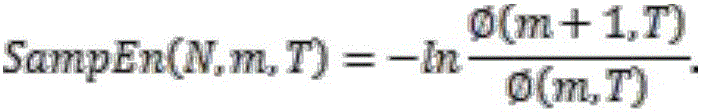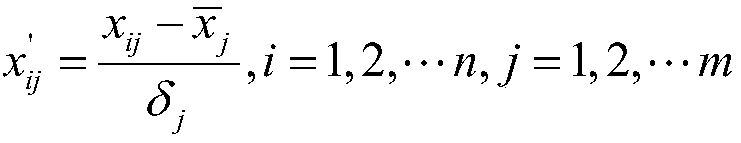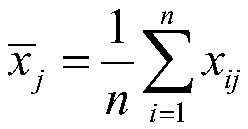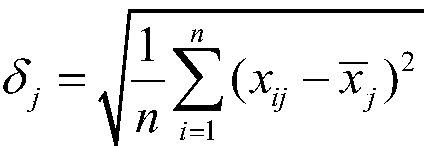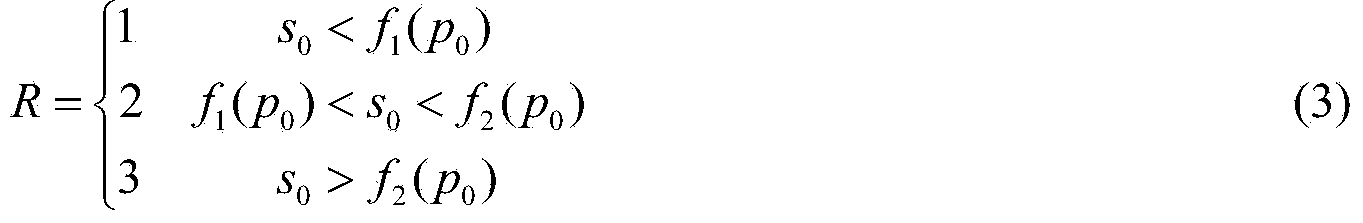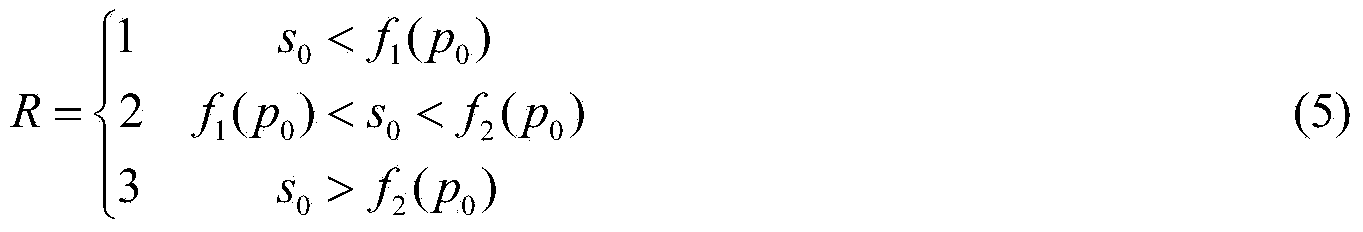Patents
Literature
44 results about "Medium Risk" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Medium risk definition, medium risk meaning | English dictionary. medium. n anything acceptable as a measure of value and a standard of exchange for goods and services in a particular country, region, etc.
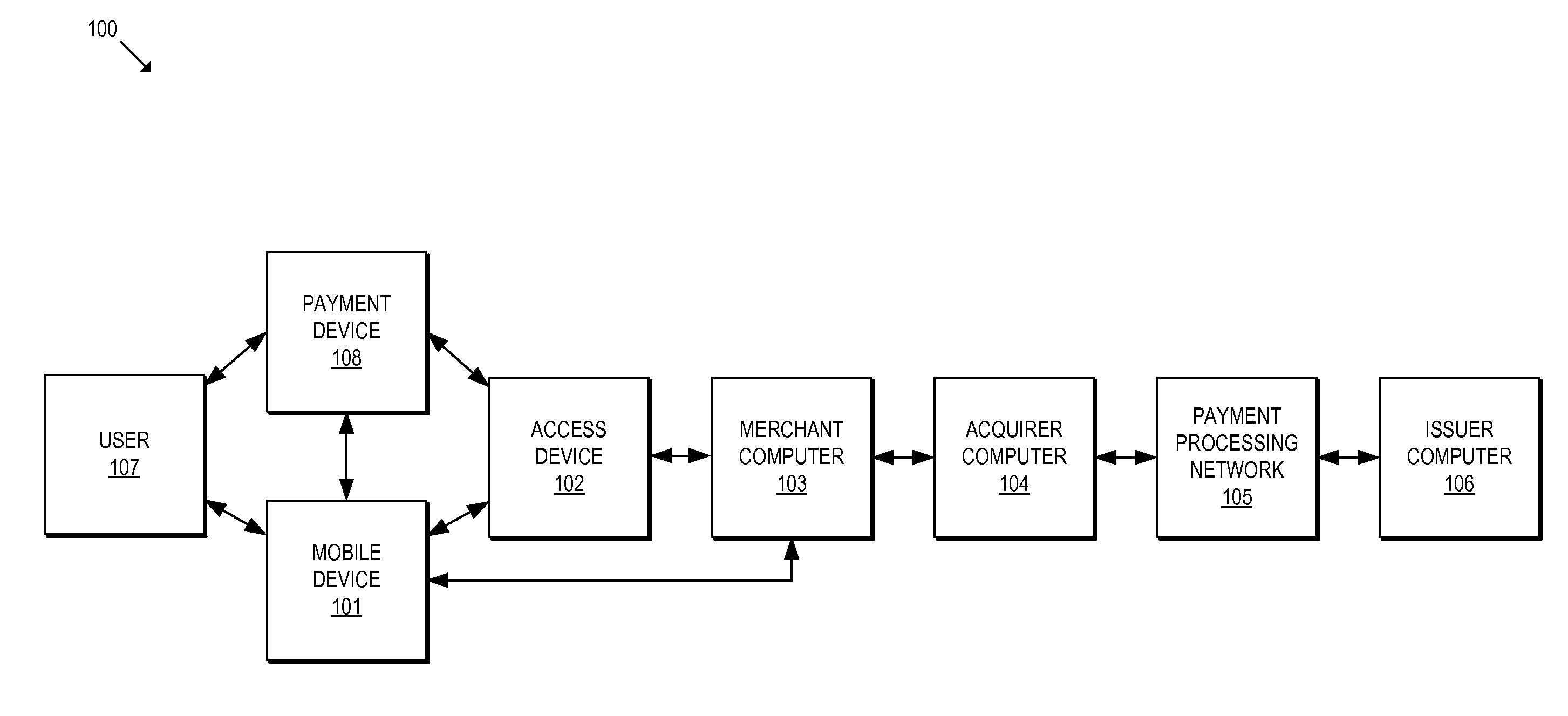
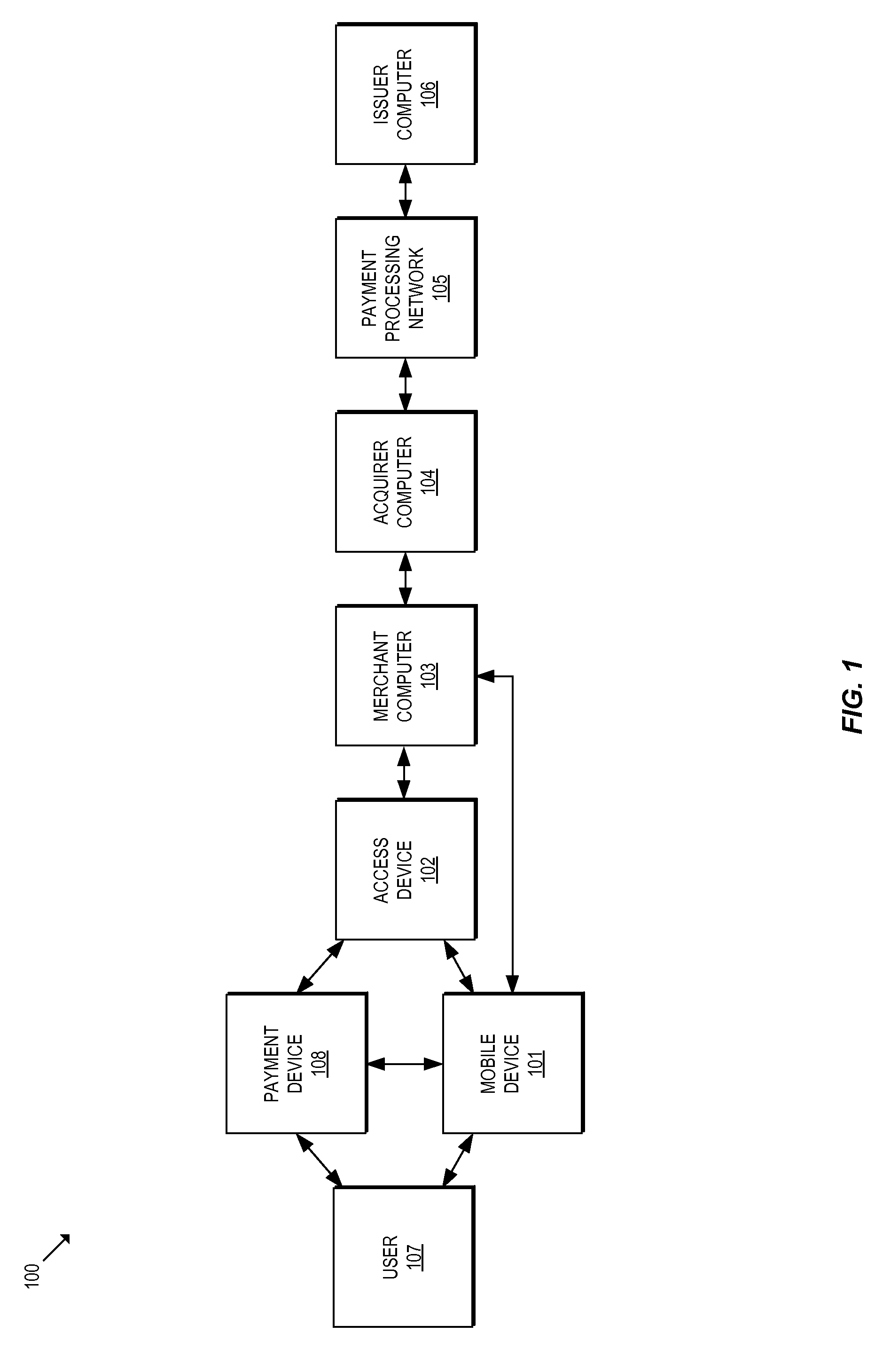
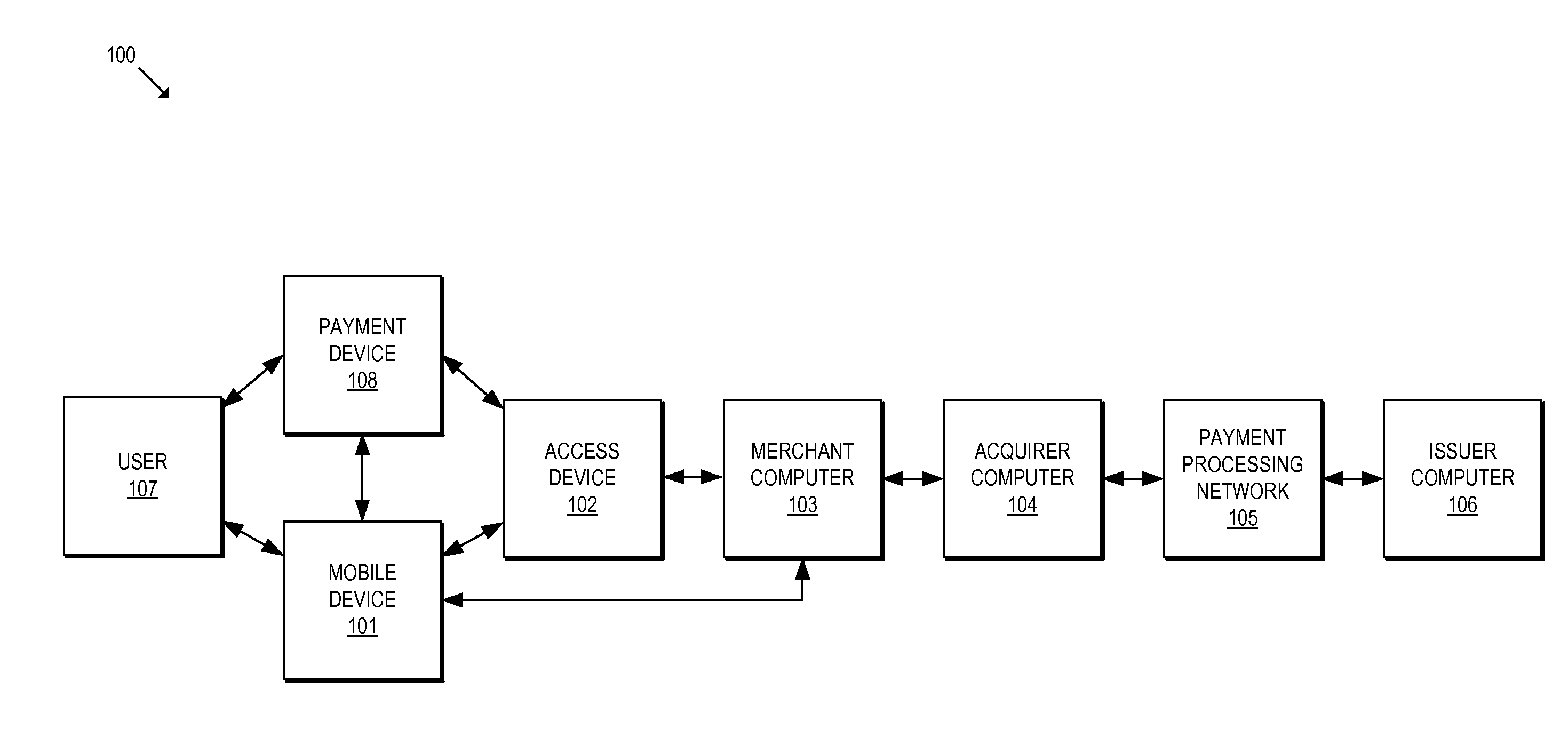
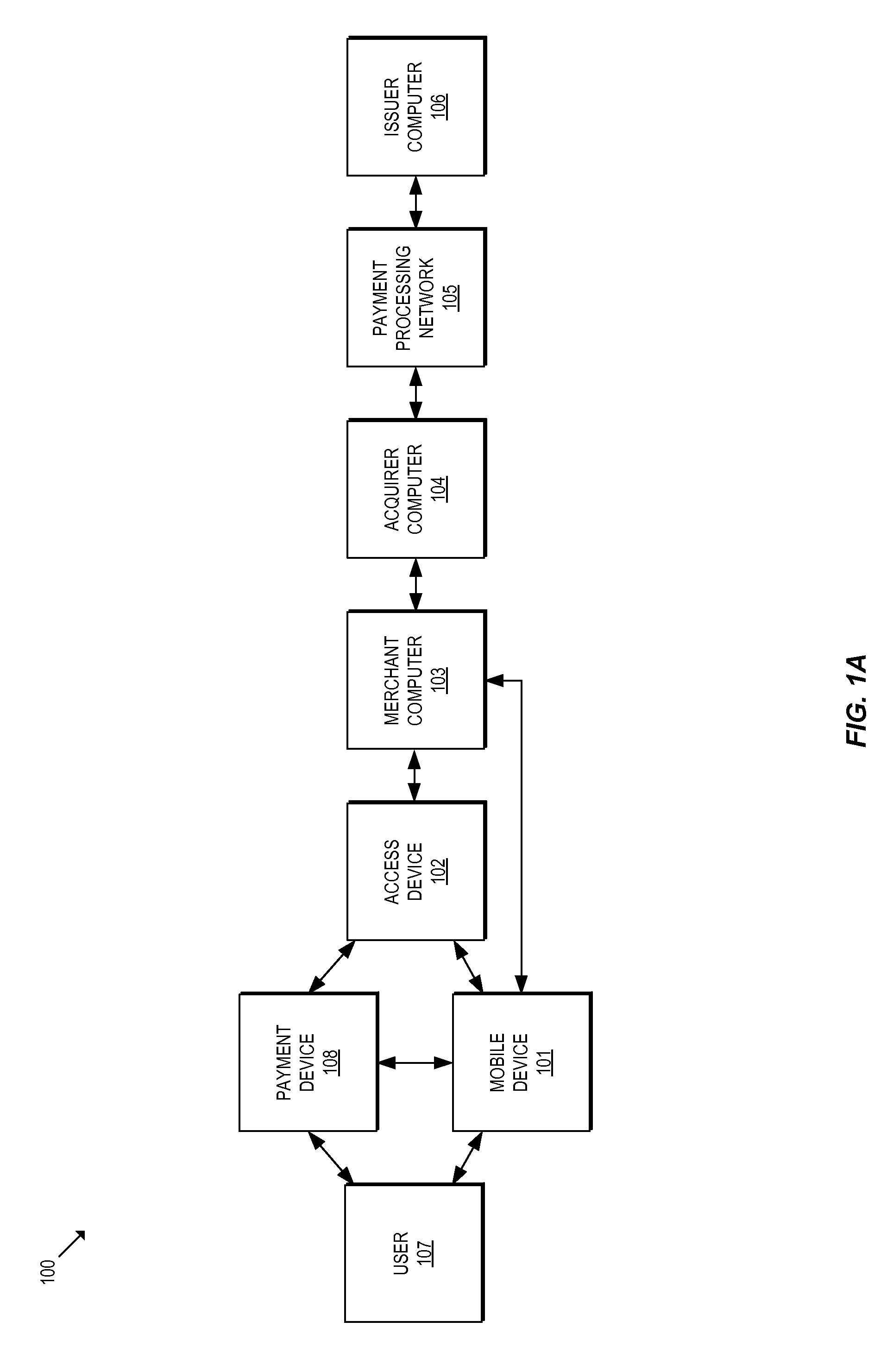
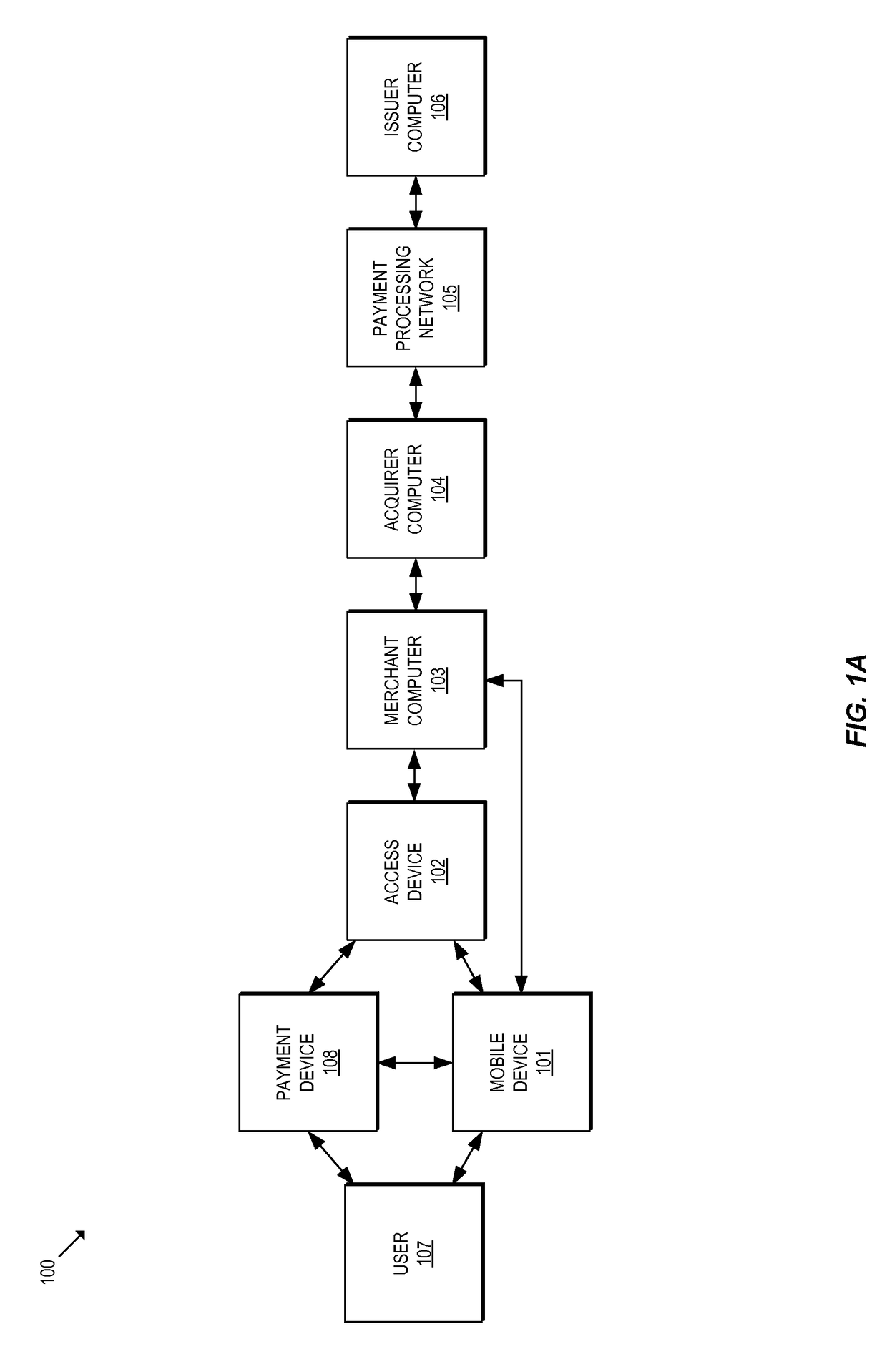
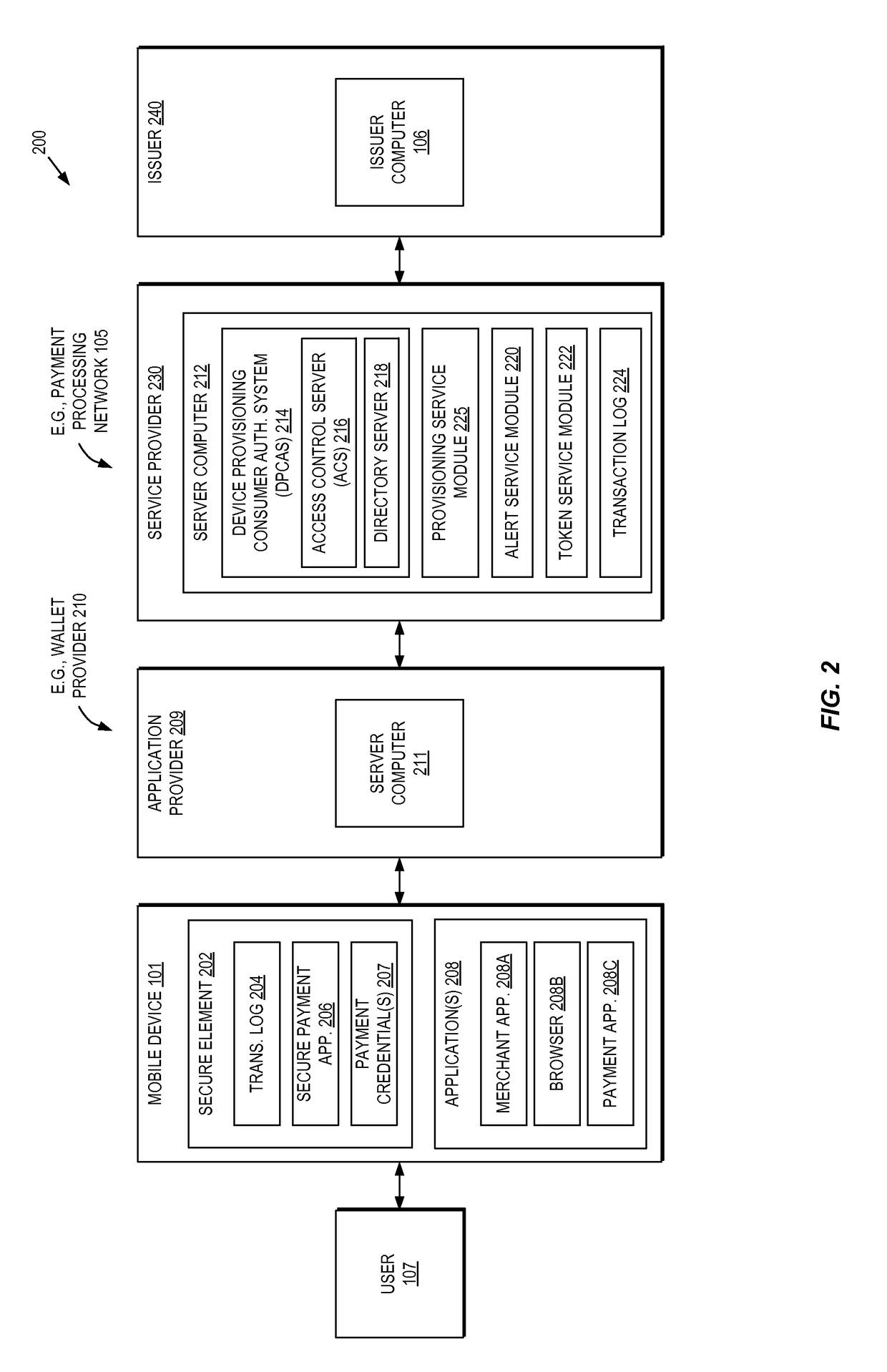
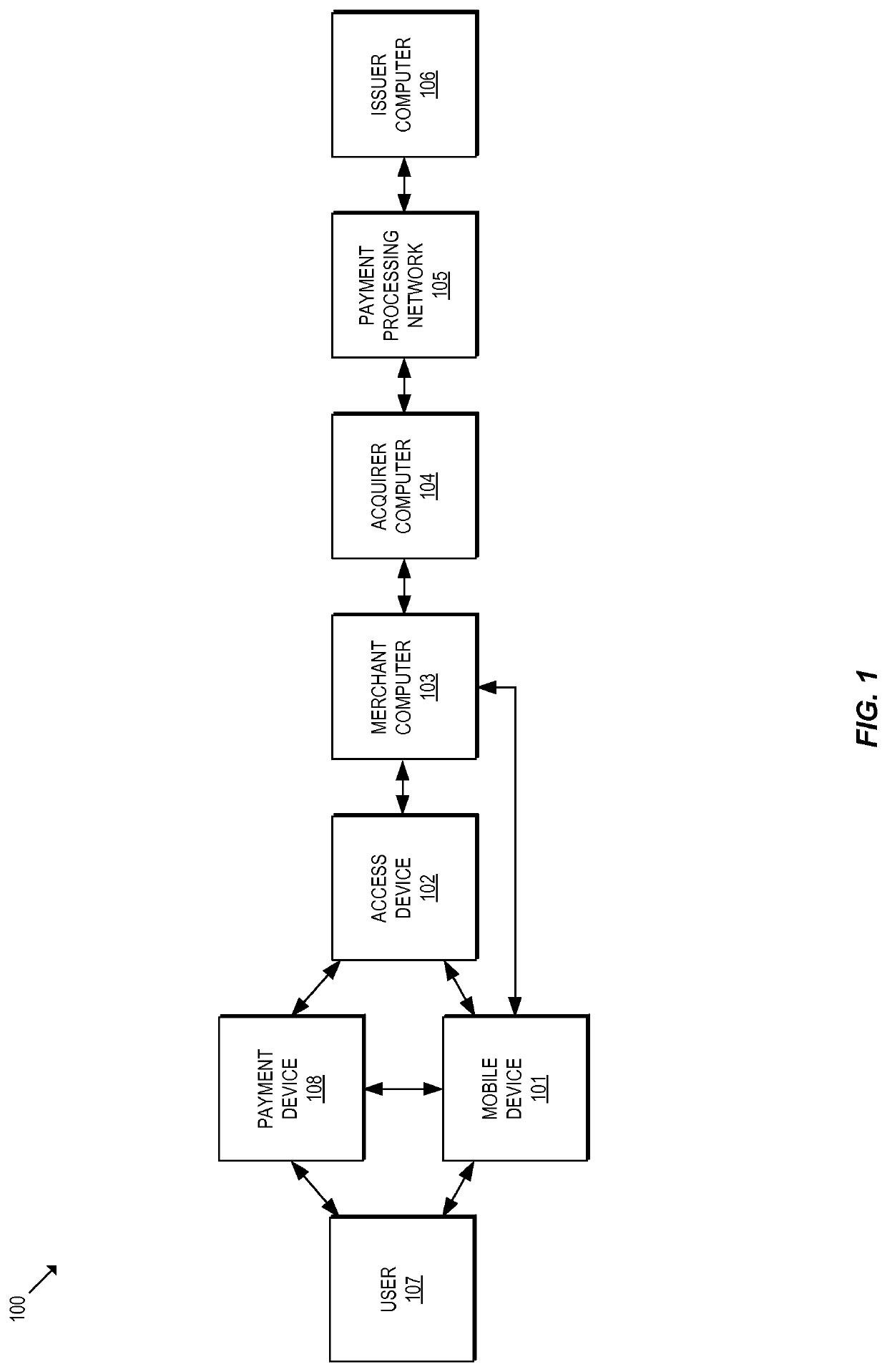
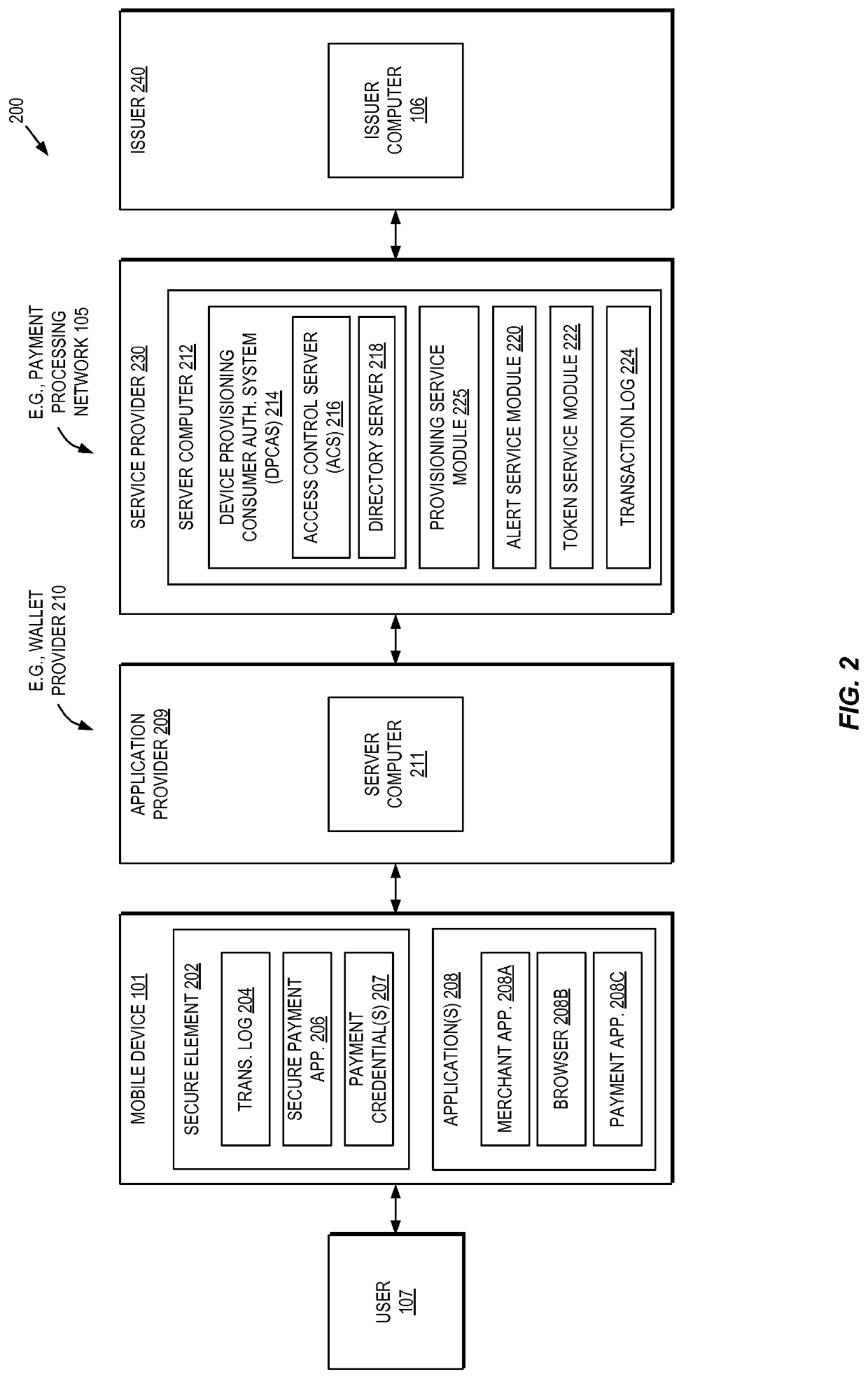
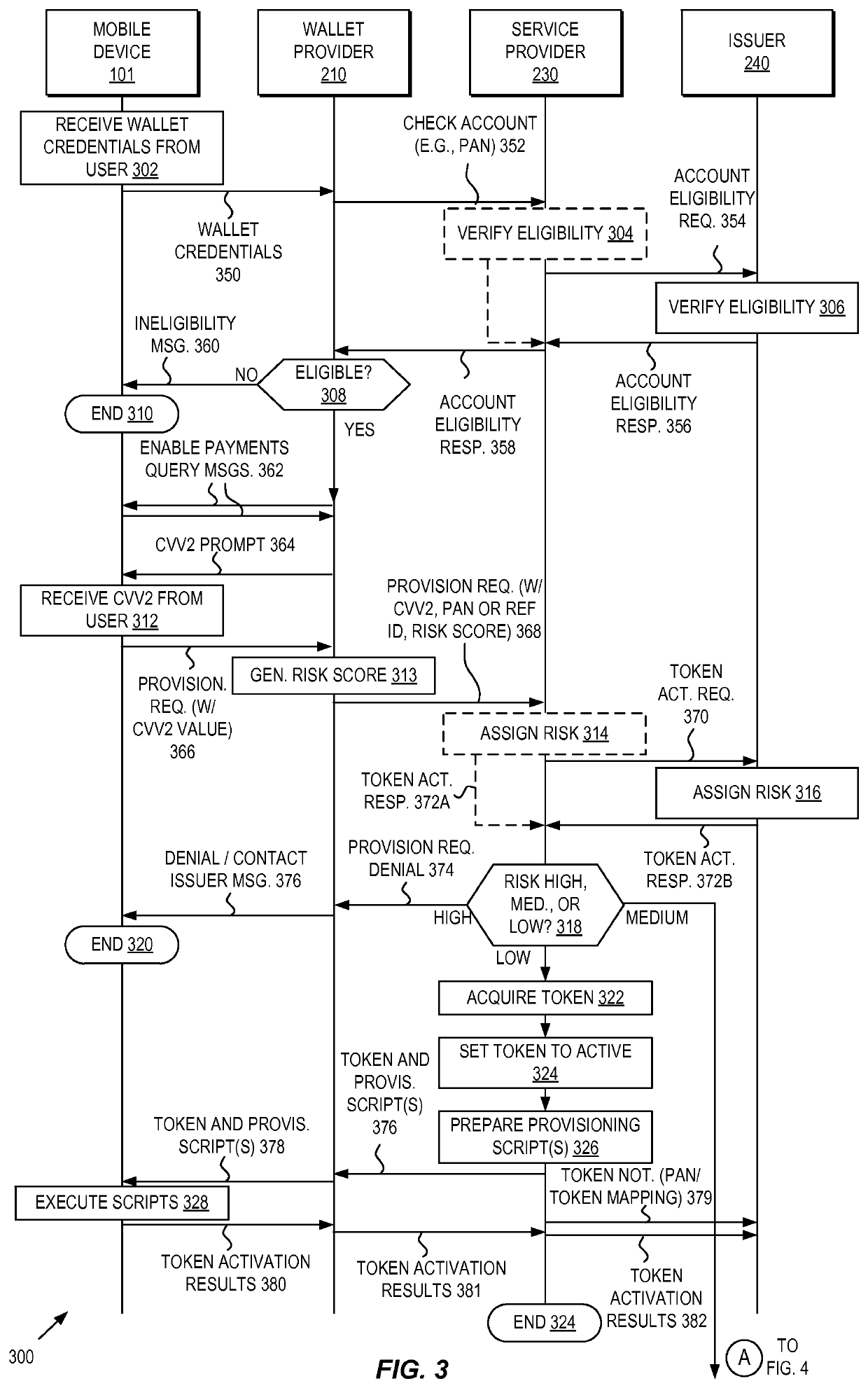
Methods and systems for provisioning mobile devices with payment credentials
ActiveUS20150046339A1Unnecessary delayProcessing speedFinanceElectronic credentialsPaymentMedium Risk
Embodiments are described that are directed to optimizing the provisioning of payment account credentials to mobile devices utilizing mobile wallets. In some embodiments, one of multiple provisioning schemes may be selectively chosen for payment account credential provisioning based upon a determined risk involved with a particular provisioning request. A low risk provisioning request leads to an immediate provisioning of a payment credential, whereas a provisioning request of high risk results in the provisioning request being denied. In some embodiments, medium risk provisioning requests will cause an additional user authentication to be performed before the payment account provisioning is finalized. The additional user authentication may occur using a separate communication channel than the channel in which the provisioning request was received.
Owner:VISA INT SERVICE ASSOC
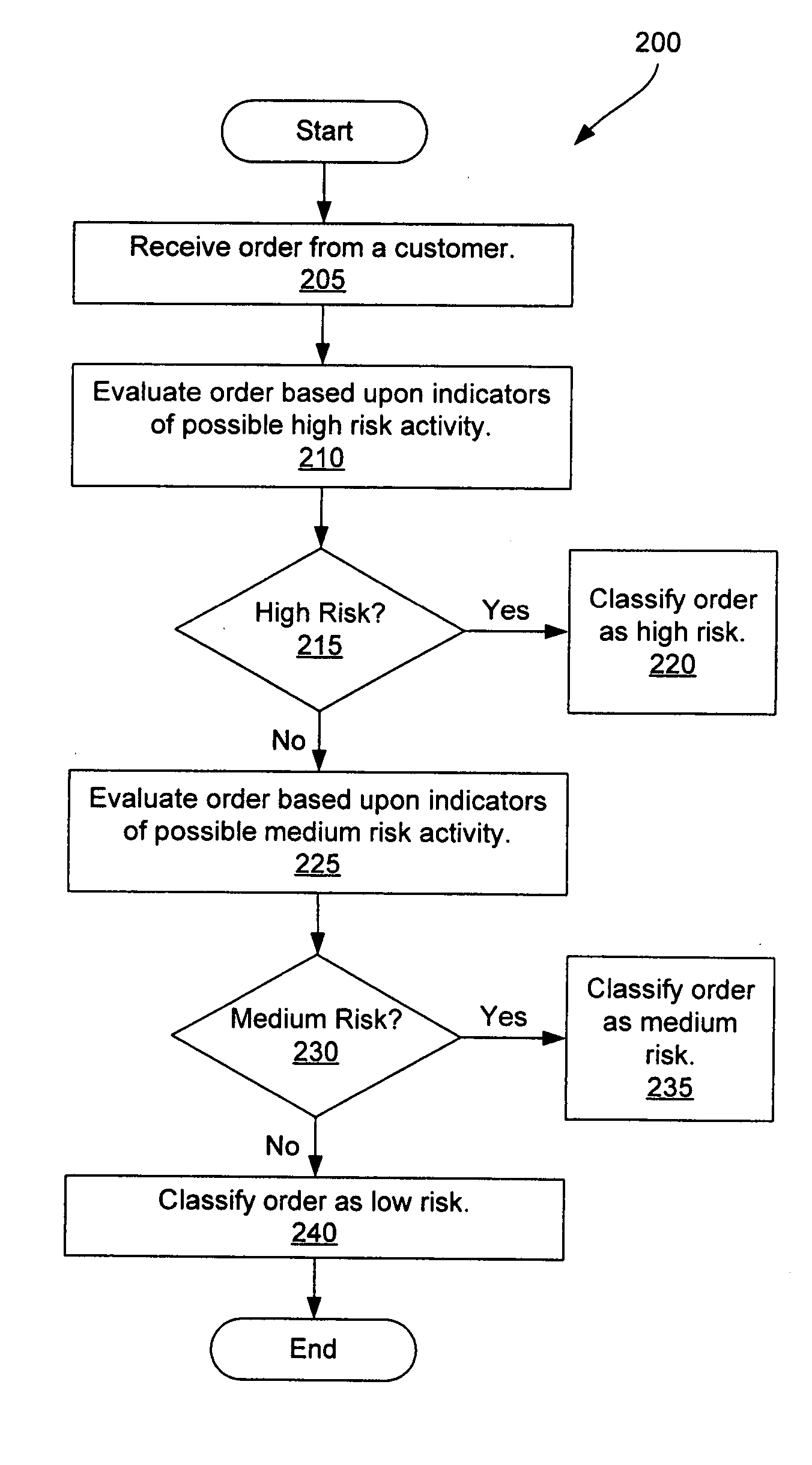
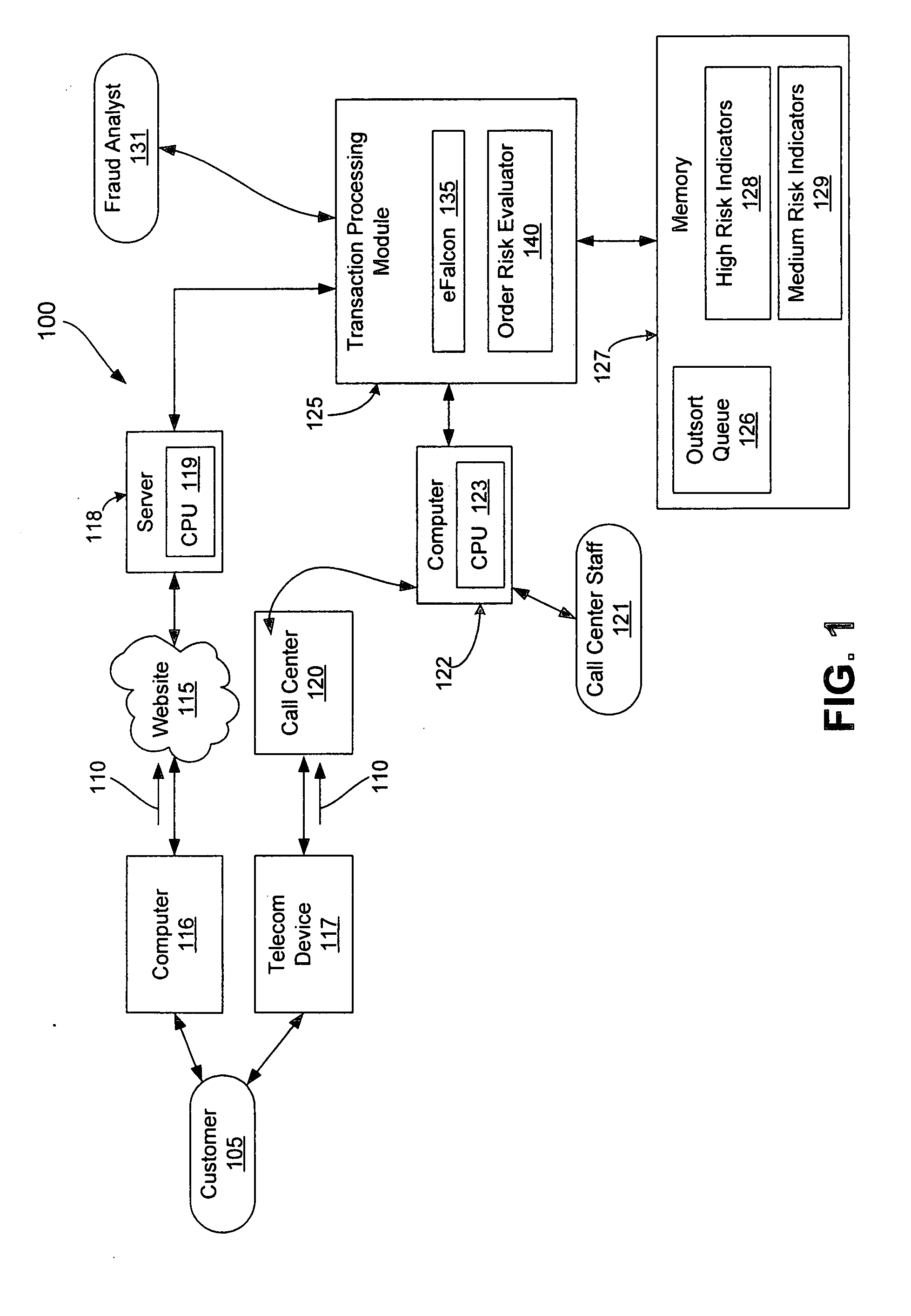
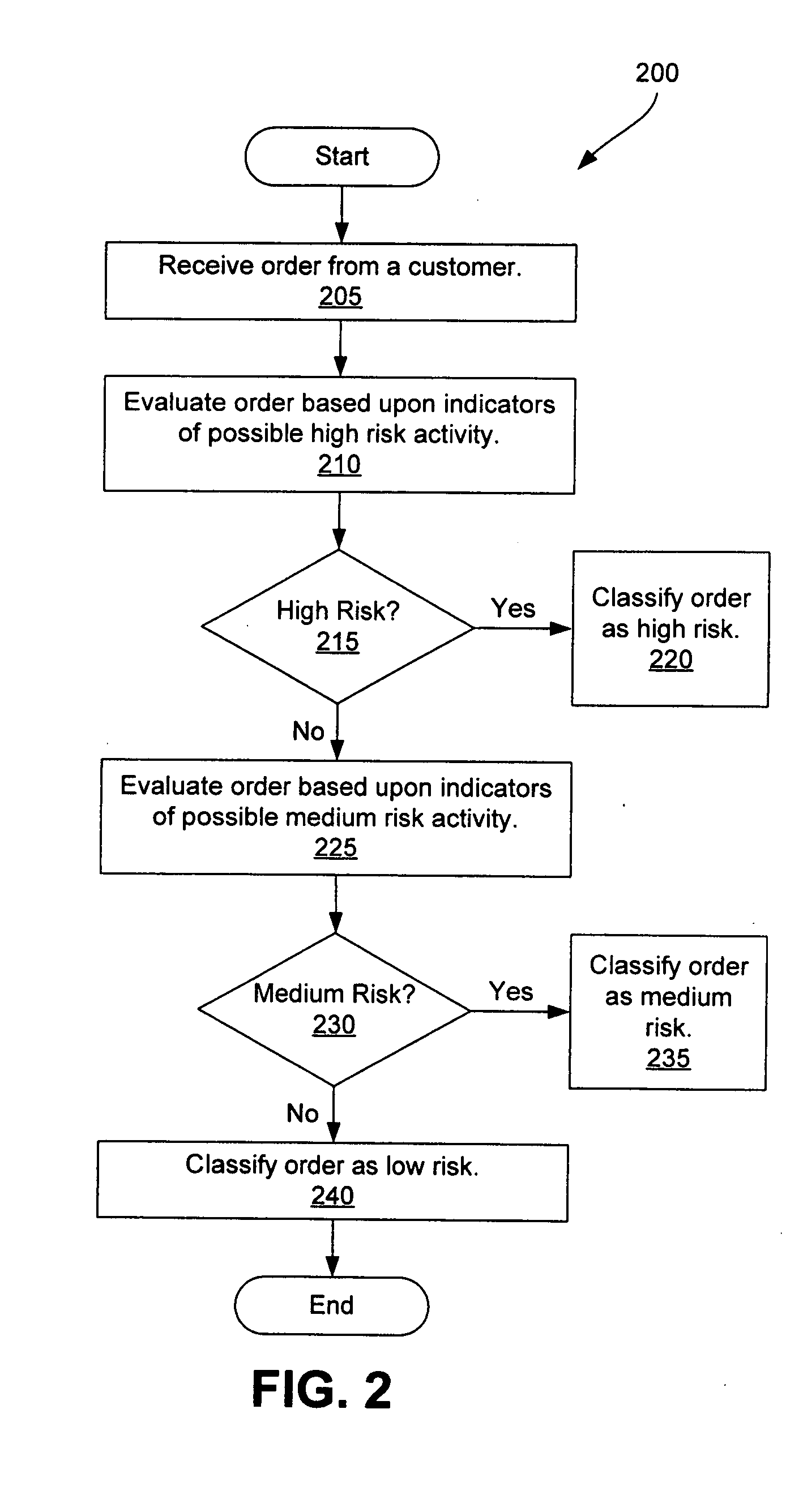
Order risk determination
InactiveUS20050108178A1Readily apparentPayment architectureBuying/selling/leasing transactionsMedium RiskLower risk
In one embodiment, the invention provides a method of determining a risk for fraud for an order, including: receiving an order from a customer; evaluating an order based upon indicators of possible high risk activities; if the order is not classified as a high risk order, then evaluating the order based upon indicators of possible medium risk activities; and if the order is not classified as a medium risk activity, then classifying the order as a low risk order.
Owner:HEWLETT PACKARD CO
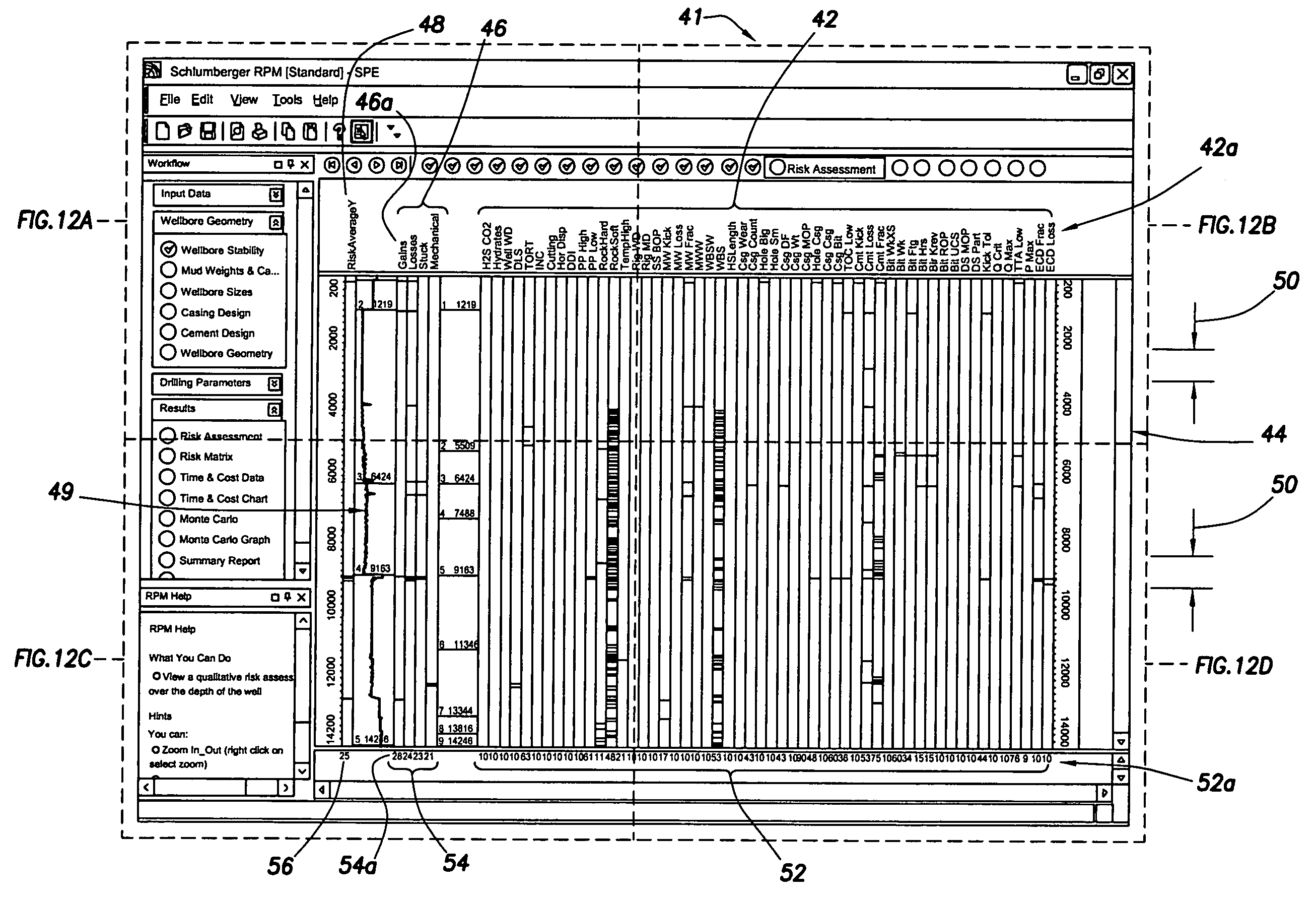
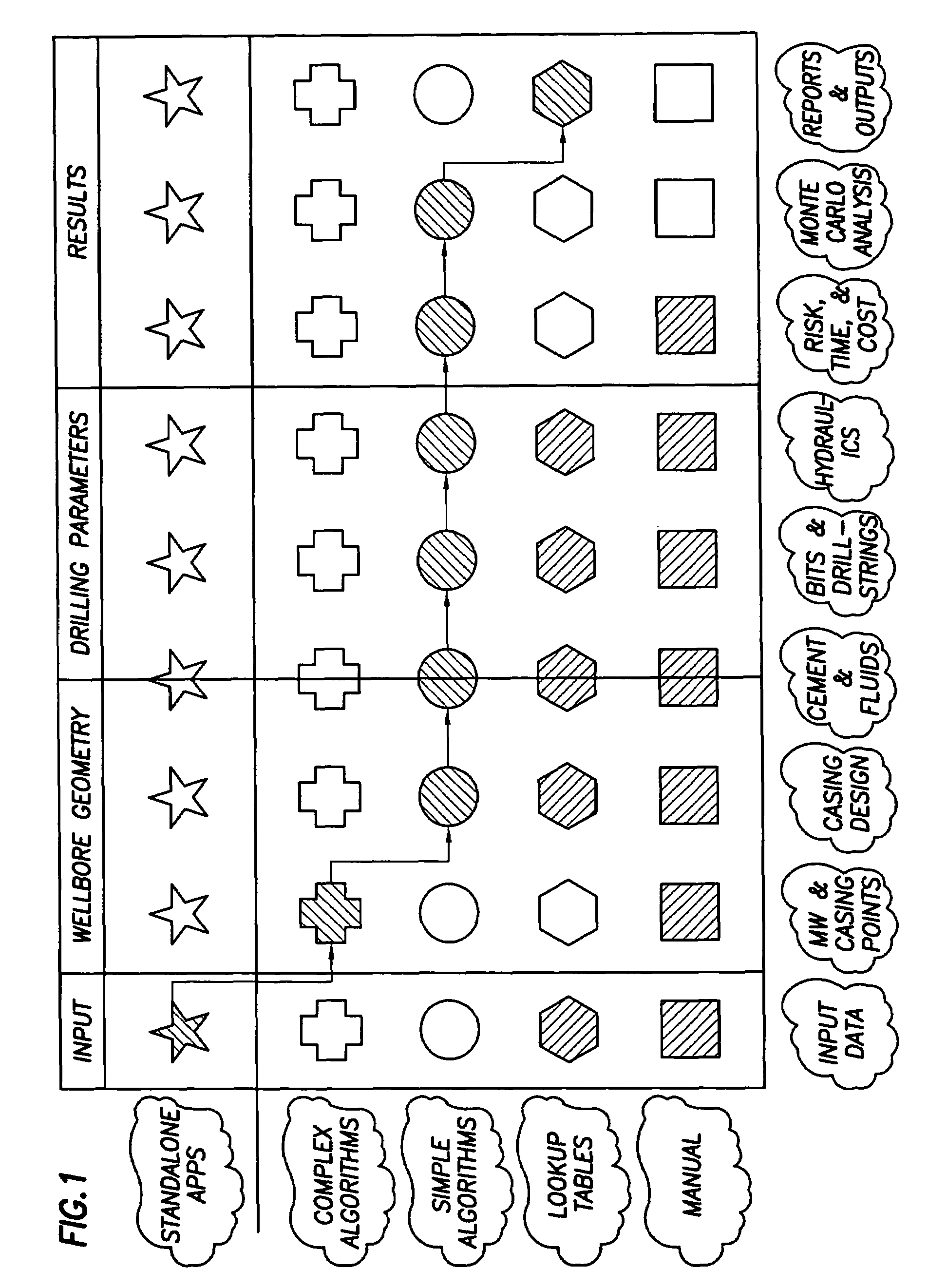
Method and apparatus and program storage device adapted for visualization of qualitative and quantitative risk assessment based on technical wellbore design and earth properties
Owner:SCHLUMBERGER TECH CORP
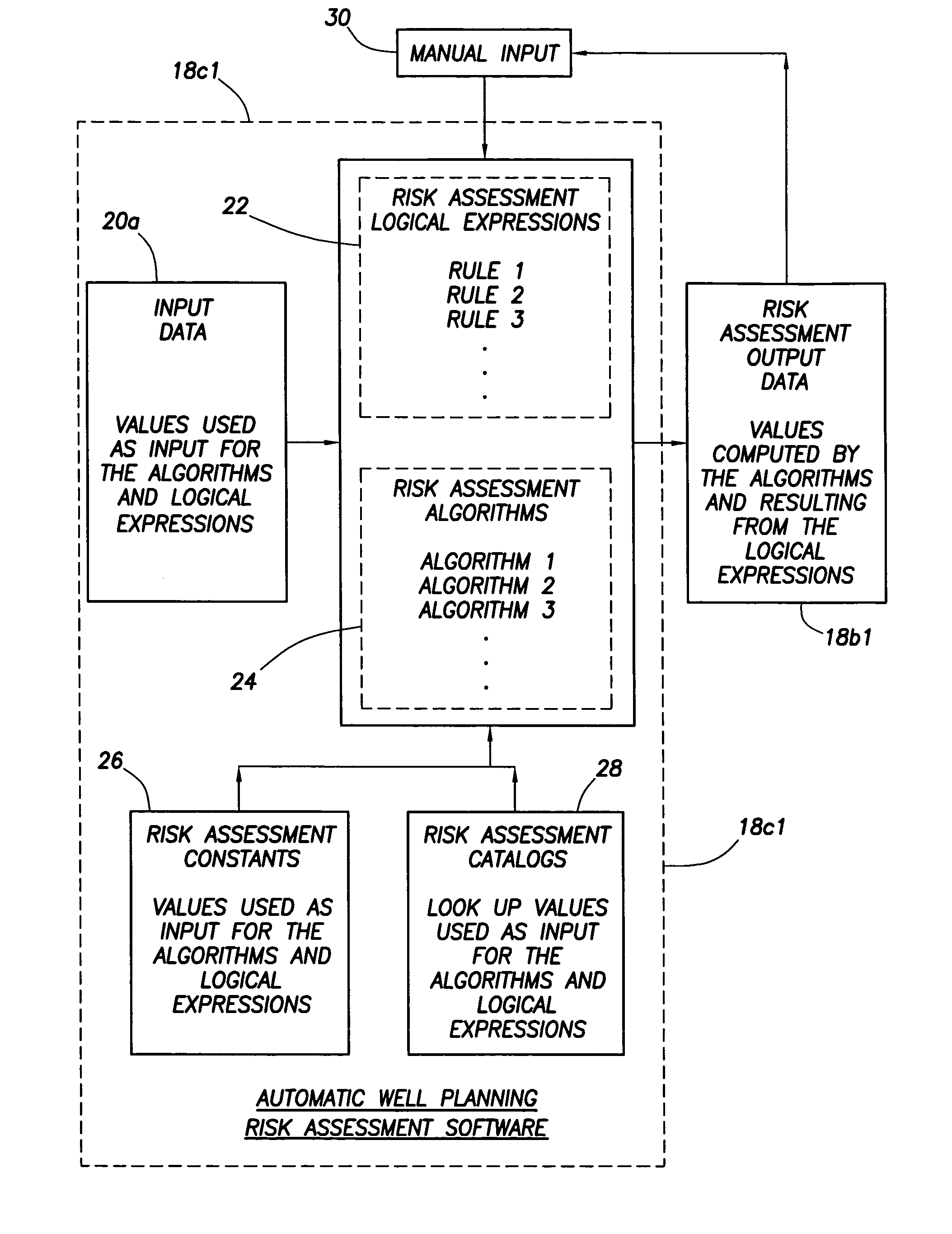
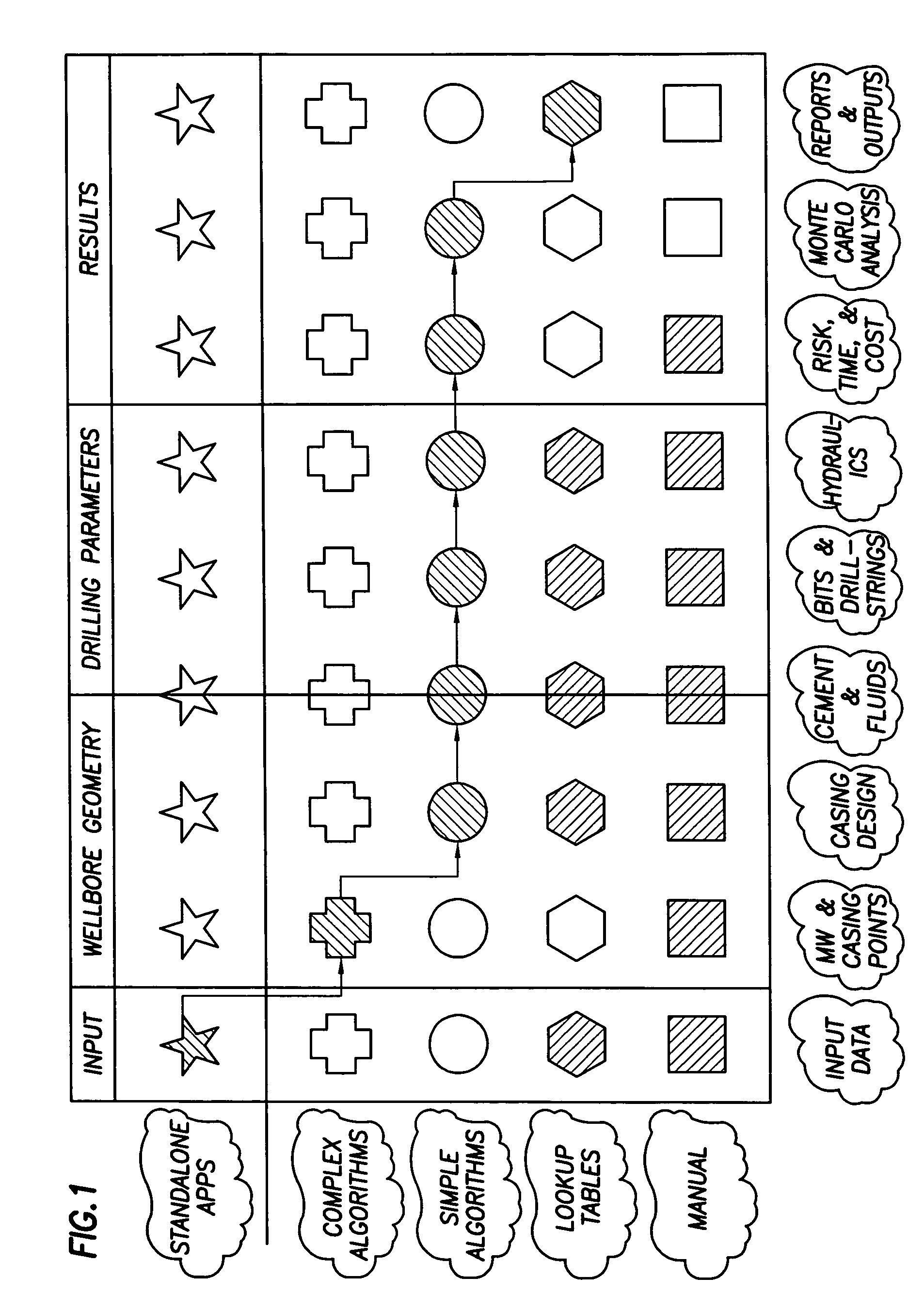
Method and apparatus and program storage device adapted for automatic qualitative and quantitative risk assessment based on technical wellbore design and earth properties
A Software System, known as an Automatic Well Planning Risk Assessment Software System, is adapted to determine and display risk information in response to a plurality of input data by: receiving the plurality of input data, the input data including a plurality of input data calculation results; comparing each calculation result of the plurality of input data calculation results with each logical expression of a plurality of logical expressions; ranking by the logical expression the calculation result; and generating a plurality of ranked risk values in response thereto, each of the plurality of ranked risk values representing an input data calculation result that has been ranked by the logical expression as either a high risk or a medium risk or a low risk; generating the risk information in response to the plurality of ranked risk values; and displaying the risk information.
Owner:SCHLUMBERGER TECH CORP
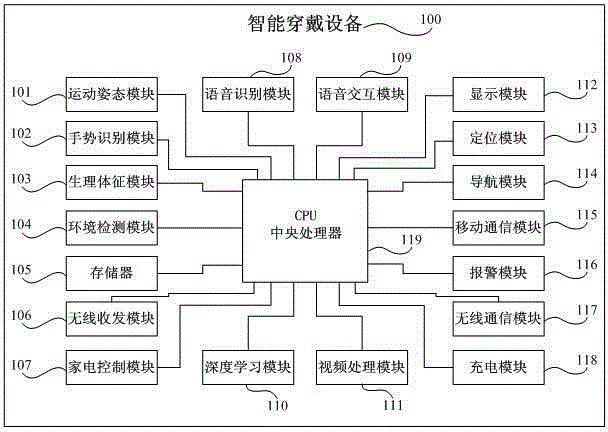
Intelligent health service system and alarming reliable detection method
ActiveCN104799826AEffective filteringReduce the impactSensorsTelemetric patient monitoringRisk levelMedium Risk
The invention discloses an intelligent health service system and an alarming reliable detection method. The method comprises a falling detection method and a platform alarming method. The falling detection method comprises the following steps: collecting an accelerated speed and angular speed data of a wearer at fixed time, monitoring a parameter and recording a changing data sequence; judging if a falling process exceeds a falling threshold value thereof; if the falling process exceeds the falling threshold value, judging if heart rate is abnormal, and if the heart rate belongs to an abnormal scope, setting a high-risk-level falling alarm; otherwise, setting a medium-risk-level falling alarm; if the falling process does not exceed the falling threshold value, setting a low-risk-level falling alarm; sending a falling alarm event and a physiological sign data of the wearer to a cloud health service platform. An intelligent wearing device provided by the invention can accurately confirm if a serious falling event occurs, a mistakenly reported and low-influence falling event is effectively filtered, and the alarm answering and processing pressures of the cloud health service platform and seat mould are reduced.
Owner:江西托克马克科技有限公司
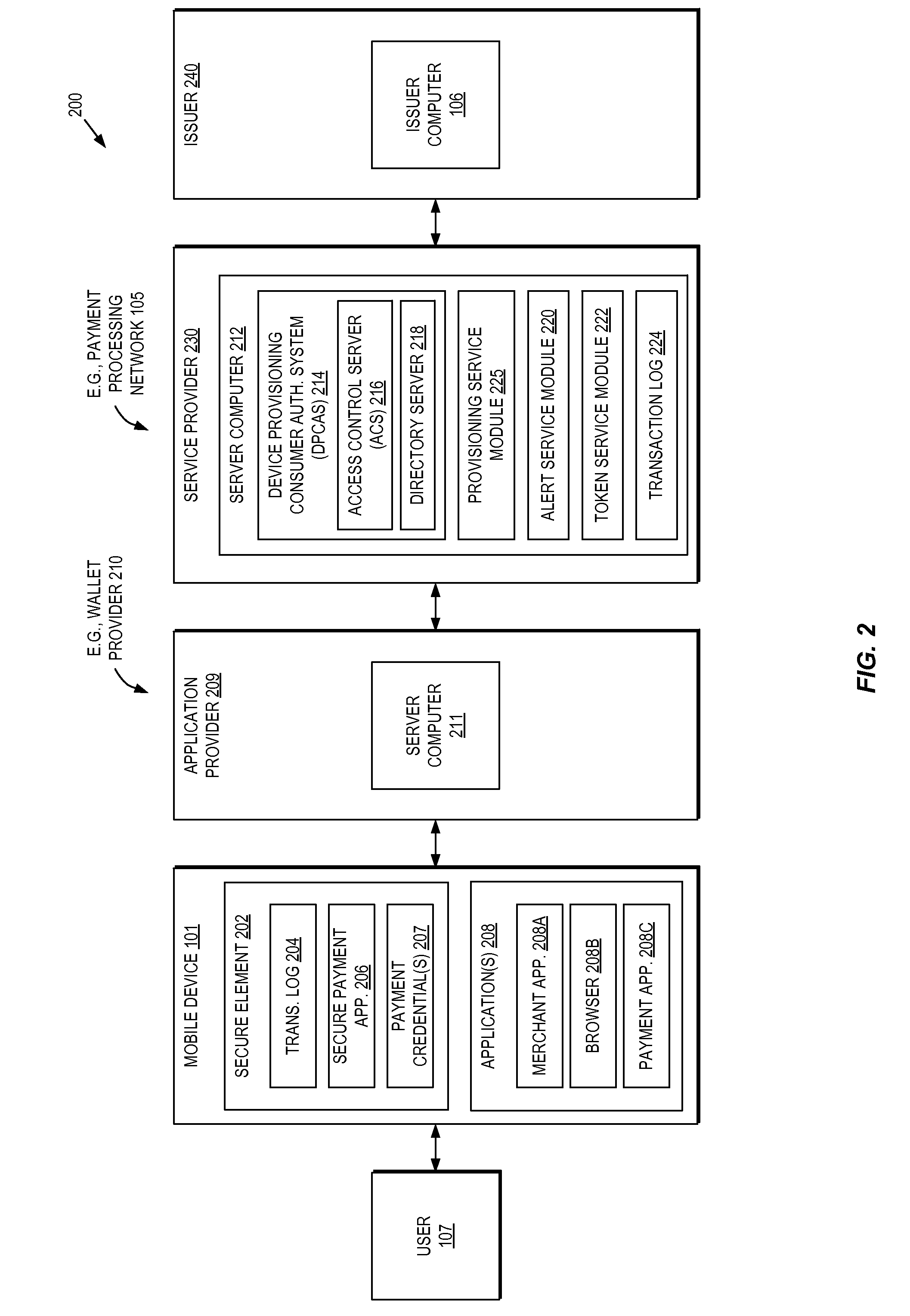
Secure Mobile Device Credential Provisioning Using Risk Decision Non-Overrides
Embodiments are directed to optimizing the secure provisioning of credentials to mobile devices through use of risk decision non-overrides. In some embodiments, a service provider receives a request from a wallet provider to provision a credential associated with an account to a mobile device. The request includes a first risk level associated with the provisioning. The service provider receives a second risk level associated with the provisioning request from an issuer of the account. Based upon determining that a non-override condition exists, the service provider uses the first risk level from the wallet provider and accordingly causes a user authentication to occur. A non-override condition may be determined based upon scenario indicators received within the provisioning request. In some embodiments, the non-override condition may be ignored when the first risk level indicates medium risk and the second risk level indicates high risk.
Owner:VISA INT SERVICE ASSOC
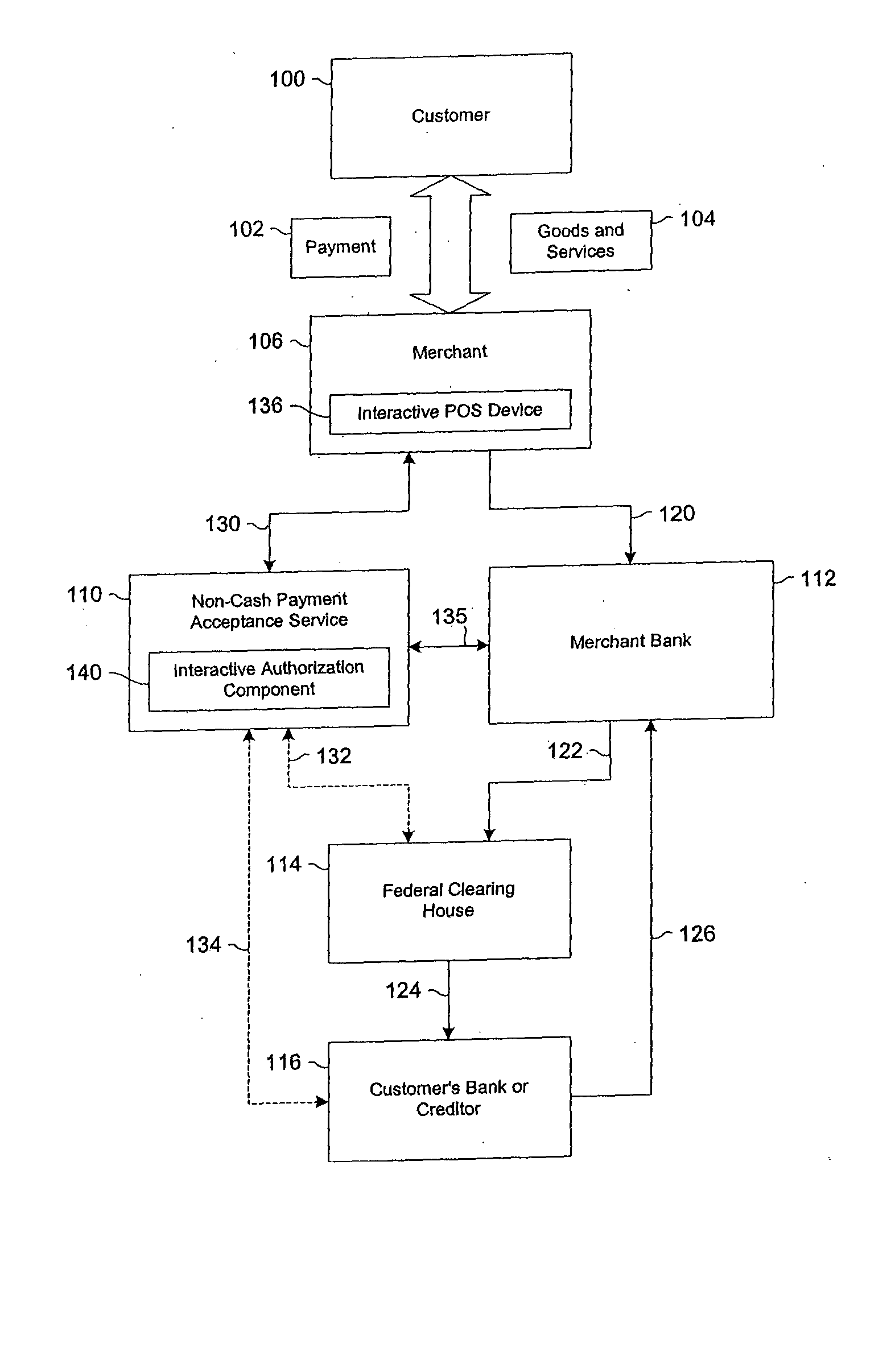
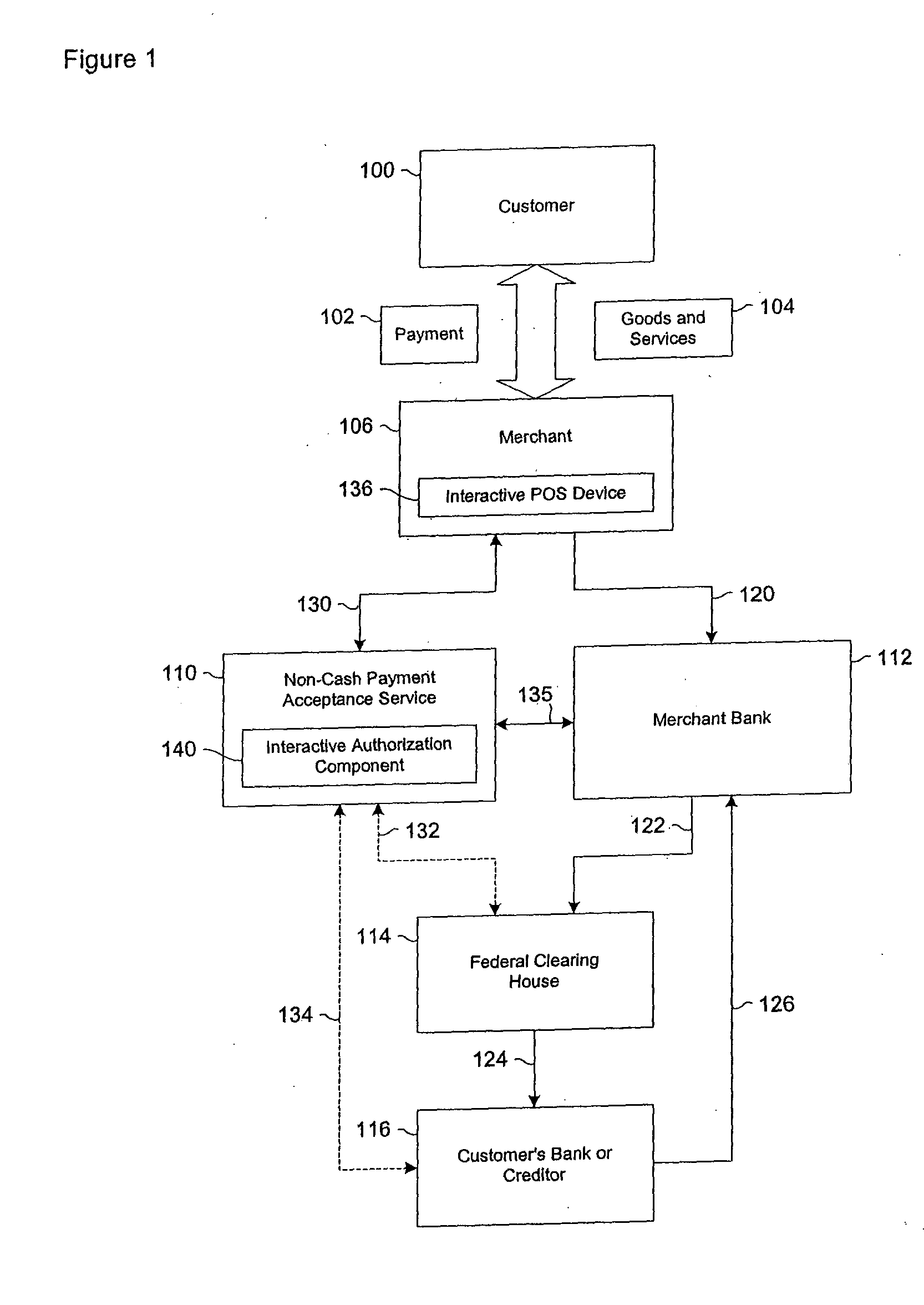
Data validation systems and methods for financial transactions
InactiveUS20050080717A1Satisfies needFinanceSpecial data processing applicationsData validationMedium Risk
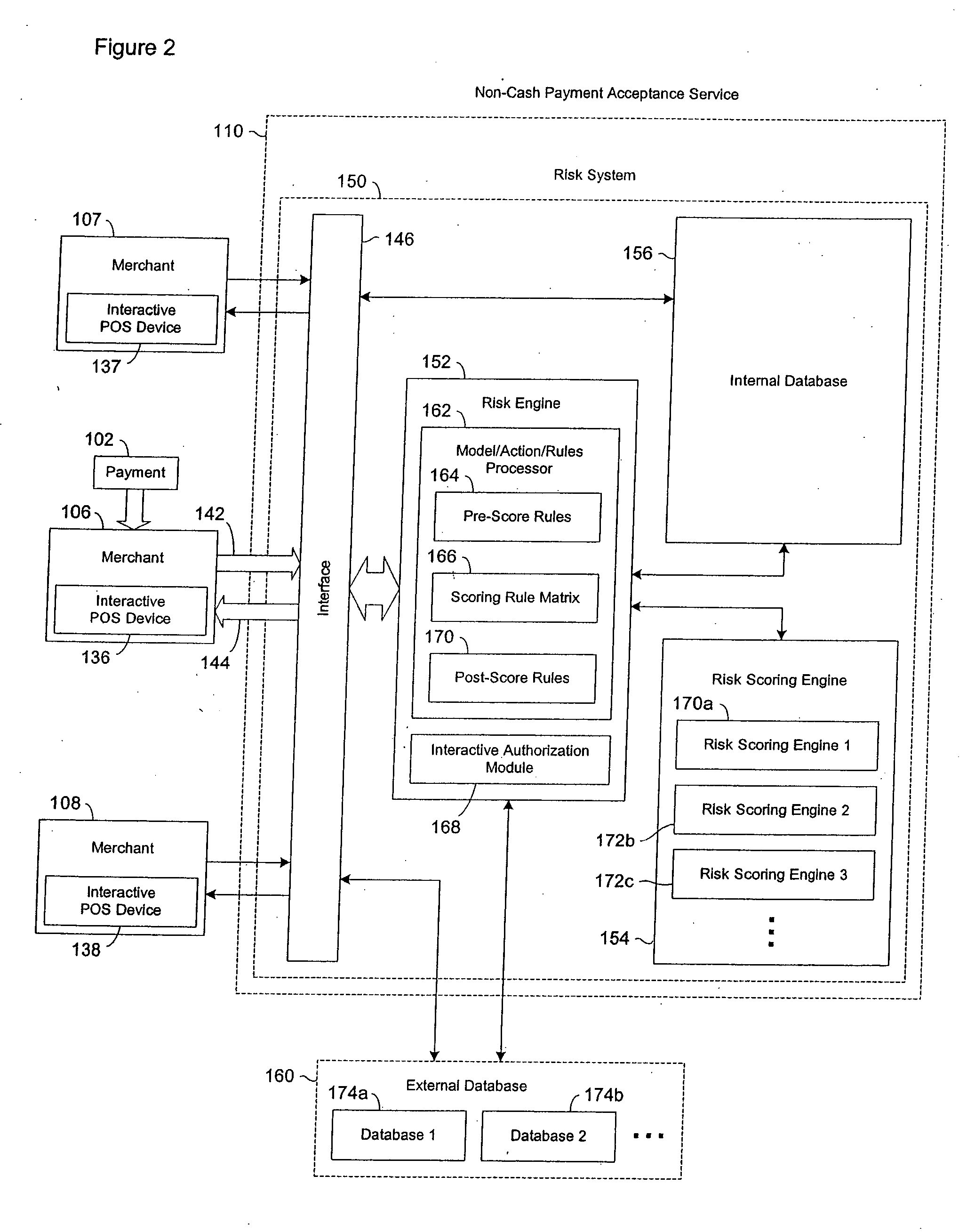
A risk system that performs a risk assessment of a financial transaction to obtain a risk score. Based on the risk score, the risk system may request additional transaction information from a customer and / or a merchant. The request is based at least in part on financial transactions that are of moderate risk to thereby provide a non-cash payment acceptance service with more information to further evaluate the financial transaction risks. Thus, moderately risky financial transactions, that are likely to benefit the non-cash payment acceptance service and the merchant that subscribes to the non-cash payment acceptance service, are authorized for increased profitability and customer satisfaction. Furthermore, the risk system may approve or authorize financial transactions that generally fail standard risk assessments that use a cut-off risk score to divide the financial transactions into either approved or declined groups. As a result, the risk system is capable of re-evaluating some of the moderate risk cases for the purpose of securing beneficial financial transactions.
Owner:FIRST DATA
Method and apparatus and program storage device adapted for automatic qualitative and quantitative risk assesssment based on technical wellbore design and earth properties
A Software System, known as an Automatic Well Planning Risk Assessment Software System, is adapted to determine and display risk information in response to a plurality of input data by: receiving the plurality of input data, the input data including a plurality of input data calculation results; comparing each calculation result of the plurality of input data calculation results with each logical expression of a plurality of logical expressions; ranking by the logical expression the calculation result; and generating a plurality of ranked risk values in response thereto, each of the plurality of ranked risk values representing an input data calculation result that has been ranked by the logical expression as either a high risk or a medium risk or a low risk; generating the risk information in response to the plurality of ranked risk values; and displaying the risk information.
Owner:SCHLUMBERGER TECH CORP
Secure mobile device credential provisioning using risk decision non-overrides
Embodiments are directed to optimizing the secure provisioning of credentials to mobile devices through use of risk decision non-overrides. In some embodiments, a service provider receives a request from a wallet provider to provision a credential associated with an account to a mobile device. The request includes a first risk level associated with the provisioning. The service provider receives a second risk level associated with the provisioning request from an issuer of the account. Based upon determining that a non-override condition exists, the service provider uses the first risk level from the wallet provider and accordingly causes a user authentication to occur. A non-override condition may be determined based upon scenario indicators received within the provisioning request. In some embodiments, the non-override condition may be ignored when the first risk level indicates medium risk and the second risk level indicates high risk.
Owner:VISA INT SERVICE ASSOC
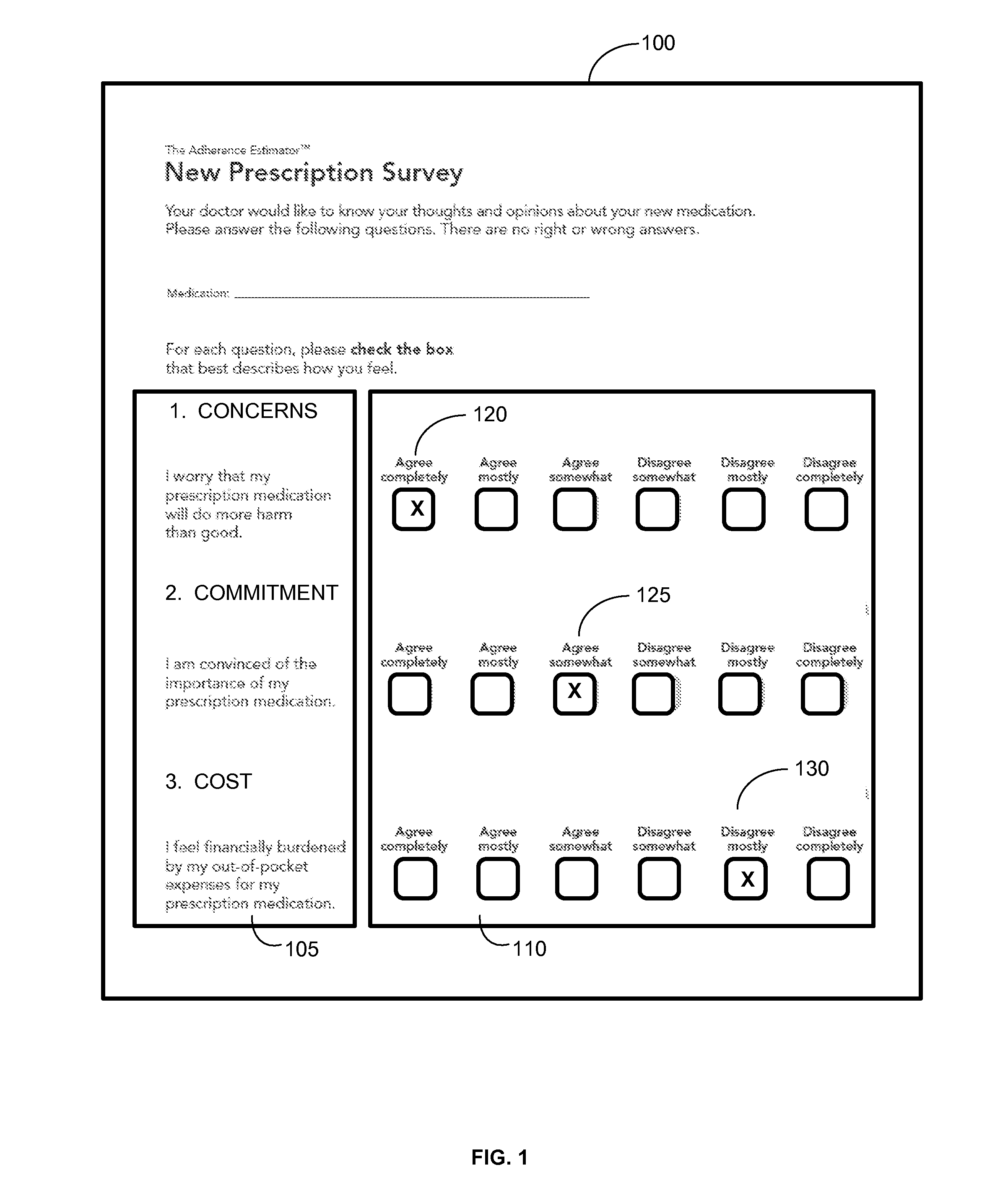
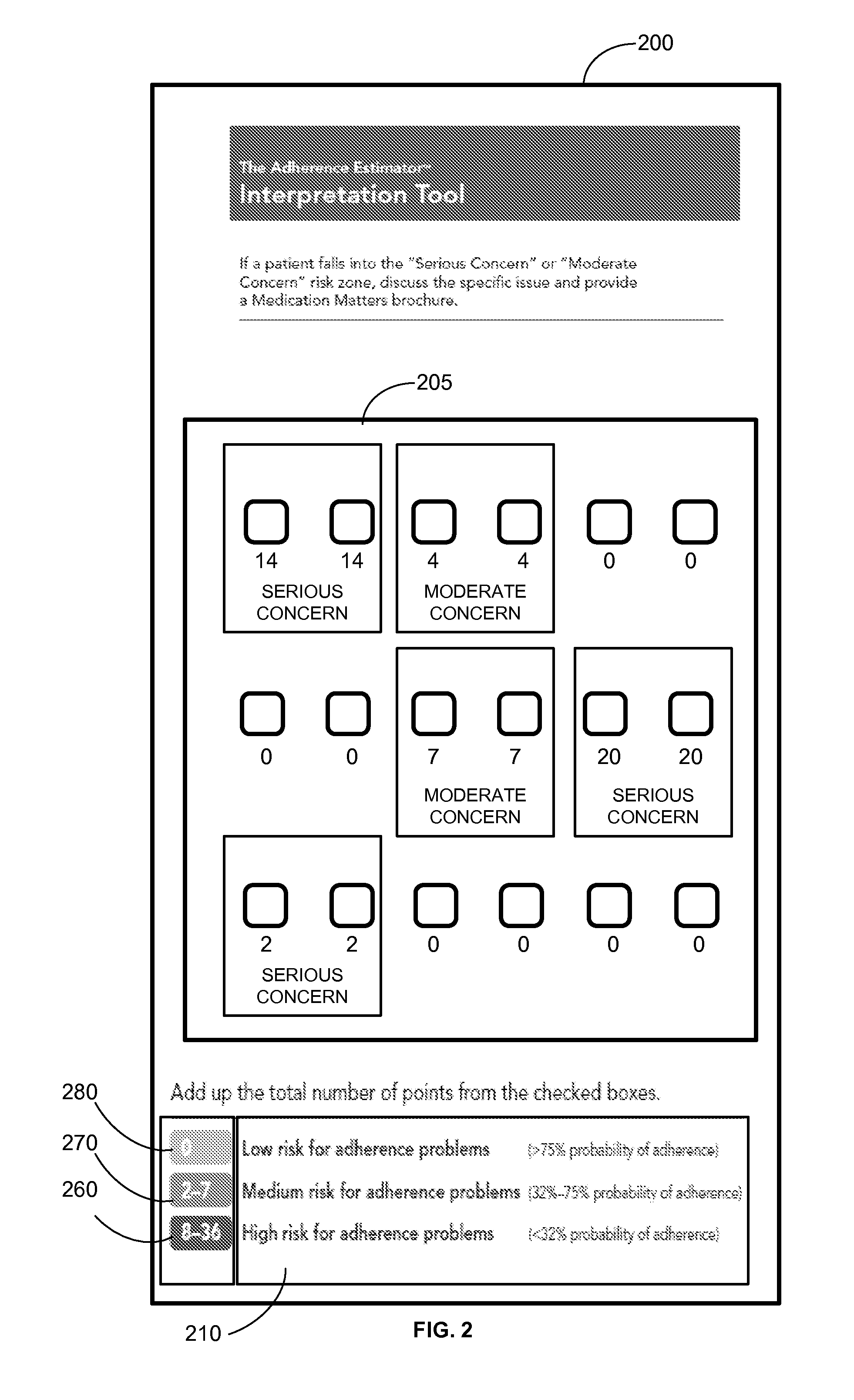
Devices and methods for determining a patient's propensity to adhere to a medication prescription
Devices and methods for determining risk groups for patients according to their propensity to adhere to a medication prescription The “Adherence Estimator™” device of the present invention comprises an incremented scale of potential total scores, a prescription survey having questions directed to assessing a patient's beliefs in respect to no more than three domains, the three domains being commitment, concerns and cost, a response recording tool, a scoring matrix and an interpretation tool Embodiments of the invention, which may be implemented in electronic or non-electronic forms, automatically score and interpret responses to the prescription survey questions in order to determine and assign patients to a high risk group, a medium risk group or a low risk group Non-electronic devices of the invention may be constructed from a variety of materials, including without limitation, paper, paper-based products, plastic, wood or metal.
Owner:MERCK SHARP & DOHME CORP
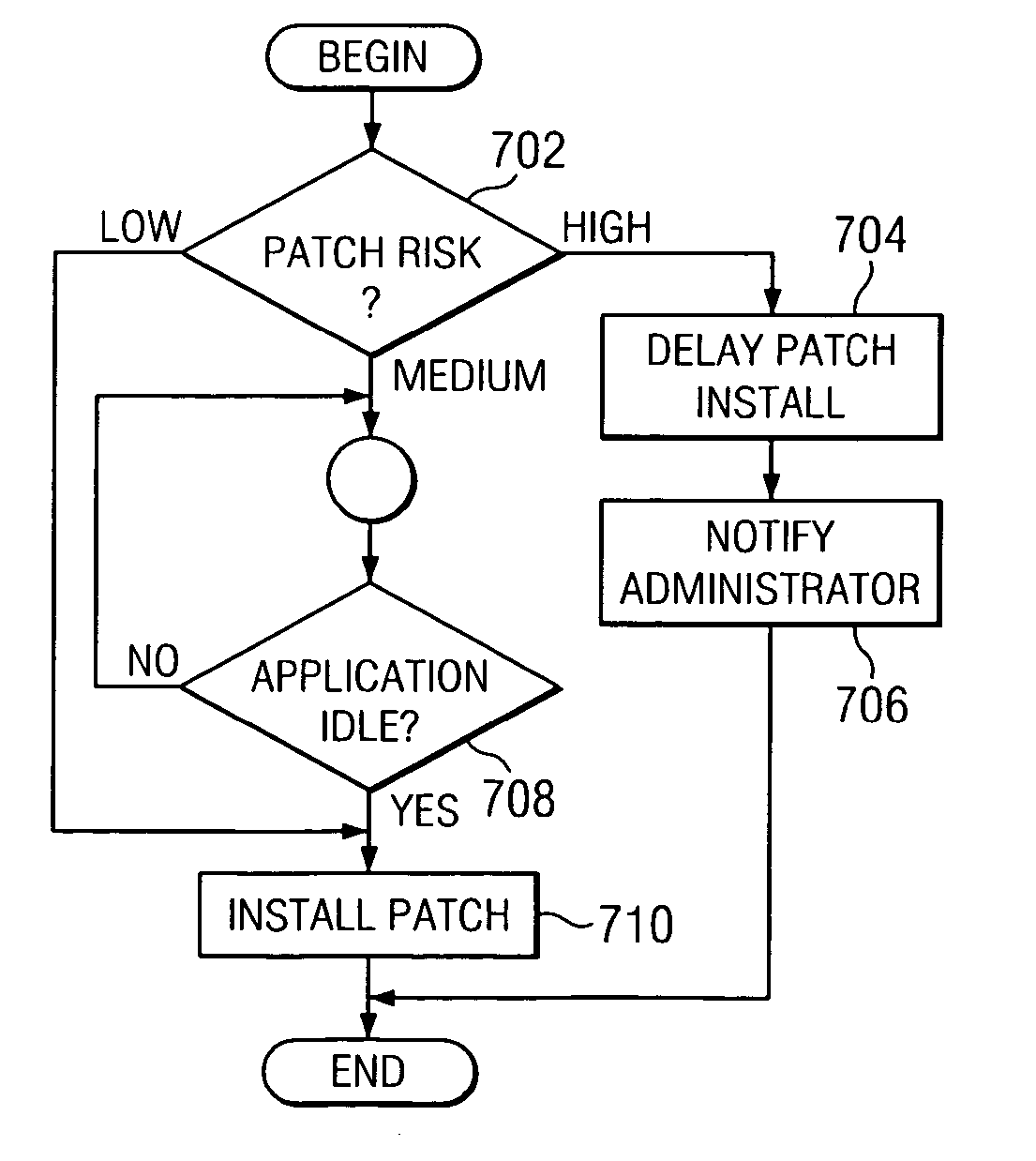
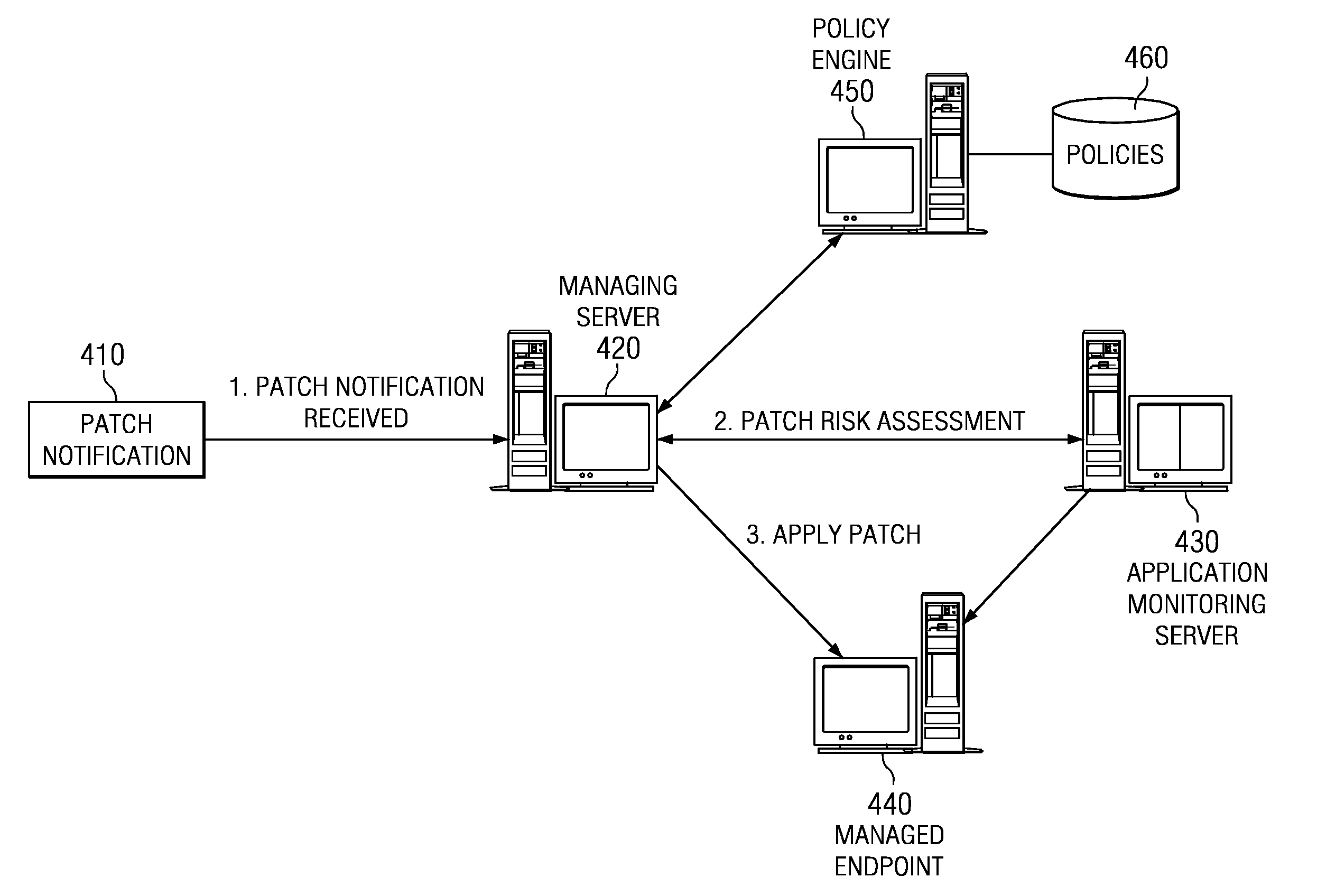
Method, apparatus, and program product for autonomic patch deployment based on autonomic patch risk assessment and policies
InactiveUS20070033635A1Recognize disadvantageComputer security arrangementsSpecial data processing applicationsMedium RiskLower risk
An automatic patch deployment system is provided that deploys a patch according to an assessed risk and a policy. The policy may specify actions to be taken to deploy the patch for different categories of risk. The automatic patch deployment system receives a patch notification, an assessment of the risk, and the policy and deploys the patch accordingly. For example, installation of a patch may be indefinitely delayed for high risk patches, rescheduled for medium risk patches, or installed immediately for low risk patches.
Owner:IBM CORP
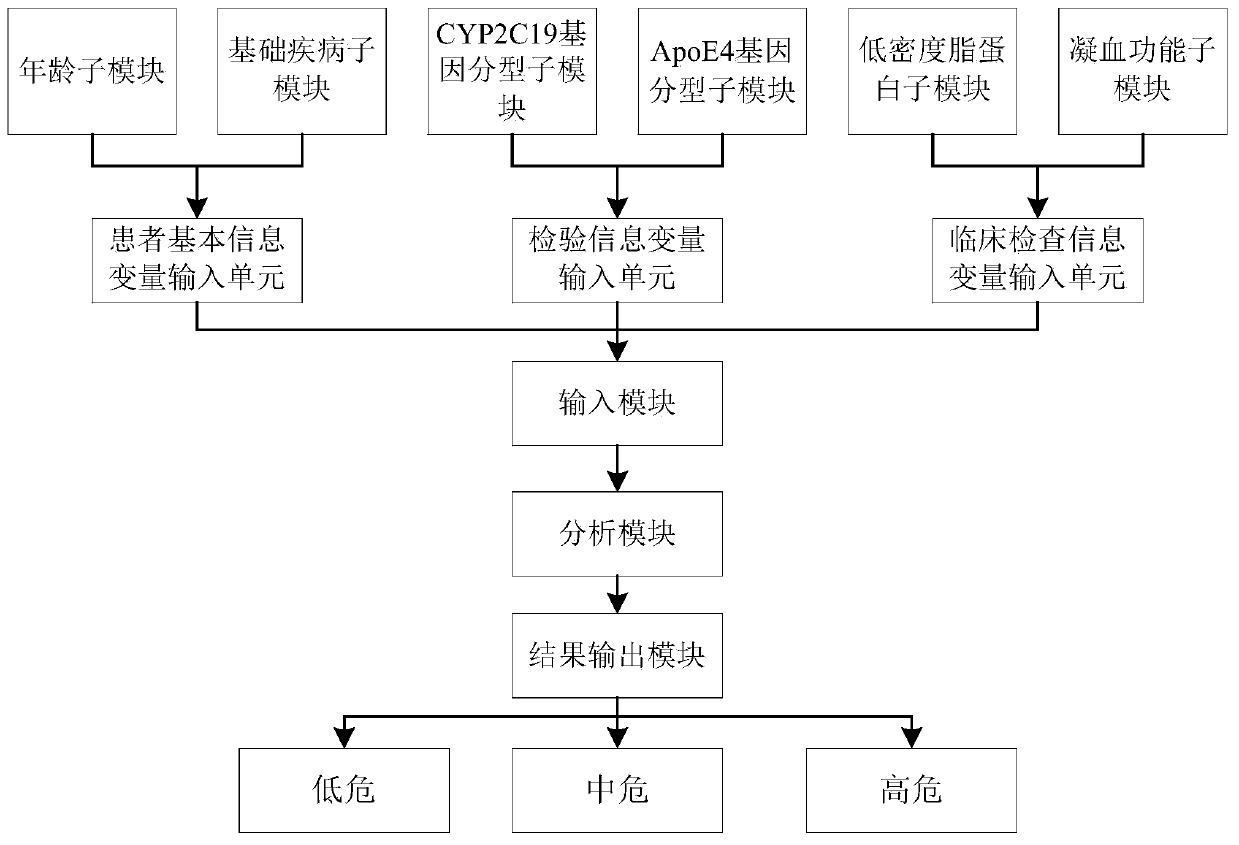
Clinical cerebral infarction patient recurrence risk early warning scoring visual model system and evaluation method thereof
InactiveCN110634573AEasy to operateEasy to handleMedical simulationHealth-index calculationLow risk groupLower risk
The invention discloses a clinical cerebral infarction patient recurrence risk early warning scoring visual model system. The system comprises an input module, an analysis module and a result output module. The invention also discloses an evaluation method of the clinical cerebral infarction patient recurrence risk early warning scoring visual model system. A clinical cerebral infarction patient recurrence risk evaluation nomogram is concise, popular and easy to understand and convenient for clinicians and patients to operate, and a current cerebral infarction recurrence risk of the patients is predicted. And meanwhile, high-risk, medium-risk and low-risk groups can be clearly distinguished according to patient risk scores calculated by a risk scoring formula in the model so that the clinicians are assisted to formulate an efficient treatment scheme. In the invention, a doctor and the patient are guided to evaluate early warning scores of the clinical cerebral infarction patient recurrence risk in combination with a statistical method, and patient data acquisition is verified through a corresponding mathematical statistical method so that the doctor and the patient can quickly grasp the clinical cerebral infarction patient recurrence risk and provide early warning information.
Owner:南昌大学第一附属医院
Method, apparatus, and program product for autonomic patch deployment based on autonomic patch risk assessment and policies
An automatic patch deployment system is provided that deploys a patch according to an assessed risk and a policy. The policy may specify actions to be taken to deploy the patch for different categories of risk. The automatic patch deployment system receives a patch notification, an assessment of the risk, and the policy and deploys the patch accordingly. For example, installation of a patch may be indefinitely delayed for high risk patches, rescheduled for medium risk patches, or installed immediately for low risk patches.
Owner:IBM CORP
Method for evaluating balance capacity of old people
InactiveCN106618487APrevent fallingEffective interventionsDiagnostic recording/measuringSensorsLow risk groupDynamic balance
The invention belongs to the technical field of rehabilitation medicine protection and particularly relates to a method for evaluating the balance capacity of old people. The method includes the following steps that A, experimental subjects are grouped into a normal group, a low-risk group, a middle-risk group and a high-risk group according an old people balance capacity test scale, plantar pressure distribution generated when the old people sit up is detected through a plantar pressure distribution detecting system, and cushion pressure generated when the old people sit up is detected through a cushion sensor; B, the old people walk on a three-dimensional dynamometry table, and kinematics parameters of the gaits generated when the old people walk are acquired through the three-dimensional dynamometry table, wherein the kinematics parameters comprise the pressure and torque in the foot vertical direction, the pressure and torque in the foot front-and-back direction and the pressure and torque in the foot inside and outside directions; C, sample entropies of the plantar pressure and torque during sitting up and walking are subjected to statistic analysis, the significant difference of the correlativity between the variable sample entropies is found, and an objective evaluation standard is obtained. The method has the advantage of being capable of evaluating dynamic balance of the old people.
Owner:BEIJING RES CENT OF URBAN SYST ENG
Novel landslide risk evaluation method
ActiveCN110489860AIn line with objective realitySuitable for real-time monitoringData processing applicationsSpecial data processing applicationsRelational modelLower risk
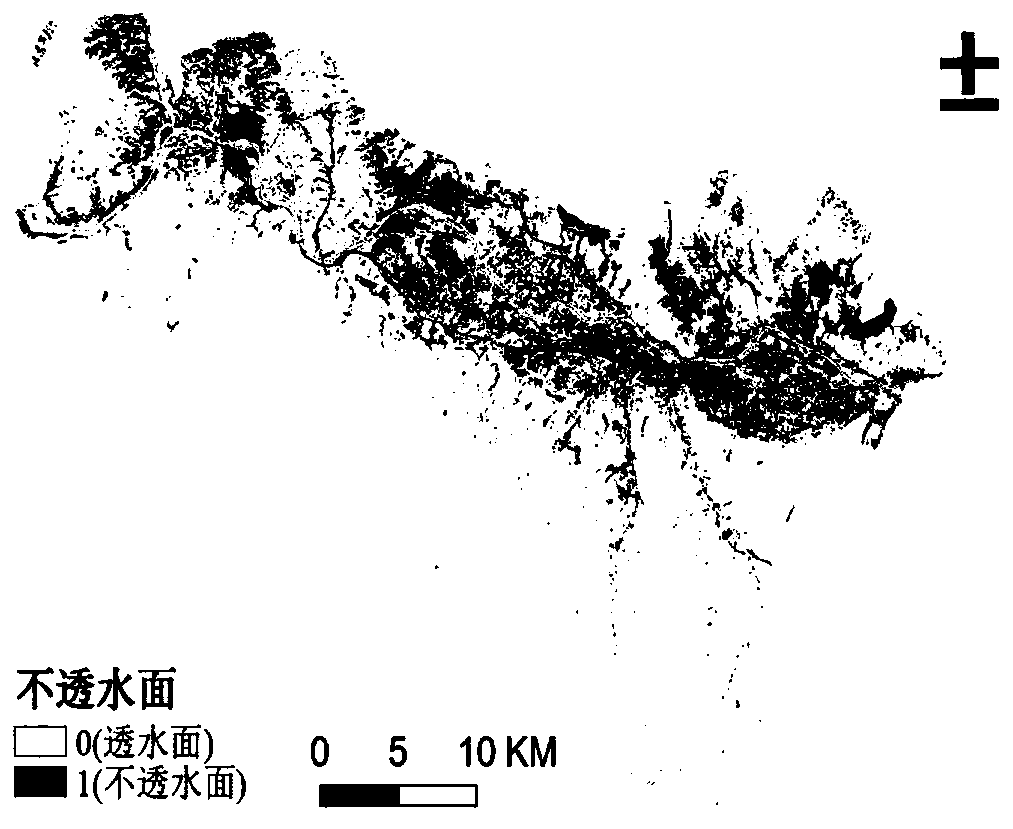
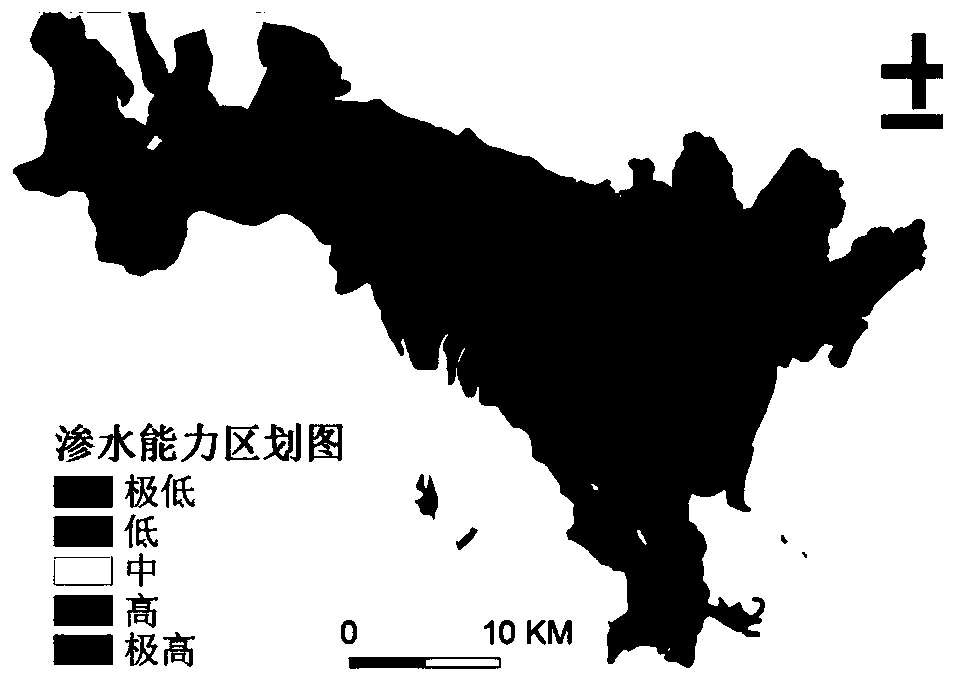
The invention discloses a novel landslide risk evaluation method, and the method comprises the following steps: S1, carrying out the statistics of effective rainfall, extracting impervious surface data, and building a water seepage capability model according to the quantitative relation among the rainfall, the impervious surface data and an infiltration relation; S2, taking the gradient, the slopedirection, the water seepage capability index, the vegetation index and the road influence as parameters, and selecting related data of a plurality of points where landslide occurs and does not occurto train the model; and S3, carrying out model construction by using a Logistic regression function to obtain landslide risk divisions, and dividing the landslide risk levels into five risk levels, that is, an extremely low risk level, a low risk level, a medium risk level, a high risk level and an extremely high risk level. According to the method, the rainfall parameters are introduced into theinfiltration relation model, the corresponding landslide risk regionalization map is displayed in real time according to different rainfall, and a certain guiding effect is provided for landslide prevention. Compared with a traditional slope model and a change model for monitoring vertical displacement and horizontal displacement of a region, the landslide risk evaluation model is more suitable for large-scale real-time monitoring.
Owner:LANZHOU JIAOTONG UNIV
Embedded system firmware security analysis method and system
The invention discloses an embedded system firmware security analysis method and system, wherein the evaluation steps comprise determining a factor set, determining a comment set, determining weightsof each factor, calculating relative weights between evaluation indexes and comprehensive evaluation, and determining the factor set, that is, an evaluation index system set U. For example, a TROMML tool is used to analyze firmware, and the firmware analysis report lists 13 main vulnerability threats U, and determining that the evaluation value of each indicator is different, so that the evaluation value of each indicator will often form a different level. For example, the evaluation of safety grade has super high risk, high risk, medium risk, low risk, safety, etc. A collection of different decisions is called a set of comments.
Owner:NAT COMP NETWORK & INFORMATION SECURITY MANAGEMENT CENT
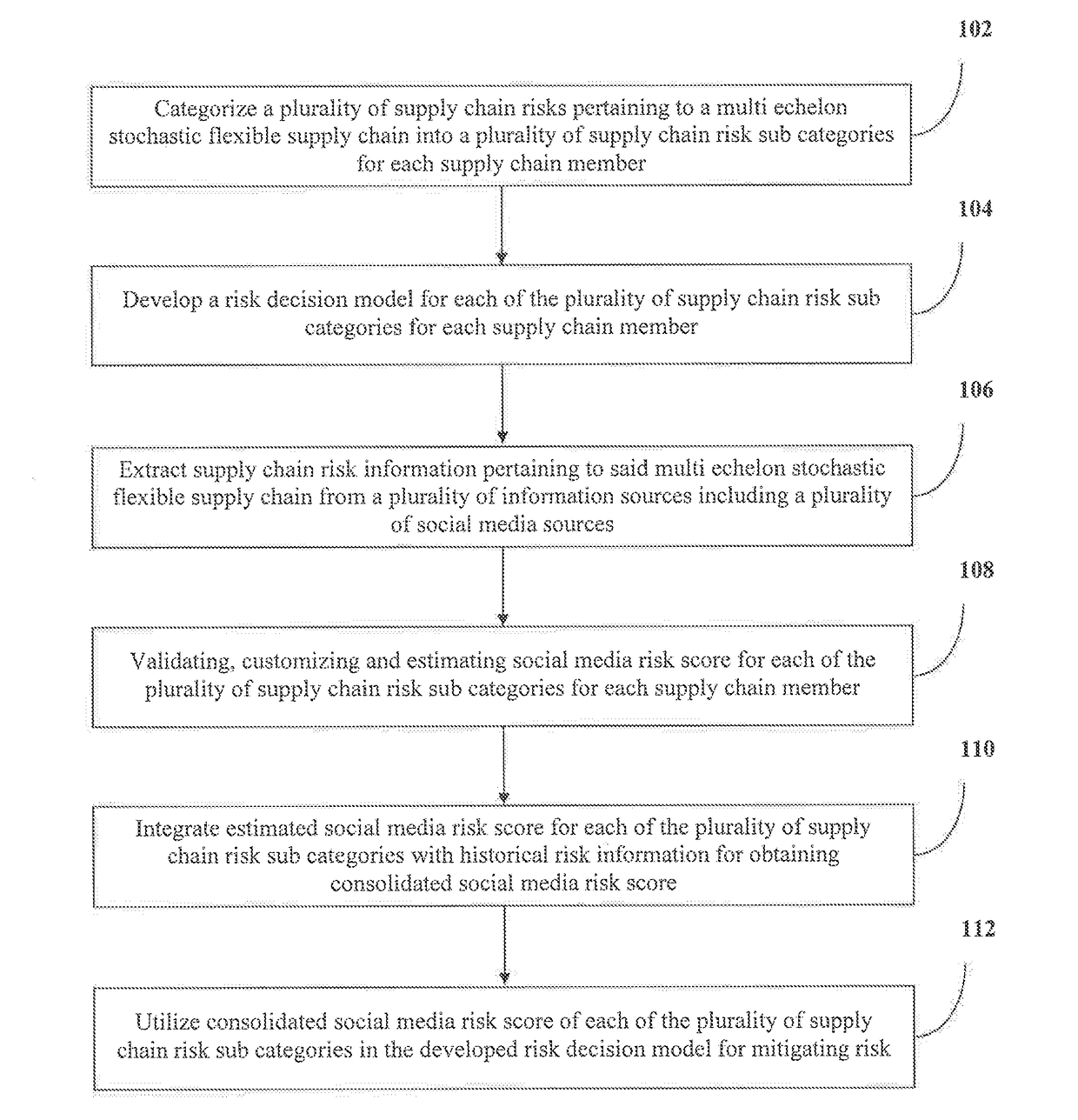
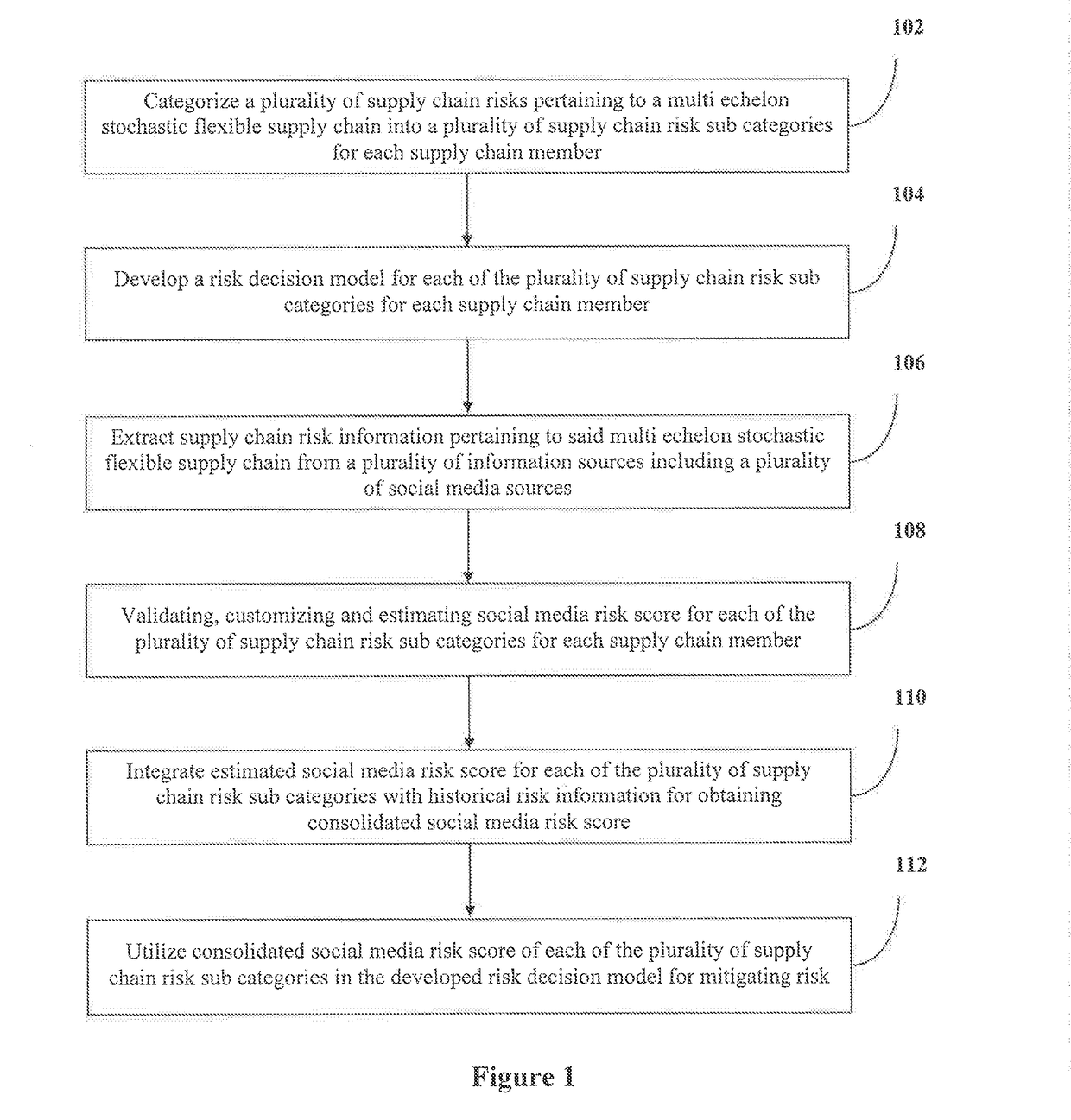
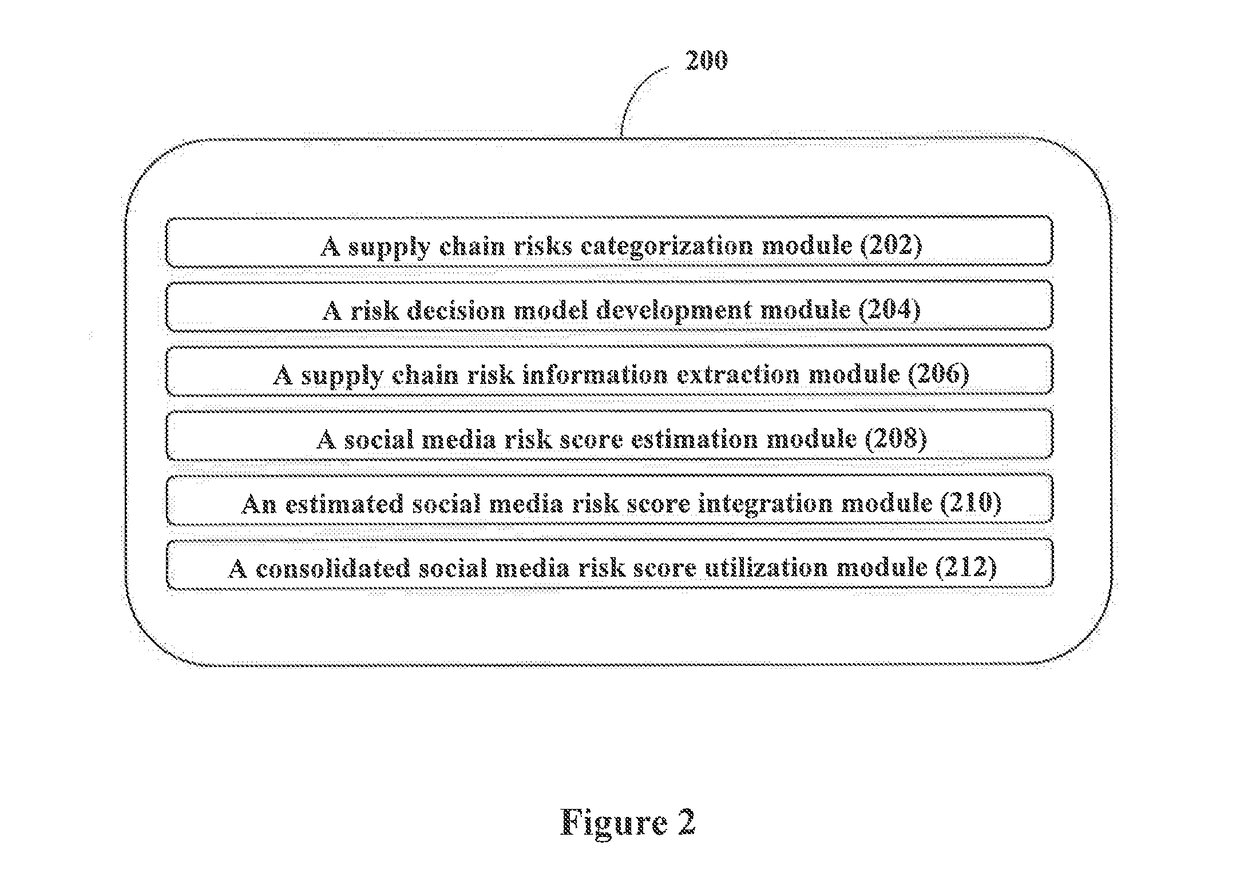
Method and system for mitigating risk in a supply chain
InactiveUS20170124495A1Reduce riskMinimizing uncertainty and disruptionResourcesMedium RiskSocial media
A method and system is provided for mitigating risk in a supply chain. The present application provides a method and system for mitigating risk in a multi echelon stochastic flexible supply chain, comprises categorizing a plurality of supply chain risks pertaining into a plurality of supply chain risk sub categories; developing a risk decision model for each of the plurality of supply chain risk sub categories; extracting supply chain risk information from a plurality of information sources including a plurality of social media information sources; validating, customizing and estimating social media risk score for each of the plurality of supply chain risk sub categories; integrating estimated social media risk score for each of the plurality of supply chain risk sub categories for each supply chain member; and utilizing consolidated social media risk score in the developed risk decision model for mitigating risk.
Owner:TATA CONSULTANCY SERVICES LTD
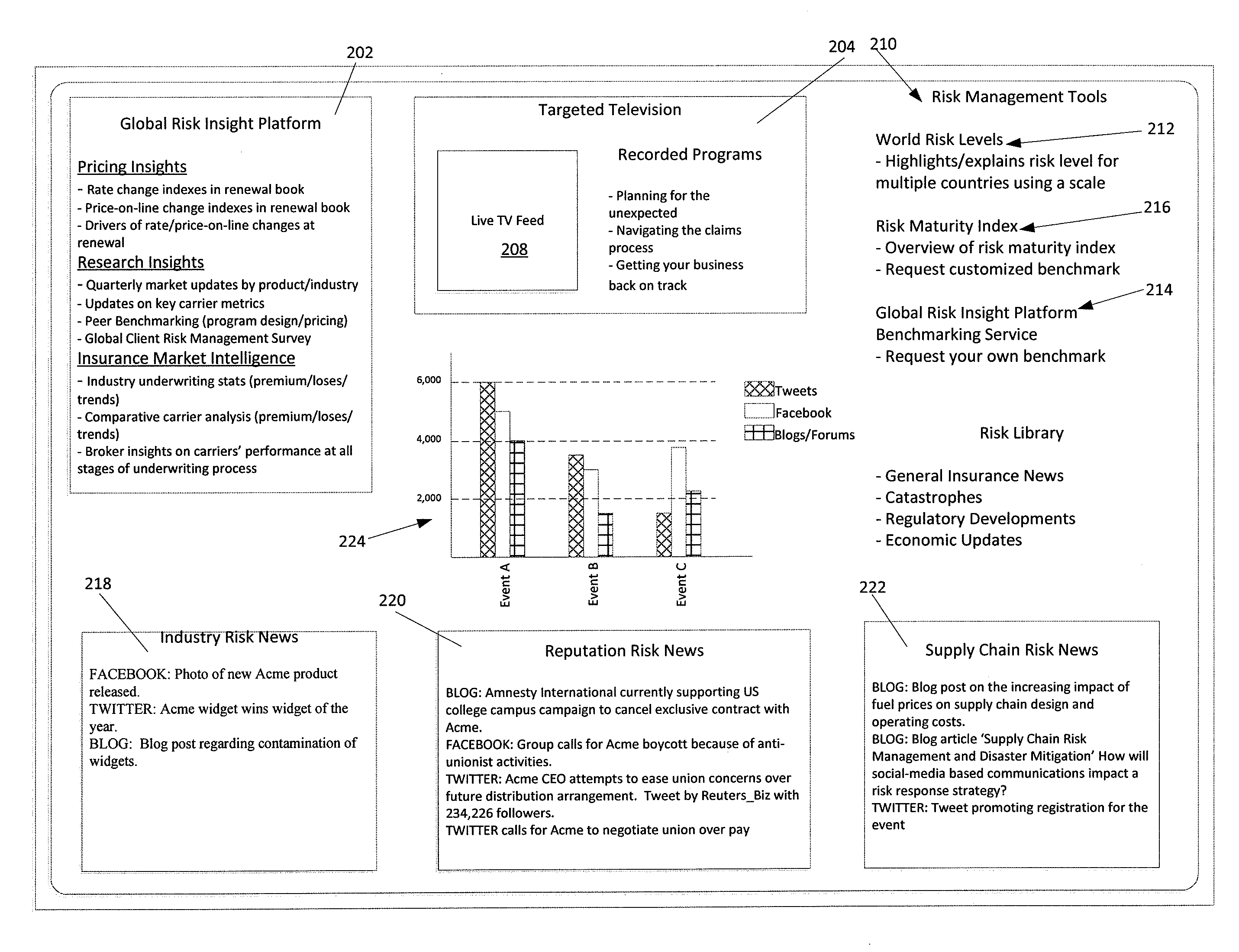
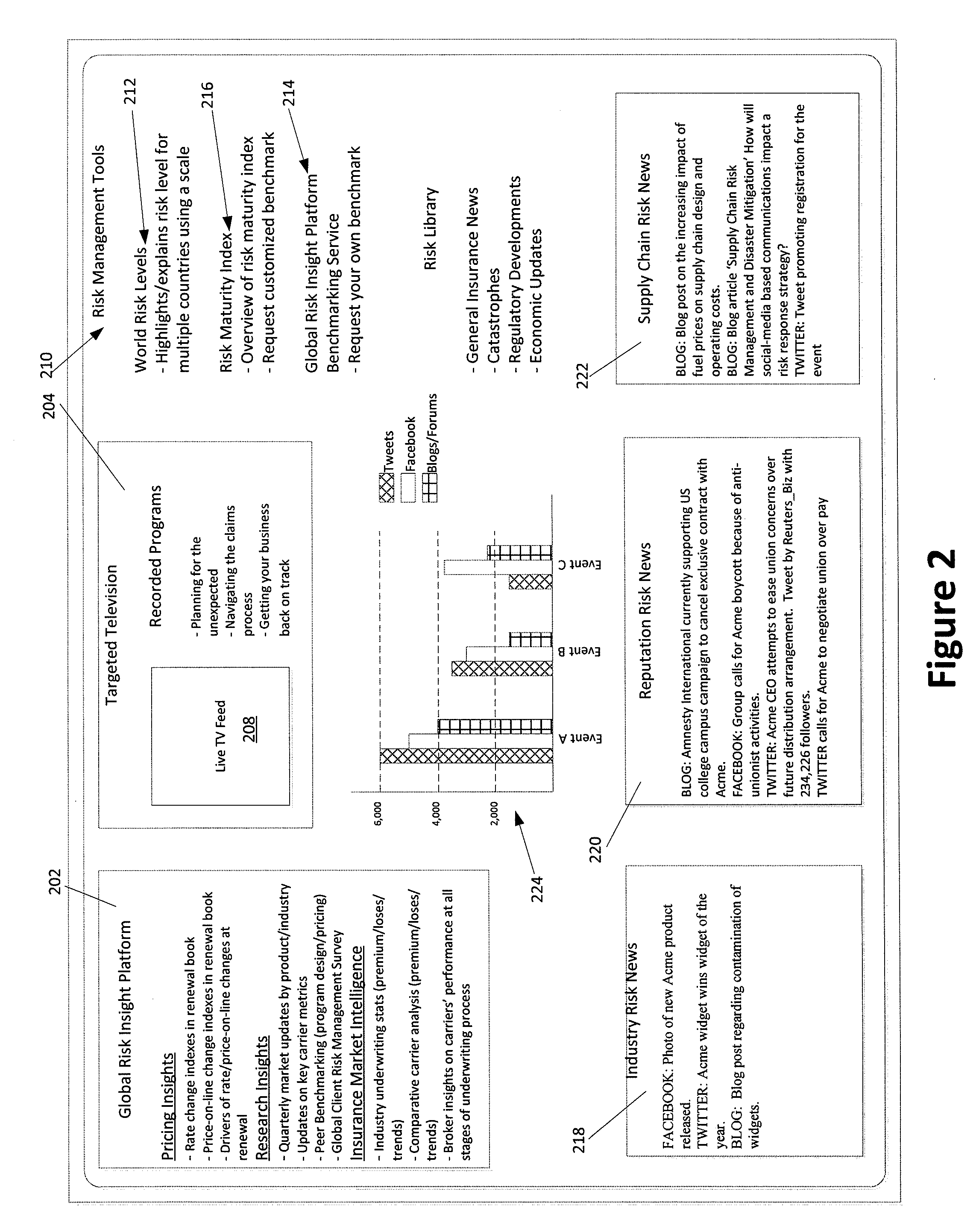
Risk Portal Including Social Media
Risk information portal systems and methods are provided. The portal allows business managers and others to track, organize and review risks. One or more social media news feeds may provide risk information that is found from social media sources. The portal may also provide research tools and interactive tools to locate industry pricing information. A risk maturity index tool also allows users to obtain a risk maturity score.
Owner:AON GLOBAL OPERATIONS LTD SINGAPORE BRANCH
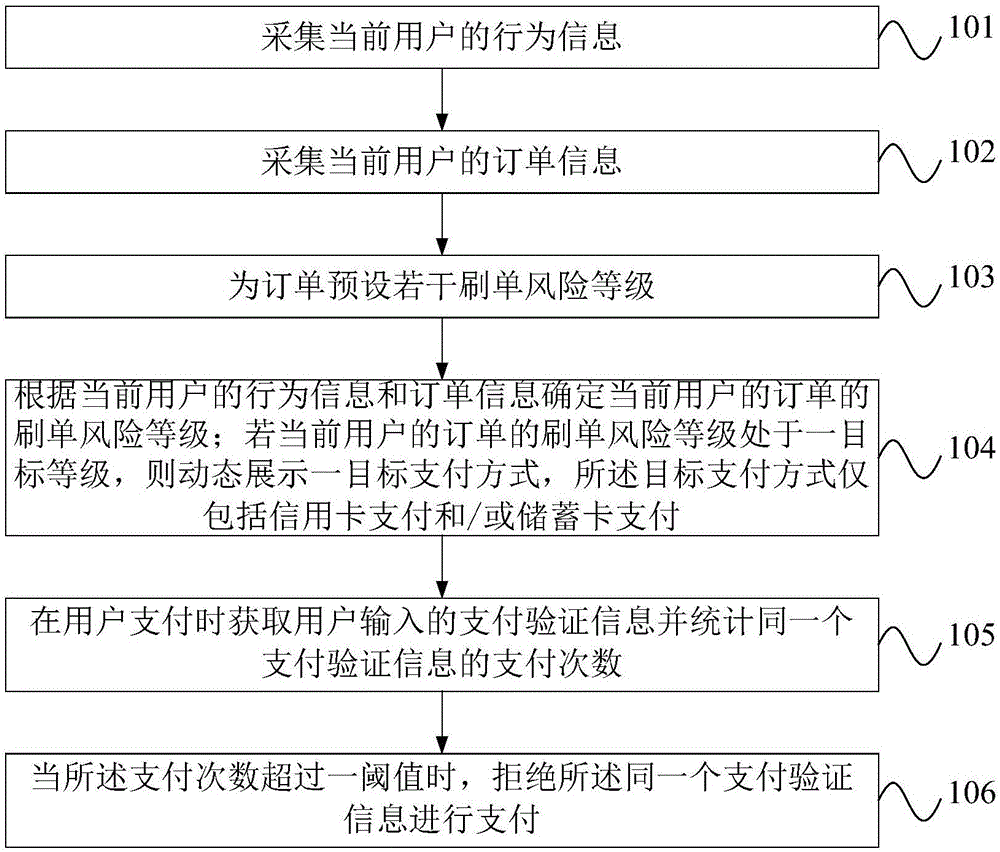
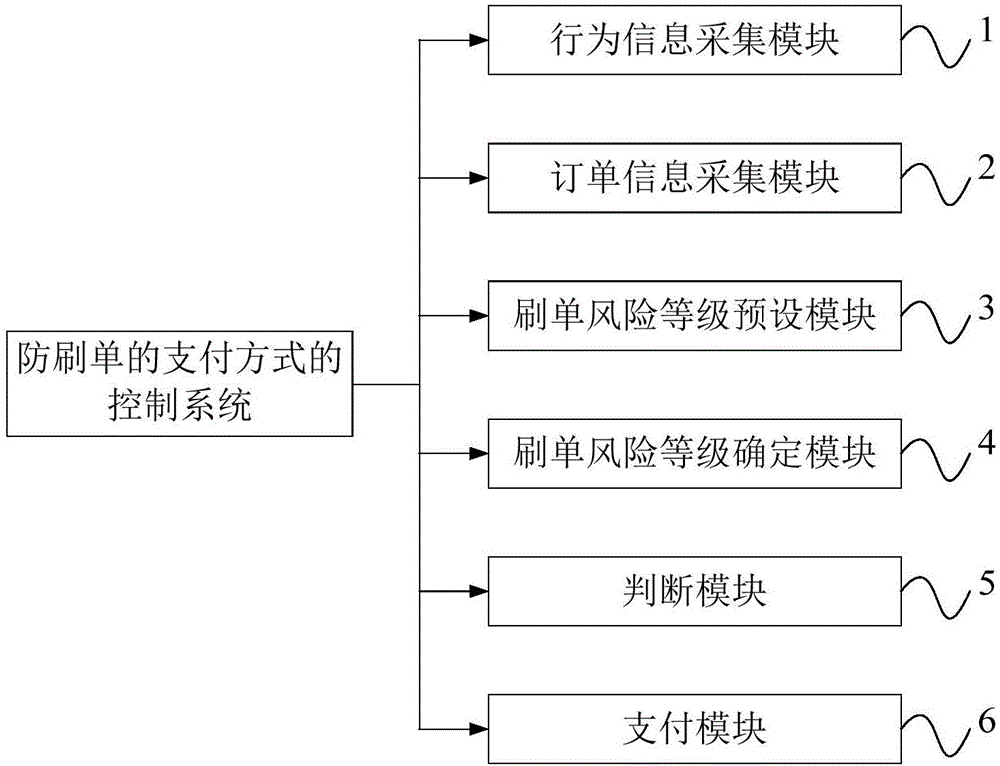
Order-scalping-preventing payment mode control method and control system
The invention discloses an order-scalping-preventing payment mode control method and control system. The order-scalping-preventing payment mode control method comprises the following steps that behavior information of a current user is acquired; order information of the current user is acquired; multiple order scalping risk levels are preset for the order; the order scalping risk level of the order of the current user is determined according to the behavior information and the order information of the current user; and if the order scalping risk level of the order of the current user is at the target level, a target payment mode is dynamically displayed, wherein the target payment mode only includes credit card payment and / or deposit card payment. Three order scalping risk levels are set for the user order according to the behavior information and the order information of the user, the normal business logic is adopted for the low risk and high risk orders, the payment mode is dynamically displayed for the medium risk orders and the same bankcard is only limited to successfully pay for the fixed number of times of orders so that the scalping orders can be reduced and the influence on the business can be reduced.
Owner:SHANGHAI CTRIP COMMERCE CO LTD
Methods and systems for provisioning mobile devices with payment credentials
ActiveUS10510073B2Processing speedUnnecessary delayElectronic credentialsProtocol authorisationPaymentMedium Risk
Embodiments are described that are directed to optimizing the provisioning of payment account credentials to mobile devices utilizing mobile wallets. In some embodiments, one of multiple provisioning schemes may be selectively chosen for payment account credential provisioning based upon a determined risk involved with a particular provisioning request. A low risk provisioning request leads to an immediate provisioning of a payment credential, whereas a provisioning request of high risk results in the provisioning request being denied. In some embodiments, medium risk provisioning requests will cause an additional user authentication to be performed before the payment account provisioning is finalized. The additional user authentication may occur using a separate communication channel than the channel in which the provisioning request was received.
Owner:VISA INT SERVICE ASSOC
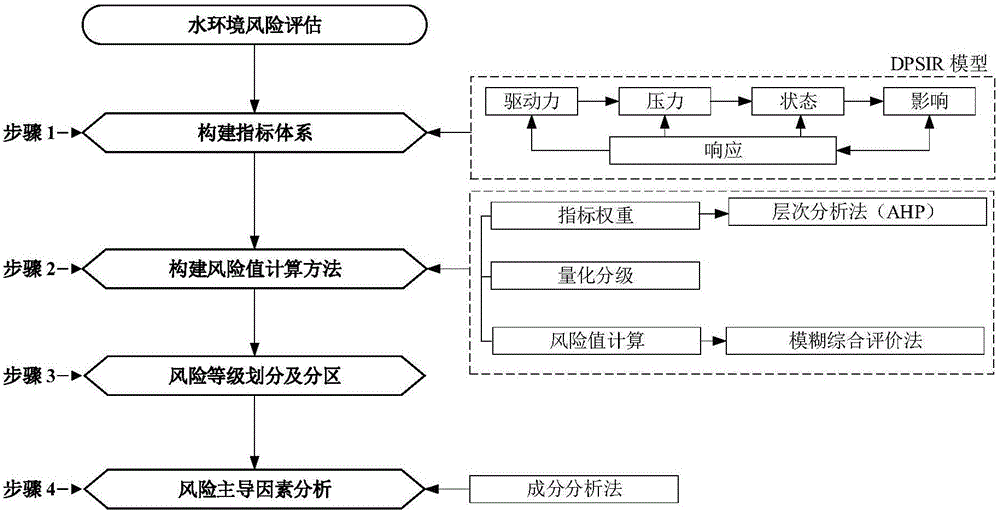
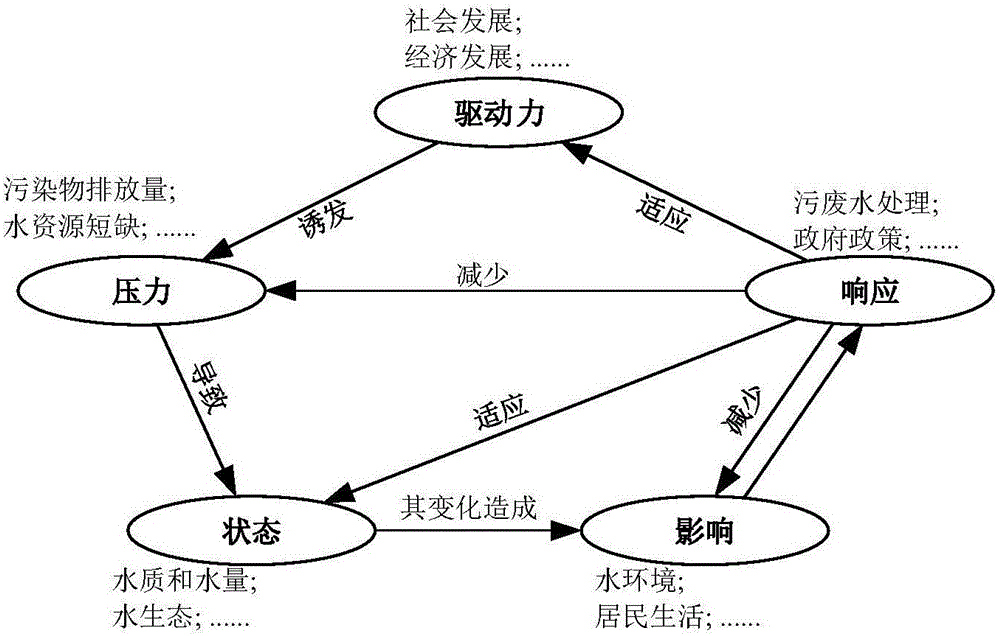
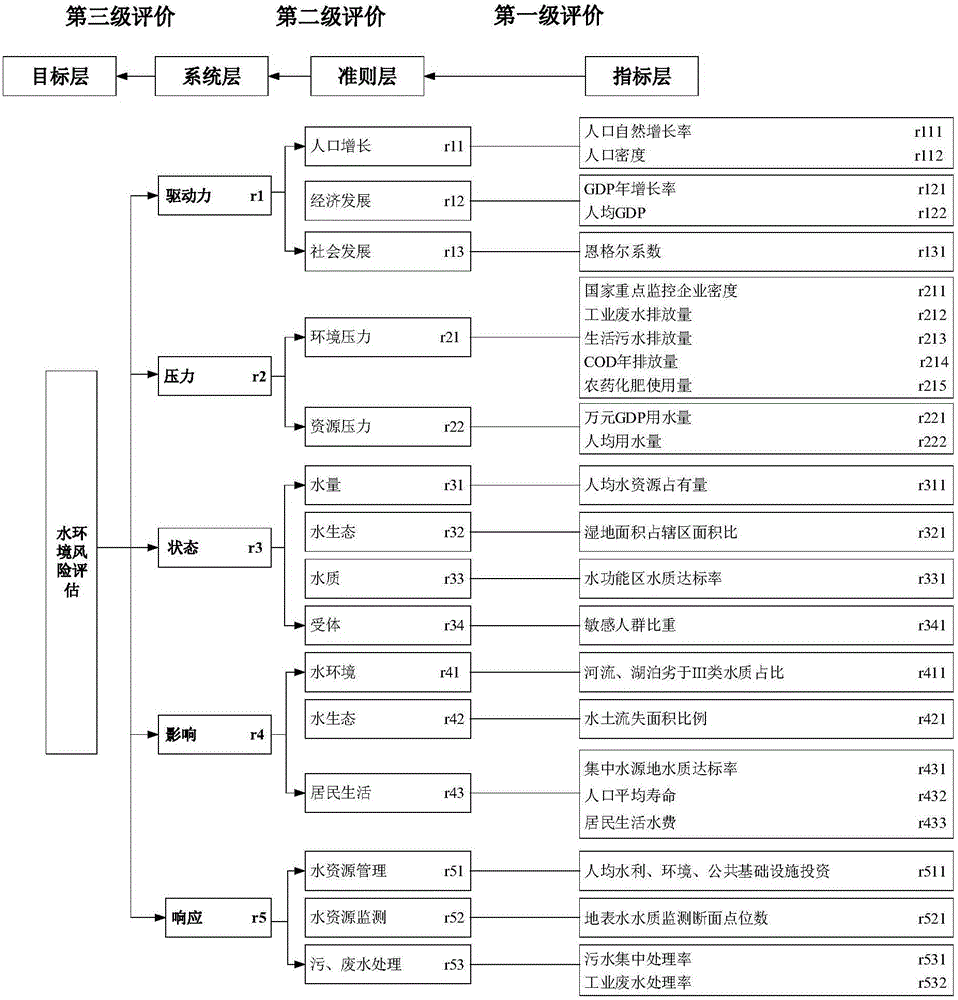
Regional water environment risk zoning method
The invention provides a regional water environment risk zoning method comprising the steps that a driving force factor, a pressure factor, a state factor, an impact factor and a response factor of a DPSIR module are determined; a regional water environment risk assessment index system is constructed, and the constructed regional water environment risk assessment index system comprises a target layer, a system layer, a criterion layer and an index layer which reflect the regional water environment risk from different angles; the weight of each index is calculated by using the analytic hierarchy process and value assignment is performed, and then all the index systems are quantitatively graded; then the regional water environment risk value is calculated through a fuzzy comprehensive evaluation method; and the regions are divided into a high-risk region, a medium-risk region, a low-risk region and a no-risk region in a decreasing order according to the risk with ArcGIS acting as an auxiliary tool. According to the scheme, the regional water environment can be more accurately assessed so as to provide accurate basis for decision.
Owner:BEIJING NORMAL UNIVERSITY
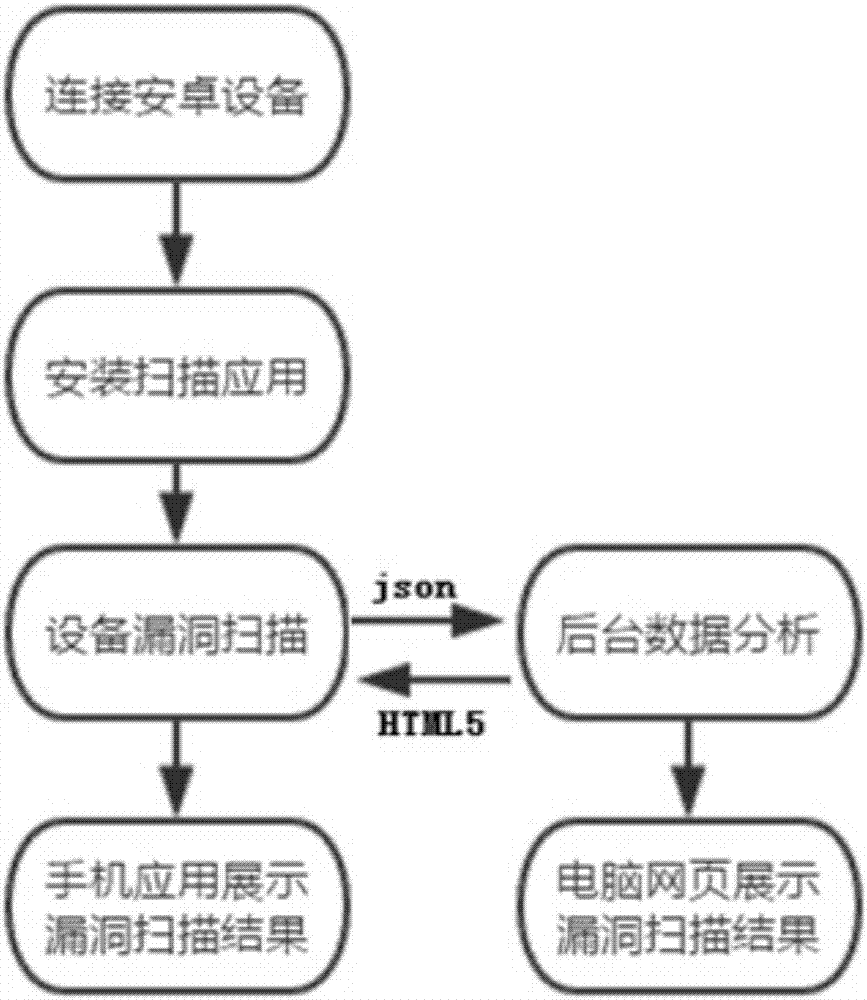
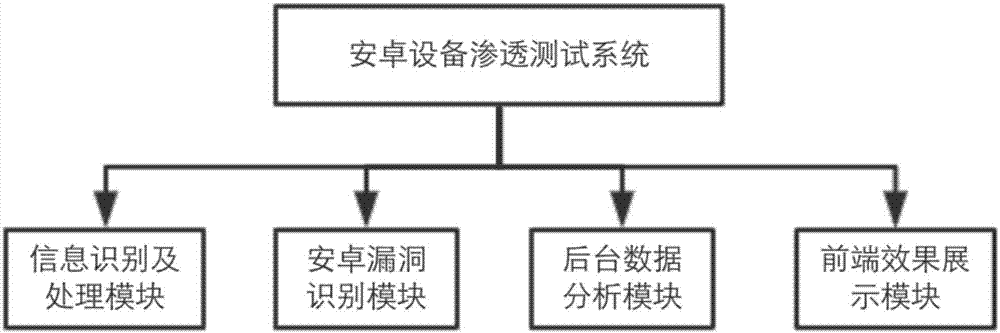
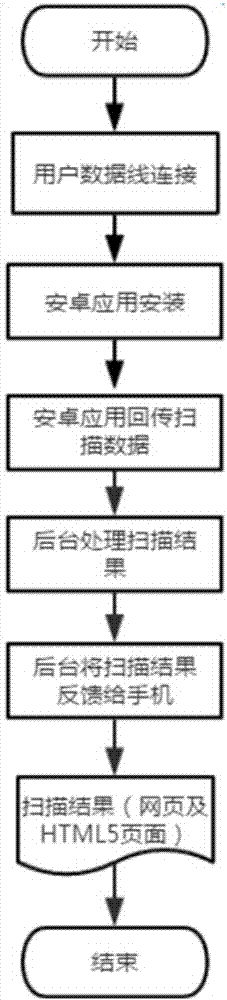
Android device penetration test system and automatic penetration test method based thereon
ActiveCN107392033AImprove compatibilityEffective Safety Analysis ResultsPlatform integrity maintainanceMedium RiskComputer module
The invention relates to vulnerability scanning and security rating techniques for Android devices and is intended to provide an Android device penetration test system and an automatic penetration test method based thereon. The Android device penetration test system comprises an information recognition and processing module, an Android vulnerability recognition module, a background data analysis module and a frontend effect display module. Numbers of high risk, medium risk and low risk vulnerabilities, device security coefficient, a repair scheme and security recommendations can be acquired for any Android device in seconds just through connection with the Android device penetration test system via a data line. The Android device penetration test system is high in efficiency and compatibility, supports plug and play, allows full-automatic execution and outputting of valid security analysis results, and allows a common user to master the situation of an Android device in seconds.
Owner:杭州安恒车联网安全技术有限公司
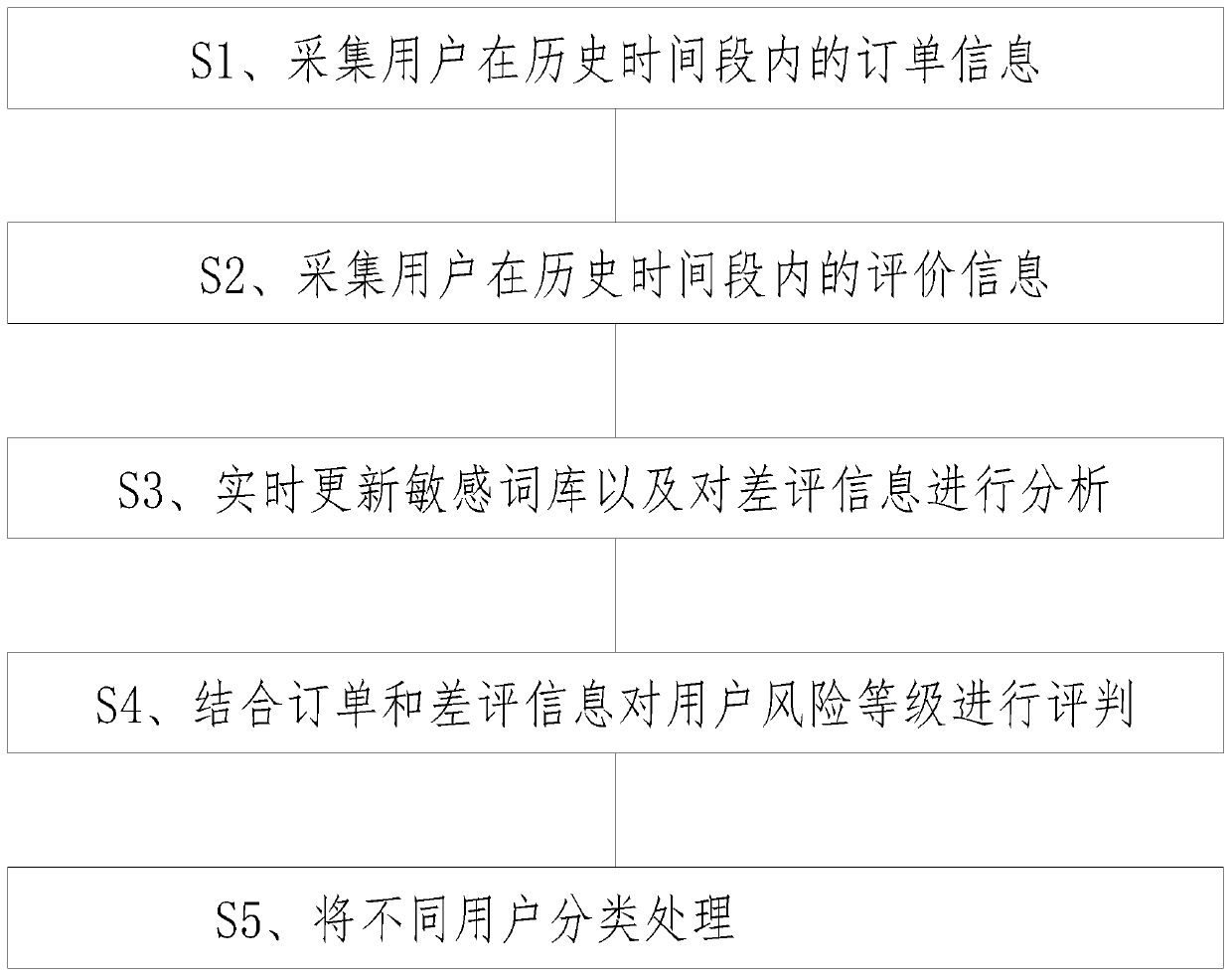
Method for identifying malicious users according to negative comments of users
InactiveCN110288431AImprove recognition rateNatural language data processingBuying/selling/leasing transactionsRisk levelMedium Risk
The invention discloses a method for identifying the malicious users according to the negative comments of the users. The method comprises the following steps of S1, acquiring the order information of a user in a historical time period; S2, collecting the evaluation information of the user in the historical time period; S3, updating a sensitive word bank in real time and analyzing the negative comment information; S4, judging the risk level of the user by combining the order and the negative comment information; and S5, classifying different users. By utilizing the negative comment records in the specified historical time period of the user and combining the user order dimension attributes to formulate a negative comment risk user level, the blacklist management is carried out on the high-risk risk users; by marking a medium-risk user as a risk, and waiting for the manual checking processing, the low-risk user is not processed and is filtered automatically; meanwhile, in combination with the sensitive word bank, the word bank has the characteristic of dynamic updating, the word segmentation is conducted on the user negative comment data through a word segmentation device, and the weighted calculation is conducted on the user risks through the sensitive words, so that the high-risk user recognition rate is effectively increased.
Owner:达疆网络科技(上海)有限公司
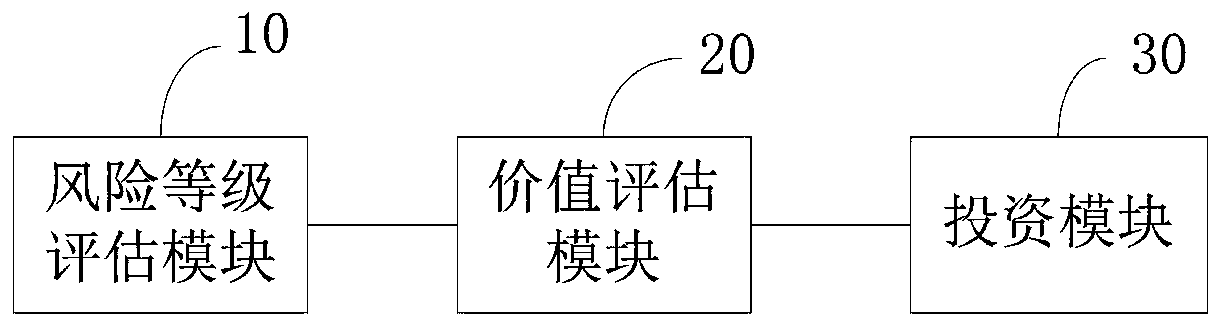
High-safety risk investment system and method
InactiveCN110009504AImprove risk management levelIncrease incomeFinanceResourcesRisk levelEvaluation result
The embodiment of the invention provides a high-safety risk investment system and method. The high-safety risk investment system comprises a risk grade evaluation module, a value evaluation module andan investment module; the risk level assessment module is used for assessing the risk level of the invested project based on the risk index and deciding whether to invest the investor or not, whereinthe risk indexes comprise a technical risk, a production risk, a market risk, a management risk, a financial risk and an environmental risk, the risk levels comprise a low risk, a medium risk and a high risk, and the low risk is that the integration value of each risk index is within a set first threshold range, the moderate risk is that the integration value of each risk index is within a set second threshold range, and the height risk is that the integration value of each risk index is within a set third threshold range; the value evaluation module evaluates the value of the invested project based on the risk level evaluation result; and the investment module carries out risk investment according to the value evaluation result and the risk level of the invested project.
Owner:湖北风口网络科技有限公司
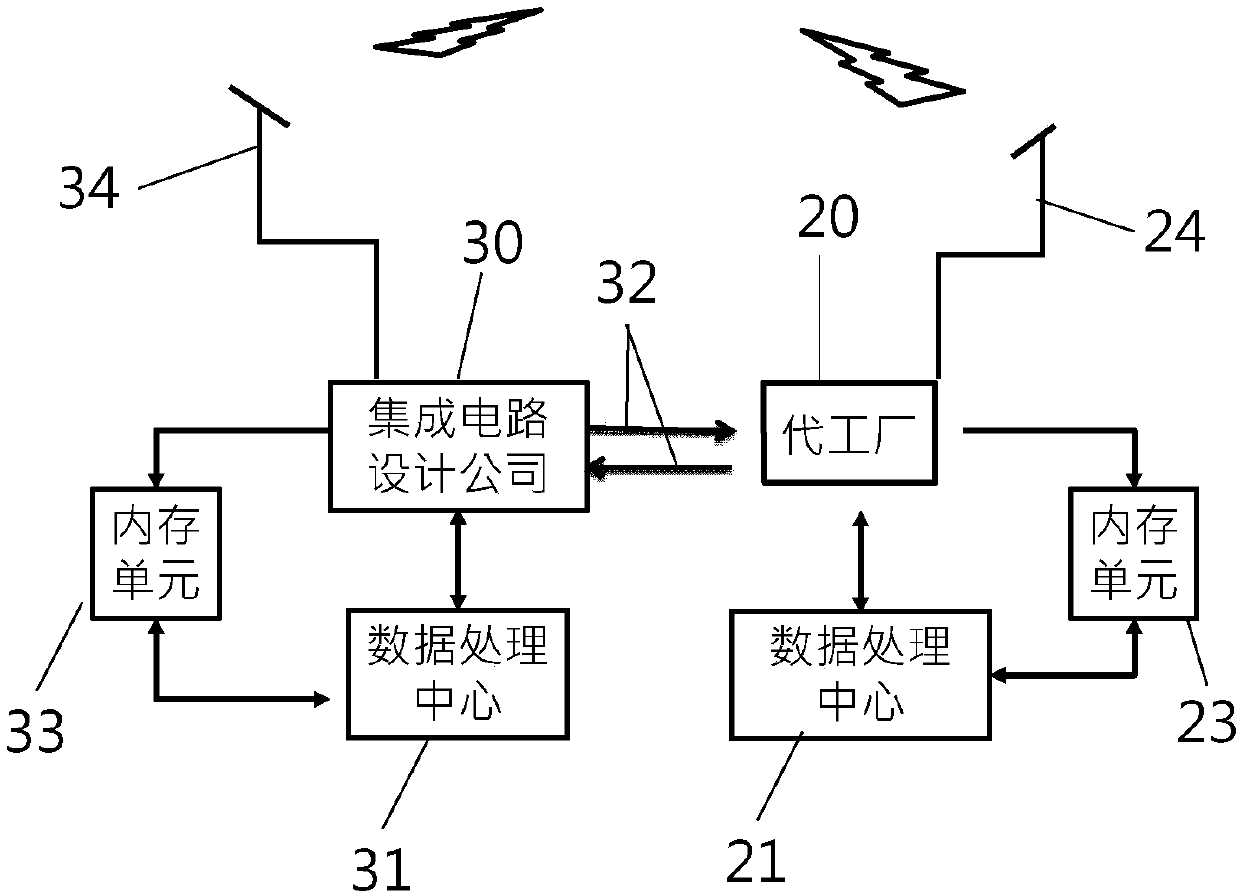
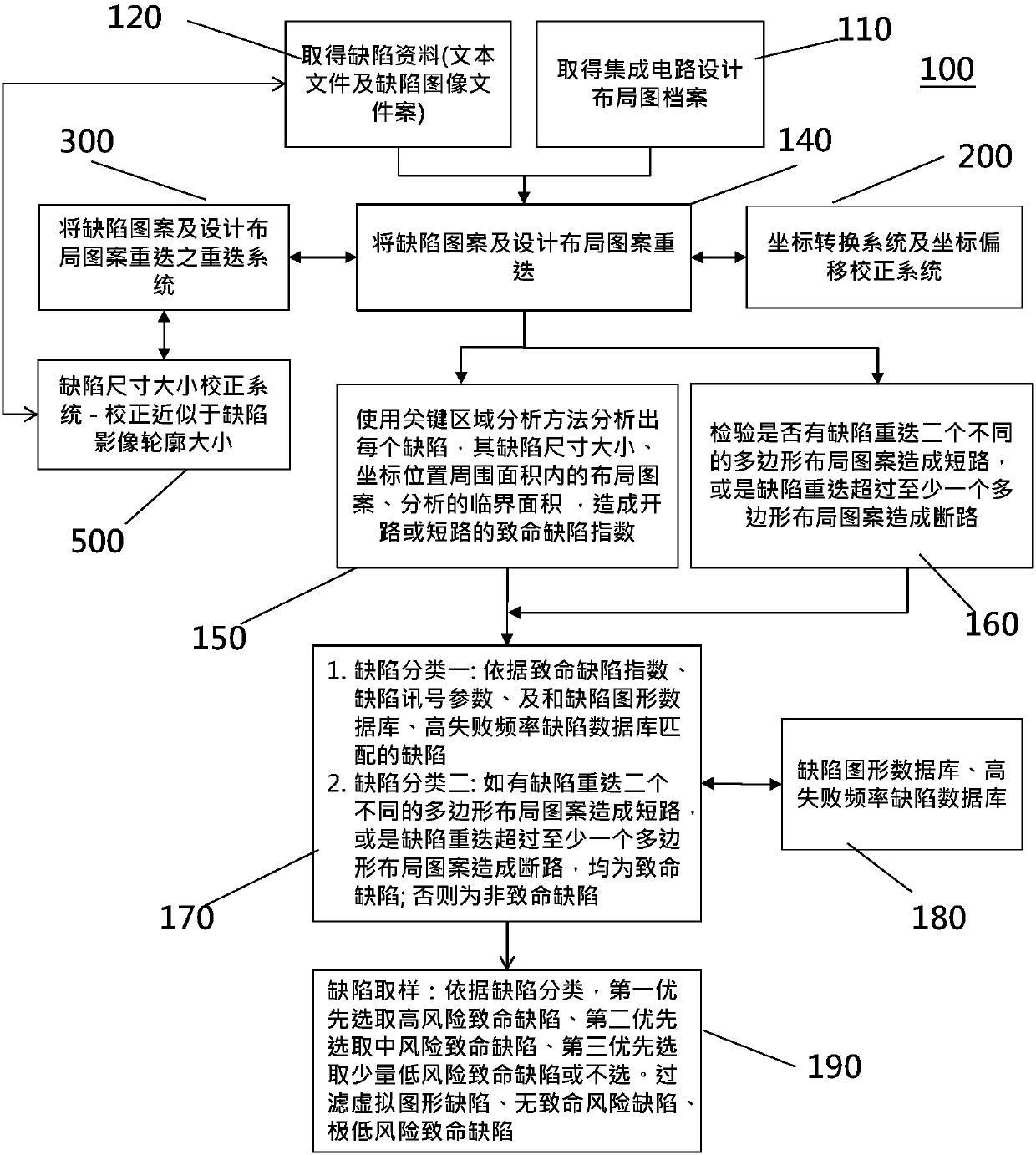
Intelligent defect correction system an implementation method thereof
ActiveCN109616426ASemiconductor/solid-state device testing/measurementSemiconductor/solid-state device manufacturingMedium RiskImage correction
The invention provides an intelligent semiconductor defect correction system and an implementation method thereof. The method comprises the following steps: receiving a plurality of defect data sent by the manufacturing factory, and receiving IC design layout diagram data of an integrated circuit design company, and the defect data are subjected to defect coordinate conversion correction and defect image correction, and analyzing and correcting the corrected defect data and the design layout graph through key region analysis, and is used for improving the accuracy of the key region analysis and accurately judging the critical defect indexes of the failure of the broken or short circuit caused by all the defect images.; and then according to the critical defect index and the defect signal parameters, and distinguishing the critical defects into high-risk defects, medium-risk defects, low-risk defects and the like, and the aims of improving the accuracy and precision of the intelligent defect correction system and the implementation method of the intelligent defect correction system are achieved.
Owner:ELITETECH TECH
Human papillomavirus (HPV) primer and molecular beacon combination based on isothermal amplification, kit and detecting method
InactiveCN110387436AReduced temperature control requirementsHigh sensitivityMicrobiological testing/measurementMicroorganism based processesHuman papillomavirusFluorescence
The invention belongs to the technical field of biology, and discloses a primer and molecular beacon combination for quickly detecting human papillomaviruses (HPVs) based on an isothermal amplification technology, a kit and a detecting method. The primer and molecular beacon combination is shown as SEQ ID No.1-17, and can specifically recognize the 13 different types of high-risk HPVs and two types of medium-risk genotypes with the high incidence in Chinese population; and according to the kit and the method for real-timely detecting the HPVs through fluorescence based on the isothermal amplification technology, the 15 types of medium-and-high-risk HPVs can be detected within the short time (1.5 h), accuracy is good, sensitivity is high, repeatability is high, specificity is good, no nonspecific reaction with clinically similar pathogens exists, using is convenient, only an extracted template sample needs to be added into a reaction tube, the manual operation time is less than 5 min, the requirement of isothermal amplification for temperature control over an instrument is not high, and thus the primer and molecular beacon combination, the kit and the detecting method can be appliedto instant detection well.
Owner:中生方政生物技术股份有限公司
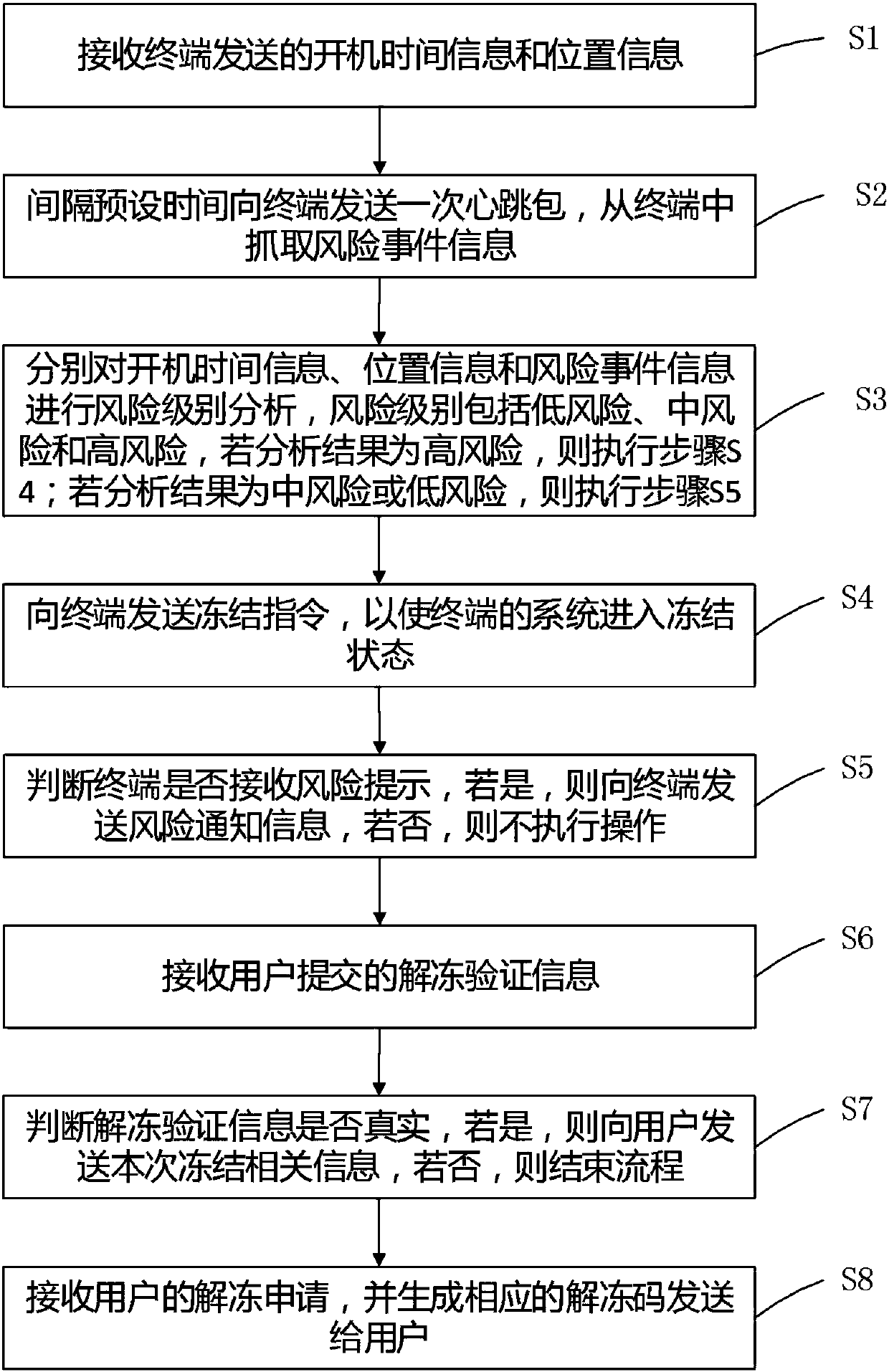
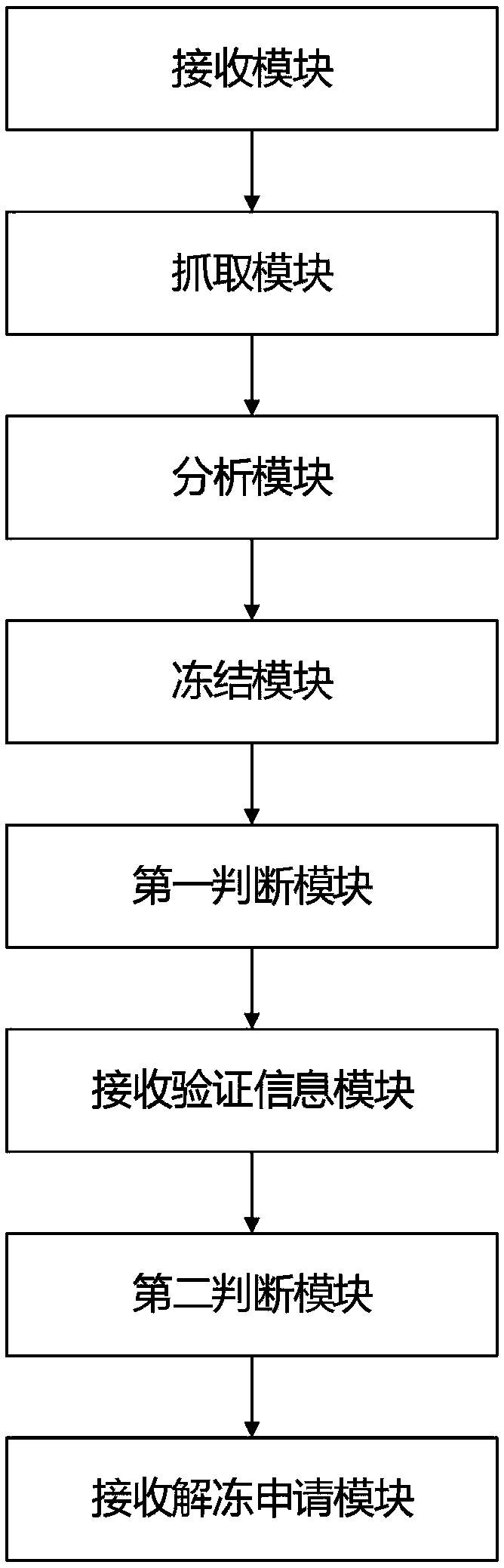
Data processing method and device based on risk management and user terminal
InactiveCN107657524AImprove securityImprove reliabilityFinanceSubstation equipmentTime informationRisk level
The invention discloses a data processing method and device based on risk management and a user terminal. The method comprises the following steps: S1) receiving boot time information and position information sent by the terminal; S2) sending a heartbeat package once to the terminal at an interval of a preset time, and capturing risk event information from the terminal; S3) carrying out risk levelanalysis on the boot time information, the position information and the risk event information, risk levels comprising low risk, medium risk and high risk, if the analysis result is the high risk, carrying out the step S4), and if the analysis result is the medium risk or the low risk, carrying out the step S5); S4) sending a freeze instruction to the terminal to enable the terminal system to enter a freeze mode; and S5) judging whether the terminal receives a risk warning, if so, sending risk notification information to the terminal, and if not, not carrying out operation. The method and device realize automatic identification and processing of risk events of the terminal device, thereby enhancing safety and reliability of the terminal device.
Owner:GUANGDONG YOUMAI INFORMATION COMM TECH
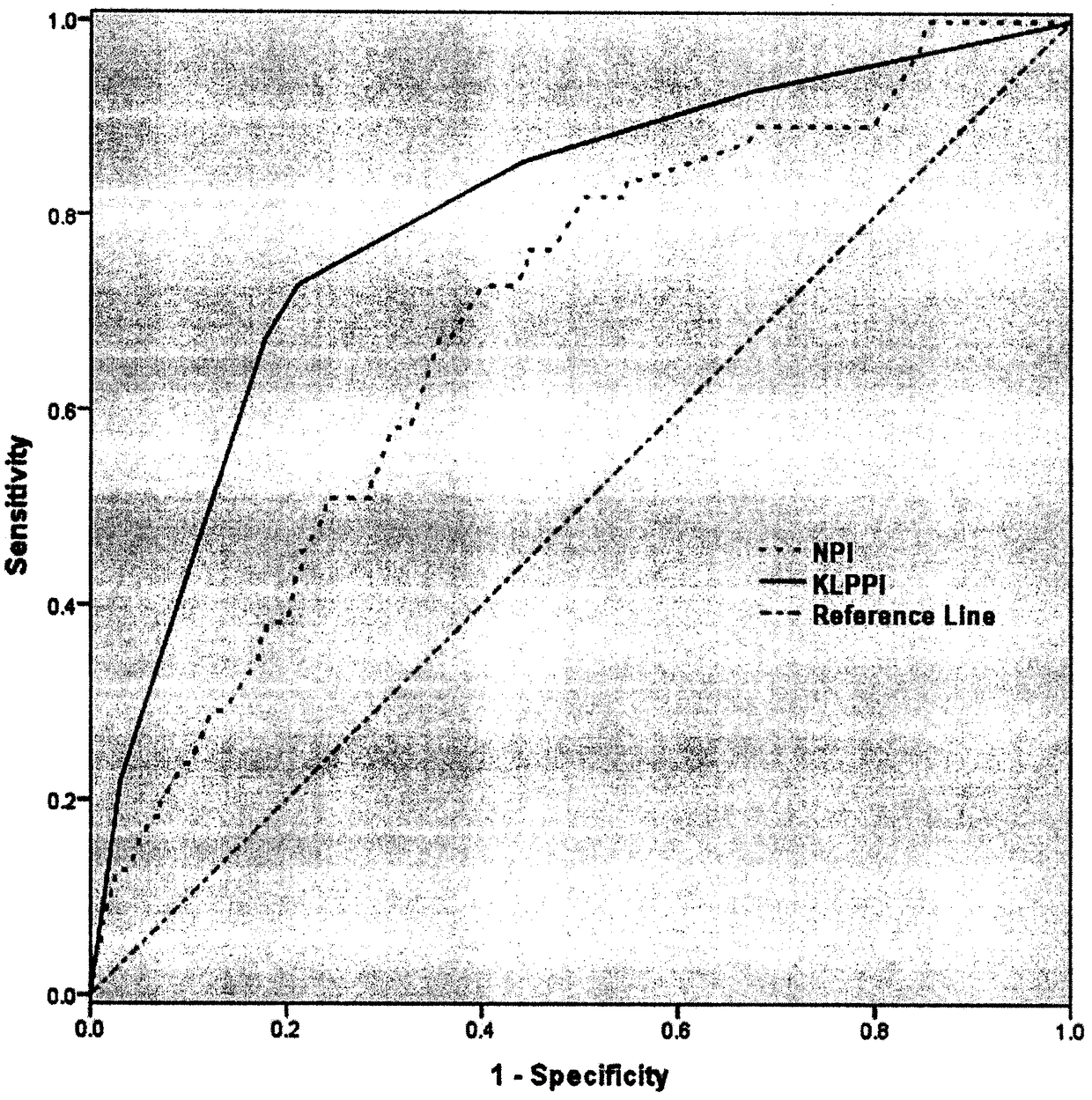
Luminal B type HER-2 negative breast cancer prognostic prediction model KLP-PI
InactiveCN108305685AEasy to distinguishEasy to identifyHealth-index calculationMedical automated diagnosisLuminal bNode metastasis
The invention discloses a luminal B type HER-2 negative breast cancer prognostic prediction model KLP-PI and relates to the field of COX algorithm prognostic prediction. The luminal B type HER-2 negative breast cancer prognostic prediction model KLP-PI is obtained based on the Chinese population. KLP-PI=1.0*KI-67LI+1.5*LN+1*PR status, according to a tumor KI-67 proliferation index, KI-67 LI is assigned with a value of 1 if the tumor KI-67 proliferation index is larger than 30%, the KI-67 LI is assigned with a value of 0 if the tumor KI-67 proliferation index is smaller than 30%, LN representslymph node metastasis, the LN is assigned with a value of 1 if the metastasis exists and is assigned with a value of 0 if the metastasis does exist, PR status represents the condition of a progesterone receptor, the PR status is 0 for a positive condition and is 1 for a negative condition, a results KLP-PI value is divided into three groups, scores 0 to 1.5 are in a low-risk group, scores 2 to 2.5are in a medium-risk group, and scores 3 to 5 is in a high-risk group.
Owner:王莹豪
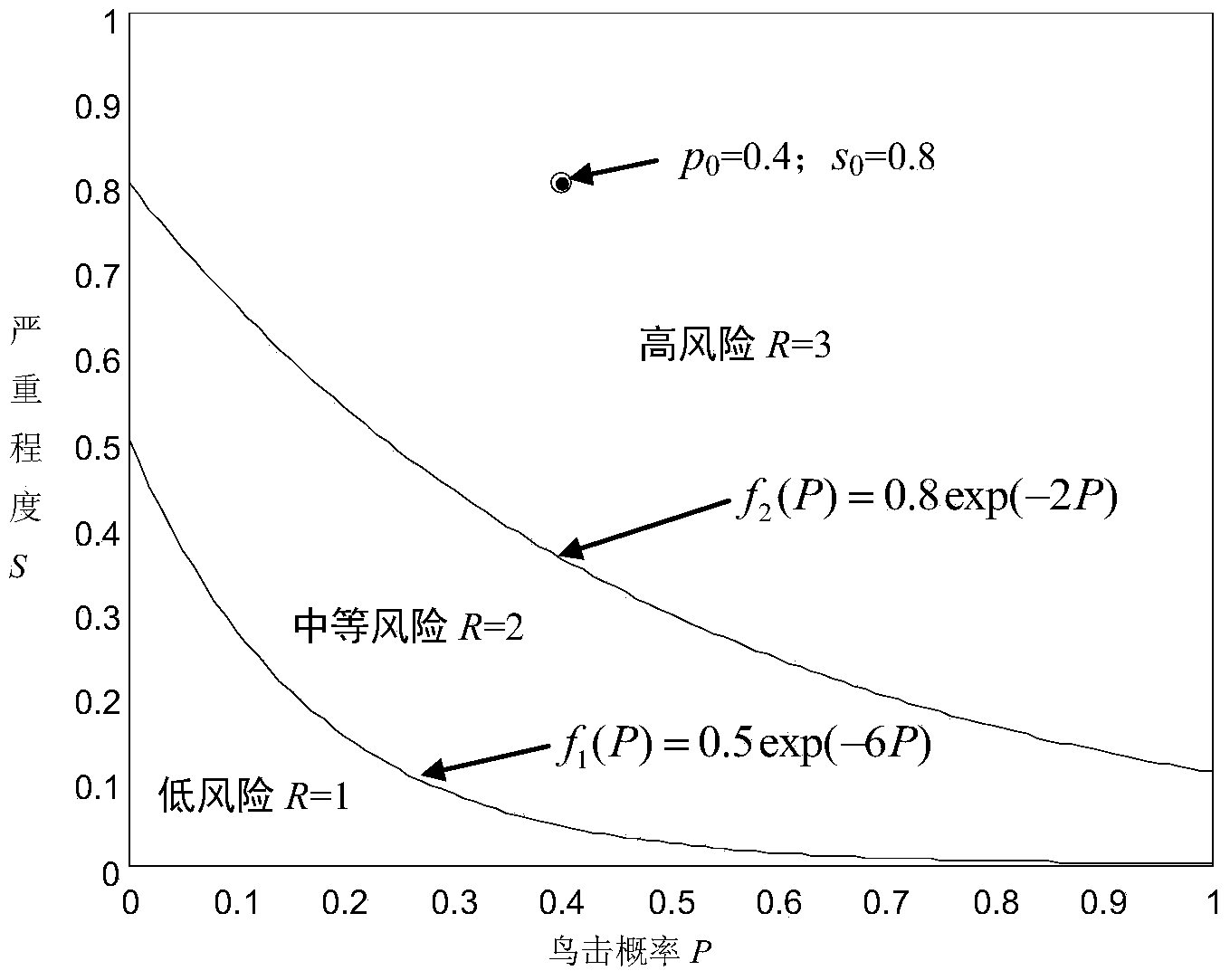
Bird strike risk evaluation method based on exponential function
ActiveCN103914626ASafe take-off and landingAvoid Bird StrikesSpecial data processing applicationsAviationMedium Risk
The invention provides a bird strike risk evaluation method based on an exponential function. The bird strike risk evaluation method based on the exponential function is used for bird strike risk evaluation in aviation. The bird strike risk evaluation method is characterized in that a bird strike risk evaluation model is established by use of an exponential function curve, the bird strike risk is divided into three grades of low risk, medium risk and high risk, and the grade of the bird strike risk is evaluated in real time based on a bird strike probability and a bird strike severity degree value both estimated in real time. The bird strike risk evaluation method is capable of estimating the bird strike risk in real time relatively accurately, and therefore, the bird strike accidents and accident proneness are effectively avoided and safety of take-off and landing of flights are guaranteed.
Owner:CHINA ACAD OF CIVIL AVIATION SCI & TECH
A traditional Chinese medicine preparation for preventing and treating cardiac and cerebrovascular disease in the elderly and a preparing method thereof
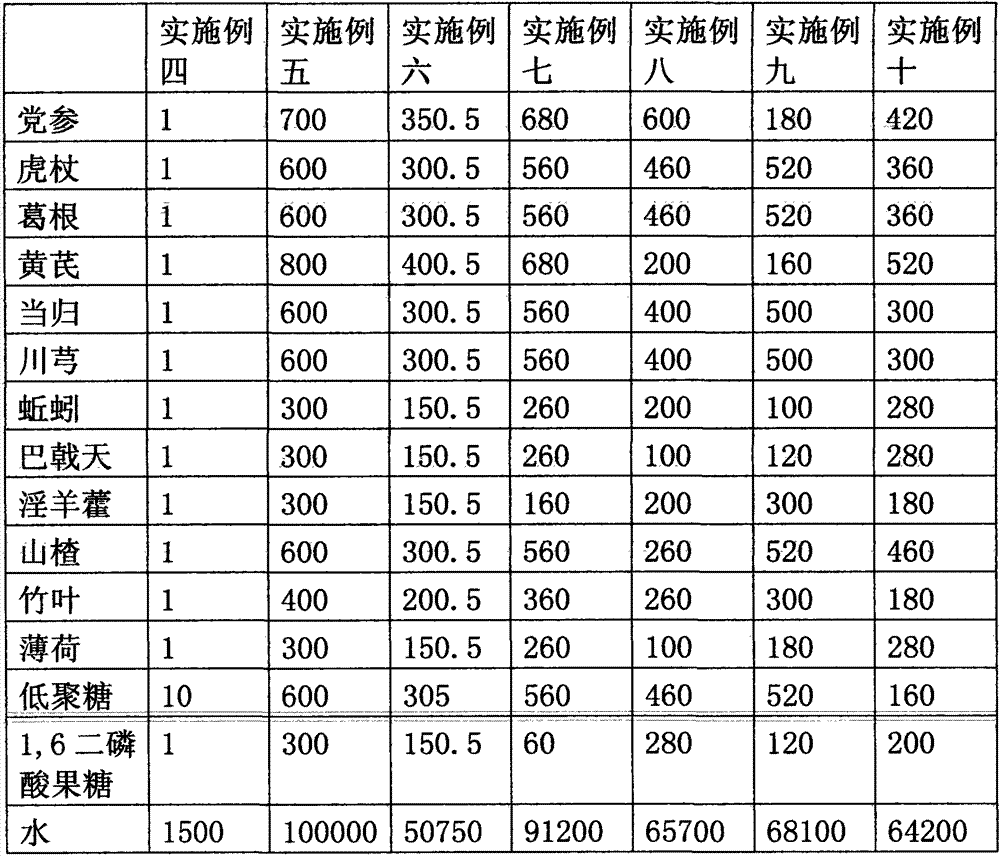
A traditional Chinese medicine preparation for preventing and treating cardiac and cerebrovascular disease in the elderly and a preparing method thereof are disclosed. The preparation is prepared from following raw materials by weight: 1-700 parts of radix codonopsis, 1-600 parts of giant knot weed, 1-600 parts of root of kudzu vine, 1-800 parts of radix astragali, 1-600 parts of Chinese angelica, 1-600 parts of ligusticum wallichii, 1-300 parts of earthworm, 1-300 parts of morinda officinalis, 1-300 parts of herba epimedii, 1-600 parts of hawthorn, 1-400 parts of bamboo leaf, 1-300 parts of mint, 10-600 parts of oligosaccharides, 1-300 parts of fructose-1,6-diphosphate and 1500-100000 parts of water. The preparation and the preparing method have characteristics of low cost, convenient carrying dosage, stable content, reliable curative effects, capability of verification and being natural, and no toxicity. The preparation is suitable for long-term medication of the elderly with cardiovascular and cerebrovascular diseases in the low-risk period and the medium-risk period in the masses, and suitable for combined treatment of traditional Chinese medicines and western medicines in the high-risk period.
Owner:万光瑞
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com