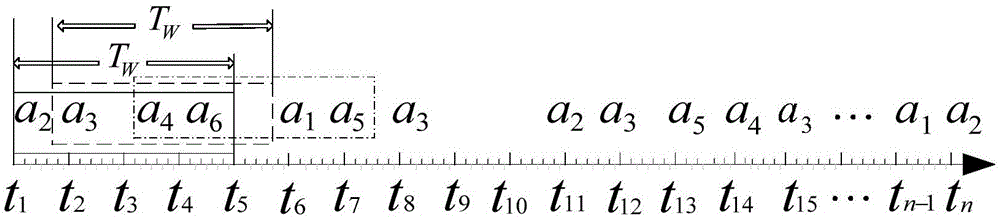Patents
Literature
639 results about "Quantitative assessment" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Quantitative Assessment: A quantitative assessment measures the monetary value of all the elements combined in a risk assessment as well as the assets and threats of a risk analysis. Components of the risk analysis process include: property value; residual damage; rate of occurrence (threats); safeguard effectiveness; safeguard expenses;
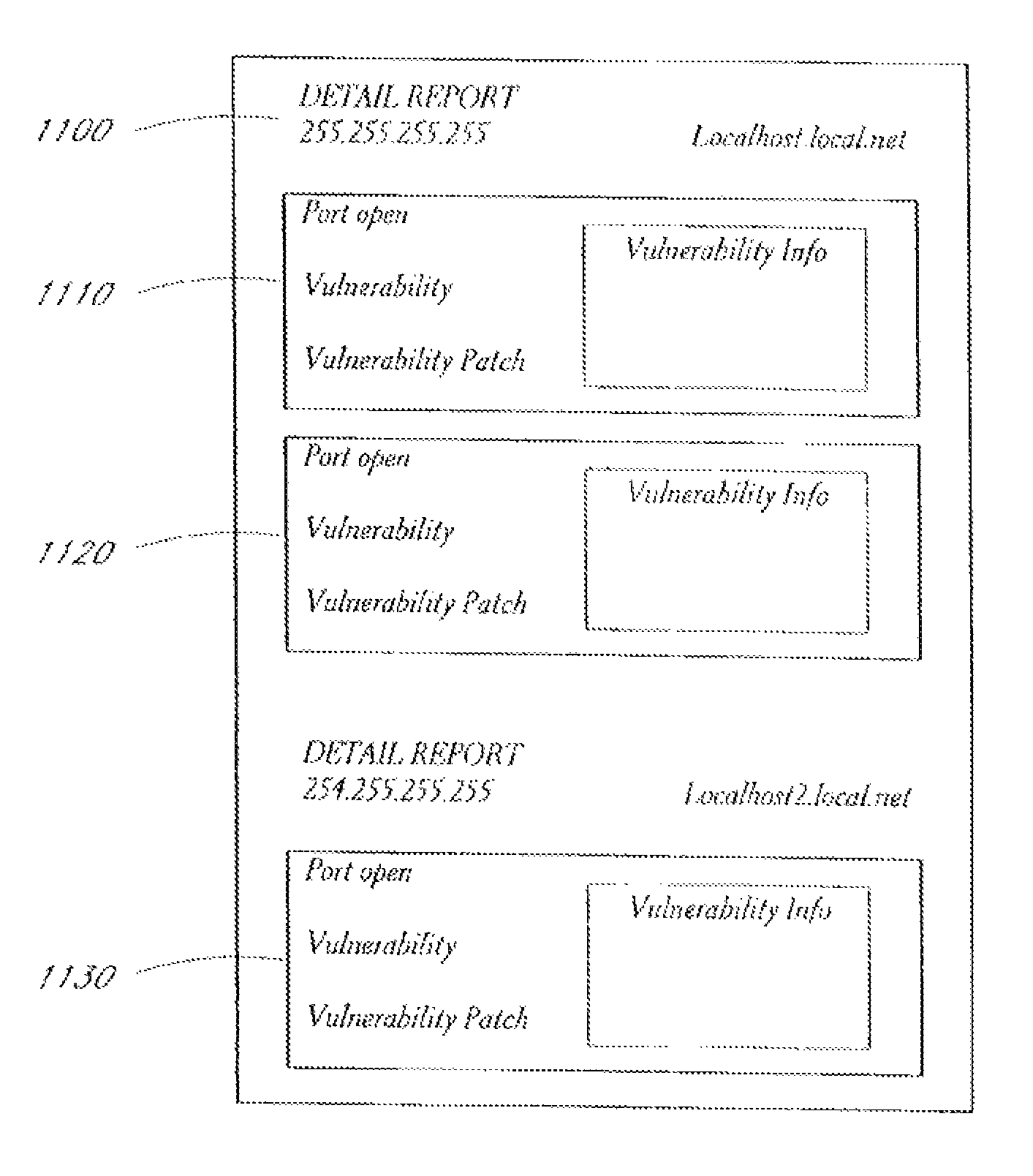
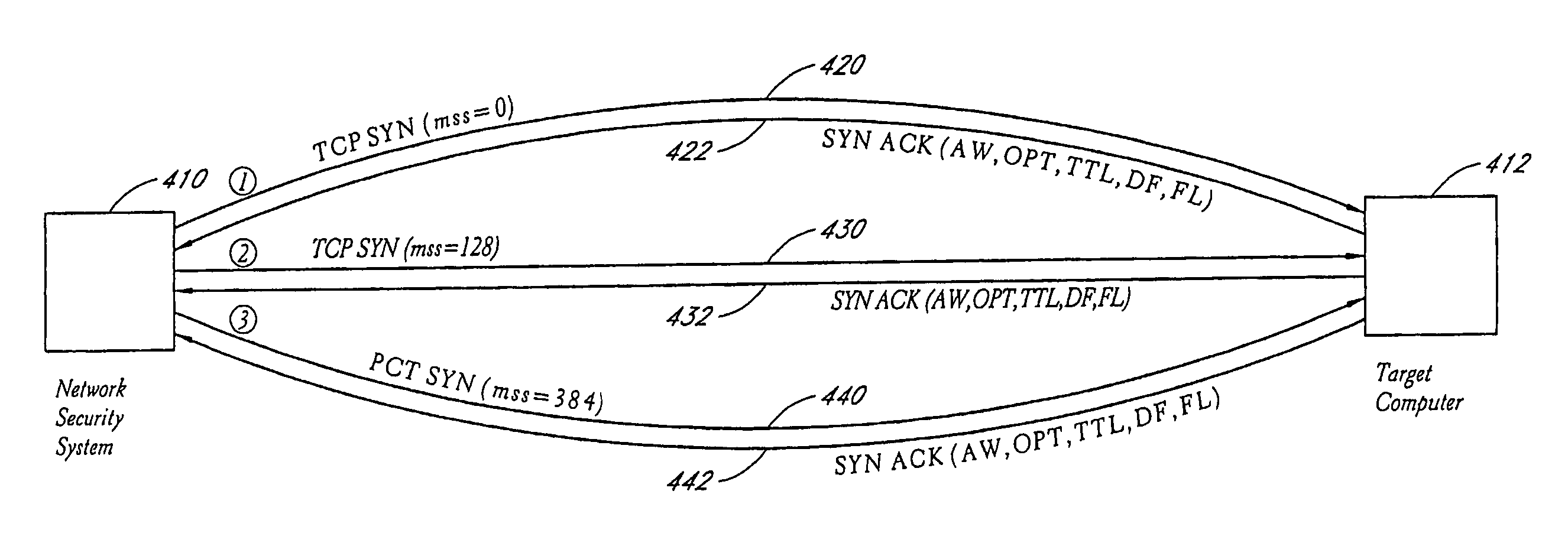
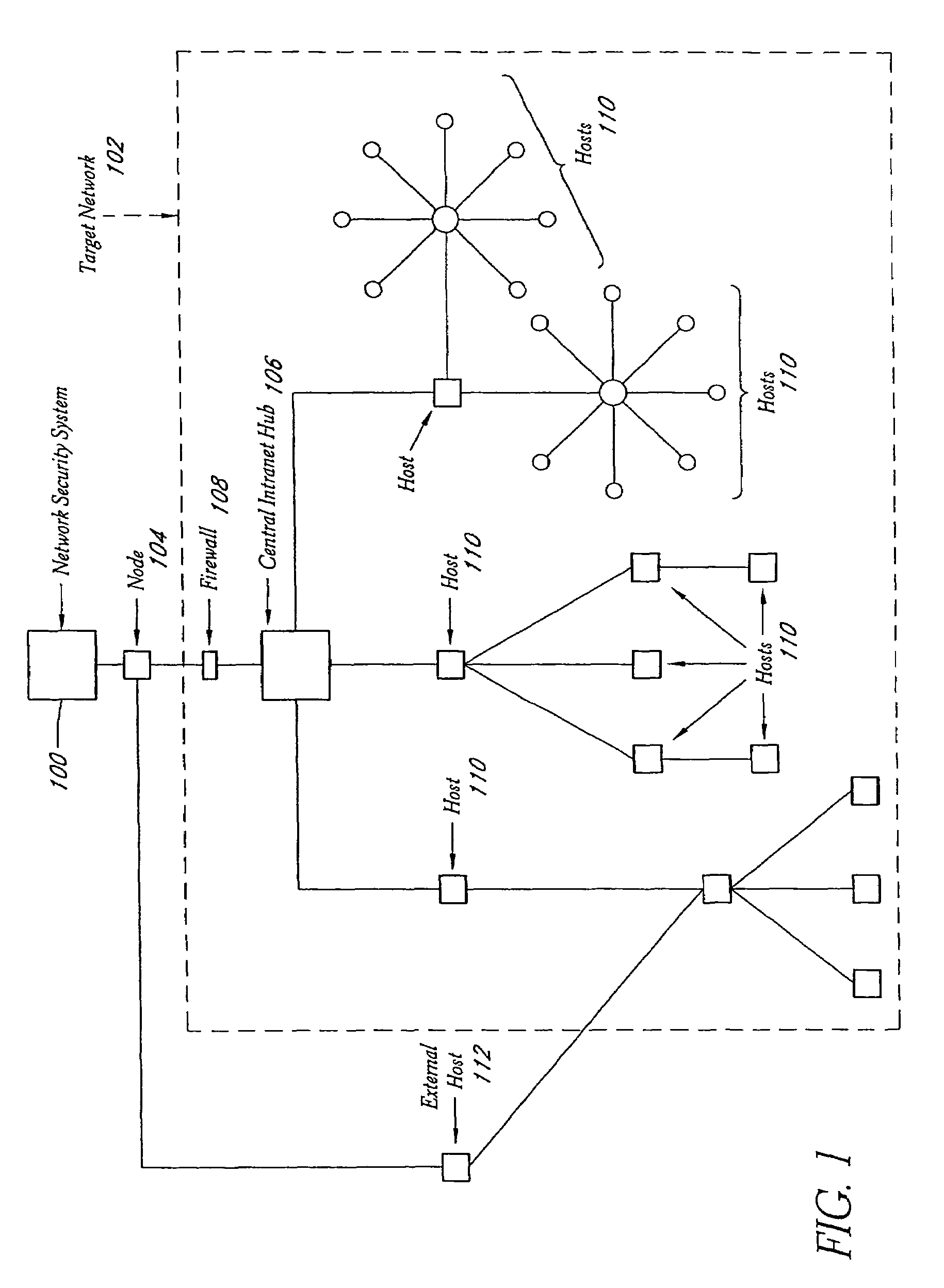
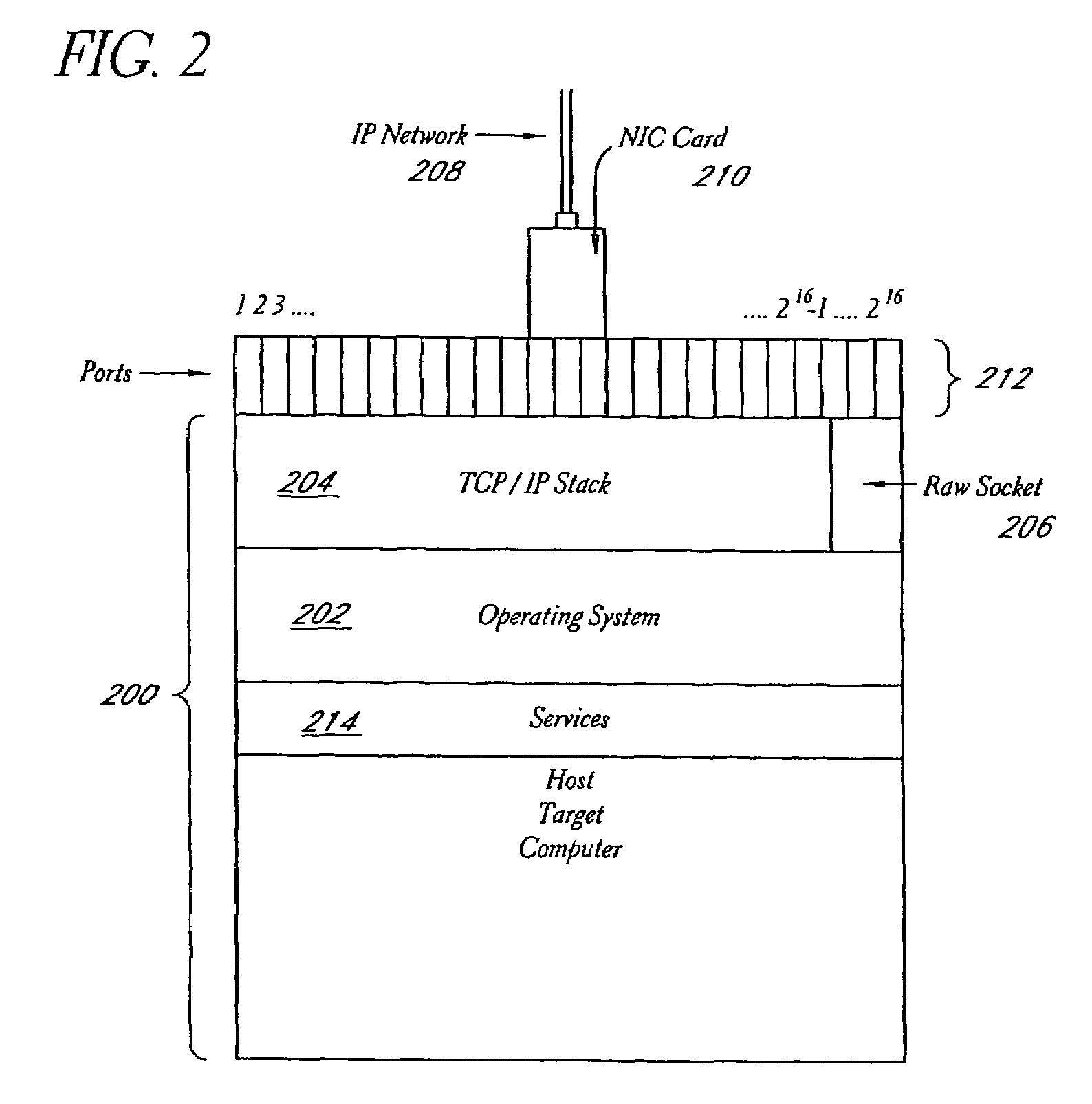
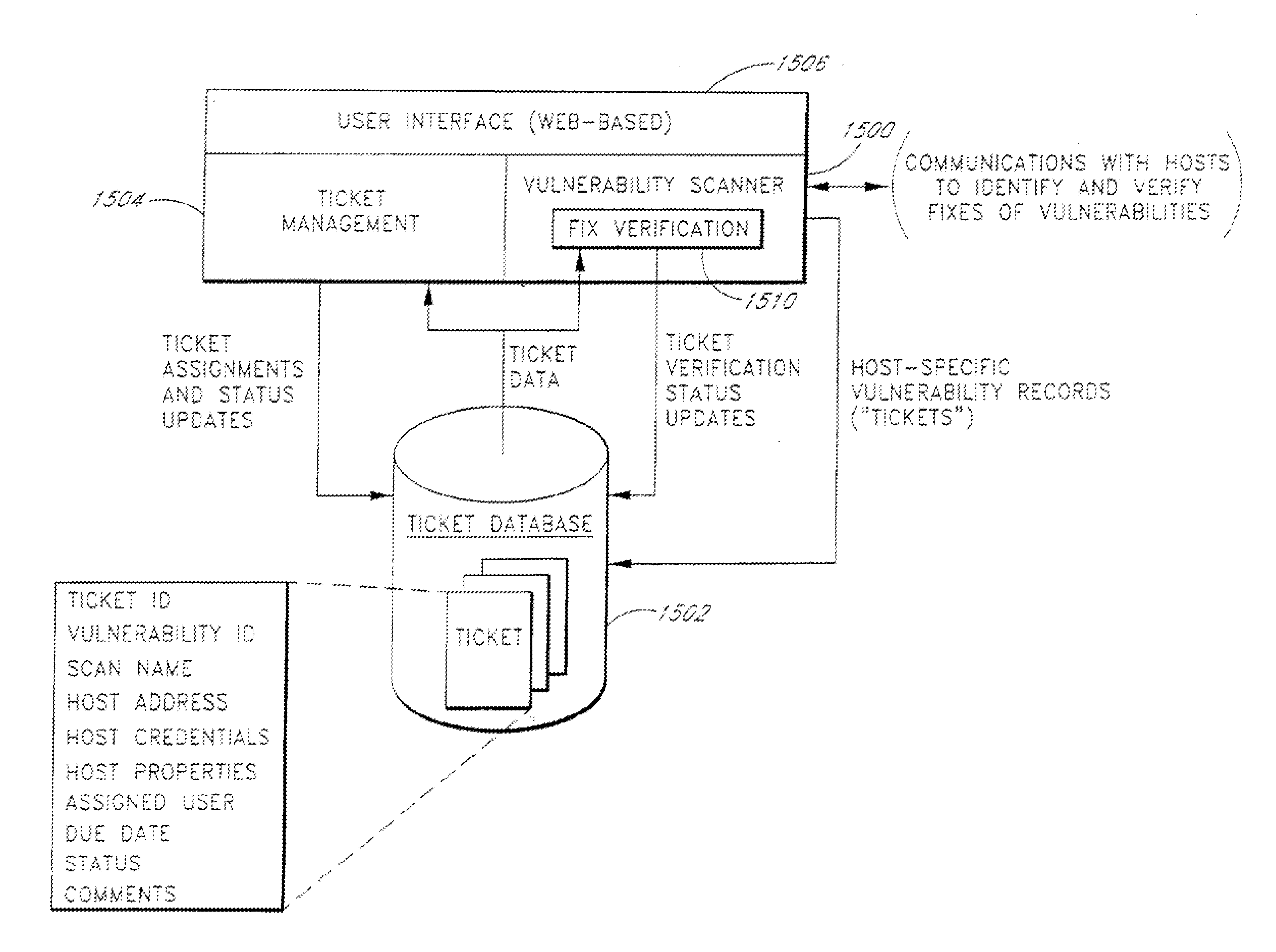
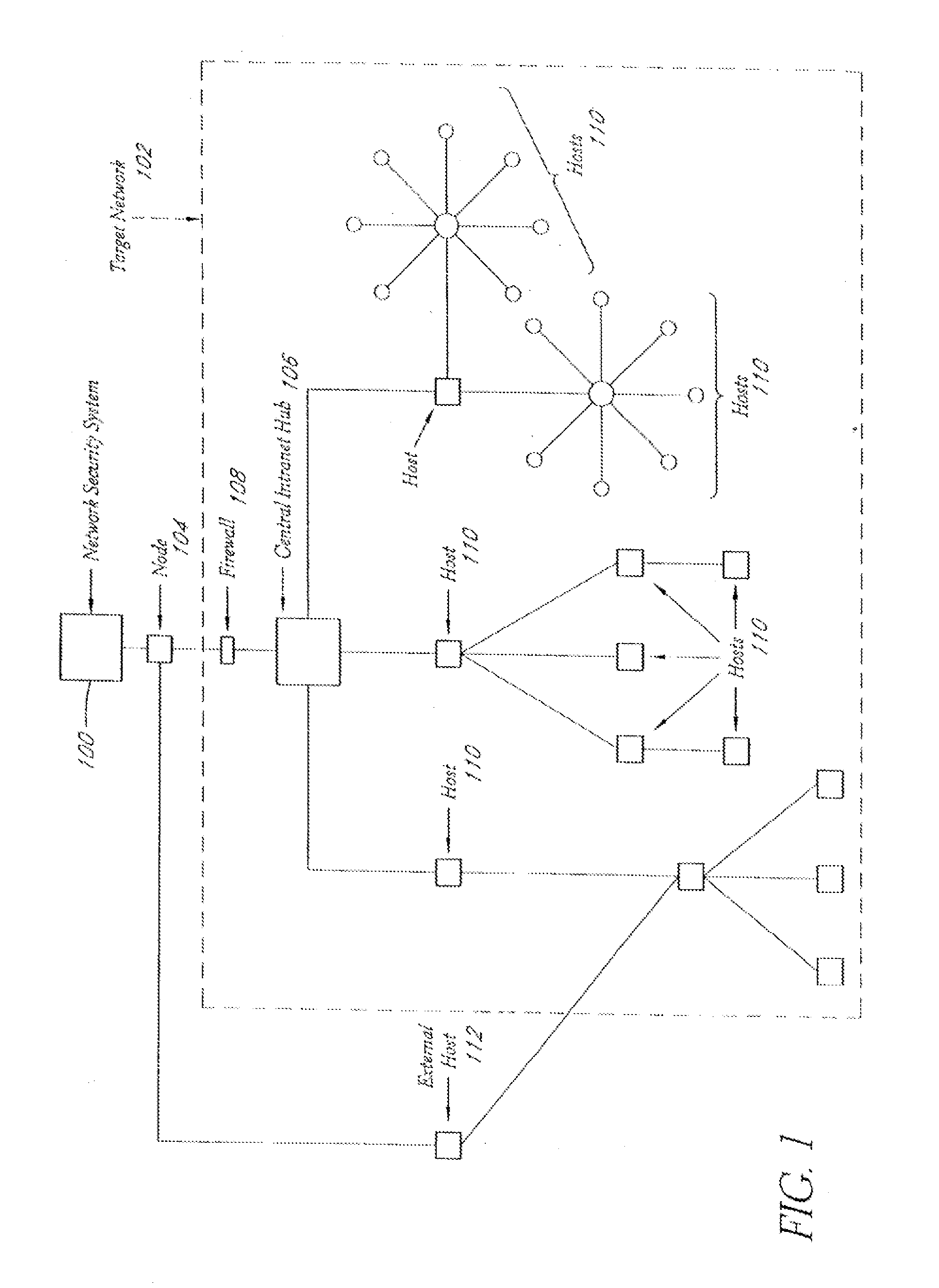
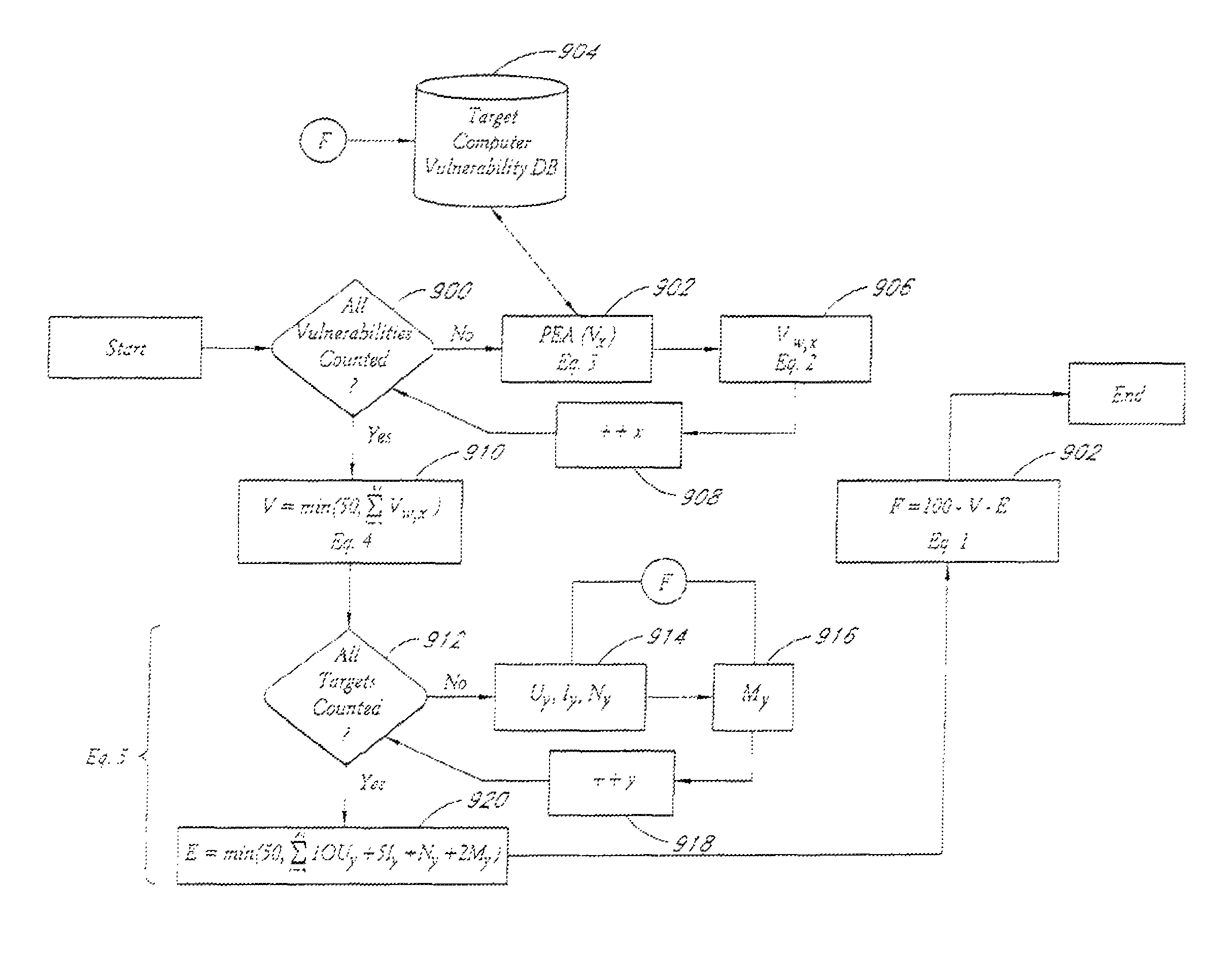
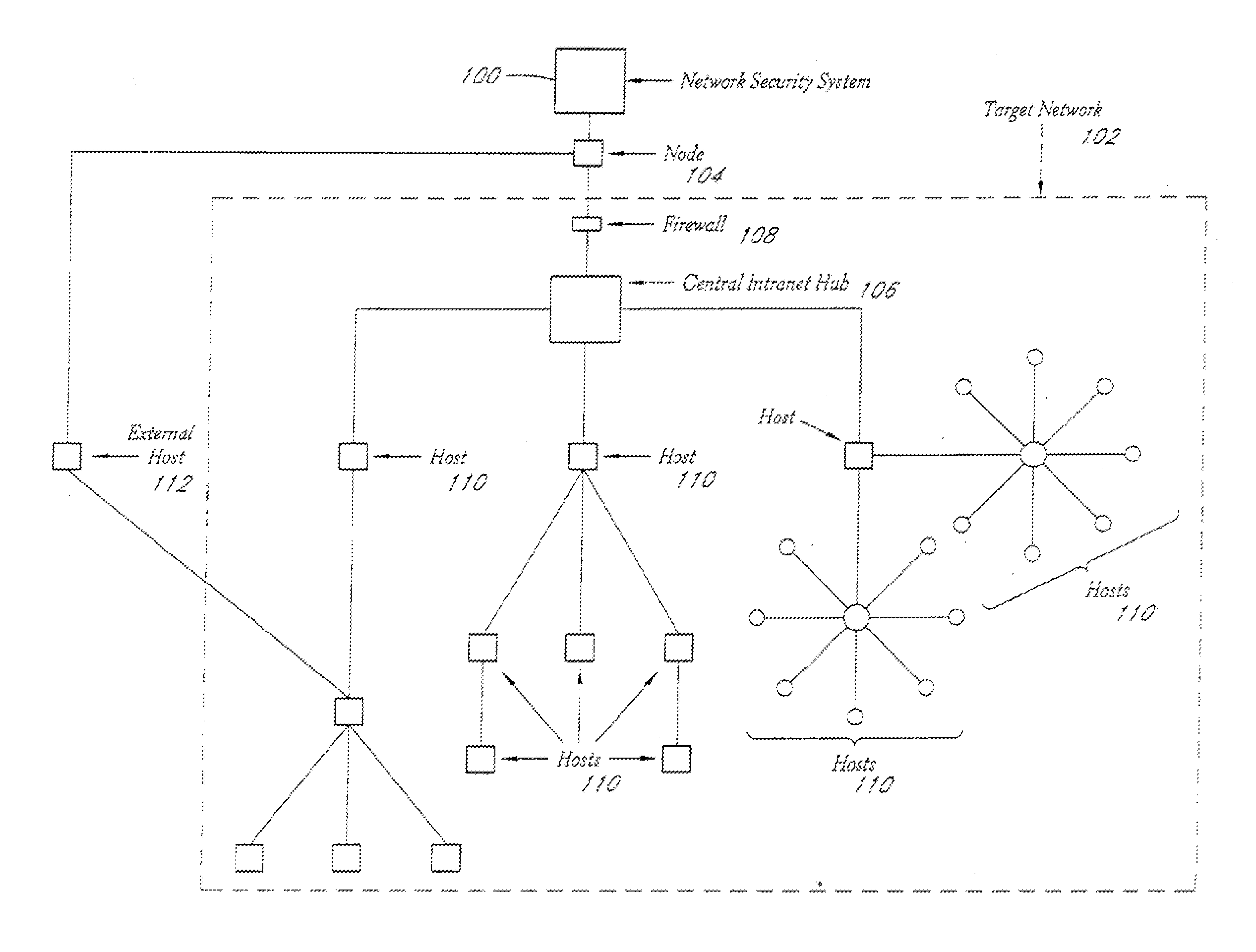
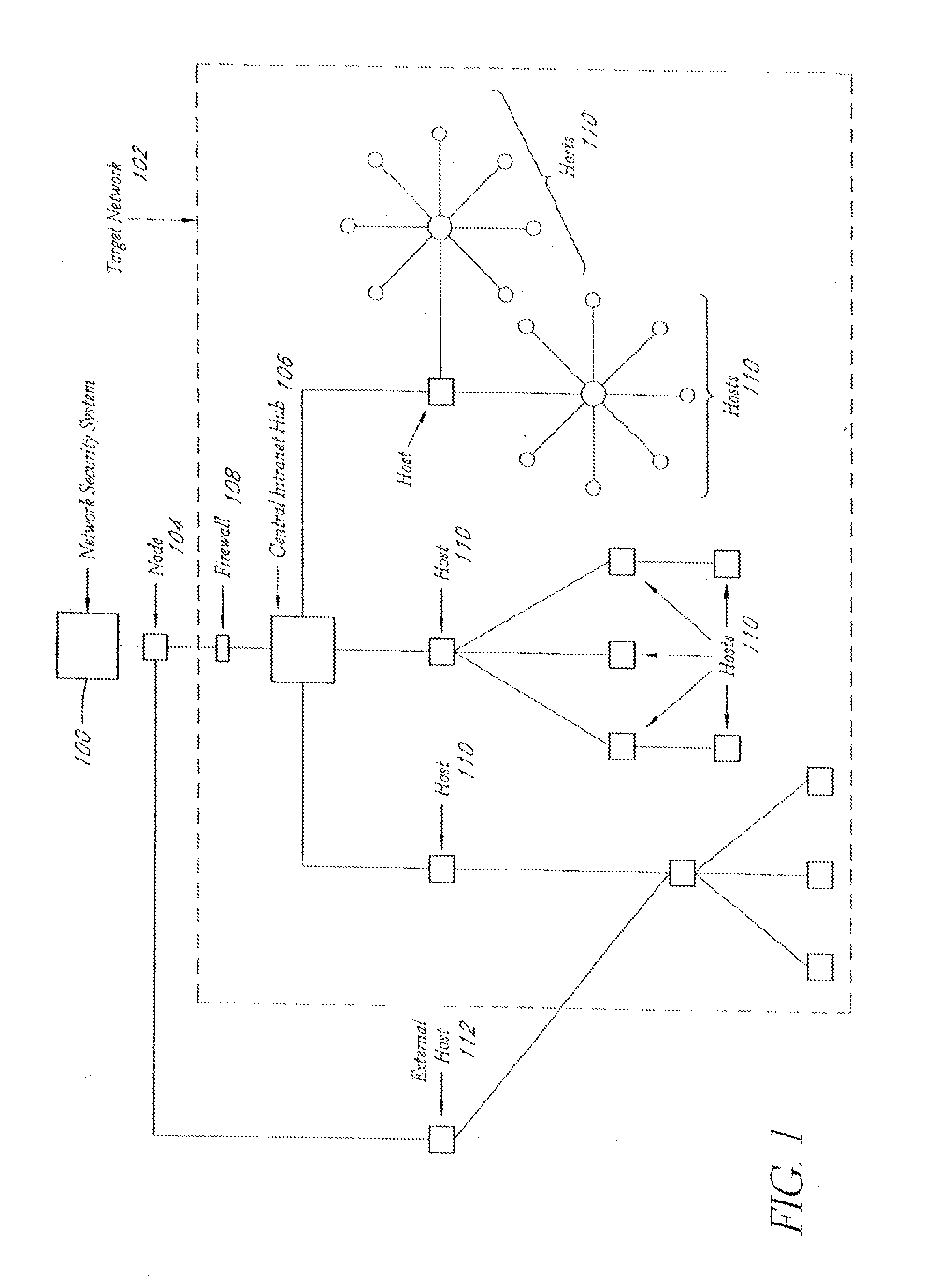
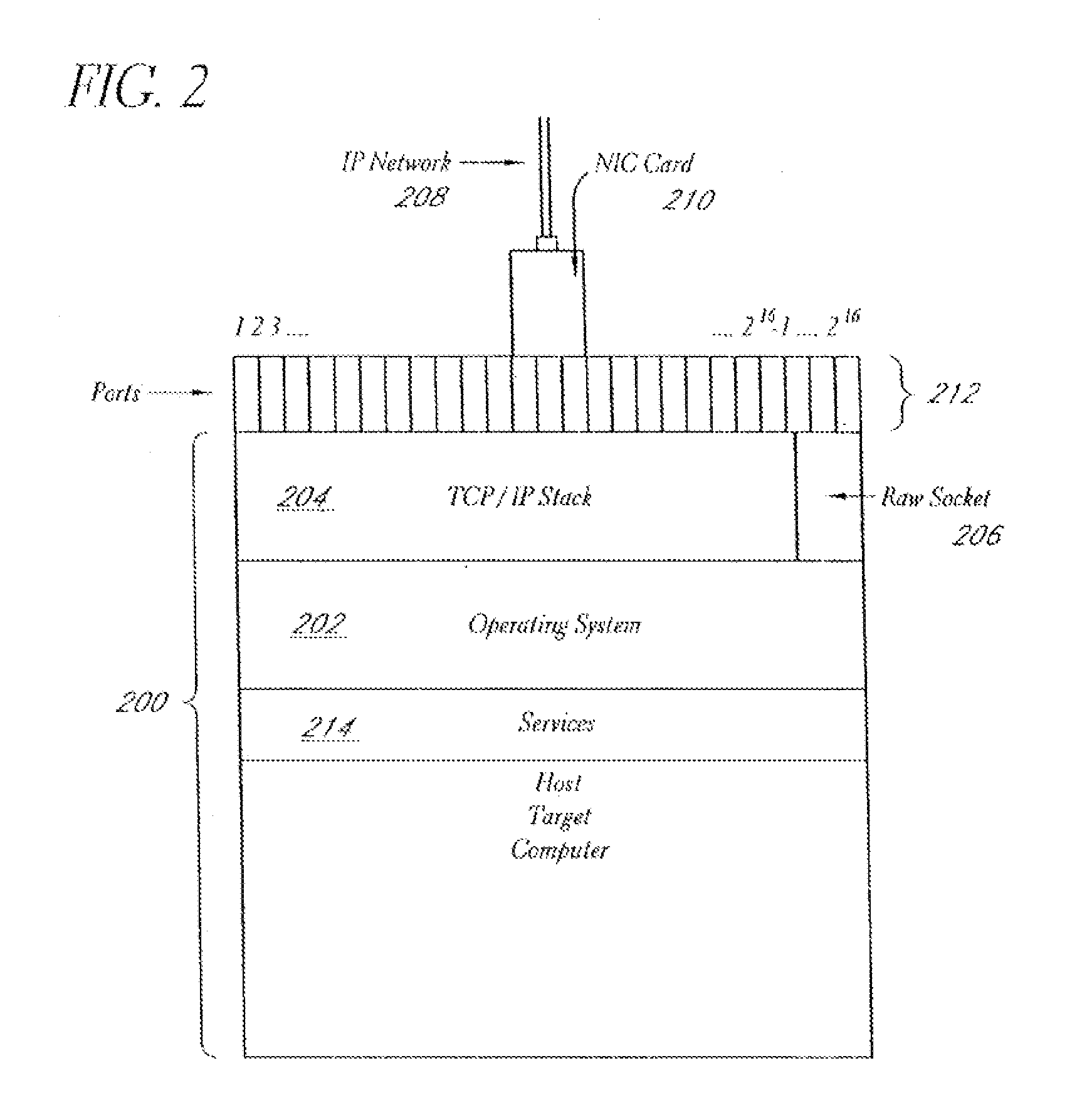
System and method for network vulnerability detection and reporting
ActiveUS7257630B2Reduce the possibilityReliably determinedMemory loss protectionError detection/correctionGraphicsOperational system
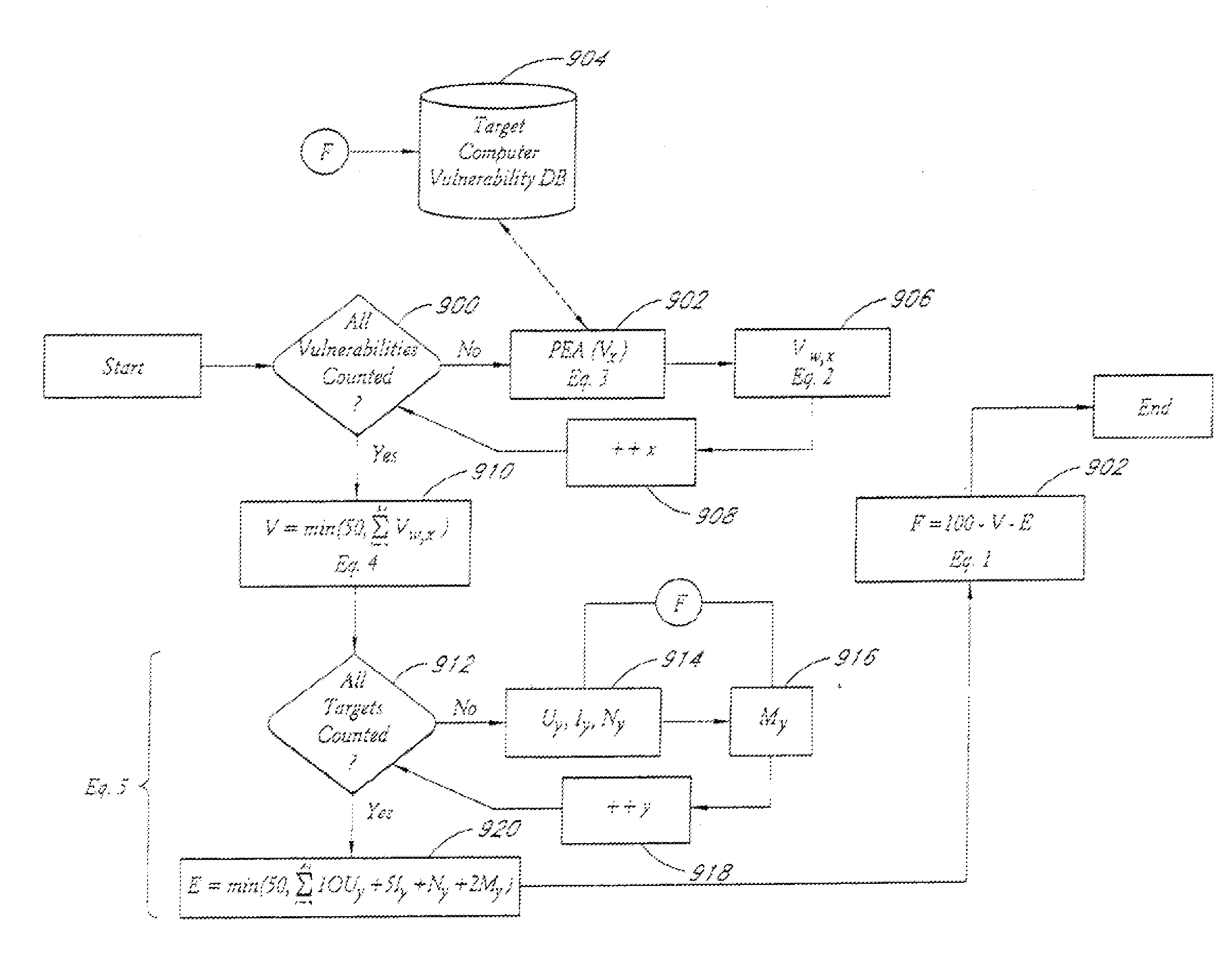
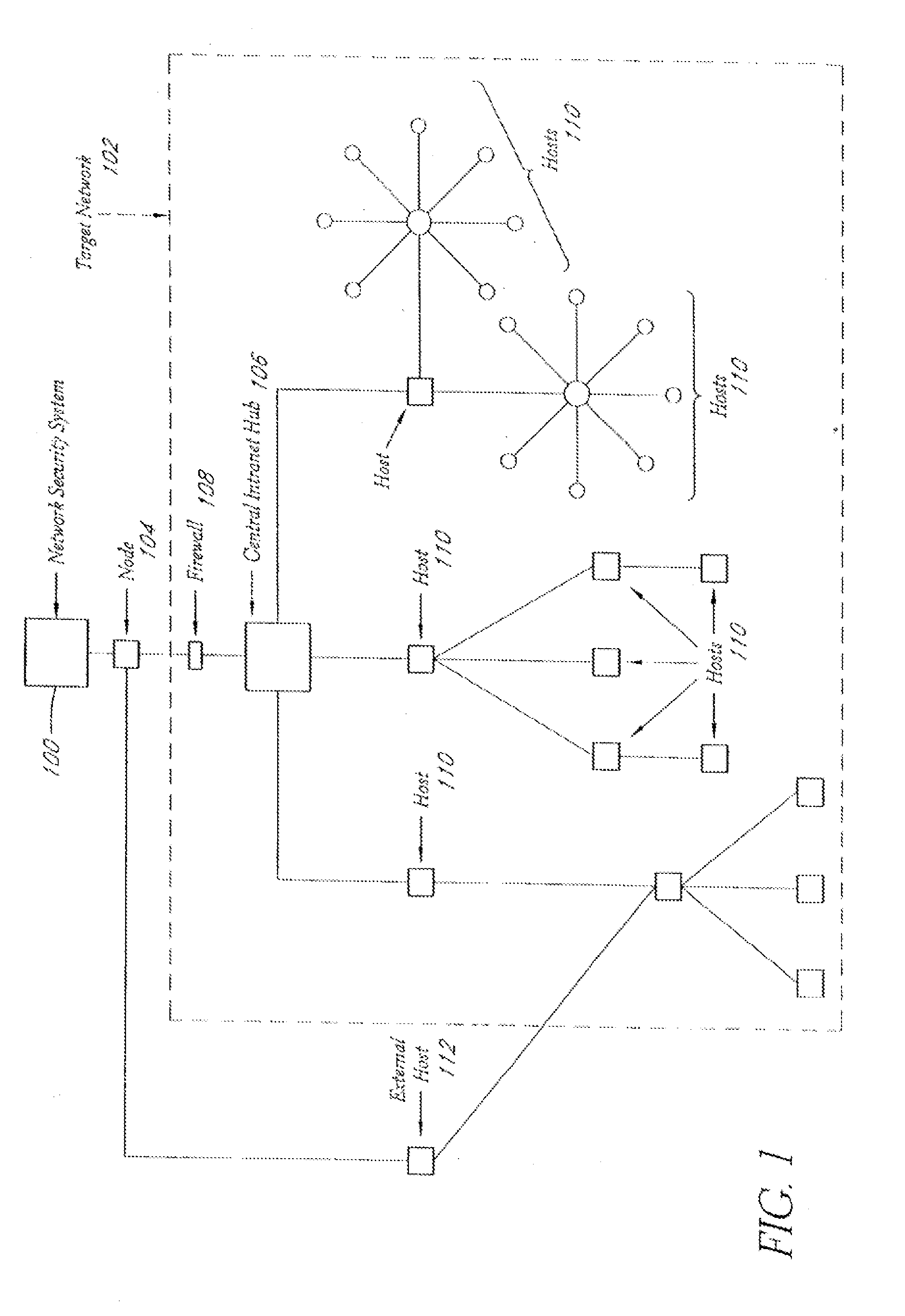
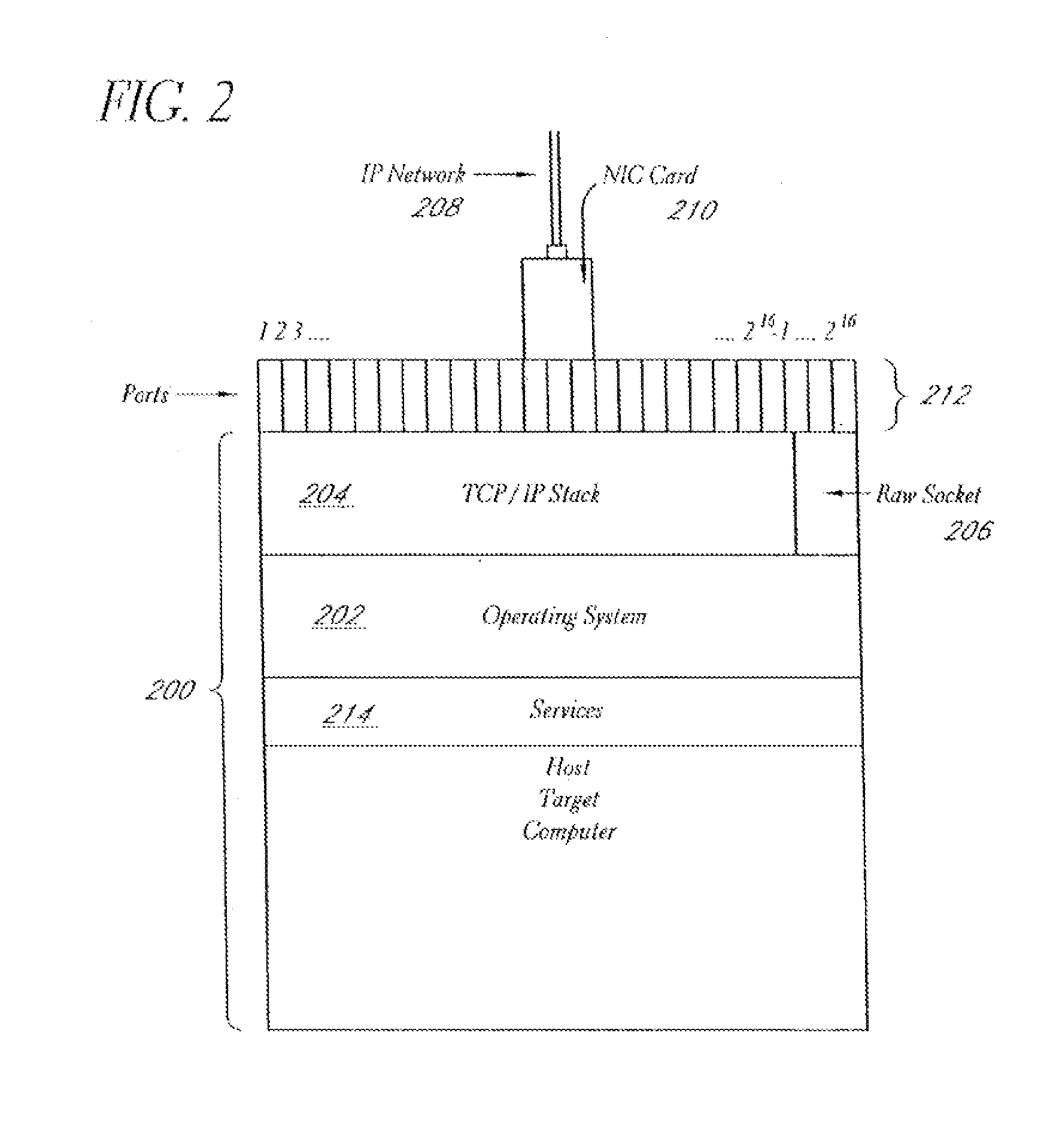
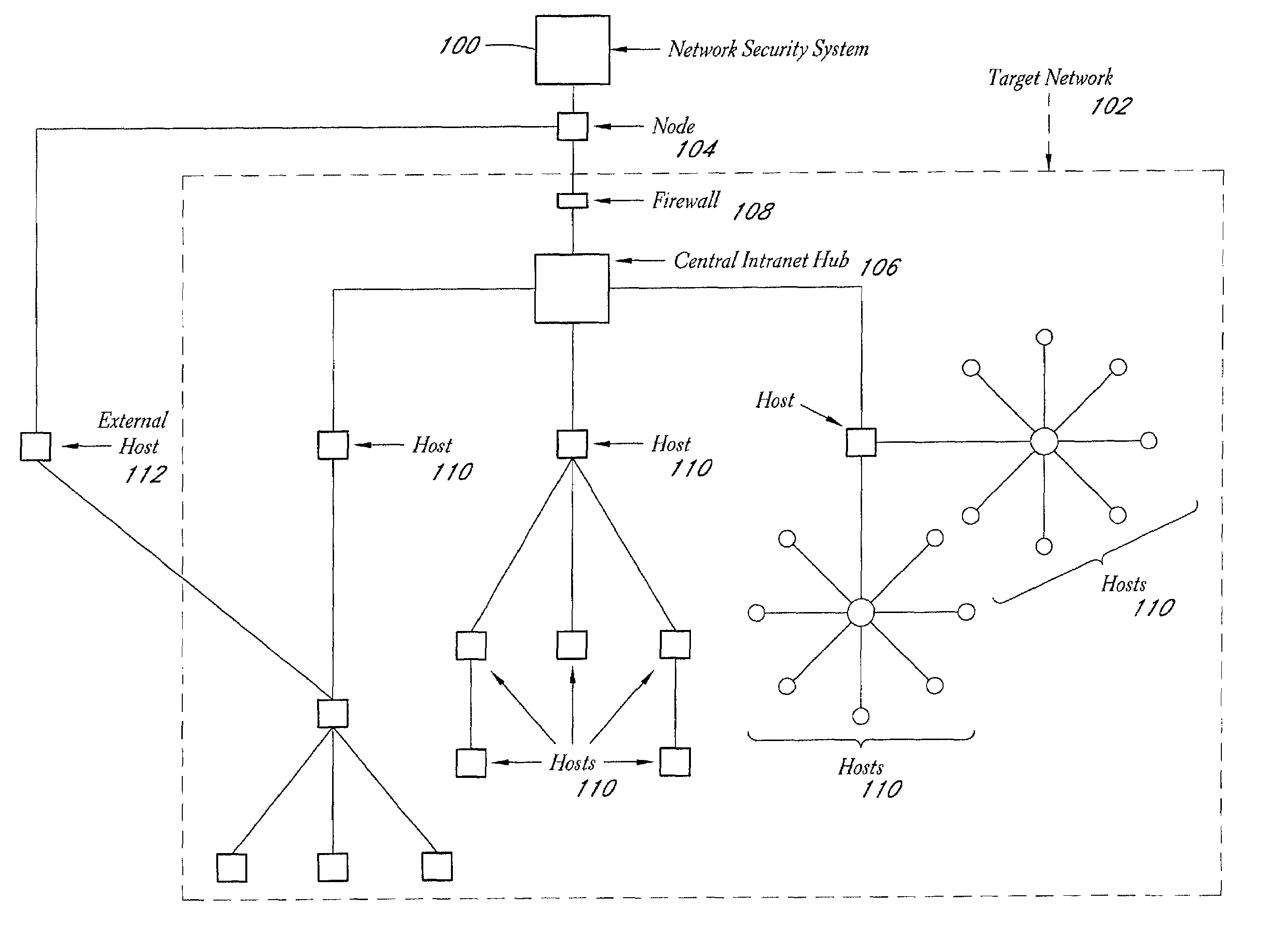
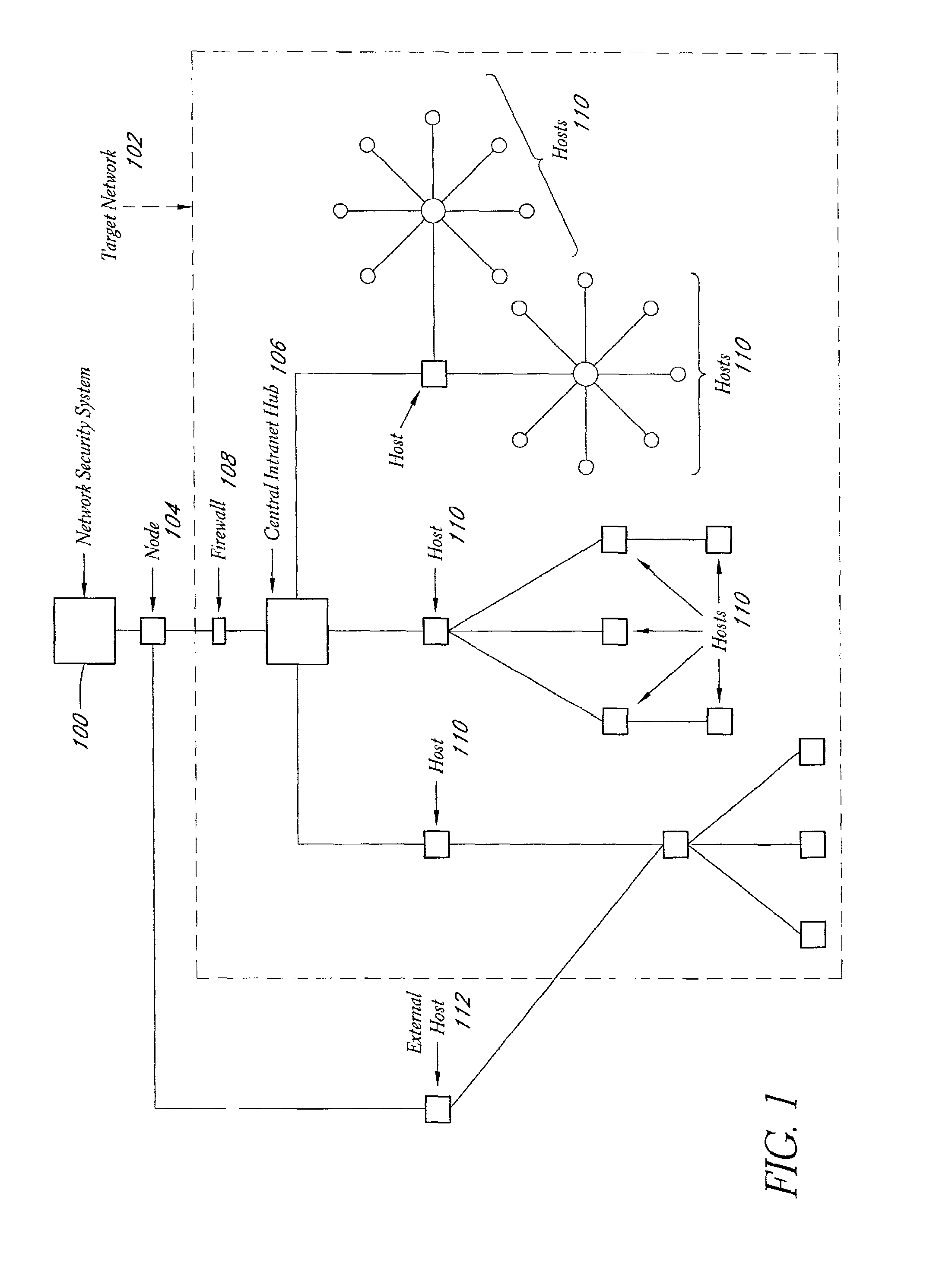
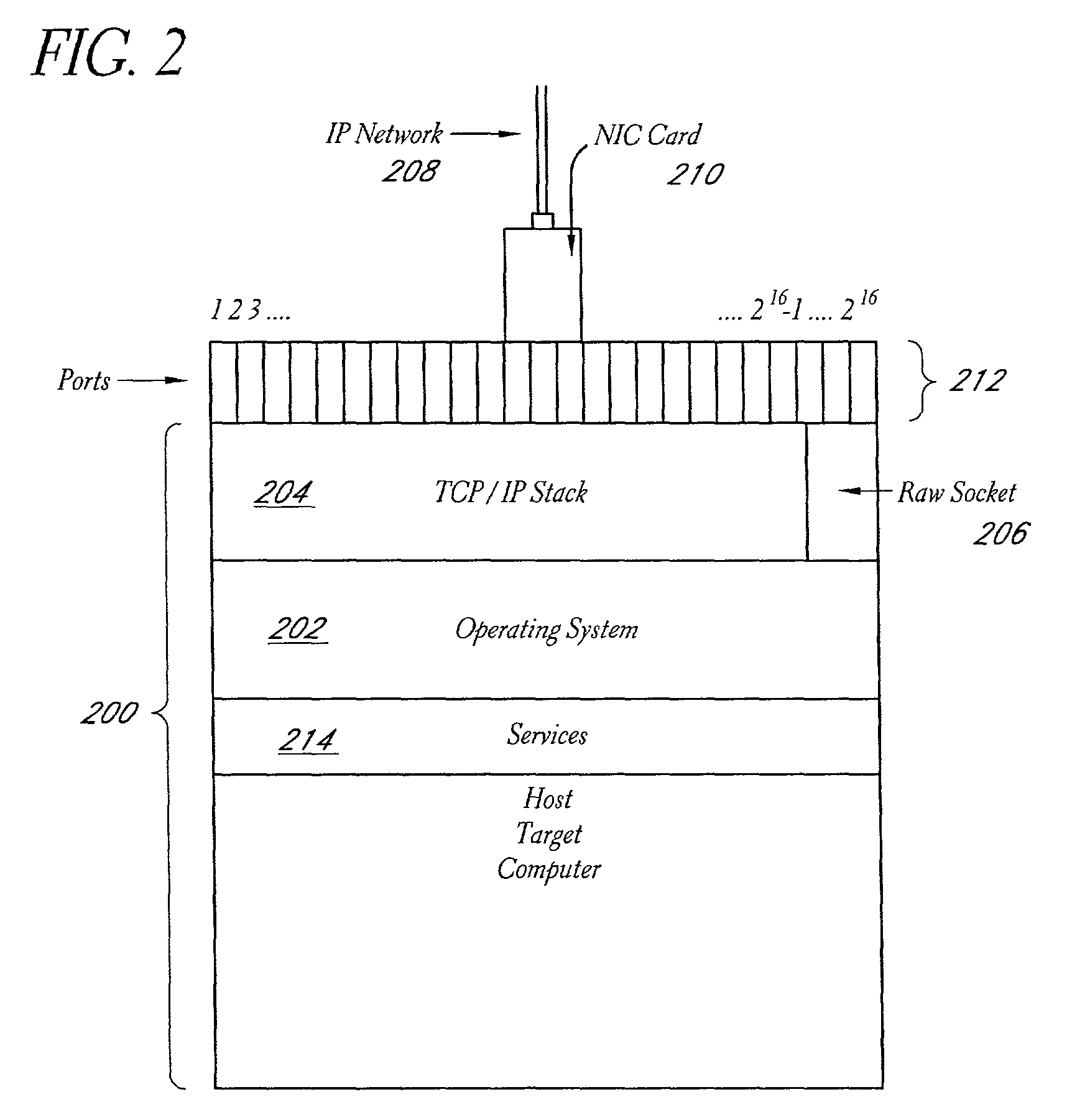
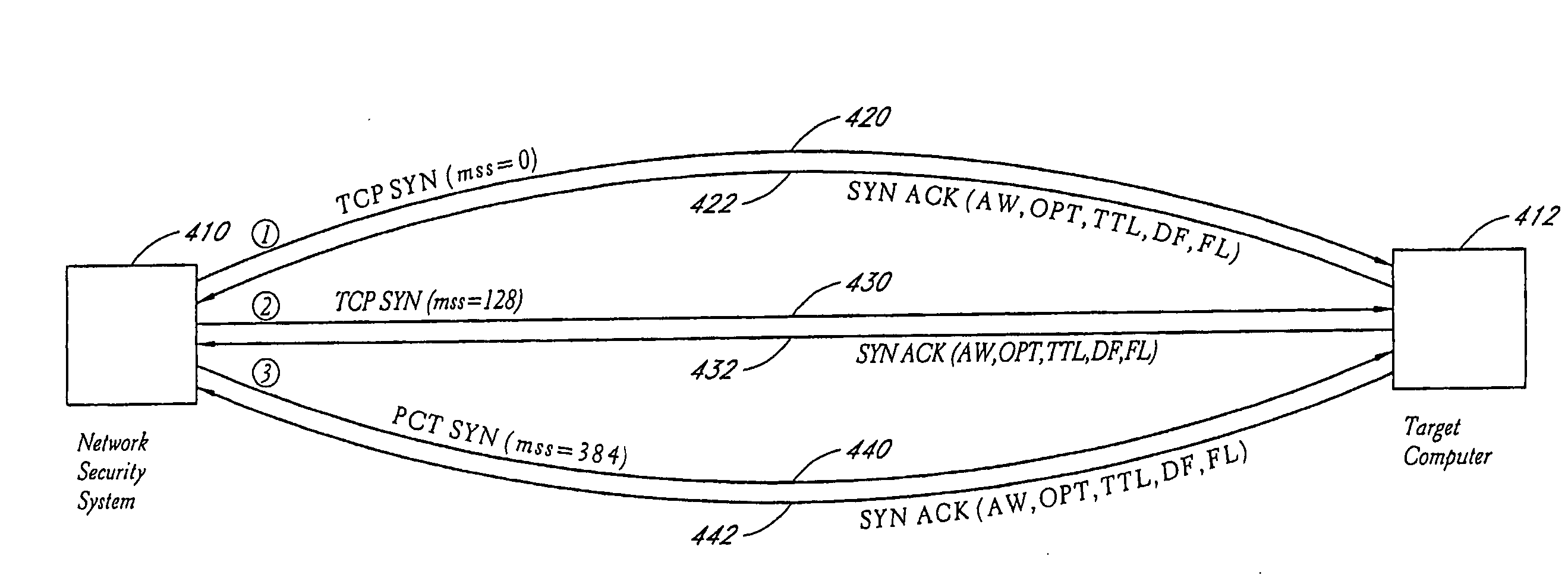
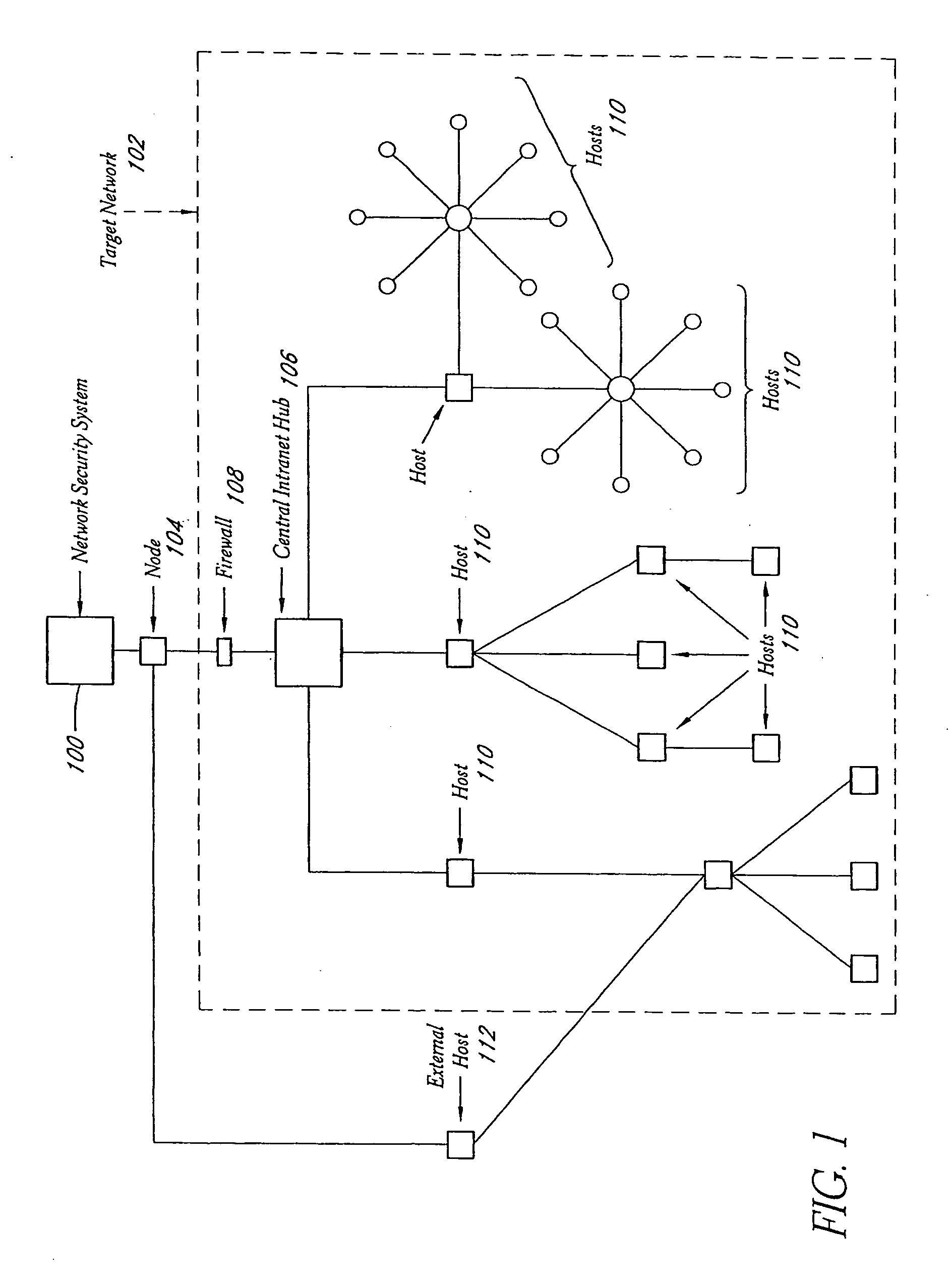
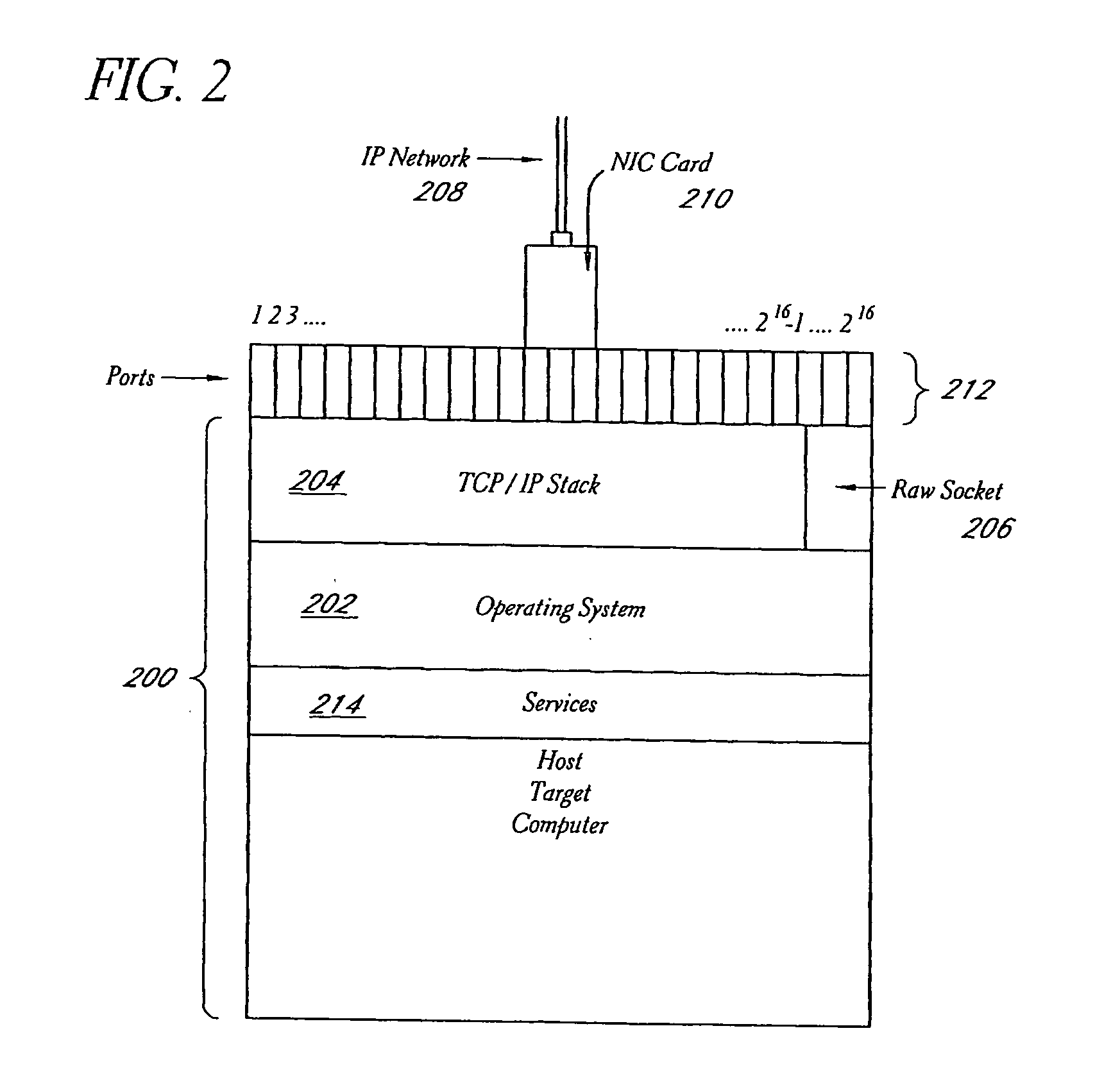
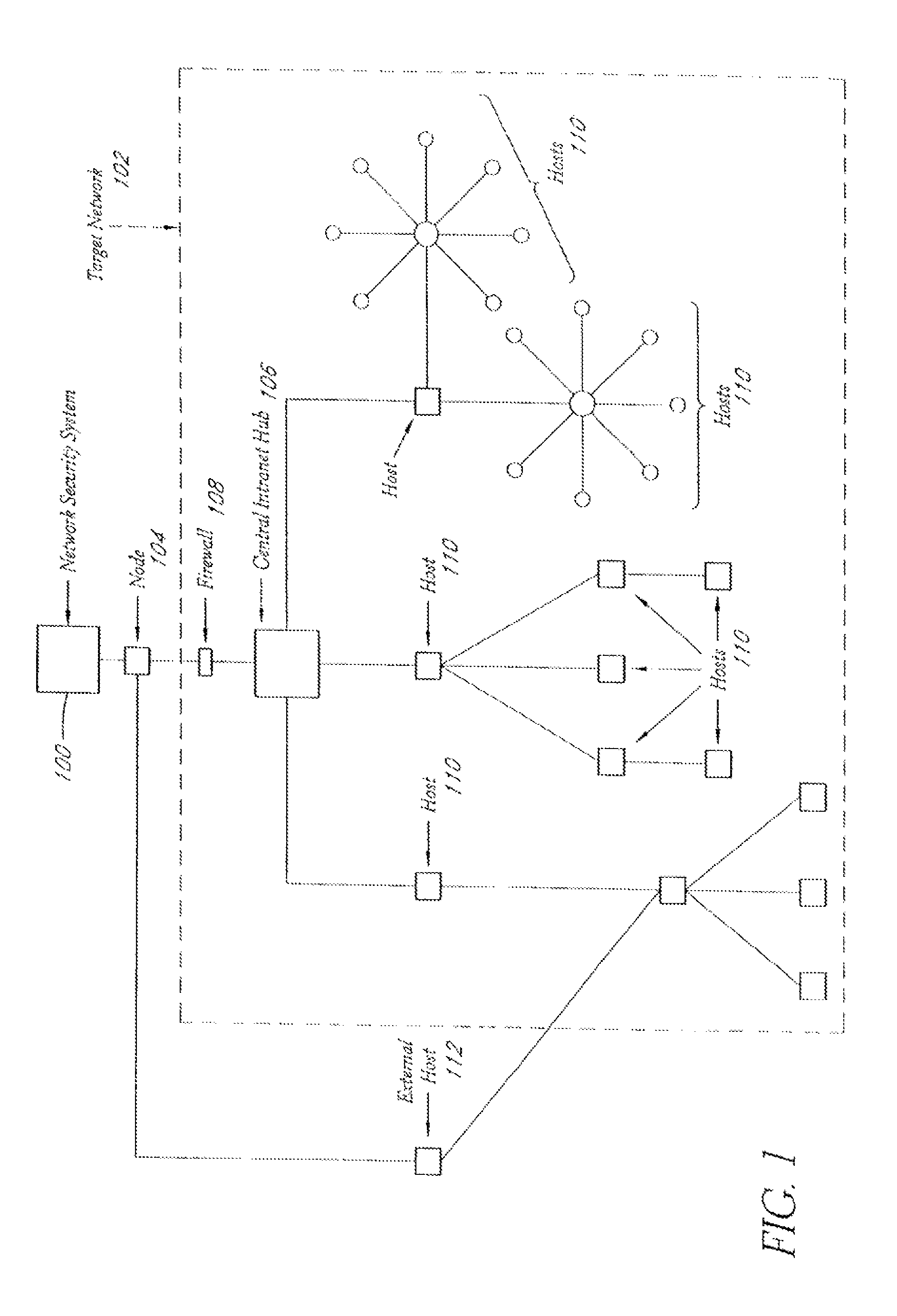
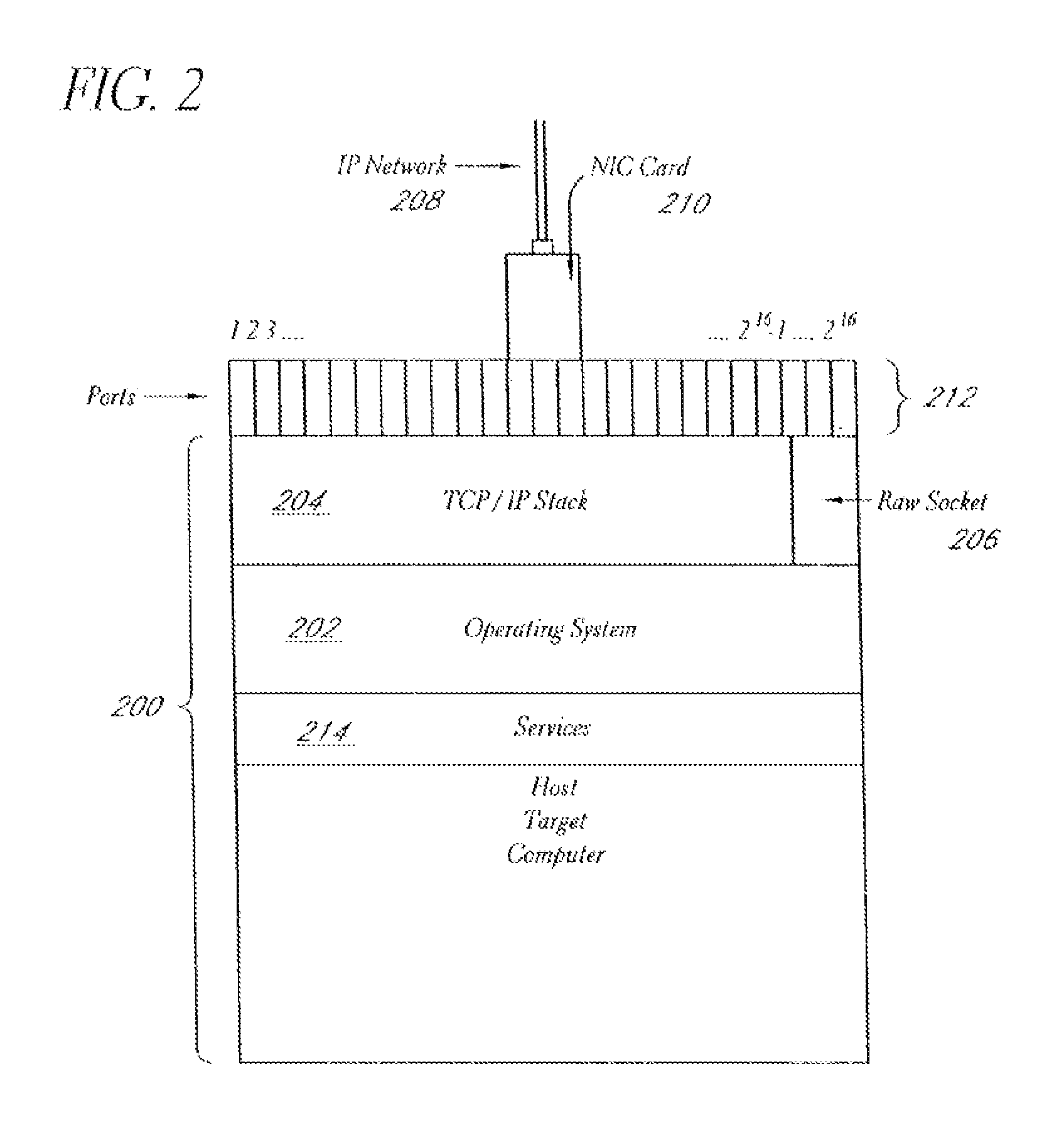
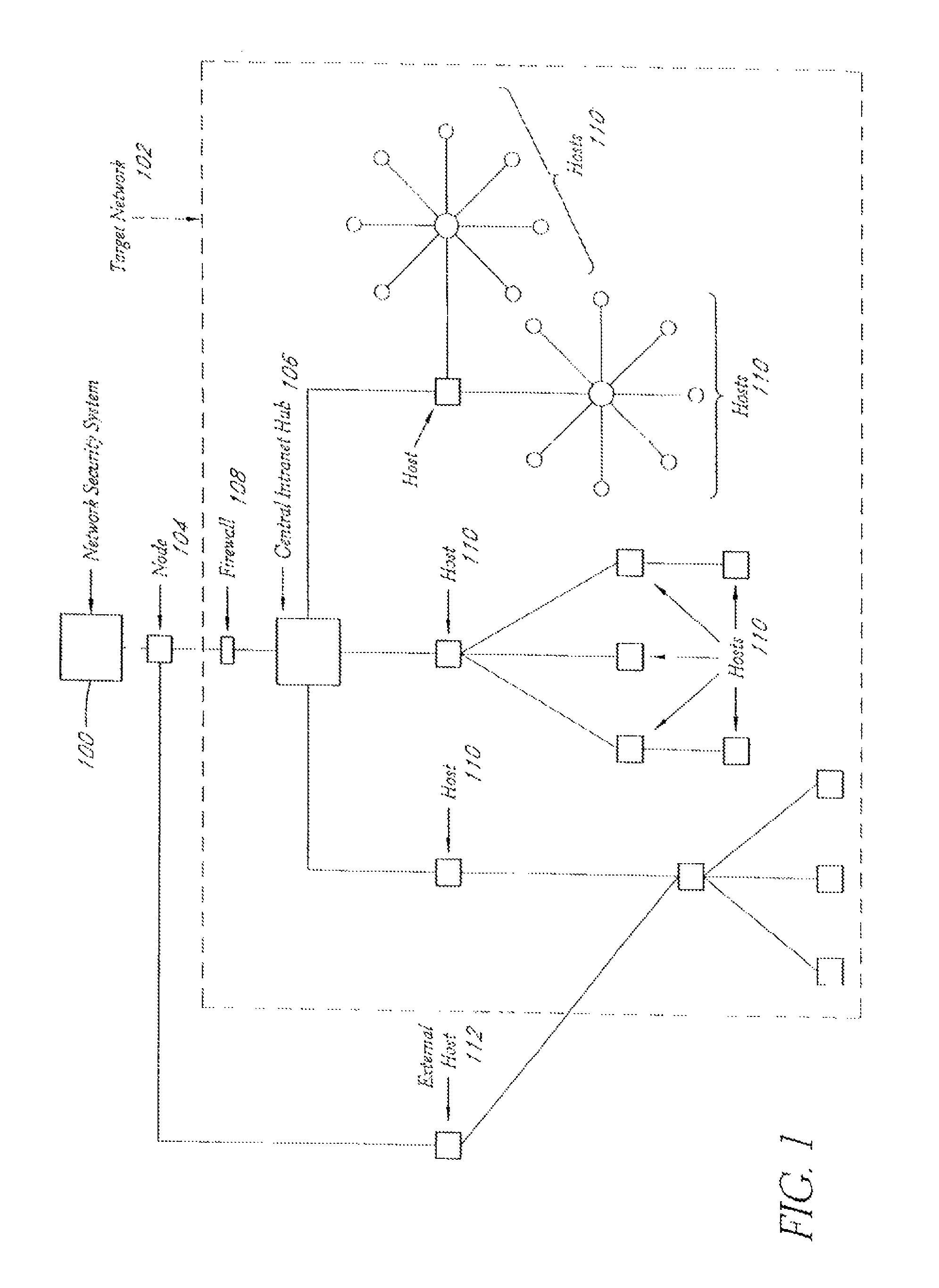
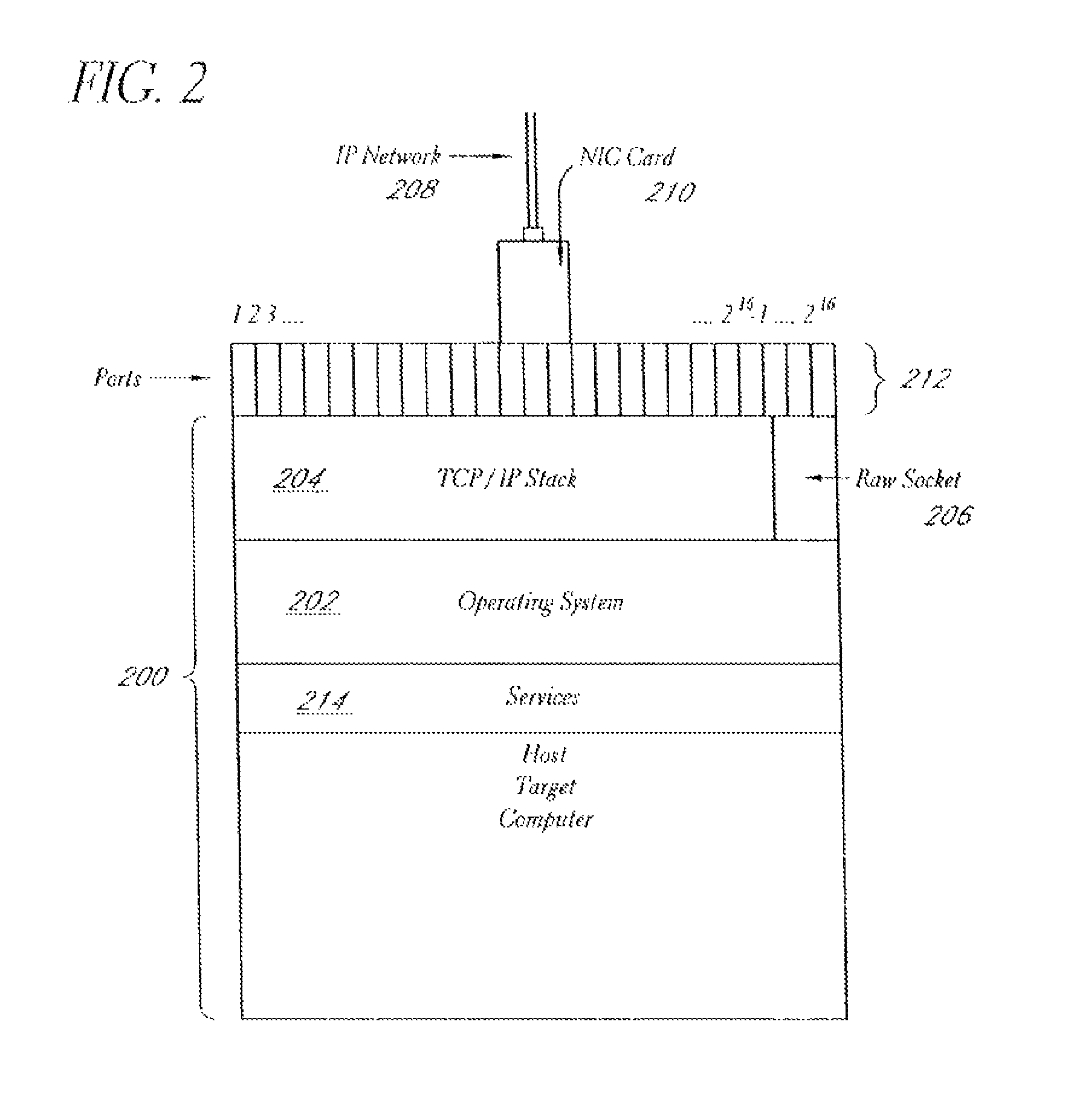
A system and method provide comprehensive and highly automated testing of vulnerabilities to intrusion on a target network, including identification of operating system, identification of target network topology and target computers, identification of open target ports, assessment of vulnerabilities on target ports, active assessment of vulnerabilities based on information acquired from target computers, quantitative assessment of target network security and vulnerability, and hierarchical graphical representation of the target network, target computers, and vulnerabilities in a test report. The system and method employ minimally obtrusive techniques to avoid interference with or damage to the target network during or after testing.
Owner:MCAFEE LLC
System and method for network vulnerability detection and reporting
ActiveUS7152105B2Easy to useReliably determinedElectric signal transmission systemsImage analysisGraphicsOperational system
A system and method provide comprehensive and highly automated testing of vulnerabilities to intrusion on a target network, including identification of operating system, identification of target network topology and target computers, identification of open target ports, assessment of vulnerabilities on target ports, active assessment of vulnerabilities based on information acquired from target computers, quantitative assessment of target network security and vulnerability, and hierarchical graphical representation of the target network, target computers, and vulnerabilities in a test report. The system and method employ minimally obtrusive techniques to avoid interference with or damage to the target network during or after testing.
Owner:MCAFEE LLC
Method and tool for network vulnerability analysis
InactiveUS7013395B1Avoid low successLow “ effort ” costMemory loss protectionUnauthorized memory use protectionLimited resourcesCountermeasure
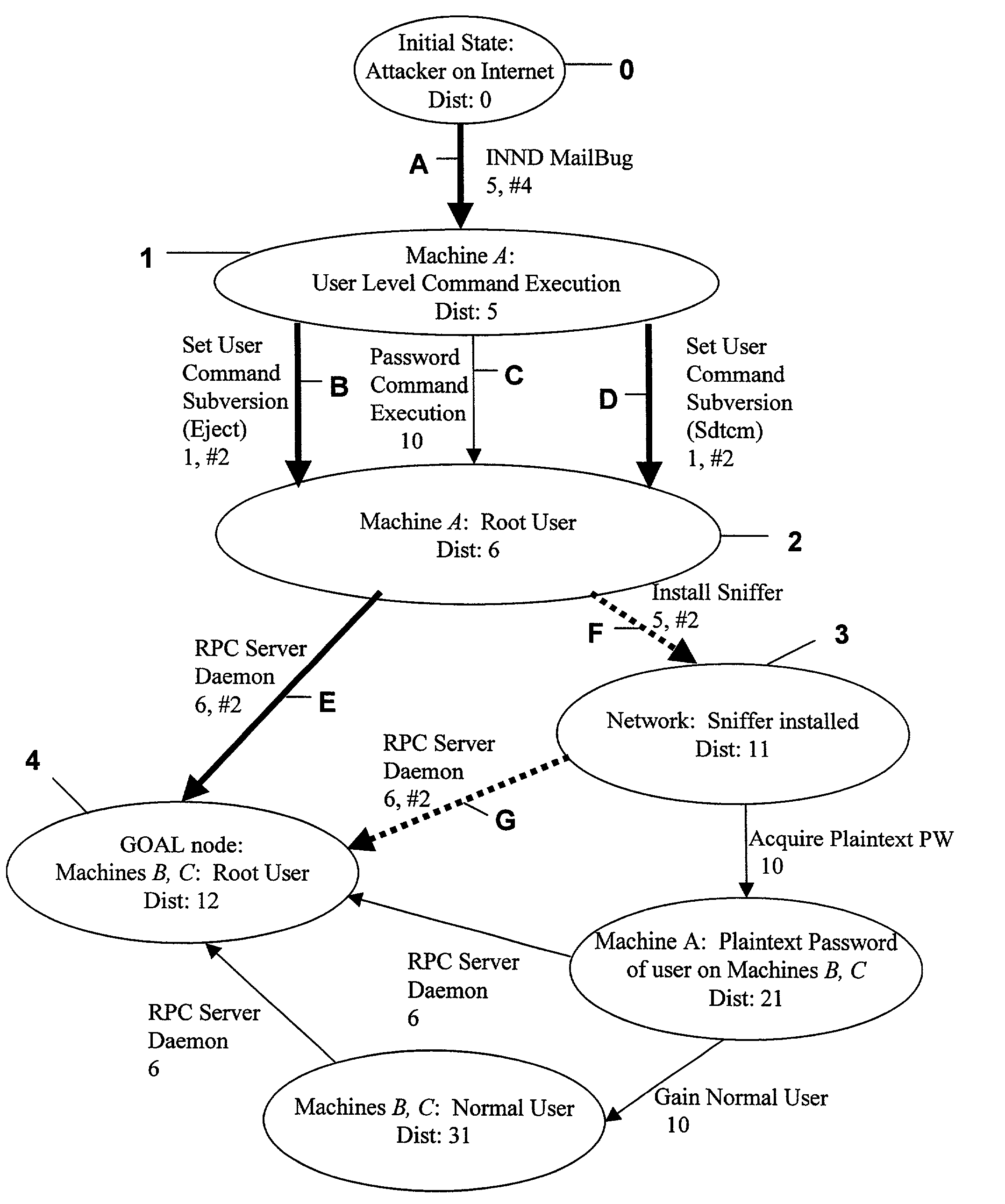
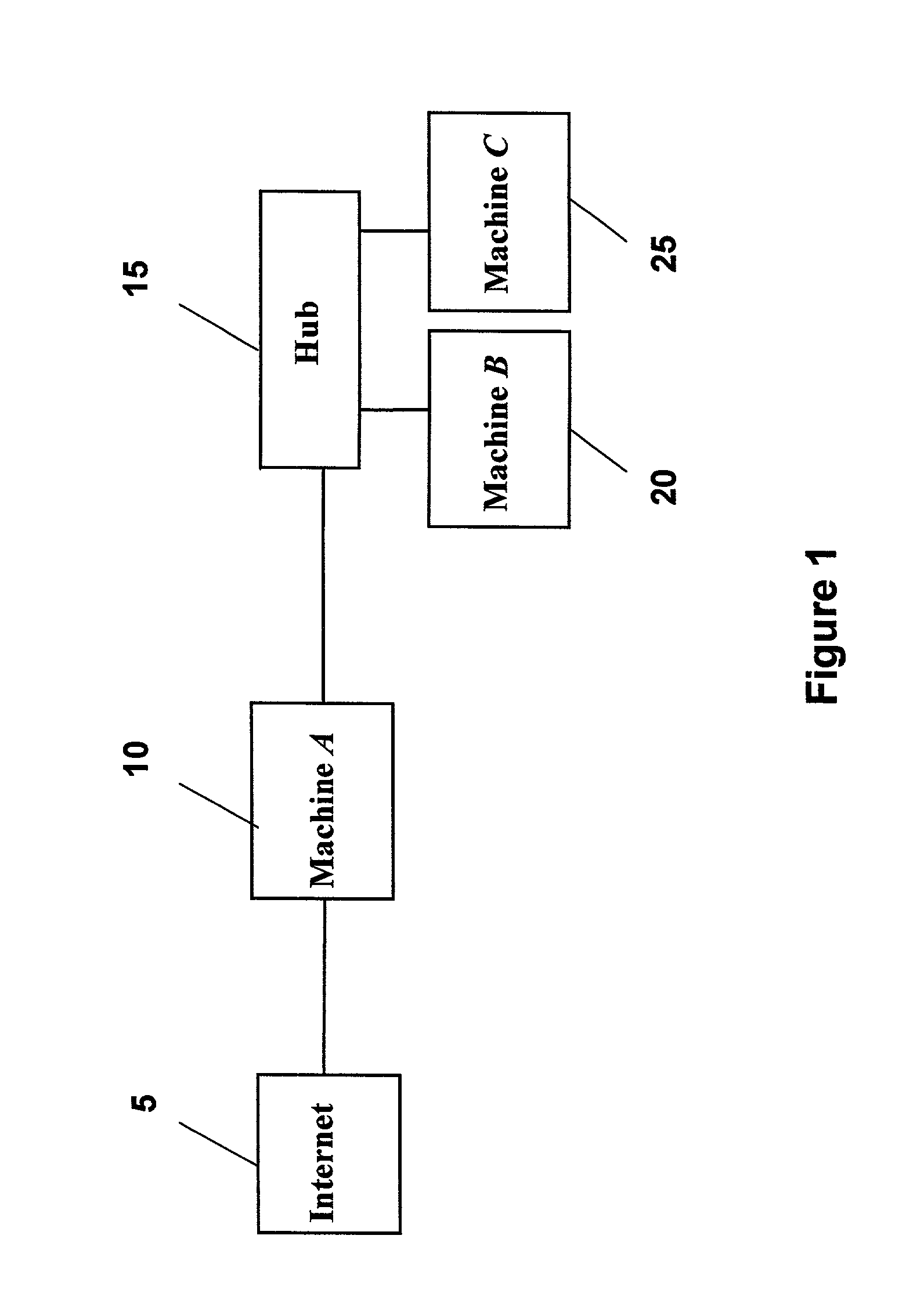
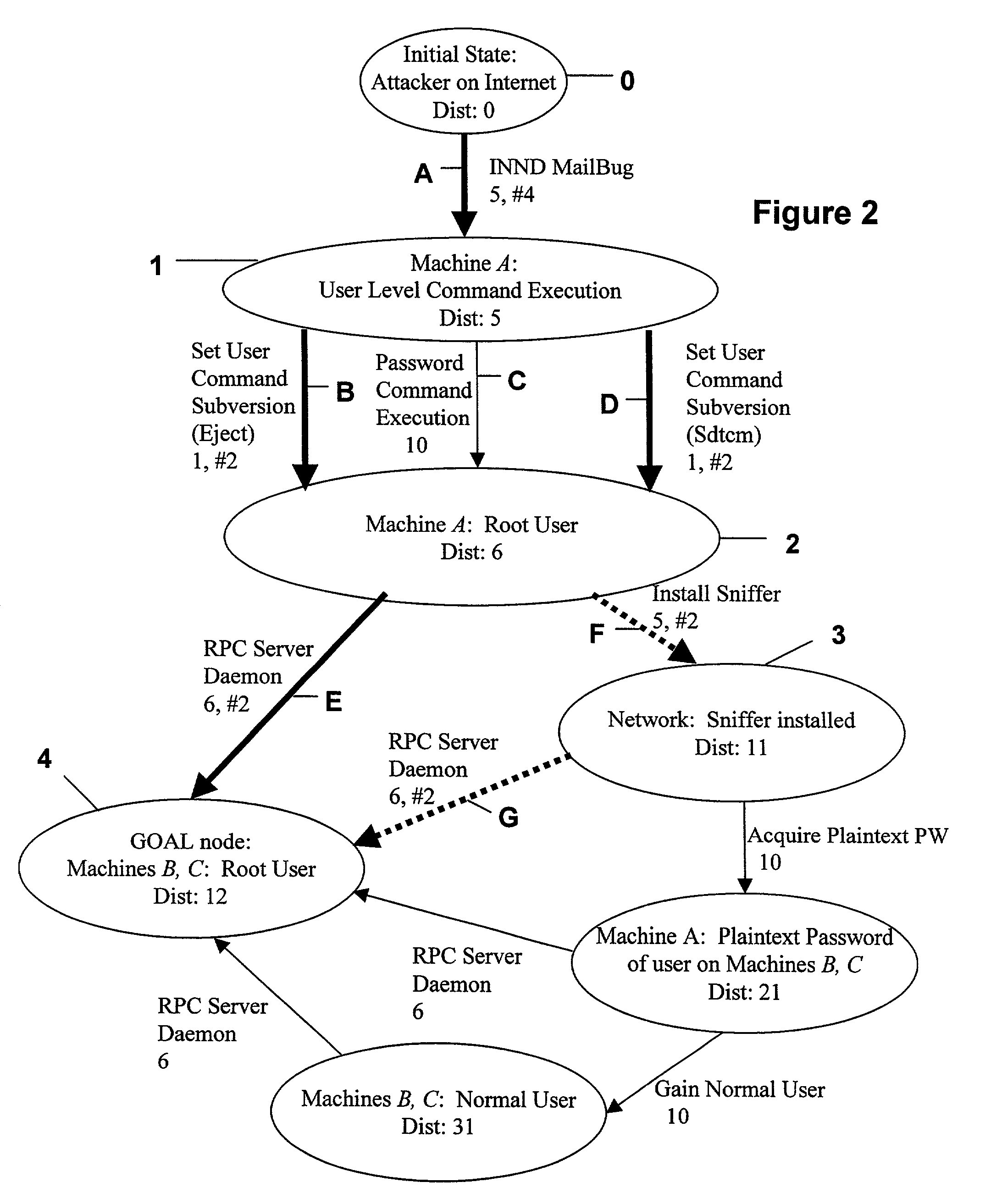
A computer system analysis tool and method that will allow for qualitative and quantitative assessment of security attributes and vulnerabilities in systems including computer networks. The invention is based on generation of attack graphs wherein each node represents a possible attack state and each edge represents a change in state caused by a single action taken by an attacker or unwitting assistant. Edges are weighted using metrics such as attacker effort, likelihood of attack success, or time to succeed. Generation of an attack graph is accomplished by matching information about attack requirements (specified in “attack templates”) to information about computer system configuration (contained in a configuration file that can be updated to reflect system changes occurring during the course of an attack) and assumed attacker capabilities (reflected in “attacker profiles”). High risk attack paths, which correspond to those considered suited to application of attack countermeasures given limited resources for applying countermeasures, are identified by finding “epsilon optimal paths.”
Owner:SANDIA NAT LAB
Scaleable method for maintaining and making consistent updates to caches
InactiveUS6256712B1High degreeData processing applicationsDigital data information retrievalData synchronizationExtensibility
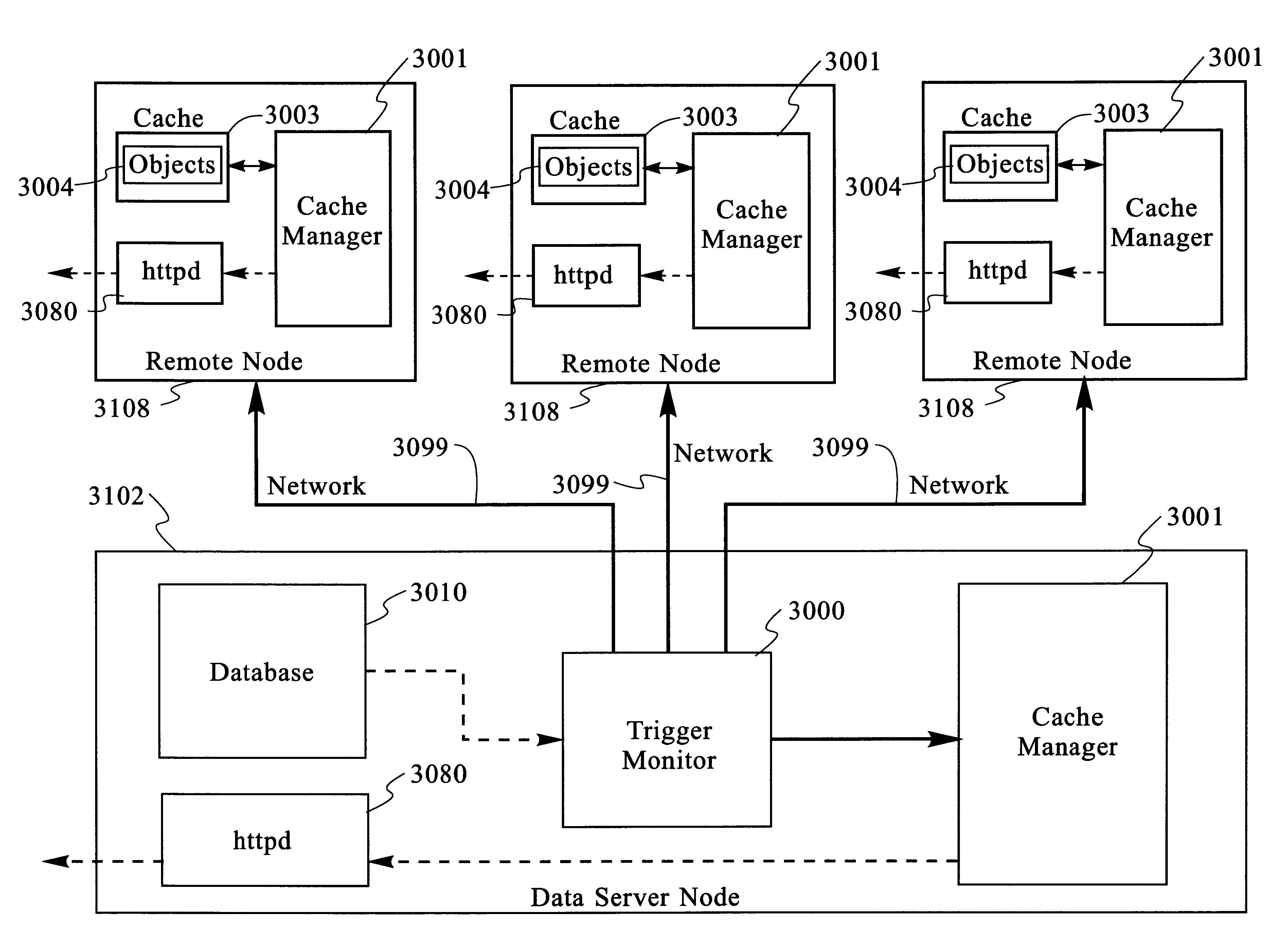
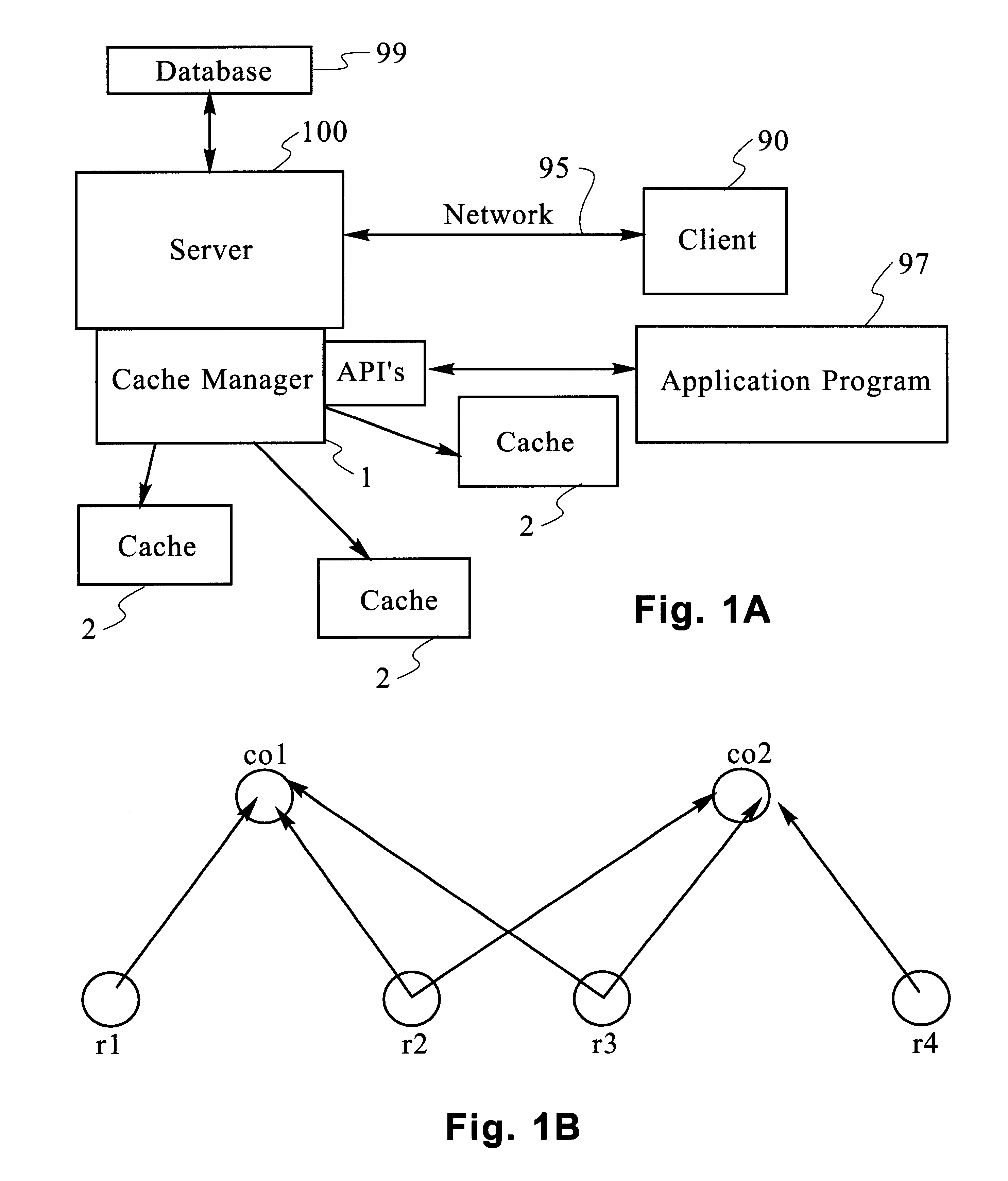
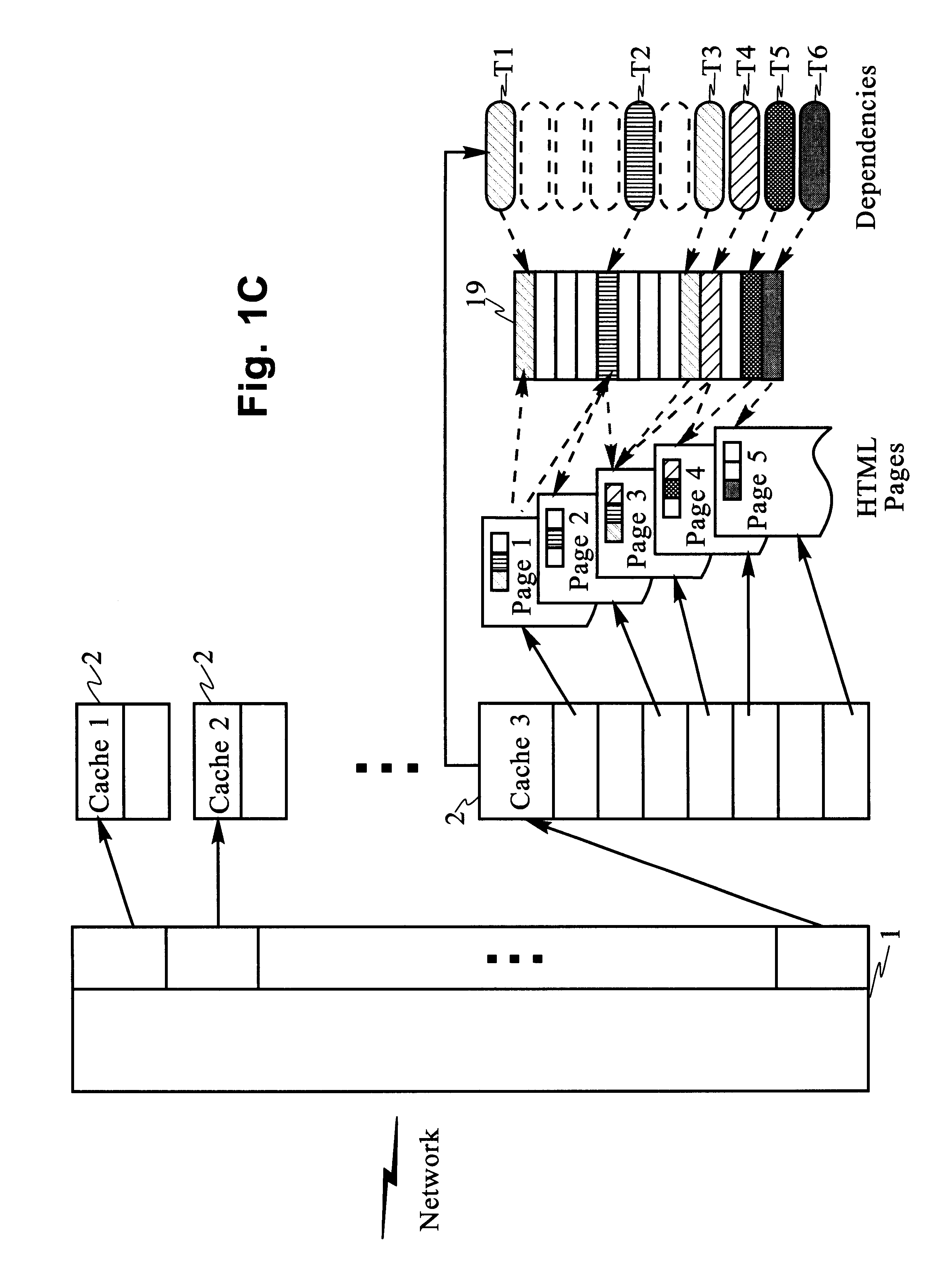
A determination can be made of how changes to underlying data affect the value of objects. Examples of applications are: caching dynamic Web pages; client-server applications whereby a server sending objects (which are changing all the time) to multiple clients can track which versions are sent to which clients and how obsolete the versions are; and any situation where it is necessary to maintain and uniquely identify several versions of objects, update obsolete objects, quantitatively assess how different two versions of the same object are, and / or maintain consistency among a set of objects. A directed graph called an object dependence graph, may be used to represent the data dependencies between objects. Another aspect is constructing and maintaining objects to associate changes in remote data with cached objects. If data in a remote data source changes, database change notifications are used to "trigger" a dynamic rebuild of associated objects. Thus, obsolete objects can be dynamically replaced with fresh objects. The objects can be complex objects, such as dynamic Web pages or compound-complex objects, and the data can be underlying data in a database. The update can include either: storing a new version of the object in the cache; or deleting an object from the cache. Caches on multiple servers can also be synchronized with the data in a single common database. Updated information, whether new pages or delete orders, can be broadcast to a set of server nodes, permitting many systems to simultaneously benefit from the advantages of prefetching and providing a high degree of scaleability.
Owner:IBM CORP
System and method for network vulnerability detection and reporting
InactiveUS20070011319A1Easy to useReliably determinedDigital computer detailsPolarising elementsGraphicsOperational system
A system and method provide comprehensive and highly automated testing of vulnerabilities to intrusion on a target network, including identification of operating system, identification of target network topology and target computers, identification of open target ports, assessment of vulnerabilities on target ports, active assessment of vulnerabilities based on information acquired from target computers, quantitative assessment of target network security and vulnerability, and hierarchical graphical representation of the target network, target computers, and vulnerabilities in a test report The system and method employ minimally obtrusive techniques to avoid interference with or damage to the target network during or after testing.
Owner:MCAFEE LLC
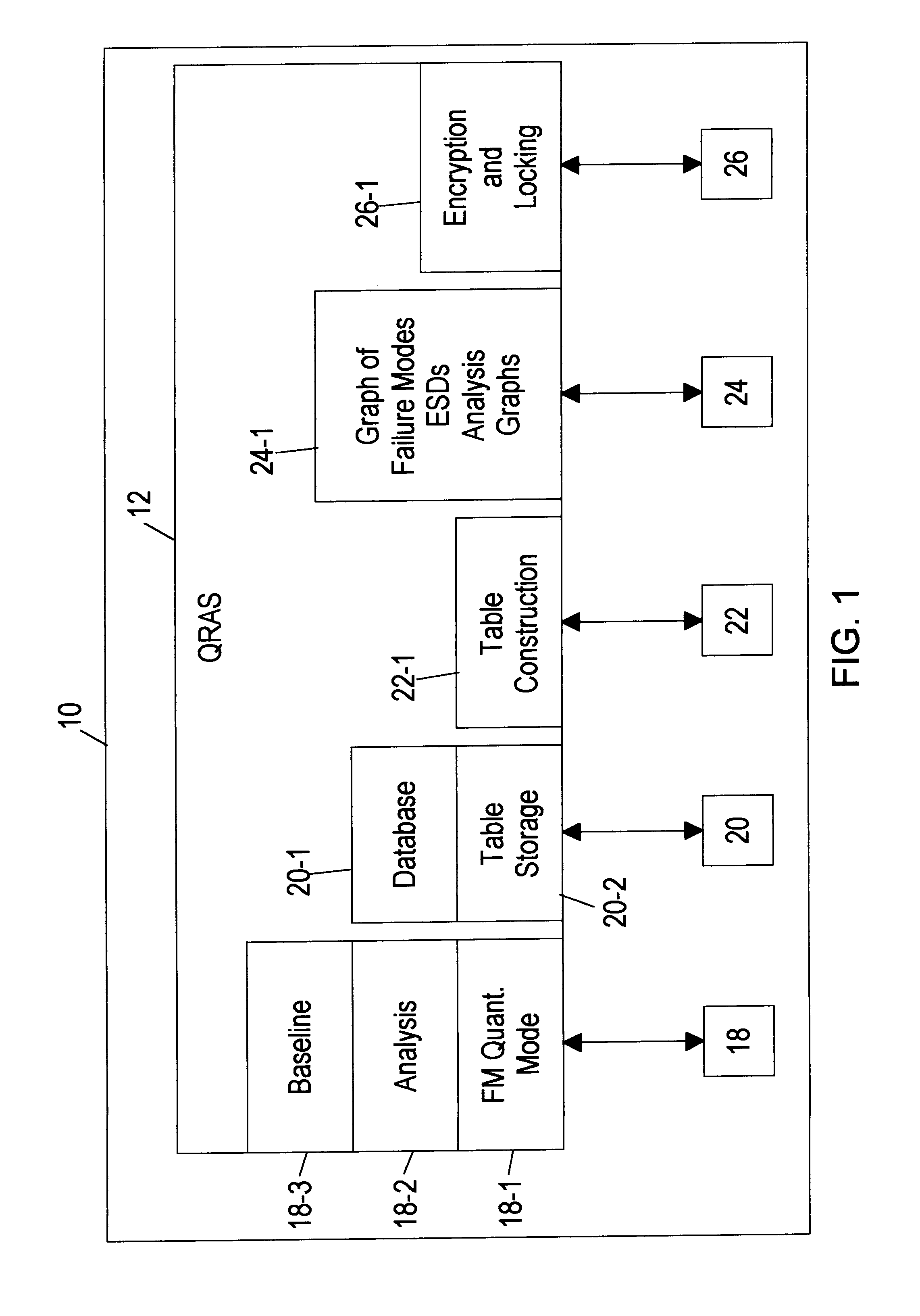
Quantitative risk assessment system (QRAS)
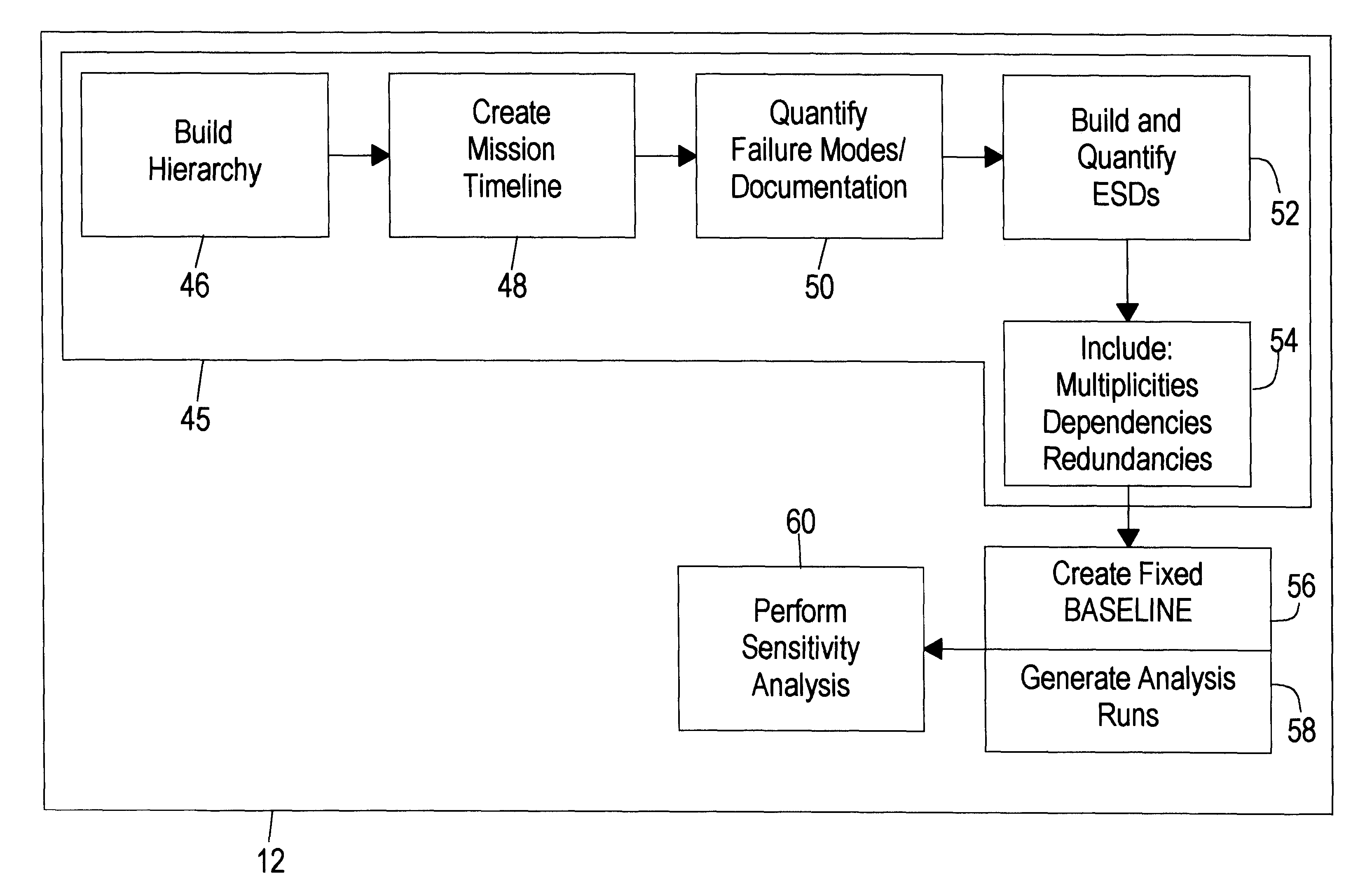
A quantitative risk assessment system (QRAS) builds a risk model of a system for which risk of failure is being assessed, then analyzes the risk of the system corresponding to the risk model. The QRAS performs sensitivity analysis of the risk model by altering fundamental components and quantifications built into the risk model, then re-analyzes the risk of the system using the modifications. More particularly, the risk model is built by building a hierarchy, creating a mission timeline, quantifying failure modes, and building / editing event sequence diagrams. Multiplicities, dependencies, and redundancies of the system are included in the risk model. For analysis runs, a fixed baseline is first constructed and stored. This baseline contains the lowest level scenarios, preserved in event tree structure. The analysis runs, at any level of the hierarchy and below, access this baseline for risk quantitative computation as well as ranking of particular risks. A standalone Tool Box capability exists, allowing the user to store application programs within QRAS.
Owner:NAT AERONAUTICS & SPACE ADMINISTATION U S GOVERNMENT AS REPRESENTED BY THE ADMINISTATOR +1
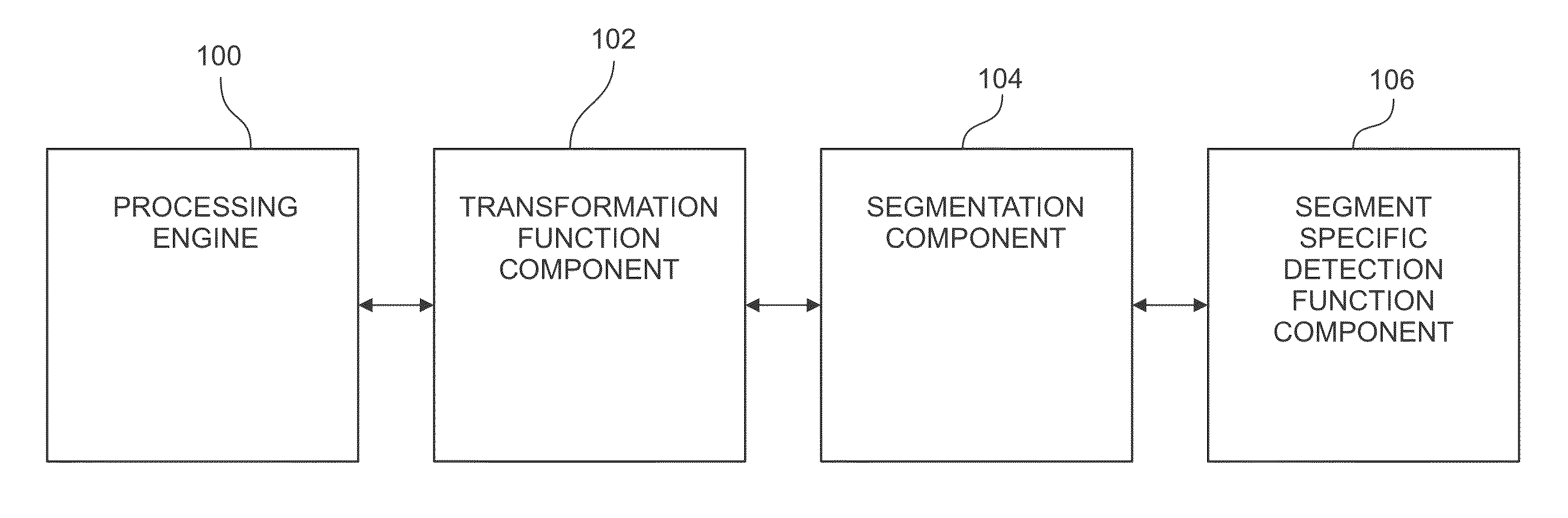
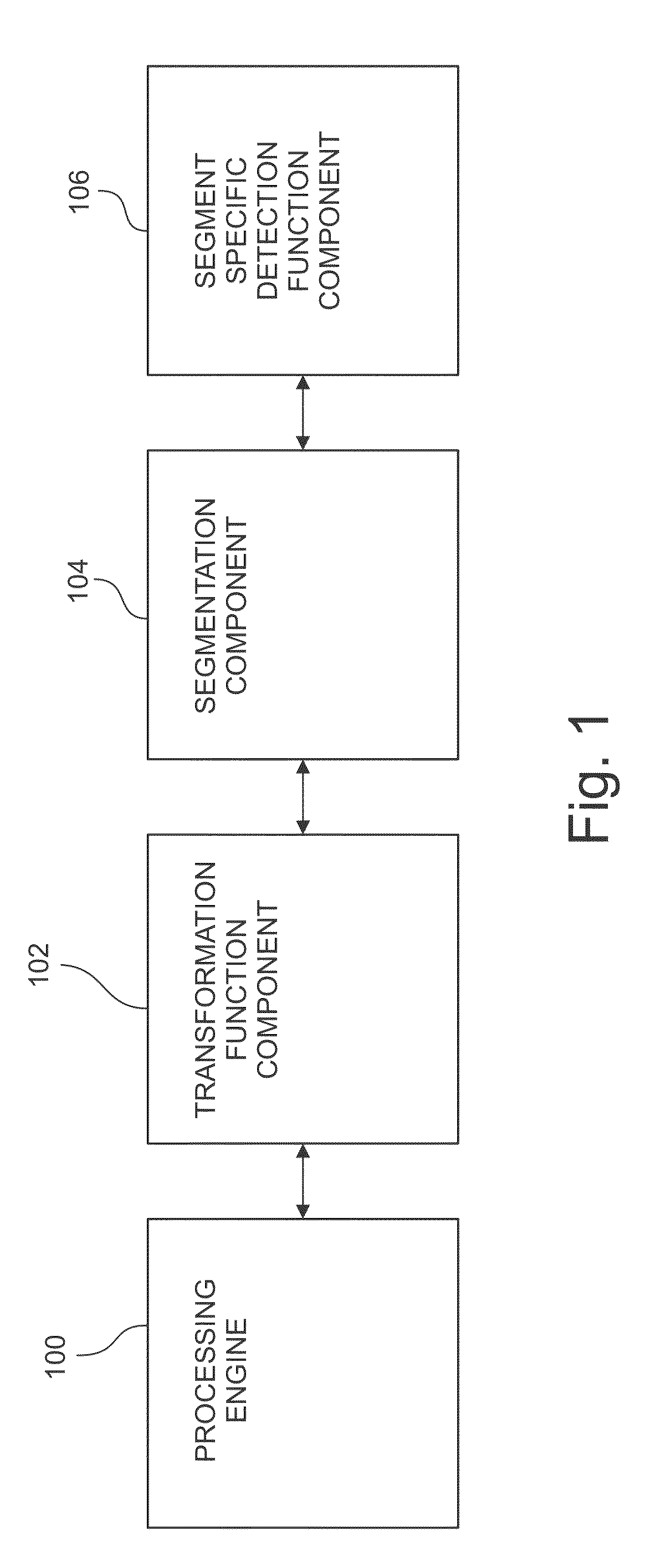
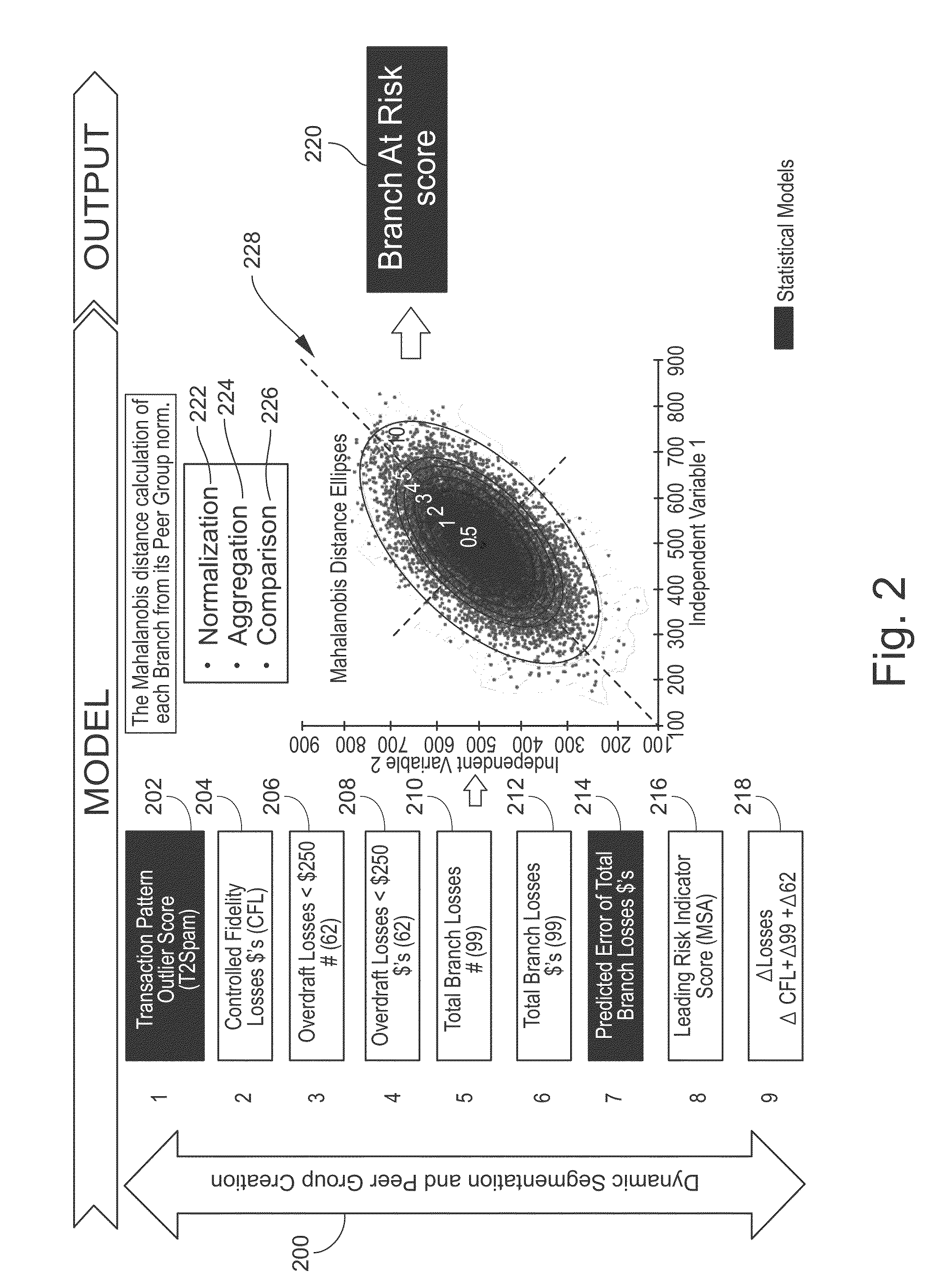
Methods and Apparatus for Quantitative Assessment of Behavior in Financial Entities and Transactions
Methods and apparatus for assessing behavior, such as fraud and risk, in financial entities and transactions involve, for example, receiving, using a processing engine computer having a processor coupled to memory, data related to a plurality of entities. The plurality of entities is segmented into a plurality of entity peer groups based at least in part on a plurality of behavior components identified for each entity in the received data. For each entity, a behavior norm is created based on the entity history and its relationship to its corresponding peer group. All of the behavior components for each of the entities are normalized, and aggregated and a behavior score generated for each entity based on a continuous comparison of behavior values of each entity to a behavior norm for the entity peer group into which the entity is segmented. Based on new data received from time-to-time, this apparatus dynamically adapts the plurality of entities which may be re-segmented, the behavior components may be re-normalized, and a new behavior score may be generated for each entity.
Owner:CITIBANK
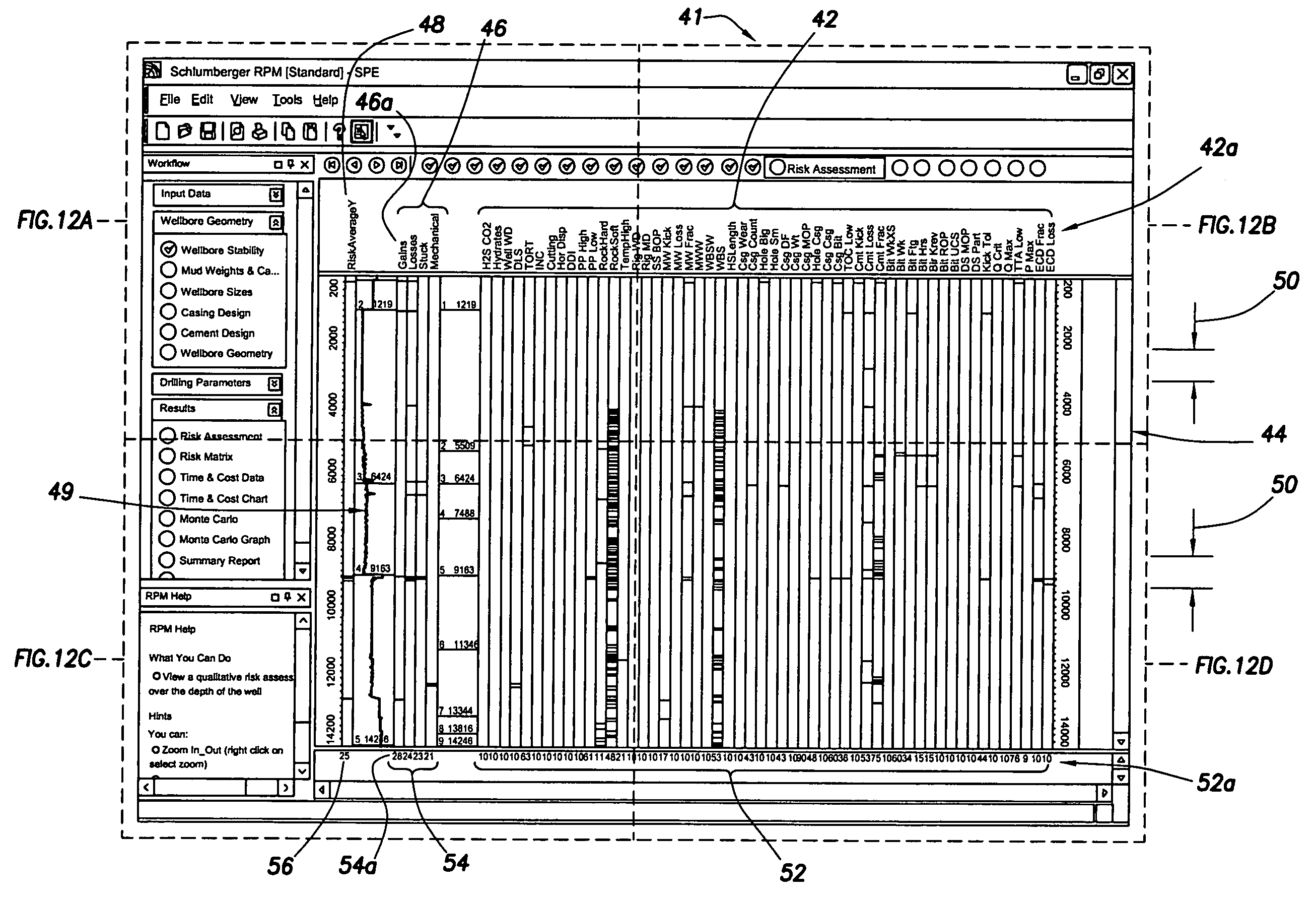
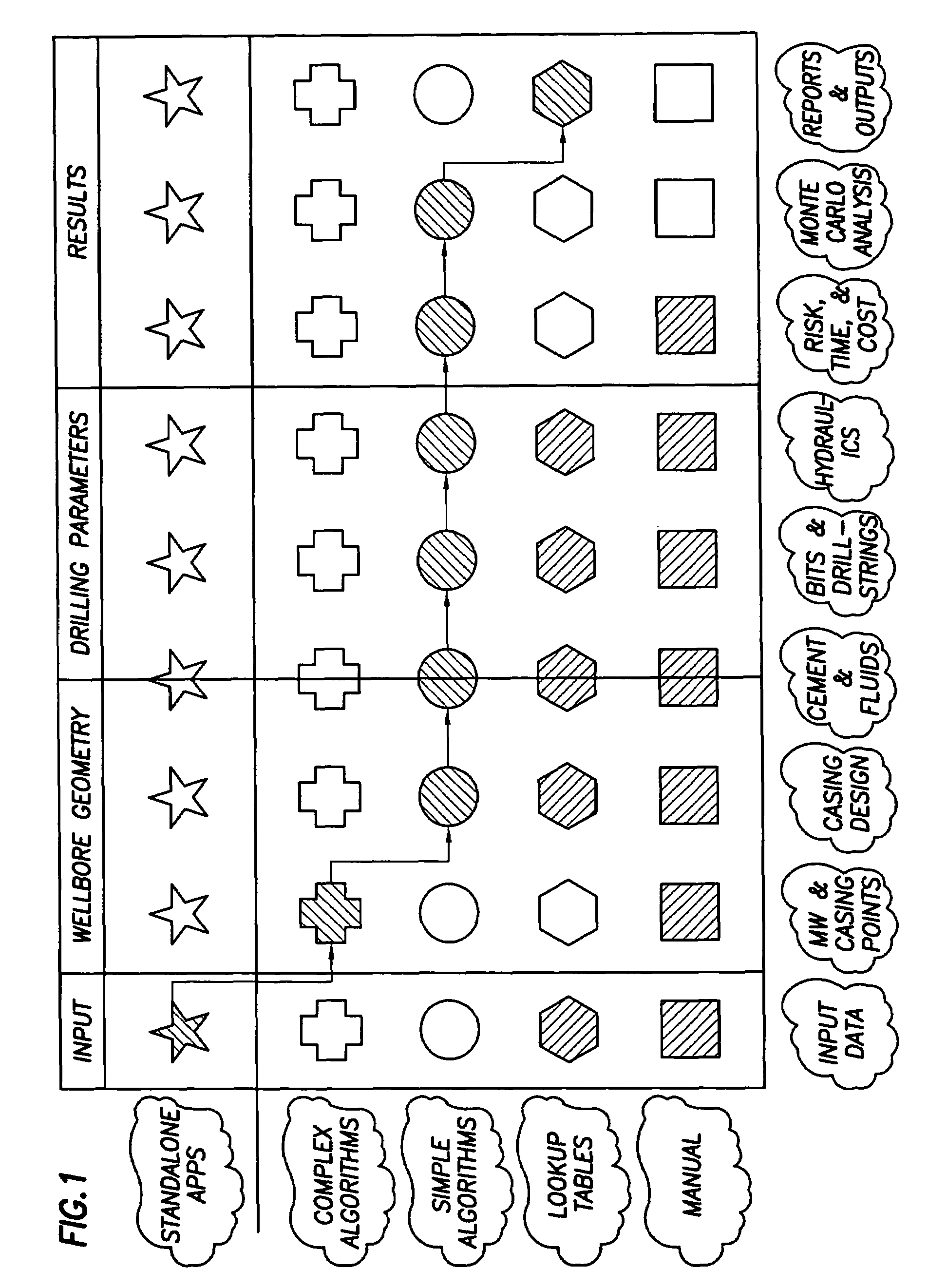
Method and apparatus and program storage device adapted for visualization of qualitative and quantitative risk assessment based on technical wellbore design and earth properties
Owner:SCHLUMBERGER TECH CORP
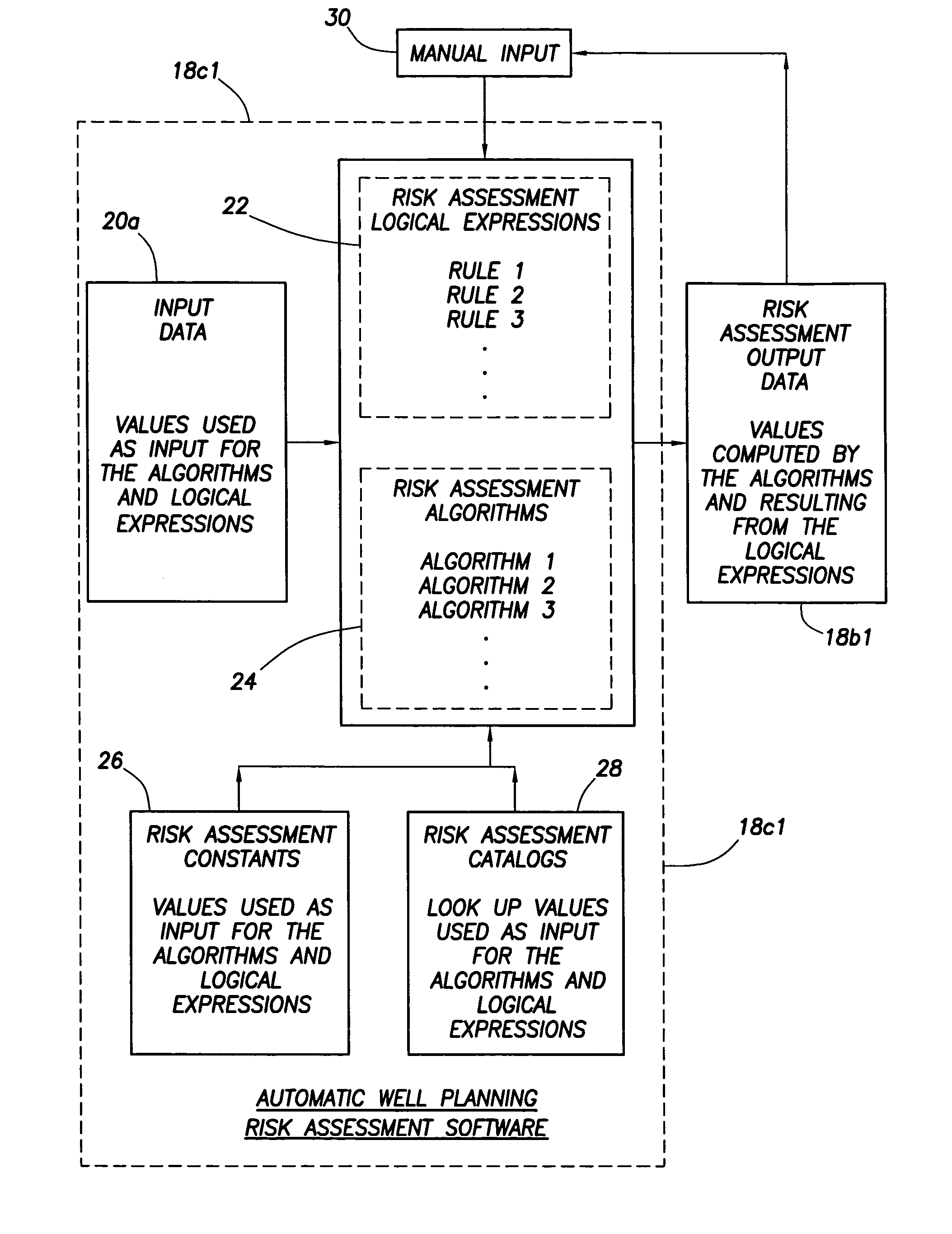
Method and apparatus and program storage device adapted for automatic qualitative and quantitative risk assessment based on technical wellbore design and earth properties
A Software System, known as an Automatic Well Planning Risk Assessment Software System, is adapted to determine and display risk information in response to a plurality of input data by: receiving the plurality of input data, the input data including a plurality of input data calculation results; comparing each calculation result of the plurality of input data calculation results with each logical expression of a plurality of logical expressions; ranking by the logical expression the calculation result; and generating a plurality of ranked risk values in response thereto, each of the plurality of ranked risk values representing an input data calculation result that has been ranked by the logical expression as either a high risk or a medium risk or a low risk; generating the risk information in response to the plurality of ranked risk values; and displaying the risk information.
Owner:SCHLUMBERGER TECH CORP
System and method for network vulnerability detection and reporting
ActiveUS7664845B2Reduce the possibilityReliably determinedMemory loss protectionError detection/correctionGraphicsOperational system
A system and method provide comprehensive and highly automated testing of vulnerabilities to intrusion on a target network, including identification of operating system, identification of target network topology and target computers, identification of open target ports, assessment of vulnerabilities on target ports, active assessment of vulnerabilities based on information acquired from target computers, quantitative assessment of target network security and vulnerability, and hierarchical graphical representation of the target network, target computers, and vulnerabilities in a test report. The system and method employ minimally obtrusive techniques to avoid interference with or damage to the target network during or after testing.
Owner:MCAFEE LLC
Brachytherapy applicator for delivery and assessment of low-level ionizing radiation therapy and methods of use
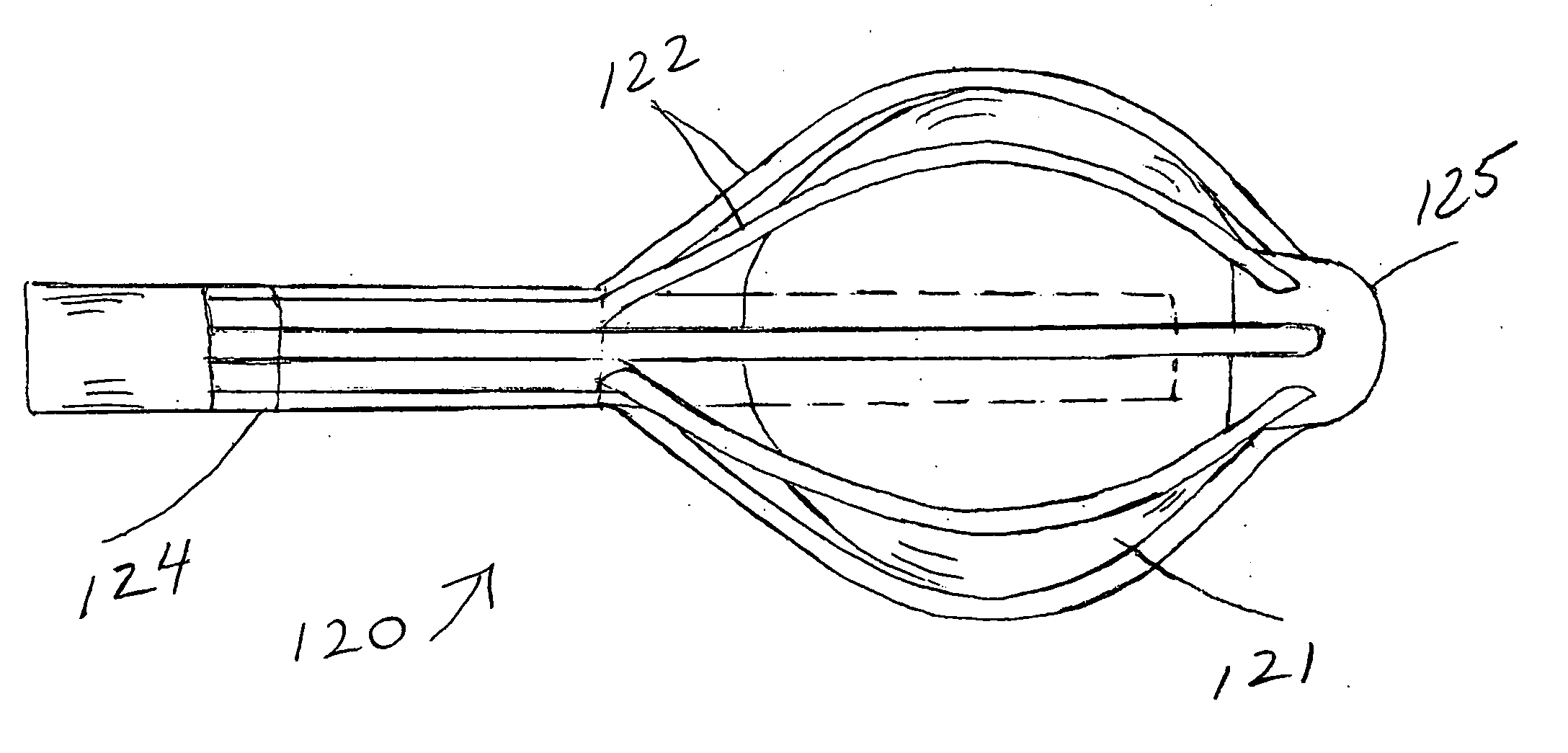
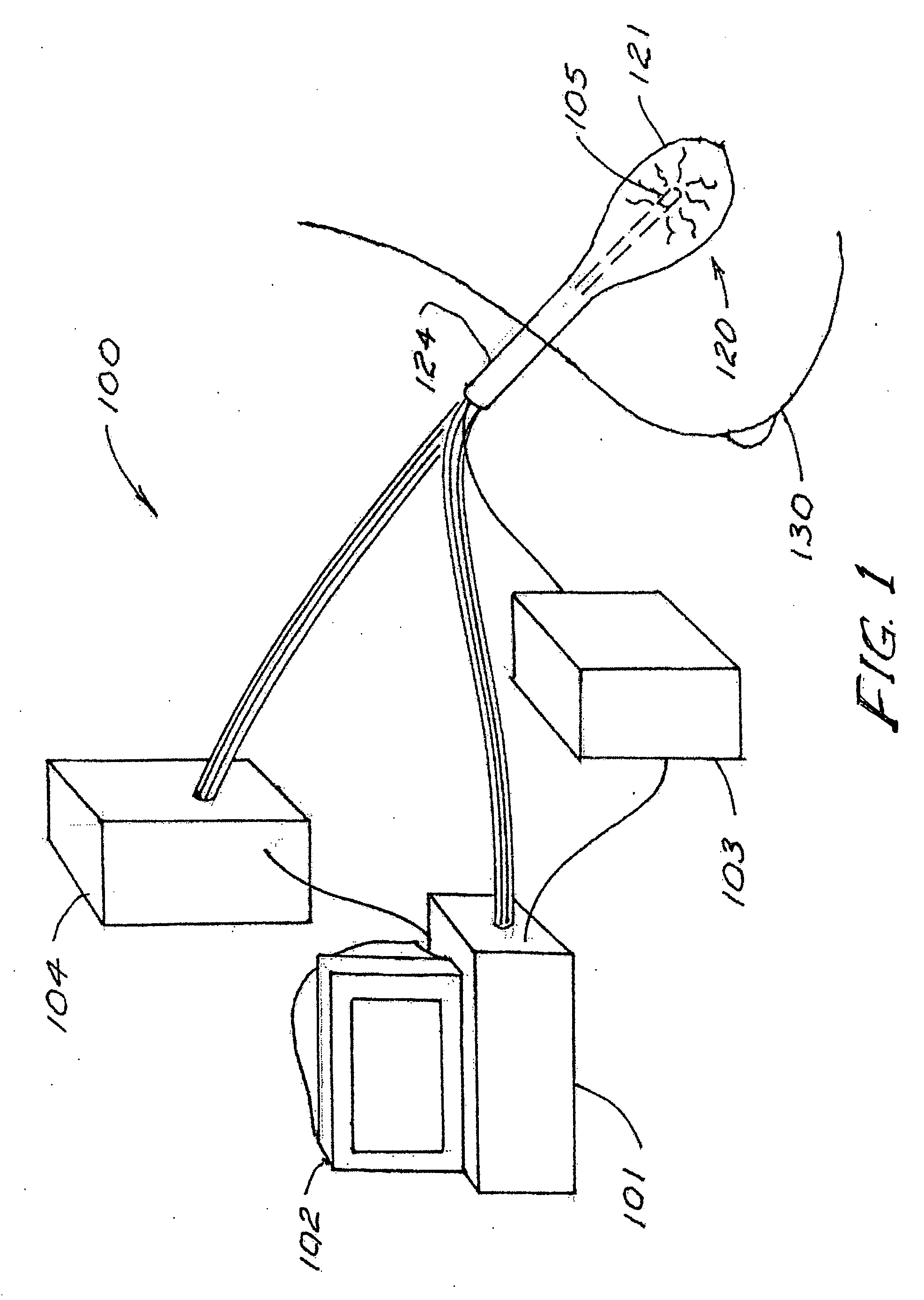
ActiveUS20060173233A1Minimize the tissue being excisedX-ray/gamma-ray/particle-irradiation therapyBrachytherapy deviceQuantitative assessment
Applicators for ionizing radiation therapy and their methods of use are provided for expedient preparation of precise treatment plans and for quantitative assessment of therapy delivered to natural or surgically-created, intra-corporeal cavities or lumina. Feedback capability is provided for timely treatment control and for verification of treatment to plan using sensors on the applicators.
Owner:XOFT INC
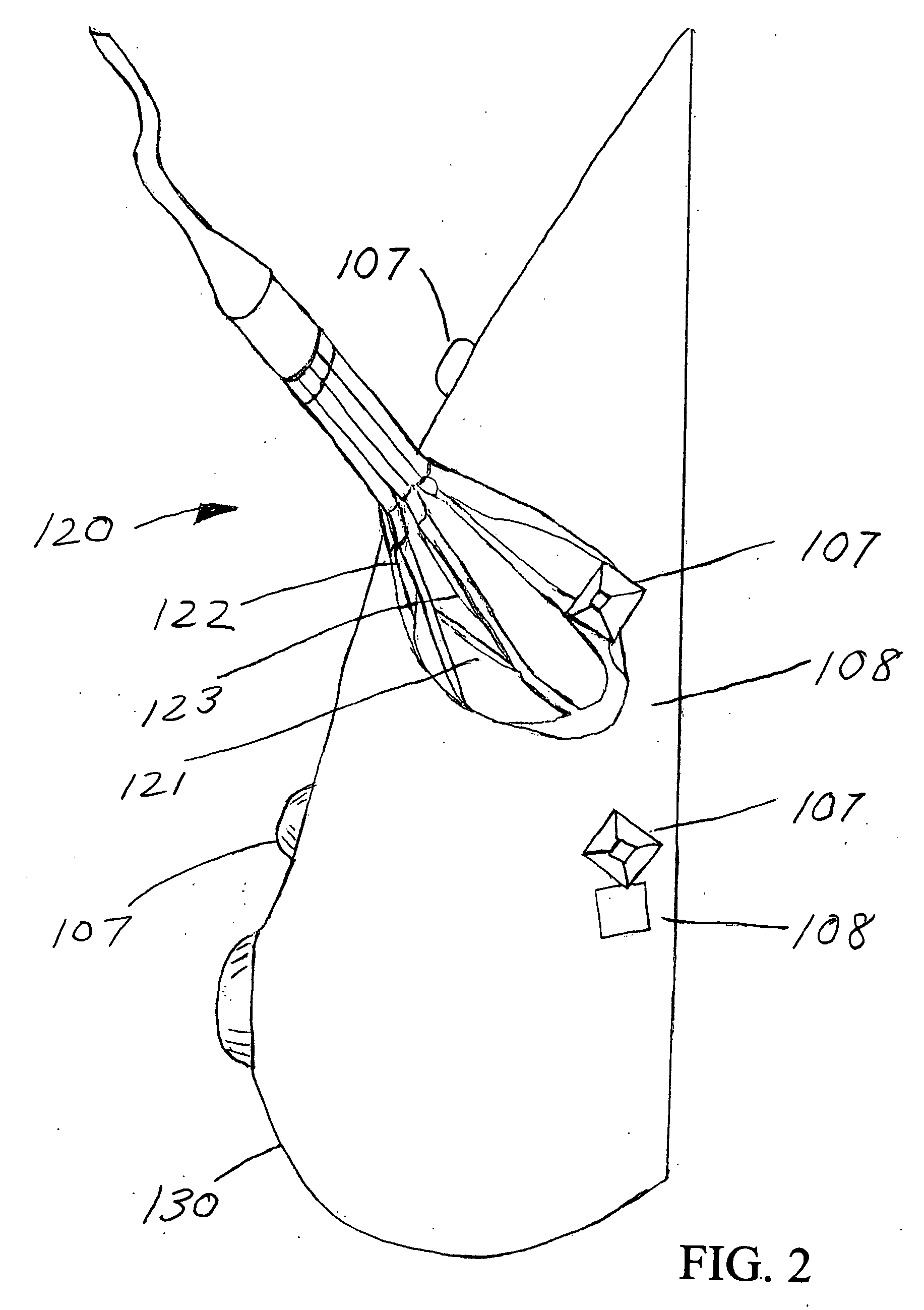
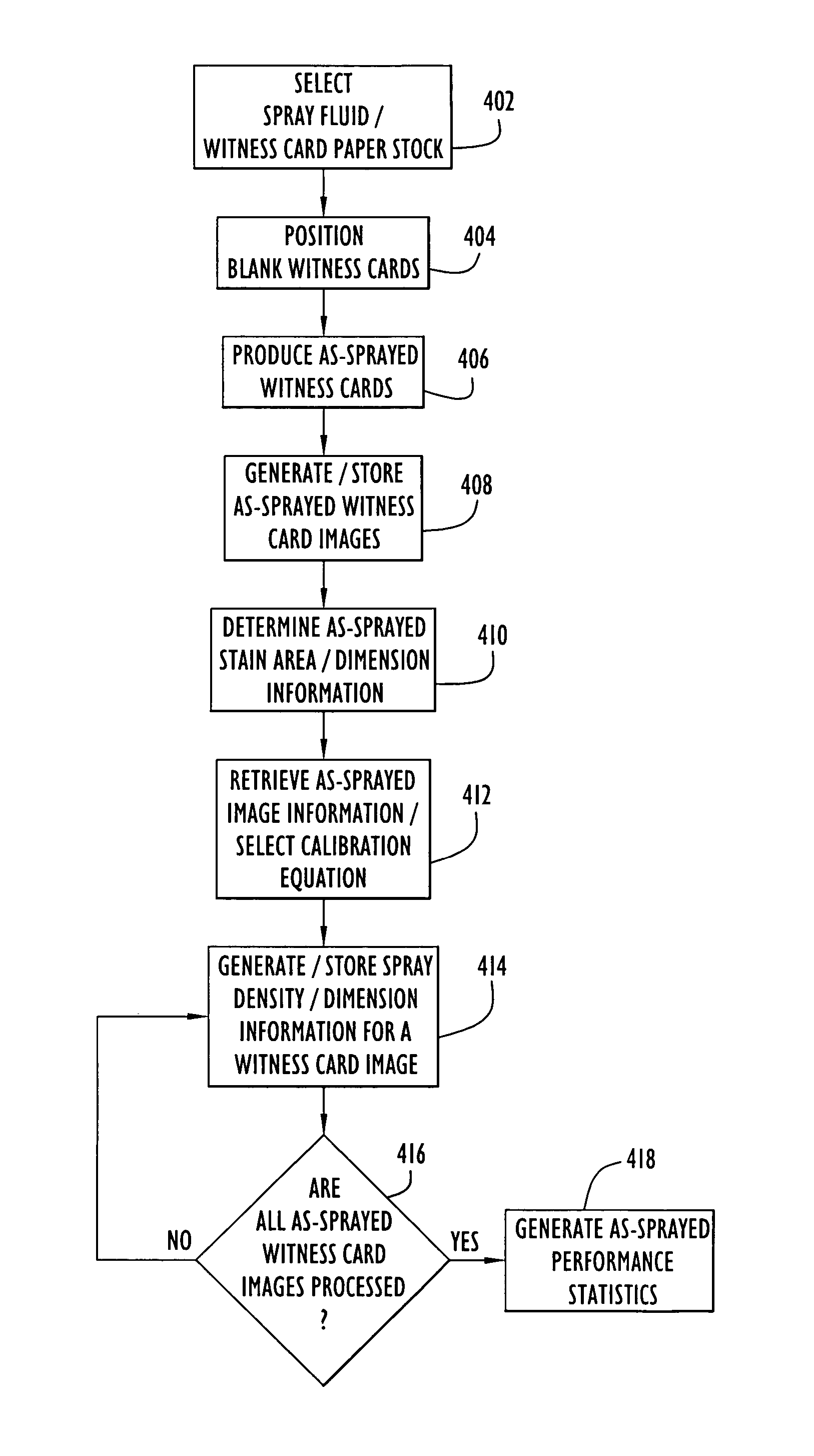
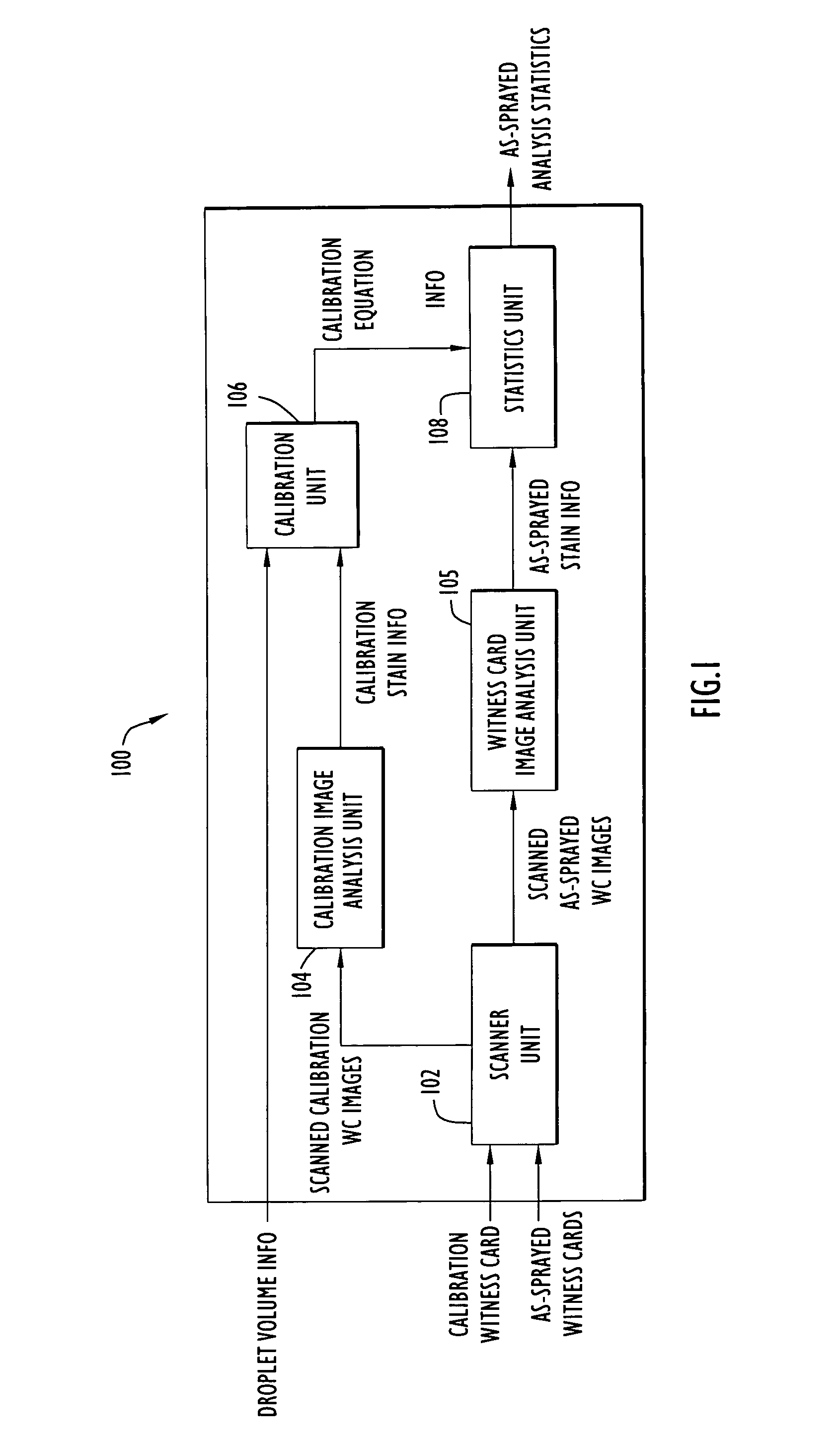
Method and apparatus for witness card statistical analysis using image processing techniques
ActiveUS7277570B2Reduce analysisShorten the timeParticle separator tubesMaterial analysis by optical meansImaging processingStatistical analysis
A method and apparatus for performing witness card statistical analysis using image processing techniques to quickly and efficiently generate as-sprayed performance statistics for a spray device, or spray, based upon a comprehensive analysis of as-sprayed witness card stains. Calibration and as-sprayed witness cards are scanned to produce images that are processed using image processing techniques to identify stain areas / dimensions. Calibration stain data is associated with known calibration droplet volumes and used to generate a set of calibration equations that model an observed relationship between the area of calibration stains upon a witness card and the volume of the respective fluid droplets that produced the stains. As-sprayed stain area / dimension information is processed using the developed calibration equations to approximate the volume of as-sprayed droplets. The approach provides a direct quantitative assessment of spray device performance based upon a comprehensive assessment of as-sprayed witness cards, resulting in highly accurate, timely spray device performance statistics.
Owner:PERATON INC
System and method for network vulnerability detection and reporting
InactiveUS7543056B2Reliably determinedSimple methodMemory loss protectionError detection/correctionGraphicsOperational system
Owner:MCAFEE LLC
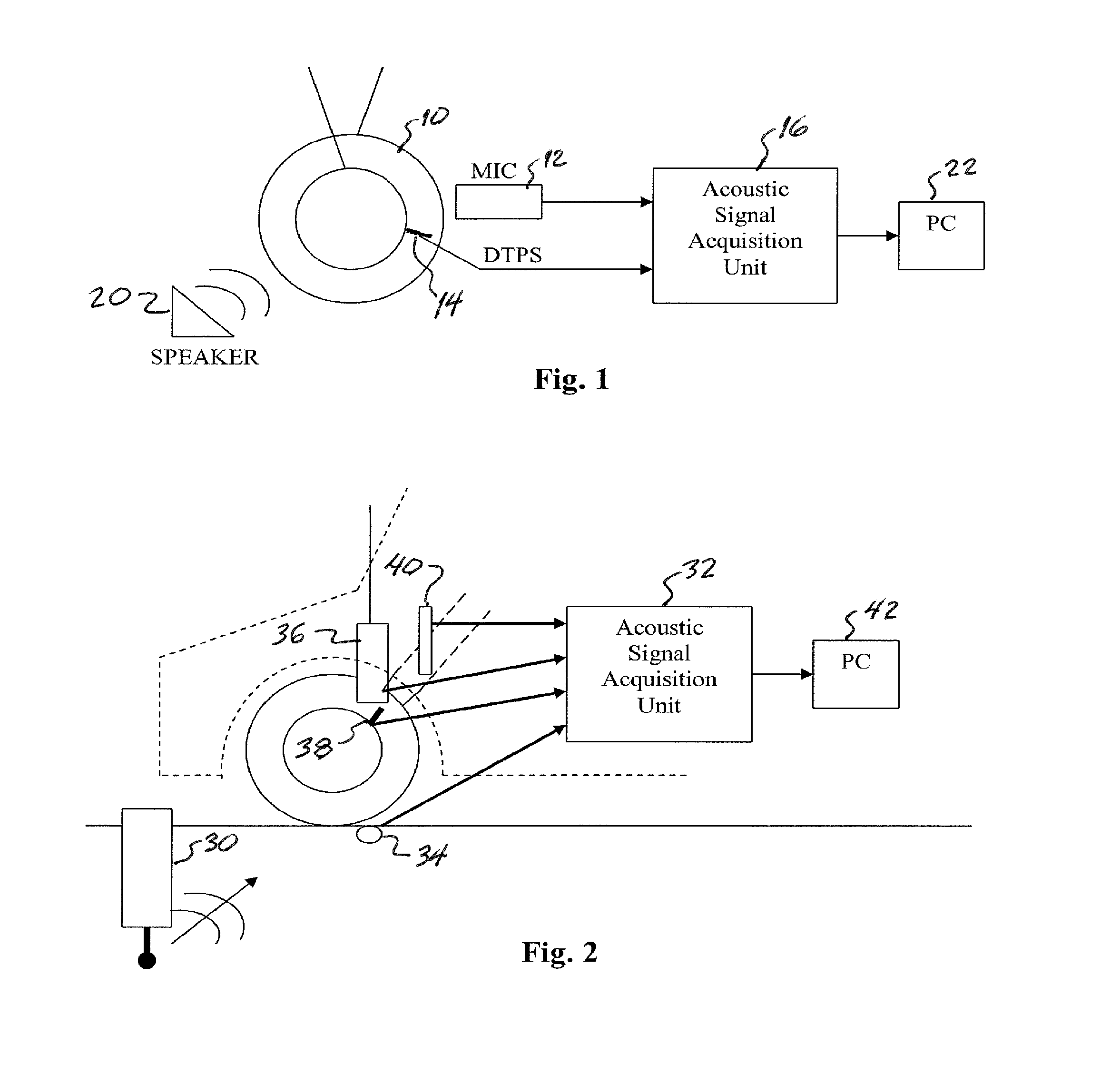
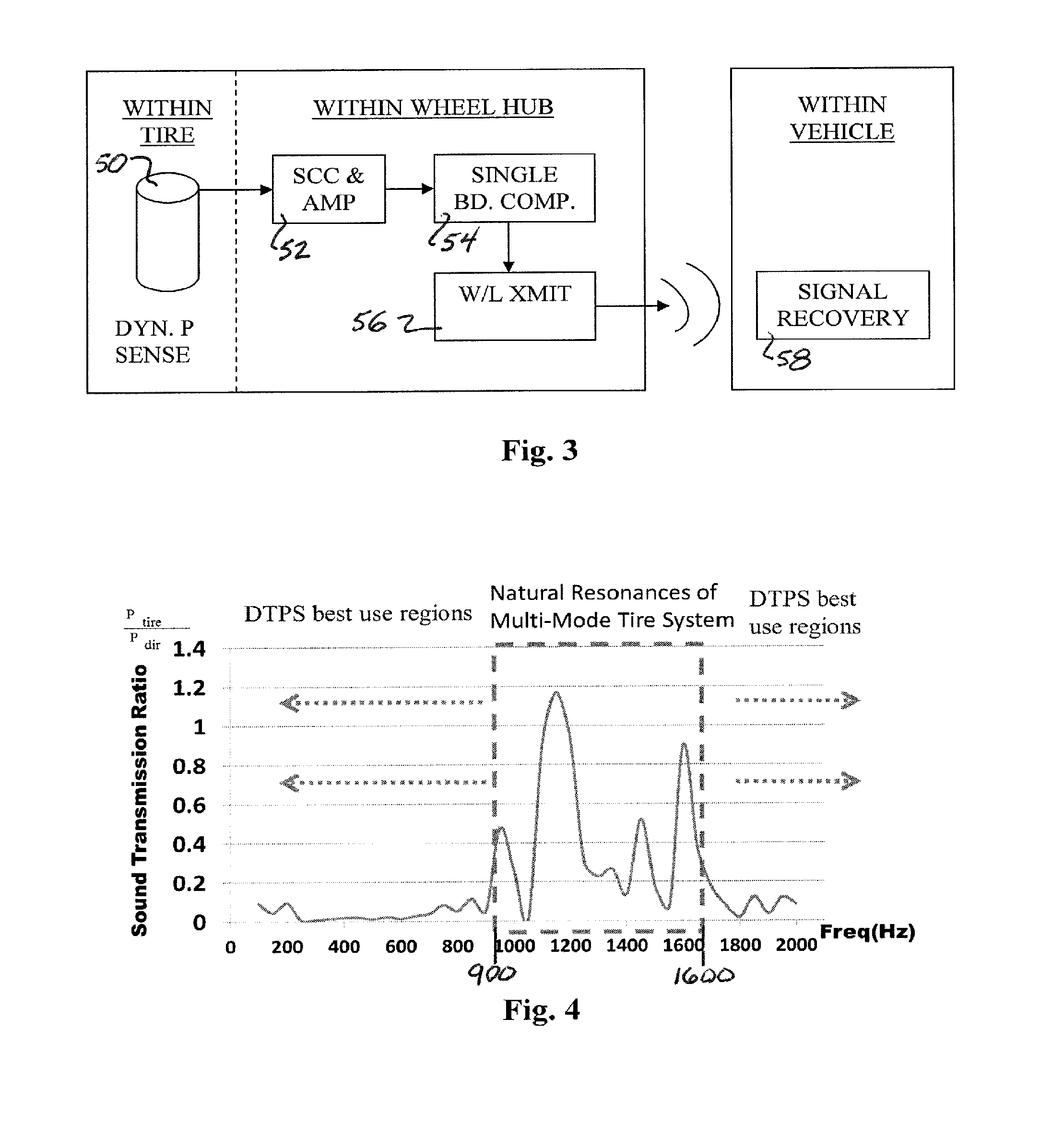
Real-time wireless dynamic tire pressure sensor and energy harvesting system
ActiveUS20140070935A1Quick testImprove detection accuracyBatteries circuit arrangementsMaterial analysis using sonic/ultrasonic/infrasonic wavesAuditory radiationEnergy harvester
An instantaneous / real-time wireless dynamic tire pressure sensor (DTPS) for characterizing pavement qualities and for detecting surface and subsurface pavement defects under normal driving conditions. Signal processing provides quantitative assessment of surface conditions. DTPS includes a vehicle tire valve stem-mounted pressure sensor and wheel hub-mounted signal conditioning, amplification, and transmitting circuitry. A signal processing computer within the vehicle is wirelessly coupled to the hub-mounted circuitry. Tire pressure changes caused by ground vibration excitation from the interaction between the tire and pavement at normal driving speeds are detected. When acoustic radiation from a surface wave is significantly stronger than acoustic noise, subsurface information can be extracted. An energy harvester based on strong magnetostatic coupling between a high permeability core solenoid, fixed proximate a vehicle wheel, and a bias magnet array, fixedly mounted in conjunction with a dust shield, can provide power the DIPS.
Owner:NORTHEASTERN UNIV
System And Method For Network Vulnerability Detection And Reporting
ActiveUS20070283441A1Reliably determinedSimple methodMemory loss protectionError detection/correctionGraphicsOperational system
A system and method provide comprehensive and highly automated testing of vulnerabilities to intrusion on a target network, including identification of operating system, identification of target network topology and target computers, identification of open target ports, assessment of vulnerabilities on target ports, active assessment of vulnerabilities based on information acquired from target computers, quantitative assessment of target network security and vulnerability, and hierarchical graphical representation of the target network, target computers, and vulnerabilities in a test report. The system and method employ minimally obtrusive techniques to avoid interference with or damage to the target network during or after testing.
Owner:MCAFEE LLC
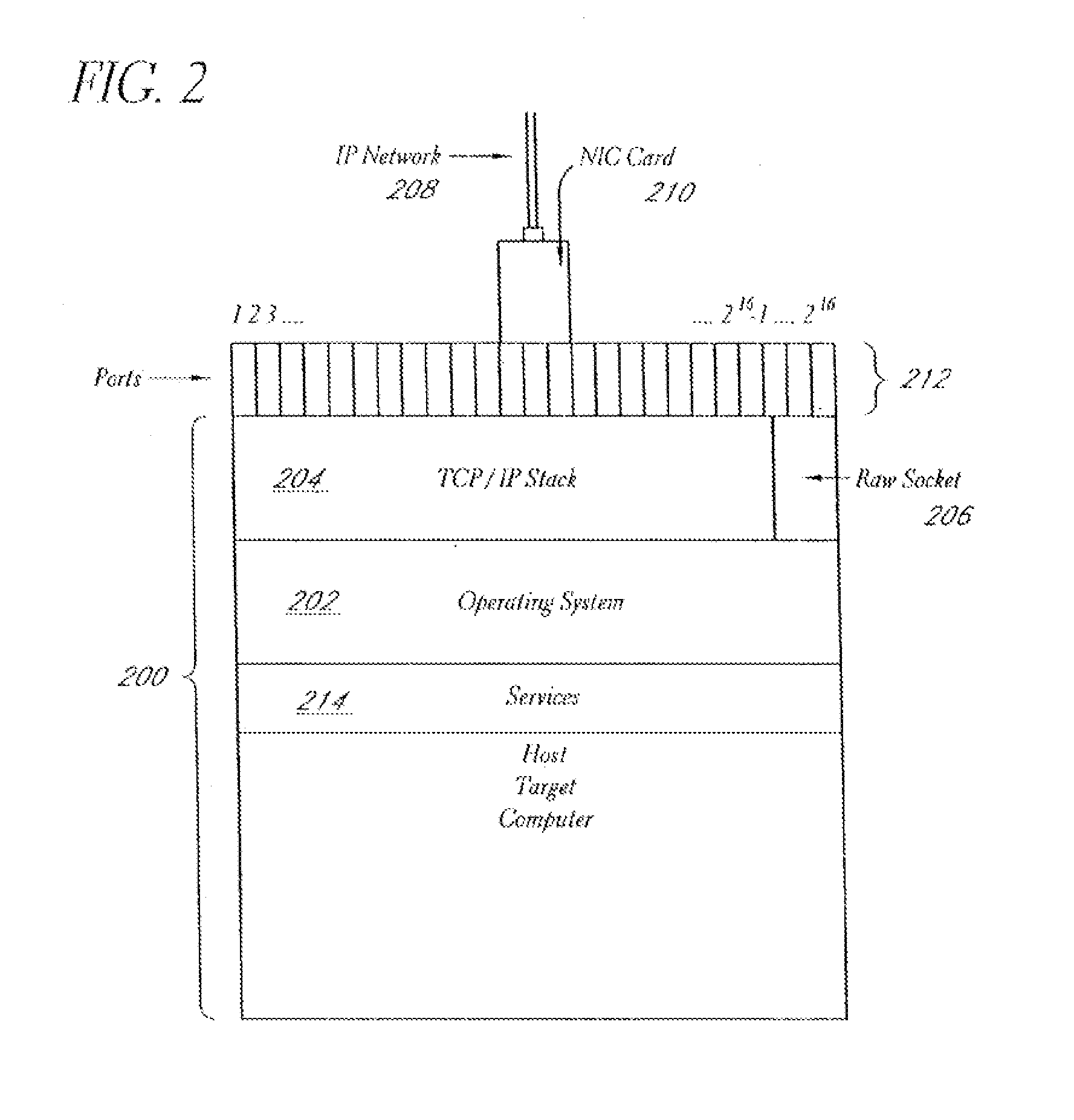
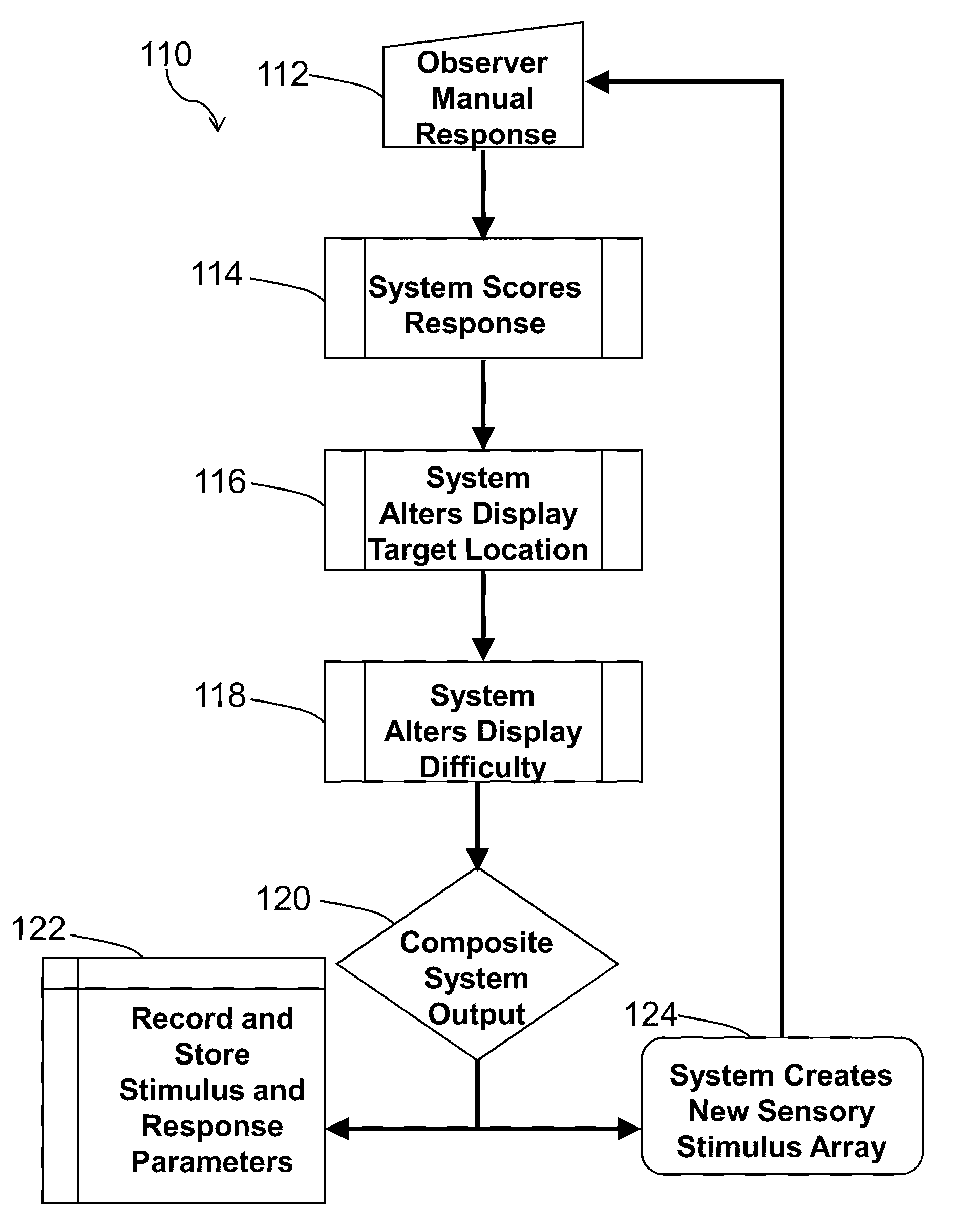
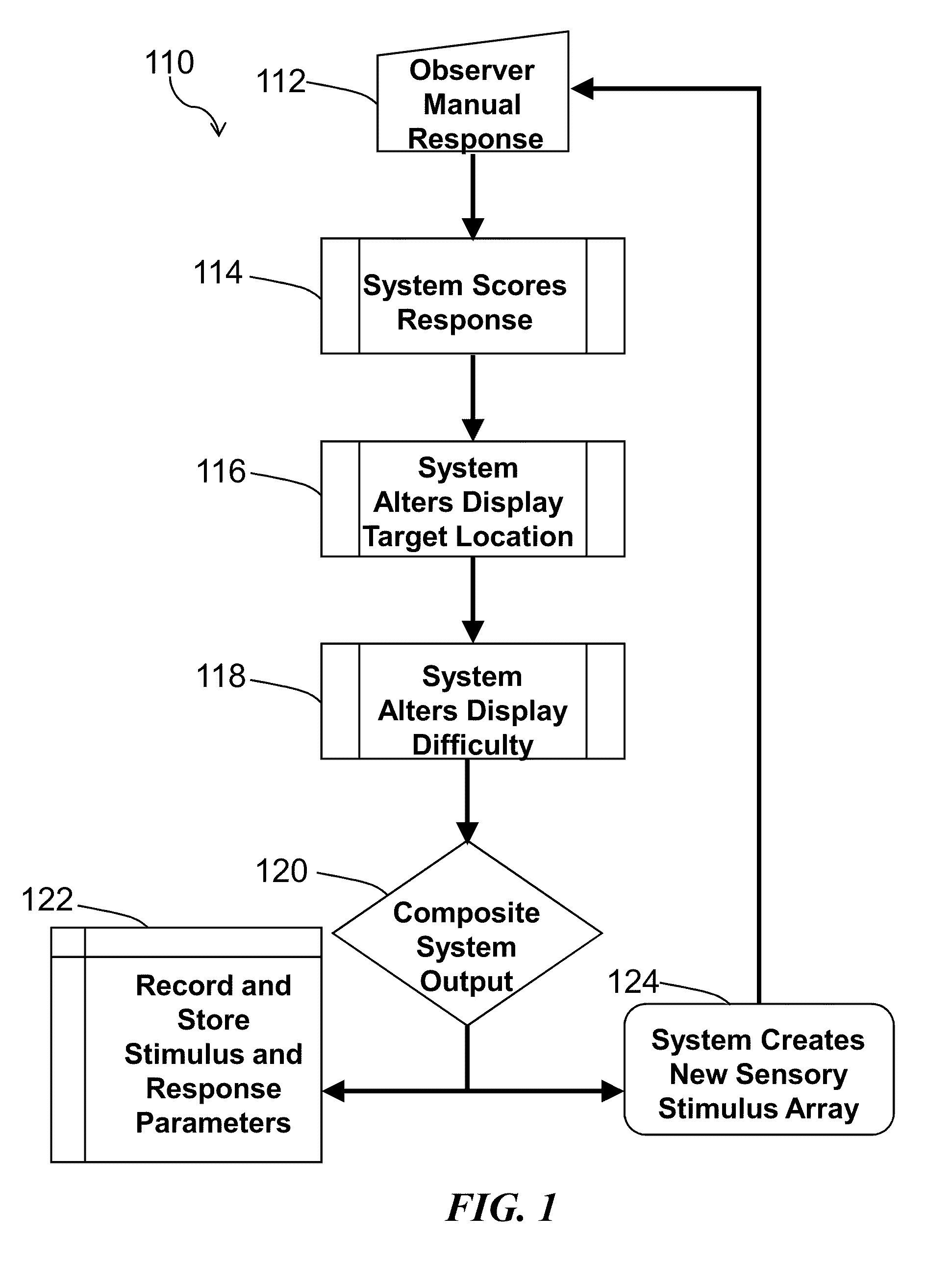
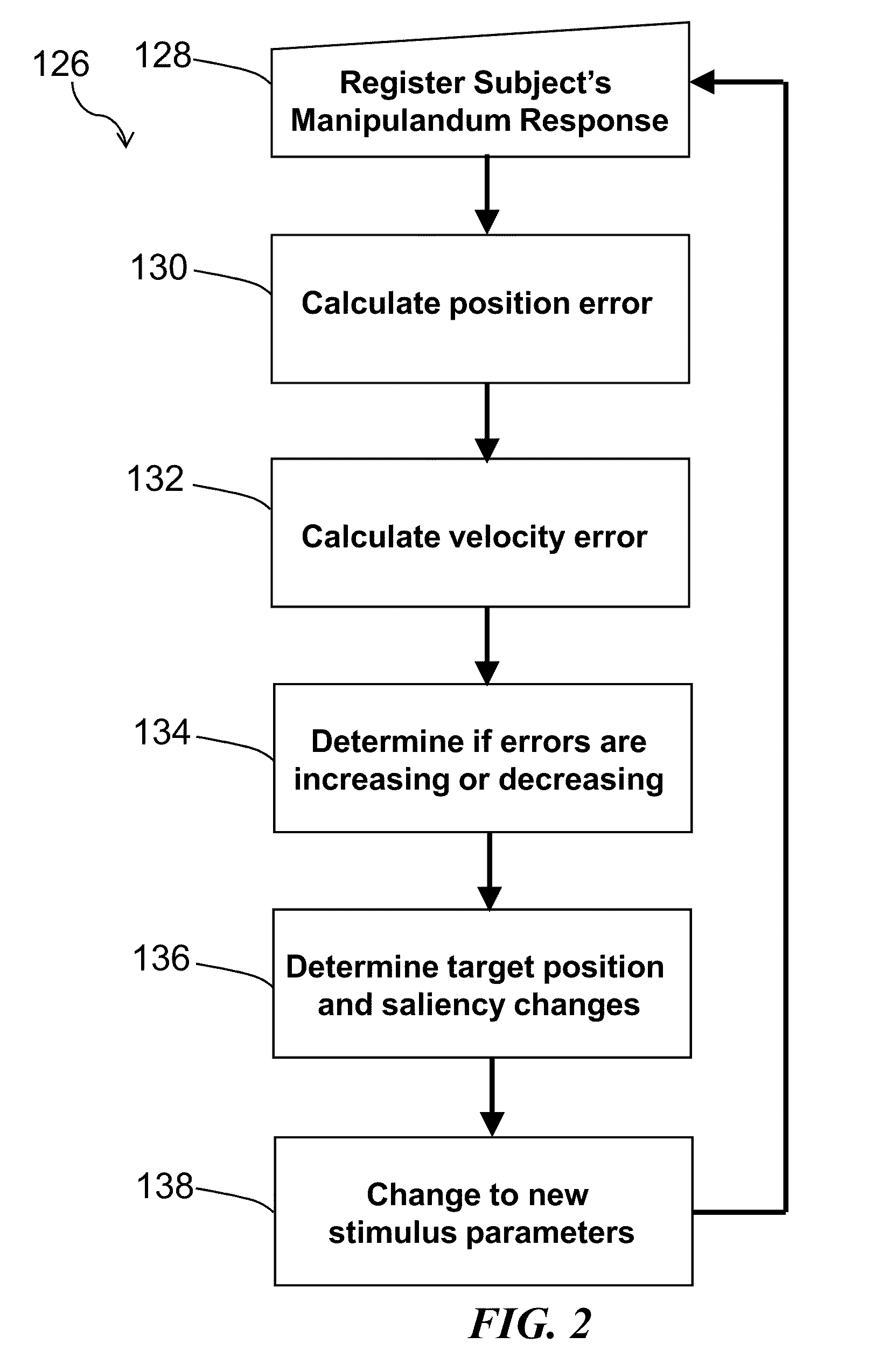
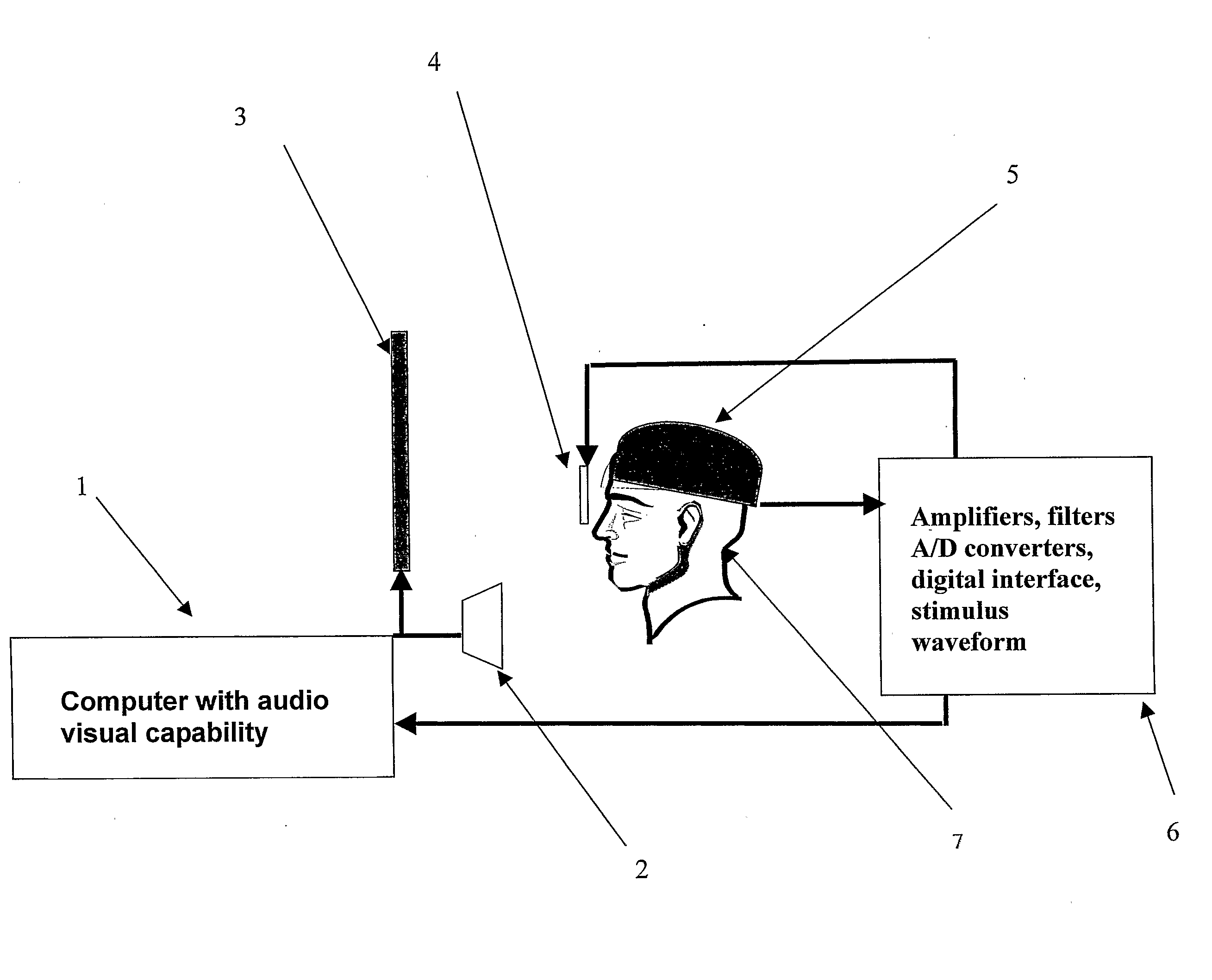
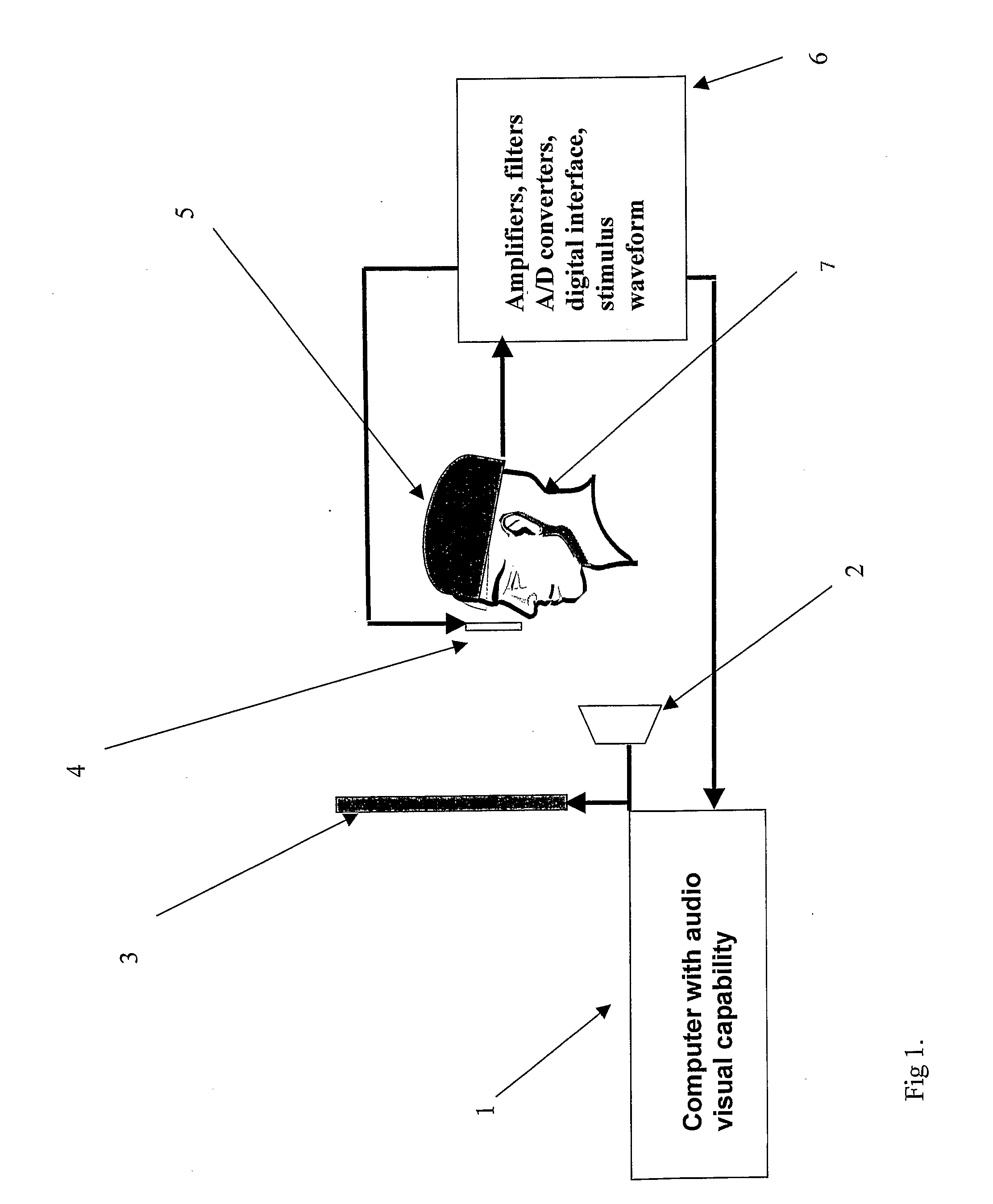
Method and system for quantitative assessment of visual contrast sensitivity
ActiveUS20110063571A1Improves and simplifies complex experimental paradigmImproved and simplifiedDiagnostic recording/measuringSensorsDisplay deviceVisual contrast sensitivity
A method is presented to address quantitative assessment of visual contrast sensitivity in a subject, where the method comprises the steps of: (1) presenting at least one scene to the subject on a display, the scene comprising a plurality of elements and a background; (2) modulating the contrast of at least one element; (3) receiving feedback from the subject via at least one input device; (4) quantitatively refining the received feedback relative to the scene; (5) adjusting the contrast relative to accuracy of the quantitatively refined feedback; (6) calculating a critical threshold parameter for the subject; and (7) recording a critical threshold parameter onto a tangible computer readable medium. An apparatus for quantitative assessment of visual contrast sensitivity of a subject comprising a display device, an input device, a control device, and a tangible computer readable medium. In its simplest sense, quantitative assessment profile of visual contrast sensitivity by psychophysical responses is generated on a tangible computer readable medium.
Owner:COGNIVUE INC
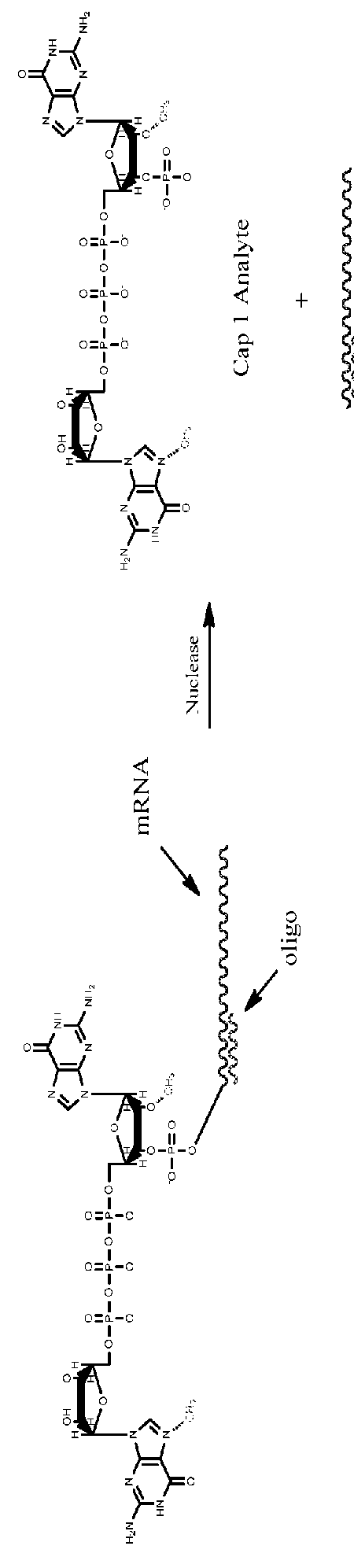
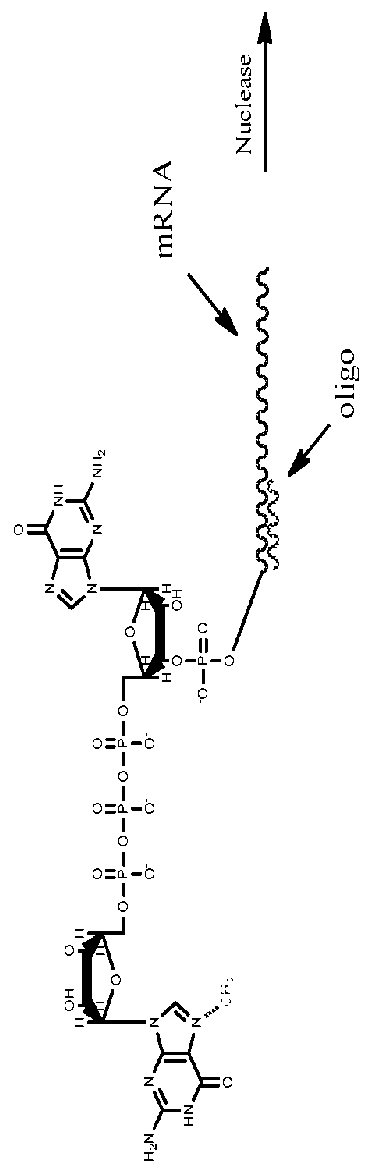
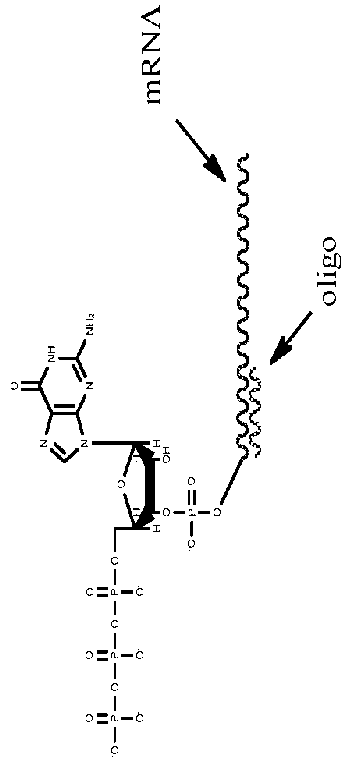
Quantitative assessment for cap efficiency of messenger RNA
ActiveUS20160032356A1Accurate quantitative determinationSimple and reliable and efficientSugar derivativesMicrobiological testing/measurementMessenger RNAQuantitative assessment
The present invention provides, among other things, methods of quantitating mRNA capping efficiency, particularly for mRNA synthesized in vitro. In some embodiments, the methods comprise chromatographic methods of quantifying capping efficiency and methylation status of the caps.
Owner:TRANSLATE BIO INC
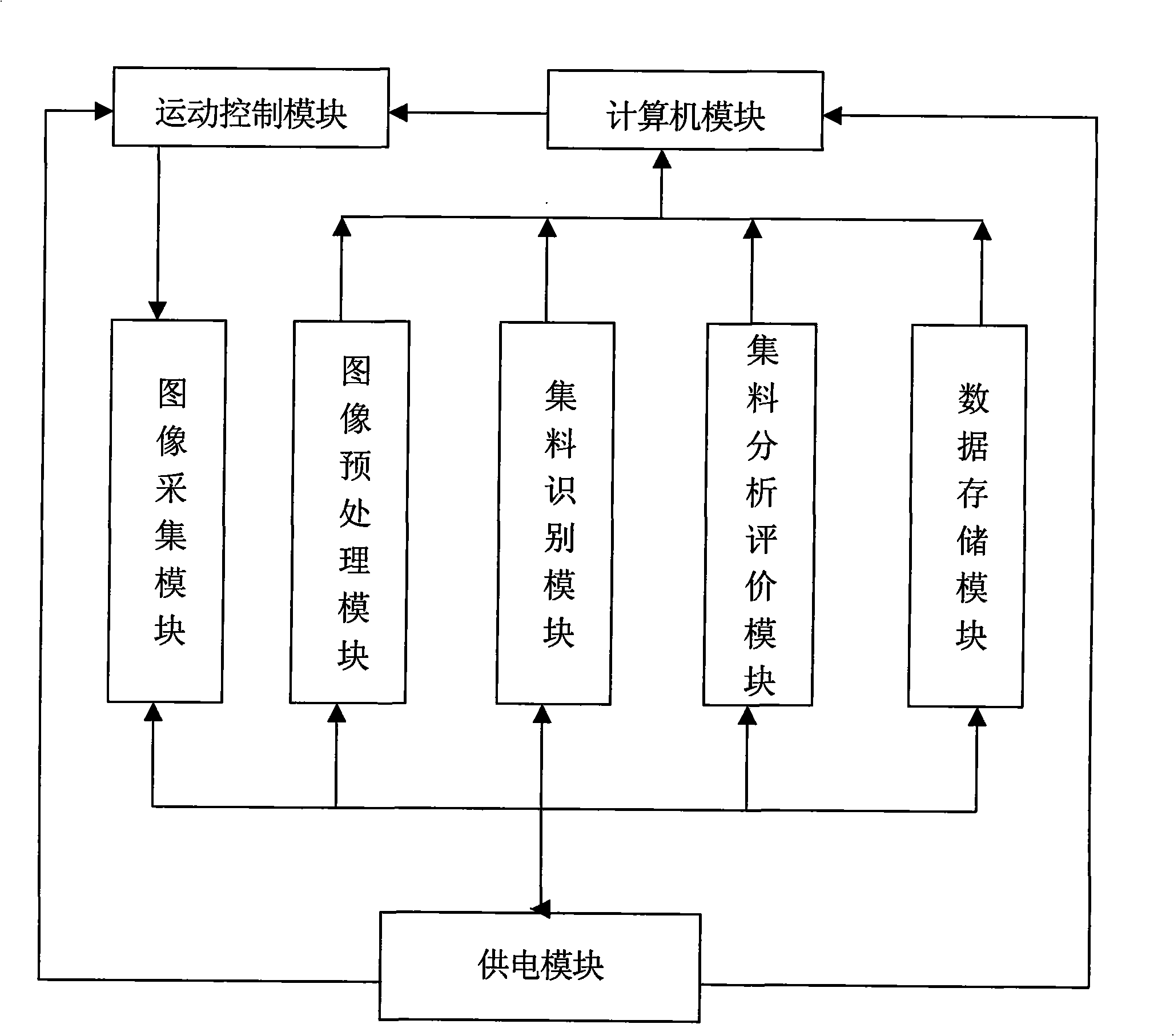
Method and system for evaluating aggregate digital image
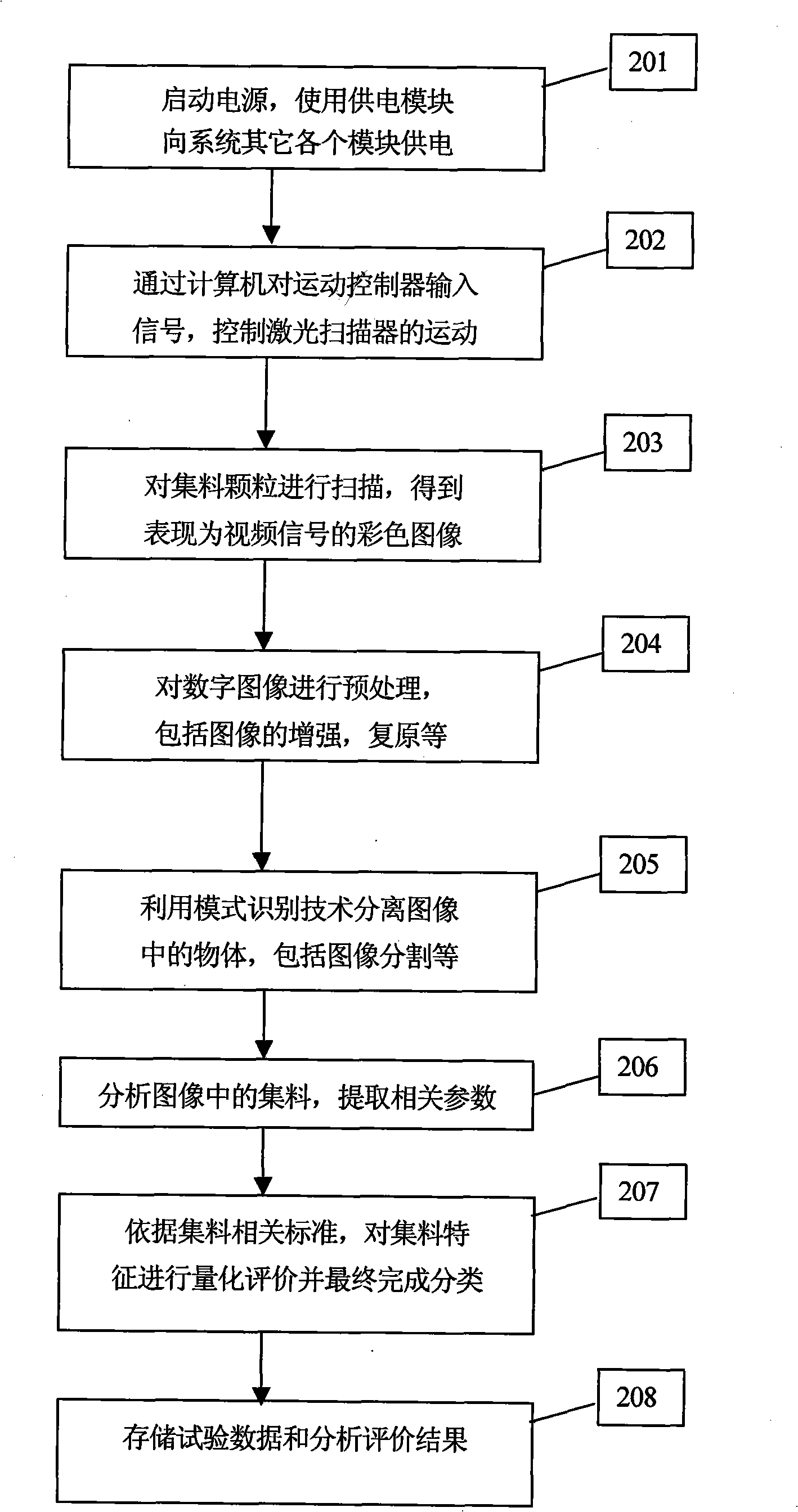
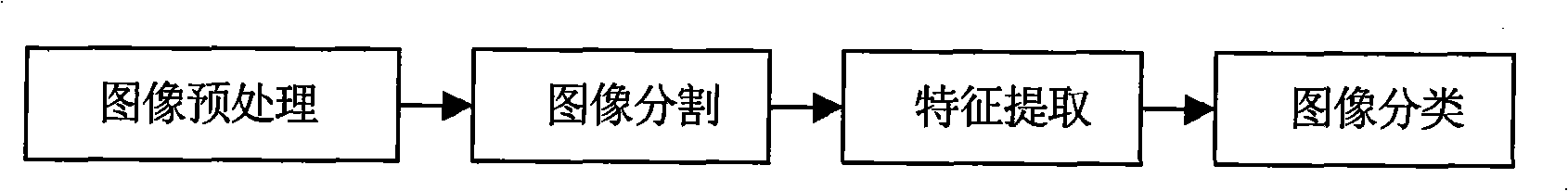
InactiveCN101354241AGuaranteed accuracyAccurately obtainedImage analysisCharacter and pattern recognitionLaser scanningMotion controller
The invention discloses an aggregate digital image assessment system which comprises a motion control module, a computer module, an image acquisition module and a power supply module, an image preprocessing module, an aggregate identity module, an aggregate analysis and evaluation module and a data storage module. The assessment method includes that: a computer sends an instruction to a motion controller for controlling the linear sliding of a laser scanner; a CCD camera takes a picture of aggregate on a scanning board and transforms the image to a digital image; the digital image is transformed to a grey-scale map, And an edge detecting operator is utilized for carrying out image enhancement and restoration to the transformed grey-scale map so as to transform the grey-scale map to a binary image; the aggregate in the binary image is projected and the image of the aggregate in the binary image is detected and separated; IPP image processing and analysis software is used for calculating the three-dimensional coordinate of the surface of the aggregate; quantitative assessment category is carried out to the characteristics of the aggregate to obtain the gradation, the shape, the corner angle and the texture of the aggregate; the computer stores experimental data as well as analysis and assessment results. The aggregate digital image assessment system of the invention can be used for analysis and assessment of the aggregate.
Owner:CHANGAN UNIV
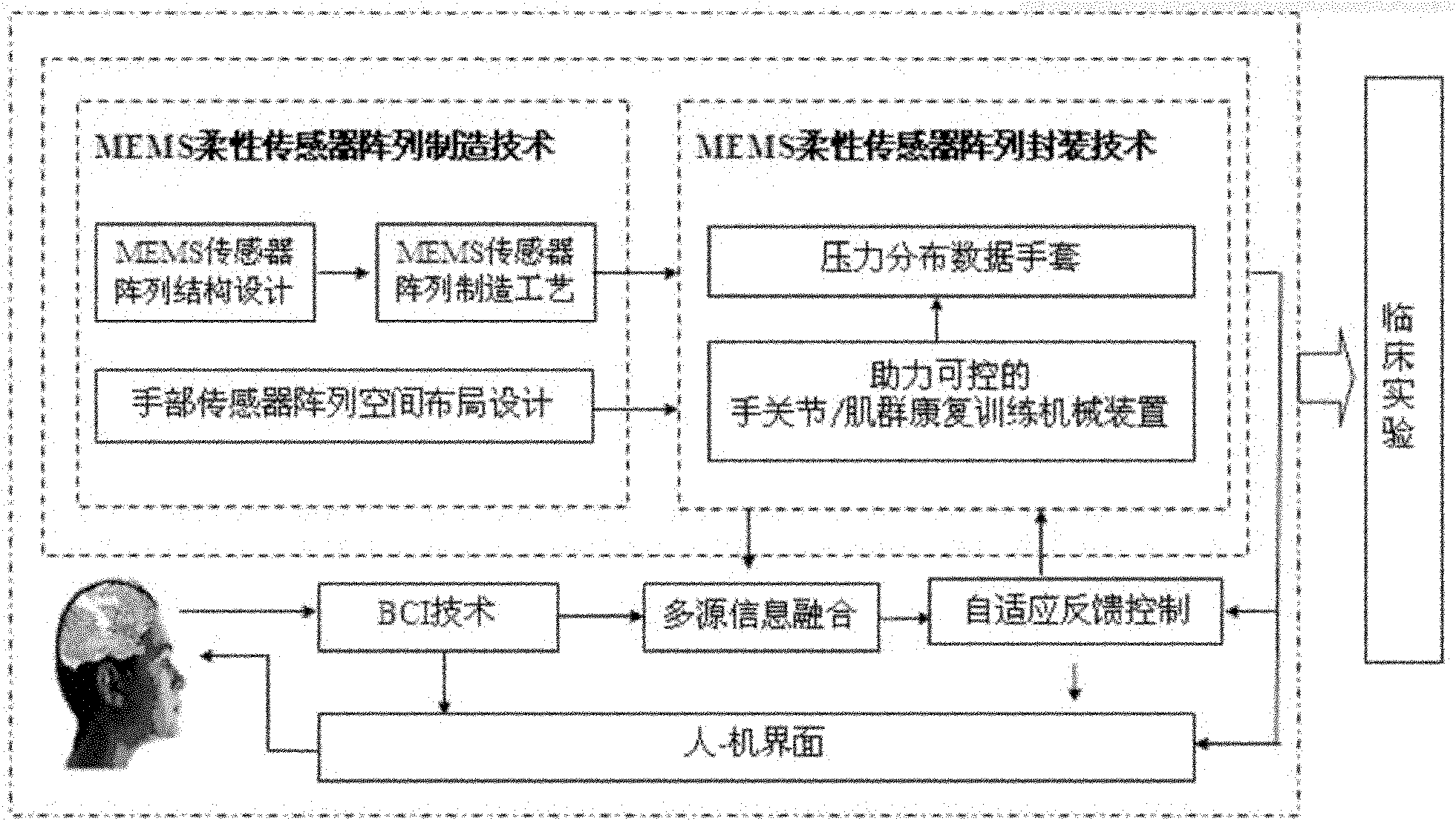
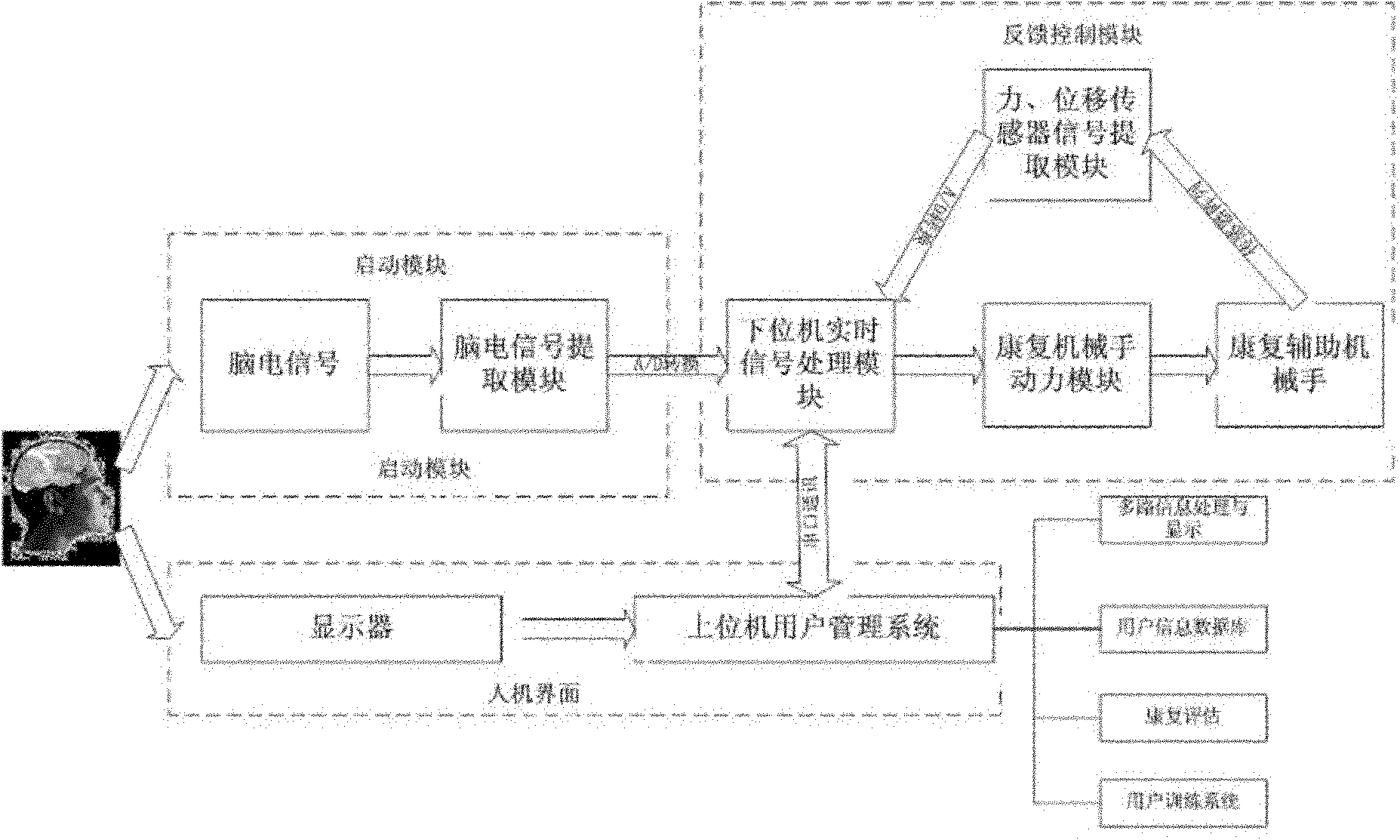
Intelligentized rehabilitation training equipment for hand functions of patients suffering from cerebral injury
InactiveCN102138860AHigh measurement accuracyObjective methodChiropractic devicesDiagnostic recording/measuringSensor arrayMuscle force
The invention relates to hand function rehabilitation training equipment based on a spontaneous movement imagery electroencephalograph. Hardware of the instrument consists of an electroencephalograph signal acquisition and processing module, a hand force signal real-time detection sensor array, a control module based on multisource information fusion and a rehabilitation manipulator module, and software for supporting the active rehabilitation training of hand functions is arranged in a computer. The rehabilitation training equipment provides external compensation assistance or resistance hierarchically by taking movement imagery electroencephalographs of patients who suffer from cerebral injury as a starting signal and the muscle force of hands as a feedback signal in a self-adaptive mode according to the myasthenia state of the patients to assist patients who suffer from dyskinesia in performing passive, assisted and active rehabilitation training, displays the state information of the hand movement functions and the provided external power information for doctors and the patients and provides an objective and quantitative assessment method and an index for clinical rehabilitation diagnosis and treatment. The instrument is easy to use, has a friendly interface and is accepted by the doctors and the patients easily. A user can operate a system of the instrument without programming experiences, and the operating environment is not complex.
Owner:XI AN JIAOTONG UNIV
Method for evaluating the effectiveness of commercial communication
InactiveUS20100094702A1Assess the effectiveness of the featuresElectroencephalographySensorsTime functionPhase difference
A method of quantitatively assessing the effectiveness of an audiovisual, visual or audio advertisement including the steps of: presenting the advertisement to a plurality of subjects, the advertisement having a sequence of audiovisual, visual and / or audio features which occur as a function of time; obtaining, during presentation of the advertisement, EEG signals from the subjects from predetermined scalp sites thereof; calculating SSVEP amplitudes and / or phase differences from EEG signals obtained from the predetermined scalp sites in order to obtain output signals which represent predetermined psychological states of each subject to the features as a function of time; combining the output signals from the subjects to obtain pooled output signals; and displaying the pooled output signals to thereby enable quantitative assessment of the subjects' responses to the features of the advertisement in order to assess the effectiveness of the features of the advertisement.
Owner:NEUROINSIGHT
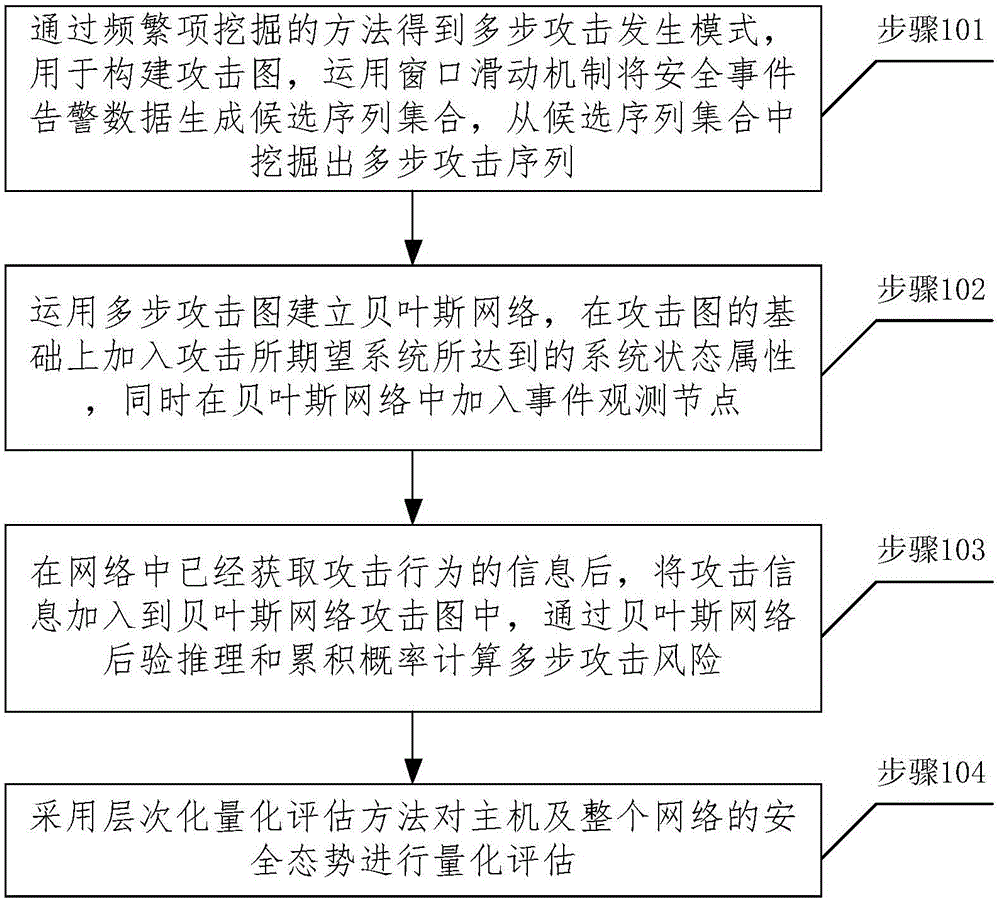
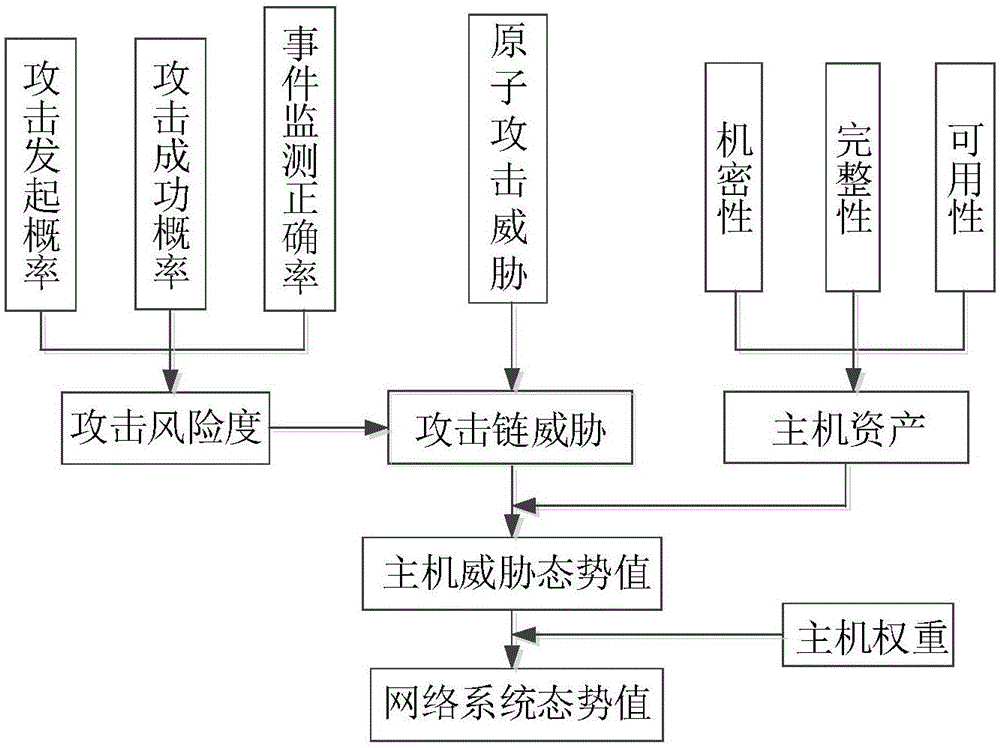
Bayesian network-based multi-step attack security situation assessment method
ActiveCN106341414AReal-time assessmentEffective assessmentPlatform integrity maintainanceTransmissionAttack graphCorrelation analysis
The invention relates to a network security situation assessment method, in particular, a Bayesian network-based multi-step attack security situation assessment method. The method includes the following steps that: multi-step attack generating patterns are mined through association analysis, so that an attack graph can be constructed; a Bayesian network is established according to the multi-step attack graph, attack wills, probability of success of attacks and the accuracy of event monitoring are defined as the probability attributes of the Bayesian network; based on the event monitoring, a multi-step attack risk is calculated according to the posterior reasoning and cumulative probability of the Bayesian network; and the security situations of a host and the whole network are quantitatively assessed according to a hierarchical quantitative assessment method. With the method of the invention adopted, the problem of lack of correlation analysis in a network security situation assessment process can be solved. According to the method of the invention, monitoring events are taken into risk assessment, and a network security situation assessment model is accurately established, and therefore, the effectiveness and real-time performance of the method of the invention can be enhanced.
Owner:CHONGQING UNIV OF POSTS & TELECOMM
System and method for network vulnerability detection and reporting
InactiveUS8135823B2Reliably determinedSimple methodDigital computer detailsPolarising elementsGraphicsOperational system
Owner:MCAFEE LLC
Method for estimating anti-seismic ability of building and its usage
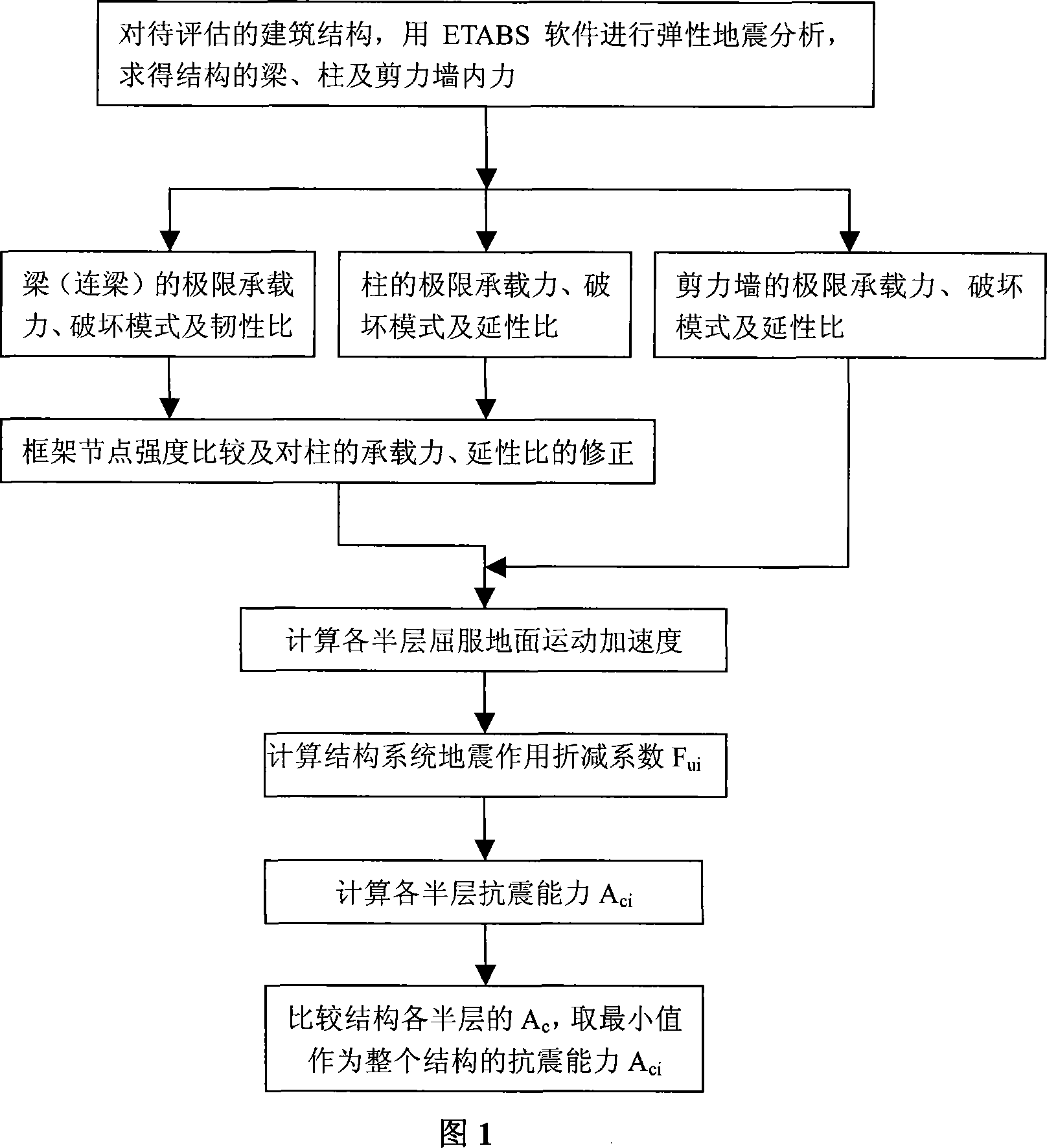
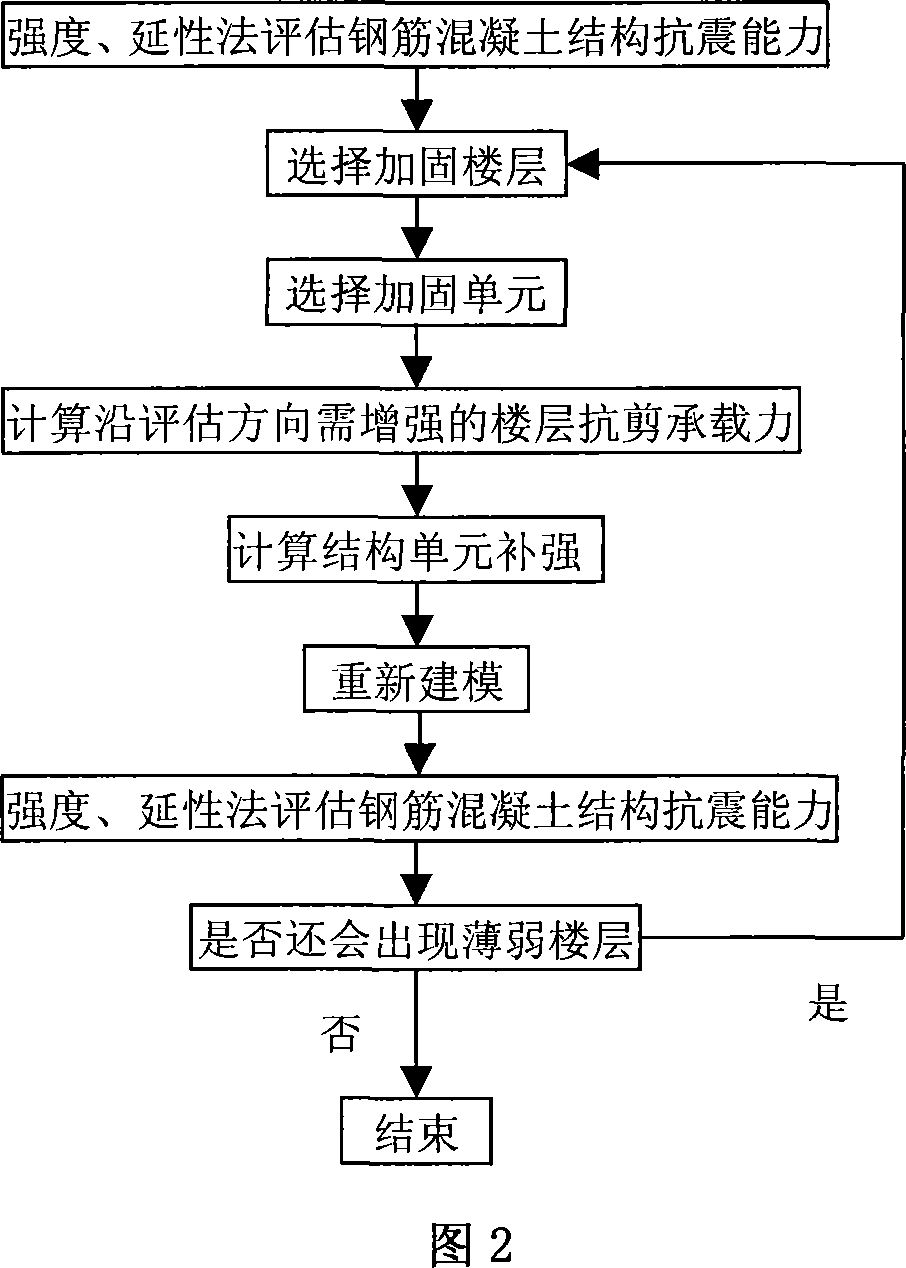
InactiveCN101074995AThe comprehensive seismic capacity index of the floor is clearRealize quantitative evaluationSeismic signal processingSpecial data processing applicationsReinforced concreteMan machine
A method for estimating anti-seismic ability of building includes integrating anti-seismic ability estimation, analysis and reinforcement of weak floor and weak unit, simplified ability chart, etc on the same software platform; utilizing man-machine interactive program to carry out quantitative estimation on anti-seismic ability of steel concrete structure for realizing anti-seismic ability estimation of building.
Owner:杨仕升
Method for reorganizing tasks for optimization of resources
A method of reorganizing a plurality of task for optimization of resources and execution time in an environment is described. In one embodiment, the method includes mapping of each task to obtain qualitative and quantitative assessment of each functional elements and variables within the time frame for execution of each tasks, representation of data obtained from the mapping in terms of a matrix of dimensions N×N, wherein N represents total number of tasks and reorganizing the tasks in accordance with the represented data in the matrix for the execution, wherein reorganizing the tasks provides for both static and dynamic methodologies. It is advantageous that the present invention determines optimal number of resources required to achieve a practical overall task completion time and can be adaptable to non computer applications.
Owner:KPIT TECH LTD
Measurement of functional microcirculatory geometry and velocity distributions using automated image analysis
ActiveUS20100104168A1Less user interactionReduces observer biasImage enhancementImage analysisImaging analysisVideo sequence
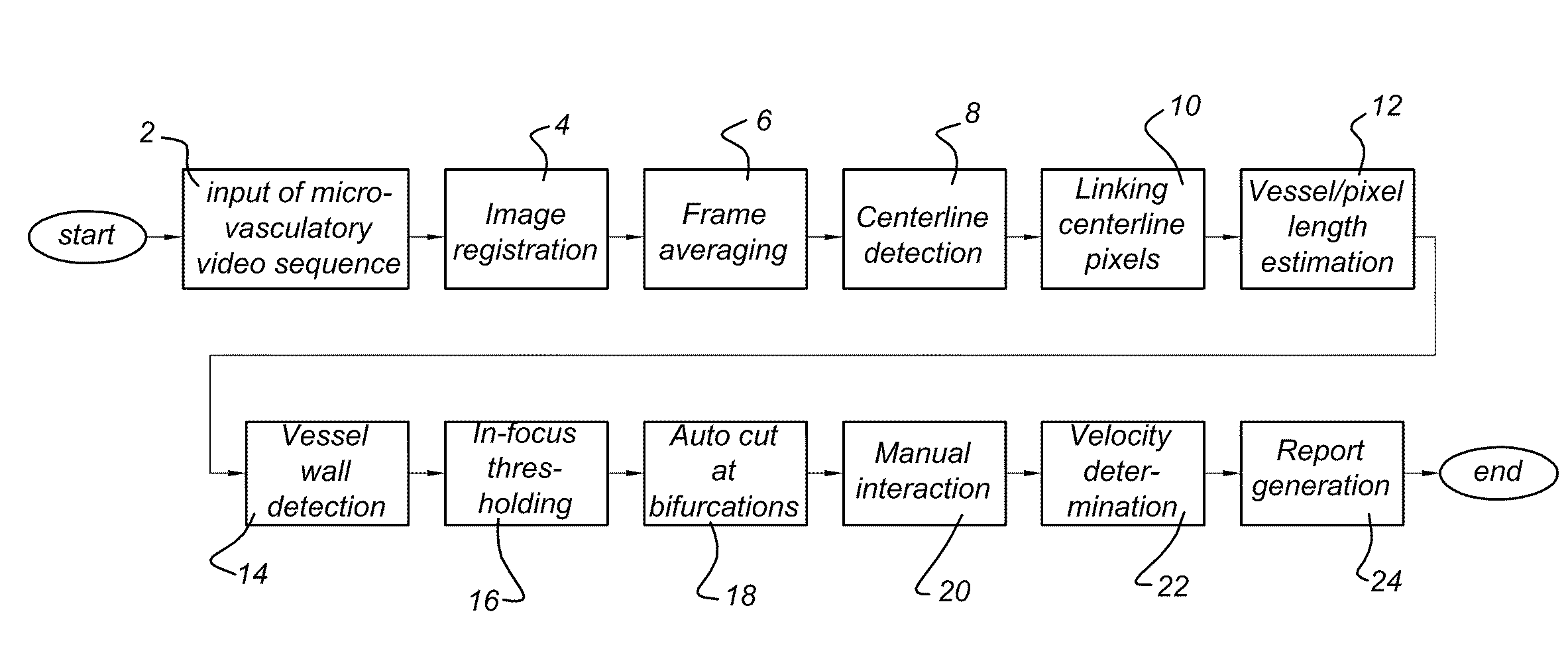
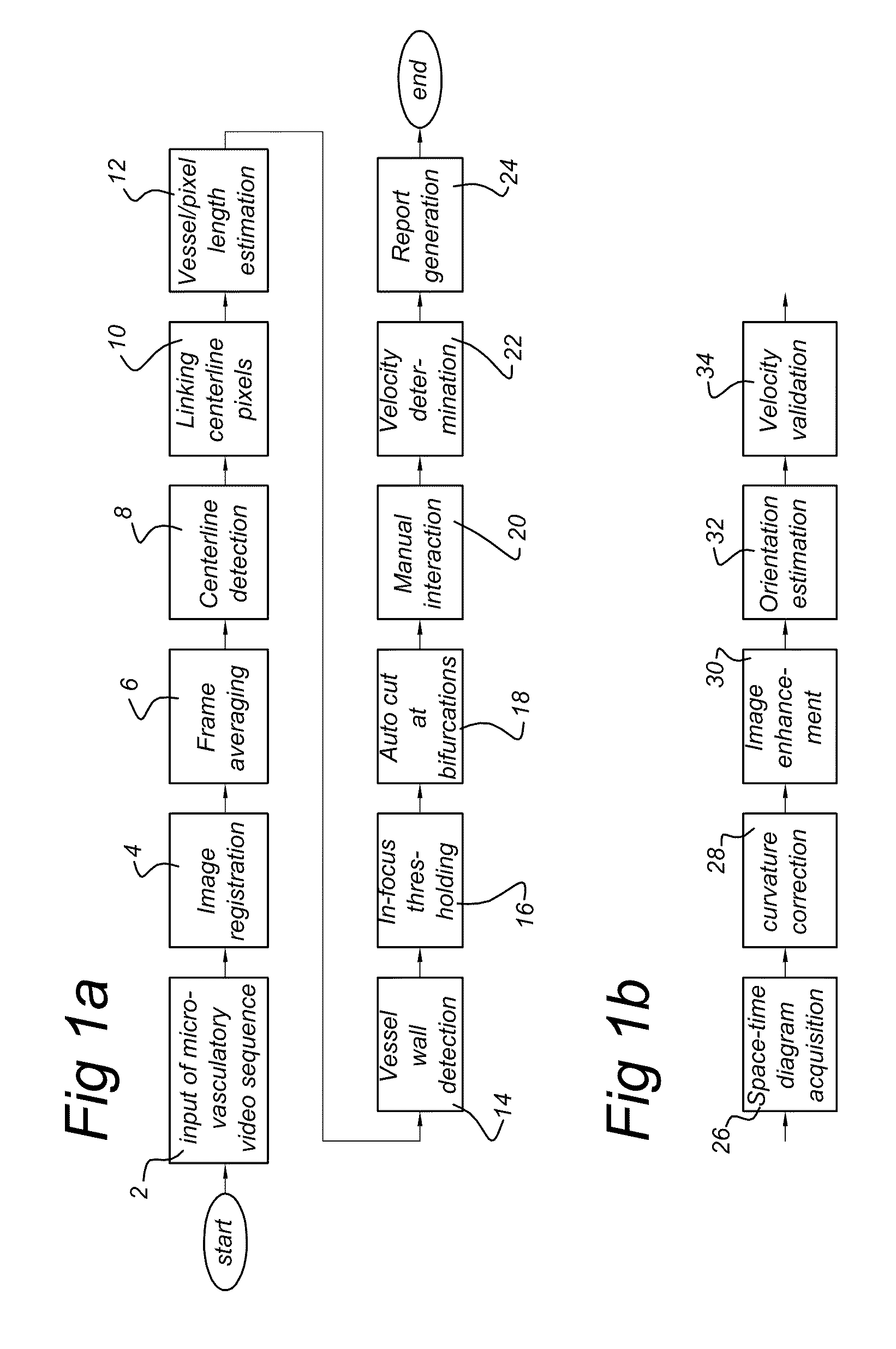
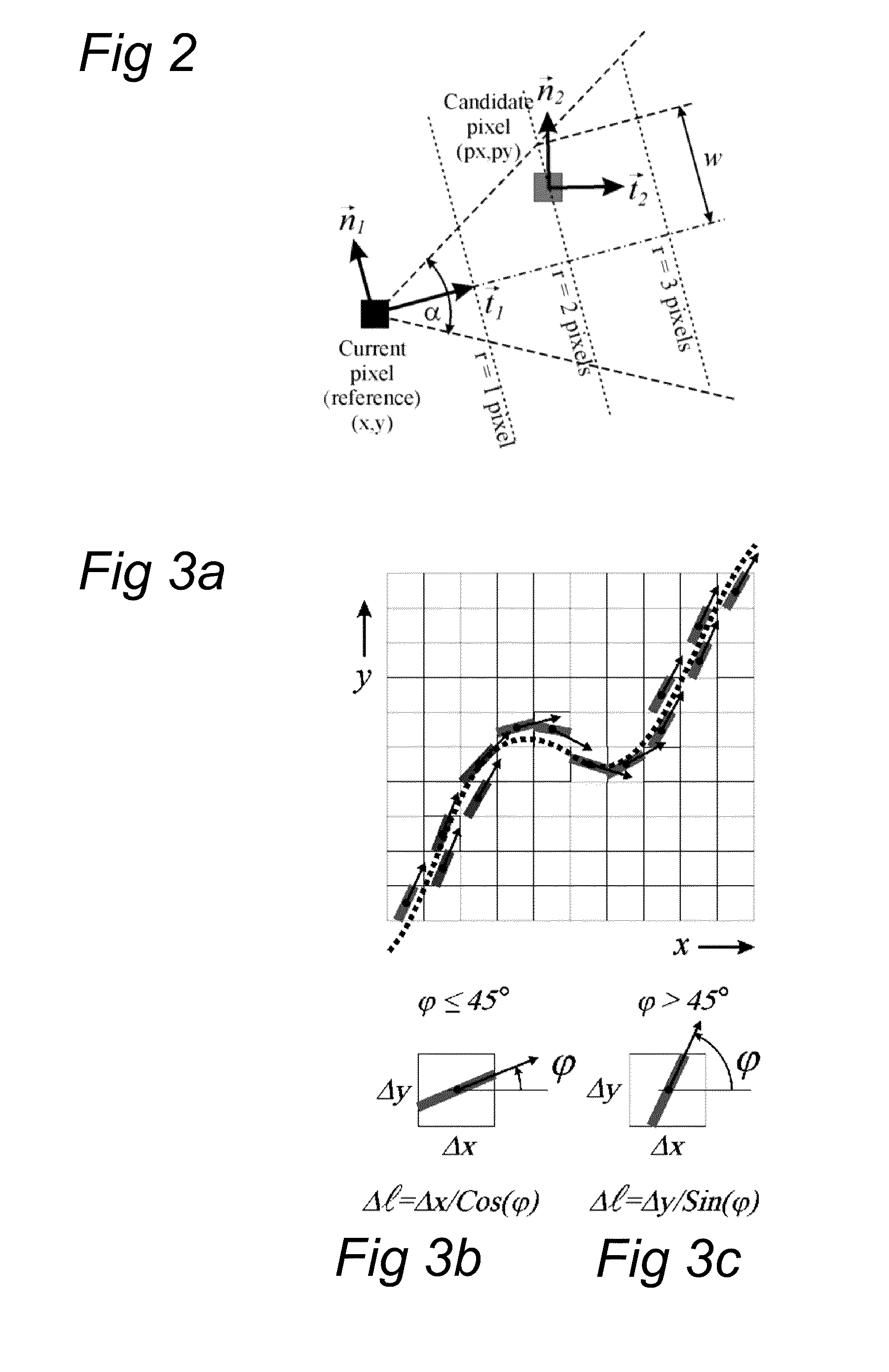
The invention provides analysis algorithms for quantitative assessment of microvasculatory video sequences that provide vessel thickness, vessel length and blood velocity per vessel segment. It further provides a method of for calculating the functional microvasculatory density and blood velocity as distributed over vessels with different thickness, in the field of view.
Owner:MVM
System And Method For Network Vulnerability Detection And Reporting
InactiveUS20070283007A1Reliably determinedSimple methodError detection/correctionDigital computer detailsGraphicsOperational system
A system and method provide comprehensive and highly automated testing of vulnerabilities to intrusion on a target network, including identification of operating system, identification of target network topology and target computers, identification of open target ports, assessment of vulnerabilities on target ports, active assessment of vulnerabilities based on information acquired from target computers, quantitative assessment of target network security and vulnerability, and hierarchical graphical representation of the target network, target computers, and vulnerabilities in a test report. The system and method employ minimally obtrusive techniques to avoid interference with or damage to the target network during or after testing.
Owner:MCAFEE LLC
Data gloves for function rehabilitation training and assessment of hands and monitoring method thereof
InactiveCN103251419AReactivityReflect resistanceDiagnostic recording/measuringSensorsNormal resistanceMuscle force
The invention discloses data gloves for function rehabilitation training and assessment of hands. Each data glove further comprises bent sensor groups which are arranged on the hand back side inside the each data glove in a packaged mode and flexible pressure sensor groups which are arranged on the palm side inside each data glove. The bent sensor groups are placed on finger joints, the pressure sensor groups are placed on the a plurality of key nodes where a hand is in contact with an object when the object is grabbed, and lead-out lines of the bent sensor groups and lead-out lines of the pressure sensor groups are packaged inside each data glove, collected to the outer side of a forearm via the hand back side, and connected with a subsequent hardware processing circuit. The data gloves for the function rehabilitation training and the assessment of the hands are strong in wearability and capable of collecting finger bending angle information and palm pressure information of the hands of a patient, the finger bending angle information and the palm pressure information are used in the hand function rehabilitation training under a virtual environment, and quantitative assessment results of a muscle force range from no joint movement to movement capable of resisting normal resistance can be given.
Owner:RES INST OF XIAN JIAOTONG UNIV & SUZHOU +2
Airplane hard landing indication system
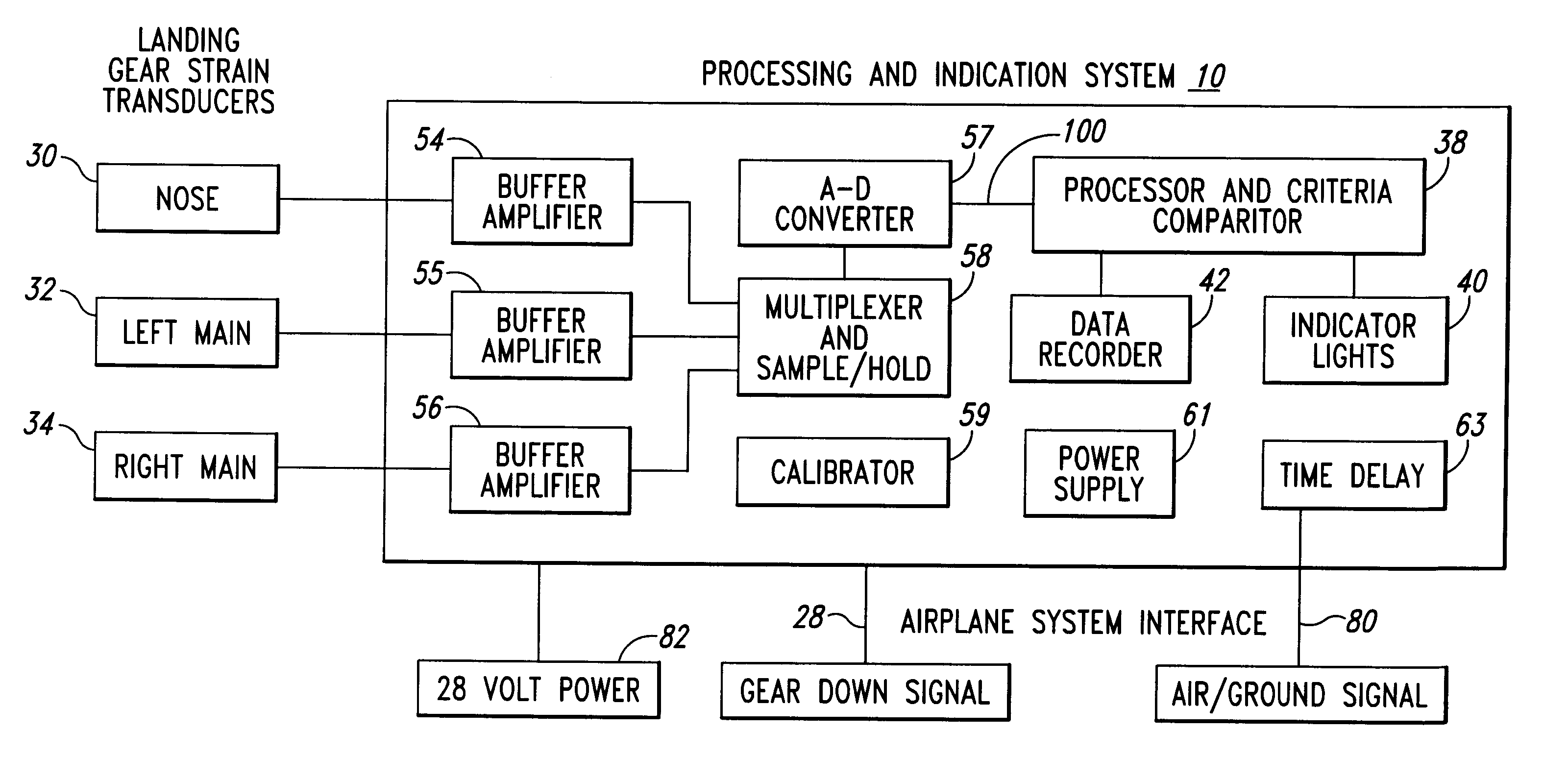
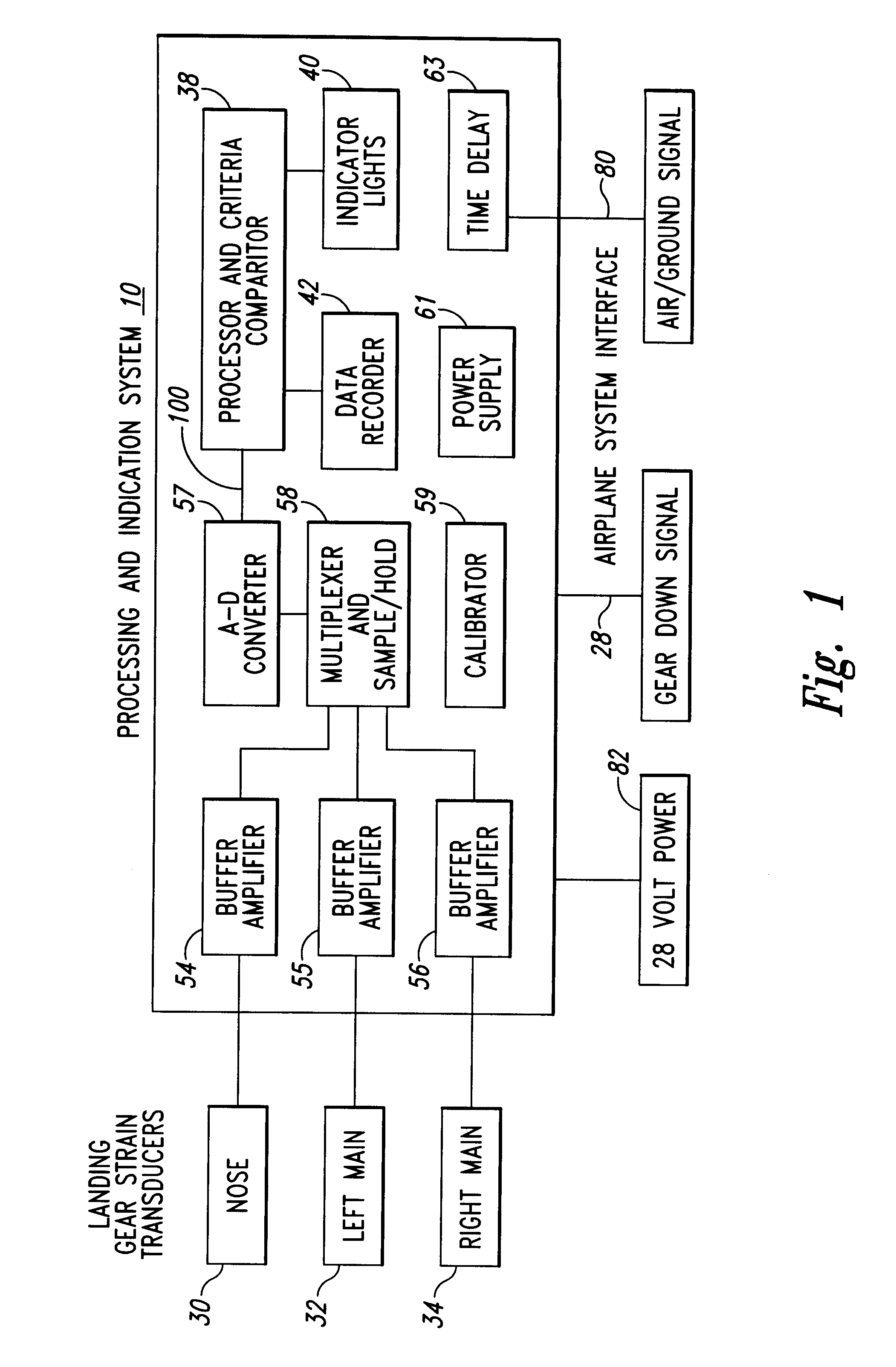
This invention relates to a hard landing indication system that will provide a quantitative assessment that a hard landing did or did not occur at the last landing of an airplane. A hard landing can cause structural damage to an airplane. An airplane that has been declared to have a hard landing must be grounded until an inspection of the structure has been made to determine if repairs are required.
Owner:THE BOEING CO
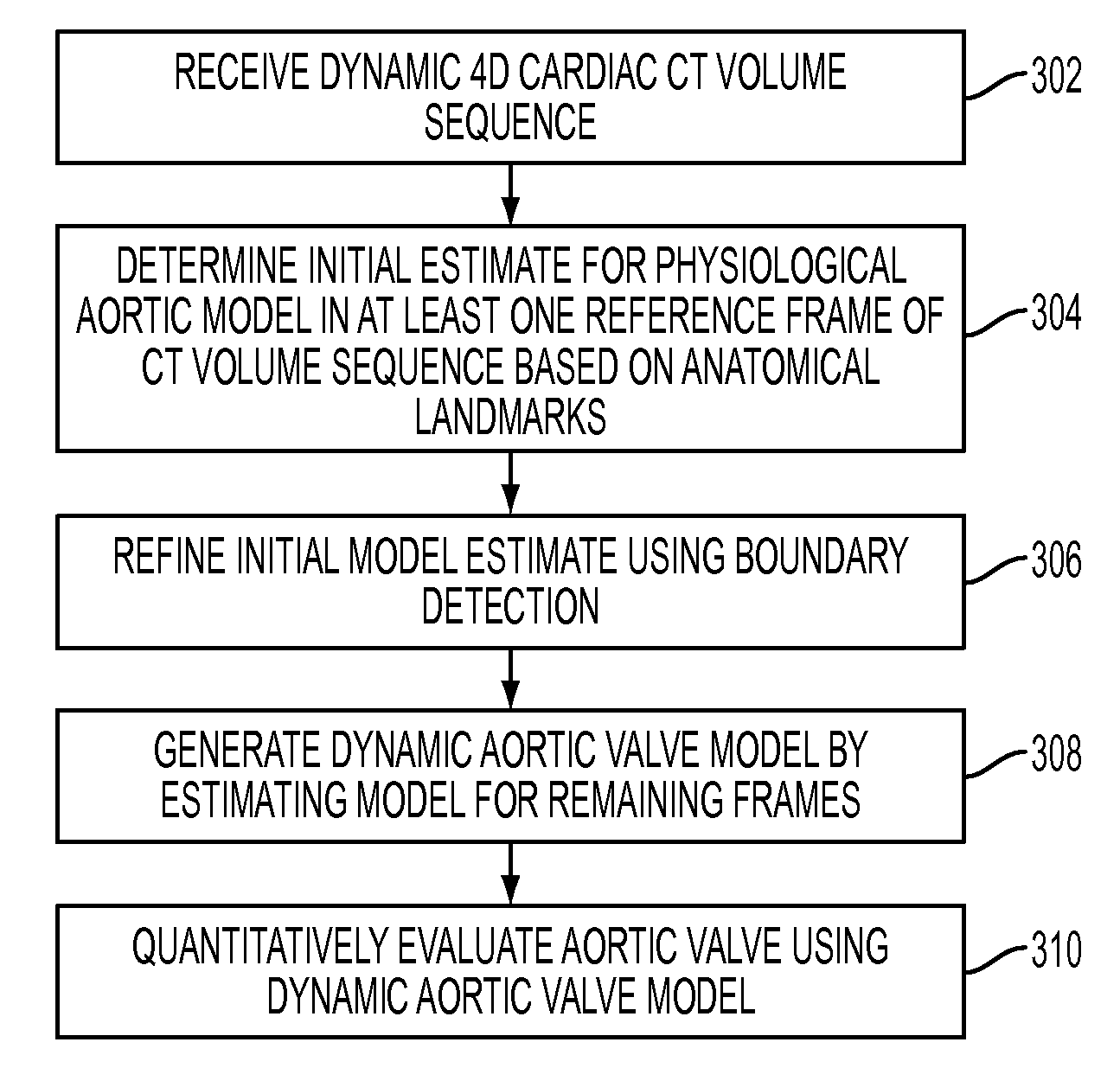
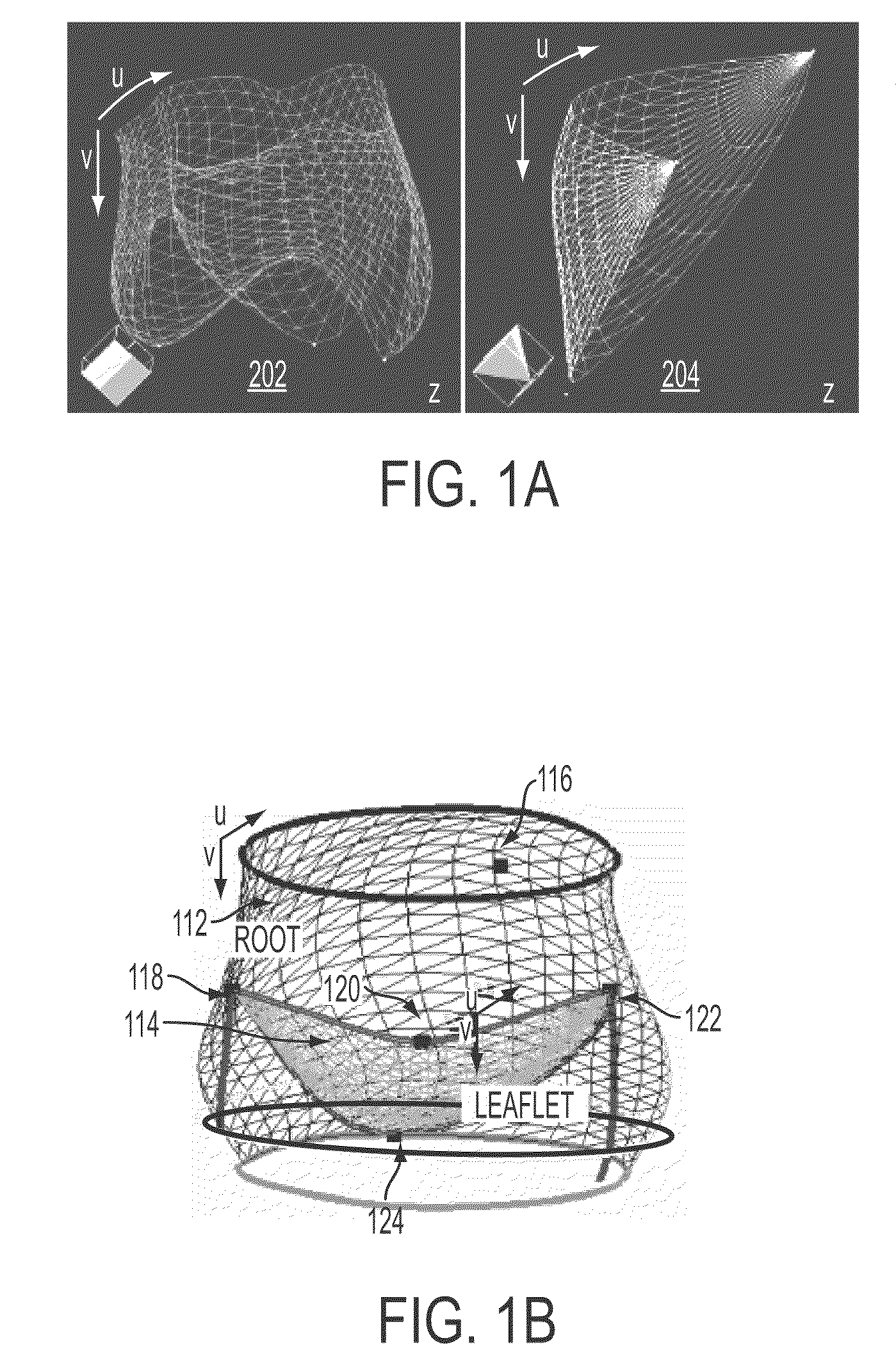
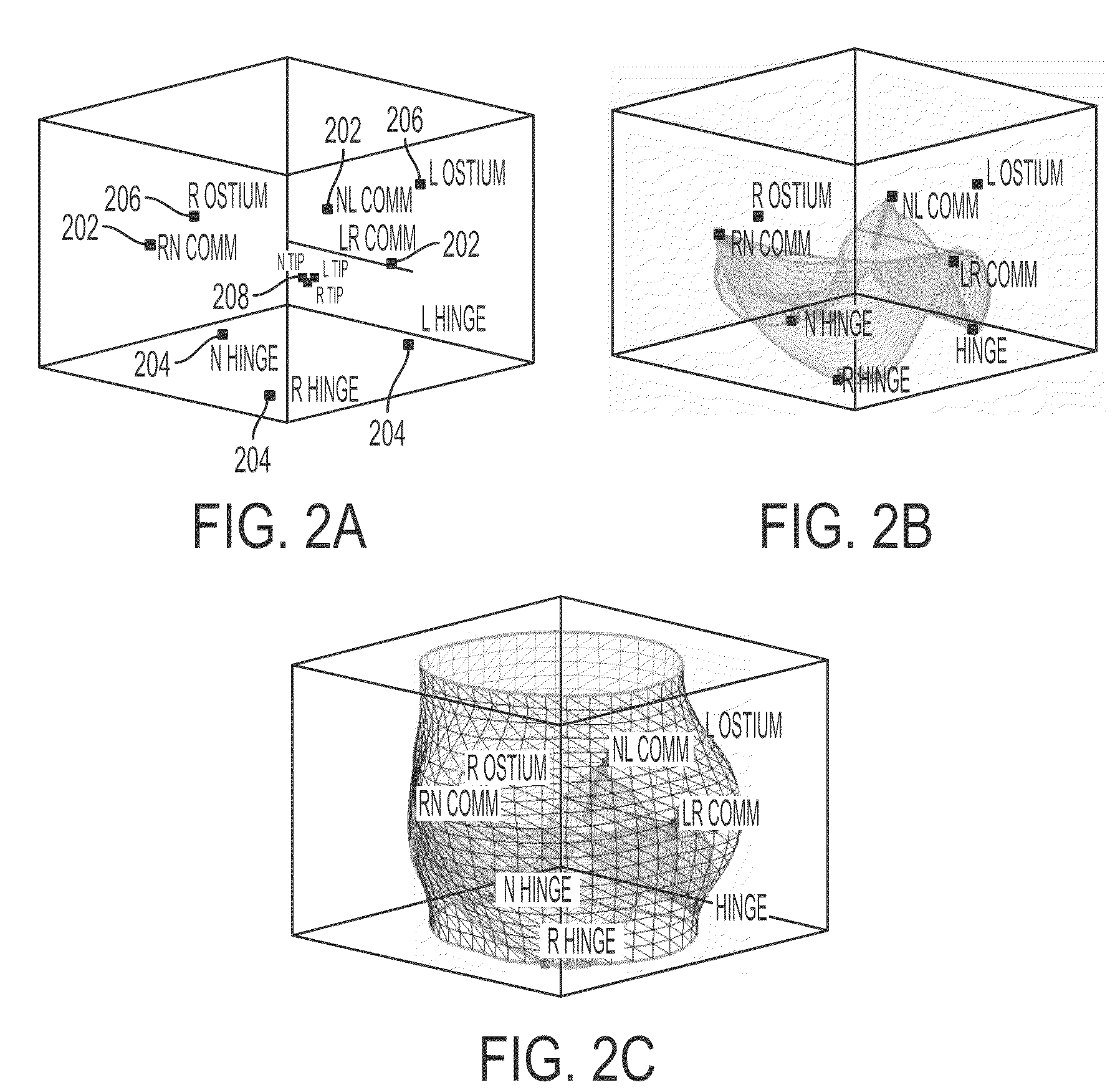
Method and system for automatic quantification of aortic valve function from 4D computed tomography data using a physiological model
A method and system for modeling the aortic valve in 4D image data, such as 4D CT and echocardiography, is disclosed. An initial estimate of a physiological aortic valve model is determined for at least one reference frame of a 4D image sequence based on anatomic features in the reference frame. The initial estimate is refined to generate a final estimate in the reference frame. A dynamic model of the aortic valve is then generated by estimating the physiological aortic valve model for each remaining frame of the 4D image sequence based on the final estimate in the reference frame. The aortic valve can be quantitatively evaluated using the dynamic model.
Owner:SIEMENS CORP +2
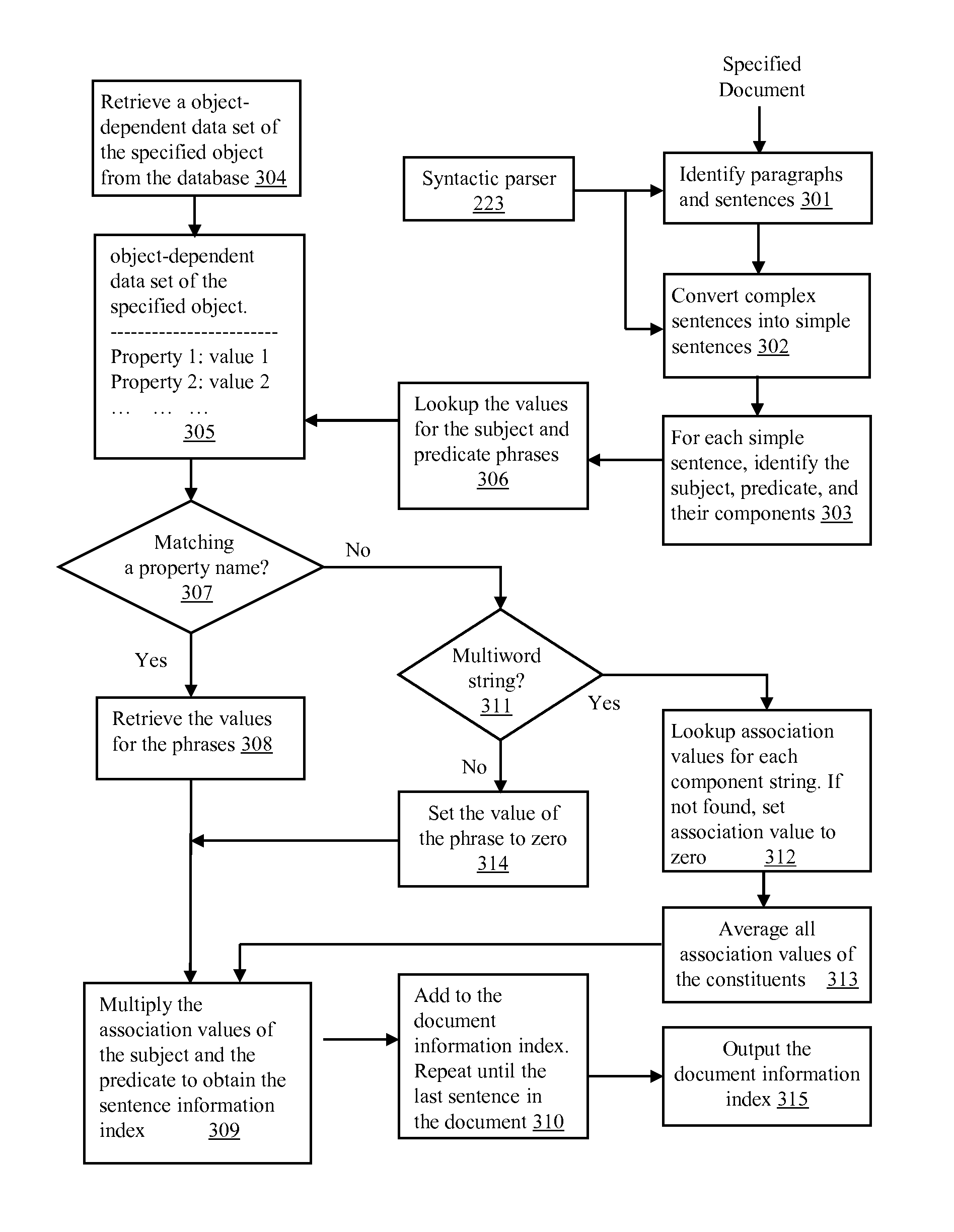
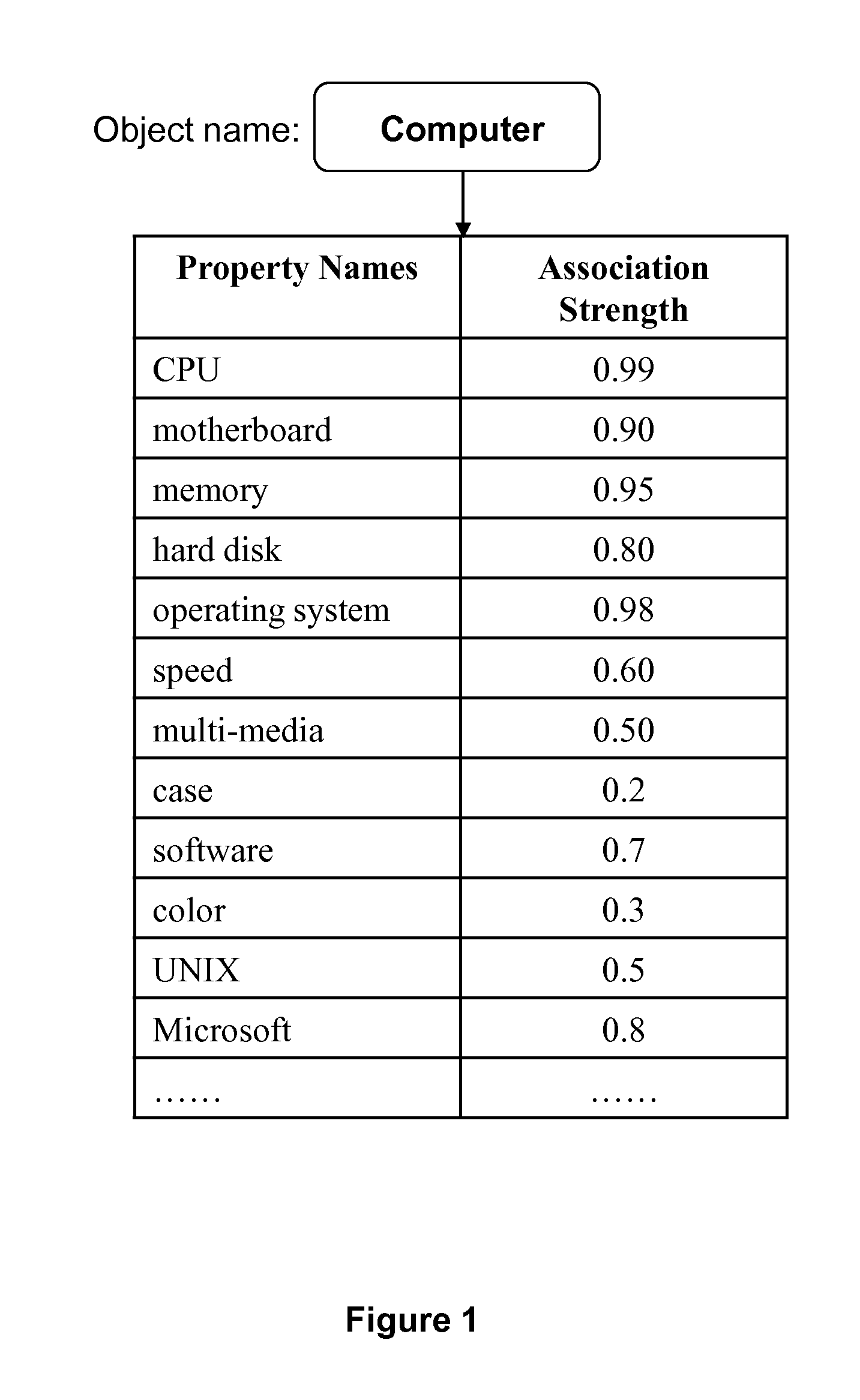
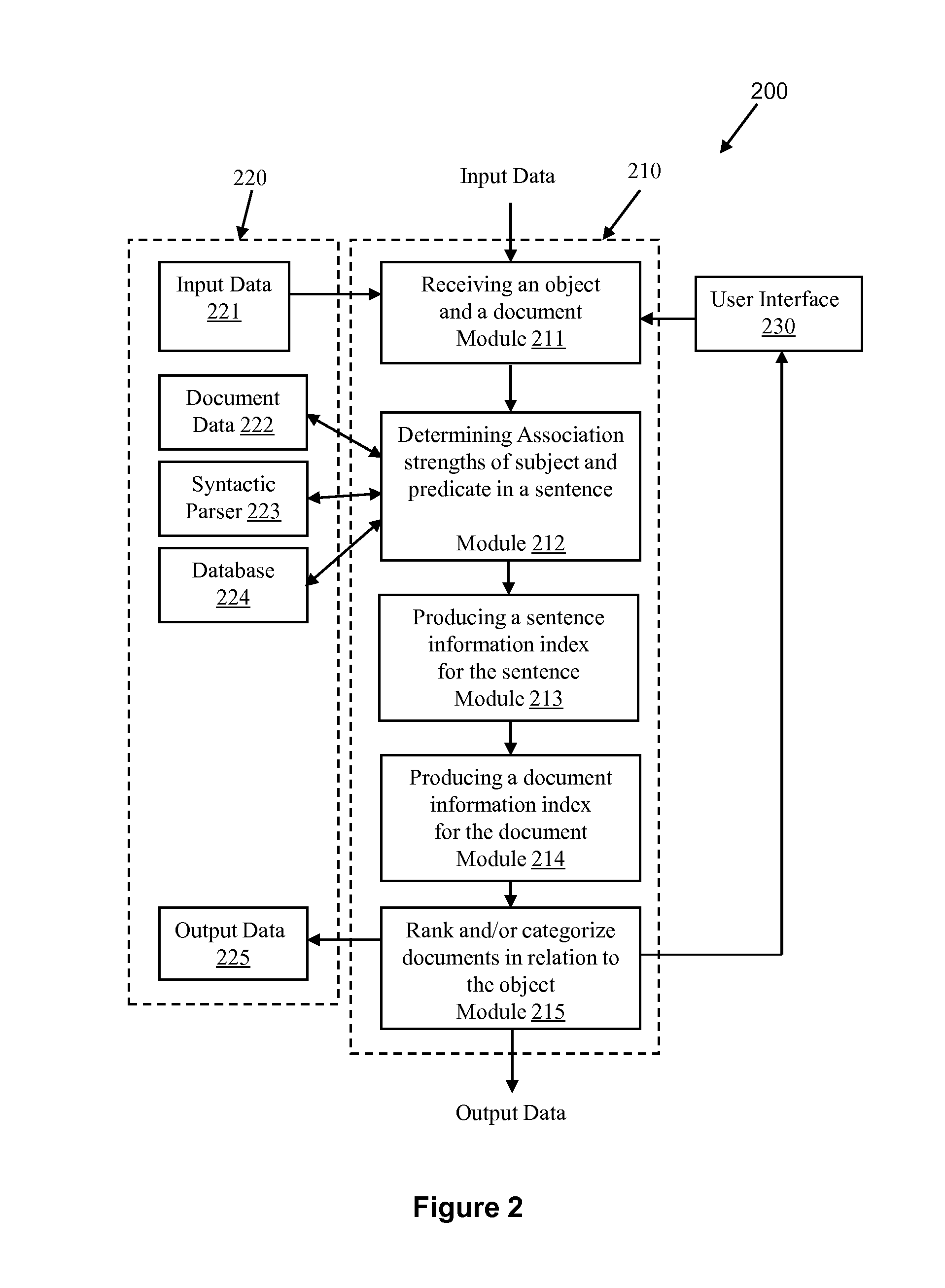
System and methods for quantitative assessment of information in natural language contents and for determining relevance using association data
ActiveUS9201927B1Improve accuracyImprove relevancy rankingSemantic analysisDigital data processing detailsData setSubject Name
System and methods are disclosed for quantitatively assessing information in natural language contents related to an object name, or a concept or topic name, and for determining the relevance between a text content and one or more concepts or topics. The methods include identifying the grammatical or semantic attributes and other contextual information of terms in the text content, and retrieving an object-specific dataset related to the object name, or an equivalent to a concept or a topic name. The data set includes property names and association-strength values. The methods further include matching the terms in the text content with the property terms in the dataset, and calculating a score as a quantitative measure of the relevance between the text content and the concept or topic.
Owner:LINFO IP LLC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com