Patents
Literature
33422results about "Software testing/debugging" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
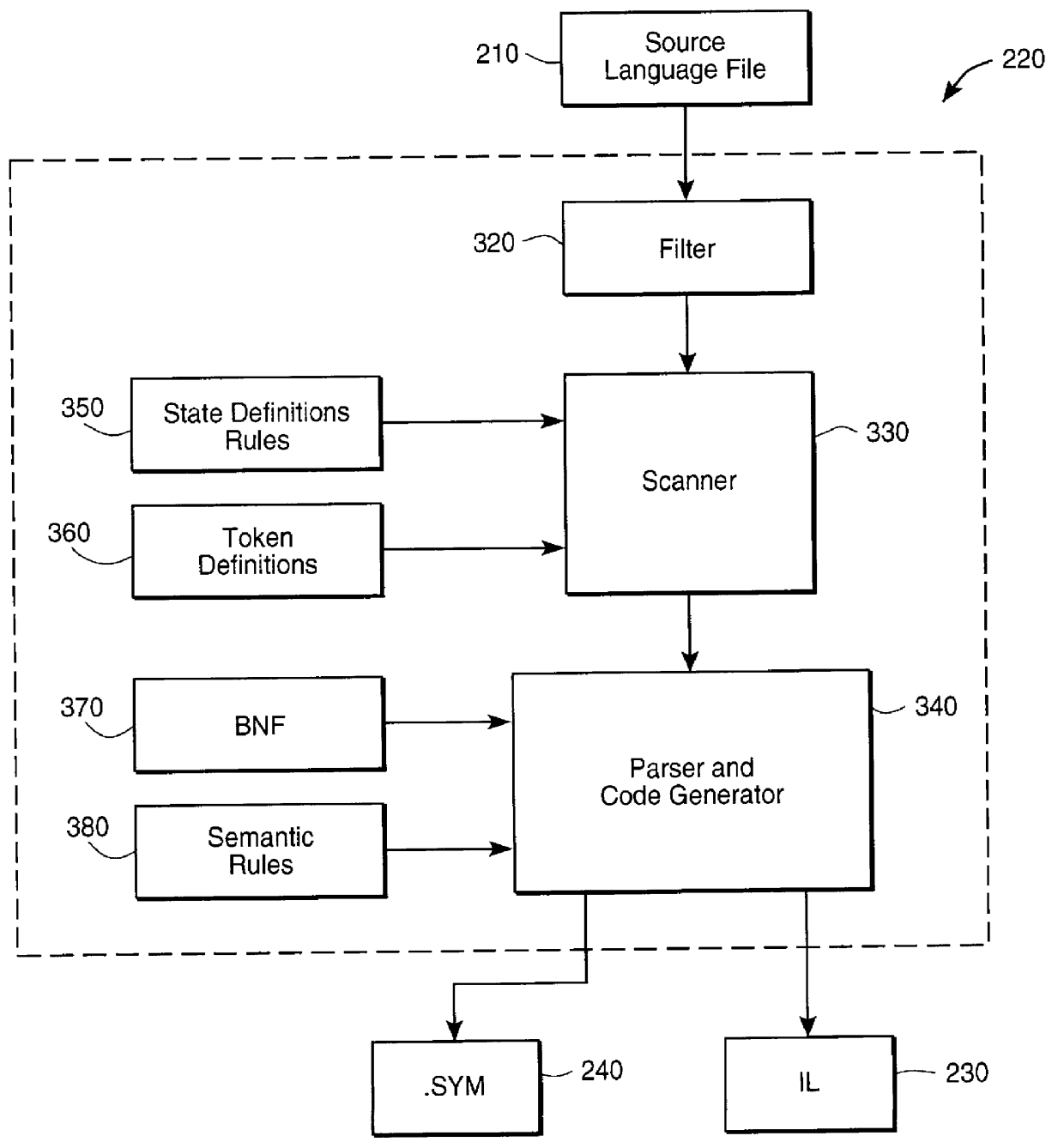
Language-driven interface for an automated testing framework
InactiveUS6907546B1Software testing/debuggingSpecific program execution arrangementsCrowdsAutomatic testing
To test the functionality of a computer system, automated testing may use an automation testing tool that emulates user interactions. A database may store words each having a colloquial meaning that is understood by a general population. For each of these words, the database may store associated computer instructions that can be executed to cause a computer to perform the function that is related to the meaning of the word. During testing, a word may be received having a colloquial meaning that is understood by a general population. The database may be queried for the received word and the set of computer instructions may be returned by the database. The automated testing tool may then perform the function returned to the colloquial meaning of the word. The words stored in the database may be in English or another language.
Owner:ACCENTURE GLOBAL SERVICES LTD
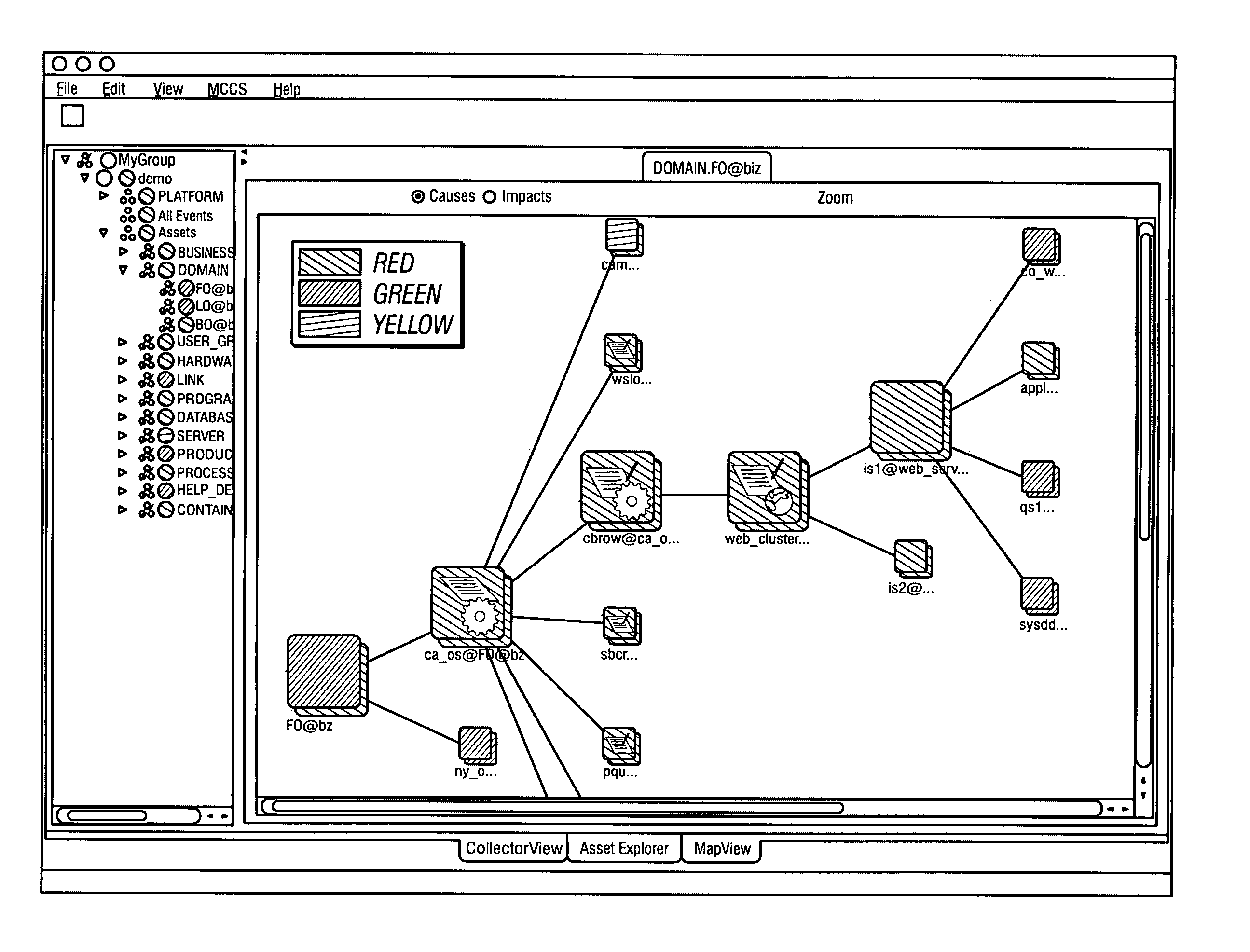
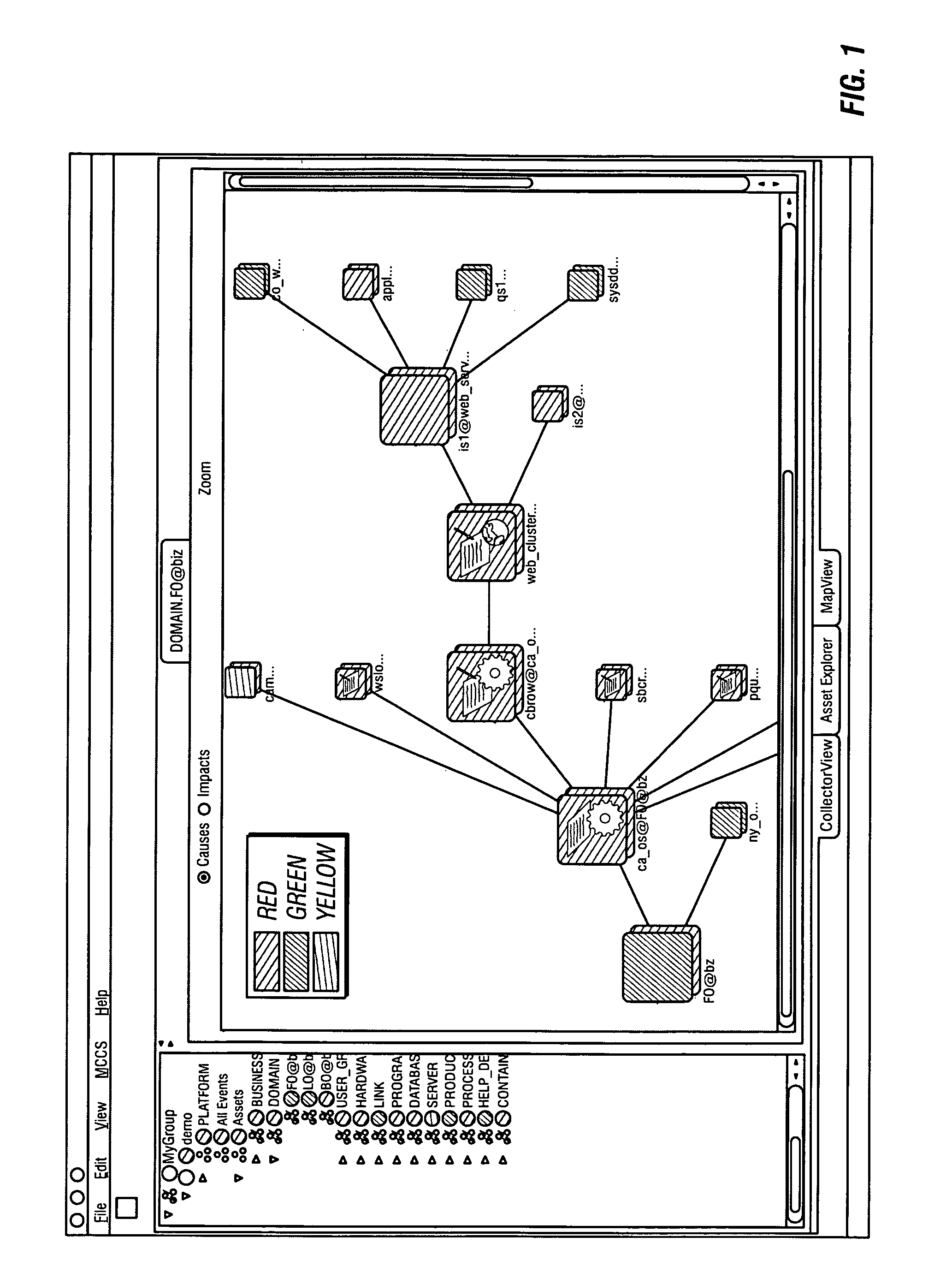
System and method for assessing and indicating the health of components
A system and method for visualization of the components of an enterprise system and the rendering of information about the health or status of the enterprise system, its components, and / or its subcomponents. The invention uses a combination of color codes or other indicators and a combination of algorithms and / or rules-based systems to control the computation of status / severities to associate to components and setup the color codes and indicators.
Owner:BMC SOFTWARE
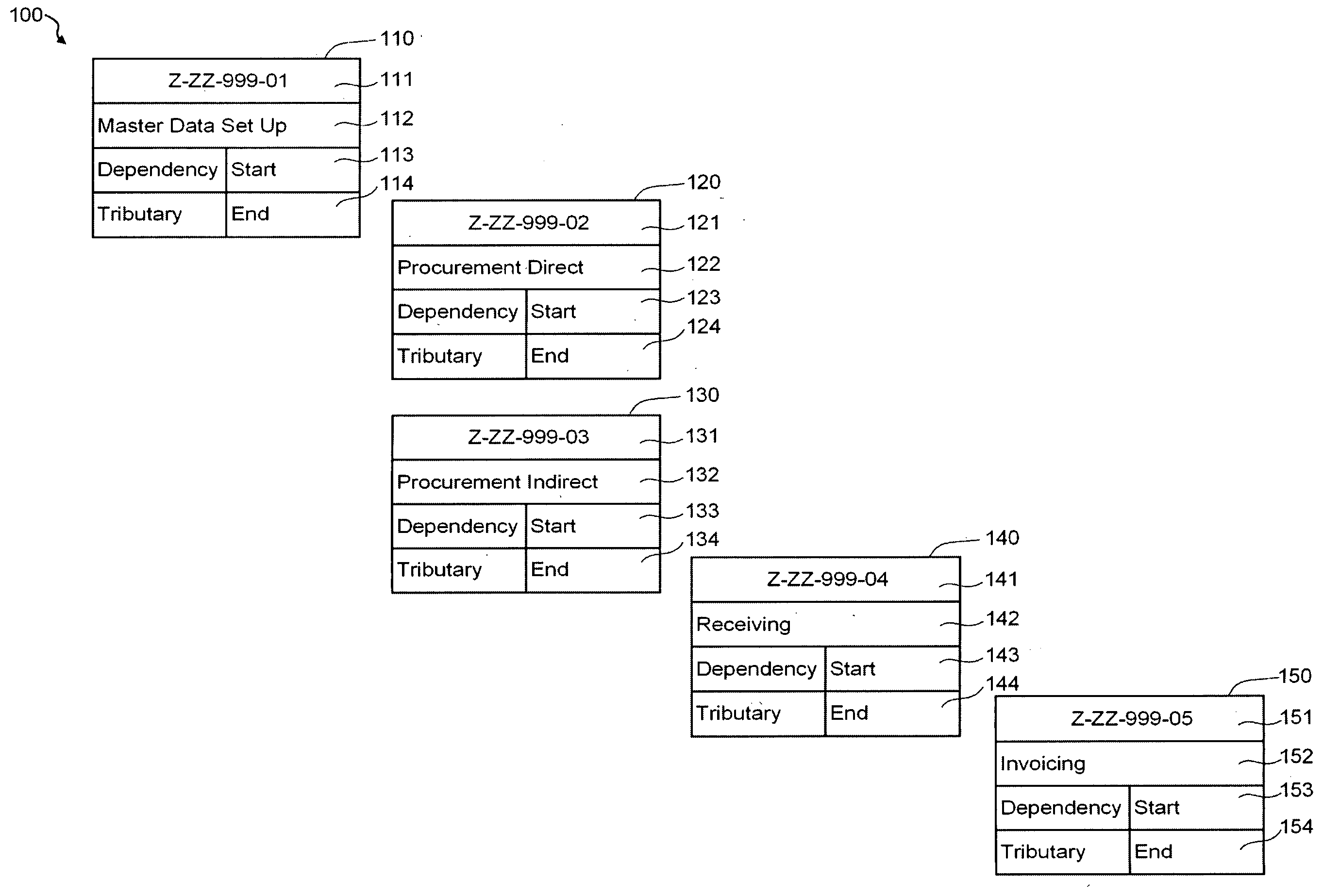
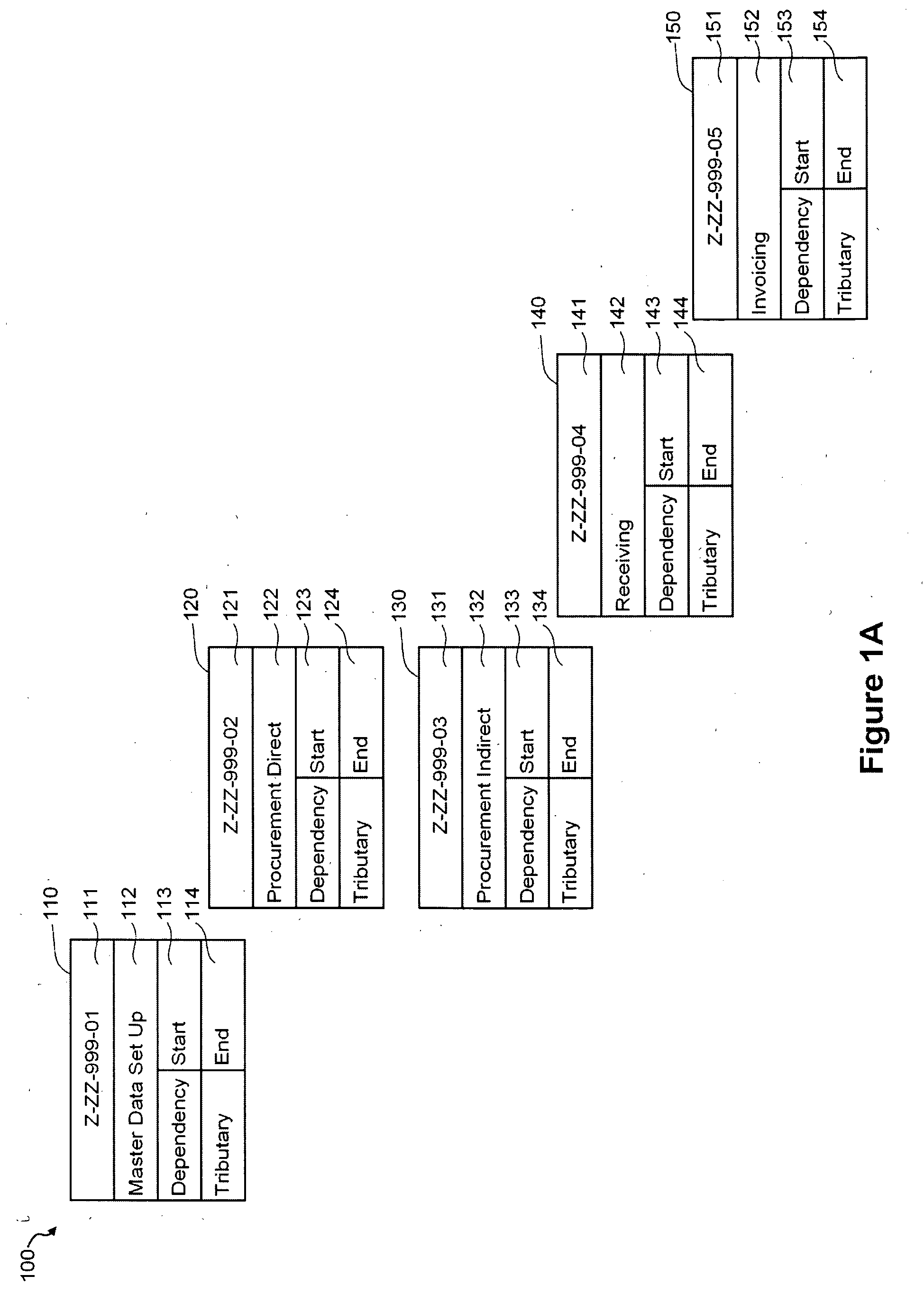
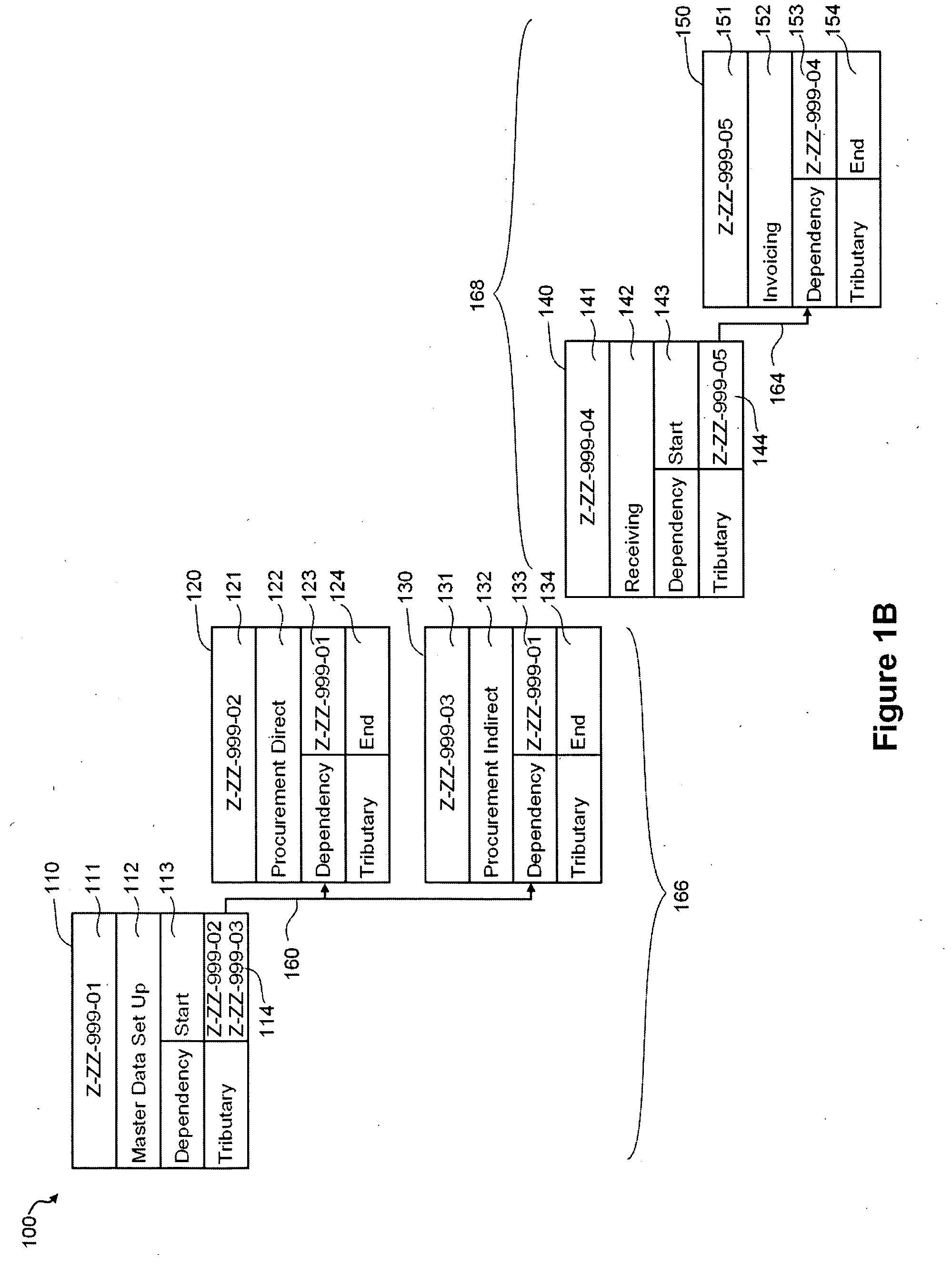
Testing tool comprising an automated multidimensional traceability matrix for implementing and validating complex software systems
InactiveUS20050166094A1Easy to createSoftware testing/debuggingSpecific program execution arrangementsSoftware systemComputer science
The present invention relates to a testing tool for testing of complex software systems having a plurality of interrelated system components and a suite of test scenarios for testing the performance of the plurality of interrelated system components. The testing tool includes an Automated Multidimensional Traceability Matrix system for determining linkages between interrelated system components, a means for identifying a change in one or more of the interrelated system components, a means for applying the Automated Multidimensional Traceability Matrix, a means for executing all of or a subset of the test scenarios associated with the interrelated system components that may be affected by the change and a means for evaluating the results of the executed test scenarios.
Owner:KIMBERLY-CLARK WORLDWIDE INC
Processor having a trace access instruction to access on-chip trace memory
InactiveUS6314530B1Hardware monitoringSoftware testing/debuggingComputerized systemParallel computing
A computer system includes a memory for storing instructions executable by a processor and an on-chip trace memory having a plurality of locations for storing trace information that indicates execution flow in the processor. A trace access instruction provides for access to the on-chip trace memory on the processor. The trace access instruction can be a write instruction or a read instruction. Typically, both read and write to the trace memory is provided. The system also has the capability to trace on start or restart of an executable thread by providing to the processor an indication of which executable thread to trace via a debug port. That indicates to the processor to provide trace information when the executable thread starts. When execution of the executable thread starts, the processor places an identifier corresponding to the executable thread into the trace memory to indicate that subsequent entries placed into the trace memory are part of said executable thread. The processor may also provide an entry indicating when the thread stops executing.
Owner:GLOBALFOUNDRIES INC
Systems and methods for software test management in cloud-based network
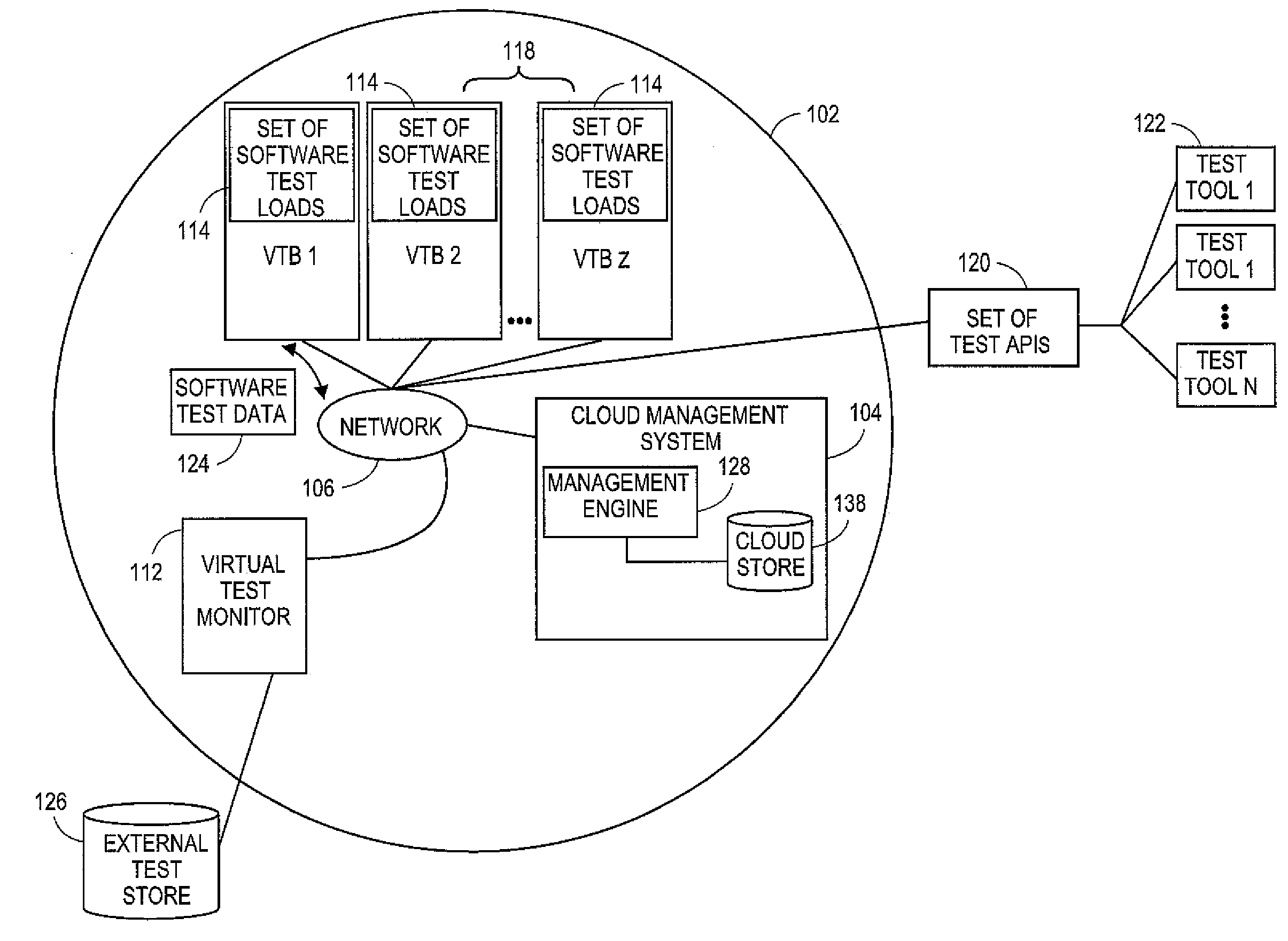
Embodiments relate to systems and methods for testing and evaluating software in the network cloud. A developer or other operator may wish to debug, modify, or update a set of test software based on testing of that software. The developer can instantiate a set of virtual servers or other test beds in the cloud, and install the subject software to the virtual test beds. A test management module can monitor the execution of the set of test software on the set of virtual test beds, to detect execution faults, measure processing performance, stress-test the software with predetermined data inputs, and manage other aspects of software life cycle development. The test management module can provide or access a set of application programming interfaces to a set of software tools external to the cloud, so that the set of test software can be tested and optimized using external programming development tools.
Owner:RED HAT
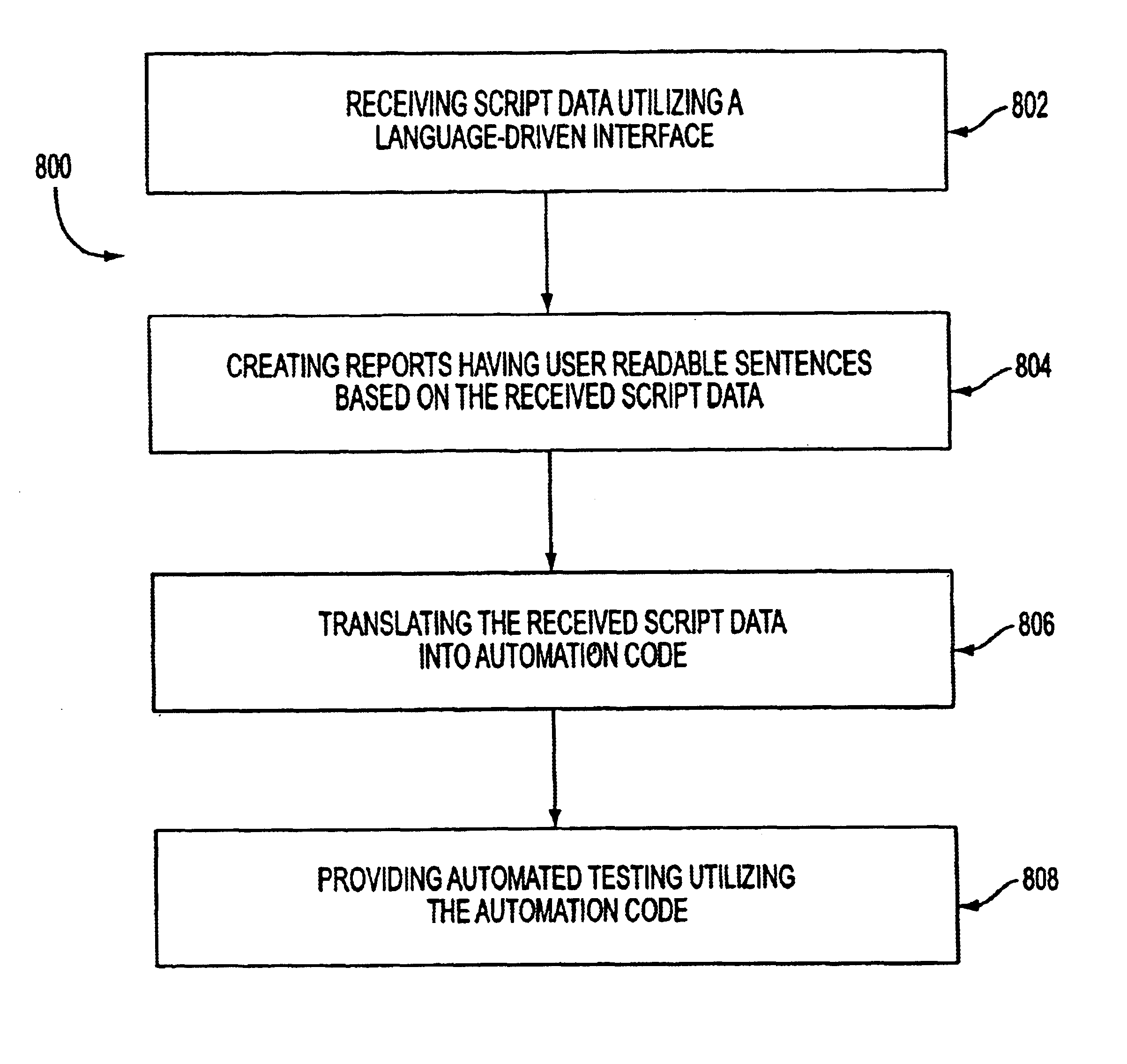
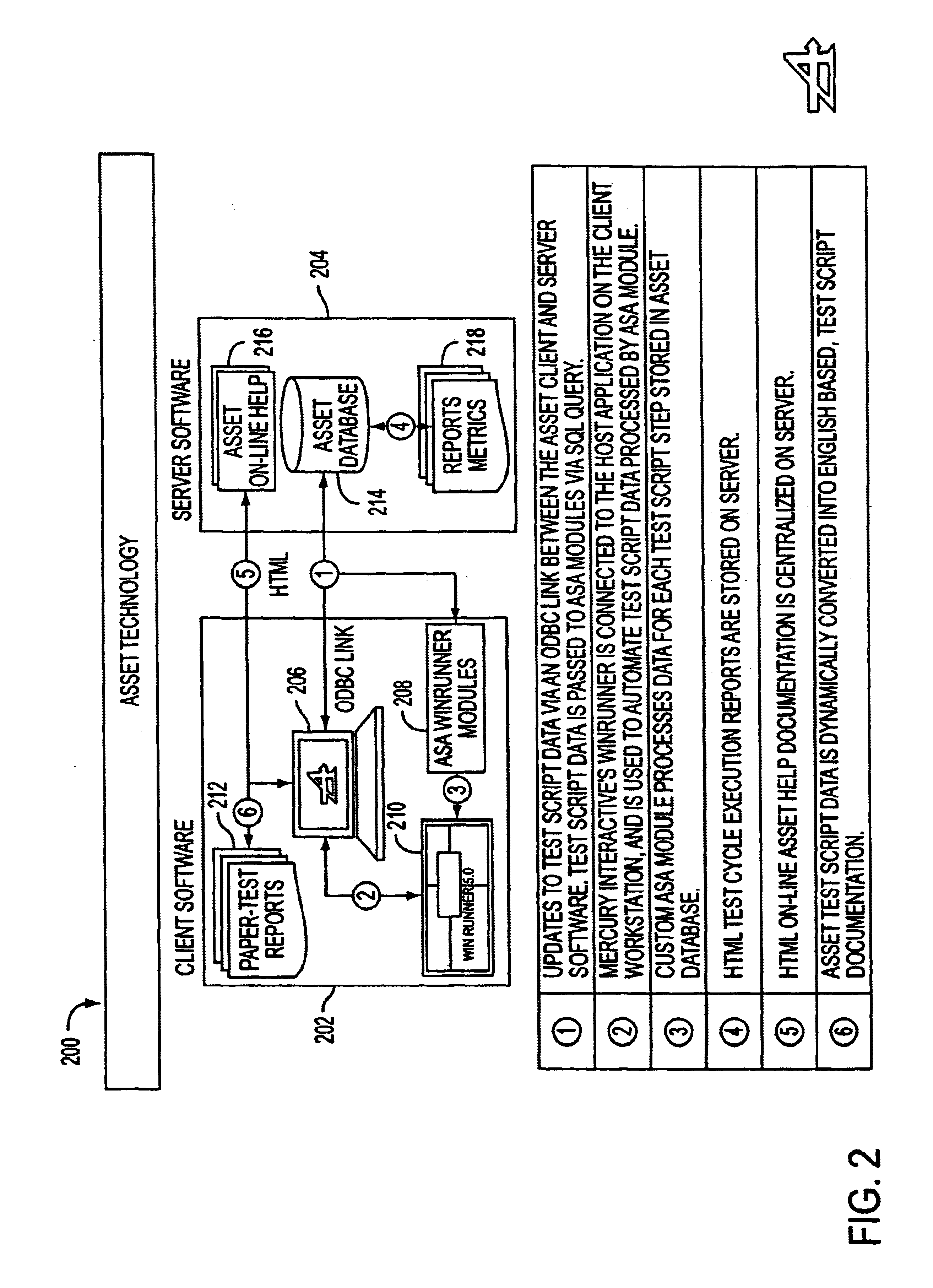
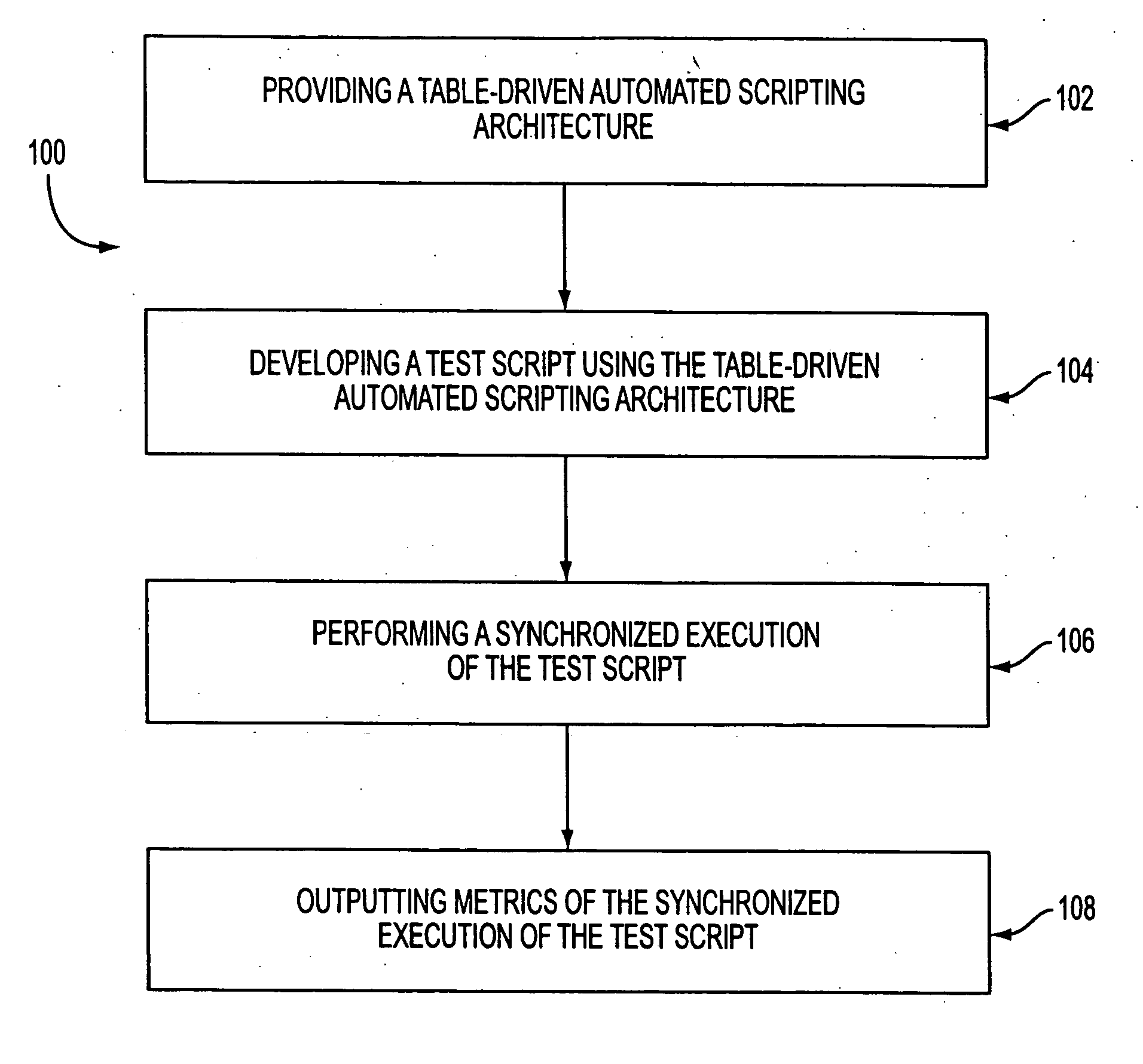
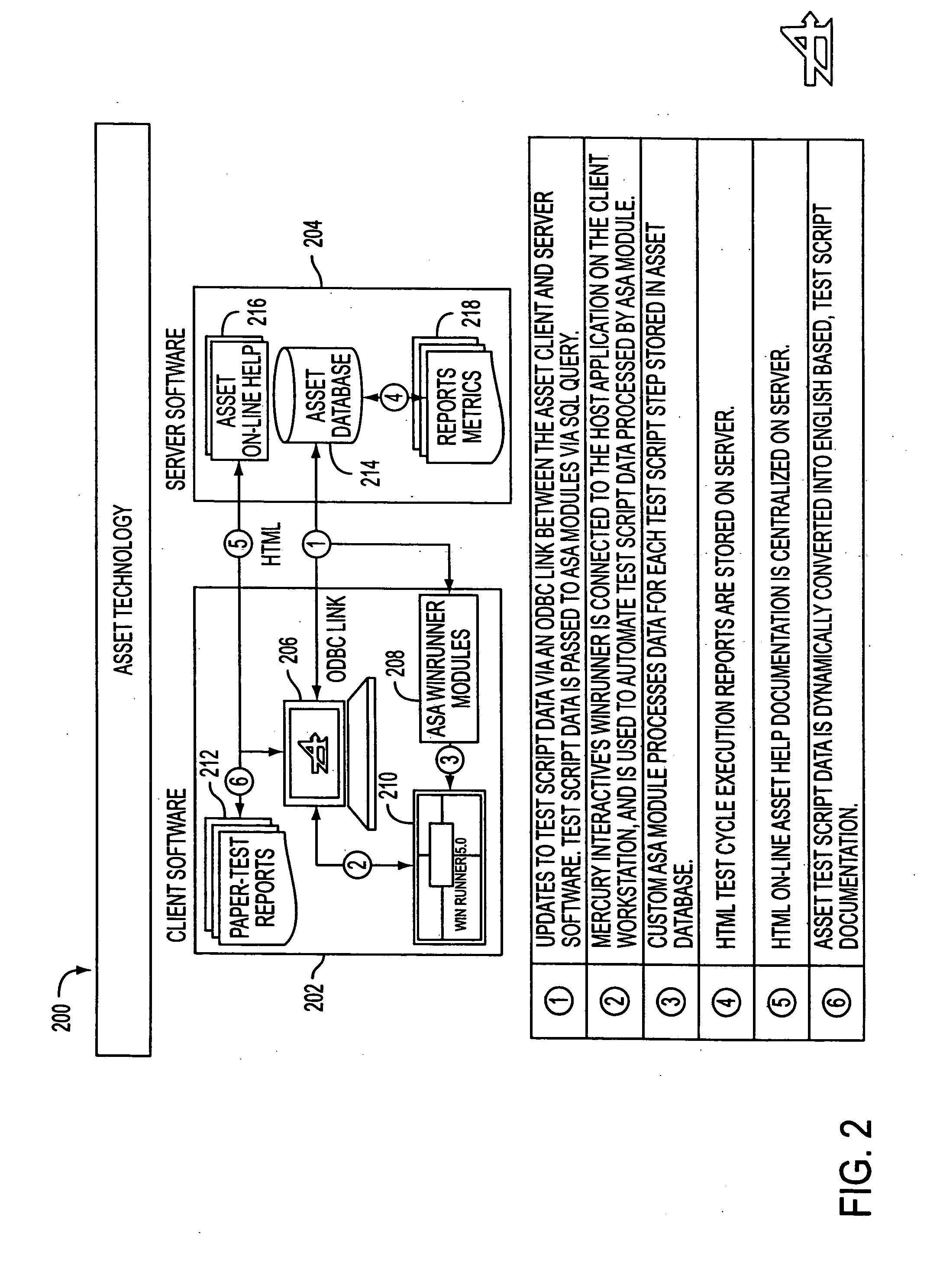
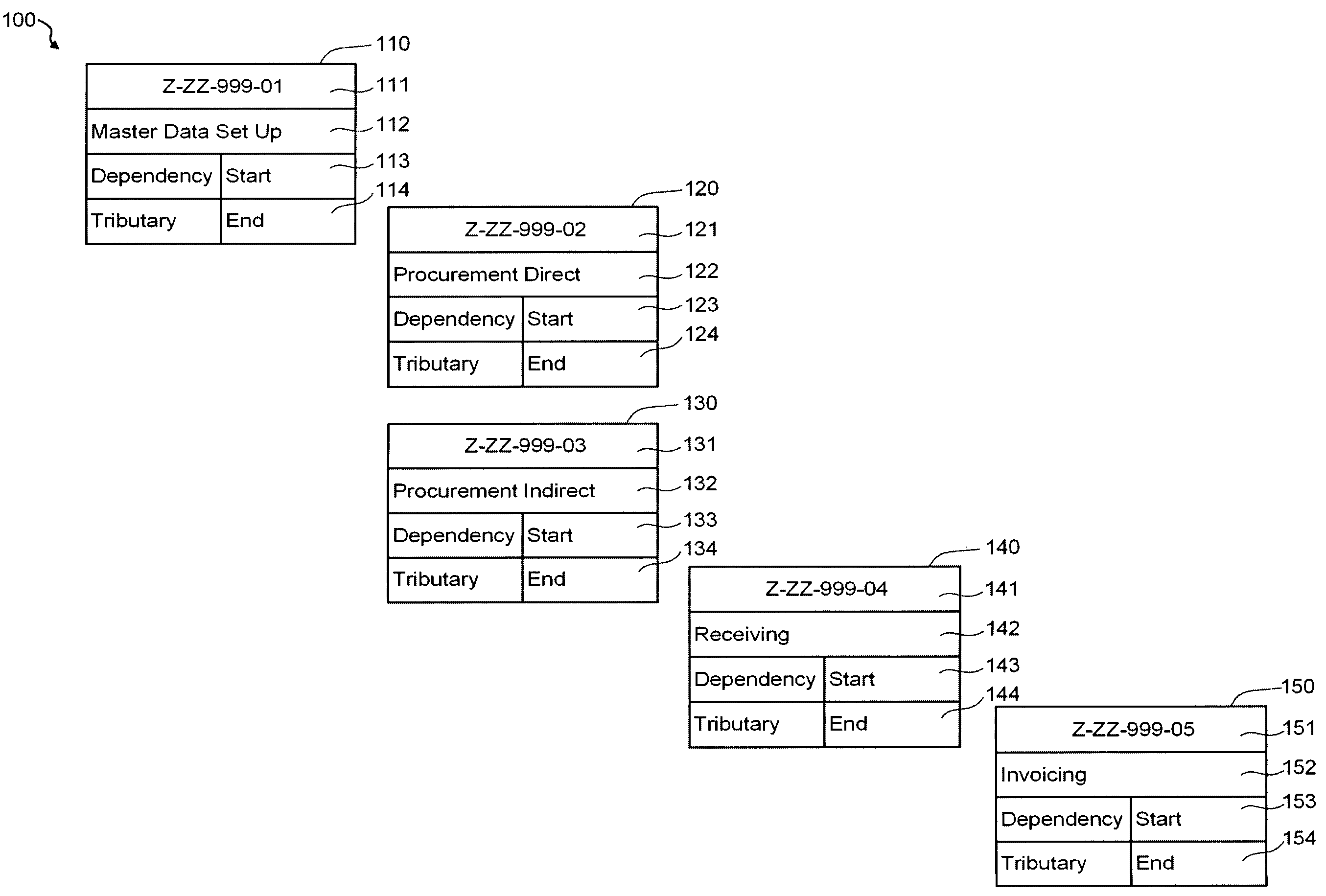
System, method, and article of manufacture for synchronization in an automated scripting framework
A system, method and article of manufacture are provided for affording synchronization in an automated scripting framework. First, script data is received utilizing a language-driven interface. Then, reports having user readable sentences are created based on the received script data. The received script data is then translated into automation code. Finally, automated testing is provided utilizing the automation code.
Owner:ACCENTURE GLOBAL SERVICES LTD
Testing tool comprising an automated multidimensional traceability matrix for implementing and validating complex software systems
InactiveUS7490319B2Easy to createSoftware testing/debuggingSpecific program execution arrangementsSoftware systemComputer science
Owner:KIMBERLY-CLARK WORLDWIDE INC
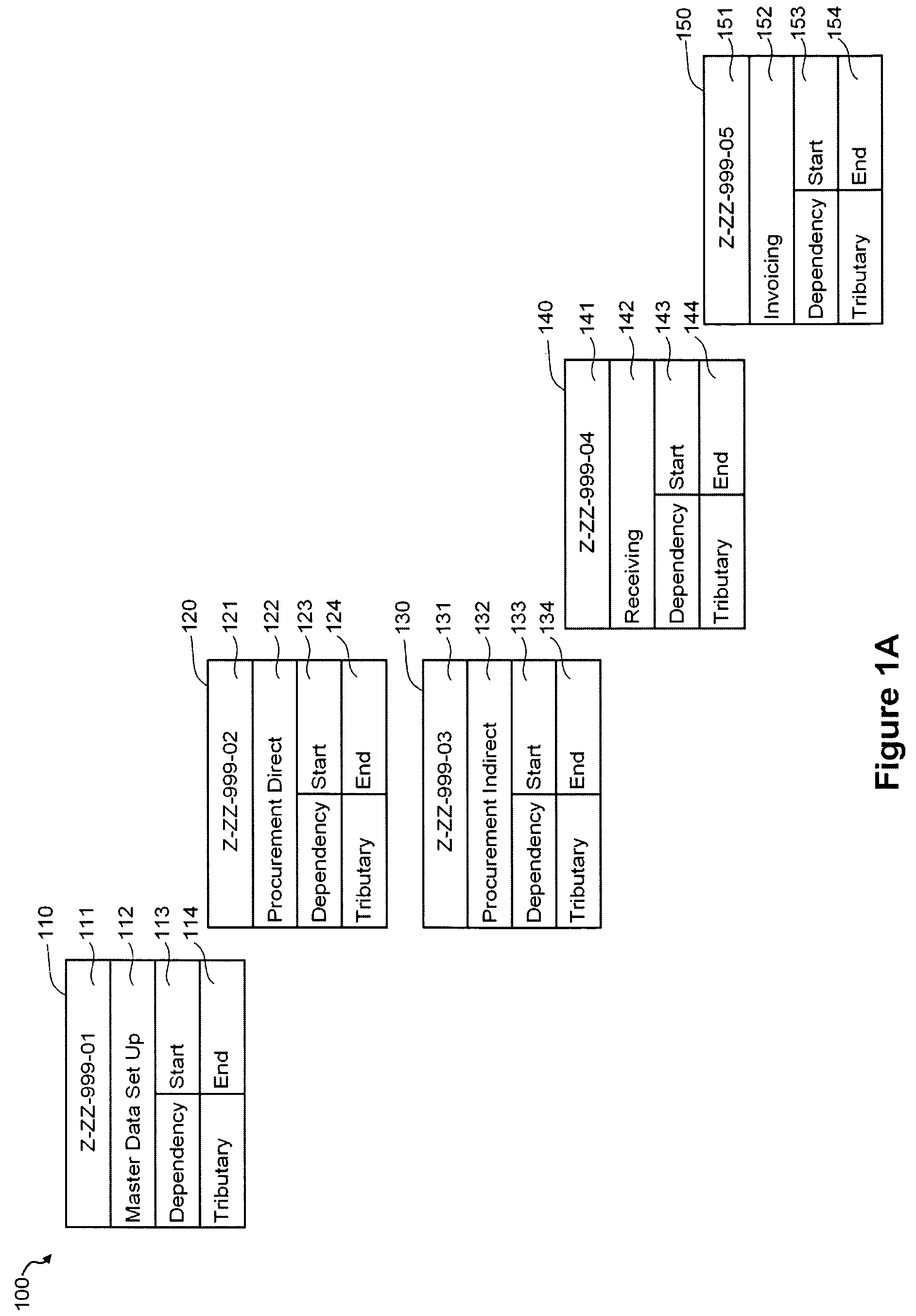
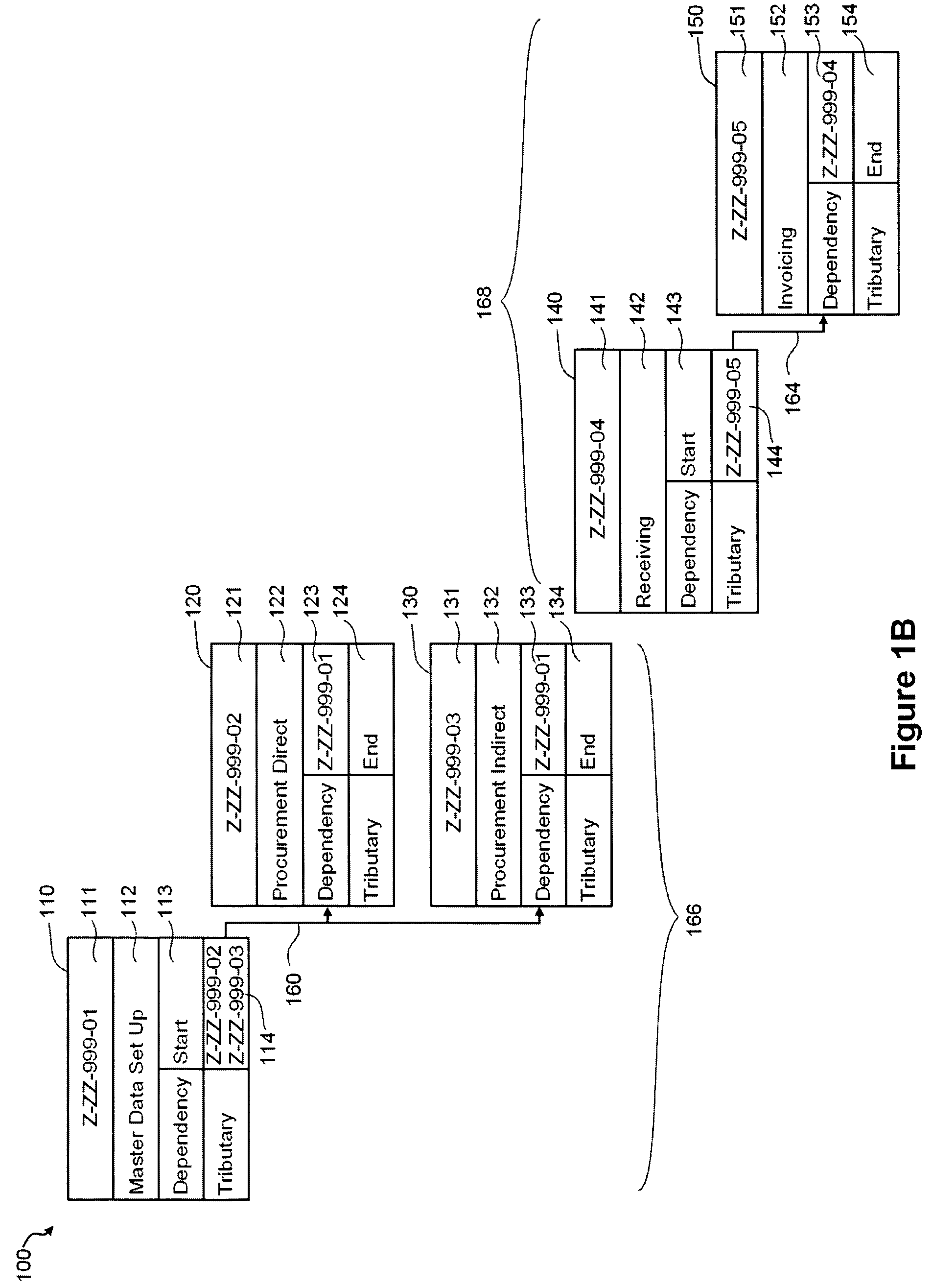
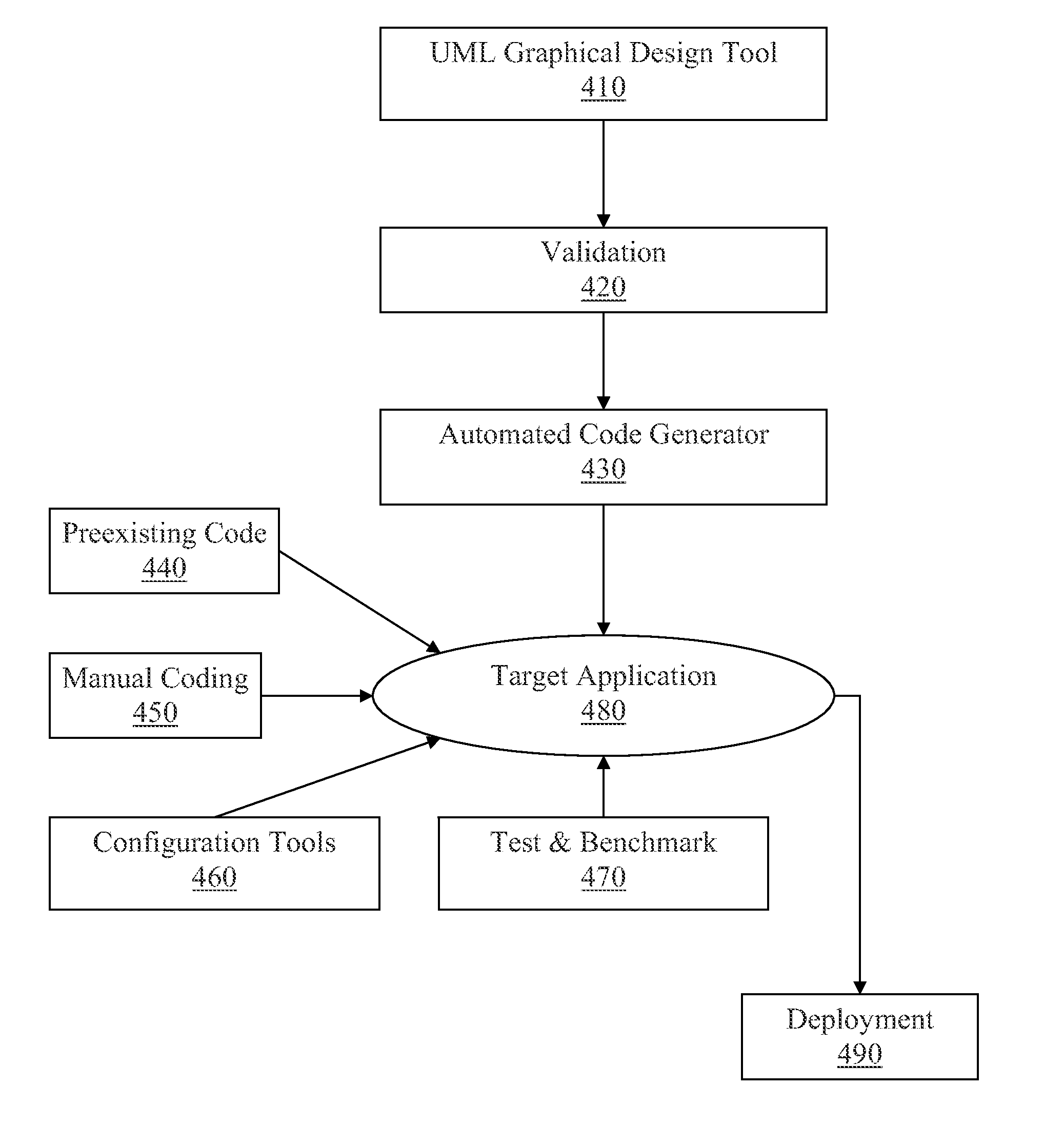
Automated Enterprise Software Development
InactiveUS20110088011A1Easy to deploySoftware testing/debuggingSoftware designGraphicsUnified Modeling Language
The preferred embodiment provides a system and method for automatically generating enterprise software applications with minimal level of manual coding. The preferred embodiment provide a graphical design tool that models an application using Unified Model Language (UML), validate the UML model, and automatically generate deployable application. The preferred embodiment also provides a framework of libraries that the target application can be build from.
Owner:VERMEG SERVICES
Debug interface including a compact trace record storage
InactiveUS6094729AReliability increasing modificationsHardware monitoringInformation typeParallel computing
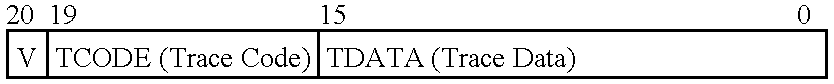
In-circuit emulation (ICE) and software debug facilities are included in a processor via a debug interface that interfaces a target processor to a host system. The debug interface includes a trace controller that monitors signals produced by the target processor to detect specified conditions and produce a trace record of the specified conditions including a notification of the conditions are selected information relating to the conditions. The trace controller formats a trace information record and stores the trace information record in a trace buffer in a plurality of trace data storage elements. The trace data storage elements have a format that includes a trace code (TCODE) field indicative of a type of trace information and a trace data (TDATA) field indicative of a type of trace information data.
Owner:GLOBALFOUNDRIES INC
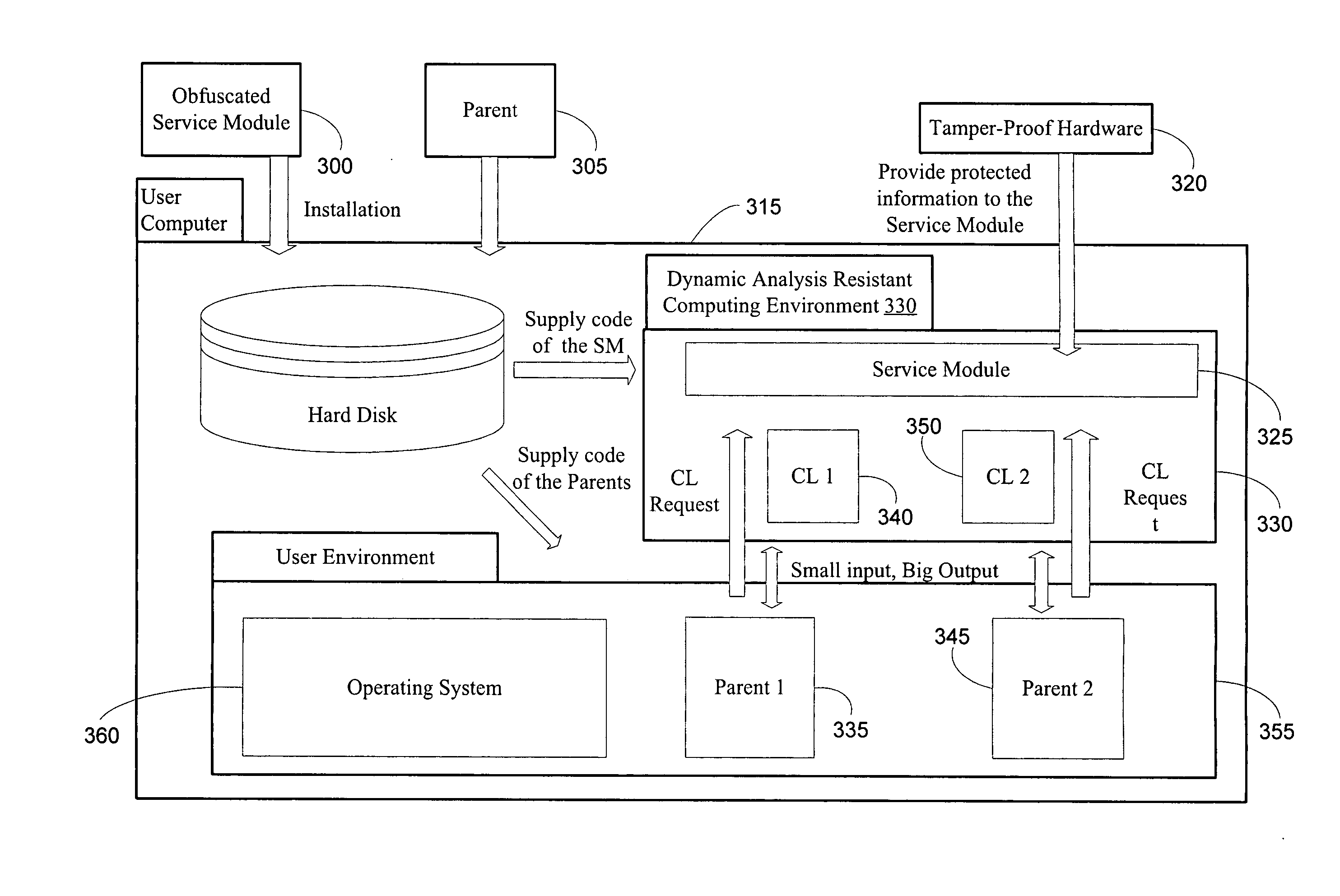
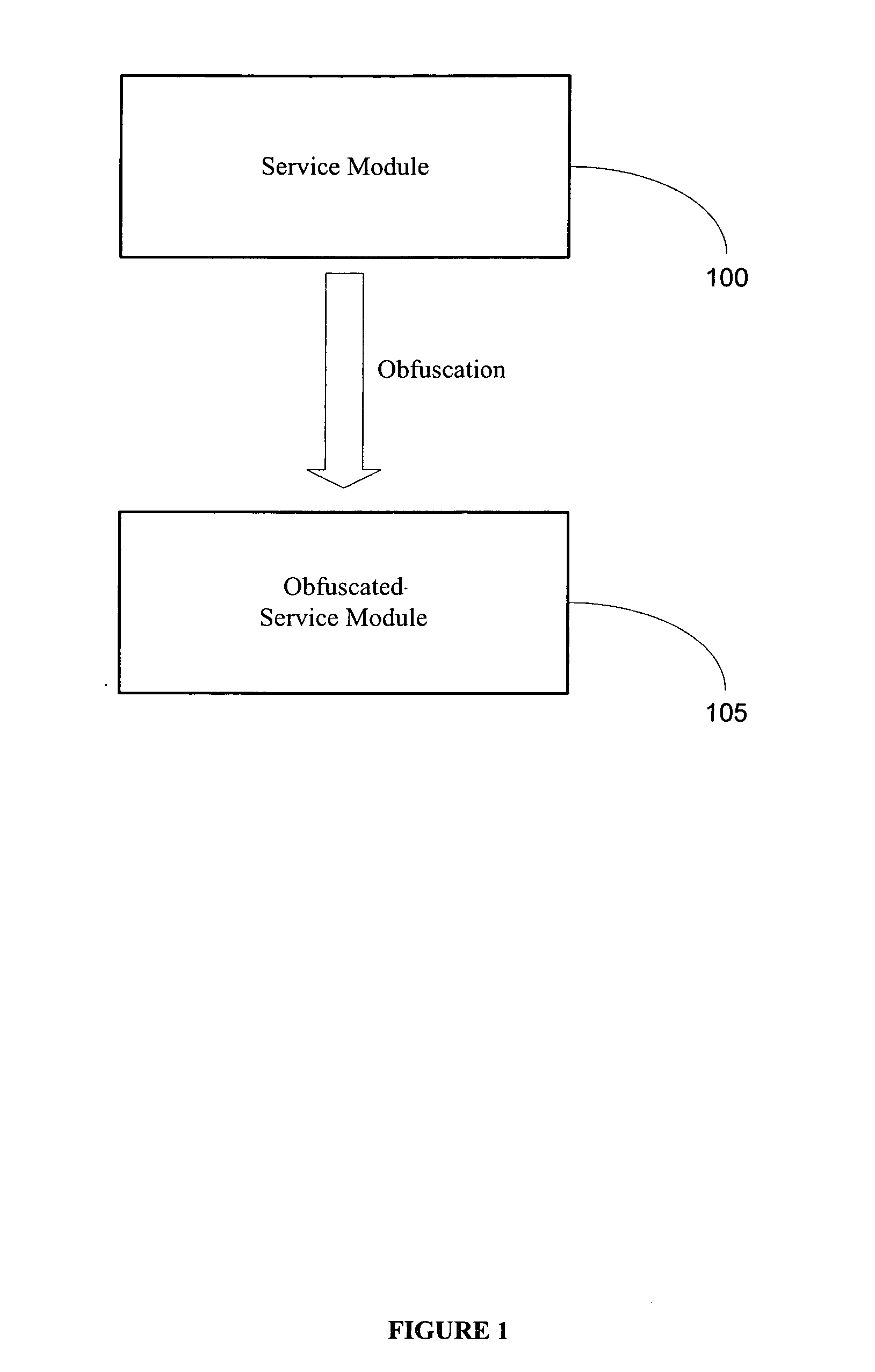
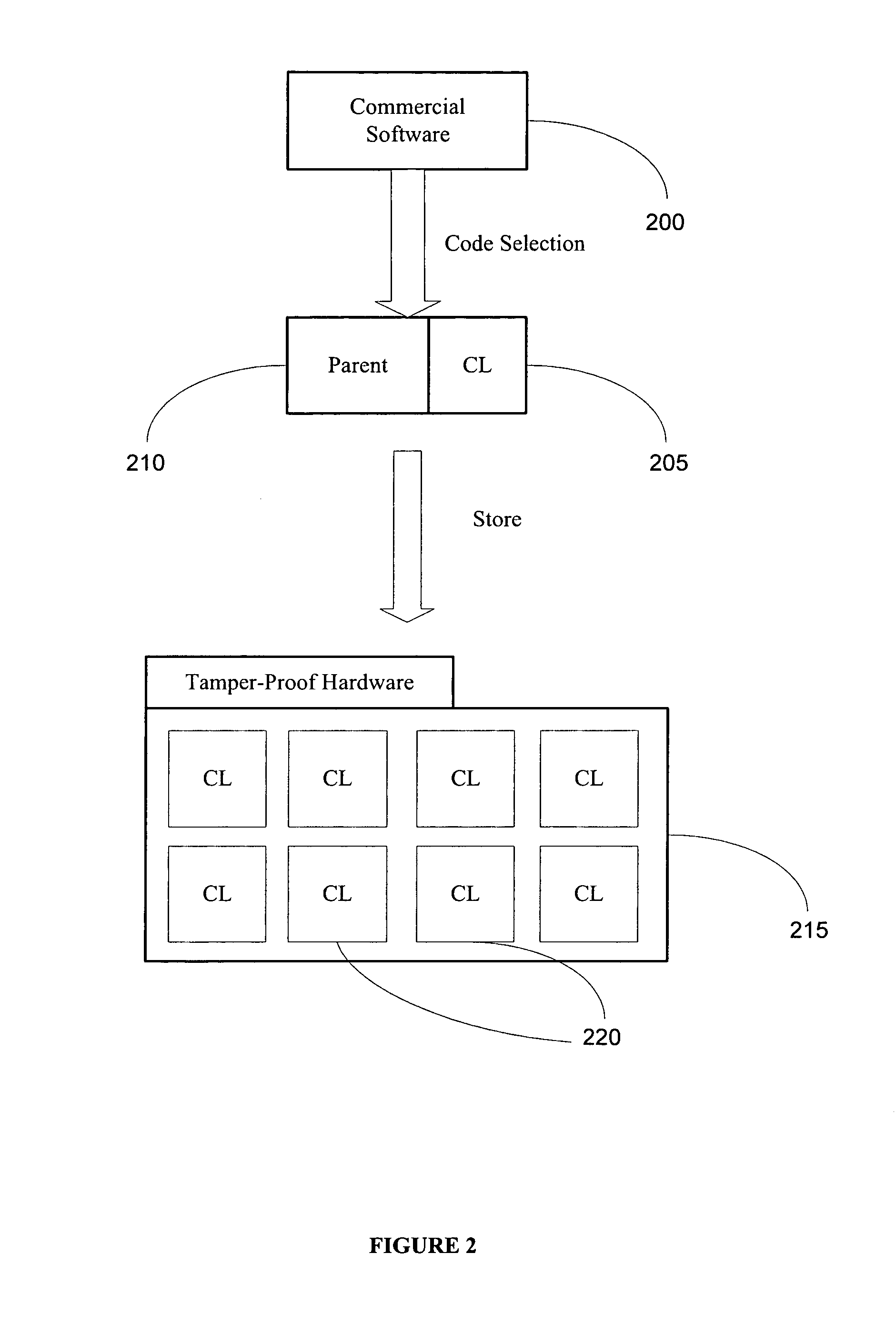
Method and system for providing tamper-resistant software
InactiveUS20060048223A1Performance penaltyImprove tamper resistanceMemory loss protectionDetecting faulty computer hardwareTamper resistanceObfuscation
A method and system for protecting only a portion of the software to be protected against tampering is described. Such a portion may be stored in a tamper-resistant physical device, with optional encryption, for downloading when needed for execution. Several layers of tamper resistance are provided without excessively impacting performance of the protected software. For instance, obfuscation is applied to the code for the service module to minimize the large expense associated with obfuscation. The invention includes embodiments that deliver critical logic, policy information and other similar information with the help of mobile agents, which may be hosted by a server in a smart card.
Owner:THE UNIVERSITY OF HONG KONG
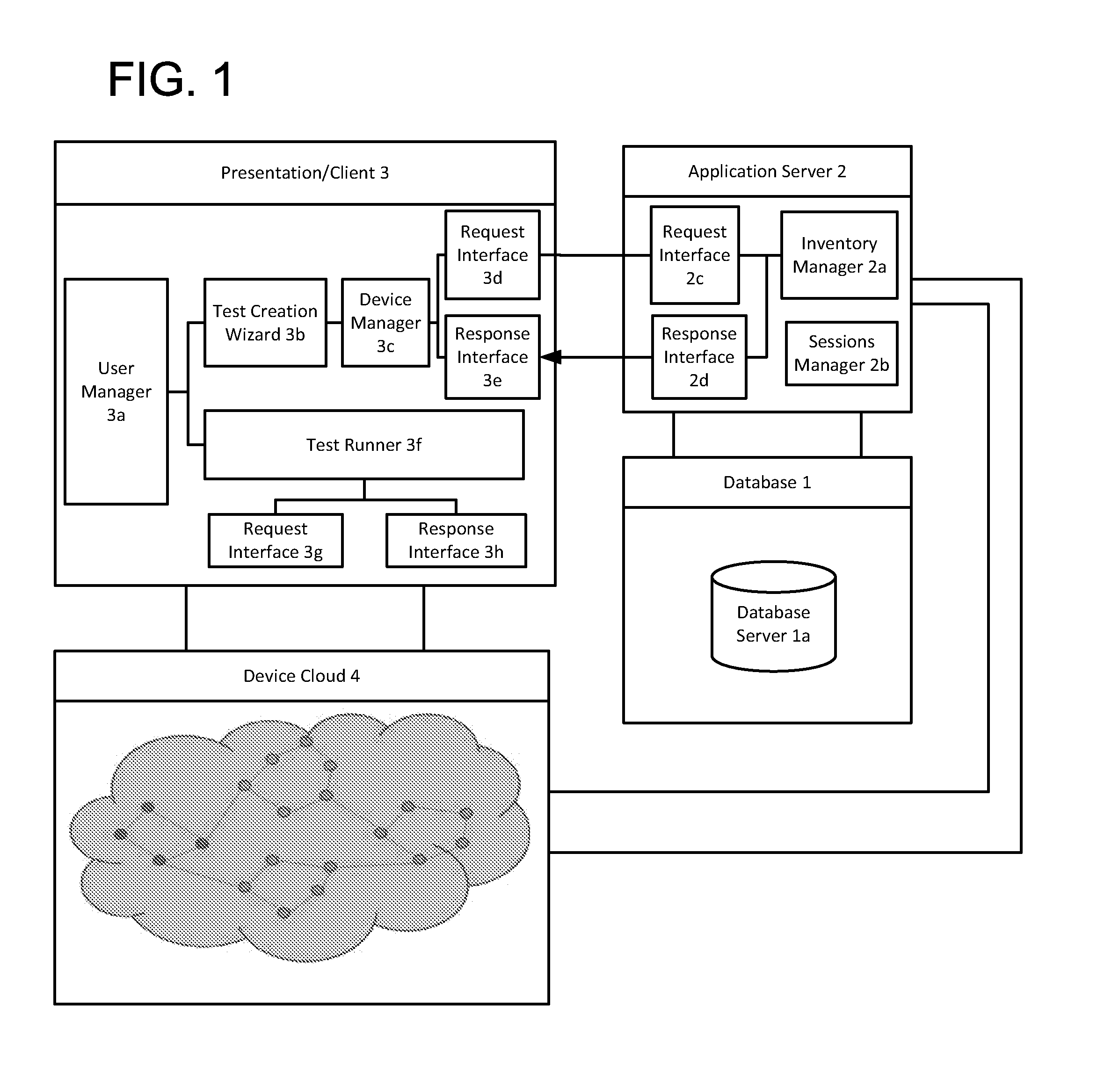
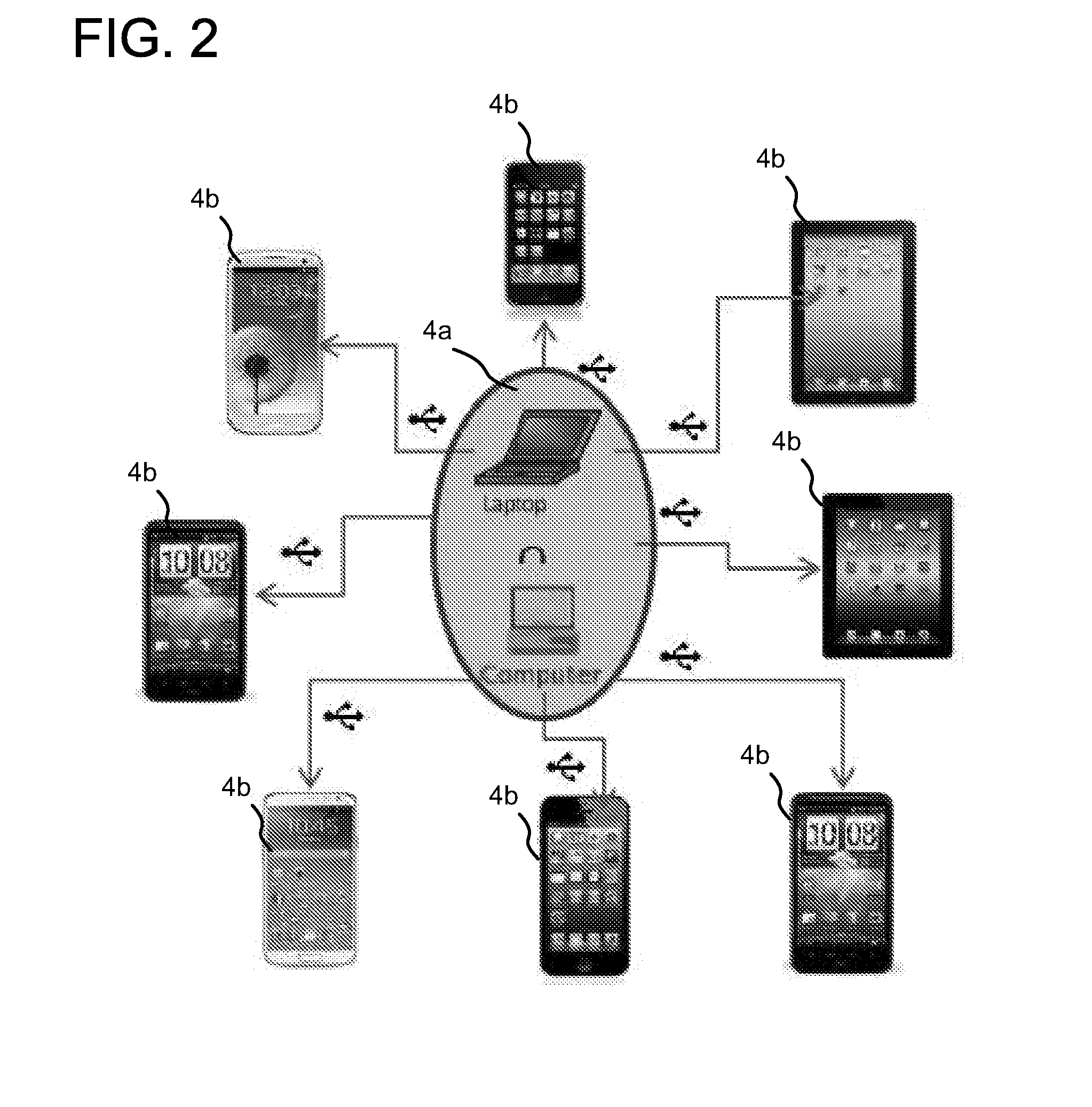
Automated application test system
An automated application test system comprises a plurality of clients (3) providing test interfaces to corresponding users, and a network of test nodes (4a) connected to the clients (3); wherein each said test node (4a) comprises one or more test devices locally connected to the test node (4a); and an agent (6) arranged to execute one or more test applications on the locally connected test devices (4b) in accordance with requests from the clients (3).
Owner:BARCLAYS EXECUTION SERVICES LTD
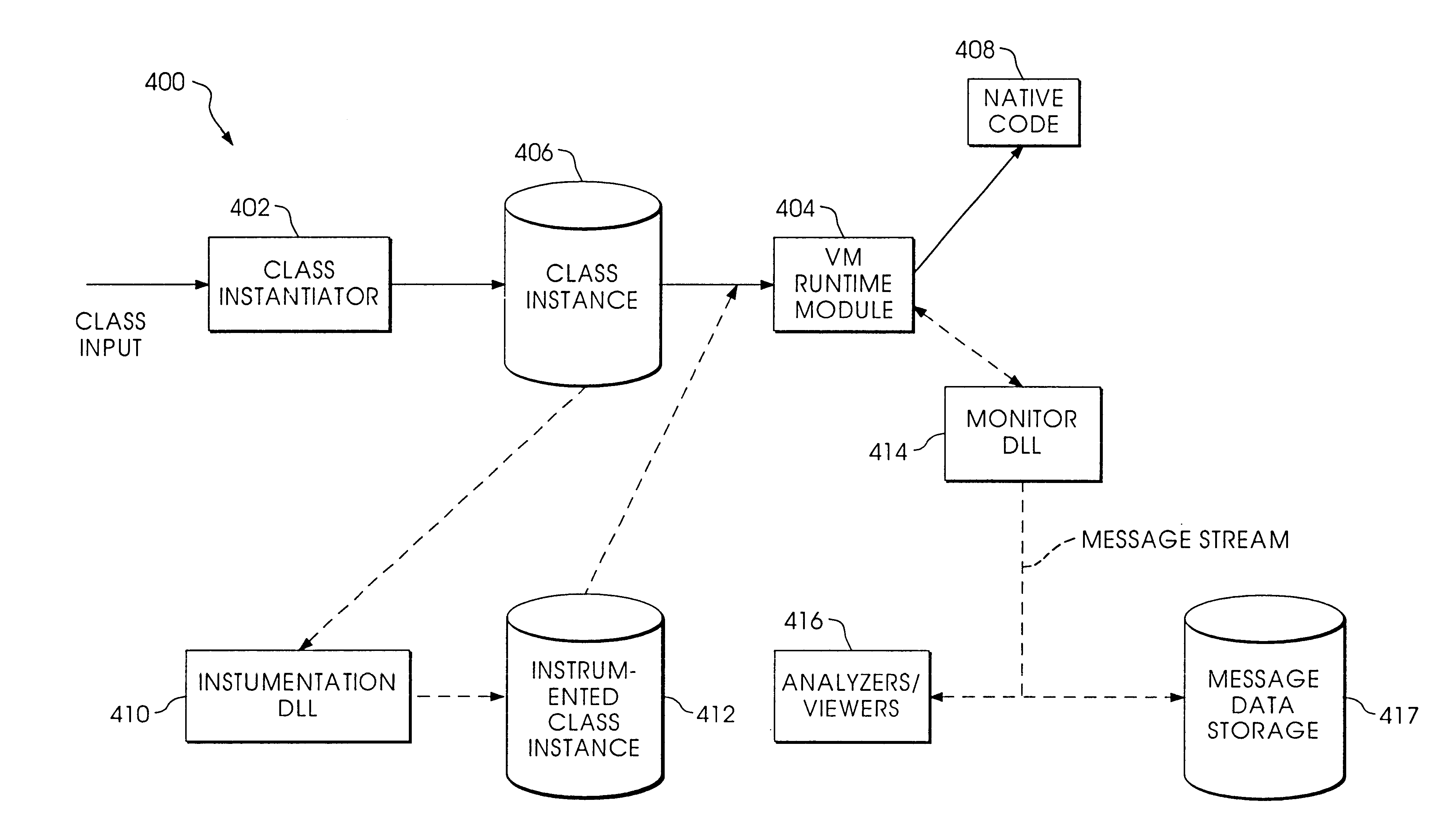
Byte code instrumentation
InactiveUS6314558B1Software testing/debuggingSpecific program execution arrangementsMessage flowTime function
Instrumenting a computer program to provide instrumented byte code includes examining the byte code, selecting portions of the byte code for instrumentation, and instrumenting the portions to provide instrumented byte code. Selecting the portions may include choosing portions of the byte code corresponding to method entry, method exit, a throw, a method call, or a new line number. Instrumenting a portion of the byte code corresponding to a method call may include instrumenting a local line number of source code corresponding to the byte code being instrumented. Instrumenting the portions may include adding calls to instrumentation runtime functions that pass parameters indicative of the portions being instrumented. At least one of the parameters that is passed may include a line number of the source code corresponding to the portion being instrumented or a object pointer for the method corresponding to the portion being instrumented. Data from instrumentation may be passed via a message stream that is viewed as the data is being generated and / or stored.
Owner:BORLAND
Integrated system for software application development
InactiveUS10001975B2Equally distributedProgram initiation/switchingVersion controlIntegrated softwareProject management
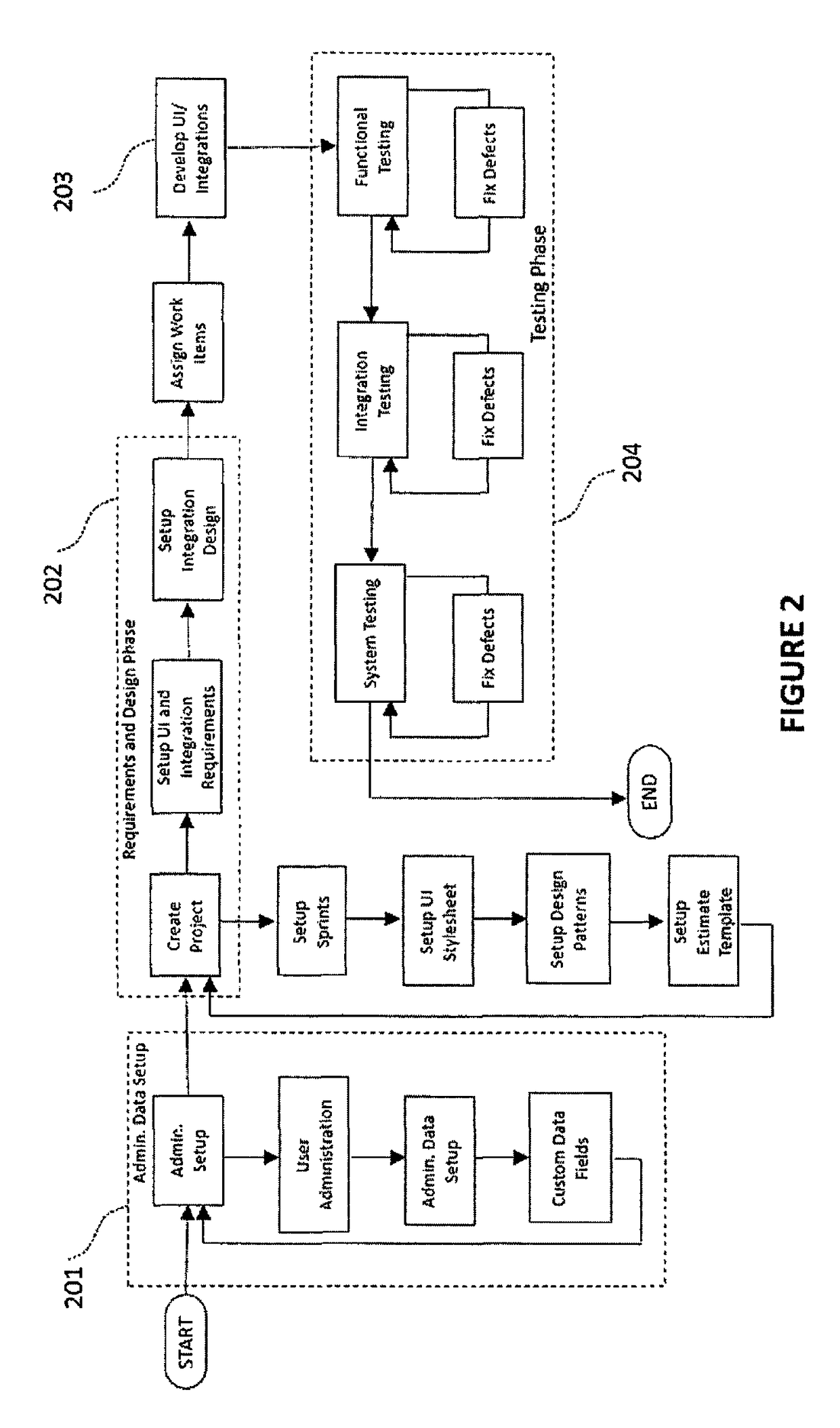
Methods and systems are disclosed for developing a software application through requirements specification, design, effort estimation, assigning and tracking work items, development, testing, collaboration and project management. The system is structured as an integrated software development system allowing for structured, systematic and user friendly set up of requirements specification (including workflow, user interface, business rules and integrations), technical design for UI features and integrations using design patterns, automated effort estimation, automated story card and task creation. The system also provides a novel, audio-video playback capability for workflow visualization. Further, the system provides visual depiction of defects and changed items side-by-side with requirements, as well as predictive modeling of defects that allows for forecasting of defect completion rate. In the preferred embodiment, the system is delivered as a multi-tenant Software as a Service.
Owner:BHARTHULWAR SHRIDHAR V
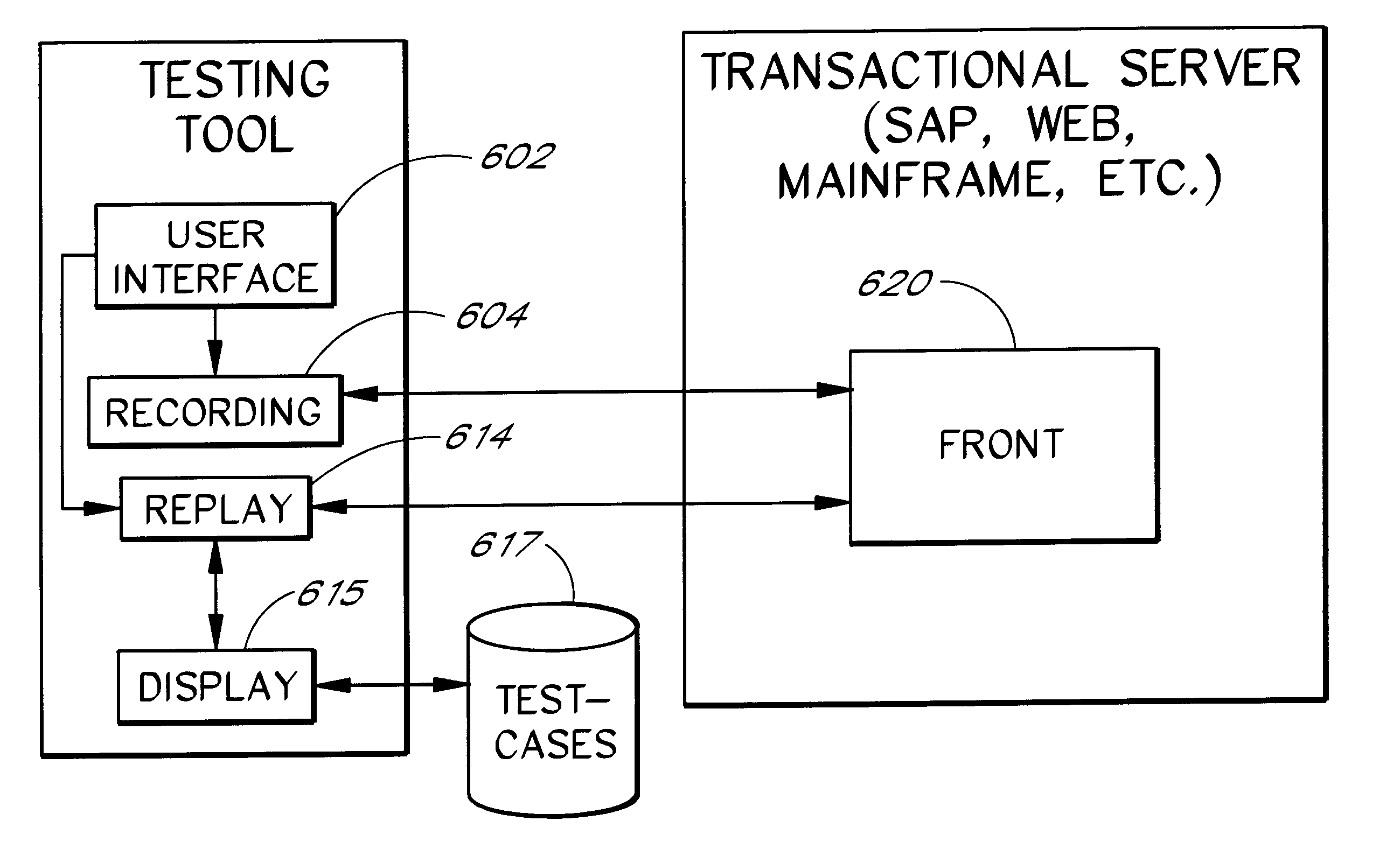
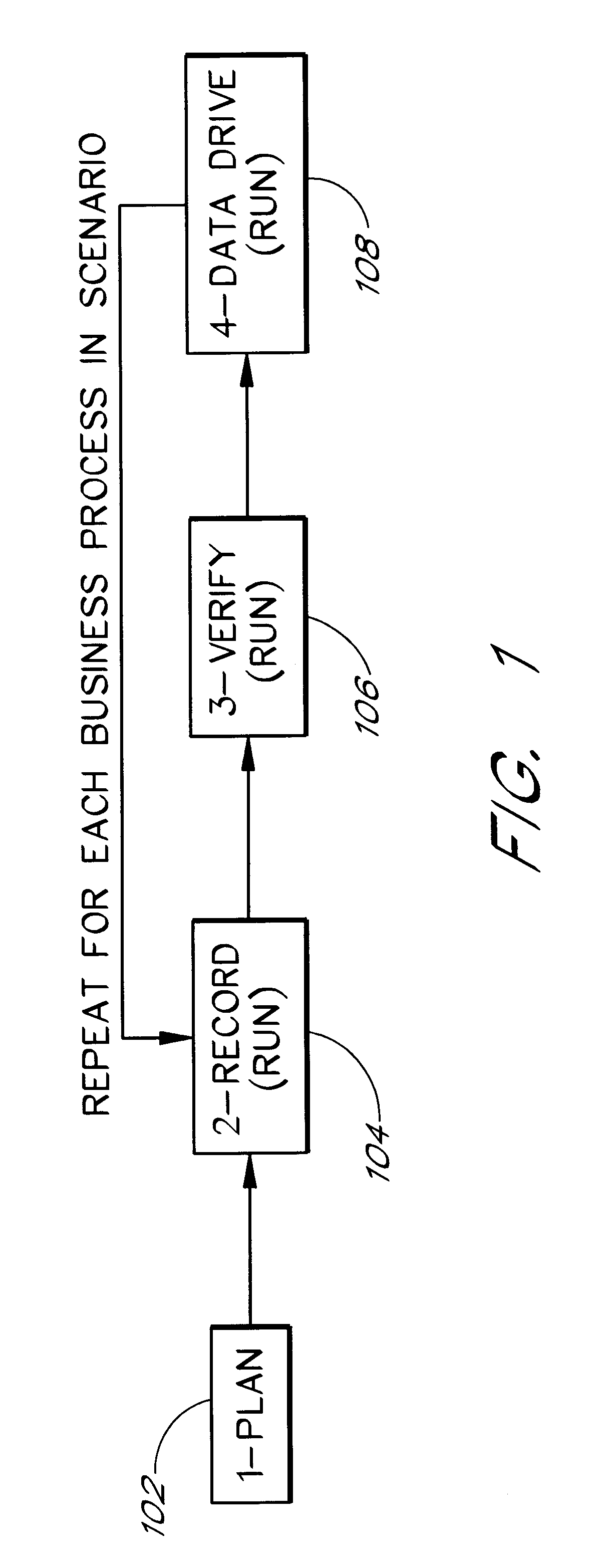
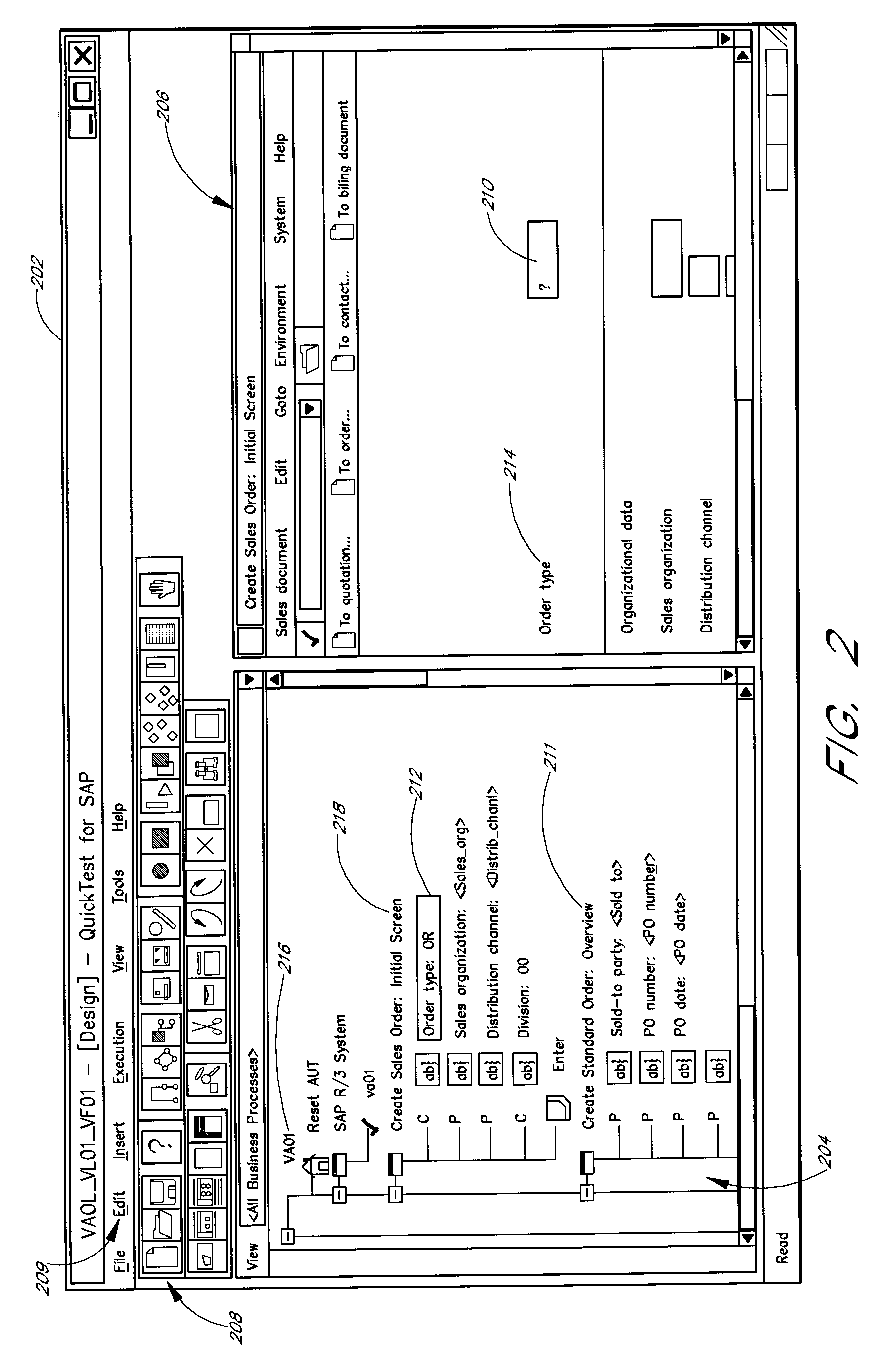
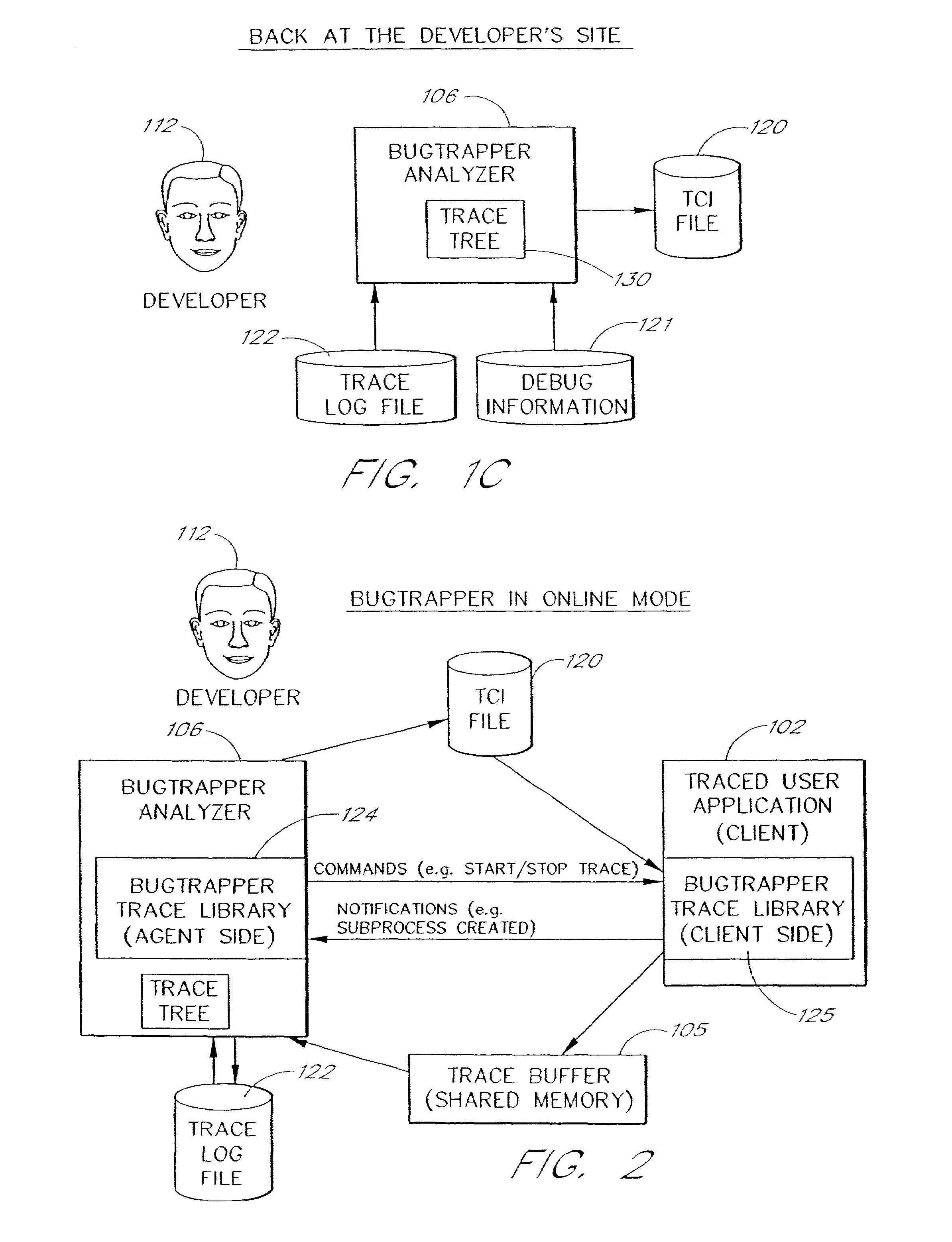
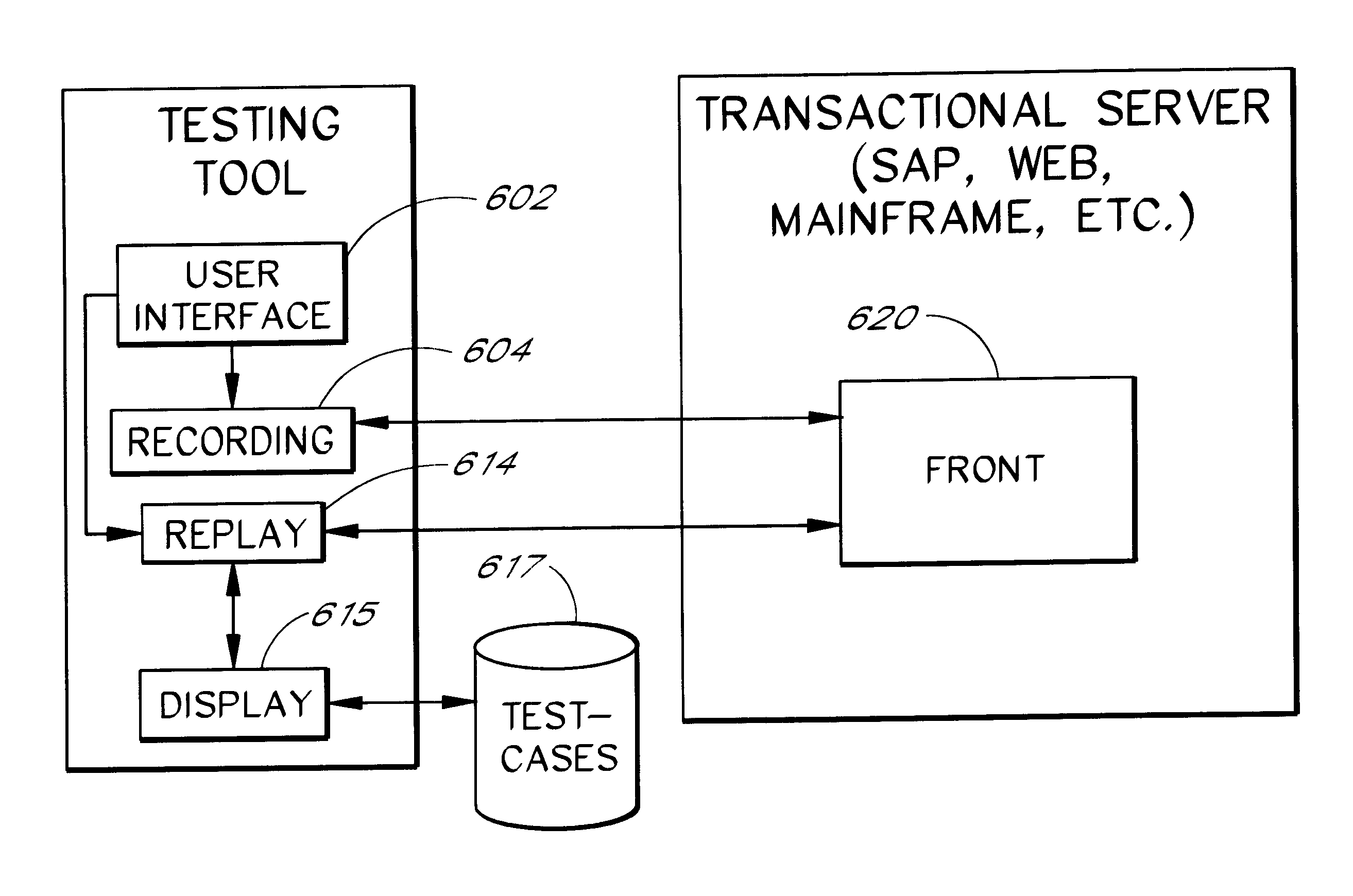
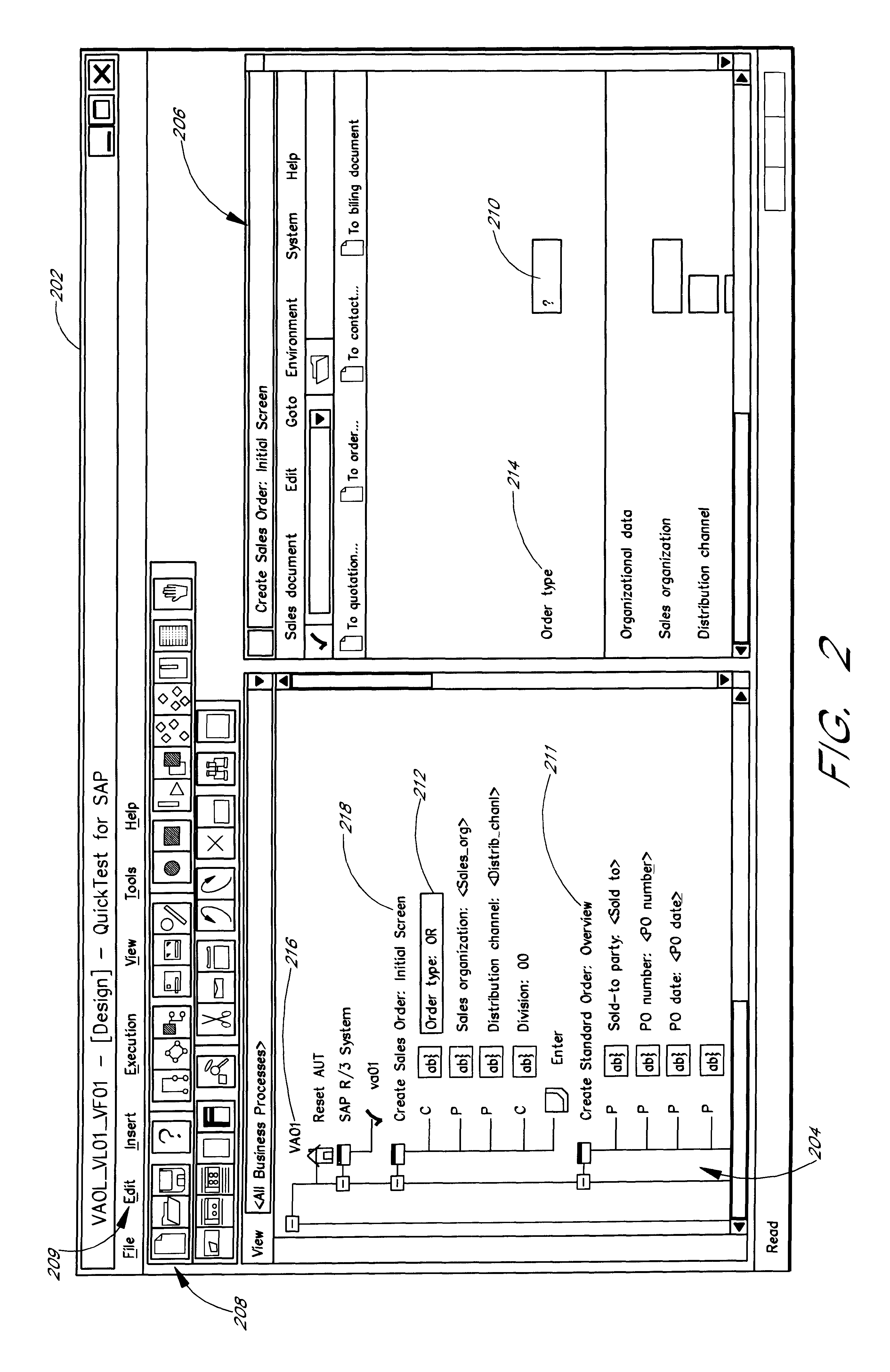
Software system and methods for testing the functionality of a transactional server
A testing tool automatically records a series of user steps taken during a user session with a transactional server and generates a test for testing the functionality of server. Through a user interface of the testing tool, the user can define verification steps to automatically test for expected server responses during test execution. The testing tool displays the test to the user as a tree having nodes (displayed as icons) which represent steps of the test. Via the user interface, the user can modify node properties and perform other types of tree edit operations to edit the test, without the need to know a scripting or other programming language. When the user selects a node that corresponds to a particular field or other object of the server screen, the testing tool automatically displays the screen with the object highlighted. The testing tool also allows the test author to use a spreadsheet to conveniently specify data sets for running multiple iterations of a test; thus, the user can record a single transaction and then automatically test the transaction with other data sets.
Owner:MICRO FOCUS LLC
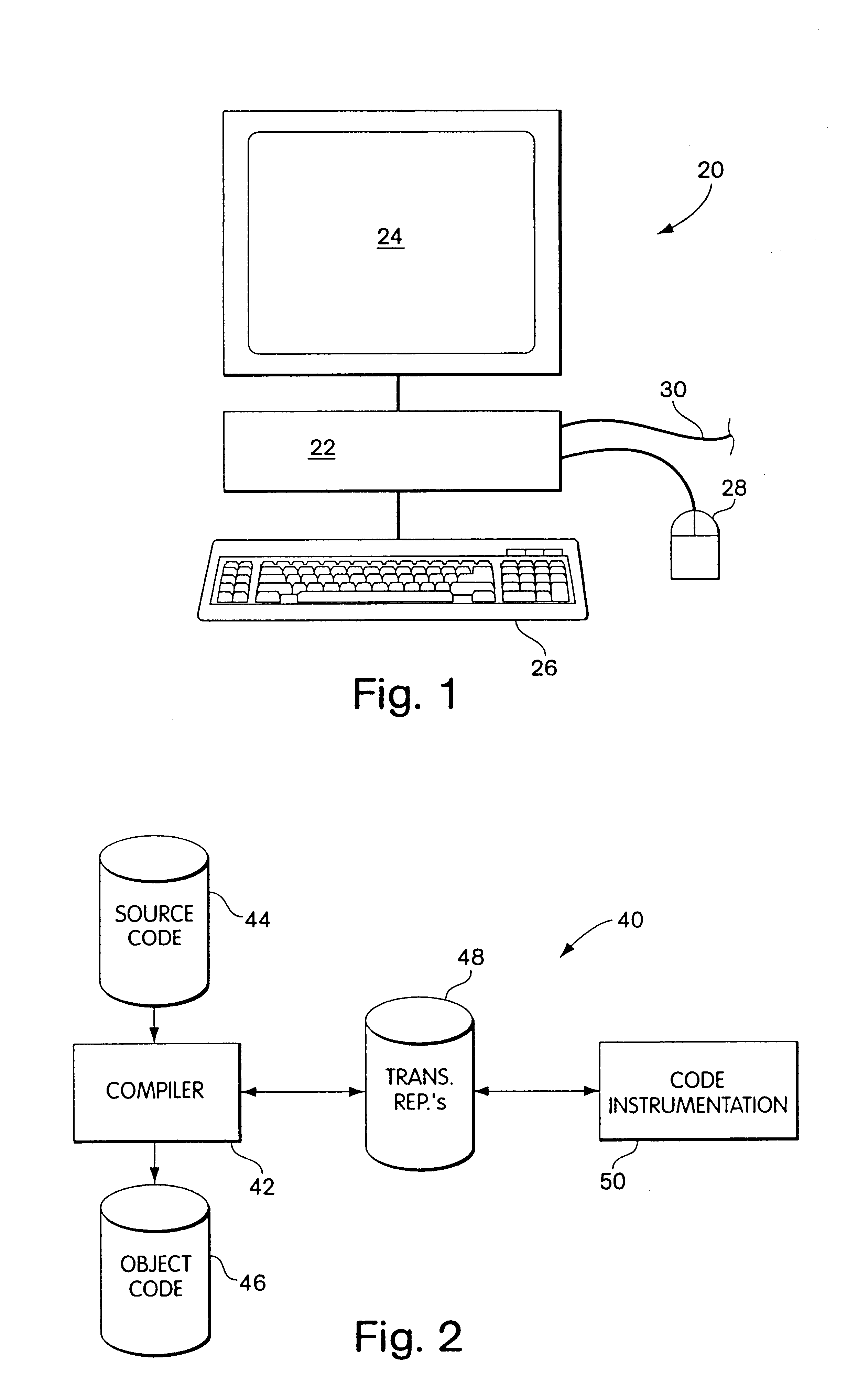
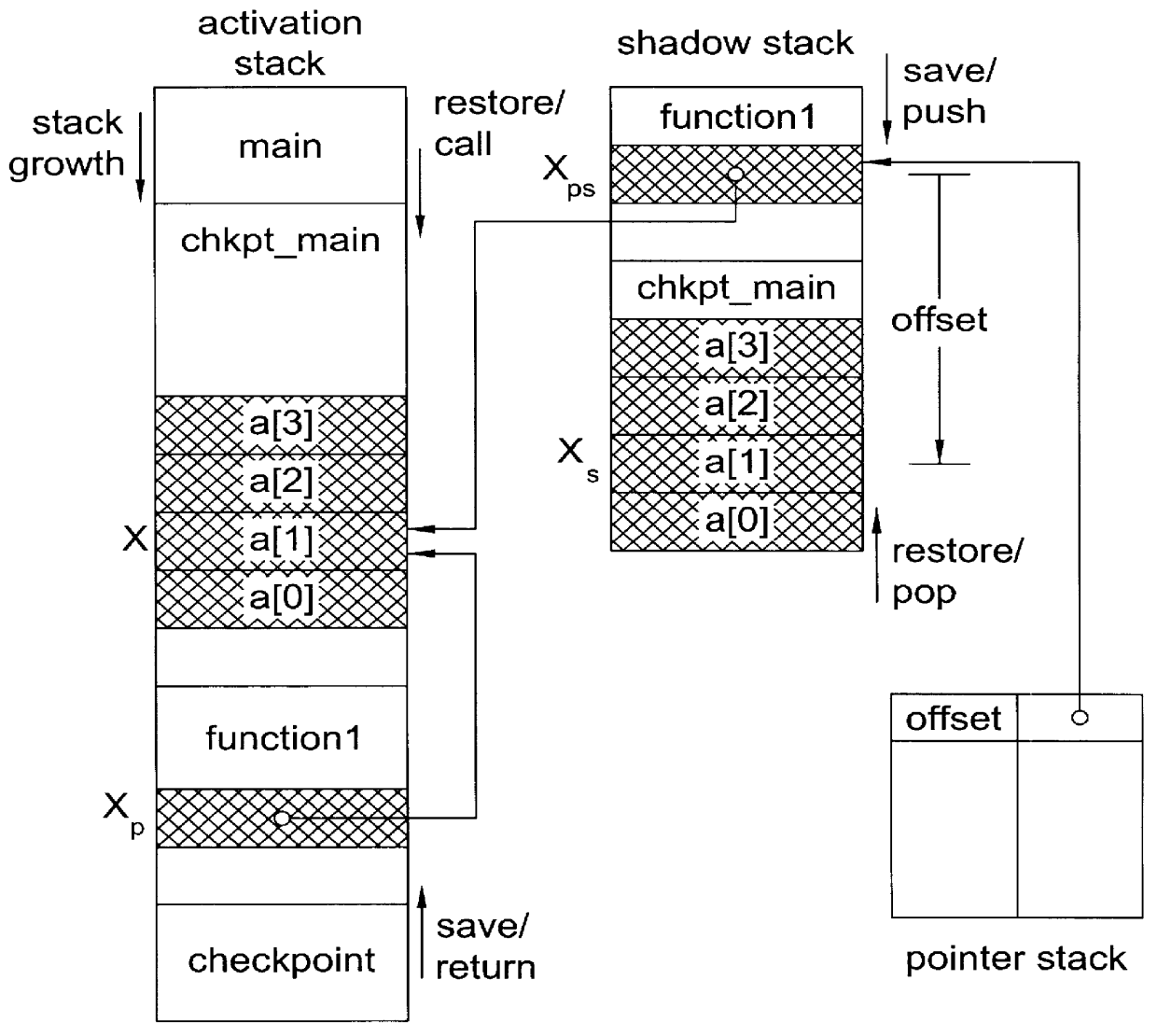
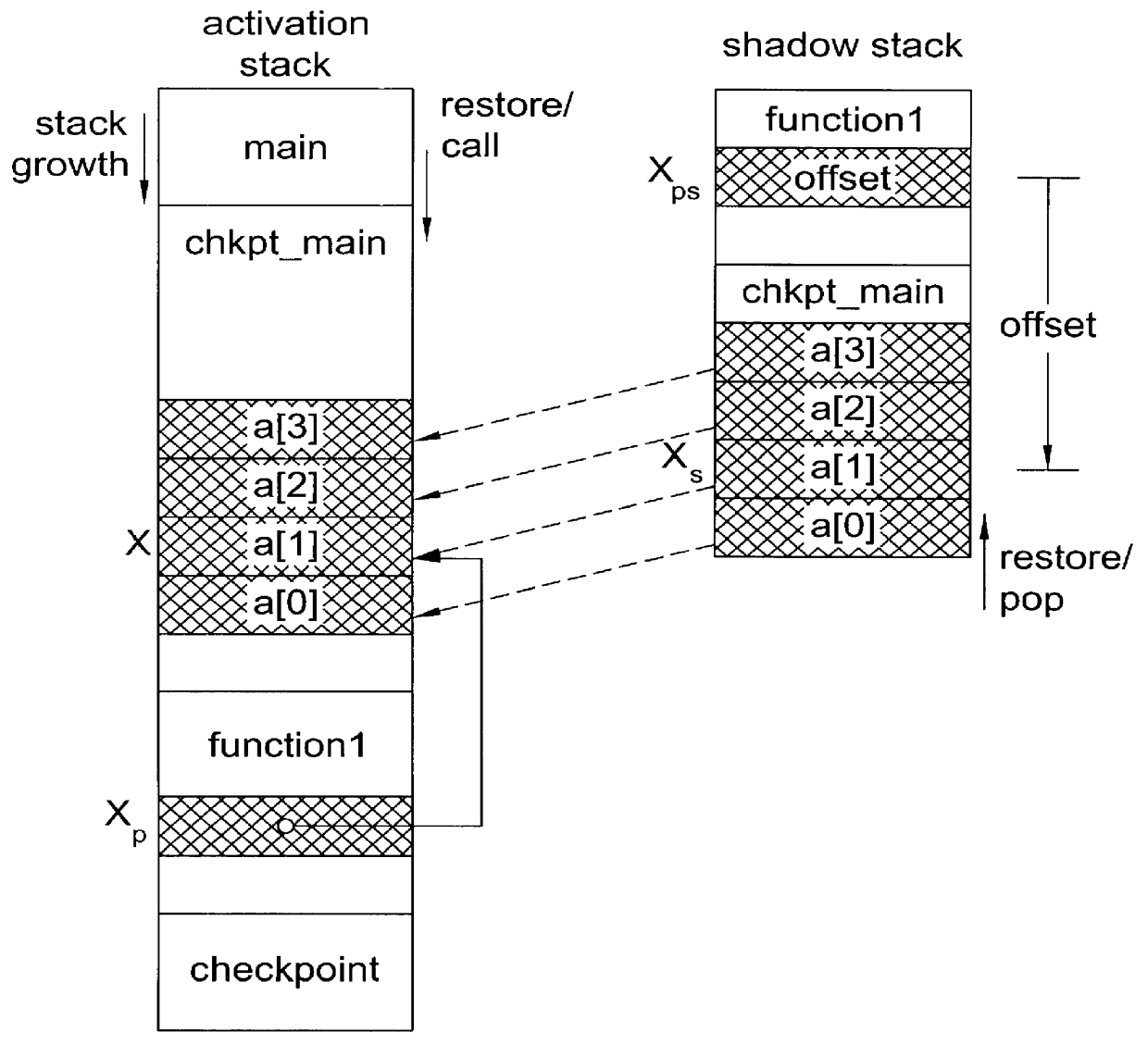
System and method for providing checkpointing with precompile directives and supporting software to produce checkpoints, independent of environment constraints
InactiveUS6161219AReduce overheadViable and practicalSoftware testing/debuggingSpecific program execution arrangementsOperational systemMinimum time
A method for portable checkpointing comprising the steps of: pre-compiling an input source code; and outputting an associated output source code which includes support for portable checkpointing. The portability of the checkpoints allows migration between systems with different hardware, software, and operating systems. The portable checkpoints are stored in a Universal Code Format (UCF) and are selectively activated at the next potential checkpoint marker after a MinTBC (Minimum Time Between Checkpoints) timer expires.
Owner:UNIV OF IOWA RES FOUND
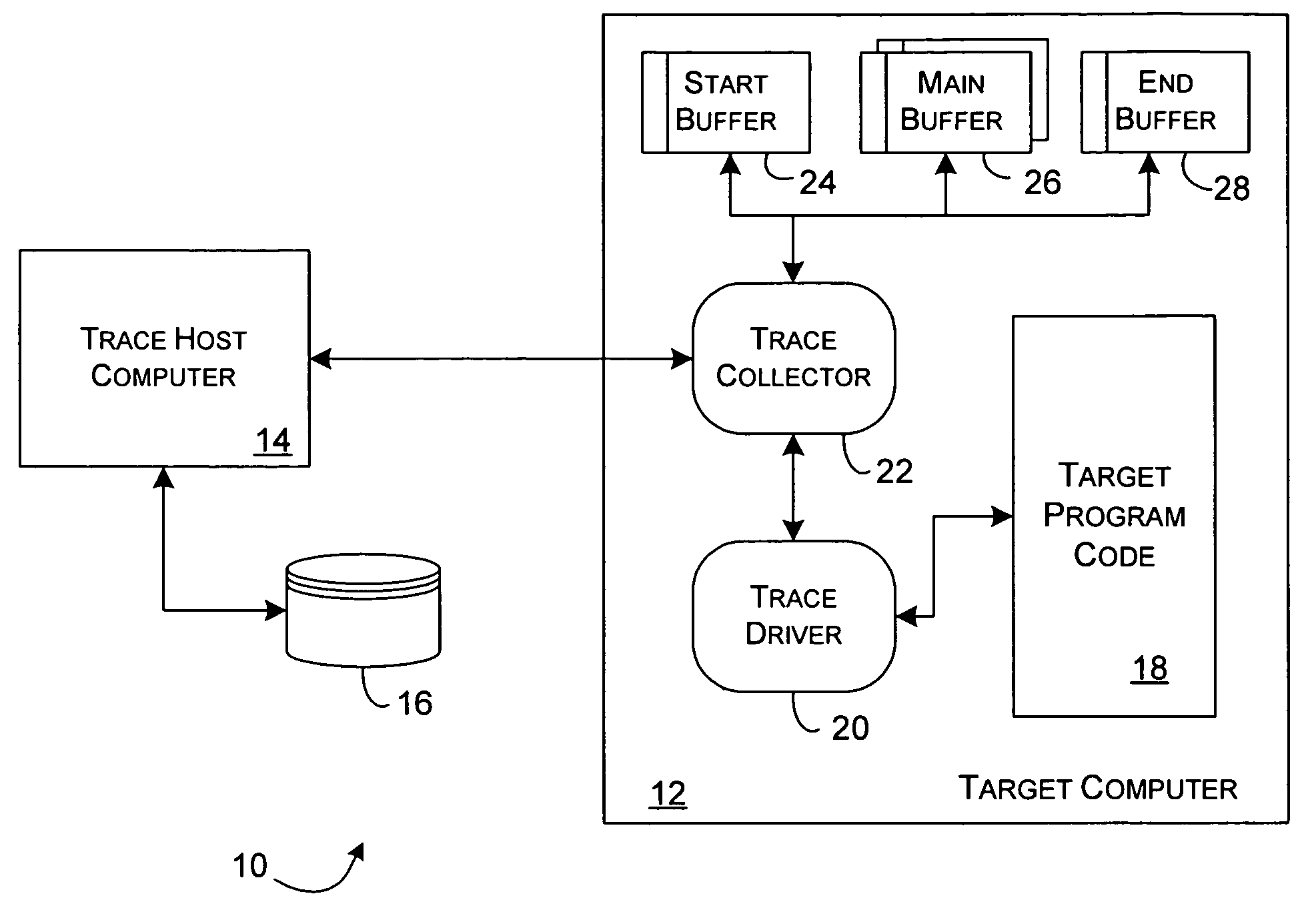
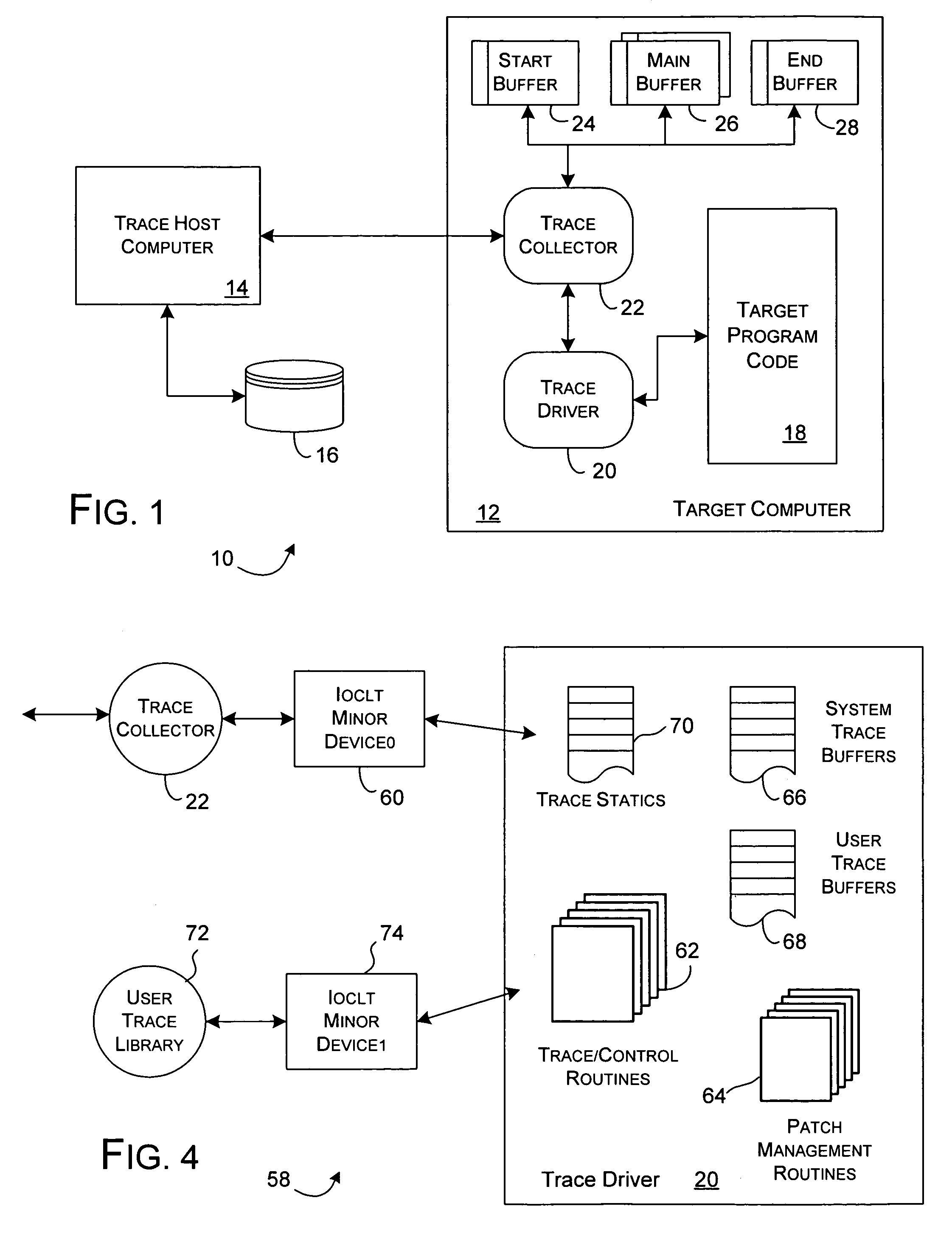
Dynamic instrumentation event trace system and methods
InactiveUS7047521B2Performance impact is minimalMaximize discriminating detectionHardware monitoringSoftware testing/debuggingDynamic instrumentationParallel computing
Program code loaded for execution by a computer can be dynamically instrumented to collect event data by inserting an instruction at a trace point within the program code as loaded in a memory space of a computer, where the trace point corresponds to the beginning of a predefined function of the program selected for event tracing. The instruction provides for the direction of the execution of said computer to a function proxy routine, which includes a call to an instance of the predefined function. Event data is collected in connection with the calling of the instance of the predefined function.
Owner:LYNX SOFTWARE TECH
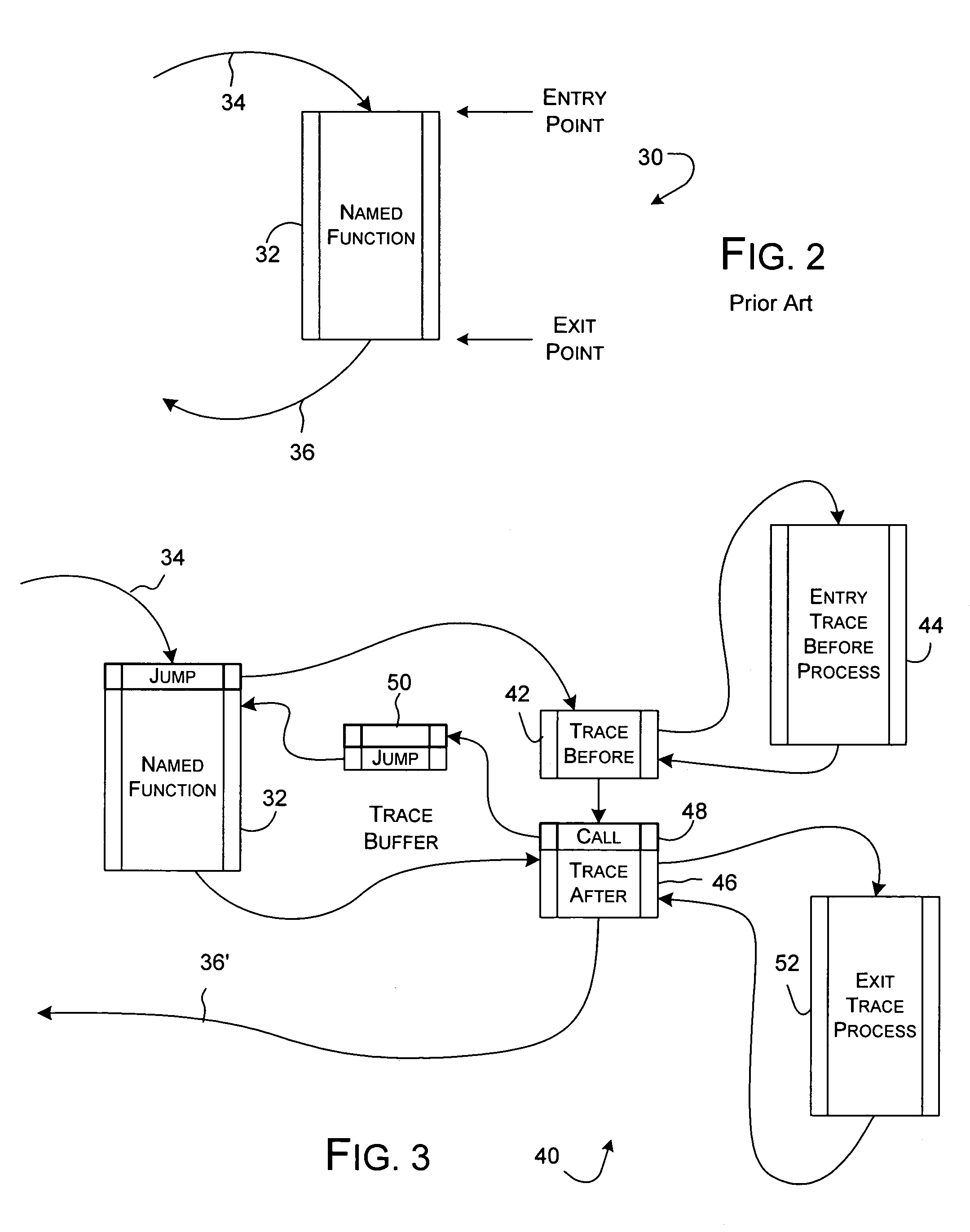
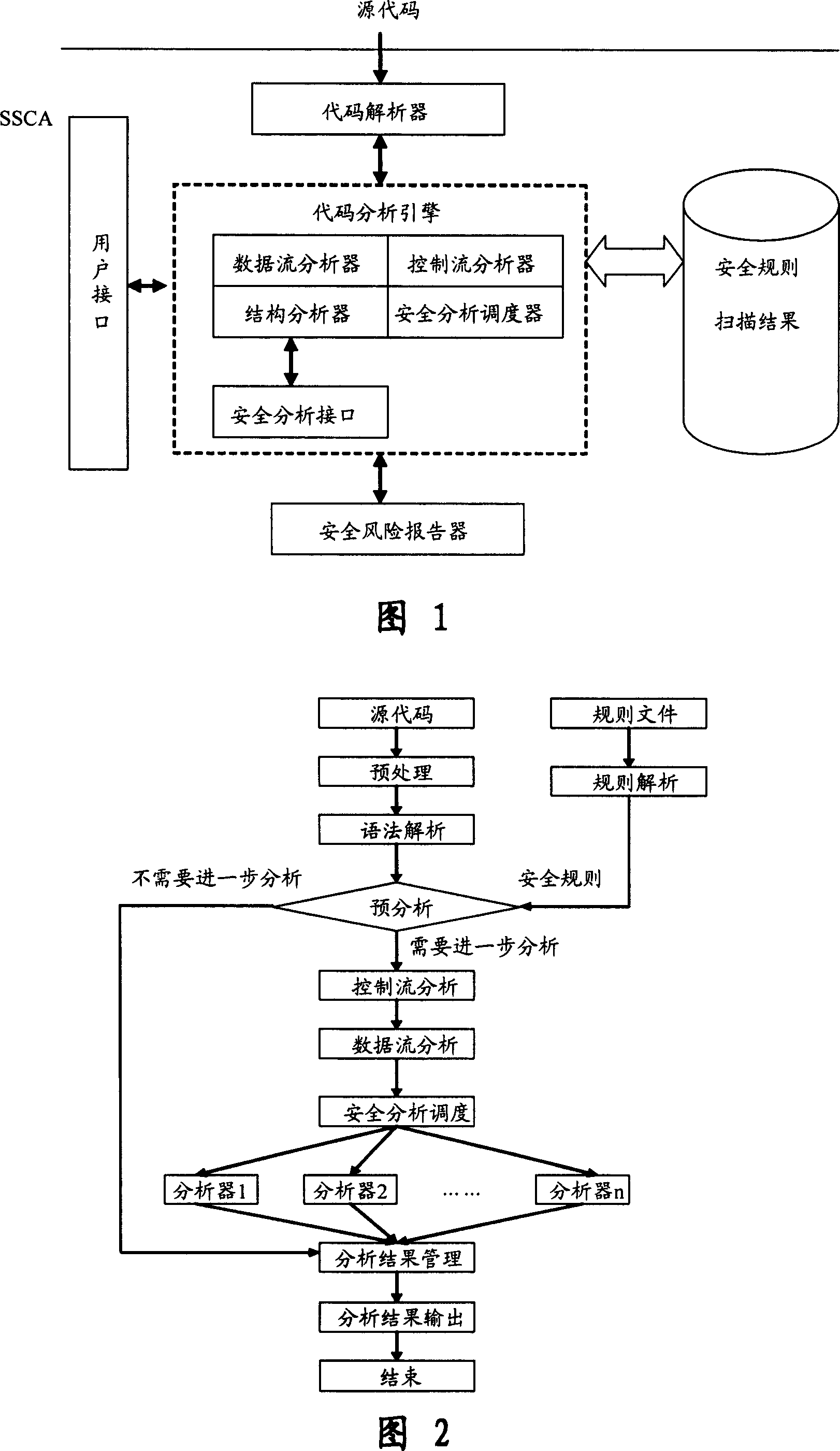
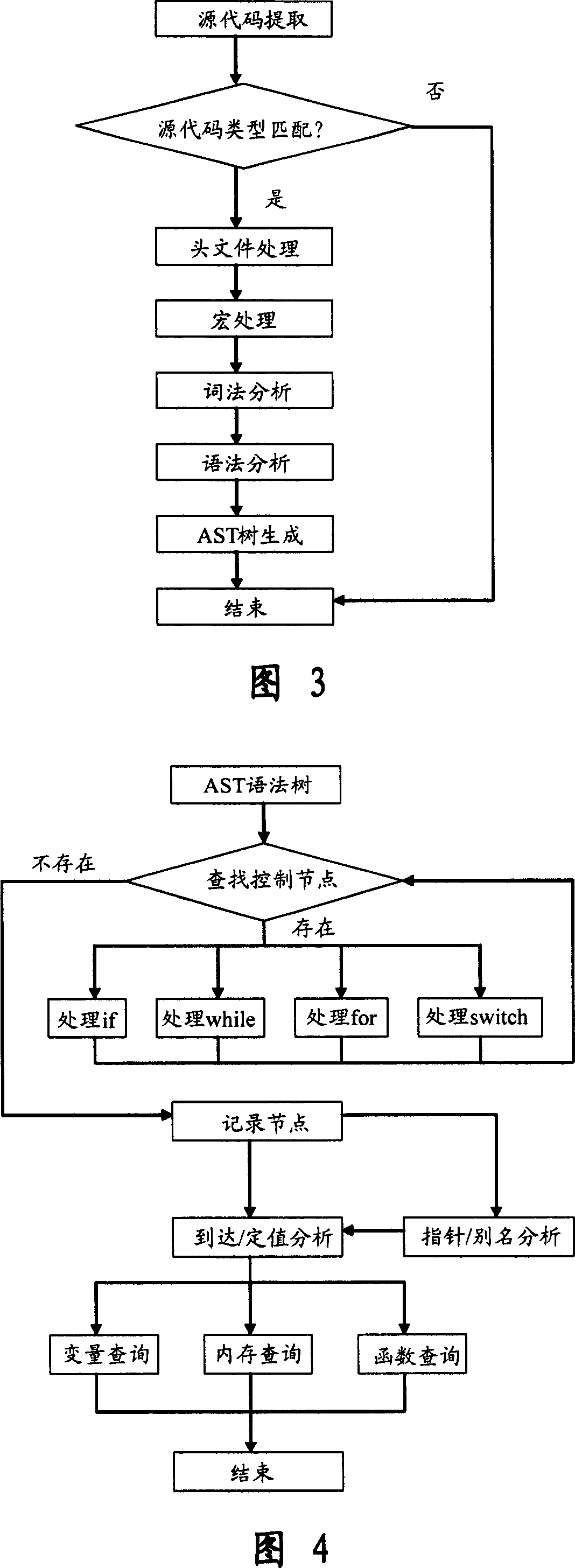
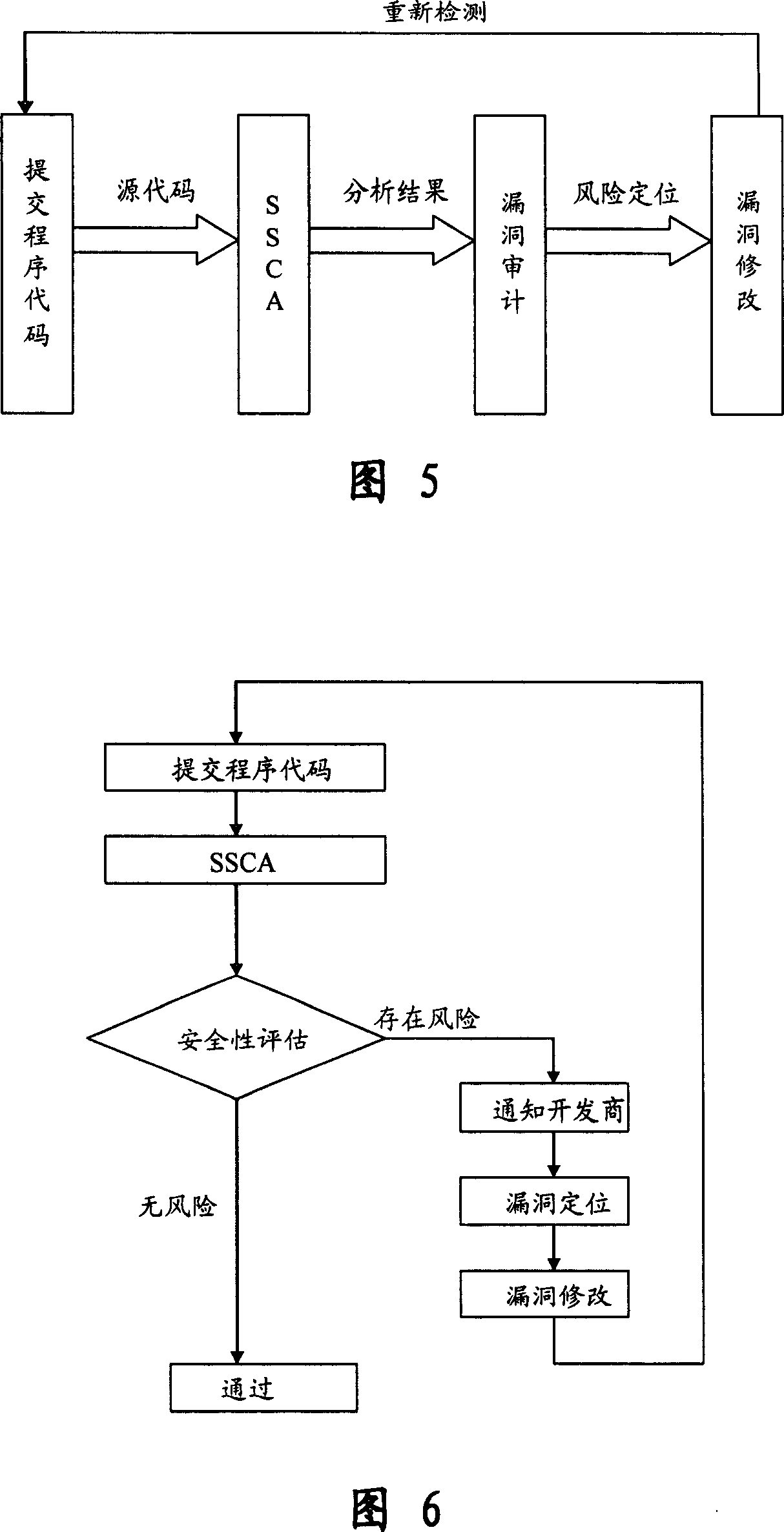
Software safety code analyzer based on static analysis of source code and testing method therefor
InactiveCN101017458AImprove accuracySupport for expansionSoftware testing/debuggingStatic timing analysisStructure analysis
This invention relates to one software analyzer and its test method based on source codes static analysis, wherein the analysis device comprises five function modules of code analysis device, codes analysis engine, safety risk report device, safety rules database and user interface; this invention gets programs safety risk to user according to the source program and grammar and meanings and delivers the safety leak to the user for audit and evaluation.
Owner:深圳北邮网络科技有限公司
Computer Platform for Development and Deployment of Sensor-Driven Vehicle Telemetry Applications and Services
InactiveUS20140380264A1Promote application developmentFacilitates vehicle anomaly detectionSoftware testing/debuggingProgram loading/initiatingCloud baseEngineering
A computing platform for intelligent development, deployment and management of vehicle telemetry applications is disclosed herein. Further, the present disclosure provides a method and system that enables provision of Intelligent Transportation Service on the Cloud-based Platform that facilitates creation and deployment of vehicle telemetry applications configured for enabling traffic measurements, traffic shaping, vehicle surveillance and other vehicle related services.
Owner:TATA CONSULTANCY SERVICES LTD
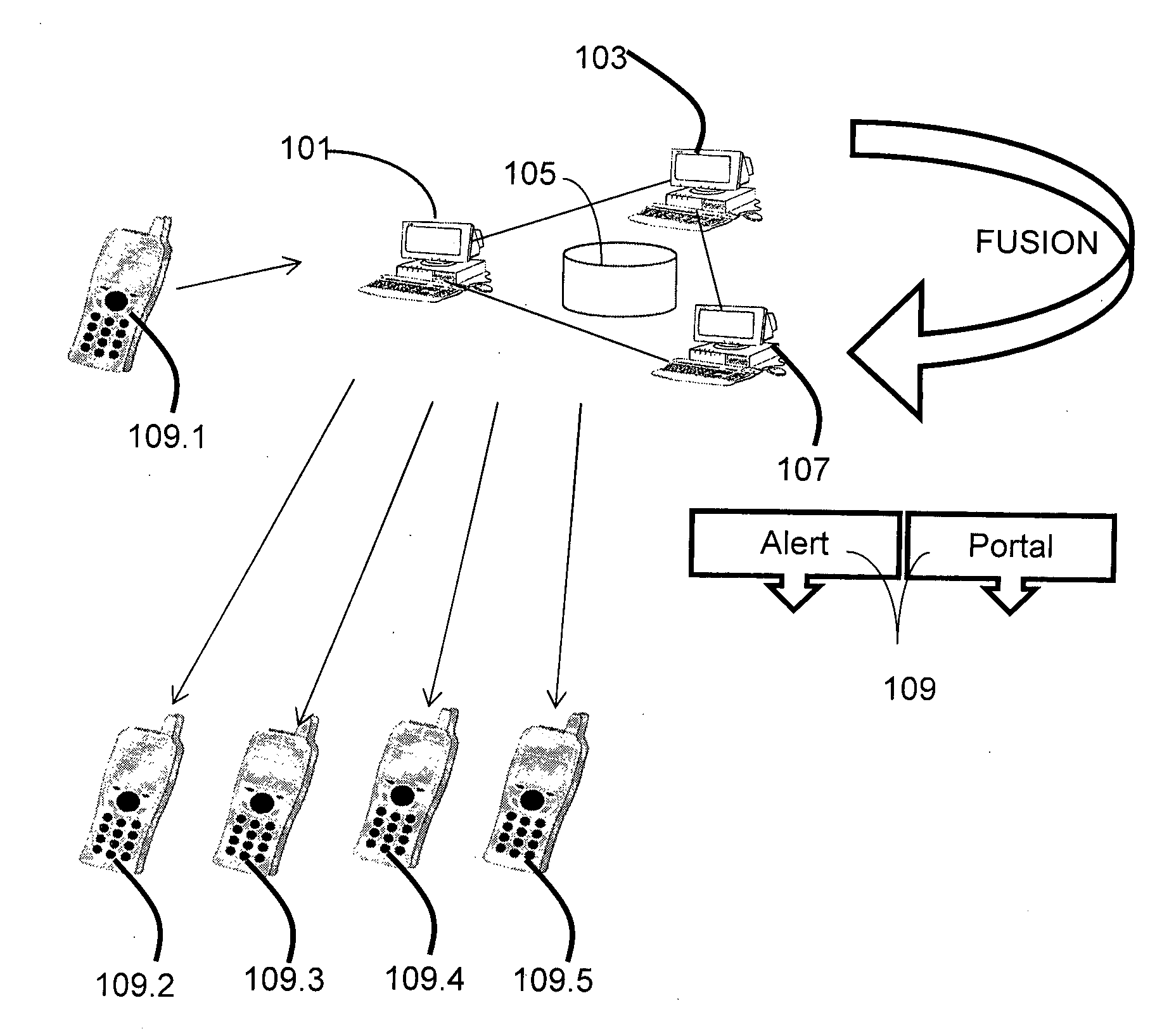
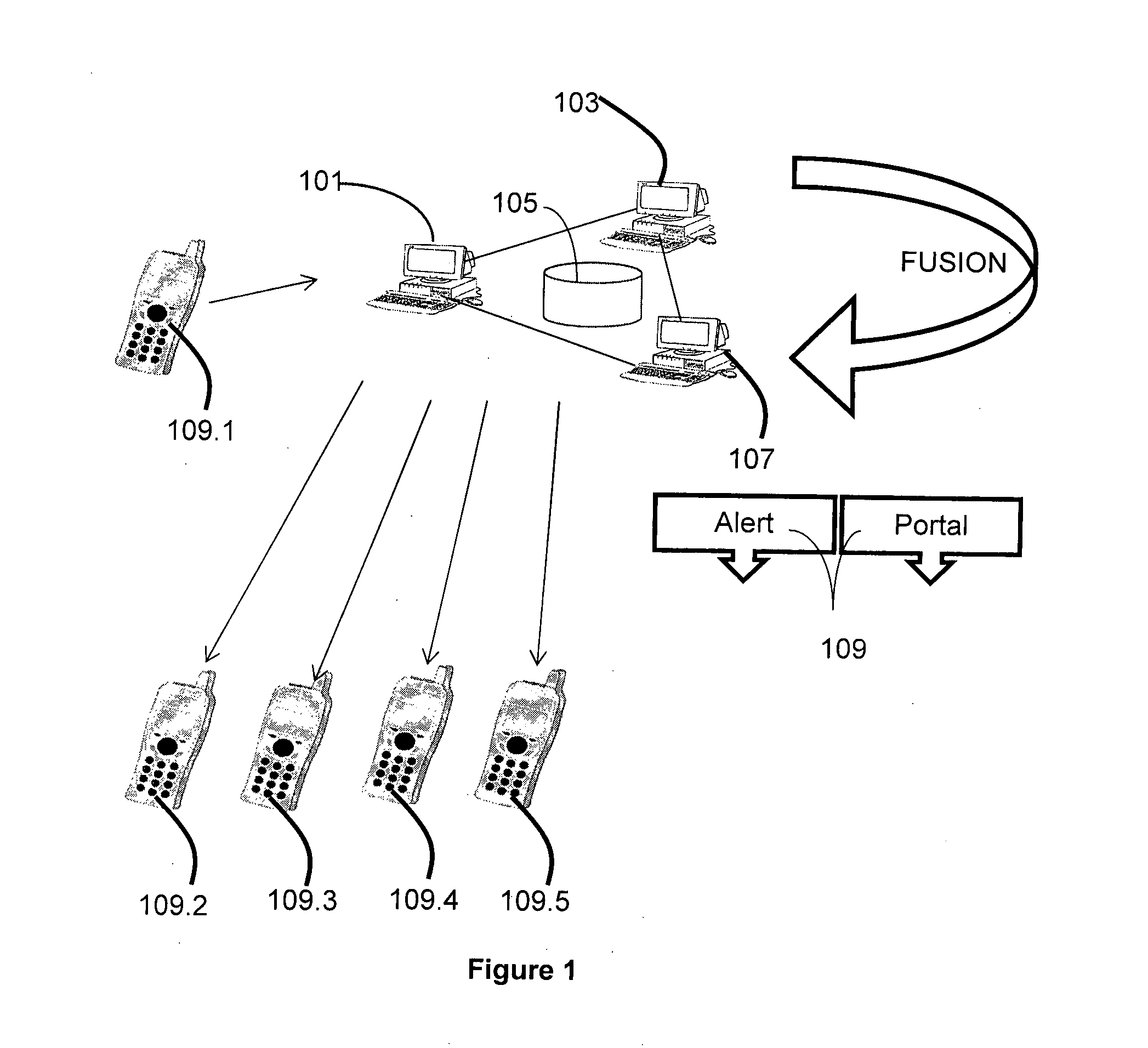
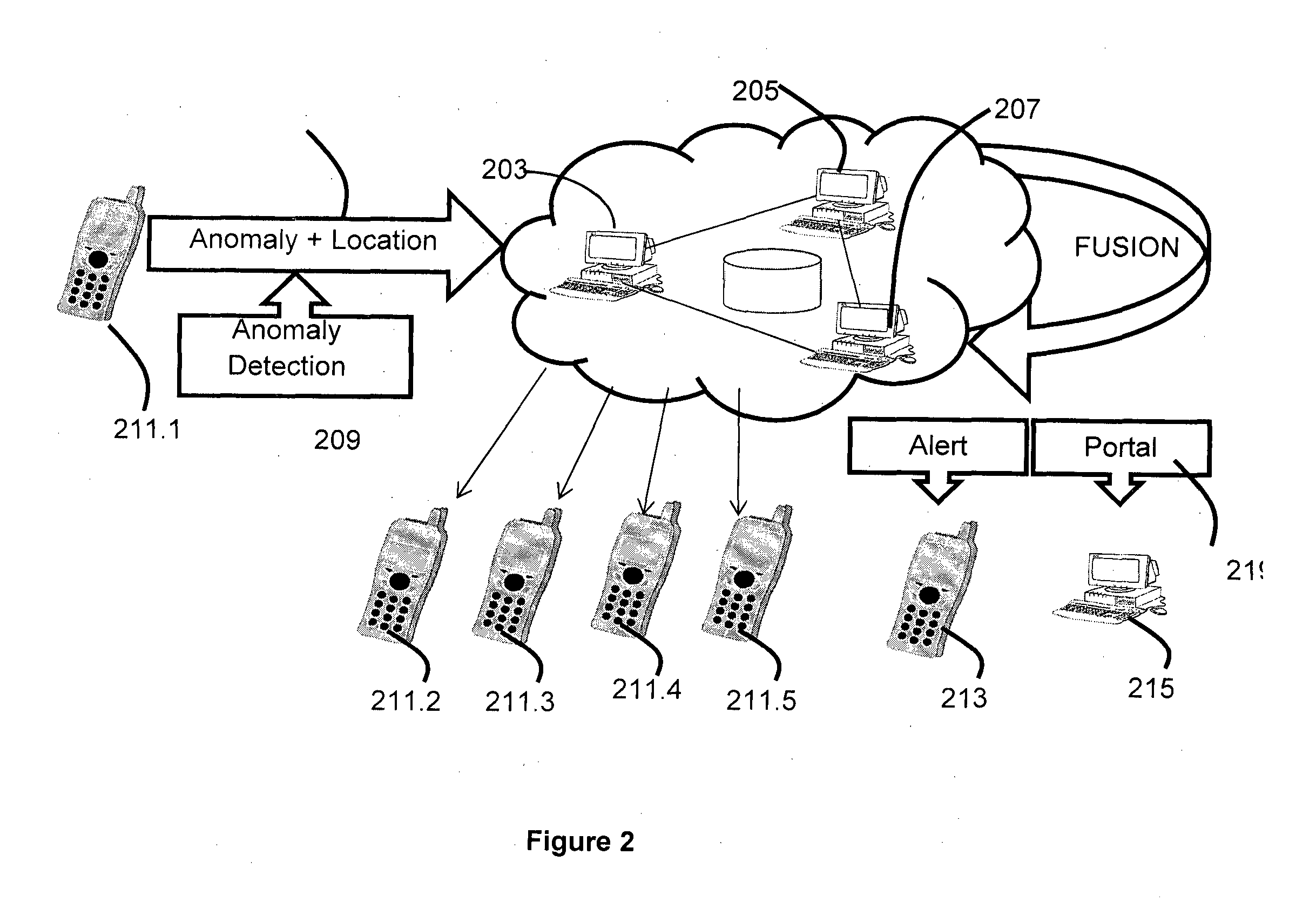
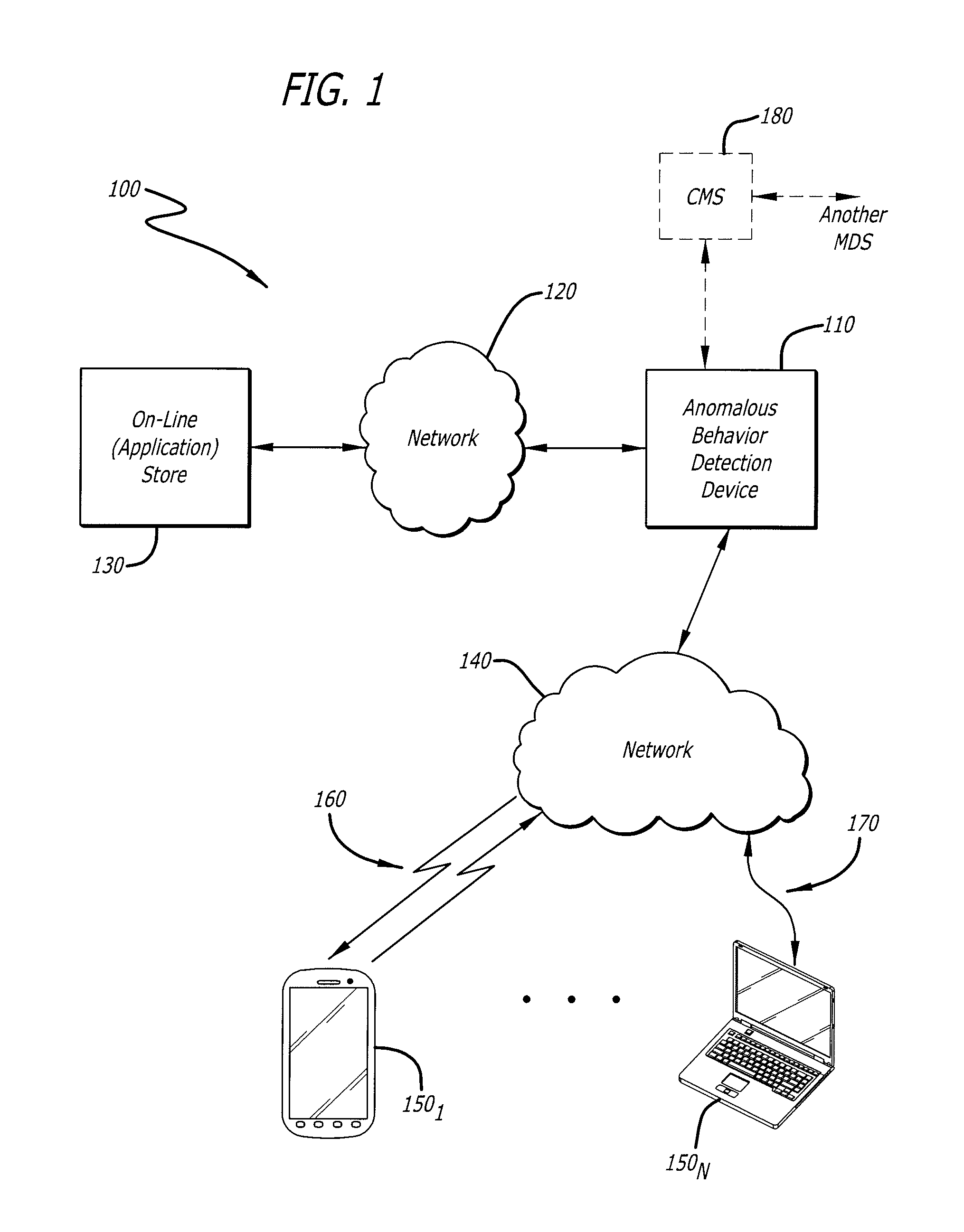
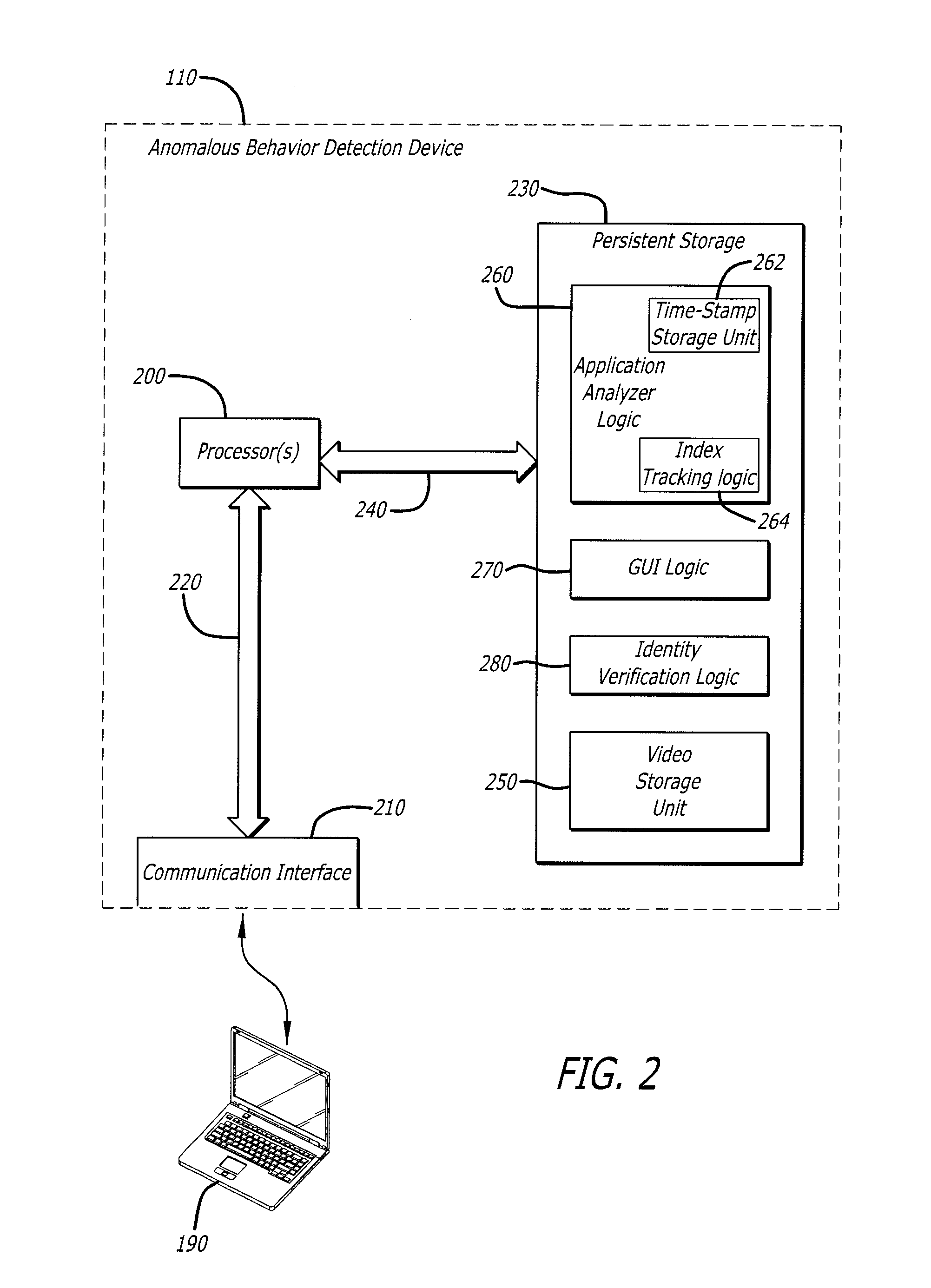
User interface with real-time visual playback along with synchronous textual analysis log display and event/time index for anomalous behavior detection in applications
ActiveUS9195829B1Television system detailsColor signal processing circuitsAnomalous behaviorApplication software
According to one embodiment, a method comprises conducting an analysis for anomalous behavior on application software and generating a video of a display output produced by the application software. The video is to be displayed on an electronic device contemporaneously with display of one or more events detected by the analysis being performed on the application software.
Owner:FIREEYE SECURITY HLDG US LLC
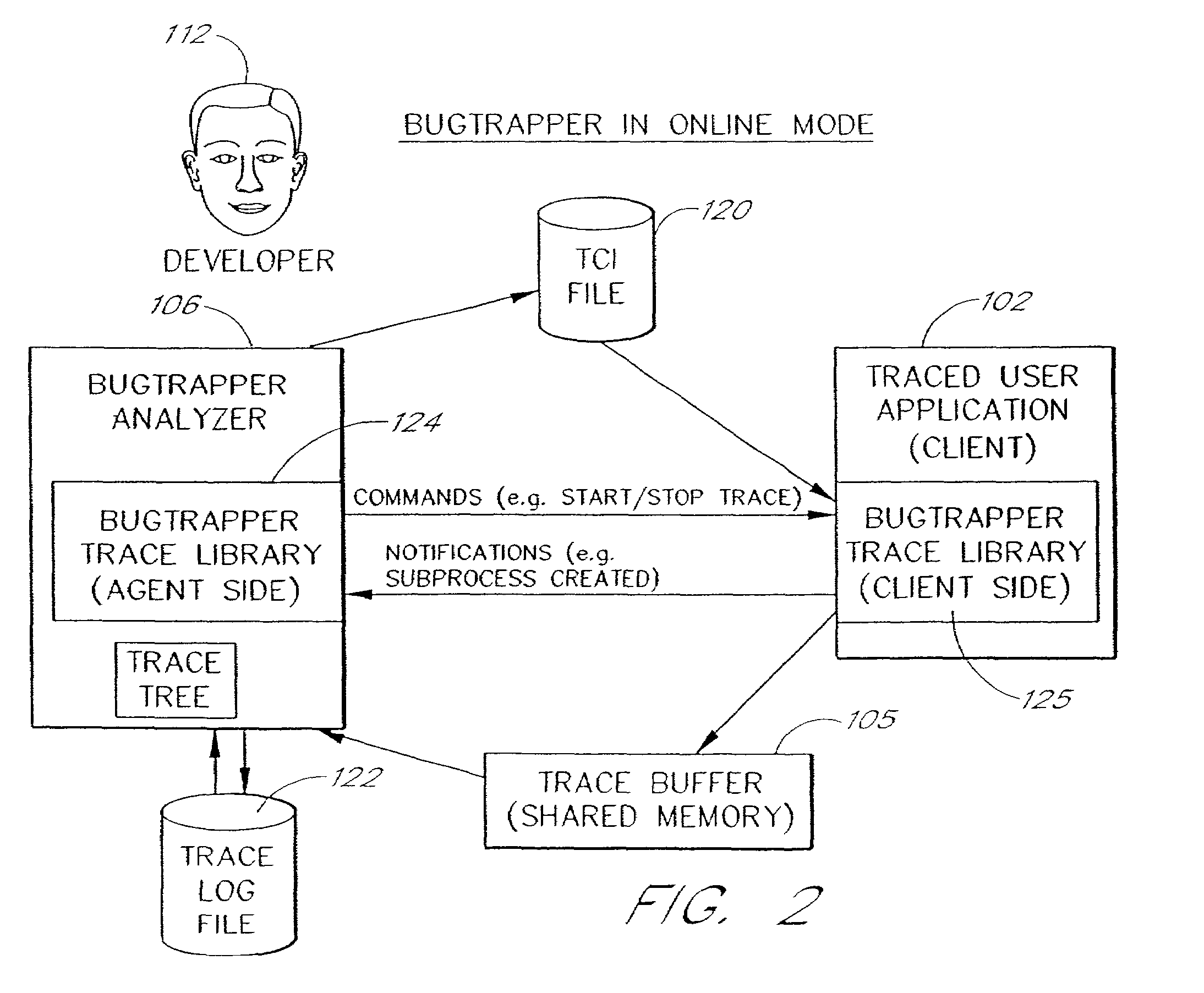
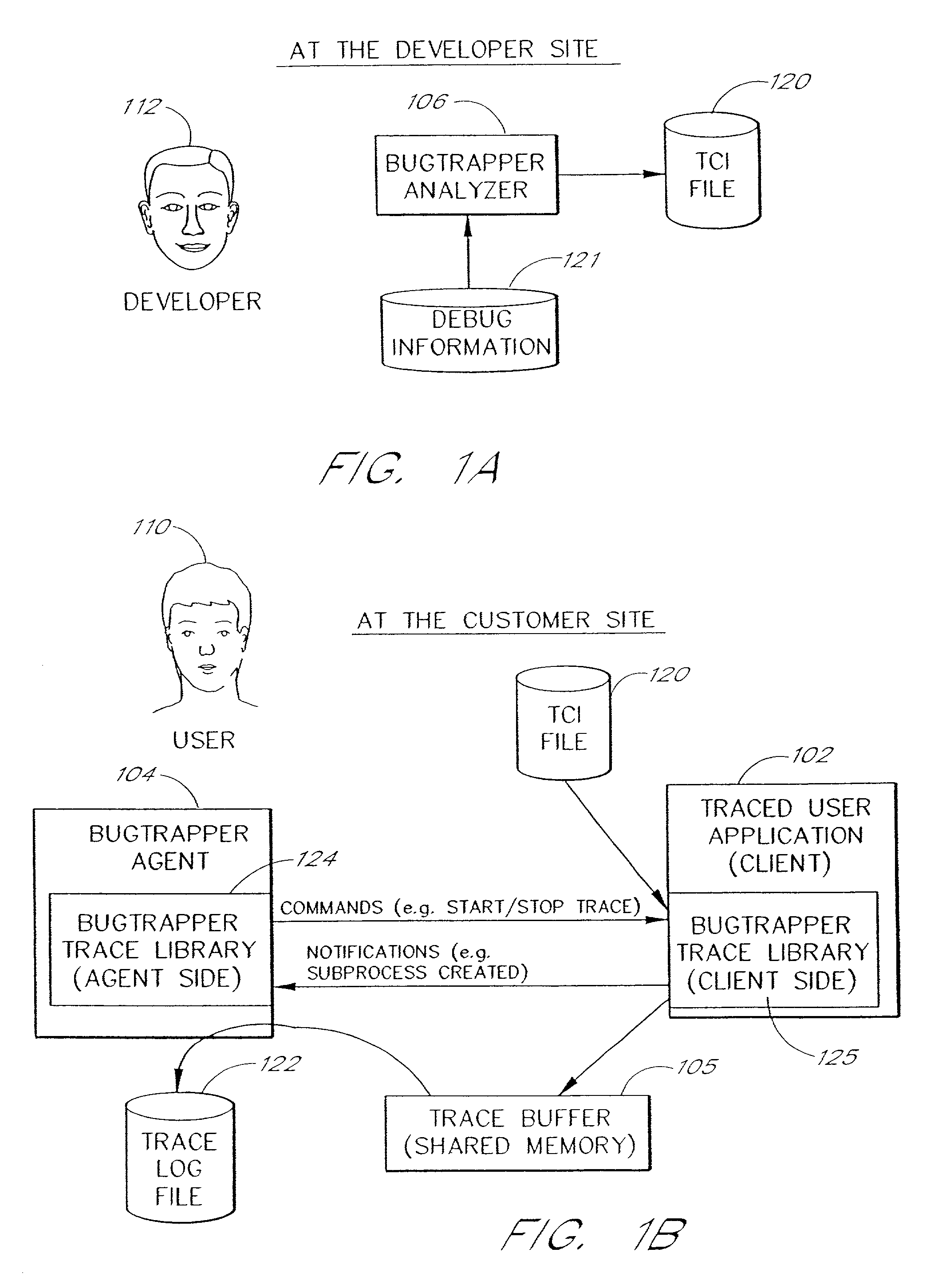
System and method for conditional tracing of computer programs
InactiveUS7058928B2Small sizeRaise the possibilitySoftware testing/debuggingProgram loading/initiatingConditional expressionApplication software
A software system is disclosed which facilitates the process of tracing the execution paths of a program, called the client. The tracing is performed without requiring modifications to the executable or source code files of the client. Trace data collected during the tracing operation is collected according to instructions in a trace options file. At run time, the tracing library attaches to the memory image of the client. The tracing library is configured to monitor execution of the client and to collect trace data, based on selections in the trace options file. Conditional tracing, through the use of triggers and actions taken in response to the triggers, allows the developer to control the tracing operation. The triggers can be conditional triggers in which the corresponding action is taken only if a conditional expression is satisfied. The system can trace multiple threads and multiple processes. The tracing system provides a remote mode and an online mode. In remote mode, the developer sends the trace control information (which can include triggers and corresponding actions) to a remote user site together with a small executable image called the agent that enables a remote customer, to generate a trace file that represents execution of the client application at the remote site. In online mode, the developer can generate trace options (including triggers and corresponding actions), run and trace the client, and display the trace results in near real-time on the display screen during execution of the client program.
Owner:BMC SOFTWARE ISRAEL LTD
Software system and methods for testing the functionality of a transactional server
A testing tool automatically records a series of user steps taken during a user session with a transactional server and generates a test for testing the functionality of server. Through a user interface of the testing tool, the user can define verification steps to automatically test for expected server responses during test execution. The testing tool displays the test to the user as a tree having nodes (displayed as icons) which represent steps of the test. Via the user interface, the user can modify node properties and perform other types of tree edit operations to edit the test, without the need to know a scripting or other programming language. When the user selects a node that corresponds to a particular field or other object of the server screen, the testing tool automatically displays the screen with the object highlighted. The testing tool also allows the test author to use a spreadsheet to conveniently specify data sets for running multiple iterations of a test; thus, the user can record a single transaction and then automatically test the transaction with other data sets.
Owner:AMAZON COM +1
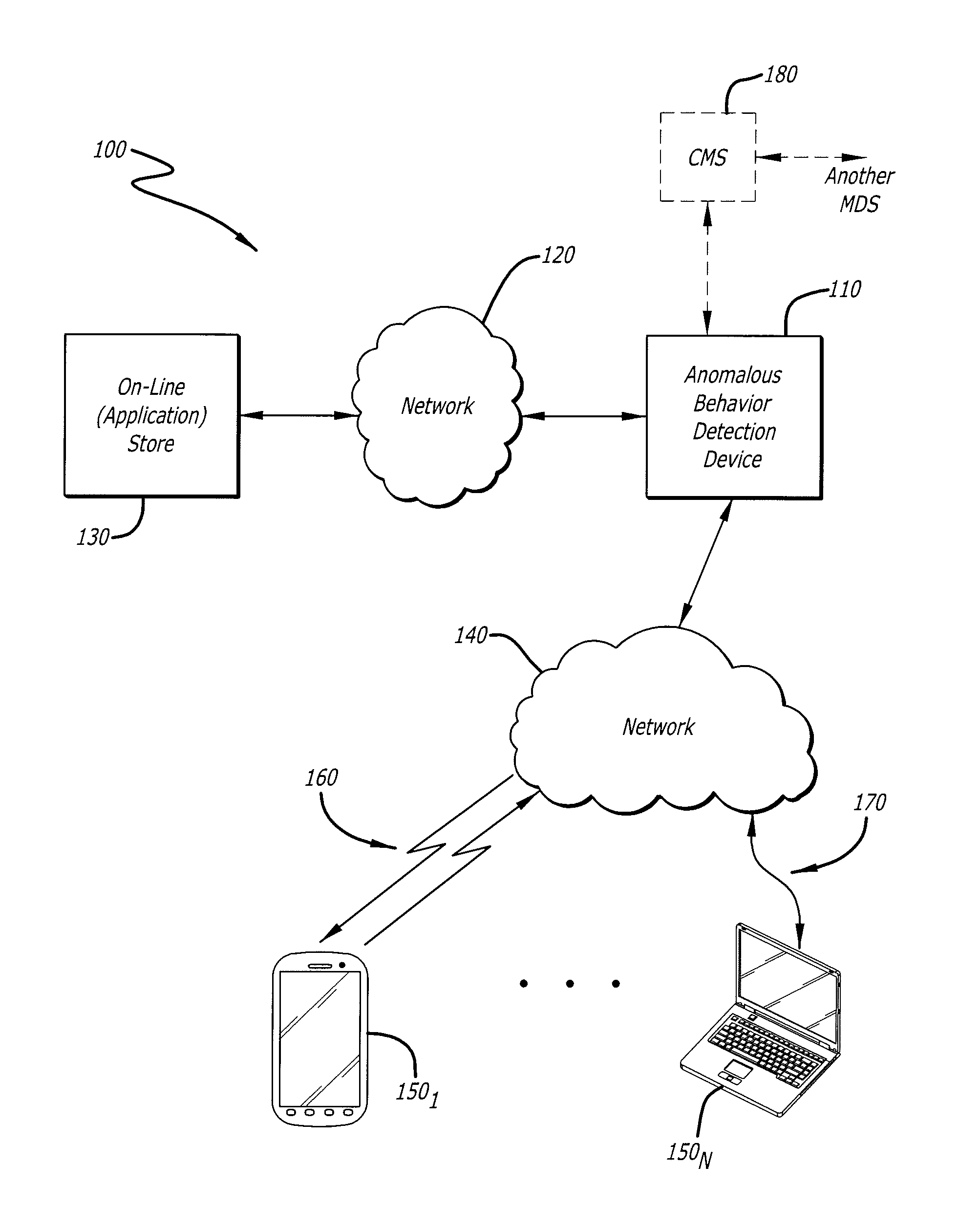
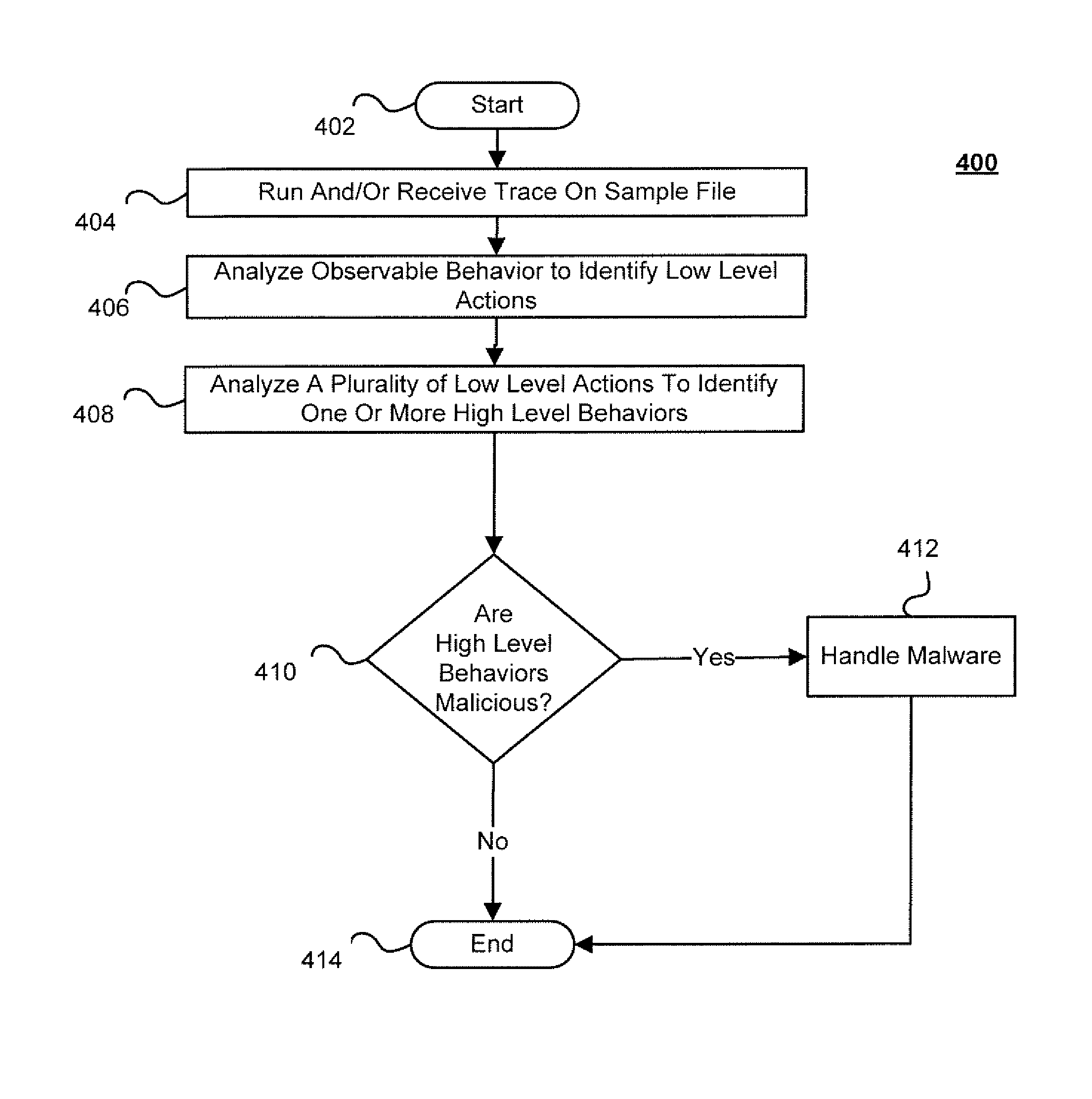
Techniques for behavior based malware analysis
ActiveUS8555385B1Avoid associationMemory loss protectionUnauthorized memory use protectionMalware analysisComputer science
Techniques for behavior based malware analysis are disclosed. In one particular exemplary embodiment, the techniques may be realized as a method for behavior based analysis comprising receiving trace data, analyzing, using at least one computer processor, observable events to identify low level actions, analyzing a plurality of low level actions to identify at least one high level behavior, and providing an output of the at least one high level behavior.
Owner:CA TECH INC
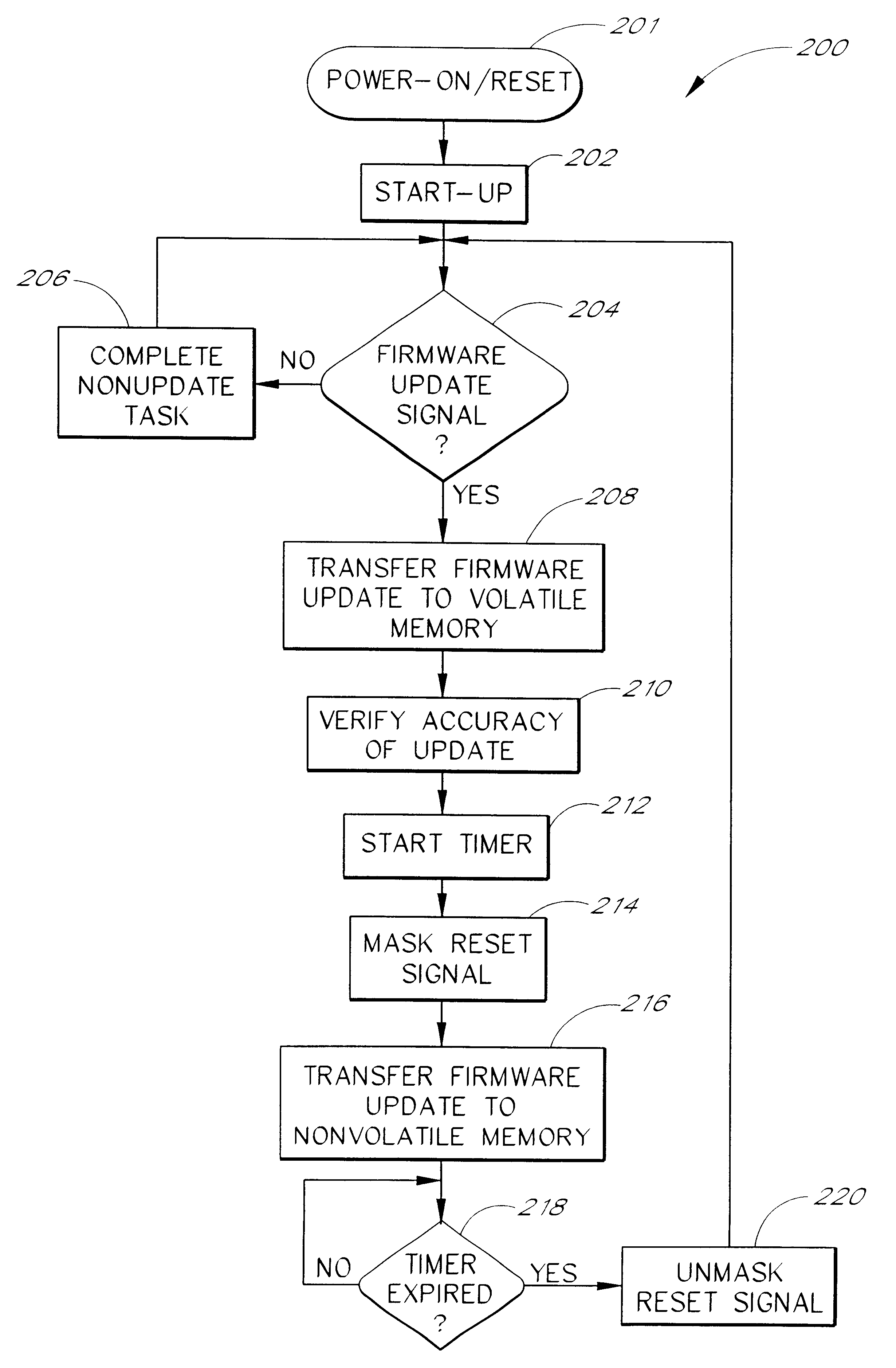
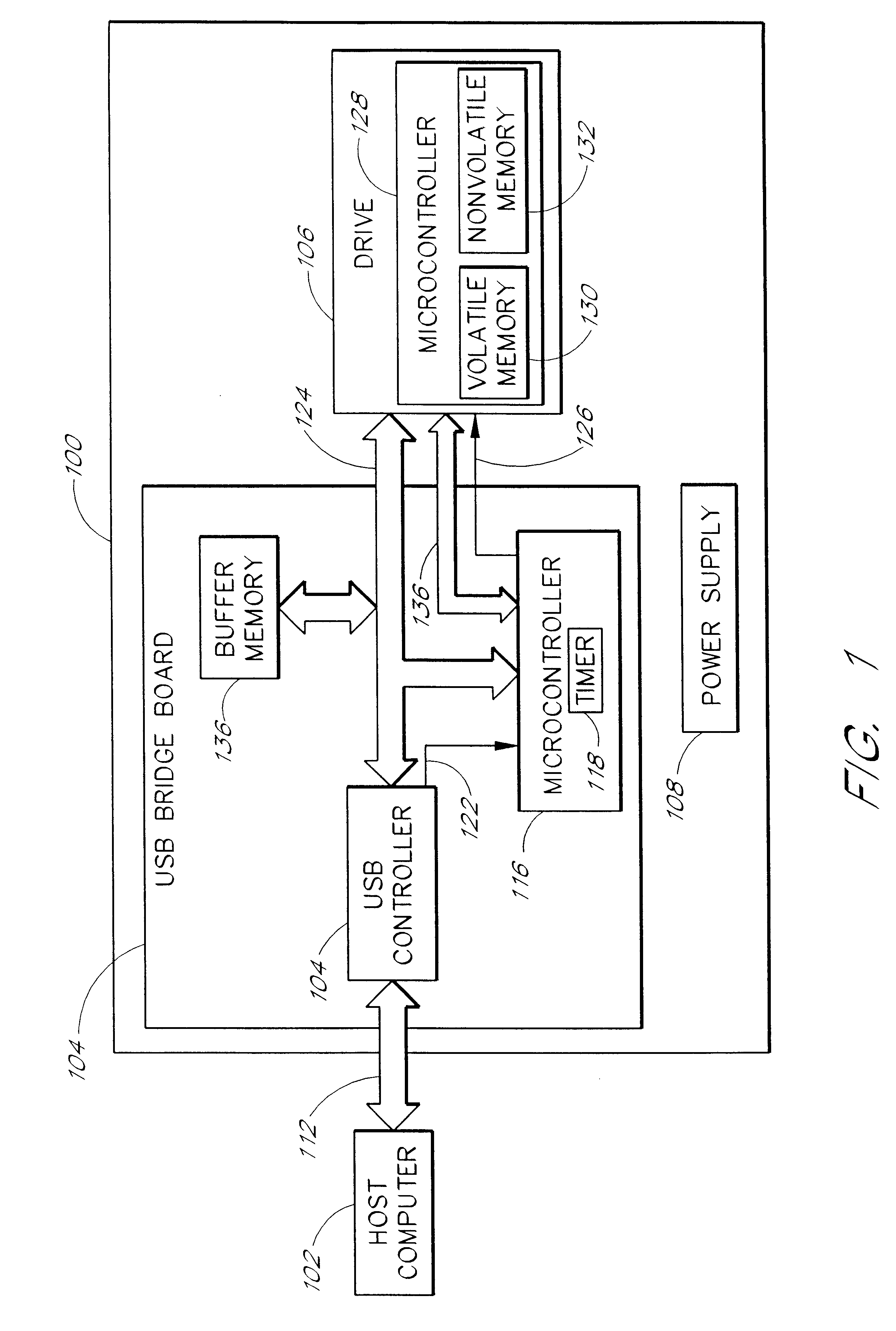
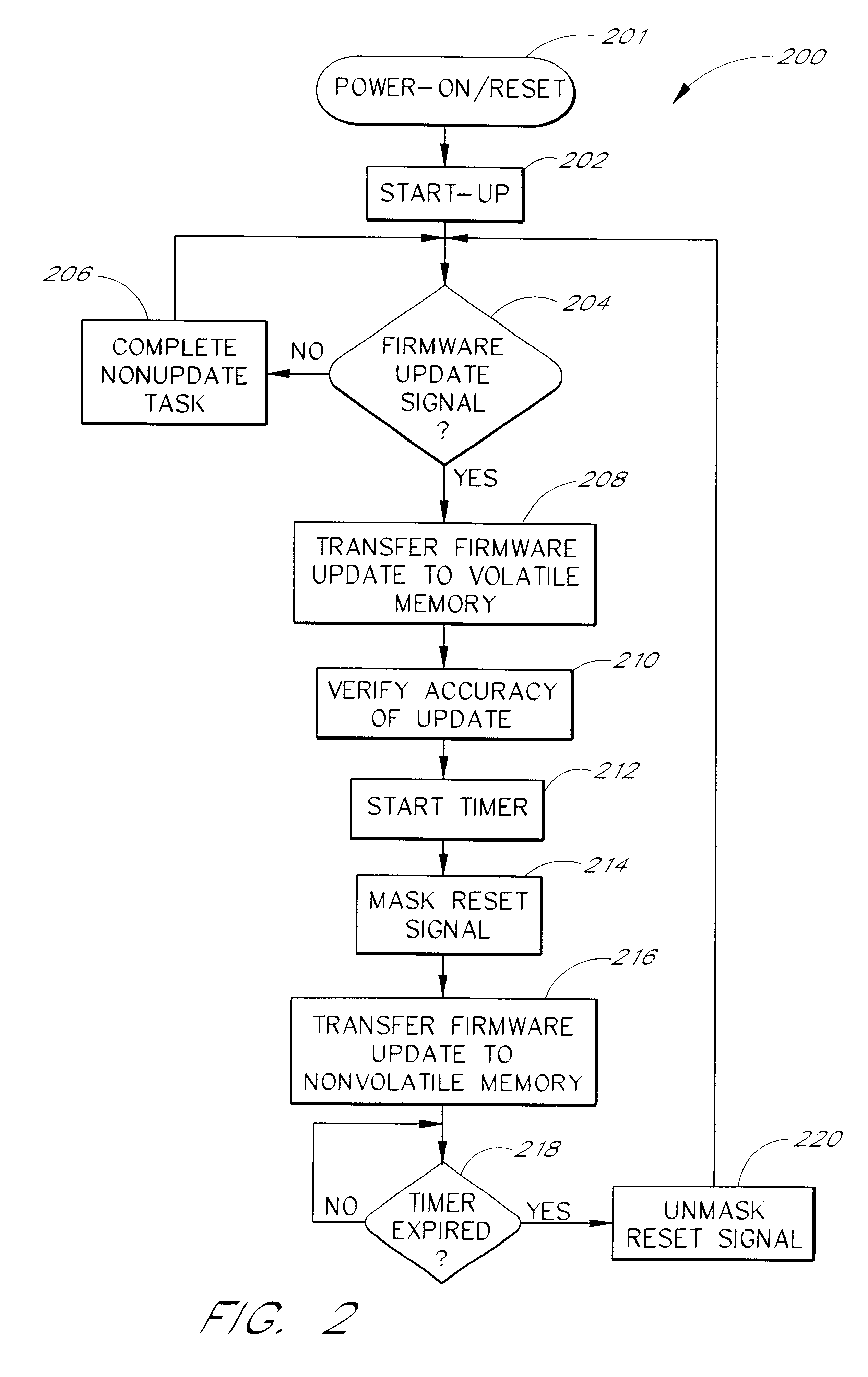
Method and system for performing a peripheral firmware update
The present invention provides systems and methods for performing a firmware update. In one embodiment, a peripheral reset signal is masked in response to a peripheral firmware update command. The firmware update is loaded into a peripheral's nonvolatile memory while the reset signal is masked.
Owner:MITSUMI ELECTRIC CO LTD
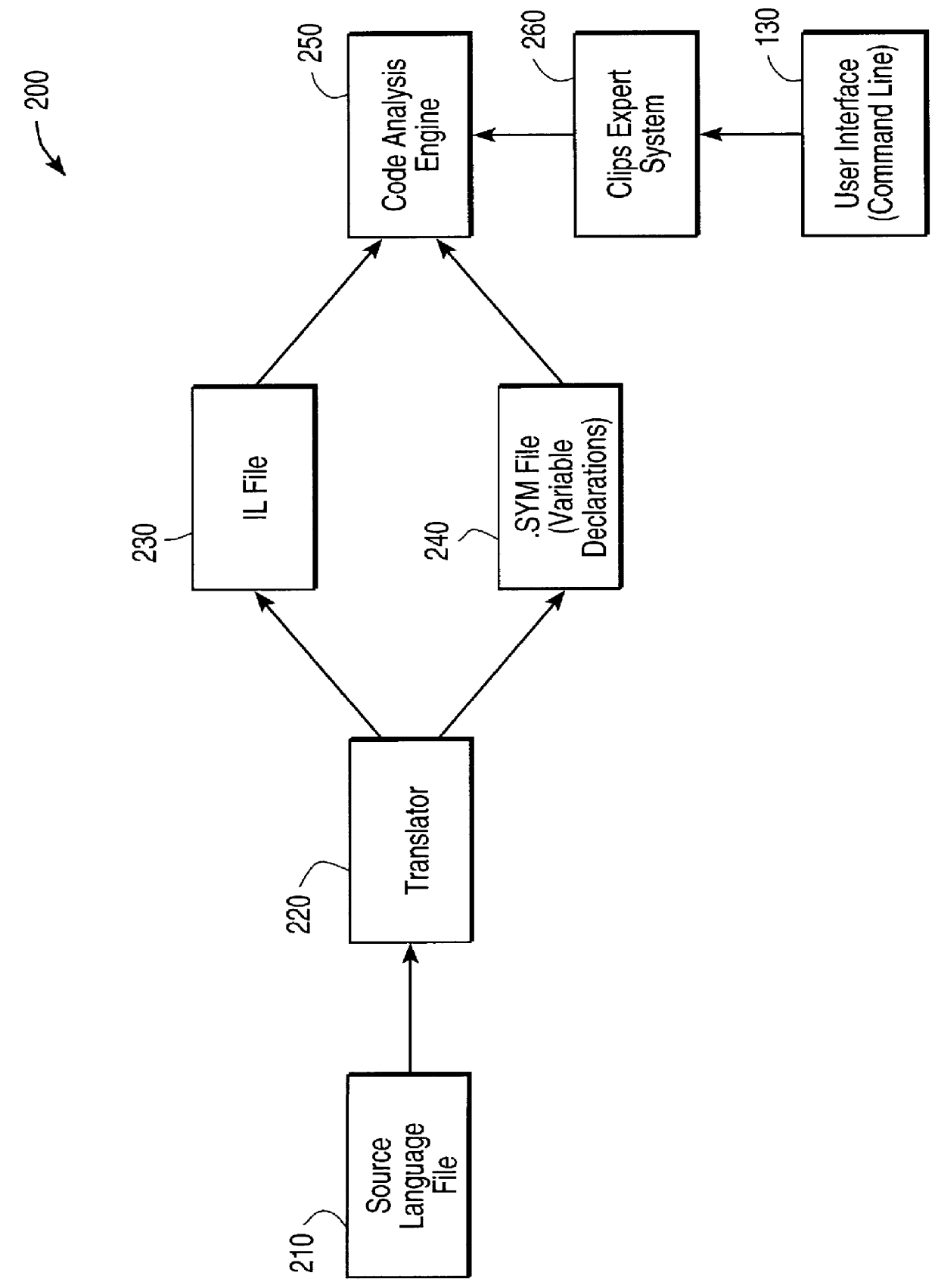
Method and apparatus for analyzing computer code using weakest precondition
An analyzer for maintaining and analyzing source code is disclosed. The analyzer includes a software translator for converting conventional source code into an intermediate language, slicing capability based upon weakest precondition determination, dual direction flow analysis and incorporation of a computational model to facilitate iterative code.
Owner:WELLS FARGO FOOTHILL
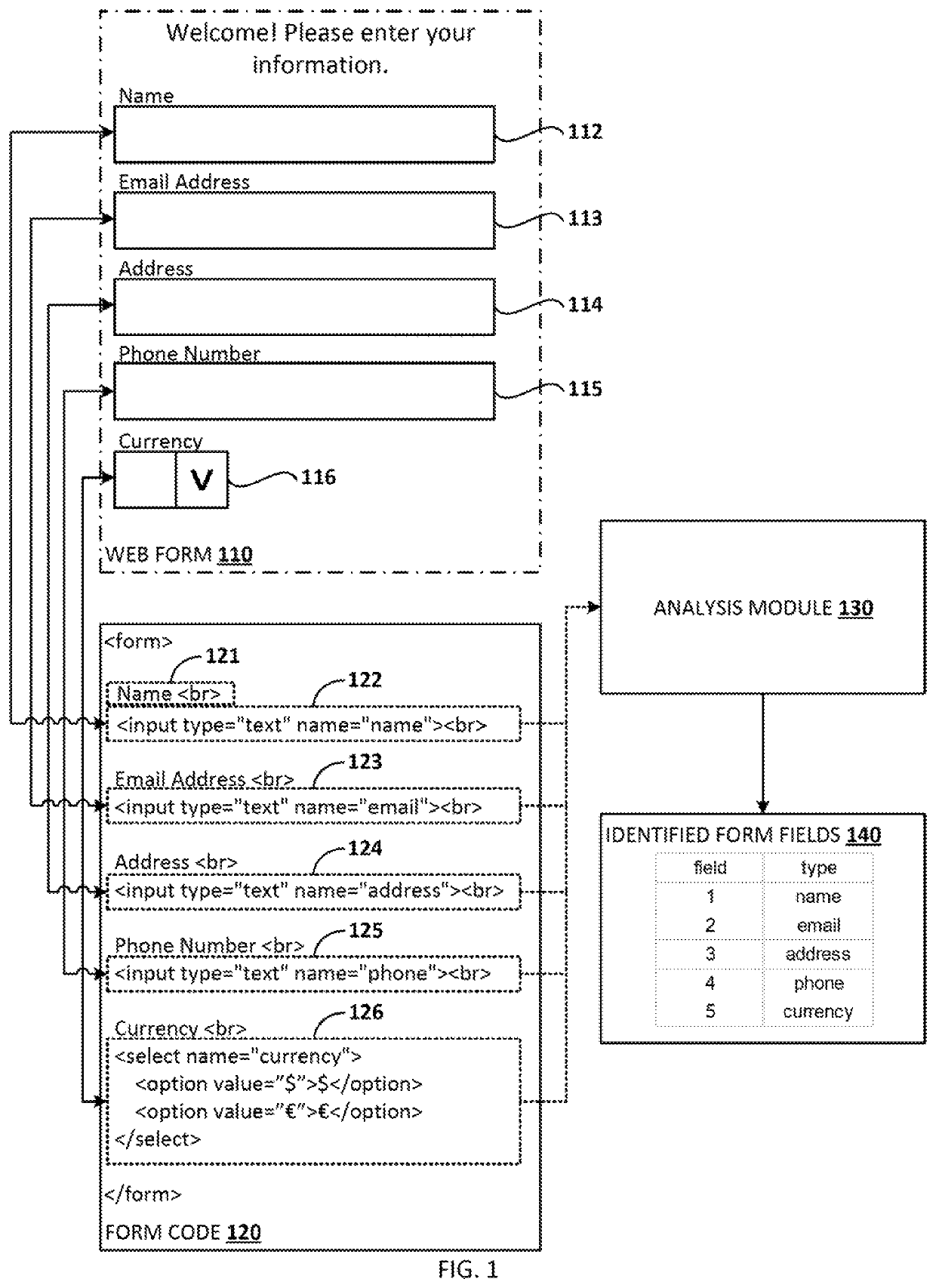
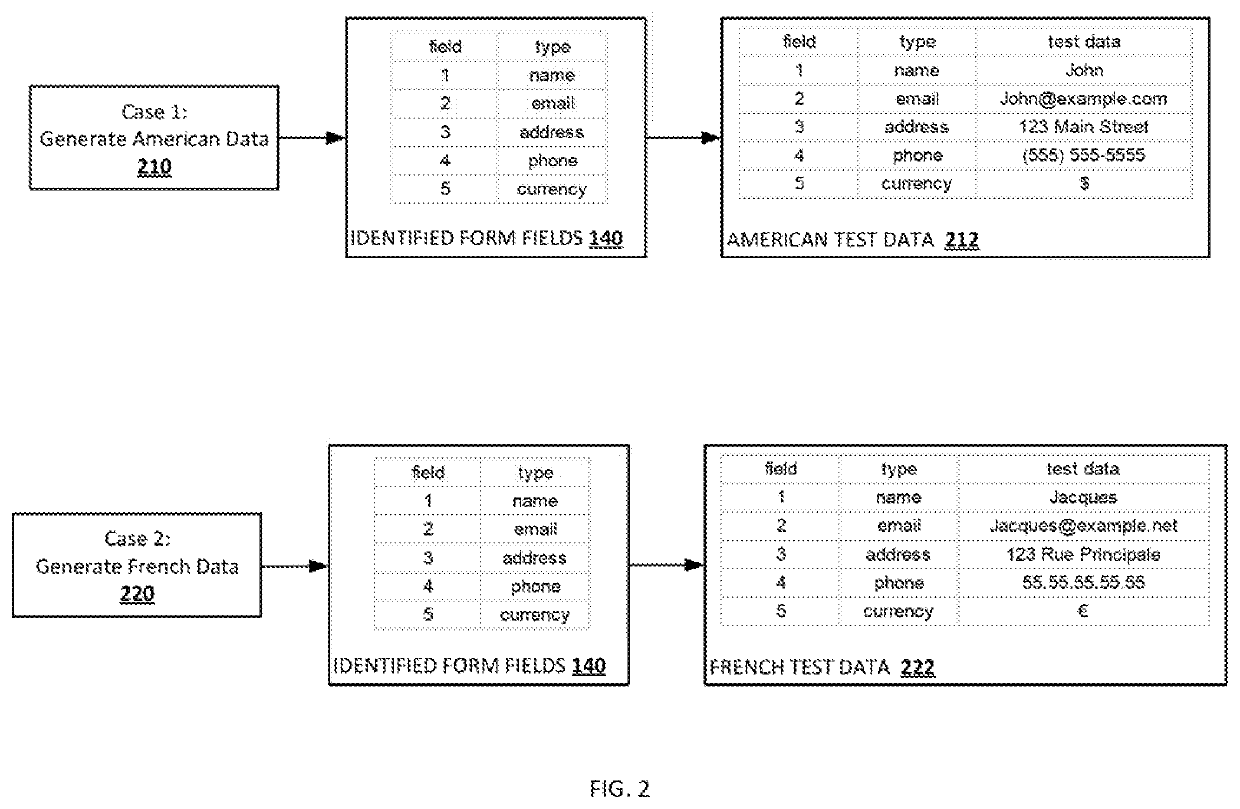
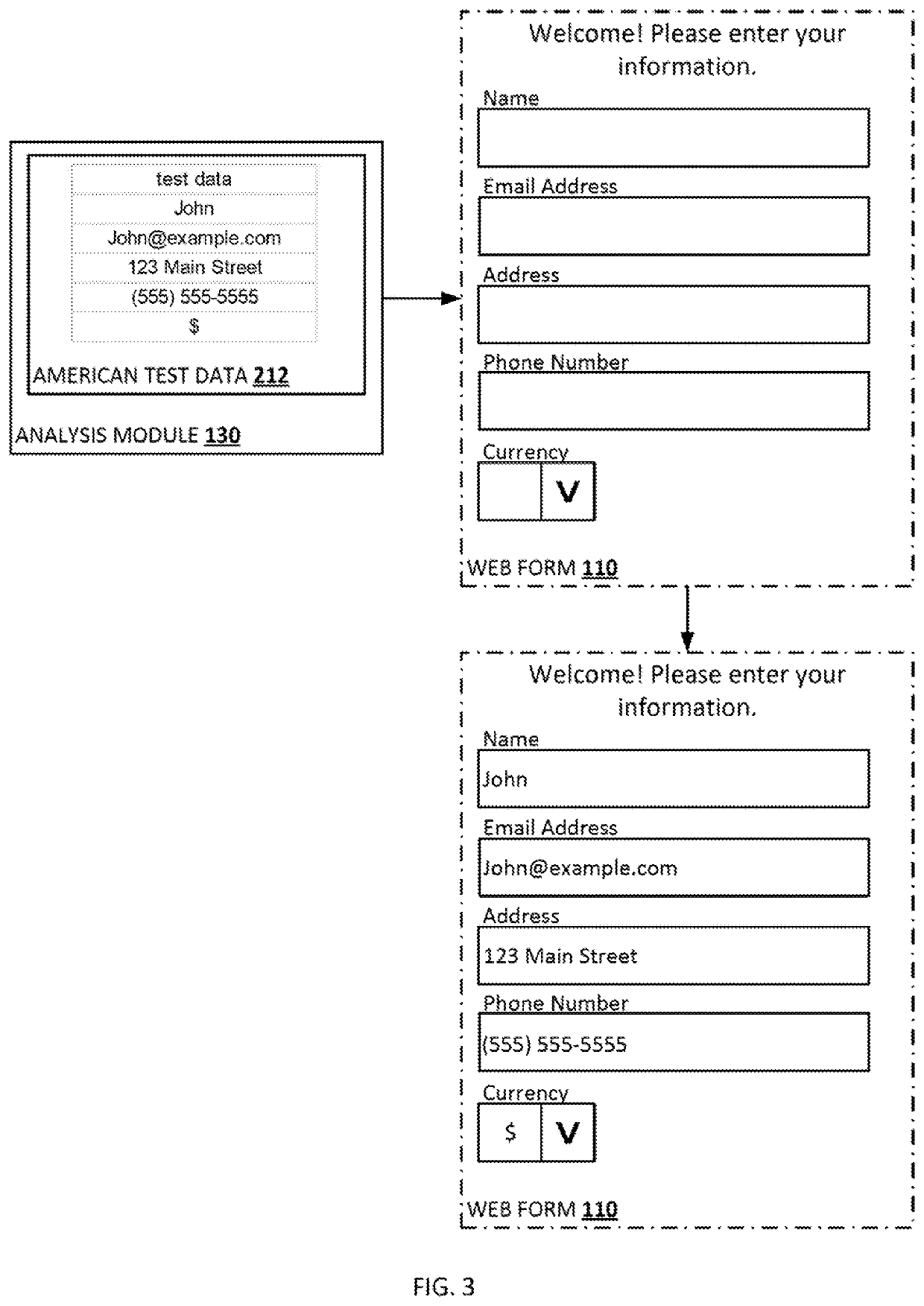
Autonomous testing of web-based applications
Certain aspects of the present disclosure provide techniques for autonomously testing a web-based application. The techniques generally include an analysis module searching a page of the web-based application for one or more fillable form fields and identifying a fillable form field in the page. The analysis module determines a field type associated with the fillable form field, determines a field data format based on the field type of the fillable form field and generates a test data entry based on the field data format. The analysis module then enters the test data entry into the respective fillable form field and submits the test data entry to a server.
Owner:INTUIT INC
Method, system, and program for logging statements to monitor execution of a program
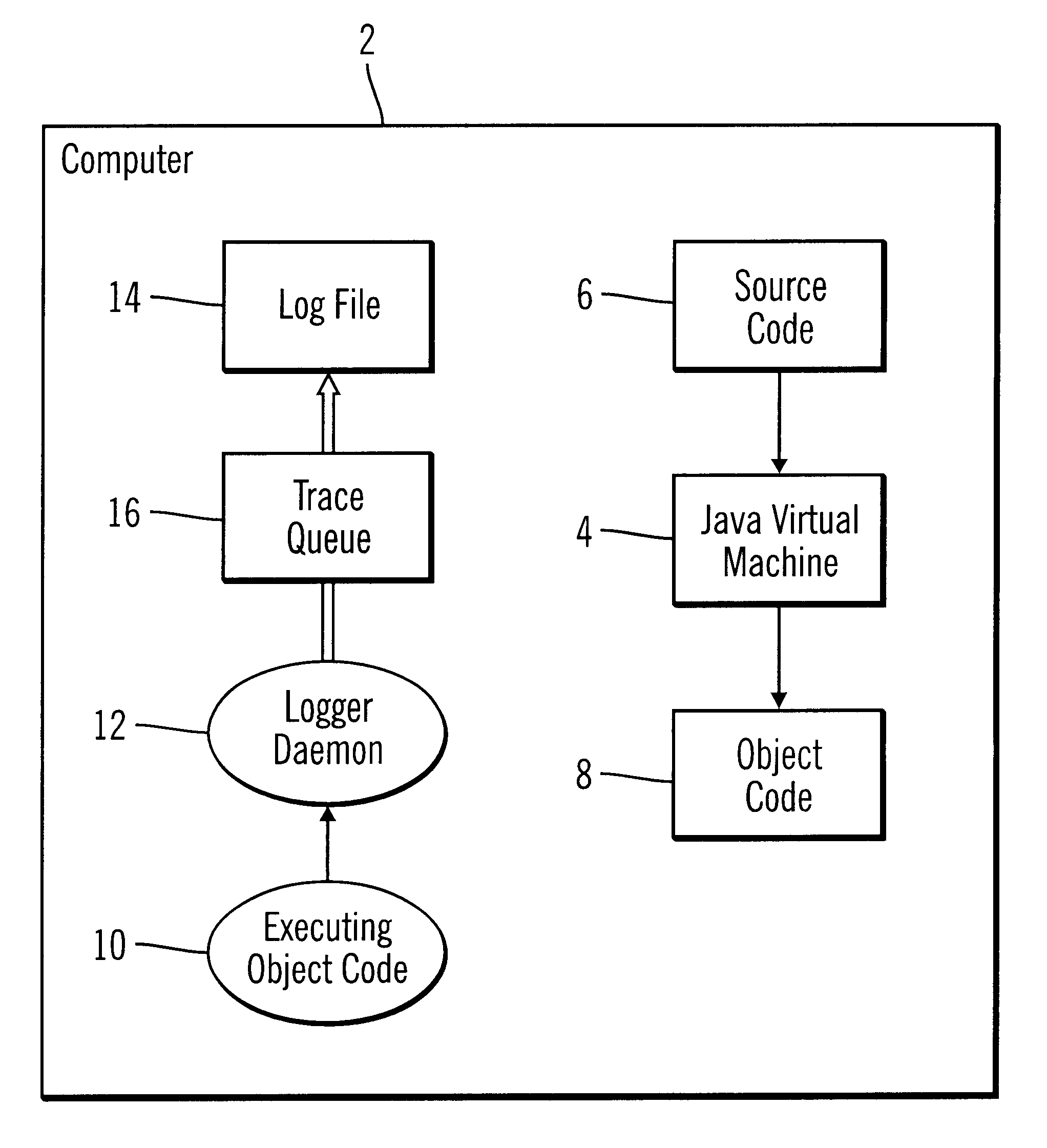
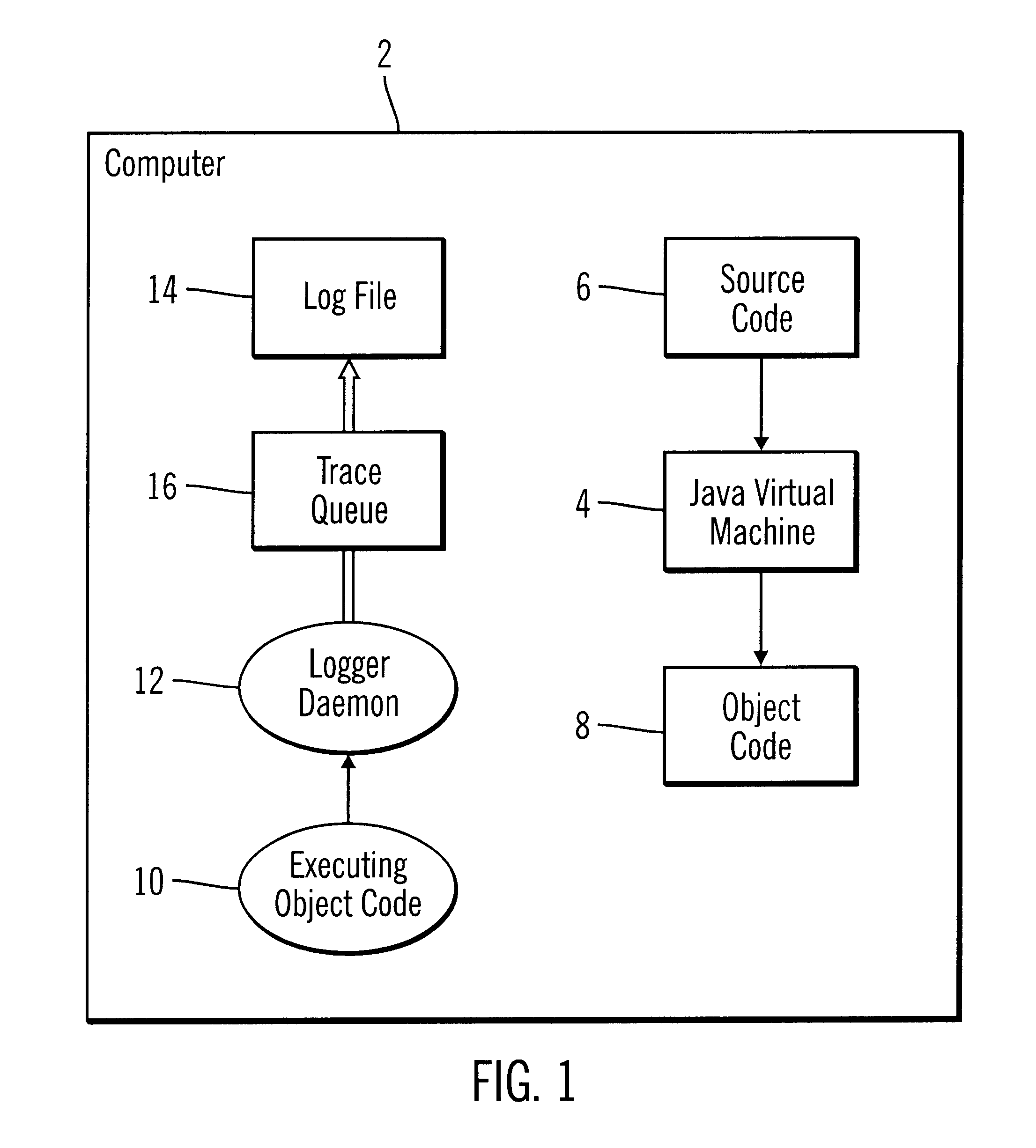
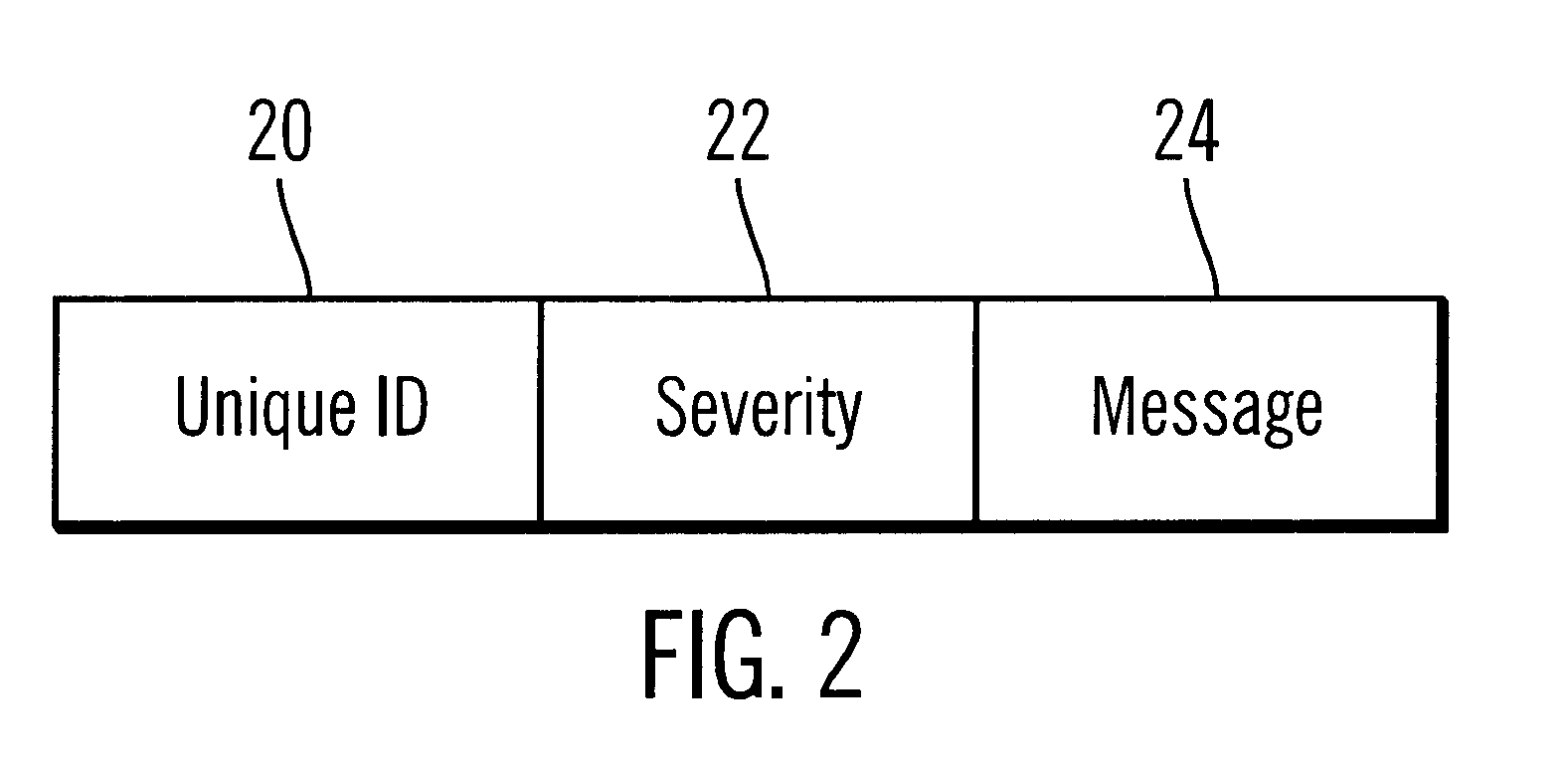
InactiveUS6539501B1Shorten the timeImprove space utilizationHardware monitoringSoftware testing/debuggingProgramming languageLogfile
Disclosed is a system, method, and program for generating trace statements to a log file. A log method in a program, such as a Java program, including an identifier parameter is processed. The program includes multiple instances of the log method to trace the execution of the program during debugging operations. A determination is made as to whether a variable indicates that log methods called with the identifier parameter should be processed. The class and method from which the log method was called is determined if the variable indicates that log methods called with the identifier parameter should be processed. Information on the identifier parameter and determined class and method are written to the log file.
Owner:IBM CORP
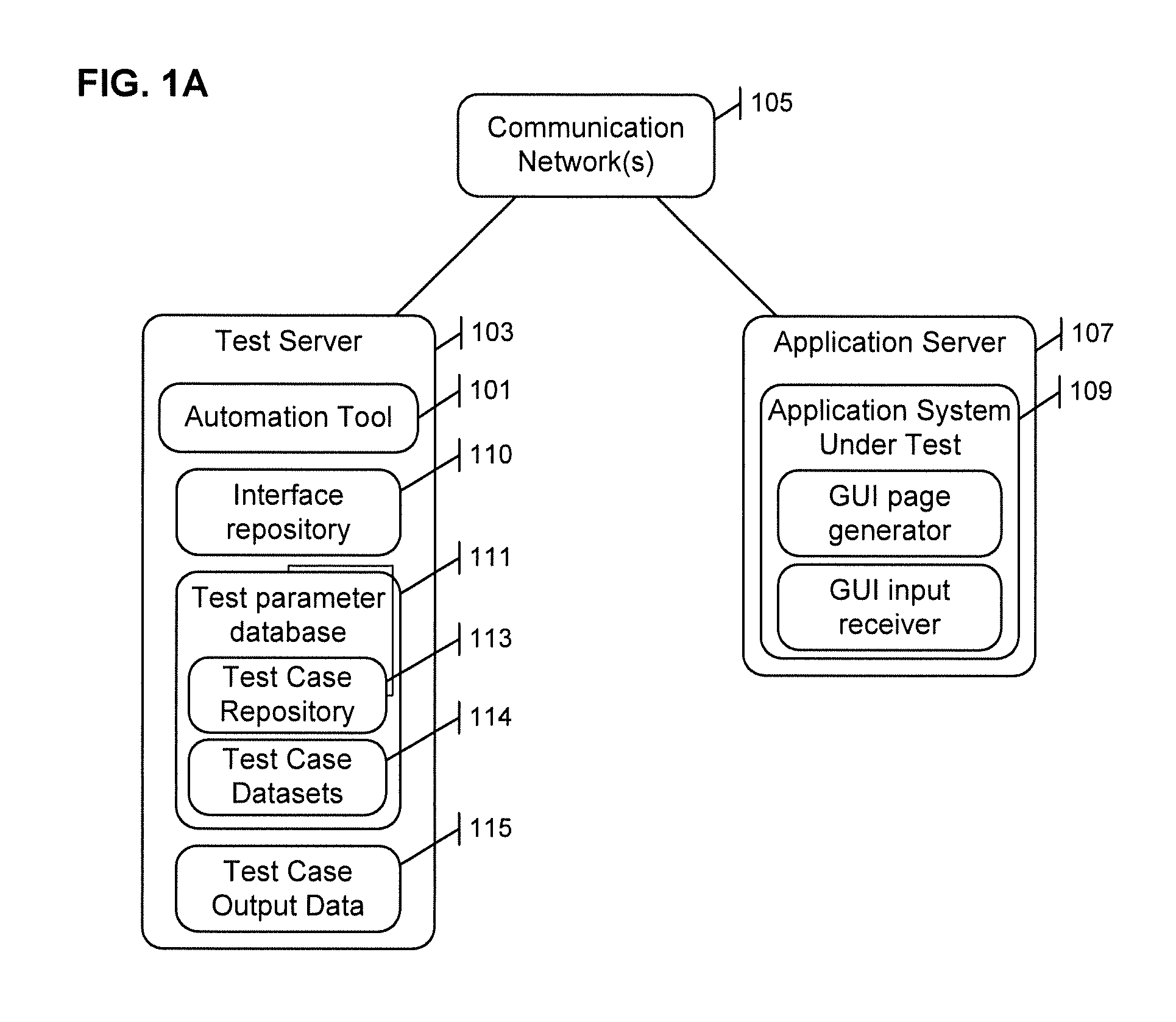
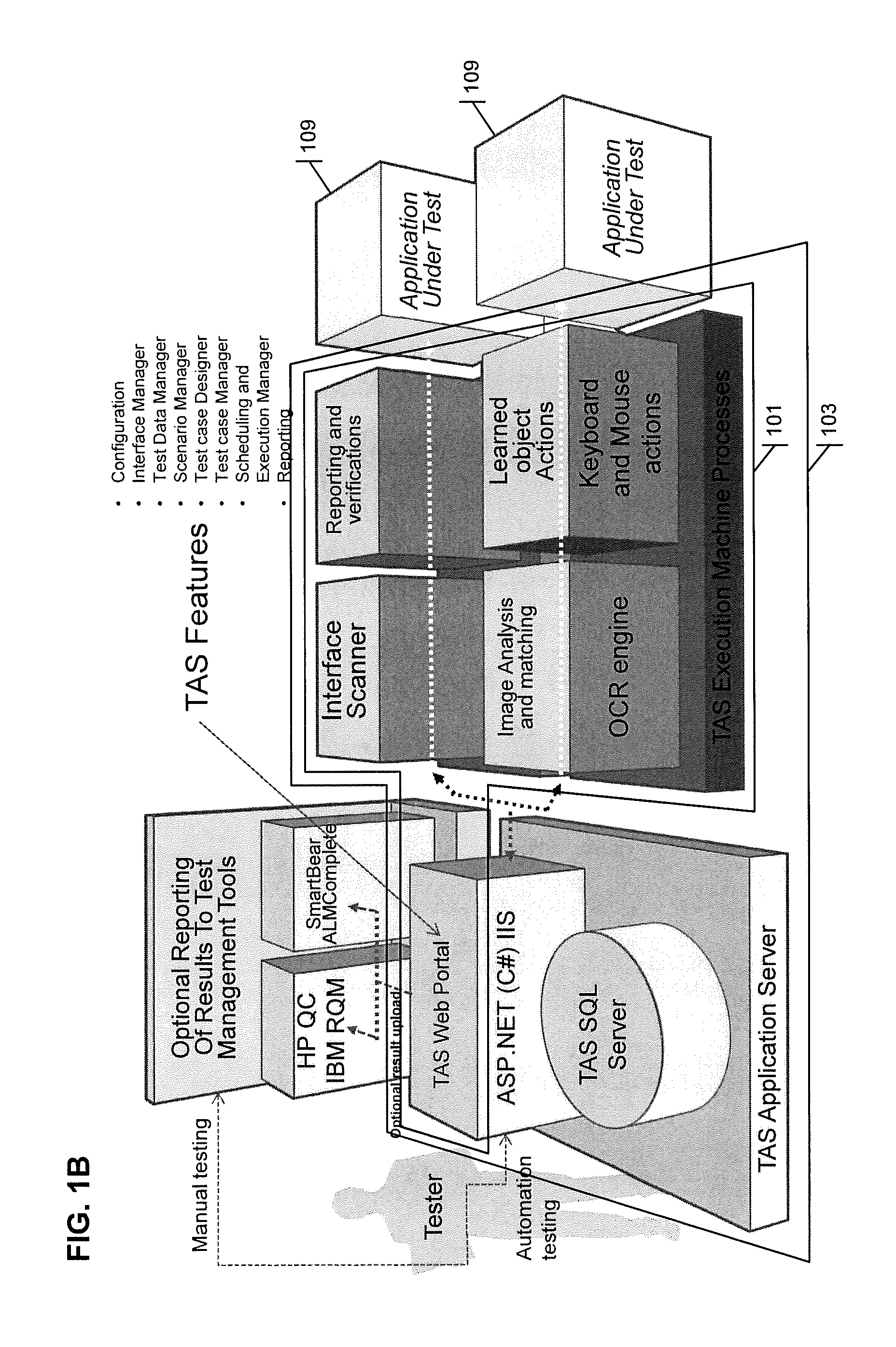
Automated testing of an application system
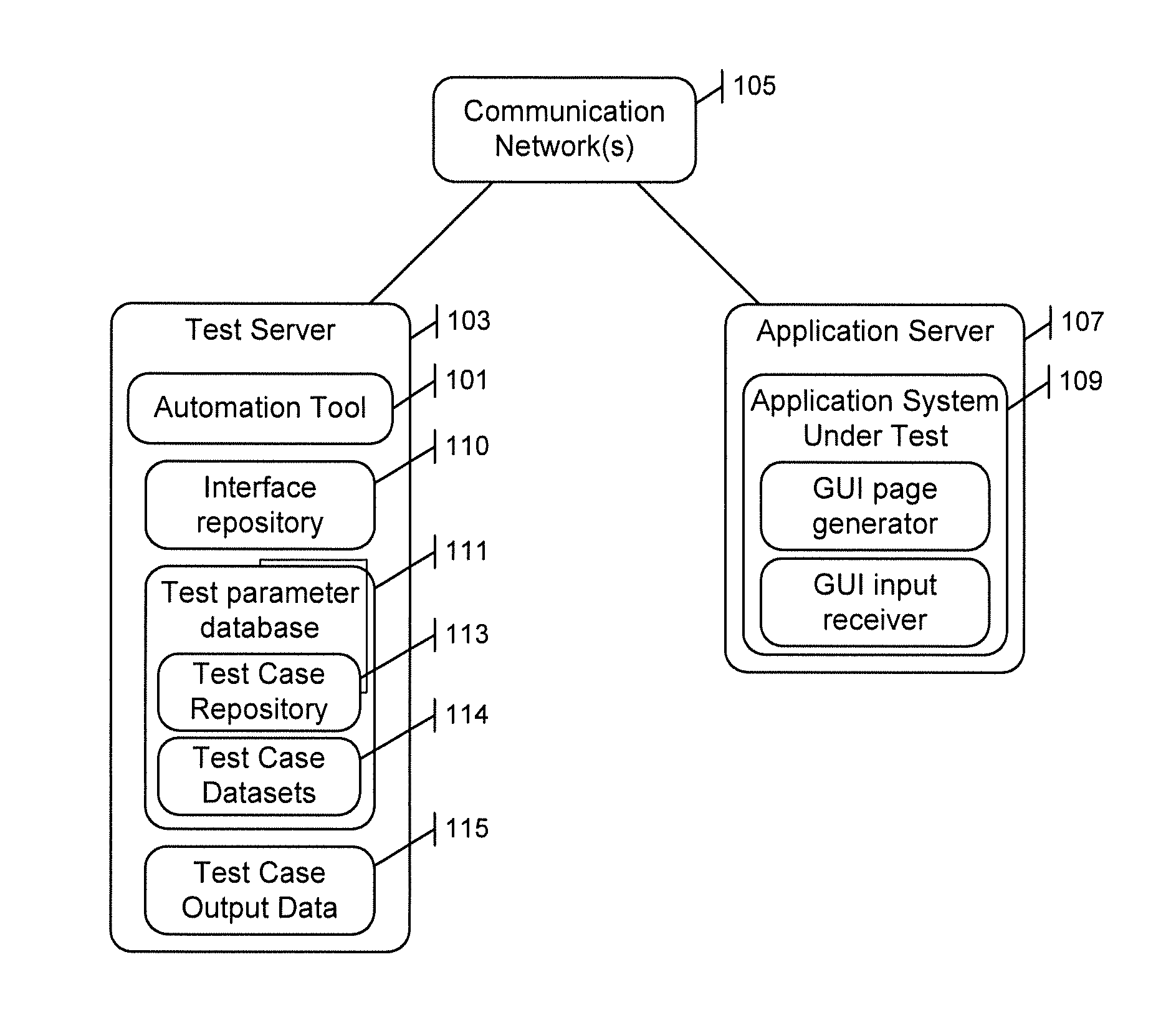
ActiveUS20150339213A1Software testing/debuggingSpecific program execution arrangementsGraphicsApplication server
A system for automatically testing an application system graphical user interface (GUI) includes first and second application servers communicatively connected across a communication network. The second application server retrieves a GUI page provided by the first application server as part of the application system, and identifies text elements and user input objects in an image of the retrieved GUI page. Each user input object is then associated with a text element. Test parameter values are retrieved from a database storing test parameter data, and the application system is tested. In particular, for each user input object of the GUI page, a respective test parameter value is provided that is associated in the database with a same text element as is associated with the user input object. A response of the application system is then monitored.
Owner:CGI TECH & SOLUTIONS
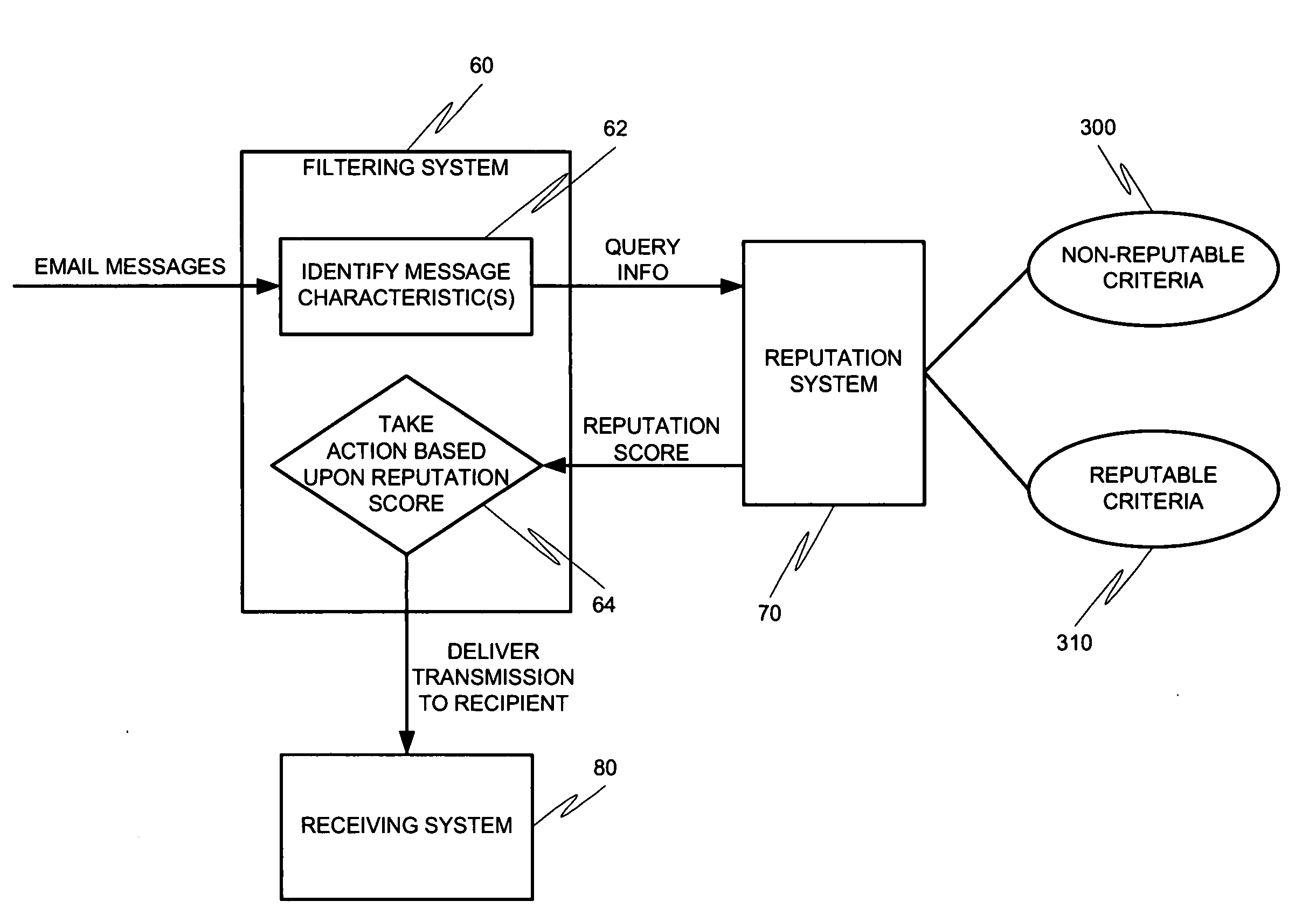
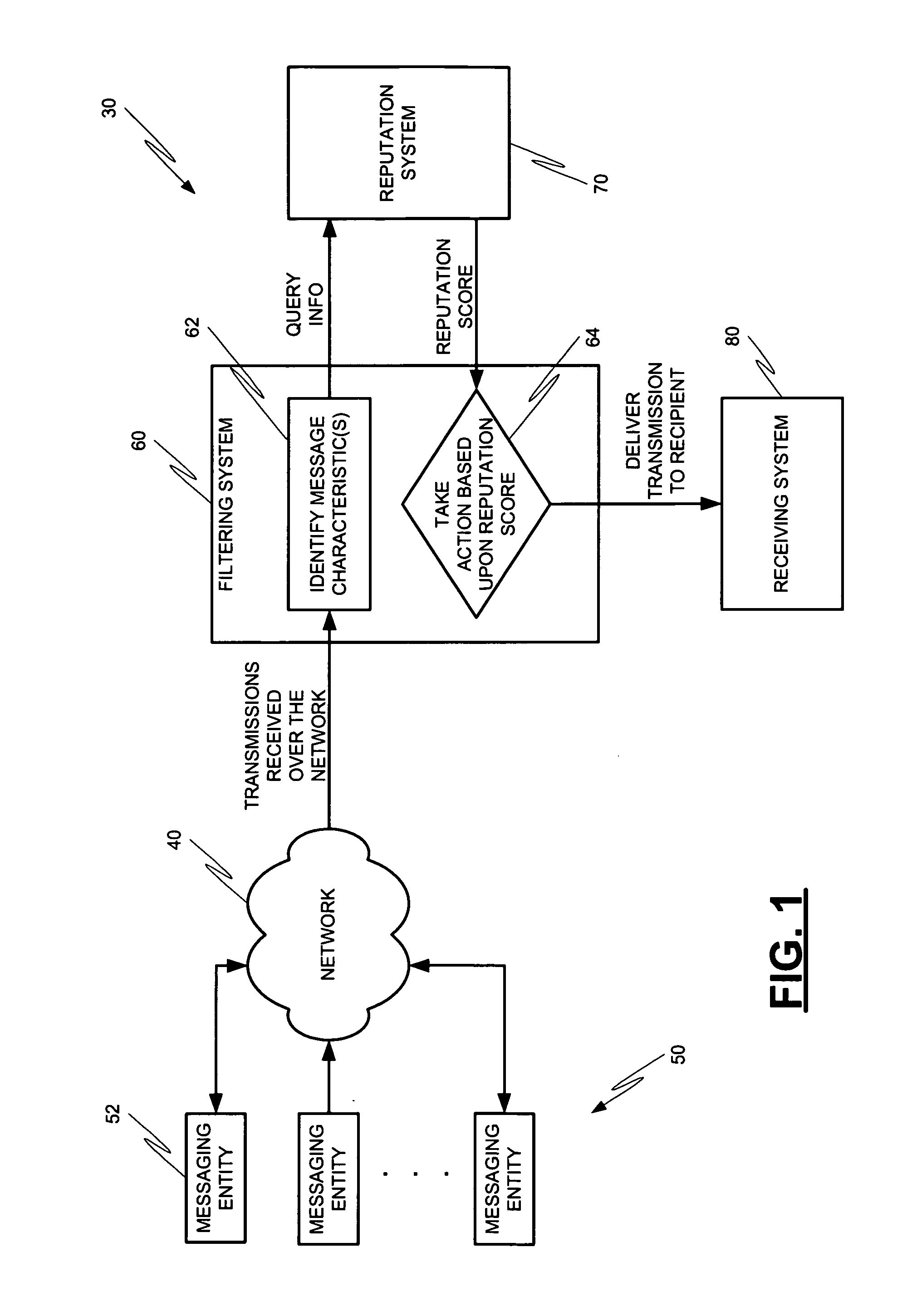
Systems and methods for classification of messaging entities
InactiveUS20060015942A1Memory loss protectionUser identity/authority verificationData treatmentMessage passing
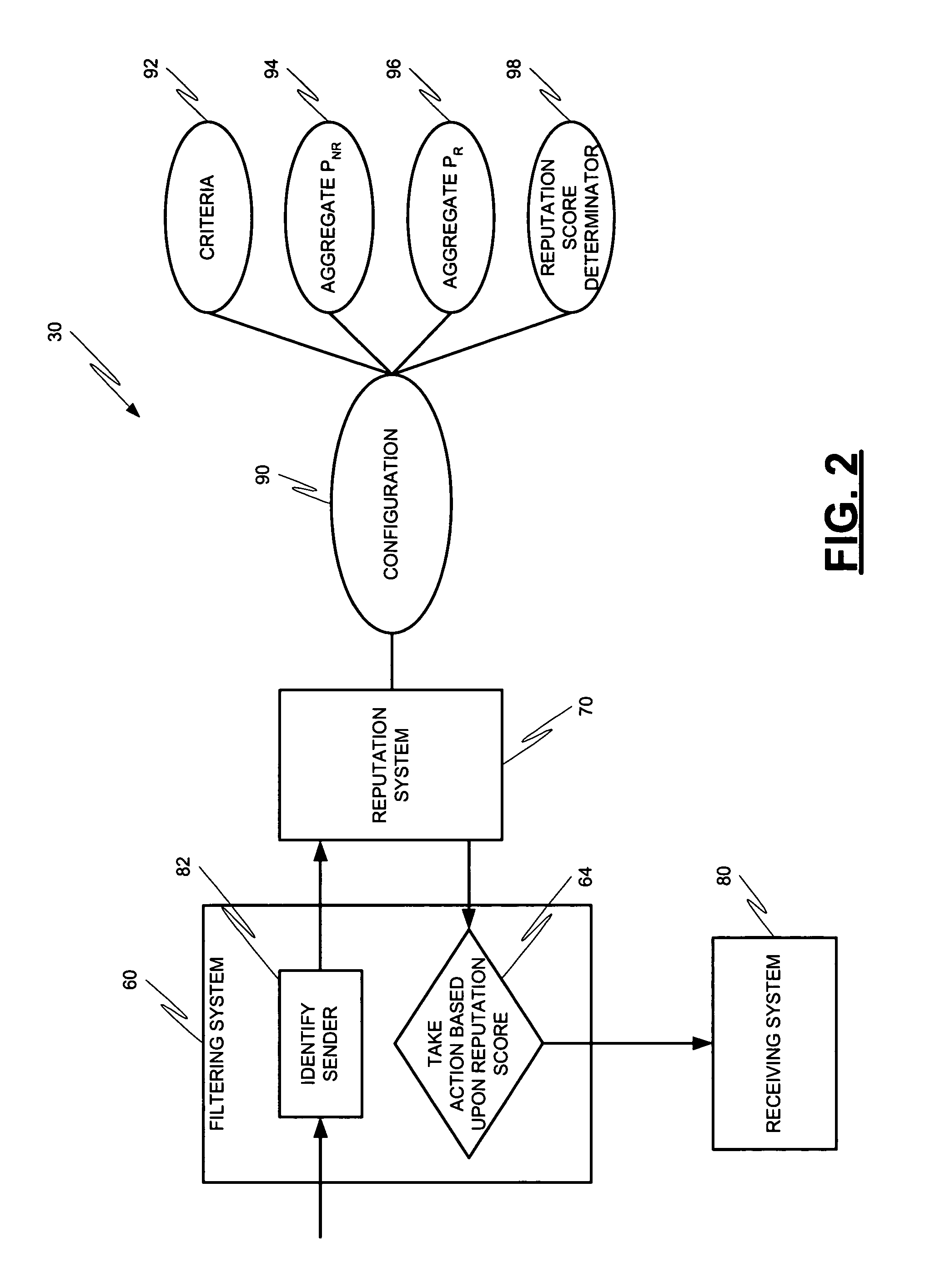
Methods and systems for operation upon one or more data processors for assigning a reputation to a messaging entity. A method can include receiving data that identifies one or more characteristics related to a messaging entity's communication. A reputation score is determined based upon the received identification data. The determined reputation score is indicative of reputation of the messaging entity. The determined reputation score is used in deciding what action is to be taken with respect to a communication associated with the messaging entity.
Owner:MCAFEE INC
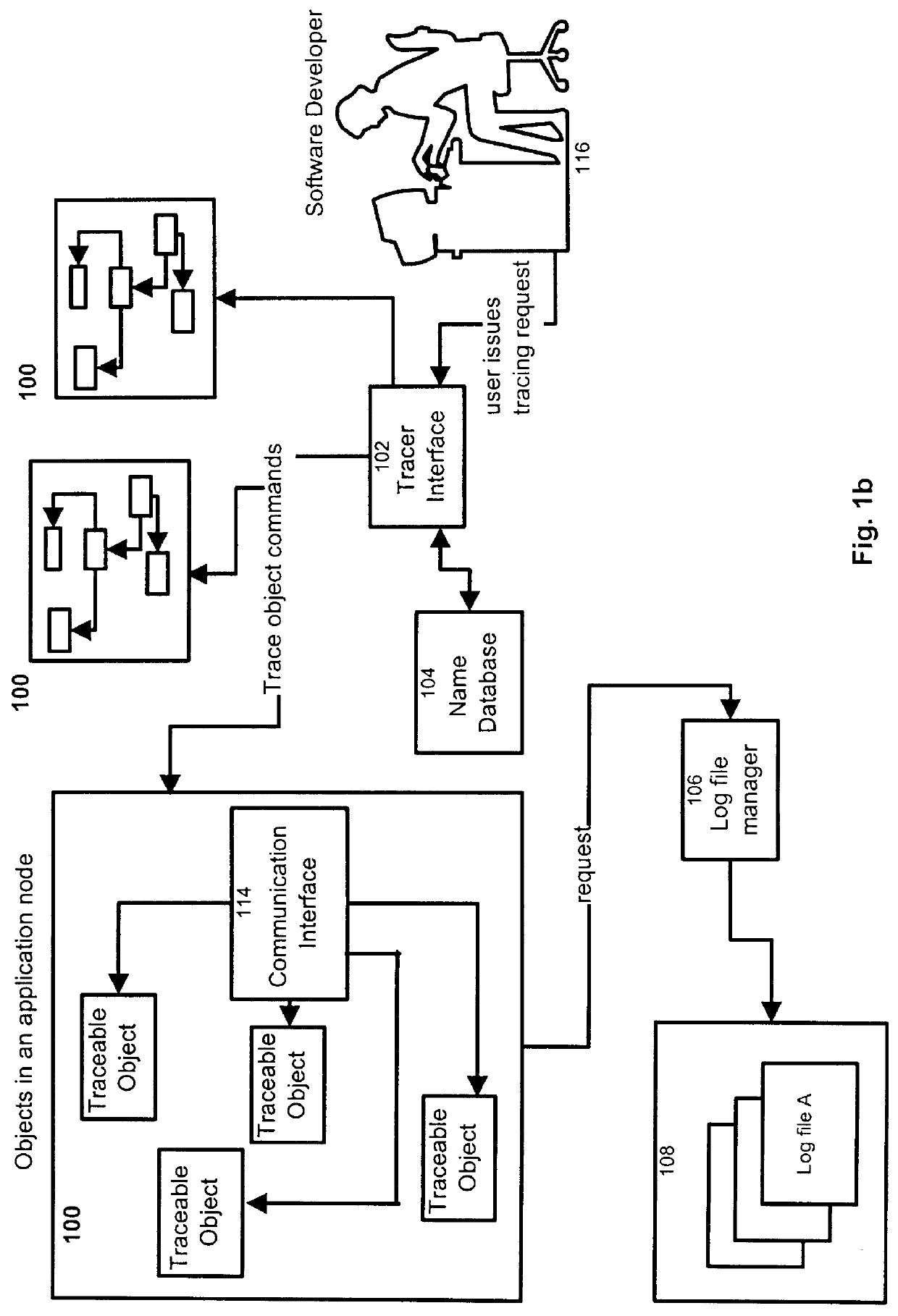
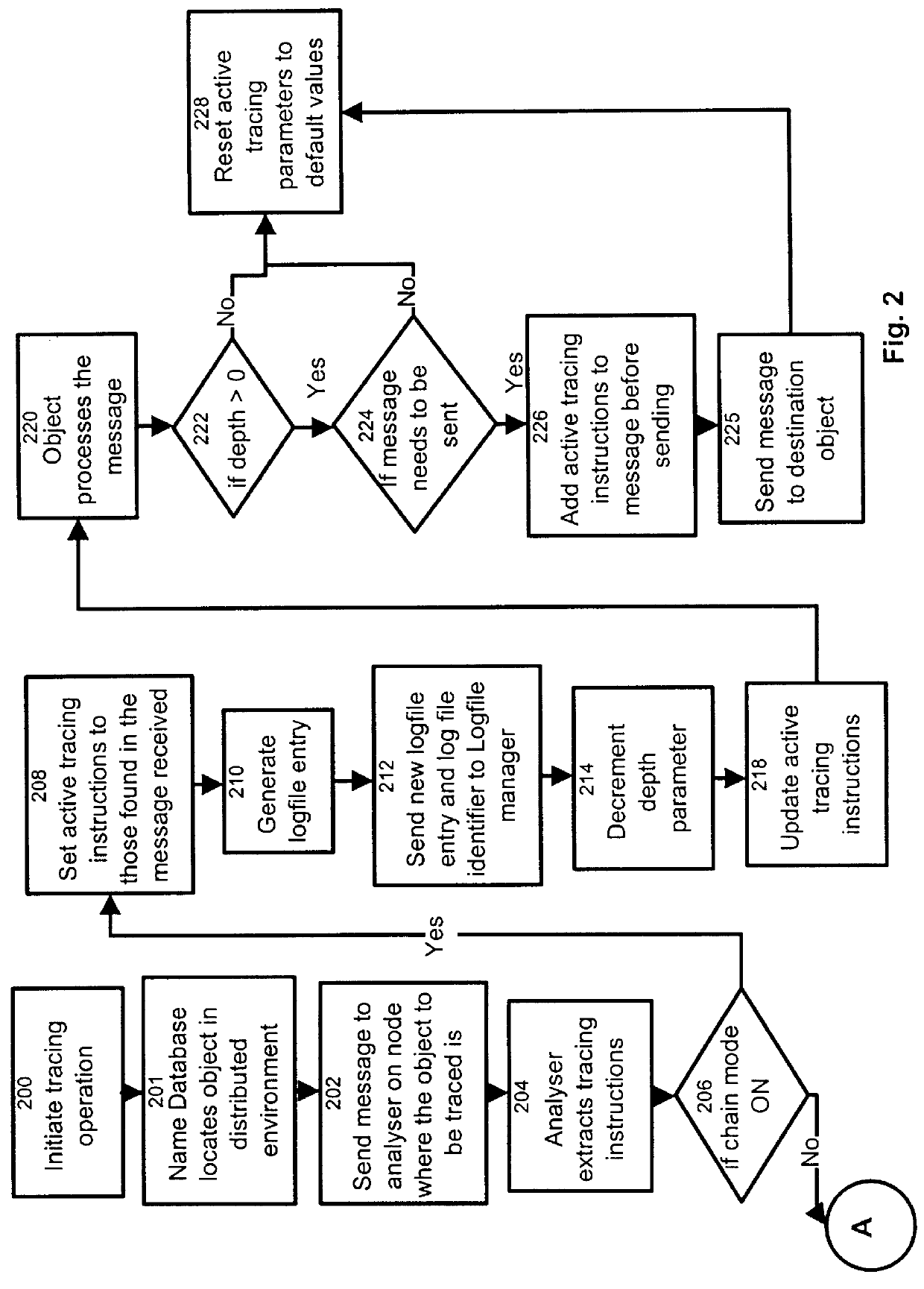
Process and apparatus for tracing software entities in a distributed system
InactiveUS6083281AHardware monitoringSoftware testing/debuggingControl flowDistributed Computing Environment
The invention relates to a process and apparatus for tracing software entities, more particularly a tracing tool providing tracing capabilities to entities in an application. The object-tracing tool provides software components to allow tracing the execution of an application. Tracing software entities is important for software developers to permit the quick localization of errors and hence facilitate the debugging process. It is also useful for the software user who wishes to view the control flow and perhaps add some modifications to the software. Traditionally, software-tracing tools have been confined to single node systems where all the components of an application run on a single machine. The novel tracing tool presented in this application provides a method and an apparatus for tracing software entities in a distributed computing environment. This is done by using a network management entity to keep track of the location of the entities in the system and by using a library of modules that can be inherited to provide tracing capabilities. It also uses a log file to allow the program developer or user to examine the flow, the occurrence of events during a trace and the values of designated attributes. The invention also provides a computer readable storage medium containing a program element to direct a processor of a computer to implement the software tracing process.
Owner:RPX CLEARINGHOUSE
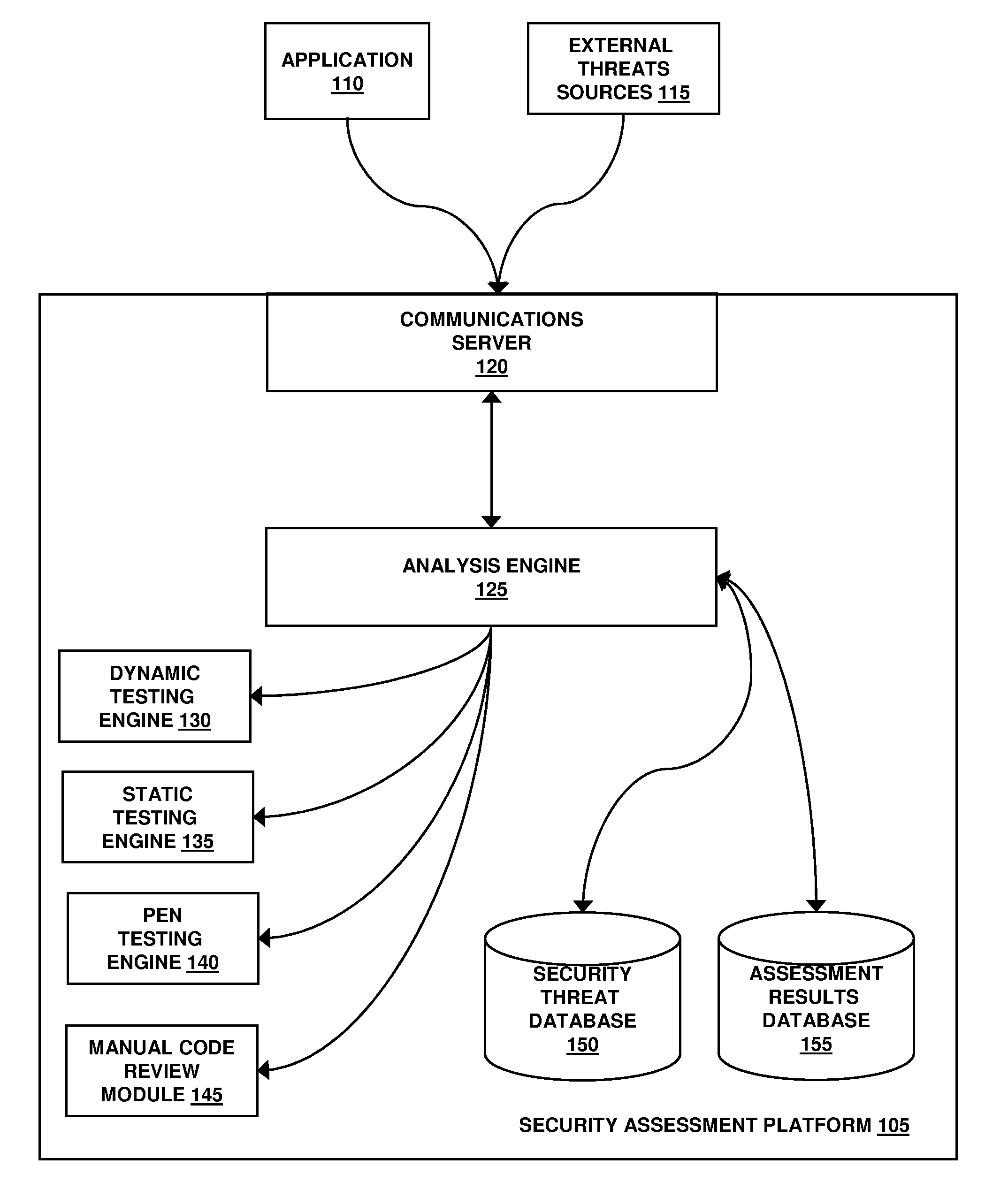
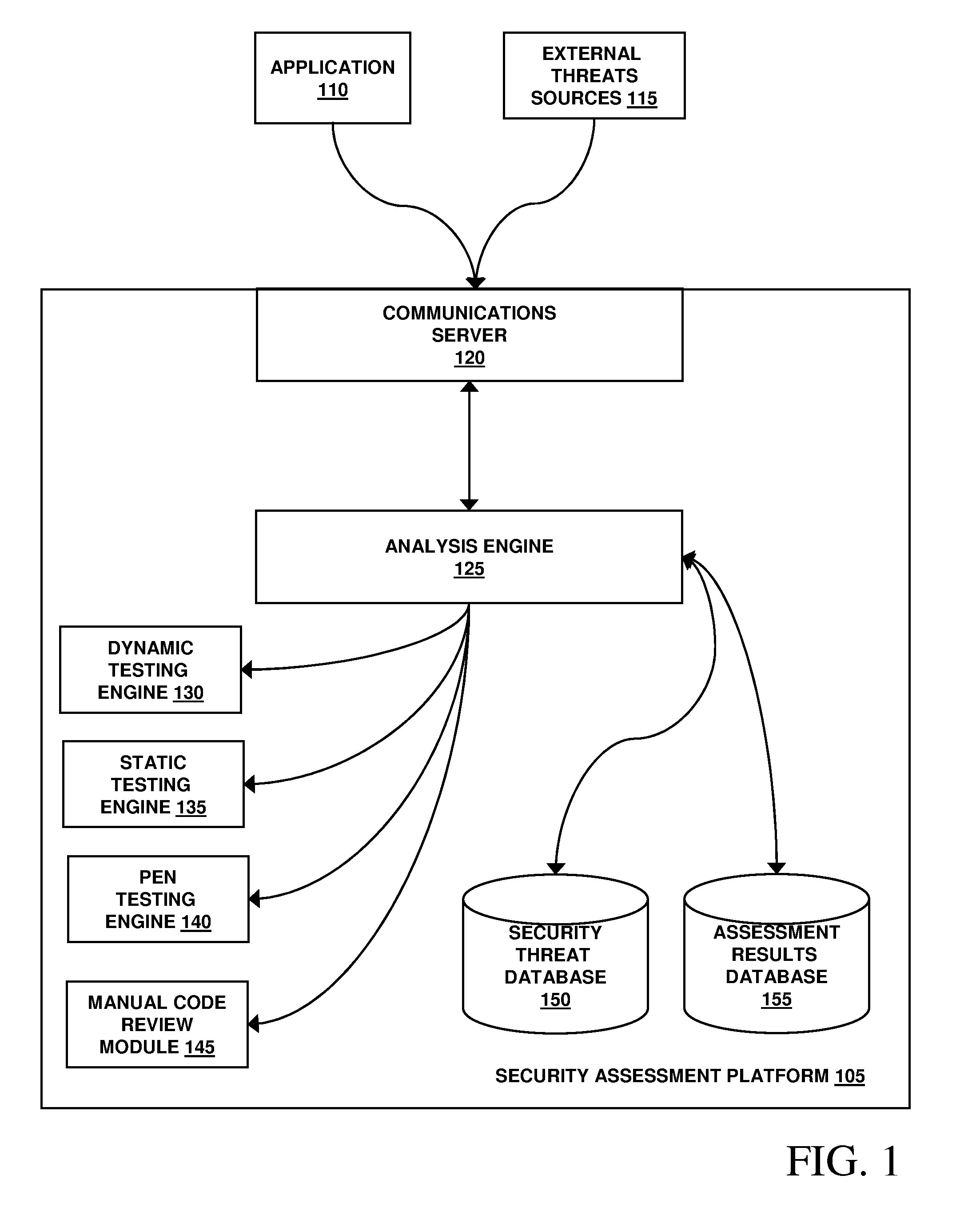
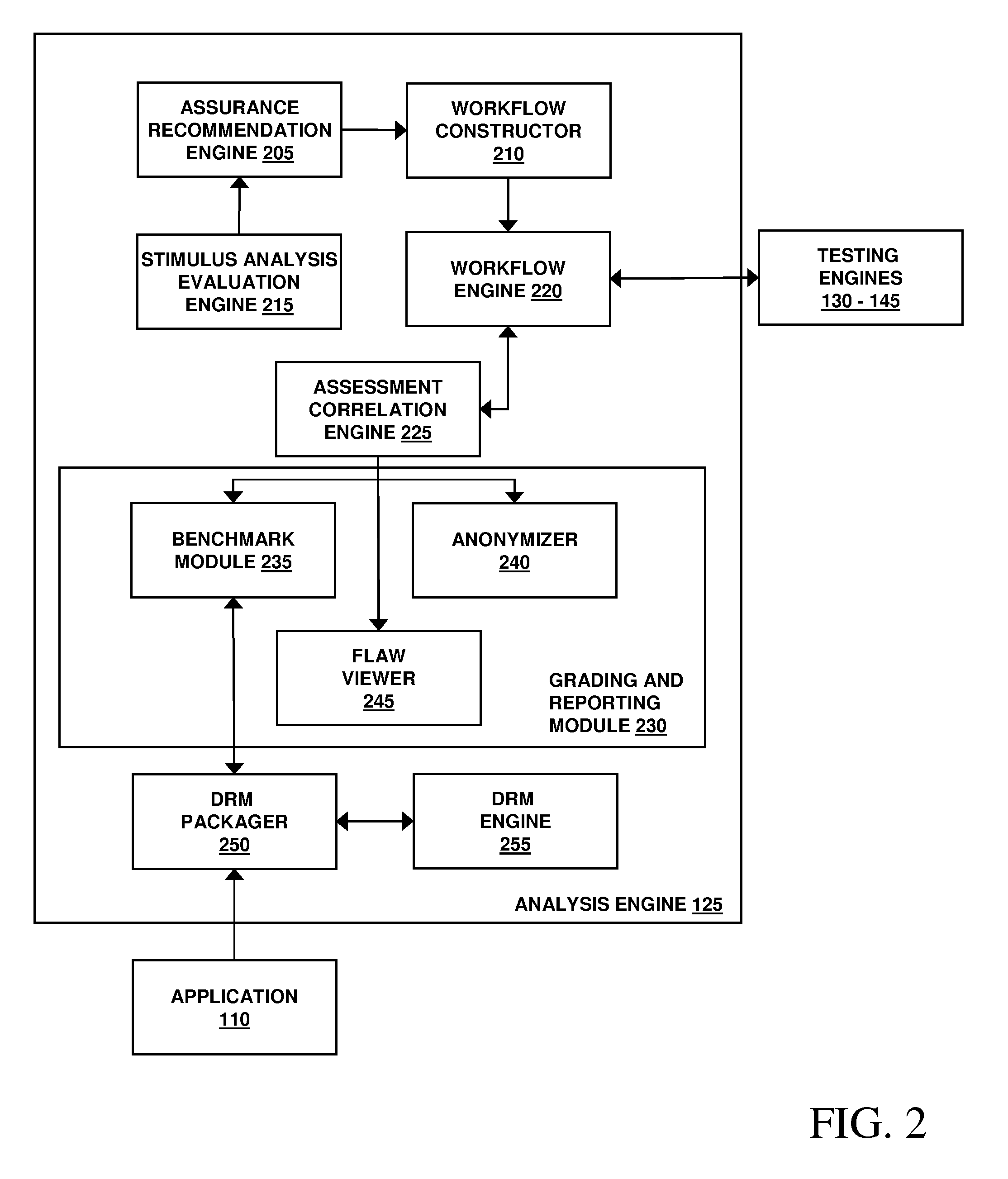
Assessment and analysis of software security flaws
ActiveUS20080209567A1Facilitates security assessment and vulnerability testingFacilitates benchmarkingMemory loss protectionUnauthorized memory use protectionApplication specificApplication software
Security assessment and vulnerability testing of software applications is performed based at least in part on application metadata in order to determine an appropriate assurance level and associated test plan that includes multiple types of analysis. Steps from each test are combined into a “custom” or “application-specific” workflow, and the results of each test may then be correlated with other results to identify potential vulnerabilities and / or faults.
Owner:VERACODE
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com