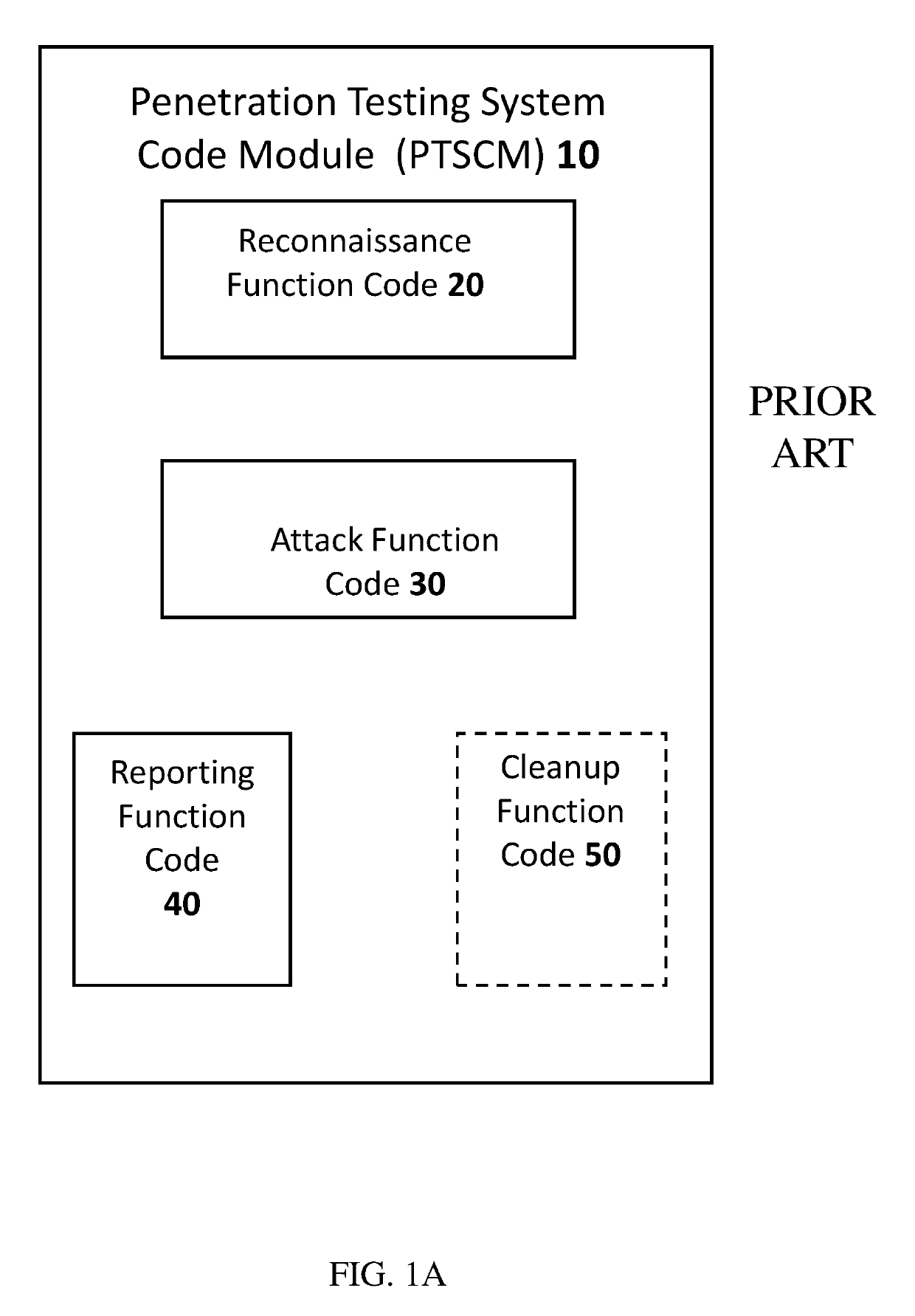
Patents
Literature
613 results about "Penetration test" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
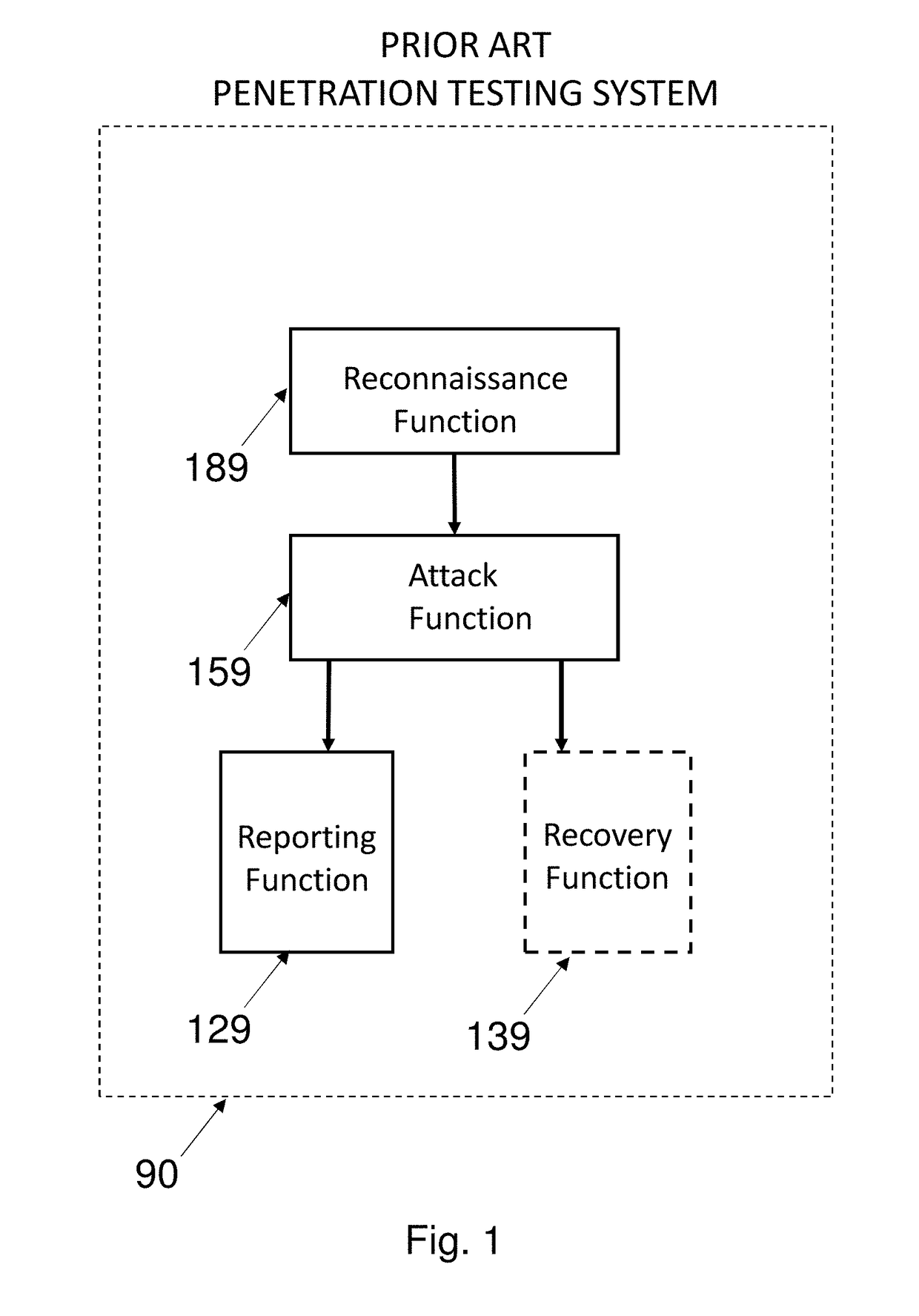
A penetration test, colloquially known as a pen test, pentest or ethical hacking, is an authorized simulated cyberattack on a computer system, performed to evaluate the security of the system. The test is performed to identify both weaknesses (also referred to as vulnerabilities), including the potential for unauthorized parties to gain access to the system's features and data, as well as strengths, enabling a full risk assessment to be completed.
Threat analysis
InactiveUS7530104B1Memory loss protectionUnauthorized memory use protectionChain reactionPenetration test
Virtual penetration testing using threat analysis is disclosed. Threat analysis may be achieved by evaluating attack paths and chain reactions of compromised assets created by threats, threat agents, or threat mechanisms. A threat agent having an existing access level is identified. The existing access level is used to analyze an attack path between the threat agent and an asset. The existing access level is updated if the analysis of the attack path between the threat agent and the asset indicates that an attack along the path would be successful.
Owner:GEN DIGITAL INC
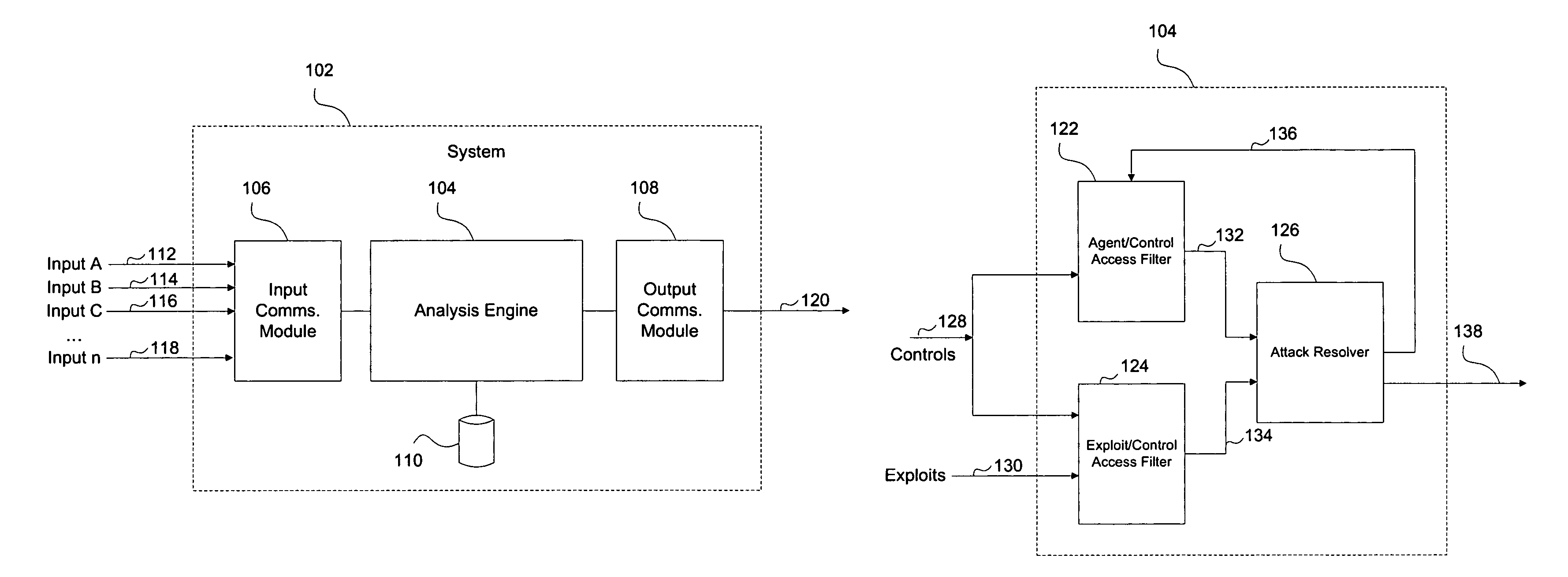
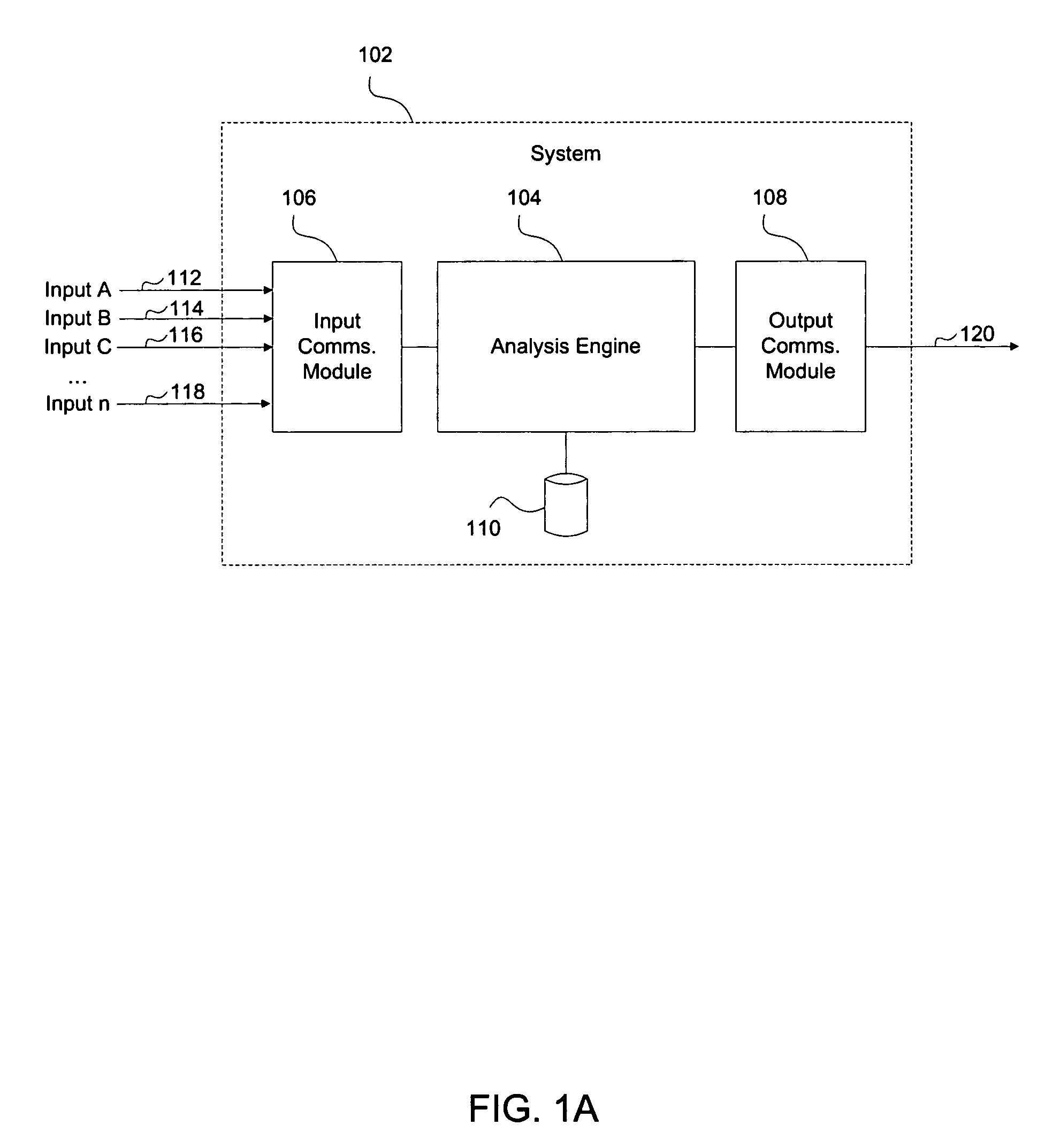
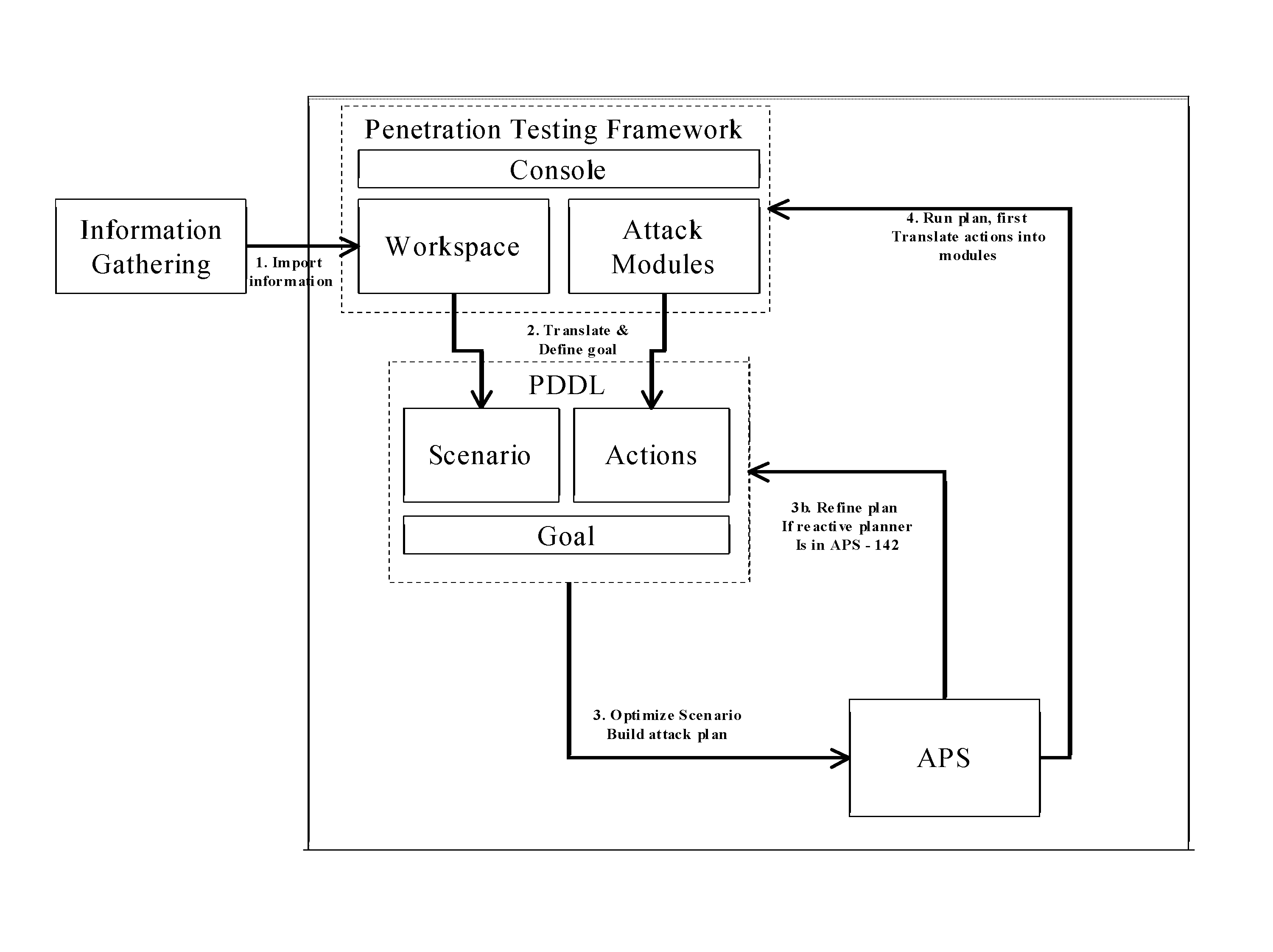
System and method for extending automated penetration testing to develop an intelligent and cost efficient security strategy
ActiveUS20110035803A1Memory loss protectionError detection/correctionProgram planningSecurity policy
A system and method for extending automated penetration testing of a target network is provided. The method comprises: computing a scenario, comprises the steps of: translating a workspace having at least one target computer in the target network, to a planning definition language, translating penetration modules available in a penetration testing framework to a planning definition language, and defining a goal in the target network and translating the goal into a planning definition language; building a knowledge database with information regarding the target network, properties of hosts in the network, parameters and running history of modules in the penetration testing framework; and running an attack plan solver module, comprising: running an attack planner using the scenario as input, to produce at least one attack plan that achieves the goal, and executing actions defined in the at least one attack plan against the target network from the penetration testing framework.
Owner:FORTRA LLC
Soil one-dimensional consolidation, penetration and stress looseness comprehensive test apparatus and method of use thereof
InactiveCN1699997AEliminate the effects of excessive errorEarth material testingMaterial strength using tensile/compressive forcesCombined testSoil science
The invention discloses a soil one-dimensional consolidation, penetration, stressing relaxation combined test instrument and usage, which posits punch inside a punch cavity at the bottom of pressure container. It can do consolidation and compression to the same soil sample K0, it also can do soil sample penetration test and stressing relaxation test directly and simultaneously. It can test the soil sample's value of coefficient of static lateral pressure K0 and the process of pore water pressure followed by time. The test instrument and method can arrange soil's consolidation characteristic parameter by test outcome and using theoretical formula penetration method. It can do soil's theological behavior analysis by the outcome of stressing relaxation test.
Owner:CHANGAN UNIV
System and method for probabilistic attack planning
ActiveUS8490193B2Memory loss protectionUnauthorized memory use protectionProgram planningNetwork attack
Owner:FORTRA LLC
System and Method for Providing Application Penetration Testing
InactiveUS20080263671A1Memory loss protectionError detection/correctionOperational systemNetwork agent
A system and method provide application penetration testing. The system contains logic configured to find at least one vulnerability in the application so as to gain access to data associated with the application, logic configured to confirm the vulnerability and determine if the application can be compromised, and logic configured to compromise and analyze the application by extracting or manipulating data from a database associated with the application. In addition, the method provides for penetration testing of a target by: receiving at least one confirmed vulnerability of the target; receiving a method for compromising the confirmed vulnerability of the target; installing a network agent on the target in accordance with the method, wherein the network agent allows a penetration tester to execute arbitrary operating system commands on the target; and executing the arbitrary operating system commands on the target to analyze risk to which the target may be exposed.
Owner:HELP SYST LLC
Method and device for system penetration testing
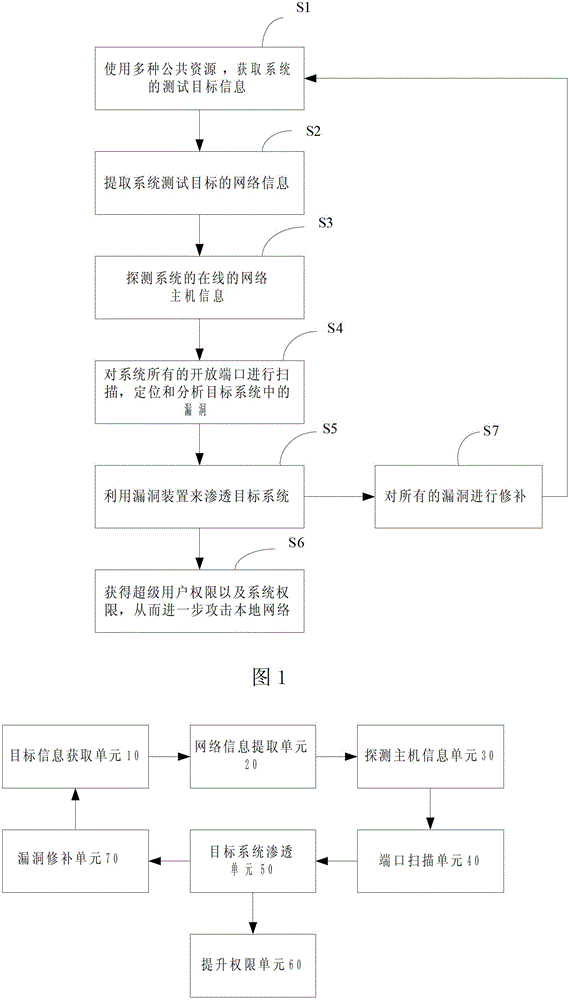
ActiveCN104009881ASpotting weaknessesDiscover securityData switching networksSystem testingPublic resource
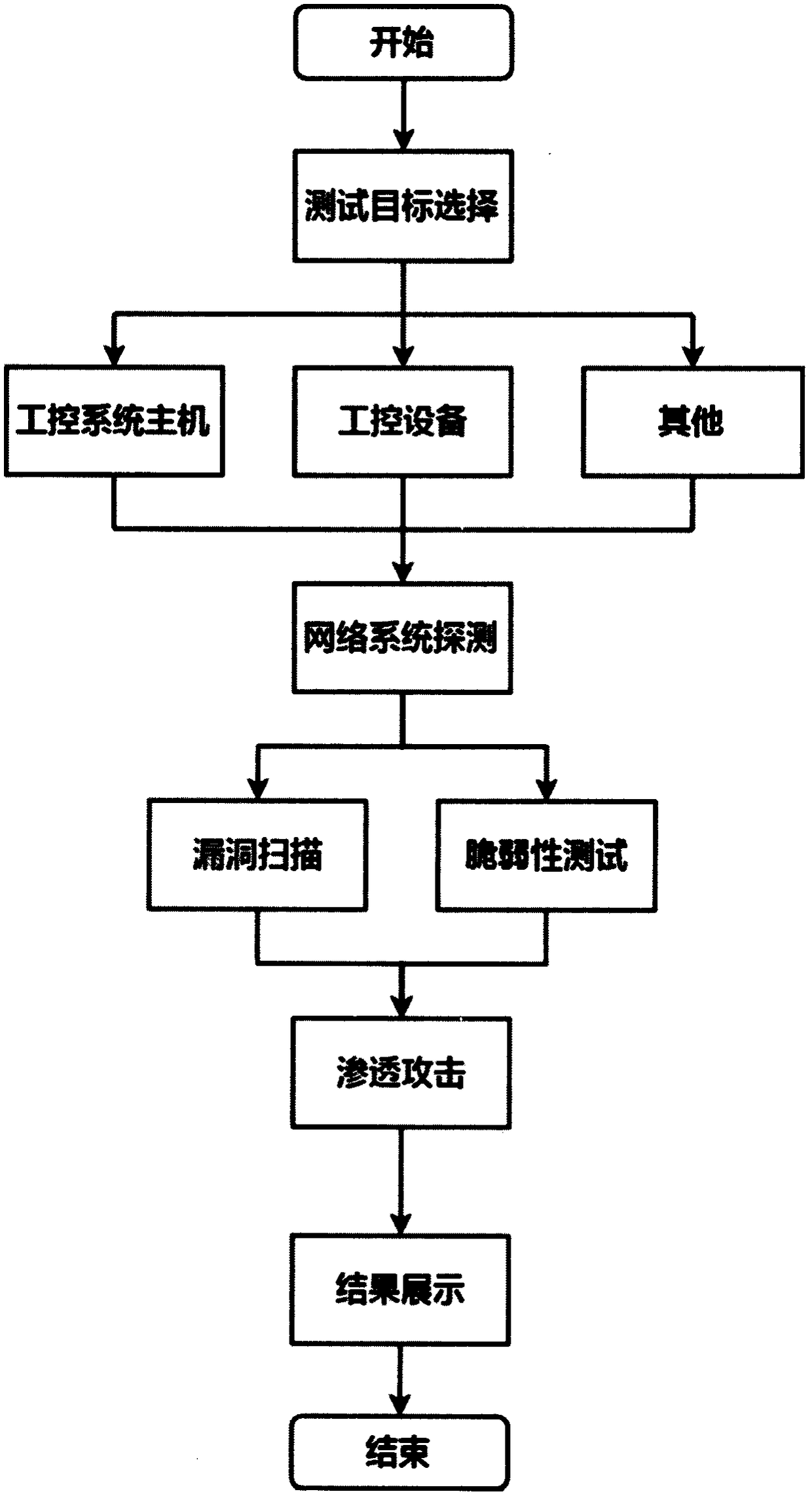
The invention discloses a method for system penetration testing, comprising the following steps: S1, test target information of a system is acquired by use of a variety of public resources; S2, network information of a system test target is extracted; S3, online network host information of the system is detected; S4, all open ports of the system are scanned, and all services are enumerated through all the ports to position and analyze a loophole in the target system; and S5, the target system is penetrated by a loophole device. The invention further discloses a device for system penetration testing. By adopting the method and the device, provided by the invention, for system penetration testing, through static analysis of a source code, on one hand, potential risks can be identified, software can be detected from inside, and the safety of the code can be improved, and on the other hand, the quality of the code can be further improved, and the software security can be greatly improved.
Owner:GUANGDONG POWER GRID CO LTD INFORMATION CENT
Automatic penetration testing method for information system security
InactiveCN103532793AImprove integritySpend less timeData switching networksTarget controlGoal system
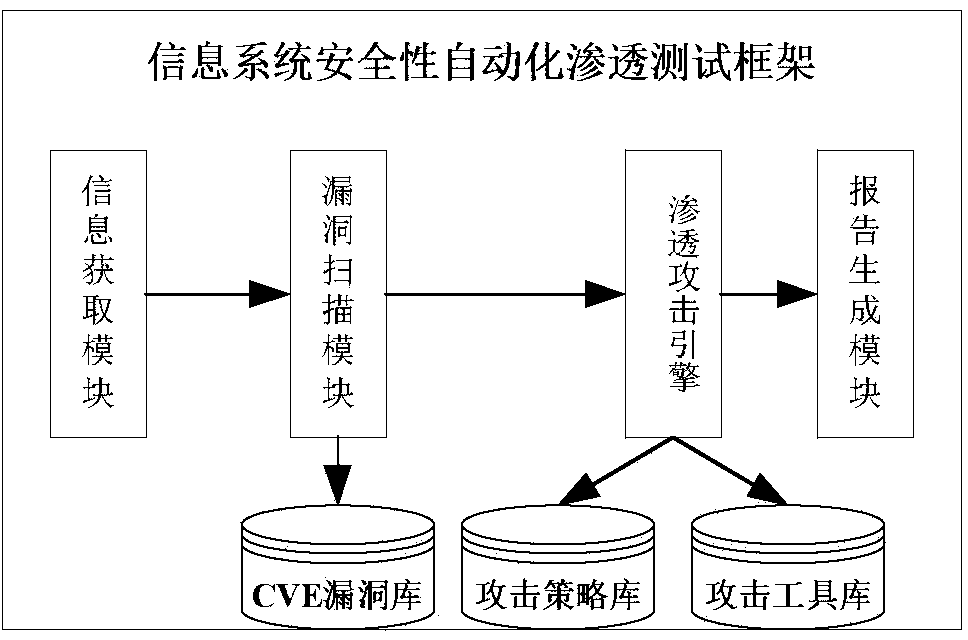
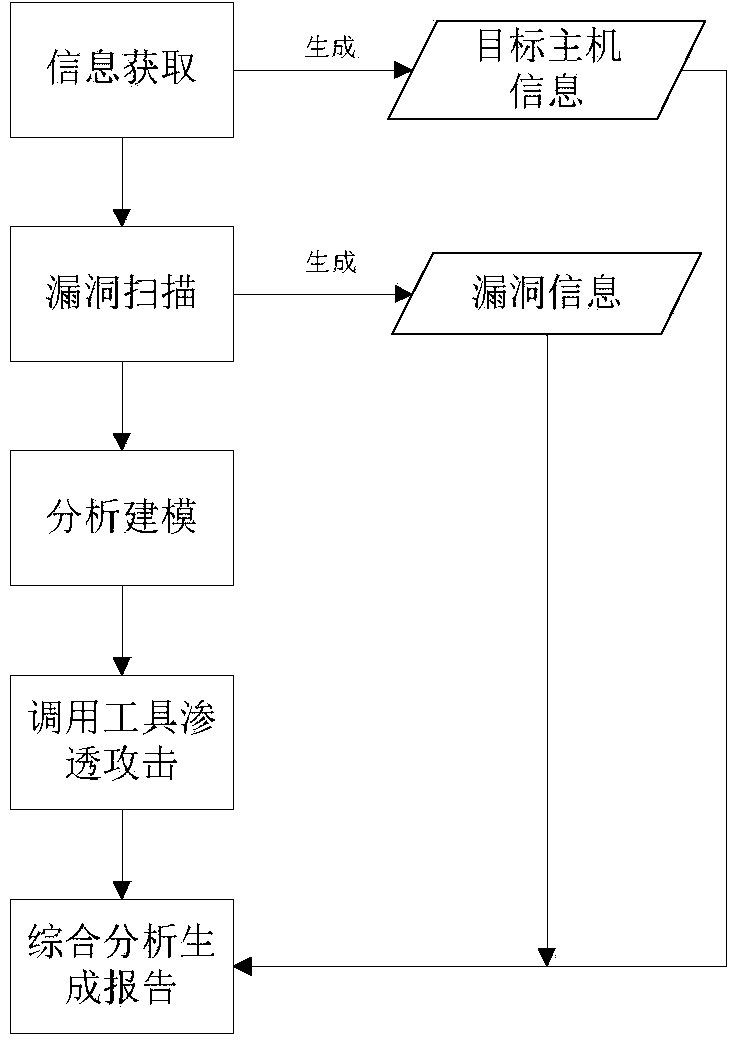
The invention belongs to the technical field of network security and discloses an automatic penetration testing method for information system security. A penetration testing platform is built to automatically scan the mainframe state of an information system and the security loopholes of a topological structure and the information system, to analyze the loophole information, to automatically transfer a verification script in a loophole verification base for attacking a target system, to obtain and improve the target control authority and to remove the access trace after finishing the penetration attack. Finally, the whole penetration testing process and result are recorded and analyzed to generate a testing report. According to the method, the penetration testing flow is comprehensively considered and the existing security analyzing tools are fully utilized to design various tools for packing an automatic penetration testing module, so that the automatic transfer and execution of the tools are achieved, and the completeness of the penetration testing process is improved. Through the exchange utilization of data among different modules and the automatic analysis and arrangement of the result output of the security analyzing tools, the efficiency and automatic degree of the penetration testing are improved.
Owner:706 INST SECOND RES INST OF CHINAAEROSPACE SCI & IND
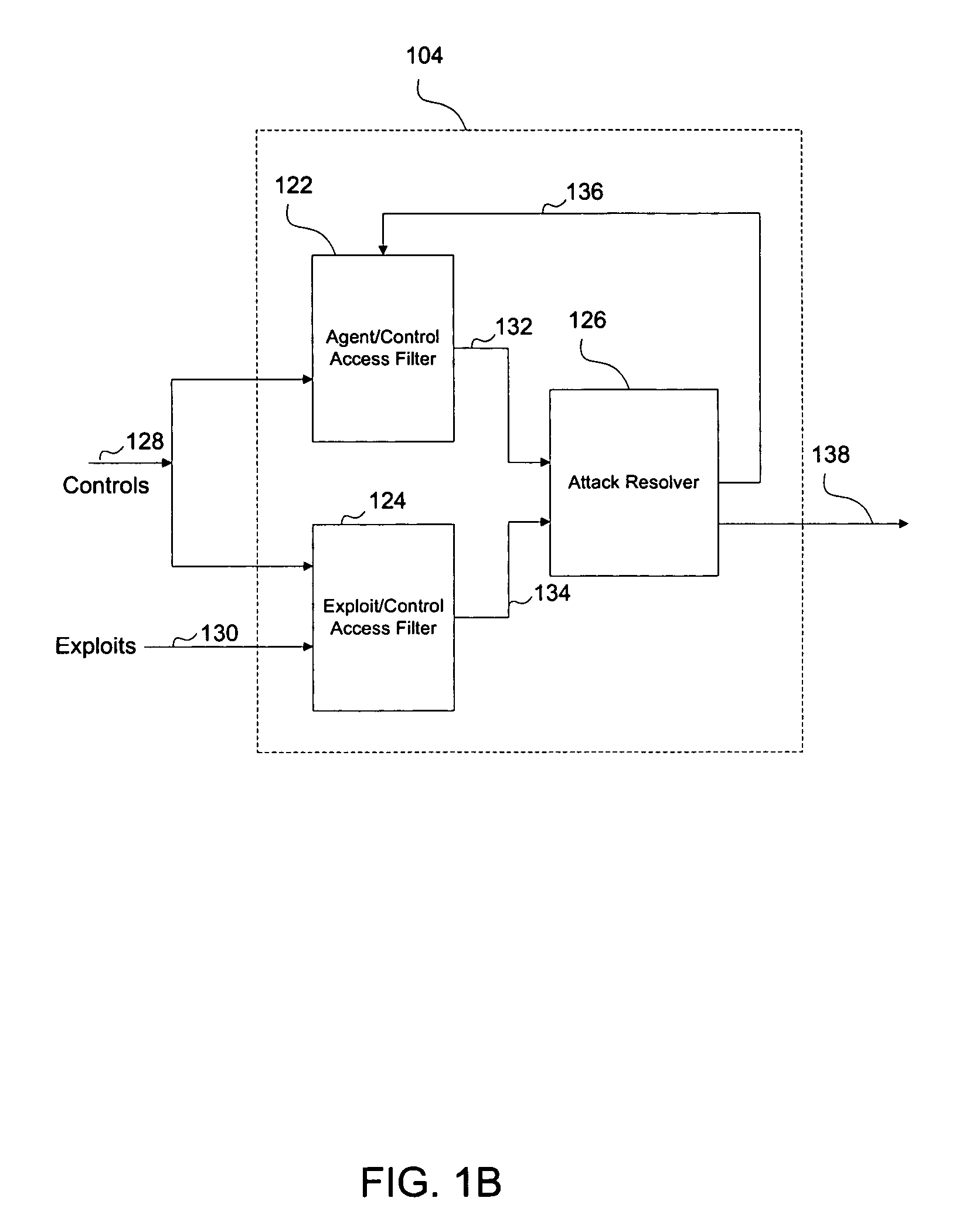
System and method for probabilistic attack planning
ActiveUS20110061104A1Minimize the numberMemory loss protectionUnauthorized memory use protectionNetwork attackRunning time
A system and method for automated probabilistic planning of network attacks against infrastructures of computer networks and applications is provided. The embodiments automate the analysis and probabilistic planning of multi-step attacks to computer and application networks (in particular in the context of automating penetration tests), optimizing with respect to one of the following metrics: the probability of success of the actions, a numerical parameter that must be minimized (e.g., running time), or the number of logs generated by the control devices in the target network.
Owner:FORTRA LLC
Cross-site script vulnerability detection method based on percolation test
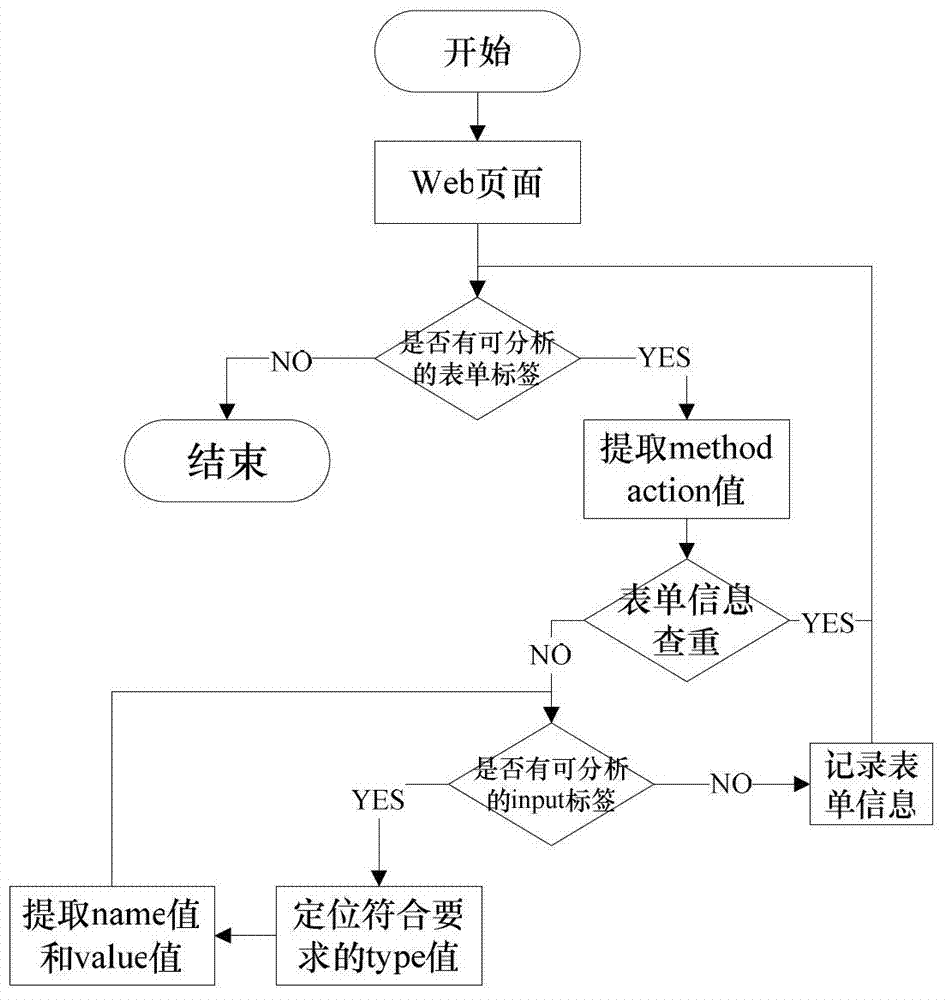
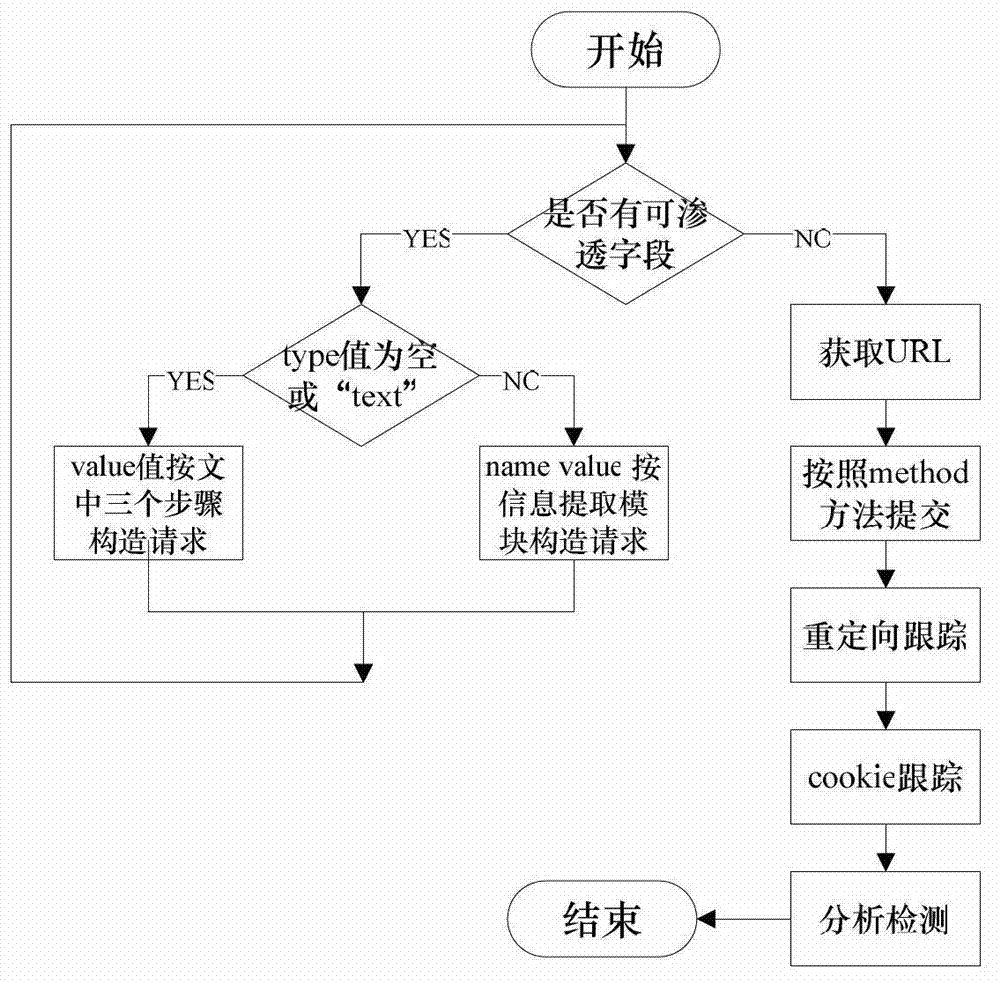
InactiveCN102819710AReduce incomplete analysisImprove detection efficiencyComputer security arrangementsSoftware testing/debuggingWeb siteComputer science
The invention discloses a cross-site script vulnerability detection method based on a percolation test. According to the cross-site script vulnerability detection method, the technical problem of low detection efficiency in a traditional cross-site script vulnerability detection method is solved. The technical scheme provided by the invention is that the cross-site script vulnerability detection method comprises the following steps of: firstly, acquiring a page; secondly, extracting form information and carrying out the percolation test on the extracted form; and finally, carrying out session retaining and redirection tracking. Due to the adoption of a session retaining and redirection tracking method, the conditions that the analysis for Web pages is incomprehensive are reduced, all pages of a Web site are analyzed and detected and further the automatic detection capability is improved. According to a percolation test strategy, the detection range of the XSS (Cross-Site Script) is gradually narrowed and the depth detection for the safe pages is avoided. While test statements are injected, test statements for closing HTML (Hypertext Markup Language) statements are actively constructed according to the returned page information, so that interaction frequencies with a server are reduced and the detection efficiency of the XXS vulnerabilities of large complex Websites is improved.
Owner:NORTHWESTERN POLYTECHNICAL UNIV
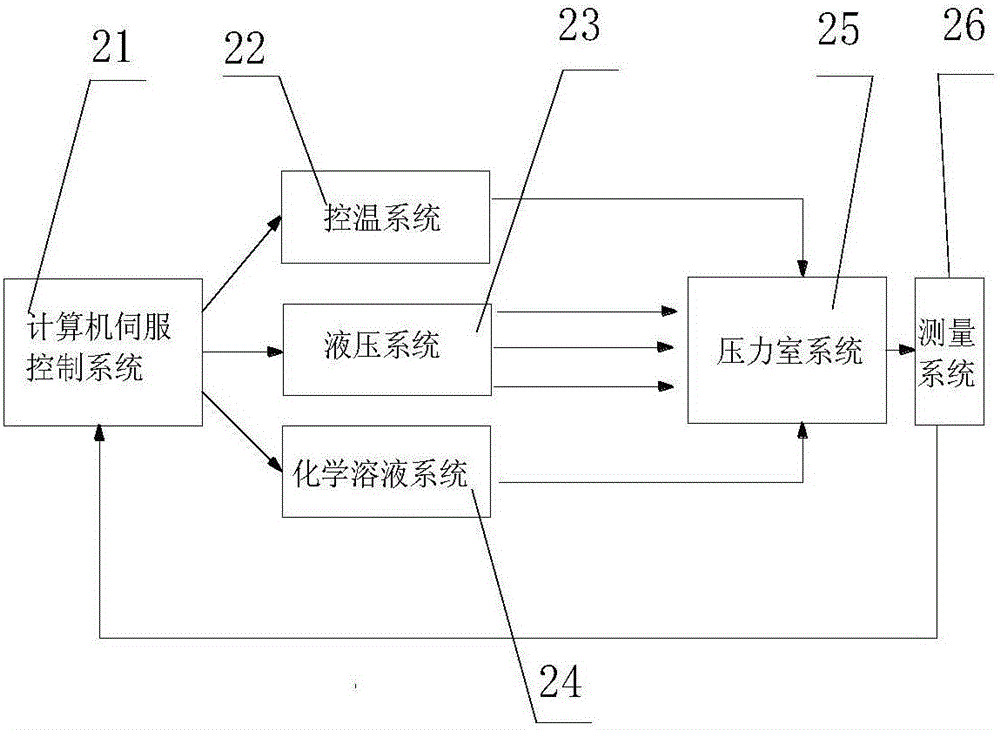
Multi-field coupling penetration test device and method for cracked rock
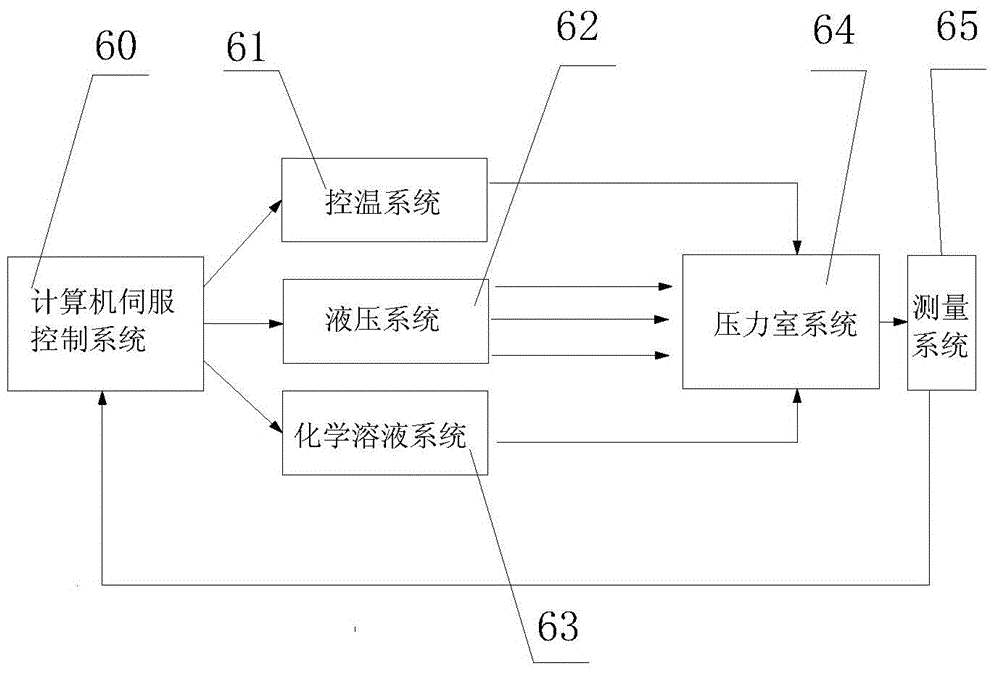
ActiveCN104819926AGuaranteed real temperaturePermeability/surface area analysisChemical solutionAxial pressure
The invention discloses a multi-field coupling penetration test device and a multi-field coupling penetration test method for cracked rock. The device comprises a computer servo control system, a confining pressure chamber, a hydraulic system, a temperature control system and a chemical solution system, wherein the hydraulic system and the confining pressure chamber are connected by virtue of a confining pressure device, an axial pressure device and a seepage device respectively; the temperature control system is arranged outside the confining pressure chamber; and the chemical solution system is connected with the seepage device. The test method comprises the following steps: opening the hydraulic system, and loading an oil source; putting a sample into a pressure chamber; loading axial pressure and confining pressure; loading the seepage pressure; loading a chemical field; applying temperature; and measuring the data. The four-field loading systems are independent from one another, the evolution test research of permeability characteristics and mechanical properties of the cracked rock can be really simulated under high water pressure, large hydraulic gradient, temperature change and water chemistry complicated conditions, and the whole-process experimental research of rock deformation damage and penetration, stress, chemistry and temperature coupling can be performed.
Owner:HOHAI UNIV
Overload test and detection device of gas gun
InactiveCN102192690ASimple and fast operationStrong reliabilityAmmunition testingOperabilityEngineering
The invention relates to an ammunition overload detection device, and in particular relates to an overload test and detection device of a gas gun, wherein the device provided by the invention can be used for solving the technical problems such as inconvenience in operation and use and the like of the existing air gun penetration test device. The overload test and detection device of the gas gun comprises a frame body which is provided with an overload test air gun launching device, a charging overload test bomb, an overload test protective box and an overload test target plate replacement device. Comprehensively, compared with the prior art, in the technical scheme provided by the invention, the target plate replacement device for an overload test, the overload test protective box and a small-size penetration test bomb are designed specially for the small-size charging and priming system air gun overload performance test, principles and methods relevant to the mechanical design are utilized, the design scheme has the characteristics of being vigorous, practicable, convenient and the like, and the overload test and detection device has the advantages of favorable practical value, reliable operability and accurate experiment result.
Owner:ZHONGBEI UNIV
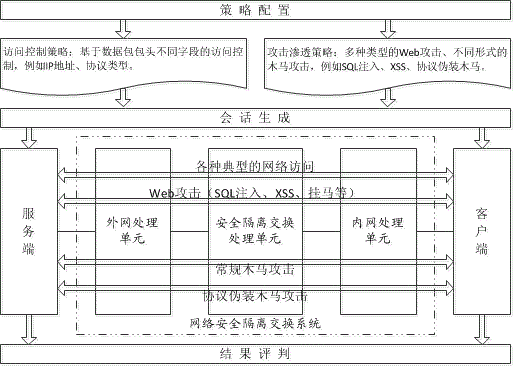
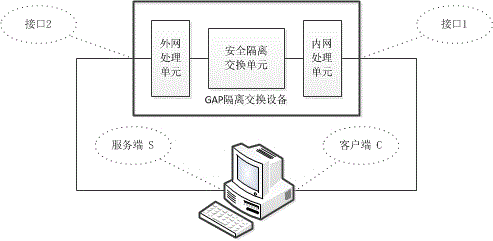
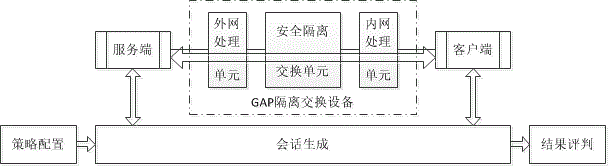
Penetration testing method for GAP isolation and exchange device
InactiveCN103916384AImplement security testingData switching networksComputer hardwareNetwork packet
The invention discloses a penetration testing method for a GAP isolation and exchange device. The method comprises the concrete steps that (a) policy configuration is tested, wherein according to the working principle, the function and the implementation mode of the tested device, applicable test cases are selected from a preset penetration testing rule base, and test environment parameters are configured; (b) a network attack session is generated, wherein an independent client program and an independent server program are established, hosts in networks at the two ends of the tested device are respectively simulated, afterwards, test plugins corresponding to the test cases are respectively called, and the test environment parameters configured in the step (a) are passed to the test plugins; the test plugins produce corresponding data packets in real time, the data packets are sent through a client or a server, and therefore the network attack session is generated; (c) test results are evaluated, wherein the test results of the test cases are evaluated according to the completion condition of the network attack session and the warning information of the tested device. By the application of the penetration testing method for the GAP isolation and exchange device, automated security testing for the GAP isolation and exchange device can be achieved.
Owner:中国人民解放军信息安全测评认证中心 +1
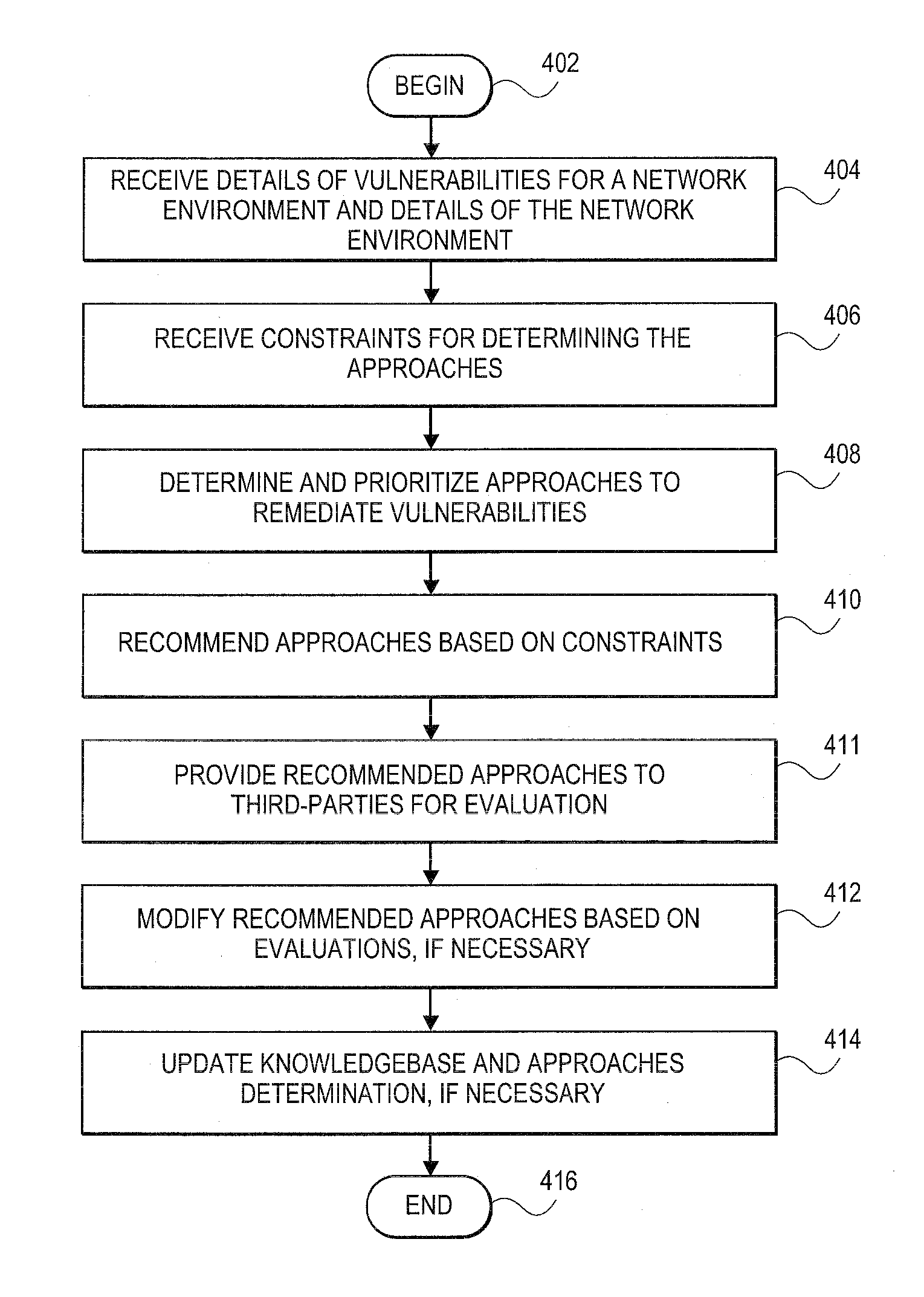
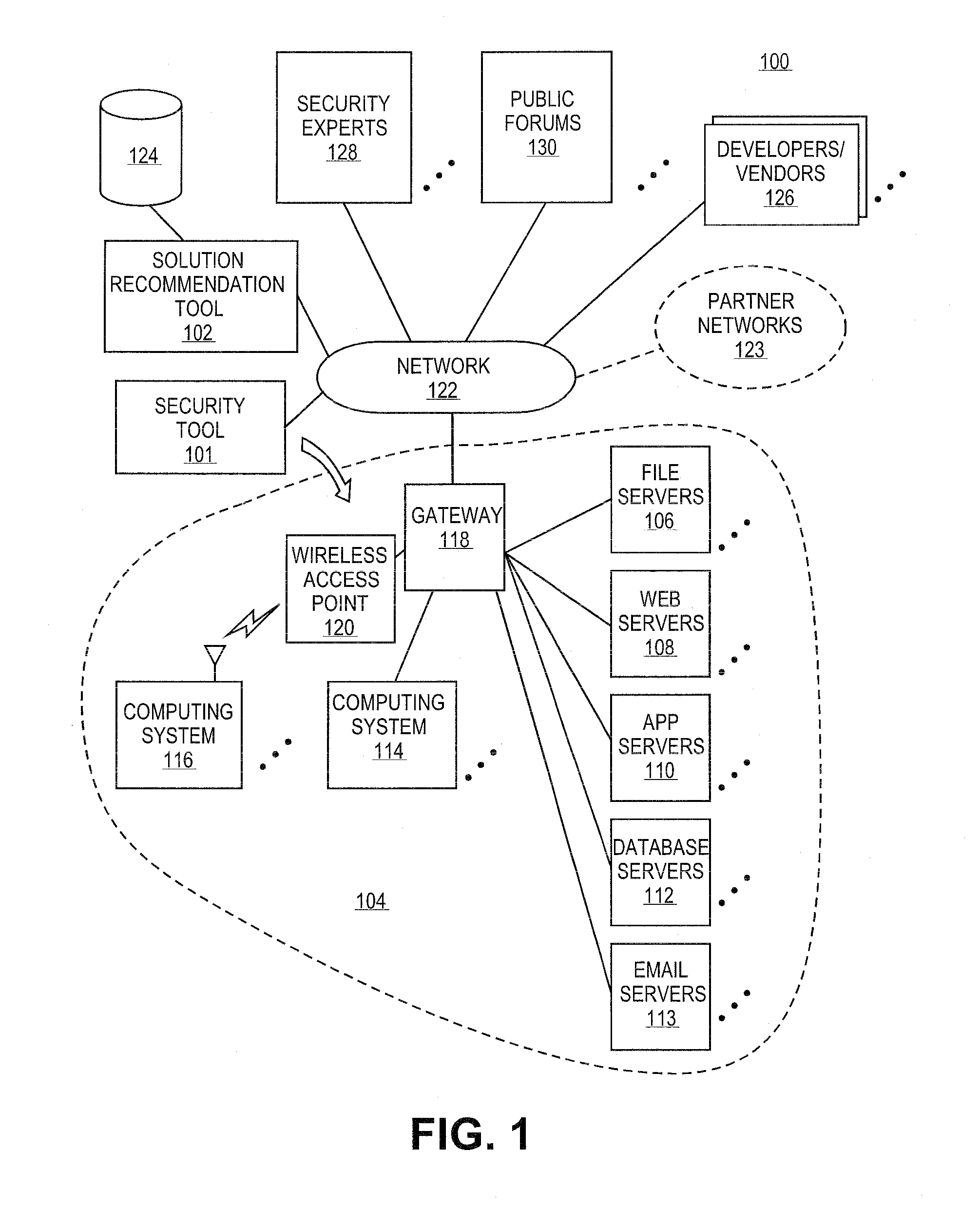
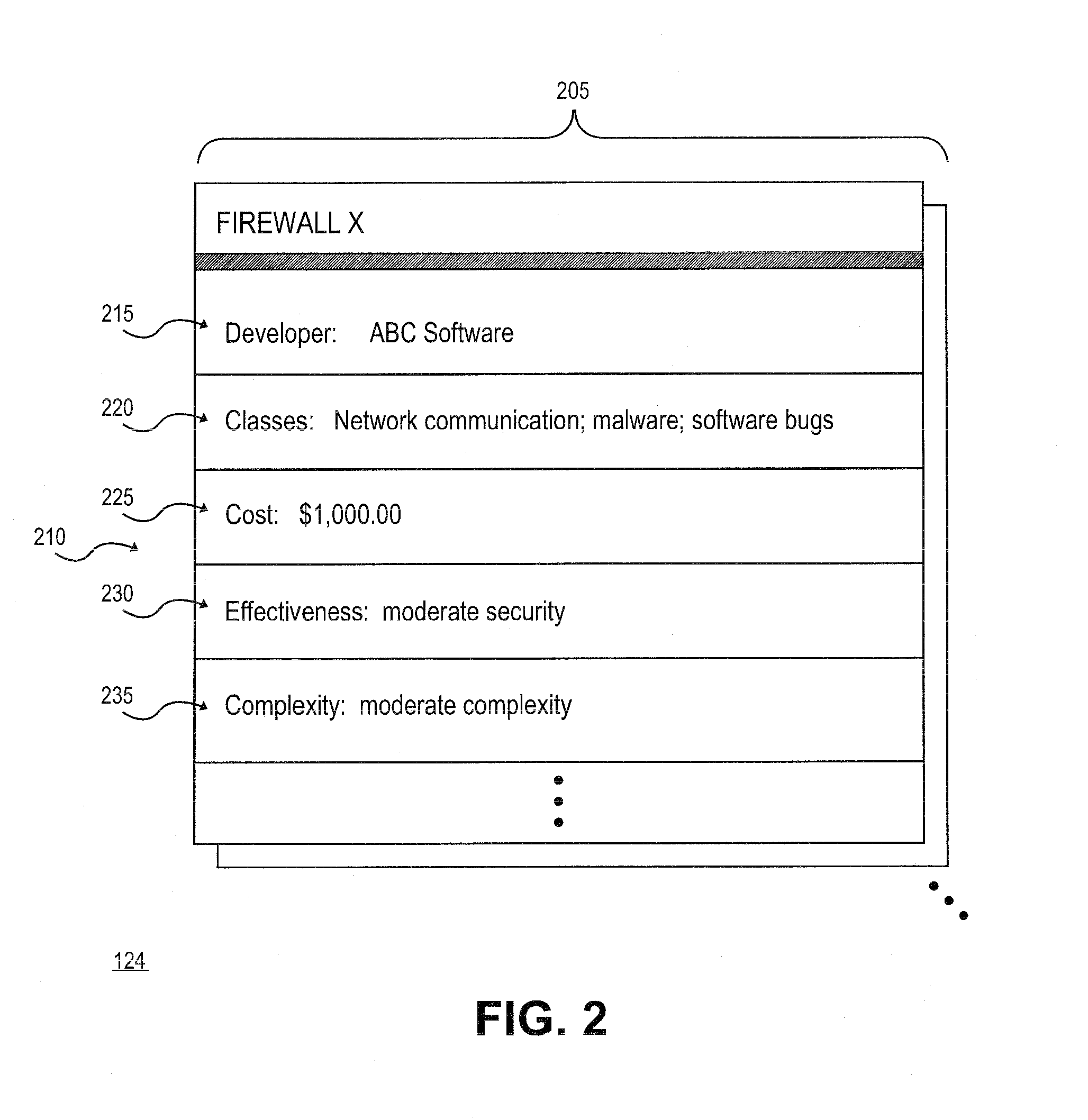
Methods and systems for providing recommendations to address security vulnerabilities in a network of computing systems
A solution recommendation (SR) tool can receive vulnerabilities identified by a vulnerability scanner and / or penetration testing tool. The SR tool can determine various approaches for remediating or mitigating the identified vulnerabilities, and can prioritize the various approaches based on the efficiency of the various approaches in remediating or mitigating the identified vulnerabilities. The SR tool can recommend one or more of the prioritized approaches based on constraints such as cost, effectiveness, complexity, and the like. Once the one or more of the prioritized approaches are selected, the SR tool can recommend the one or more prioritized approaches to third-party experts for evaluation.
Owner:RAPID7
Testing for Risk of Macro Vulnerability
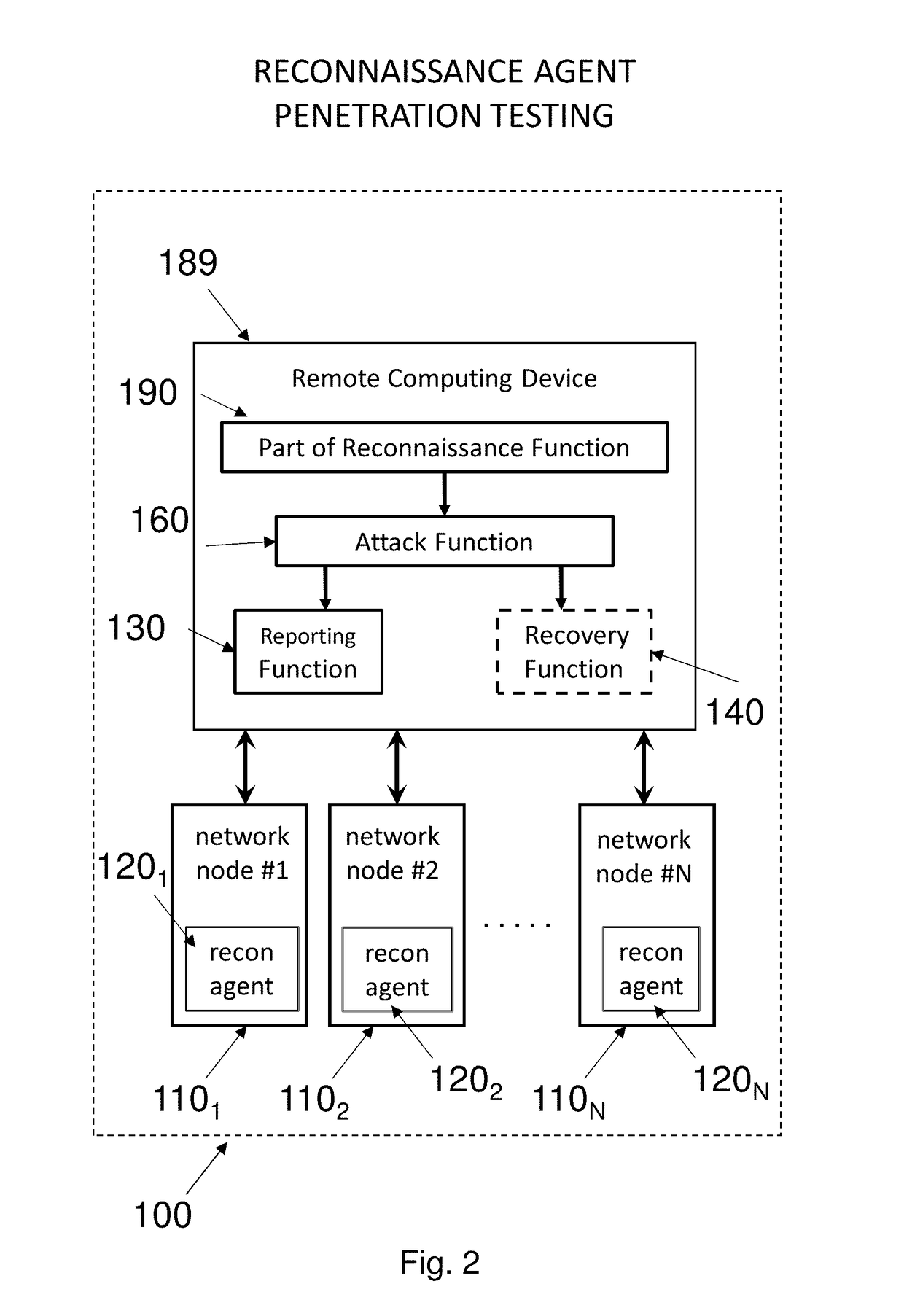
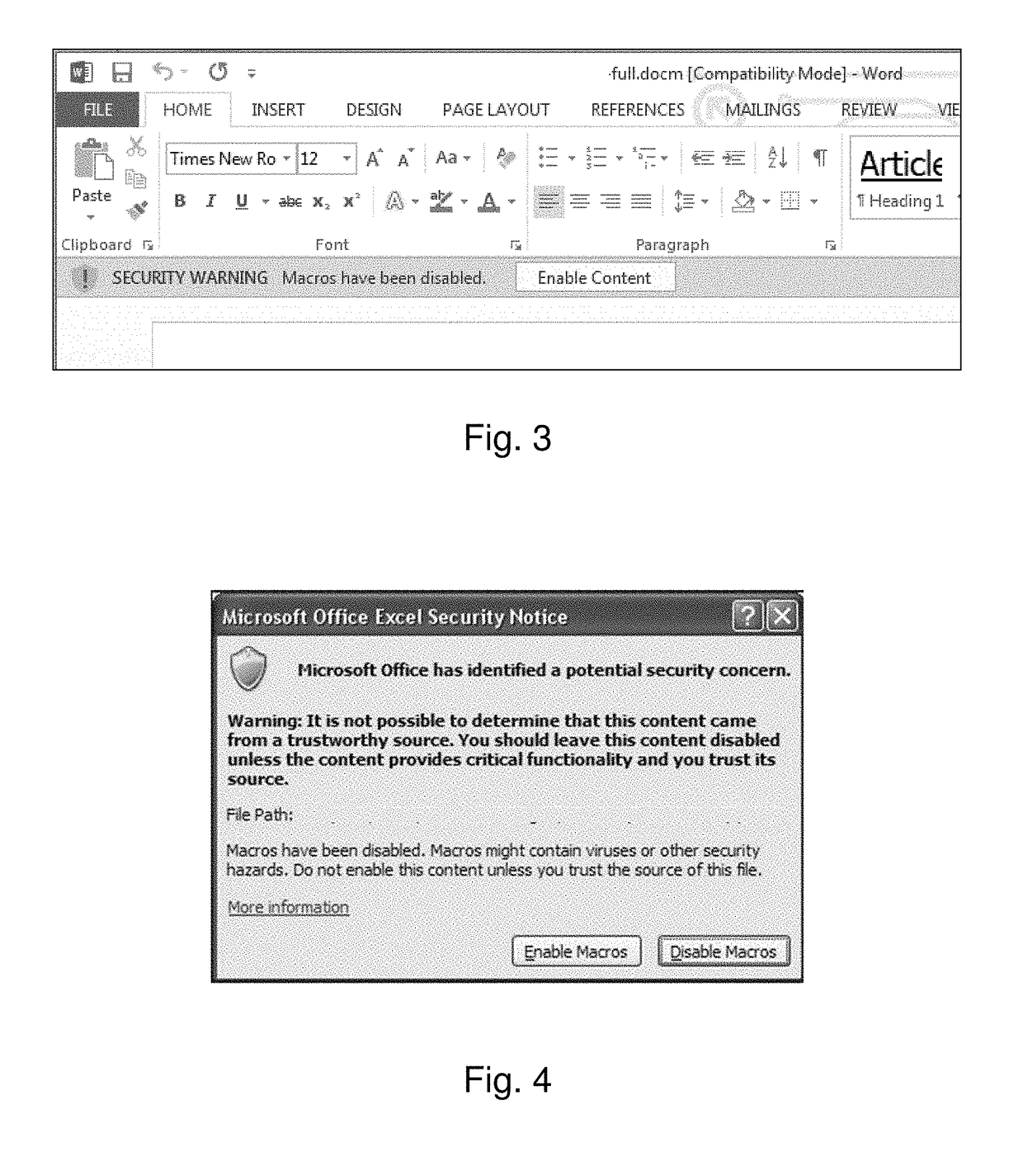
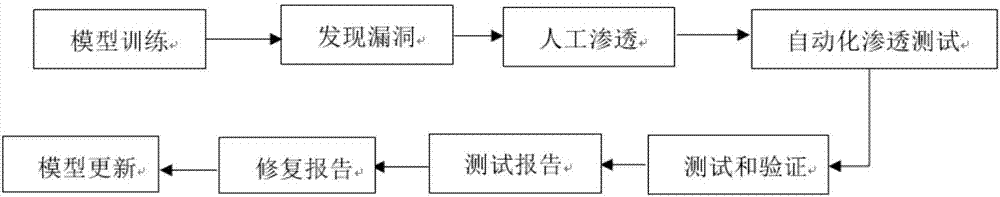
ActiveUS20180365429A1Runtime instruction translationPlatform integrity maintainanceApplication softwarePenetration test
Methods and systems are disclosed for penetration testing of a network node by a penetration testing system to determine vulnerability of network nodes to macro-based attacks. A reconnaissance agent runs in a network node to prompt user responses to macro warnings upon detecting file openings by macro-supporting software applications of files not containing auto-executing macros, and the responses are used for determining vulnerability.
Owner:XM CYBER LTD
Automated safety penetration test method
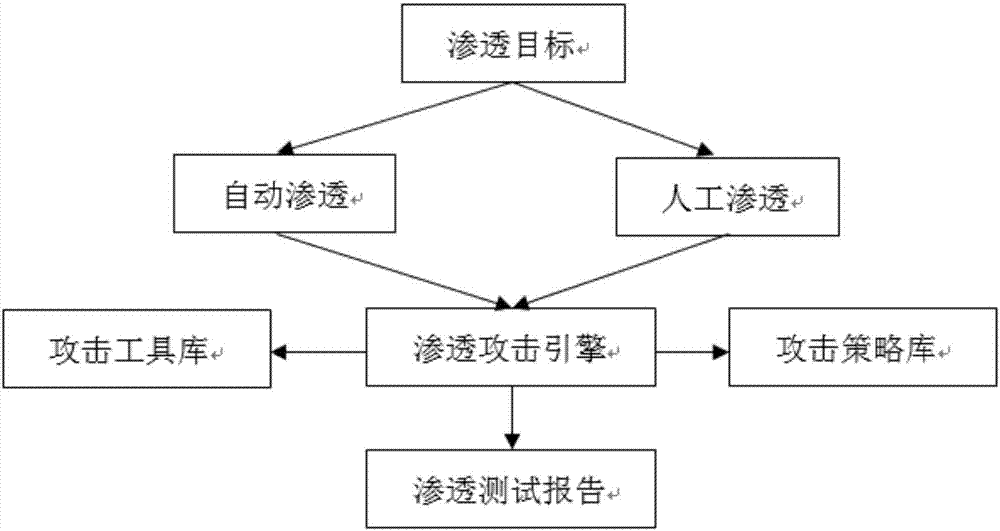
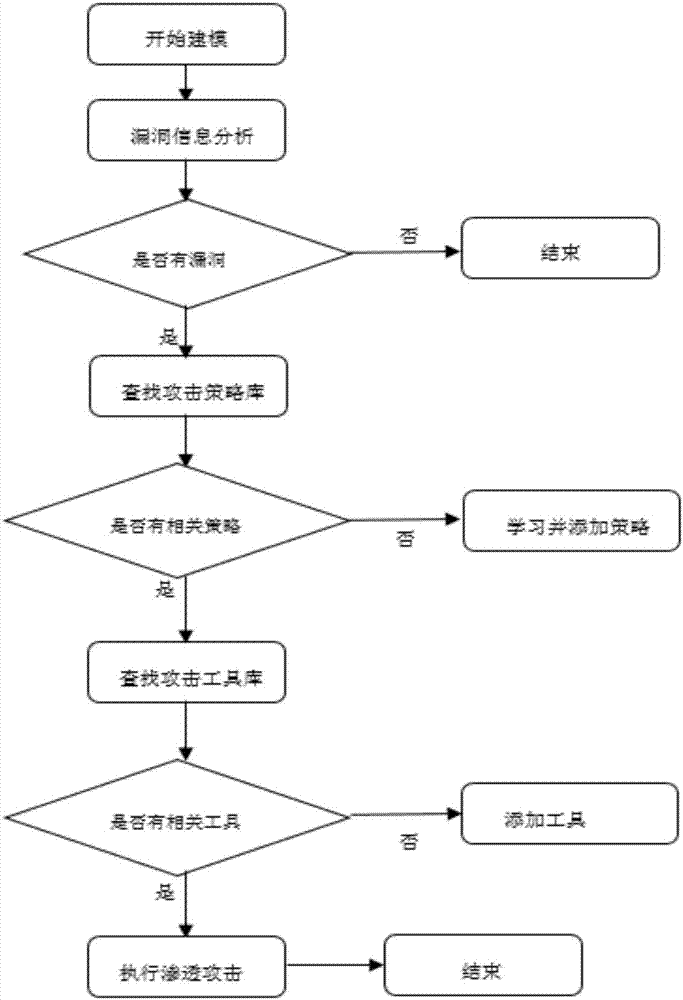
ActiveCN107426227ARealize automatic callAchieve executionPlatform integrity maintainanceData switching networksAttack modelAttack strategy
The invention discloses an automated safety penetration test method, comprising: step 1, training an automated response model, establishing a corresponding model; step 2, scanning a target information system, obtaining host information; step 3, scanning vulnerability of the target information system, obtaining vulnerability information; step 4, according to the host information and the vulnerability information obtained in the step 2 and step 3, combined with an attack strategy library, establishing an attack model, according to the attack model, trying to attack the target information system, obtaining an attack feedback result; step 5, performing comprehensive analysis on a penetration test overall process, generating a penetration test report and teasing test steps and intermediate results, analyzing system security, providing a related solution; step 6, the response model updating in an adaptive manner, and regulating a response strategy.
Owner:CHINA INFOMRAITON CONSULTING & DESIGNING INST CO LTD
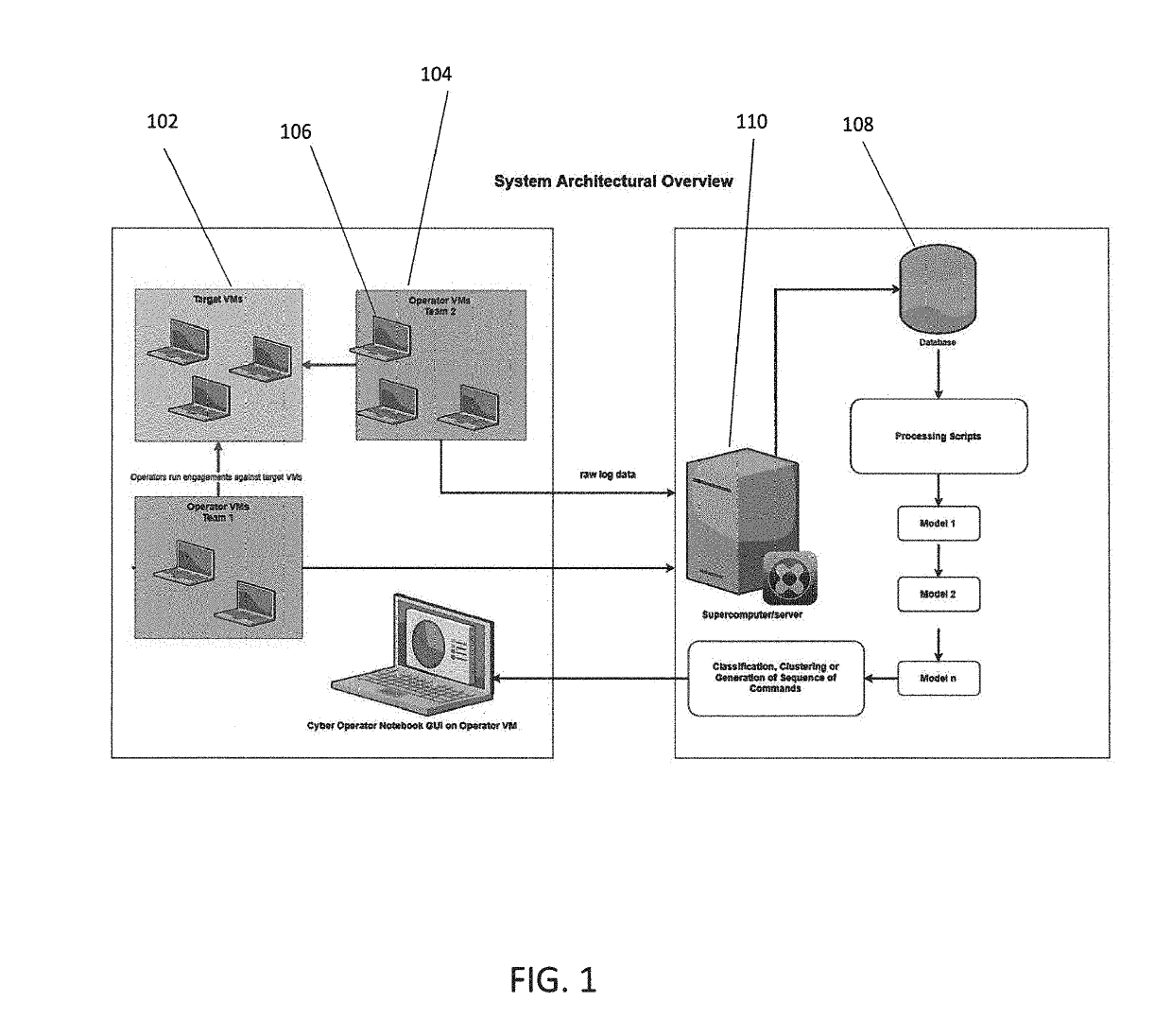
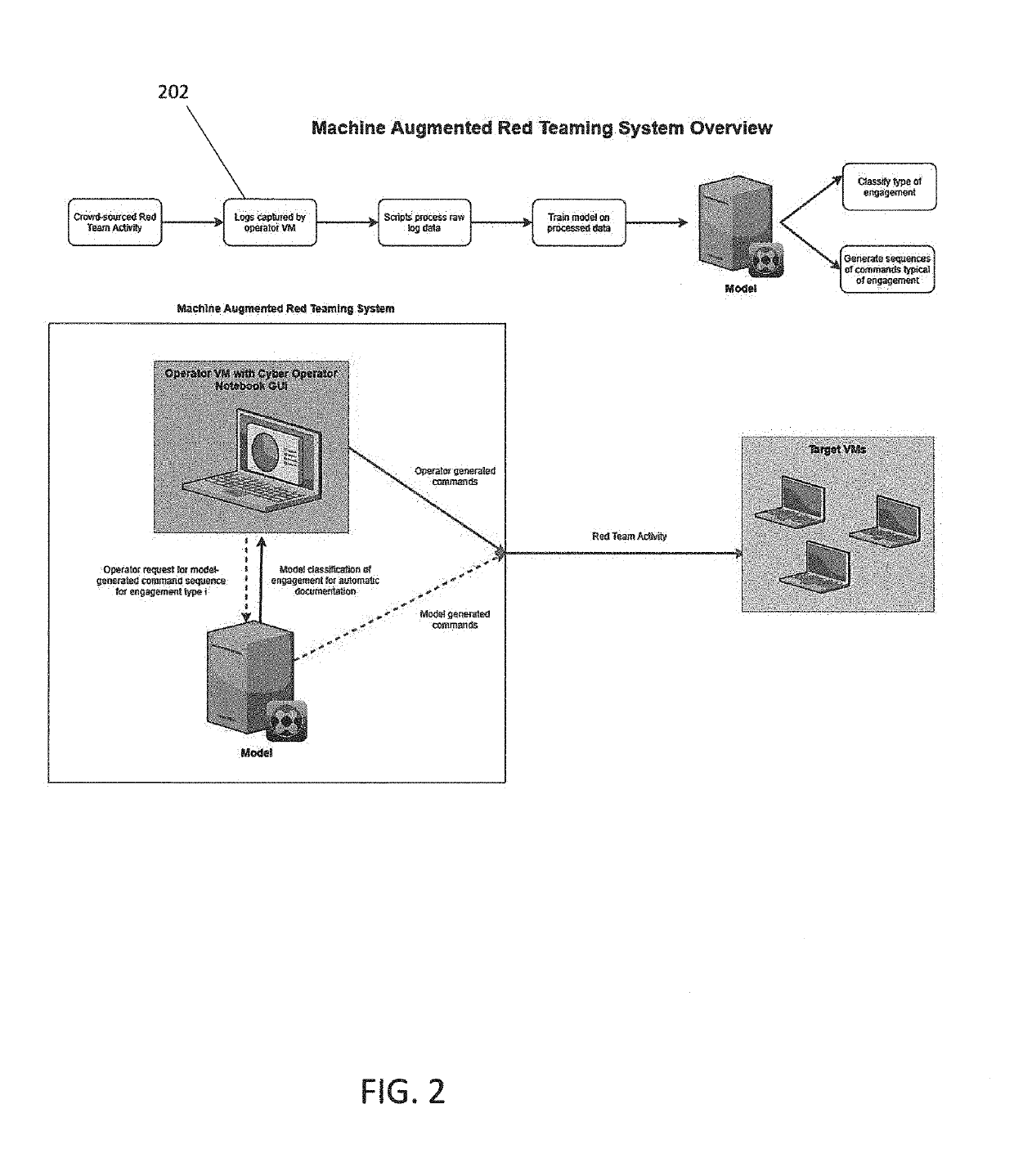
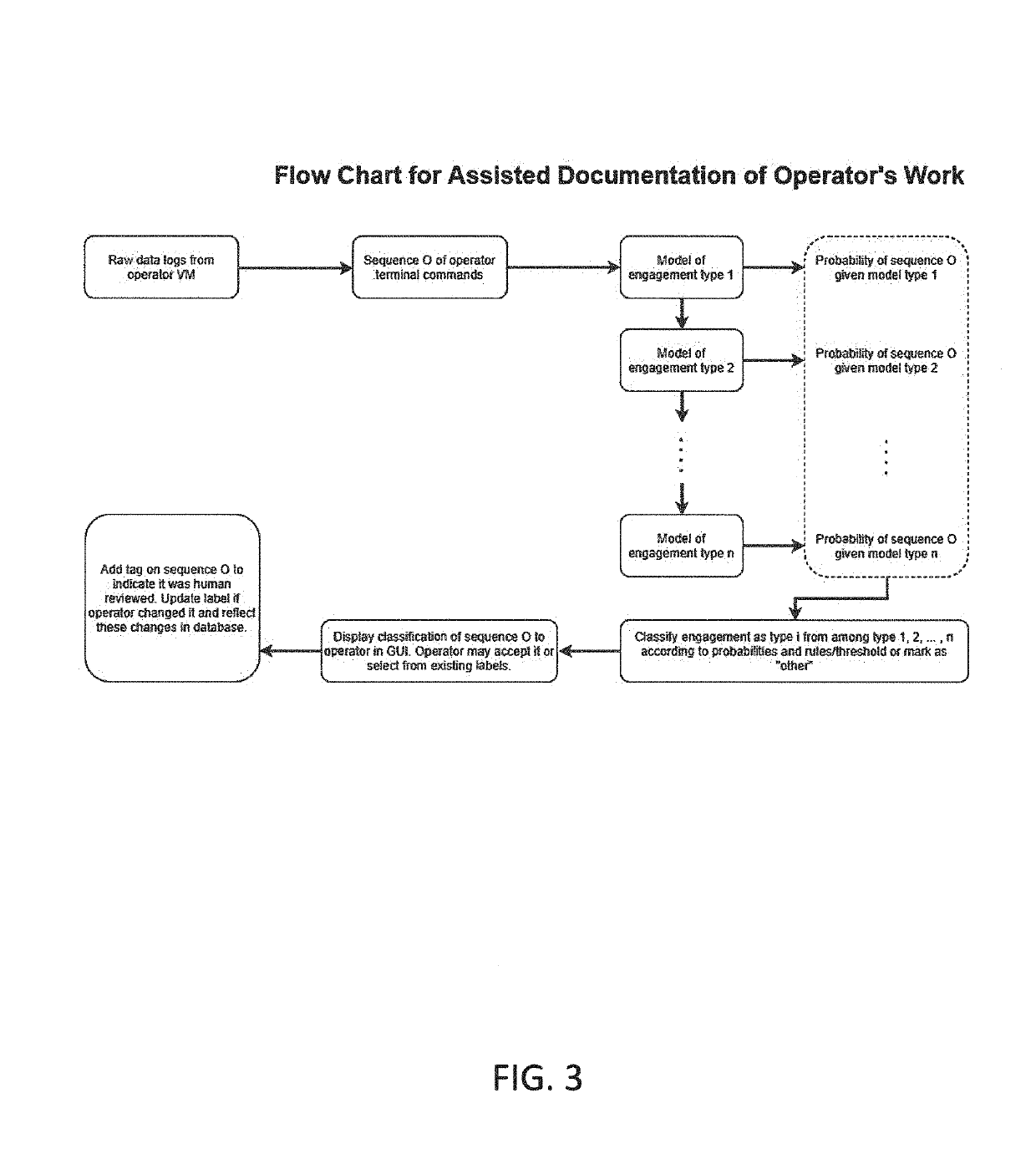
Method and system for penetration testing classification based on captured log data
Aspects of the invention comprise methods and systems for collecting penetration tester data, i.e. data from one or more simulated hacker attacks on an organization's digital infrastructure in order to test the organization's defenses, and utilizing the data to train machine learning models which aid in documenting tester training session work by automatically logging, classifying or clustering engagements or parts of engagements and suggesting commands or hints for an tester to run during certain types of engagement training exercises, based on what the system has learned from previous tester activities, or alternatively classifying the tools used by the tester into a testing tool type category.
Owner:CIRCADENCE
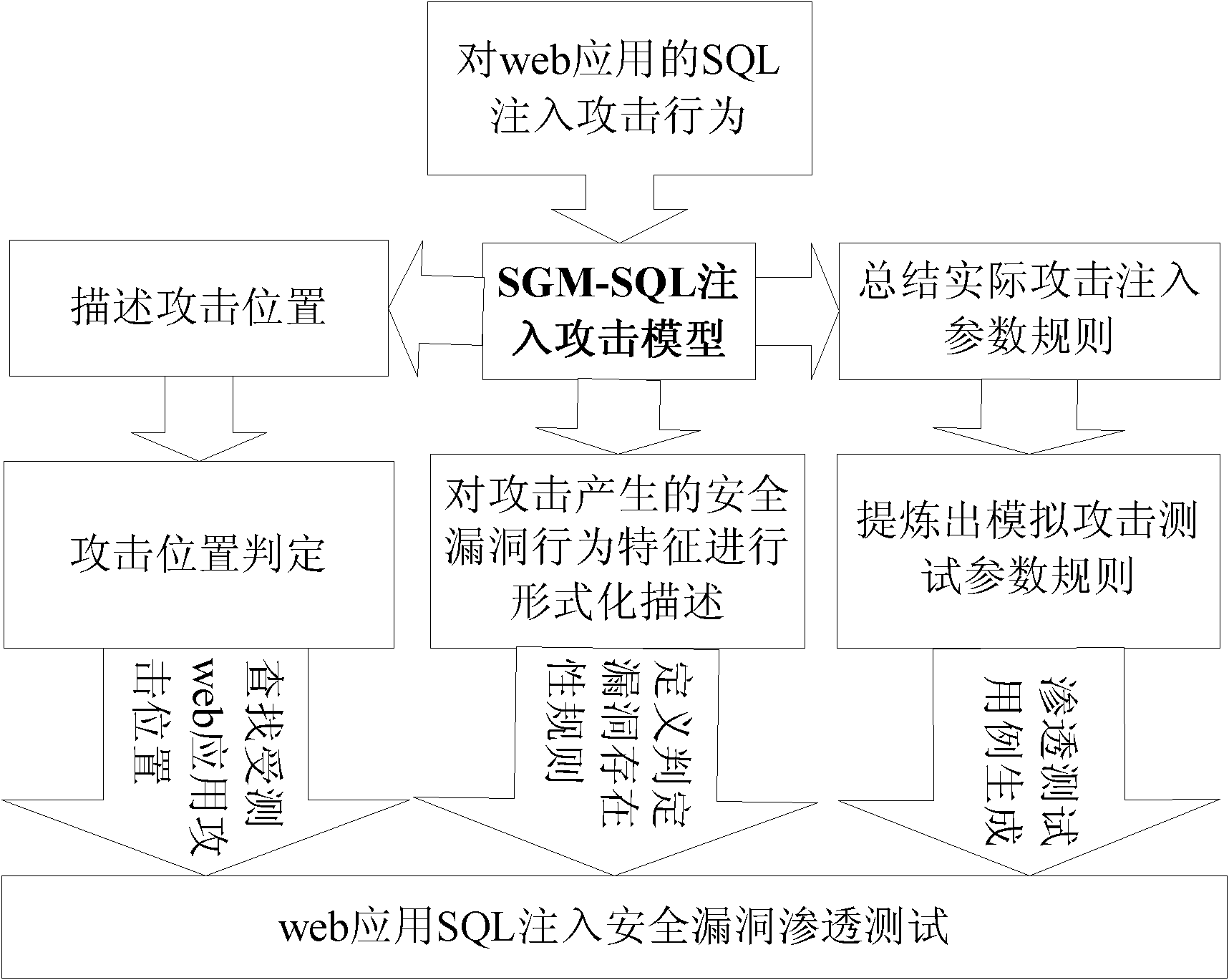
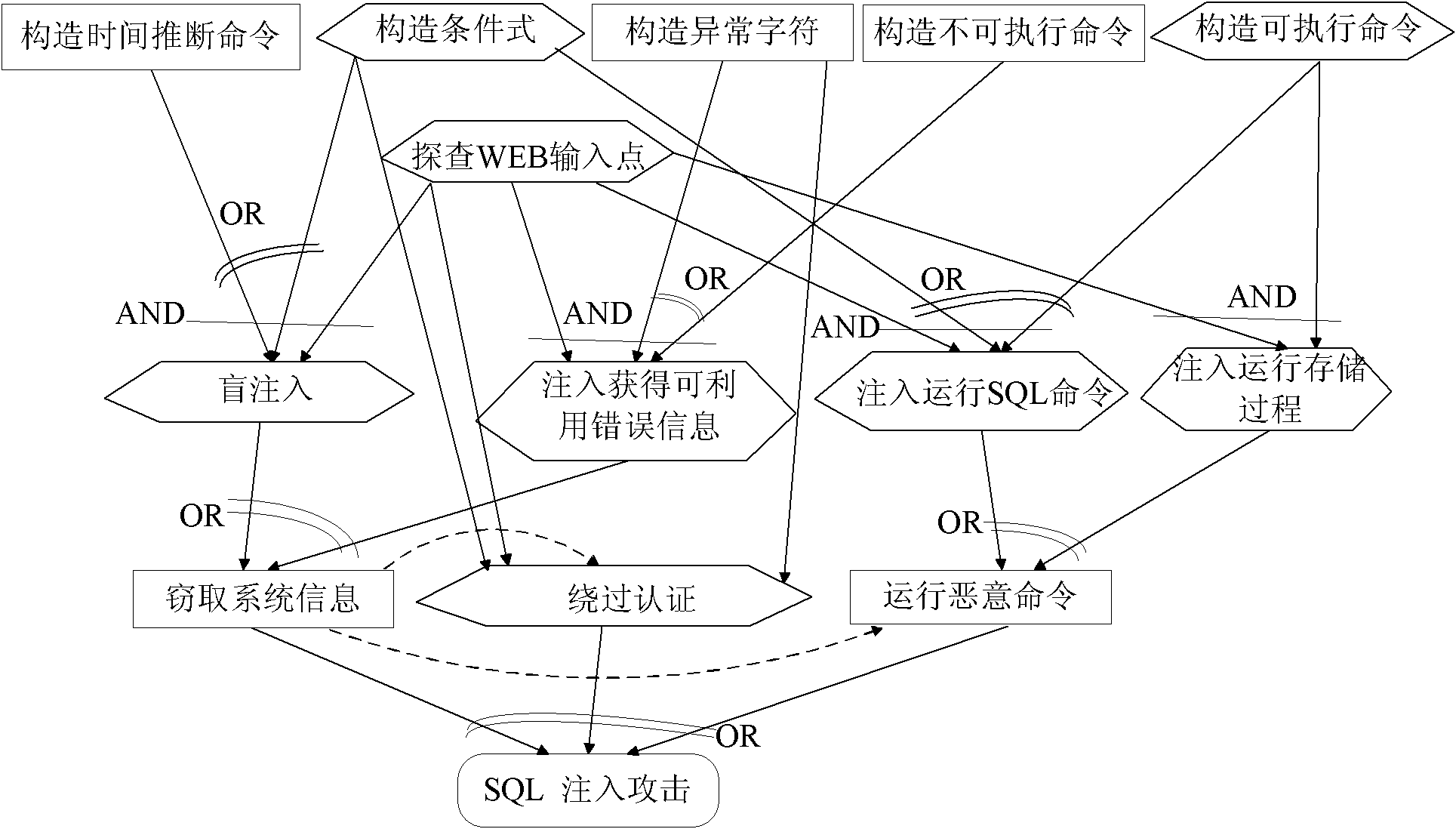
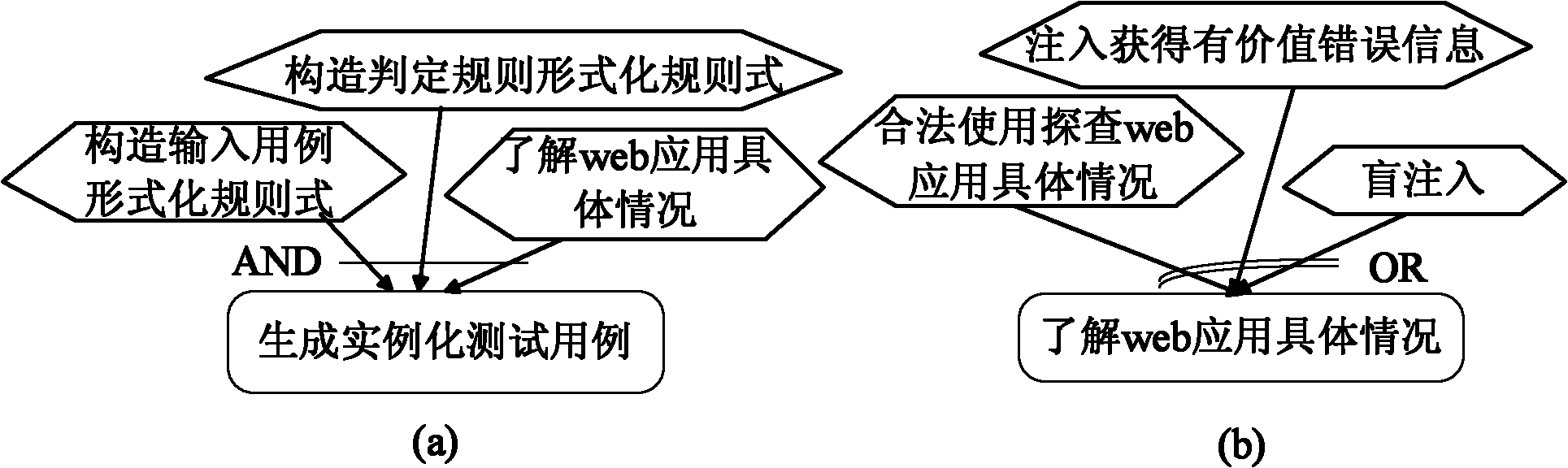
Method for driving web application penetration testing by applying SGM-SQL (sage grant management-structured query language) injection model
InactiveCN102136051AImprove accuracyMake up for the shortcomings of low accuracySoftware testing/debuggingPlatform integrity maintainanceAttack modelRDF query language
The invention relates to a method for driving web application penetration testing by applying an SGM-SQL (sage grant management-structured query language) injection model, in the method, a web application penetration test framework driven by an SGM-SQL injection attack model is defined; by defining the SGM-SQL injection attack model in the framework and guiding the definition of a formalized definition set of SQL injection safety loopholes and a formalized description system of penetration test cases thereof, the accurate criterion for judging existence of the safety loopholes and the orderedcomplete test cases are further provided for the penetrating testing, and an SQL injection safety loophole penetration test algorithm driven by the SGM-SQL injection attack model is accordingly provided, thereby improving the accuracy of the web application SQL injection safety loophole penetration testing. Practices prove that the method is credible, systematic and complete, and can be applied in the field of the web application safety loophole penetration testing.
Owner:NANKAI UNIV +1
Antiperspirant compositions and methods for making same
Owner:PROCTER & GAMBLE CO
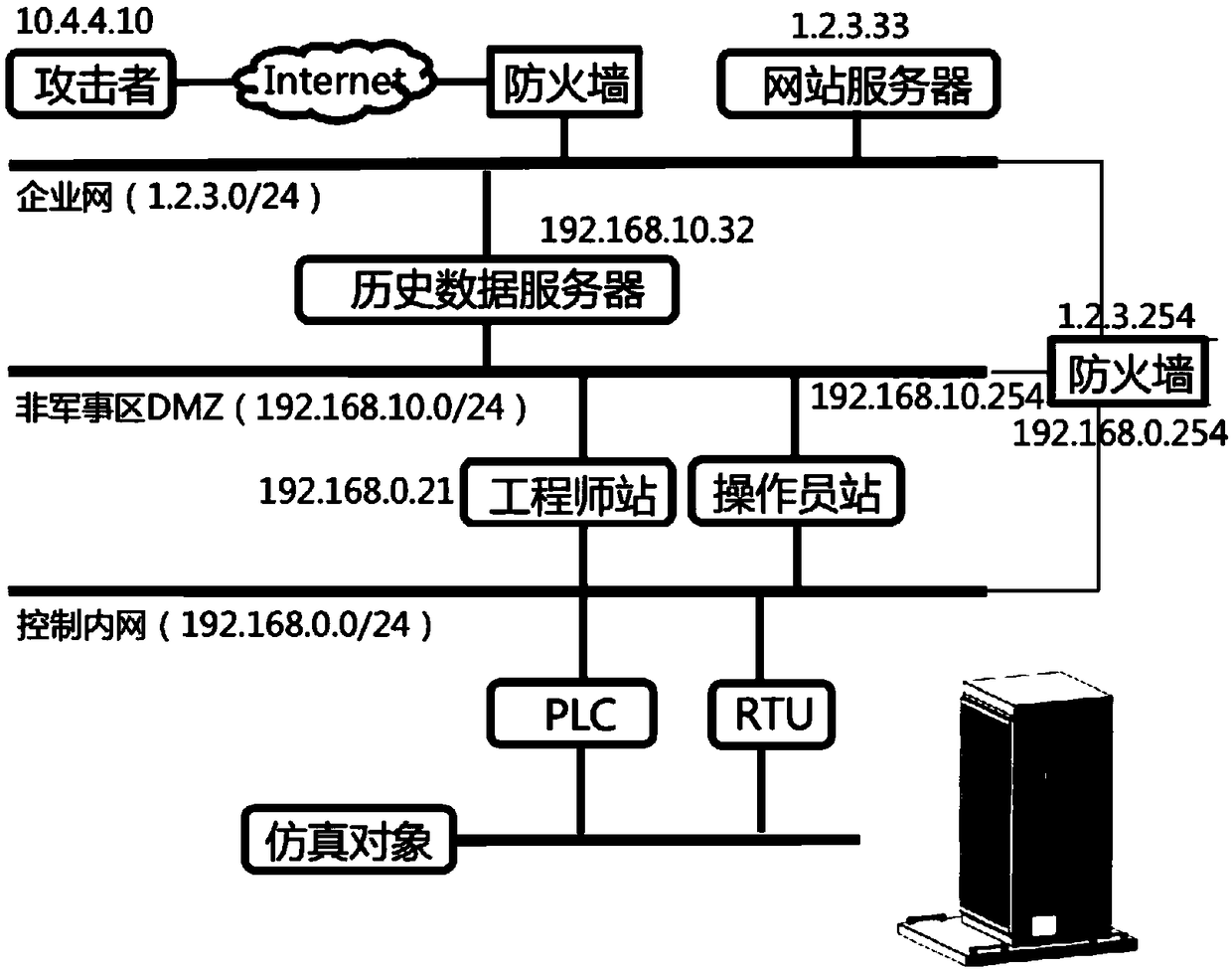
Industrial control system security experiment platform for penetration testing
ActiveCN108769022AImprove scalabilityEnsure safetyData switching networksData acquisitionPhysical model
The invention discloses an industrial control system security experiment platform for penetration testing. The platform comprises a virtual industrial control network, a control device, a control object, an attacker module, a data acquisition module and an anomaly detection module, wherein the virtual industrial control network is a three-layer network structure, which is successively an enterprise network, a demilitarized zone, and a control intranet from the outside to the inside; the enterprise network with the demilitarized zone, and the demilitarized zone with the control intranet are allconnected through a gateway; the control device is connected to the control intranet through an Ethernet protocol; the control object comprises a physical model and a simulation model and communicates with the control device; the attacker module is connected to a public network, simulates an attacker, and performs penetration testing on the industrial control system; the data acquisition module collects network flow data of the gateway; and the anomaly detection module is used for implementing anomaly detection of industrial control systems based on network flow data. The platform of the invention can deeply dig into the safety hazards of the industrial control system and has a positive effect on protecting the safety performance of the industrial control system.
Owner:ZHEJIANG UNIV
Multifunctional integrated cap pressing type pressure chamber in rock coupling penetration test and test method
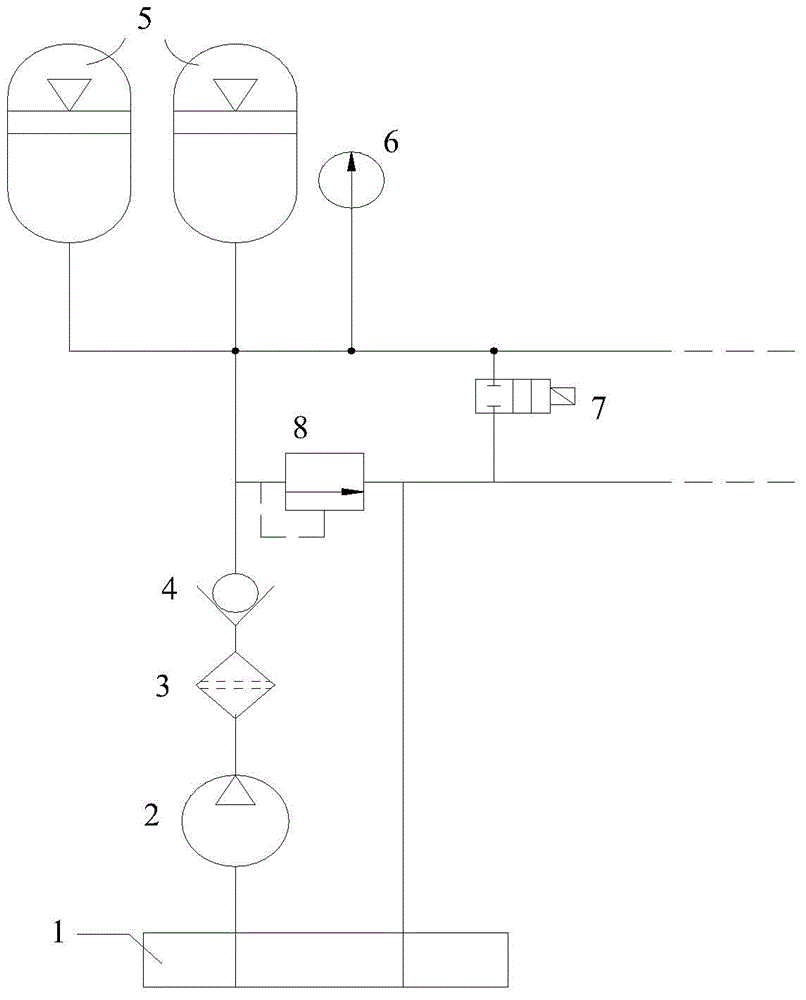
InactiveCN106018236AEasy to assemble and disassemblePrevent leakagePermeability/surface area analysisVolume variationEngineering
The invention belongs to the field of penetration experimental apparatuses and specifically relates to a multifunctional integrated cap pressing type pressure chamber in a rock coupling penetration test and a test method. The multifunctional integrated cap pressing type pressure chamber comprises a pressure chamber body, a pressure chamber base, a pressure chamber cover, a confining pressure oil inlet, a seepage outlet, a seepage inlet, a pressure chamber lock cap, a hoisting cylinder, an upper pressing head, an upper penetrating plate, a test part, a lower penetrating plate and a lower pressing head, wherein the pressure chamber base is located at the bottom of the pressure chamber; the pressure chamber cover is located at the top of the pressure chamber; the confining pressure oil inlet and the seepage outlet are located at the bottom of the pressure chamber; the seepage inlet is located close to the top of the pressure chamber; the pressure chamber lock cap is located on the outer side of the pressure chamber base and is connected with the pressure chamber base; the hoisting cylinder is arranged at the top of the pressure chamber; the upper pressing head, the upper penetrating plate, the test part, the lower penetrating plate and the lower pressing head are successively arranged in the pressure chamber body; the seepage outlet is successively connected with a cooling water tank and a volume variation gauge. The invention provides a pressure chamber with high safety, degree of automation and multifunction and the test method; complex operation and potential safety hazards are avoided; the pressure chamber is fit for the rock tri-axial coupling penetration test under the coupling effect of temperature-seepage-stress- chemistry (THMC).
Owner:HOHAI UNIV
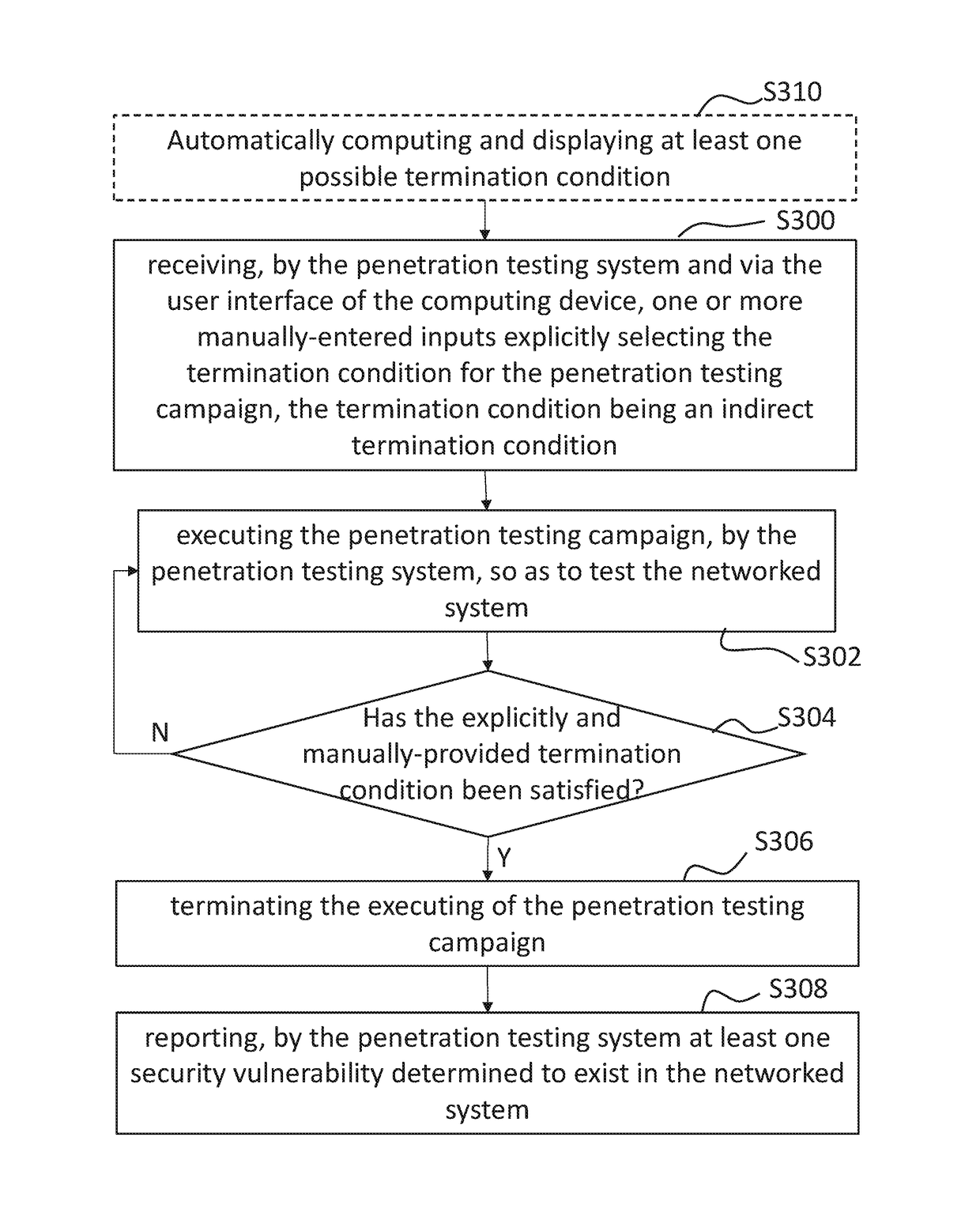
Systems and methods for selecting a termination rule for a penetration testing campaign
Systems and methods of penetration testing of a networked system by a penetration testing system that is controlled by a user interface of a computing device so that a penetration testing campaign is executed until a termination condition is satisfied, the termination condition being manually and explicitly selected and being an indirect termination condition.
Owner:XM CYBER LTD
Visual uniaxial penetrating test-based bituminous mixture homogeneity evaluation method
InactiveCN105806861AThe evaluation result is accurateHigh industrial applicabilityMaterial analysis by transmitting radiationFractographyTomography
The invention discloses a visual uniaxial penetrating test-based bituminous mixture homogeneity evaluation method, which comprises the following steps: carrying out indoor molding or drilling a cylindrical core sample on site, acquiring two-dimensional horizontal section images of a plurality of bituminous mixture test pieces through tomoscan of an industrial CT machine, and then preprocessing and intensifying the two-dimensional horizontal section images acquired by the CT machine to generate gray images; recognizing and segmenting the processed bituminous mixture section gray images to obtain a boundary coordinate of each aggregate and gap in the bituminous mixture section images, establishing a three-dimensional discrete element model of the bituminous mixture and carrying out a virtual uniaxial penetration test, and evaluating the bituminous mixture homogeneity by using the uniaxial penetration strength index variable coefficient obtained by the test. The bituminous mixture homogeneity evaluation method is based on the visual uniaxial penetrating test, and the bituminous mixture homogeneity is quantitatively evaluated by using the uniaxial penetration strength index variable coefficient, so the industrial practicability and maneuverability are very strong.
Owner:ZHEJIANG UNIV
Systems and methods for using multiple lateral movement strategies in penetration testing
Methods and systems for carrying out multiple campaigns of penetration testing using different lateral movement strategies for discovering and reporting security vulnerabilities of a networked system, the networked system comprising a plurality of network nodes interconnected by one or more networks.
Owner:XM CYBER LTD
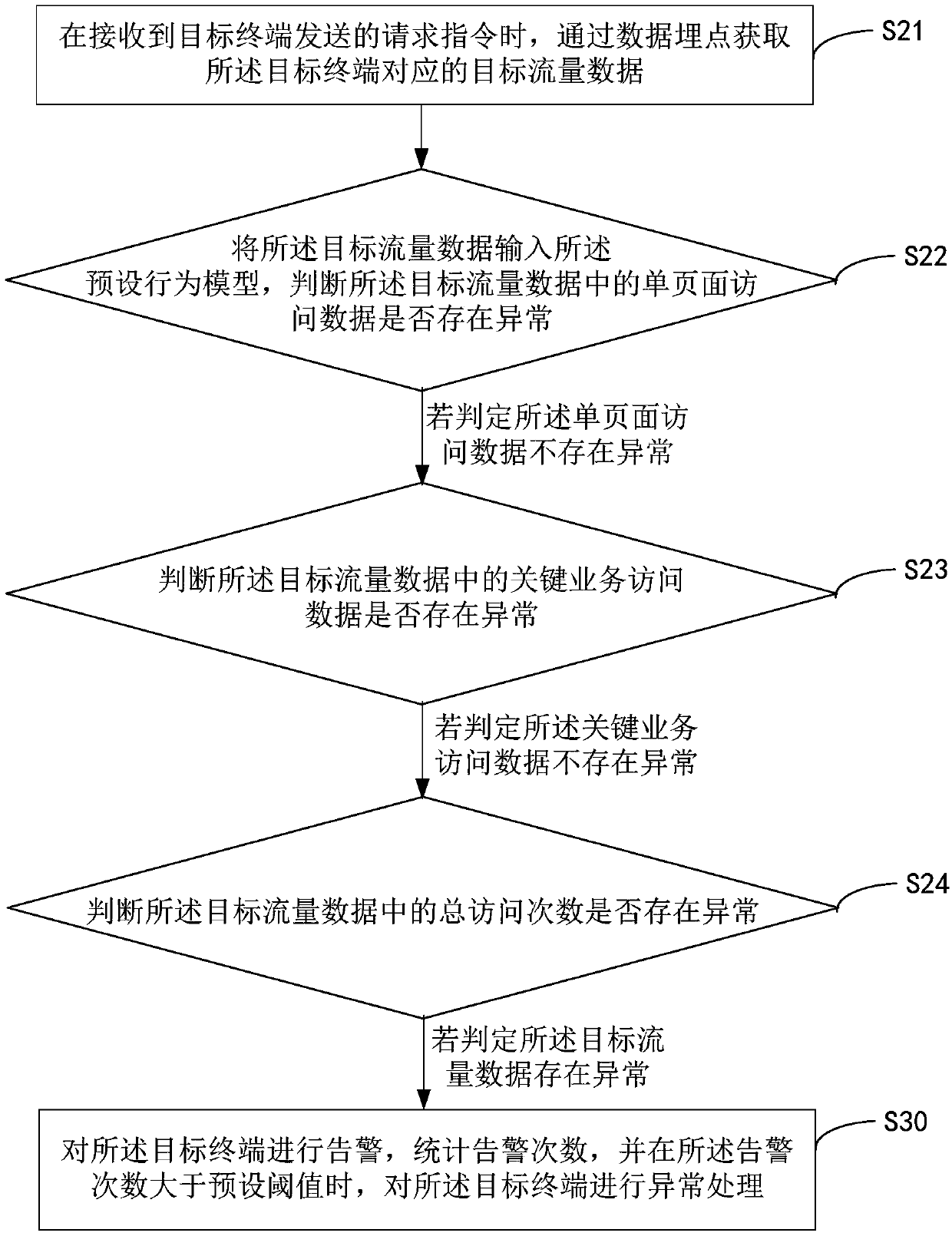
Abnormal behavior detection method, apparatus and device, and storage medium
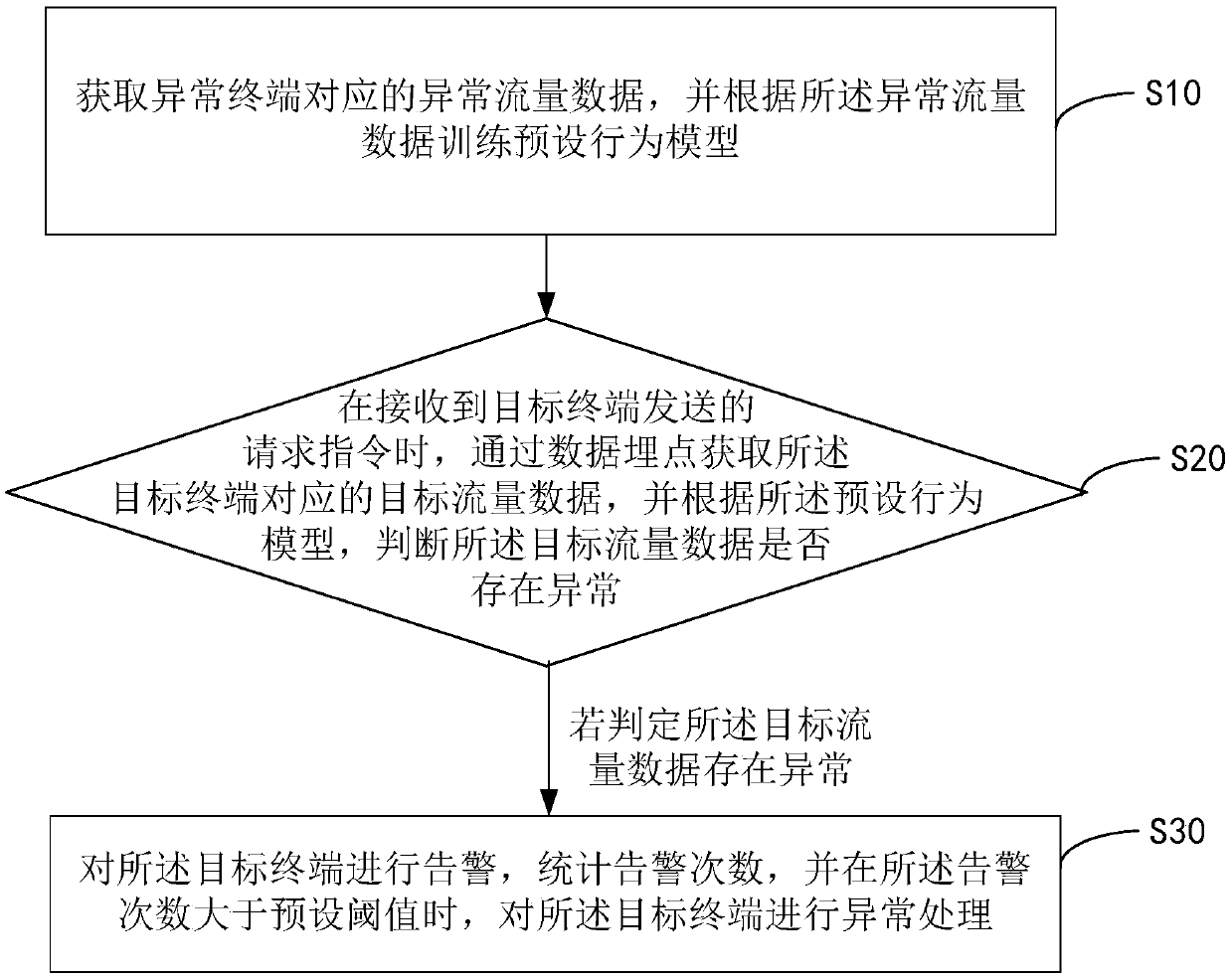
InactiveCN109660502AReduce the risk of finding system vulnerabilitiesSolve the technical problem of not taking corresponding measures for the detection behavior of permeabilityTransmissionInformation securityException handling
The invention provides an abnormal behavior detection method, apparatus and device, and a computer readable storage medium. A preset behavior model is trained through abnormal flow data correspondingto an abnormal behavior in advance; when a request instruction sent by a target terminal is received, target flow data corresponding to the target terminal is obtained through a buried point; whetherthe target flow data is abnormal or not is judged through the preset behavior model; and when the target flow data is abnormal, an alarm is given to a target application and an alarm frequency is subjected to statistics. When the alarm frequency exceeds a preset threshold value, the target terminal is subjected to abnormal processing. The flow data containing unknown security problems can be judged to ensure the network security; the abnormal behavior of intrusion is detected to reduce the risk that a hacker searches for system vulnerabilities in a penetration test mode; and early warning is carried out on the abnormal behavior to improve the information security in a system.
Owner:PING AN TECH (SHENZHEN) CO LTD
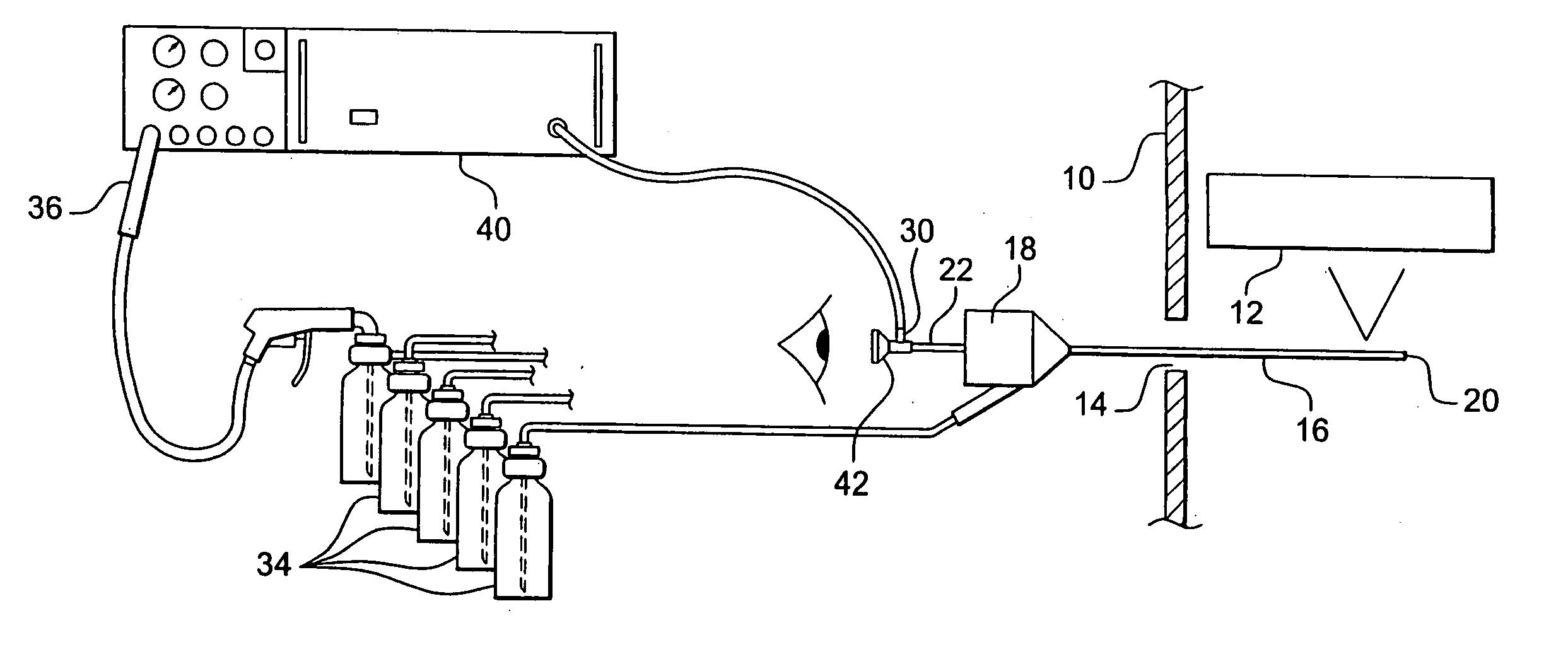
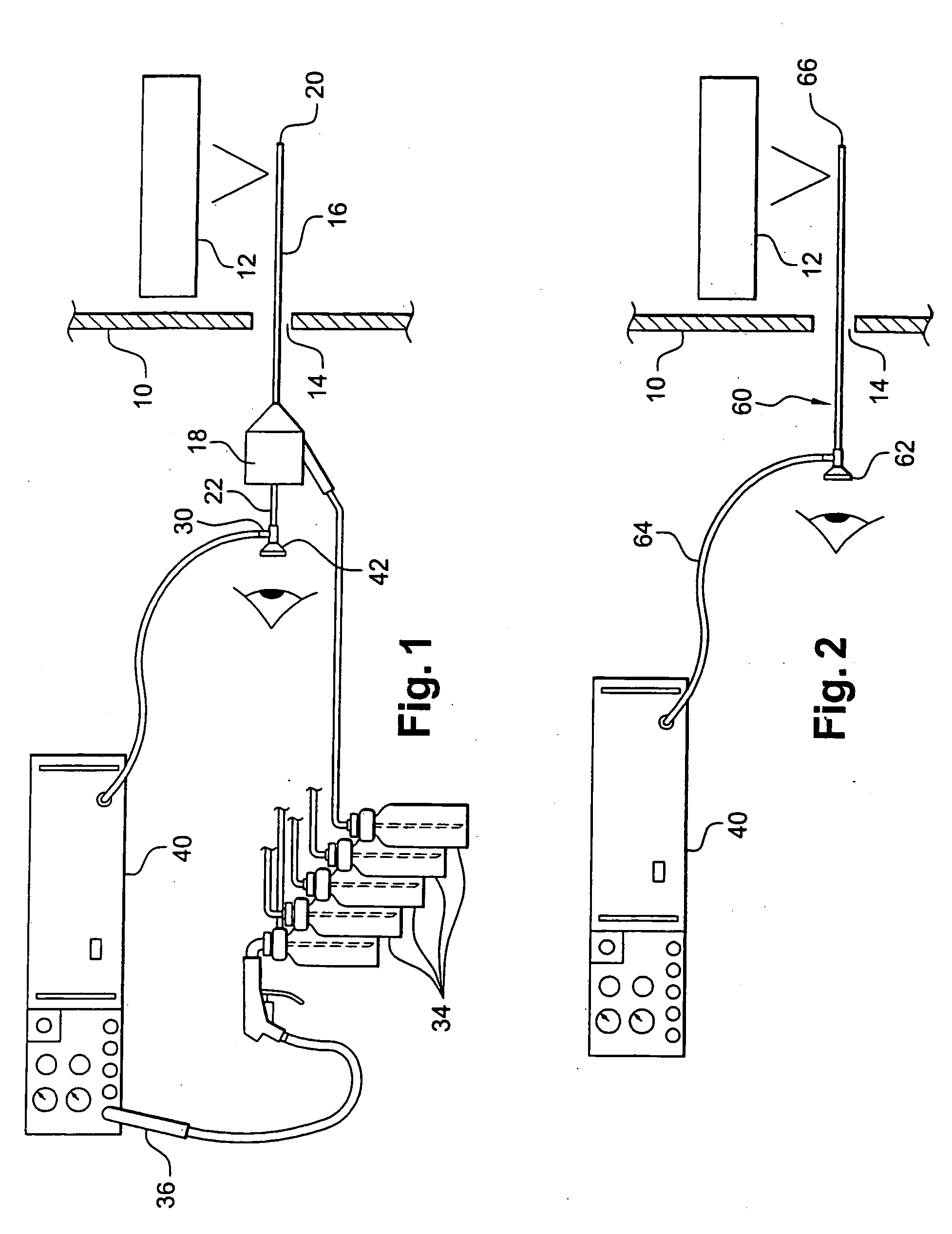
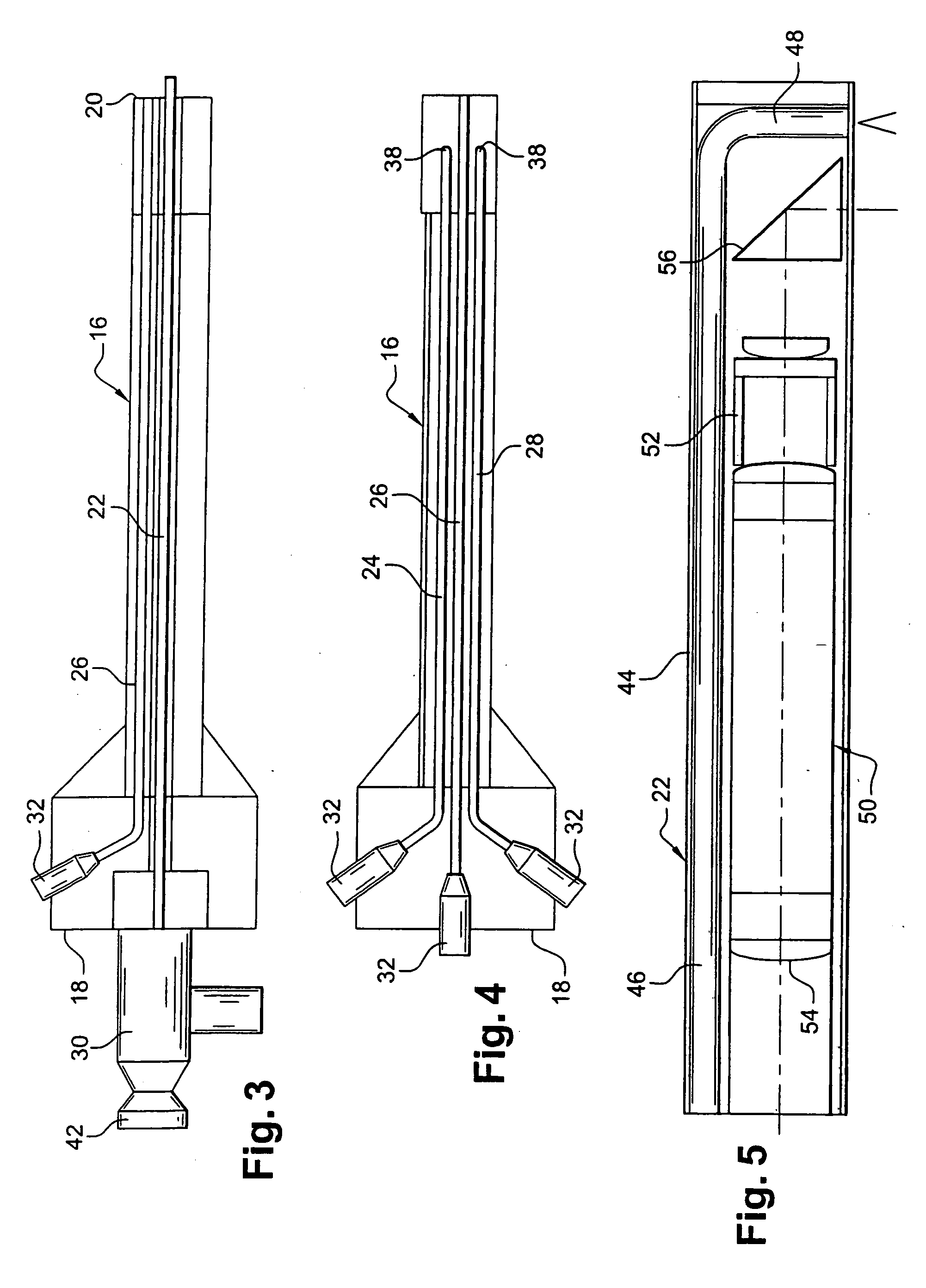
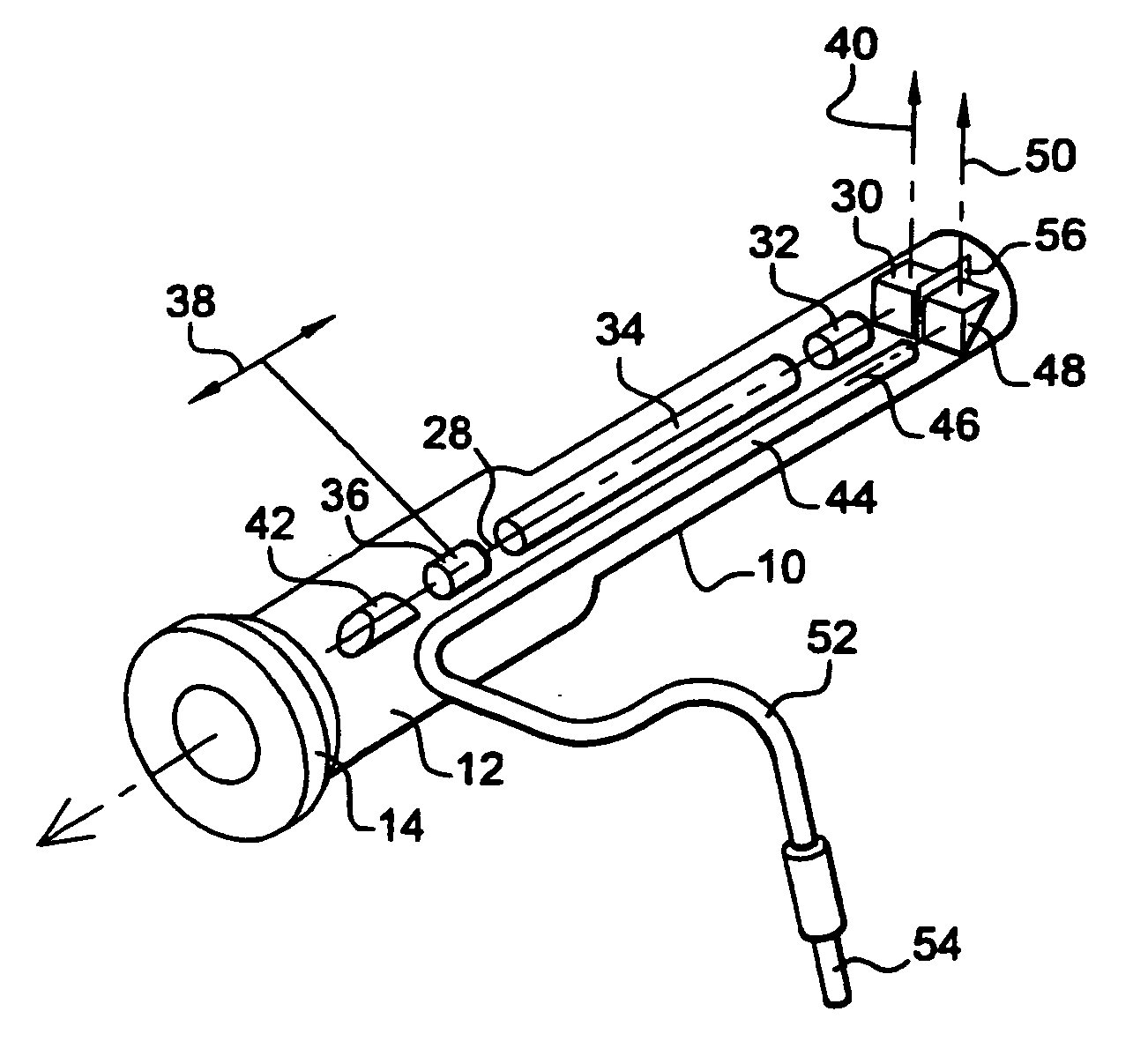
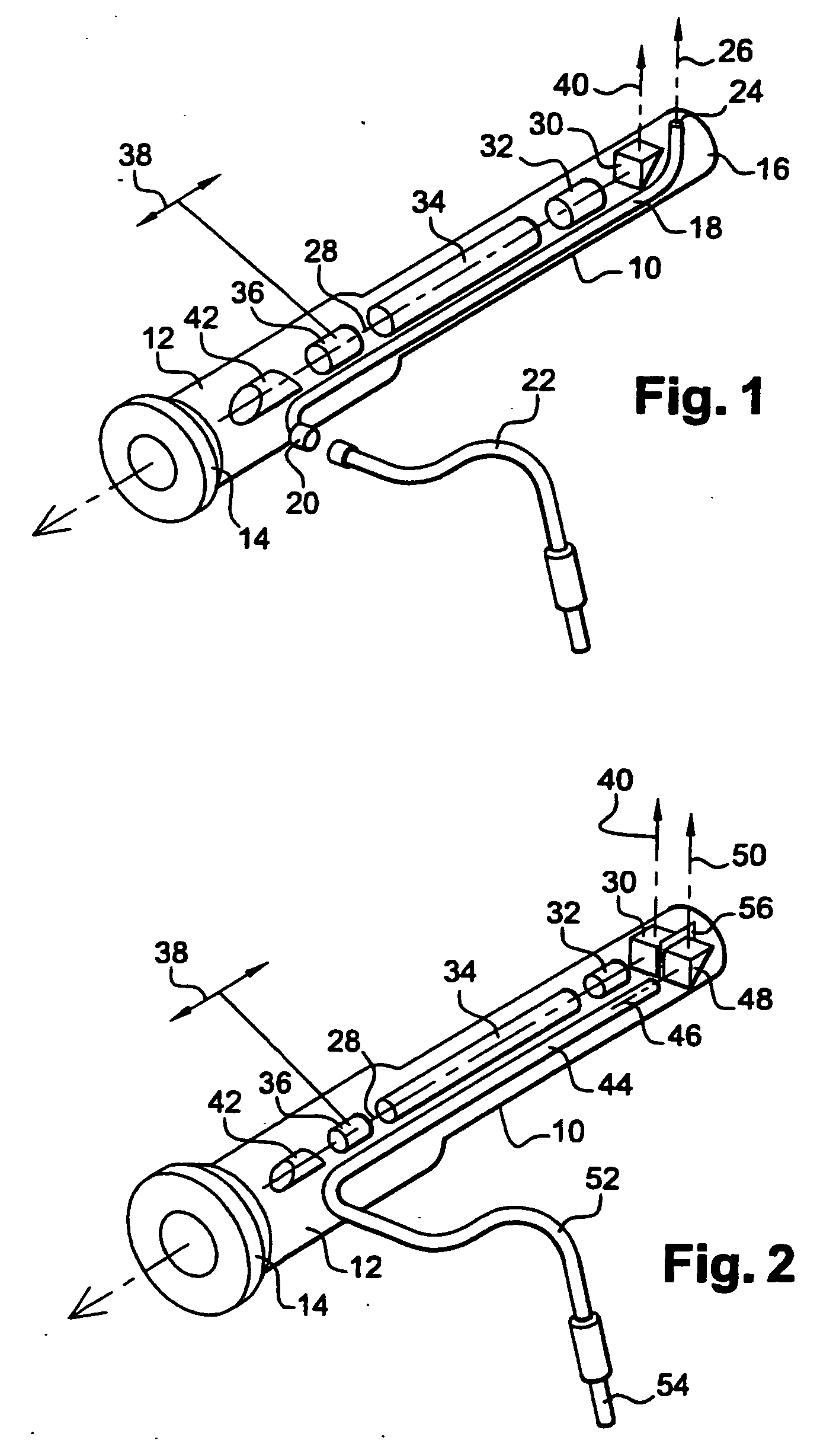
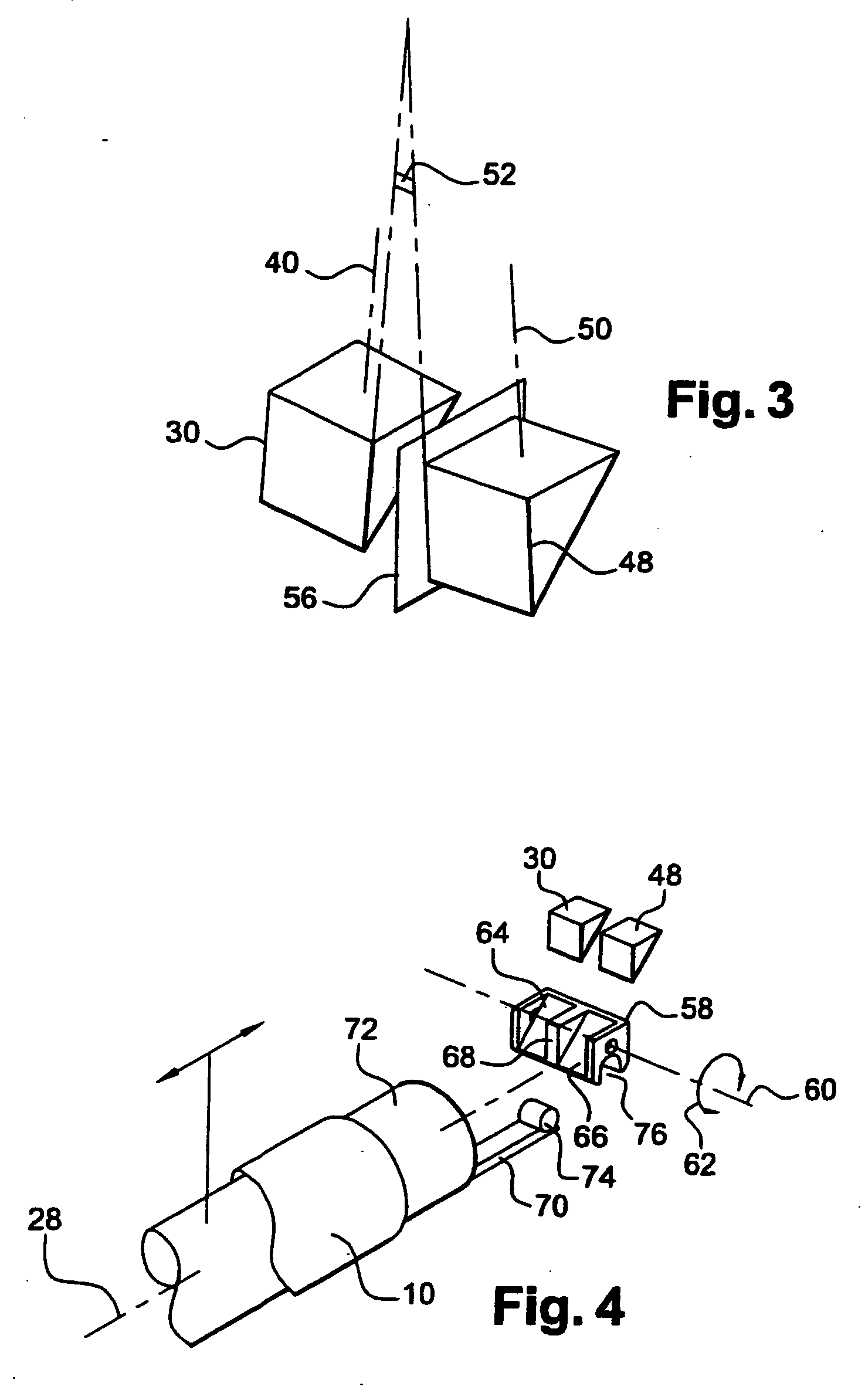
Apparatus for searching for and detecting defects in parts by endoscopy
ActiveUS20050200842A1Improve performanceSimple and satisfactory and inexpensiveRadiation pyrometrySurgeryFlexible endoscopeMedicine
Apparatus for searching for and detecting defects on parts that are substantially inaccessible, being located behind a wall, the apparatus comprising a first endoscope for illumination in visible light and for observation, the first endoscope and pipes for feeding and spraying penetration test substances being housed together in a rod which can be passed through an orifice in the wall in order to examine a part, the apparatus further comprising a second endoscope independent of the first endoscope and the rod for illuminating in ultraviolet light and for observing the portion of the part that has been treated by the penetration test substances.
Owner:SN DETUDE & DE CONSTR DE MOTEURS DAVIATION S N E C M A
System and method for controlling on-demand security
InactiveUS20070028300A1Ensure isolationMemory loss protectionError detection/correctionService provisionProgram security
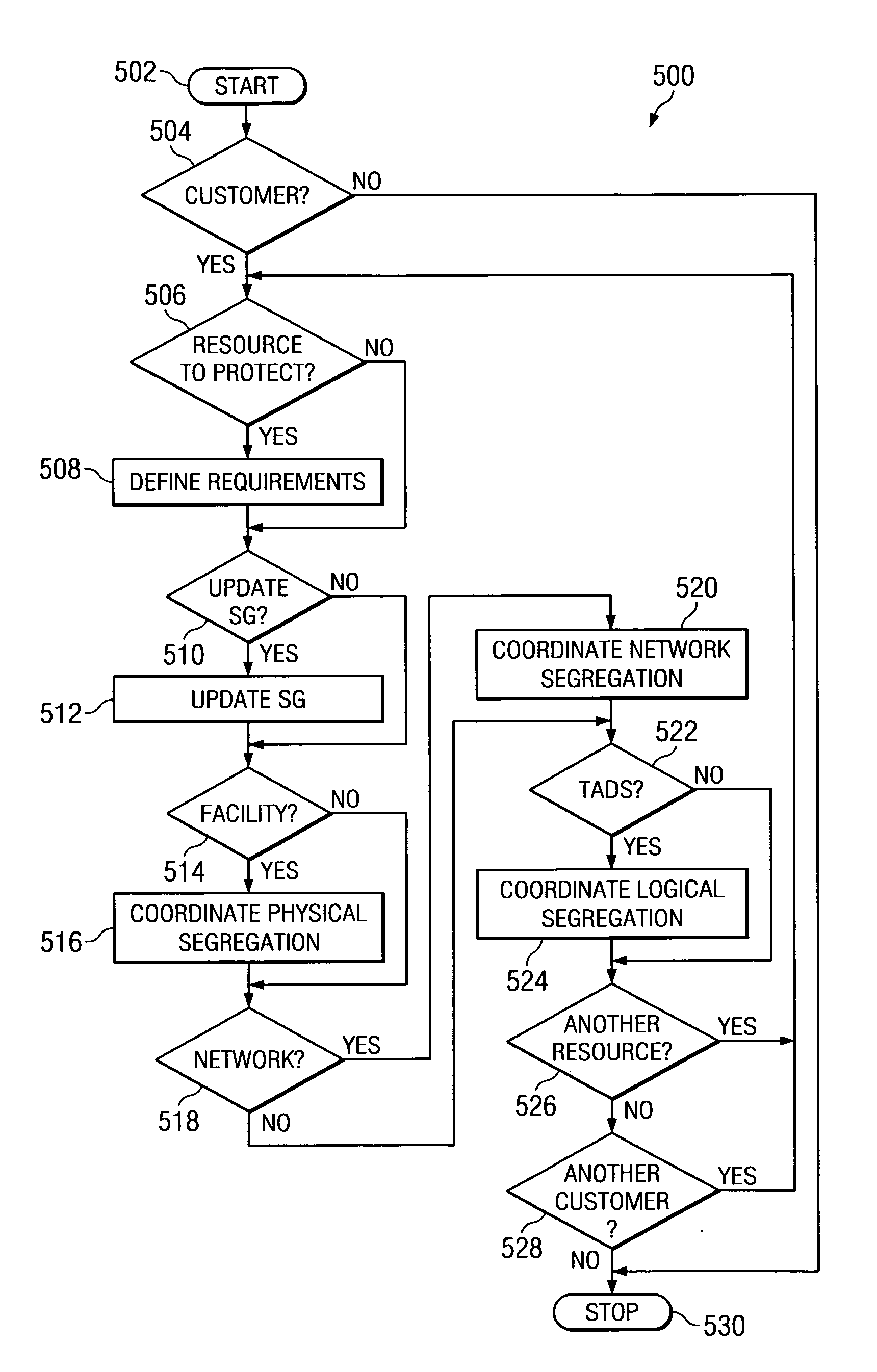
An on-demand security service ensures isolation of the service provider's customers where the customers share resources at the system, subsystem, and storage level. The security service is provided in a pre-production phase and in a post production phase. The pre-production phase takes place prior to boarding the customer. In the pre-production phase the resources to be protected are defined in a security guide, and using the security guide, physical segregation at the facility, network, and technical and delivery support levels is planned and then implemented. In the post production phase, on going activities are proactive and reactive. Proactive activities include maintaining physical segregation by reviewing and updating the security guide, and testing physical segregation by performing security audits and penetration tests. Observations and finding of the audits and penetration tests are resolved. Reactive activities include identifying isolation failures, coordinating appropriate actions, and resolving the isolation failure. The service may be embodied in a system and in a computer implemented process comprising a security guide file (SGF), a security guide application (SGA), a security implementation application (SIA), a security validation application (SVA), and an event coordination application (ECA).
Owner:IBM CORP
Method for determining shear strength of asphalt mixture
InactiveCN1873390ATest results are stableSignificant application valueMaterial strength using steady shearing forcesMaterial testing goodsRoad surfaceUltimate tensile strength
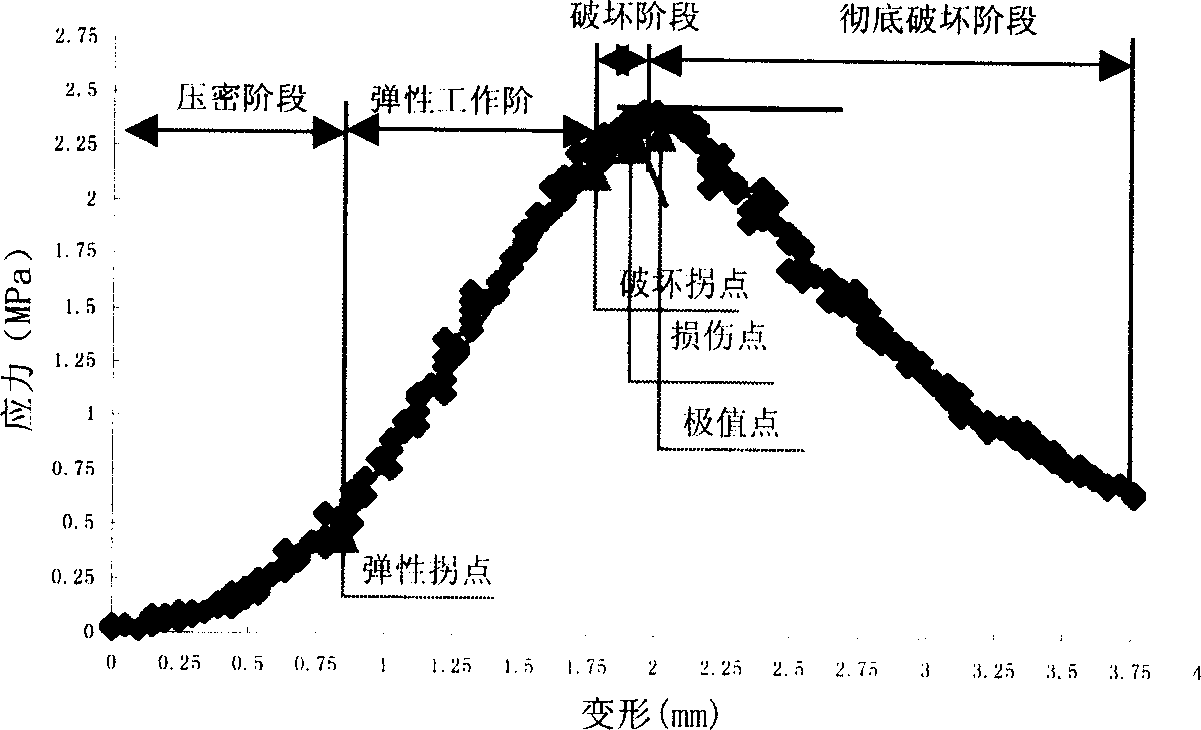
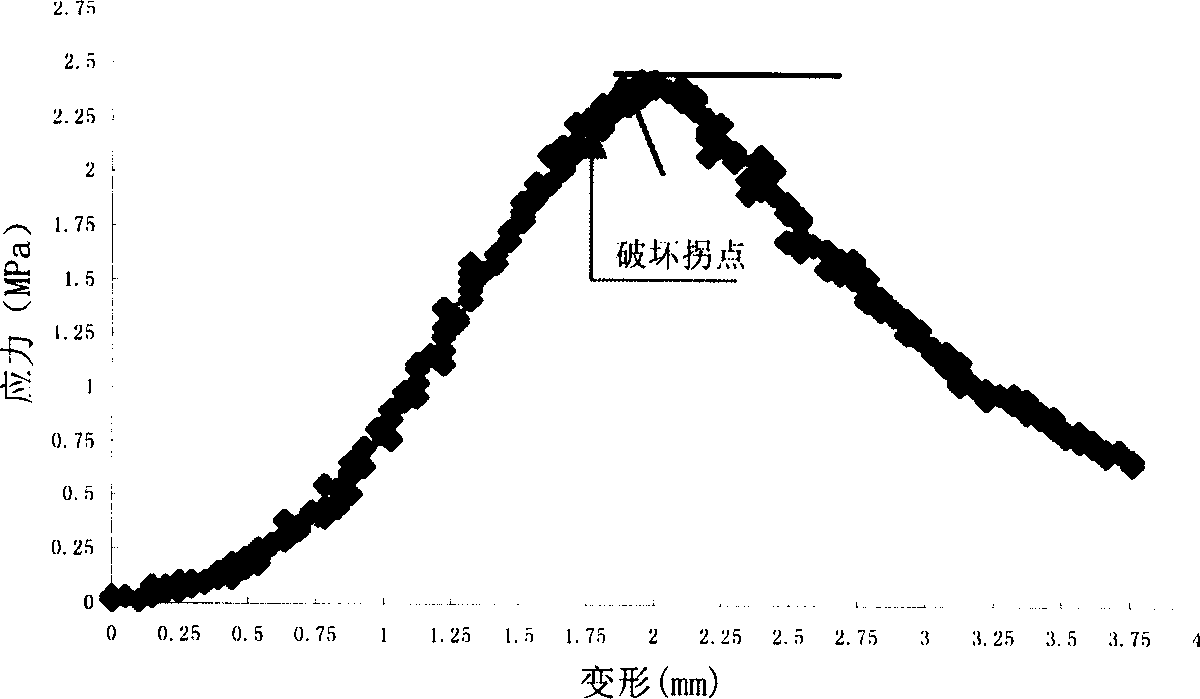
The invention relates to the method used to confirm asphalt mixture shear strength, which adopts single shaft penetration test firstly. It includes the following steps: laying a steel pressure head on the test piece and pressurizing; calculating the shear strength by three-dimensional finite element calculation and mechanics formula derivation. This can confirm that the diameter of the steel pressure head is 28.5mm; the size of the test piece is 100*100mm; penetration strength is 1MPa; Poisson ratio is 0.35. The calculating formula of the shear strength is as follows: Tau=intensive parameter*penetration pressure. The penetration pressure is the damage inflection point value of the penetration strength curve.
Owner:TONGJI UNIV
Penetration test framework suitable for industrial control system
InactiveCN108809951AStrong targetingValid device version informationTransmissionNetwork topologyVulnerability scanning
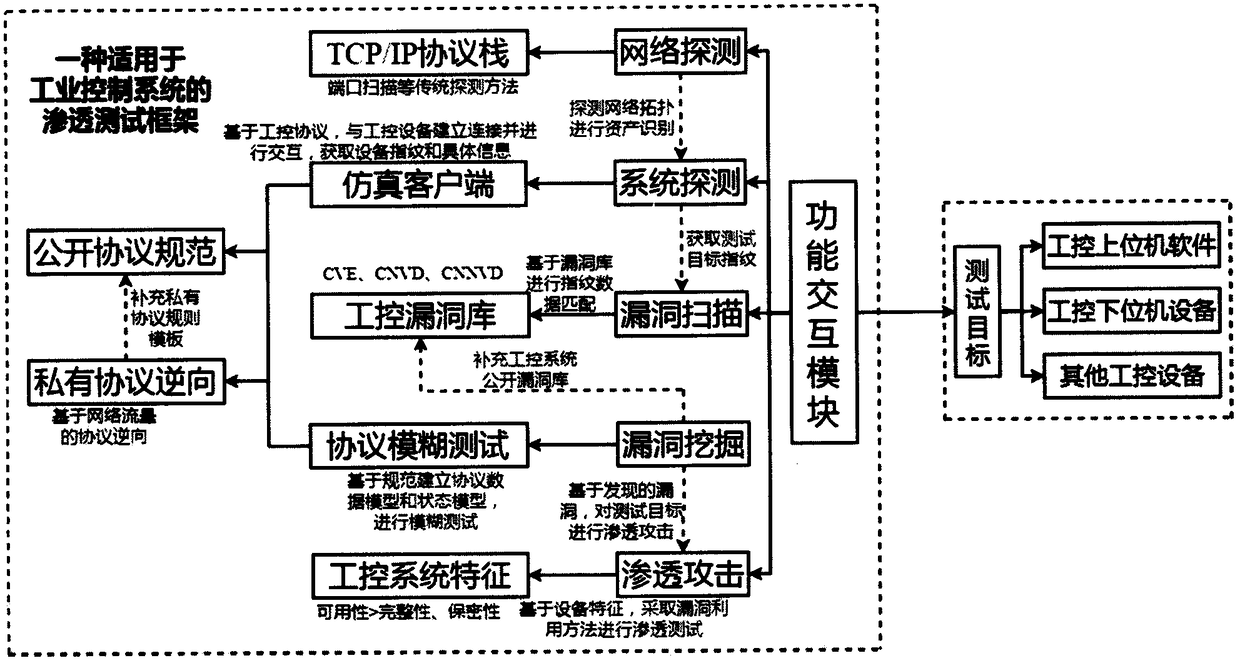
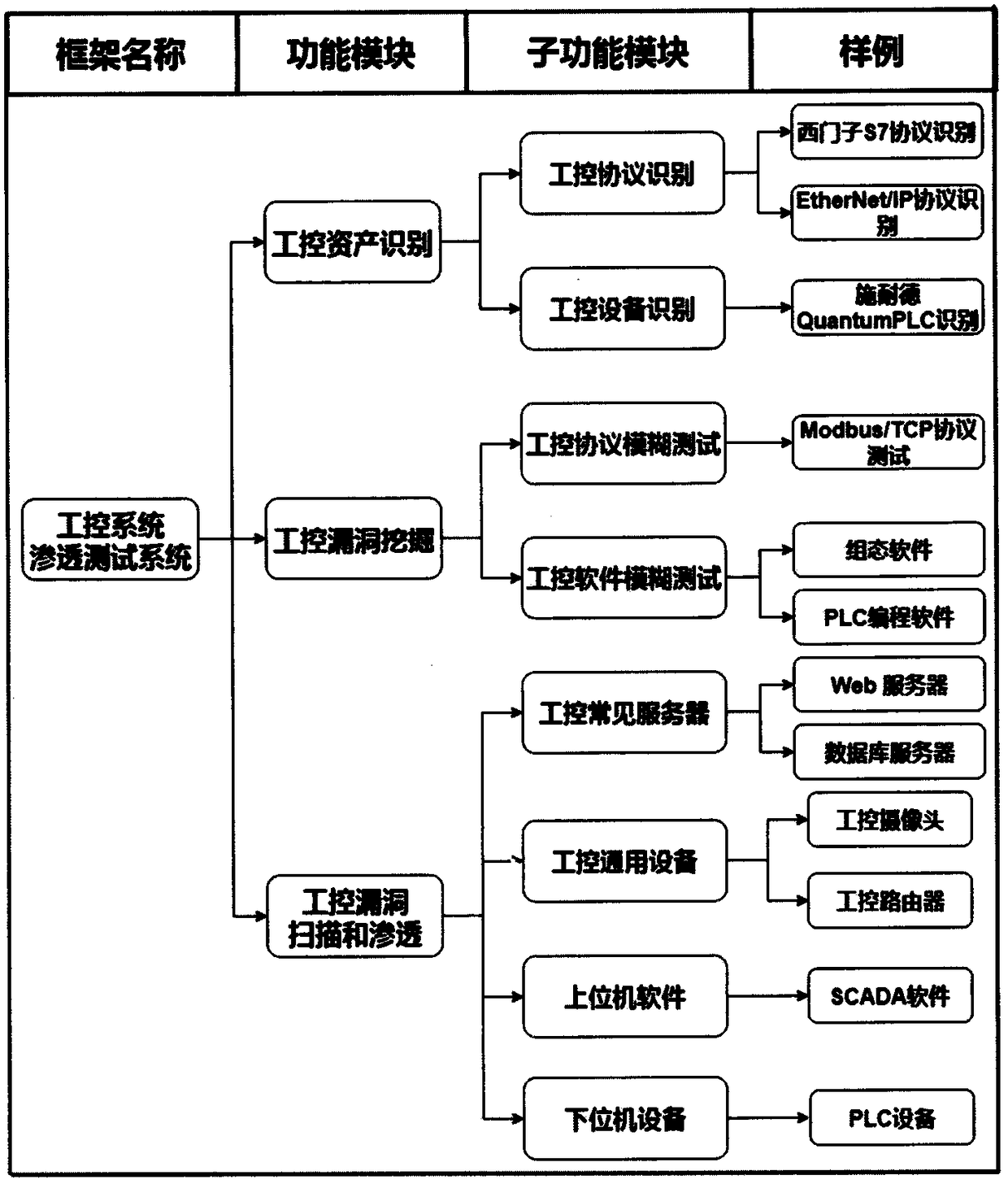
The invention discloses a penetration test framework suitable for an industrial control system. The penetration test framework comprises the following modules: (1) a functional interaction module based on a test target; (2) asset identification and network topology detection on a target network based on a TCP / IP protocol stack; (3) system detection based on an industrial control simulation client,and acquisition of target fingerprint information through a feature data packet; (4) vulnerability scanning based on an industrial control vulnerability library; (5) vulnerability mining based on anindustrial control proprietary protocol, and a blurring test of an industrial Ethernet protocol test; and (6) penetration attack based on features of the industrial control system, and an effective simulation attack on the test target. The framework can perform an effective penetration test on the industrial control system, and solve the problems of of low detection efficiency of the industrial control system, low coverage of industrial control vulnerabilities, difficult detection of industrial control environment vulnerability and single use of vulnerabilities of the existing penetration testtools.
Owner:NANJING UNIV +3
Grading optimization method for asphalt mixture under virtual state
ActiveCN106950120AEasy to operateStrong representativeMaterial strength using tensile/compressive forcesMaterial strength using steady shearing forcesOperabilityVirtual state
The invention discloses a grading optimization method for an asphalt mixture under virtual state. The method includes the steps of: on the basis of grading that needs to optimize according to practical demand, in three-dimensional discrete element software PFC3D, randomly generating an asphalt mixture mechanical test three-dimensional discrete element model (including uniaxial penetration test, low temperature split test, uniaxial compression test and shear fatigue test) which satisfies a target grading, wherein the generation process of the three-dimensional discrete element model, which satisfies the target grading, is the base of asphalt mixture grading optimization; and comparing mechanical performance evaluation results of various grading to obtain a grading having best mechanical performance. The method has strong operability, convenience and representativeness.
Owner:ZHEJIANG UNIV
Endoscope with ultraviolet illumination
ActiveUS20050085698A1Convenient lightingGood for observationSurgeryEndoscopesLight beamUltraviolet lights
An endoscope with deflected distal viewing, comprises a rigid tube containing observation means, themselves comprising a distal deflector prism having a viewing axis that is inclined relative to the axis of the tube, and ultraviolet light guide means housed in the tube and opening out at their distal end onto a prism for deflecting the illuminating light beam in a direction that is substantially parallel to the viewing axis. The invention applies in particular to inspecting parts by the penetration test technique in the aviation field.
Owner:SN DETUDE & DE CONSTR DE MOTEURS DAVIATION S N E C M A
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com