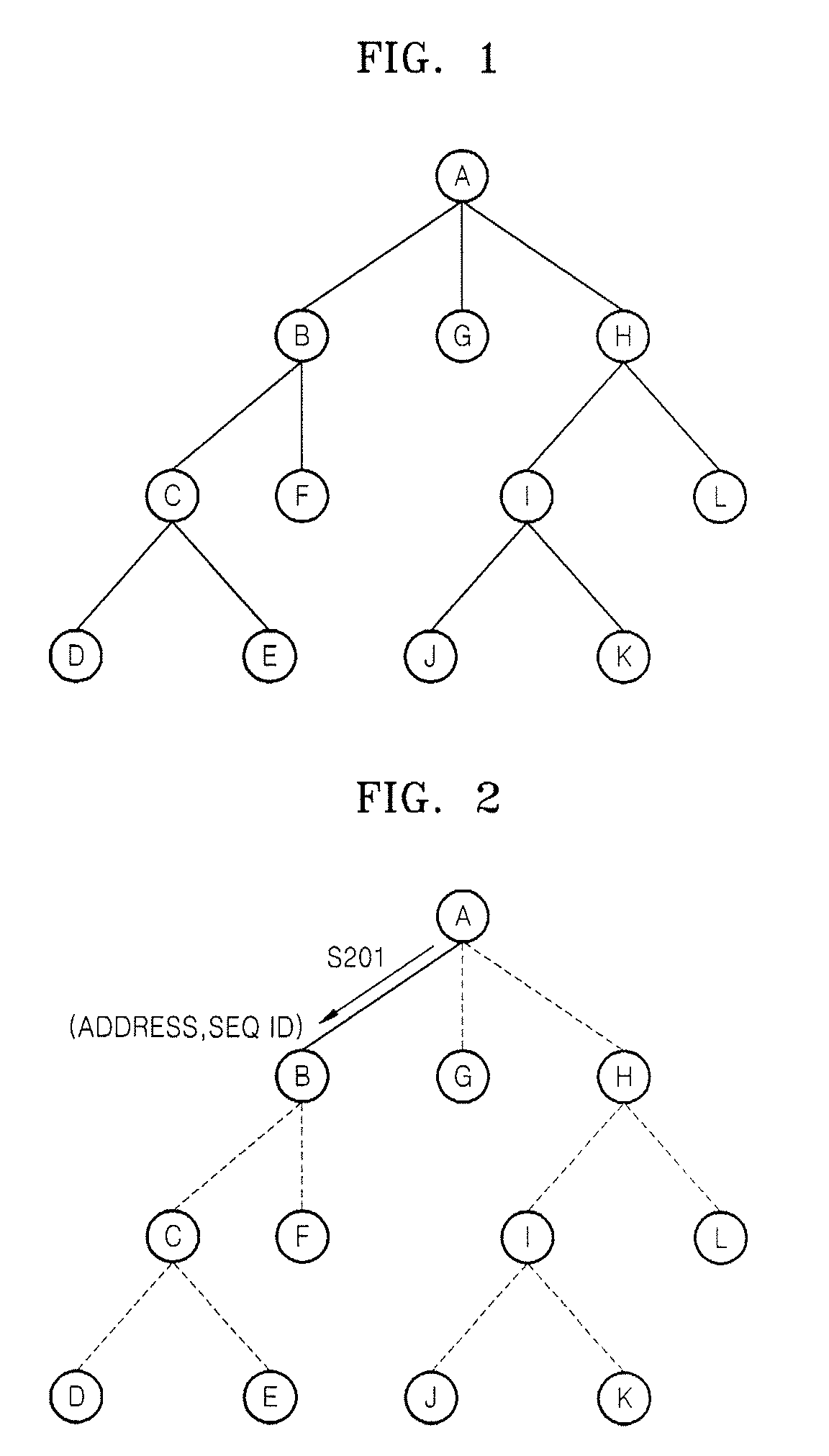
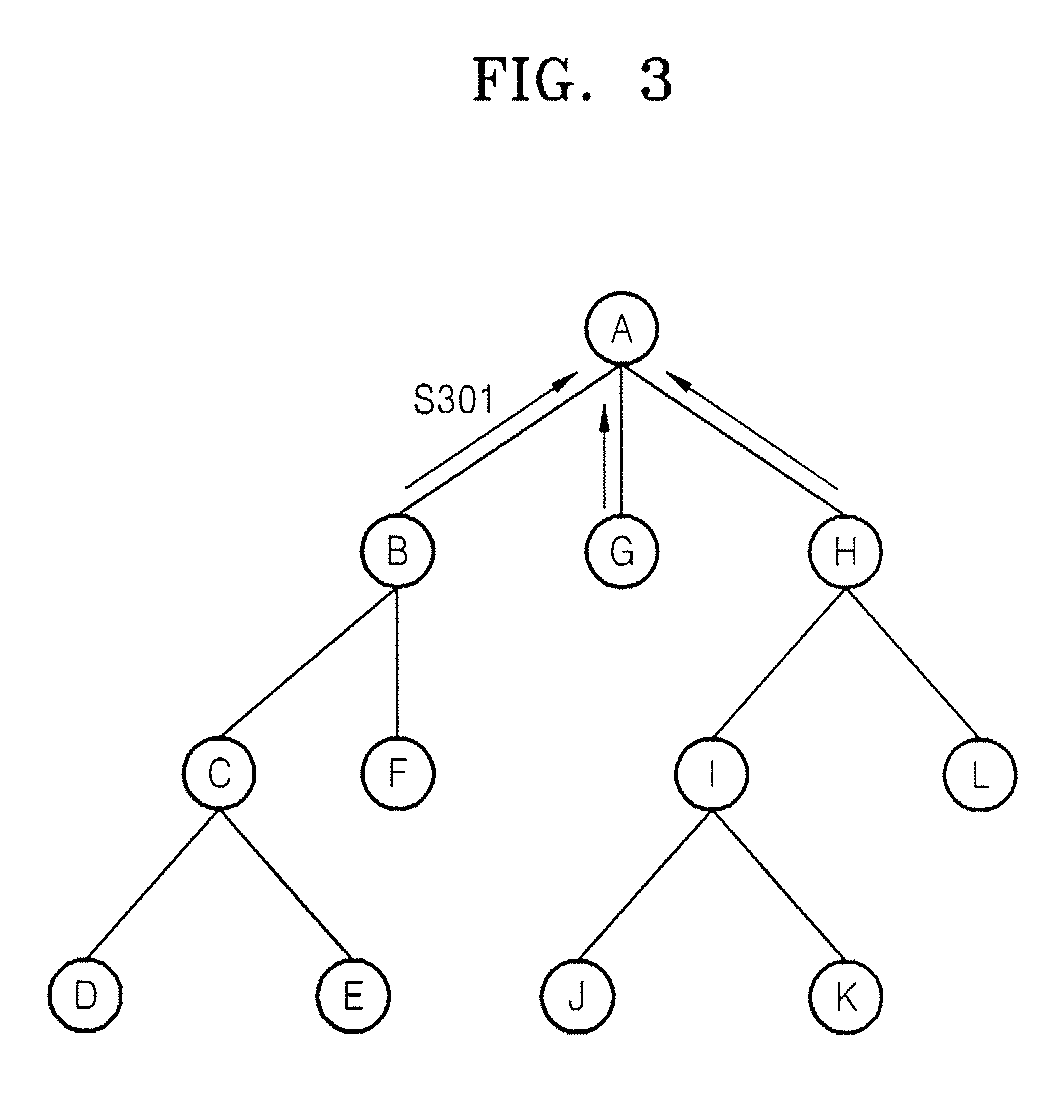
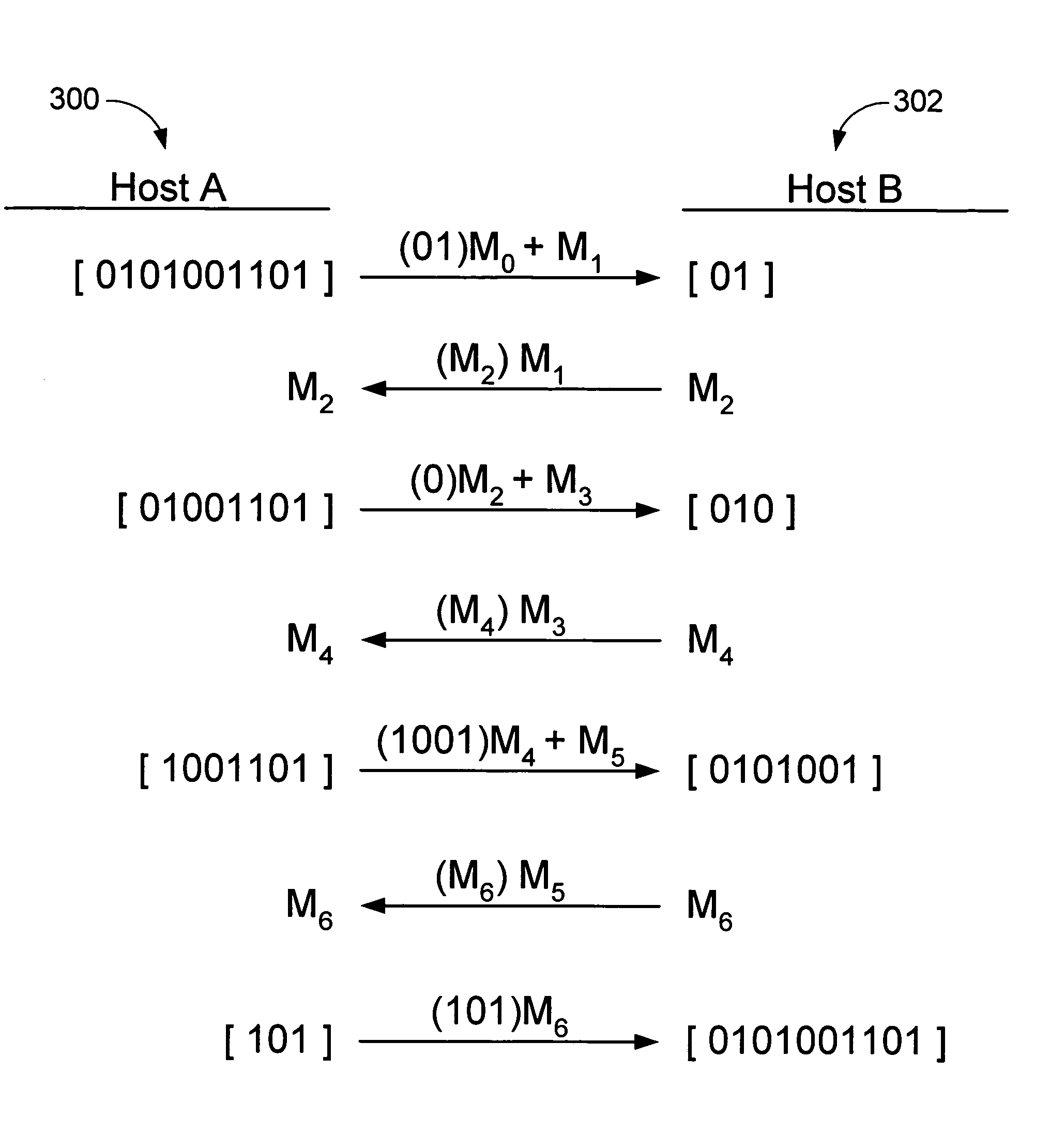
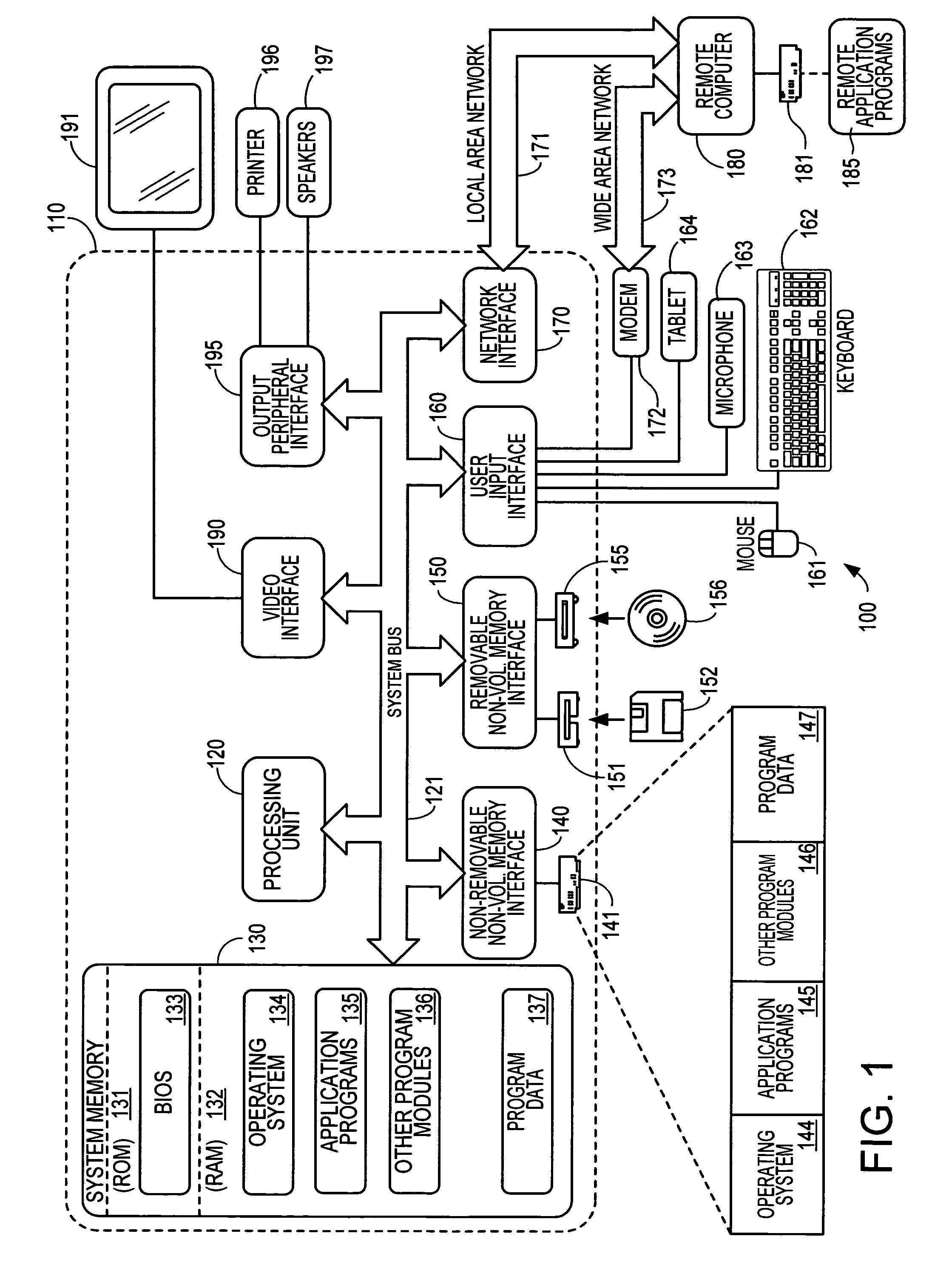
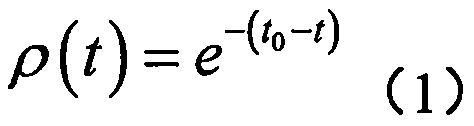Patents
Literature
207 results about "Value assignment" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
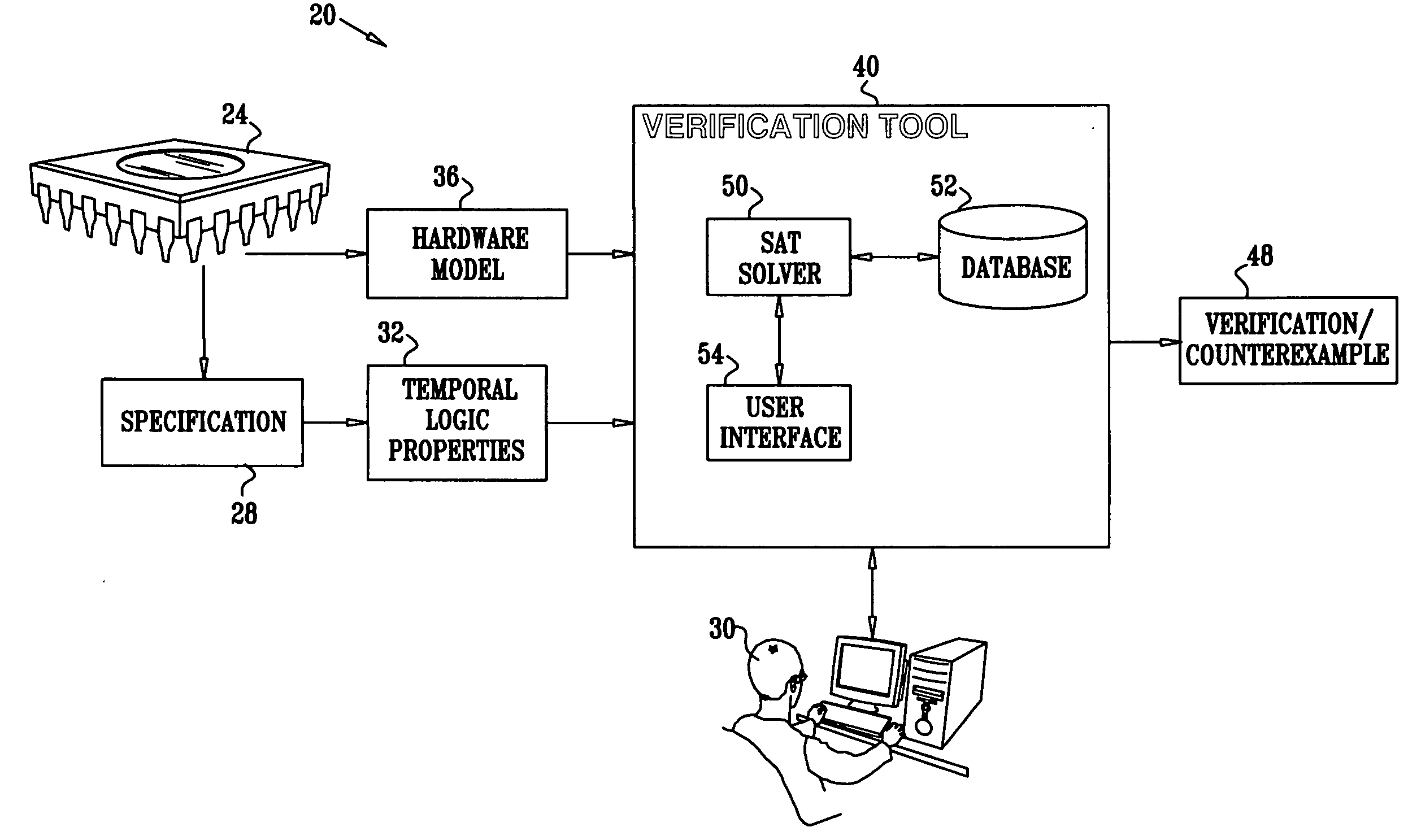
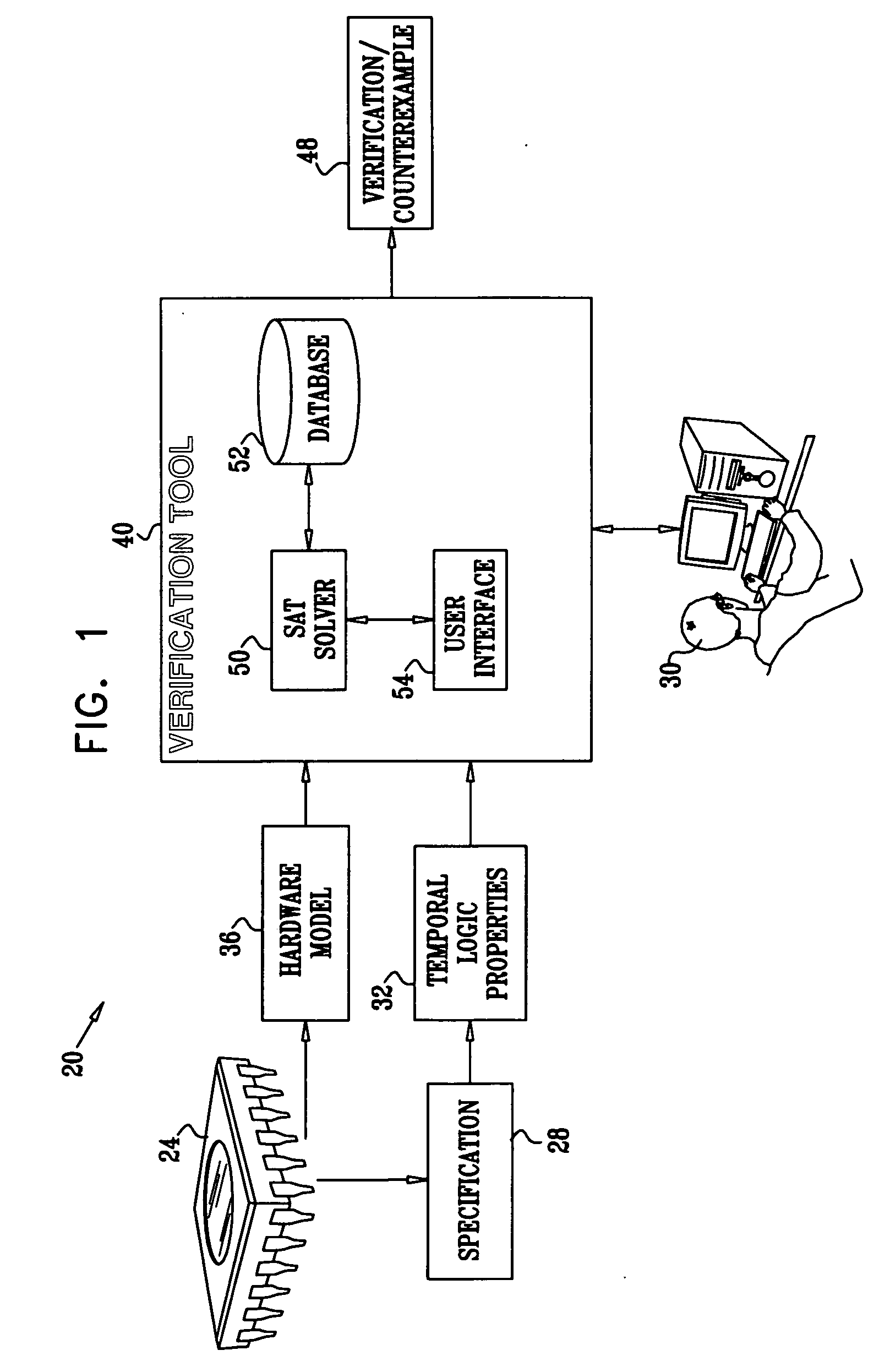
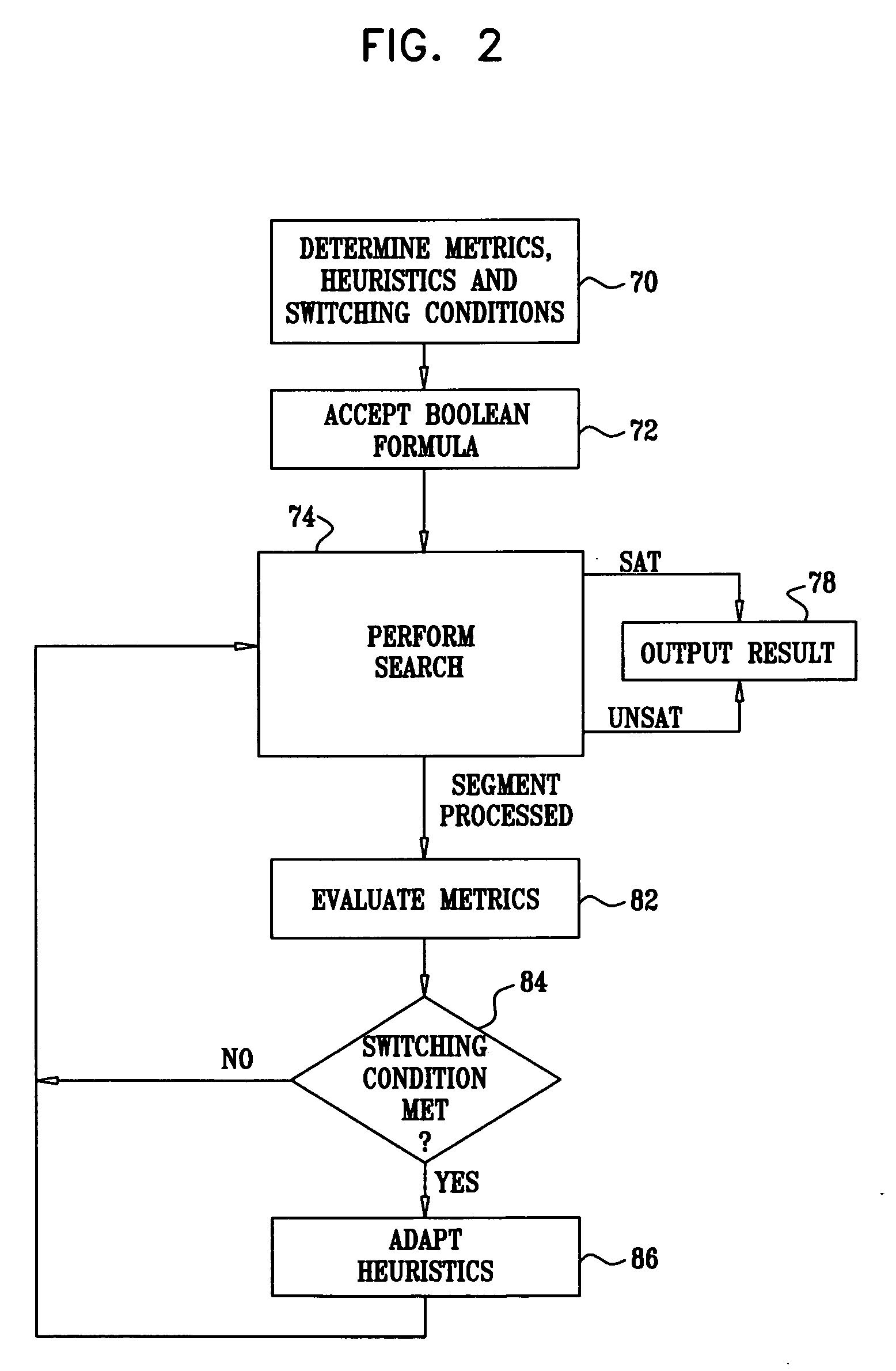
Adaptive application of SAT solving techniques
InactiveUS20070011629A1Computer aided designSoftware simulation/interpretation/emulationValue assignmentGoal system
A computer-implemented method for solving a satisfiability (SAT) problem includes defining a formula, including variables, which refers to properties of a target system. Using a chosen search strategy, a search process is performed over possible value assignments of the variables for a satisfying assignment that satisfies the formula. A performance metric estimating an effectiveness of the search process is periodically evaluated during the search process. The strategy of the search process is modified responsively to the evaluated performance metric. The method determines, using the search process, whether the formula is satisfiable on the target system.
Owner:GOOGLE LLC
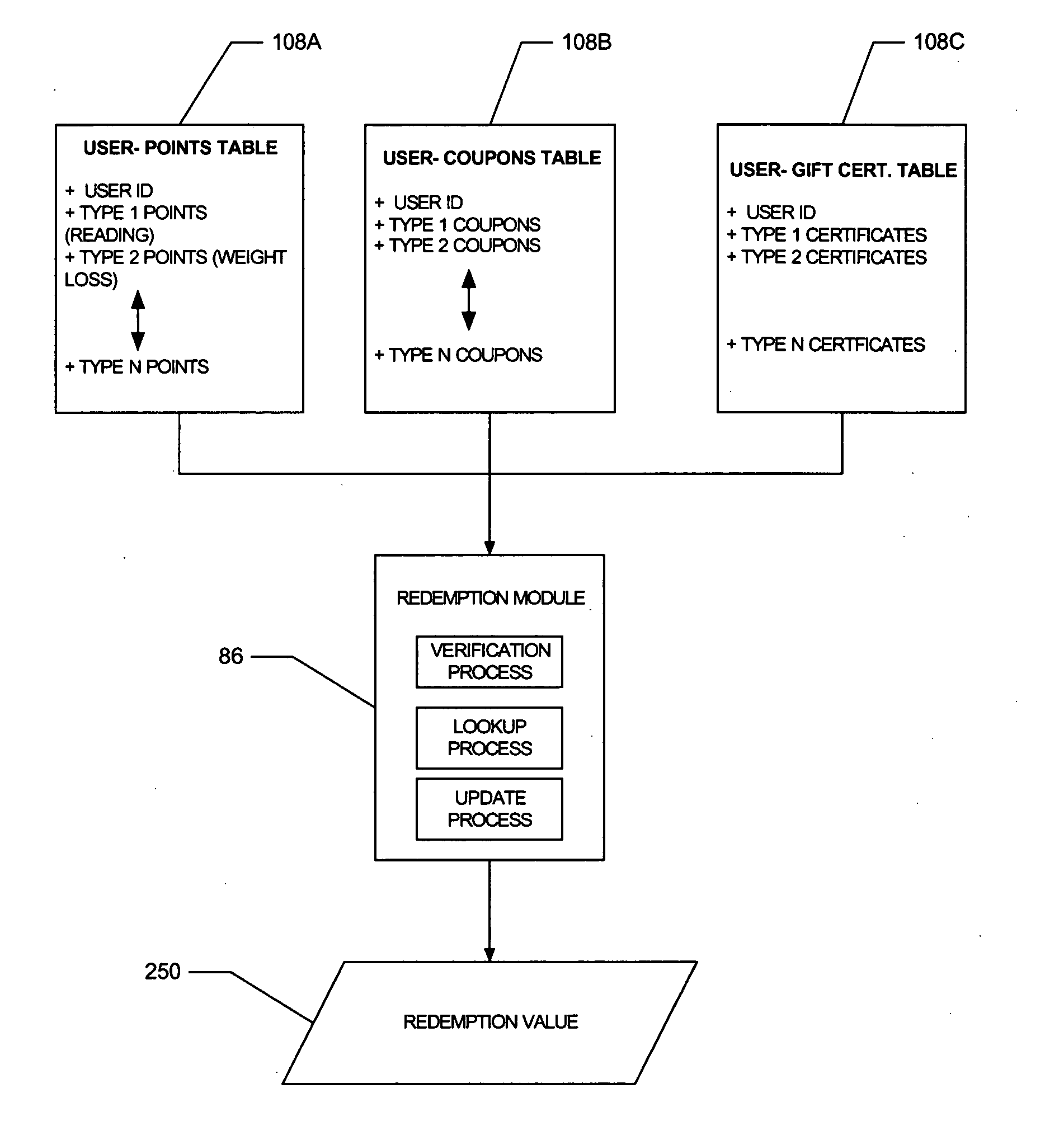
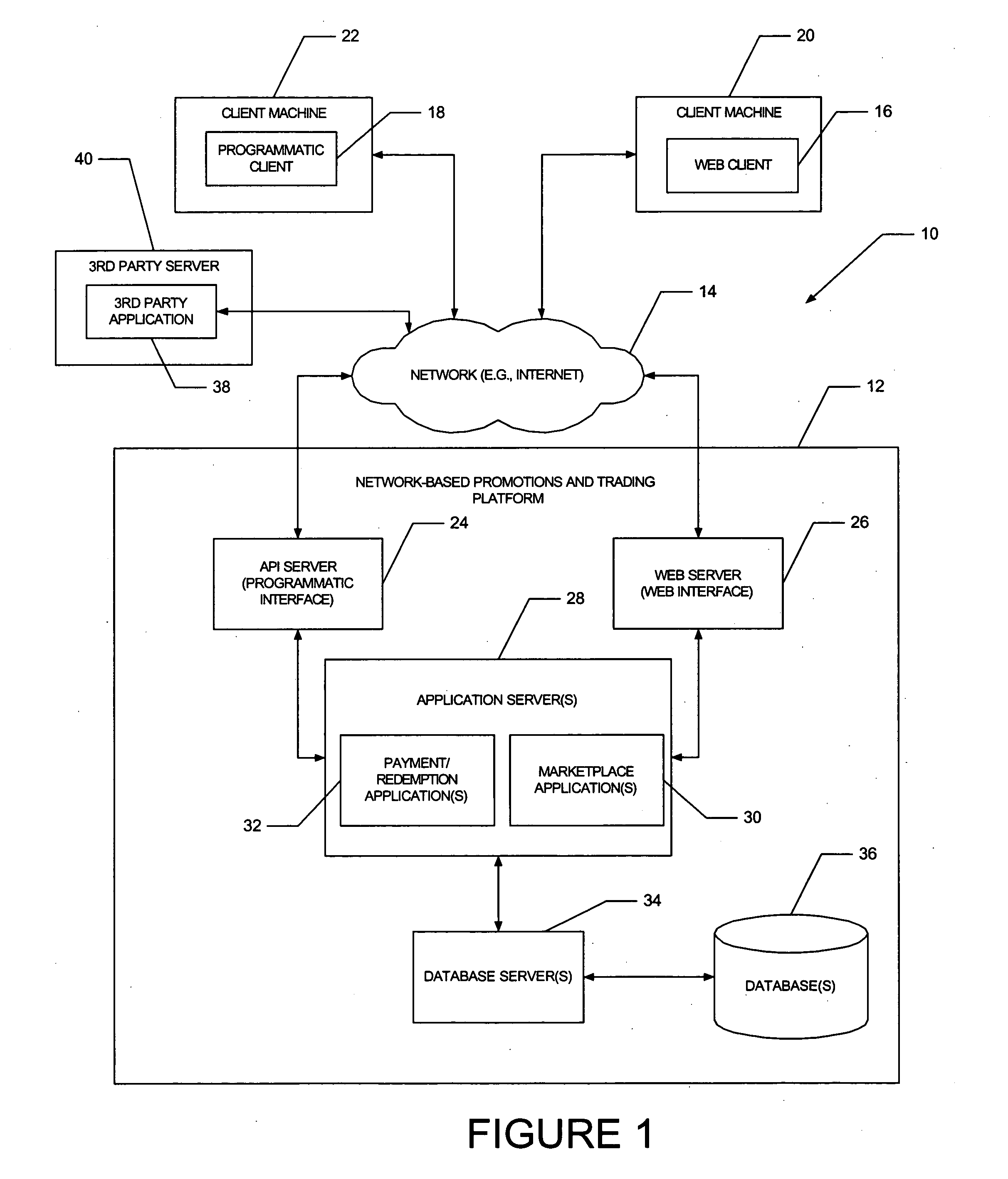
Method and apparatus to facilitate the electronic accumulation and redemption of a value in an account
An automated system to facilitate redemption of value against a single purchase price includes a first module to allocate a first value, of a first value type, to a user within a transaction system. The first module is further to allocate a second value, of a second value type different from the first value type, to the user within the transaction system. A second module is to enable a user to redeem both the first value and the second value against a single purchase price.
Owner:PAYPAL INC
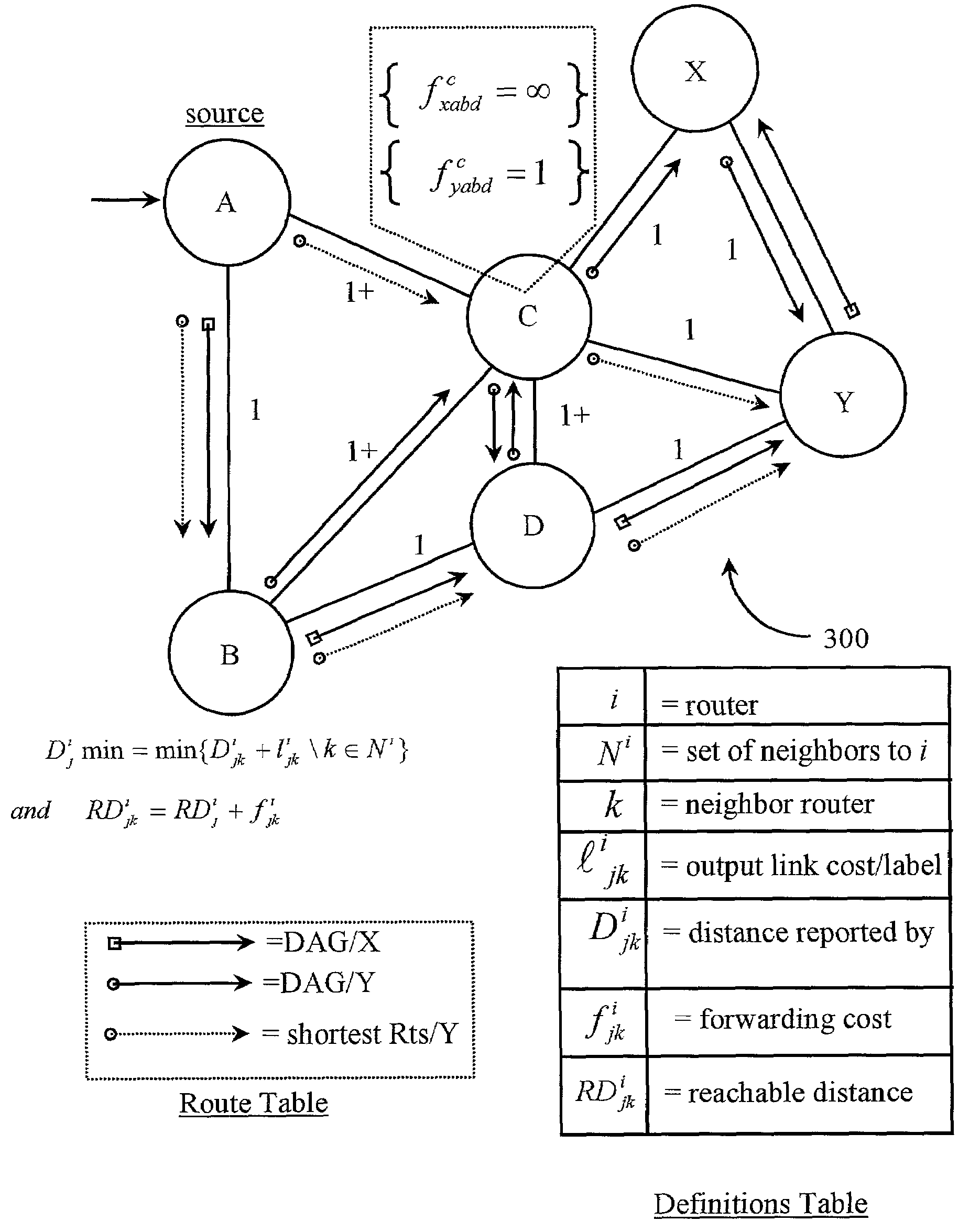
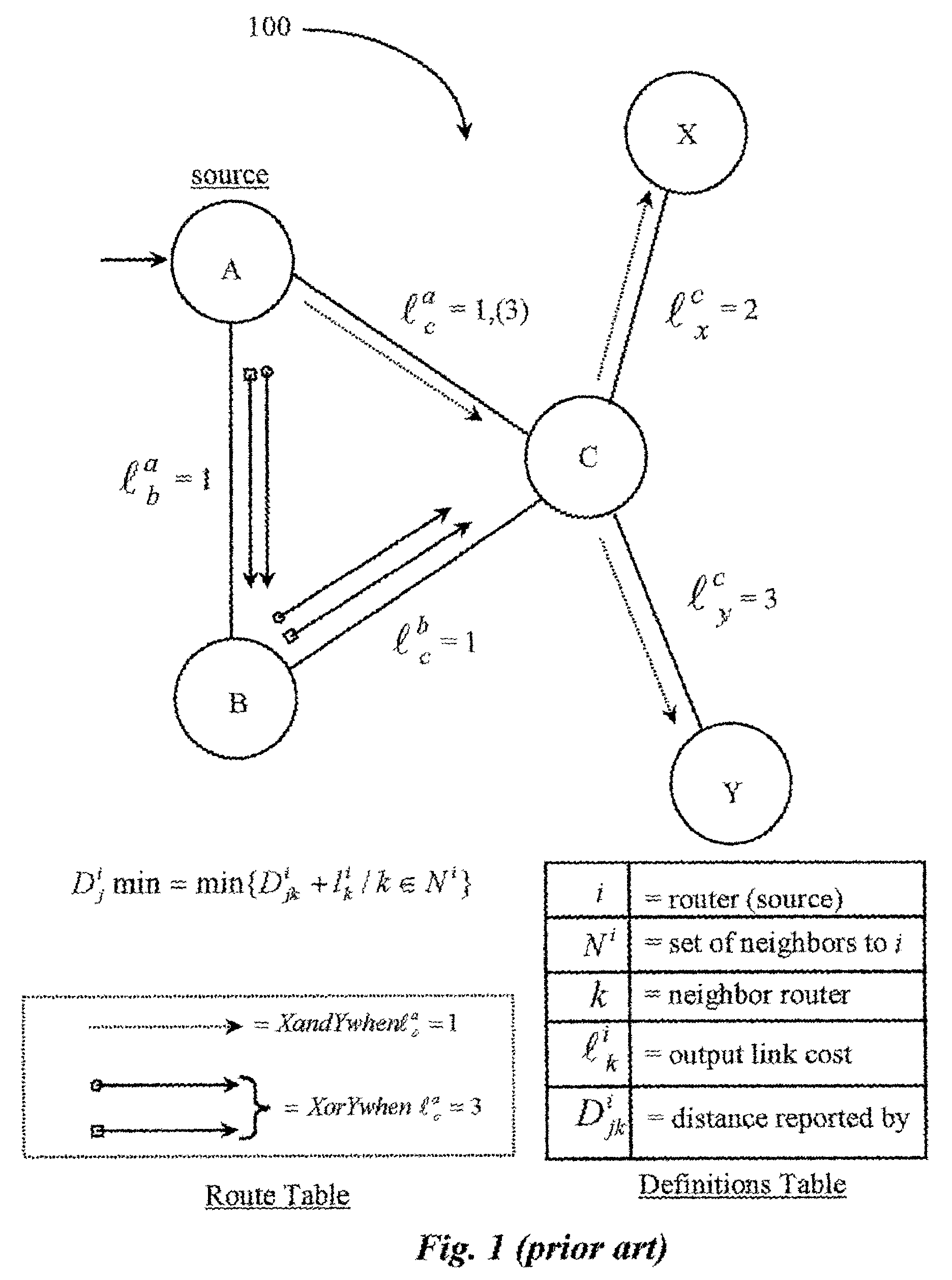
Control method for data path load-balancing on a data packet network
ActiveUS7111074B2Increased administrative controlData switching by path configurationMultiple digital computer combinationsControl systemNetwork packet
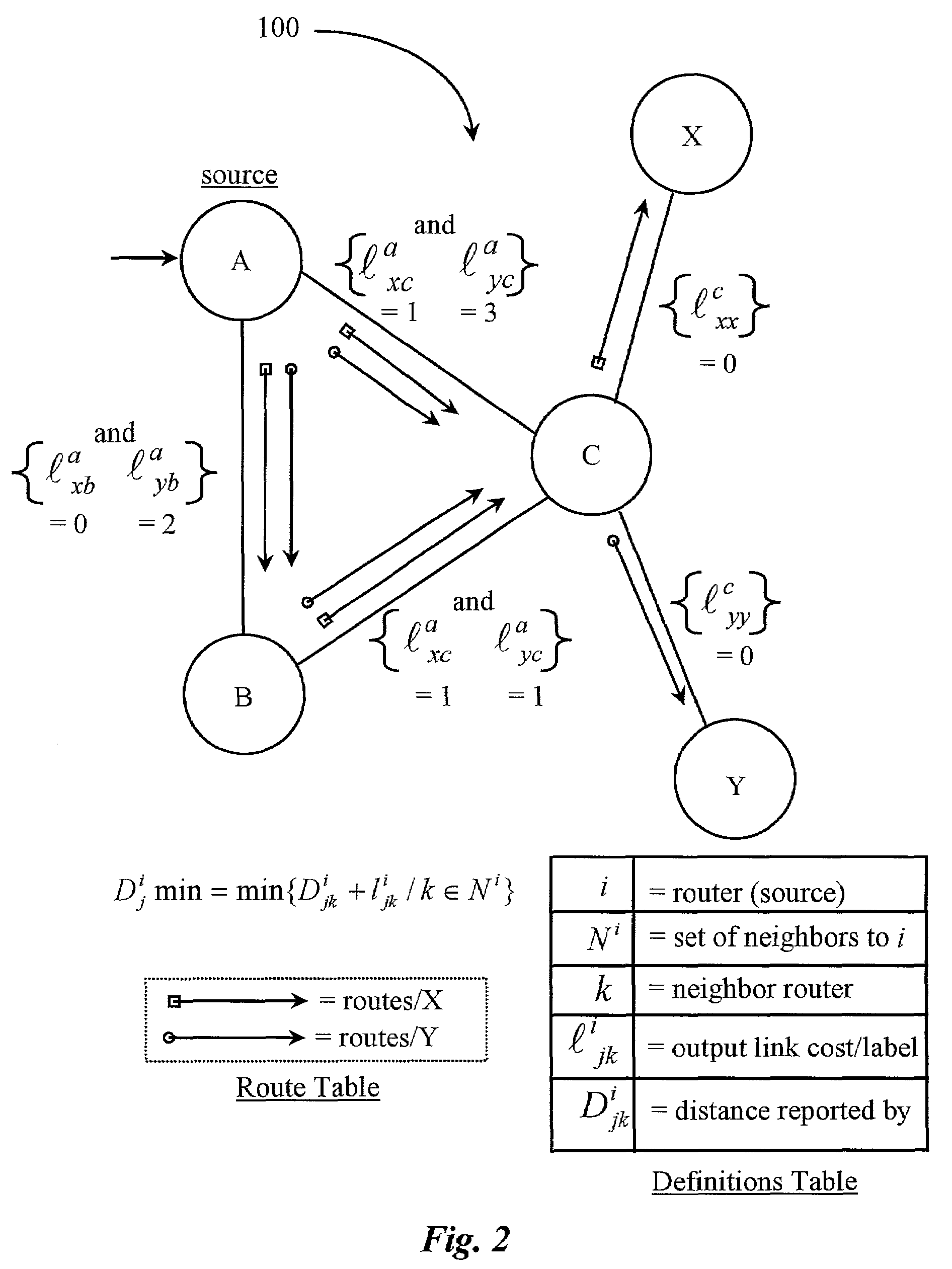
A control system is disclosed for controlling data flow over a data-packet-network according to specific destinations. The system has a network monitoring system for monitoring network performance parameters; a network access system for accessing specific nodes in the network; and a control software executable on the network access system for assigning and changing cost parameters at selected nodes in the network. A network administrator uses the network access system and control software to assign and implement cost values at the selected nodes, the values associated individually with a specific destination or destinations, the values establishing forwarding costs to be incurred at the selected nodes, and link costs to be incurred per data link between the nodes such that manipulation of such cost value assignments enables load balancing of data traveling through the network. In one embodiment the data-packet-network is internal to a router and nodes comprise internal router cards.
Owner:PLURIS
Text keyword extraction method, apparatus and device, and storage medium
InactiveCN108563636AImprove accuracyNatural language data processingSpecial data processing applicationsPart of speechValue assignment
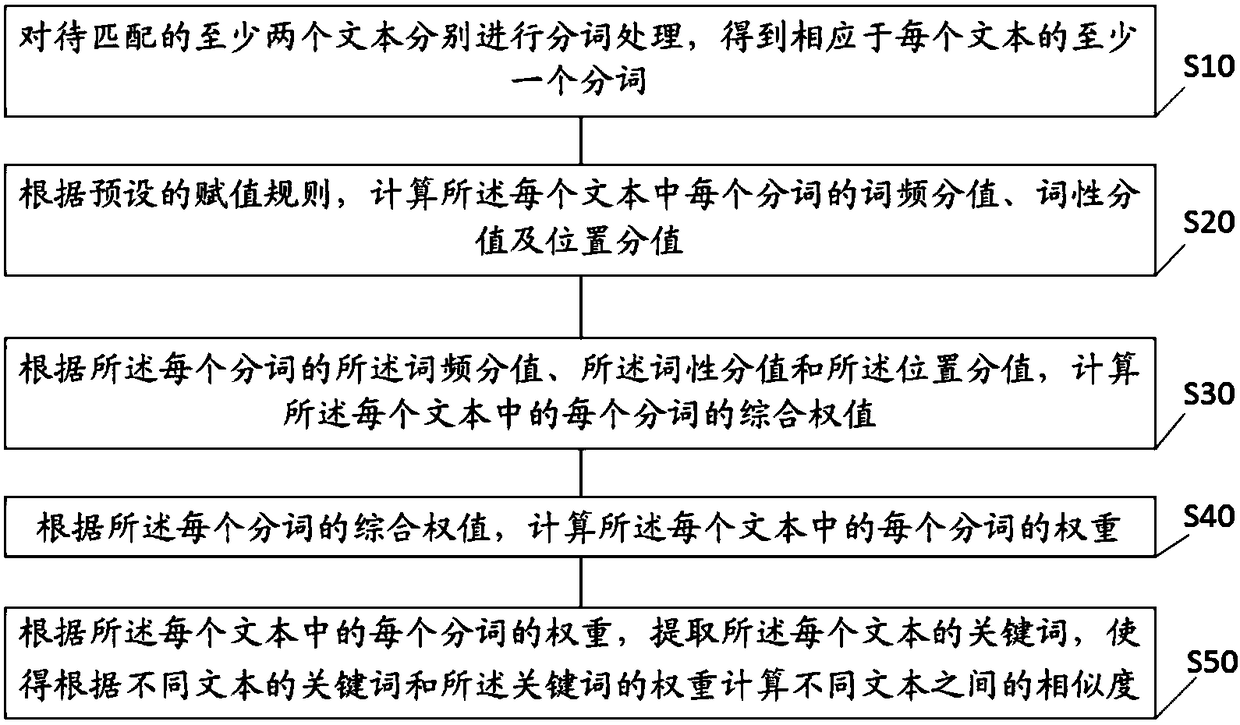
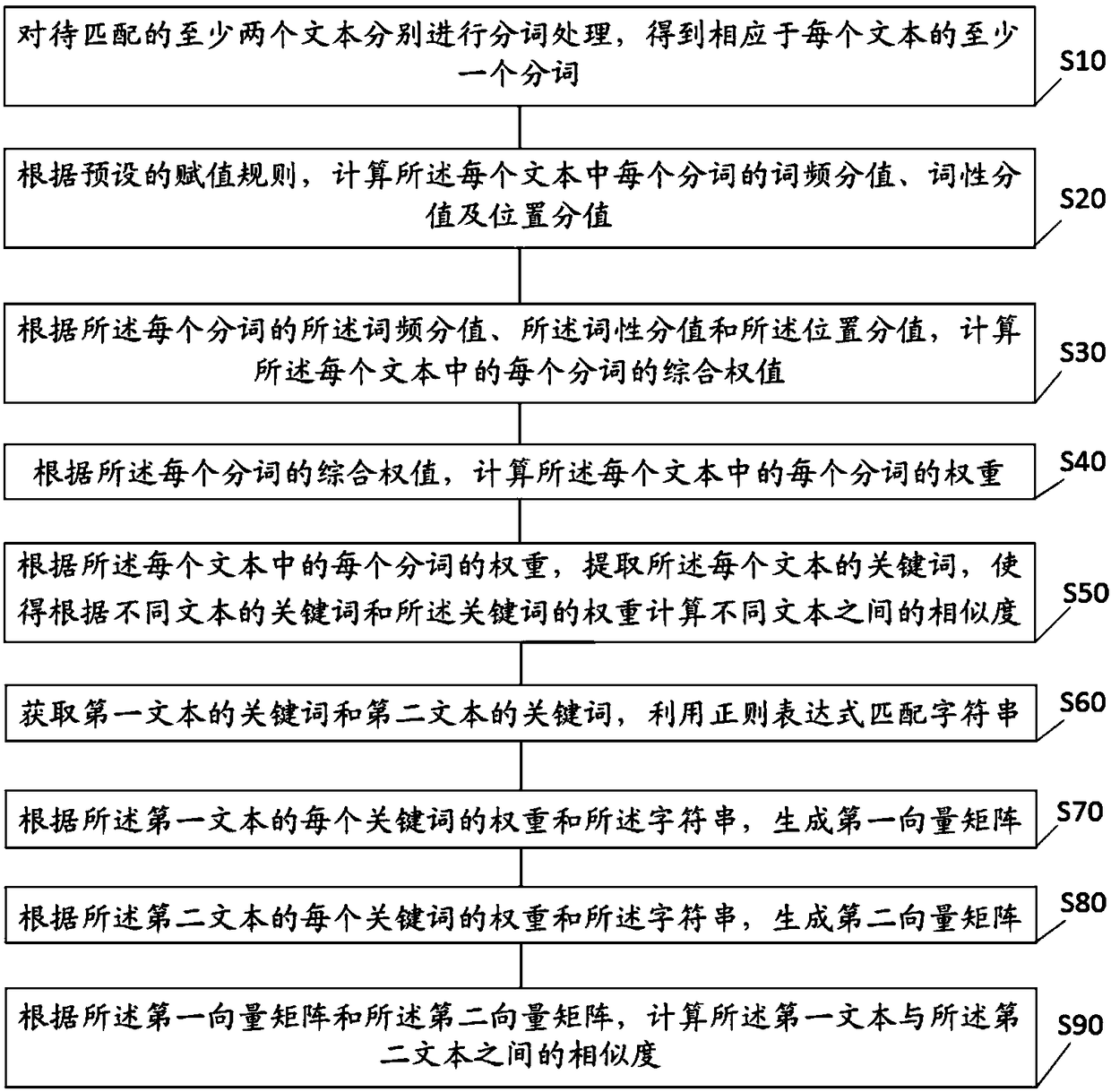
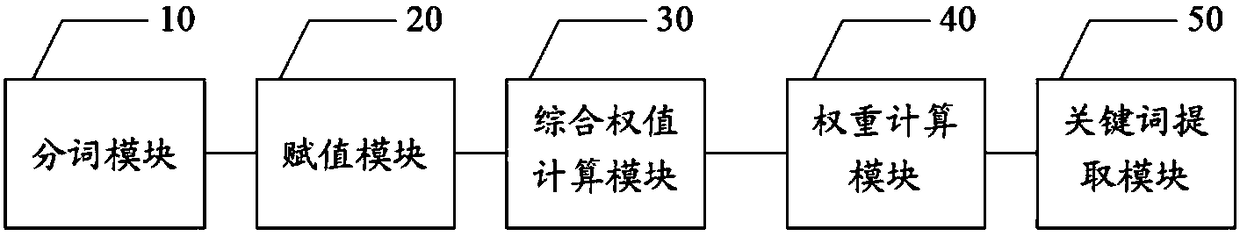
The invention discloses a text keyword extraction method. The method comprises the steps of performing word segmentation processing on at least two to-be-matched texts to obtain at least one segmentedword corresponding to each text; according to a preset value assignment rule, calculating a word frequency score, a part-of-speech score and a position score of each segmented word in each text; according to the word frequency score, the part-of-speech score and the position score of each segmented word, calculating a comprehensive weight value of each segmented word in each text; according to the comprehensive weight value of each segmented word, calculating a weight of each segmented word in each text; and according to the weight of each segmented word in each text, extracting a keyword ofeach text. The invention furthermore discloses a text keyword extraction apparatus and device, and a storage medium. The problem of inaccurate document keyword extraction can be solved, so that the measurement of the similarity between different documents is more accurate.
Owner:GCI SCI & TECH +1
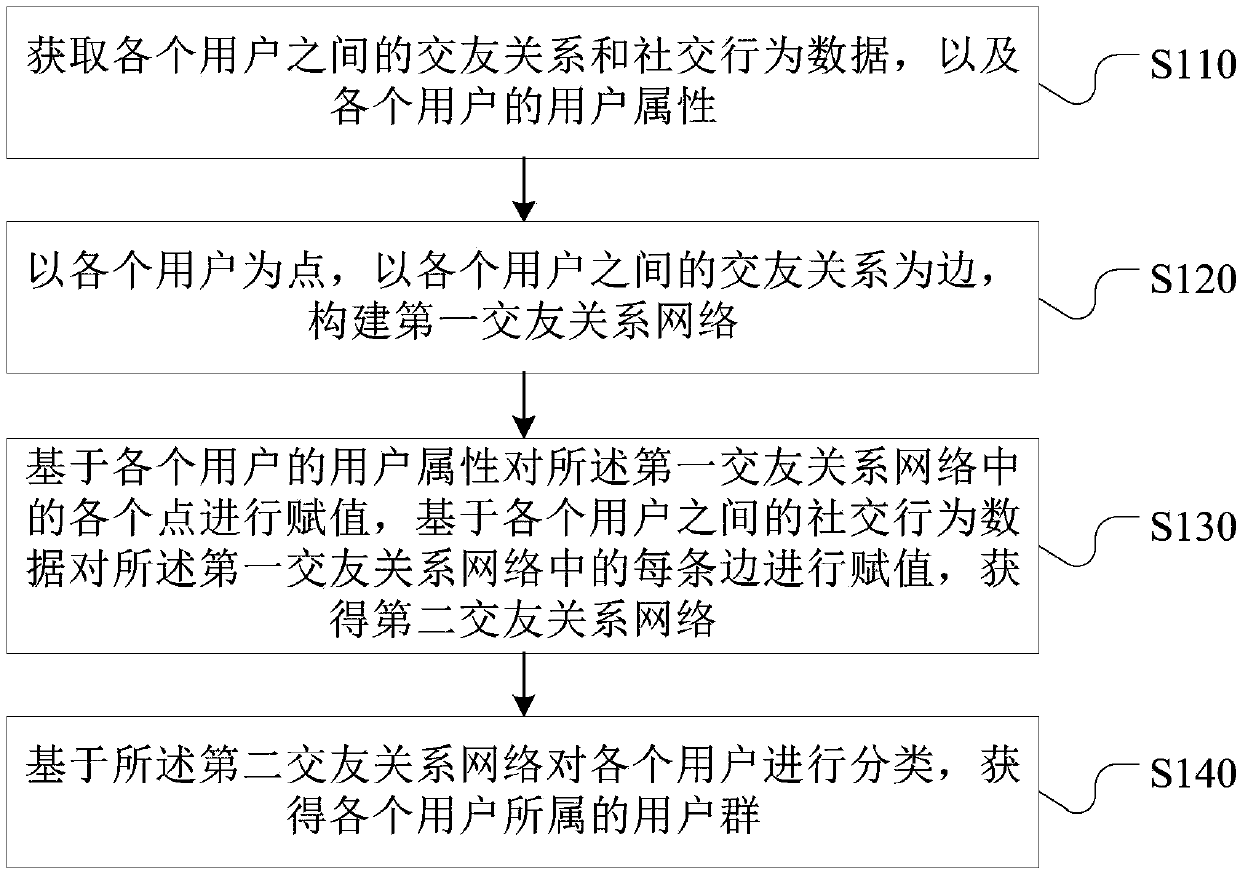
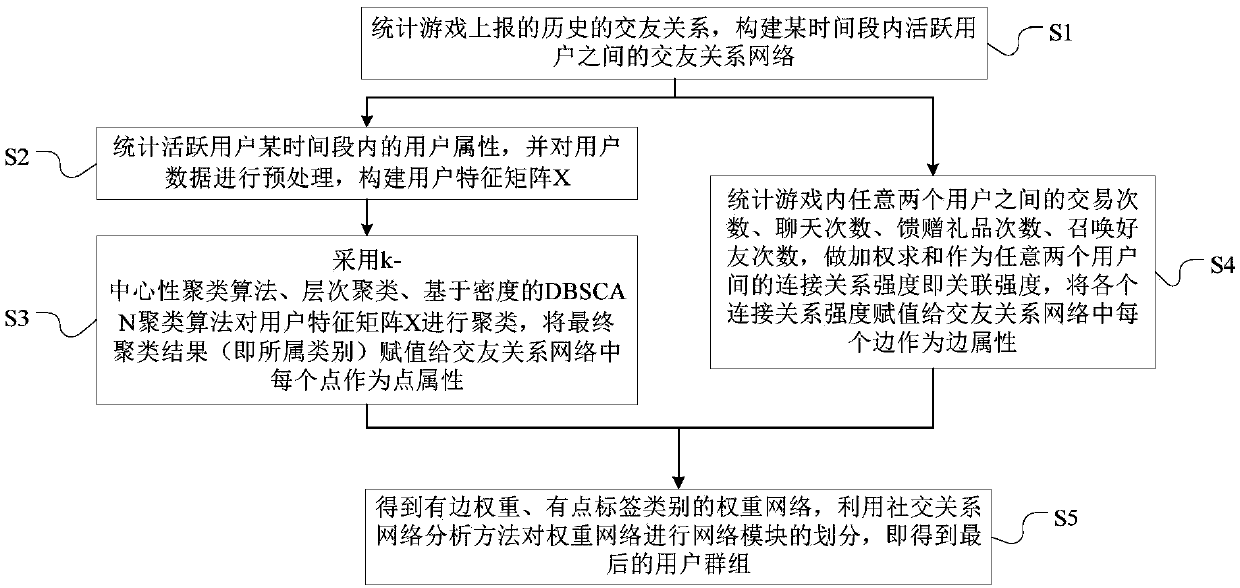
User group classification method, storage medium and terminal
ActiveCN108197224AAvoid churnImprove recallData processing applicationsSpecial data processing applicationsClassification methodsValue assignment
The invention provides a user group classification method, a storage medium and a terminal, and aims to solve the problem of poor usage efficiency of user groups in the prior art. The method comprisesthe steps of obtaining friend-making relationships and social behavior data among users, and user attributes of the users; by taking the users as points and the friend-making relationships among theusers as edges, establishing a first friend-making relationship network; based on the user attributes of the users, performing value assignment on the points in the first friend-making relationship network, and based on the social behavior data among the users, performing value assignment on the edges in the first friend-making relationship network, thereby obtaining a second friend-making relationship network; and based on the second friend-making relationship network, classifying the users to obtain the user groups which the users belong to. Therefore, the usage efficiency of the user groupsis improved.
Owner:GUANGZHOU HUYA INFORMATION TECH CO LTD
Method for creating numerical control programs
ActiveUS20110046766A1Special data processing applicationsNumerical controlNumerical controlLaser processing
A method for creating an NC program for controlling a test run for determining, optimizing and / or validating processing parameters and / or control parameters of a processing operation on a laser processing machine comprises accessing a base NC program that includes at least one contour variable for the at least one test contour to be produced in the test run and at least one decision function for value assignment of a contour parameter to the contour variable, providing a selection function for selection by an operator of a combination of input values that are characteristic of the processing operation, and creating the NC program from the base NC program by automatic execution of the at least one decision function for assigning a contour parameter to the contour variable, the contour parameter being determined based on the combination of input values.
Owner:TRUMPF SCHWEIZ AG
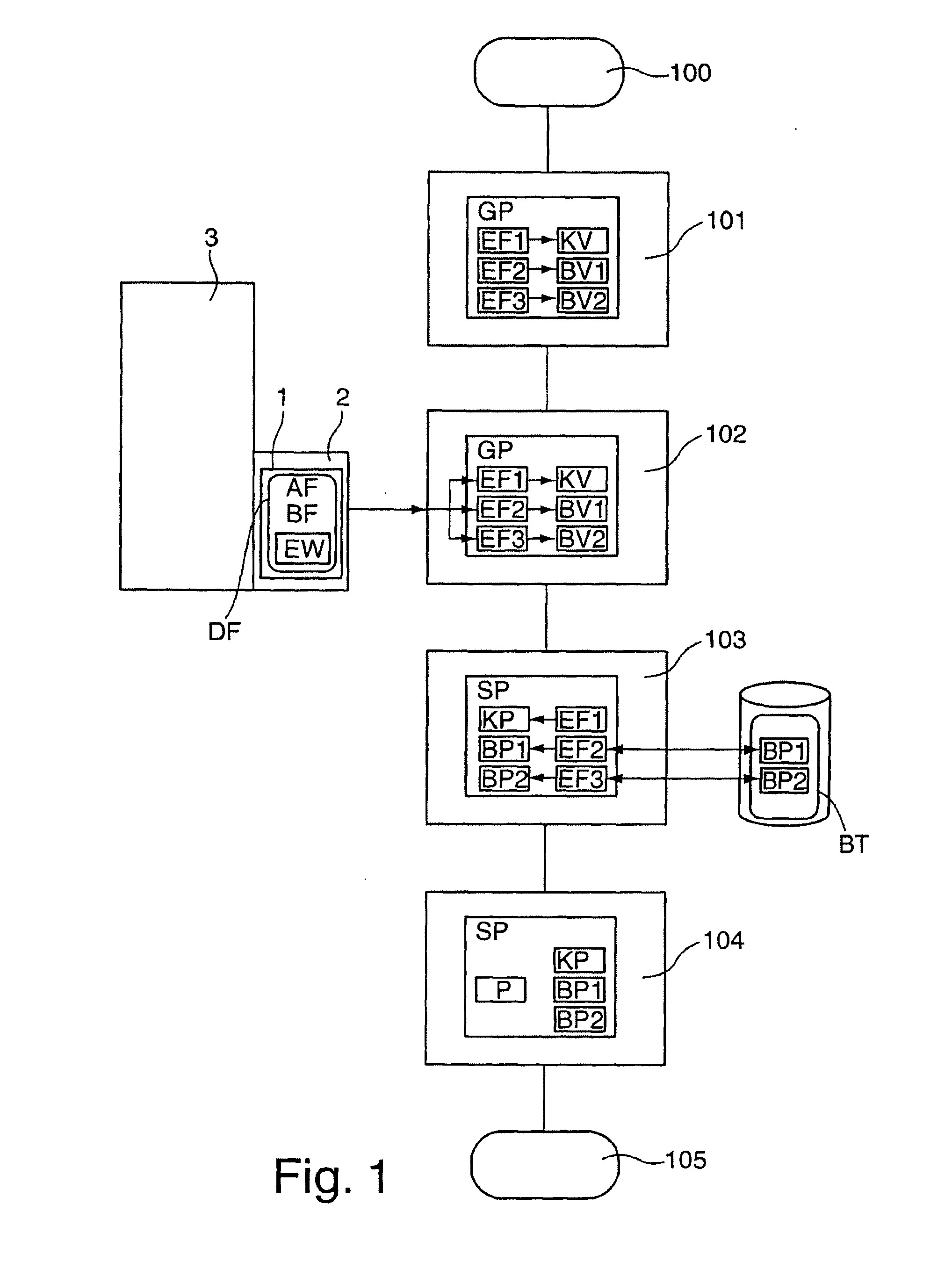
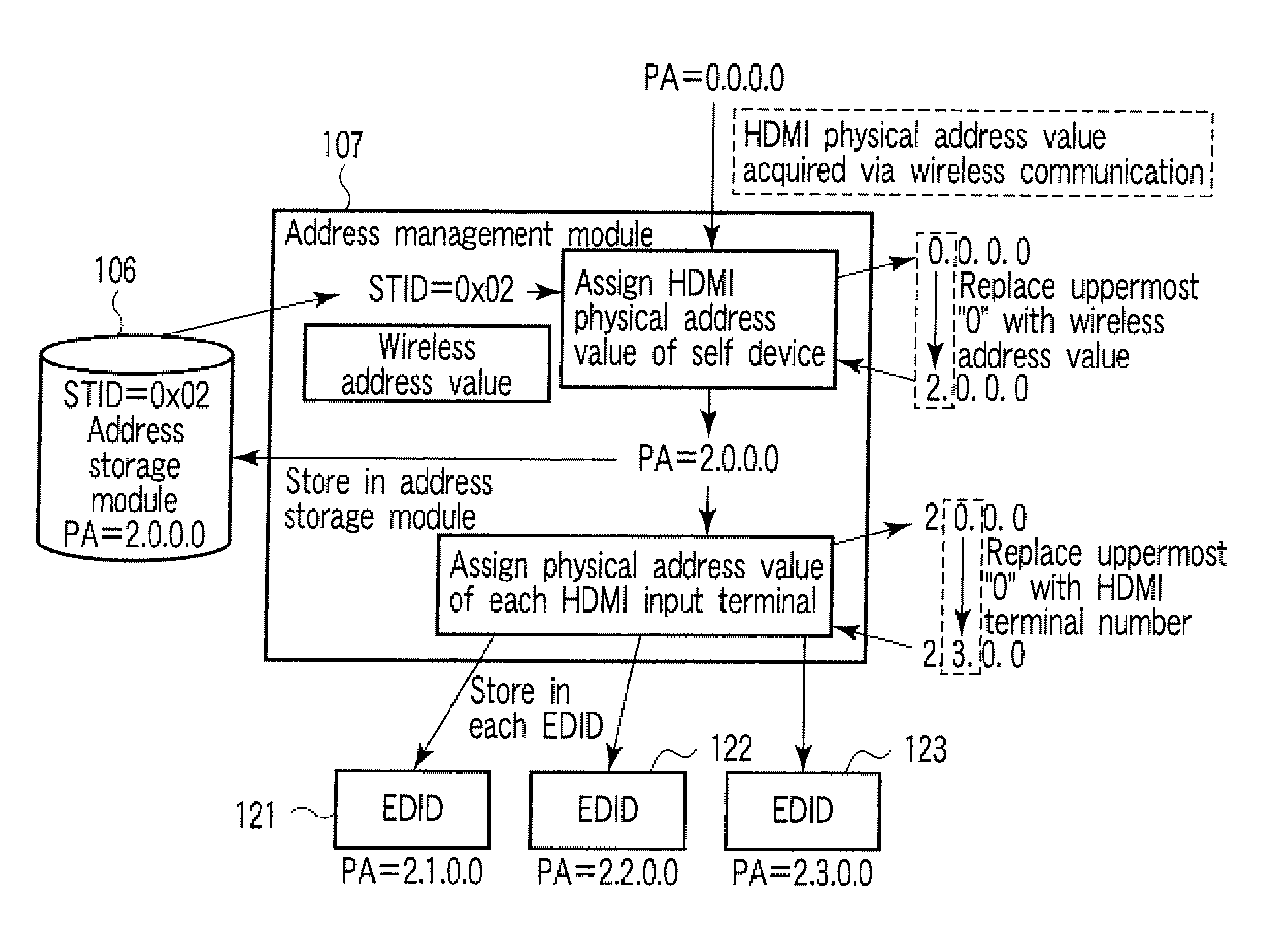
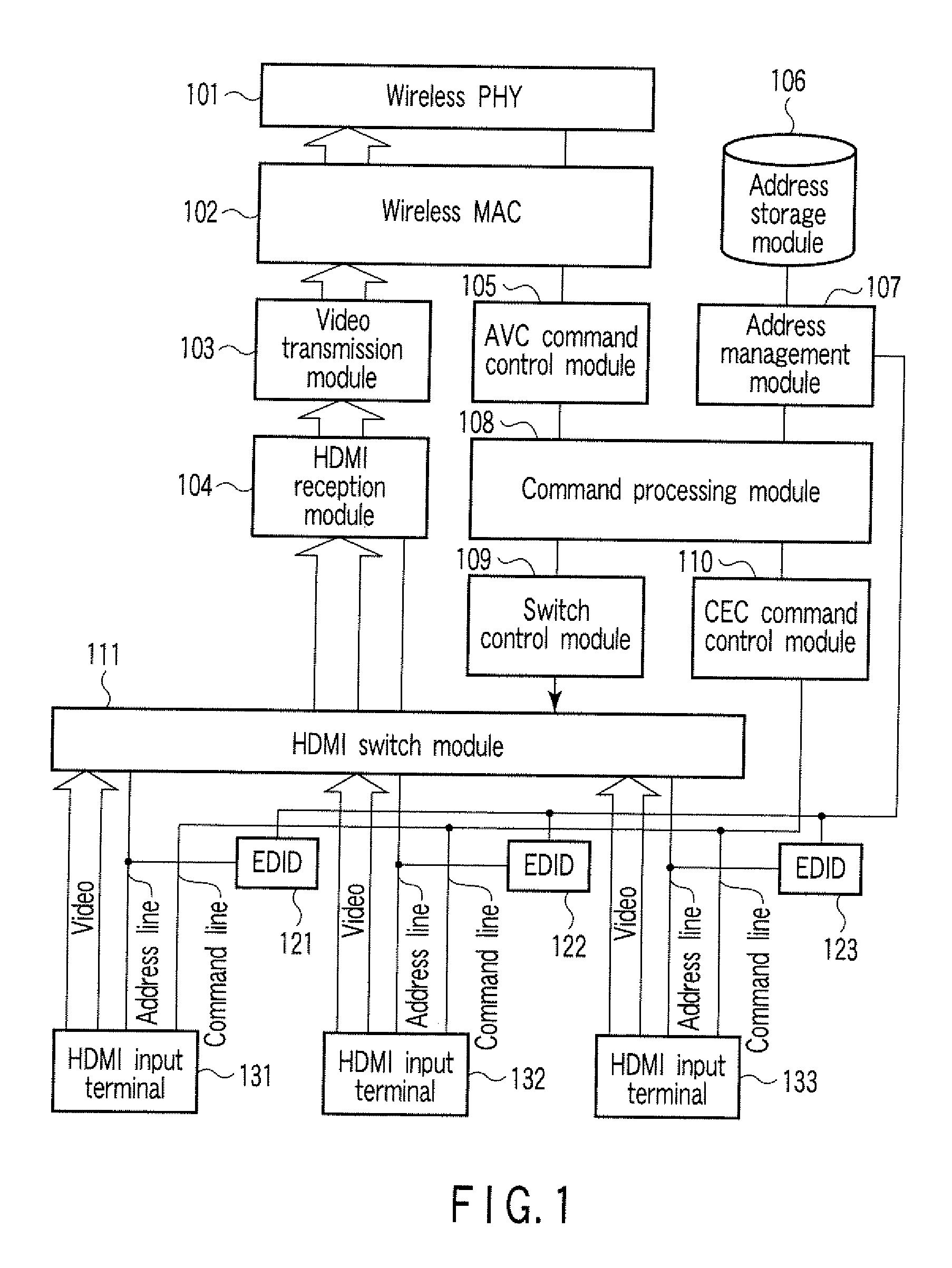
Communication Apparatus
ActiveUS20090271530A1Cathode-ray tube indicatorsMultiple digital computer combinationsValue assignmentE communication
According to one embodiment, a communication apparatus includes a first communication module configured to communicate with at least one partner device by a first communication scheme, a second communication module configured to communicate with at least one partner device by a second communication scheme, and an address management module configured to assign an address value for the second communication scheme to at least one partner device connected via the second communication module based on the address value for the first communication scheme of the self device, which is assigned based on an address value assignment scheme defined by the first communication scheme.
Owner:KK TOSHIBA
Method for Domain Trading
A method for domain portfolio trading involving the assessment of risk level based on various tangible criteria and applying this determination to the assignment of a value. Once the aggregated level of risk and actual value number are determined, a real-time, online domain portfolio trading mechanism allows those involved to track, move, implement and otherwise conduct business in an instantaneous environment.
Owner:MANRIQUEZ GREGORY +1
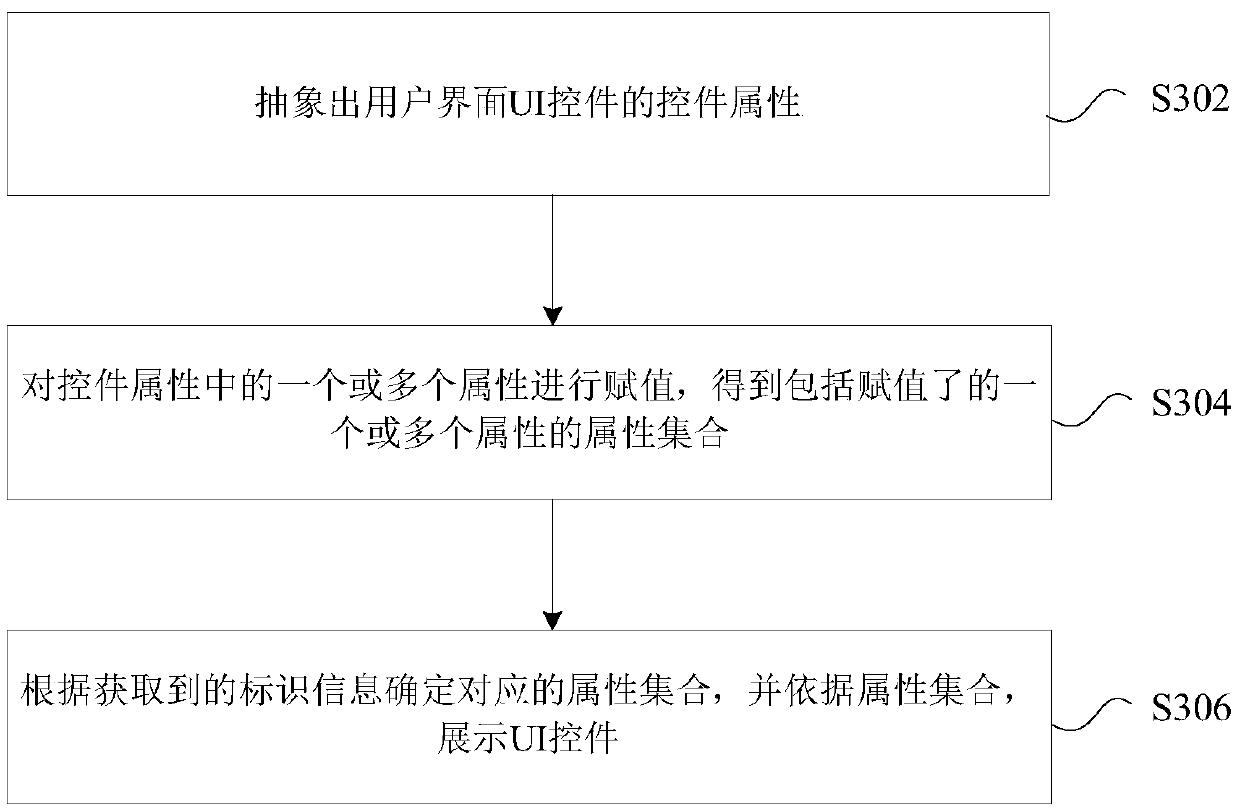
User interface control display method and device
ActiveCN105511873AReduce consumptionSolve the problems of high resource consumption and low development efficiencyExecution for user interfacesResource consumptionValue assignment
The invention provides a user interface control display method and device. The method includes the steps that control attributes of a UI control of a user interface are extracted; value assignment is conducted on one or more attributes in the control attributes, and an attribute set including the one or more attributes to which values are assigned is obtained; the corresponding attribute set is determined according to the obtained identification information, and the UI control is displayed according to the attribute set. By means of the user interface control display method and device, the problems that in the prior art, resource consumption is high, and development efficiency is low when the control is operated are solved, and thus the effects that resource consumption is reduced, and development efficiency is improved are achieved.
Owner:NETEASE (HANGZHOU) NETWORK CO LTD
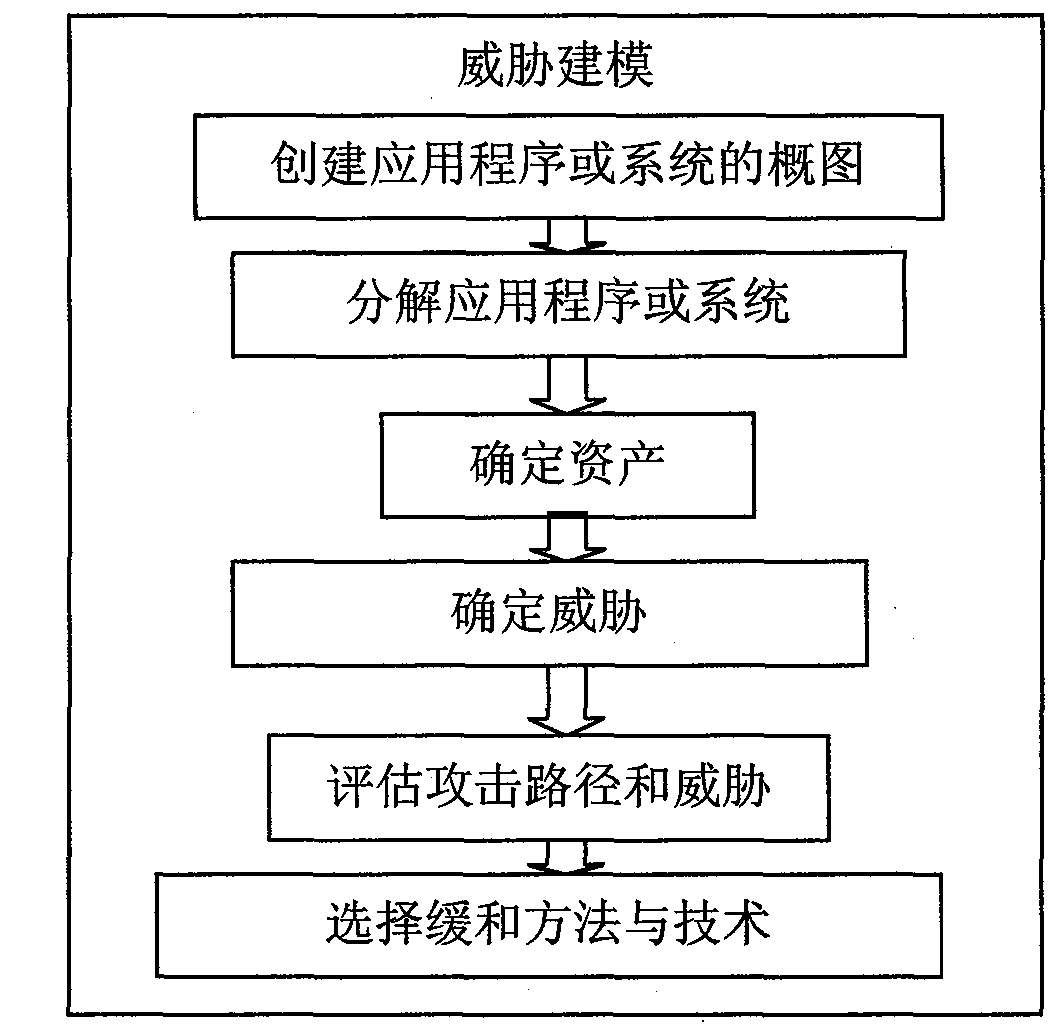
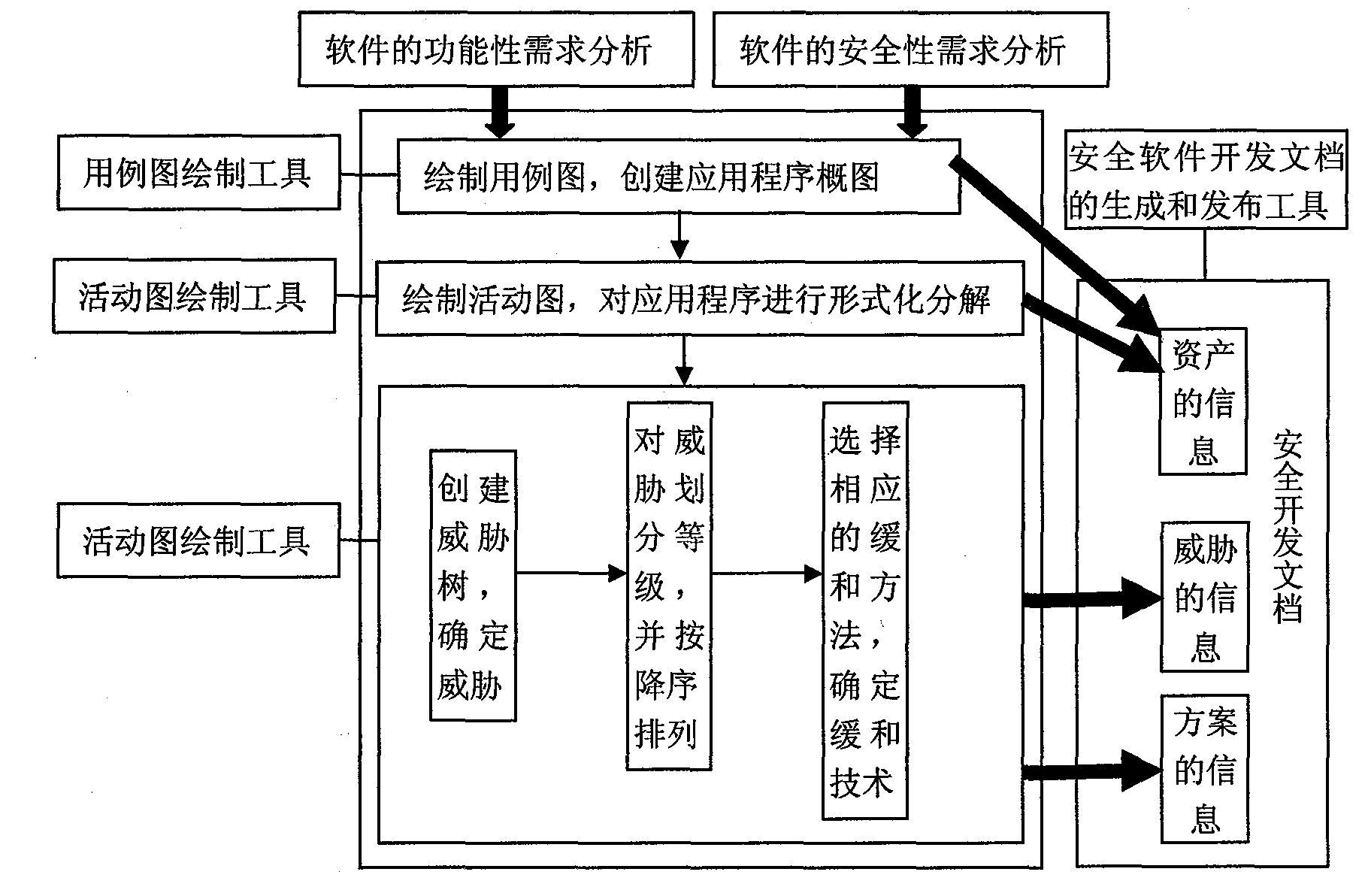
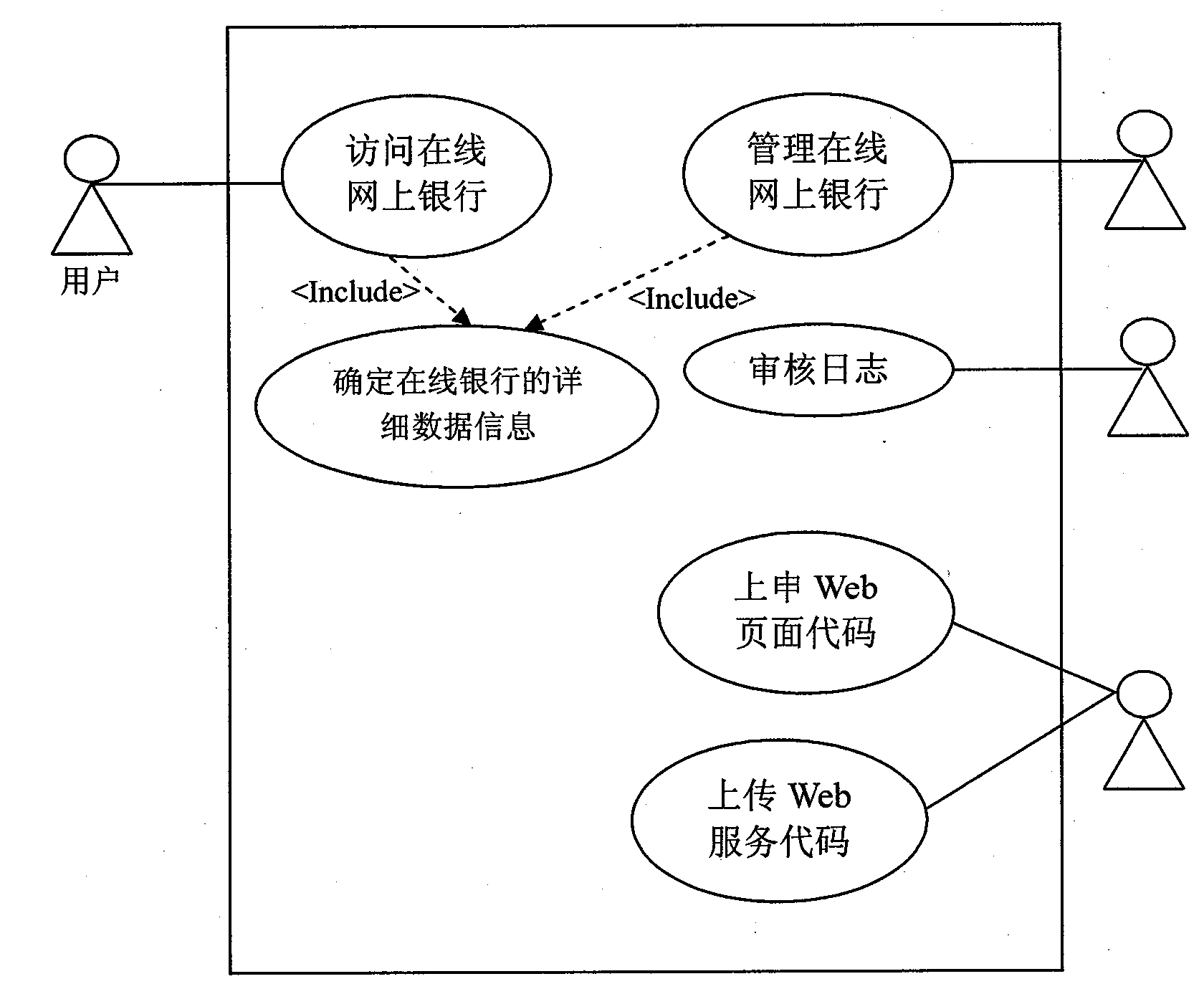
Threat modeling method added with attack path formalization analysis
InactiveCN101655787AReduce security flawsQuality improvementComputer security arrangementsSpecific program execution arrangementsApplicability domainSoftware design pattern
The invention discloses a threat modeling method added with attack path formalization analysis. In software design stage, software defect information is extracted by UML active graph decomposition application or system and threat modeling is carried out. The method includes the following steps: creating and modeling use case; creating silhouette of application or system; decomposing the application or system by using the active graph; using the acquired key asset information as threat object, creating a threat tree by taking the threat object as root node and assigning value to all nodes in the threat tree including value assignment on root nodes and leaf nodes; classifying and evaluating the threat object; and calculating the attack path of the threat tree. Compared with the prior art, the invention can reduce software product safety defect and improve software quality, improves application range of threat modeling, obtains more comprehensive and accurate threat relaxation scheme, realizes threat modeling automation and greatly reduces technical threshold, cost and development period of trusted software development.
Owner:TIANJIN UNIV
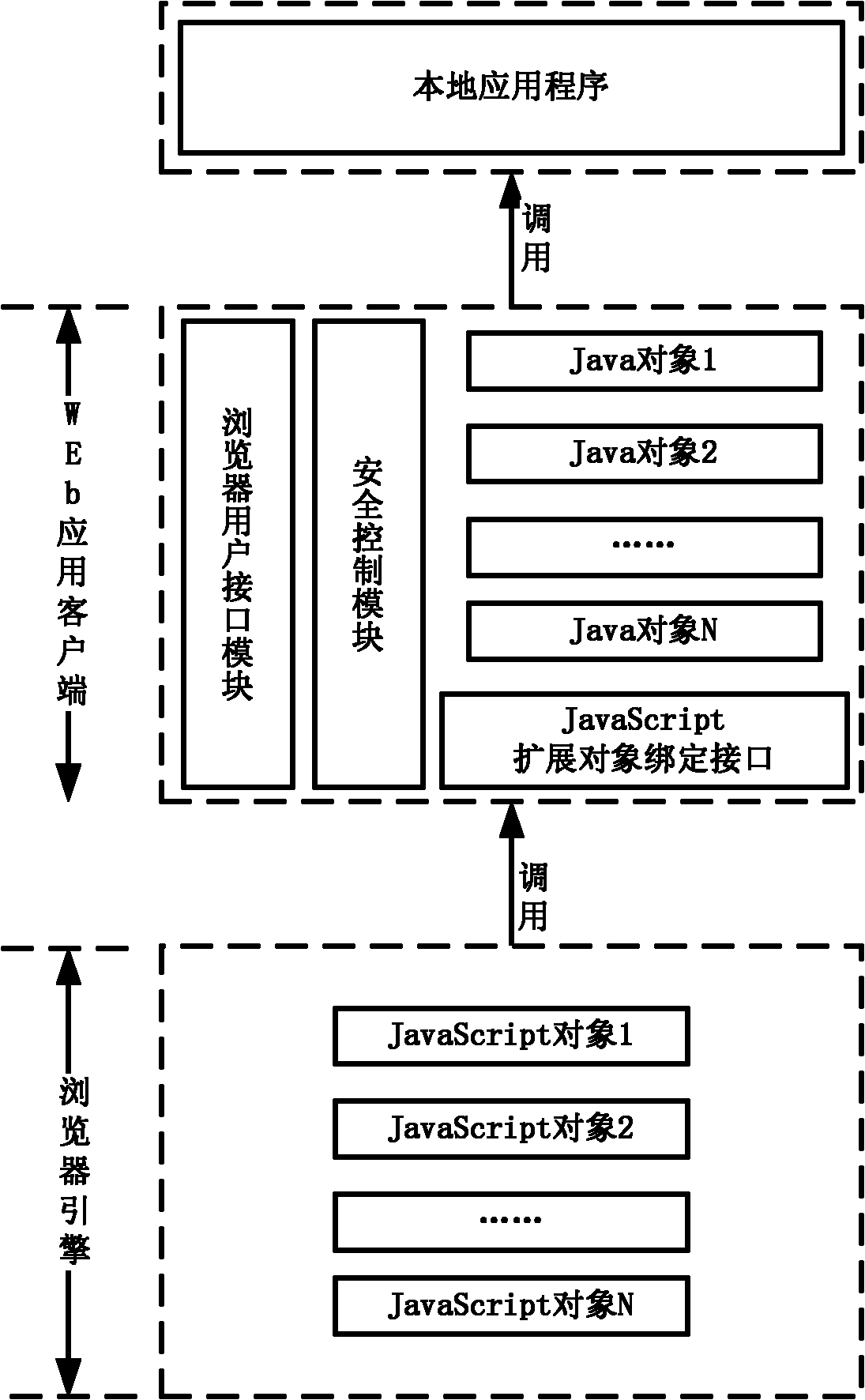
Realizing method of JavaScript extended object based on Android platform, and binding interface structure
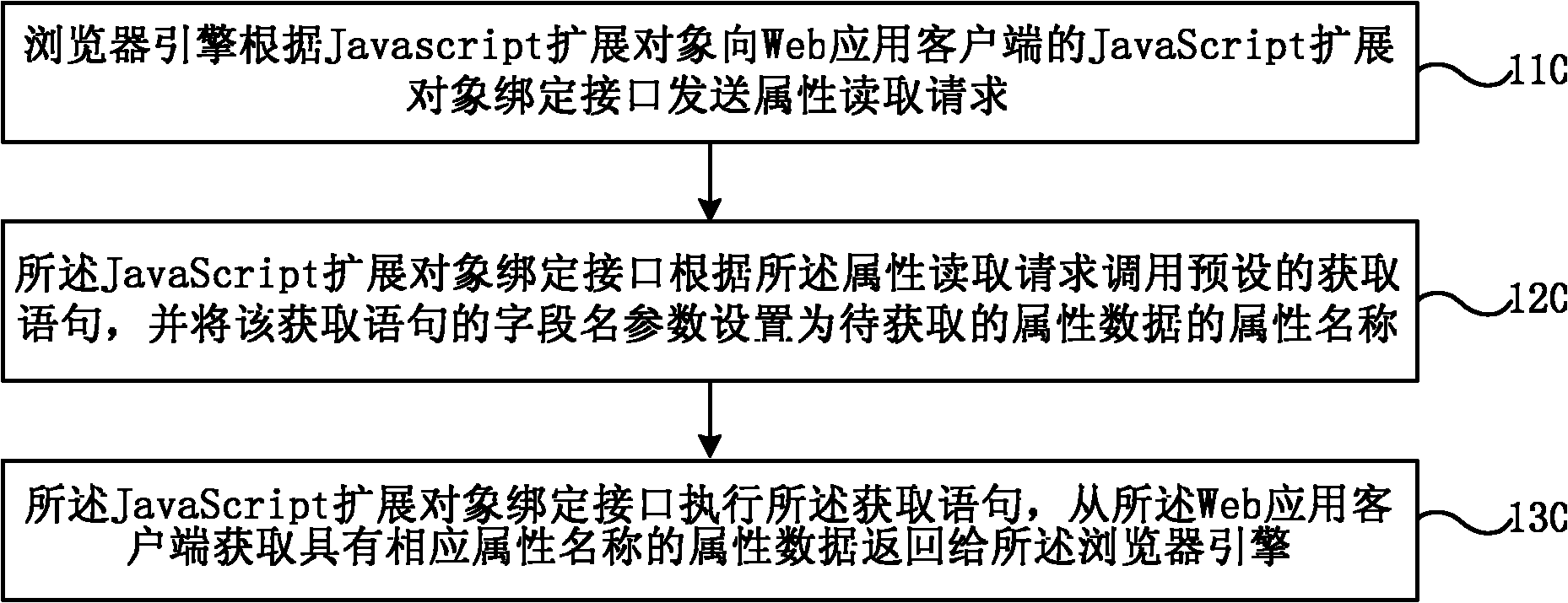
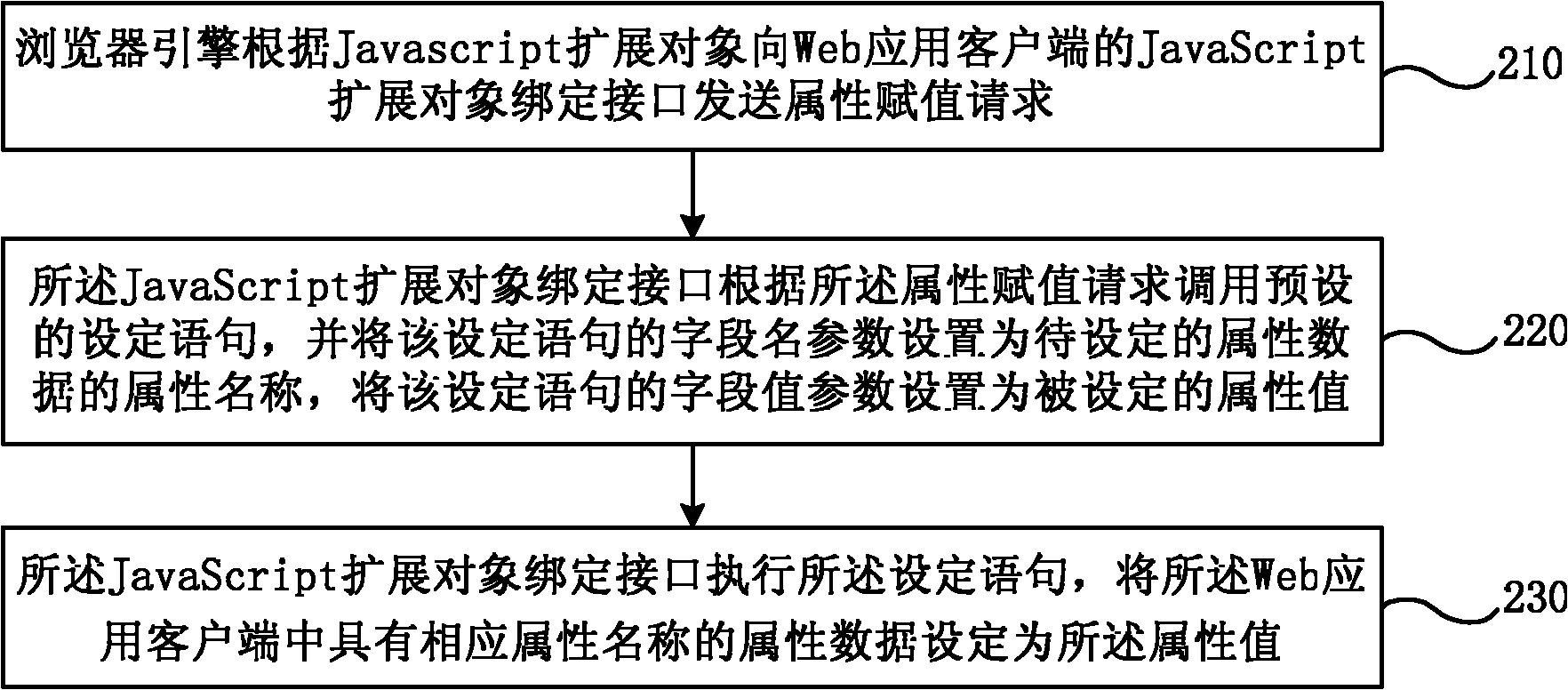
ActiveCN102207873ADirect readRealize assignmentSpecific program execution arrangementsWeb applicationValue assignment
The invention provides a realizing method of a JavaScript extended object based on an Android platform, and a binding interface structure. The realizing method of the JavaScript extended object based on the Android platform comprises the following steps of: sending an attribute reading request to the binding interface of the JavaScript extended object of a Web application client by a browser engine according to the JavaScript extended object; calling a pre-set acquisition statement by the binding interface of the JavaScript extended object according to the attribute reading request and setting field name parameters of the acquisition statement to be an attribute name of attribute data to be acquired; and executing the acquisition statement and returning the attribute data which has the corresponding attribute name and is acquired from the Web application client back to the browser engine. According to the realizing method and the binding interface structure, the direct reading and value assignment of the attribute date of the Java object are realized so that the conditions for realizing more abundant extending function are created.
Owner:CHINA UNITED NETWORK COMM GRP CO LTD
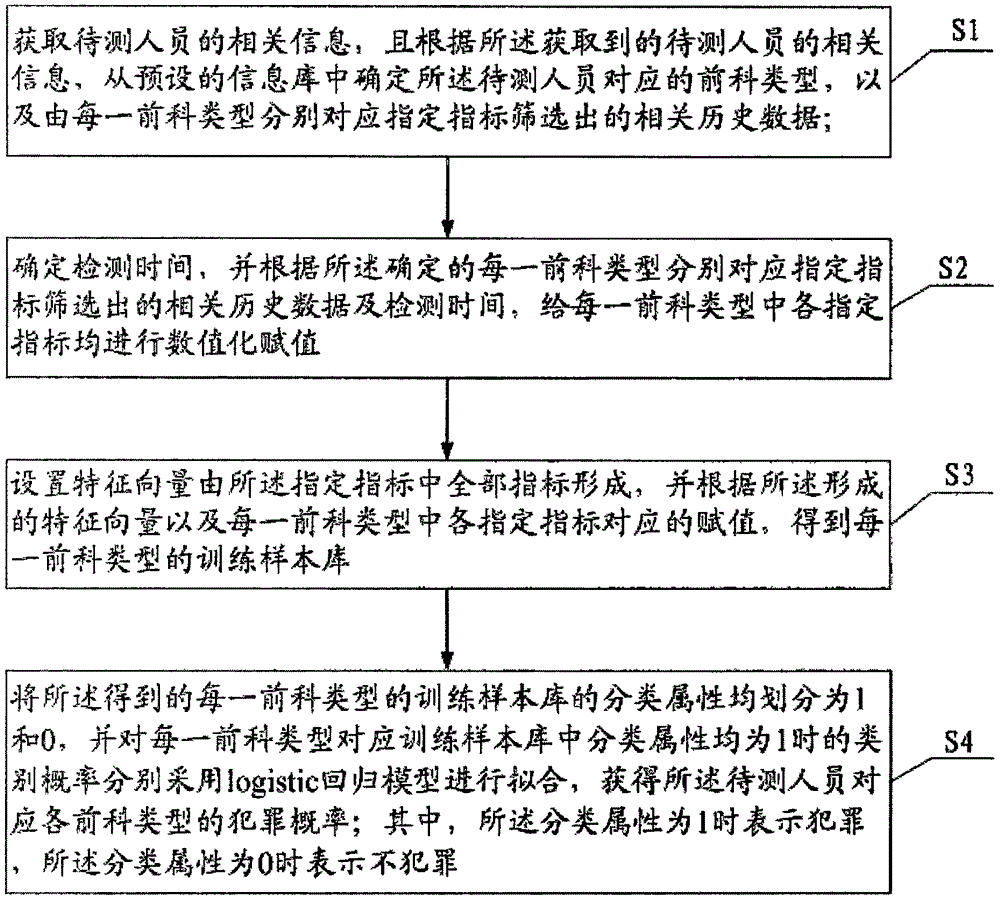
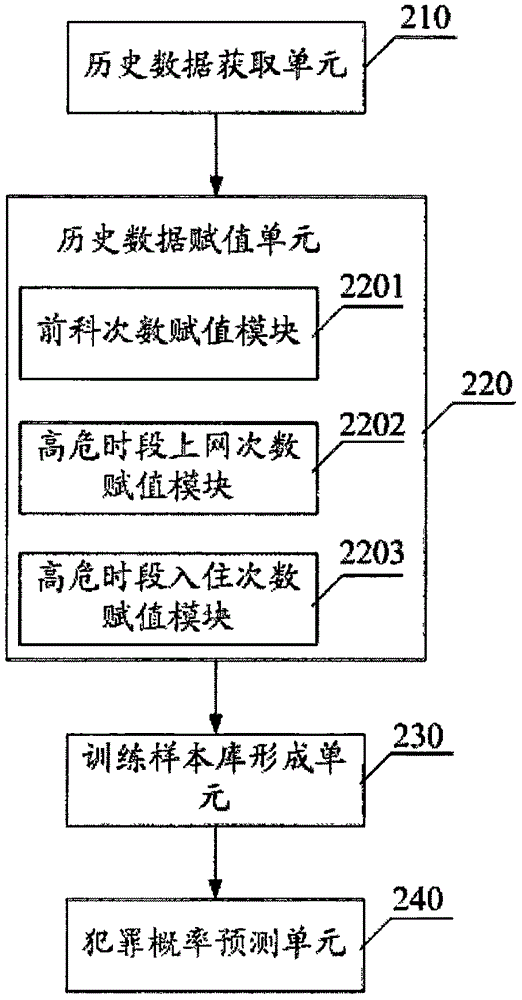
Criminal suspicion probability prediction method and system
The invention provides a criminal suspicion probability prediction method, and the method comprises the steps: obtaining the related information of a to-be-detected person, determining the corresponding criminal record types of the to-be-detected person according to the related information, and also determining the related historical data screened through a specified index corresponding to each criminal record type; determining the detection time, and carrying out the numerical value assignment of the specified indexes of all criminal record types according to the related historical data; setting a characteristic vector which is formed by all the specified indexes, and obtaining the training sample library of each criminal record type according to the characteristic vector and the values of all specified indexes; enabling the classification attribute of the training sample library of each criminal record type to be divided into 1 and 0, carrying out the fitting of the classification probability of the classification attribute (1) in the training sample library corresponding to each criminal record type through employing a logistic regression model, and obtaining the crime probability of all criminal record types of the to-be-detected person. According to the invention, the method can accurately detect the crime type and probability of the to-be-detected person, and provides onsite guide for public security officers to carry out key inspection.
Owner:WENZHOU POLYTECHNIC
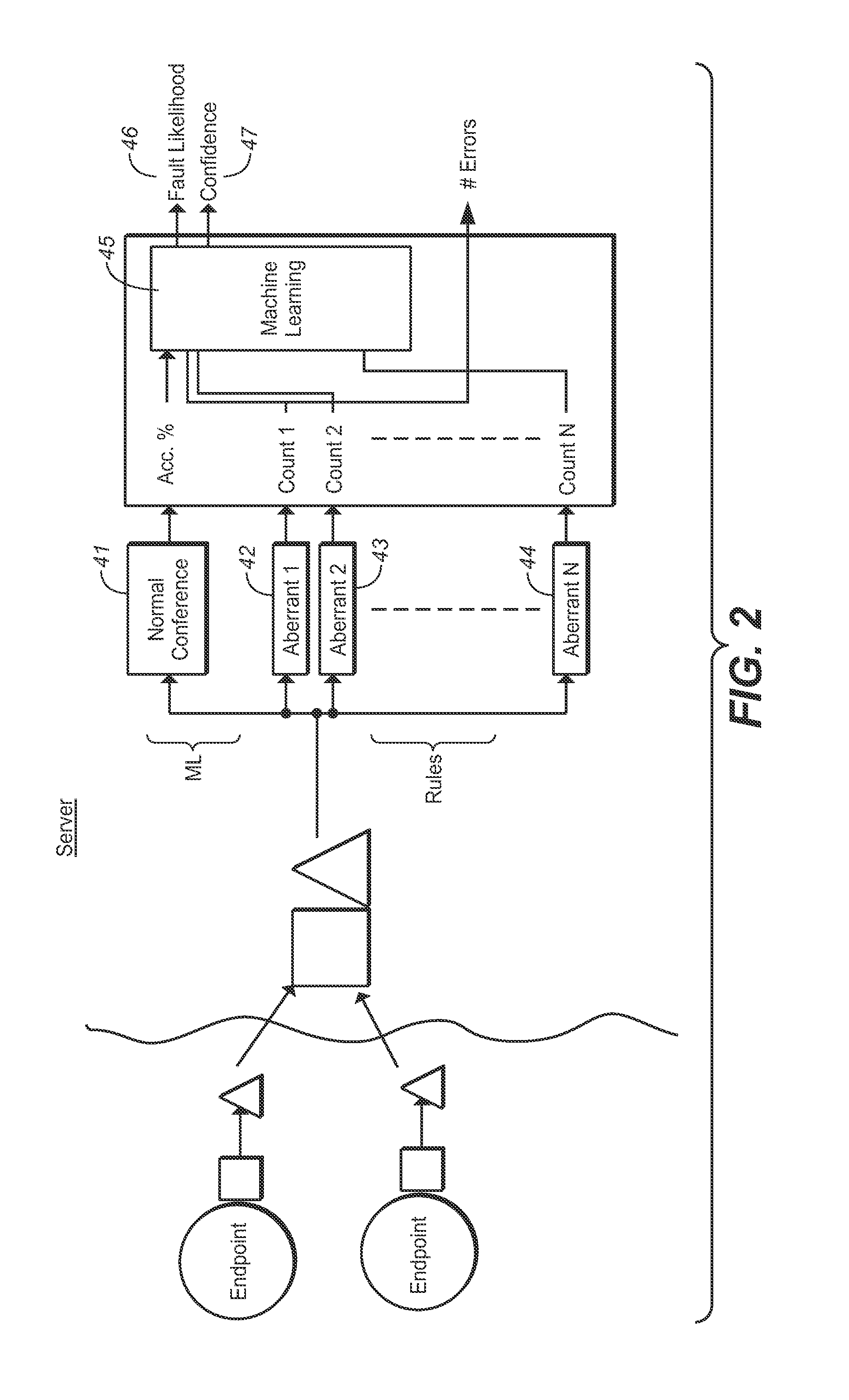
Detecting Conference Call Performance Issue from Aberrant Behavior
ActiveUS20160337510A1Improve the level ofReduce user experienceSpeech analysisSpecial service for subscribersValue assignmentAnomalous behavior
In a conference call having a plurality of participants interacting in a conference exchange of information in a digital transmission environment, the interaction being across a variable network transmission resource, a method of allocating the level of transmission resource, the methods including the steps of: (a) monitoring predetermined aspects of the participant's behavior during the conference call; (b) determining a divergence of participants behavior from normative values; (c) utilising any divergence as an indicator of aberrant operation of the participants; and (d) allocating the resource determinative on the divergence of participants behavior from normative values.
Owner:DOLBY LAB LICENSING CORP
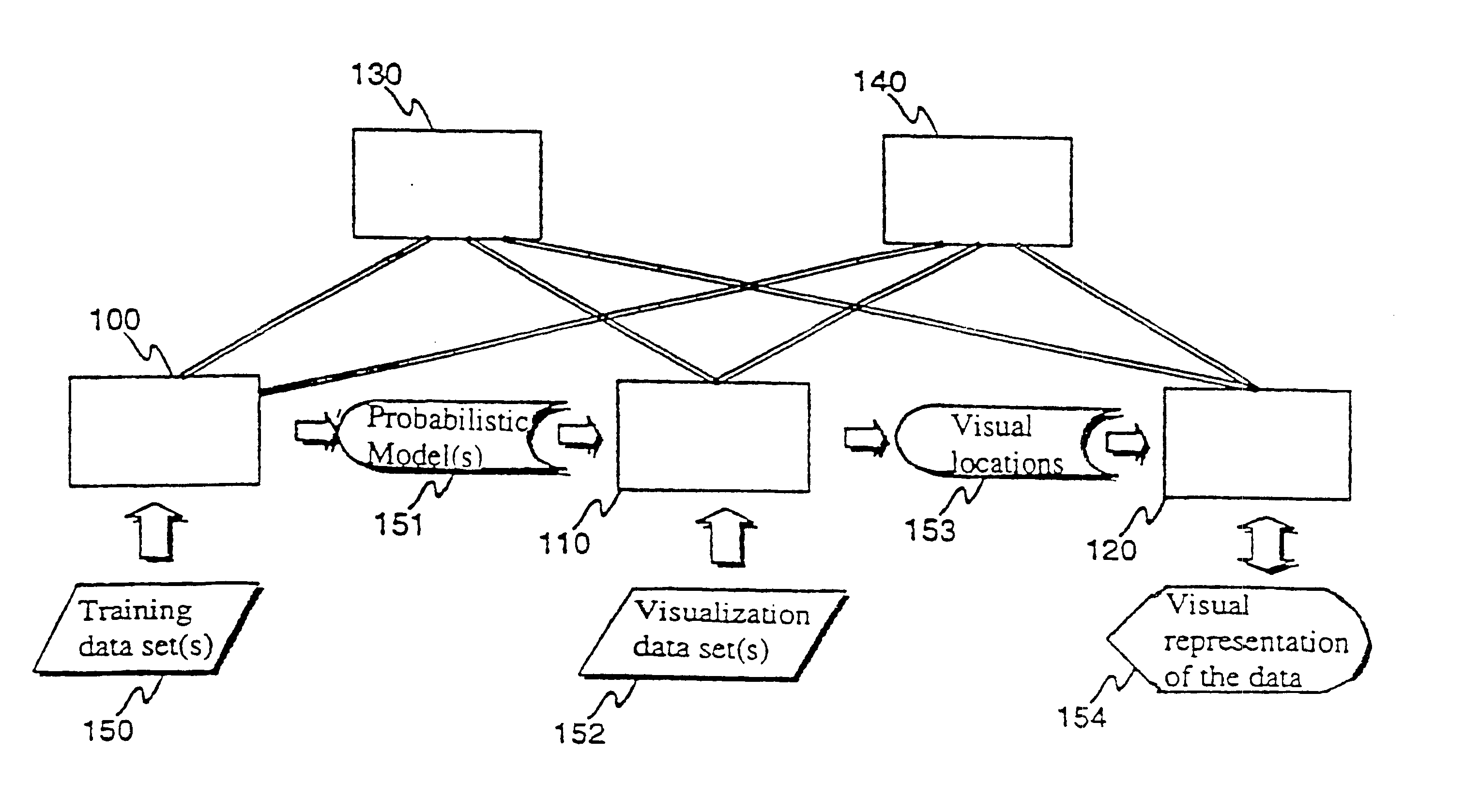
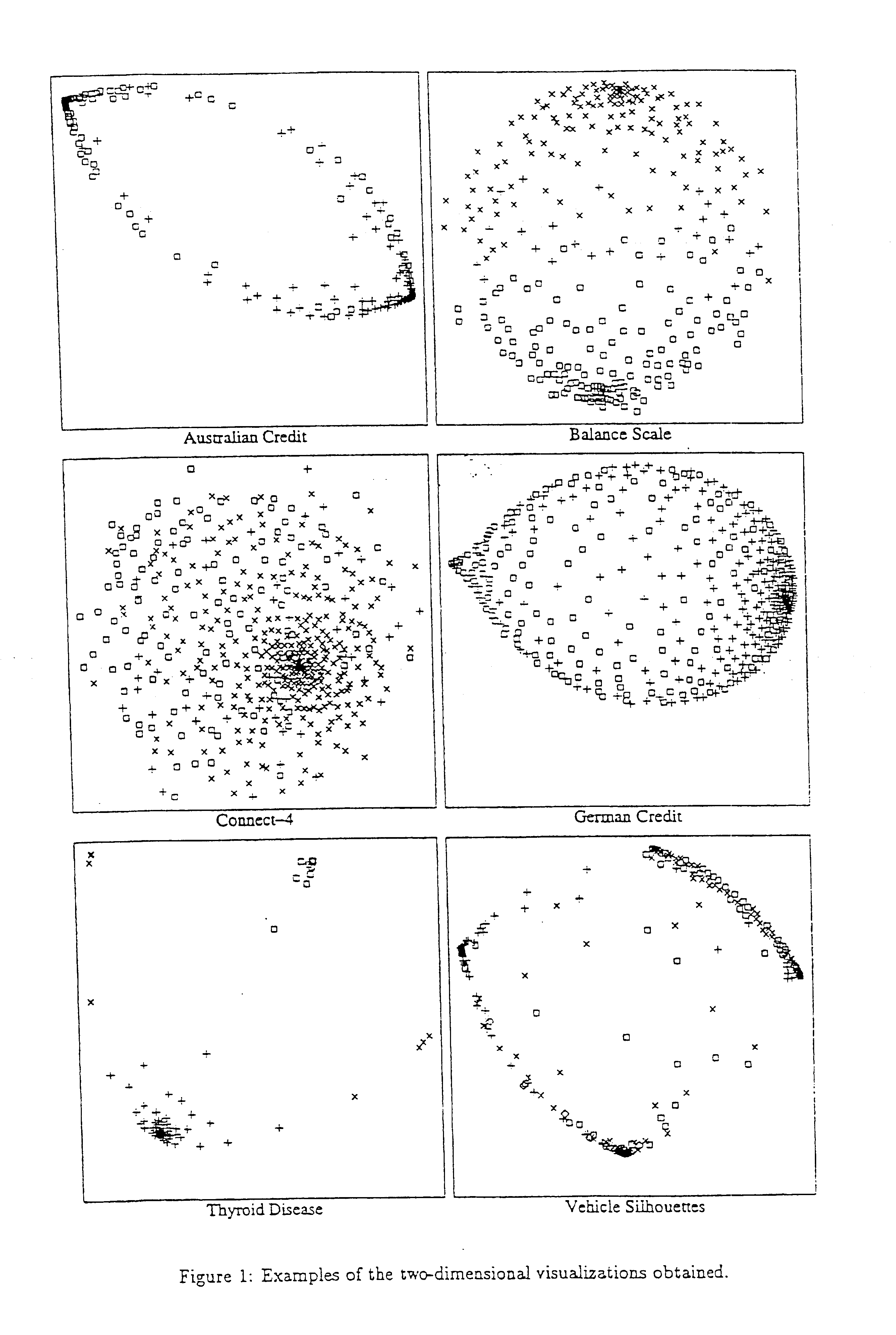
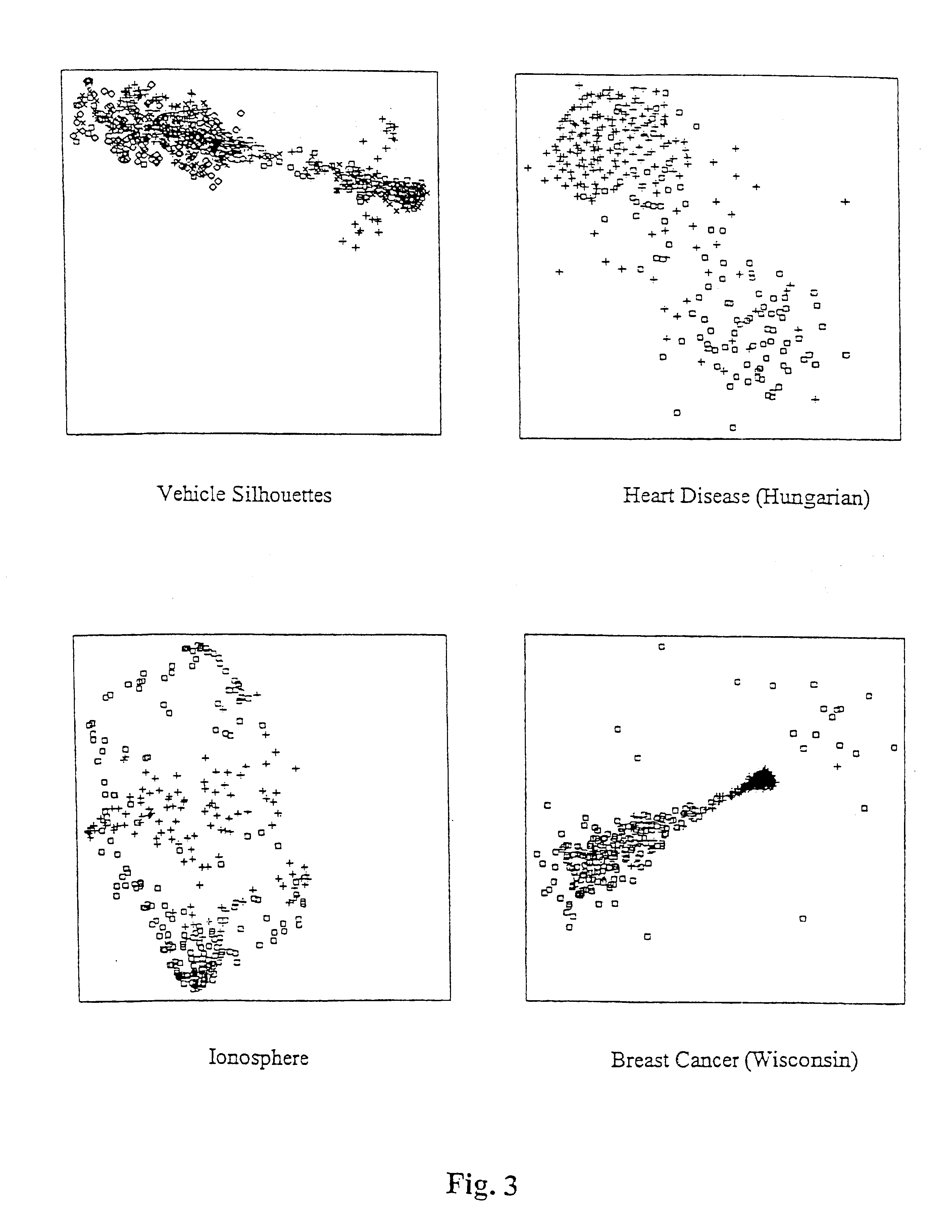
Visualization method and visualization system
InactiveUS6873325B1Flexible processFlexible approachDrawing from basic elementsCharacter and pattern recognitionProbit modelValue assignment
A method and system for transforming a multivariate data domain into a low-dimensional visual representation. Probabilistic models of the data domain are utilized, and at least one probabilistic model is used to produce at least one predictive distribution. The predictive distributions are used as inputs to the visualization process, where the multidimensional space is converted to a low-dimensional space. In this process data vectors are considered similar, for example, if the corresponding instances of a predictive distribution, conditioned with the variable value assignments found in the data vectors, are similar. Consequently, similarity is not defined directly using the physical properties of the data vectors, but indirectly through the probabilistic predictive model(s).
Owner:BAYES INFORMATION TECH
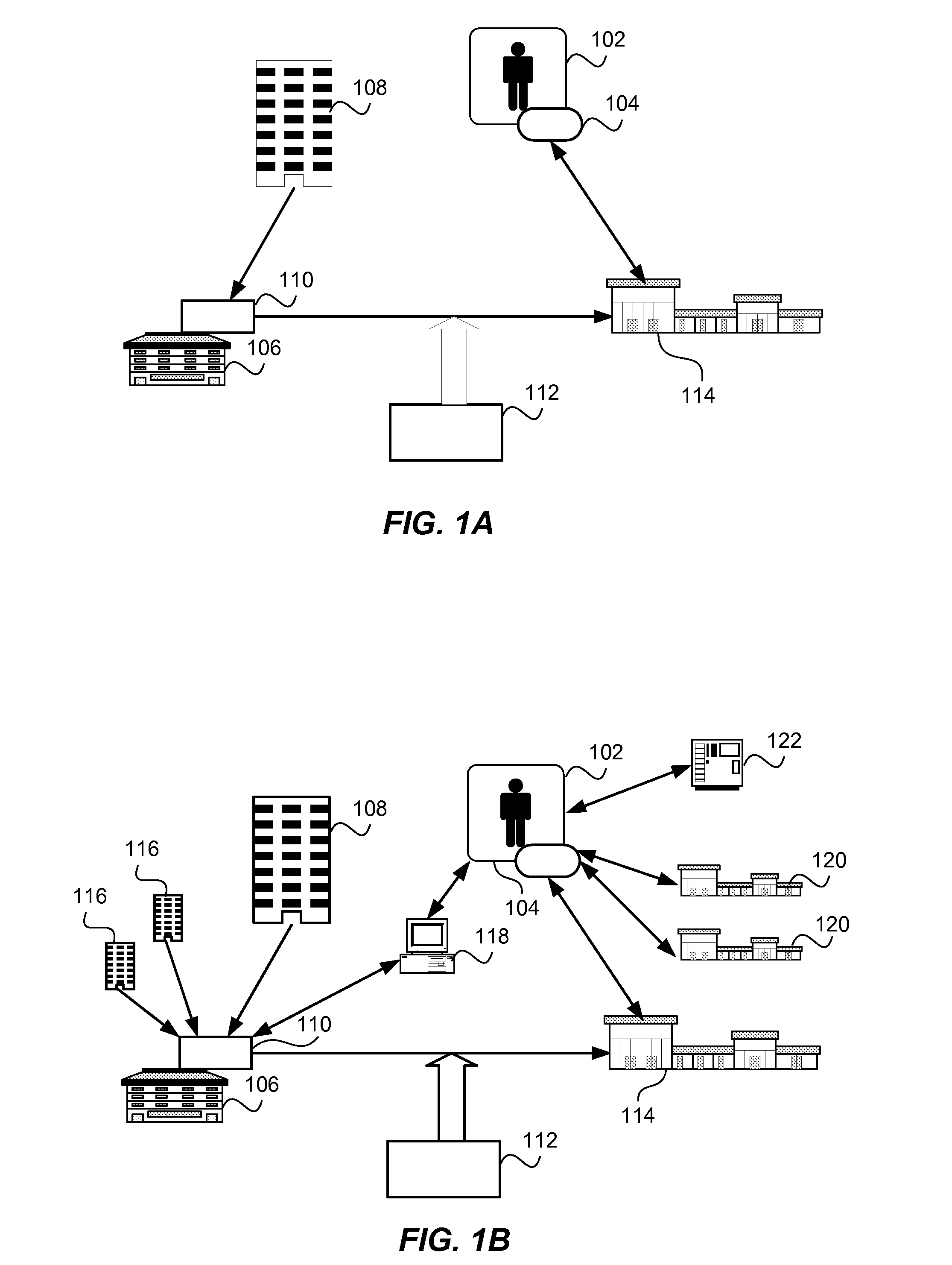
Payer-Based Account Porting To Portable Value Distribution Systems And Methods
A value distribution method includes enrolling a payee into a source program through which the payee receives funds from a payer. The source program includes a stored value account into which the payer deposits the payee's funds. The stored value account has account information associated therewith. The method also includes receiving a porting trigger, and, in response to the porting trigger, establishing a target program for the payee. The target program includes a target account into which entities in addition to the payer may deposit funds. The method also includes porting at least a portion of the account information from the source program to the target program.
Owner:MONEY NETWORK FINANCIAL
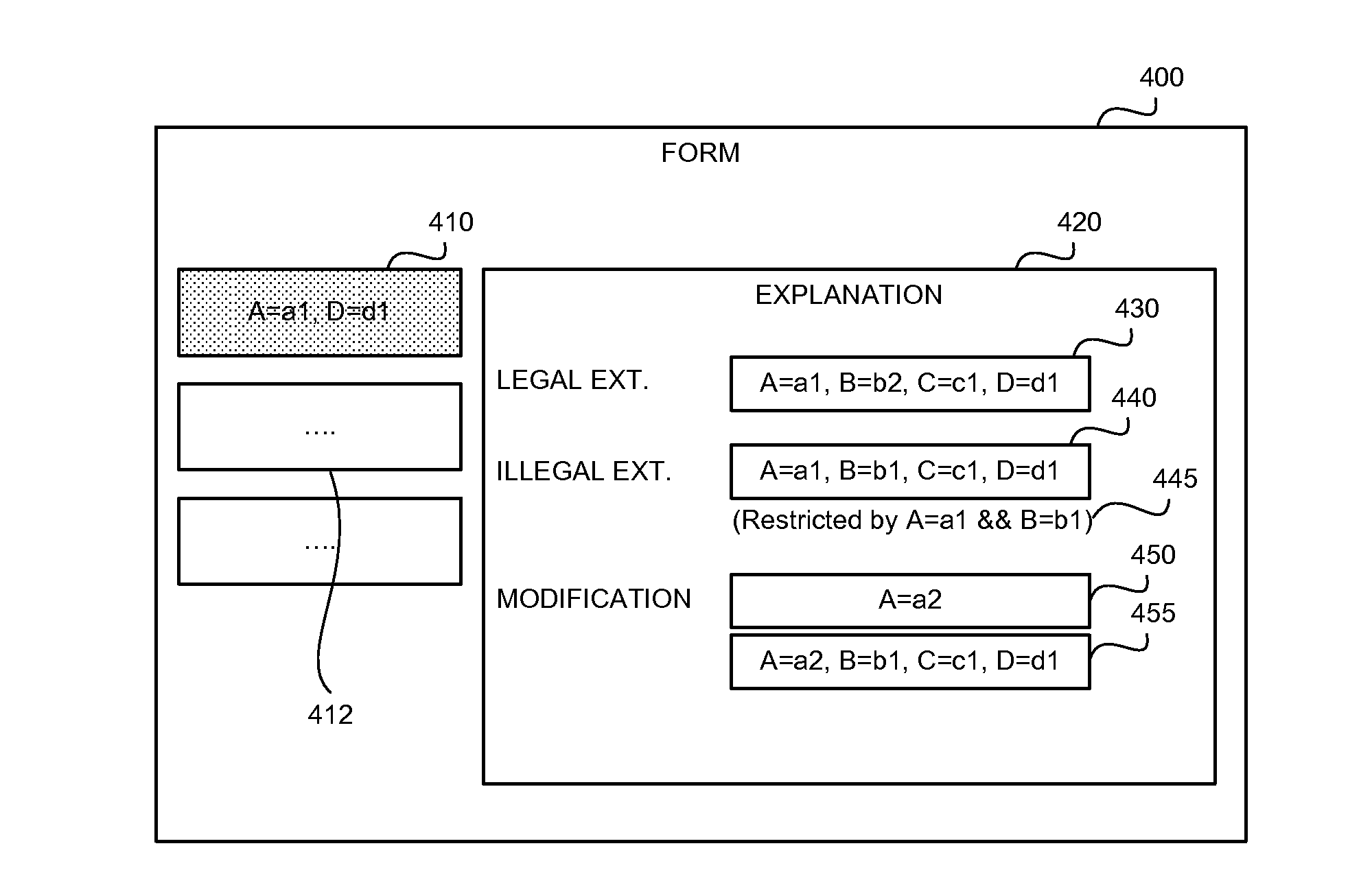
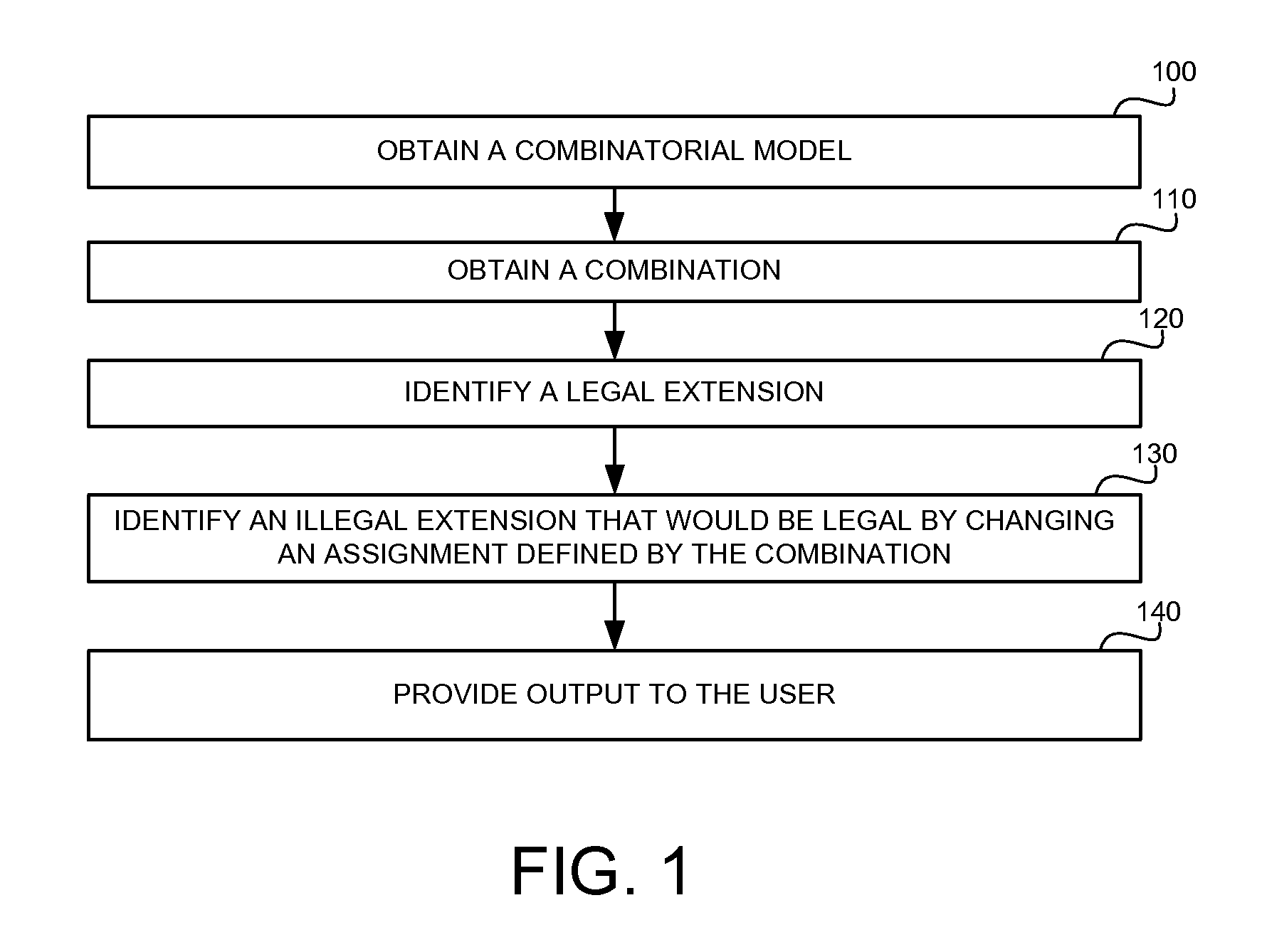
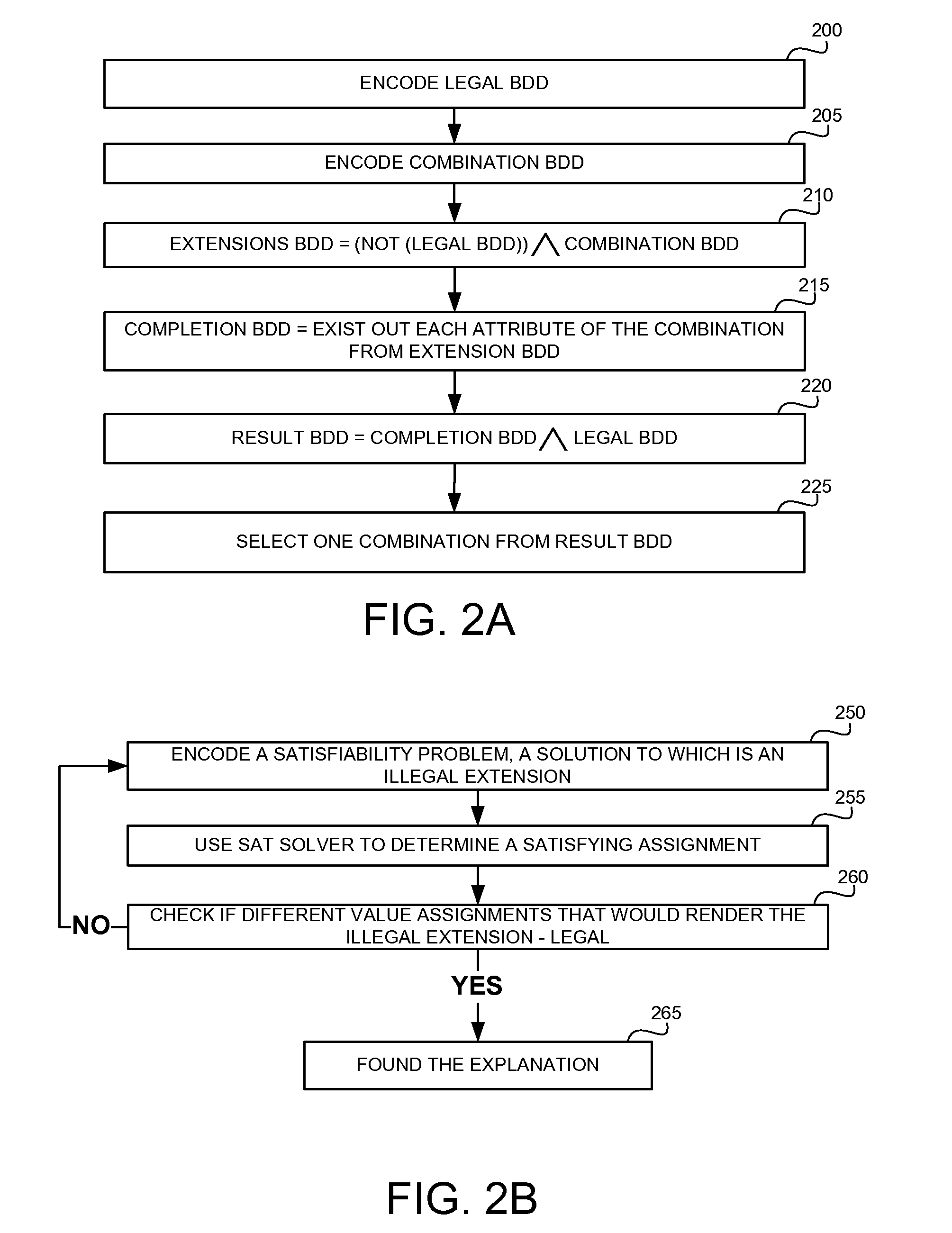
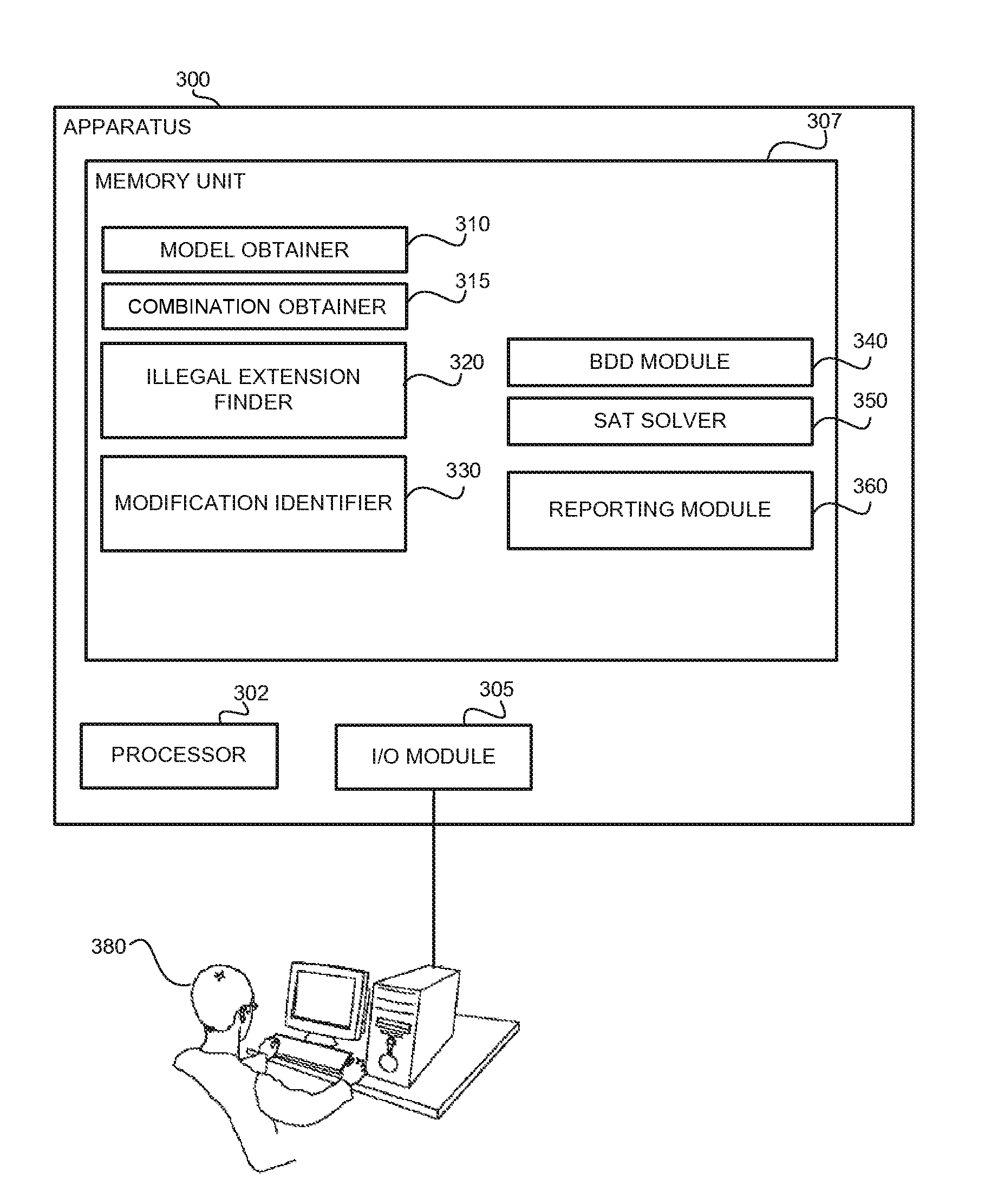
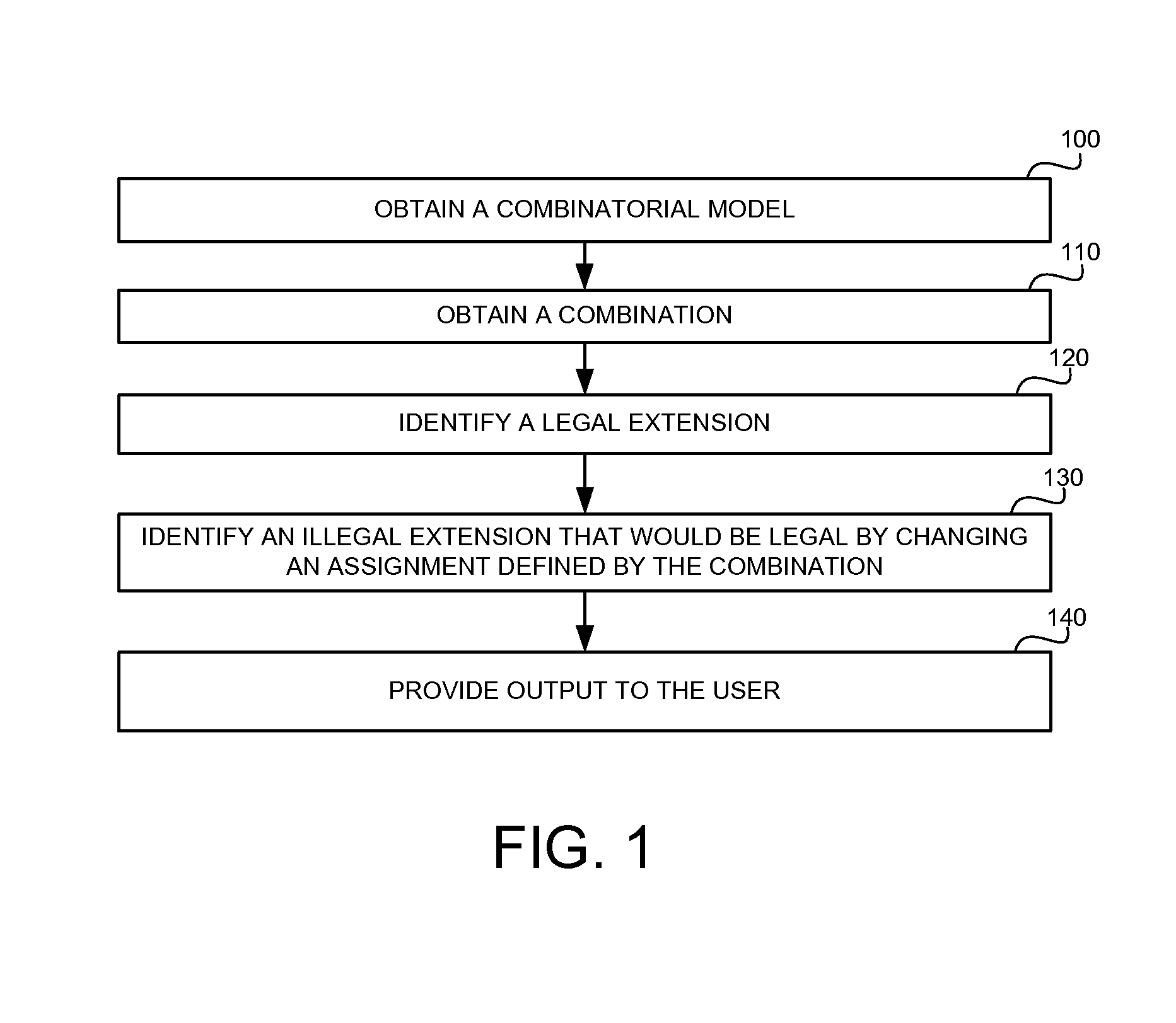
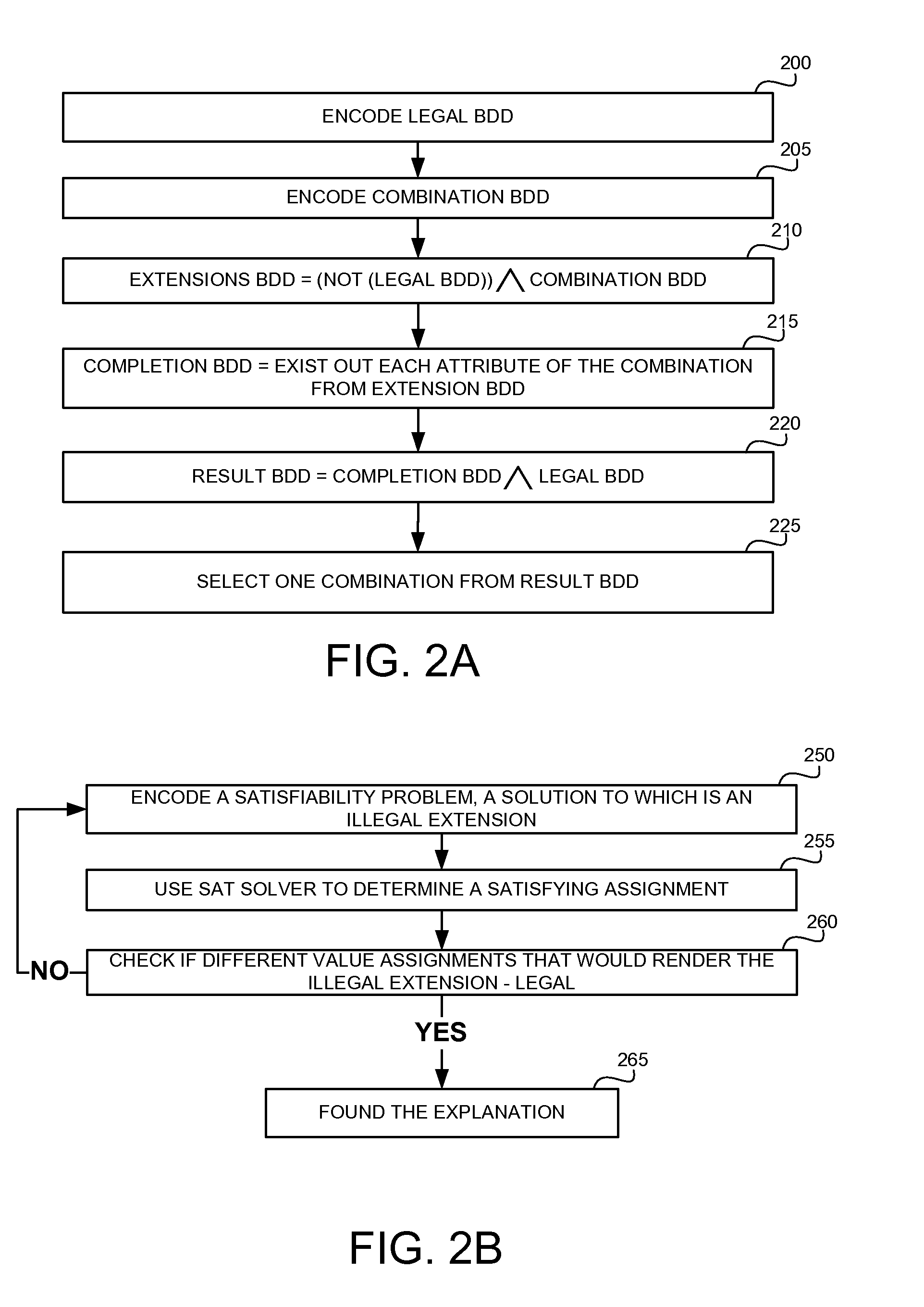
Explaining partially illegal combinations in combinatorial models
A methods, apparatus and product for explaining partially illegal combinations in combinatorial models. The method comprising: obtaining a combinatorial model defining a legal test space, the combinatorial model comprising a set of attributes, a respective domain for each attribute defining possible values for the attribute, and a set of restrictions, wherein the restrictions define a combination of values of the attributes that are illegal and are excluded from the legal test case; obtaining a partially illegal combination defining value assignments to a portion of the attributes; automatically identifying an extension of the partially illegal combination, wherein the extension is excluded from the legal test space, wherein the extension can be modified to become legal by changing a portion of the value assignments defined by the partially illegal combination; and outputting the extension.
Owner:GLOBALFOUNDRIES INC
Value allocation method and system for smart contracts
InactiveCN107292622ASolve the problem of not being able to fully trust each otherSolve problems that can't be finerUser identity/authority verificationProtocol authorisationComputer architectureValue assignment
The invention discloses a value allocation method for smart contracts. The method comprises: providing an interface for mutual cooperation between different smart contracts, thus guaranteeing more effective and efficient interaction between the smart contracts; providing an allocation system for realizing open and transparent allocation between partners, thus ensuring accuracy and integrity of complete trusting allocation between the partners; and providing a model for controlling an allocation strategy more finely between the partners, thus ensuring fine allocation and relatively real-time value allocation between the partners. The method is suitable for mutual cooperation with smart contracts, and can realize more effective, efficient, open and transparent value allocation for cooperation between the smart contracts and realize a fine controlled allocation strategy.
Owner:武汉凤链科技有限公司
Mass vector data partition method and system based on Hadoop
ActiveCN106021567AImprove Spatial Index EfficiencyImprove storage efficiencySpecial data processing applicationsPartition matrixValue assignment
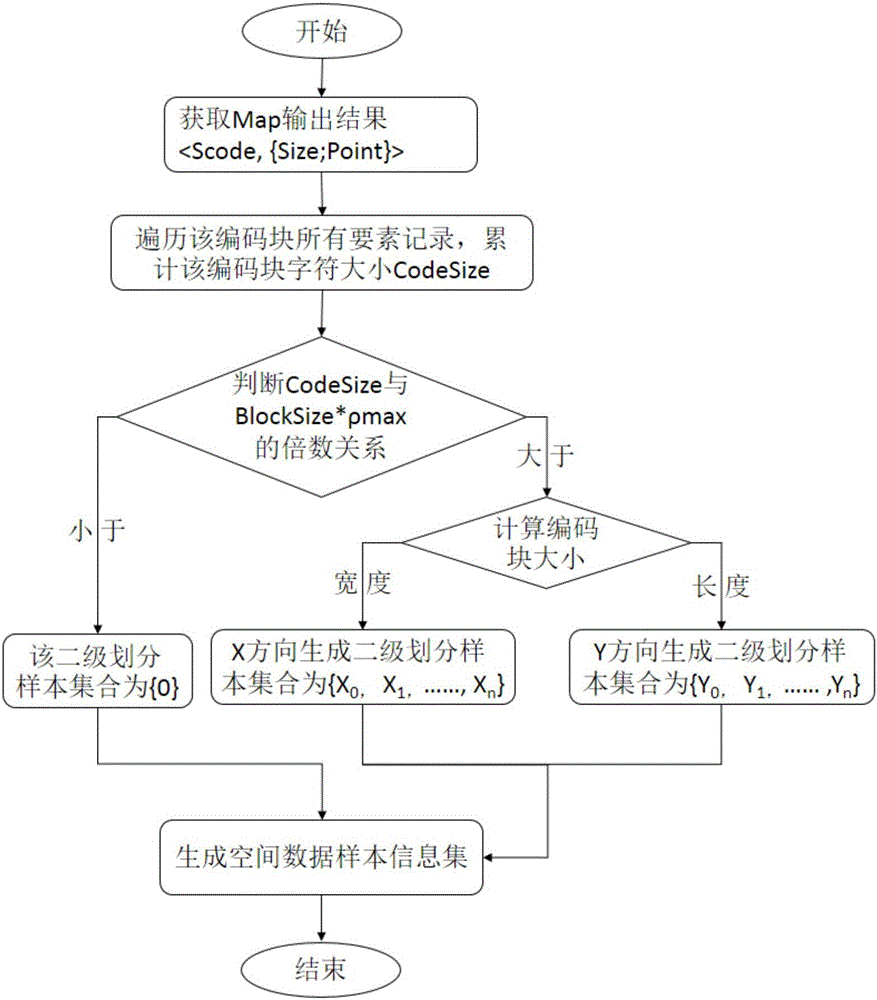
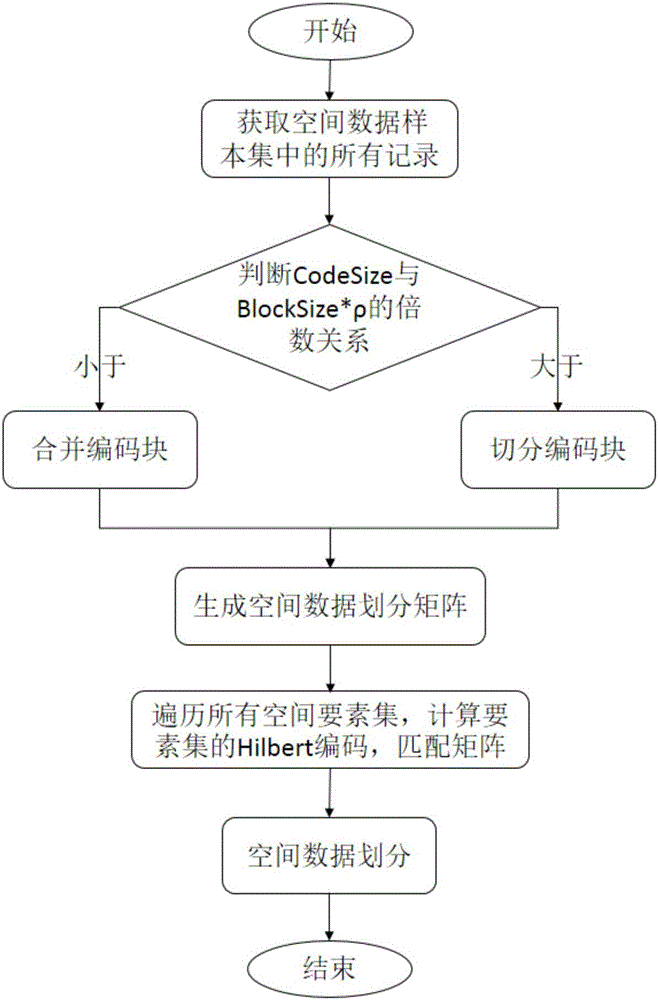
The invention relates to a mass vector data partition method and system based on Hadoop. The method comprises the steps that space encoding is conducted on space data-concentrated space elements on the basis of a Hilbert space filling curve; key value assignment on the space elements is achieved through a Map function and a Reduce function, and a space data sample information set is generated; space data partition matrixes are generated according to the space data sample information set; the space elements are partitioned in corresponding storage data blocks according to the space data partition matrixes, and meanwhile every two adjacent data blocks are distributed in a same cluster node. According to the system, the Hilbert space filling curve is introduced into a data sampling and partitioning rule, the influence factors such as the space position relation of adjacent objects of the space data, the self size of the space objects and the space object number of same encoding blocks are fully taken into account, therefore, the space distribution characteristics of the sample information set are guaranteed, the space index efficiency of the mass vector data is improved, and meanwhile load balance based on HDFS data block storage is guaranteed.
Owner:CHINA AGRI UNIV
Health assessment method, assessment device and system for rehabilitation
InactiveCN109166627AHealth status assessment is accurateFast and effective rehabilitationMedical data miningHealth-index calculationEvaluation resultState dependent
The present invention provides a health state assessment method based on physiological data and psychological data, a health state assessment device, and a system for rehabilitation. The health stateassessment method includes the following steps that: physiological data and psychological data related to health states are acquired, the physiological data are normalized, and data dimensionality reduction and / or data cleaning is performed on the psychological data; data weighting and value assignment are performed on the normalized physiological data and the psychological data which have been subjected to the data reduction and / or data cleaning; and health state assessment is carried out according to physiological and psychological comprehensive data which have been subjected to the weighting and value assignment. The health state assessment method is in line with the actual situation of each patient; the evaluation result of the method is more accurate; and rapid and effective rehabilitation can be achieved.
Owner:SUZHOU ZHONGKE ADVANCED TECH RES INST CO LTD
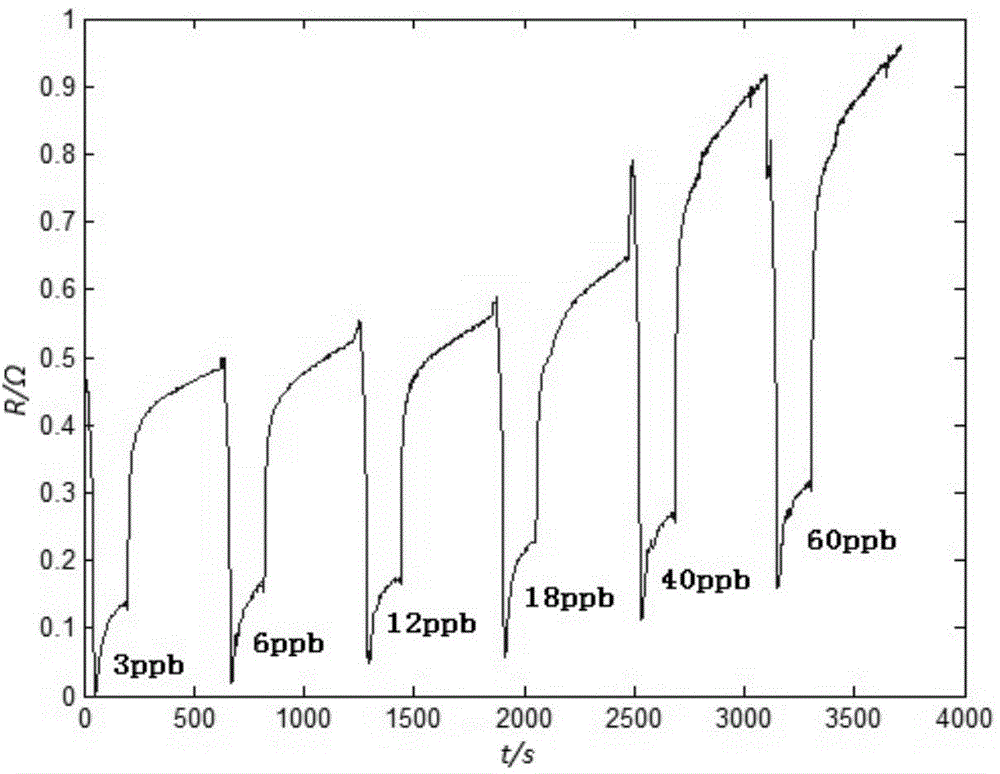
Low-concentration gas detection method based on double threshold stochastic resonance
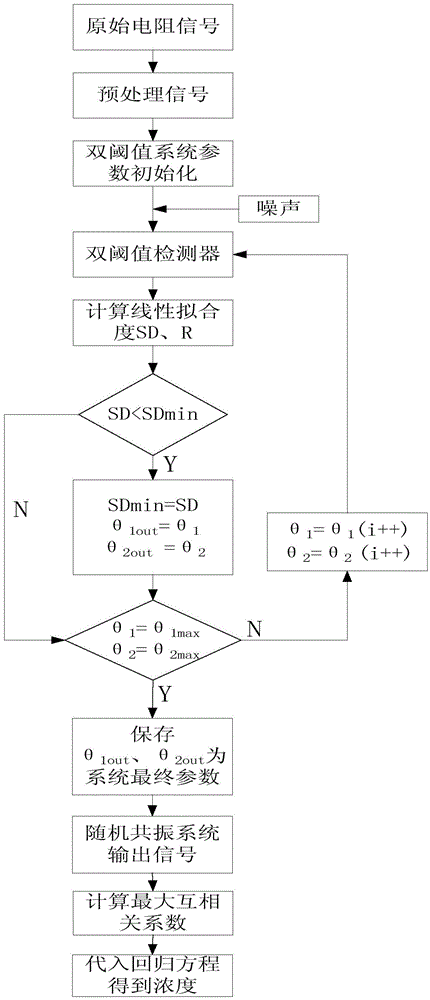
The invention discloses a low-concentration gas detection method based on double threshold stochastic resonance. The method includes the steps: measuring resistance values of a gas-sensitive sensor under different concentrations of reference gas; inputting the measured resistance values as signals, carrying out normalization processing on the signals, and then carrying out curve fitting to obtain a periodic function by Fourier series; carrying out discretization processing on the periodic function to obtain an input function; inputting the input function and added gaussian white noise into a double threshold stochastic resonance system, carrying out value assignment by using a double threshold detector, taking a value-assignment signal as an output signal, and calculating a cross-correlation coefficient of the double threshold stochastic resonance system; searching an optimal double threshold to make the cross-correlation coefficient maximal, and building a linear regression equation with the maximal cross-correlation coefficient and a corresponding gas concentration; and selecting to-be-measured low-concentration gas, acquiring a corresponding maximal cross-correlation coefficient of the to-be-measured low-concentration gas, introducing into the linear regression equation, and calculating out the concentration of the to-be-measured low-concentration gas.
Owner:连云港欧亚气体有限公司
Method and apparatus for obtaining L users having optimum communication influence
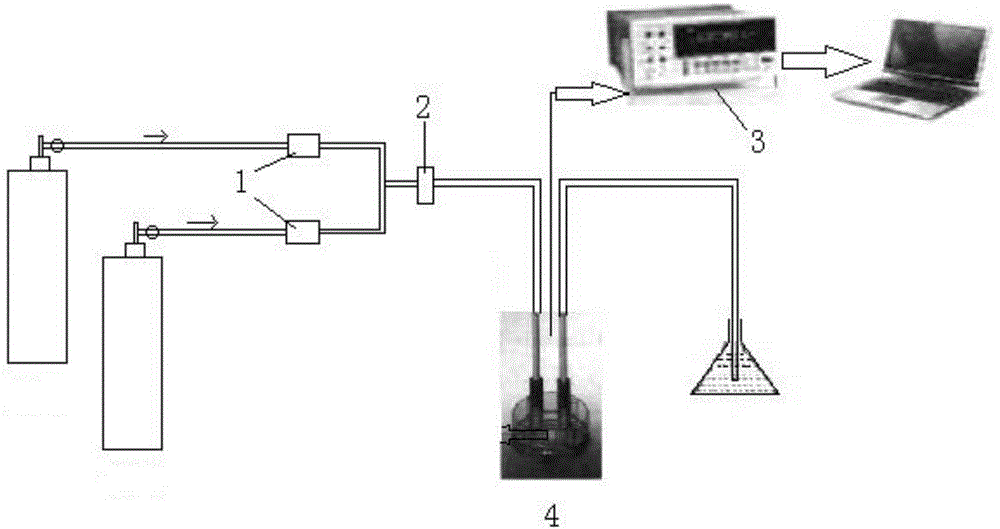
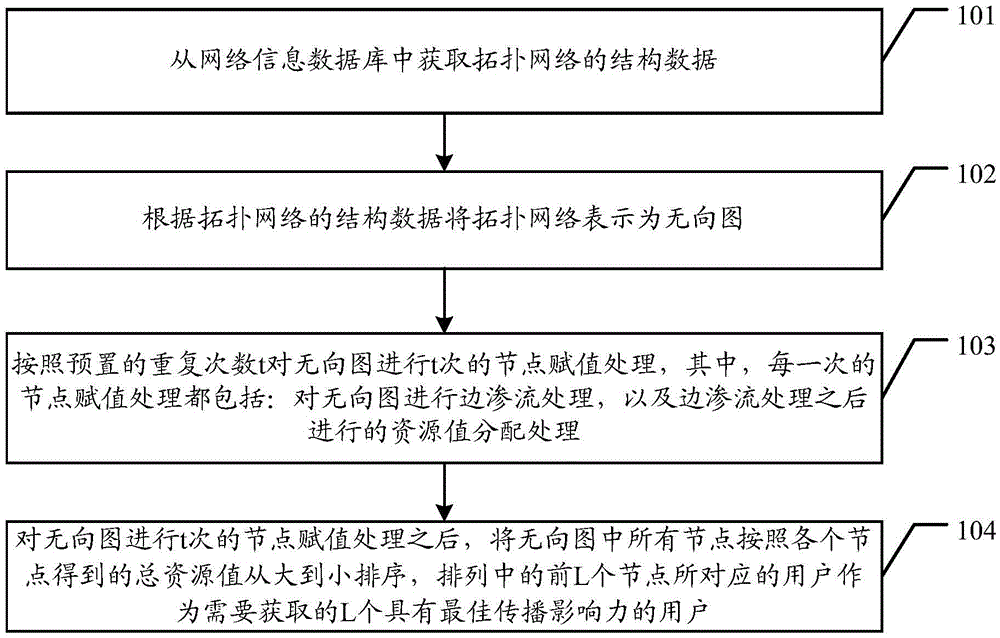
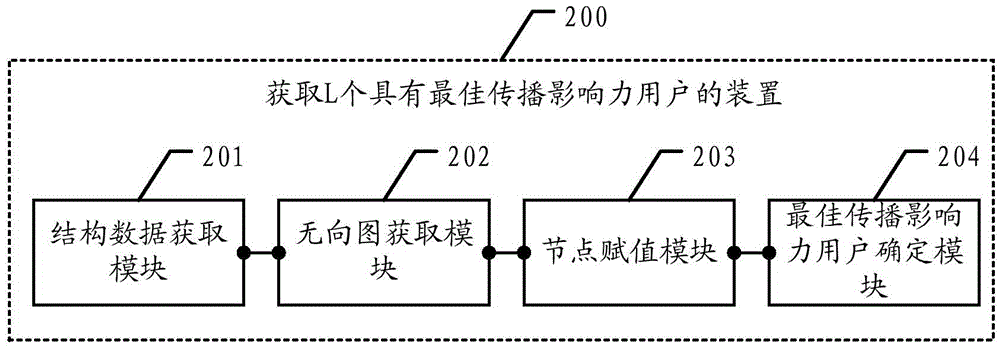
ActiveCN105528407AGood communication influenceVectoral format still image dataSpecial data processing applicationsUndirected graphValue assignment
The present invention discloses a method and apparatus for obtaining L users having optimum communication influence. The method and apparatus are used for simultaneously obtaining a plurality of users having the optimum communication influence, and information communication efficiency is improved. The method comprises the steps of obtaining structure data of a topology network from a network information database; representing the topology network as an undirected graph according to the structure data of the topology network; performing node assignment treatment on the undirected graph for t times according to preset repetition times t, wherein the node assignment treatment every time comprises bond percolation treatment on the undirected graph, and resource value assignment treatment after the bond percolation treatment; and ordering all nodes in the undirected graph on basis of total resource values obtained by the nodes from large to small after the node assignment treatment on the undirected graph is performed for t times, and selecting users corresponding to the top L nodes in the ordering as the L users having the optimum communication influence which are required to be obtained.
Owner:HANGZHOU NORMAL UNIVERSITY
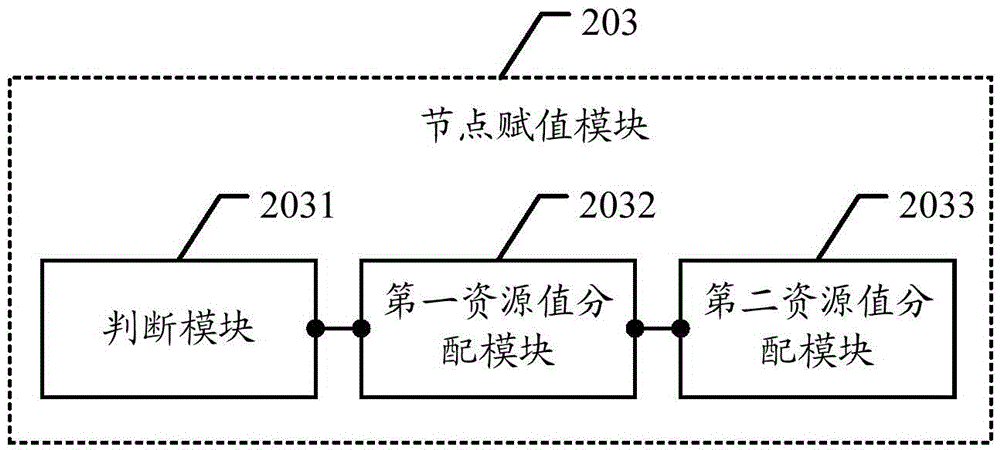
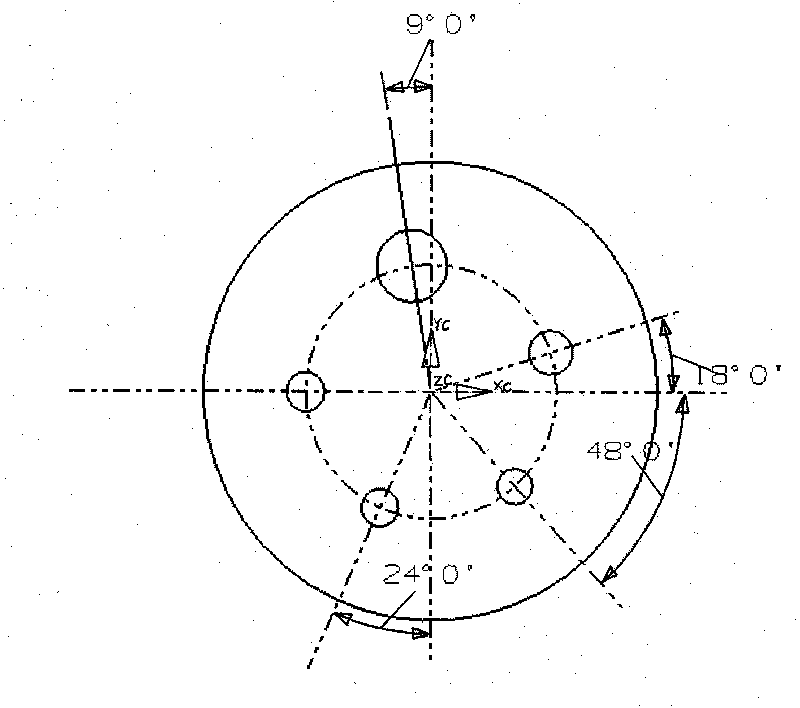
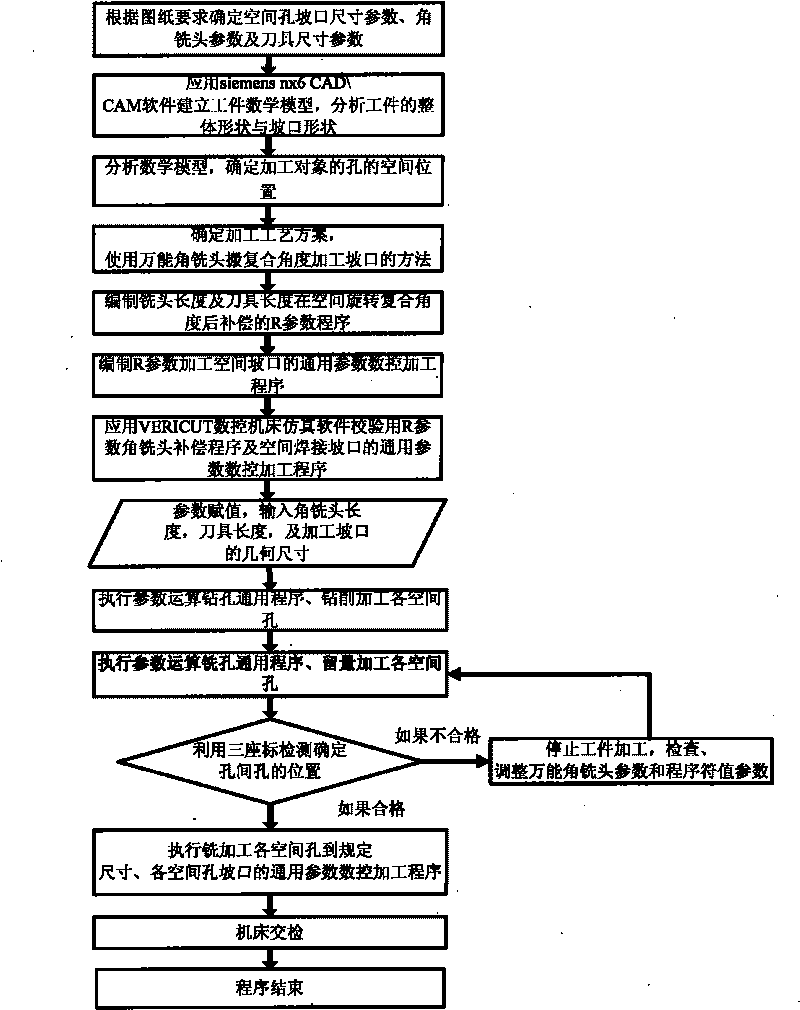
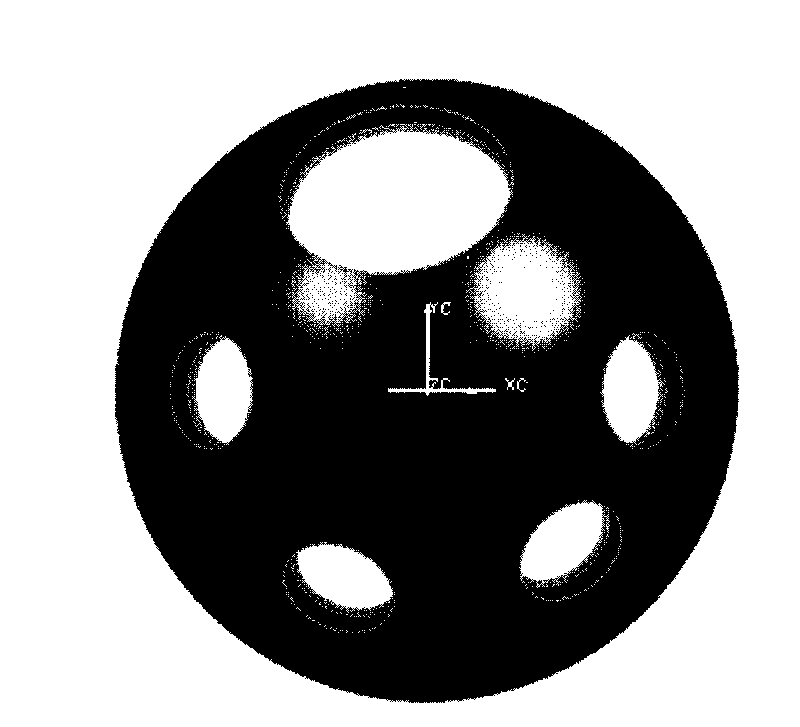
Numerical-control processing method of multi-space hole welding groove on large-scale spherical space curved surface
ActiveCN101710236AGuaranteed positionGuaranteed shape accuracyProgramme controlComputer controlNumerical controlSpherical space
The invention discloses a numerical-control processing method of a multi-space hole welding groove on a large-scale spherical space curved surface, comprising the following steps of: establishing a mathematical model of a workpiece; analyzing the mathematical model; compiling a space curved surface numerical-control processing procedure of a basic hole with a common parameter; compiling an after-compensation R parameter procedure of a rotary compound angle; compiling a general parameter numerical-control processing procedure of a R parameter processing space hole groove; applying simulation software of a VERICUT numerical-control machine tool to carry out verification; and executing the general procedures to process space holes and the groove. In the invention, because the R parameter form of a universal angle cutter head for compensation is calculated by the R parameter function of a control system of the numerical-control processing machine tool, and the processing of the welding groove is also compiled in a parameter form, the value assignment is performed according to the positions, the shapes and the sizes of the grooves of the space holes, the length of actually measured angle cutter head and the length of a cutter on a drawing so that the purpose that the grooves of multiple space holes are clamped once for processing is realized, and the shape precision of the space holes is ensured.
Owner:CHINA FIRST HEAVY IND +1
Explaining partially illegal combinations in combinatorial models
InactiveUS9454466B2Software testing/debuggingComputation using non-denominational number representationValue assignmentData mining
A methods, apparatus and product for explaining partially illegal combinations in combinatorial models. The method comprising: obtaining a combinatorial model defining a legal test space, the combinatorial model comprising a set of attributes, a respective domain for each attribute defining possible values for the attribute, and a set of restrictions, wherein the restrictions define a combination of values of the attributes that are illegal and are excluded from the legal test case; obtaining a partially illegal combination defining value assignments to a portion of the attributes; automatically identifying an extension of the partially illegal combination, wherein the extension is excluded from the legal test space, wherein the extension can be modified to become legal by changing a portion of the value assignments defined by the partially illegal combination; and outputting the extension.
Owner:GLOBALFOUNDRIES INC
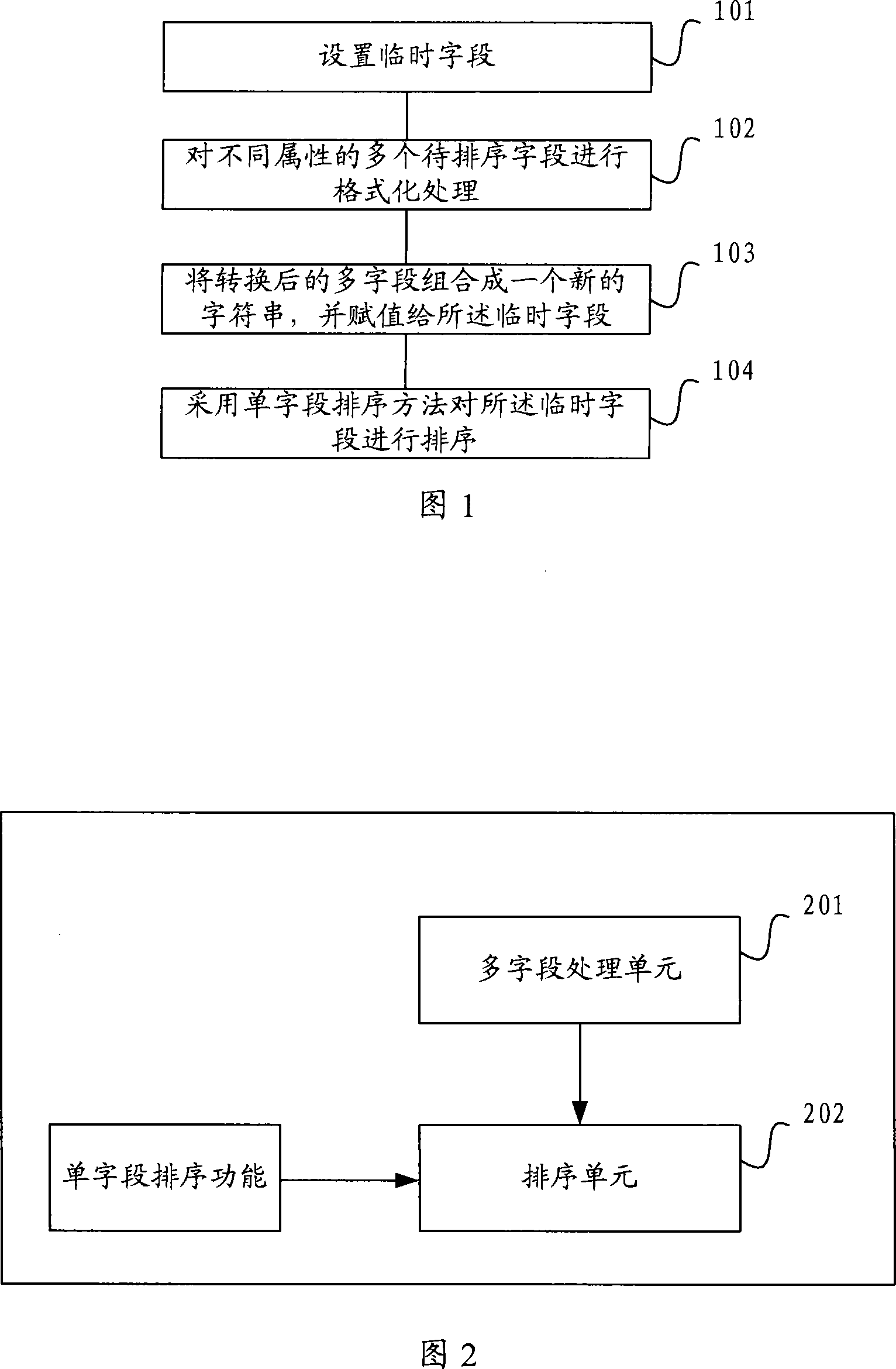
Ordering method and system for different attribute haracter
ActiveCN101136035ARelieve pressureThe sorting method is simple and easySpecial data processing applicationsMulti fieldValue assignment
The method is used for making the order setting for multi fields with different attributes. It comprises: setting a temporary field, and making format conversion for the multi fields with different attributes; combining the converted multi fields to form a character string; making the value assignment for the temporary field; using the single field ordering method to order said temporary field. Comparing with the method of calling database to order the multi fields, the invention has no needs to save the object to data base, and it can directly make ordering in the memory so as to reduce the pressure on the data base.
Owner:KINGDEE SOFTWARE(CHINA) CO LTD
Test data encoding compression method
InactiveCN102592682ADouble compressionIncrease the compression ratioStatic storageComputer hardwareBaseline data
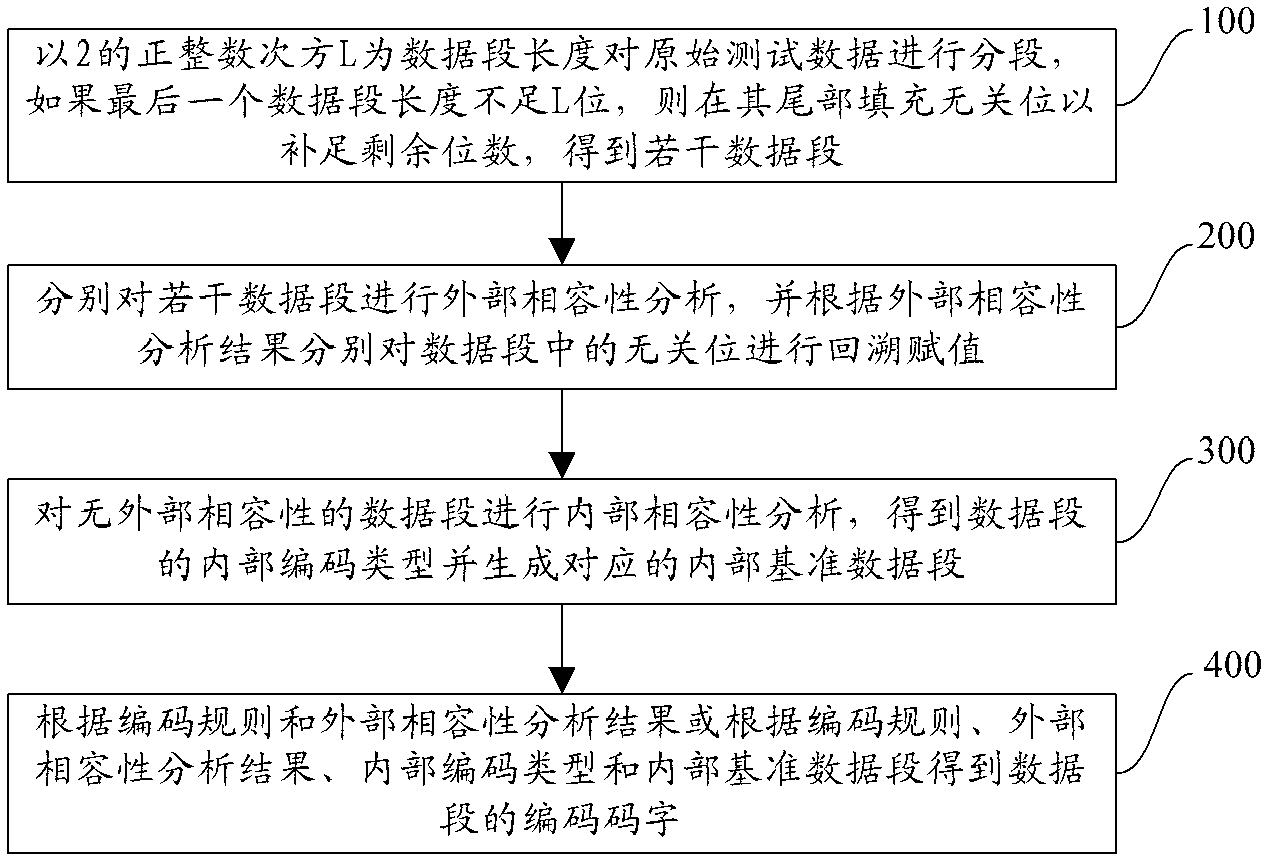
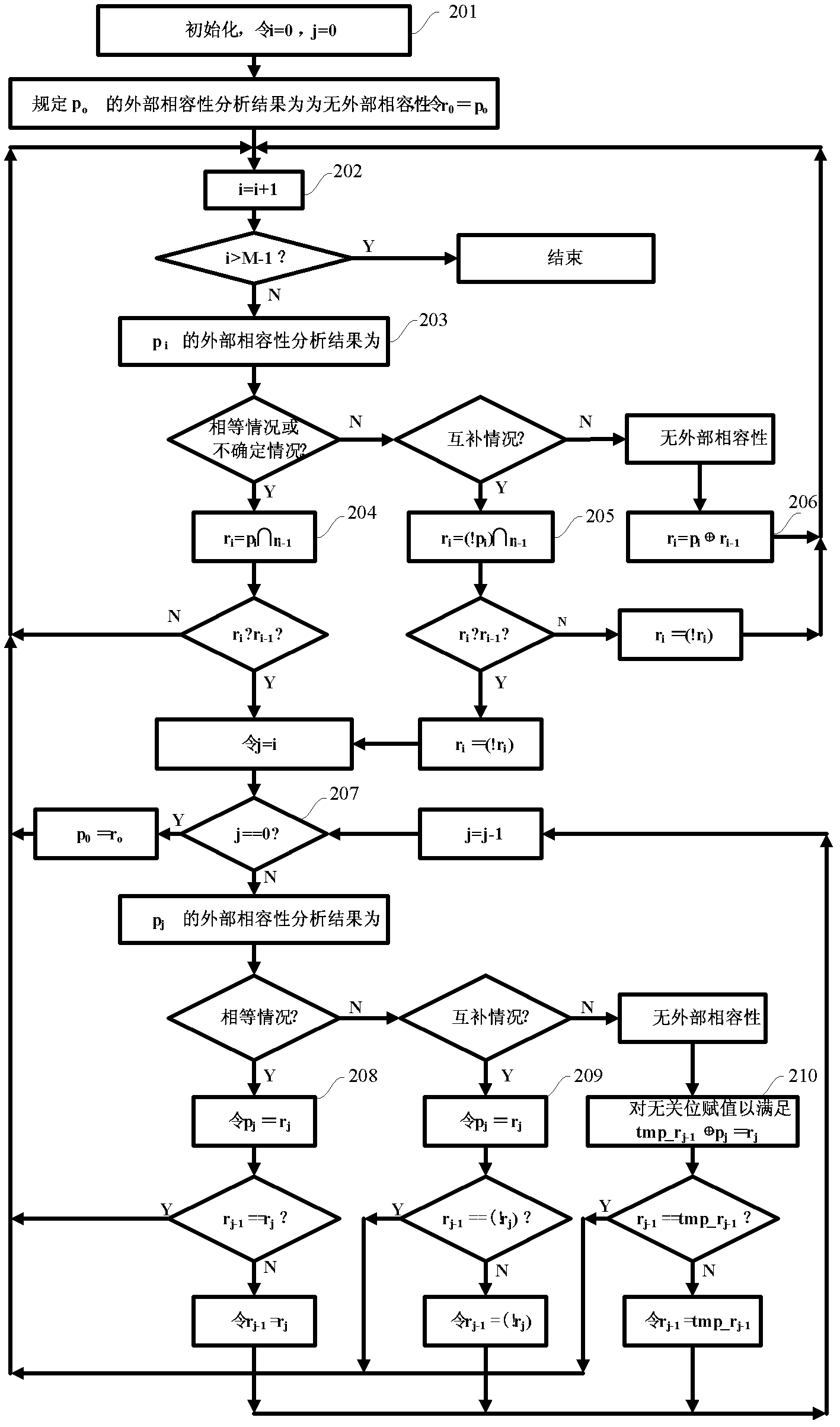
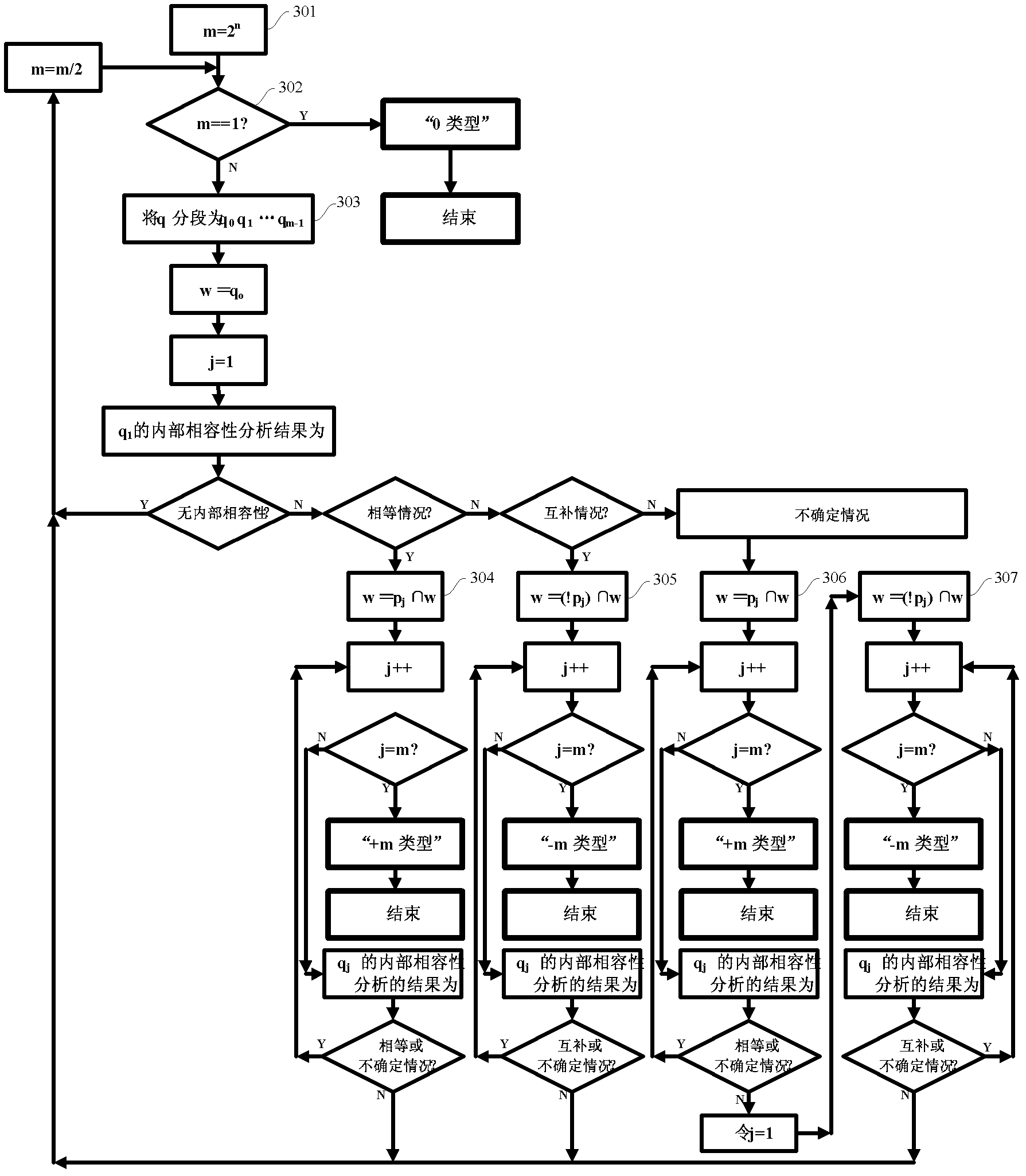
The invention relates to a test data encoding compression method. The test data encoding compression method comprises the following steps of: segmenting original test data by using L as a data section length, wherein L is a positive integer power of 2; if the length of the last data section is less than L bits, then filling X-bits at the tail part of the last data section to complement the residual bits, and obtaining a plurality of data sections; respectively carrying out external compatibility analysis on the plurality of data sections, carrying out backtracking and value assignment on the X-bits in the data sections according to an external compatibility analysis result; carrying out internal compatibility analysis on the data sections without external compatibility to obtain internal encoding types of the data sections and generate corresponding internal reference data sections; and obtaining encoding code words of the data sections according to an encoding rule and the external compatibility analysis result or according to the encoding rule, the external compatibility analysis result, the internal encoding types and the internal reference data sections. The invention has the characteristics of realizing double compression of the test data and improving test data compression ratio.
Owner:INST OF ACOUSTICS CHINESE ACAD OF SCI
Method of managing address spaces of incommunicable nodes in zigbee network
InactiveUS20080080416A1Inefficient managementPreventing situationData switching by path configurationRadio/inductive link selection arrangementsManagement processValue assignment
Provided is a method of managing addresses of incommunicable nodes in a ZigBee network, and more particularly, a method of managing address values of a plurality of nodes that form a ZigBee network by efficiently withdrawing address values from nodes which are incommunicable for reasons of abnormality. An address management process can be performed using two methods. According to a first method, a parent node withdraws address values of child nodes that do not transmit a hello message for a predetermined period of time. According to a second method, a parent node transmits a periodic or non-periodic request message to child nodes, and the child nodes, which receive the request message, immediately transmit a hello message to the parent node. Then, the parent node withdraws address values of child nodes that do not respond to the request message sent by the parent node more than a predetermined number of times. An address value assignment process and a process for nodes that have their address values withdrawn are also provided.
Owner:ELECTRONICS & TELECOMM RES INST
Domino scheme for wireless cryptographic communication and communication method incorporating same
ActiveUS7680278B2Simple processExhaustive searchSecret communicationTelevision systemsComputer hardwareSecure communication
A system and method for secure wireless cryptographic communication among participants in a wireless computing network is presented. This secure communication method is based on a random modulation technique and a domino match. Once the initial modulation scheme is selected, each data transmission includes an indication of what modulation scheme should be used for the next data transmission. If a given number of bits are to be used, the modulation scheme for the final transmission may be limited to complete the bit transfer. The bit value assignments within particular modulation schemes may also be varied for each subsequent transmission.
Owner:MICROSOFT TECH LICENSING LLC
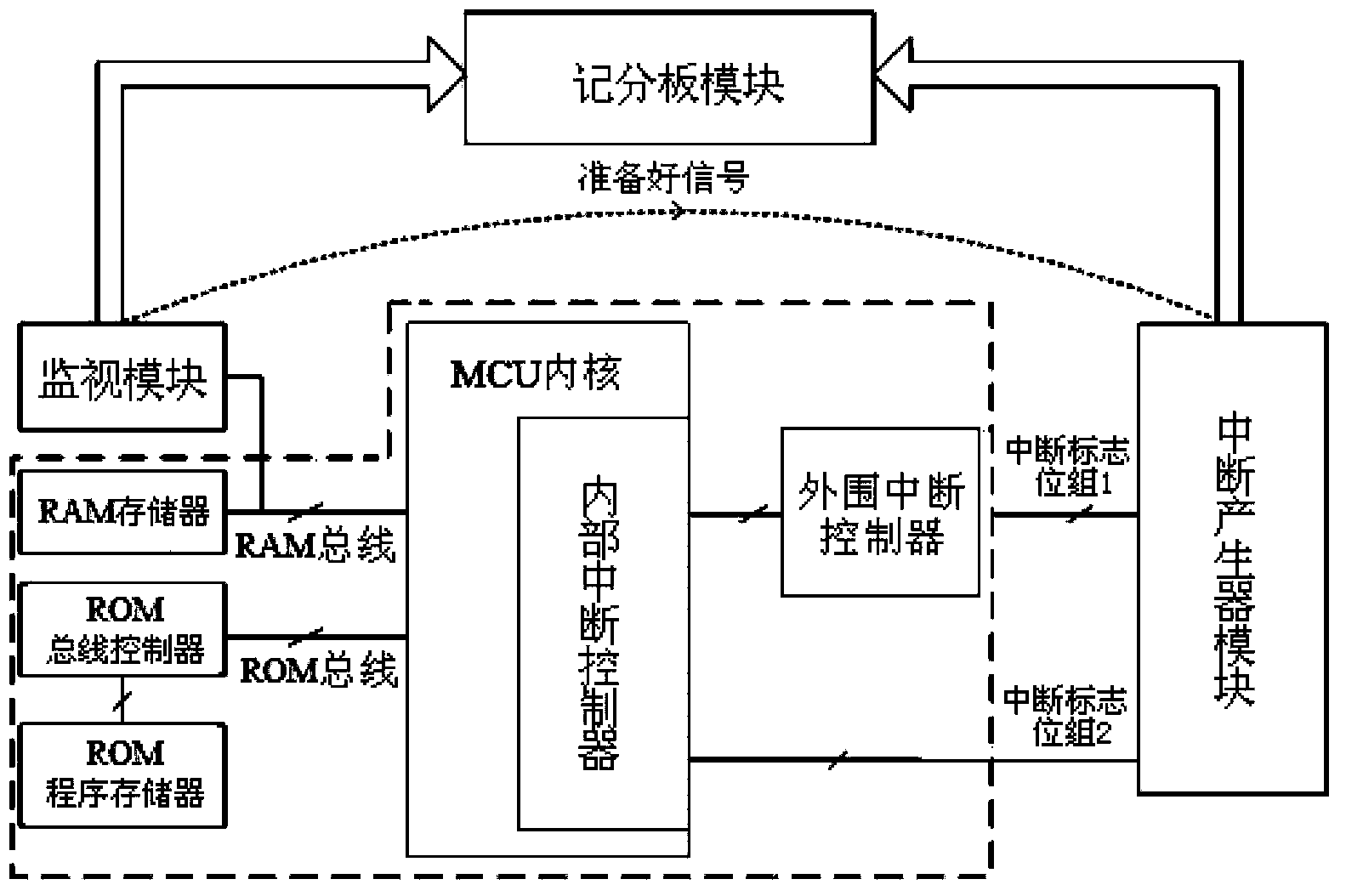
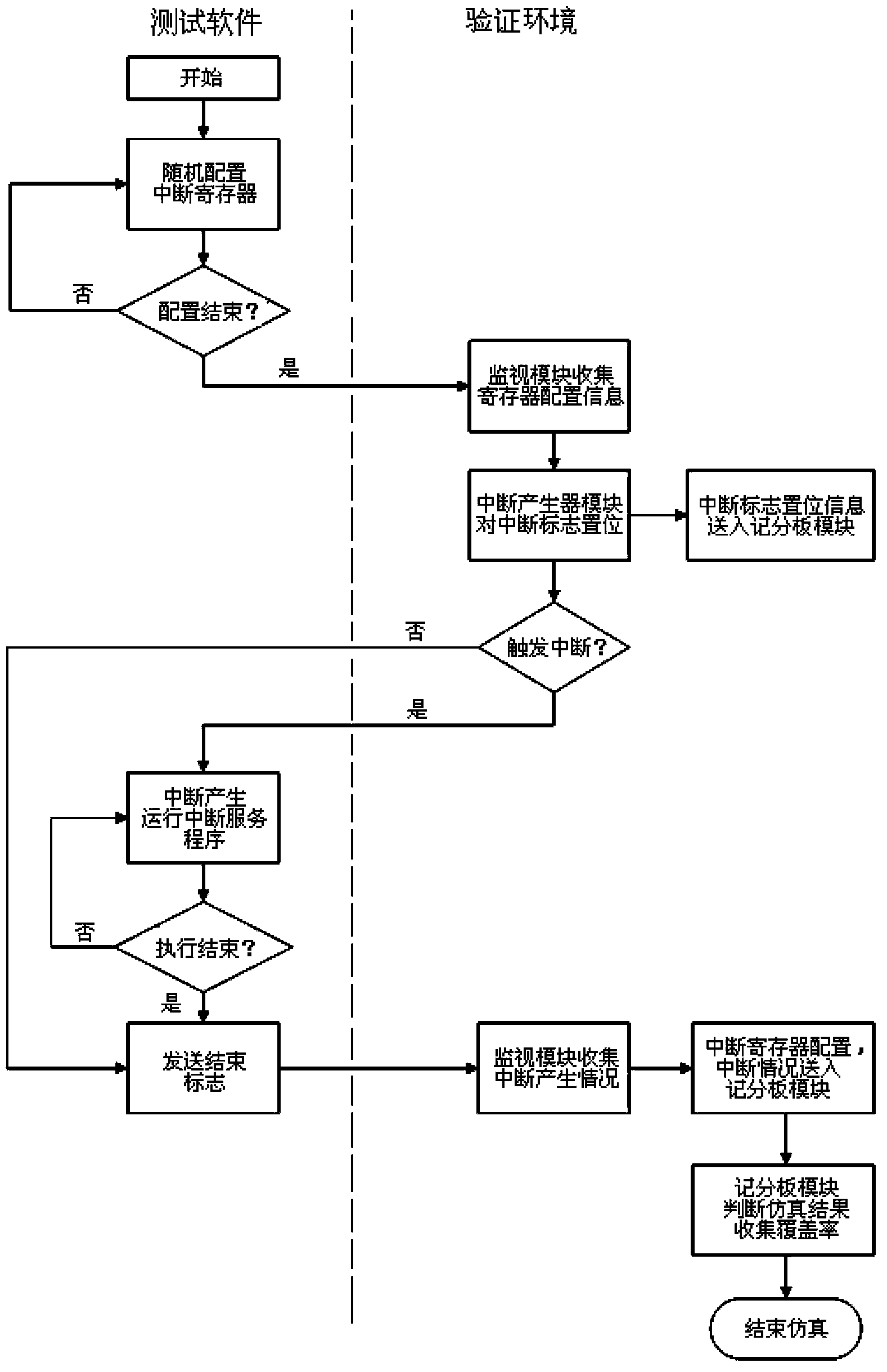
Simulation verification system and method for interrupt controller of hard-core MCU
ActiveCN103838899AImprove reusabilityIncrease coverageSpecial data processing applicationsRegister allocationValue assignment
The invention discloses a simulation verification system for an interrupt controller of a hard-core MCU. The simulation verification system comprises testing software and a simulation verification environment module. The testing software comprises a main program and an interrupt service routine. Value assignment is performed on a relevant interrupt register by the main program in a random mode, and the main program transmits interrupt register configuration, interrupt processing information and a software ready signal to the simulation verification environment module; the interrupt service routine records an interrupt mark number and an interrupt sequence; the simulation verification environment module produces interrupt setting information in a random mode and directly sets all interrupt flag bits in the simulation verification system; the testing software obtains the interrupt processing information in cooperation with the simulation verification environment module, and simulation verification of the interrupt controller is collaboratively completed under a certain flow control. The invention further discloses a simulation verification method for the interrupt controller of the hard-core MCU. According to the simulation verification system and method for the interrupt controller of the hard-core MCU, verification efficiency can be enhanced, the coverage rate can be increased, and reusability is quite high.
Owner:SHANGHAI HUAHONG INTEGRATED CIRCUIT
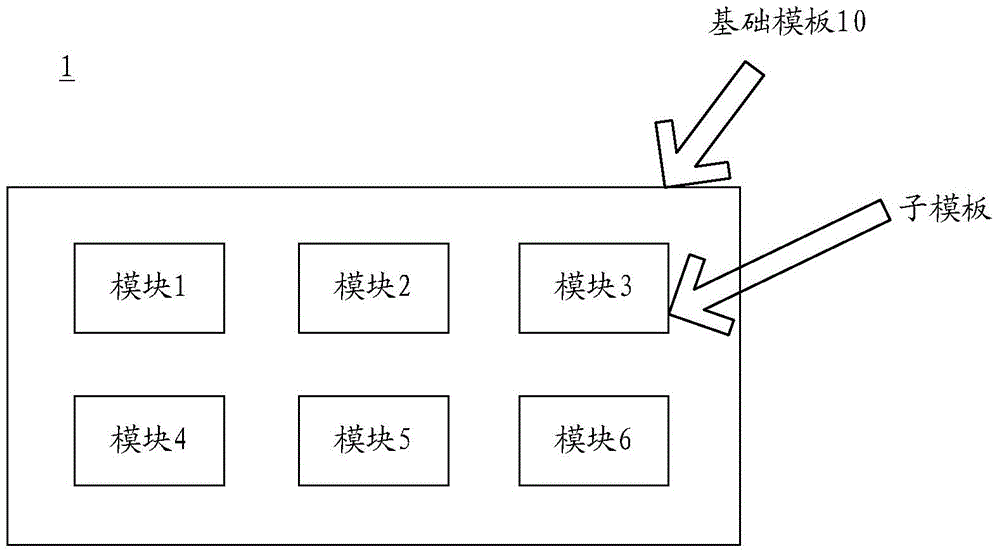
Method and device for generating webpage based on webpage template
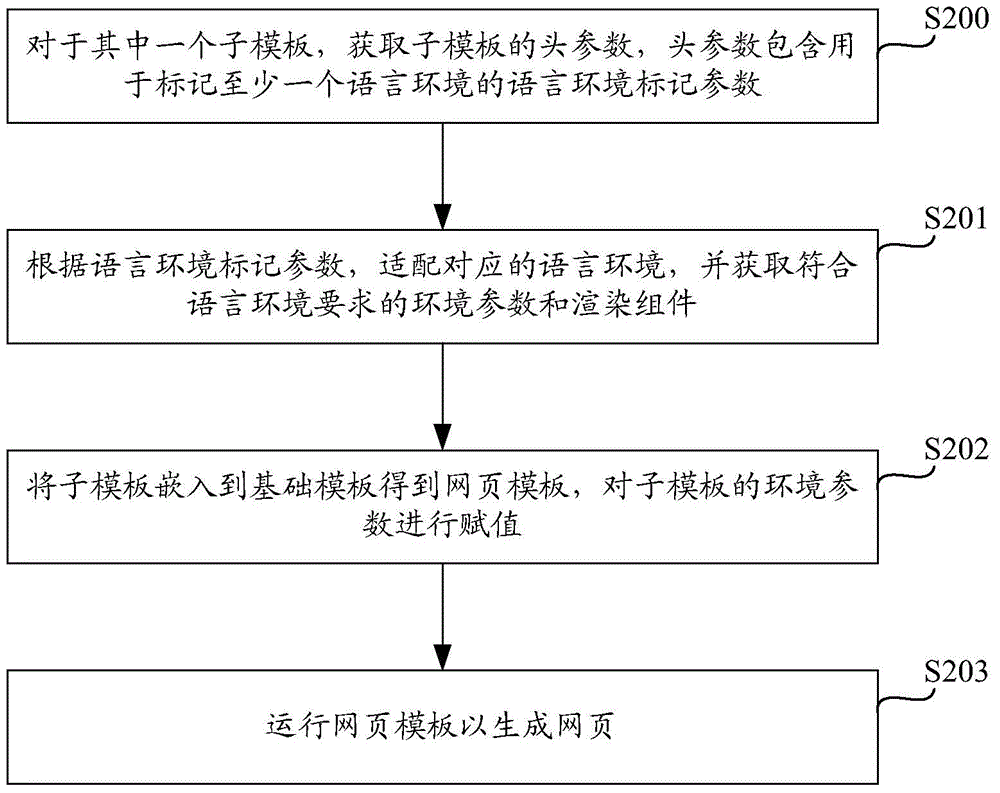
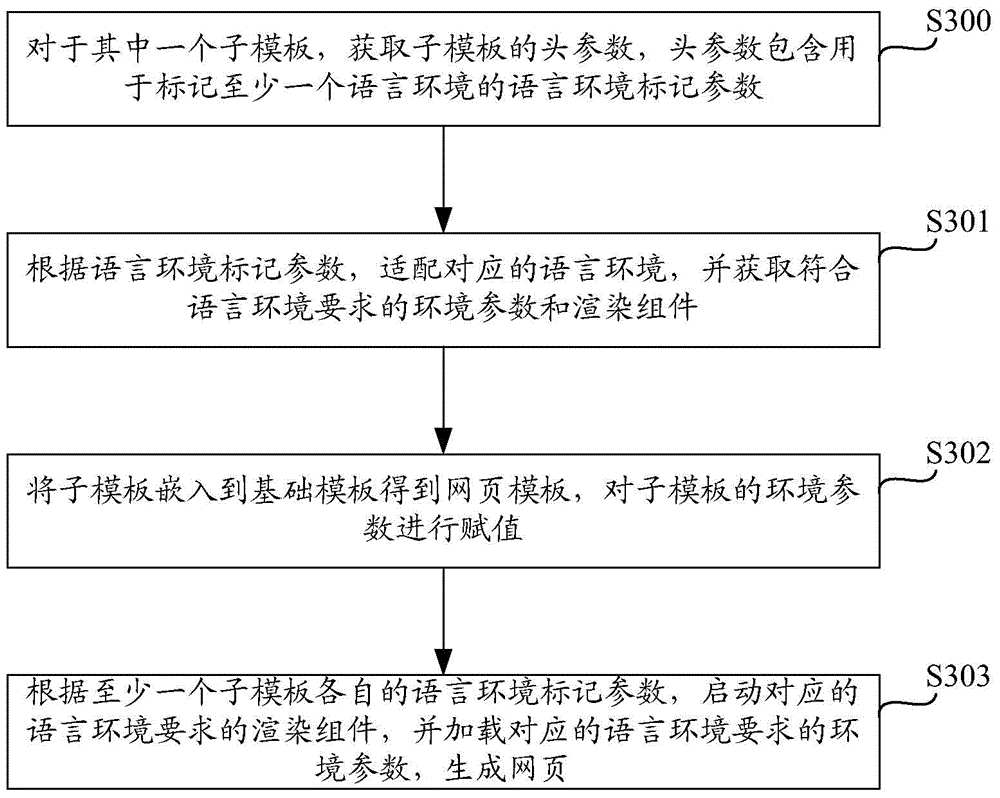
ActiveCN105095497ARelieve pressureReduce the burden onWebsite content managementSpecial data processing applicationsProgramming languageValue assignment
The invention discloses a method and device for generating a webpage based on a webpage template. The webpage template comprises a foundation template and one or more subtemplates. The method comprises the steps that a head parameter of one of the subtemplates is obtained, and the head parameter comprises language environment tagging parameters used for tagging one or more language environments; according to the language environment tagging parameters, the corresponding language environments are matched, and environment parameters and rendering components which accord with the language environment requirements are obtained; the webpage template is obtained by inserting the subtemplates into the foundation template, and value assignment is conducted on the environment parameters of the subtemplates; the webpage template is run so that the webpage can be formed. According to the method and device for generating the webpage based on the webpage template, the language environments are matched according to programming languages, a designer can design the webpage template according to the mastered programming languages, and the defect that in the prior art, due to the fact that a fixed language can be used for design and matching of the language environments cannot be conducted automatically when other languages are used for the design, an error occurs is overcome.
Owner:BEIJING QIHOO TECH CO LTD
Automatic construction method and system for road network of open mine
ActiveCN105139434ASolve technical problems that cannot be built accuratelyAutomate the process2D-image generationForecastingValue assignmentRoad networks
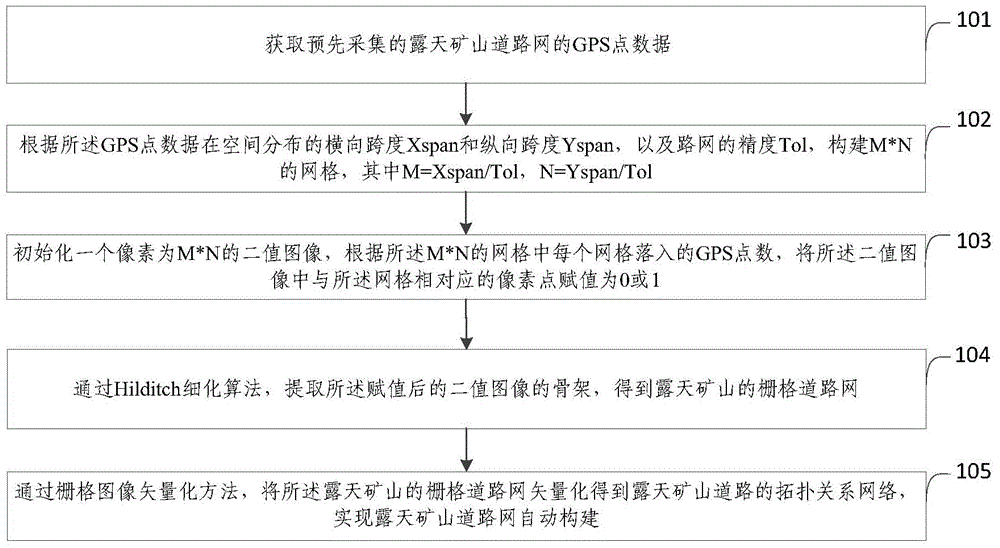
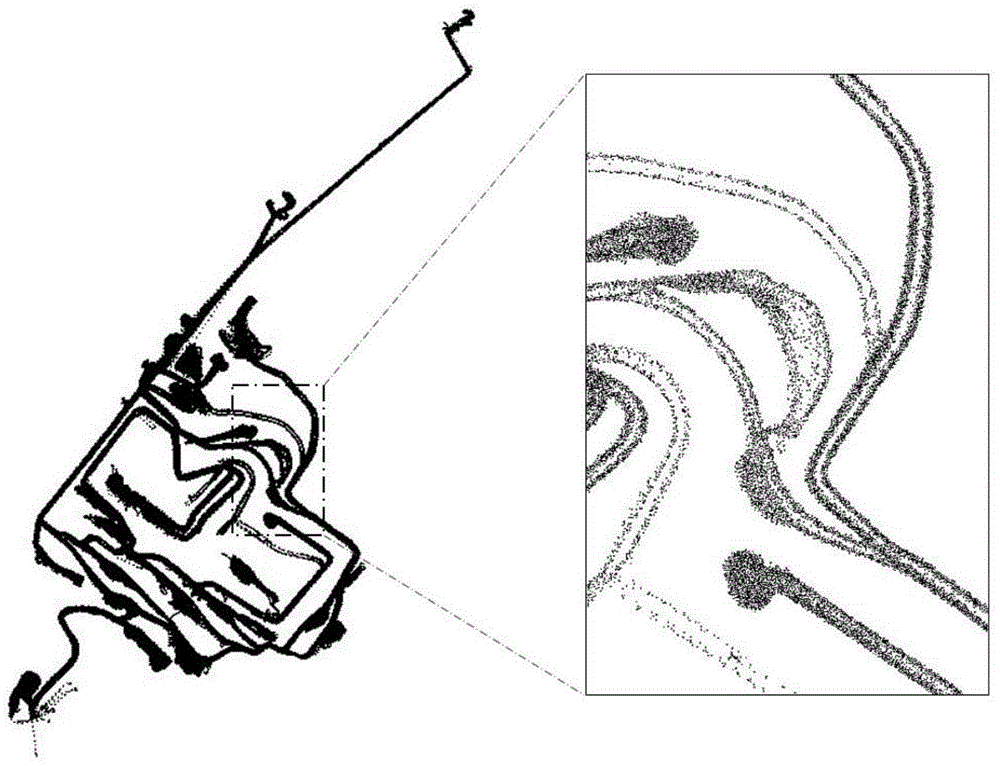
The invention provides an automatic construction method and system for a road network of open mine. The method comprises: obtaining pre-acquired GPS point data of the road network of the open mine; according to a transverse span Xspan and a longitudinal span Yspan of the GPS data distributed in space and the precision Tol of the road network, constructing M*N grids; initializing a binary image with a pixel of M*N, and according to the number of GPS points located in each of the M*N grids, assigning a pixel point corresponding to the grid in the binary image with a value of 0 or 1; by using a Hilditch thinning algorithm, extracting a framework of the assigned binary image subjected to value assignment, and obtaining the grid road network of the open mine; and by using a grid image vectorization method, vectorizing the grid road network of the open mine to obtain a topological relationship network of an open mine road. The automatic construction method for the road network of the open mine can realize automatic construction of the road network of the open mine.
Owner:CHANGSHA DIGITAL MINE
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com