Patents
Literature
153 results about "Correctness" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
In theoretical computer science, correctness of an algorithm is asserted when it is said that the algorithm is correct with respect to a specification. Functional correctness refers to the input-output behavior of the algorithm (i.e., for each input it produces the expected output).
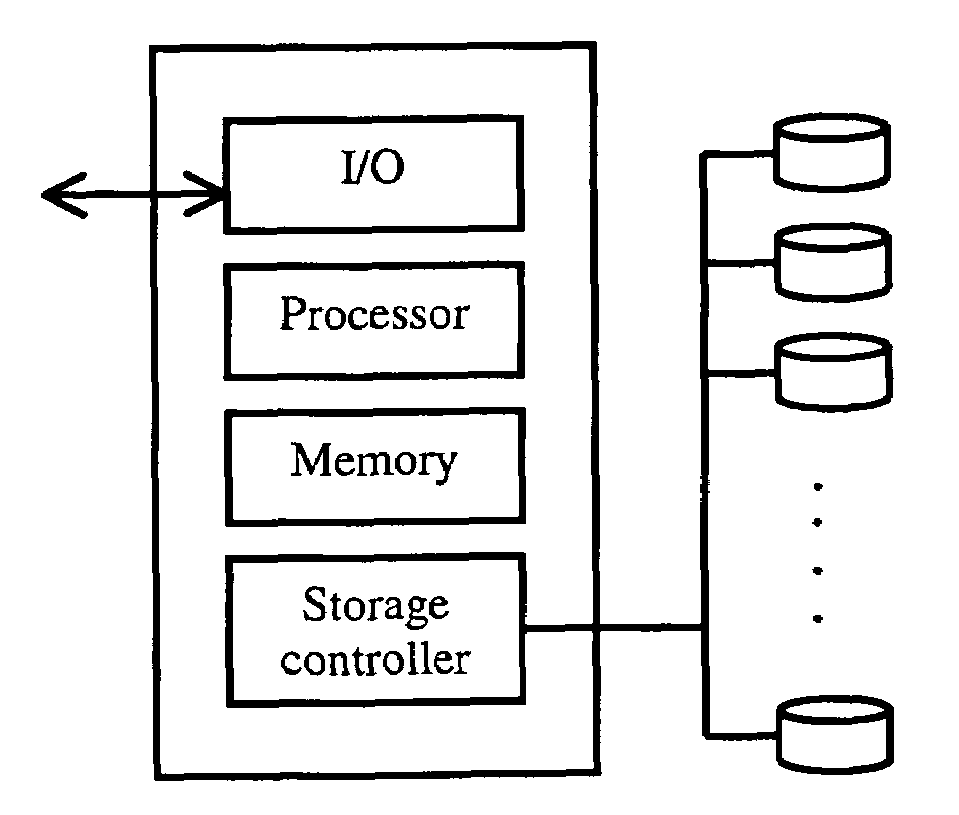
Multiply redundant raid system and XOR-efficient method and apparatus for implementing the same
InactiveUS7219289B2Efficient, high-redundancy erasure codeEasy to calculateCode conversionError correction/detection using linear codesRAIDTheoretical computer science
Owner:TANDBERG DATA
Multiply redundant raid system and XOR-efficient method and apparatus for implementing the same
InactiveUS20060218470A1Efficient executionEffective calculationError detection/correctionCode conversionDecoding methodsRAID
An improved and extended Reed-Solomon-like method for providing a redundancy of m≧3 is disclosed. A general expression of the codes is described, as well as a systematic criterion for proving correctness and finding decoding algorithms for values of m>3. Examples of codes are given for m=3, 4, 5, based on primitive elements of a finite field of dimension N where N is 8, 16 or 32. A Horner's method and accumulator apparatus are described for XOR-efficient evaluation of polynomials with variable vector coefficients and constant sparse square matrix abscissa. A power balancing technique is described to further improve the XOR efficiency of the algorithms. XOR-efficient decoding methods are also described. A tower coordinate technique to efficiently carry out finite field multiplication or inversion for large dimension N forms a basis for one decoding method. Another decoding method uses a stored one-dimensional table of powers of α and Schur expressions to efficiently calculate the inverse of the square submatrices of the encoding matrix.
Owner:TANDBERG DATA
Information sharing and secure multi-party computing model based on block chain
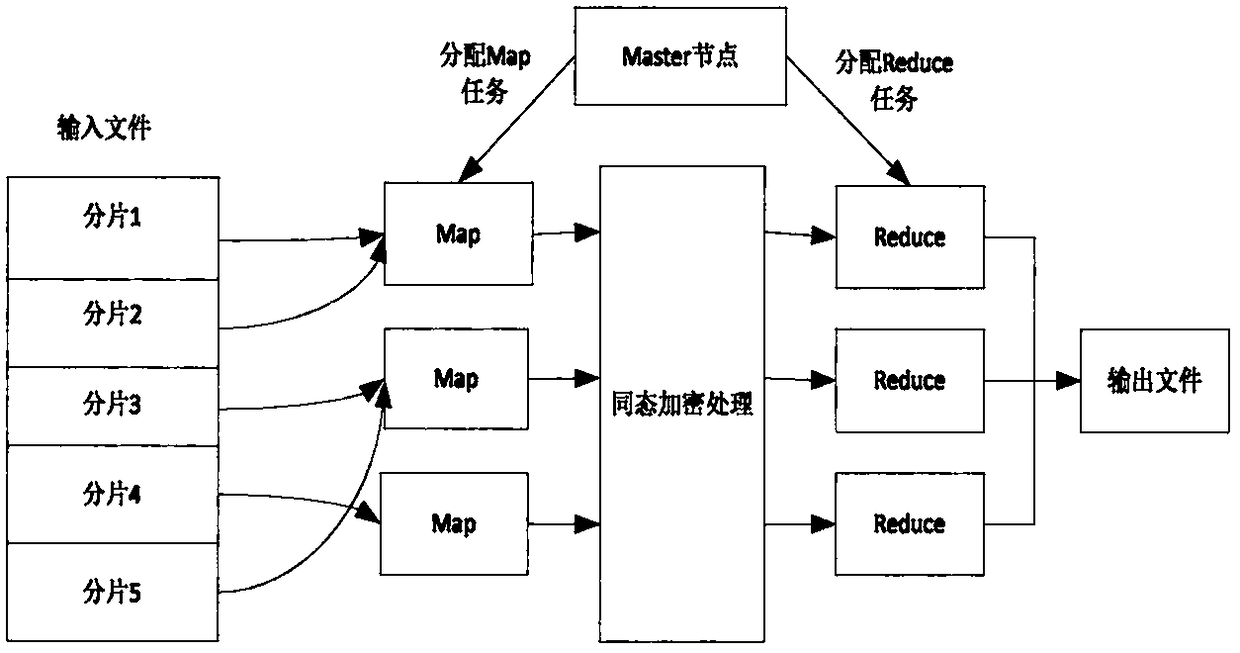
The invention discloses an information sharing and safe multi-party computing protocol based on a block chain, mainly solves the problem that the existing secure multi-party computation is easy to cause the user to be unable to control the data independently that is easy to get the data by the third party. The technical solutions are as follows: 1) constructing the storage model, and storing the index table information on the chain and the database under the chain in the way. 2) constructing a data sharing model,wherein users can access their data by authorizing a third party or revoke their privileges at any time. 3) using the consensus mechanism of the block chain to ensure the consistency among nodes; 4) Based on the correctness of nodes, using MapReduce programming model, the model isdivided into two phases: Map and Reduce, and the master node assigns the tasks of Map and Reduce to the nodes; 5) Map node uses the improved homomorphic encryption algorithm for encryption calculation; 6) Reduce node integrates the encrypted data to output data files.
Owner:全链通有限公司
Systems and methods for validating objects models
ActiveUS20050125806A1Avoid less flexibilityImprove performanceDigital data processing detailsMultiprogramming arrangementsDEVSValidation rule
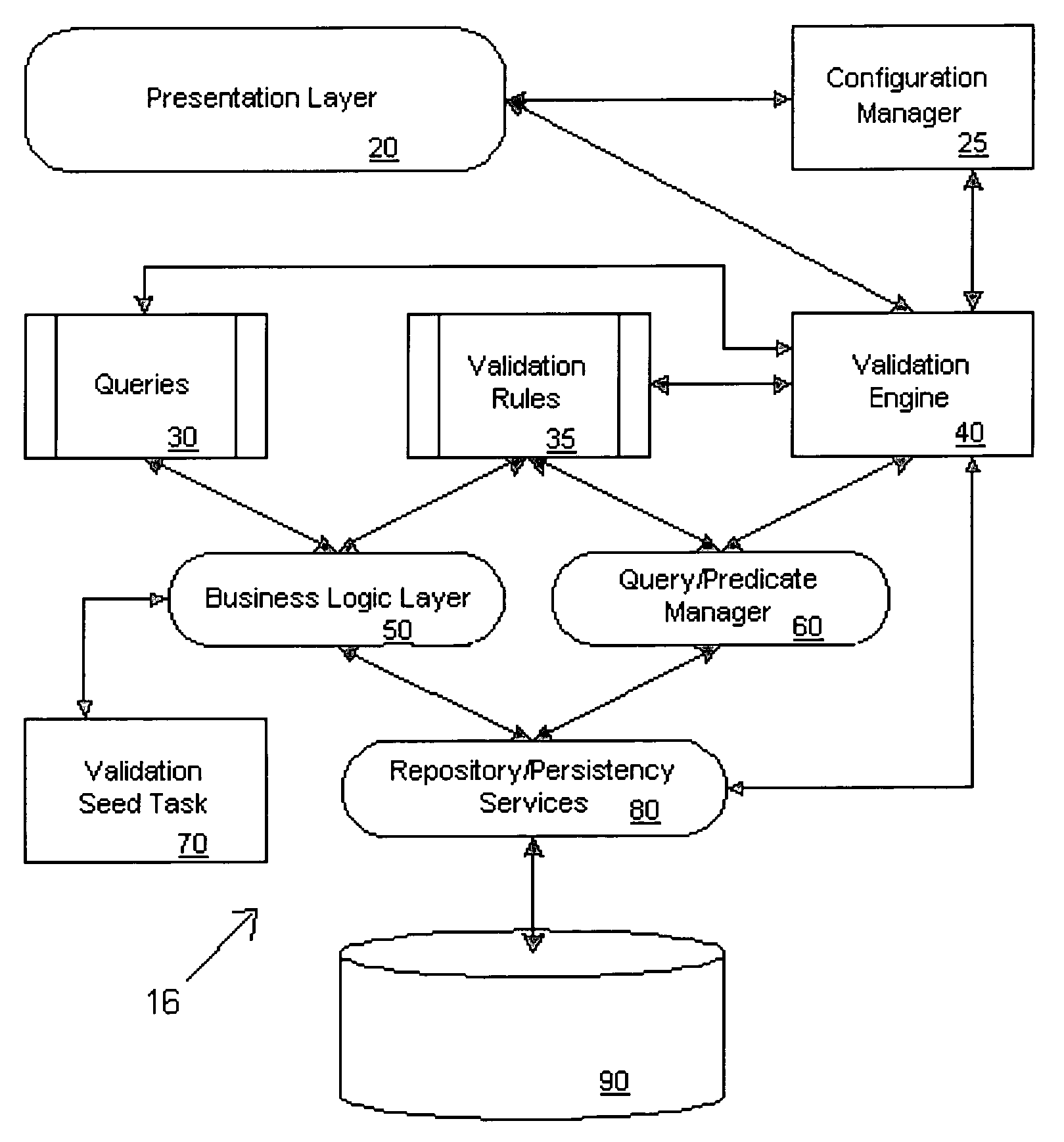
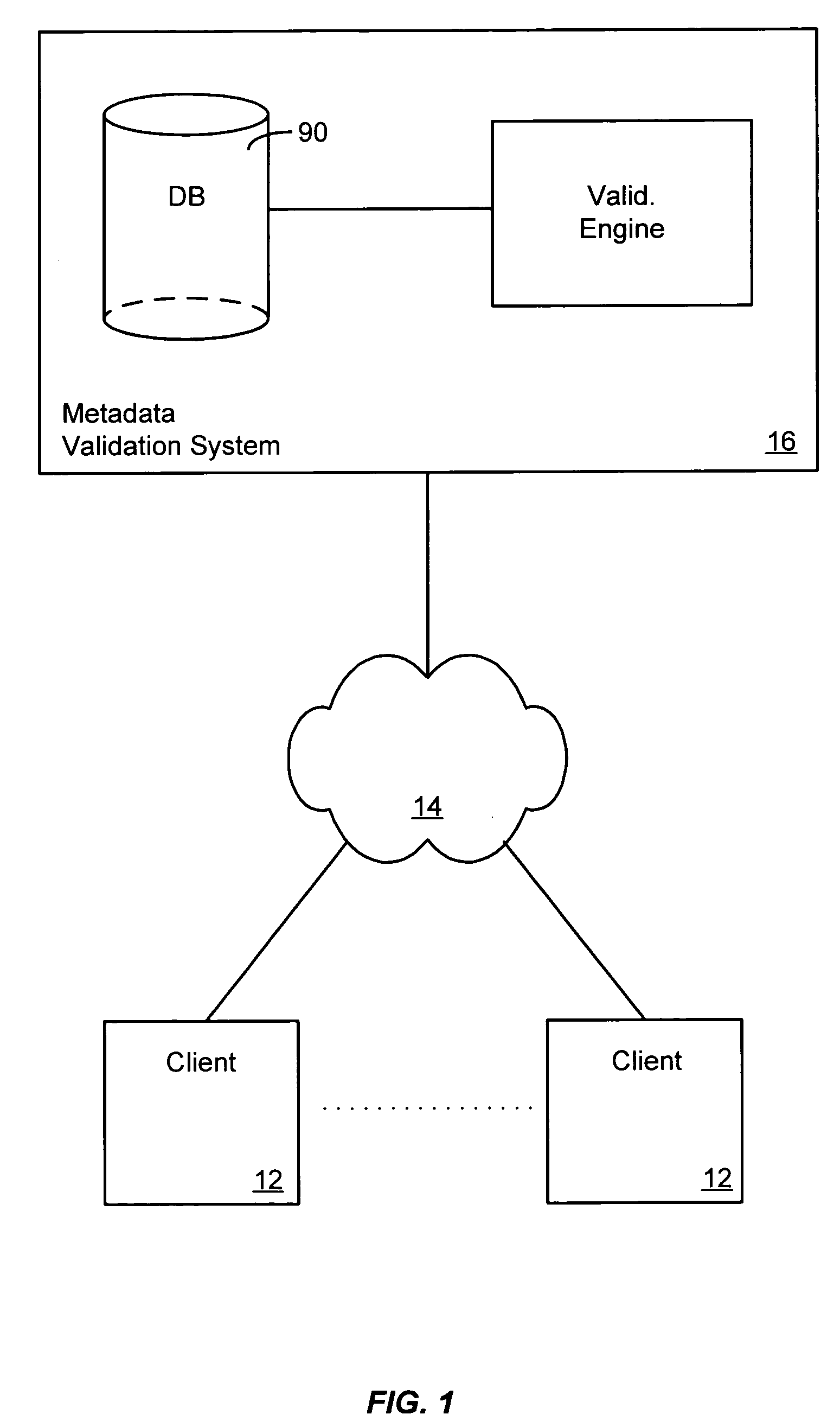
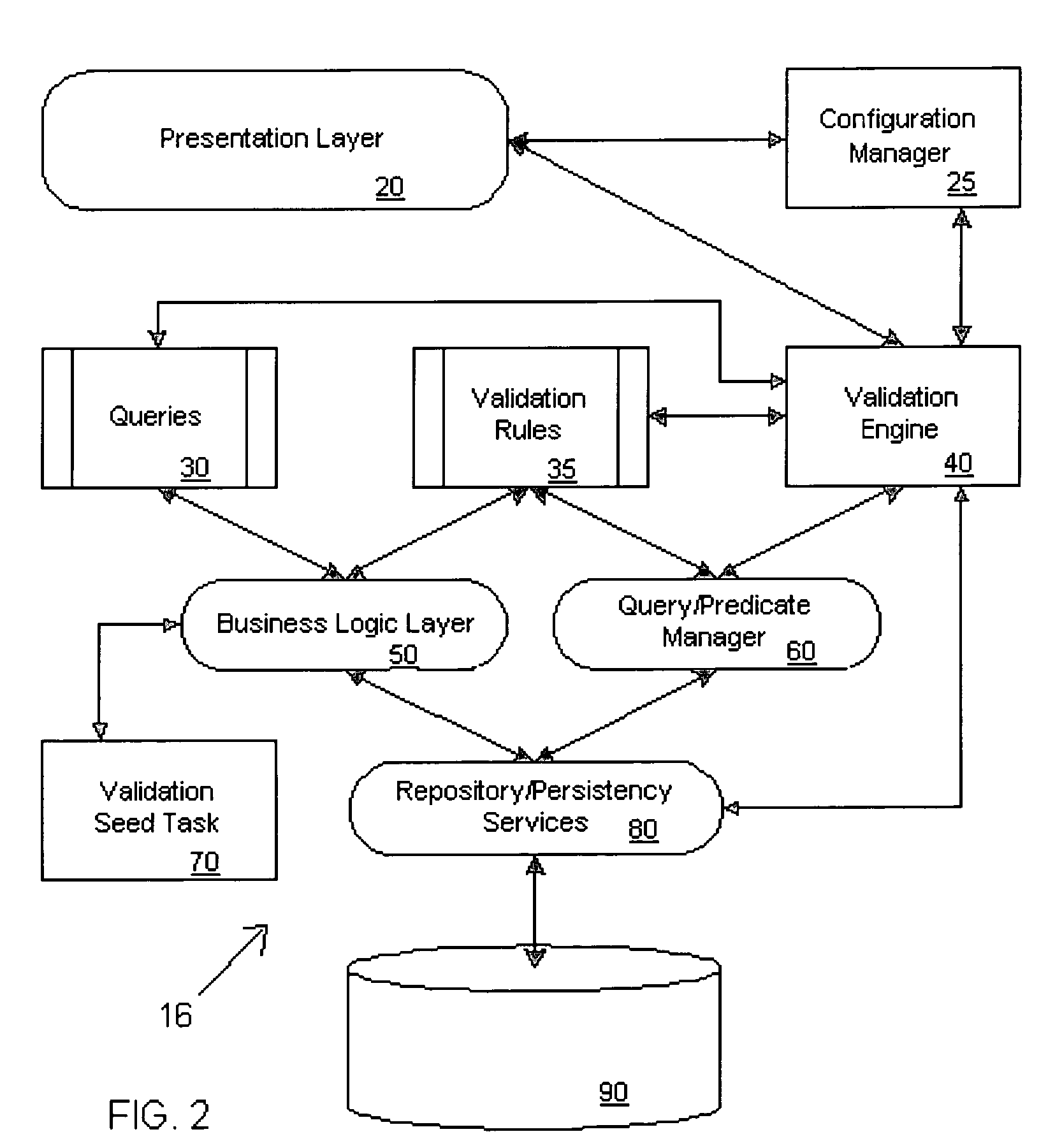
A metadata validation process that allows for deferring object model validation until after the objects are created. The process also allows for multi-threaded processing of the validation rules, thus increasing overall performance. Validation is performed by enforcing a series of validation rules on an appropriate subject. Rules are specified according to the subject that they are validating (i.e., attribute level, association level, object level or collection level). The metadata driven validation process implements several validation types on different validation units. Correctness validation rule types ensure that a validation unit satisfies all semantic rules defined for it. Completeness validation rule types ensure that a validation unit contains all the necessary data and is ready for further use. At design time, only correctness type validation is performed. Thus, the present invention advantageously allows for incomplete objects to be created at design time. The developer, however, in this case may opt to perform completeness validation at any time. In general, a developer may opt to perform completeness and / or correctness validation at any time independent of deployment processing. In another aspect, full validation (e.g., completeness and correctness) is automatically performed on the objects during the process of creating a configuration prior to deployment.
Owner:ORACLE INT CORP
Malicious code detection method and system
ActiveCN110348214AAccurate detectionAccurate descriptionCharacter and pattern recognitionPlatform integrity maintainanceFeature vectorData set
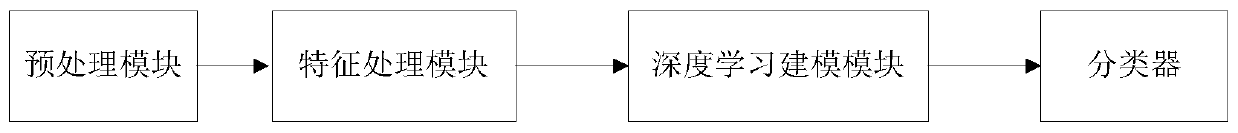
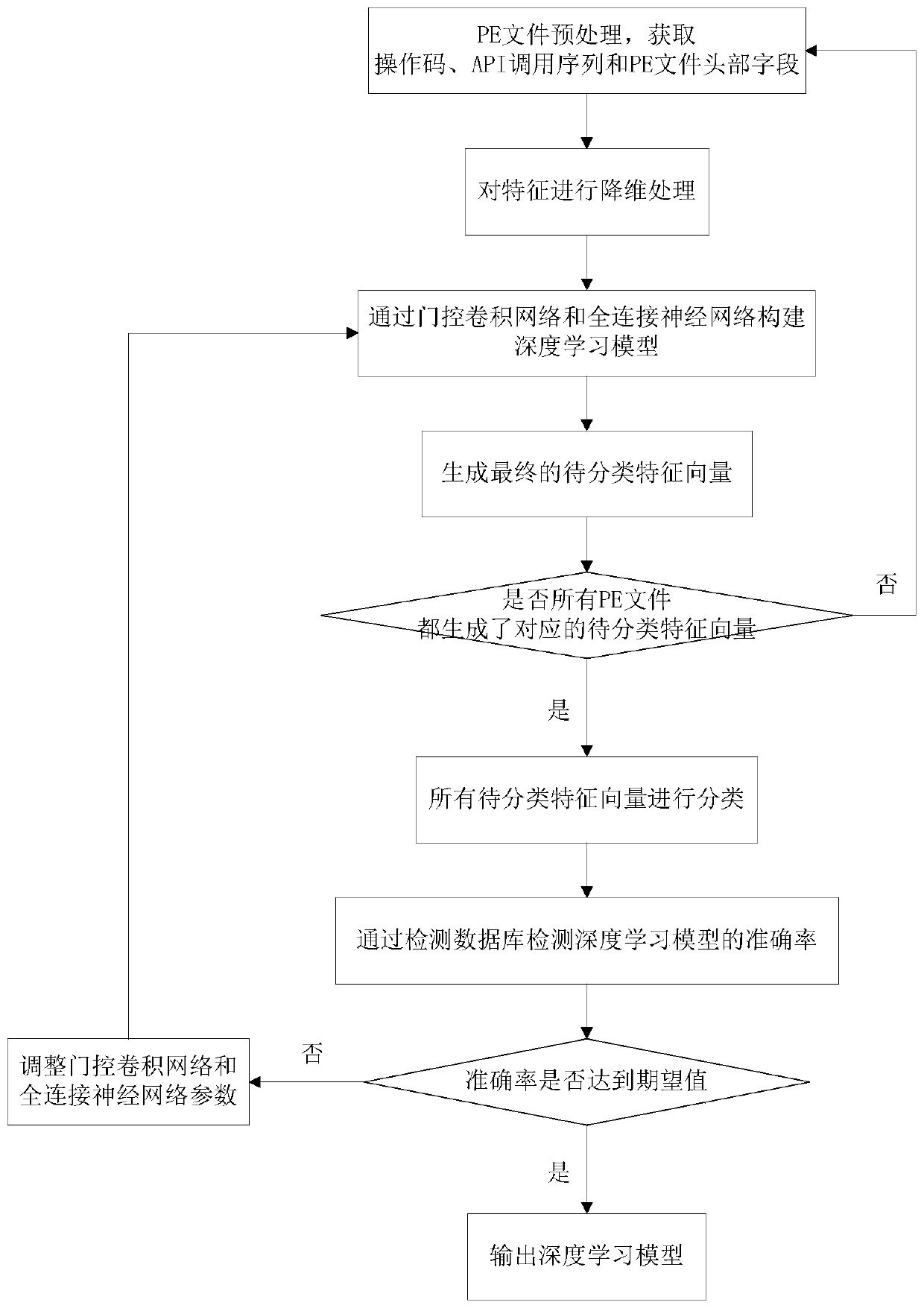
The invention relates to a malicious code detection method and system. The method comprises the steps that A, extracting corresponding features from binary data of a single PE file in a training dataset; b, performing dimension reduction processing on the features; c, extracting the features of the binary data as the front half part of the deep learning model through a gated convolutional network; d, combining the features after dimension reduction with the feature vectors obtained in the step C, inputting the combined features into a full-connection neural network serving as the rear half part of the deep learning model, and generating final feature vectors to be classified; e, generating corresponding to-be-classified feature vectors for all PE files; and F, classifying all the to-be-classified feature vectors, comparing the classified feature vectors with known categories in the test data set to verify the correctness of the deep learning model, and obtaining an optimal deep learning model by adjusting parameters. According to the method, the influence of malicious code instruction transformation can be avoided, whether the unknown software contains the malicious code or not can be accurately detected, and the detection efficiency is also improved.
Owner:UNIV OF ELECTRONICS SCI & TECH OF CHINA
A verifiable fully homomorphic encryption method based on matrix operation
ActiveCN109787743AVerifiableImprove efficiencyKey distribution for secure communicationPlaintextComputer science
The invention discloses a verifiable fully homomorphic encryption method based on matrix operation. The method comprises the following steps: preprocessing and converting plaintext data into vectors to obtain a vector set; Then selecting a non-zero random real number and each vector to construct a triangular matrix, and encrypting each triangular matrix to obtain an encrypted matrix set; Generating verification evidences by utilizing the triangular matrix set according to the calculation function type; Performing matrix operation on each encryption matrix according to a certain rule to obtainan encrypted operation result; And finally, decrypting the encrypted operation result to obtain a plaintext of the result, and verifying the correctness of the result by comparing whether the verification evidence is equal to the value of the calculation result. The method has privacy security and result verifiability; Simulation experiment results show that the method has high efficiency in the stages of secret key generation, decryption and verifiability, and the effectiveness and feasibility of the scheme are shown.
Owner:GUANGXI UNIV
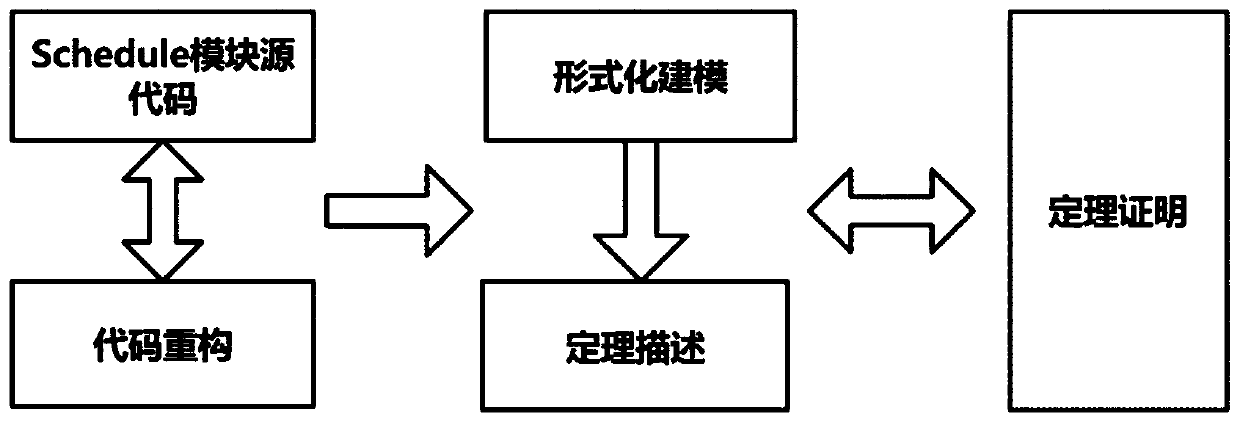
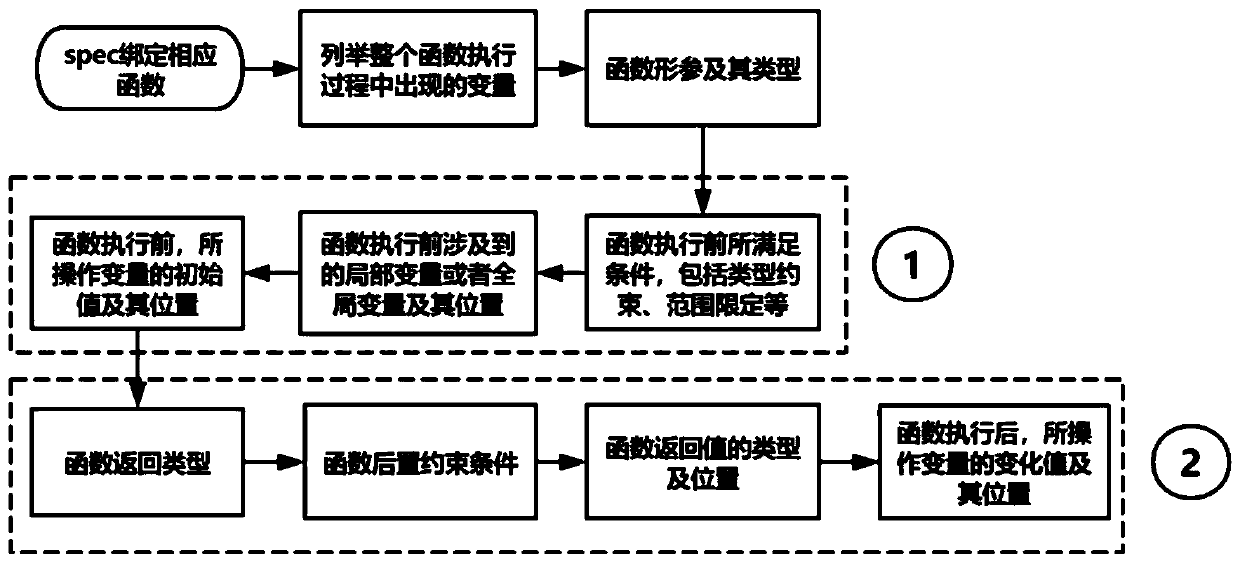
Theorem proving-based formal verification method
InactiveCN110989997AVerified conclusions are credibleProgramming languages/paradigmsOperational systemValidation methods
The invention discloses a theorem proving-based formal verification method. The method is applied to the field of secure operating systems. The invention aims to solve the security problem of an existing operating system. The theorem proving-based formal verification method comprises the following steps that: source codes are reconstructed; formal modeling is conducted on a function; theorem description is conducted on the function; and finally, formal certification is conducted. According to the method of the invention, the semi-automatic proving of human-computer interaction is adopted; by means of an isomorphic relationship between a type system and logic, a proof constructing process is converted into a program writing process; proof correctness check is changed into a type check problem; although a large amount of manual labor is needed to construct the proof, the method provided by the invention does not need to sacrifice the expression ability of protocols and codes, particularly logic with very strong expression ability can be used in a program to realize representation; the proof itself has display representation in a machine; the correctness of the proof itself can be automatically checked; and a verified conclusion is more credible.
Owner:UNIV OF ELECTRONICS SCI & TECH OF CHINA
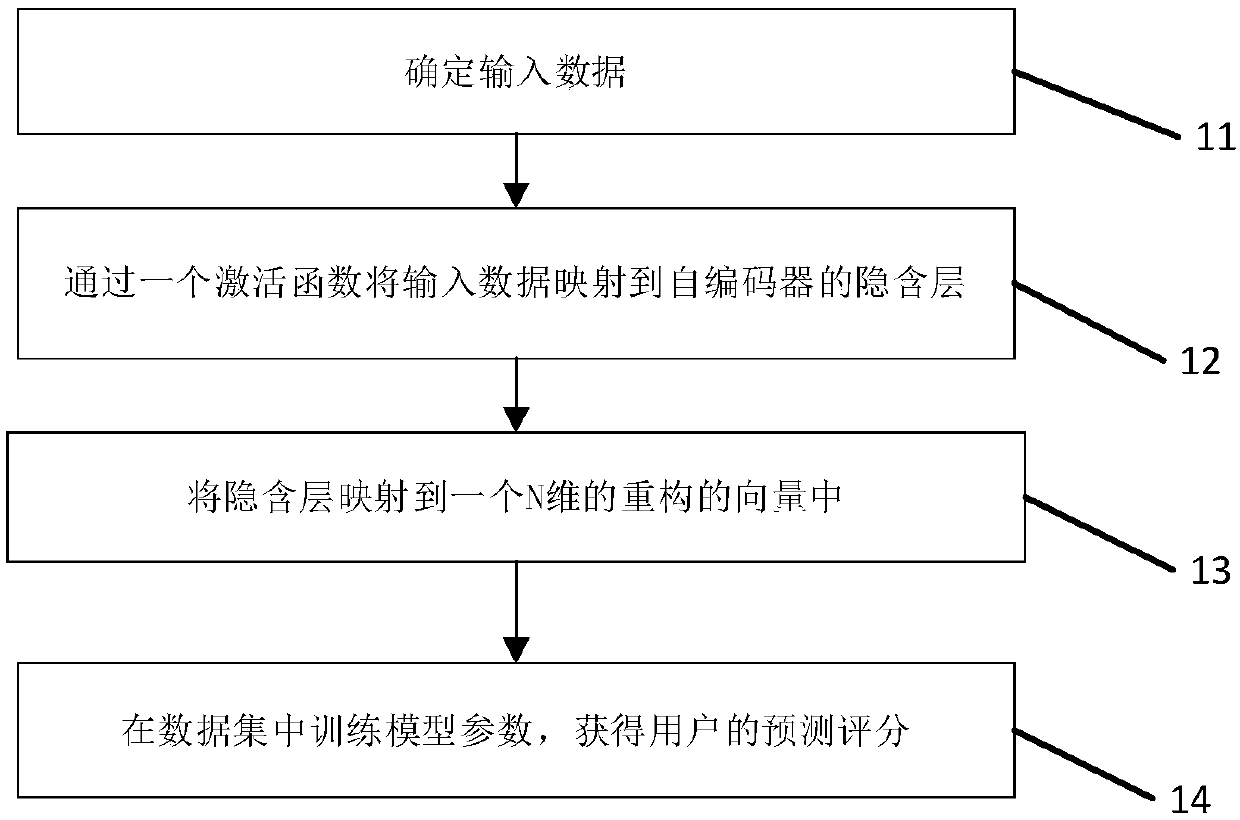
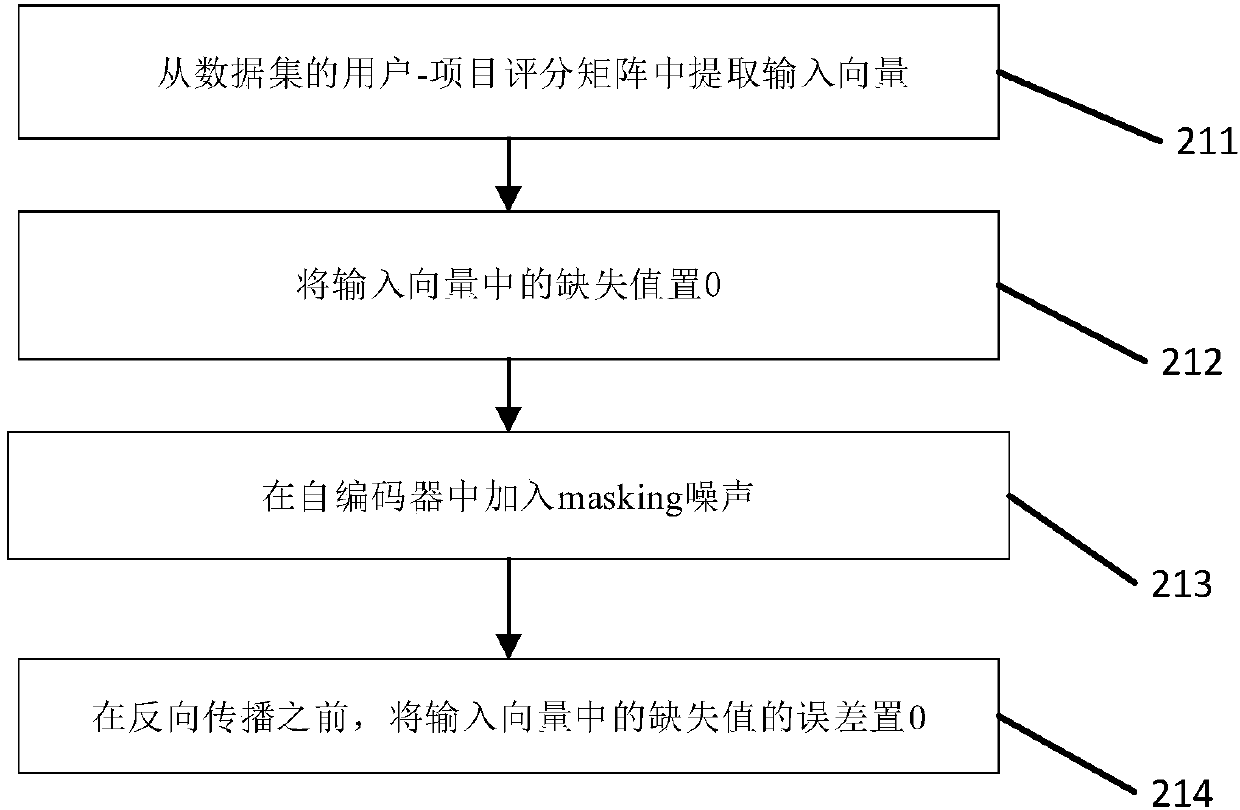
User recommendation method
ActiveCN107943897AImprove robustnessRich relevant informationBuying/selling/leasing transactionsNeural architecturesActivation functionData set
The invention discloses a user recommendation method. The method specifically comprises the following steps of: determining input data of an auto-encoder; mapping the input data to an implicit layer of the auto-encoder through an activation function; mapping the implicit layer into a one-dimensional reconstructed vector; and training model parameters in a data set to obtain a predicted score of auser, wherein the step of training model parameters is carried out through minimizing a reconstruction error. The step of training the model parameters comprises the following steps of: carrying out sparseness on the input data of the auto-encoder; and carrying out training by combining score data of the data set and explicit trust information. The step of carrying out sparseness on the input dataof the auto-encoder comprises the following sub-steps of: extracting an input vector from a user-project score matrix in the data set; setting a missing value in the input value to be zero; adding masking noise in the auto-encoder; and before counter-propagation, setting an error of the missing value in the input vector to be zero. The method is capable of achieving the effect of improving the recommendation correctness.
Owner:NORTHEAST NORMAL UNIVERSITY
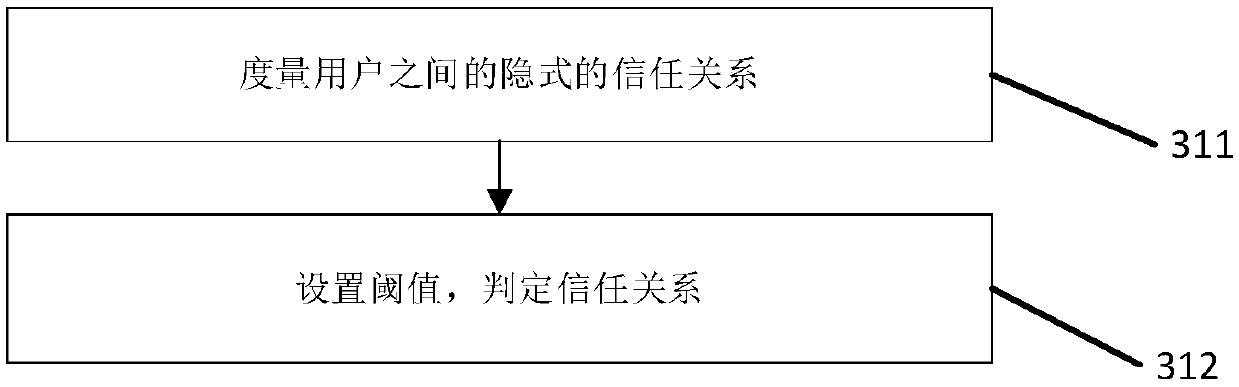
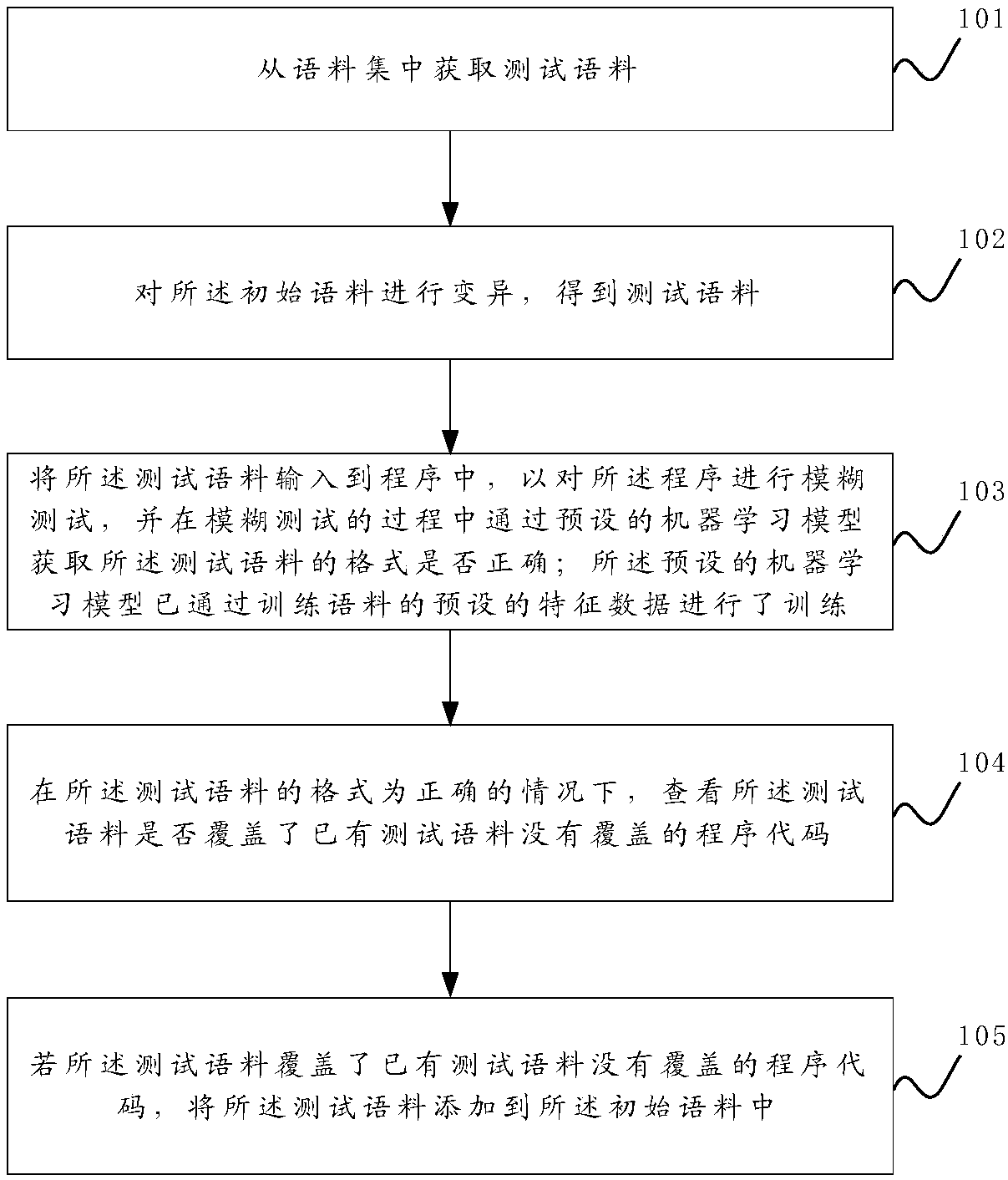
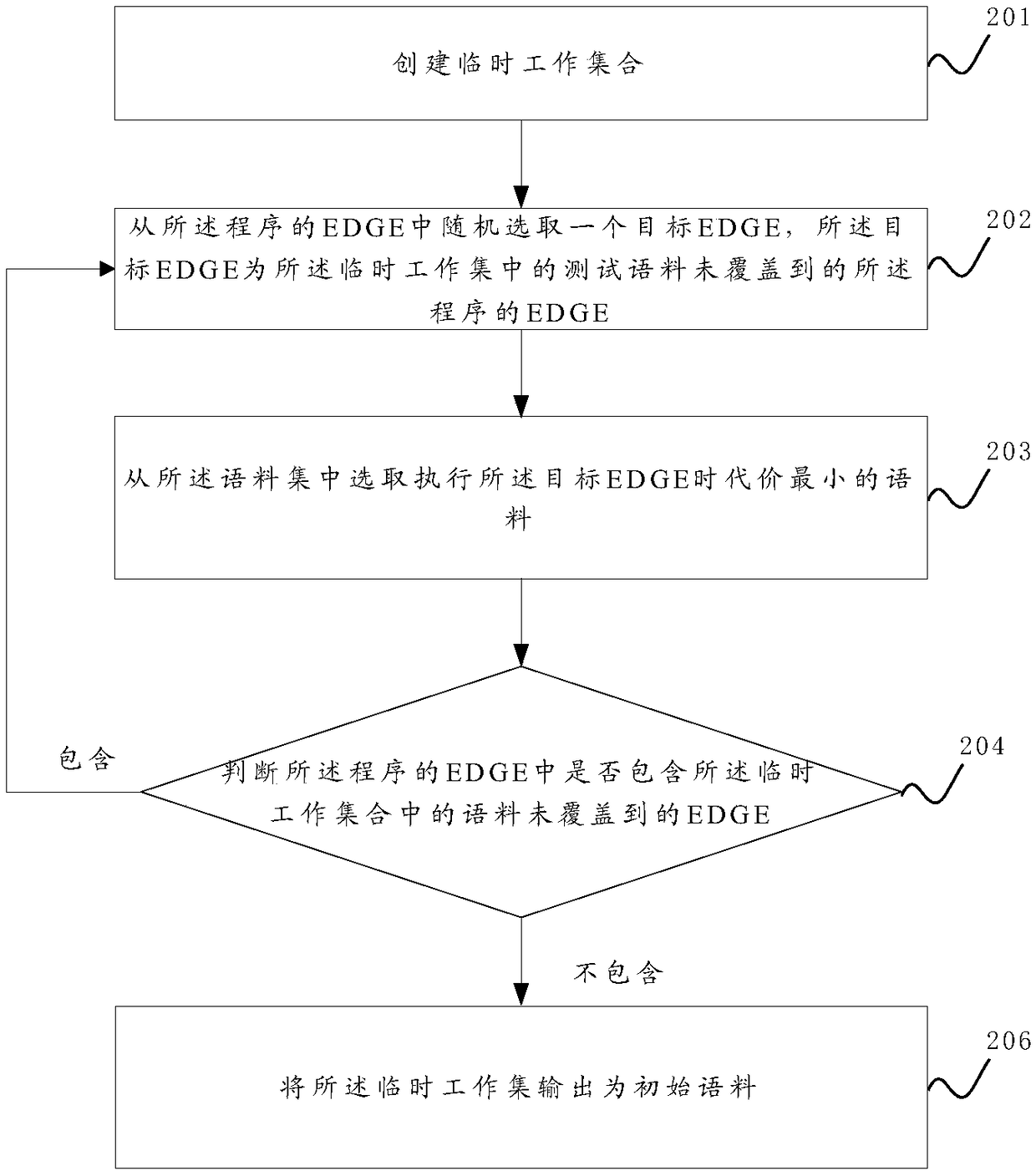
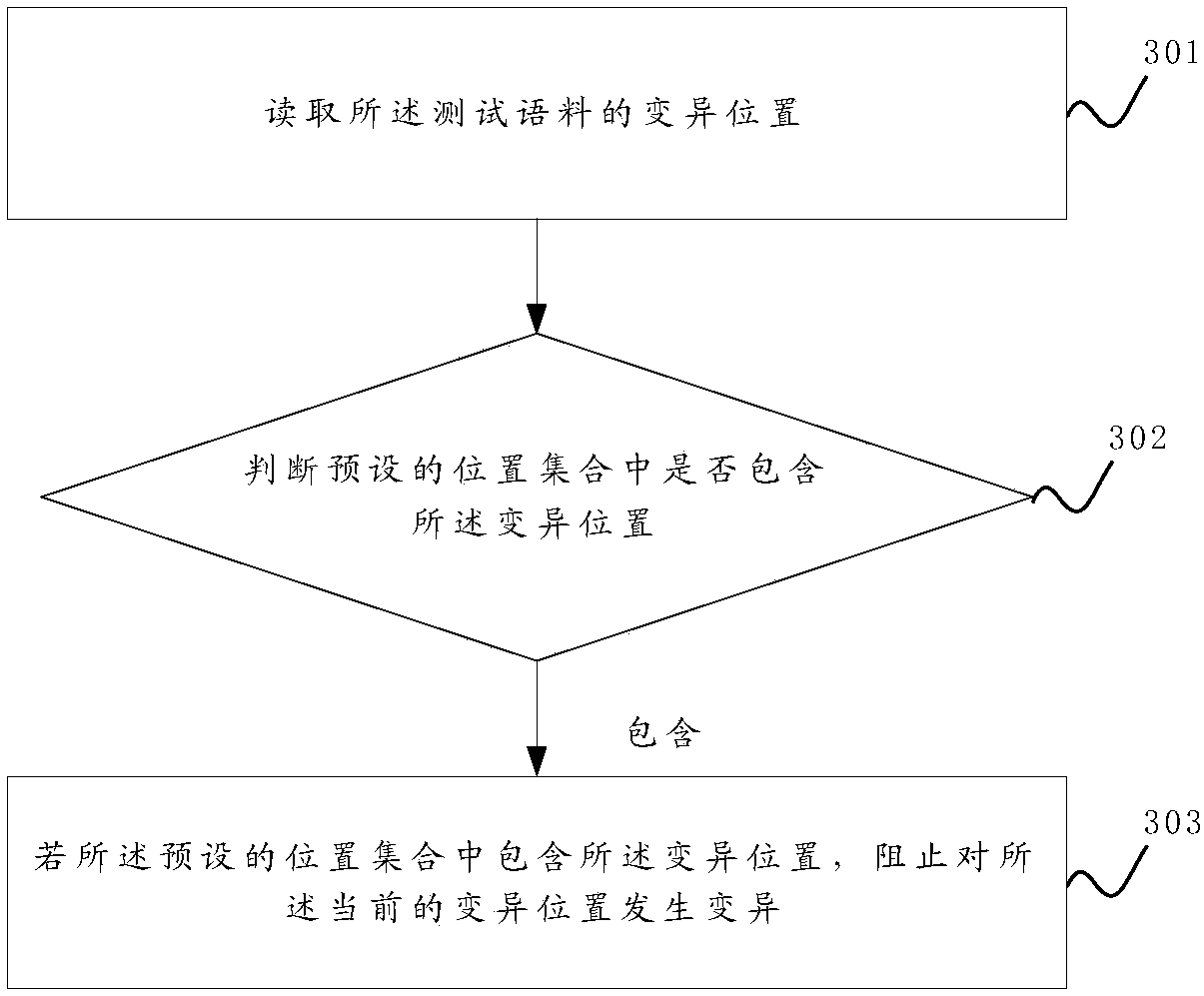
Sample format protection method and device for gray box fuzzy test
ActiveCN108171064AGuaranteed correctnessImprove fuzz testing efficiencySoftware testing/debuggingPlatform integrity maintainanceTest efficiencyTheoretical computer science
The invention discloses a sample format protection method and device for a gray box fuzzy test. The sample format protection method comprises the steps of training a machine learning model to enable the model to recognize the correctness of the format of a testing corpus; when the fuzzy test is conducted on a program, obtaining an initial corpus from a corpus set and mutating the initial corpus toobtain the testing corpus; using the testing corpus to conduct the fuzzy test on the program, and in the process of the fuzzy test, determining whether the format of the testing corpus is correct ornot through the model. When the format of the testing corpus is correct and the testing corpus covers a program code uncovered by an existing testing corpus, the testing corpus is added into the corpus set, and the process is repeated. In this way, the corpuses, with the correct format, determined in each fuzzy test is added into the corpus set, the correctness of the formats of the corpuses in the corpus set is guaranteed to the greatest extent, and the efficiency of the fuzzy test is improved. Moreover, through a position set, the mutation of the initial corpus is guided, an invalid mutationoperation is avoided, and the testing efficiency is further improved.
Owner:PLA STRATEGIC SUPPORT FORCE INFORMATION ENG UNIV PLA SSF IEU
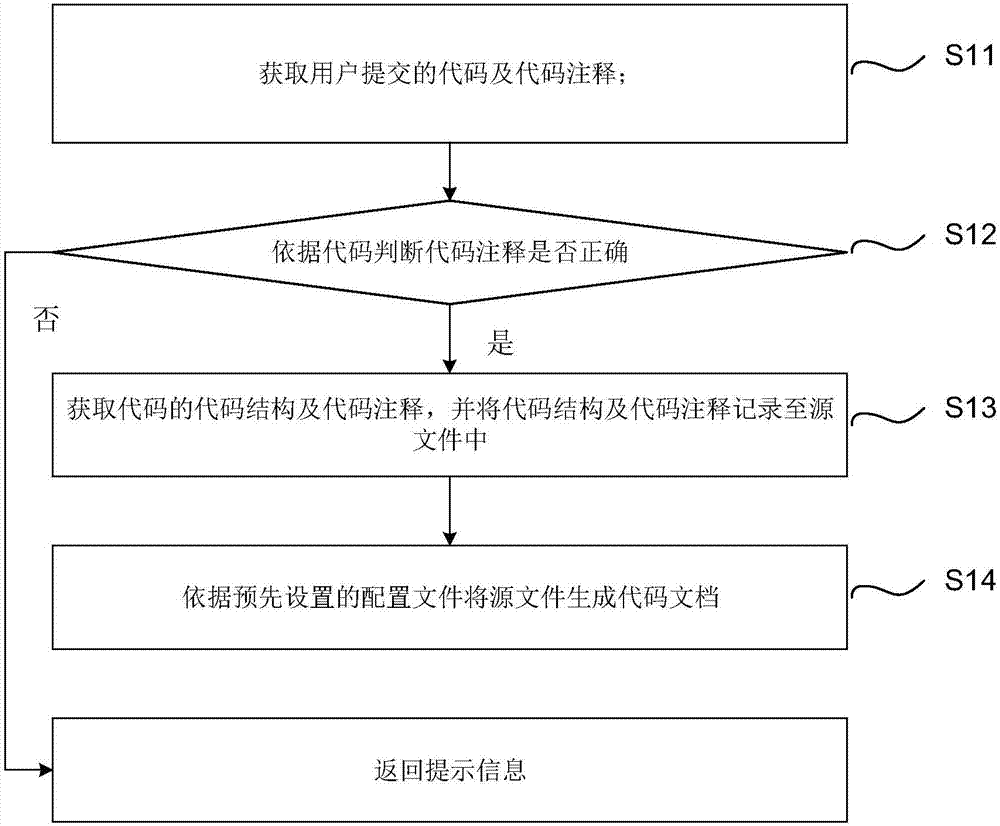
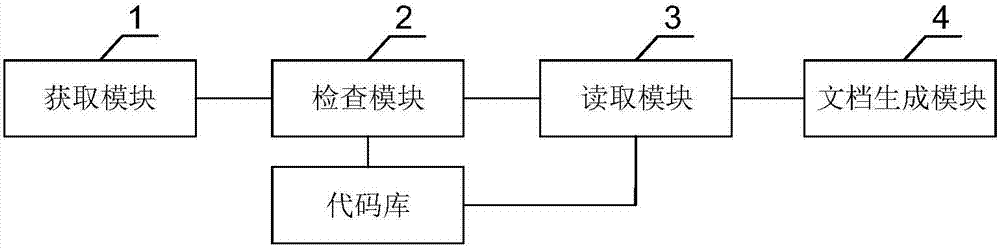
Method, device and system for generating code documents in continuous integration
InactiveCN107256160AImprove accuracyEnsure consistencyProgram documentationSpecific program execution arrangementsDatabaseCode annotation
Embodiments of the invention disclose a method, device and system for generating code documents in continuous integration. The method comprises the following steps of: obtaining a code and a code annotation submitted by a user; judging whether the code annotation is correct or not according to the code; if the judging result is positive, storing the code and the code annotation into a code library and executing the next step; if the judging result is negative, returning prompt information; obtaining a code structure and the code annotation, and recording the code structure and the code annotation into a source file; and generating the source file into a code document according to a preset configuration file. According to the method, the code and the code annotation submitted by the users are verified to ensure the consistency between the code annotation and the code; after the verification passes, the source file is generated according to the code structure and the code annotation, submitted by a worker, of the code; and the source file is generated into the code document according to the preset configuration information. According to the method, device and system disclosed by the invention, the automatic generation and timely updating of code documents are realized, so that the manpower resources are saved, and the working efficiency and the correctness of the code documents are improved.
Owner:ZHENGZHOU YUNHAI INFORMATION TECH CO LTD
Fault-resistant exponentiationi algorithm
InactiveUS20120321075A1Digital data processing detailsSecret communicationRight-to-leftComputer science
A method for performing a m-ary right-to-left exponentiation using a base x, a secret exponent d and a modulus N, wherein m is a power of 2. A device having a processor and m+1 registers R[0]-R[m] in at least one memory: initializes register R[0] to h for a chosen value h, wherein the order of the value h is a divisor of m*(m−1) / 2, register R[m] to x(m−1) and the registers other than R[0] and R[m] to the value h; updates register R[r] to R[r] times x, wherein r is the remainder of a division of d by (m−1) mod N; obtains a working exponent q that is the quotient of the division of d by (m−1); performs l iterations, starting at i=0, of: setting R[qi] to R[qi] times R[m] and raising R[m] to the power of m, where l is the length of q in base m and qi is the i-th digit of the representation of q in base m and ql−1 is non-zero; verifies the correctness of the result by checking that R[m] equals the product of registers R[0]-R[m−1] to the power of m−1; and outputs the product of R[l]j, where 1≦j≦m−1, only if the correctness is successfully verified.
Owner:MAGNOLIA LICENSING LLC
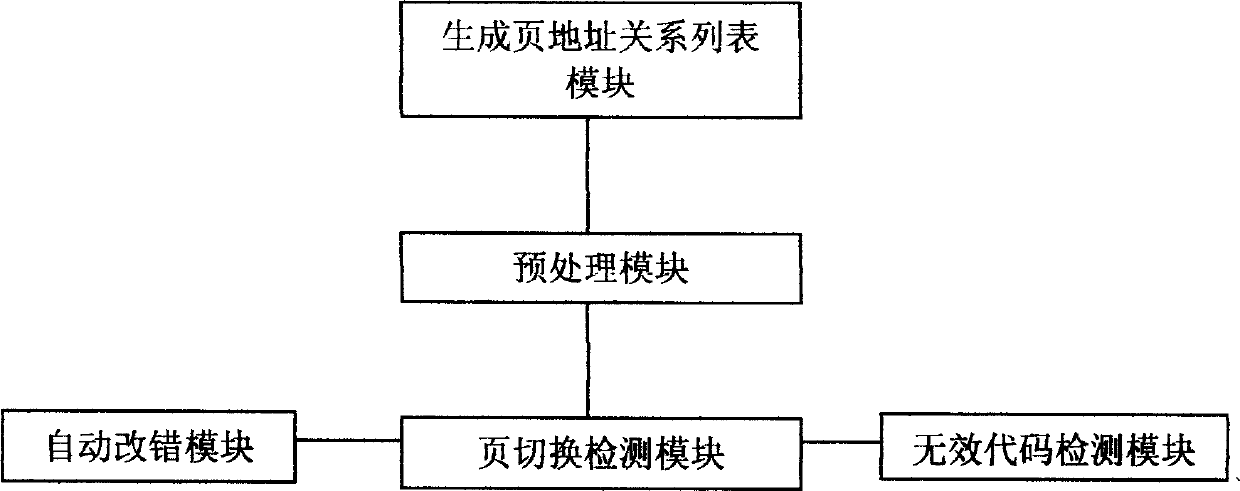
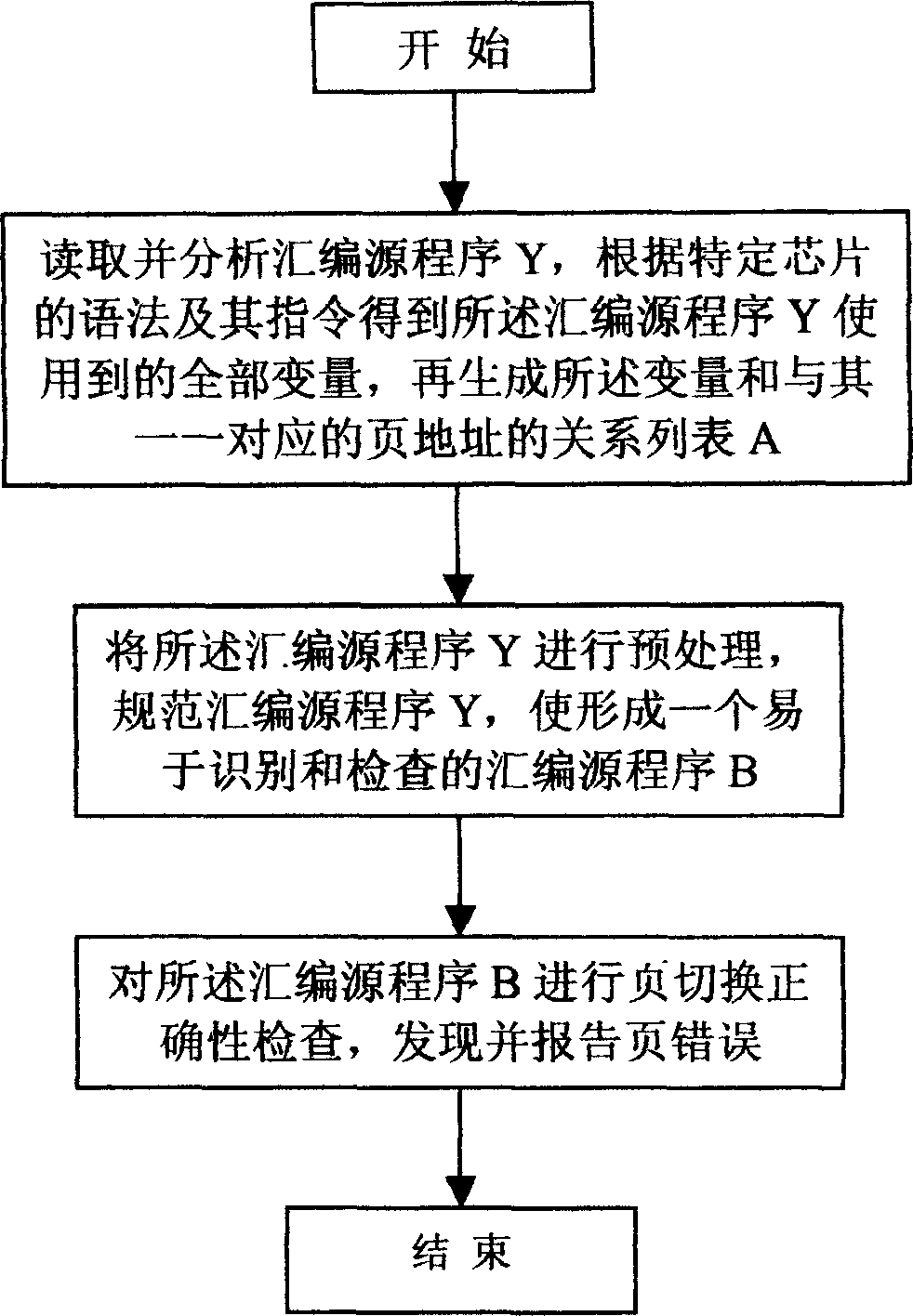
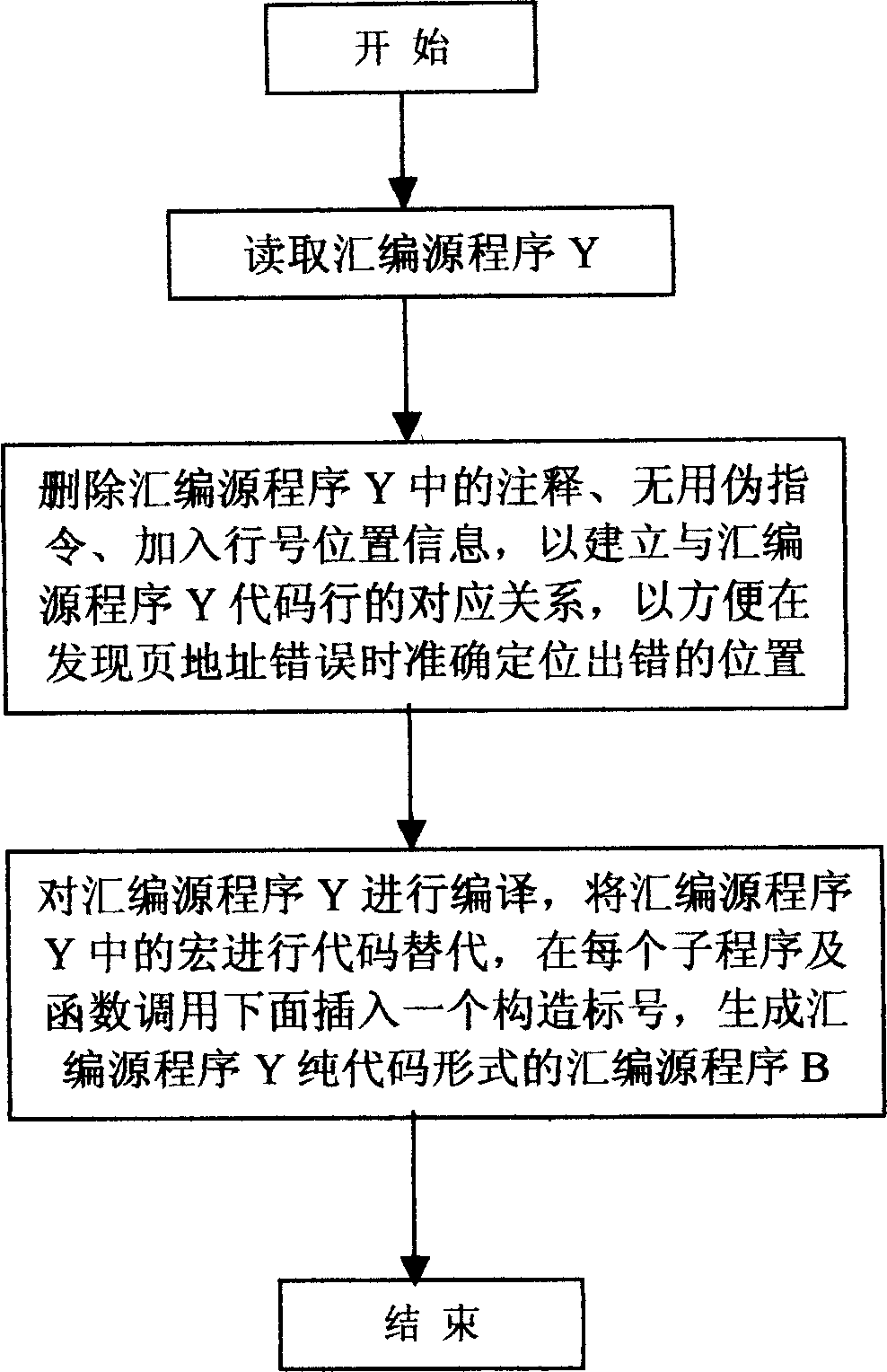
Automatic debugging and mistake correcting method and system for assembly program in embedded module
InactiveCN1632763AAccurate checkSave human effortSoftware testing/debuggingDead codeProgramming language
It is an assembler program automatic fault-finding method, which comprises the following steps: to read and analyze the assembler program Y and to get the said whole variables of the said program according to the grammar and orders of the special chip and to generate the relation form A between the variable and the web address; to pre-process the assembler program and standardize the program to form one assembler program easy to be identified and inspected; to test the web page accuracy of the program and to fine the error of the report page.
Owner:时仁帅
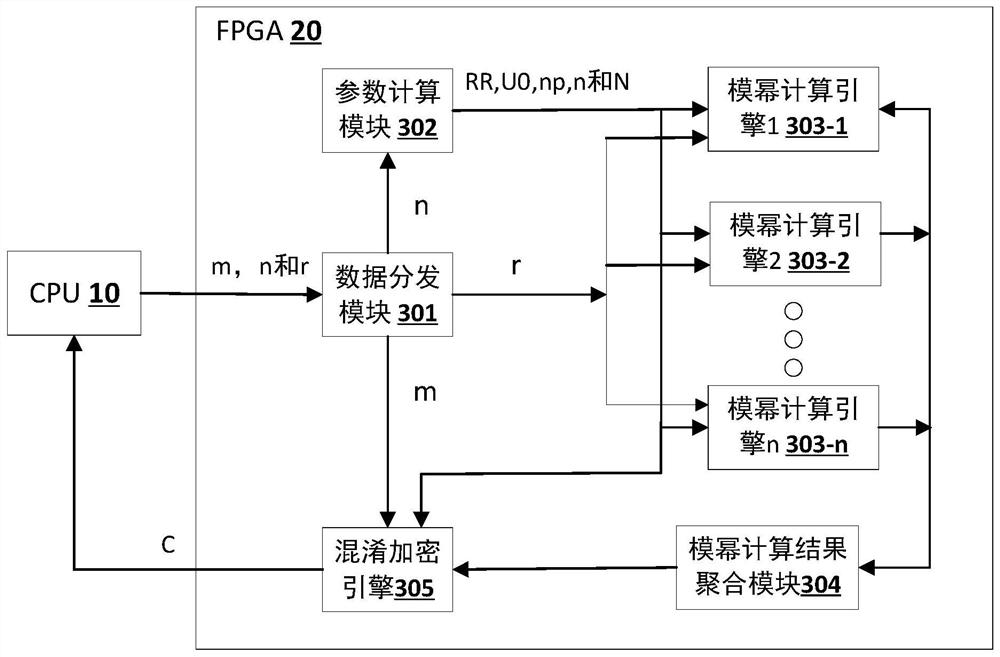
Algorithm verification method and system for federated learning heterogeneous processing system
PendingCN112286752AEnsemble learningError detection/correctionTheoretical computer scienceCorrectness
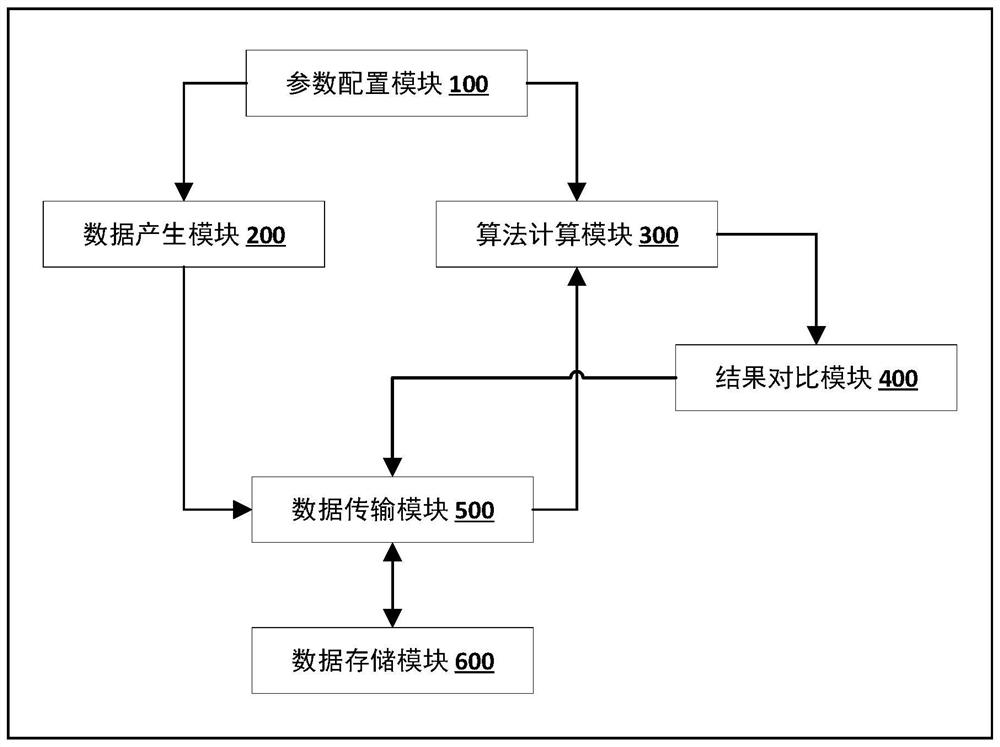
The embodiment of the invention provides an Algorithm verification method and system for federated learning heterogeneous processing system, which is applied to verifying the correctness of an FPGA heterogeneous computing chip algorithm in the heterogeneous processing system, and comprises the following steps: acquiring configuration information which comprises an algorithm type, each input parameter and the bit width of each input parameter; randomly generating input parameter data according to the bit width configuration information of each input parameter; performing calculation based on astandard operation library according to the input parameter data to obtain a standard value; based on an actual algorithm of an FPGA heterogeneous computing chip, calculating according to the input parameter data to obtain an actual value; and comparing the standard value with the actual value, if the standard value is consistent with the actual value, determining that the algorithm verification is passed, and if the standard value is inconsistent with the actual value, sending error information. According to the scheme, the correctness of algorithm implementation on the heterogeneous computing chip can be automatically verified, and the engineering verification efficiency is improved.
Owner:CLUSTAR TECH LO LTD
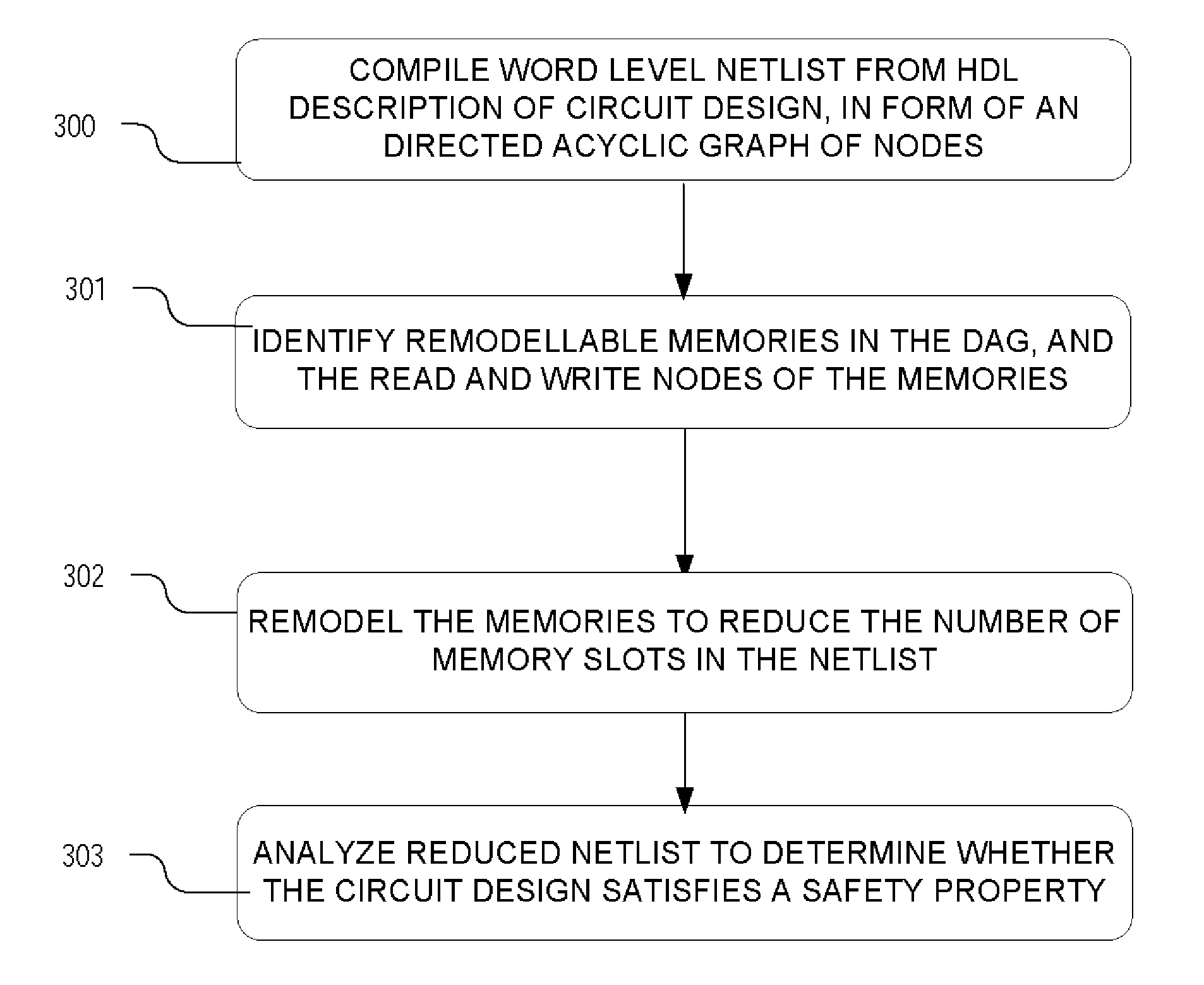
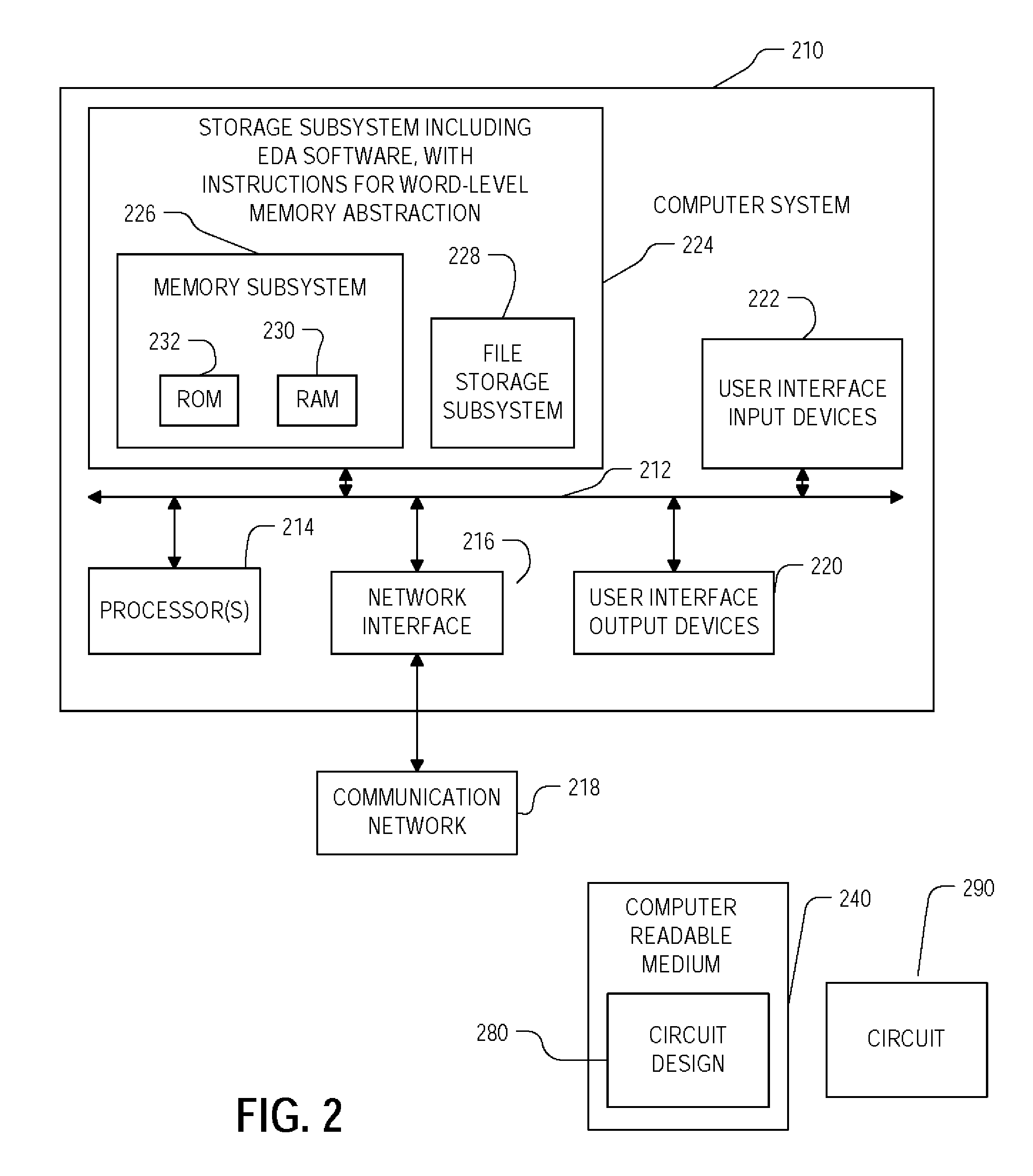
Method and apparatus for memory abstraction and verification using same
ActiveUS20100107131A1Reduce decreaseReduced netlistComputer aided designSoftware simulation/interpretation/emulationNetlistCircuit design
A computer implemented representation of a circuit design including memory is abstracted to a smaller netlist, which can be analyzed by standard verification tools and by other tools that operate on netlists. The correctness of such systems can require reasoning about a much smaller number of memory entries than exist in the circuit design, and by abstracting such memories to a smaller number of entries, the computational complexity of the verification problem is substantially reduced.
Owner:SYNOPSYS INC
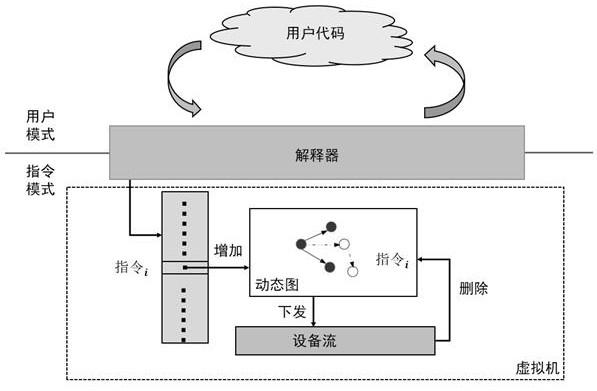
Dynamic graph execution method and device for neural network calculation
ActiveCN114461351AMeet the needs of just-in-time debuggingSatisfy the correctness of instant verification algorithmProgram initiation/switchingBiological neural network modelsScheduling instructionsTheoretical computer science
The invention discloses a dynamic graph execution method and device for neural network calculation. The method comprises the following steps: S1, constructing and distributing operators and tensors; s2, deriving an operator execution process by an operator interpreter; s3, the operator interpreter constructs an instruction of the virtual machine during operation; s4, the operator interpreter sends the instruction to the runtime virtual machine; s5, a virtual machine dispatch instruction; and S6, releasing the executed instruction by the virtual machine. According to the dynamic graph execution method and device for neural network calculation provided by the invention, the runtime is abstracted as the virtual machine, and the virtual machine obtains the sub-graph scheduling of each step established by the user through the interpreter in real time and issues and executes each sub-graph, so that the instant debugging requirement of the user is met, local adjustment and optimization can be realized, and the user experience is improved. And obtaining an optimal local model. And the requirements of algorithm researchers for instantly verifying the algorithm correctness and the local performance of the model in the model development process are met.
Owner:ZHEJIANG LAB
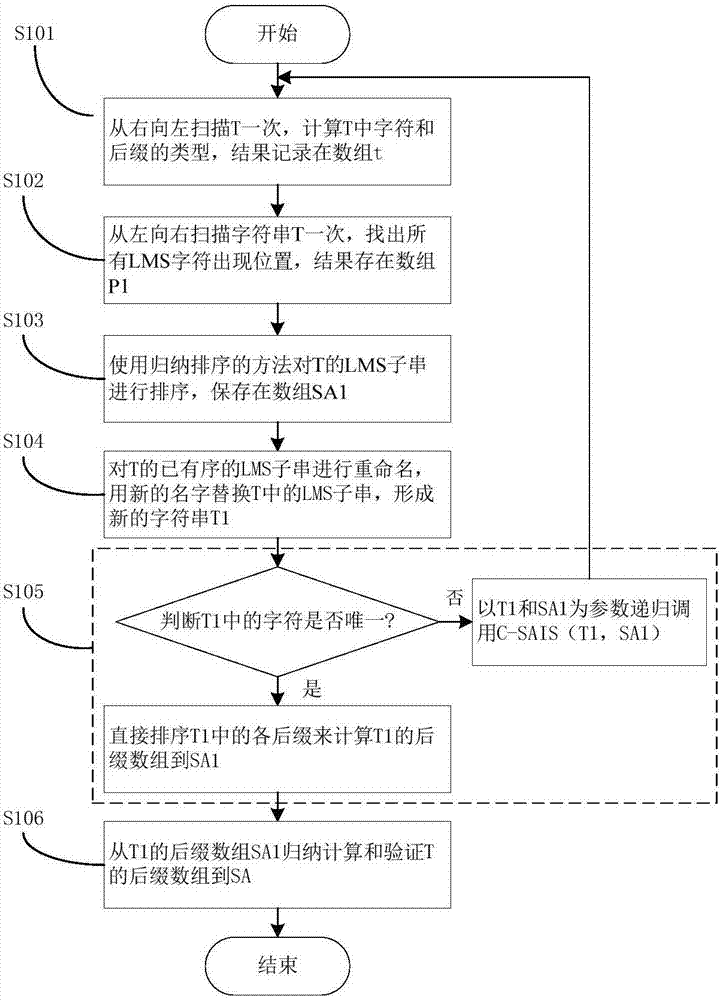
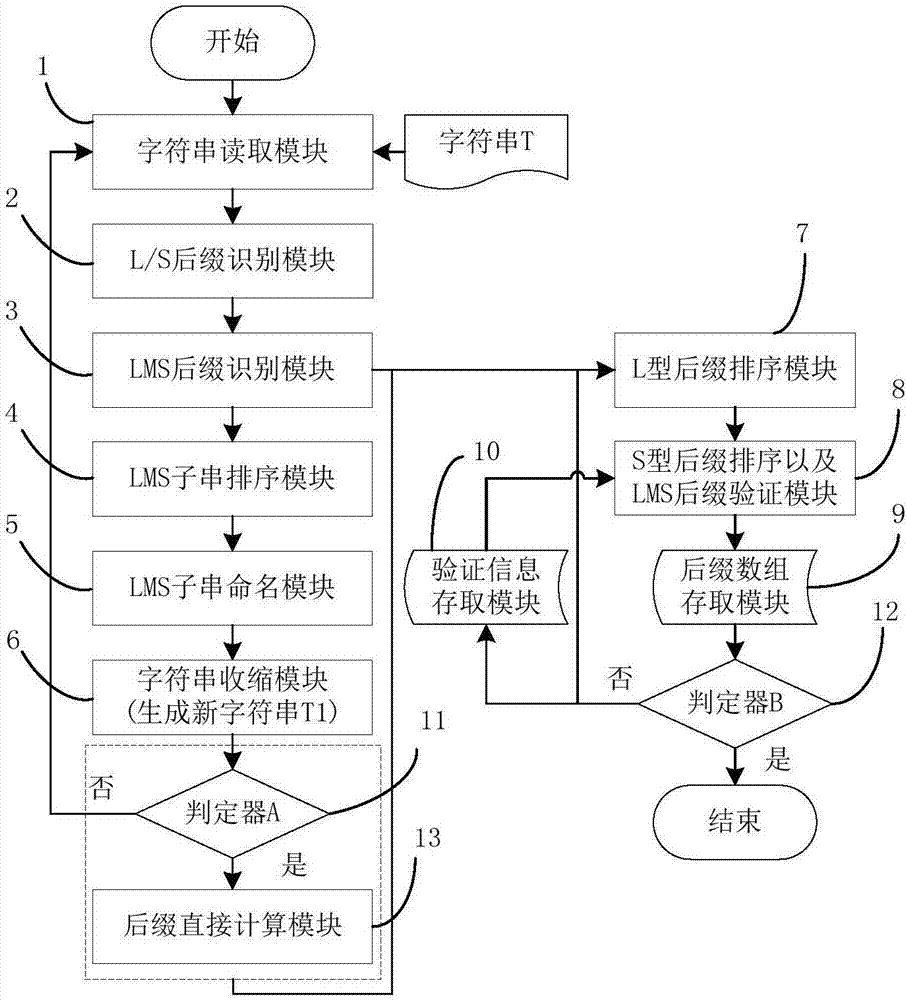
Correctness verification method and system of suffix array
ActiveCN107015951AImplement correctness verificationShorten the timeNatural language data processingSpecial data processing applicationsParallel computingCorrectness
The invention relates to a correctness verification method and system of a suffix array. The method includes the steps that T is scanned once from right to left, the size of a currently scanned character T[i] and the size of a subsequent character T[i+1] are compared according to the definition of suffix types, and the types of the characters T[i] and suf(T, i) of T are calculated and recorded in t[i]; T is scanned once from left to right, the positions of all LMS characteristics are found, and first-character pointers of all LMS sub-strings are obtained accordingly and recorded with an array P1; according to arrays P1, B and SA, the LMS sub-strings of T are sorted through an inducting and sorting method, and the result is saved in an array SA1; SA is scanned from left to right, and if SA[i] is of an LMS type, SA[i] is saved in SA1; whether characters in T1 are unique or not is judged, if yes, SA1 is directly calculated according to the name of T1, and an array C is updated through SA1; the suffix array SA of T is inductively calculated according to T1 and SA1, the correctness of SA is verified through the array C in the calculation process, and if SA is correct, the array C is updated through SA.
Owner:SYSU CMU SHUNDE INT JOINT RES INST +1
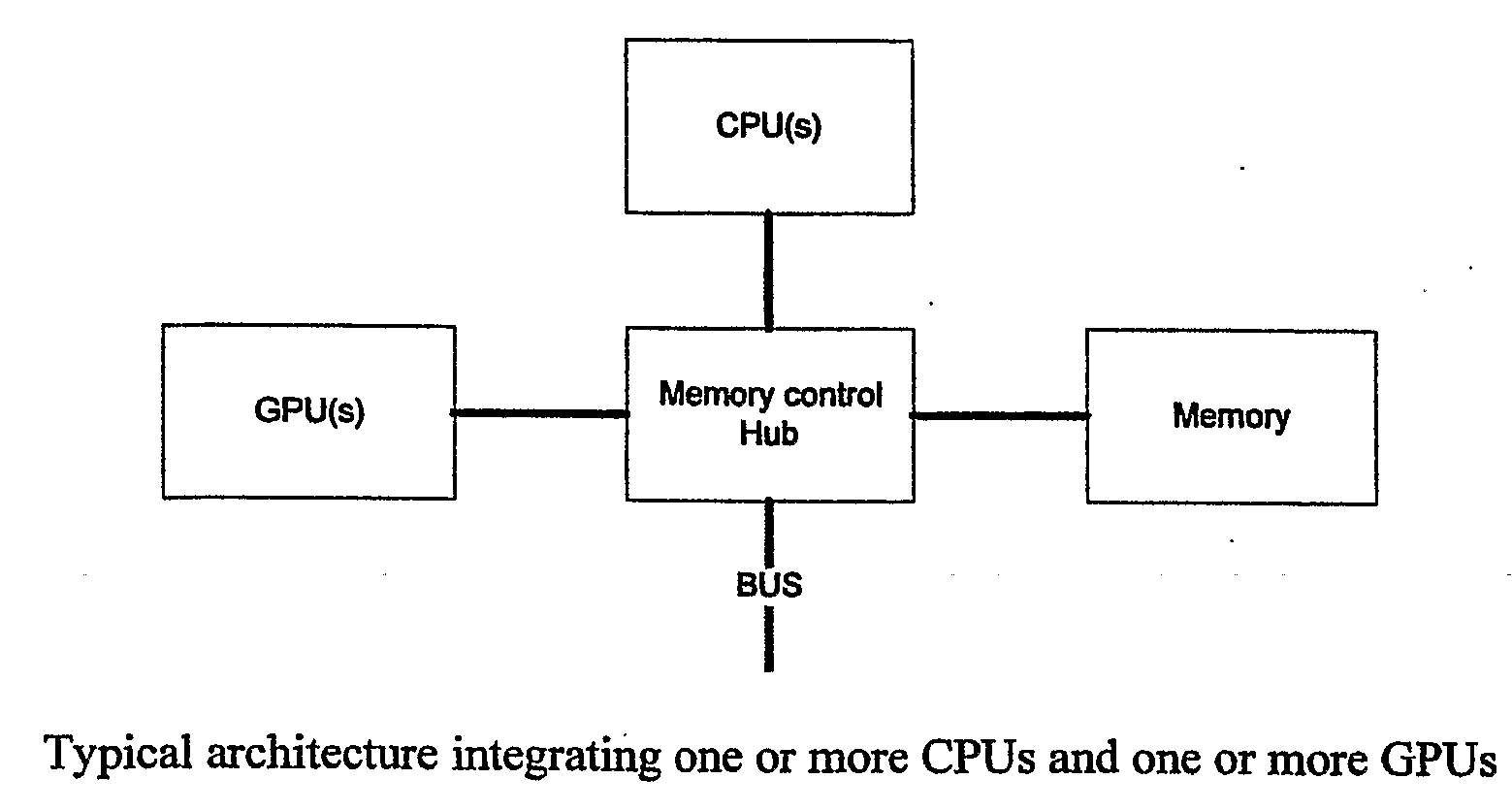
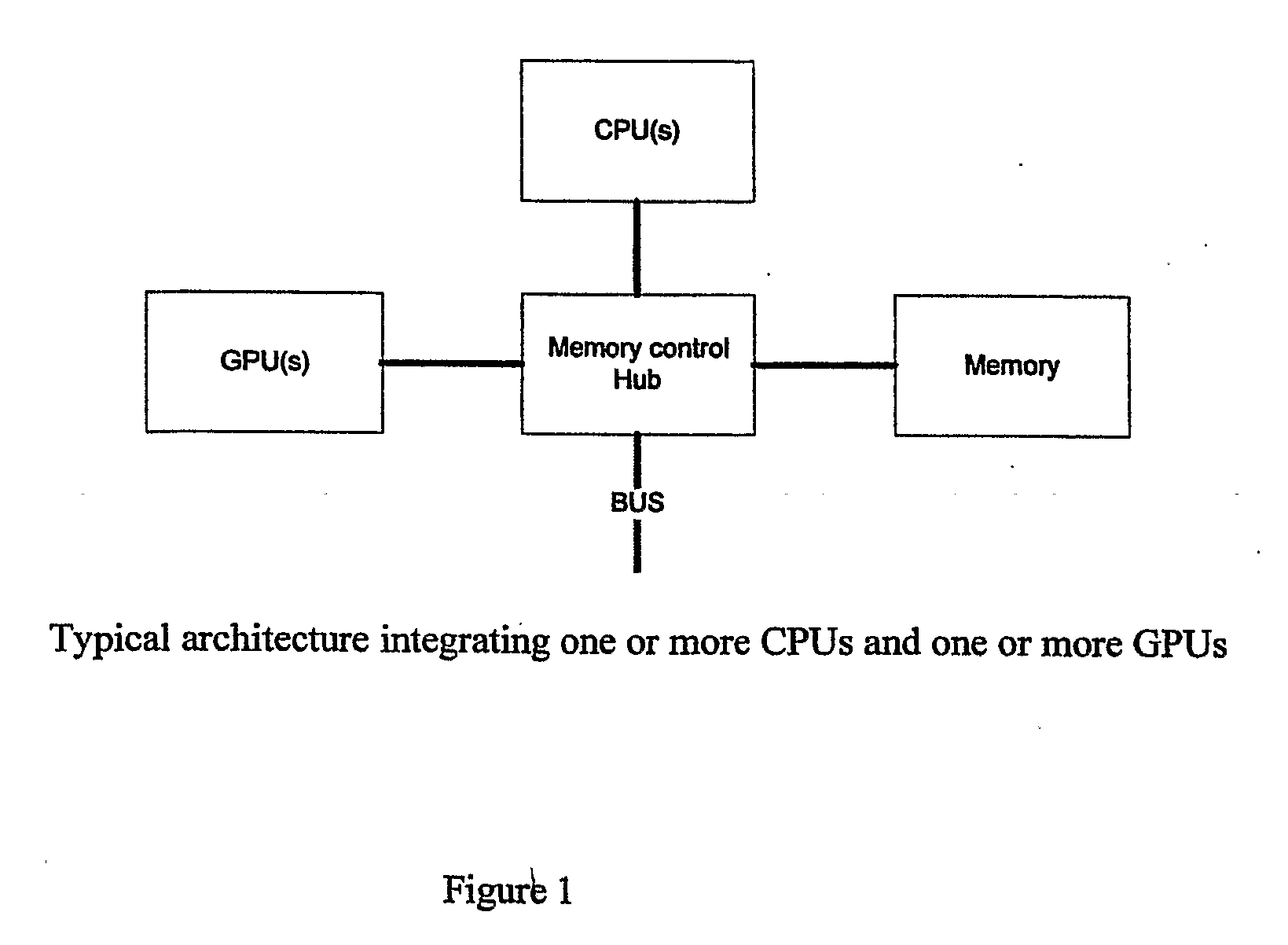
Apparatus and Method for Determining Intersections
InactiveUS20080259078A1Increase speedGuarantee qualityMultiple digital computer combinationsImage data processing detailsNormal fieldCriss-cross algorithm
In a data processing system for determining intersections between geometric objects, the work is split between a CPU and a stream processor. The intersection determination is controlled by the CPU. Data processing intensive parts of intersection algorithms, such as checking possible overlap of objects, checking overlap of normal fields of objects, approximating the extent of an object, approximating the normal fields of an object, or making conjectures for intersection topology and / or geometry between objects, are run on the stream processor. The results of the algorithmic parts run on the stream processor are used by the part of the algorithms run on the CPU. In cases where conjectures for the computational result are processed on the stream processor, the conjectures are checked for correctness by algorithms run on the CPU. If the correctness check shows that the result found is incomplete or wrong, additional parts of the algorithm are run on the CPU and possibly on the stream processor.
Owner:SINVENT AS
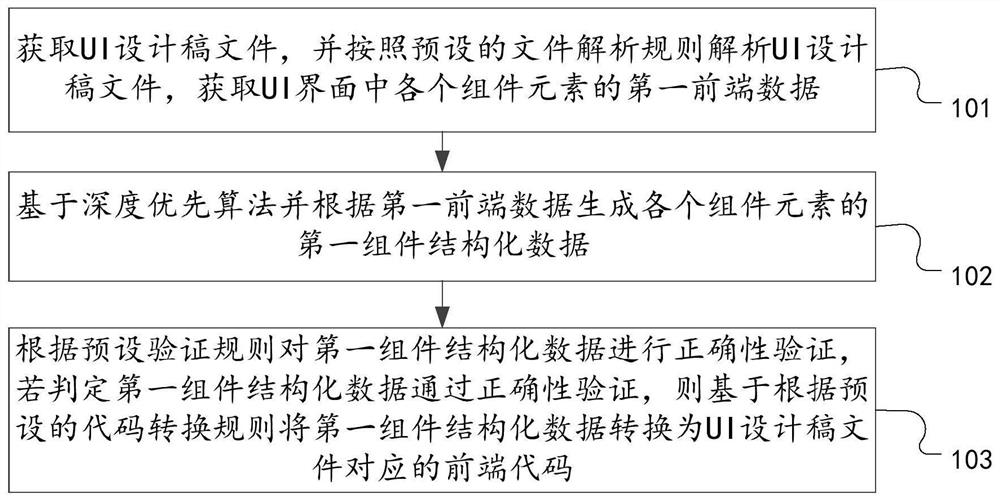
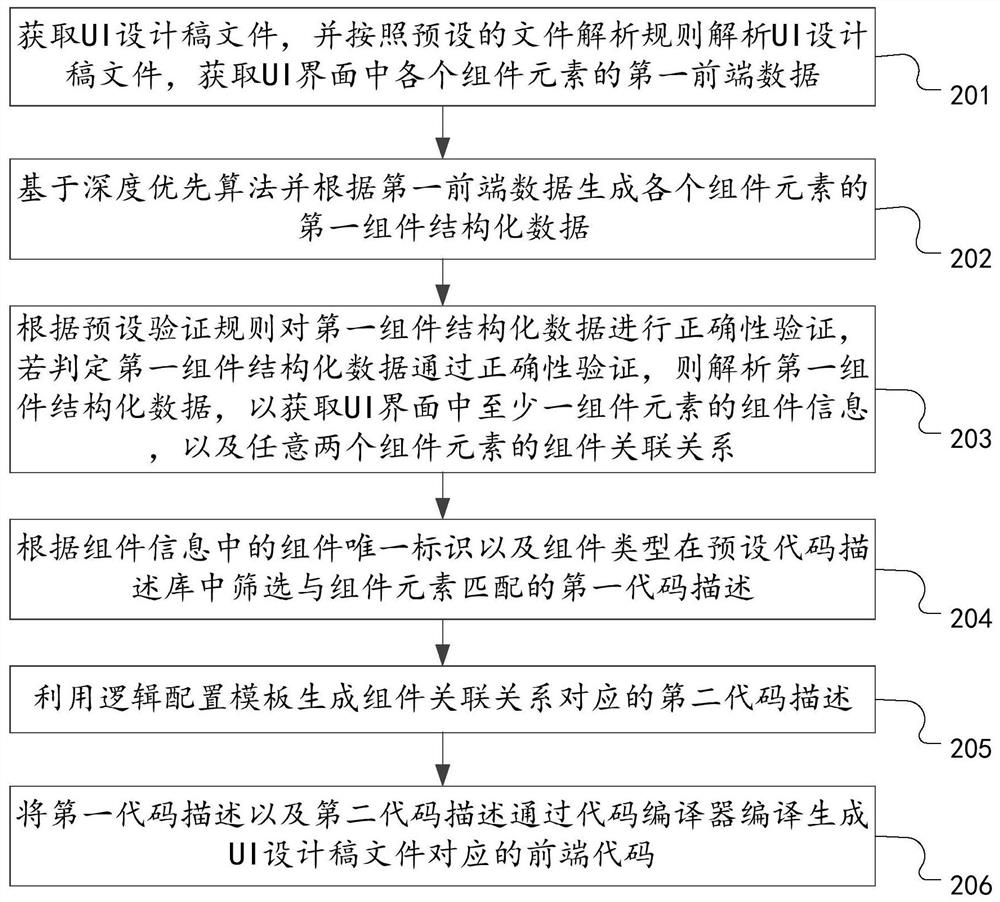
Front-end code generation method and device and computer equipment
ActiveCN113805871AReduce learning costsImprove efficiencyVisual/graphical programmingEnergy efficient computingCode generationData transformation
The invention discloses a front-end code generation method and device and computer equipment, relates to the technical field of computers, and can solve the technical problems that the code generation efficiency is low and the workload is large due to the fact that an existing front-end code generation mode has a repeated labor part. The method comprises the following steps: acquiring a UI design draft file, analyzing the UI design draft file according to a preset file analysis rule, and acquiring first front-end data of each component element in a UI interface; based on a depth-first algorithm and according to the first front-end data, generating first component structured data of each component element; and performing correctness verification on the first component structured data according to a preset verification rule, and if it is judged that the first component structured data passes the correctness verification, converting the first component structured data into a front-end code corresponding to the UI design draft file based on a preset code conversion rule. The invention is suitable for automatic generation of front-end codes.
Owner:PINGAN INT SMART CITY TECH CO LTD
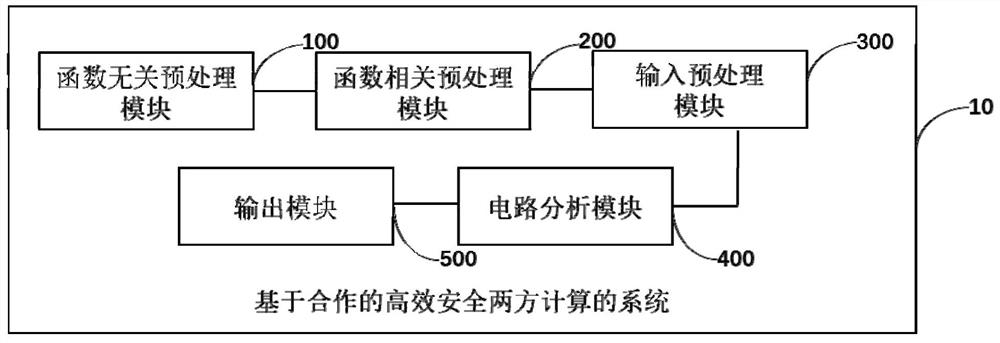
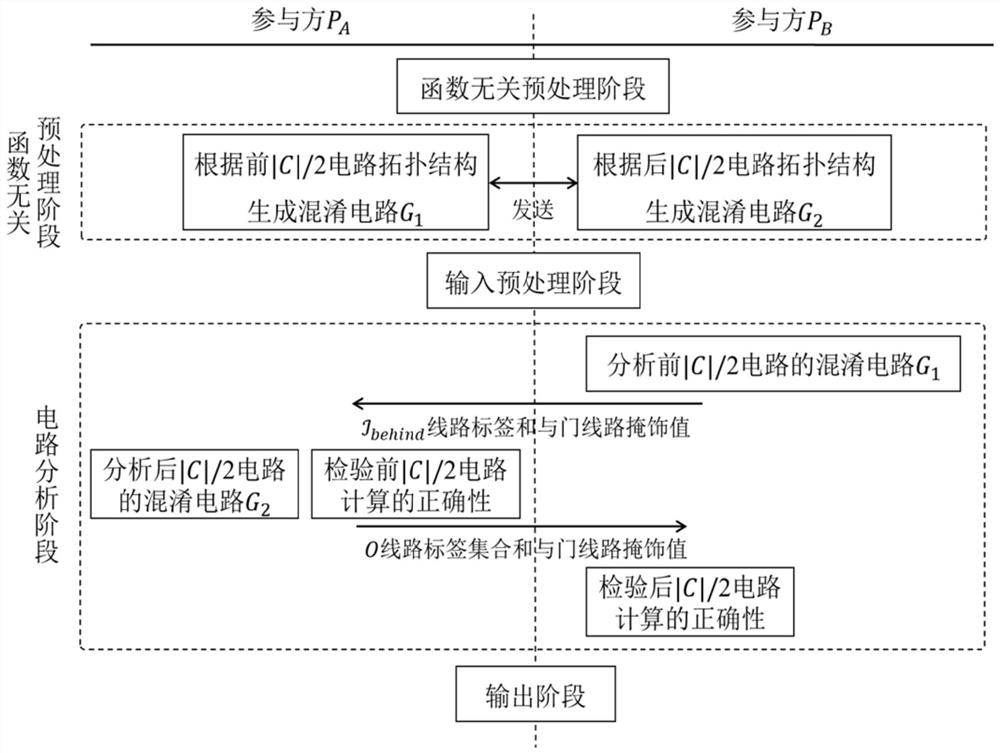
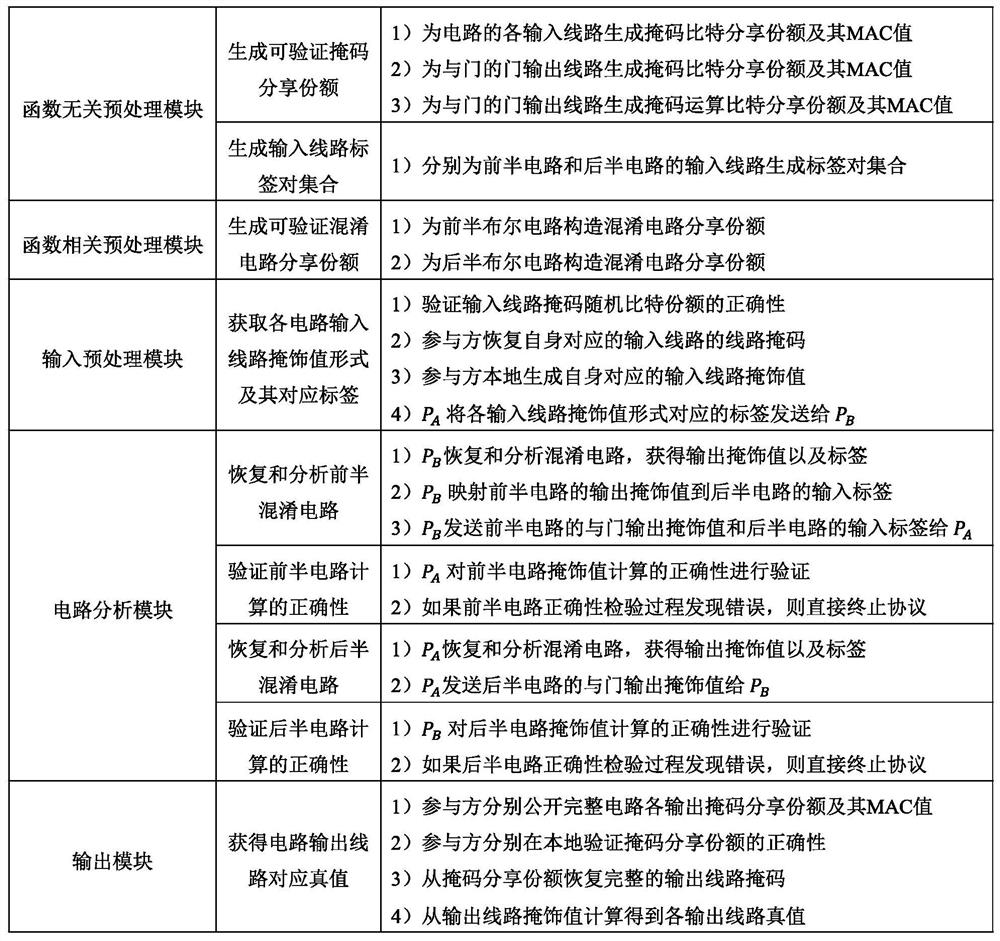
Efficient and safe two-party computing system and computing method based on cooperation
PendingCN113591146AReduce complexityReduce communication delayDigital data protectionSecuring communicationCorrectnessComputing systems
The invention discloses an efficient and safe two-party computing system and method based on cooperation, and the system comprises: a function-independent preprocessing module which is used for pre-generating verifiable random bit sharing shares and a label pair set of an input line, which are needed by safe computing, for two communication parties; a function correlation preprocessing module, wherein participants serve as confusion parties respectively, and verifiable confusion circuit sharing shares are generated for the first half circuit and the second half circuit respectively; an input preprocessing module, wherein a calculation side obtains a label set corresponding to a true value masking value form of each input line of the circuit; a circuit analysis module, wherein participants serve as calculation parties in sequence, confusion circuits of a front half circuit and a rear half circuit are recovered and analyzed respectively, and the correctness of circuit calculation is verified; and an output module, wherein the two communication parties obtain the corresponding masking values from the output line labels and recover the output true values. According to the system, circuit calculation correctness and input privacy can be ensured, communication complexity is low, both parties share calculation pressure, safety calculation efficiency is high, and malicious opponents can be resisted.
Owner:BEIHANG UNIV
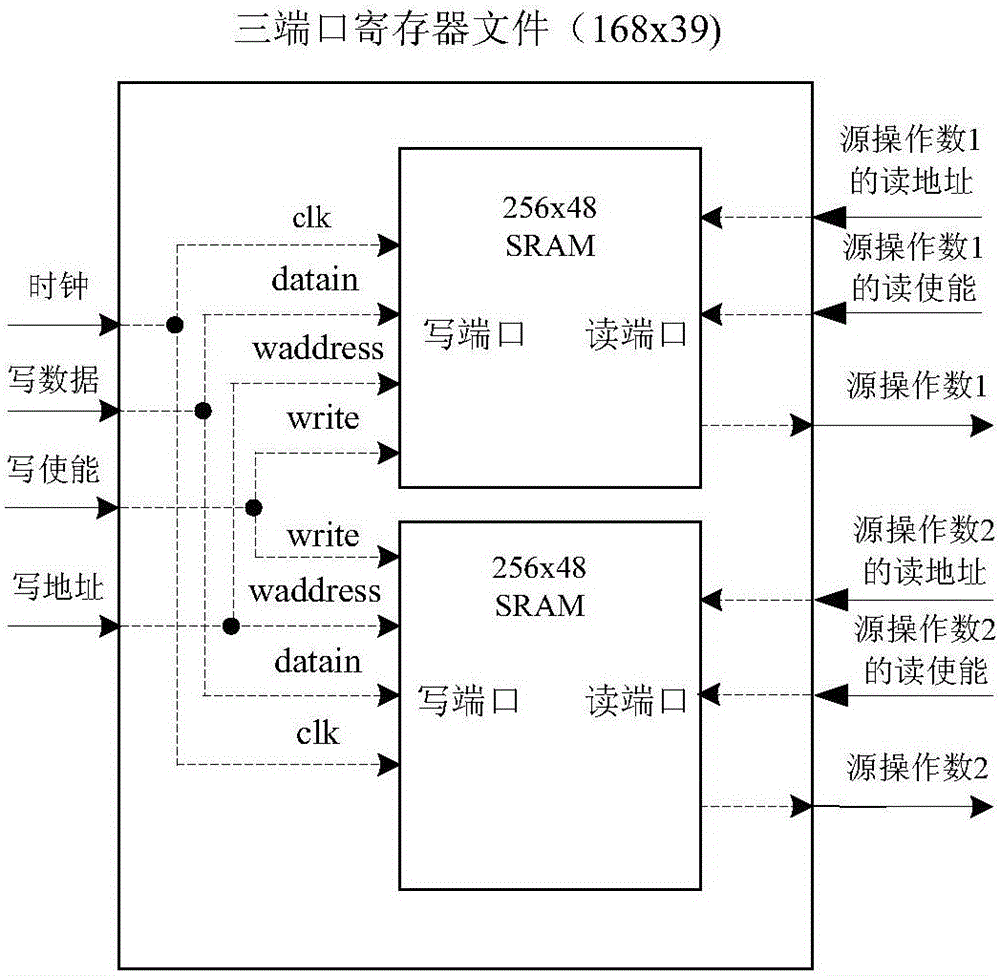
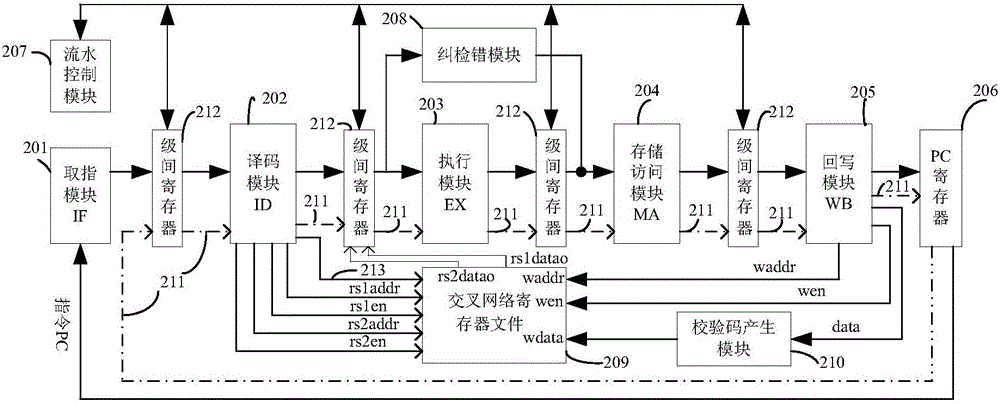
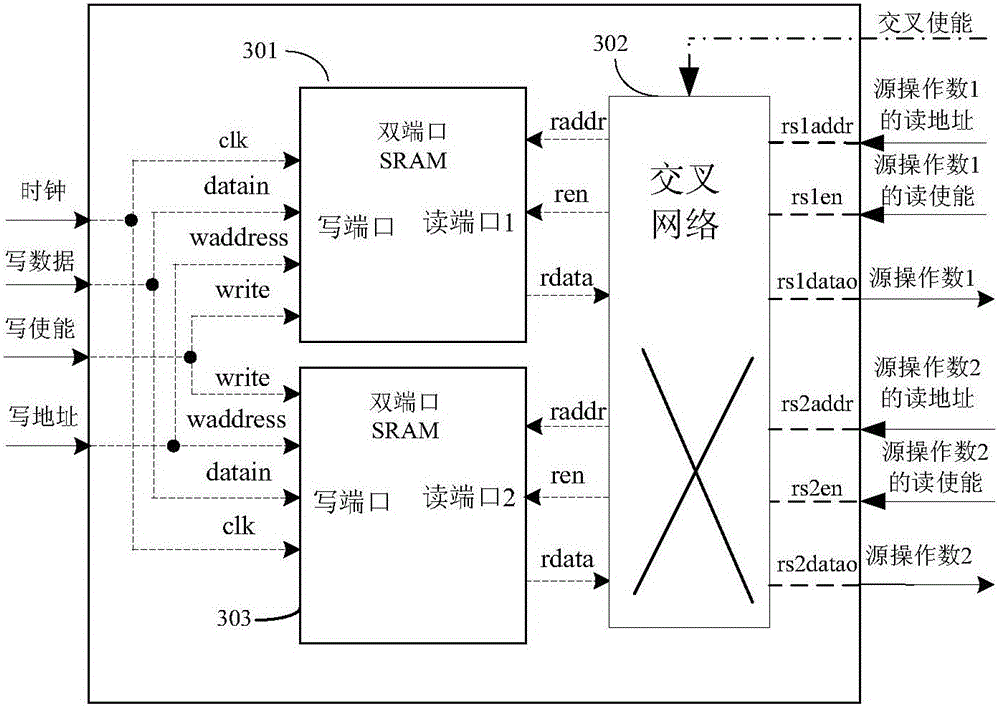
Processor based on semi-custom register file and fault-tolerant method
ActiveCN104991844AHigh data reliabilityFully excavatedRedundant hardware error correctionMachine execution arrangementsProcessor registerOperand
The invention discloses a processor based on a semi-custom register file, which comprises a five-stage assembly line, an error detecting-and-correcting module, a crossover network register file and a check code generation module, wherein a processor fault-tolerant method comprises following steps: when an error that can be corrected occurs in datum of the register file, the assembly line is restarted to correct the error and related instructions are re-performed; when an error that can't not be corrected occurs in the datum of the register file, the assembly line is restarted to detect the backup datum of the error datum of the register file; if the backup datum are right, the subsequent processor processing is performed with the backup datum; if an error that can't be corrected also occurs in the backup datum, the processor will enter trap processing program; and the error is recovered by software. By a plurality of rollbacks and restarts of the assembly line, and the scheduling to an operand access address, the error that can be corrected is refreshed and the backup datum are polled correctly; and a data backup in rebundant hardware is dug out, thus the data reliability of the register file is improved.
Owner:NO 771 INST OF NO 9 RES INST CHINA AEROSPACE SCI & TECH
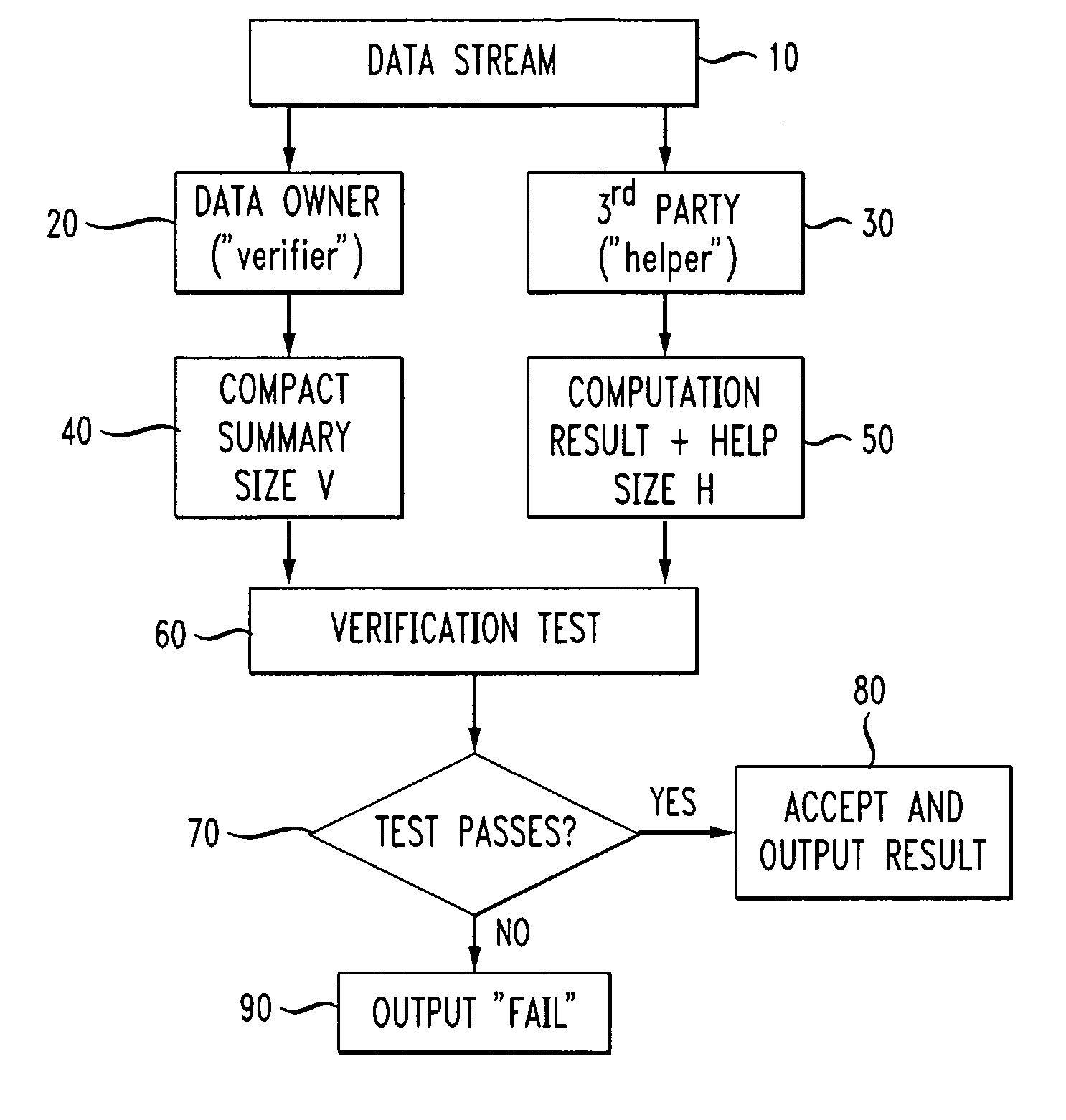
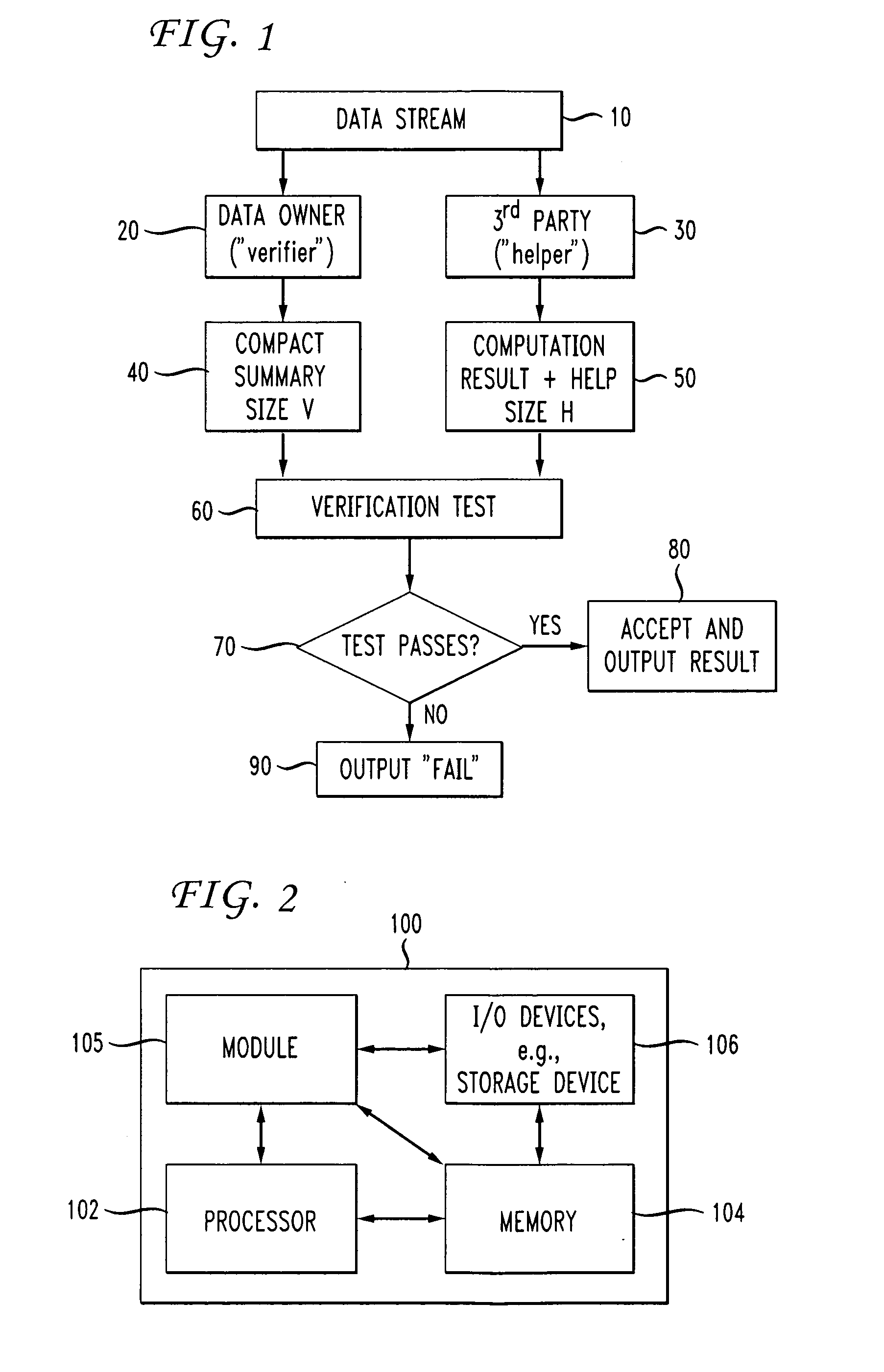
Verification Of Data Stream Computations Using Third-Party-Supplied Annotations
A third party that performs data stream computation is requested to return not only the solution to the computation, but also “annotations” to the original data stream. The annotations are then used by the data owner (in actuality, a “verifier” associated with the data owner) to check the results of the third party's computations. As implemented, the verifier combines the annotations with the original data, performs some computations, and is then assured of the correctness of the provided solution. The cost of verification is significantly lower to the data owner than the cost of fully processing the data “in house”.
Owner:TRUSTEES OF DARTMOUTH COLLEGE THE +1
Flow verification system and method
InactiveCN1760903AAvoid normal workPrevent execution problemsResourcesValidation methodsWeight coefficient
Based on weight coefficients calculated for corresponding nodes of first flow, nodes of multiple flows and nodes of second flow, the method compares the weight coefficients. Then, the method validates whether weight coefficients of nodes of second flow are equal to weight coefficients of nodes of first flow so as to obtain validity and correctness. Through the above inspection in advance, the invention prevents problem in execution in future caused by design error of workflow. The invention provides validation method for projector of workflow to build collect workflow. The invention is also applicable to workflow includes program in cascaded sign and sign jointly. Thus, diversified workflow can be designed to be suitable to practical need.
Owner:VIA TECH INC
Method and device for debugging parallel programs based on application logical orders
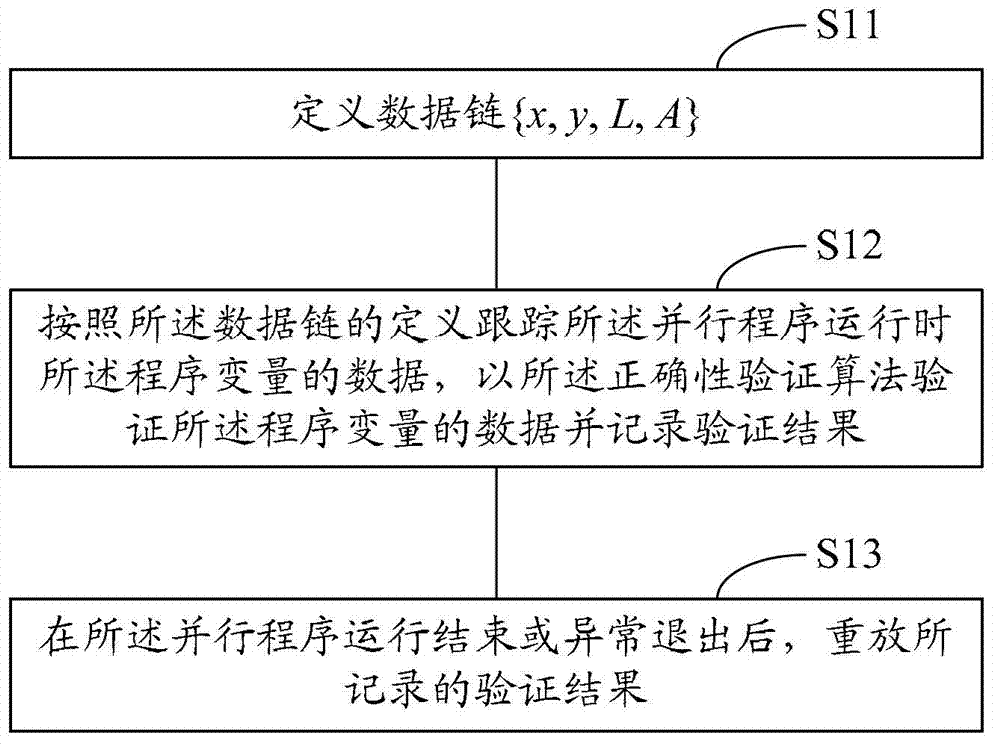
ActiveCN102929780AReduce overheadEasy to locate errorsSoftware testing/debuggingParallel computingApplication logic
The invention discloses a method and a device for debugging parallel programs based on application logical orders. The method for debugging parallel programs includes defining data chains and abstractly describing semantic logics of complex parallel programs, wherein the data chains comprise application logical orders, logic fragment assembles and a correctness verification algorithm, and the application logical orders are iteration step orders or data flow orders; data of program variables during parallel program operation are tracked according to definitions of the data chains, and the data of the program variables are verified by the correctness verification algorithm and verification results are recorded; and the recorded verification results are reset when the parallel program stops operation or is exited abnormally. The method and the device are based on a reset debugging plan of parallel application system semantic logics, error locating of parallel programs is facilitated, and storage and analysis expenditures are saved.
Owner:JIANGNAN INST OF COMPUTING TECH
System and method for enforcement of correctness for key derivation
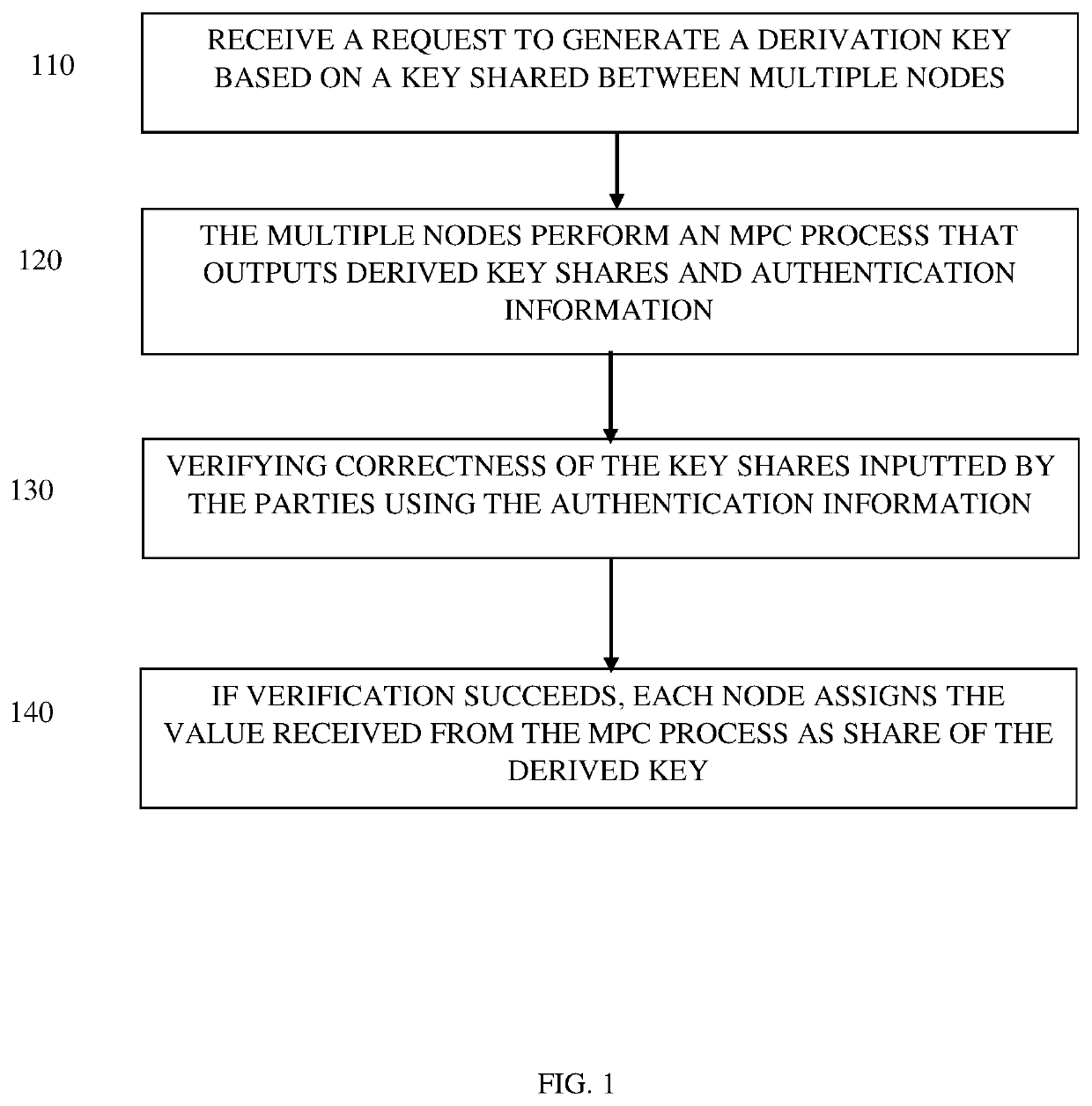
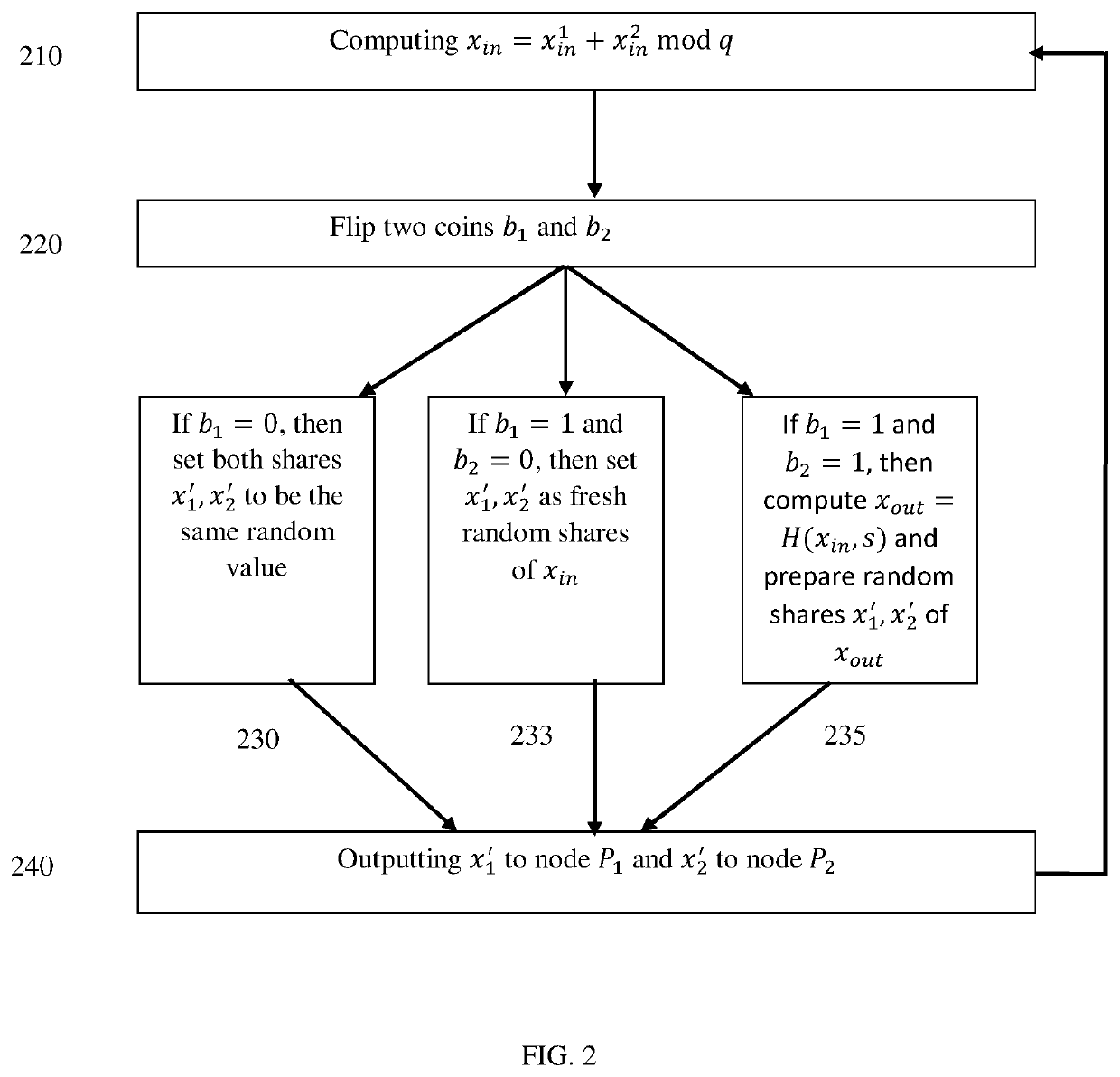
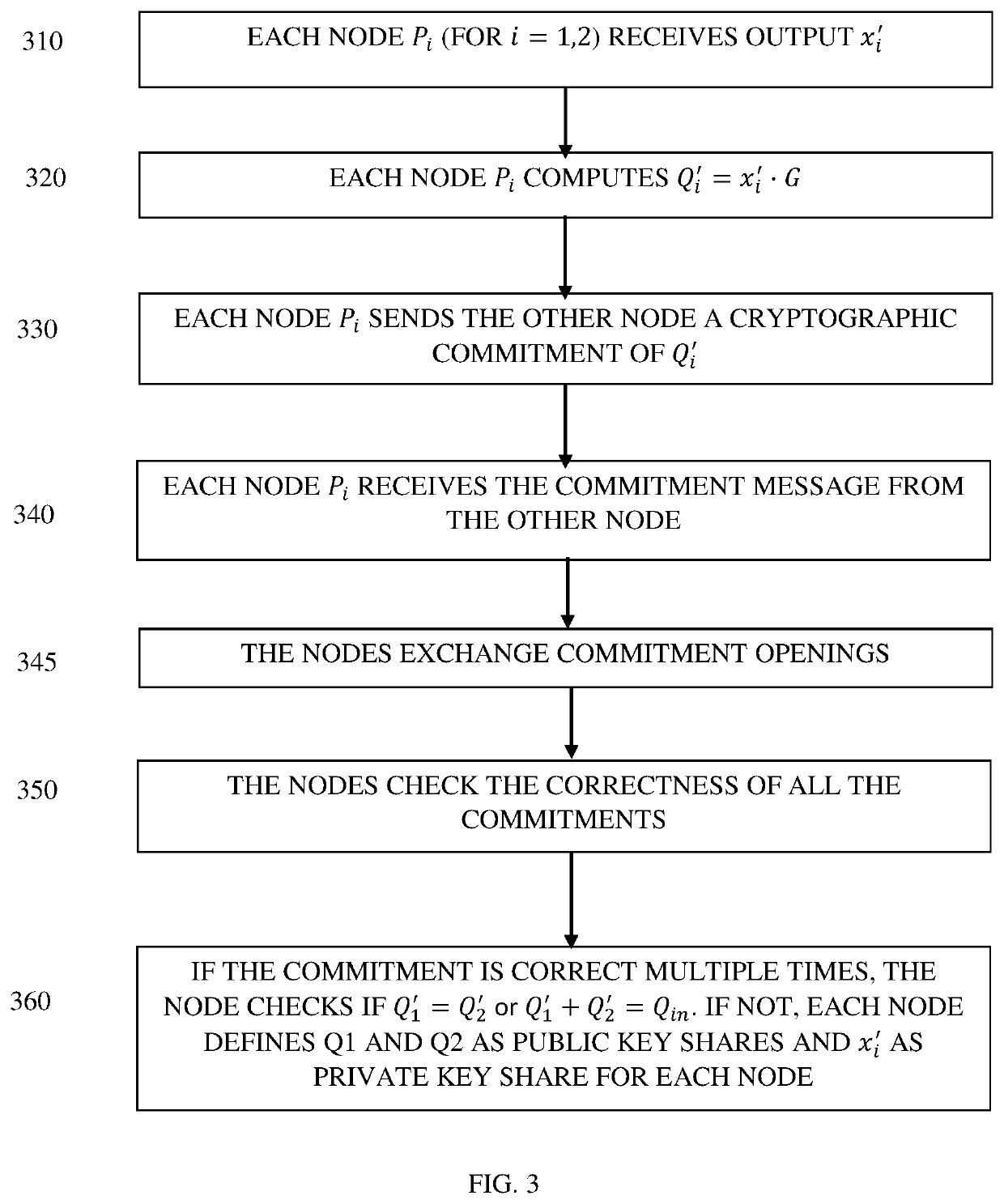
ActiveUS10630471B1Key distribution for secure communicationEncryption apparatus with shift registers/memoriesTheoretical computer scienceCorrectness
The subject matter discloses a system for enforcing correctness of a derivation key, comprising multiple computerized nodes, comprising a storage module configured to store a share of a key used as an input of a function generating the derivation key, a communication module configured to exchange information between the multiple computerized nodes, and a processing module configured to receiving a request to create the derivation key, performing an MPC process between the multiple computerized nodes, said MPC process is performed multiple times, in each time the MPC process comprises receiving the key shares as input, randomly selecting a function, outputting the outputs of the selected function to the multiple computerized nodes, the multiple computerized nodes lack access to the selected function, the multiple computerized nodes perform computations on the received outputs and exchange outputs of the computations to estimate correction of the key shares inputted into the MPC process.
Owner:COINBASE IL RD LTD
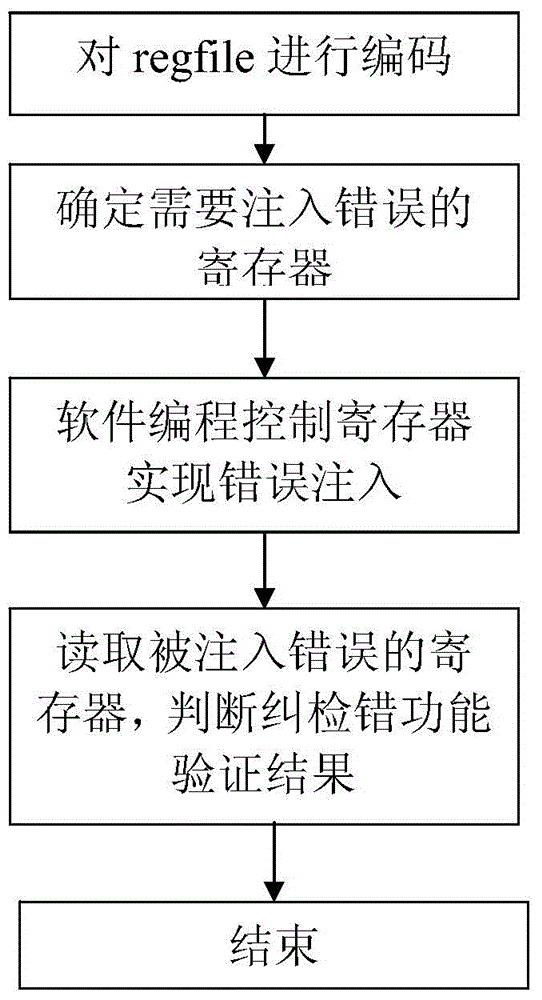
Method for verifying error correction and detection function of regfile of SPARC V8 processor
ActiveCN104484256AImplement error injectionAccurate Functional Verification ObjectError detection/correctionError processingProcessor register
The invention discloses a method for verifying an error correction and detection function of a regfile of a SPARC V8 processor. The method includes generating and injecting error into a register of the regfile by a software programming method, simulating error of the regfile, reading the error injected into the regfile, triggering the error correction and detection function of the regfile, and judging accuracy of the error correction and detection function of the regfile according to executing results of the software program. By the method, accurate error injection into data bits and check bits of the regfile of the highly reliable SPARC V8 processor can be realized, and the error correction and detection function of the regfile can be verified. The method completed by software is convenient, low in cost and high in speed and can be combined with applications to verify the error processing program function of the regfile in the applications.
Owner:BEIJING MXTRONICS CORP +1
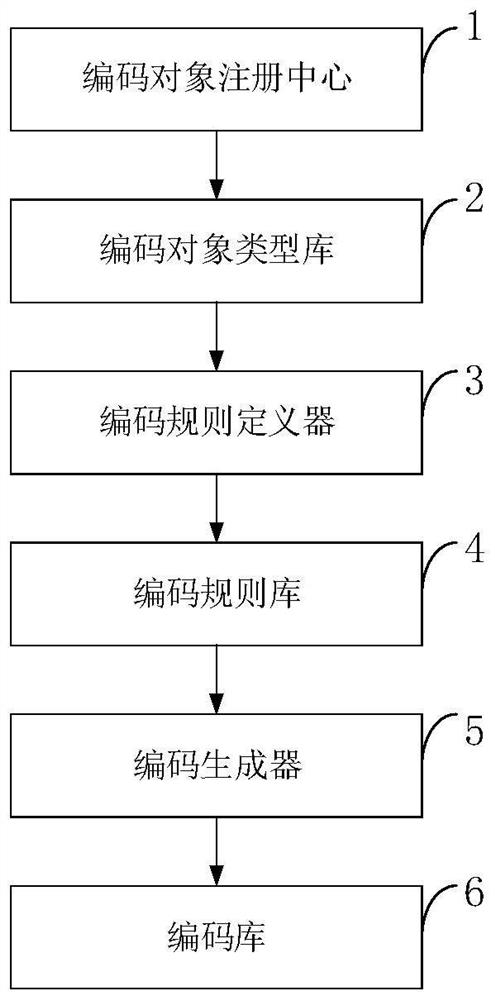
Extensible universal code generation system and method
PendingCN111859861AGuaranteed correctnessUniqueness guaranteedNatural language data processingCode generationInformatization
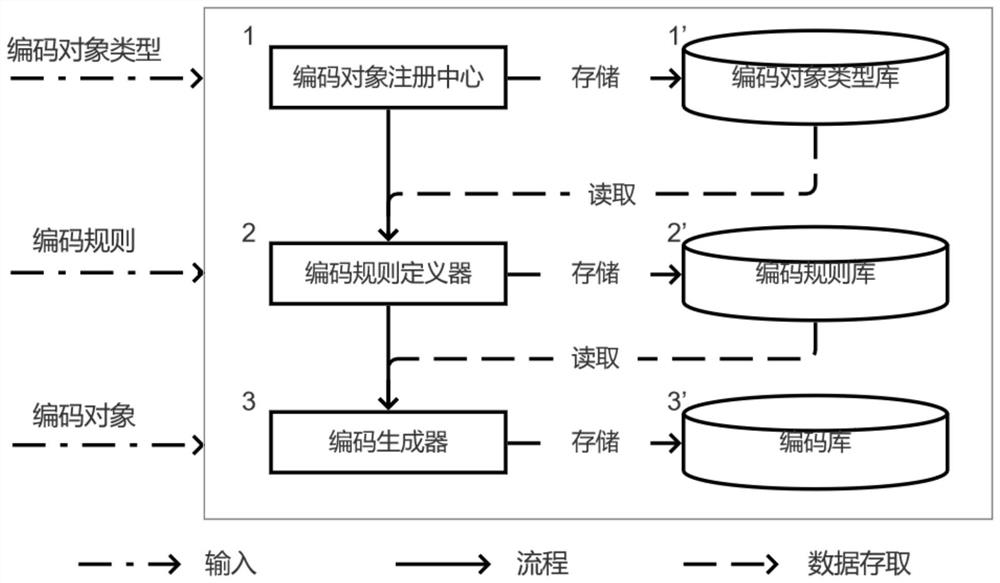
The invention belongs to the technical field of computer science informatization, and discloses an extensible universal code generation system and method, and the method comprises the steps that a code object registration center manages all object type information needing to be coded; the coding rule definition device defines a coding rule; a code generator obtains a corresponding attribute valuefrom an object to be coded according to the definition of a coding rule, obtains a new code value through attribute calculation, code conversion and fragment combination, and distributes the new codevalue to a code applicant, wherein the coding object type library stores all registered object types; the encoding rule base stores all encoding rule definitions; the code library stores the code andgenerates an object attribute value of the code. According to the invention, a new coding object type can be dynamically registered according to business requirements, a coding generation rule is customized, a new code is generated, the management of the coding object type, the coding rule and the code is provided, and the correctness, uniqueness and consistency of the code are ensured.
Owner:HUAZHONG UNIV OF SCI & TECH +1
Text style processing method and device, electronic equipment and storage medium
PendingCN112528605ANatural language data processingNeural architecturesDecision modelTheoretical computer science
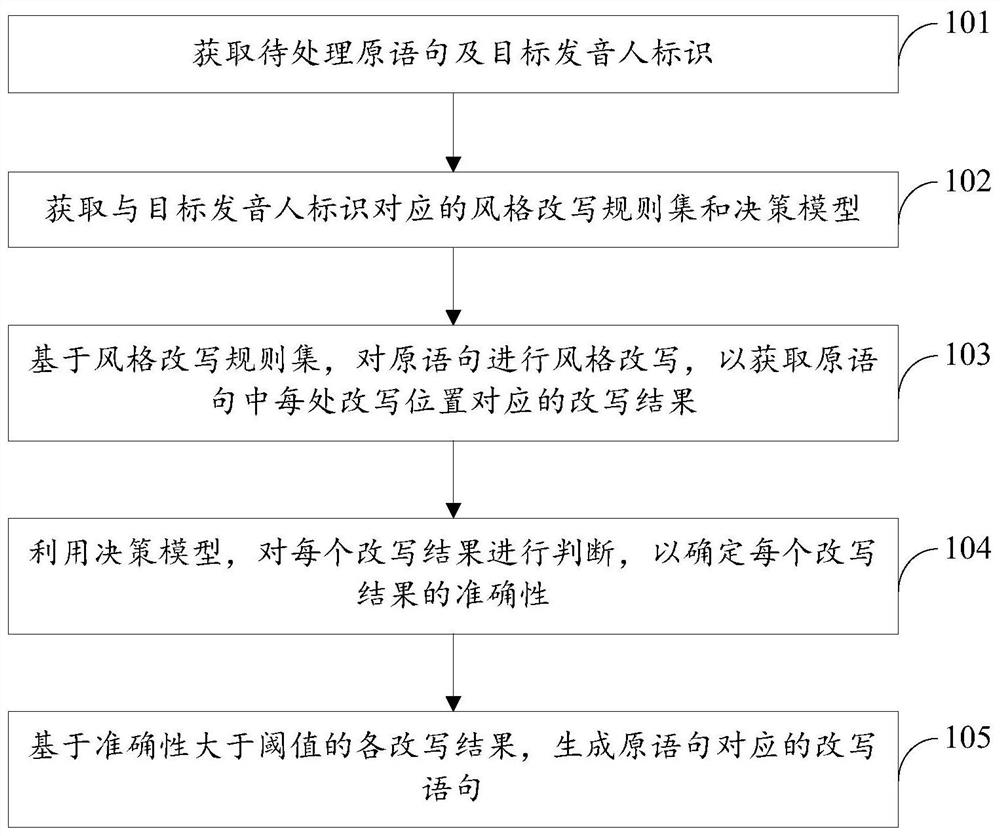
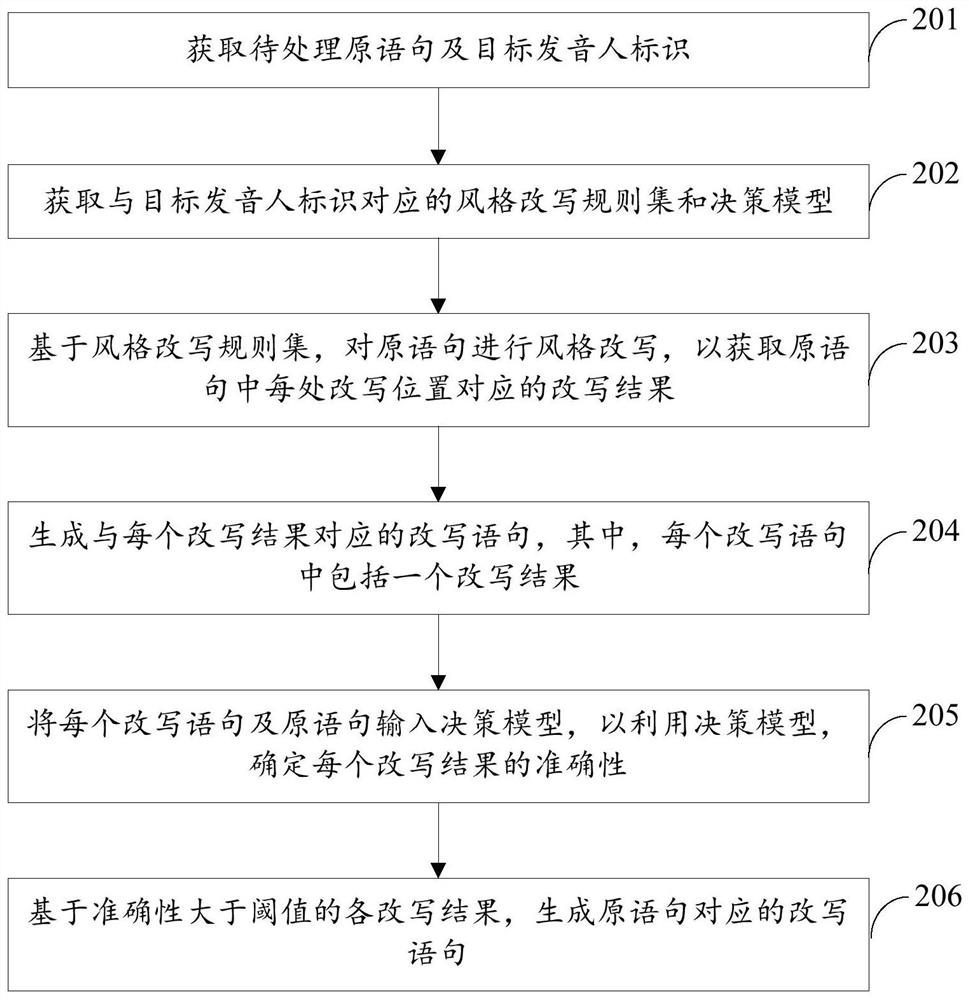
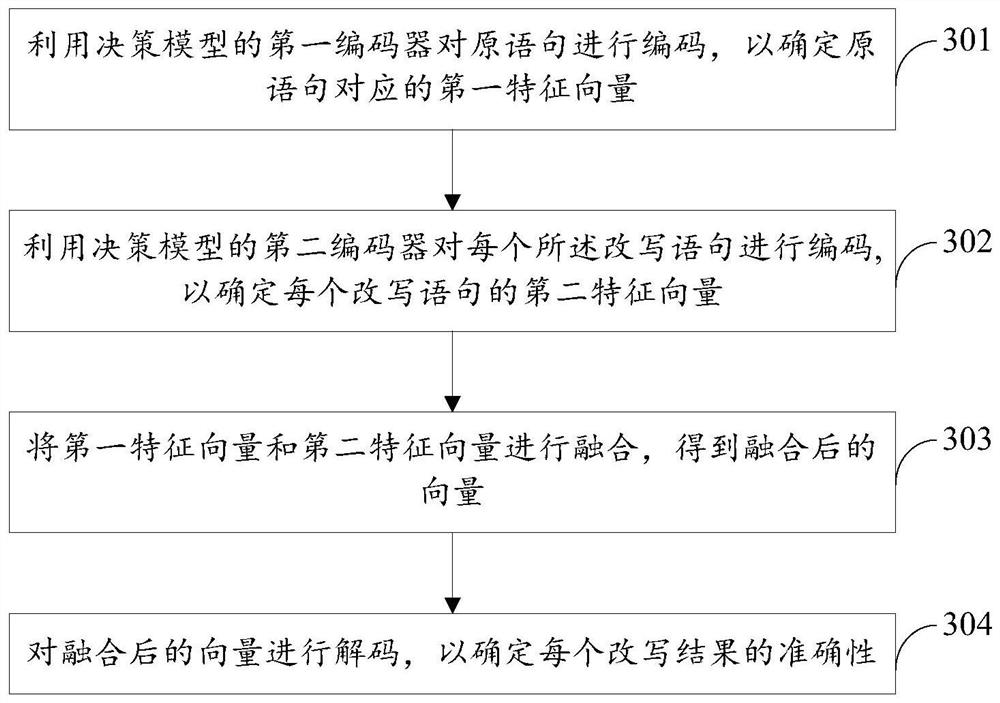
The invention discloses a text style processing method and device, electronic equipment and a storage medium, relates to the computer technology, and particularly relates to the technical field of artificial intelligence such as natural language processing and deep learning, and the method comprises the steps: obtaining a to-be-processed original statement and a target speaker identifier; obtaining a style rewriting rule set and a decision model corresponding to the target speaker identifier; performing style rewriting on the original statement based on the style rewriting rule set to obtain arewriting result corresponding to each rewriting position in the original statement; utilizing the decision model to judge each rewriting result so as to determine the accuracy of each rewriting result; and generating a rewriting statement corresponding to the original statement based on each rewriting result of which the accuracy is greater than a threshold. According to the method, the controllability of the result is guaranteed by utilizing rule rewriting, whether the rewriting result is adopted or not is judged by utilizing the decision model, the long-distance modeling advantage of the model is exerted, the correctness of rewriting is improved, the rewriting effect of the text style is integrally improved, and the text is better matched with the voice library.
Owner:BEIJING BAIDU NETCOM SCI & TECH CO LTD
MCAD and ECAD interaction design method
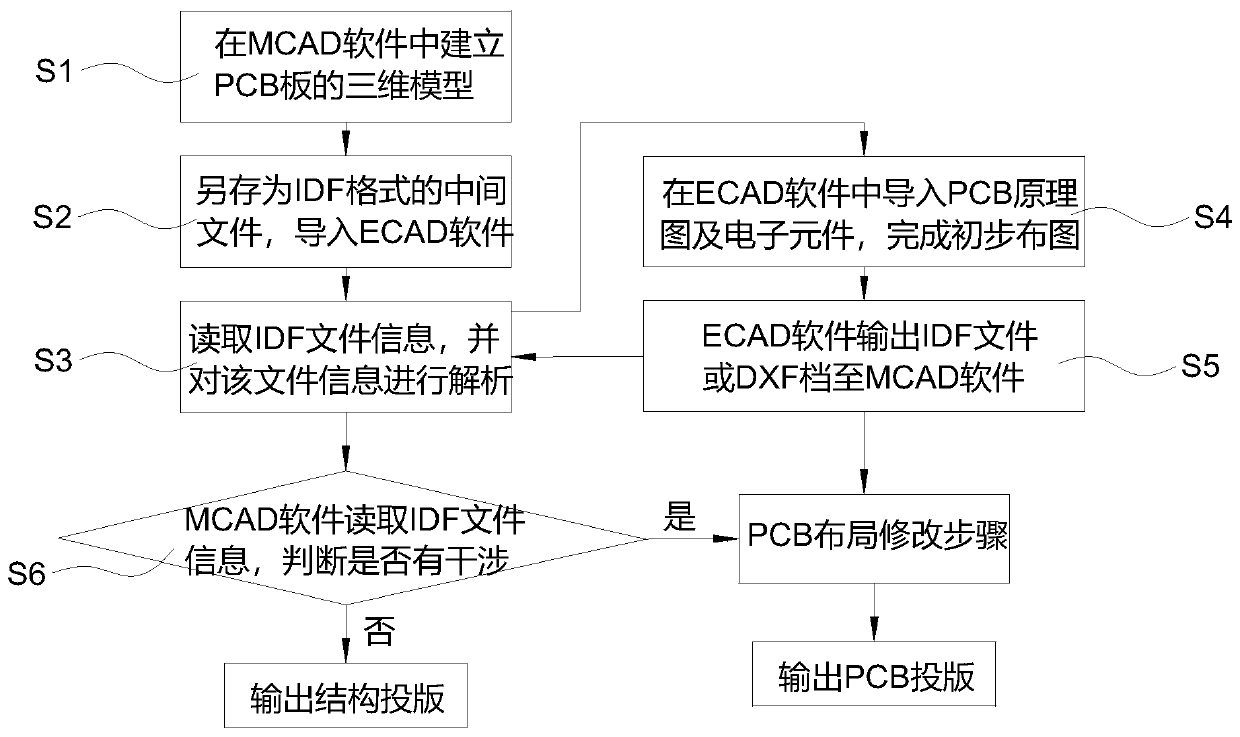
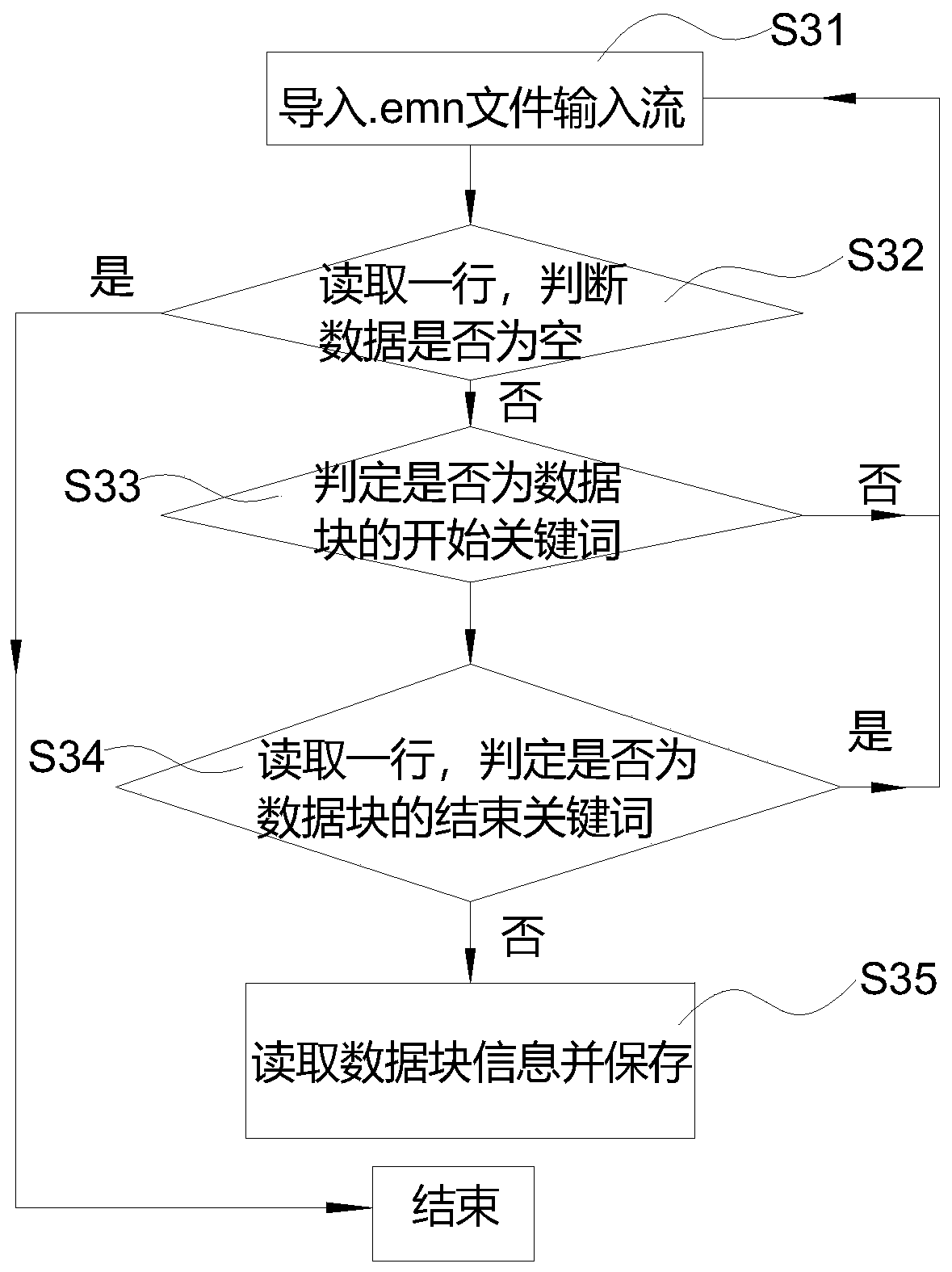
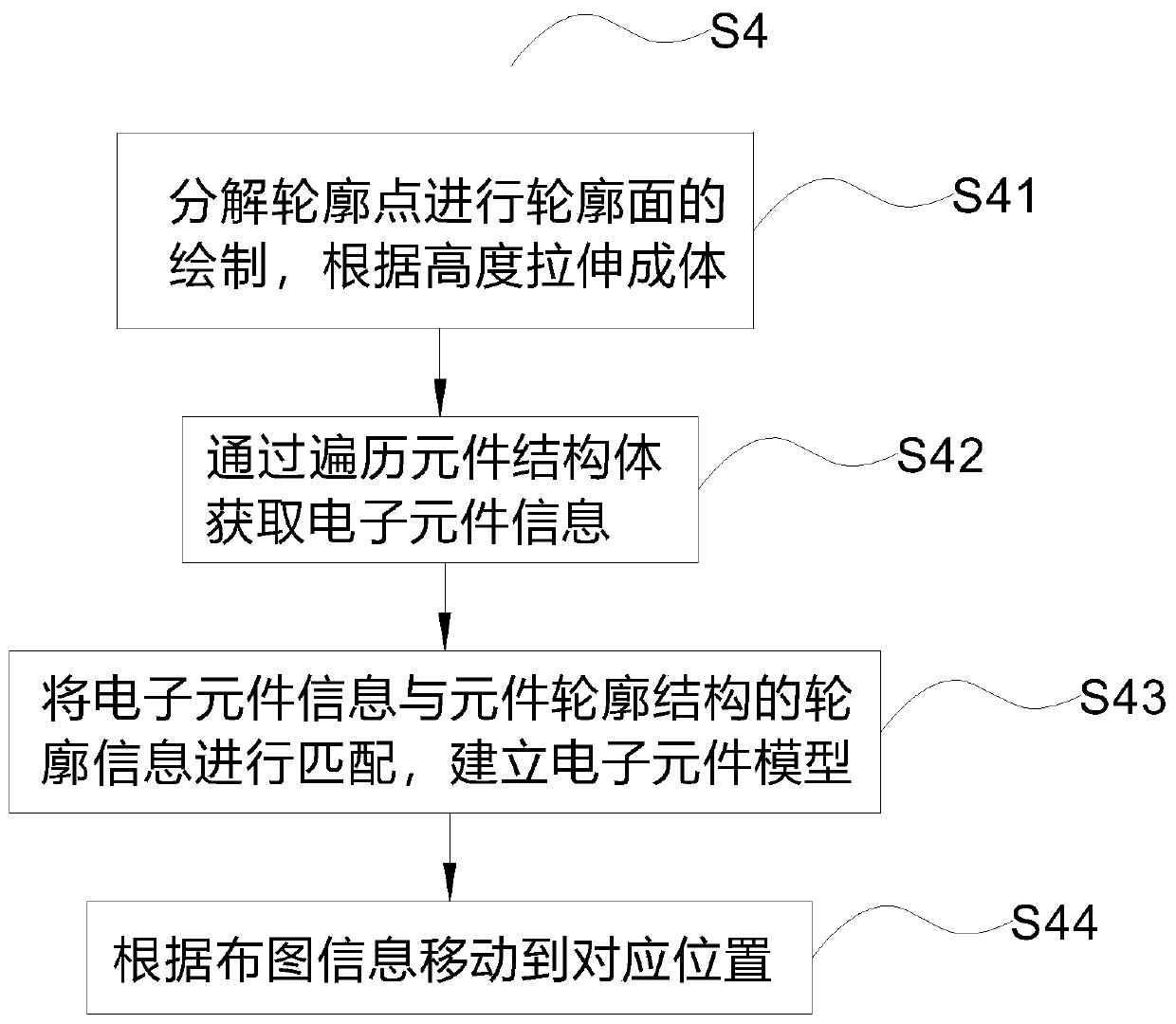
PendingCN111062179AResolve interferenceEasy to importGeometric CADSpecial data processing applicationsInteraction designCorrectness
The invention provides an MCAD and ECAD interaction design method. The MCAD and ECAD interaction design method comprises the following steps that S31, importing Emn file input streams; S32, reading arow, judging whether the data is empty, if yes, ending, and otherwise, entering S33; S33, judging whether the keyword is a start keyword of the data block, if yes, entering S34, and otherwise, returning to S31; S34, reading a row, judging whether the row is an end keyword of the data block, if yes, returning to S1, and otherwise, entering S35; and S35, reading and storing the data block information. According to the method, the design data exchange of the PCB between MCAD software and ECAD software can be realized, the problem of interference between PCBs and mechanism space can be solved, theinterference problem of electronic components of the PCBs is reduced, and the working efficiency and correctness in the design process are improved.
Owner:北京浩瀚深度信息技术股份有限公司
Algorithm library testing method
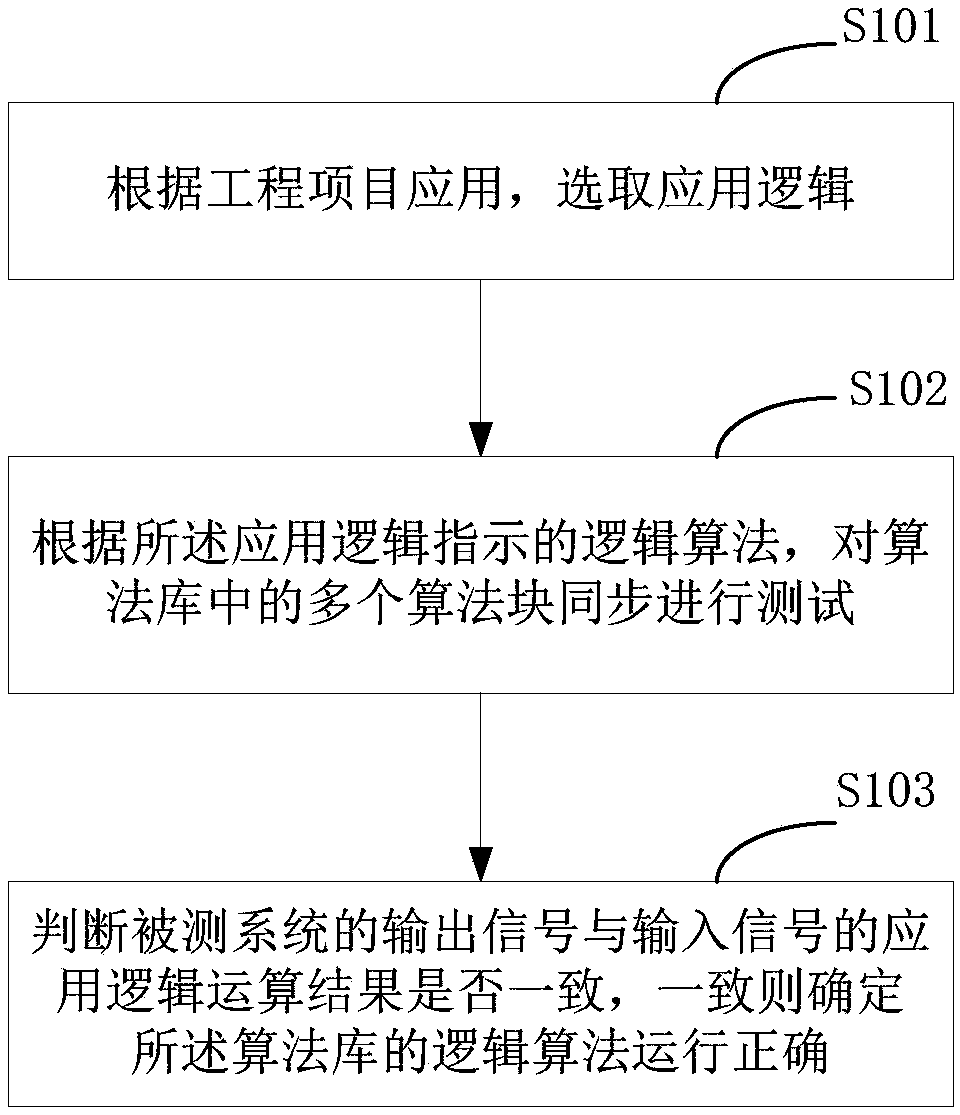
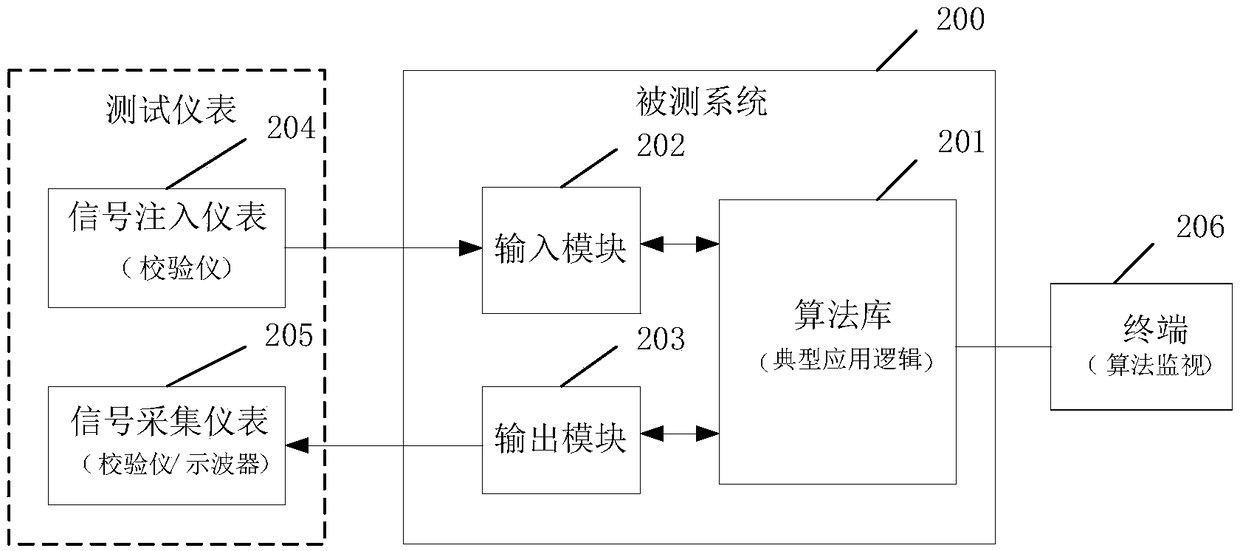
InactiveCN109375606AOvercome the functional defects that cannot guarantee the correct operation of multiple algorithm blocks used in series and parallelImprove accuracyElectric testing/monitoringSystem under testDependability
The invention relates to an algorithm library testing method. The method comprises the following steps that: an application logic is selected based on application of an engineering project; accordingto a logic algorithm indicated by the application logic, a plurality of algorithm blocks in an algorithm library are tested synchronously; whether application logic operation results of the output signal and the input signal of a tested system are consistent is determined; and if so, the logic algorithm of the algorithm library is determined to be correct. According to the invention, for the application of the actual engineering project, testing of the plurality of algorithm blocks is carried out synchronously on the algorithm library based on the application logic function. A functional defect that the operation correctness can not be guaranteed when the plurality of algorithm blocks are used in series-parallel connection according to the existing test method is overcome; and the test accuracy and reliability are improved.
Owner:CHINA TECHENERGY +1
Program automatic debugging method
The invention relates to a program automatic debugging method which includes the following steps: 101, reading and analyzing an assembly source program Y to obtain all variables used by the assembly source program Y, and generating a relation list A of the variables and page addresses respectively corresponding to the variables; 102, preprocessing and standardizing the assembly source program Y to form an assembly source program B easy to distinguish and check; and 103, performing page switching correctness check for the assembly source program B and finding and reporting page faults. By aid of the program automatic debugging method, page address faults in the programs can be fast and accurately checked, further invalid codes in the programs can be checked easily, manpower is saved, and efficient proceeding of development work is ensured. The program automatic debugging method is wide in application range and can be widely used for debugging of the programs with data spaces or program spaces having distinguishing of pages or section. The program automatic debugging method includes page address fault check for the programs with page / section characteristic storage spaces and of chips of digital signal processors (DSPs), micro-programmed control units (MCUs), microprocessor units (MPUs) and the like.
Owner:徐下兵
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com