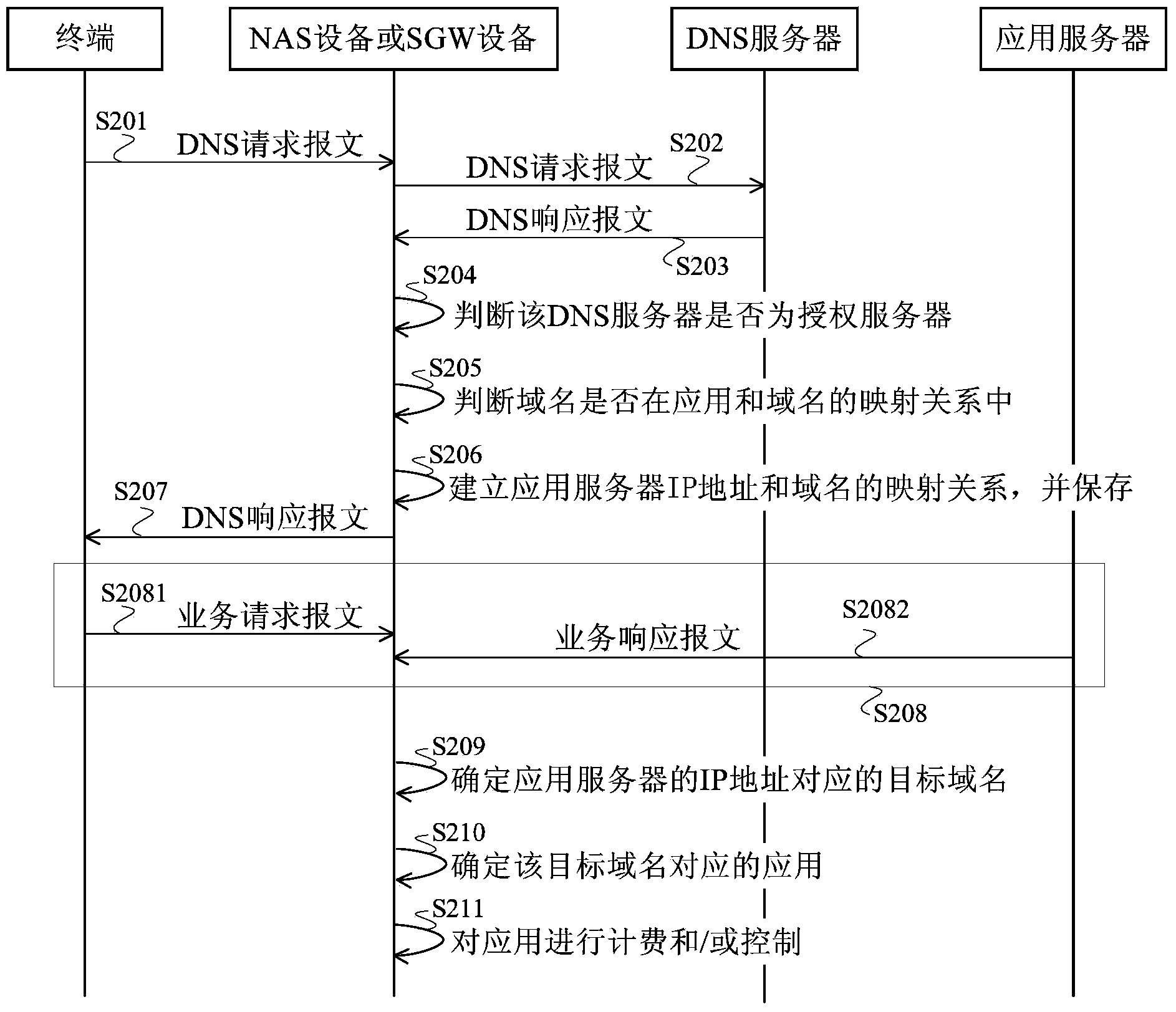
Application identification method and device
The embodiment of the invention provides an application identification method and device. The method comprises the following steps: a service message is received, wherein the service message carries a network protocol IP address of an application server; according to the mapping relation between the IP address of the application server and a domain name, a target domain name corresponding to the IP address of the application server is determined; according to the preset mapping relation between an application and the domain name, the application corresponding to the target domain name is determined. According to the IP address of the application server carried in the service message, the mapping relation between the IP address of the application server and the domain name and the mapping relation between the application and the domain name, the application corresponding to the IP address of the application server is determined, and therefore the application identification method and device realize application identification for communication adopting a proprietary protocol or an encryption protocol.
Owner:HUAWEI TECH CO LTD
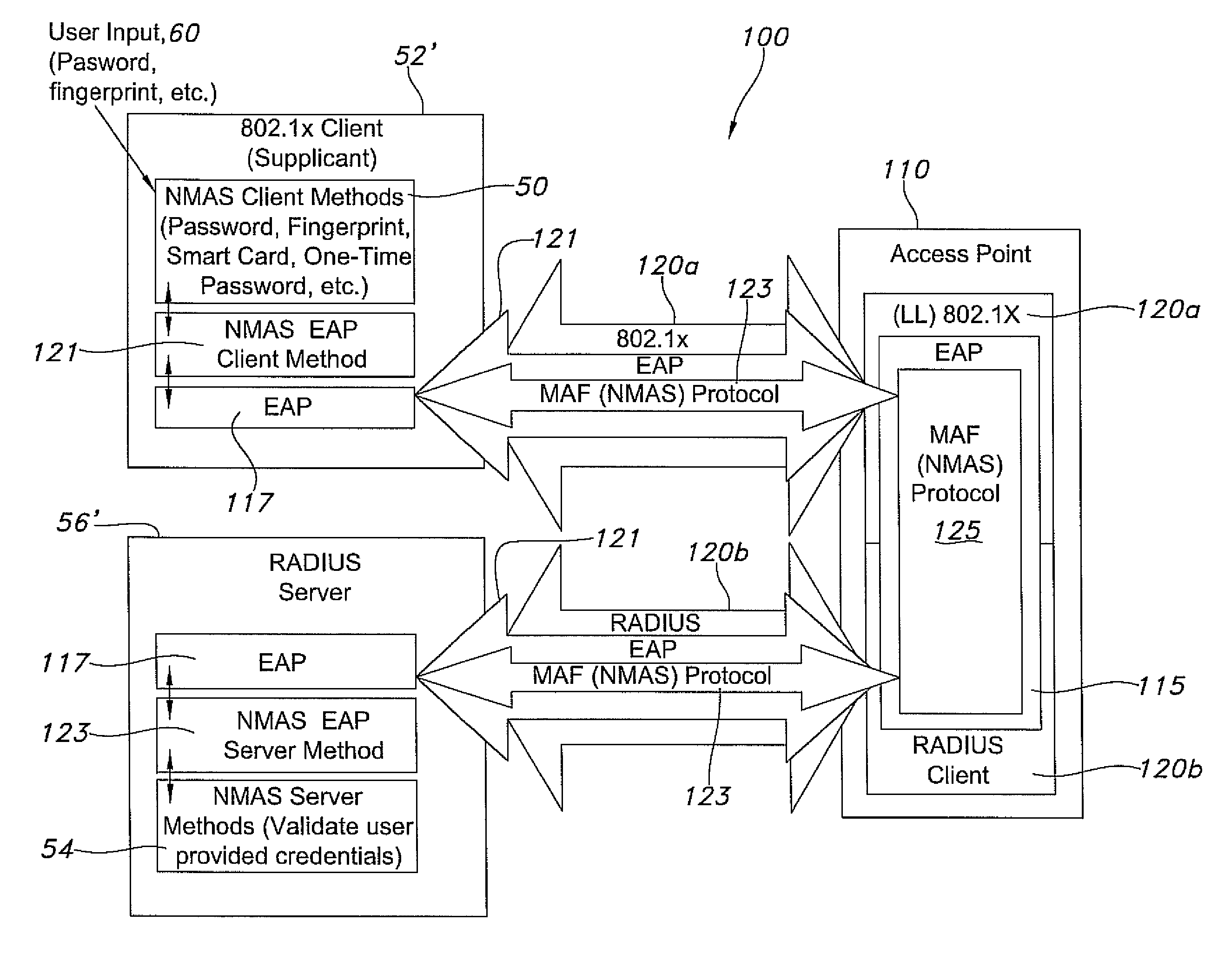
Proprietary protocol tunneling over eap
Methods and apparatus provide tunneling one authentication framework over a more widely accepted framework (e.g., EAP). In this manner, pluralities of strong authentication protocols are wirelessly enabled between a supplicant and server that are not otherwise wirelessly enabled. During use, packets are wirelessly transmitted and received between the supplicant and server according to EAP's prescribed message format, including a wireless access point. In a tunnel, various authentication protocols form the payload component of the message format which yields execution capability of more than one protocol, instead of the typical single protocol authentication. Certain tunneled frameworks include NMAS, LDAP / SASL, Open LDAP / SLAPD, or IPSEC. Computer program products, computing systems and various interaction between the supplicant and server are also disclosed.
Owner:EMC CORP
I/O data interface for packet processors
InactiveUS8848726B1Efficient and simple and flexible and scalableTime-division multiplexData switching by path configurationInformation processingProtocol for Carrying Authentication for Network Access
Systems and methods to process packets of information use an on-chip information processing system configured to receive, resolve, convert, and / or transmit packets of different packet-types in accordance with different protocols. A first packet-type may use a protocol for wired local-area-networking (LAN) technologies, such as Ethernet. A second packet-type may use a proprietary protocol. The proprietary protocol may be used to exchange information with one or more packet processing engines, such as neural processing engines.
Owner:FRIDAY HARBOR LLC
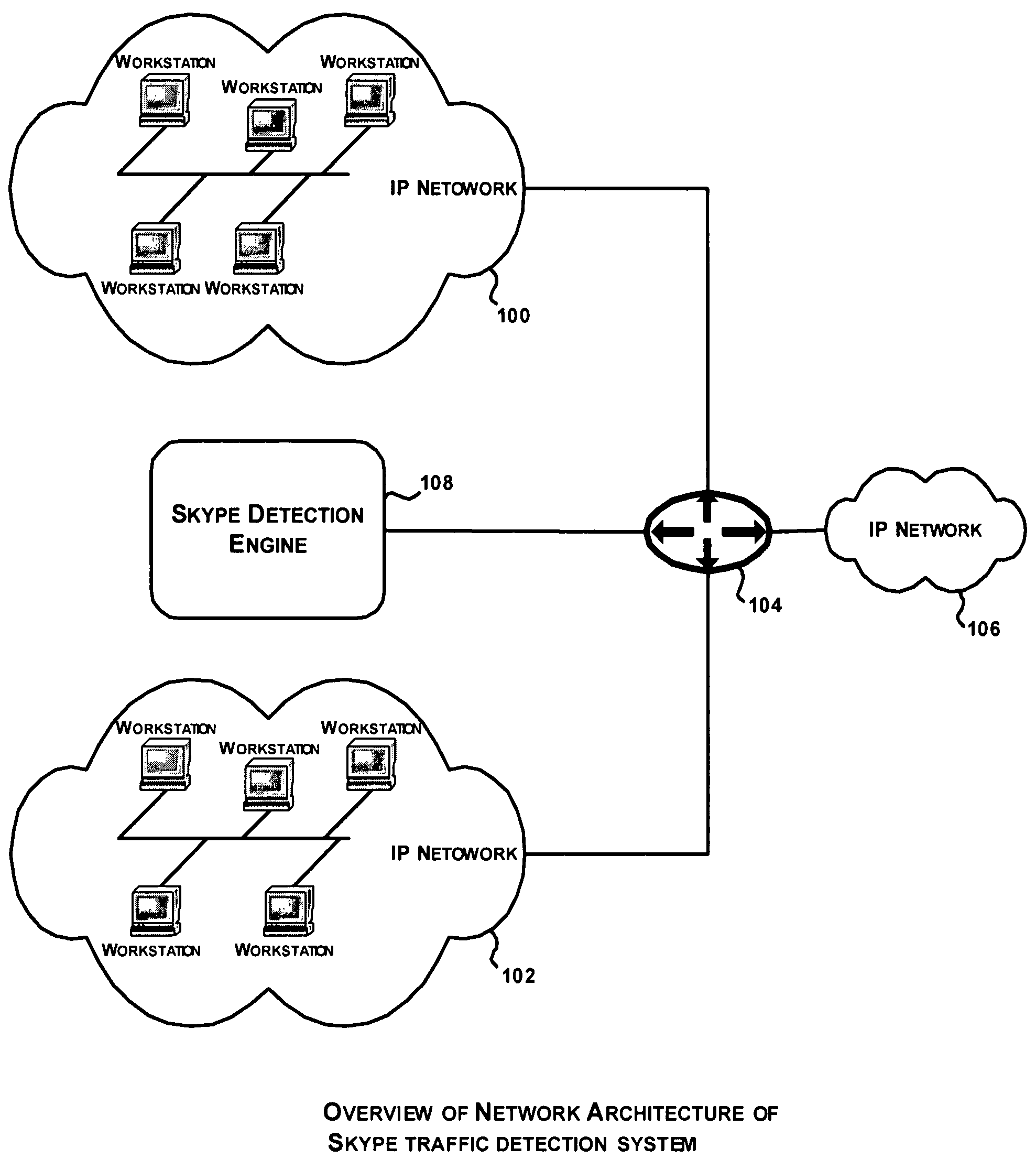
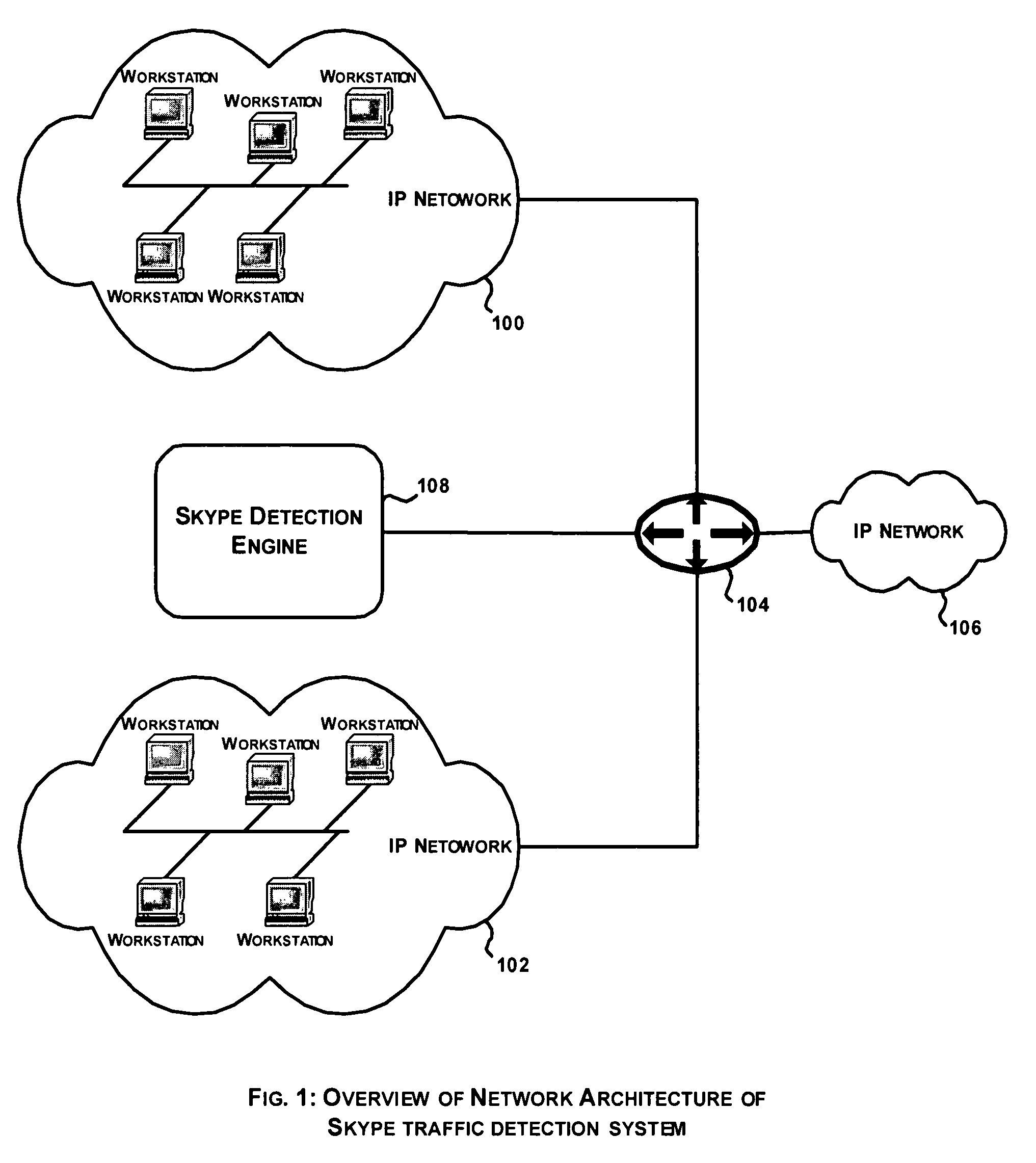
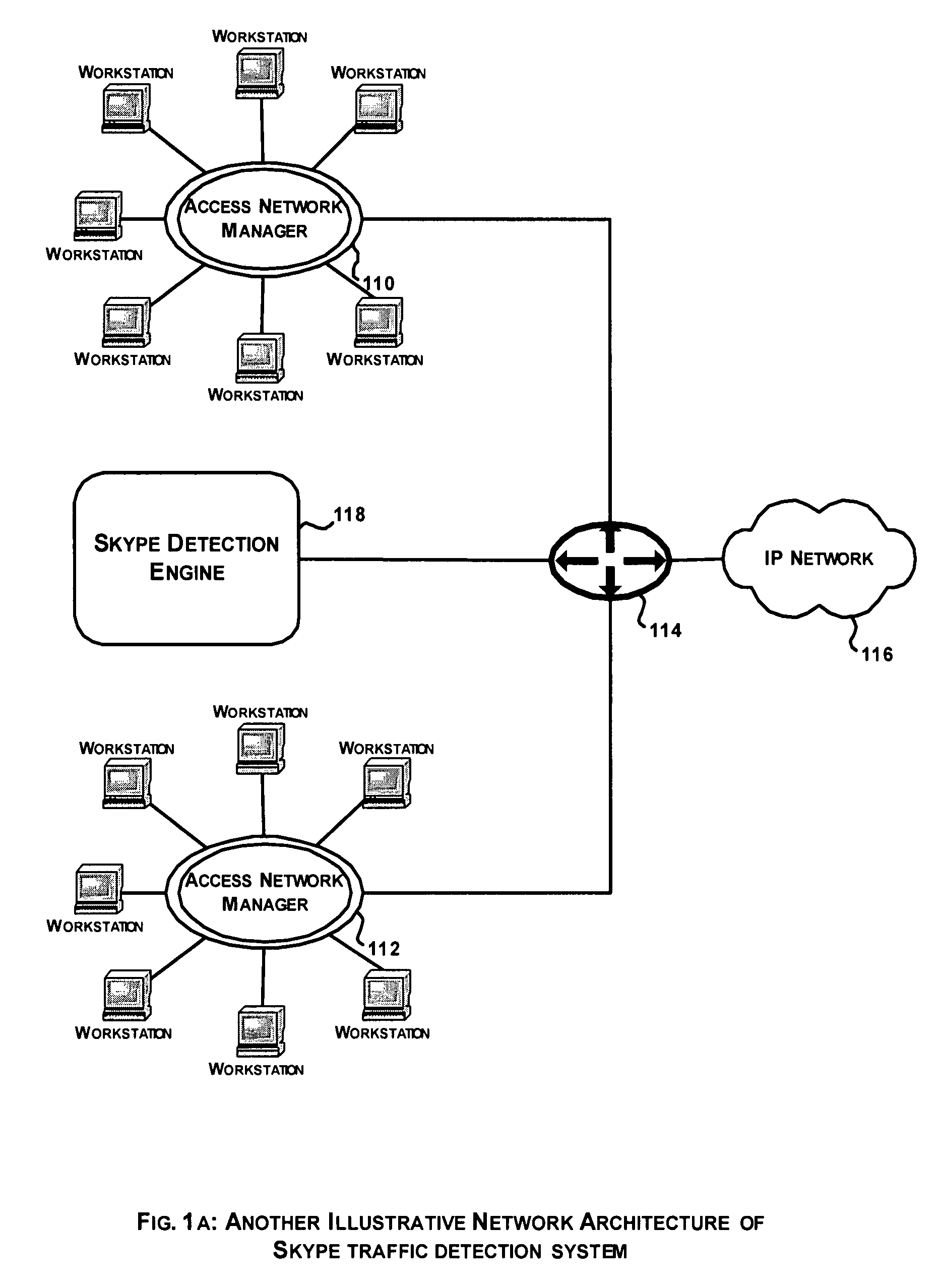
System and method for Skype traffic detection
Networks carry various kinds of traffic and ISPs are keen to analyze the traffic so as to be able to support QoS on the distinct traffic flows. Traffic can be broadly categorized into two types: plain traffic and encrypted traffic. Further, each of these traffic types is based on either a standard protocol or a proprietary protocol. While it is fairly straightforward to analyze traffic that are based on standard protocols, it is extremely difficult to analyze encrypted traffic based on proprietary protocols. A system for Skype traffic detection involves analyzing encrypted traffic based on proprietary peer to peer protocol. The proposed approach is based on building Skype traffic models and using the same to determine Skype traffic in the network traffic.
Owner:TECH MAHINDRA INDIA
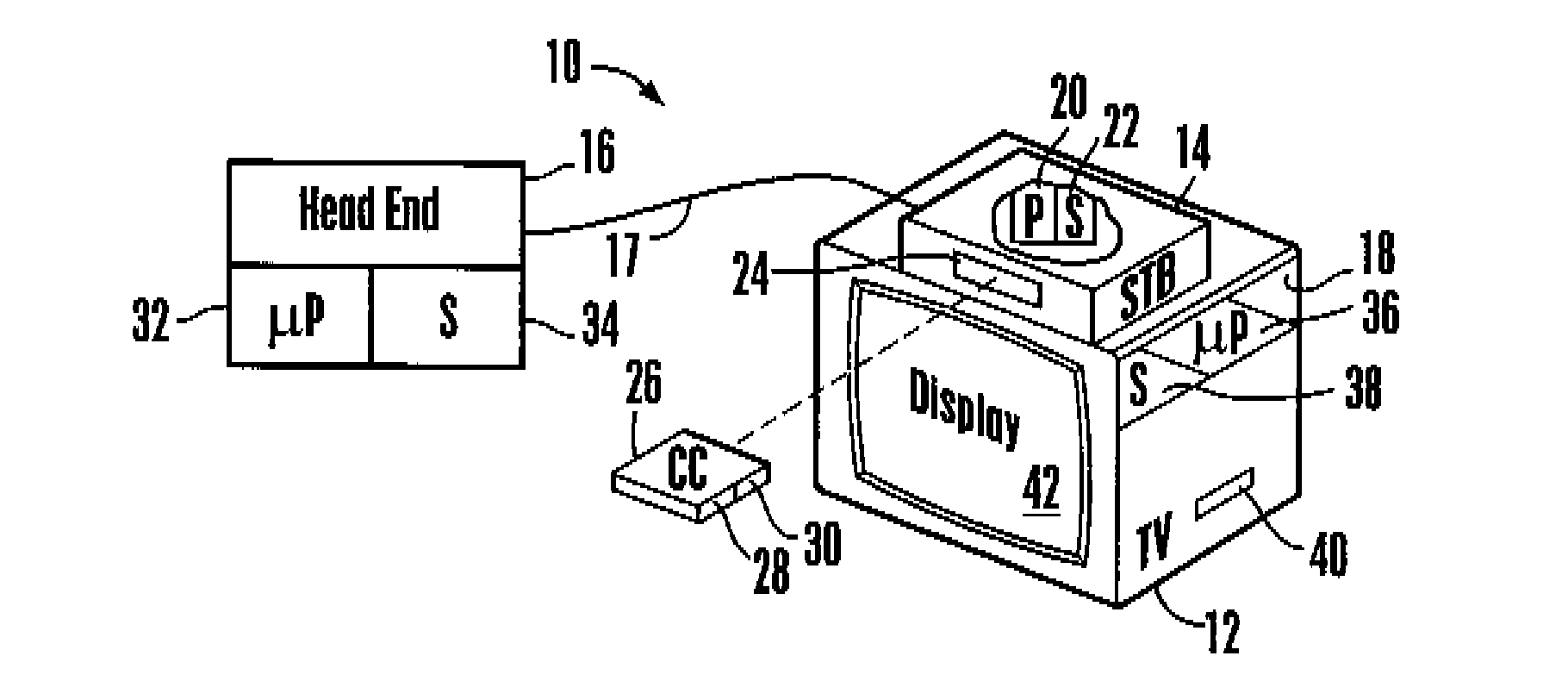
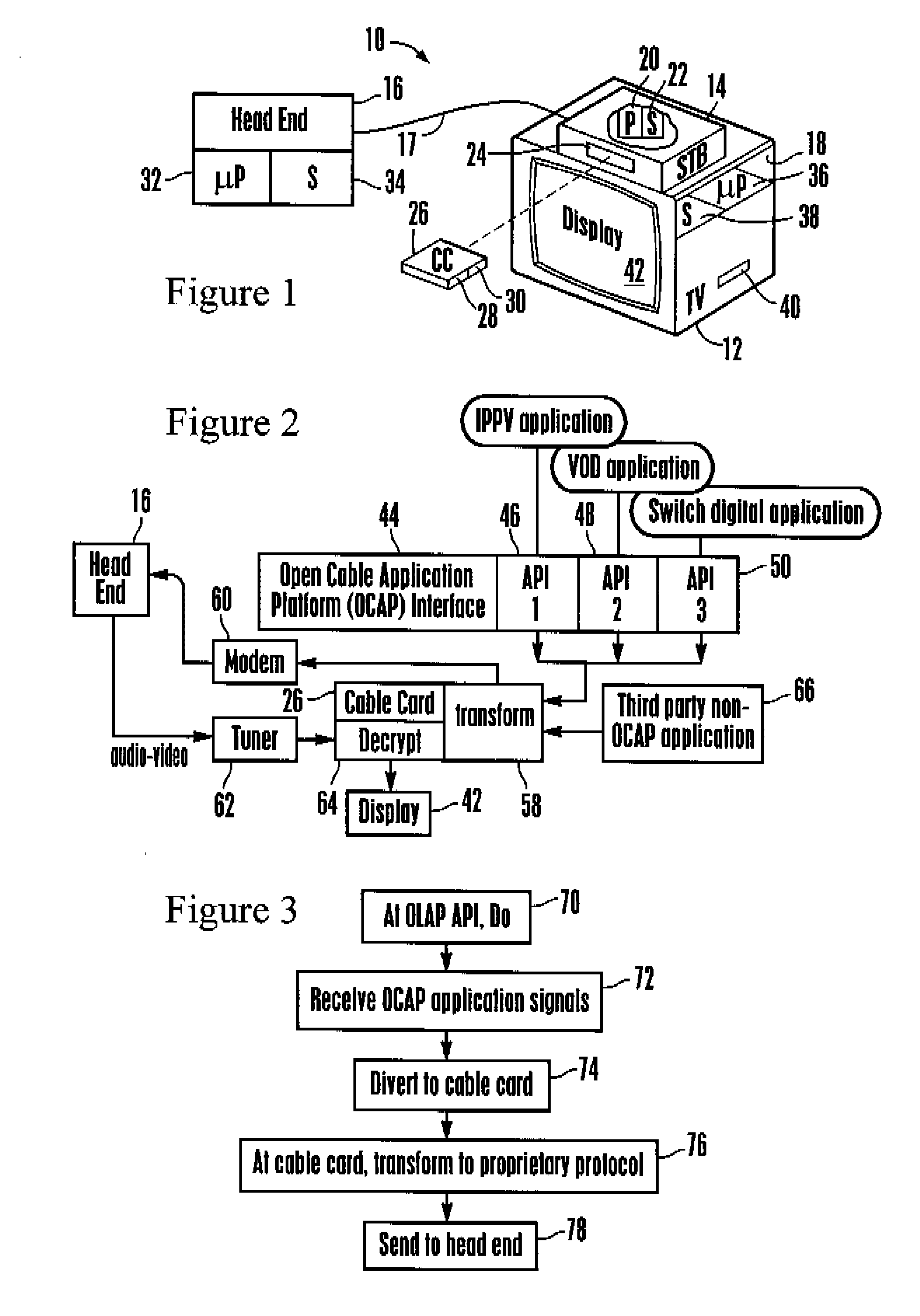
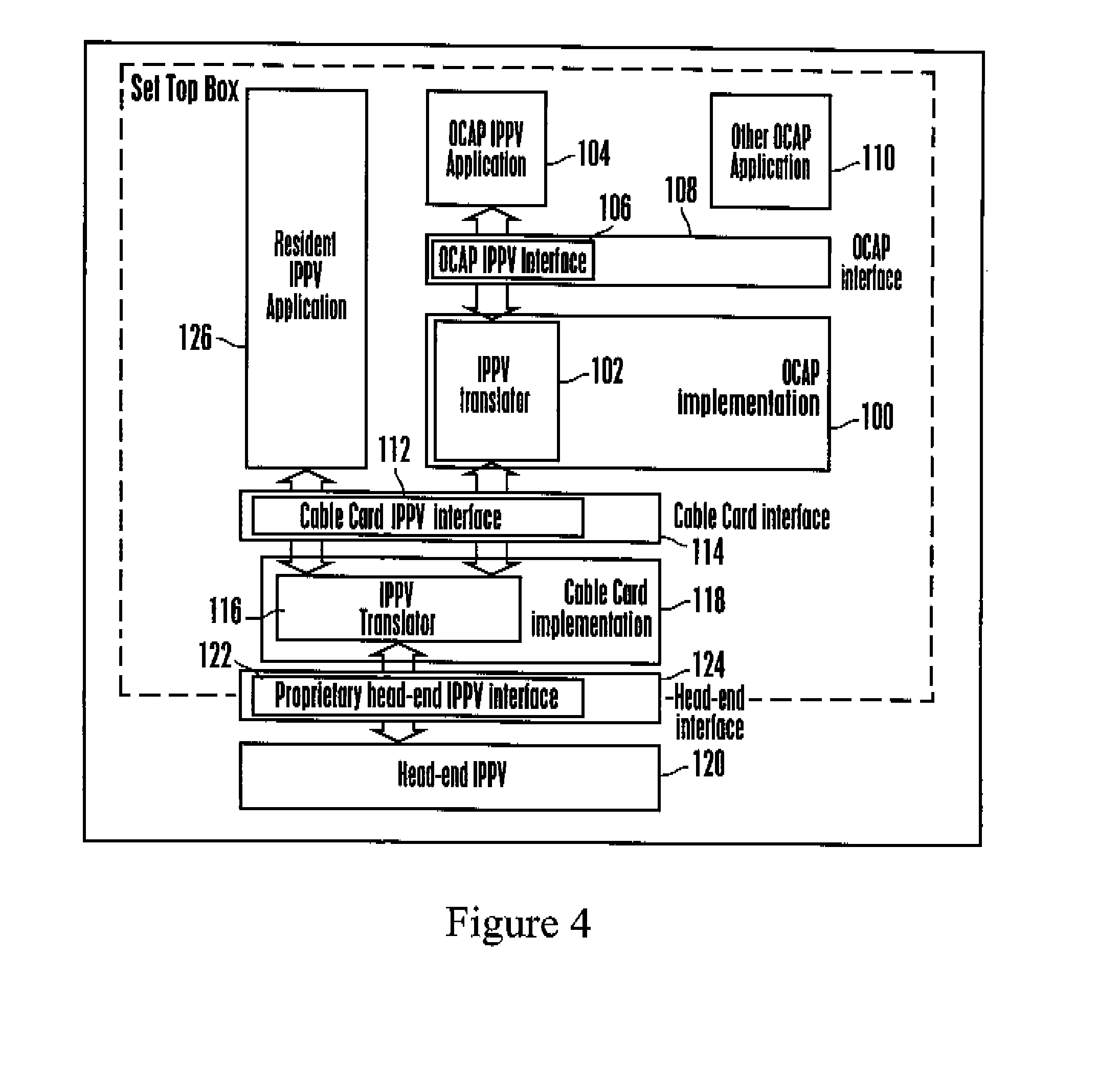
TV receiver using cable card for abstracting open cable application platform (OCAP) messages to and from the head end
InactiveUS20090064262A1Guaranteed to workTwo-way working systemsSelective content distributionDigital videoTelevision receivers
A TV receiver such as a set-top box has an Open Cable Application Platform (OCAP) programming interface that communicates with interactive digital video applications such as pay-per-view applications to enable a viewer to communicate requests, purchase orders, and the like to a head end. A cable card provides both decryption of incoming video from the head end as well as translation functionality that transforms standardized messages into a proprietary protocol recognizable to the head end. The OCAP has an API that interfaces with the application and that directs standardized messages from the application to the standardized interface of the removable cable card ensuring common reliance on the translation functionality built in to the cable card.
Owner:SONY CORP +1
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com