Method and device for deduplication of cookie access
A technology for configuring information and fields, applied in the computer field, can solve problems such as unsatisfactory effect, low processing efficiency, and many invalid data, and achieve ideal and efficient deduplication effect.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
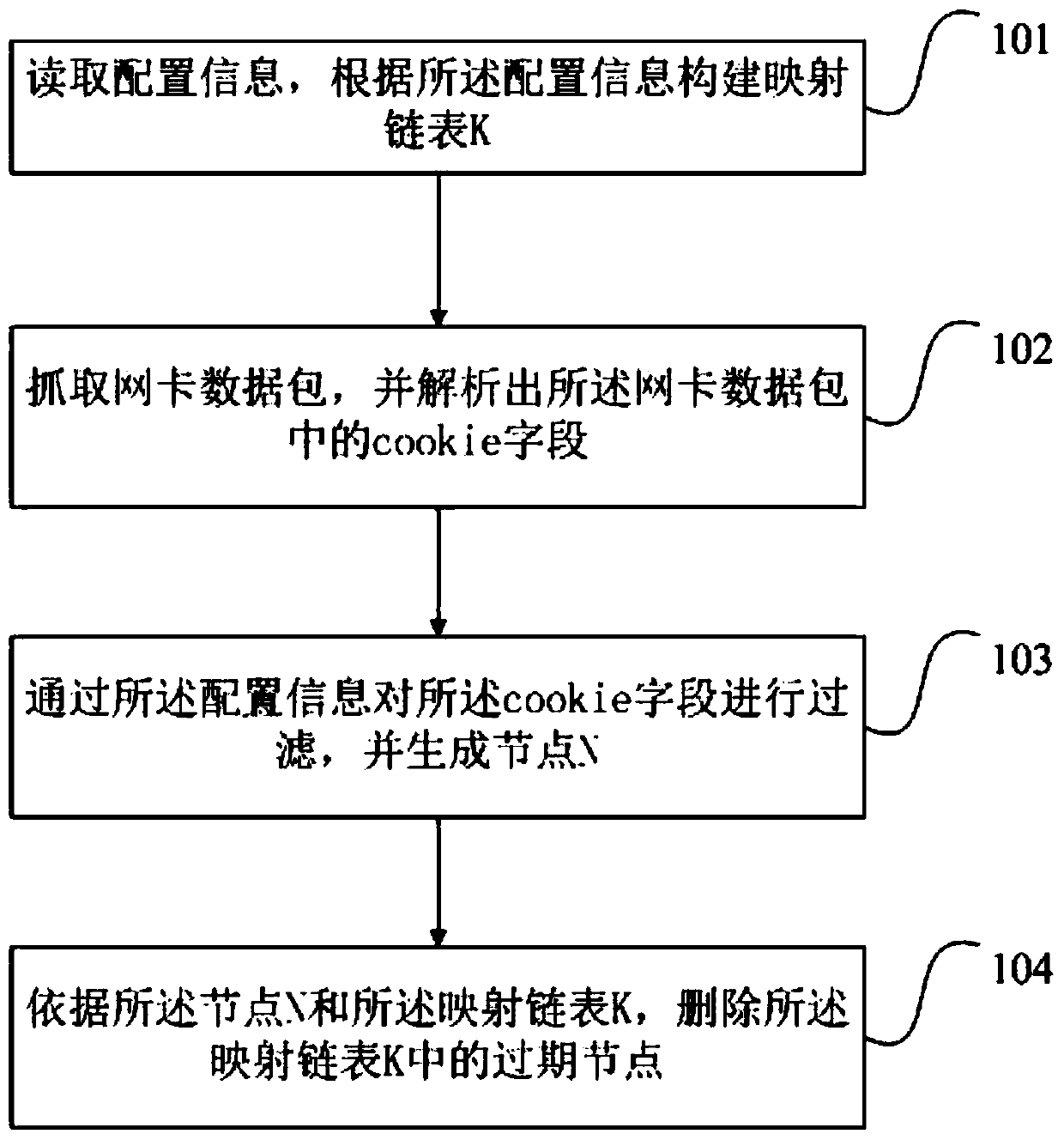
[0042] figure 1 This is a flowchart of the cookie access deduplication method provided in the first embodiment of the present invention. This embodiment can be applied to a scenario where a website collects statistics on user access. The method can be executed by a computing device such as a server, and specifically includes the following steps:
[0043] Step 101: Read configuration information, and construct a mapping linked list K according to the configuration information.
[0044] Among them, the configuration information is used to configure the attributes of the web application. Exemplarily, the configuration information may be an xml configuration file, which may include the following content: environmental parameter initialization, servlet configuration, filter configuration, listener configuration, JNDI configuration, session configuration, JSP web page related configuration, MIME TYPE configuration, welcome file Checklist and error handling, etc. Among them, the mapping ...
Embodiment 2
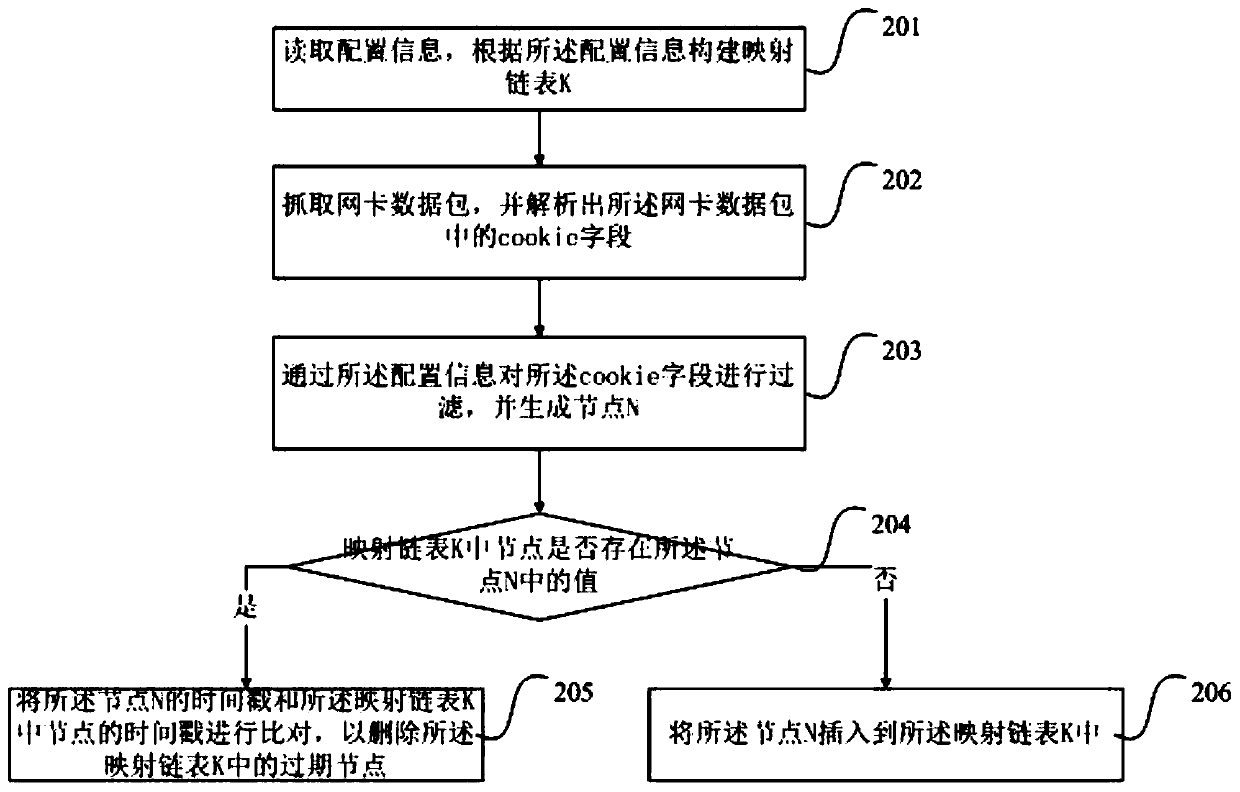
[0055] figure 2 This is a flowchart of the cookie access deduplication method provided in the second embodiment of the present invention. Based on the first embodiment, this embodiment provides a specific method for deduplication based on the node N and the mapping list K, which specifically includes as follows:
[0056] Step 201: Read configuration information, and construct a mapping linked list K according to the configuration information.
[0057] Step 202: Grab the network card data packet, and parse the cookie field in the network card data packet.
[0058] Step 203: Filter the cookie field based on the configuration information, and generate a node N.
[0059] Step 204: Determine whether the node in the mapping linked list K has the value in the node N, if it exists, execute step 205, otherwise execute step 206.
[0060] Step 205: Compare the timestamp of the node N with the timestamp of the node in the mapping list K to delete the expired node in the mapping list K. Among the...
Embodiment 3
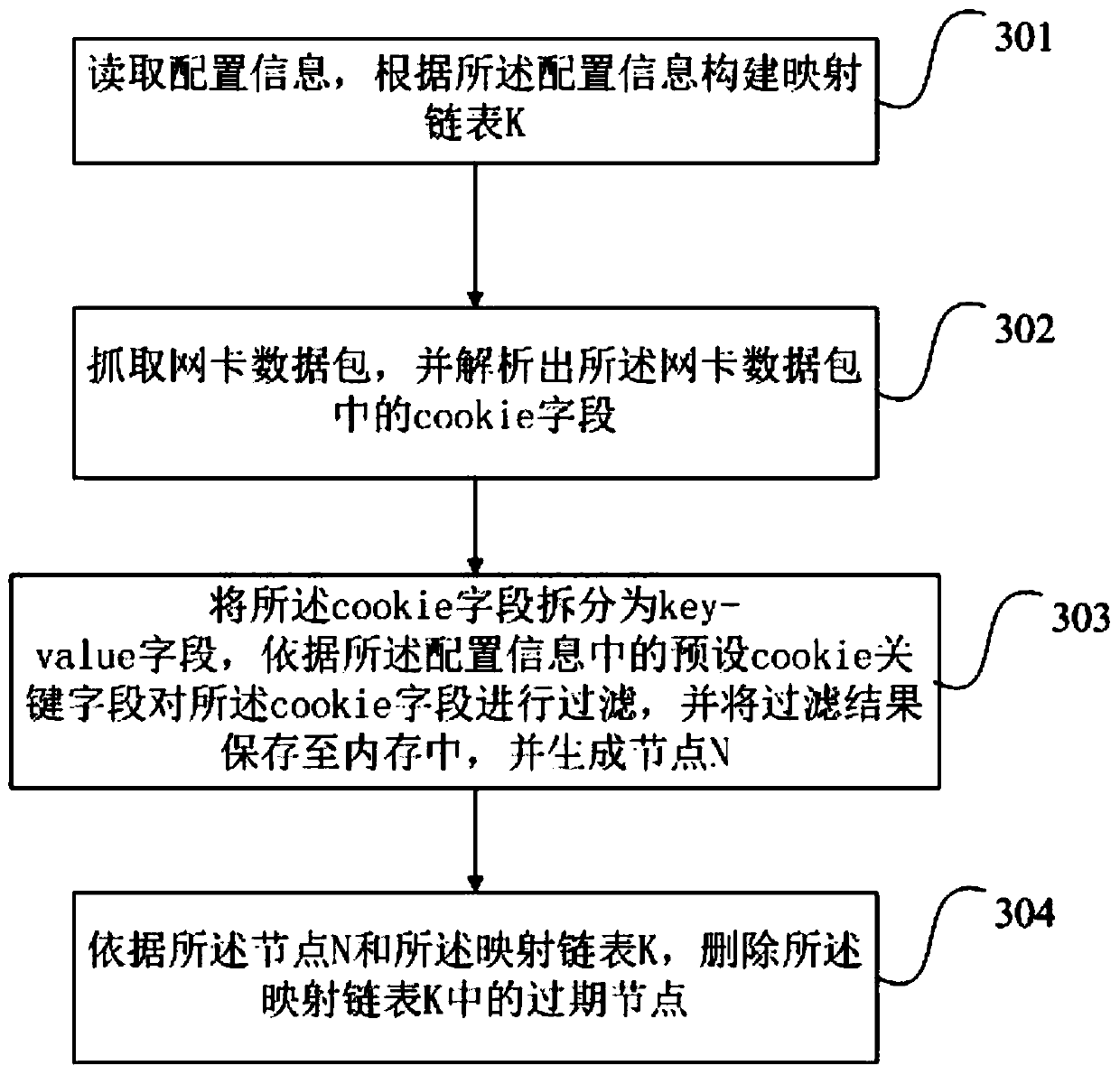
[0065] image 3 Shown is a flowchart of cookie access deduplication provided in the third embodiment of the present invention. Based on the above embodiments, this embodiment provides a specific method for filtering cookie fields through configuration information, which specifically includes as follows:
[0066] Step 301: Read configuration information, and construct a mapping linked list K according to the configuration information.
[0067] Step 302: Grab the network card data packet, and parse the cookie field in the network card data packet.
[0068] Step 303: Split the cookie field into key-value fields, filter the cookie field according to the preset cookie key field in the configuration information, save the filtering result in the memory, and generate node N .
[0069] Among them, the key-value field is the key-value field, key represents the primary key, and value is the value corresponding to the primary key. In this step, after the cookie field is parsed in step 302, the ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com