Patents
Literature
4793 results about "Internal memory" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
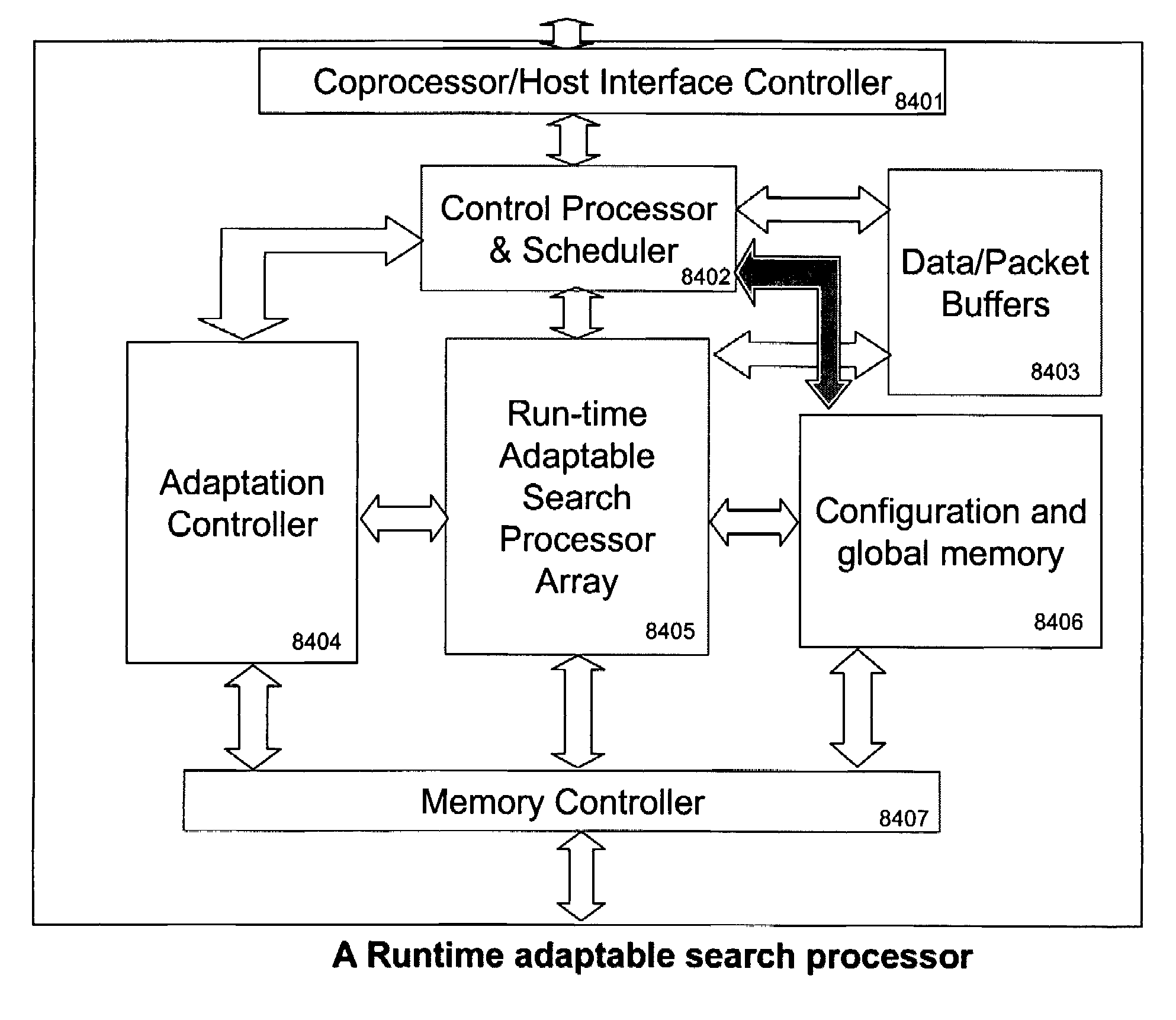
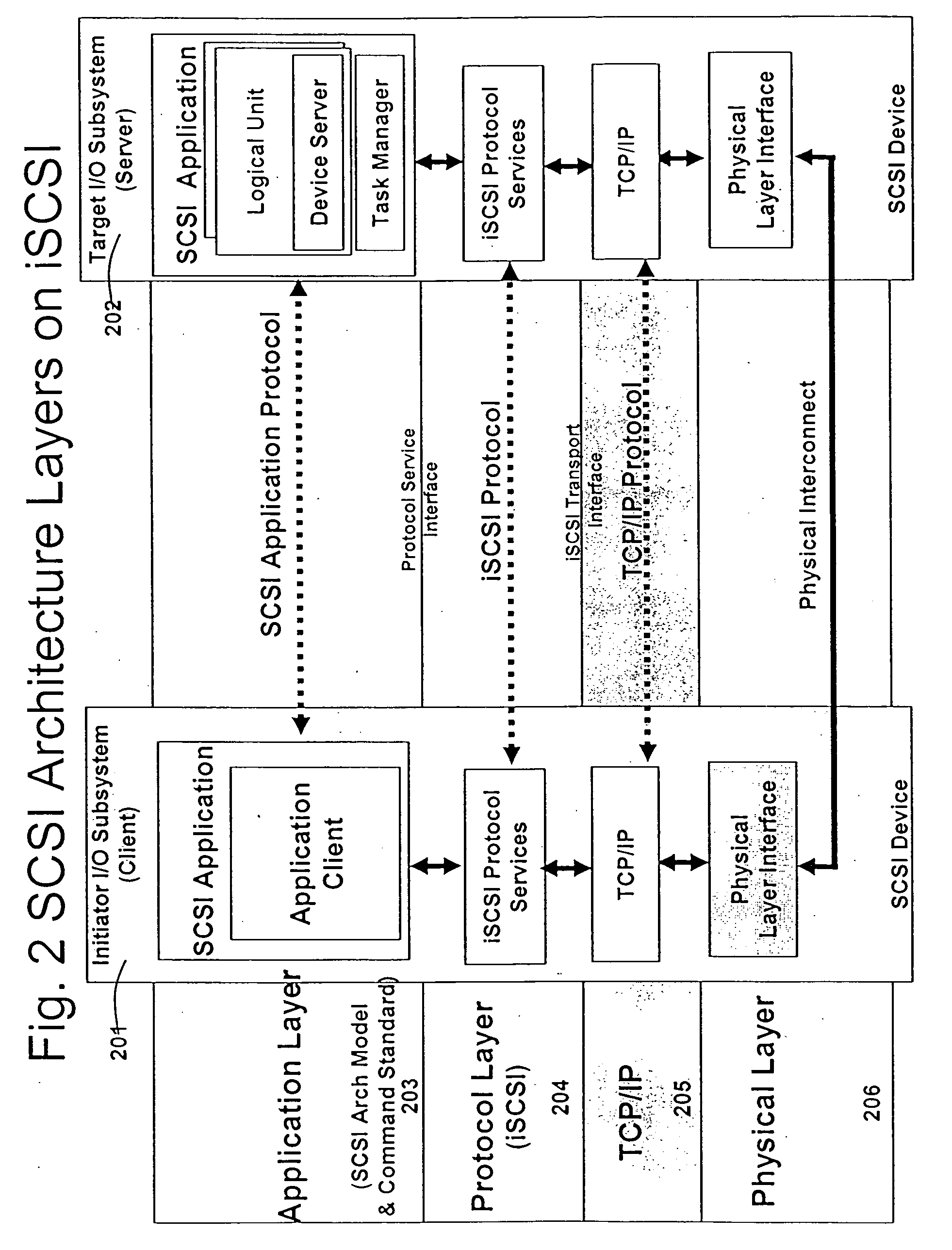
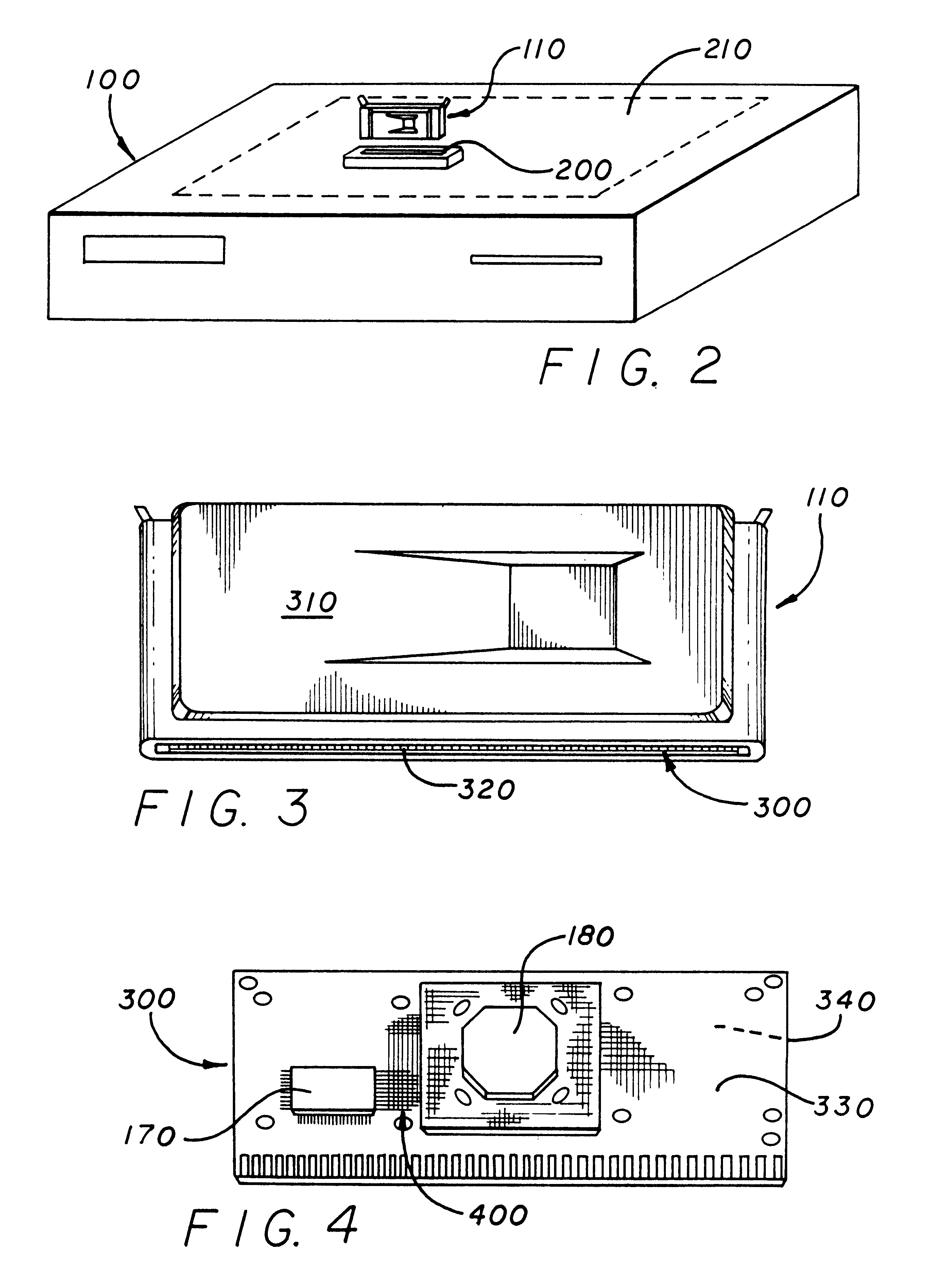
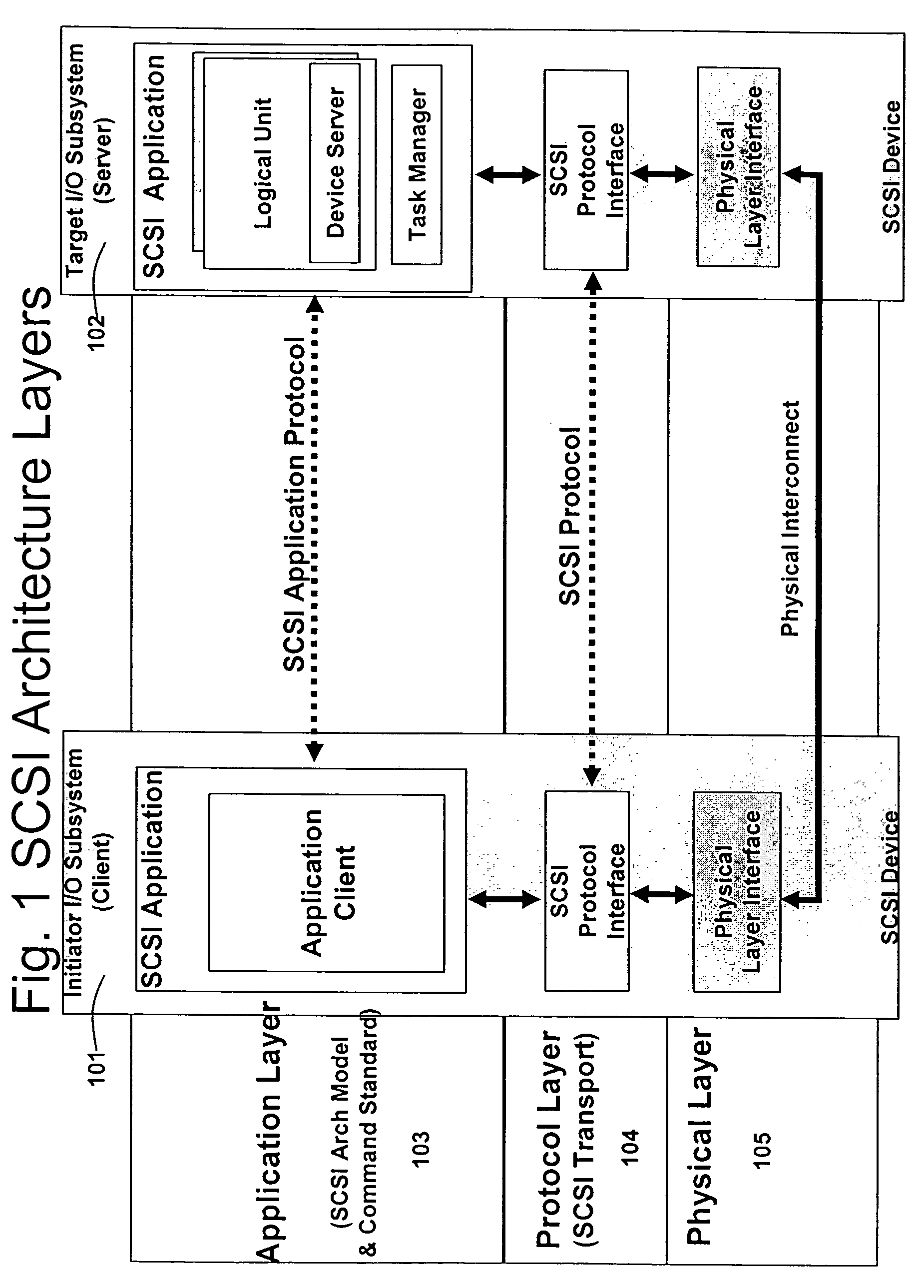
Runtime adaptable search processor
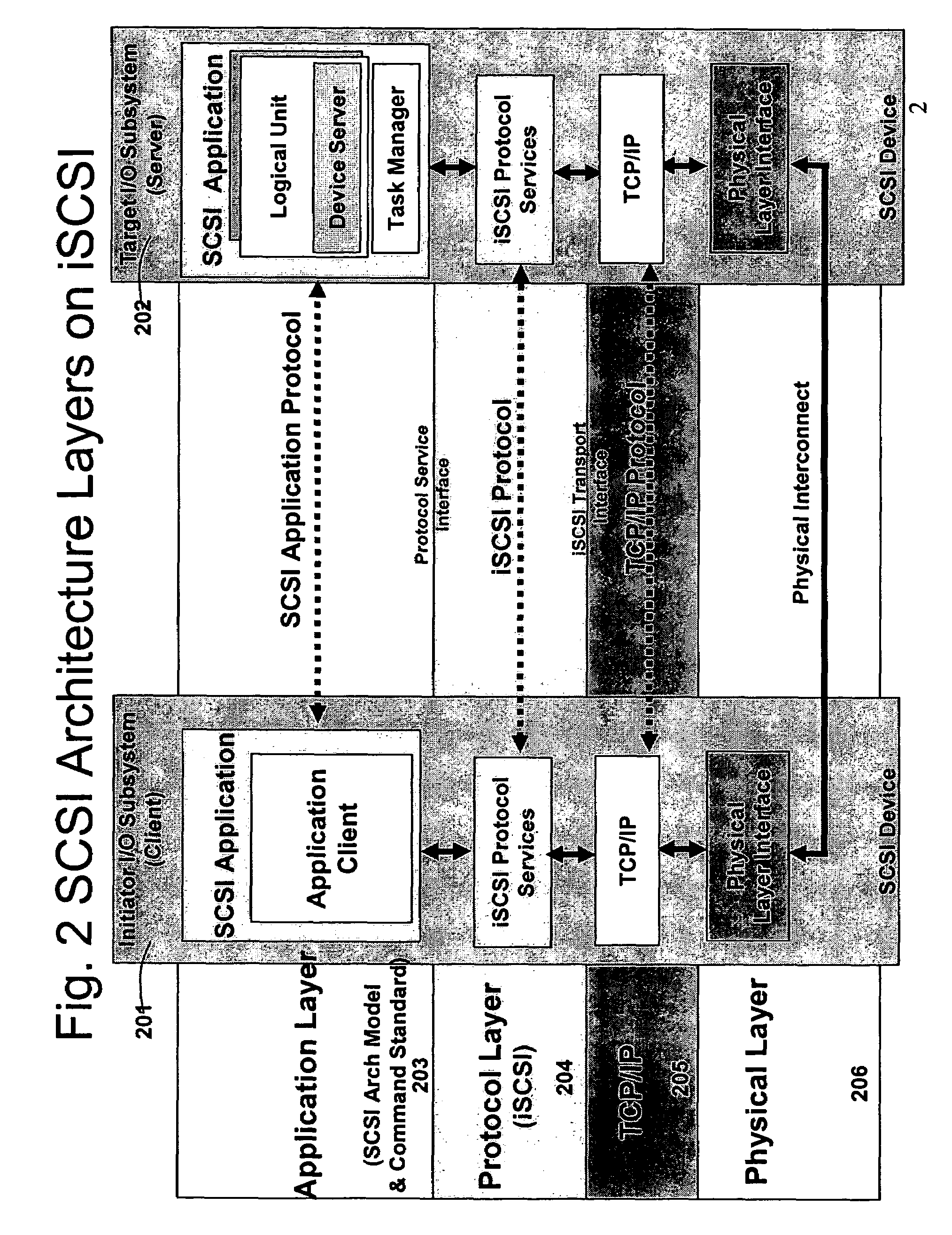
ActiveUS20060136570A1Reduce stacking processImproving host CPU performanceWeb data indexingMultiple digital computer combinationsData packInternal memory
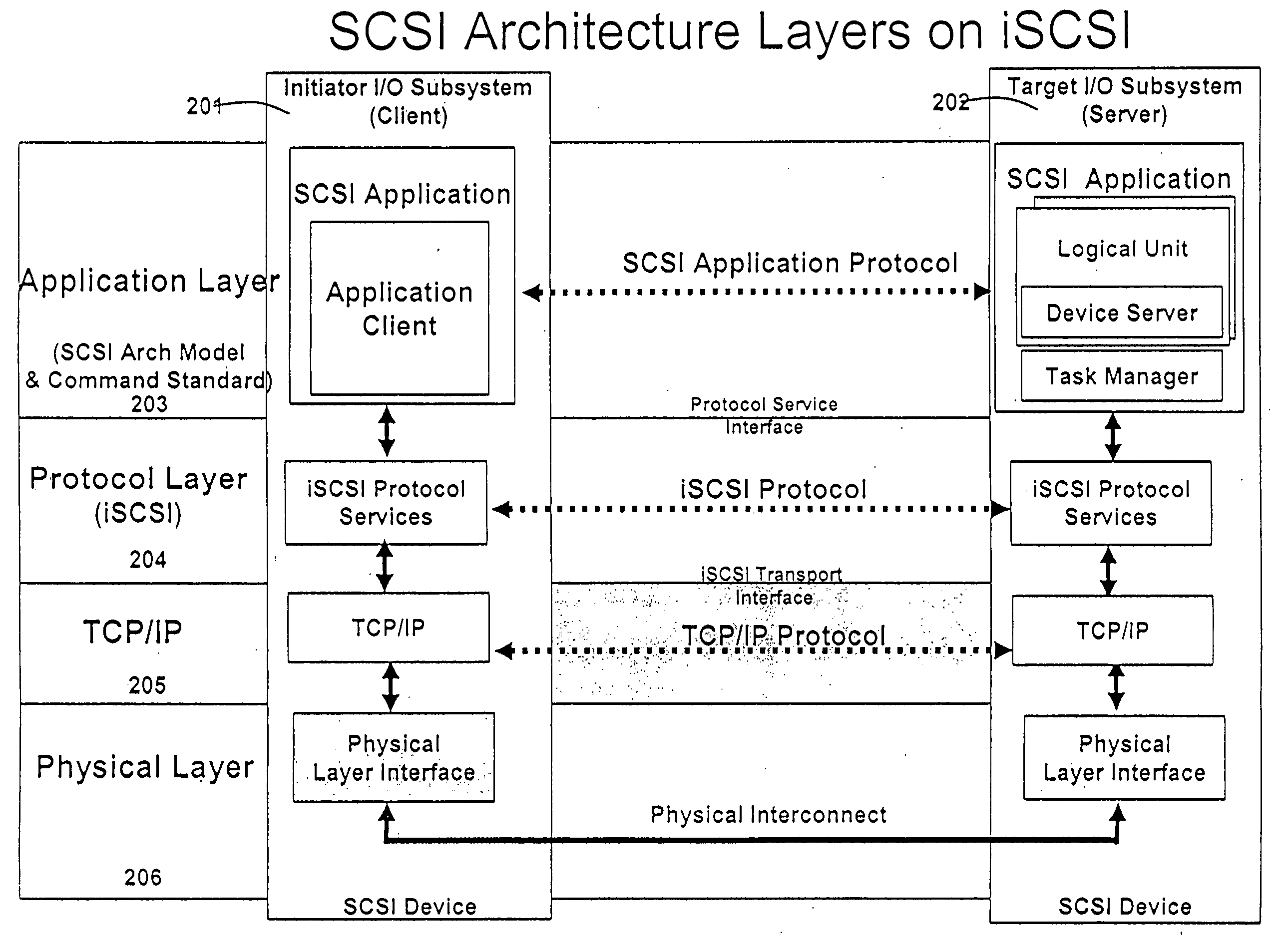
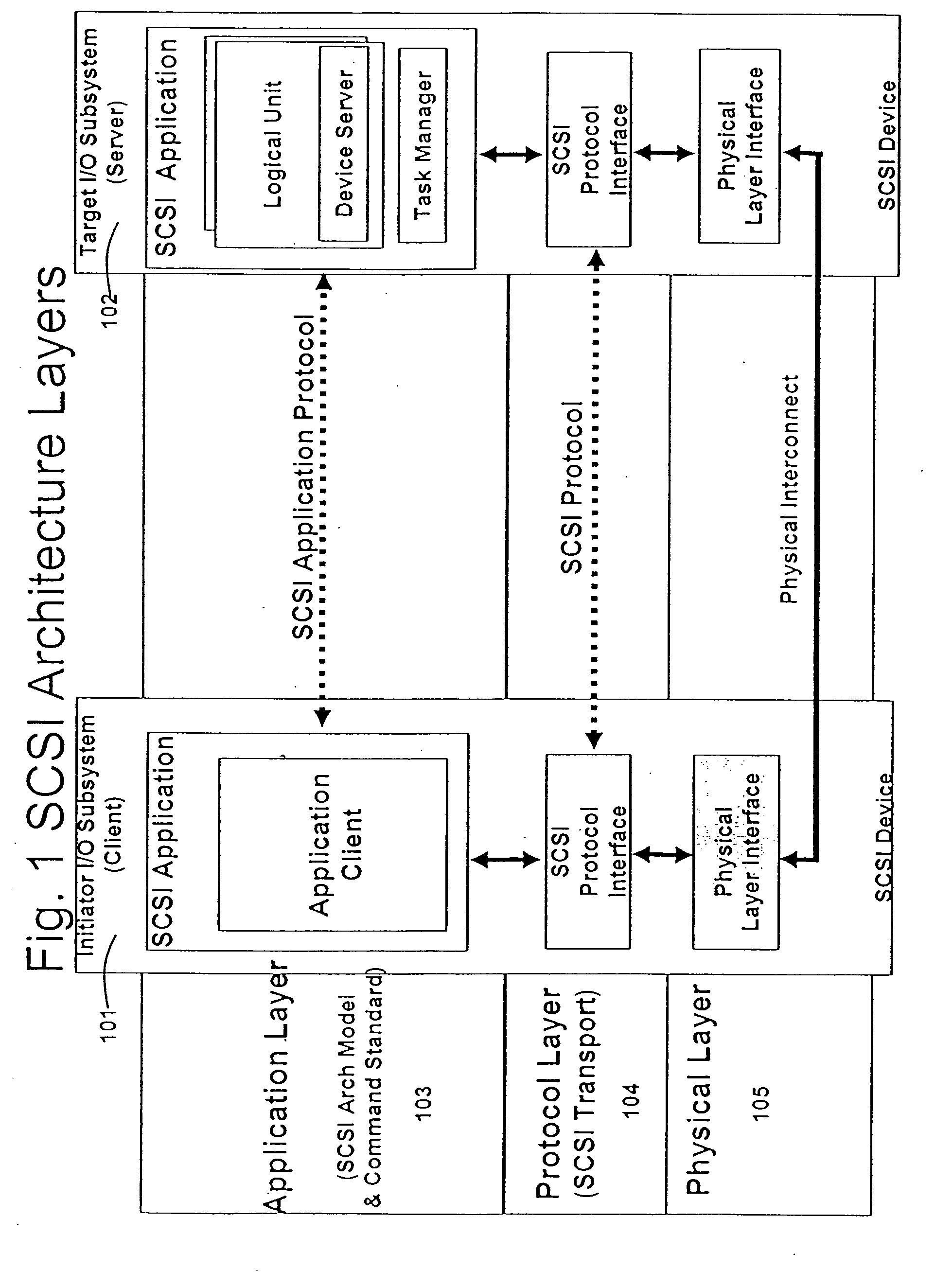
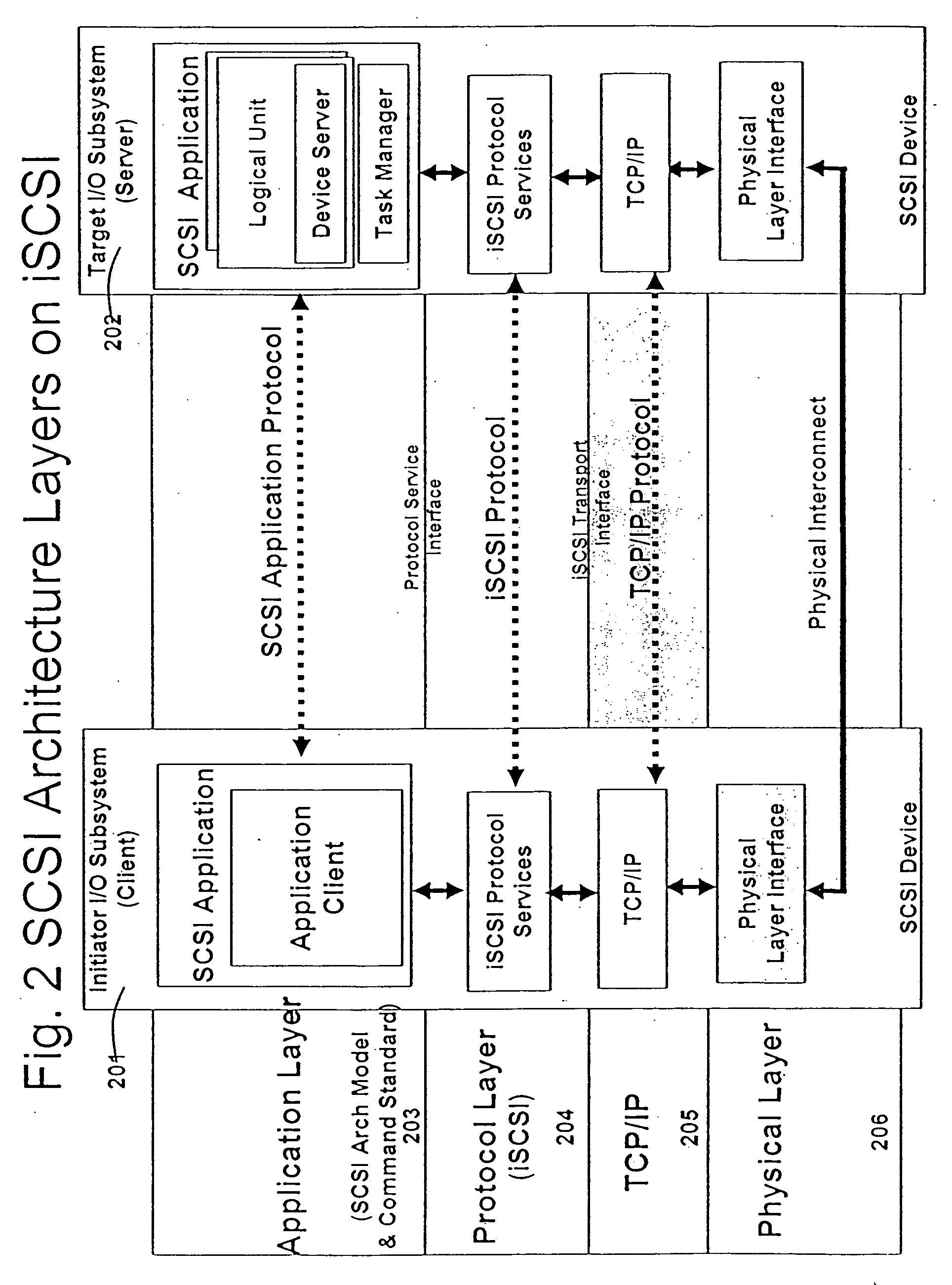
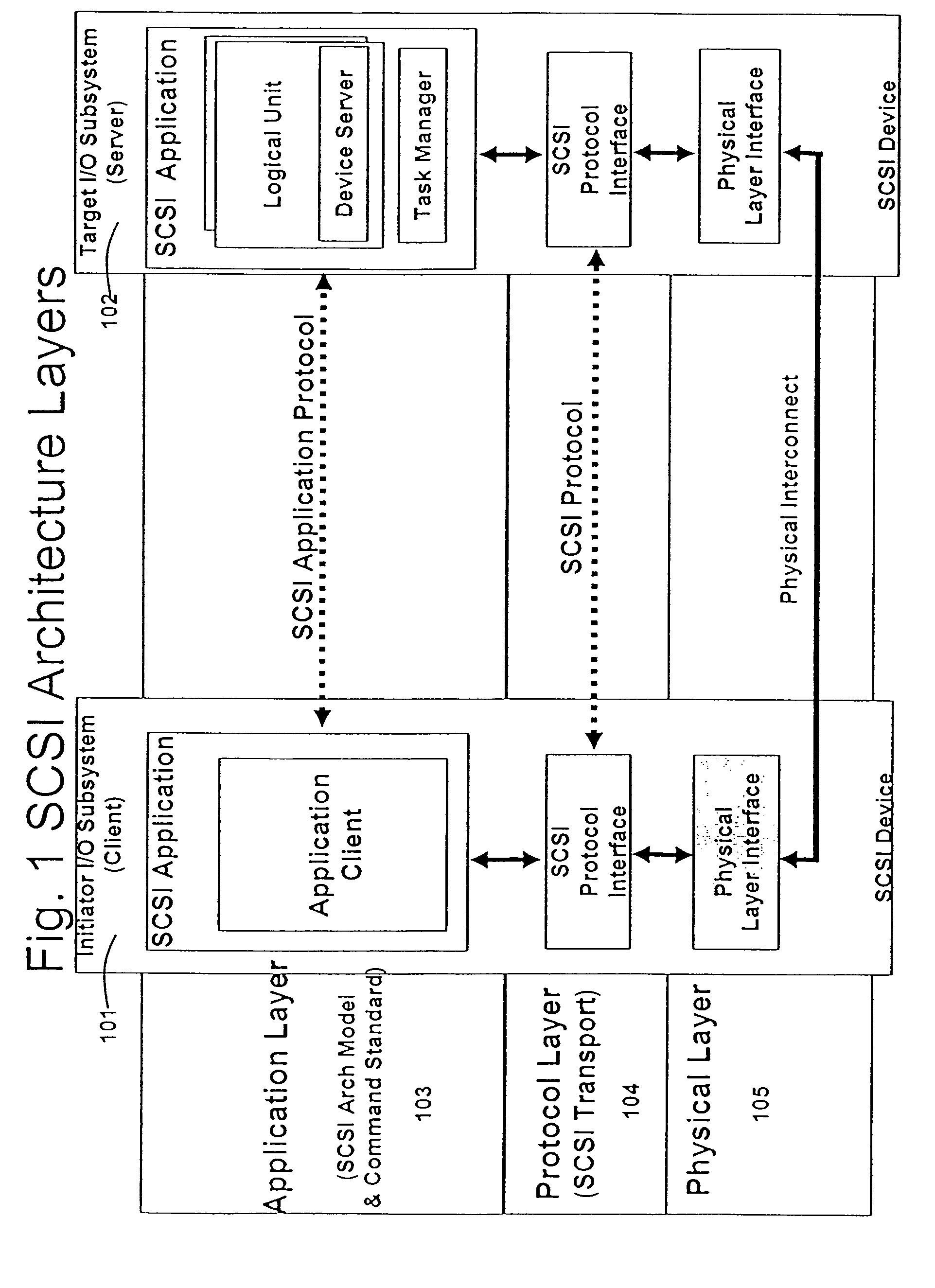
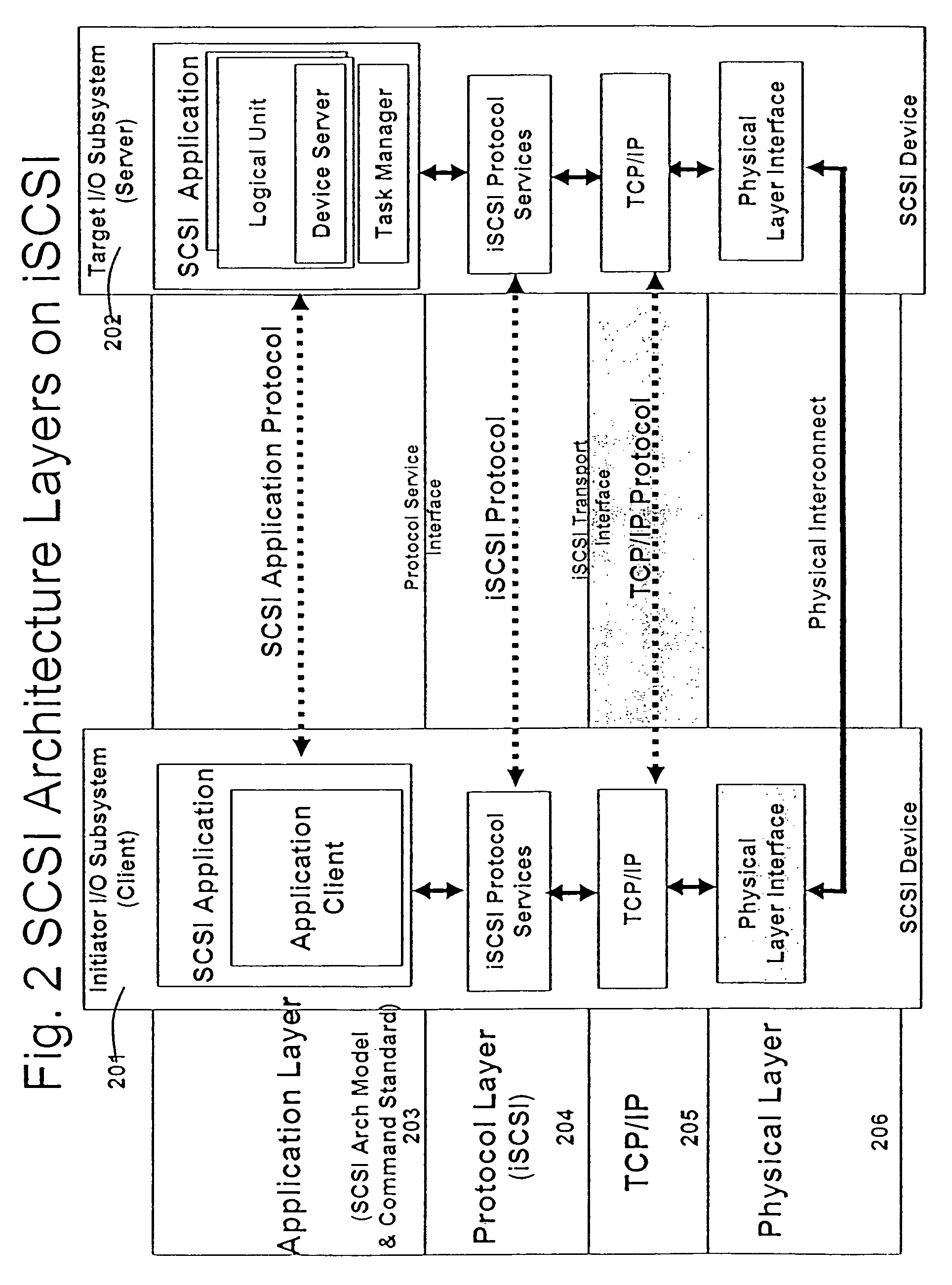
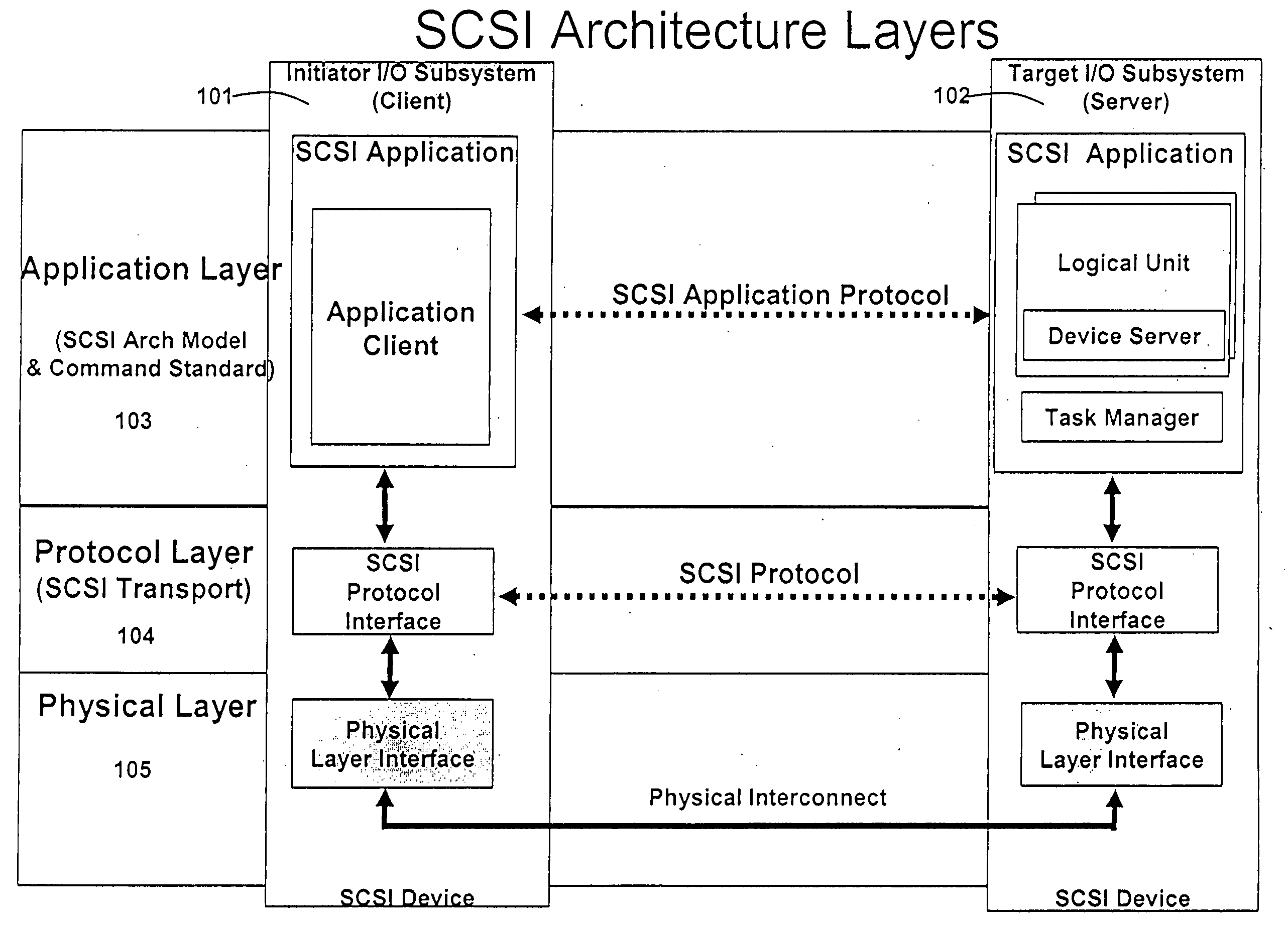
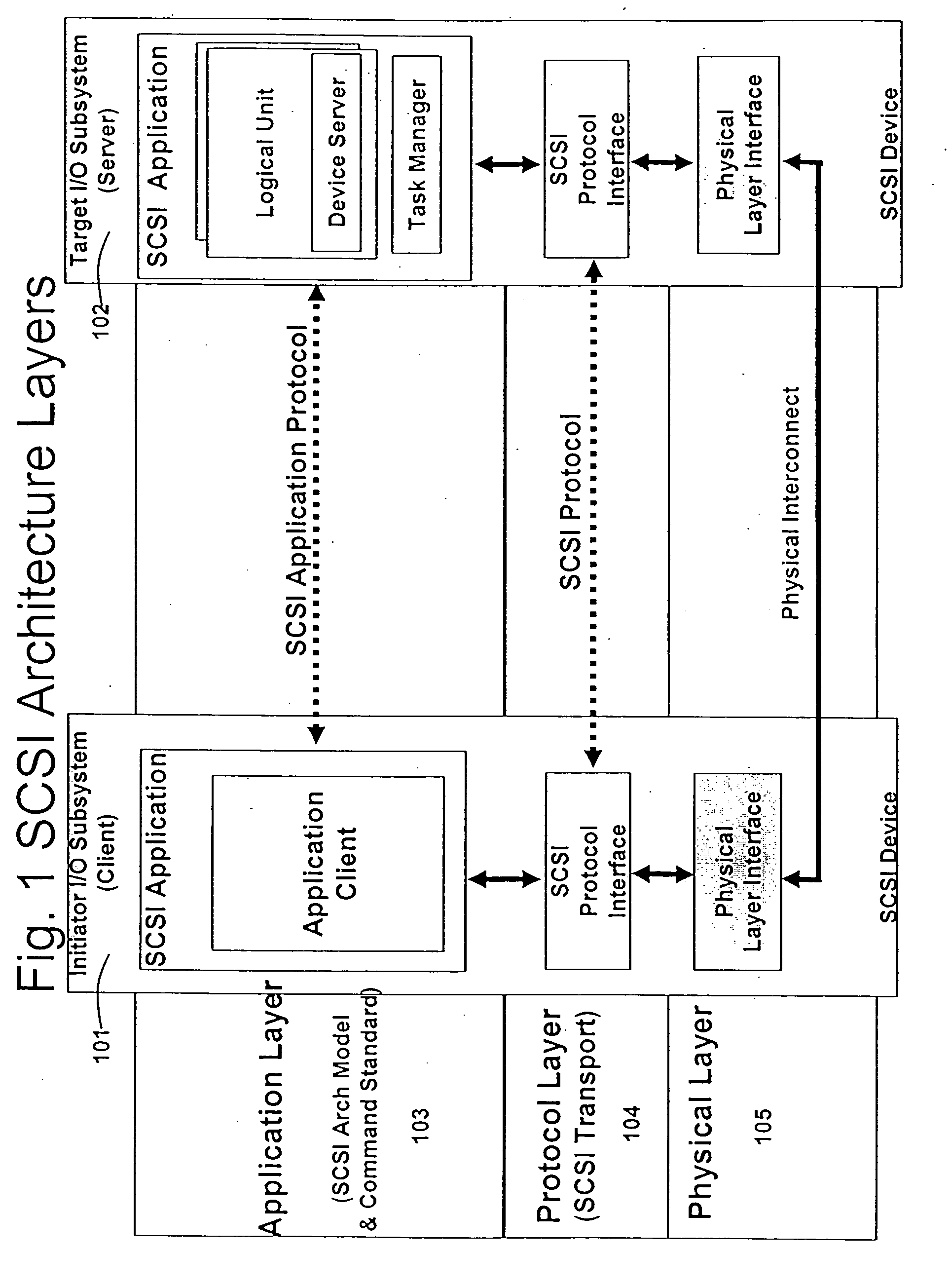
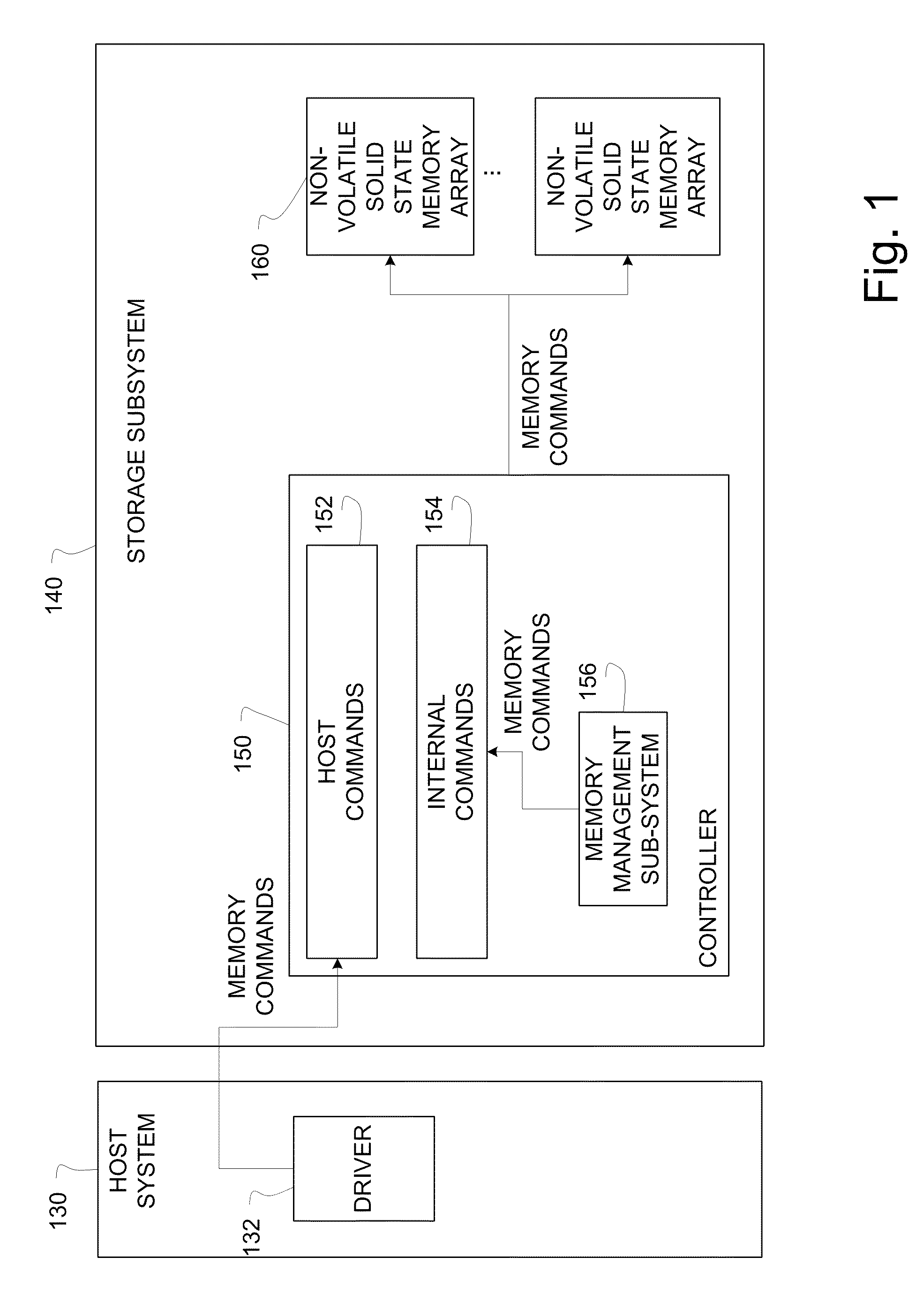
A runtime adaptable search processor is disclosed. The search processor provides high speed content search capability to meet the performance need of network line rates growing to 1 Gbps, 10 Gbps and higher. he search processor provides a unique combination of NFA and DFA based search engines that can process incoming data in parallel to perform the search against the specific rules programmed in the search engines. The processor architecture also provides capabilities to transport and process Internet Protocol (IP) packets from Layer 2 through transport protocol layer and may also provide packet inspection through Layer 7. Further, a runtime adaptable processor is coupled to the protocol processing hardware and may be dynamically adapted to perform hardware tasks as per the needs of the network traffic being sent or received and / or the policies programmed or services or applications being supported. A set of engines may perform pass-through packet classification, policy processing and / or security processing enabling packet streaming through the architecture at nearly the full line rate. A high performance content search and rules processing security processor is disclosed which may be used for application layer and network layer security. scheduler schedules packets to packet processors for processing. An internal memory or local session database cache stores a session information database for a certain number of active sessions. The session information that is not in the internal memory is stored and retrieved to / from an additional memory. An application running on an initiator or target can in certain instantiations register a region of memory, which is made available to its peer(s) for access directly without substantial host intervention through RDMA data transfer. A security system is also disclosed that enables a new way of implementing security capabilities inside enterprise networks in a distributed manner using a protocol processing hardware with appropriate security features.
Owner:MEMORY ACCESS TECH LLC
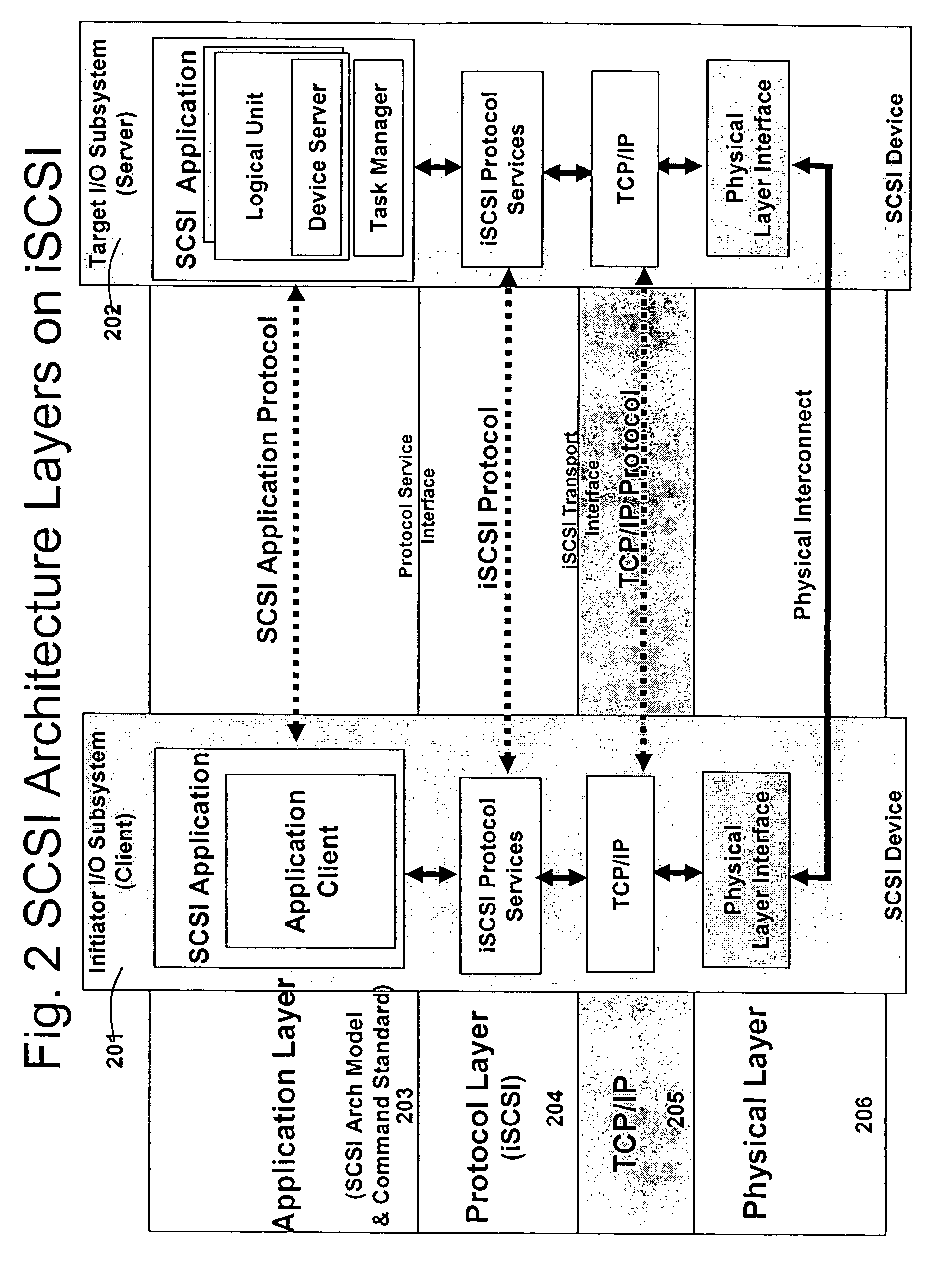
Runtime adaptable search processor
ActiveUS7685254B2Improve application performanceLarge capacityWeb data indexingMemory adressing/allocation/relocationPacket schedulingSchema for Object-Oriented XML
A runtime adaptable search processor is disclosed. The search processor provides high speed content search capability to meet the performance need of network line rates growing to 1 Gbps, 10 Gbps and higher. The search processor provides a unique combination of NFA and DFA based search engines that can process incoming data in parallel to perform the search against the specific rules programmed in the search engines. The processor architecture also provides capabilities to transport and process Internet Protocol (IP) packets from Layer 2 through transport protocol layer and may also provide packet inspection through Layer 7. Further, a runtime adaptable processor is coupled to the protocol processing hardware and may be dynamically adapted to perform hardware tasks as per the needs of the network traffic being sent or received and / or the policies programmed or services or applications being supported. A set of engines may perform pass-through packet classification, policy processing and / or security processing enabling packet streaming through the architecture at nearly the full line rate. A high performance content search and rules processing security processor is disclosed which may be used for application layer and network layer security. Scheduler schedules packets to packet processors for processing. An internal memory or local session database cache stores a session information database for a certain number of active sessions. The session information that is not in the internal memory is stored and retrieved to / from an additional memory. An application running on an initiator or target can in certain instantiations register a region of memory, which is made available to its peer(s) for access directly without substantial host intervention through RDMA data transfer. A security system is also disclosed that enables a new way of implementing security capabilities inside enterprise networks in a distributed manner using a protocol processing hardware with appropriate security features.
Owner:MEMORY ACCESS TECH LLC
Runtime adaptable security processor
InactiveUS20050108518A1Improve performanceReduce overheadSecuring communicationInternal memoryPacket scheduling
A runtime adaptable security processor is disclosed. The processor architecture provides capabilities to transport and process Internet Protocol (IP) packets from Layer 2 through transport protocol layer and may also provide packet inspection through Layer 7. Further, a runtime adaptable processor is coupled to the protocol processing hardware and may be dynamically adapted to perform hardware tasks as per the needs of the network traffic being sent or received and / or the policies programmed or services or applications being supported. A set of engines may perform pass-through packet classification, policy processing and / or security processing enabling packet streaming through the architecture at nearly the full line rate. A high performance content search and rules processing security processor is disclosed which may be used for application layer and network layer security. A scheduler schedules packets to packet processors for processing. An internal memory or local session database cache stores a session information database for a certain number of active sessions. The session information that is not in the internal memory is stored and retrieved to / from an additional memory. An application running on an initiator or target can in certain instantiations register a region of memory, which is made available to its peer(s) for access directly without substantial host intervention through RDMA data transfer. A security system is also disclosed that enables a new way of implementing security capabilities inside enterprise networks in a distributed manner using a protocol processing hardware with appropriate security features.
Owner:MEMORY ACCESS TECH LLC
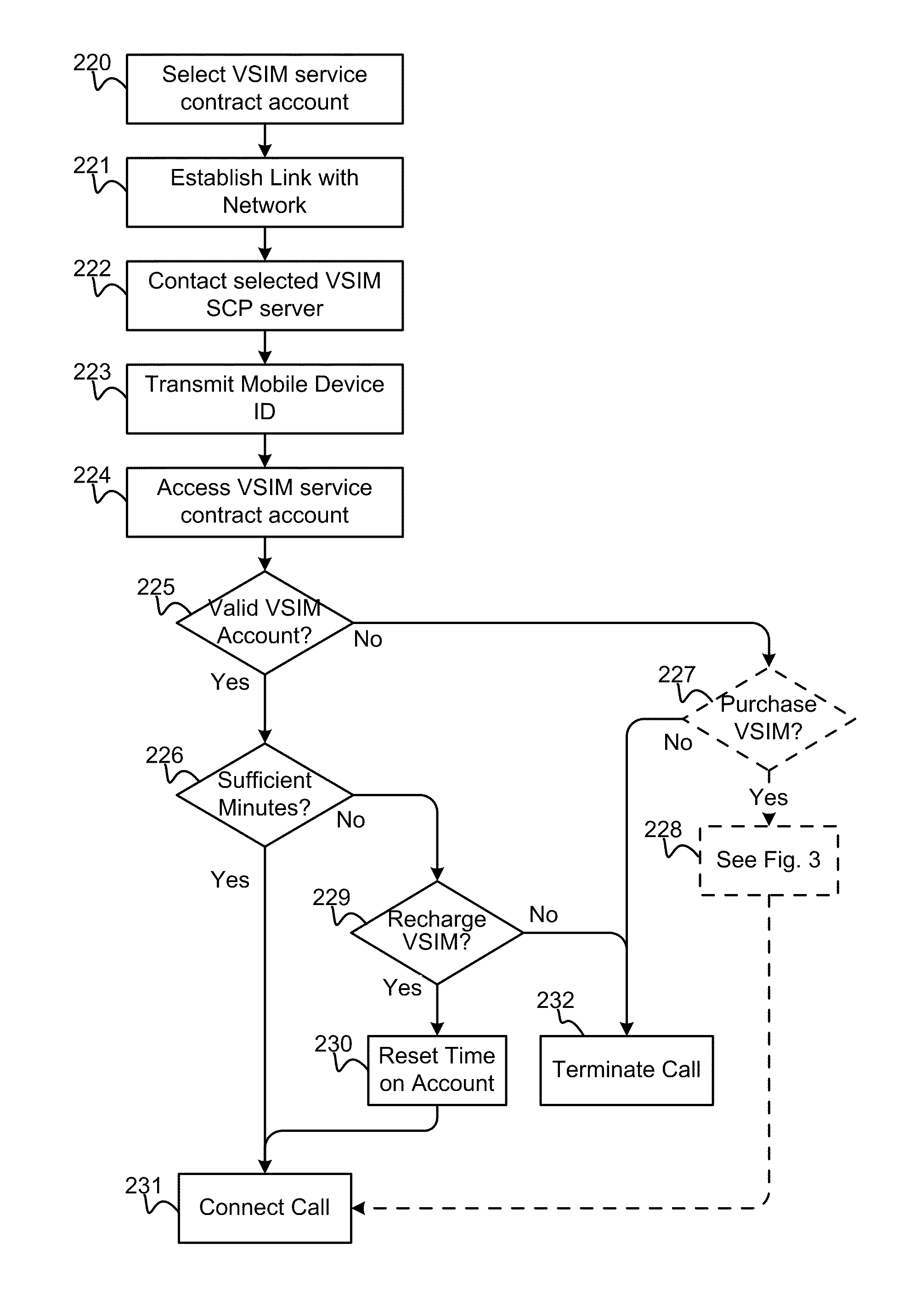
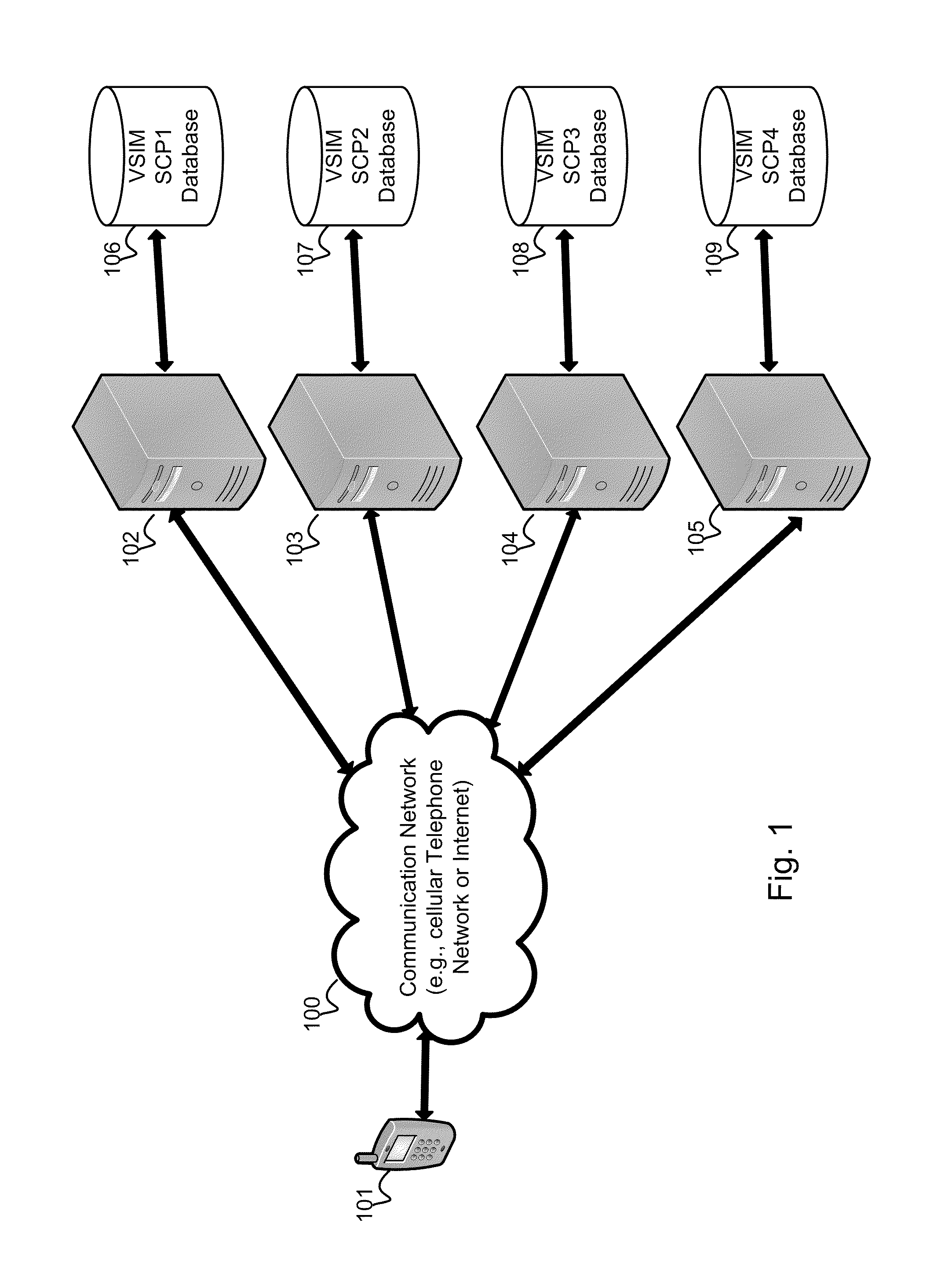
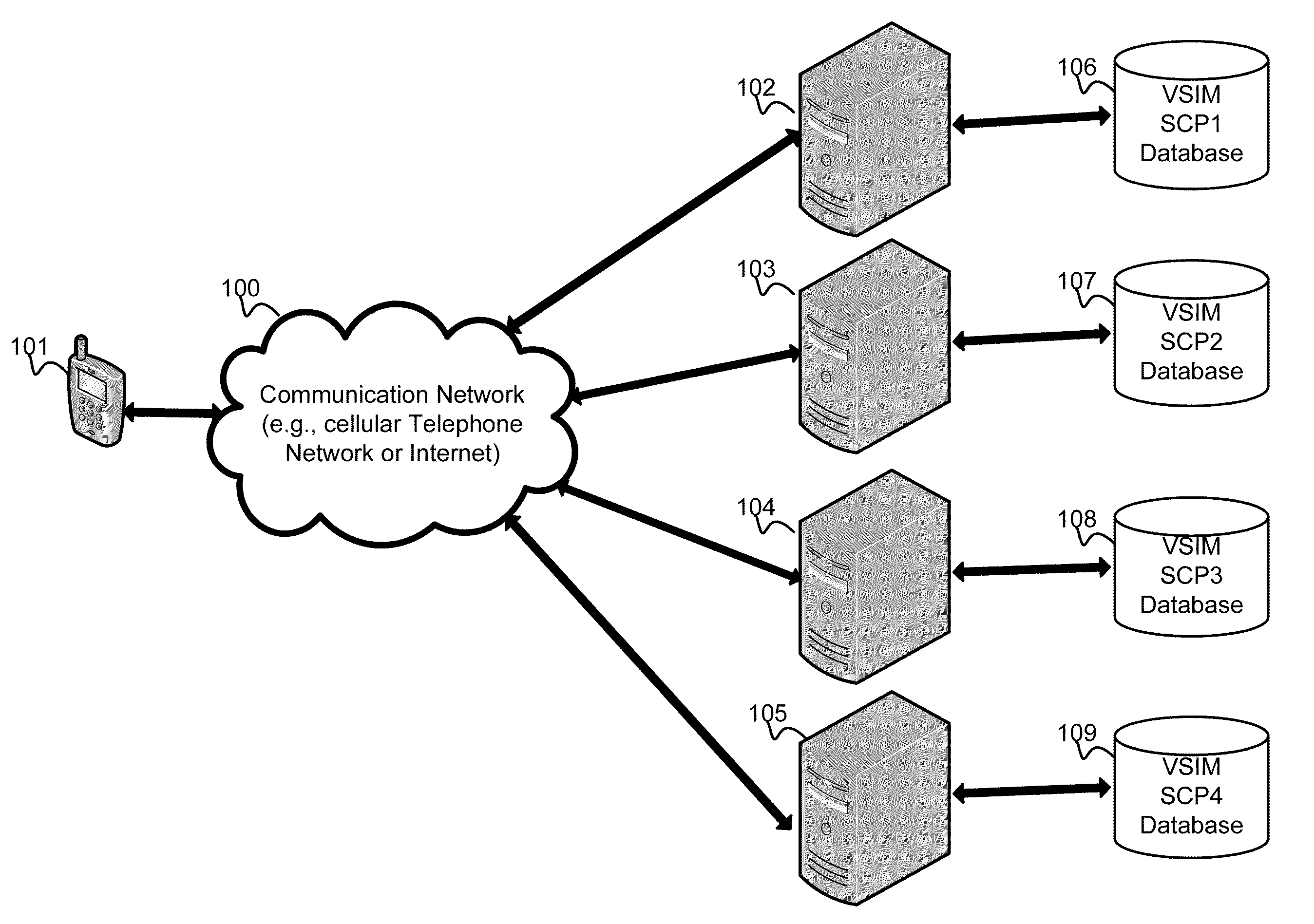
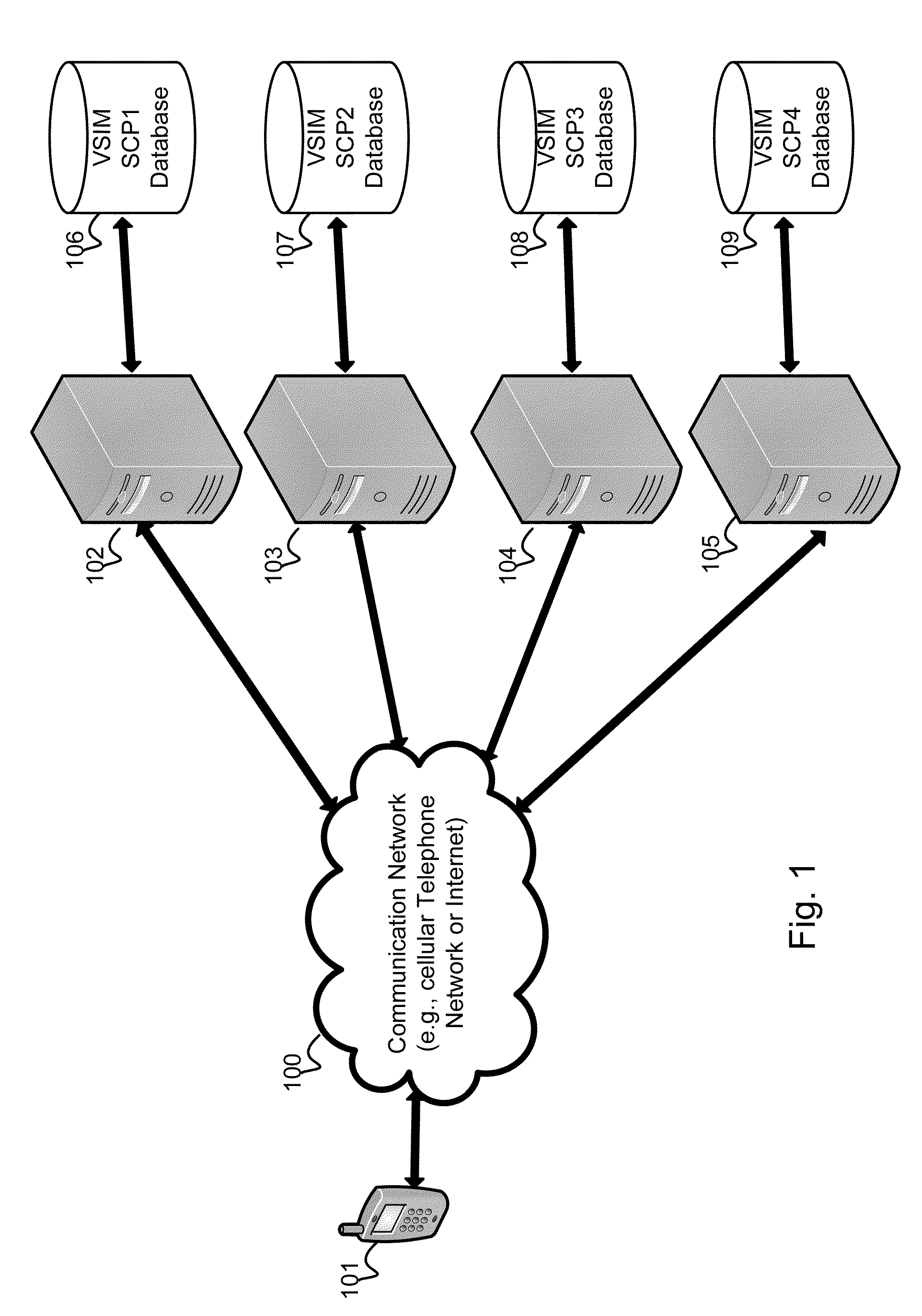
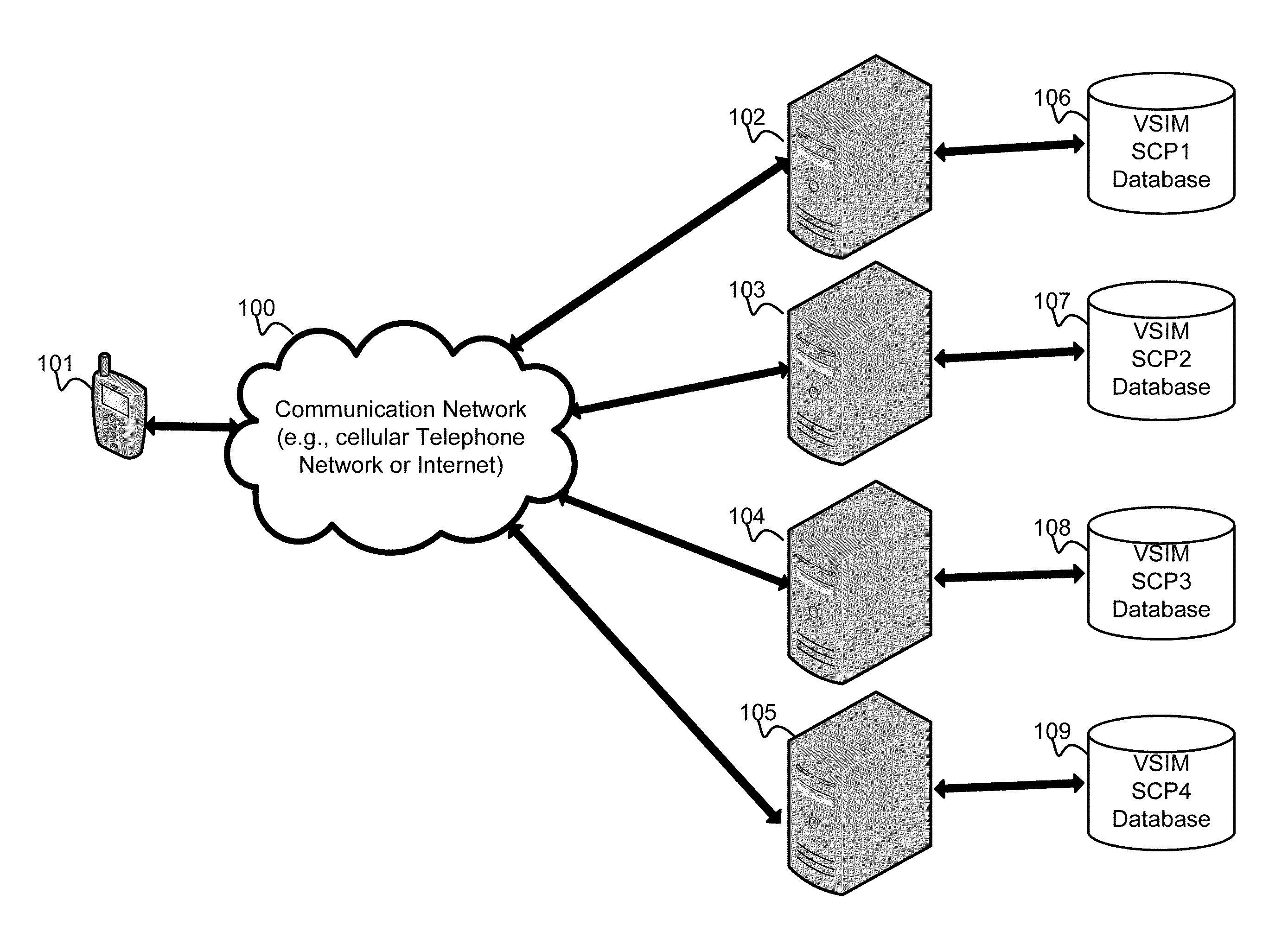
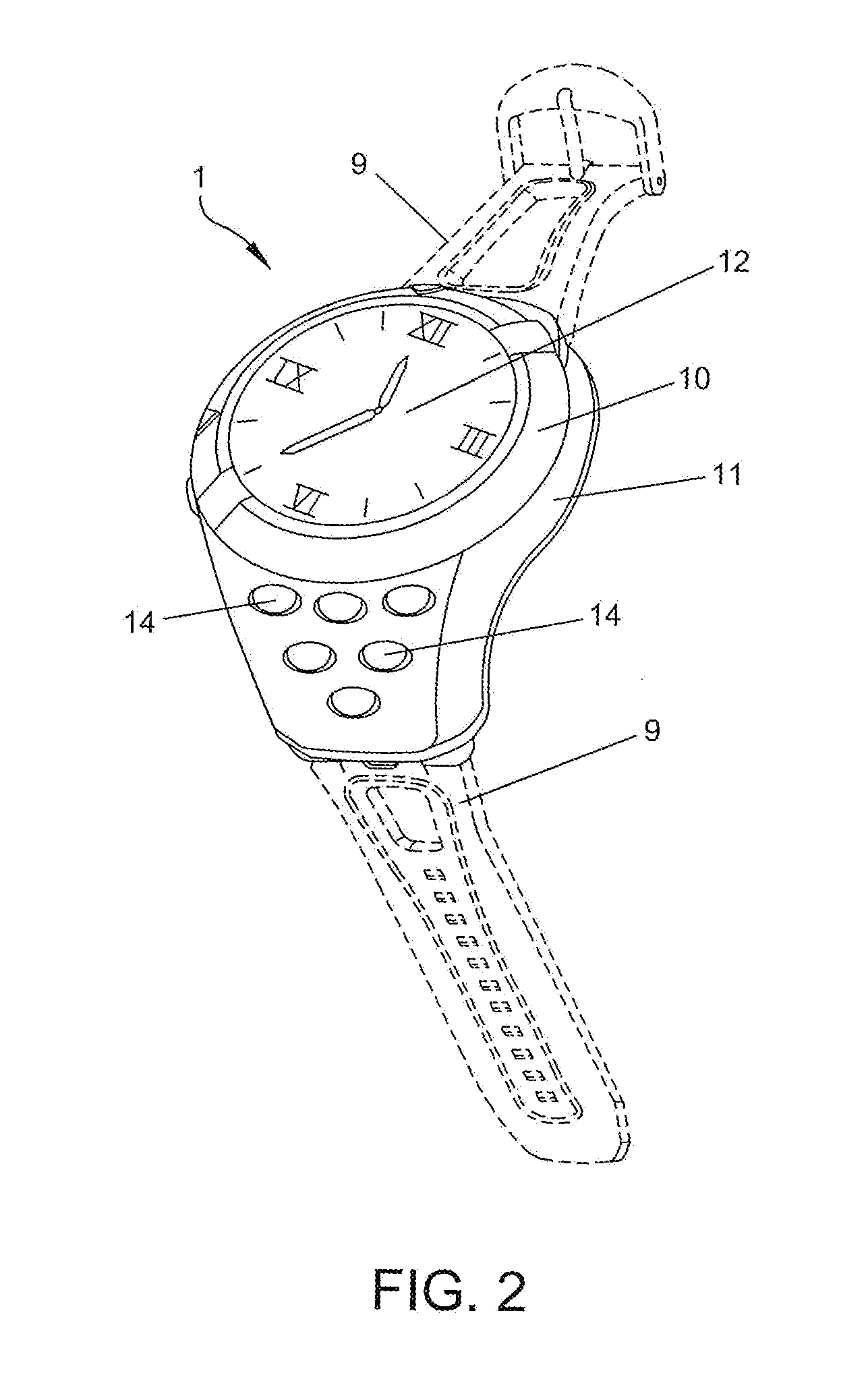
Method and apparatus for performing soft switch of virtual sim service contracts
InactiveUS20100311402A1Save battery powerEffective supportService provisioningAssess restrictionInternal memoryService provision
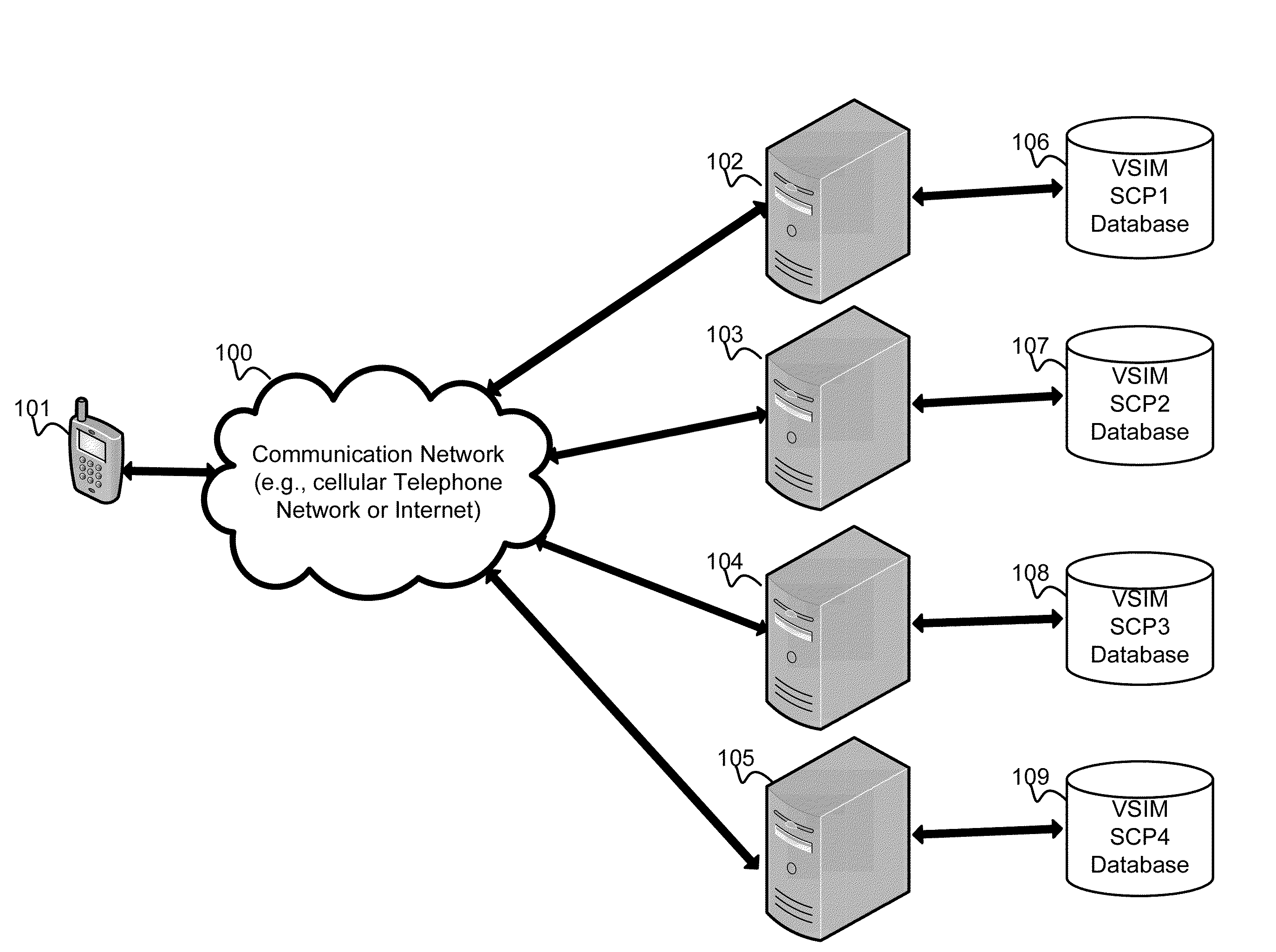
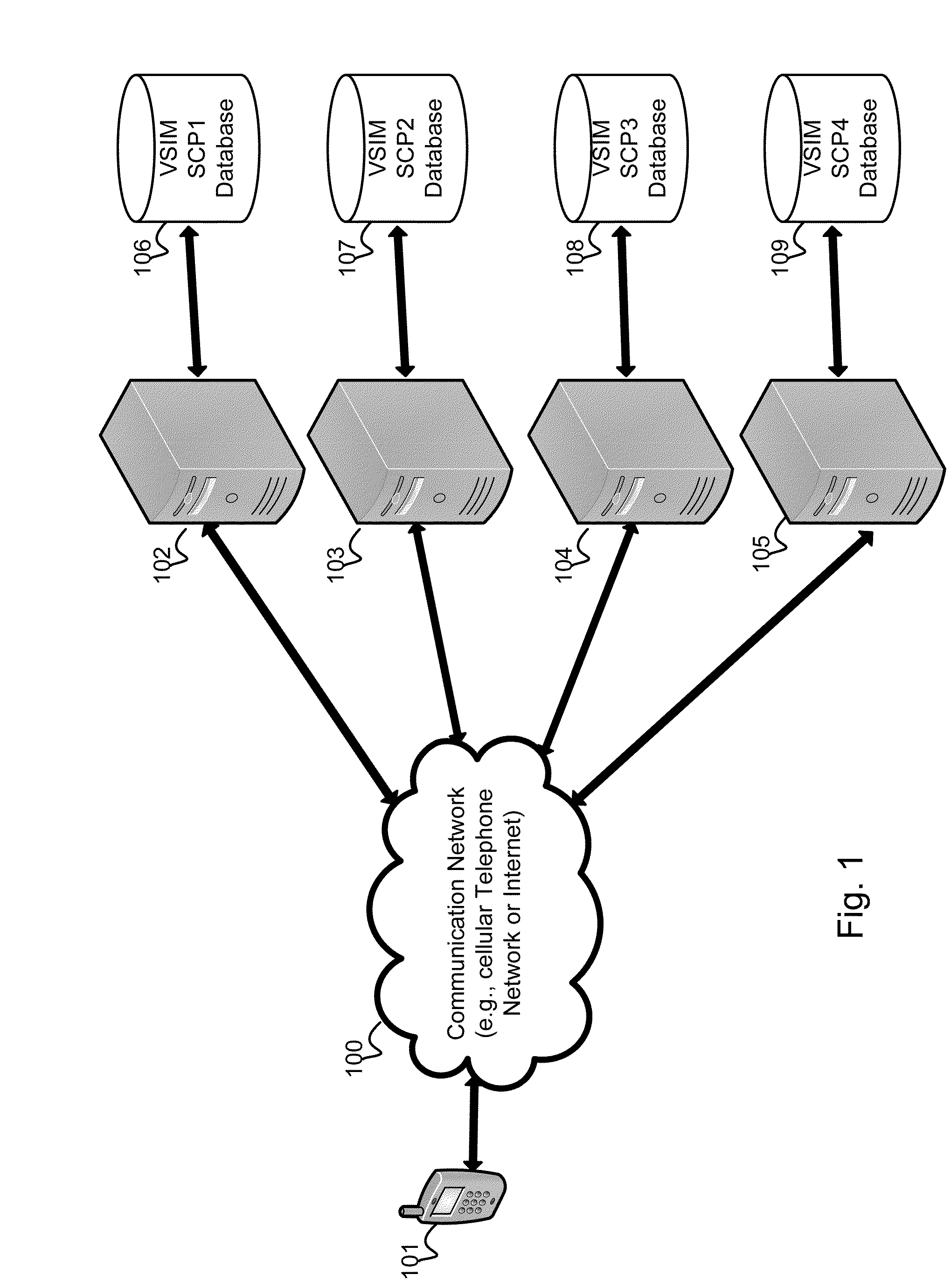
A system and method for providing updated rules governing the switching of enabled provisioning data supporting a wireless service contract. A mobile device may be initially programmed with a profile data table and priority list index data table to automatically enable provisioning data supporting one of the plurality of service providers stored in a VSIM internal memory unit to conduct a wireless communication when certain operational parameter values are satisfied. The profile data table and priority list index data table may be automatically updated in response to a variety of triggers. The profile data table and priority list index data table may be stored remotely. Operational parameters regarding each call request are collected and transmitted to a remote service contract selection server. The selection of an optimal service provider account may be made remotely in the service contract selection server and transmitted back to the mobile device.
Owner:QUALCOMM INC
Mobile phone with internal accounting
InactiveUS7245901B2Expands potential customer baseExpand its customer baseAccounting/billing servicesConnection managementInternal memoryMobile Telephone Service
A mobile phone system with a mobile phone having internal accounting capabilities for real time call debiting to account for the billing parameters of a mobile phone unit that is operated in a multi zone communication network with a complex rate structure, the mobile phone unit having an internal processor with accessible internal memory for storing the accounting program and call data for each call, a clock and circuit means for activating and deactivating the phone, the accounting program including an updatable rate table and a complex billing algorithm for calculating the account status on the fly including multiple rate structure factors such as long distance calls, international calls with country independent local charges, charges for roaming per day and / or roaming per minute, and call surcharges, where the account status of the mobile phone is calculated in real time for decrementing a debit account or calculating an account charge on demand, the mobile debit phone having a signal for alerting the user of account status which is preferably a display of real time account status, the mobile phone system including a communication system for activating and programming a new phone unit over the airways and upgrading the account status in rate table in the phone unit over the airways.
Owner:TRACFONE WIRELESS
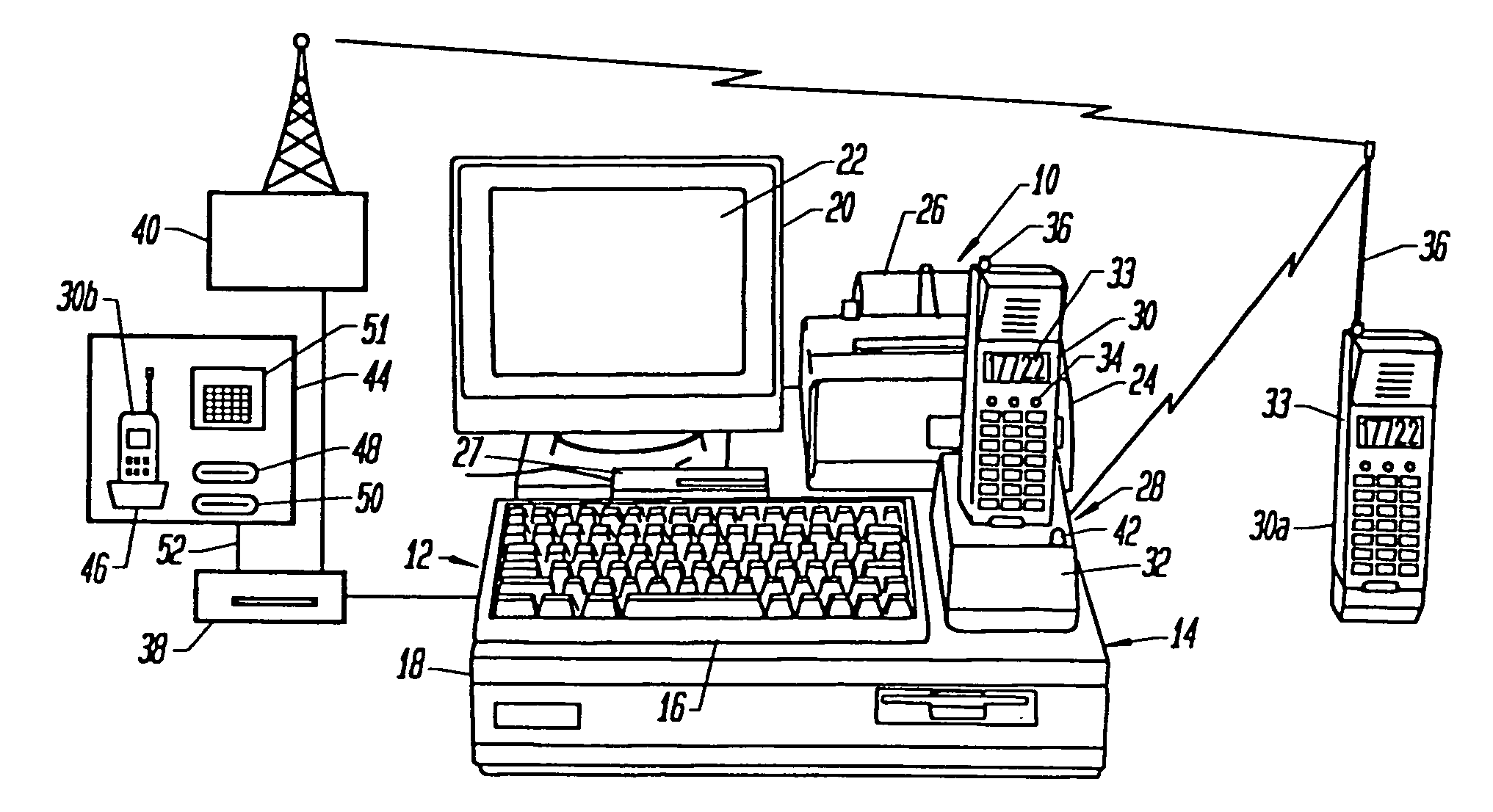
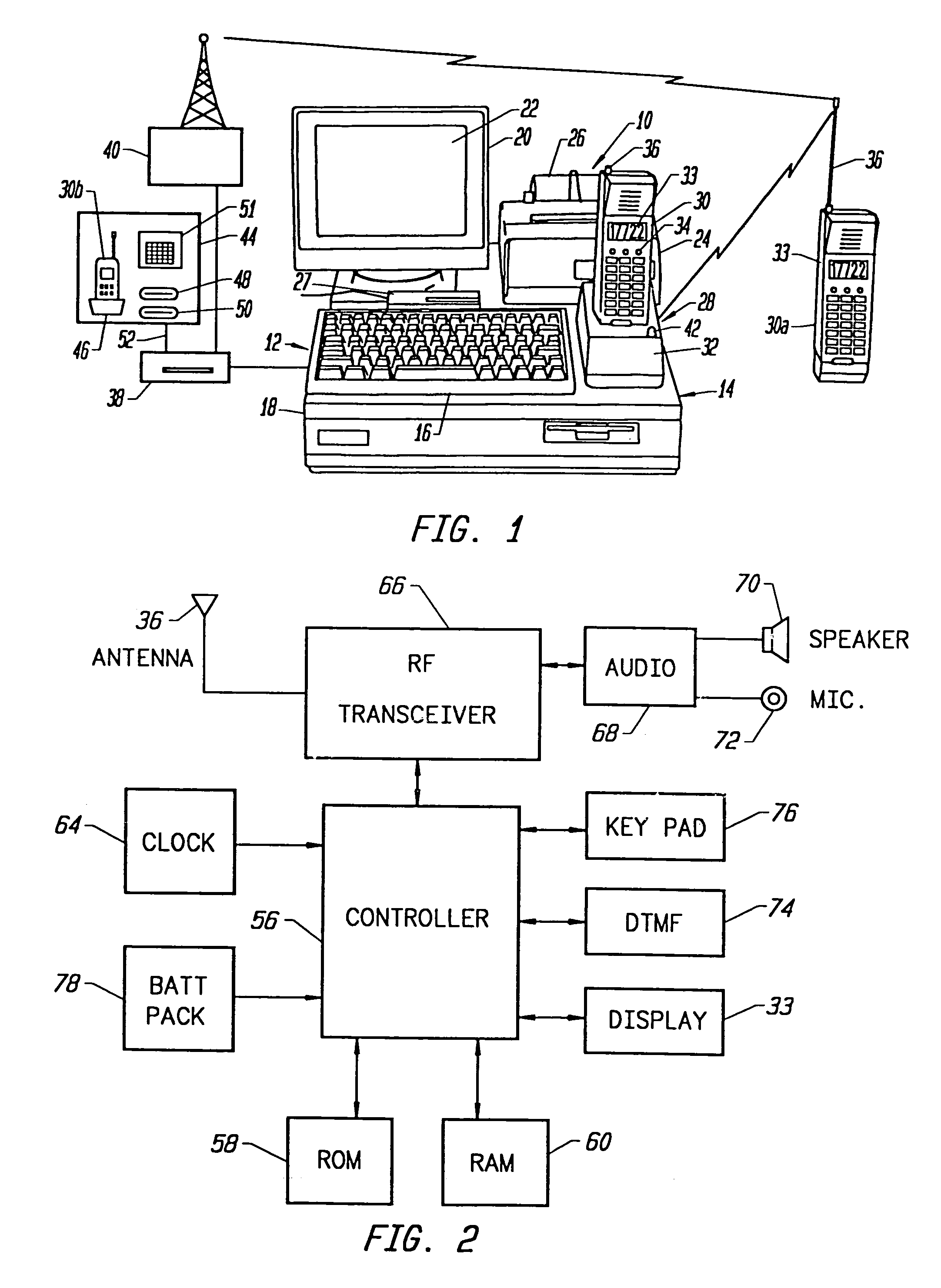
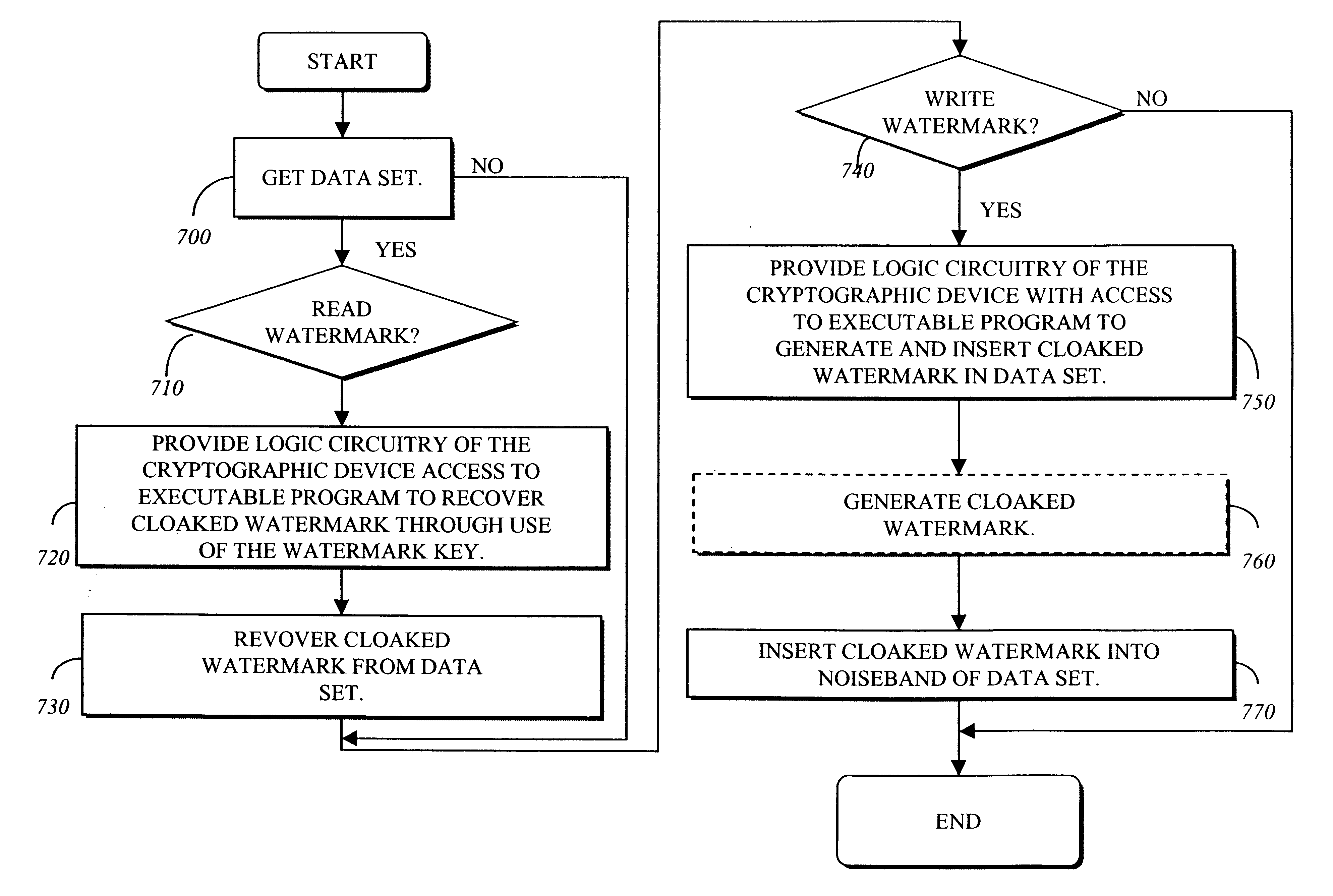
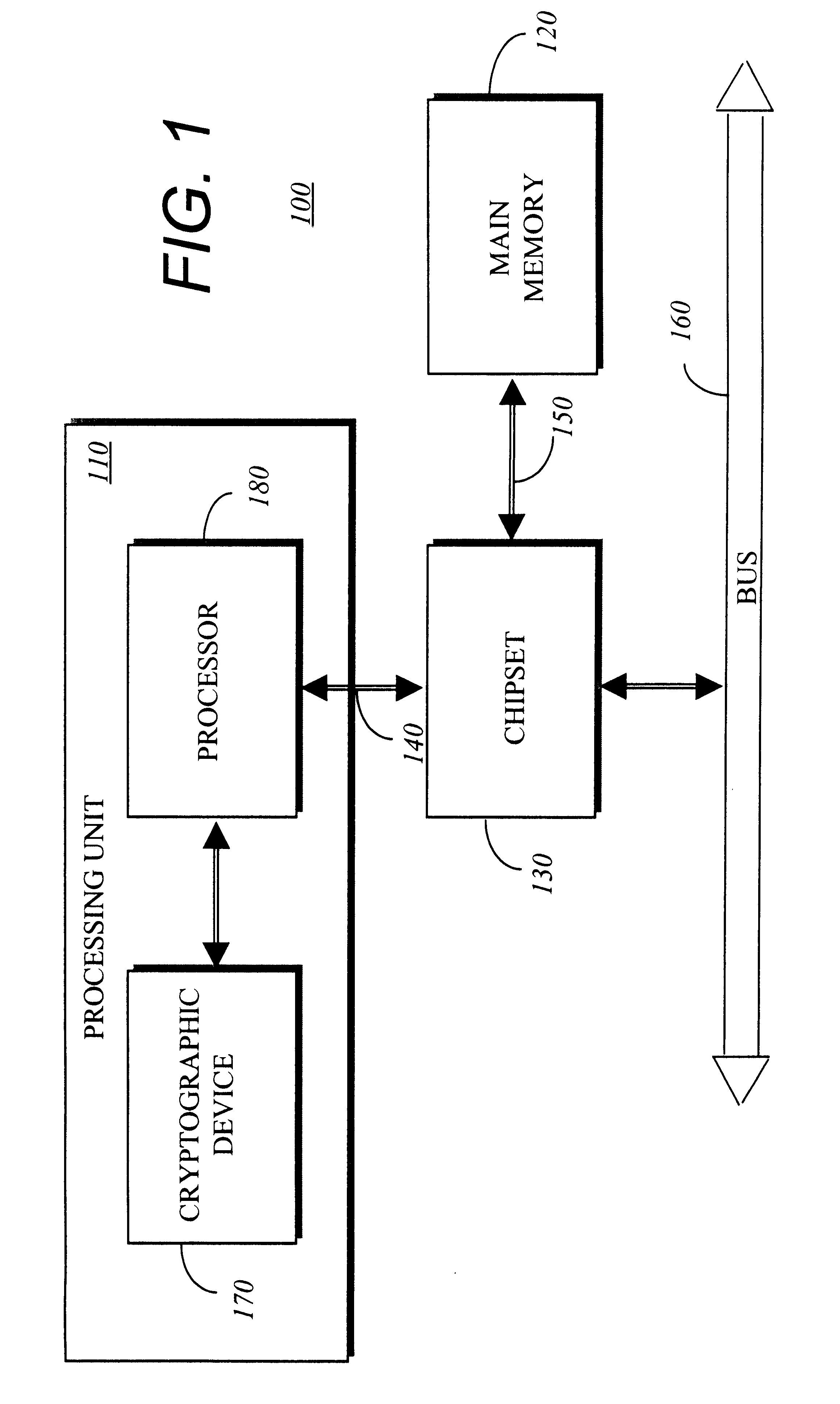
Secure public digital watermark
A cryptographic device and corresponding method for producing a cloaked watermark which is a private watermark having the functionality of a public watermark. In one embodiment, the cryptographic device comprises an internal memory and a processor contained in a package. The internal memory provides a region for storage of key information used at least to produce the cloaked watermark. The processor is coupled to the internal memory and is responsible for producing a cloaked watermark based on the key and for inserting the cloaked watermark into an outgoing data set.
Owner:INTEL CORP
Virtual sim card for mobile handsets
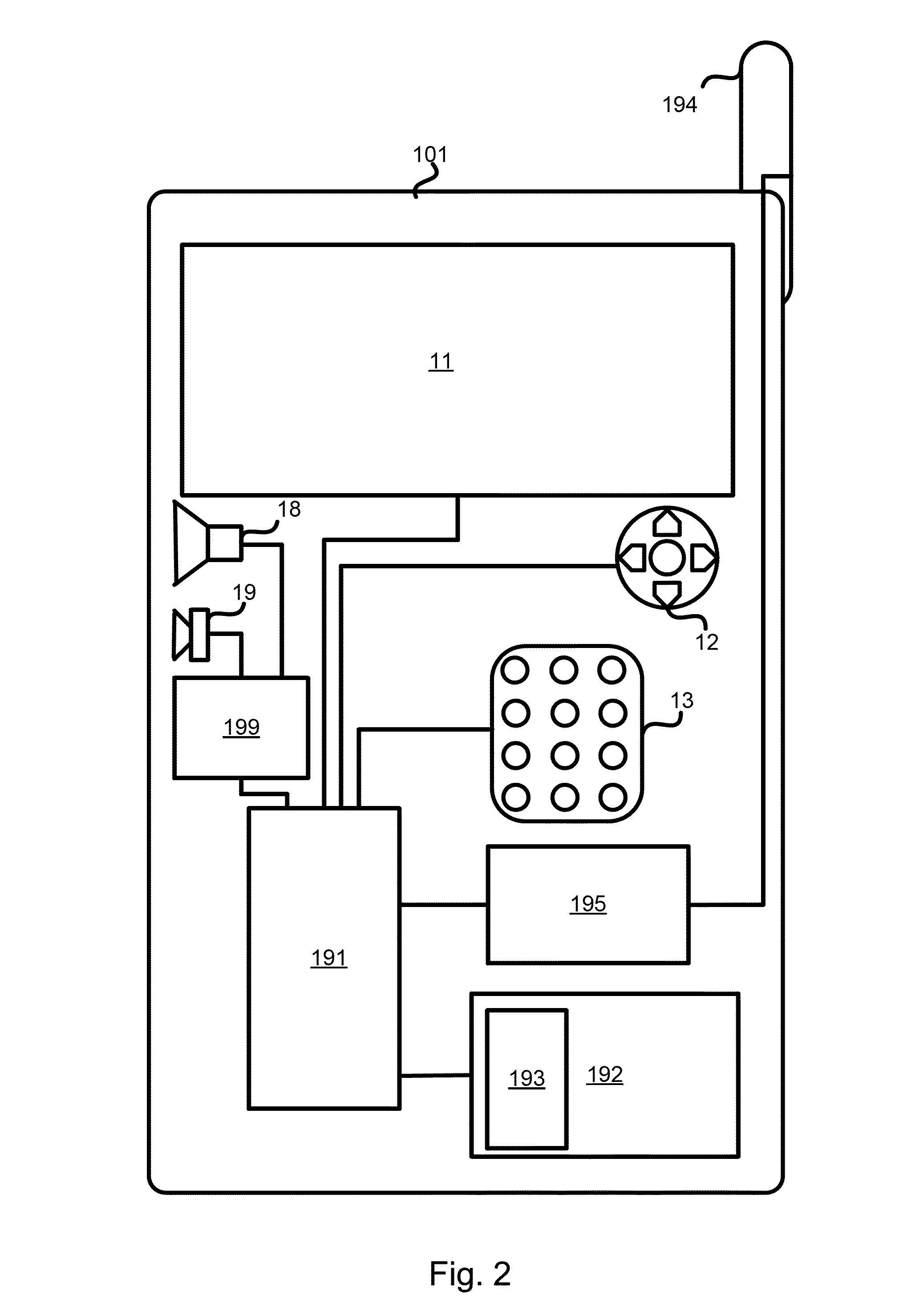
A system and method store provisioning data supporting a plurality of service providers in a VSIM internal memory unit of a mobile device. A user may selectively enable provisioning data supporting one of the plurality of service providers stored in the VSIM internal memory unit to conduct a wireless communication. An embodiment permits backing up, retrieving and restoring personal data in the VSIM internal memory unit using a remote database. Another embodiment allows a mobile device to select an optimal service provider to conduct a wireless communication. The optimal service provider may be determined based upon mobile device location, communication usage request and / or time and date.
Owner:QUALCOMM INC
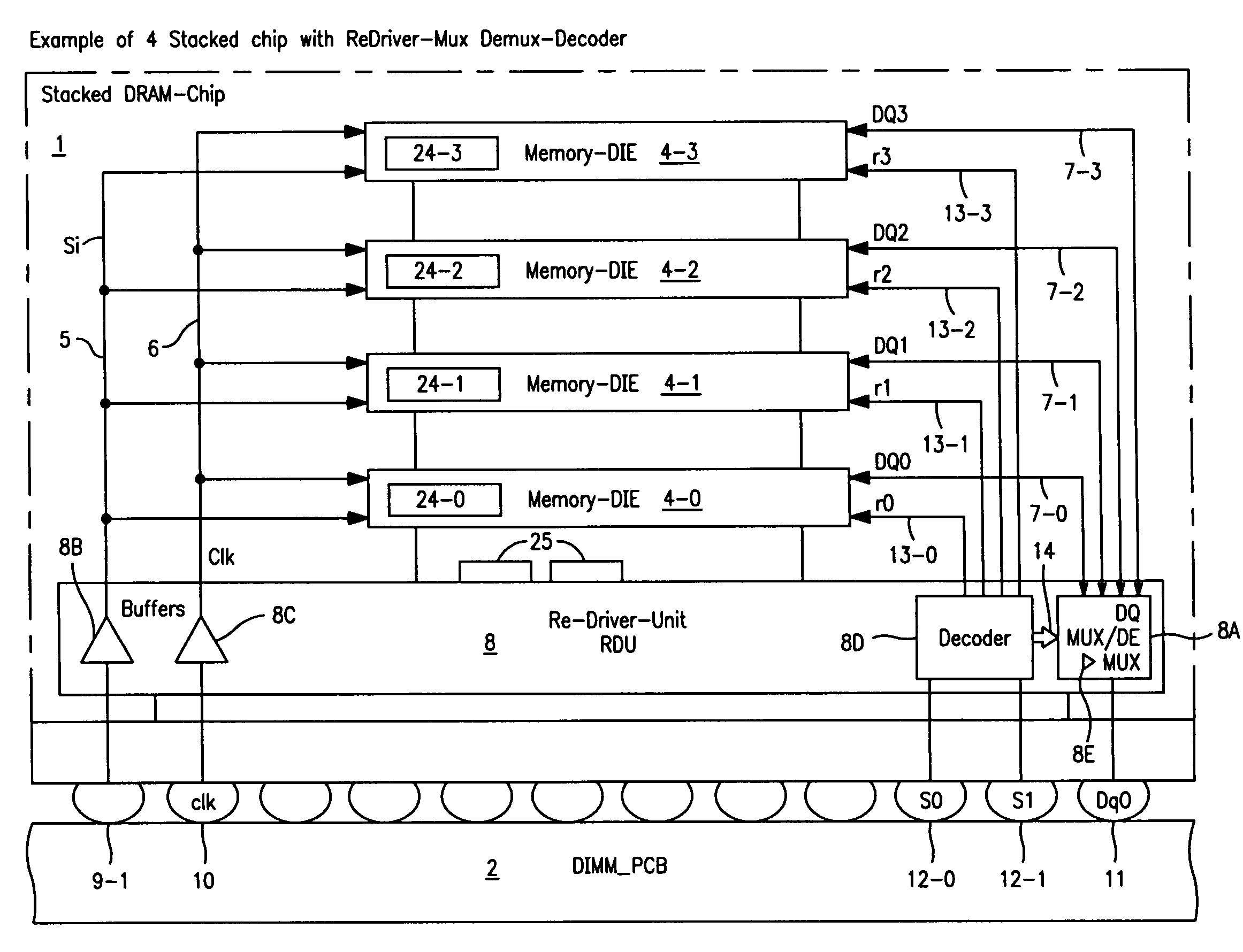
Stacked DRAM memory chip for a dual inline memory module (DIMM)
ActiveUS7200021B2Increase the number ofSmall sizeSemiconductor/solid-state device detailsNanoinformaticsInternal memoryMemory chip
A stacked DRAM memory chip for a Dual In Line Memory Module (DIMM) is disclosed. According to one aspect, the DRAM memory chip comprises at least four stacked DRAM memory dies. Further, the memory dies are each selectable by a corresponding internal memory rank signal. Each memory die comprises an array of memory cells. A common internal address bus is provided for addressing the memory cells and is connected to all stacked DRAM memory dies. Internal data buses are provided for writing data into the memory cells and reading data out of the memory cells of the DRAM memory dies. An integrated redriving unit comprises buffers for all internal address lines provided for driving external address signals applied to address pads of the DRAM memory chip. A multiplexer / demultiplexer switches the internal data lines of the selected DRAM memory die. A memory rank decoder selects a corresponding memory die.
Owner:POLARIS INNOVATIONS LTD
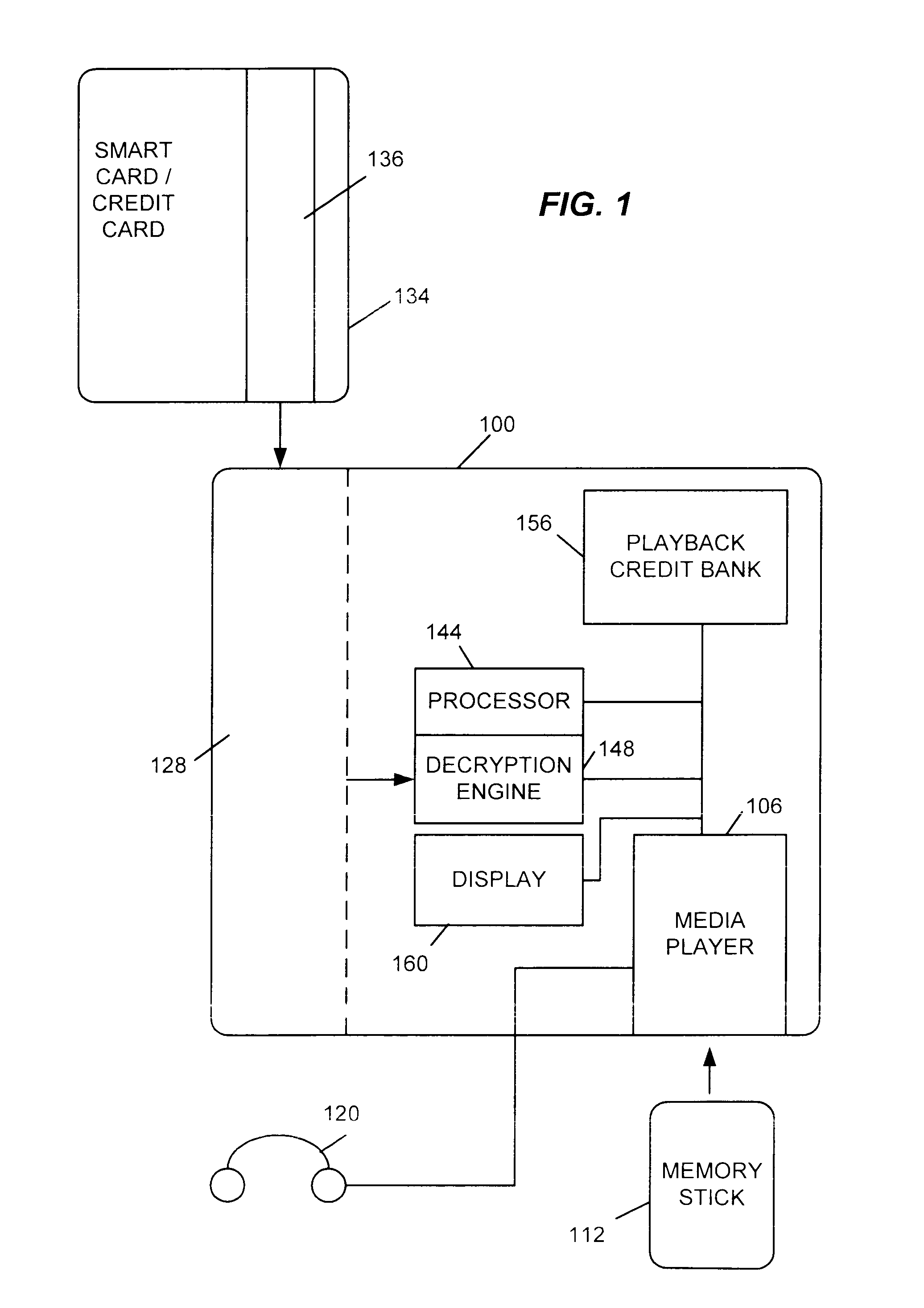
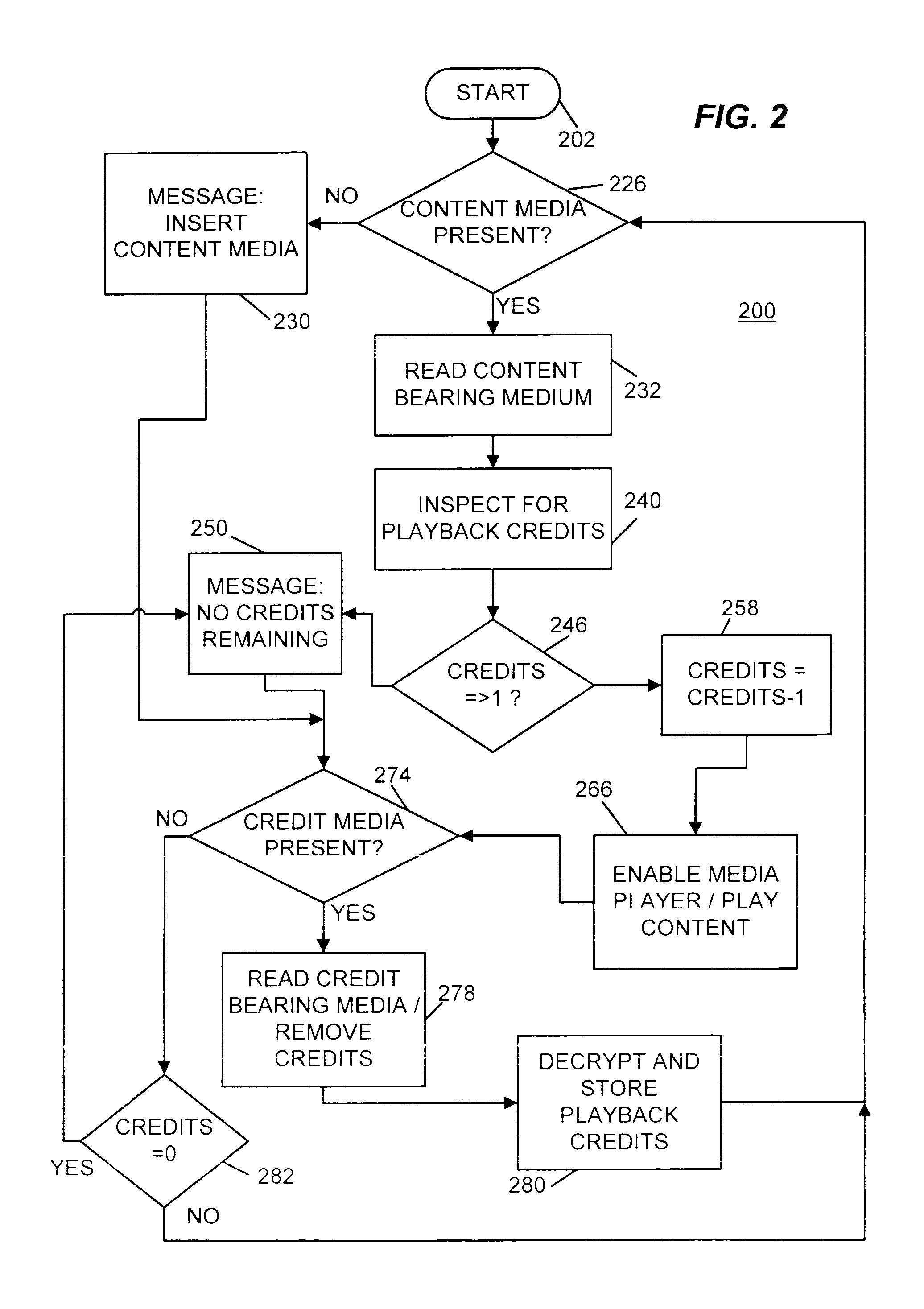
Portable music player with pay per play usage and method for purchase of credits for usage
A portable content playback device that includes the ability to accept a media with electronic playback credits, i.e. a smart card, that is pre-loaded with credits. Alternatively, the device may have internal memory that is capable of storing electronic credits. Consequently, when a user plays the content that is protected so that it may only be played only in a “pay per play” application credits are deducted from the media that manages the amount of electronic credits available to the user.
Owner:SONY CORP +1
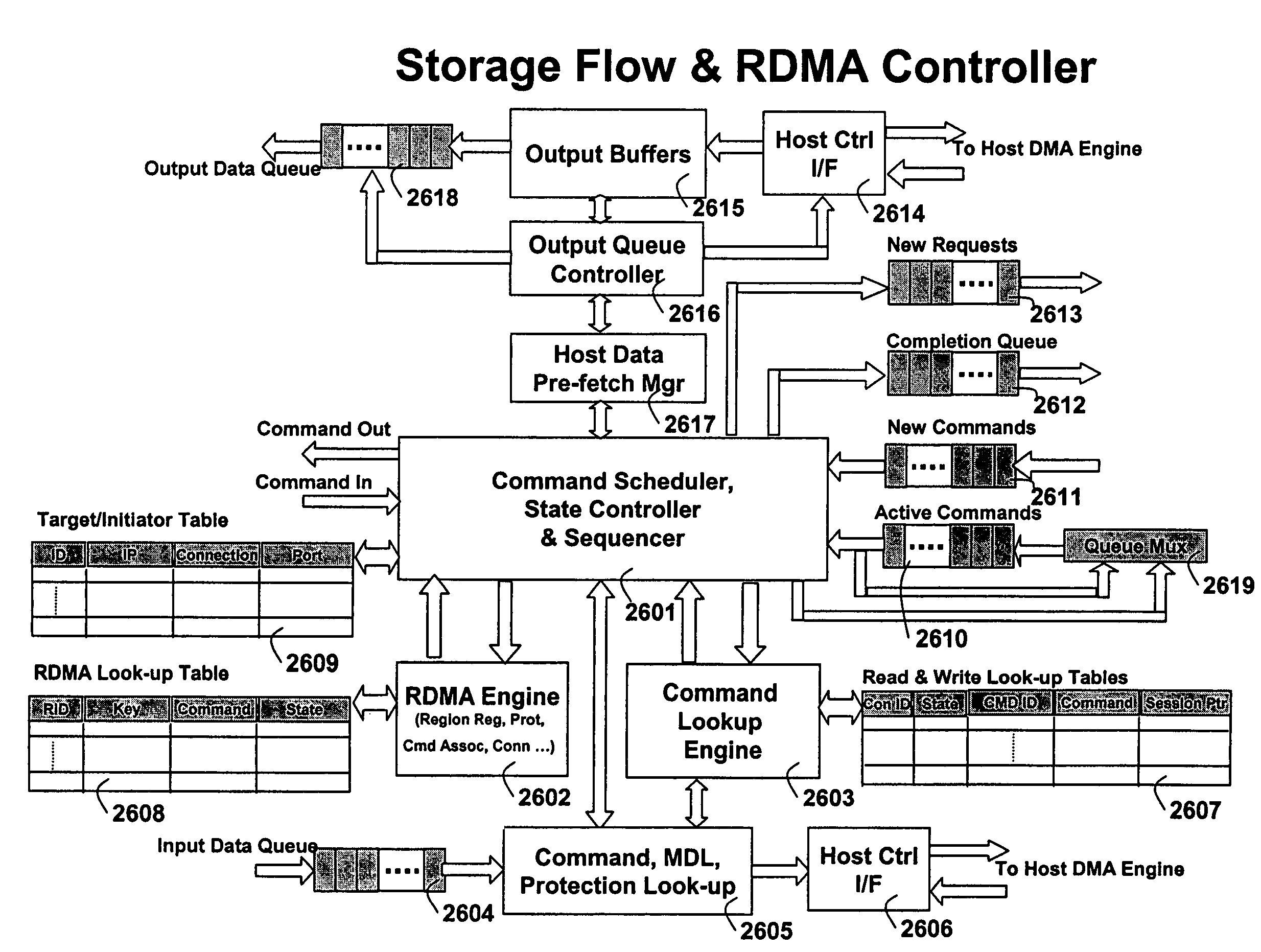
TCP/IP processor and engine using RDMA
ActiveUS7376755B2Sharply reduces TCP/IP protocol stack overheadImprove performanceMultiplex system selection arrangementsMemory adressing/allocation/relocationTransmission protocolInternal memory
A TCP / IP processor and data processing engines for use in the TCP / IP processor is disclosed. The TCP / IP processor can transport data payloads of Internet Protocol (IP) data packets using an architecture that provides capabilities to transport and process Internet Protocol (IP) packets from Layer 2 through transport protocol layer and may also provide packet inspection through Layer 7. The engines may perform pass-through packet classification, policy processing and / or security processing enabling packet streaming through the architecture at nearly the full line rate. A scheduler schedules packets to packet processors for processing. An internal memory or local session database cache stores a TCP / IP session information database and may also store a storage information session database for a certain number of active sessions. The session information that is not in the internal memory is stored and retrieved to / from an additional memory. An application running on an initiator or target can in certain instantiations register a region of memory, which is made available to its peer(s) for access directly without substantial host intervention through RDMA data transfer.
Owner:MEMORY ACCESS TECH LLC
Method and apparatus for updating rules governing the switching of virtual sim service contracts
A system and method for providing updated rules governing the switching of enabled provisioning data supporting a wireless service contract. A mobile device may be initially programmed with a profile data table and priority list index data table to automatically enable provisioning data supporting one of the plurality of service providers stored in a VSIM internal memory unit to conduct a wireless communication when certain operational parameter values are satisfied. The profile data table and priority list index data table may be automatically updated in response to a variety of triggers.
Owner:QUALCOMM INC
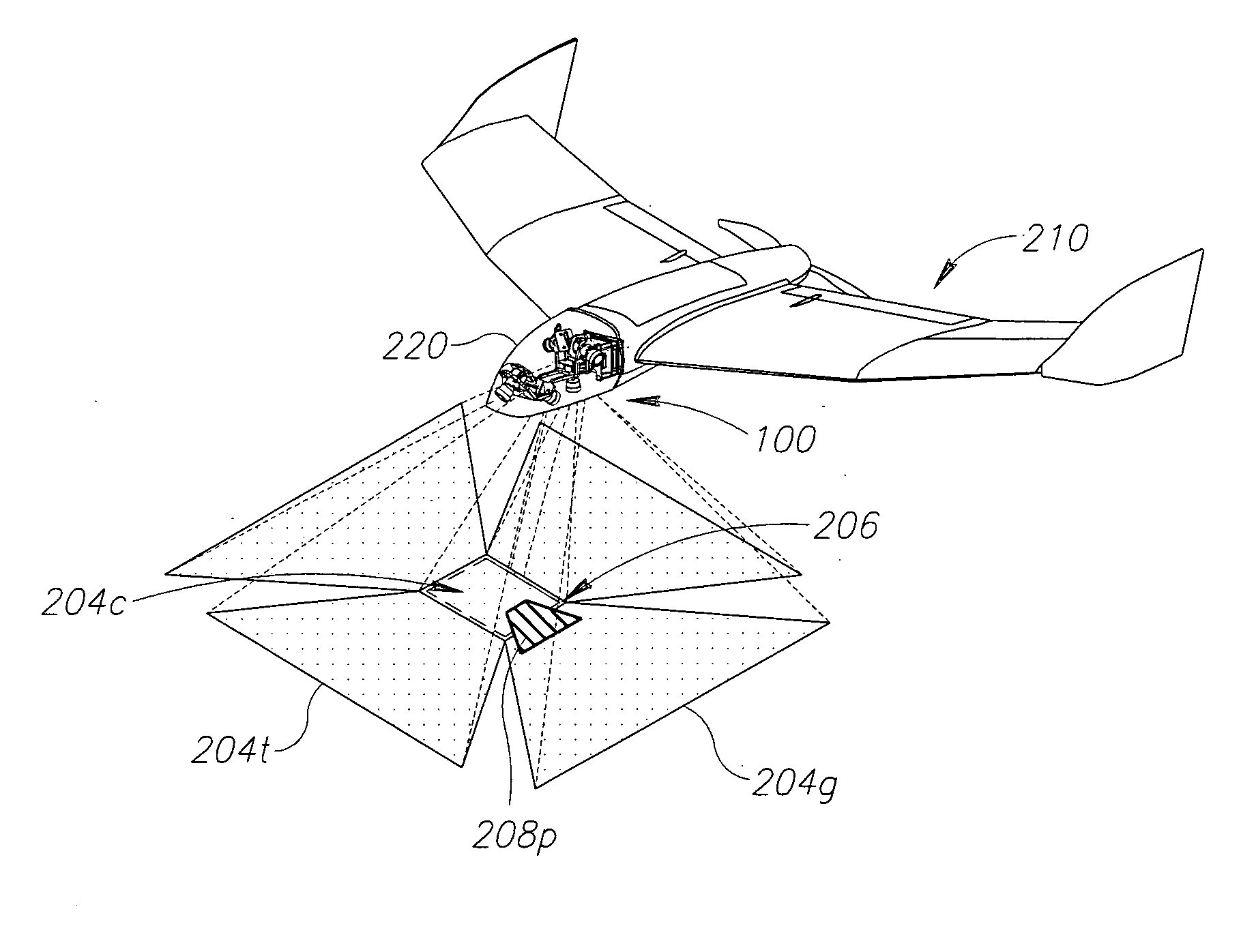
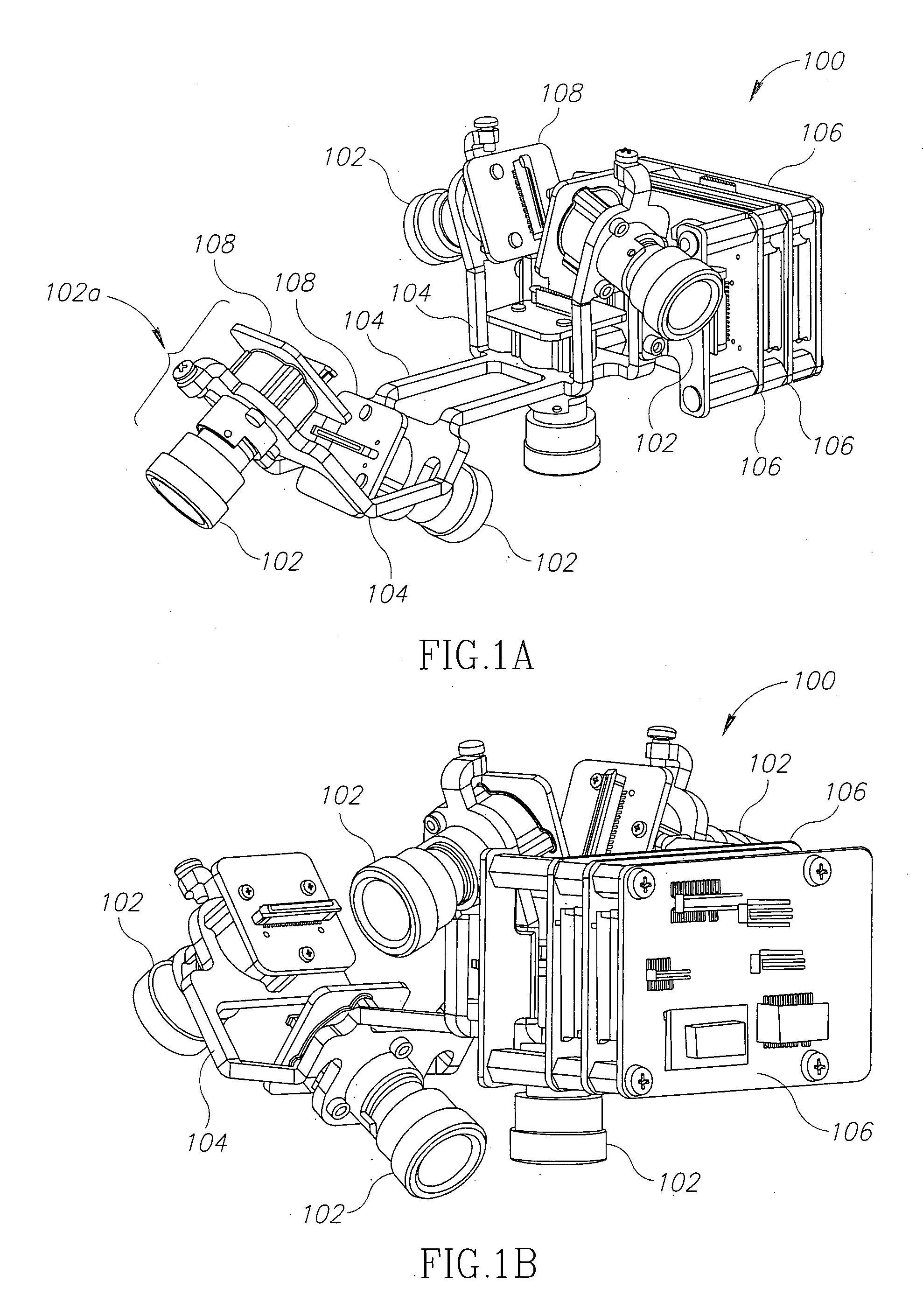
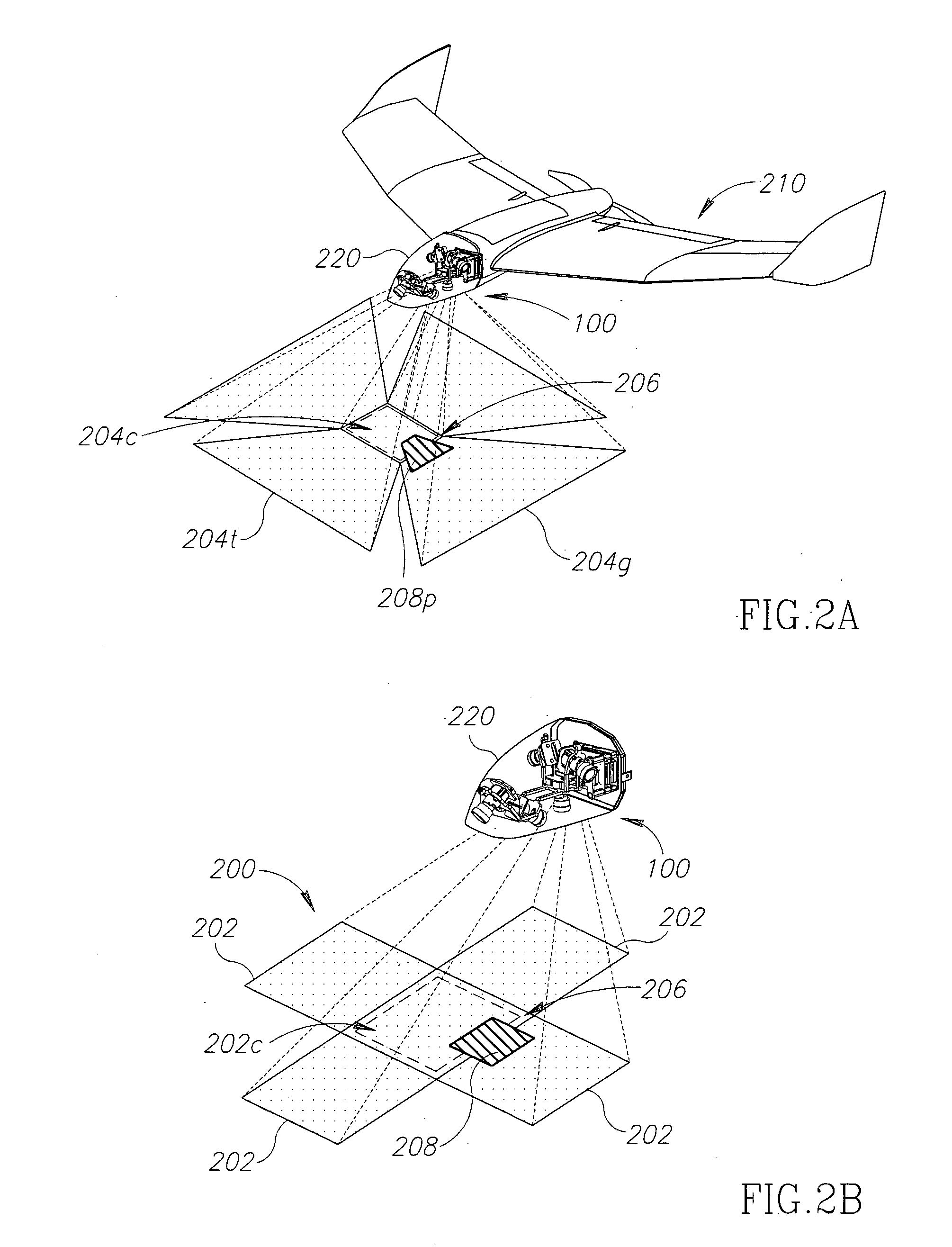
Imaging system for UAV
InactiveUS20120200703A1Increase frame rateEasy to handleTelevision system detailsColor television detailsInternal memoryHigh frame rate
There is provided herein a system for providing a stabilized video image with continuously scrollable and automatically controllable Line-Of-Site (LOS) and adjustable Field-Of-View (FOV) for use in an Unmanned Aerial Vehicle (UAV), with no moving parts. The system comprising a plurality of fixed oriented sensors disposed in one or more of orientations, a computing unit comprising processor adapted to define a position of a window of interest (WOI) within one or more field-of-views of said plurality of sensors, read pixels data from said WOI, compensate, in real time, for changes in a target position relative to the UAV and for the UAV attitude by continuously scrolling the position of said WOI and provide a continuous high frame rate video image based on the pixels data from said WOI. The system may also provide retrievable high resolution images of the scene, to be stored in internal memory for later retrieve or transmitted to a Ground Control Station in parallel to the real-time video.
Owner:BLUEBIRD AERO SYST
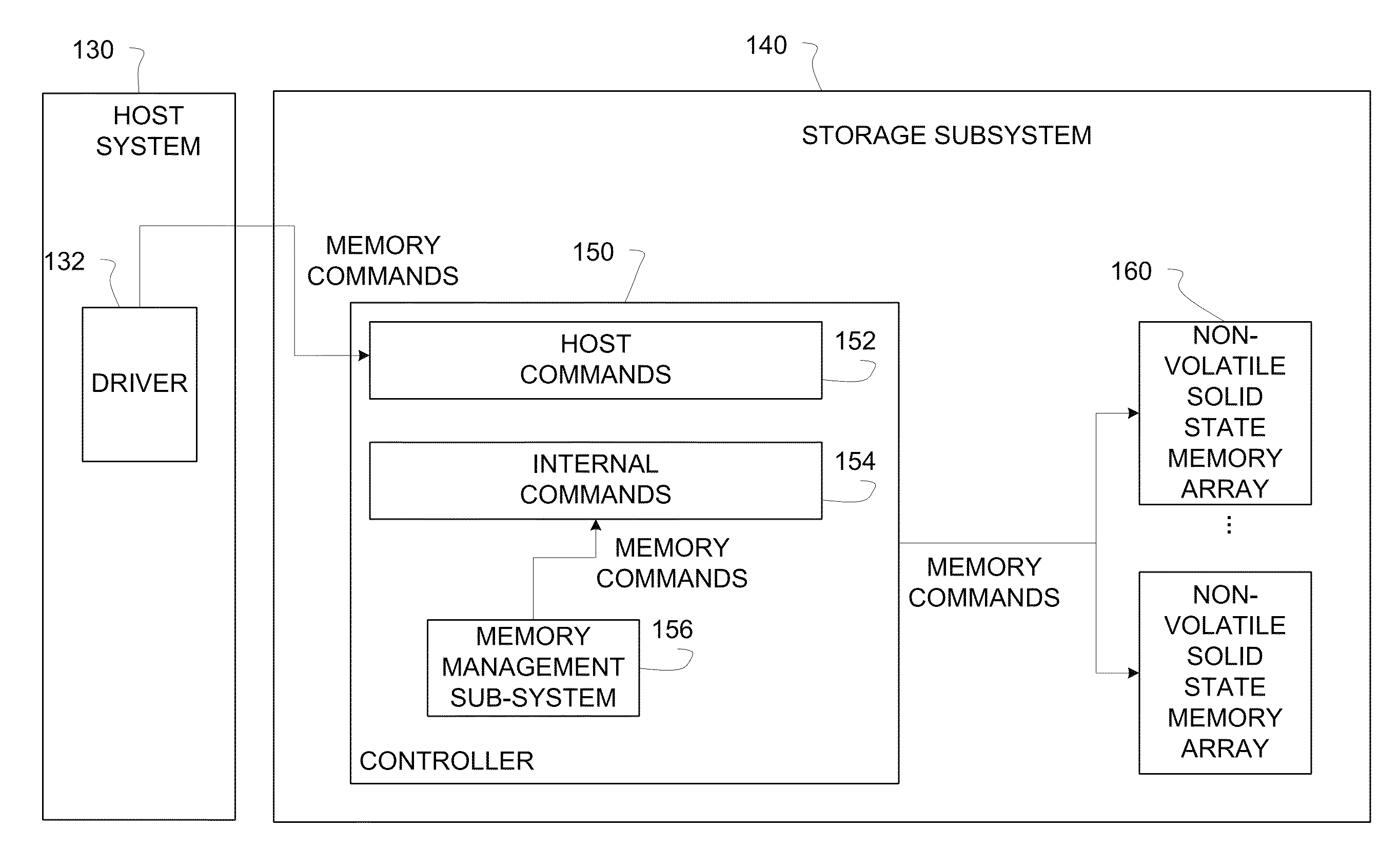
System and method for reducing contentions in solid-state memory access
ActiveUS8769190B1Memory architecture accessing/allocationMemory systemsInternal memorySolid-state storage
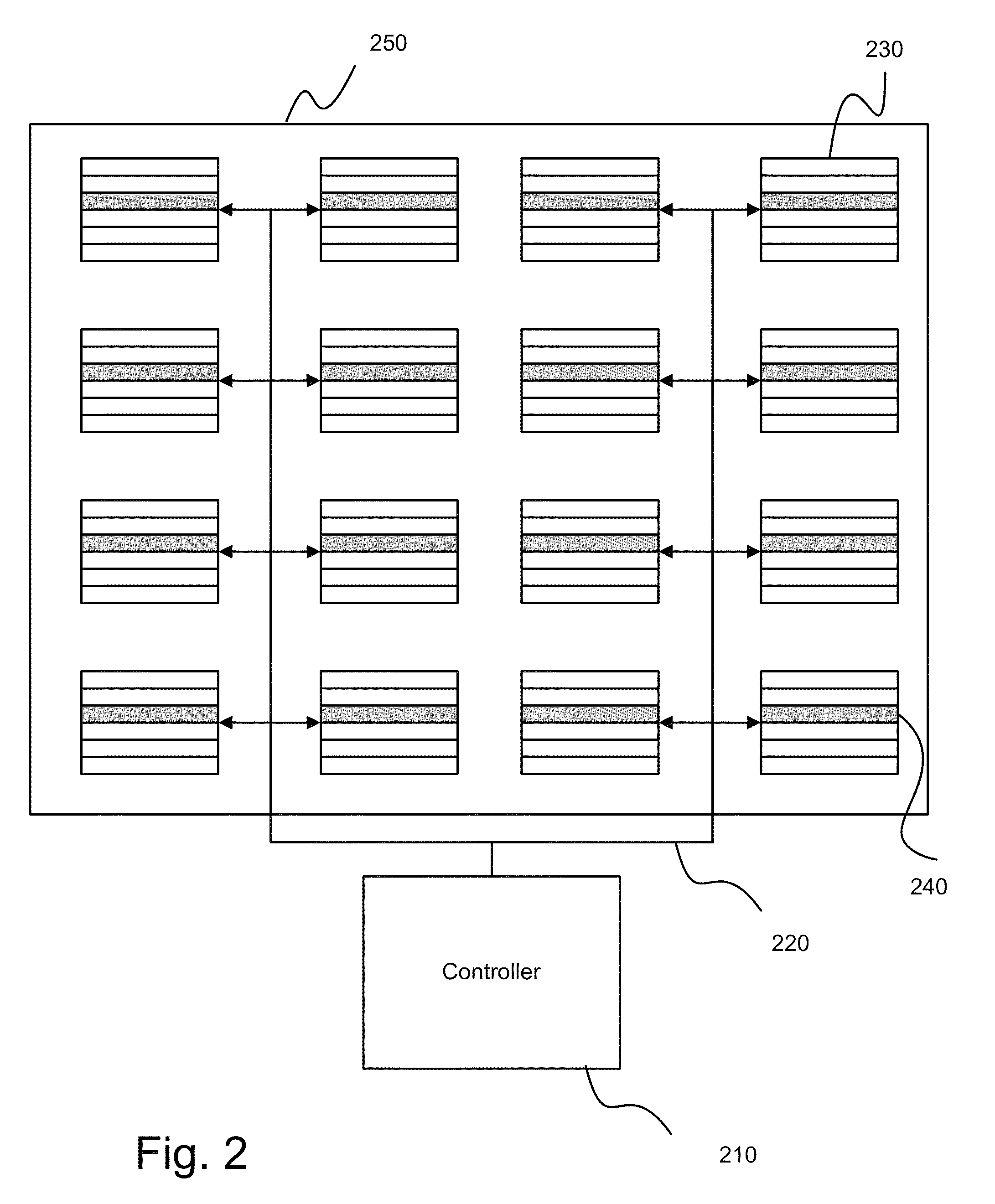
Embodiments of the invention are directed to enabling concurrent commands from command requesters in a non-volatile solid-state storage subsystem in a manner that reduces contentions among the commands. Embodiments group blocks of memory into multiple sets of superblocks and associate a command requester to each superblock set. In one embodiment, the superblock sets are dynamically associated with a requester. In one embodiment, the superblock sets are dynamically associated with requesters based in part on at least one of internal memory management needs and host command throughput. In one embodiment, an erase command is executed on a superblock within a set and a simultaneous write command is executed on a superblock within another set.
Owner:WESTERN DIGITAL TECH INC
Single-chip microcomputer using adjustable timing to fetch data from an external memory
InactiveUS6125431AIncrease costEasy to operateMemory adressing/allocation/relocationProgram controlMicrocontrollerInternal memory
It is an object of the present invention to provide a one-chip microcomputer which permits the access time for an external memory to be equal to that for an internal memory. The one-chip microcomputer 10 includes an internal ROM 11, control circuit 12, output terminals 13, input terminals 14, control circuit 15, selector 16, instruction register 17, delay circuit 18, and fetch control signal select gate 19. For selection of the external ROM 30, a control arrangement 20 and a delay circuit 18 are employed in one embodiment to adjust the time at which ROM data is fetched by the instruction register 17, based on the delay time for accessing the external ROM 30.
Owner:LAPIS SEMICON CO LTD
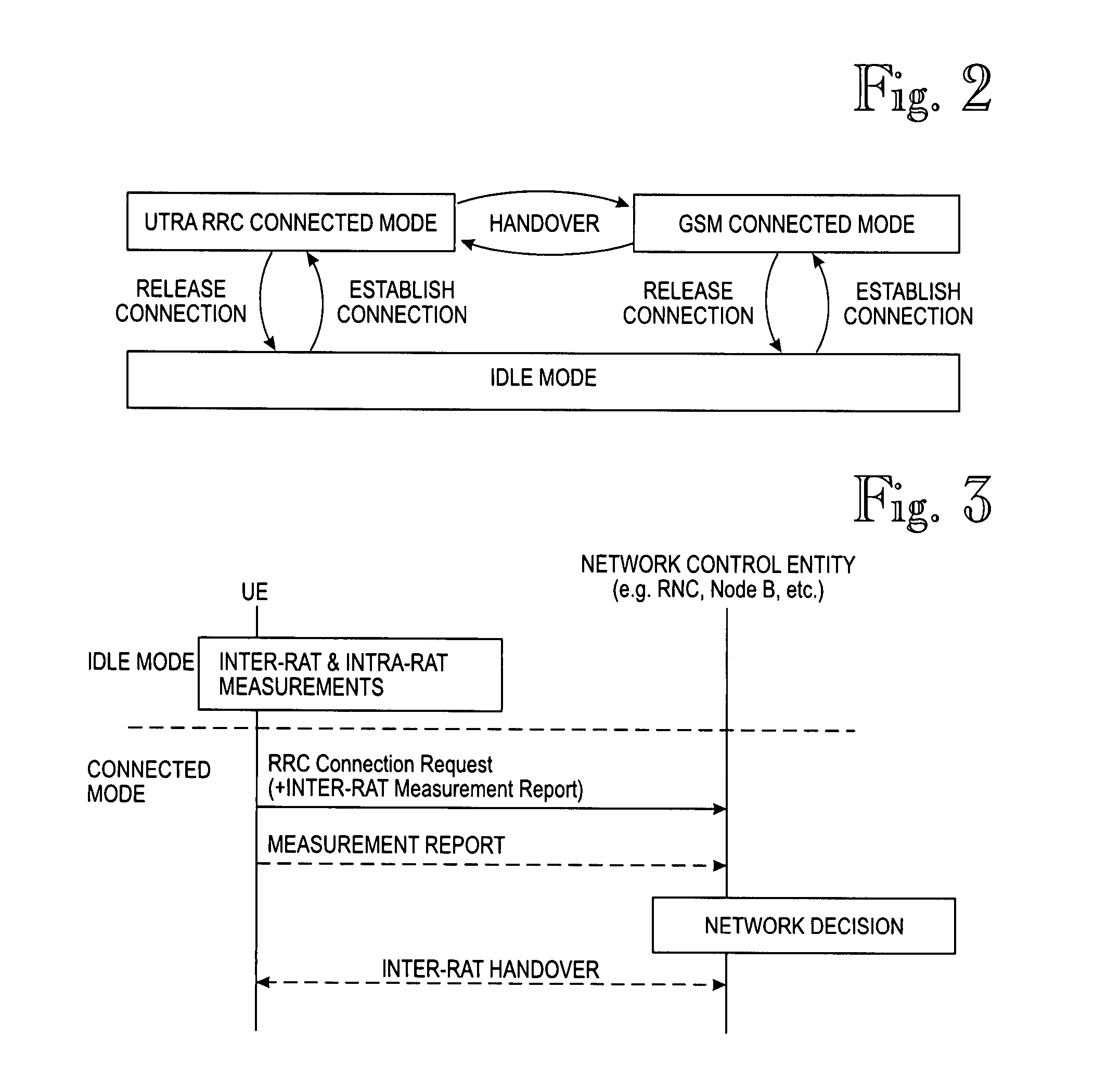
Neighbour cell measurement and reporting in a multiple radio access technologies (RAT) environment
InactiveUS20080014957A1Radio/inductive link selection arrangementsWireless communicationRadio access technologyInternal memory
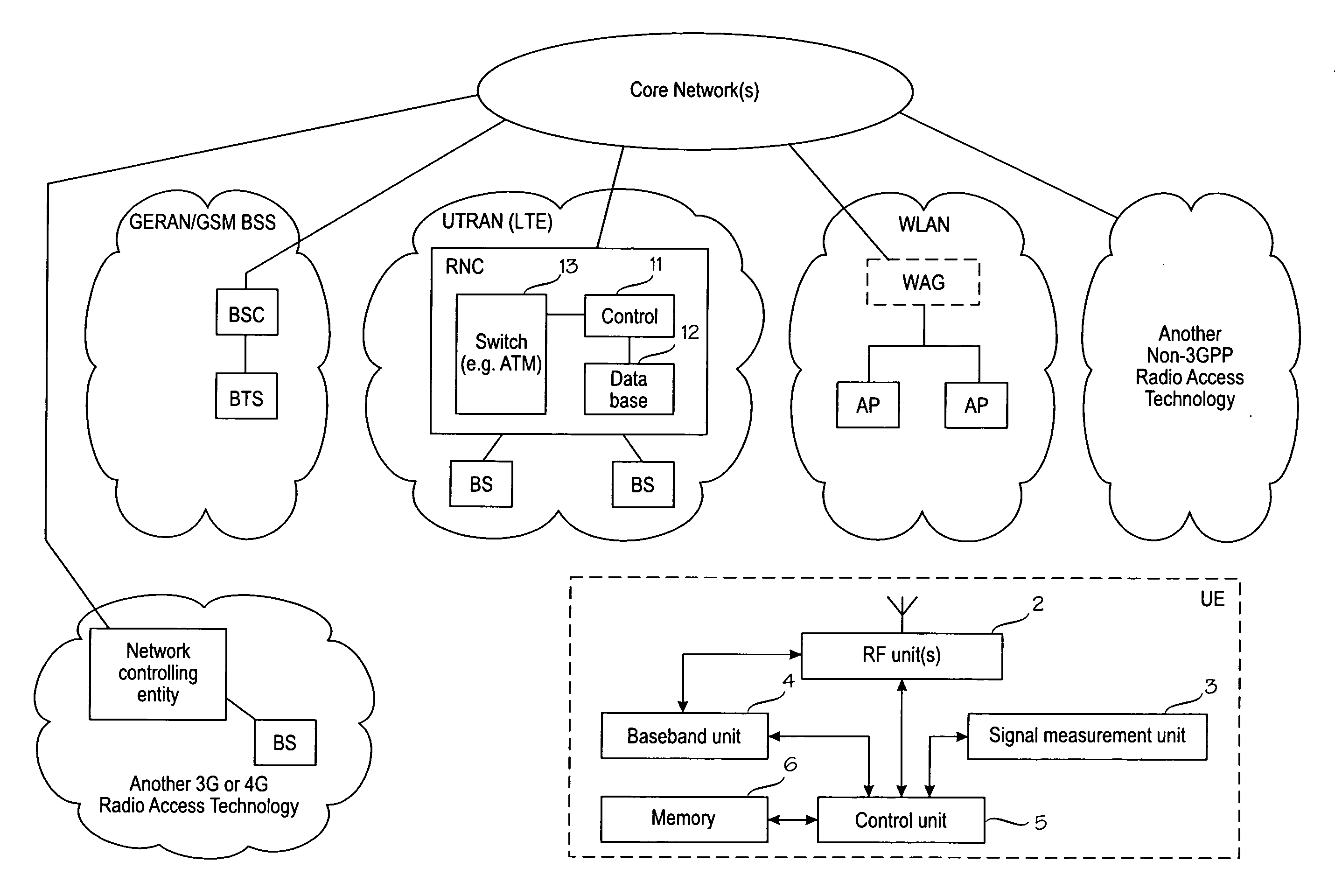
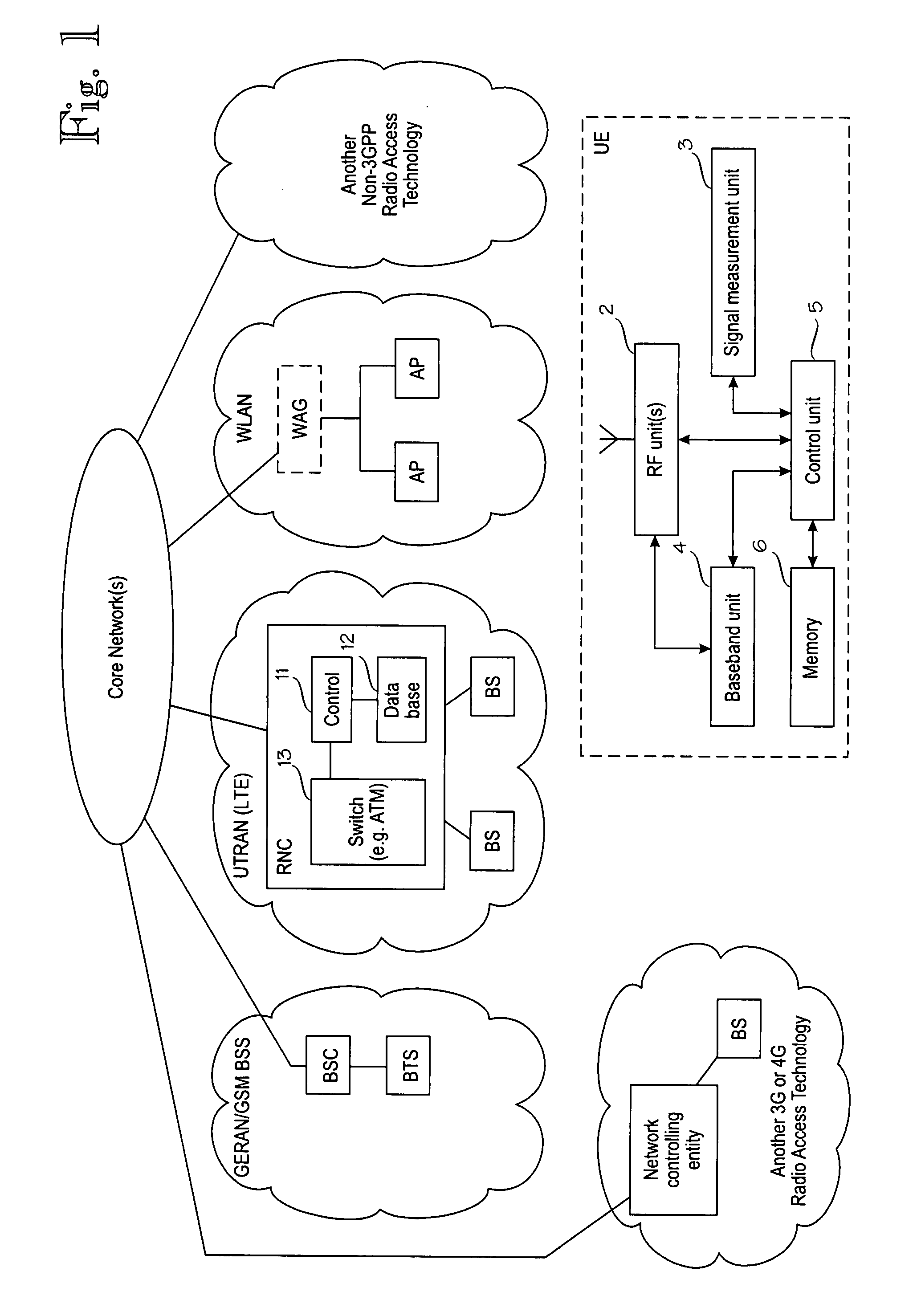
According to embodiments of the invention, user equipment (UE) performs inter-radio access technology (RAT) neighbour cell measurements during an idle mode of the UE. The inter-RAT measurement results may be stored in an internal memory of the UE during the Idle mode. When the UE initiates a connection setup, an inter-RAT measurement report containing inter-RAT measurement results obtained during the idle mode is sent to the network at the connection setup. Consequently, the inter-RAT measurement information is immediately available for a network decision at the beginning of the connected mode. For example, an inter-RAT handover can be decided and performed without a delay, based on the inter-RAT measurements made in advance during the idle mode and reported at the connection setup.
Owner:NOKIA CORP
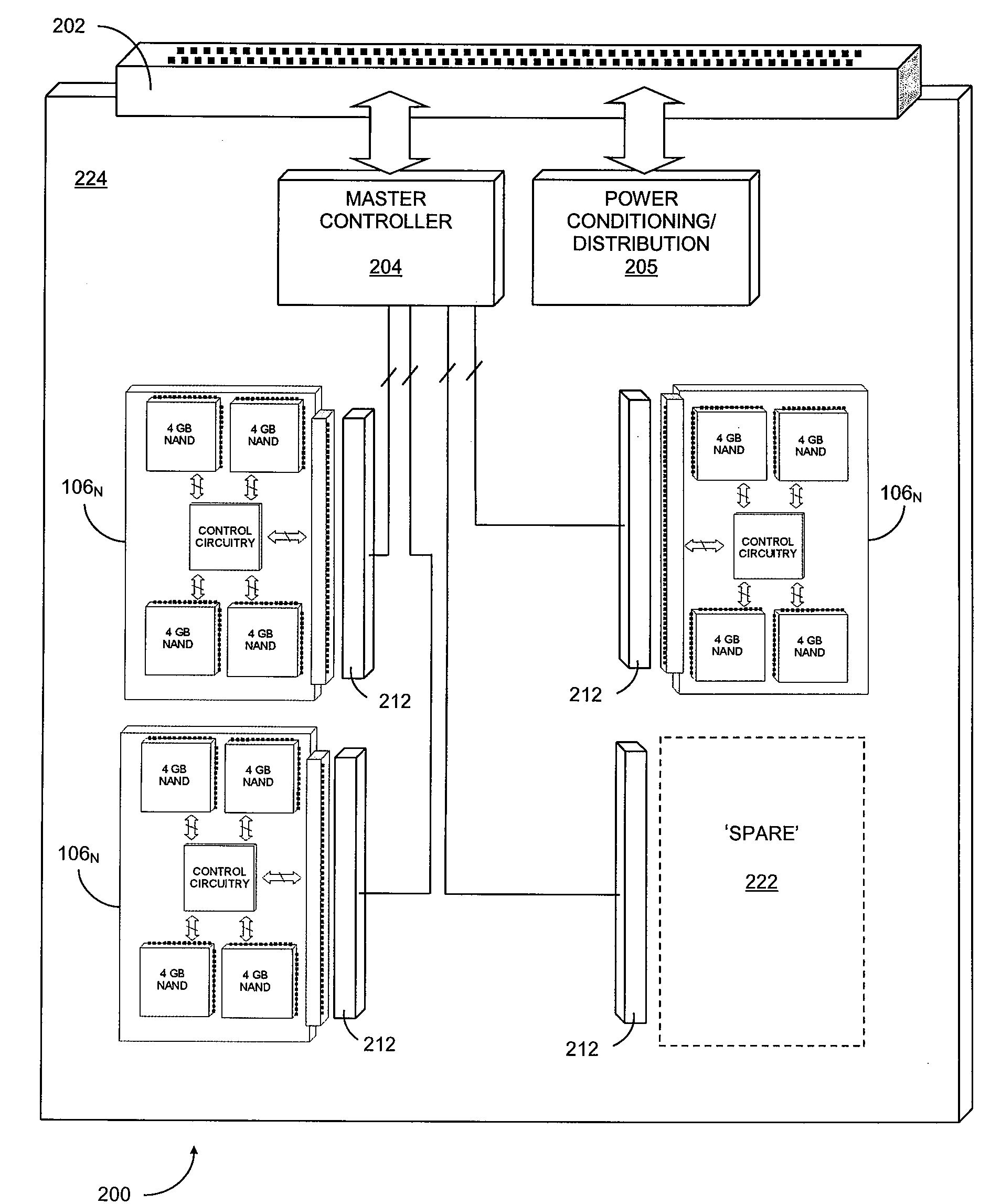
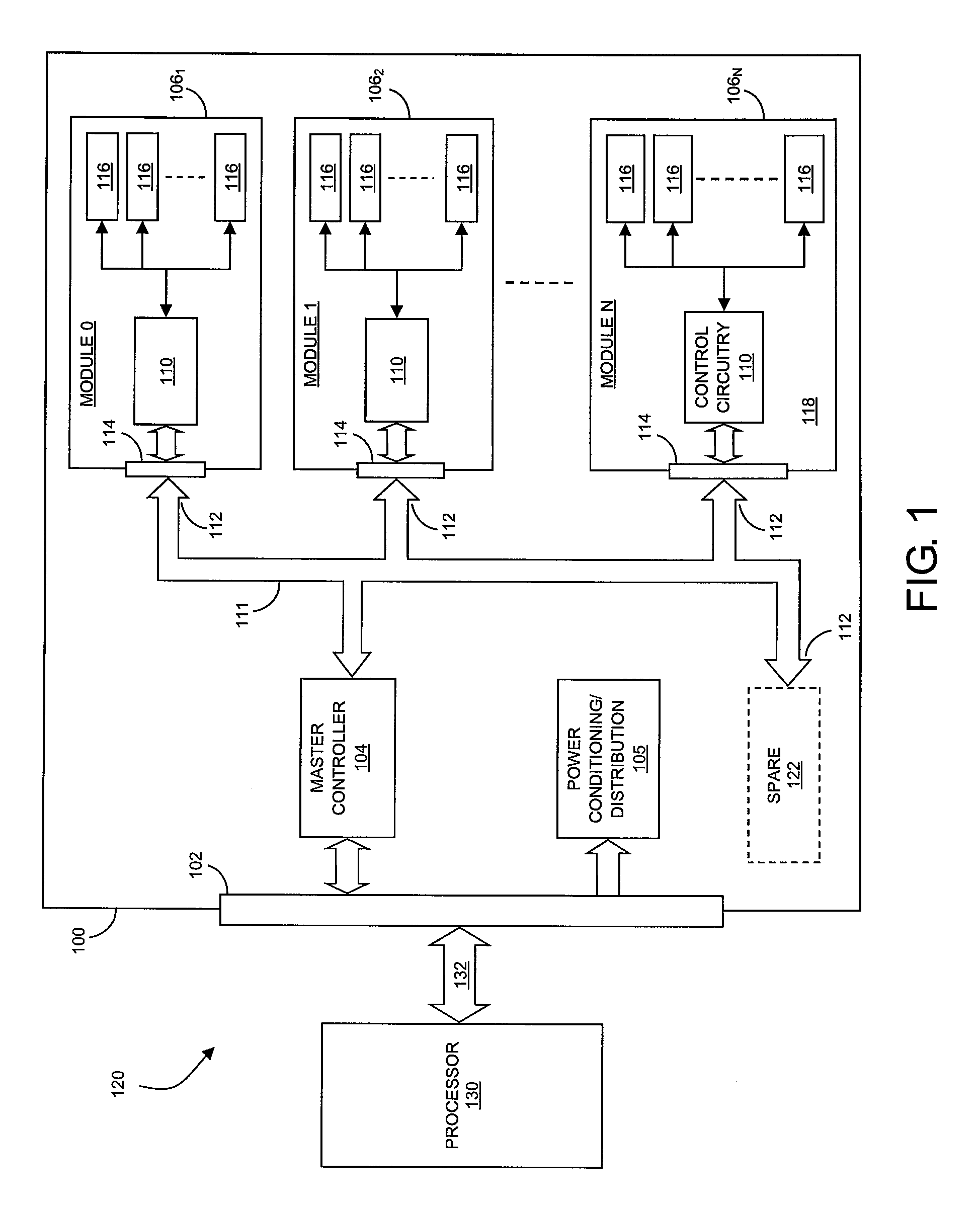
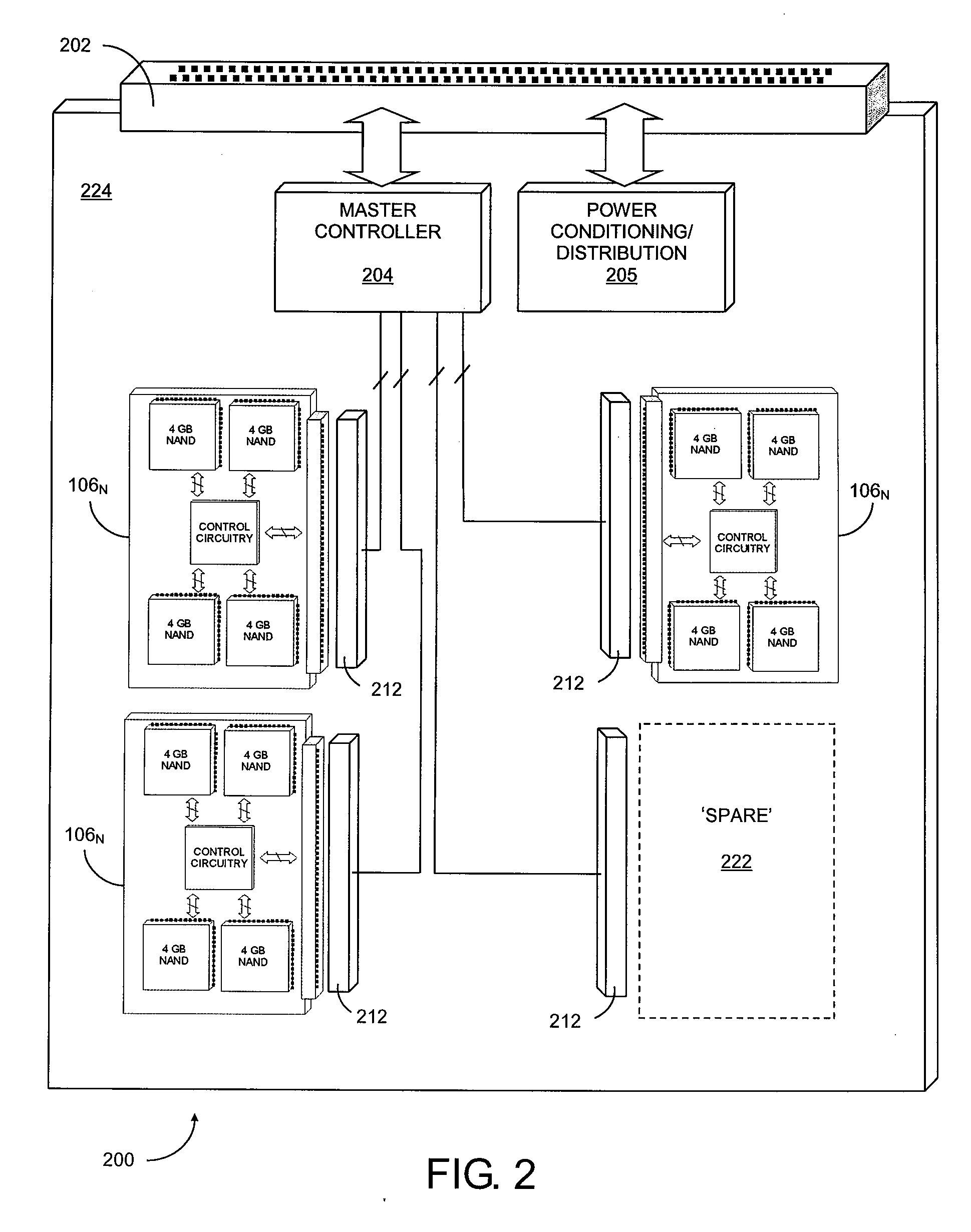
Scaleable and maintainable solid state drive
InactiveUS20090063895A1Memory adressing/allocation/relocationRedundant hardware error correctionInternal memoryEngineering
Methods and apparatus for maintaining a solid state disk drive facilitate expansion of storage capacity and maintenance of internal memory storage media, for example, are disclosed. Memory modules are adapted for removable installation in a solid state drive allowing for expansion of drive storage capacity and servicing of failed or worn out memory storage media. Data can be managed to mitigate loss during expansion, maintenance and servicing of the solid state drive.
Owner:MICRON TECH INC
Memory cards having two standard sets of contacts
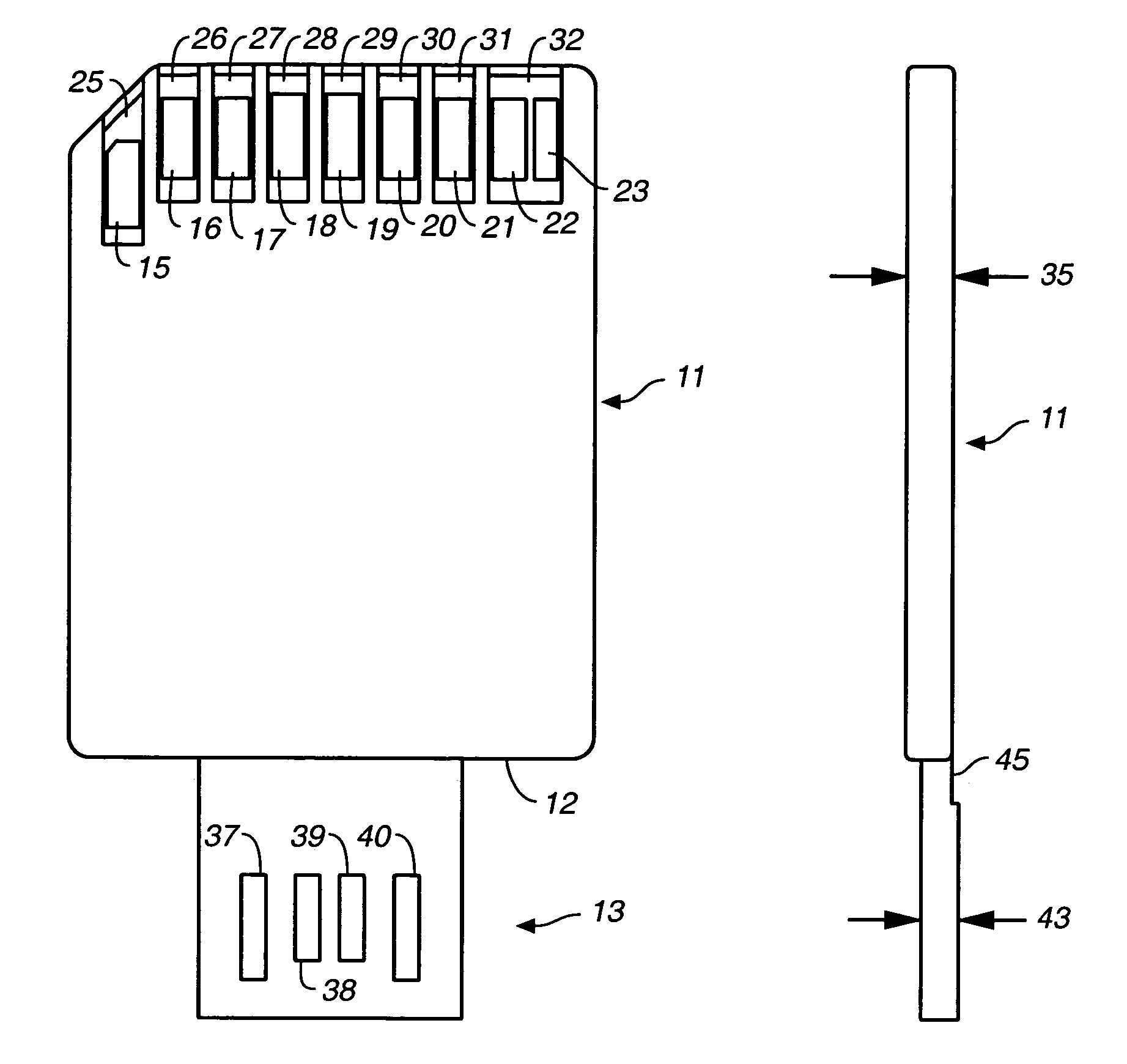
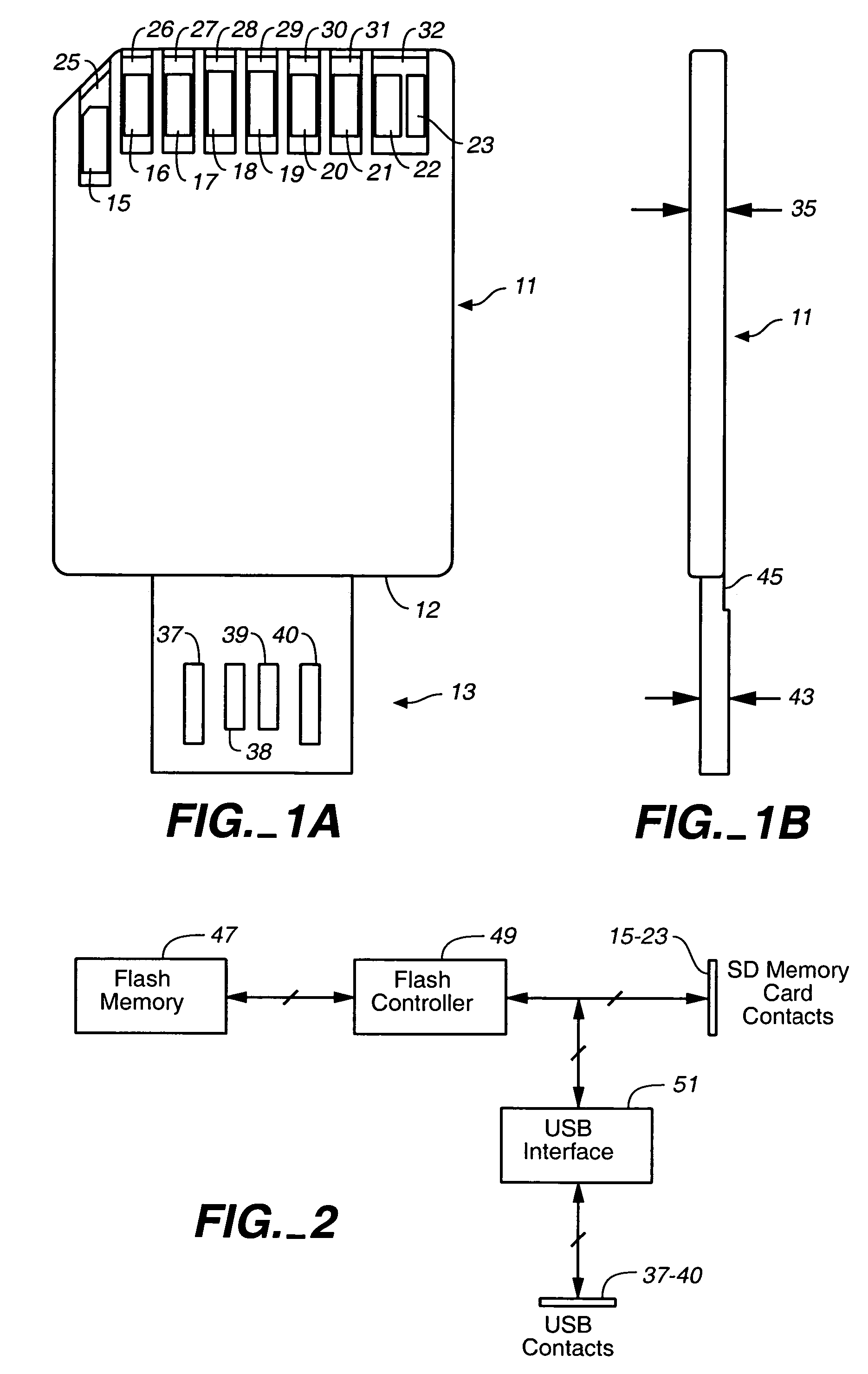
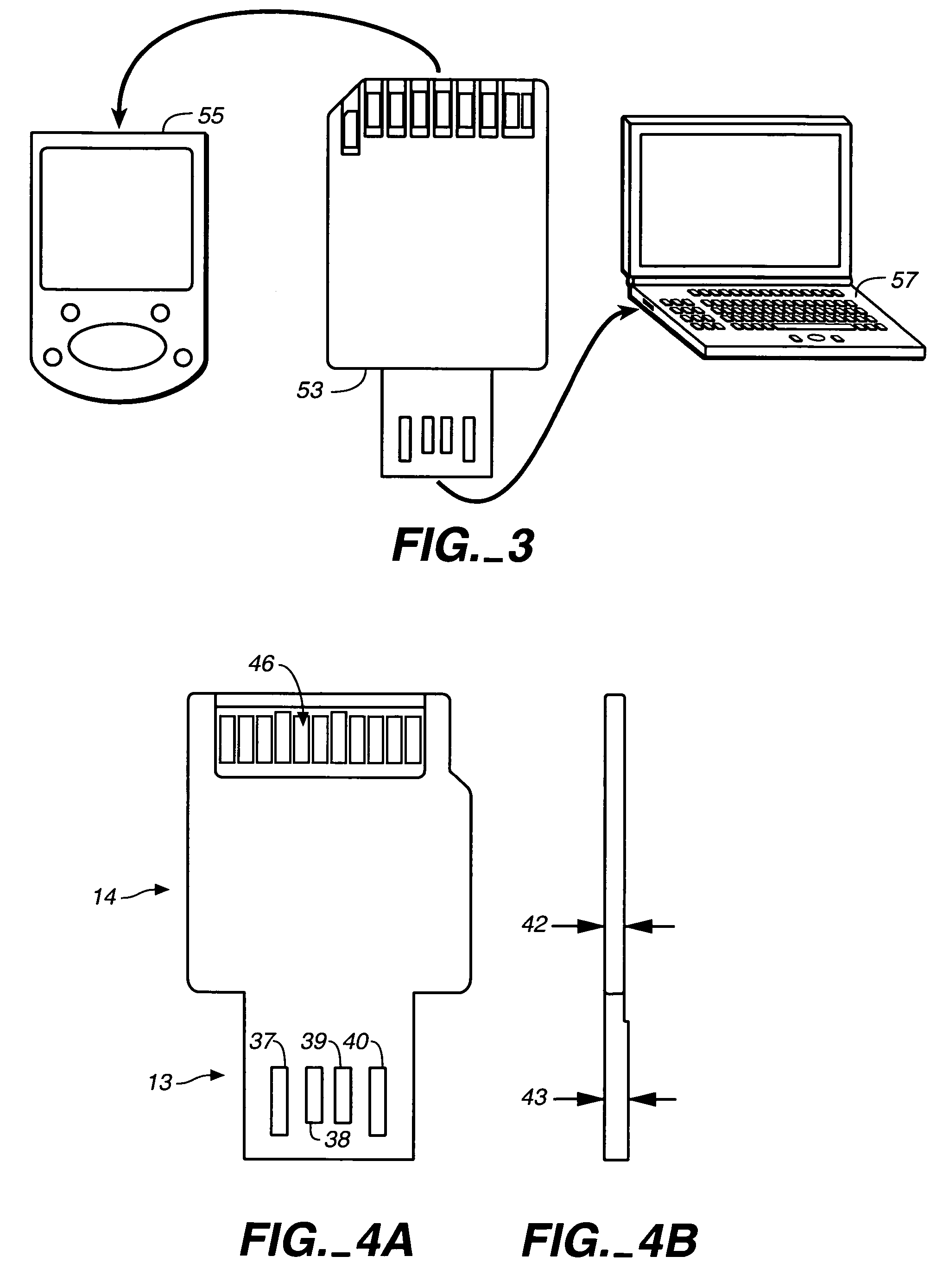
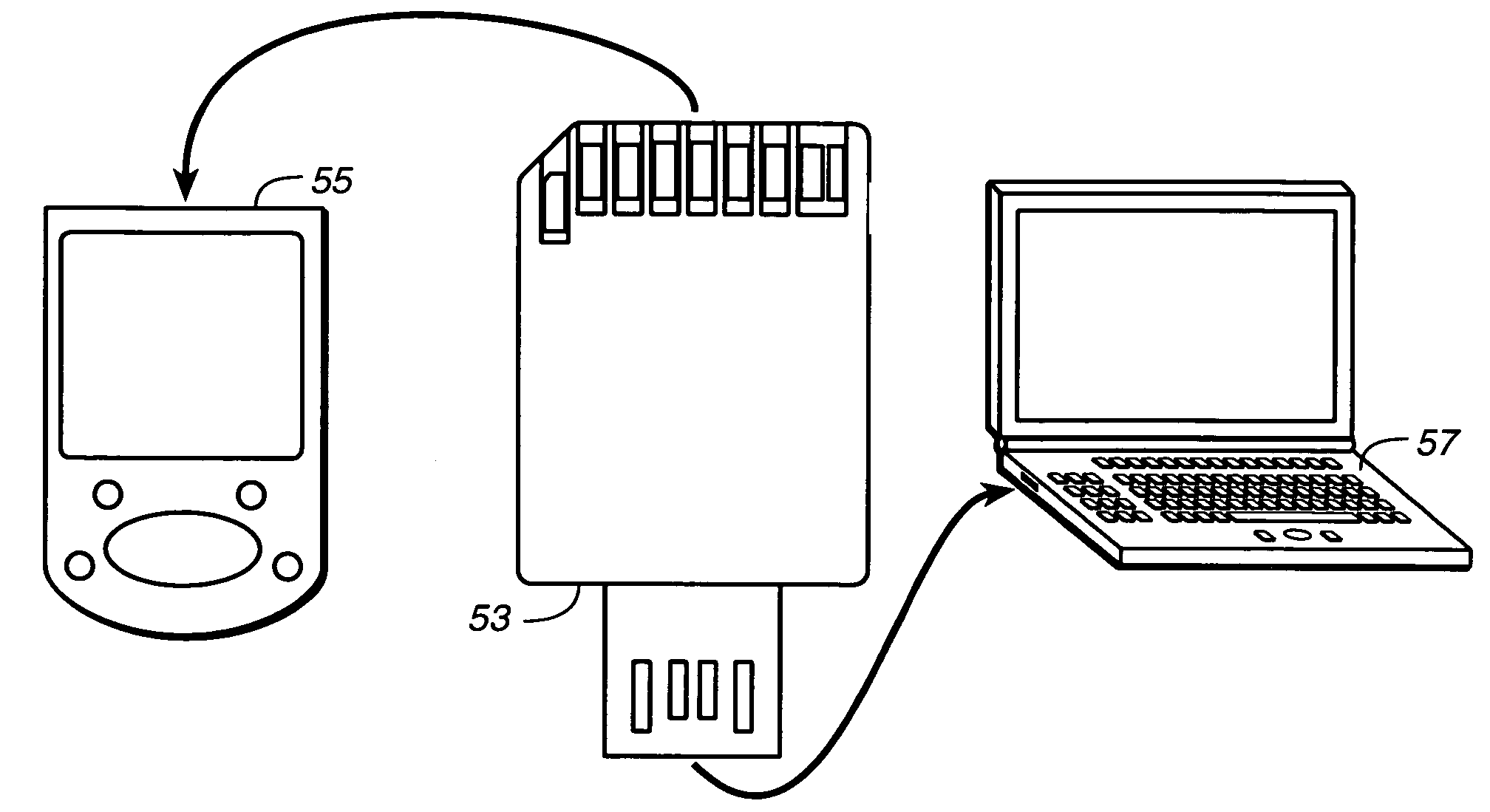
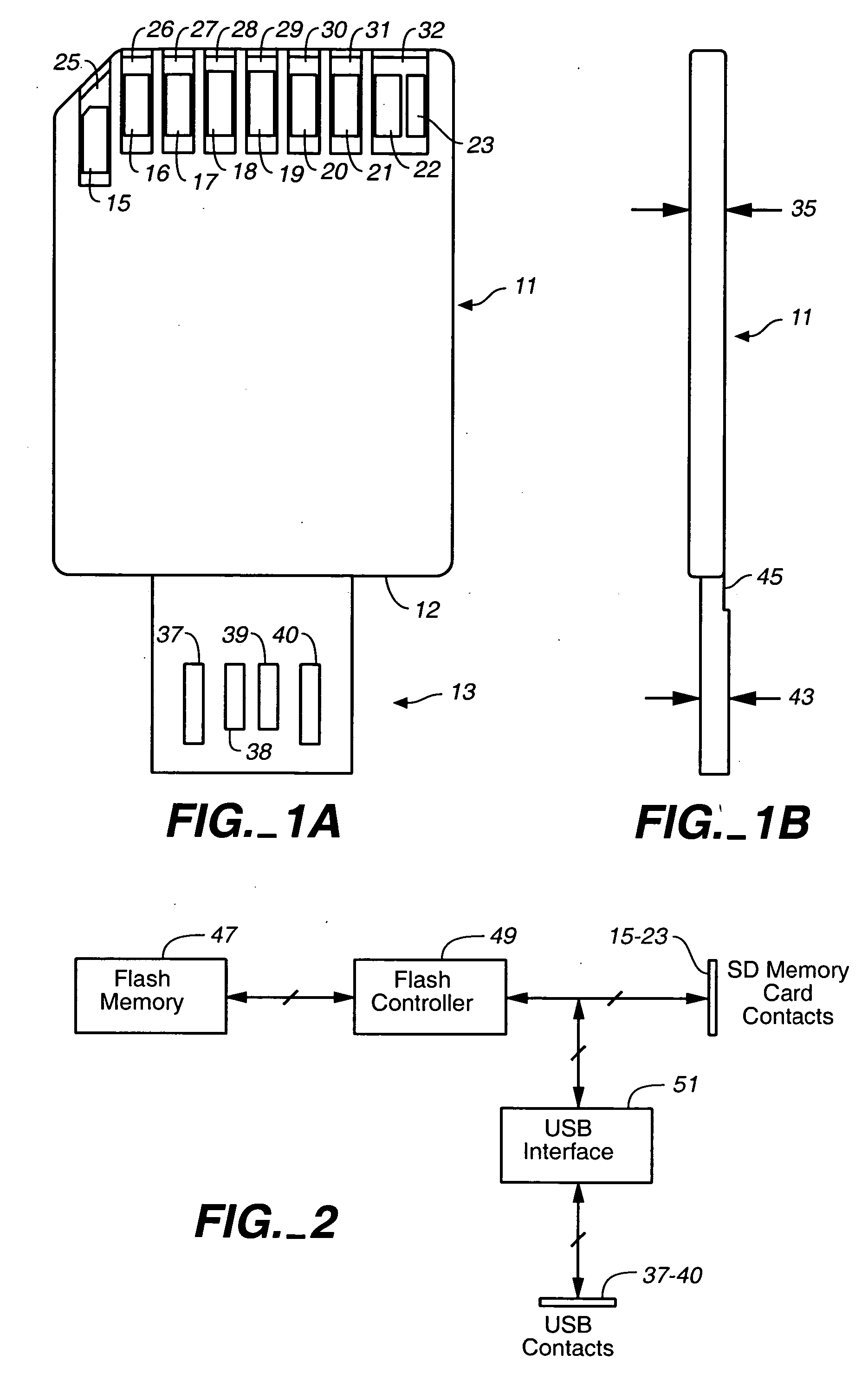
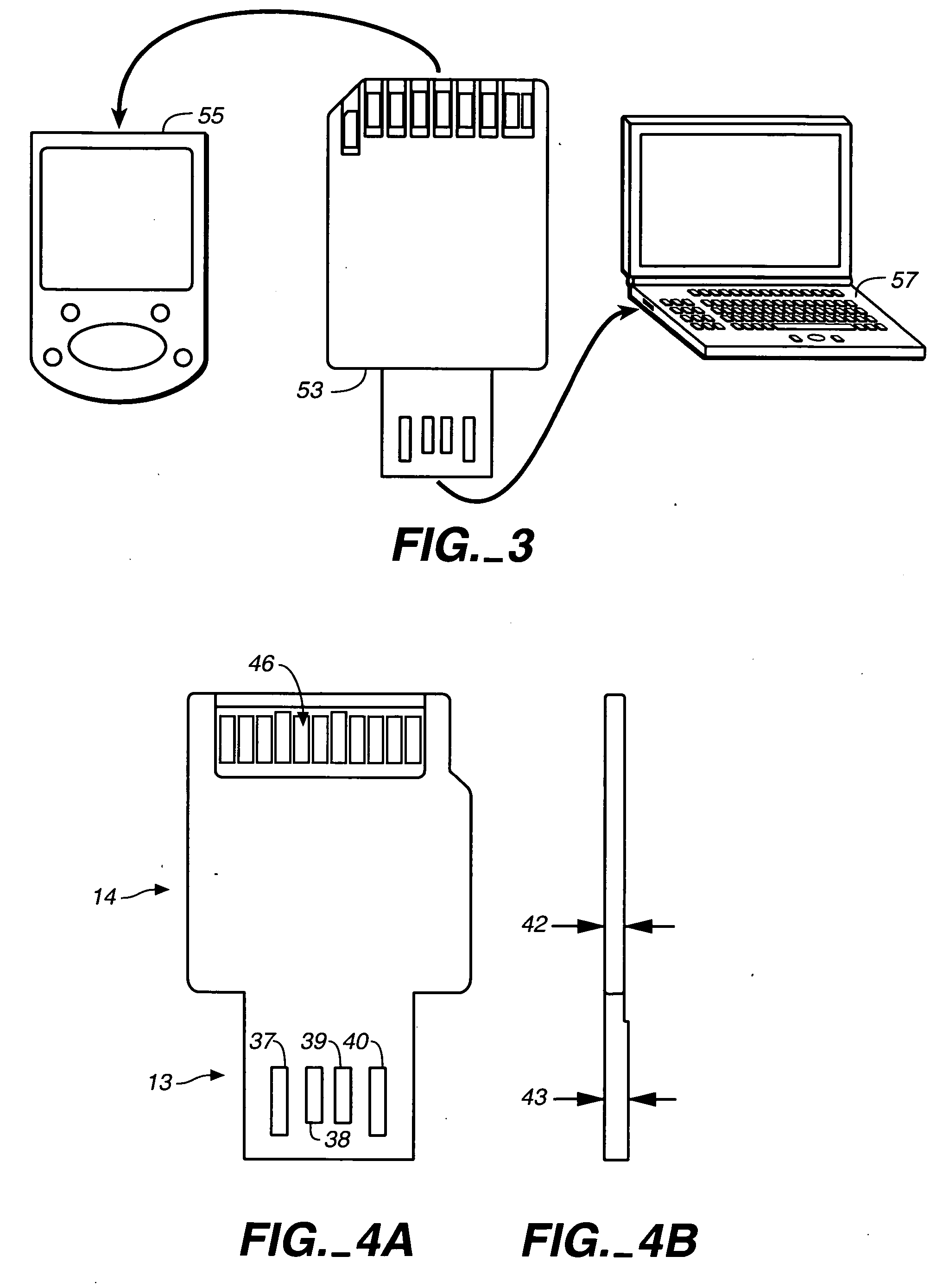
ActiveUS7152801B2Electrical connection printed elementsRecord carriers used with machinesElectricityInternal memory
Owner:SANDISK TECH LLC
Memory cards having two standard sets of contacts
ActiveUS20050230484A1Electrical connection printed elementsRecord carriers used with machinesInternal memoryElectricity
Enclosed re-programmable non-volatile memory cards include at least two sets of electrical contacts to which the internal memory is connected. The two sets of contacts have different patterns, preferably in accordance with two different contact standards such as a memory card standard and that of the Universal Serial Bus (USB). One memory card standard that can be followed is that of the Secure Digital (SD) card. The cards can thus be used with different hosts that are compatible with one set of contacts but not the other. A sleeve that is moveable by hand may be included to expose the set of contacts being used.
Owner:SANDISK TECH LLC
Electronic Health Journal
A system for creating an electronic health journal comprising: at least one sensor configured to monitor an objective physiological parameter of a user and generate signals indicative of the monitored objective physiological parameter; a mobile electronic device comprising: input means for entering information relating to a subjective physiological condition of the user; an internal memory device configured to store the information relating to the subjective physiological condition of the user and the signals indicative of the monitored objective physiological parameter as a data log; and a transmitter; a local base station; and a remote data store, wherein the local base station is configured to automatically receive the data log from the mobile electronic device upon the mobile electronic device coming into communication proximity with the local base station and wherein the local base station is configured to transmit the data log to the remote data store.
Owner:IMPAK HEALTH
Method and apparatus for switching virtual sim service contracts based upon a user profile
A system and method store provisioning data supporting a plurality of service providers in a VSIM internal memory unit of a mobile device. A user may specify a user profile to automatically enable provisioning data supporting one of the plurality of service providers stored in the VSIM internal memory unit to conduct a wireless communication when certain criteria values are satisfied. The automatic enabling of provisioning data may be determined based upon mobile device location, communication usage request and / or time and date.
Owner:QUALCOMM INC
Remote storage for electronics
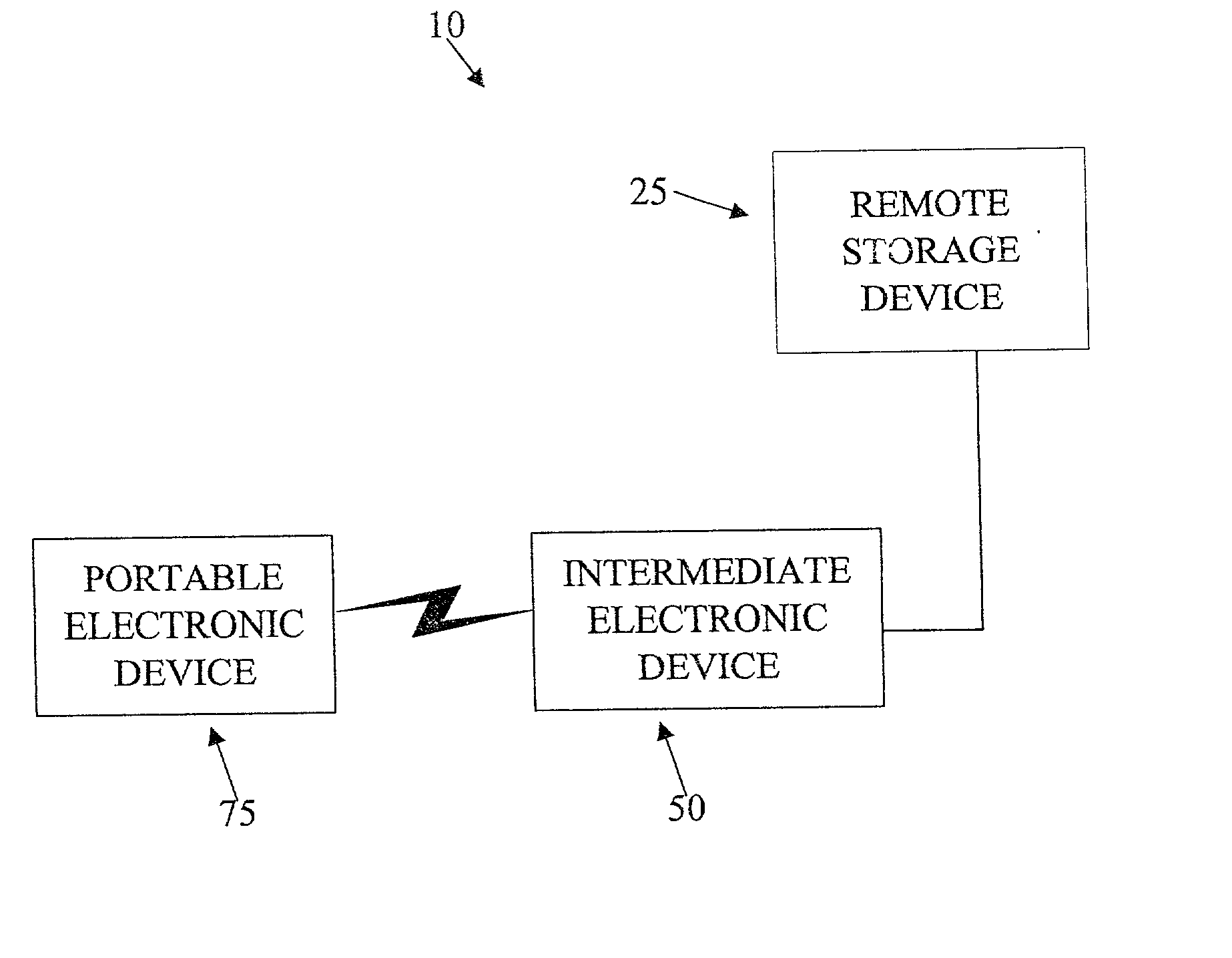
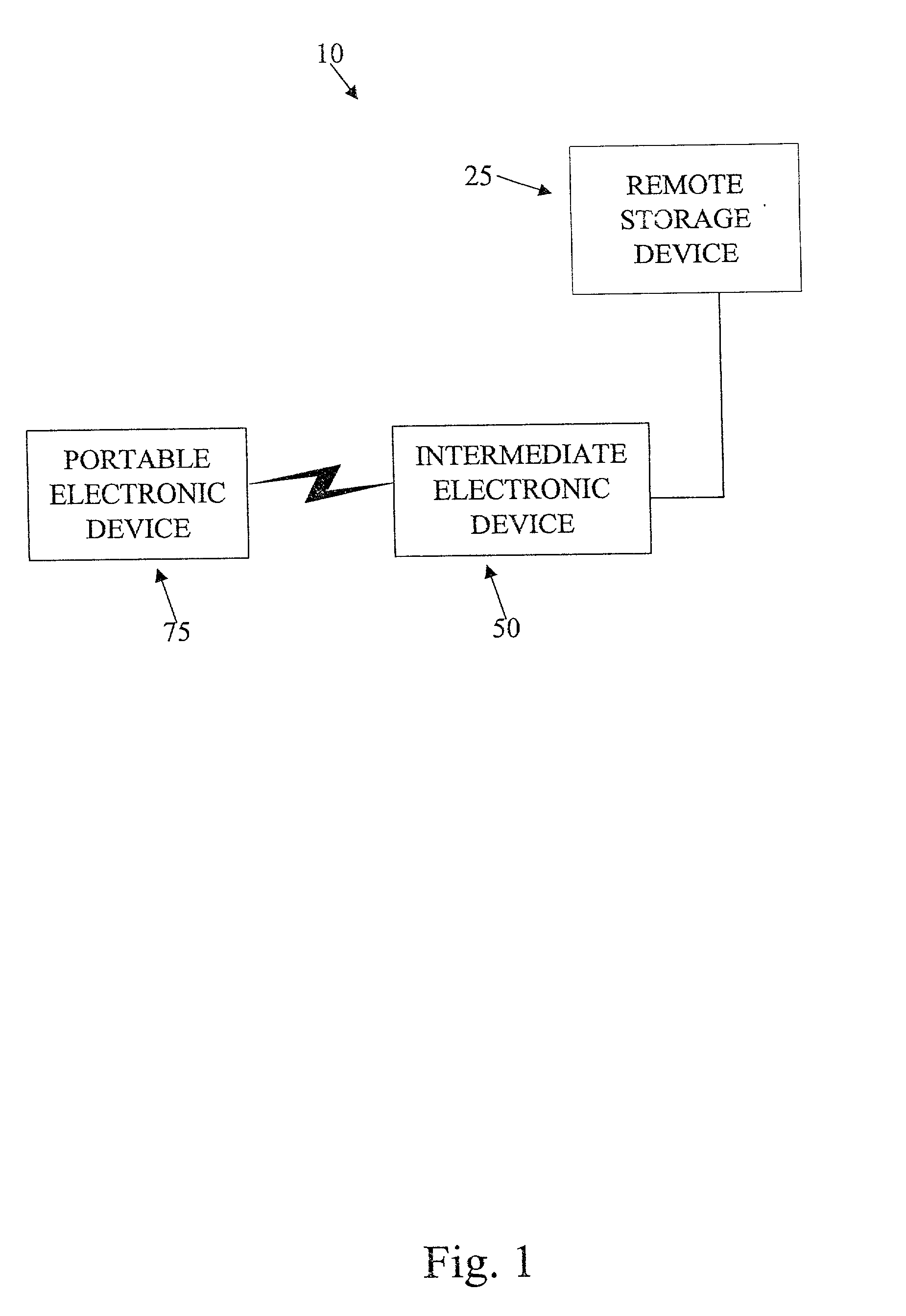
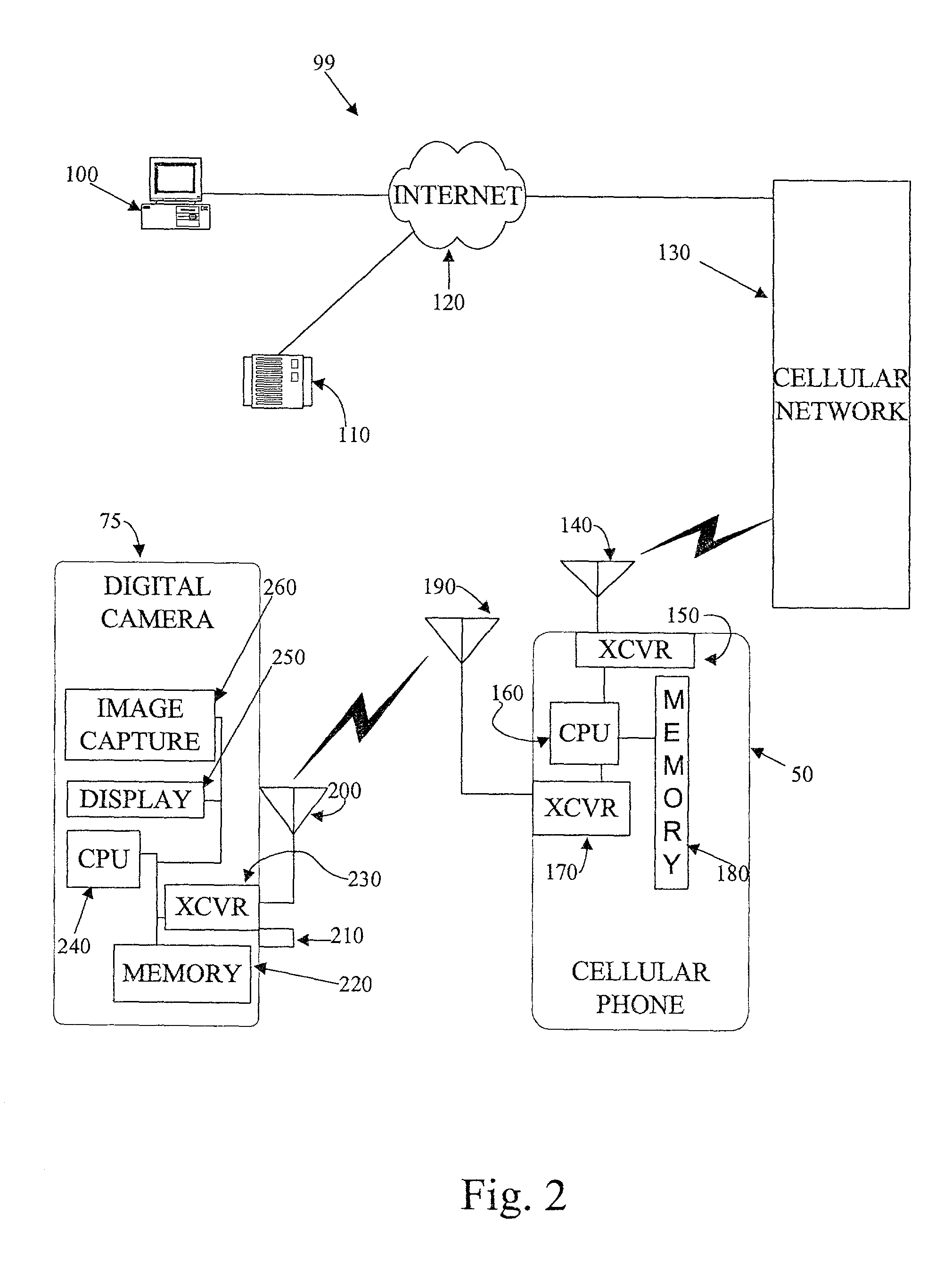
ActiveUS20030157960A1Easy accessReduce dependenceSubstation equipmentTransmissionInternal memoryThe Internet
A system and a method for remotely storing information from portable electronics using a multi-point wireless link. The method and system involves a Bluetooth-enabled camera that communicates to a 3G cellular telephone via a Bluetooth wireless link, the telephone then uses the 3G wireless link to connect to a remote storage device via the Internet. Using this concept, the internal memory of the portable device is used as a buffer memory without needing to be in the vicinity of a computer because the cellular telephone can act as a go between from the portable device to the storage space via the Internet.
Owner:QUALCOMM INC
Apparatus and method for gathering and utilizing data
InactiveUS7117374B2Minimal unit costSpeed up preparationKey distribution for secure communicationConveying record carriersWeb siteInternal memory
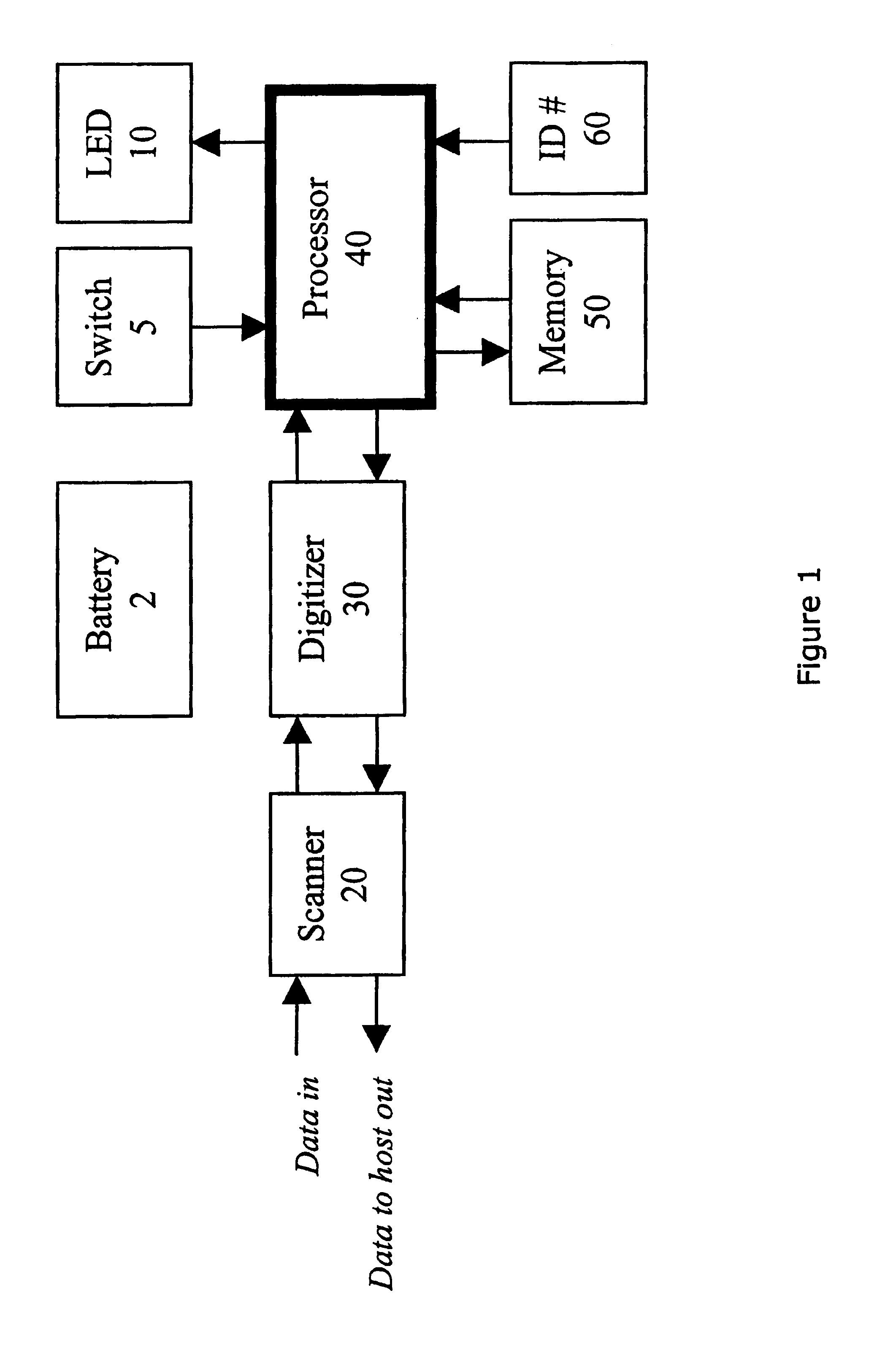
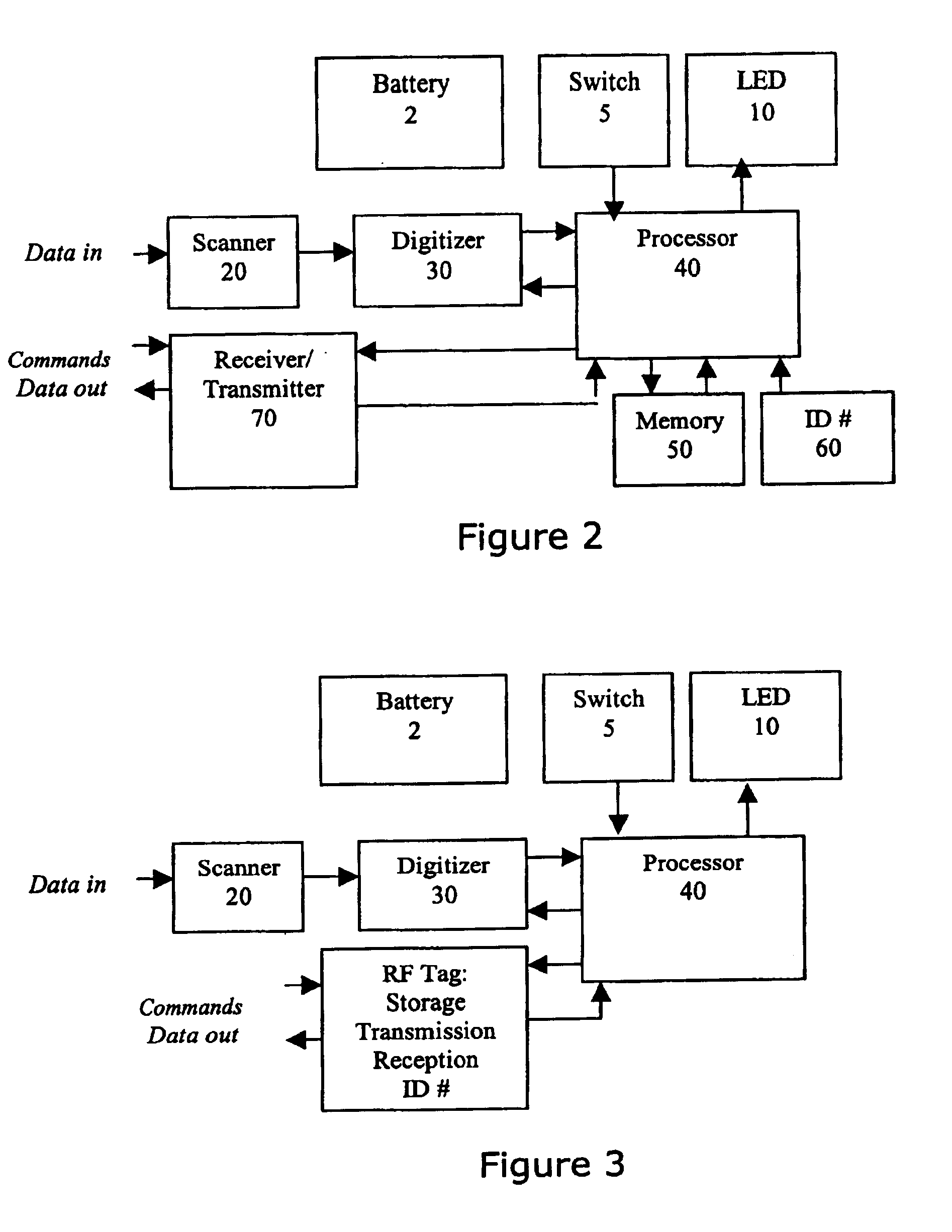
Disclosed is a device and method for obtaining and utilizing data. A handheld device which is capable of optically scanning or receiving RFID signals from an object, storing the data in an internal memory, and then re-transmitting the data is disclosed. The re-transmitted data may trigger access to an internet web site or other database which provides a user with detailed information relating to the scanned object. The device is also usable as a re-configurable electronic key or may be built into electronic devices to allow reconfiguration by scanning a symbol.
Owner:INTERMEC IP
Image capture device with artistic template design
InactiveUS20110029635A1Automating tedious stepTelevision system detailsColor television detailsInternal memoryComputer graphics (images)
An image capture system with processing and memory system components for storing digital image template files. Each of these files include data describing a digital image template, a number, location, and shape of openings in the template. Each of the openings include image attribute requirements for images that will he placed there. A display screen showing a GUI of the capture system displays digital image templates that a user can select. Captured images are stored in the system and a processor automatically places a captured image into one of the openings in based on the attribute requirements and the actual attributes of the image. The system automatically searches for other stored images that satisfy the attribute requirements for other openings. The completed template with images is stored in an internal memory or removable memory.
Owner:INTELLECTUAL VENTURES FUND 83 LLC
Runtime adaptable security processor
InactiveUS20120117610A1Sharply reduces TCP/IP protocol stack overheadImprove performanceComputer security arrangementsSpecial data processing applicationsInternal memoryApplication software
A runtime adaptable security processor is disclosed. The processor architecture provides capabilities to transport and process Internet Protocol (IP) packets from Layer 2 through transport protocol layer and may also provide packet inspection through Layer 7. A high performance content search and rules processing security processor is disclosed which may be used for application layer and network layer security. A scheduler schedules packets to packet processors for processing. An internal memory or local session database cache stores a session information database for a certain number of active sessions. The session information that is not in the internal memory is stored and retrieved to / from an additional memory. An application running on an initiator or target can in certain instantiations register a region of memory, which is made available to its peer(s) for access directly without substantial host intervention through RDMA data transfer.
Owner:MEMORY ACCESS TECH LLC
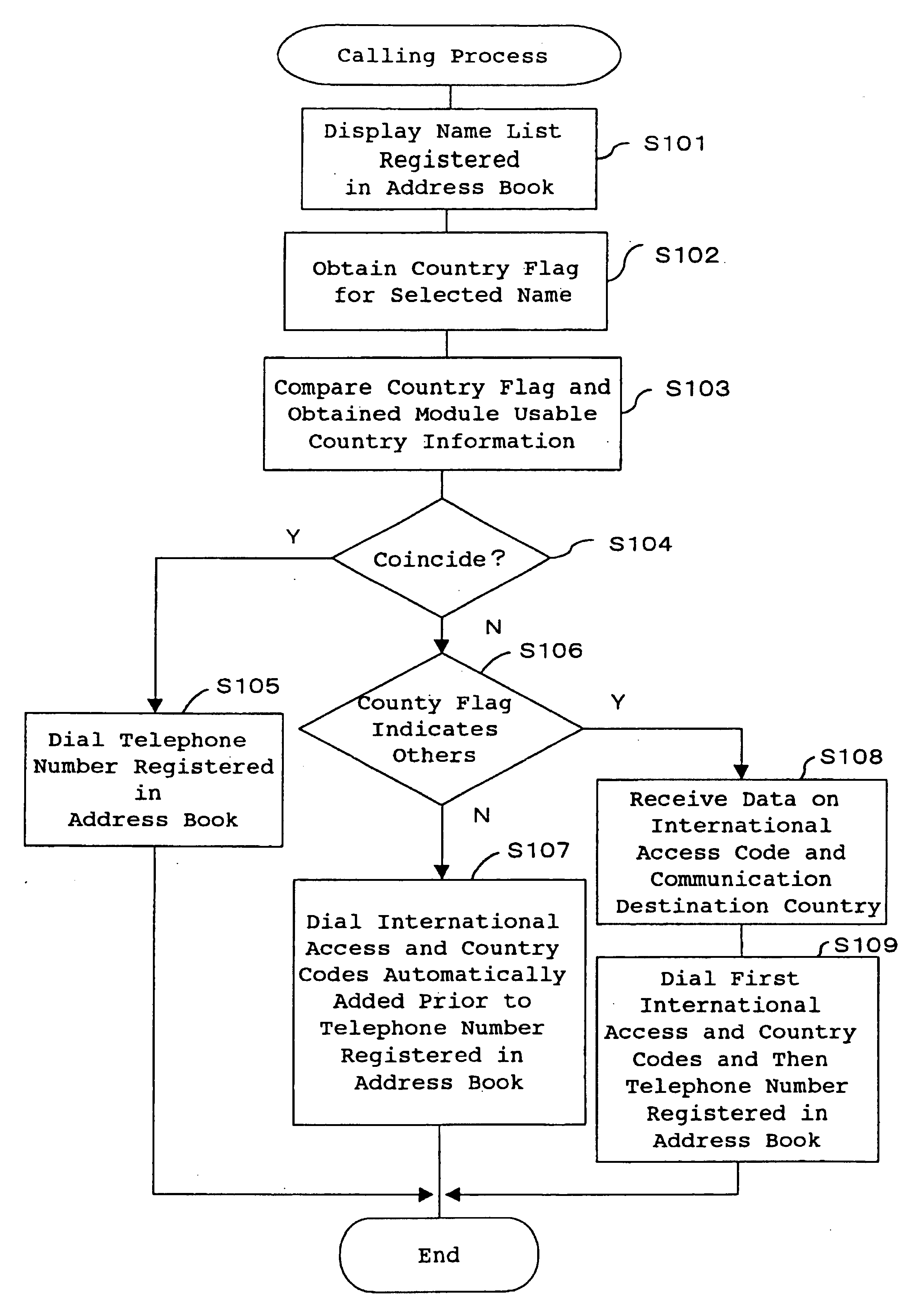
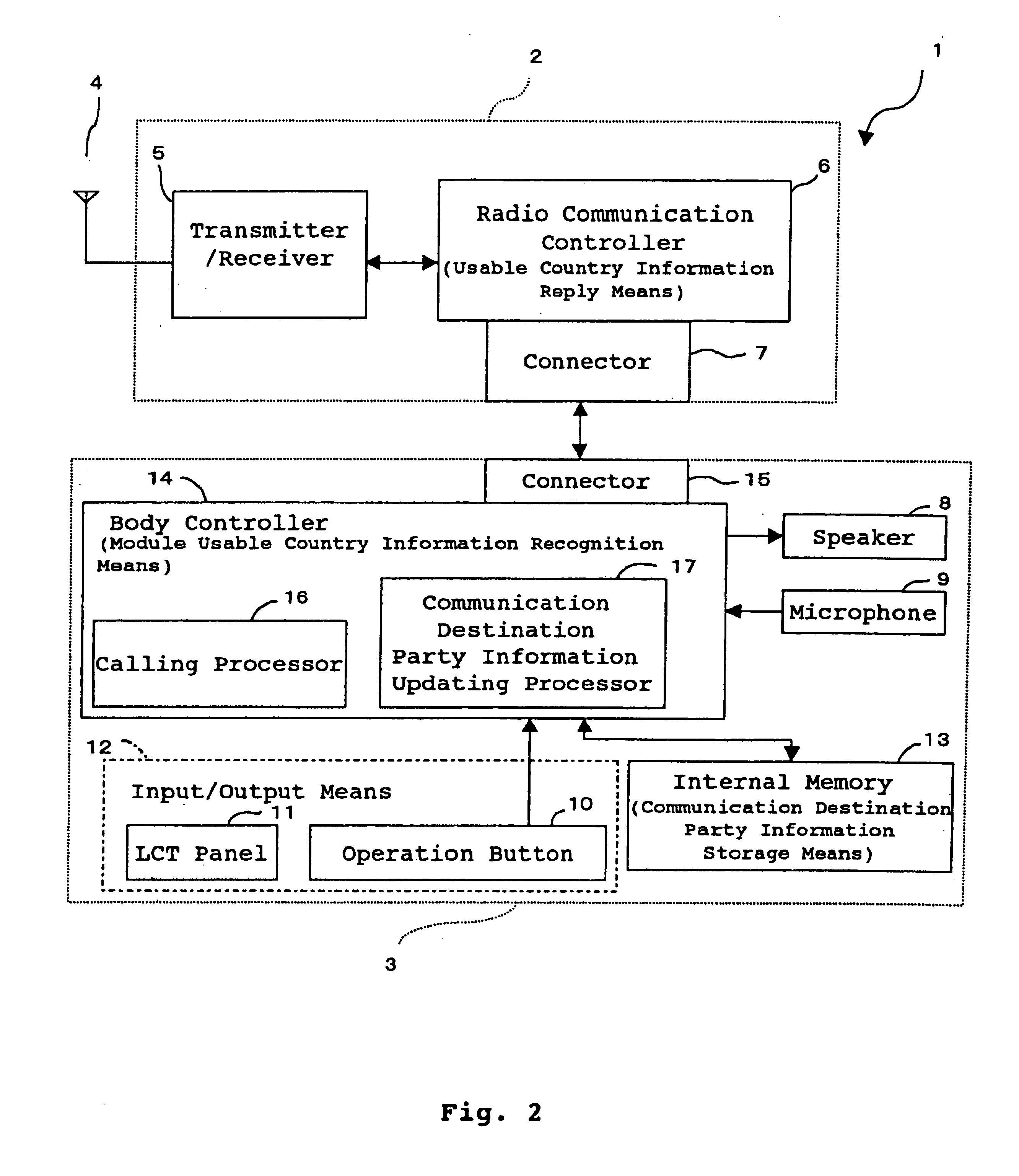
Portable communication device for domestic and international communications and automatic calling method for domestic and international calls
InactiveUS7120469B1Effectively “dial”Reduce the amount requiredSpecial service for subscribersCalling susbscriber number recording/indicationInternal memoryTelecommunications
An internal memory has an address book table for registering data regarding a communication destination party, a telephone number, and a country flag indicative of a country where the communication destination party is present, in a manner that they are shown corresponding to one another. A calling processor compares a country flag attached to a communication destination party selected using a memory dial function, and information obtained from an RF module regarding a country where the communication circuit can be established. When the flag information and the information from the Rf module coincide, the calling processor determines that the ongoing call is a domestic call, and thus dials the telephone number as registered in the address book table and, when they do not coincide, the calling processor determines that the ongoing call is an international call, and thus dials international access and country codes prior to the telephone number registered in the address book table. Using a portable communication device having the above arrangement, the user can automatically place a call to a party in or out of the country where the user is present even when the destination party information for each communication destination candidate party is registered only in a single formation.
Owner:MITSUBISHI ELECTRIC CORP
Runtime adaptable protocol processor
ActiveUS7631107B2Sharply reduces TCP/IP protocol stack overheadImprove performanceComputer controlTime-division multiplexInternal memoryData pack
A runtime adaptable protocol processor is disclosed. The processor architecture provides capabilities to transport and process Internet Protocol (IP) packets from Layer 2 through transport protocol layer and may also provide packet inspection through Layer 7. Further, a runtime adaptable processor is coupled to the protocol processing hardware and may be dynamically adapted to perform hardware tasks as per the needs of the network traffic being sent or received and / or the policies programmed or services or applications being supported. A set of engines may perform pass-through packet classification, policy processing and / or security processing enabling packet streaming through the architecture at nearly the full line rate. A scheduler schedules packets to packet processors for processing. An internal memory or local session database cache stores a session information database for a certain number of active sessions. The session information that is not in the internal memory is stored and retrieved to / from an additional memory. An application running on an initiator or target can in certain instantiations register a region of memory, which is made available to its peer(s) for access directly without substantial host intervention through RDMA data transfer. A security system is also disclosed that enables a new way of implementing security capabilities inside enterprise networks in a distributed manner using a protocol processing hardware with appropriate security features.
Owner:MEMORY ACCESS TECH LLC
Placement and optimization of process dummy cells
ActiveUS8225255B2Reduce probabilityImprove toleranceSolid-state devicesStatic storageInternal memoryVirtual cell
A method for laying out process dummy cells in relationship to inside memory cells of a memory array includes (a) calculating an initial process performance parameter for the memory array; (b) changing dummy cell layout configuration for a layer electrically connected to inside cells; (c) applying lithographic simulation and yield model for both the inside memory cells and the changed layout configuration process dummy cells; and (d) repeating steps (b) and (c) until yield is maximized. Checks may be performed to ensure that there is enough room to make the change and that there is no significant adverse effect to neighboring circuits. The process performance parameter may be yield or a process window for the inside memory cells.
Owner:GLOBALFOUNDRIES U S INC
Tcp/ip processor and engine using rdma
InactiveUS20080253395A1Sharply reduces TCP/IP protocol stack overheadImprove performanceDigital computer detailsTime-division multiplexInternal memoryTransmission protocol
A TCP / IP processor and data processing engines for use in the TCP / IP processor is disclosed. The TCP / IP processor can transport data payloads of Internet Protocol (IP) data packets using an architecture that provides capabilities to transport and process Internet Protocol (IP) packets from Layer 2 through transport protocol layer and may also provide packet inspection through Layer 7. The engines may perform pass-through packet classification, policy processing and / or security processing enabling packet streaming through the architecture at nearly the full line rate. A scheduler schedules packets to packet processors for processing. An internal memory or local session database cache stores a TCP / IP session information database and may also store a storage information session database for a certain number of active sessions. The session information that is not in the internal memory is stored and retrieved to / from an additional memory. An application running on an initiator or target can in certain instantiations register a region of memory, which is made available to its peer(s) for access directly without substantial host intervention through RDMA data transfer.
Owner:MEMORY ACCESS TECH LLC
Background application automatic clearing method based on mobile phone and mobile phone
InactiveCN102946486ASave powerReduce trafficInterprogram communicationSubstation equipmentInternal memorySimulation
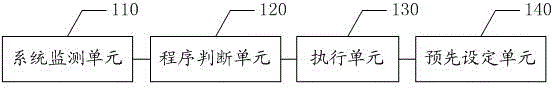
The invention discloses a background application automatic clearing method based on a mobile phone and the mobile phone. The background application automatic clearing method comprises the steps of monitoring the occupancy rate of a central processing unit (CPU) or an internal memory of a mobile phone system and periodically judging whether the occupancy rate of the CPU or the internal memory of the mobile phone system at present exceeds a preset threshold value or not; and invoking an universal interface for closing a system application program to close a judged system non-application program when the occupancy rate of the CPU or the internal memory of the mobile phone system at present exceeds the preset threshold value. By means of the method, the background application program of the mobile phone is automatically cleared, the operation speed of the system is improved, electric quantity and internet surfing flows of the mobile phone can be saved, and the mobile phone with good performance is provided for a user.
Owner:HUIZHOU TCL MOBILE COMM CO LTD
Method and apparatus for switching virtual sim service contracts when roaming
InactiveUS20100311418A1Avoid roaming feeService provisioningAssess restrictionInternal memoryTelecommunications
A system and method store provisioning data supporting a plurality of service providers in a VSIM internal memory unit of a mobile device. The mobile device may automatically enable provisioning data supporting one of the plurality of service providers stored in the VSIM internal memory unit to conduct a wireless communication so as to avoid roaming fees.
Owner:QUALCOMM INC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com