Industrial control network-oriented Quantitative evaluation method and system for influence of multi-mode attack mode on state of industrial control system
An industrial control system, quantitative evaluation technology, applied in the field of information security, can solve the problem of lack of correlation evaluation and analysis of abnormal state characteristics
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0120] A method for quantitatively evaluating the impact of multi-mode attacks on industrial control networks on the state of industrial control systems, including the following steps:
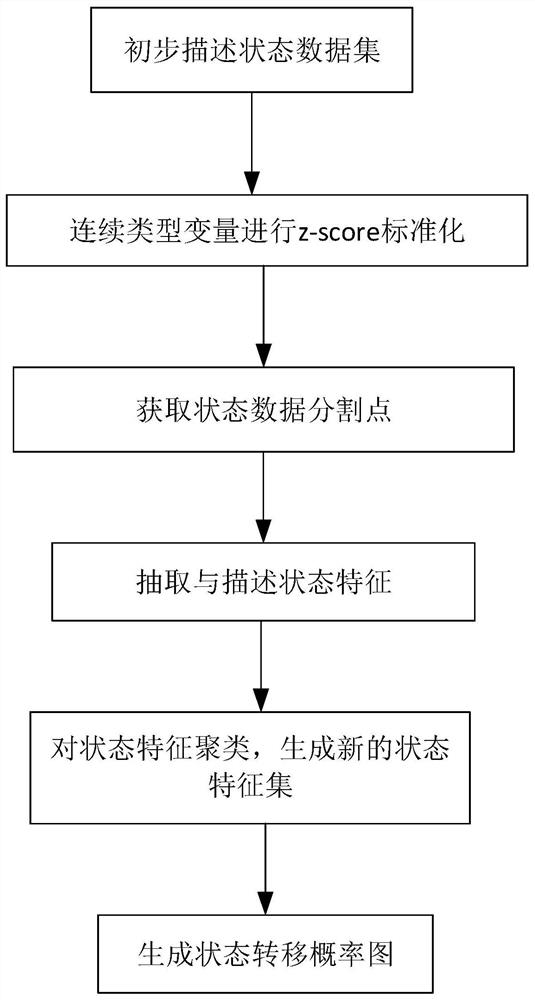
[0121] (1) Preliminary description and extraction of the state characteristics, that is, the state data set of the industrial control system, and obtain the state data segmentation point;
[0122] (2) Clustering the status features;
[0123] (3) Construct a state transition probability map;
[0124] (4) Quantitatively assess the impact on the system state based on abnormal characteristics and damage degree indicators.
[0125] The process of generating a state transition probability map from the original state data set is as follows: figure 1 shown.
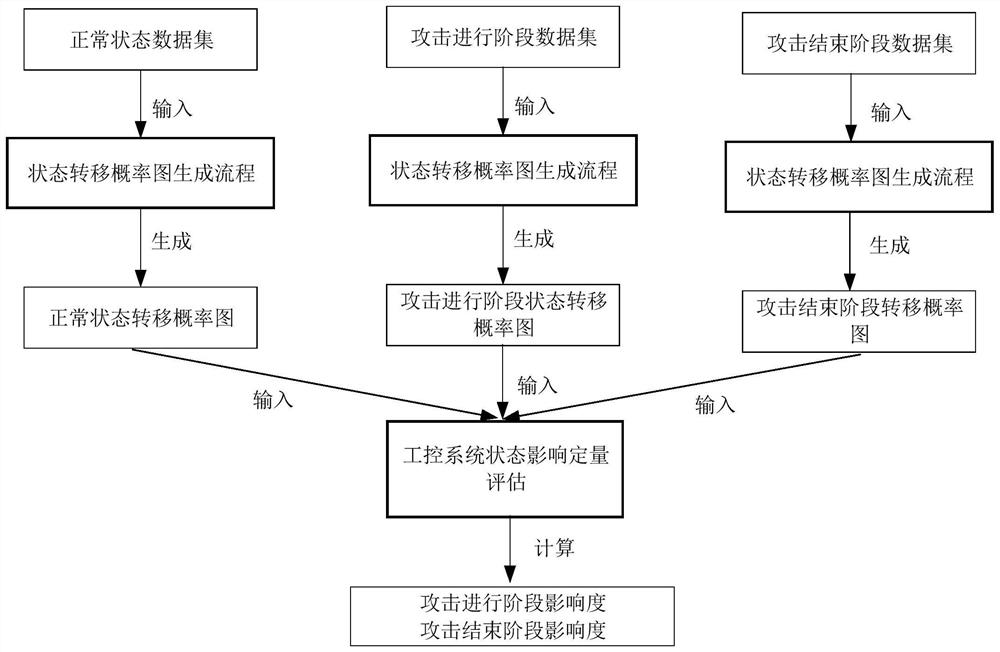
[0126] The flow of the quantitative evaluation method for the impact of multi-mode attack methods on industrial control networks on the state of industrial control systems is as follows: figure 2 shown, including:
[0127] First of all, whe...
Embodiment 2
[0132] According to the method for quantitatively evaluating the impact of an industrial control network-oriented multi-mode attack on the status of an industrial control system described in Embodiment 1, the difference is that:
[0133] The specific implementation process of step (1) includes:
[0134] A. A preliminary description of the state data set of the industrial control system refers to:
[0135] The state data set of the industrial control system is expressed as DS={CM,D,TDS}, TDS represents a period of time, where tds i Indicates the specific moment, i=1,2,...n t ; n t is the number of moments and the length of the time period TDS; CM represents the collection of continuous type variables in the industrial control system in the TDS time period, Indicates the continuous type variable in the industrial control system in the TDS time period, n c is the number of continuous type variables; D represents the set of discrete type variables in the industrial cont...
Embodiment 3
[0229] A quantitative evaluation system for the impact of multi-mode attack methods on industrial control networks on the state of industrial control systems, such as Figure 8 As shown, it is used to realize the quantitative evaluation method for the impact of the industrial control network-oriented multi-mode attack mode on the state of the industrial control system described in Embodiment 1 or 2, including the preliminary description of the state data and the extraction unit, the clustering unit, and the construction of the state transition probability map unit and quantitative assessment unit;
[0230] The state data preliminary description and extraction unit is used to perform step (1); the clustering unit is used to perform step (2); the state transition probability map construction unit is used to perform step (3); the quantitative evaluation unit is used to perform step (4) .
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com