Patents
Literature
330 results about "Traffic shaping" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Traffic shaping is a bandwidth management technique used on computer networks which delays some or all datagrams to bring them into compliance with a desired traffic profile. Traffic shaping is used to optimize or guarantee performance, improve latency, or increase usable bandwidth for some kinds of packets by delaying other kinds. It is often confused with traffic policing, the distinct but related practice of packet dropping and packet marking.
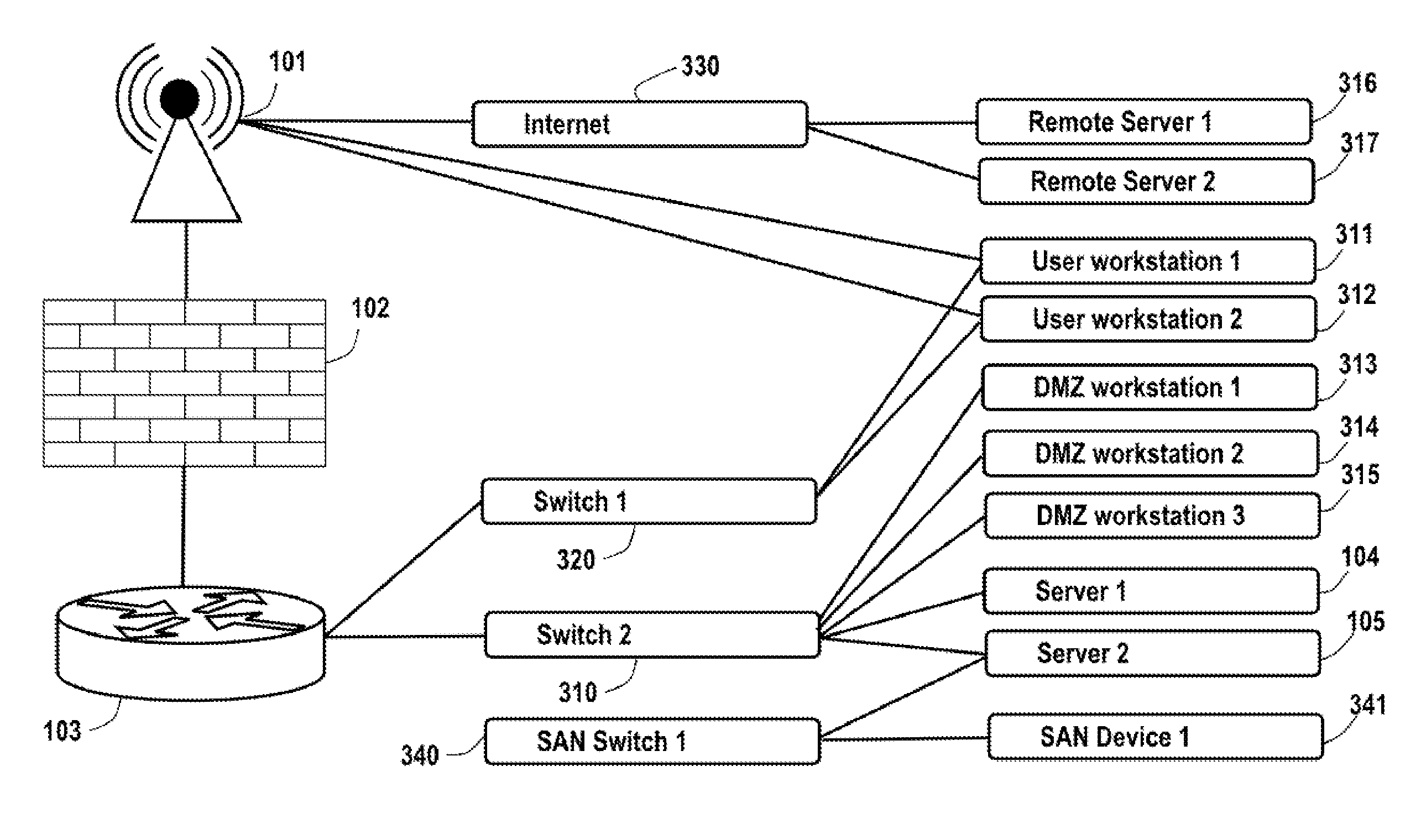
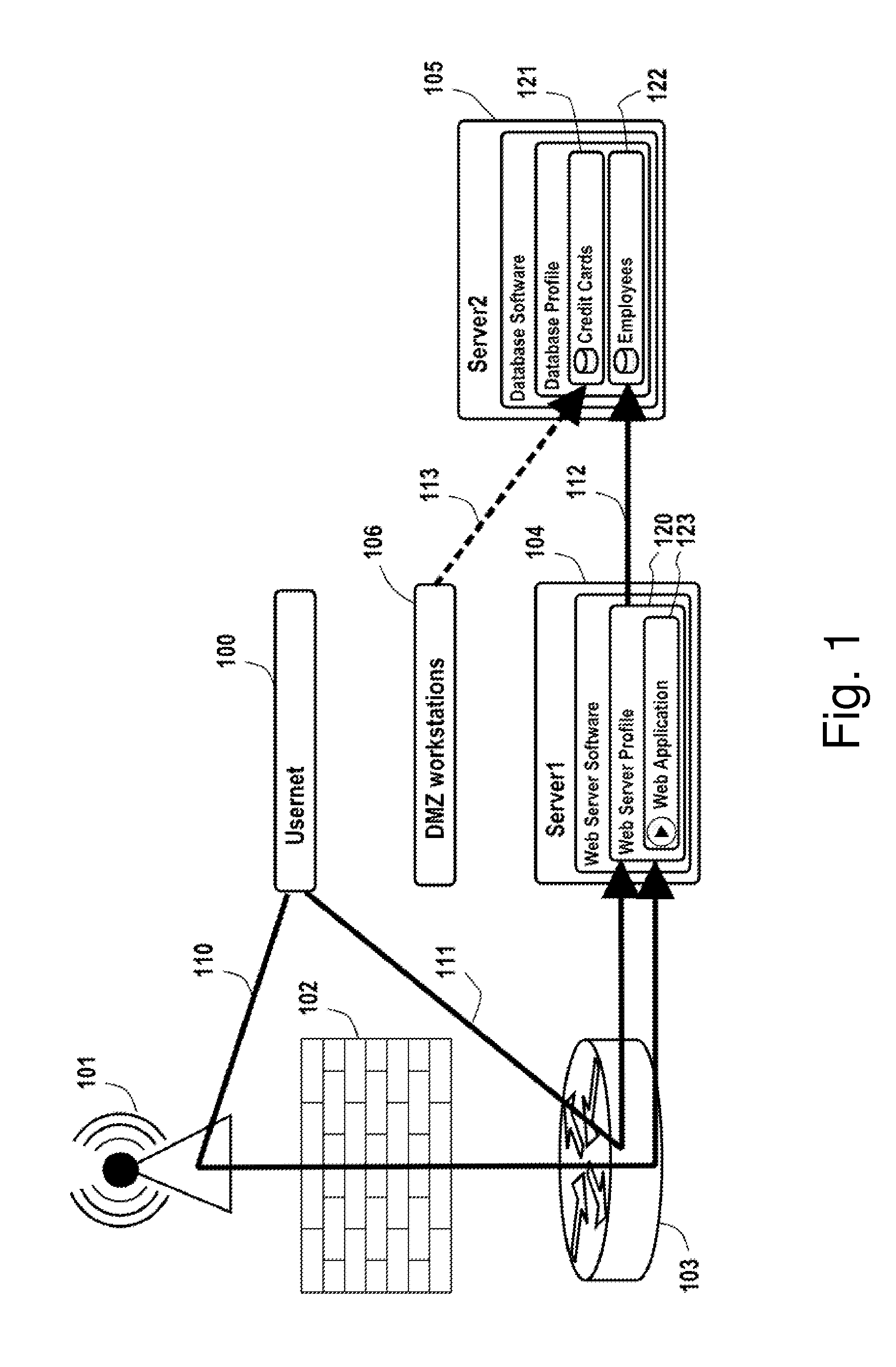
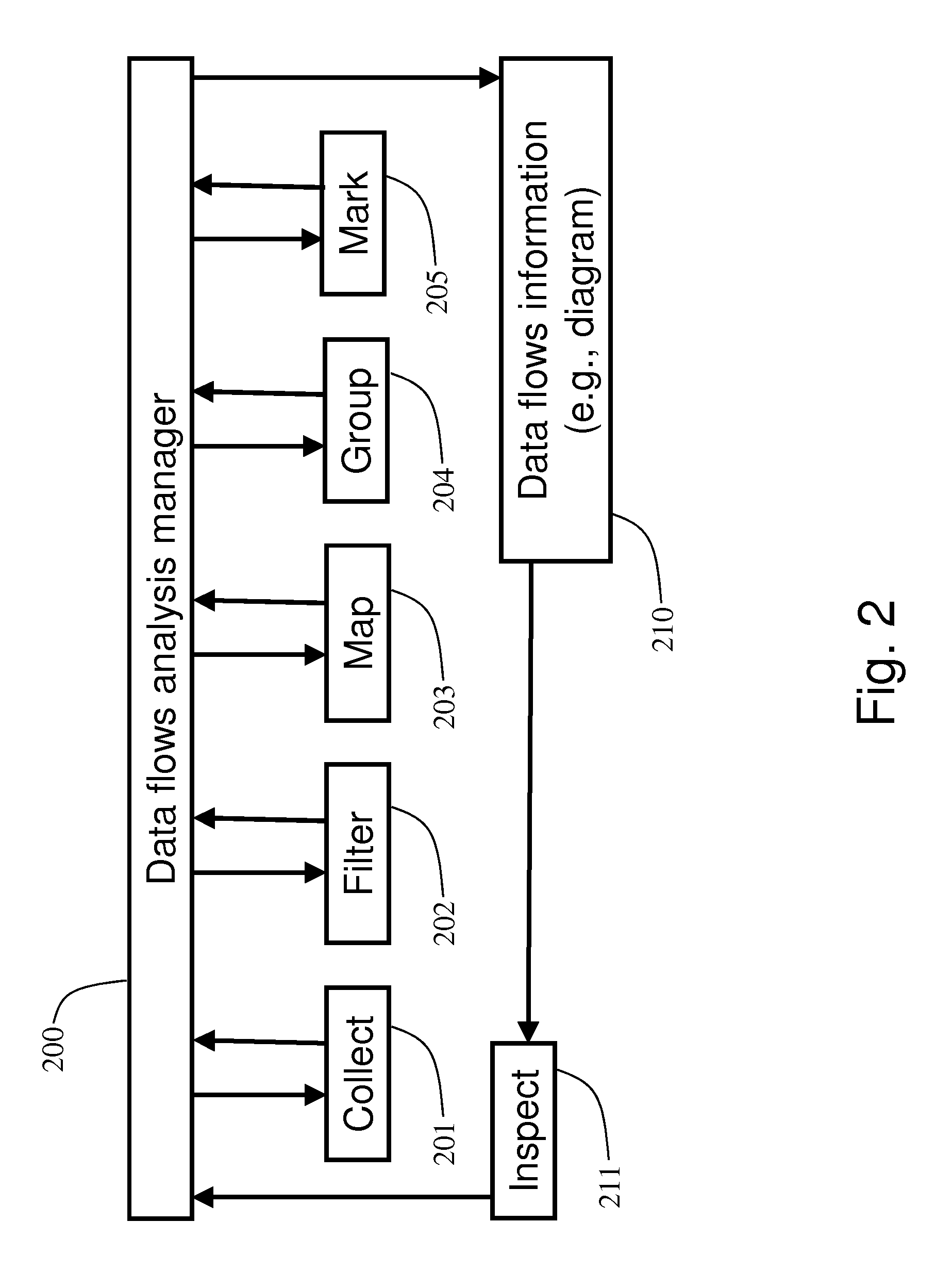
Analysis of data flows in complex enterprise it environments
The present technology enables identification, visualization, and analysis of data flows via network components in complex enterprise IT environments including but not limited to servers, workstations, switches, routers, wireless access points, traffic shapers, firewalls, storage systems and SAN systems. The technology is based on a combination of information collection, information filtering, mapping, grouping, marking, report generation, and verification.
Owner:MODELIZEIT INC
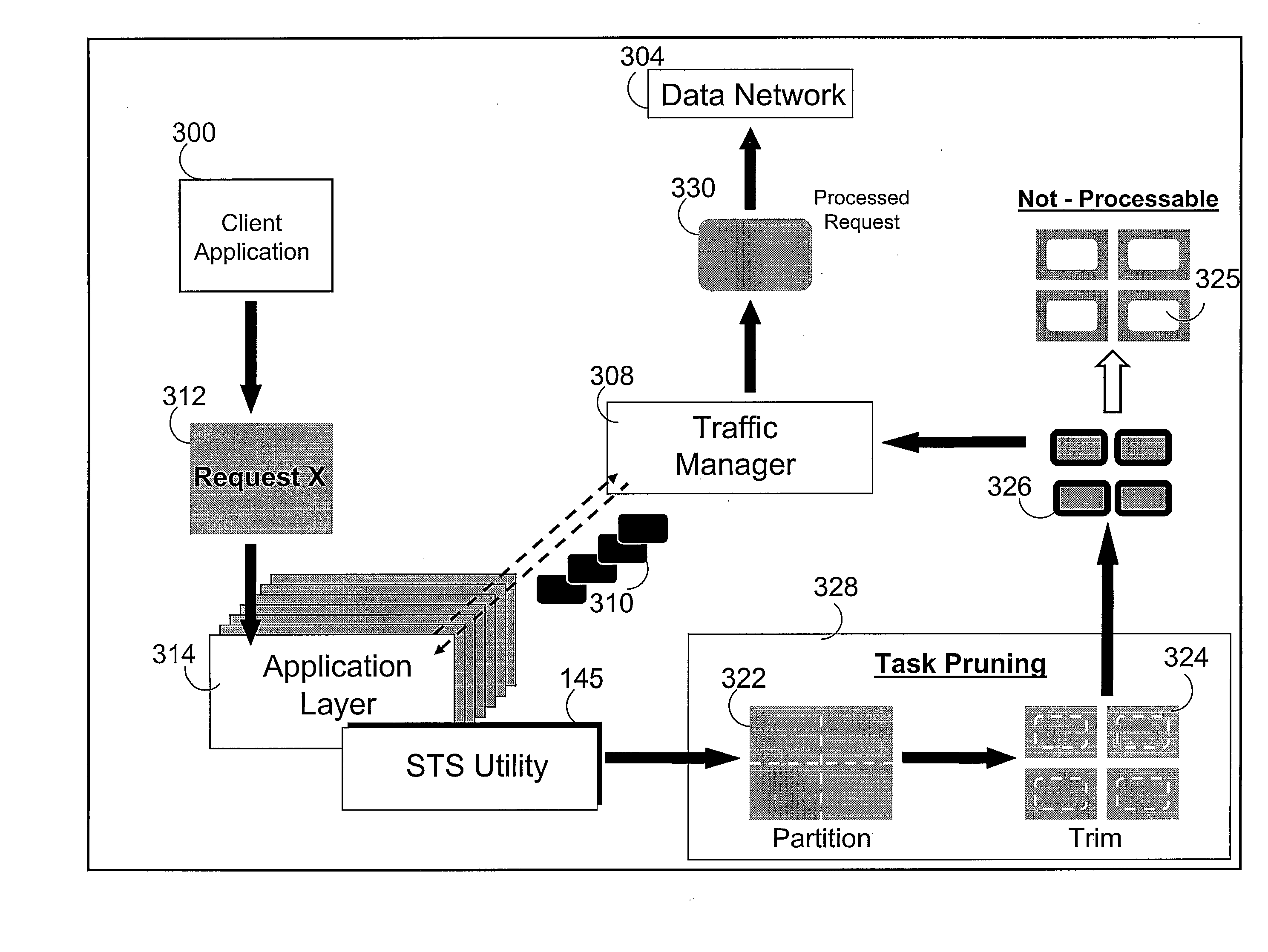
Method for application layer synchronous traffic shaping
InactiveUS20080212470A1Avoid network congestionError preventionTransmission systemsProtocol ApplicationDistributed computing
A method, a system, and a computer program product implements traffic shaping by processing as a synchronous request, tasks representing one or more units of work contained within the request. Before a request is sent through the network, the request is inspected in order to derive the amount of work that the request would generate in the network. A traffic manager queries the amount of work in that request compared to the amount of work that the network can support and generates a number of traffic envelopes. Based on the results of this query, “task pruning” may be implemented to break the request into smaller manageable task that fit into the traffic envelopes. Task pruning may also enable only a subset of the work to be performed. Thus, a measure of the amount of work, rather than the amount of data, within a request is considered when scheduling the request.
Owner:IBM CORP
Computer Platform for Development and Deployment of Sensor-Driven Vehicle Telemetry Applications and Services
InactiveUS20140380264A1Promote application developmentFacilitates vehicle anomaly detectionSoftware testing/debuggingProgram loading/initiatingCloud baseEngineering
A computing platform for intelligent development, deployment and management of vehicle telemetry applications is disclosed herein. Further, the present disclosure provides a method and system that enables provision of Intelligent Transportation Service on the Cloud-based Platform that facilitates creation and deployment of vehicle telemetry applications configured for enabling traffic measurements, traffic shaping, vehicle surveillance and other vehicle related services.
Owner:TATA CONSULTANCY SERVICES LTD
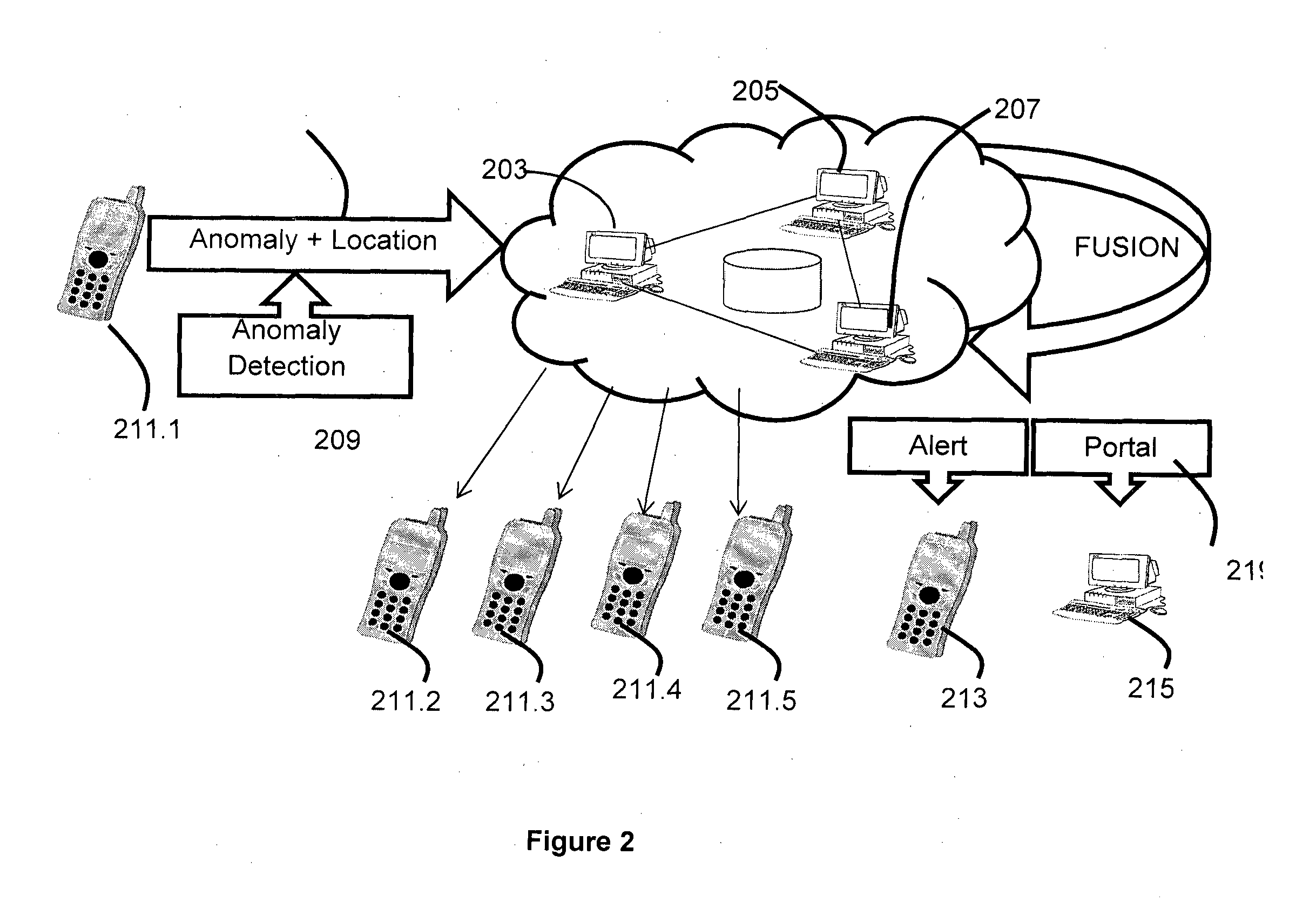
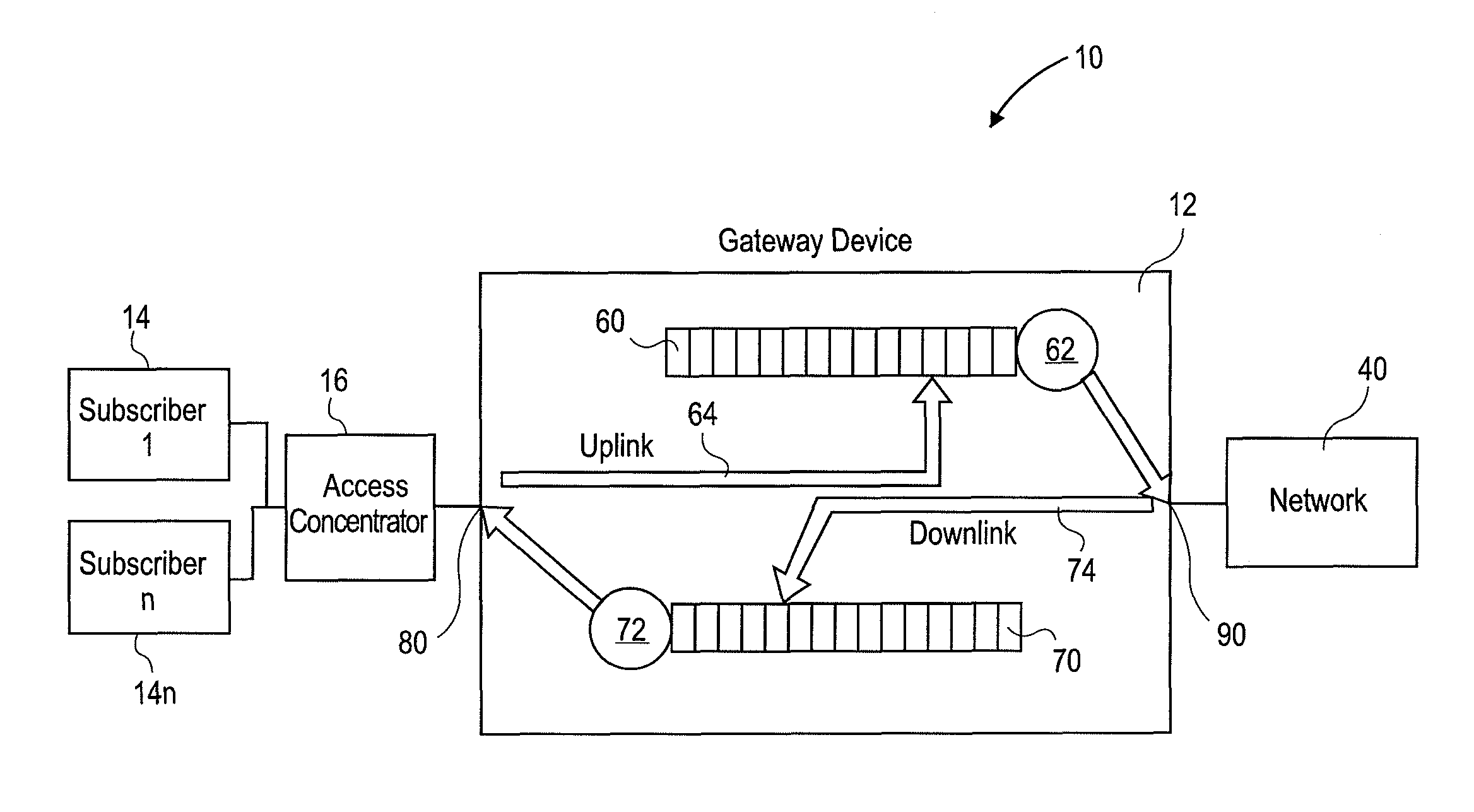
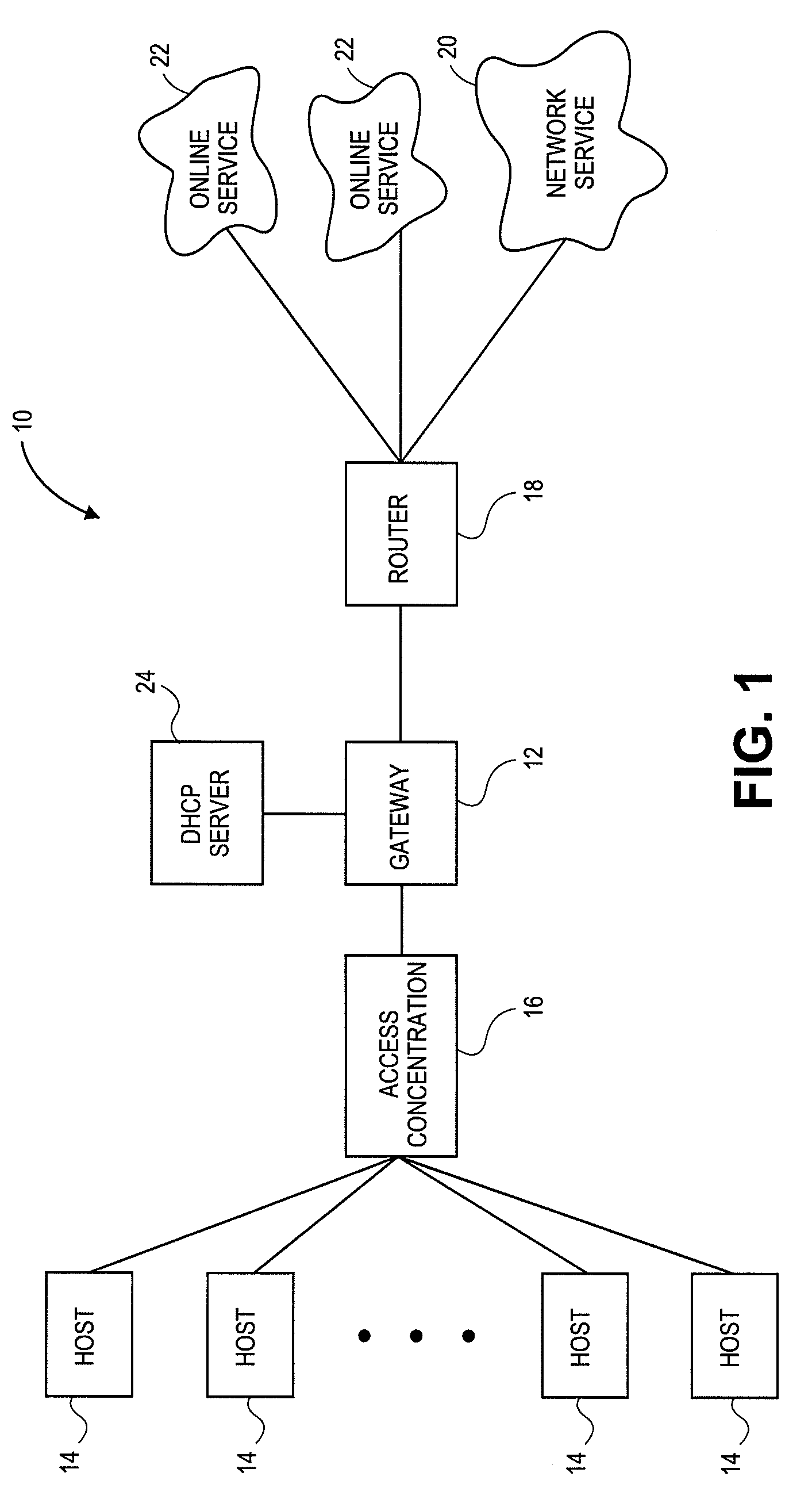
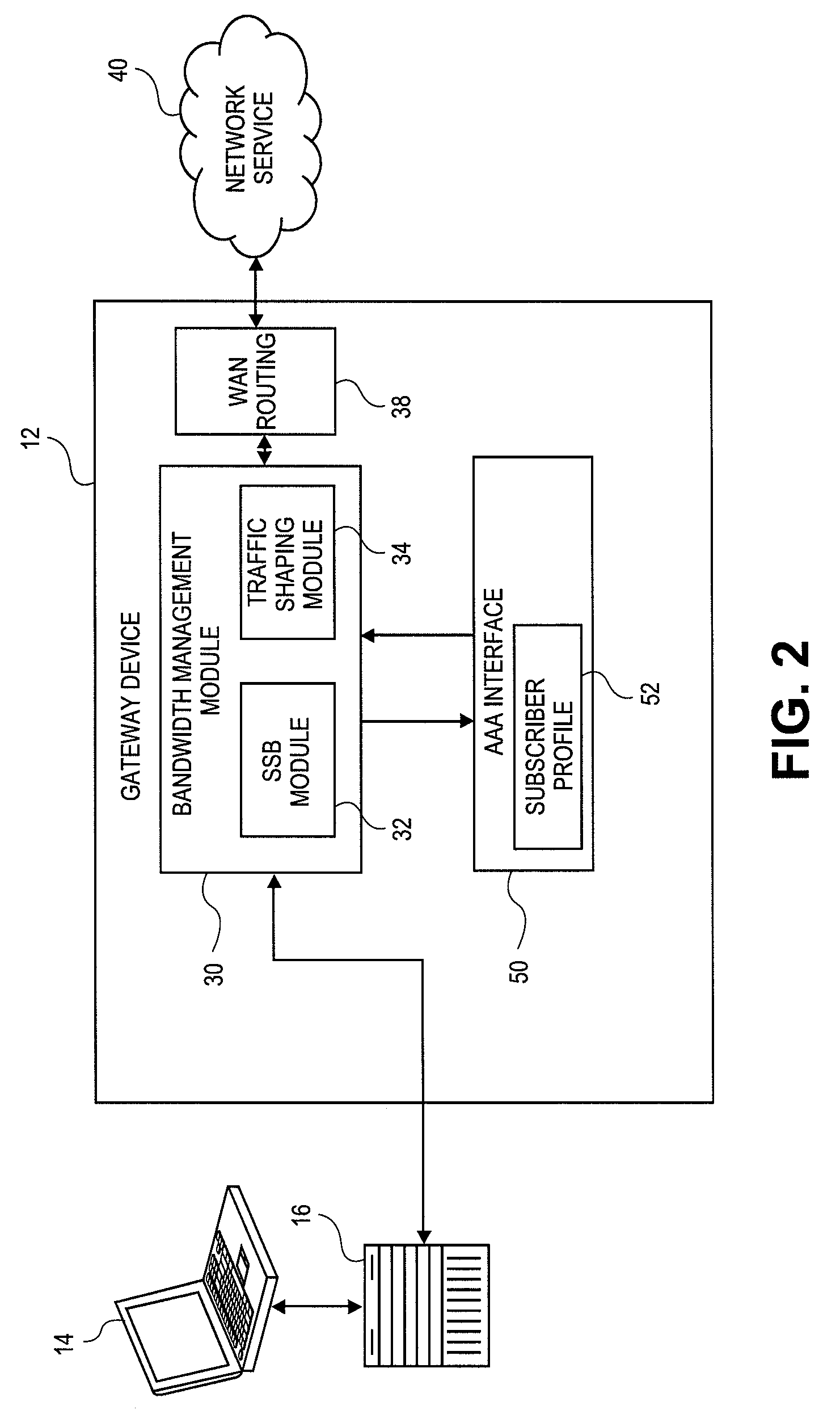
Systems and methods for dynamic bandwidth management on a per subscriber basis in a communications network
InactiveUS7739383B1Efficient managementImprove throughputMetering/charging/biilling arrangementsMultiple digital computer combinationsUplink transmissionNetwork management
A subscriber bandwidth management process and device that allows users / subscribers in a communications network to dynamically alter bandwidth limits independently in both the uplink and downlink data transmission paths. This is accomplished by providing for a single queue in the uplink transmission path and a single queue in the downlink transmission path. Thus, the user / subscriber can efficiently manage their network access according to the specific activity on the network. The network manager benefits from being able structure bandwidth allocation on a per subscriber basis so that overall data transmission is made more efficient. In addition, the bandwidth manager provides active management of the delivery of data (also known as and referred to herein as traffic shaping) to increase throughput from a gateway device onto the network.
Owner:NOMADIX INC
System and method for traffic shaping based on generalized congestion and flow control
ActiveUS7088678B1Overcome problemsError preventionFrequency-division multiplex detailsPacket arrivalModem device
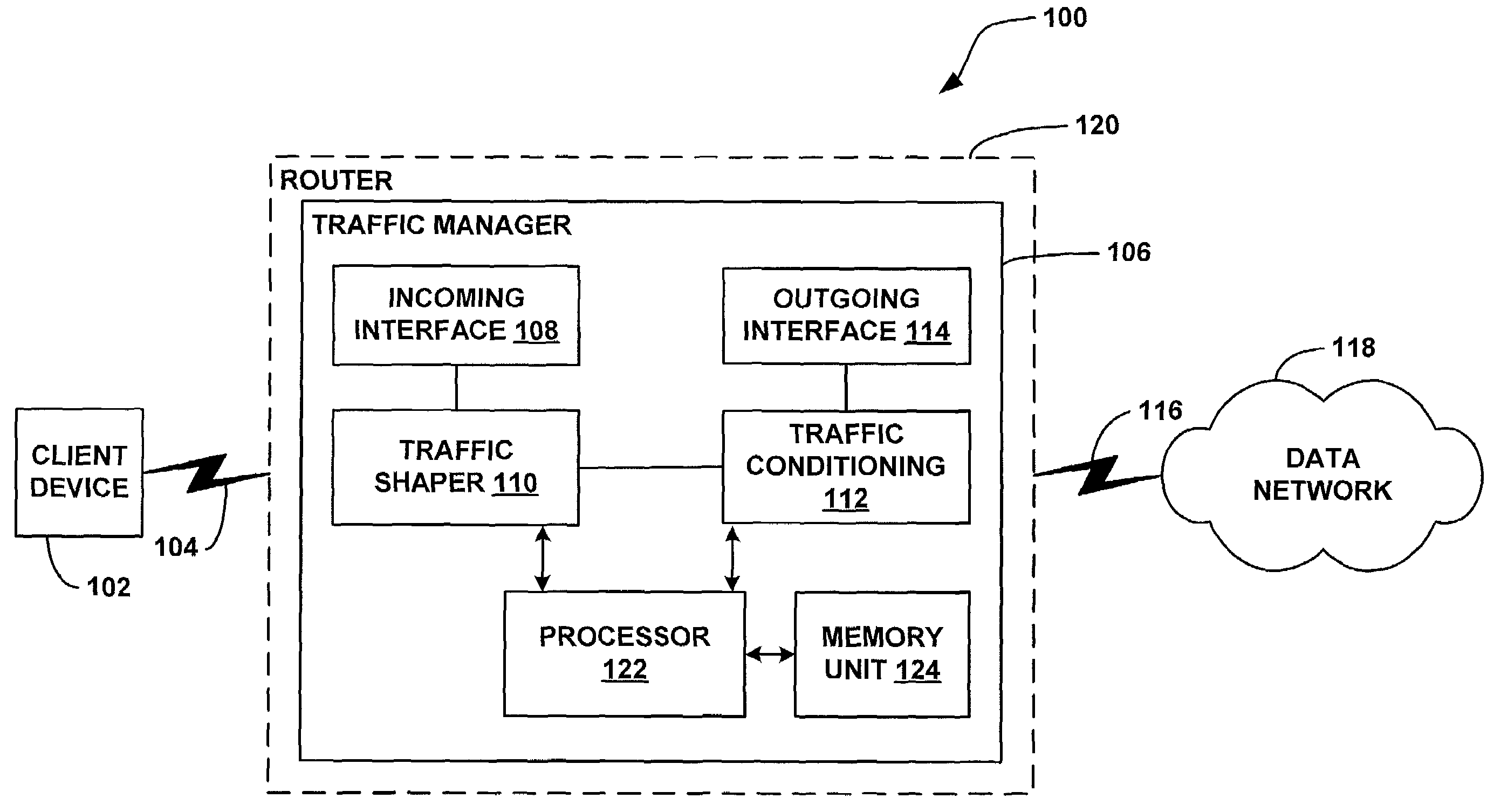
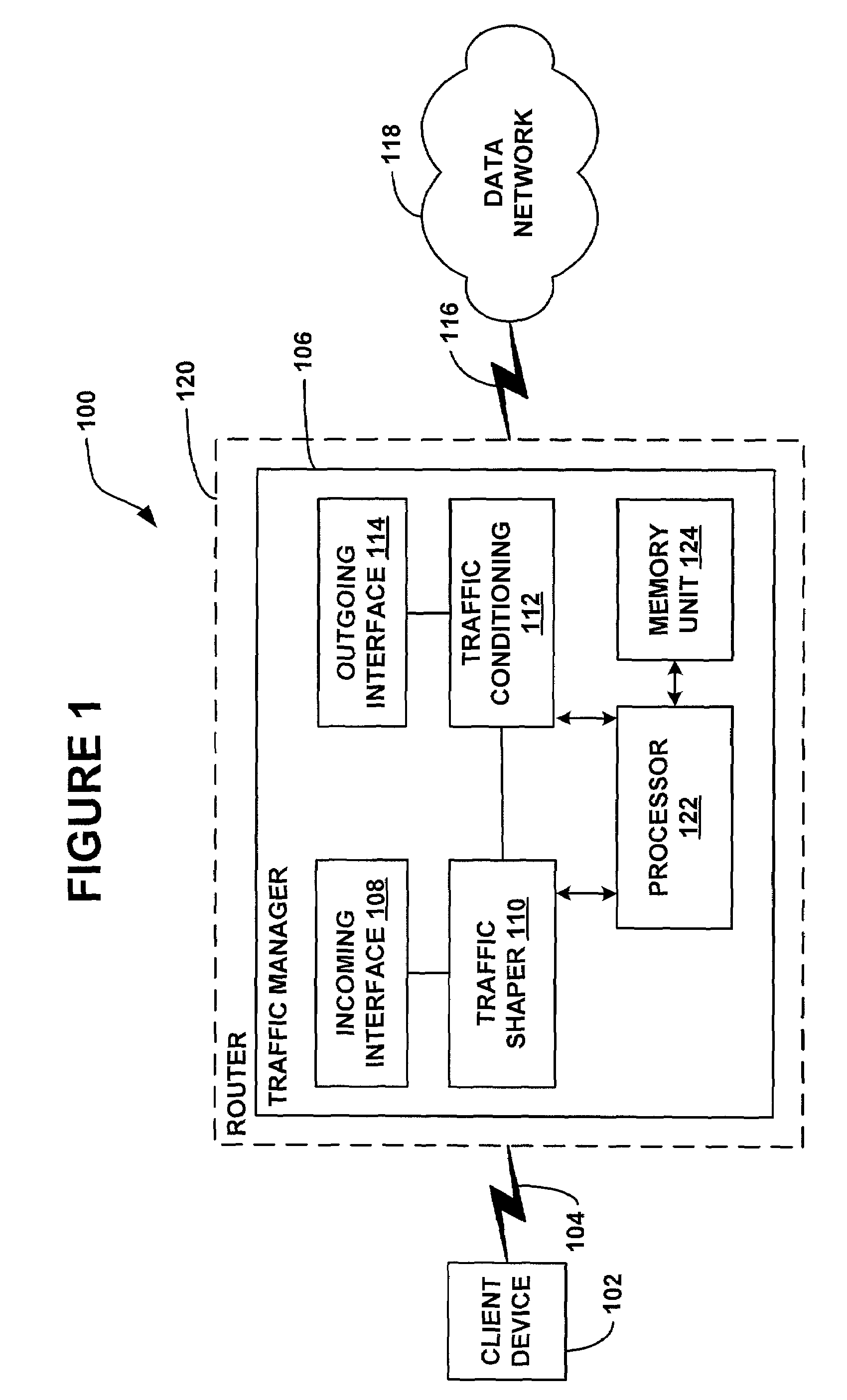
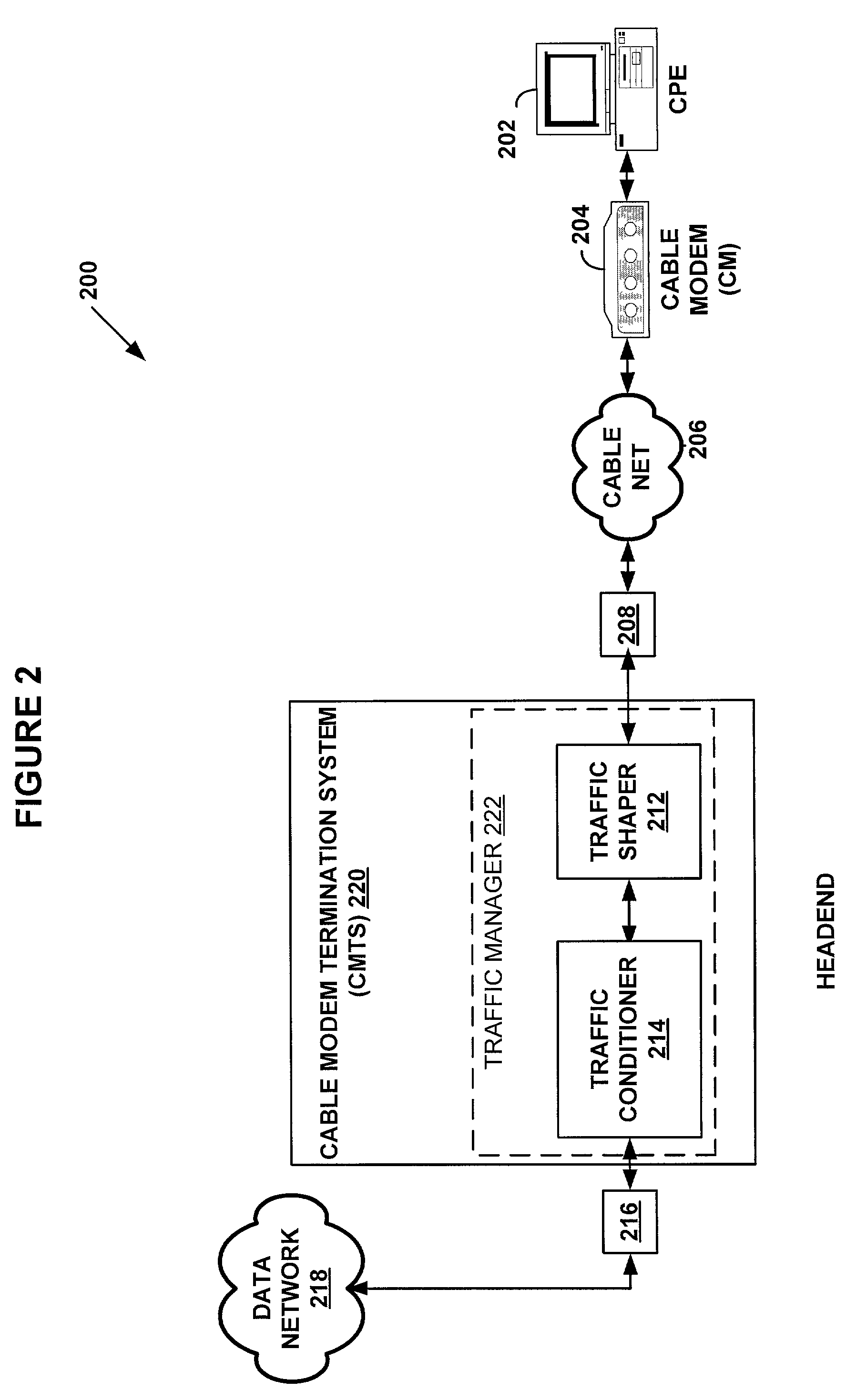
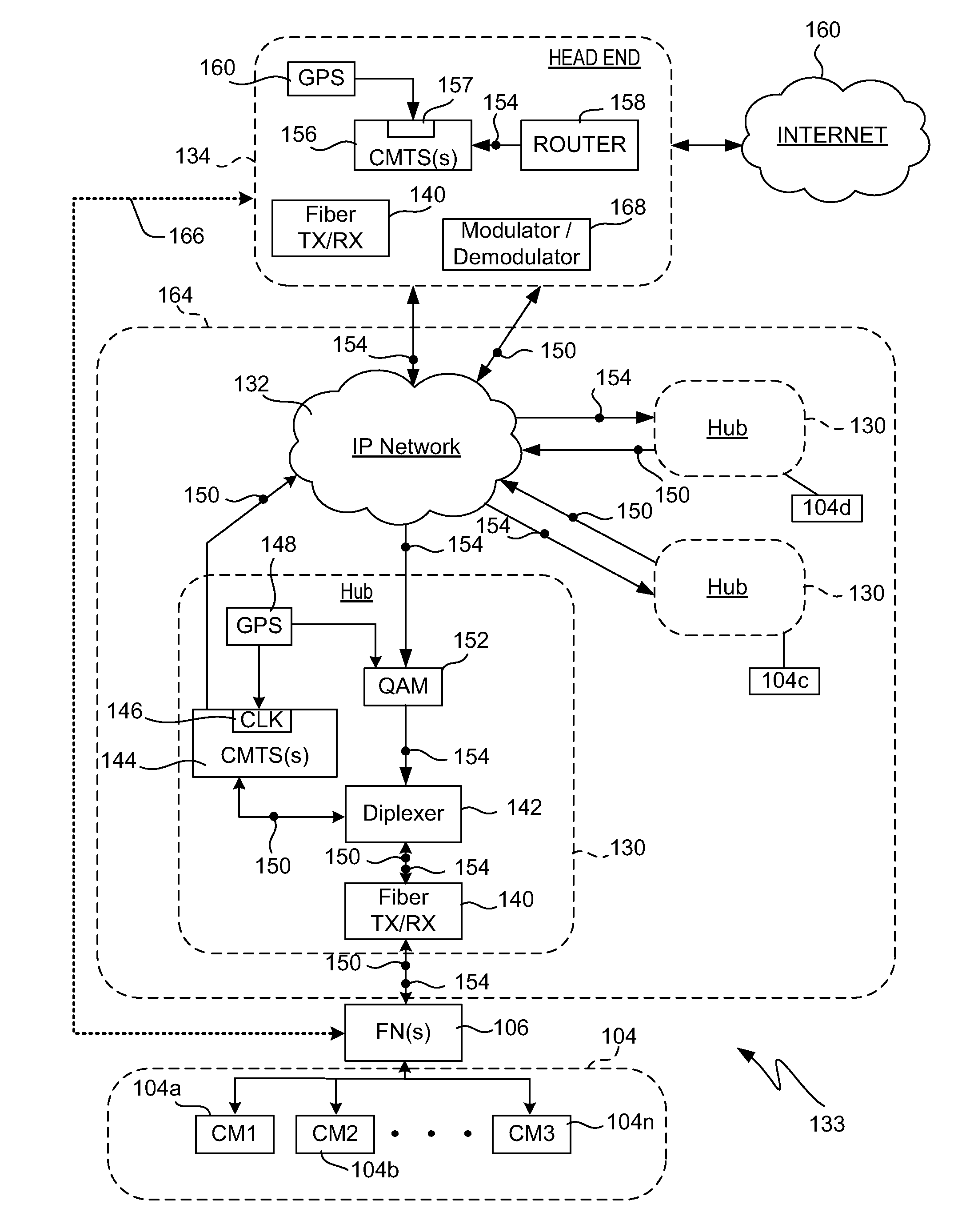
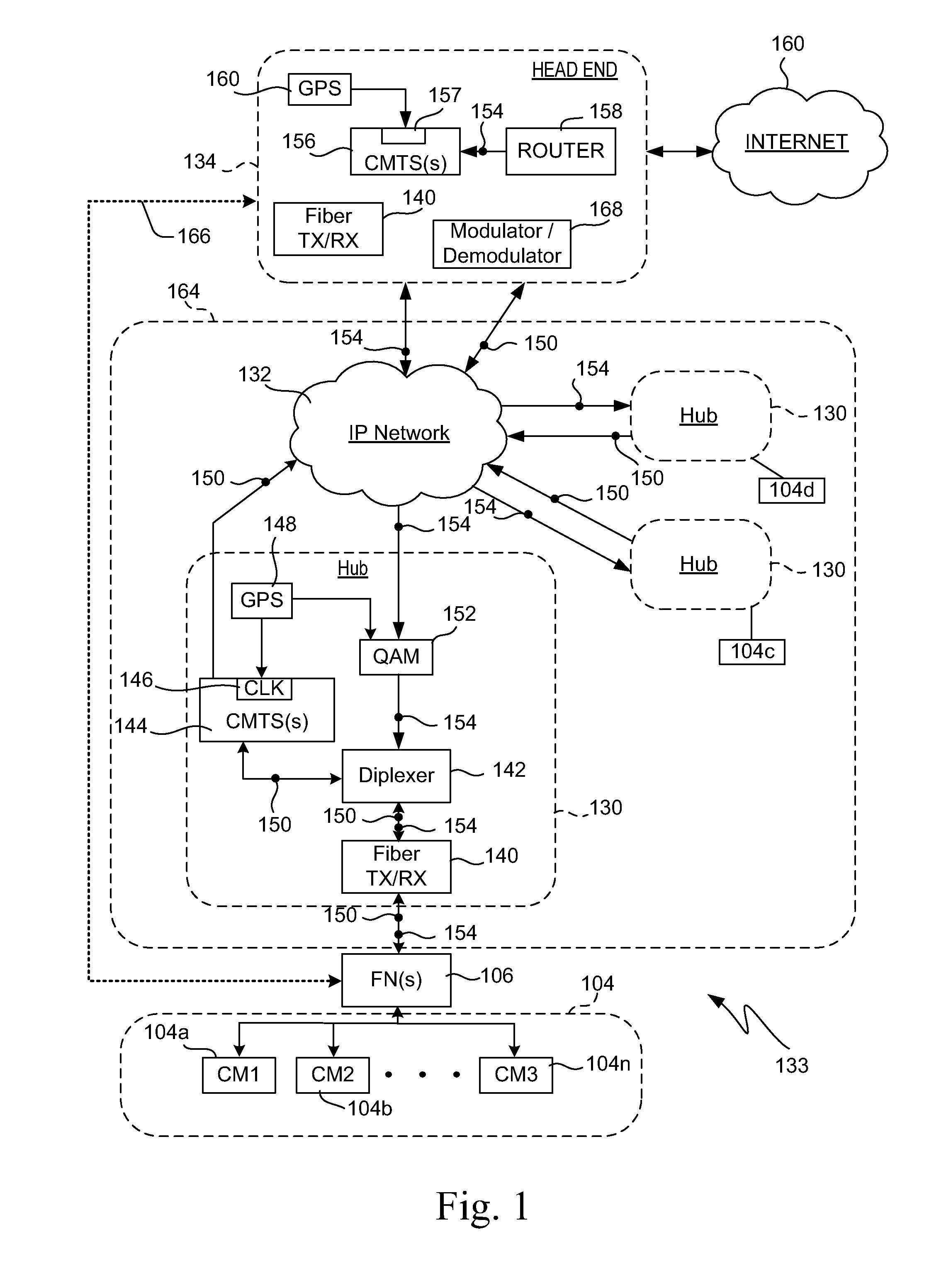
A system and methods are shown for traffic shaping and congestion avoidance in a computer network such as a data-over-cable network. A headend of the data-over-cable system includes a traffic shaper configured to calculate a packet arrival rate from a cable modem and a traffic conditioner configured to calculate an average queue size on an output interface to an external network. For example, the traffic shaper compares the packet arrival rate to three packet arrival thresholds including a committed rate threshold, a control rate threshold and a peak rate threshold. If the calculated packet arrival rate falls between the committed threshold and control rate threshold, the traffic shaper applies a link layer mechanism, such as a MAP bandwidth allocation mechanism, to lower the transmission rate from the cable modem.
Owner:VL COLLECTIVE IP LLC
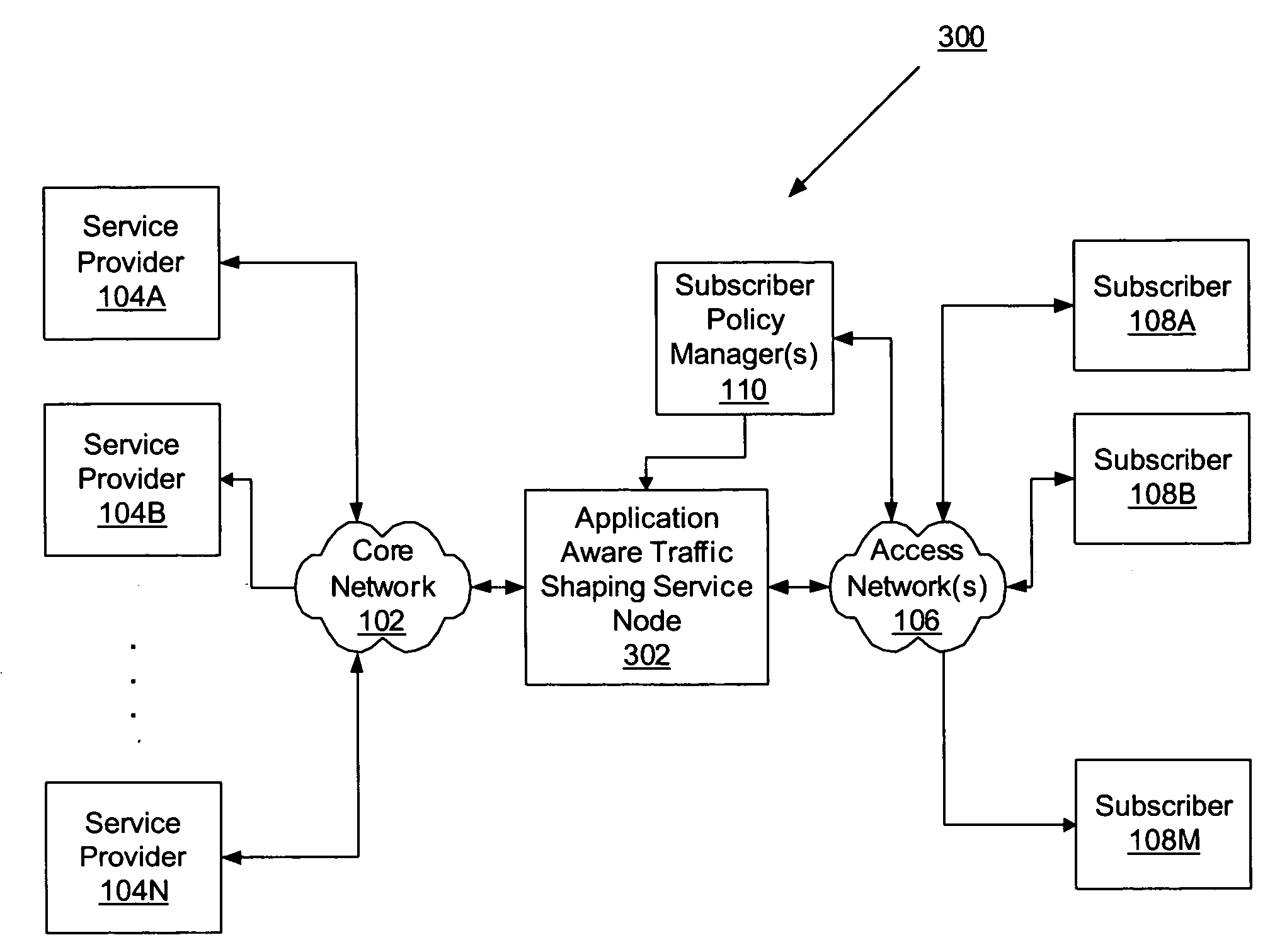
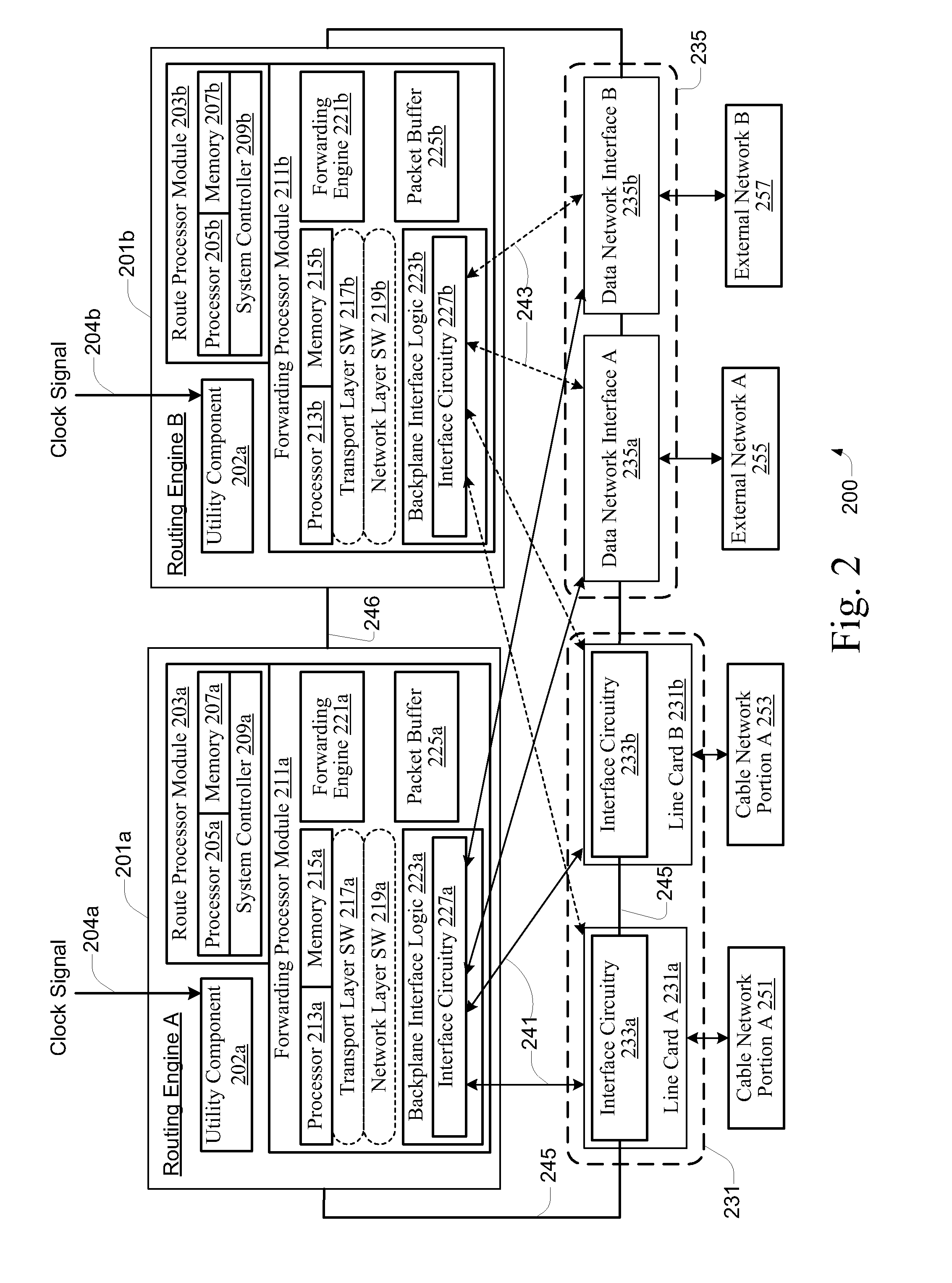
Network element architecture for deep packet inspection
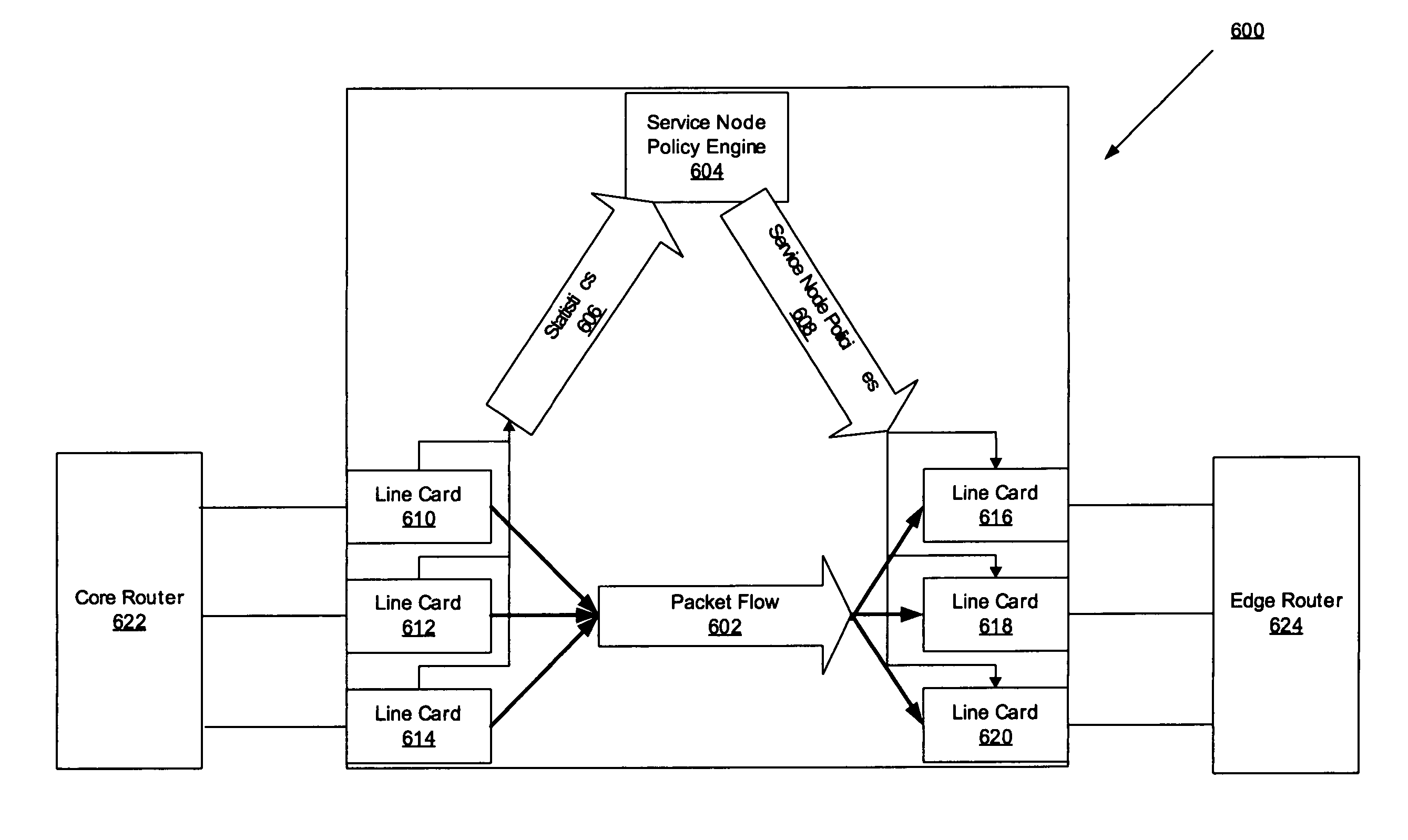
A method and apparatus for an application aware traffic shaping service node architecture is described. One embodiment of the invention, the service node architecture includes a set of one or more line cards, a set of one or more processor cards and a full mesh communication infrastructure coupling the sets of line and processor cards. Each link coupling the sets of line and processor cards is of equal capacity. A line card includes a physical interface and a set of one or policy network processors, with the network processors performing deep packet inspection on incoming traffic and shaping outgoing traffic. Processors cards include a set of one or more policy generating processors. According to another embodiment of the invention, the service node generates a set of statistics based on the incoming traffic and continually updates, in real-time, traffic shaping policies based on the set of statistics.
Owner:TELLABS COMM CANADA
Network element architecture for deep packet inspection
ActiveUS20060233101A1Equal capacityError preventionFrequency-division multiplex detailsTraffic capacityNetwork architecture
A method and apparatus for an application aware traffic shaping service node architecture is described. One embodiment of the invention, the service node architecture includes a set of one or more line cards, a set of one or more processor cards and a full mesh communication infrastructure coupling the sets of line and processor cards. Each link coupling the sets of line and processor cards is of equal capacity. A line card includes a physical interface and a set of one or policy network processors, with the network processors performing deep packet inspection on incoming traffic and shaping outgoing traffic. Processors cards include a set of one or more policy generating processors. According to another embodiment of the invention, the service node generates a set of statistics based on the incoming traffic and continually updates, in real-time, traffic shaping policies based on the set of statistics.
Owner:TELLABS COMM CANADA
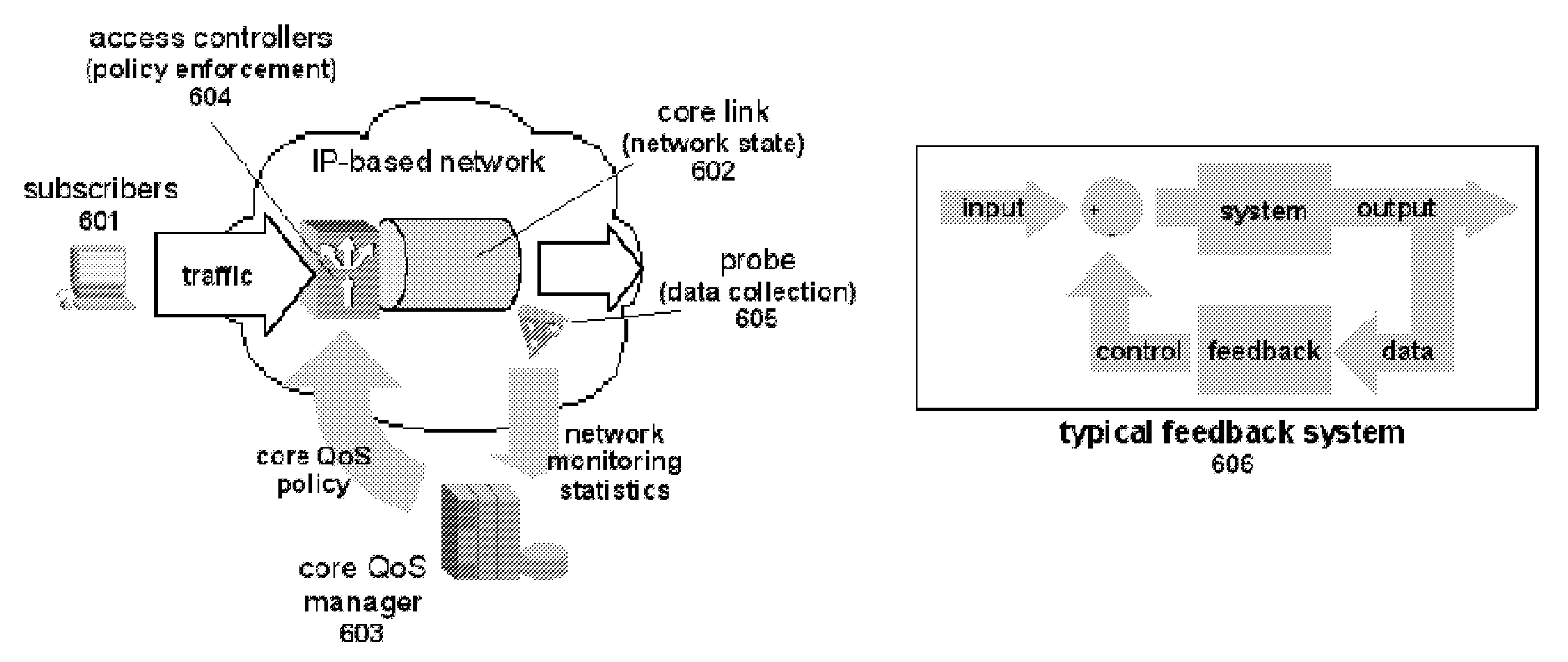
Methods and systems for providing quality of service in packet-based core transport networks
InactiveUS7599290B2Effective carryFair sharingEnergy efficient ICTError preventionService-level agreementTraffic capacity
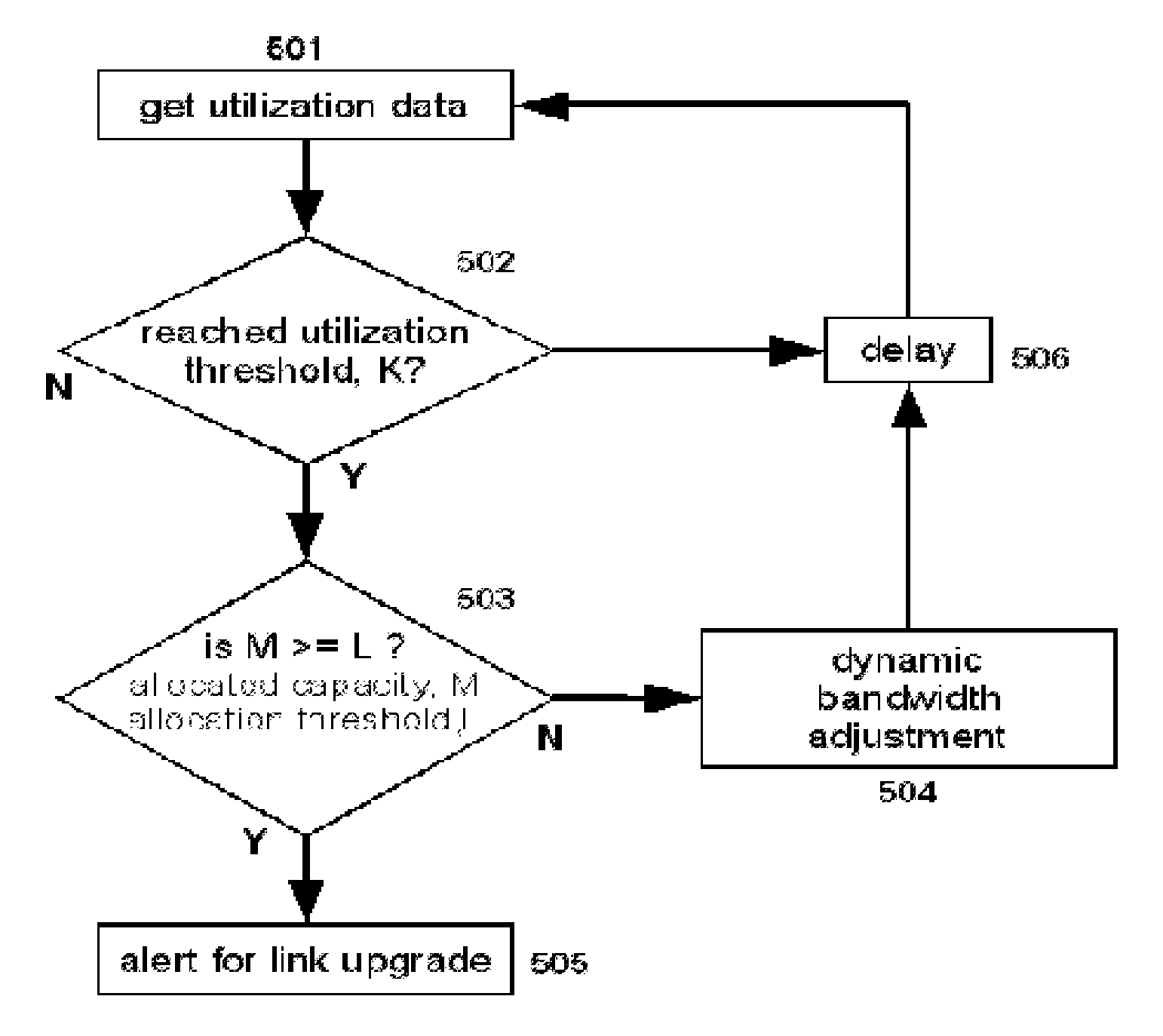
Methods and systems for providing necessary and sufficient quality-of-service (QoS), in a packet-based core transport network that utilizes dynamic setting of bandwidth management pipes or thresholds to obviate link congestion are disclosed. Congestion avoidance is a necessary and sufficient requirement in order to guarantee Quality of Service (QoS) in packet-based core networks.A typical network is composed of a plurality of backbone links connecting edge nodes where backhaul links are aggregated. The backhaul links connect the backbone links to the remote sites serving the subscribers. In order to enforce bandwidth management policies, Access Controllers, which perform traffic shaping, are situated on each remote site.In the event of a violation of certain link threshold settings, dynamic adjustment of the bandwidth management policies on affected Access Controllers is enforced. Various algorithms in determining the correlation between the link nearing congestion and the source or destination of traffic streams are also discussed. This invention implements a feedback control loop wherein probes at various points in the network checks for congestion states to guide bandwidth management threshold decisions in order to maintain the condition of non-congestion throughout the network. Capacity planning and congestion avoidance mechanisms work hand-in-hand to fulfill Service Level Agreements (SLA).
Owner:LATITUDE BROADBAND
Method and apparatus for traffic shaping in a broadband fiber-based access system
InactiveUS6229788B1Increased complexityIncrease costError preventionFrequency-division multiplex detailsFiberTraffic capacity
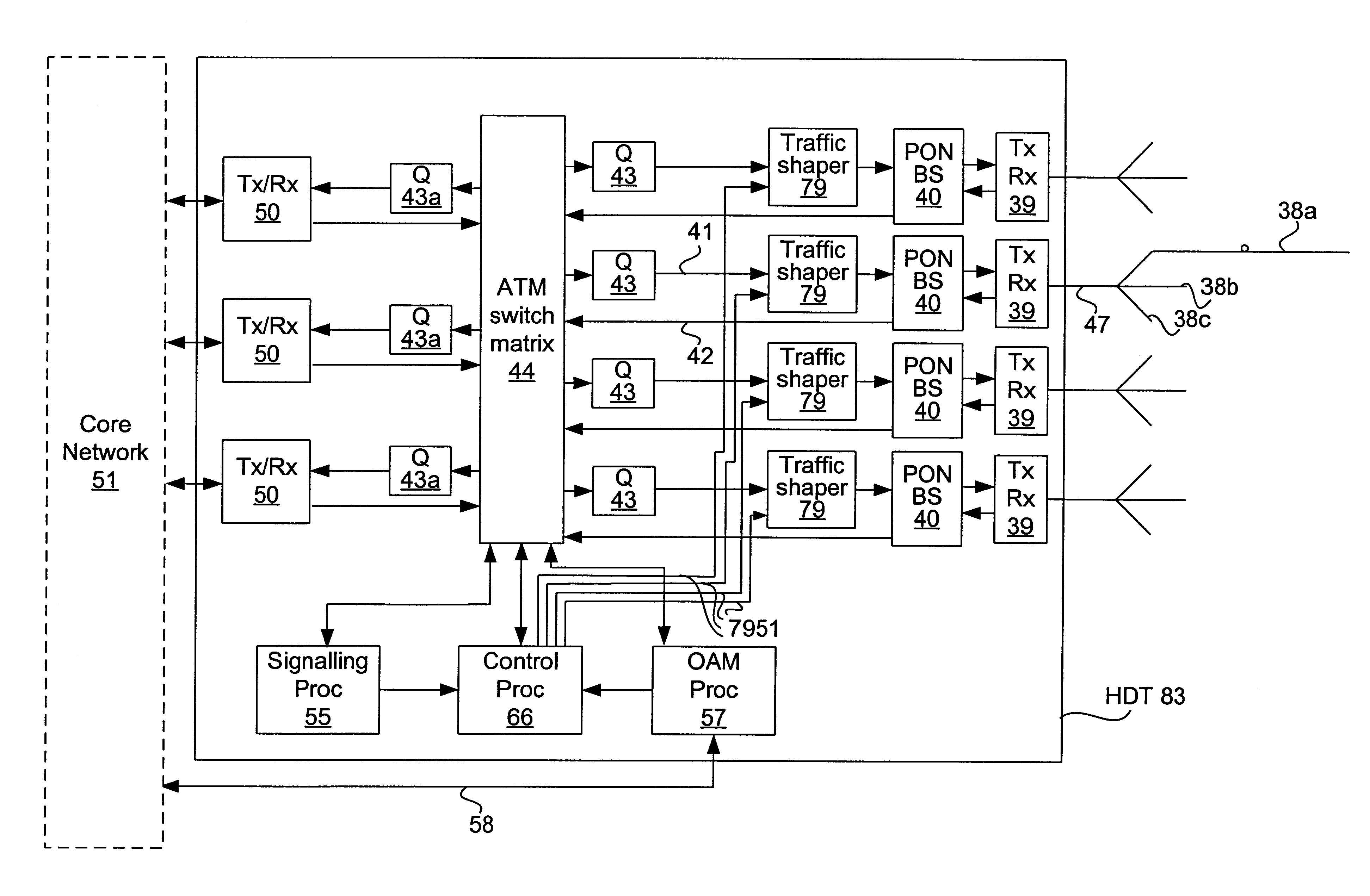
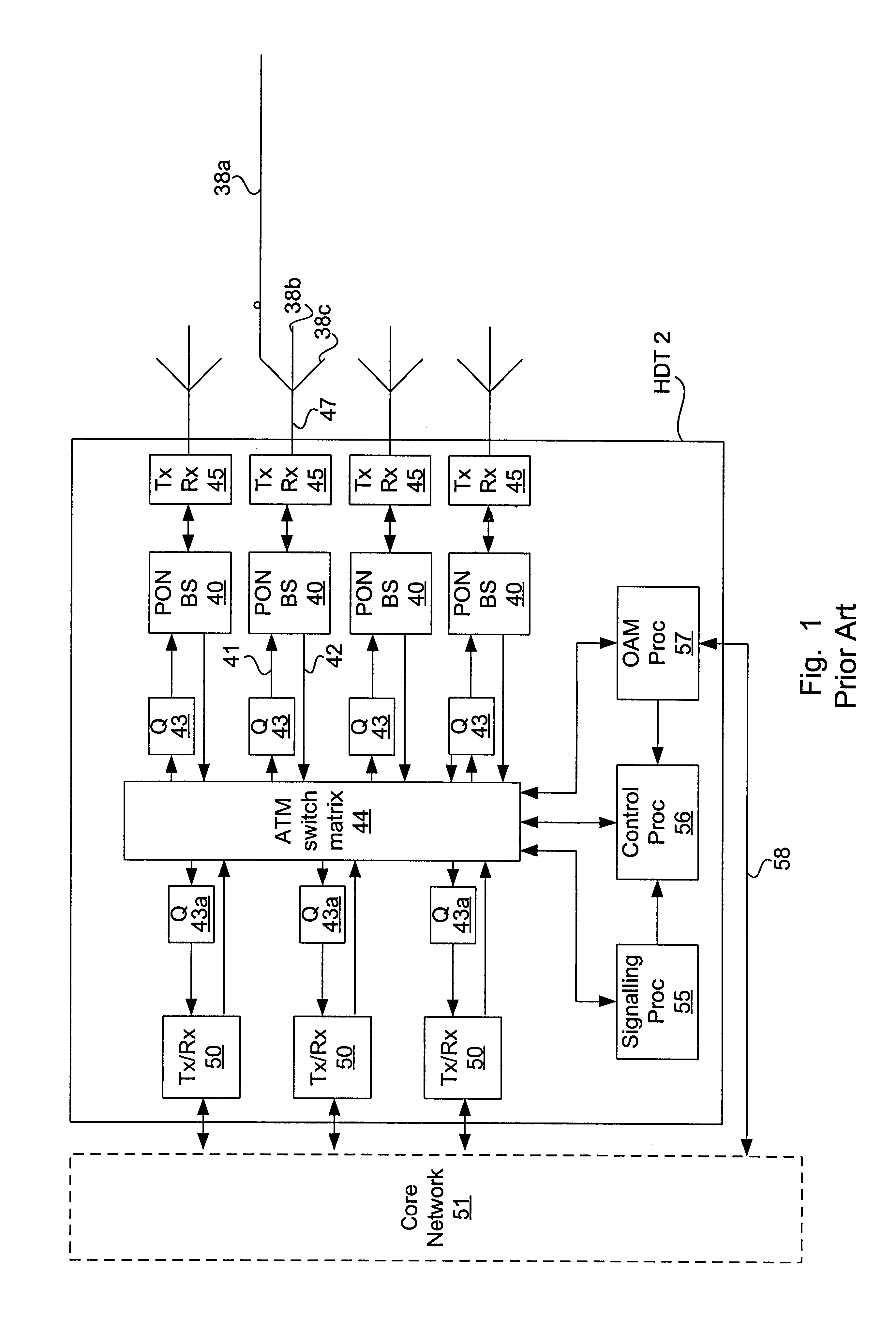
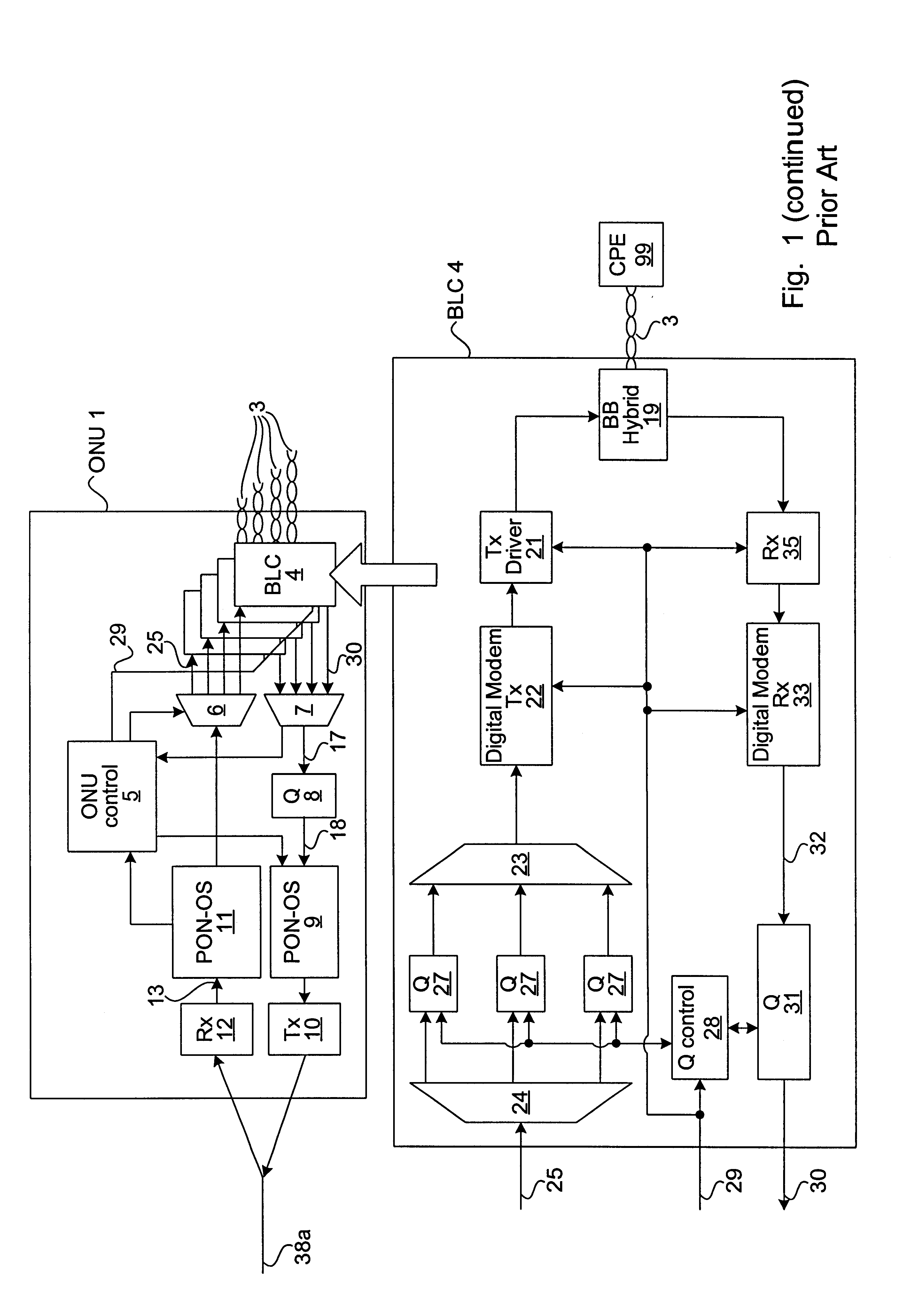
The invention is a novel method and apparatus for controlling the flow of traffic between a host digital terminal (HDT) and a plurality of optical network units (ONUs). Each ONU is connected to the HDT by optical fiber and to a plurality of subscribers by a respective plurality of subscriber drops (typically pre-existing copper twisted pairs). The bandwidth on the fiber, although large, is usually inferior to the total bandwidth that can be transmitted across the subscriber drops. Therefore, both upstream and downstream traffic may become congested at various "choke points" under certain circumstances of usage. Ordinarily, the data is buffered at the choke points, leading to the installation of large queues within each ONU. This solution is not only expensive, but is inadequate since the required queue size is dependent on the maximum transaction size, which has no hard upper bound. In contrast, the present invention provides a traffic shaper located in the HDT, which gives centralized control of the traffic flowing to and from the ONUs. Consideration of the priority and destination of each traffic cell is taken into account by the traffic shaper to ensure that the capacity of the fiber and of the individual drops is never exceeded, irrespective of the transaction sizes, thereby eliminating the need for costly buffers in the outside plant. Any maintenance or repairs of the traffic shaper can be easily effected without field visits, due to its centralized location.
Owner:RPX CLEARINGHOUSE
Systems and methods for dynamic bandwidth management on a per subscriber basis in a communications network
InactiveUS7698432B2Efficient managementImprove throughputMetering/charging/biilling arrangementsMultiple digital computer combinationsUplink transmissionNetwork management
A subscriber bandwidth management process and device that allows users / subscribers in a communications network to dynamically alter bandwidth limits independently in both the uplink and downlink data transmission paths. This is accomplished by providing for a single queue in the uplink transmission path and a single queue in the downlink transmission path. Thus, the user / subscriber can efficiently manage their network access according to the specific activity on the network. The network manager benefits from being able structure bandwidth allocation on a per subscriber basis so that overall data transmission is made more efficient. In addition, the bandwidth manager provides active management of the delivery of data (also known as and referred to herein as traffic shaping) to increase throughput from a gateway device onto the network.
Owner:NOMADIX INC
Methods And Systems For Providing Quality Of Service In Packet-Based Core Transport Networks
InactiveUS20080037552A1Effective carryFair sharingEnergy efficient ICTError preventionService-level agreementTraffic capacity
Methods and systems for providing necessary and sufficient quality-of-service (QoS), in a packet-based core transport network that utilizes dynamic setting of bandwidth management pipes or thresholds to obviate link congestion are disclosed. Congestion avoidance is a necessary and sufficient requirement in order to guarantee Quality of Service (QoS) in packet-based core networks.A typical network is composed of a plurality of backbone links connecting edge nodes where backhaul links are aggregated. The backhaul links connect the backbone links to the remote sites serving the subscribers. In order to enforce bandwidth management policies, Access Controllers, which perform traffic shaping, are situated on each remote site.In the event of a violation of certain link threshold settings, dynamic adjustment of the bandwidth management policies on affected Access Controllers is enforced. Various algorithms in determining the correlation between the link nearing congestion and the source or destination of traffic streams are also discussed. This invention implements a feedback control loop wherein probes at various points in the network checks for congestion states to guide bandwidth management threshold decisions in order to maintain the condition of non-congestion throughout the network. Capacity planning and congestion avoidance mechanisms work hand-in-hand to fulfill Service Level Agreements (SLA).
Owner:LATITUDE BROADBAND
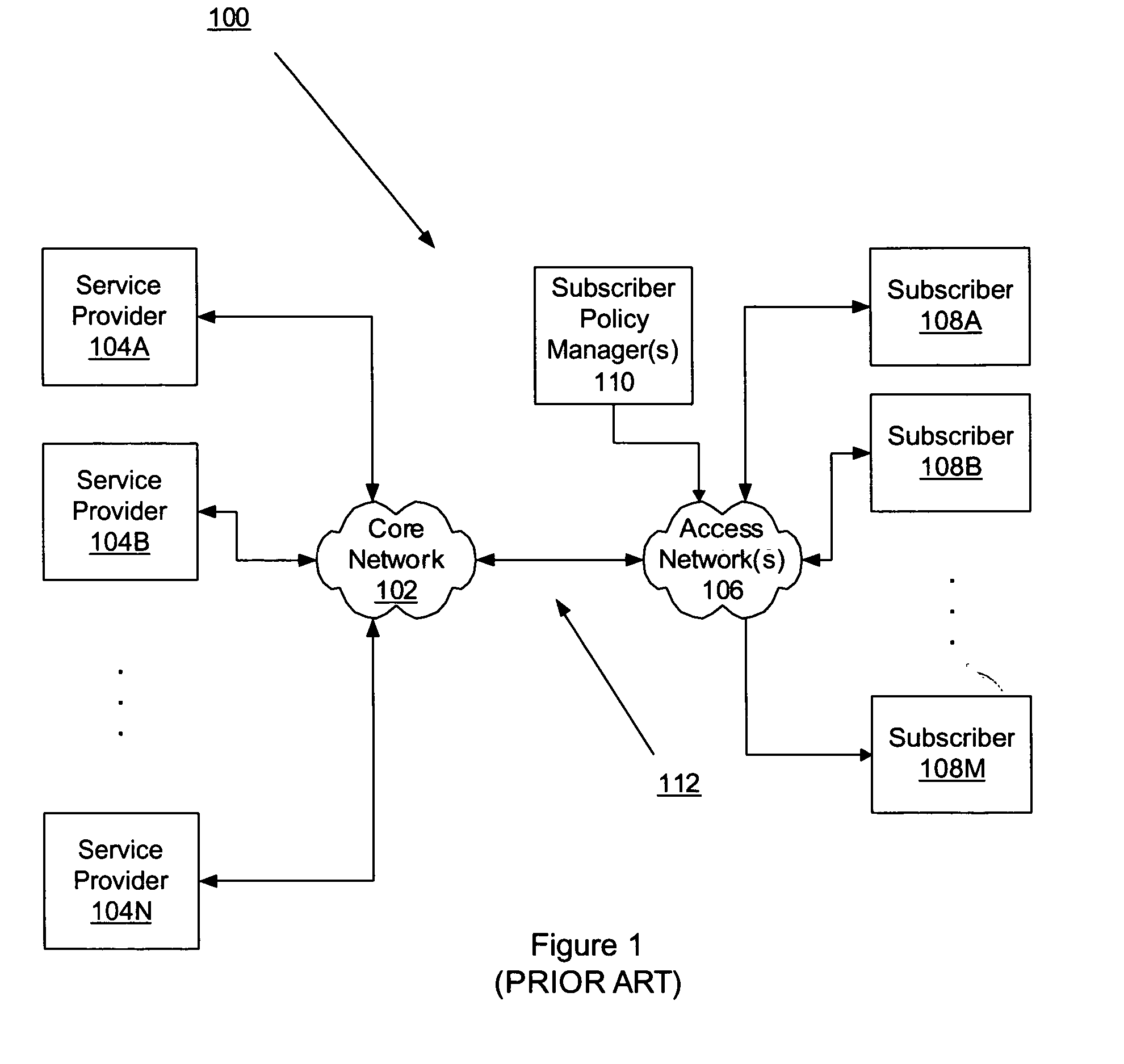
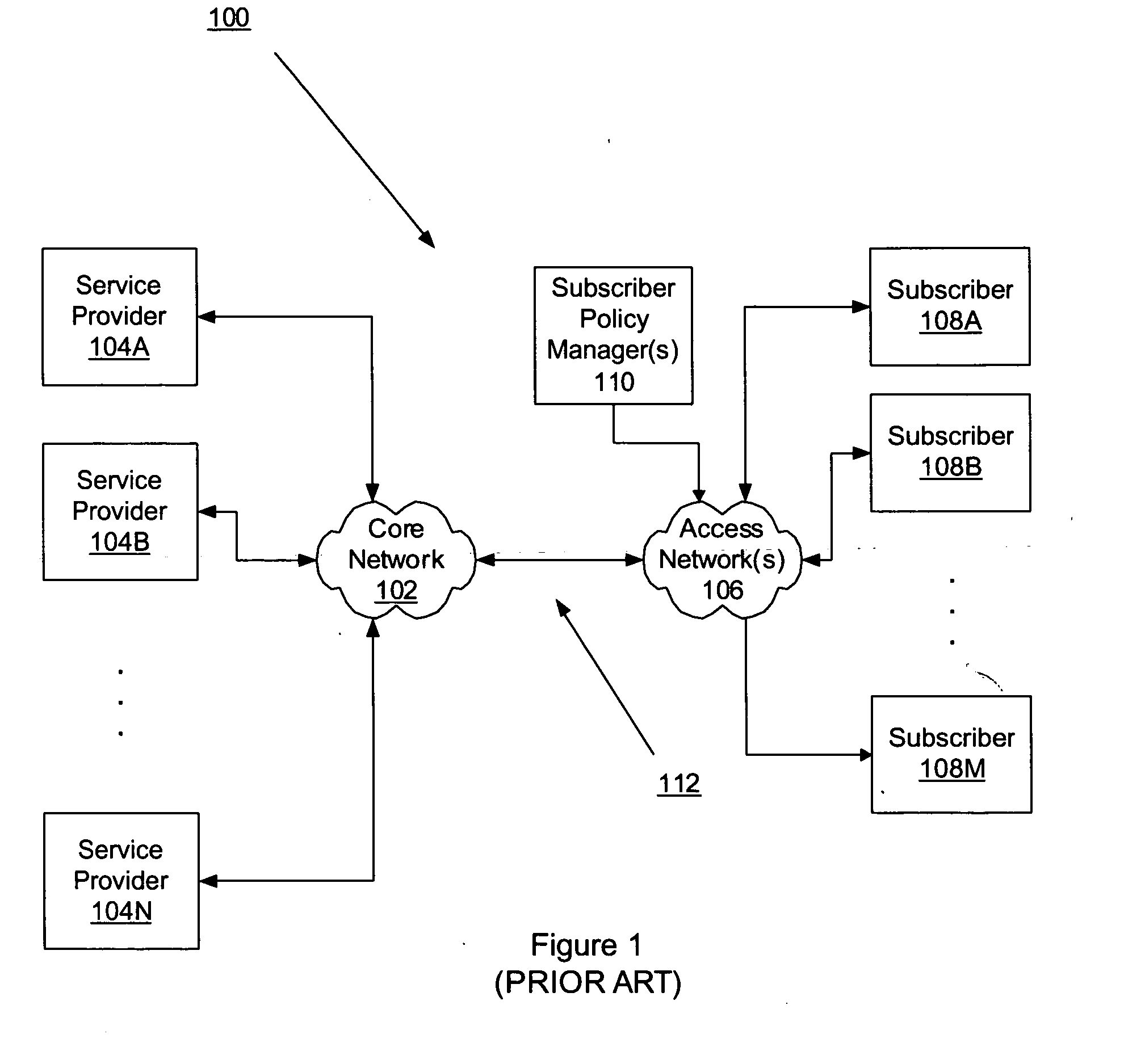
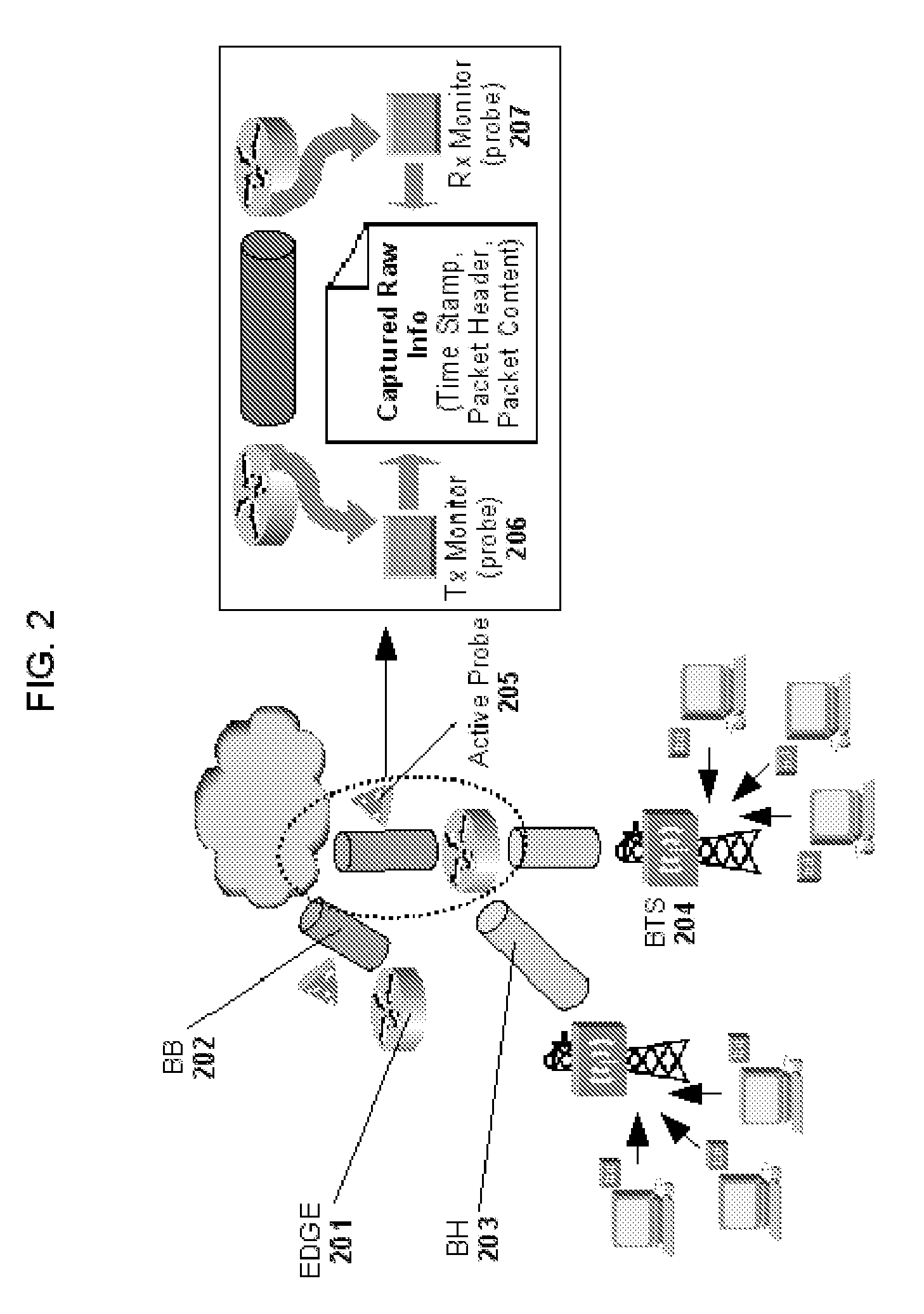
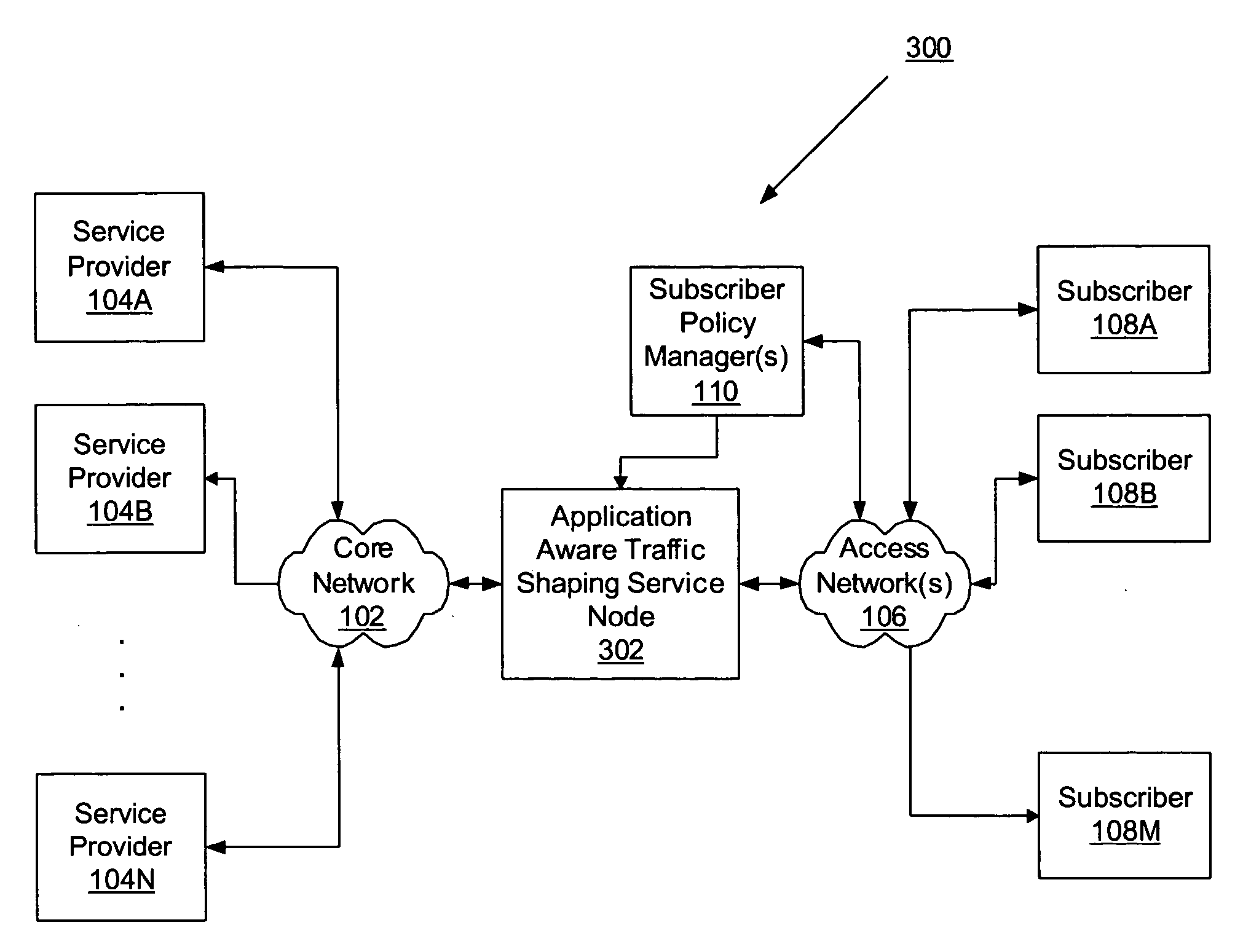
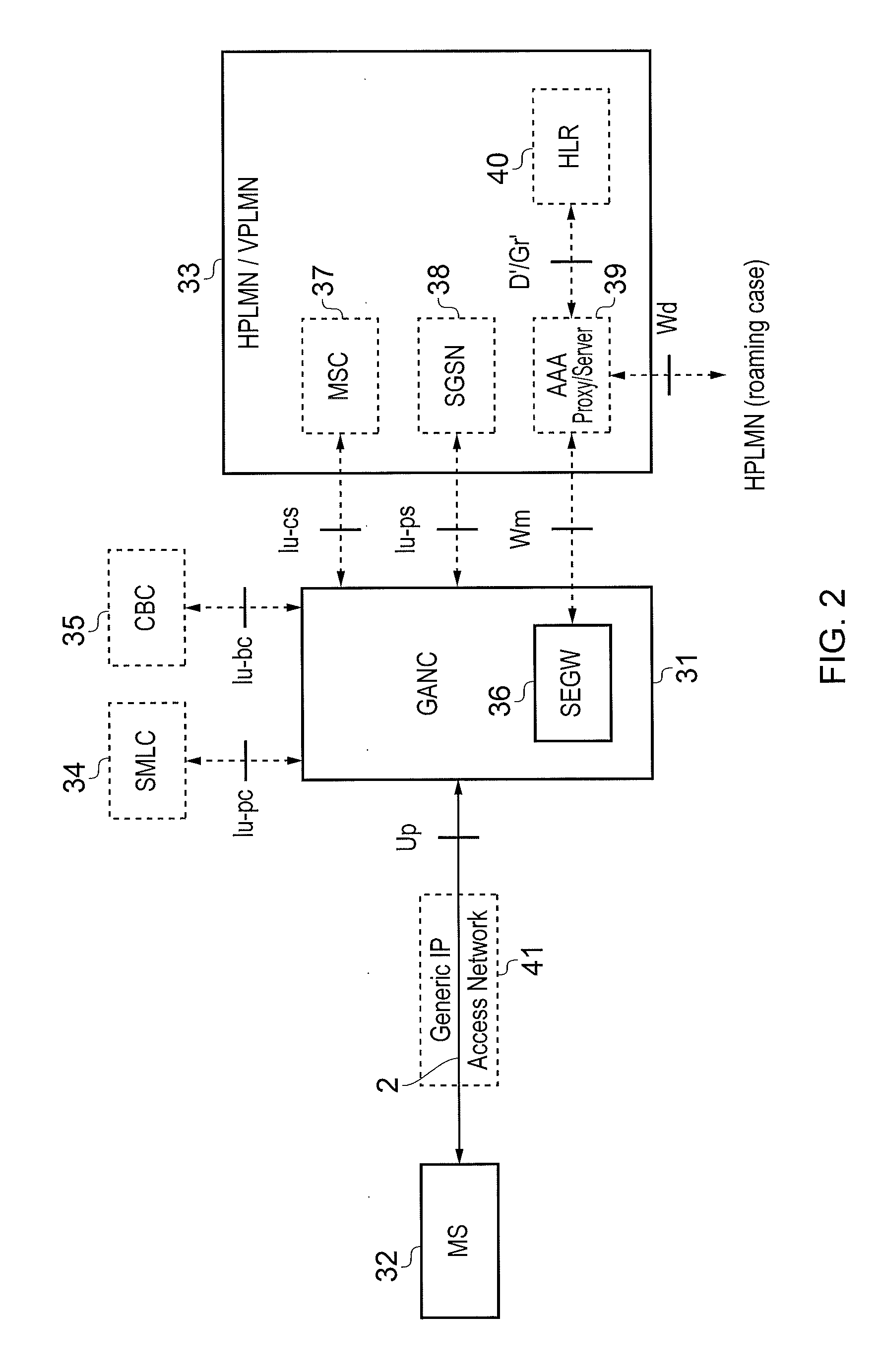
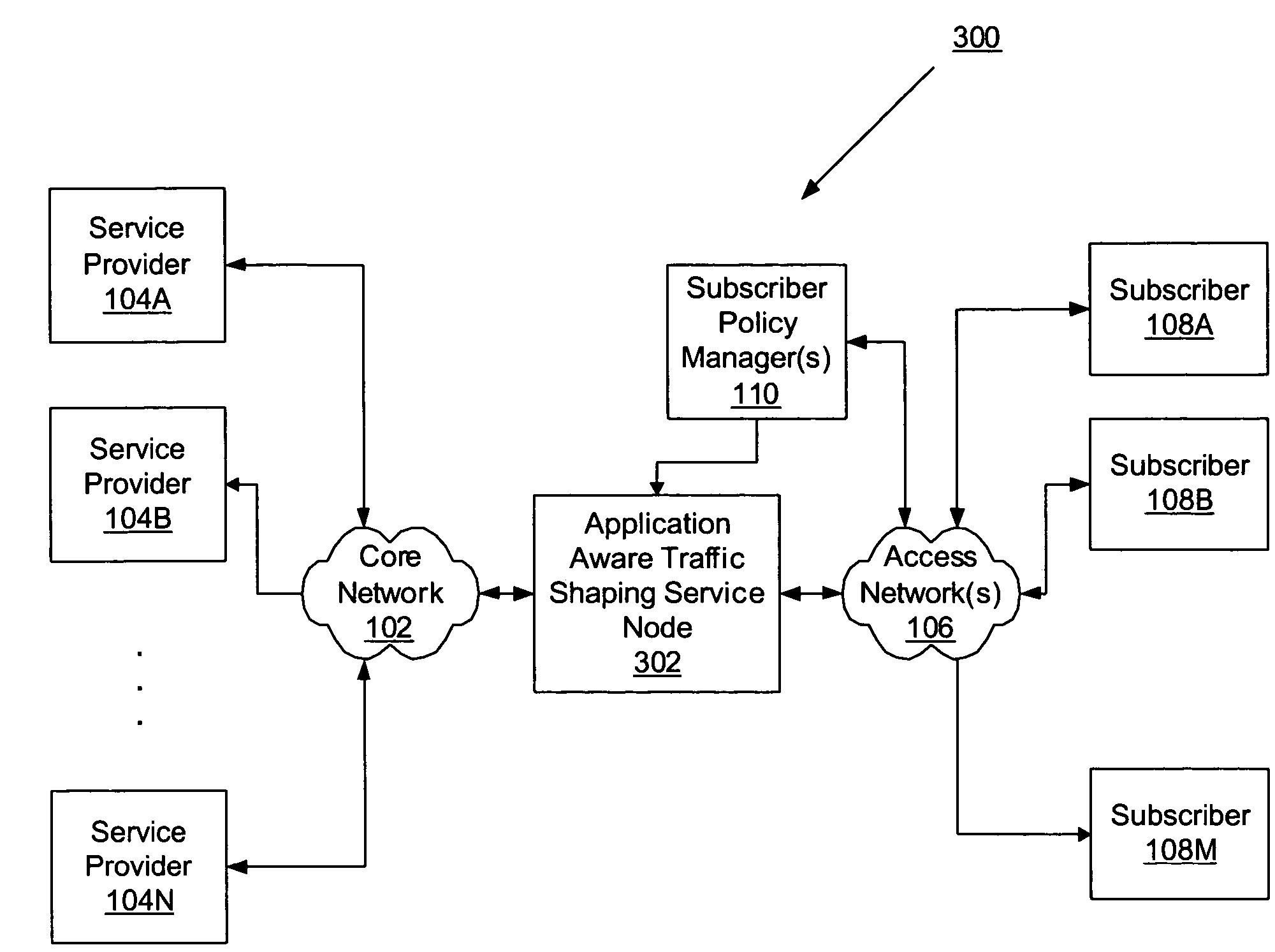
Application aware traffic shaping service node positioned between the access and core networks
ActiveUS20060233100A1Error preventionFrequency-division multiplex detailsGPRS core networkData traffic
A method and apparatus for an application aware traffic shaping service node positioned between the access and core networks is described. One embodiment of the invention enforces a per subscriber, per application traffic policy for network traffic between one or more subscribers communicatively connected through an access network and a set of one or more service providers communicatively connected through a core network. According to another embodiment of the invention enforcement of the per subscriber, per application traffic policy comprises classifying the network traffic into application level subscriber flows, maintaining real-time statistics on the application level subscriber flows and overall network element congestion, updating, in real-time, the per subscriber, per application traffic policy based on the real-time statistics and restricting bandwidth and dropping packets on the application level subscriber flows as necessary to enforce the per subscriber, per application traffic policy. Another embodiment of the invention is a passthrough mode where the data traffic is transmitted by the traffic in the same manner as received by the traffic shaping service node. Yet another embodiment of the invention is a combined service node with integral edge routing and traffic aggregator.
Owner:TELLABS COMM CANADA
Traffic shaper
InactiveUS6704321B1Decreasing cell delay variationError preventionFrequency-division multiplex detailsCell delayDistributed computing
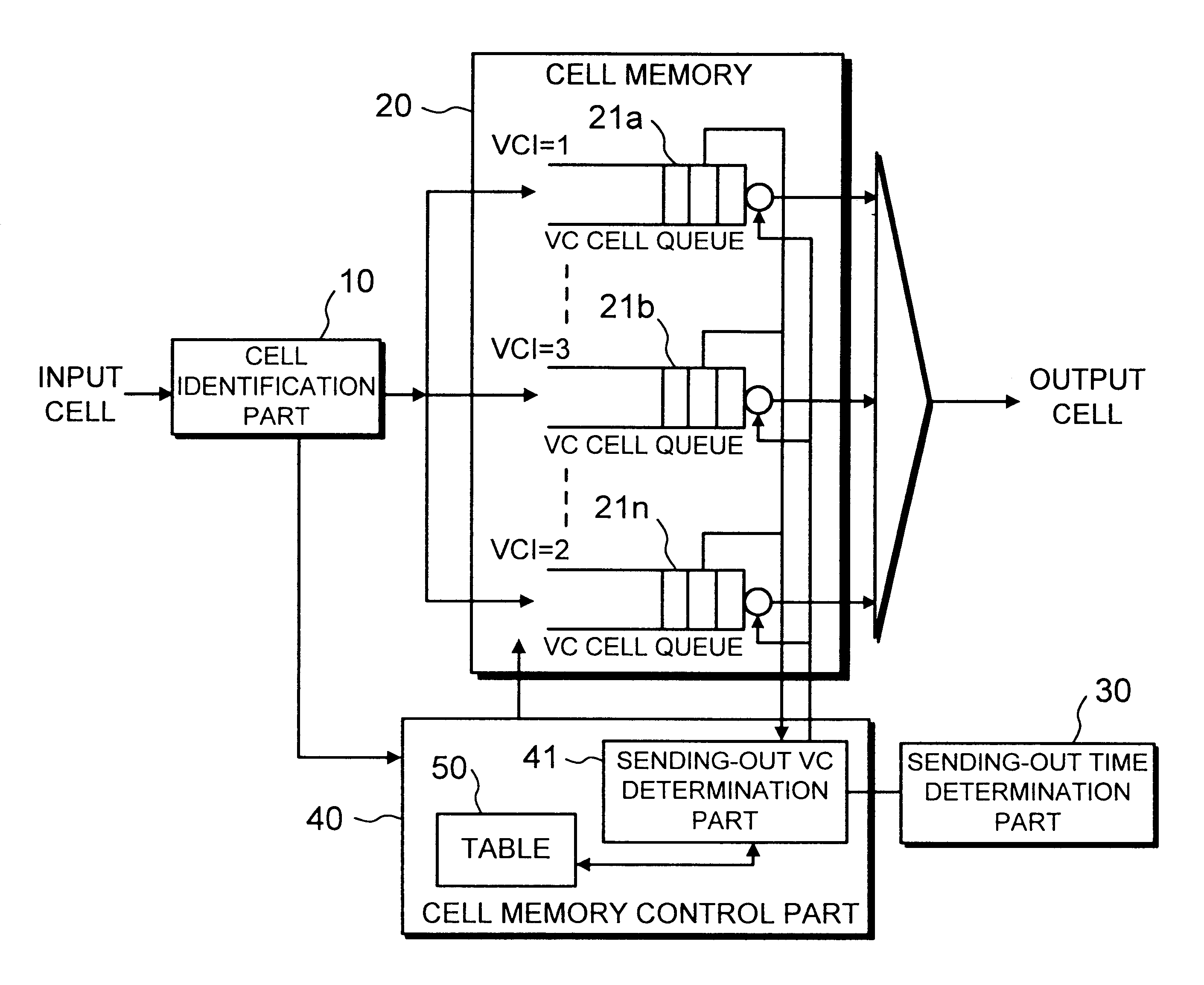
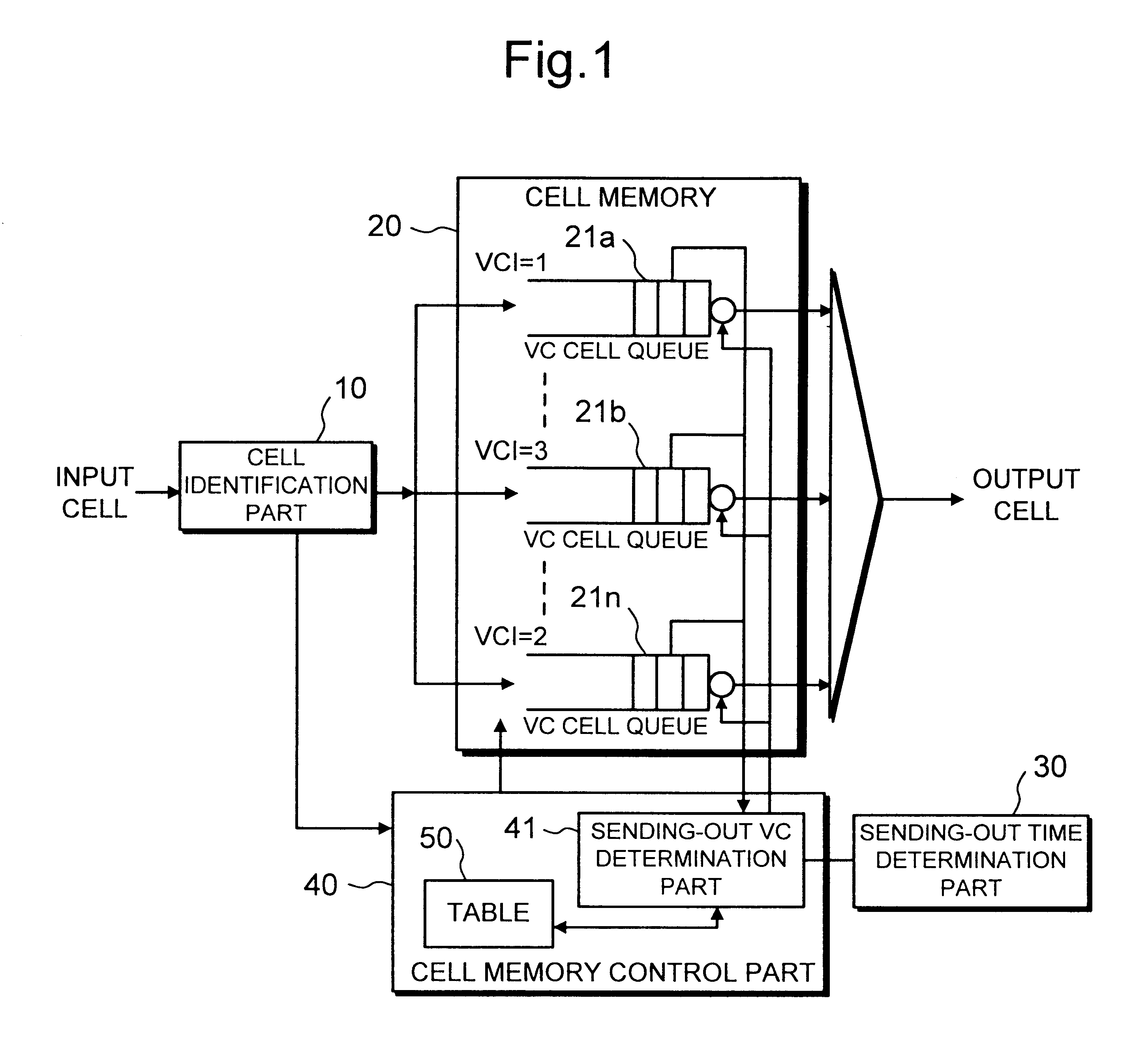
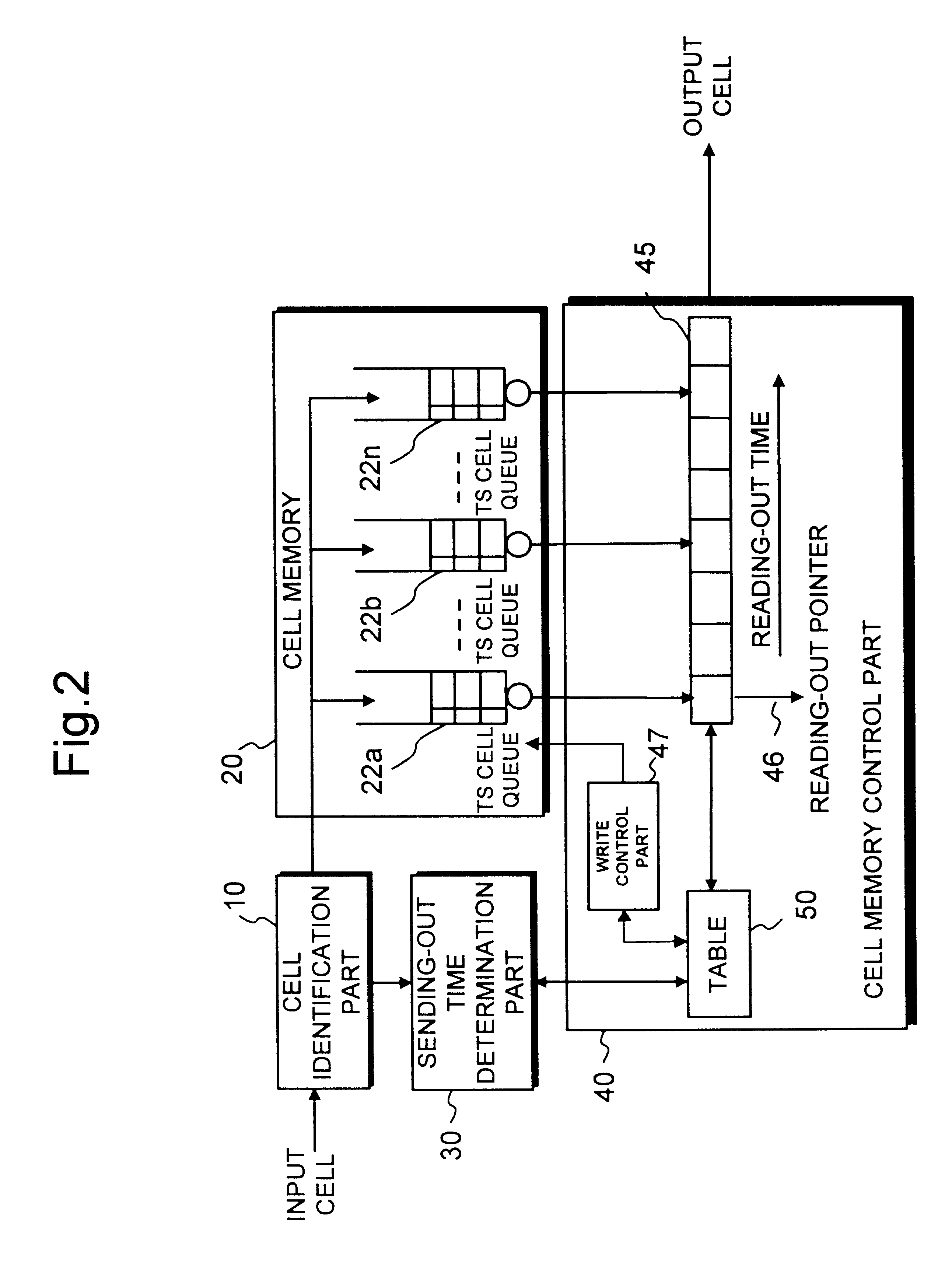
A traffic shaper for absorbing a cell delay variation of cell flow in each of virtual connections in an ATM (asynchronous transmission mode) network is realized. The traffic shaper comprises a cell identification part, a cell memory, a sending-out time determination part and a cell memory control part. The cell identification part is provided for identifying a virtual connection allocated to an input cell, the cell memory is provided for storing input cells into respective virtual queues, each queue is corresponding to the virtual connection, in accordance with the identified virtual connection of each input cell, the sending-out time determination part is provided for determining a sending-out time for each cell stored in the cell memory on the virtual connection basis, and the cell memory control part is provided for performing a cell output from each virtual queue in accordance with the sending-out time determined for each cell, and performing an output competition control by selecting a cell to be output among cells having the same sending-out time in different virtual queues in accordance with a predetermined output priority assigned to each virtual connection.
Owner:JUMIPER NETWORKS INC
Method to automatically map business function level policies to it management policies
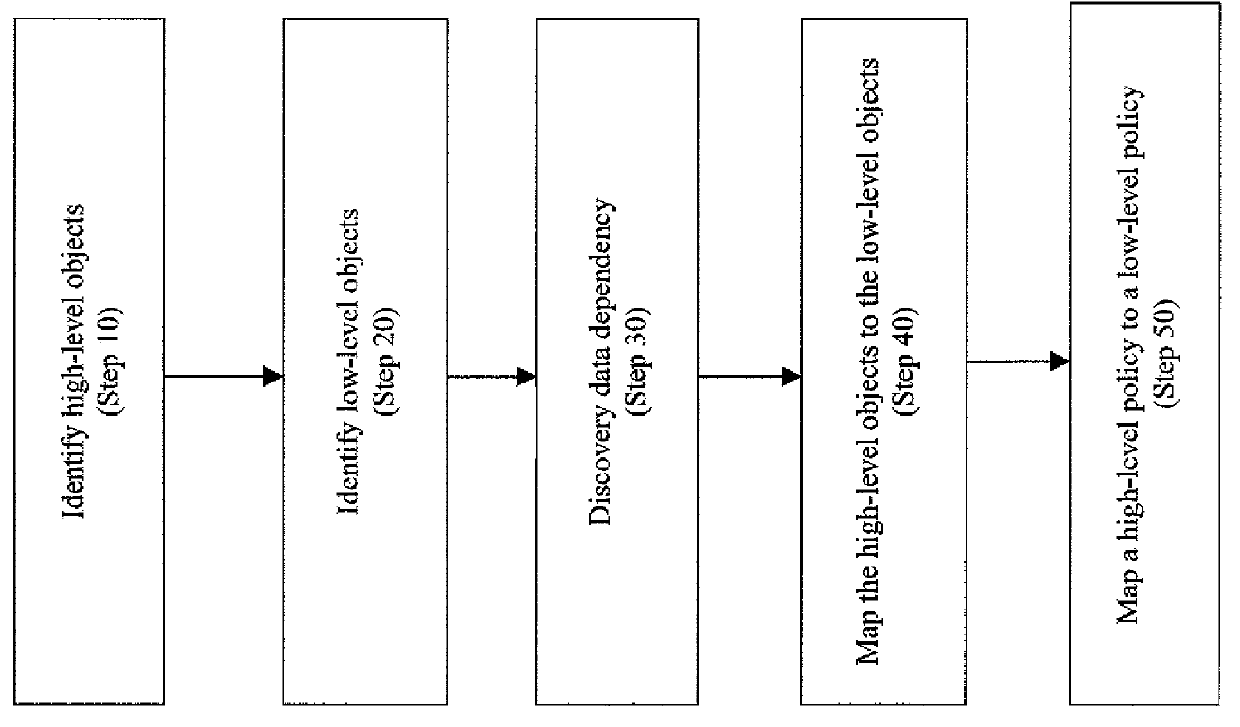
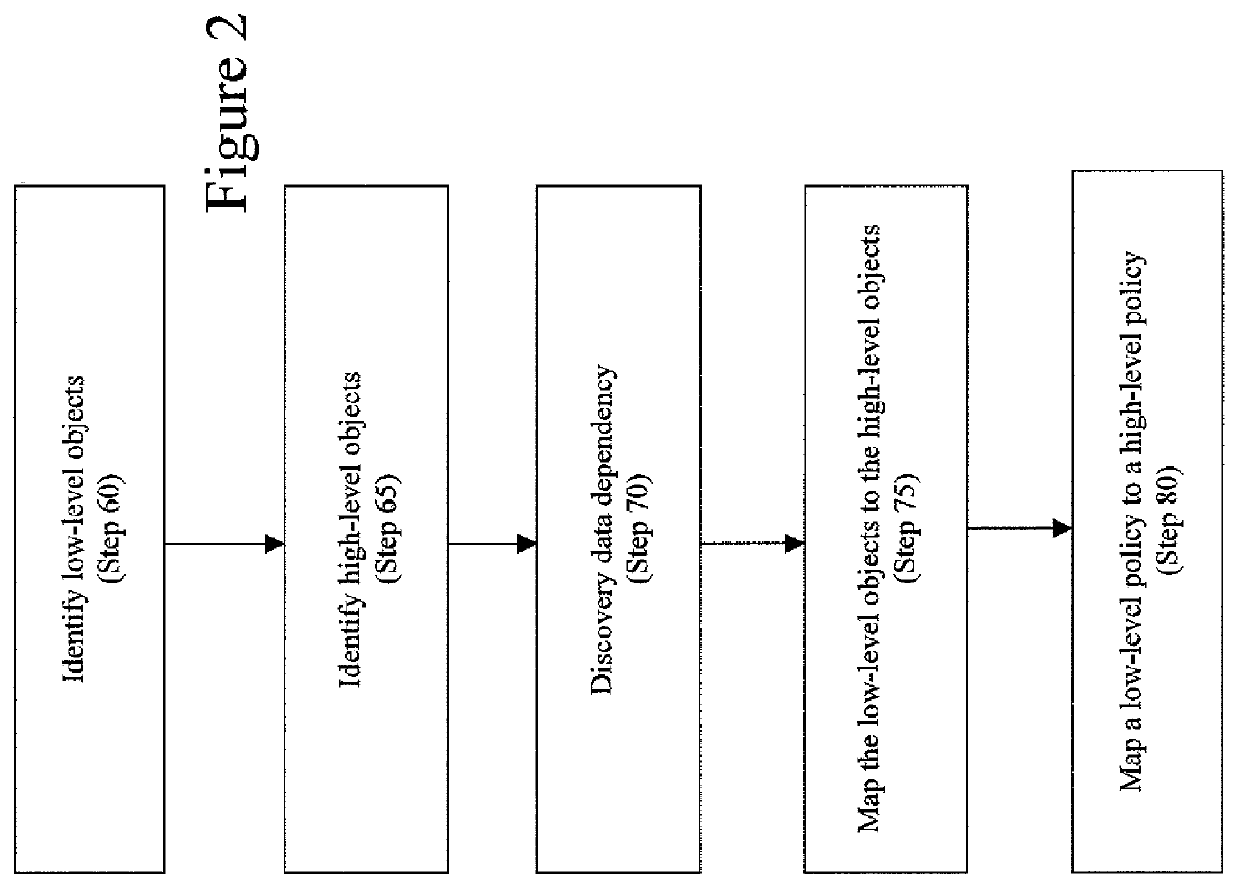
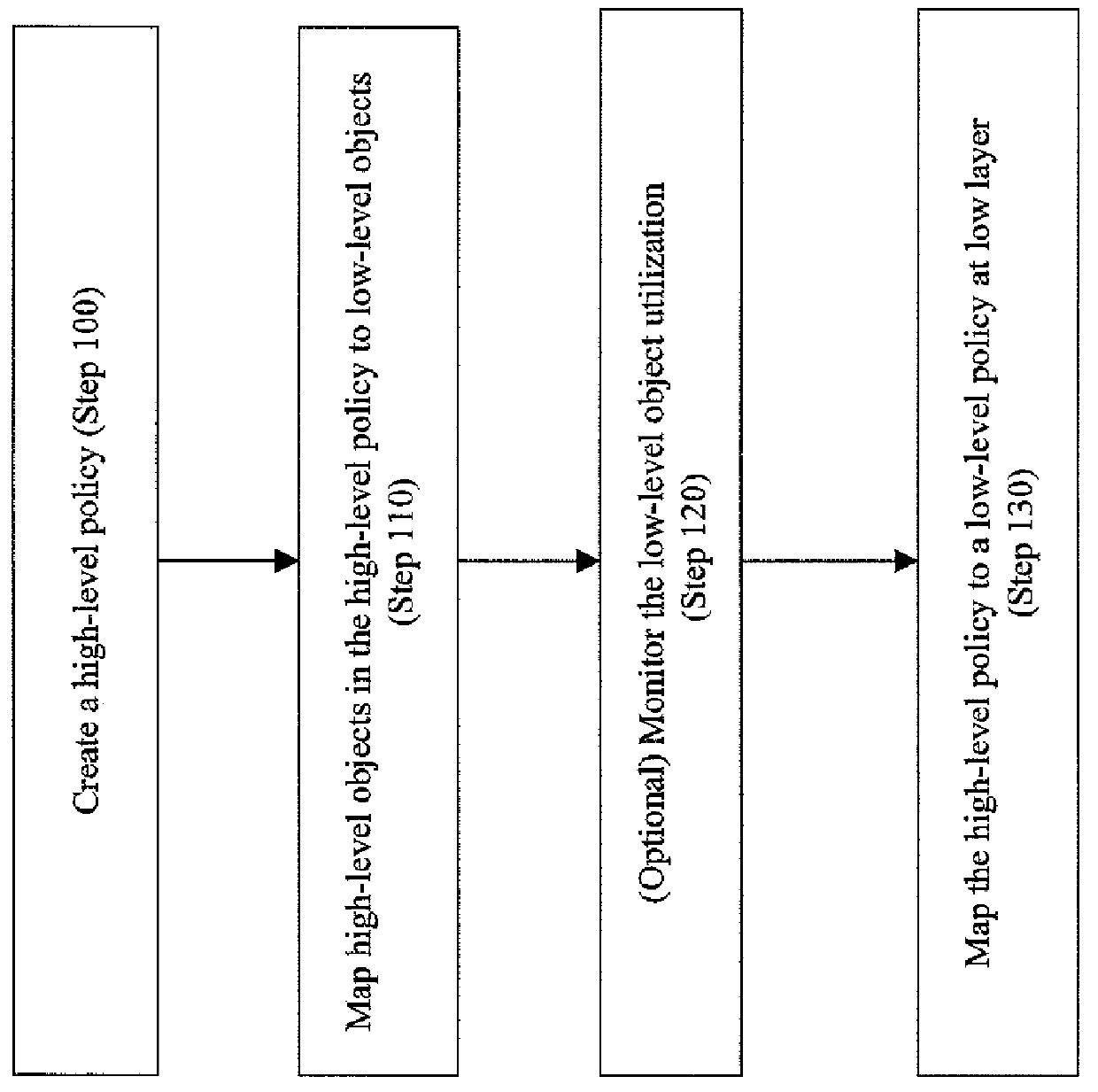
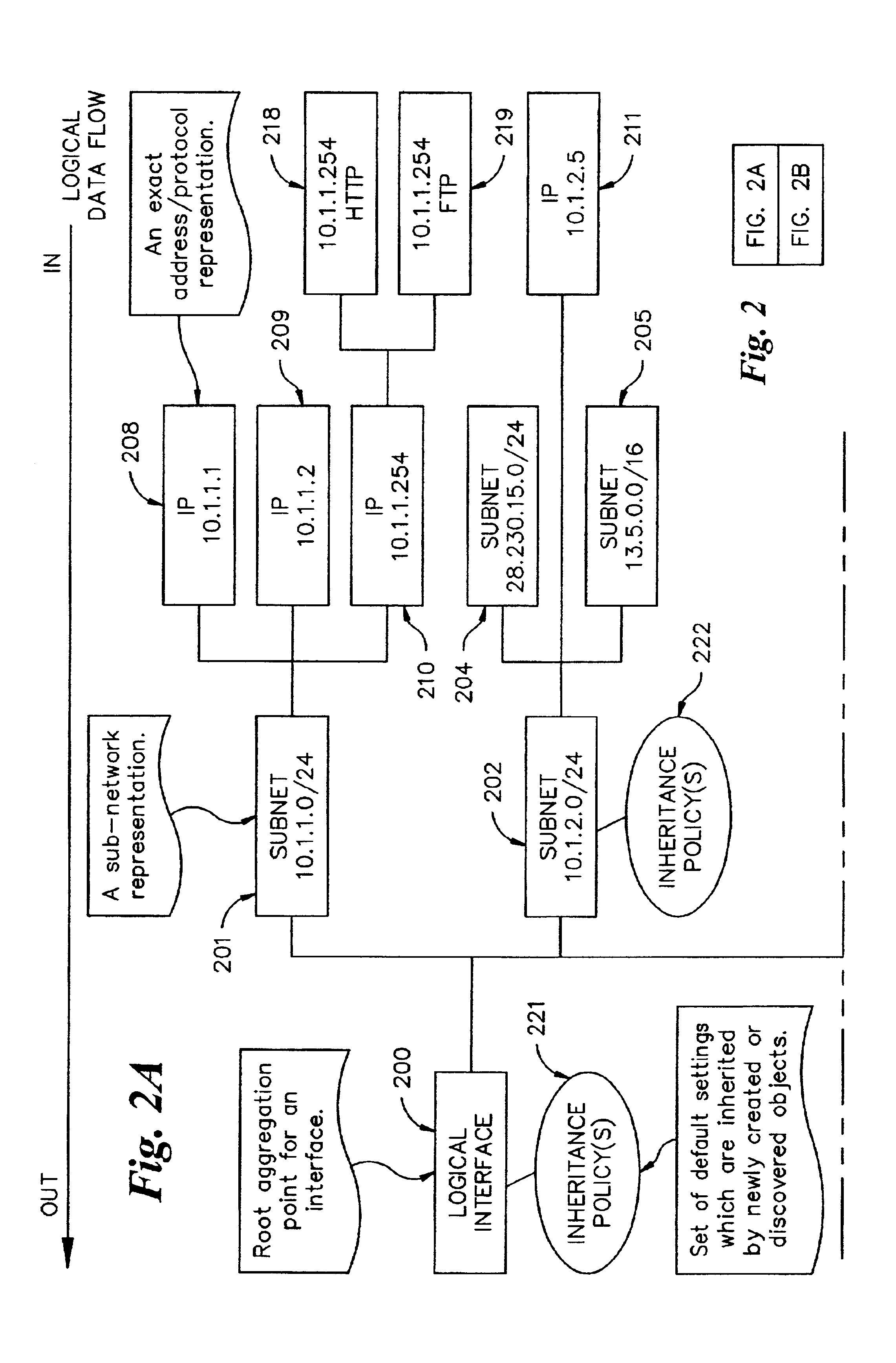
A method, system, computer program product, and computer program storage device for transforming a high-level policy associated with a high layer to a low-level policy associated with a low layer. Mapping between high-level objects in a high layer and low-level objects in a low layer is derived by an automated discovery tool. The high-level policy is mapped to the low-level policy according to the mapping (e.g., by substituting the high-level objects with the low-level objects and by performing a syntax transformation). In one embodiment, a low-level policy is transformed to a high-level policy according to the mapping. As exemplary embodiments, policy transformations in traffic shaping and data retention are disclosed.
Owner:INT BUSINESS MASCH CORP
Mobile Device and Method
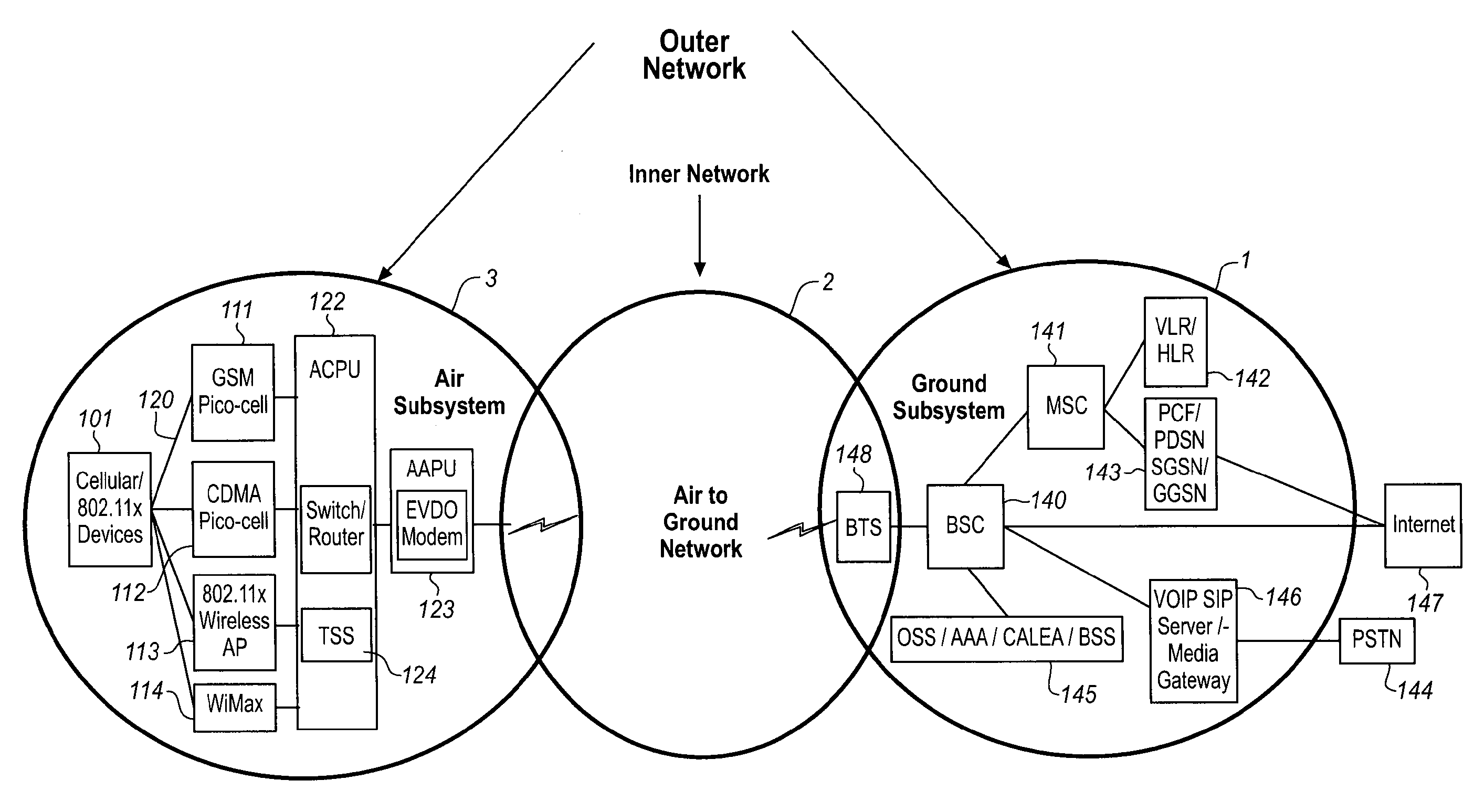
ActiveUS20110306386A1Reduce operating costsNetwork traffic/resource managementSubstation equipmentService protocolAir interface
Systems, methods and a mobile device for using policy defined by the operator to control the interfaces on which data is sent and received by the device are provided. The policy can be dynamically updated by the operator, by pushing new policy to the device for implementation. The policy can define that the device should switch certain data between two or more available interfaces at certain times, or when certain data may be sent or received over a particular interface. The device may receive new policy from the operator in order to help with the operator's own operational objectives, such as traffic shaping or other traffic limitation to ease congestion or enforce service agreements. A policy implementing corresponding traffic limitation or shaping on the air interface between the mobile device and network base stations can be sent to the mobile device so as to reduce signaling congestion on the air-interface.
Owner:CARNEGIE TECH UK
Application aware traffic shaping service node positioned between the access and core networks
A method and apparatus for an application aware traffic shaping service node positioned between the access and core networks is described. One embodiment of the invention enforces a per subscriber, per application traffic policy for network traffic between one or more subscribers communicatively connected through an access network and a set of one or more service providers communicatively connected through a core network. According to another embodiment of the invention enforcement of the per subscriber, per application traffic policy comprises classifying the network traffic into application level subscriber flows, maintaining real-time statistics on the application level subscriber flows and overall network element congestion, updating, in real-time, the per subscriber, per application traffic policy based on the real-time statistics and restricting bandwidth and dropping packets on the application level subscriber flows as necessary to enforce the per subscriber, per application traffic policy. Another embodiment of the invention is a passthrough mode where the data traffic is transmitted by the traffic in the same manner as received by the traffic shaping service node. Yet another embodiment of the invention is a combined service node with integral edge routing and traffic aggregator.
Owner:TELLABS COMM CANADA
Traffic shaping of cellular service consumption through modification of consumer behavior encouraged by cell-based pricing advantages
ActiveUS20060030291A1Increase profitAccounting/billing servicesSpecial service for subscribersCell specificProgram planning
Changes in wireless service user behavior are encouraged and produced to shape utilization patterns among cells within a rate plan region by using shaping rules which define potential discounts from a standard charge rate under certain cell-specific utilization conditions, analyzing the shaping rules and utilization statistics of a cell upon service initiation, generating a discount from the standard rate for underutilized cells. The user is notified of these discount opportunities using text messages, icons, or other means. Over time, the users learn that at certain places and times, significant discounts are offered, and thus changes their behavior to take advantage of those discounts, thereby shaping traffic in a manner desired by the service provider.
Owner:D-LINK
Automatic adaptive network traffic prioritization and shaping
InactiveUS20090067328A1Error preventionFrequency-division multiplex detailsTraffic capacityData stream
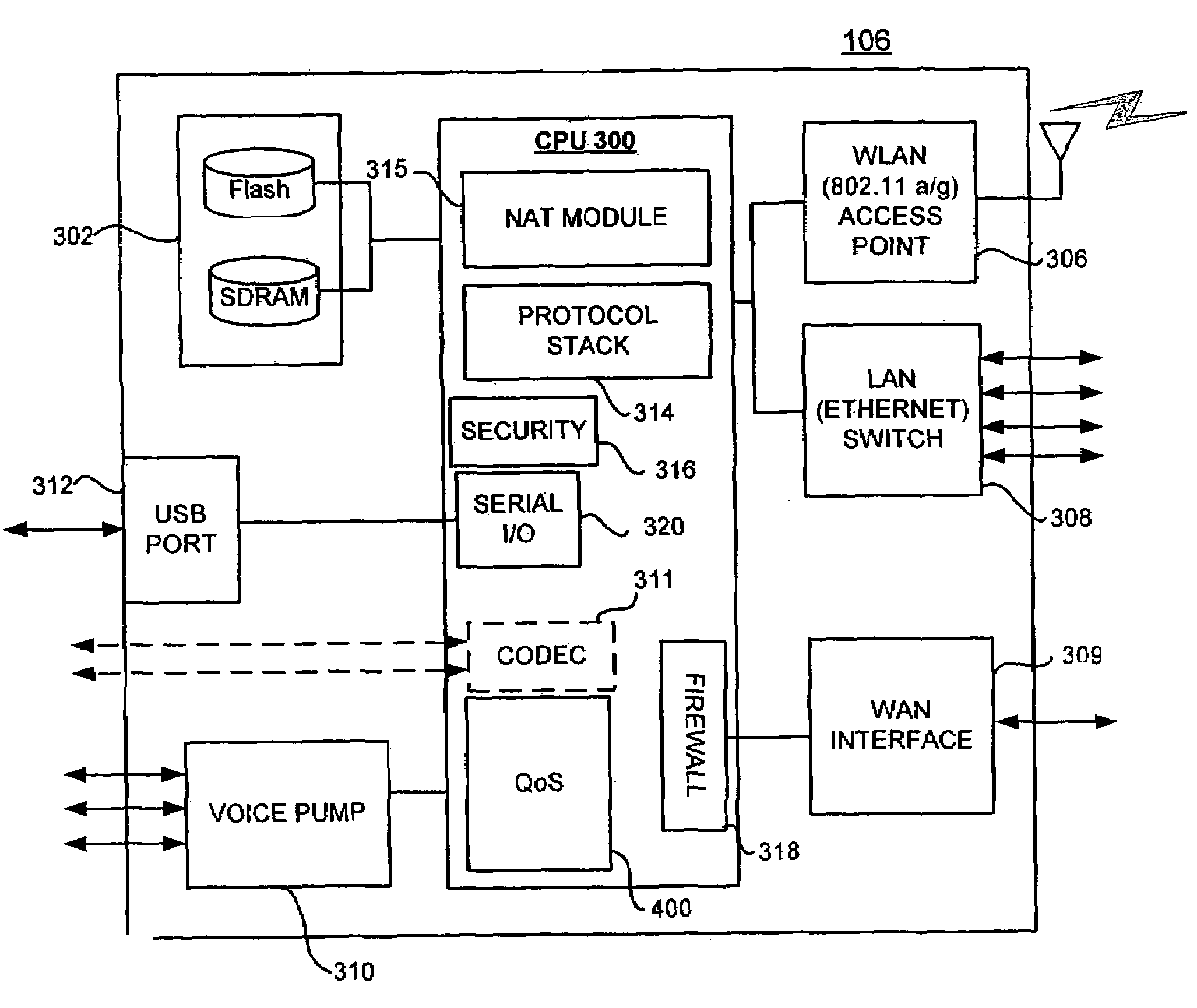
A local area network includes computers and peripherals networked in a high-speed LAN with access to a WAN through a slower connection via a broadband modem. A LAN gateway device manages data traffic between the local computers and peripherals and between the LAN and the WAN. The LAN gateway device provides multiple features, such as wired or wireless links, security, firewall, NAT, DCHP, traffic management, and the like. Traffic management features include an automatic quality of service priority classification scheme. A quality of service module automatically assigns priorities to the data streams based on analysis of the data packets. A configuration access list can be provided with pre-configured priorities for some streams. Initially, all streams are given highest priority and subsequently the priority is automatically adapted to the results of the packet analysis. Traffic shaping techniques control the LAN gateway upstream output and enable IP fragmentation of TCP packets according to measured upstream channel conditions.
Owner:QUALCOMM INC
Method and apparatus for applying quality of service to multicast streams transmitted in a cable network
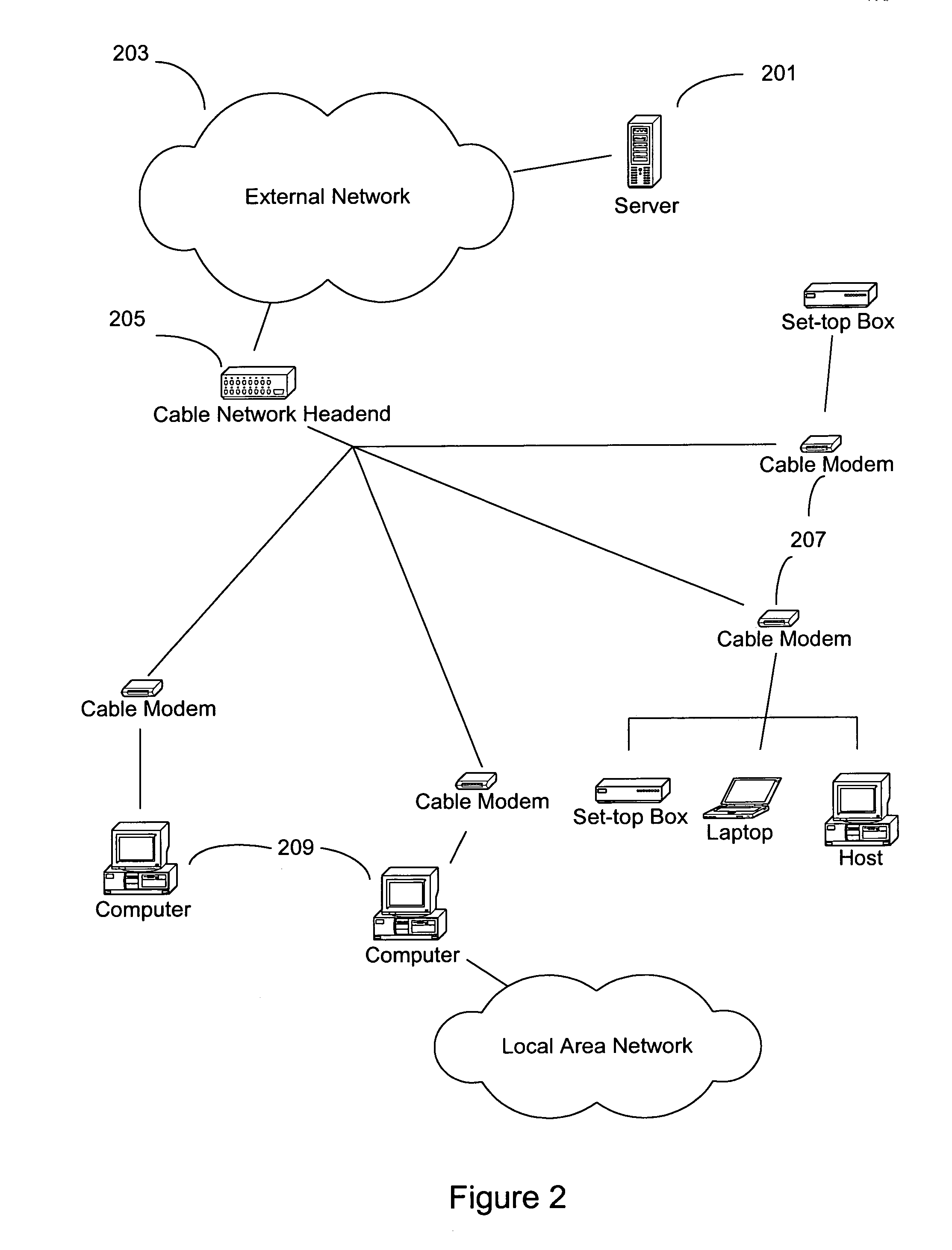
ActiveUS7012891B1Meet actual needsSpecial service provision for substationError preventionQuality of serviceFiber
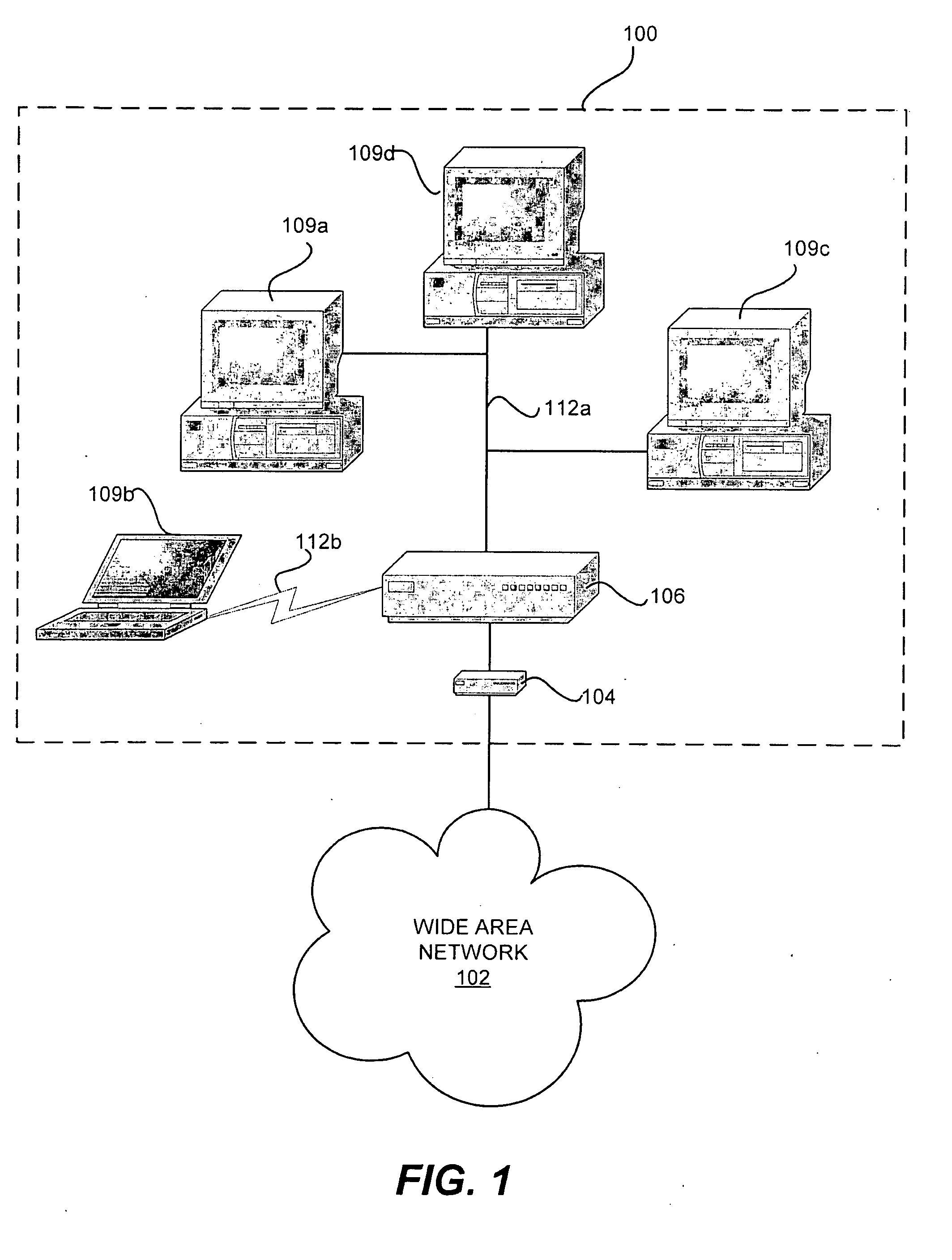
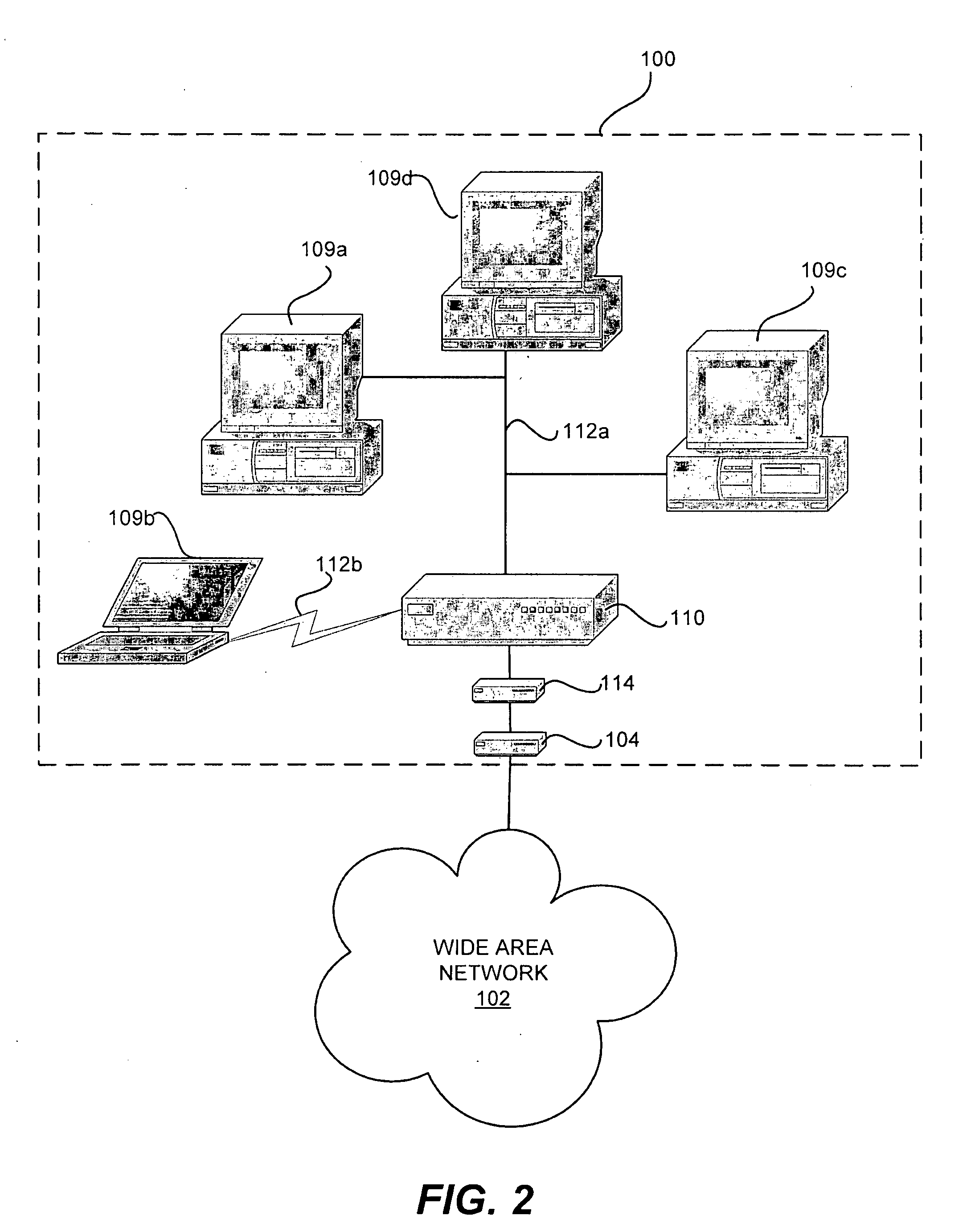
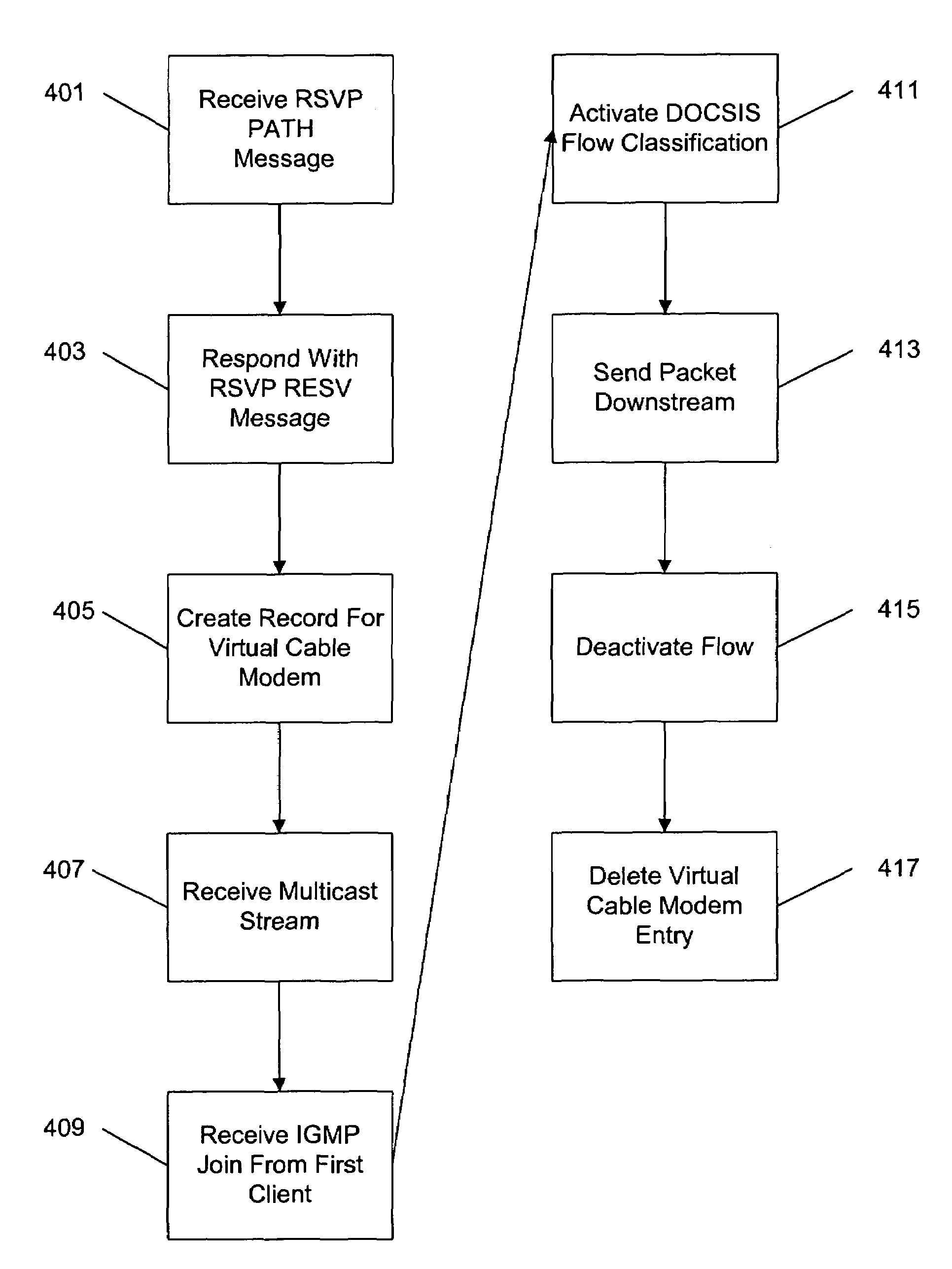
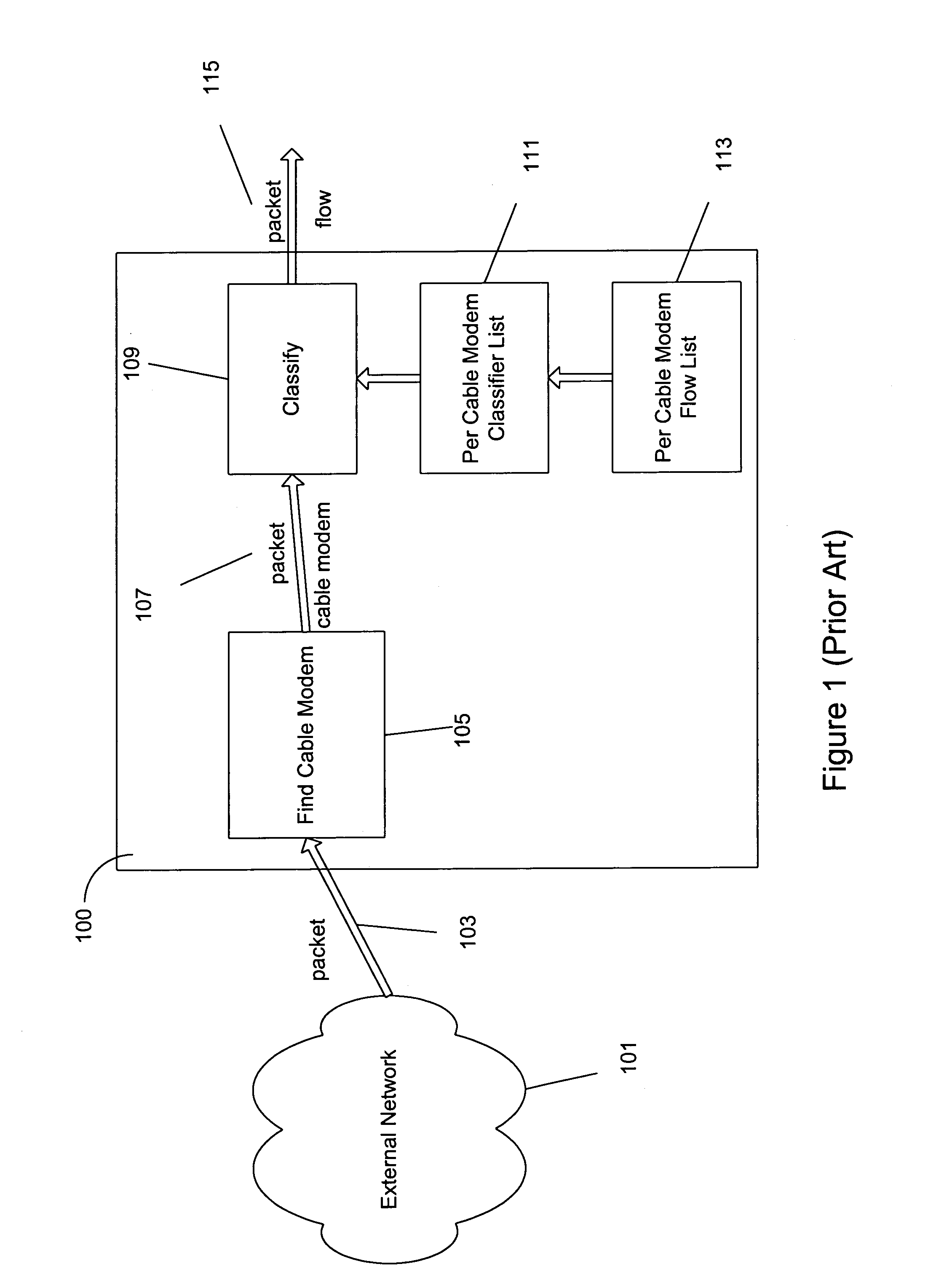
A method and apparatus for providing quality of service parameters for transmissions of multicast streams on a cable network is provided. A cable network headend connects an external network to a hybrid fiber coax or cable network. The cable network headend maintains a table of cable modems with entries associating each cable modem with one or more quality of service parameters. Virtual cable modem entries are created for multicast streams when indications of quality of service for multicast streams are received by the cable network headend. Multicast packets arriving at the cable network headend are processed using the stored quality of service parameters for the corresponding multicast stream. The multicast packets may then be transmitted, queued, or dropped depending on the specified parameters and traffic shaping or policing algorithms.
Owner:CISCO TECH INC
Bandwidth control system
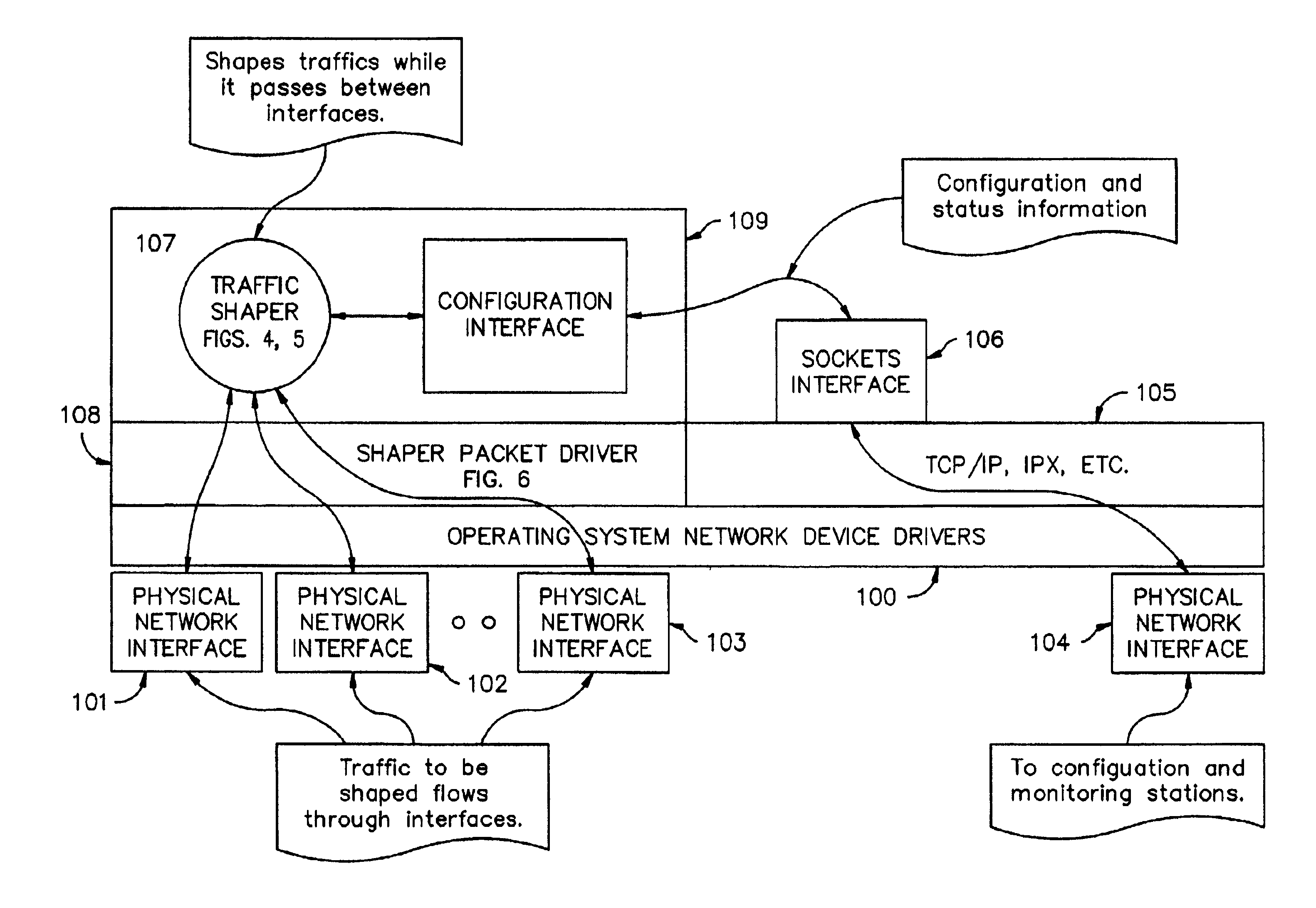
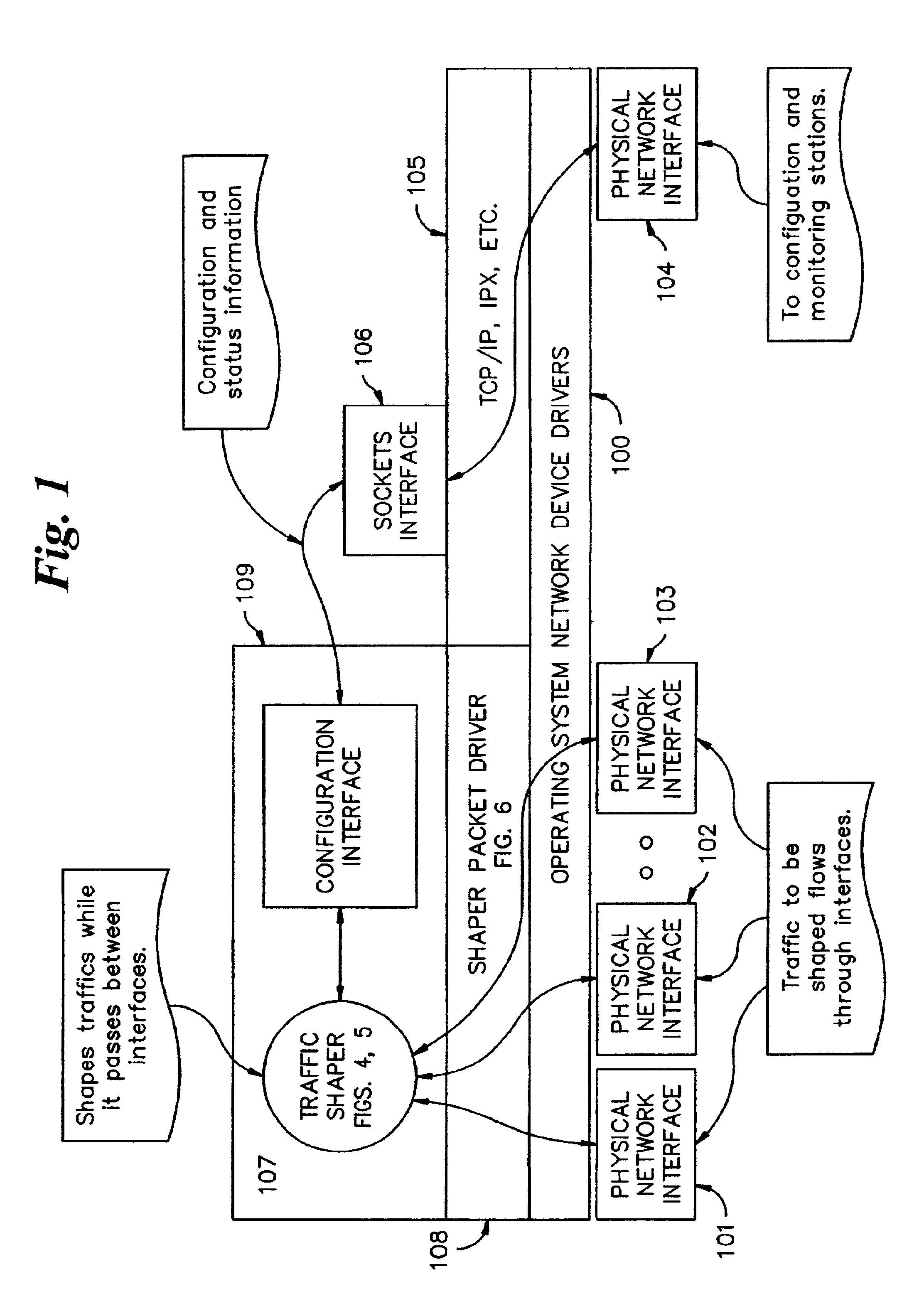
InactiveUS6954429B2Error preventionFrequency-division multiplex detailsTraffic capacityNetwork packet
A bandwidth control system for a network, the network having a host computer that includes a first network interface and a second network interface. A packet driver adapted to be executed on the host computer is logically connected to the first network interface and the second network interface. The packet driver captures packets received from the network on the first network interface. A traffic shaper adapted to be executed on the host computer maintains a topology representation of the network, the topology representation including one or more nodes. The traffic shaper performs priority and packet rate metering functions on the captured packets to match a set of rate conditions unique to each node in the topology representation of the network. The captured packets are returned to the packet driver for transmission to the network on the second network interface.
Owner:DYBAND CORP
IP platform for advanced multipoint access systems
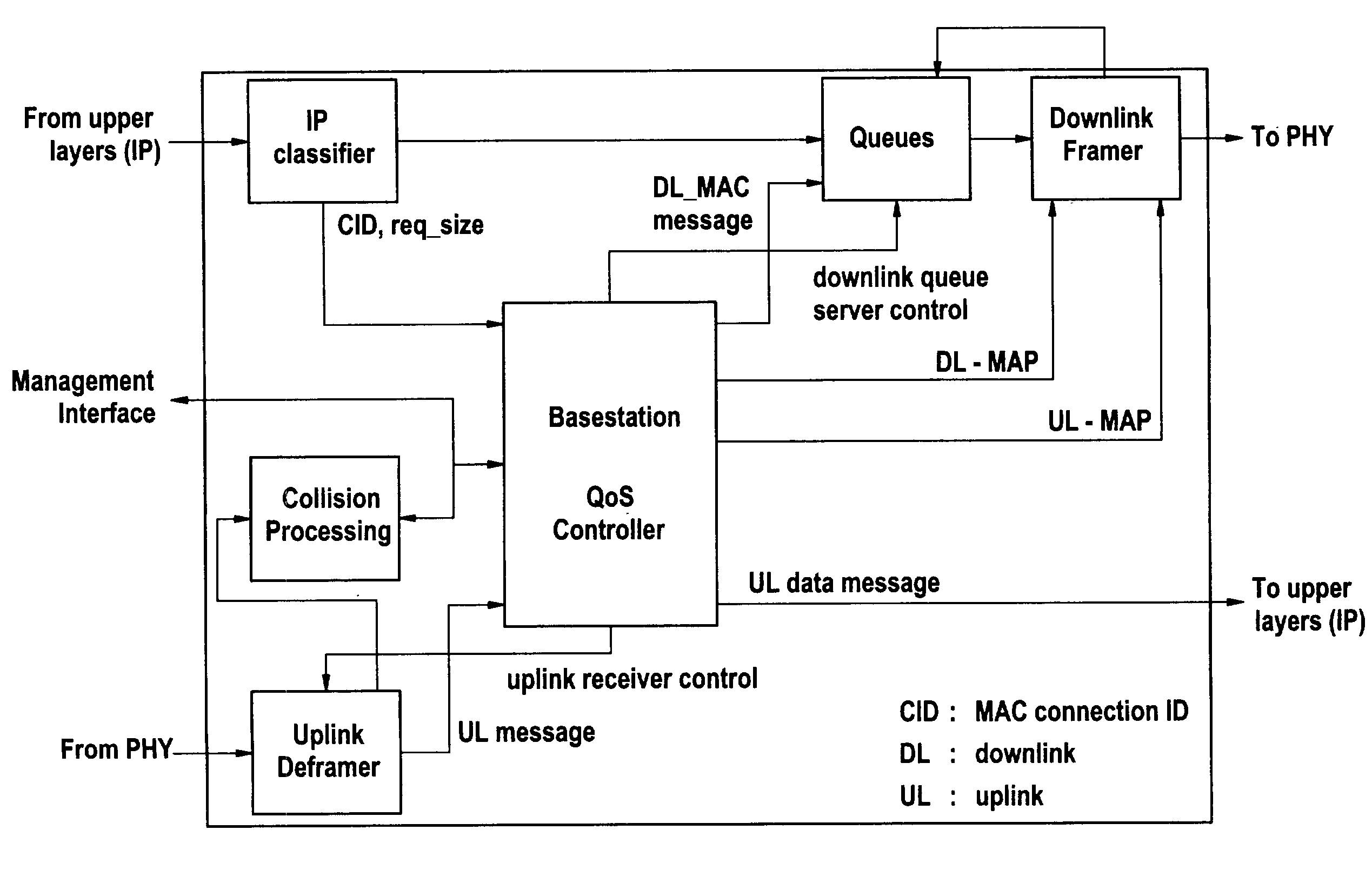
InactiveUS7266087B2Minimum amount of memory spaceError preventionFrequency-division multiplex detailsNetwork terminationTraffic capacity
In LMDS systems the downlink bandwidth is continuously varying in time because each downlink burst uses a network termination individual modulation and coding (Physical layer) scheme, the higher layer (IP) functions cannot perform service priority respecting traffic shaping. The invention proposes mainly to combine both framing and IP layer functions within one inter-layer framer. The combination of both information ensures QoS provisioning in case of multi-modulation and multi-coding environment. The QoS queue server gets always informed on the actual amount of available data frame bits from the downlink framer and therefore, the QoS queue server is able to decide on the next IP packet or packet fraction to transport. This decision is always based on service priority aspects. As soon as the downlink frame is filled—supposing that the maximum downlink frame rate is always lower than the internal processing in the inter-layer framer—the QoS server stops the data delivery.
Owner:WSOU INVESTMENTS LLC
Traffic shaping of cellular service consumption through delaying of service completion according to geographical-based pricing advantages
InactiveUS20060040641A1Low costMaximum convenienceAccounting/billing servicesFinanceProgram planningClass of service
Changes in user behavior of usage of wireless services from a mobile device are encouraged in order to effect shaping of traffic and utilization patterns among a plurality of cells within a rate plan region, wherein a discount indicator disposed in said mobile device is provided to notify a user of a discount available for consuming wireless service from a given cell. A geo-cost policy is established for that user or mobile device in which rules and conditions according to the available discounts and class of service are defined. A service completer queues services and automatically completes queued services upon present conditions meeting said geo-cost policy rules, such as delaying and later delivering messages when the mobile device is relocated to a cell where discounts are being offered.
Owner:IBM CORP
Automatic adaptive network traffic prioritization and shaping
A local area network includes computers and peripherals networked in a high-speed LAN with access to a WAN through a slower connection via a broadband modem. A LAN gateway device manages data traffic between the local computers and peripherals and between the LAN and the WAN. The LAN gateway device provides multiple features, such as wired or wireless links, security, firewall, NAT, DCHP, traffic management, and the like. Traffic management features include an automatic quality of service priority classification scheme. A quality of service module automatically assigns priorities to the data streams based on analysis of the data packets. A configuration access list can be provided with pre-configured priorities for some streams. Initially, all streams are given highest priority and subsequently the priority is automatically adapted to the results of the packet analysis. Traffic shaping techniques control the LAN gateway upstream output and enable IP fragmentation of TCP packets according to measured upstream channel conditions.
Owner:QUALCOMM INC
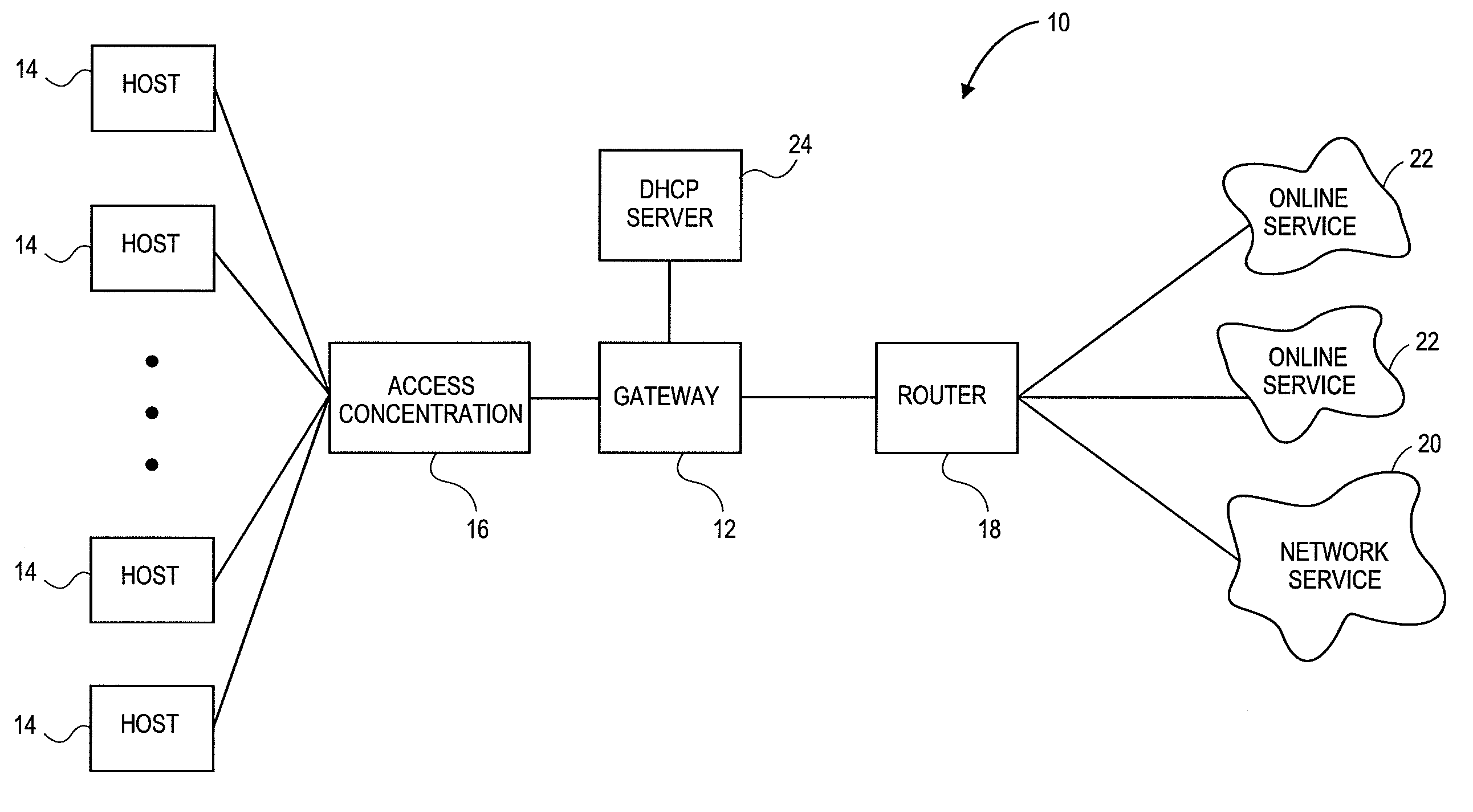
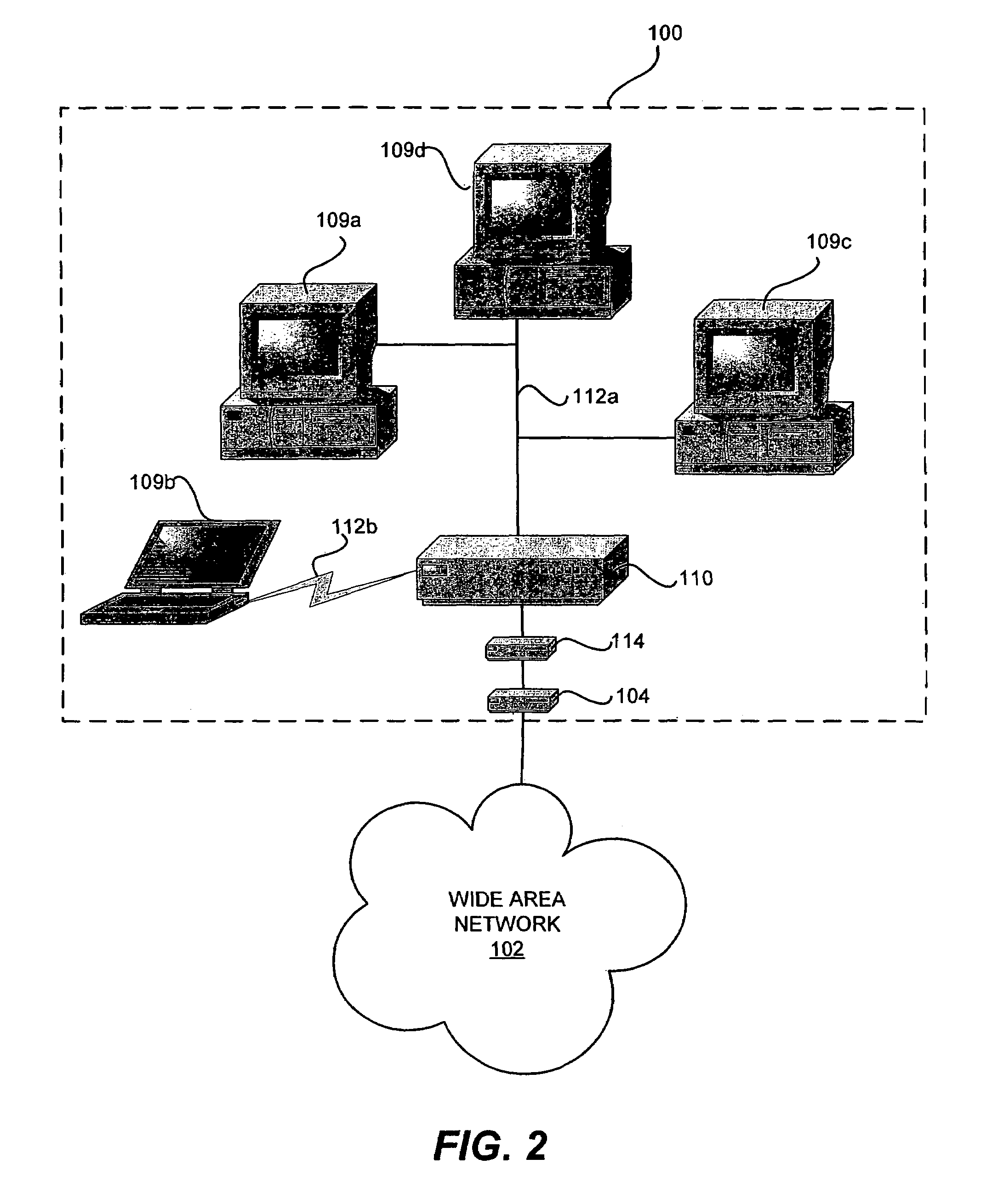
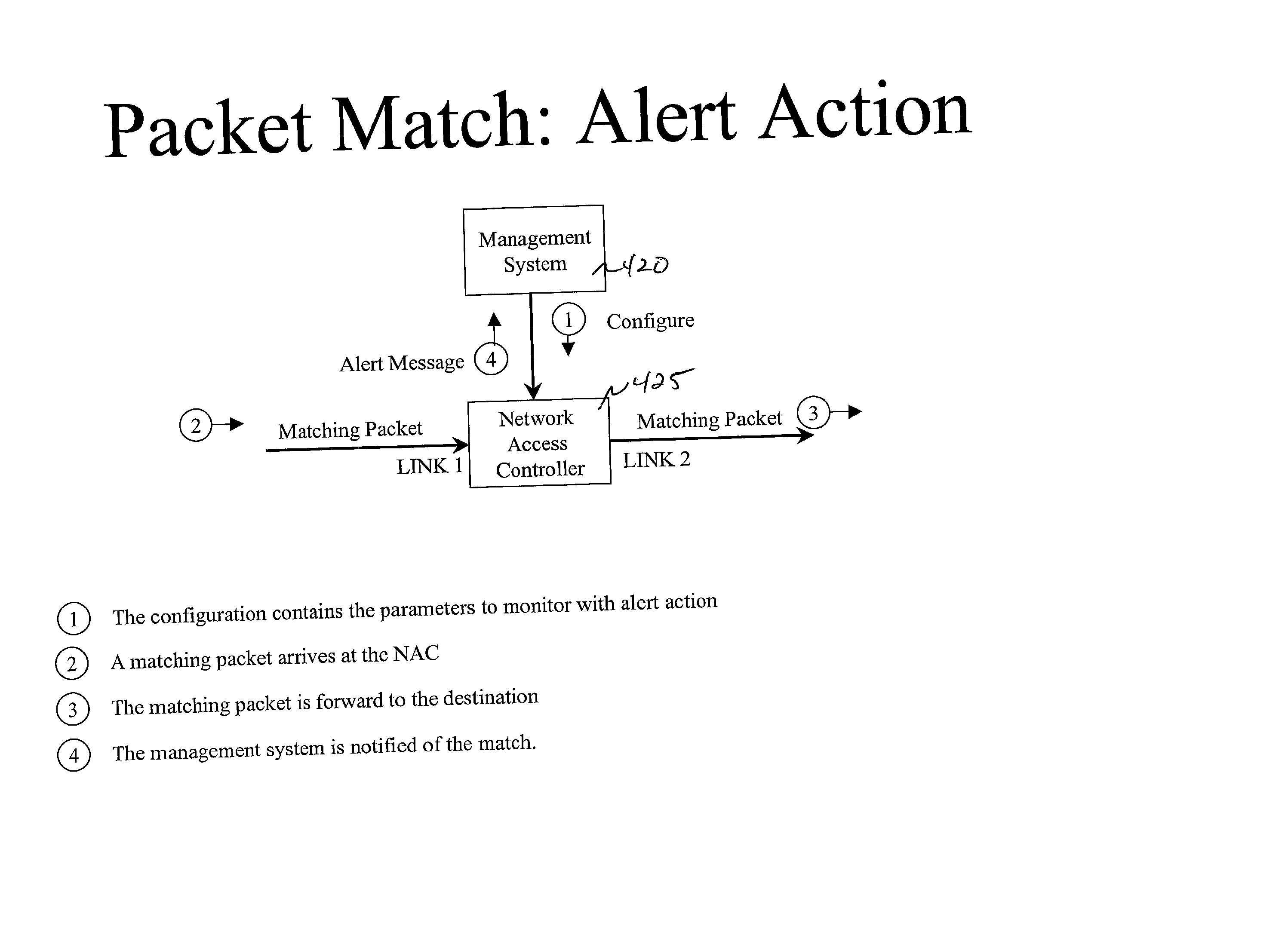
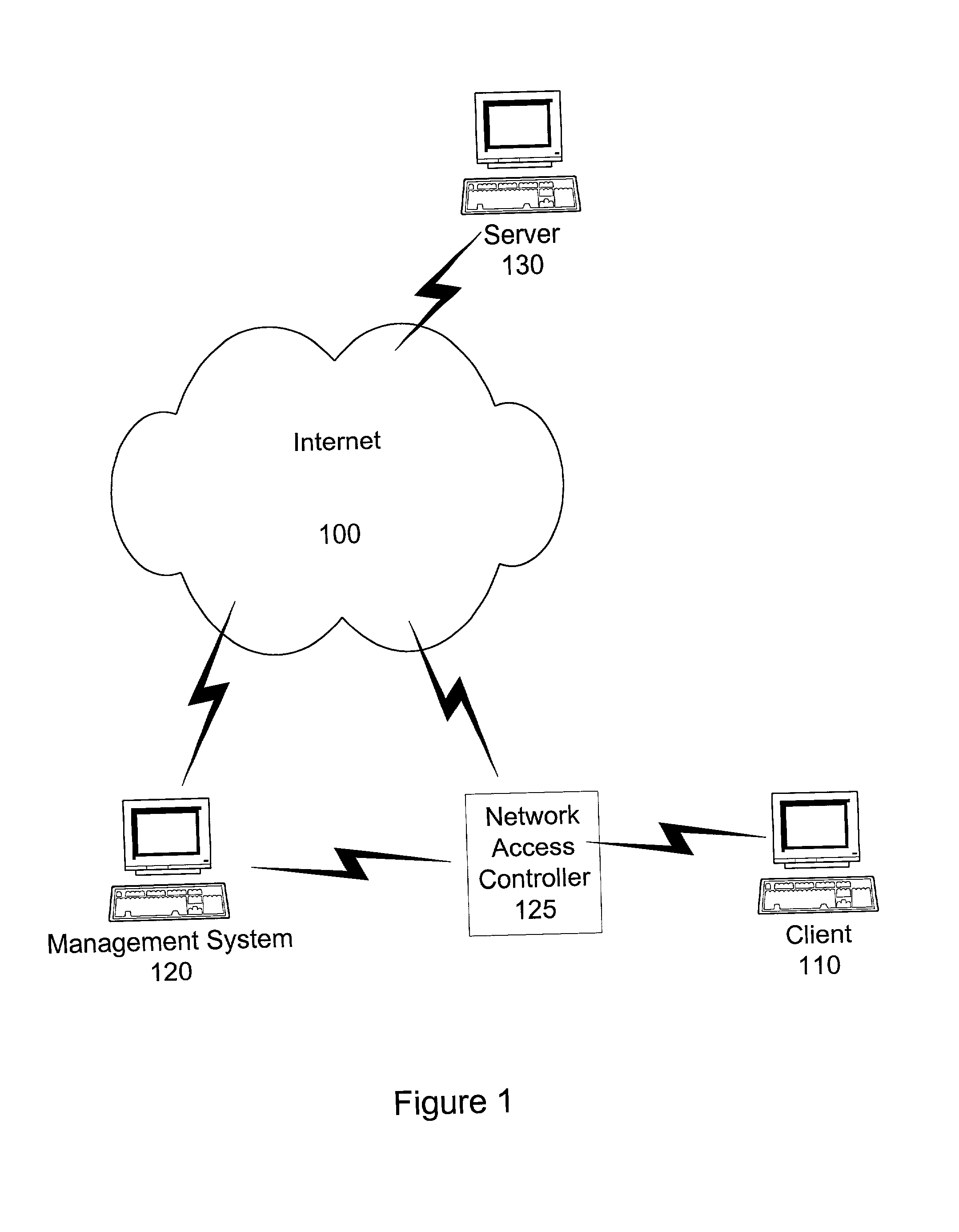
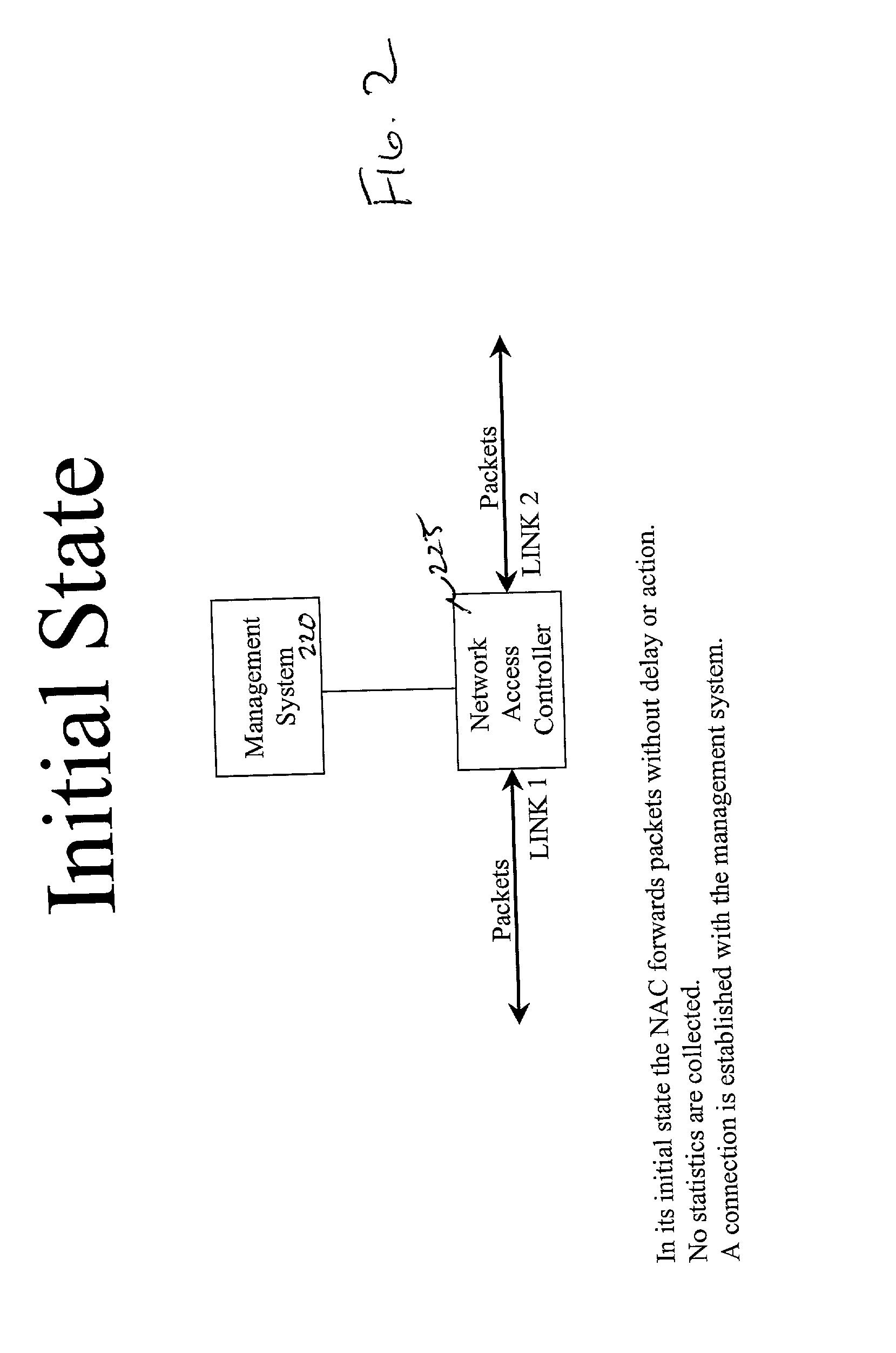
System and method for delivery and usage based billing for data services in telecommunication networks
InactiveUS20020116488A1Improved automated ordering and delivery and usage based billingMetering/charging/biilling arrangementsMultiple digital computer combinationsService flowQuality level
A system and method for delivering and charging for data services over a netword system. A hardware device called "network access controller" (NAC) can be configured by a management system with information regarding data services available on a per-user, per-customer, or per-service basis. The access controller is able to read all data packets coming into the network and figure out whether they indicate the start of any premium service session like video on demand or whether they are from a premium user who needs special treatment. The access controller is able to process incoming data packets without leading to any degradation in performance or throughput. Once it detects the start of a specific type of data service session, then the access controller signals to the management system that this data service flow has started and supplies additional information extracted from the incoming data packet. Using this information and additional information on the capacity of the transport network and server resources, the number of service sessions already active and availability of credit, such as billing authorization information from a billing system, the management system can determine whether to allow the start of this service or not. The management system communicates this decision to the access controller and alters the Access Control Lists (ACLs) in traffic shapers appropriately. If the data service request is admitted into the network, then additional bandwidth is opened in The traffic shapers so that the end user receives the appropriate quality level for the service. If the service request is denied access, then the end user will not be able to gain access to the premium service.
Owner:ALCATEL USA SOURCING
Traffic Flow Scheduling Techniques Implemented on Bonded Channels of a Shared Access Cable Network
Owner:CISCO TECH INC
Traffic scheduling system for wireless communications
InactiveUS20110116373A1Optimize and guarantee performanceOptimize and guarantee and low latencyError preventionFrequency-division multiplex detailsTraffic capacityTime segment
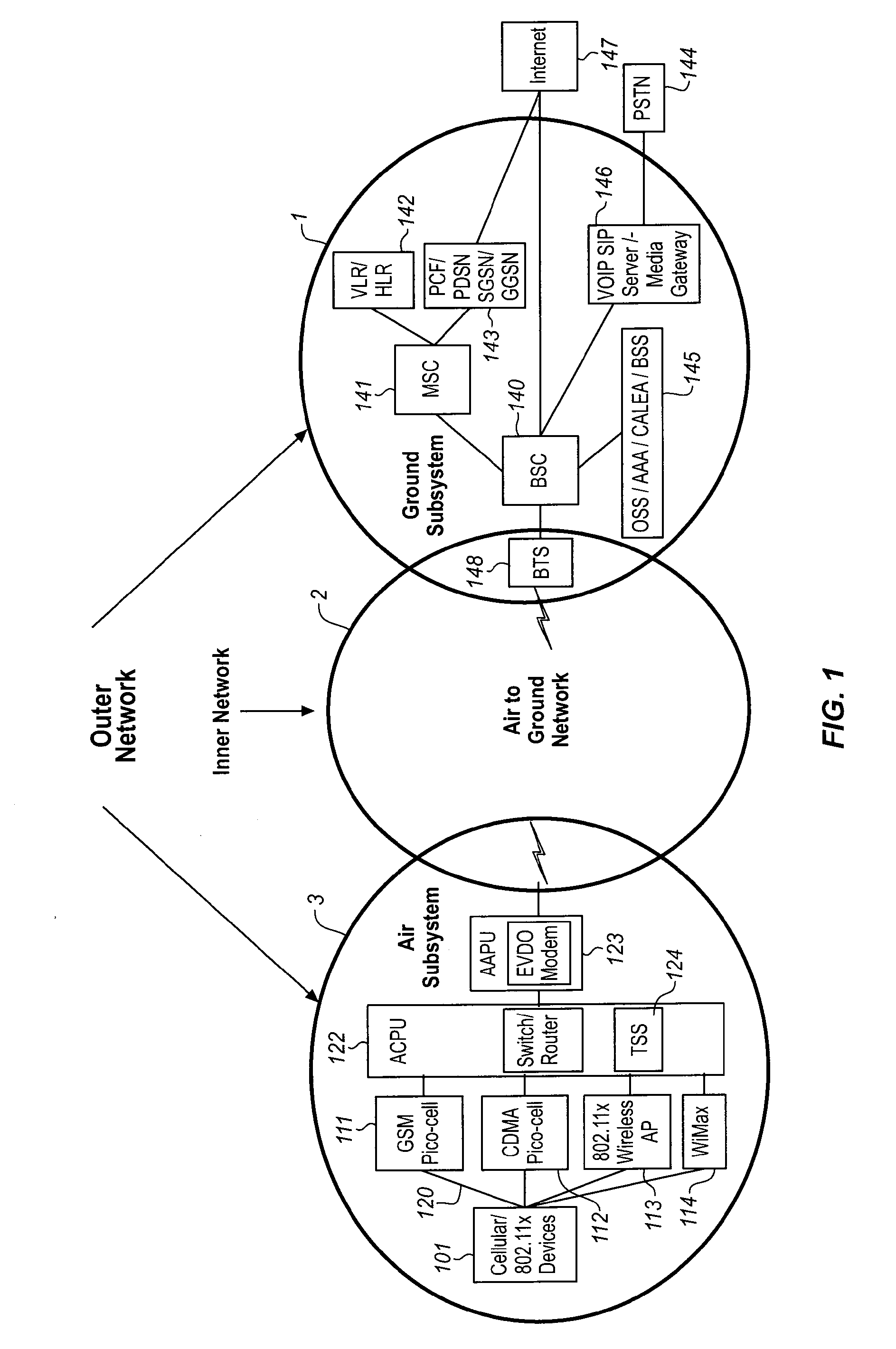
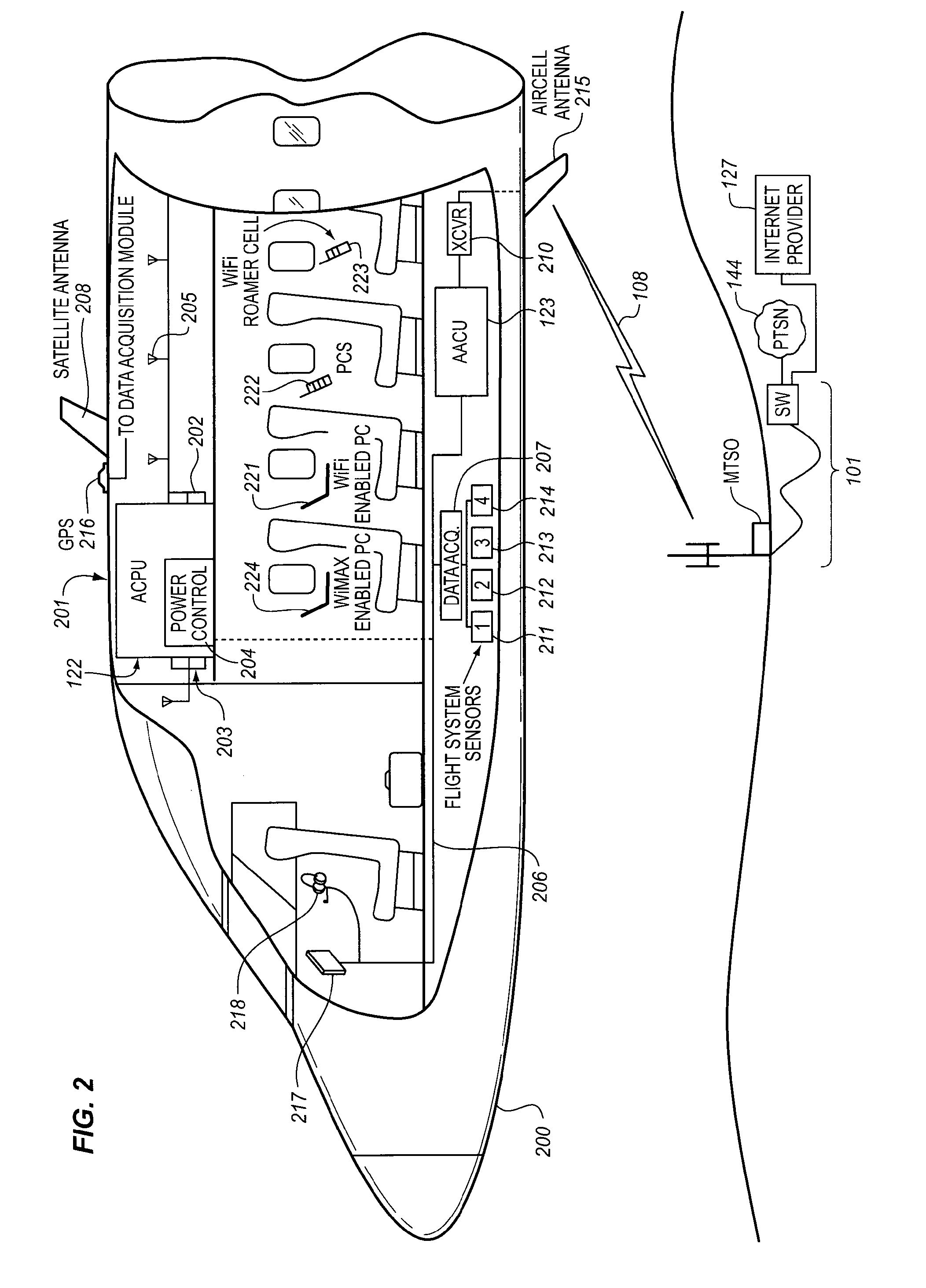
The Traffic Scheduling System executes a multi-step process first to identify the bandwidth intensive traffic. The identification of the bandwidth intensive traffic is effected at the stream level by measuring the byte volume of the stream over a predetermined period of time and using this data to classify the stream into one of a plurality of usage categories. The classification of bandwidth intensive traffic is network neutral in that all data is classified at the stream level (source IP, destination IP, source port, destination port). Otherwise, the data is not inspected. Once streams have been classified by the Traffic Scheduling System, the Bandwidth Intensive and Near Real Time traffic can be controlled by a simple Traffic Shaping process executed by the Traffic Scheduling System, using a traffic management parameter such as via the Round-Trip Time of the next higher priority queue, in the set of queues.
Owner:GOGO BUSINESS AVIATION LLC
Systems and methods for traffic shaping
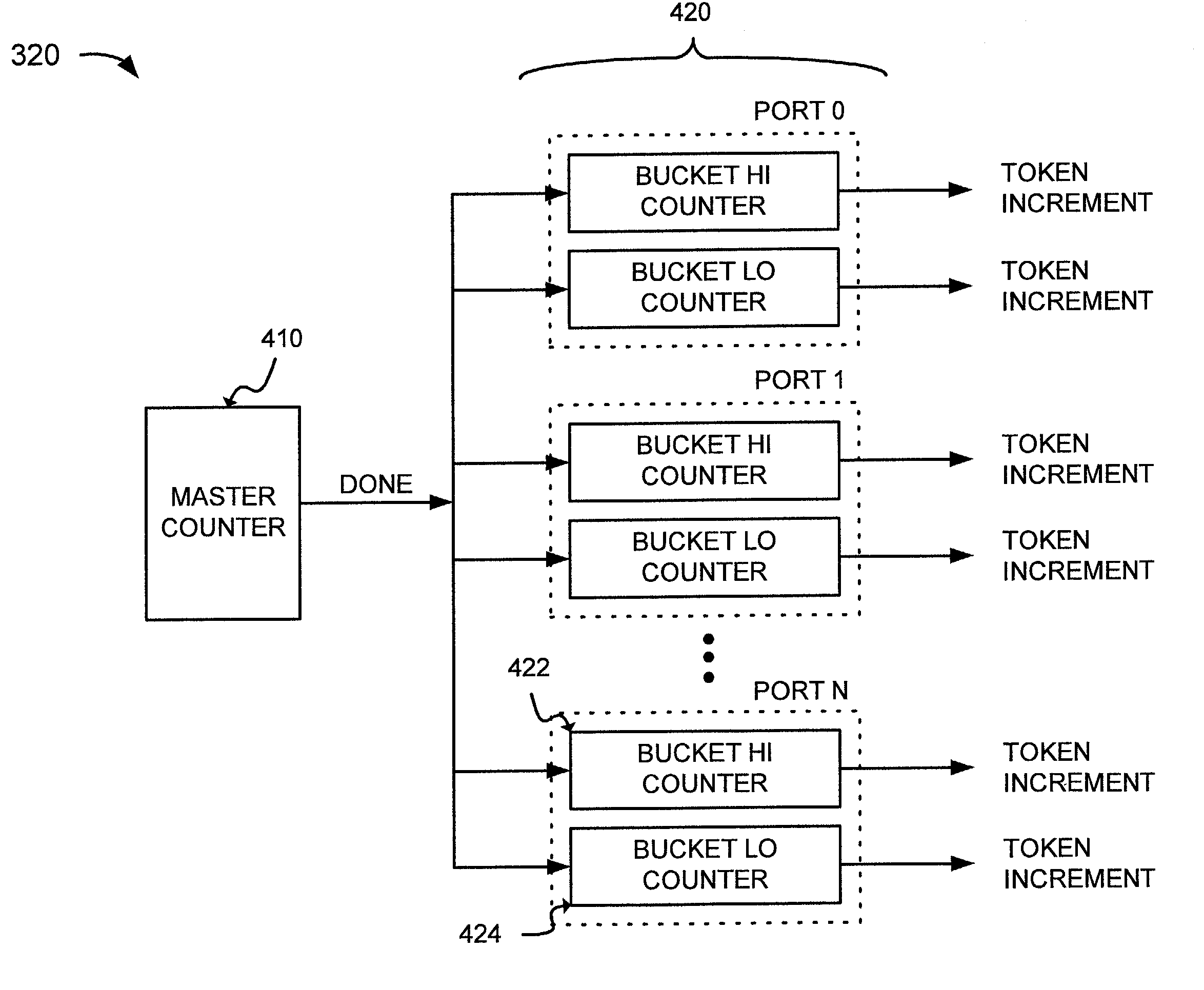
InactiveUS6925055B1To offer comfortError preventionFrequency-division multiplex detailsByteControl logic
A system shapes traffic in a multiport network device. The system includes multiple token buckets and token bucket logic. The token buckets correspond to multiple priority queues of the multiple output ports of the network device and store one or more tokens. Each of the tokens corresponds to a byte of one or more received packets to be transmitted by the network device. The token bucket control logic generates the tokens for the token buckets. The token bucket control logic includes a master counter and multiple bucket counters. The master counter counts to a first count value and generates a done signal when the count reaches the first count value. The bucket counters, corresponding to the token buckets, receive the done signal, count to a second count value, and generate a token increment signal for storing a token in the corresponding token buckets when the count reaches the second count value.
Owner:ADVANCED MICRO DEVICES INC
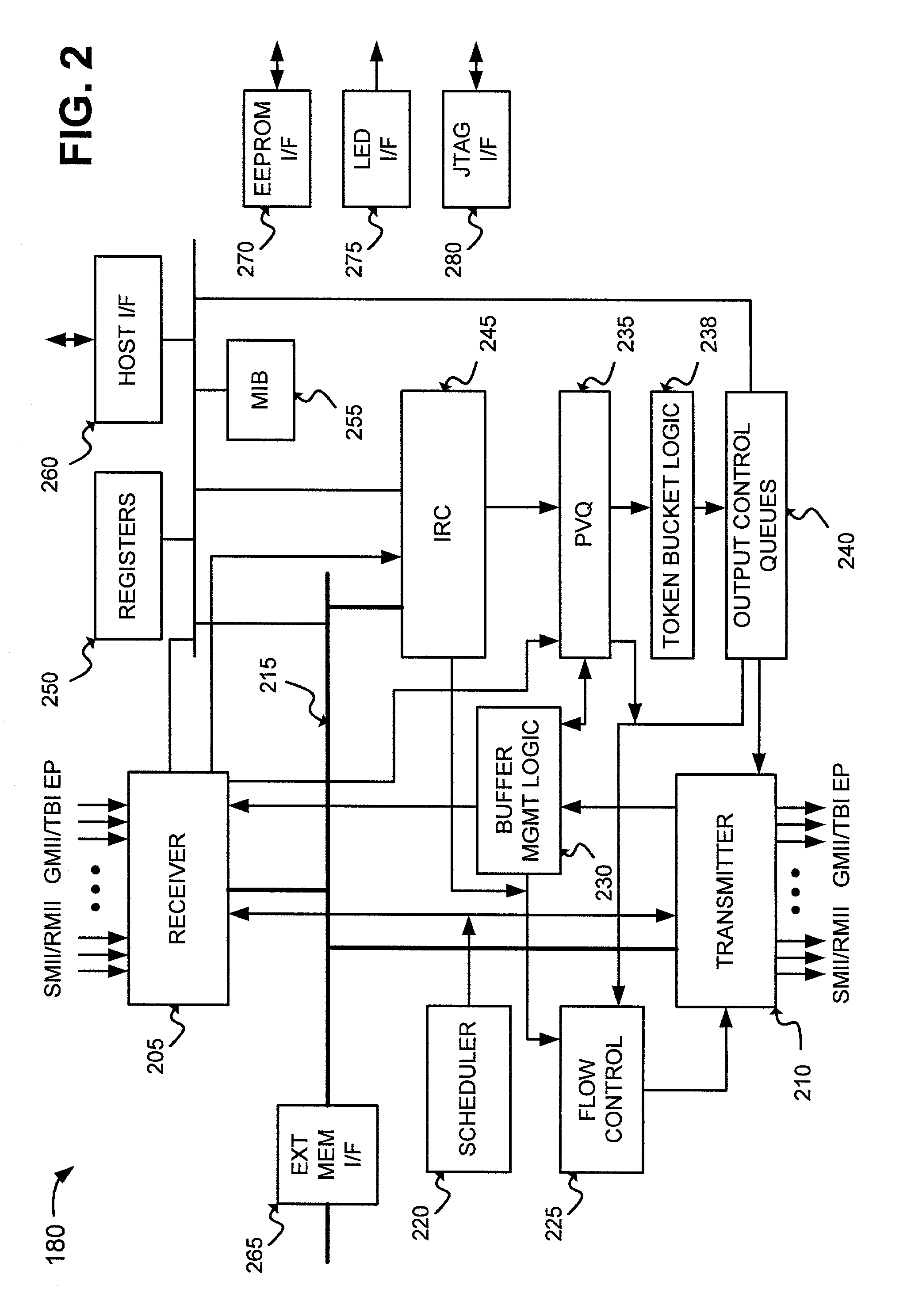
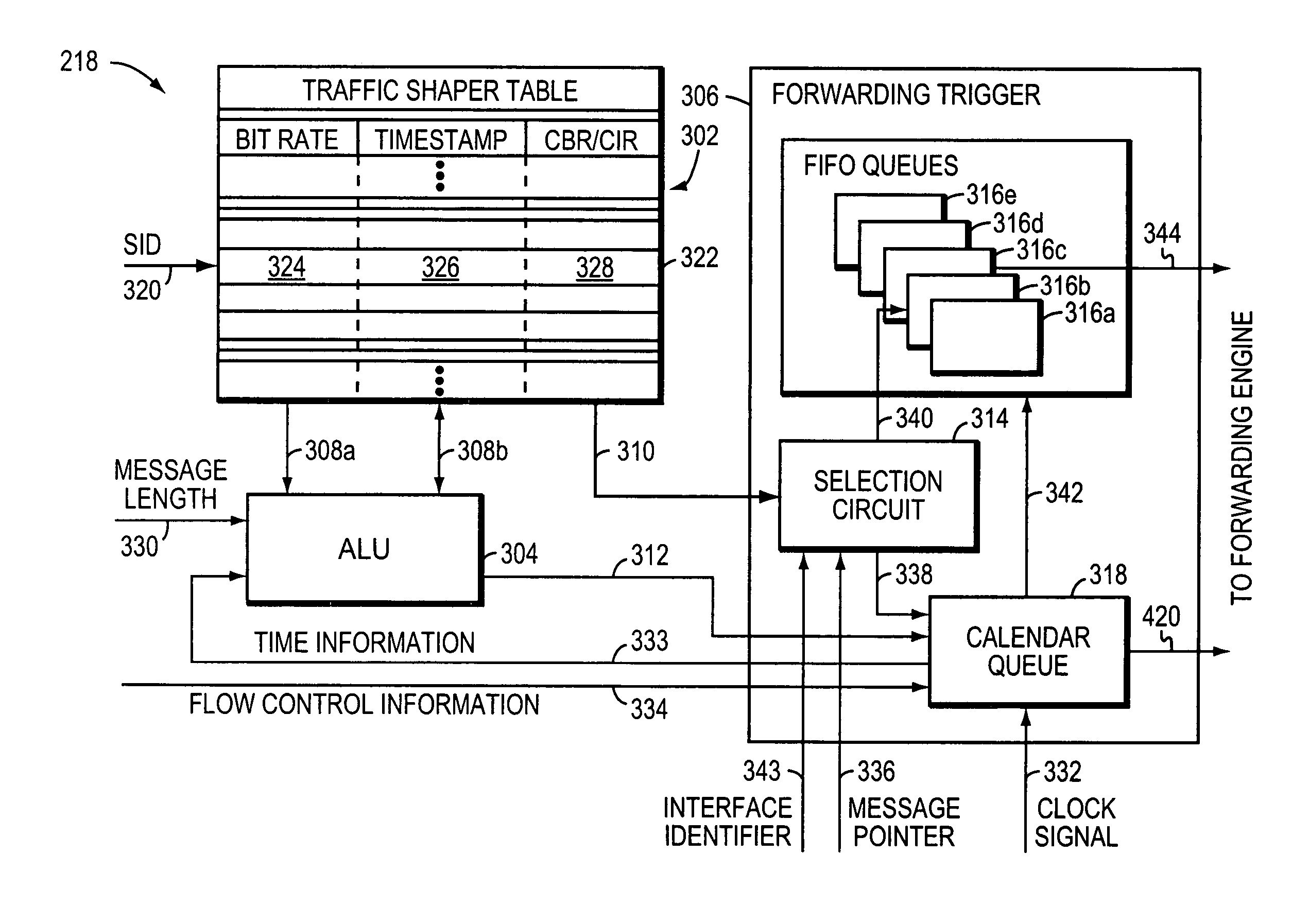
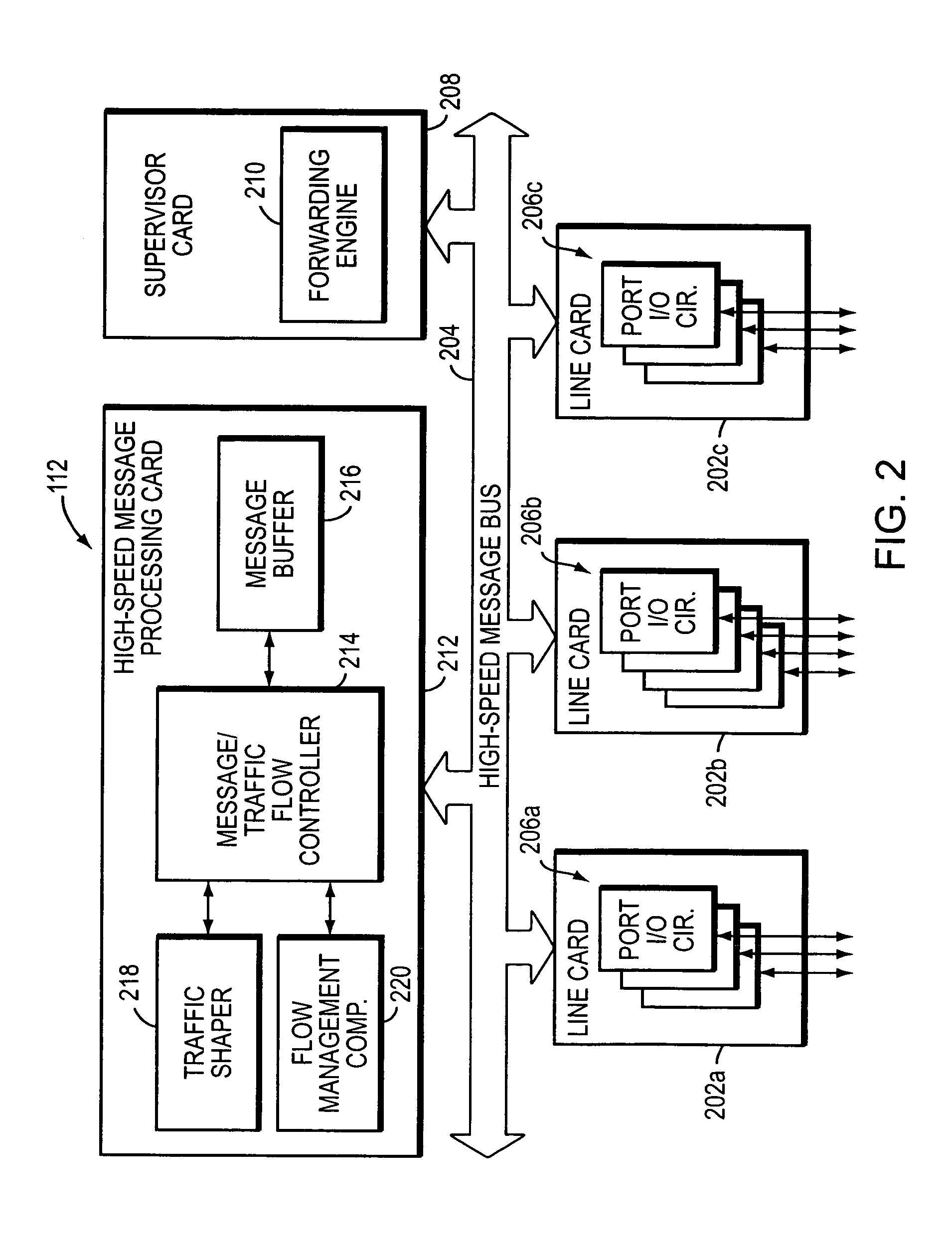
Method and apparatus for performing high-speed traffic shaping
A network traffic shaper for shapping transmission of network messages includes a system time generator for generating a system time, an arithmetic logic unit (ALU) for computing a transmission start time for each network message in response to the system time, and a retrieve time generator adapted to increment a retrieve time at a rate faster than the system time. As network messages are received, they are stored in a queue along with an associated transmission start time for each message. A forwarding trigger transmits a store network messages when its associated transmission start time matches the retrieve time. Alternately, a second transmission start time representing an excess bandwidth transmission start time may be computed for each network message. If excess bandwidth is detected, a message may be transmitted when its second transmission start time matches the retrieve time.
Owner:CISCO TECH INC
Quality of service for server applications
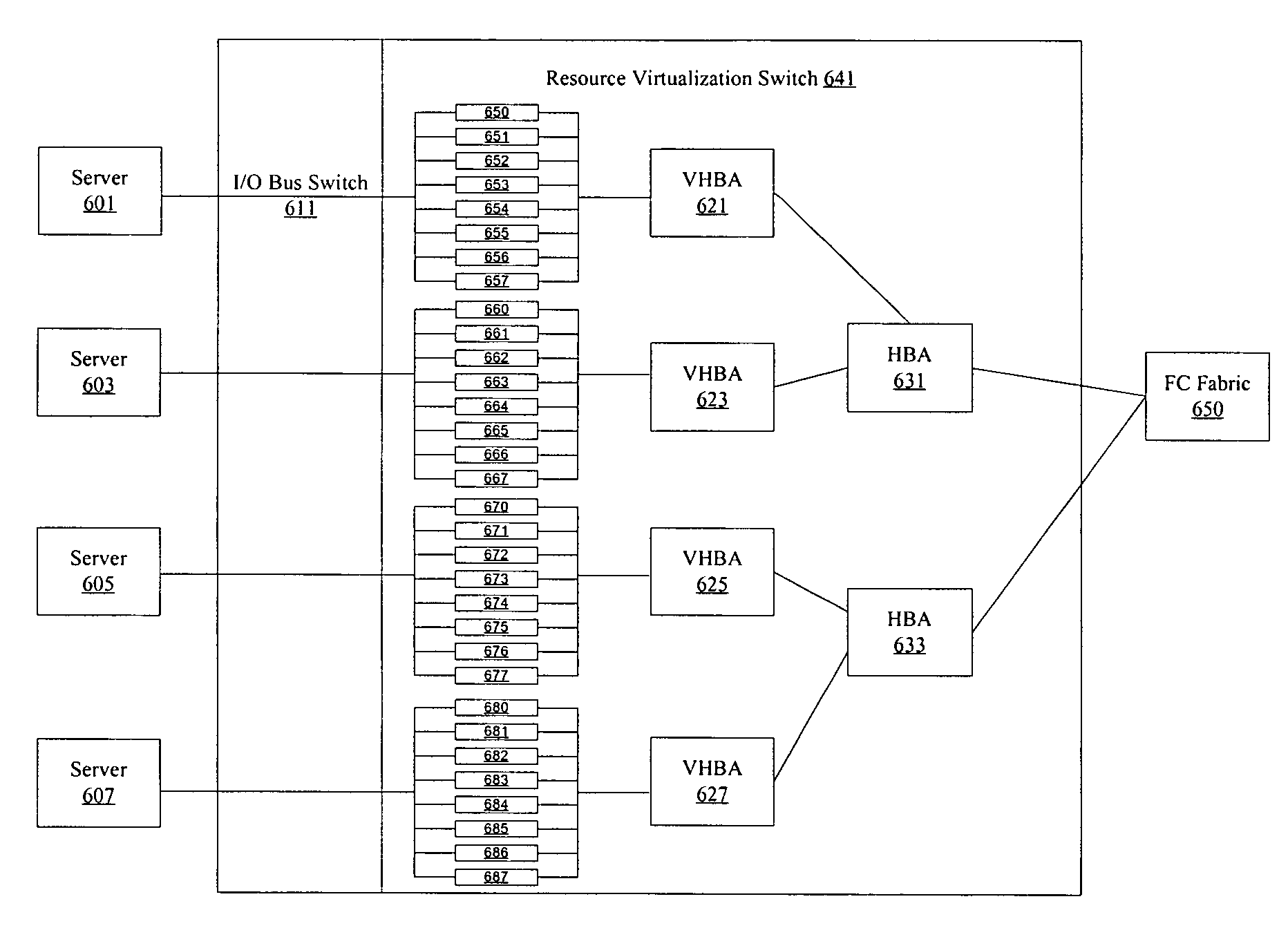
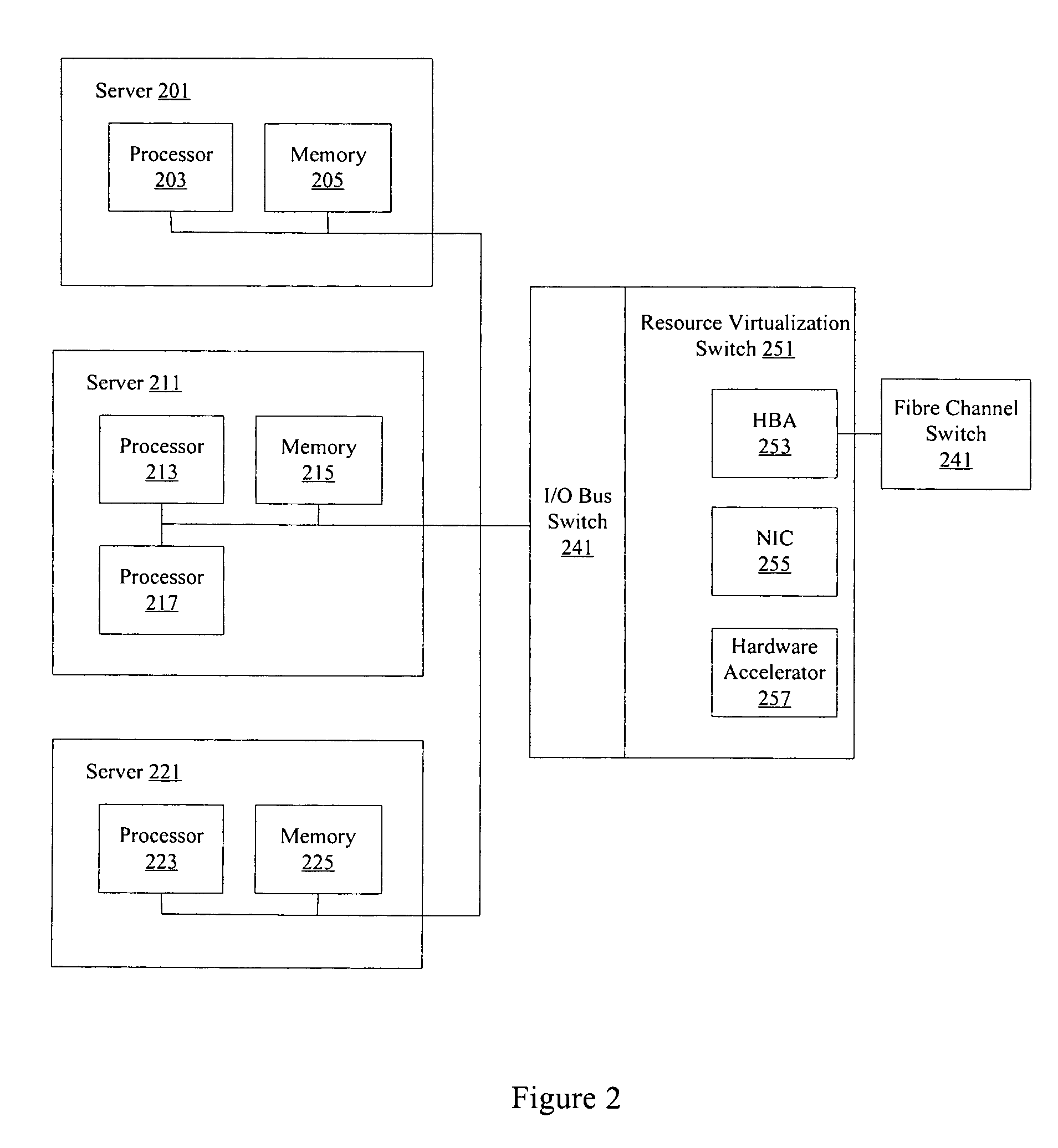
ActiveUS7602774B1Multiplex system selection arrangementsData switching by path configurationQuality of serviceTraffic capacity
Methods and apparatus are provided for allowing quality of service (QoS) configuration for storage applications running on servers connected to a storage area network (SAN). Resources such as host bus adapters (HBAs) are offloaded from individual servers onto a resource virtualization switch. Servers are connected to the resource virtualization switch using an I / O bus connection. The resource virtualization switch provides storage applications running on connected servers with different quality of service levels. The resource virtualization switch can also apply traffic shaping policies associated with QoS.
Owner:ORACLE INT CORP
Automatic network traffic characterization
InactiveUS7633869B1Overcome problemsError preventionTransmission systemsQuality of serviceModem device
A local area network includes computers and peripherals networked in a high-speed LAN with access to a WAN through a slower connection via a broadband modem. A LAN gateway device manages data traffic between the local computers and peripherals and between the LAN and the WAN. The LAN gateway device provides multiple features, such as wired or wireless links, security, firewall, NAT, DCHP, traffic management, and the like. Traffic management features include an automatic quality of service priority classification scheme. A quality of service module automatically assigns priorities to the data streams based on analysis of the data packets. Traffic shaping techniques control the LAN gateway upstream output and enable IP fragmentation of TCP packets according to measured upstream channel conditions. The traffic shaping techniques estimate available upstream data rate, available downstream data rate, and the size of datagrams being used on the network link.
Owner:QUALCOMM INC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com