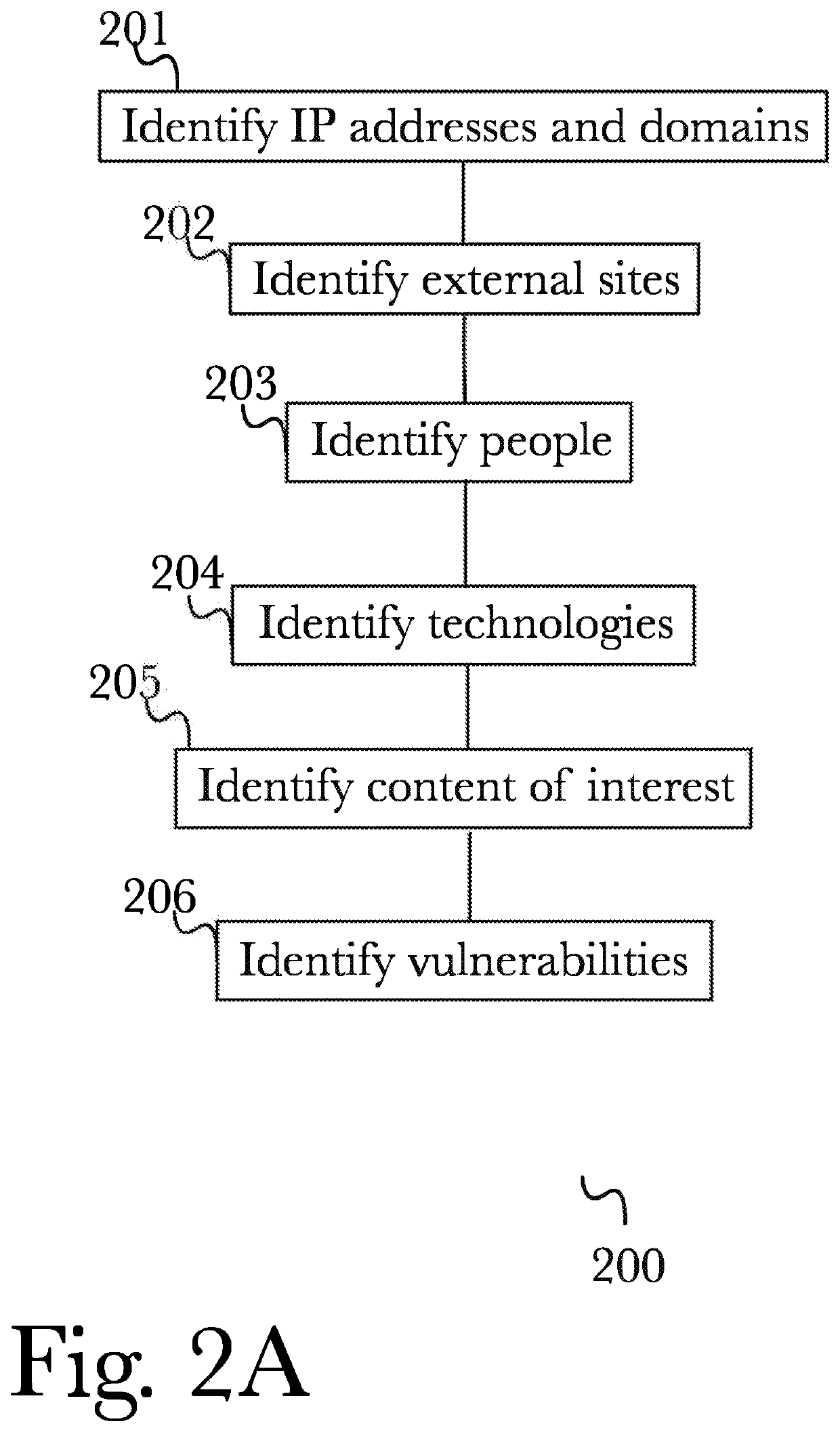
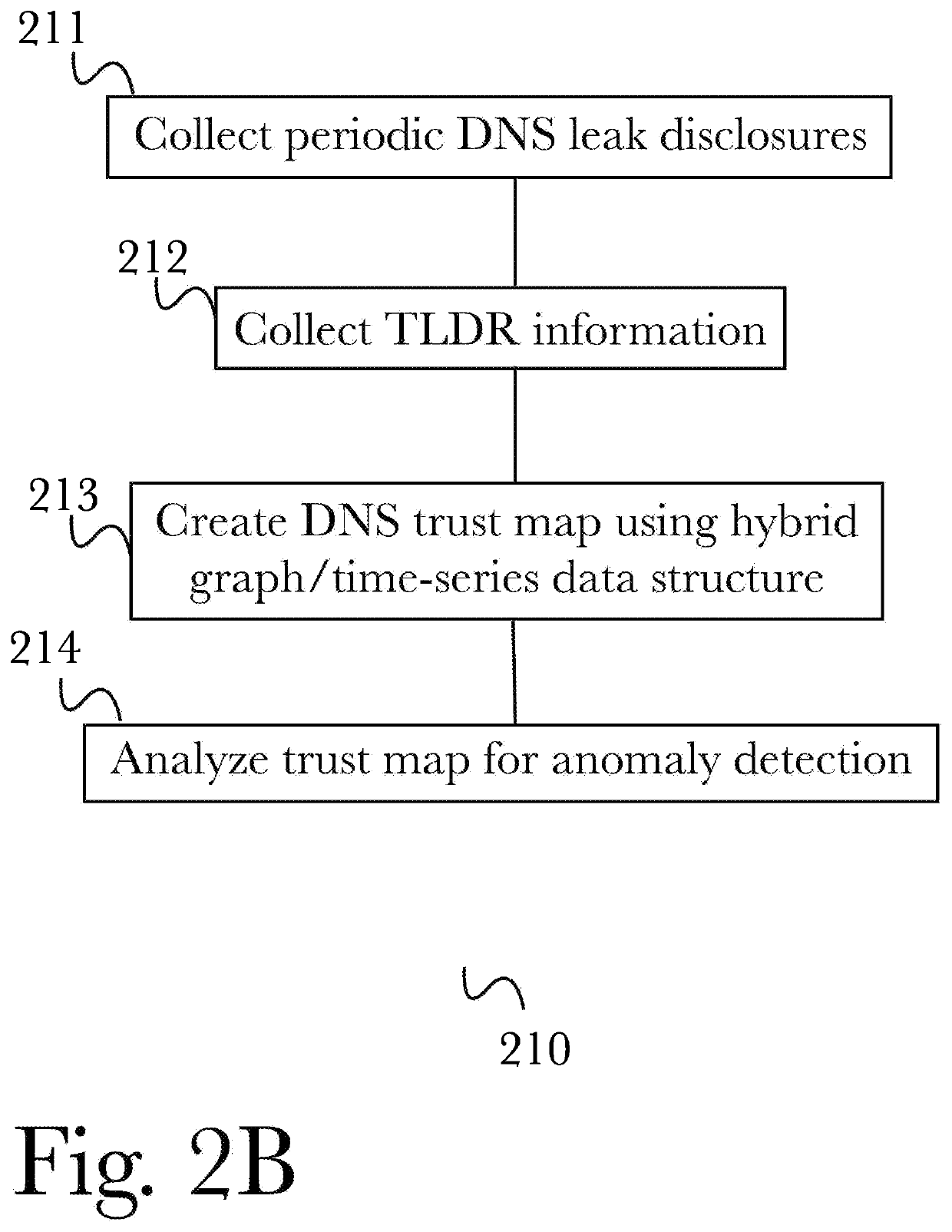
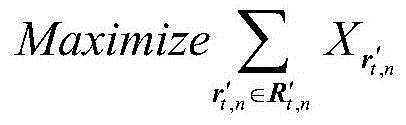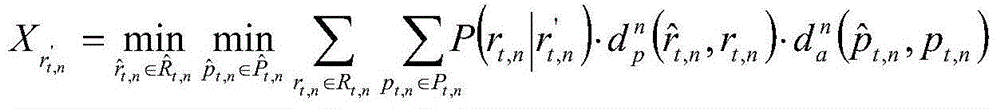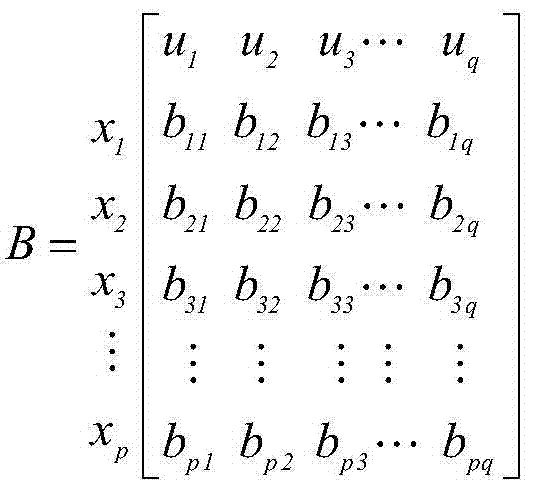Patents
Literature
137 results about "Attack strategy" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
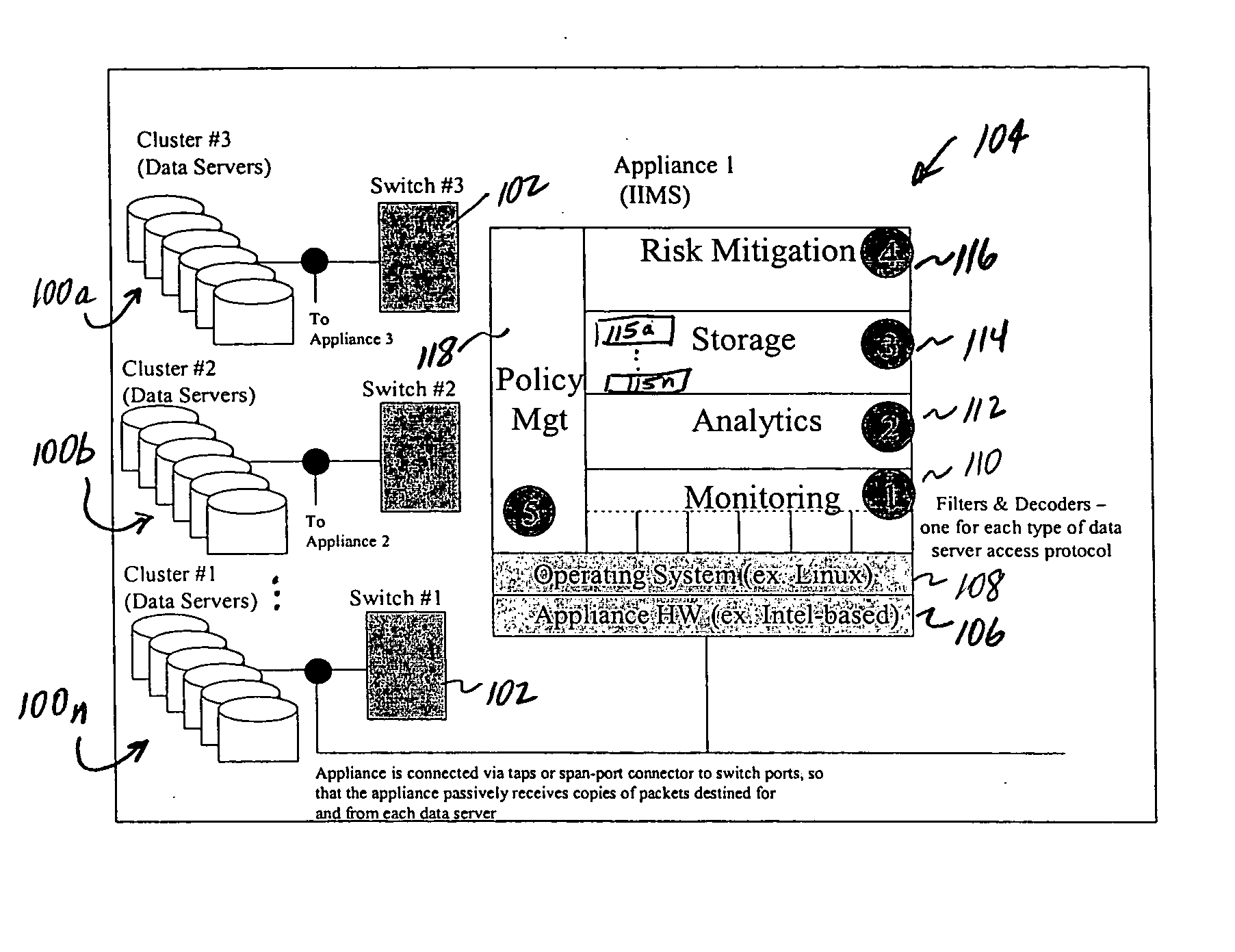
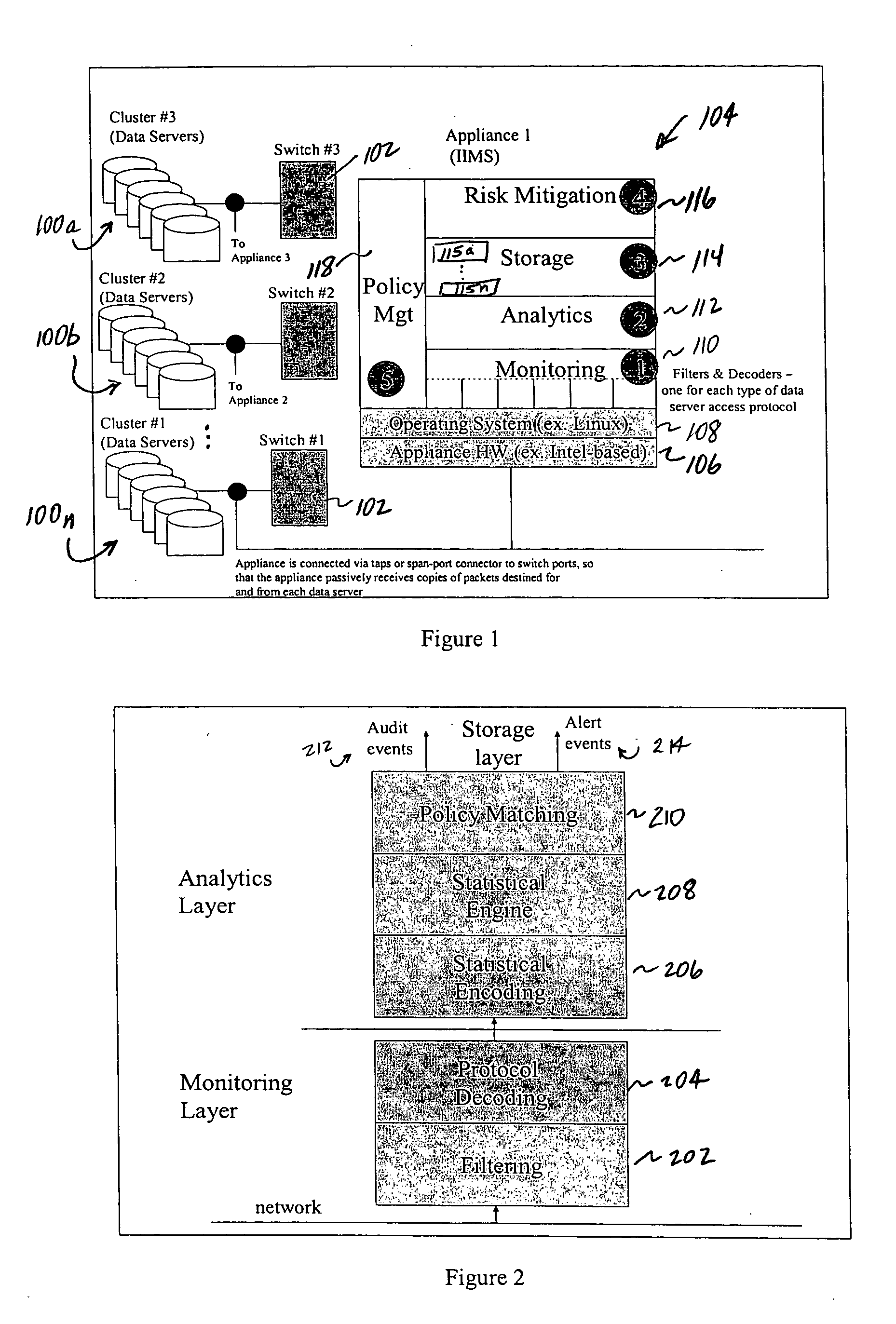
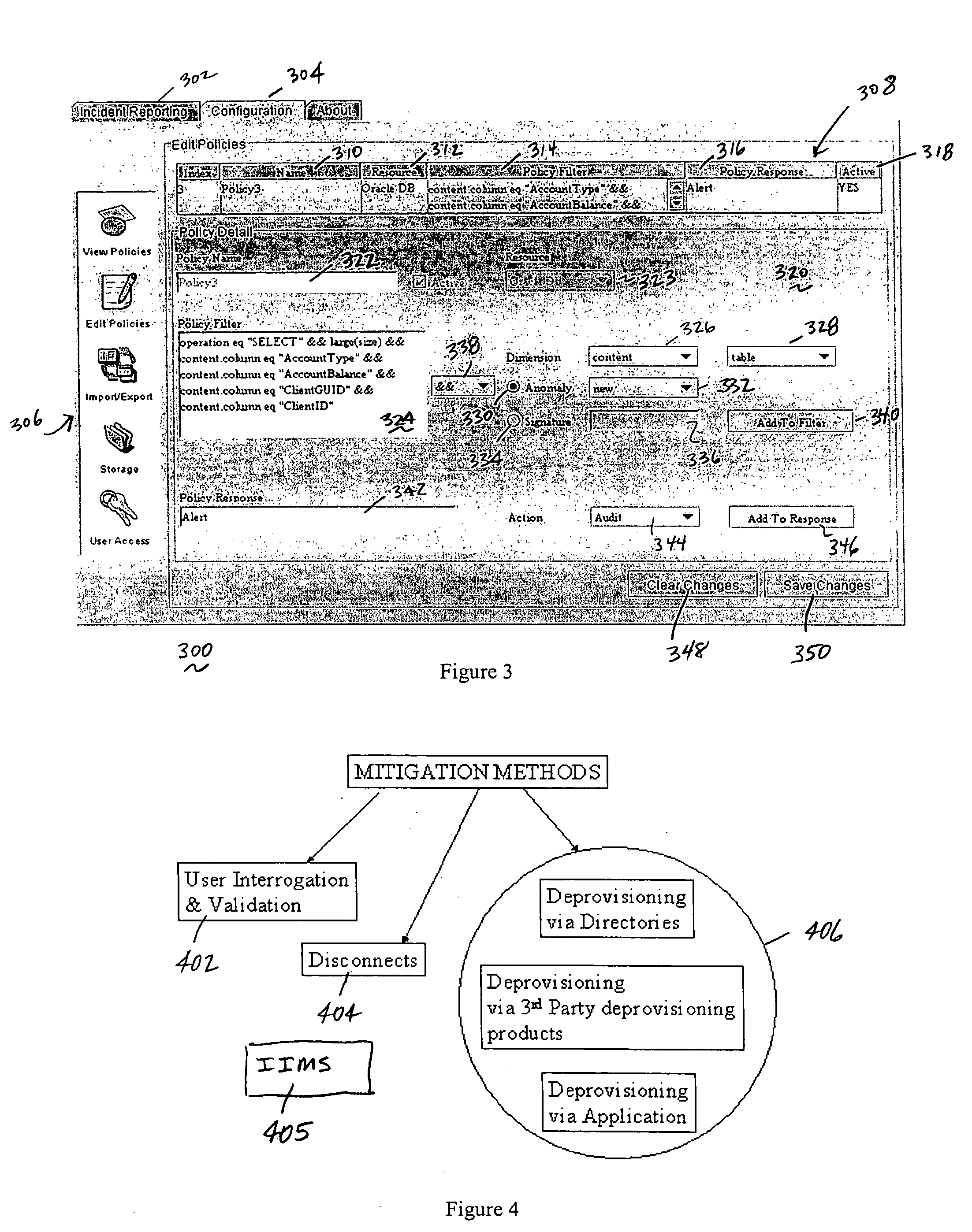
Method of and system for enterprise information asset protection through insider attack specification, monitoring and mitigation
ActiveUS20050071643A1Reduce harmComputer security arrangementsSecret communicationData accessAttack strategy
The present invention provides a policy specification framework to enable an enterprise to specify a given insider attack using a holistic view of a given data access, as well as the means to specify and implement one or more intrusion mitigation methods in response to the detection of such an attack. The policy specification provides for the use of“anomaly” and “signature” attributes that capture sophisticated behavioral characteristics of illegitimate data access. When the attack occurs, a previously-defined administrator (or system-defined) mitigation response (e.g., verification, disconnect, de-provision, or the like) is then implemented.
Owner:SOFTWARE LABS CAMPUS UNLIMITED CO
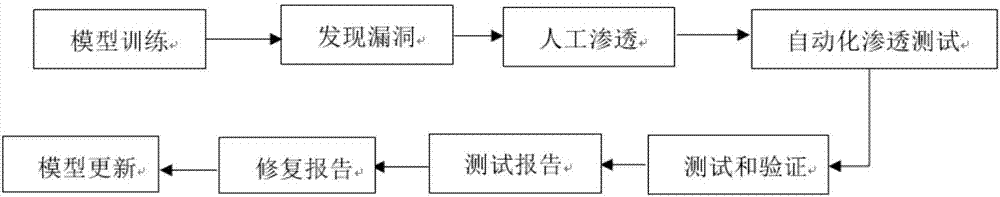
Automated safety penetration test method
ActiveCN107426227ARealize automatic callAchieve executionPlatform integrity maintainanceData switching networksAttack modelAttack strategy
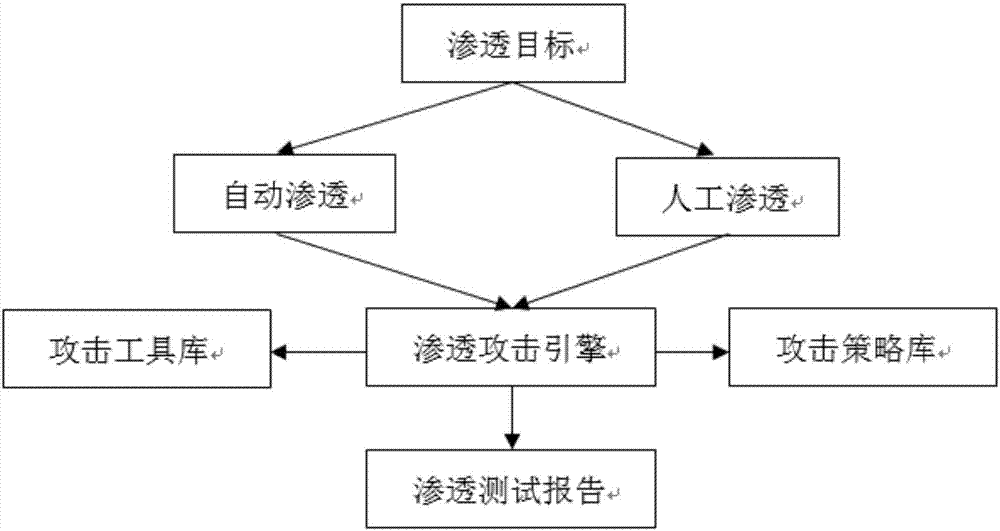
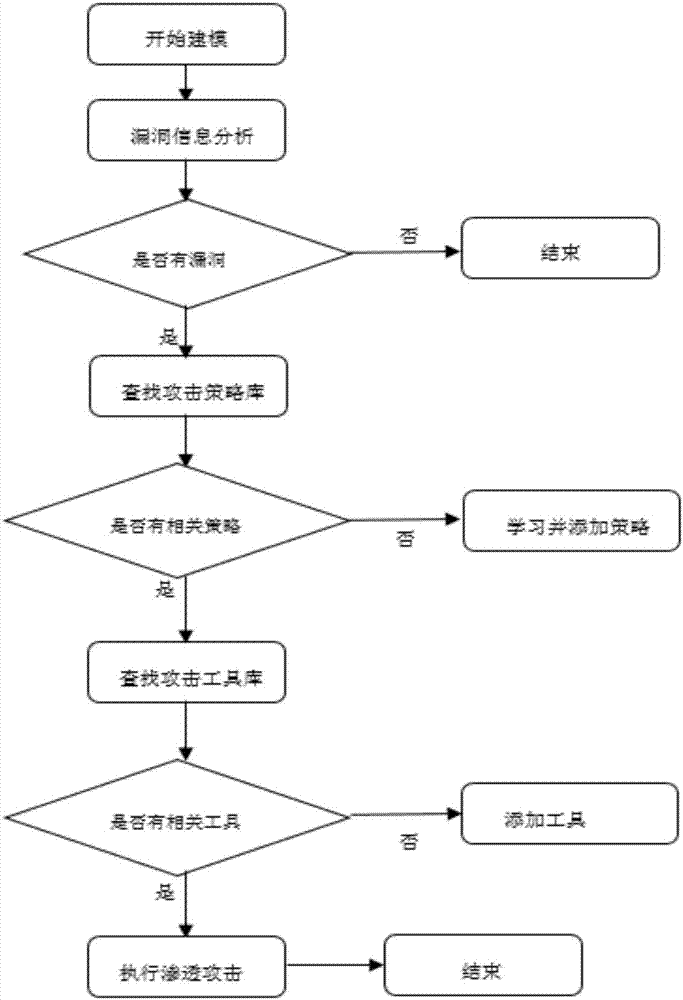
The invention discloses an automated safety penetration test method, comprising: step 1, training an automated response model, establishing a corresponding model; step 2, scanning a target information system, obtaining host information; step 3, scanning vulnerability of the target information system, obtaining vulnerability information; step 4, according to the host information and the vulnerability information obtained in the step 2 and step 3, combined with an attack strategy library, establishing an attack model, according to the attack model, trying to attack the target information system, obtaining an attack feedback result; step 5, performing comprehensive analysis on a penetration test overall process, generating a penetration test report and teasing test steps and intermediate results, analyzing system security, providing a related solution; step 6, the response model updating in an adaptive manner, and regulating a response strategy.
Owner:CHINA INFOMRAITON CONSULTING & DESIGNING INST CO LTD
Method for selecting optimized protection strategy for network security
InactiveCN101820413AAccurate and effective strategic performanceData switching networksStatistical analysisAttack strategy
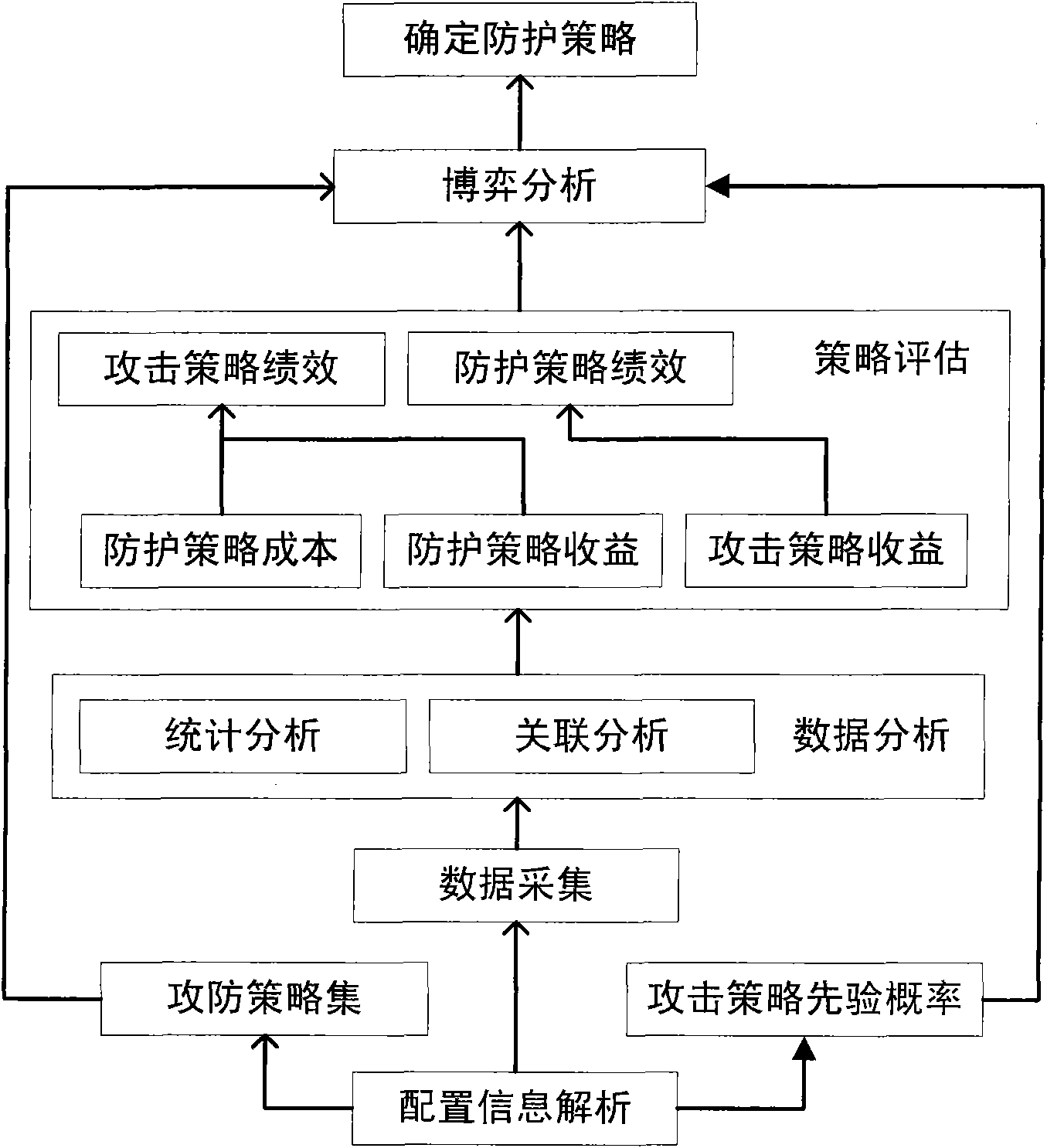
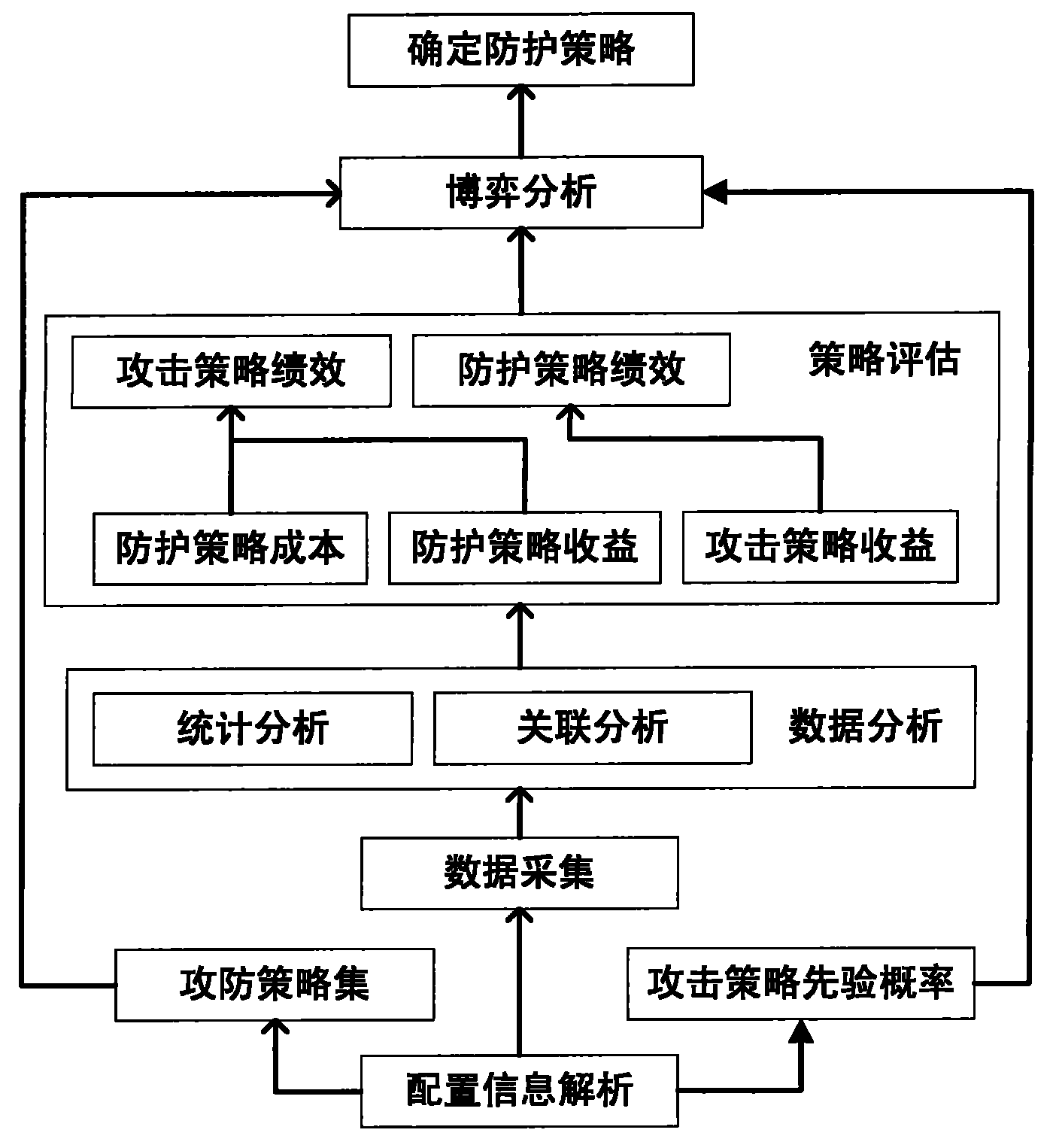
The invention discloses a method for selecting an optimized protection strategy for network security and belongs to the technical field of the network security. The method for selecting the optimized protection strategy for the network security comprises the following steps of: 1) analyzing user configuration information, and acquiring host information, link information, service information, protection system information, economic cost information and property importance information in the attack-defense process; 2) performing statistic analysis and association analysis on the acquired information, and outputting an analysis result; 3) calculating the protection strategy performance and attacking strategy performance according to the analysis result; 4) establishing a static Bayesian game model for the attacking party and the defending party according to the user configuration information and the calculated result in the step 3); and 5) calculating Bayesian Nash equilibrium according to the established static Bayesian game model, and determining the protection strategy during the Bayesian Nash equilibrium as the network security protection strategy. Compared with the prior art, the method for selecting the optimized protection strategy for the network security integrates various factors to provide the optimized protection strategy for a network security manager.
Owner:INST OF SOFTWARE - CHINESE ACAD OF SCI
Malicious scanning defense method and system based on adaptive IP address conversion
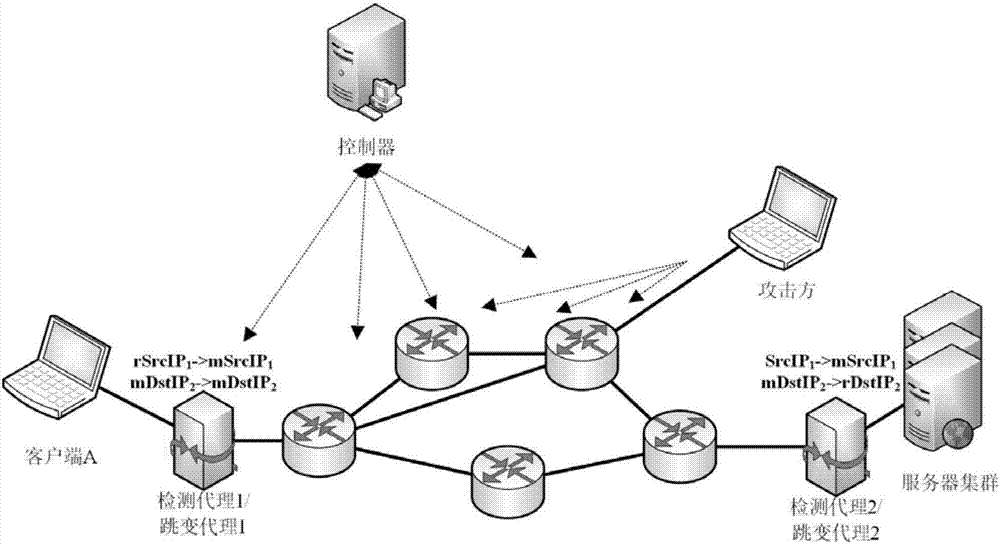
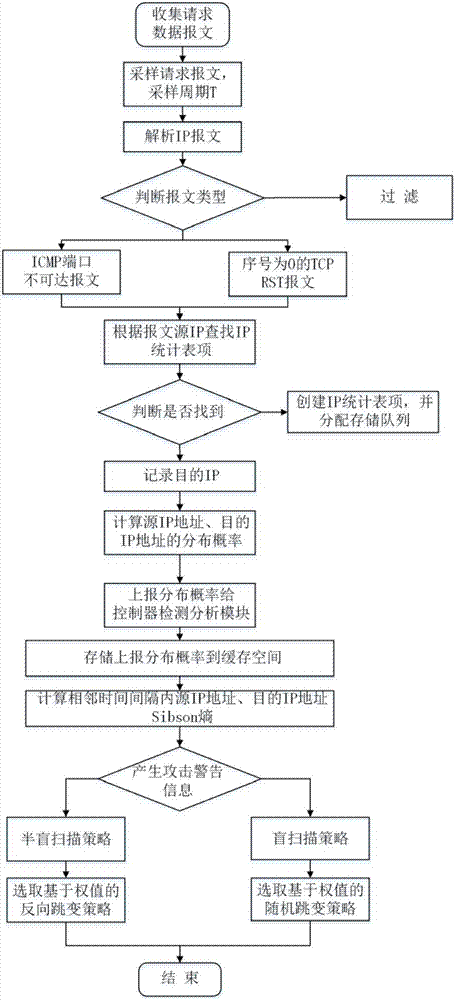
InactiveCN106982206AImprove manageabilityImprove Adaptive HopTransmissionAttack strategyVirtual IP address
The invention provides a malicious scanning defense method based on adaptive IP address conversion, applied to an SDN. The method comprises the following steps: 1) in the case of a scanning attack, sampling a request data packet from each subnet of the SDN, and analyzing the request data packet to generate statistical data within different time intervals; 2) calculating the distribution of a source IP address, a destination IP address and a destination port number within each time interval according to the statistical data; 3) calculating the Sibson entropy of the same distribution of the source IP addresses, the destination IP addresses and the destination port numbers within adjacent time intervals, and judging a scanning attack strategy accordingly; and 4) generating an IP address transfer strategy according to the scanning attack strategy, and implementing virtual IP address conversion according to the IP address transfer strategy. Meanwhile, the invention further provides a system for implementing the method. The system comprises constructing a controller, hopping proxy and detection proxy in the SDN architecture for implementing the steps in the method.
Owner:INST OF INFORMATION ENG CAS
Security policy dynamic acquisition method of process control system based on attack-defense game
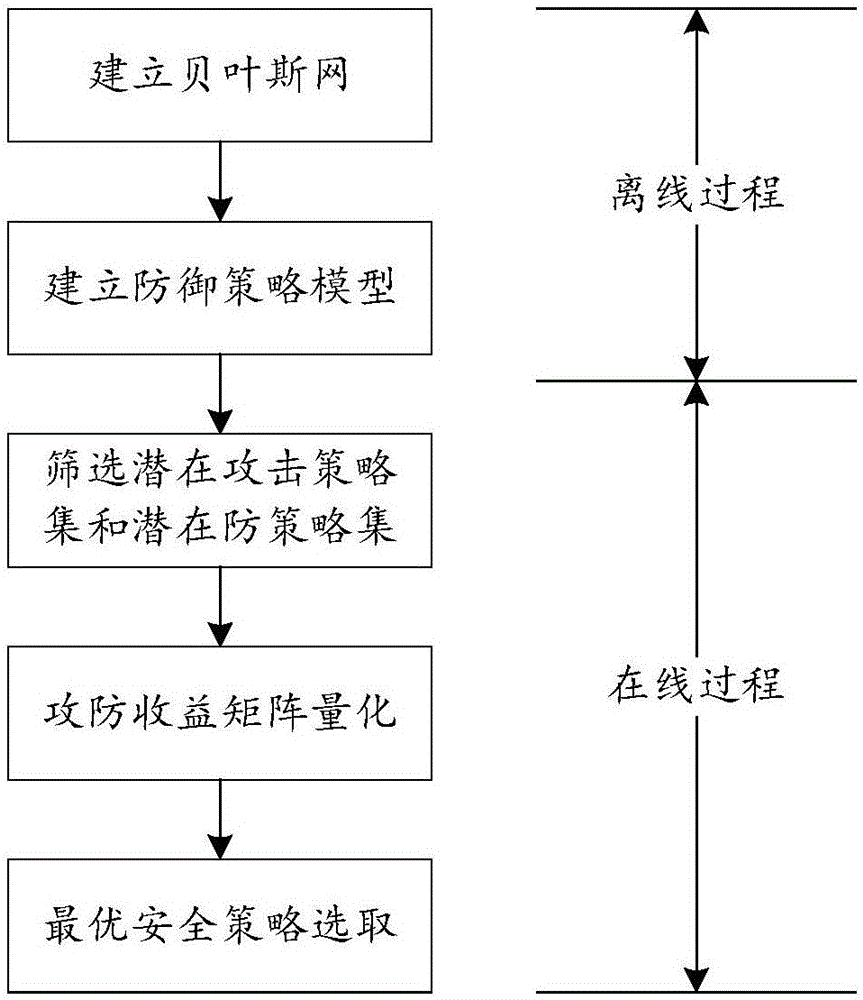
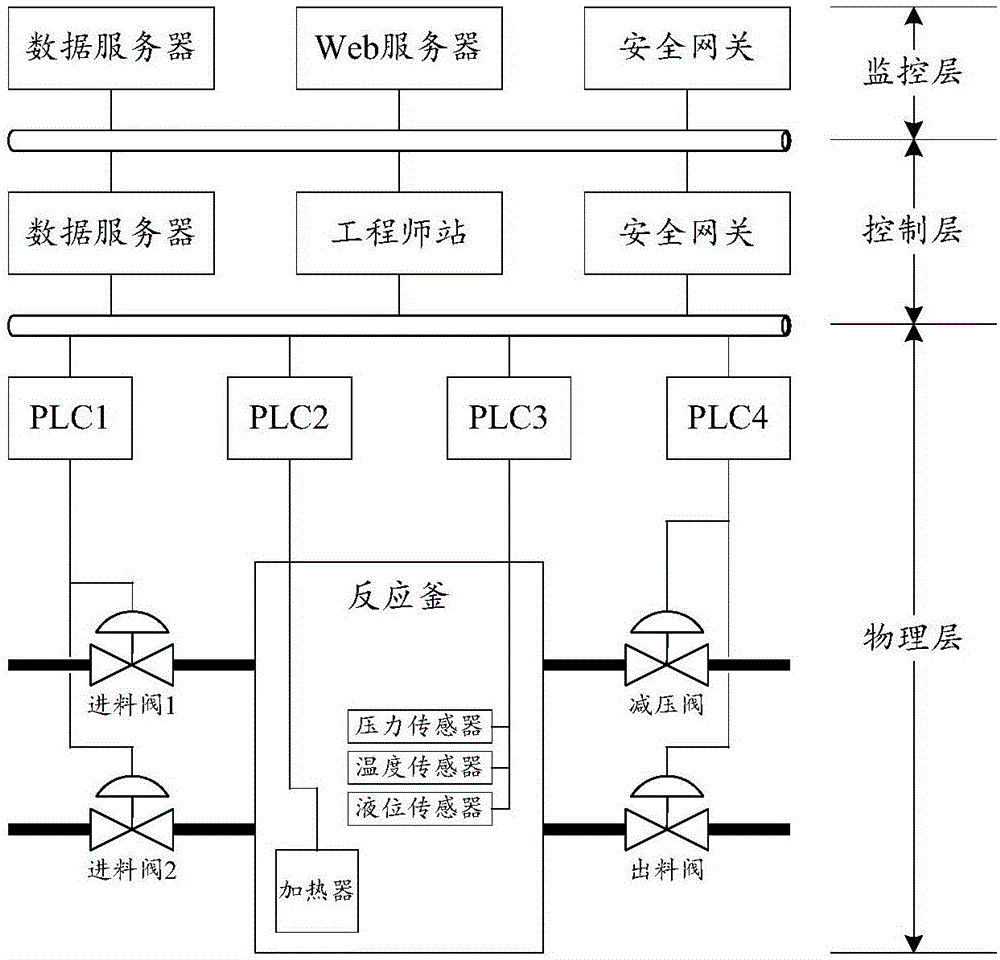
ActiveCN106453379ARealize unified scale quantificationExcellent security policyTransmissionProgramme total factory controlControl systemResponse method
The invention discloses a security policy dynamic acquisition method of a process control system based on an attack-defense game. The method comprises an offline process and an online process; the method comprises the following steps: firstly, analyzing the process control system and establishing a Bayesian network; secondly, building a defense strategy model; thirdly, screening a potential attack strategy set and a potential defense strategy set; fourthly, quantizing an attack-defense payoff matrix; and finally, according to the attack-defense payoff matrix, establishing an equation solution and acquiring an optimal security strategy. The method of the invention comprehensively considers various consequences caused by the attack-defense strategy, and performs uniform scale quantization; an idea of an attack-defense game theory is introduced to a solving process of the optimal security strategy, so that the problems that the traditional dynamic strategy decision is excessive responsive, and the response mode of a dynamic decision response method is fixed and easily exploited by attackers are solved; and besides, the Bayesian network and the attack-defense strategy model are used for screening the potential attack-defense strategy, so that the number of alternative attack-defense strategies can be greatly reduced, thereby reducing the computing time of cost-benefit quantification of the attack-defense strategies, and improving the real-time performance of a dynamic decision.
Owner:HUAZHONG UNIV OF SCI & TECH
Threat detection and alert method and system based on big data analysis
The invention discloses a threat detection and alert method and system based on big data analysis. The system comprises an alert aggregation assembly, a scene extraction assembly, a study and detection assembly, a prediction assembly and a new attack strategy digging assembly. According to the threat detection and alert method and system, the big data technology is adopted to predict and alert network attacks to government and enterprise information systems in real time, thereby greatly covering the shortage of the existing information security alert analysis technology on one hand; and on the other hand, false alerts generated by information security equipment such as an intrusion detection system can be identified and unknown malicious attacks can be analyzed, and therefore, the accuracy and the credibility of the alerts can be improved and the security risks of the information systems can be sensed.
Owner:NANJING LIANCHENG TECH DEV
Adversarial sample defense method based on spoofing attacker
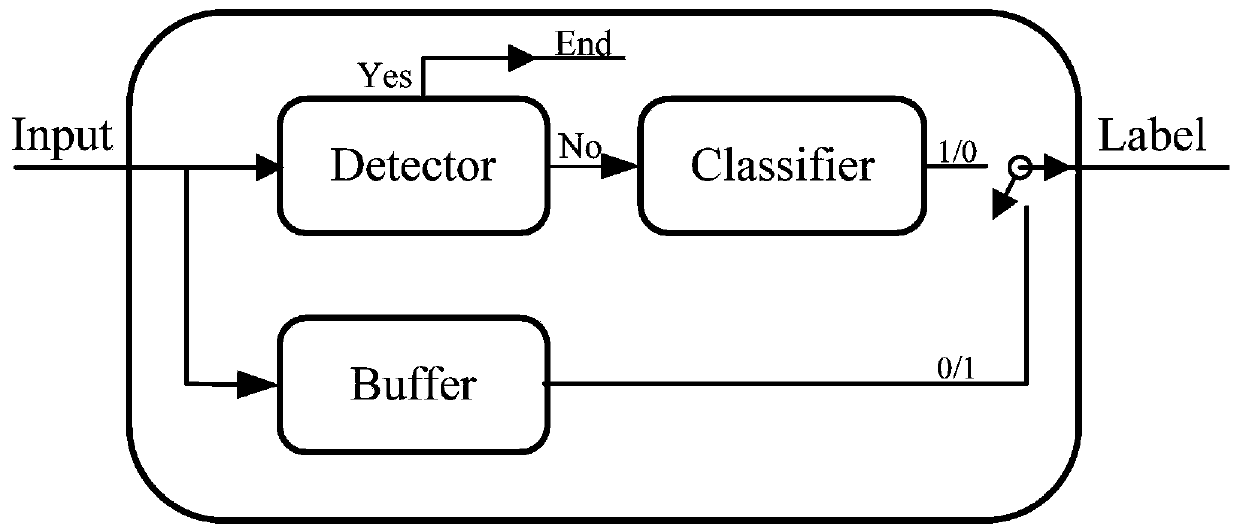
ActiveCN110852363ADefense Gradient AttackEfficient Gradient AttackCharacter and pattern recognitionGeneration processAlgorithm
The invention discloses an adversarial sample defense method based on a spoofing attacker, and belongs to the technical field of computer image processing. According to the technical scheme, a classification system is constructed on the basis that the classification performance of an original classifier is not changed, a buffer is added into the classification system in a parallel mode, and an attacker is well cheated by constructing a classifier 2 poor in generalization performance with the original classifier; an additional detector is arranged in front of an original classifier, single-stepattacks are defended, the difficulty of the attack process is improved, and only the original classifier is adopted to classify images classified into normal labels by the detected device; a comparator or an ensemble learning block is adopted to replace a detector, better classification performance and non-gradient return characteristics are obtained, and the comparator does not bear any specificattack strategy and disturbance mode. The method has the beneficial effects that the generation process of the adversarial sample is hindered by adopting the buffer, the comparator and the like, andthe defensive performance of the classification network on the adversarial sample is improved under the condition that the classification performance of the normal sample is not influenced.
Owner:DALIAN UNIV OF TECH
APT defense method based on game system
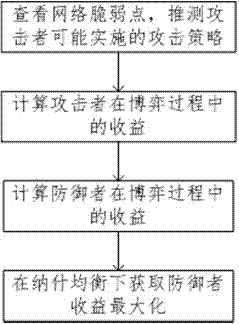
ActiveCN107147670ADefender's profit maximizationMaximize the benefitsTransmissionAttack strategyNetwork topology
The invention relates to an APT defense method based on a game system. The optimal response measure can be obtained according to the Nash equilibrium strategy, and the low efficiency caused by manual intervention on the detection of the traditional invasion system can be effectively solved. The APT defense method provided by the invention comprises the following steps: checking a fragile point of a network, and obtaining all possible attack strategies of an attacker according to a network topology structure; calculating an attacker benefit in the game system according to factors affecting the attacker benefit; calculating a defender benefit according to the factors affecting the attacker benefit; and obtaining the maximum defender benefit under the premise of Nash equilibrium.
Owner:福建中信网安信息科技有限公司
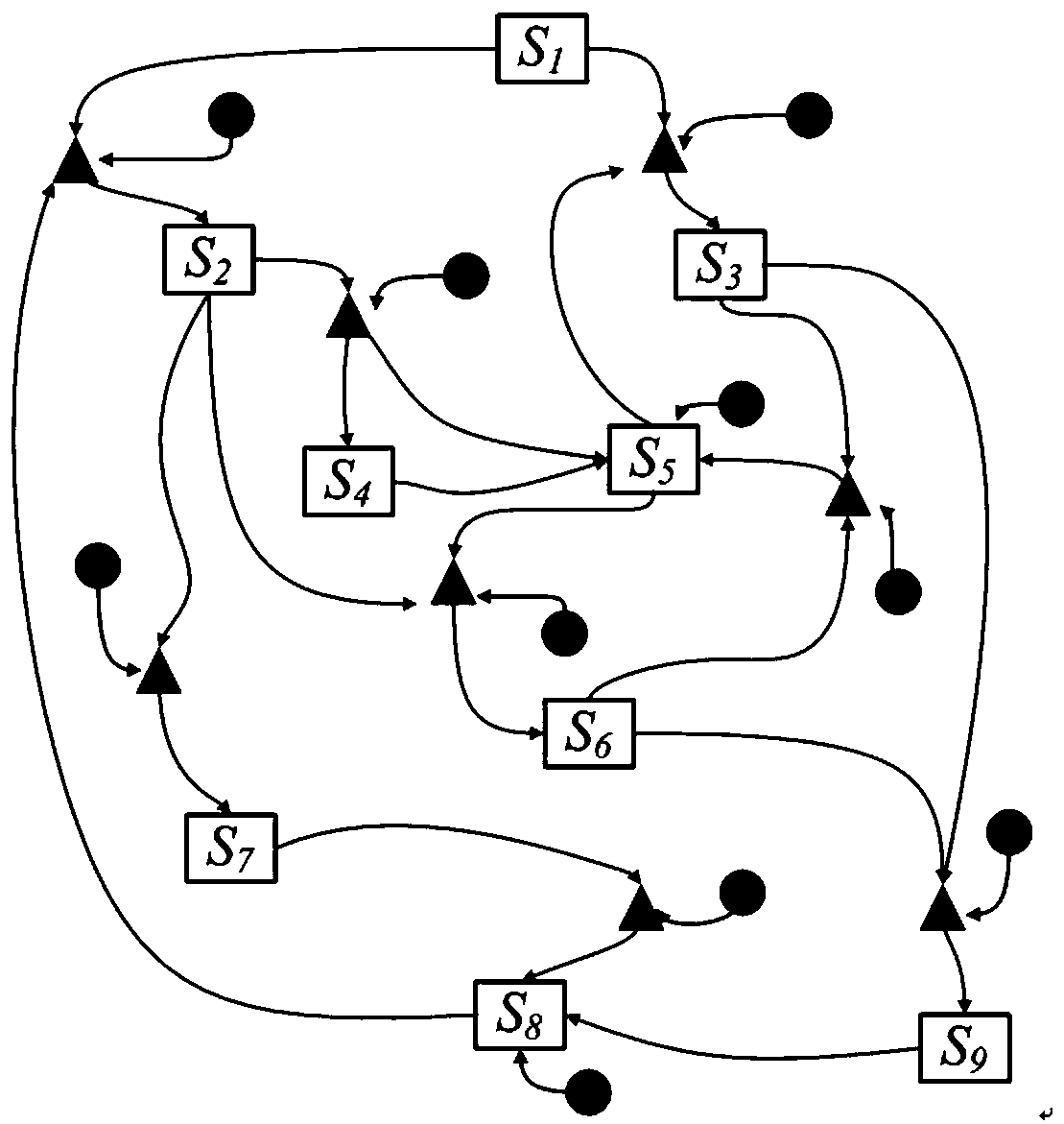
Method for comprehensively analyzing and processing real-time alarms on basis of attack strategy graphs and intrusion detection system thereof
InactiveCN103914649AImprove accuracySolve the split problemPlatform integrity maintainanceTransmissionGraphicsAlgorithm
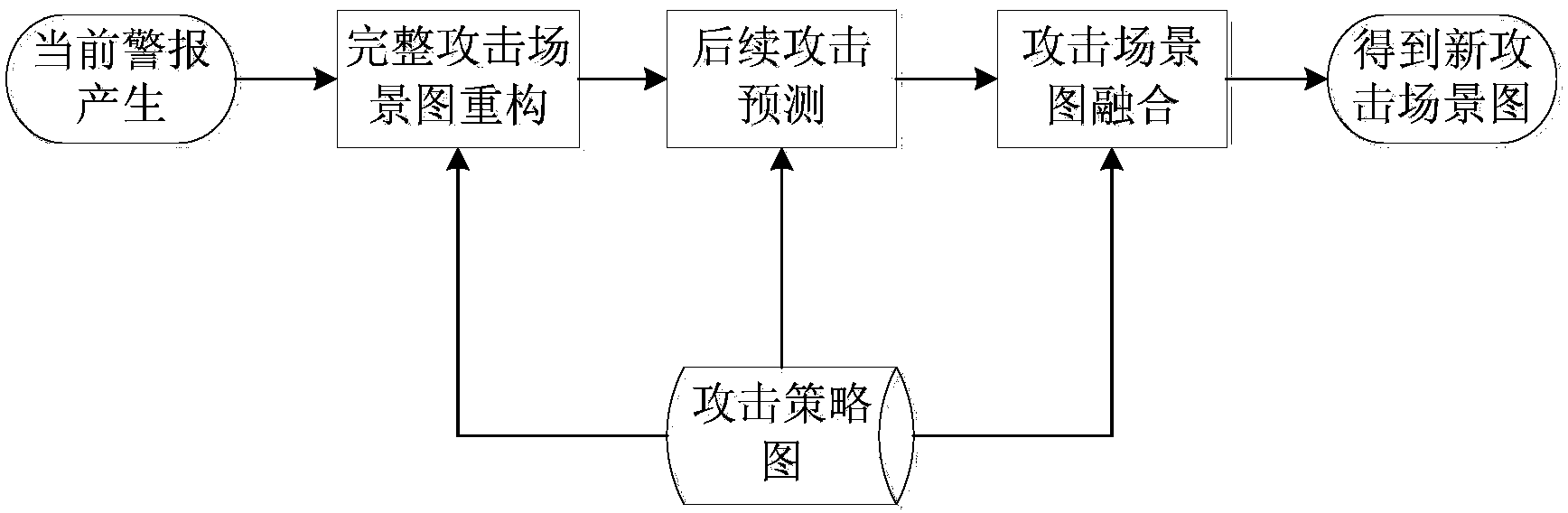
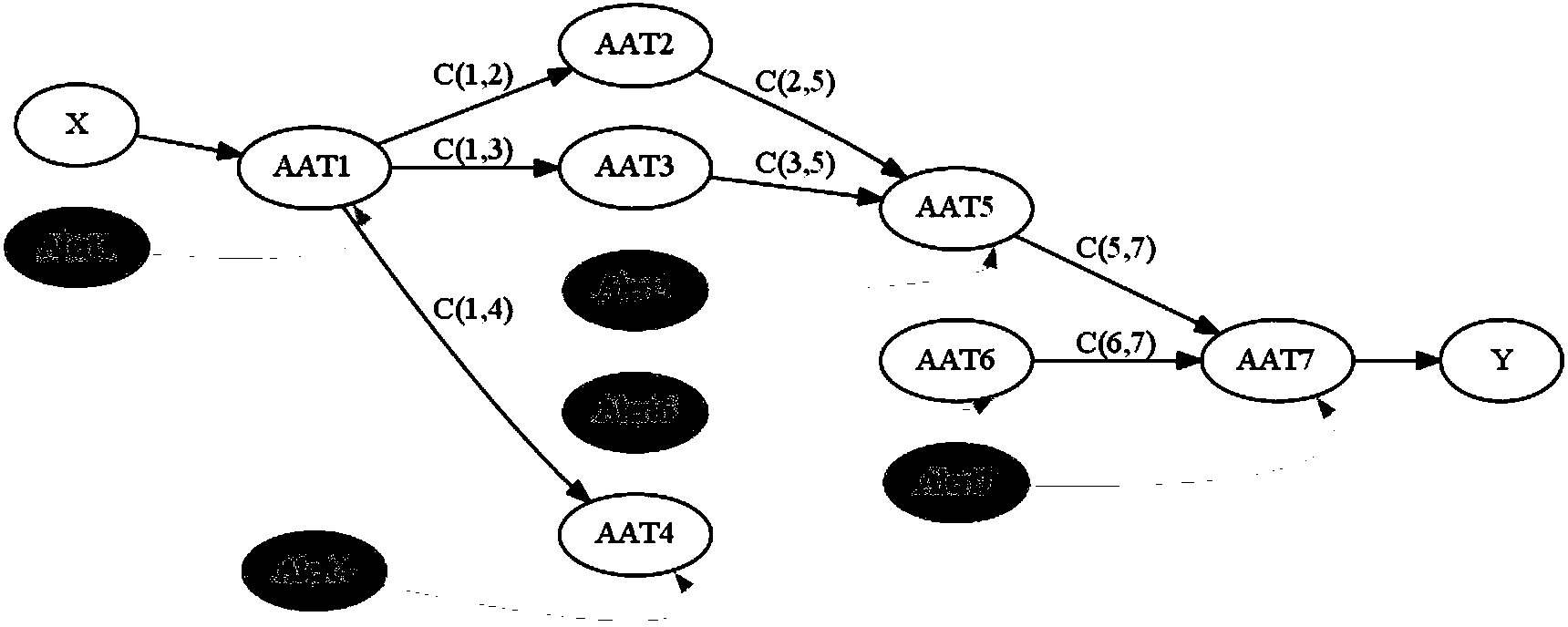
The invention provides a method for comprehensively analyzing and processing real-time alarms on the basis of attack strategy graphs and an intrusion detection system thereof; splitting of attack scene graphs can be effectively prevented, the complete attack scene graphs can be reconstructed, the subsequent attack can be predicted, attack scenes can be fused with one another, and alarm information capable of being directly utilized can be accurately provided for analysts. The method for comprehensively analyzing and processing the real-time alarm includes steps of (1), constructing the attack strategy graphs; (2), reconstructing attack scene graphs, adding missing alarms or inferences of attack links omitted deliberately by an attacker, utilizing inference results as inference alarms and adding the inference alarms into alarm sets to be associated; (3), predicting subsequent attacks; (4), fusing the attack scene graphs, expressing fused associated records by graphs, and acquiring fresh attack scene graphs. The method and the intrusion detection system have the advantages that splitting of attack scene graphs can be effectively prevented, and analyzing accuracy can be improved. The intrusion detection system is used for analyzing and processing safety events to alarms generated by the system by the analyzing and processing method.
Owner:XIDIAN UNIV
Method and system for three-in-one smart card anti-side-channel-attack protection
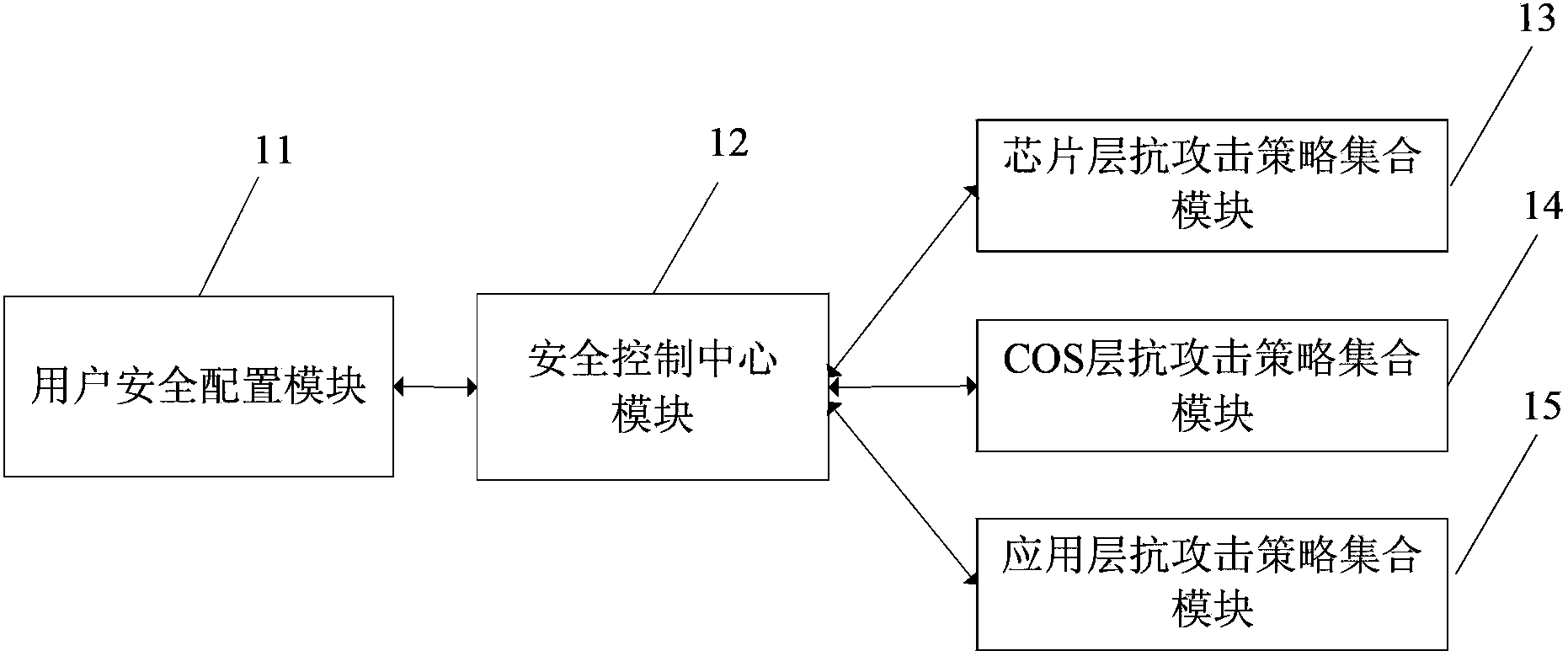
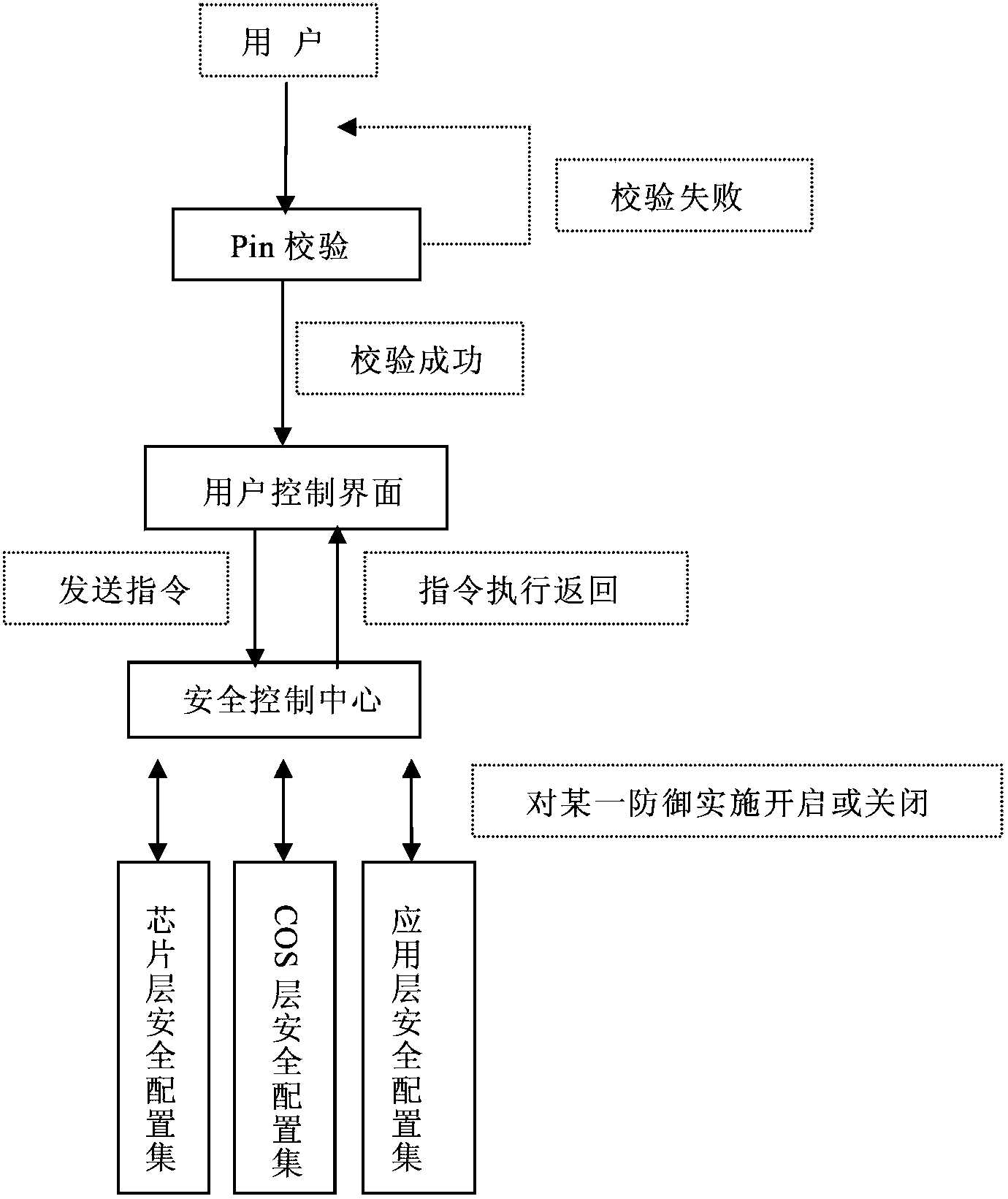
InactiveCN103903043AOptimizationIncrease the difficultyEncryption apparatus with shift registers/memoriesRecord carriers used with machinesAttack strategySmart card
The invention relates to a method and a system for three-in-one smart card anti-side-channel-attack protection. According to the method and the system of the invention, a security control center is arranged in a COS layer so as to configure and manage anti-attack strategies of a chip layer, the COS layer and an application layer in a unified mode. A legitimate user can configure the security control center through a user security configuration interface after PIN verification so as to realize flexible and unified three-in-one anti-attack strategy management. By adopting the method and the system of the invention, the overall security of smart cards can be promoted, and the difficulty for smart cards to resist side channel attack is increased.
Owner:BEIJING WATCH DATA SYST
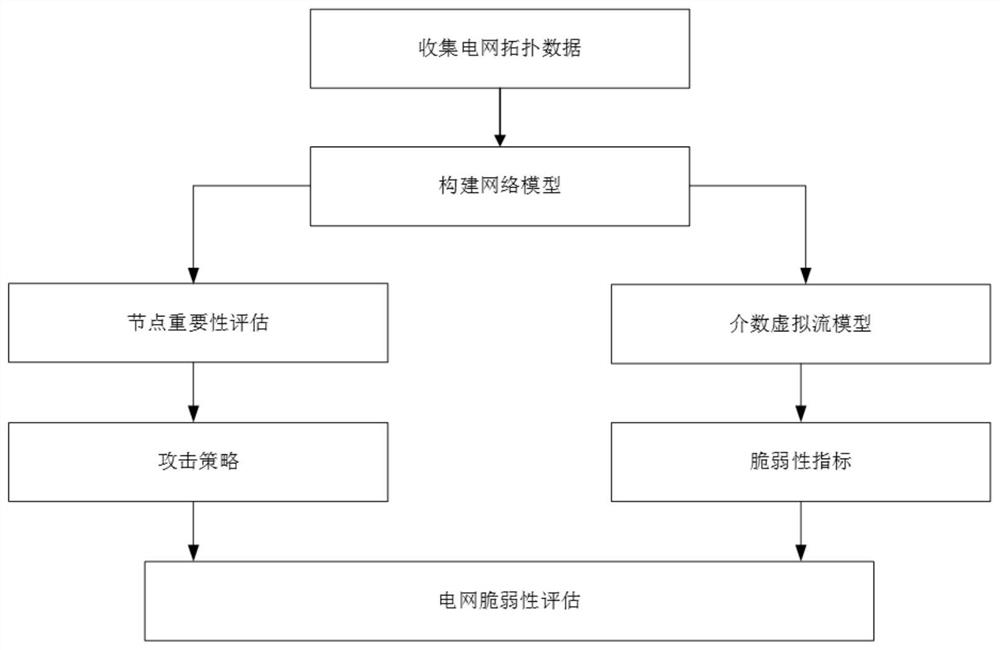
Power network vulnerability evaluation method based on multiple attack strategies
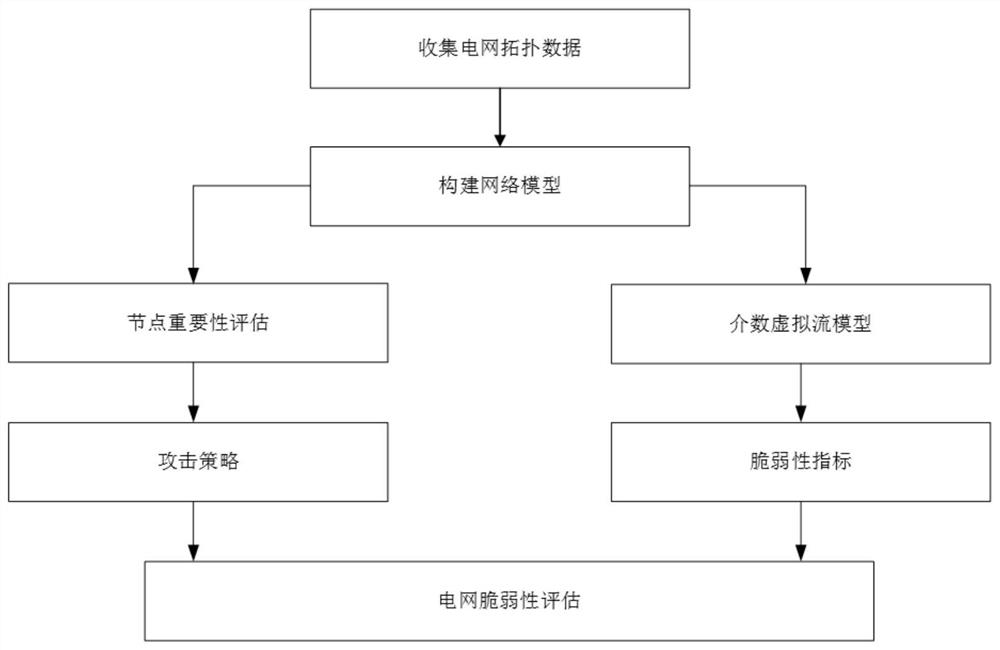
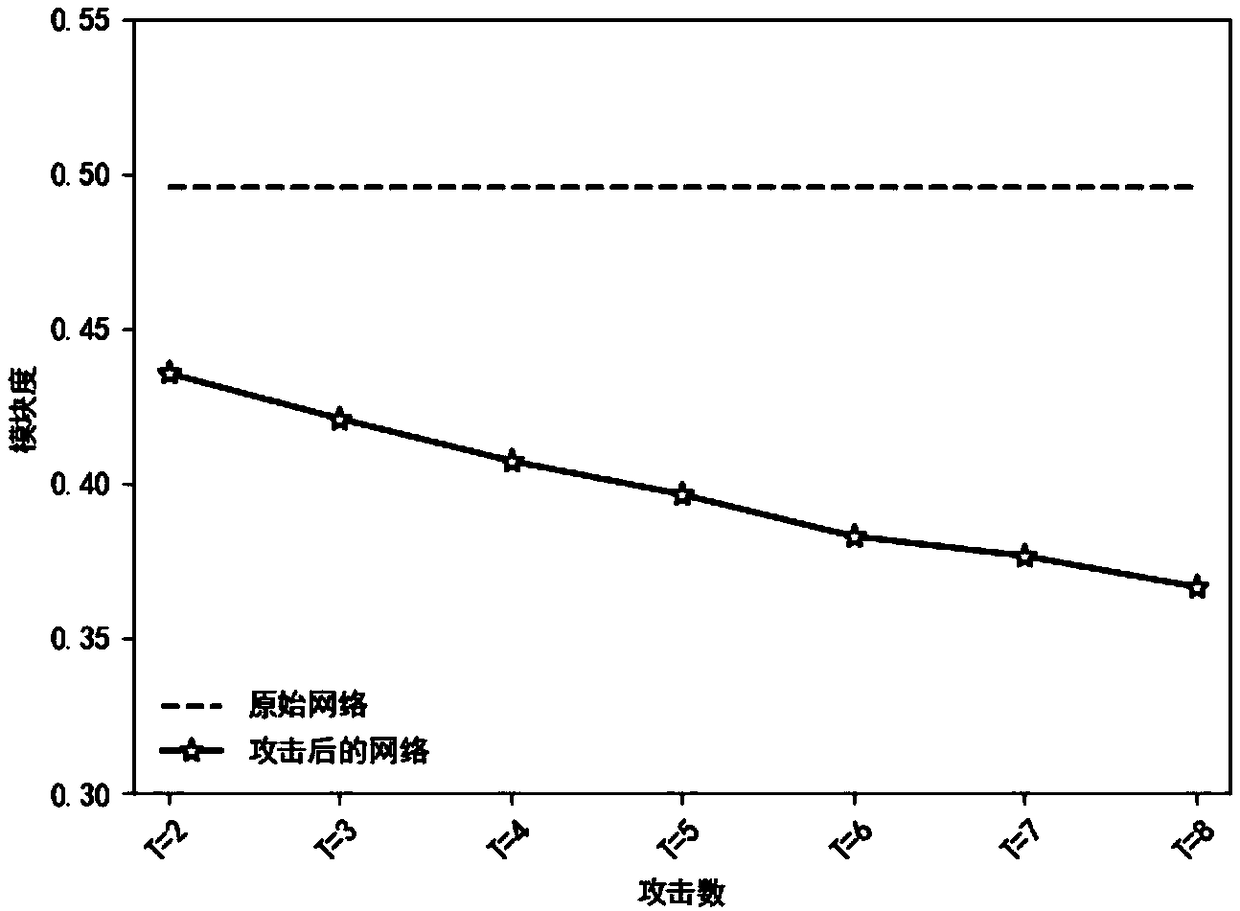
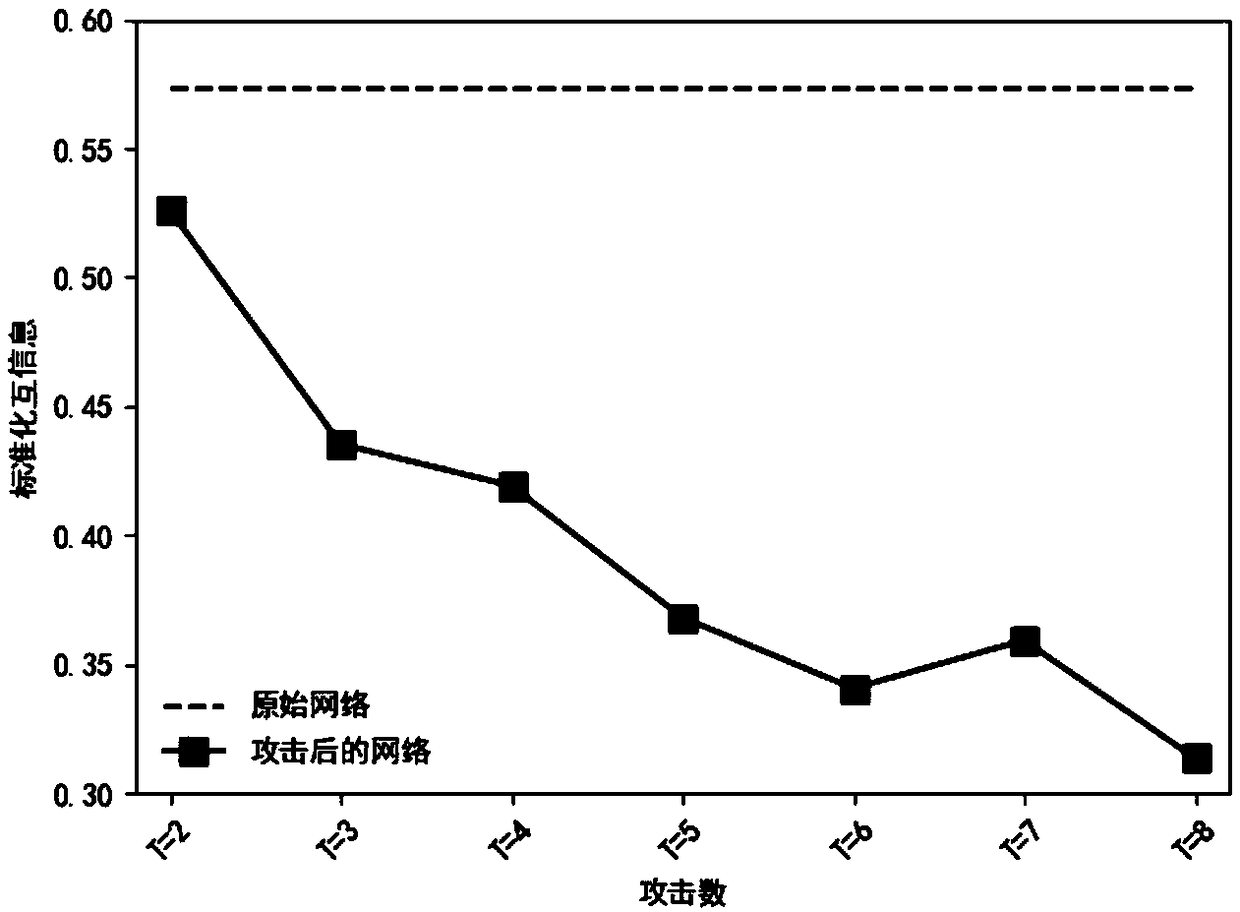
InactiveCN111950153AFacilitate identificationFeatures at the functional levelDesign optimisation/simulationResourcesElectric power systemAttack
The invention discloses a power system vulnerability evaluation method based on multiple attack strategies. The method comprises the following steps: 1) constructing a power grid model; 2) evaluatingthe importance of nodes in the network from four aspects of node degree, betweenness, local centrality and node fault loss, and completing the formulation of an attack strategy according to the importance of the network nodes; 3) establishing a betweenness virtual flow model to simulate a cascade fault propagation process in a power system; and 4) establishing a vulnerability index based on the betweenness virtual flow model, simulating a network attack by adopting a plurality of attack strategies, and evaluating the vulnerability of the IEEE300 power system network according to the change ofthe vulnerability index. Aiming at the vulnerability of the power network under the condition of various attack strategies, the betweenness virtual flow model and the various attack strategies are established to analyze the performance change of the power grid under the cascade failure. The importance of nodes in a power network can be identified, and decision support is provided for maintenance work of power system managers and power system fault prevention of designers.
Owner:XUZHOU NORMAL UNIVERSITY
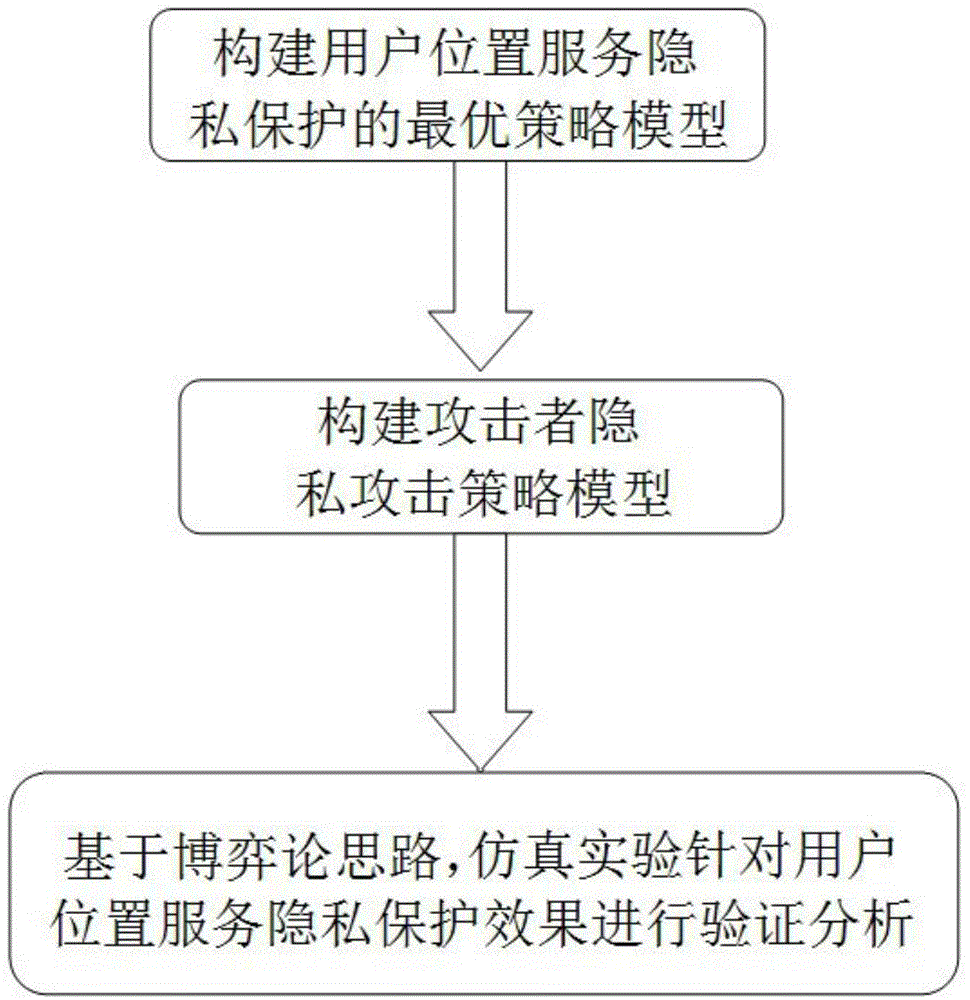
Privacy protection quantitative analysis method in location-based service
ActiveCN104918214AThe design idea is simpleEasy to understandLocation information based serviceSecurity arrangementPrivacy protectionAttack strategy
The invention relates to a privacy protection quantitative analysis method in a location-based service. Firstly, an optimal strategy model of user location-based service privacy protection is designed and built; according to corresponding design, an attacker privacy attack strategy model is built then; and, finally, based on game theory thinking, a simulation test is performed aiming at the optimal strategy model of the user location-based service privacy protection and the attacker privacy attack strategy model, the verification analysis is performed aiming at a simulation result, evaluation aiming at a user location-based service privacy protection effect is achieved, a user's specific mobile behavior is analyzed aiming at an attacker by utilizing user historical trajectory data, a condition that a user uses a location privacy protection algorithm is known, and evaluation aiming at user's privacy protection effects of multiple positions in a period of time can be achieved well.
Owner:南京嗯哇智能科技有限公司
Multiple module encryption method
InactiveUS7190790B1Preserve invulnerability characteristicLimited computing powerEncryption apparatus with shift registers/memoriesPublic key for secure communicationPower analysisAttack strategy
The present invention proposes an encryption / decryption method able to resist against various attack strategies such as Simple Power Analysis, Timing Analysis or Differential Power Analysis. The method is carried out by a plurality of encryption / decryption modules arranged in series, wherein an encryption / decryption module, different from the first module, starts encryption / decryption operations as soon as said module receives a part of the results of encryption / decryption operations from the immediately preceding encryption / decryption module.
Owner:NAGRAVISION SA
Multi-step attack dynamic defense decision selection method and system for network attack and defense
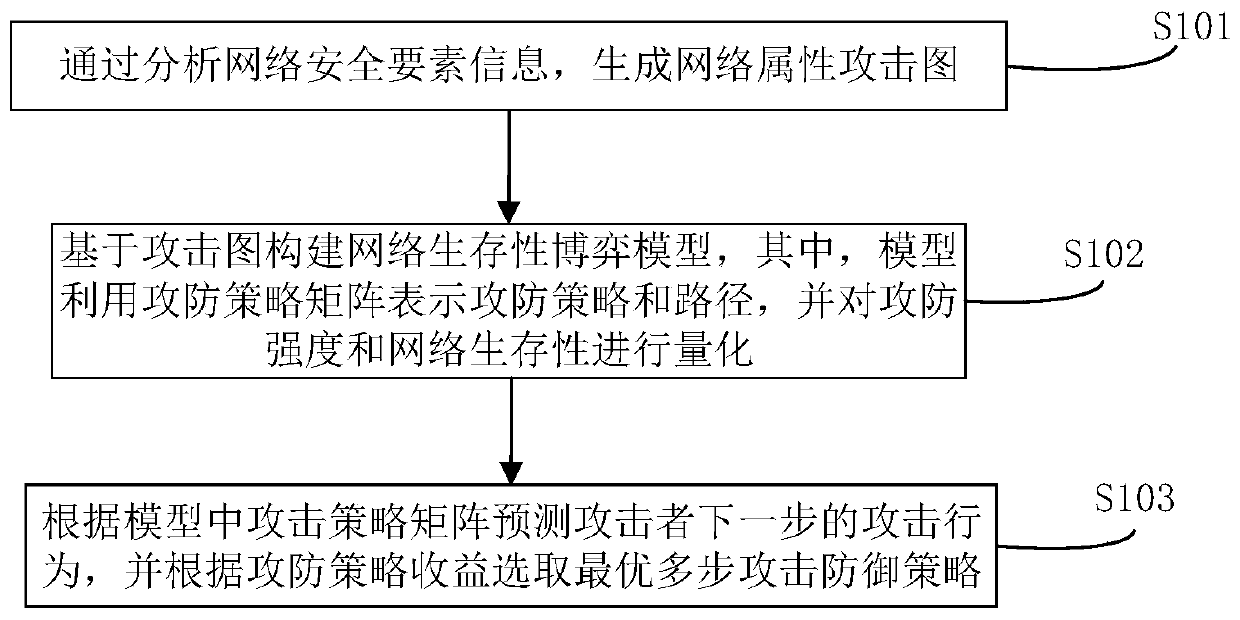
ActiveCN110602047AImprove defenseImprove security governance capabilitiesData switching networksAttack graphAttack strategy
The invention belongs to the technical field of network security, and particularly relates to a multi-step attack dynamic defense decision selection method and system for network attack and defense, and the method comprises the steps: generating a network attribute attack graph through the analysis of network security element information; constructing a network survivability game model based on the attack graph, representing an attack and defense strategy and a path by the model by utilizing an attack and defense strategy matrix, and quantifying attack and defense intensity and network survivability; predicting the next attack behavior of an attacker according to the attack strategy matrix in the model, and selecting the optimal multi-step attack defense strategy according to the attack defense strategy cost. The attack and defense strategy is implemented around the network survivability, the situation pre-judgment and defense strategy can be adjusted according to the dynamically changing attack and defense situation of the network, an easily understood and reasonable defense decision is provided for network security management personnel, the network defense capability is improved,the application prospect is good, and the method has important guiding significance and value for the network security technology.
Owner:PLA STRATEGIC SUPPORT FORCE INFORMATION ENG UNIV PLA SSF IEU
Multi-target air-to-ground semi-supervised machine adaption independent decision-making real-time attack method
The invention discloses a multi-target air-to-ground semi-supervised machine adaption independent decision-making real-time attack method. The method comprises the steps that the target attack necessity is calculated by adopting the six main indexes, namely, the number nh of fire units, the reliability K, the survivability S, the search capability F, the damage capacity H and the antijamming capability G; the target attack necessity is calculated through an analytic hierarchy process; a semi-supervised machine adaption decision-making system carries out air-to-ground attack decision making on multiple targets; a semi-supervised machine self-adaption system is constructed, and the target attack necessity is automatically sorted through the constructed semi-supervised machine self-adaption system; the attack effectiveness of an unmanned aerial vehicle is analyzed through an information balance weight algorithm; the comprehensive weight is calculated through the information balance weight algorithm, and a decision matrix is constructed; the multi-target unmanned aerial vehicle attack strategy is comprehensively considered, independent decision-making is carried out on the attack sequence of the unmanned aerial vehicle, and the unmanned aerial vehicle is dispatched to attack. The method has the advantage that multi-batch precise attacks are carried out according to the sequence of the target attack necessity.
Owner:LANZHOU JIAOTONG UNIV
Method and device for resisting cooperative type sensing data falsification attack through cognitive wireless network
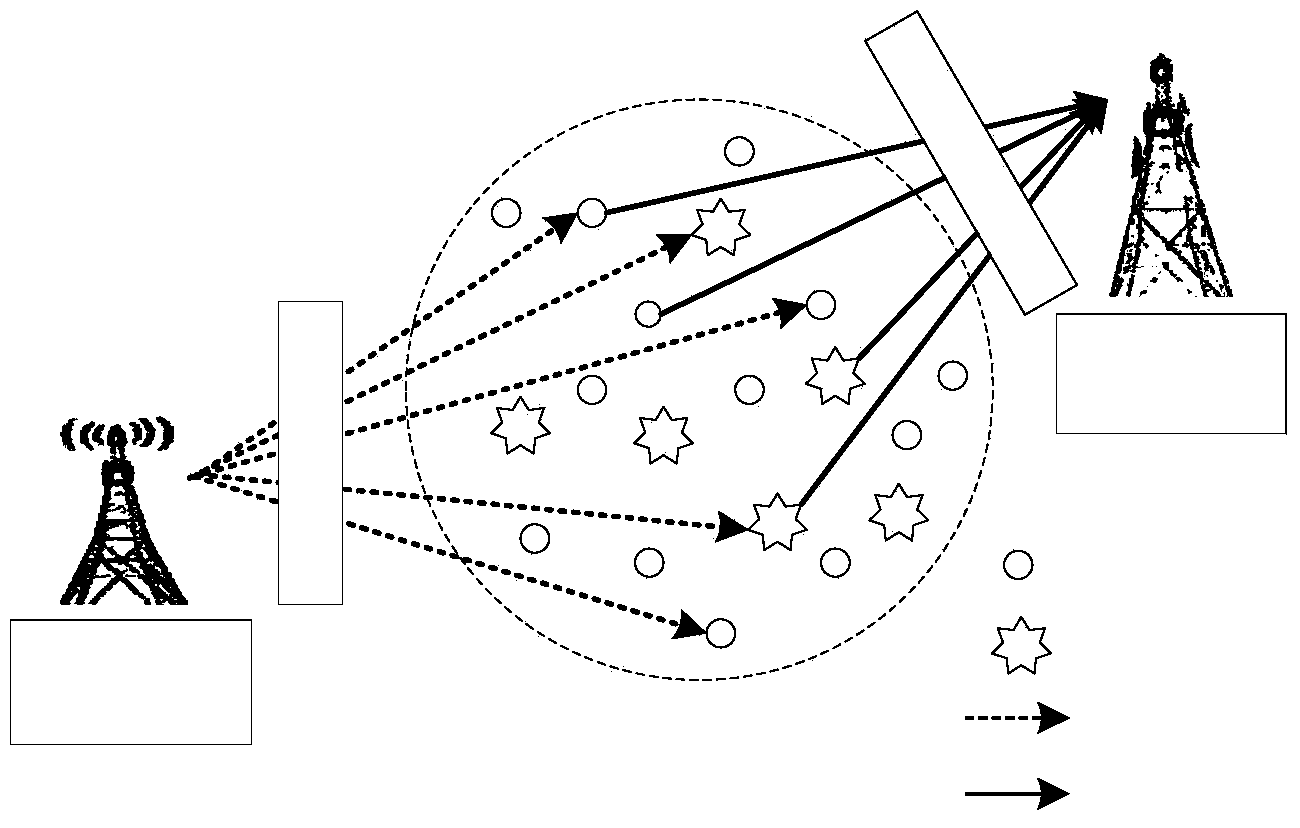
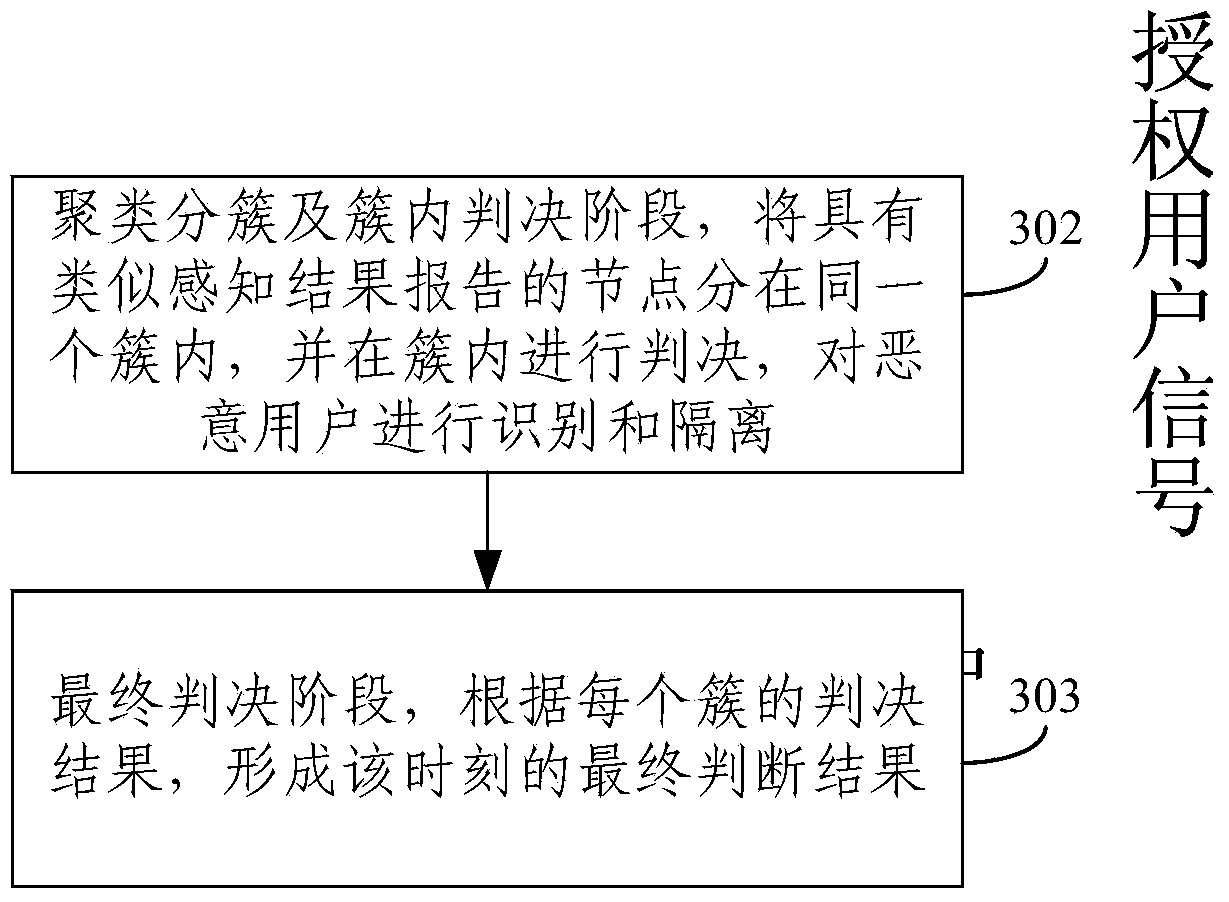
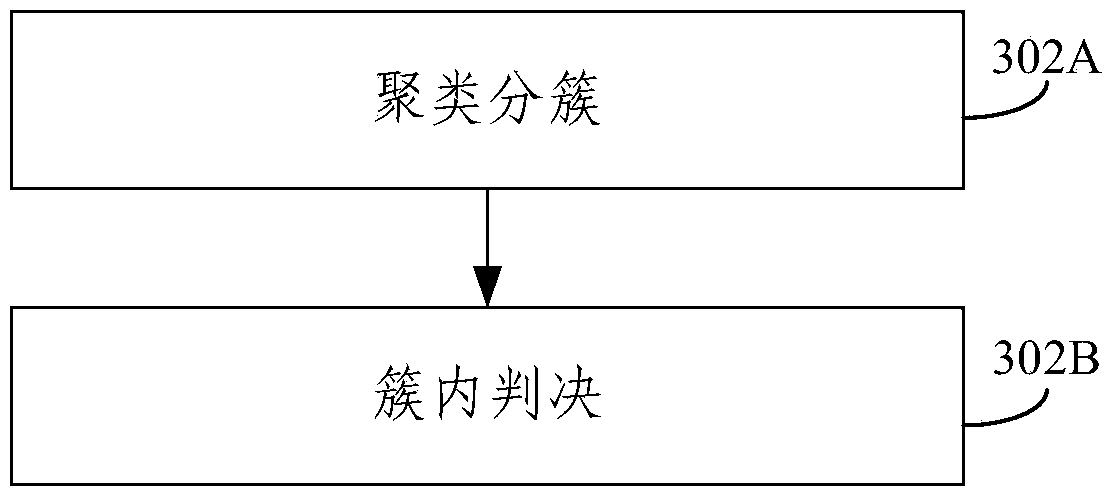
InactiveCN103731834AImprove perceptionImprove detection rateSecurity arrangementSensing dataAttack strategy
The invention relates to the technical field of wireless communication, in particular to a method and device for resisting cooperative type sensing data falsification attack through a cognitive wireless network. The method includes the steps of clustering sensing results and judging the sensing results within clusters, dividing sensing users with similar sensing result reports into the same clusters, recognizing and isolating malicious users, and then judging the real channel occupancy state of main users according to the judgment result of each cluster. According to the method, the malicious users are recognized and isolated by means of the self-adaption clustering technology by fully using sensing report historical data of the sensing users under the condition that prior knowledge such as the number of attackers and the attack strategies does not exist; all aspects of sensing performance of the system is improved, the aims of lowering system false alarm probability and improving system detection probability are achieved, and therefore the cooperative type sensing data falsification attack is effectively defended.
Owner:CHONGQING UNIV OF POSTS & TELECOMM
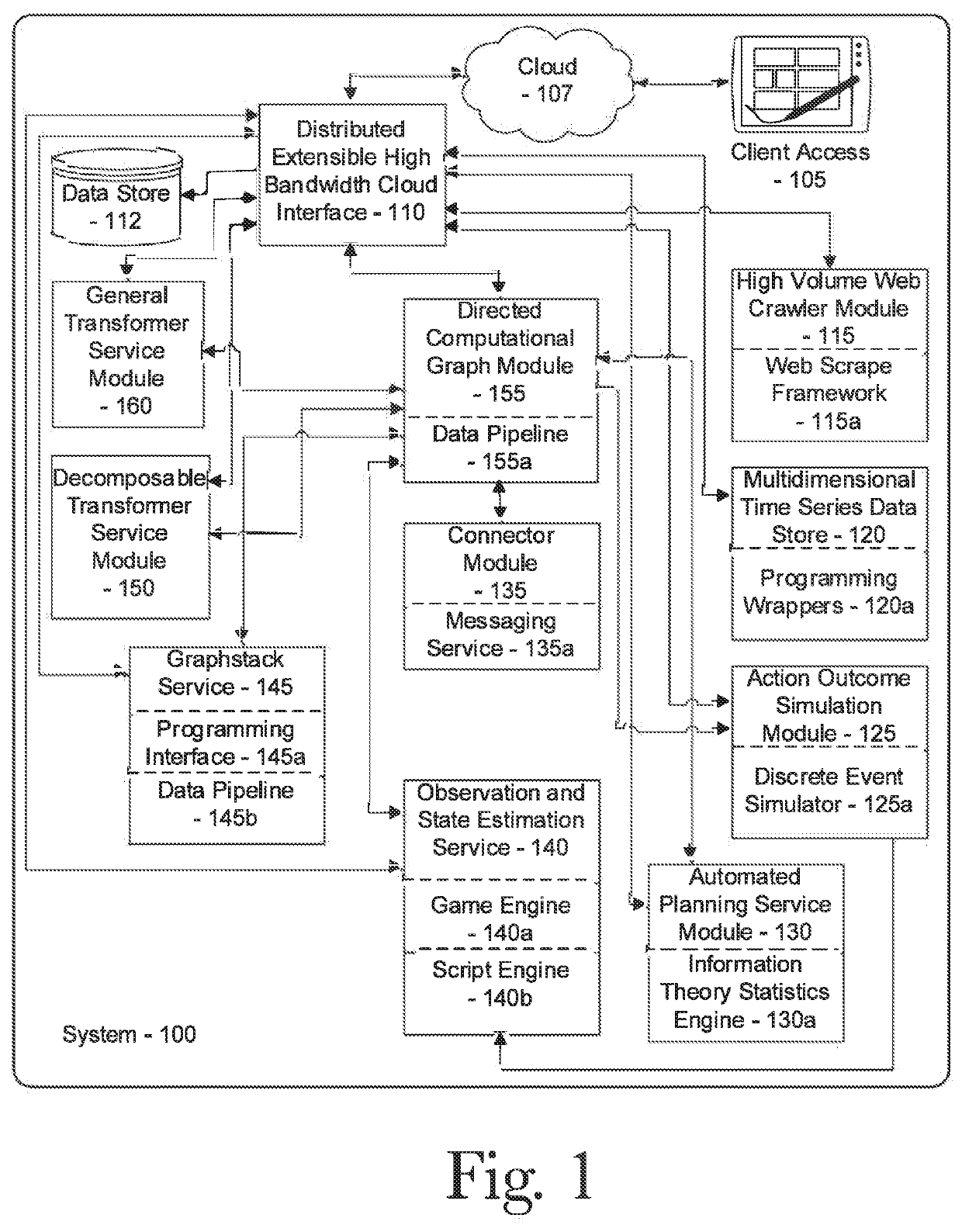
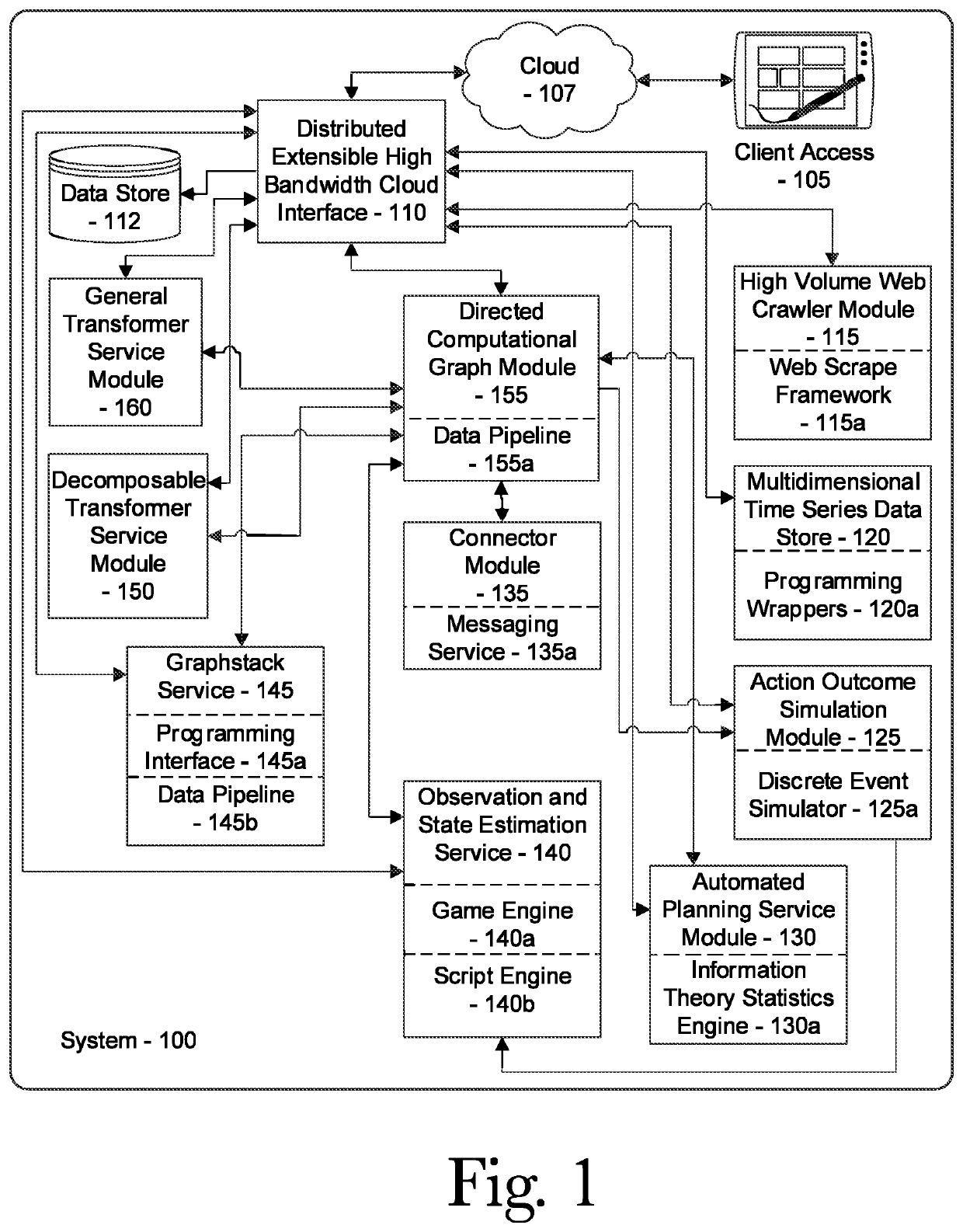
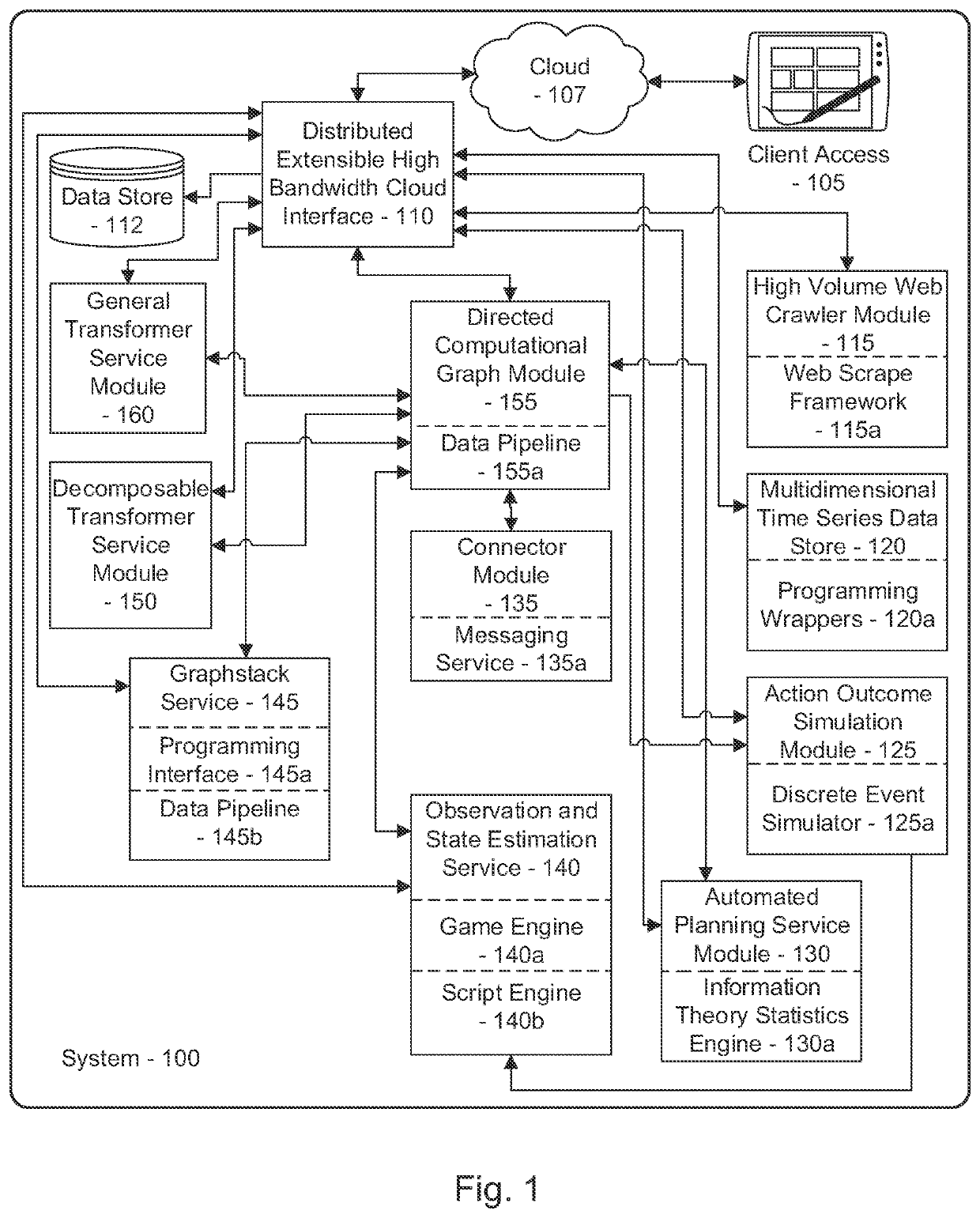
Ai-driven defensive cybersecurity strategy analysis and recommendation system
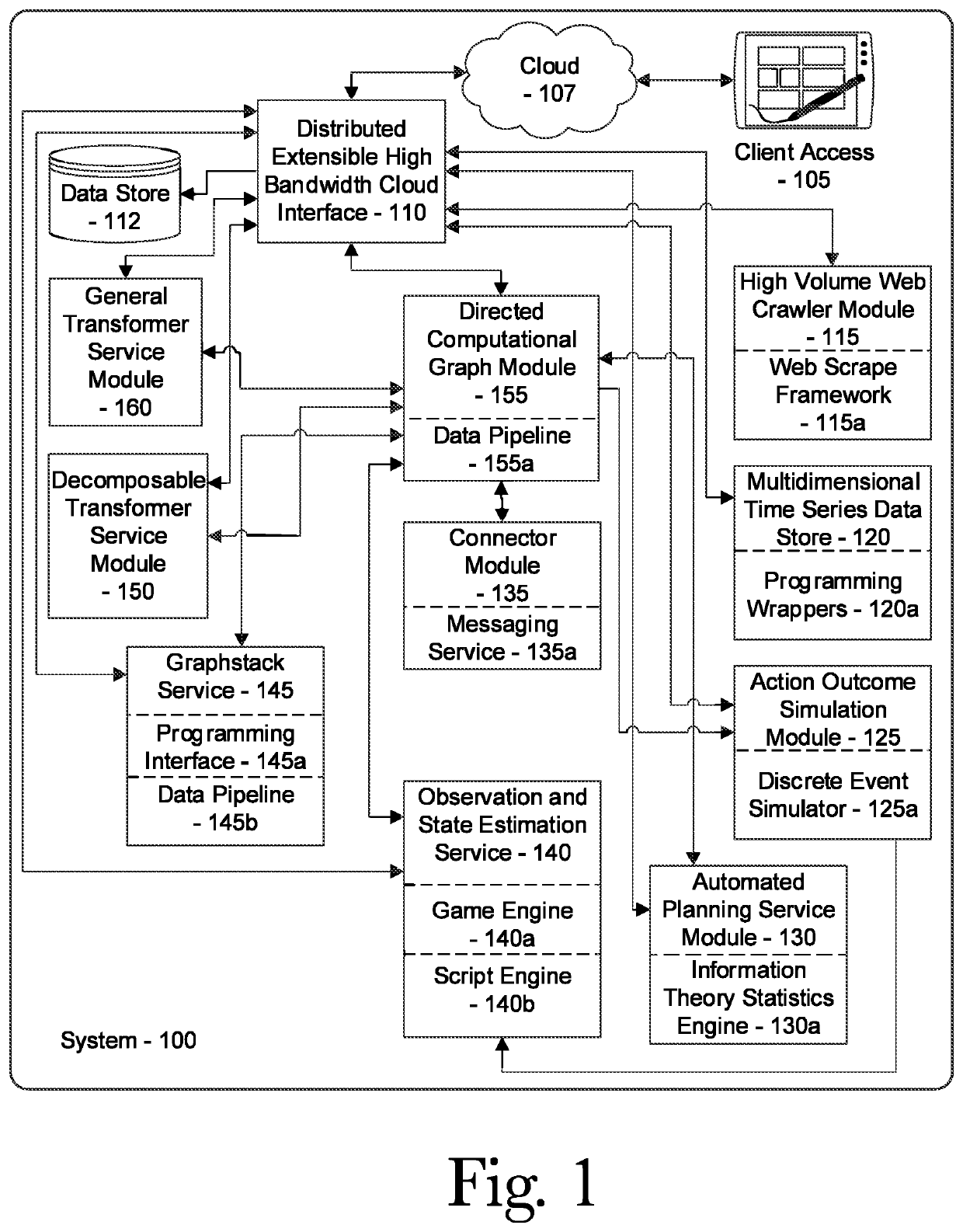
A system and method for automated cybersecurity defensive strategy analysis that predicts the evolution of new cybersecurity attack strategies and makes recommendations for cybersecurity improvements to networked systems based on a cost / benefit analysis. The system and method use machine learning algorithms to run simulated attack and defense strategies against a model of the networked system created using a directed graph. Recommendations are generated based on an analysis of the simulation results against a variety of cost / benefit indicators.
Owner:QPX LLC
Ai-driven defensive penetration test analysis and recommendation system
PendingUS20220201042A1Reduce sensitivityWeb data indexingComputer security arrangementsAttackNetworked system
A system and method for automated defensive penetration test analysis that predicts the evolution of new cybersecurity attack strategies and makes recommendations for cybersecurity improvements to networked systems based on a cost / benefit analysis. The system and method use captured system data to classify networked system based upon their susceptibility to privilege escalation attacks measured against the networked system's response to a penetration test. The system and method use machine learning algorithms to run simulated attack and defense strategies against a model of the networked system created using a directed graph. Recommendations are generated based on an analysis of the simulation results and system classifications against a variety of cost / benefit indicators.
Owner:QOMPLX INC
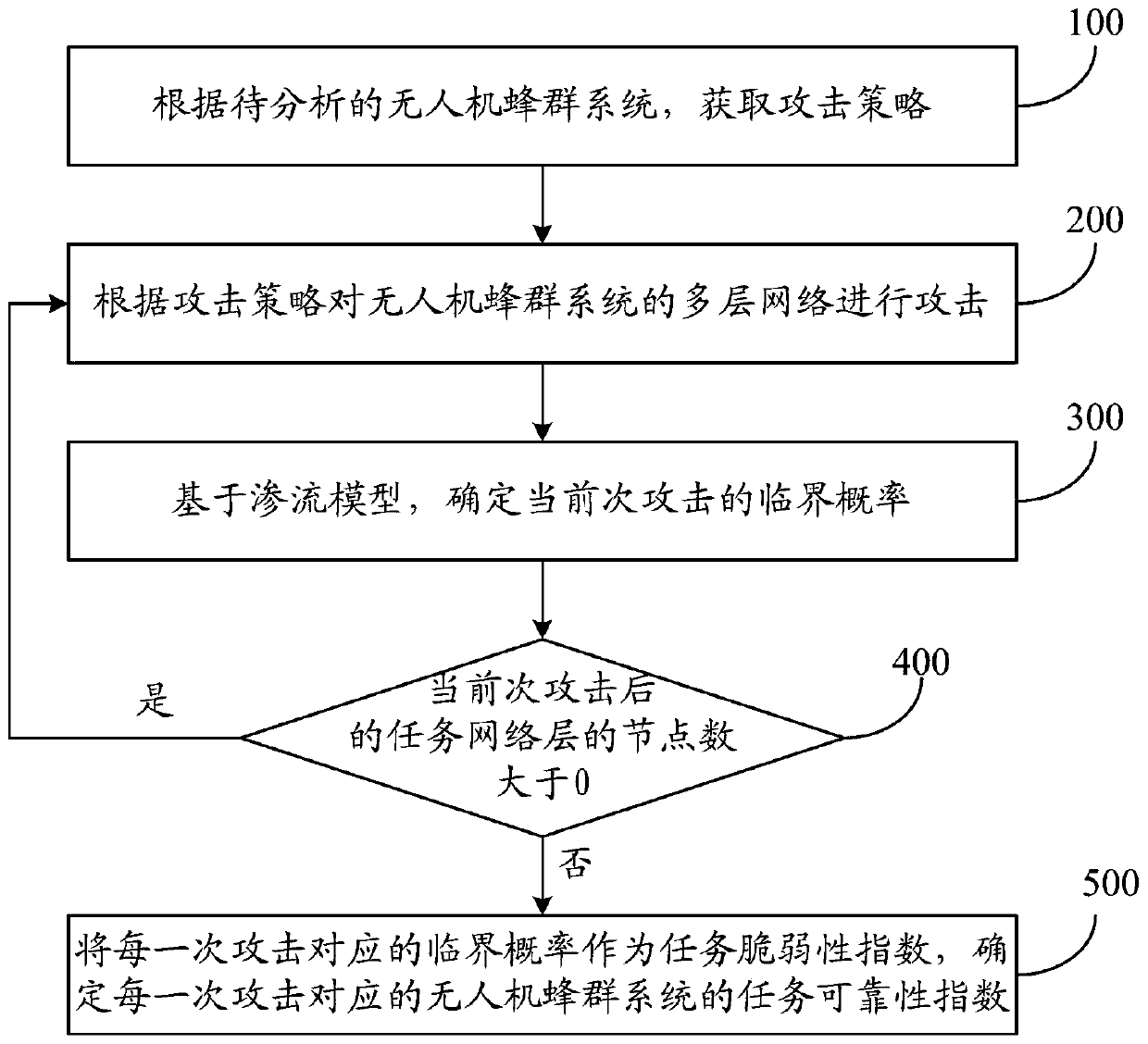
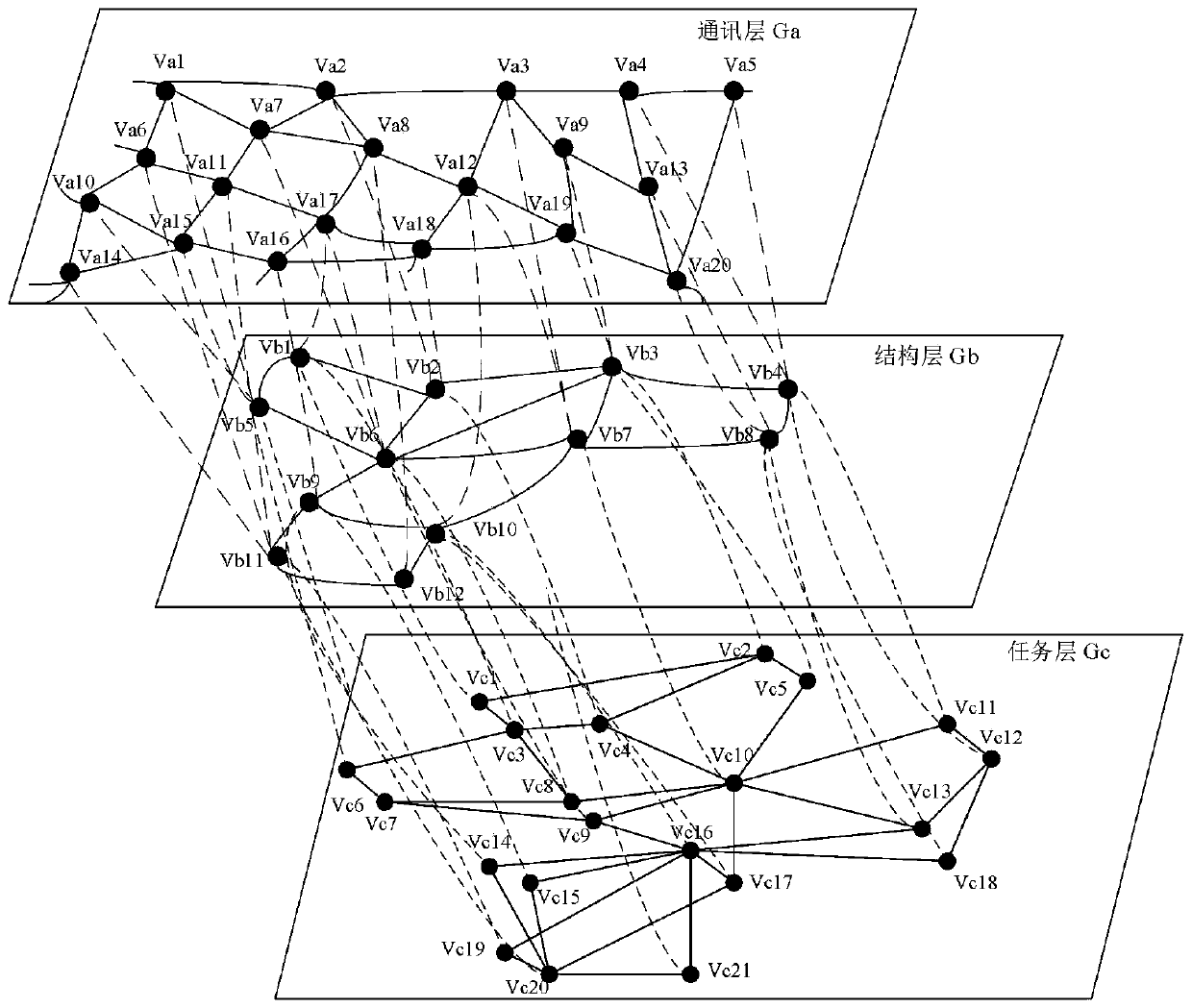
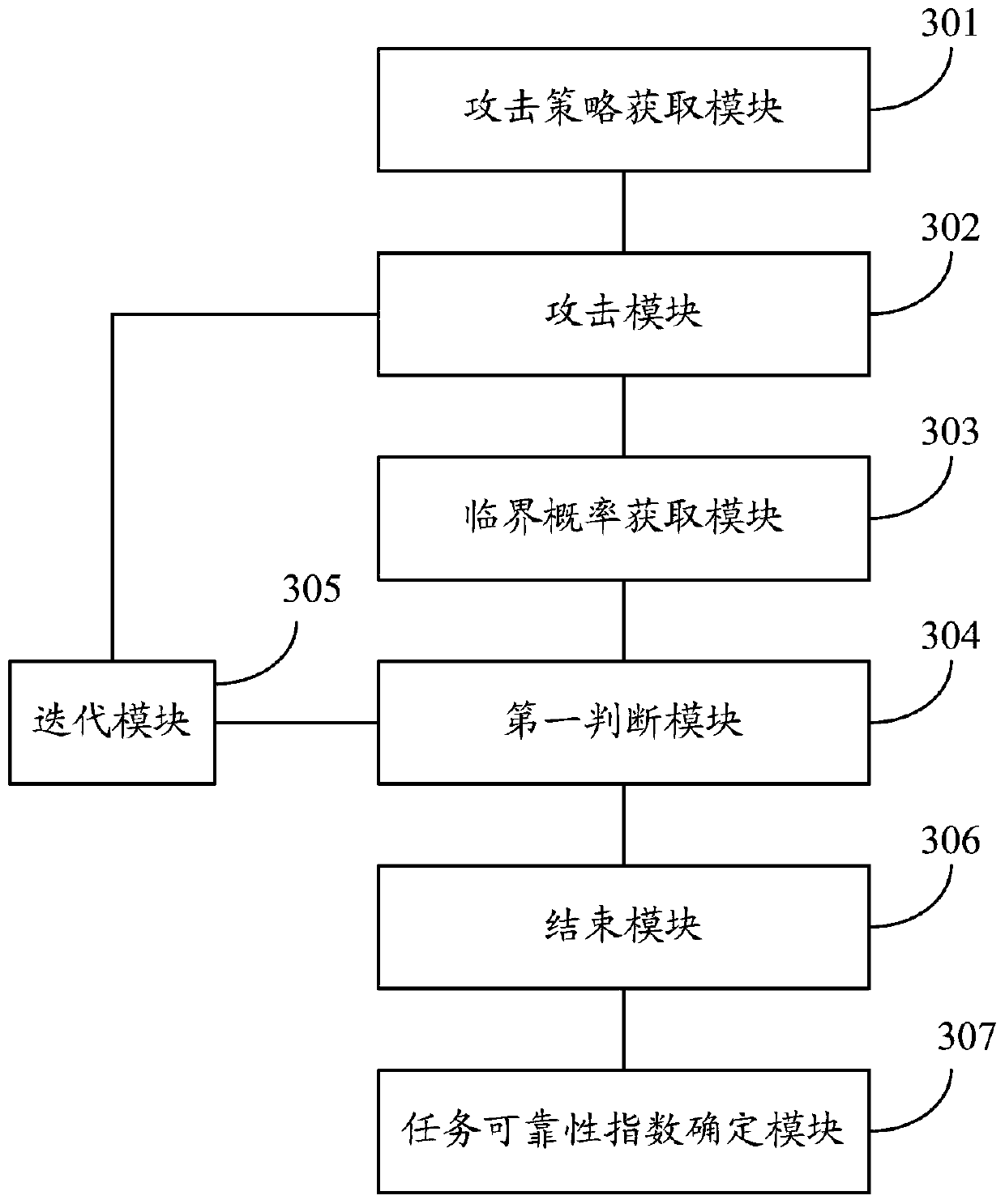
Task reliability analysis method and system based on unmanned aerial vehicle swarm system
PendingCN110795823AImprove accuracyAccurate and effective quantitative basisDesign optimisation/simulationProbabilistic CADSimulationUncrewed vehicle
The invention discloses a task reliability analysis method and system based on an unmanned aerial vehicle swarm system. The analysis method comprises the steps of obtaining an attack strategy according to a to-be-analyzed unmanned aerial vehicle swarm system; attacking the multi-layer network of the unmanned aerial vehicle swarm system according to the attack strategy; determining the critical probability of the current attack based on the seepage model; judging whether the node number of the task network layer after the current attack is greater than 0 or not, and if so, carrying out the nextattack according to an attack strategy; if not, ending the attack; taking the critical probability corresponding to each attack as a task vulnerability index, and determining a task reliability indexof the unmanned aerial vehicle swarm system corresponding to each attack; wherein the task reliability index corresponding to each attack is inversely proportional to the task vulnerability index, and the higher the task reliability index is, the higher the reliability of task execution of the unmanned aerial vehicle swarm system is. The method can be well applied to an unmanned aerial vehicle swarm system, and the accuracy of a reliability analysis result is improved.
Owner:BEIHANG UNIV
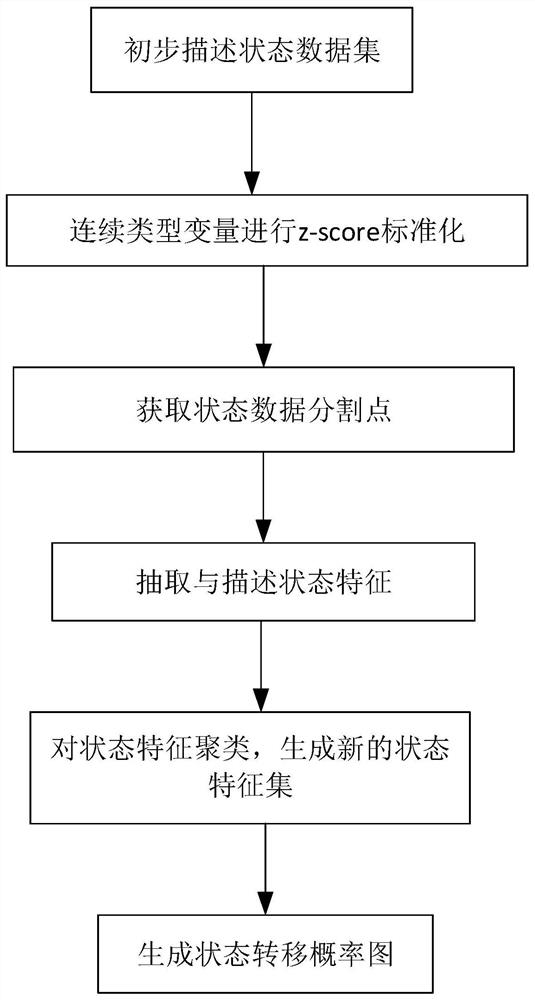
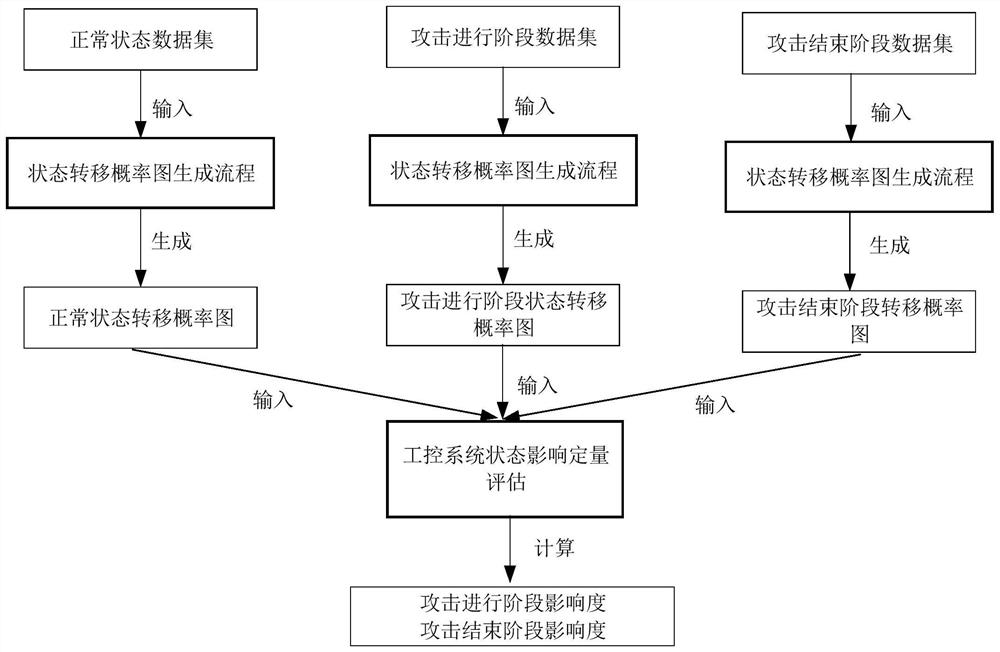
Industrial control network-oriented Quantitative evaluation method and system for influence of multi-mode attack mode on state of industrial control system
ActiveCN113486352ASolve problems that are difficult to accurately assessConsensus assessment resultsPlatform integrity maintainanceEvaluation resultData set
The invention relates to an industrial control network-oriented quantitative evaluation method and system for influence of a multi-mode attack mode on a state of an industrial control system, and the method comprises the following steps: (1) carrying out the preliminary description and extraction of a state feature, i.e., a state data set of the industrial control system, and obtaining a state data segmentation point; (2) clustering the state features; (3) constructing a state transition probability graph; and (4) carrying out quantitative evaluation on the influence of the system state based on the abnormal characteristics and the damage degree index. According to the method and system, for various industrial control network attack strategies, the state abnormal characteristics are taken as main indexes, the actual state change of the system in the attack proceeding stage and the attack ending stage is quantitatively evaluated, and the problem that the influence of various attack strategies on the system state is difficult to accurately evaluate is solved. According to the method and system, a formula for evaluating the influence of the attack strategy on the system state is provided, state abnormal characteristics and threat damage degrees are associated, evaluated and analyzed, and an evaluation result consistent with the actual state influence is obtained.
Owner:SHANDONG COMP SCI CENTNAT SUPERCOMP CENT IN JINAN
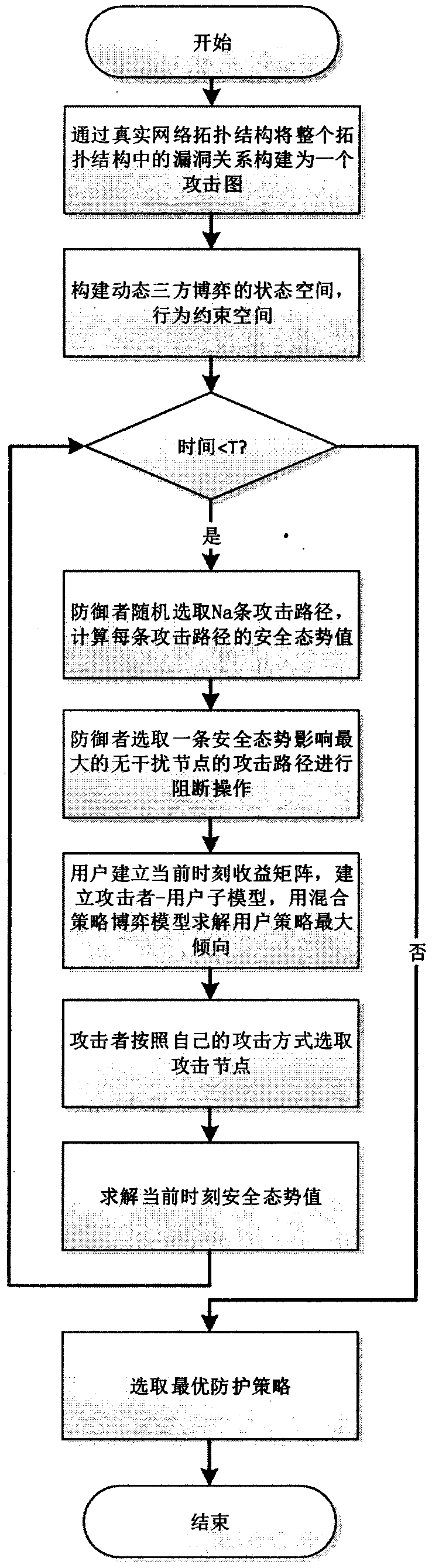
Defense strategy generation method based on three-party dynamic game
PendingCN111245828ARemove uncertaintyImprove the coupling effectData switching networksComplex mathematical operationsGeneration processRisk prevention
The invention discloses a defense strategy generation method based on a three-party dynamic game, and belongs to the field of network security. According to the method, internal and external threats are comprehensively considered, and the internal threats are instantiated in the strategy generation process. In the node value measurement process of the initialization stage, the influence of multiple targets on the node is balanced so as to reduce the bias problem in node value calculation. In the sequential game process, the defense party uses a heuristic method to obtain the path with the maximum threat in the plurality of attack paths for blocking; a user side models a strategy of a user by using a mixed strategy game model, so the coupling of a stealth attack and an internal threat is improved; for attackers, uncertainty of behavior modes of the attackers is increased, three attack strategies are used for simulating attack behaviors of different attackers respectively, and finally, defense strategies in each time period are combined to generate a final protection strategy set. According to the invention, through dynamic analysis of three-party behaviors, decision suggestions withhigher risk prevention capability are provided for an administrator.
Owner:NANJING UNIV OF AERONAUTICS & ASTRONAUTICS
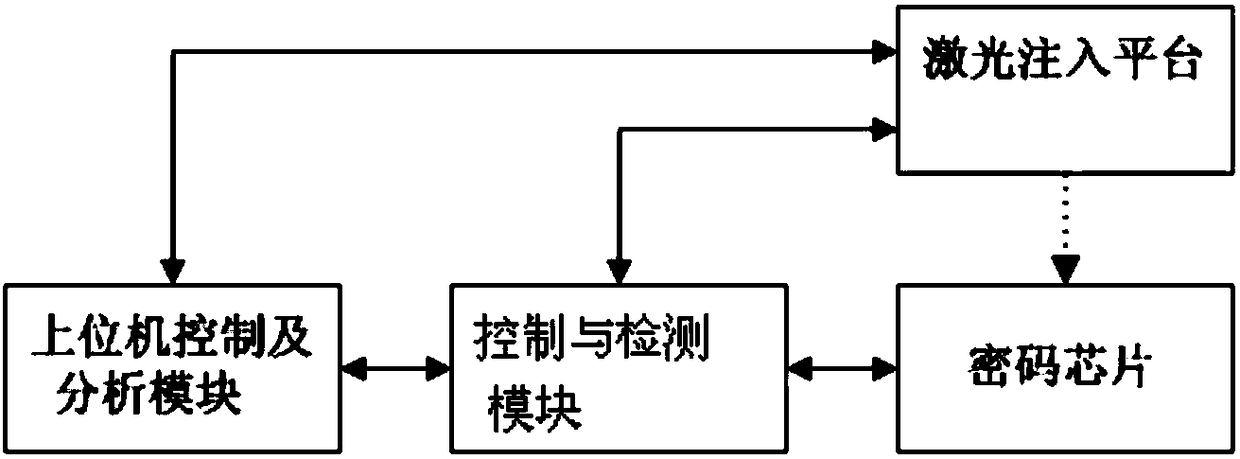
Safety detection method and device for cipher chip
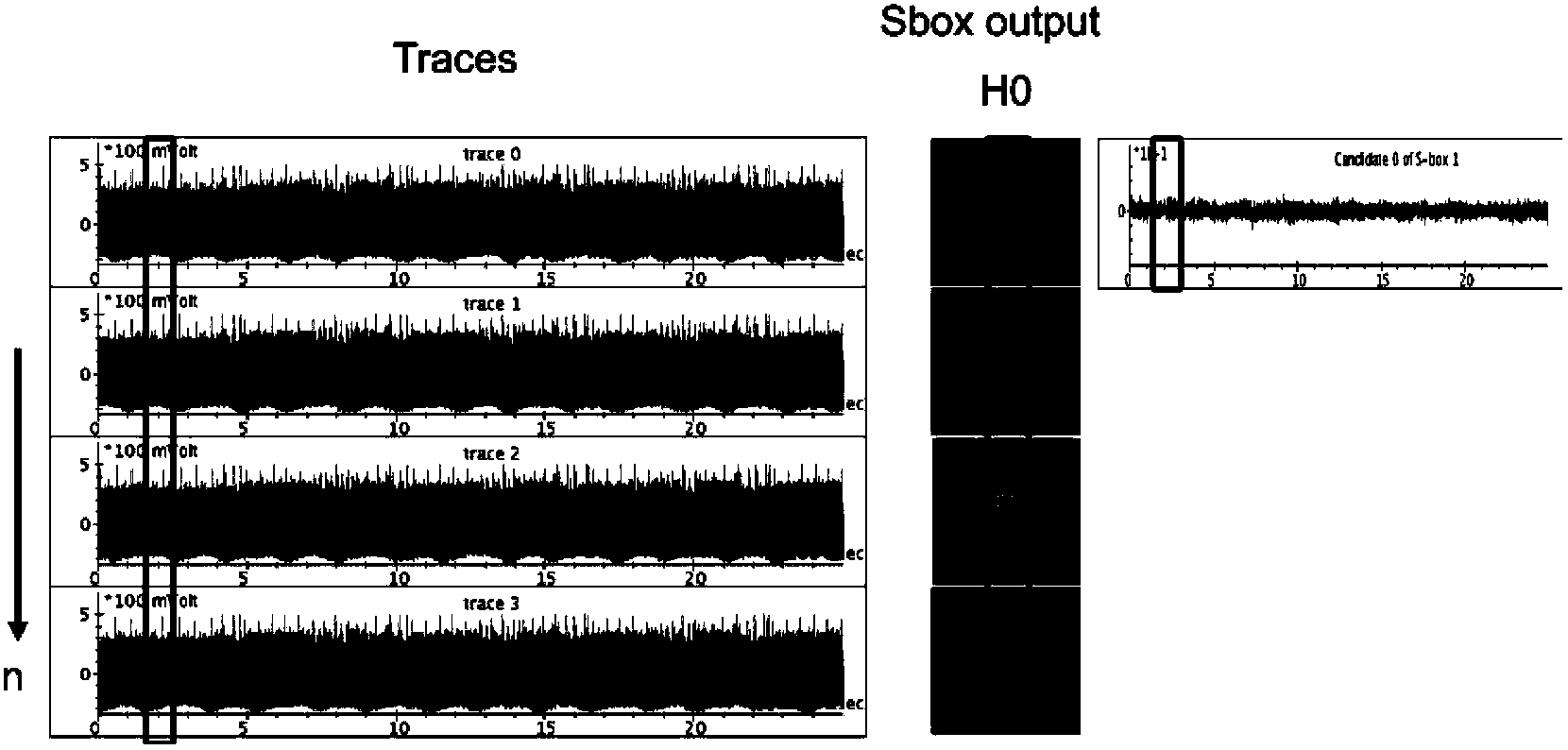
ActiveCN108173645APrecision injectionEfficient Laser Scanning ImplantationKey distribution for secure communicationCryptographic attack countermeasuresCiphertextInjection point
The invention relates to a safety detection method for a cipher chip. The method comprises the following steps: carrying out laser injection on the cipher chip at one or more first laser injection points according to a laser attack strategy, so that the cipher chip generates one or more first cipher texts; analyzing the one or more first cipher texts, and screening out one or more second laser injection points, which comply with the laser attack strategy, from the one or more first cipher texts, wherein the one or more first cipher texts are respectively associated with the one or more first cipher texts; carrying out laser injection on the cipher chip at the one or more second laser injection points at different laser triggering times; screening out one or more third laser injection points, which comply with the different laser triggering times, from the one or more second cipher texts generated by the cipher chip, wherein the one or more second cipher texts are respectively associated with the one or more second laser injection points; and carrying out key analysis according to the one or more third laser injection points to obtain a key for recovering the cipher chip.
Owner:NAT SPACE SCI CENT CAS
Ai-driven defensive cybersecurity strategy analysis and recommendation system
PendingUS20220210200A1Web data indexingPlatform integrity maintainanceTheoretical computer scienceNetworked system
A system and method for automated cybersecurity defensive strategy analysis that predicts the evolution of new cybersecurity attack strategies and makes recommendations for cybersecurity improvements to networked systems based on a cost / benefit analysis. The system and method use machine learning algorithms to run simulated attack and defense strategies against a model of the networked system created using a directed graph. Recommendations are generated based on an analysis of the simulation results against a variety of cost / benefit indicators. The recommendation engine runs continuously, makes suggestions, and takes adjustably autonomous actions to go further and actuate parts of the system using an orchestration service employing a distributed computational graph and actuation plugins based on generated plans. Actions are validated as required or as prudent from appropriate simulation modeling services.
Owner:QOMPLX INC
System and method for collaborative cybersecurity defensive strategy analysis utilizing virtual network spaces
A system and method for collaborative cybersecurity defensive strategy analysis that predicts the evolution of new cybersecurity attack strategies and creates a virtual network space that provides a virtual reality environment for collaborative insights into network dynamics during a cyberattack. makes recommendations for cybersecurity improvements to networked systems based on a cost / benefit analysis. The system and method use machine learning algorithms to run simulated attack and defense strategies against a virtual network space model of the networked system created using a virtual network space manager. A simulation interaction server can facilitate secure sharing of virtual network spaces and simulations between and among various real and virtual actors to provide a collaborative space where one or more organization's network can be tested for resilience and mitigation. Recommendations are generated based on an analysis of the simulation results against a variety of cost / benefit indicators.
Owner:QOMPLX INC
Power network vulnerability evaluation method based on multiple attack strategies
InactiveCN112507552AEasy to identifyFeatures at the functional levelDesign optimisation/simulationResourcesComputer networkElectric power system
The invention discloses a power system vulnerability evaluation method based on multiple attack strategies. The method comprises the following steps: 1) constructing a power grid model; 2) evaluatingthe importance of nodes in the network from four aspects of node degree, betweenness, local centrality and node fault loss, and completing the formulation of an attack strategy according to the importance of the network nodes. 3) establishing a betweenness virtual flow model to simulate a cascade fault propagation process in the power system. and 4) establishing a vulnerability index based on thebetweenness virtual flow model, simulating a network attack by adopting a plurality of attack strategies, and evaluating the vulnerability of the IEEE300 power system network according to the change of the vulnerability index. Aiming at the vulnerability of the power network under the condition of various attack strategies, the betweenness virtual flow model and the various attack strategies are established to analyze the performance change of the power grid under the cascade failure. The importance of nodes in a power network can be identified, and decision support is provided for maintenancework of power system managers and power system fault prevention of designers.
Owner:XUZHOU NORMAL UNIVERSITY
A method for preventing a community structure in a complex network from being deeply mined
ActiveCN109376544AAvoid over diggingGood attack performanceDigital data information retrievalData processing applicationsCluster algorithmComputer network
The invention provides a method for preventing a community structure in a complex network from being deeply mined. The method comprises the following steps: (1) for a given network, initializing a population according to a set coding mode, sequentially selecting an initial population, crossing, mutating and reserving an elite to obtain an optimal individual, namely, an optimal attack strategy of acomplex network clustering algorithm; (2) according to the optimal individuals, adding or deleting the corresponding edges in the network to obtain the new network after camouflage so as to prevent the community structure in the complex network from being accurately mined. The method for preventing the community structure in the complex network from being excavated in depth provided by the invention effectively reduces the performance of the complex network clustering algorithm and guarantees the privacy safety of the community in the network.
Owner:ZHEJIANG UNIV OF TECH
A method for acquiring an intelligent driving system test case
ActiveCN109902018ARealize black box attackGuaranteed scalabilityBiological neural network modelsSoftware testing/debuggingState of artNerve network
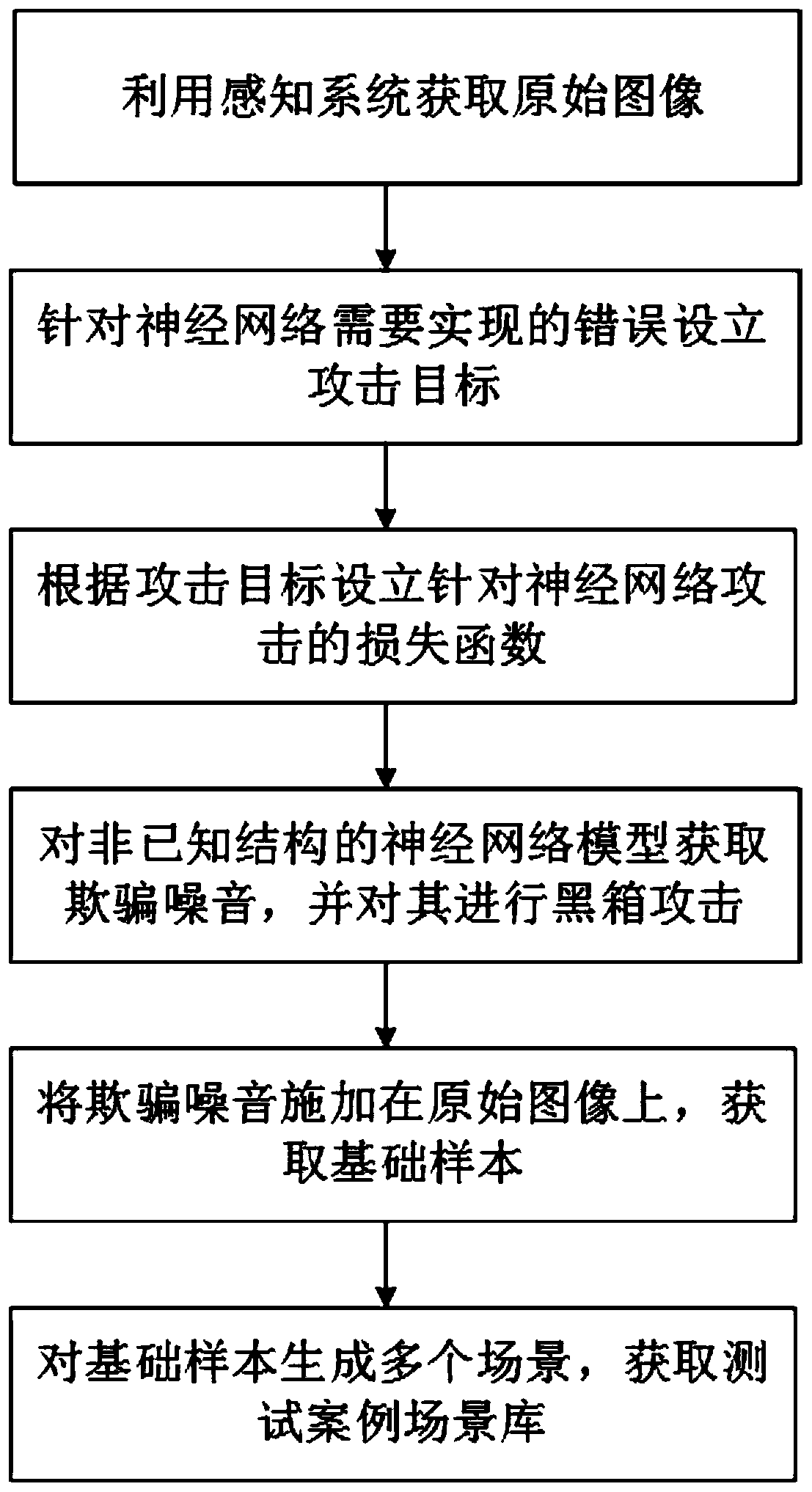
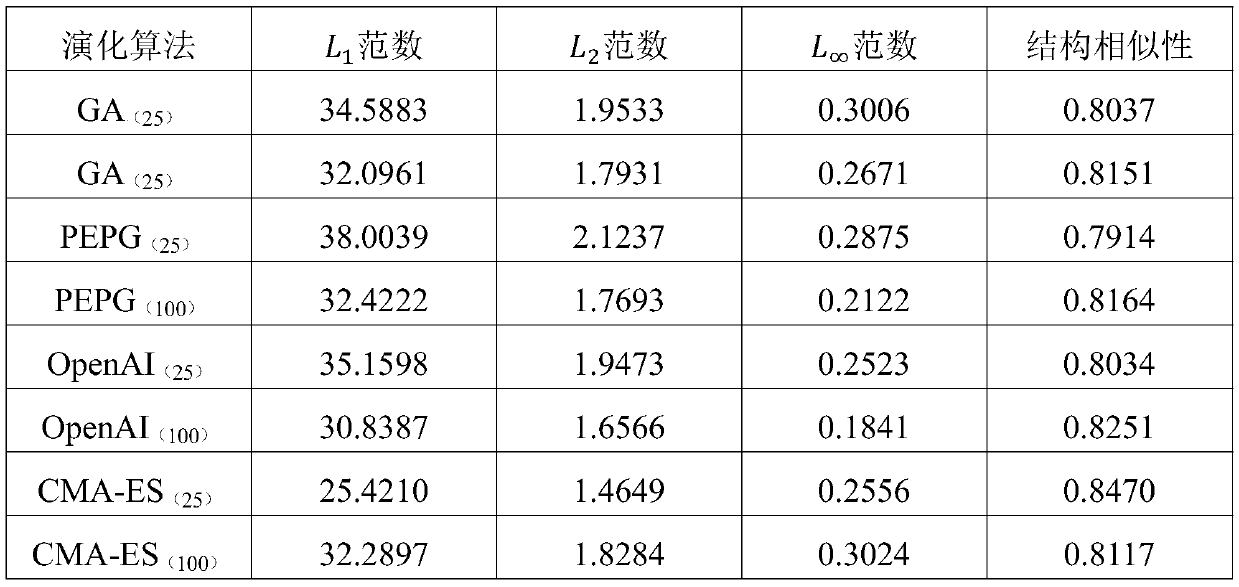
The invention relates to a method for acquiring an intelligent driving system test case, and the method comprises the steps: enabling a neural network model attack problem to be formalized into an optimization problem for an image classification problem; achieving black box confrontation of the neural network model through iterative operation of an evolutionary algorithm, and meanwhile generatinga test library of the intelligent vehicle in a sample guidance mode based on the neural network confrontation. Compared with the prior art, the method can automatically obtain an effective test case library, and has the advantages of ensuring the expandability of the attack strategy while ensuring that the target model is attacked at the success rate of 100%, and the like.
Owner:TONGJI UNIV
Attack test method and device for industrial control network
ActiveCN112422557AAccurately reflect the communication statusImprove attack test effectSemi-structured data mapping/conversionData switching networksAttackNetwork communication
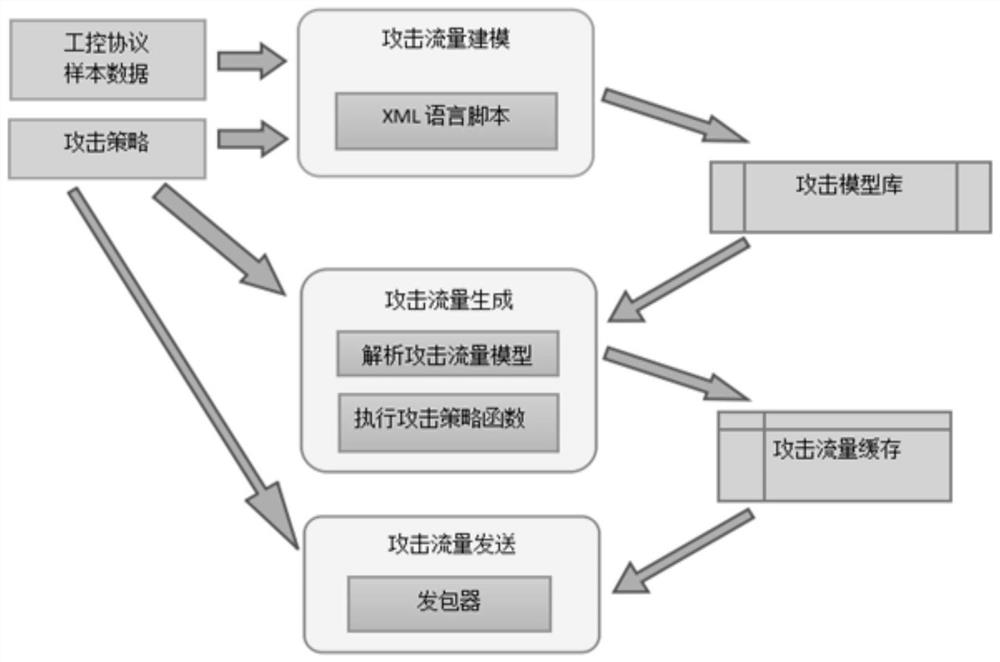
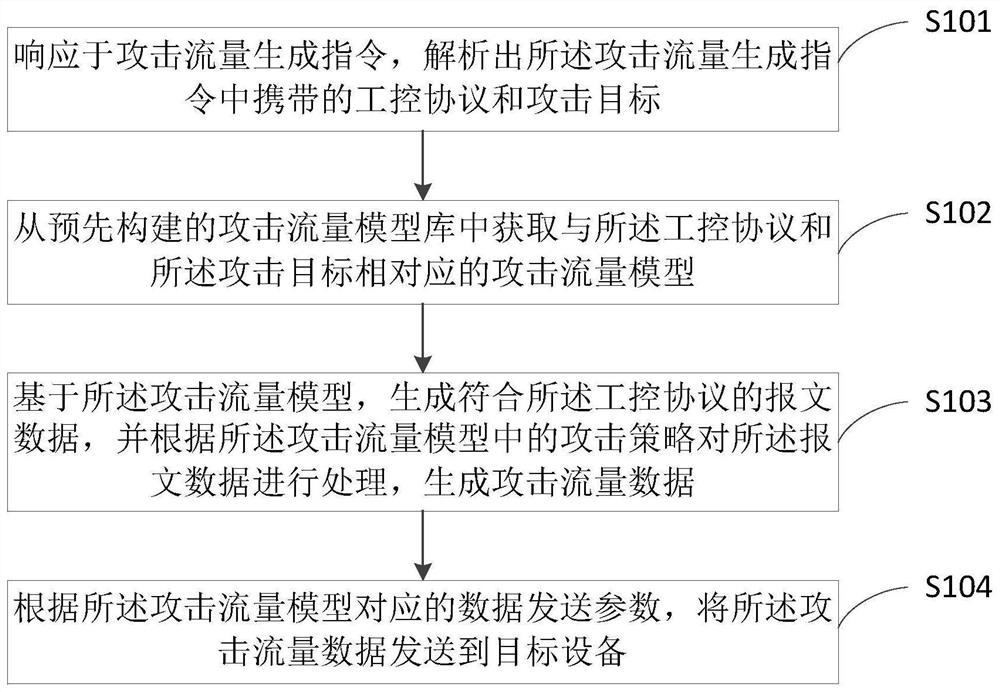
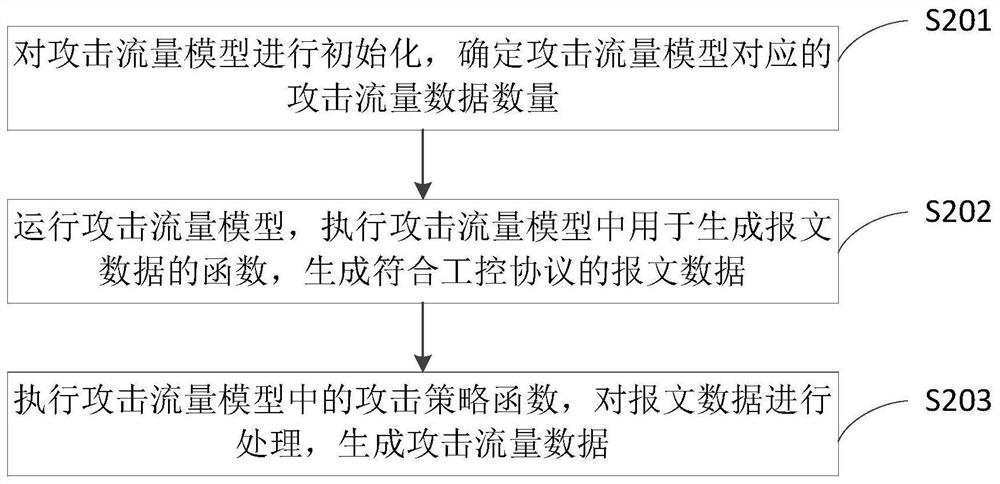
The invention provides an attack test method and device for an industrial control network, and the method comprises the steps: building an attack flow model library in advance for an industrial control protocol and an attack target of the industrial control network, wherein the attack flow model library comprises attack flow models corresponding to different combinations of the industrial controlprotocol and the attack target; wherein the attack traffic data, which is generated based on the attack traffic model, accords with the industrial control protocol and is implanted with the attack strategy can accurately reflect the real network communication state of the attack target under the corresponding industrial control protocol, thereby improving the attack test effect.
Owner:CHINA INFORMATION TECH SECURITY EVALUATION CENT +1
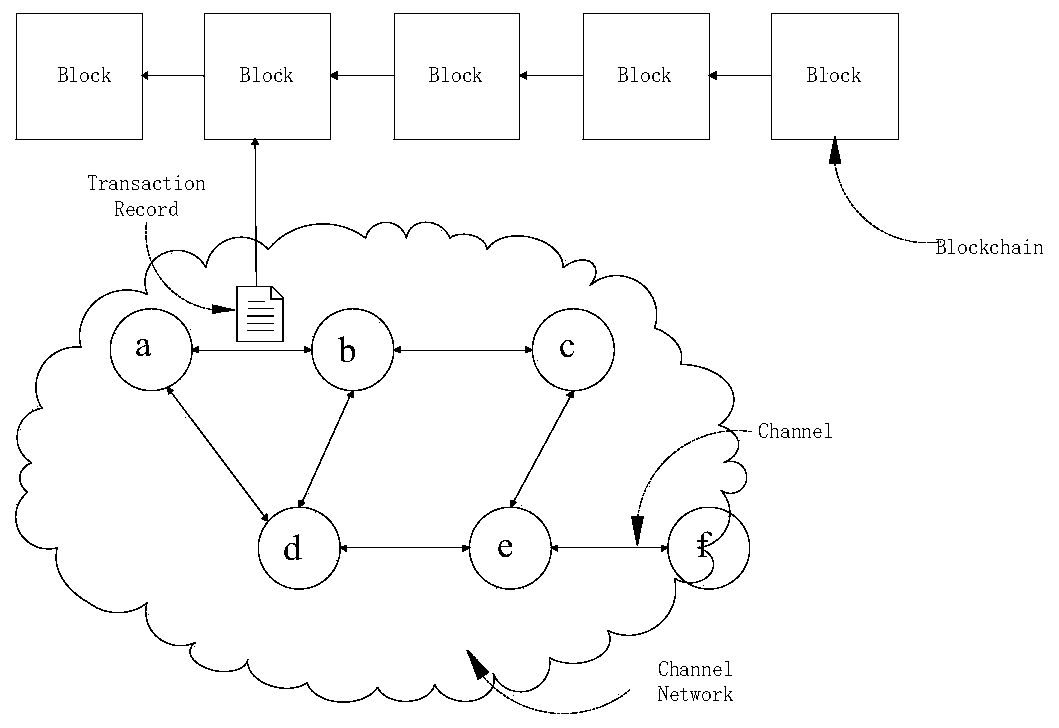
Channel network steady-state evolutionary game method in blockchain environment
The invention discloses a channel network steady-state evolutionary game method in a blockchain environment. Based on finite rationality and a replication dynamic mechanism of a biological evolution process, node transactions in the channel network are modeled into a dynamic evolutionary game model, the model designs a channel network dynamic defense mechanism based on evolutionary game, the mechanism adds a defense strategy to a strategy space of an I-type node, and under the condition of considering the attack cost and success rate of the II-type node under the condition of deploying the defense strategy, and the defense mechanism can help the I-type node to resist attack behaviors of the II-type node at a certain probability. The nodes of the model have limited and rational evolutionarylearning capability, and can dynamically adjust respective strategies to achieve effective defense according to different attack strategies of attackers.
Owner:ANHUI NORMAL UNIV
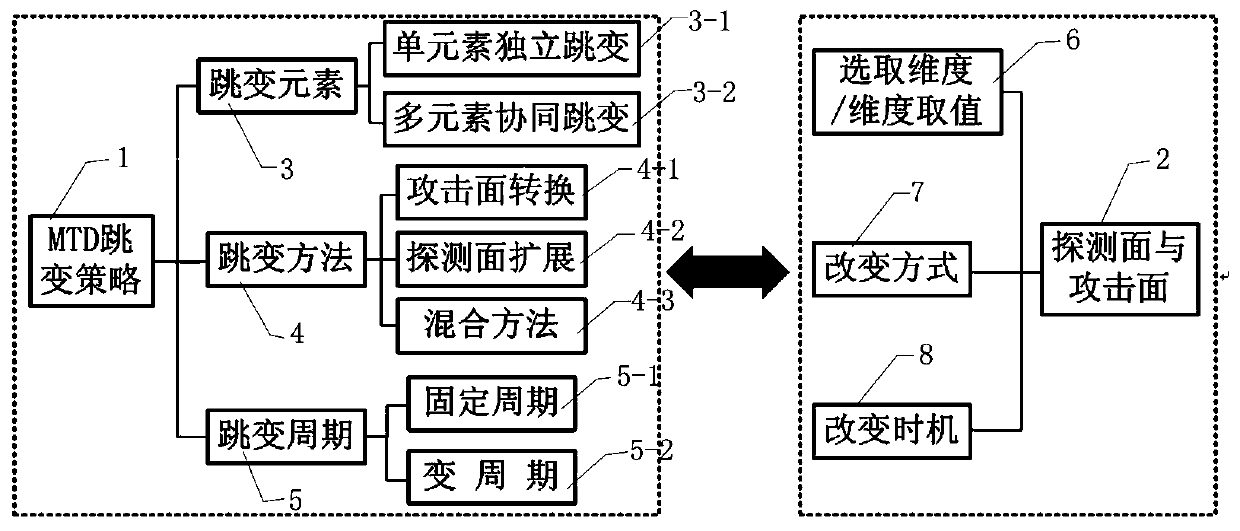
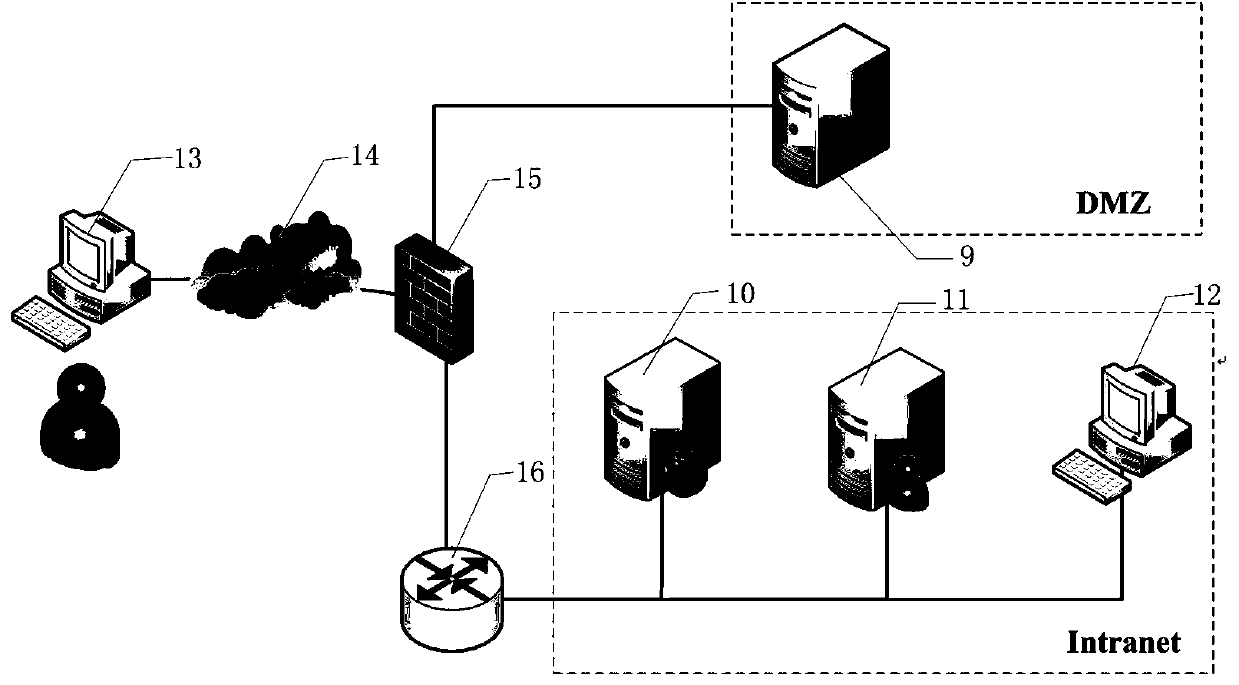
Decision method for dynamic network transformation under full information conditions and system thereof
InactiveCN109379322AEfficient analysisAccurately describe the offensive and defensive confrontation processData switching networksAttack strategyData mining
The invention belongs to the technical field of network safety and specifically relates to a decision method for dynamic network transformation under full information conditions and a system thereof.The decision method comprises the following steps: obtaining state transition probability according to the network state, an attack strategy and a defense strategy; using a game theory to describe gains of both sides of the offensive and defensive game during moving target defense; constructing a moving target defense model based on a Markov game in combination with the state transition probability; transforming the solution of the moving target defense model into an equivalent of a target function and obtaining an optimal moving target defense strategy. According to the method and the systemin the invention, the moving target defense model based on the Markov game is constructed according to the state transition probability and both the sides of the offensive and defensive game; furthermore, the optimal moving target defense strategy is obtained by solving so as to realize balance of network performance overheads and moving target defense gains and solve the technical problem of howto select the optimal defense strategy based on limited network resources.
Owner:PLA STRATEGIC SUPPORT FORCE INFORMATION ENG UNIV PLA SSF IEU
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com