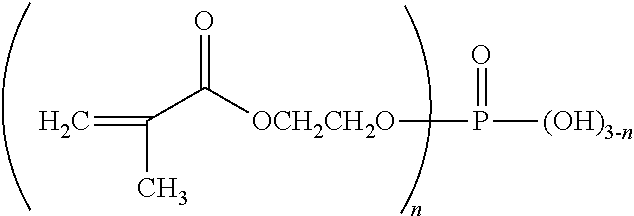
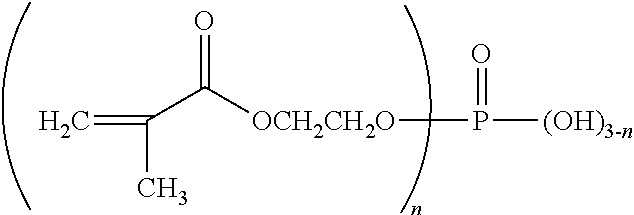
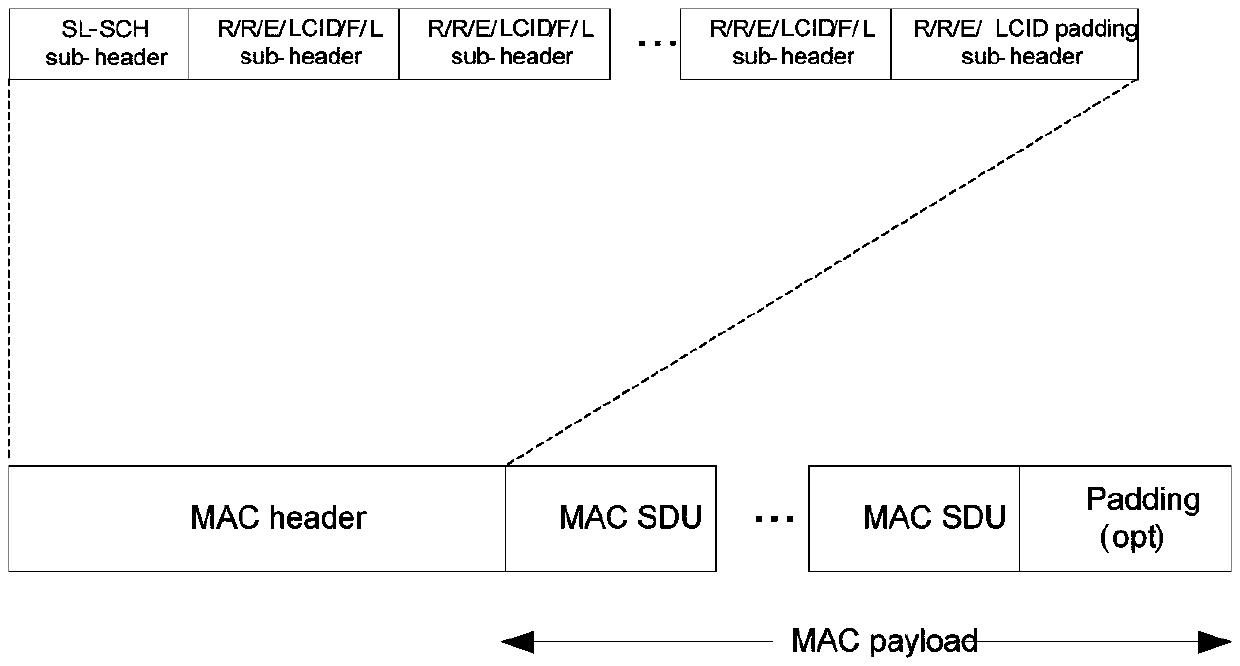
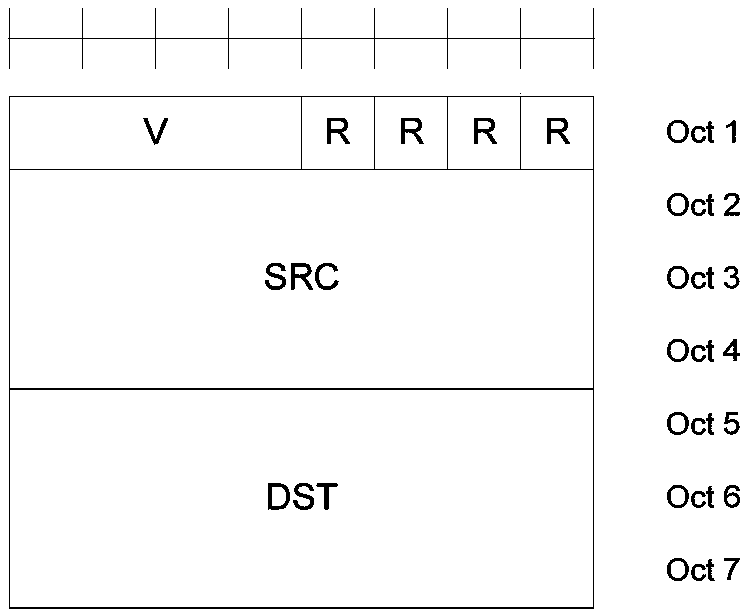
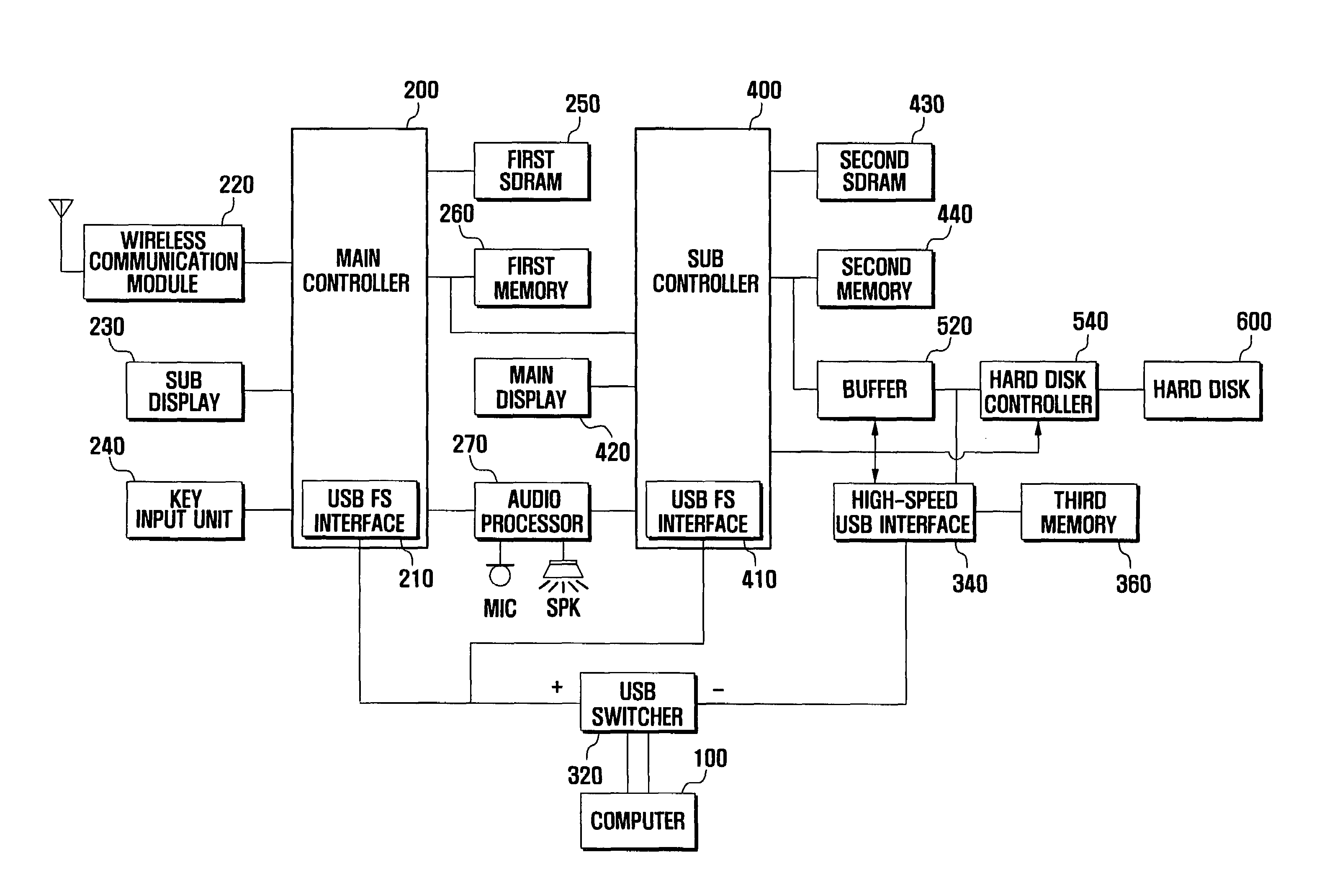
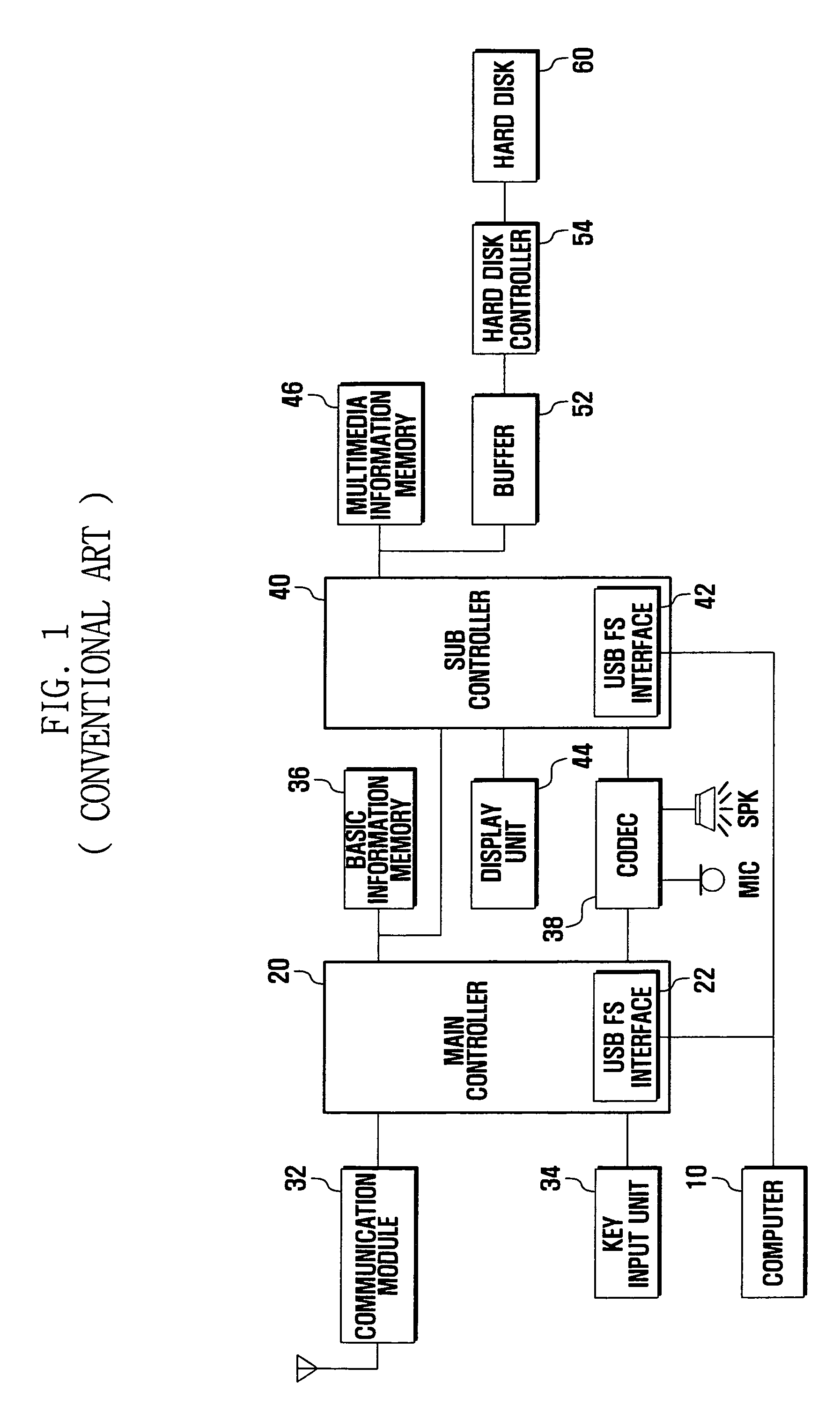
Patents
Literature
92results about How to "Avoid association" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
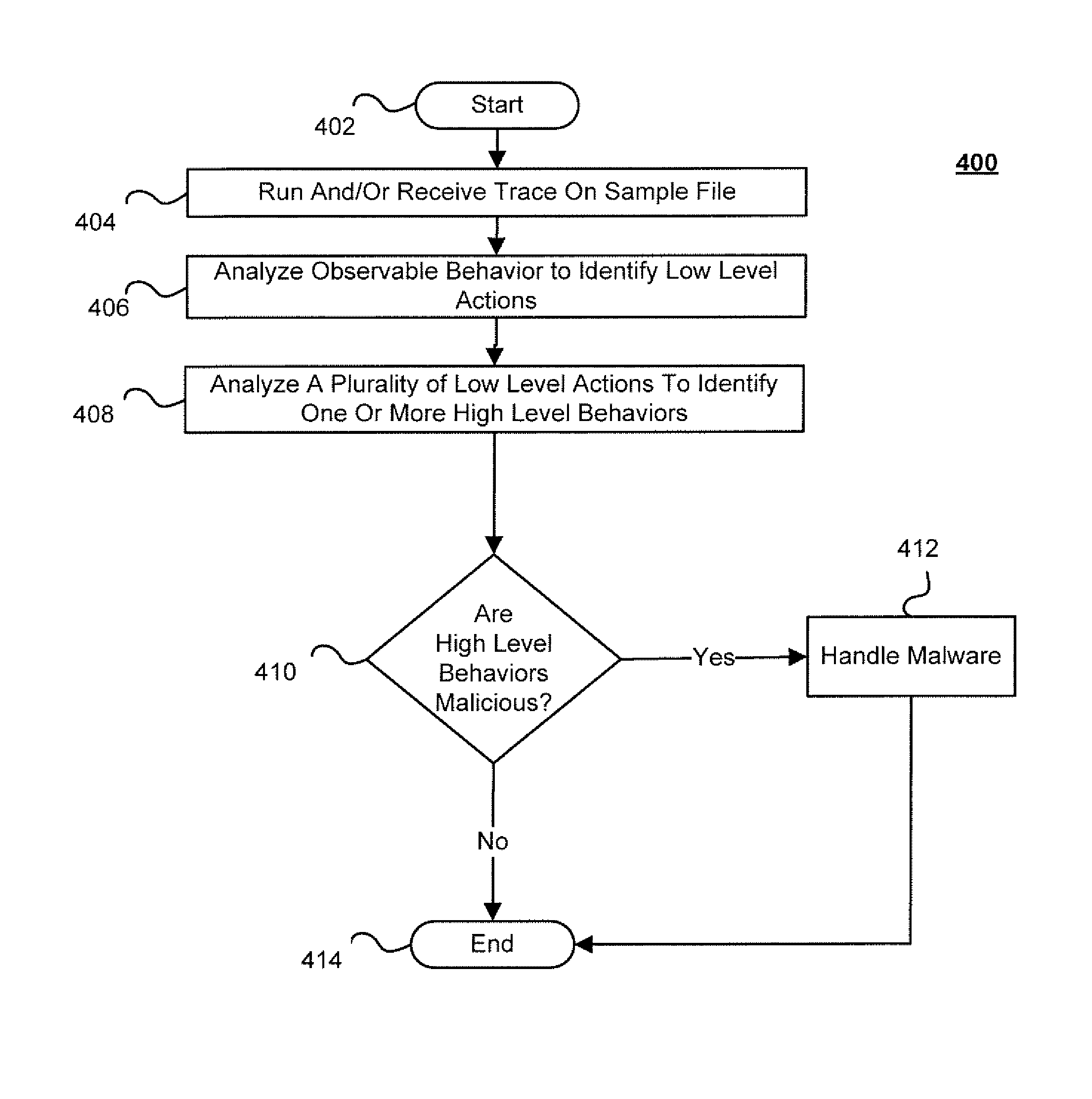
Techniques for behavior based malware analysis
ActiveUS8555385B1Avoid associationMemory loss protectionUnauthorized memory use protectionMalware analysisComputer science
Techniques for behavior based malware analysis are disclosed. In one particular exemplary embodiment, the techniques may be realized as a method for behavior based analysis comprising receiving trace data, analyzing, using at least one computer processor, observable events to identify low level actions, analyzing a plurality of low level actions to identify at least one high level behavior, and providing an output of the at least one high level behavior.
Owner:CA TECH INC
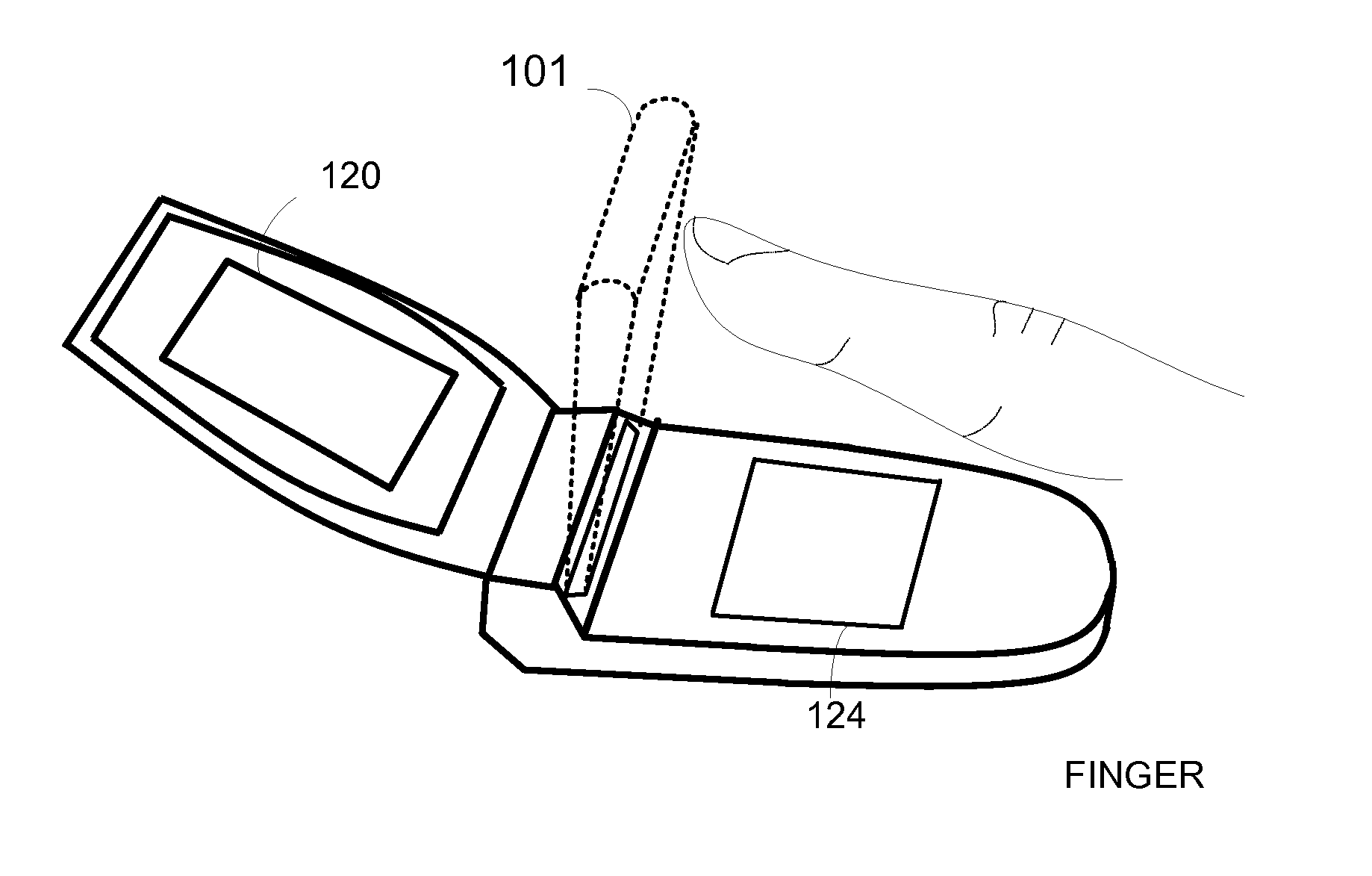
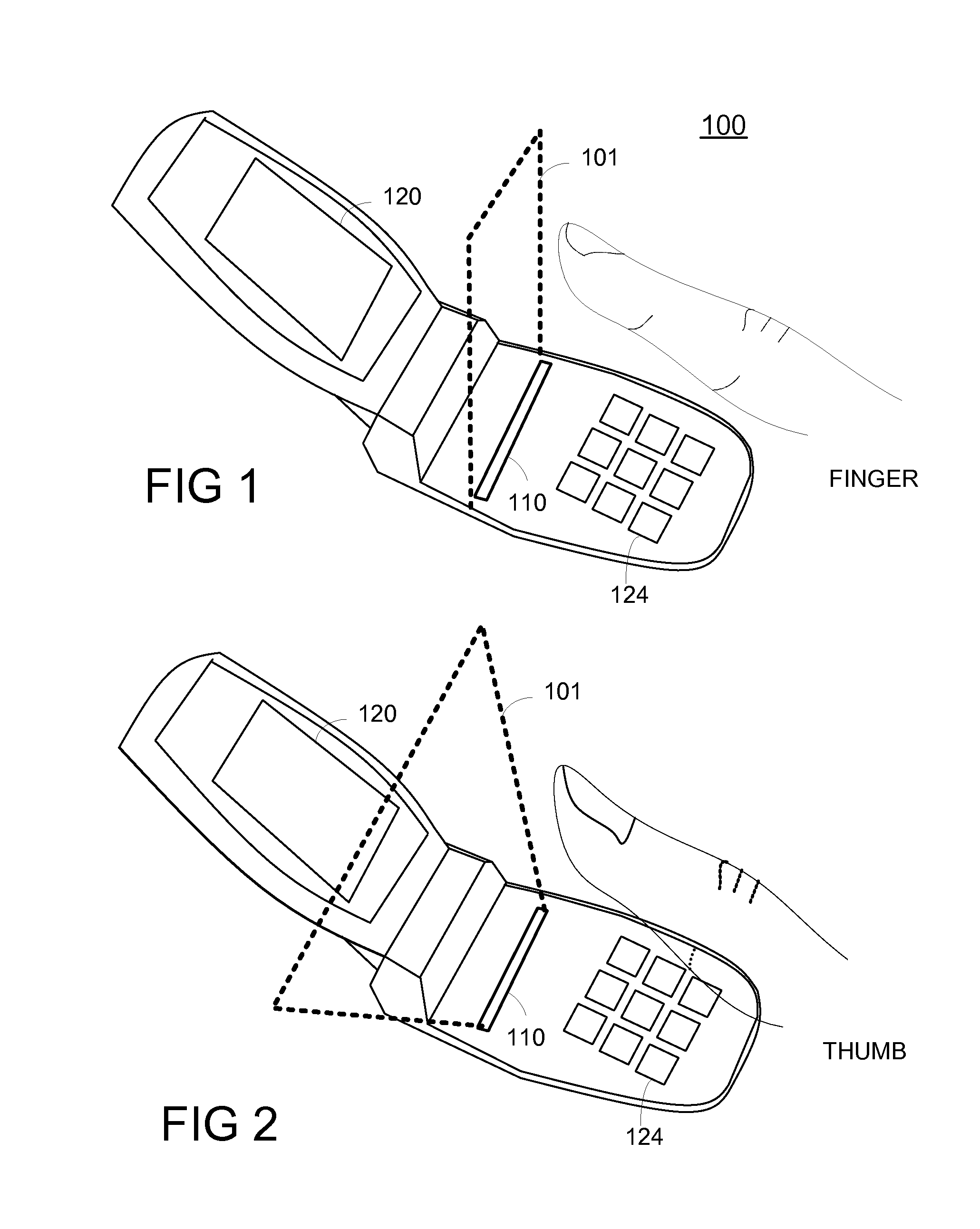
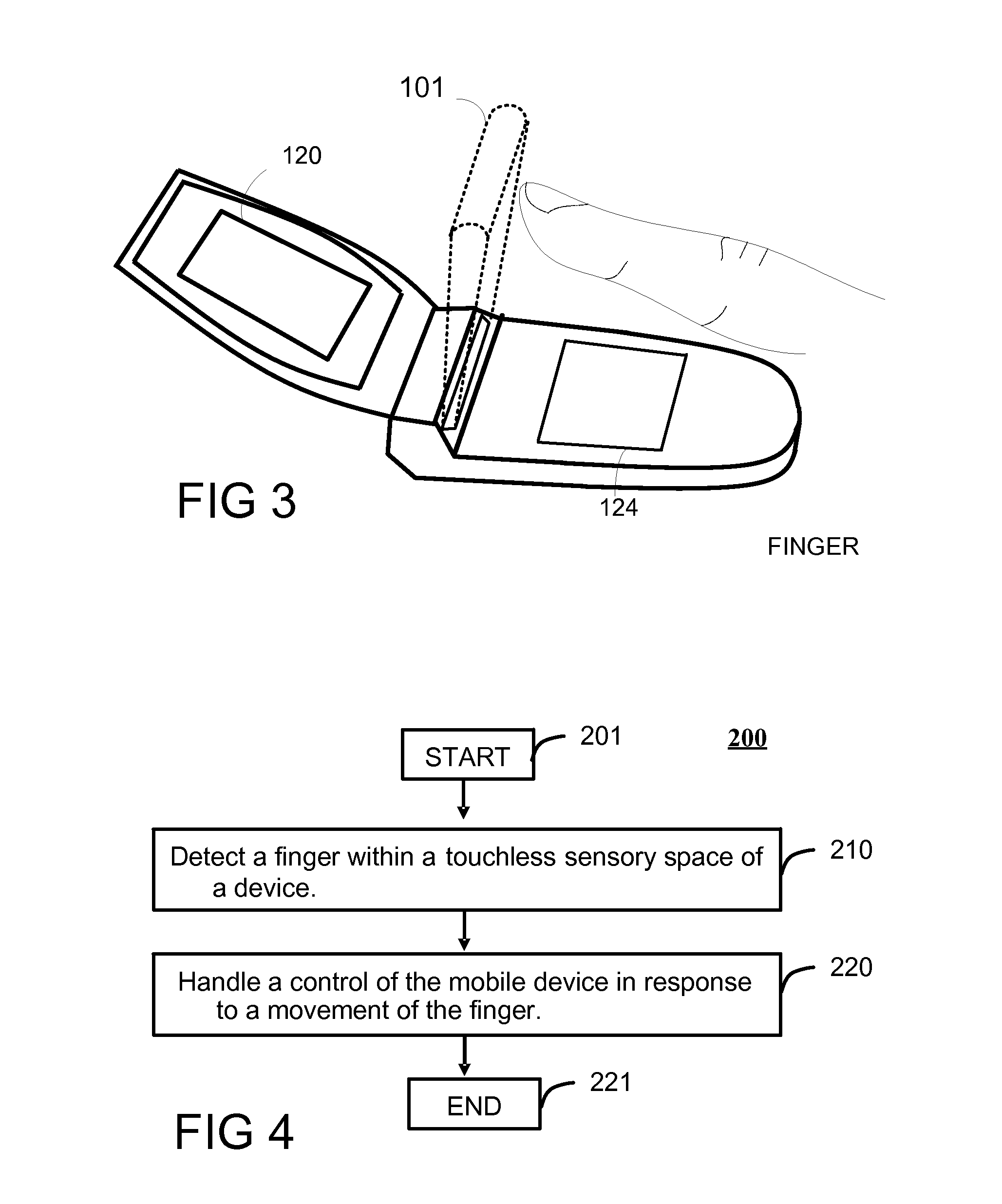
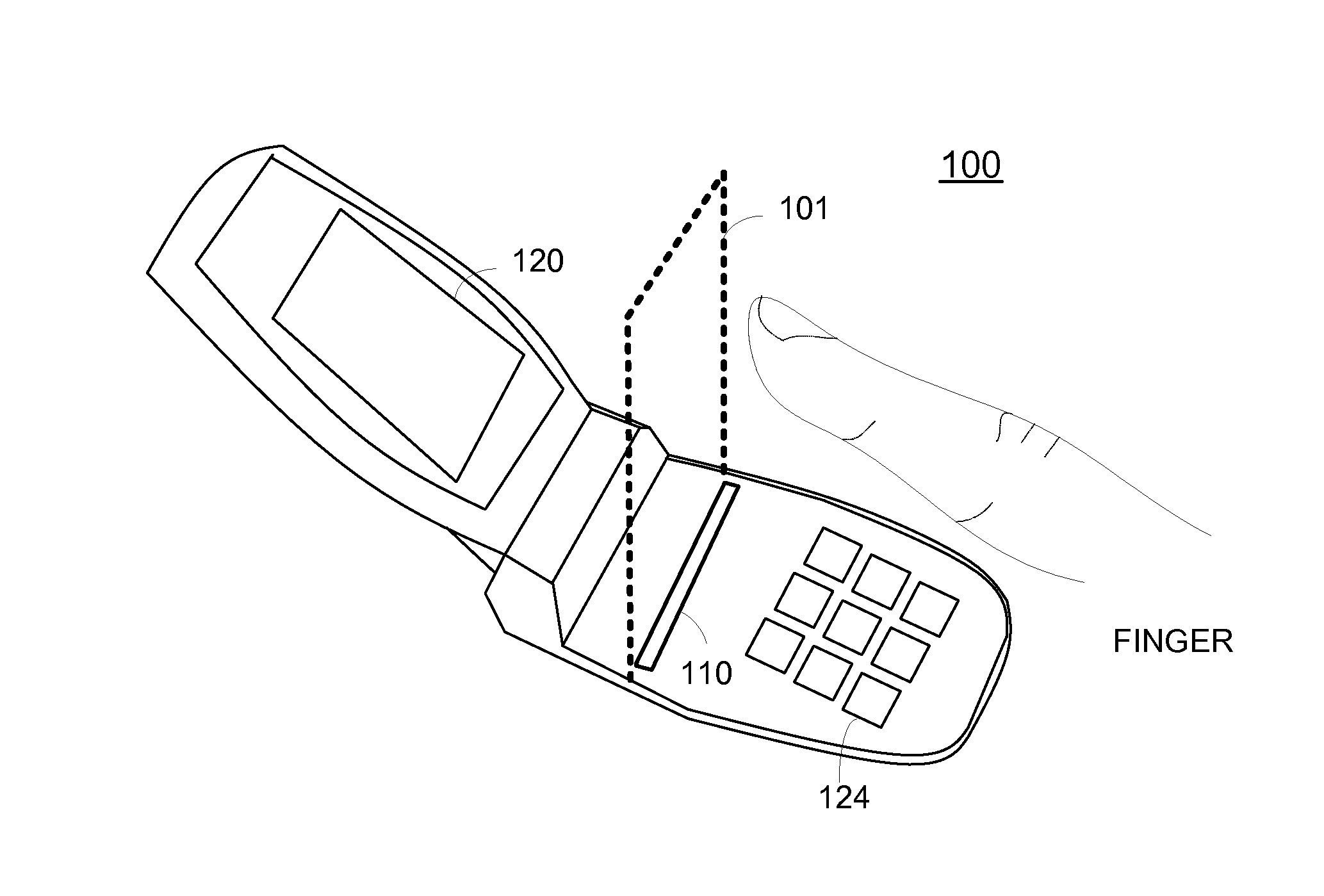
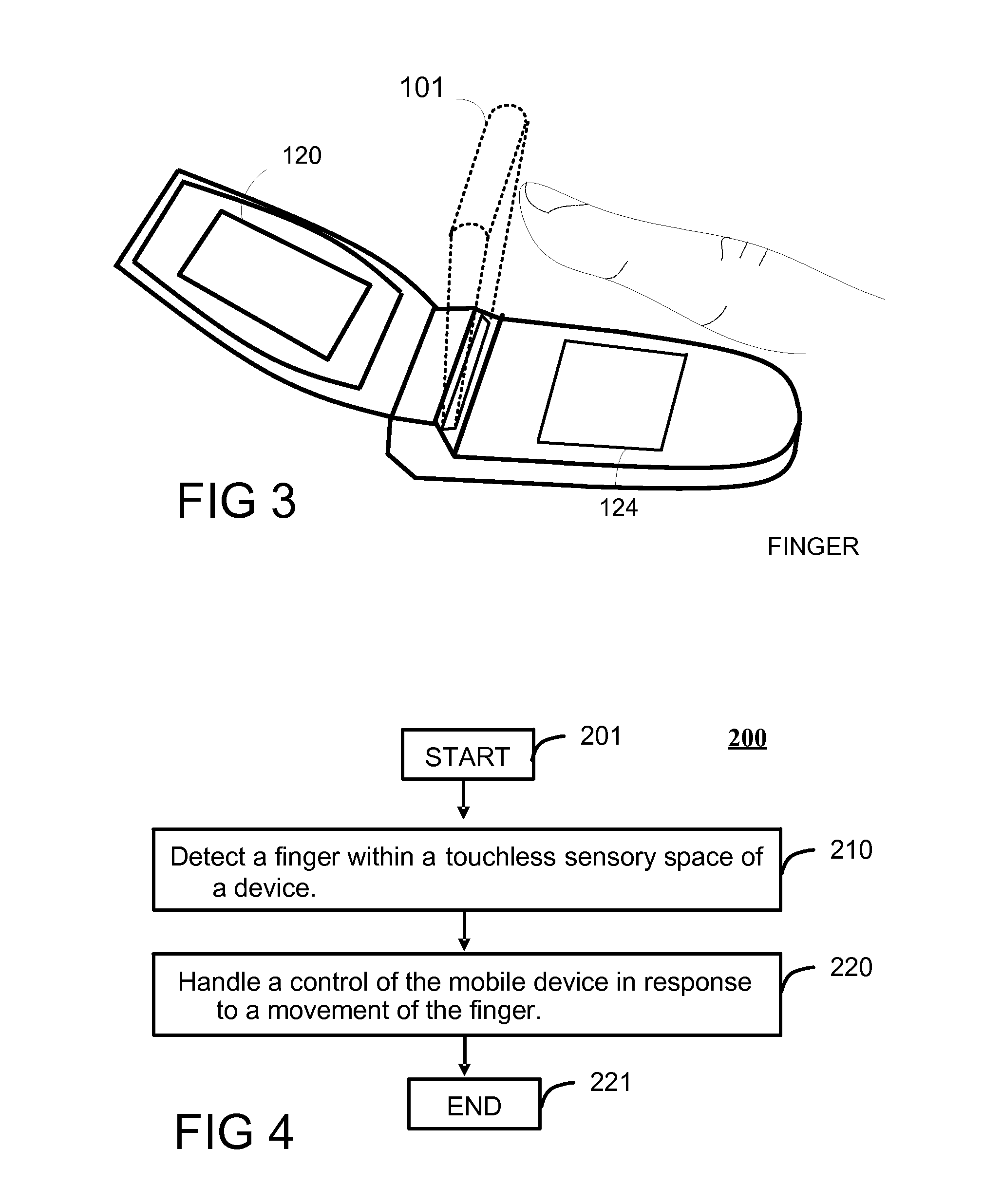
Method and Apparatus for Touchless Control of a Device
InactiveUS20080059915A1Avoid associationCathode-ray tube indicatorsInput/output processes for data processingEngineeringFinger movement
A touchless sensing unit (110) and method (200) for operating a device via touchless control is provided. The method can include detecting (210) a finger (310) within a touchless sensory space (101), and handling (220) a control of the device (100) in accordance with a movement of the finger. A first finger movement can be recognized for acquiring a control, and a second finger movement for selecting a control. The method can include estimating (230) a location of the finger in the touchless sensory space for acquiring the control, and identifying a finger movement (250) of the finger at the location for selecting the control.
Owner:NAVISENSE
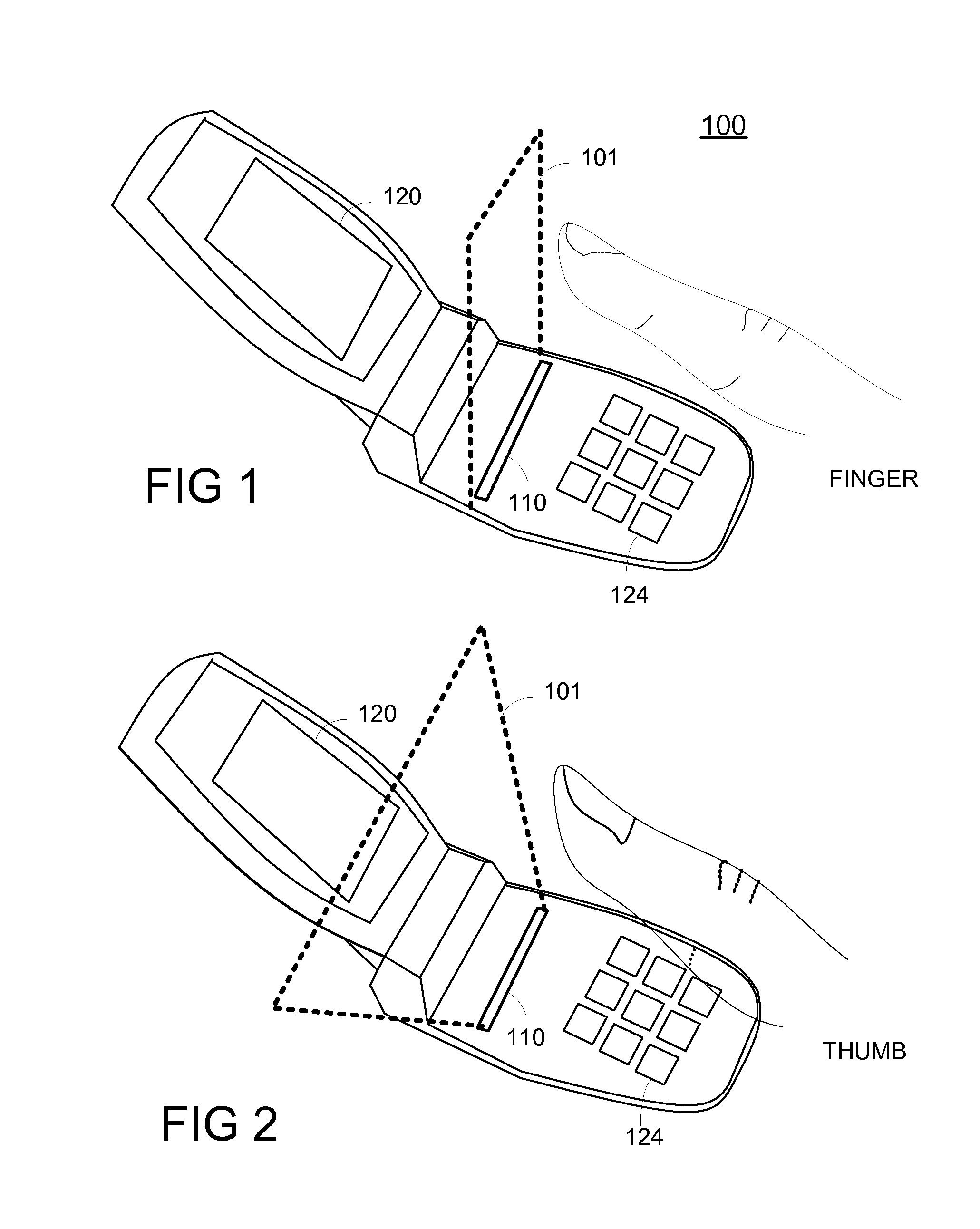
Method and apparatus for touchless control of a device
InactiveUS8316324B2Avoid associationCathode-ray tube indicatorsInput/output processes for data processingEngineeringFinger movement
Owner:NAVISENSE
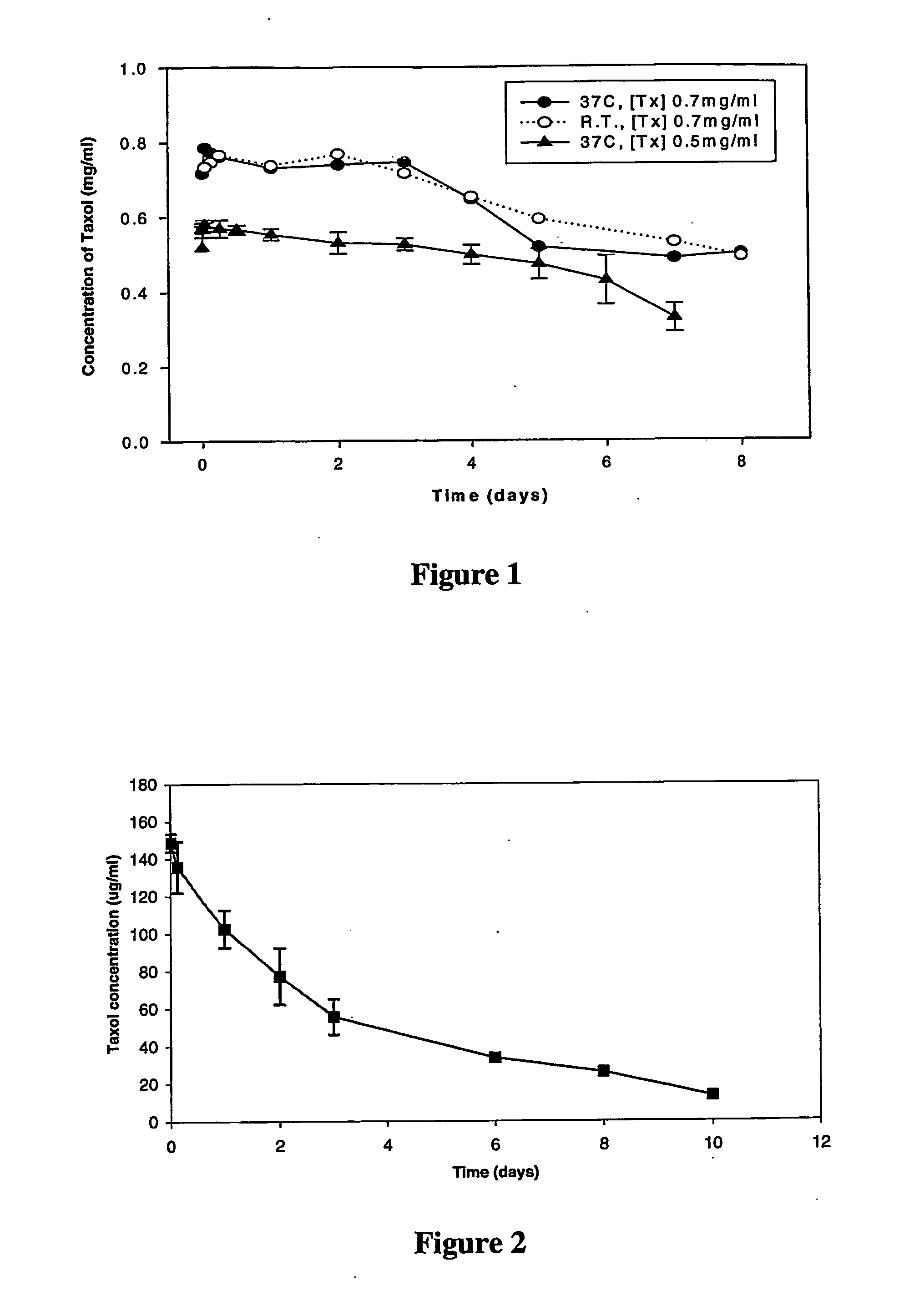
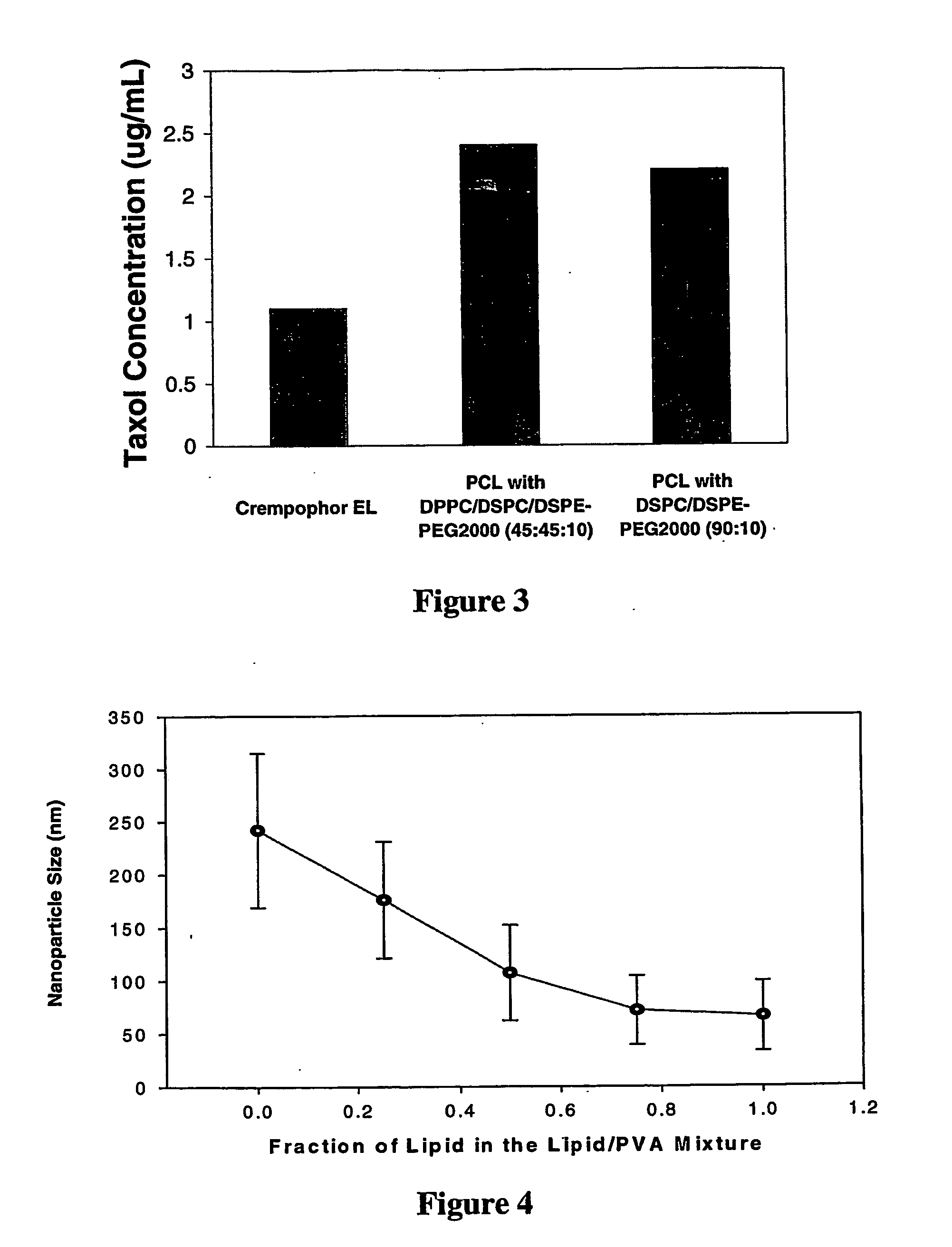
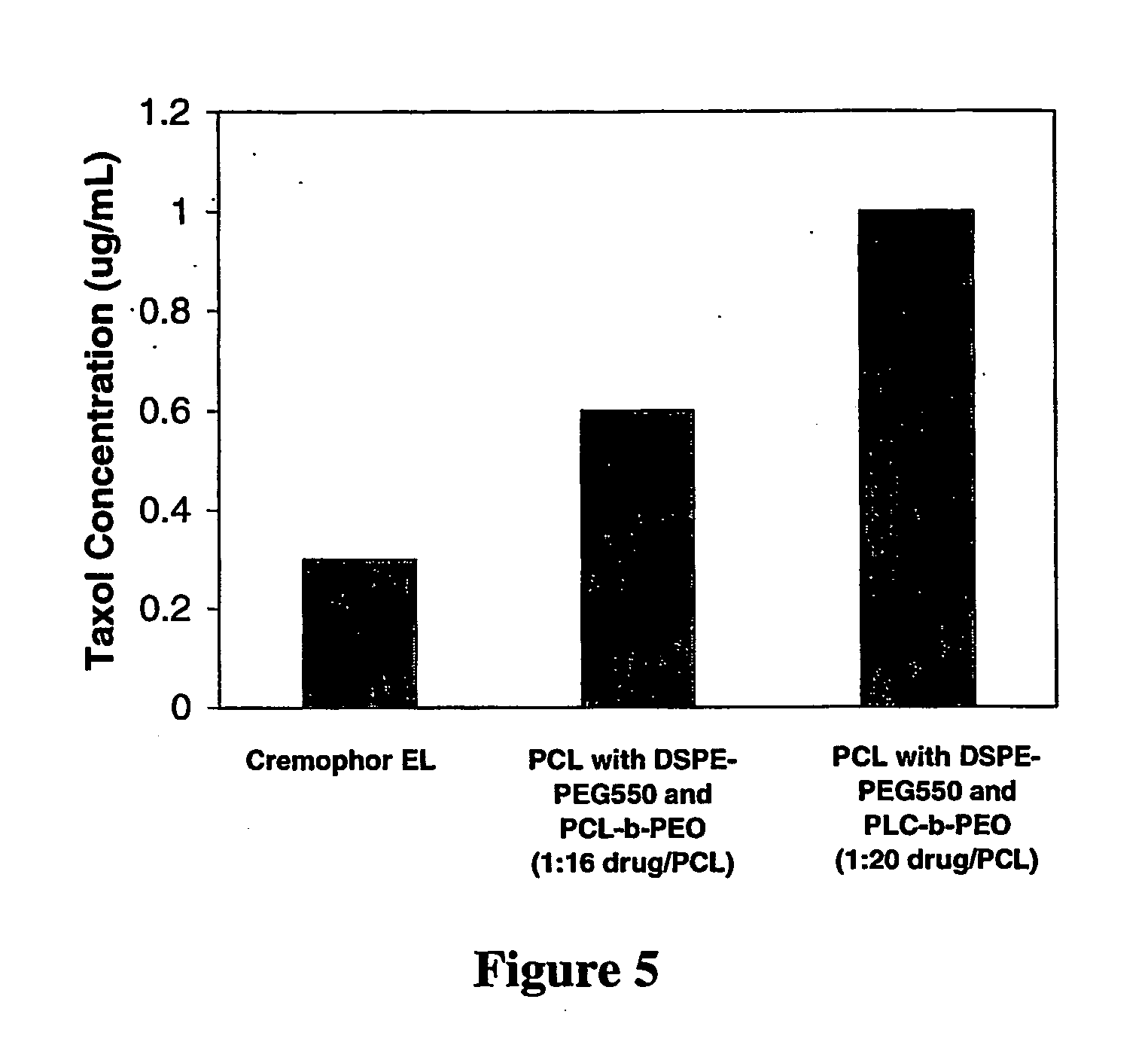
Polymer-lipid delivery vehicles
InactiveUS20060177495A1Improve pharmacokineticsEfficient deliveryHeavy metal active ingredientsOrganic active ingredientsLipid formationHydrophobic polymer
Delivery vehicles comprising nanoparticles which are composed of: (a) a biodegradable hydrophobic polymer forming a core, and; (b) an outer amphiphilic layer surrounding the polymer core containing a stabilizing lipid are suitable for delivering active agents.
Owner:CELATOR PHARMA INC
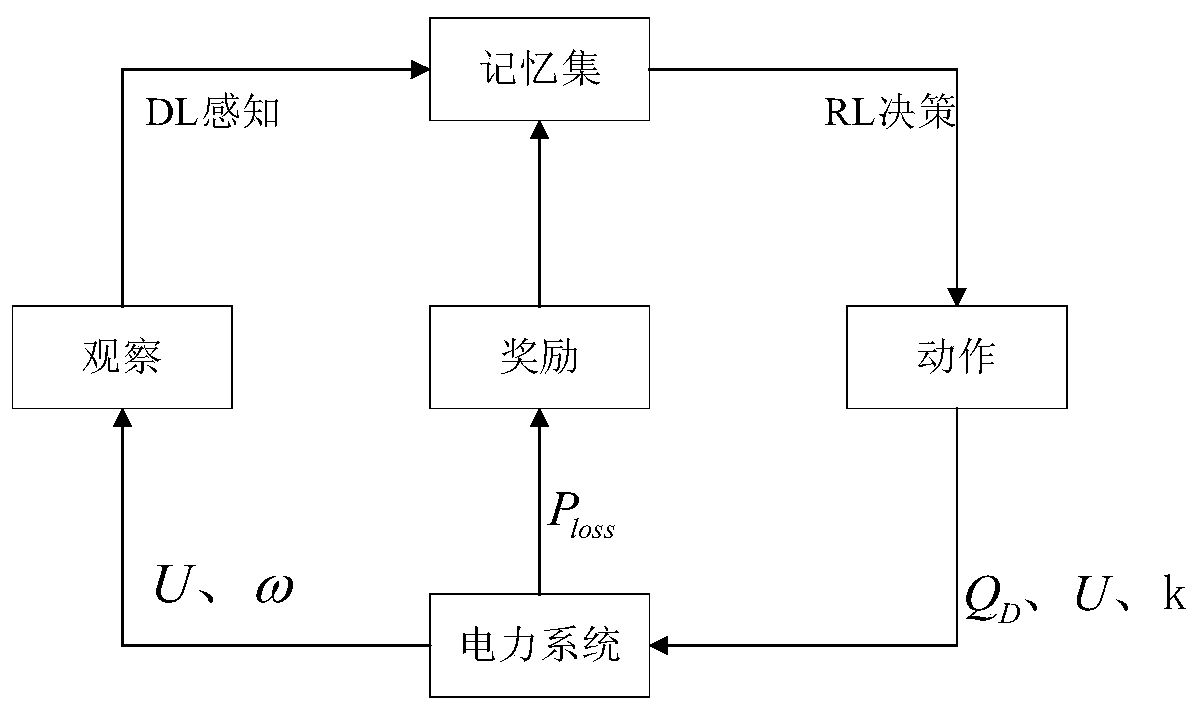
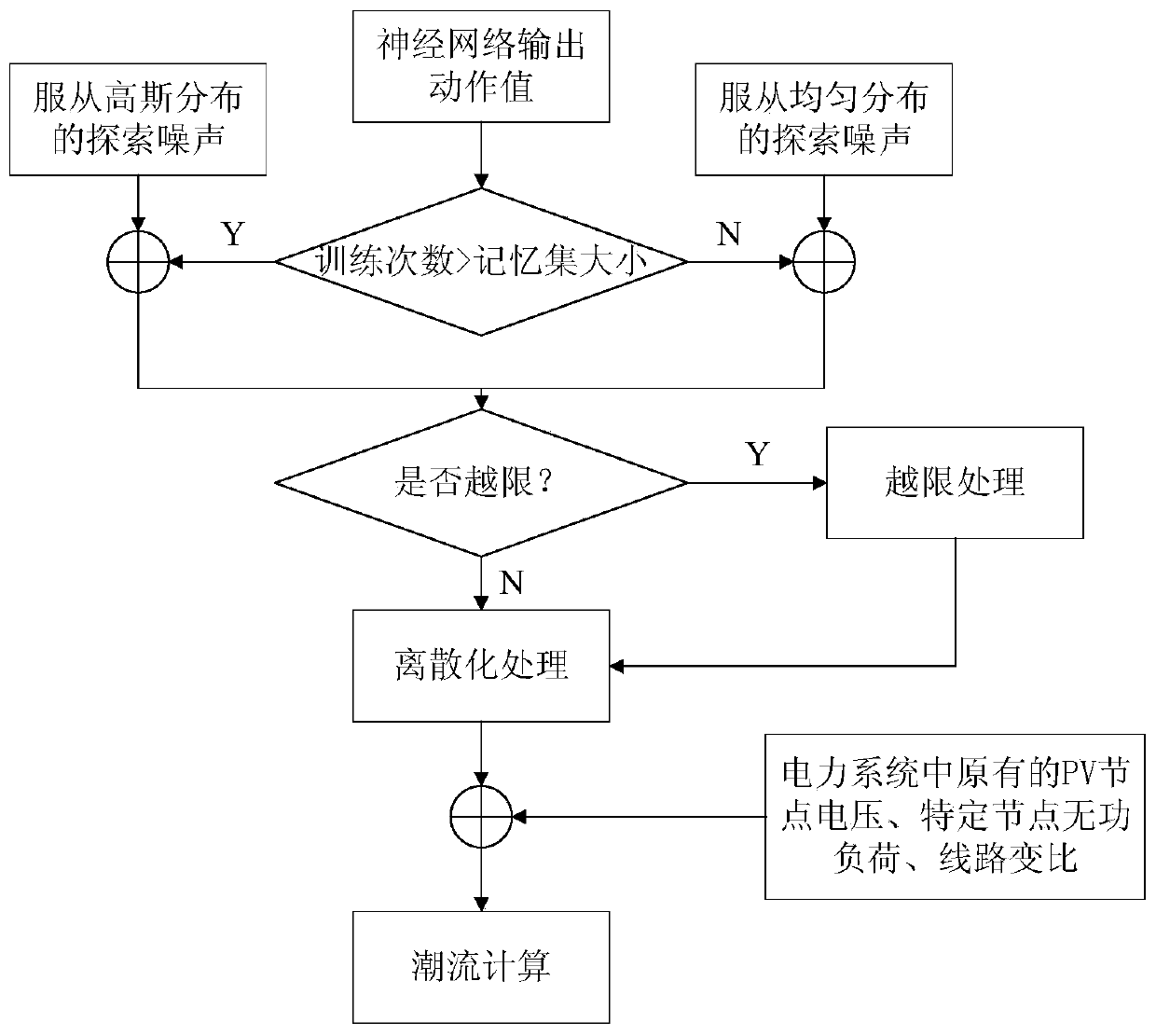
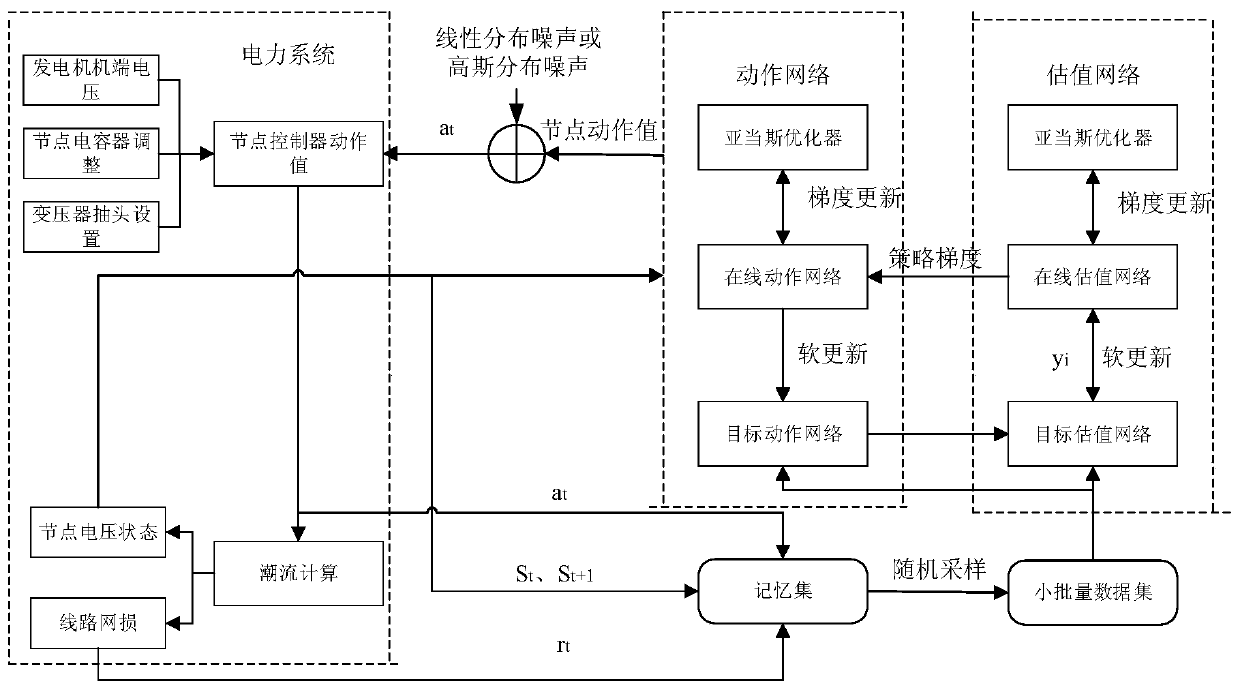
Power system reactive power optimization method based on depth determination strategy gradient reinforcement learning
ActiveCN110535146AAchieve information exchangeImprove power utilizationReactive power adjustment/elimination/compensationReactive power compensationTerminal voltageTransformer
The invention provides a power system reactive power optimization method based on depth determination strategy gradient reinforcement learning. A deterministic depth gradient strategy algorithm is applied to the traditional power system reactive power optimization problem. The voltage state of the power system is sensed through a depth neural network, a corresponding action decision is then made by using a reinforcement learning method, a correct generator terminal voltage adjustment action, a node capacitor bank switching action and a transformer tapping point adjustment action are made to adjust reactive power distribution in the power system, the active power network loss of the power system is minimized. As the neural network is divided into an online network and a target network, association between parameter updating and adjacent training in each training process of the neural network is avoided, and the problem that reactive power optimization of the power system is caught in local optimization is avoided. On the premise of conforming to the security constraint of the power system, the economical efficiency of the operation of the power system is improved by reducing the network loss of the power system.
Owner:HARBIN INST OF TECH +1
Elastic plastics blended antioxidation modified bituminous water-proof coiled material
InactiveCN1354203AGood low temperature flexibilityImprove high temperature resistanceOther chemical processesBuilding insulationsBituminous waterproofingThermoplastic elastomer
The present invention relates to a modified water-proofing asphalt roll material (called SA roll material for short), and is characterized by that in the raw material formula of asphalt 4-15% of thermoplastic elastomer polystyrene-butadiene-styrene block copolymer (SBS), 3-12% of atactic polypropylene (APP), 1-8% of light shielding agent, 0.05-3% of antioxidant, 0.05-3% of light stabilizer and 0.05-3% of UV absorbing agent. Said water-proofing roll material possesses low-temp. resistance, high-temp. resistance. UV-resisting property and good ageing resistance.
Owner:CHONGQING CITY NEW TYPE WATER PROOFING MATERIAL
Cement admixture and cement composition
InactiveUS6919388B2Stable maintenanceImprove the level ofOrganic chemistryInksMaterials scienceUltimate tensile strength
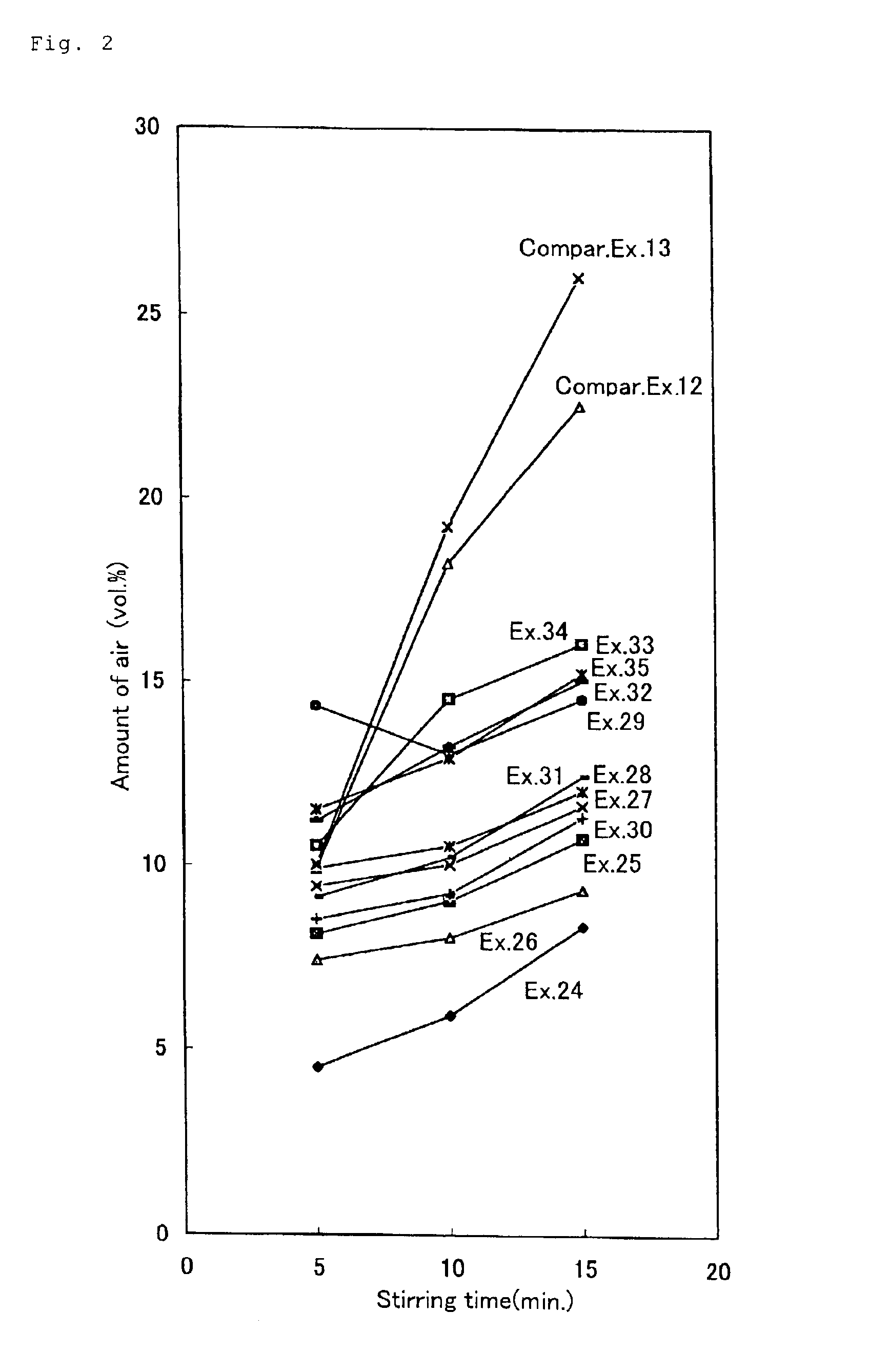
The admixtures for a cementitious composition of the invention, which have the above-mentioned constitutions, can suitably be used in cement pastes, mortar, concrete and like cement compositions and can stabilize the amount of air entrained with the lapse of time and thus facilitate the quality control of cement compositions and, further, can improve the workability of cement compositions owing to their excellent dispersing capacities. The cement compositions of the invention which comprise such admixture for a cementitious composition are excellent in water-reducing ability and workability and can give hardened products excellent in strength and durability and, further, can stably maintain the amount of air entrained without allowing increases in the amount of air even when the time of kneading is prolonged in the production.
Owner:NIPPON SHOKUBAI CO LTD
Method for accessing access pint (AP) into access controller (AC) in local area network, AC and AP
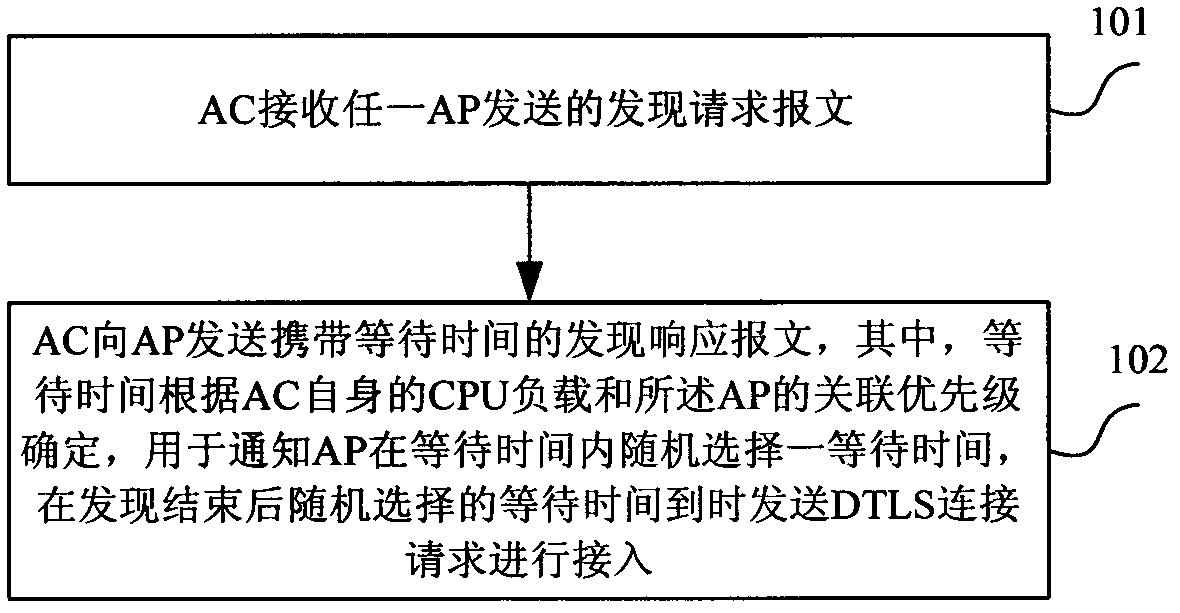
ActiveCN102316549AEasy maintenanceAvoid associationAssess restrictionNetwork topologiesCpu loadComputer science
The invention discloses a method for accessing an access pint (AP) into an access controller (AC) in a local area network, which comprises the following steps that: the AC receives discovery request messages sent by any one AP and sends discovery response messages carrying the waiting time to the AP, wherein the waiting time is determined according to the self central processing unit (CPU) load of the AC and the association priority of the AP and is used for notifying the AP to randomly select a waiting time in the waiting time, and datagram transport layer security (DTLS) connection requests are sent when the randomly selected waiting time is reached after the discovery completion for carrying out the access. Based on the same invention idea, the invention also provides the AC and the AP. The problem of simulation correlation of the AC by a large number of APs can be avoided, and convenience is brought for the network maintenance.
Owner:NEW H3C TECH CO LTD
Target track optimization method based on dual-fusion maximum entropy fuzzy clustering JPDA
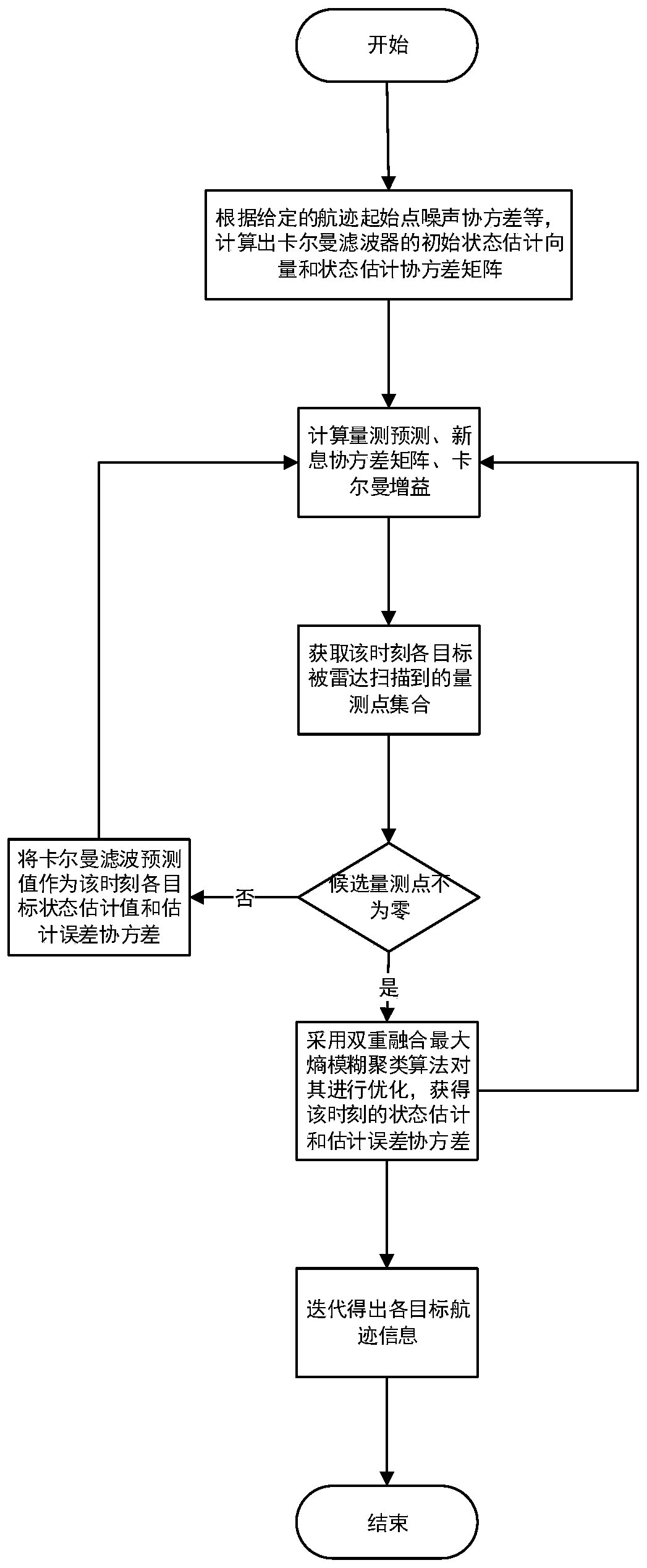
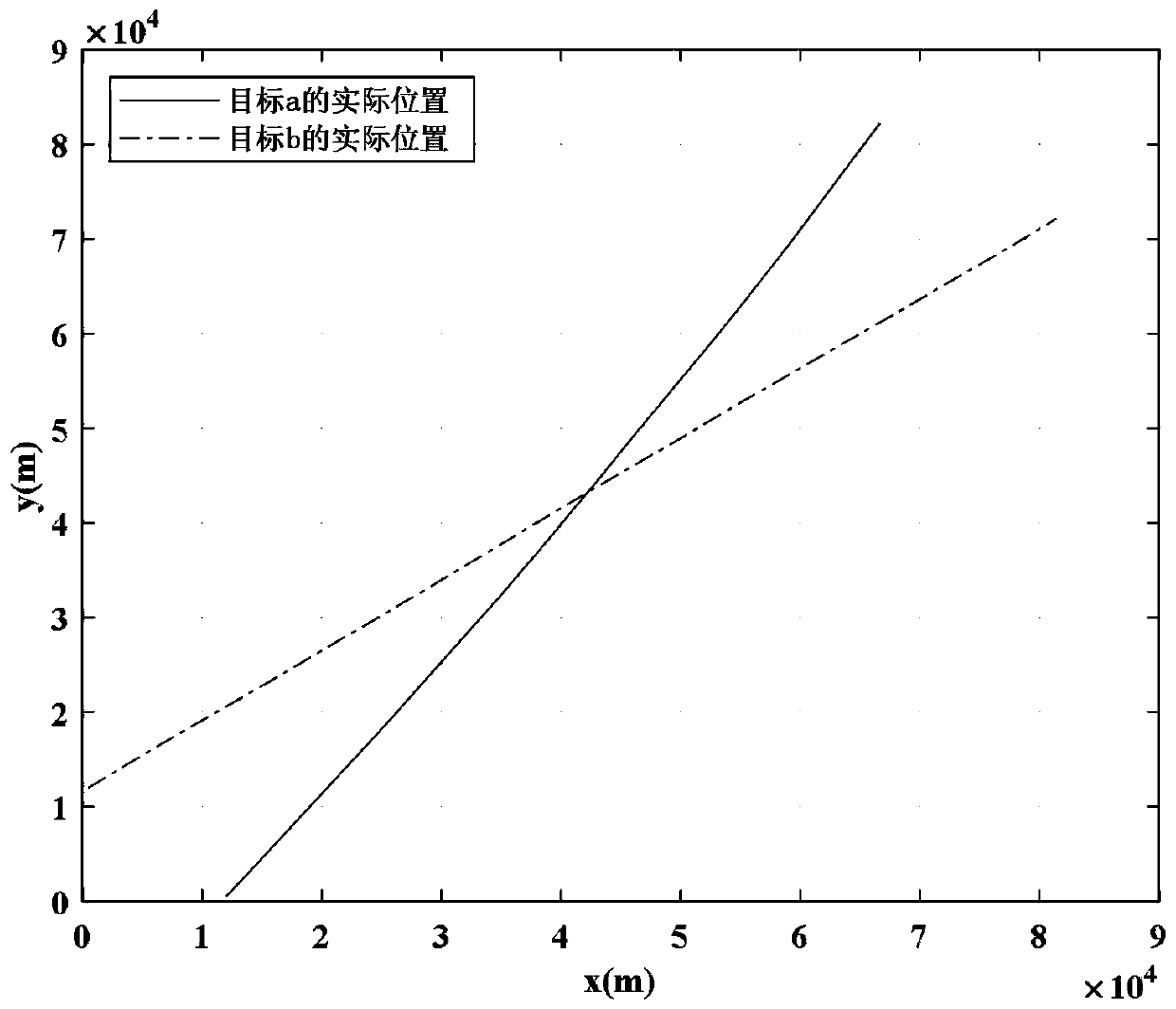
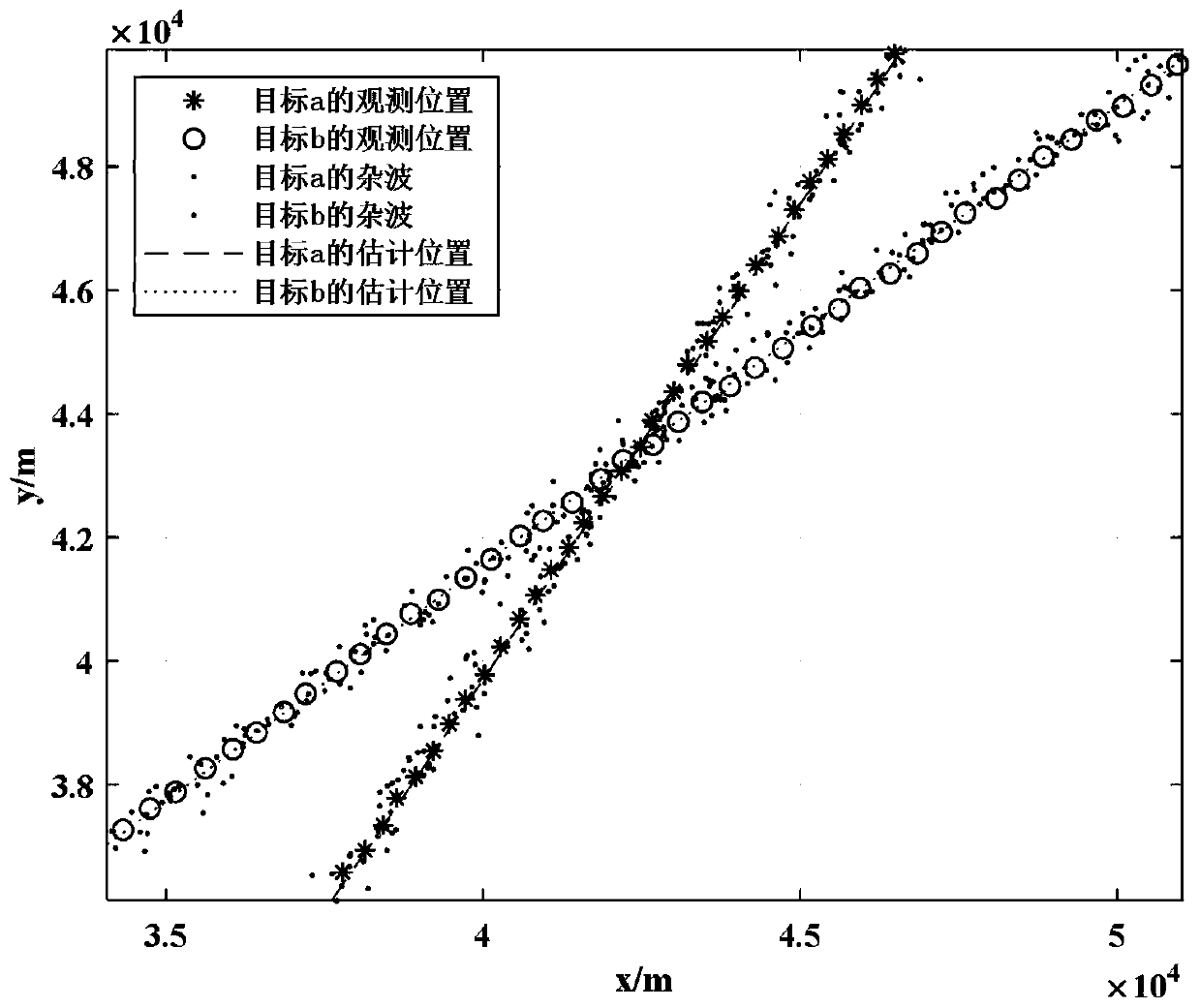
ActiveCN111007495AAvoid associationImprove the speed of associationInternal combustion piston enginesRadio wave reradiation/reflectionKaiman filterState prediction
The invention belongs to the technical field of radar. The invention relates to a flight path optimization method, in particular to a target track optimization method based on dual-fusion maximum entropy fuzzy clustering JPDA. The method comprises the following steps: (1) performing state prediction and updating by adopting a Kalman filter on the basis of a maximum entropy fuzzy clustering method,and performing preliminary screening on a target trace point set obtained at a moment k + 1according to an elliptical wave gate rule during scanning and tracking; (2) multiplying the measurement membership degree taking the wave gate center as the clustering center by the corresponding position of the wave gate membership degree taking the effective measurement data as the clustering center to obtain the bidirectional membership degree between each effective measurement and all the wave gate centers; and (3) analyzing clutter distribution and combining the bidirectional membership degree to obtain a final association probability, obtaining state estimation and estimation error covariance of the target according to a standard JPDA algorithm filtering program, and finally iterating trackingtrack information of the target. The method is high in tracking precision, and avoids complex correlation matrix splitting.
Owner:XIDIAN UNIV
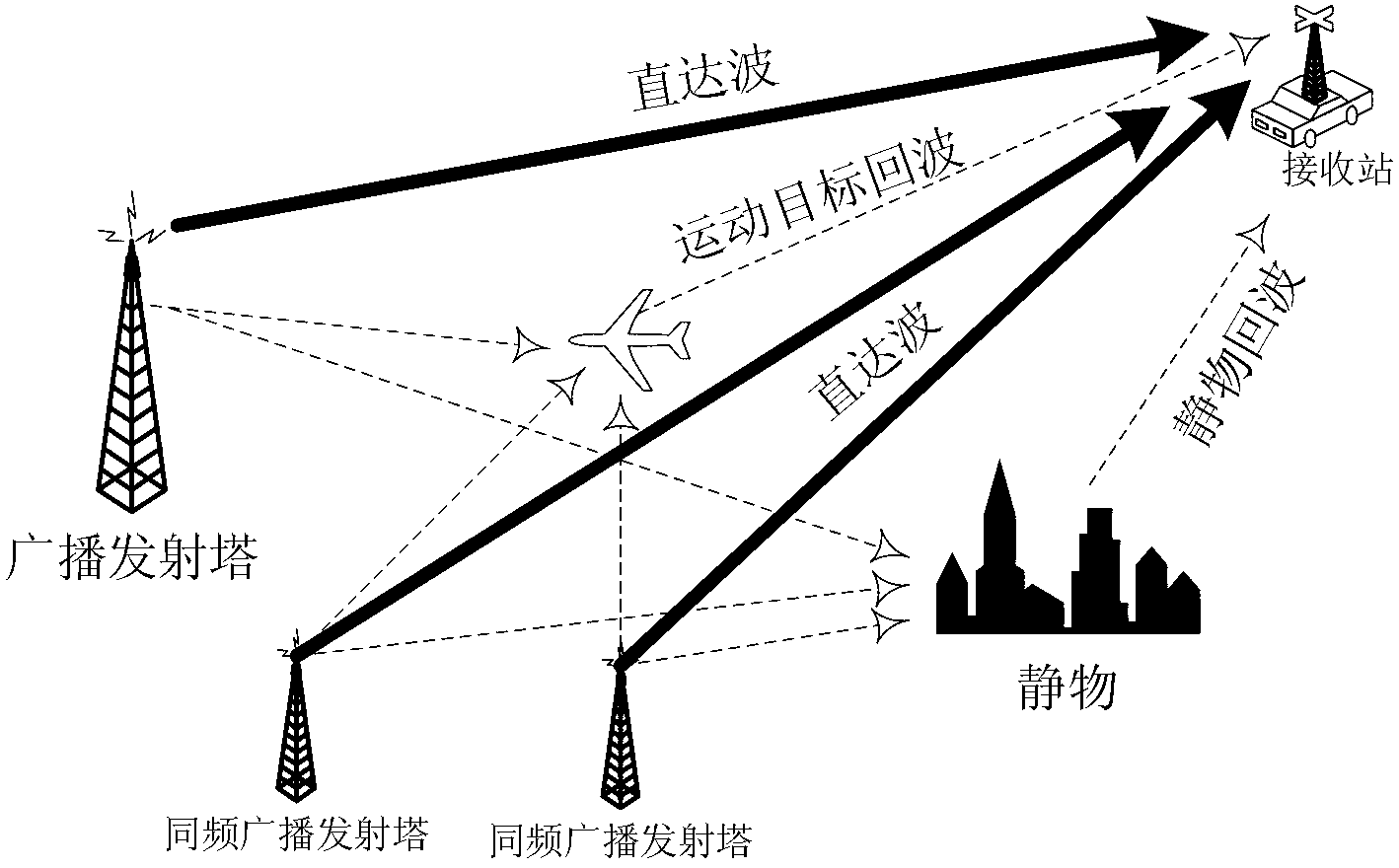
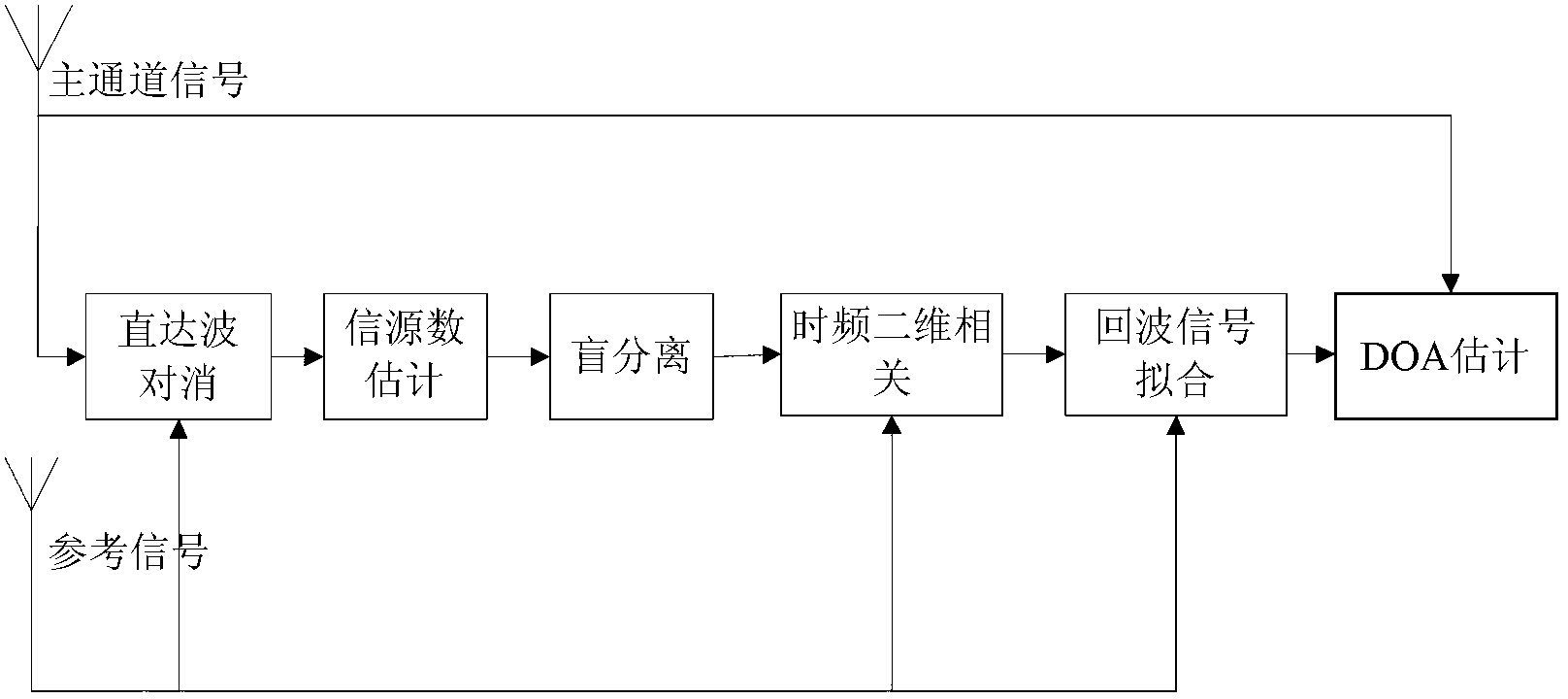
Method for estimating weak signal separation on basis of positioning for external radiation sources
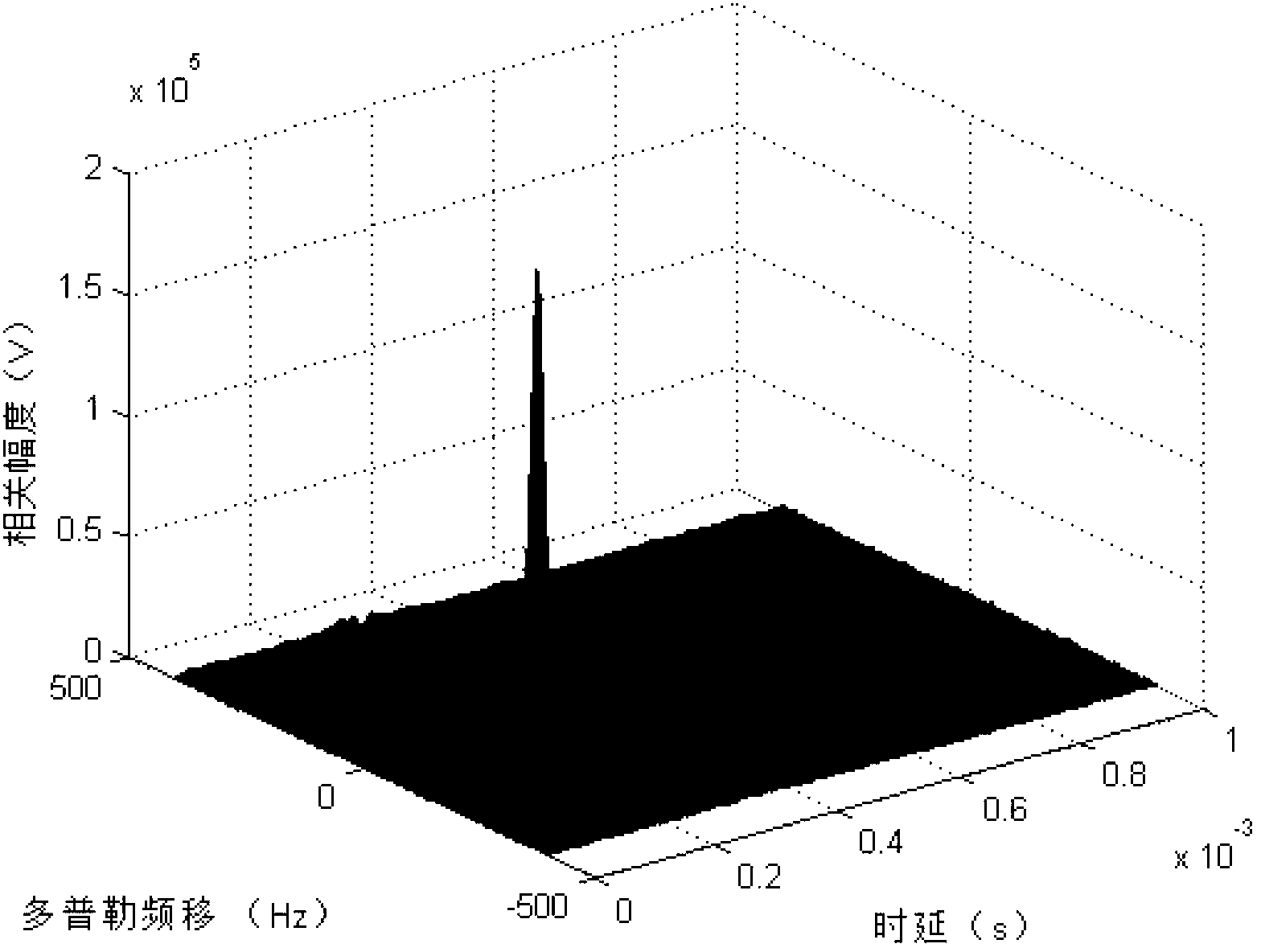
InactiveCN103235294AHelp delayDoppler shiftWave based measurement systemsMain channelSample sequence
The invention provides a method for estimating weak signal separation on the basis of positioning for external radiation sources. The method includes steps of performing direct-wave and multi-path cancellation for a sample sequence x (t) of a main channel by means of NLMS (normalized least mean square) to obtain output signals y<NLMS>(t); estimating the number of source signals of the output signals y<NLMS>(t) by an AIC (Akaike information criterion) or an MDL (minimum description length) criterion, preliminarily whitening the output signals y<NLMS>(t) to obtain whitened signals z(t), and updating a separation matrix W by an ICA (independent component analysis) algorithm to obtain M channels of estimated signals y(t); respectively performing time-frequency two-dimensional correlation for the M channels of estimated signals y<1>(t), ..., y<M>(t) and reference signals s<ref>(t); and searching a peak point in absolute correlation values phi(tau, f) corresponding to the M channels of estimated signals, and determining time delay and Doppler frequency shift which correspond to the peak point as time delay and Doppler frequency shift of a target when a signal-to-noise ratio of a certain channel of signals is larger than or equal to a threshold value.
Owner:UNIV OF ELECTRONICS SCI & TECH OF CHINA
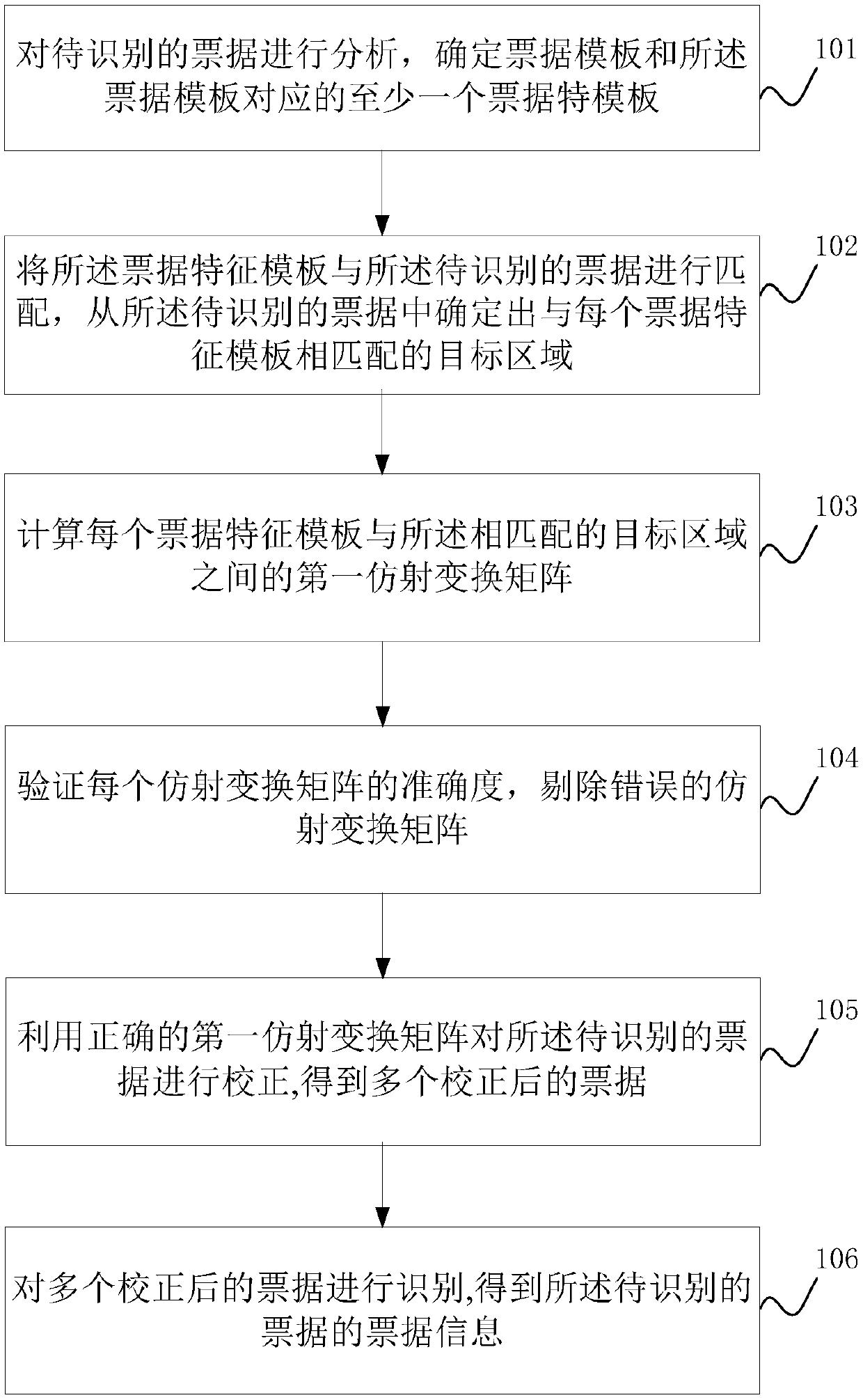
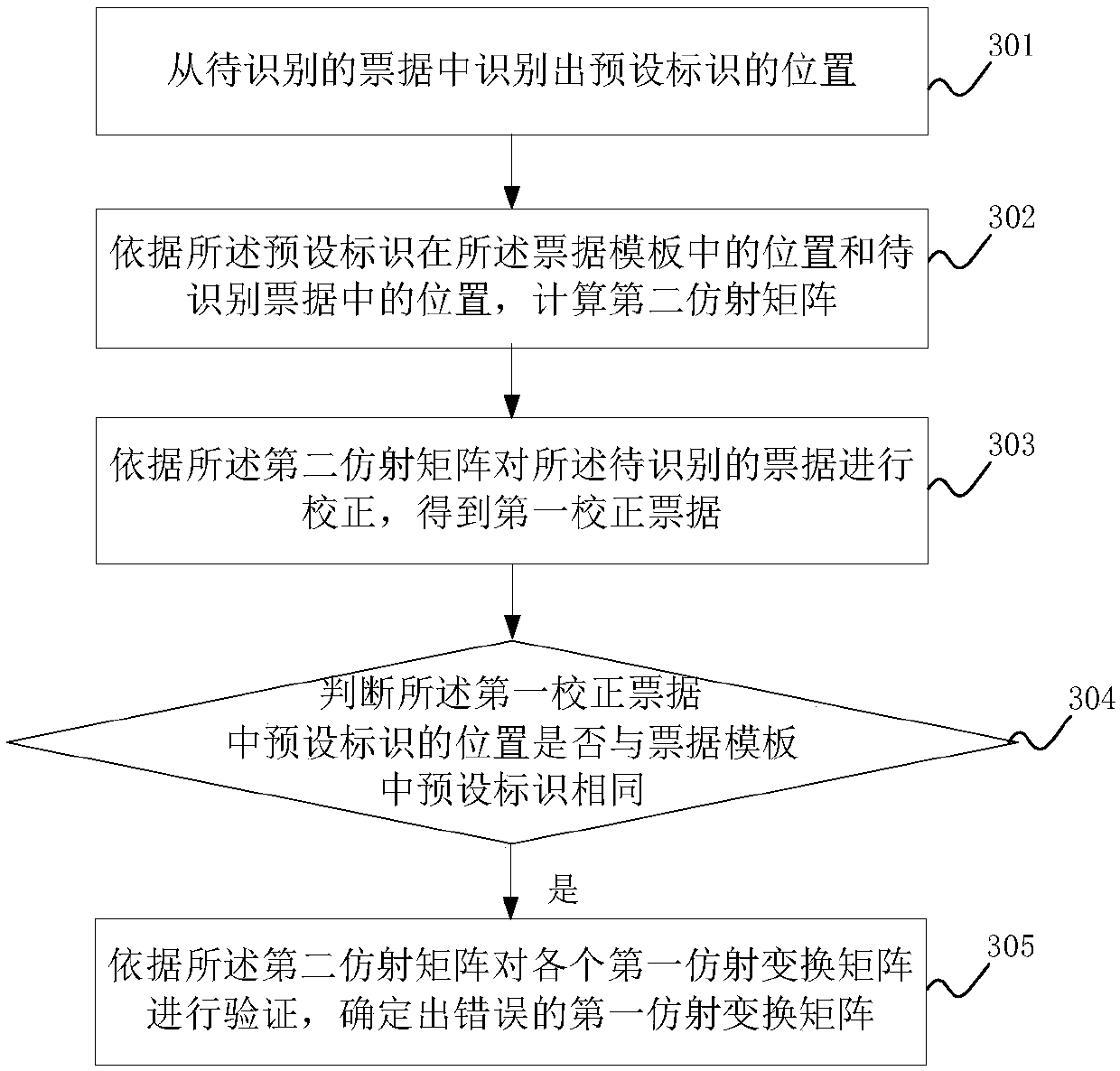
Bill identification method and device thereof
ActiveCN109658584AAchieve precise positioningImprove robustnessPaper-money testing devicesTemplate matchingComputer science
An embodiment of the invention discloses a bill identification method and a device thereof. A to-be-identified bill is corrected through a multi-characteristic template. An affine transformation matrix between the characteristic template and the to-be-identified bill is calculated according to a template matching result. Correctness of the affine transformation matrix is verified. Furthermore according to a proximity principle, which characteristic template with the corrected bill image which comprises a to-be-interrupted identification information block is determined through a distance relation between the characteristic template and an identification information block is determined, and accurate positioning of a bill surface identification information block is realized, thereby improvingrobustness of a positioning algorithm. Furthermore an algorithm correlating problem in a pipe type manner is prevented.
Owner:TAIKANG LIFE INSURANCE CO LTD +1
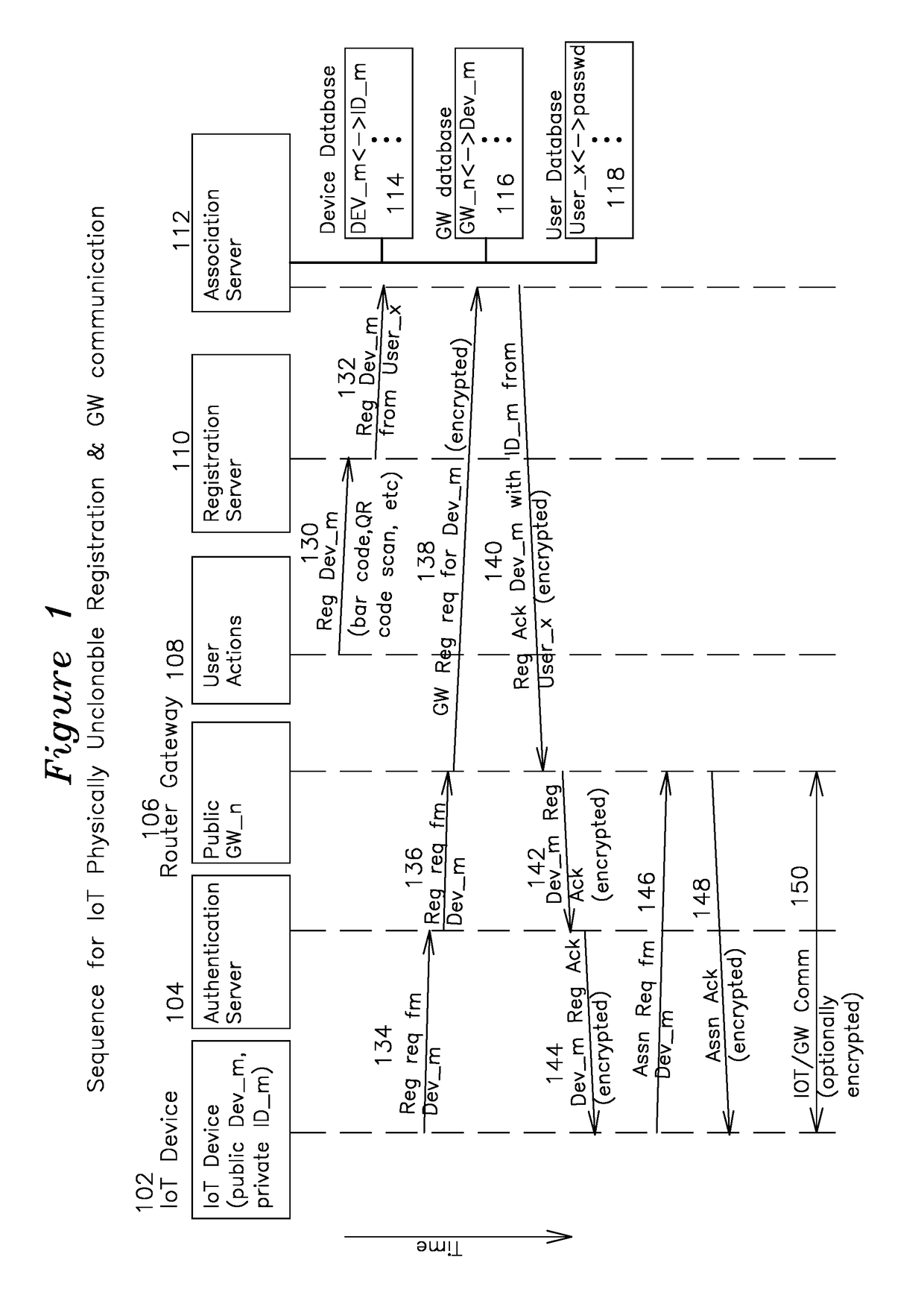
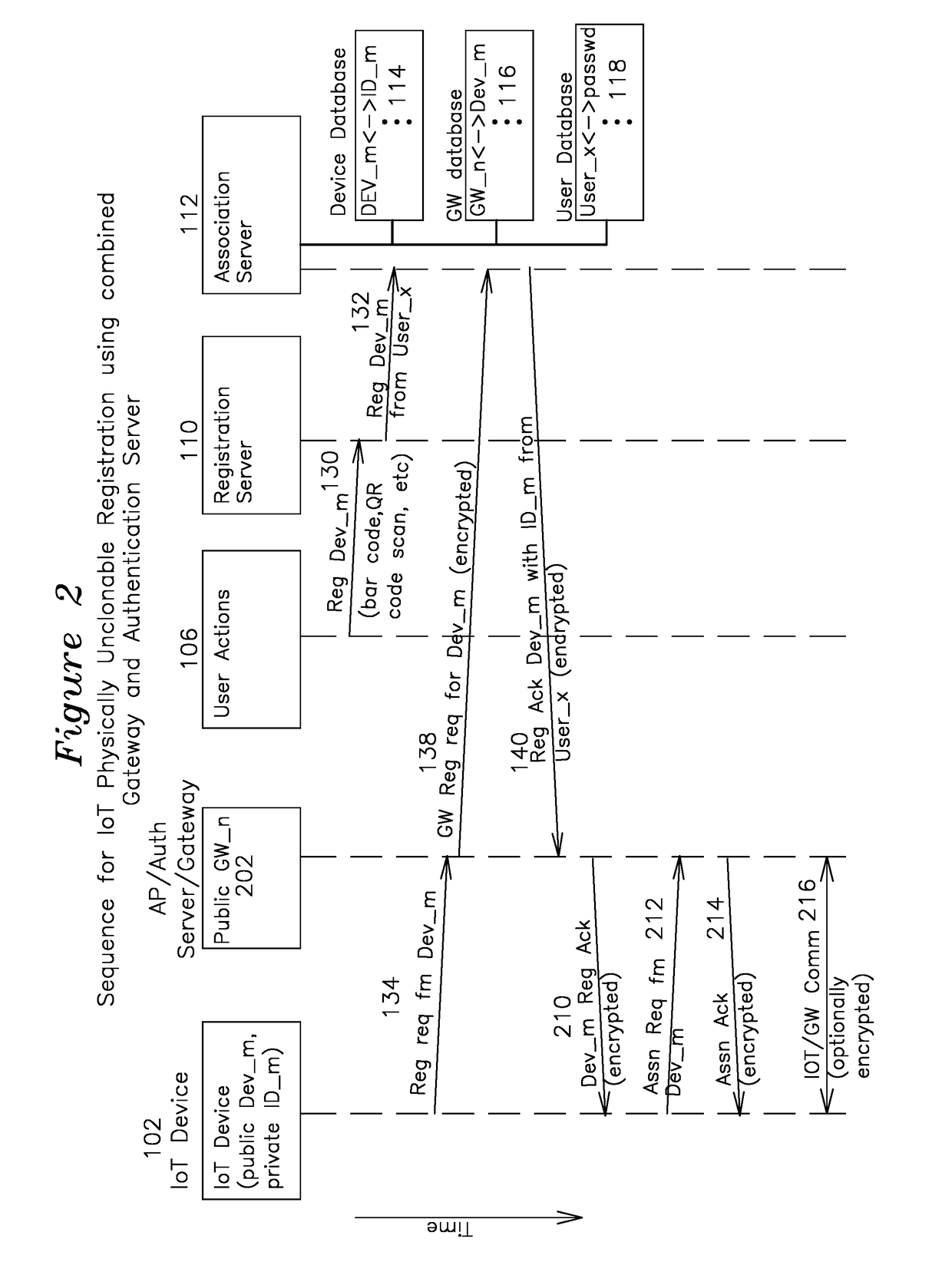
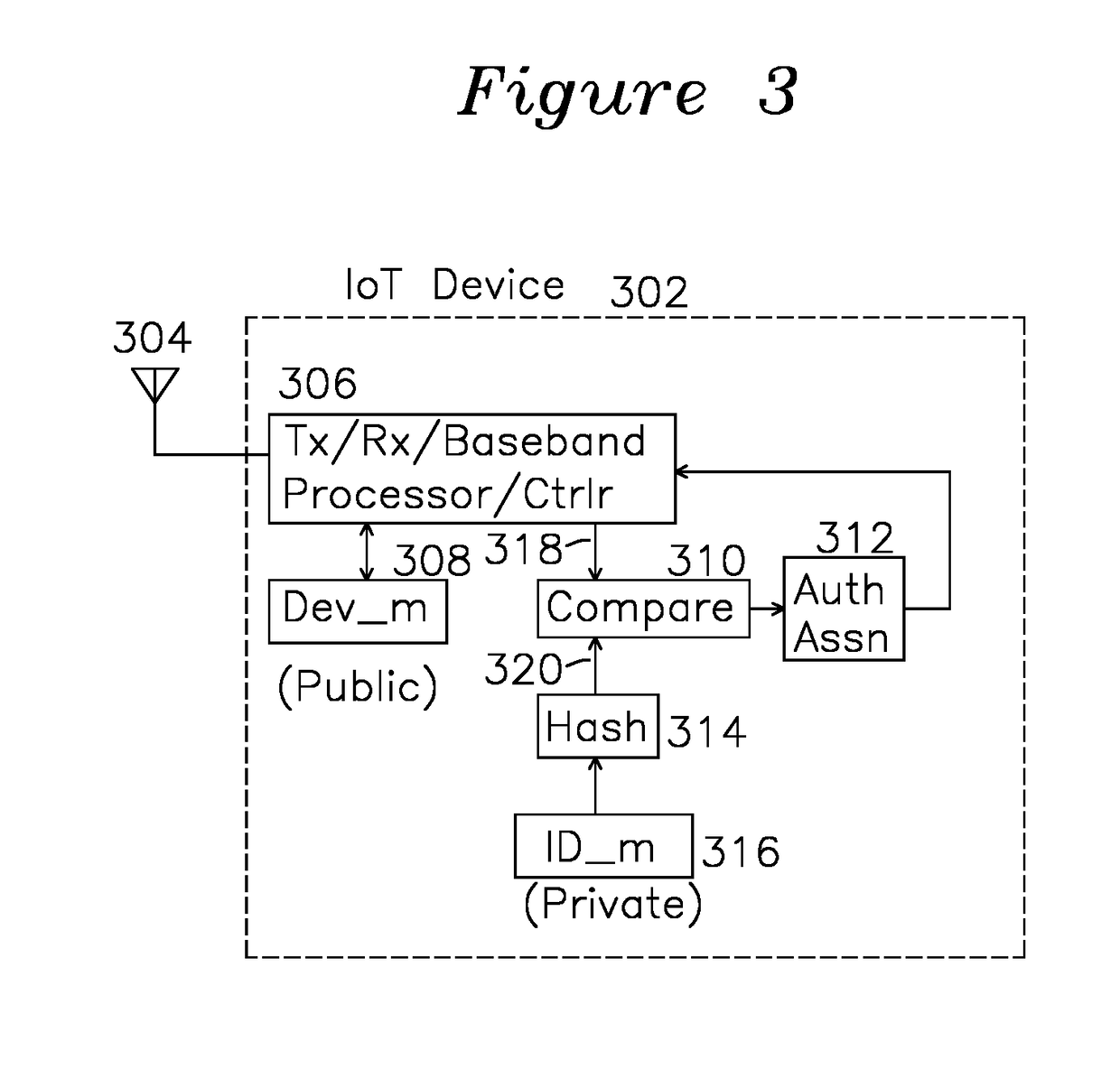
Uncloneable Registration of an Internet of Things (IoT) Device in a Network
ActiveUS20190068592A1Avoid associationTransmissionSecurity arrangementComputer securityInternet of Things
An IoT device has a public device identifier and a private device identifier, where the public device identifier is publicly available and the private device identifier is secret but kept in a secure device database as a correspondence. A registration request is sent from the IoT device to an association server in communication with the device database having an association between IoT public identifier and a corresponding IoT private identifier. The association server which receives the registration request responds with a registration acknowledgement containing, in encrypted form, the private device identifier of the original request and, optionally, the public device identifier associated with the registration request. The requesting IoT device receives the association acknowledgement, decrypts the private device identifier, compares it to its own device identifier, and if they match, sends one or more association requests.
Owner:SILICON LAB INC
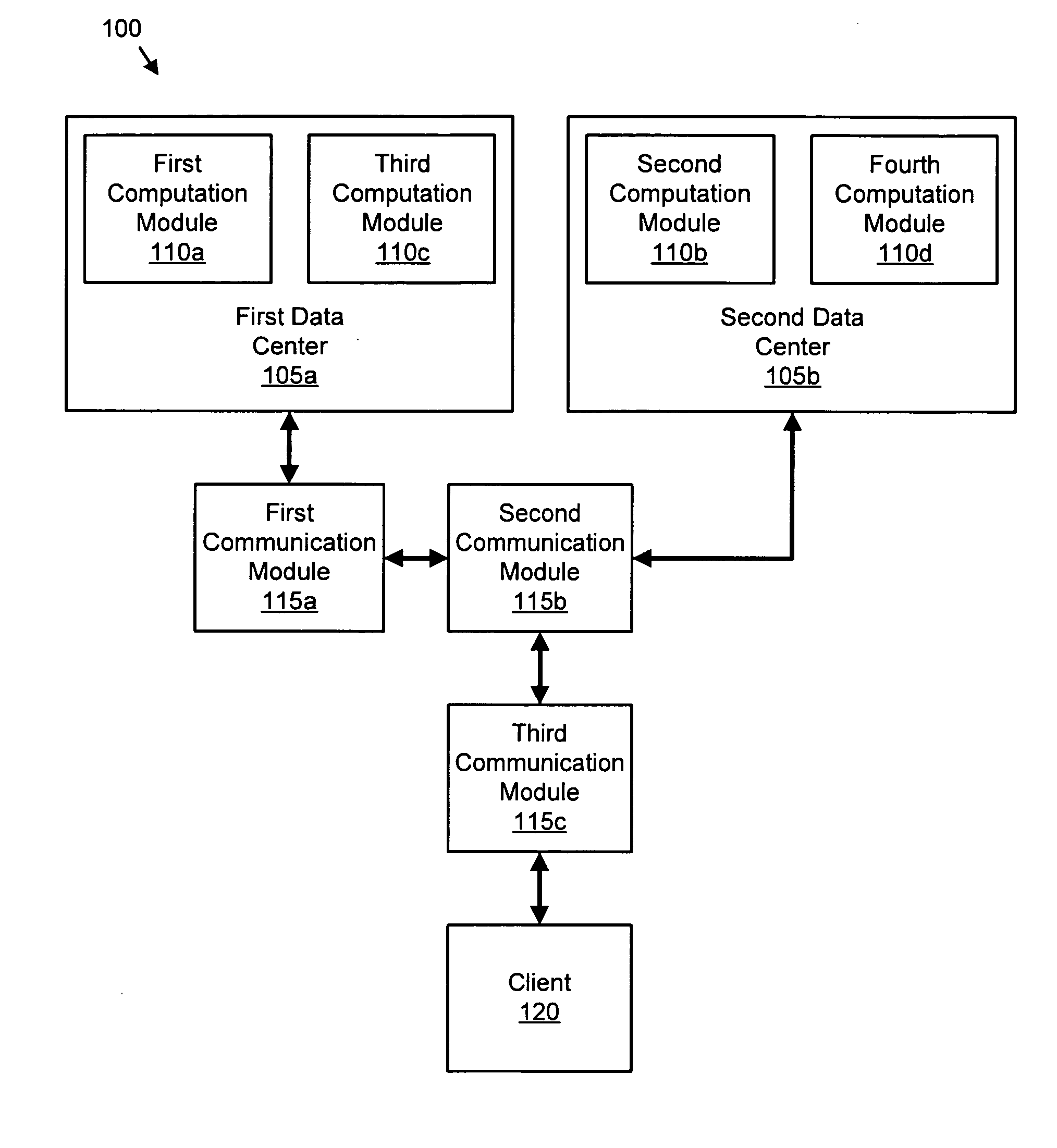
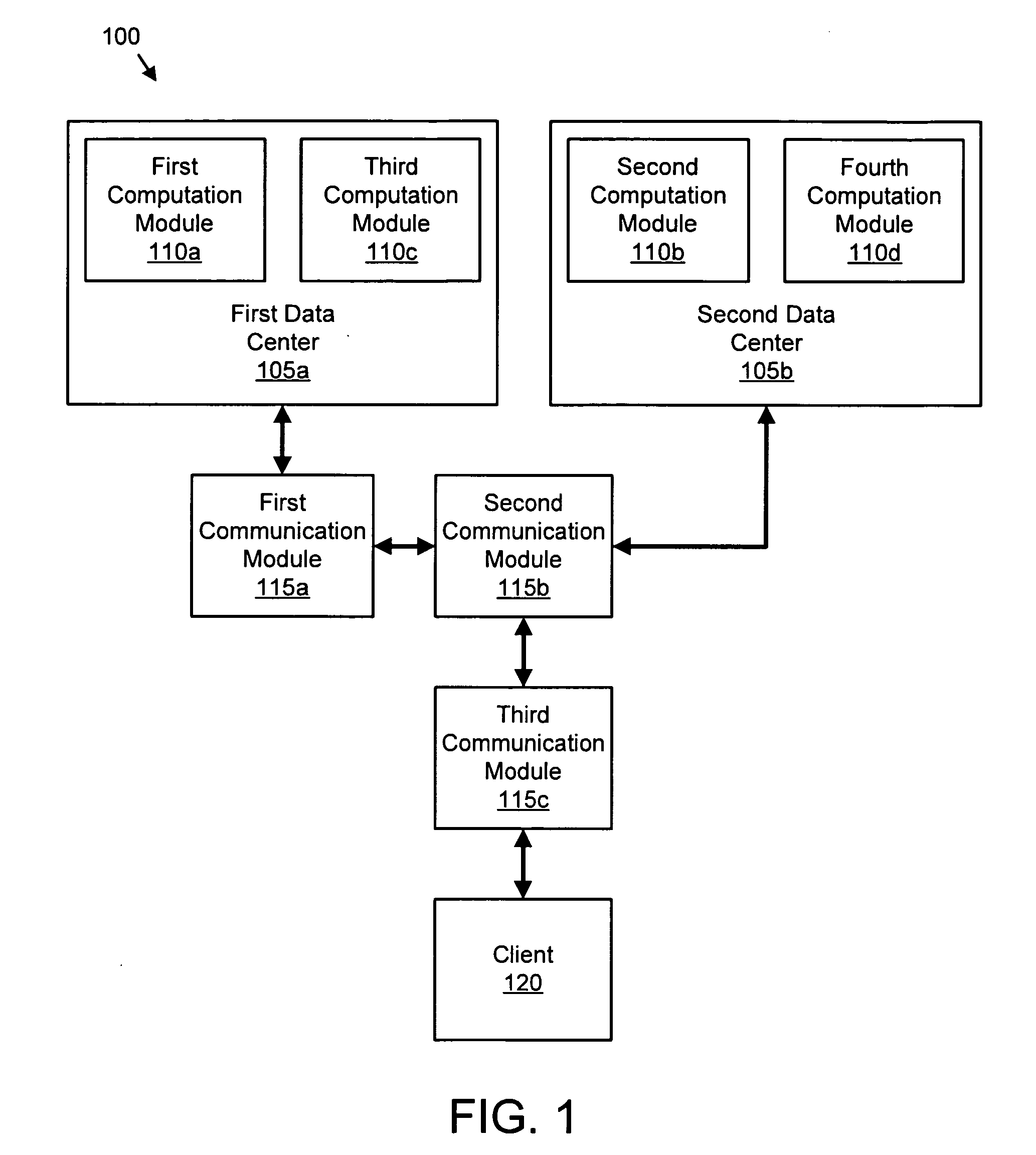
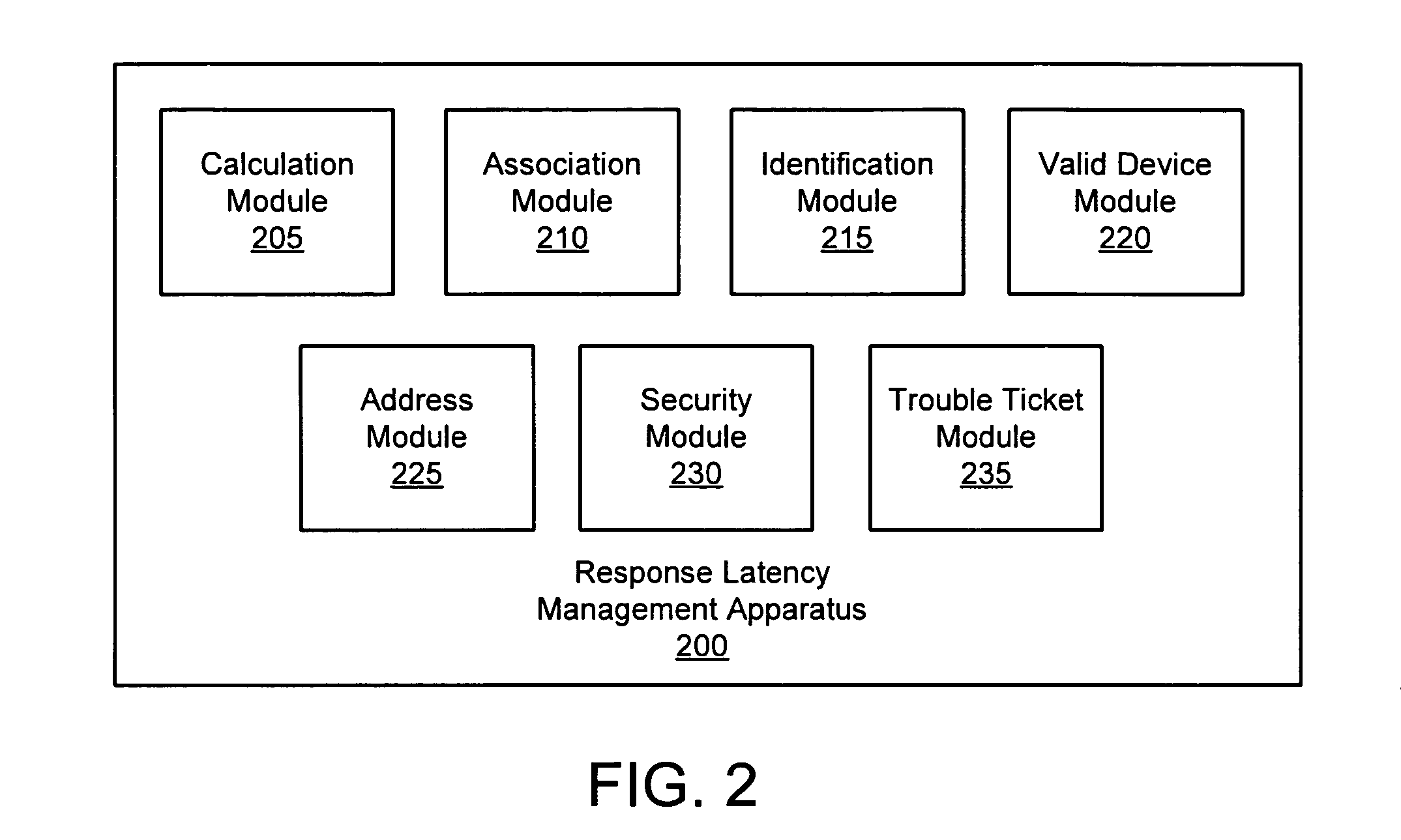
Apparatus, system, and method for managing response latency
InactiveUS20070101019A1Response latencyAvoid associationDigital computer detailsTransmissionData packClient-side
An apparatus, system, and method are disclosed for managing response latency. An identification module identifies a computation module that may communicate with a client through one or more communication modules. A calculation module calculates the number of communication modules that transceive a packet between the computation module and the client as a hop count. An association module associates the client with the first computation module in response to the hop count satisfying a count range of a response policy. In one embodiment, a trouble ticket module generates a trouble ticket in response to a specified number of clients having a hop count greater than the count range.
Owner:IBM CORP
Modified Titanium Oxide Microparticle and Photoelectric Transducer Making Use of the Same
InactiveUS20080110497A1Increase the open circuit voltageHigh voltageElectrolytic capacitorsFinal product manufactureTransducerSilicon oxide
[PROBLEMS] To develop metal microparticles useful in dye-sensitized solar cell, etc. and to provide a photoelectric transducer capable of exhibiting enhanced release voltage in dye-sensitized solar cell.[MEANS FOR SOLVING PROBLEMS] There are provided modified titanium oxide microparticles comprised of titanium oxide and one or two or more types of nontitanic metal oxides (including silicon oxides) selected from the group consisting of periodic-table group IB oxides, group IIA oxides, group IIB oxides, group IIIA oxides, group IIIB oxides, group IVA oxides other than titanium oxides, group IVB oxides, group VIA oxides, group VIII oxides and vanadium oxides.Further, there is provided a photoelectric transducer making use of the modified titanium oxide microparticles.
Owner:NIPPON KAYAKU CO LTD
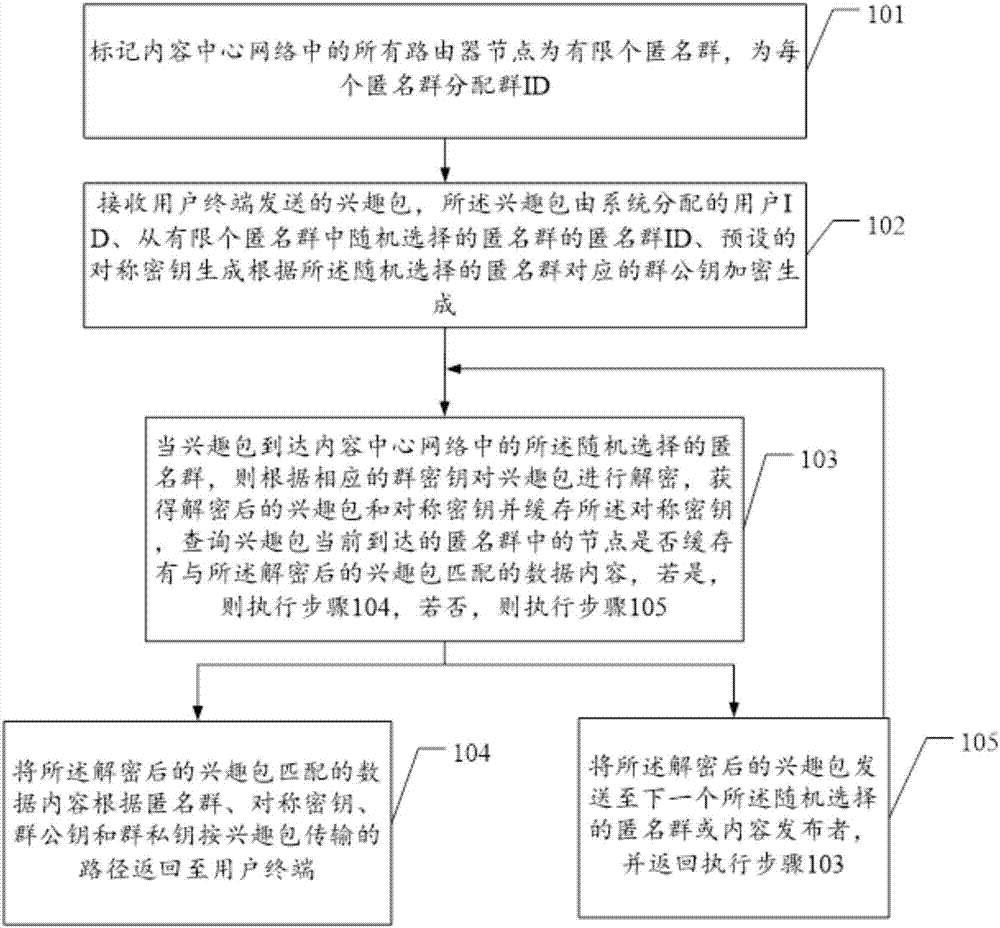
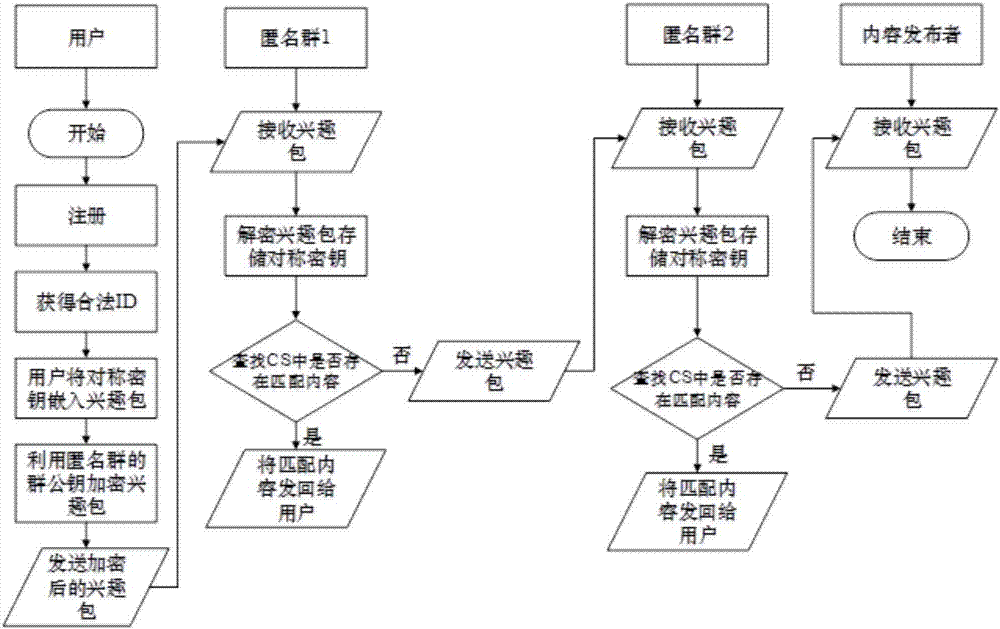
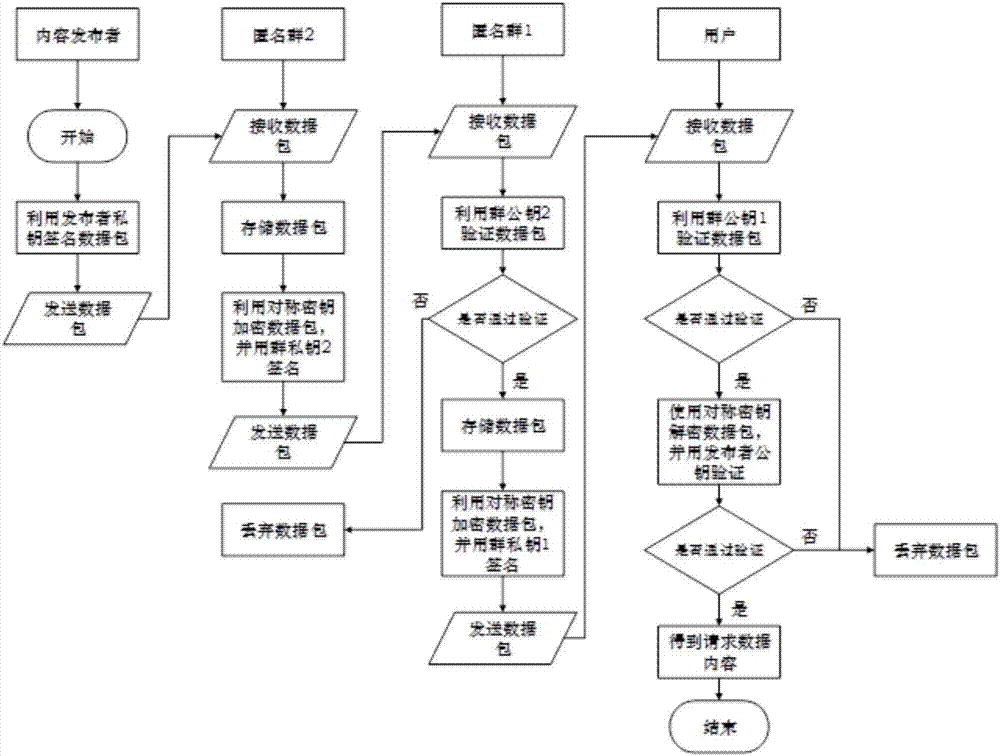
Content centric network privacy protection method based on hybrid encryption and anonymous group
The embodiment of the invention provides a content centric network privacy protection method based on hybrid encryption and an anonymous group. An interest packet is transmitted through the anonymous group, and decrypted into a plaintext interest packet layer by layer in a node of the anonymous group, thereby effectively preventing an attacker from getting association between the interest packet and a user. Hybrid encryption is performed on the interest packet and a data packet through encryption methods such as a user ID, a public key and a private key of a publisher, a symmetric key, and a public key and a private key of the anonymous group, so that the data packet can be protected from being modified in a process from signature to reception by the user, and plaintext content cannot be cracked inversely within certain time even though the attacker gets encrypted communication content by eavesdropping, thereby protecting the privacy of communication data. In the embodiment of the invention, the identity privacy information of a signer is protected through construction of the anonymous group, and meanwhile unlinkability between communication content and both communication parties is realized through a hybrid encryption method.
Owner:GUANGDONG UNIV OF TECH
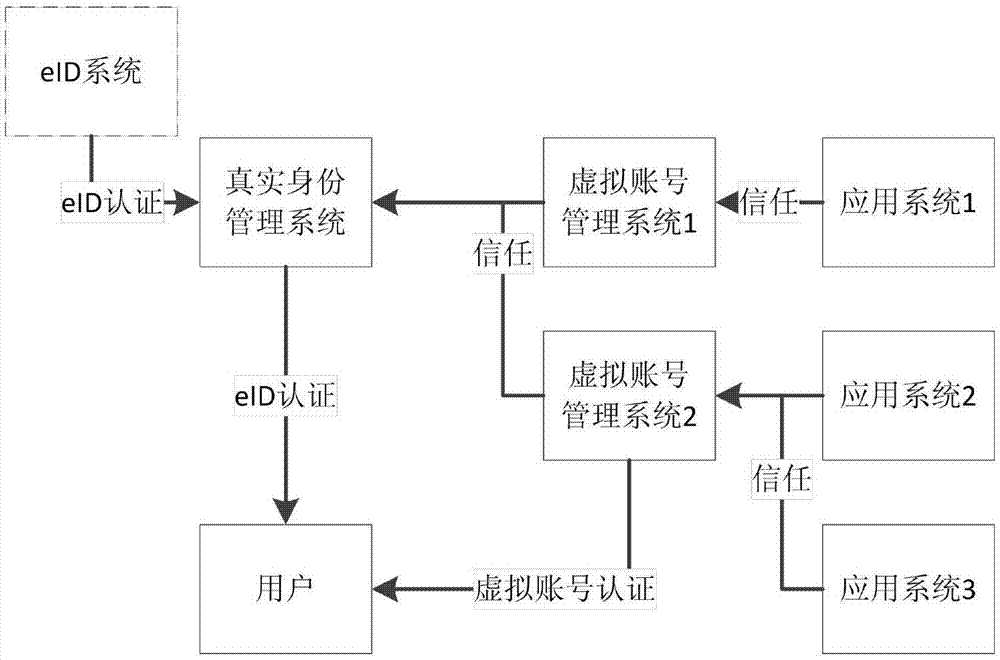
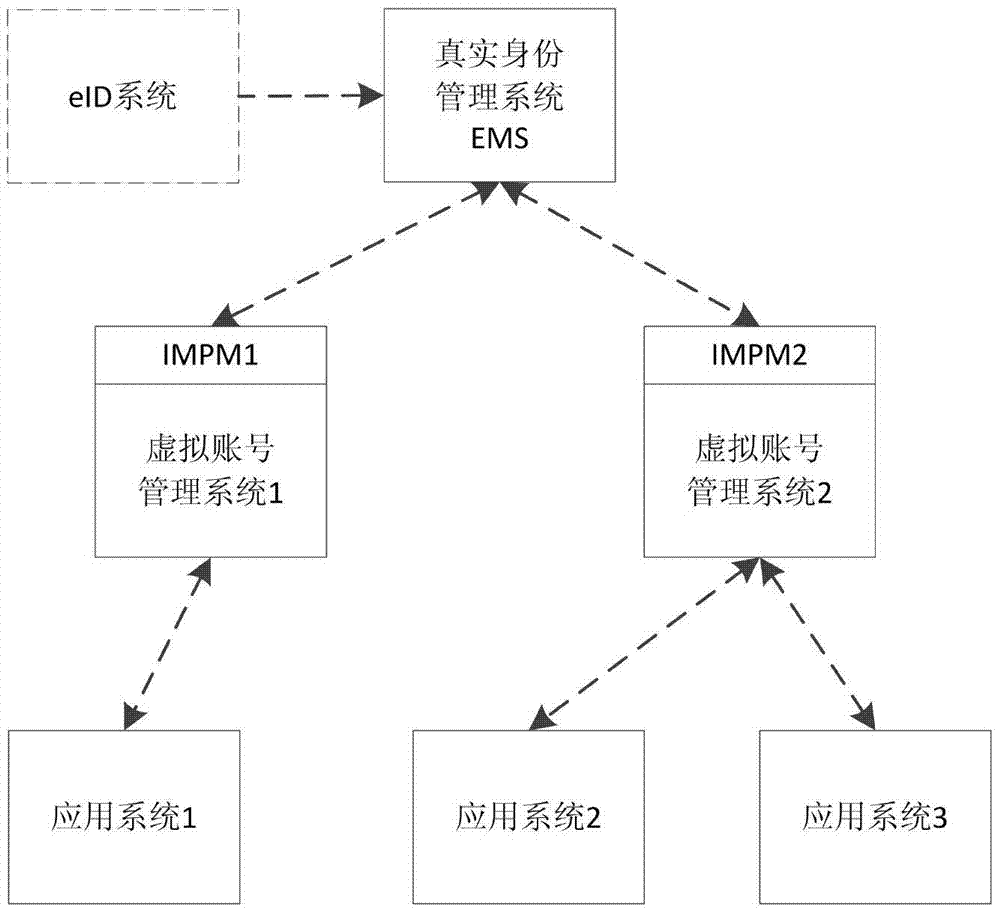
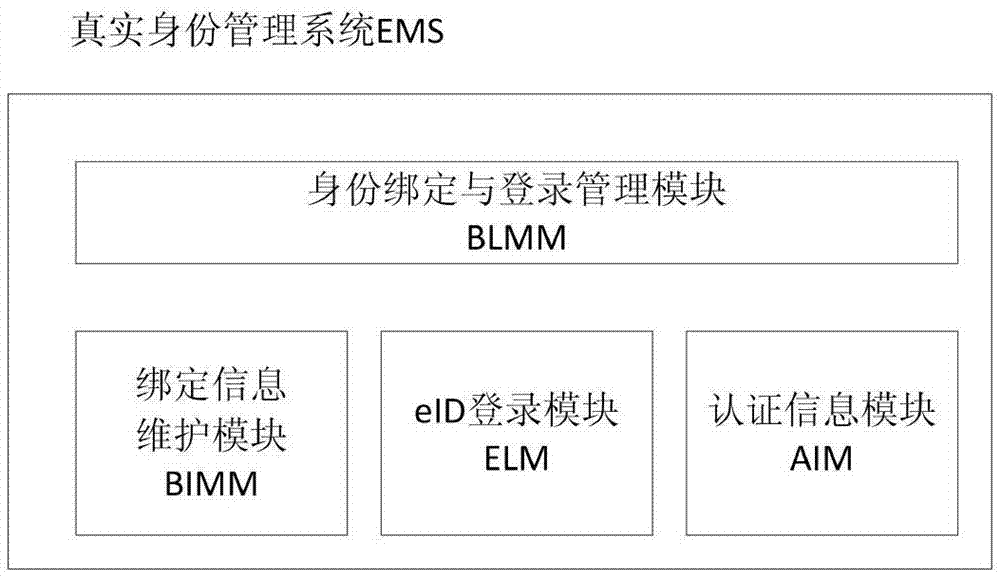
EID security control method and system based on eID
The invention discloses an EID security control method and system based on eID. The system comprises a virtual identity management system VIMS and an EID management system EMS of a target application system AS, wherein the VIMS is used for authenticating a user; if authentication is passed, a binding request is generated, and sent to the EMS; when the user accesses the AS, a login request is generated, and sent to the EMS; the EMS is used for authenticating the user according to the binding request; if authentication is passed, the Ie of the eID identity of the user is returned; then, the Ie is bound with account numbers Iv and V included in the binding request; then, a binding result is sent to the VIMS; the user is authenticated according to the login request; if authentication is passed, authentication result information is generated according to a returned virtual account number set {I} and the identifier E of the EMS, and returned to the VIMS; and the VIMS obtains the virtual account number Iv included therein, and processes access of the user.
Owner:INST OF SOFTWARE - CHINESE ACAD OF SCI
Infusion line systems
ActiveUS20180177938A1Avoid associationAvoid misidentificationMechanical apparatusInfusion devicesLight signalIdentification system
An IV line identification system to enable ready identification of an IV line and its associated fluid source and output and to enable distinguishing the IV line from other IV lines and their fluid sources and outputs. The IV line identification system includes a first light source and a second light source communicatively coupled to one another via a wireless connection. The light sources are configured such that when one is activated so as to generate a light signal, the other is automatically activated to generate a corresponding light signal. Each light source may be placed on opposite ends of an IV line to enable ready identification of each end of the same IV line.
Owner:ORION INNOVATIONS INC
Oral Care Compositions
ActiveUS20170151158A1Reduce deliveryAvoid associationCosmetic preparationsToilet preparationsStainingCosmetic ingredient
This application provides, among other things, novel aqueous oral care compositions useful for combining and delivering poorly compatible ingredients, for example to deliver effective levels of cationic antibacterial agents in combination with anionic polymers that protect against erosion and staining, by addition of a stabilizing amount of a polyamine, e.g., lysine, and methods for making and using the same.
Owner:COLGATE PALMOLIVE CO
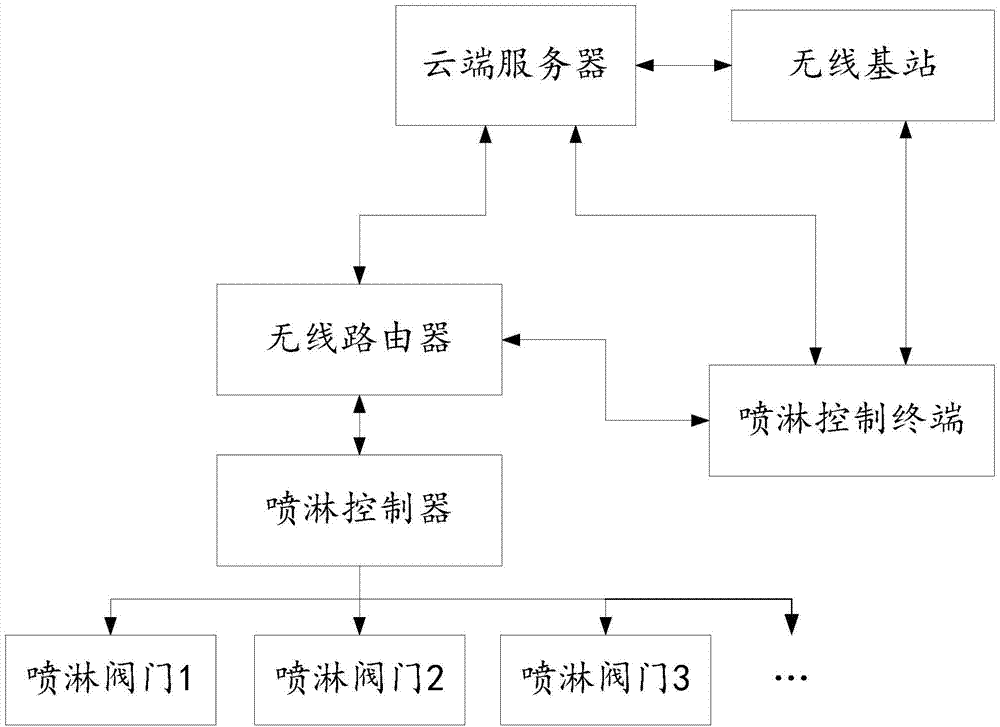
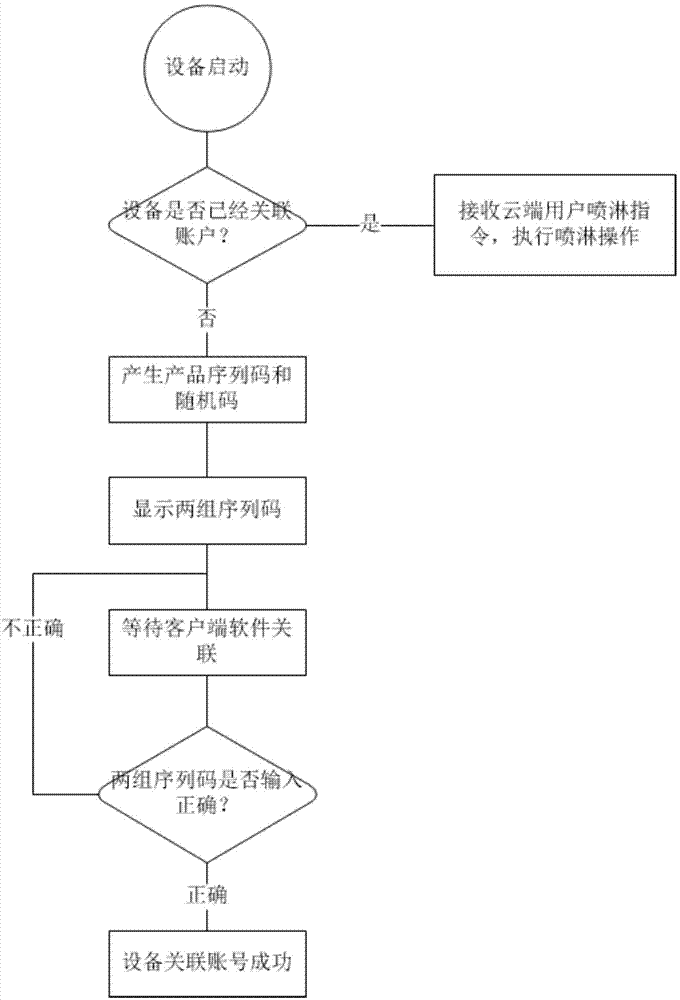
Device recognition method based on internet of things spraying control system
InactiveCN104125073AImprove accuracyEliminate hidden dangersUser identity/authority verificationInternet of ThingsRecognition sequence
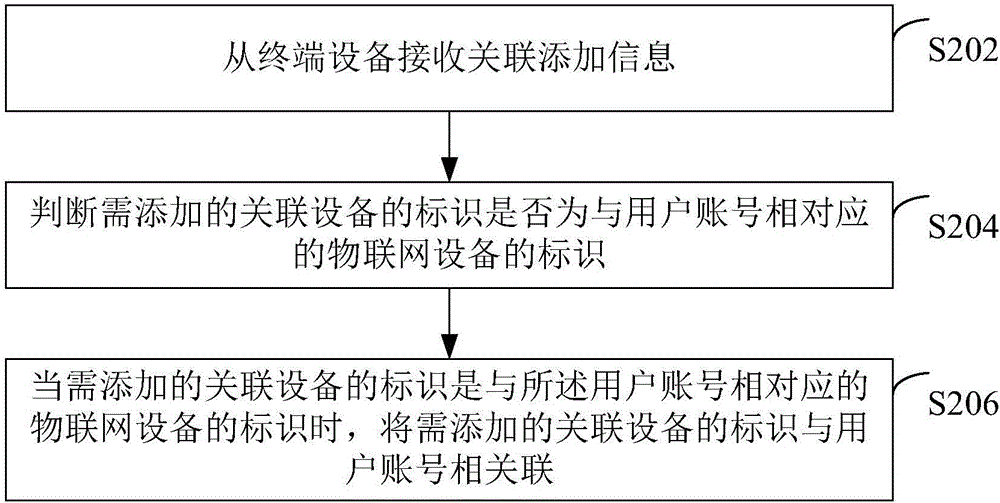
The invention relates to a device recognition method based on an internet of things spraying control system, and belongs to the technical field of wireless communication. The method comprises the following steps: sending a mainboard recognition sequence code and a generated random sequence code to a server through a spraying controller and displaying in a display screen together; inputting the two sequence codes through a user after logging in client operational software; determining the input through the server; successfully associating a device with an account through a cloud server after two groups of character strings input by the user are completely consistent with the contents displayed in the display screen of the spraying controller; accurately sending all control commands sent by the client software to the specified spraying controller after the device and the account are associated successfully. With the adoption of the method, the user can accurately realize the association (binding) of the account and the device, and any safety problem caused by mis-operation of the device can be avoided.
Owner:NANJING YUCHAO NETWORK CO LTD
Ink and ink jet recording method
InactiveUS7926931B2Improve ejection effectEnhance the imageMeasurement apparatus componentsDuplicating/marking methodsThermal energyLiquid medium
An ink used in an ink jet recording method in which ink droplets are ejected from a recording head by the action of thermal energy to record an image on a recording medium; the ink being characterized by containing (a) a pigment, (b) a dispersing agent, (c) a liquid medium, (d) a polyglycerol and (e) at least one selected from a potassium salt of a carboxylic acid, a rubidium salt of a carboxylic acid and a cesium salt of a carboxylic acid.
Owner:CANON KK
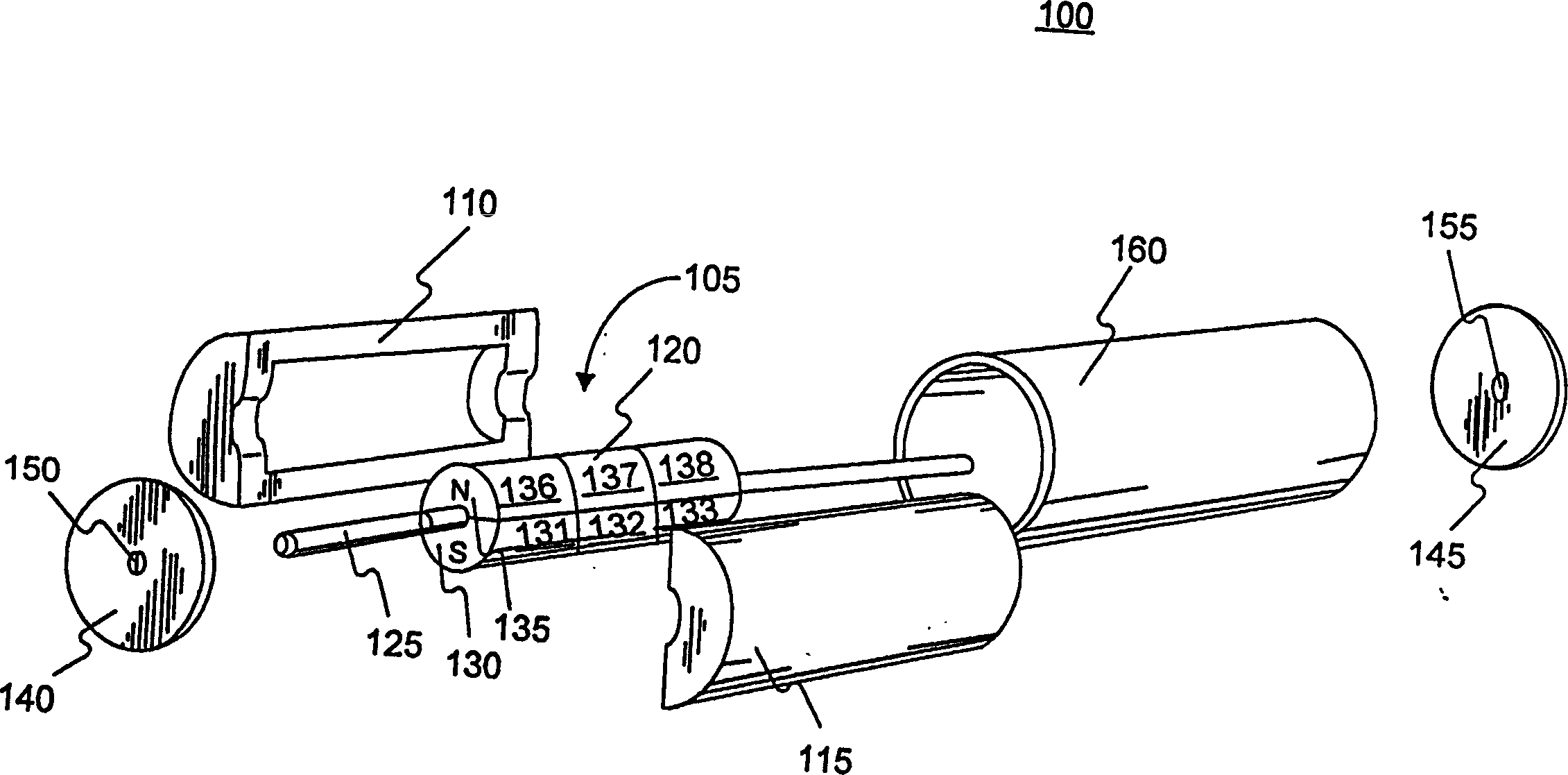
Axial vibration AC motor
An AC motor of axial vibration consists of a rotator with permanent magnetic rotating along longitudinal shaft, a stator coil coordinating to periphery of rotator and basically setting in coaxial with rotator longitudinal shaft and a stator coordinating to periphery of stator coil and basically setting in coaxial with longitudinal shaft of rotator. It features that variation between rotator vibration angles under end value of stator coil Ac frequency range and under initial value of stator coil AC frequency range is not greater than 30 %.
Owner:快乐响应美国公司
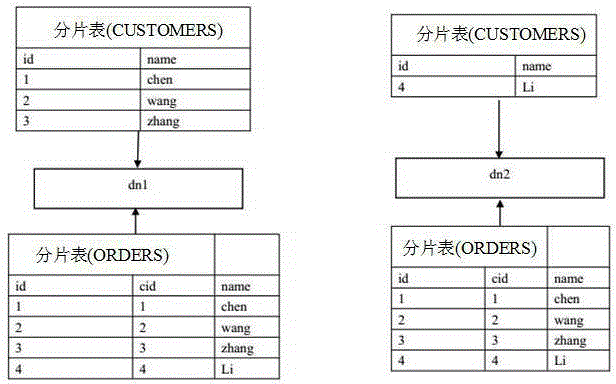
Method for solving correlated query of distributed cross-database fragment table
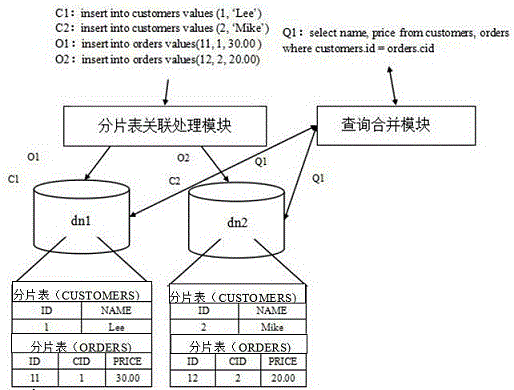
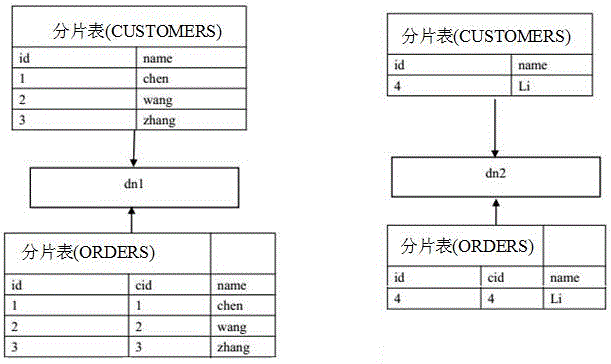
InactiveCN105404638AImprove query efficiencyImplement relational querySpecial data processing applicationsDatabaseForeign key
The invention discloses a method for solving the correlated query of a distributed cross-database fragment table. The method comprises the following steps: constructing a correlated relationship between a CUSTOMERS fragment table and an ORDERS fragment table; appointing the table name, all distributed nodes, the fragment field and the fragment rule of the CUSTOMERS fragment table; meanwhile, appointing the table name, the foreign key listing and the listing of a list quoted by a foreign key of the ORDERS fragment table; and causing a storage operation of the CUSTOMERS fragment table to be the normal storage operation, and causing the storage operation of the ORDERS fragment table to be executed according to a node where associated CUSTOMERS fragment table data is positioned, wherein the CUSTOMERS fragment table is a conventional fragment table, and the CUSTOMERS fragment table needs to be associated with the conventional fragment table.
Owner:GOSUNCN TECH GRP
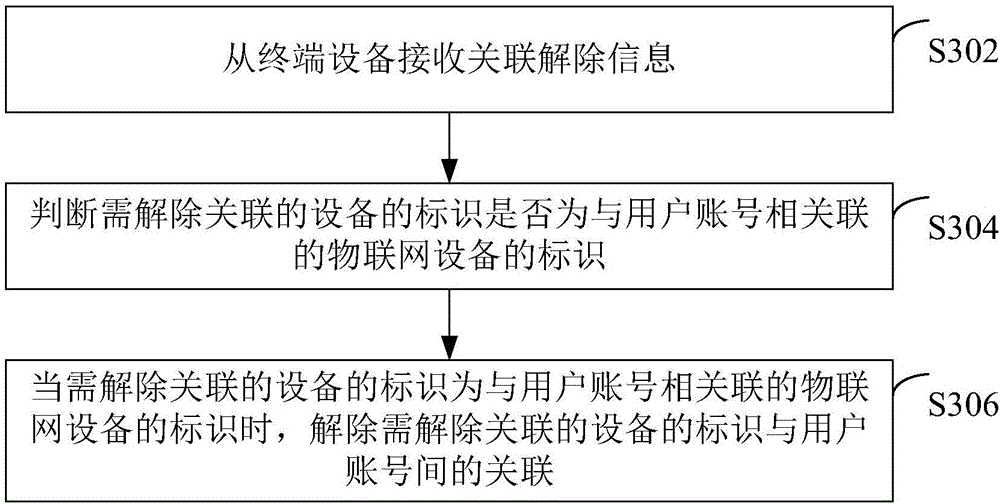
Method and device for associating Internet of Things equipment with user account
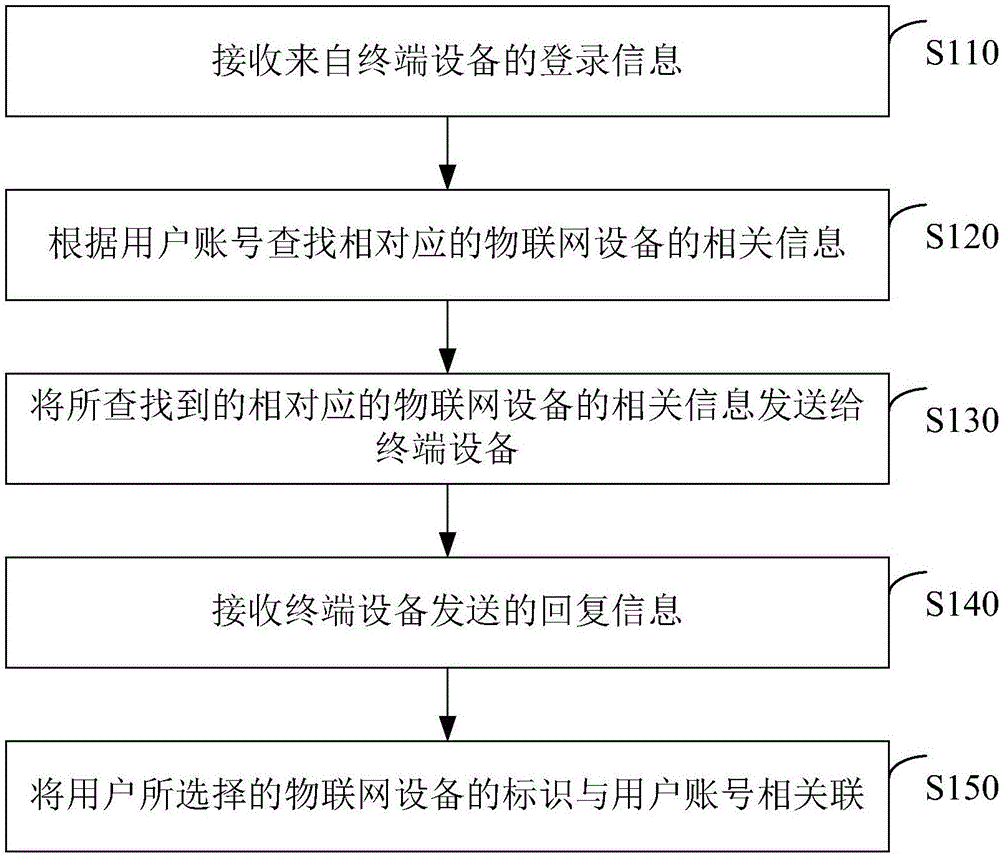
ActiveCN106534349ARealize automatic associationImprove securityHome automation networksTerminal equipmentThe Internet
The invention relates to the technical field of Internet of Things and discloses a method and a device for associating Internet of Things equipment with a user account. The method is used for a server and comprises the following steps of receiving login information from terminal equipment, wherein the login information comprises the user account; searching related information of the corresponding Internet of Things equipment according to the user account; sending the related information of the corresponding searched Internet of Things equipment to the terminal equipment; receiving a replay message sent by the terminal equipment, wherein the reply message comprises the user account and an identifier of the Internet of Things equipment, which is selected from the corresponding Internet of Things equipment on the terminal equipment by a user; and associating the identifier of the Internet of Things equipment, which is selected by the user, with the user account. According to the method and the device, the automatic association between the Internet of Things equipment and the user account is realized, the operation efficiency is improved, and the associated Internet of Things equipment is selected from the Internet of Things equipment corresponding to the user account, so that the association between the user account and the uncorrelated Internet of Things equipment is avoided, and the network security is improved.
Owner:MIDEA SMART TECH CO LTD +1
Ink and ink jet recording method
InactiveUS20080260948A1Improve ejection effectHigh fastnessMeasurement apparatus componentsDuplicating/marking methodsThermal energyLiquid medium
An ink used in an ink jet recording method in which ink droplets are ejected from a recording head by the action of thermal energy to record an image on a recording medium; the ink being characterized by containing (a) a pigment, (b) a dispersing agent, (c) a liquid medium, (d) a polyglycerol and (e) at least one selected from a potassium salt of a carboxylic acid, a rubidium salt of a carboxylic acid and a cesium salt of a carboxylic acid.
Owner:CANON KK
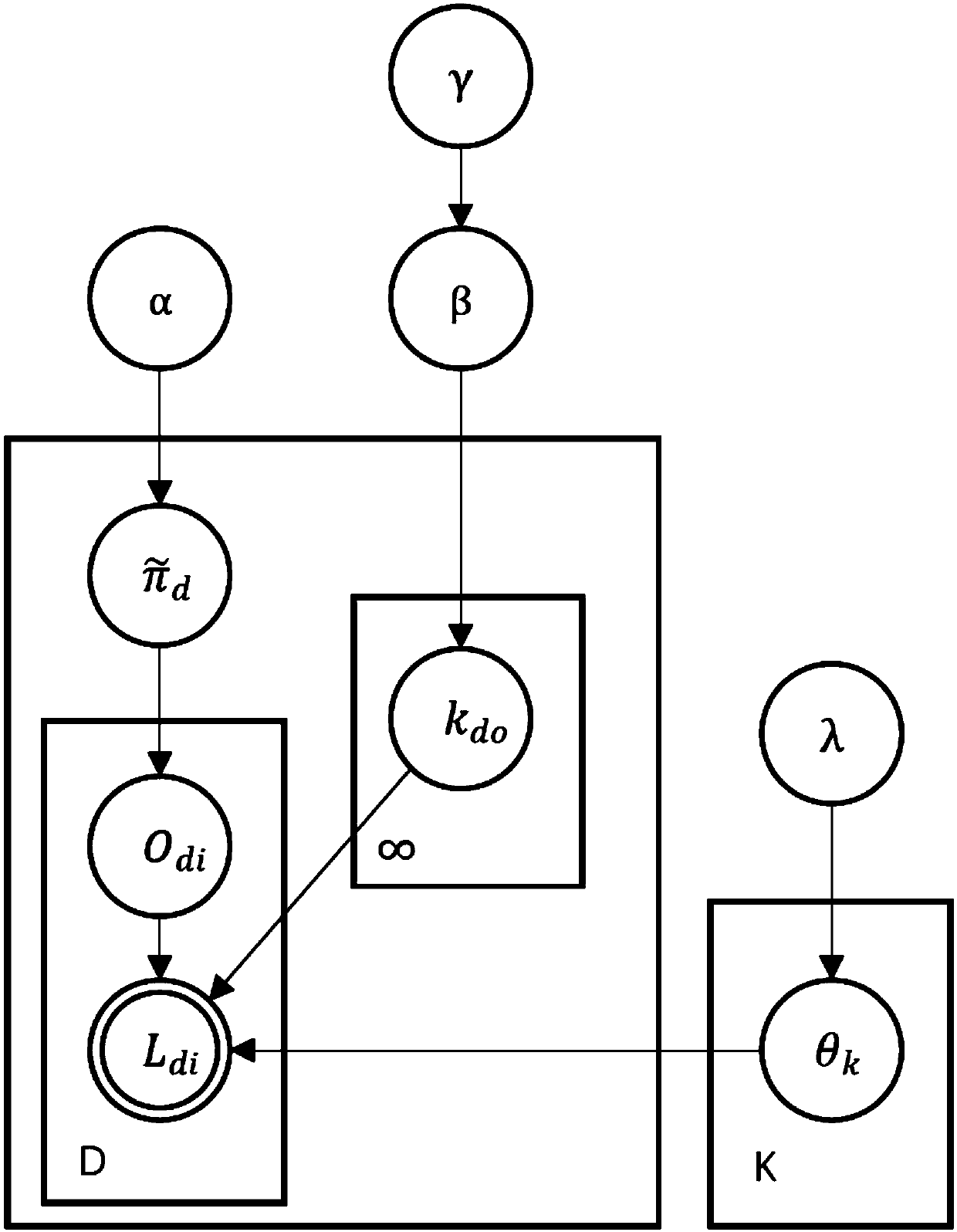
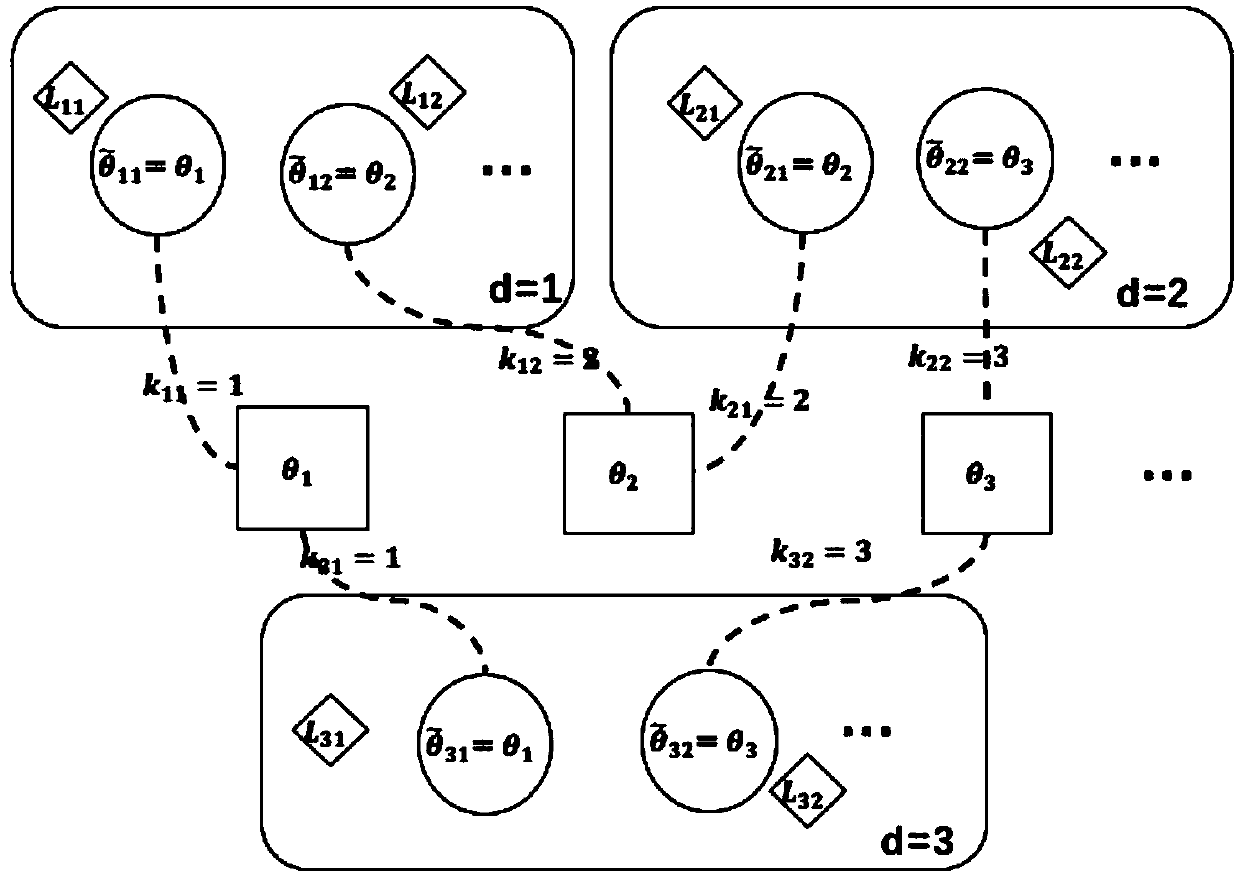
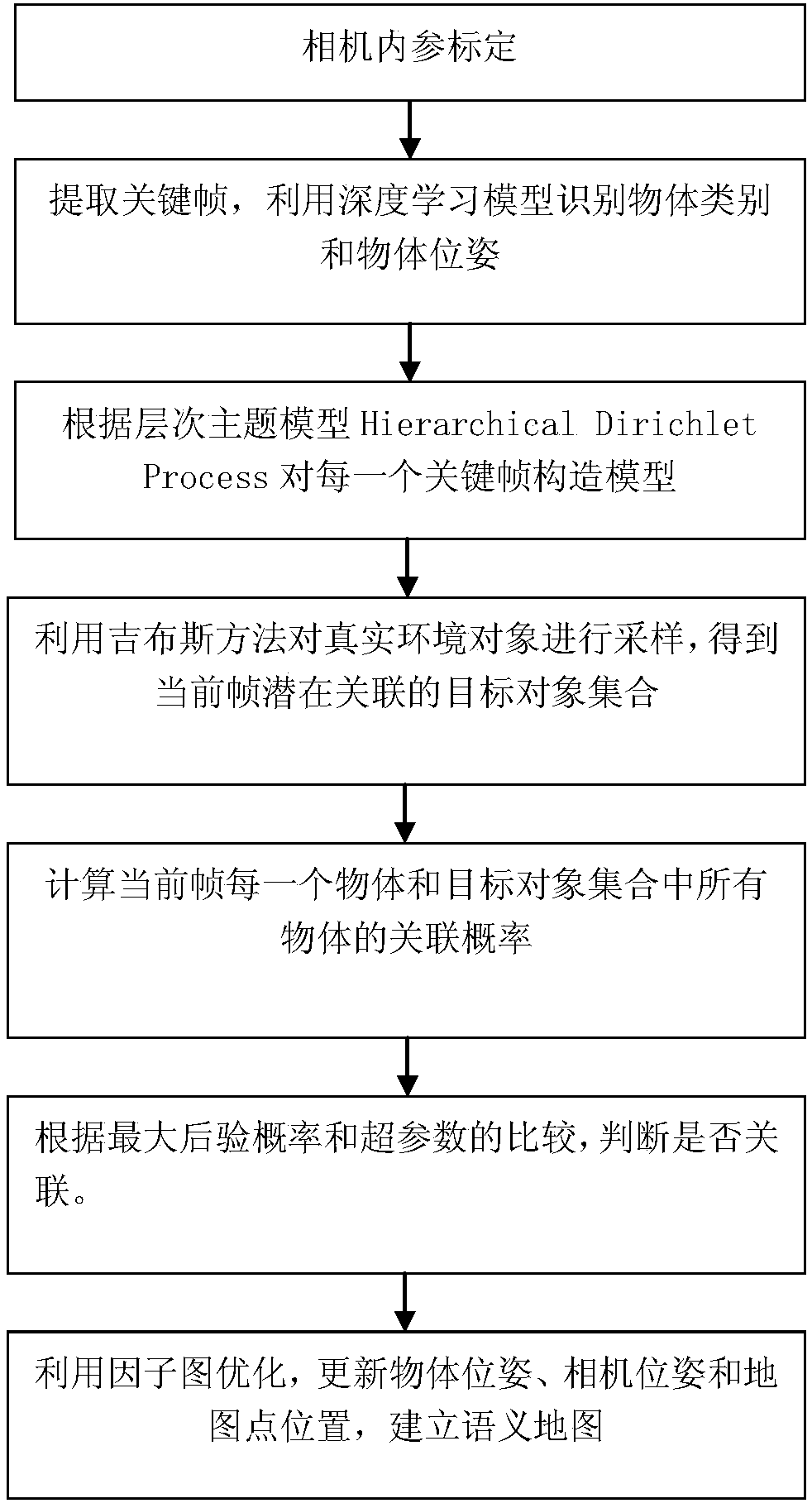
A semantic SLAM object association method based on a hierarchical topic model
ActiveCN109544632AFacilitating Camera Pose EstimationObject association is accurateImage enhancementImage analysisTopic modelLearning models
A semantic SLAM object association method based on a hierarchical topic model uses a depth learning model to detect objects in key frames and predict their positions and postures, When processing eachframe object, the Gibbs sampling method is used to sample the real environment object set with potential associated object according to the principle of view overlap, and the object association method is used to calculate for each object in the current frame, and the maximum posteriori probability is used to judge whether the object is associated or not. Factor maps are constructed for objects, cameras, and map points, and observations between them are used as edges to optimize object posture, camera posture, and map point positions. Finally, a complete semantic map including object information and camera trajectory is constructed. The invention can realize object association with high precision and avoids redundant object association. It can promote the camera pose estimation of semanticSLAM, and the optimized object pose can make the object association more accurate, so as to build a more accurate semantic map.
Owner:ZHEJIANG UNIV OF TECH
Association analysis system and method
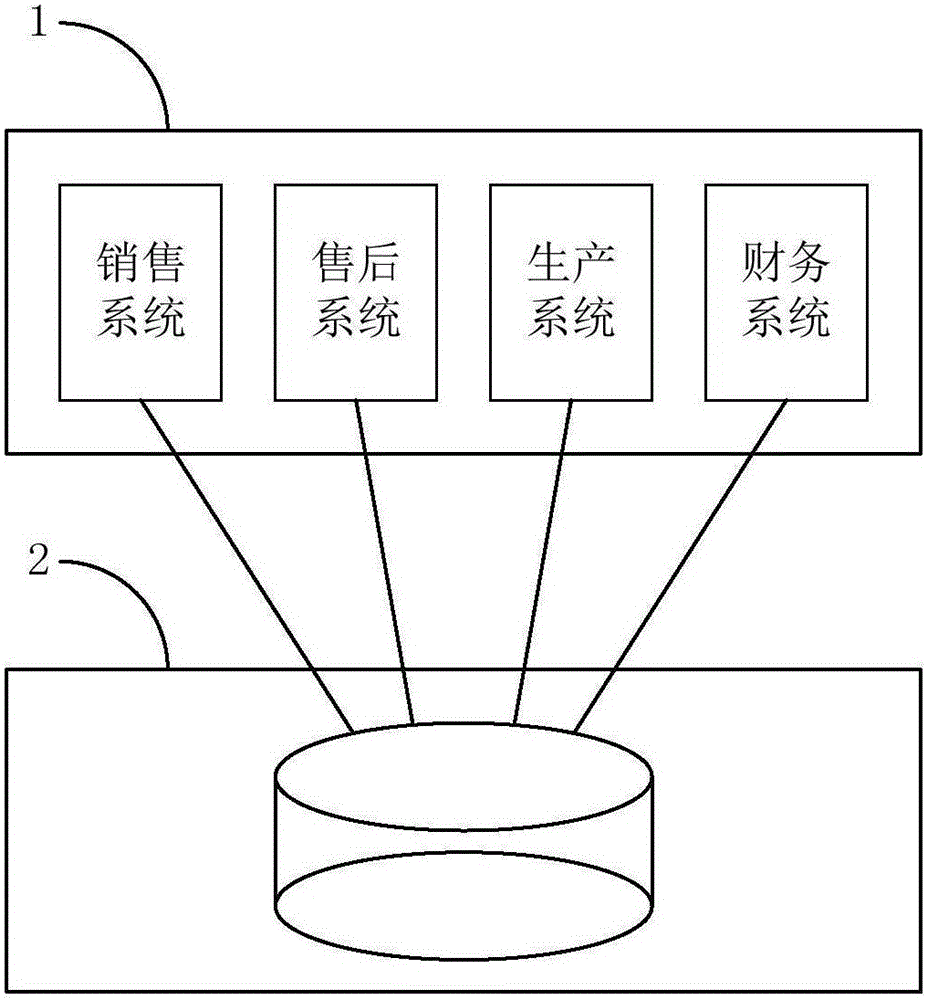
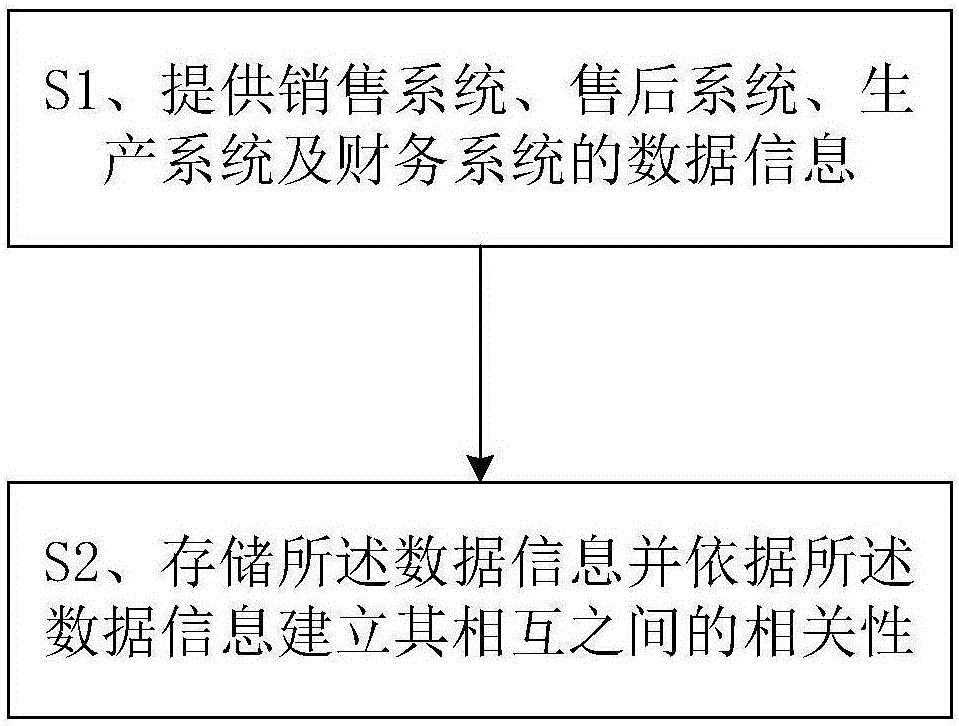
InactiveCN105069138ARapid positioningQuick modificationResourcesSpecial data processing applicationsFunctional changeData information
The present invention provides an association analysis system and method. The system comprises: an application platform used for providing data information to a sales system, an after-sale system, a production system and a financial system; and a data platform used for storing the data information and establishing mutual association among the data information on the basis of the data information. The association analysis system and method have the beneficial effects that business people can quickly locate a functional change range caused by the change of demands, without missing any associated demand; a developer can quickly analyze modified content of an associated function, without missing any modification, so as to avoid any associated problem caused by the change; and a database designer can systematically control functions such as data standards, database design specifications, and automatic generation of execution scripts. In summary, with the adoption of the association analysis system and method, the associated problems caused by the change can be reduced, the probability of errors is lowered, and the change efficiency is improved.
Owner:SHENZHEN LAN YOU TECH
Dormitory electric quantity usage statistical system based on card-inserting electricity utilization
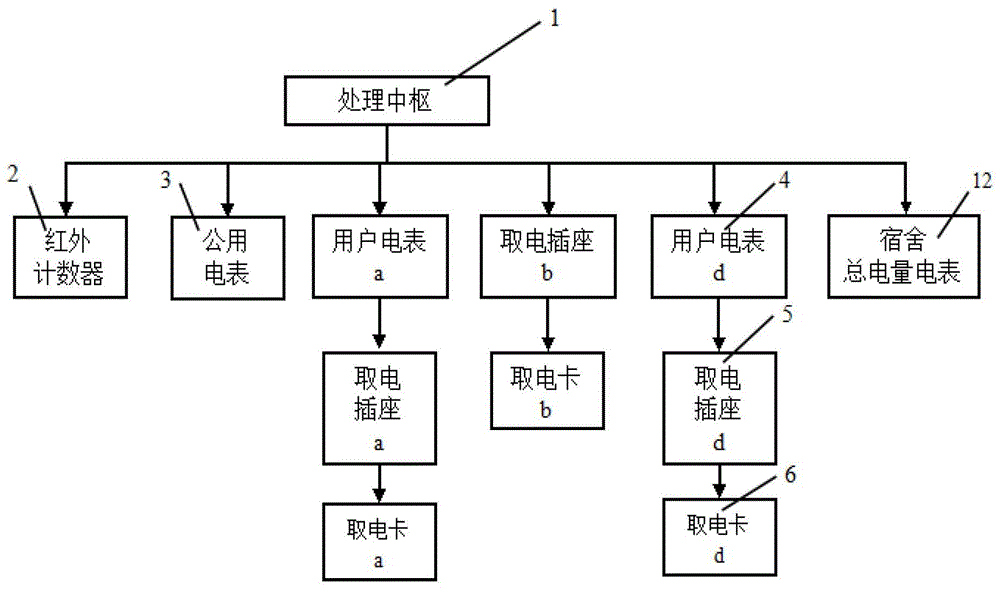
InactiveCN104866958AGuaranteed reasonablenessAvoid interferenceIndividual entry/exit registersResourcesElectricityMicrocomputer
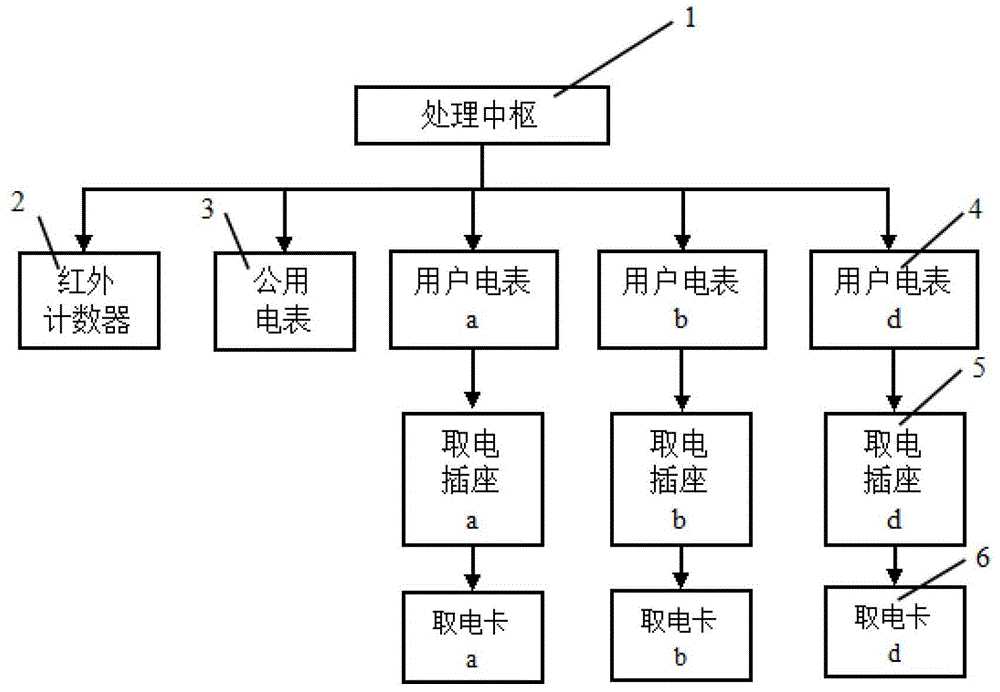
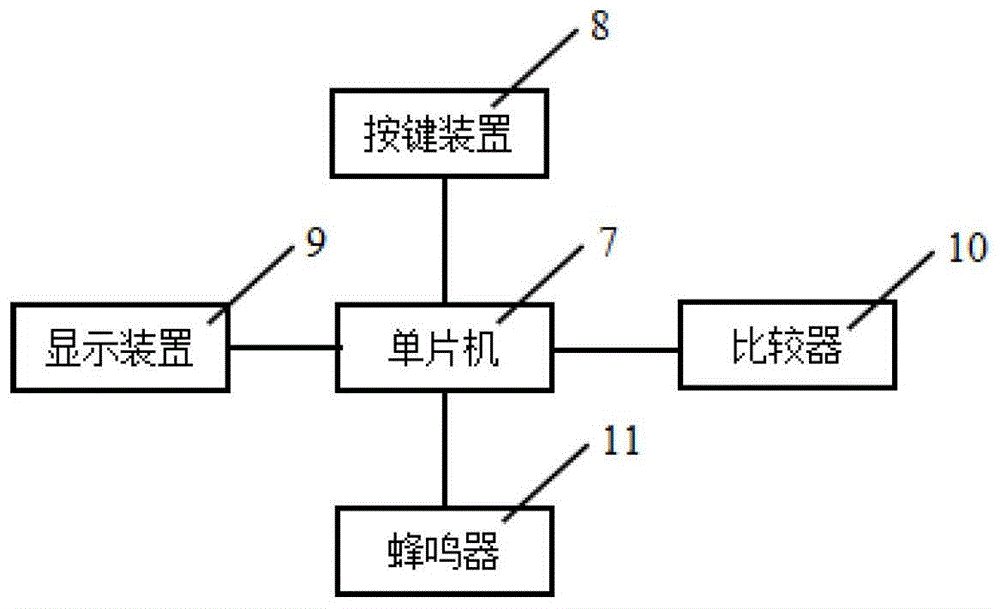
The invention discloses a dormitory electric quantity usage statistical system based on card-inserting electricity utilization. The dormitory electric quantity usage statistical system is characterized in that the dormitory electric quantity usage statistical system comprises card-inserting electricity utilization sockets, electricity utilization cards, a processing center, an infrared counter, user ammeters and a public ammeter, wherein the processing center comprises a single-chip microcomputer, a button device, a display device, a comparator and a buzzer. According to the invention, the electricity utilization cards matched with the card-inserting electricity utilization sockets for usage are adopted to identify dormitory members, then improvement is carried out on an electric quantity usage statistical algorithm, identification time sequence when members enter the dormitory and the like, and the electric quantity used by each dormitory member is accurately calculated, so that the problems of unreasonable electric quantity usage statistics and subsequent electricity charge distribution in the dormitory is effectively solved; in addition, the dormitory electric quantity usage statistical system is simple in structure, convenient to use, low in manufacturing cost and very suitable for various kinds of dormitories.
Owner:HUAZHONG UNIV OF SCI & TECH
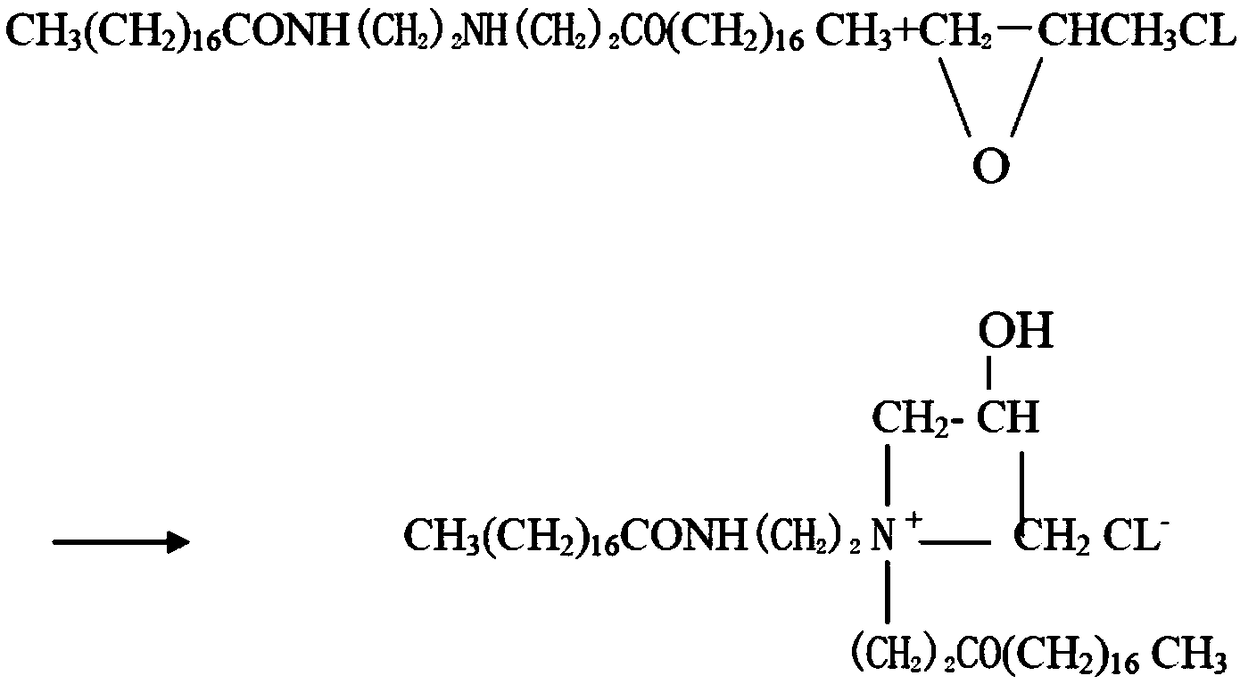
Preparation method of novel papermaking sizing agent
InactiveCN108221474AGood self retentionImprove waterproof performanceWater-repelling agents additionSurfactants additionEpoxyStearic acid
A preparation method of a novel papermaking sizing agent belongs to the technical field of papermaking sizing agents and includes the steps of: A) preparing raw materials including, by weight, 60-80 parts of stearic acid, 2-3 parts of diethanolamine, and 6-14 parts of diethylenetriamine, and performing a reaction at 140-220 DEG C for 4-6 h, cooling the product to obtain a reaction material liquidfor later use; B) mixing 100 parts by weight of water and 2-10 parts by weight of starch, gelatinizing the starch, cooling the liquid to 50 DEG C to obtain gelatinized starch liquid, or mixing 100 parts by weight of water and 0.5-10 parts of a high-polymer, heating the mixture to 50 DEG C to prepare a mixture liquid; C) adding 5-14 parts of the reaction material liquid in the step A) to the gelatinized starch liquid or the mixture liquid, adding 0.2-1 part of a compound surfactant and dropwise adding 3-10 parts of epoxy chloropropane, heating the mixture to 70 DEG C and performing heat-insulation reaction for 2-5 h, adding 5 parts of water, and cooling the mixture to produce the papermaking sizing agent. The preparation method has simple operations and has gentle and stable reaction processes. The papermaking sizing agent has good sizing effect and better damp-proof effect, and can satisfy demands in process of papermaking with waste pulp.
Owner:石家庄德旺科技有限公司
Resource selection method, base station and terminal
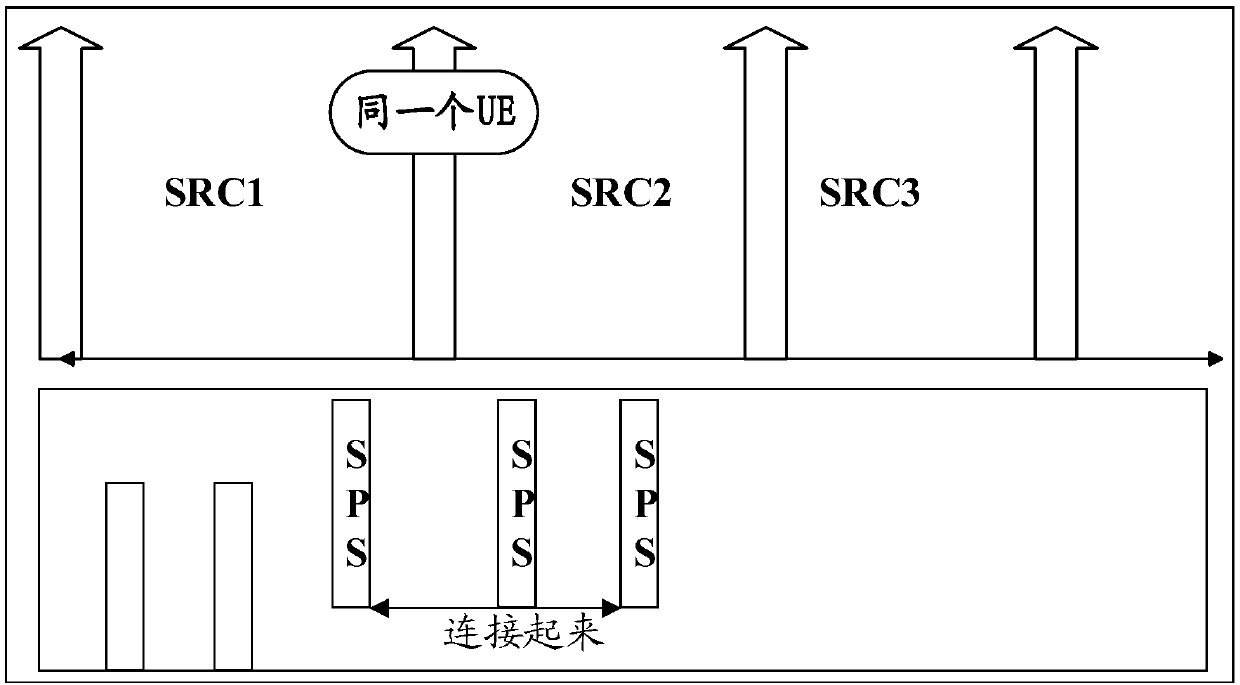
ActiveCN110740522AReduce the probability of continuous trackingAvoid associationConnection managementTransmission path sub-channels allocationEngineeringDistributed computing
The invention provides a resource selection method, a base station and a terminal, solving the problem that in an SPS mechanism mode, a malicious terminal may track the geographic position of a targetterminal by continuously determining information monitoring on resources, resulting in privacy leakage of the target terminal. The resource selection method comprises the step of triggering SPS resource reselection when a layer 2 ID is changed or the duration of semi-persistent scheduling SPS resources reaches the preset maximum duration. According to the resource selection method, when the layer2 ID changes or the duration of semi-persistent scheduling (SPS) resources reaches the preset maximum duration, the layer 2 ID is changed; and SPS resource reselection is triggered, so that the SPS resource is prevented from being kept unchanged for a long time, and the situation that the receiving node can associate different layer 2 IDs is avoided, and the probability of continuous tracking ofthe malicious terminal to the target terminal is reduced.
Owner:DATANG MOBILE COMM EQUIP CO LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com