Automated safety penetration test method
A penetration testing and security technology, applied in the field of network security, can solve the problems of inconsistent data format, lack of test platform, and inability to carry out autonomous interaction, so as to improve efficiency and automation, realize automatic invocation and execution, improve integrity and The effect of accuracy
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0057] The present invention will be further described below in conjunction with the accompanying drawings and embodiments.
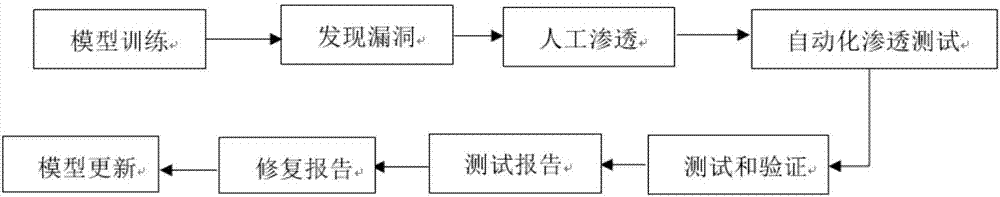
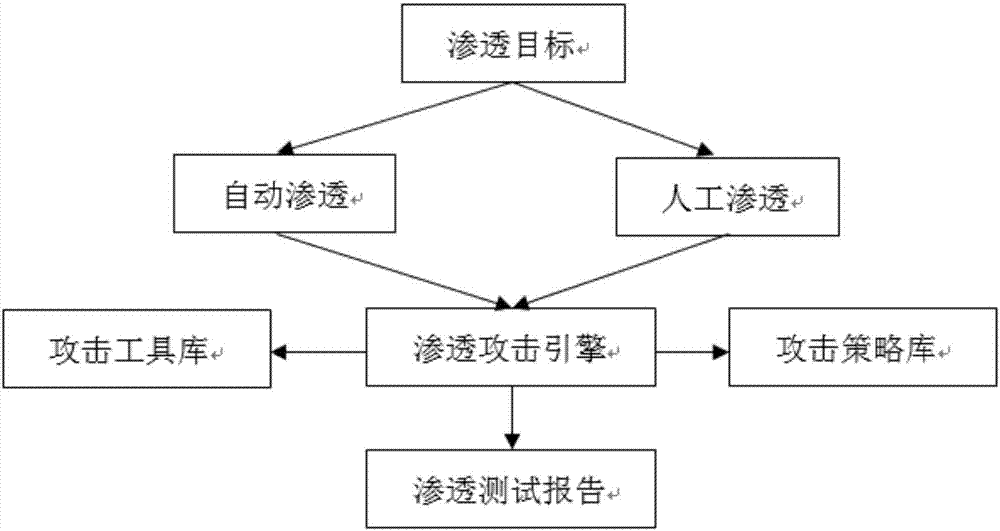
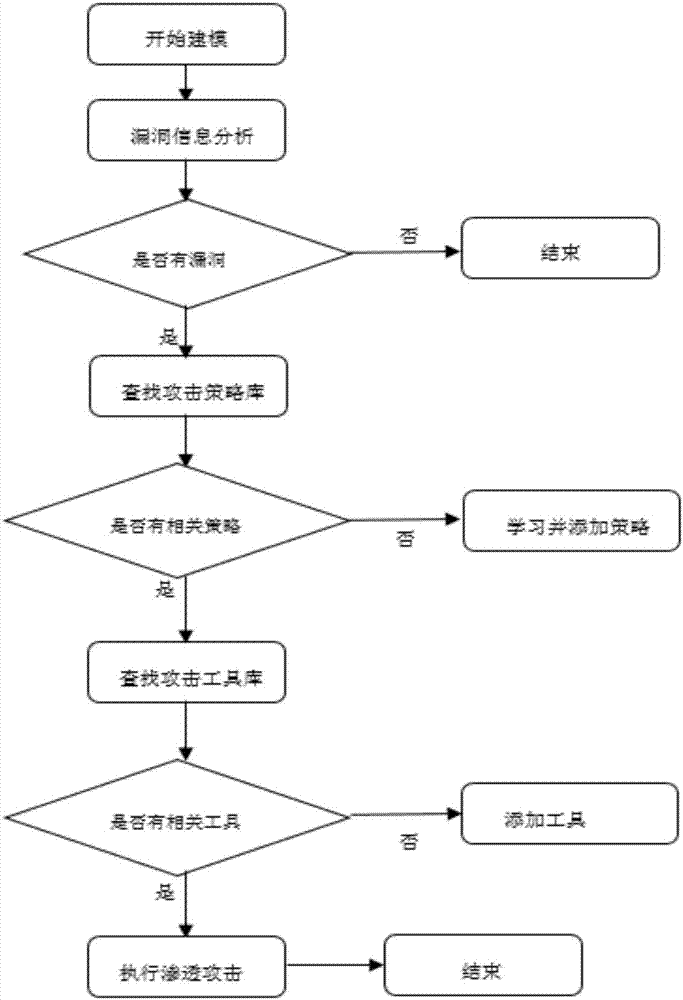
[0058] Such as figure 1 , figure 2 and image 3 As shown, the method of the present invention adopts the scripting language Ruby to develop, adopts the standard interface, and can be docked with other security systems (Nessus, Nexpose, Appscan, WVS, etc.). The invention supports the combination of manual and automatic penetration methods, covers common penetration testing methods, and can perform penetration testing on networks, WEB applications, databases, network equipment, mobile terminals, and the like. All functions of the present invention are modeled development, support multi-user and multi-task operation, and can meet different penetration testing requirements. The specific process is as follows:
[0059] Step 0: Automatically respond to model training and establish a corresponding model.
[0060] Step 0.1: Continuously collect process inf...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com