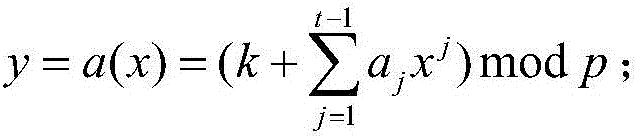Patents
Literature
328 results about "Key sharing" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
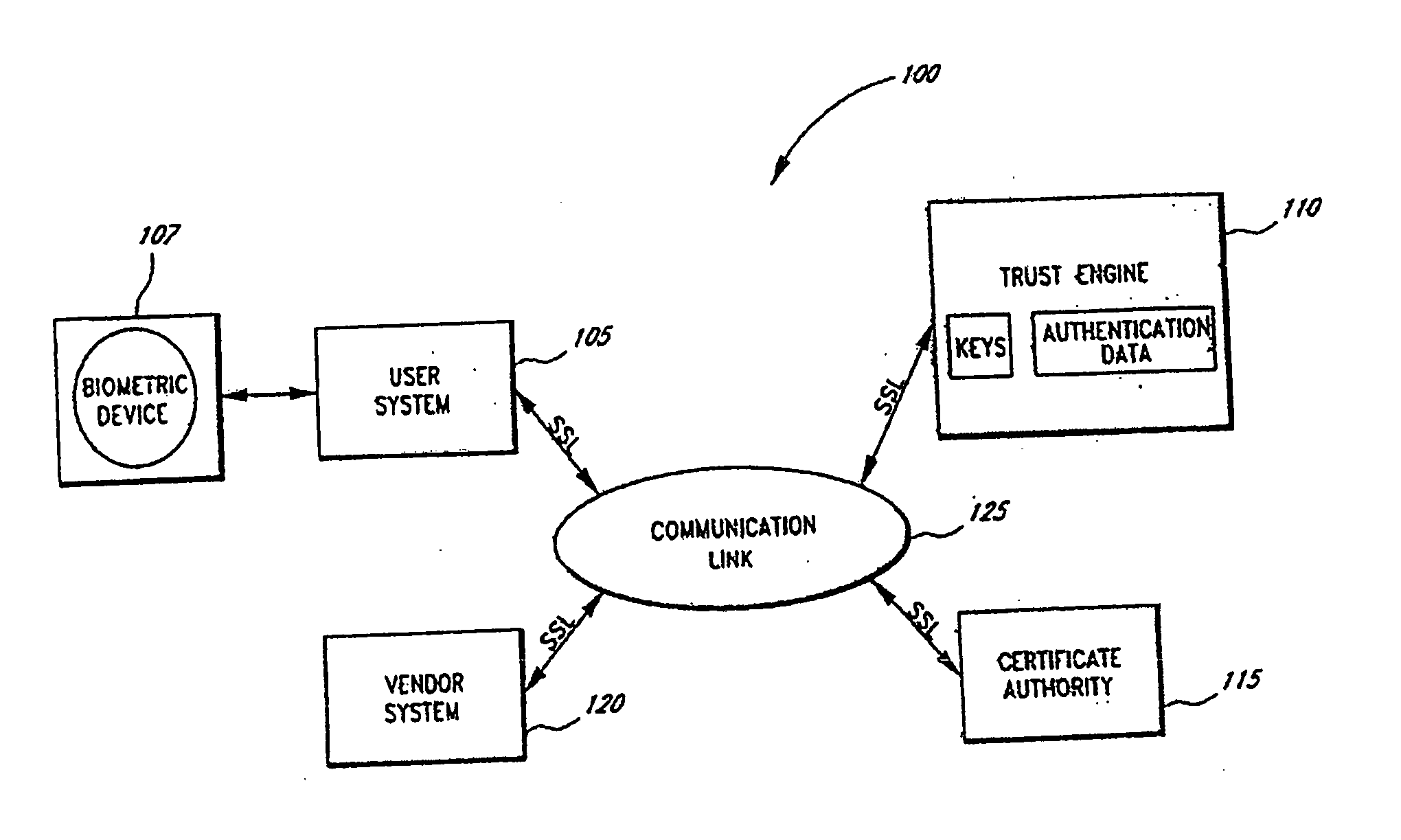
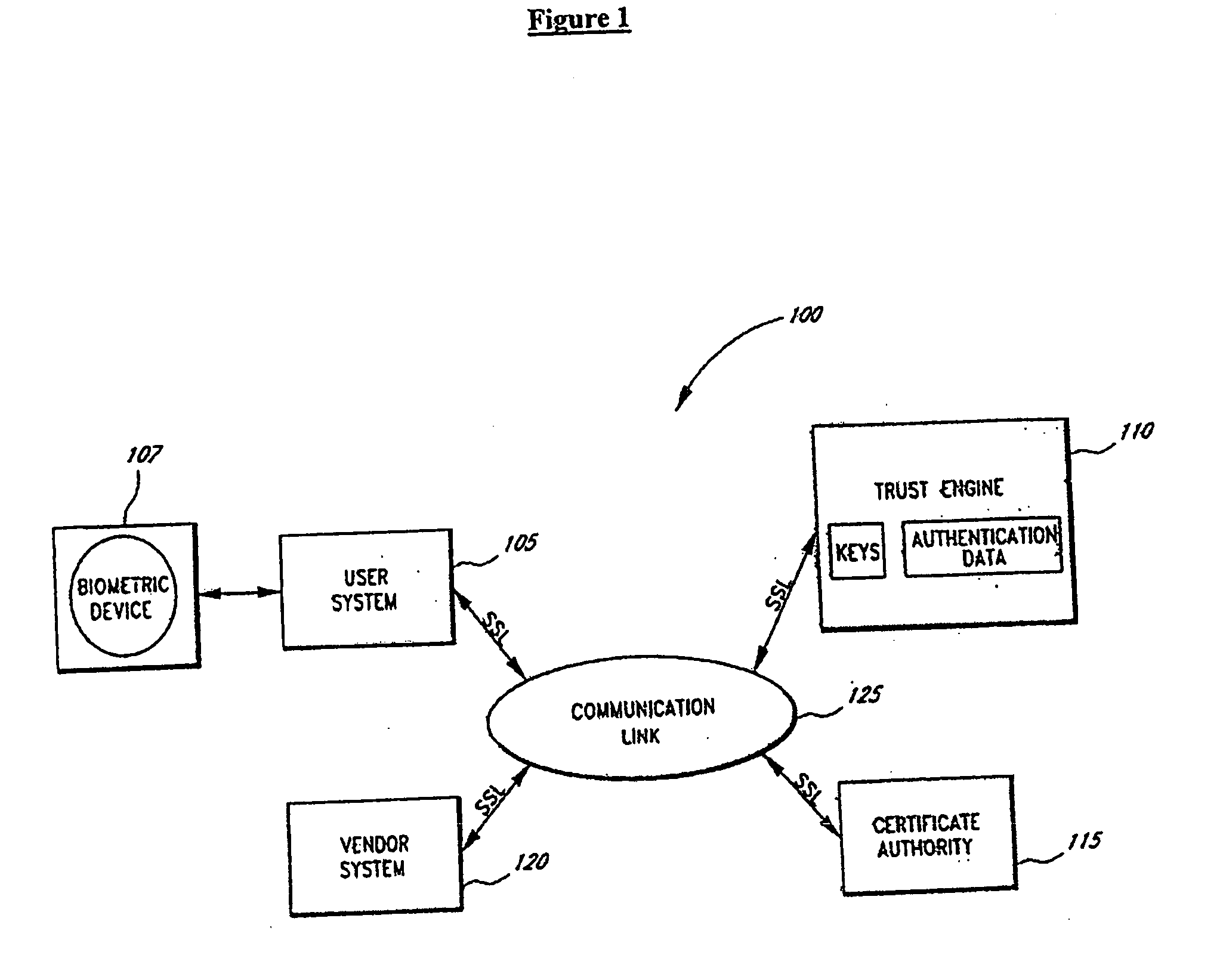
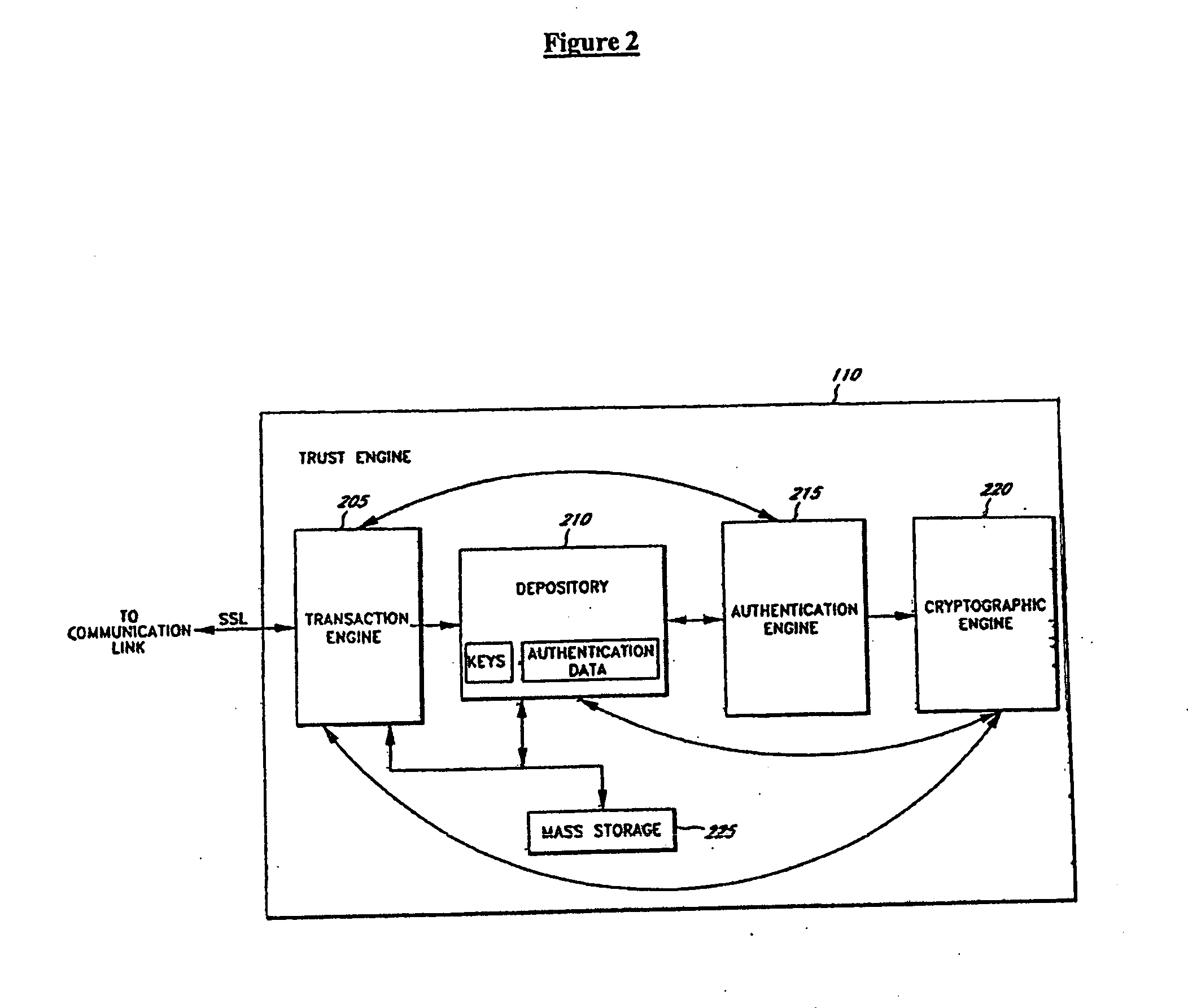
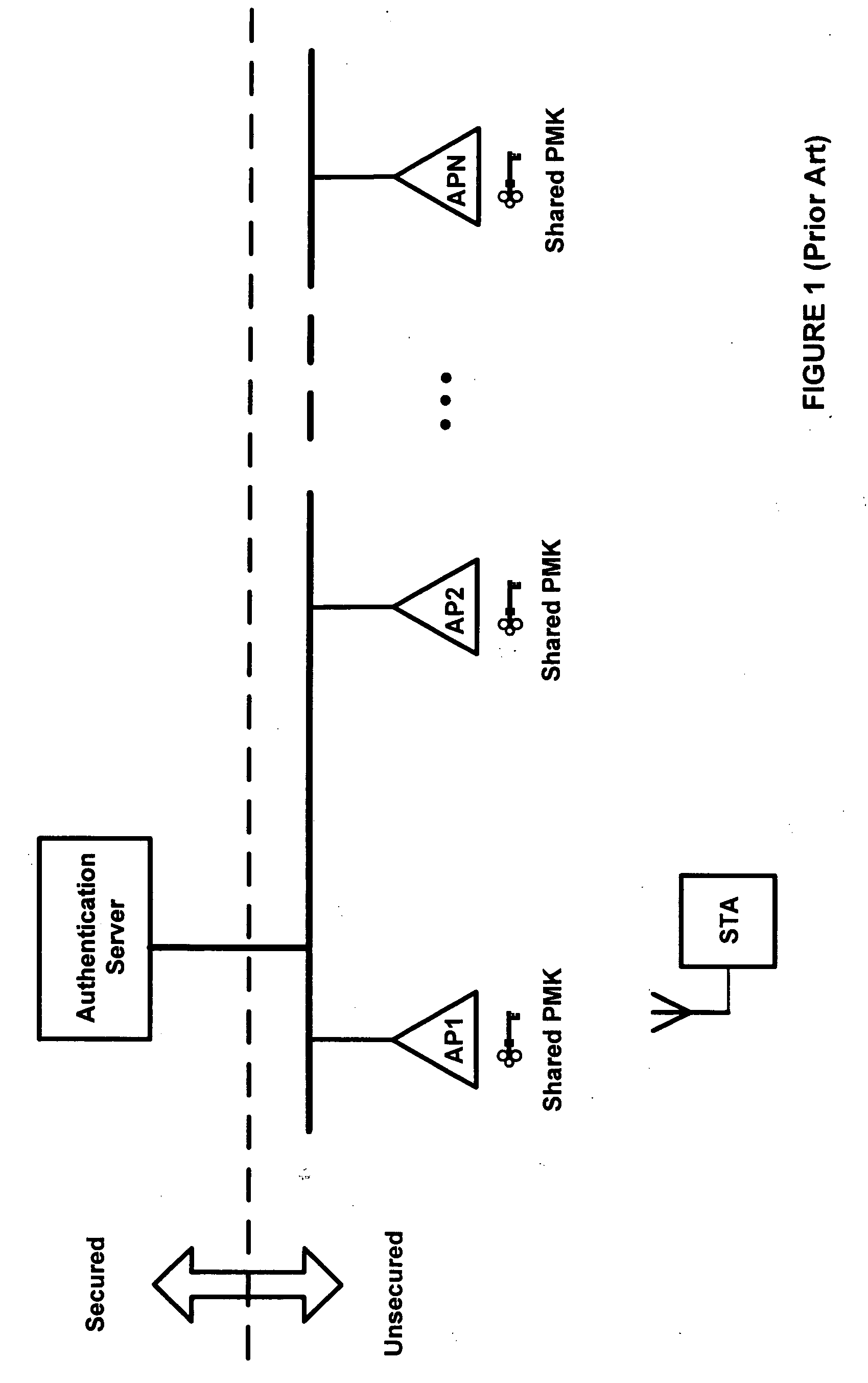
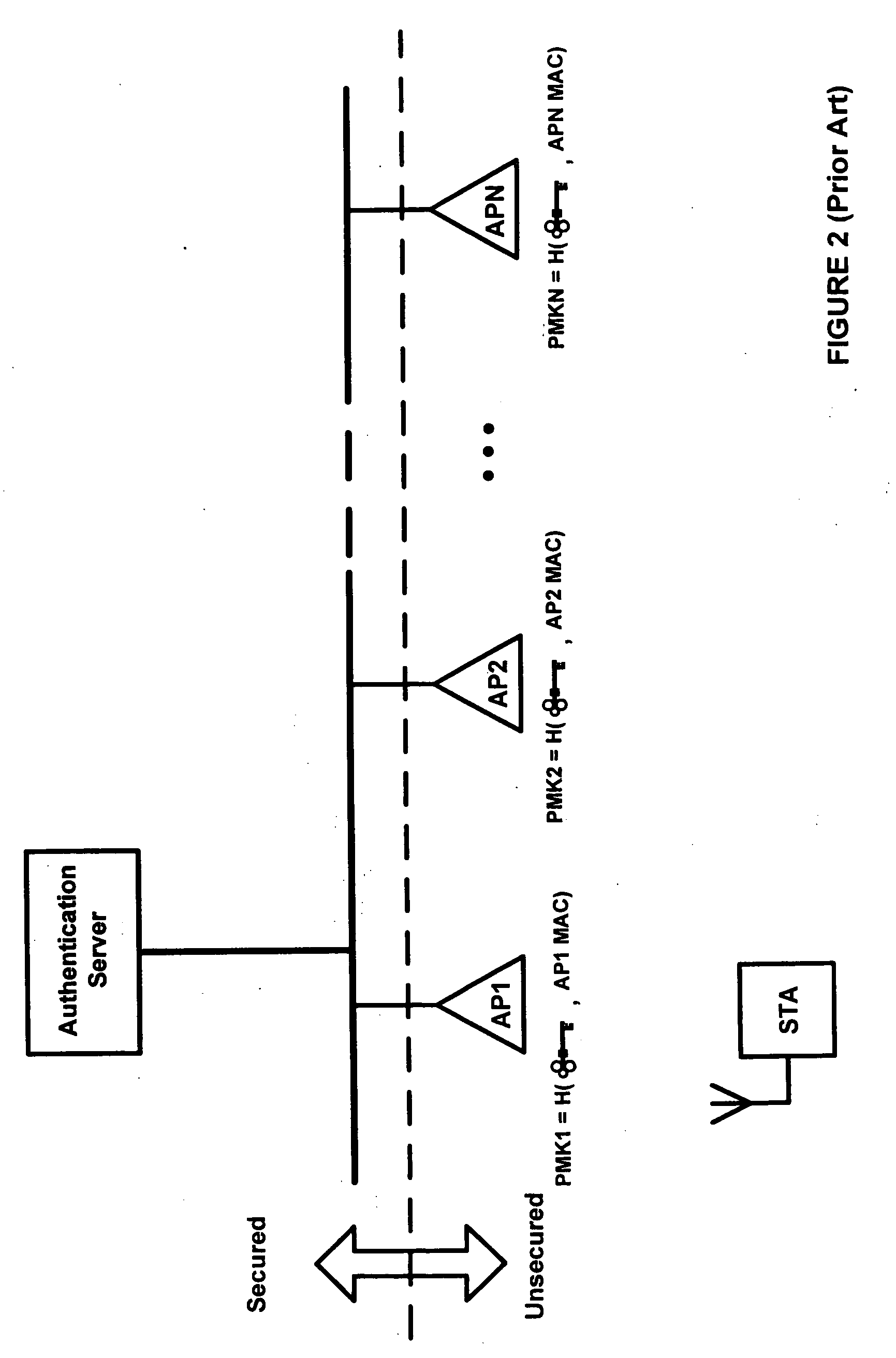
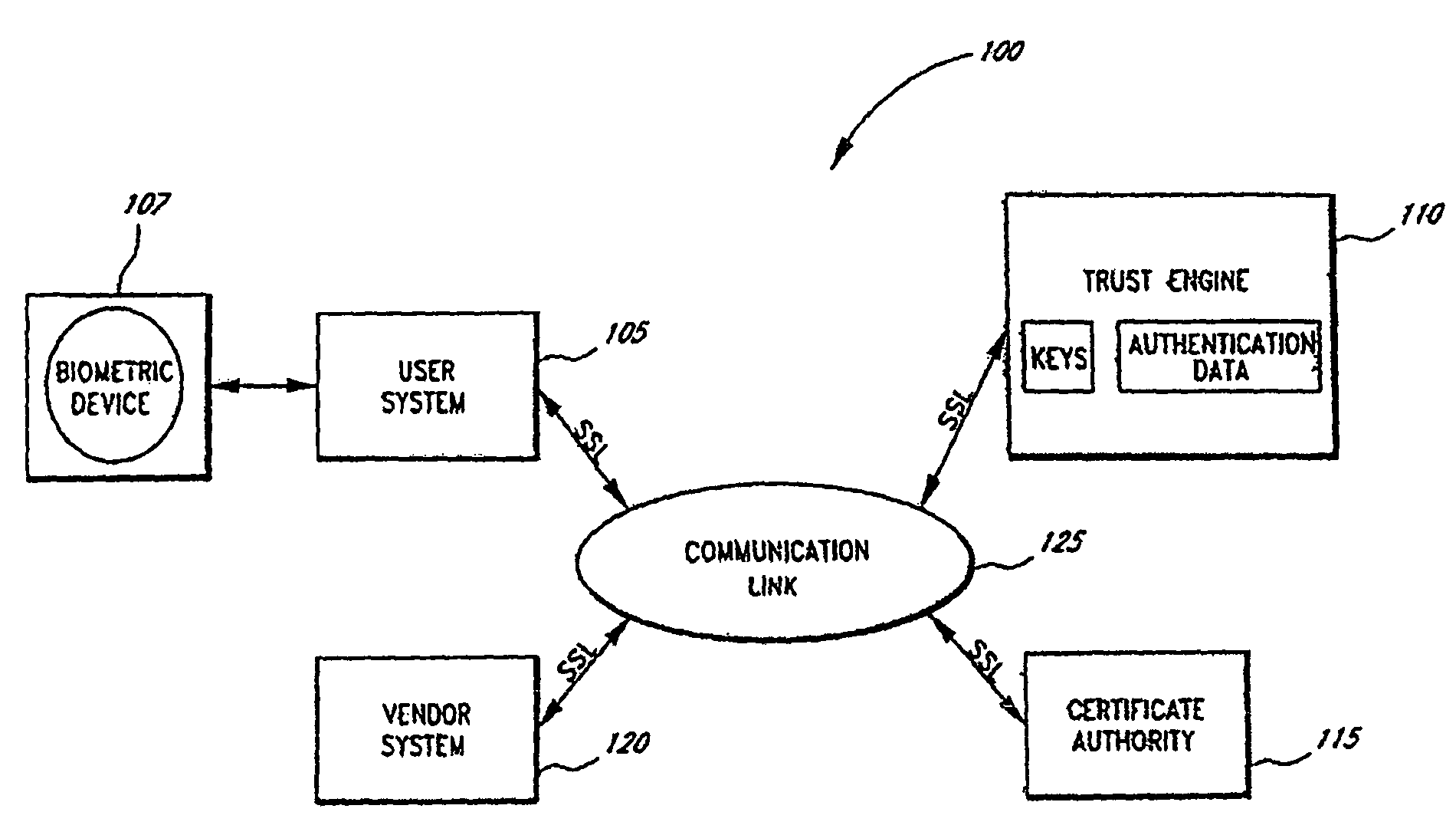
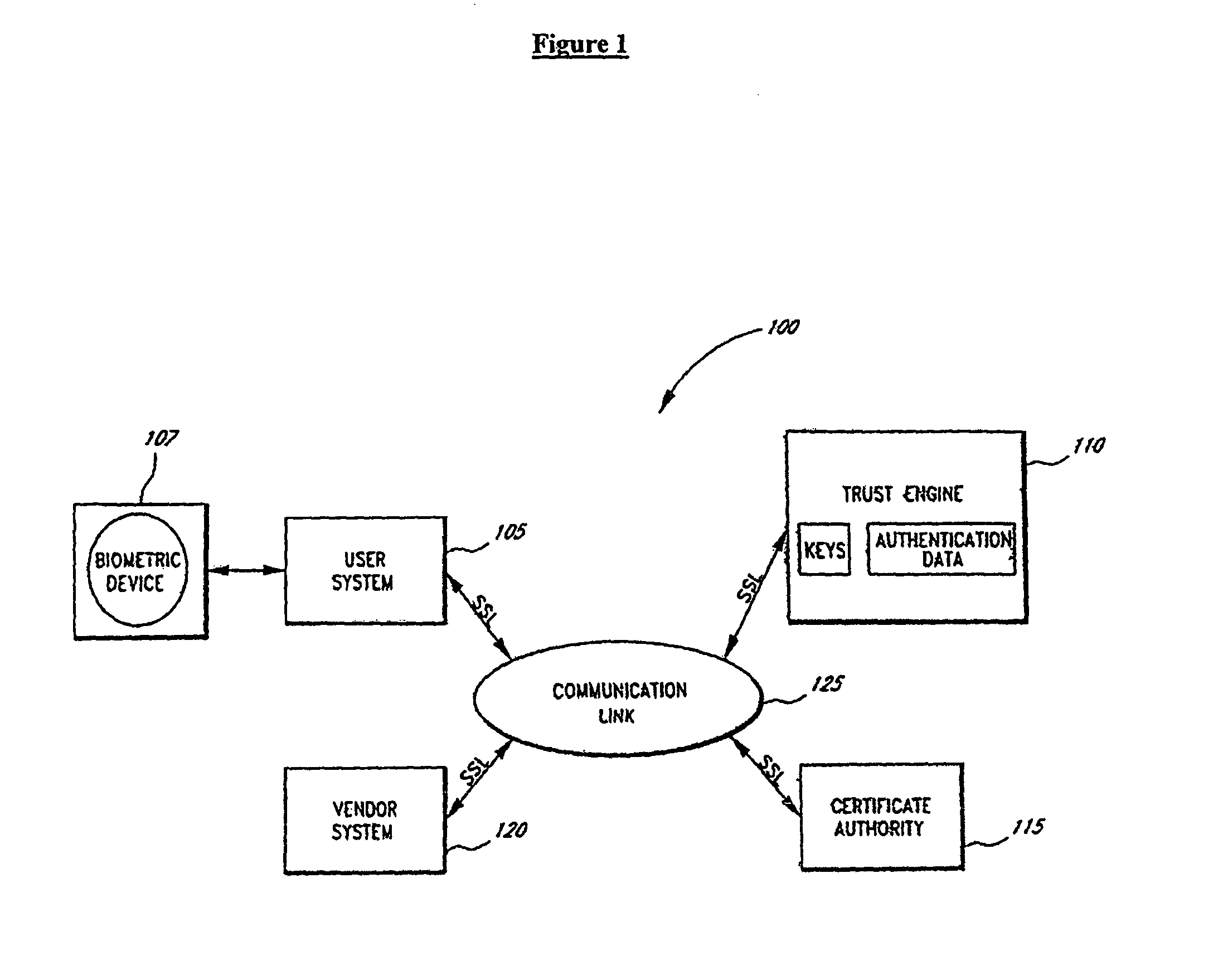
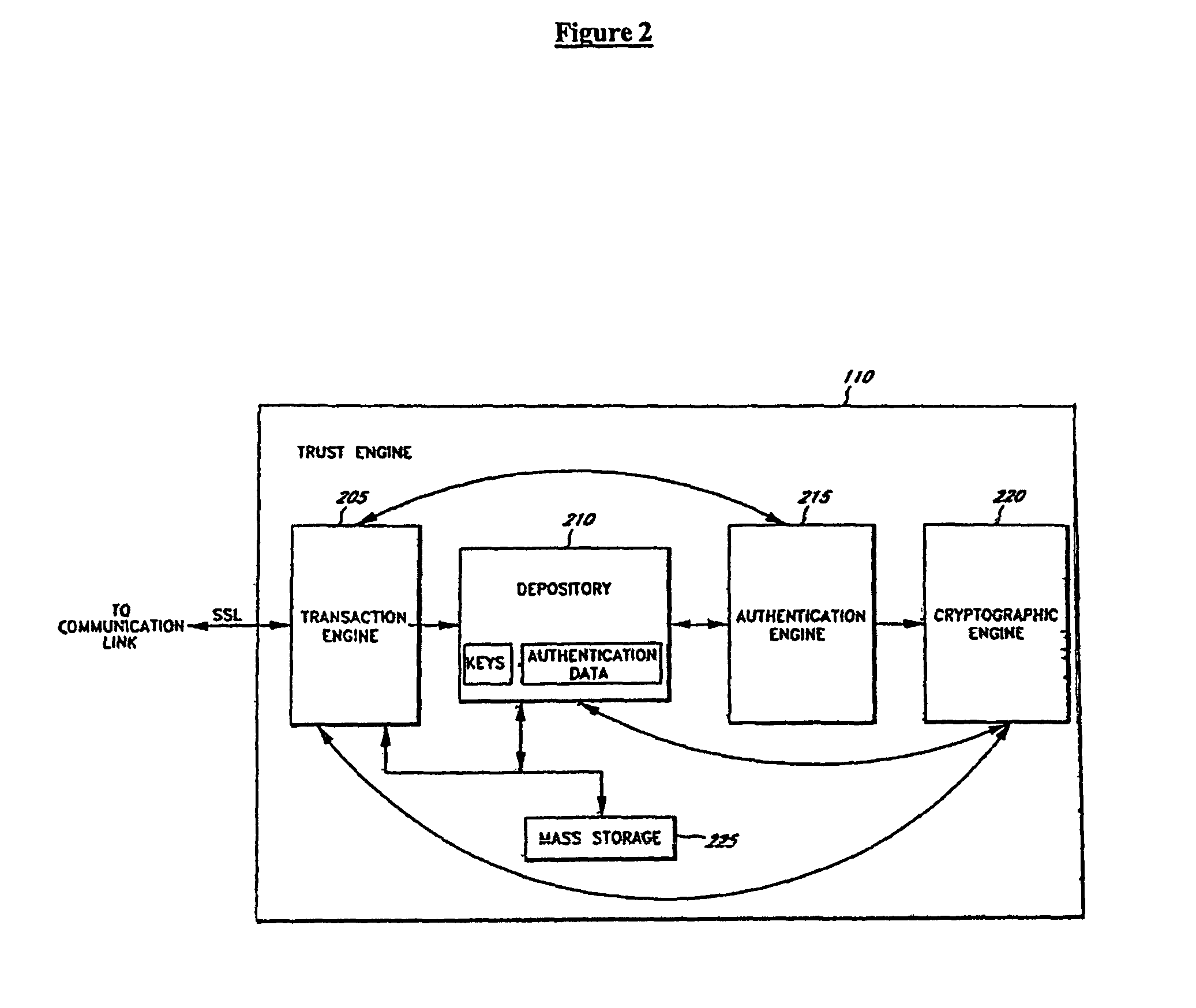
Systems and methods for distributing and securing data
ActiveUS20080137857A1Key distribution for secure communicationRandom number generatorsInformation dispersalCiphertext
A robust computational secret sharing scheme that provides for the efficient distribution and subsequent recovery of a private data is disclosed. A cryptographic key may be randomly generated and then shared using a secret sharing algorithm to generate a collection of key shares. The private data may be encrypted using the key, resulting in a ciphertext. The ciphertext may then be broken into ciphertext fragments using an Information Dispersal Algorithm. Each key share and a corresponding ciphertext fragment are provided as input to a committal method of a probabilistic commitment scheme, resulting in a committal value and a decommittal value. The share for the robust computational secret sharing scheme may be obtained by combining the key share, the ciphertext fragment, the decommittal value, and the vector of committal values.
Owner:SECURITY FIRST INNOVATIONS LLC
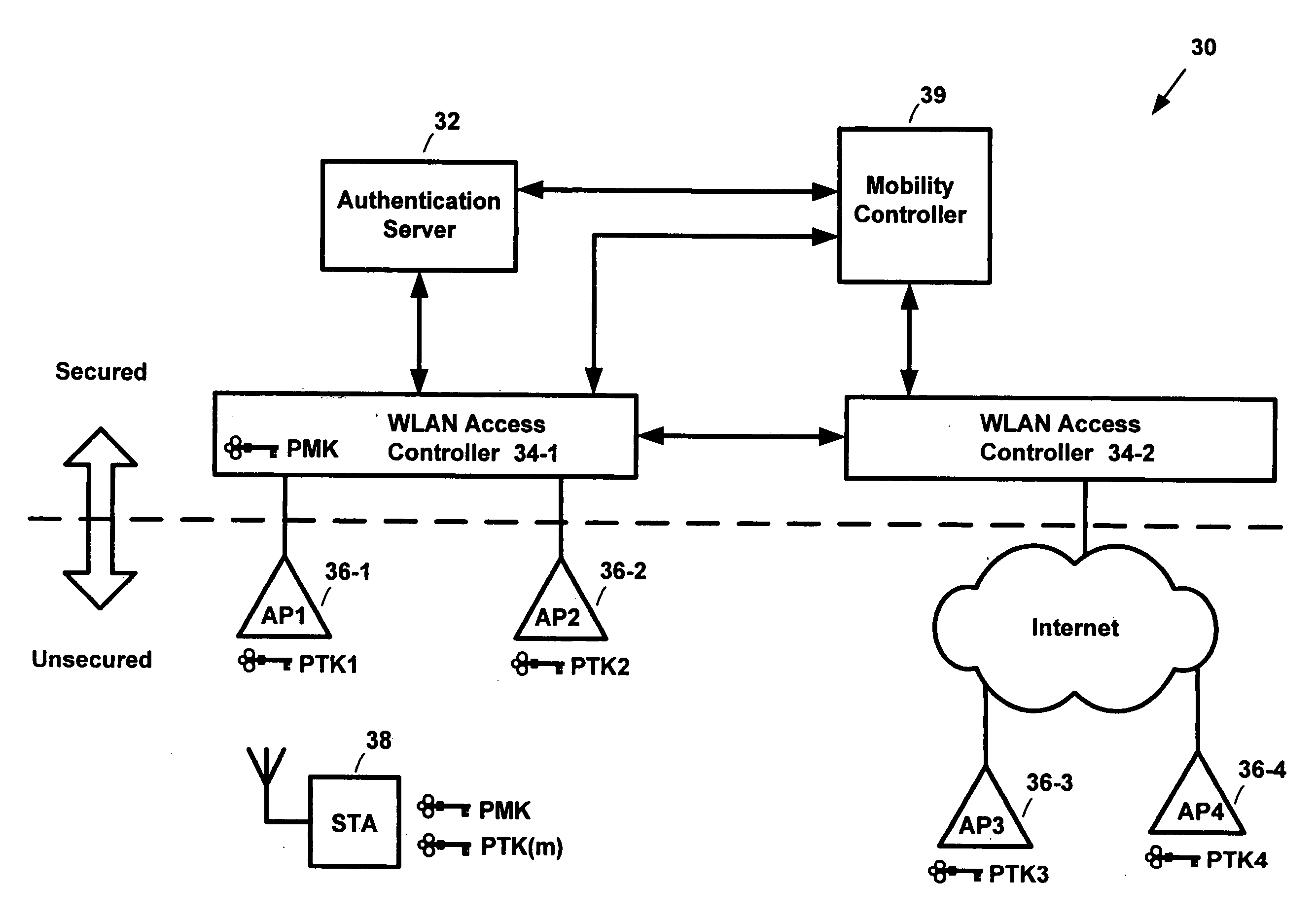
Pre-authentication of mobile clients by sharing a master key among secured authenticators
InactiveUS20050254653A1Key distribution for secure communicationUser identity/authority verificationAuthentication serverClient-side
Systems and methods for pre-authenticating a mobile client in a wireless network. Authenticators in a secured section of the wireless network share a master key generated during an authentication session between a mobile client and an authentication server. The shared master key is not allowed to reside on any devices located outside the secured section of the network. Accordingly, the likelihood that the master key may be hijacked is essentially eliminated. A first session encryption key is derived from the master key and used by the mobile client and a first access point during a first communications session. When the mobile client roams to a second access point, a fast authentication process is performed. The fast authentication process retrieves the shared master key and generates a second session encryption key. A full authentication process between the authentication server and the mobile client is not required. The second session encryption key is used by the mobile client and a second access point during a second communications session.
Owner:MOTOROLA INC
Methods and Systems for Making, Tracking and Authentication of Products
InactiveUS20080046263A1Easy to manufactureUser identity/authority verificationCo-operative working arrangementsSecure authenticationKey sharing
The invention foresees the labeling of each manufactured good with a digitally verified unique numeric identifier, and a central checking center allowing users to verify the authenticity of a particular cigarette pack or case by means of a cell phone interface. A system of secret key sharing allows secure authentication of each item and prevents code breaking or misuse.
Owner:PHILIP MORRIS USA INC
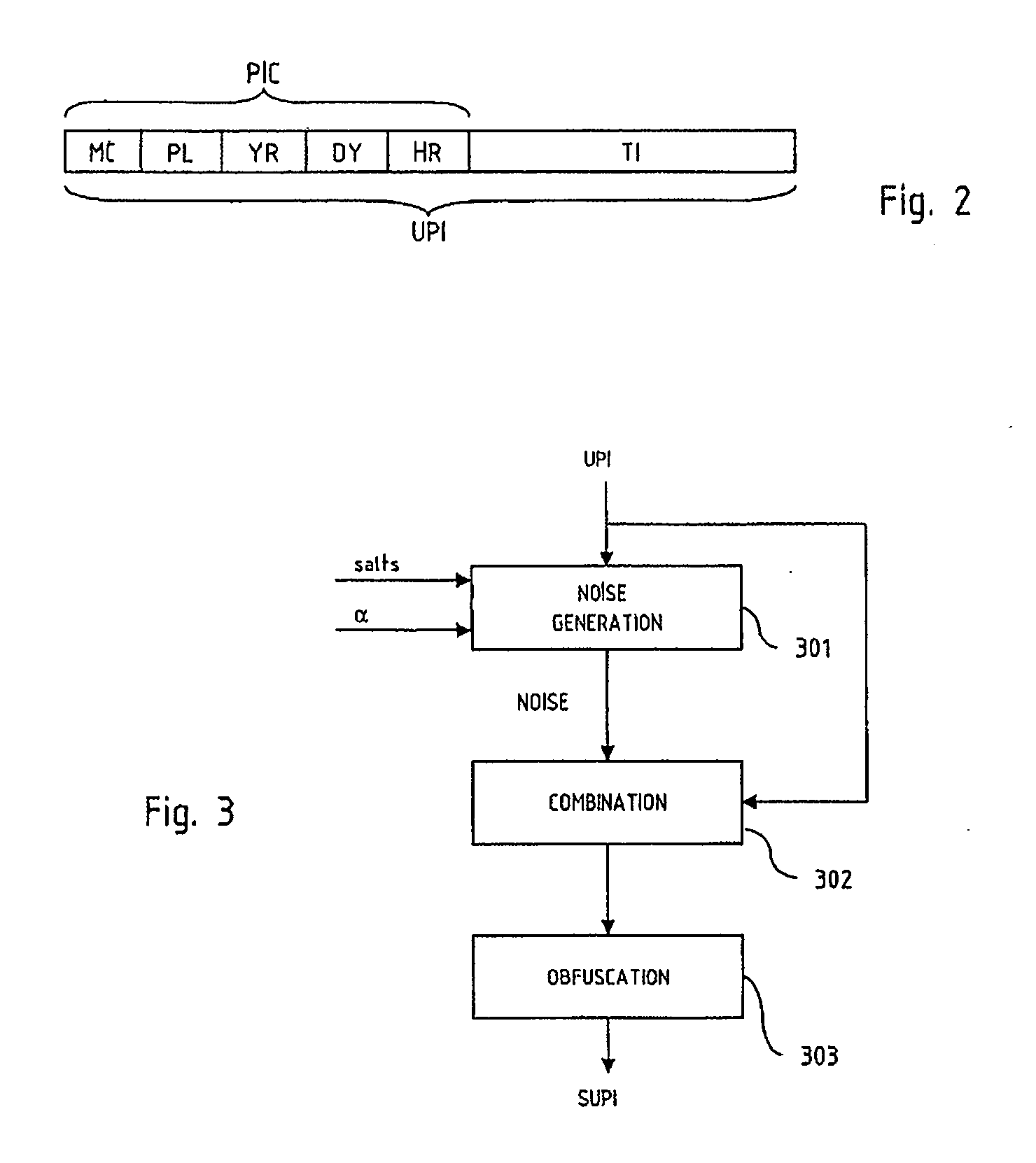
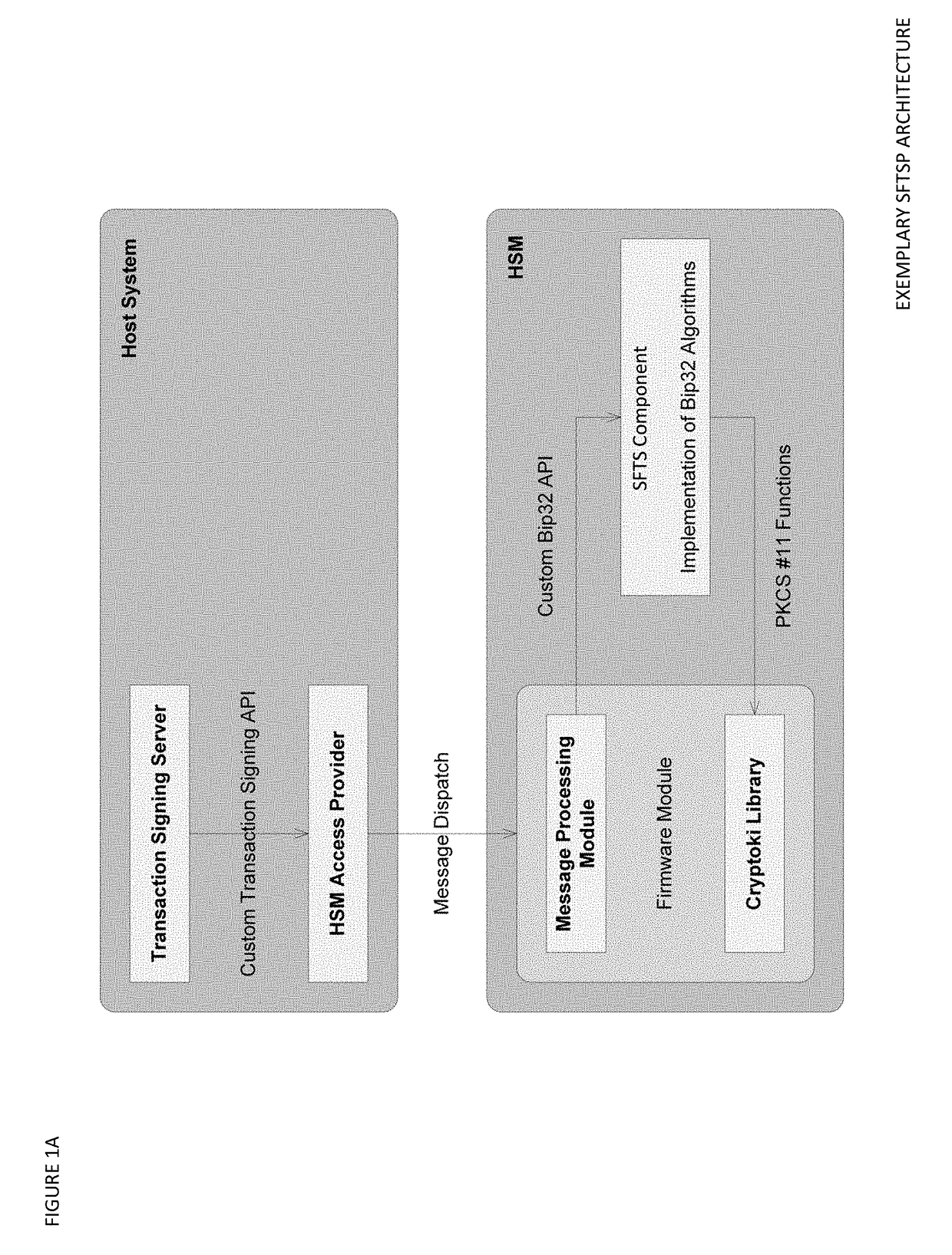
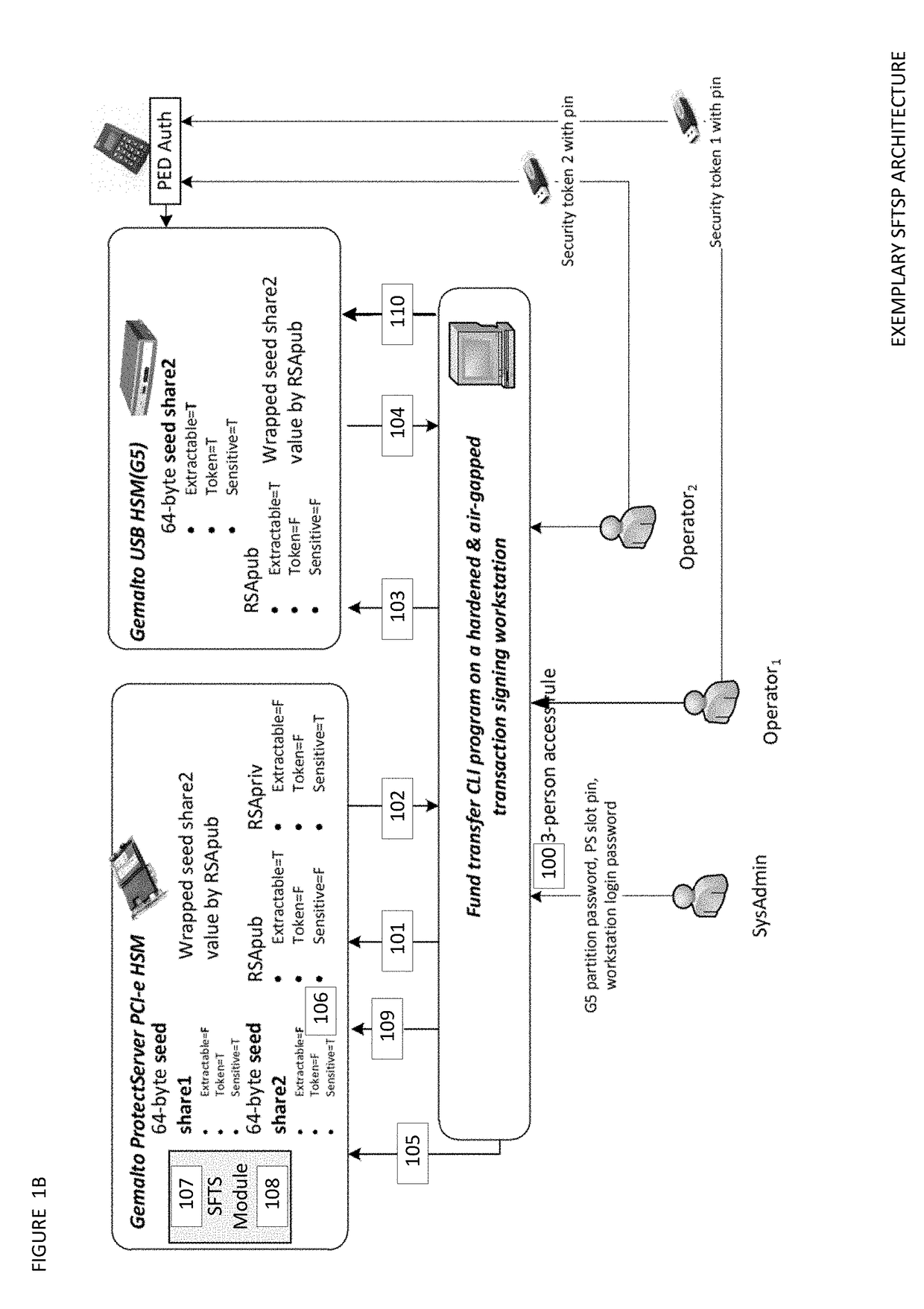
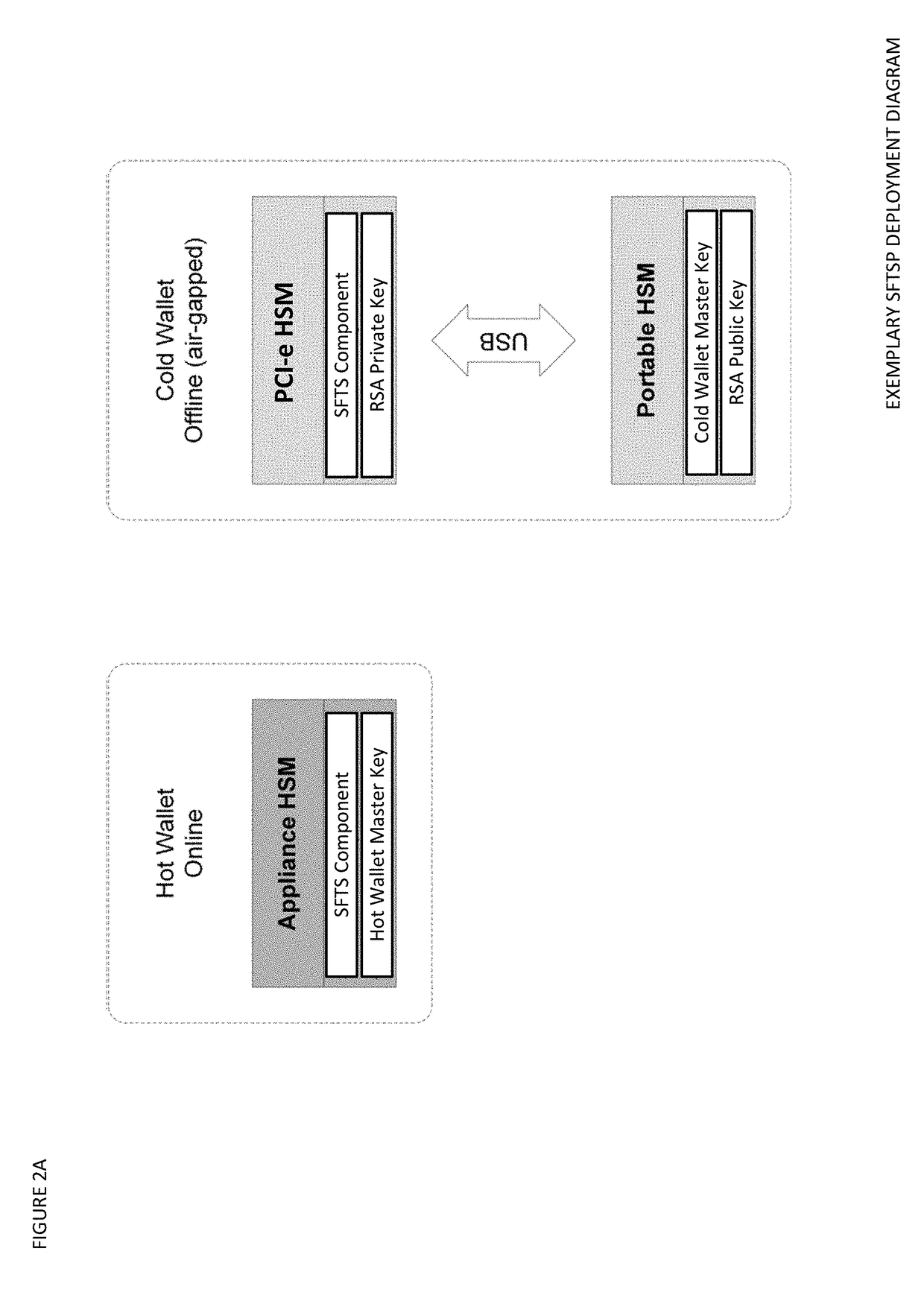
Seed splitting and firmware extension for secure cryptocurrency key backup, restore, and transaction signing platform apparatuses, methods and systems
ActiveUS20180367316A1Improve network efficiencyProlong lifeKey distribution for secure communicationEncryption apparatus with shift registers/memoriesMaster keyKey sharing
The Seed Splitting and Firmware Extension for Secure Cryptocurrency Key Backup, Restore, and Transaction Signing Platform Apparatuses, Methods and Systems (“SFTSP”) transforms transaction signing request, key backup request, key recovery request inputs via SFTSP components into transaction signing response, key backup response, key recovery response outputs. A transaction signing request message for a transaction is received by a first HSM and includes an encrypted second master key share from a second HSM whose access is controlled by M-of-N authentication policy. The encrypted second master key share is decrypted. A first master key share is retrieved. A master private key is recovered from the master key shares. A transaction hash and a keychain path is determined. A signing private key for the keychain path is generated using the recovered master private key. The transaction hash is signed using the signing private key, and the generated signature is returned.
Owner:FMR CORP
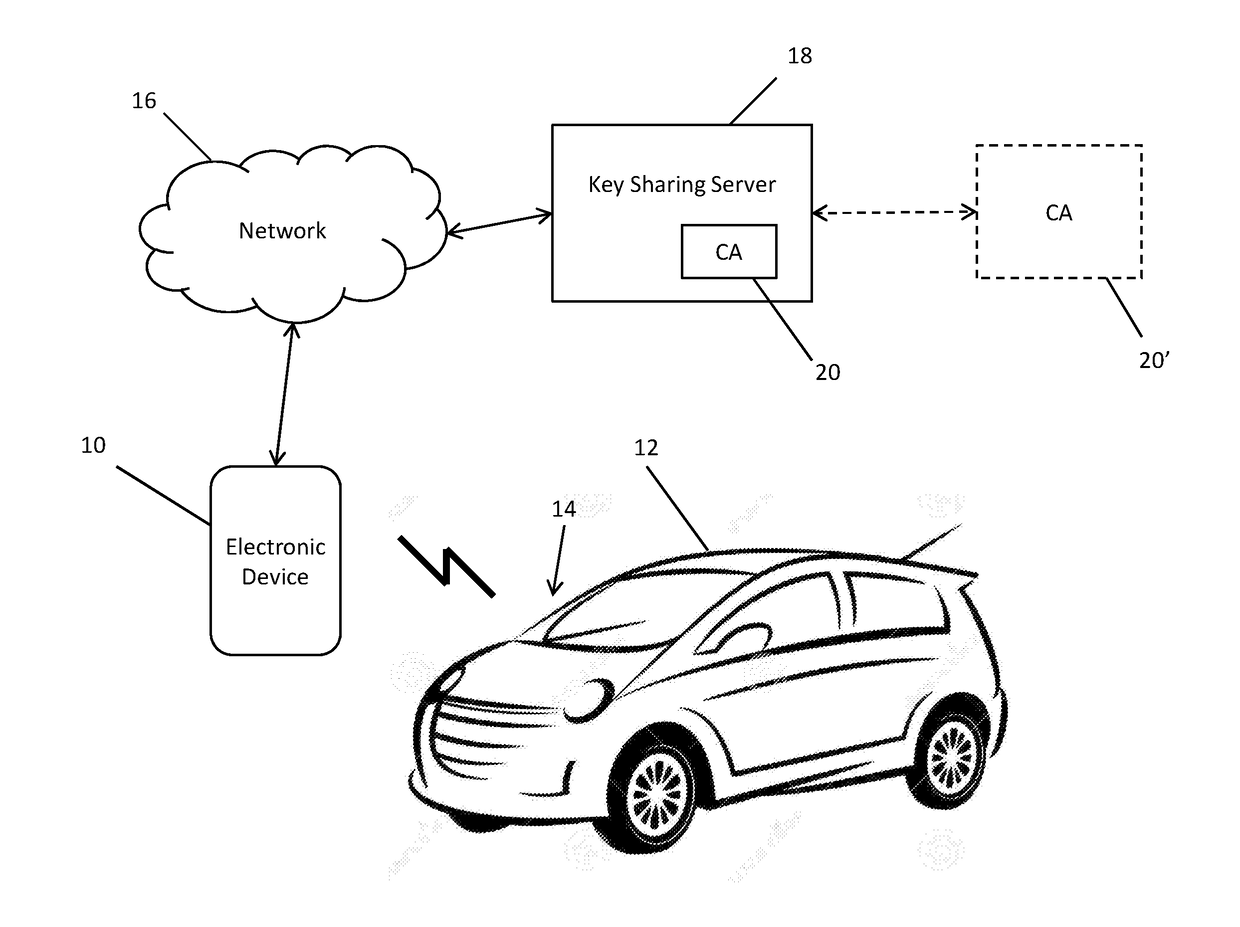
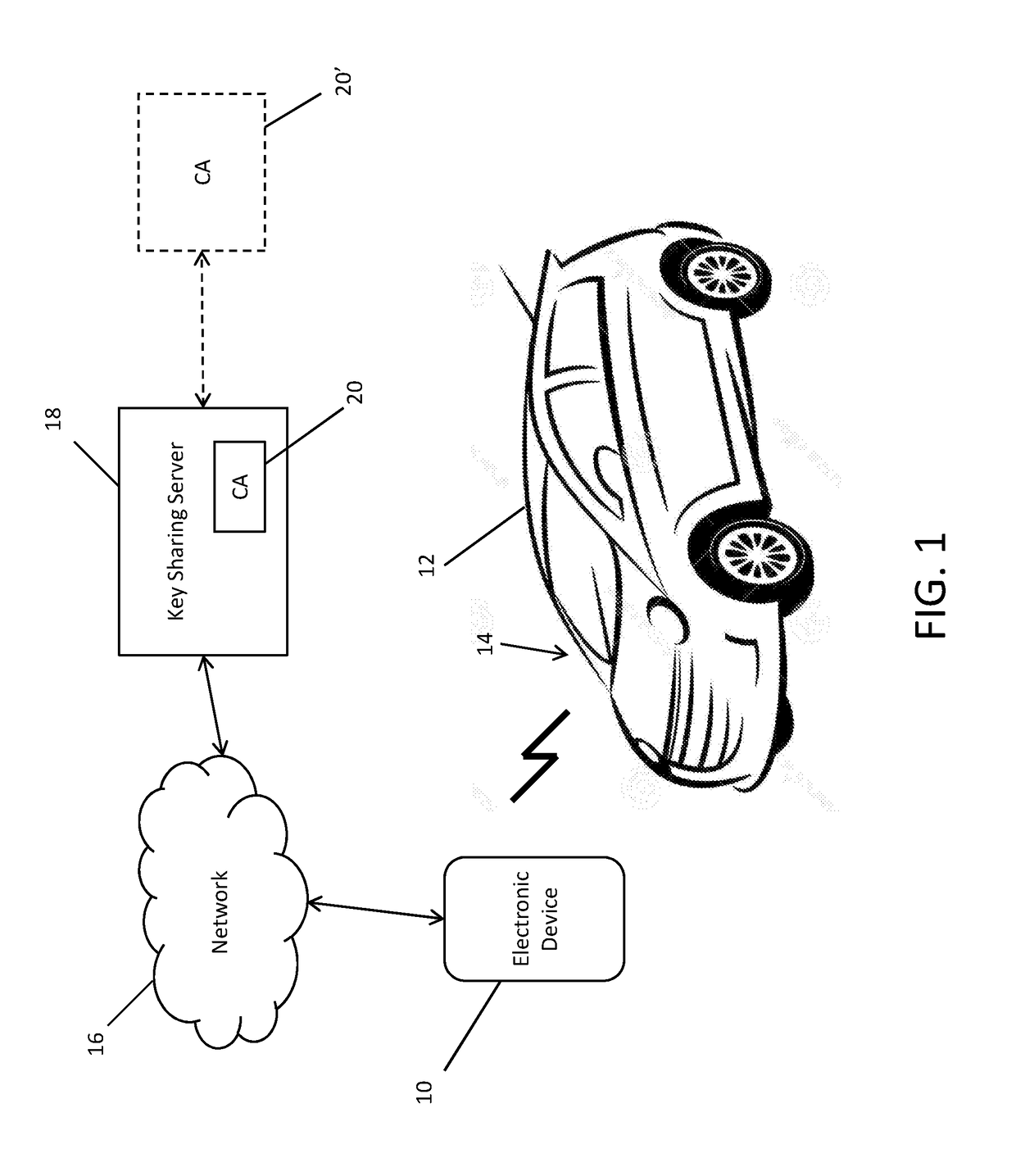
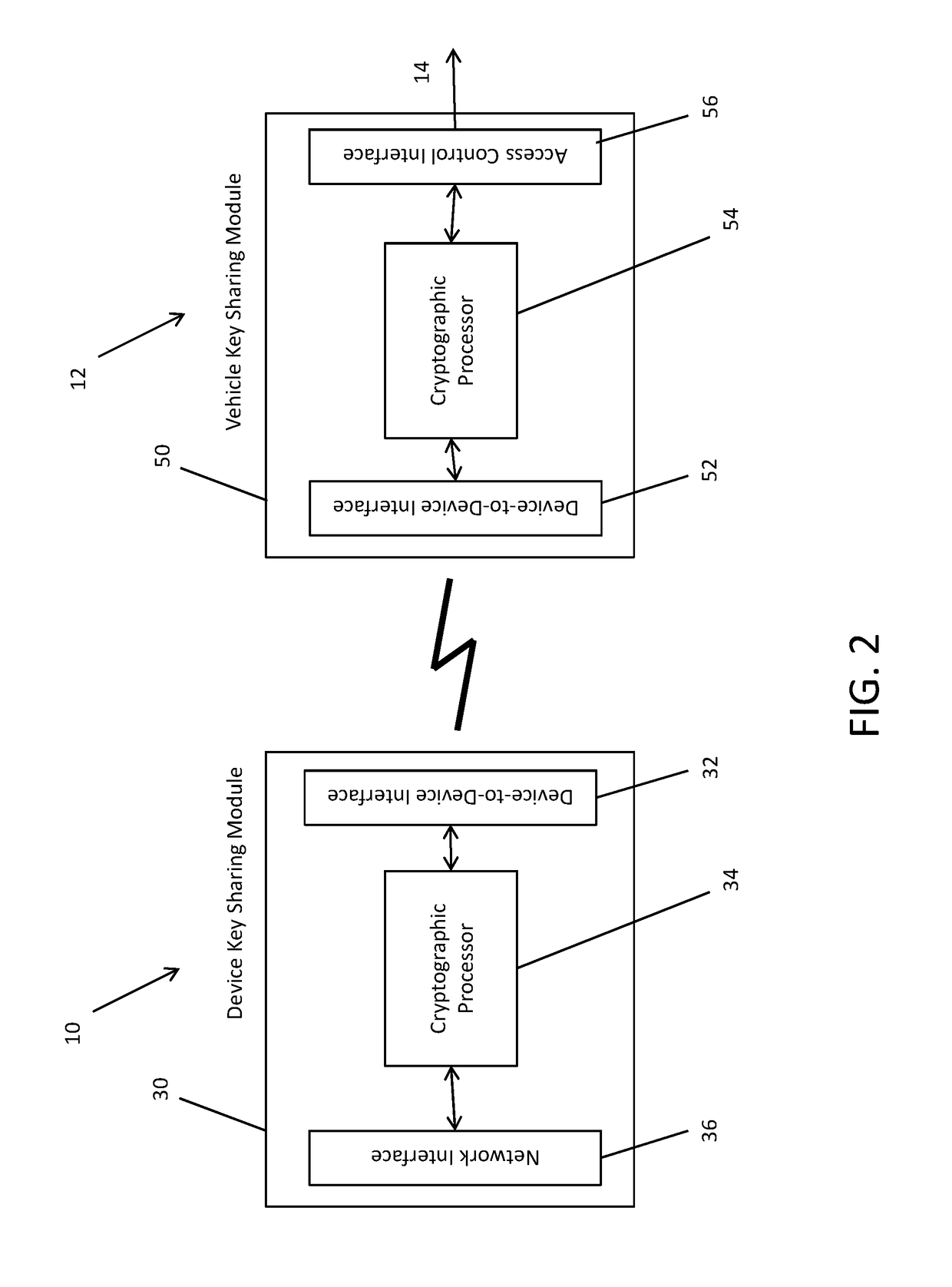
System and Method for Digital Key Sharing for Access Control
ActiveUS20170104589A1Key distribution for secure communicationParticular environment based servicesCommunications systemKey sharing
A communication system involving an access point, a vehicle and a user is provided. The vehicle and user possess a registration code, the user possesses a public and private key pair, and the access point and vehicle possess certificates and associated private keys. The access point issues a certificate to the user associated with the user's public and private keys, and the certificate of the access point is known and trusted by the vehicle. The access point signs a message granting ownership of the vehicle to the user, and the identity of the user indicates the user's certificate. The vehicle conditionally accepts the ownership registration request of the user.
Owner:ETAS EMBEDDED SYST CANADA INC
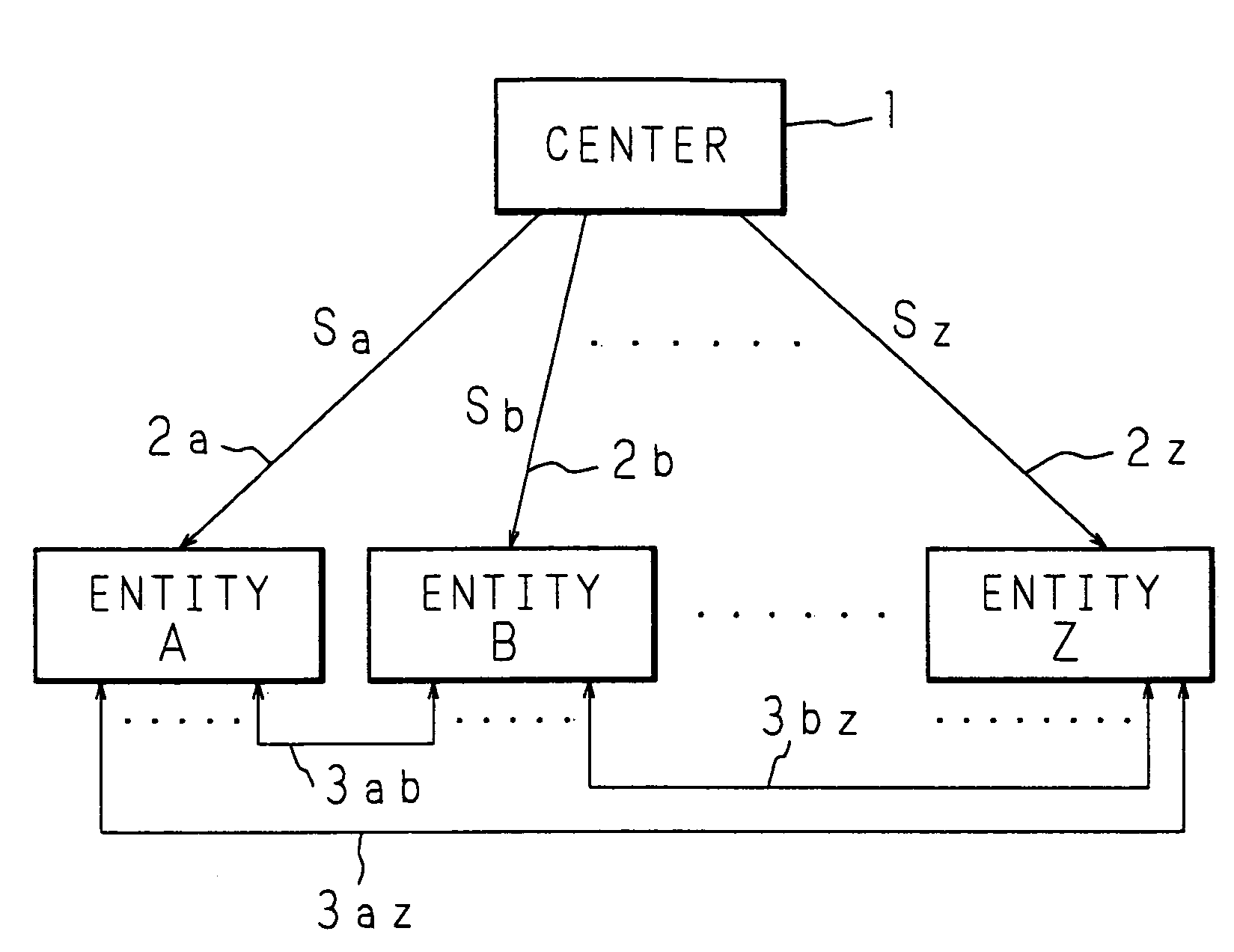
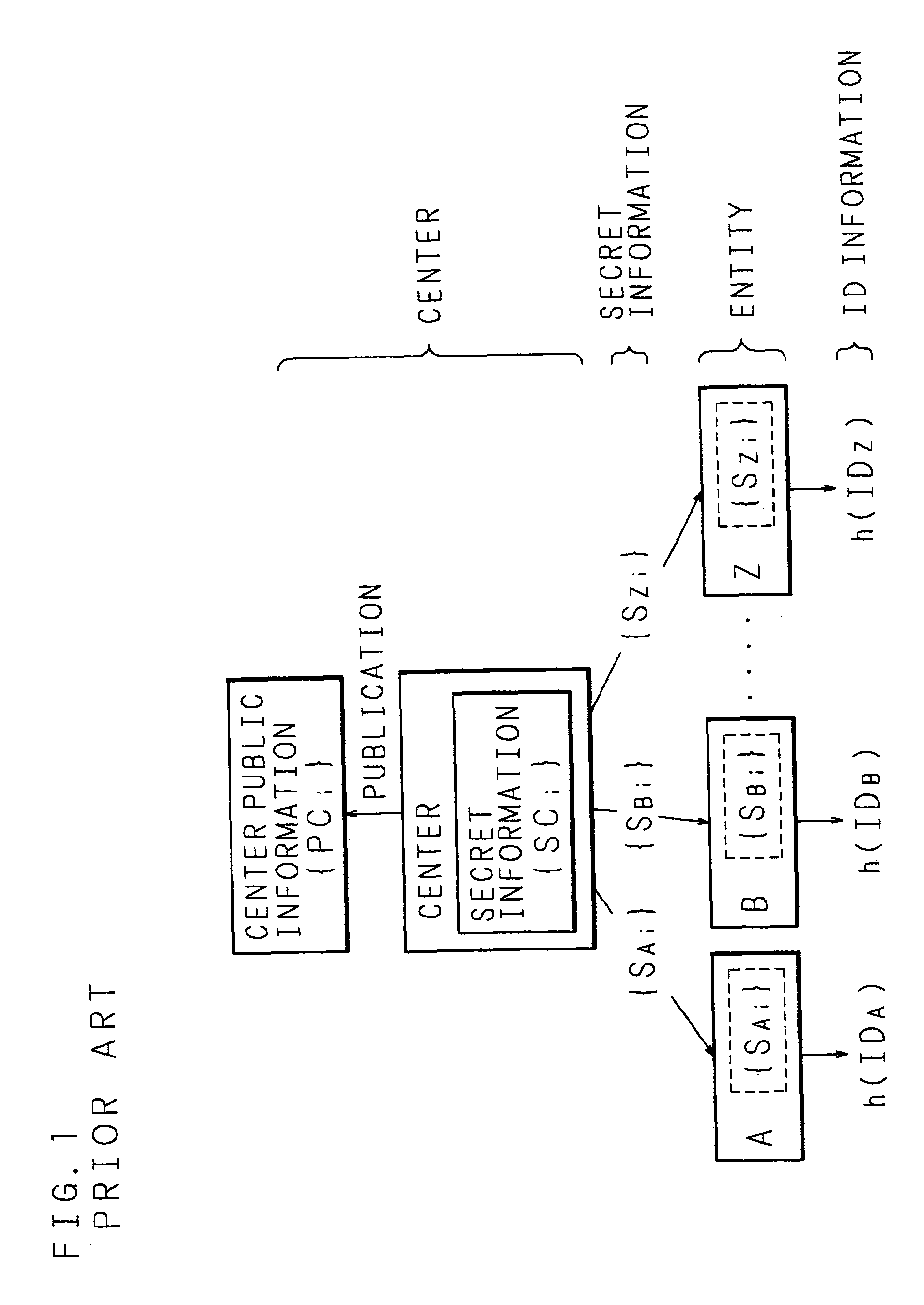
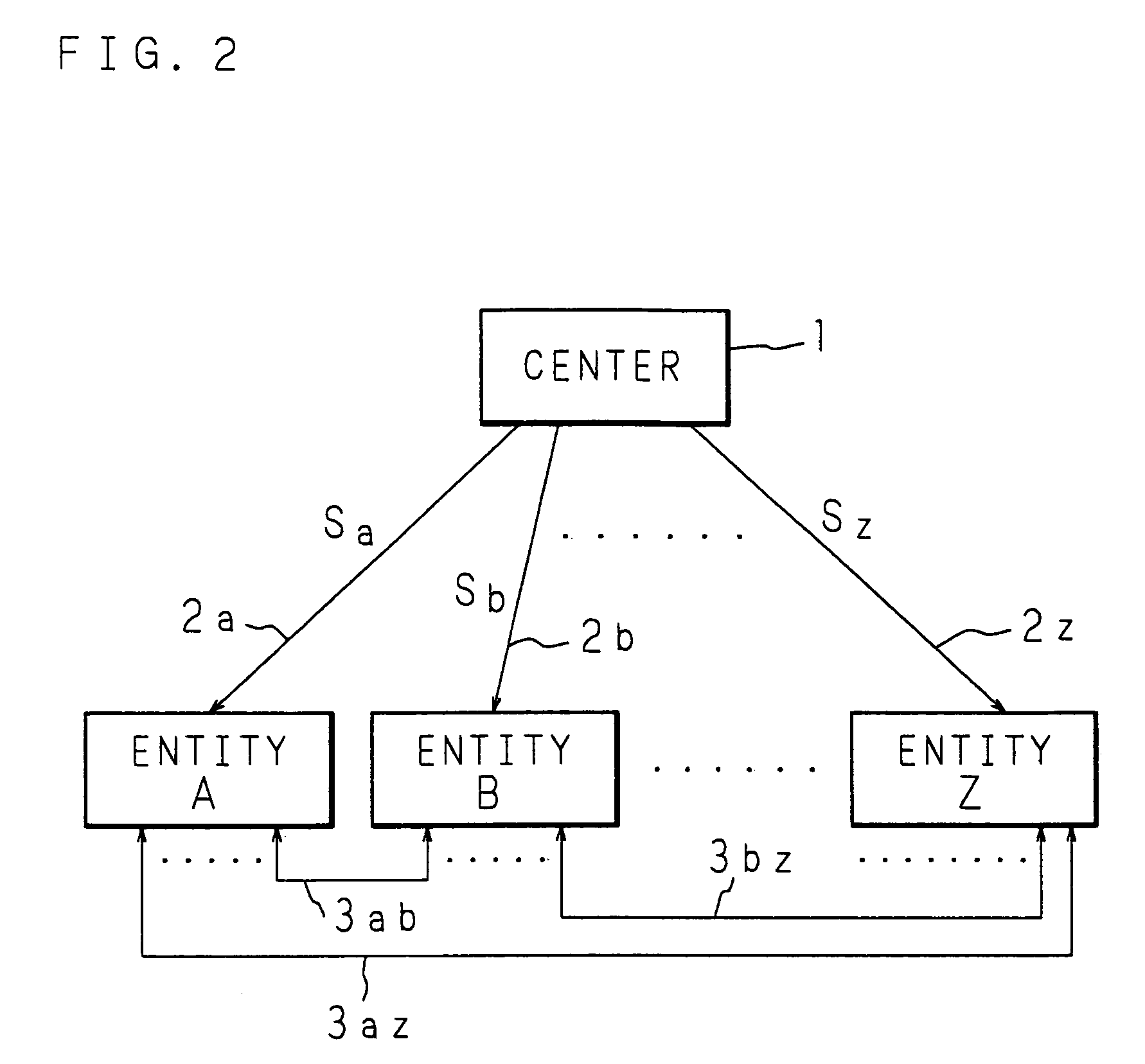
Key sharing method, secret key generating method, common key generating method and cryptographic communication method in ID-NIKS cryptosystem
InactiveUS7239701B1Easy to shareImprove securityKey distribution for secure communicationSecret communicationCryptosystemKey generation
Mapping is carried out at a point on an elliptic curve to be utilized for elliptic encryption based on identity information (ID information) of each entity and a mapping value is set to be a public key of the entity. By using the mapping value and secret information, a secret key of each entity is generated. The entity generates a common key to be used for an encrypting process and a decrypting process by utilizing the self-secret key and the public key to be the mapping value obtained by mapping at a point on the elliptic curve based on ID information of a communication participate. In this case, pairing on the elliptic curve is utilized.
Owner:NIPPON TELEGRAPH & TELEPHONE CORP
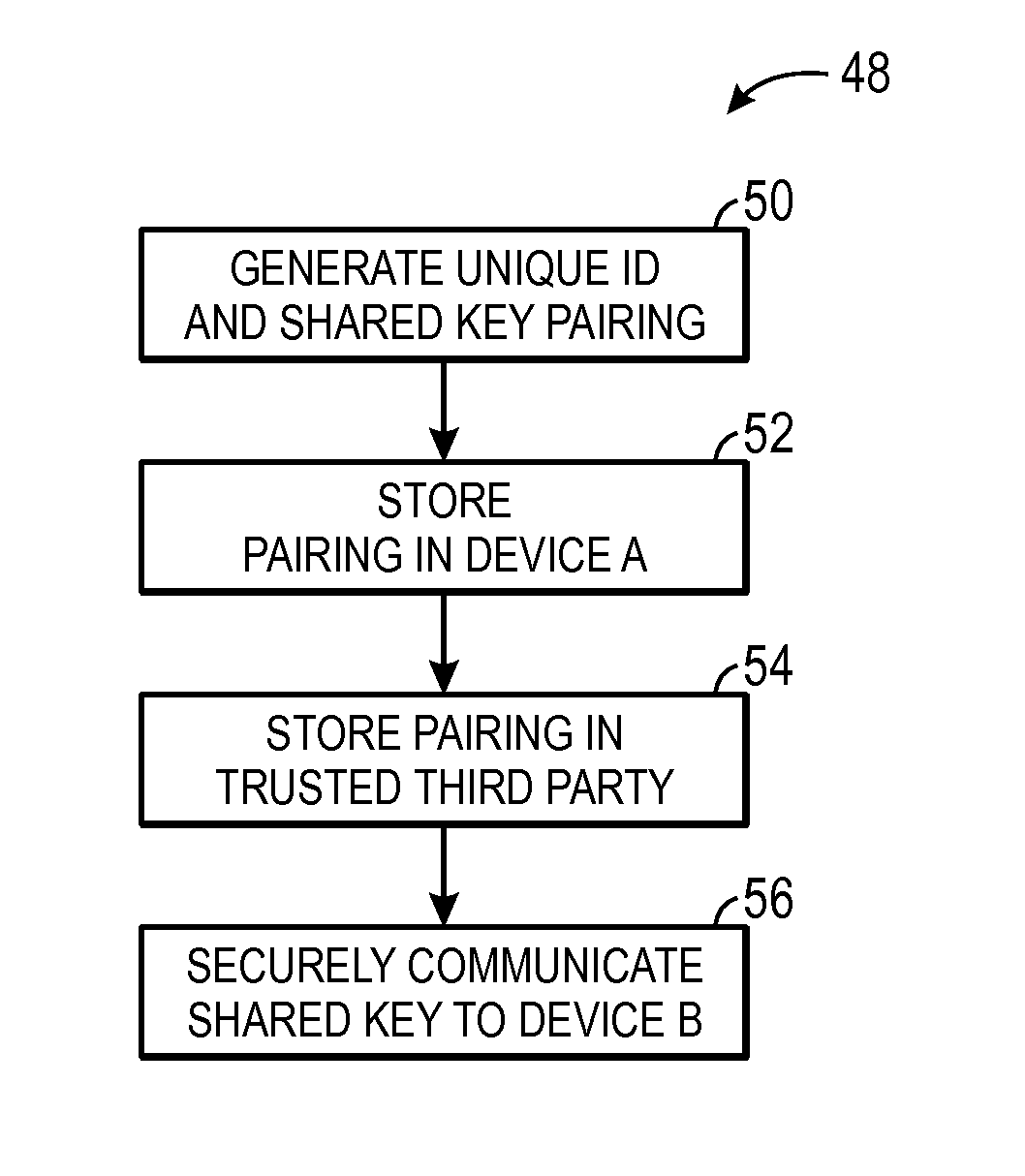
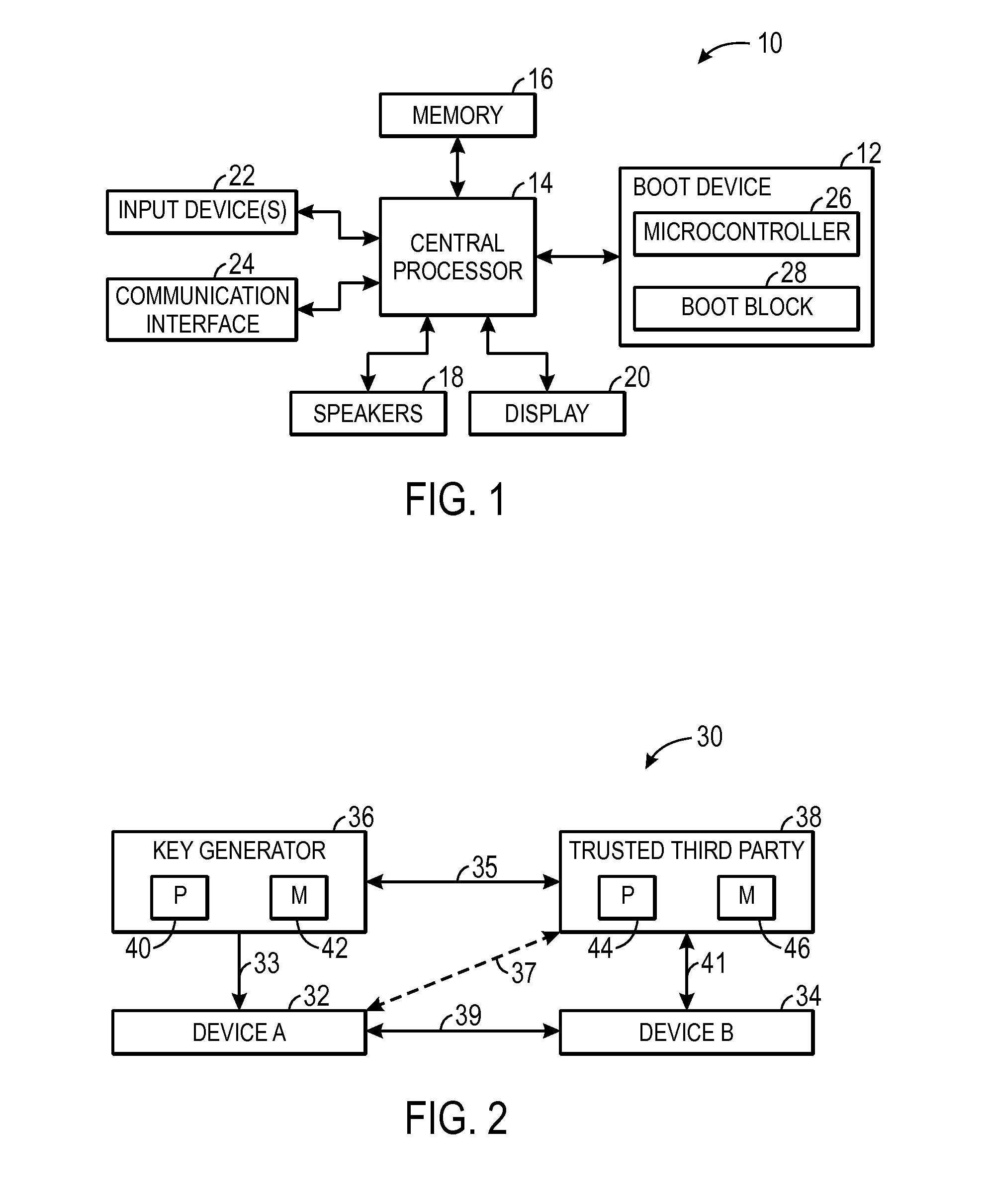
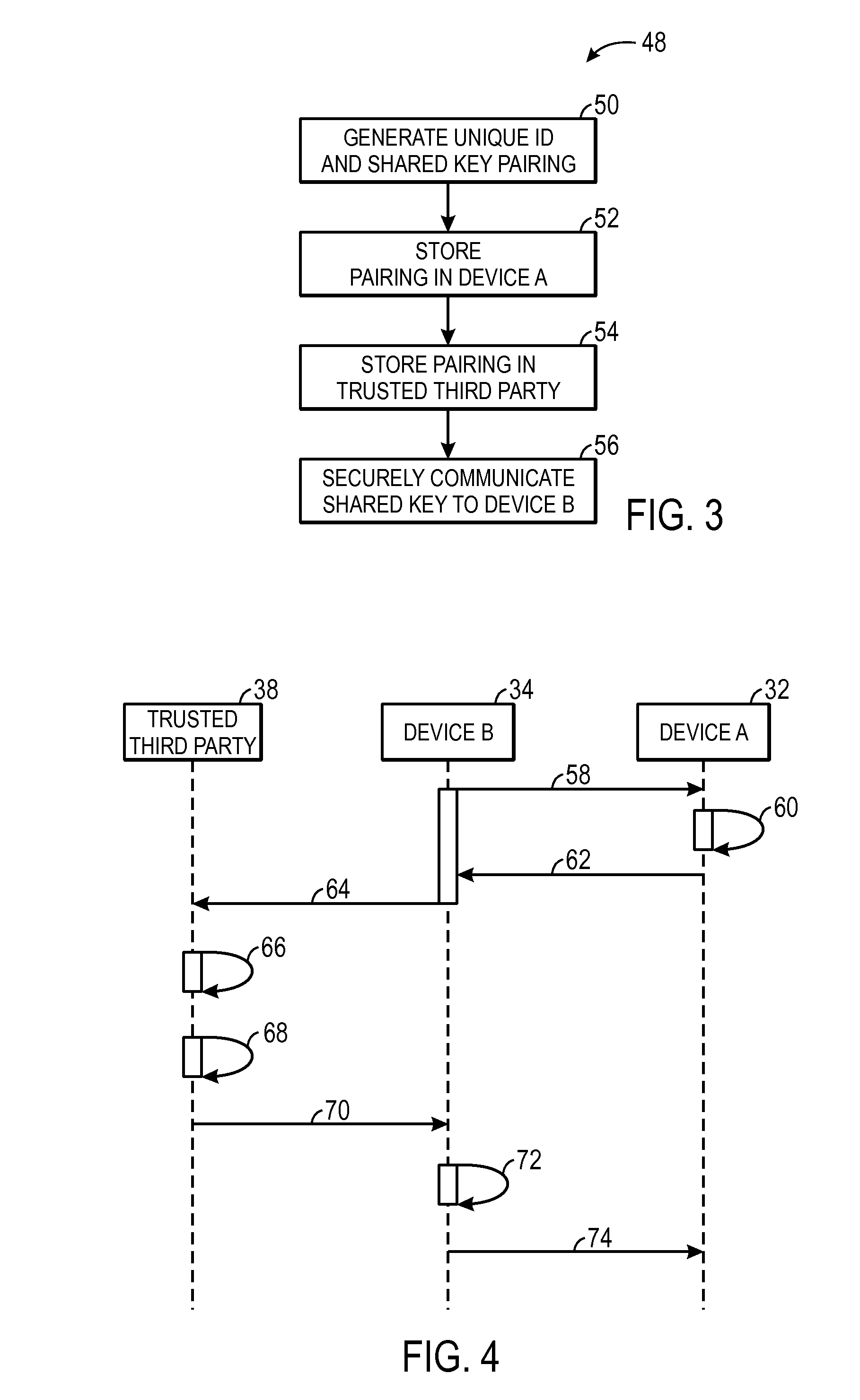
Secure shared key sharing systems and methods
ActiveUS20160099922A1User identity/authority verificationComputer security arrangementsThird partyUnique identifier
Systems and methods used to securely communicate a shared key to devices. One embodiment describes a method to securely communicate a shared key to a first device and a second device that includes receiving, using the first device, a shared key and unique identifier pairing associated with the first device from a key generator; receiving, using a trusted third party, the shared key and unique identifier pairing from the key generator; generating, using the first device, a signature using the unique identifier and the shared key; transmitting, using the first device, the signature and the unique identifier to the trusted third party; verifying, using the trusted third party, the unique identifier based on the signature; determining, using the trusted third party, the shared key when the unique identifier is verified; and transmitting, using the trusted third party, the shared key to the second device to enable the first device and the second device to communicate securely by encoding and decoding communicated data using the shared key.
Owner:MICRON TECH INC
Systems and methods for distributing and securing data
ActiveUS8155322B2Key distribution for secure communicationRandom number generatorsInformation dispersalCiphertext
A robust computational secret sharing scheme that provides for the efficient distribution and subsequent recovery of a private data is disclosed. A cryptographic key may be randomly generated and then shared using a secret sharing algorithm to generate a collection of key shares. The private data may be encrypted using the key, resulting in a ciphertext. The ciphertext may then be broken into ciphertext fragments using an Information Dispersal Algorithm. Each key share and a corresponding ciphertext fragment are provided as input to a committal method of a probabilistic commitment scheme, resulting in a committal value and a decommittal value. The share for the robust computational secret sharing scheme may be obtained by combining the key share, the ciphertext fragment, the decommittal value, and the vector of committal values.
Owner:SECURITY FIRST INNOVATIONS LLC
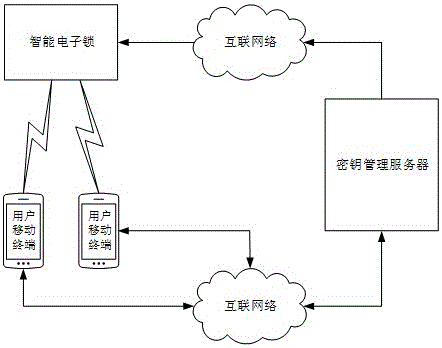
Electronic key sharing service system for house renting
ActiveCN105915344AMeet the needs of useRealize identification verificationKey distribution for secure communicationPublic key for secure communicationUser - individualKey sharing
The invention provides an electronic key sharing service system for house renting. Asymmetric encryption operation is carried out by using user identification information to generate a uniquely corresponding public renting key and a uniquely corresponding private renting key, wherein the private renting key is used for generating an electronic private key with an established unique corresponding relationship between an individual user and an intelligent electronic lock in an encrypted mode and the public renting key is used for executing delocking identification verification with user individual variation for decryption of the electronic key by the smart electronic lock. The private renting key is kept by a private key management server to guarantee security of the distribution and delocking process of the electronic key. Possible different using requirements for randomness, individual variation, and security in house renting sharing can be met well; convenience of the system in house renting sharing application is improved; the convenience degree of housing renting is enhanced; and development of the intelligent door lock industry can be promoted. Therefore, the system has the broad market promotion and application prospects.
Owner:CHONGQING JINOU SCI & TECH DEV
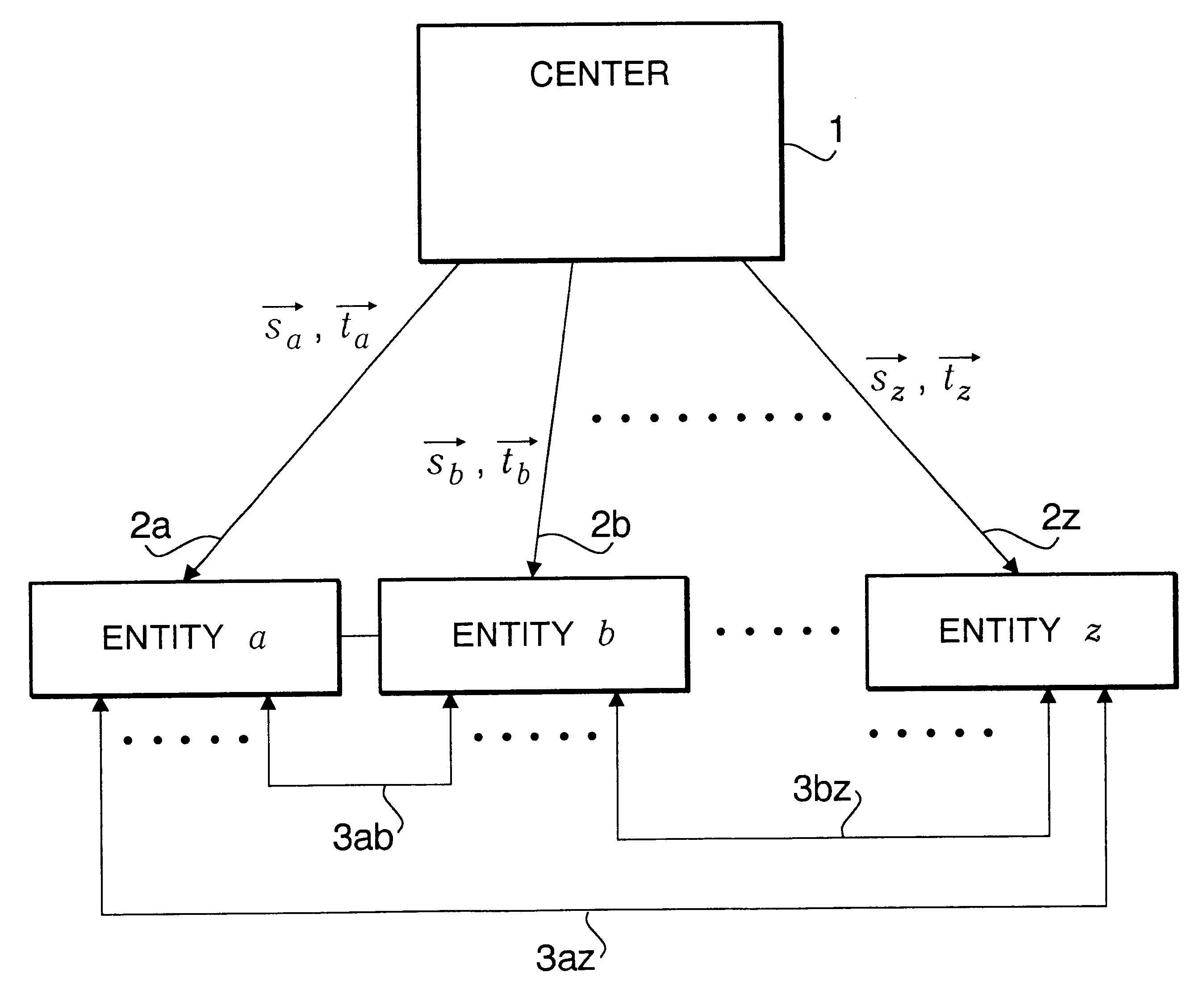
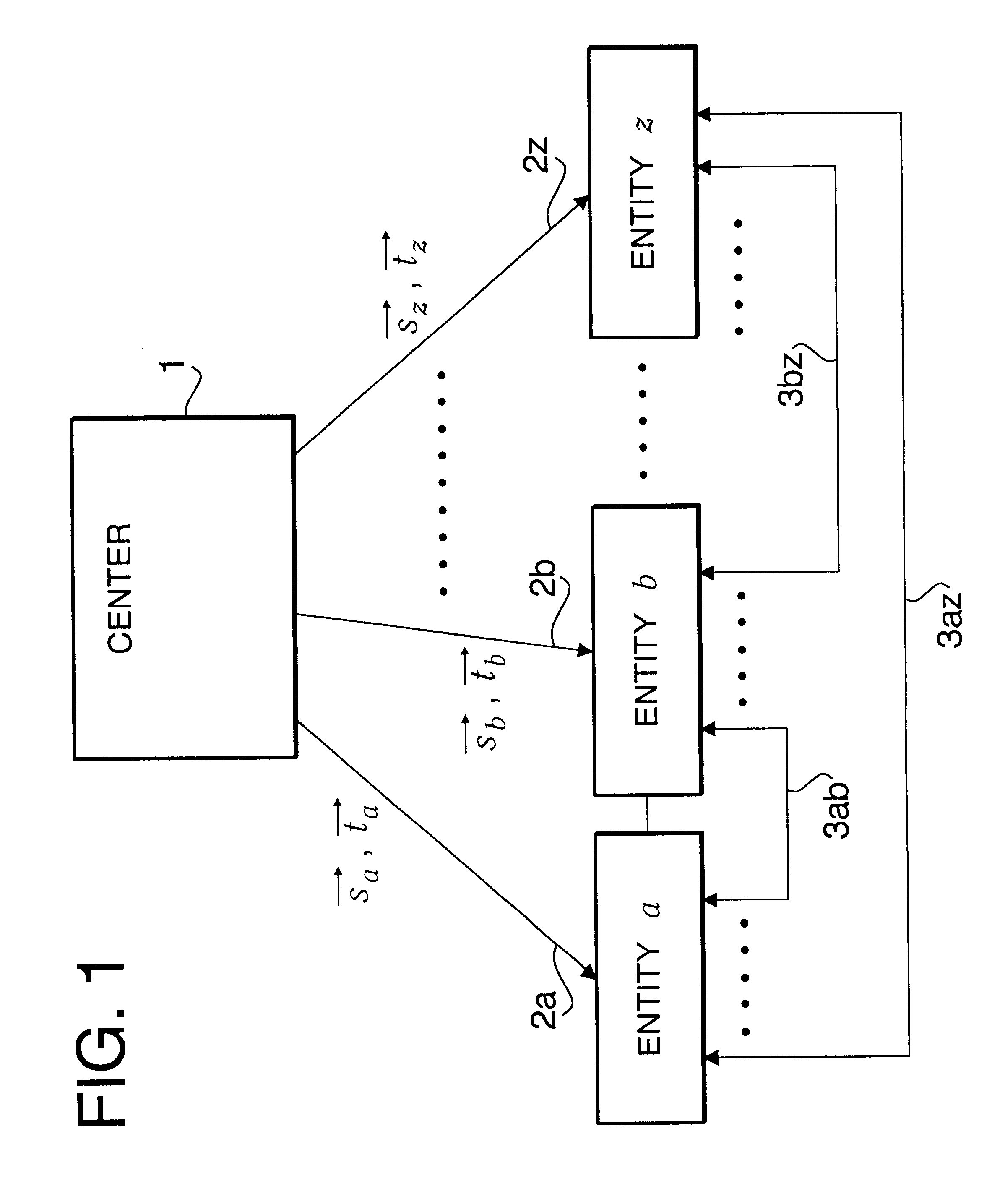
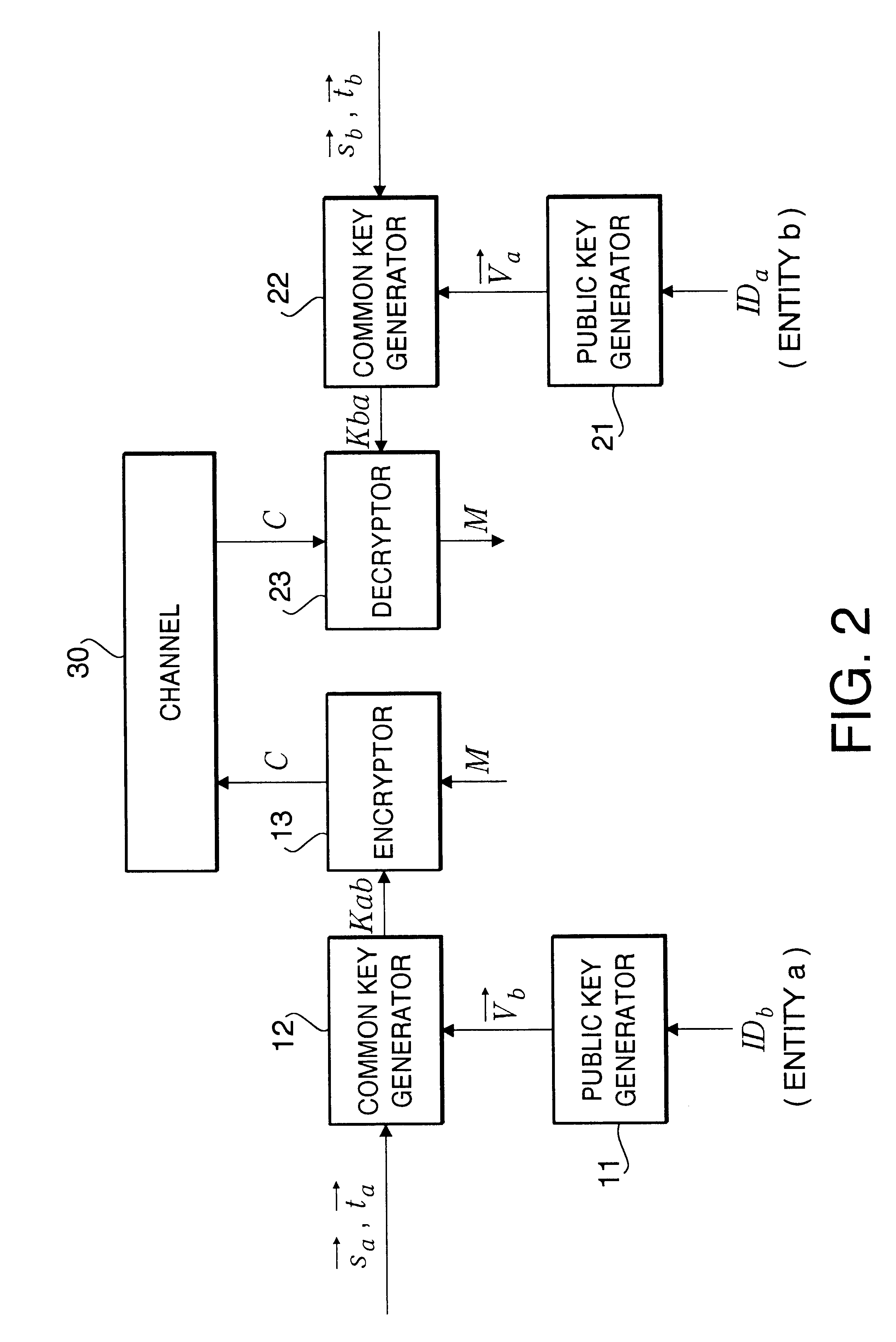
Cryptographic communication method, encryption method, and cryptographic communication system
InactiveUS6788788B1Key distribution for secure communicationPublic key for secure communicationPlaintextCommunications system
A novel cryptographic communication system including ID-NIKS system with high security. Secret key generation functions and key sharing functions are not separable. Key sharing is also probabilistically possible. A center uses entity-specific random numbers and entity-specific public keys based on ID information for each entity to generate two types of secret key (vectors s and t) in which two numbers serve as the moduli, respectively. The center then sends these secret keys to each entity, and each entity uses these two types of its own entity-specific secret key sent from the center and disclosed public key of another entity (the entity who receives a ciphertext or sends a ciphertext) to generate a common key that is shared by two entities for use in the encrypting of a plaintext into a ciphertext and in the decrypting of a ciphertext into a plaintext.
Owner:MURATA MASCH LTD
Credible data access control method applied to cloud storage of mobile devices
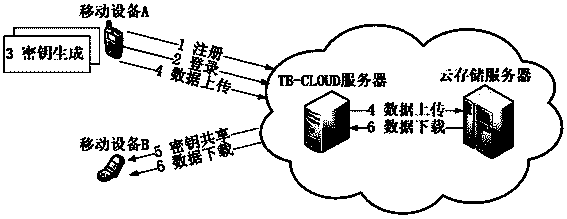
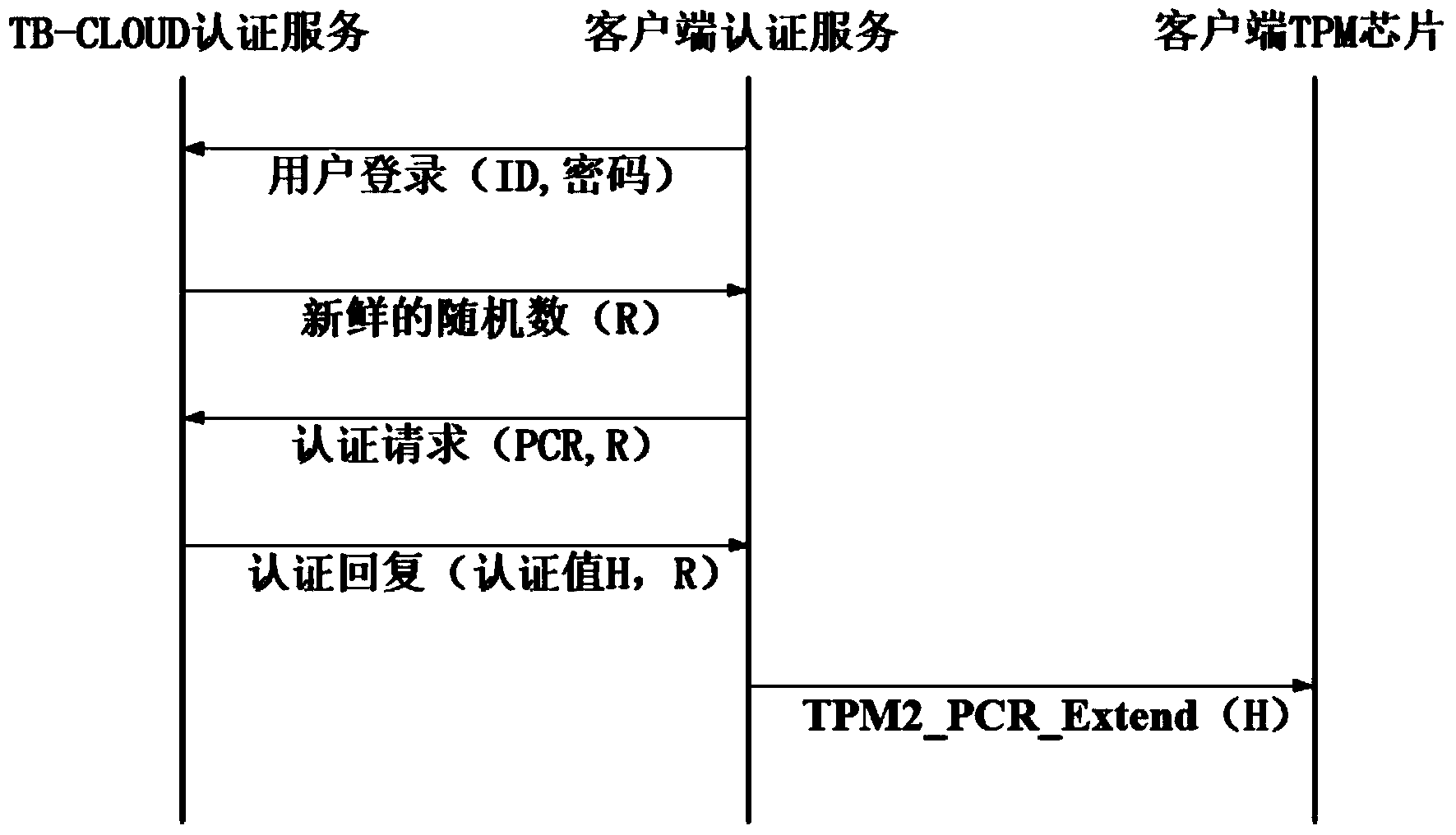
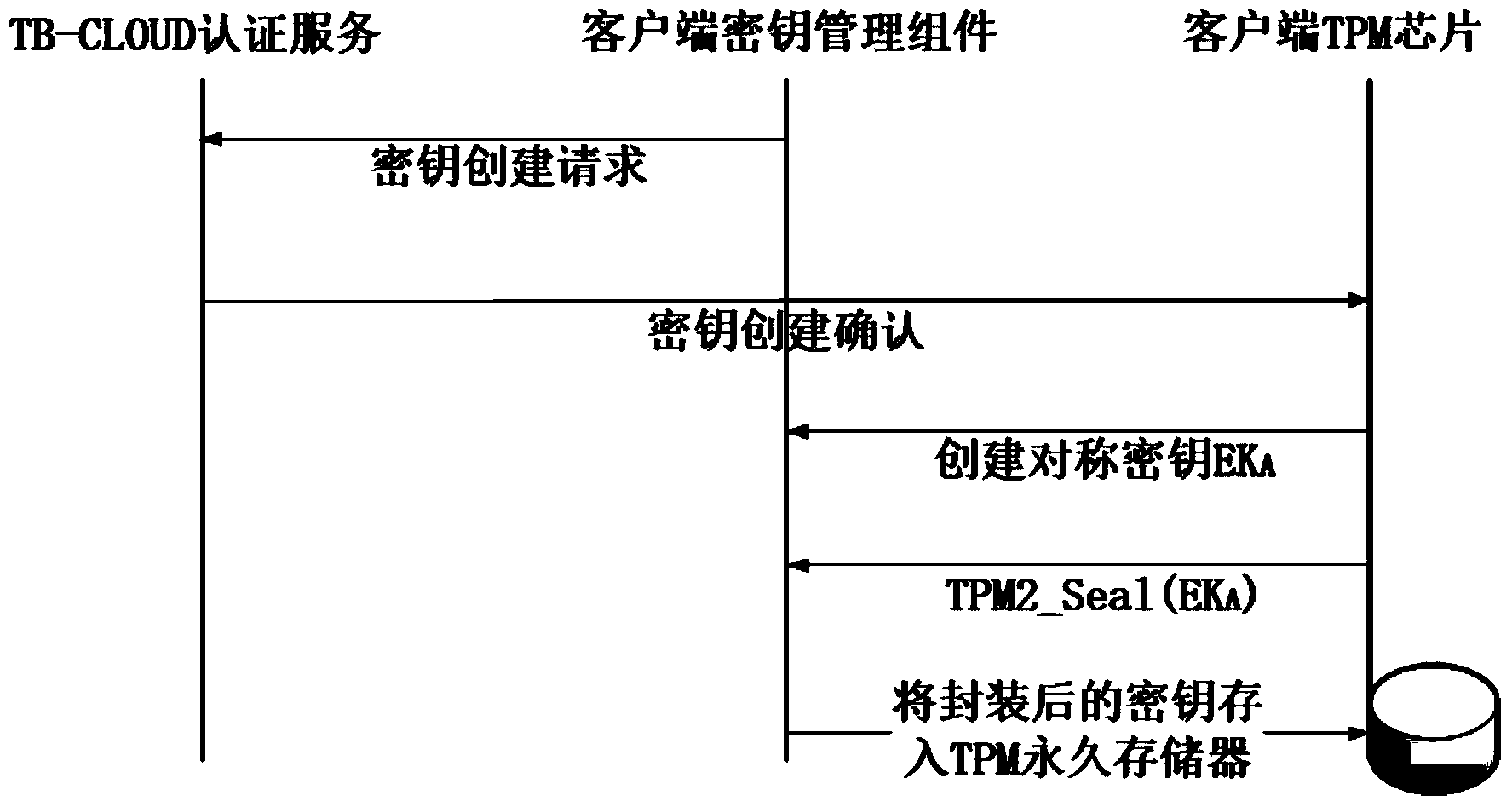
ActiveCN103763315AReduce the amount of data interactionConfidenceTransmissionCryptographic key generationKey size
The invention relates to a credible data access control method applied to cloud storage of mobile devices. The credible data access control method includes six steps including user registering, user login, secret key generation, data encryption uploading, data downloading and decryption in three stages. The first step is user registering, the second step is user login with an authentication process, the third step is encryption secret key generation, the fourth step is user data encryption uploading, the fifth step is secret key sharing among the multiple mobile devices, and the sixth step is data downloading and decryption. According to the credible data access control method, transmitting of a credible chain in the secret key exchanging process is guaranteed by a user through a mobile TPM chip, the length of a secret key is reduced through encryption based on a elliptic curve, it is guaranteed that the multiple mobile devices can safely share the secret key, compared with a traditional server terminal or client terminal data encryption method provided by a cloud storage service provider, the credible data access control method is safe, reliable, high in confidence degree and small in interaction data amount, and the good practical value and the wide application prospect are achieved in the technical field of cloud storage safety.
Owner:BEIHANG UNIV
Quantum key distribution system, quantum key distribution method and device
ActiveCN105871538AReduce the possibility of obtaining and maliciously leaking user dataEnsure safetyKey distribution for secure communicationPasswordKey distribution
The invention discloses a quantum key distribution system, a quantum key distribution method and a quantum key distribution device. The system includes a quantum security key management device, quantum security key distribution devices and a quantum security key service device; the quantum security key management device is used for splitting a system private key into at least two system sub private keys according to a threshold key sharing mechanism and distributing the system sub private keys to the quantum security key distribution devices through a quantum key negotiation mode; the quantum security key service device is used for forwarding authorized private key acquisition requests to other quantum security key distribution devices; and the quantum security key distribution devices are used for acquiring identity-based authorized sub keys from the other quantum security key distribution devices through the quantum key negotiation mode and reconstructs an identity-based authorized private key through adopting the threshold key sharing mechanism. With the above system adopted, the risk that a classic password is cracked can be resisted, and the likelihood that an administrator maliciously leaks user data can be decreased.
Owner:ALIBABA GRP HLDG LTD
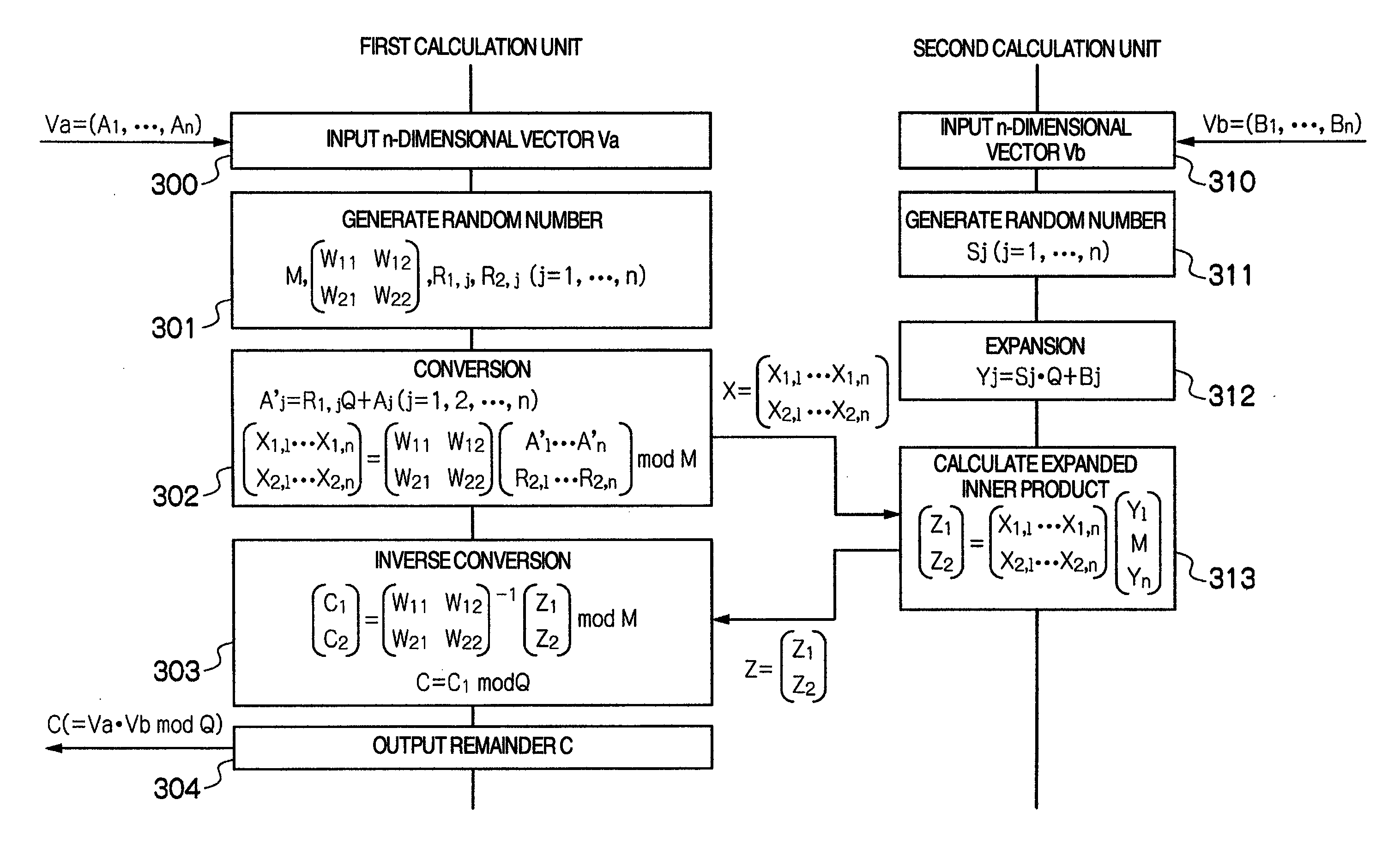
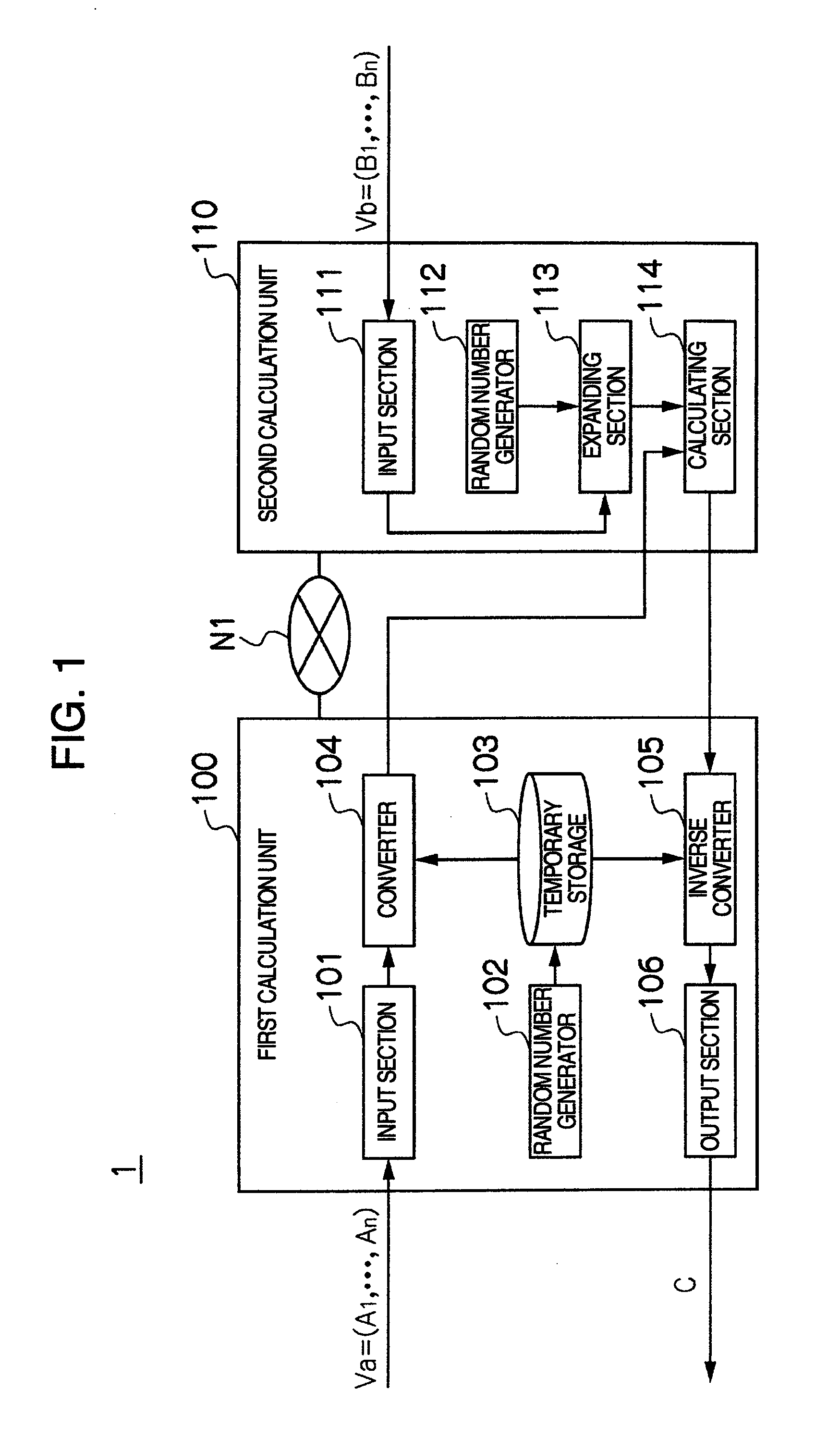
Privacy-preserving scalar product calculation system, privacy-preserving scalar product calculation method and cryptographic key sharing system
InactiveUS20090279694A1Calculation cost is highReduce computing costKey distribution for secure communicationRandom number generatorsScalar ValuePrivacy preserving
A privacy-preserving scalar product calculation system is provided. A first unit linearly transforms an n-dimensional vector Va into an n-dimensional vector based on a scalar value based on a random number Wi and a random number Rj to calculate a remainder by dividing each element of the linearly transformed n-dimensional vector by a random number Mi, and transmits an n-dimensional converted vector X including each of the remainders as its element to the second unit, the second unit calculates an inner product value Z based on the received n-dimensional converted vector X and an n-dimensional vector Vb, and transmits the inner product value Z to the first unit, and the first unit further calculates, based on a reciprocal of the scalar value and the receive inner product value, a scalar value and which calculates a remainder by dividing the scalar value by the random number Mi.
Owner:HITACHI LTD
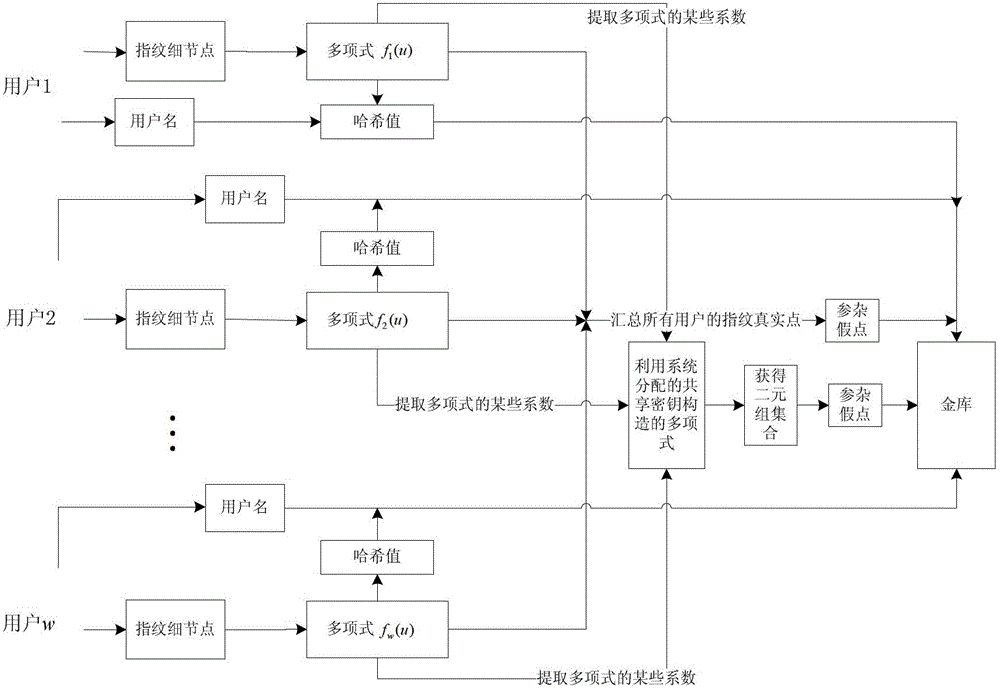
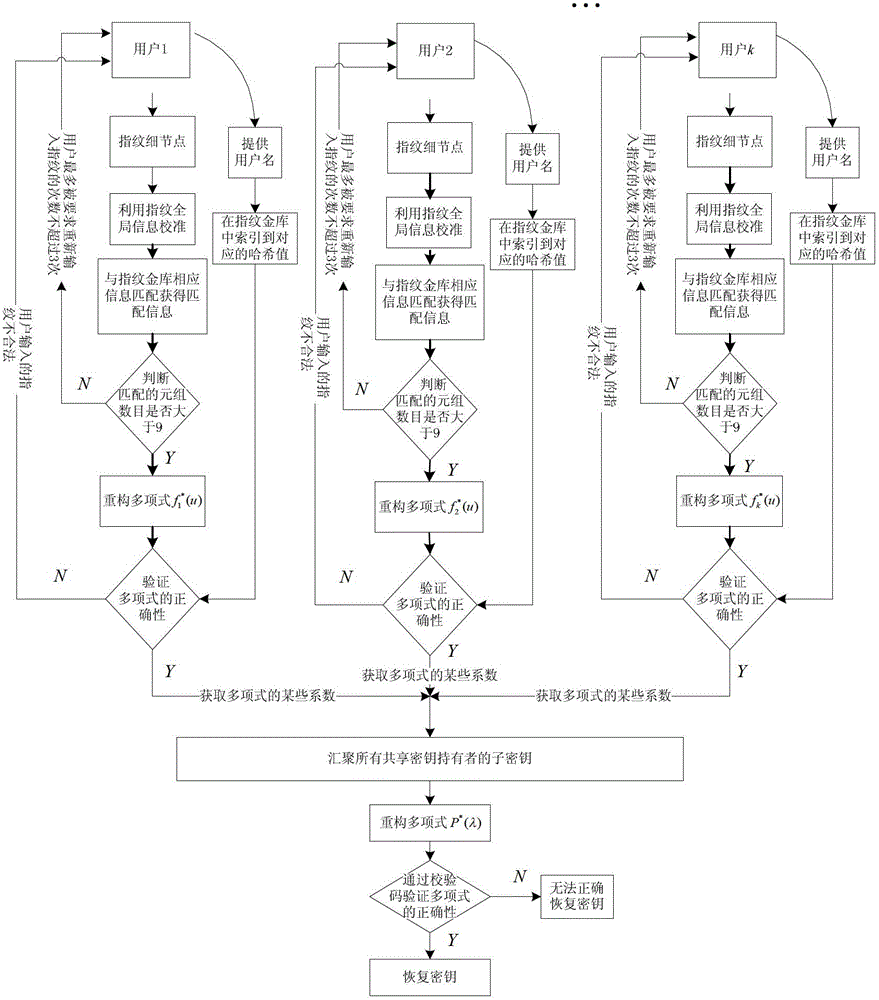
Fingerprint fuzzy vault method based on (k, w) threshold secret sharing scheme
ActiveCN102946310AKey distribution for secure communicationCharacter and pattern recognitionKey distributionKey sharing
The invention relates to a fingerprint fuzzy vault method based on a threshold secret sharing scheme. The method comprises a shared key distribution phase and a shared key reconstruction phase. The shared key distribution phase further comprises a binding process of the fingerprint fuzzy vault and a user subkey, and a shared key binding process. The shared key reconstruction phase further comprises a releasing process of partial user subkeys and a releasing process of the shared key. When the fingerprint fuzzy vault method is used to protect the shared key, the shared key is safely and conveniently released through fingerprint characteristics of the user. The releasing process of the key is very simple, and thus the key sharing scheme is more practical.
Owner:海宁鼎丞智能设备有限公司
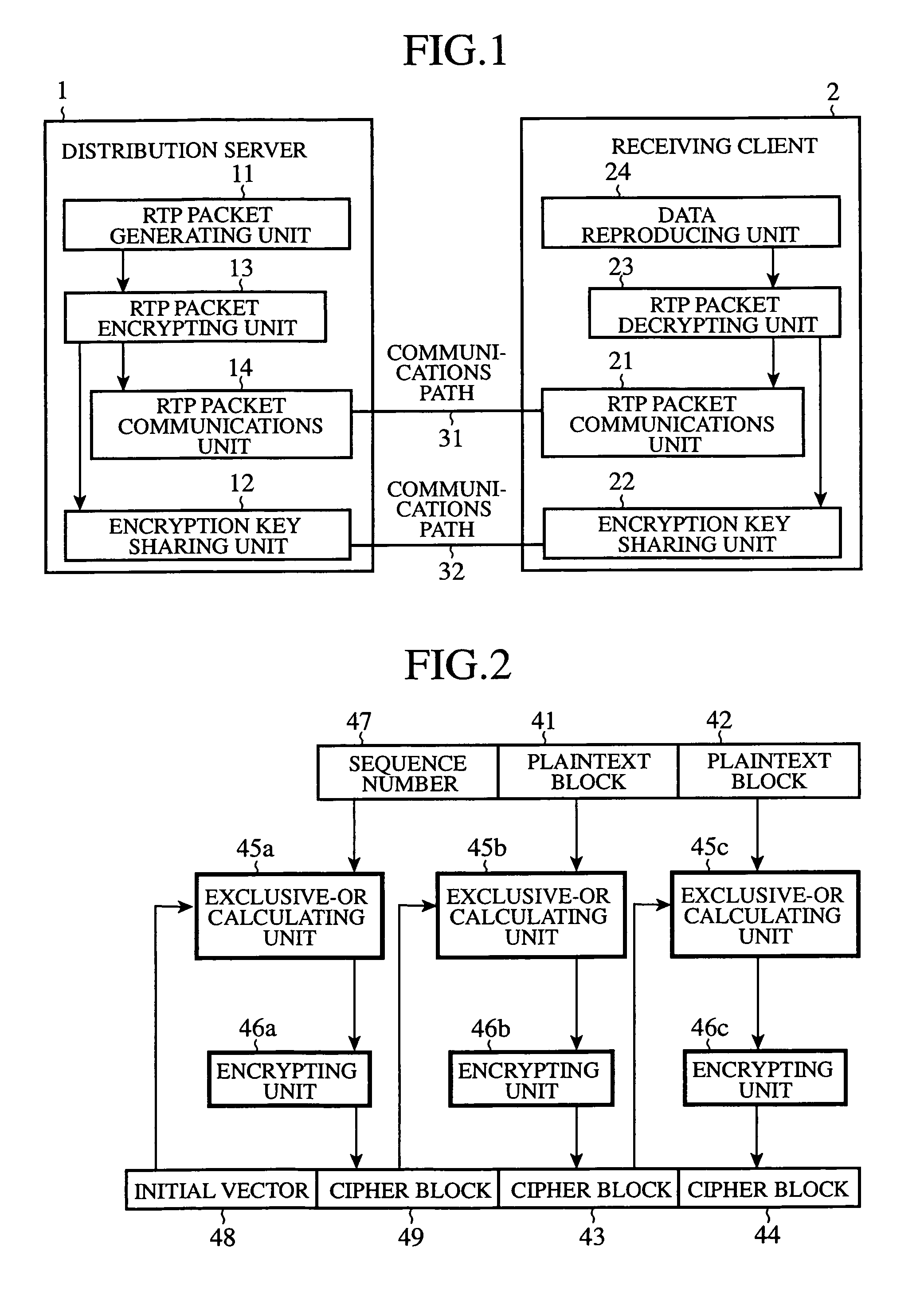
Data distribution apparatus and data communications system
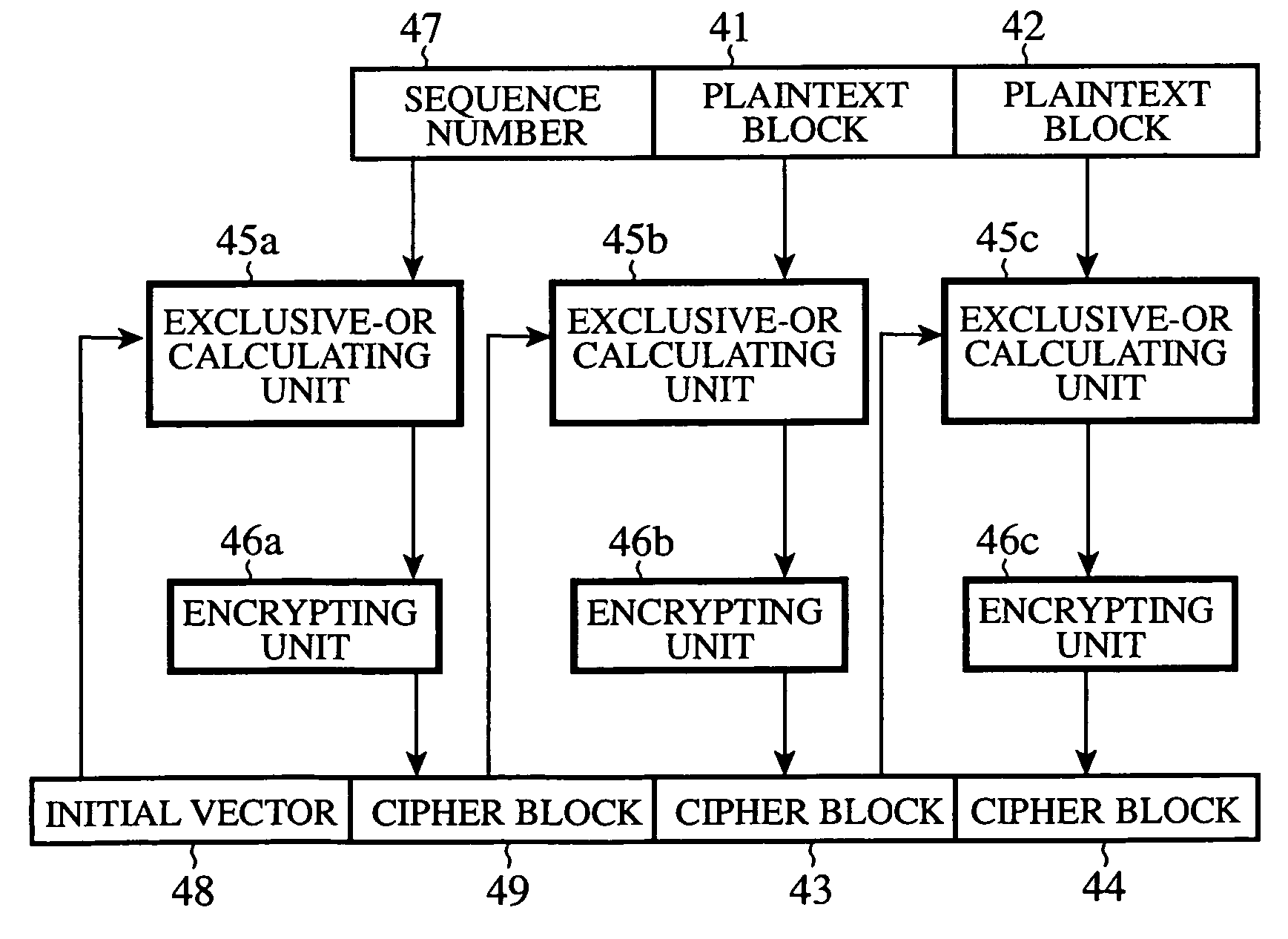
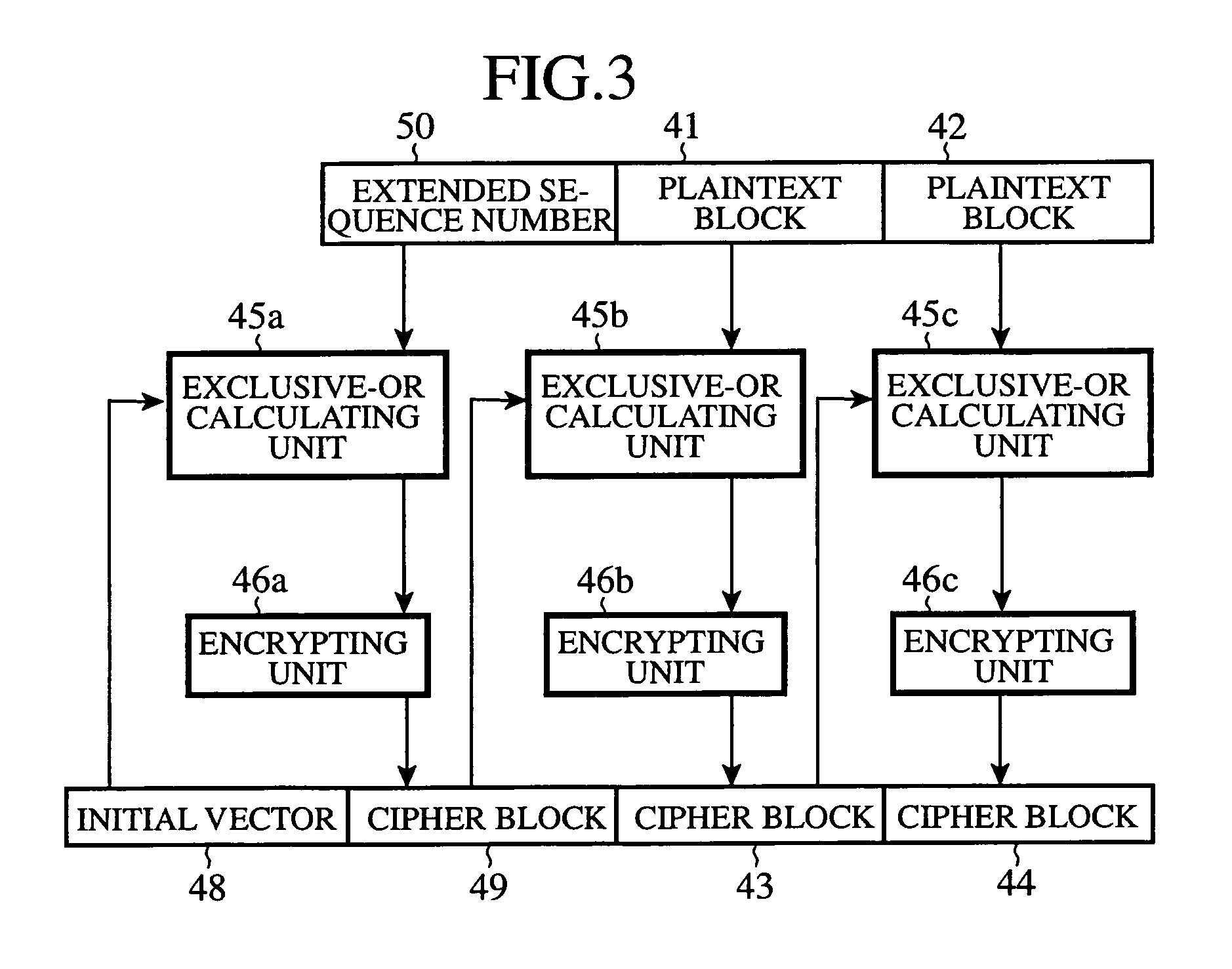
ActiveUS20070033391A1Improve security levelUnauthorized memory use protectionHardware monitoringCommunications systemClient-side
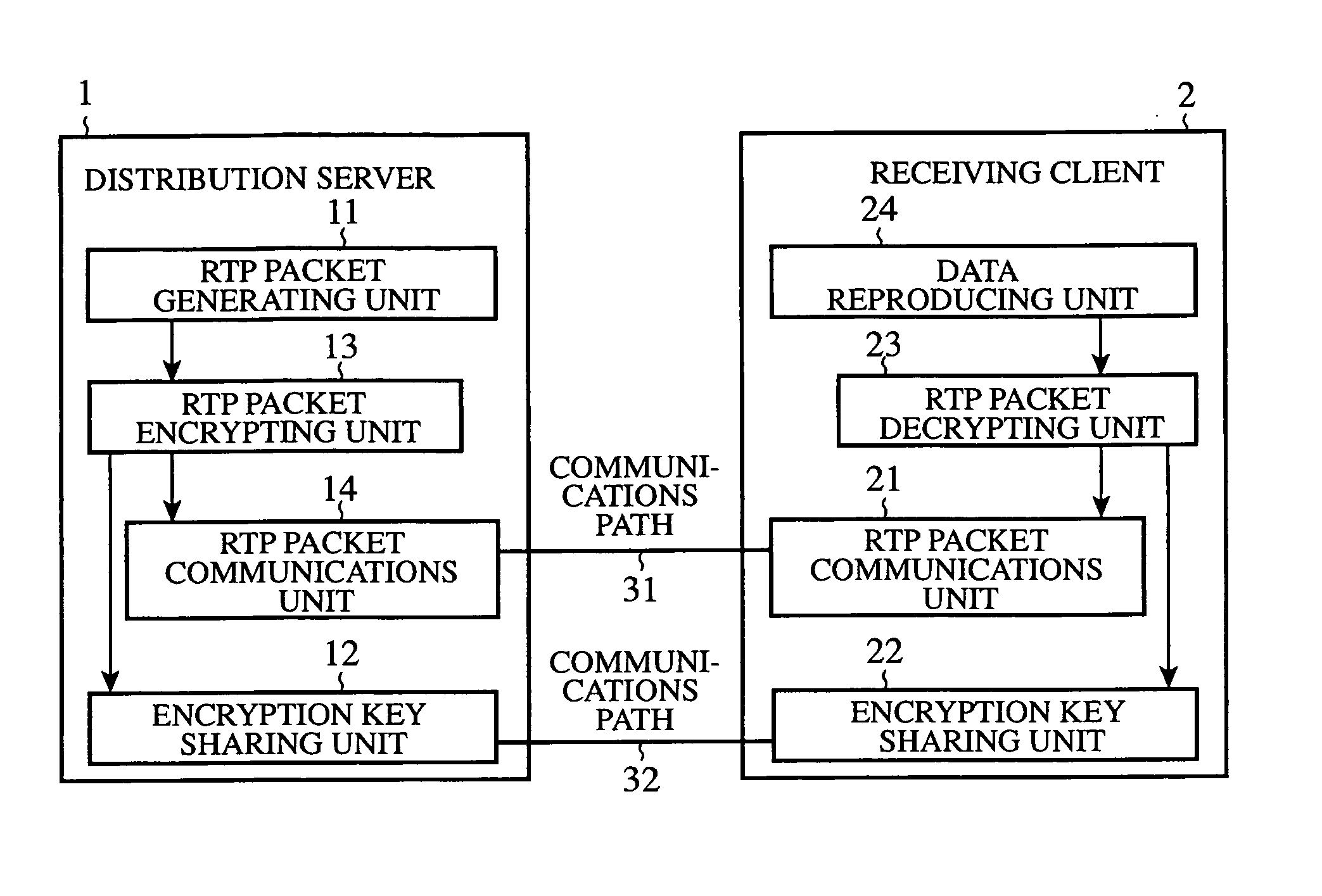
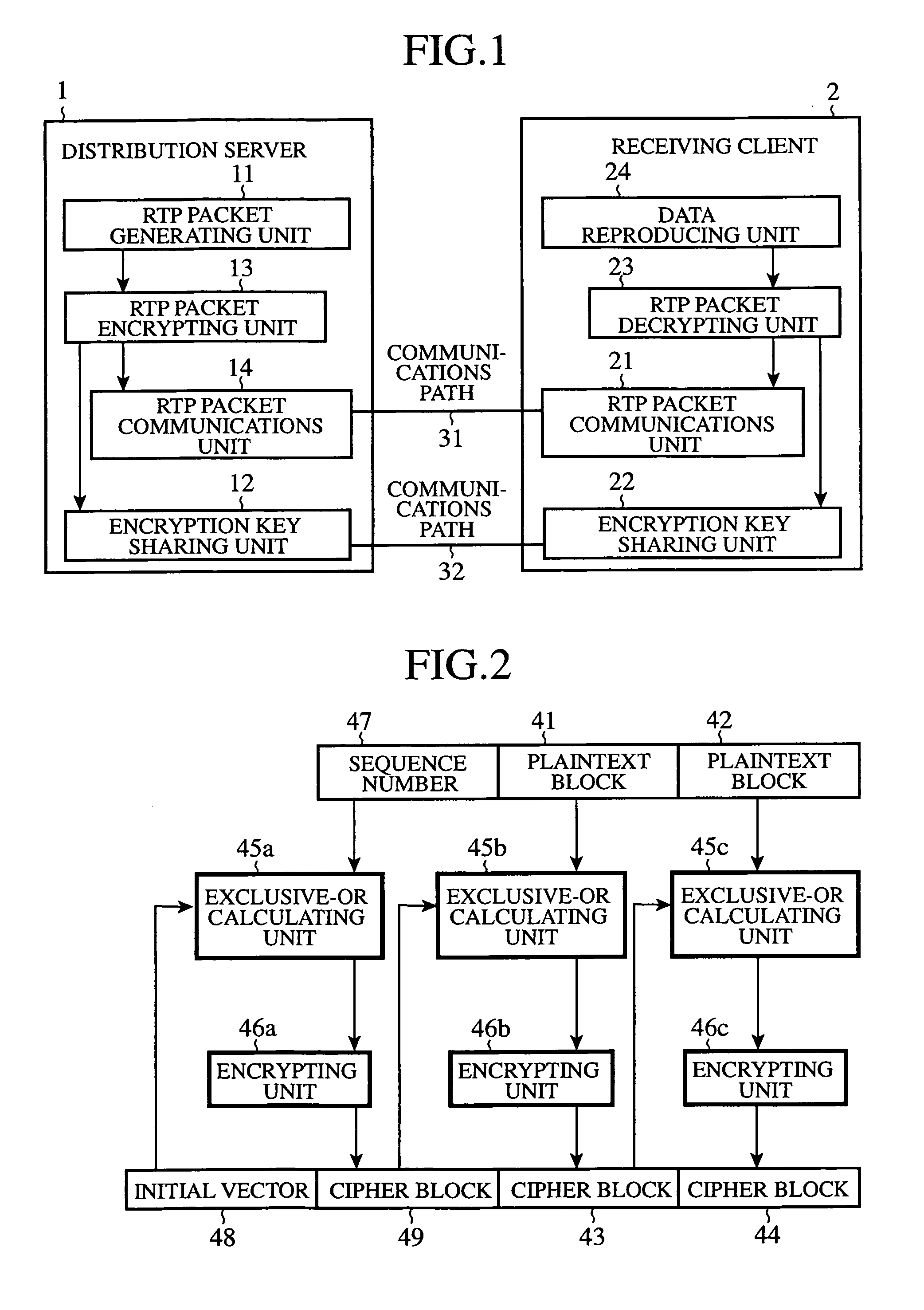
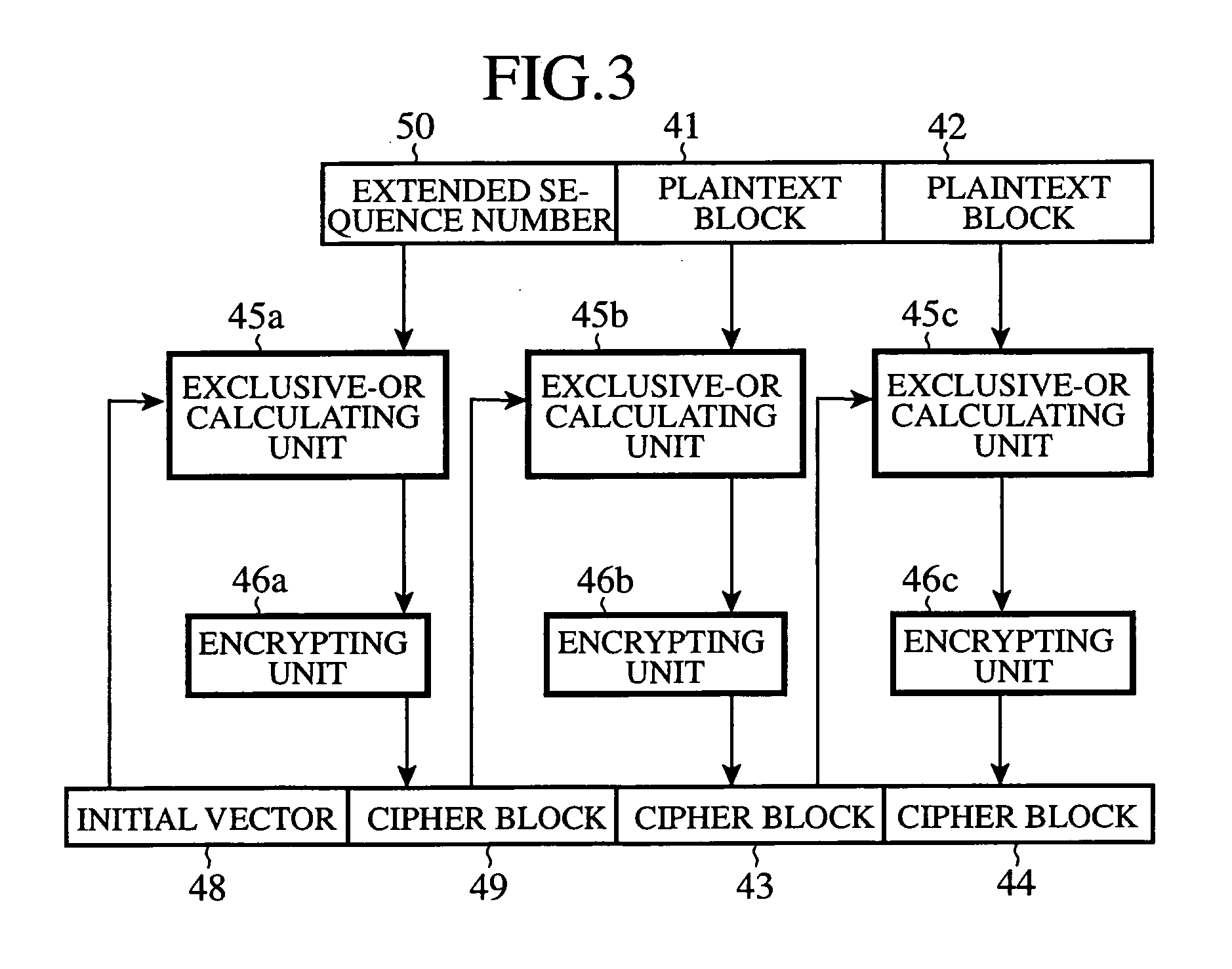
An RTP packet generating unit 11 packetizes data into packets, and adds identification information to the header of each of the packets, the identification information identifying each of the packets. An RTP packet encrypting unit 13 divides data included in each of the generated packets into blocks, and encrypts the data included in each of the packets on a block-by-block basis using an encryption key which an encryption key sharing unit 12 shares with a receiving client in such a manner that, when encrypting a first block of the data, the packet encrypting unit encrypts it using the identification information for identifying each of the packets, which is contained, as an initial vector, in the header of each of the packets, and, when encrypting each subsequent block of the data, encrypts it according to an encryption method which uses an immediately-previously-encrypted block.
Owner:MITSUBISHI ELECTRIC CORP
Automobile digital cloud key sharing system
InactiveCN106301781AAchieve sharingResolve deliveryAnti-theft devicesUser identity/authority verificationComputer moduleComputer terminal
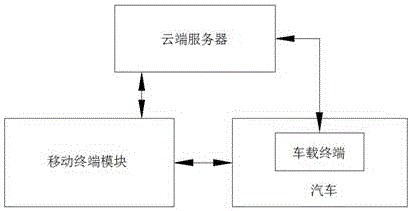
The invention discloses an automobile digital cloud key sharing system. The system comprises a cloud server, a mobile terminal module and a vehicle-mounted module. The cloud server is connected with the mobile terminal module and the vehicle-mounted module and used for generating an automobile digital cloud key and an authorization digital certificate. When the mobile terminal module and the vehicle-mounted module are bound, the mobile terminal module acquires the automobile digital cloud key and the authorization digital certificate from the cloud server through wireless data transmission. The automobile digital cloud key is used for achieving control on an automobile. The authorization digital certificate is used for verifying identify of a user. The mobile terminal module is connected with the vehicle-mounted module through a communication module, and comprises a main intelligent terminal and multiple sub-intelligent terminals. According to the invention, automobile digital cloud key sharing is achieved, and the automobile digital cloud key sharing system can be completely suitable for all kinds of uncertain environments and suitable for promotion.
Owner:山东尼格电子技术有限公司
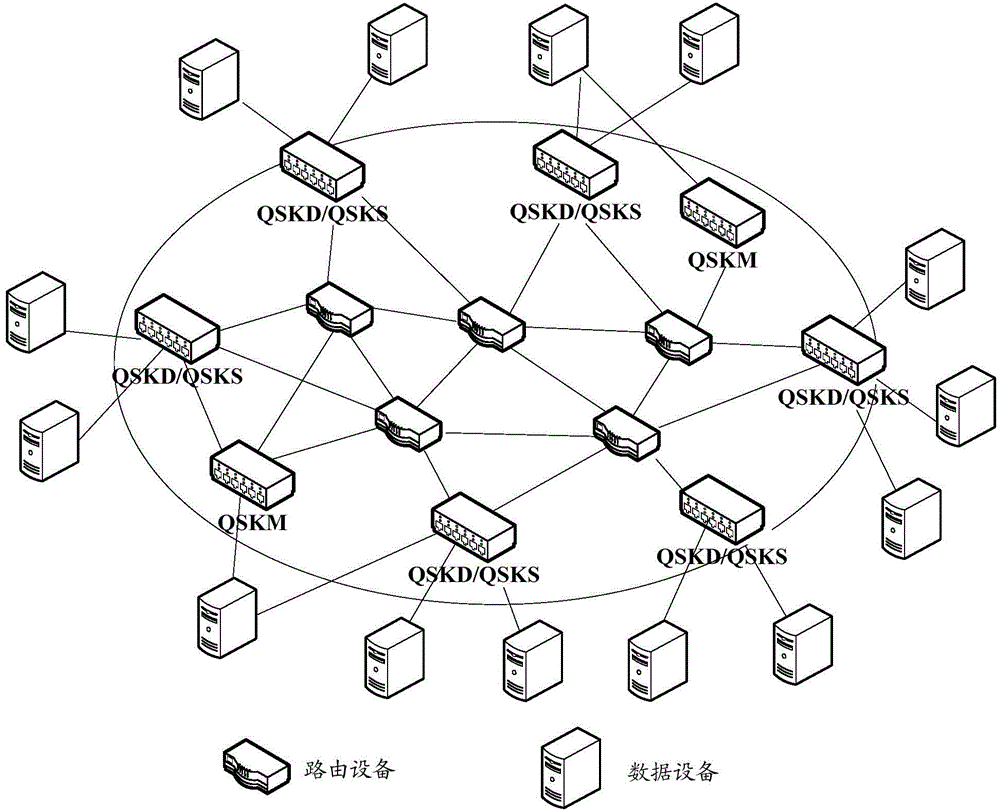
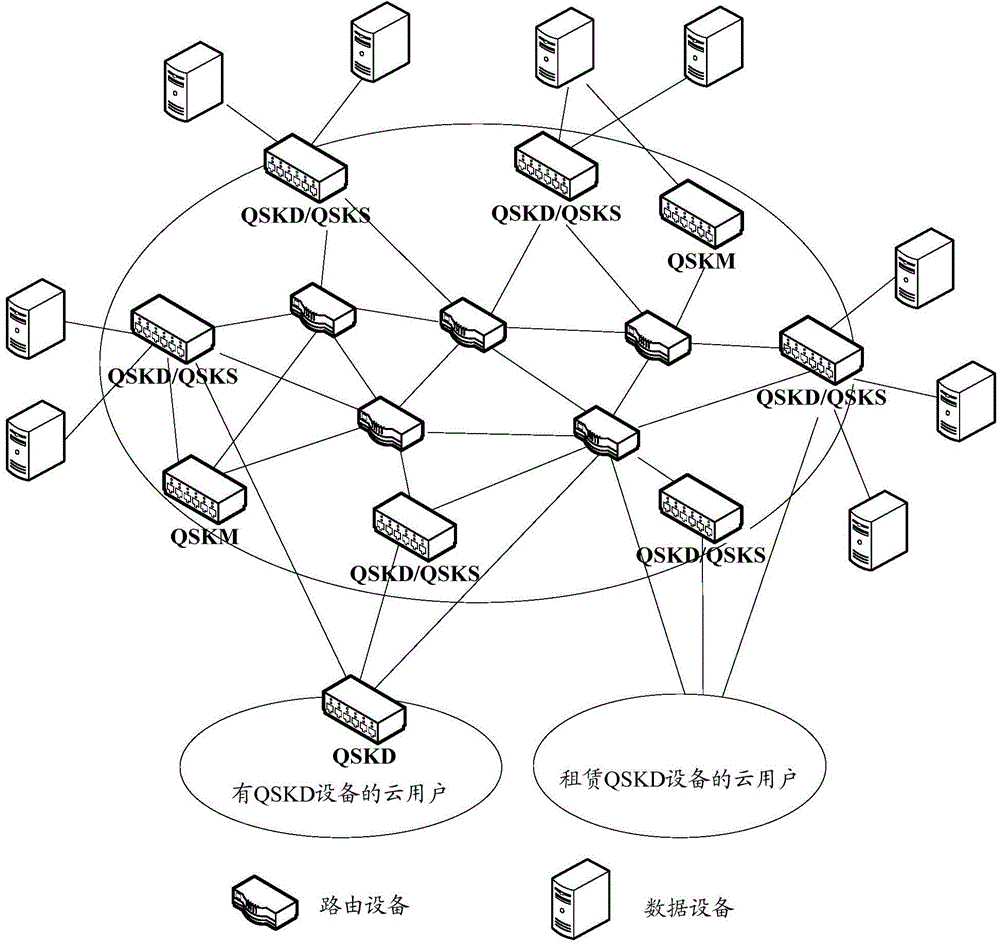
Expandable multi-user quantum key distribution network system and key distribution method thereof
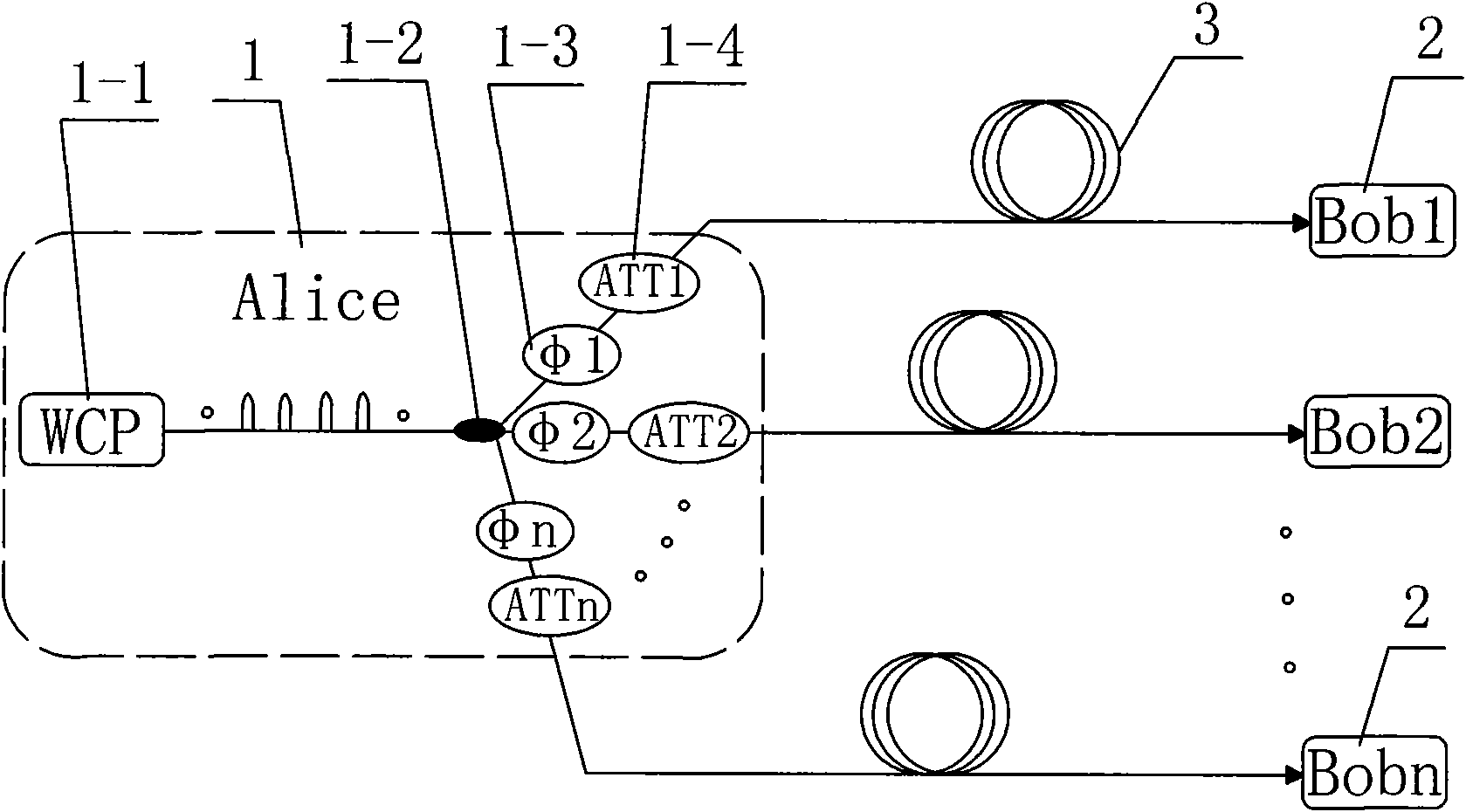
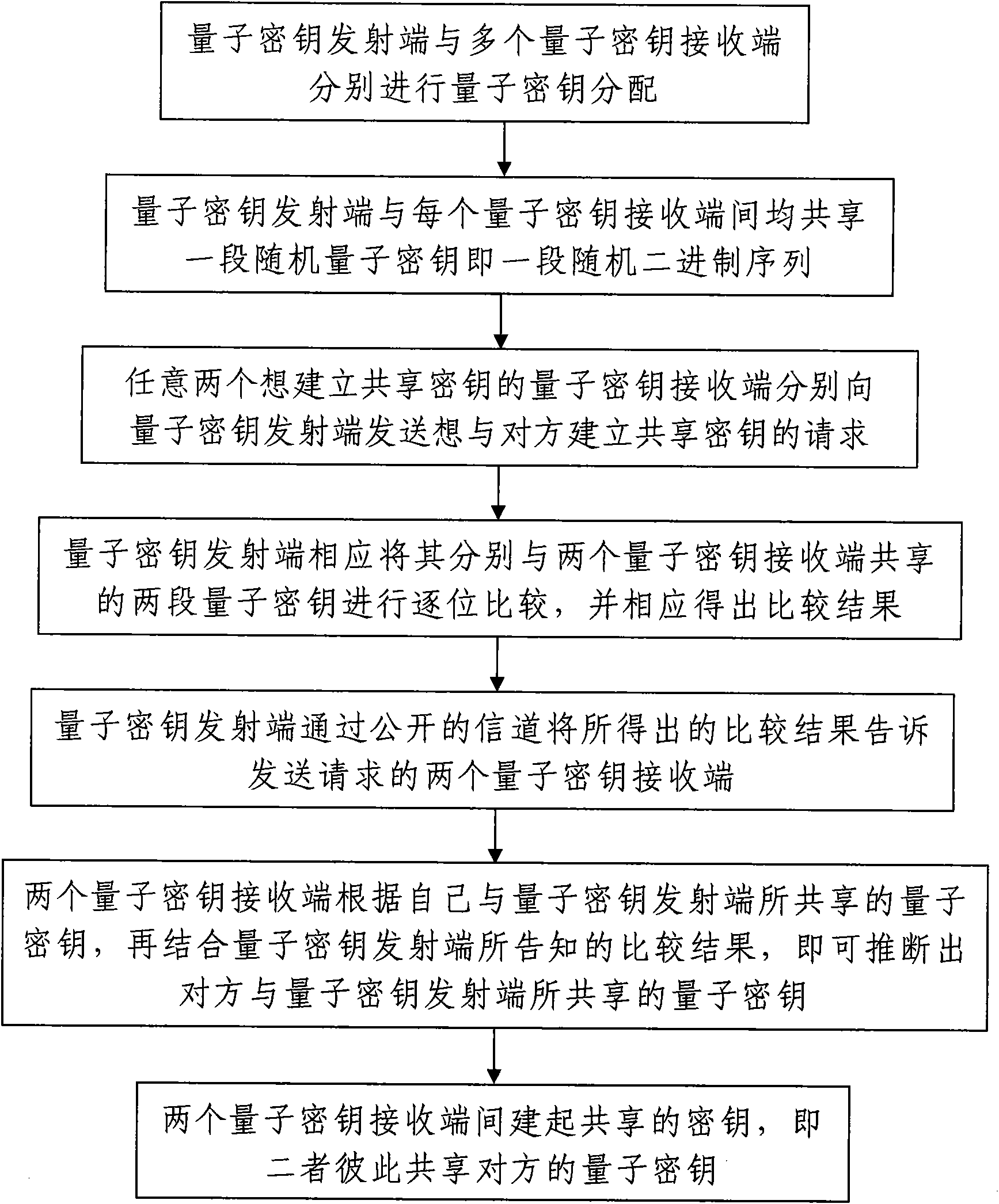
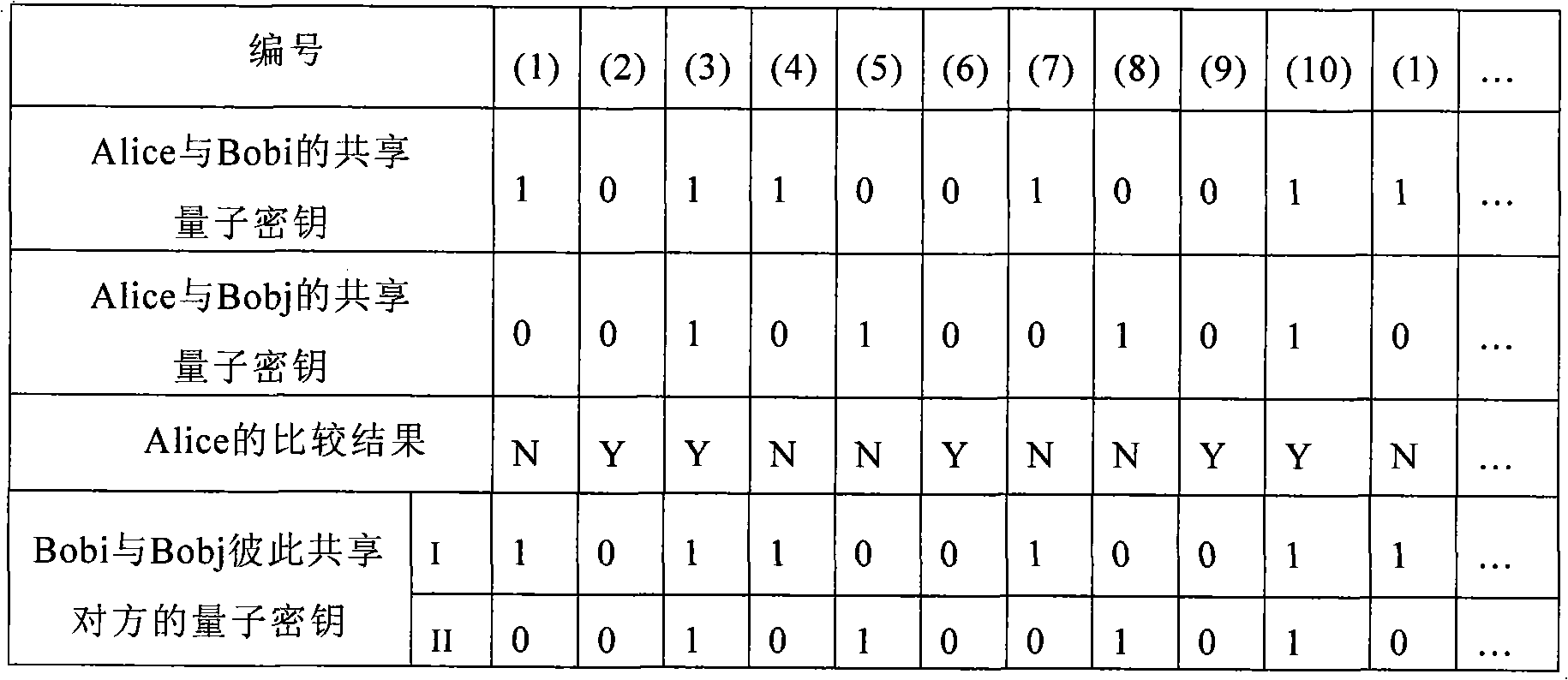
InactiveCN101599826AUnlimited expansionNo longer affects allocation rateKey distribution for secure communicationComputer hardwareKey distribution
The invention discloses an expandable multi-user quantum key distribution network system and a key distribution method thereof; wherein the system comprises a point-to-multipoint quantum key distribution system composed of a quantum key transmitting terminal and a plurality of quantum key receiving terminals. The key distribution method includes the steps: firstly, the quantum key transmitting terminal namely the transmitter and a plurality of quantum key receiving terminals namely the receivers carry out quantum key distribution, the transmitter and each receiver all share a random quantum key; secondly, any two receivers send a request to the transmitter, the transmitter compares the two quantum keys shared with the receivers bit by bit and sends the comparison result to the two receivers, and the two receivers can obtain the quantum key shared by the transmitter and the other receiver by combining the own quantum key shared with the transmitter. The invention is reasonable in design and convenient in use and operation, and has strong user capacity expansion capability, long transmission distance and good user functionality; and any two legal receivers can share the key.
Owner:SHAANXI UNIV OF TECH
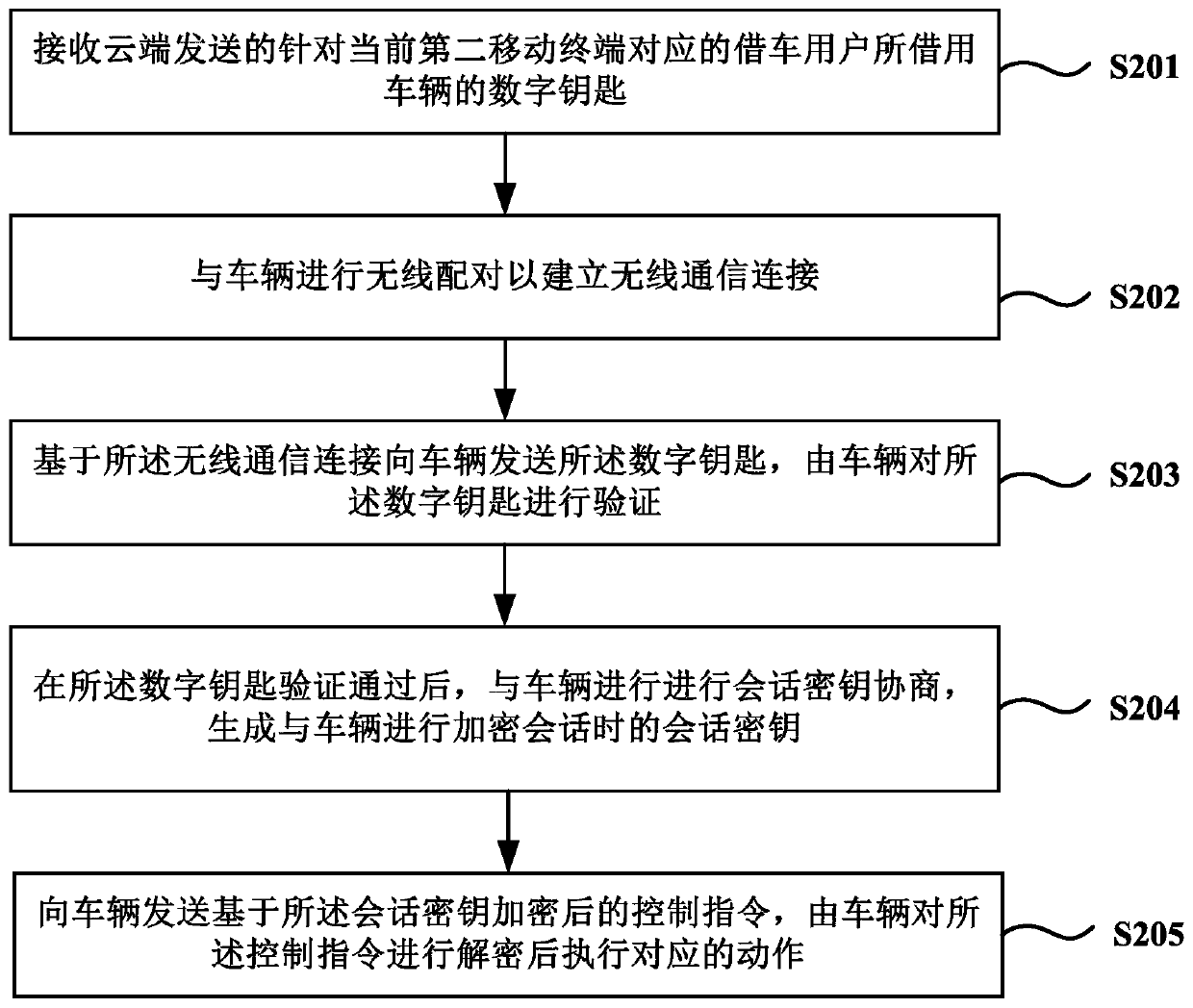
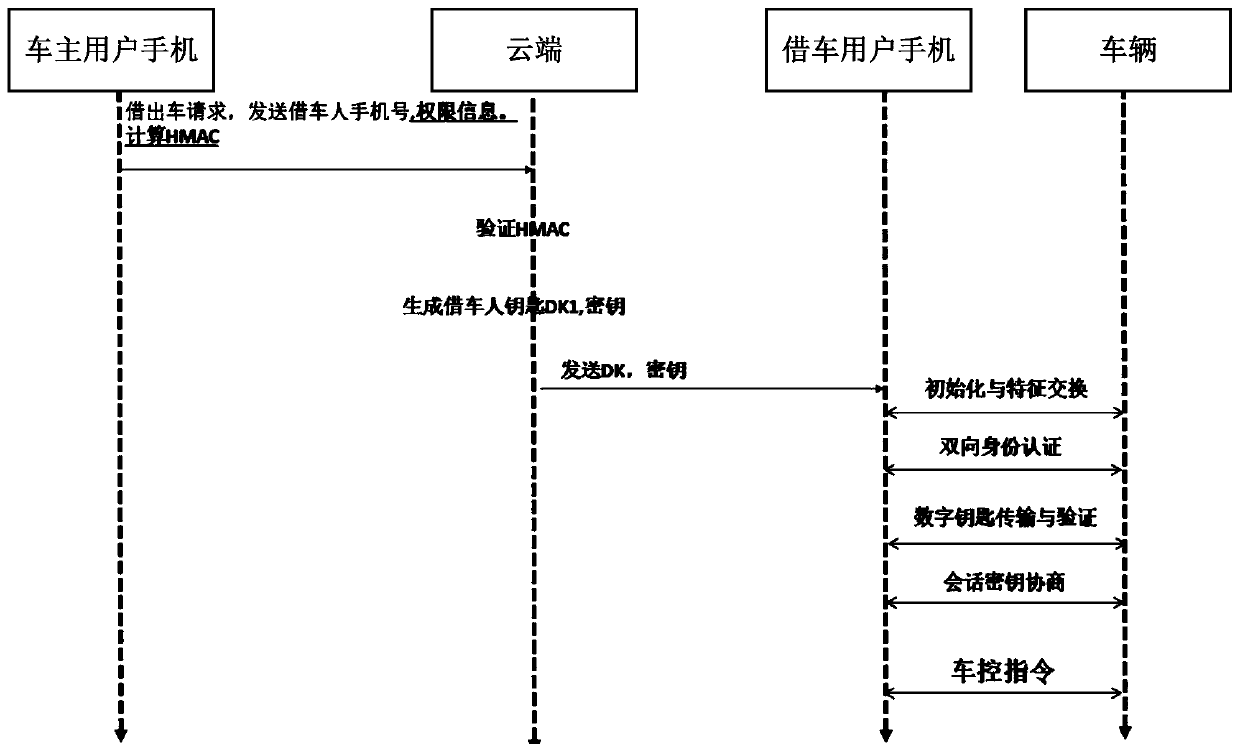
Vehicle digital key sharing method and system and mobile terminal
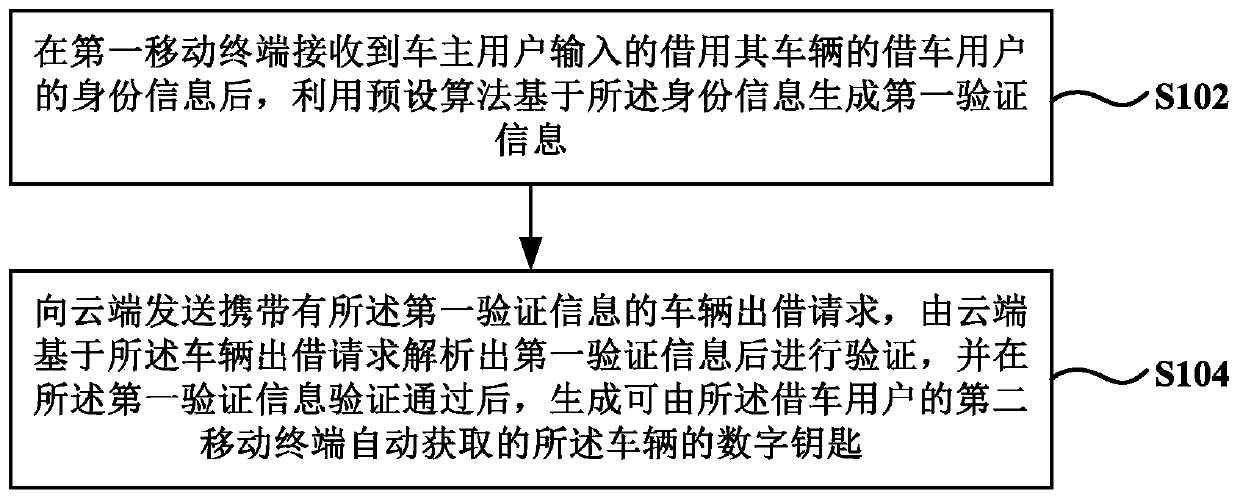
InactiveCN110290525AEnsure safetyIndividual entry/exit registersTransmissionUser inputComputer terminal
The invention provides a vehicle digital key sharing method and system and a mobile terminal, and the method comprises the steps: after a first mobile terminal receives the identity information of a vehicle borrowing user who borrows a vehicle and is input by a vehicle owner user, generating first verification information based on the identity information by using a preset algorithm; sending a vehicle lending request carrying the first verification information to a cloud, and enabling the cloud to analyze the first verification information based on the vehicle lending request and then verify the first verification information, and generate a digital key of the vehicle which can be automatically acquired by a second mobile terminal of the vehicle lending user after the first verification information passes the verification. Based on the scheme provided by the invention, the cloud needs to verify the identity of a vehicle owner user, feature exchange, key transmission and verification and session key negotiation are also needed between the second mobile terminal of the vehicle borrowing user and the vehicle, then the vehicle control instruction can be sent, and the security of the digital key is ensured through multi-key encryption and verification.
Owner:ECARX (HUBEI) TECH CO LTD
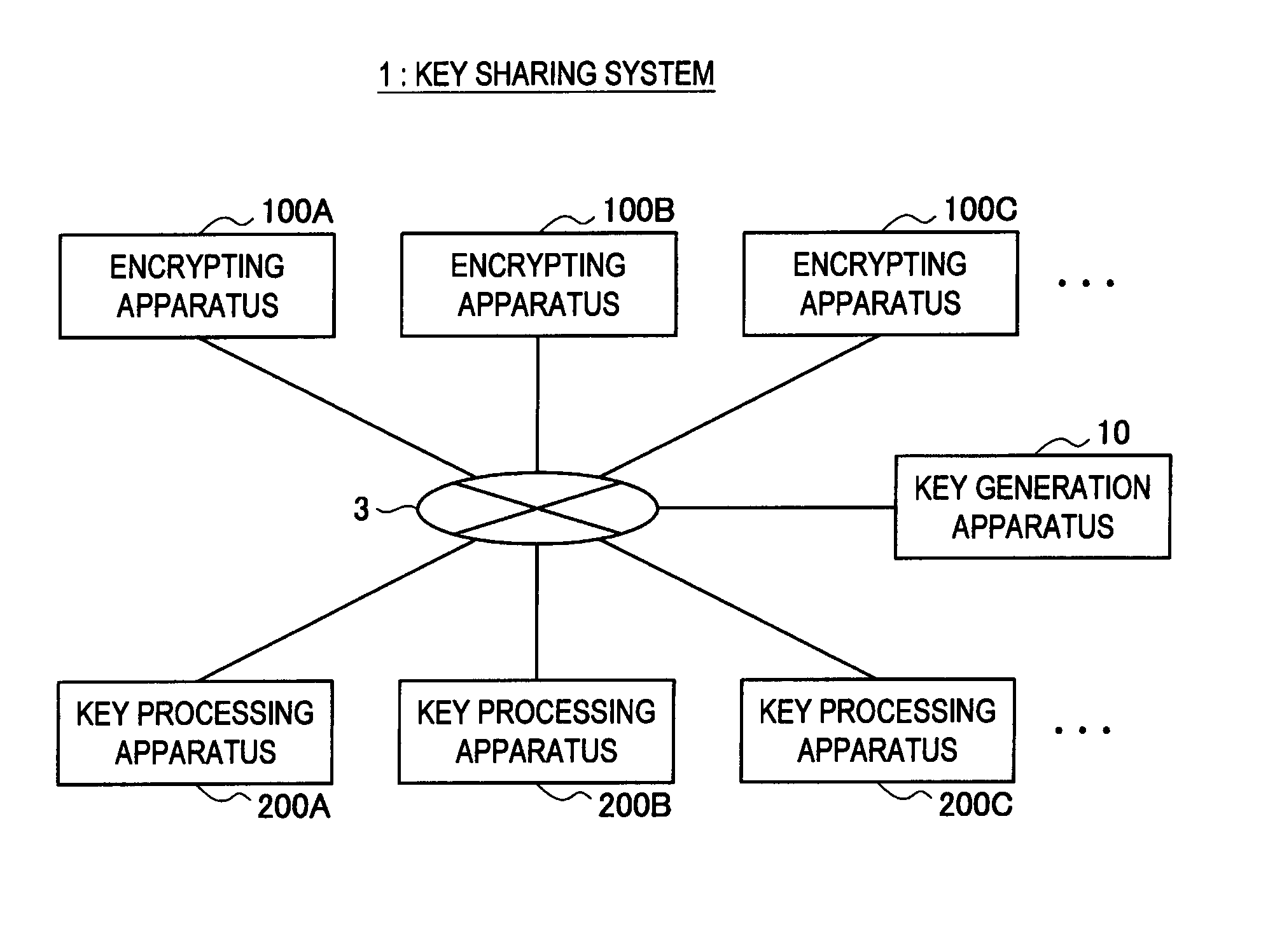
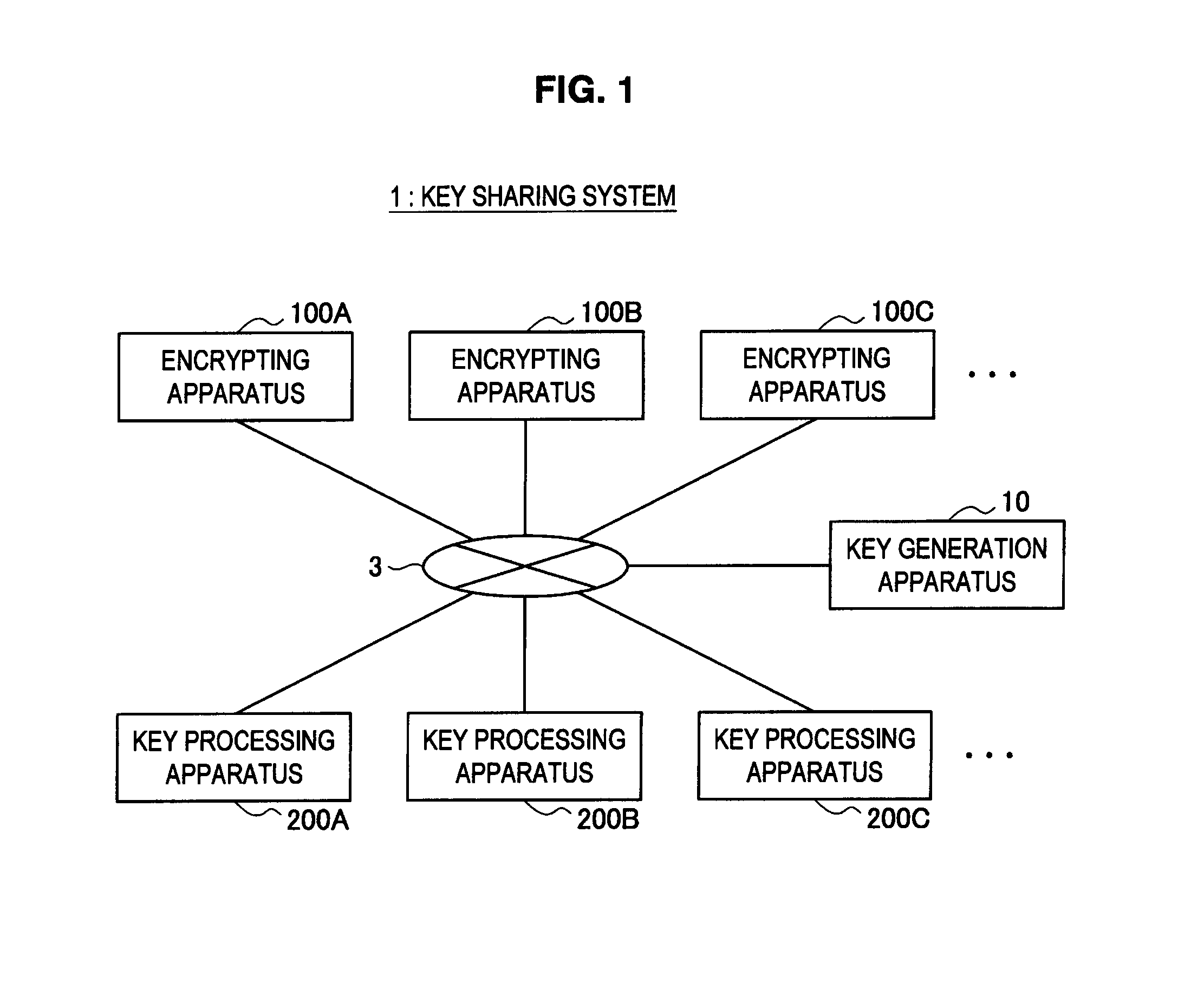
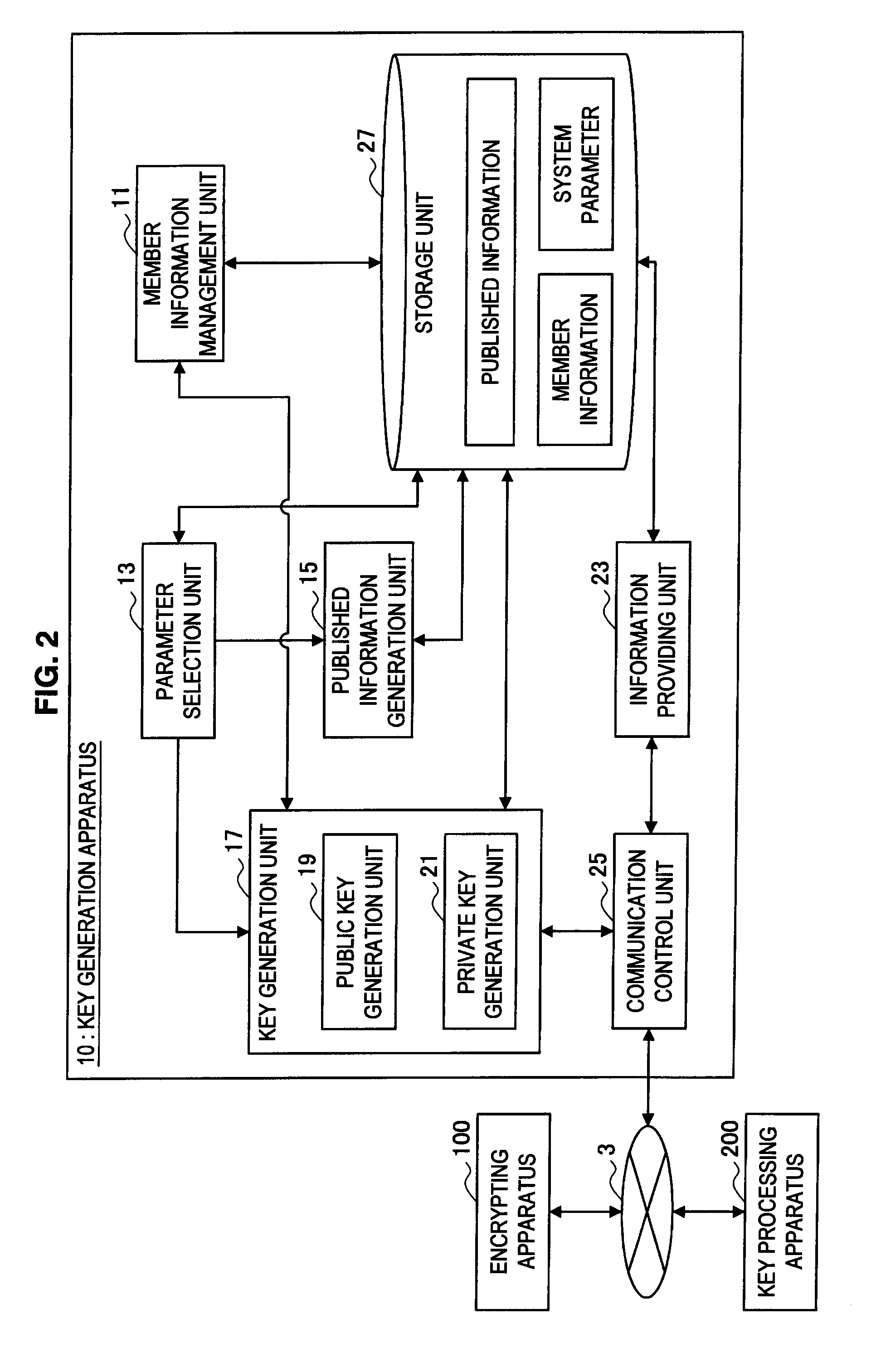
Key Sharing System
InactiveUS20110194698A1Improve securityKey distribution for secure communicationKey sharingInformation needs
When each apparatus generates session information needed for calculating a session key used in a simultaneous communication, an encrypting apparatus and a key processing apparatus according to the present invention causes each piece of session information to include a value dependent upon a private key unique to each apparatus, which is assigned to each apparatus in advance. Therefore, this provides protection against spoofing attempt by a member within a group.
Owner:SONY CORP
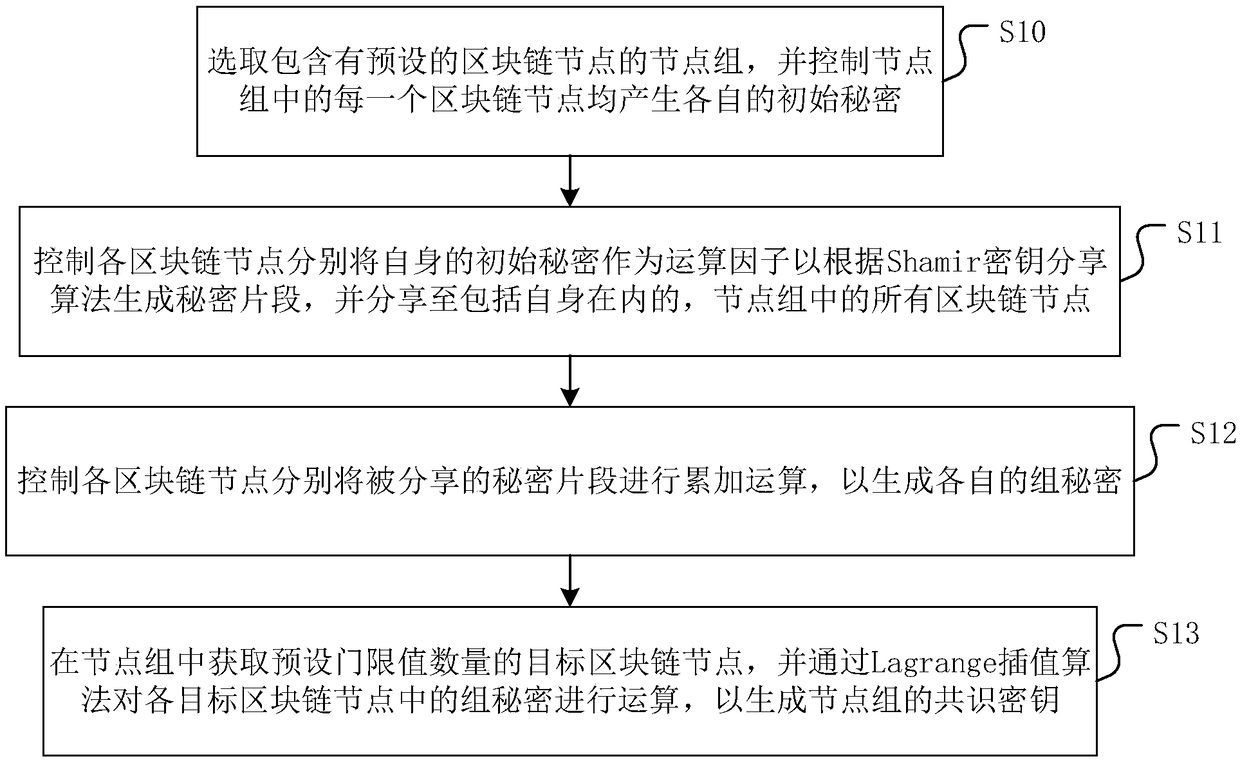
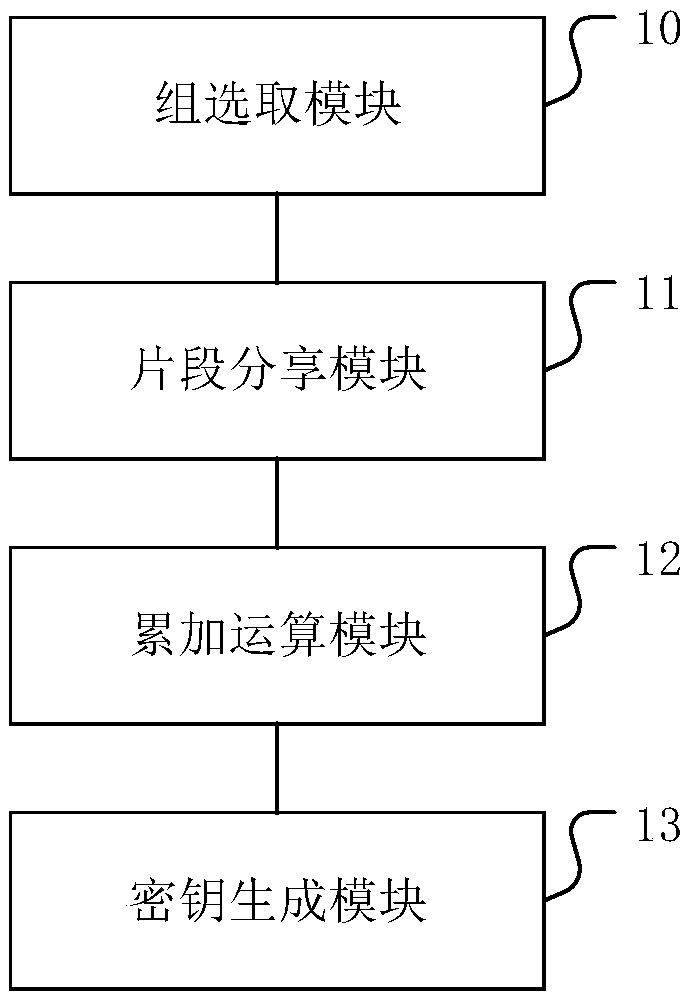
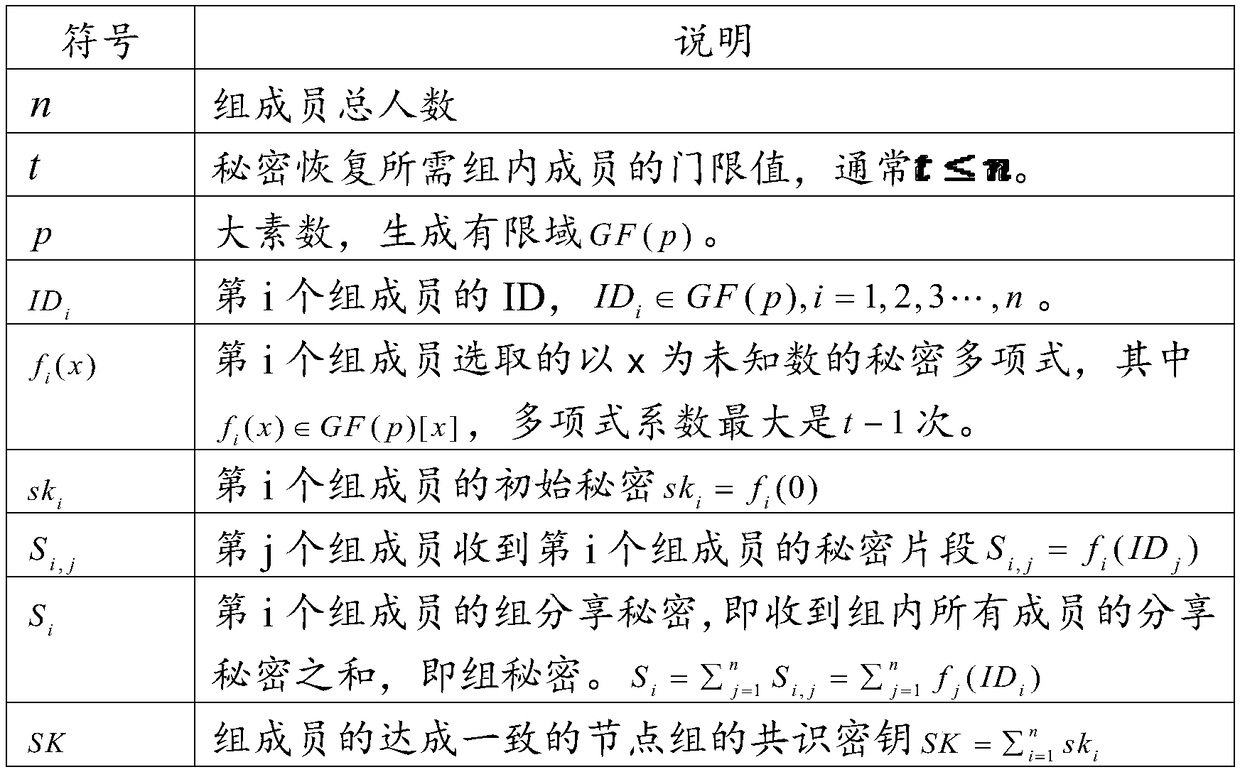
Blockchain-based key generation method and apparatus, and medium
ActiveCN108712261AEnsure safetyGuaranteed reliabilityKey distribution for secure communicationUser identity/authority verificationKey sharingKey generation
The invention discloses a blockchain-based key generation method and apparatus, and a medium. The method comprises the following steps: selecting a node group comprising preset blockchain nodes, and controlling each blockchain node in the node group to generate a respective initial secret; controlling the blockchain nodes to respectively use the own initial secrets as operation factors to generatesecret fragments according to the Shamir key sharing algorithm, and to share the secret fragments with all blockchain nodes containing themselves in the node group; controlling the blockchain nodes to perform accumulation operation on the shared secret fragments to generate a group secret; obtaining a preset threshold number of target blockchain nodes in the node group, and generating a consensuskey of the node group through the Lagrange interpolation algorithm. By adoption of the method disclosed by the invention, the security and reliability of the node group key generated under the blockchain mechanism are ensured. In addition, the invention further provides a blockchain-based key generation apparatus and a medium, which have the same beneficial effects as described above.
Owner:吕晟珉
Key management method based on convergence encryption for use in cloud storage data duplication elimination
InactiveCN106100832AEfficient deduplicationReduce storage overheadKey distribution for secure communicationEncryption apparatus with shift registers/memoriesCloud storage systemClient-side
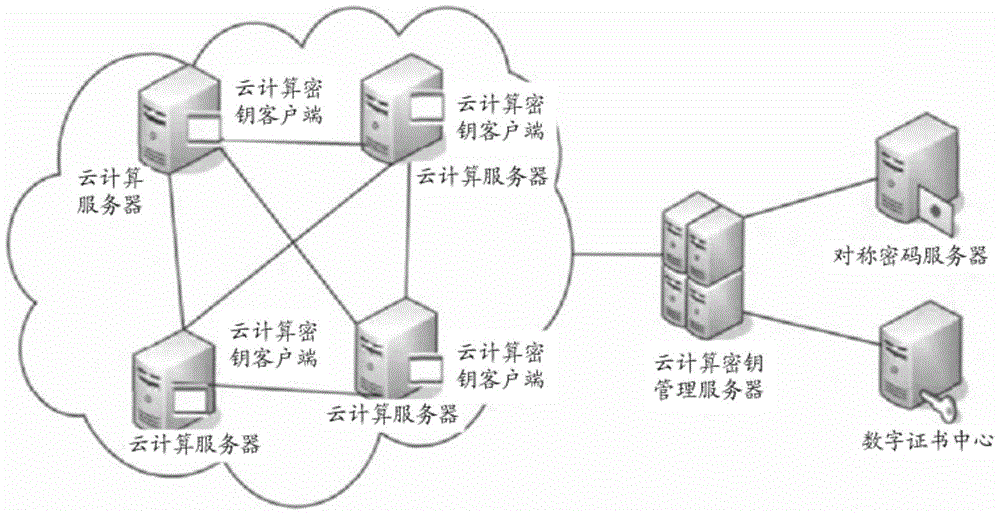
The invention relates to a key management method based on convergence encryption for use in cloud storage data duplication elimination. The method comprises the following steps: adding n key servers into a cloud storage system, wherein the servers are used for storing key shares distributed by a client, and the key shares are obtained by the client in a way of executing a Share algorithm based on (n, k, r)-RSSS, segmenting an original key and performing encoding, a key recovery algorithm is a Recover algorithm for recovering the shares into an original key S, the key shares of any k (k is less than n) servers can be recovered to the original key S, a part of n servers are allowed to fail or be damaged but safe running of k (exceeding a minimum threshold) servers needs to be ensured, and r pseudo-random shares are generated by the Share algorithm to replace random shares of RSSS; and performing duplication elimination management on convergence keys according to a key distributed management method for use in cloud storage system duplication elimination, and executing a duplication elimination operation on file data blocks to be stored.
Owner:GUANGDONG UNIV OF TECH
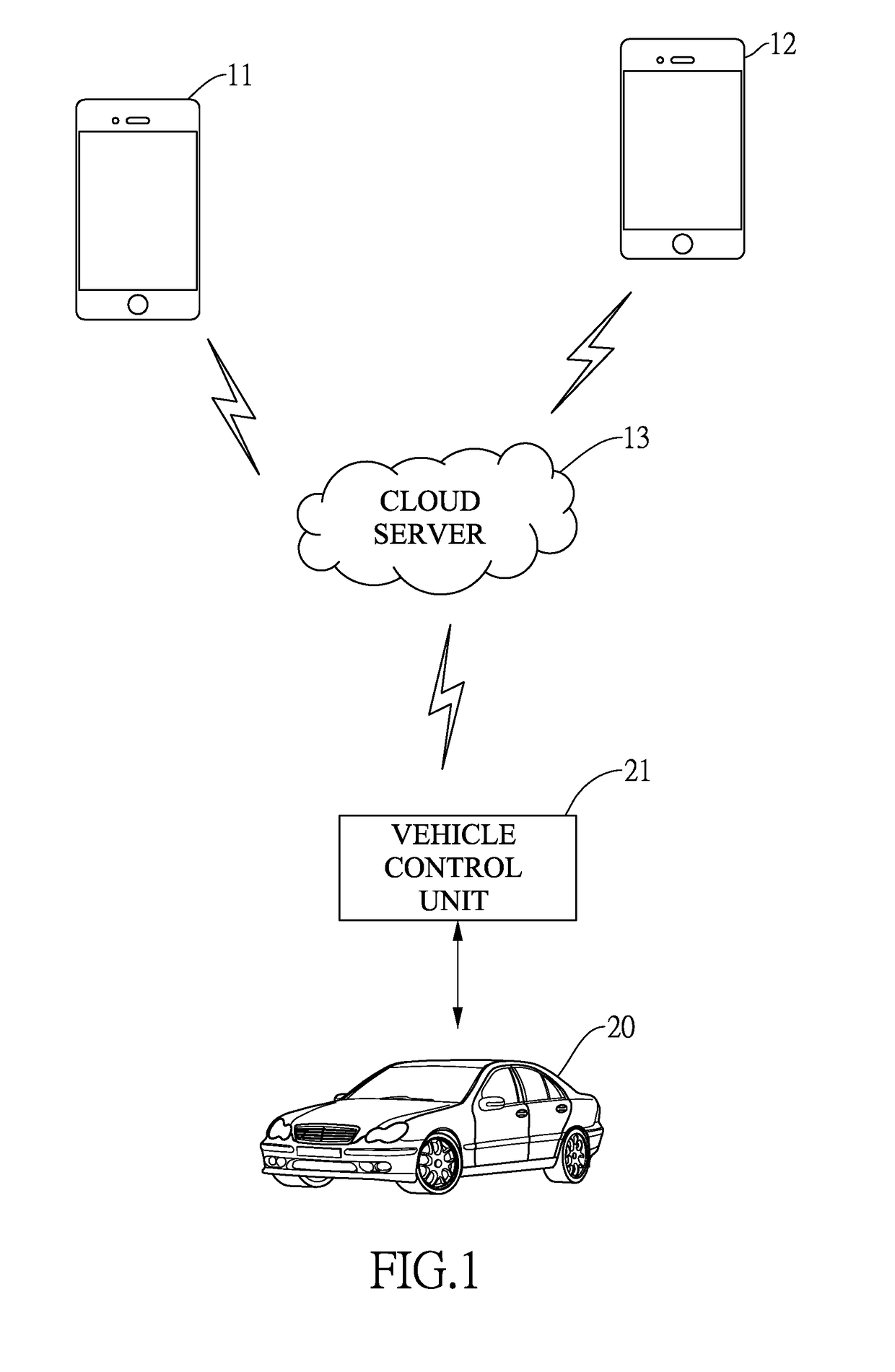
Intelligent vehicular electronic key system
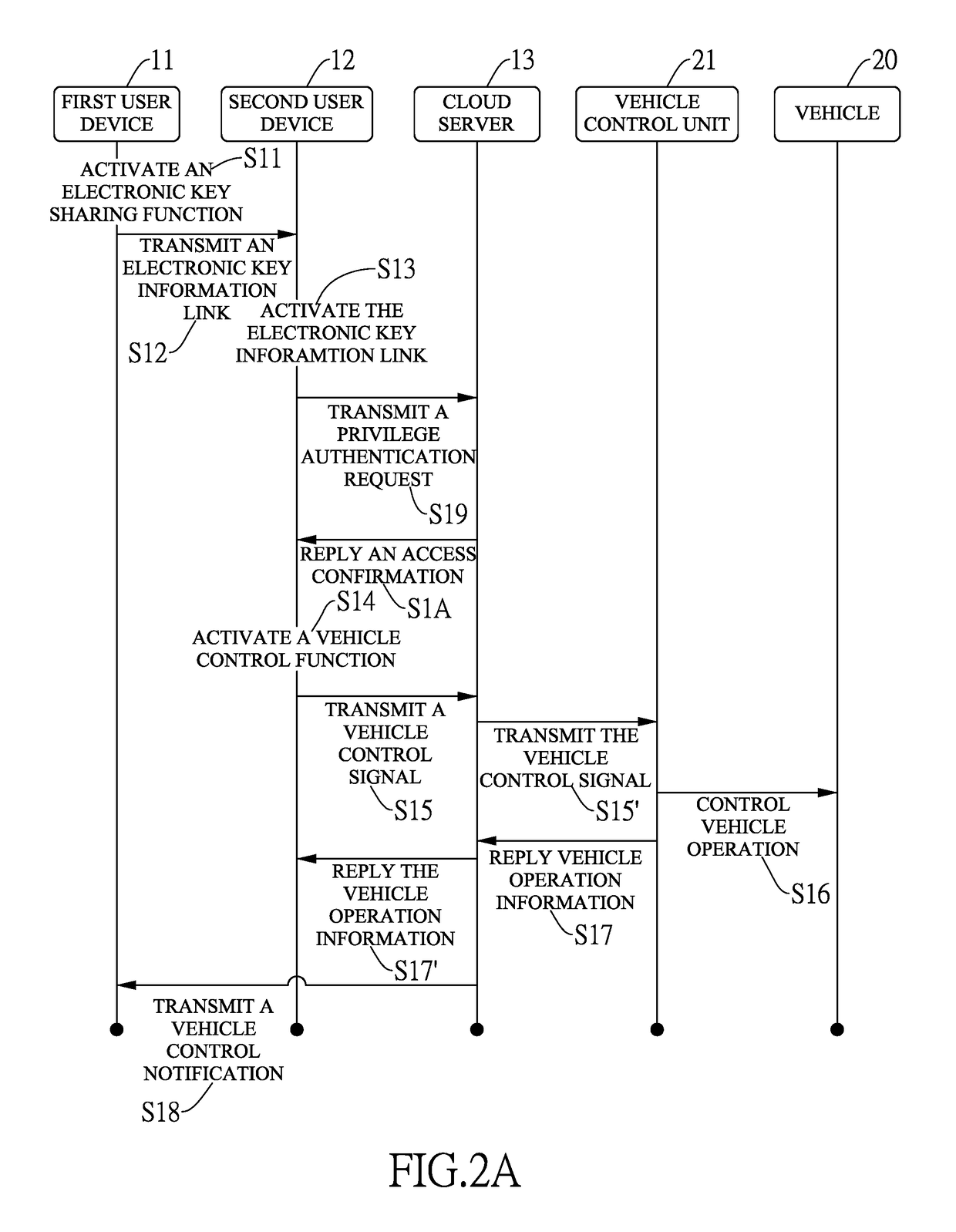
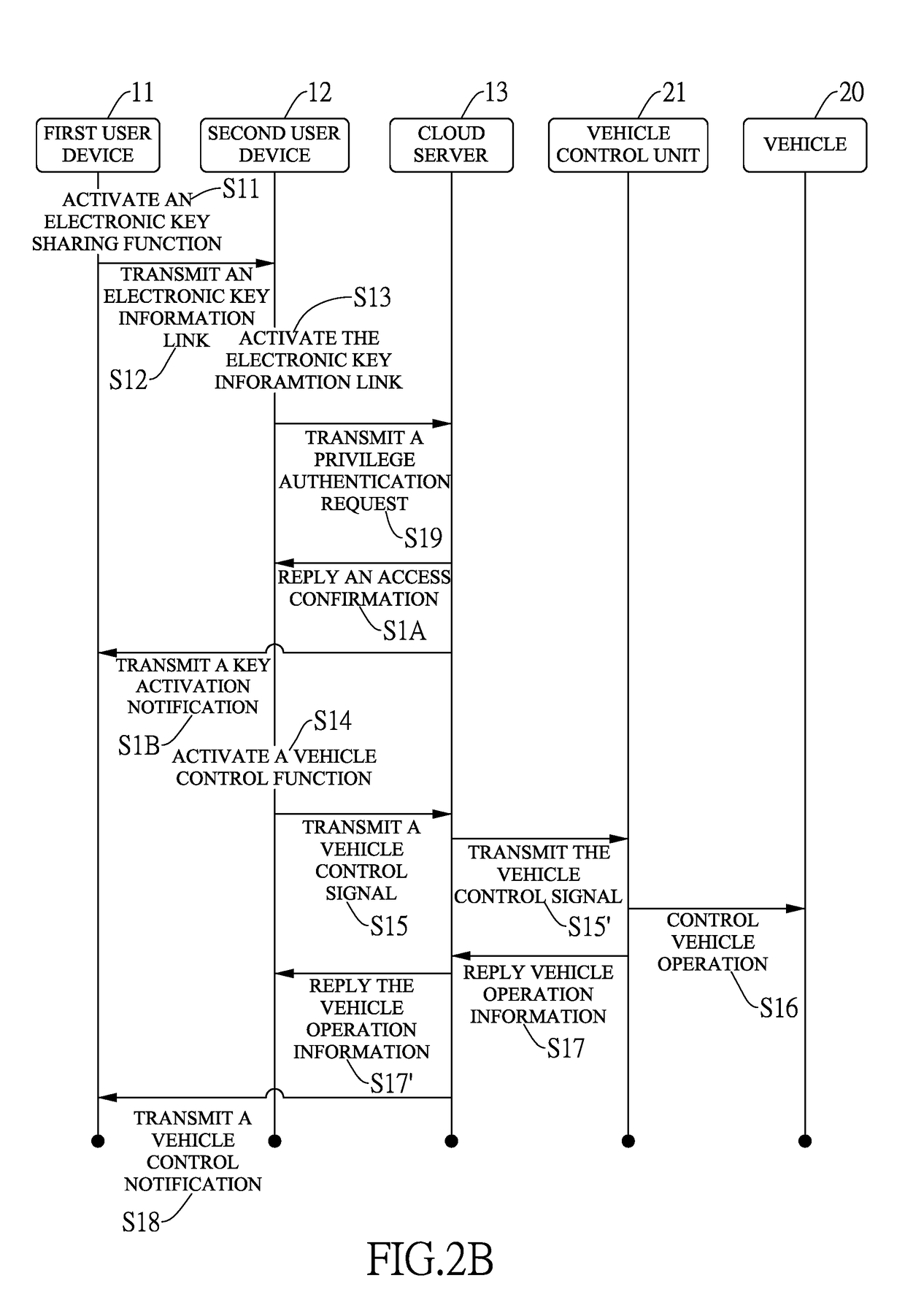
ActiveUS20180357846A1Unexpected riskImprove security and convenienceRegistering/indicating working of vehiclesParticular environment based servicesUser deviceControl signal
An intelligent vehicular electronic key system includes a cloud server, a first user device, a second user device and a vehicle control unit. The vehicle control unit is installed inside a vehicle and is connected to the cloud server through the Internet. When activating an electronic key sharing function, the first user transmits an electronic key information link to the second user device. After activating the electronic key information link, the second user device transmits a privilege authentication request and receives an access confirmation to and from the cloud server. The second user device further activates a vehicle control function and transmits a vehicle control signal to the vehicle control unit through the cloud server for the vehicle control unit to control operation of the vehicle. Accordingly, sharing access privilege of the electronic key enhances operation convenience of the vehicle.
Owner:IVTES LTD
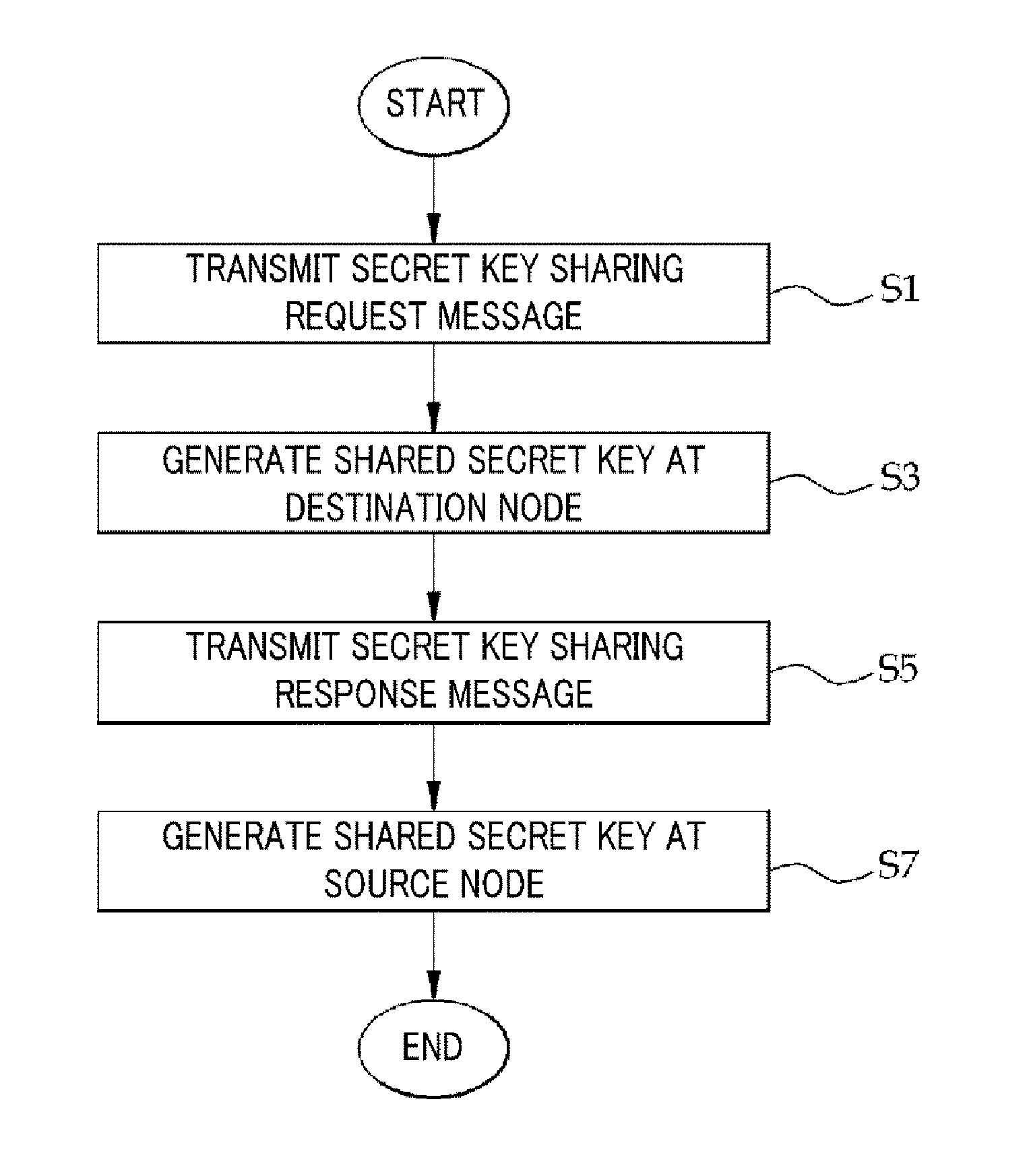
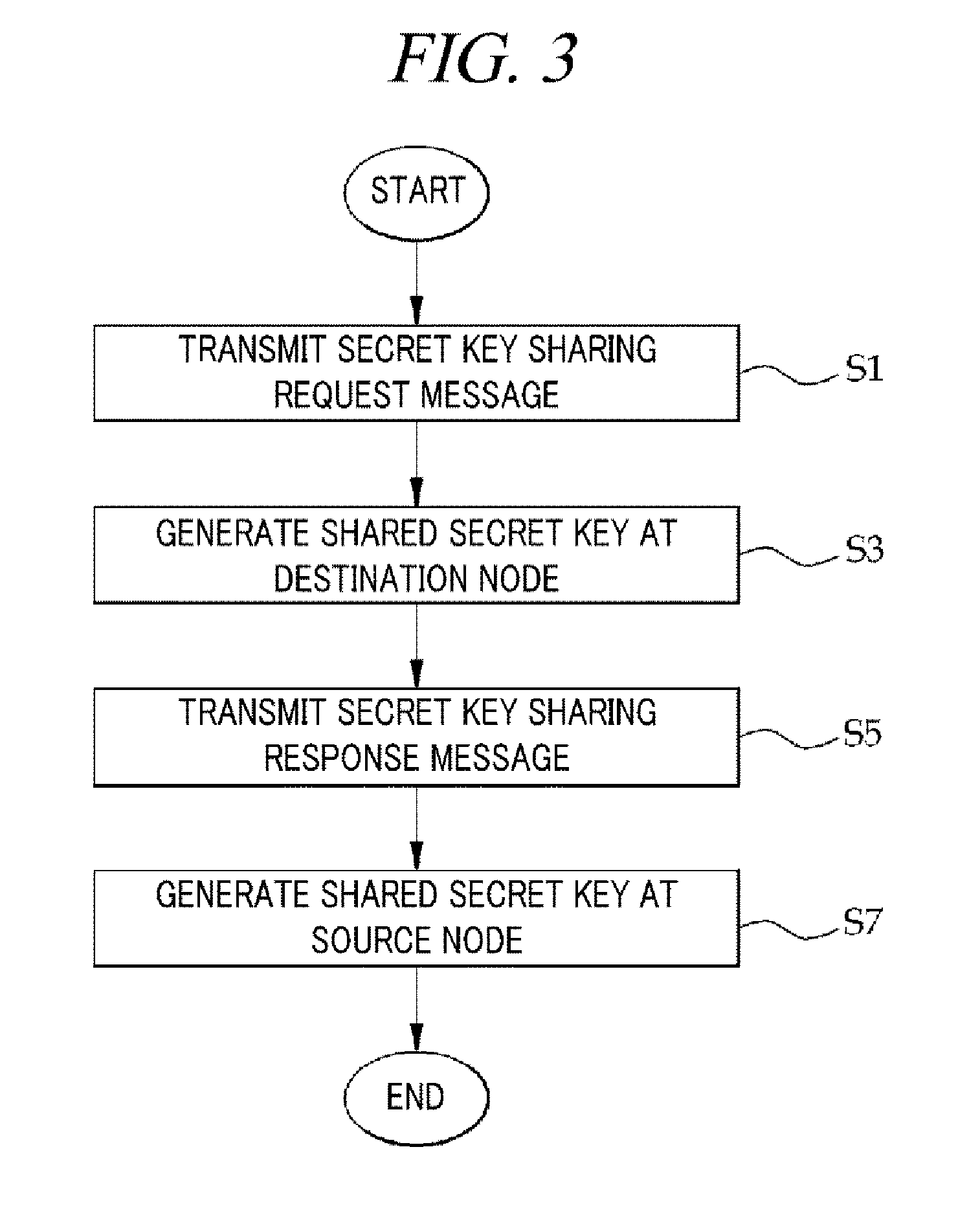
Method for sharing secret values between sensor nodes in multi-hop wireless communication network
InactiveUS20130173910A1Reduce energy consumptionPrevent hackingEnergy efficient ICTPower managementSensor nodeKey sharing
A method for sharing a secret key between a source node and a destination node includes (a) adding, at each forward intermediate node, a secret key between the forward intermediate node and a node before the forward intermediate node to the secret key sharing request message; (b) generating a shared secret key between the source node and the destination node from the secret key between the forward intermediate node and the node before the forward intermediate node added in the secret key sharing request message; (c) adding, at each backward intermediate node, a secret key between the backward intermediate node and a node before it to the secret key sharing response message; and (d) generating the shared secret key between the destination node and the source node from the secret key between the backward intermediate node and the node before it added in the secret key sharing response message.
Owner:INTELLECTUAL DISCOVERY CO LTD
Data distribution apparatus and data communications system
ActiveUS7693278B2Improve security levelUnauthorized memory use protectionAnalogue secracy/subscription systemsCommunications systemClient-side
An RTP packet generating unit 11 packetizes data into packets, and adds identification information to the header of each of the packets, the identification information identifying each of the packets. An RTP packet encrypting unit 13 divides data included in each of the generated packets into blocks, and encrypts the data included in each of the packets on a block-by-block basis using an encryption key which an encryption key sharing unit 12 shares with a receiving client in such a manner that, when encrypting a first block of the data, the packet encrypting unit encrypts it using the identification information for identifying each of the packets, which is contained, as an initial vector, in the header of each of the packets, and, when encrypting each subsequent block of the data, encrypts it according to an encryption method which uses an immediately-previously-encrypted block.
Owner:MITSUBISHI ELECTRIC CORP
Phase-polarization multi-freedom-degree-modulation QKD network system and method
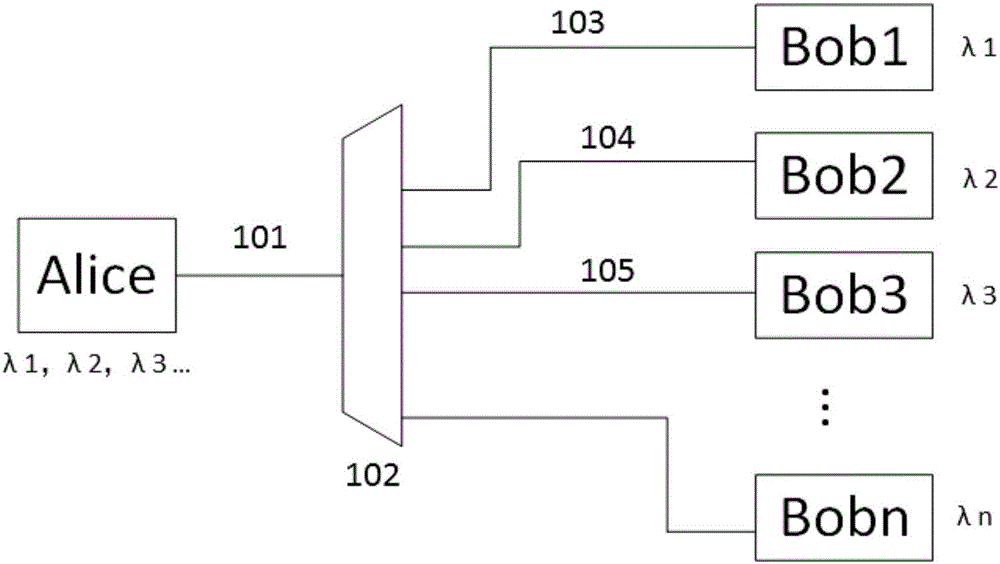
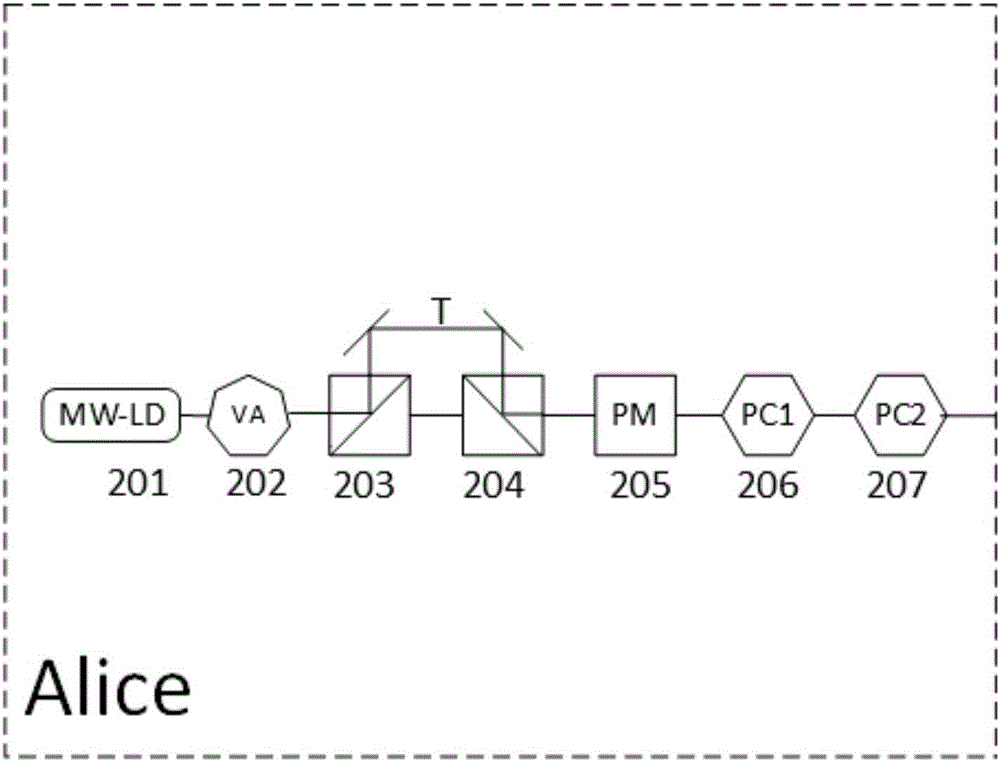
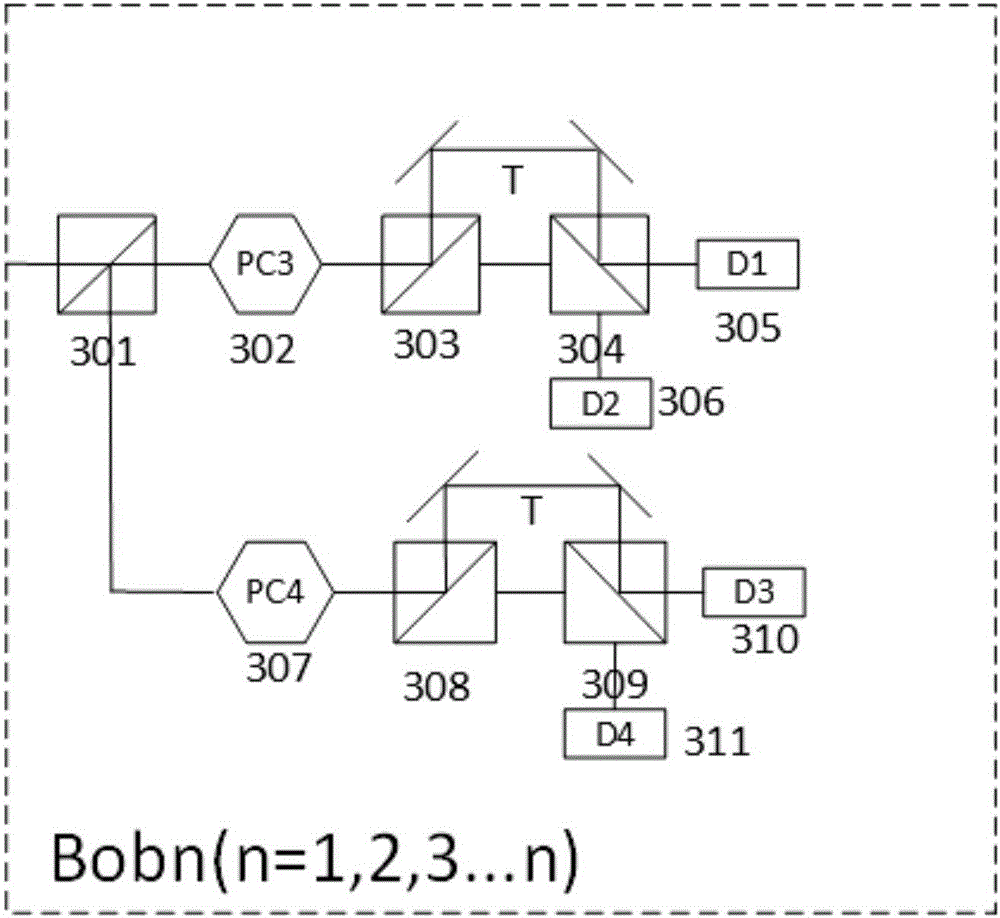
ActiveCN106685655AAchieve sharingExpand delivery capacityKey distribution for secure communicationPhotonic quantum communicationEngineeringOptical polarization
The invention relates to a phase-polarization multi-freedom-degree-modulation QKD (quantum key distribution) network system and method. The system comprise an Alice transmitting end, a WDM (wavelength division multiplexing) unit and a multi-user Bob end, wherein the Alice end is connected with the multi-user Bob end through the WDM unit, and the Alice end comprises a multi-wavelength laser generating device, an attenuator, a first polarization beam splitter, a first beam combiner, a phase modulator, a first polarization controller and a second polarization controller; the WDM unit comprises a wavelength selecting device; the multi-user Bob end comprises a plurality of unit Bob user ends for receiving different wavebands, and each unit Bob user end comprises a second polarization controller, a third polarization controller, a fourth polarization controller, a third polarization beam splitter, a fourth polarization beam splitter, a second beam combiner, a third beam combiner, a first photon detector, a second photon detector, a third photon detector and a fourth photon detector. The QKD network system has the advantages that one-to-many quantum key sharing, information transmission capacity is expanded effectively, and the system is applicable to a phase-polarization multi-freedom-degree-modulation QKD scheme and other QKD schemes.
Owner:GUANGDONG INCUBATOR TECH DEV CO LTD
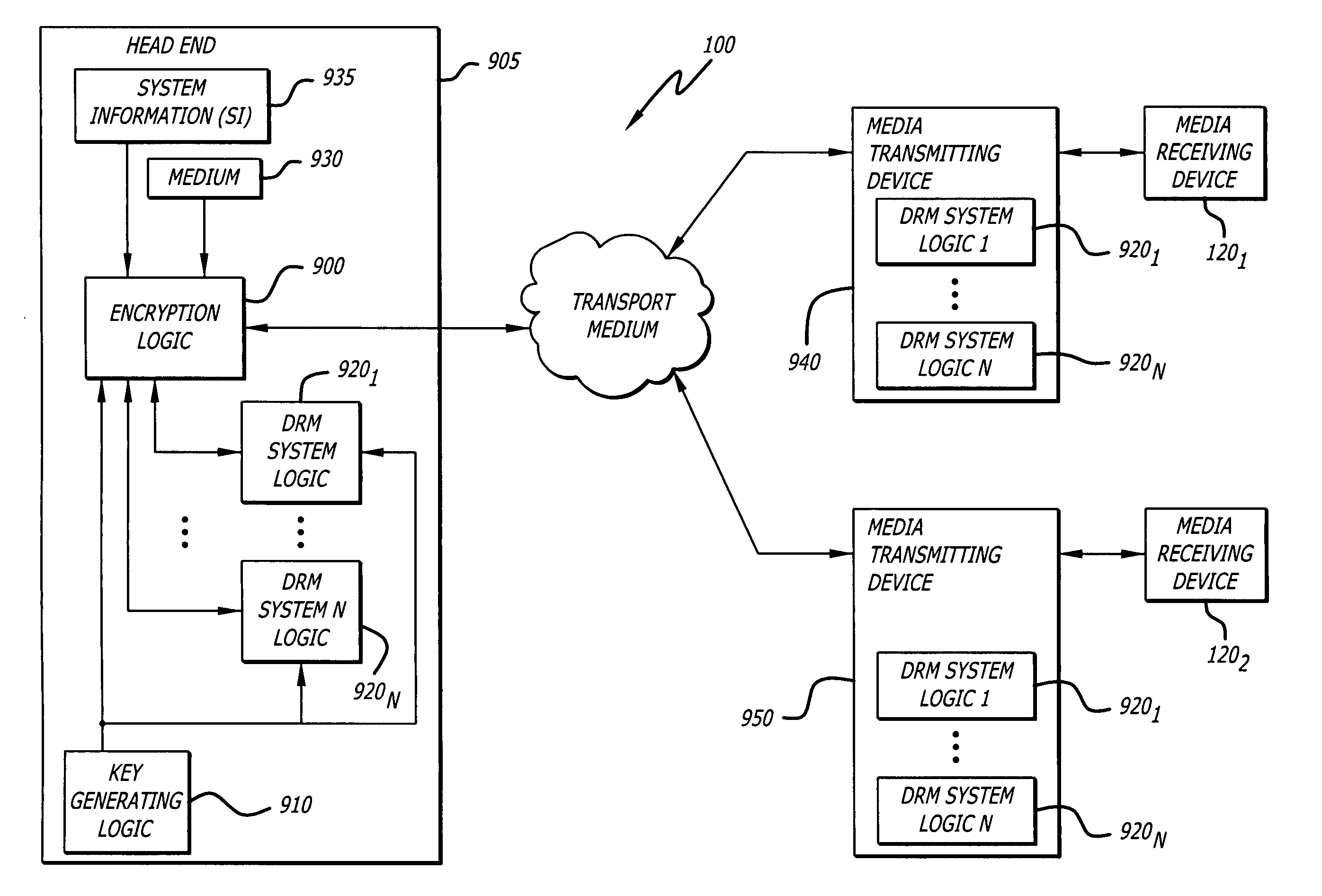
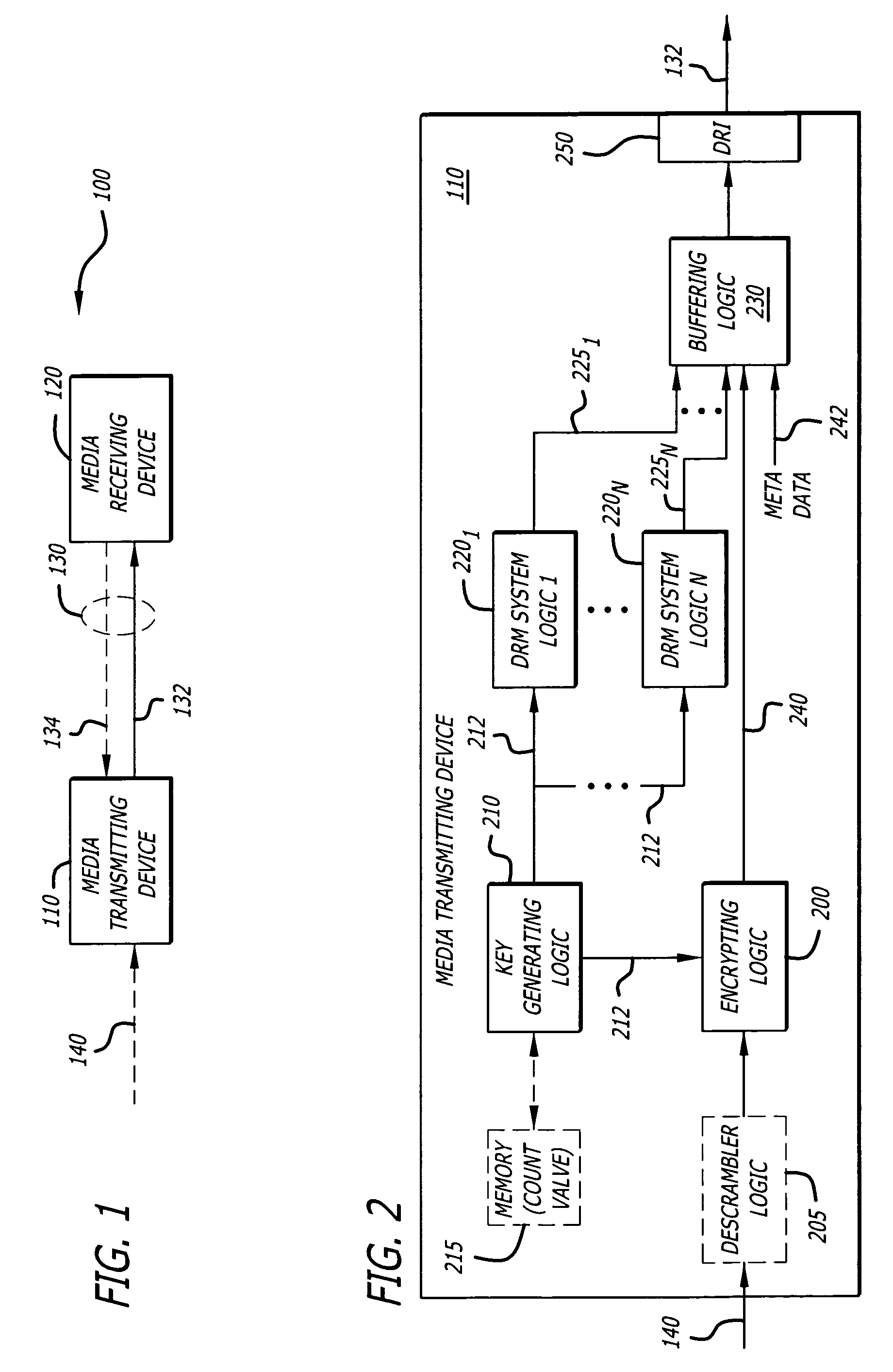
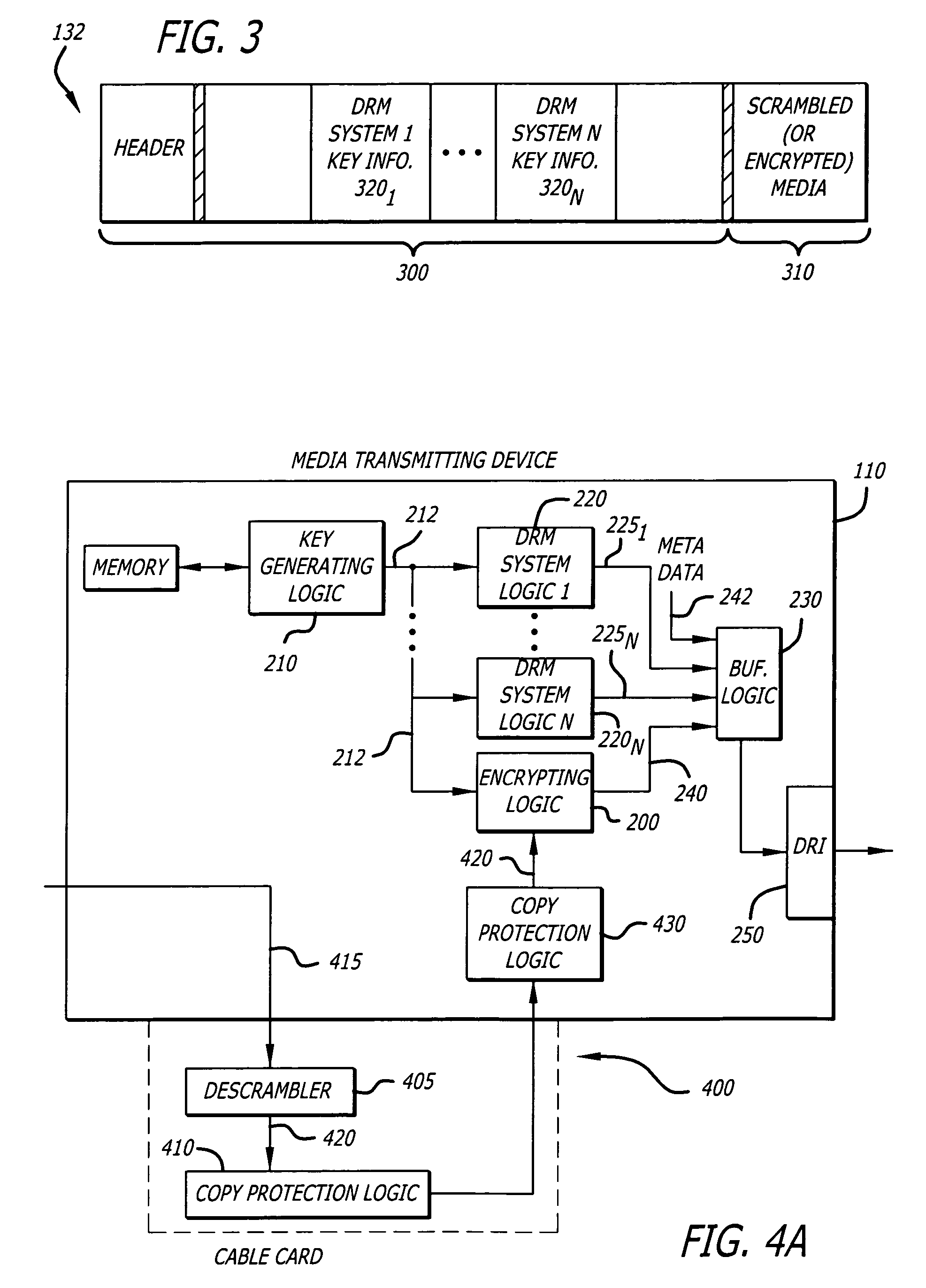
Key sharing for DRM interoperability
InactiveUS7840489B2Key distribution for secure communicationData processing applicationsComputer hardwareDigital rights management
According to one embodiment, a method comprises generating a cryptographic key and sharing the cryptographic key with a plurality of digital rights management (DRM) systems supplied by different providers. This provides flexibility in using any DRM system by media receiving devices targeted to receive media.
Owner:SONY CORP +1
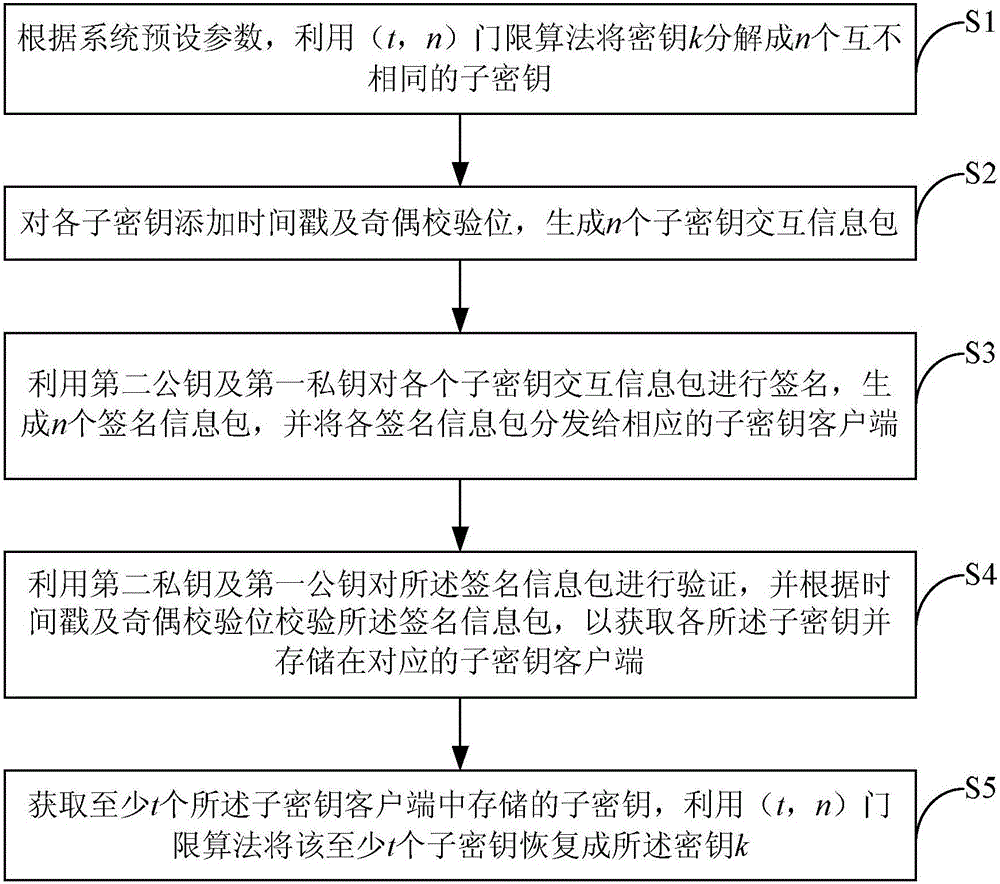
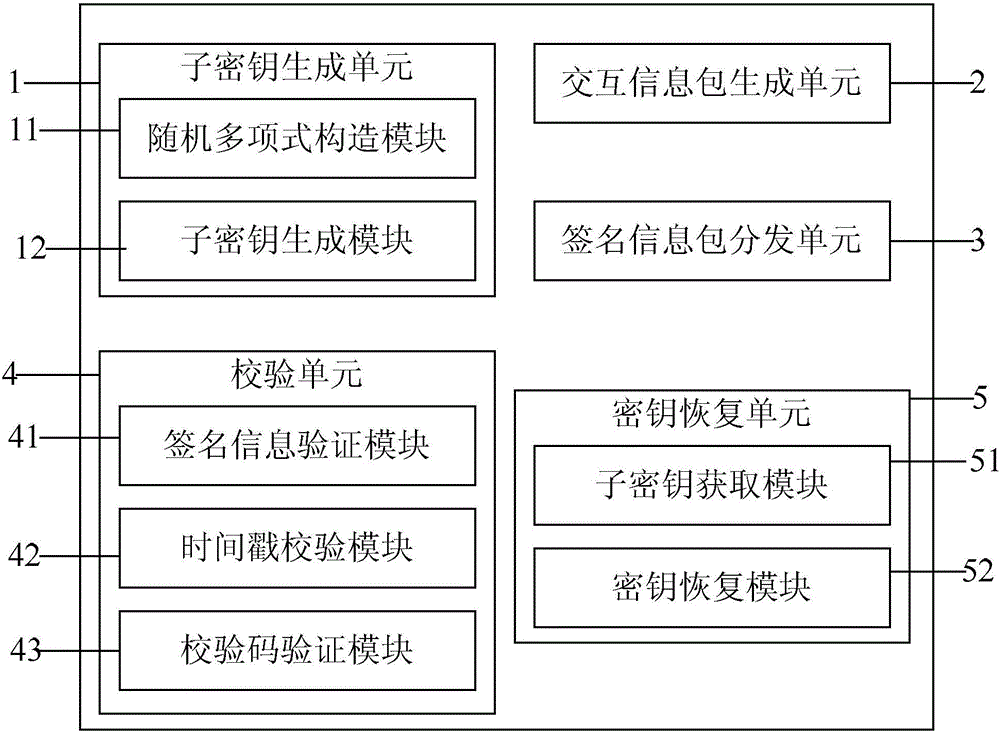
Key sharing method and device
ActiveCN106027245AGuaranteed correctnessEnsure safetyKey distribution for secure communicationKey sharingParity bit
The invention provides a key sharing method and device. The method comprises the steps of decomposing a key k into n mutually different sub-keys by employing a (t, n) threshold algorithm according to preset parameters of a system; adding time stamps and parity check bits to the sub-keys, thereby generating n sub-key interaction information packets; signing the sub-key interaction information packets by employing a second public key and a first private key, thereby generating n signed information packets, and distributing the signed information packets to corresponding sub-key clients; verifying the signed information packets by employing a second private key and a first public key and checking the signed information packets according to the time stamps and the parity check bits, thereby obtaining the sub-keys, and storing the sub-keys in the corresponding sub-key clients; and obtaining the sub-keys stored in at least t sub-key clients, restoring the at least t sub-keys to the key k by employing the (t, n) threshold algorithm, wherein the first private key and the first public key are a mutually matching key pair, and the second private key and the second public key are a mutually matching key pair.
Owner:INDUSTRIAL AND COMMERCIAL BANK OF CHINA
Network smart lock system
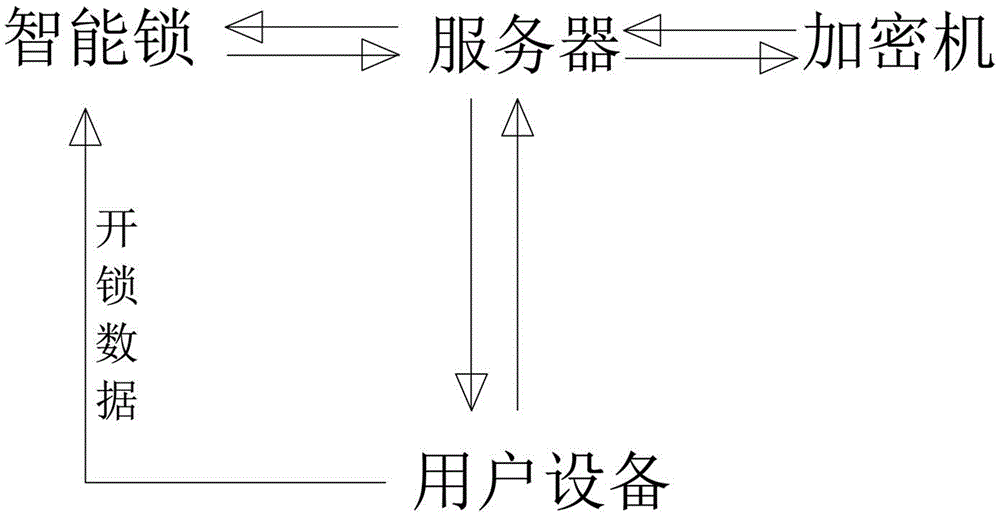
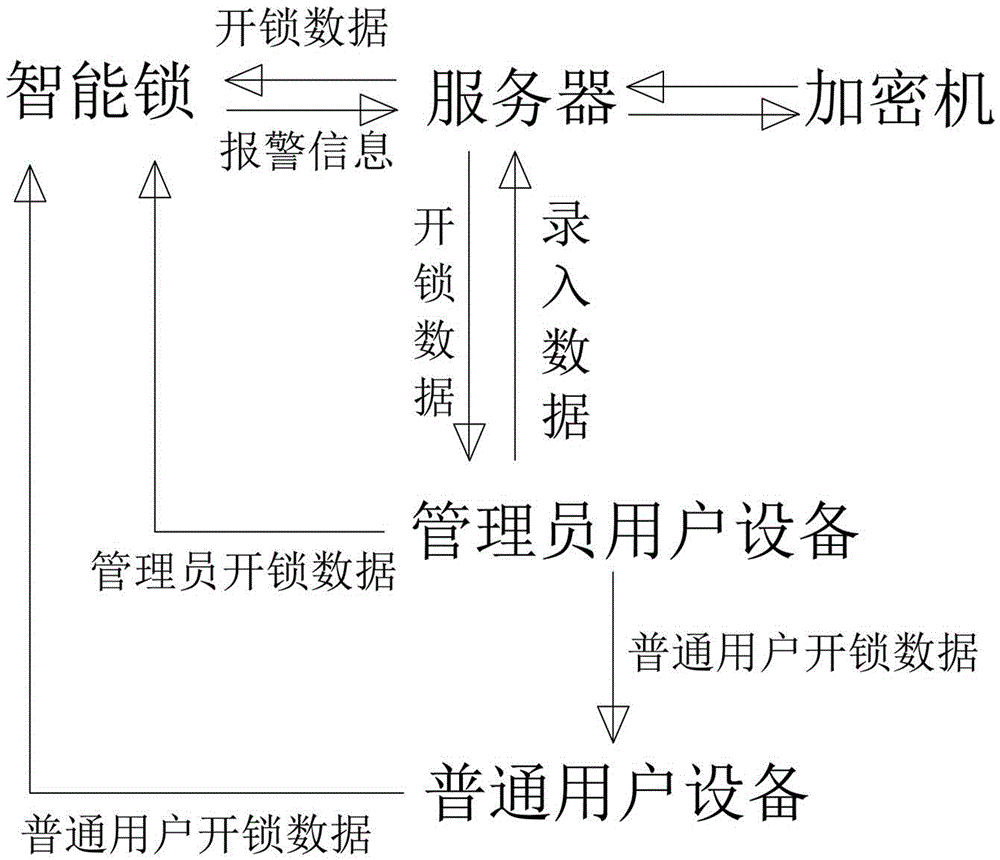
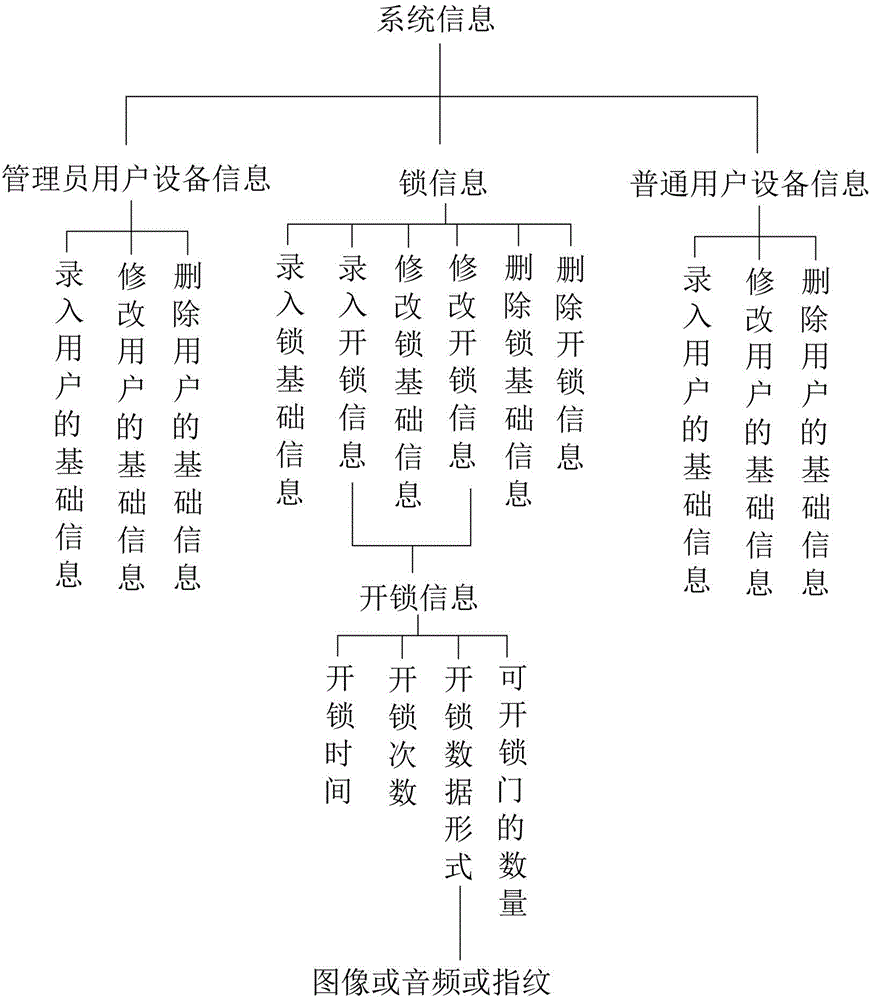
InactiveCN105261096AImprove securityImprove convenienceIndividual entry/exit registersTransmissionComputer networkUser equipment
The invention discloses a network smart lock system. The network smart lock system comprises a smart lock, a server and user equipment. The server is in communication with the smart lock and the user equipment through a network. The user equipment comprises the administrator user equipment and the common user equipment. The administrator user equipment sends input data containing unlocking information to the server, the server receives the input data, encrypts the input data and then sends administrator unlocking data, common user unlocking data and related data to the administrator user equipment and the smart lock, and the common user unlocking data are forwarded to the common user equipment by the administrator user equipment. The administrator user equipment utilizes the administrator unlocking data for unlocking, and the common user equipment utilizes the common user unlocking data for unlocking. Through the network smart lock system, the functions of non-entity key entering and exiting and digital key sharing can be achieved, and therefore practicability and safety are greatly improved.
Owner:DONGGUAN DIANKAI NETWORK TECH CO LTD
Quantum secure communication method and apparatus
ActiveCN106533565AAchieve sharingKey distribution for secure communicationFibre transmissionComputer hardwareSecure communication
The invention provides a quantum secure communication method and apparatus. A relay device is respectively arranged on a quantum secure communication sending terminal and receiving terminal. The relay devices negotiate quantum keys with a directly connected upstream device and a downstream device respectively, and key relay processing and transmission are executed according to the quantum key negotiated with the directly connected upstream device and the downstream device and a key relay processing signal sent by the upstream device. End-to-end communication key sharing and quantum key communication are realized. Long-distance quantum key communication is realized through multi-core fibers and relay devices.
Owner:CHINA ACADEMY OF INFORMATION & COMM
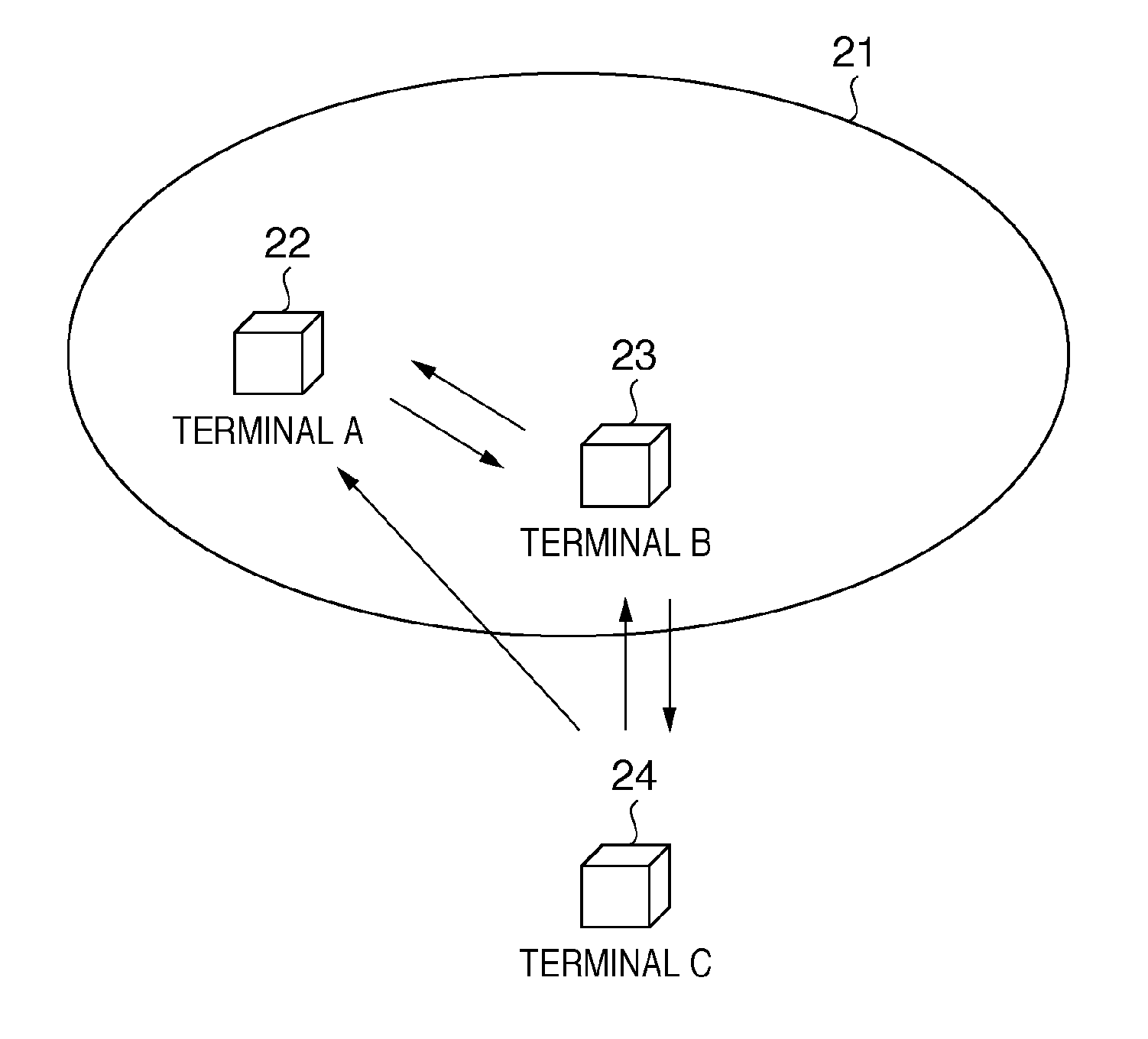
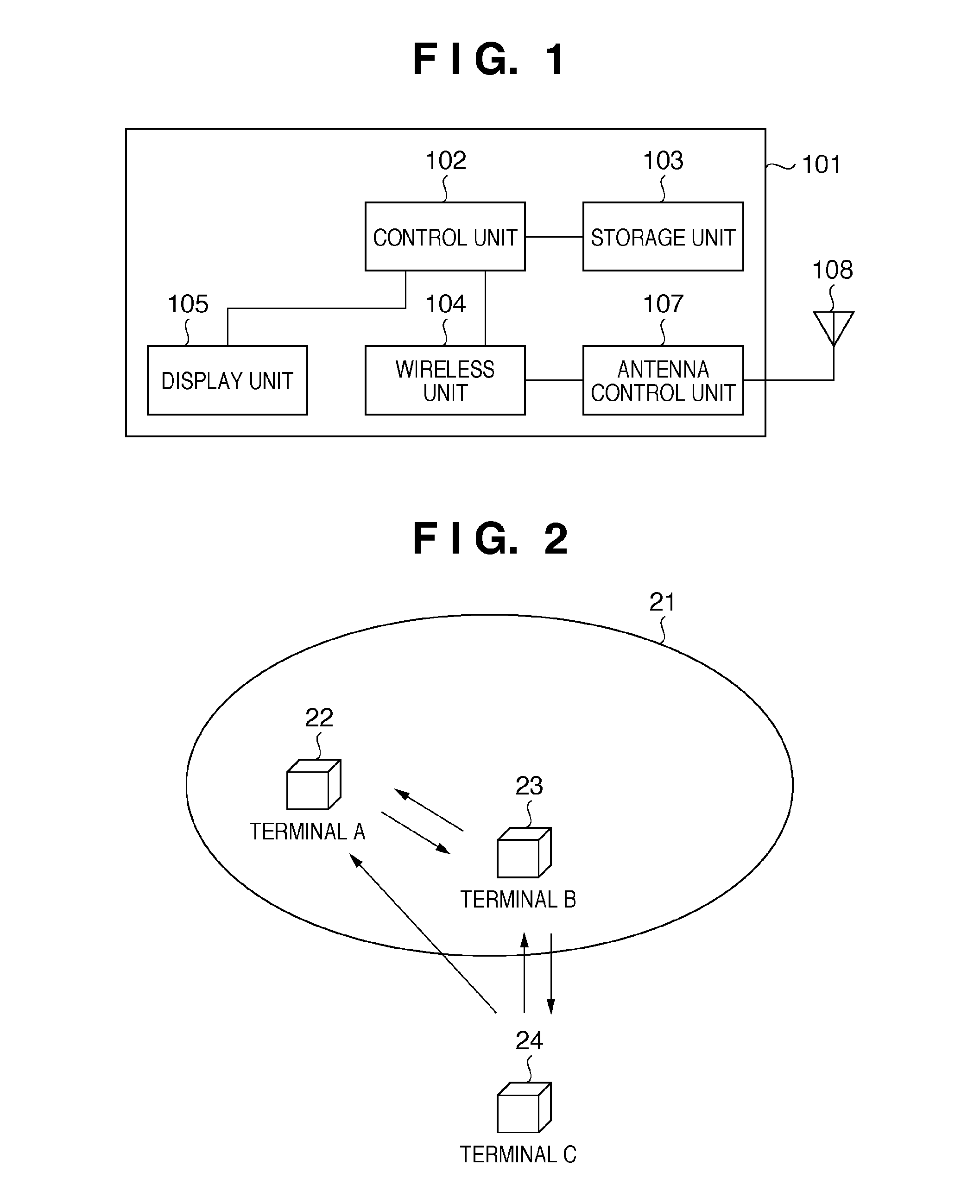
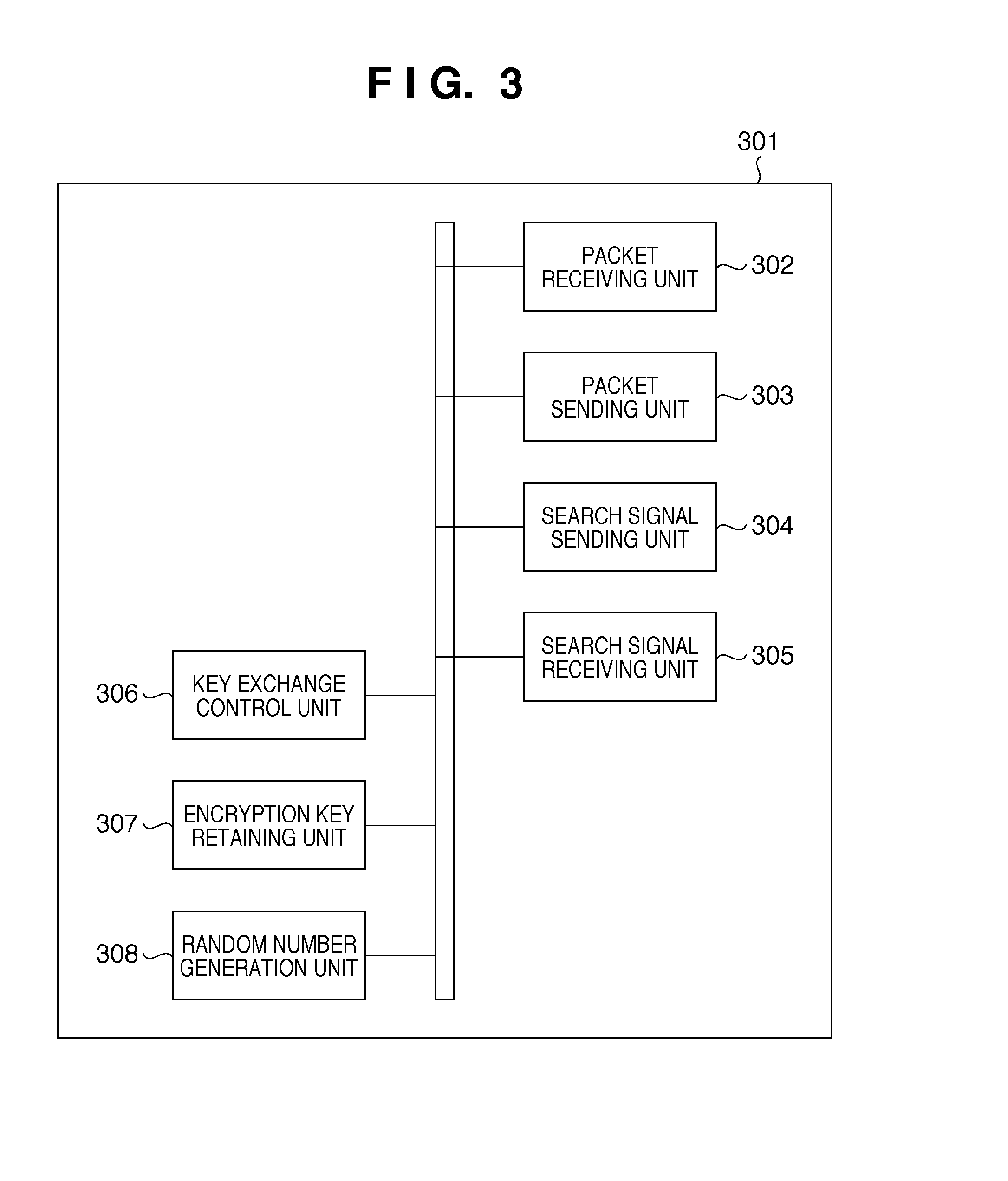
Communication apparatus and control method thereof
InactiveUS20100208896A1Key distribution for secure communicationNetwork topologiesComputer hardwareKey sharing
A first communication apparatus that functions as a providing apparatus that provides an encryption key or as a receiving apparatus that receives an encryption key provided by a providing apparatus, and that performs a key sharing process for sharing an encryption key with another apparatus, the first communication apparatus includes: acquisition means for acquiring identification information of a second communication apparatus that functioned as the providing apparatus in the key sharing process performed among a plurality of apparatuses present on a network which the first communication apparatus is to join; and determination means for determining whether the first communication apparatus is to function as the providing apparatus or as the receiving apparatus based on the result of a comparison between the identification information of the second communication apparatus acquired by the acquisition means and identification information of the first communication apparatus.
Owner:CANON KK
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com