Key management method based on convergence encryption for use in cloud storage data duplication elimination
A technology of convergent encryption and key management, applied to encryption devices with shift registers/memory, key distribution, can solve problems such as single point failure, inability of key storage management to be fault-tolerant, etc., and achieve the effect of reducing storage overhead
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
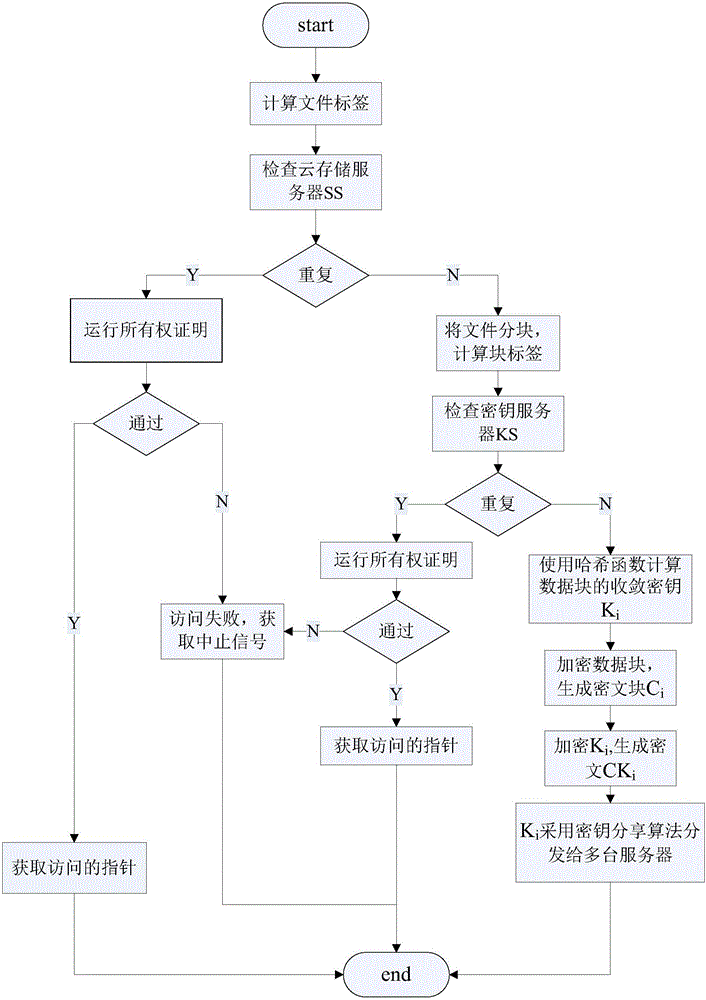
[0035] A key management method Dekey based on convergent encryption in cloud storage data deduplication, comprising:
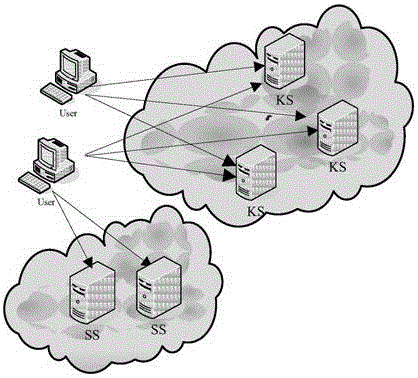
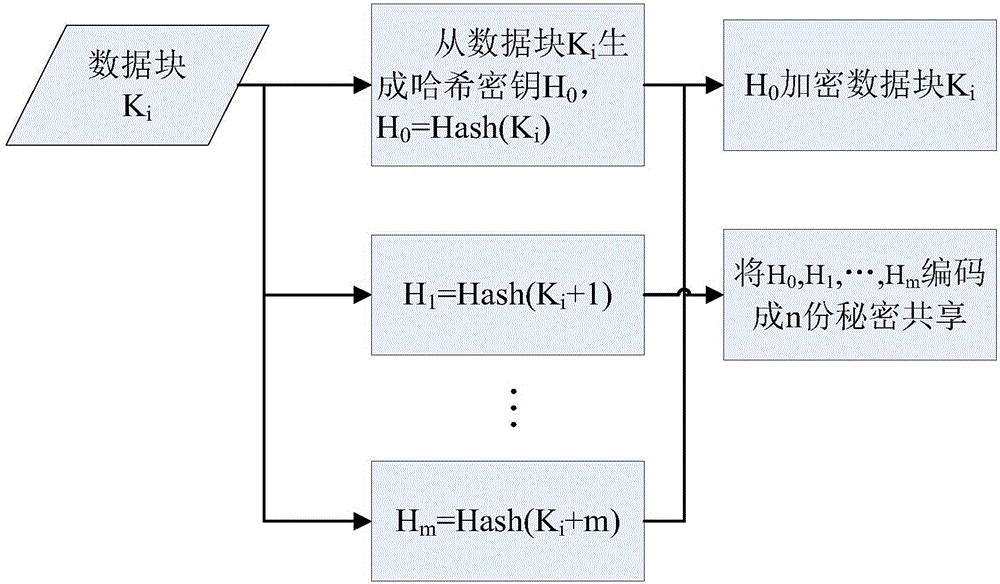
[0036] A. Add n key servers in the cloud storage system, and the server is used to store the key sharing share distributed by the client, wherein the key sharing share is performed by the client based on (n, k, r)-RSSS Share Algorithm, the original key is divided and encoded; the key recovery algorithm is the Recover algorithm, which restores the shared share to the original key S; the shared key share of any k (k<n) servers can restore the original key S , some of the n servers can be allowed to fail or be damaged, but it is necessary to ensure the safe operation of k servers exceeding the minimum threshold, in which the Share algorithm generates r pseudo-random shares instead of RSSS random shares;
[0037] B. According to the distributed management method of the deduplication key in the cloud storage system, the deduplication management of the converged key a...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com