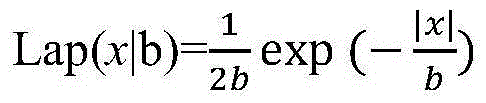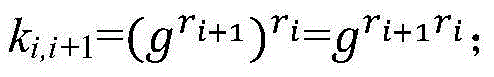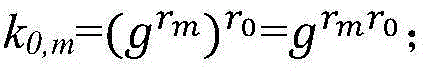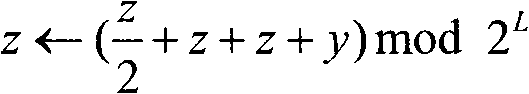Patents
Literature
298results about How to "Reduce the number of communications" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
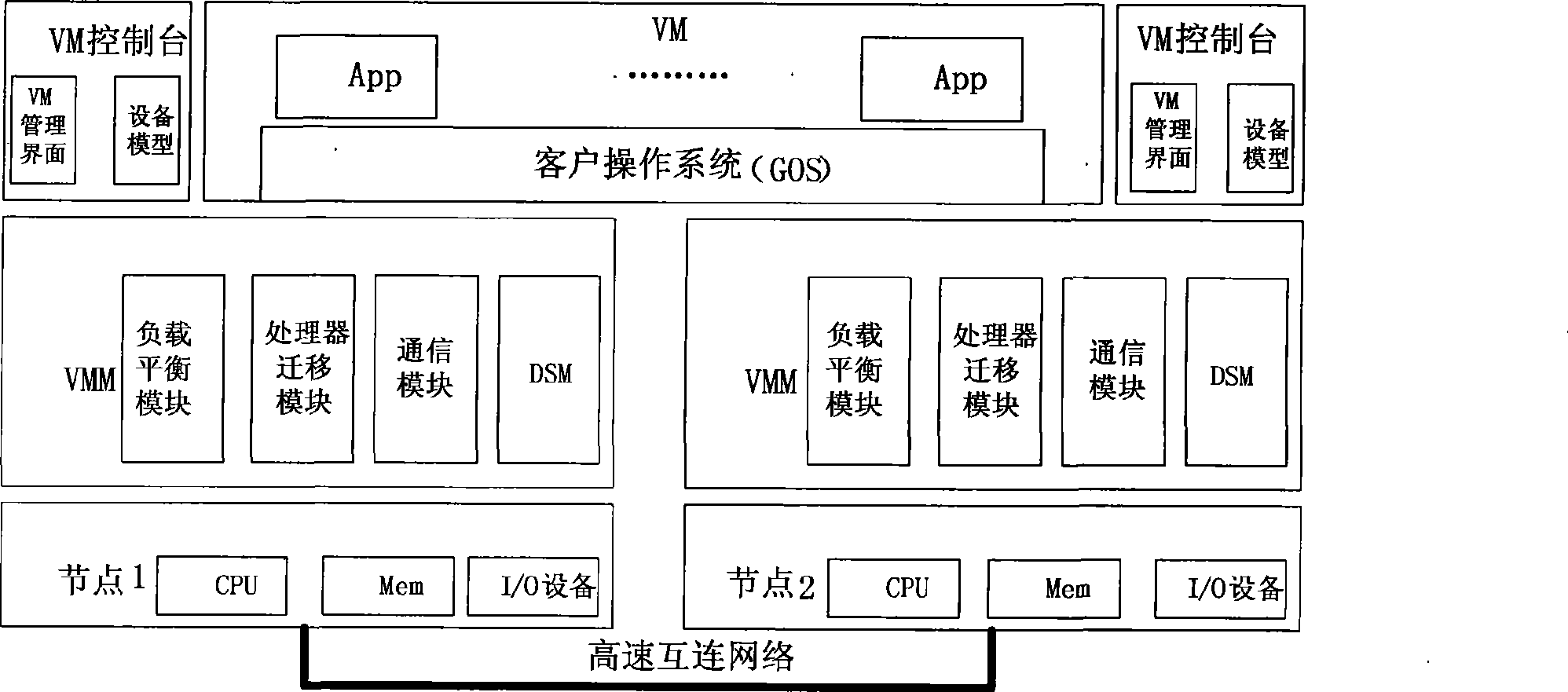
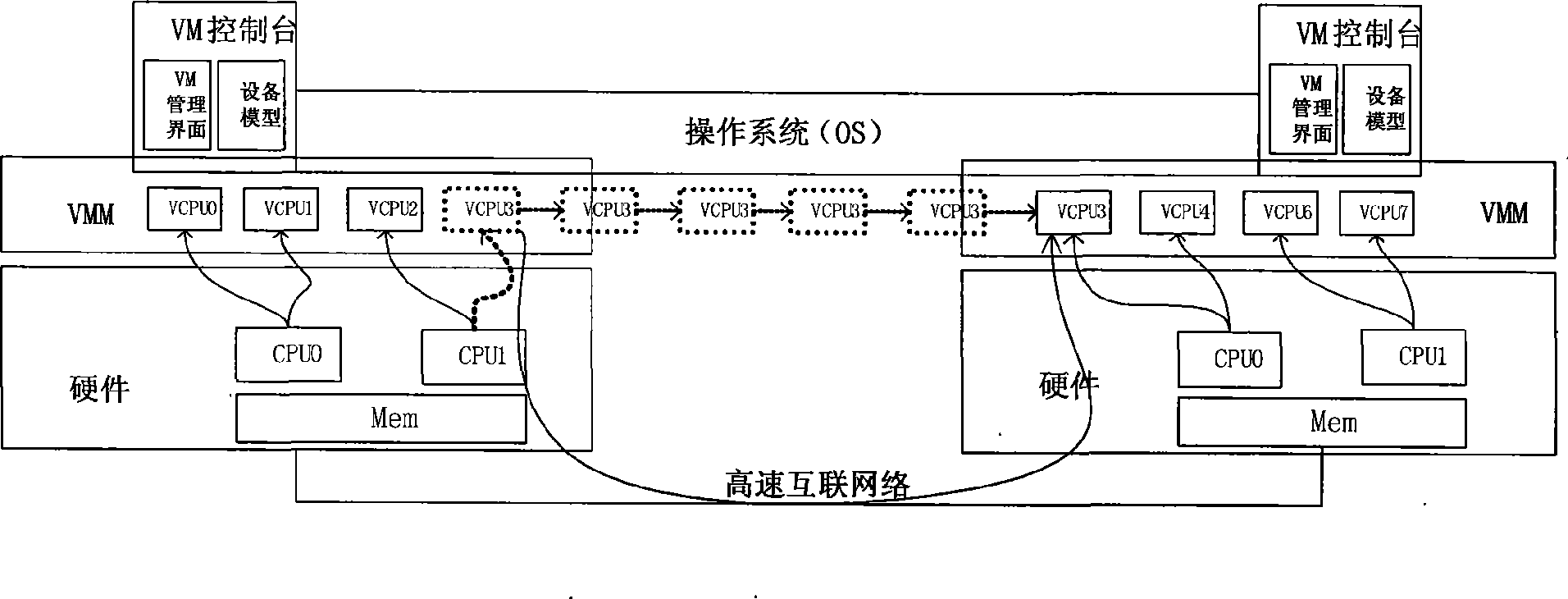
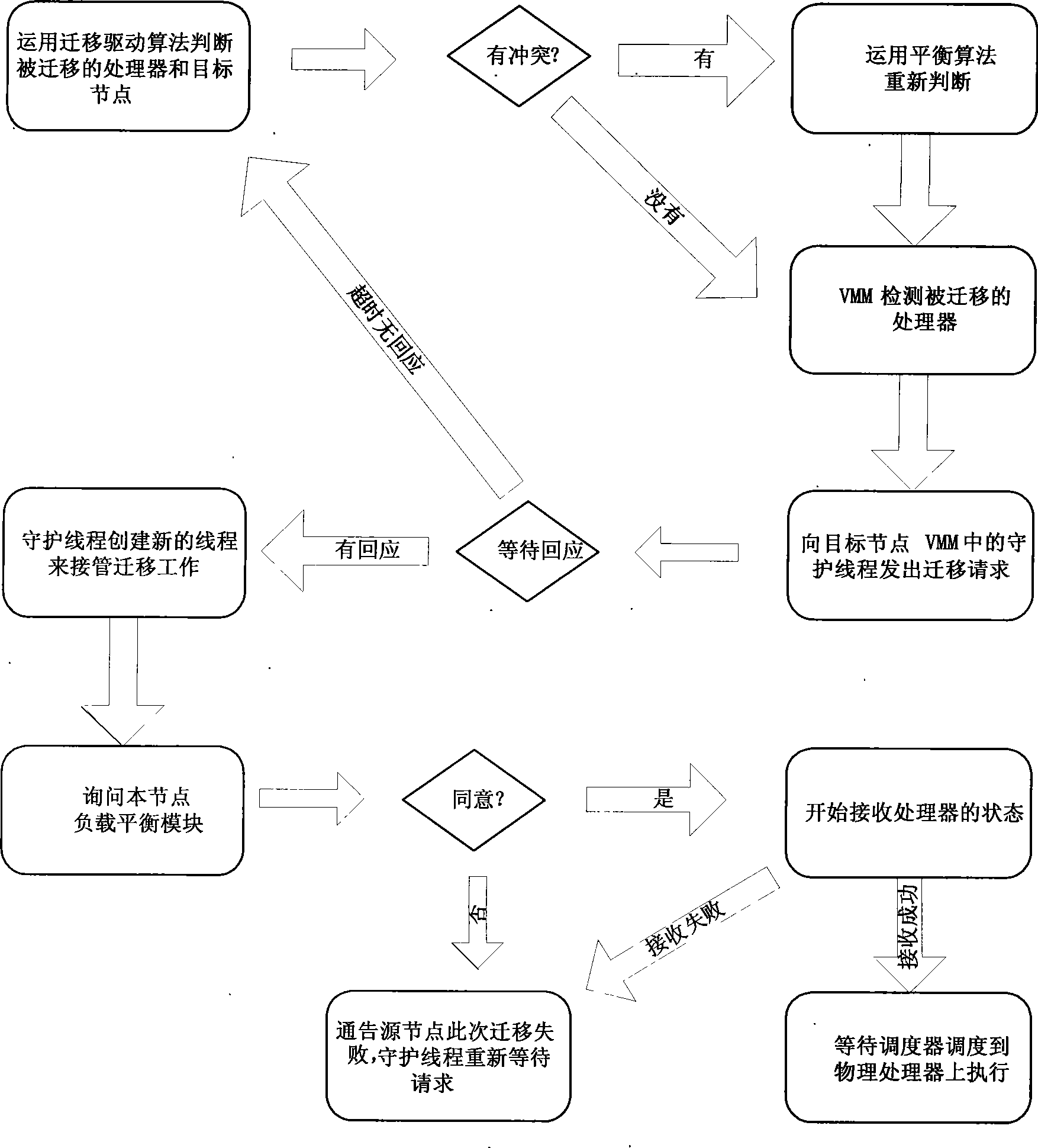
Cluster load balance method transparent for operating system
InactiveCN101452406AImplement a load balancing strategyIncrease profitResource allocationVirtualizationOperational system
The present invention provides a cluster load balancing method transparent to an operation system. Main functional modules comprise a load balancing module, a processor migrating module and a communication module. The method is characterized by comprising the following steps: 1, driving a virtual processor to migrate; 2, driving balance migration; 3, sending a migrating request to a target node and negotiating; 4, storing and restoring a state of the virtual processor; and 5, communicating. The method better solves the problem of low resource utilization rate of a cluster system. Along with the development of more popularization of the cluster system and the continuous development of hardware virtualization technology in the future, the method can be a good solution for the low resource utilization rate of the cluster system and has good application prospect.
Owner:HUAWEI TECH CO LTD
Mobile ad hoc authentication method, network and system
InactiveCN101192928AImprove efficiencyMake the most of processing resourcesEnergy efficient ICTUser identity/authority verificationNetwork structureMobile ad hoc network
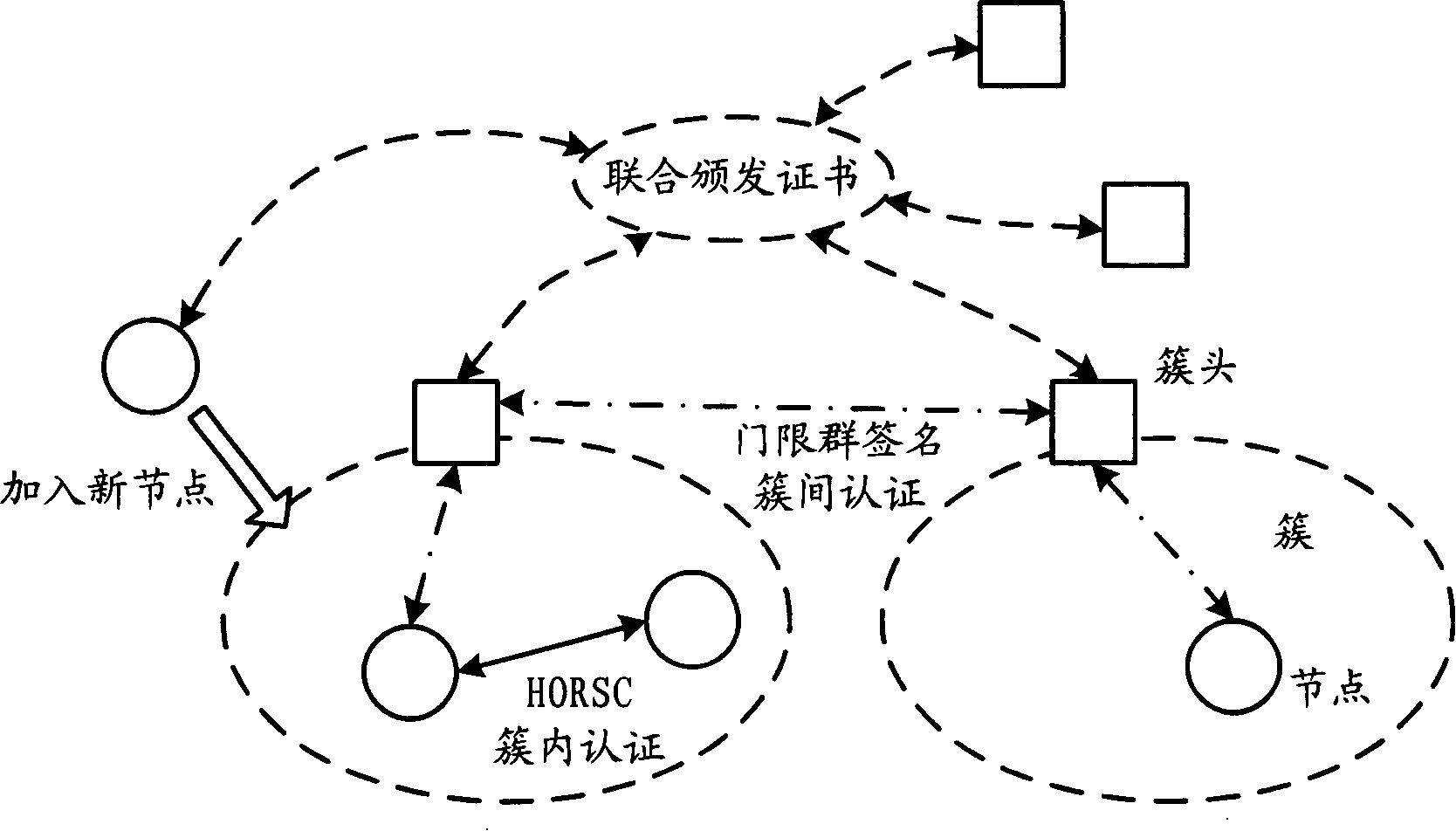
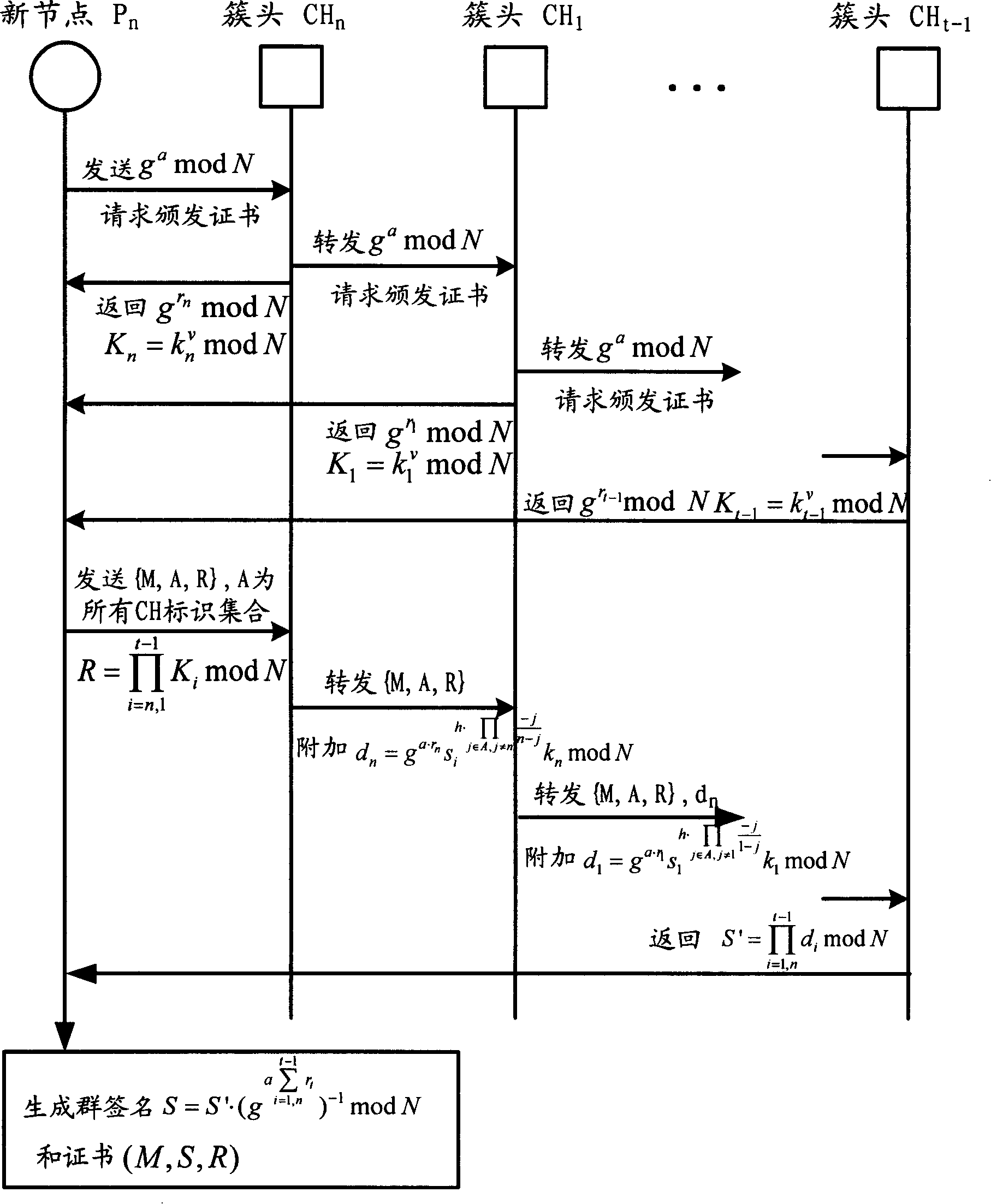
The invention relates to the communication field and discloses an authentication method, a network and a system of mobile ad hoc network, which ensures the realization of layer distribution type authentication scheme of cluster mobile ad hoc network; and the requirement on computer processed resources is rational, which can be realized in practical application environment. The invention adopts a group network structure of cluster mobile ad hoc network and advocates layer distribution identity authentication scheme; and the inter-cluster communication used an improved new threshold group signature protocol which improves the original threshold group signature method based on GQ and decreases power index calculation times, improves calculation parallelism and reduces the requirement on processed resources; at the time of initialization, a certificate and a sub key are issued by the system uniformly; cluster heads which have enough numbers of sub keys can jointly recover system keys, thereby carrying out the group signature to issue certificates to new added nodes and using multi-leap serial communication for realizing united group signature.
Owner:HUAWEI TECH CO LTD +1
Block chain system consensus method and device based on improved clustering algorithm
ActiveCN110113388AImprove work efficiencyControl consumptionUser identity/authority verificationCanopy clustering algorithmCluster algorithm
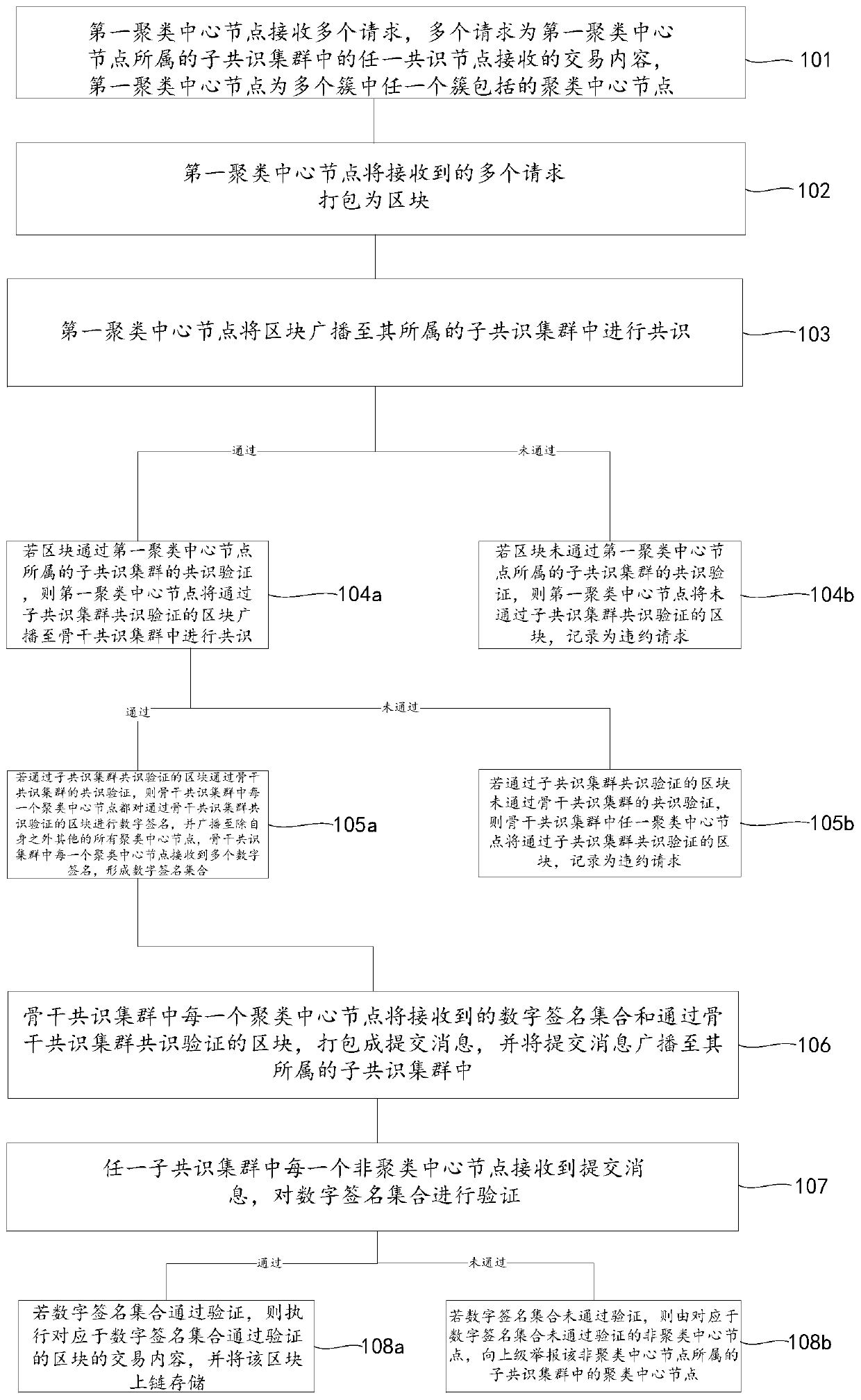
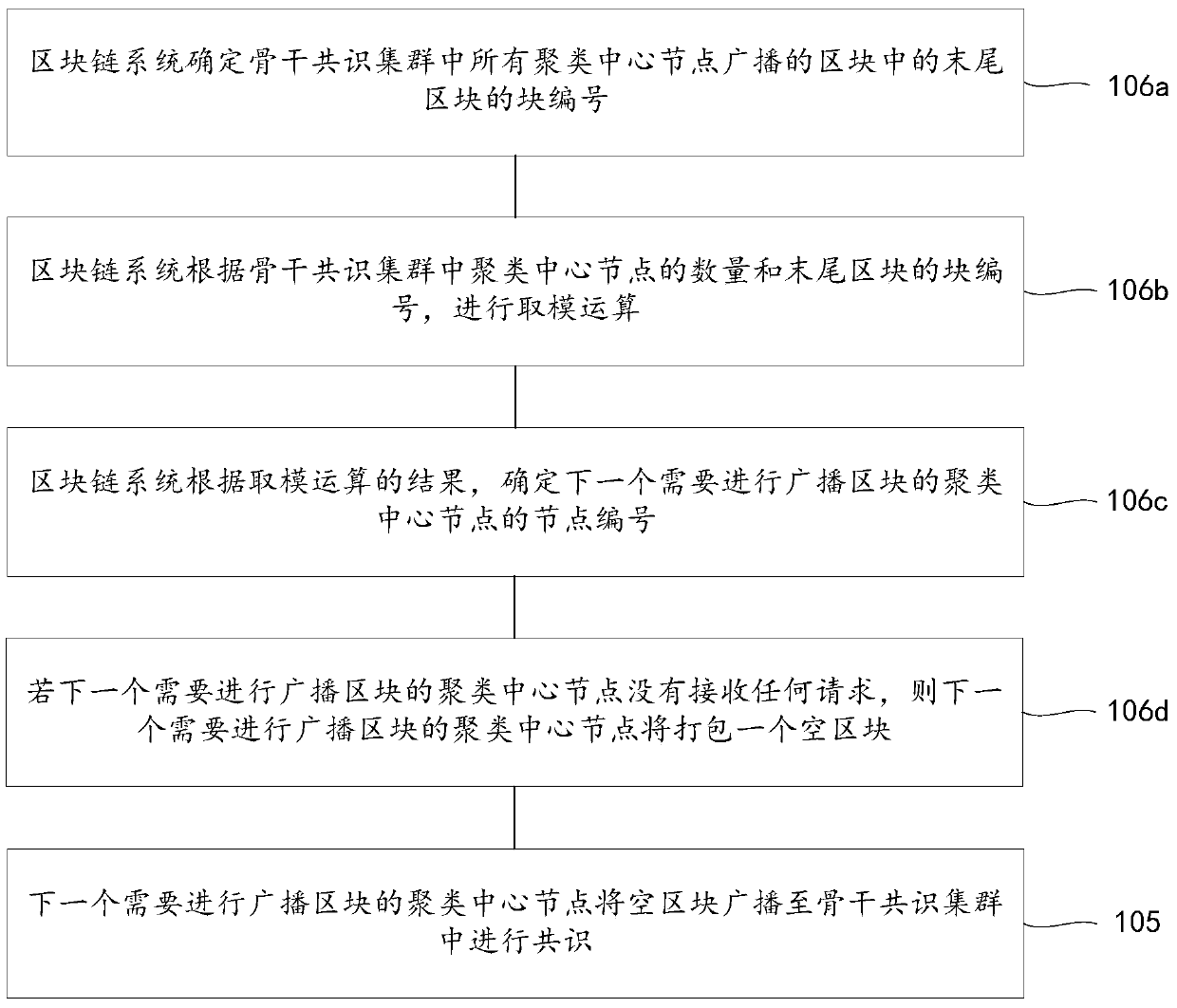
The invention discloses a block chain system consensus method and device based on an improved clustering algorithm. The invention relates to the field of block chains. The method comprises the following steps: enabling the first clustering center node to receive a plurality of requests, packaging the plurality of requests into blocks; broadcasting to the subconsensus cluster to which the subconsensus cluster belongs for consensus; if the block passes the consensus, enabling the block to pass the consensus, broadcasting the blocks to a backbone consensus cluster for consensus; if the consensusof the backbone consensus cluster is passed, enabling each clustering center node to digitally sign and broadcast the block; packaging the received digital signature set and the block into a submission message, broadcasting the submission message to a sub-consensus cluster to which the submission message belongs, receiving the submission message by each non-clustering center node, verifying the digital signature set, and if the transaction content of the block is verified and executed, storing the block in a chain. According to the block chain system consensus based on the improved clusteringalgorithm, the communication frequency and the data transmission amount required by single consensus are reduced, and the working efficiency of the whole block chain system is greatly improved.
Owner:SICHUAN UNIV
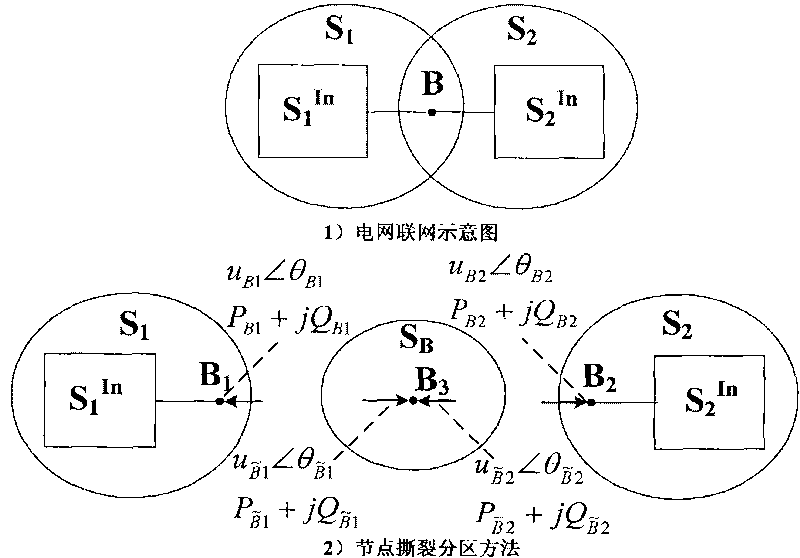
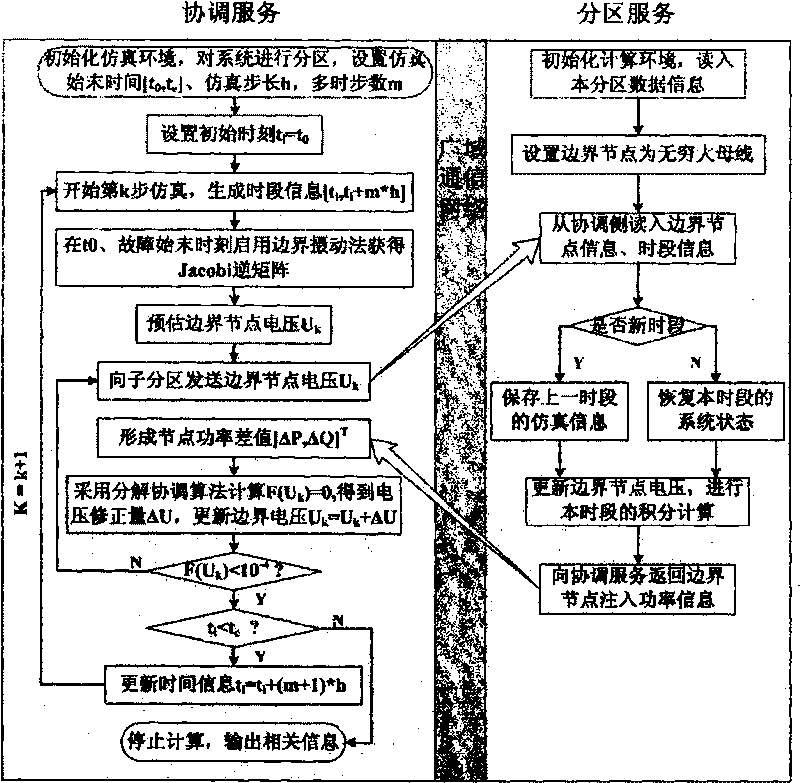
Method for distributed tidal current analyzing by exchange boundary node state and net damage information
ActiveCN101141064AFlexible handlingThe problem of flexible unbalanced power distributionData processing applicationsSpecial data processing applicationsDecompositionData source
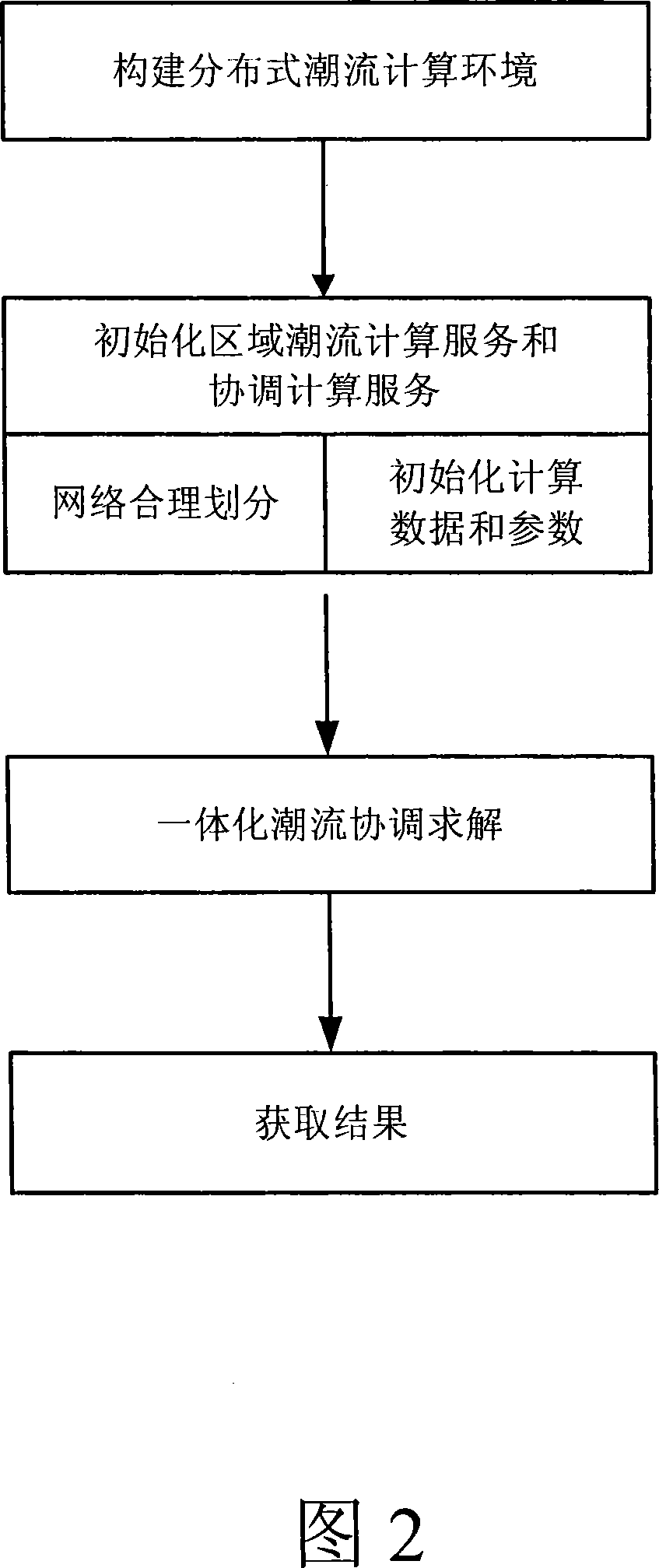
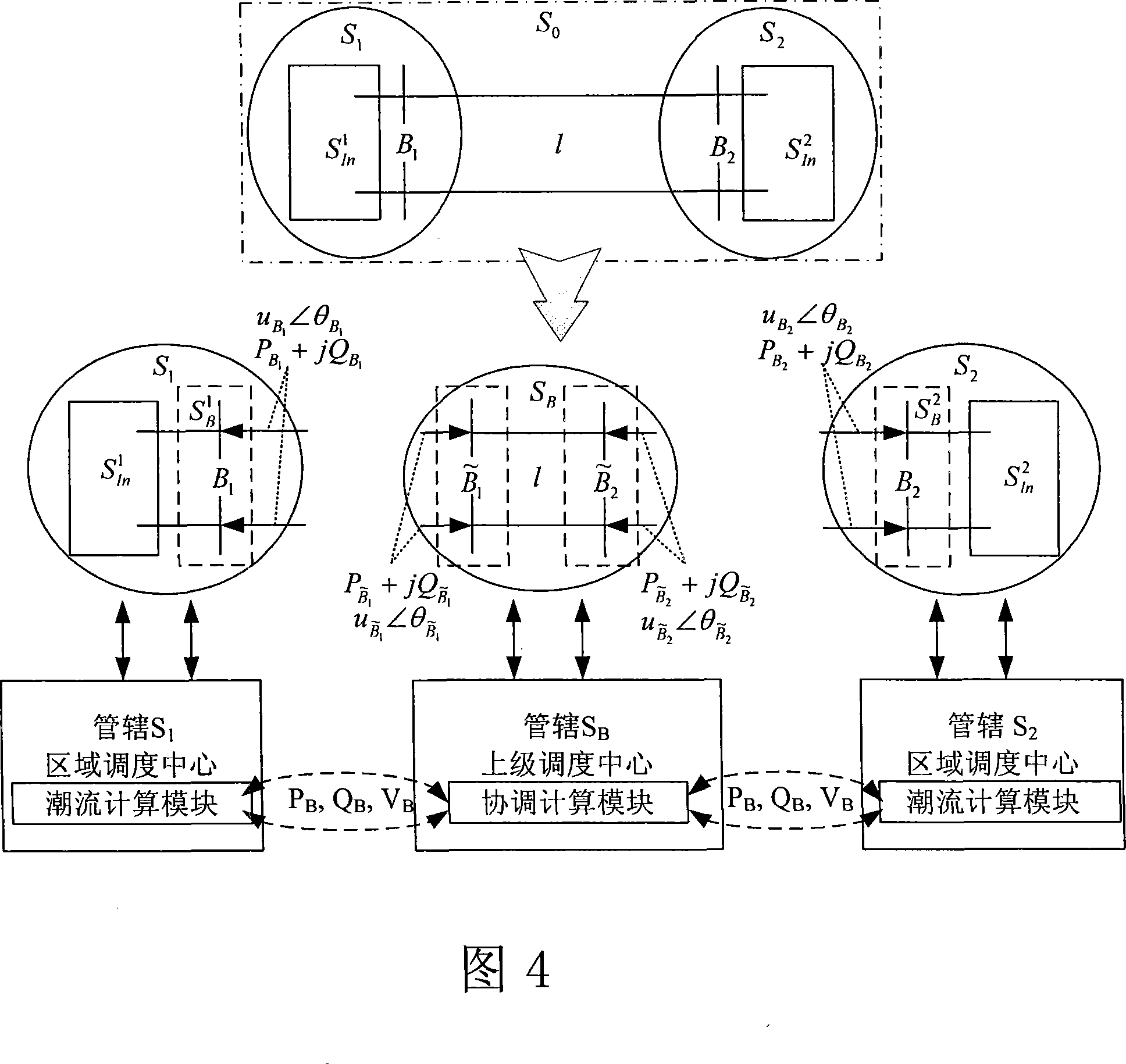
The invention discloses a method of completing the distributed tide analysis by exchanging the border node state and the network damage information, which comprises: establishing a distributed tide analyzing system according to the actual scheduling management manner of the electric power system; based on the topology connection relations of the electric power system and the operation situations of the practical system, dividing the interconnected electric network by the dividing method with border area, and clarifying the counting objects and the data sources of the counting server and the coordinating counting server; a domain tide counting server and the superior coordinating counting server are initialized by counting data and parameters, while the coordinating counting server calls the domain tide counting server to together complete the network integrative tide decomposition coordinating solve; besides, the servers call the processes, the domain tide counting server feeds back the result to the coordinating counting server so as to make the coordinating counting server obtain the convergent network integrative tide result.
Owner:TSINGHUA UNIV
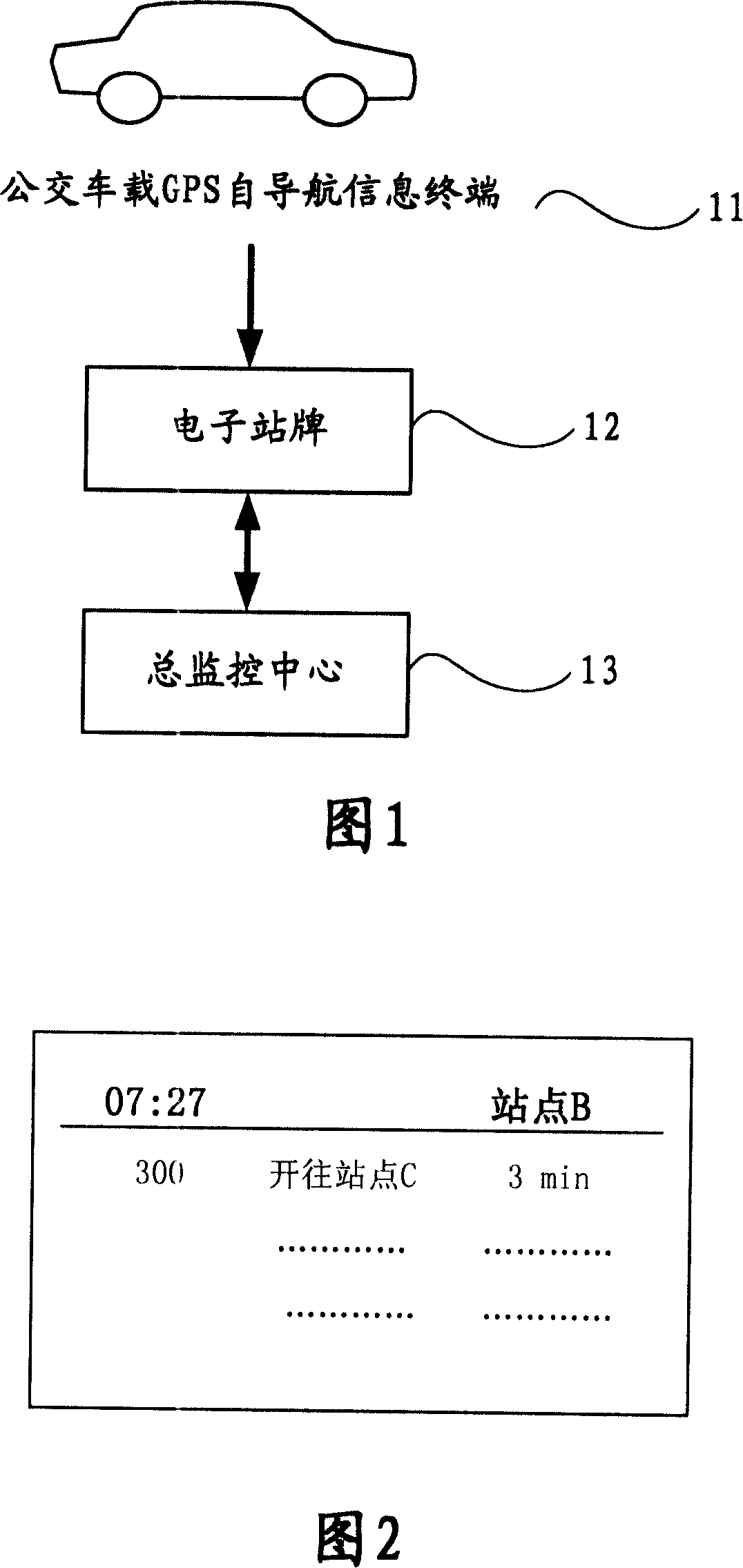
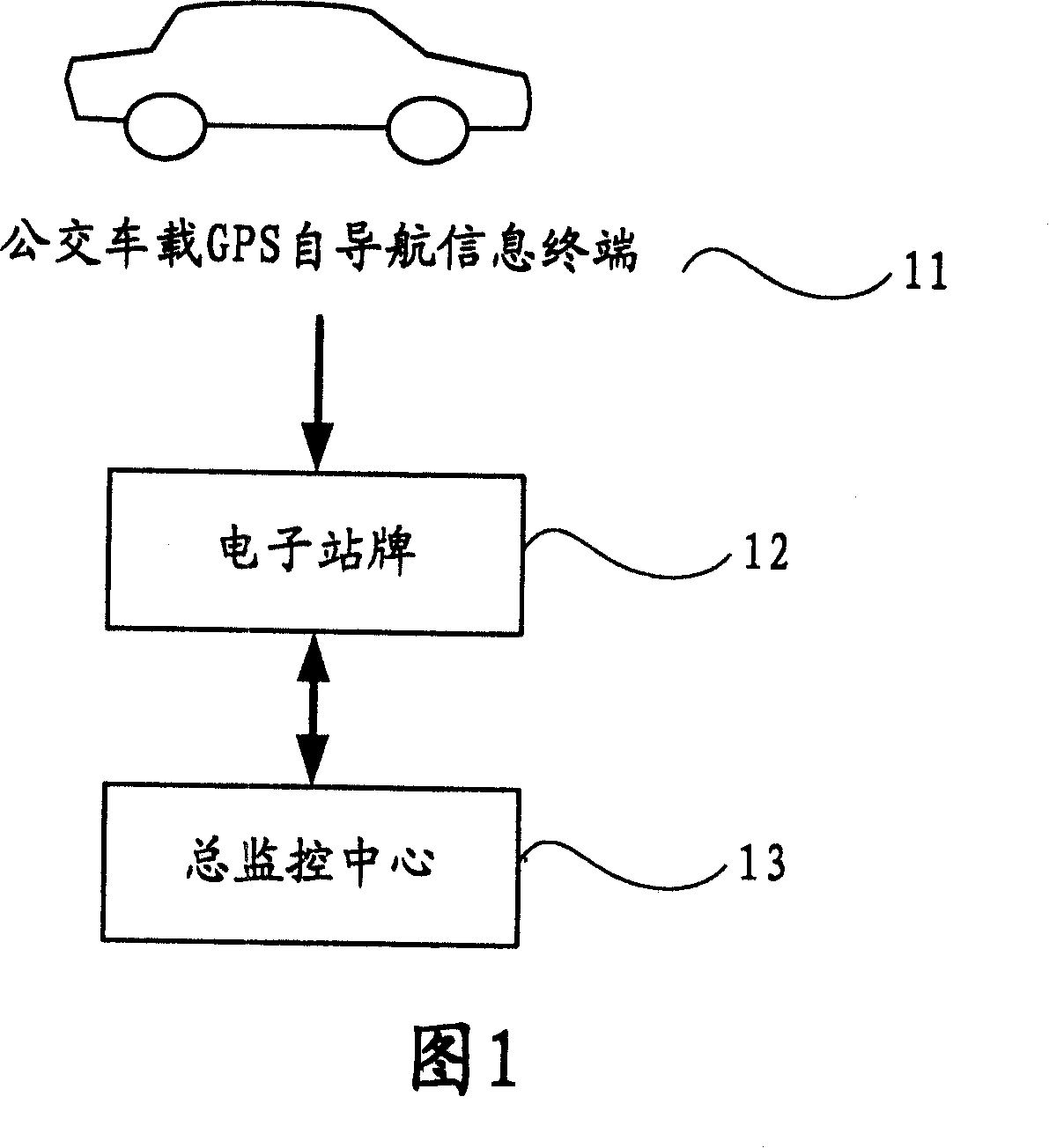
A forecast method for station reach time in digital bus system
InactiveCN101123515AAccurate forecastReduce operating costsSpecial service provision for substationRoad vehicles traffic controlOn boardArrival time
The present invention provides a forecast method of the bus arrival time of a digital public transportation system that comprises at least one on-board information device mounted on a bus, at least one electronic bus station and an information management system. The forecast method of the bus arrival time includes three steps. Firstly, the electronic bus station sends bus arrival information to the information management system via a wireless communication network; secondly, after successfully obtaining the bus arrival information, the data processing unit of the information management system processes the bus arrival information; finally, the estimated time when the bus arrives every electronic bus station ahead is calculated, and arrival forecast information is generated and then sent to every electronic bus station ahead for display via the wireless communication network. The present invention combines the data of realtime road condition and historic statistics and dynamically obtains the time needed for an operating bus to reach every station, thus accurately forecasting the arrival time.
Owner:新世界(中国)科技传媒有限公司
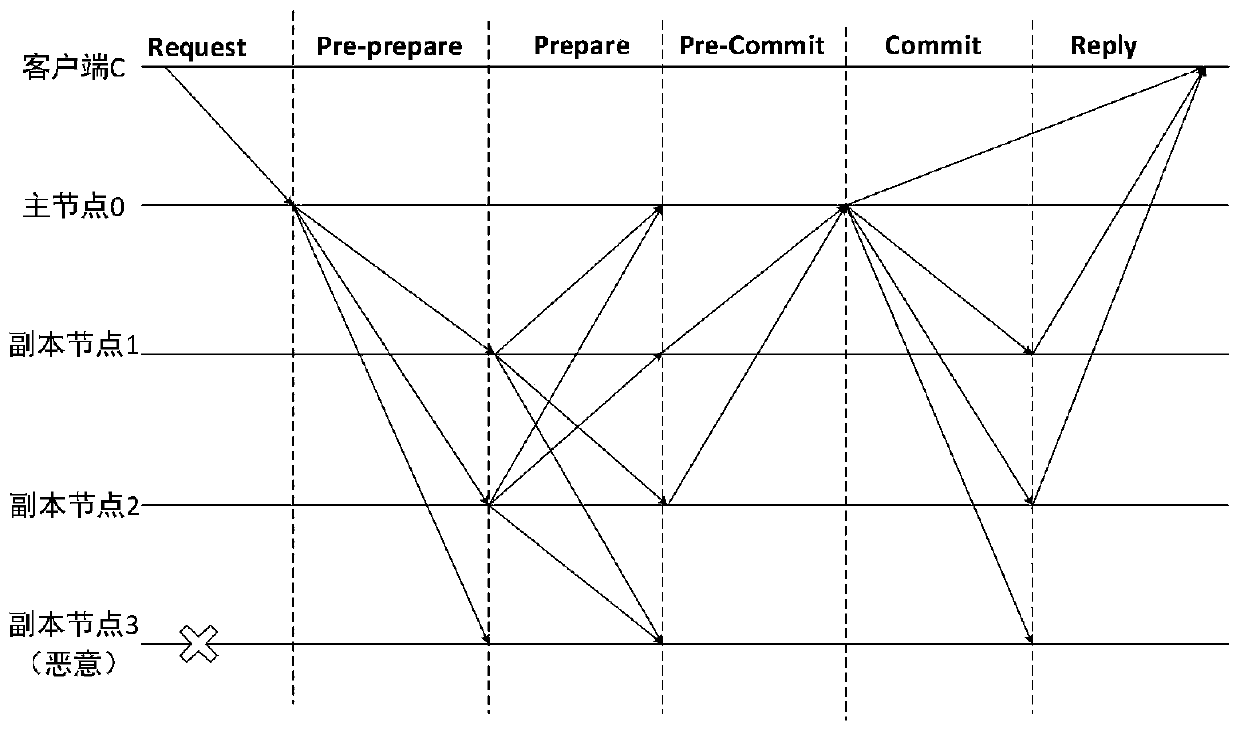
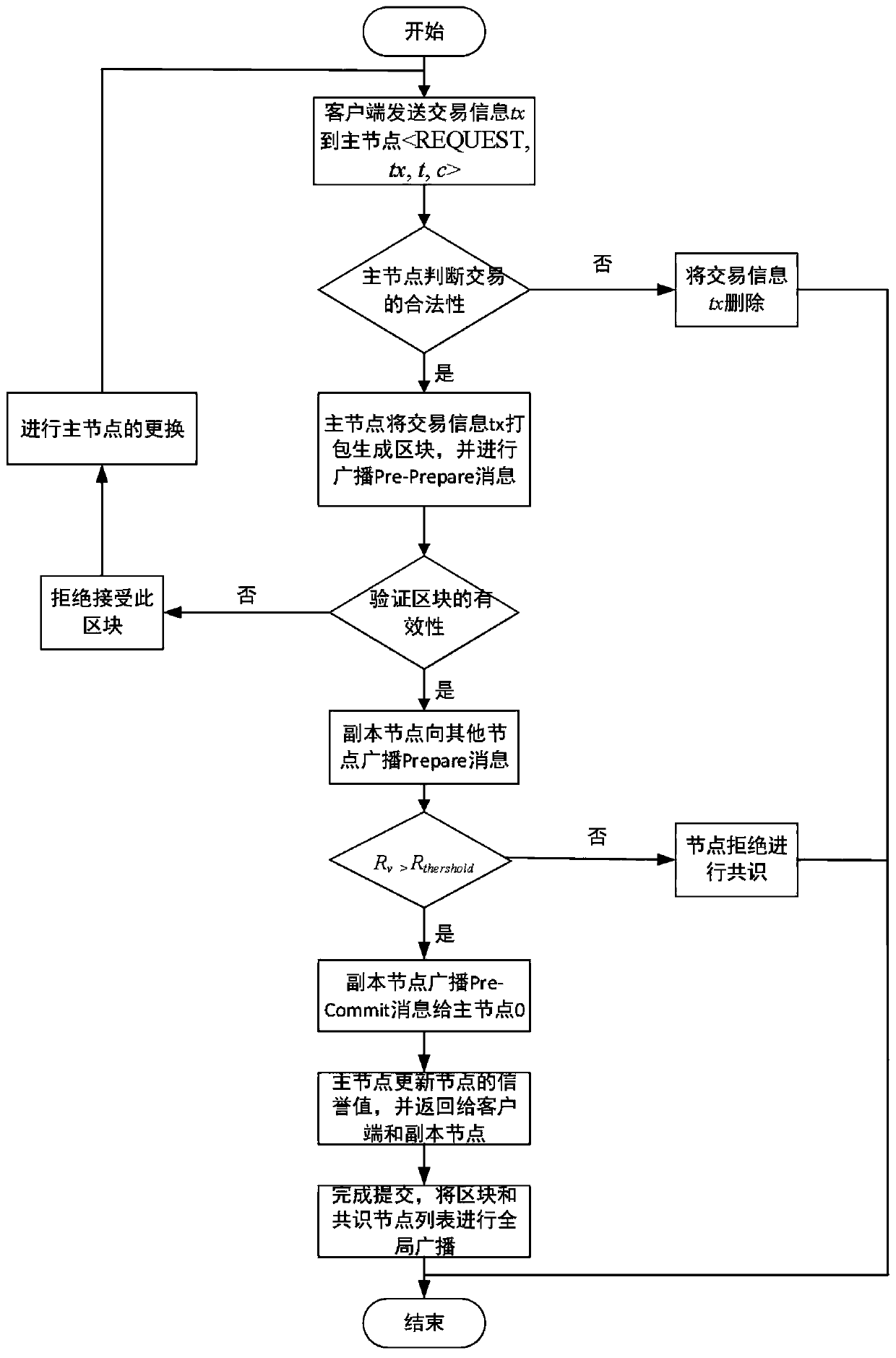
Method for defending Sybil attacks in block chain based on improved PBFT algorithm
InactiveCN110493198AEffective attackReduce the number of communicationsTransmissionBlockchainSybil attack
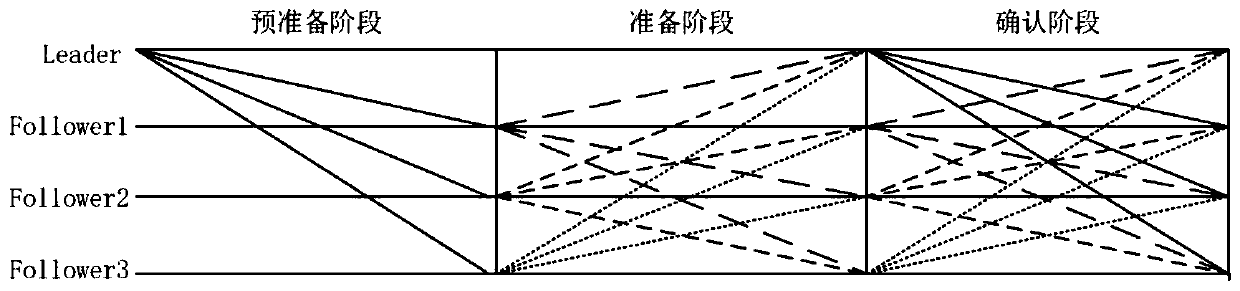
The invention discloses a method for defending Sybil attacks in a block chain based on an improved PBFT algorithm. According to the method, a PBFT algorithm is improved, an original view change mechanism in the algorithm is deleted, a main node Sp is randomly selected through the credible state of a consensus node, and meanwhile, a Pre-Commit stage is added in a consensus protocol to reduce the communication frequency between nodes; secondly, a reputation model is established to count comprehensive information of each consensus node to calculate a reputation value of the node, and due to the fact that the reputation values of the nodes are different, owned speaking rights are different, and the nodes achieve consensus through voting so as to defend Sybil attacks in the blockchain. According to the method, the frequency of communication between the nodes is reduced, the voting weight of the consensus node corresponds to the owned reputation value by referring to the consensus thought based on share certification in the public chain, and different speaking rights are allocated to the nodes according to the reputation value of the consensus node, so that Sybil attacks in the blockchain can be effectively defended.
Owner:BEIJING UNIV OF TECH
Transient stability distributed simulation method of electric power system
ActiveCN101699448AFast convergenceKeep Data Interface SimpleSpecial data processing applicationsInformation technology support systemEngineeringTransient stability analysis
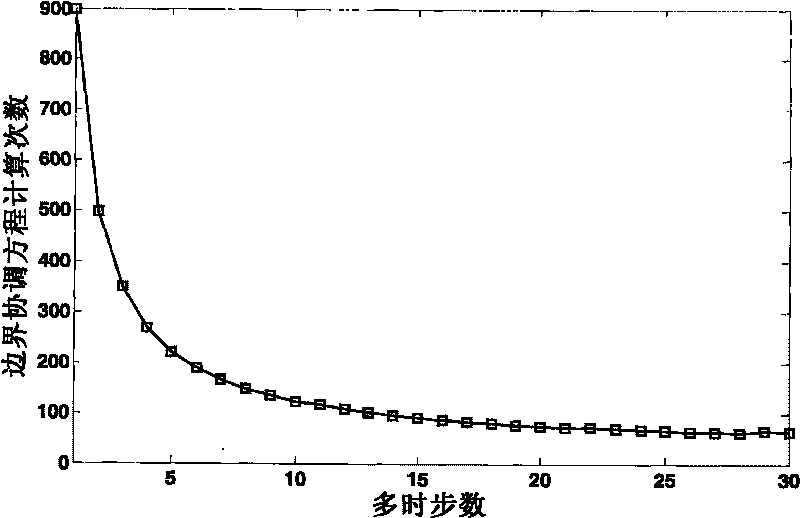
The invention relates to a transient stability distributed simulation method of an electric power system, belonging to the transient stability analysis technical field of the electric power system; the transient stability distributed simulation method is characterized in that: variable dimension of boundary coordination equation is reduced to one half of that of a partitioning method based on connecting line by using the partitioning method based on a node decomposing method, so as to improve the simulation efficiency; the accurate initial Jacobi inverse matrix is obtained by using a boundary perturbation method, so as to reduce iterations; the calculation process is accelerated by comprehensively adopting the methods that the boundary node voltage value of the next time step is pre-estimated and the Jacobi inverse matrix is coordinated and dynamically updated simultaneously in multiple time steps; by adopting coordination algorithm based on inverse Broyden quasi-Newton method, the solving times of the boundary coordination equation are reduced greatly, so as to improve the simulation efficiency. In the technical proposal, the data interface is simple, the data transmission capacity is low, the system model is simplified, superlinear convergence speed close to the newton method is provided, and hyper real-time simulation can be realized in a wide area communication network, therefore, the method is conveniently applied to the practical electric power system.
Owner:TSINGHUA UNIV
Method for tracking moving targets in wireless sensor networks
InactiveCN102638863AReduce energy consumptionReduce the number of communicationsNetwork topologiesHigh level techniquesLocation determinationEnergy consumption
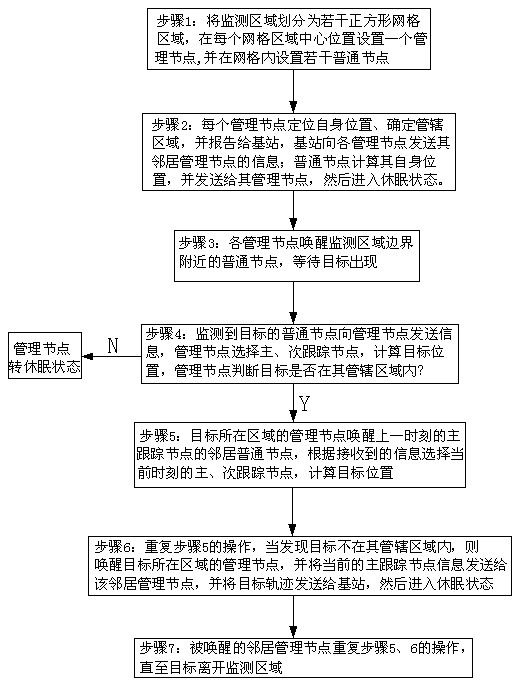
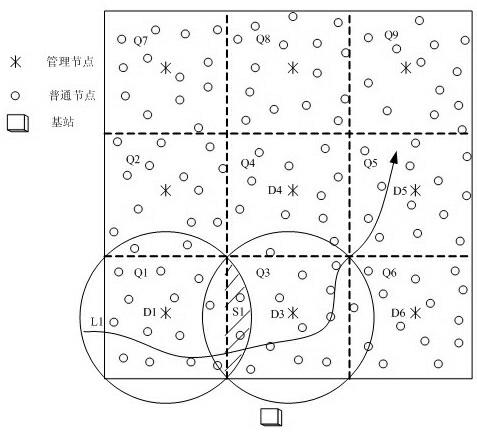
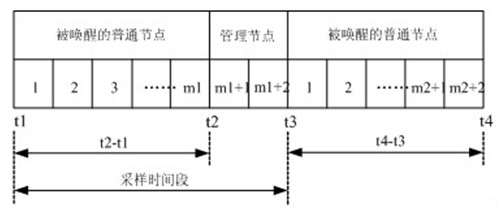
The invention discloses a method for tracking moving targets in wireless sensor networks. Monitoring areas are subjected to partition management, a management node is in charge of tracking tasks of an area, and position information of all nodes is not needed to be acquired by a base station; management nodes determine nodes needed to be awakened in the next sampling time period according to positions of main tracking nodes in the previous sampling time period. During each sampling time period, only a small part of nodes is in monitoring or moving states while most of the nodes remain dormant; ordinary nodes monitoring targets only need to send information to the management nodes, and information exchange is not needed; when the targets are lost, searching in one area is performed firstly, then whole network tracking is performed when the area searching fails. By the method for tracking moving targets in the wireless sensor networks, energy consumption of the nodes and communication times among the nodes are reduced, life circle of the networks is prolonged, and communication resources are saved.
Owner:SOUTHEAST UNIV
Multiple AUV cooperative positioning method based on underwater sound double pass range finding
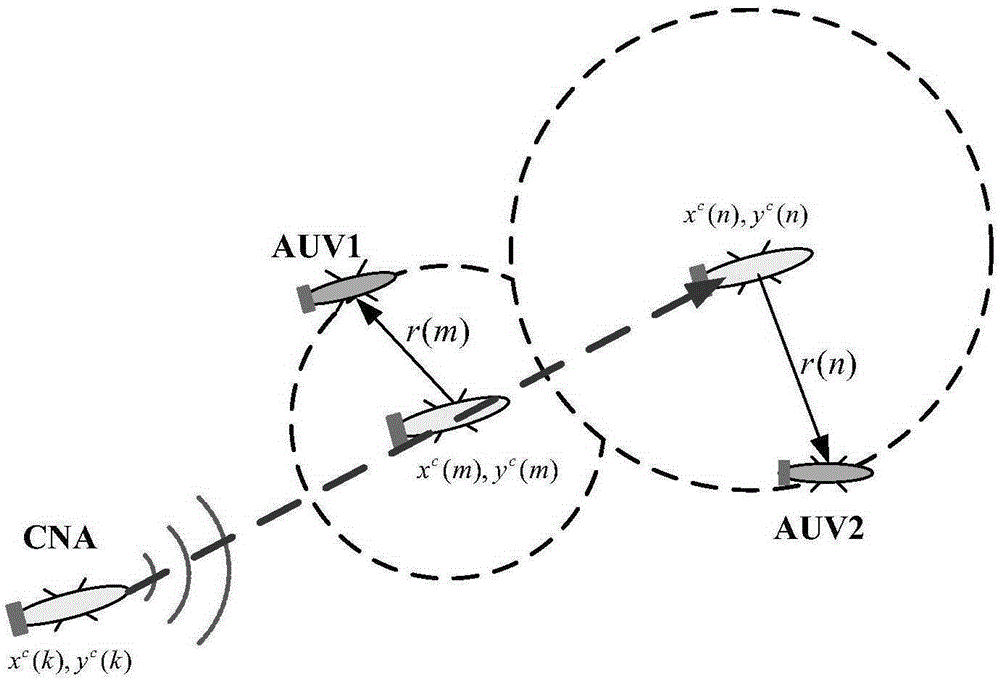
ActiveCN105319534AAvoid Synchronization RequirementsEasy to implementWaterborne vesselsPosition fixationCurrent timeDouble pass
The invention discloses a multiple AUV cooperative positioning method based on underwater sound double pass range finding, comprising: synchronizing time of all AUV systems; determining the priority of each AUV system, and setting corresponding range finding response delay time according to levels of priorities; when not receiving the underwater sound information of a main AUV, a slave AUV performing dead reckoning according to the measurement information of a self sensor; the slave AUV receiving the underwater sound information of the main AUV, decoding the position information, speed information and time information of information sending time of the main AUV, and then performing range finding on the main AUV; when measuring the distance information between the main AUV and the slave AUV, the slave AUV recording a current time t (n), and reckoning the main AUV position information xc (n) at the current time; and performing cooperative positioning according to the distance information between the main AUV and the slave AUV, and the main AUV position information xc (n), and correcting a self dead reckoning error through the information fusion technology. The multiple AUV cooperative positioning method has the advantages of simple realization, high positioning precision, and small energy consumption.
Owner:HARBIN ENG UNIV
Network coding-based multicast routing method applied to vehicular ad hoc network
InactiveCN101883330AHigh success rateImprove efficiencyError preventionNetwork topologiesNetwork codeDistributed computing
The invention provides a network coding-based multicast routing method applied to a vehicular ad hoc network by combining the characteristics of the vehicular ad hoc network. The method comprises the following steps of: acquiring information of two-hop neighboring nodes of a node sending a data packet to form a two-hop neighbor information sheet by the node sending the data packet; selecting a routing mode according to the relationship between the number of the neighboring nodes and the threshold value of the number of the nodes existing in every kilometer, which is recorded in the two-hop neighbor information sheet, if the number is more than the threshold value, entering a network coding mode, and otherwise entering an opportunistic routing mode; determining a forward node set and then determining the data sending rate k and local topological max-flow min-cut value n of the current node in the network coding mode; calculating a minimum finite field by combining maximum distance separable codes and selecting nonzero elements from the field to construct an overall coding matrix which meets k-row linear independence relationship; transmitting a coding rule according to the coding matrix by the node and coding in strict accordance with the rule by a downstream node; and repeating the processes until information arrives at a target node. The routing method has the advantages of expandability, high efficiency and high adaptability.
Owner:HUNAN UNIV
Update method of mobile object location based on traffic network and GPS
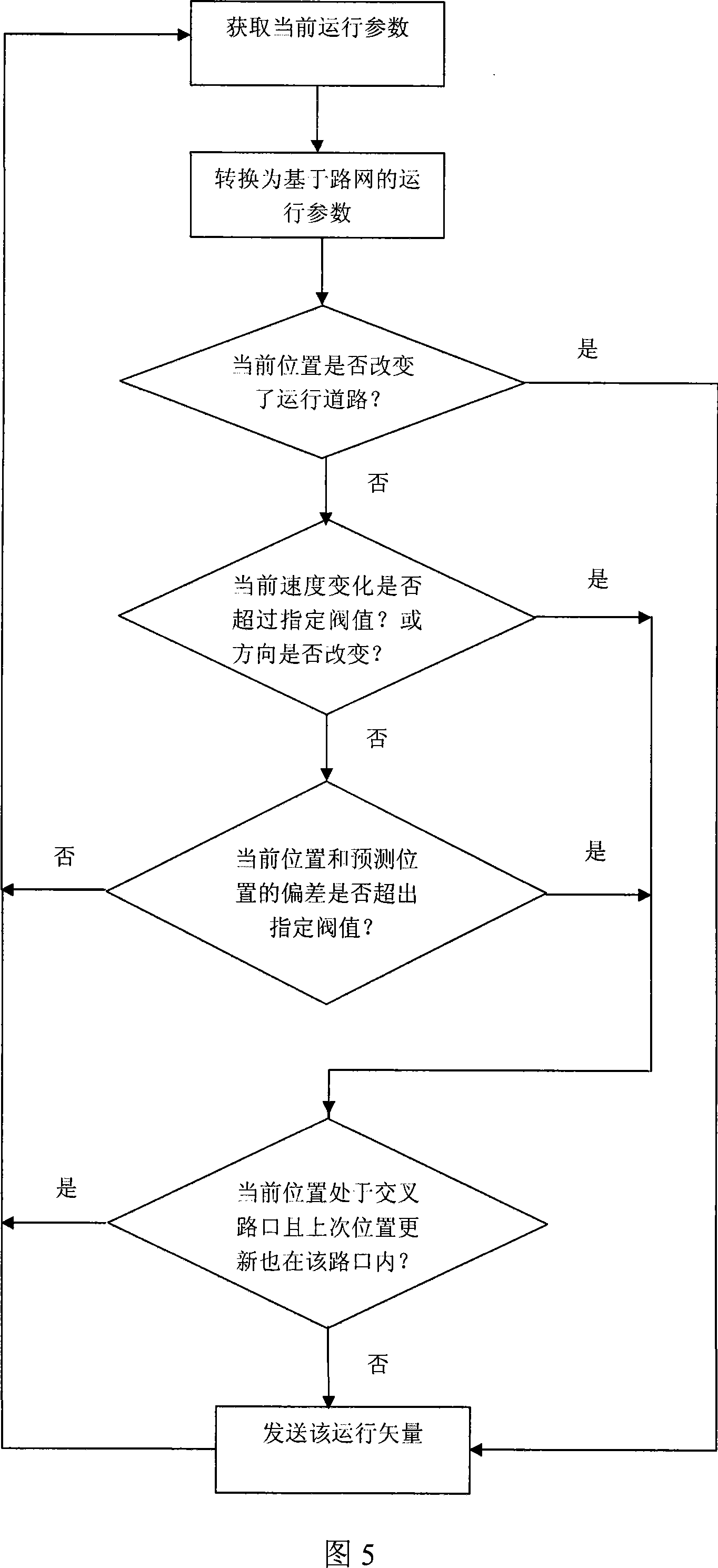
InactiveCN101128051AGuaranteed accuracyReduce calculation errorsBeacon systems using radio wavesPosition fixationObject basedTraffic network
The utility model discloses an updating method for a moving object based on the road transportation network and GPS, aiming at enabling a central server to trace the former and current position of the moving objects. The utility model is characterized in that the moving object uses GPS to measure the latest running data continuously, through matching with the transportation network, the coordinate of the latitude and the longitude and the direction data are converted into the data format based on the road network, then the current running vector is compared with the running data submitted by the updating on the last position according to the principle of the inertia, and the position updating condition is determined, the current running vector of the moving object is reported to the central server only when the moving object does not keep running as the principle of the inertia. Additionally, the utility model optimizes the updating of the position in the road crossing, only one time position updating of the moving object is performed at most in the road crossing. The utility model has advantages of reducing the communication frequency and improving the data processing efficiency under the premises of securing the processing precision compared with the prior art.
Owner:INST OF SOFTWARE - CHINESE ACAD OF SCI
Network file system and method based on certificate-free public key infrastructure
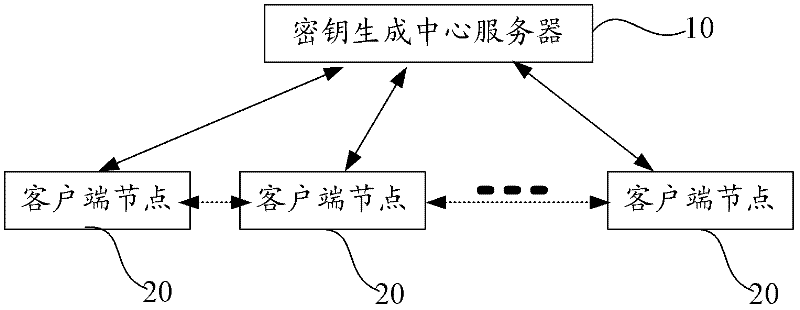
InactiveCN102420810ANo hosting issuesEliminate redundancyUser identity/authority verificationNetwork File SystemClient-side
The invention provides a network file system and method based on a certificate-free public key infrastructure. All client side nodes are registered in a key generating centre server, and node public keys and node private keys of the client side nodes are generated according to system public keys and partial private keys in system parameters generated by the key generating centre server; no key hosting problem exists, the node public keys and identities of the client side nodes are not needed to be bound by certificates, thus the certificate redundancy problem brought by certificate utilization is eliminated, and a secure channel is not needed to be built between the key generating centre server and each client side node; the identity authentication of two communicating client side nodes is directly finished according to the node public keys, the node private keys and the system parameters, and the key generating centre server is not needed anymore; the communication frequency for mutual authentication of the client side nodes is greatly reduced, the bandwidth resources used in the identity authentication process are lowered, and the calculation amount is reduced and higher efficiency is obtained.
Owner:SHANGHAI SHENGPAY E PAYMENT SERVICE CO LTD
Wireless positioning method and device
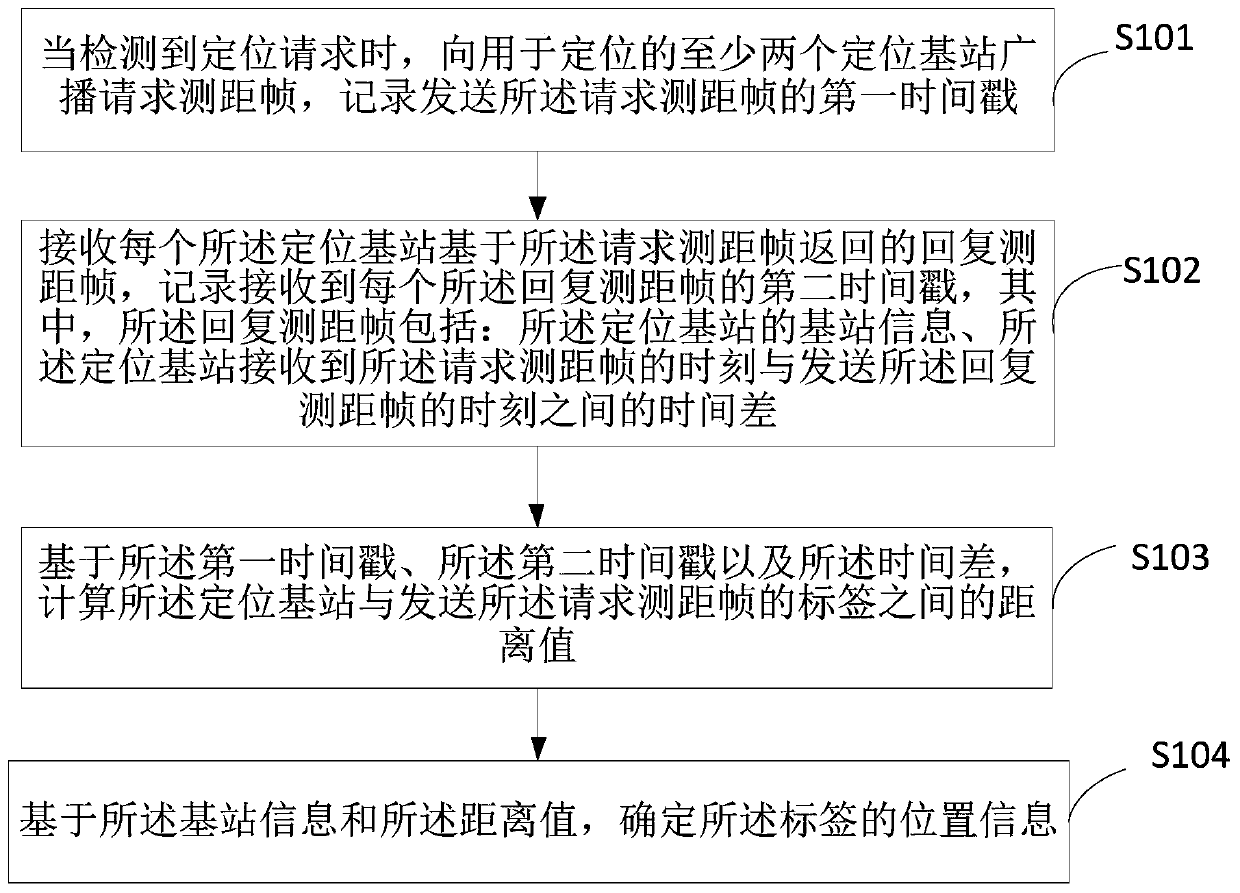
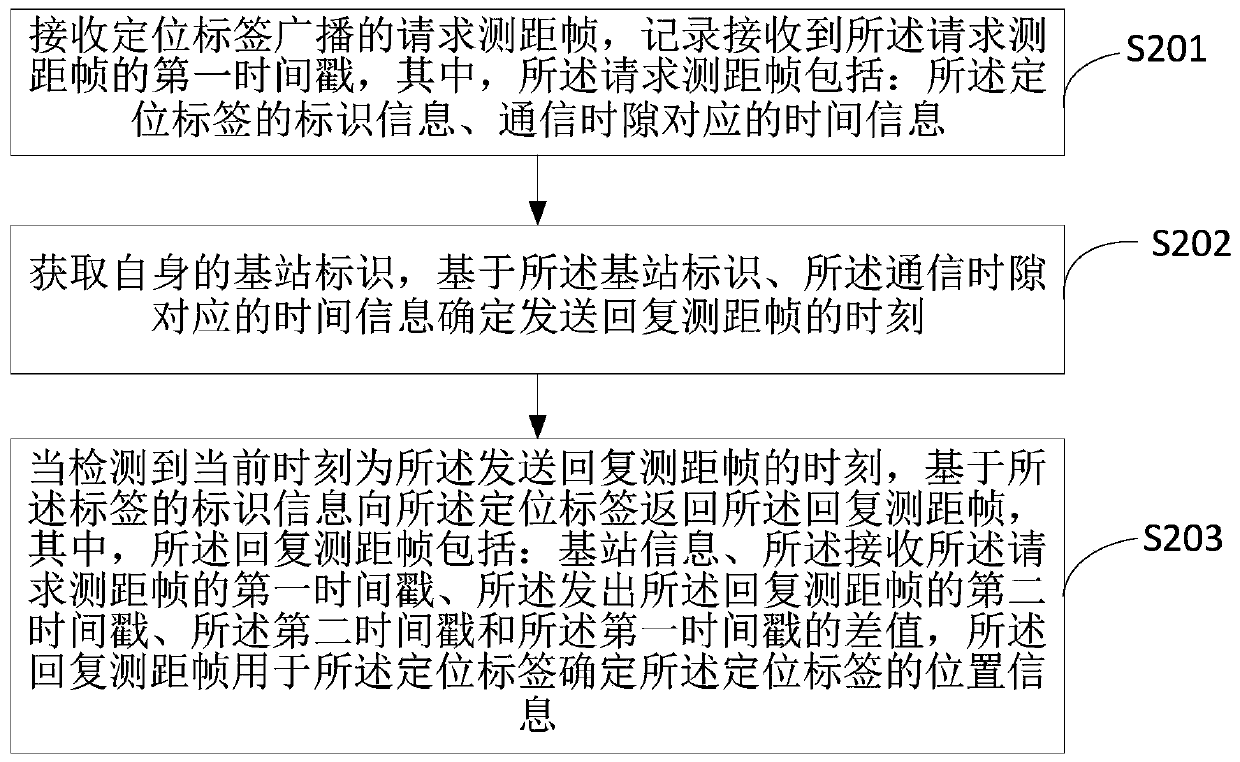
InactiveCN111372185AReduce power consumptionReduce the number of communicationsPower managementSynchronisation arrangementBroadcastingWireless positioning
The invention is suitable for the technical field of communication, and provides a wireless positioning method and device, and the method comprises the steps: broadcasting a range finding request frame to at least two positioning base stations for positioning when a positioning request is detected, and recording a first time stamp for transmitting the range finding request frame; receiving a replyranging frame returned by each positioning base station based on the request ranging frame, and recording a second timestamp of each reply ranging frame; based on the first timestamp, the second timestamp and the time difference, calculating a distance value between the positioning base station and a label sending the request ranging frame; and determining the position information of the label based on the base station information and the distance value. According to the above mode, the label can determine the position information of the label through one-time broadcasting and receiving of the reply ranging frames of the plurality of positioning base stations, the frequency of wireless communication is reduced, the positioning time is saved, and the power consumption of the positioning label is reduced.
Owner:UBTECH ROBOTICS CORP LTD
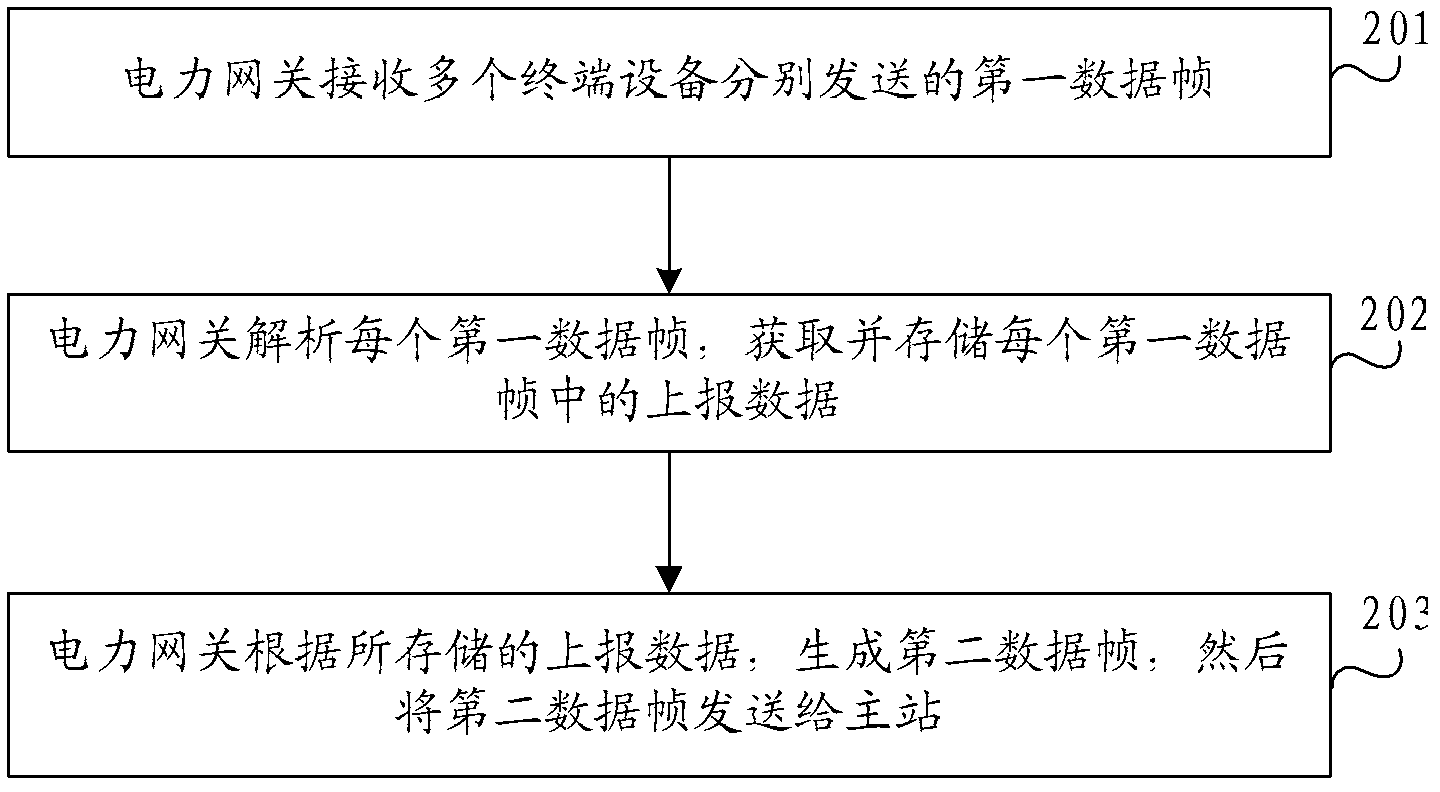
Data transmission method and system, electrical gateway and master station
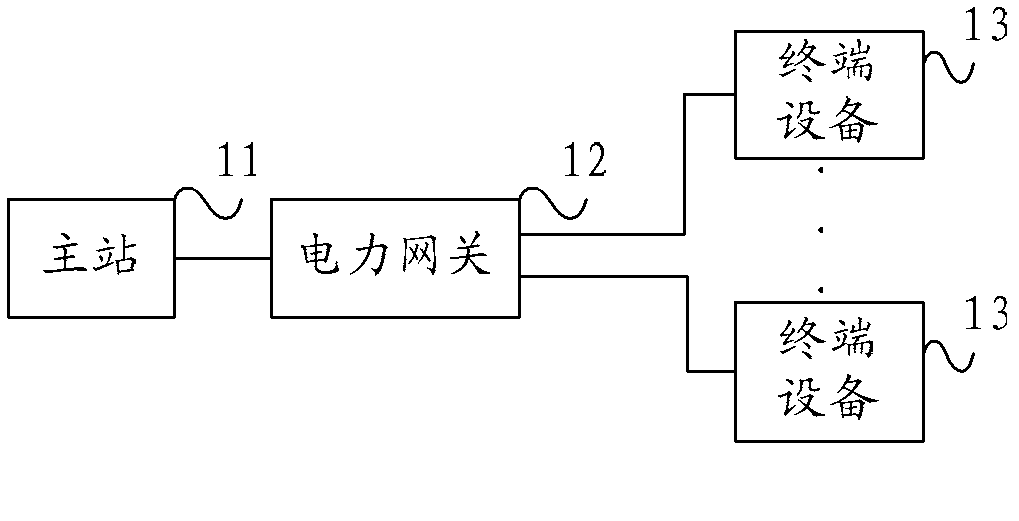
InactiveCN102714814AReduce the number of connections establishedReduce communication trafficNetwork traffic/resource managementNetwork connectionsTraffic capacityComputer hardware
Provided in the embodiments of the present invention are a data transmission method and system therefor, an electrical gateway and a master station. The method comprises: an electrical gateway receiving first data frames sent from a plurality of terminal devices respectively, the data portion of each such data frame including the reporting data of a terminal device; the electrical gateway analysing each first data frame and acquiring and storing the reporting data from each such frame; on the basis of the stored reporting data, the electrical gateway generating a second data frame, the data portion whereof includes a plurality of reporting data sets, then sending the second data frame to the master station. Under the technical solution of the present invention, an electrical gateway, by means of storing reporting data from terminal devices and transmitting in a single connection to a master station the reporting data from a plurality of terminal devices, reduces the number of communications between itself and the master station, thus also reducing wireless network traffic and limiting waste of network resources.
Owner:HUAWEI DEVICE CO LTD
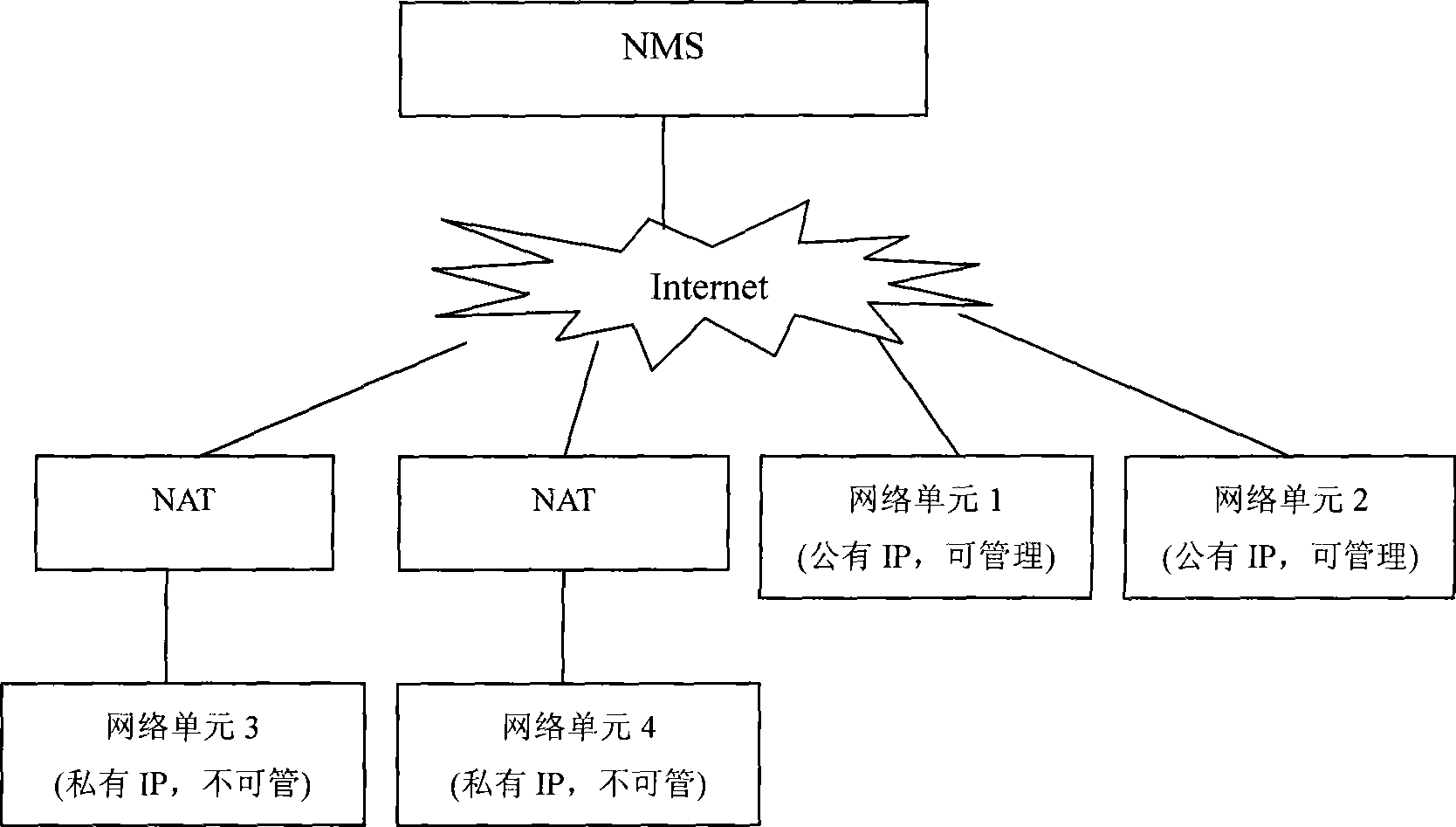
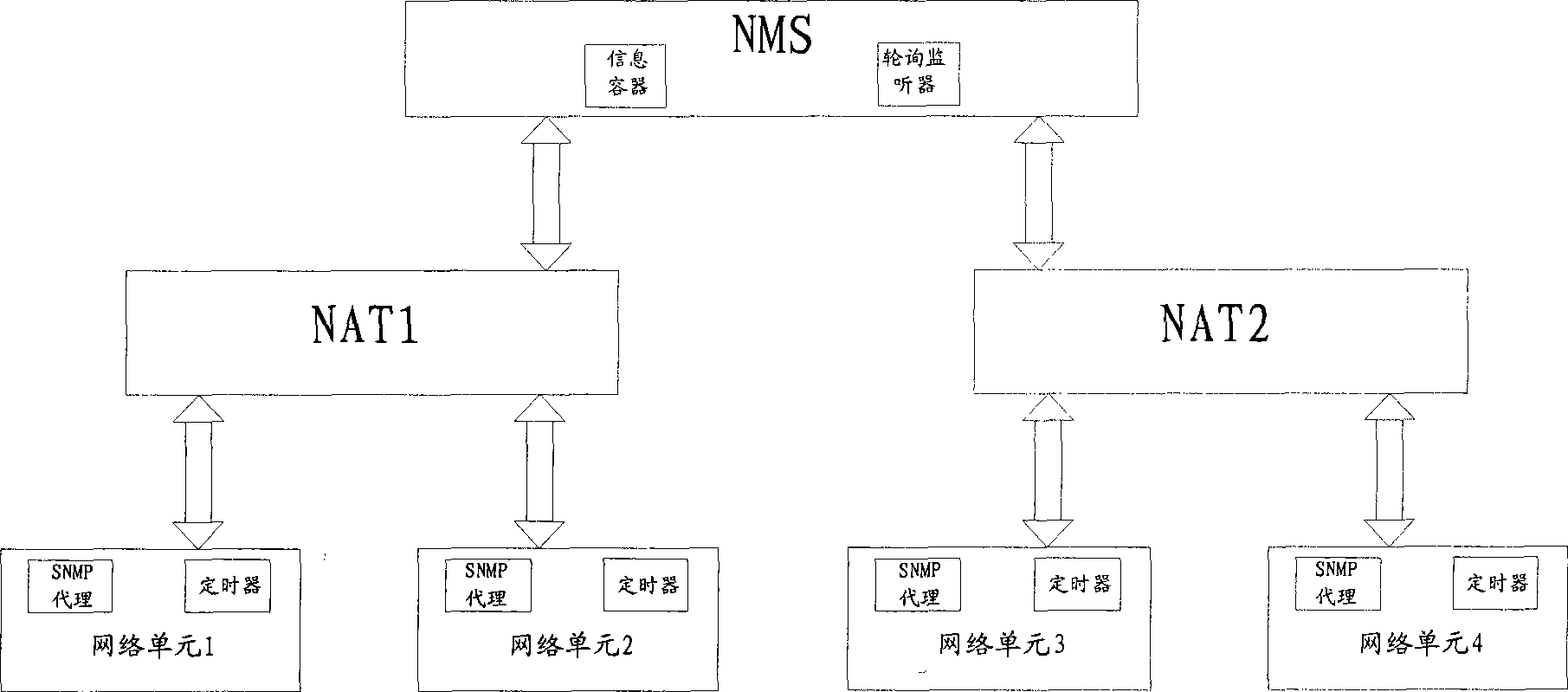
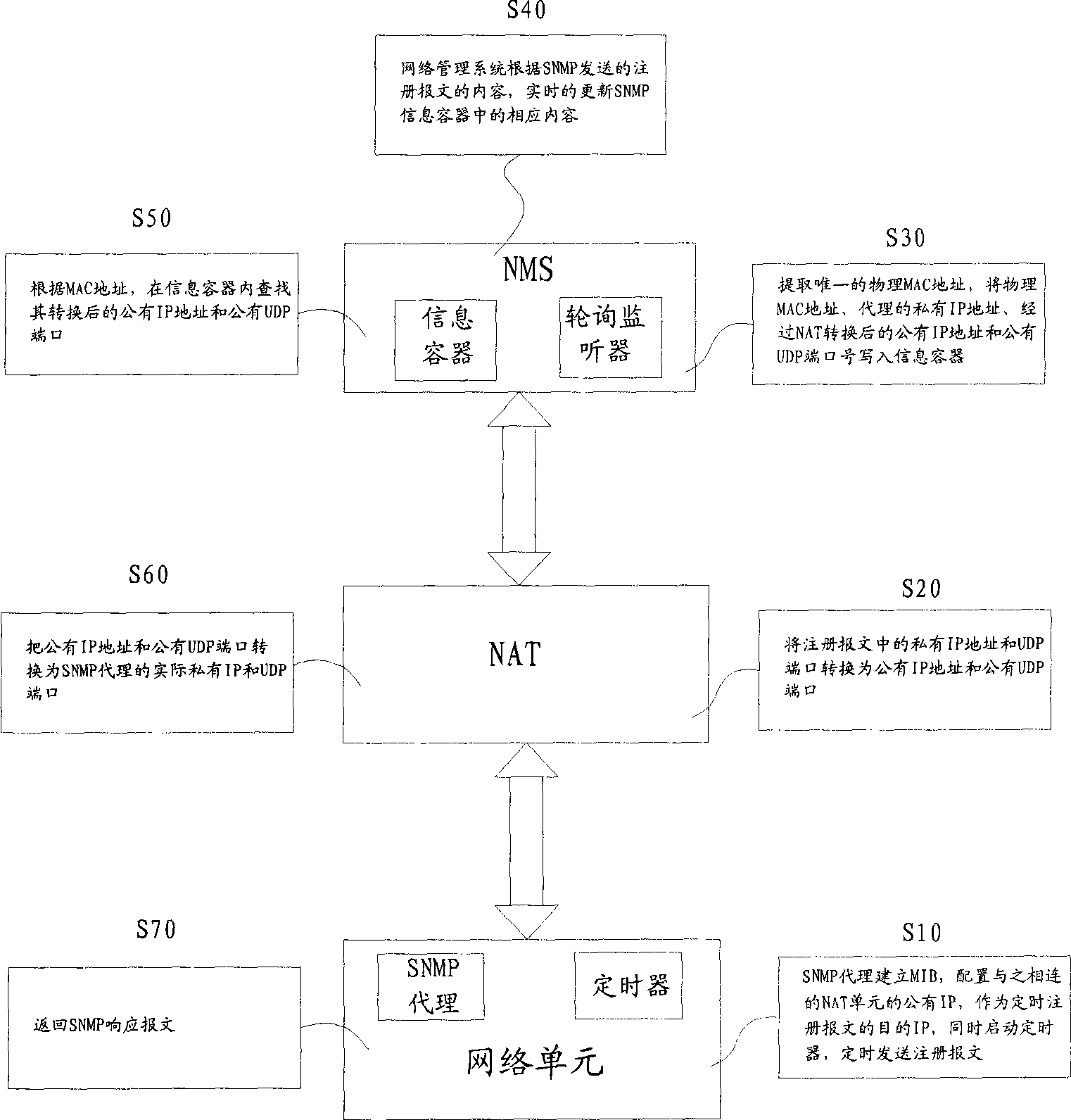
Network management system and implementing method for SNMP traversing NAT
InactiveCN101442443AIncrease profitReduce the number of communicationsNetwork connectionsPrivate IPIp address
The invention discloses a network management system of which SNMP traverses NAT. The system comprises a plurality of equipment under management, a plurality of NAT units and NMSs, each NMS is provided with an SNMP information container and a polling monitor, wherein the SNMP information container comprises a mapping list used for storing a physical MAC address substituted by the SNMP, a private IP address substituted by the SNMP, a public IP address conversed by NAT, and a UDP interface number. The invention also provides a realizing method for the system; through the system and method provided by the invention, the mutual communication between a network management platform of the public IP address and an SNMP agent of the private IP addresses can be realized, thereby achieving the management on a great number of SNMP agents, and efficiently saving IP addresses and the cost of network running and maintenance, and improving the efficiency of network management.
Owner:FENGHUO COMM SCI & TECH CO LTD
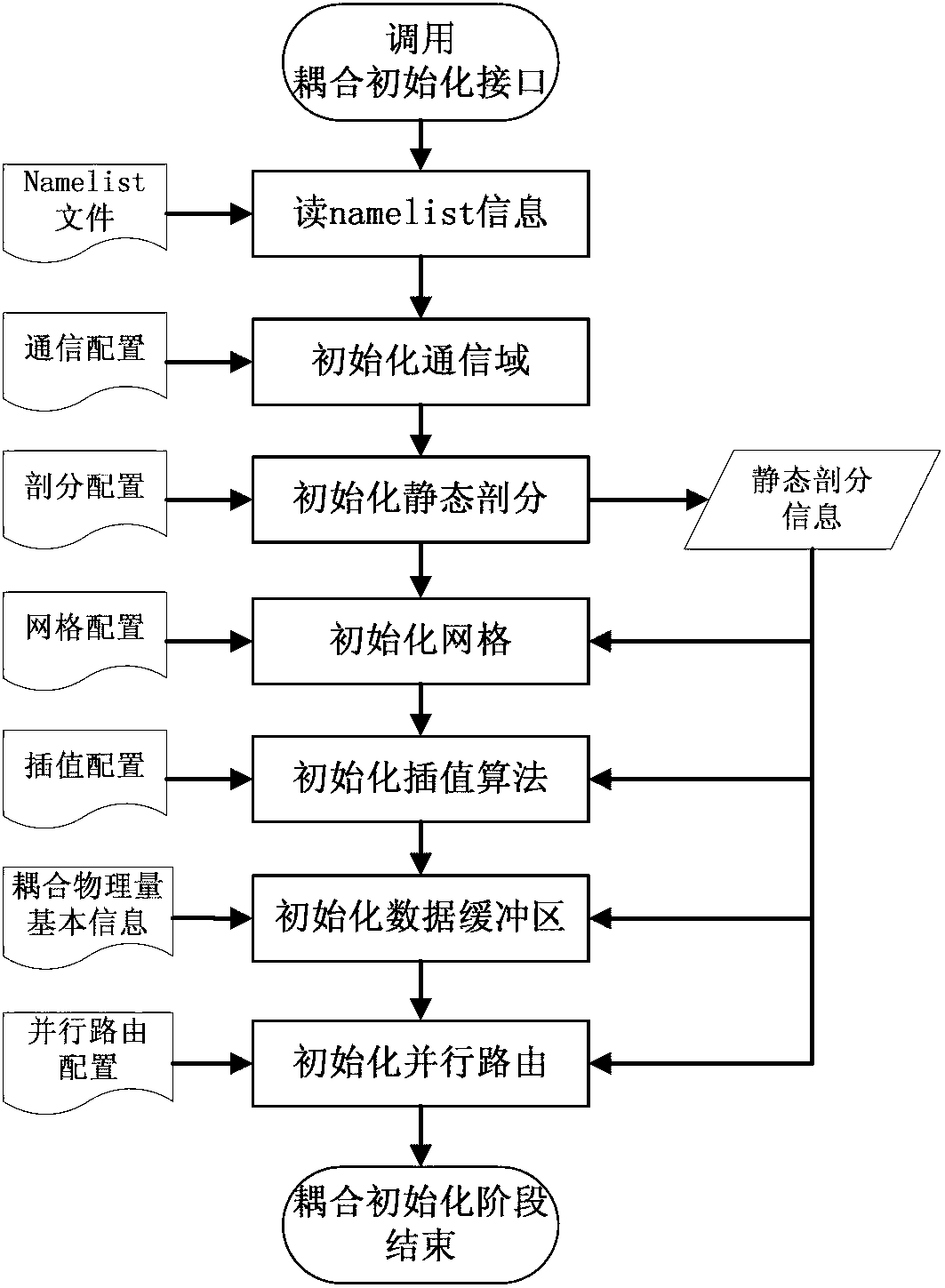
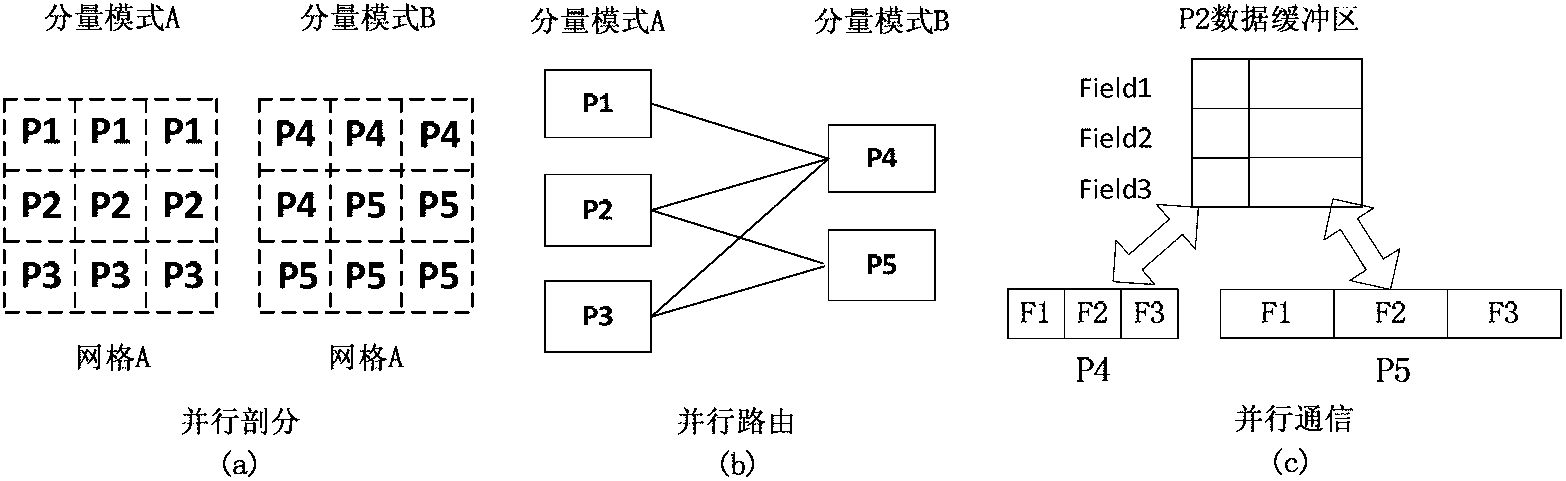
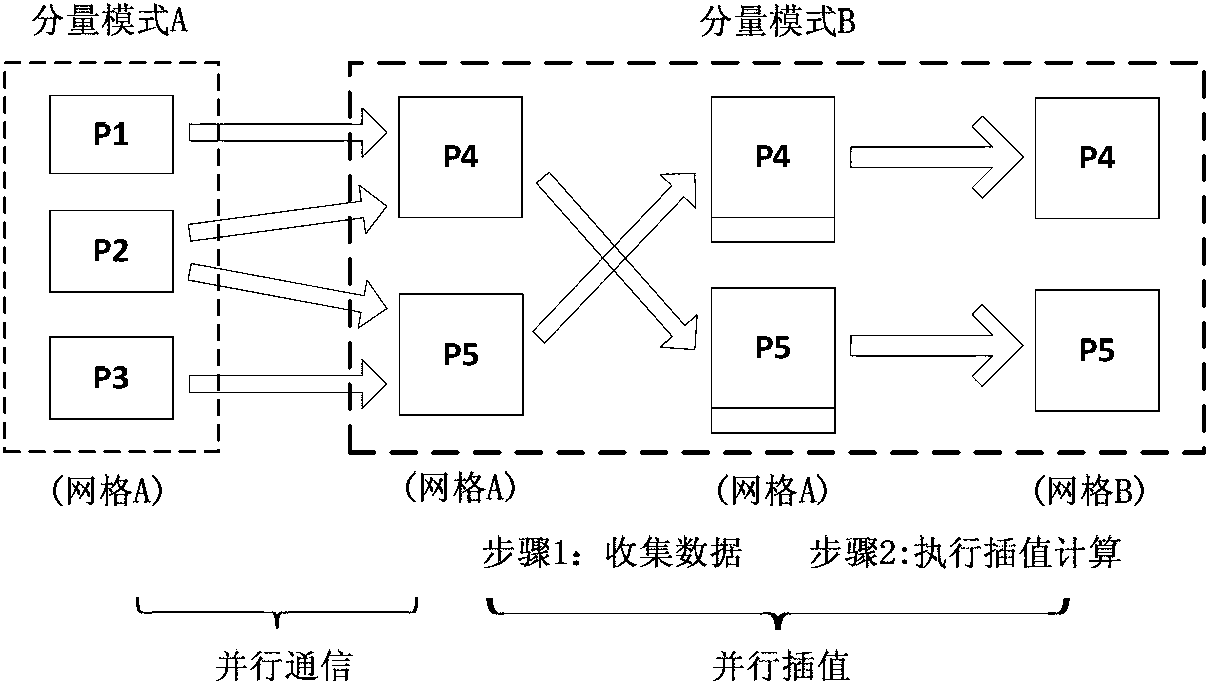
Parallel coupling method for global system mode
ActiveCN102707932AEliminate communication operationsReduce the number of communicationsInterprogram communicationConcurrent instruction executionEnd stagesCoupling
Owner:TSINGHUA UNIV
Method for controlling heliostats in tower type solar-powered heat collecting device
ActiveCN102997453AReduce the number of communicationsGuaranteed accuracySolar heating energySolar heat collector controllersHeliostatTracking model
The invention relates to a method for controlling heliostats in a tower type solar-powered heat collecting device. A list of the change data of the height angle and azimuth angle of each heliostat is established by using a relevant mathematical model, so that the heliostats can accurately track sunlight and project light spots onto specified positions in a heat collector at any moment; the face mass center positions of the heliostats with mechanical errors are founded, and a novel tracking model method is provided for the positions, so that mechanical errors of the heliostats are eliminated; and a heliostat control data optimizing method matched with mechanical transmission is given under the condition of meeting controllable accuracy for tolerating influences caused by mechanical errors of a control system, so that the system cost is lowered, and the system reliability is enhanced.
Owner:陕西西科博尔科技有限责任公司
Event-driven coal mine underground wireless sensor network system
InactiveCN106376048AReduce the number of communicationsReduce collectionPower managementNetwork topologiesSafety monitoringCoal
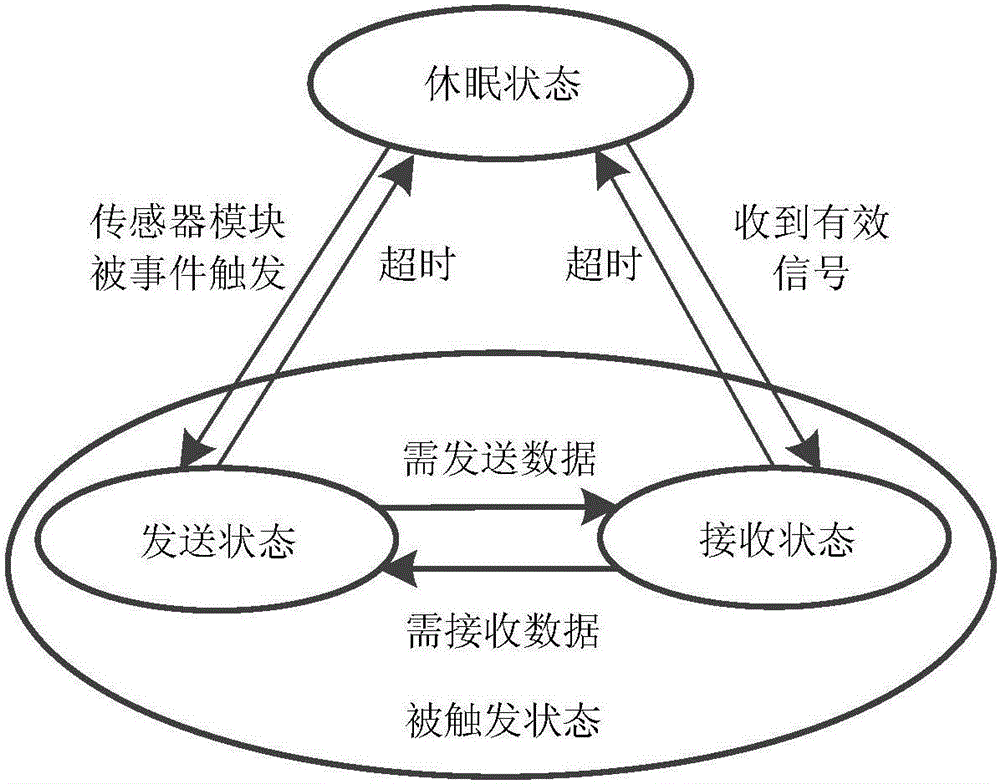
The invention discloses an event-driven coal mine underground wireless sensor network system which comprises a base station device and an underground node device. An underground node wireless communication module comprises a sending state, a receiving state and a hibernation state. Three working states of the underground node wireless communication module can be converted to each other. An event-driven wireless sensor network in operation determines whether to trigger an event and transmit data to a base station by monitoring and judging whether data exceed a threshold value. The system has the characteristics of high communication efficiency and low operation energy consumption. According to the invention, the system is combined with coal mine underground safety production needs; through reasonable threshold setting and an improved routing protocol, the number of times of invalid communication among nodes is remarkably reduced; the communication efficiency is improved; the energy consumption of the nodes is reduced; the service life of a network is prolonged; collected useless data are reduced; in the case of an accident or alarm, useful alarm data can be quickly extracted; the event-driven network technology is applied to coal mine underground safety monitoring; and the system is an efficient coal mine safety monitoring system.
Owner:CHINA UNIV OF MINING & TECH (BEIJING)
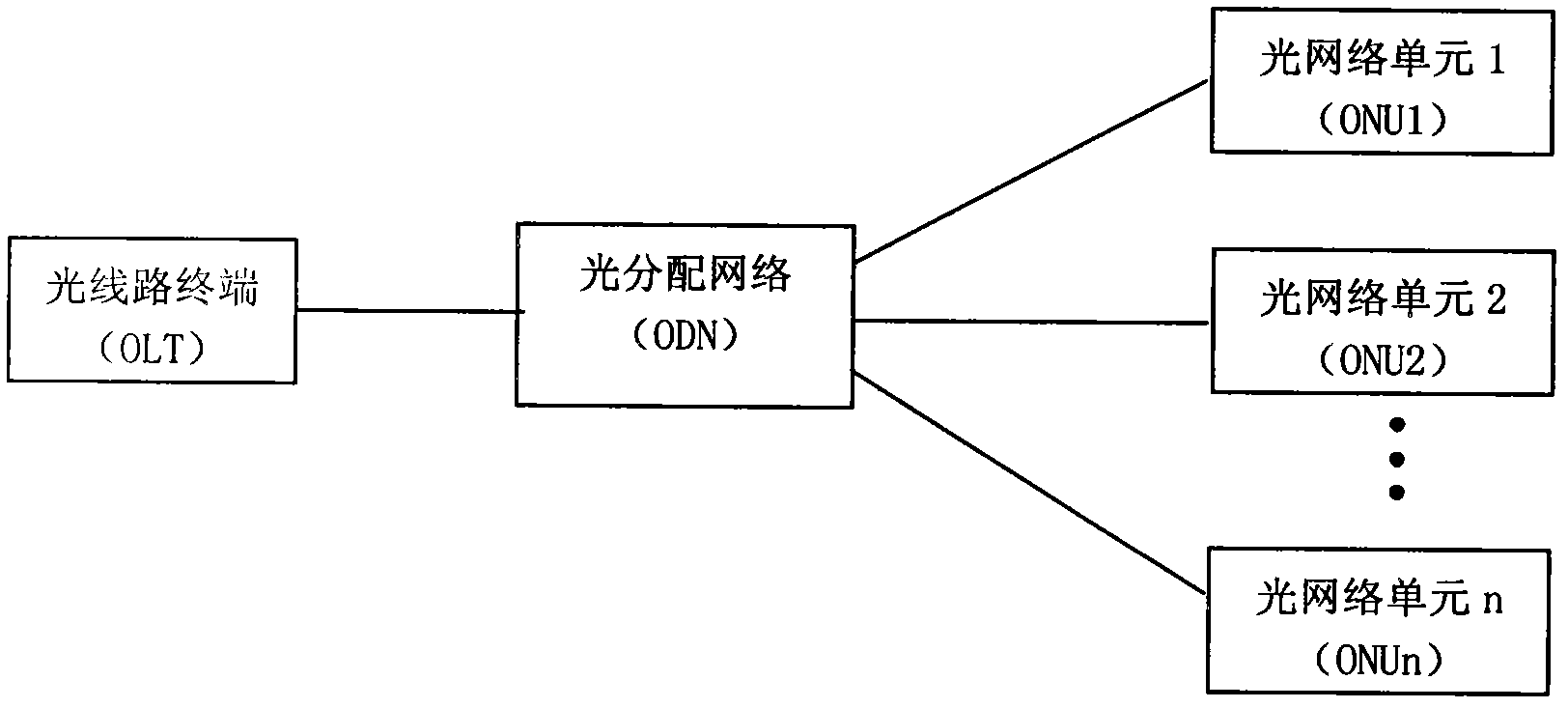
Optical network unit (ONU) energy-saving method for improving bandwidth utilization rate
InactiveCN101969584AIncrease profitSimplified Interaction ProtocolMultiplex system selection arrangementsElectromagnetic transmissionStart timeData needs
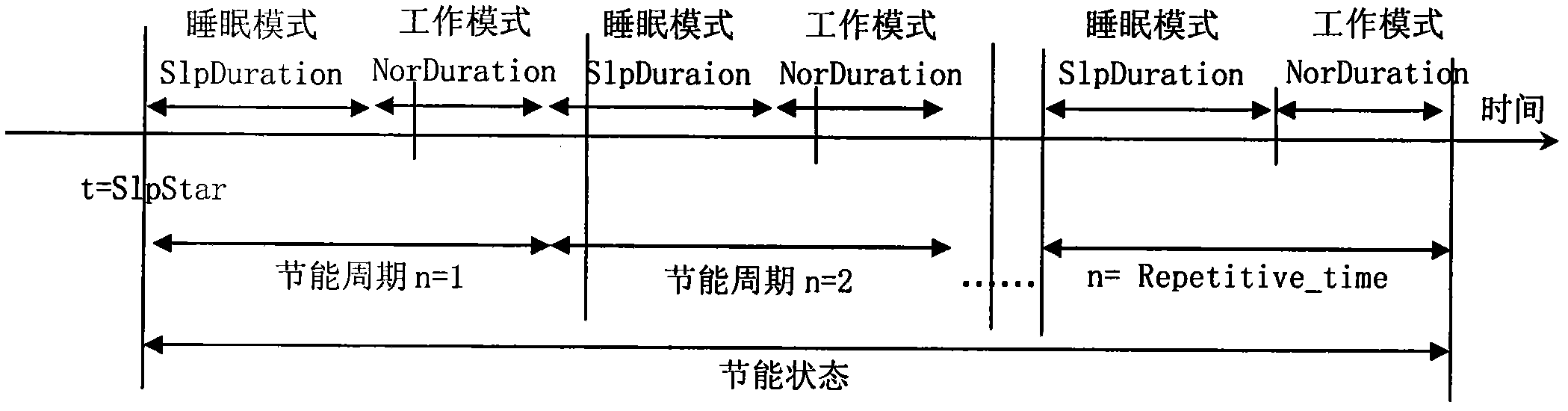
The invention relates to an optical network unit (ONU) energy-saving method for improving bandwidth utilization rate, which comprises the following steps that: an optical line terminal (OLT) sets a judgment condition that the ONU enters an energy-saving state; the OLT respectively sets the starting time of a first energy-saving period when the ONU enters the energy-saving state, the duration of a sleep mode, the duration of a work mode, and the times of the energy-saving period and sets a minimum authorization interval T1; when the ONU meets the judgment condition of the energy-saving state, the OLT sends a permission message for entering the energy-saving state; after receiving the permission message, the ONU checks whether data needing sending exists or not at the time; if the data needing sending do not exist, the ONU is switched to the energy-saving state from a normal state in the set time of the first energy-saving period; after entering the sleep mode, the ONU is immediately switched to the normal state if the data needing sending exist; and when the periodic alternate times of the sleep mode and the work mode reach a set value, whether the energy-saving condition is met or not is rejudged. By the method, the communication times between the OLT and the ONU can be reduced and the bandwidth utilization rate is improved.
Owner:FENGHUO COMM SCI & TECH CO LTD
Distributed w-event differential privacy infinite streaming data distribution method
ActiveCN105095447AEasy to deployPrevent leakageWebsite content managementSpecial data processing applicationsStreaming dataData center
The invention discloses a distributed w-event differential privacy infinite streaming data distribution method. Through adopting a function monitoring technology based on a geometrical method to assist privacy budget allocation of users, the synchronization distribution of privacy budget among the users can be achieved. Meanwhile, the data distribution scheme of the invention is independent on a credible data centre, and all transmitted data is data containing noise and has higher safety. The invention provides two high available w- event differential privacy distribution schemes which are a dBD scheme and a dBA scheme, and can be flexibly selected according to characteristics of actual data.
Owner:WUHAN UNIV
Self-adaptive electric power carrier wave concentrator
InactiveCN101136723AReduce the number of communicationsImprove communication success rateNon-electrical signal transmission systemsCode division multiplexCode division multiple accessCarrier signal
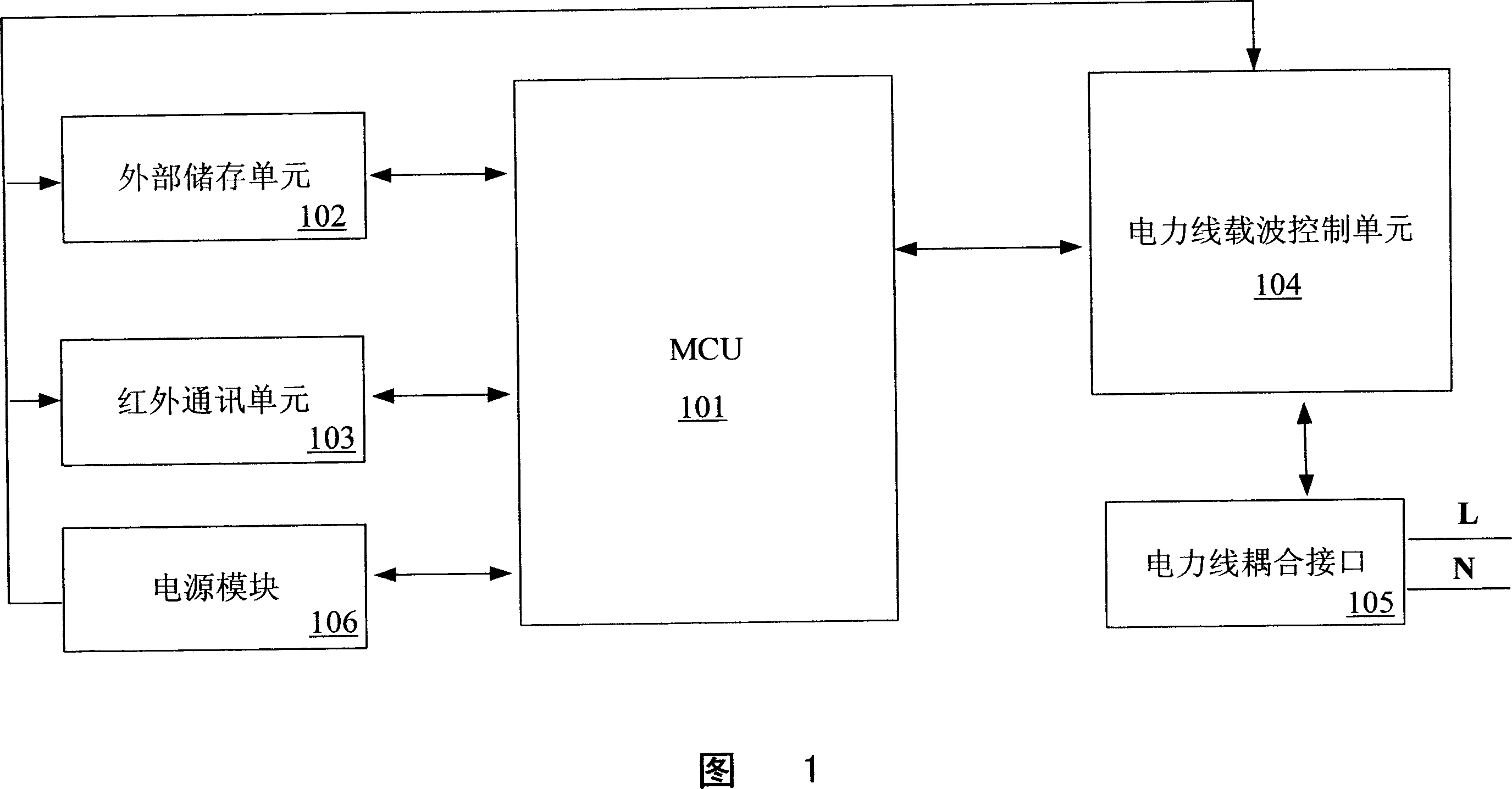
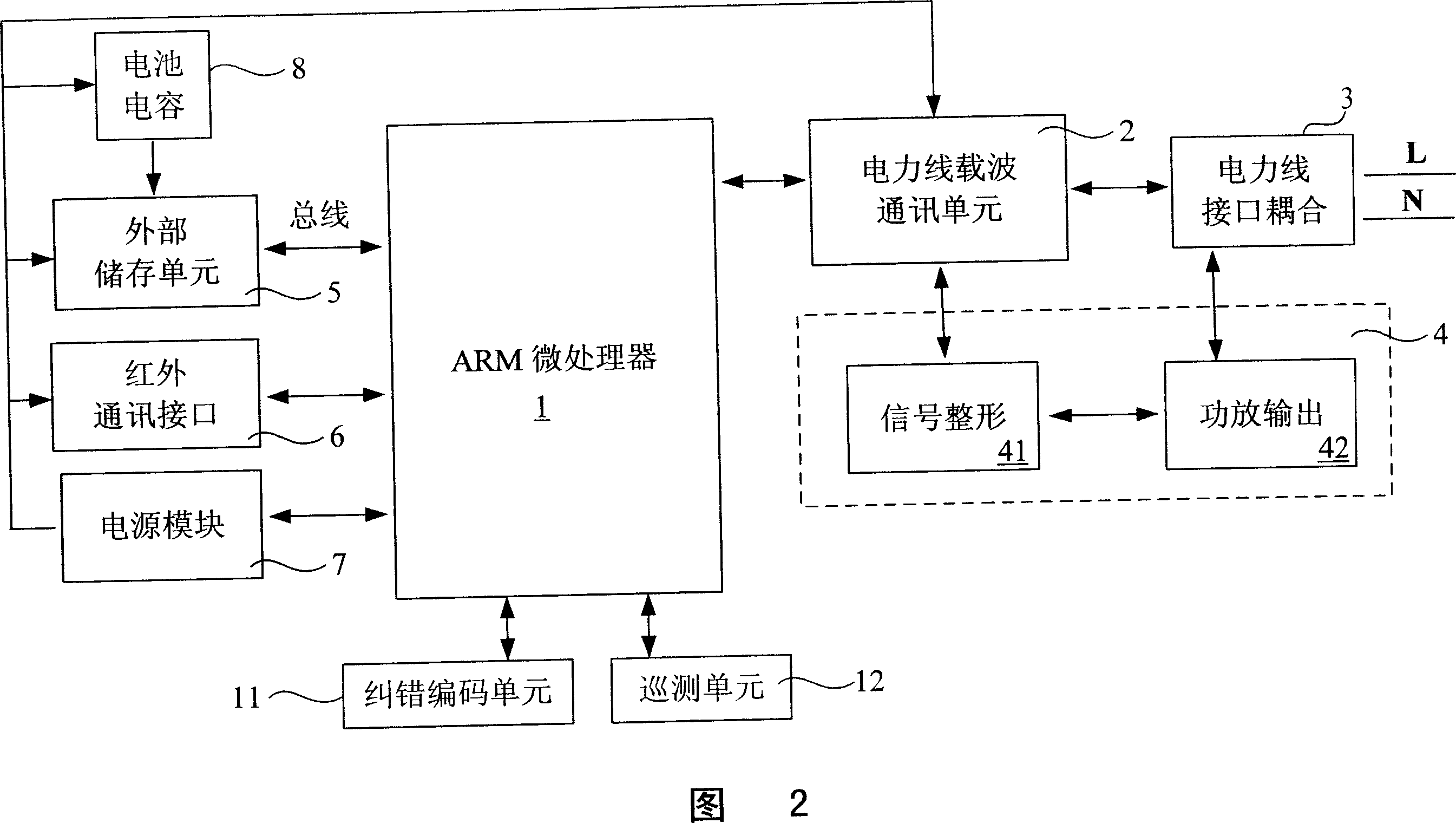
The concentrator includes microprocessor, electric power carrier communication unit (EPCCU) connected to microprocessor, external memory unit, infrared communication interface, power line coupling interface (PLCI) connected to EPCCU, and power amplifier circuit connected between EPCCU and PLCI. Characters are that being composed of dedicated frequency extended carrier wave chip, EPCCU is in use for communicating with each meter-reading terminal (MRT) in CDMA frequency extended mode; being composed of amplifying circuit in sine wave, power amplifier circuit is in use for carrying out sine wave amplification for signal output from EPCCU; the concentrator also includes an error correction coding unit; a polling unit in use for executing polling step, and establishing routing list communicated with each MRT. The invention raises stability of communication under condition without raising transmission power so as to be in favor of reducing harmonic wave pollution of power line.
Owner:SHANGHAI XIETONG TECH
Anti-collision method for identifying multiple radio frequency identification (RFID) tabs
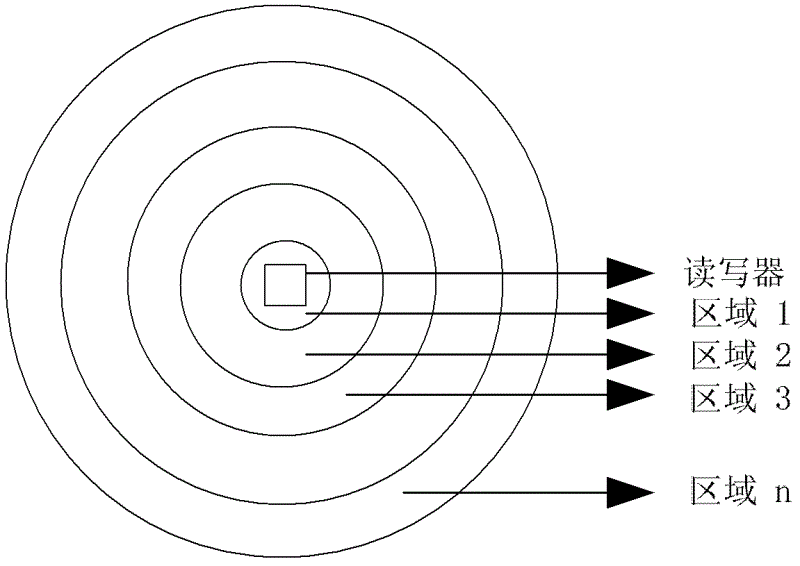
InactiveCN102622564AImprove efficiencyImprove communication stabilitySensing record carriersTime rangeReceived signal strength indication
The invention discloses an anti-collision method for identifying multiple radio frequency identification (RFID) tabs, which is characterized in that according to the index of a radio signal strength indicator (RSSI) communicating between the RFID tabs and a reader, regional division is performed on the induction range of the reader to form a plurality of different induction areas; the RFID tabs covered by each induction area form a corresponding tab group; and moreover, data are transmitted by the RFID tabs in different tab groups at different time ranges, whereas data transmission is realized between the RFID tabs in the same one group and the reader by adopting a conventional anti-collision algorithm. The problem that normal communication cannot be realized because signal collision is generated in the communication process of a great number of tabs and the reader can be effectively solved, the identification efficiency under such the condition is greatly increased, and the misreading rate can be effectively reduced. The reader is higher in reading efficiency and communication stability when reading the information of a great amount of tabs.
Owner:SHANGHAI MARITIME UNIVERSITY
Safety verification method, device and system based on non-interactive zero-knowledge
ActiveCN104717067AEnhanced anonymityAchieve traceabilityKey distribution for secure communicationUser identity/authority verificationNon-interactive zero-knowledge proofCentral node
The invention discloses a safety verification method, device and system based on non-interactive zero-knowledge, and relates to the field of electronic safety verification. The method includes the steps of public secret keys and private secret keys of a central node device and other local node devices; sending the identity (ID) and the identity commitment value of any local node device I to the central node device after the local node device I obtains the identity commitment value with the ID of the local node device I as the commitment object; sending certificate information to the local node device I through the central node device according to the private secret key of the central node device, the ID of the local node device I and the identity commitment value of the local node device I; establishing the non-interactive zero-knowledge proof based on the certificate commitment value after the local node device I obtains the certificate commitment value with the certificate information as the commitment object, and conducting signing on key information on service according to the non-interactive zero-knowledge proof, the public secret key of the local node device I and the private secret key of the local node device I; sending the key information on the signed service to a verification device through the local node device I.
Owner:LIAONING MOBILE COMM
TDOA (Time difference of Arrival) positioning method and system based on time correction and device
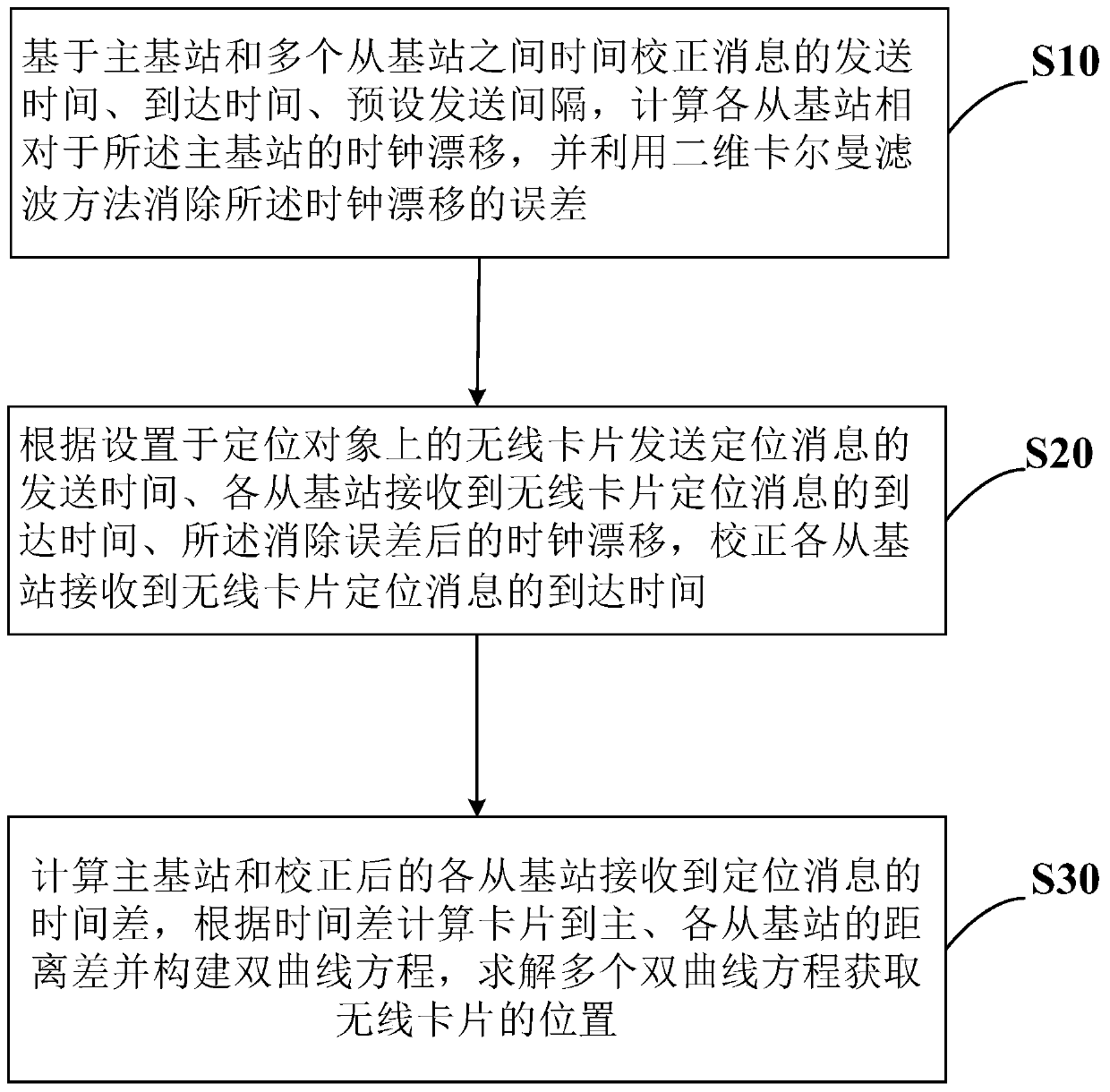
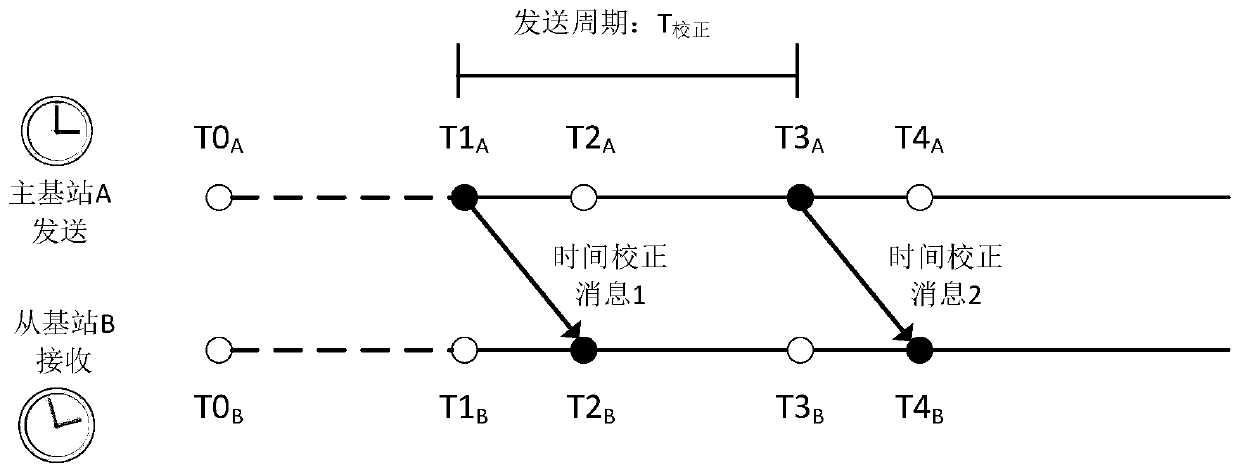
InactiveCN110174641AHigh precisionReduce power consumptionPosition fixationClock driftSystems approaches
The invention belongs to the technical field of indoor wireless positioning, particularly relates to a TDOA (Time Difference of Arrival) positioning method and system based on time correction, and a device, and aims to solve the problems of high TDOA positioning power consumption and low positioning time synchronizing accuracy. The method comprises the following steps: calculating clock drift based on the sending time, time of arrival and preset sending interval of a time correction message between a main station and a plurality of slave stations, and eliminating the clock drift error by usinga two-dimensional Kalman filtering method; correcting time when positioning messages are received from the slave stations according to positioning message sending time of a wireless card, the receiving time of each slave station and the error-eliminated clock drift; and calculating the difference between time when the main station and each corrected slave station receive the positioning message,calculating the distance between the card to each slave station according to the time difference, building dual-curve equations, and solving the plurality of dual-curve equations to obtain the position of the wireless card. Through adoption of the method, the positioning power consumption of the TDOA is lowered, and the positioning time synchronizing accuracy is improved.
Owner:INST OF AUTOMATION CHINESE ACAD OF SCI
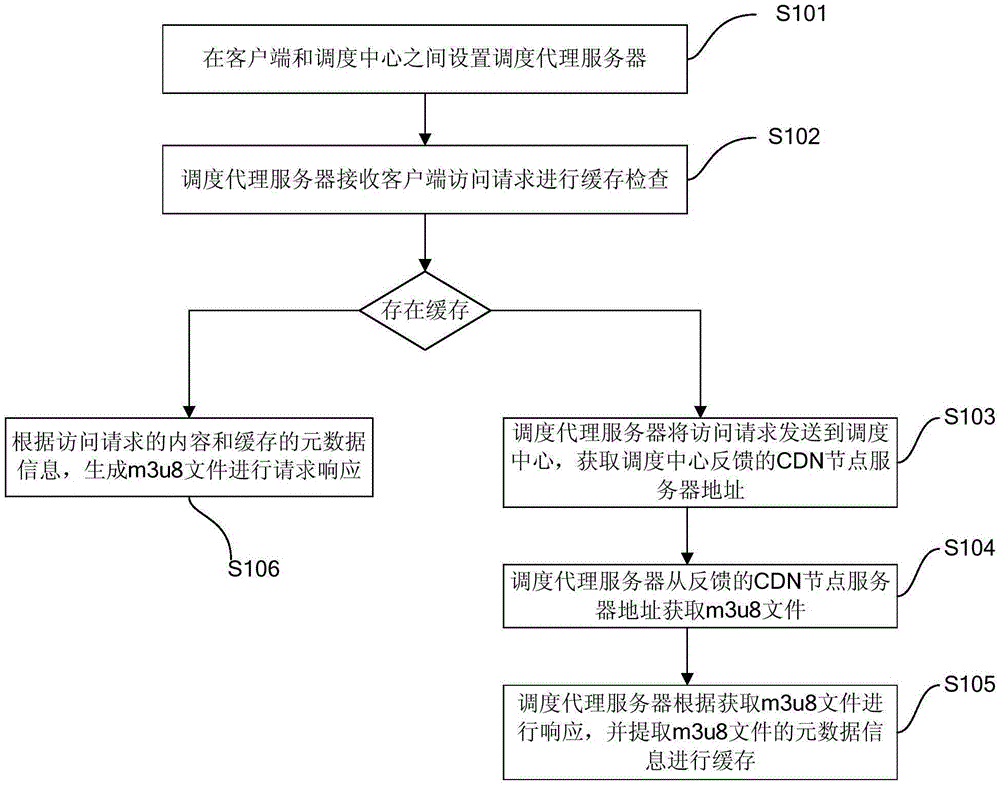
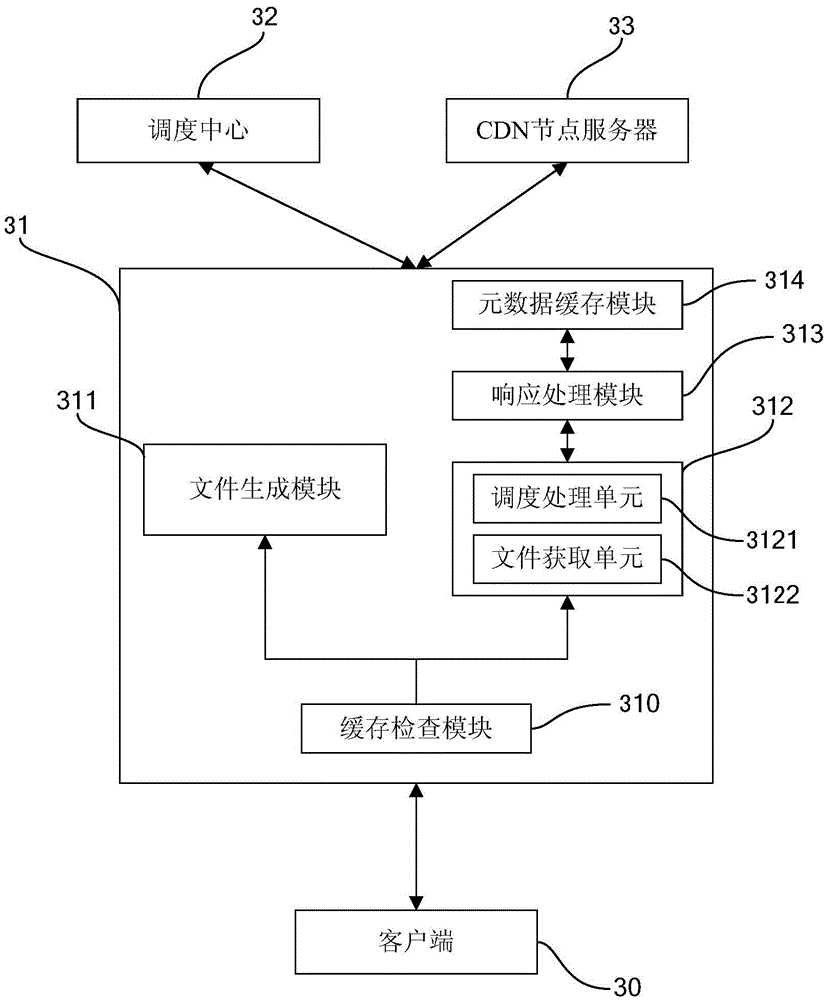
Response processing method and system and scheduling proxy server for CDN platform
InactiveCN105897850AReduce the number of communicationsHigh speedTransmissionClient-sideProxy server
The invention provides a response processing method and system and scheduling proxy server for a CDN platform. The CDN platform comprises a scheduling center and CDN nodes. The method is characterized in that the scheduling proxy server is configured for the scheduling center; the scheduling proxy server receives an access request, interacts with the scheduling center and obtains an m3u8 file from the CDN nodes; and the scheduling proxy server responds to the access request according to the obtained m3u8 file. Through the method, system and the scheduling proxy server, interaction frequency between a client and the server can be reduced, communication stability and smoothness are improved, and response efficiency is guaranteed.
Owner:LETV CLOUD COMPUTING CO LTD
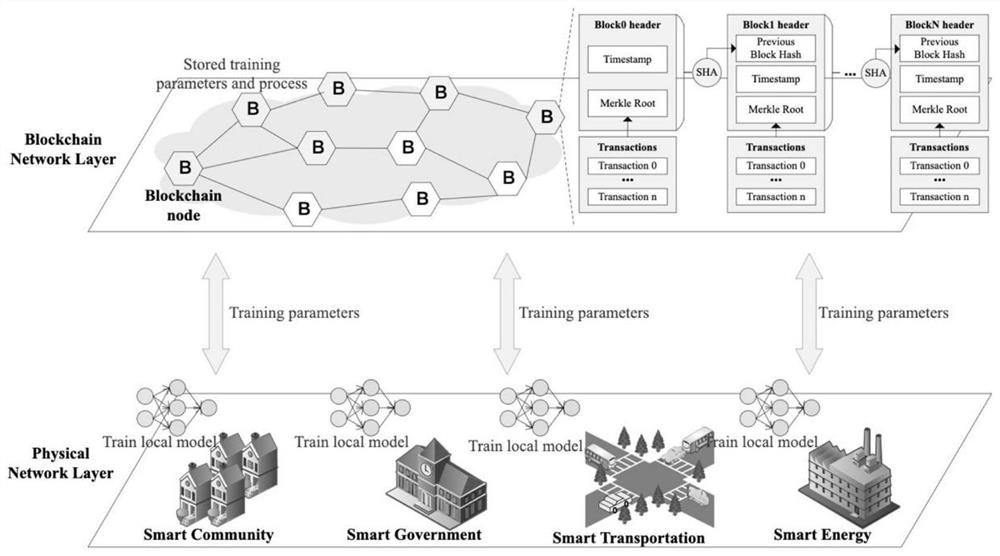
Industry Internet of Things data lightweight trusted sharing technology based on block chain
ActiveCN112395640AReduce the number of communicationsIncrease motivationFinanceInterprogram communicationComputer networkPrivacy protection
The invention discloses an industry Internet of Things data lightweight trusted sharing mechanism based on a block chain. The mechanism utilizes the block chain and a federated learning algorithm to realize data sharing and privacy protection. The Raft algorithm is optimized in the aspects of owner selection, log replication and safety, the consensus efficiency is improved, and the requirements ofa smart city for time delay and safety are met. A transaction mechanism is designed based on a smart contract, thus standardizing a transaction process, and improving the enthusiasm of an Internet ofThings data holder to participate in data sharing through excitation.
Owner:STATE GRID HEBEI ELECTRIC POWER CO LTD +2
A digital bus system based on private SMS communication and its working method
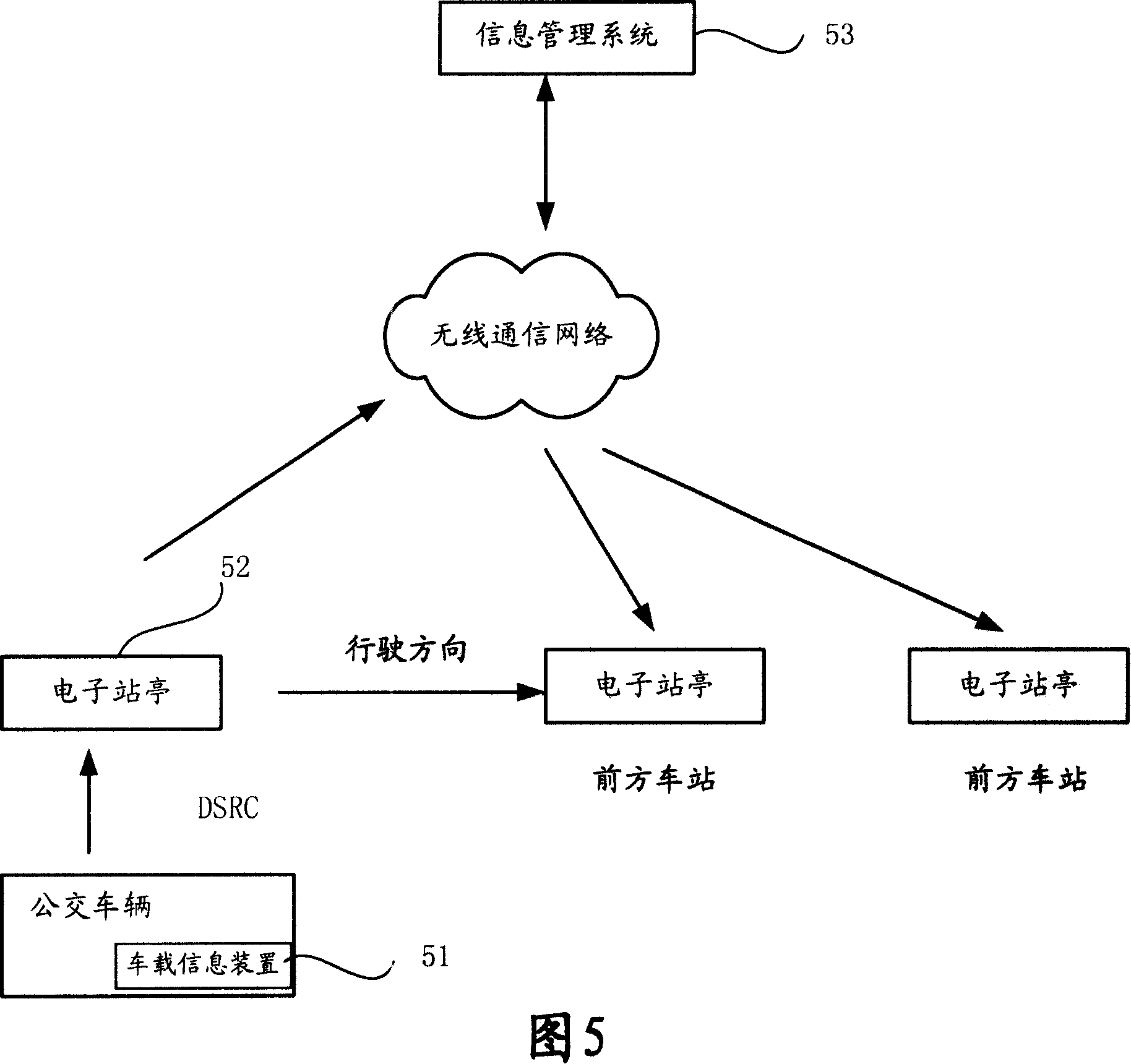
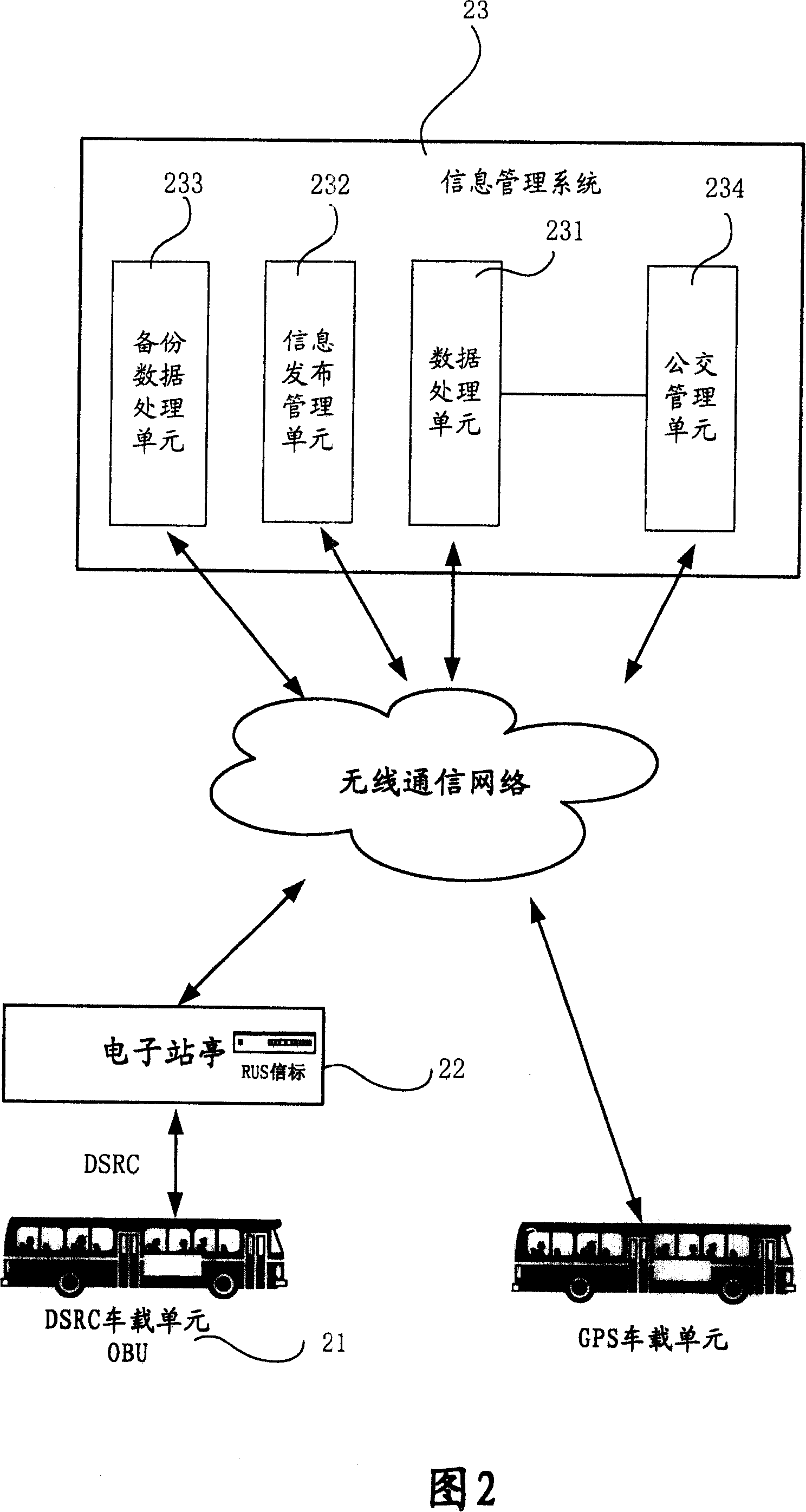
InactiveCN101123516AAvoid troubleSave coordination time and engineering effortSpecial service provision for substationTelephonic communicationEmbedded systemWireless communication systems
The present invention a digital public transportation system based on the dedicated short-range communication and a working method. The system comprises at least one on-board information device mounted on a bus, at least one electronic bus station and an information management system. The electronic bus station exchanges information with the on-board information device via a dedicated short-range communication network to record bus arrival information, which is then sent to the information management system for processing via a wireless communication network; and the information management system comprising at least one data processing unit collects and stores the realtime information of the bus, processes the received arrival information sent by the electronic bus station, calculates the estimated time when the bus arrives every electronic bus station ahead and generates arrival forecast information, which is then sent to every electronic bus station ahead for display via the wireless communication network. The present invention uses the mature and stable DSRC wireless short-range communication technology and accurately forecasts the arrival of the bus, the stability of the system is good, and the cost of construction is low.
Owner:新世界(中国)科技传媒有限公司
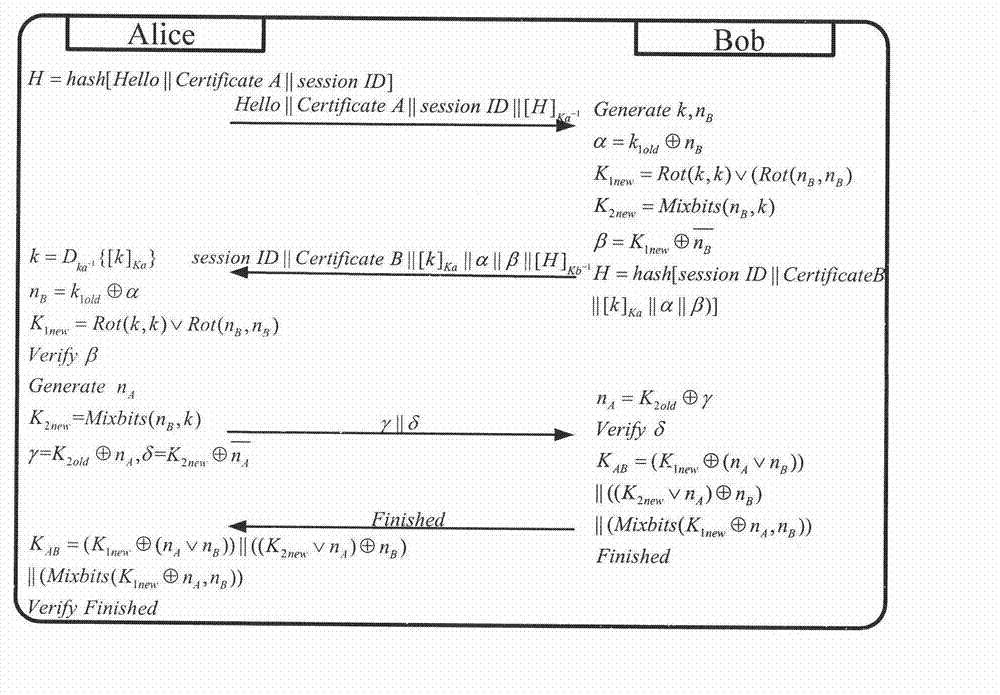
Wireless network lightweight class authentication key negotiation protocol based on digital certificate
InactiveCN102833748AReduce the number of communicationsSmall amount of calculationSecurity arrangementKey-agreement protocolPassword
The invention relates to a wireless network lightweight class authentication key negotiation protocol based on a digital certificate. A user identity is subjected to dual authentication through a 'certificate private key and protection key' dual authentication system and a 'protection key' dynamic negotiation mechanism by sharing a dynamic protection key according to a public key password; a user proves the session holdness and the private key owning property by exchanging the certificate according to a private key signature, so that primary authentication is executed; and due to protection key sharing, secondary authentication is executed. Important parameters are protected by two parties through the protection key after the last session is finished; the correctness of the key is confirmed through a new protection key calculated at the session; during each communication, when the parameters are exchanged, the correctness can be checked. Negotiation for key groups and parameter exchange adopt simple bit computation; and the key updating is confirmed by Finished messages. According to the protocol, a dynamic ID is set to dynamically select whether the shared old parameters are used for calculating the key of the session; and safety and high efficiency are guaranteed, and the flexibility of the protocol is improved.
Owner:BEIJING UNIV OF POSTS & TELECOMM
Safe and efficient consensus mechanism implementation method and system
ActiveCN112329051AReduce the number of communicationsImprove consensus efficiencyDatabase management systemsDatabase distribution/replicationComputer networkSecret share
The invention discloses a safe and efficient consensus mechanism implementation method and system, and the method comprises the steps that each node calculates a random number of a current round according to a secret value revealed by a main node of a previous round, and determines the main node of the current round; each round of master node is responsible for collecting votes of each node to a block extracted by the previous round of master node, proposing a new block, revealing an original secret value, selecting a new secret value and disclosing a new secret value commitment; if each nodedoes not collect the voting result sent by the main node within the specified time, each node broadcasts a decryption secret sharing value to recover the secret value of the current main node, calculates the main node of the next round, and votes again. According to the method, the leader replacement process is organically coupled with the normal process, the introduced PVSS scheme can still recover the random number of the current round under the condition that the main node does not respond, the communication traffic and the communication time required for confirming one block are reduced through the chained Hotsuff thought, the communication frequency required in the consensus process is reduced, and the consensus efficiency, performance and safety are improved.
Owner:DATA ASSURANCE & COMM SECURITY CENT CHINESE ACADEMY OF SCI
Small file combination method for spatio-temporal data in smart city
ActiveCN108460121AReduce the number of communicationsThe merge algorithm is simple and efficientCharacter and pattern recognitionData miningAccess timeSmart city
The invention discloses a small file combination method for spatio-temporal data in a smart city. A small file is combined to serve as a microscopic data layout mechanism, system I / O performance of the system can be effectively improved, and a user access time delay is reduced. The characteristics of the spatio-temporal data are analyzed, historical user access information is subjected to parametric representation and spatio-temporal attribute extraction, the access information is subjected to hierarchy clustering by an AGNES (AGglomerative NESting) algorithm in a spatio-temporal attribute domain, a clustering result is subjected to weighted calculation based on access density, and a relevant spatio-temporal range is found. Finally, the spatio-temporal range is used for guiding the combination of small files. An experiment result indicates that the algorithm is simple and efficient, and the access efficiency of the spatio-temporal data small file in the system is greatly improved.
Owner:CHONGQING UNIV OF POSTS & TELECOMM
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com