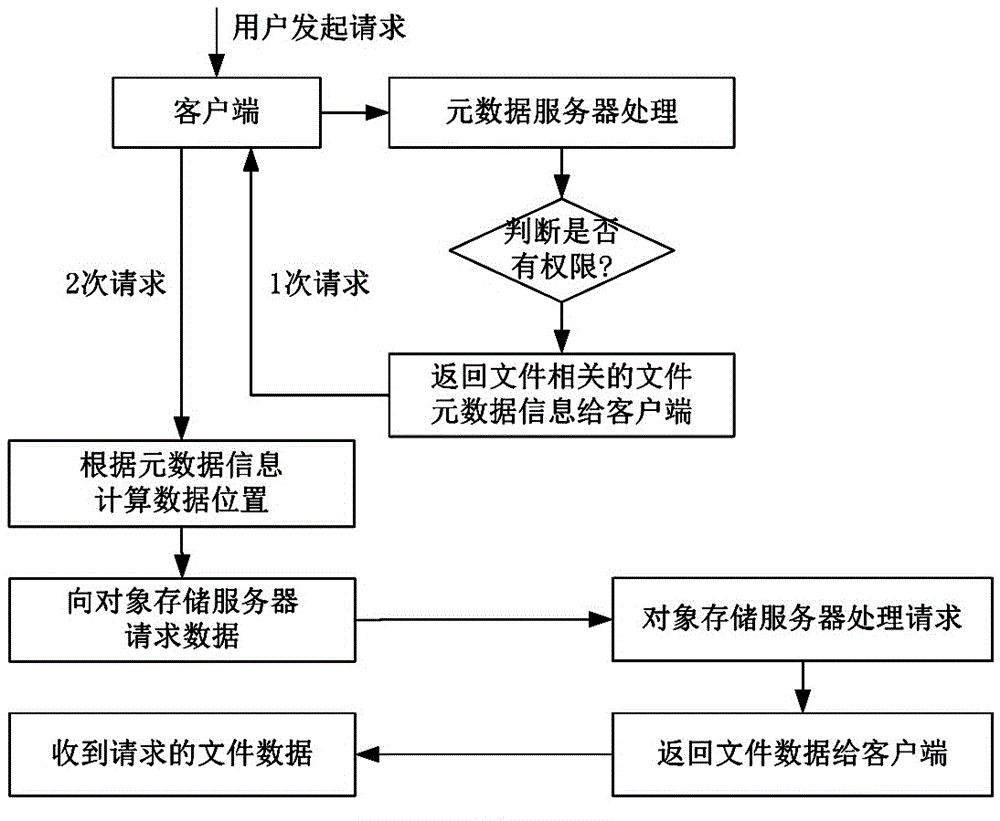
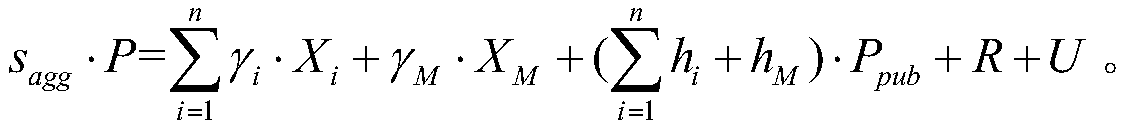Patents
Literature
565results about How to "Reduce communication delay" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
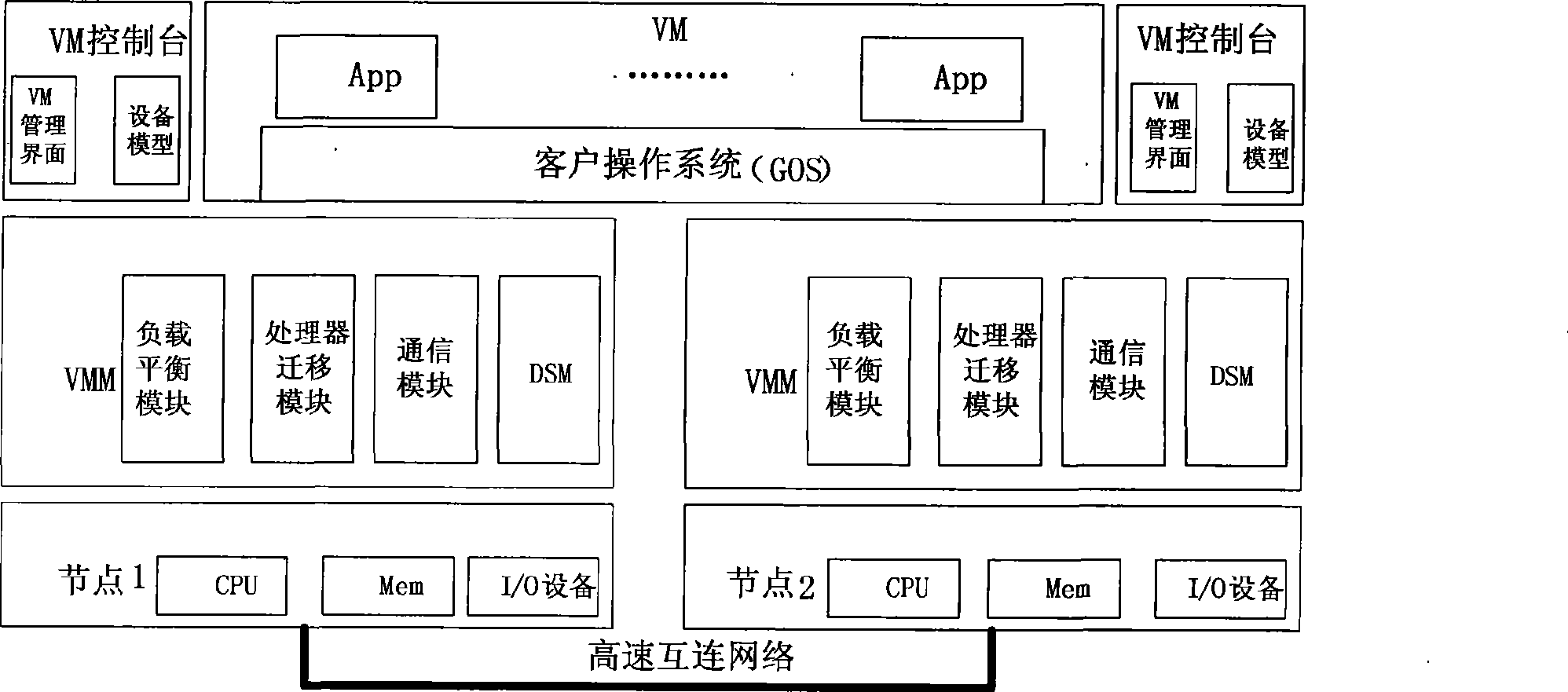
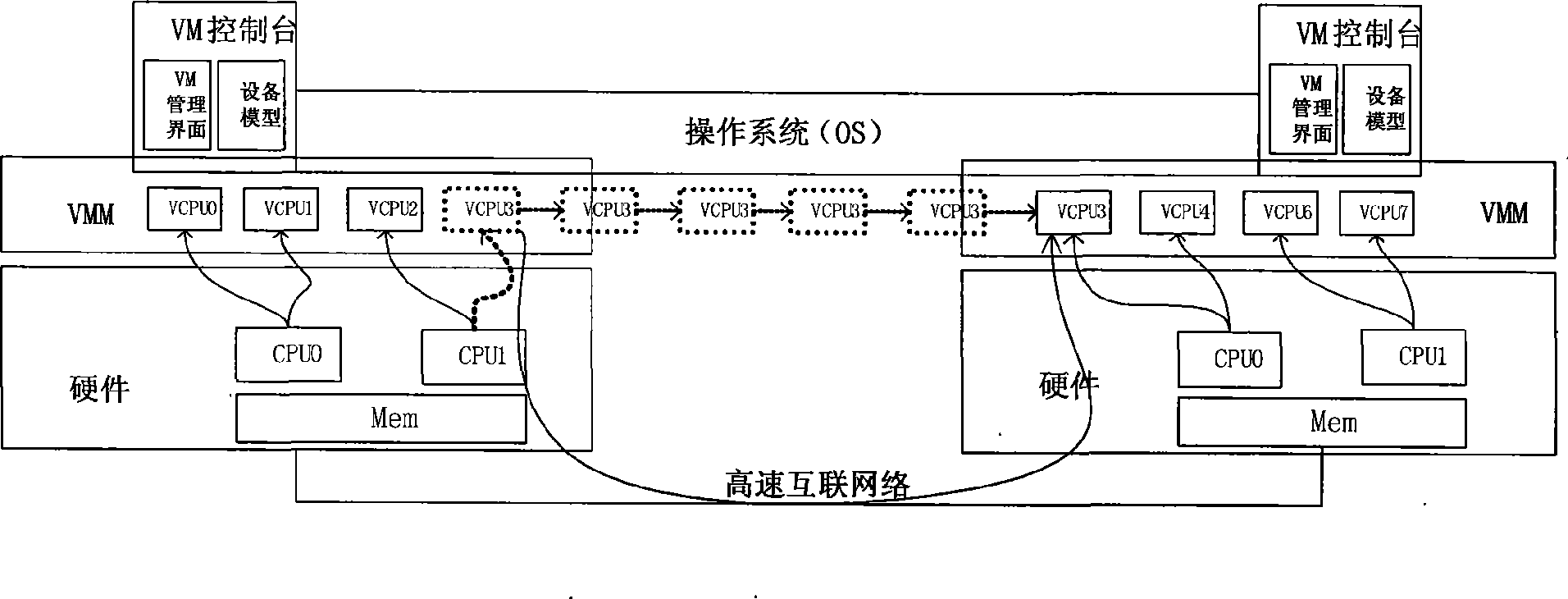
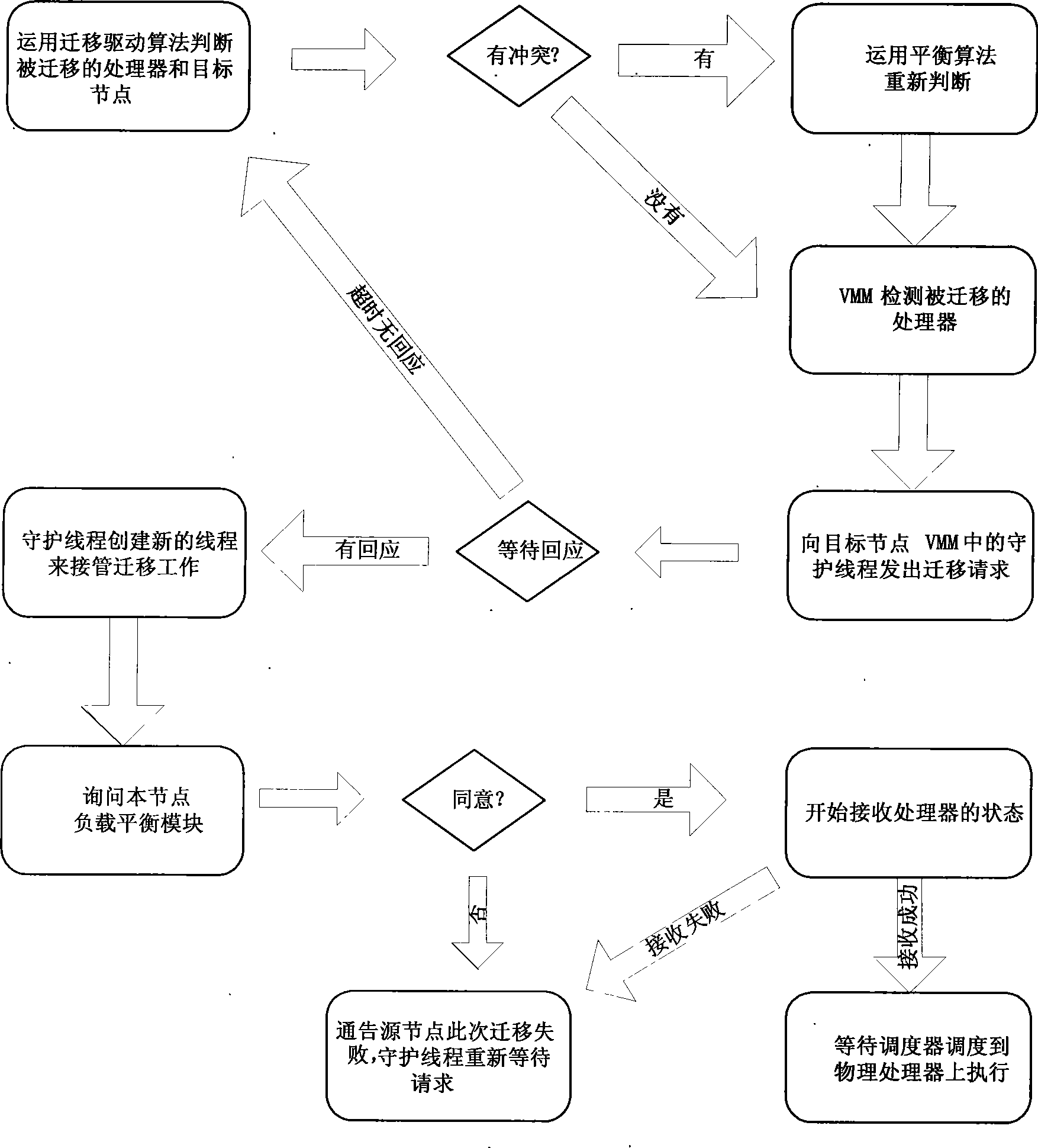
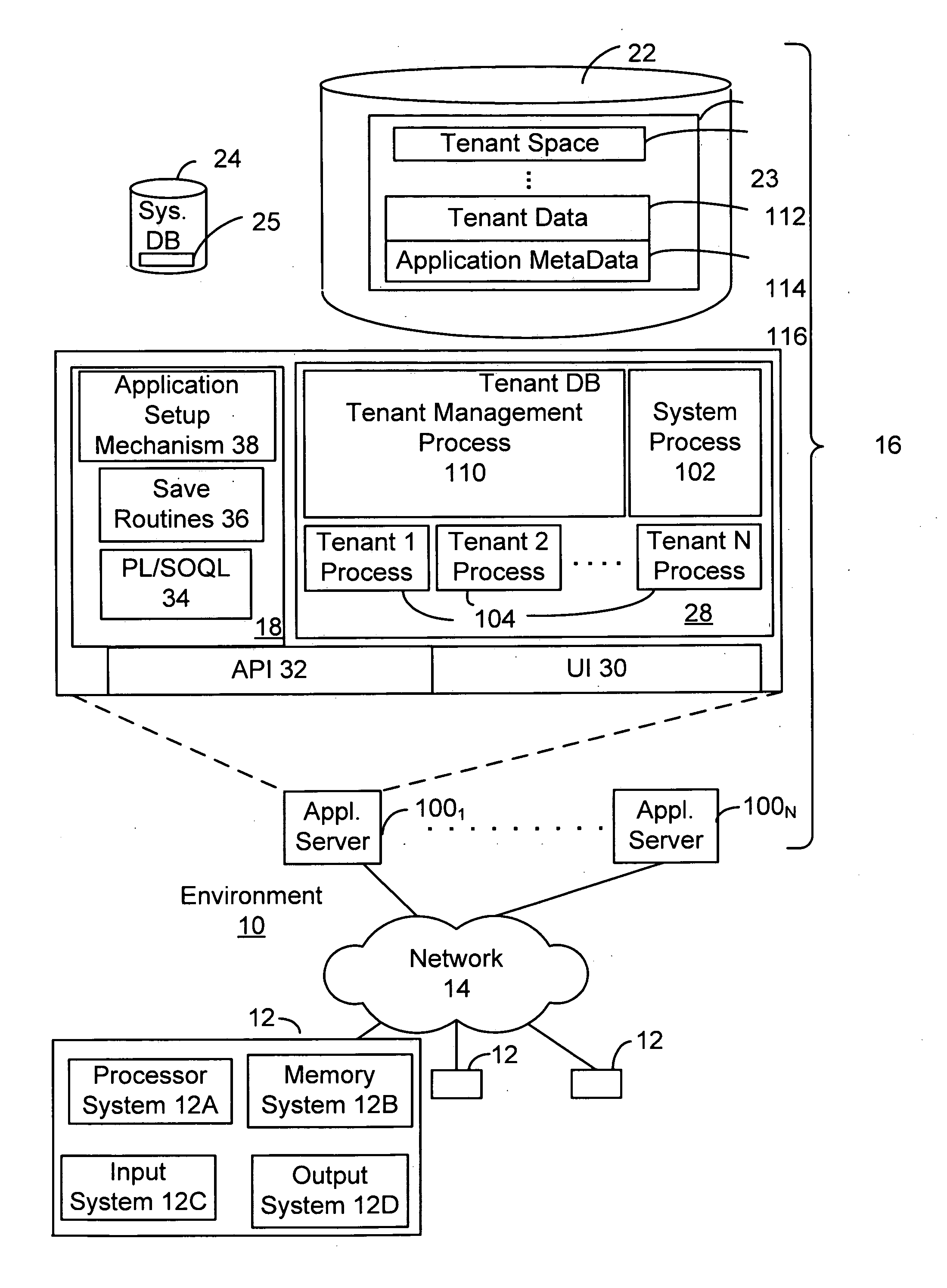
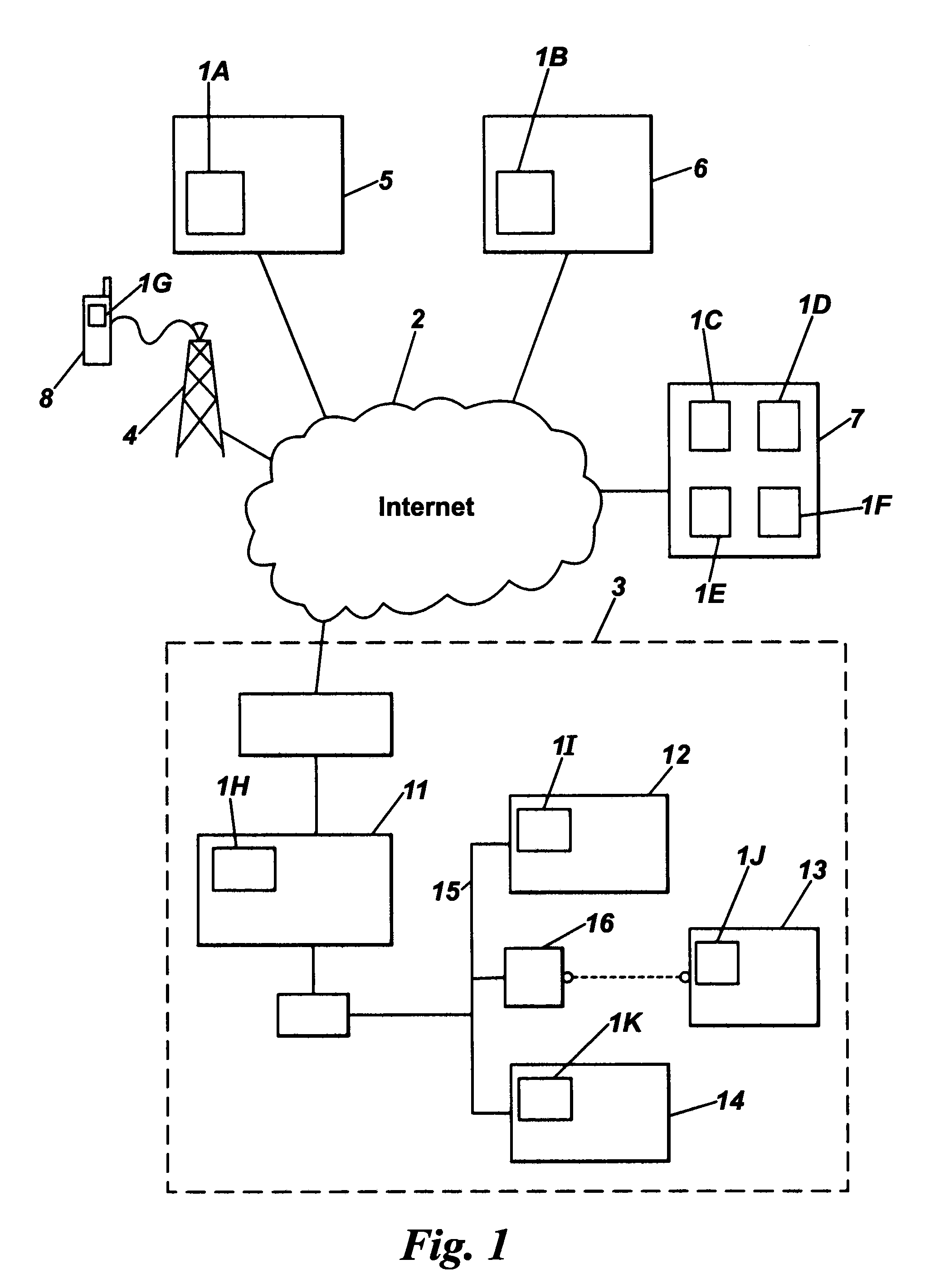
Cluster load balance method transparent for operating system
InactiveCN101452406AImplement a load balancing strategyIncrease profitResource allocationVirtualizationOperational system
The present invention provides a cluster load balancing method transparent to an operation system. Main functional modules comprise a load balancing module, a processor migrating module and a communication module. The method is characterized by comprising the following steps: 1, driving a virtual processor to migrate; 2, driving balance migration; 3, sending a migrating request to a target node and negotiating; 4, storing and restoring a state of the virtual processor; and 5, communicating. The method better solves the problem of low resource utilization rate of a cluster system. Along with the development of more popularization of the cluster system and the continuous development of hardware virtualization technology in the future, the method can be a good solution for the low resource utilization rate of the cluster system and has good application prospect.
Owner:HUAWEI TECH CO LTD
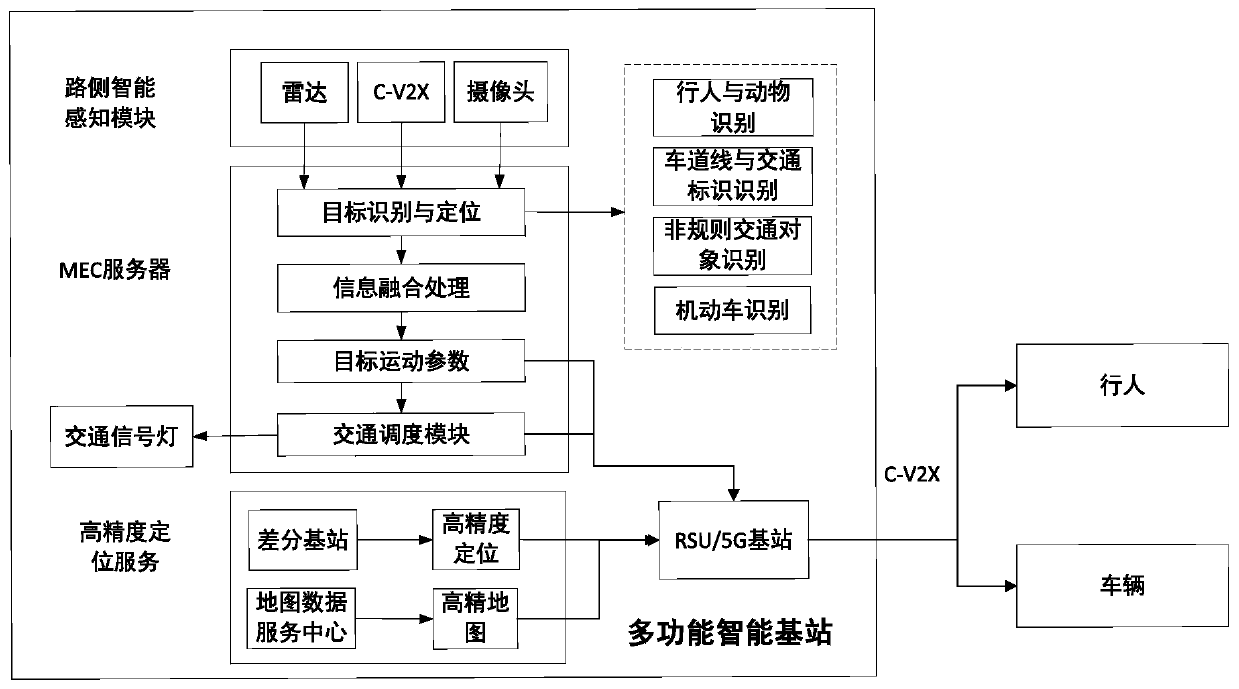
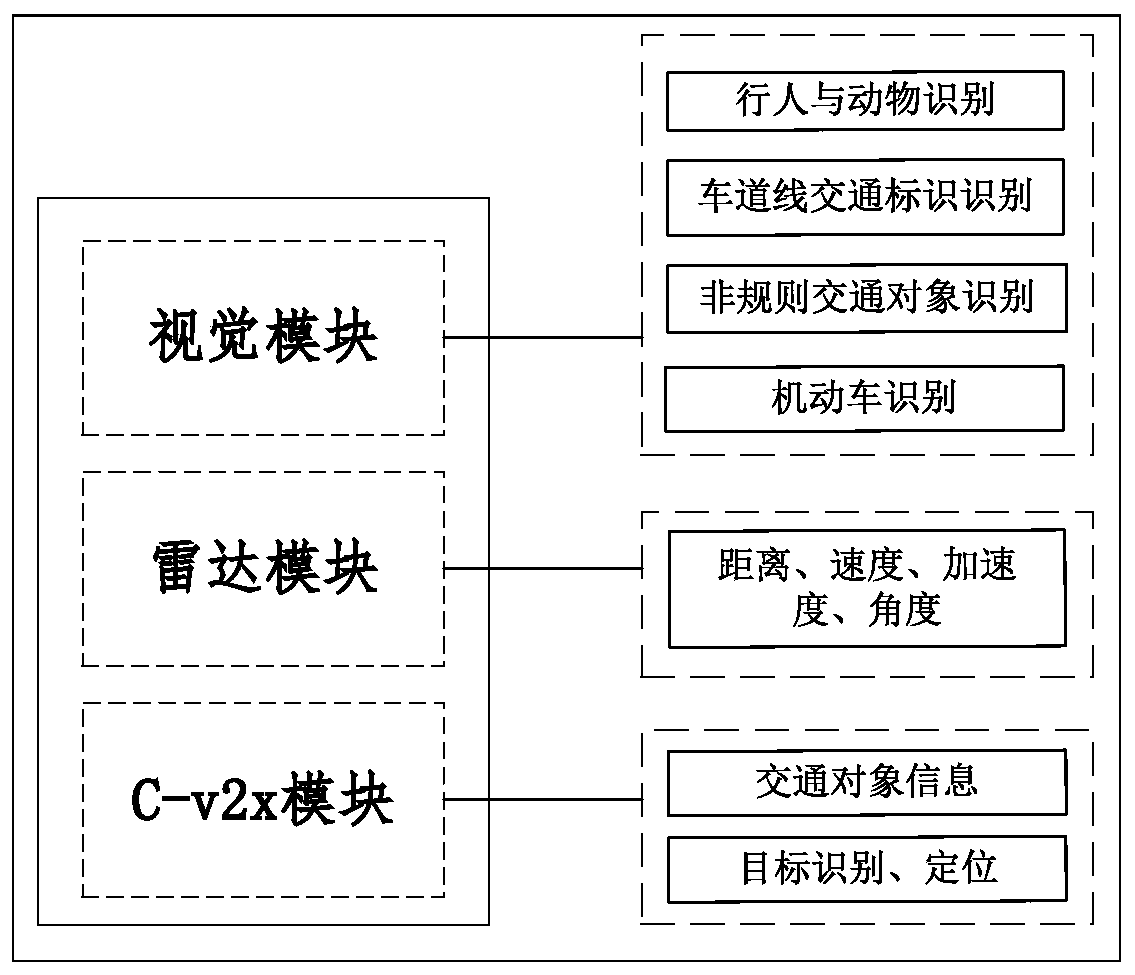
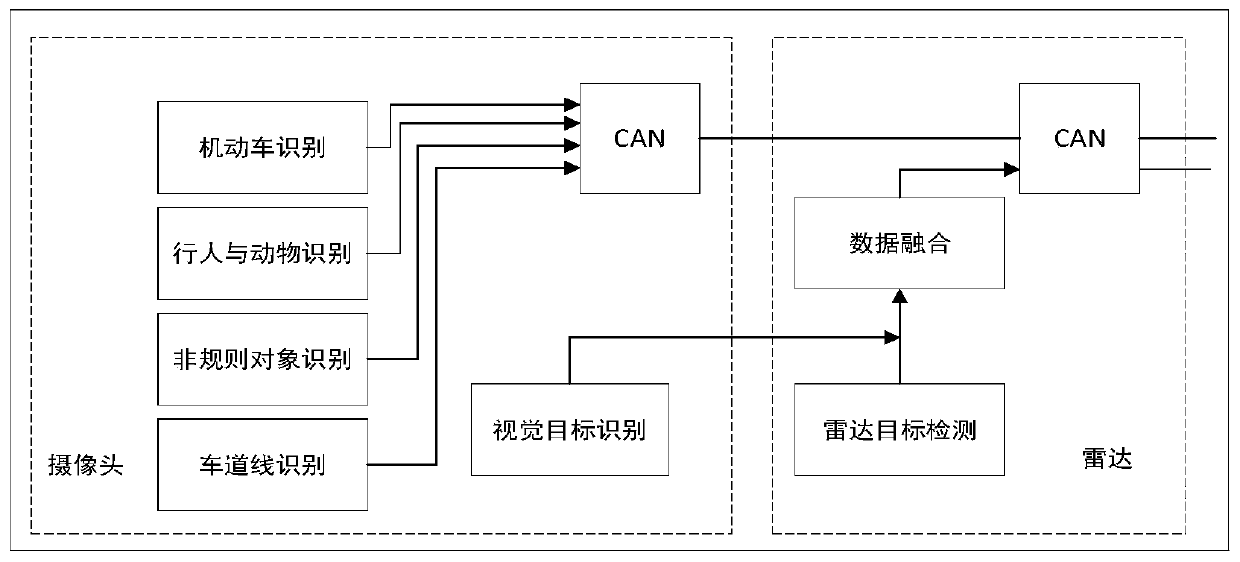
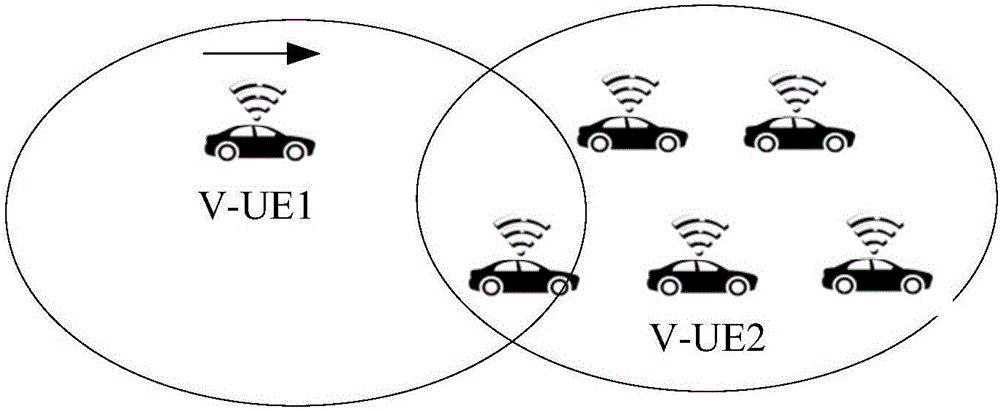
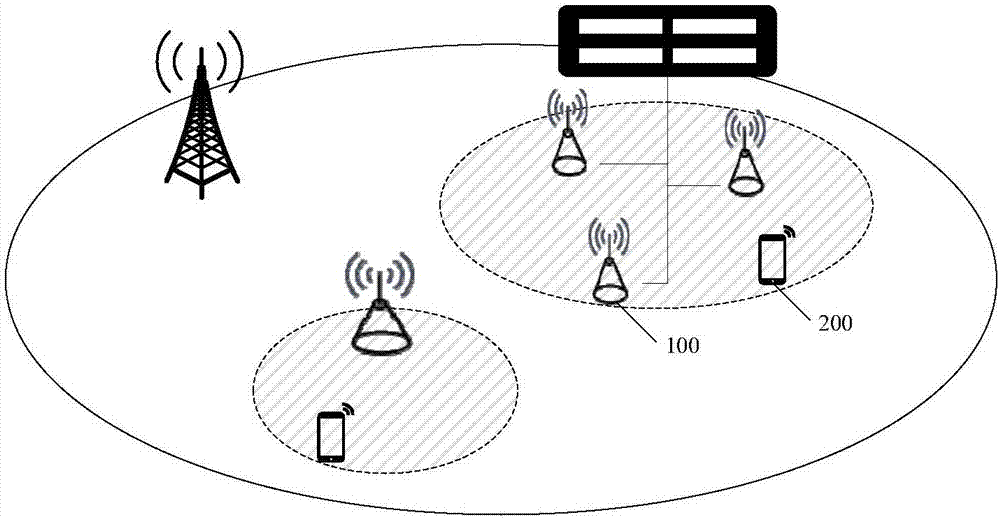
Multifunctional V2X intelligent roadside base station system
ActiveCN111554088AImprove object detection accuracyImprove accuracyControlling traffic signalsDetection of traffic movementVehicle drivingData format
The invention requests to protect a multifunctional V2X intelligent roadside base station system. The system comprises roadside sensing equipment, an MEC server, a high-precision positioning service module, a multi-source intelligent roadside sensing information fusion module and a 5G / LTE-V communication module. An intelligent roadside device integrating C-V2X communication, environmental perception and target recognition, high-precision positioning and the like is designed, and the problem that multi-device information fusion and integration are inconvenient in intelligent transportation is solved. In the system, a C-V2X intelligent road side system architecture and a target layer multi-source information fusion method are designed. Road side multi-source environment cooperative sensing is combined, real-time traffic scheduling of the intersection is realized by using a traffic scheduling module in the MEC server, and communication and high-precision positioning services are providedfor vehicle driving, and finally the target information after fusion processing is broadcasted to other vehicles or pedestrians through a C-V2X RSU (LTE-V2X / 5G V2X and the like) according to an application layer standard data format, so the driving and traffic safety is improved.
Owner:CHONGQING UNIV OF POSTS & TELECOMM
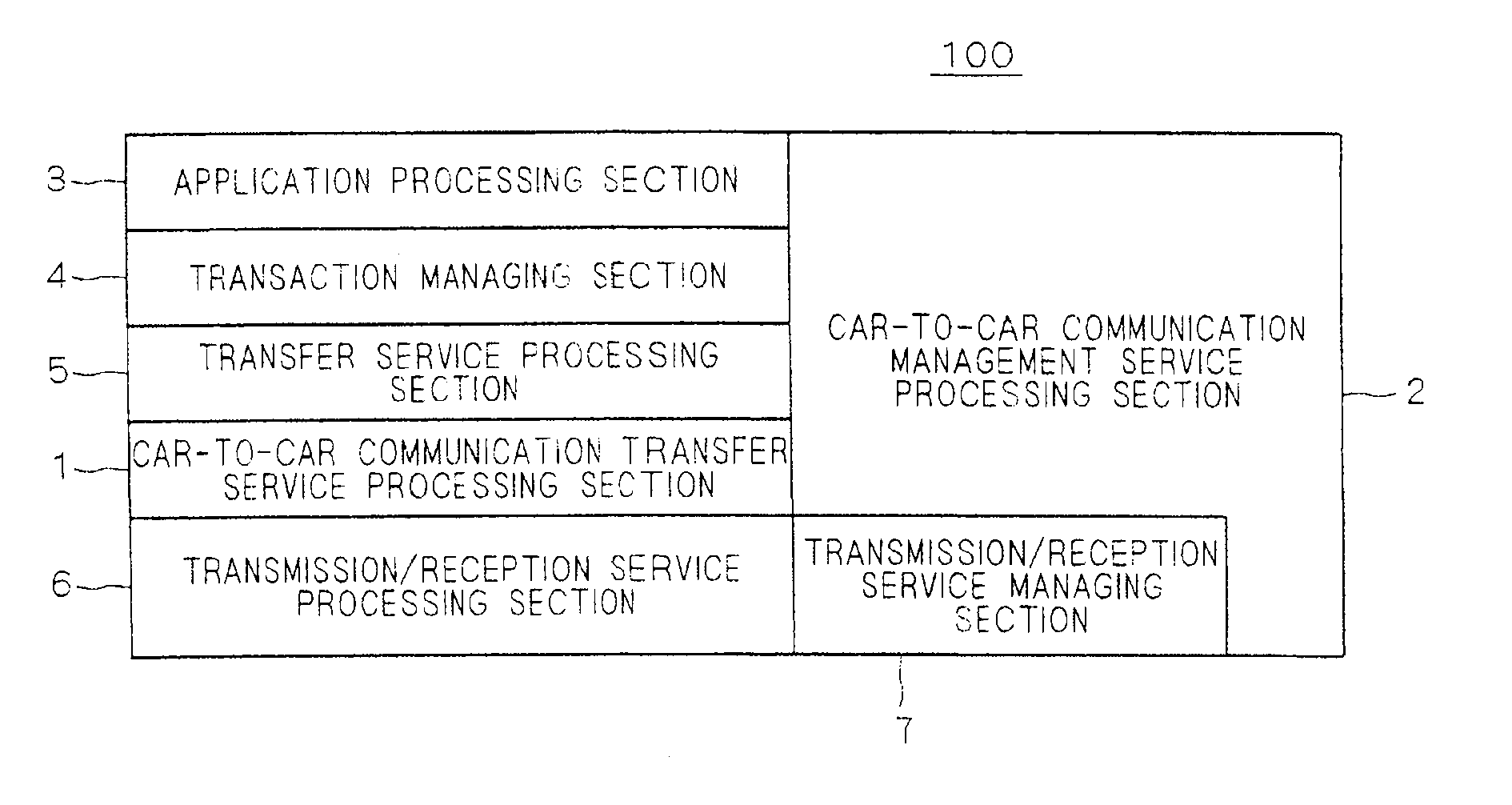
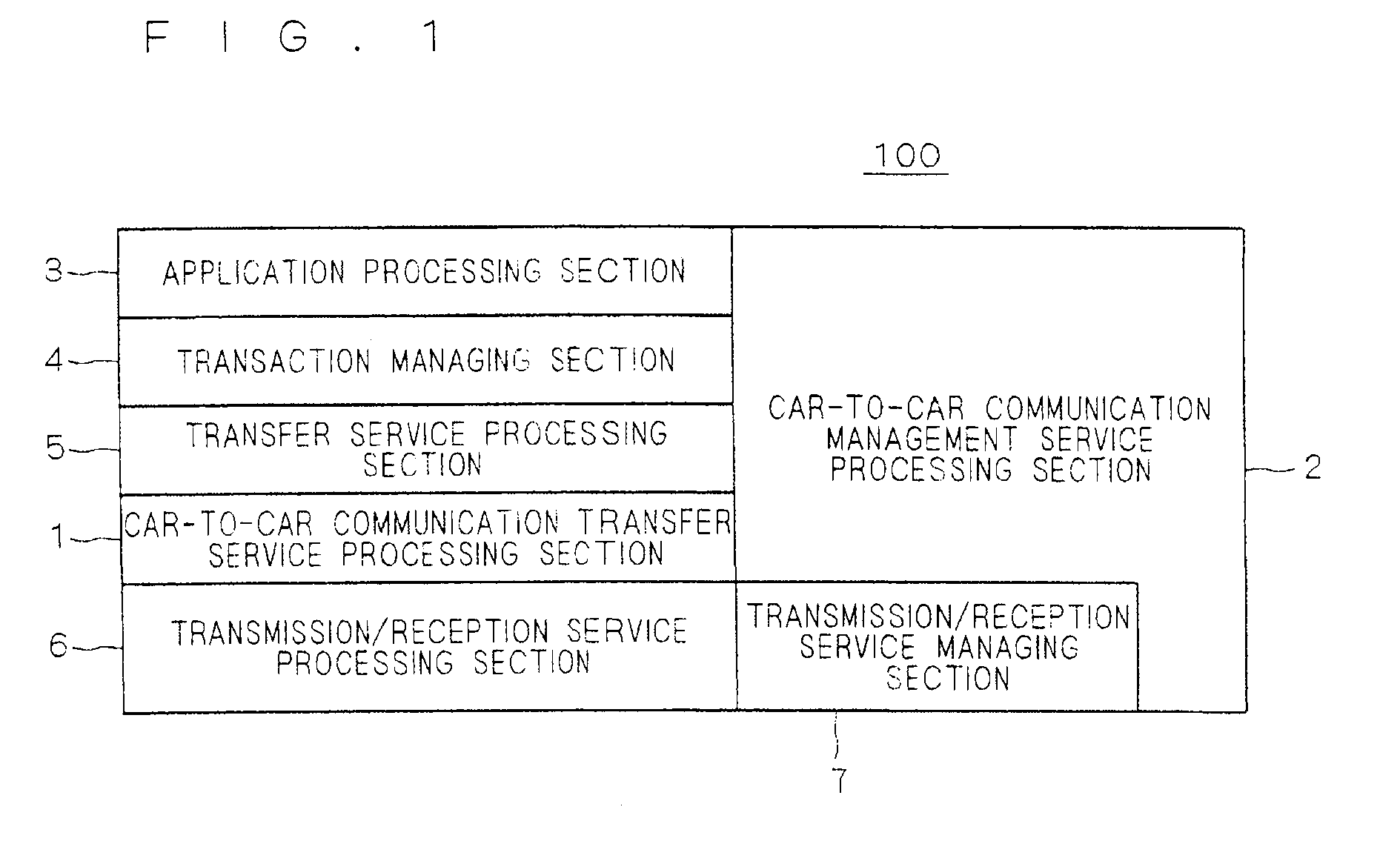
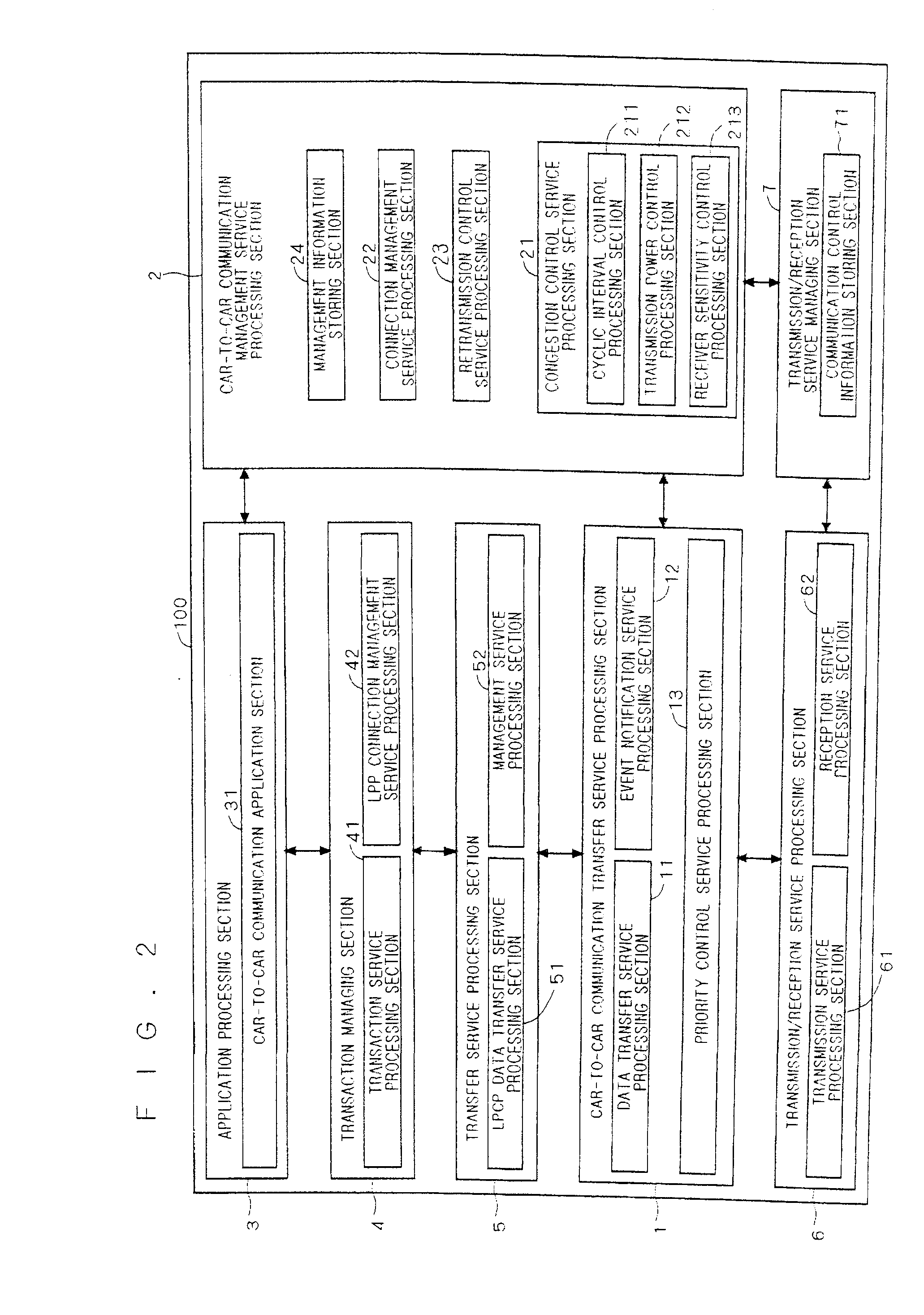
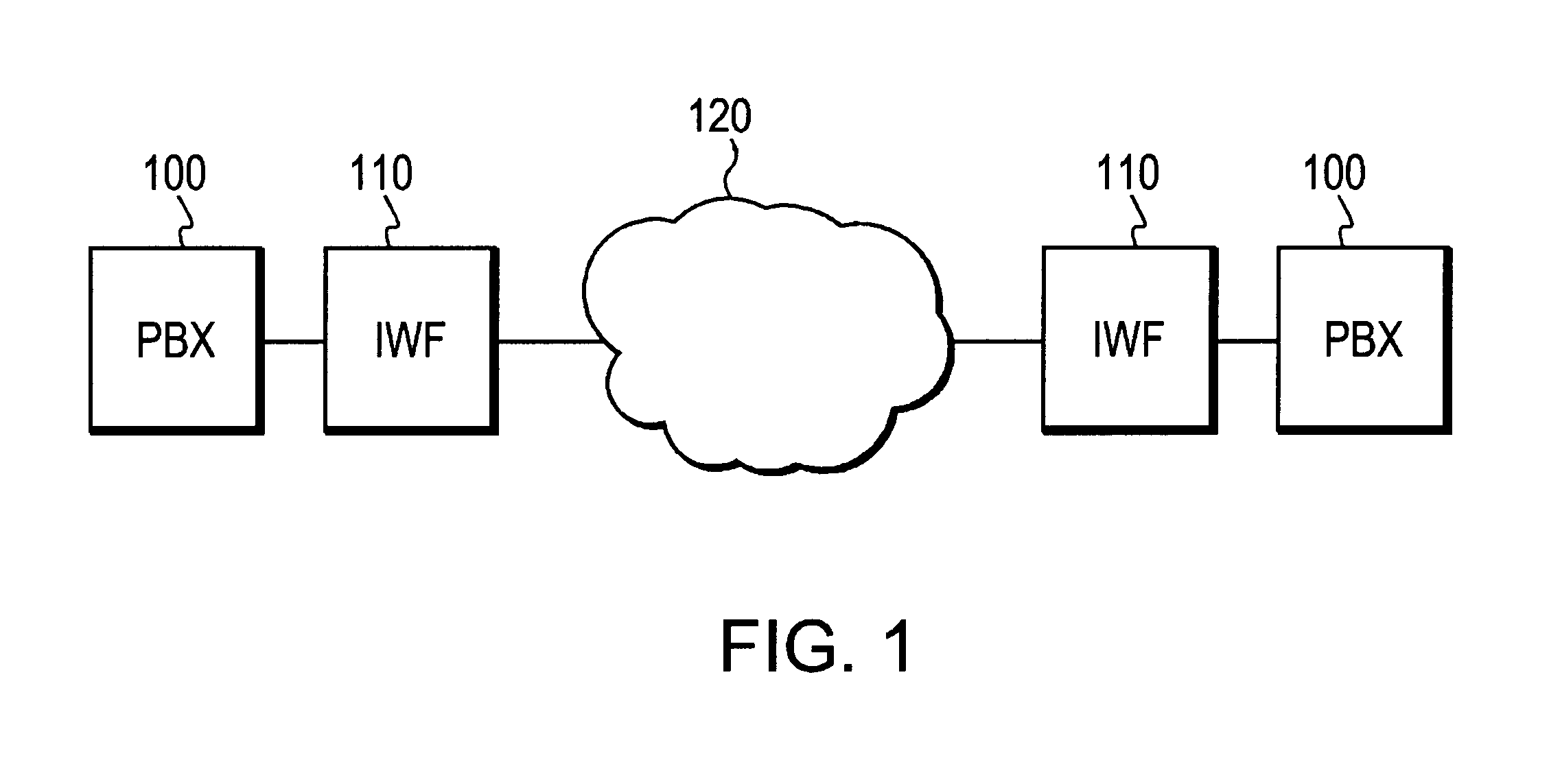
On-board communication device and cooperative road-to-vehicle/vehicle-to-vehicle communication system
ActiveUS20110034201A1Reduce communication delayRoad vehicles traffic controlWireless network protocolsCommunications systemOn board
The present invention has an object to provide an on-board communication device and a cooperative road-to-vehicle / car-to-car communication system that are adaptable to a road-to-vehicle communication system and a car-to-car communication system. An on-board communication device (100) includes a car-to-car communication transfer service processing section (1), a car-to-car communication management service processing section (2), an application processing section (3), a transaction managing section (4), a transfer service processing section (5), a transmission / reception service processing section (6) and a transmission / reception service managing section (7), in which the car-to-car communication transfer service processing section (1) and the car-to-car communication management service processing section (2) include interfaces to the transfer service processing section (5) that is an existing road-to-vehicle communication protocol.
Owner:MITSUBISHI ELECTRIC CORP
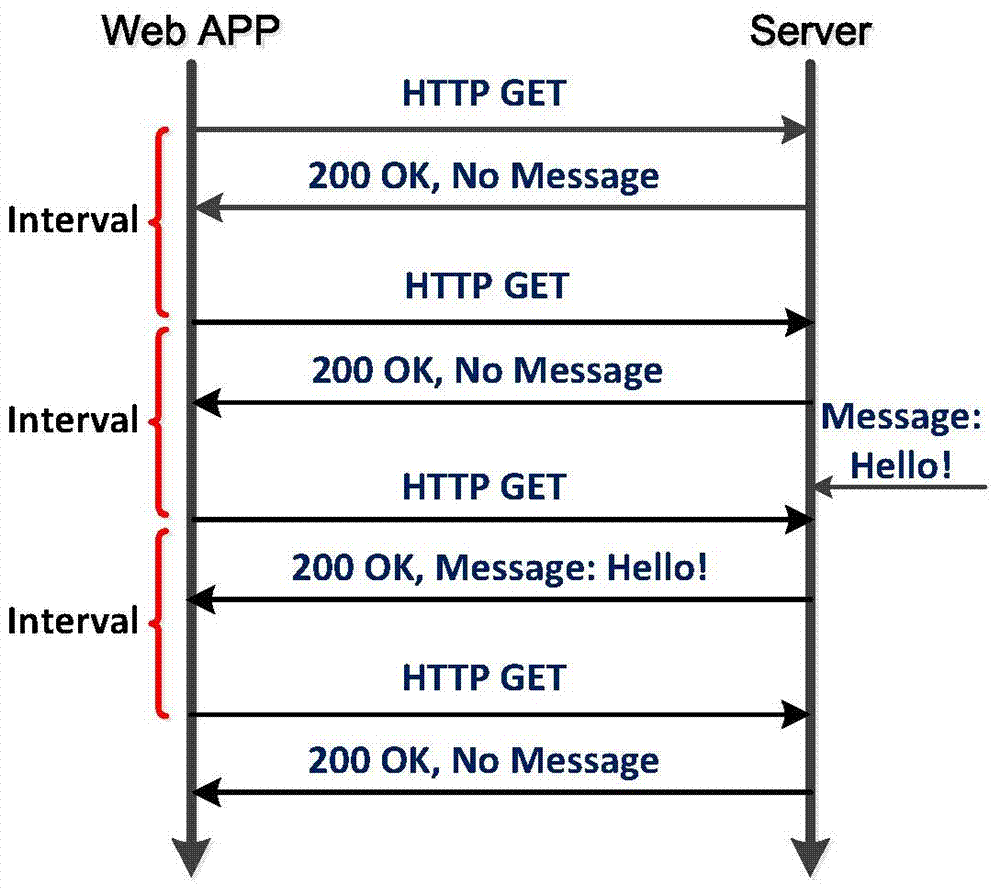
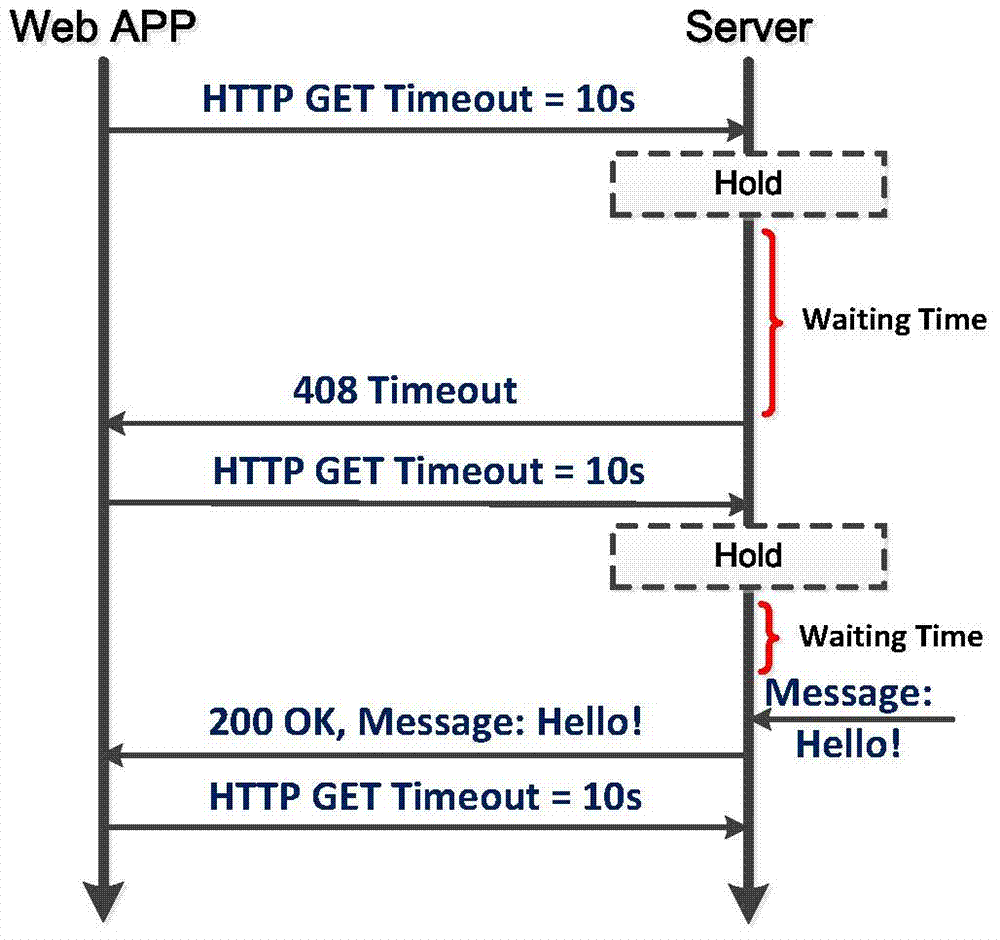
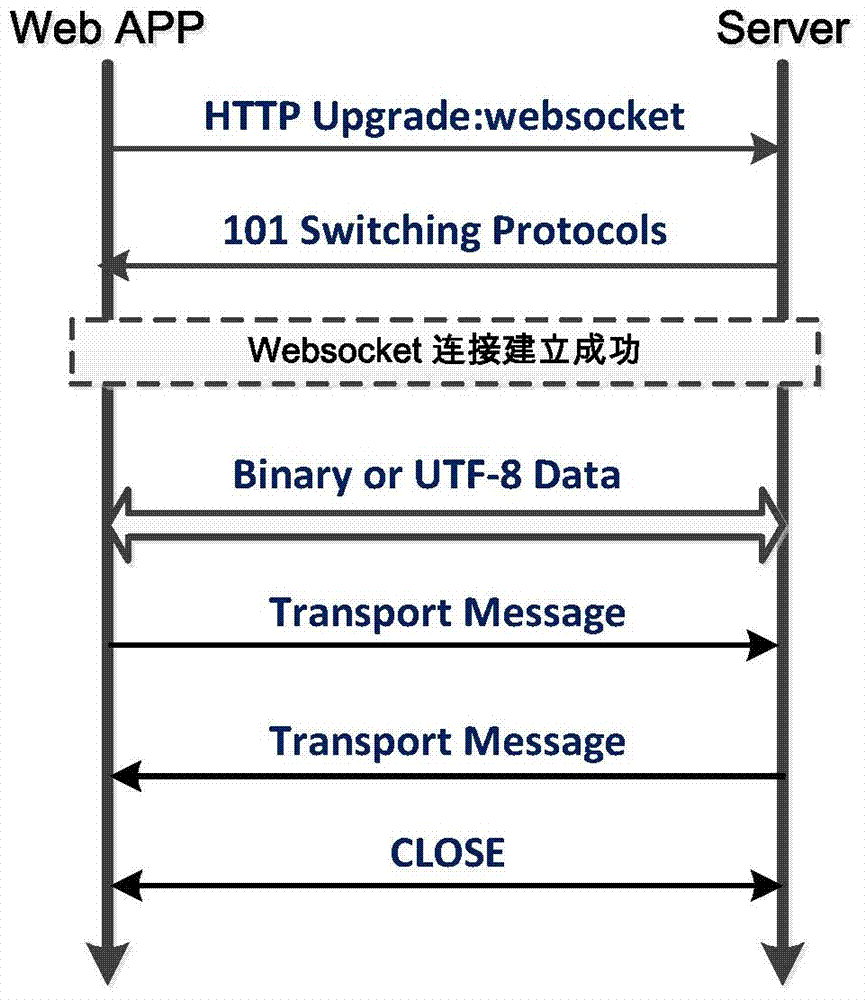
Dynamic self-adapting method for connection of Web RTC (Real Time Communication) client
ActiveCN103945003AFunction increaseImprove intelligenceTransmissionHyper text transport protocolLow delay
The invention provides a dynamic self-adapting method for the connection of a Web RTC (Real Time Communication) client, belonging to the technical fields of a Web RTC, an HTML (Hypertext Markup Language) 5 web Socket and the like. An entity related by the method comprises a Web RTC client, a browser and a real-time communication server, wherein the Web RTC client can support three connecting ways, including an HTTP (Hyper Text Transport Protocol) polling, an HTTP long connection and a Web Socket, and the HTTP long connection comprises an HTTP stream; according to the method, the connecting way with lowest delay of the HTTP polling, the HTTP long connection and the Web Socket can be optimally selected, and the Web RTC client and the real-time communication server are connected by using the connecting way with the lowest delay. Under the premise of guaranteeing timeliness, the communication delay can be reduced, the functions of the client can be enhanced, and the intelligence of the client can be improved.
Owner:BEIJING UNIV OF POSTS & TELECOMM
Secure client-side communication between multiple domains
ActiveUS20110246772A1Reduce communication delayCommunication securityDigital data processing detailsUser identity/authority verificationData integrityClient-side
Methods and systems for secure client-side communication between multiple domains is provided. Such methods and systems can provide for decreased communication latency particularly effective for dynamic multi-domain and / or multi-tenant environments while allowing for granular security or specific security of messages and operations with regard to users, user sessions, groups, organizations, permissions sets, applications, or any other logical delineation. Such methods and systems may involve a variety of security components, for example, at least one set of instructions including a plurality of defined instruction to be utilized by users of the set of instructions to communicate, and cryptographic construct data in order to verify the data integrity and the authenticity of messages sent and received using the secure client-side communication between multiple domains.
Owner:SALESFORCE COM INC
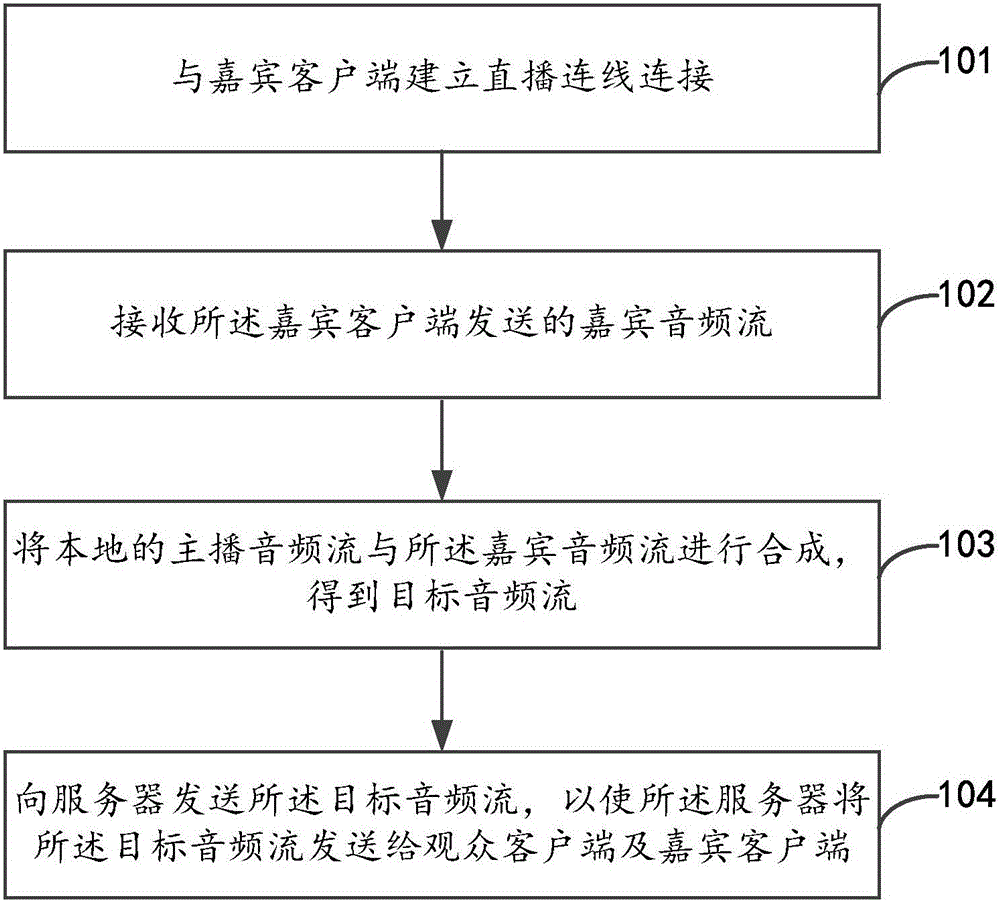
Live broadcast processing method, device and system and terminal equipment
InactiveCN106131583AImprove user experienceTroubleshoot communication delaysSelective content distributionTerminal equipmentComputer terminal
The present disclosure relates to a live broadcast processing method, device, terminal equipment and system. The method includes: establishing a live connection with the guest client; receiving the guest audio stream sent by the guest client; synthesizing the local anchor audio stream and the guest audio stream to obtain the target audio stream; sending the audio stream to the server The target audio stream, so that the server sends the target audio stream to the audience client and the guest client. The solution of the present disclosure can solve the problem of communication delay during multi-person live broadcast and improve user experience.
Owner:BEIJING XIAOMI MOBILE SOFTWARE CO LTD
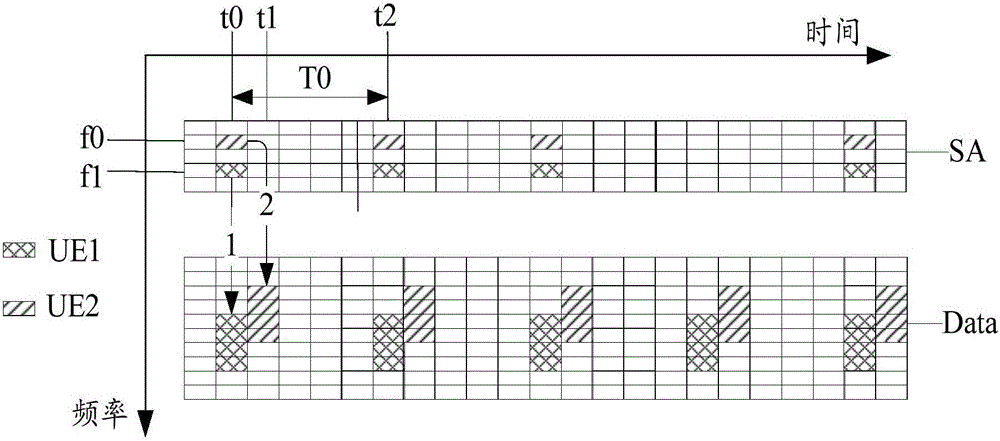
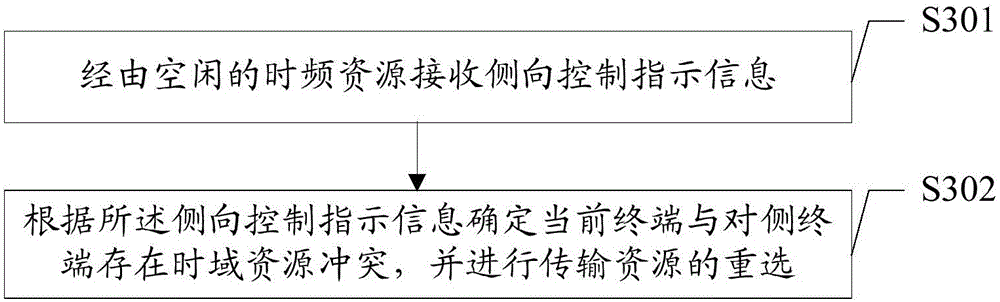
D2D communication resource reselecting method, apparatus and terminal
The invention provides a D2D communication resource reselecting method, an apparatus and a terminal wherein the D2D communication resource reselecting method comprises: receiving the side direction control and indication information from the idle time-frequency resource; according to the side direction control and indication information, determining that time-domain resource conflict exists between the current terminal and the opposite side terminal and reselecting the transmission resource wherein the opposite side terminal communicates with the current terminal through the use of D2D. The technical schemes of the invention can increase the efficiency of D2D communications.
Owner:BEIJING SPREADTRUM HI TECH COMM TECH CO LTD
Satellite network based on distributed-type SDN and construction method thereof
ActiveCN107294592ARealize Converged DeploymentReduce the burden onRadio transmissionData switching networksTotal delaySurvivability
Owner:DALIAN UNIVERSITY
Intersection bus signal priority control system and control method based on C-V2X
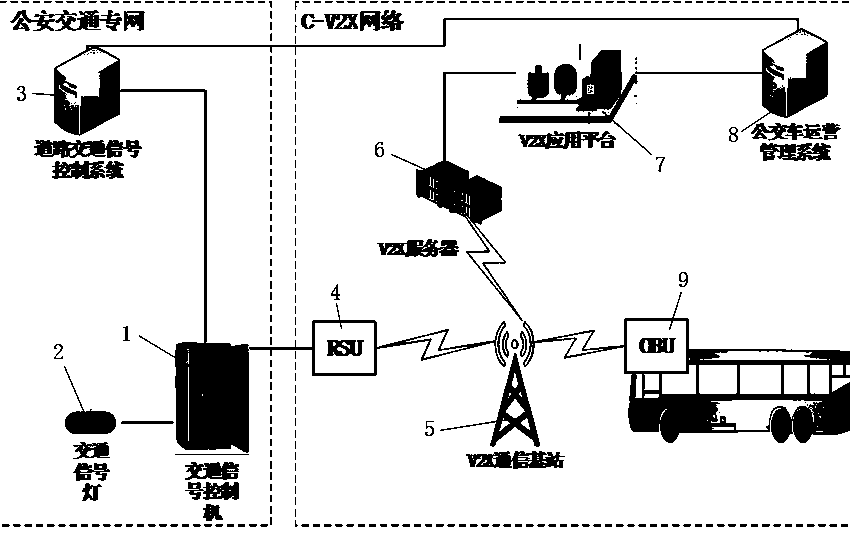
ActiveCN108898824AHigh positioning accuracyImprove anti-interference abilityRoad vehicles traffic controlTraffic signalControl system
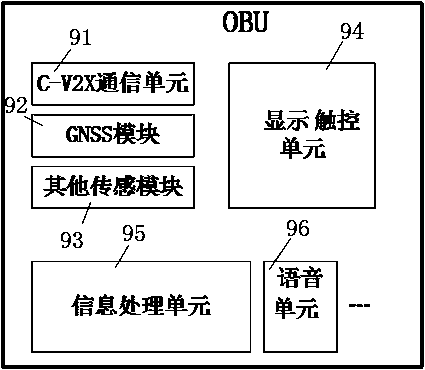
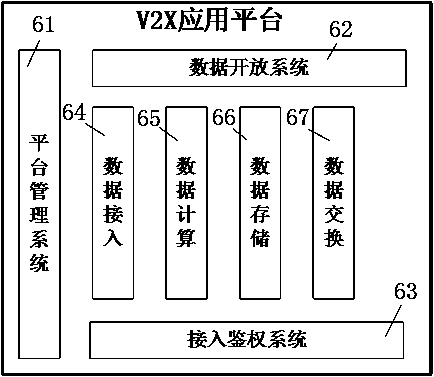
The invention provides an intersection bus signal priority control system and control method based on C-V2X. Instrumentation from buses to a road traffic signal control machine and interconnection between a signal control center system and a bus operation management system are supported, dynamic priority adjustment of bus signals and active bus priority are achieved, the intersection bus signal priority control system comprises the road traffic signal control machine, traffic signal lamps, a road traffic signal control system, a RSU device, a C-V2X communication base station, a V2X server, a V2X application platform, the bus operation management system and a OBU device, the OBU device uploads bus information and sends the bus information to the road traffic signal control system, the roadtraffic signal control system is in interaction with the bus operation management system and sends bus signal priority requests and estimated time of arrival to the road traffic signal control machine, and the road traffic signal control machine makes decisions to respond to the priority requests or not to respond to the priority requests, gives out a priority control strategy to adjust phase positions of the traffic signal lamps and gives bus traffic priority.
Owner:TRAFFIC MANAGEMENT RES INST OF THE MIN OF PUBLIC SECURITY
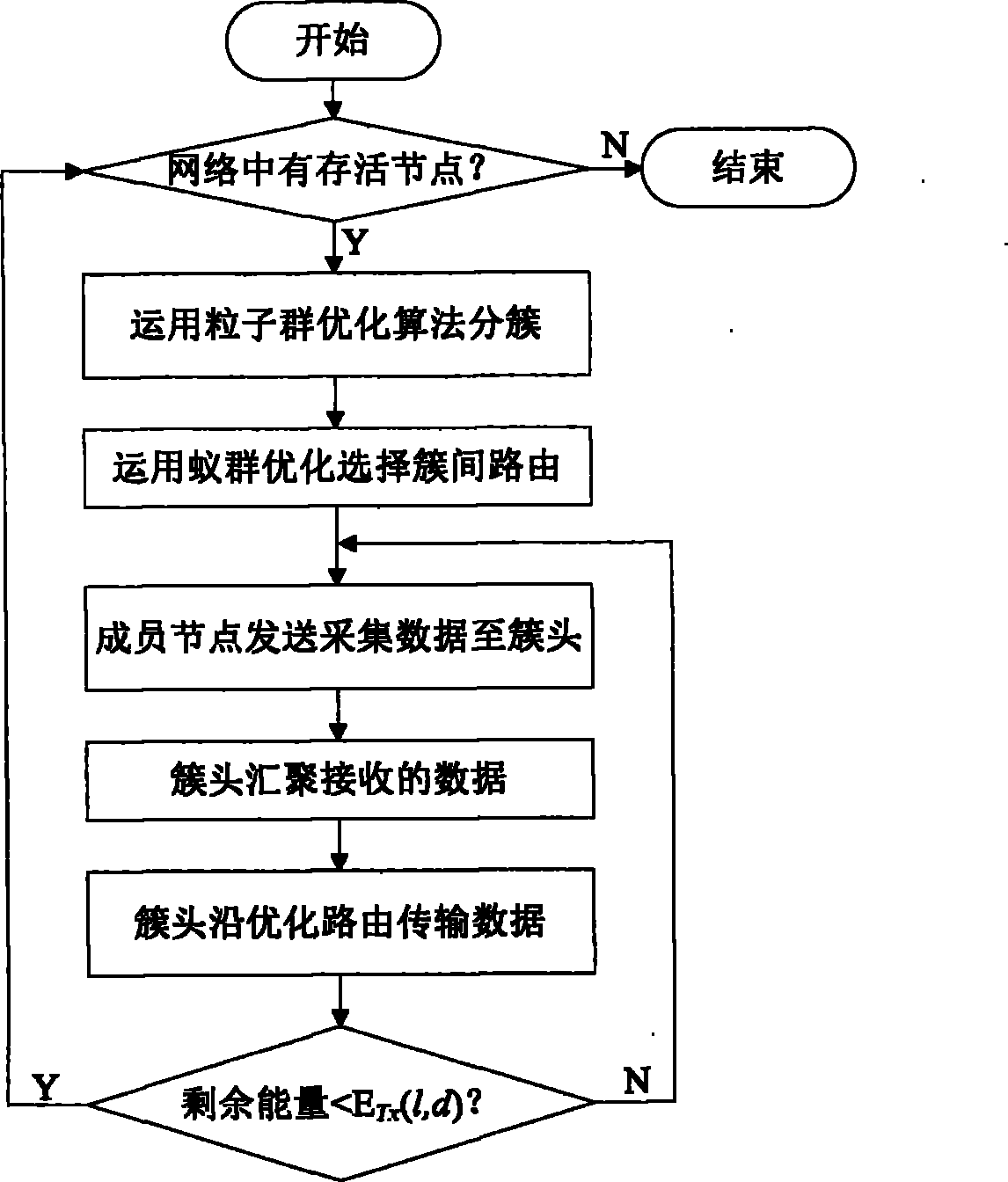
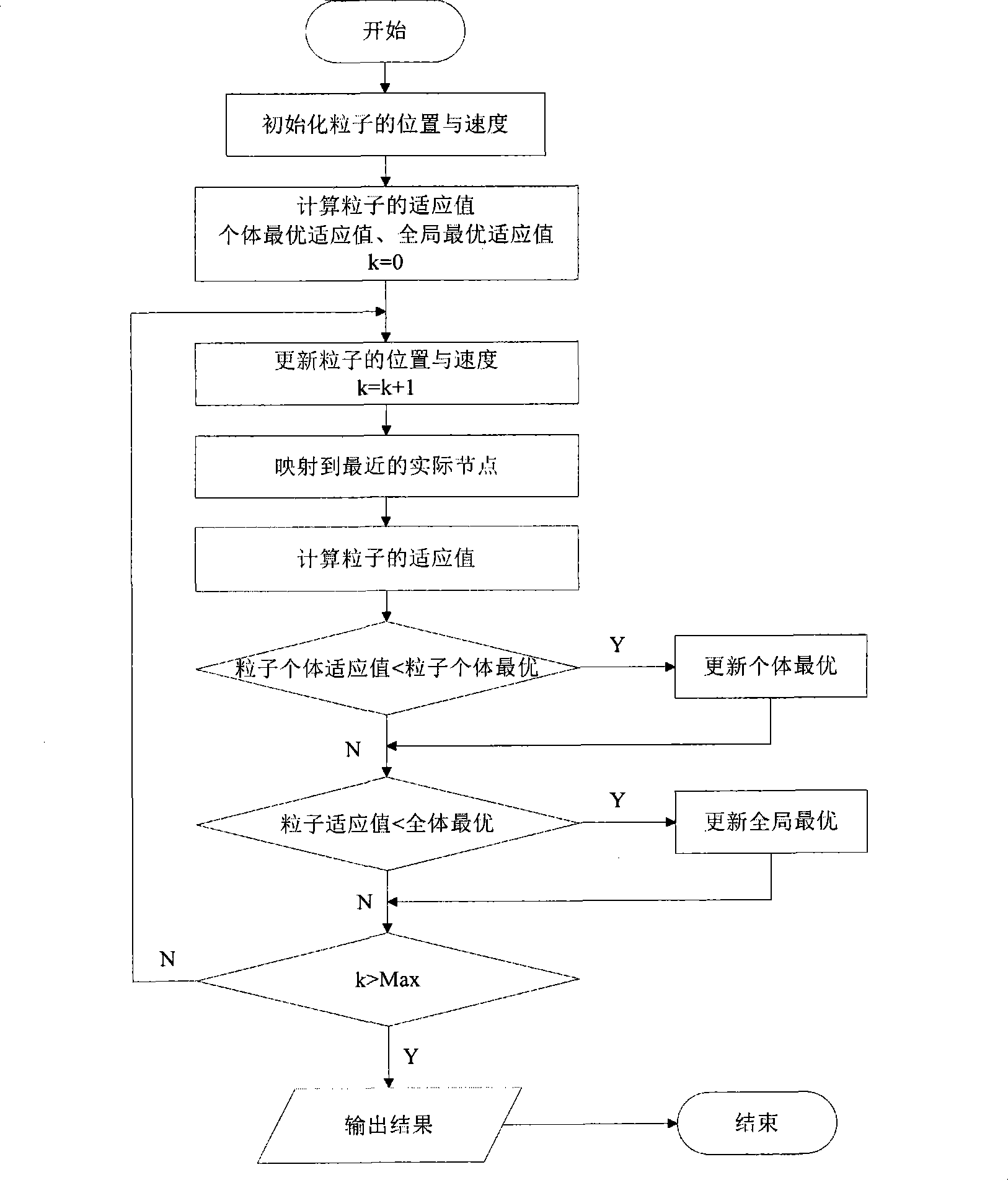
Wireless sensor network clustering routing method based on particle swarm optimization and ant colony optimization
InactiveCN103228023AProlong survival timeIncrease profitNetwork topologiesHigh level techniquesNODALWireless mesh network
The invention discloses a wireless sensor network clustering routing method based on particle swarm optimization and ant colony optimization, and belongs to the technical field of wireless sensor networks. The method is characterized in that the method comprises the steps that the optimal cluster quantity of an animal breeding environment detection system is decided dynamically; factors influencing energy consumption are analyzed earnestly; an adaptive value function is constructed; clustering is optimized by using a particle swarm optimization algorithm; and then routing between clusters is optimized by operating an ant colony algorithm in a cluster head node. Therefore, the energy consumption of a sensor node in a network is equalized; the survival time of the network is prolonged; a path with small communication delay is selected; the flow of the network is equalized; and a utilization ratio of a wireless sensor network for animal breeding environment detection is increased.
Owner:QINGDAO AGRI UNIV
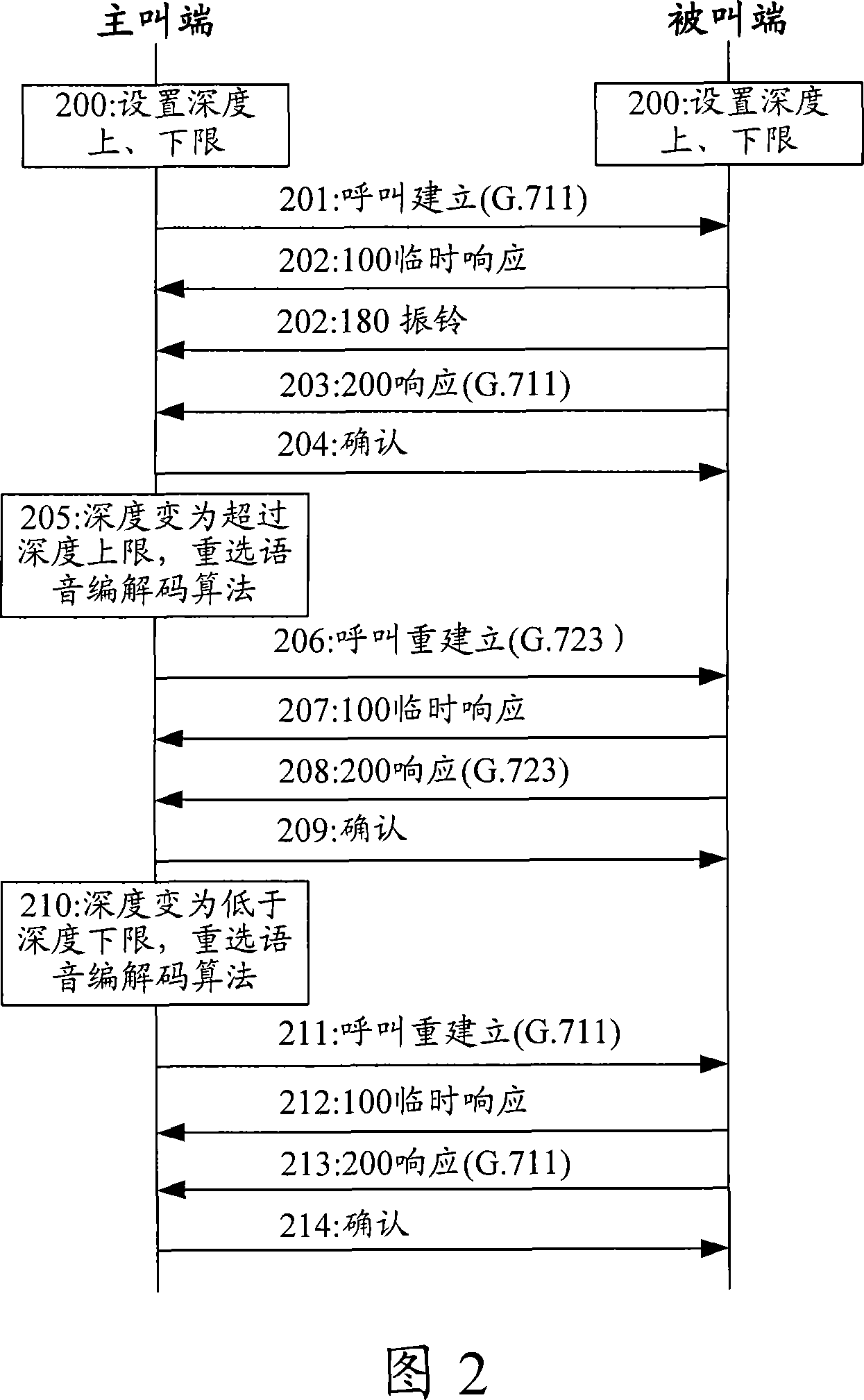
Data transfer method and device
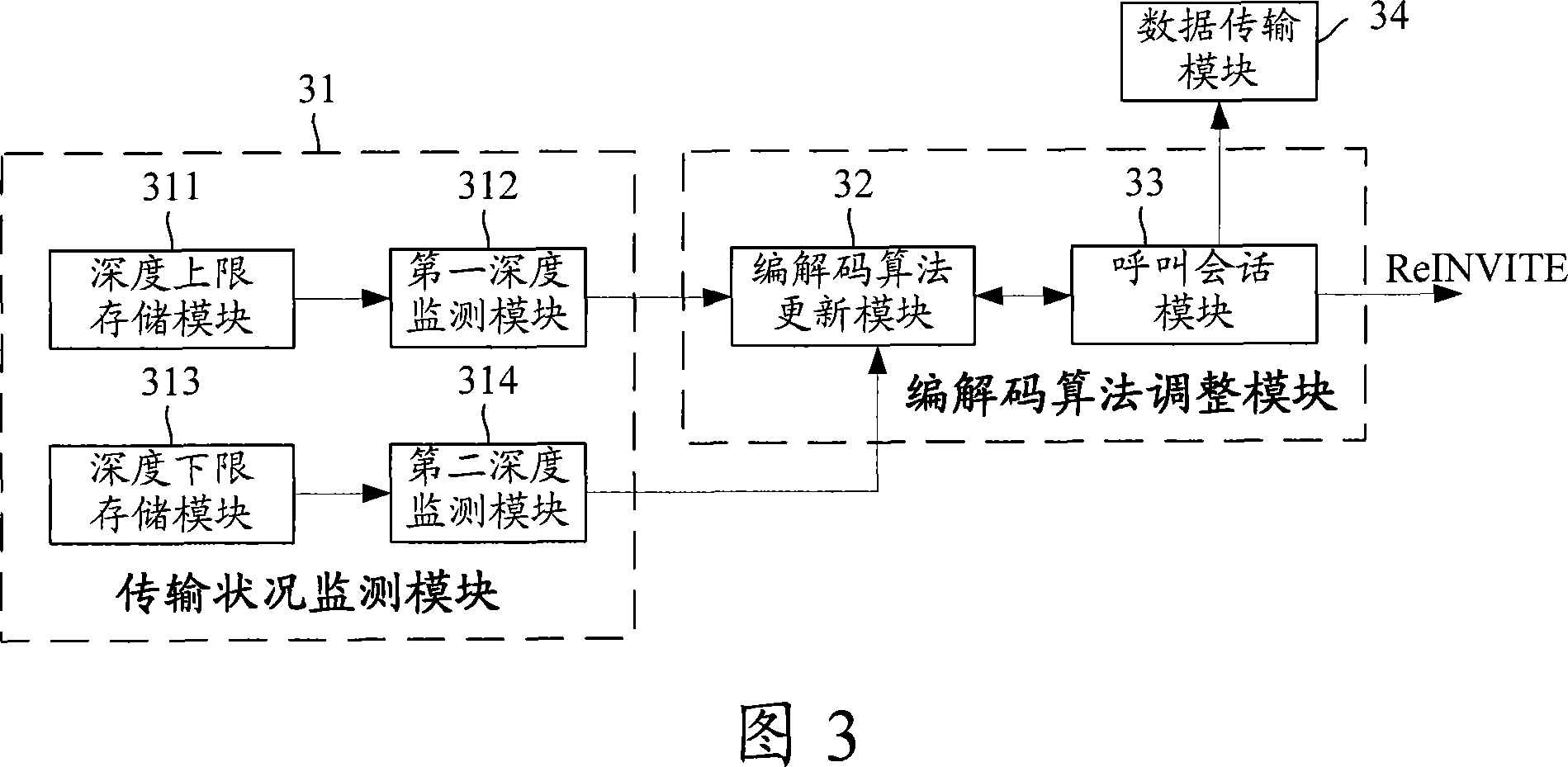
InactiveCN101035086ARelieve stressFast shrinkageError preventionData switching networksData informationNetwork conditions
The invention discloses a data transmitting method, comprising: when detecting the change of data transmission network conditions, selecting an encoding / decoding algorithm whose compression ratio is suitable for the current network conditions, and adopting the selected encoding / decoding algorithm to make the follow-up data transmission. And the invention also discloses a data transmitting device, comprising: network condition monitoring module, encoding / decoding algorithm regulating module, and data transmitting module. And the invention raises the data transmitting rate. When the network conditions turn bad, it selects an encoding / decoding algorithm whose compression ratio is higher than that of the current encoding / decoding algorithm to reduce the network bandwidth occupied by the data transmission, to a certain extent, relieving network pressure, increasing Jitter Buffer depth shrinking rate, and reducing communication delay; when the network conditions turn good, it selects an encoding / decoding algorithm whose compression ratio is higher than that of the current encoding / decoding algorithm to increase transmitted data information and improving the received data quality. And the invention is simple to implement and easy to apply without adding any hardware equipment.
Owner:NEW H3C TECH CO LTD
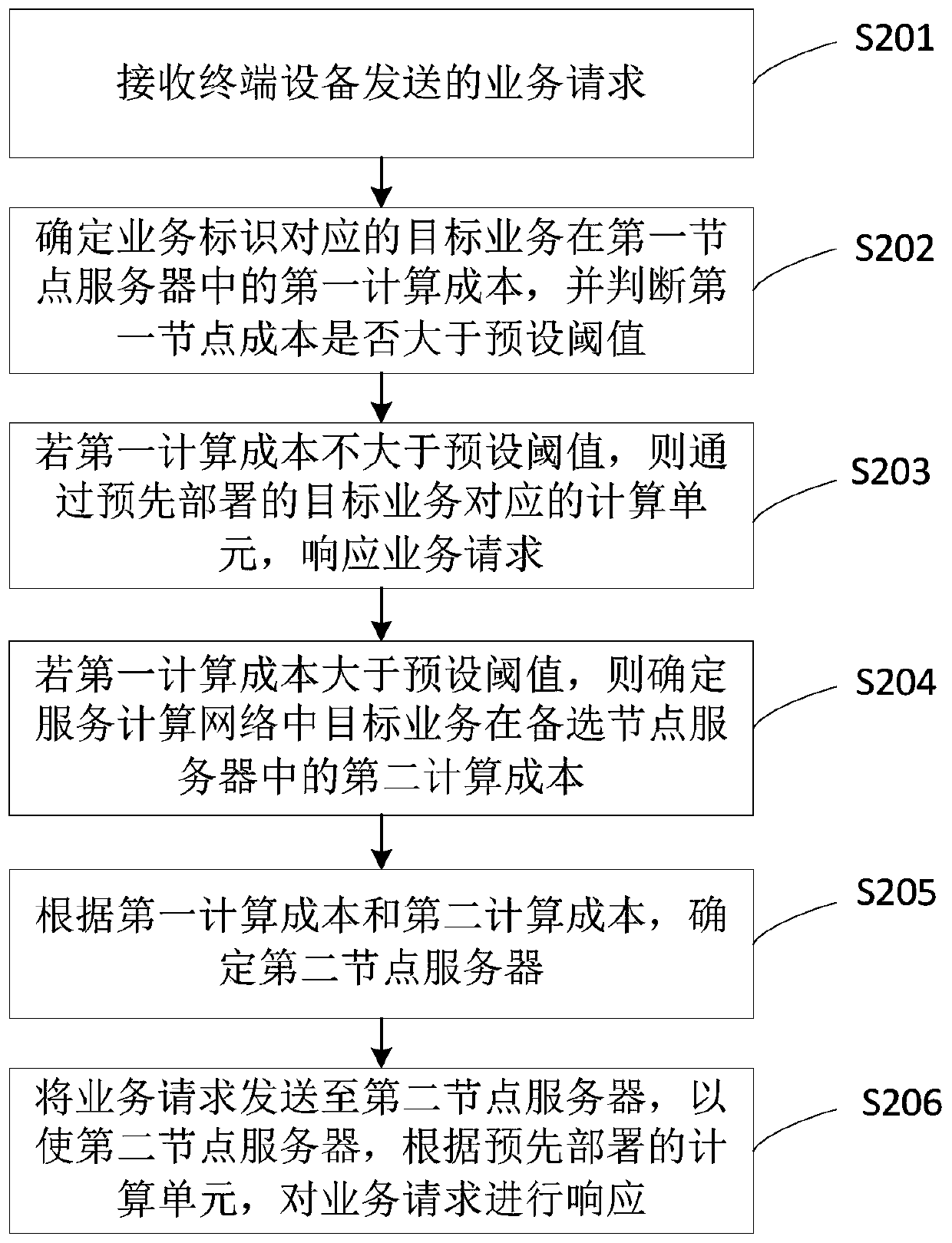
Service deployment and task scheduling method and device based on edge computing
The embodiment of the invention provides a service deployment and task scheduling method and device based on edge computing. The method comprises the steps of responding to a service request when a first calculation cost of a target service in a first node server is not greater than a preset threshold; if the first calculation cost is greater than the preset threshold, determining a second node server; and sending the service request to the second node server, so that the second node server responds to the service request according to a pre-deployed computing unit. According to the scheme, thedevice comprises a base, the calculation cost of the first node server and the calculation cost of the alternative node server for the service request are compared; a calculation unit is selected anddeployed; and the node server of the service request can be efficiently and timely processed, so that the condition that the node server is overloaded and the service request cannot be timely processed after the service request is migrated to a certain node server is avoided, the communication delay can be effectively reduced, the network load can be balanced, and the network service quality canbe improved.
Owner:BEIJING UNIV OF POSTS & TELECOMM
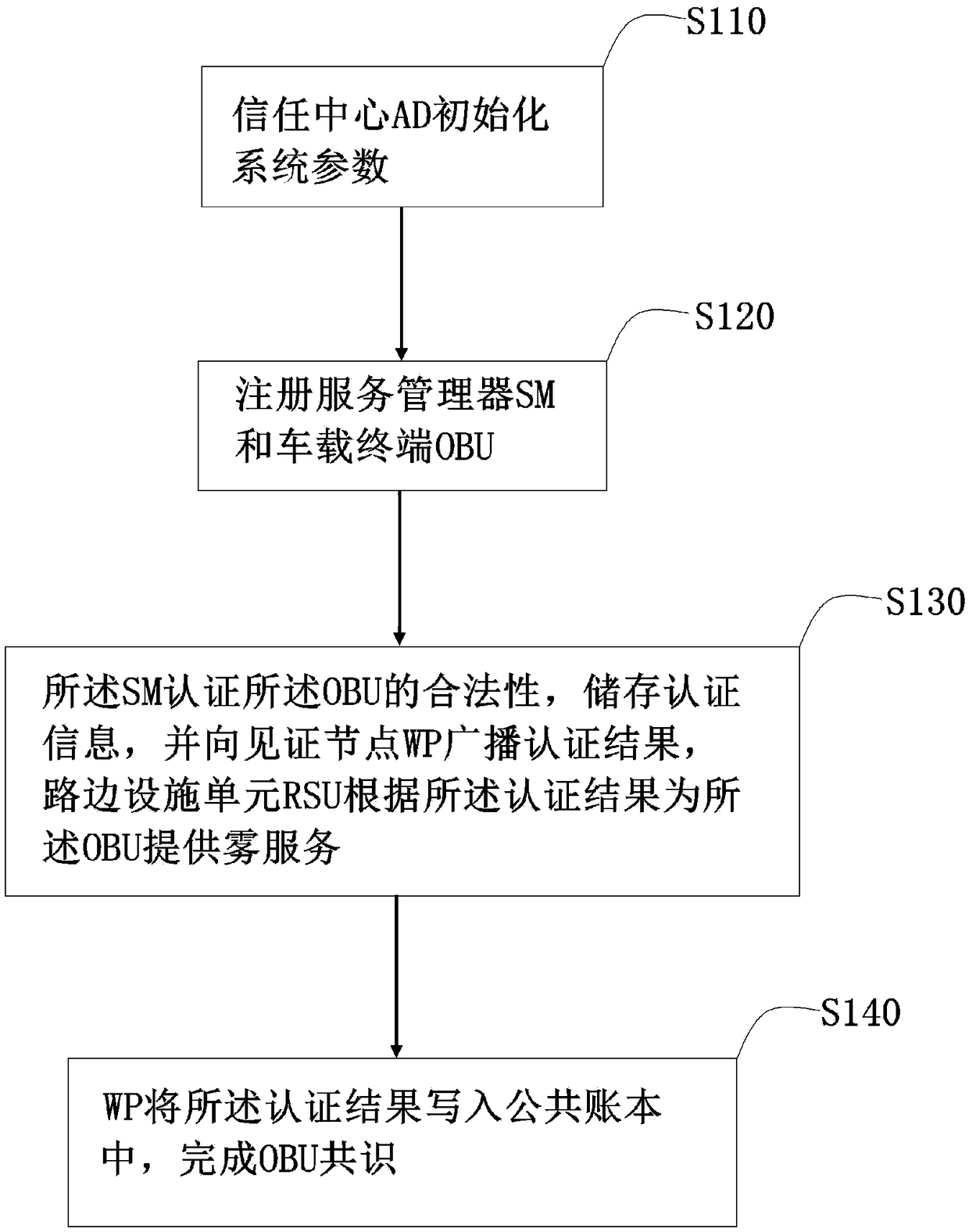
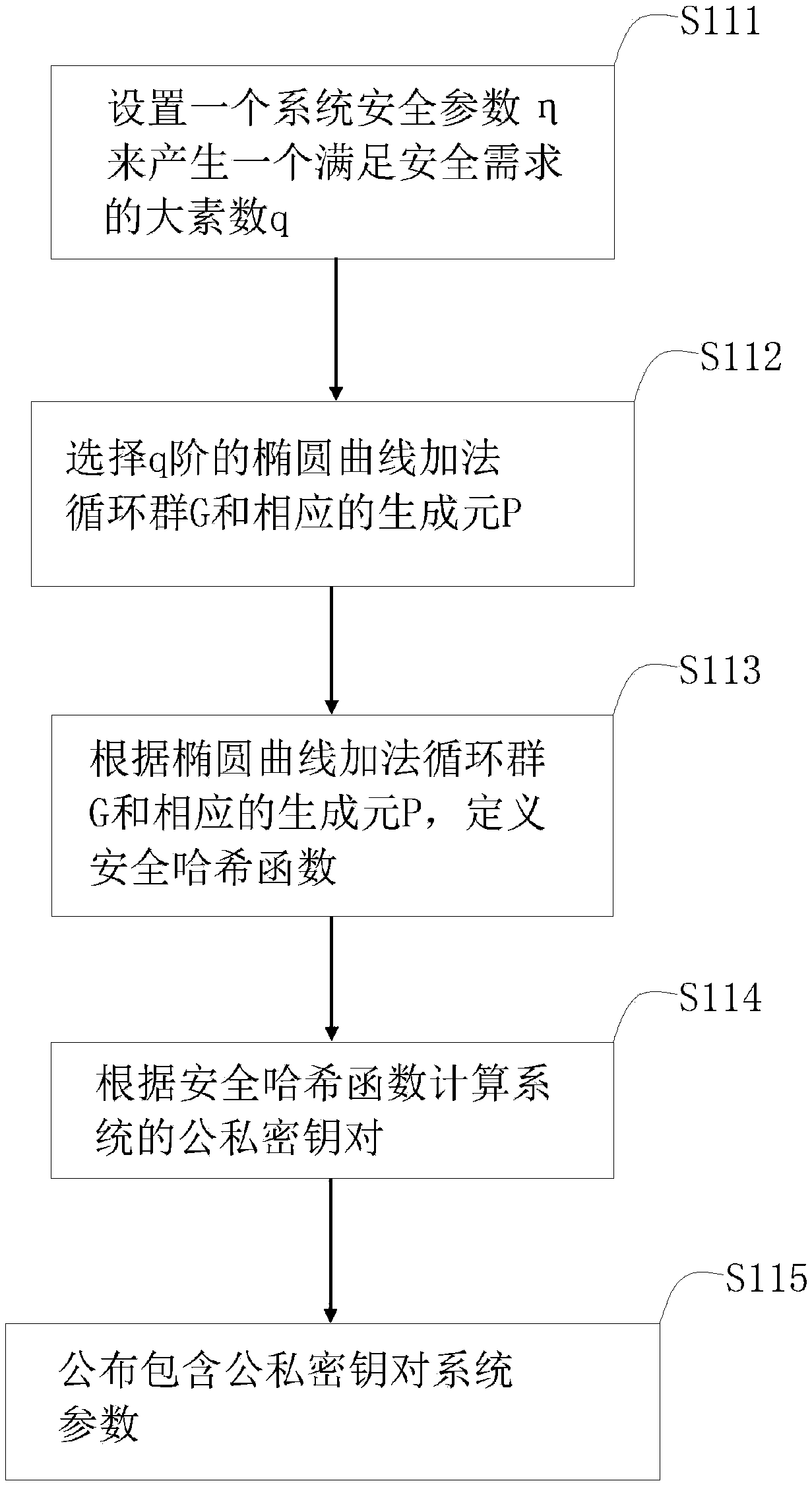
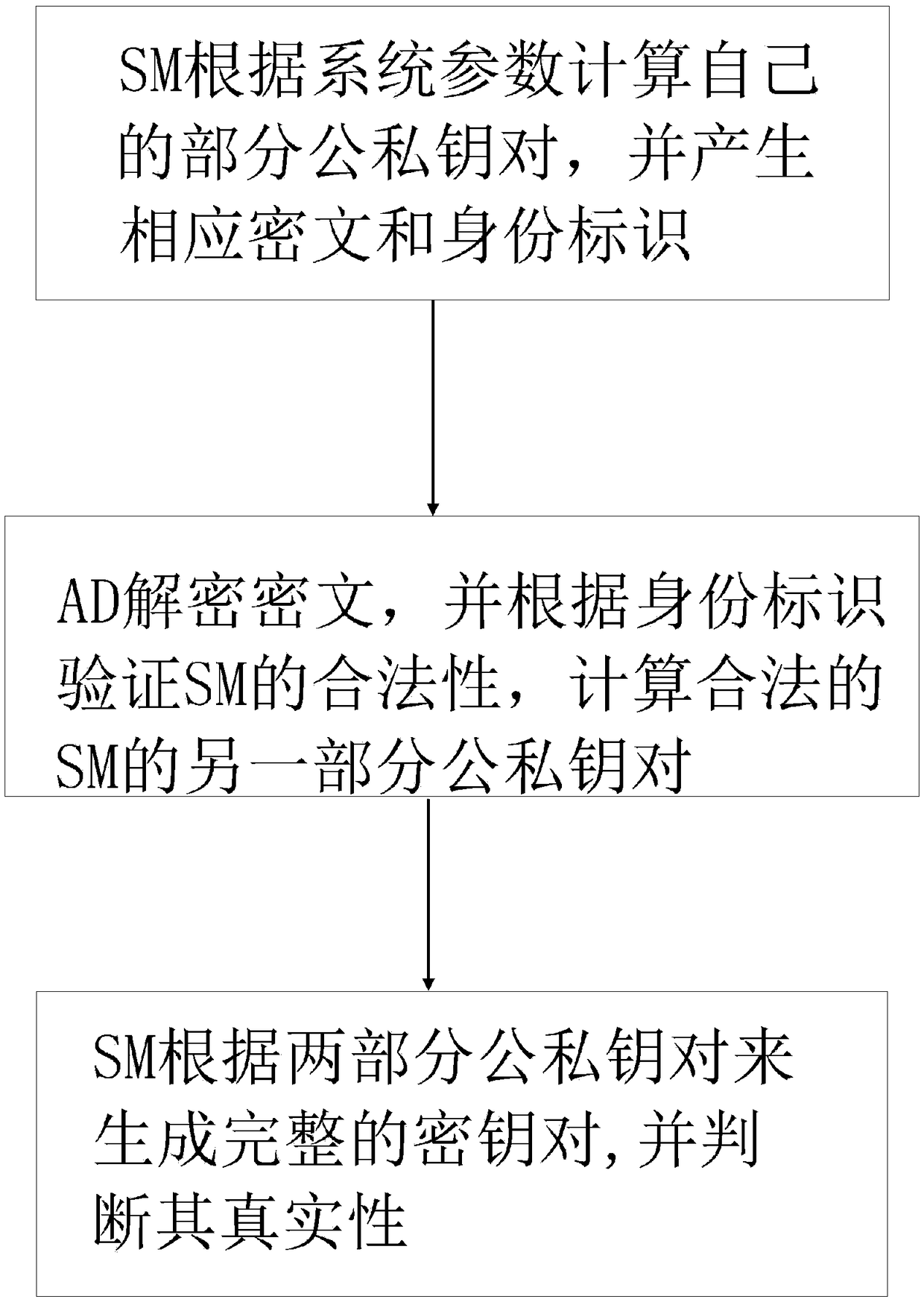
Vehicle fog data light-weight anonymous access authentication method based on blockchain assistance
InactiveCN109194610AProtect private informationEnhanced anonymityKey distribution for secure communicationEncryption apparatus with shift registers/memoriesPublic accountOn board
The present invention provides a vehicle fog data light-weight anonymous access authentication method based on blockchain assistance, and relates to the technical field of network communication safetyof urban traffic operation management. The method comprises the steps of: arranging one witness node (WP) in a management range of each service manager (SM), initializing system parameters through antrusted center AD, and registering the SM and a OBU (On Board Unit); allowing the SM to authenticate the validity of the OBU, storing the authentication information, broadcasting an authentication result to the WP, and providing fog service to the OBU according to the authentication result by a roadside facility unit RSU; and writing the authentication result into a public account by the WP to complete OBU consensus. The vehicle fog data light-weight anonymous access authentication method based on blockchain assistance can protect the user privacy information while ensuring the identity authenticity of a vehicle user accessing the fog service so as to achieve the vehicle anonymous authentication and allow users to select the time and the frequency of replacement of the pseudonym by themselves; the non-interactive autonomous cross-domain authentication is achieved, and the communication delay is effectively reduced; and moreover, the authentication information management is simplified,and the risk that a single database is tampered is effectively avoided.
Owner:BEIJING JIAOTONG UNIV
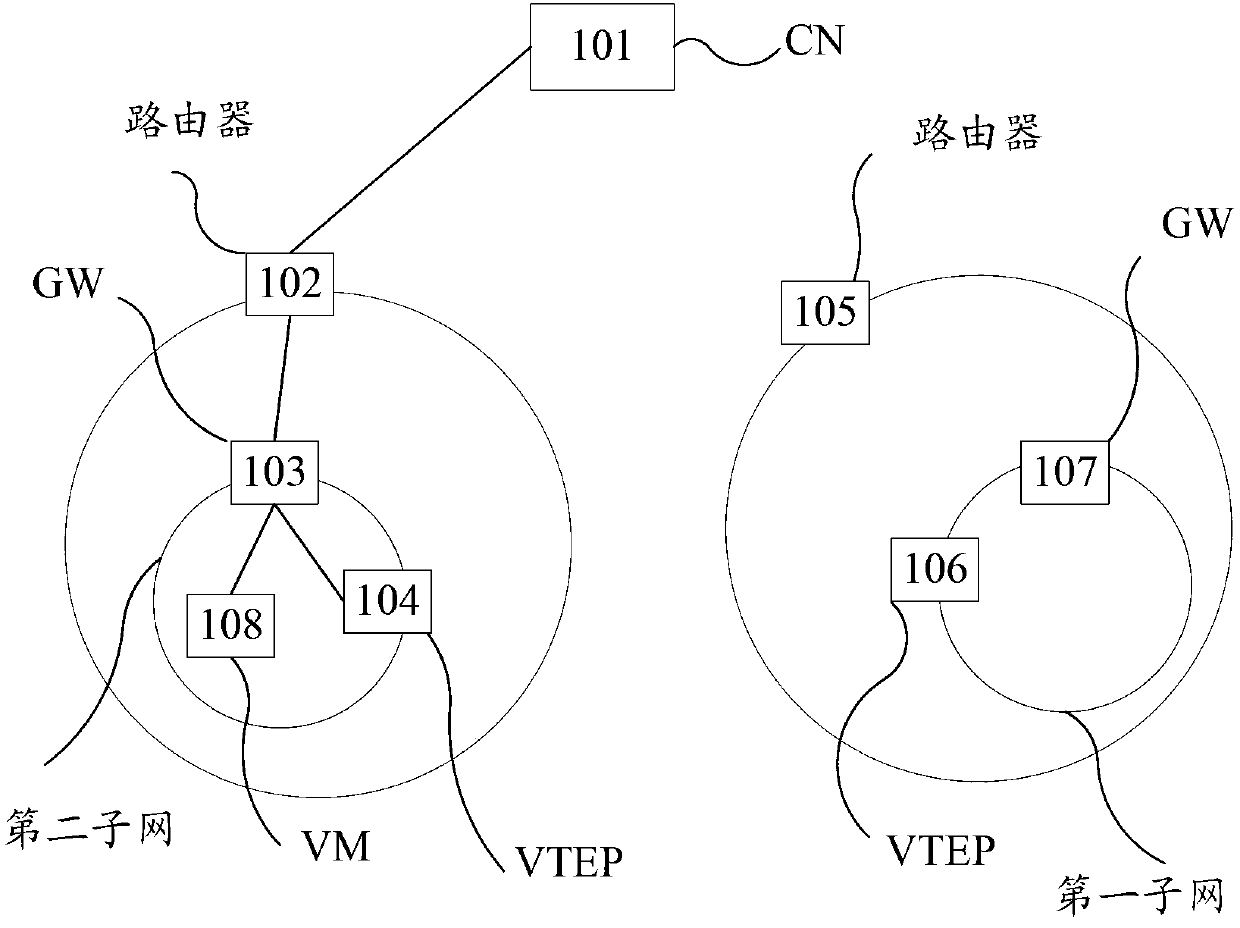
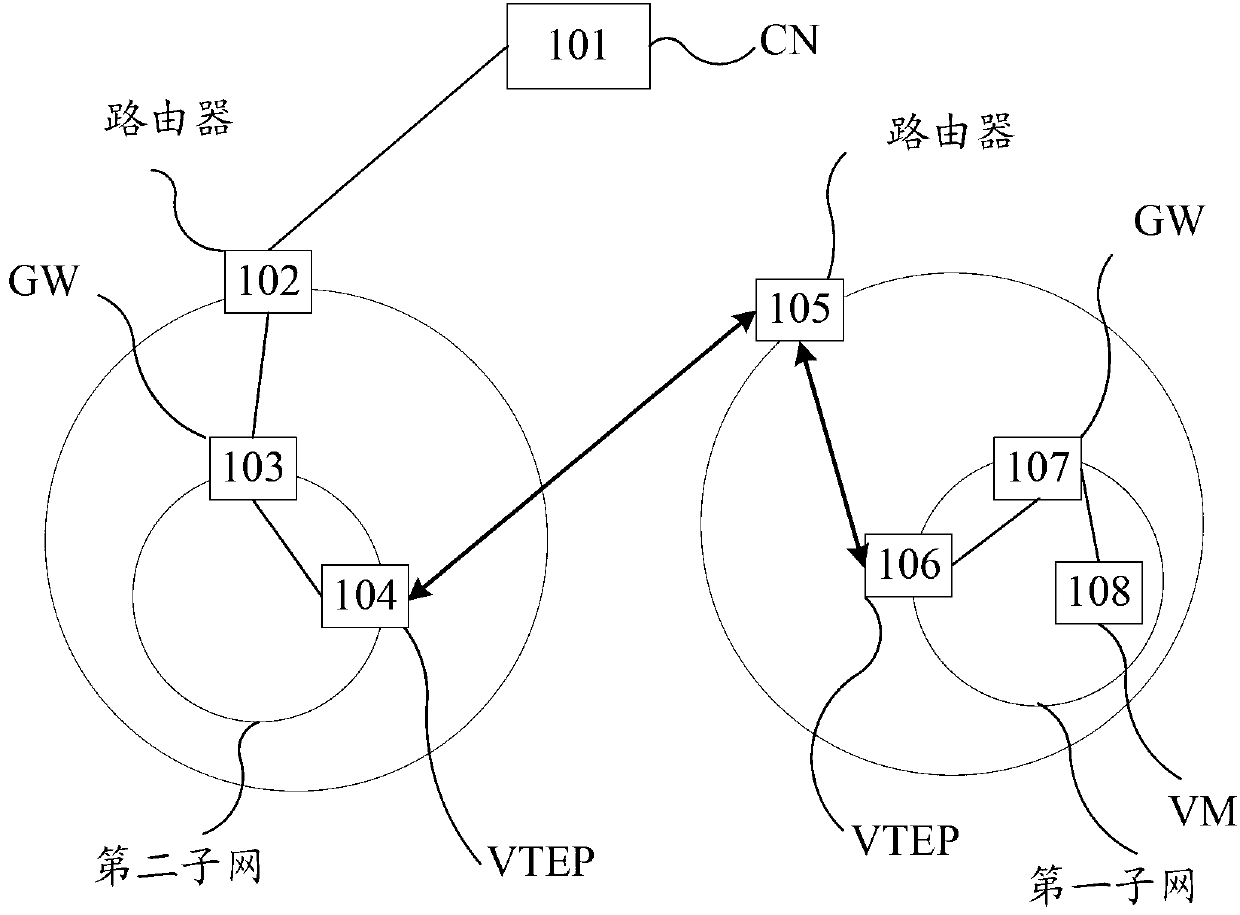
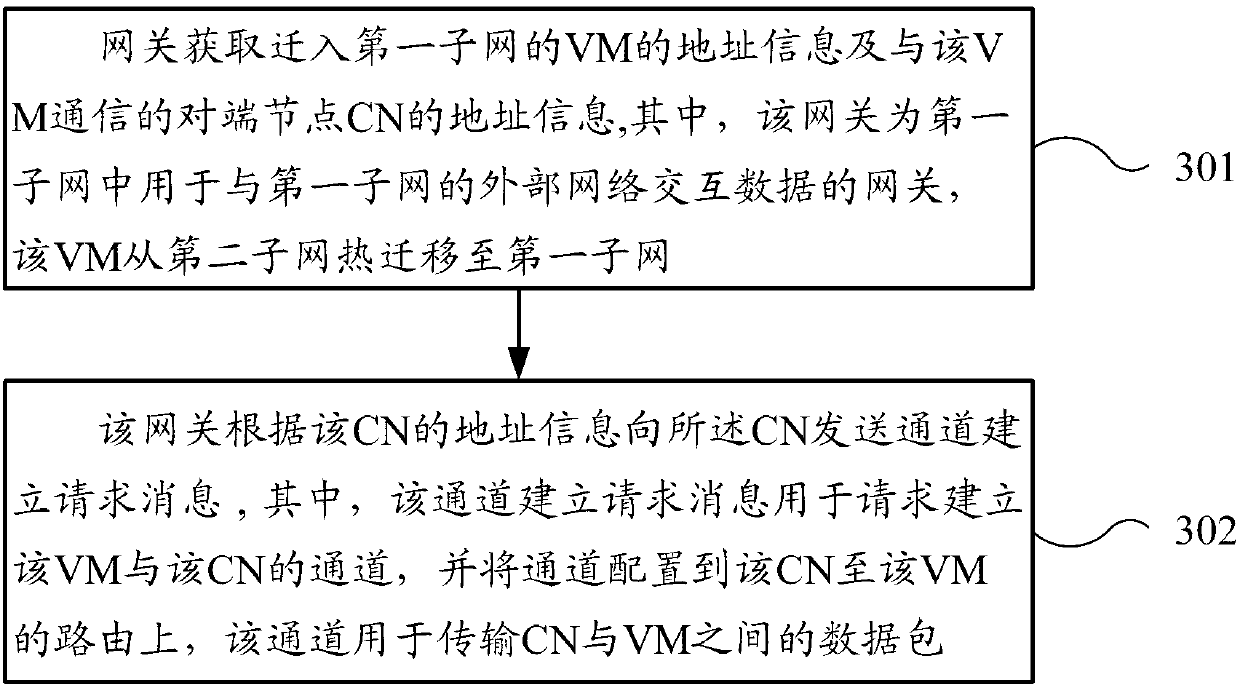
Route configuration method and gateway after thermal migration of virtual machine in large two-layer network
ActiveCN103346900AReduce communication delayShorten routing pathNetworks interconnectionNetwork connectionsVirtual machineReal-time computing
The invention provides a route configuration method and a gateway after thermal migration of a virtual machine in a large two-layer network. The method includes the following steps that the gateway obtains address information of a VM migrating into a first subnet and address information of a CN performing communication with the VM; the VM thermally migrates from a second subnet into the first subnet. The gateway sends a message of requesting set-up of a channel to the CN according to the address information of the CN; the message of requesting set-up of the channel is used for requesting set-up of a channel between the gateway and the CN and configures the channel to a route from the CN to the VM. According to the route configuration method and the gateway after thermal migration of the virtual machine in the large two-layer network, the gateway sets up the channel between the gateway and the CN and configures the channel to the route between the CN and the VM by obtaining the address information of the VM migrating into the subnet where the gateway exists and the address information of the CN which performs communication with the VM and sending the message of requesting set up of the channel to the CN. The path of the route between the CN and the VM is shortened and communication delay after the thermal migration of the VM of the large two-layer network is reduced to a certain degree.
Owner:HUAWEI TECH CO LTD
Mixed mobile agent-based wireless sensor network data transmission method
InactiveCN101039321AEfficient data transferReduce data volumeEnergy efficient ICTData switching by path configurationTime informationSelf navigation
A data transmission method of wireless sensor network based on multiple mobile agents introduces the mobile agents into the data collection and transmission for network. The main strategies of the method are: 1. collecting local data through self-equipped processing capability of software mobile agents and carrying out local processing; 2. starting hardware agents for continuously carrying out data collection and transmission for a local part of the network during a period with requirement of massive data collection and transmission. Thereby, the traditional mode pattern of distributed user terminal / server of a system is changed, data flow transmitted from a sensor node to a base station (or a gateway) is greatly decreased, the manner of data transmission is simplified and the purpose of energy saving and efficiency is realized. On condition of that once these matters occur in the network, the user needs to obtain accurate and real-time information, a self-navigation mechanism of the hardware agent can get to the occurring area, and the hardware agent can speedily collect and transmit the data cared by the user based on its excellent capability of management and communication.
Owner:NANJING UNIV OF POSTS & TELECOMM
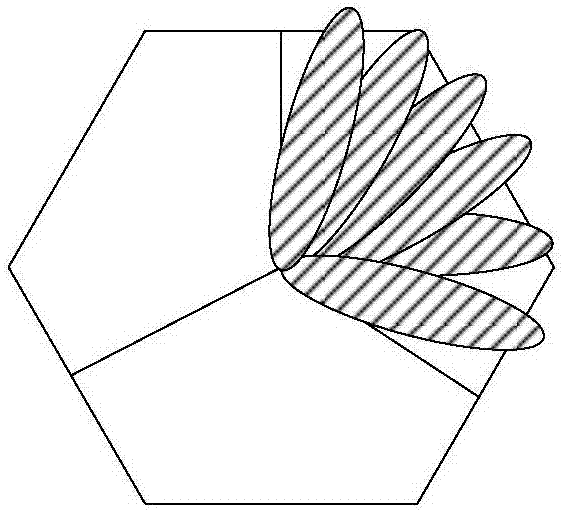
Radio resource selection method and device
ActiveCN107889130AReduce communication delaySolve the real problemAssess restrictionSignal allocationCommunication qualityBiological activation
The invention relates to a radio resource selection method and device. The method comprises the following steps that a terminal obtains a measurement result of a beam, and the terminal sends first indication information for indicating deactivation or deletion of the beam to network equipment, wherein the beam meets a first quality condition, so that the network equipment can deactivate or delete the beam according to the indication of the first indication information, and thus the influence on normal communication between the terminal and the network equipment due to the fact that the communication quality of the beam does not meet the requirement is avoided. In addition, the terminal obtains the measurement result of the beam and sends second indication information for indicating activation or increase of the beam to the network equipment in order to indicate the network equipment to activate or increase the beam with better communication quality for communication with the terminal, so that the communication quality between the terminal and the network equipment can be improved.
Owner:HUAWEI TECH CO LTD
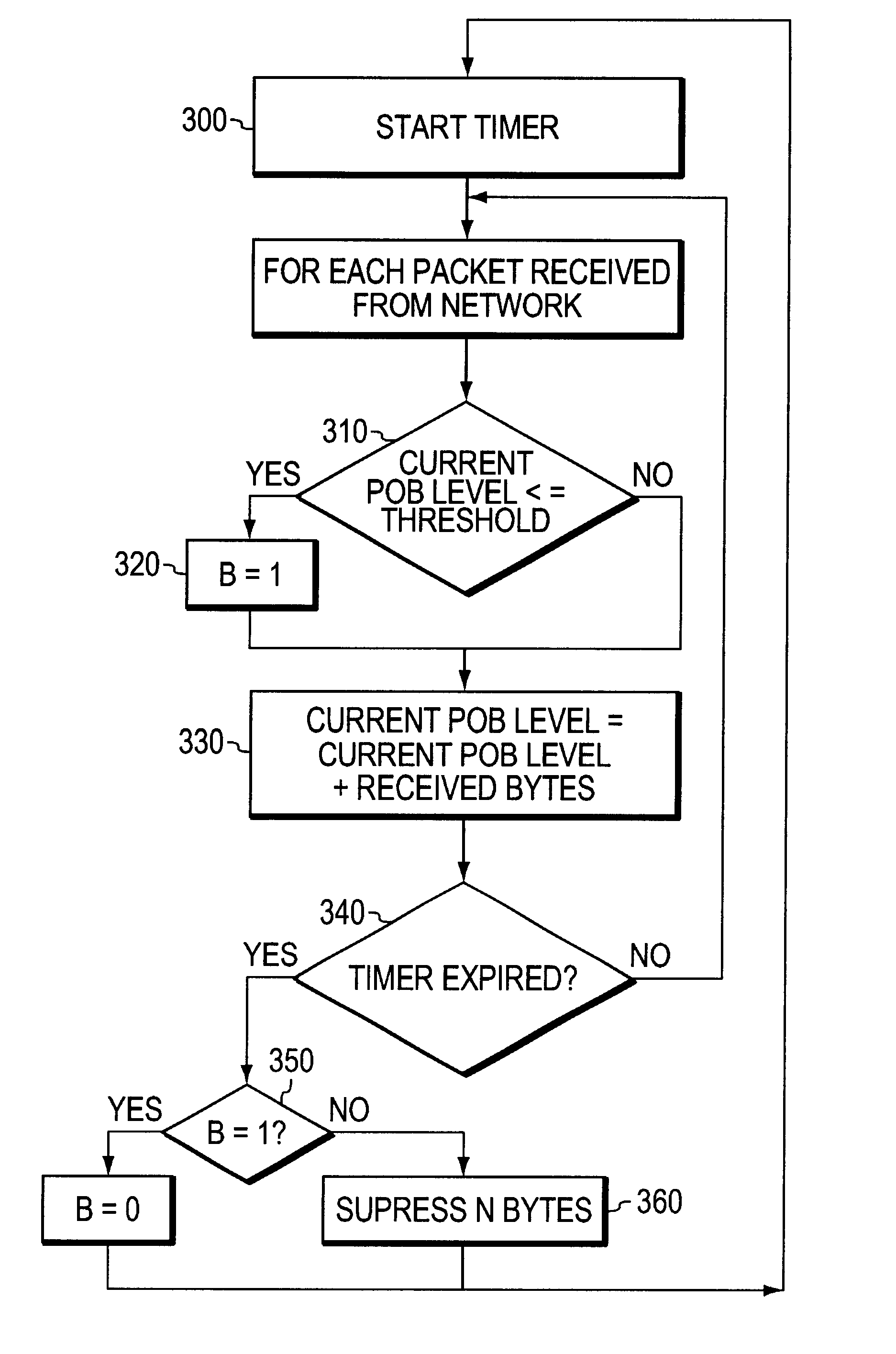
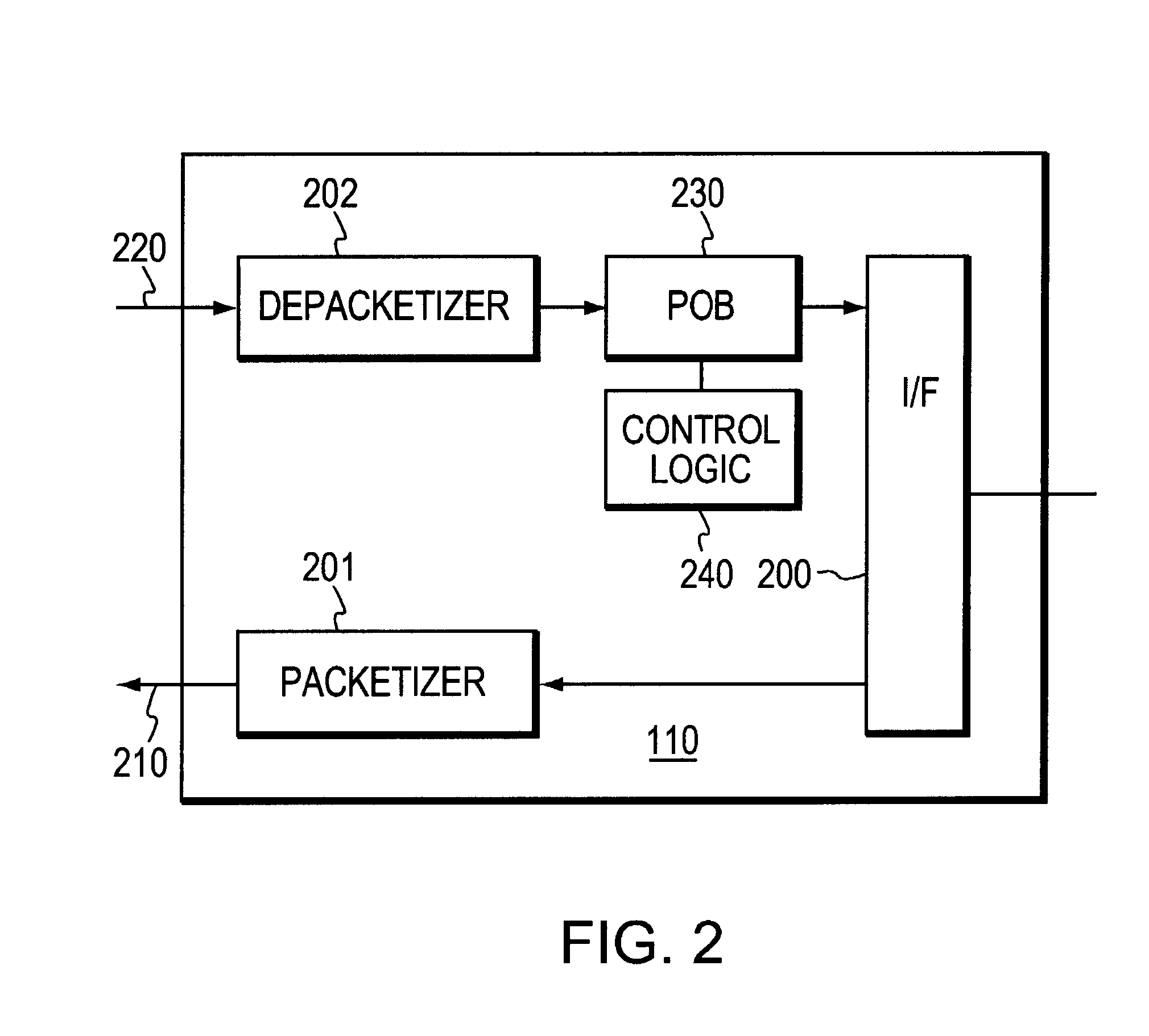
Adaptive playout buffer and method for improved data communication
InactiveUS6912224B1Level of filling is reducedReduce the impactData switching by path configurationTime segmentEdge node
An adaptive apparatus and method for managing a playout buffer (POB) in an edge node of a packet-based data communications network, such as an ATM network, in order to reduce the end-to-end communication delay introduced thereby and to allow the POB filling level to be corrected in the event of clock speed differences. A monitoring mechanism determines if the minimum filling level of the playout buffer over a time period whereby the average filling level of the playout buffer is reduced according to the minimum filling level of the playout buffer over the time period.
Owner:CISCO TECH INC
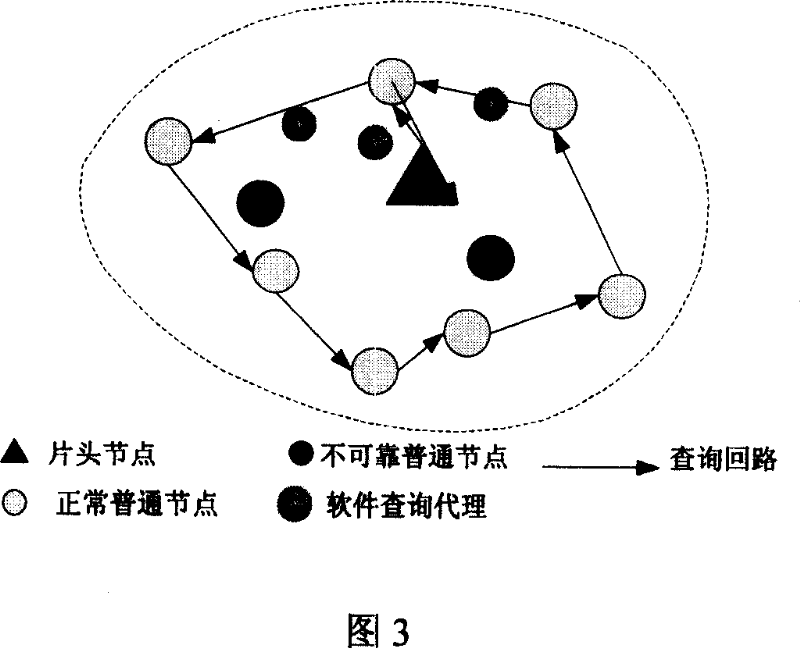
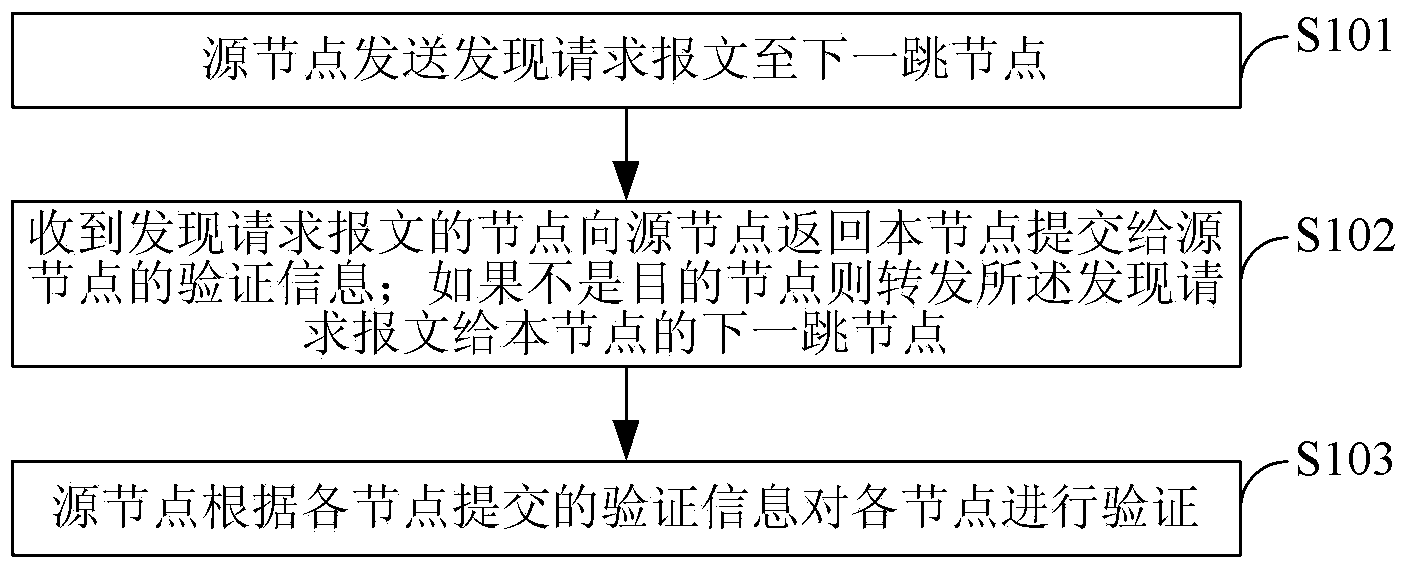
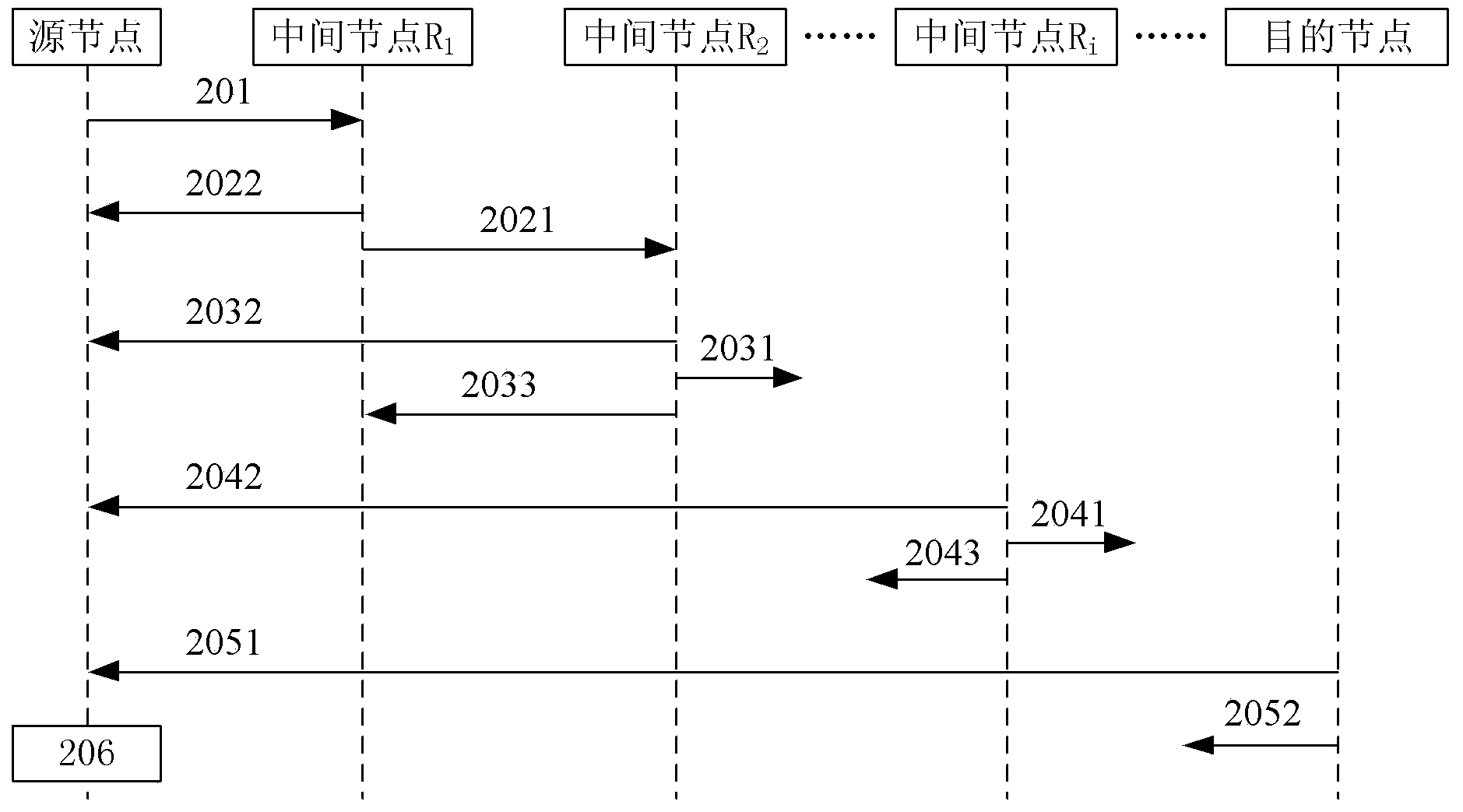
Node discovering method and system in communication network
ActiveCN103701700AAchieve mutual authenticationSafe and reliable communication transmissionUser identity/authority verificationData switching networksComputer networkComputer science
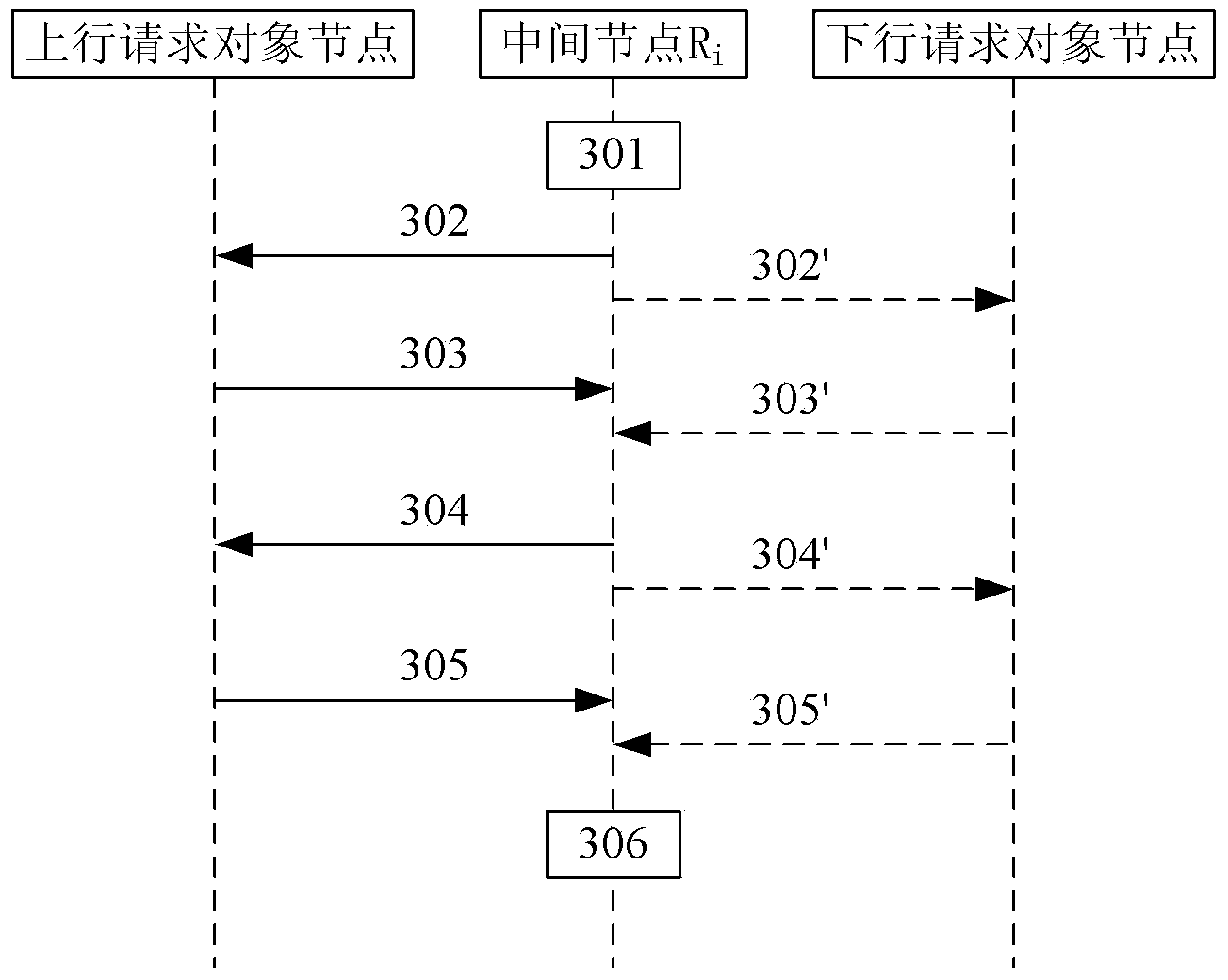
The invention provides a node discovering method and a node discovering system in a communication network. The method comprises the following steps that a source node sends discovery request messages to a next hop of node, and the discovery request messages carry the address information of the source node, the identity information of the source node, the address information of a target node and the challenge value generated by the source node; a node receiving the discovery request messages returns verification information, submitted to the source node by the node, to the source node; whether the node is a target node or not is judged according to the address information, and if the node is not the target node, the discovery request messages are transferred to the next hop of node of the node; after the source node receives the verification information returned by the target node, each node is verified according to the verification information submitted by each node; if the verification is completely passed, each node is determined to be trusted nodes. The method and the system provided by the invention have the advantages that the safety and the reliability of the communication transmission between network equipment can be ensured, and the communication delay is reduced.
Owner:INST OF INFORMATION ENG CAS +1
Transmission message generating device and vehicle on-board transmission system
InactiveCN103959718AReduce trafficReduce communication delaySubstation remote connection/disconnectionNetworks interconnectionCommunications systemOn board
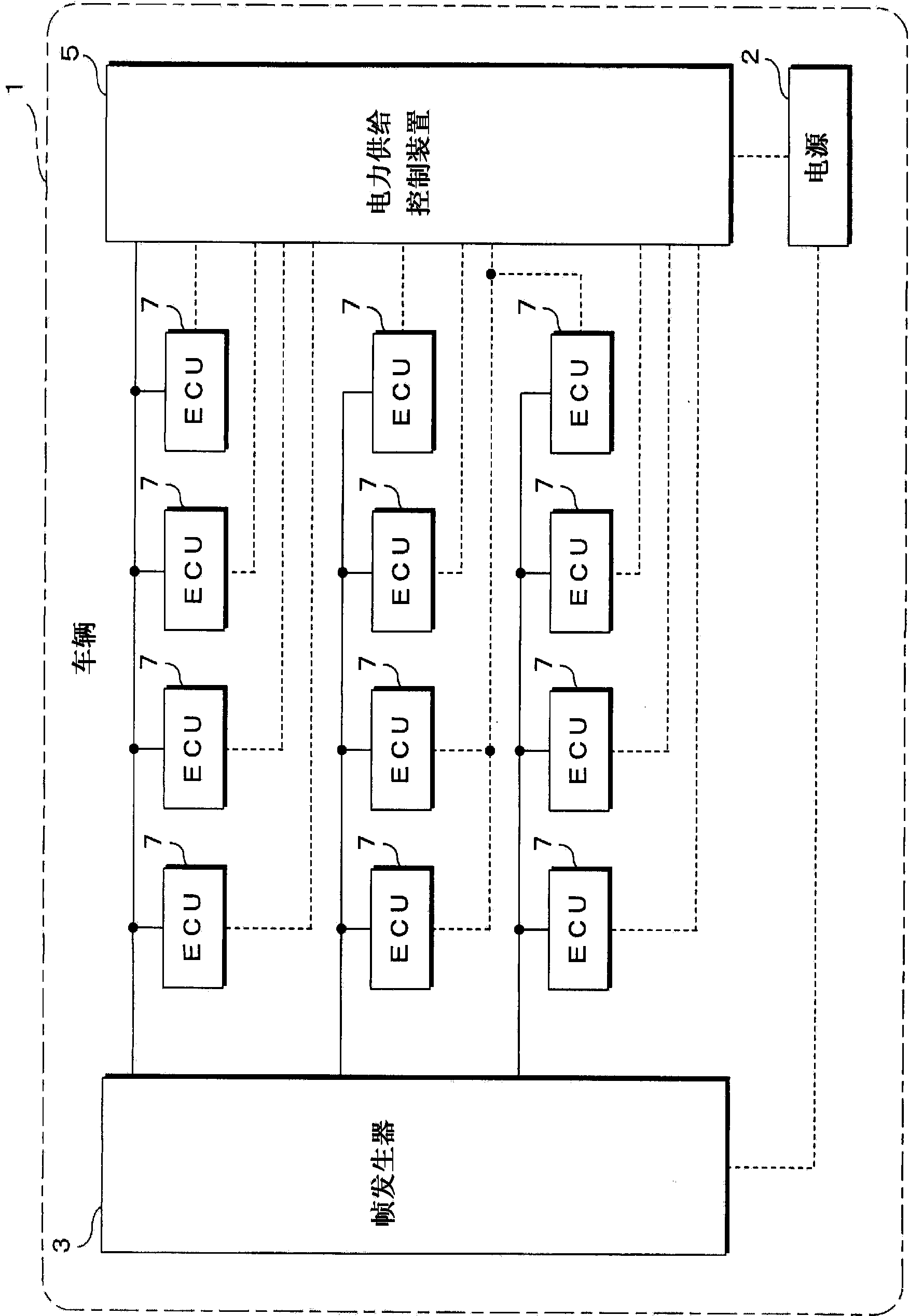
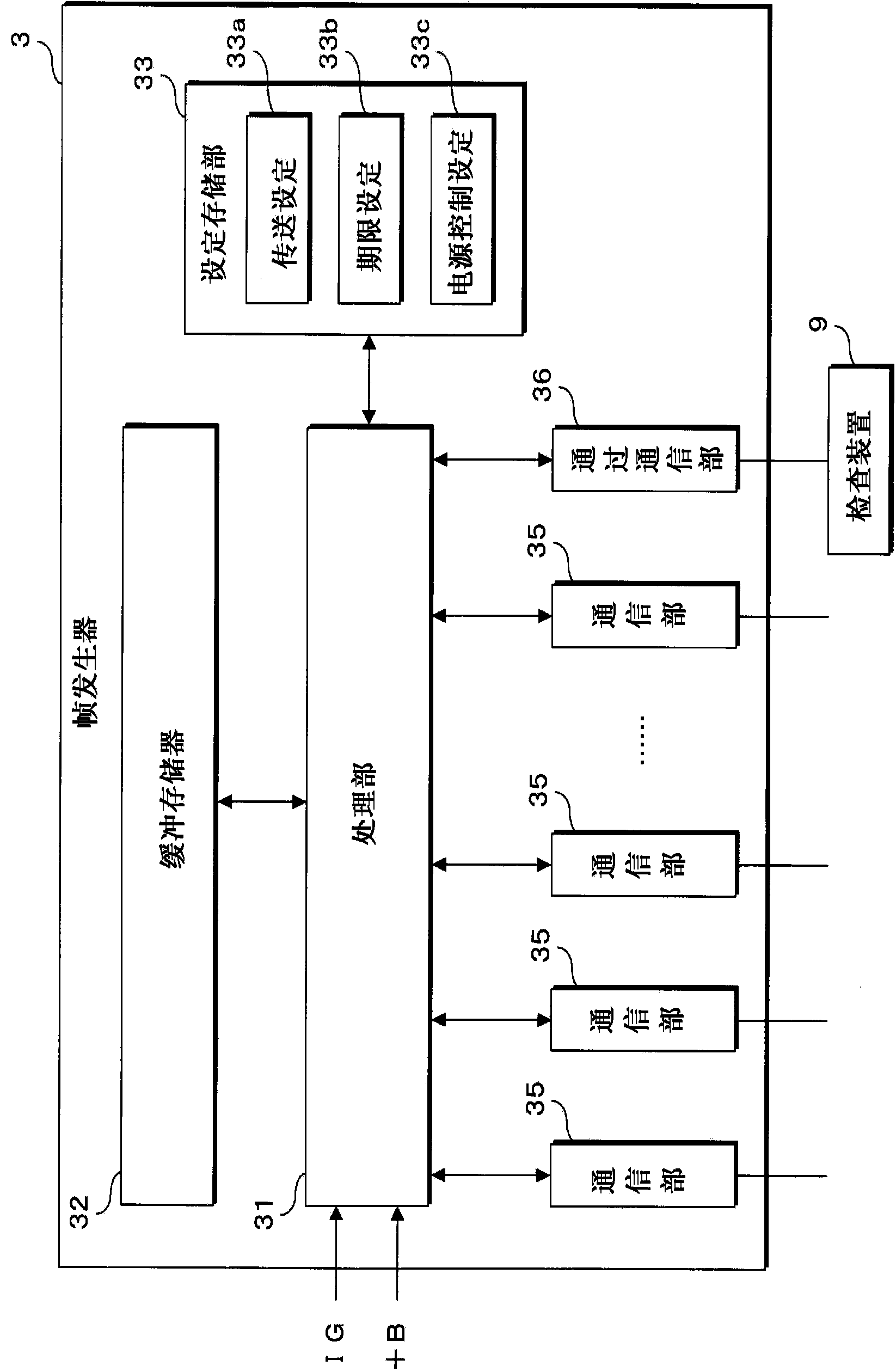
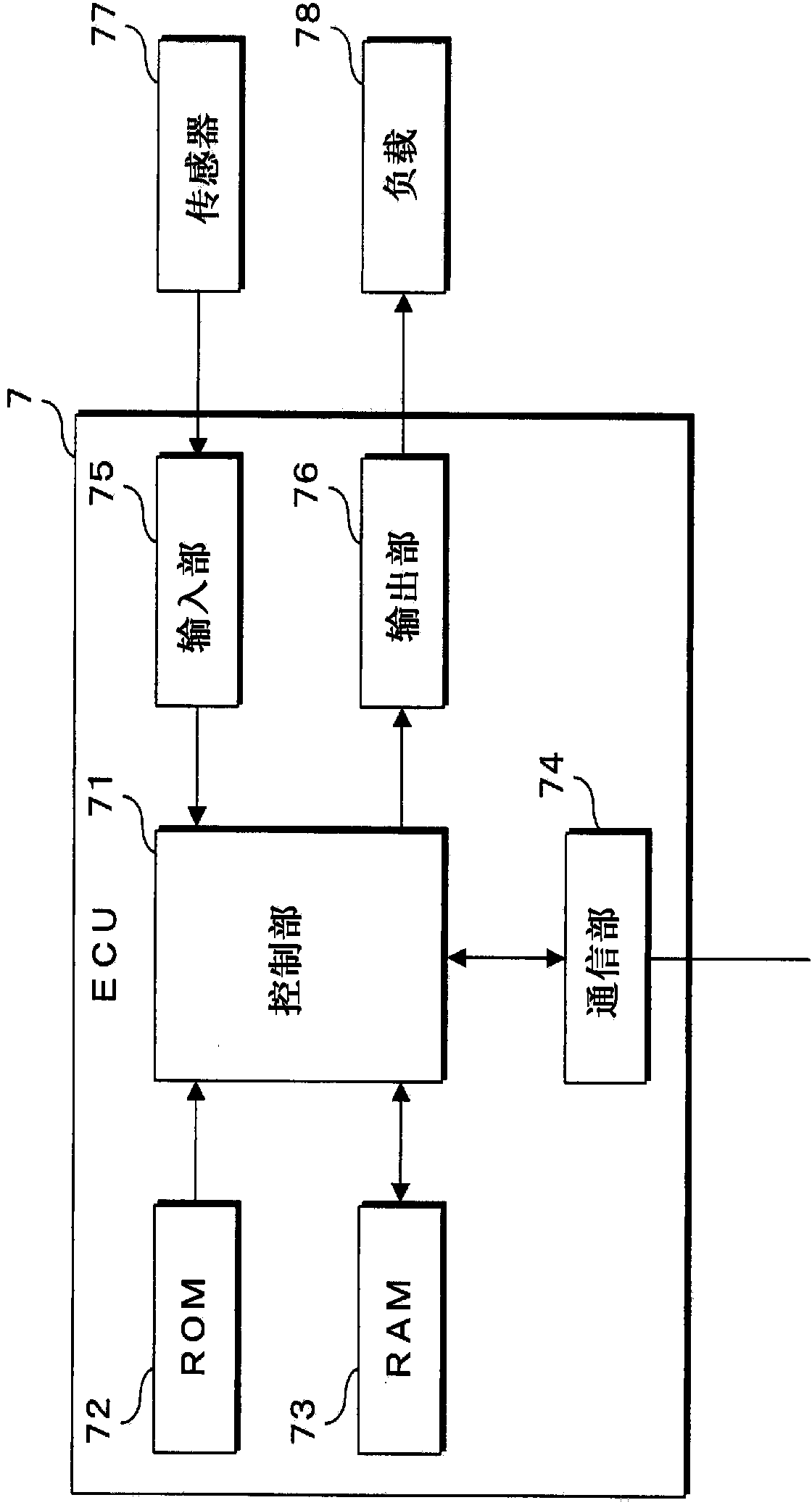
Provided are a transmission message generating device and a vehicle on-board transmission system that can reduce unnecessary sending and receiving of messages between communication devices, as well as preventing information leakage to the outside, or improper intrusion from the outside. Each ECU (7) transmits a frame to a frame generator (3), whereupon the frame generator (3) disassembles the data contained in the received frames, and stores messages of each type in a buffer memorys. The frame generator (3) generates and transmits a message containing data to be transmitted to each ECU (7). According to the state of a signal indicating a power supply state, the frame generator (3) controls enabling / disabling of the transmission process in such a way that frames are not transmitted to ECU (7) not being supplied with power by a power supply control unit (5). In a case in which an abnormal frame has been received by any communication portion, the frame generator (3) does not include the data contained in frames subsequently received by this communication portion, in frames generated for sending to other communication portions.
Owner:AUTONETWORKS TECH LTD +2
Method for enabling local security context
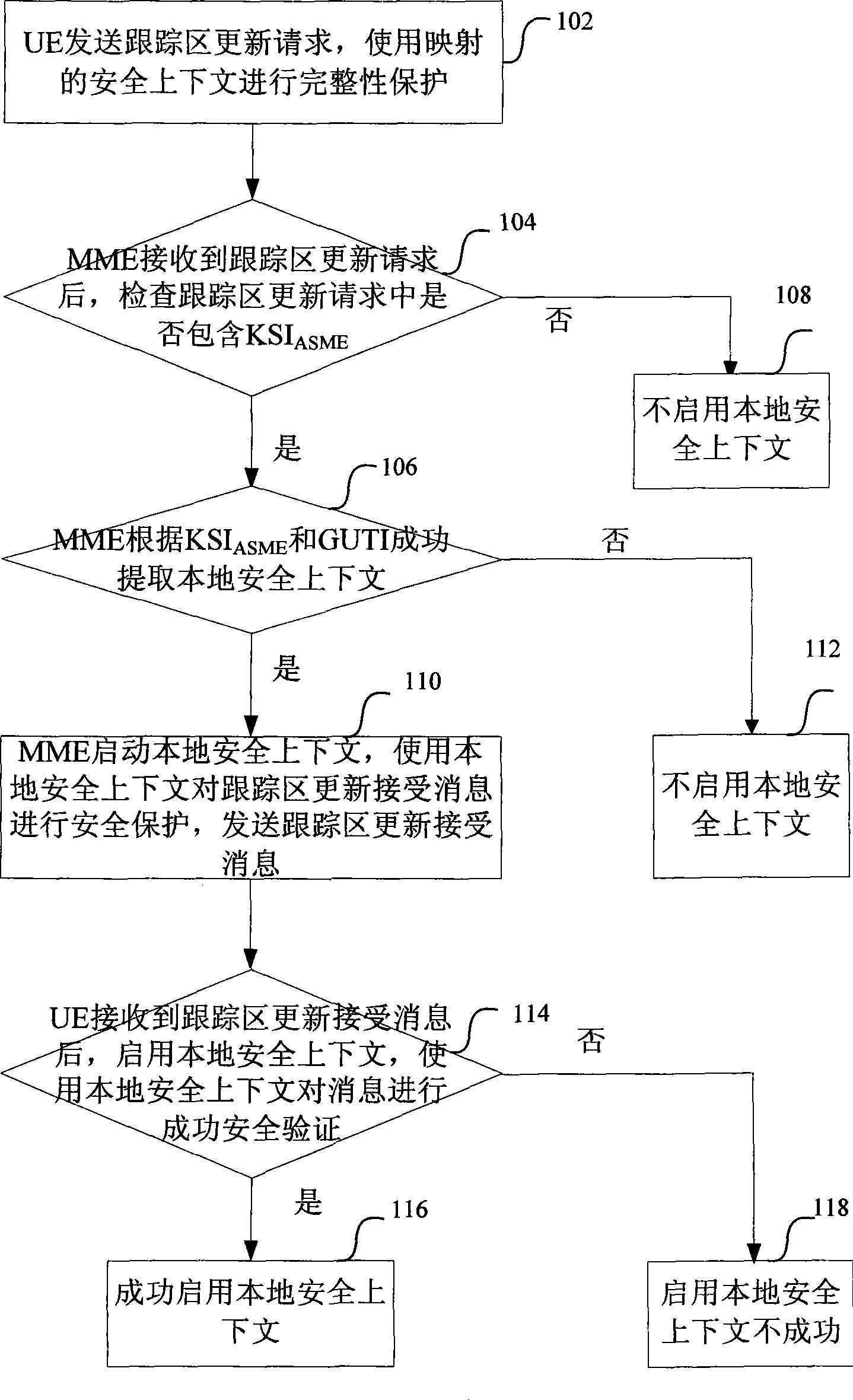
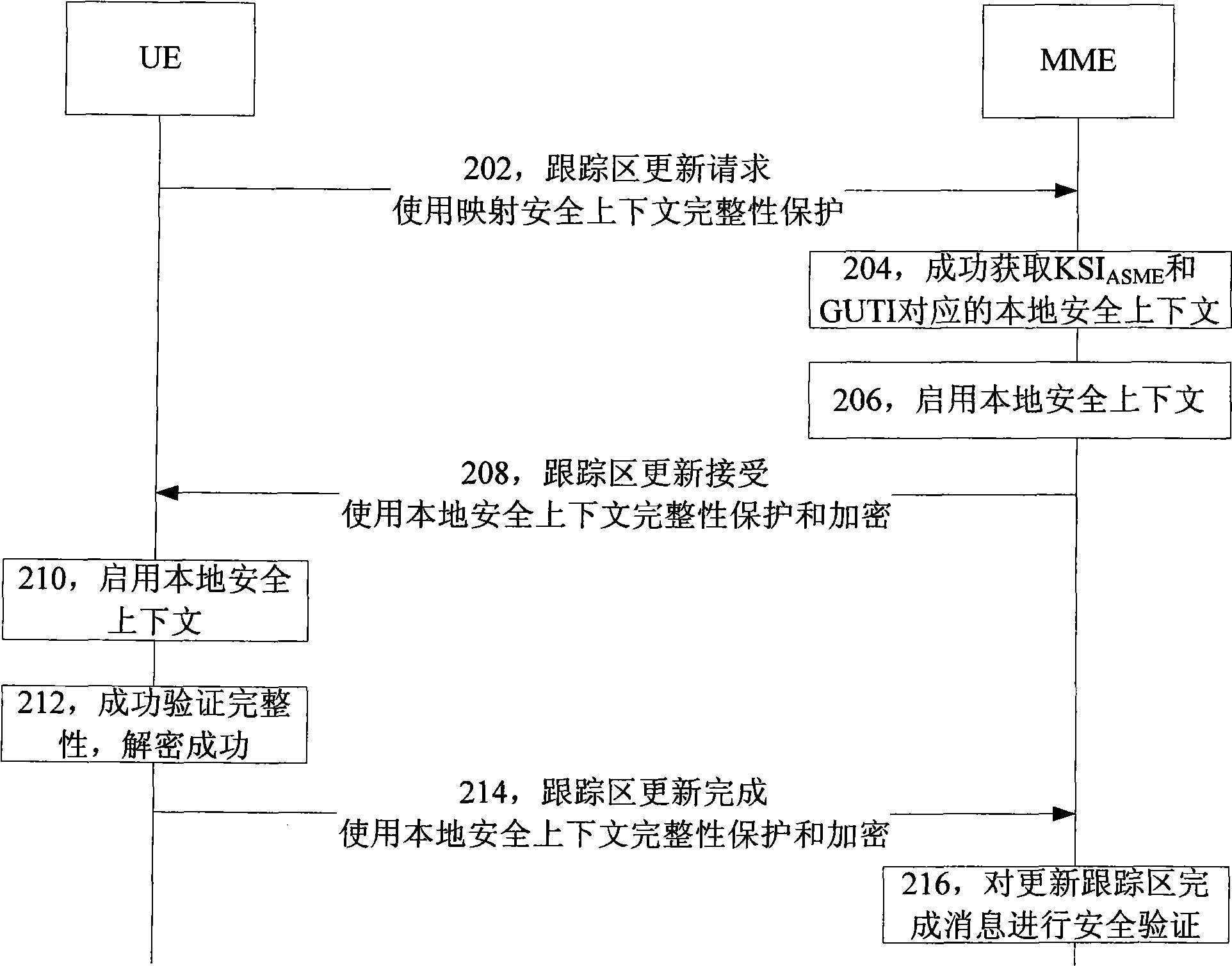
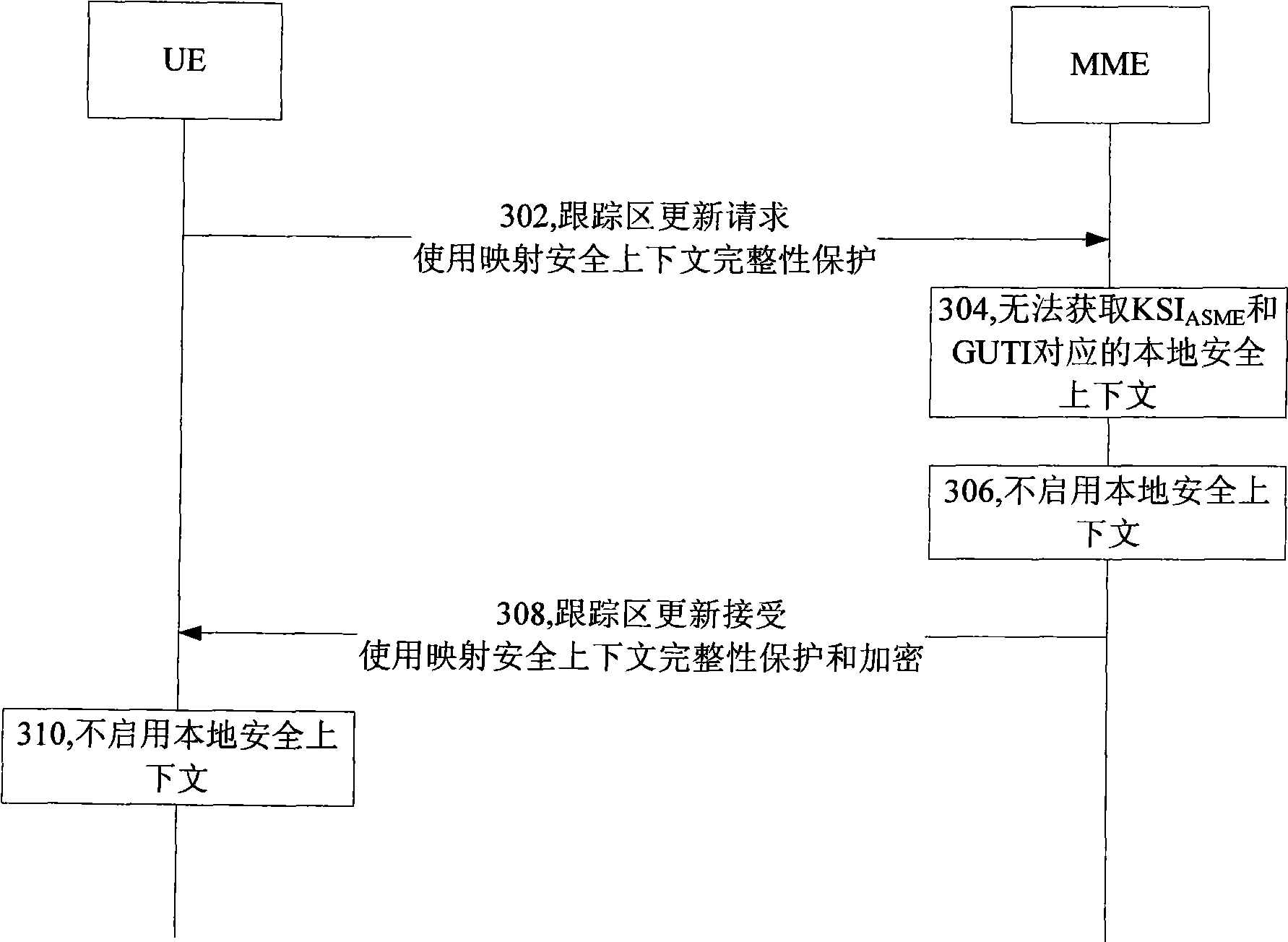
ActiveCN101521873AReduce loadReduce communication delaySecurity arrangementNetwork data managementKey switchSecurity context
The invention provides a method for enabling a local security context, which comprises the following steps that user equipment (UE) sends a tracking area updating request information to a mobility management entity (MME), and when the MME knows that the MME and the UE share the local security context which corresponds to the key switch-in access security management entity (KSIASME) and the global unique temporary identification (GUTI), the MME enables the local security context which corresponds to the KSIASME and the GUTI. The invention improves the tracking area updating process, has the function of enabling the local security context so as to be in a non-access stratum from switch flow among systems and remove the security mode command procedure of the non-access stratum, thereby achieving the effects of alleviating signaling traffic of systems, reducing communication delay and optimizing the communication process.
Owner:ZTE CORP
Parallel Processing
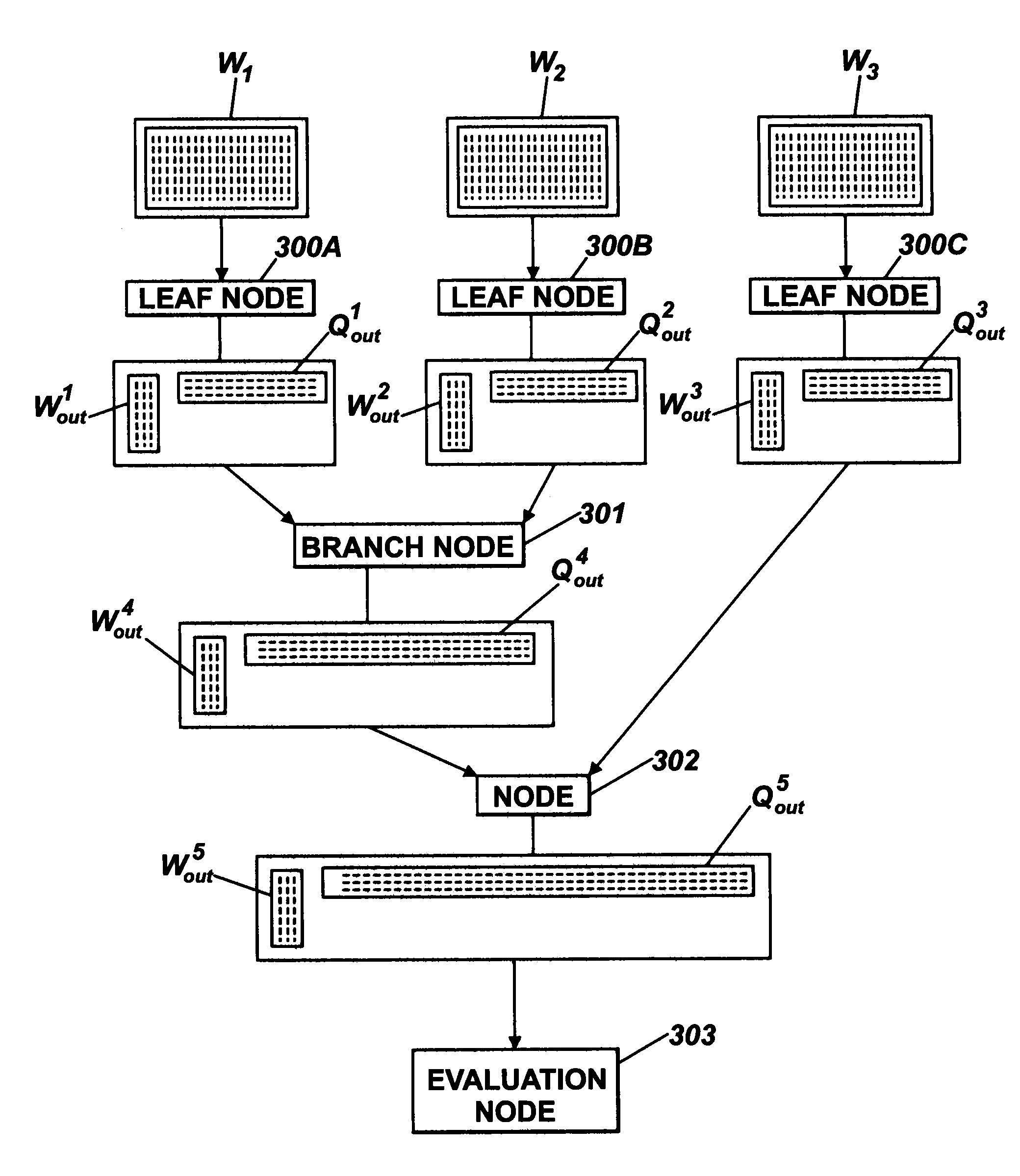
InactiveUS20090216996A1Reduce communication delayAvoid complex processProgram control using wired connectionsGeneral purpose stored program computerParallel processingData mining
A system and methods comprising a plurality of leaf nodes in communication with one or more branch nodes, each node comprising a processor. Each leaf node is arranged to obtain data indicative of a restriction A|IS of a linear map from Rn to Rm represented by a first matrix, A, to a subspace IS of Rn and to carry out a calculation of data indicative of at least a leading part of the SVD of a matrix representation of the restriction A|IS. One or more of the plurality of leaf nodes or branch nodes is arranged to use results of the calculations to compute data indicative of a subspace OS of each node input subspace IS and to pass that data and a corresponding restriction A|OS of A to one of a plurality of the one or more branch nodes. Each of the one or more branch nodes is arranged to receive data indicative of node output spaces OS1, . . . , OSk and the corresponding restrictions A|OS1, . . . , A|OSk for k≧2, to use this data to form a further node input space IS=OS1+ . . . +OSk, and to carry out a further calculation indicative of the leading part of the SVD of a matrix representation of a further restriction A|IS, of the linear map A to the further node input space IS. One or more of the one or more branch nodes is arranged to these results of the further calculations to compute data indicative of a further node output space OS of the further node input space IS and, if further processing of the data indicative of a further node output space OS is required, to pass the data indicative of the further node output space OS and a corresponding restriction A|OS of A to one or a plurality of the one or more branch nodes.
Owner:ISIS INNOVATION LTD
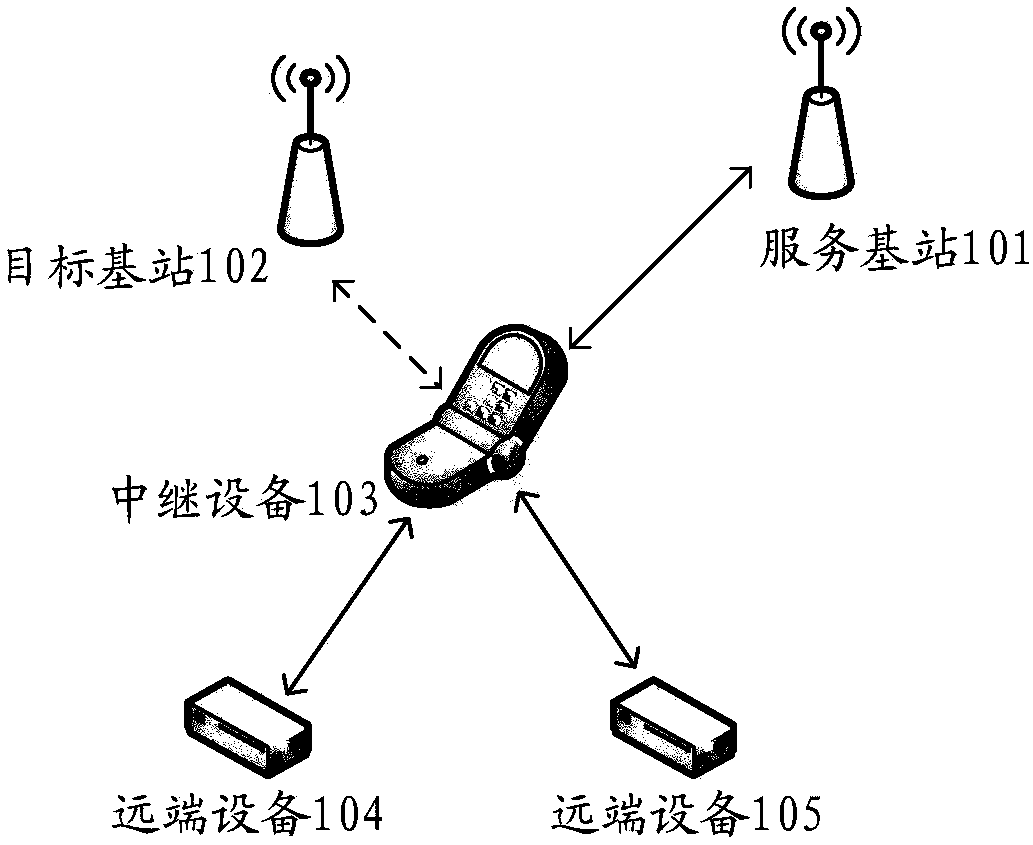
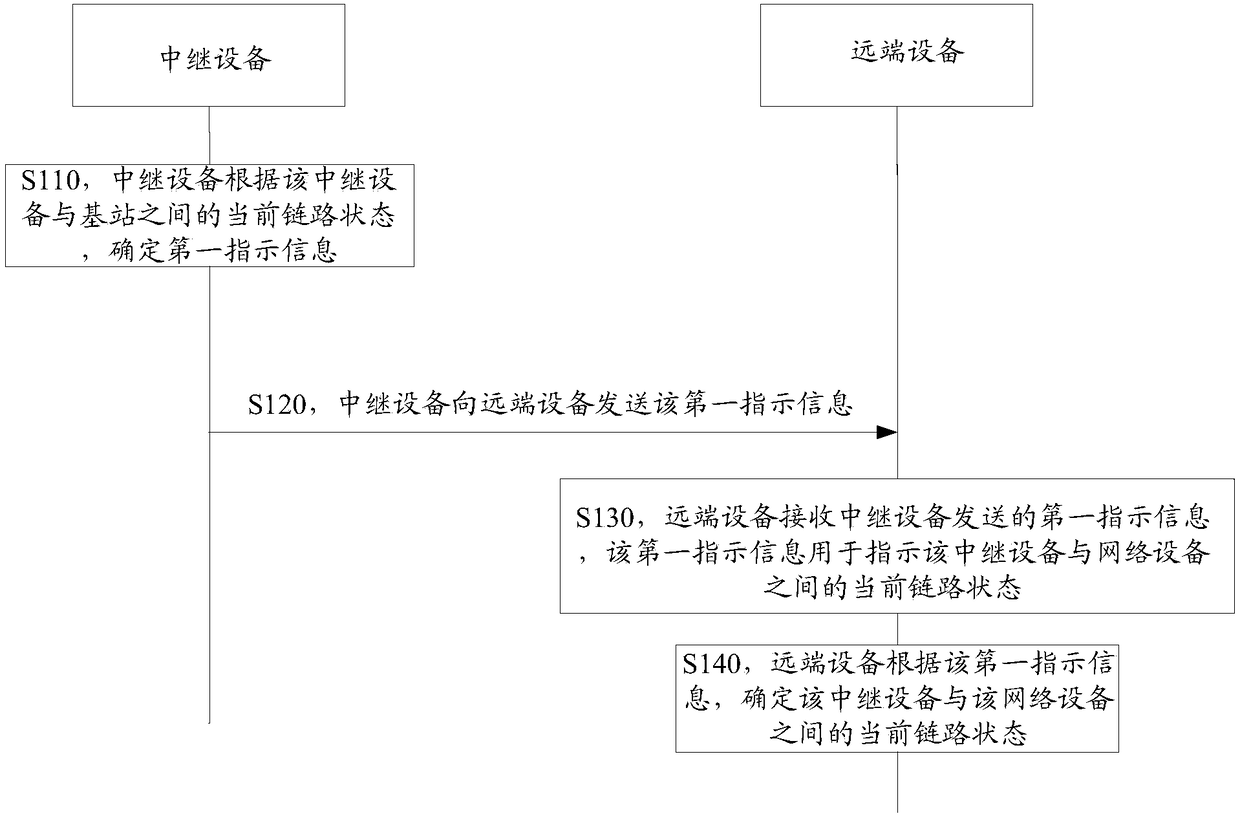
Information indication methods and devices
ActiveCN108924962AReduce communication delayImprove communication efficiencyConnection managementTerminal equipmentRadio link failures
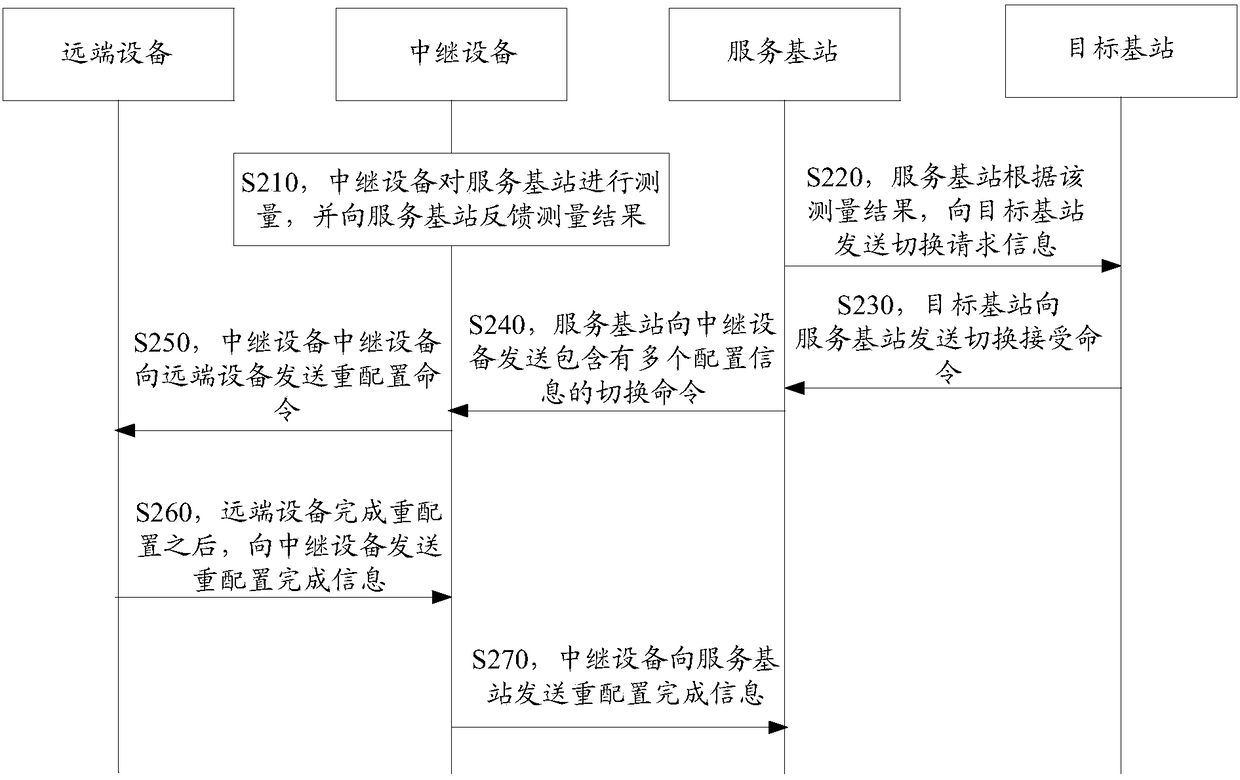
The embodiment of the invention provides information indication methods and devices. A method comprises the following steps: first terminal equipment determines first indication information accordingto a current link state between the first terminal equipment and network equipment, wherein the current link state is link reconfiguration failure, link switching failure, current switching, radio link failure or radio resource control connection reestablishment failure; and the first terminal equipment sends the first indication information to second terminal equipment, wherein the first indication information is used for notifying the current link state between the first terminal equipment and the network equipment to the second terminal equipment, and the first terminal equipment is the equipment capable of assisting the second terminal equipment to communicate with the network equipment. The second terminal equipment determines a coping policy according to the current link state between the first terminal equipment and the network equipment, so communication delay of the second terminal equipment is reduced, and communication efficiency is improved.
Owner:HUAWEI TECH CO LTD
Method, device and system for key agreement
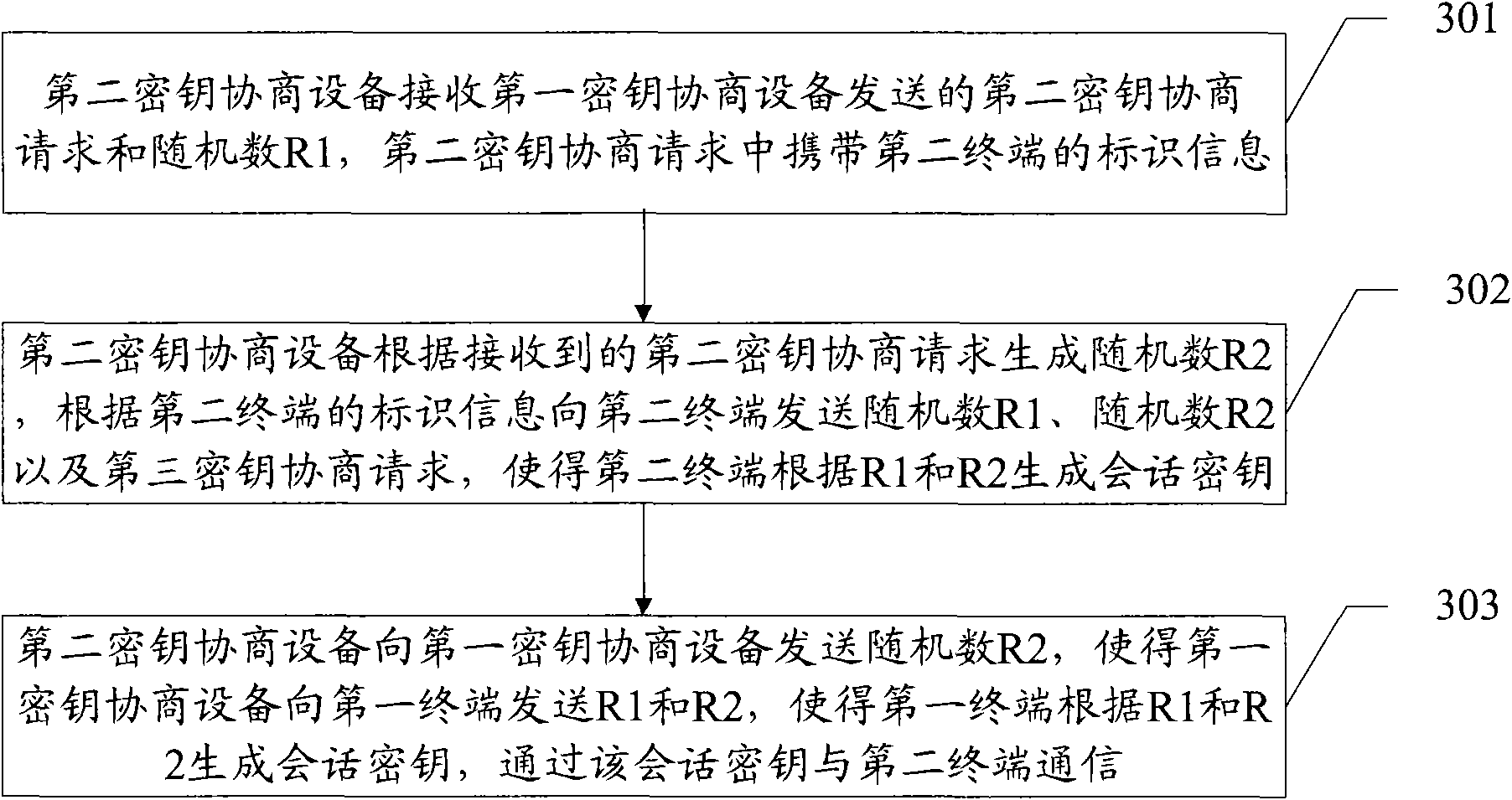
InactiveCN101895877ASimplify the encryption processReduce communication delayConnection managementTransmissionComputer hardwareSession key
The invention discloses a method, a device and a system for key agreement. The method comprises the following steps: a first key agreement device receives a first key agreement request sent by a first terminal, wherein the identification information of a second terminal is contained in the first key agreement request; the first key agreement device generates a random number R1 according to the received first key agreement request and sends a second key agreement request and the random number R1 to a second key agreement device corresponding to the second terminal according to the identification information of the second terminal; the second key agreement device generates a random number R2 and sends the random numbers R1 and R2 and a third key agreement request to the second terminal; the second terminal generates a session key according to the random numbers R1 and R2; the first key agreement device receives the random number R2 sent by the second key agreement device and sends the random numbers R1 and R2 to the first terminal; and the first terminal generates a session key according to the random numbers R1 and R2 and communicates with the second terminal on the basis of the session key. Accordingly, the invention can achieve the encrypted communication between the first terminal and the second terminal.
Owner:HUAWEI TECH CO LTD
Vehicle and pedestrian collision avoidance method based on edge computing
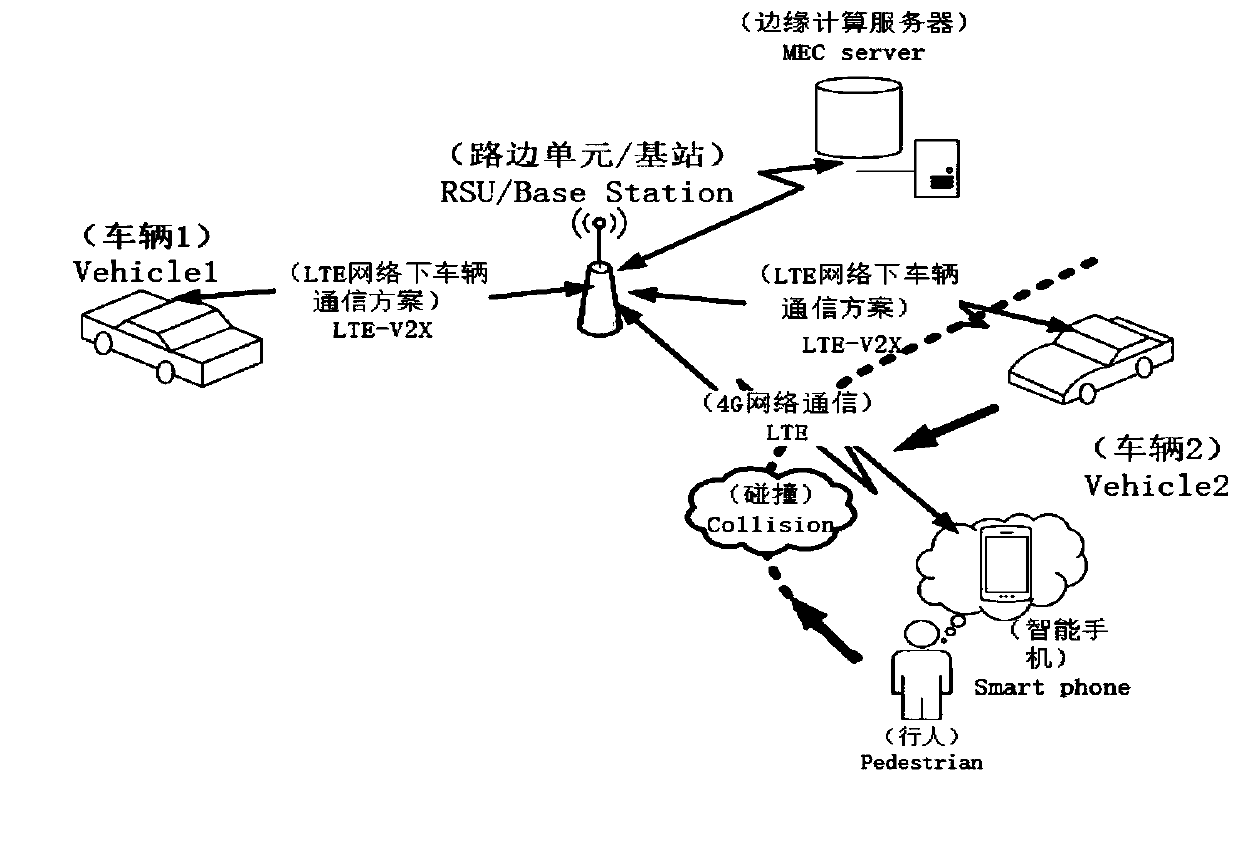
InactiveCN111489585AImprove accuracyReduce communication delayParticular environment based servicesAnti-collision systemsEdge serverEdge computing
The invention discloses a vehicle and pedestrian collision avoidance method based on edge computing, and belongs to the field of Internet of Things. In an edge computing environment, communication between a vehicle and pedestrian equipment is realized through an edge server, communication delay is reduced, kalman filtering is adopted to predict the position of the vehicle, and the track of a pedestrian is predicted by using a sensor on the pedestrian equipment, so that restriction of line of sight is overcome, the collision detection precision is improved, and the method is suitable for most non-line-of-sight (NLOS) scenes. In addition, a collision risk model based on the time to collision (TTC) is established according to the relative motion relationship between the vehicle and the pedestrian. The simulation result shows that the collision avoidance algorithm provided by the invention can effectively reduce the collision risk of the vehicle and the pedestrian.
Owner:KUNMING UNIV OF SCI & TECH
Method, device and system for accessing memory
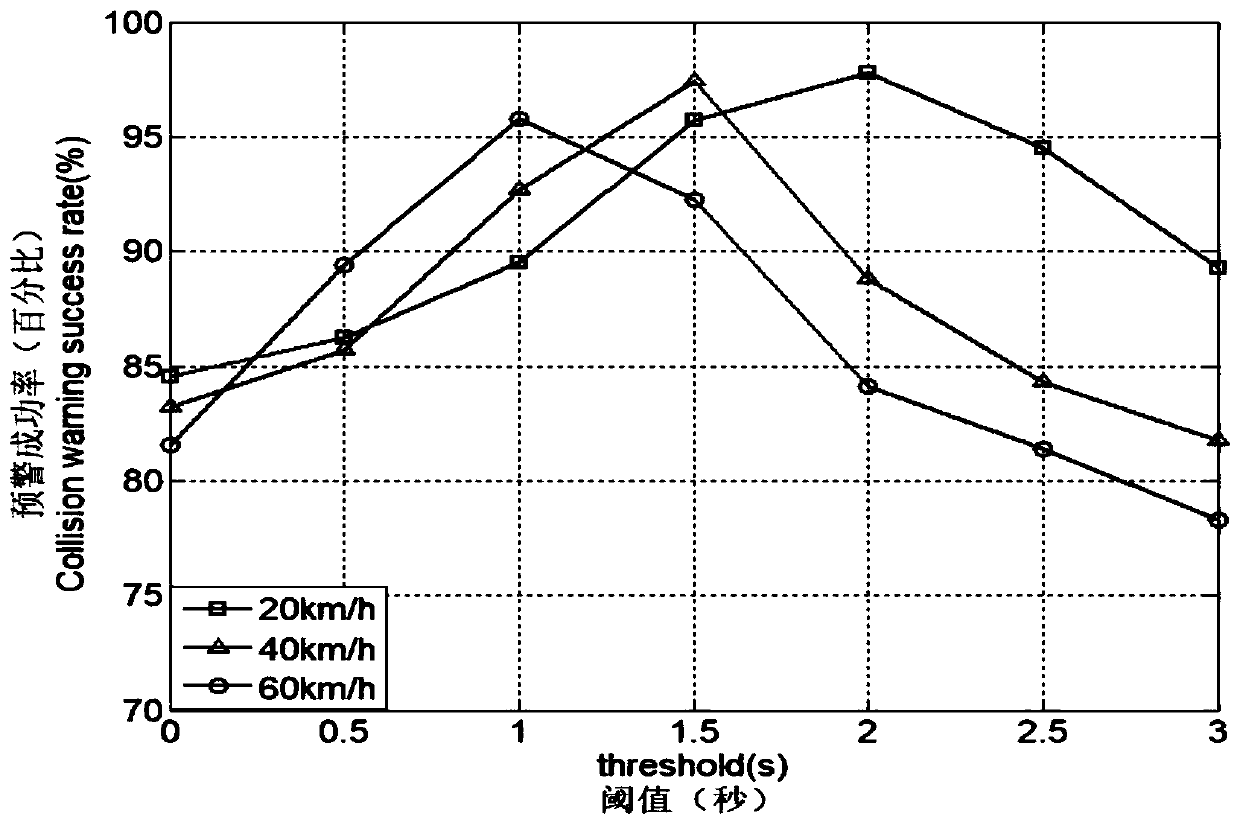
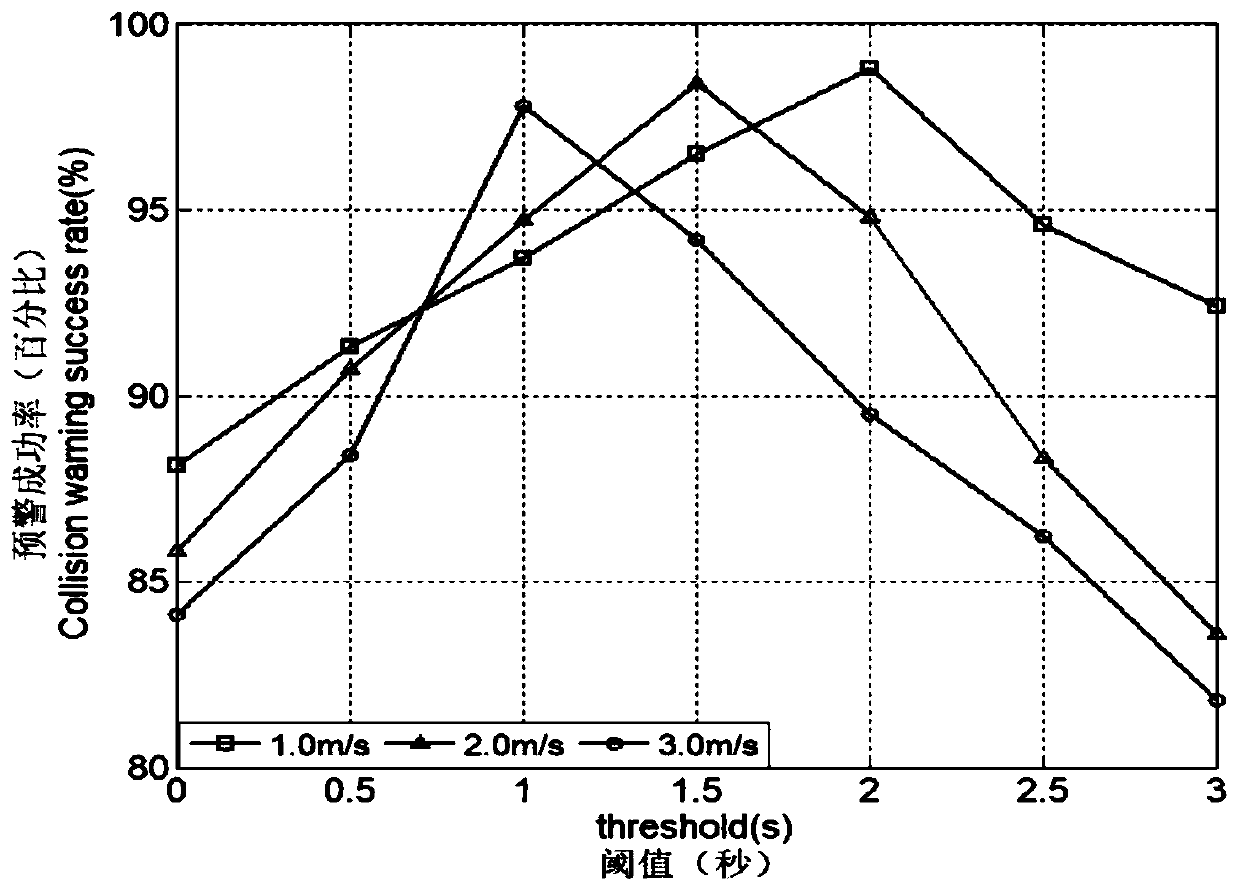
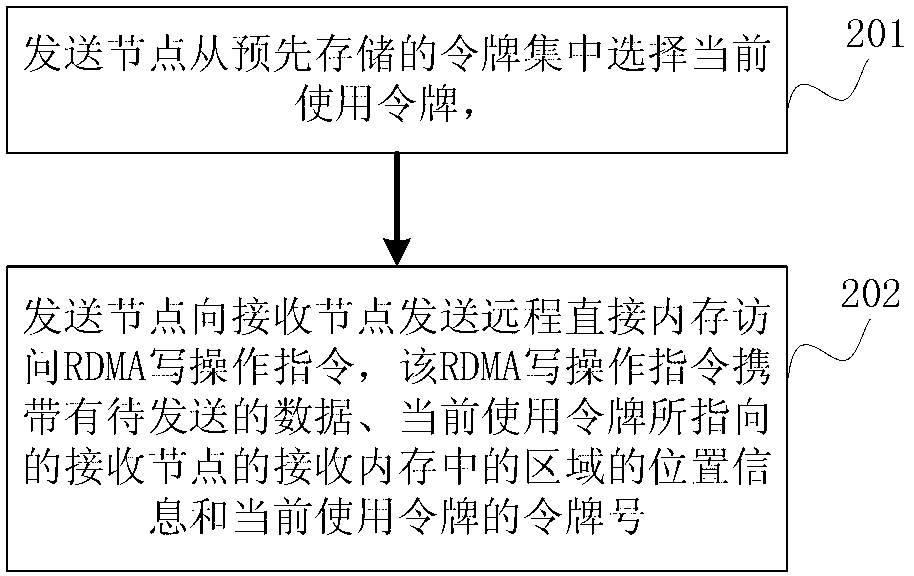
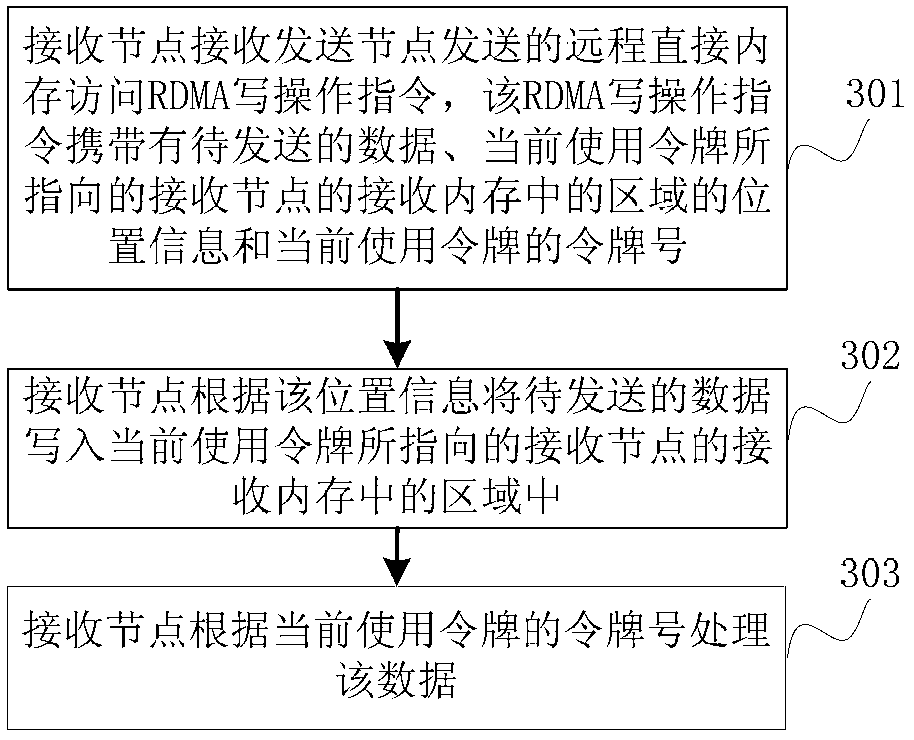
ActiveCN103227778AReduce inefficienciesImprove efficiencyTransmissionElectric digital data processingDirect memory accessOperating instruction
The invention discloses a method, device and system for accessing memory, and belongs to the field of network technology. The method comprises the following steps: a sending node selects a current using token from prestored tokens in a centralized manner; an RDMA (Remote Direct Memory Access) written operating instruction is sent to a receiving node, wherein the RDMA written operating instruction carries to-be-sent data, information of the position which the current using token points to and a token number of the current using token to enable the receiving node to receive the RDMA written operating instruction conveniently; and the data is processed according to the token number of the current using token. According to the invention, the RDMA written operating instruction carries the token number of the current using token, and the sending node just needs to send the RDMA written operating instruction once to perform direct memory access to the receiving node, so that communication delay in the process of RDMA is reduced, and the communication efficiency is improved.
Owner:HUAWEI TECH CO LTD
Certificateless aggregation signature LTE-R network group authentication key negotiation method
InactiveCN110149214AReduce overheadReduce communication delayKey distribution for secure communicationEncryption apparatus with shift registers/memoriesDigest access authenticationUser equipment
A certificateless aggregation signature LTE-R network group authentication key negotiation method comprises the following main operation steps: A, system establishment and participant registration: anentity participating in authentication completing registration at a key generation center, and obtaining public and private key information; B, initial access authentication: the user equipment beinguniformly accessed to LTE-before departure of a train; when R network is carried out, executing the certificateless signature algorithm to generate respective signatures, sending the signatures to the relay server, and the relay server executing the certificateless aggregation signature algorithm to realize rapid mutual authentication among the user equipment, the relay server and the roadside base station and negotiating to share the key; C, switching authentication: in the running process of the train, the user equipment being always stably connected with the relay server, and the relay server and the roadside base station realizing quick and frequent switching authentication by executing a certificateless signature algorithm; D, terminating the session. The method is high in authentication efficiency, low in signaling overhead and good in security.
Owner:CHINA ACADEMY OF RAILWAY SCI CORP LTD +1
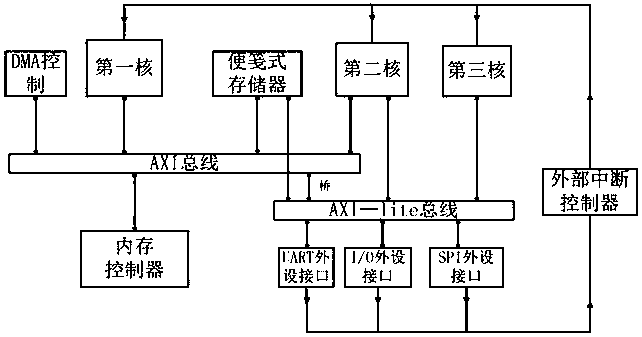
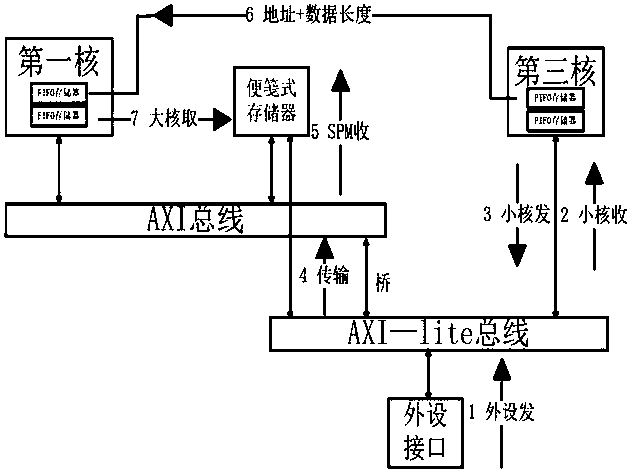
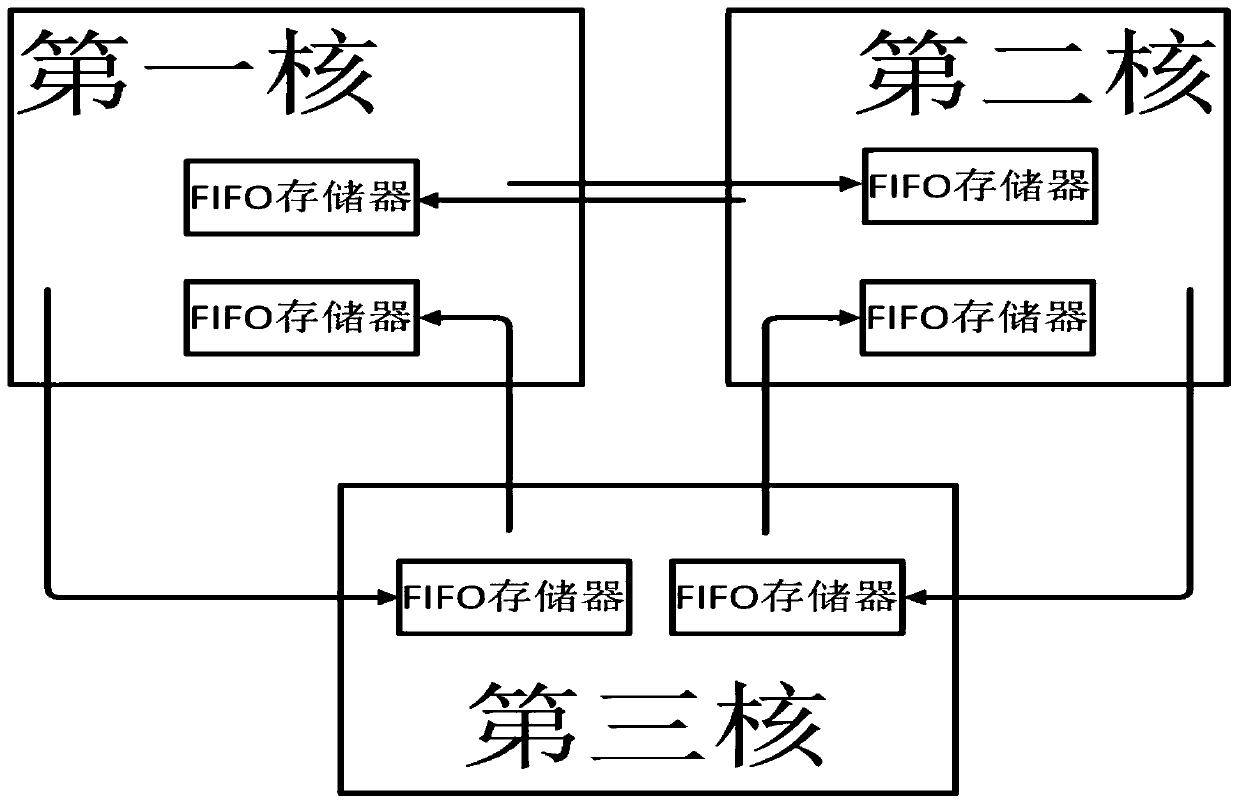
Heterogeneous multi-core microprocessor based on multi-layer bus
ActiveCN110347635AImprove processing efficiencyImprove computing powerDigital computer detailsElectric digital data processingProcessing coreNetwork packet
The invention discloses a heterogeneous multi-core microprocessor based on a multilayer bus. The heterogeneous multi-core microprocessor comprises a plurality of processing cores for uniform addressing, wherein the plurality of processing cores have different pipeline structures; the plurality of processing cores are connected through an AXI bus with bridge connection; the AXI bus with bridge connection is connected with a notepaper type memory; data packets are sent and read between every two processing cores through a scratch pad memory; a data packet head address and a data packet length are directly sent between every two processing cores so as to assist in completing the transmission of a data packet between the two processing cores; and the AXI bus with bridging is also connected with a peripheral interface, and the processing cores perform access control on external equipment through the peripheral interface. According to the heterogeneous multi-core microprocessor based on themulti-layer bus, disclosed by the invention, the communication delay can be reduced.
Owner:XIAN UNIV OF TECH
System and method for mobility in multihop networks
InactiveUS20090290494A1Improve communication throughputReduce communication delayError preventionFrequency-division multiplex detailsNetwork controlWireless connectivity
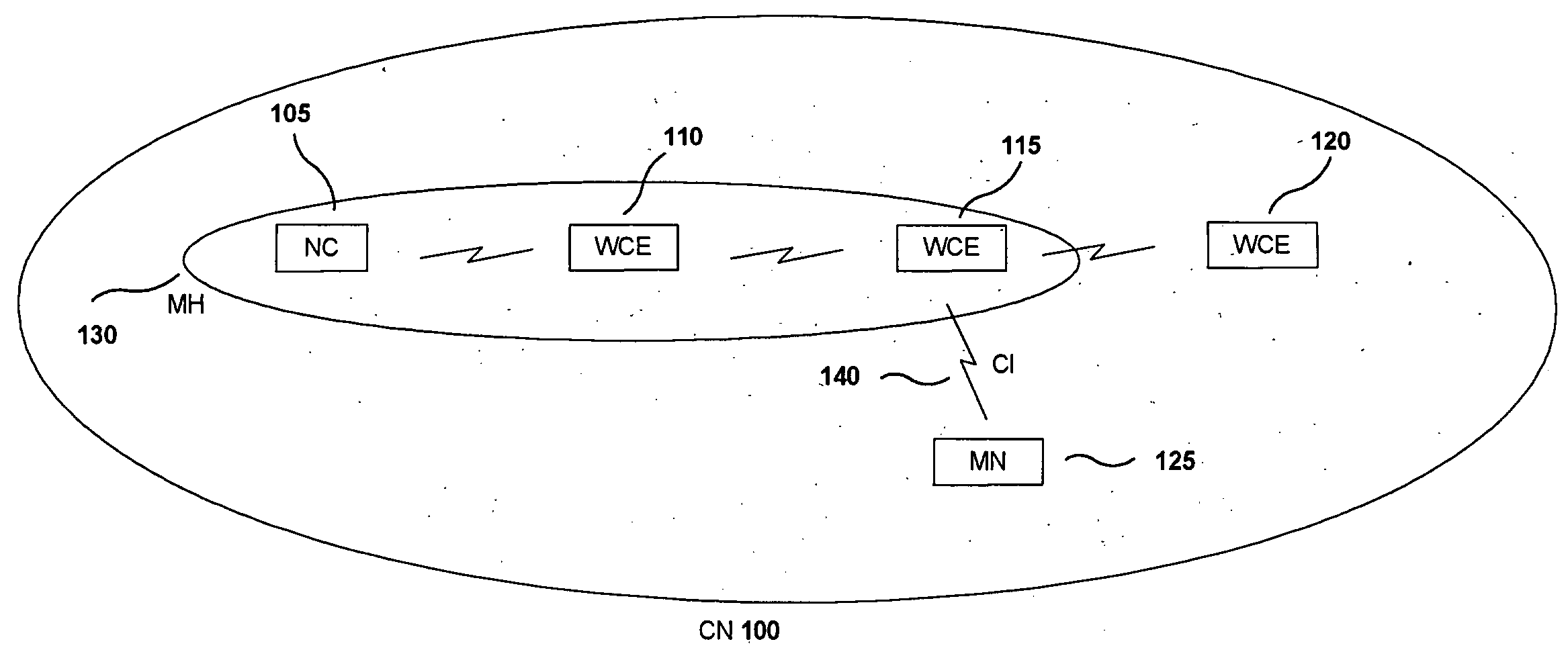
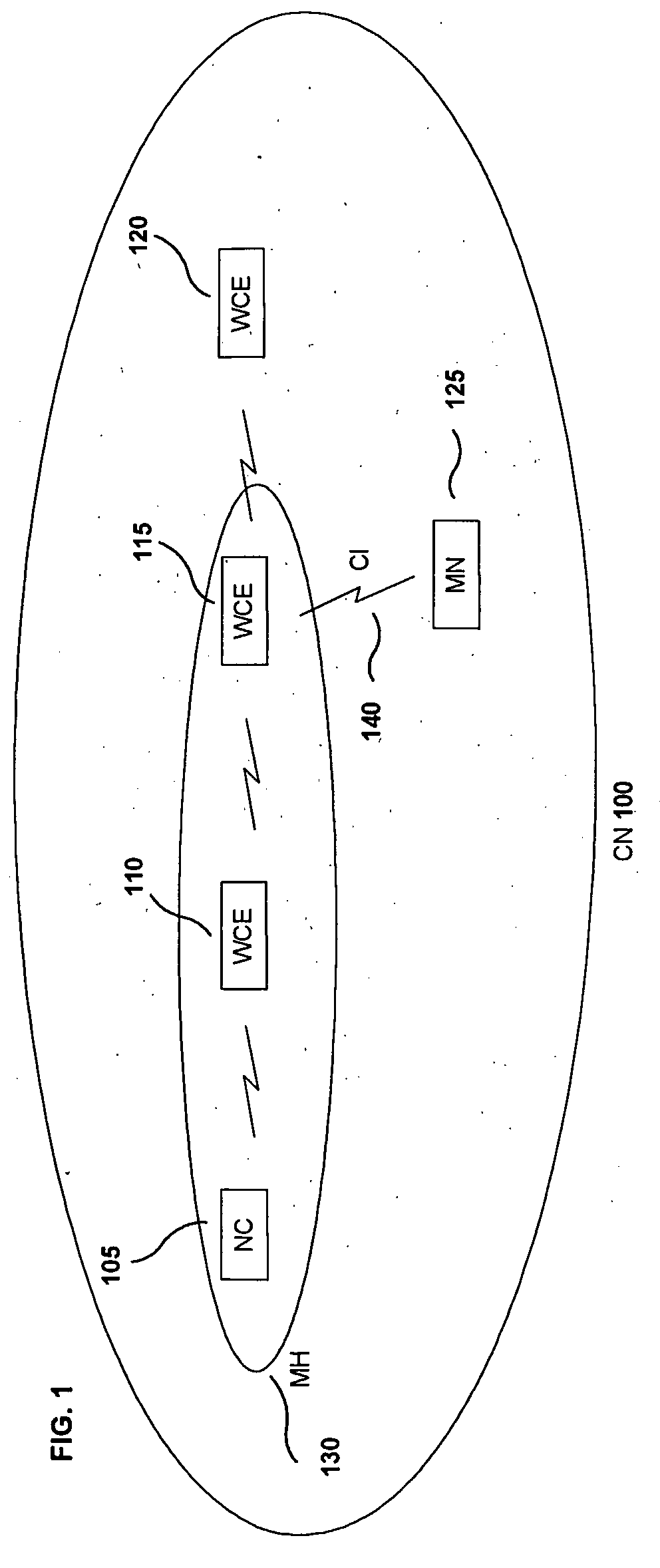
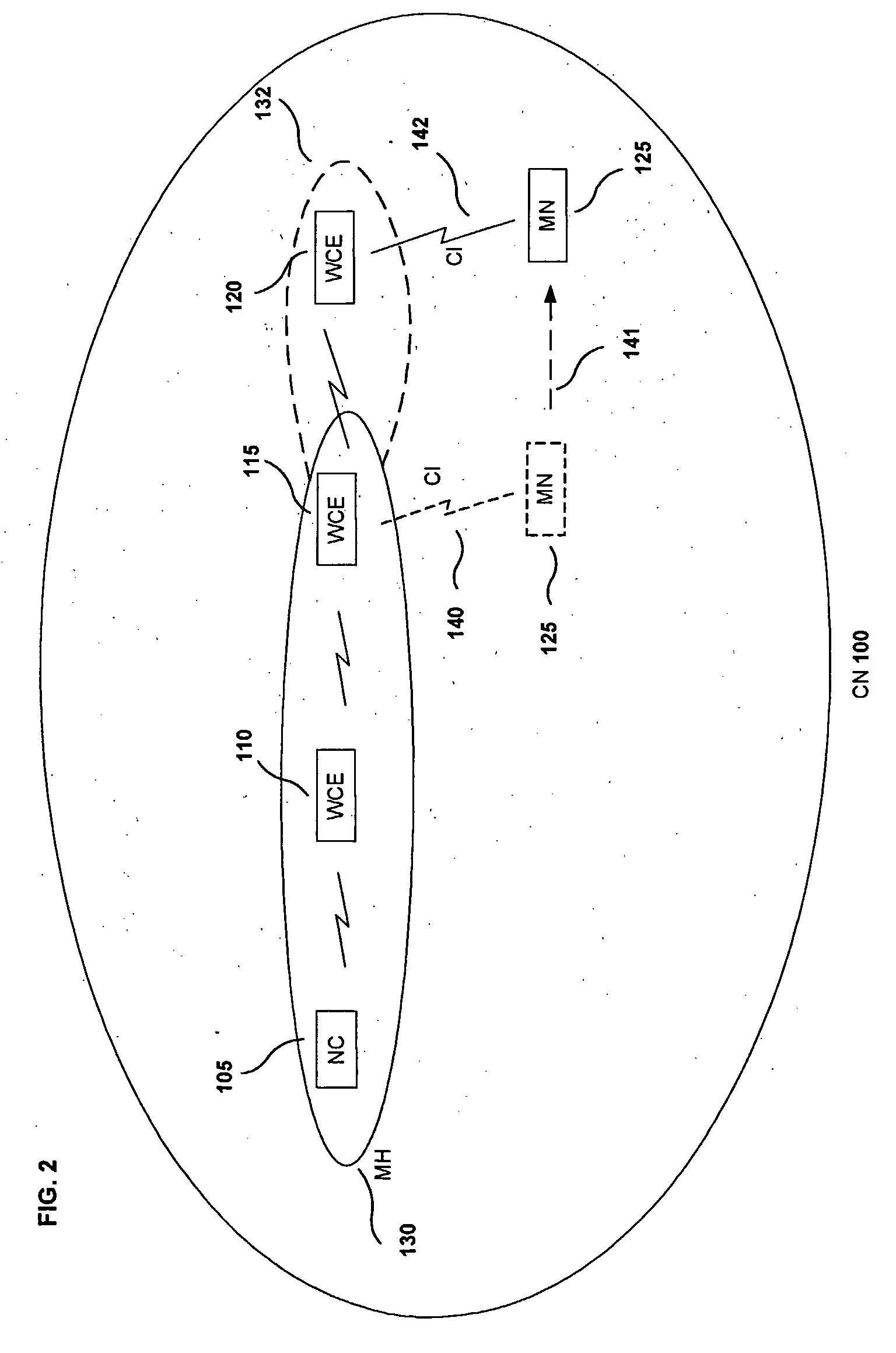
A network controller (NC) (105) that reduces the overhead exchanges for mobility events in a communications network is disclosed. Such a communications network is constituted by a wireless multihop communications network comprising a multihop chain (MH) (130) that wirelessly connects in series wireless communications entities (WCE) (110, 115) for relaying and the network controller as a first entity. Within the wireless multihop communications network a mobile node (MN) (125) wirelessly communicates with the wireless communications entity (115) located at the end of the multihop chain (130). In a communications network, the network controller (105) manages the multihop chain (130), and upon determining that the communications path has to be changed by a mobility event (ME) (141), it establishes a wireless communication between the mobile node (125) and a wireless communications entity (120) by expanding (132) the multihop chain (130).
Owner:PANASONIC CORP
Small file access method accelerated based on solid state disk for distributed file system
ActiveCN106775446AImprove access performanceReduce computing timeInput/output to record carriersAccess methodDistributed File System
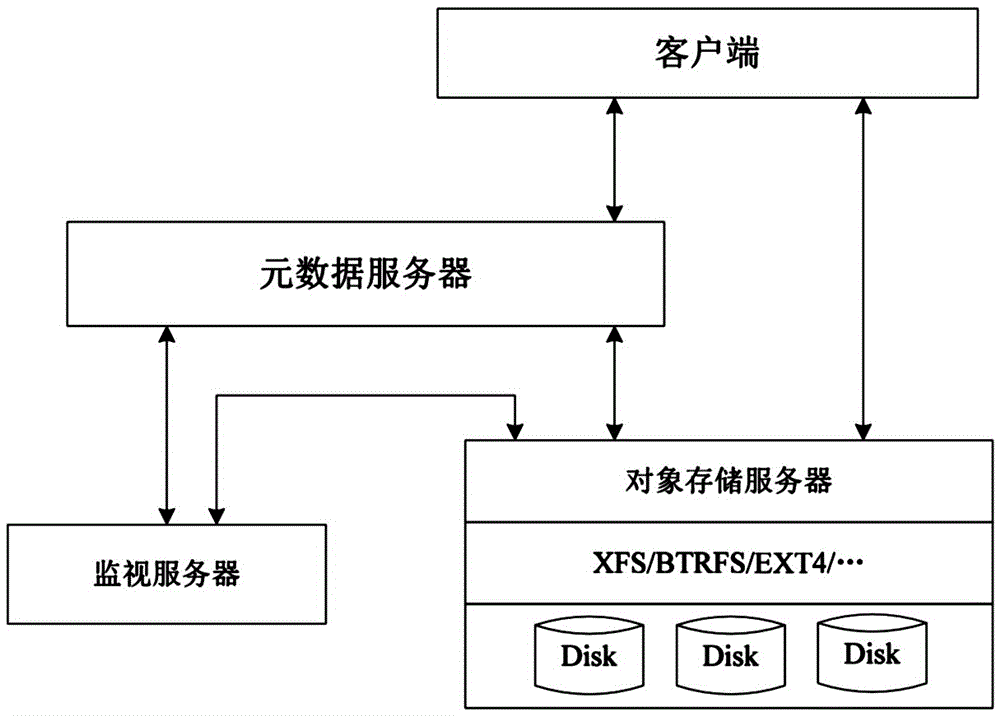
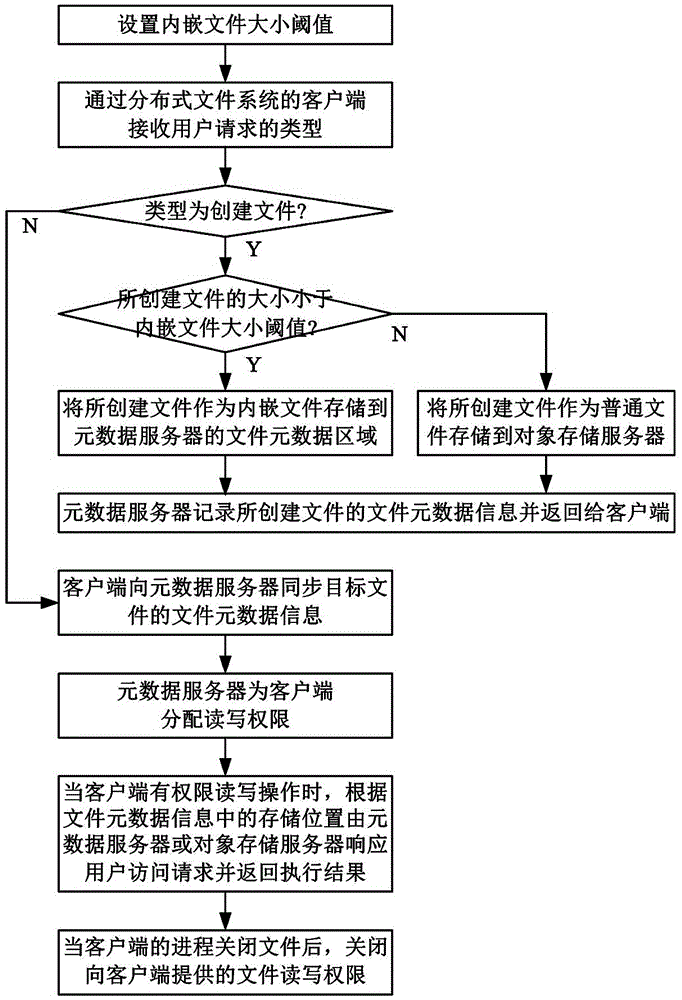
The invention discloses a small file access method accelerated based on a solid state disk for a distributed file system. The small file access method comprises the following steps of setting the threshold value of the size of an embedded file; when a client establishes a file, if the size of the established file is less than the threshold value of the size of the embedded file, embedding and storing the established file in a file metadata area, which is located in the solid state disk, of a metadata server as the embedded file, otherwise, storing the established file in an object storage server; when a process of the client opens the file, according to a storage position in file metadata information, responding to the access request of a user and returning an execution result by the metadata server or the object storage server. According to the small file access method, the data of a small file are directly stored in a metadata area of the solid state disk; the computing time of the storage position of the data of the small file is saved; the access communication time delay of the small file is saved; the access performance of the small file is promoted; the small file is conveniently optimized; the load of the metadata server cannot be aggravated; the overall performance of the distributed file system cannot be decreased.
Owner:NAT UNIV OF DEFENSE TECH
Adaptive rate control method based on mobility and DSRC/WAVE network relevance feedback
InactiveCN105791143AImprove utilizationAccurately control the targetData switching networksGeneration rateSignal-to-noise ratio (imaging)
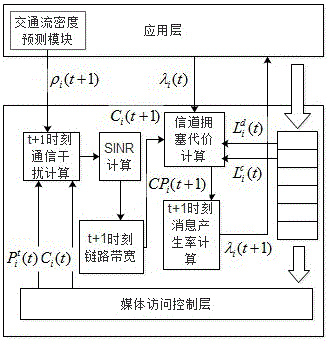
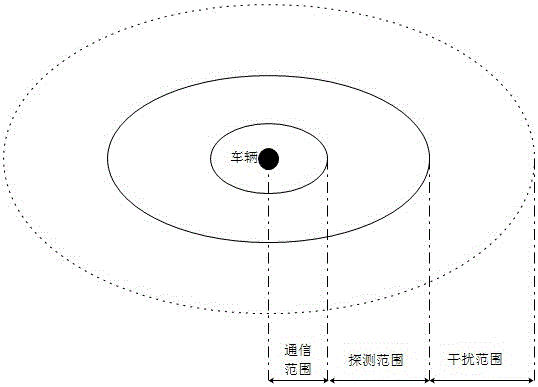
The invention, which belongs to the technical field of car networking communinication, relates to an adaptive rate control method based on mobility and DSRC / WAVE network relevance feedback. The method comprises establishment of a traffic flow density prediction module, a t+1 time communication interference calculation module, an SINR calculation module, a t+1 time available link bandwidth calculation module, a channel congestion cost calculating module and an adaptive message generation rate calculation module. A traffic flow density value at a next time is predicted; according to the density value of the next time, a transmitting power, and a rate, an interference module of a communication process is established, a signal to noise ratio is calculated, and an available link bandwidth of a node at the next time is predicted; on the basis of mismatching of a transmission rate and mismatching of a transmission queue length, a channel congestion cost module is established, so that a message generation rate at the next time is adjusted adaptively. According to the method, adaptive rate adjustment is carried out in advance by using the prediction technology, so that the channel congestion is avoided; and the low communication delay and the high data packet transmission rate are guaranteed with the low calculation time and cost.
Owner:DALIAN UNIV OF TECH
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com