Patents
Literature
7433 results about "Traffic flow" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
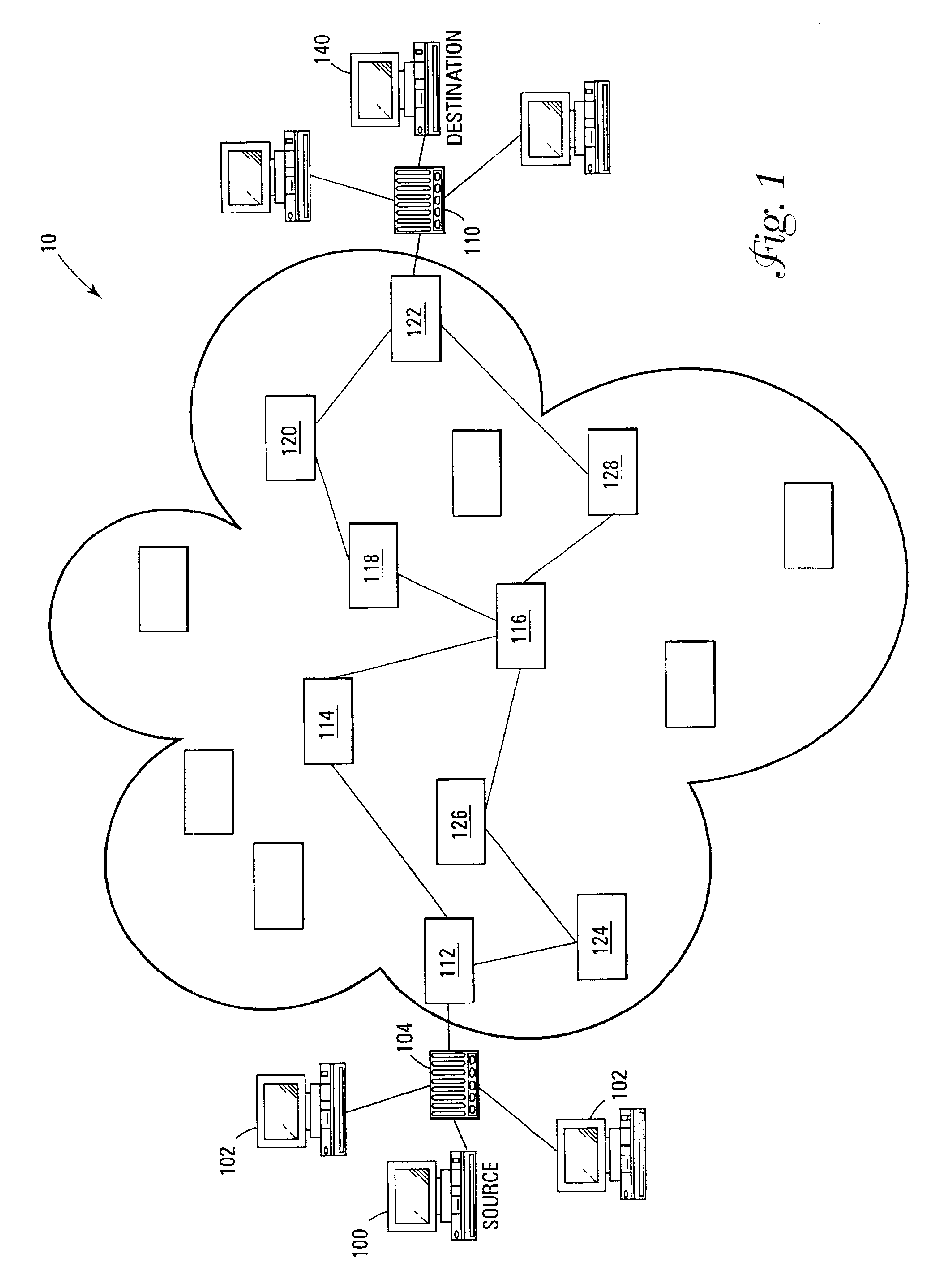
In mathematics and transportation engineering, traffic flow is the study of interactions between travellers (including pedestrians, cyclists, drivers, and their vehicles) and infrastructure (including highways, signage, and traffic control devices), with the aim of understanding and developing an optimal transport network with efficient movement of traffic and minimal traffic congestion problems.
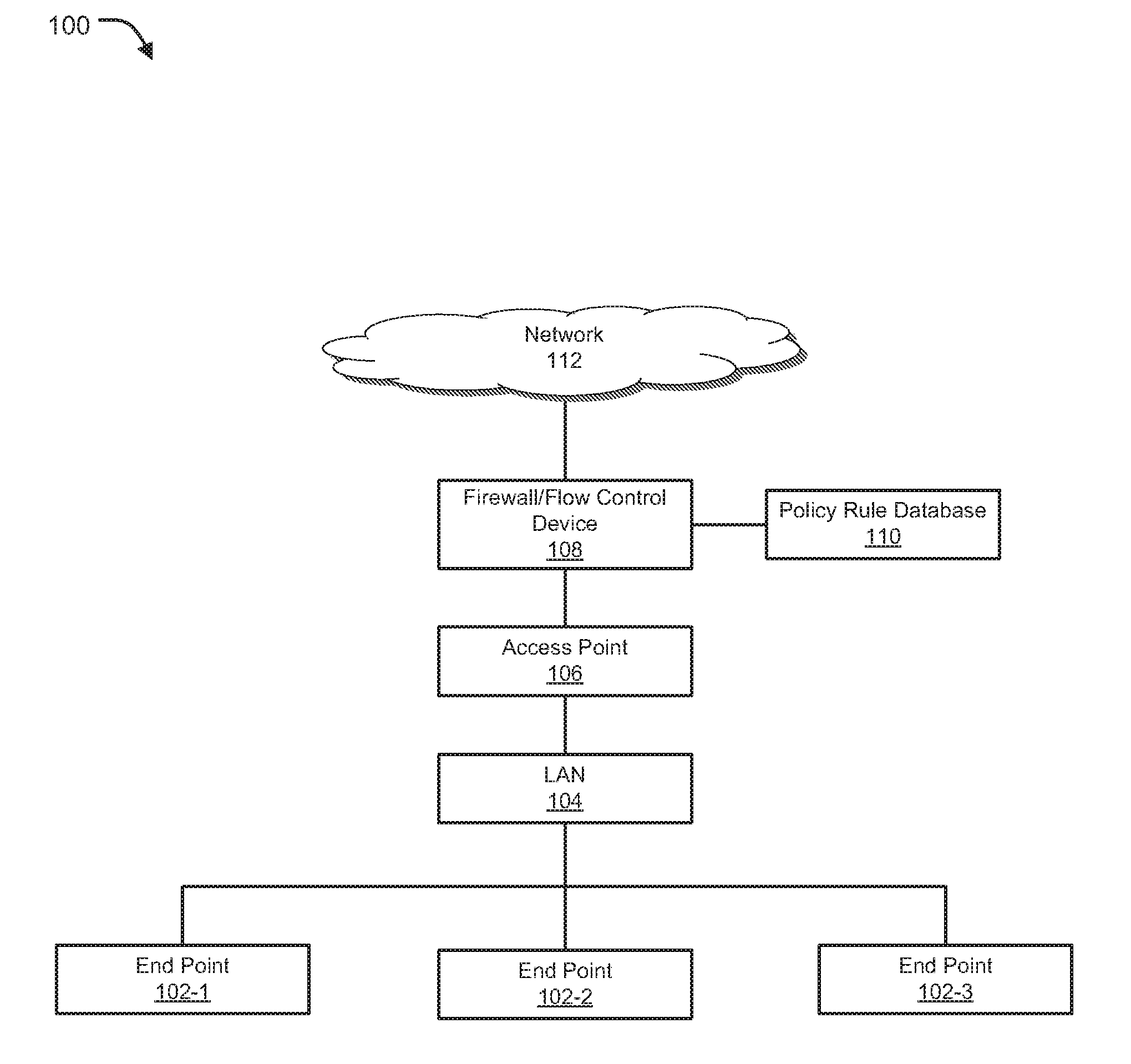
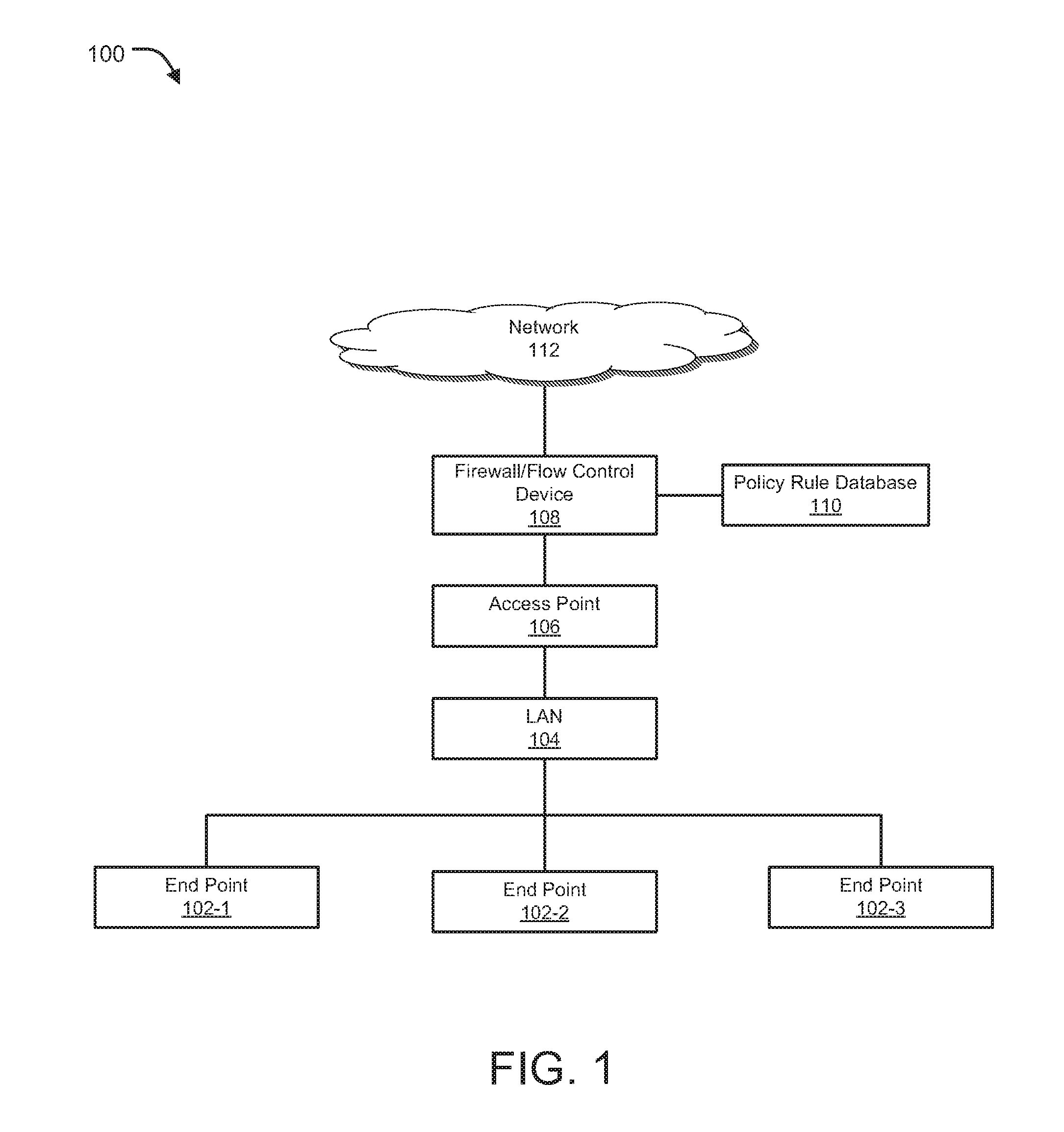
System and method for optimizing network capacity in a cellular wireless network
InactiveUS20050007993A1Easy to adaptNetwork traffic/resource managementPower distribution line transmissionQuality of serviceFiber
Owner:CHAMBERS MAHDI +1
Robust anomaly detection and regularized domain adaptation of classifiers with application to internet packet-flows
InactiveUS20120284791A1Maximize aggregate statistical significanceMaximizesMathematical modelsMemory loss protectionCredit cardAlgorithm
Sound, robust methods identify the most suitable, parsimonious set of tests to use with respect to prioritized, sequential anomaly detection in a collected batch of sample data. While the focus is on detecting anomalies in network traffic flows and classifying network traffic flows into application types, the methods are also applicable to other anomaly detection and classification application settings, including detecting email spam, (e.g. credit card) fraud detection, detecting imposters, unusual event detection (for example, in images and video), host-based computer intrusion detection, detection of equipment or complex system failures, as well as of anomalous measurements in scientific experiments.
Owner:PENN STATE RES FOUND
Lane-level vehicle navigation for vehicle routing and traffic management
ActiveUS20140278052A1Improves other aspectSimple methodInstruments for road network navigationRoad vehicles traffic controlTraffic signalTransportation planning
A lane-level vehicle routing and navigation apparatus includes a simulation module that performs microsimulation of individual vehicles in a traffic stream, and a lane-level optimizer that evaluates conditions along the candidate paths from an origin to a destination as determined by the simulation module, and determines recommended lane-level maneuvers along the candidate paths. A link-level optimizer may determines the candidate paths based on link travel times determined by the simulation module. The simulation may be based on real-time traffic condition data. Recommended candidate paths may be provided to delivery or service or emergency response vehicles, or used for evacuation planning, or to route vehicles such as garbage or postal trucks, or snowplows. Corresponding methods also may be used for traffic planning and management, including determining, based on microsimulation, at least one of (a) altered road geometry, (b) altered traffic signal settings, such as traffic signal timing, or (c) road pricing.
Owner:CALIPER CORPORATION
Traffic policing in a mobile ad hoc network
InactiveUS7068600B2Hinders its propagationError preventionTransmission systemsTraffic flowMobile ad hoc network
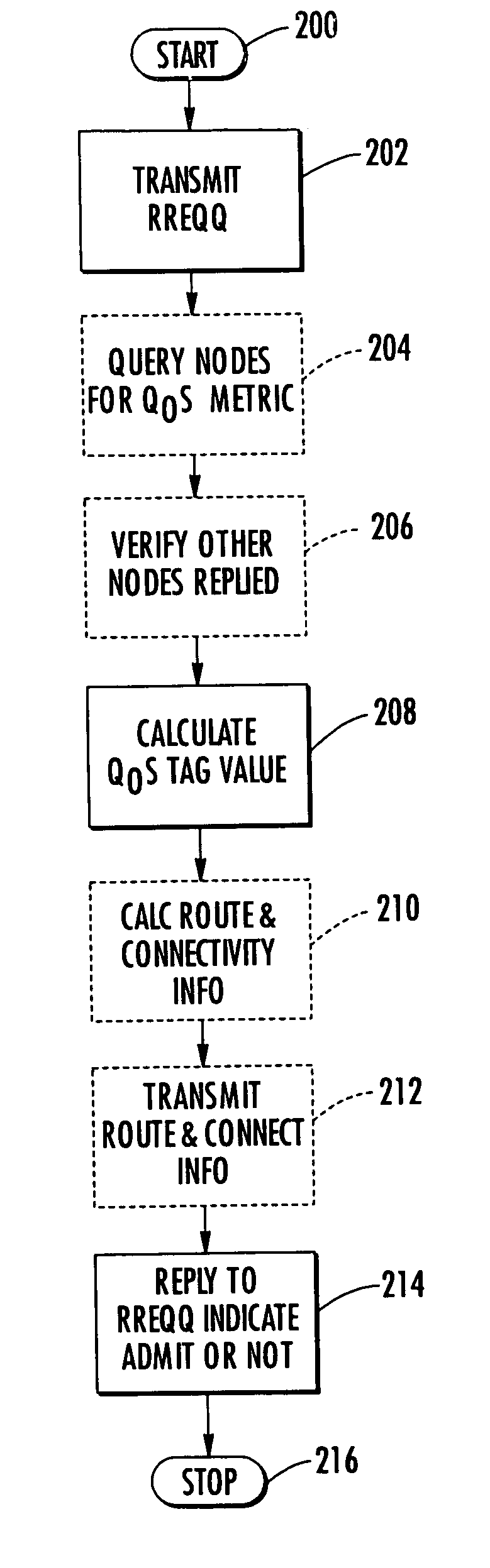
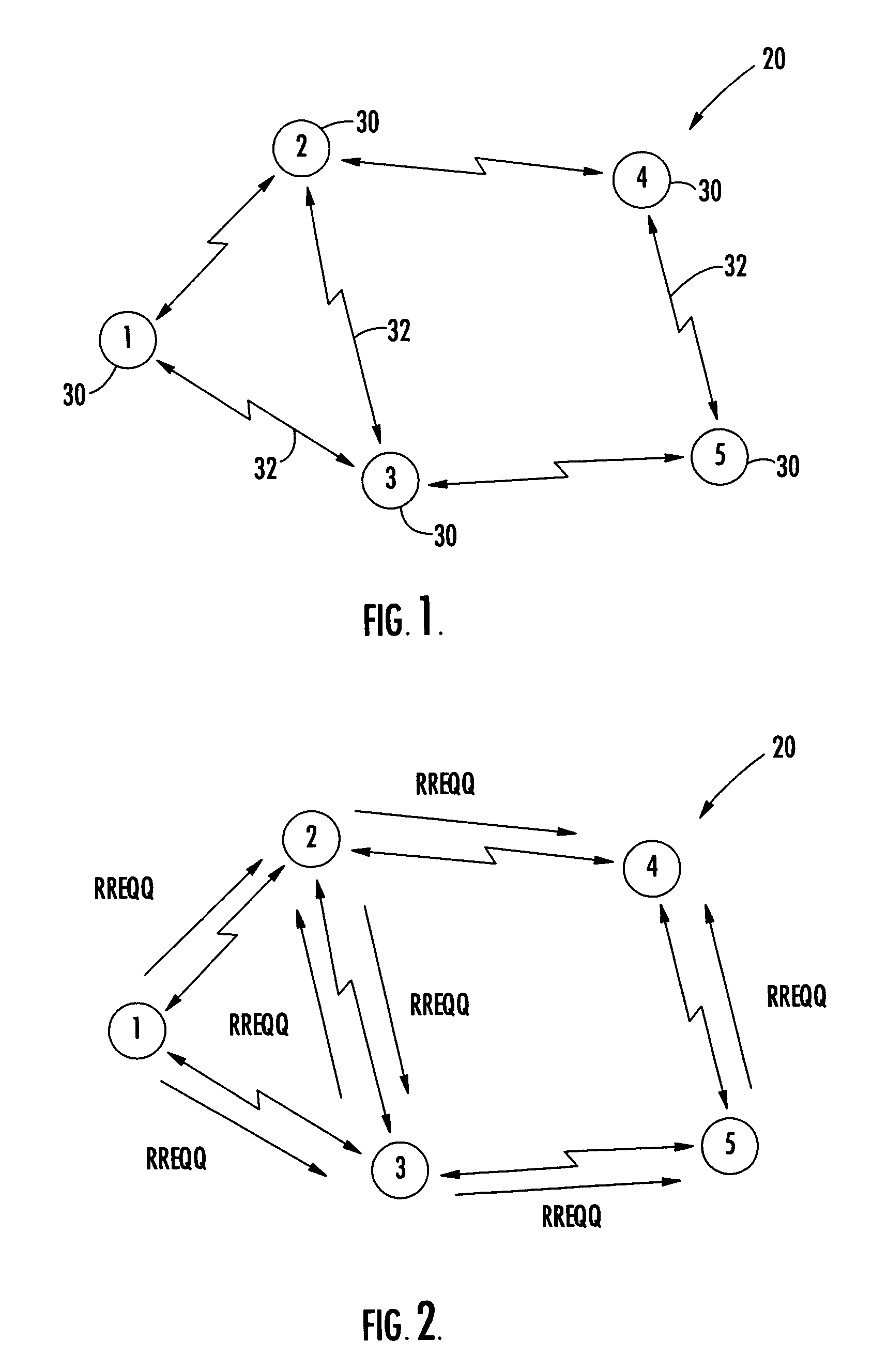
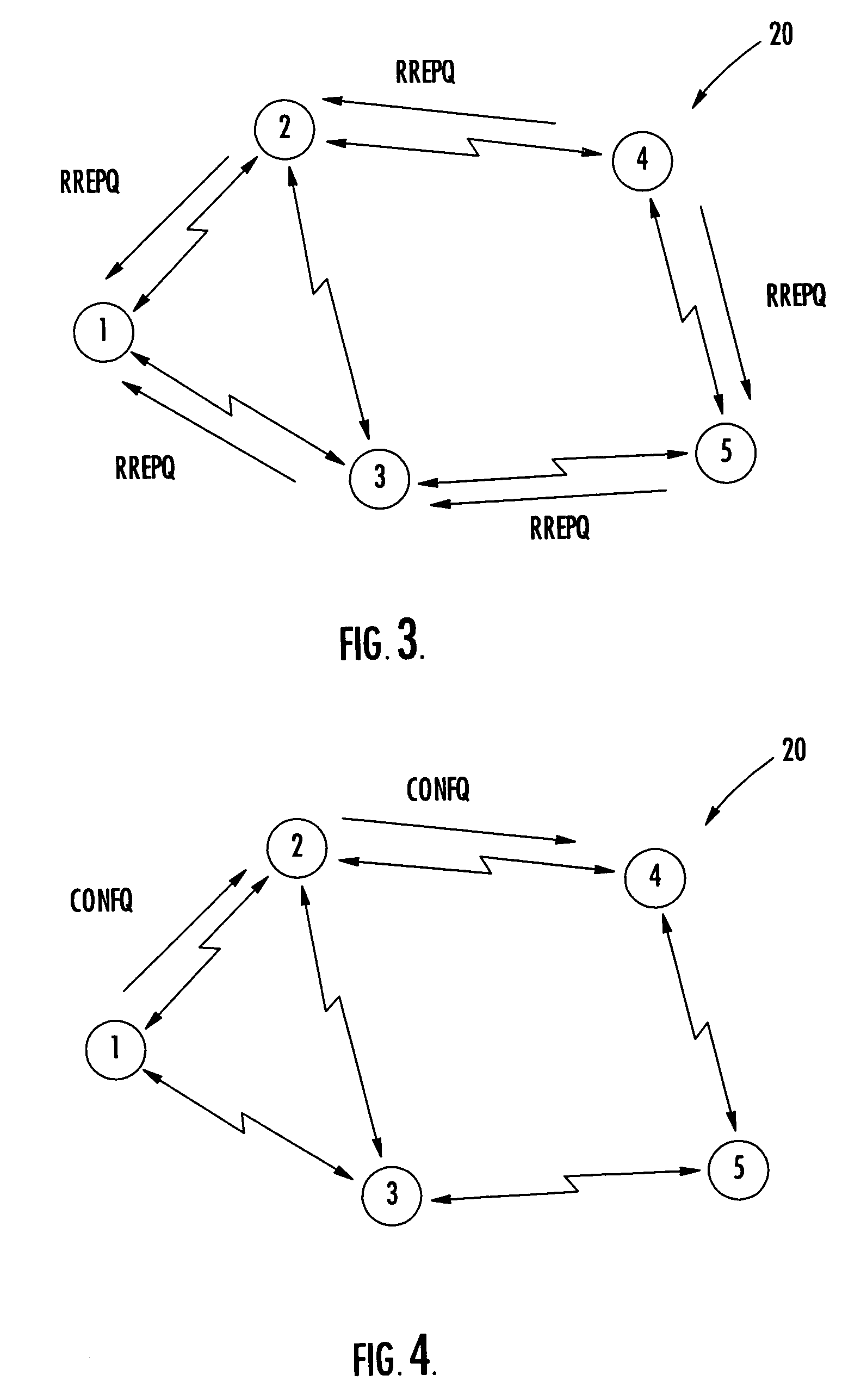
The method includes nodes transmitting quality-of-service (QoS) route requests to discover traffic routing based upon a QoS parameter, and the QoS route requests including a traffic flow identifier. Each node calculates a node QoS tag value to make traffic admission control decisions, and each node determines whether to admit traffic in response to QoS route requests based upon the calculated QoS tag value and the QoS parameter of QoS route requests. Also, each node replies to QoS route requests to indicate whether the node can support the QoS parameter of the route request and admit the traffic, and each node polices admitted traffic based upon the traffic flow identifier to ensure that admitted traffic does not exceed the QoS parameter of the QoS route request.
Owner:STINGRAY IP SOLUTIONS LLC
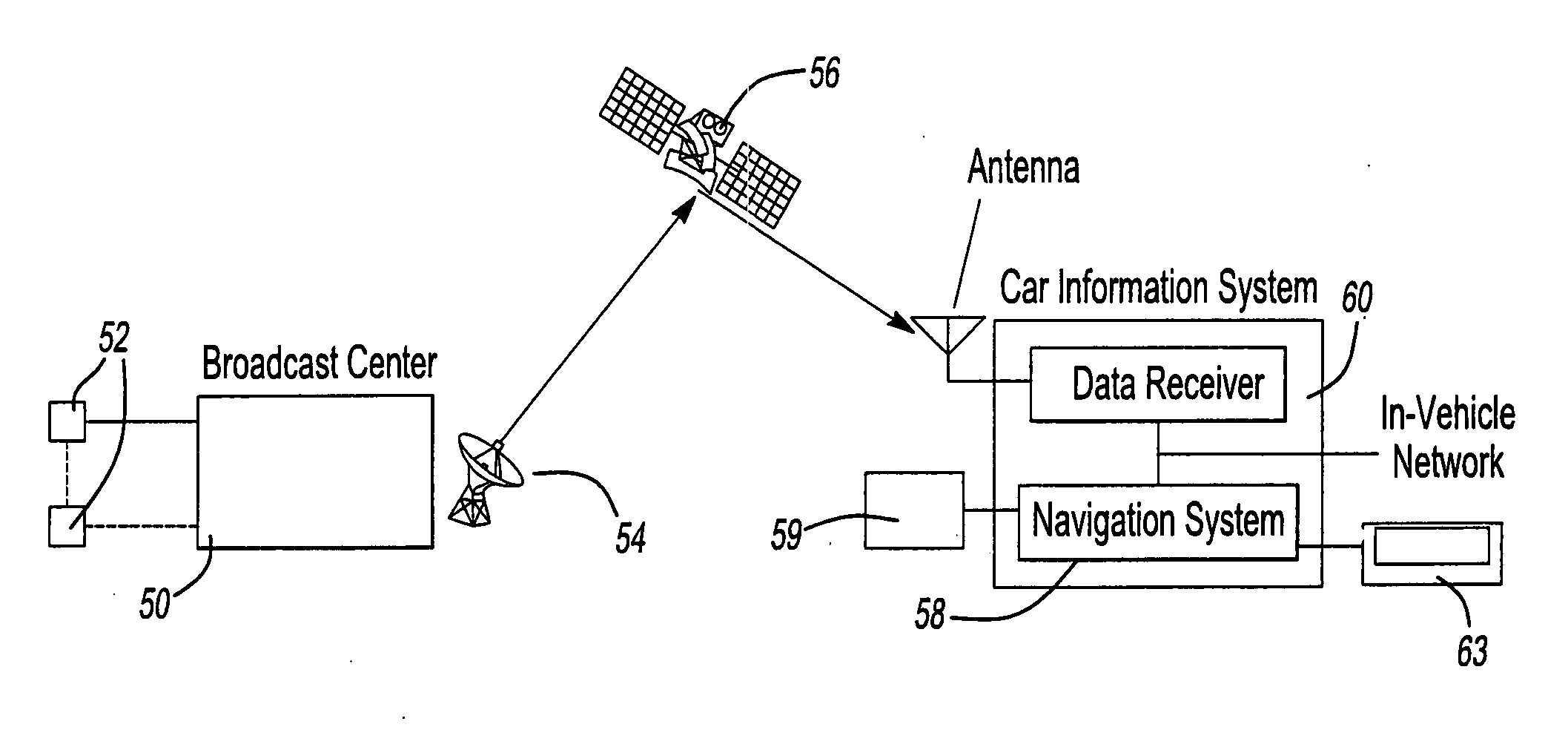
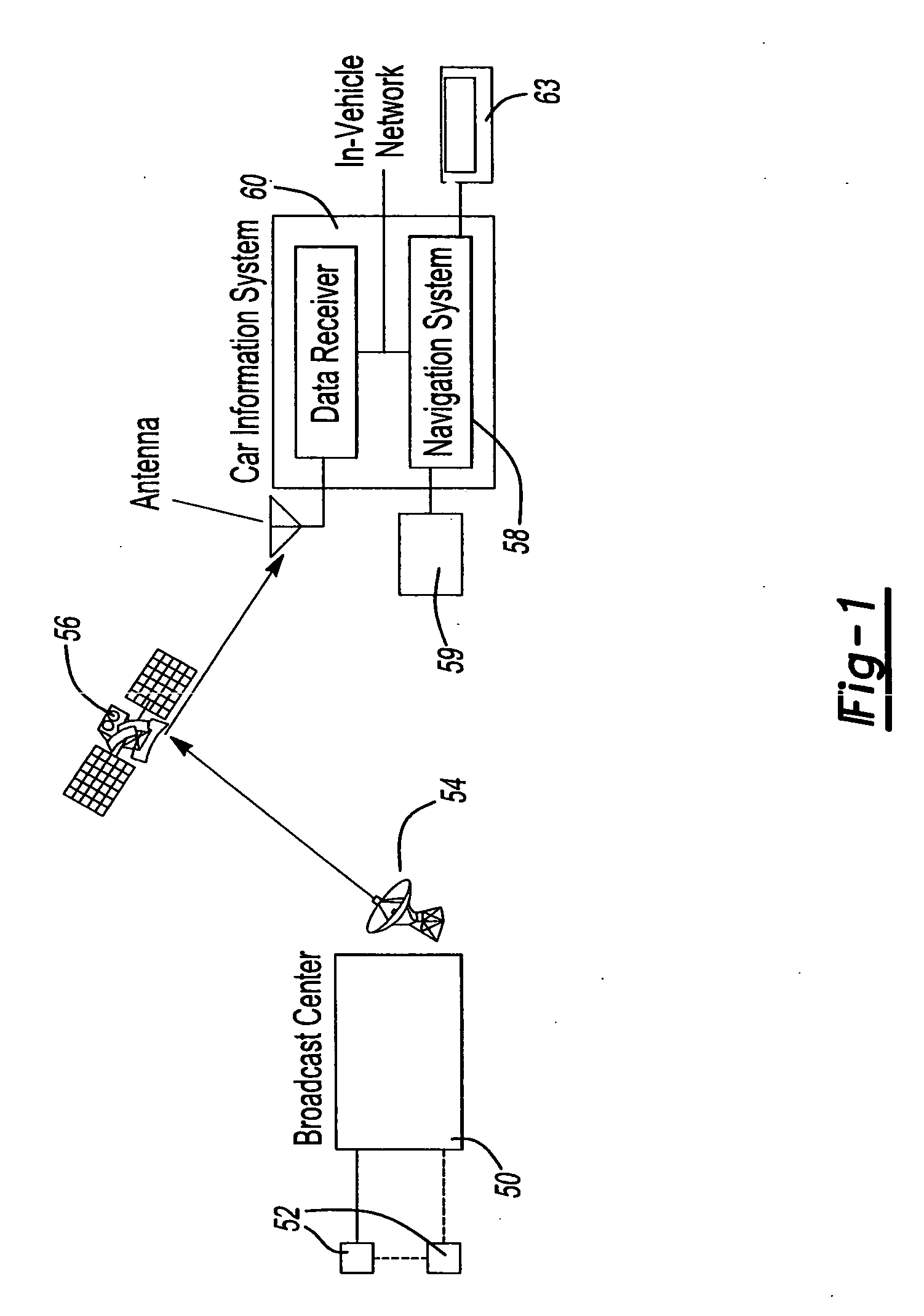
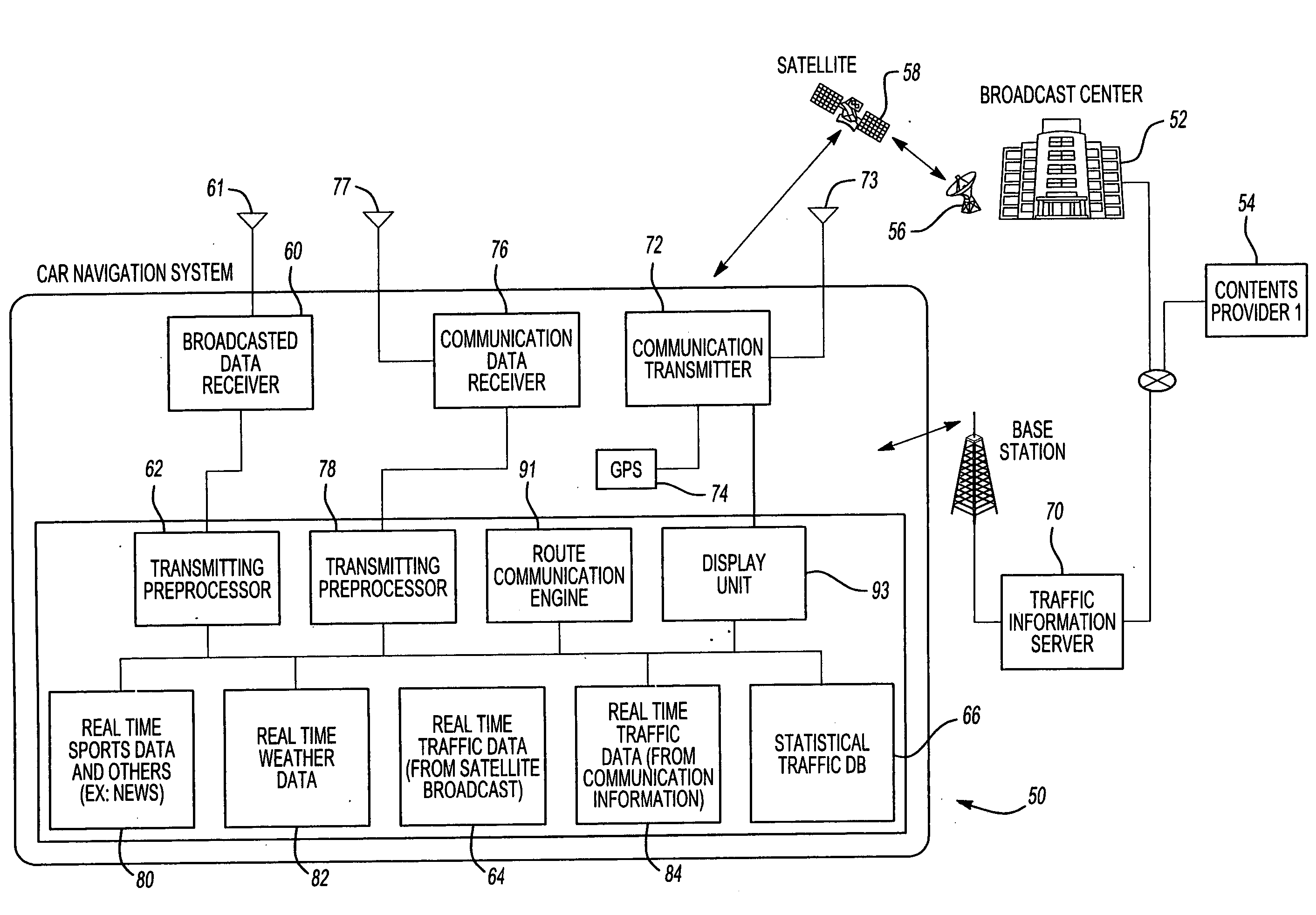
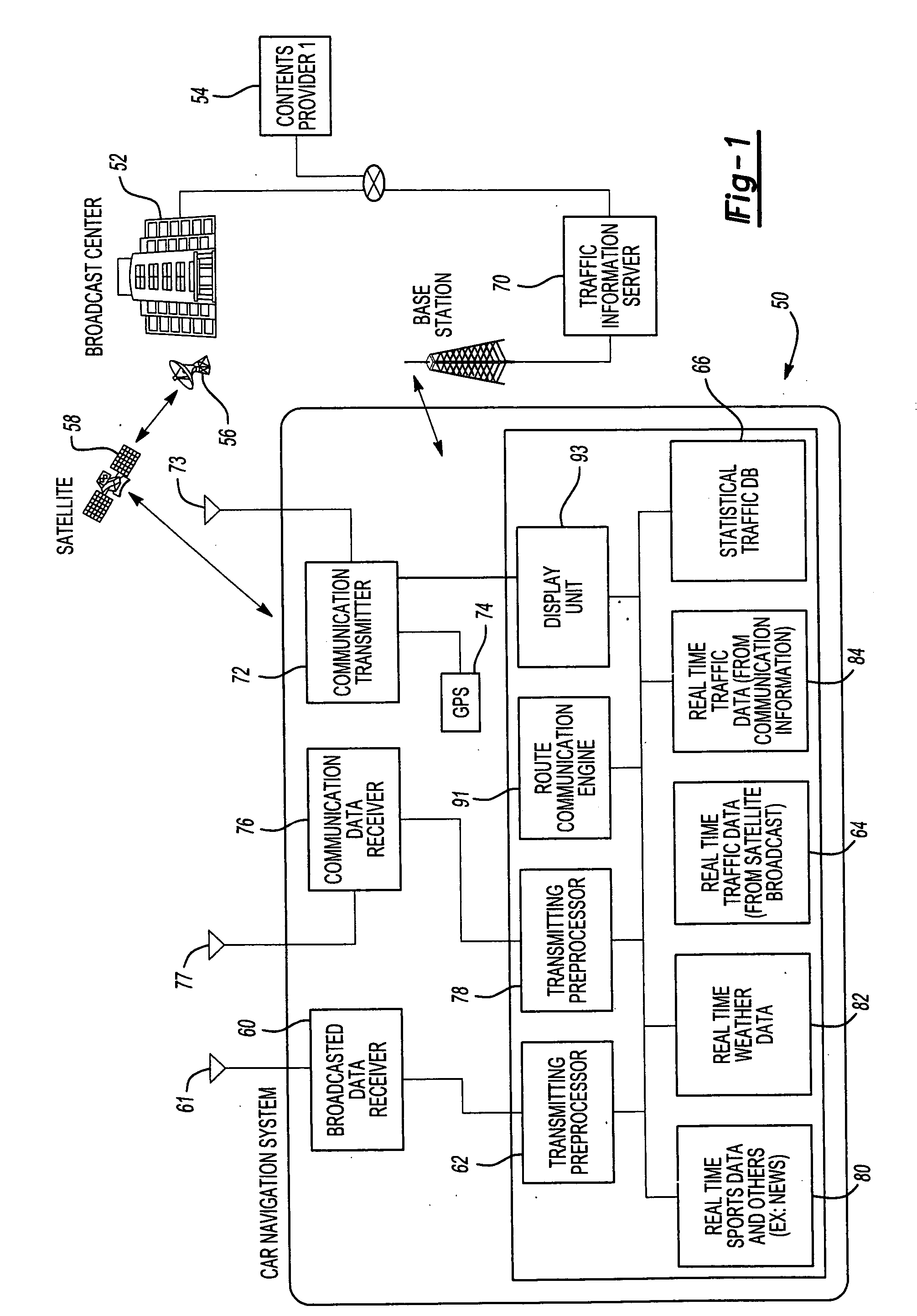
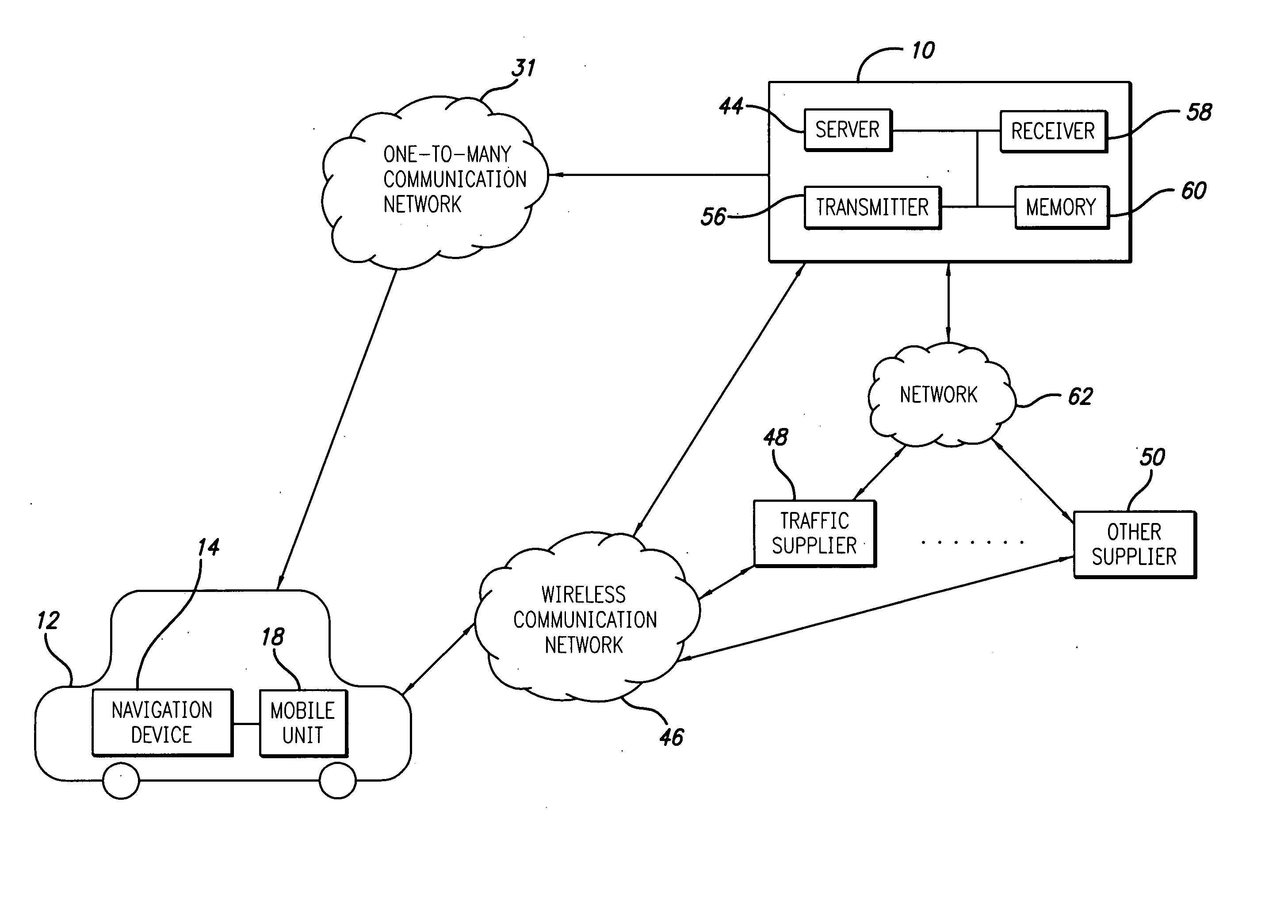
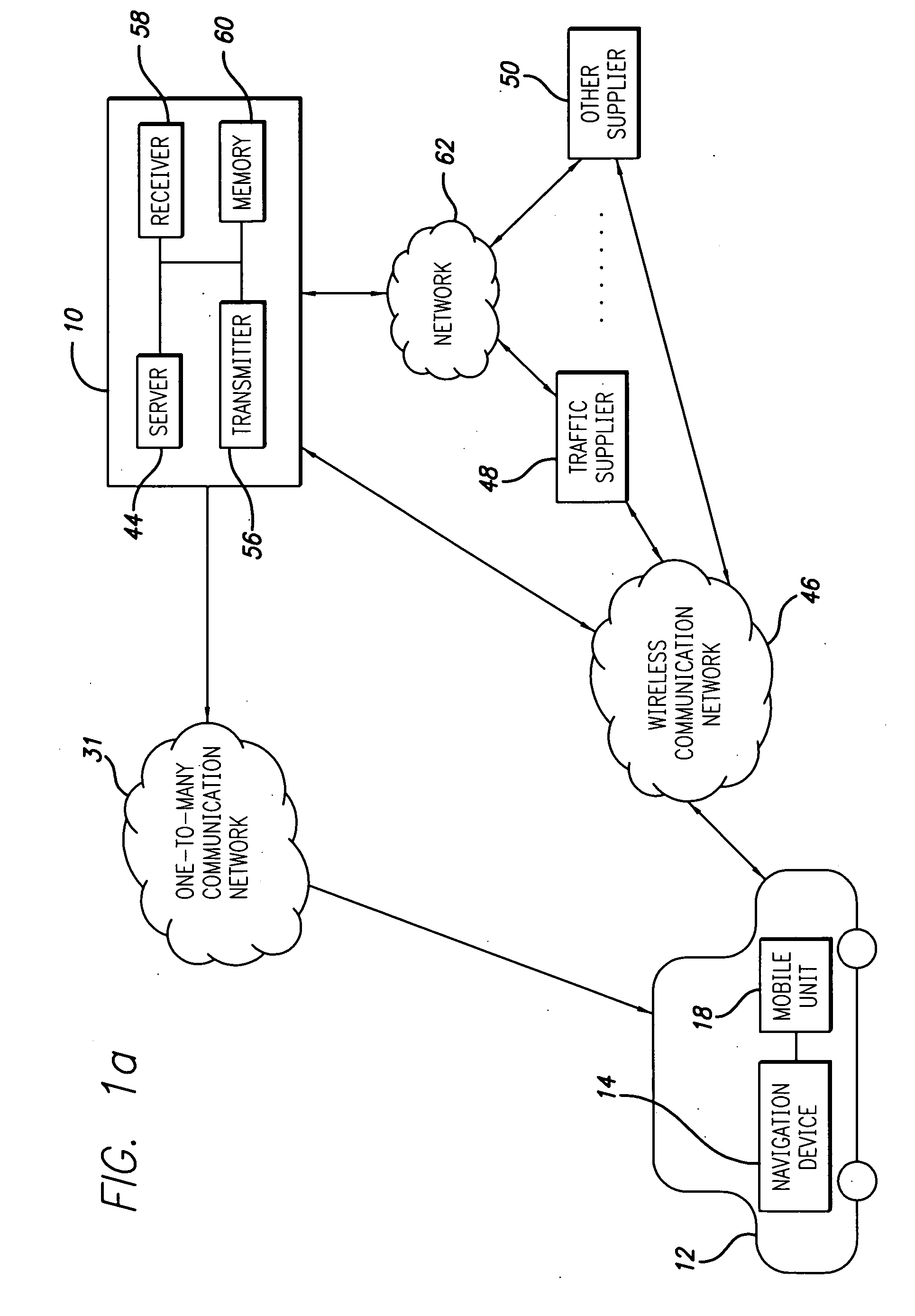
System and method for processing and displaying traffic information in an automotive navigation system
InactiveUS20060055565A1Analogue computers for vehiclesArrangements for variable traffic instructionsDisplay deviceTraffic flow
A system and method for displaying traffic information in an automotive navigation system having a display, memory and a data receiver. The method includes the first step of storing in a traffic speed table in memory at least two speed threshold limits wherein each speed threshold limit represents a different traffic flow category. The receiver receives data representative of the vehicle speed on at least one road segment and compares that received vehicle speed data with the traffic speed table to determine the traffic flow category corresponding to the received speed data for the road segment. A visual indicator is then displayed on the display which corresponds to the traffic flow category for the road segment. The user is able to customize the speed threshold limits through a GUI. These speed threshold limits are further user modifiable as a function of weather, day of the week, road conditions, type of road, as well as other factors.
Owner:CLARION CO LTD
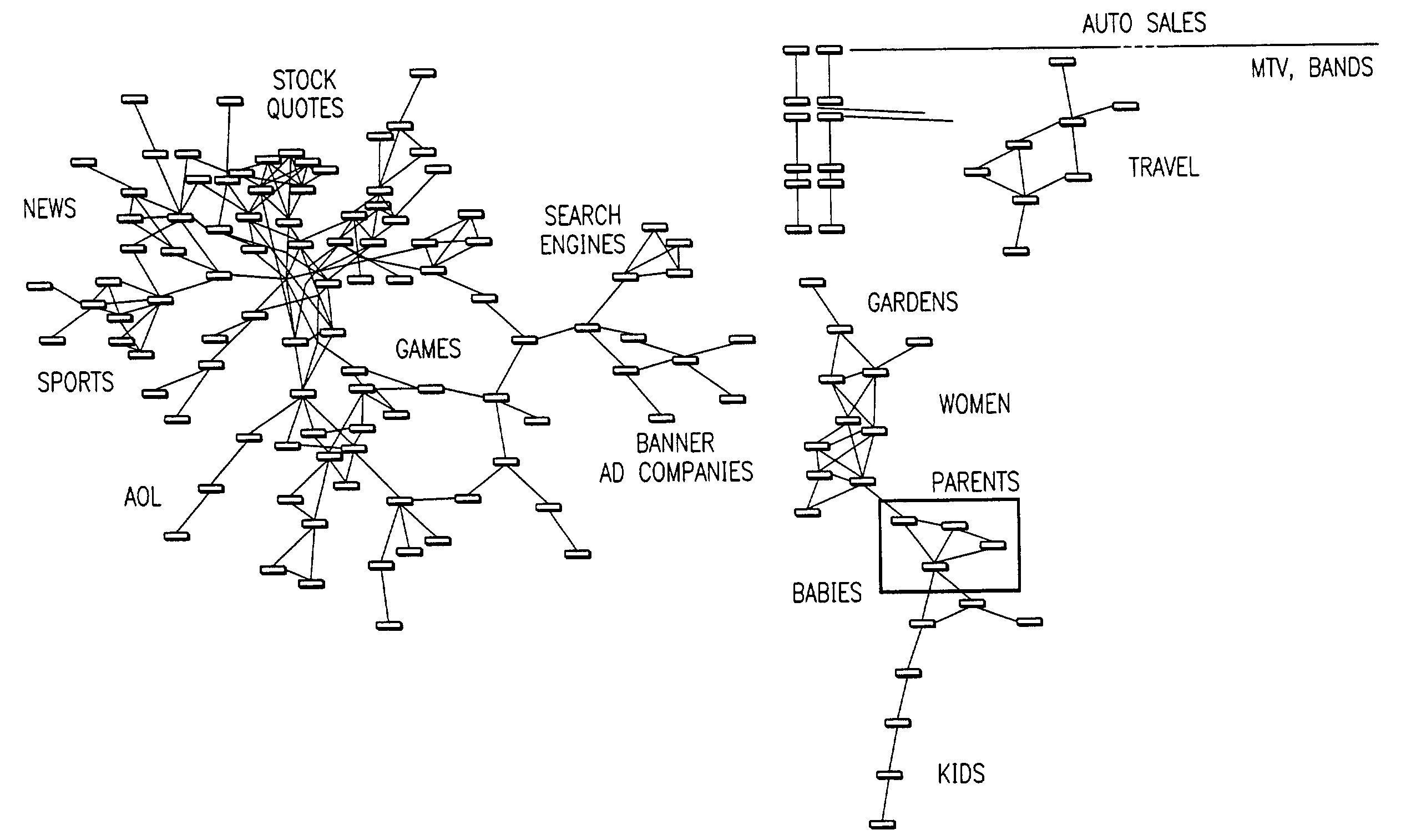
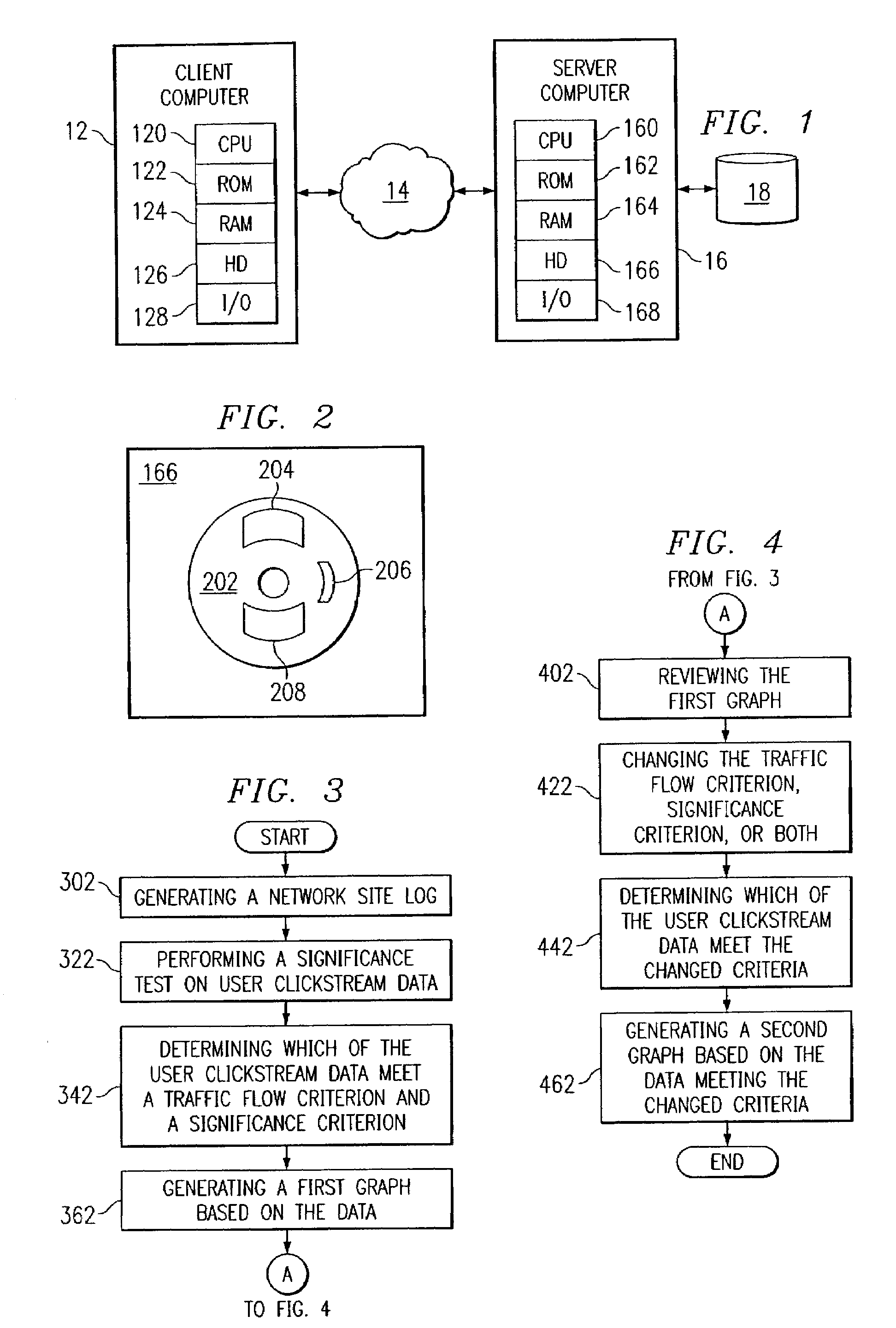
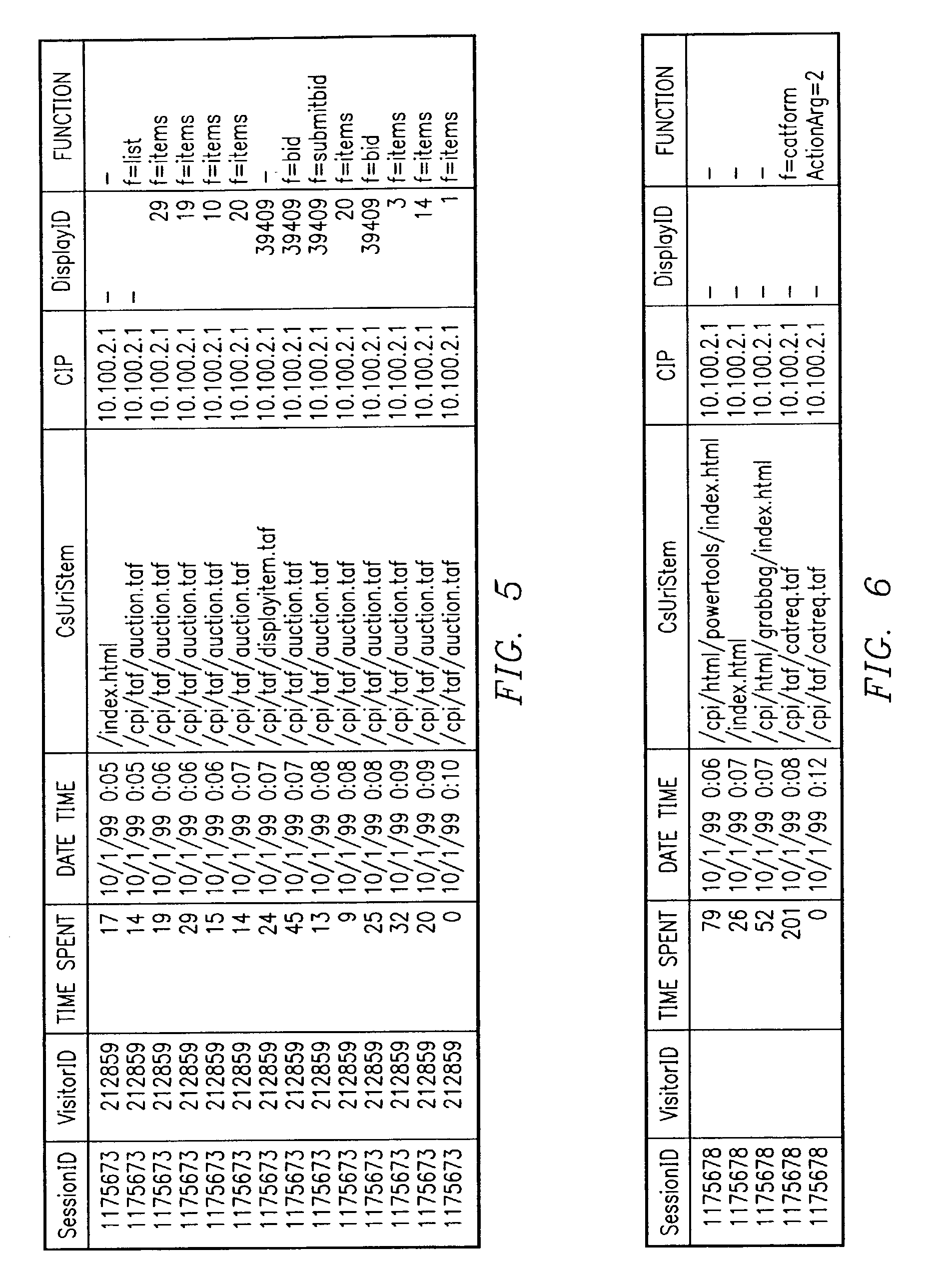
Visualization and analysis of user clickpaths
Methods and data processing system readable media have been created to graph user clickstream data over a network or at a network site to yield meaningful and visually esthetic information. In one set of embodiments, the method can comprise (i) performing a significance test on data from a network log and generating significance results. The method can also comprise (ii) determining which of network addresses and clicktrails between network addresses meet a traffic flow criterion. The data that meet a significance criterion, traffic criterion, or both can form (iii) graphable addresses and relationships. The method can further comprise (iv) generating statistics about the graphable addresses and relationships. The method can still further comprise (v) generating a graph based on the statistics about the graphable addresses and relationships, and (vi) changing any or all of the traffic flow, significance criterion, and statistics being computed, and regenerating the graph.
Owner:OPEN TEXT SA ULC
System and Method for Vehicular Communications
InactiveUS20070242339A1Reduce decreaseReduce impactElectric signal transmission systemsDigital data processing detailsData streamControl system
A method for communicating with a vehicle has a generator for producing a data stream that can indicate, street sign information, house number, lead vehicle information, traffic information, oncoming vehicle information, juxtaposed vehicle information, a voice channel, etc. vehicle information can indicate braking, low beam requests, direct or indirect traffic flow information, adjacency, partial adjacency, or presence of nearby vehicles, etc. This signal is generated by at least one of: the sign, house number, oncoming vehicle, lead vehicle, operator of the lead vehicle, operator of the oncoming vehicle, operator of the juxtaposed vehicle, a traffic control system. A device for generating such data streams is discussed, as well as, a device for receiving such data streams. Information pertinent to the people in the vehicles or operation of the vehicle can be modulated on the link.
Owner:BRADLEY JAMES ROY
Consistent sampling for network traffic measurement
InactiveUS6873600B1Reduce ambiguityIncrease choiceError preventionFrequency-division multiplex detailsHash functionNetwork measurement
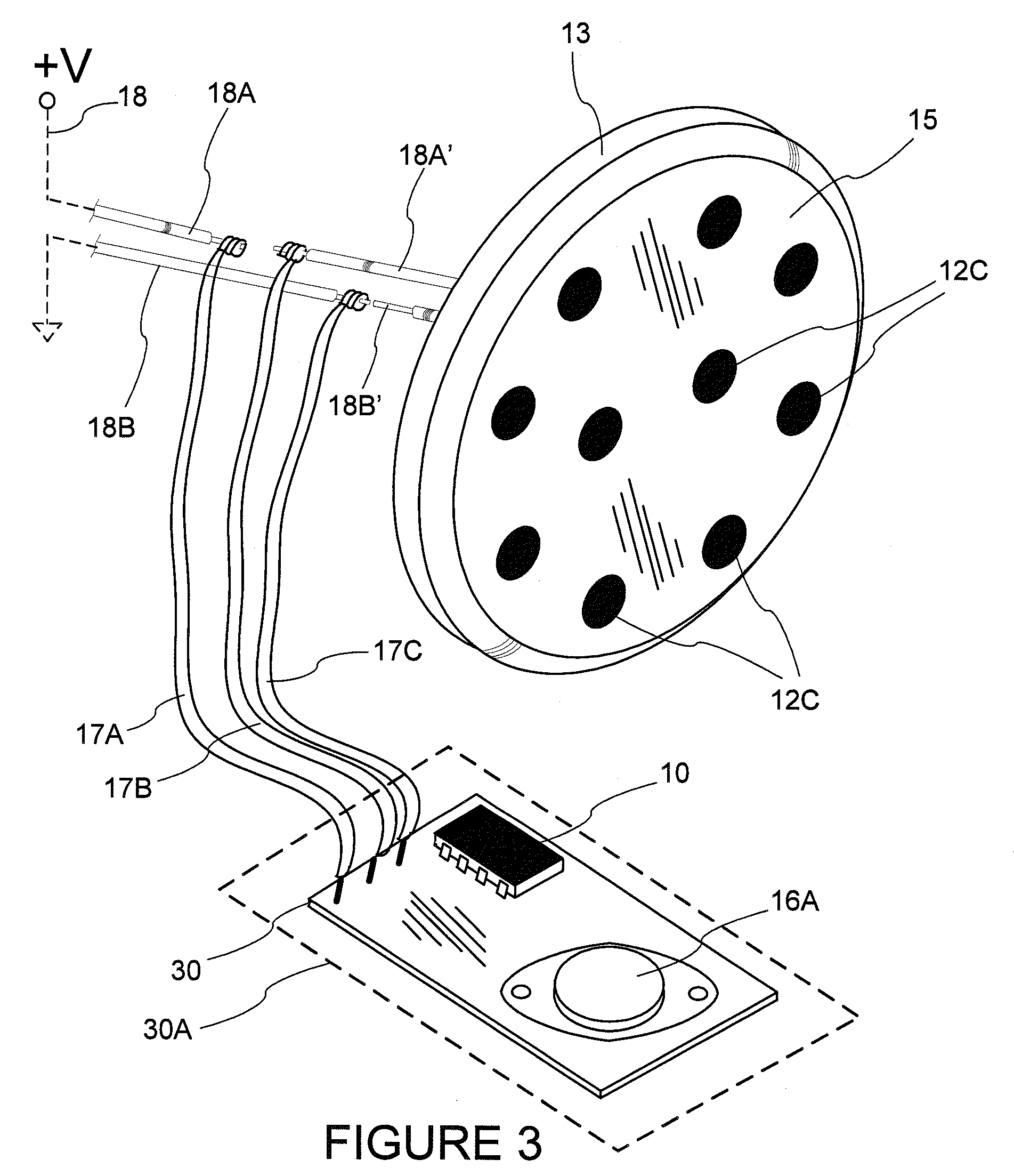
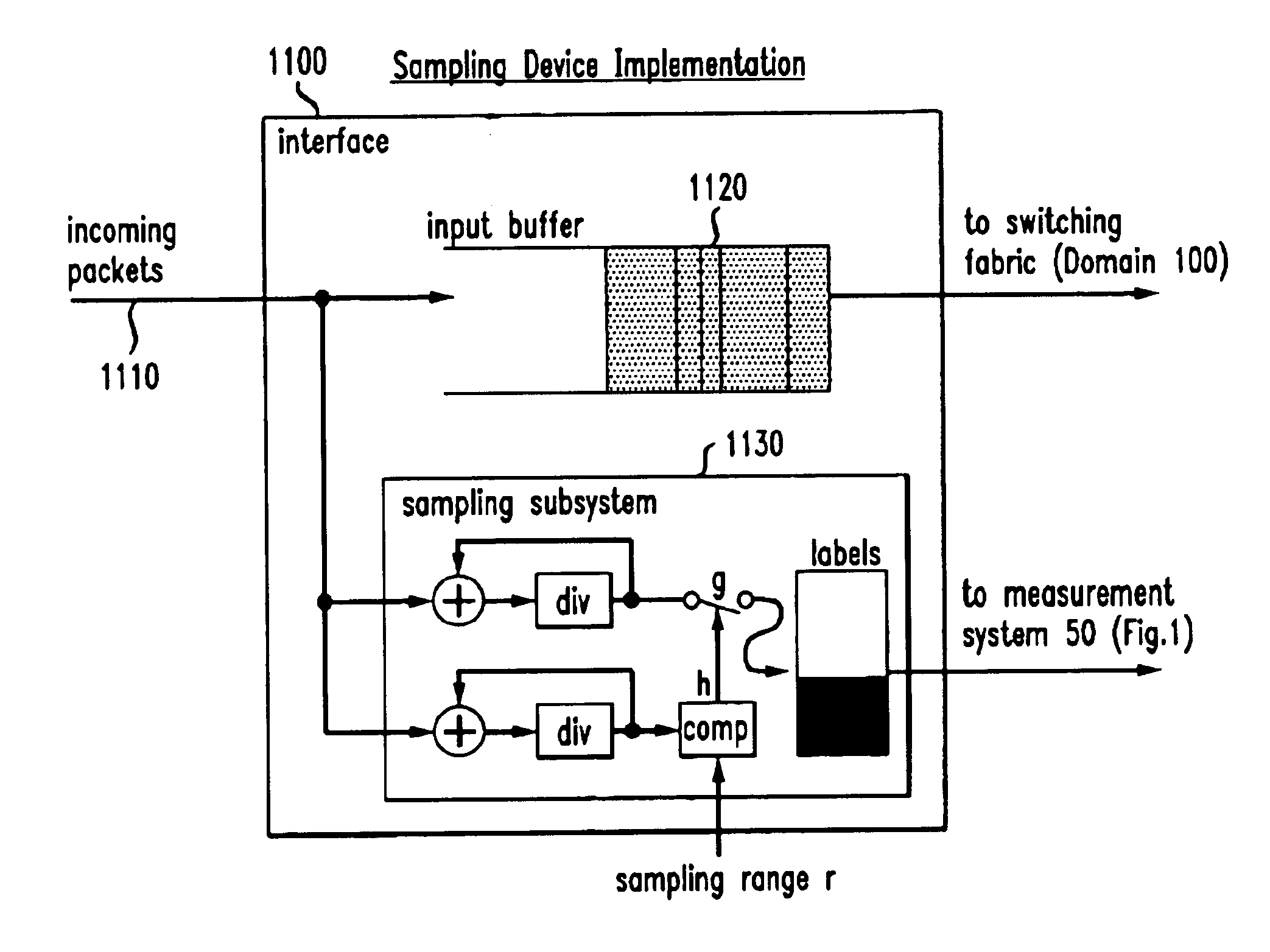
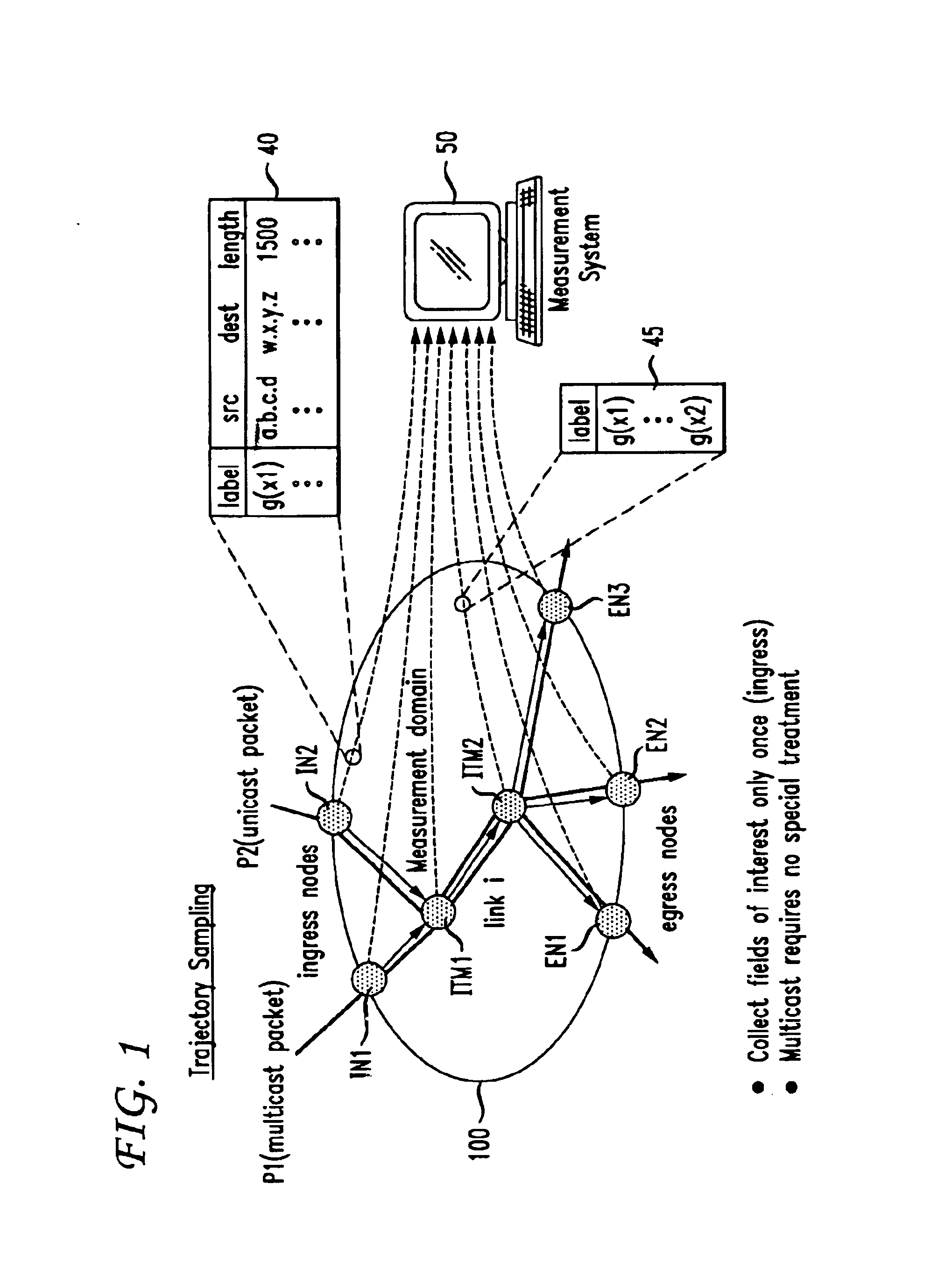
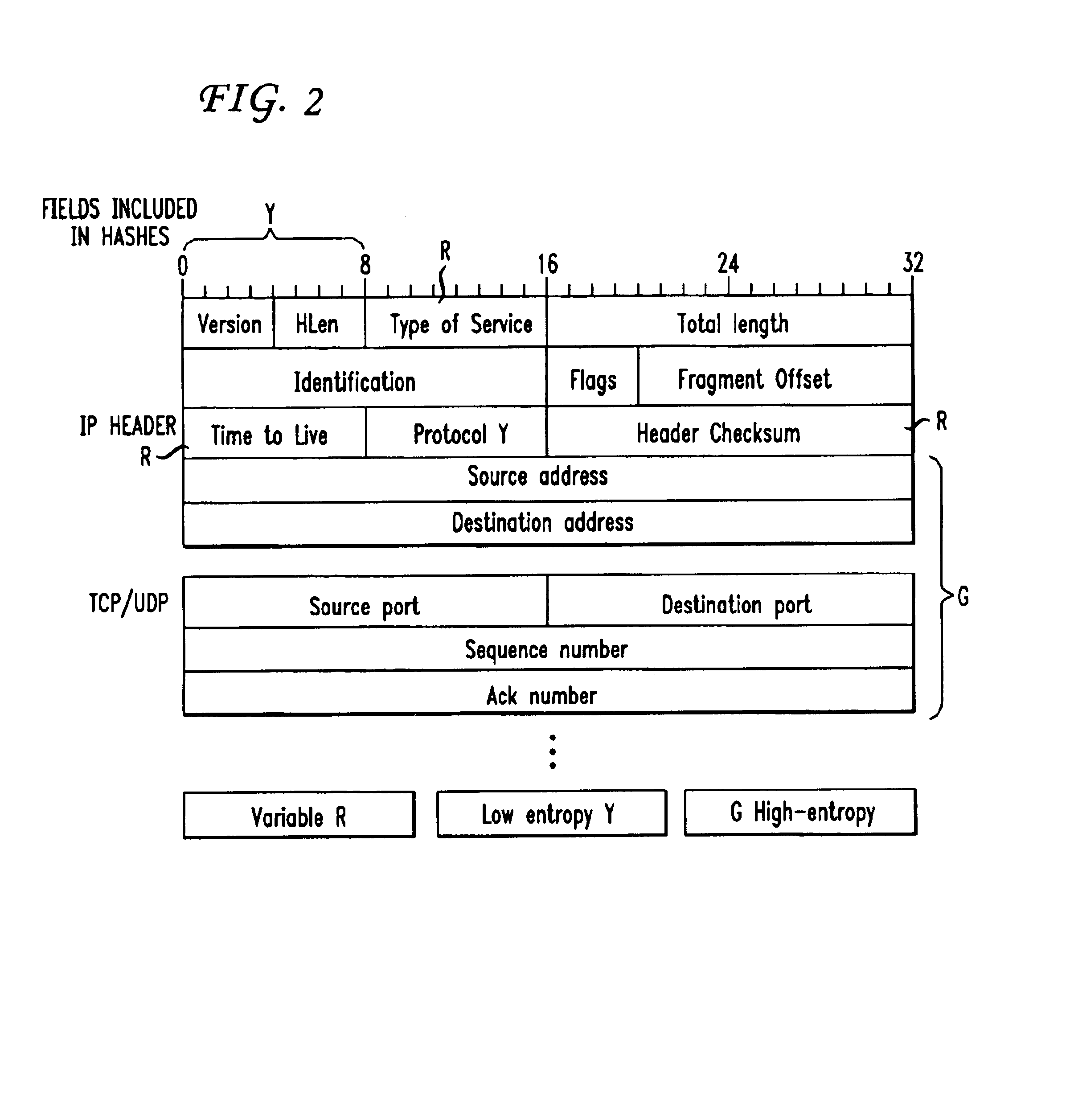
Traffic measurement should make it possible to obtain the spatial flow of traffic through the domain, i.e., the paths or trajectories followed by packets between any ingress and egress point of the domain. A method of sampling packet trajectories in a packet switching network allows the direct inference of traffic flows through a measurement domain by observing the trajectories of a subset of all packets traversing the network. A method which assumes that the measurement domain does not change comprises the steps of selecting packets for sampling in accordance with a sampling function of the packet content and generating a practically unique label for each sampled packet. The method does not rely on routing state, its implementation cost is small, and the measurement reporting traffic is modest and can be controlled precisely. Using the same hash function will yield the same sample set of packets in the entire domain, and enables us to reconstruct packet trajectories. An alternate embodiment which assumes no constraints and that the measurement domain may change comprises the steps of applying a sampling function and altering an invariant bit position as a signaling flag in each packet selected for sampling.
Owner:AMERICAN TELEPHONE & TELEGRAPH CO
V2v safety system using learned signal timing
ActiveUS20170243485A1More dataPower managementRoad vehicles traffic controlCommunications securityIp address
A vehicle-to-vehicle (V2V) communication transponder for use in V2V communication, safety, optimization and anti-collision systems wherein the transponder records and shares observed traffic signal timing and phasing, and uses this information to make recommendations or perform automatic operation to optimize parameters such as safety, gas mileage, travel time, and overall traffic flow. Methods for sharing and making recommendations are described. Embodiments include considerations of traffic and road history in recommendations. No central authority, road-side equipment, (RSU), or pre-determined lane maps are required. Embodiments include a hybrid protocol using both TDMA and CSMA. Some embodiments are free of MAC and IP addresses. Embodiments include equipped vehicles and V2V system using the transponder.
Owner:ZETTA RES & DEV - FORC SERIES
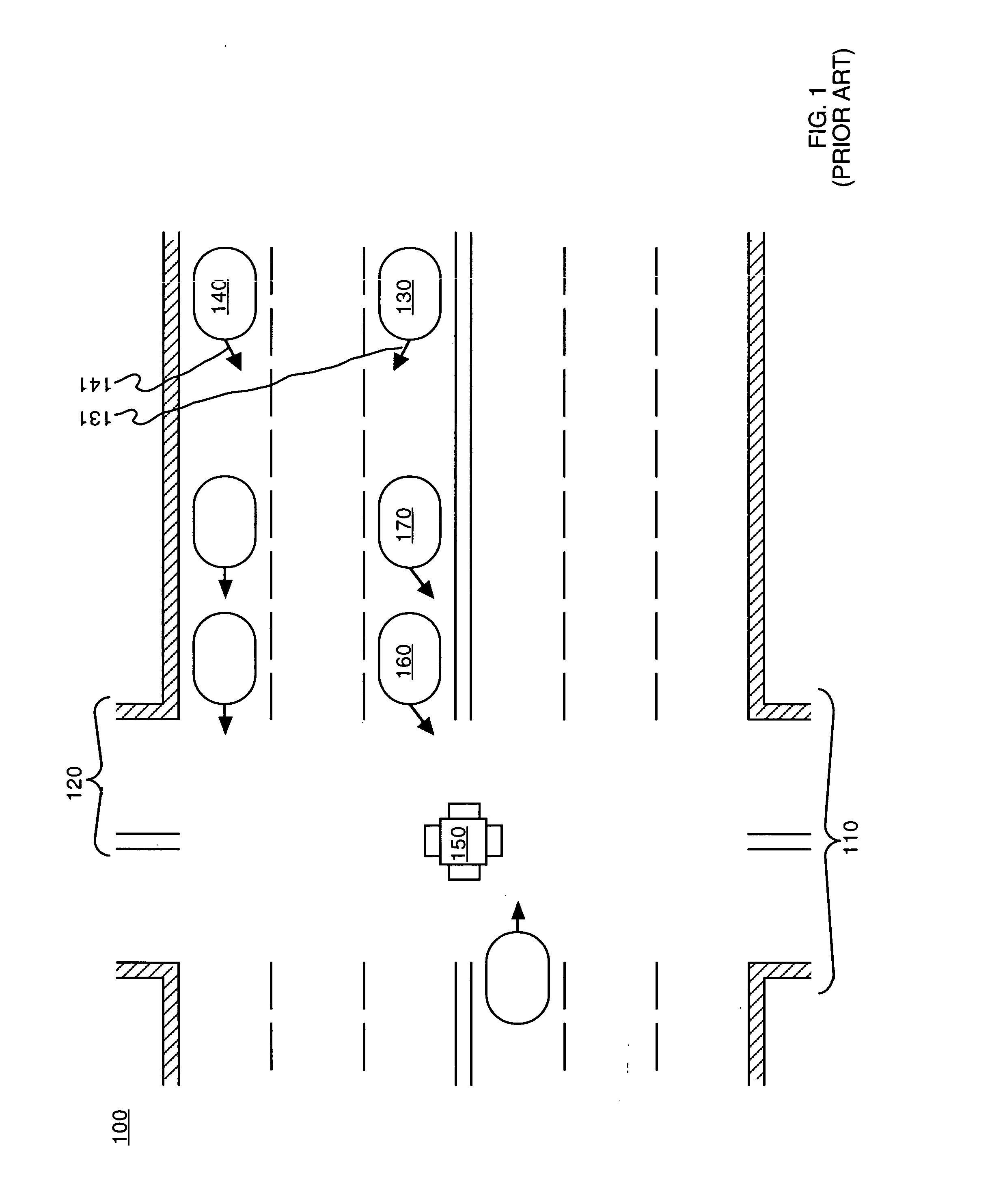
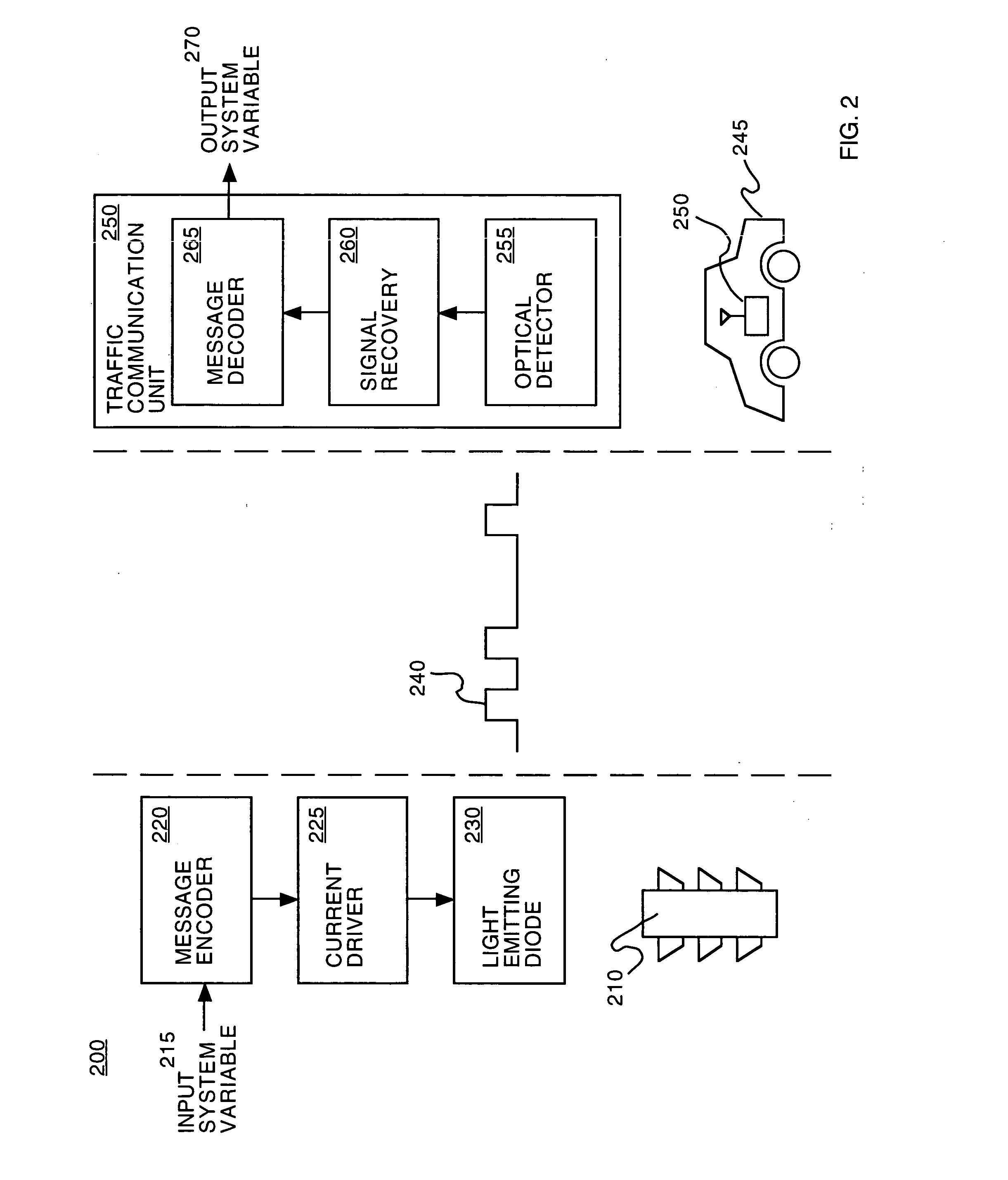
Traffic communication system
InactiveUS20050187701A1Improve securityImprove traffic efficiencyAnalogue computers for vehiclesAnalogue computers for trafficCommunications systemDriver/operator
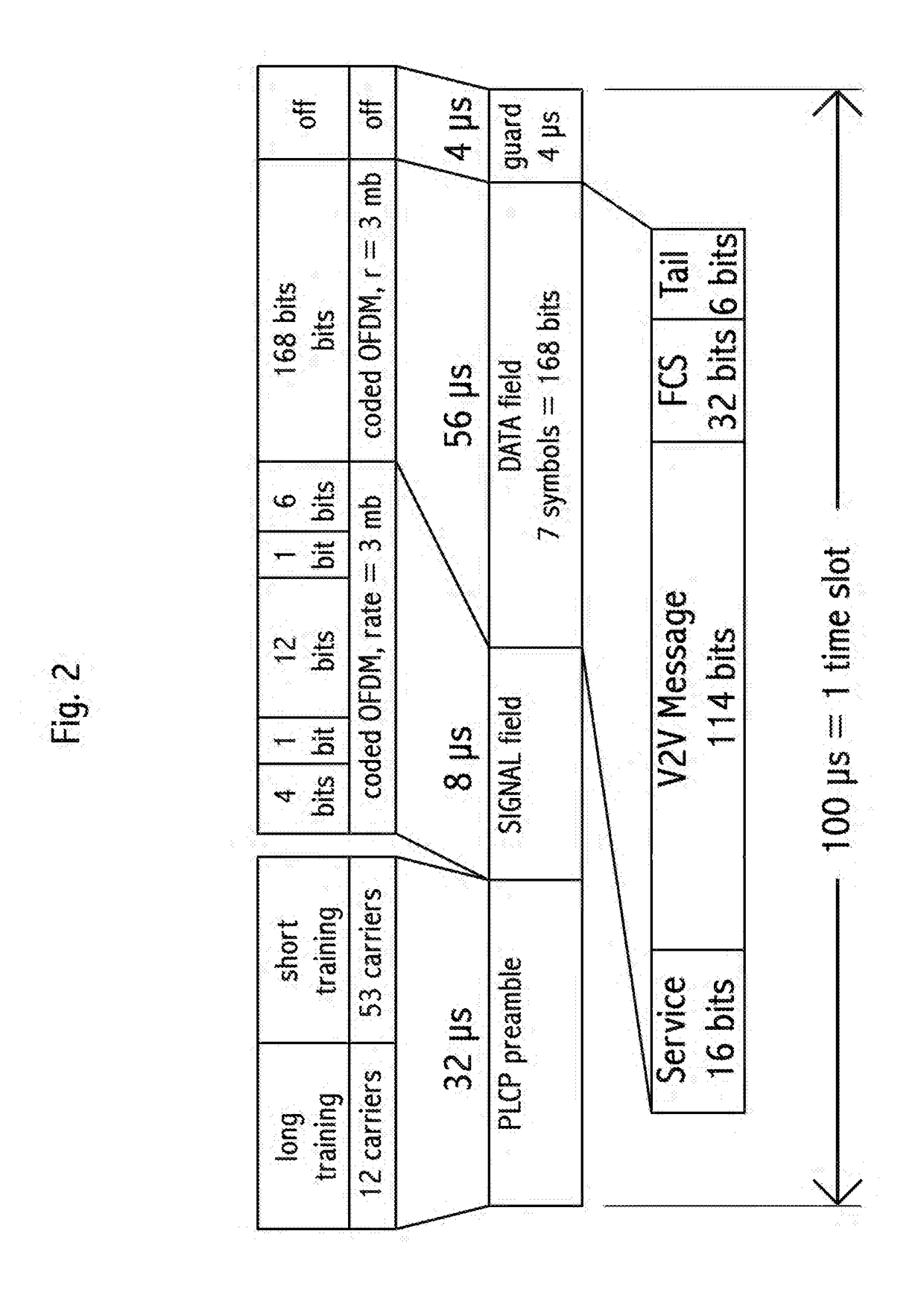
Embodiments in accordance with the invention provide communication between vehicles and traffic control devices and / or other vehicles. The communication system provides for communication of system variables such as: signal setting (e.g., red / yellow / green light), signal direction, time to signal change, signal sequence (e.g., next traffic flow), red light runner alert, signal failure, driver urgency, vehicle presence, absolute vehicle location, toll collection information, vehicle speed, roadway condition (e.g., ice on bridge surface), traffic impairments (e.g., delay ahead). The communication system also provides for communication of system variables such as: speed, acceleration / deceleration, braking, lane change with direction, malfunction (e.g., stall). The system communicates utilizing wireless optical, acoustic and / or radio frequency signaling methods.
Owner:AGILENT TECH INC
Method for Configuring an Optical Network
InactiveUS20090296719A1Huge complexityHuge timeData switching by path configurationOptical multiplexObject definitionNetwork model
A network model for the planning and / or the provisioning of traffic flows in a communication network includes nodes interconnected with each other by links according to a given network topology. The network model uses a graph defined by arc objects storing information related to both the links and adjacent nodes thereof.
Owner:TELECOM ITALIA SPA
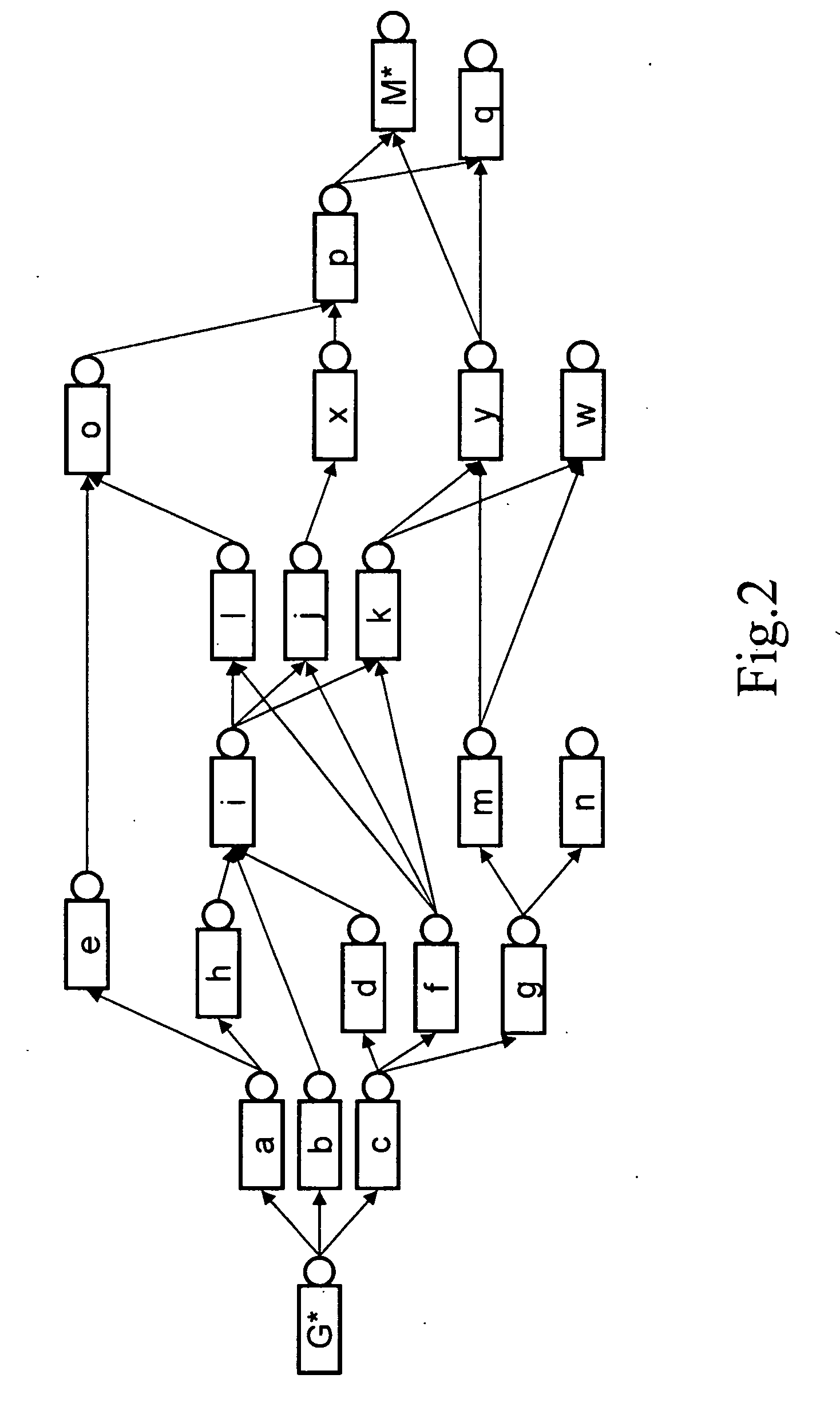
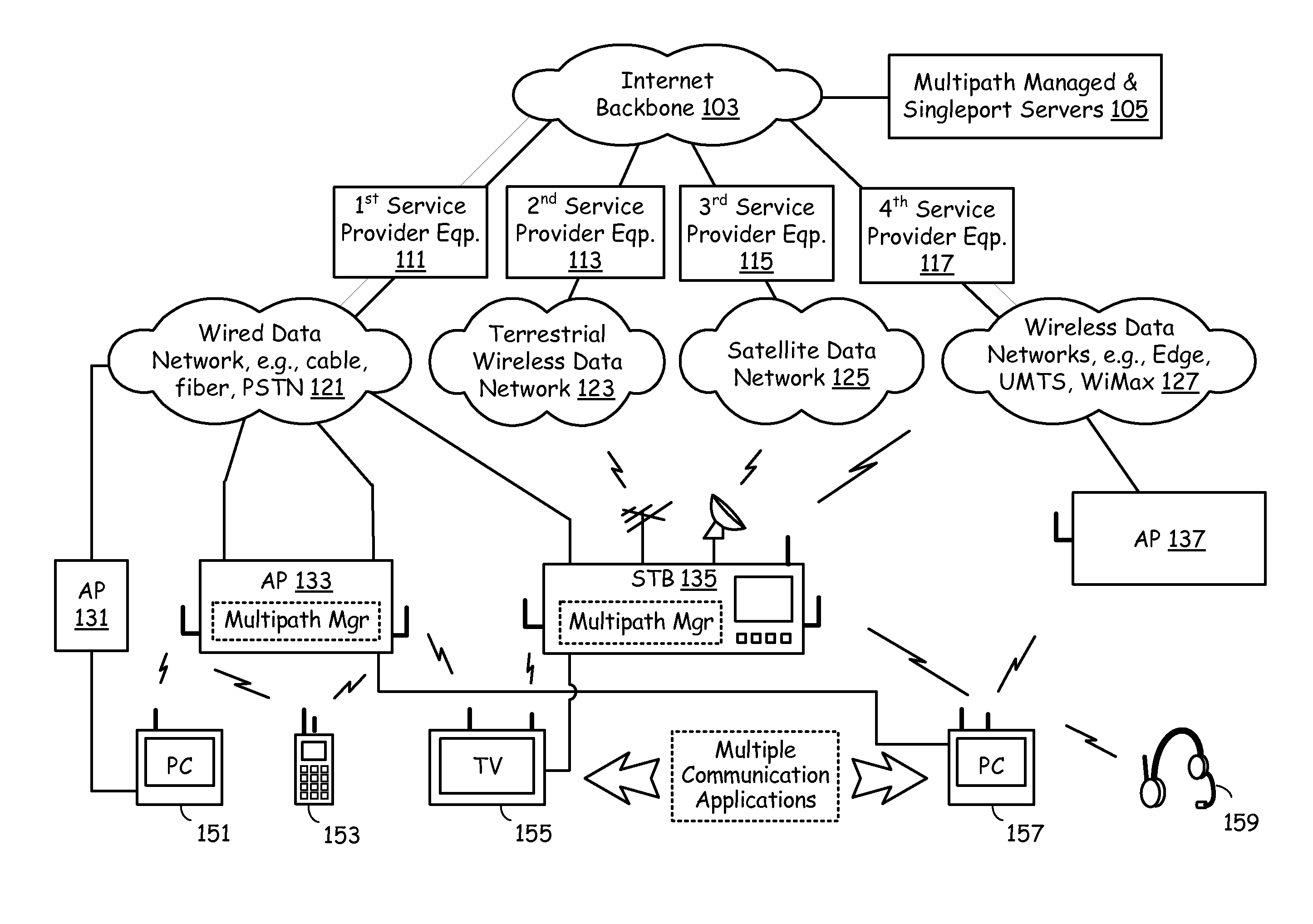
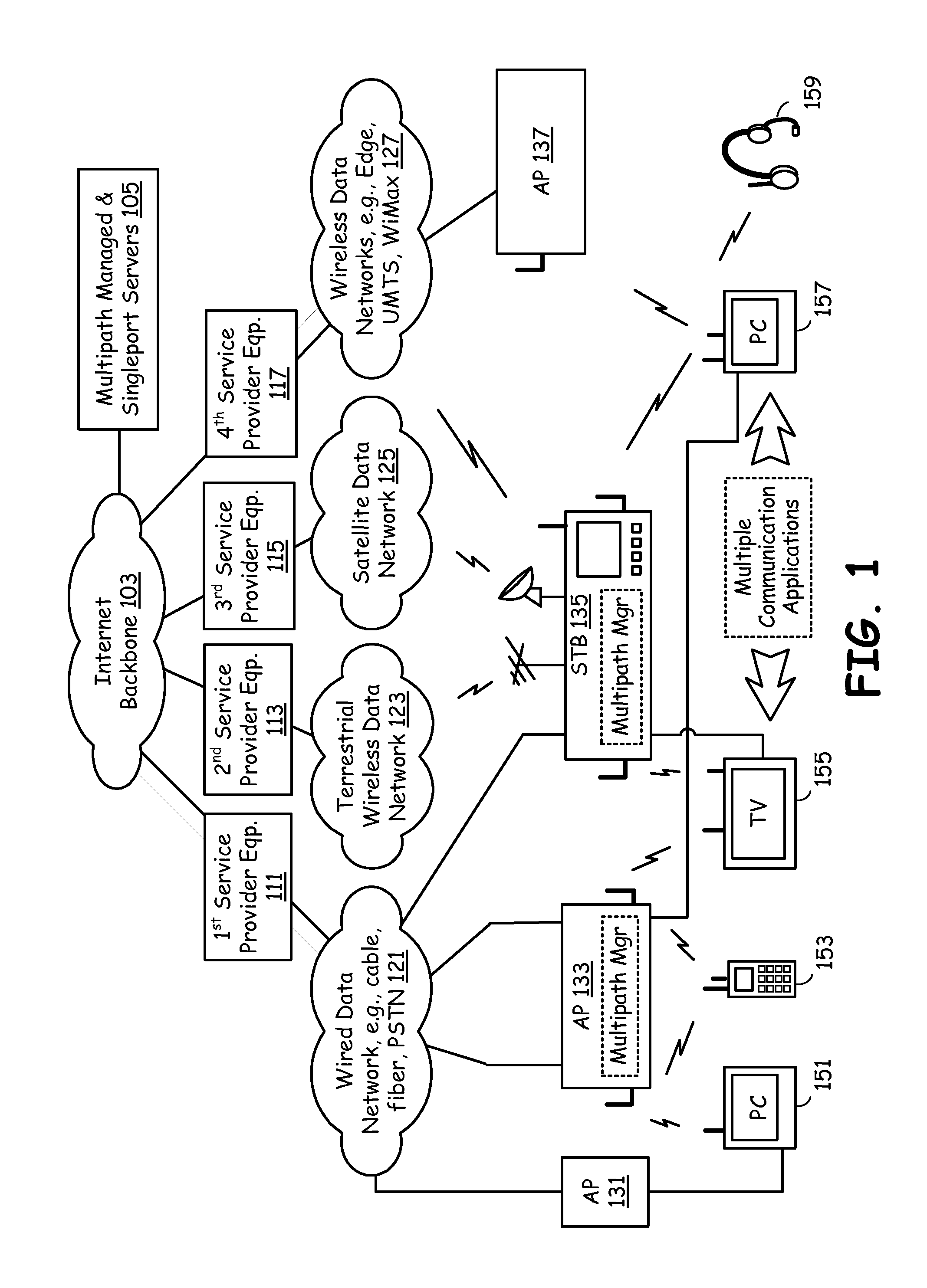
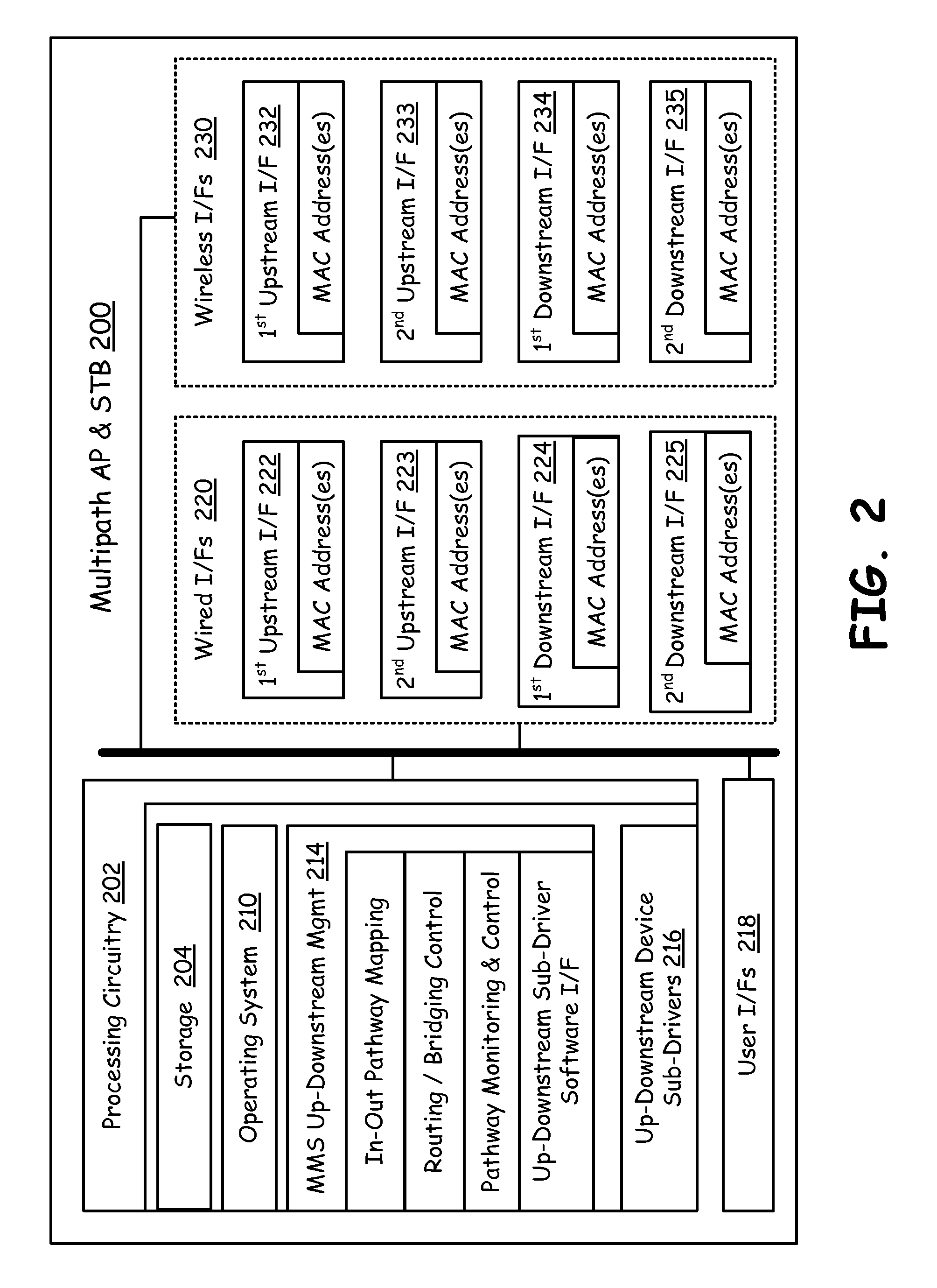
Network nodes cooperatively routing traffic flow amongst wired and wireless networks
InactiveUS20110110309A1Wireless commuication servicesData switching networksWireless mesh networkNetwork conditions
End-point devices, access points and other types of network nodes each employ multi-path management software to manage communication via multiple possible paths to the Internet backbone from communication applications that run on an end-point device. The multi-path management software on an end-point device may operate independently and / or cooperate with the local communication applications and the multi-path management software located on the access points or other network nodes to select one or more pathways for the local communication applications. The multi-path management software depending on data types and data requirements also supports selection and maintenance of two or more paths that simultaneously serve a single communication application. The multi-path management software of an end-point device may pass all or a portion of multi-path management responsibility to a local communication application and / or to multi-path management software of another network node. In addition to managing the selection of one or more pathways, the multi-path management software seamlessly switches pathways as may become necessary to meet changing network conditions or bandwidth demands.
Owner:AVAGO TECH WIRELESS IP SINGAPORE PTE
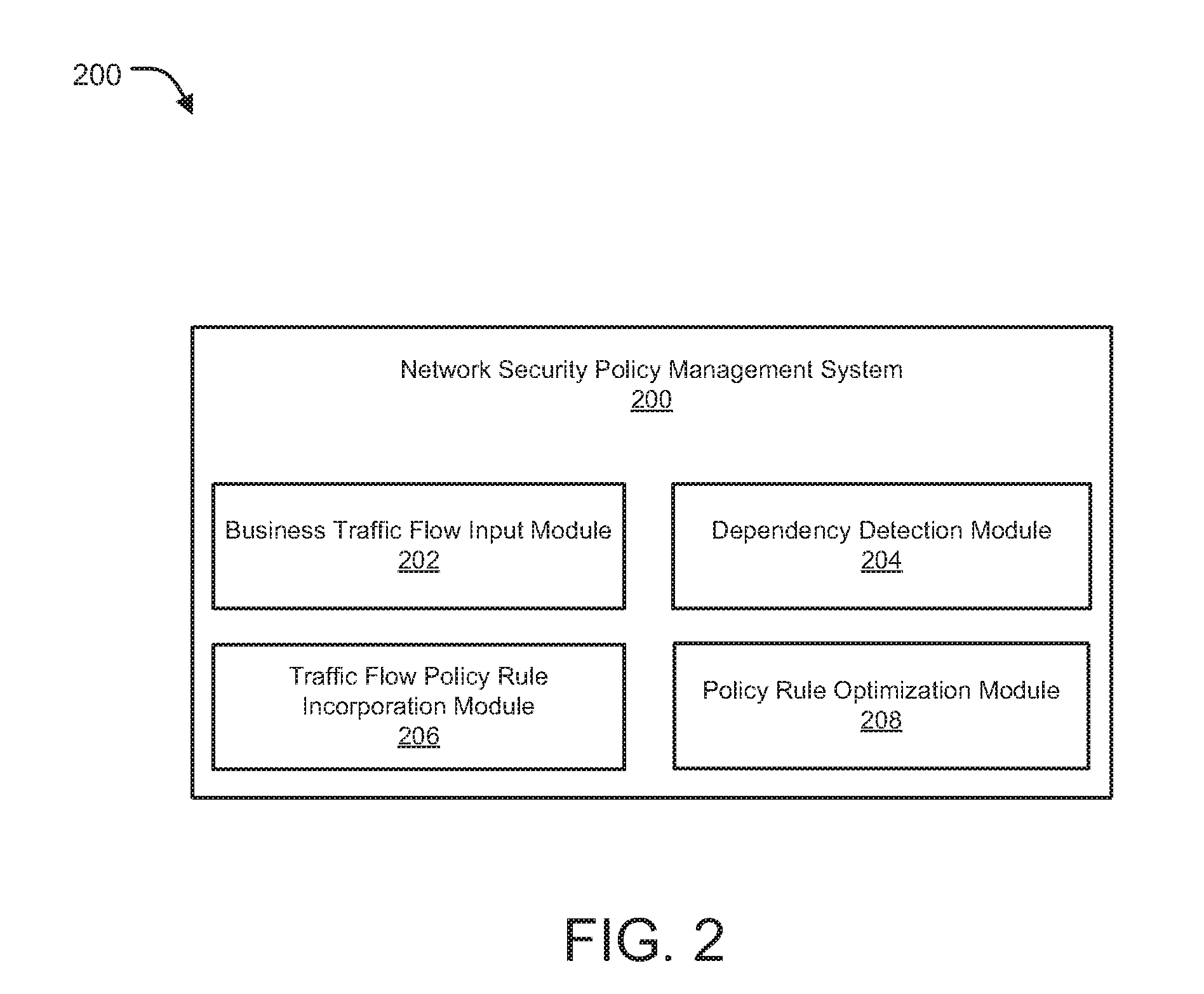
Dynamically optimized security policy management
ActiveUS20160191466A1TransmissionSpecial data processing applicationsTraffic characteristicPriority setting
Methods and systems for dynamically optimized rule-based security policy management are provided. A request is received by a network security management device to add a new traffic flow policy rule to multiple existing policy rules managed by the network security management device. Dependencies of the new traffic flow policy rule on the existing policy rules are automatically determined. An updated set of policy rules is formed by incorporating the new traffic flow policy rule within the existing policy rules based on the dependencies. The updated set of policy rules is then optimized by grouping, reordering and / or deleting a sub-set of policy rules of the updated set of policy rules based on one or more of weights assigned to particular types of traffic, preference settings, priority settings, network traffic characteristics and usage statistics for each policy rule of the updated set of policy rules.
Owner:FORTINET
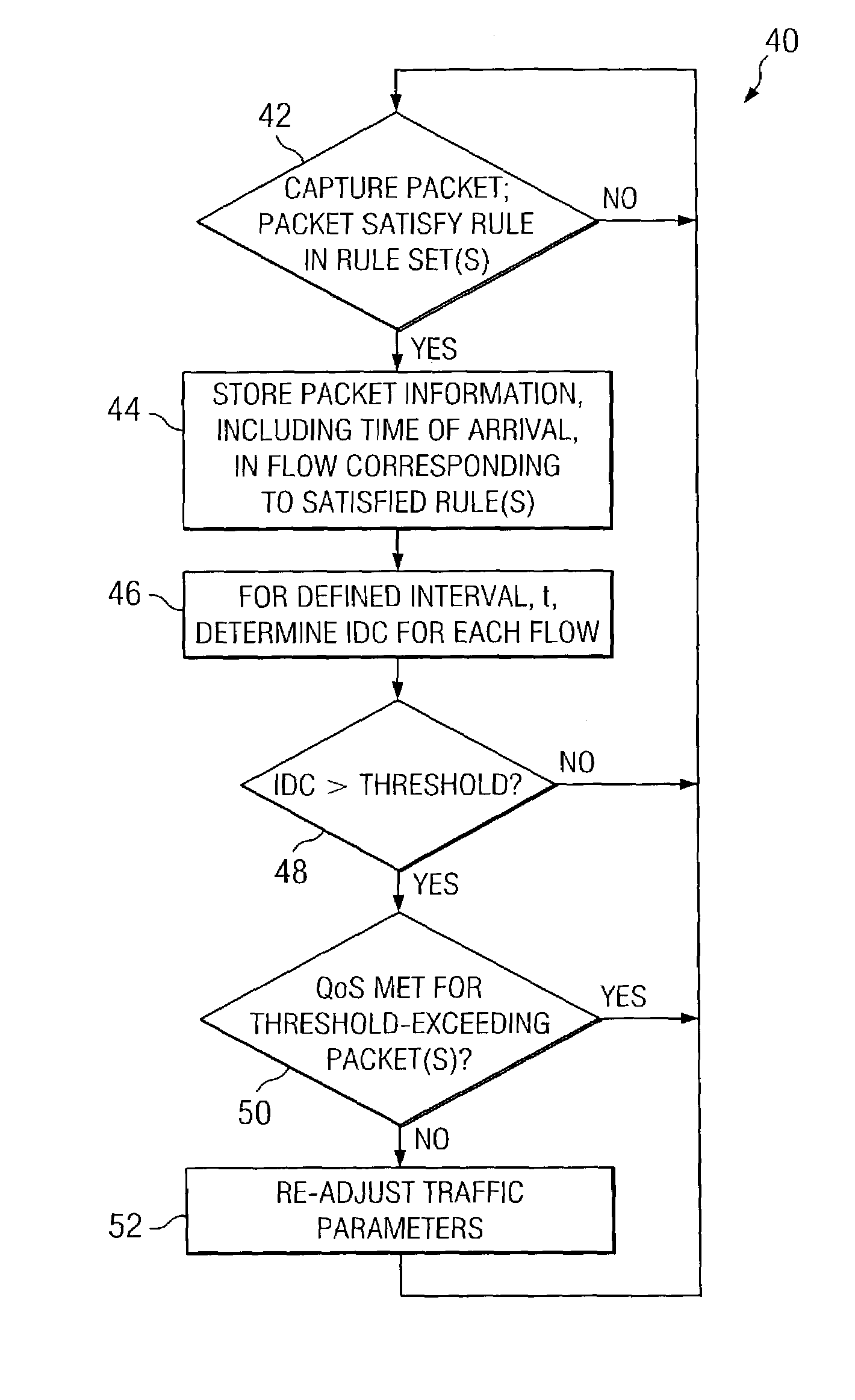
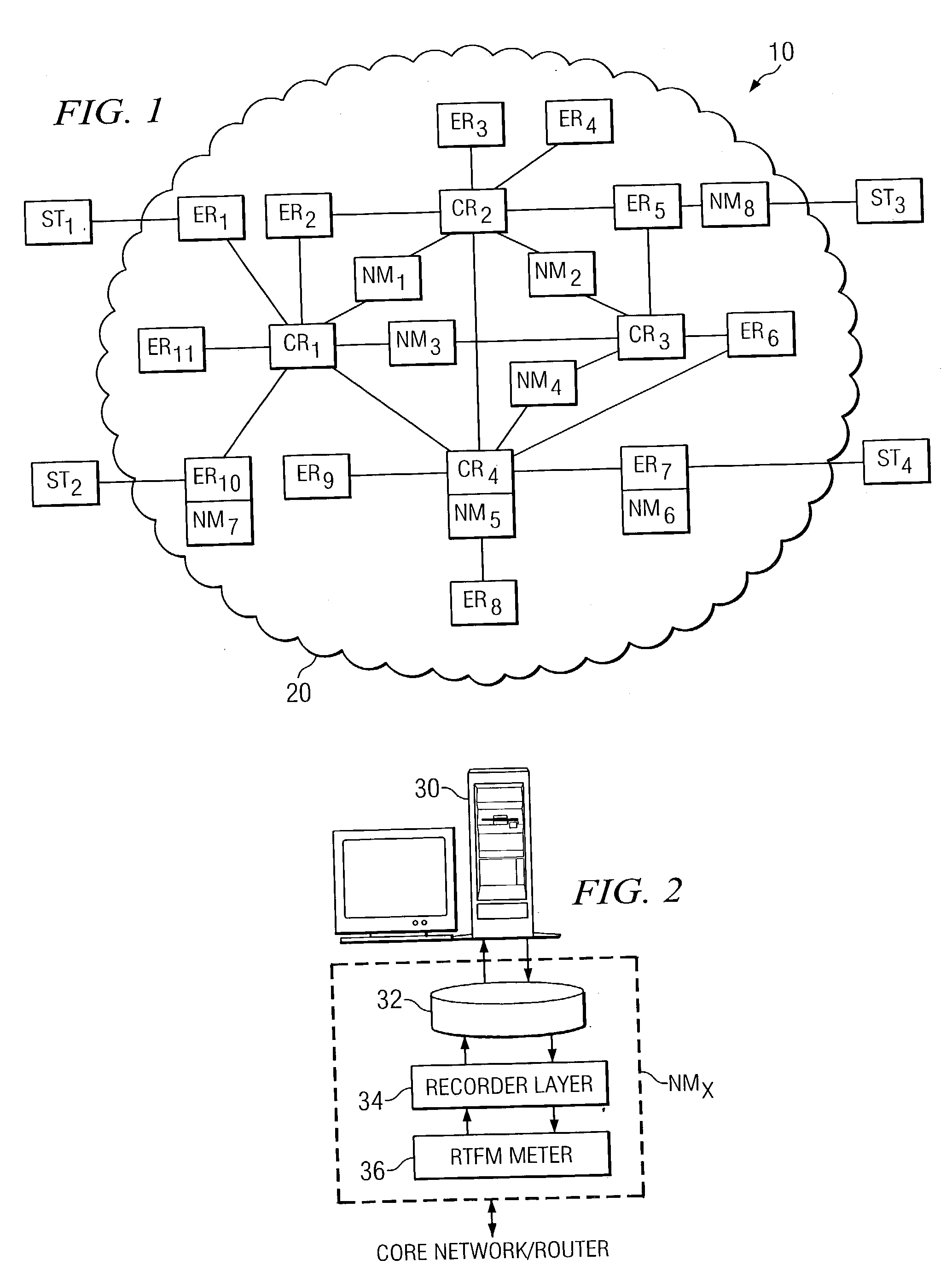
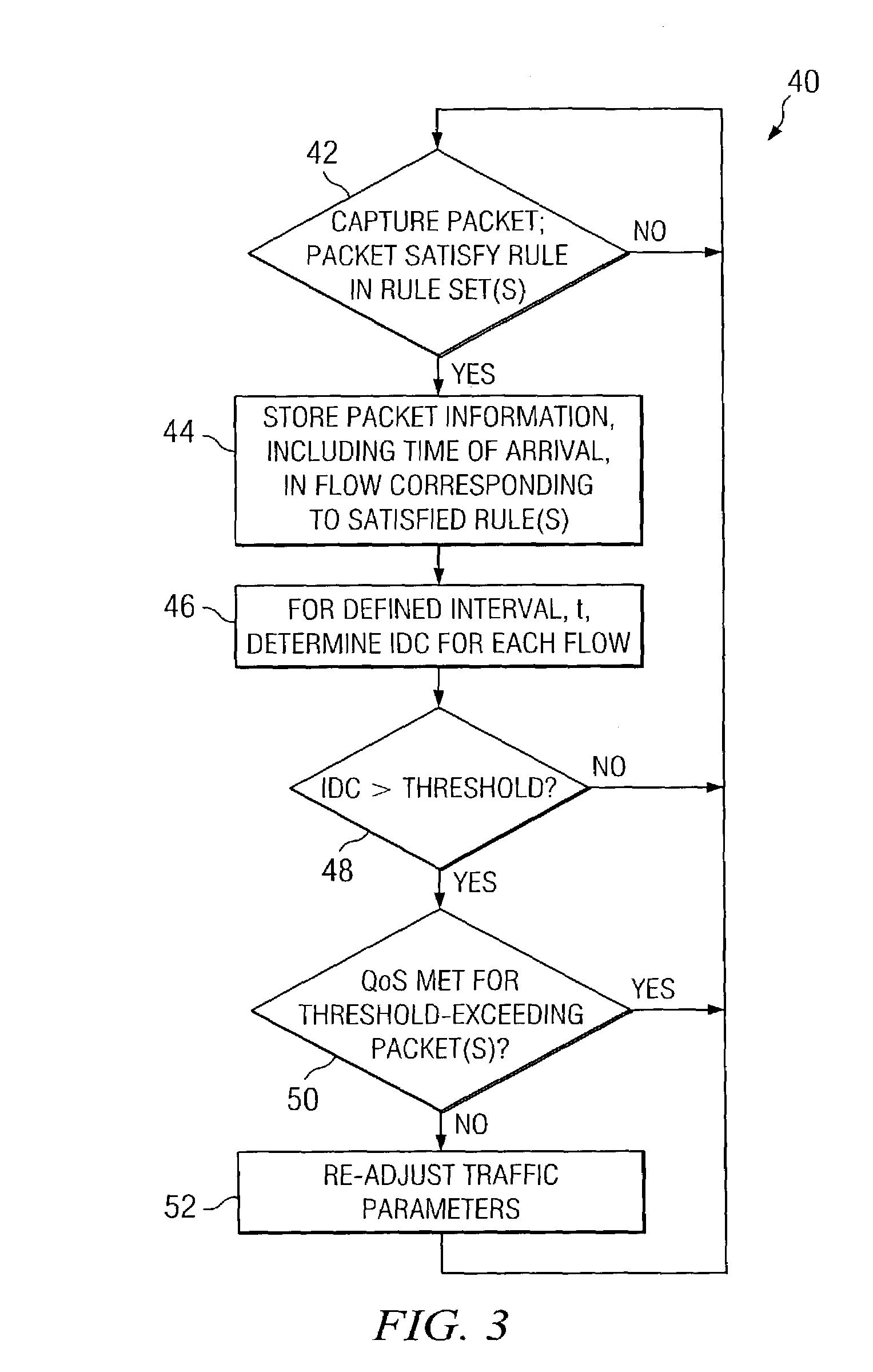
Network monitoring system responsive to changes in packet arrival variance and mean
InactiveUS7242668B2Error preventionFrequency-division multiplex detailsPacket arrivalMonitoring system
A network monitoring system (10) for monitoring a network along which network traffic flows in a form of packets. The system comprises circuitry (36, 42) for receiving a packet communicated along the network and for determining whether the received packet satisfies a set of conditions. The system further comprises circuitry (36 / 30, 46), responsive to a determination that the received packet satisfies the set, for determining a measure, wherein the measure is determined over a defined time interval and comprises a ratio of packet arrival variance and a mean of packets arriving during the time interval and for comparing the measure to a threshold. Lastly, the system comprises circuitry (36, 52), responsive to the measure exceeding the threshold, for adjusting network resources.
Owner:WSOU INVESTMENTS LLC
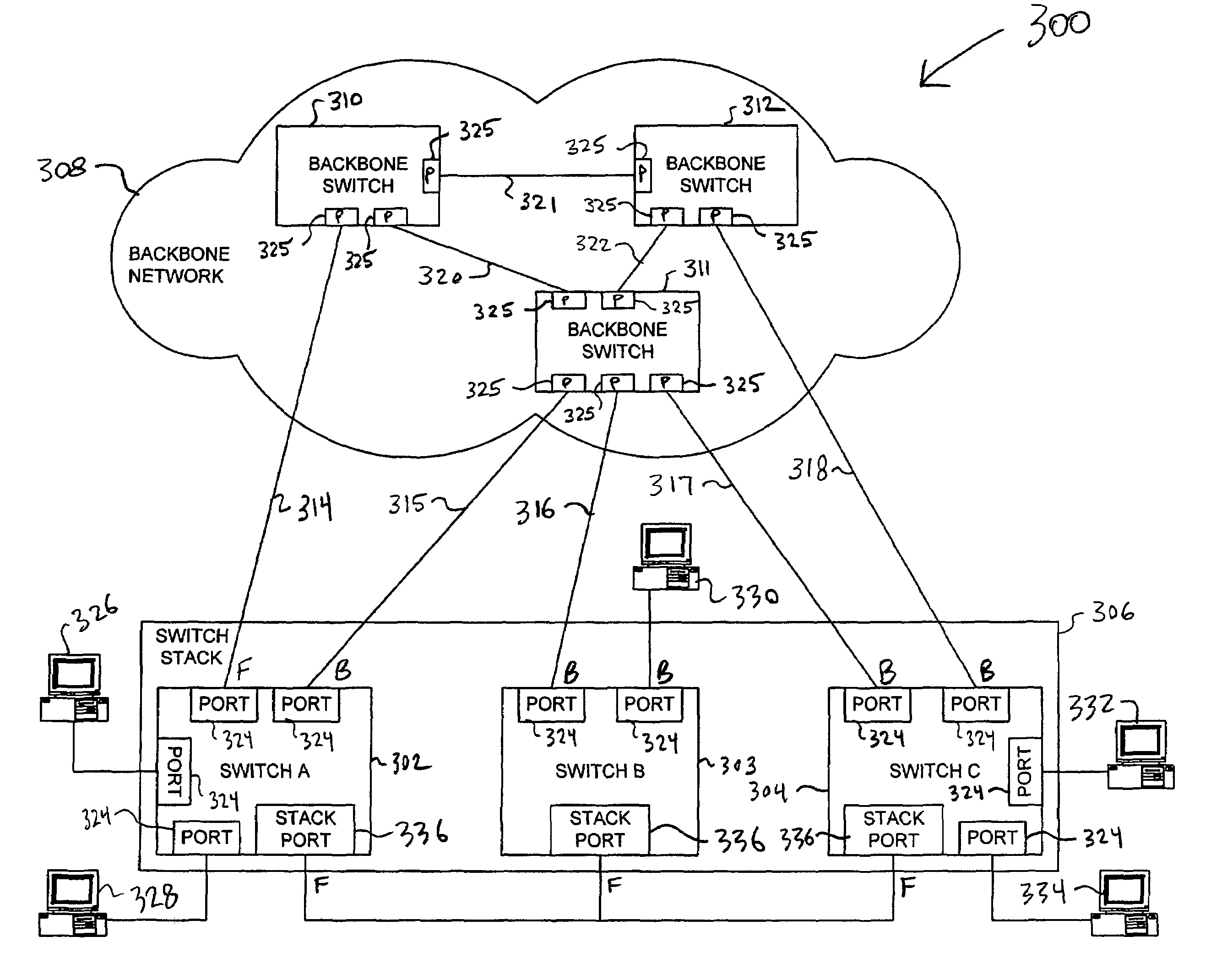
Cross stack rapid transition protocol
ActiveUS7480258B1Fast rebuildError preventionFrequency-division multiplex detailsTraffic flowComputer science
A cross stack rapid transition protocol is provided for permitting multiple network devices organized as a stack to rapidly transition their ports in response to network changes so as to minimize traffic flow disruptions while avoiding loops. Each switch in the stack has a stack port that connects the switch to another switch in the stack, and a plurality of ports for connecting the switch to other entities of the computer network. Each switch includes a Spanning Tree Protocol (STP) entity that transitions the ports of the switch among a plurality of states including a forwarding state and a blocking state. Each switch also tracks which other switches are members of the switch stack. The stack port of each switch is transitioned to the forwarding state, and a single switch having connectivity to a root is elected to be a Stack Root. One or more other switches may have Alternate Stack Root Ports, that provide alternate paths to the root. If the current Stack Root loses connectivity to the root, the switch whose Alternate Stack Root Port represents the next best path to the root issues one or more proposal messages to the other members of the switch stack. These other members respond with an Acknowledgement, and the former Stack Root transitions its port to the blocking state. Once the proposing switch receives an Acknowledgment from all other active members of the switch stack, it transitions its Alternate Stack Root Port to the forwarding state so that network messages can be forwarded to and from switch stack.
Owner:CISCO TECH INC
Vehicle-to-vehicle safety transceiver free of IP addresses
ActiveUS20130279392A1Highly efficient and reliable time slot based allocationIncrease flexibilityPower managementRoad vehicles traffic controlTransceiverIp address
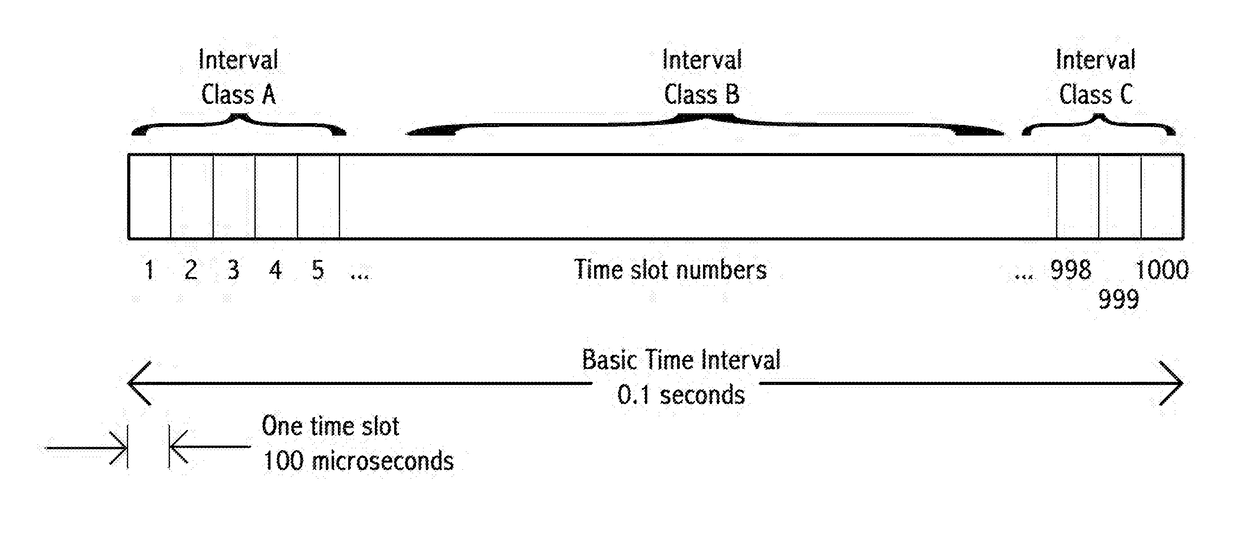
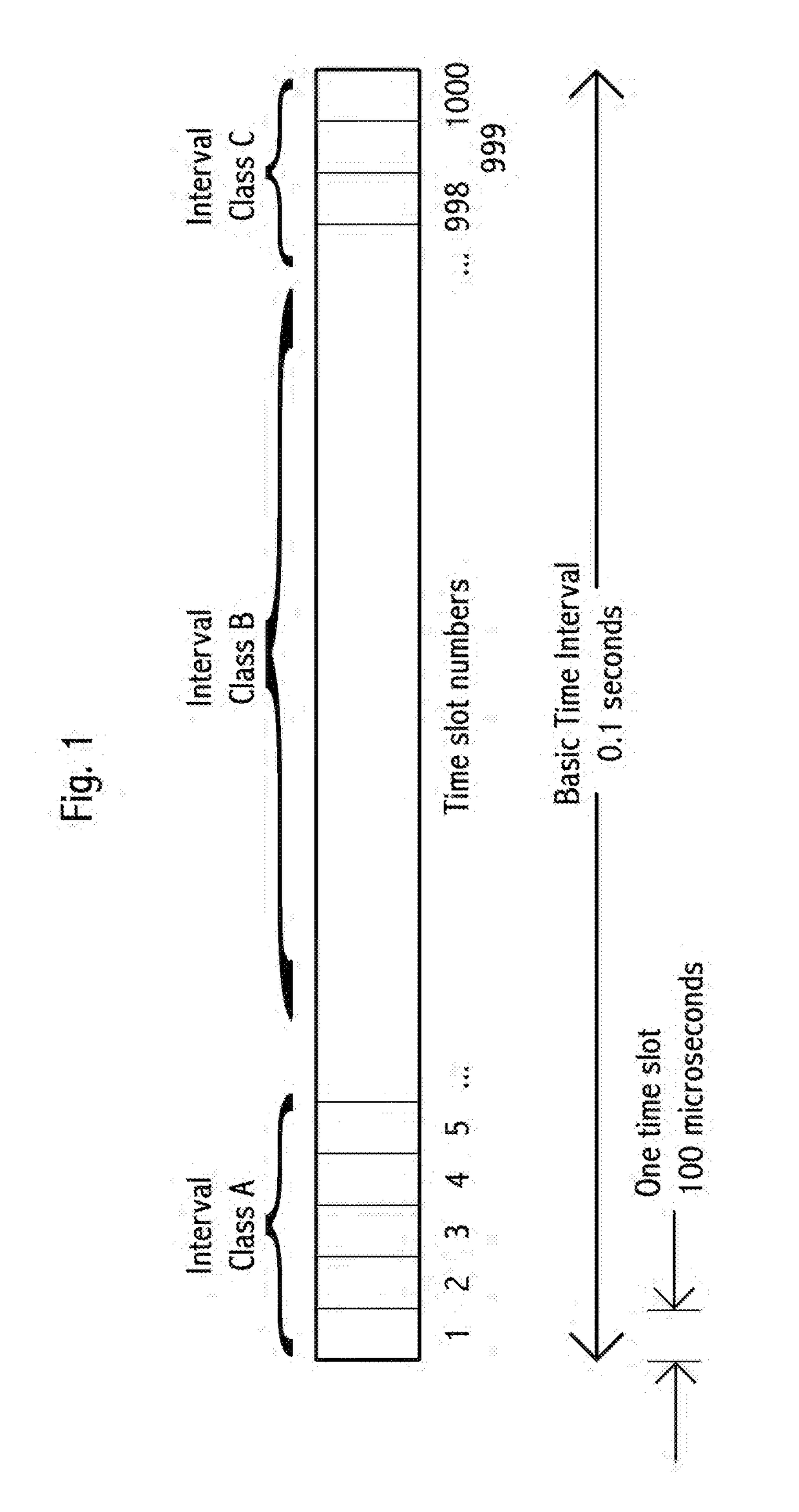
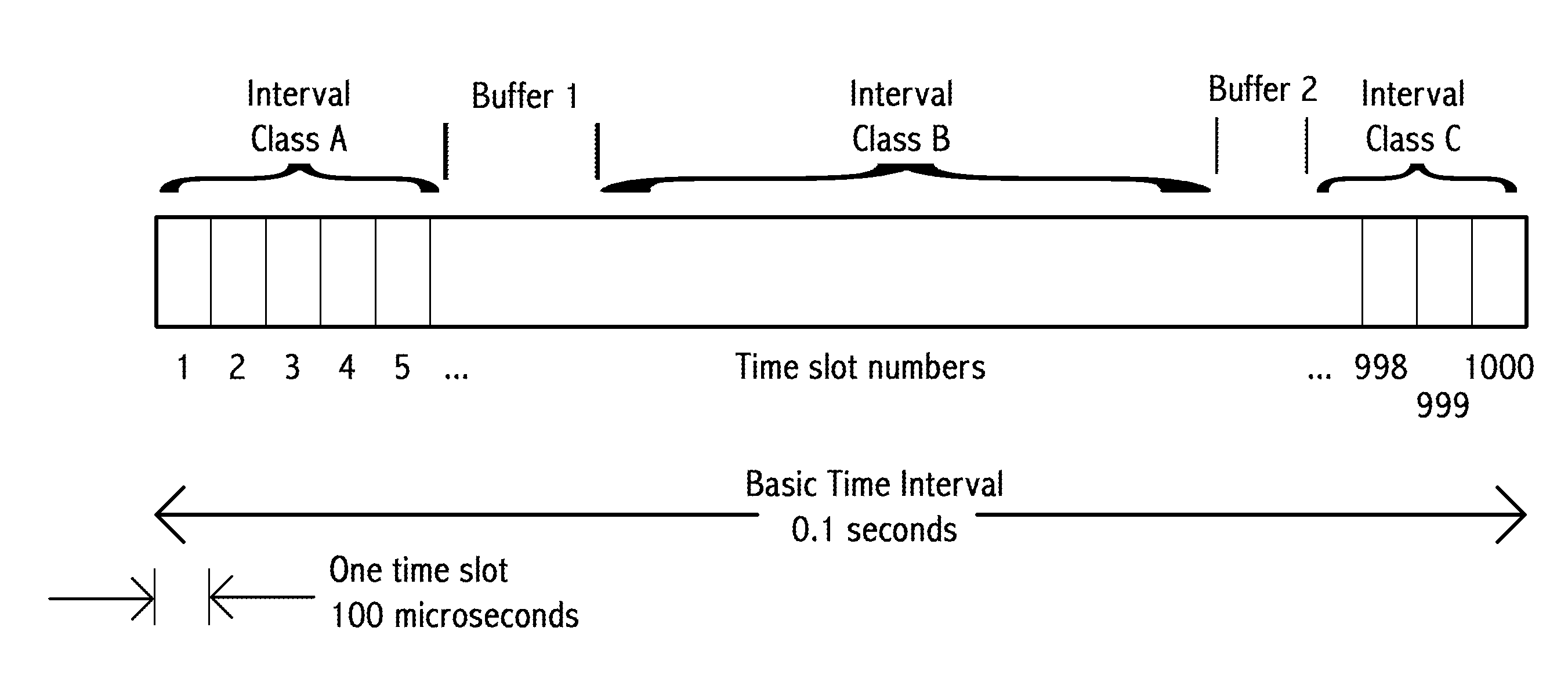
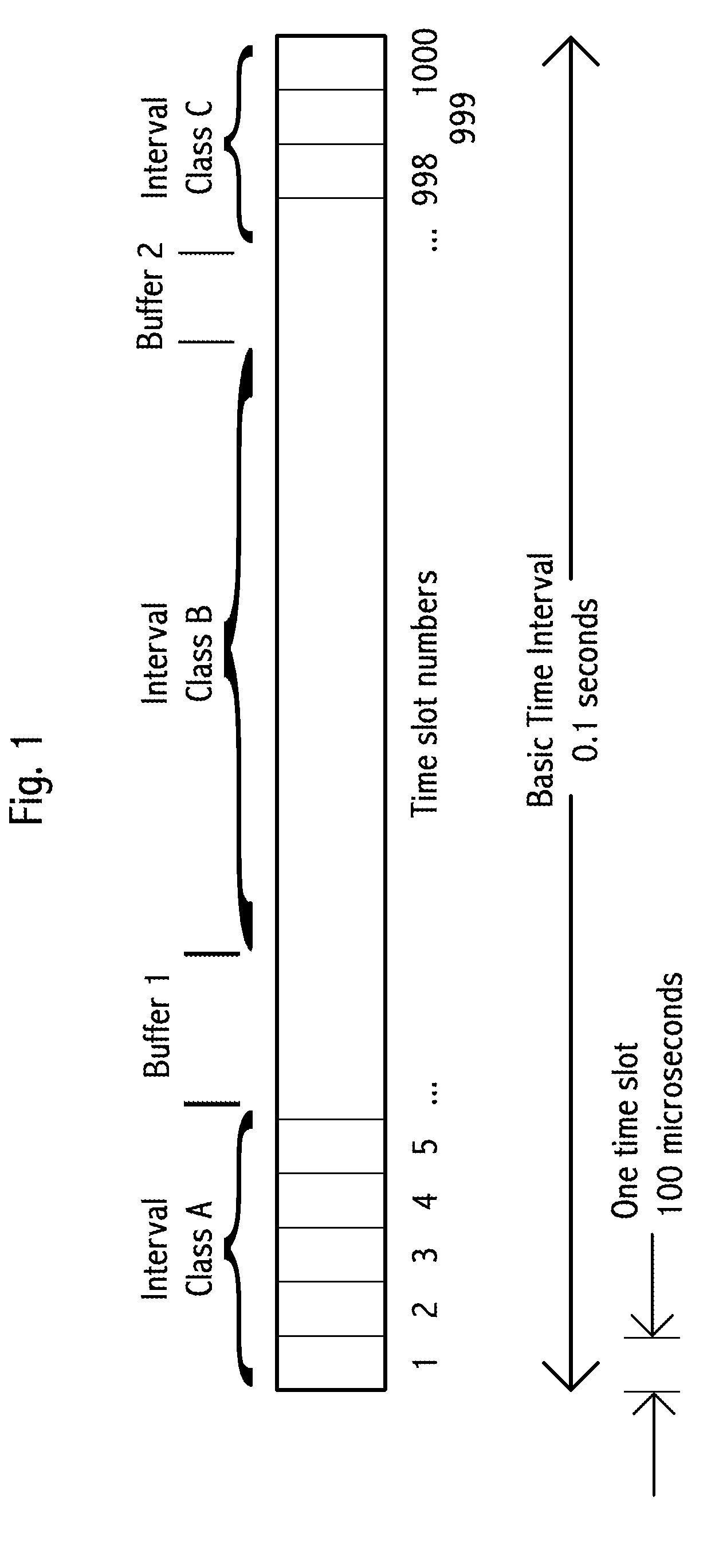
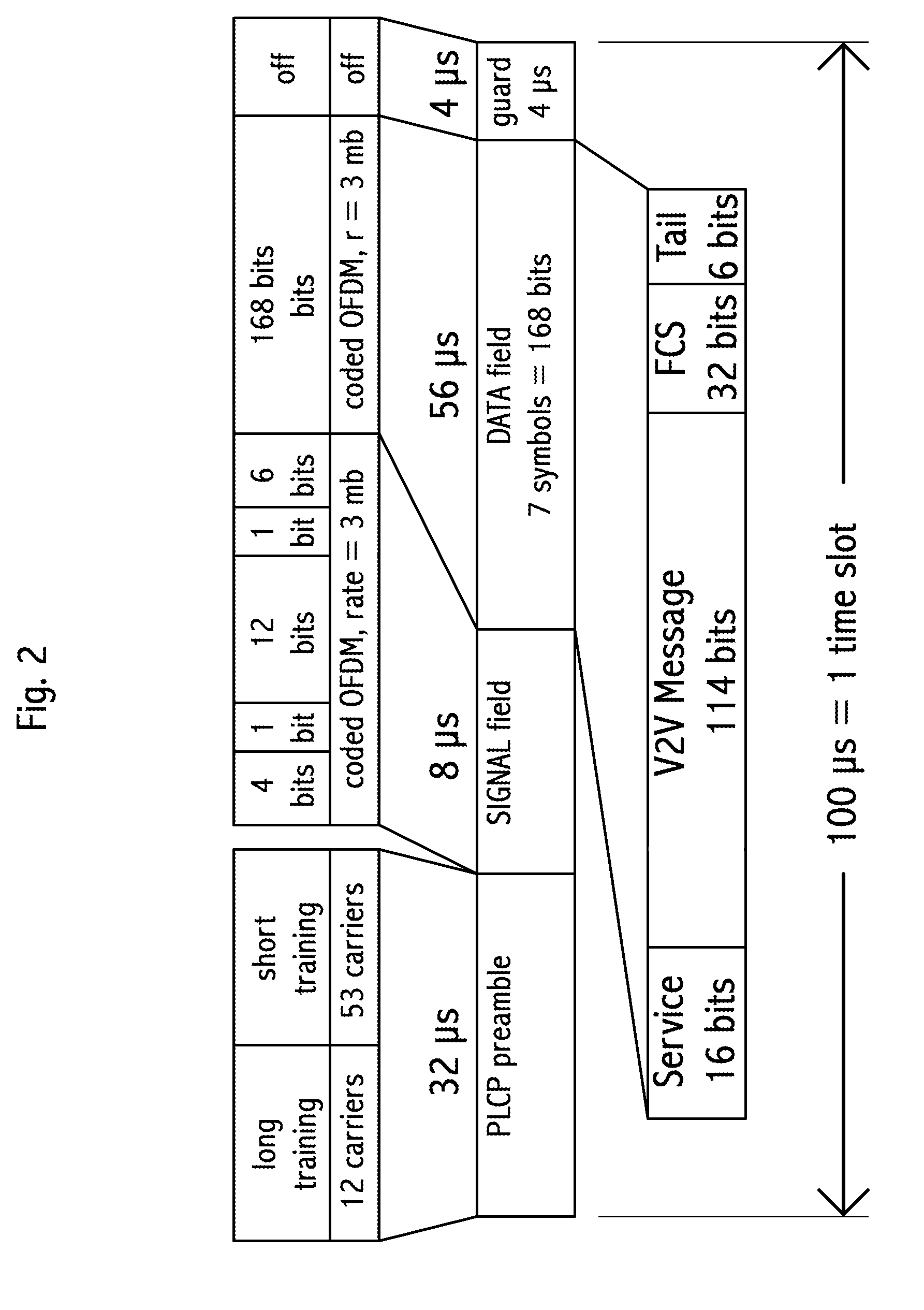
A transceiver in a vehicle-to-vehicle (V2V) communication and safety system that regularly broadcasts safety messages, comprising location, heading and speed, of a subject vehicle, that are free of MAC and IP addresses. The V2V system uses the location of the subject vehicle for vehicle identification, in place of a pre-assigned vehicle ID. Some embodiments broadcast safety message in self-assigned time slots in a synchronized TDMA broadcast architecture, with unusually short inter-message gaps and unusually short messages. The TDMA frame is partitioned into three prioritized time interval classes with differing priorities and dynamically changing sizes based on demand of higher-priority messages. Time slot selection uses weighted algorithms. Selected time slots are held until either a message collision or a timeout occurs. A transceiver equipped vehicle may proxy a different subject vehicle. Embodiments include optimized traffic flow and signal timing.
Owner:ZETTA RES & DEV - FORC SERIES
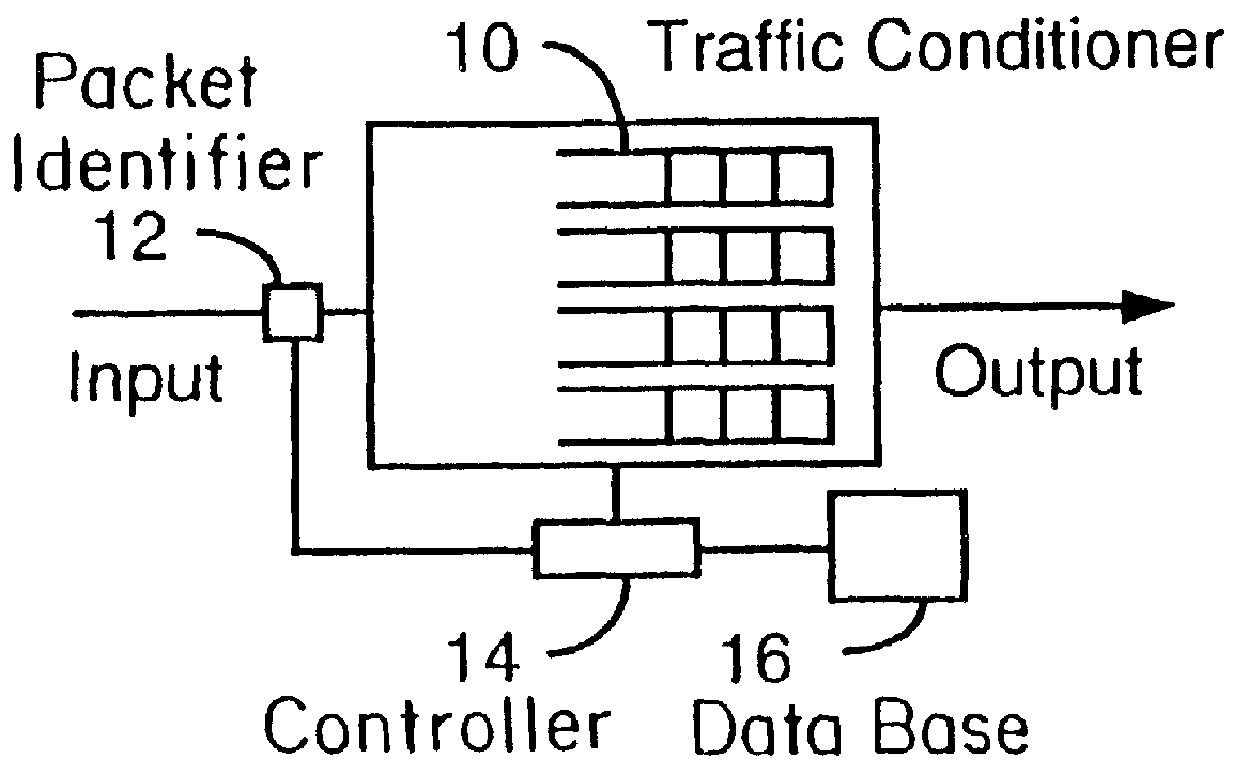
Dynamic traffic conditioning
Multi-media networks will require that a data flow be given certain quality-of-service (QOS) for a network connection but pre-negotiation of this sort is foreign to the current data networking model. The real time traffic flow in the data network requires distinct limits on the tolerance to delay, and the variations in that delay. Interactive voice and video demand that the total delay does not exceed the threshold beyond which human interaction is unacceptably impaired. The present invention allows the network to discover the nature of the service for each traffic flow, classifies it dynamically, and exercises traffic conditioning by means of such techniques as admission control and scheduling when delivering the traffic downstream to support the service appropriately.
Owner:RPX CLEARINGHOUSE
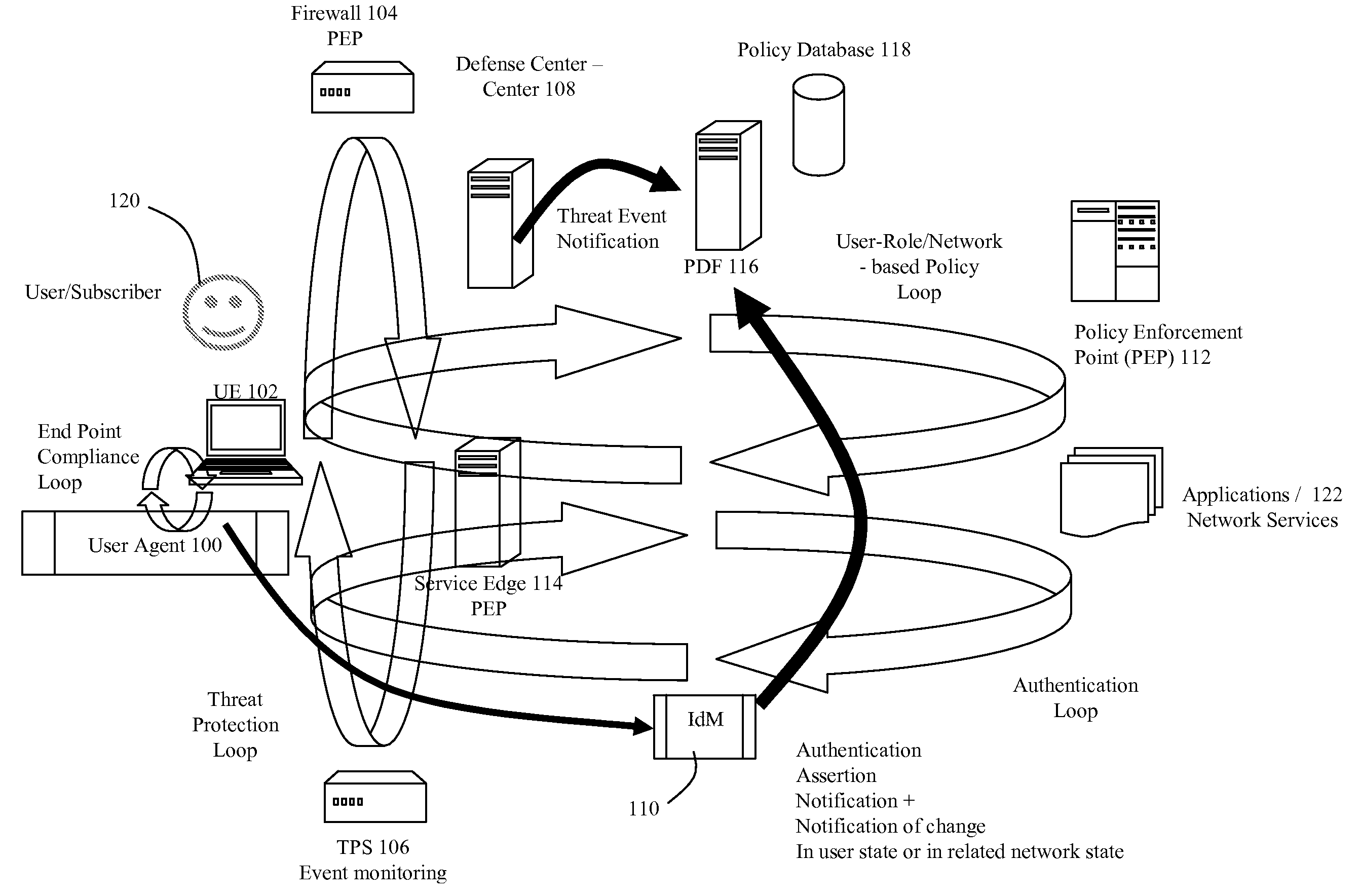
Dynamic Network Identity and Policy management
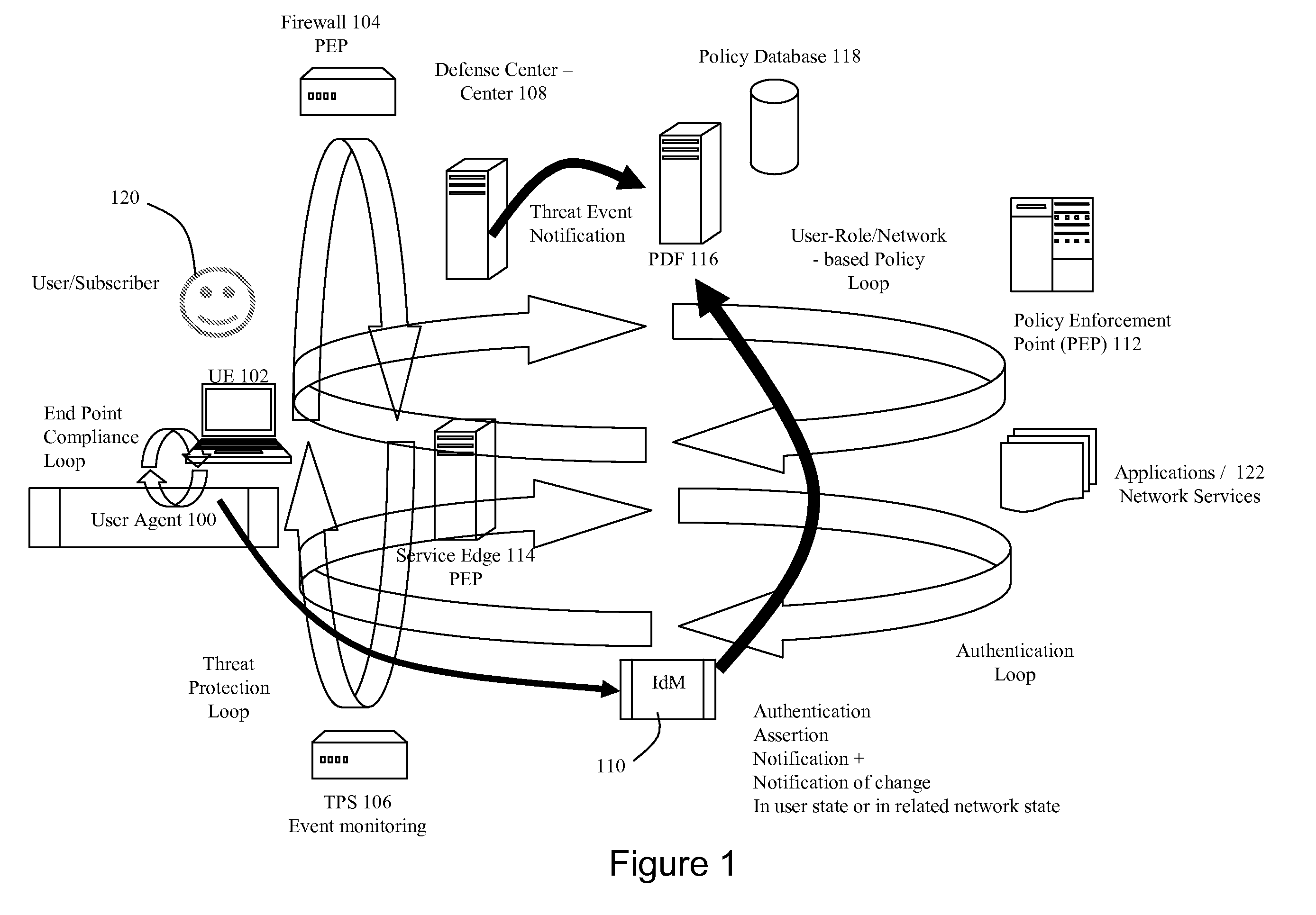
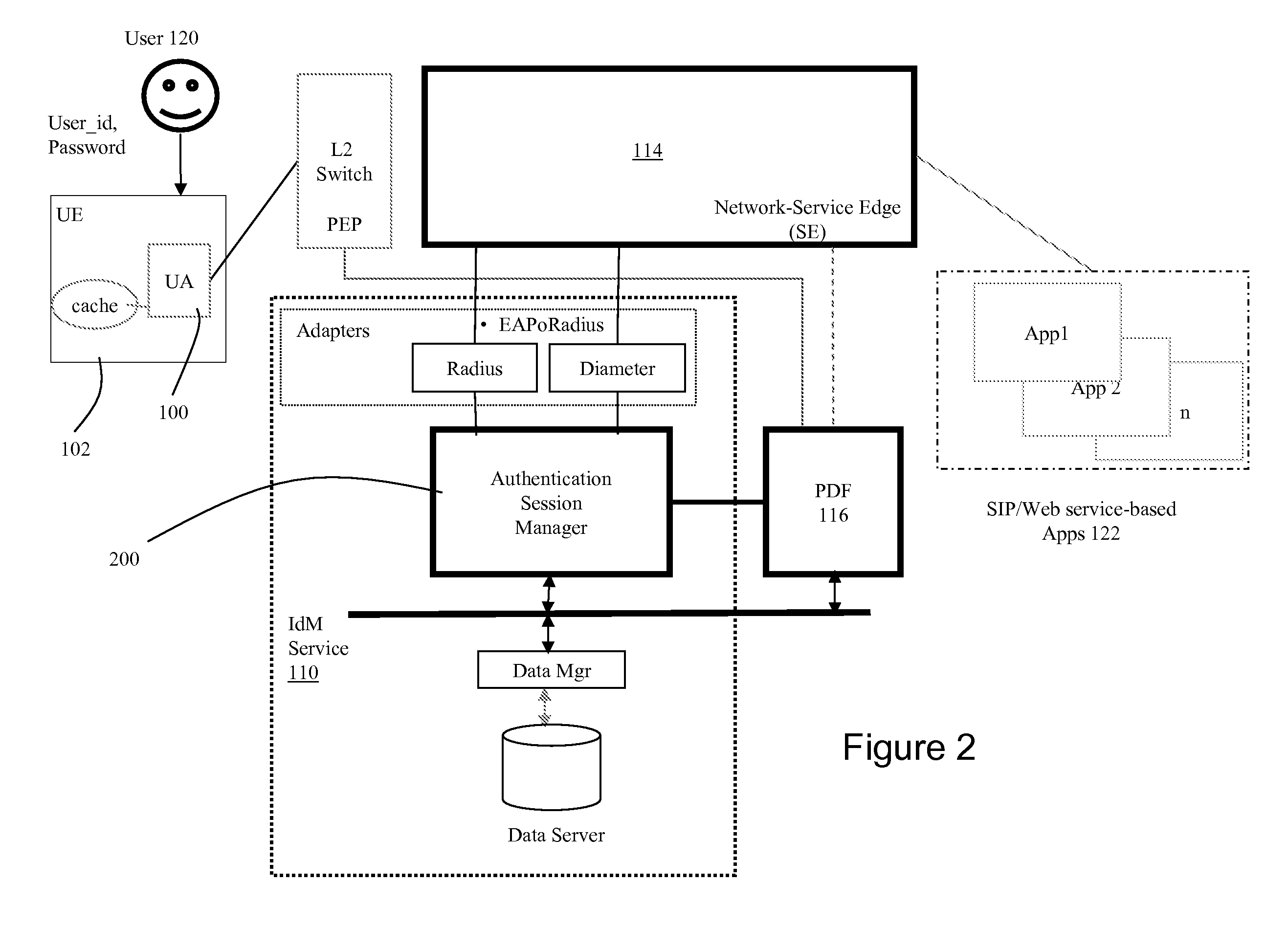
InactiveUS20070150934A1Network resource is limitedSpecial data processing applicationsSecurity arrangementTarget ResponsePassword
Network policies are managed based at least in-part on user / entity identity information with: a state monitor operable to monitor for state change events in user / entity state and related, network state or in traffic pattern and traffic flow state; an identity manager operable to obtain and validate user credentials; and a policy manager operable in response to a state change event detected by the state monitor (either the identity manager or a defense center) to select a policy based in-part on the user identity obtained by the identity manager or security context obtained by the defense center, and to prompt application of the selected policy. The policies are indicative of user / device authorization entitlements and restrictions to utilization of certain network resources, network services or applications. Dynamic policy selection and targeted responses can be used, for example, against a user who gains network access with stolen user ID and password, and subsequently attempts malicious behavior. In particular, the malicious behavior is detected and identified, and the malicious user can then be restricted from abusing network resources without adversely affecting other users, groups, network devices, and other network services.
Owner:NORTEL NETWORKS LTD
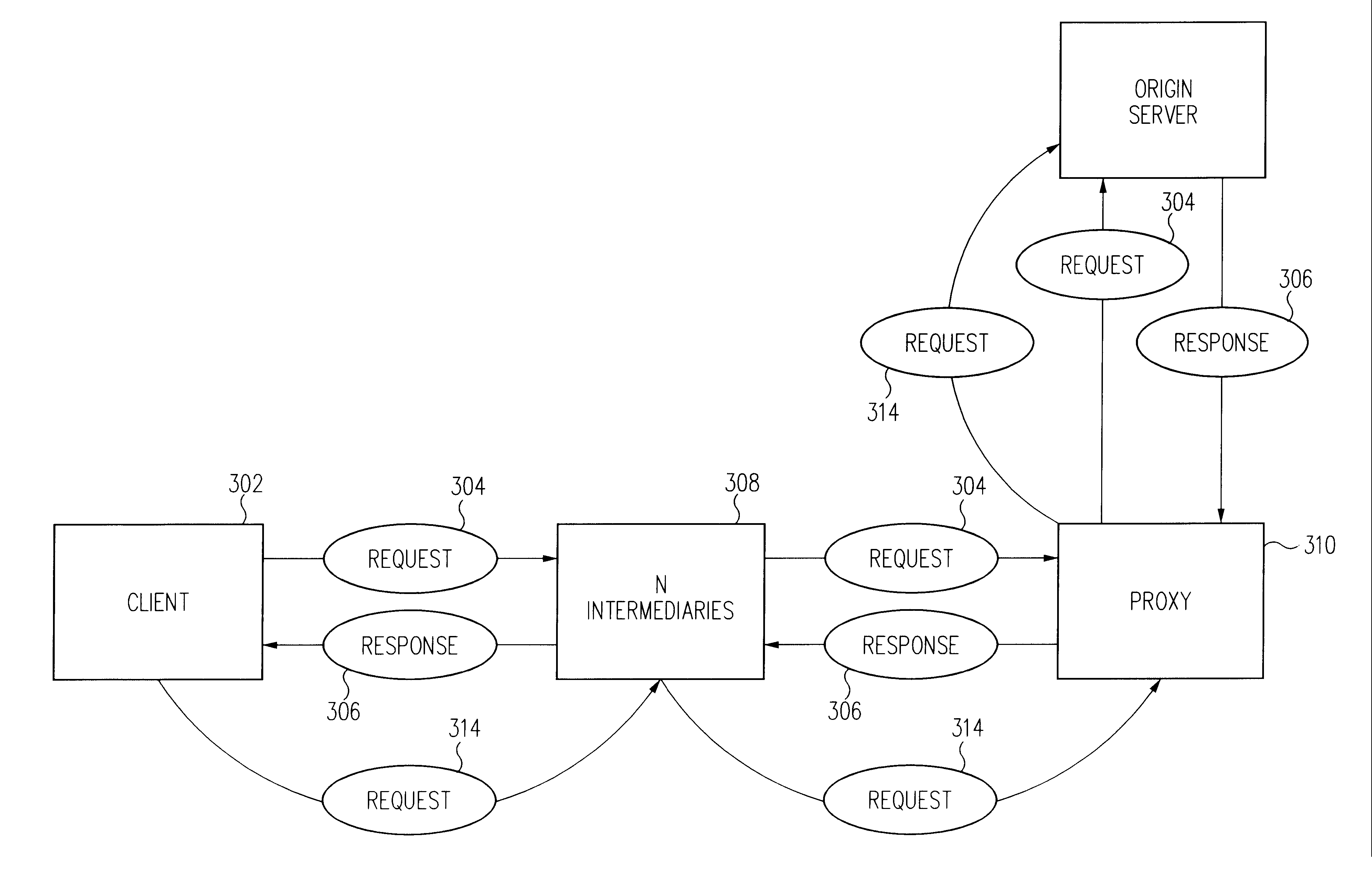
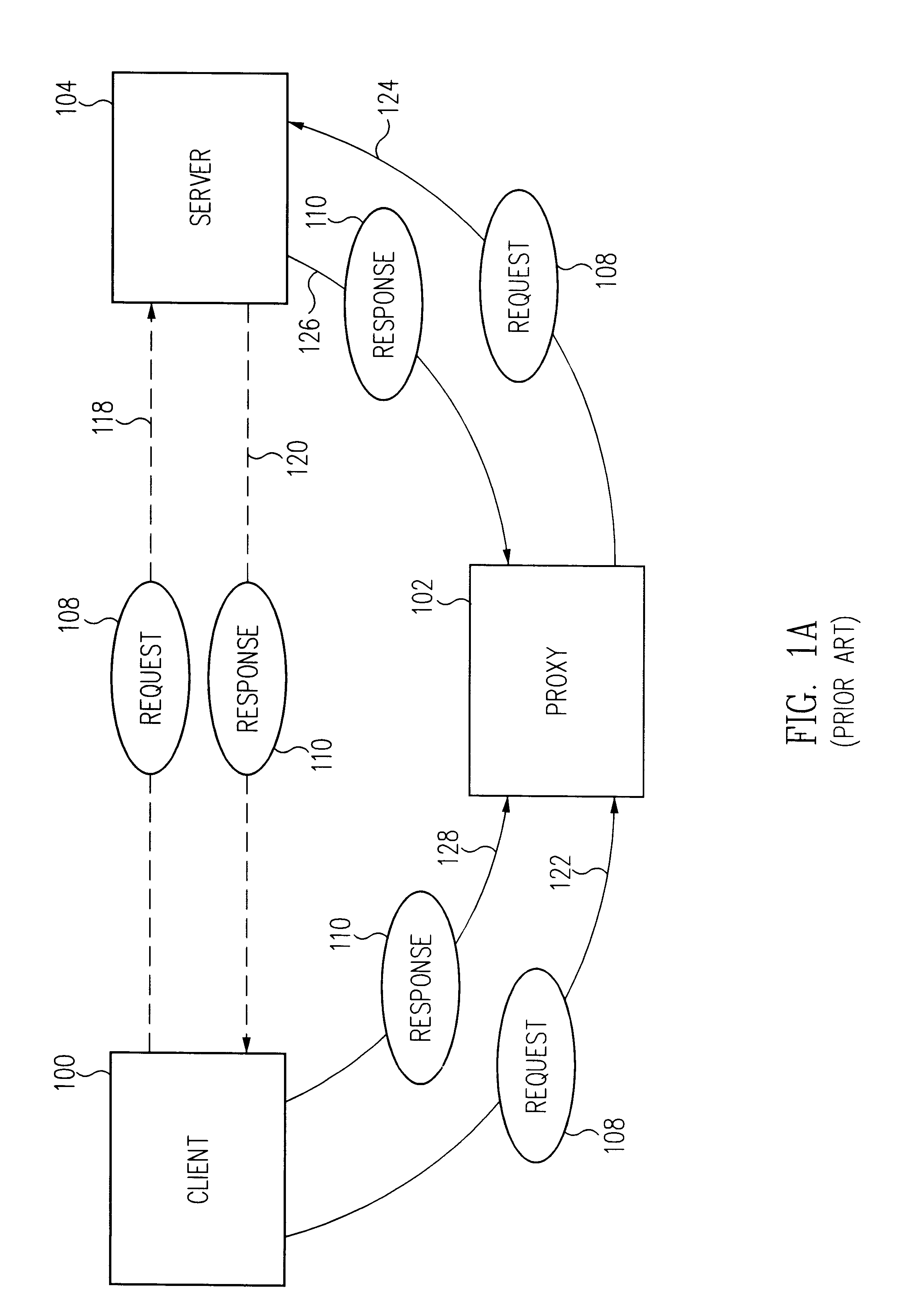
Method and apparatus for dynamic proxy insertion in network traffic flow
In embodiments of the invention, a method and apparatus for dynamic proxy insertion in network traffic path is described. According to one or more embodiments of the invention, a request and / or response message may be modified to include one or more thru-proxy tags to identify a network (or traffic) node (e.g., a proxy, server, or intermediary). For example, a request directed to a server or a response directed to a client may be altered to insert a plurality of intermediate or final destination designations. In so doing, a path of a request or response may be altered dynamically. A thru-proxy tag in a response may be inserted in a related request to identify a destination or node such that the request is sent to the destination in the thru-proxy tag before being sent to an origin server. Thru-proxy tags may be used to identify multiple and / or alternate destinations.
Owner:ORACLE INT CORP
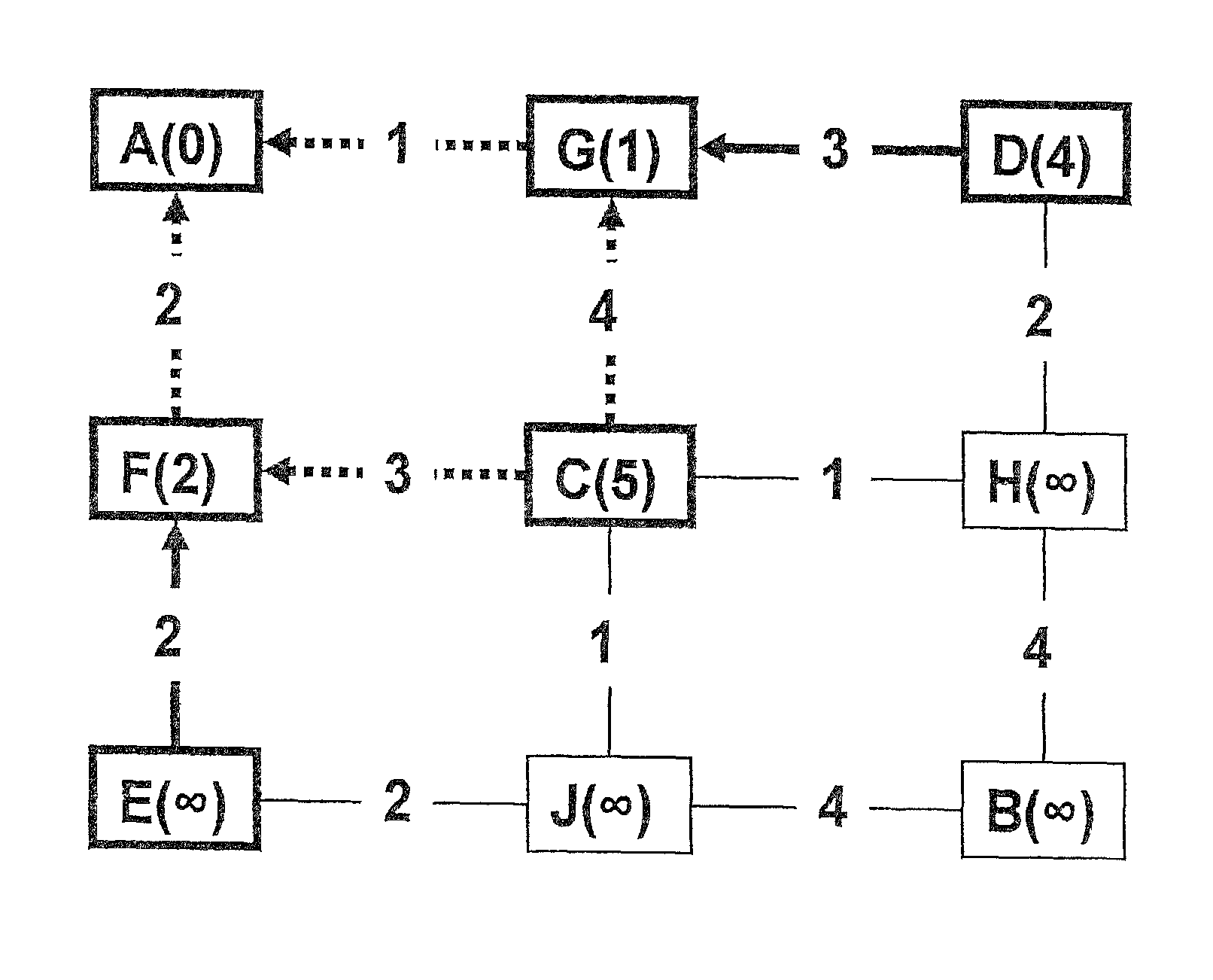
Tie-breaking in shortest path determination
InactiveUS8761022B2Simple calculationLower requirementError preventionTransmission systemsTraffic flowOrder set
A consistent tie-breaking decision between equal-cost shortest (lowest cost) paths is achieved by comparing an ordered set of node identifiers for each of a plurality of end-to-end paths. Alternatively, the same results can be achieved, on-the-fly, as a shortest path tree is constructed, by making a selection of an equal-cost path using the node identifiers of the diverging branches of the tree. Both variants allow a consistent selection to be made of equal-cost paths, regardless of where in the network the shortest paths are calculated. This ensures that traffic flow between any two nodes, in both the forward and reverse directions, will always follow the same path through the network.
Owner:RPX CLEARINGHOUSE
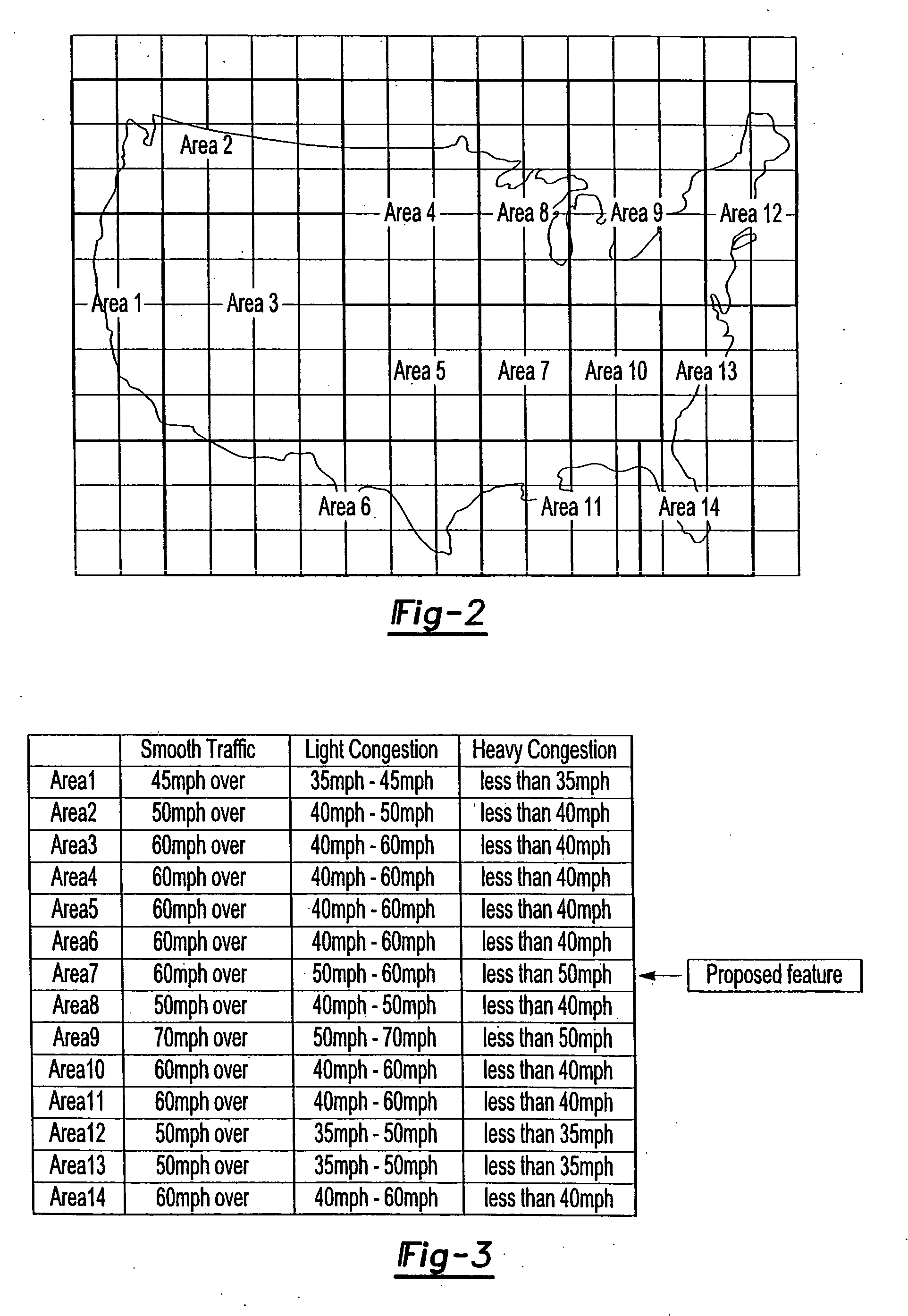
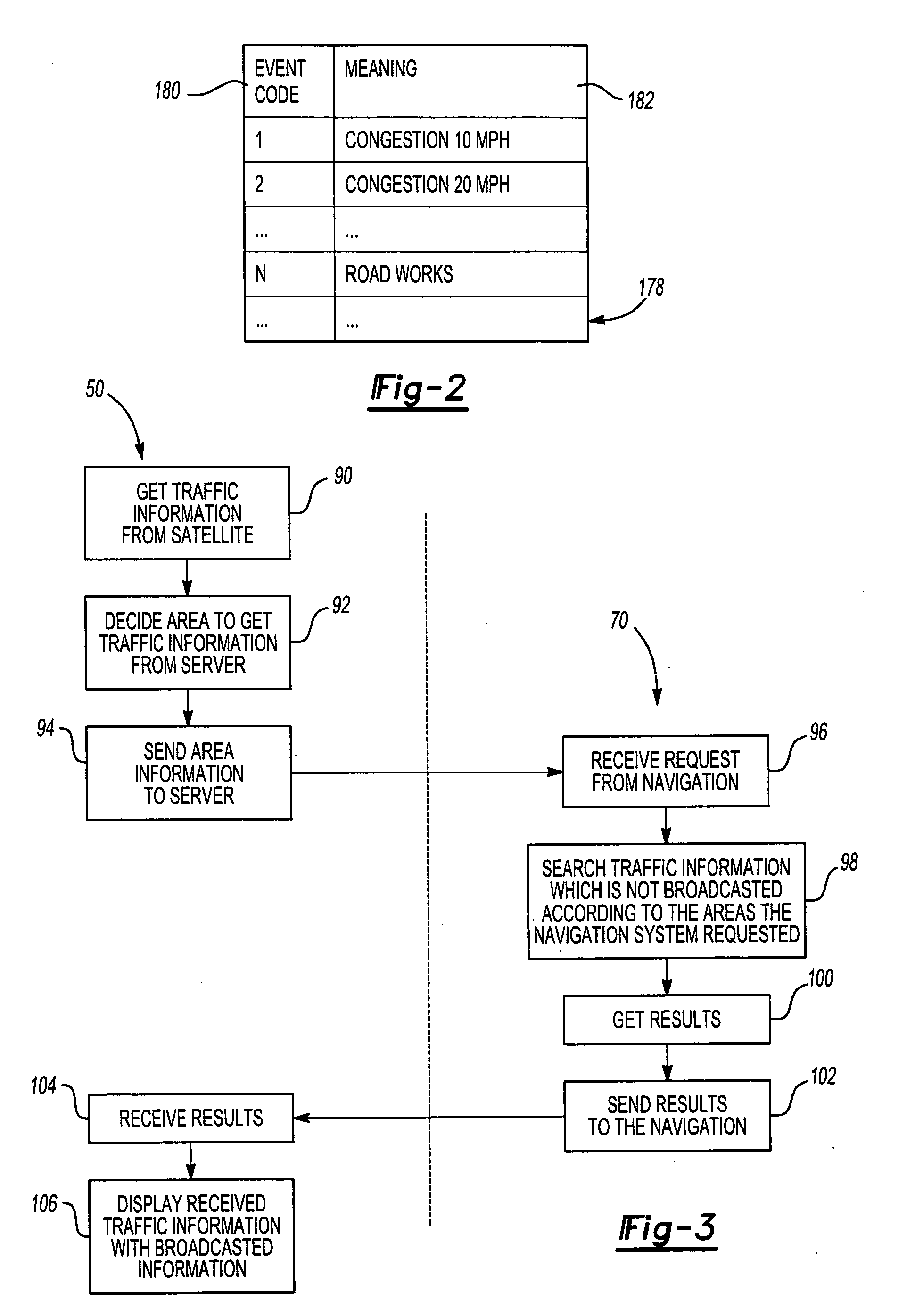
Apparatus and method for processing and displaying traffic information in an automotive navigation system
InactiveUS20060178807A1Eliminate redundant dataControlling traffic signalsAnalogue computers for vehiclesCommunications systemTraffic flow
A vehicle navigation system for use with a traffic information broadcast system which transmits traffic data relating to primary road segments and a communication system which transmits traffic data relating to road segments in a local geographic area. A broadcast receiver receives the broadcast traffic data from the broadcast system and stores the received data. A communication transmitter, when activated, transmits a data request to the communication system. A communication receiver receives the local traffic data from the communication system in response to the data request while a processor displays traffic information on a display screen corresponding to the received broadcast traffic data and the received local traffic data. The local traffic data includes both traffic information relating to local road segments as well as non-traffic temporal events, such as weather, and time-related events which affect traffic flow. A database of historic traffic flow for the road segments is periodically updated to reflect new traffic data.
Owner:CLARION CO LTD
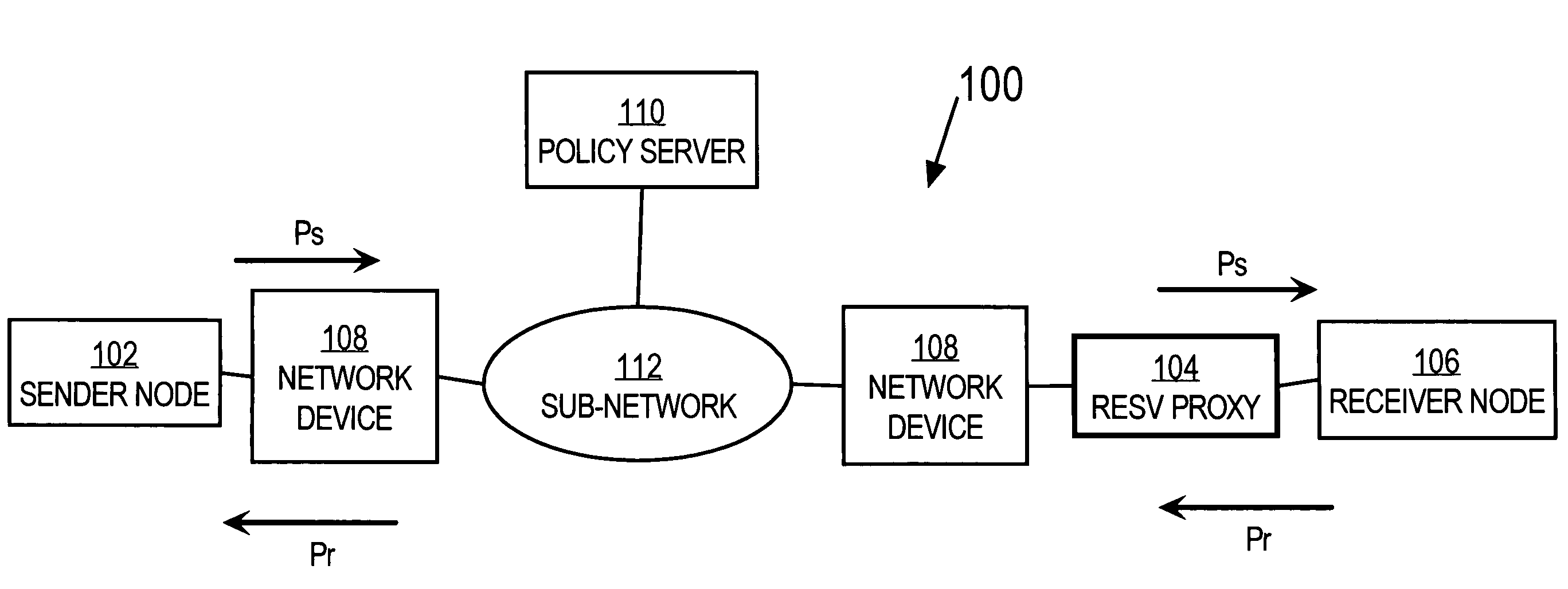
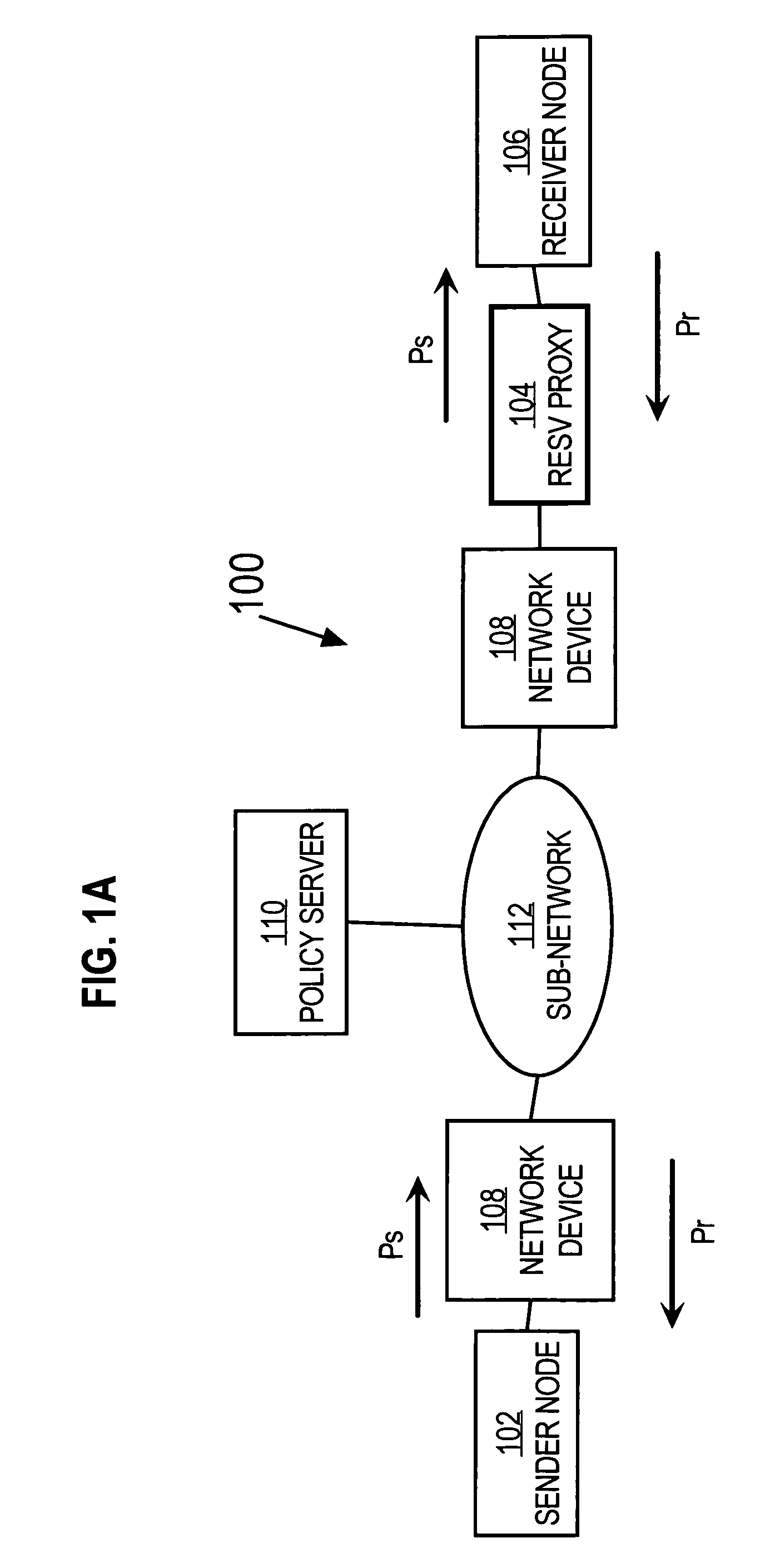
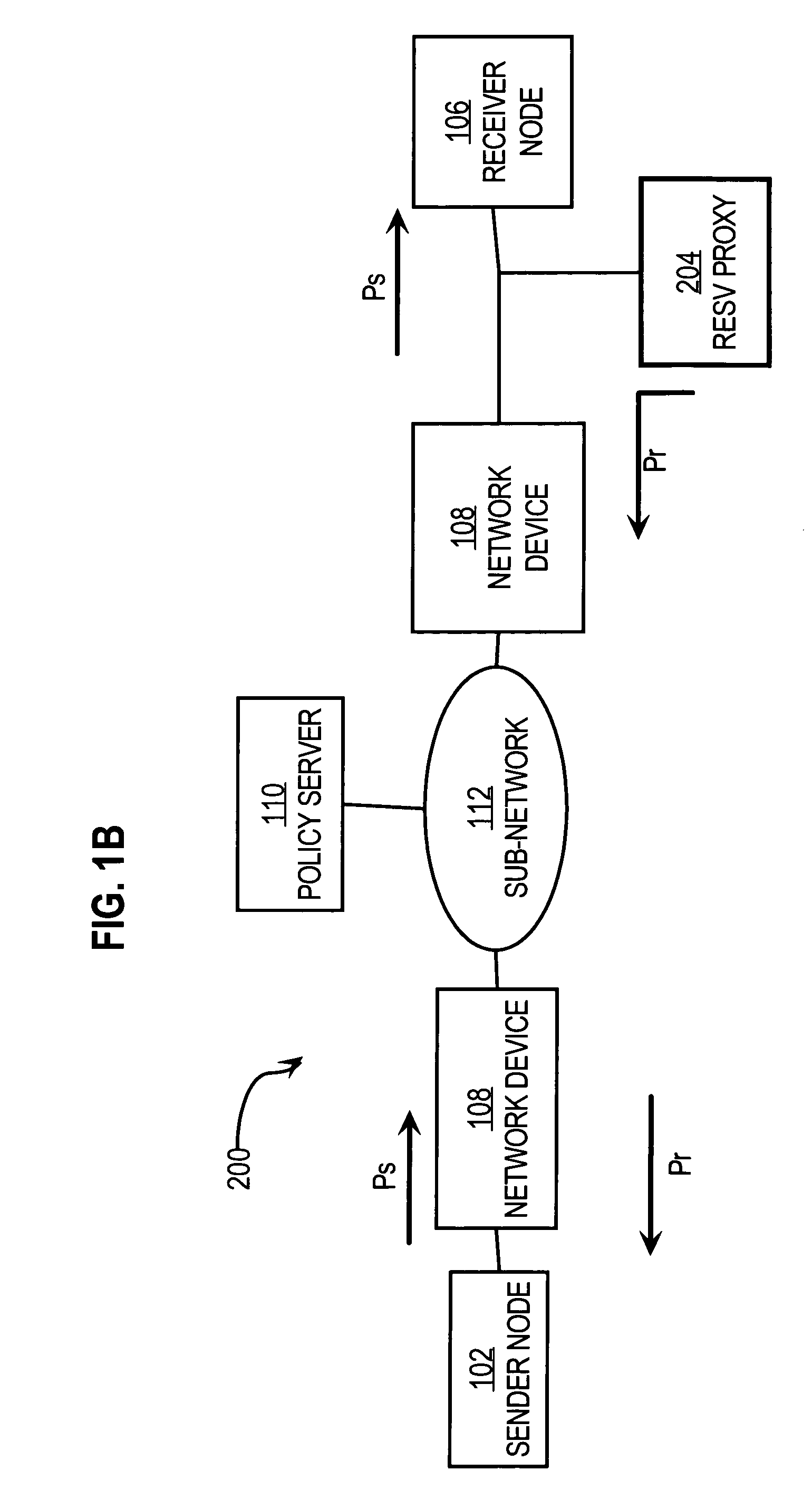
Method and apparatus providing automatic RESV message generation for non-RESV-capable network devices
A method and apparatus for providing network resource reservation capability for receiver nodes that either cannot or do not facilitate RSVP processes is provided. A RESV proxy is connected between an anticipated sender node and an anticipated receiver node in a computer network, e.g., a voice over IP network. The RESV proxy can detect an RSVP Path message and determine whether a RESV message is appropriate for the anticipated traffic flow. If it is so determined, the RESV proxy generates and communicates a RESV message through the network back to the anticipated sender node. The appropriateness of a RESV message can be based upon predetermined relationships or logic involving one or more of network parameters, transport parameters, and characteristics of the anticipated traffic flow, and other traffic flow attributes determined from analyzing the RSVP Path message. The RESV proxy can also interface with a policy server on the network to facilitate generation of the RESV message according to one or more of the anticipated traffic flow attributes. Alternatively, the RESV proxy can include the policy server functionality itself.
Owner:CISCO TECH INC
Display method and system for a vehicle navigation system
ActiveUS20050222760A1Controlling traffic signalsAnalogue computers for vehiclesDisplay deviceTraffic flow
Traffic information, including traffic flow information and traffic incident information, obtained through a traffic management system for providing and facilitating the exchange of traffic information between a remote location and a vehicle may be presented to a user on a user display in the vehicle. The traffic information may be presented to the user in several circumstances, either as cued by the user, or automatically presented by the traffic management system. The user display may also automatically display traffic flow and traffic incident information for the direction that the user is traveling or along a route calculated by the navigation device. Further, a window displaying information about an upcoming traffic incident such as distance to the incident and incident details may automatically appear in the user display. Alternately, the user may select a roadway, freeway, or area for which traffic information is desired.
Owner:HONDA MOTOR CO LTD
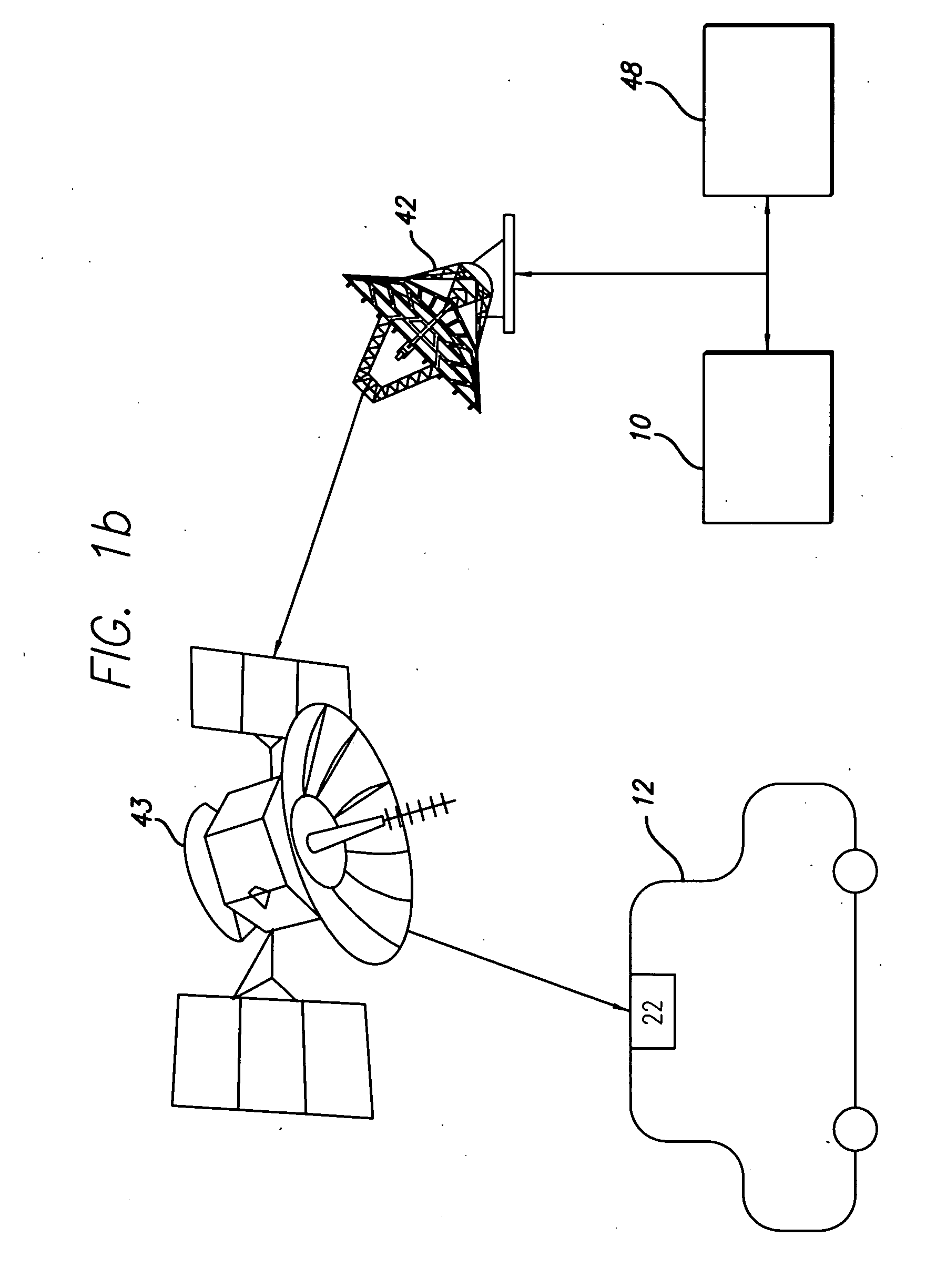
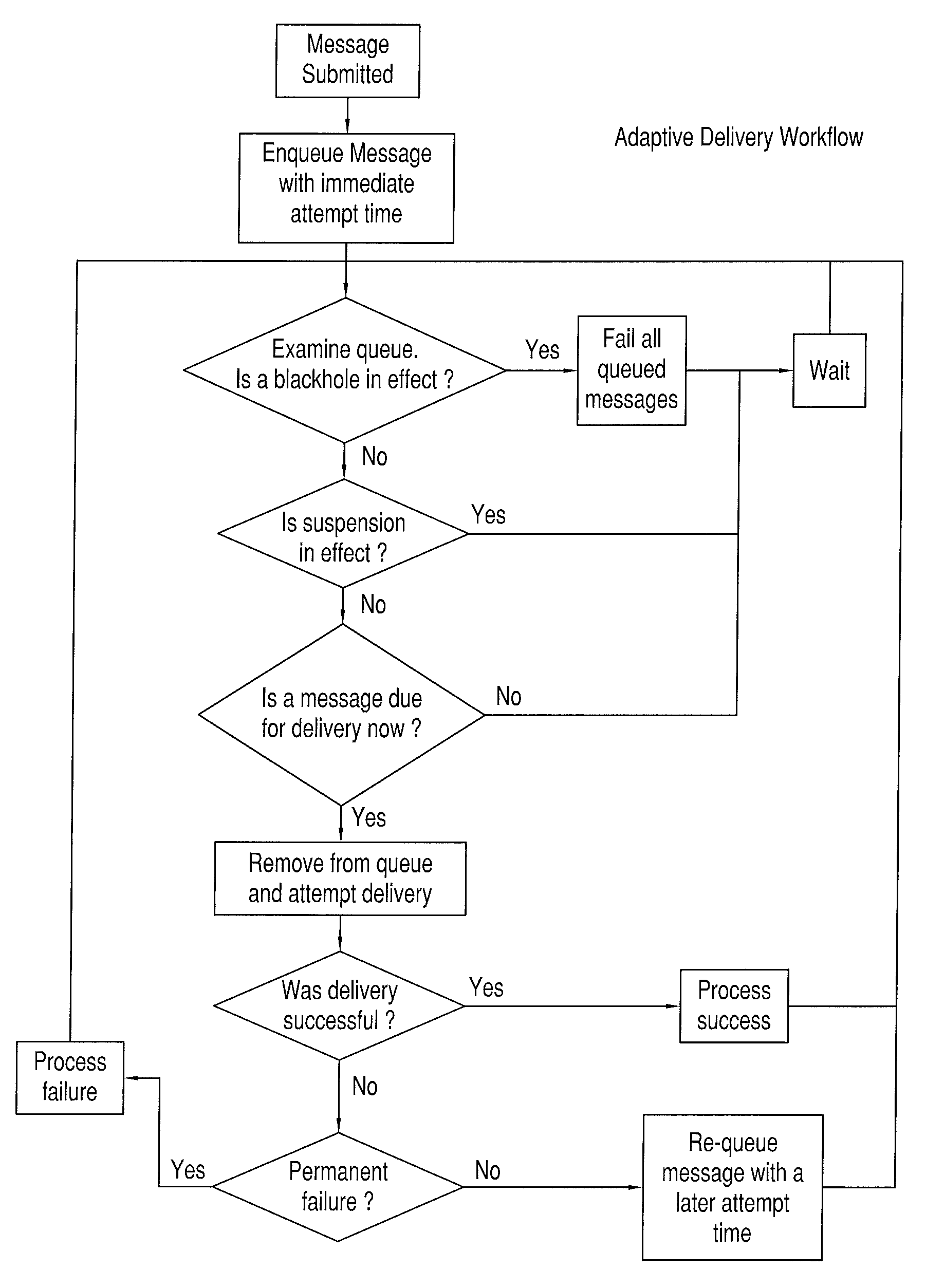
Method and system for adaptive delivery of digital messages
InactiveUS20110289162A1Convenient and flexible and effectiveMultiple digital computer combinationsData switching networksMessage flowMessage delivery
A system and method for automatically adapting digital message traffic flow evaluates message delivery disposition, latency and performance metrics such that the system operates more optimally in terms of both overall throughput as well as with respect to system sending reputation. Reputation is in the context of maintaining message flow within limits that are acceptable for a given destination, such that the sender behavior avoids being flagged as abusive or otherwise undesirable.
Owner:MESSAGE SYSTEMS
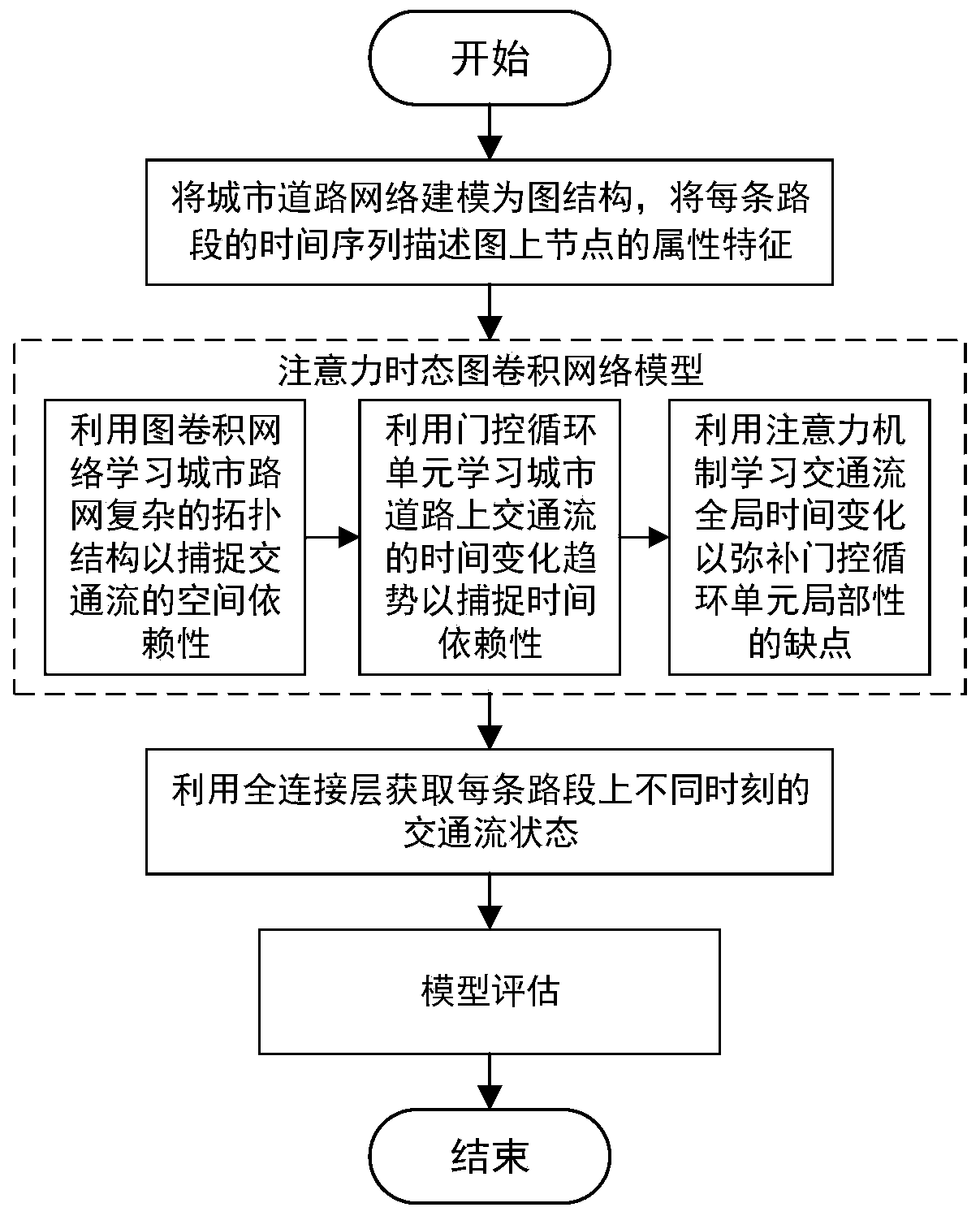
Traffic prediction method based on attention temporal graph convolutional network
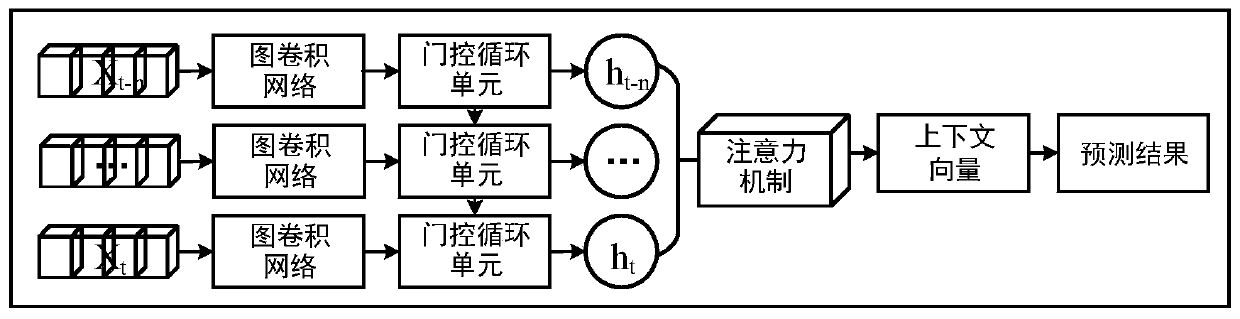
ActiveCN109754605AGain spatial dependenceGood forecastDetection of traffic movementForecastingTraffic predictionNetwork model
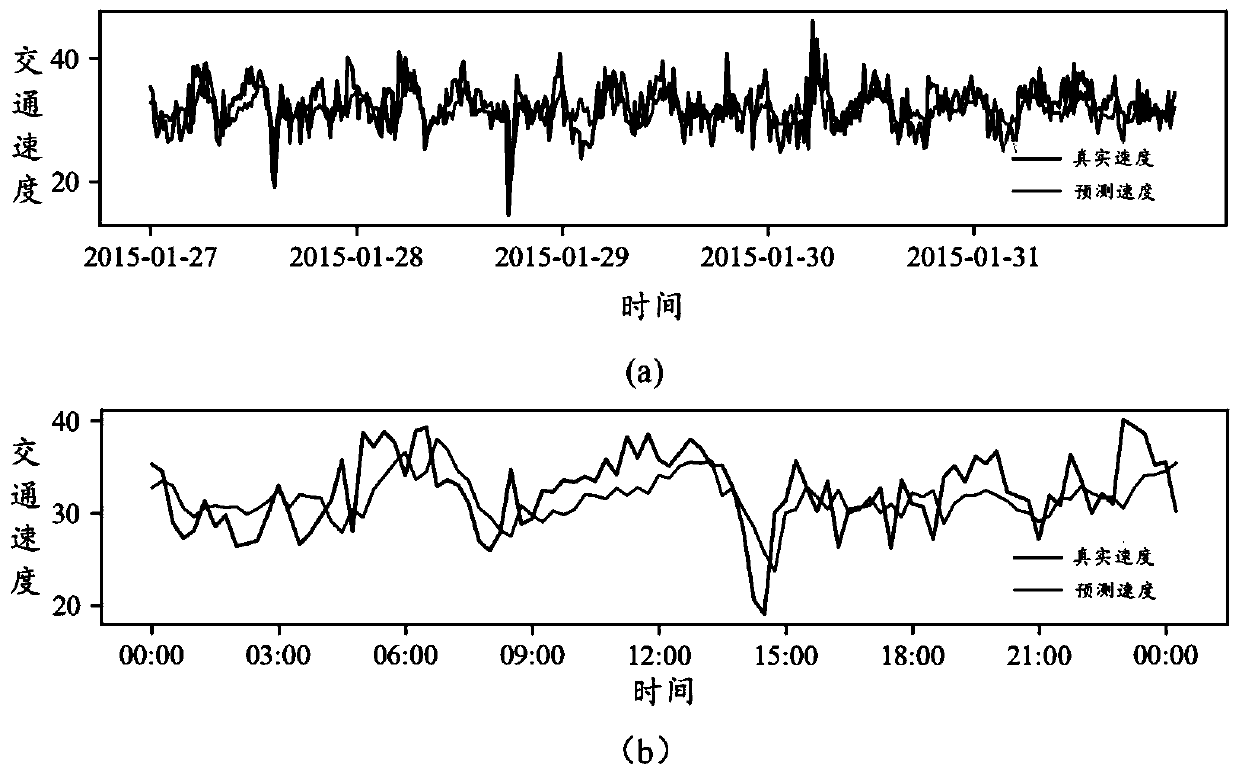
The invention belongs to the field of intelligent transportation, and discloses a traffic prediction method based on an attention temporal graph convolutional network. The method includes the following steps that: firstly, an urban road network is modeled as a graph structure, nodes of the graph represent road sections, edges are connection relationships between the road sections, and the time series of each road section is described as attribute characteristics of the nodes; secondly, the temporal and spatial characteristics of the traffic flow are captured by using an attention temporal graph convolutional network model, the temporal variation trend of the traffic flow on urban roads is learned by using gated cycle units to capture the time dependence, and the global temporal variation trend of the traffic flow is learned by using an attention mechanism; and then, the traffic flow state at different times on each road section is obtained by using a fully connected layer; and finally,different evaluation indexes are used to estimate the difference between the real value and the predicted value of the traffic flow on the urban roads and further estimate the prediction ability of the model. Experiments prove that the method provided by the invention can effectively realize tasks of predicting the traffic flow on the urban roads.
Owner:CENT SOUTH UNIV
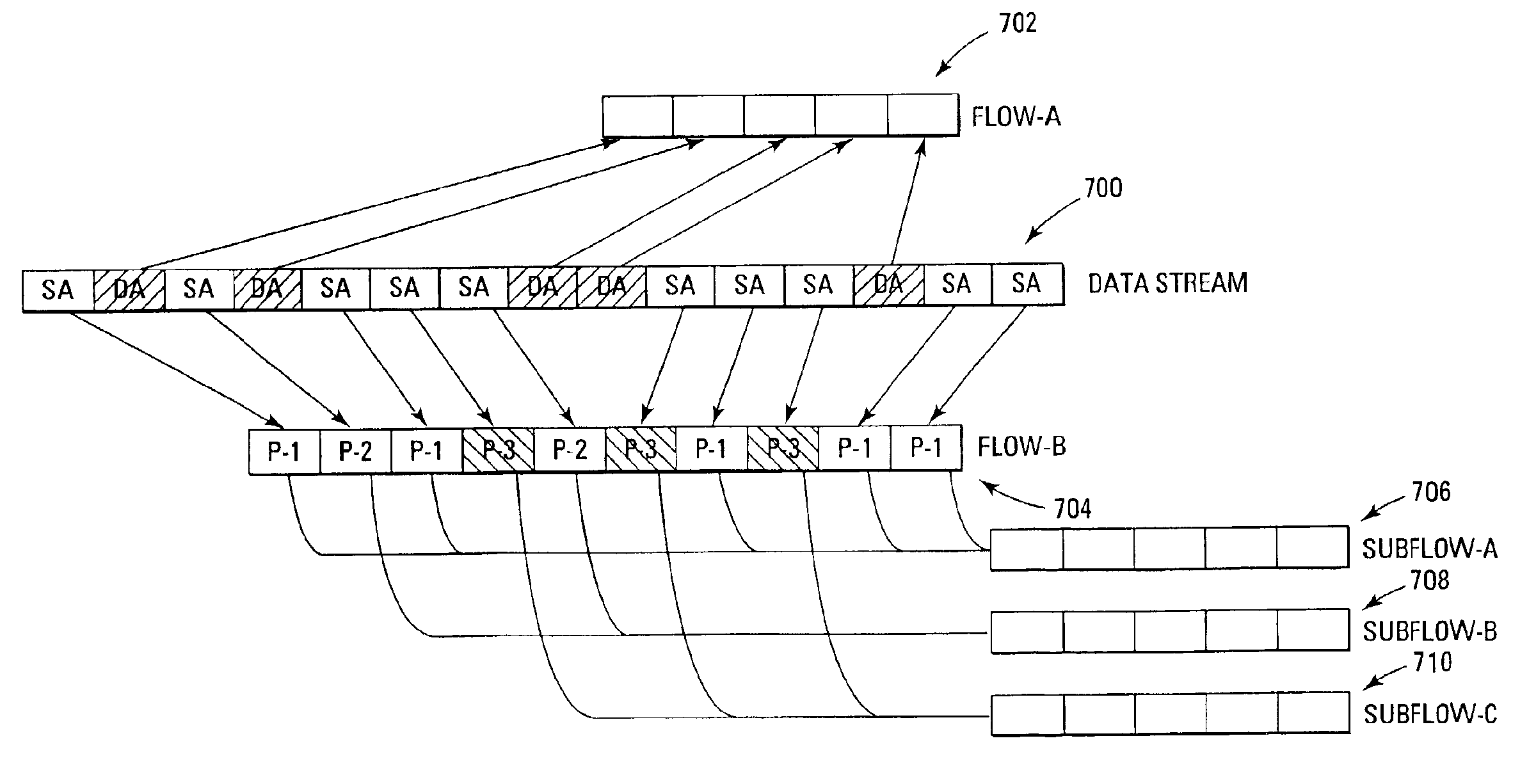
System and method for hierarchical policing of flows and subflows of a data stream
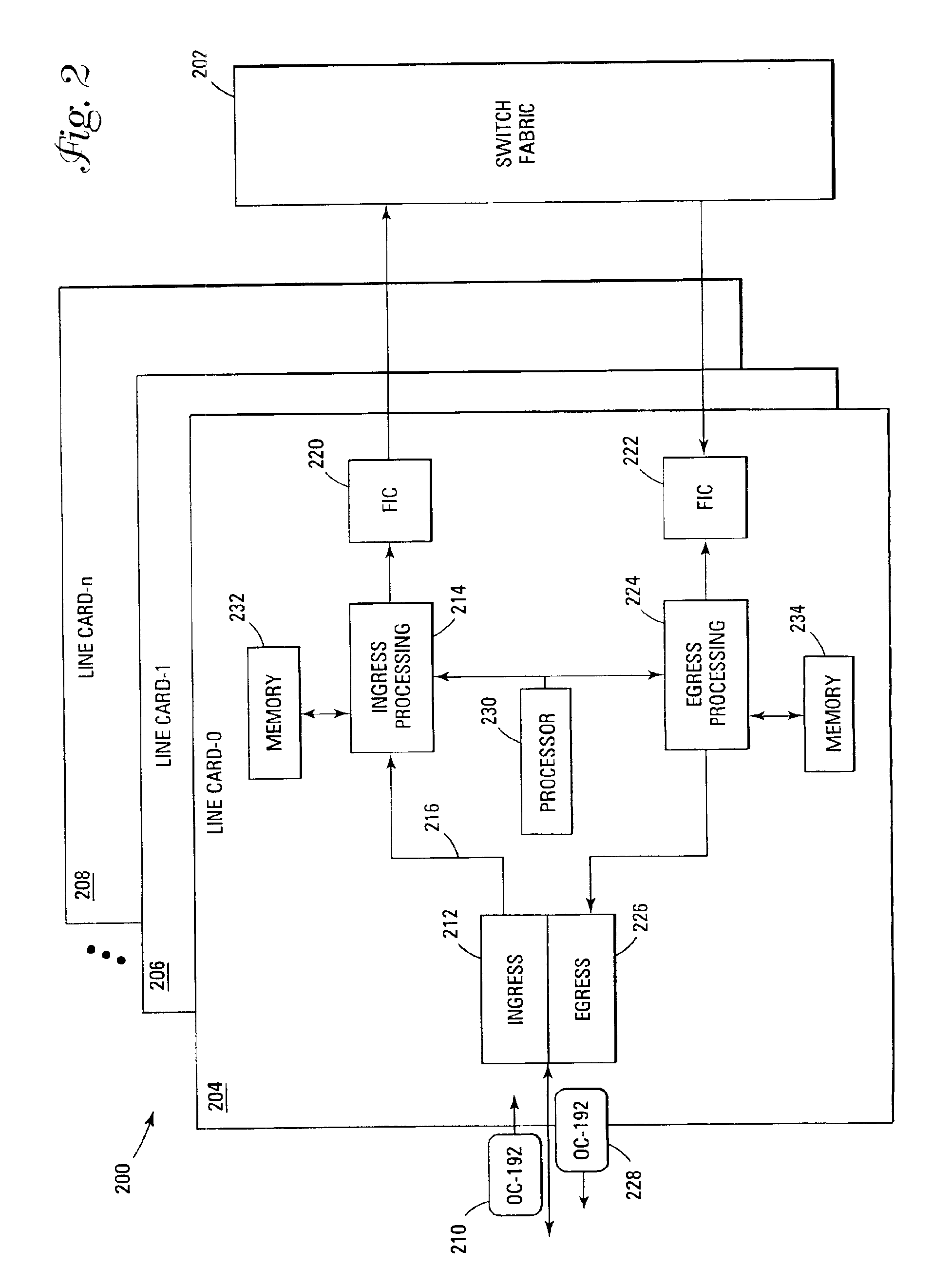
ActiveUS7042848B2Facilitating layered policingMaximizing exploitationError preventionTransmission systemsRate limitingData stream
A system and method for policing individual flows and subflows of a data stream. Data traffic streams are classified into separate traffic flows, which in turn can be further classified into subflows, thereby providing for different priority levels of subsets of the flow. The subflows may be still further classified into additional subflows, creating a hierarchical, layered prioritization that can be metered at each vertical and horizontal level of the hierarchy. A packet flow rate of each of the subflows is compared to a predefined rate limit to allow subflows of a flow to have different priorities therebetween.
Owner:RPX CORP
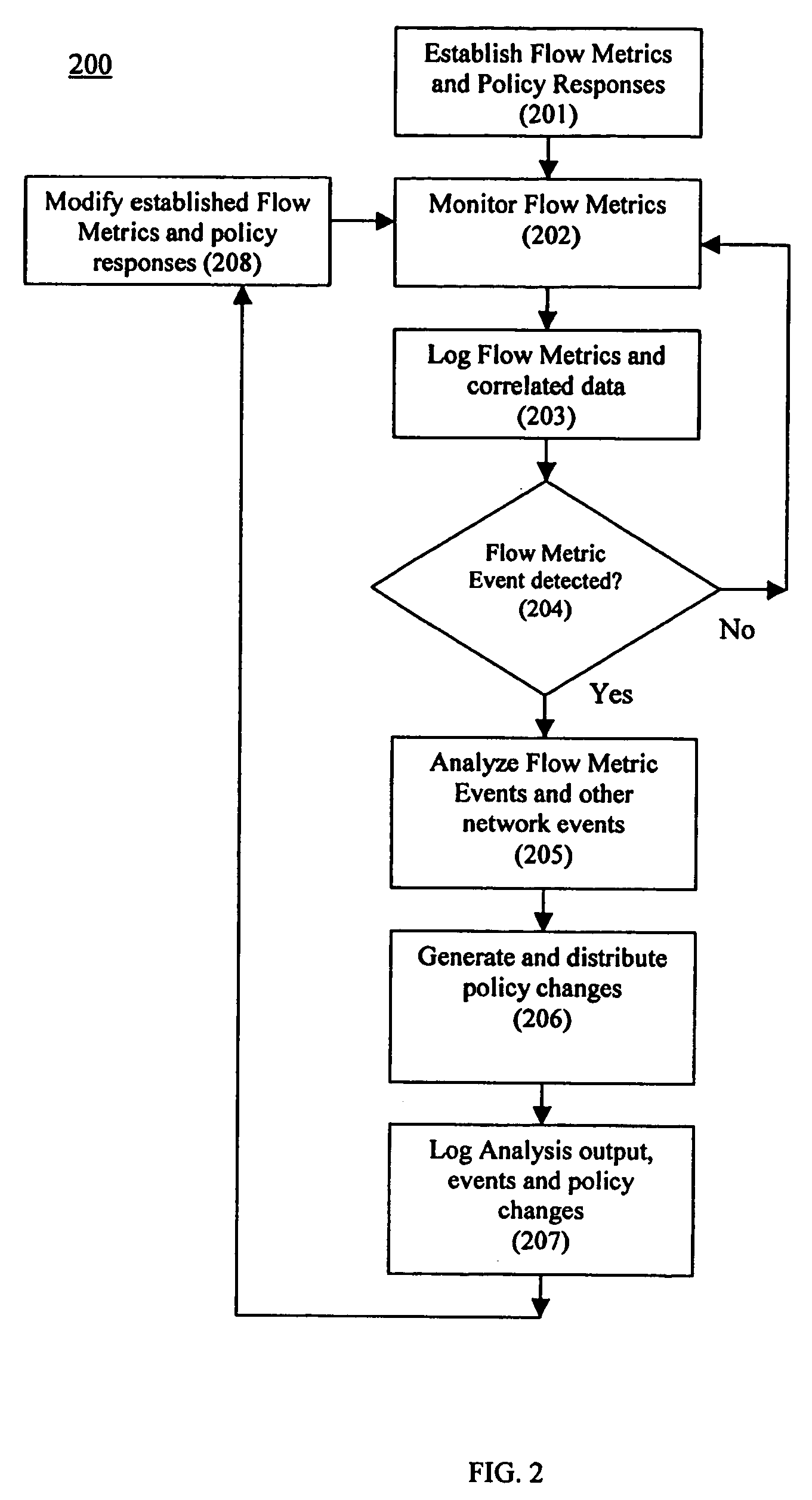
Using flow metric events to control network operation
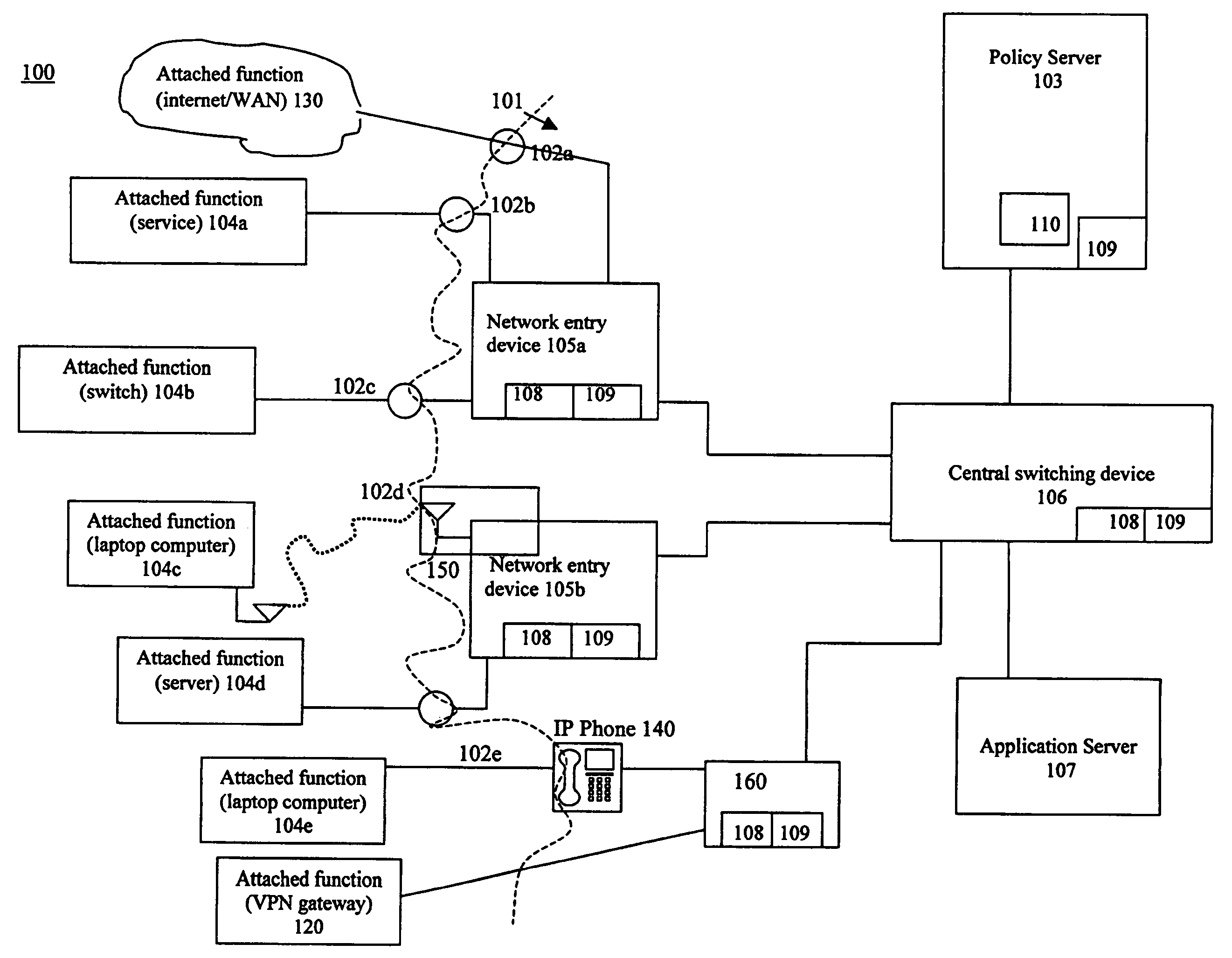
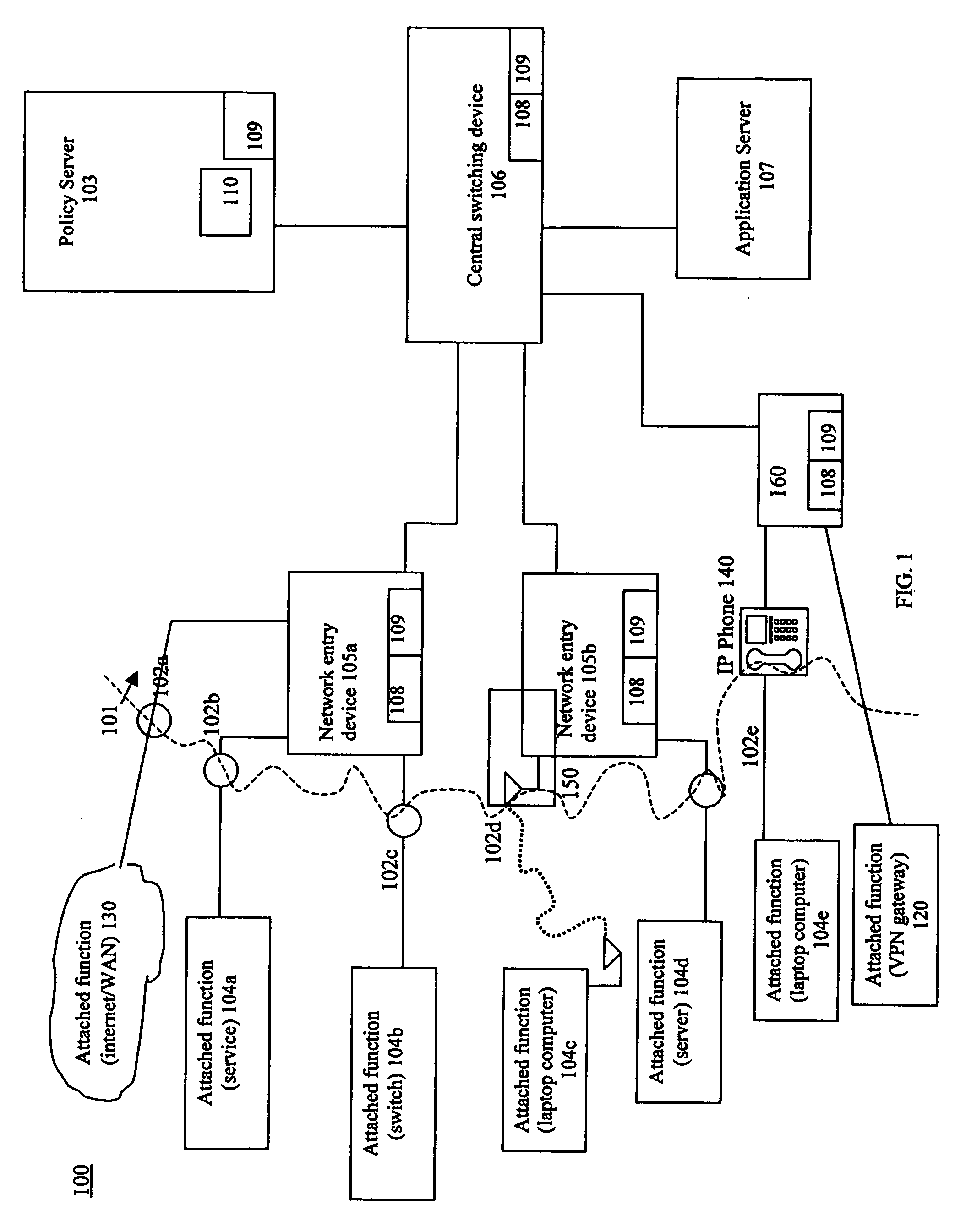
InactiveUS20060075093A1Minimize impactSlow changeDigital computer detailsTransmissionNetworked systemTraffic flow
A system and method to monitor, detect, analyze and respond to, triggering conditions associated with packet and signal flows in a network system including attached functions and a network infrastructure. The system includes a detection function, an analysis function, and a response function. The detection function includes a monitoring sub-function, a flow definition sub-function, and a monitor counter sub-function. The flow definition sub-function defines the types of activities associated with the traffic flow that may indicate a triggering condition requiring analysis and potentially a response. The monitor sub-function observes traffic flows. The monitor counter sub-function counts the defined types of activities occurring in the device. The analysis function analyzes the event from the monitored flows, flow counters, status and other network information and determines whether a response is required. The response function initiates a response to a perceived event or attack based on the events detected in the flow metrics and other data. The response function further includes a sub-function for activating changes throughout the network system based on receiving and sending event notifications. Responses generated by the response function include dynamic policy changes.
Owner:ENTERASYS NETWORKS
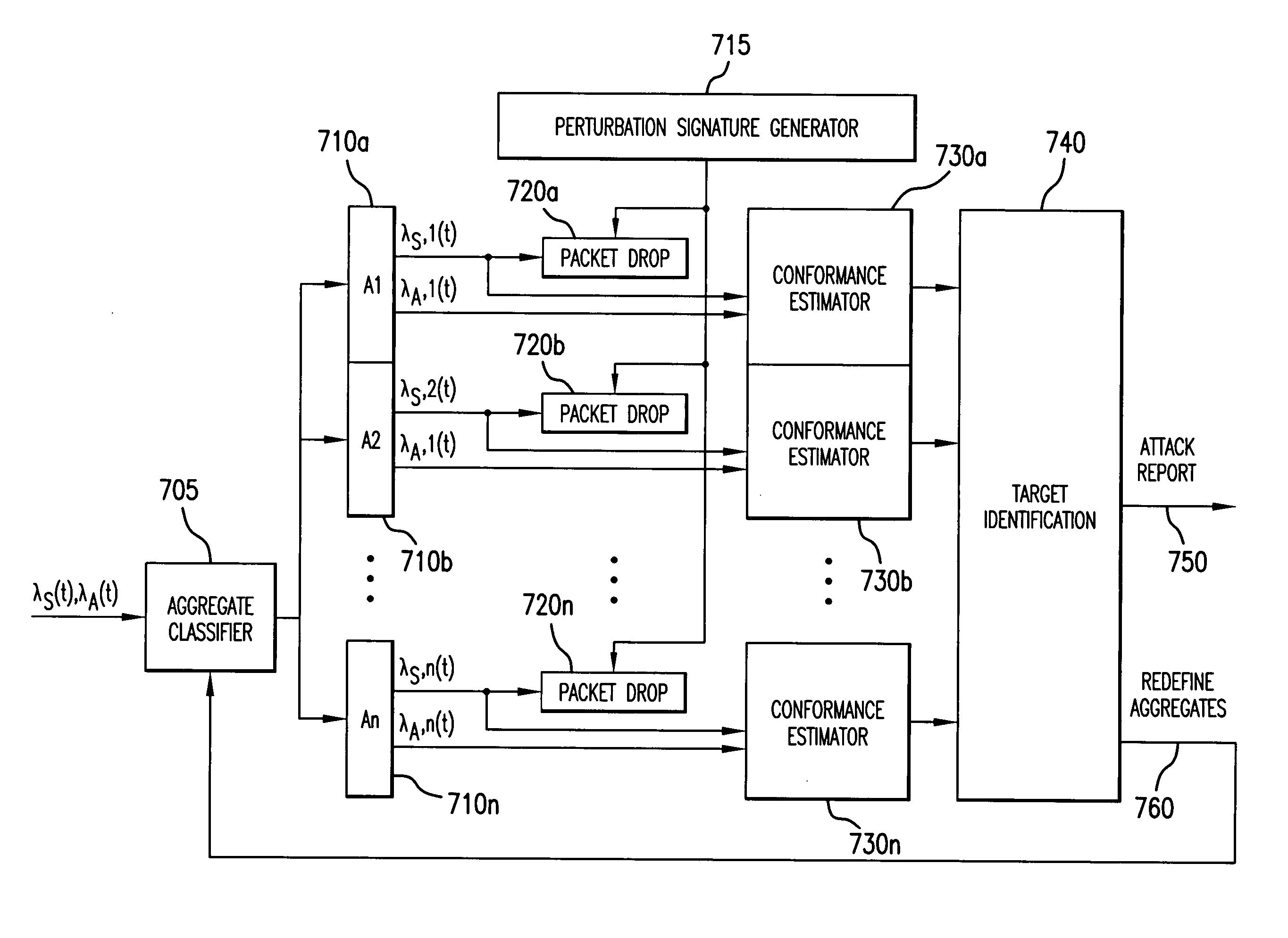
Detection of nonconforming network traffic flow aggregates for mitigating distributed denial of service attacks
An estimate of a portion of network traffic that is nonconforming to a communication transmission control protocol is used to signal that a distributed denial of service attack may be occurring. Traffic flows are aggregated and packets are intentionally dropped from the flow aggregate in accordance with an assigned perturbation signature. The flow aggregates are observed to determine if the rate of arrival of packets that have a one-to-one transmission correspondence with the dropped packets are similarly responsive to the perturbation signature. By assigning orthogonal perturbation signatures to different routers, multiple routers may perform the test on the aggregate and the results of the test will be correctly ascertained at each router. Nonconforming aggregates may be redefined to finer granularity to determine the node on the network that is under attack, which may then take mitigating action.
Owner:MARYLAND UNIV OF
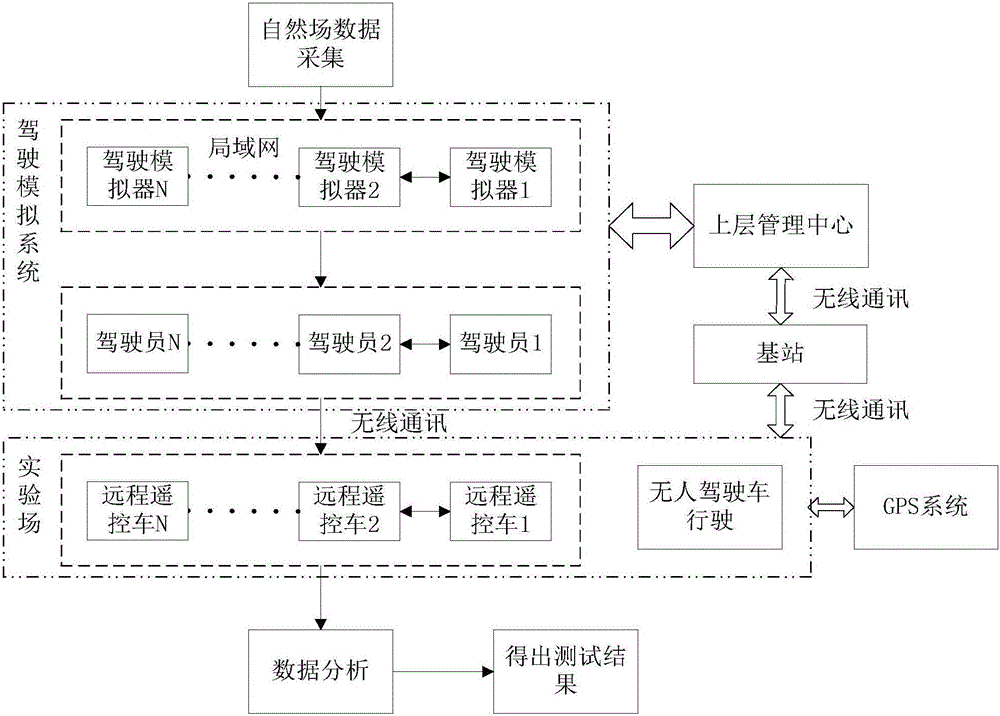
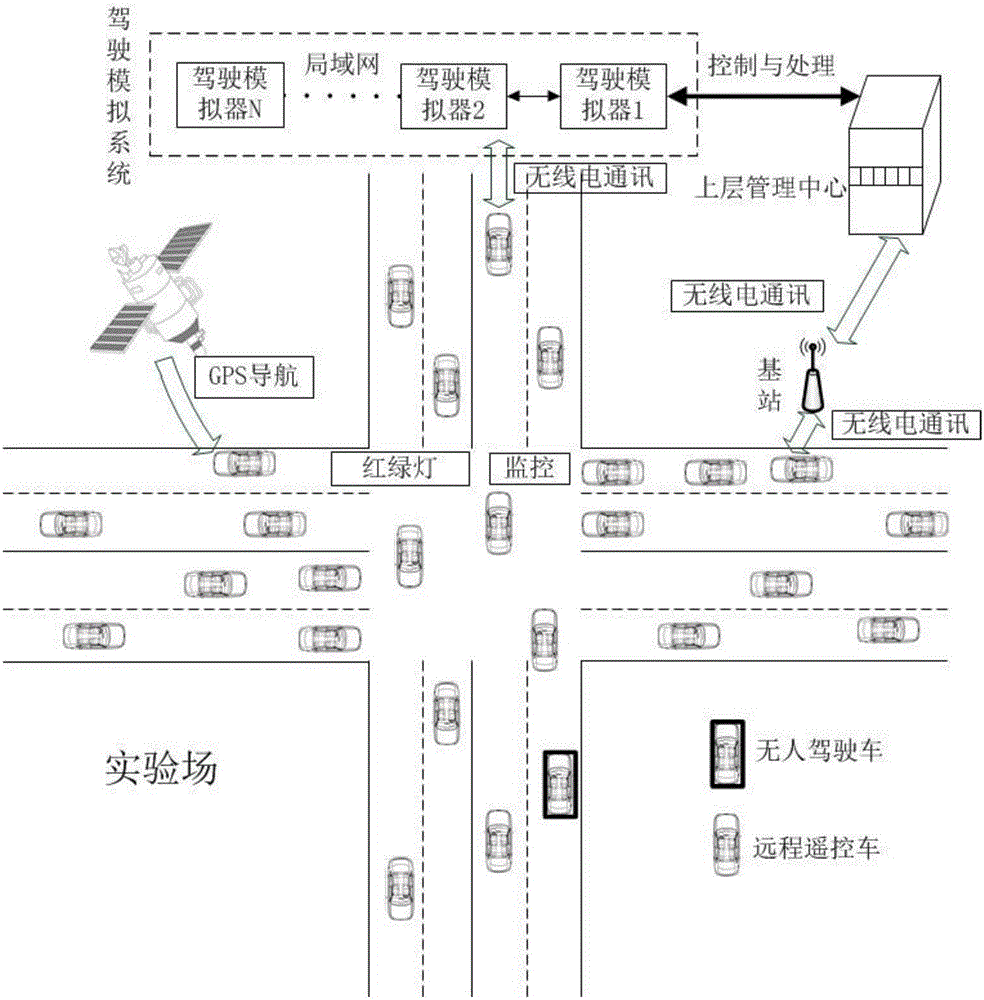
An unmanned vehicle test and verification platform and a test method thereof
ActiveCN106153352AGood for road testingNo experimental riskVehicle testingDetection of traffic movementVirtual vehicleEngineering
The invention belongs to an unmanned vehicle test and verification platform and a test method thereof in the field of unmanned vehicles. The platform comprises a driving simulation system, an experimental field, a network system, an upper level management center and an unmanned vehicle. The driving simulation system constructs a driving environment of a virtual vehicle according to the information collected in a natural scene; the traffic scene of the actual site of the experimental field coincides with the scene modeled by the driving simulation system; and the upper level management center is used for establishing a simulator driving environment, controlling the driving simulation system and processing data; the unmanned vehicle is a test vehicle and is automatically driven in the experimental field; and the driving information of the unmanned vehicle is transmitted to the upper level management center through a network system and then transmitted to the driving simulator of the driving simulation system. According to the invention, function verification and performance evaluation of the unmanned vehicle can be studied, and meanwhile, influences by the unmanned vehicle on an actual traffic flow can be studied and evaluated through the platform.
Owner:上海泽尔汽车科技有限公司
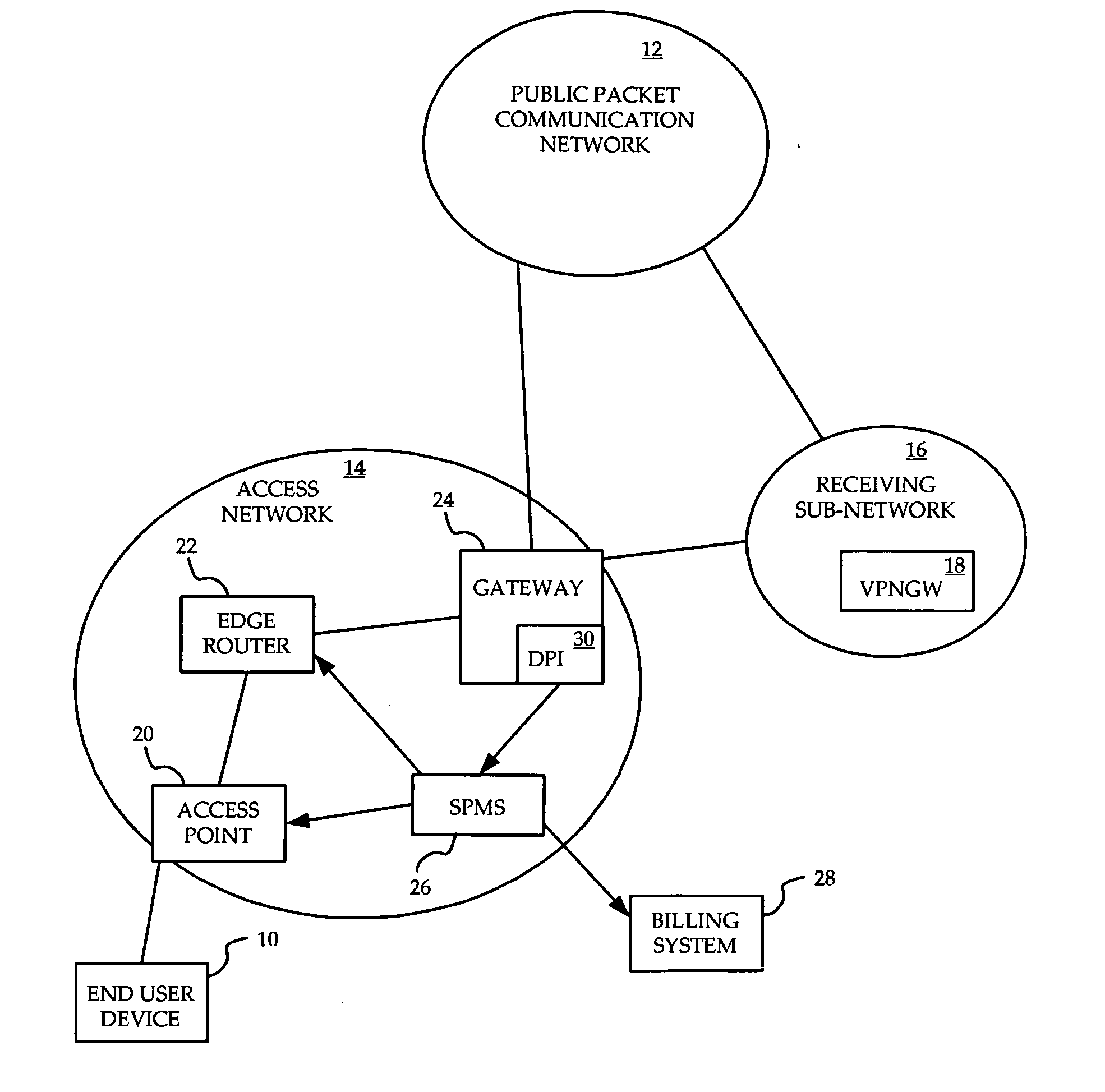
System and method for prioritization of traffic through internet access network
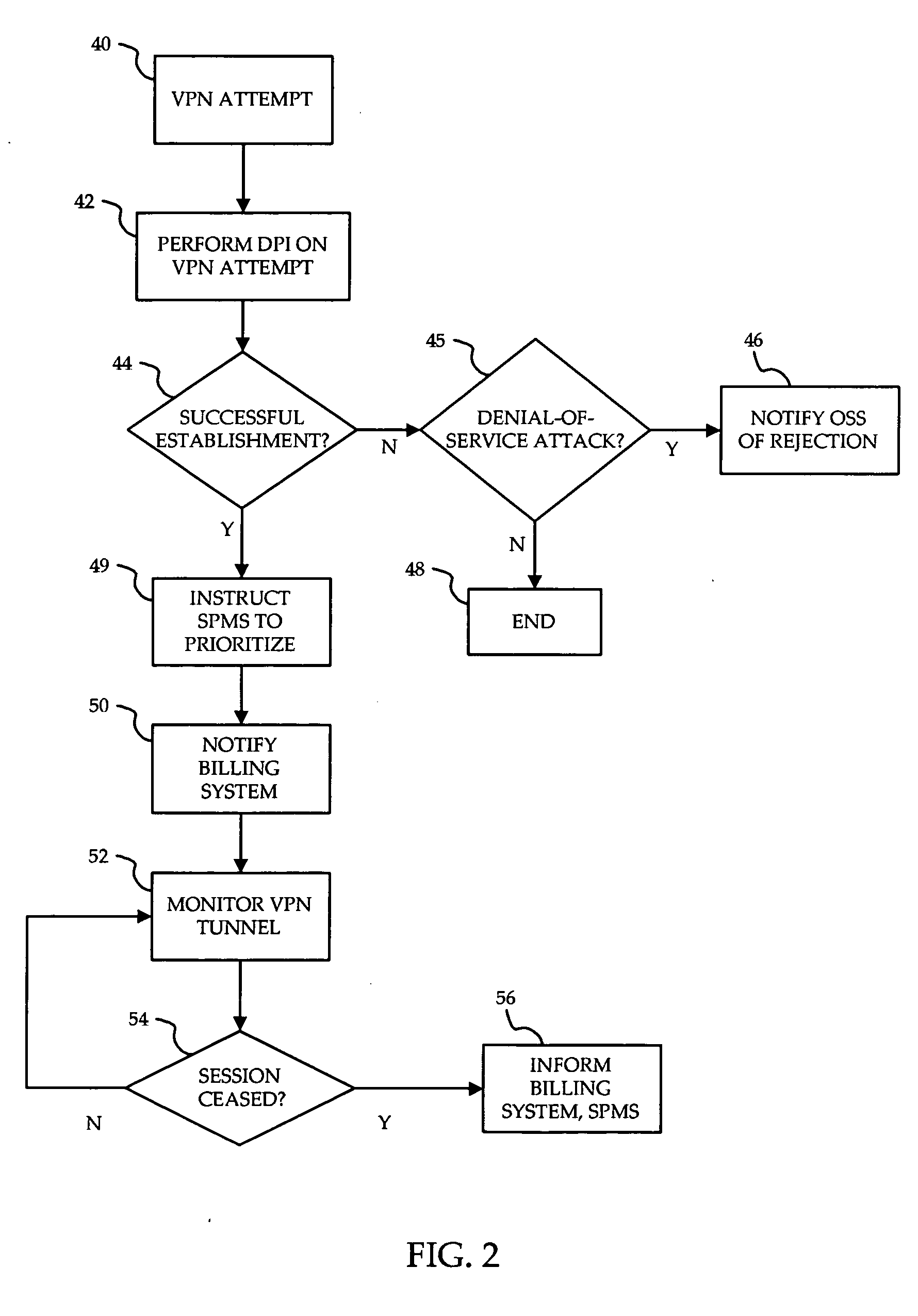
InactiveUS20070153798A1Avoid allocation problemsReduce network congestionData switching by path configurationAccess networkInternet access
A method is provided for ensuring that specific traffic flows are adequately prioritized in a public packet communication network even when the network is heavily congested. Per-flow QoS capability is added to VPN tunnels. Connection requests are routed through a specific port in an access provider's network to designated VPN gateway. Deep packet inspection is performed on traffic through the port in an attempt to determine whether the connection request was accepted. If the connection request was accepted, the traffic flows associated with that session may be given a specific priority of QoS level when transiting a packet access network.
Owner:ALCATEL LUCENT SAS
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com