Patents
Literature
974 results about "Message flow" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
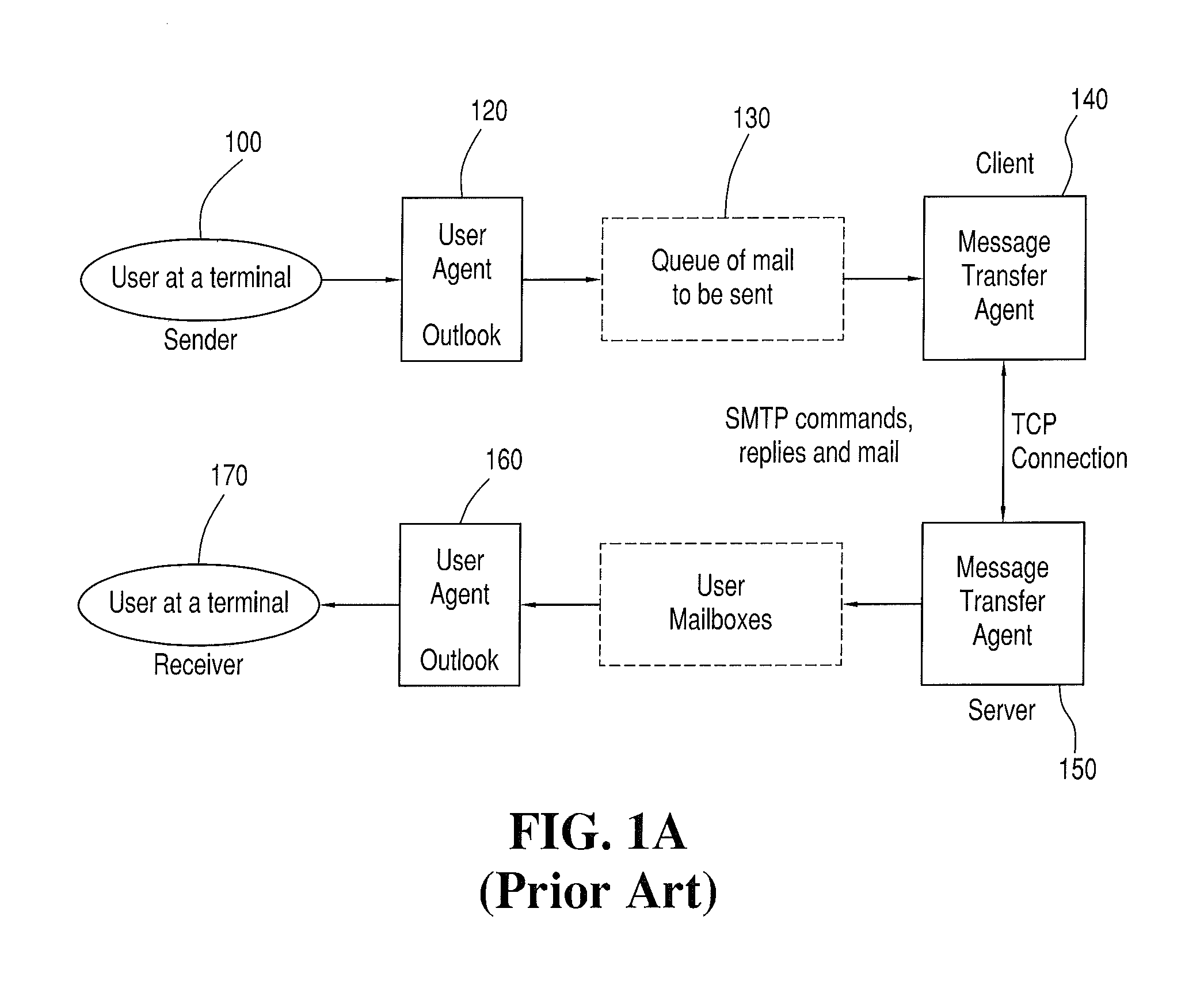
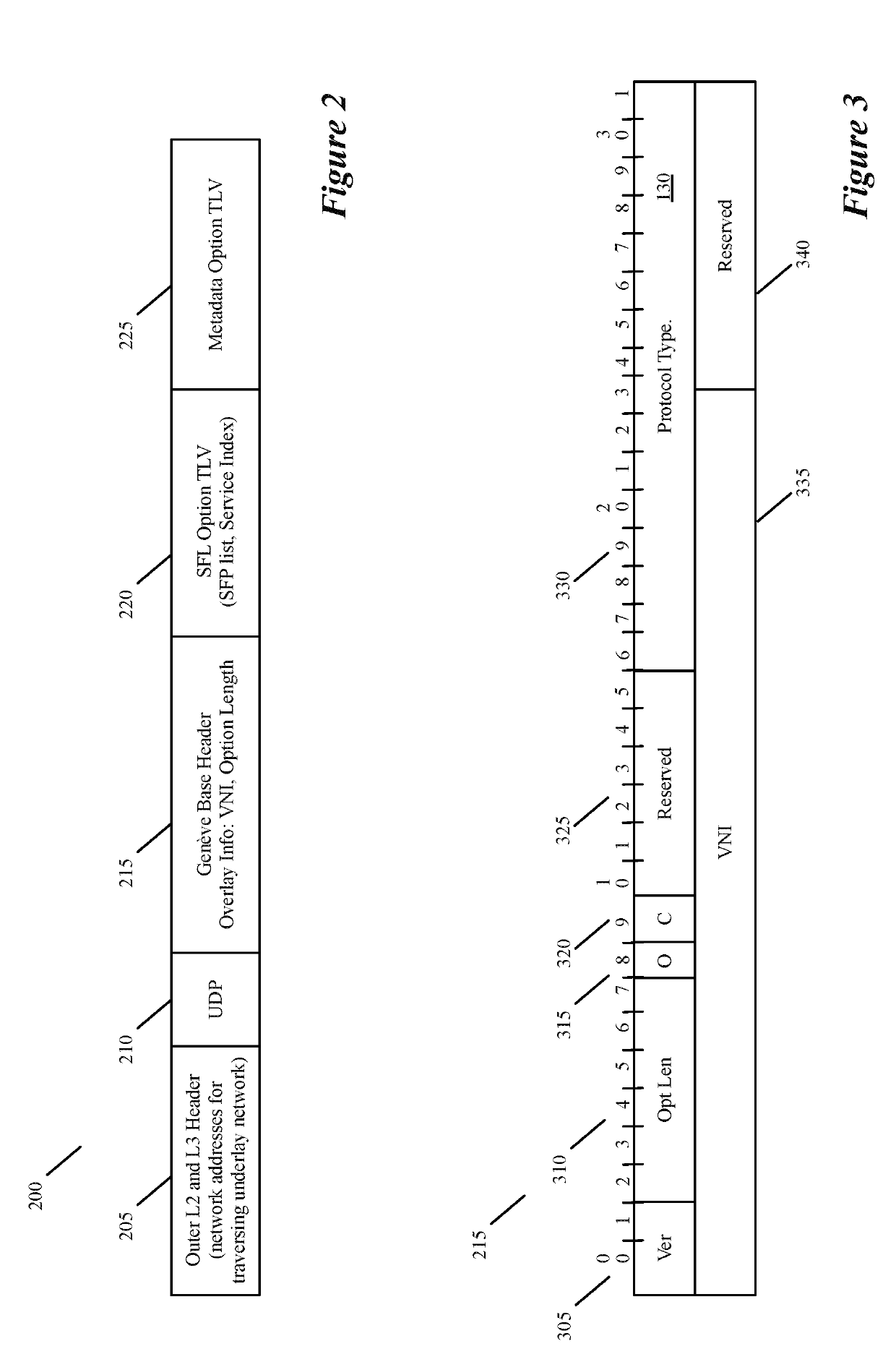
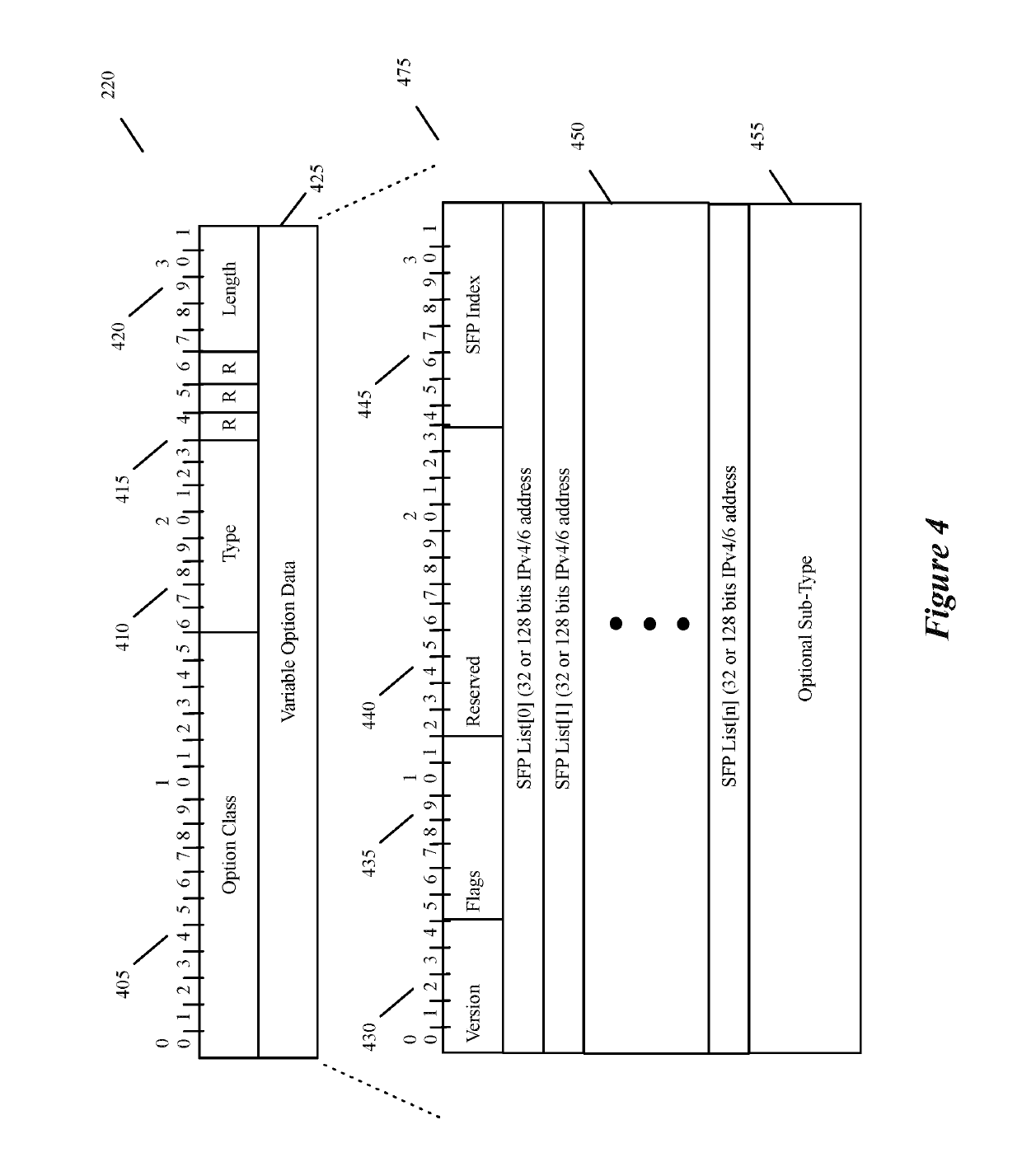
A message flow is a sequence of processing steps that run in the broker when an input message is received. You define a message flow in the IBM® Integration Toolkit by including a number of message flow nodes, each of which represents a set of actions that define a processing step.
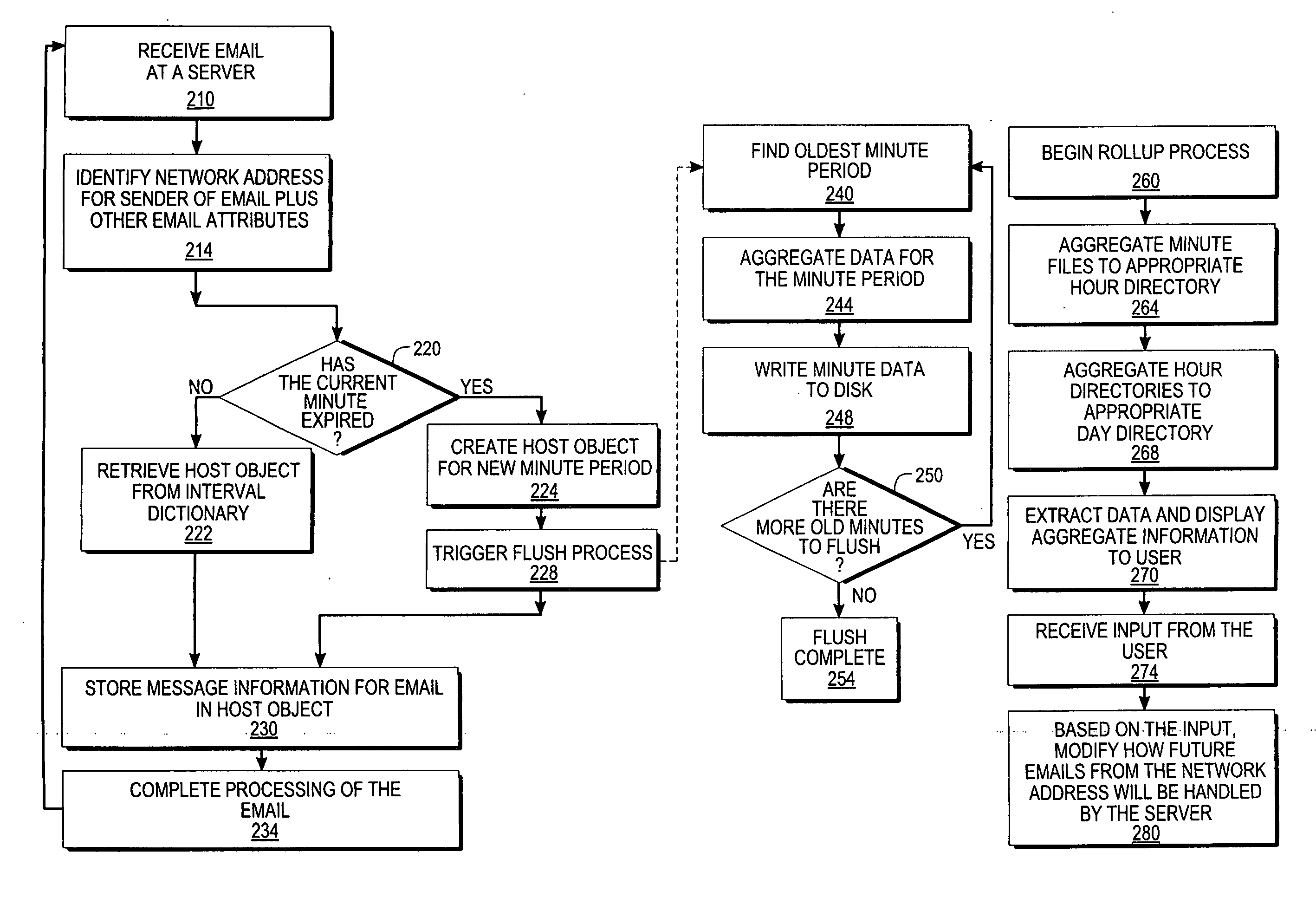
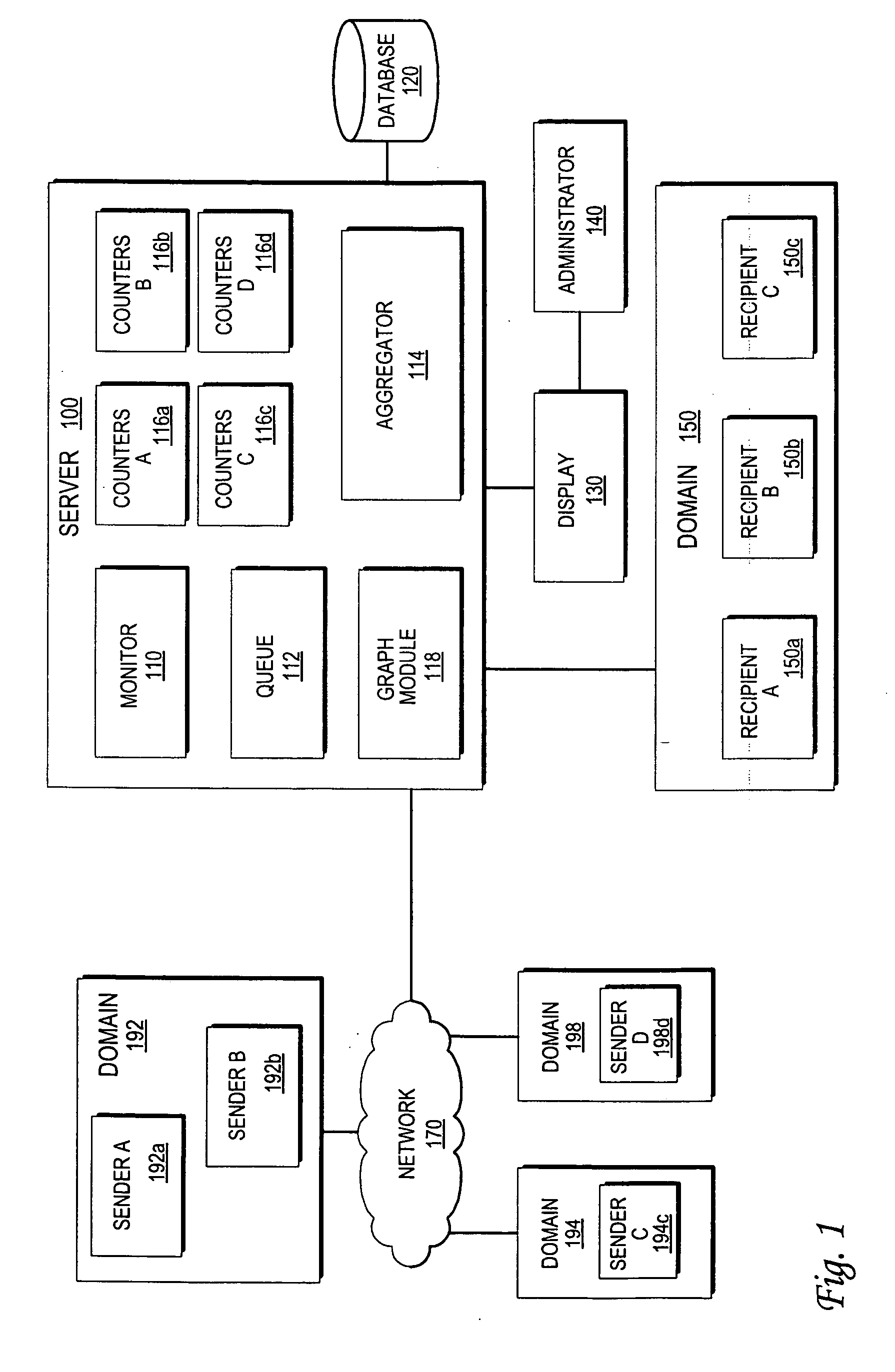
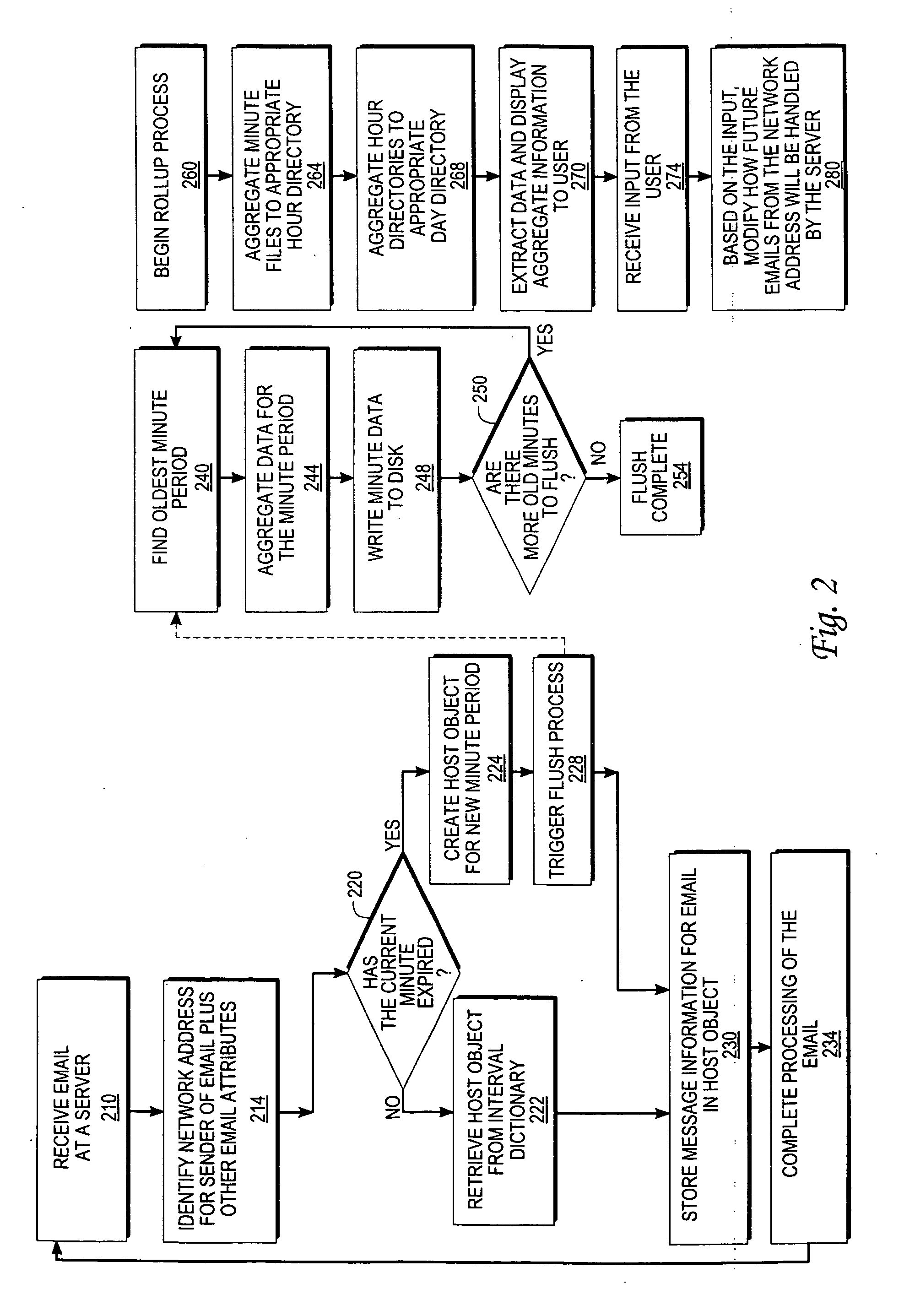
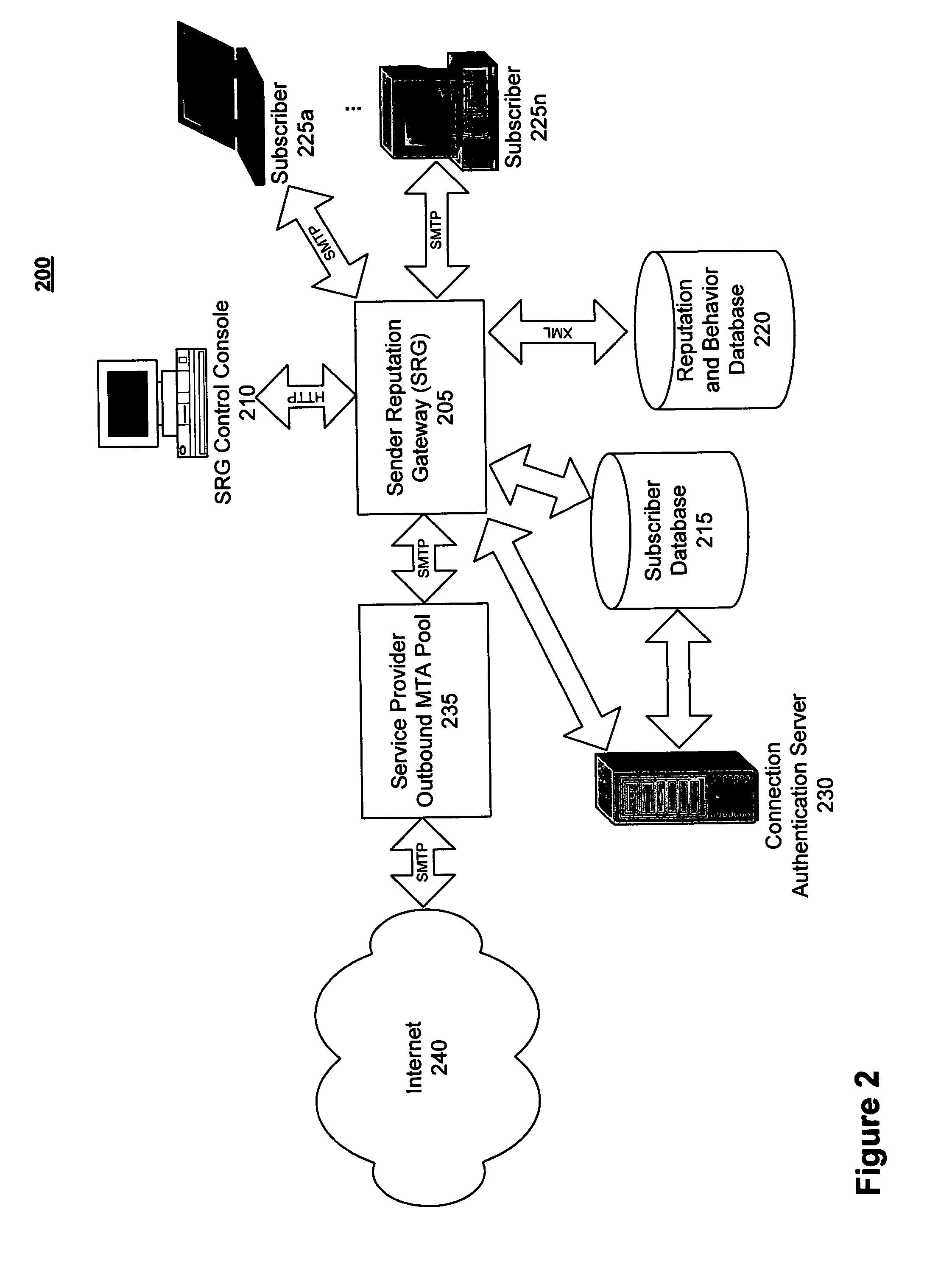
Monitoring the flow of messages received at a server
InactiveUS20060059238A1Multiple digital computer combinationsData acquisition and loggingMessage flowNetwork addressing
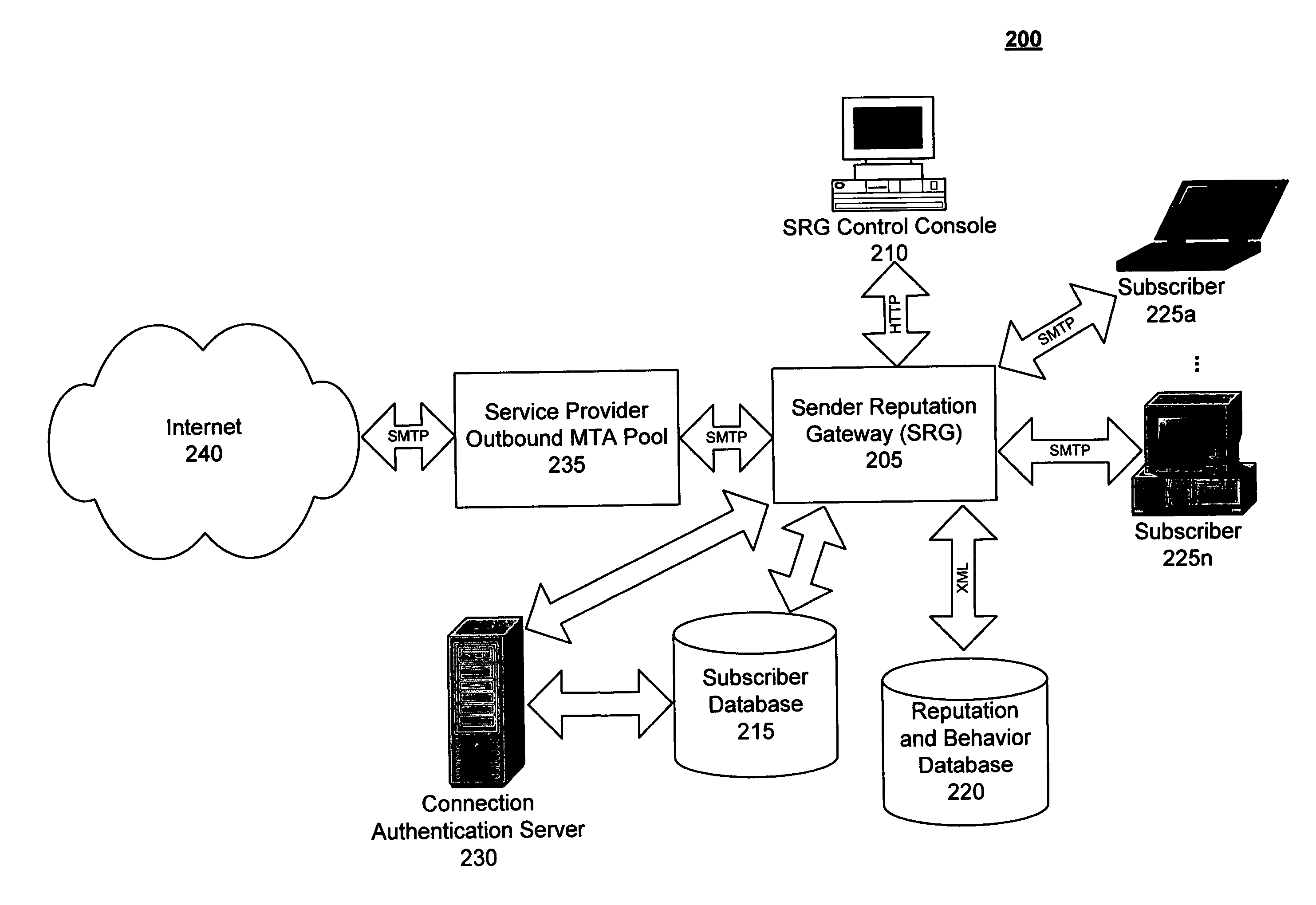
An approach for monitoring electronic messages received at a server is disclosed. Message information for a plurality of electronic messages received at the server: is determined and stored in a queue. Based on the queue, aggregate information is generated for a particular network address of a plurality of network addresses. The aggregate information is generated for each time interval of a plurality of time intervals and displayed for the plurality of time intervals. In some implementations, input from a user is received, and based on the input, a modification is made regarding how future electronic messages from the particular network address are handled by the server. In some implementations, combined aggregate information is generated for two or more network addresses and then displayed. In some implementations, aggregate policy information indicating which policies have been applied to the electronic messages is generated and displayed for the time intervals.
Owner:IRONPORT SYST
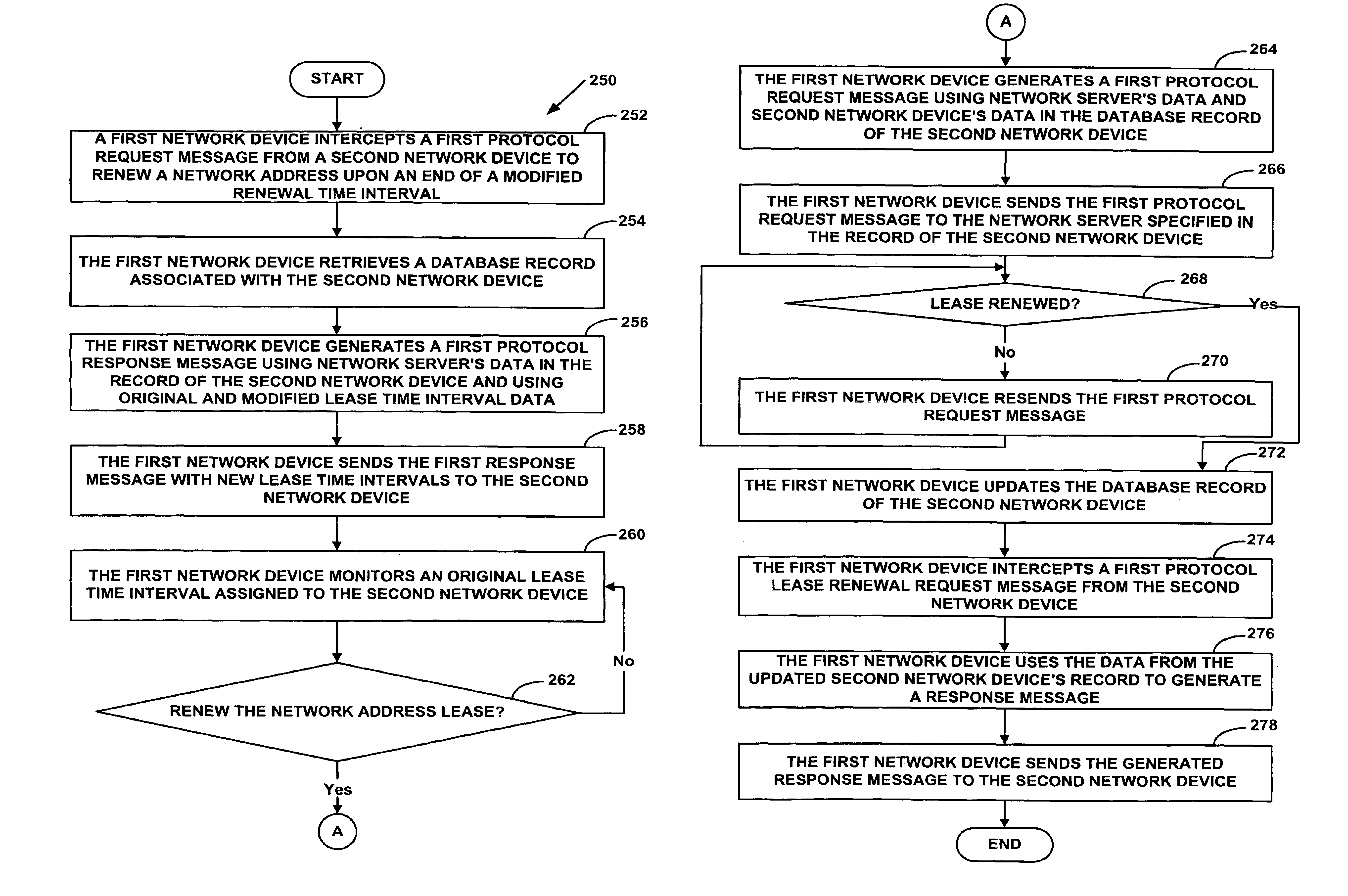
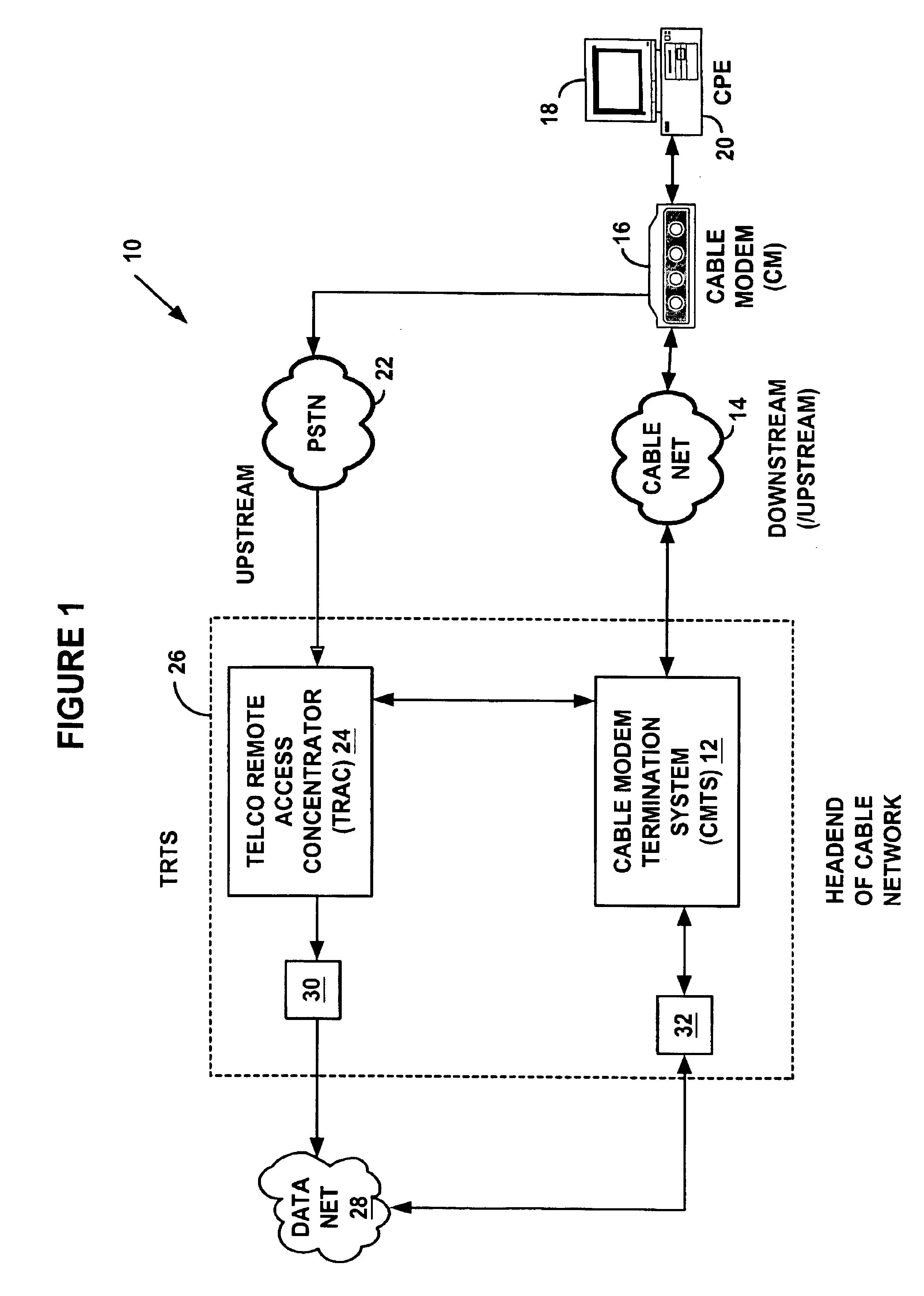
System and method for a specialized dynamic host configuration protocol proxy in a data-over-cable network
A system and method for proxying Dynamic Host Configuration Protocol (“DHCP”) network services for a network device, such as, a customer premise equipment entity, on a network device, such as, a cable modem, include creating a specialized proxy task for the customer premise equipment entity on the cable modem. One method of the present invention includes intercepting DHCP message flow between a customer premise equipment having a specialized proxy task created on the cable modem and a DHCP server selected by the customer premise equipment entity. The methods further include modifying lease time intervals prior to providing a routable network address lease to a customer premise equipment entity and renewing an initial lease for the customer premise equipment entity by a cable modem prior to expiration of the lease time interval provided by a DHCP server. The methods include using known protocols, such as, for example, the Dynamic Host Configuration Protocol.
Owner:VALTRUS INNOVATIONS LTD
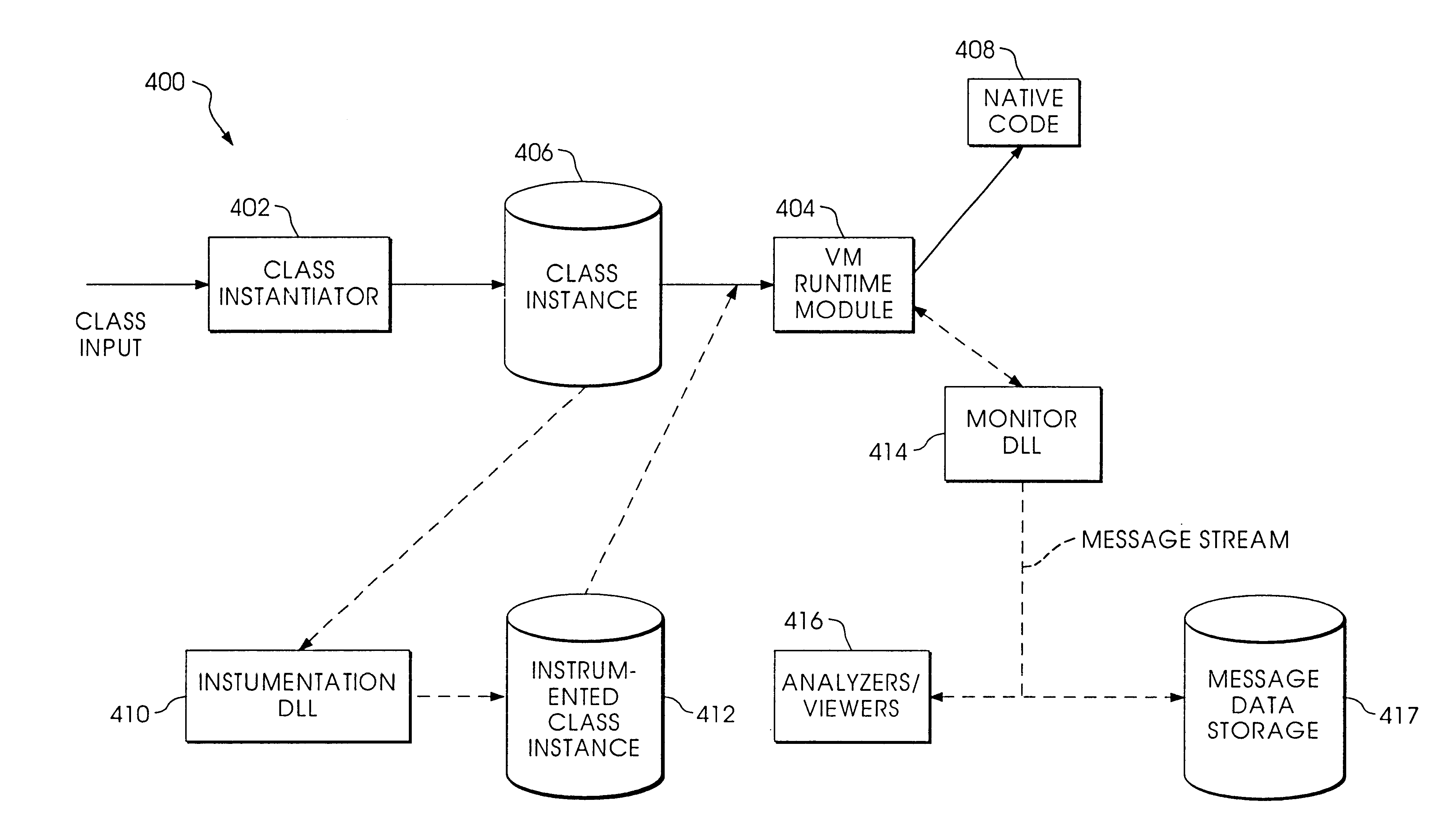
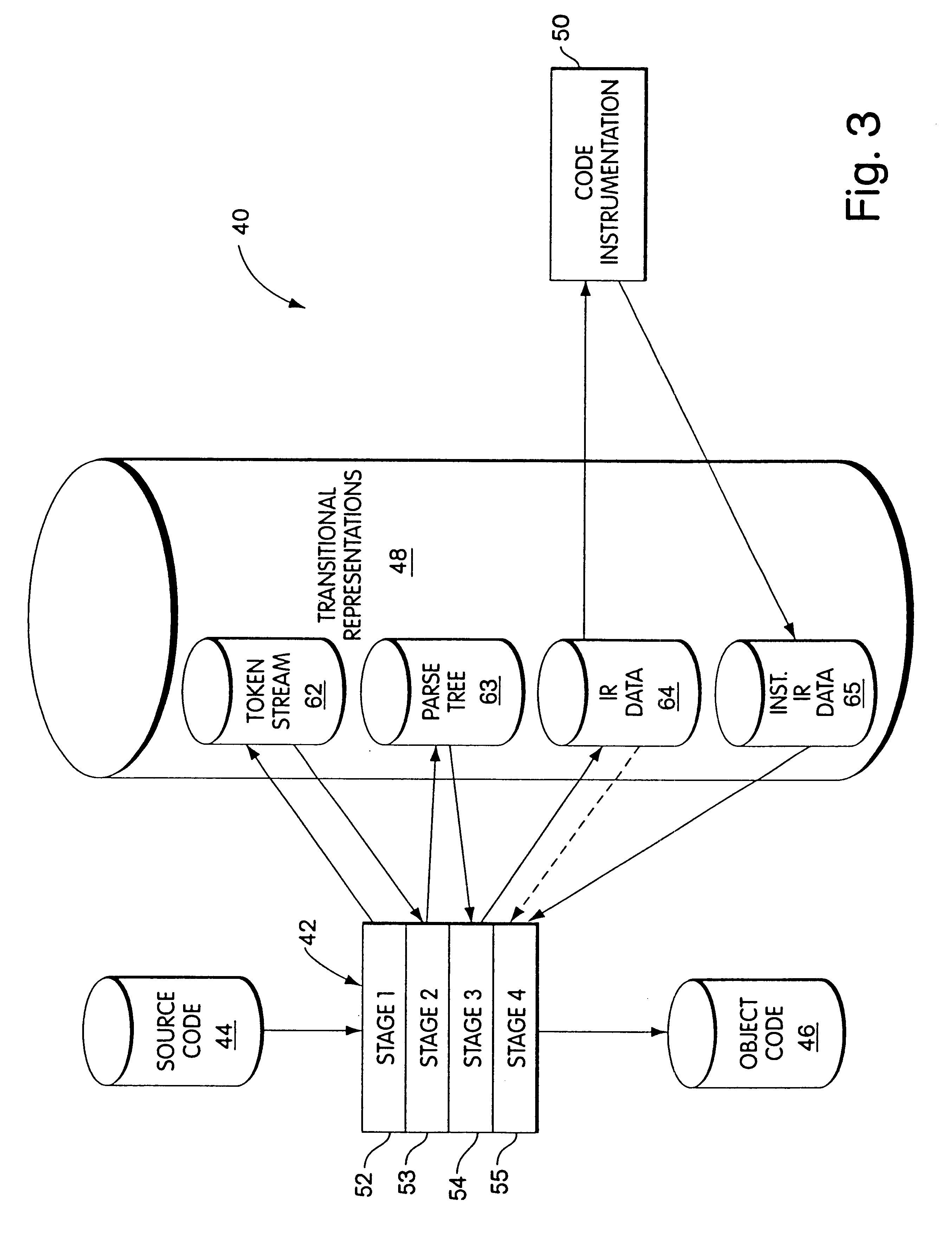
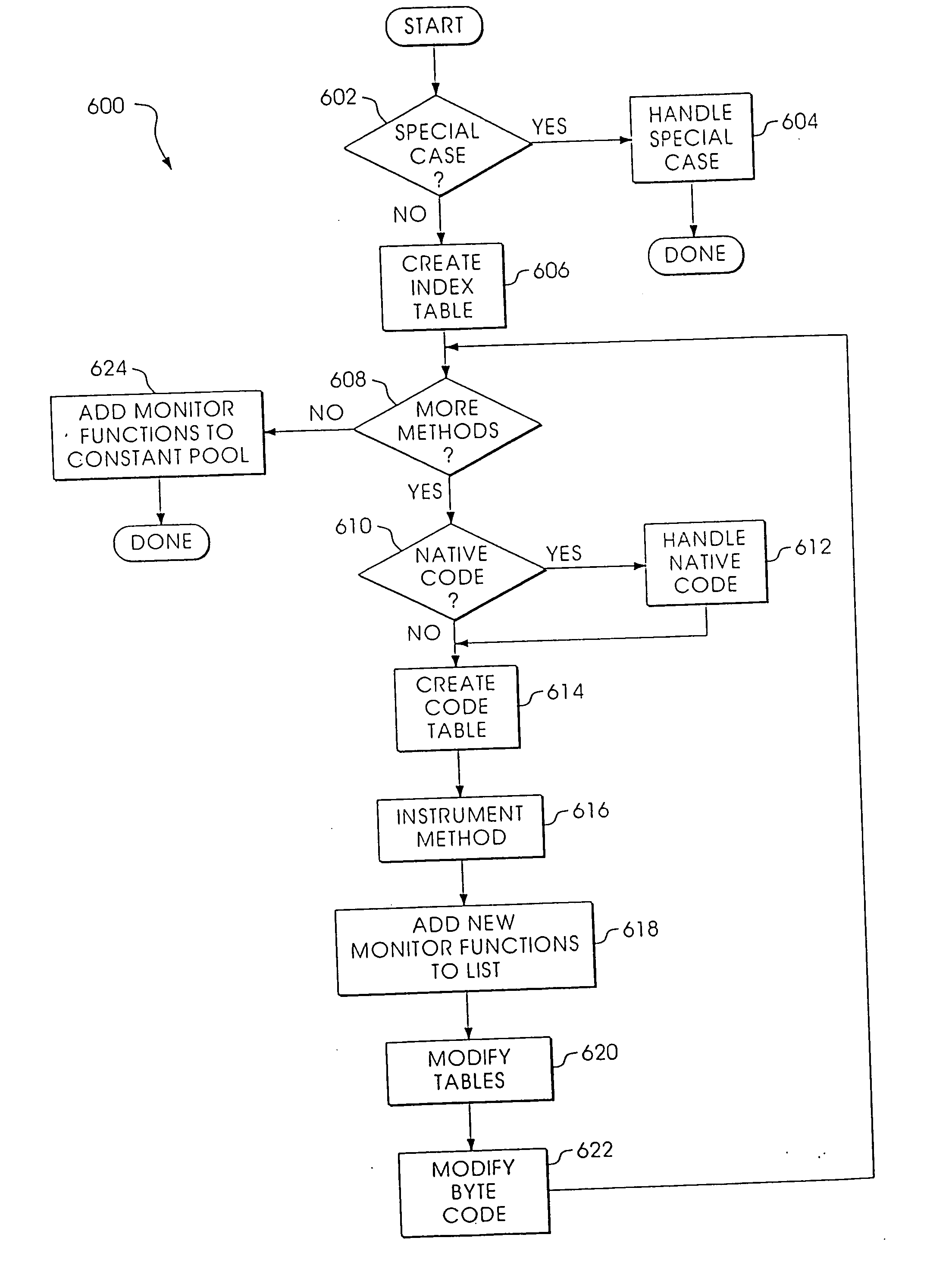
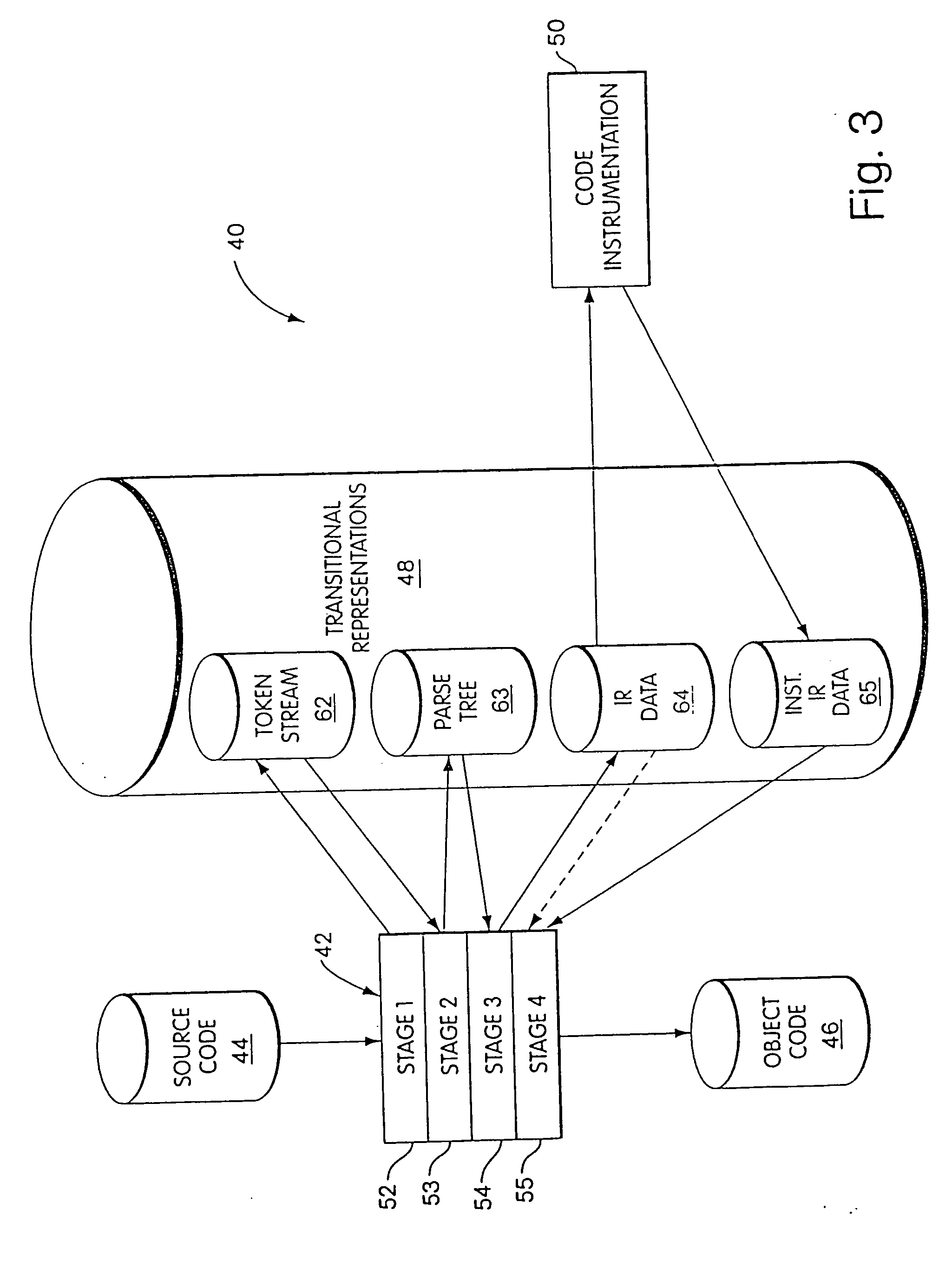
Byte code instrumentation
InactiveUS6314558B1Software testing/debuggingSpecific program execution arrangementsMessage flowTime function
Instrumenting a computer program to provide instrumented byte code includes examining the byte code, selecting portions of the byte code for instrumentation, and instrumenting the portions to provide instrumented byte code. Selecting the portions may include choosing portions of the byte code corresponding to method entry, method exit, a throw, a method call, or a new line number. Instrumenting a portion of the byte code corresponding to a method call may include instrumenting a local line number of source code corresponding to the byte code being instrumented. Instrumenting the portions may include adding calls to instrumentation runtime functions that pass parameters indicative of the portions being instrumented. At least one of the parameters that is passed may include a line number of the source code corresponding to the portion being instrumented or a object pointer for the method corresponding to the portion being instrumented. Data from instrumentation may be passed via a message stream that is viewed as the data is being generated and / or stored.
Owner:BORLAND
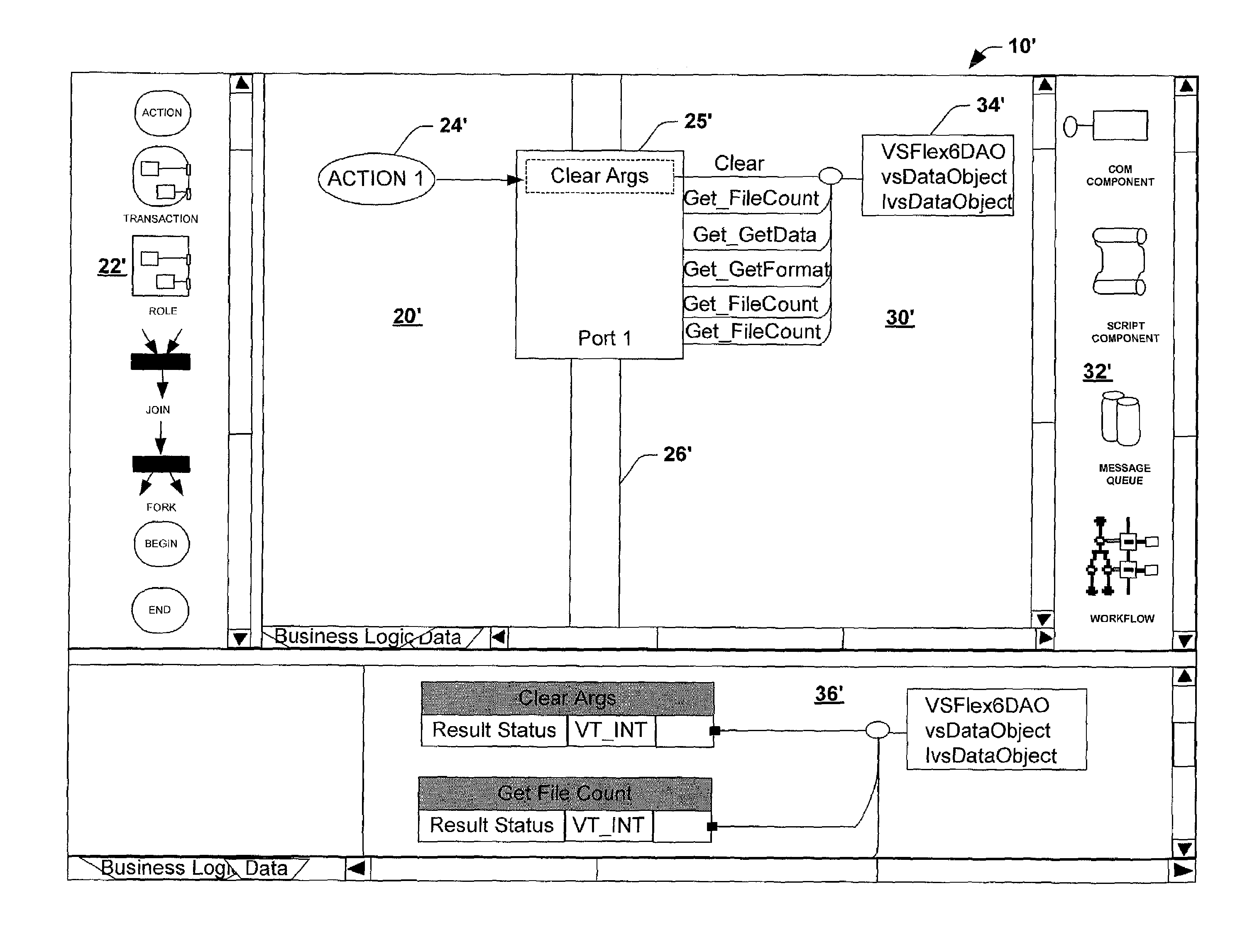
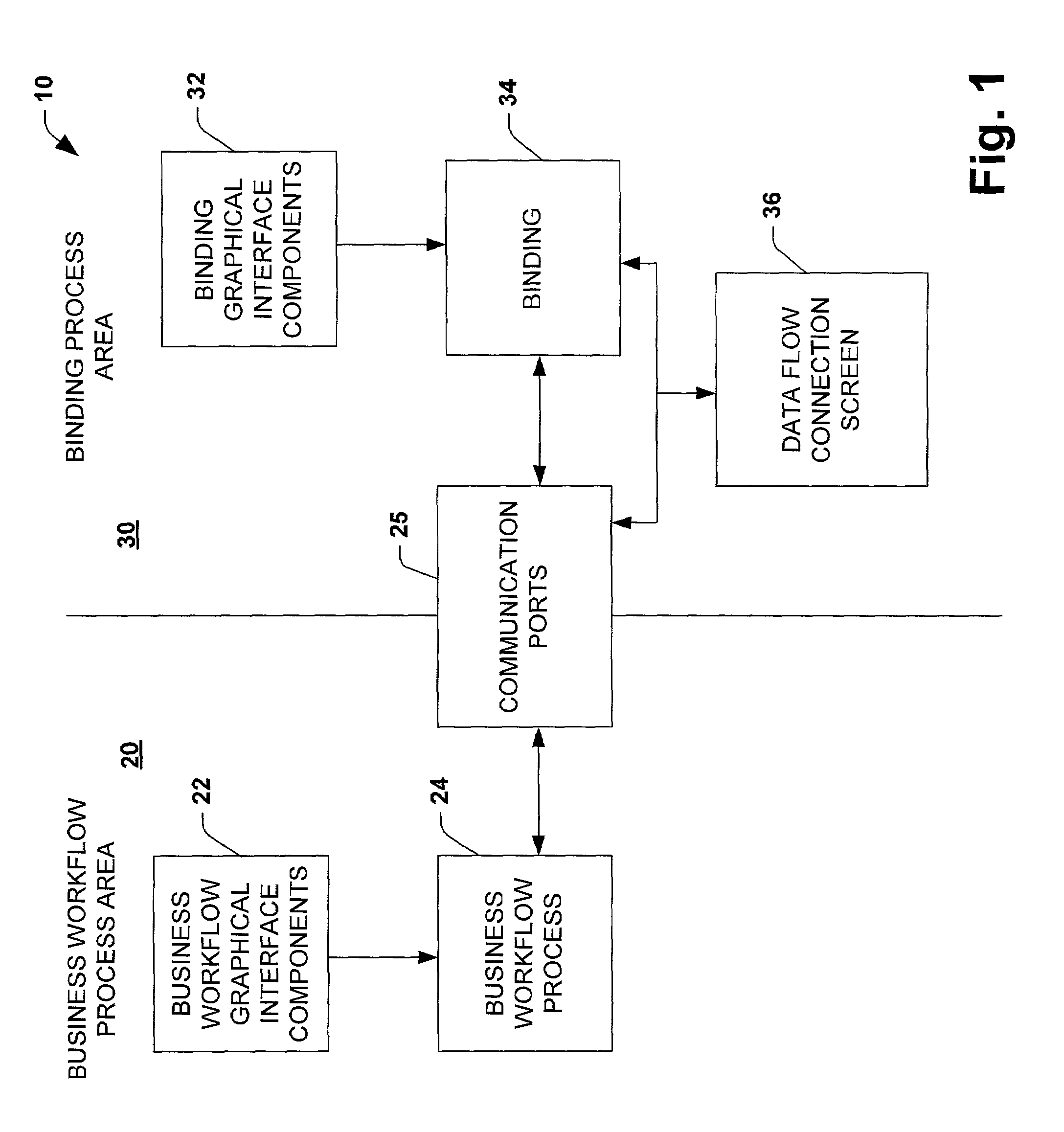
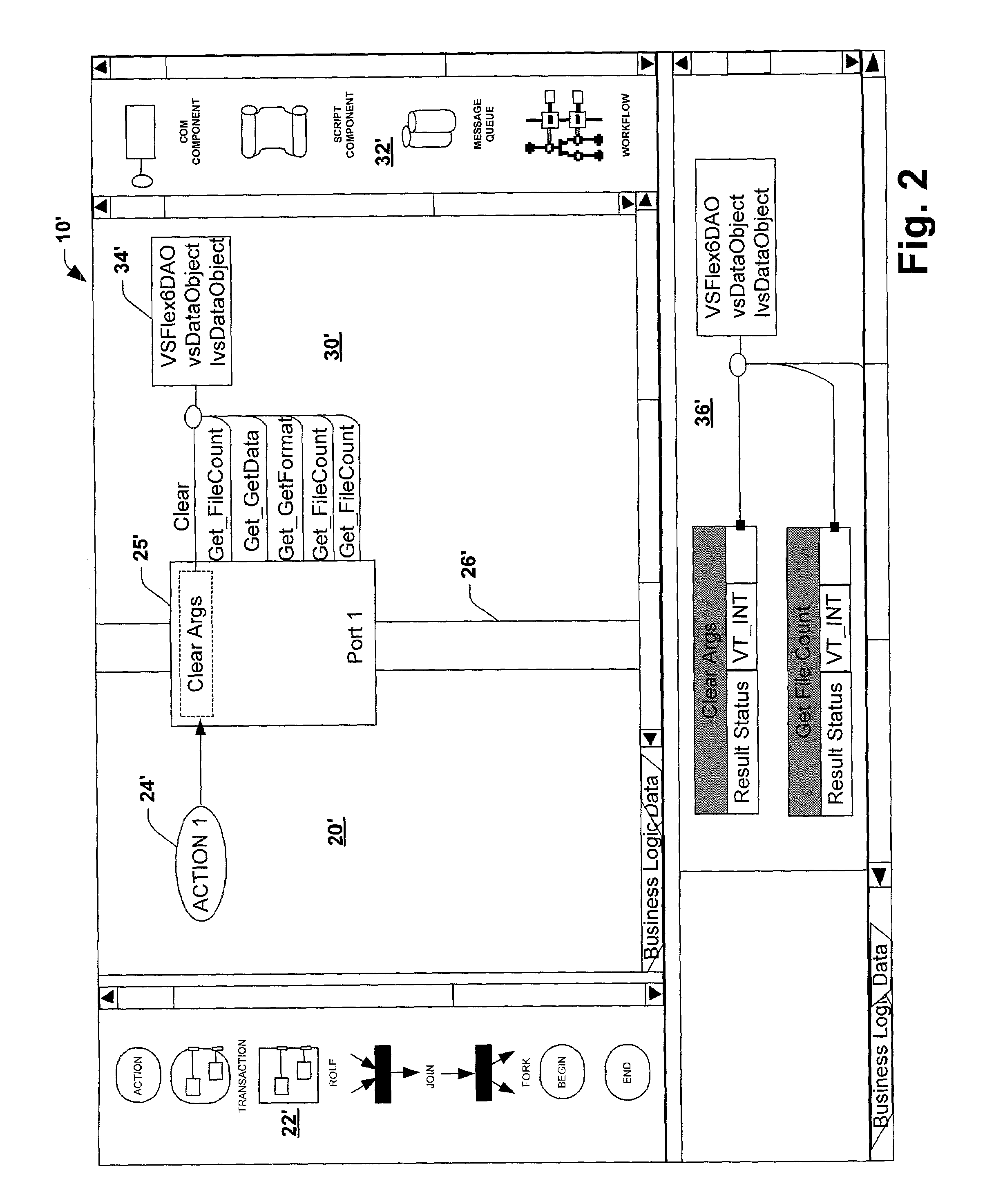
System and method utilizing a graphical user interface of a business process workflow scheduling program
InactiveUS7184967B1Promote modelOffice automationProgramme total factory controlSoftware engineeringBusiness process
A graphical user interface (GUI) scheduler program is provided for modeling business workflow processes. The GUI scheduler program includes tools to allow a user to create a schedule for business workflow processes based on a set of rules defined by the GUI scheduler program. The rules facilitate deadlock not occurring within the schedule. The program provides tools for creating and defining message flows between entities. Additionally, the program provides tools that allow a user to define a binding between the schedule and components, such as COM components, script components, message queues and other workflow schedules. The scheduler program allows a user to define actions and group actions into transactions using simple GUI scheduling tools. The schedule can then be converted to executable code in a variety of forms such as XML, C, C+ and C++. The executable code can then be converted or interpreted for running the schedule.
Owner:MICROSOFT TECH LICENSING LLC
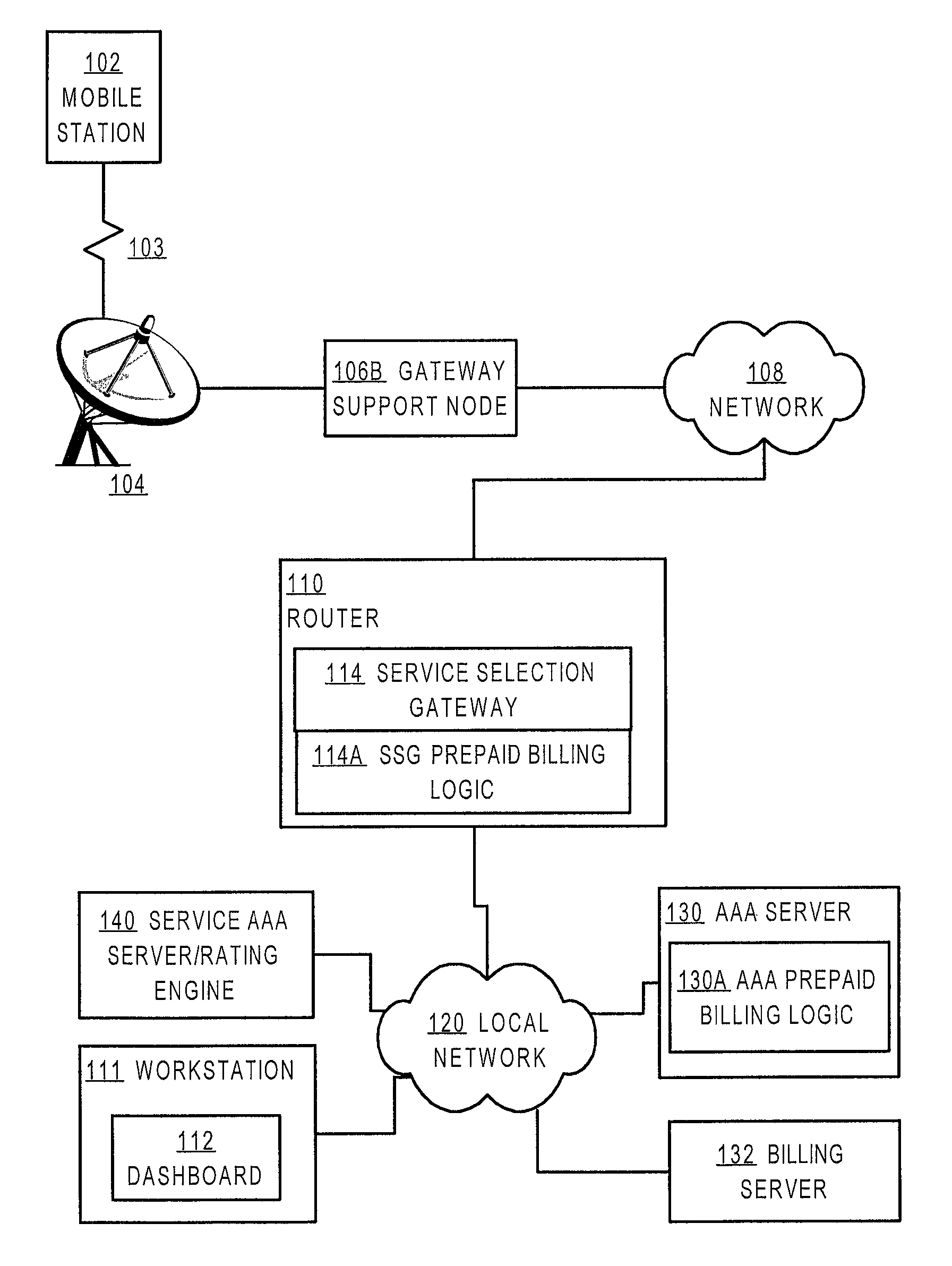
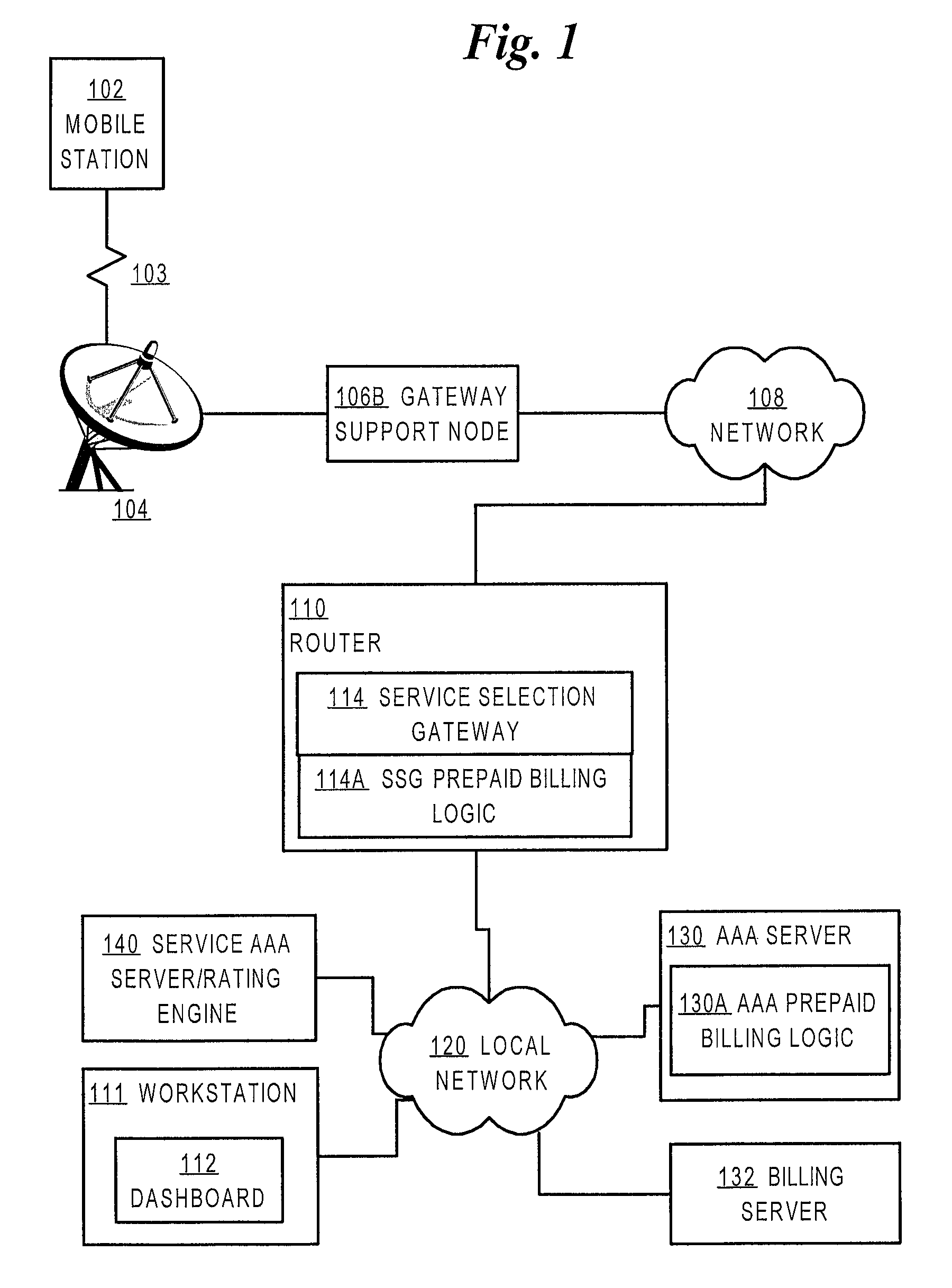
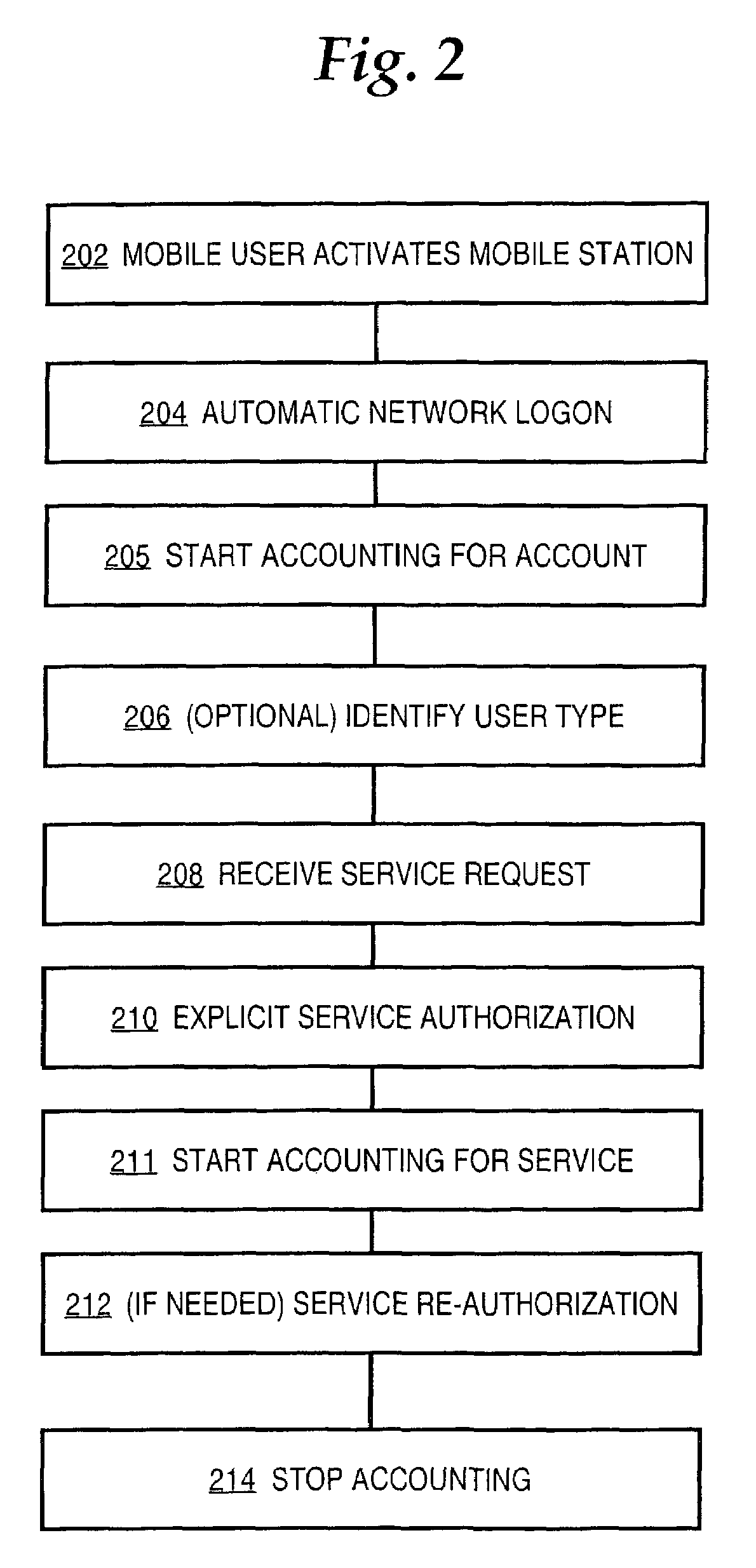
Method and apparatus providing prepaid billing for network services using explicit service authorization in an access server
ActiveUS7720960B2Complete banking machinesAccounting/billing servicesNetwork terminationTraffic capacity
A method is disclosed for authorizing a prepaid network service in a data network. A network end station issues a request for a prepaid network service. At a network node, such as a router serving as a gateway for selecting services, a determination is made about whether a user associated with the end station is authorized to access the prepaid network service. Network traffic from the end station is forwarded to a service provider only when the user is authorized to use the prepaid network service. Specific embodiments provide message flows among a mobile station, gateway support node, router, and authentication server that support providing prepaid services in a packet-switched network for mobile communication. In certain embodiments, a connection is held open for an end station while a prepaid quota value is refreshed at a portal, thereby reducing overhead and precluding the need to repeat user logon steps. Further, unused quota amounts can be returned to the authentication server for use in association with multiple concurrent connections of the same device.
Owner:CISCO TECH INC
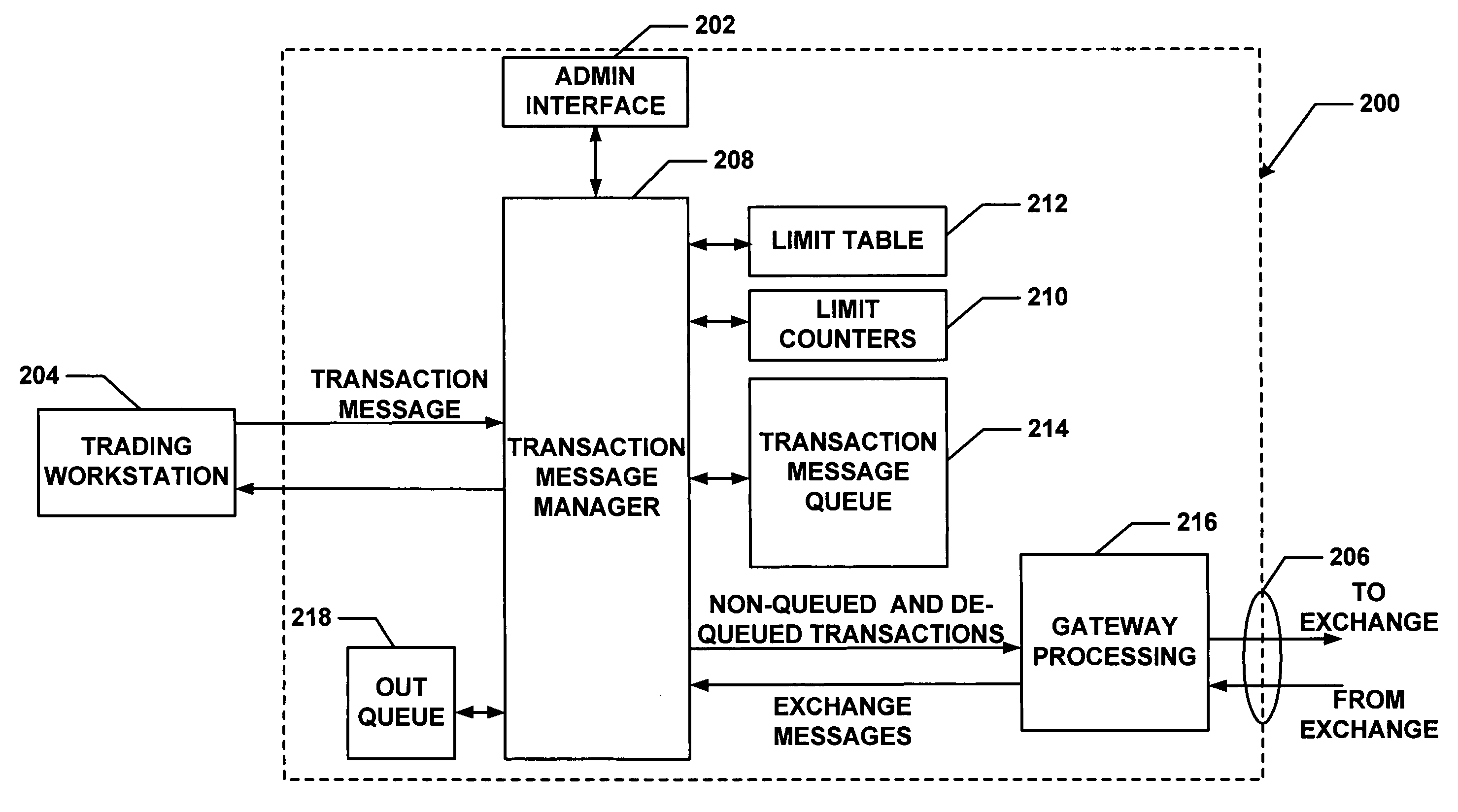
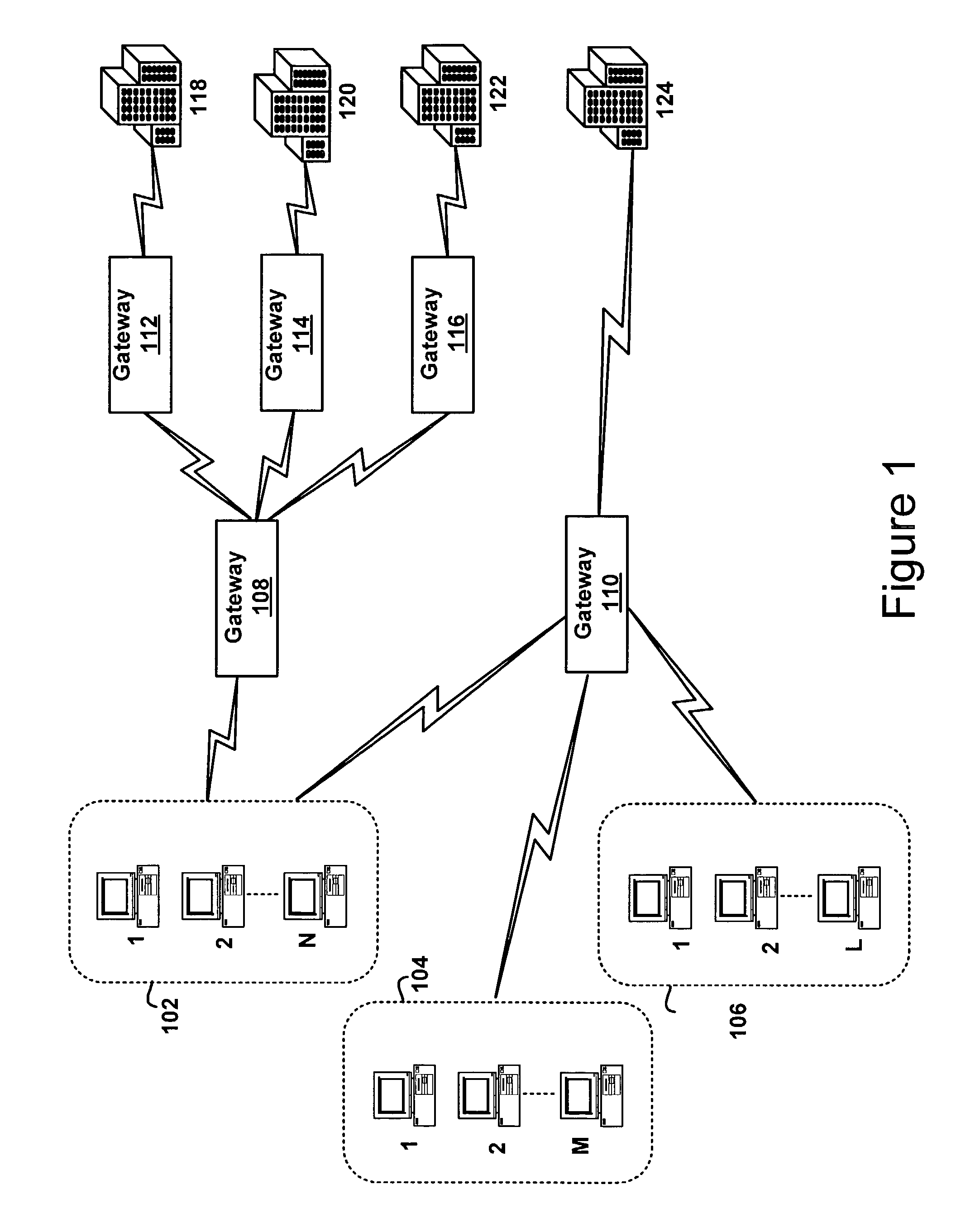
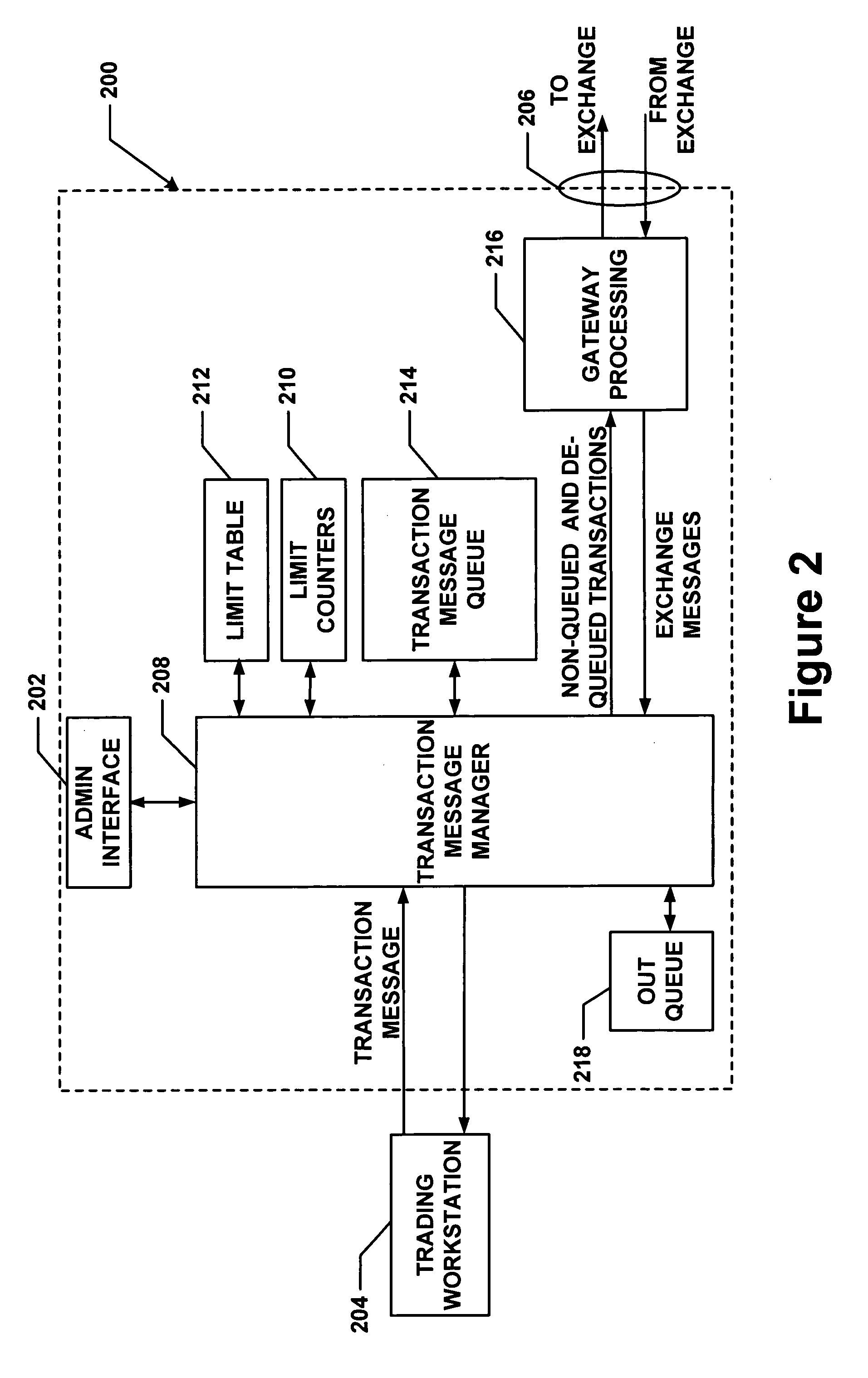
Method and apparatus for message flow and transaction queue management
Management of transaction message flow utilizing a transaction message queue. The system and method are for use in financial transaction messaging systems. The system is designed to enable an administrator to monitor, distribute, control and receive alerts on the use and status of limited network and exchange resources. Users are grouped in a hierarchical manner, preferably including user level and group level, as well as possible additional levels such as account, tradable object, membership, and gateway levels. The message thresholds may be specified for each level to ensure that transmission of a given transaction does not exceed the number of messages permitted for the user, group, account, etc.
Owner:TRADING TECH INT INC
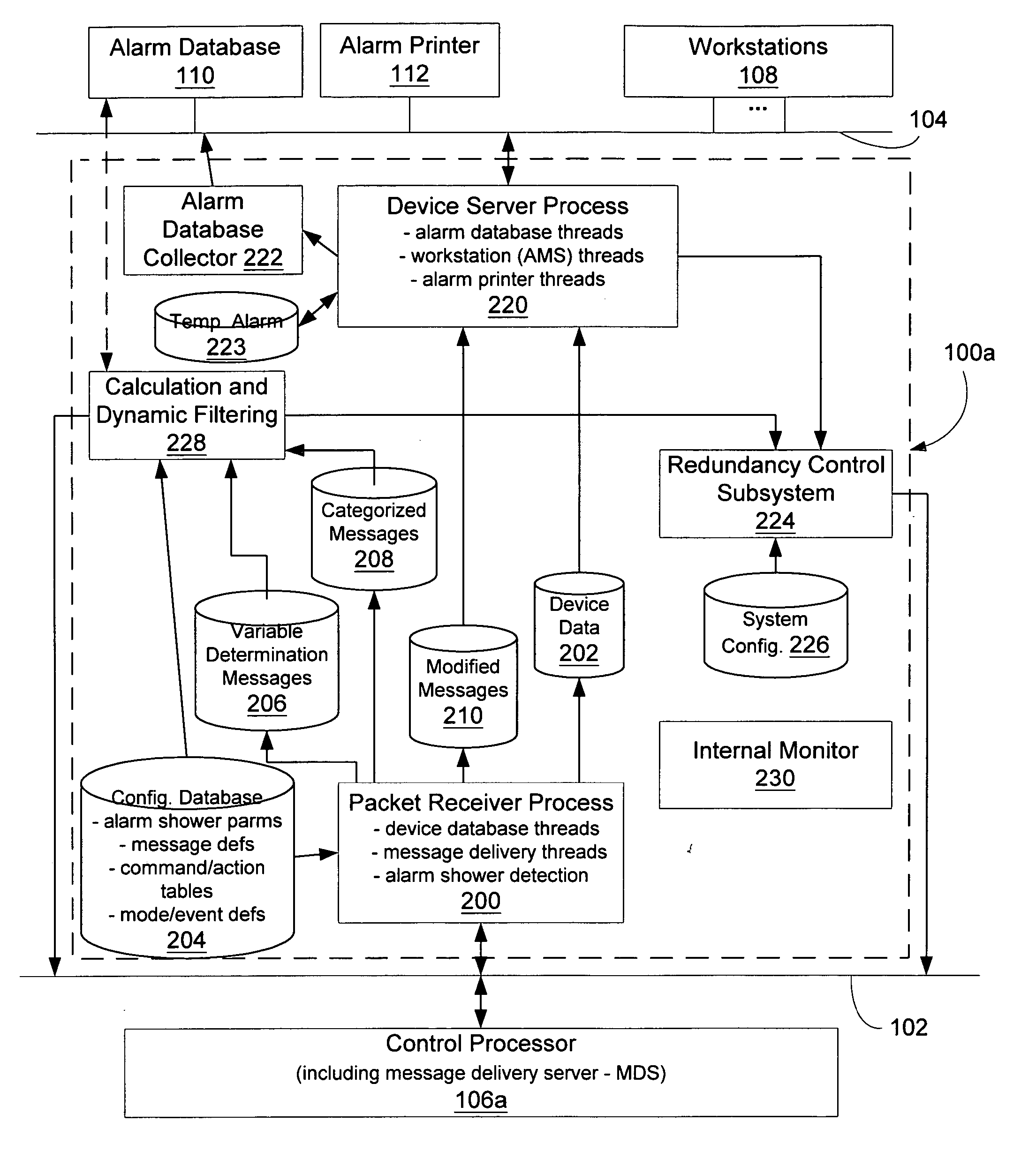
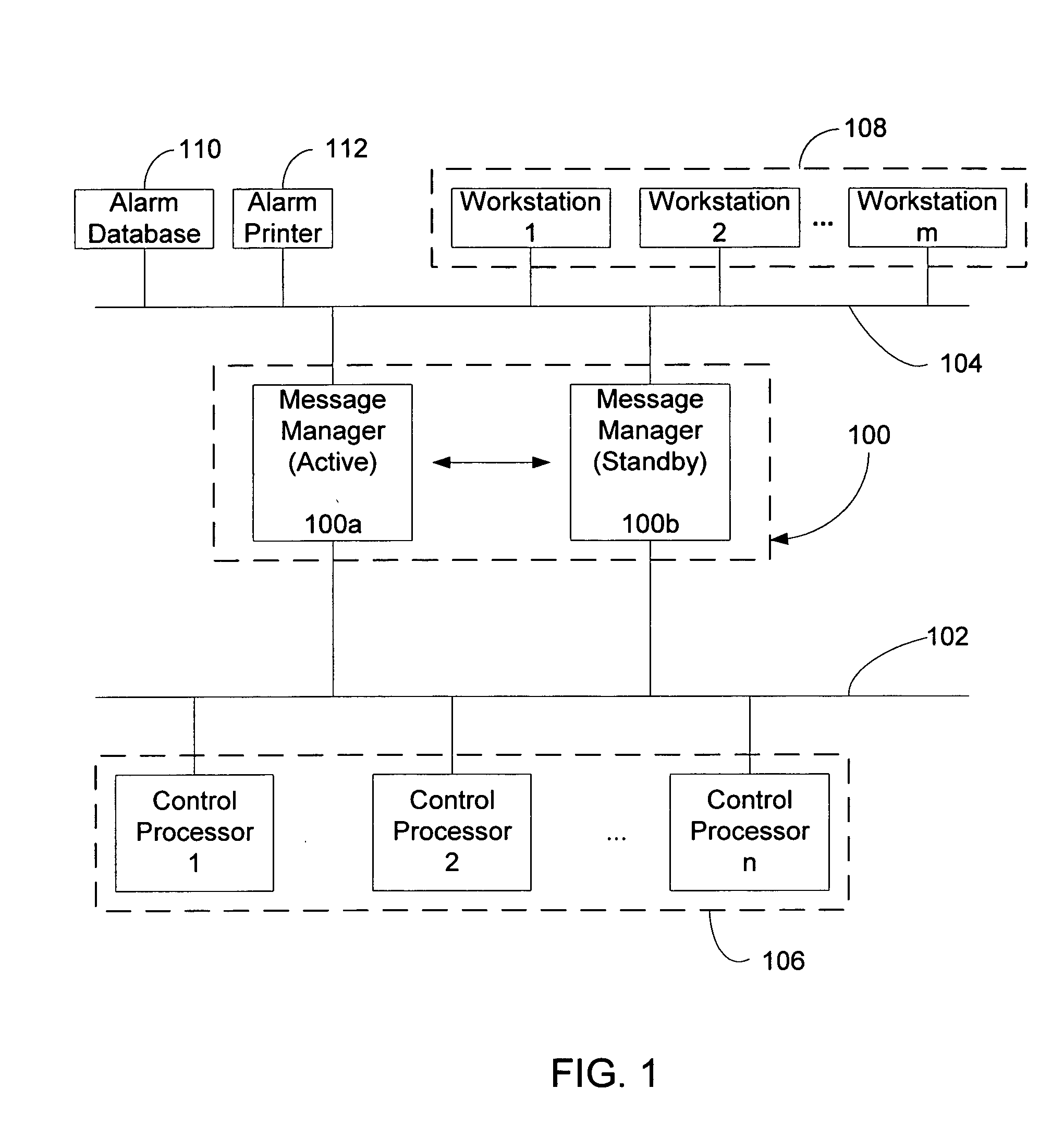
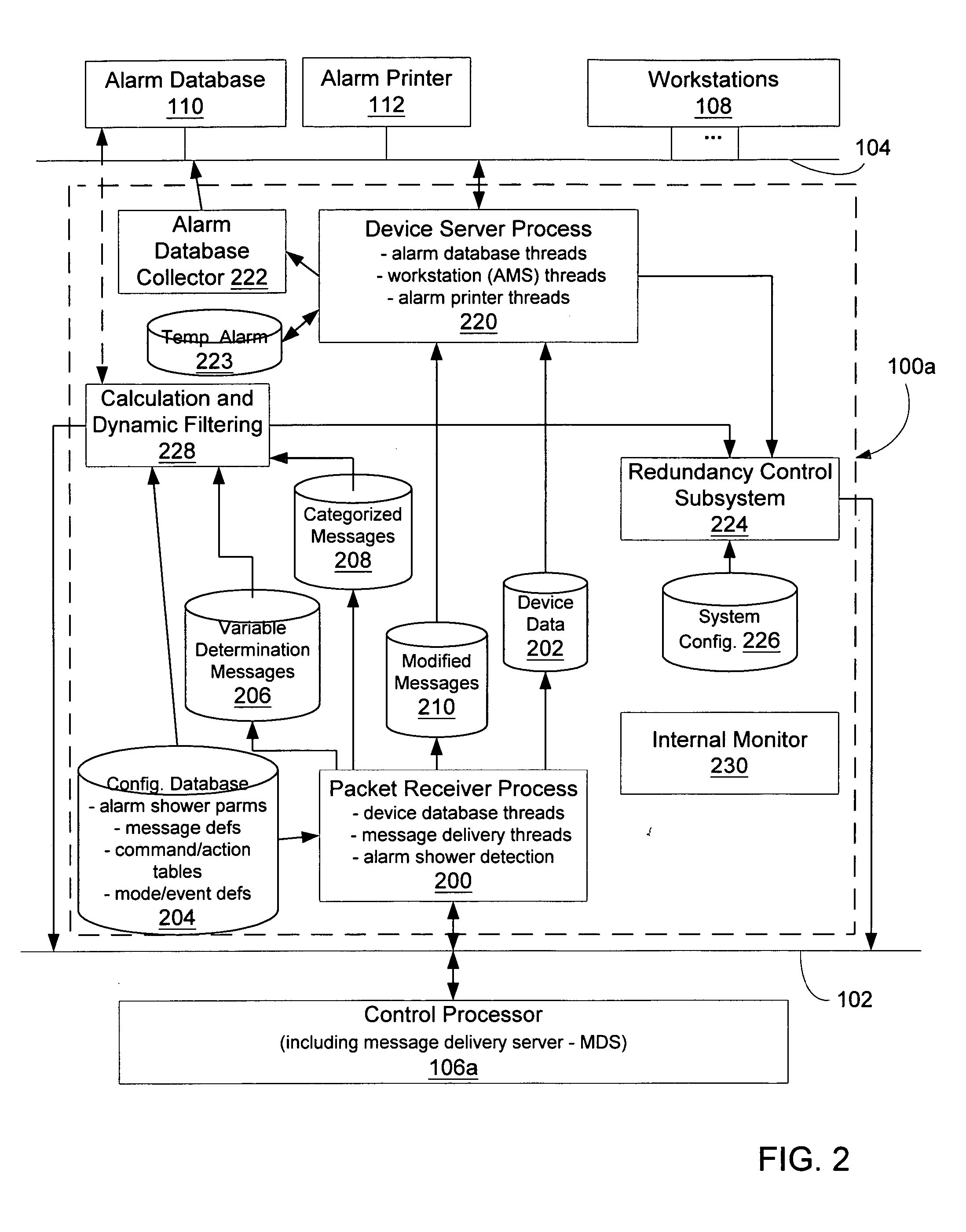
Message management facility for an industrial process control environment
InactiveUS20060168013A1Easy to implementProgramme controlTesting/monitoring control systemsAlarm messageProcess control network
A message management facility is described herein that is hosted by a networked node, in a process control network environment, that is separate from a control processor. The message management facility routes a stream of messages received from the control processor to a set of destinations on a supervisory network. By interposing the message management facility on a node that is interposed, in a message steam, between alarm message sources (control processors) and alarm message sinks (workstations, printers, historians), a number of additional functions can be implemented to carry out a number of advanced functions. Examples of such functions include: table-based routing of a single alarm to a number of destinations on an application network, suppressing alarm showers by applying a criterion to received messages when shower conditions have been sensed, invoking commands based upon a configured category assigned to particular identified messages prior to delivery of the message to its final destination, and invoking actions in response to event / mode status changes (including re-prioritizing alarms).
Owner:INVENSYS SYST INC
Multiradio control incorporating quality of service
InactiveUS20080291830A1Error preventionFrequency-division multiplex detailsQuality of serviceMessage flow
A system for managing the operation of one or more of wireless communication mediums supported by one or more radio modules integrated within a WCD. A control strategy may be employed to evaluate and manage pending communication activity down to the wireless message stream level through the creation of operational schedules. The operational schedules may be utilized by the one or more radio modules in the WCD in order to determine how resource usage should be allocated for supporting the communication activities conducted over a radio module.
Owner:NOKIA CORP
Coordinating persistent status information with multiple file servers
InactiveUS6119244APrevent mutual attempt at takeoverMemory loss protectionDigital computer detailsMessage flowEngineering
The invention provides a storage system, and a method for operating a storage system, that provides for relatively rapid and reliable takeover among a plurality of independent file servers. Each file server maintains a reliable communication path to the others. Each file server maintains its own state in reliable memory. Each file server regularly confirms the state of the other file servers. Each file server labels messages on the redundant communication paths, so as to allow other file servers to combine the redundant communication paths into a single ordered stream of messages. Each file server maintains its own state in its persistent memory and compares that state with the ordered stream of messages, so as to determine whether other file servers have progressed beyond the file server's own last known state. Each file server uses the shared resources (such as magnetic disks) themselves as part of the redundant communication paths, so as to prevent mutual attempts at takeover of resources when each file server believes the other to have failed. Each file server provides a status report to the others when recovering from an error, so as to prevent the possibility of multiple file servers each repeatedly failing and attempting to seize the resources of the others.
Owner:NETWORK APPLIANCE INC
Method for paging a device in a wireless network
InactiveUS7197025B2Avoiding all setup messagingEffective controlPower managementFrequency-division multiplex detailsWireless mesh networkMessage flow
A method for access control in a wireless network having a base station and a plurality of remote hosts includes the optional abilities of making dynamic adjustments of the uplink / downlink transmission ratio, making dynamic adjustments of the total number of reservation minislots, and assigning access priorities by message content type within a single user message stream. The method of the invention further provides for remote wireless host paging and for delayed release of active channels by certain high priority users in order to provide low latency of real-time packets by avoiding the need for repeated channel setup signaling messages. In the preferred embodiment, there are N minislots available for contention in the next uplink frame organized into a plurality of access priority classes. The base station allows m access priority classes. Each remote host of access priority class i randomly picks one contention minislot and transmits an access request, the contention minislot picked being in a range from 1 to Ni where N(i+1)<Ni and N1=N. In an alternate embodiment of a method for access control according to the present invention, each remote host of access priority class i and with a stack level that equals 0, then transmits an access request with a probability Pi where P(i+1)<Pi and P1=1.
Owner:WSOU INVESTMENTS LLC
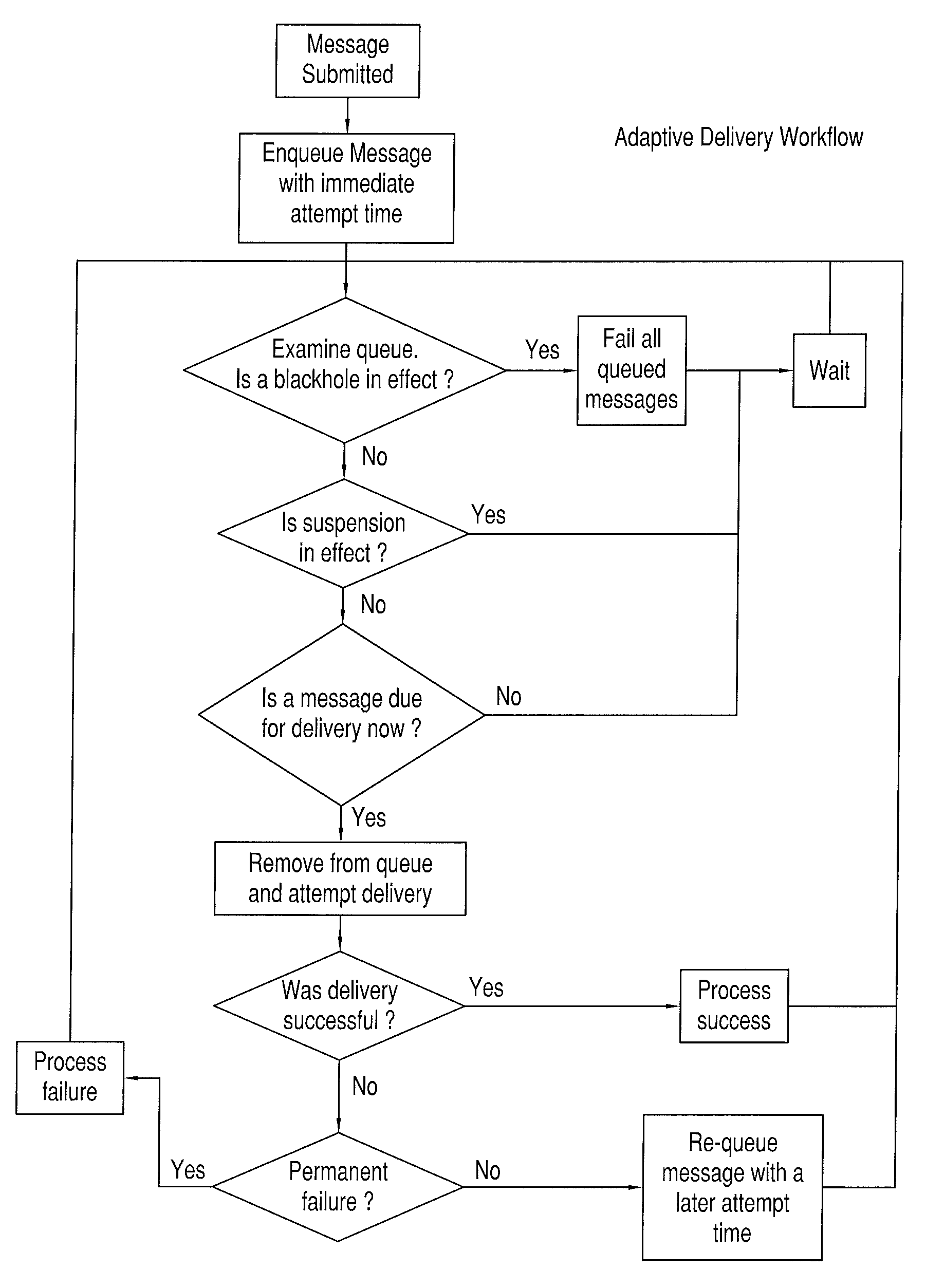
Method and system for adaptive delivery of digital messages
InactiveUS20110289162A1Convenient and flexible and effectiveMultiple digital computer combinationsData switching networksMessage flowMessage delivery
A system and method for automatically adapting digital message traffic flow evaluates message delivery disposition, latency and performance metrics such that the system operates more optimally in terms of both overall throughput as well as with respect to system sending reputation. Reputation is in the context of maintaining message flow within limits that are acceptable for a given destination, such that the sender behavior avoids being flagged as abusive or otherwise undesirable.
Owner:MESSAGE SYSTEMS
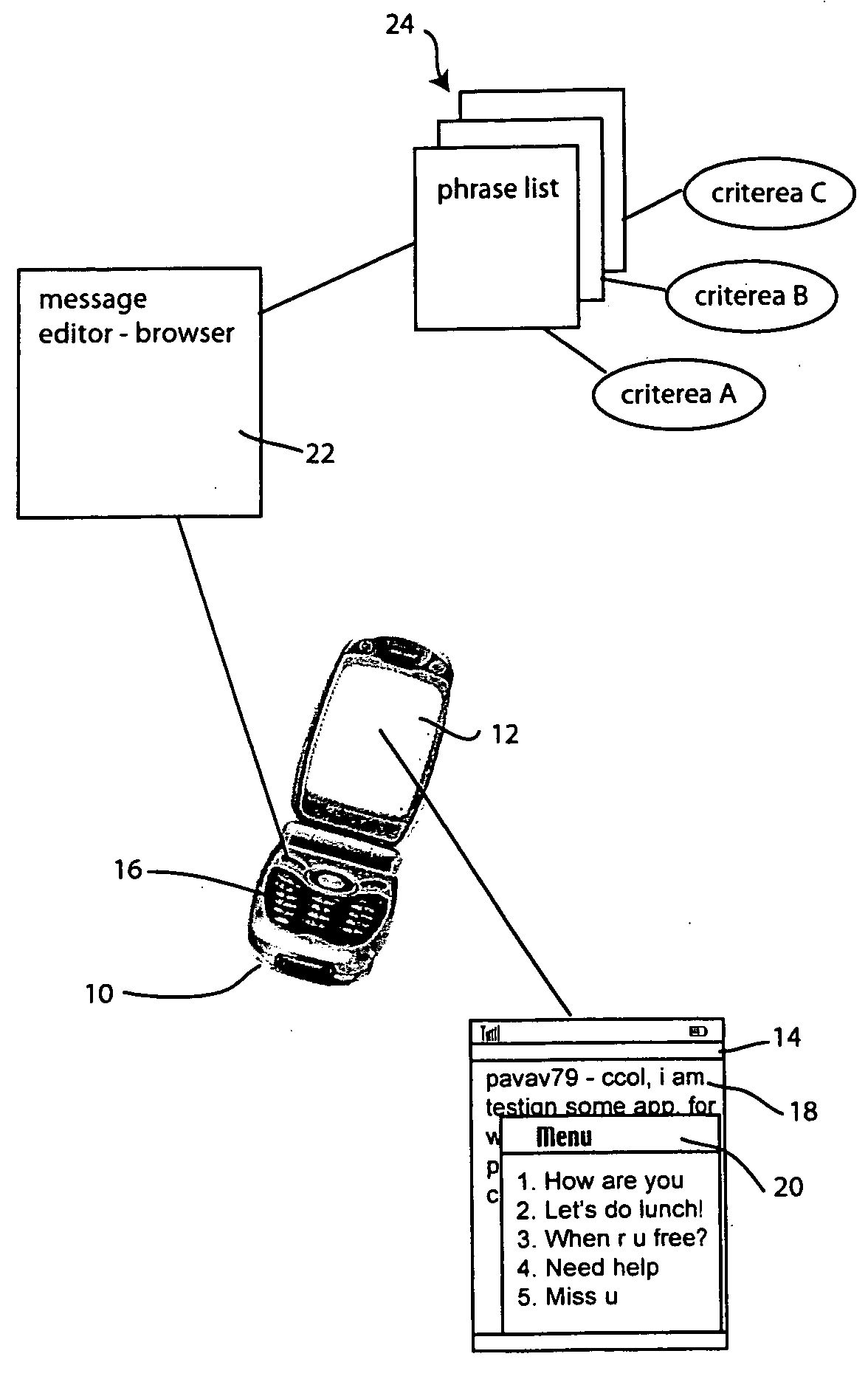
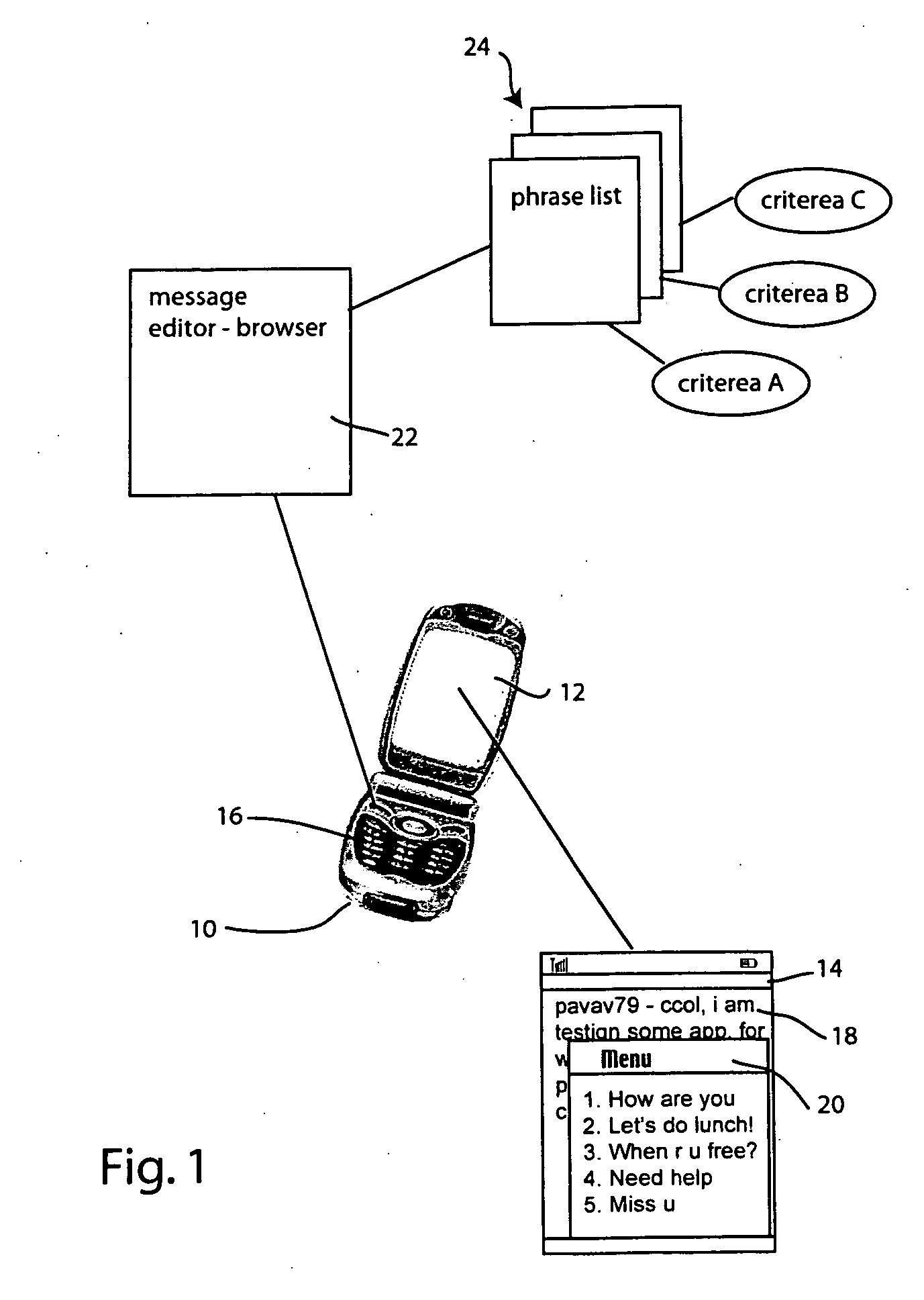
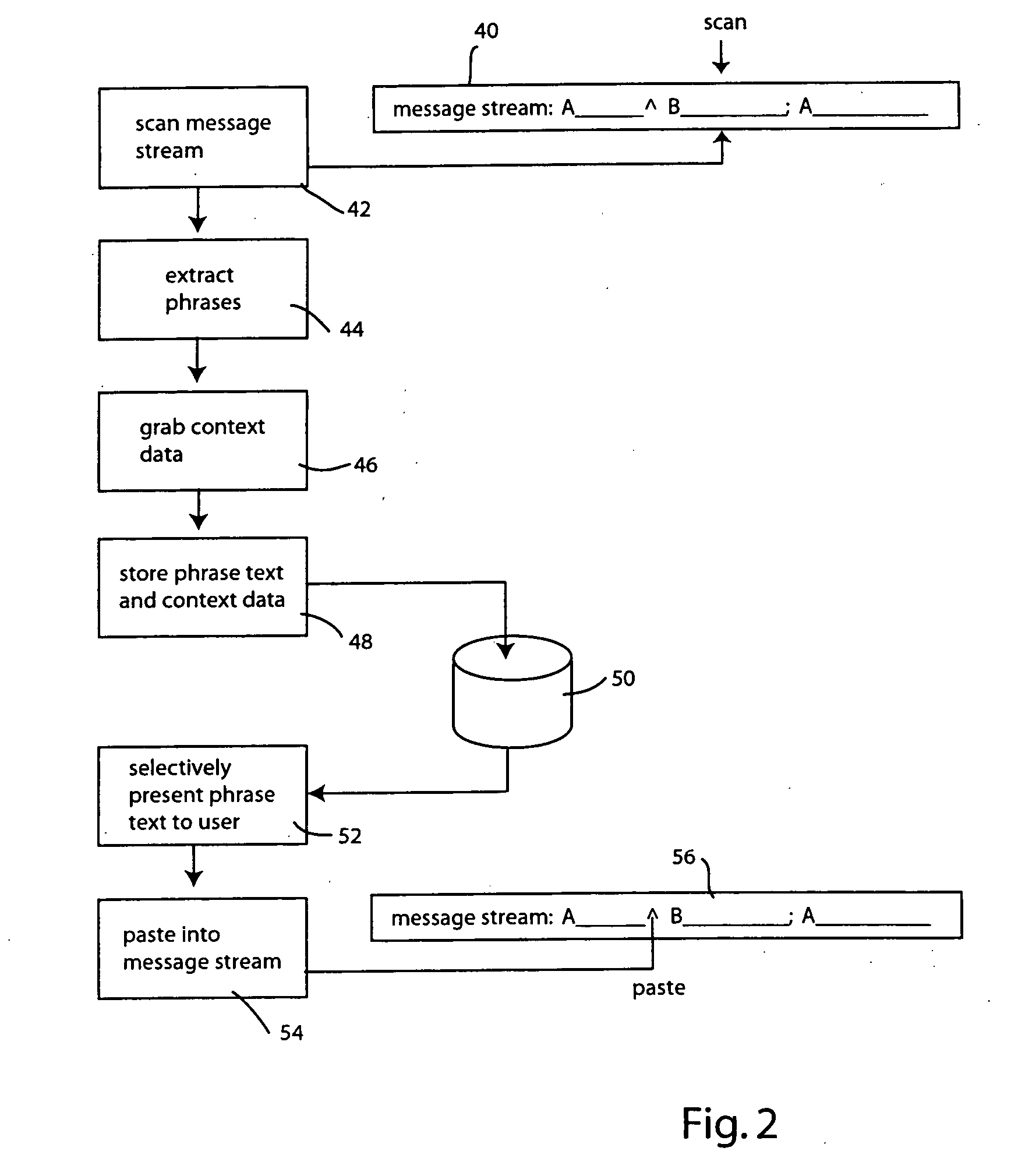
Method for creating and using phrase history for accelerating instant messaging input on mobile devices
Rapid instant messaging input is enabled through a system that displays frequently used or useful message phrases in a pop-up window from which the user may select a desired phrase to be inserted into the message stream. The system allows multiple phrase lists to be utilized and individual phrase messages are tagged with context information, allowing them to be selectively retrieved to provide only the most useful messages for a given context or scenario. The system automatically generates phrase lists by scanning the message stream data within instant messaging log files and the scanned information is then processed to select phrases for inclusion in the phrase list based on predefined heuristics.
Owner:PANASONIC CORP
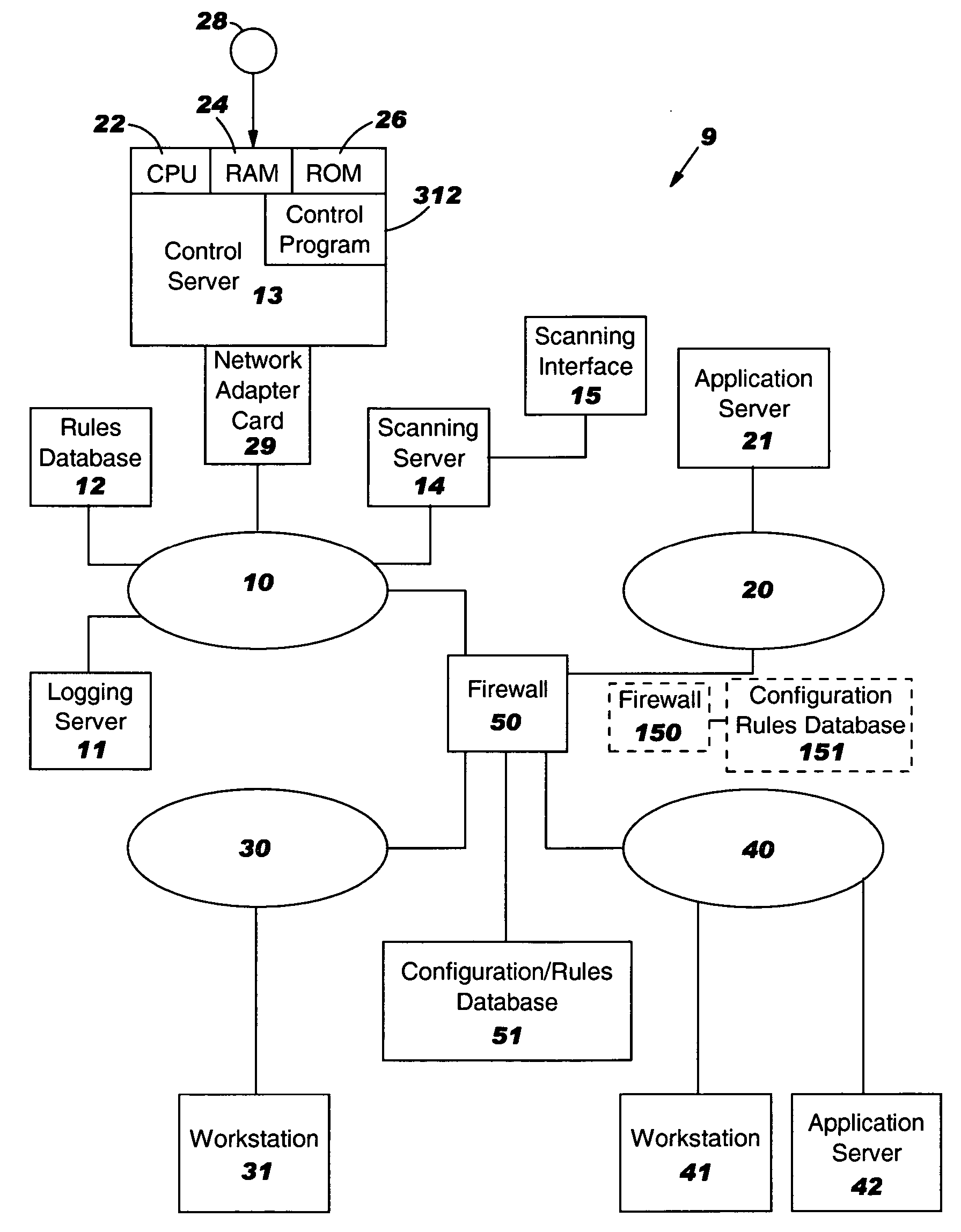
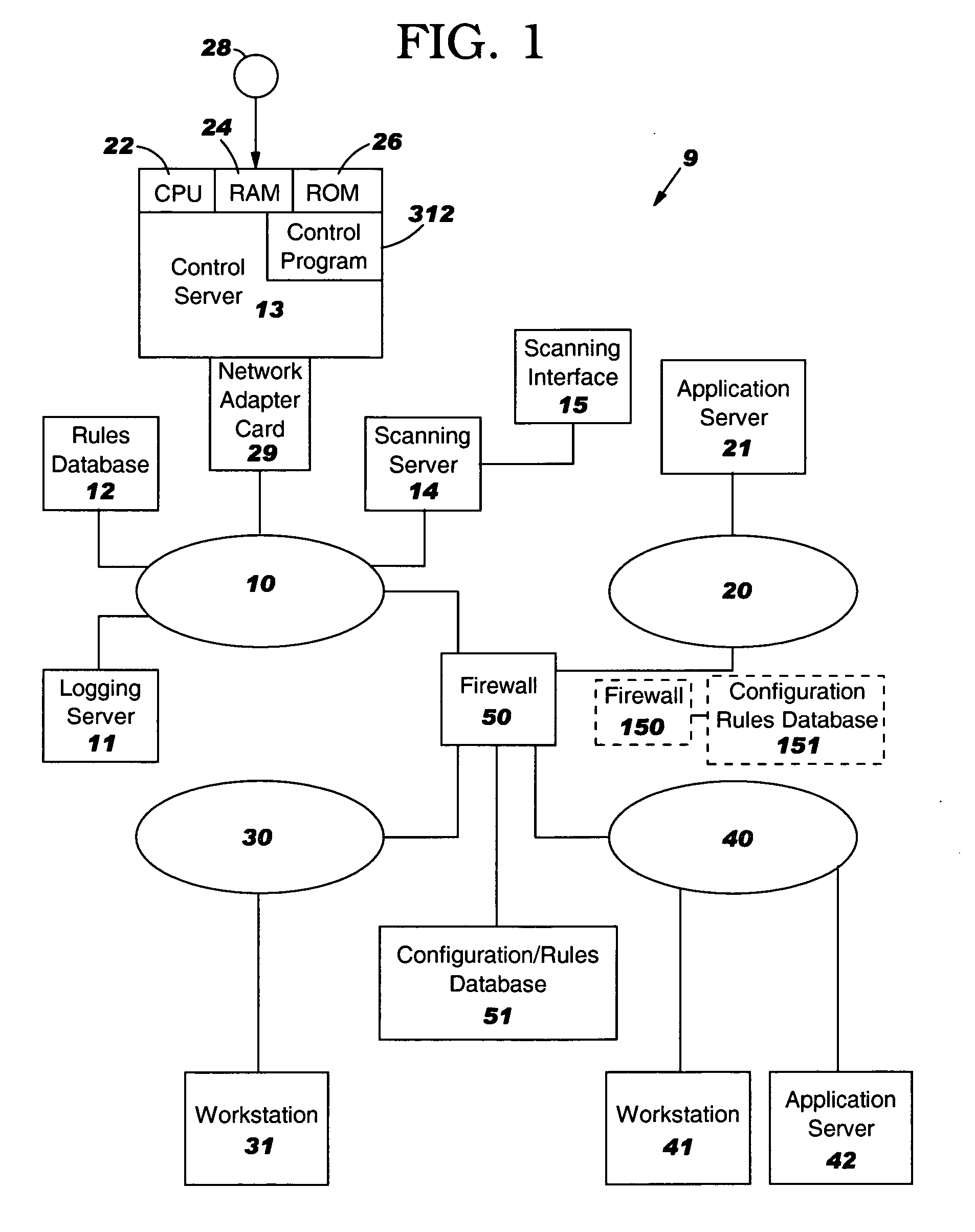
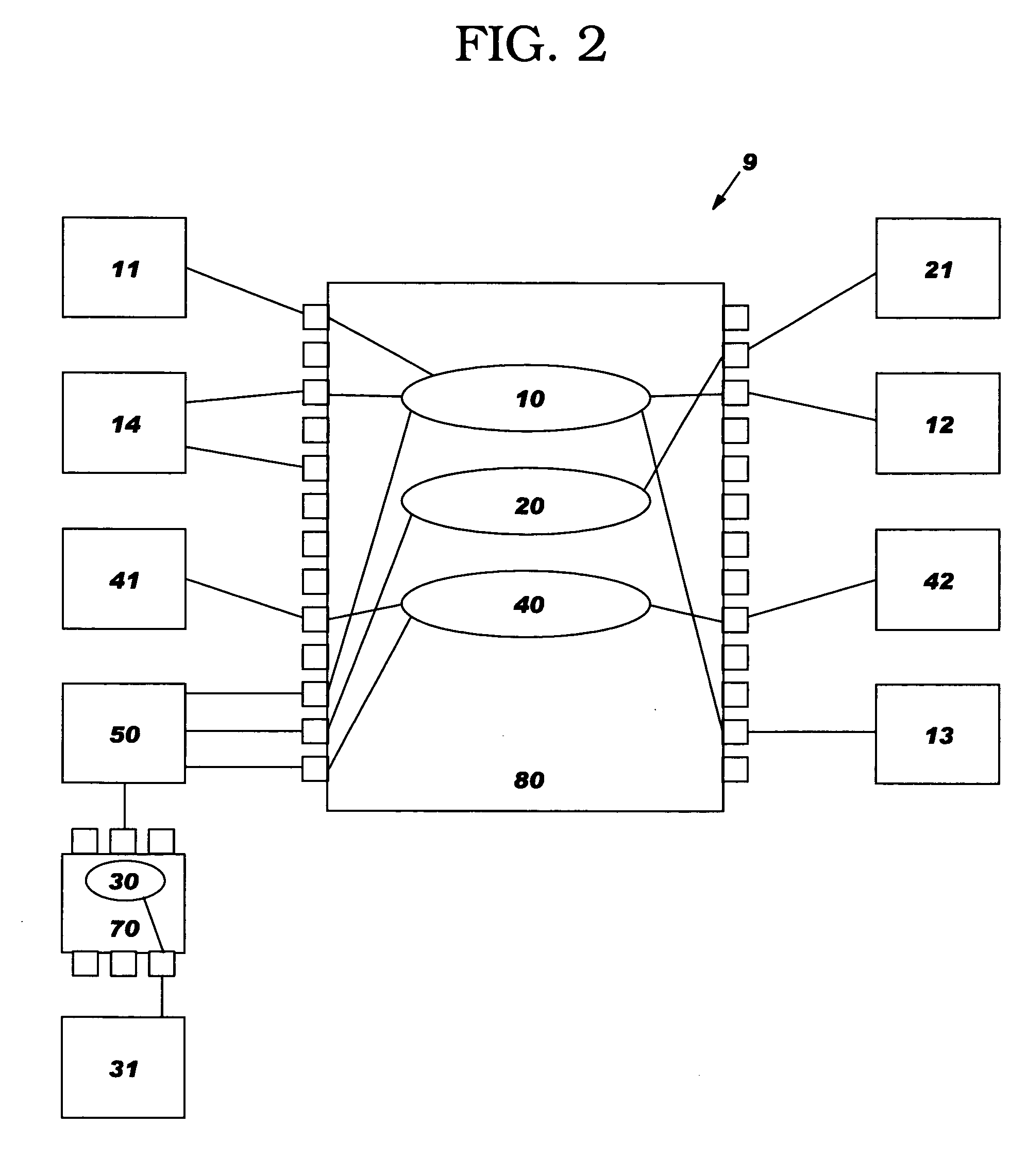
System, method and program product to identify additional firewall rules that may be needed
System, method and program product for managing a security policy of a firewall. The firewall receives a message packet addressed to a specified port of a destination IP address and determines that the firewall does not have a message flow rule which permits passing of the message packet to the port. The port is tested to determine if the port is open. If so, an administrator is queried whether the firewall should have a message flow rule which permits passing of the message packet to the port. If not, an administrator is not queried whether the firewall should have a message flow rule which permits passing of the message packet to the port. There may be first and second firewalls located between the source IP address and destination IP address. Before the port is tested, a central database is checked to learn if the central database has a record of whether the first firewall should have a message flow rule which permits passing of the message packet to the port. If not, and the port is found to be open, the central database is updated to indicate that both the first and second firewalls should have a message flow rule which permits passing of the message packet to the port. Also, the security policy of the first firewall is updated with a message flow rule which permits passing of the message packet to the port. The second firewall is not updated until it encounters a message packet addressed to the port.
Owner:KYNDRYL INC
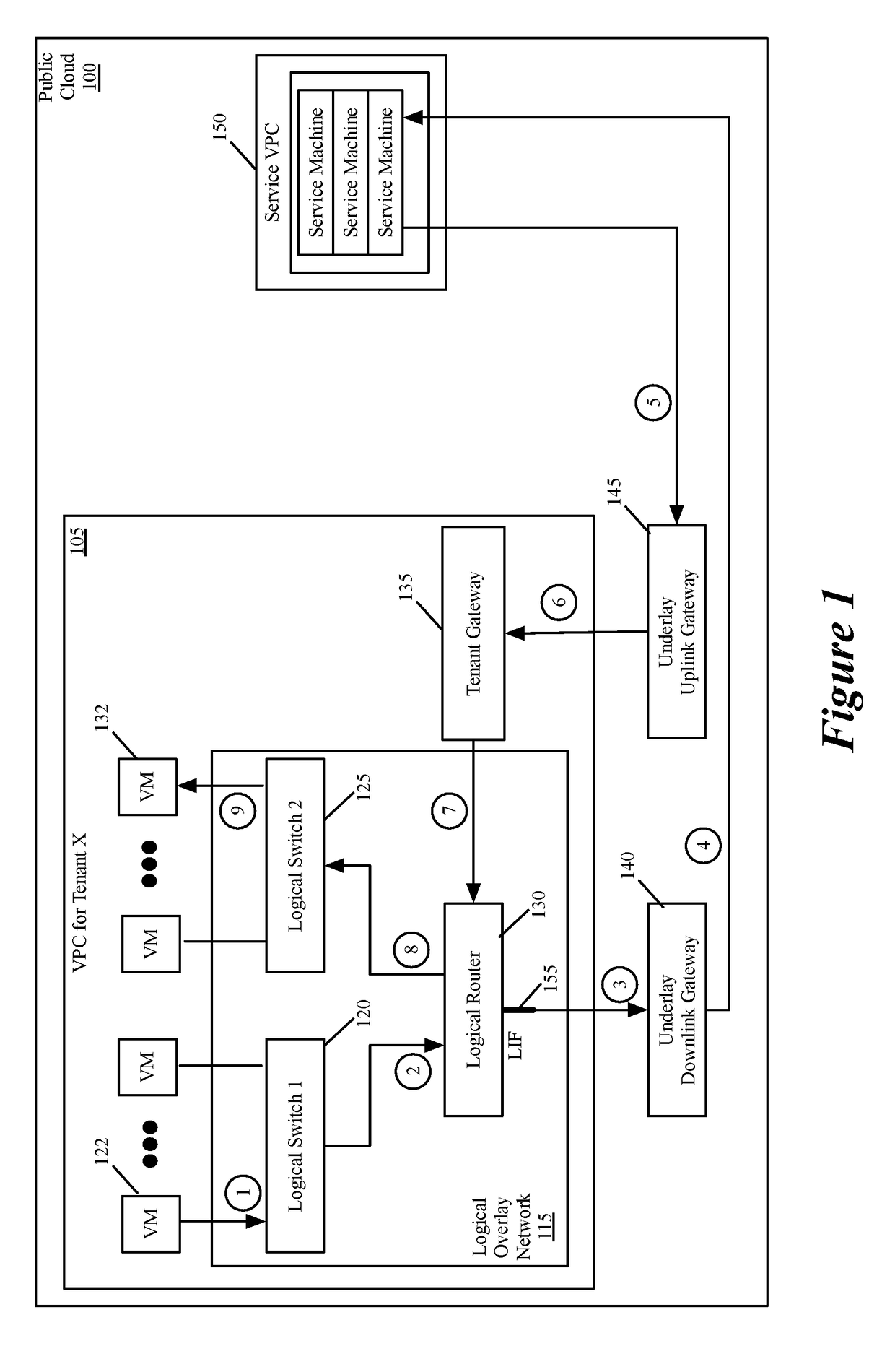
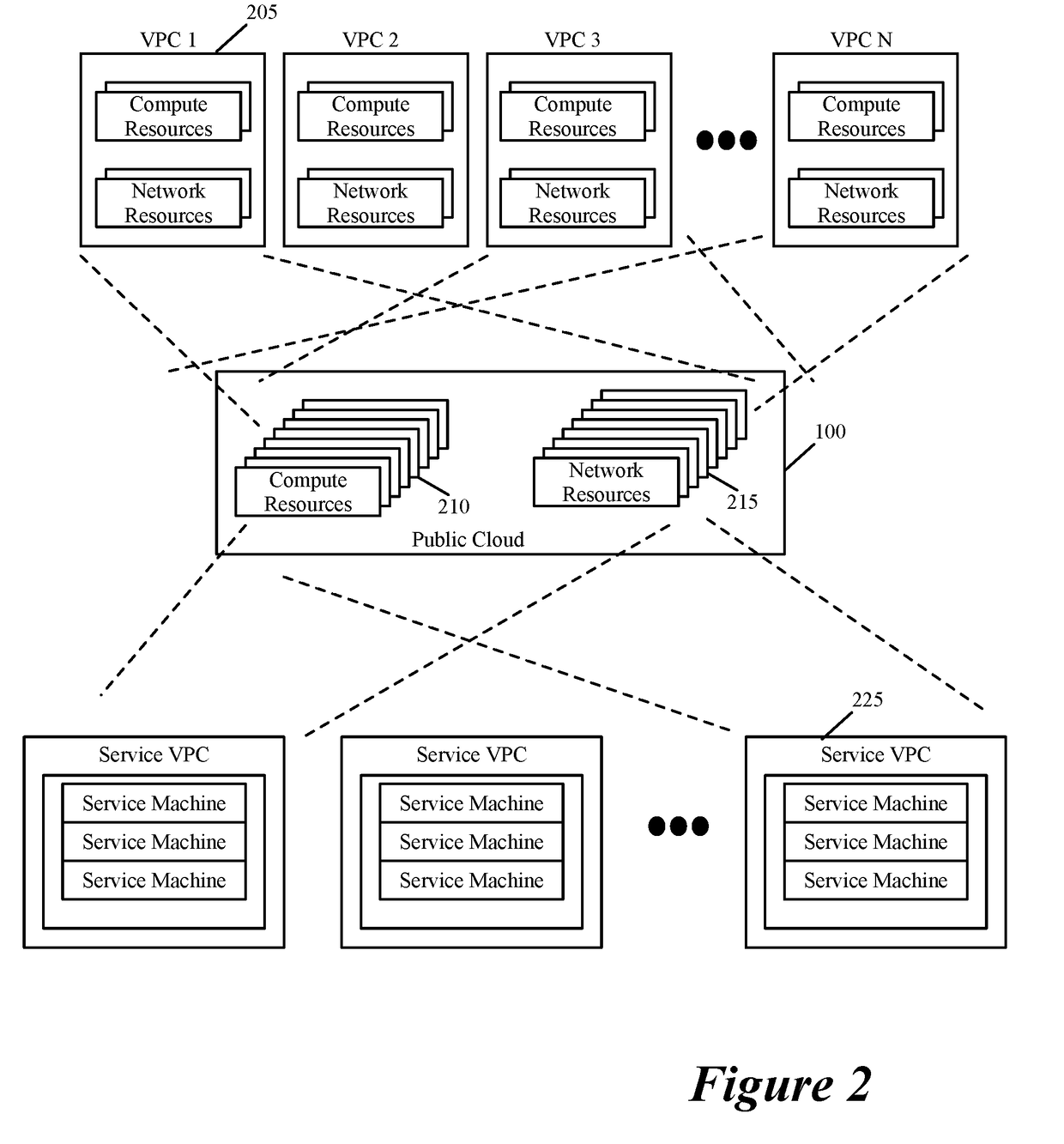
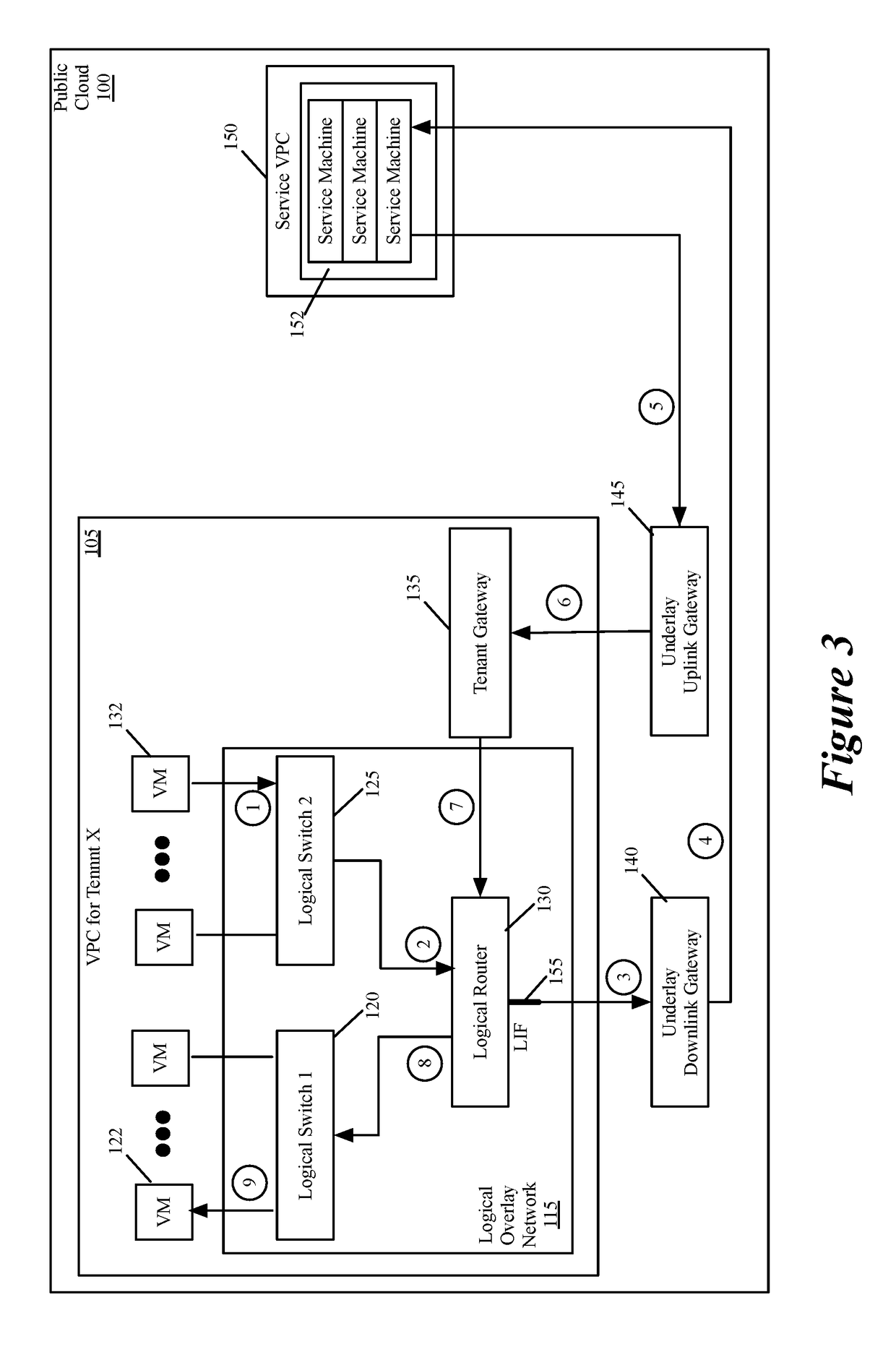
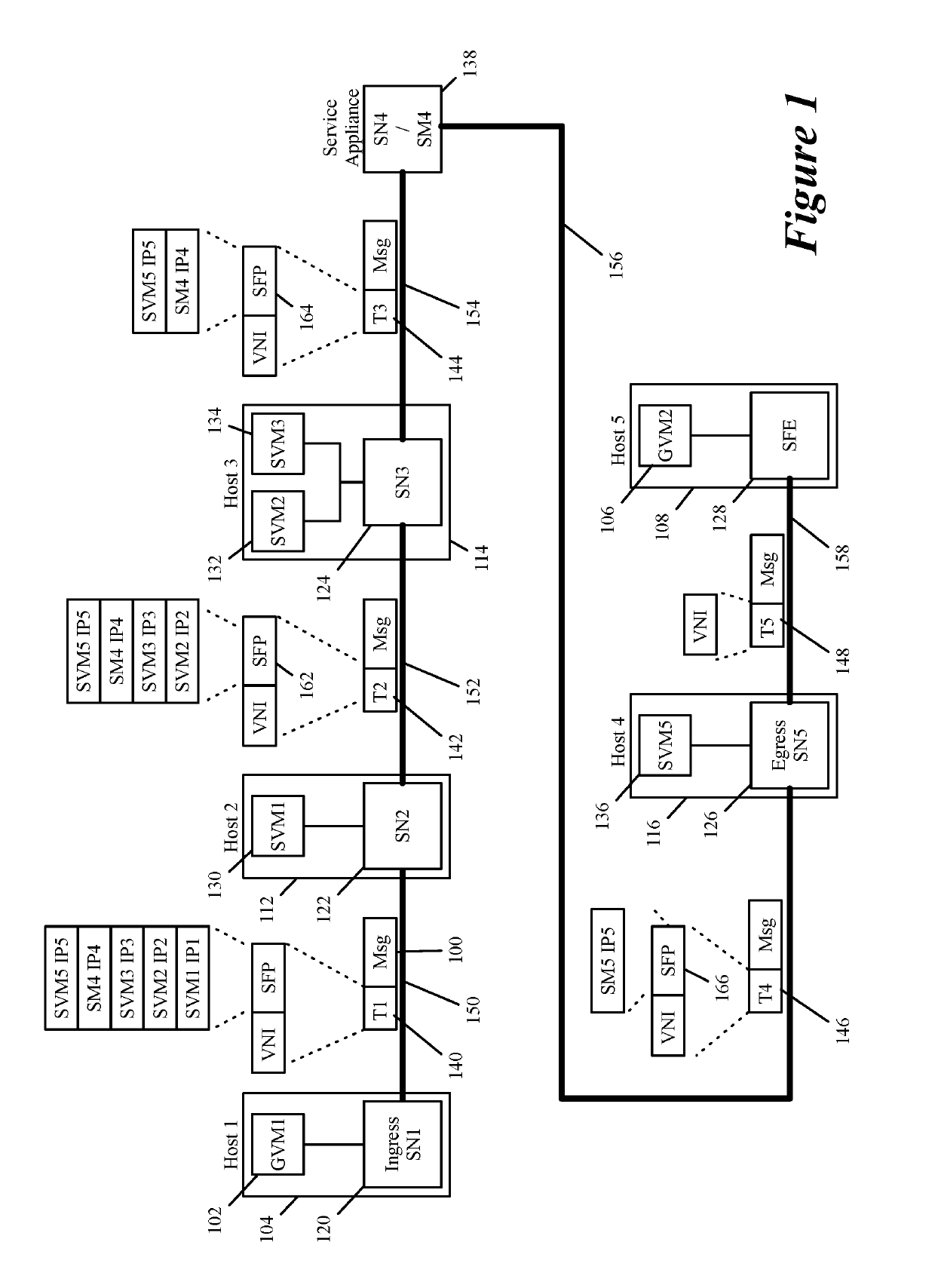
Performing in-line service in public cloud
Some embodiments provide a novel way to insert a service (e.g., a third party service) in the path of a data message flow, between two machines (e.g., two VMs, two containers, etc.) in a public cloud environment. For a particular tenant of the public cloud, some embodiments create an overlay logical network with a logical overlay address space. To perform a service on data messages of a flow between two machines, the logical overlay network passes to the public cloud's underlay network the data messages with their destination address (e.g., destination IP addresses) defined in the logical overlay network. The underlay network (e.g., an underlay default downlink gateway) is configured to pass data messages with such destination addresses (e.g., with logical overlay destination addresses) to a set of one or more service machines. The underlay network (e.g., an underlay default uplink gateway) is also configured to pass to the particular tenant's public cloud gateway the processed data messages that are received from the service machine set and that are addressed to logical overlay destination addresses. The tenant's public cloud gateway is configured to forward such data messages to a logical forwarding element of the logical network, which then handles the forwarding of the data messages to the correct destination machine.
Owner:NICIRA
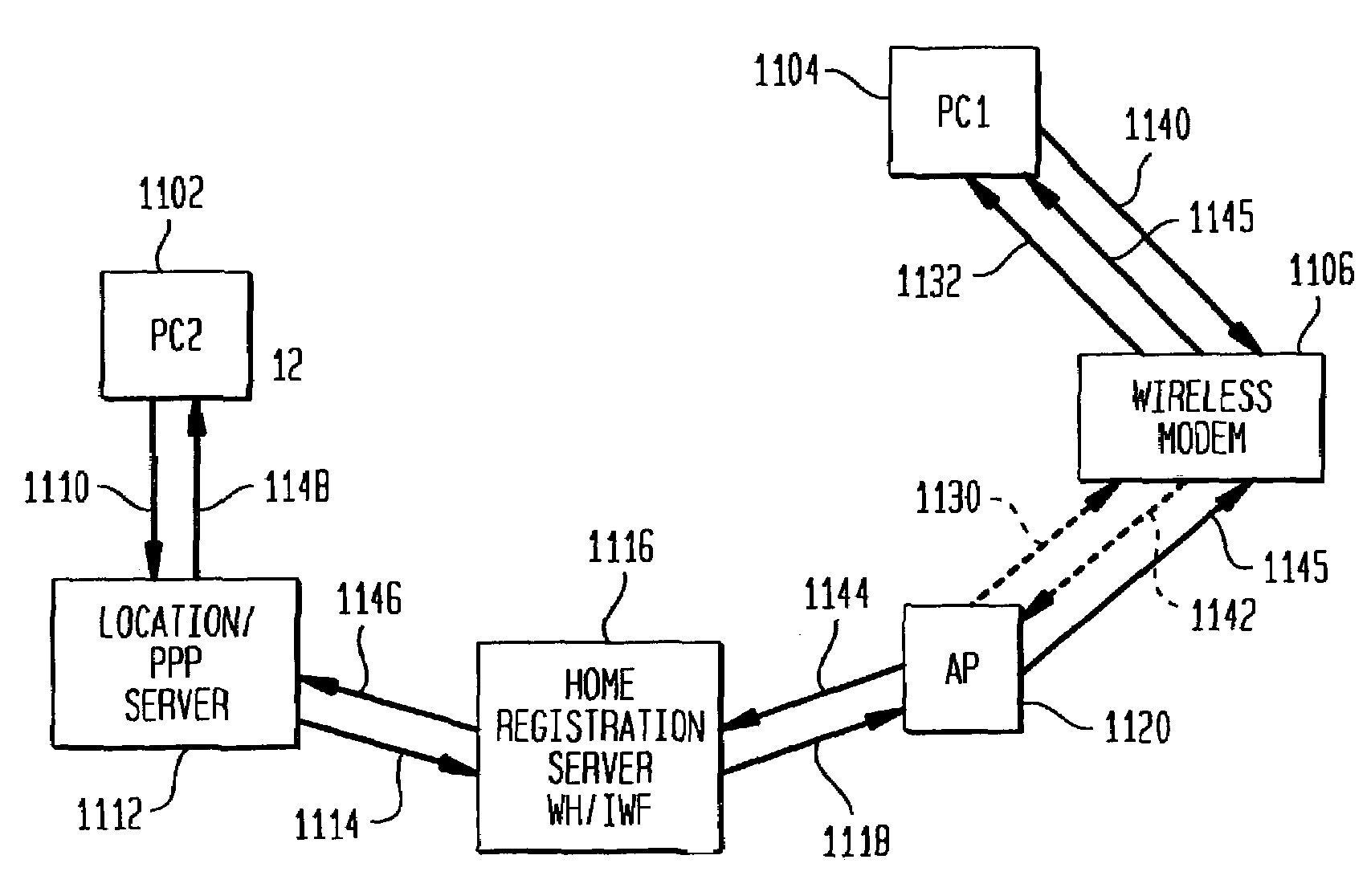
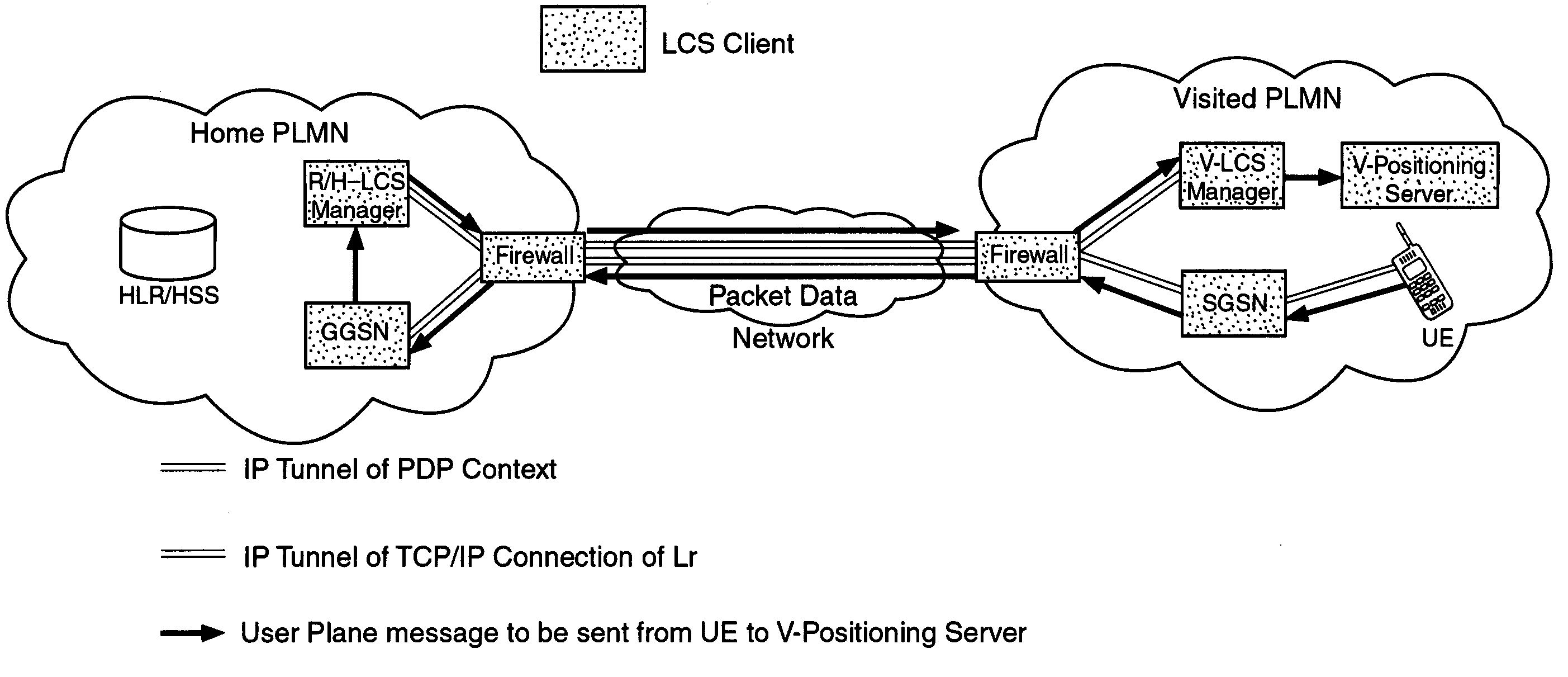
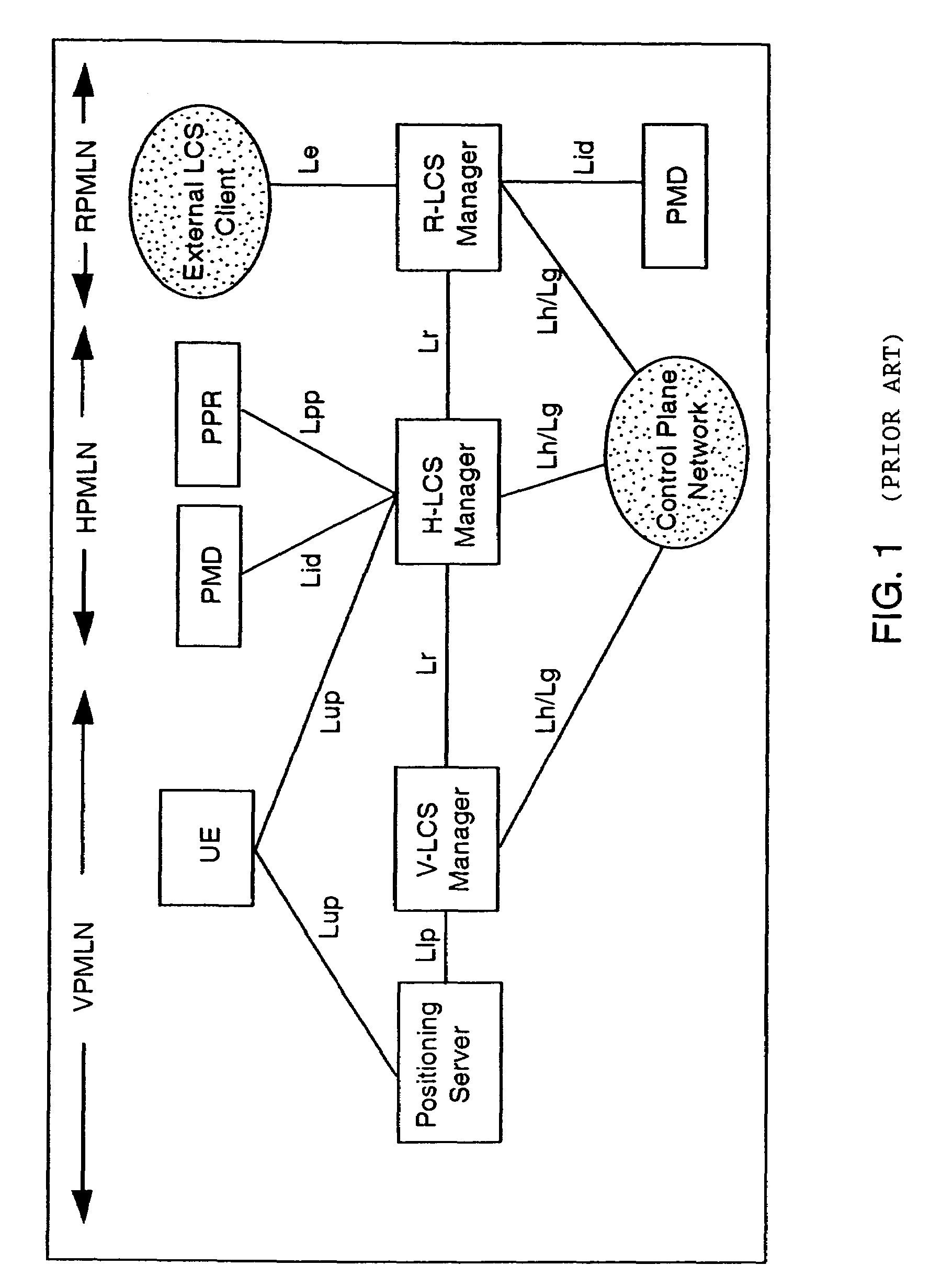
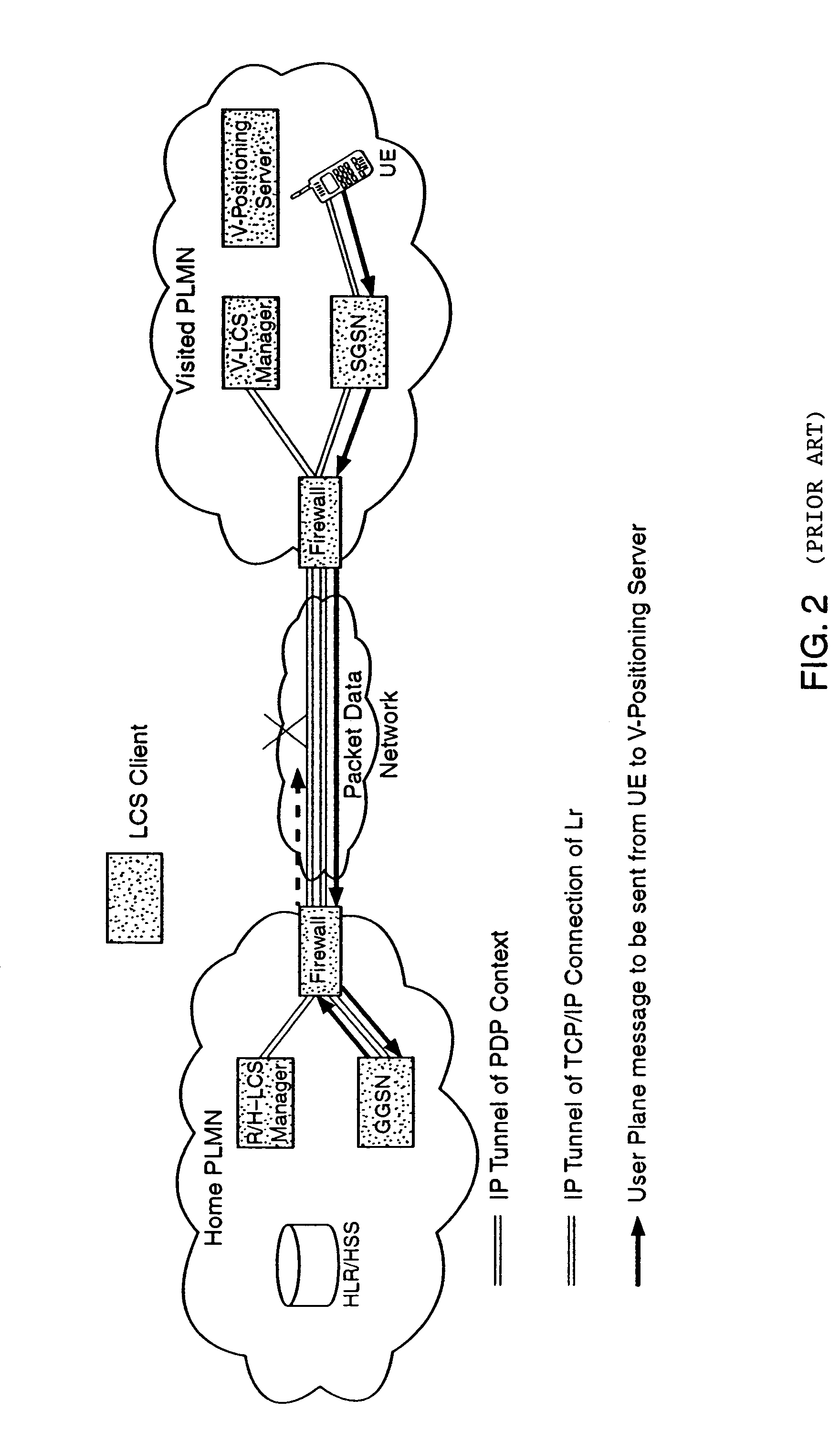
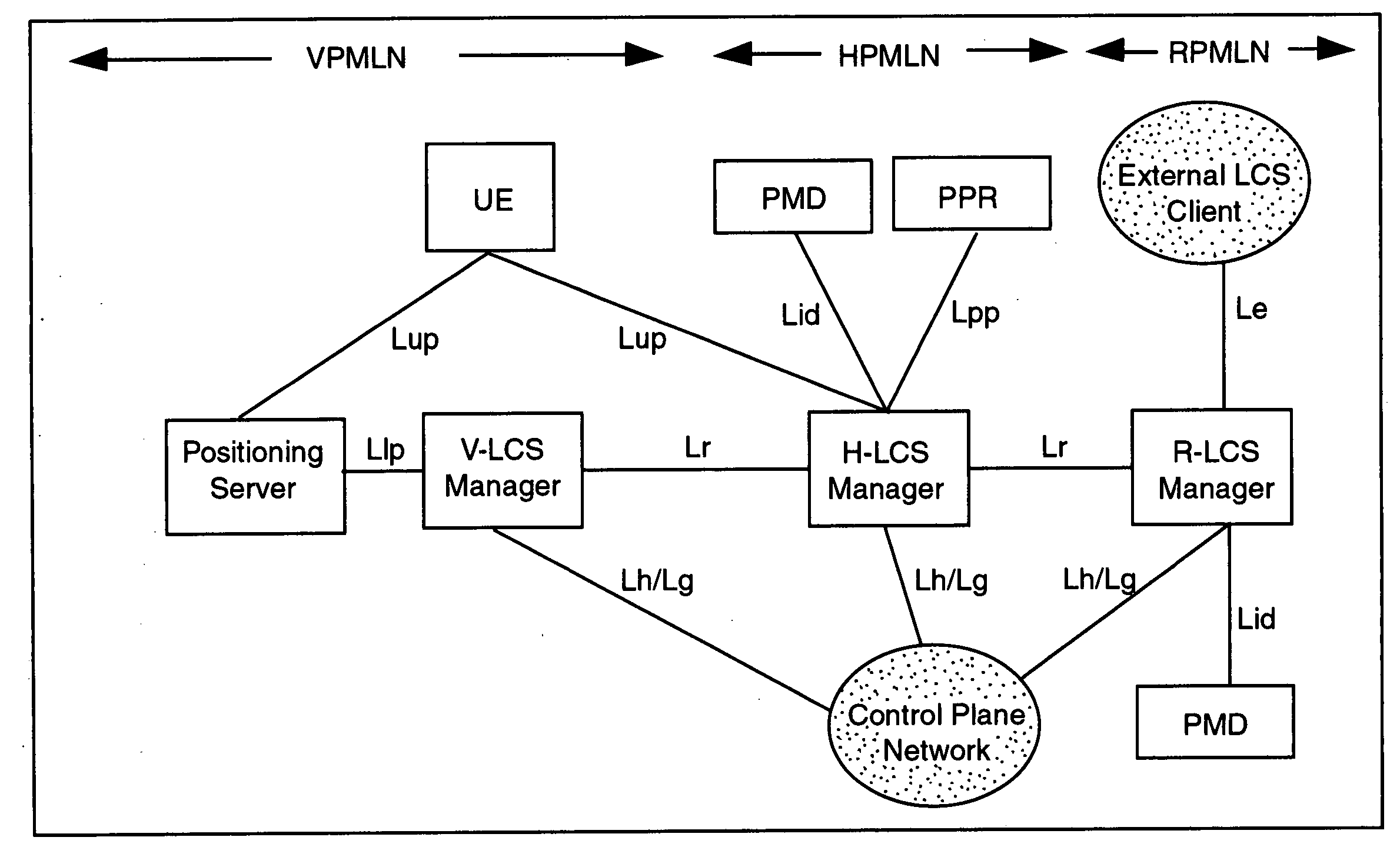
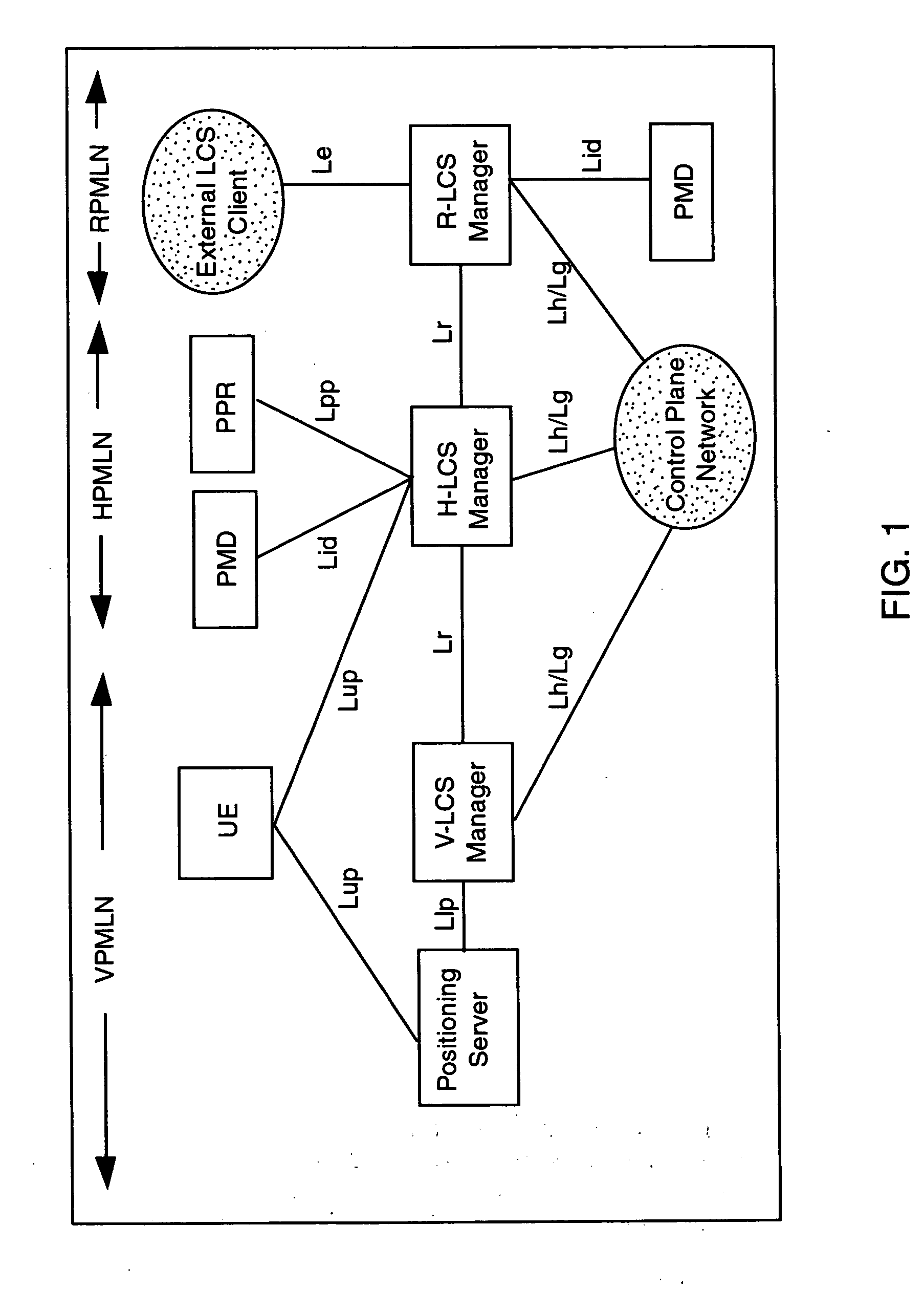
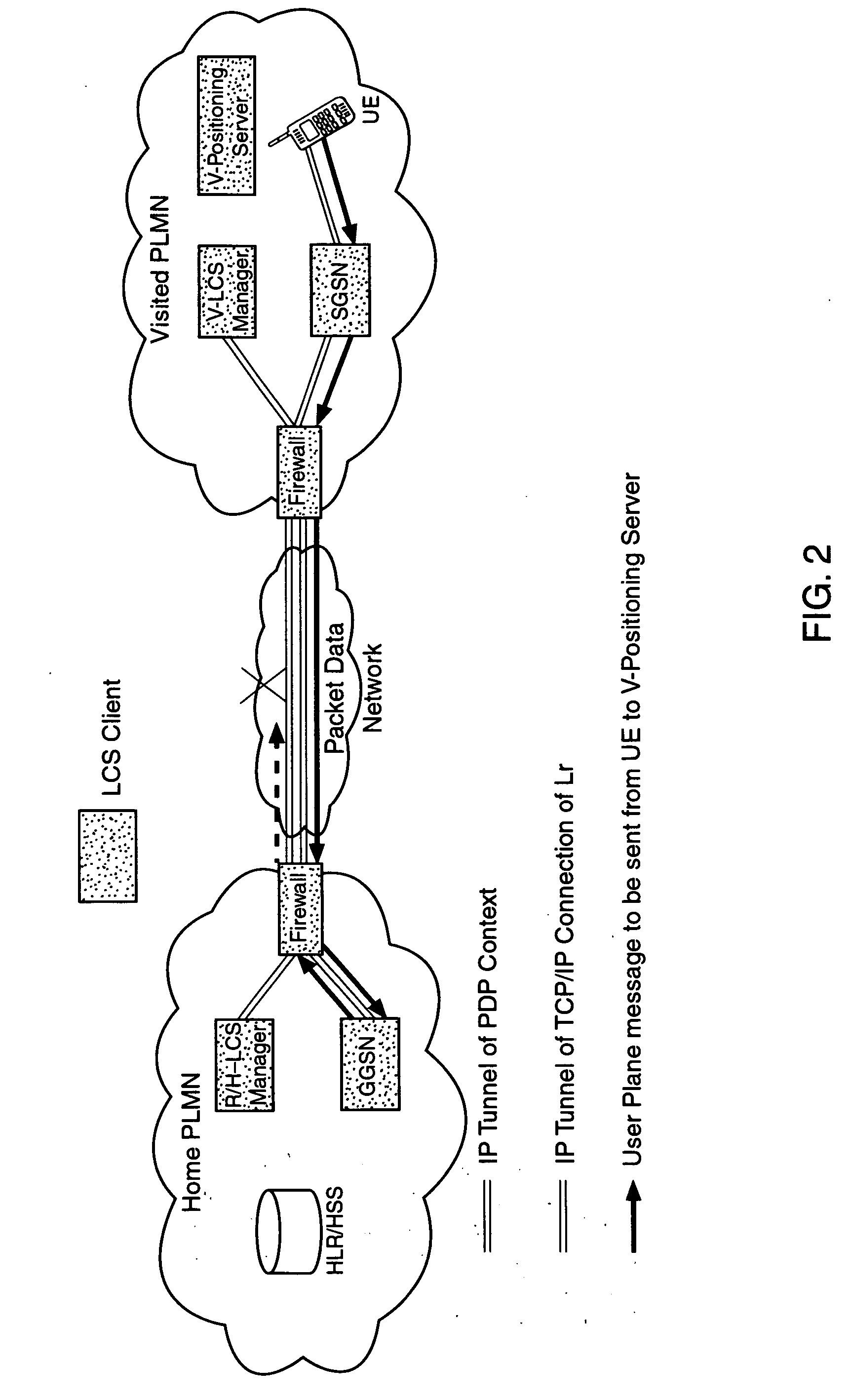
User plane location based service using message tunneling to support roaming
An improved User Plane location based service (LBS) architecture and message flow, enabling seamless User Plane location based services even when a mobile or wireless device has roamed among different carrier networks. The present invention overcomes constraints inherent in the current protocol for roaming support defined by the Secure User Plane Location Service specification. A location system is enabled to automatically fall back to a message tunneling mechanism to ensure the security of a communication path between the location service system and the target wireless device, ensuring that the communication path is uninterrupted as the wireless device travels.
Owner:ARTAX LLC
User plane location based service using message tunneling to support roaming
An improved User Plane location based service (LBS) architecture and message flow, enabling seamless User Plane location based services even when a mobile or wireless device has roamed among different carrier networks. The present invention overcomes constraints inherent in the current protocol for roaming support defined by the Secure User Plane Location Service specification. A location system is enabled to automatically fall back to a message tunneling mechanism to ensure the security of a communication path between the location service system and the target wireless device, ensuring that the communication path is uninterrupted as the wireless device travels.
Owner:ARTAX LLC
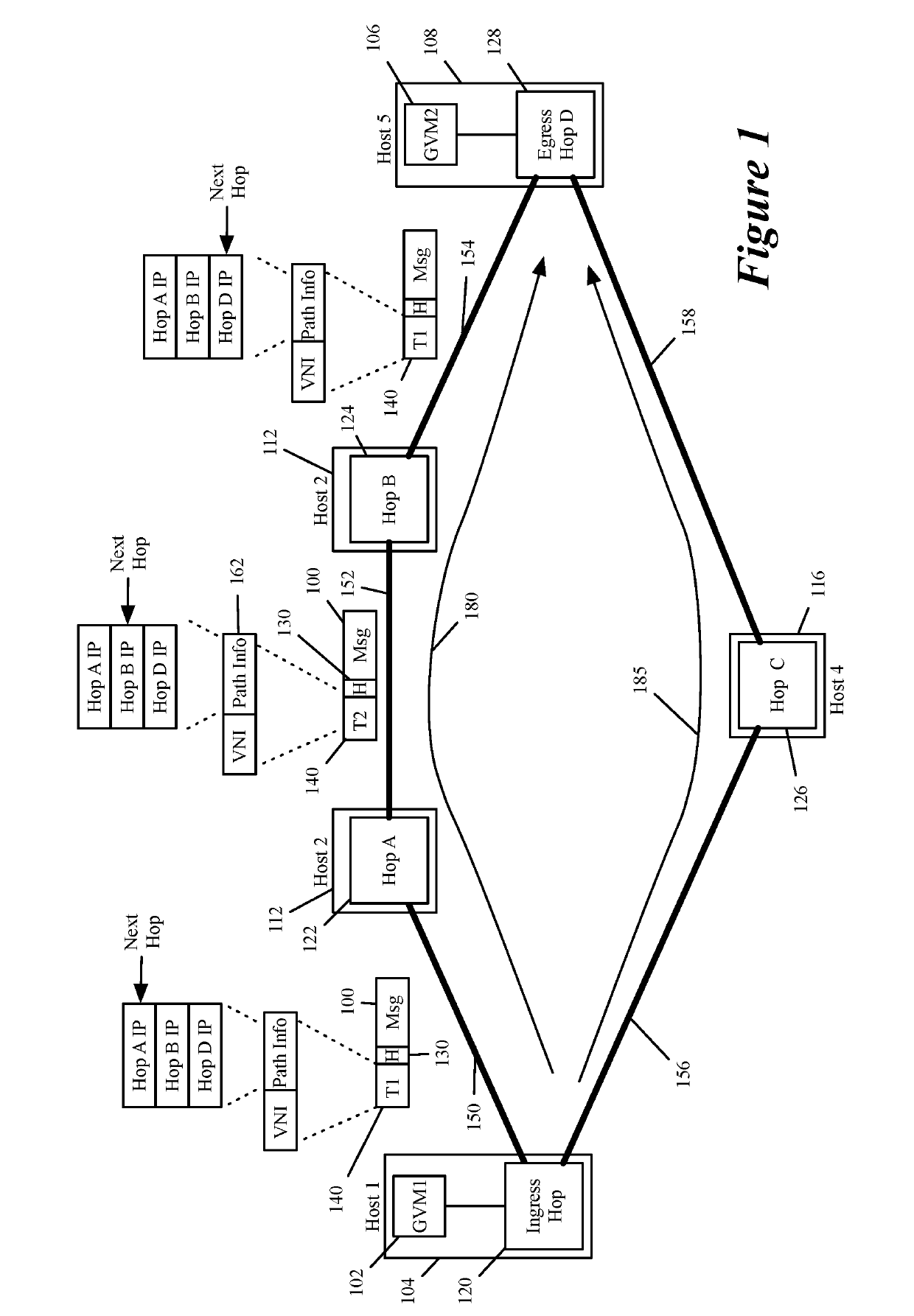
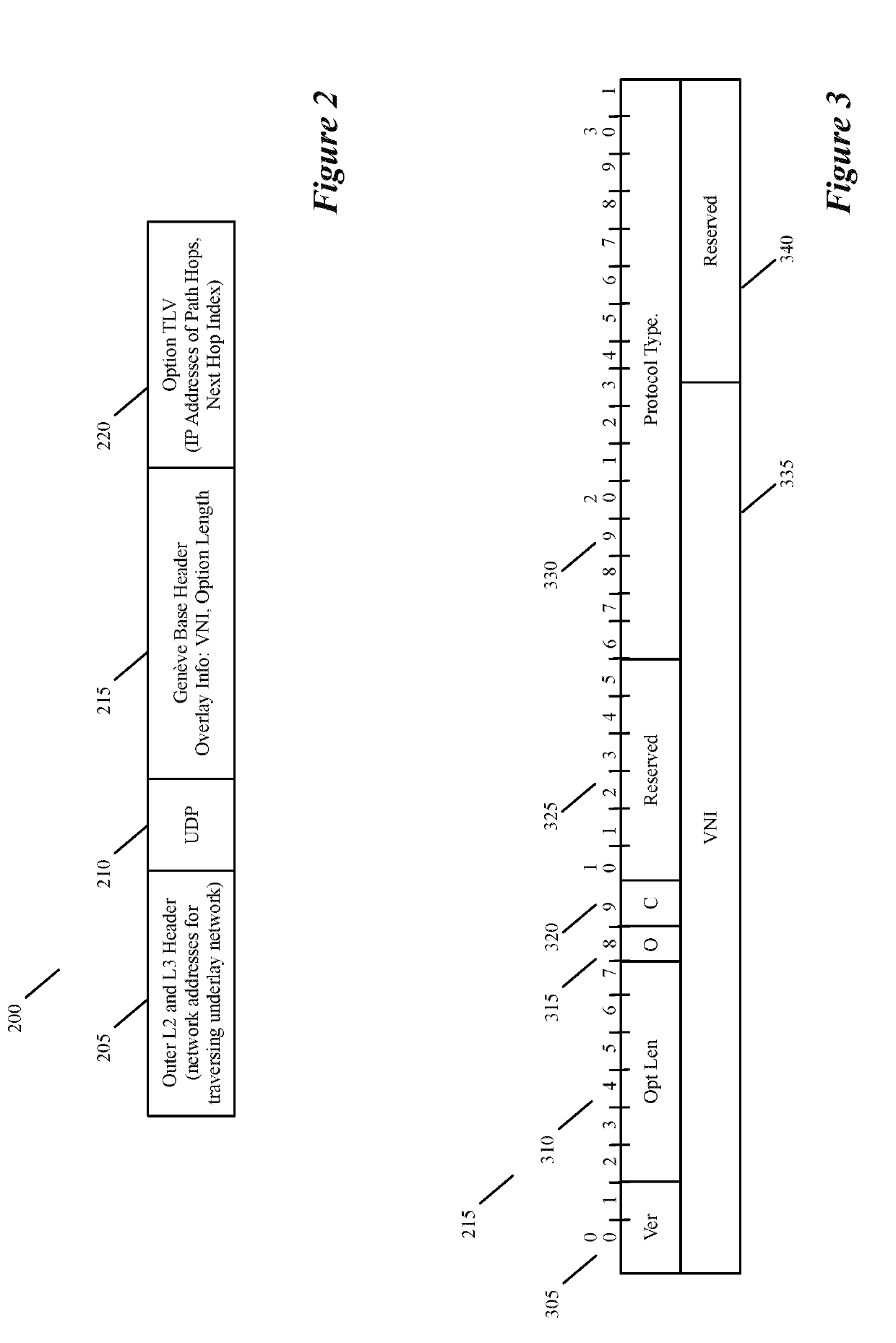
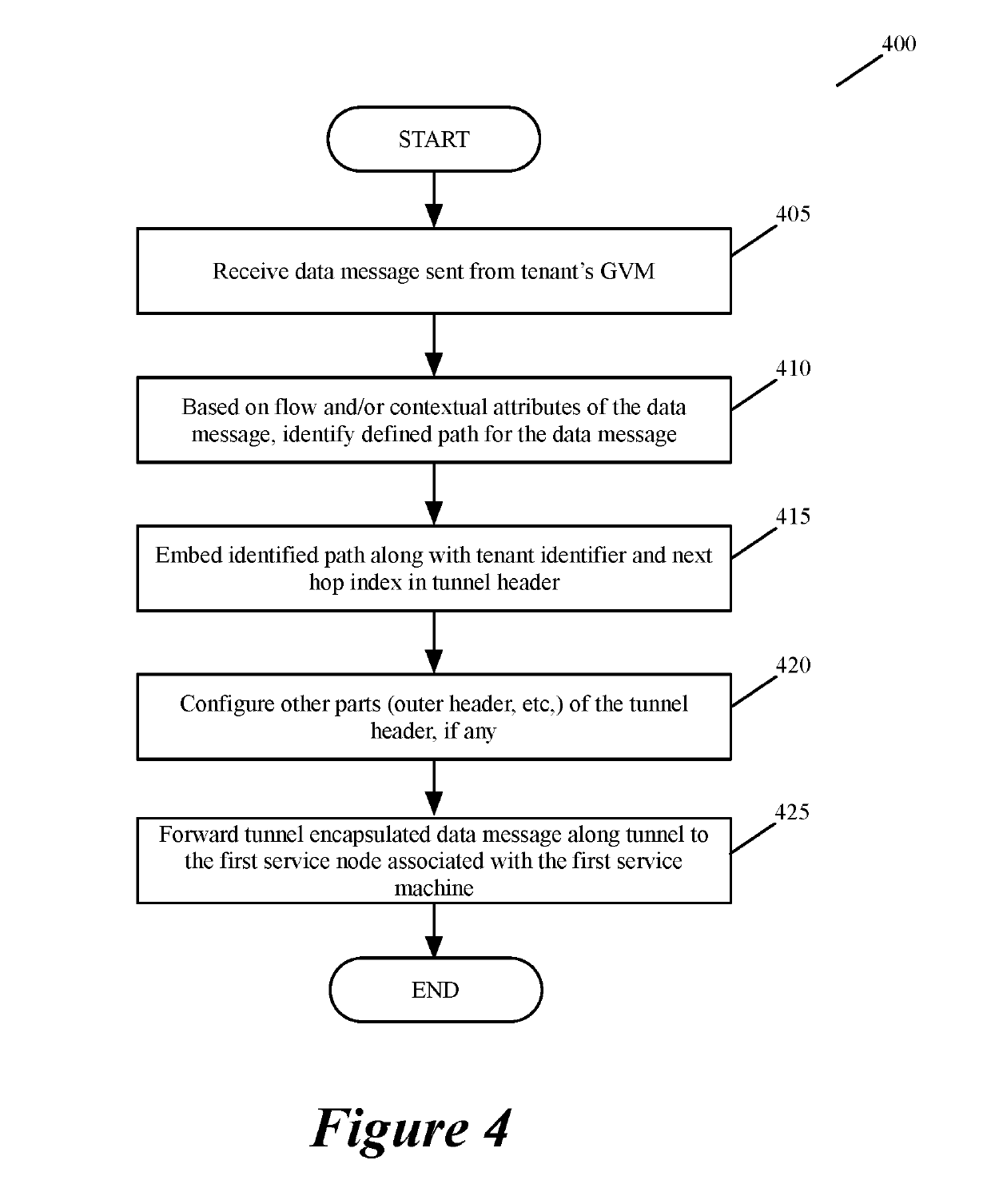
Specifying and utilizing paths through a network
For a multi-tenant environment, some embodiments of the invention provide a novel method for (1) embedding a specific path for a tenant's data message flow through a network in tunnel headers encapsulating the data message flow, and then (2) using the embedded path information to direct the data message flow through the network. In some embodiments, the method selects the specific path from two or more viable such paths through the network for the data message flow.
Owner:NICIRA
Byte code instrumentation
InactiveUS20040133882A1Reliability increasing modificationsSoftware testing/debuggingMessage flowParallel computing
Instrumenting a computer program to provide instrumented byte code includes examining the byte code, selecting portions of the byte code for instrumentation, and instrumenting the portions to provide instrumented byte code. Selecting the portions may include choosing portions of the byte code corresponding to method entry, method exit, a throw, a method call, or a new line number. Instrumenting a portion of the byte code corresponding to a method call may include instrumenting a local line number of source code corresponding to the byte code being instrumented. Instrumenting the portions may include adding calls to instrumentation runtime functions that pass parameters indicative of the portions being instrumented. At least one of the parameters that is passed may include a line number of the source code corresponding to the portion being instrumented or a thispointer for the method corresponding to the portion being instrumented. Data from instrumentation may be passed via a message stream that is viewed as the data is being generated and / or stored.
Owner:BORLAND
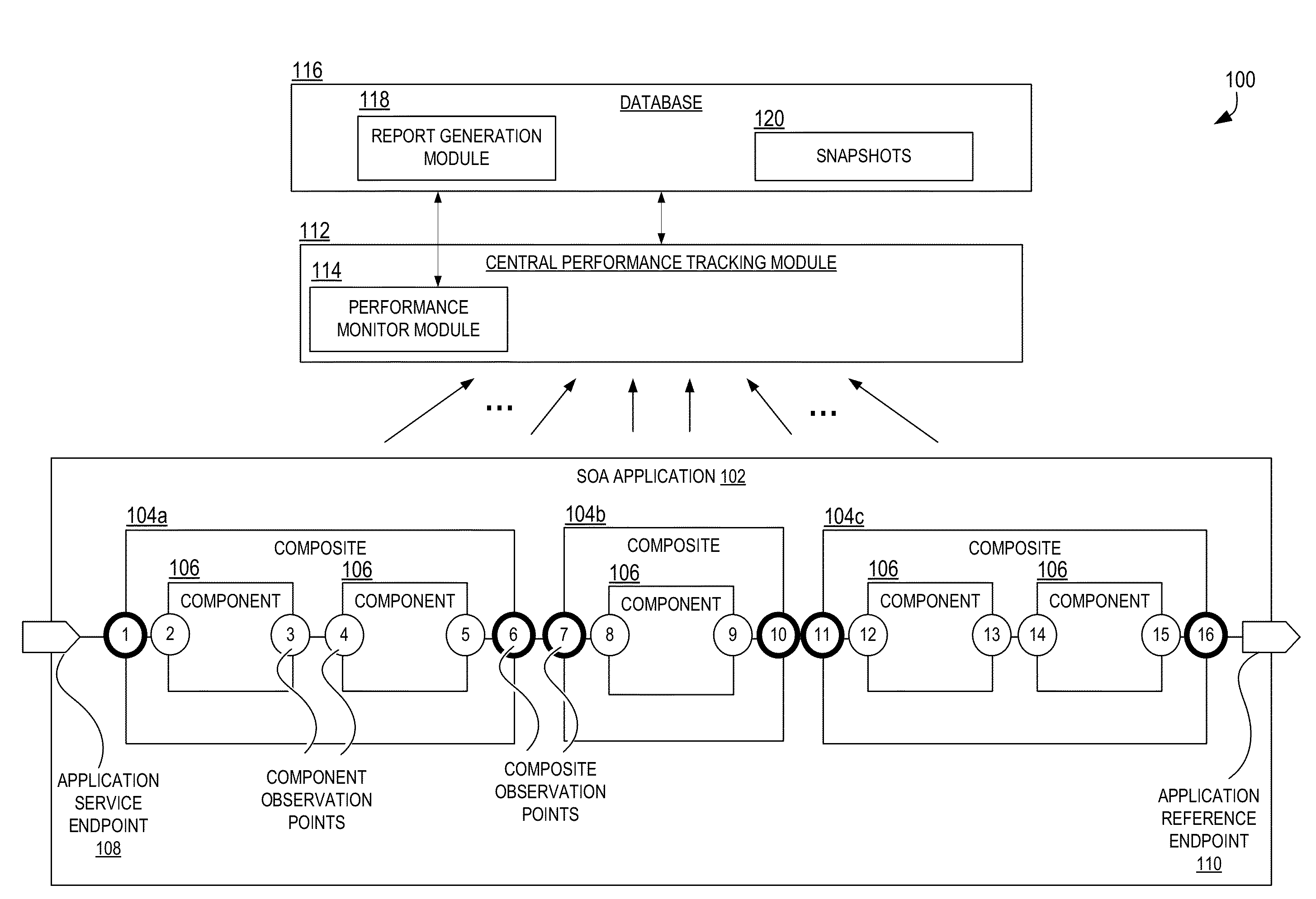
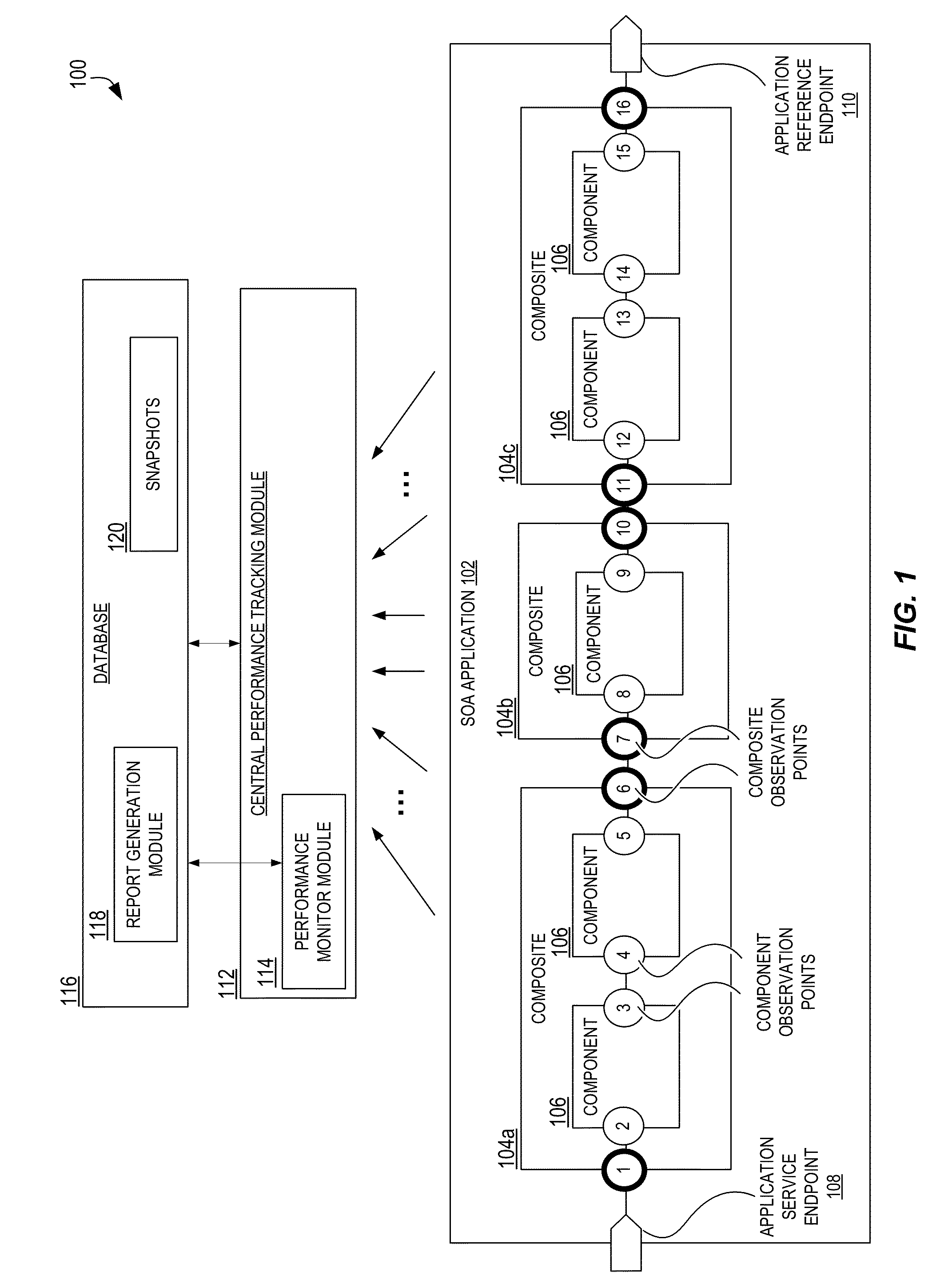
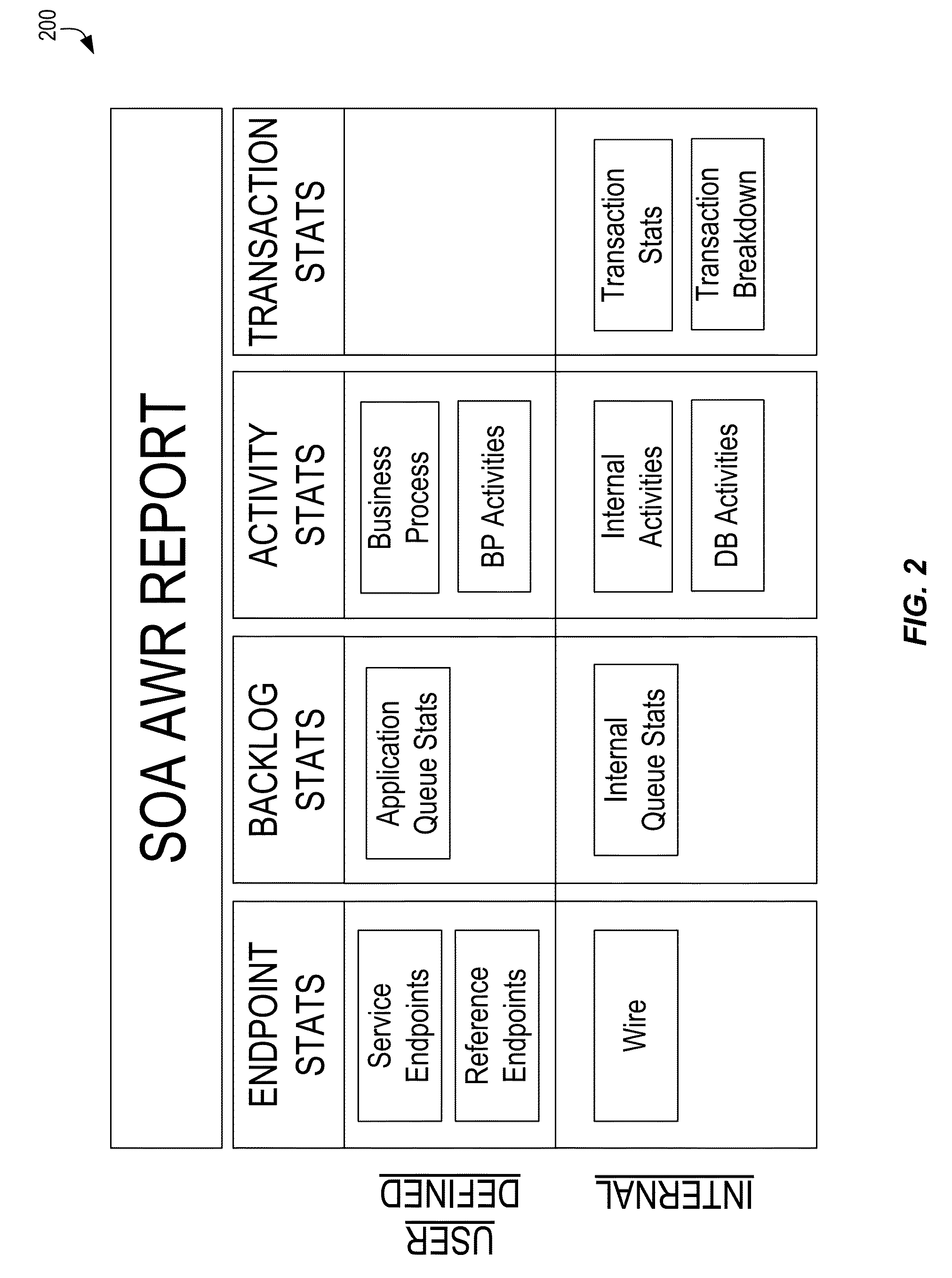
Performance analysis and bottleneck detection in service-oriented applications
ActiveUS20160182328A1Increase execution priorityDigital computer detailsData switching networksMessage flowService oriented applications
Techniques are disclosed for assembling statistics for diagnosing performance and scalability issues in SOA systems. Key statistics related to key points in a SOA system, for key activities during processing of transactions in the SOA system, are collected and aggregated. The statistics may include message flow rates and latency at key points in the system during a time interval, and execution times for key activities in the system during the time interval. The statistics for the time interval may be added to corresponding cumulative statistics, and persisted to storage. Reports may be generated based upon the statistics to present to a user. Automated processes may be implemented to use the statistics to identify the existence and likely cause of SOA application performance issues, and potentially to attempt to remediate the issues.
Owner:ORACLE INT CORP
Server monitoring virtual points of presence
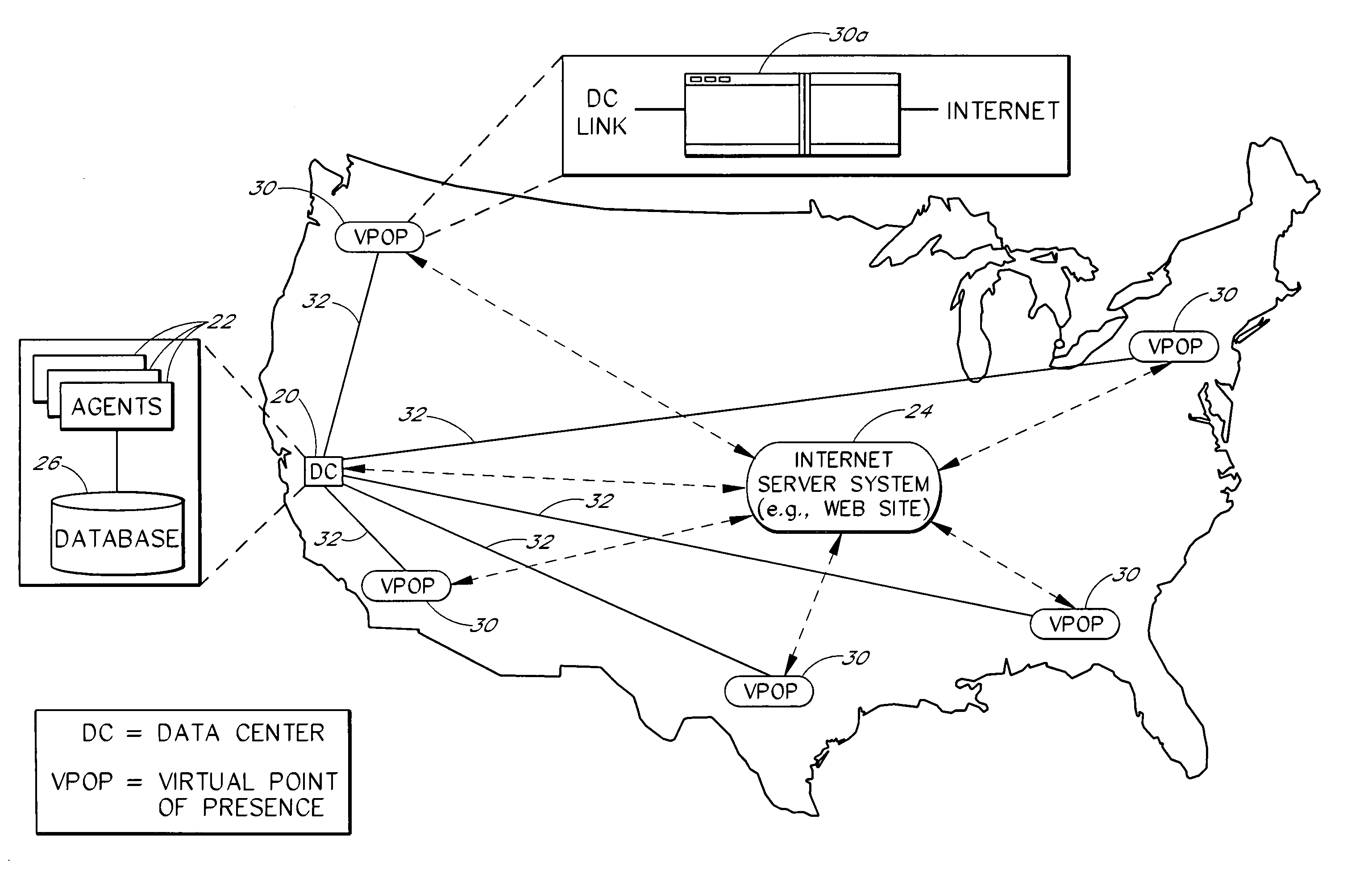
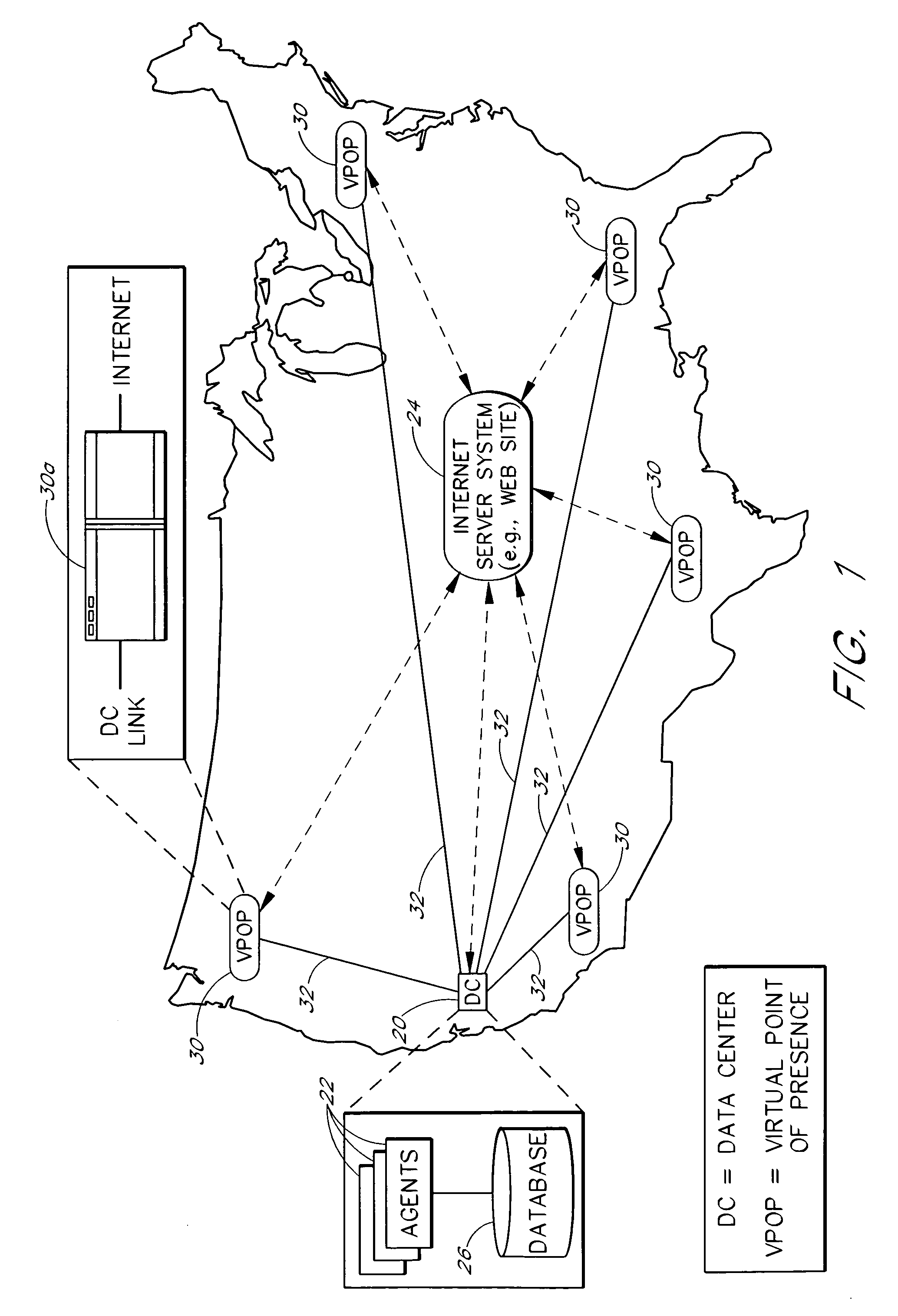
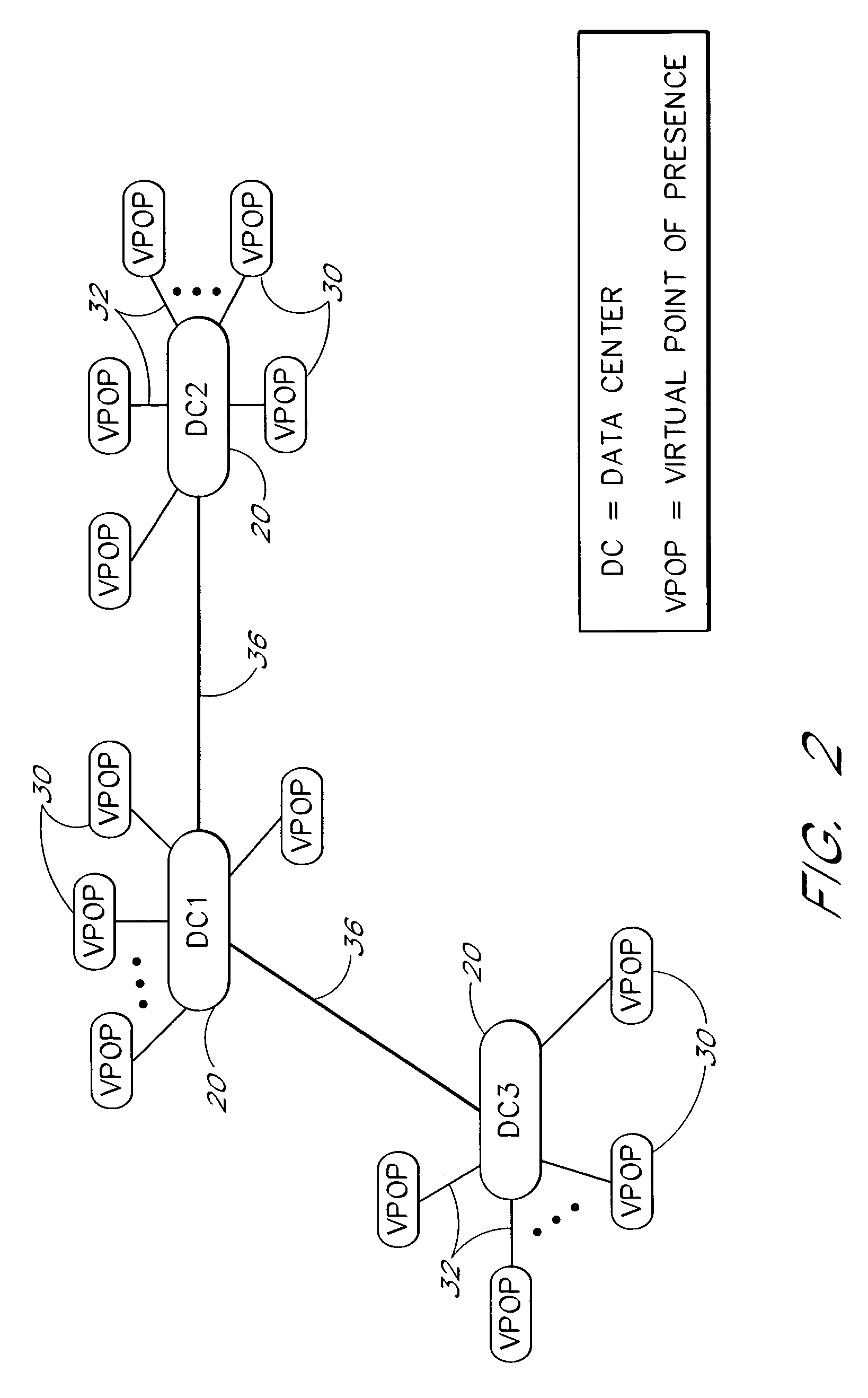
InactiveUS6973489B1CostLow costHardware monitoringMultiple digital computer combinationsTotal responsePoint of presence
A server monitoring system monitors the performance of a web site or other Internet server system, as seen by users in multiple geographic access locations, without the need for special monitoring software or hardware within such locations. Automated agents that run at a central data center generate message traffic that is used to access and monitor the server system from the multiple remote locations. The message traffic associated with a particular remote access location is transmitted from the data center to the remote location across a dedicated link, such as an ATM link, and is routed onto the Internet at a corresponding Internet access point. The server response to each request message flows back to the data center across the same link as the corresponding request message. The remote access points thus serve as virtual points of presence for monitoring purposes. Server response times as seen from the remote access locations are determined by measuring the total response times as observed from the data center, and deducting from the total response times the round-trip latencies associated with the corresponding dedicated links. The response times and other performance data generated by the agents are aggregated within a database that is local to the agents. Multiple data centers may be interconnected such that each data center services a particular continent or other region using a respective set of virtual points of presence.
Owner:MICRO FOCUS LLC
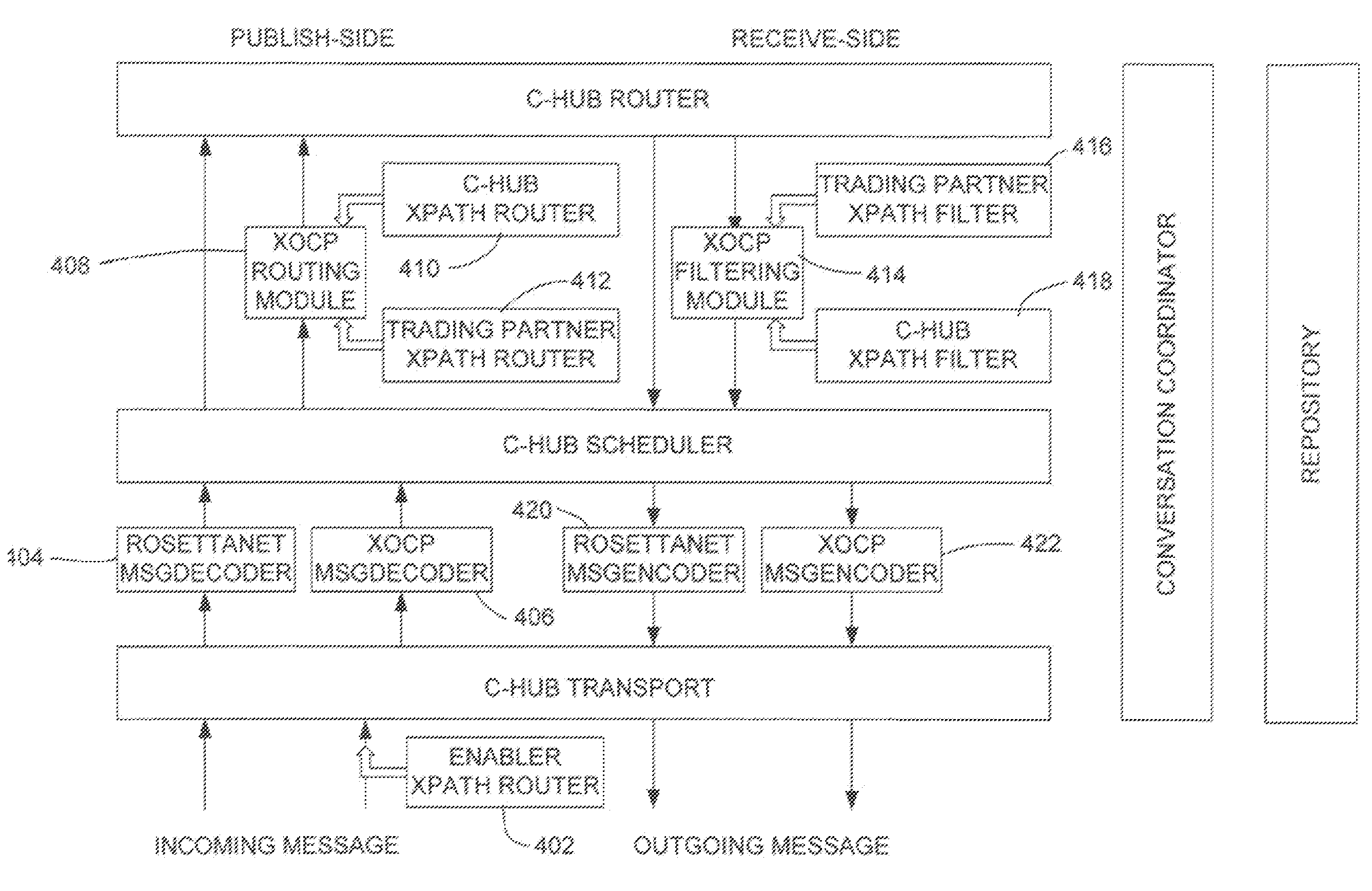
Pluggable hub system for enterprise wide electronic collaboration
InactiveUS7143186B2Increase speedEnsure qualityFinanceMultiple digital computer combinationsSession managementMessage flow
An enterprise wide electronic commerce system allows trading partners to act as participants in a complex trading process. Participants communicate with one another by joining conversations that are hosted in a collaboration space and managed by a collaboration hub. In this manner, the enterprise workflow may have an effect on, or be affected by, local workflows. The invention provides a pluggable hub system for enterprise wide electronic collaboration. An embodiment of the invention includes a collaboration hub for use with a collaboration system, comprising a hub transport for receiving messages from participants and sending messages to participants, a hub router for routing messages from a first participant to a second participant, a hub scheduler for scheduling the flow of messages between the hub router and the hub transport, a conversation manager for managing the flow of messages between participants, and a repository for storing conversation management data.
Owner:ORACLE INT CORP
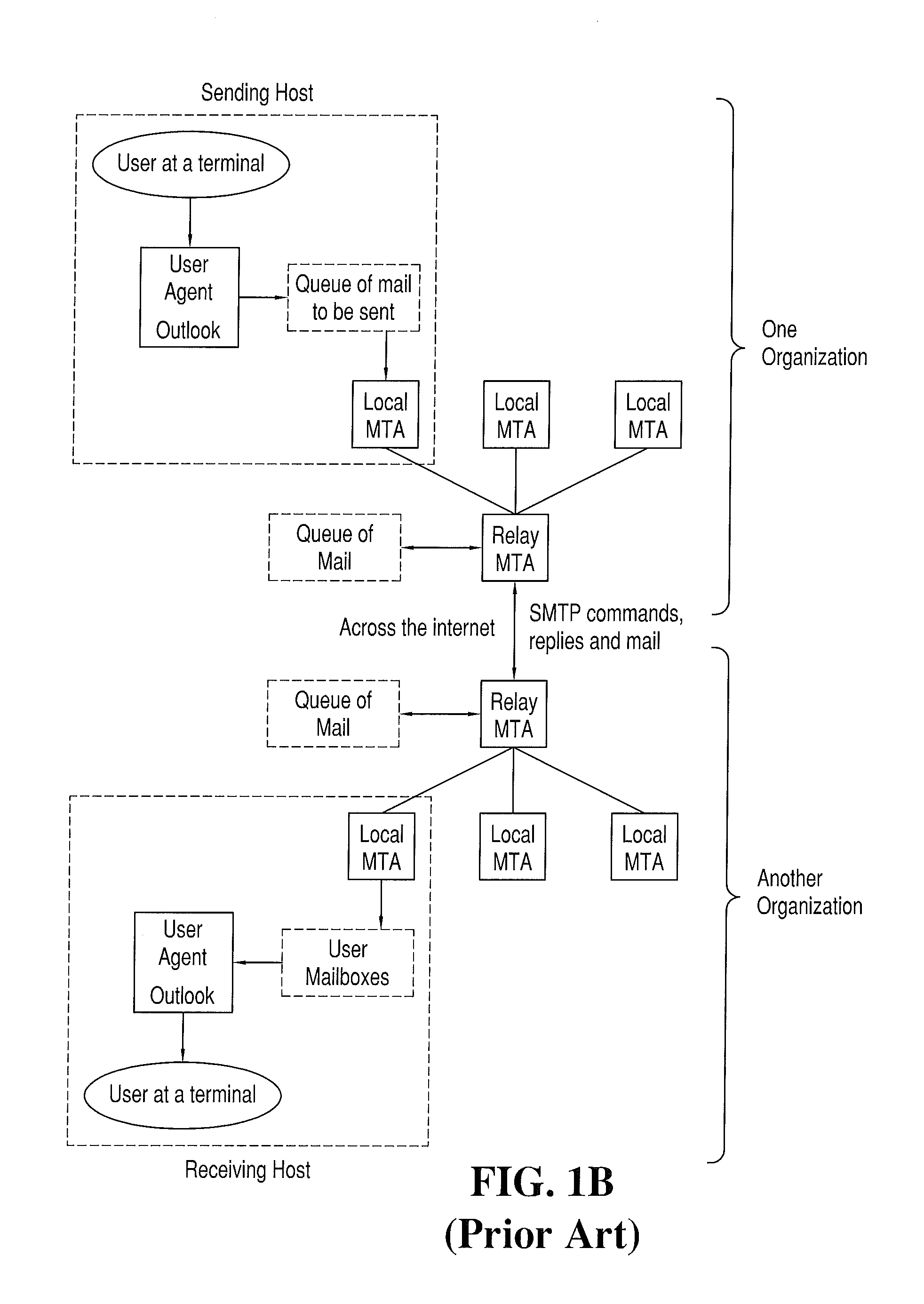
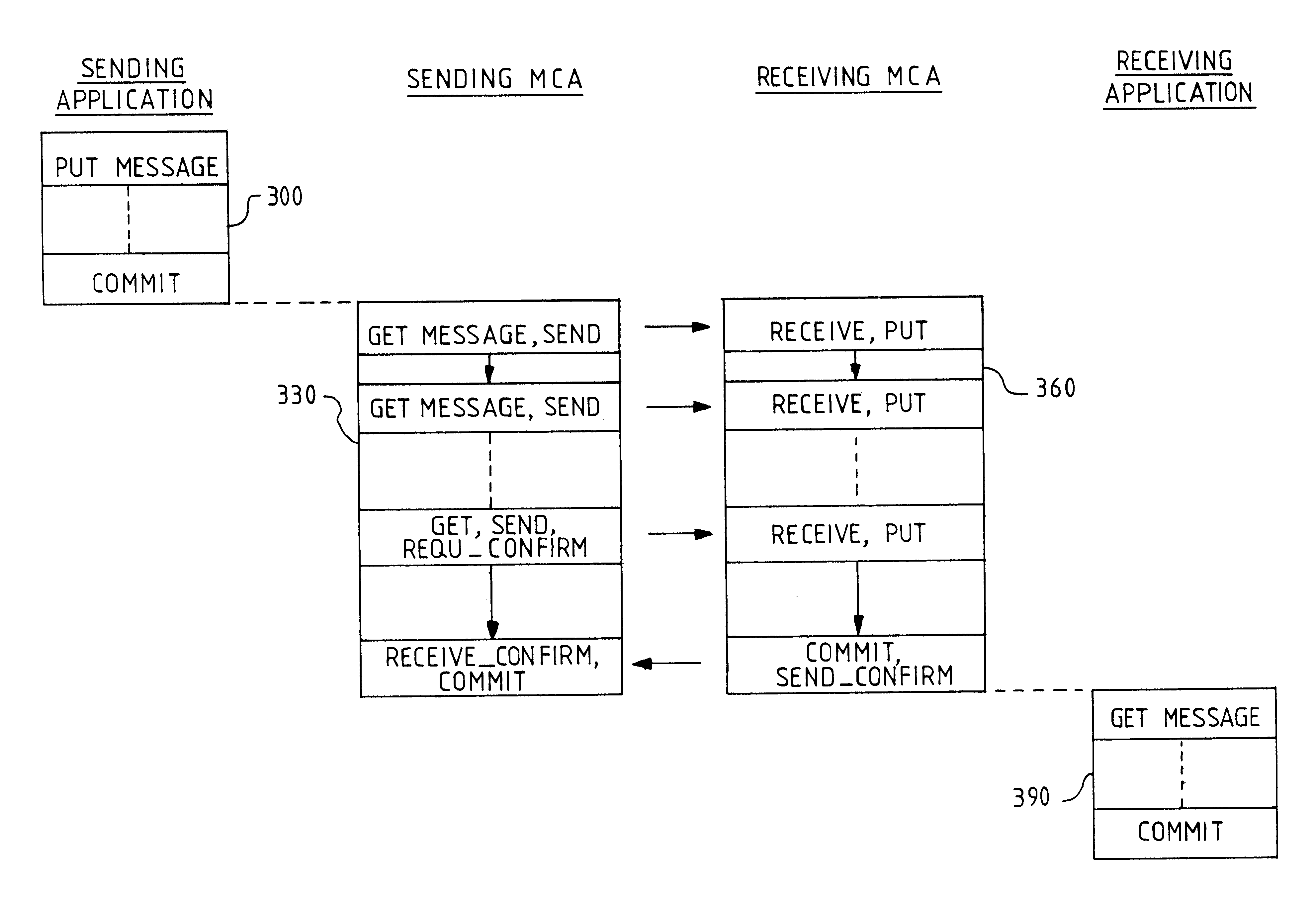
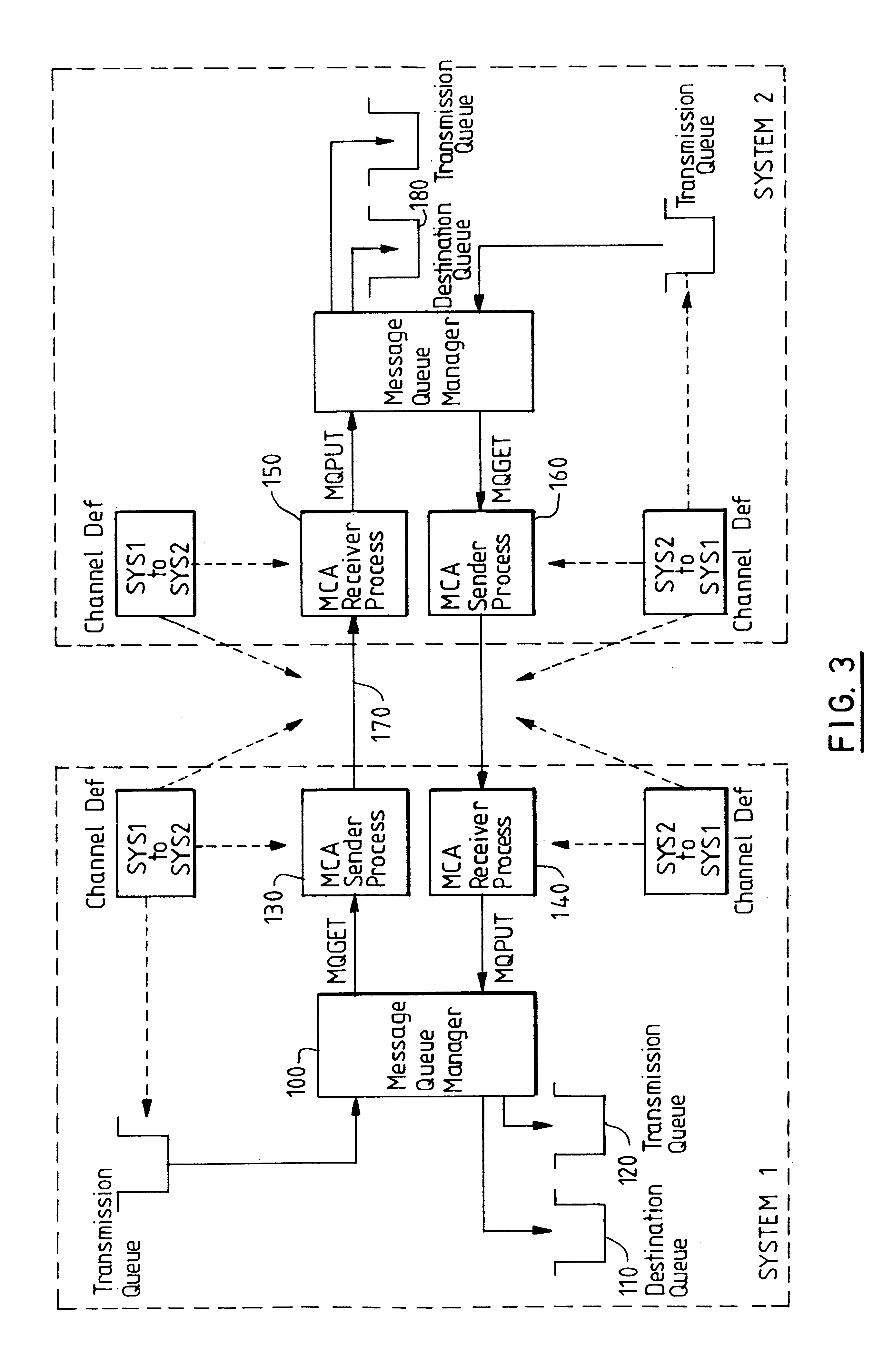
Method of transferring messages between computer programs across a network
A method of delivering messages between application programs is provided which ensures that no messages are lost and none are delivered more than once. The method uses asynchronous message queuing. One or more queue manager programs (100) is located at each computer of a network for controlling the transmission of messages to and from that computer. Messages to be transmitted to a different queue manager are put onto special transmission queues (120). Transmission to an adjacent queue manager comprises a sending process (130) on the local queue manager (100) getting messages from a transmission queue and sending them as a batch of messages within a syncpoint-manager-controlled unit of work. A receiving process (150) on the receiving queue manager receives the messages and puts them within a second syncpoint-manager-controlled unit of work to queues (180) that are under the control of the receiving queue manager. Commitment of the batch is coordinated by the sender transmitting a request for commitment and for confirmation of commitment with the last message of the batch, commit at the sender then being triggered by the confirmation that is sent by the receiver in response to the request.The invention avoids the additional message flow that is a feature of two-phase commit procedures, avoiding the need for resource managers to synchronise with each other. It further reduces the commit flows by permitting batching of a number of messages.
Owner:IBM CORP
Service operation chaining
For a multi-tenant environment, some embodiments of the invention provide a novel method for forwarding tenant traffic through a set of service machines to perform a set of service operations on the tenant traffic. In some embodiments, the method performs a classification operation on a data message flow of a tenant, in order to identify a set of service operations to perform on the data message flow. For some data message flows, the classification operation selects the identified set of service operations from several candidate sets of service operations that are viable service operation sets for similar data message flows of the tenant. In some embodiments, the classification operation is based on a set of attributes associated with the data message flow (e.g., five tuple identifier, i.e., protocol and source and destination ports and IP addresses).
Owner:NICIRA
Instant messaging system that facilitates better knowledge and task management
InactiveUS20120317499A1Improve user experienceImprove business satisfactionInput/output for user-computer interactionMultiple digital computer combinationsMessage flowTask management
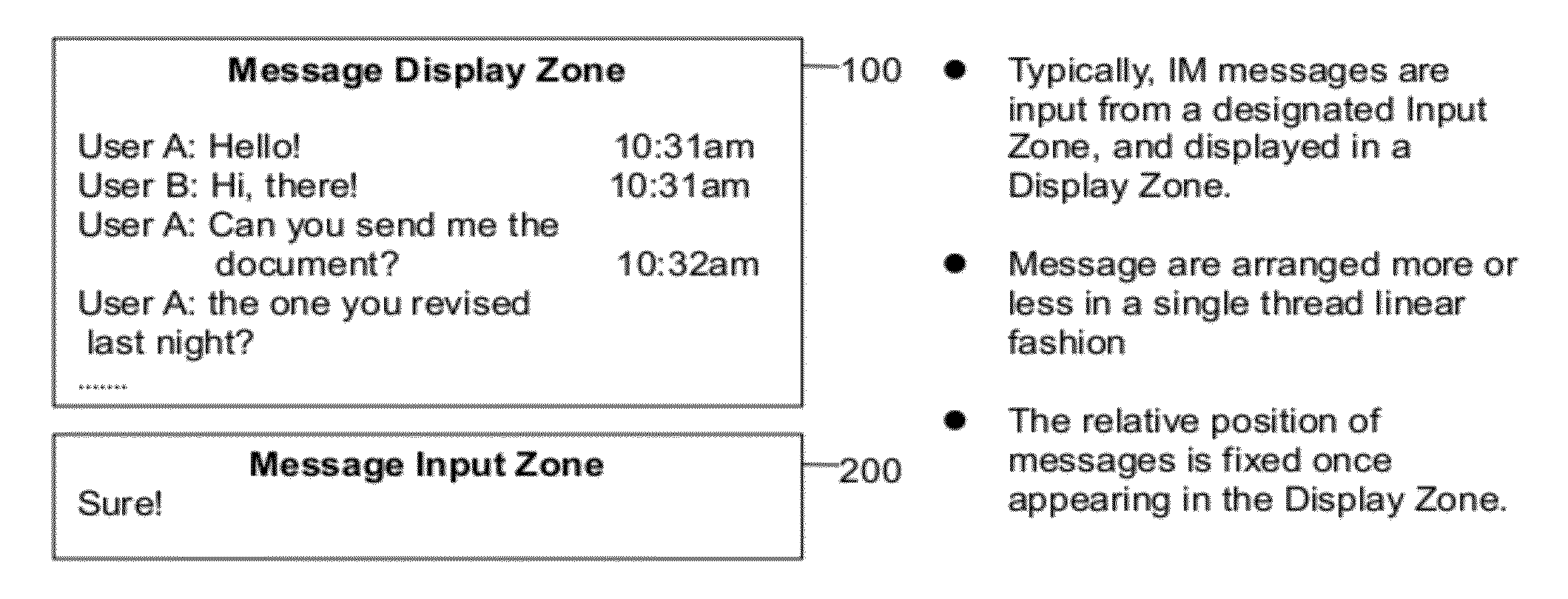
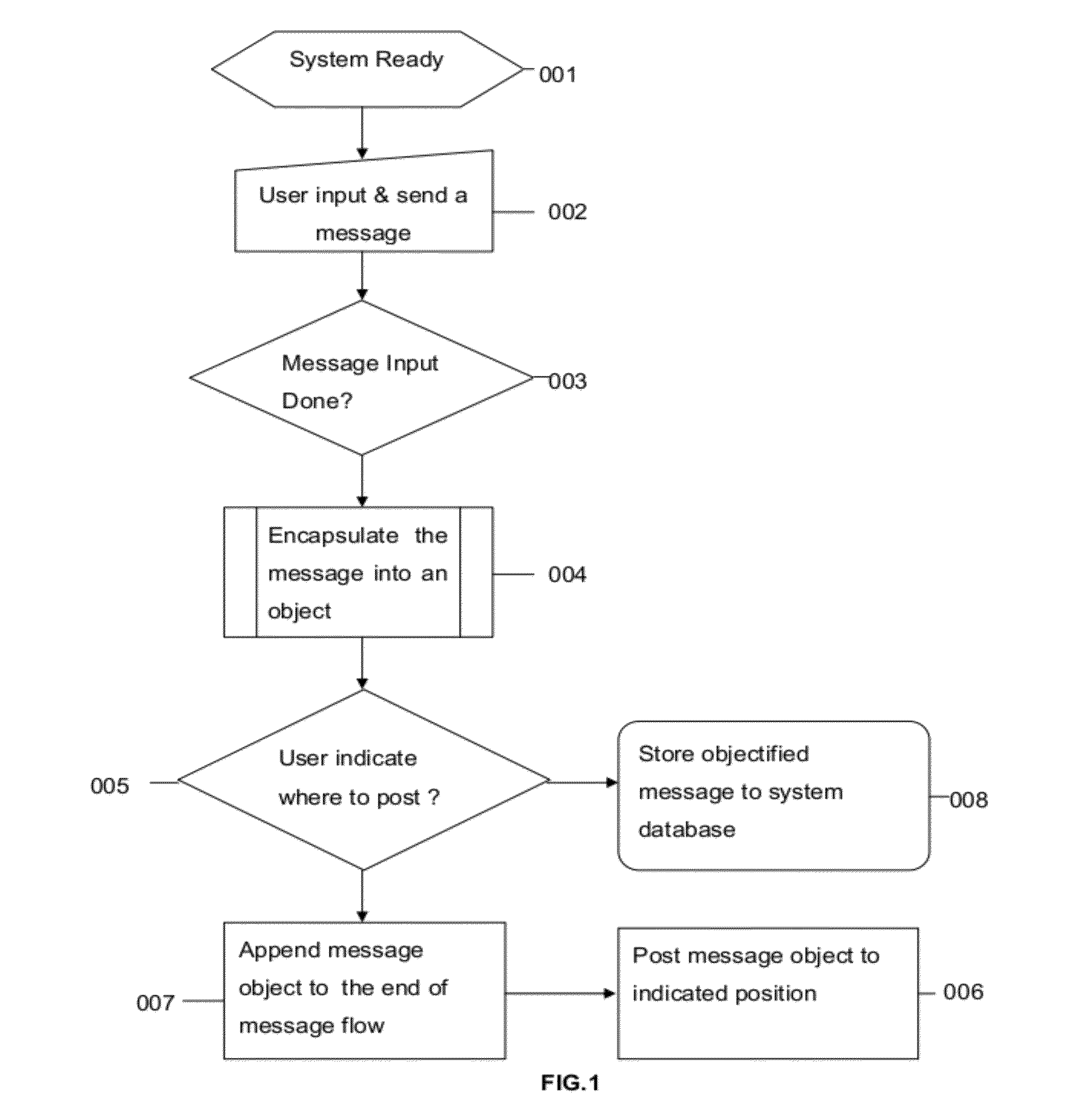
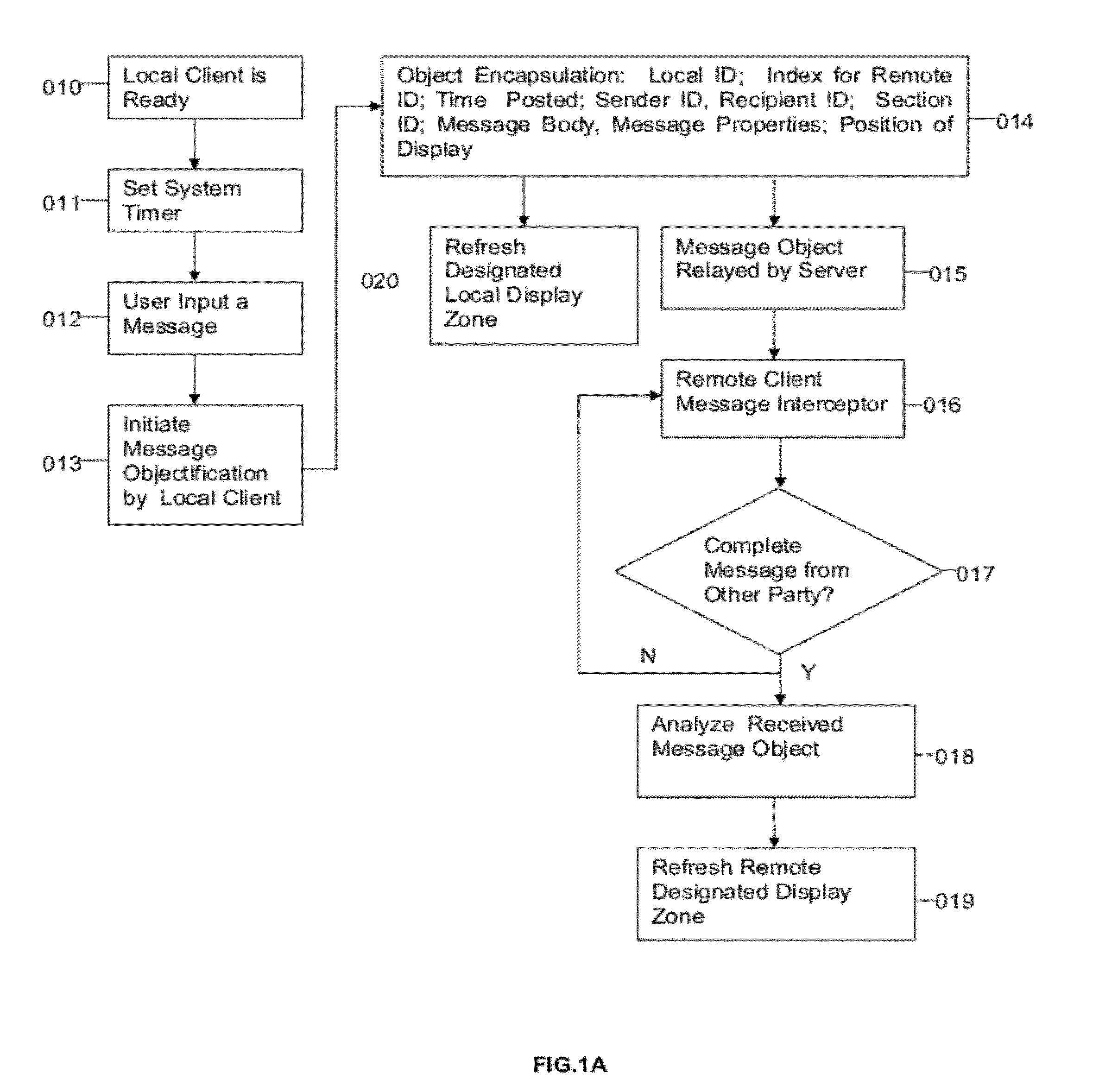
This invention discloses a novel system that is tuned for people to exchange information effectively and manage the domain knowledge and tasks productively. With a WYSIWYG-like user interface, message encapsulation into individual objects, and multithreading message flow handling, this new system is able to bring forth revolutionary features that break the limitations of traditional IM systems by knitting traditionally separated functions into an integrated business information and management platform, and hence enable new ways in building knowledge base, reading industrial specific news, and assigning and managing tasks.
Owner:SHEN JIN WEN
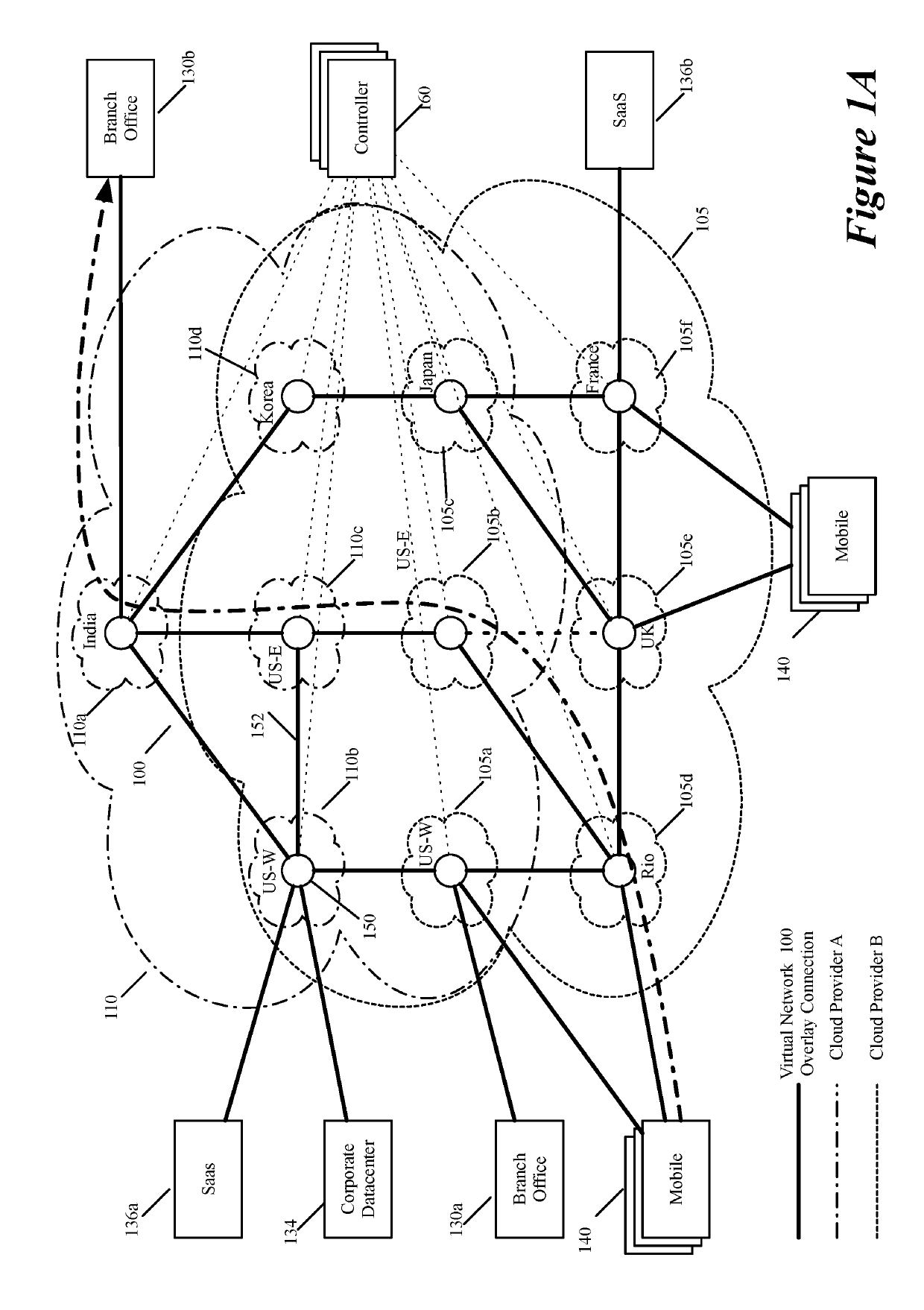
Dynamically specifying multiple public cloud edge nodes to connect to an external multi-computer node
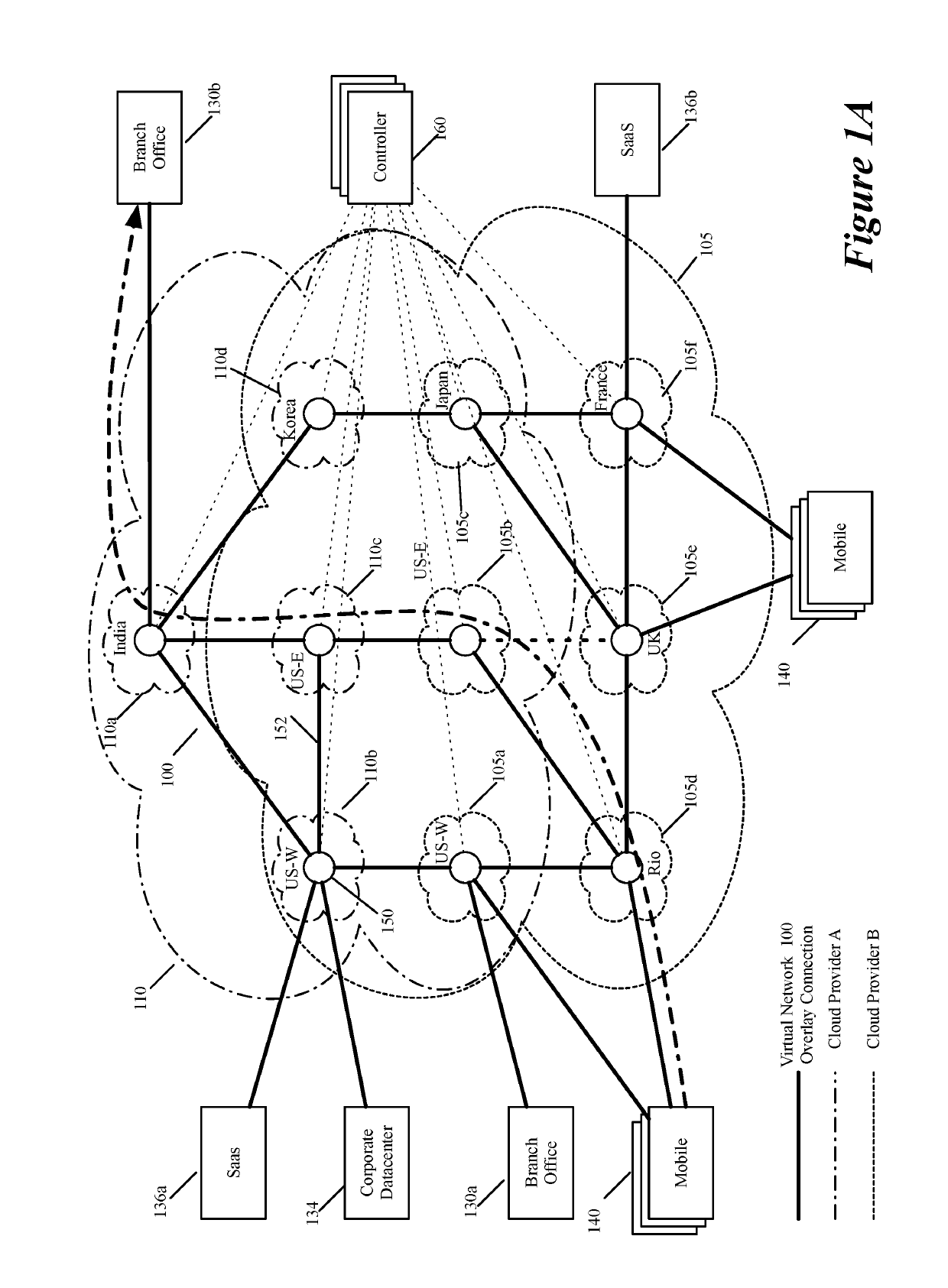
ActiveUS20190104413A1Traffic minimizationIncrease redundancyNetworks interconnectionSecurity arrangementData centerPrivate network
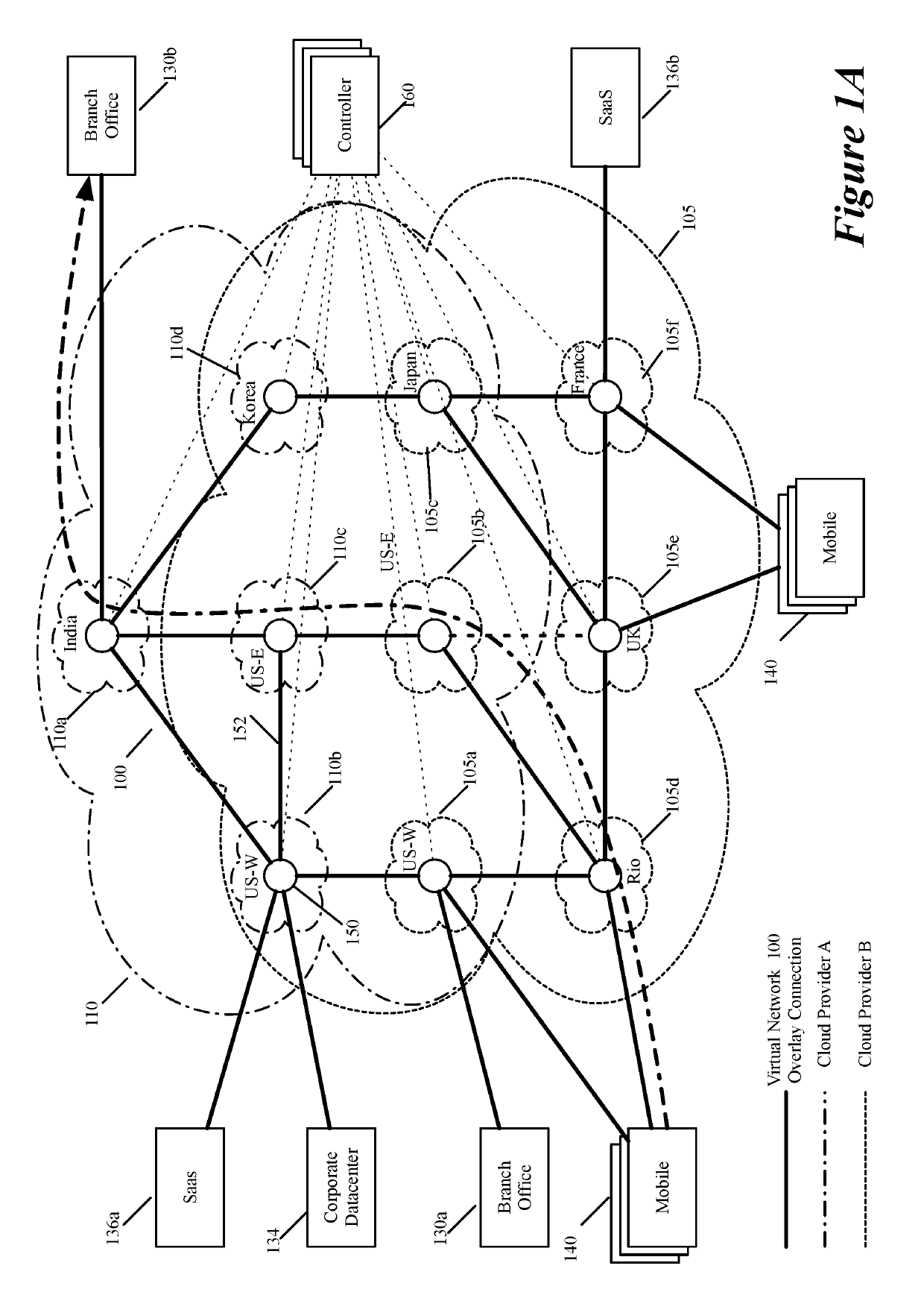
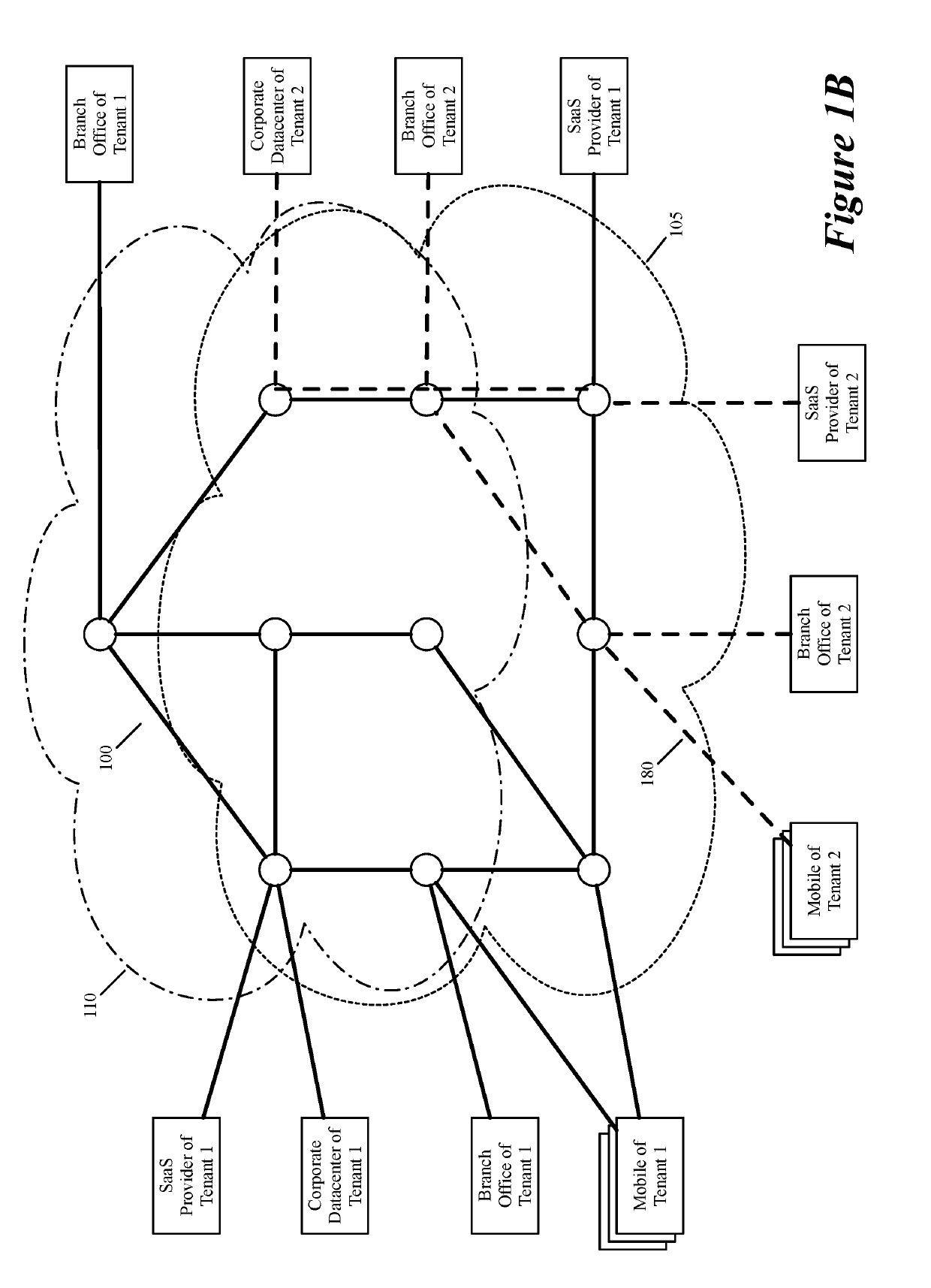
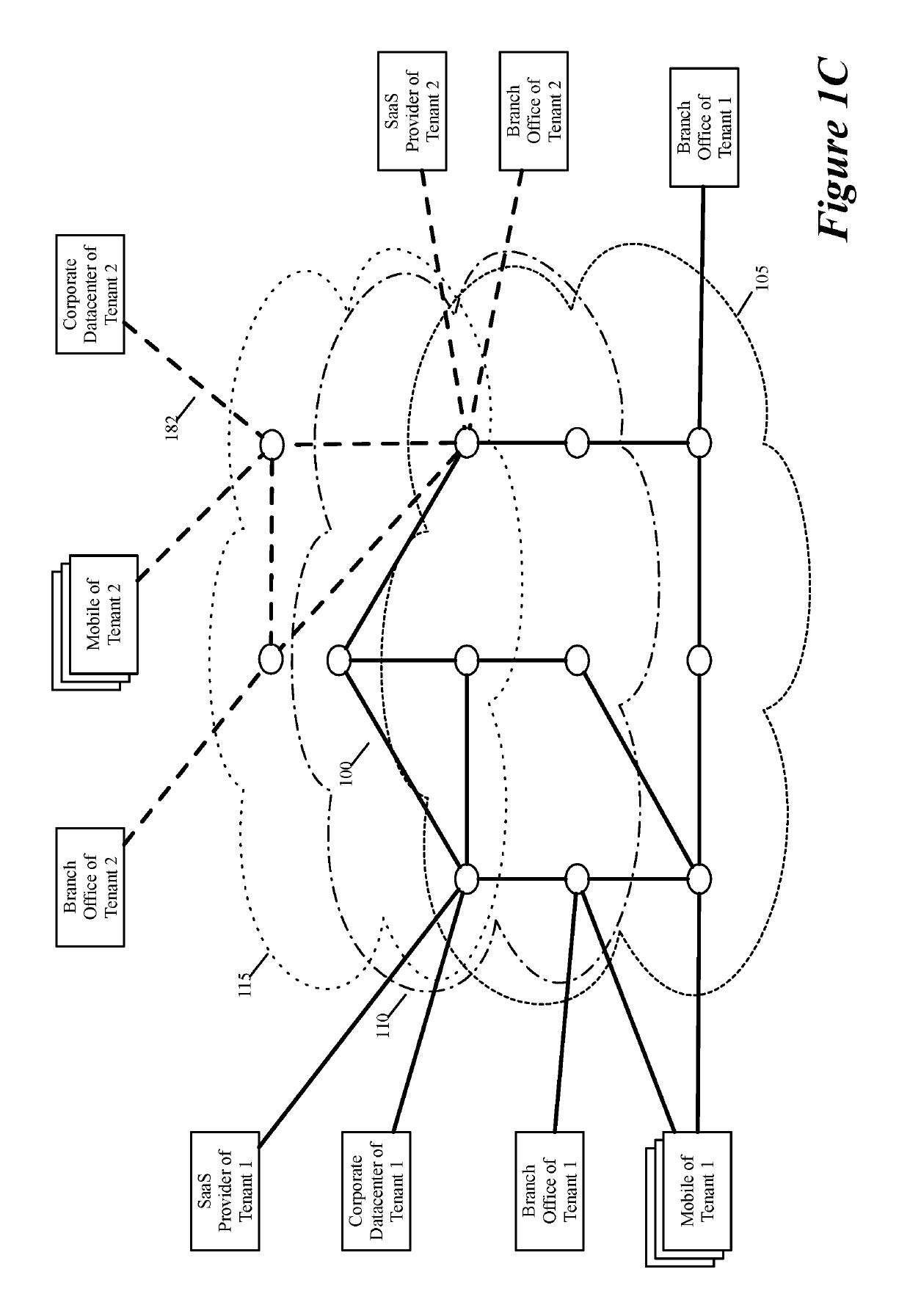
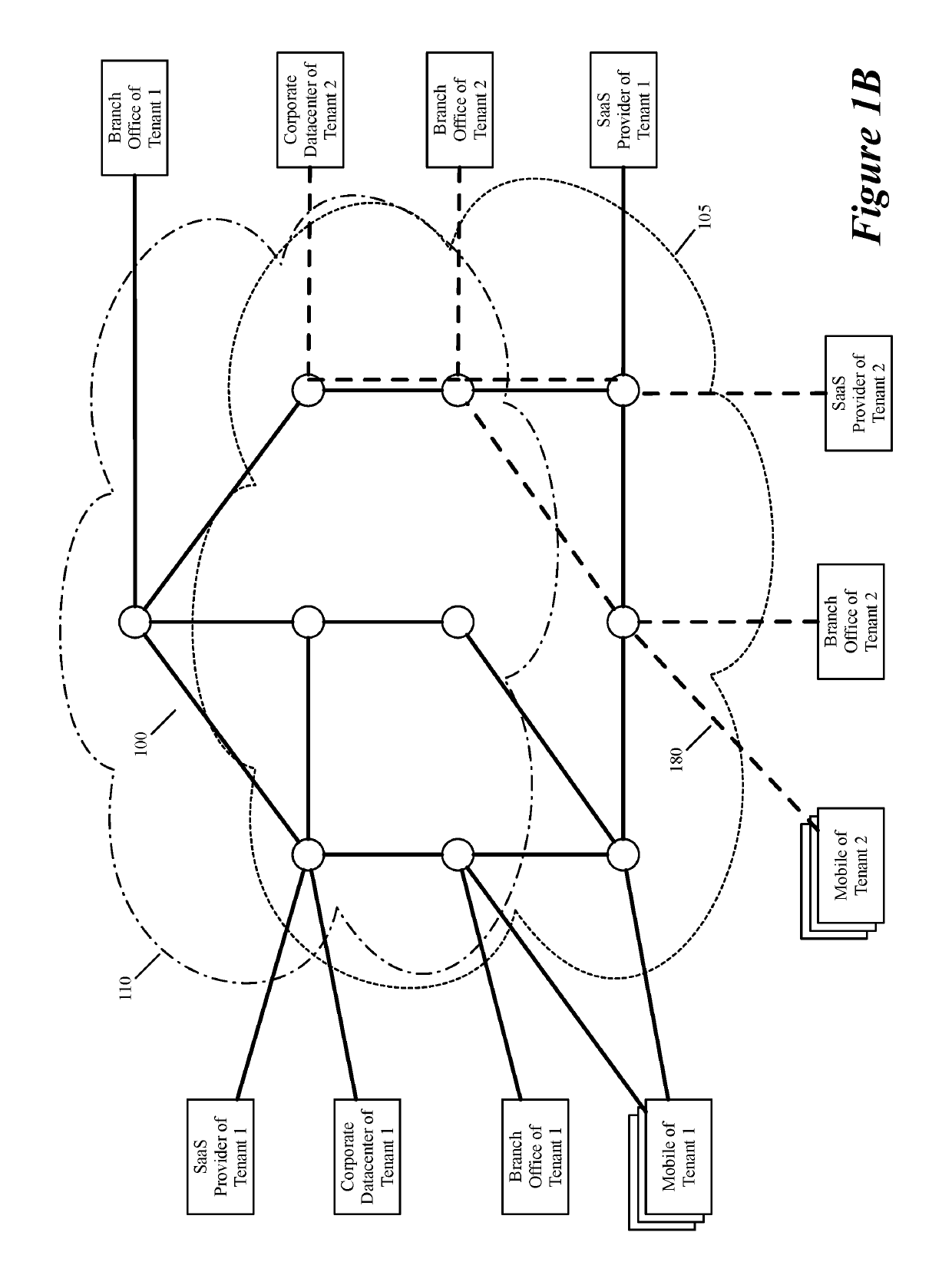
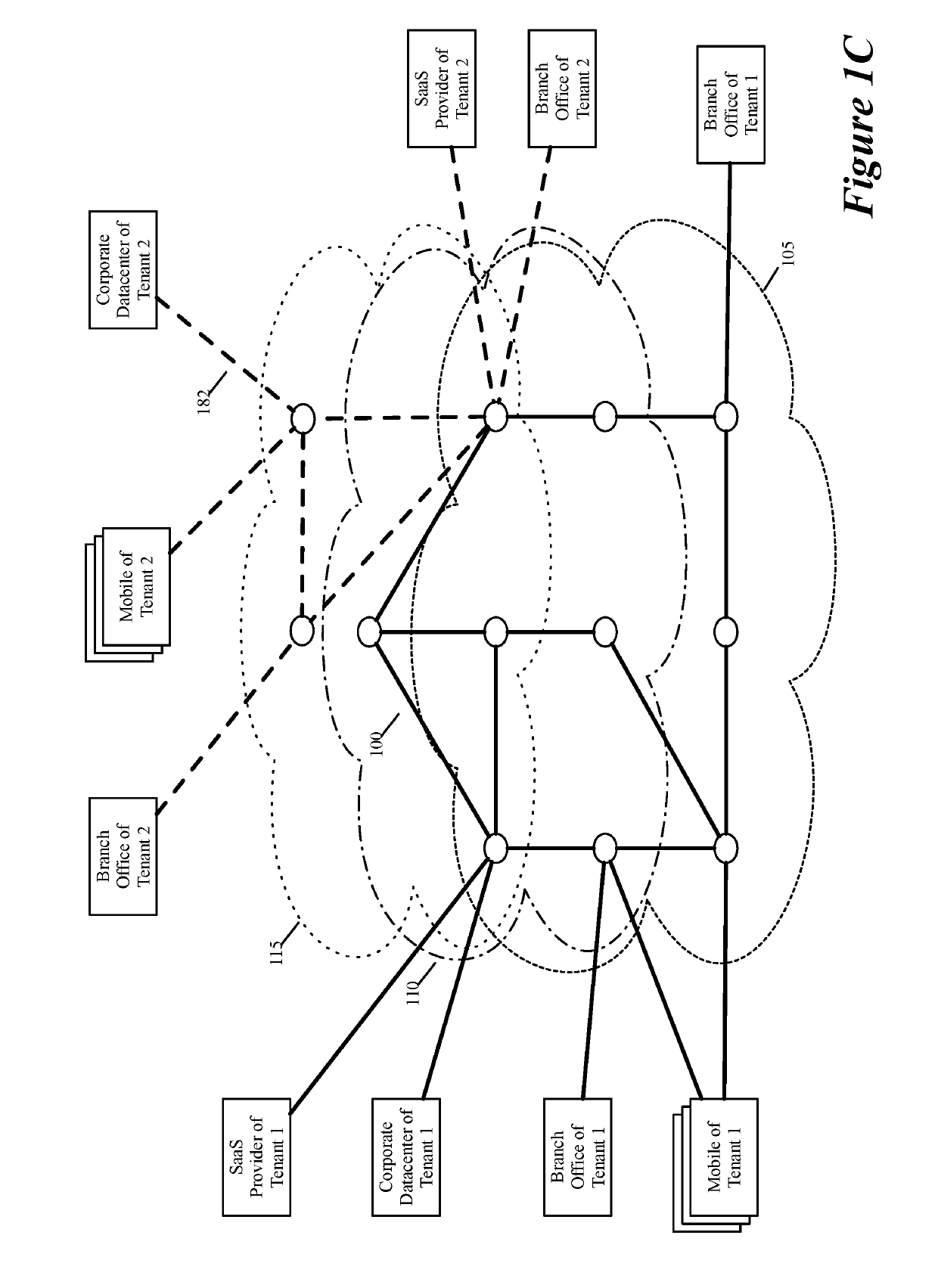
Some embodiments establish for an entity a virtual network over several public clouds of several public cloud providers and / or in several regions. In some embodiments, the virtual network is an overlay network that spans across several public clouds to interconnect one or more private networks (e.g., networks within branches, divisions, departments of the entity or their associated datacenters), mobile users, and SaaS (Software as a Service) provider machines, and other web applications of the entity. The virtual network in some embodiments can be configured to optimize the routing of the entity's data messages to their destinations for best end-to-end performance, reliability and security, while trying to minimize the routing of this traffic through the Internet. Also, the virtual network in some embodiments can be configured to optimize the layer 4 processing of the data message flows passing through the network.
Owner:VMWARE INC
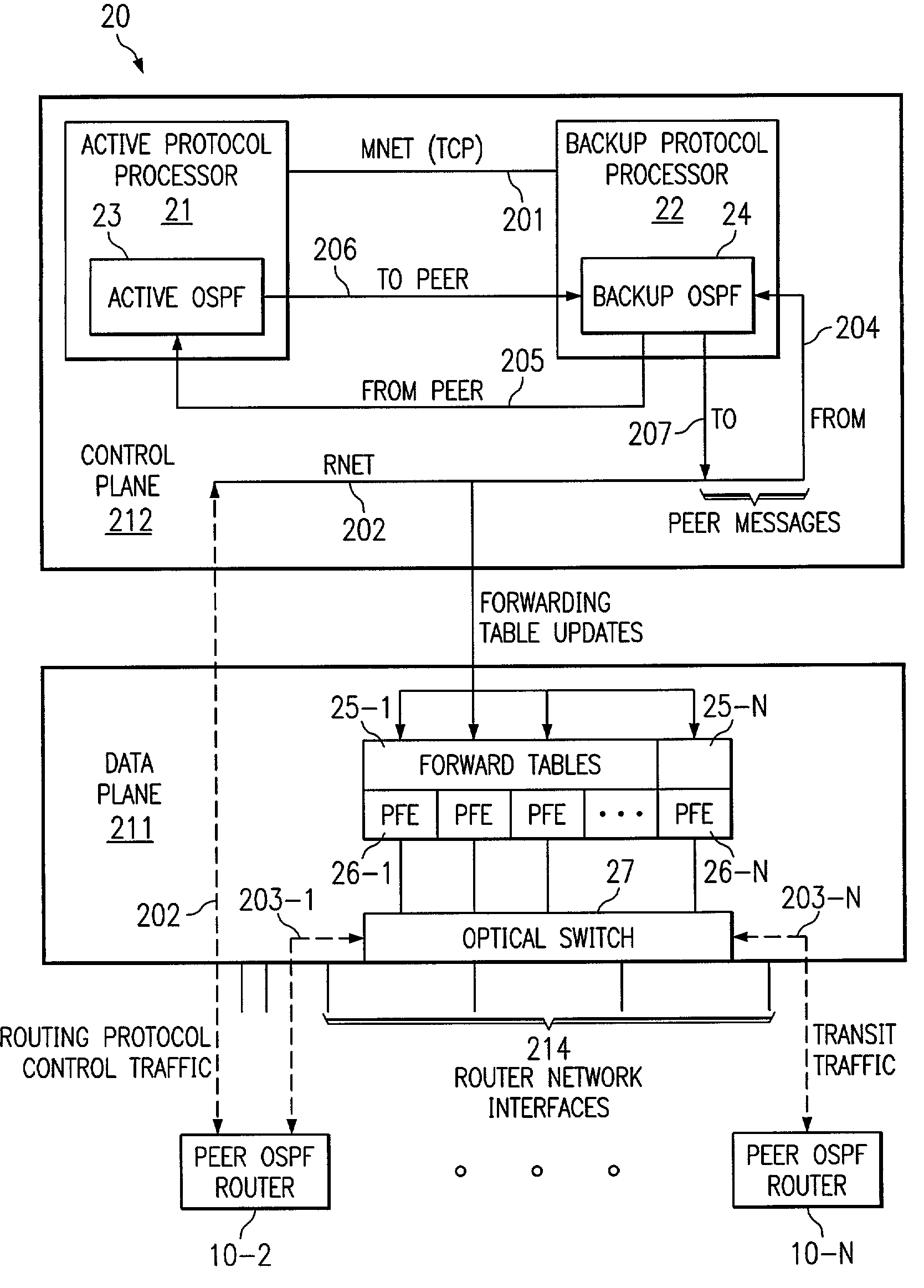
Highly-available OSPF routing protocol
InactiveUS7292535B2Error preventionFrequency-division multiplex detailsMessage flowOpen Shortest Path First
In highly-available Open Shortest Path First (OSPF) routing in a network, the dynamic state of a backup OSPF instance in a router is synchronized with the dynamic state of an active OSPF instance using explicit message transmission from the active instance to the backup instance. After this, the dynamic state synchronization of the backup OSPF instance is maintained using a combination of explicit message updates from the active OSPF instance together with a message flow-through mechanism. In the event of fail-over of the active OSPF instance, then the router recovers seamlessly without reconfiguring or interrupting traffic among peer routers in the network, by functionally substituting the synchronized backup OSPF instance for the active OSPF instance, such that the backup OSPF instance establishes itself as the new active OSPF instance.
Owner:AVAGO TECH INT SALES PTE LTD
Layer four optimization for a virtual network defined over public cloud
ActiveUS20190268421A1Better download timeImprove performanceData switching networksPrivate networkData center
Some embodiments establish for an entity a virtual network over several public clouds of several public cloud providers and / or in several regions. In some embodiments, the virtual network is an overlay network that spans across several public clouds to interconnect one or more private networks (e.g., networks within branches, divisions, departments of the entity or their associated datacenters), mobile users, and SaaS (Software as a Service) provider machines, and other web applications of the entity. The virtual network in some embodiments can be configured to optimize the routing of the entity's data messages to their destinations for best end-to-end performance, reliability and security, while trying to minimize the routing of this traffic through the Internet. Also, the virtual network in some embodiments can be configured to optimize the layer 4 processing of the data message flows passing through the network.
Owner:VMWARE INC
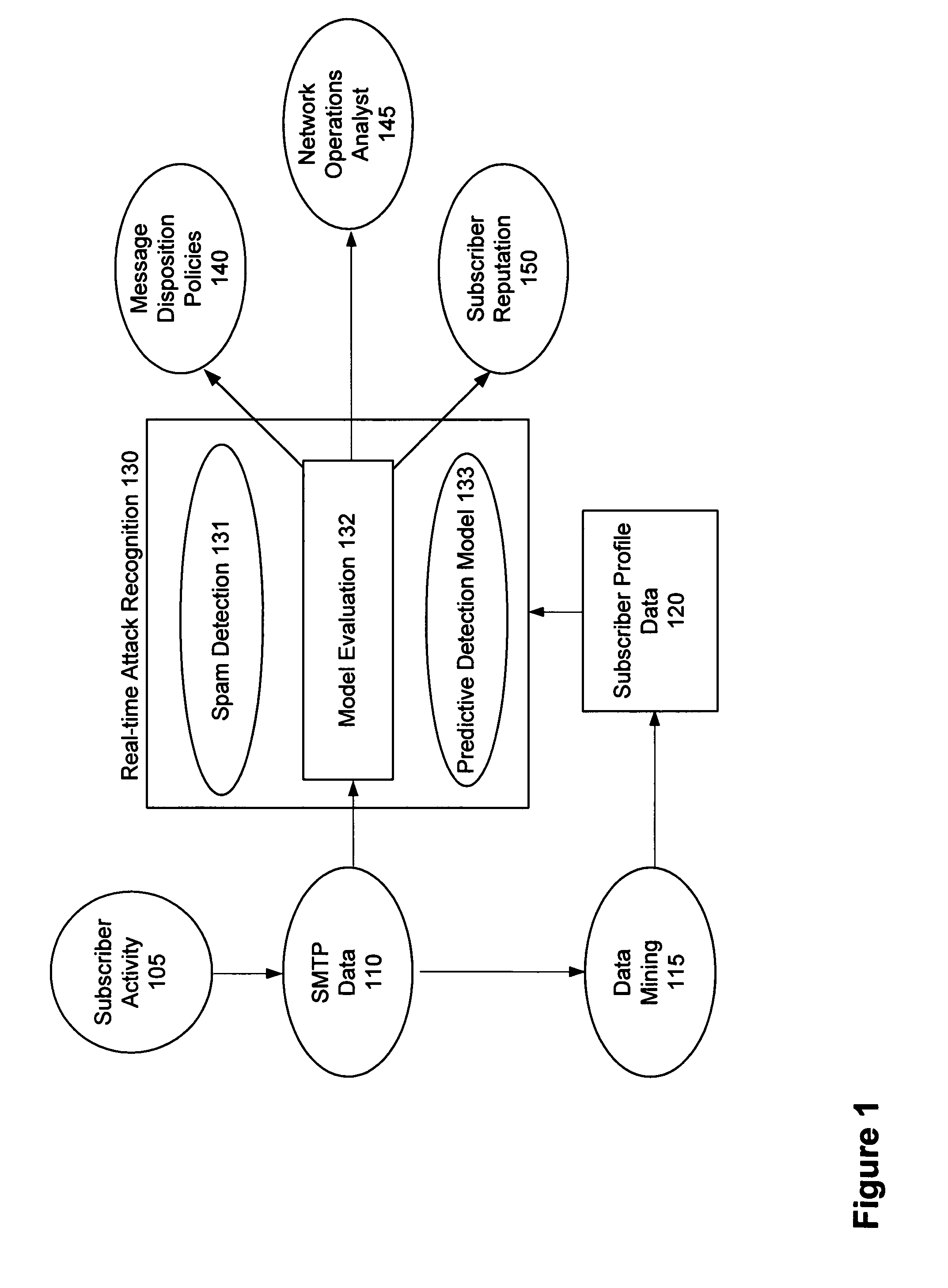
Stopping and remediating outbound messaging abuse
Systems and methods are provided for allowing subscriber message sending profiles to be maintained and used in conjunction with behavior-based anomaly detection techniques and traditional content-based spam signature filtering to enable application of appropriate message disposition policies to outbound subscriber message traffic. According to one embodiment, subscriber profiles are constructed for multiple subscriber accounts associated with a service provider based on outbound message flow originated from the subscriber accounts. Then, possible subscriber account misuse may be discovered by performing behavior-based anomaly detection, including a comparison of a subscriber profile associated with the subscriber account with recent subscriber account usage information, to identify one or more behavioral anomalies in outbound message flow originated from a subscriber account, the behavior-based anomaly detection.
Owner:MUSARUBRA US LLC
Three tiers of saas providers for deploying compute and network infrastructure in the public cloud
ActiveUS20190104035A1Increase redundancyImprove usabilityMetering/charging/biilling arrangementsTelephonic communicationPrivate networkData center
Some embodiments establish for an entity a virtual network over several public clouds of several public cloud providers and / or in several regions. In some embodiments, the virtual network is an overlay network that spans across several public clouds to interconnect one or more private networks (e.g., networks within branches, divisions, departments of the entity or their associated datacenters), mobile users, and SaaS (Software as a Service) provider machines, and other web applications of the entity. The virtual network in some embodiments can be configured to optimize the routing of the entity's data messages to their destinations for best end-to-end performance, reliability and security, while trying to minimize the routing of this traffic through the Internet. Also, the virtual network in some embodiments can be configured to optimize the layer 4 processing of the data message flows passing through the network.
Owner:VMWARE INC
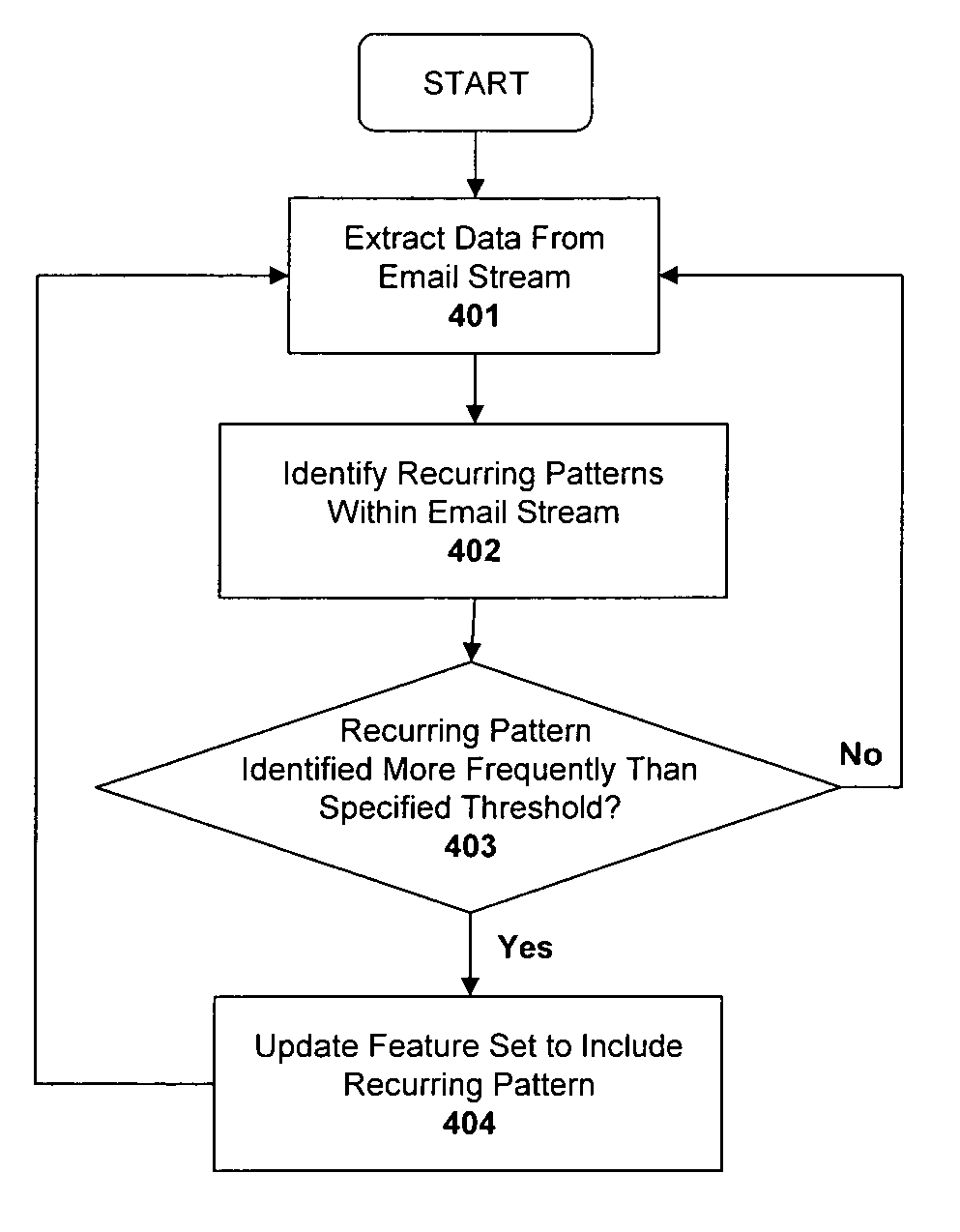
Message stream analysis for spam detection and filtering
ActiveUS7716297B1Memory loss protectionDigital data processing detailsMessage flowStatistical analysis
A system and method are described for performing a correlative statistical analysis on a stream of email messages to identify new spam campaigns. For example, a method according to one embodiment of the invention comprises: extracting a series of patterns from a stream of incoming email messages; performing a correlation between the patterns to identify recurring patterns within the stream of email messages over a specified time period; dynamically updating a spam filtering engine to include a particular recurring pattern if the number of times the particular recurring pattern is detected within the specified time period is above a first specified threshold value.
Owner:PROOFPOINT INC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com