Threat modeling method added with attack path formalization analysis
A technology of attack path and modeling method, which is applied in the direction of instruments, electronic digital data processing, computer security devices, etc., can solve problems such as exploitation, achieve the effect of reducing security defects, improving the scope of application, and lowering the technical threshold
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
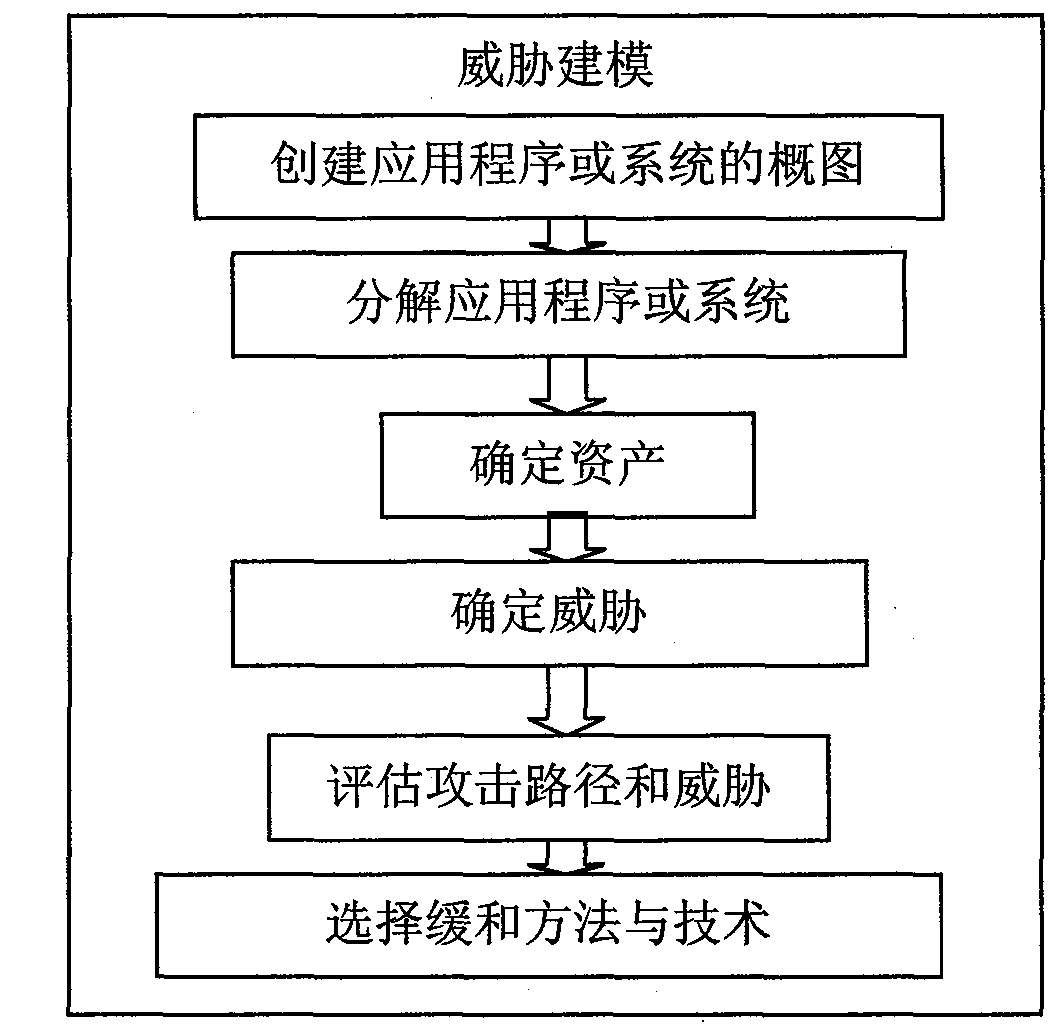
[0043] The present invention is divided into following two main processes:
[0044] (1) Threat Acquisition
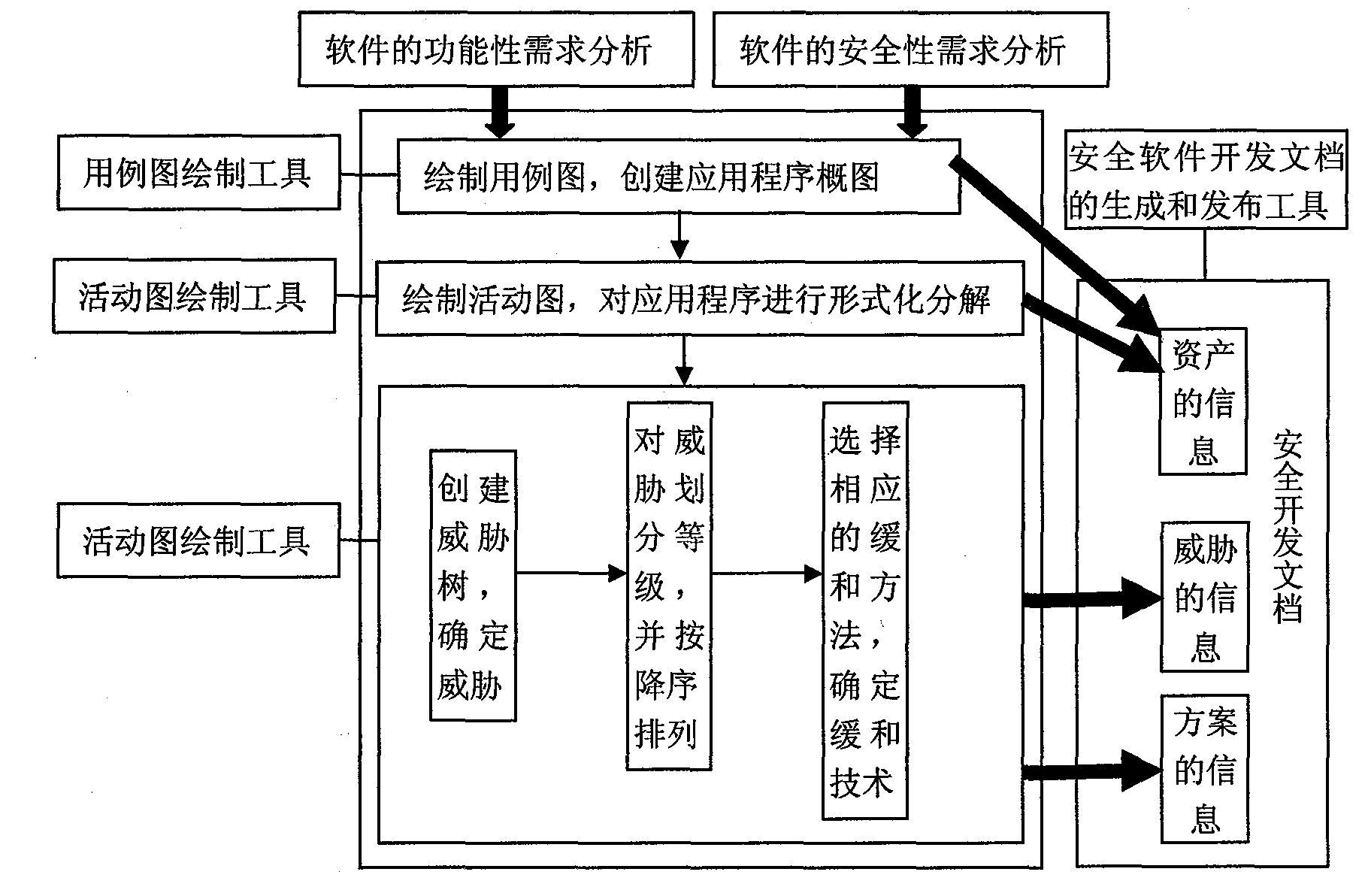
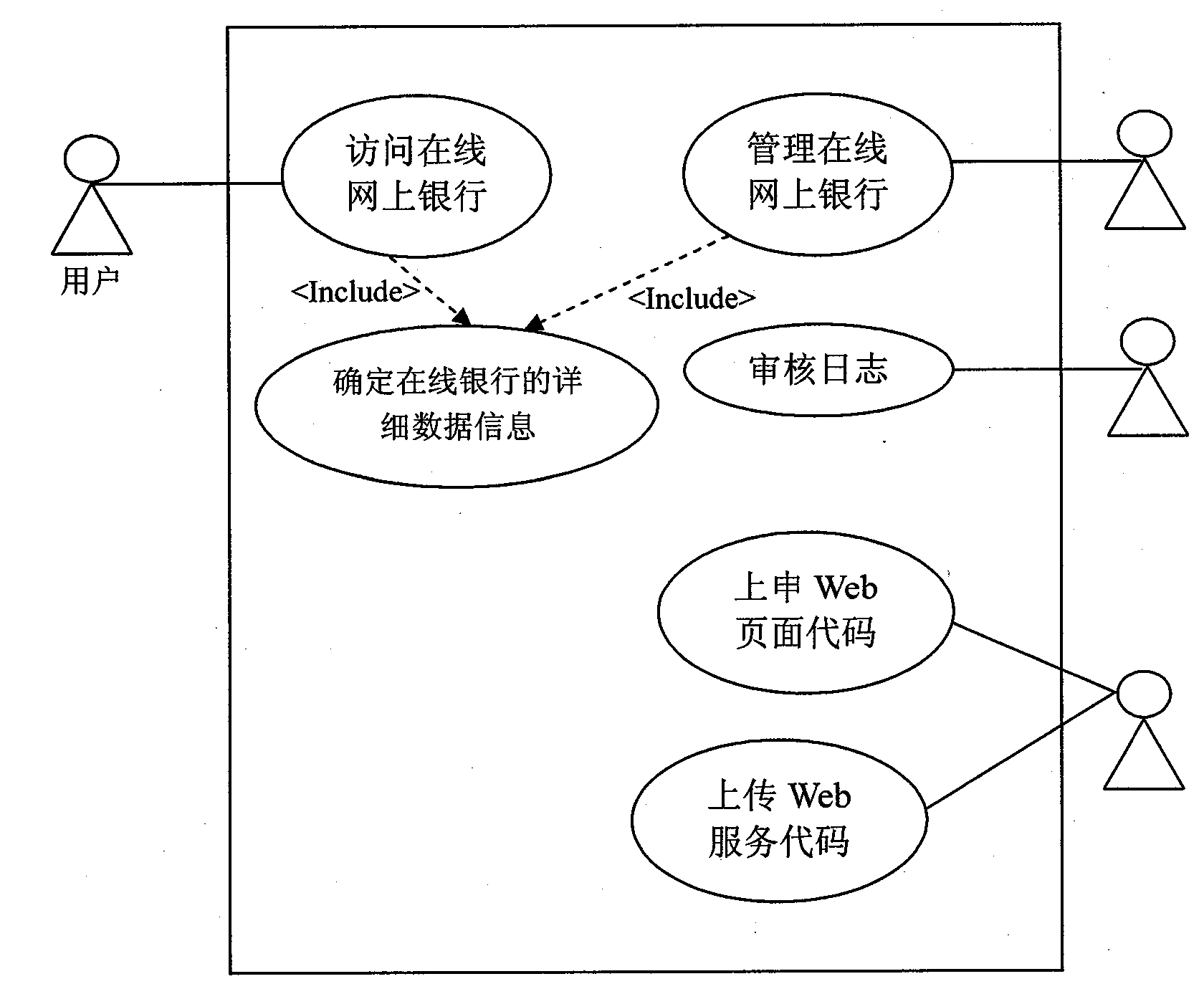
[0045] First create an overview of the application or system, described with a use case diagram. The key to drawing a use case diagram is use case modeling. The typical use case modeling process is: find out the boundaries, participants and use cases of alternative applications or systems, and iterate this process until the system boundaries, participants and use cases are stabilized. In this process, the main purpose of use-case modeling is to identify the assets of the application or system, based on which the number of iterations of use-case modeling is considered. The initial stage of use case modeling is to make an estimate of the application or system boundary to help define the modeling activities; then, iterate on the activities whose output is the use case model, including:
[0046] 1) Application or system boundary: Describe the boundary of the application o...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com