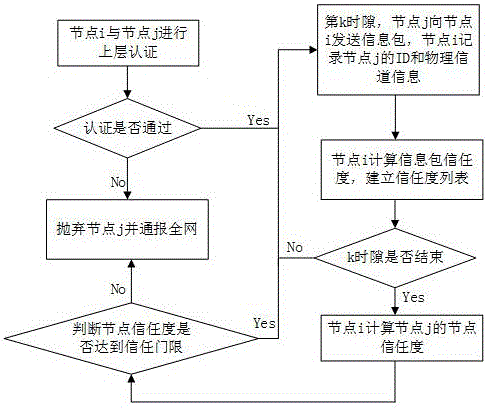
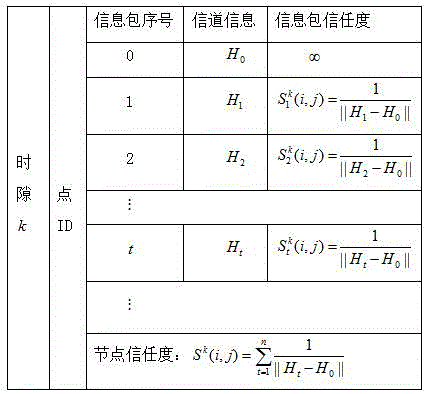
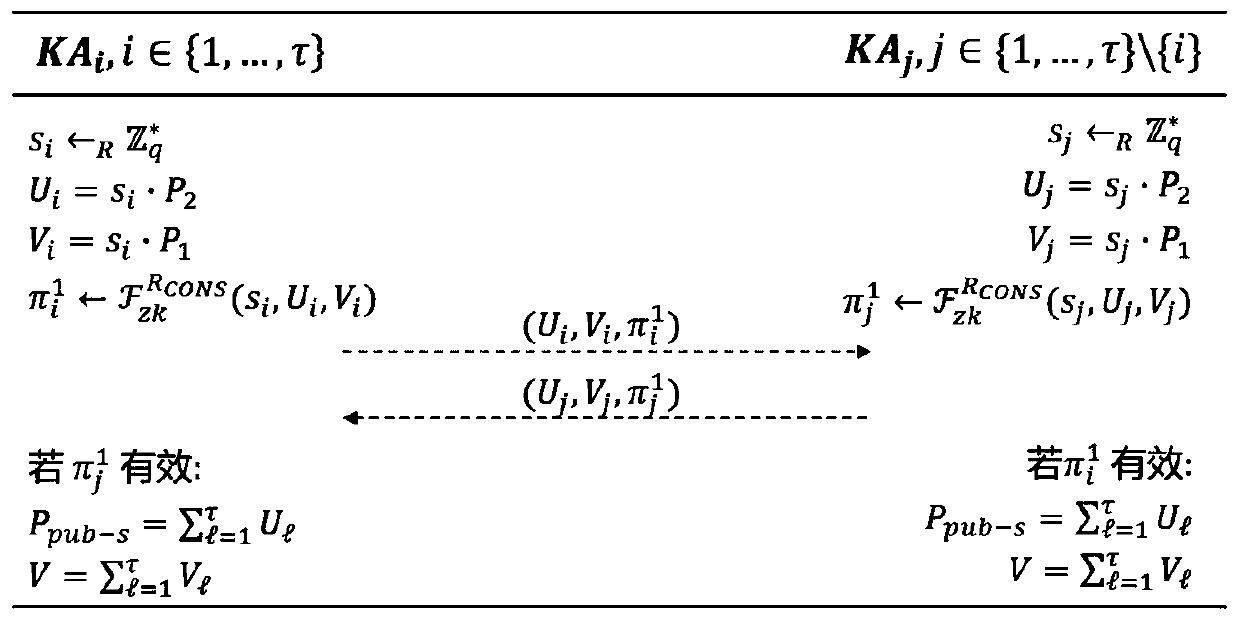
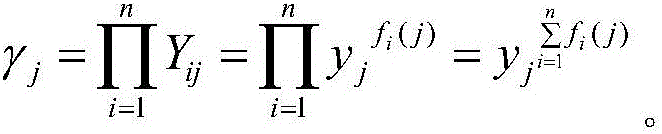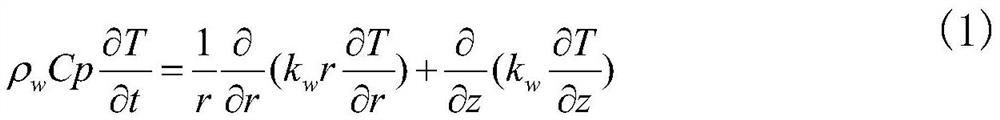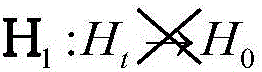Patents
Literature
64results about How to "Solve the single point of failure problem" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
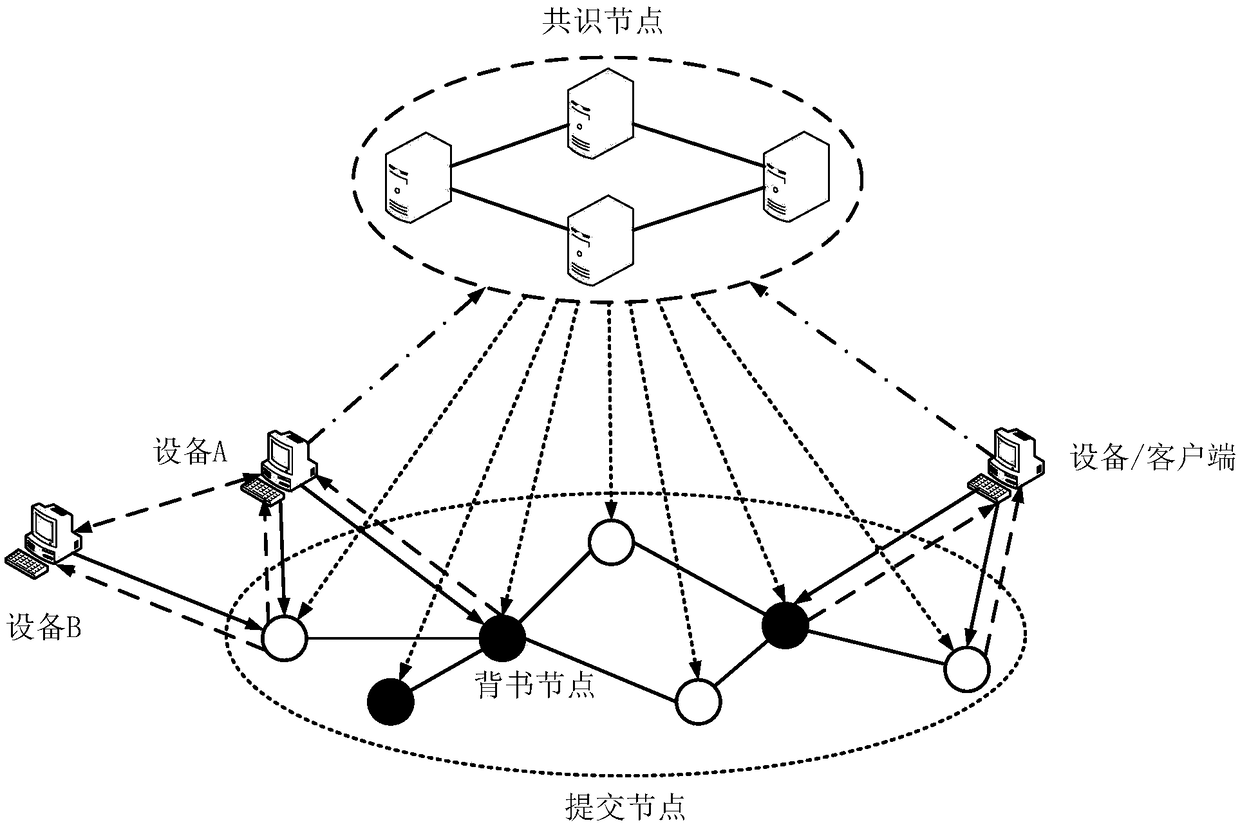
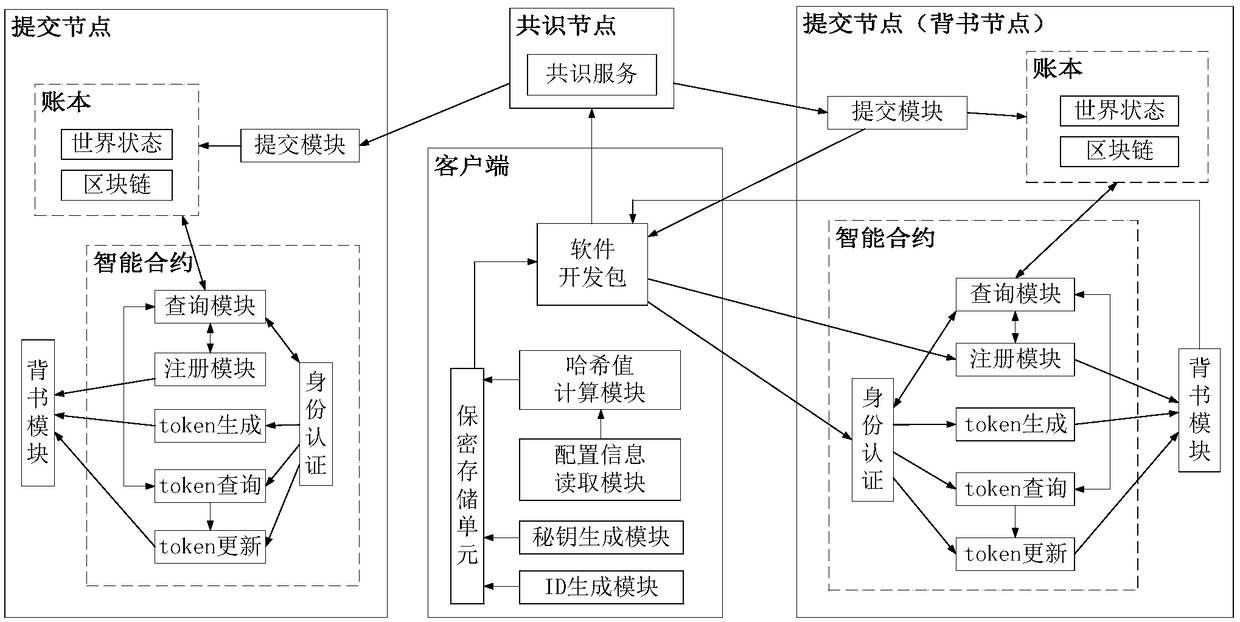
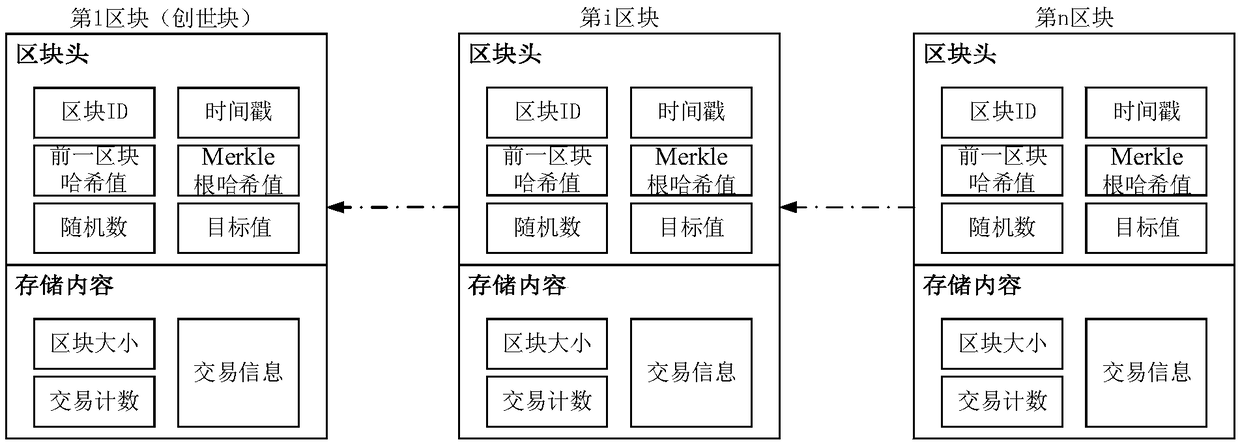
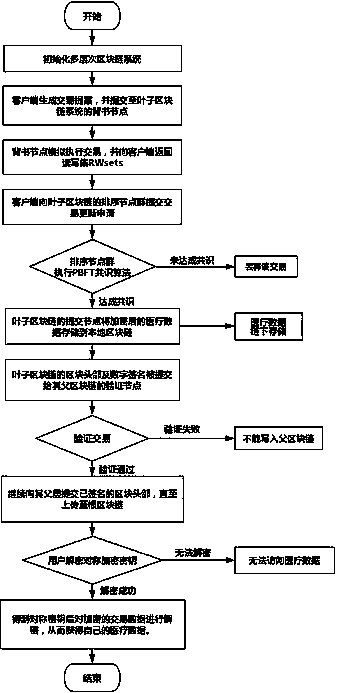
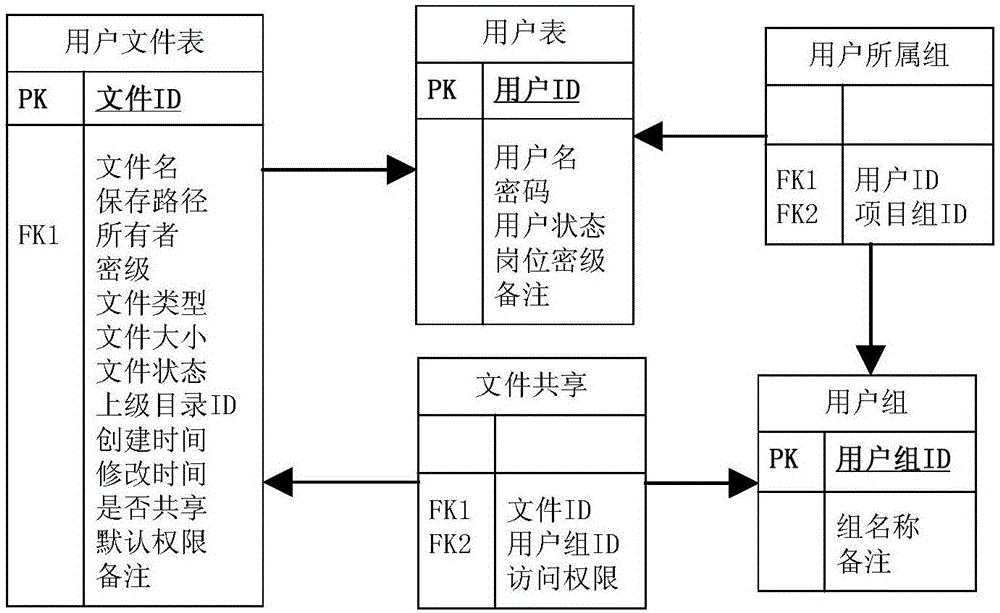
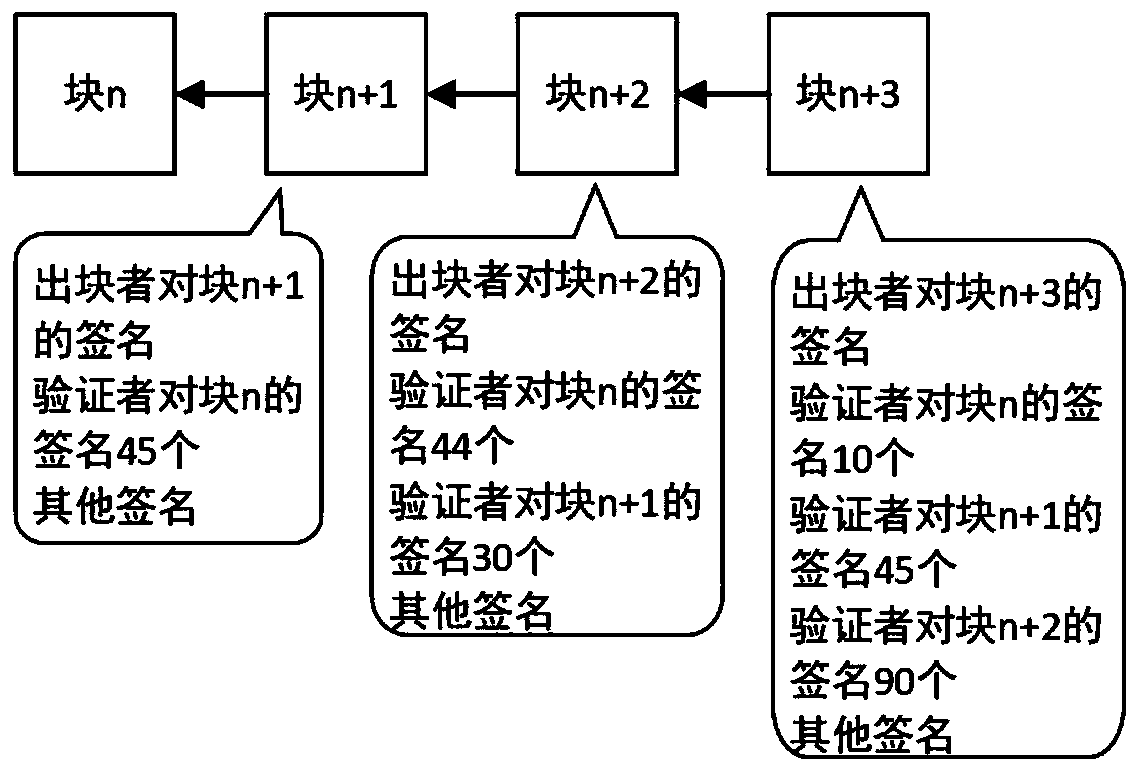
Device networking authentication method based on blockchain
ActiveCN108833081AGuaranteed legalityWill not affect operationKey distribution for secure communicationEncryption apparatus with shift registers/memoriesTimestampSmart contract
The invention discloses a device networking authentication method based on a blockchain for solving the single point failure problem existing in the current networking authentication method. The technical scheme is to deploy a blockchain network comprising a client, a submission node and a consensus node. By means of the non-tampering property of the blockchain, a device firstly registers on the blockchain before accessing the network, when the device A needs to access the network, the device sends a networking request of a device B that has accessed to the network, the device B compares the information of the device A in the networking request with the information of the device A stored in the blockchain to judge whether the identity of the device A is legal, a smart contract issues a token to the device A, a timestamp in the token ensures that the device A is valid within a certain period of time, and after the token expires, the device A needs to pass the identity authentication toaccess the network again. By adoption of the device networking authentication method disclosed by the invention, the single point failure problem existing in the traditional networking authenticationmethod can be avoided, the legality of the identity of the device is ensured, and the security of the network is improved.
Owner:NAT UNIV OF DEFENSE TECH
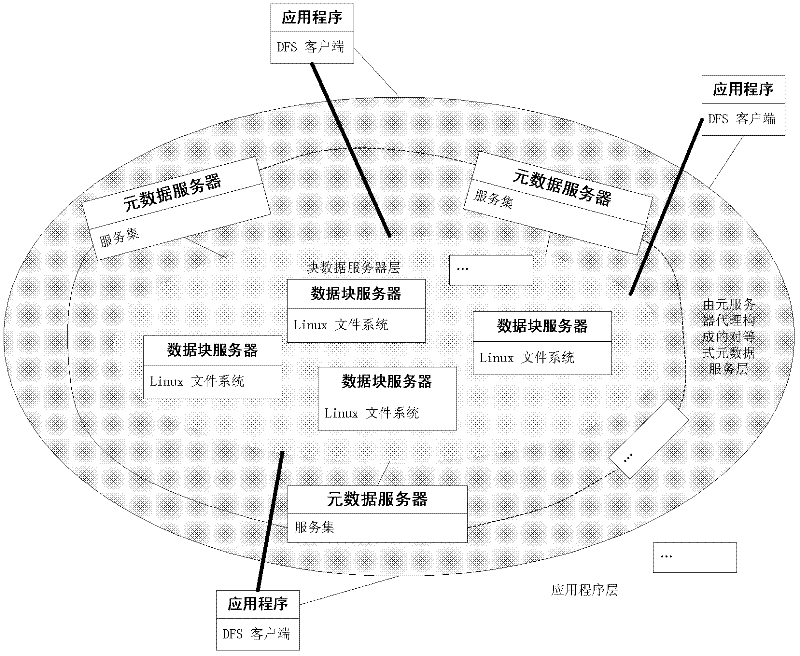
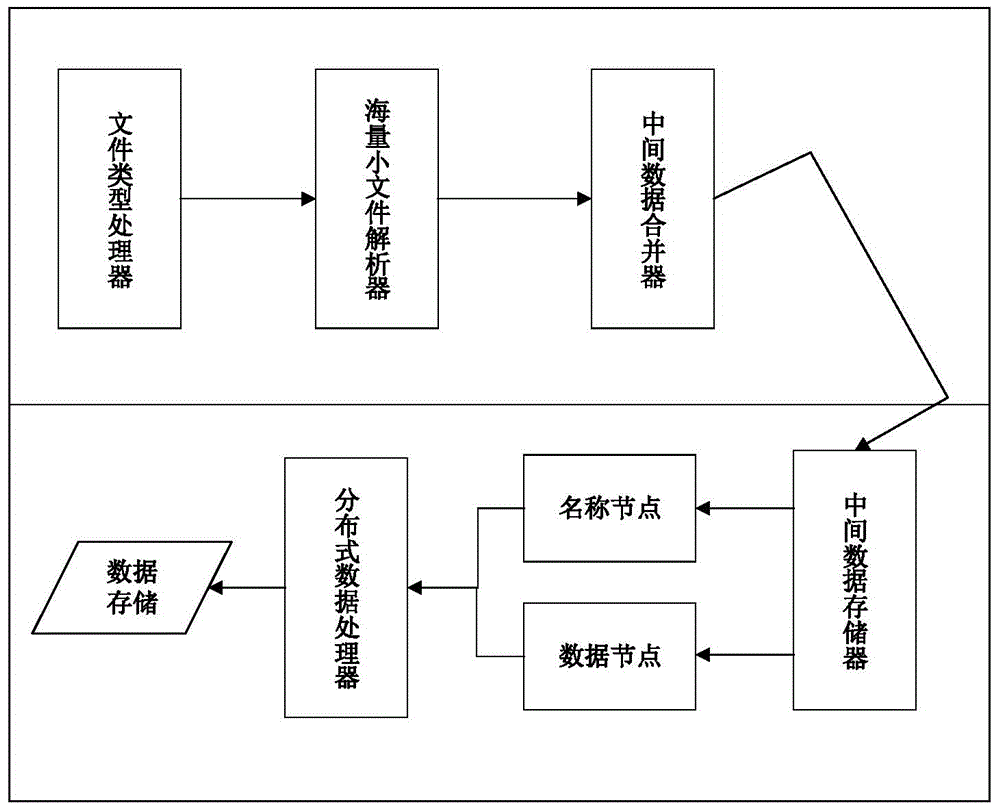
Distributed file system facing to cloud storage
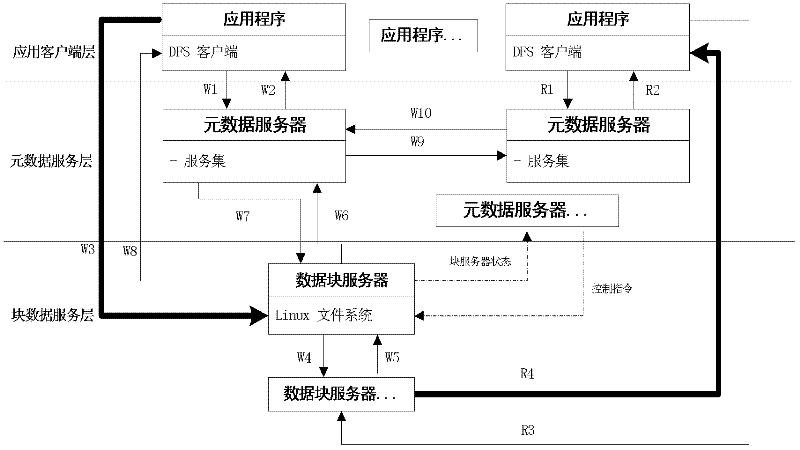
InactiveCN102420854AImprove parallel processing performanceOvercoming high load problemsTransmissionSpecial data processing applicationsSingle pointMetadata service
The invention provides a distributed file system facing to cloud storage, mainly aiming at solving the problem that the existing cloud storage system is low in performance and reliability, high in load and invalid in a single point. The system comprises a block data service layer, a metadata service layer and an application client layer, wherein the metadata service layer replaces single metadata server in a global file system (GFS) by a plurality of agent servers, and forms into peer-to-peer type service network by adopting peer-to-peer P2P network configuration; the interaction among three layers of the system comprises the following steps: the application client layer requests to write to the metadata service layer, and the metadata service layer returns block data server information; and the client layer writes the file into the block data service layer and performs the redundancy backups according to a returned result, and the metadata service layer generates metadata according to a backups result and updates local metadata and a vector clock. Therefore, the performance and the business support capacity of the existing cloud storage system can be enhanced, and the system can be used for designing and optimizing the high-performance and high-reliability cloud storage system.
Owner:XIDIAN UNIV
Intelligent medical data storage method based on multi-level blockchain system architecture
ActiveCN110727737AImprove efficiency andHigh robustness and fault toleranceDatabase distribution/replicationDigital data protectionBlockchainEncryption system
The invention discloses an intelligent medical data storage method based on a multi-level blockchain system architecture. According to the method, an existing single-chain or double-layer blockchain system design is abandoned, a multi-layer blockchain system architecture is provided based on a Hyperledger Fabric platform to solve the storage problem of medical data, efficient management of large-scale medical data is achieved, and the efficiency and expandability of the system are greatly improved. Meanwhile, a dual-key encryption system combining public key encryption and symmetric encryptionis adopted, storage and sharing of medical data are achieved under the condition that privacy of the patient is protected, and great convenience is provided for medical institutions, patients and scientific research institutions.
Owner:NANJING UNIV OF POSTS & TELECOMM
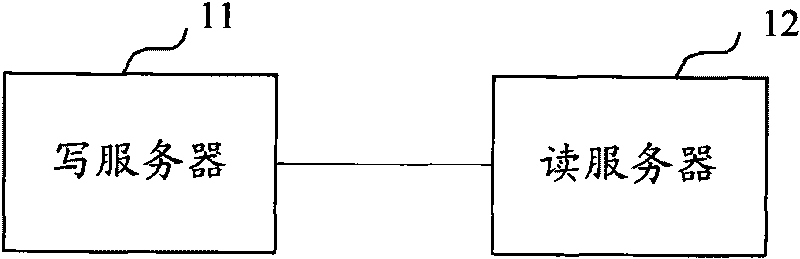
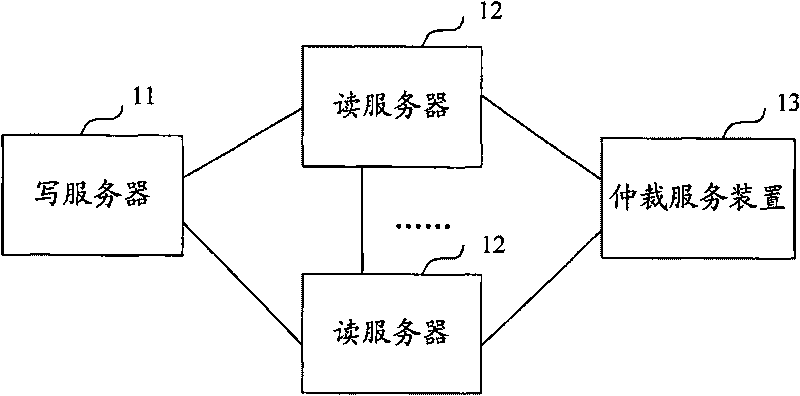
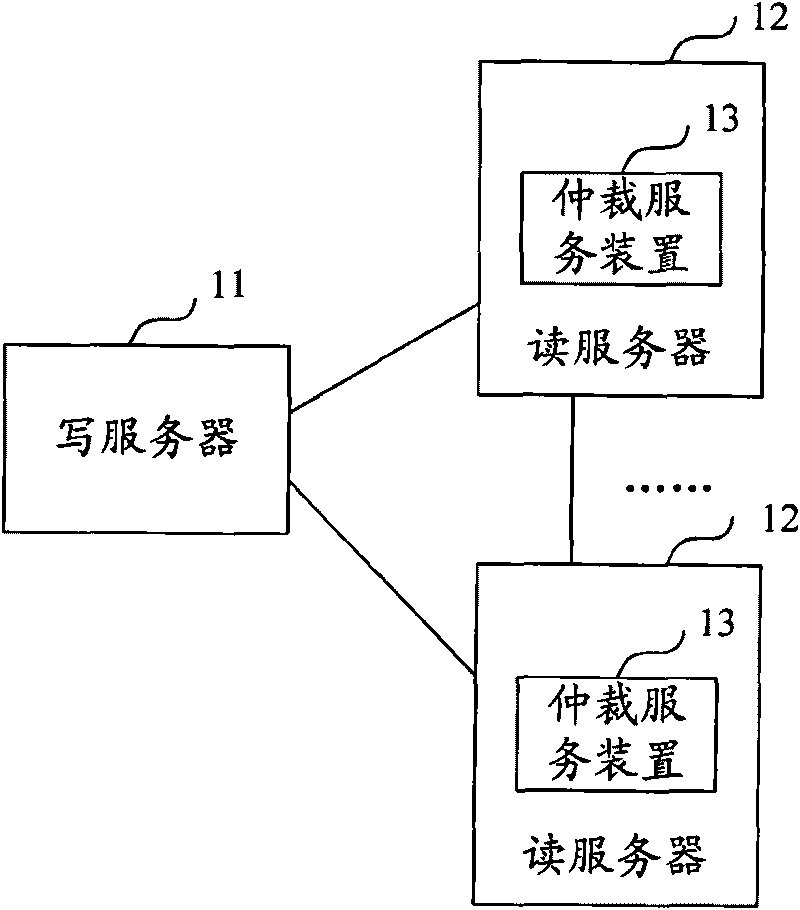
Metadata service system metadata synchronized method and writing server updating method
ActiveCN101751415ASolve the single point of failure problemMeet concurrent access requirementsSpecial data processing applicationsSingle pointMetadata service
The invention discloses a metadata service system metadata synchronized method and writing server updating method. The metadata service system provided by the invention includes a writing server and a reading server; the writing server is used for storing the metadata in a concurrent file system to receive reading access and receive writing access; correcting the metadata in the concurrent file system and synchronously updating the corrected metadata into the reading server; the reading server is used for storing the metadata and receiving reading access, receiving the synchronous updating of the writing server to the metadata, and is also used for converting into writing service when the write server is monitored to be valid. The invention solves the problem of single point failure through the mutual backup of the reading server and the writing server, and can meet high effective large-scale concurrent access demands.
Owner:CHINA MOBILE COMM GRP CO LTD
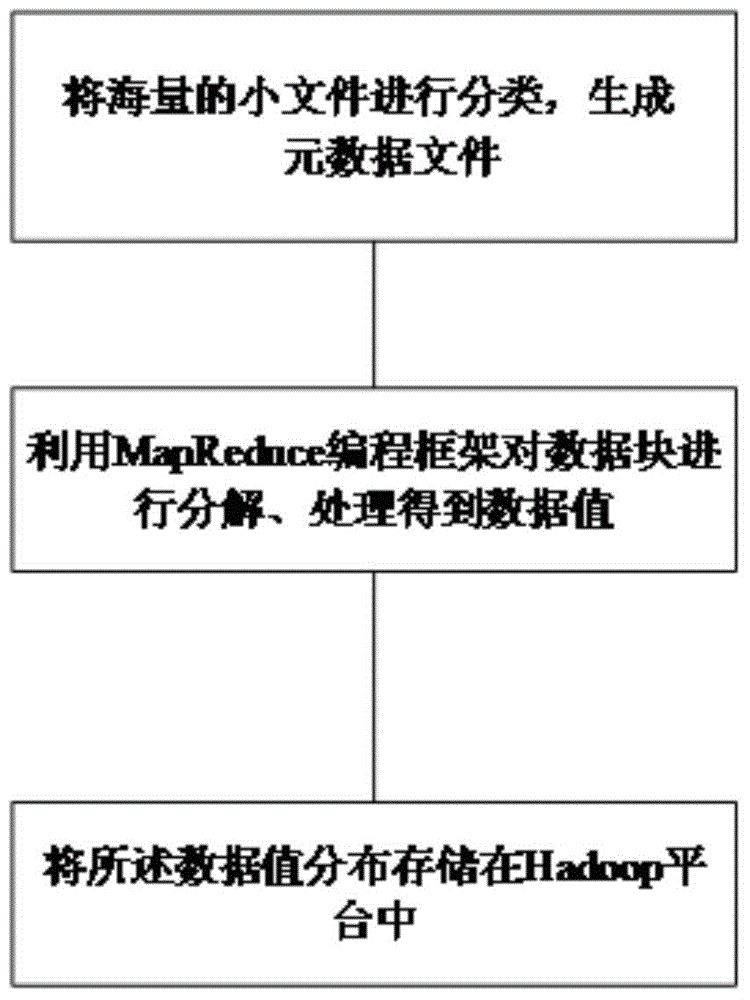
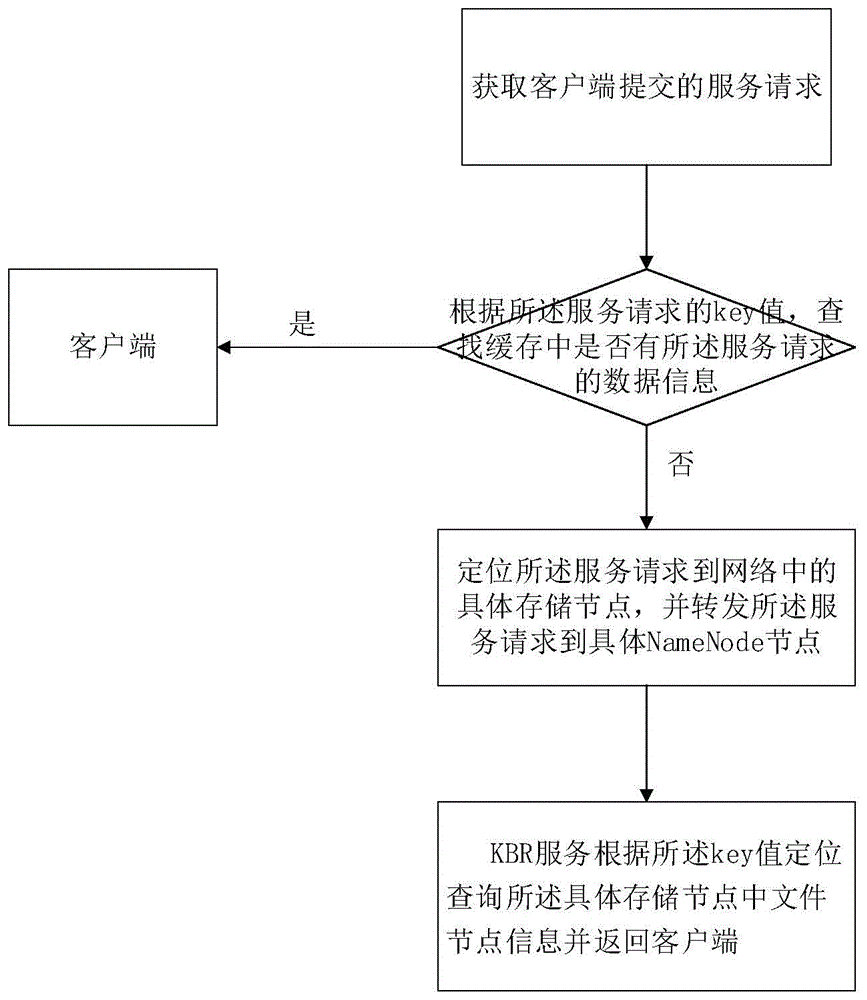
Massive small file storage and management method and system
ActiveCN104820717ALoad balancingImprove processing efficiencySpecial data processing applicationsBalancing networkPeer to peer computing
The invention provides a massive small file storage and management method and a system, wherein the massive small file storage and management method comprises that massive small files are stored, and metadata is written into a name node service network, and is managed through the name node service network, thereby achieving access request response of a client. The system comprises the name node service network and a massive small file storage system. The massive small file storage and management method and the system use peer-to-peer computing technology, prevent the problem of single point failure, provide routing lookup method based on keywords, effectively balance network load, and improve query efficiency.
Owner:GLOBAL ENERGY INTERCONNECTION RES INST CO LTD +3
Parallel execution method and device for timed task on multiple servers
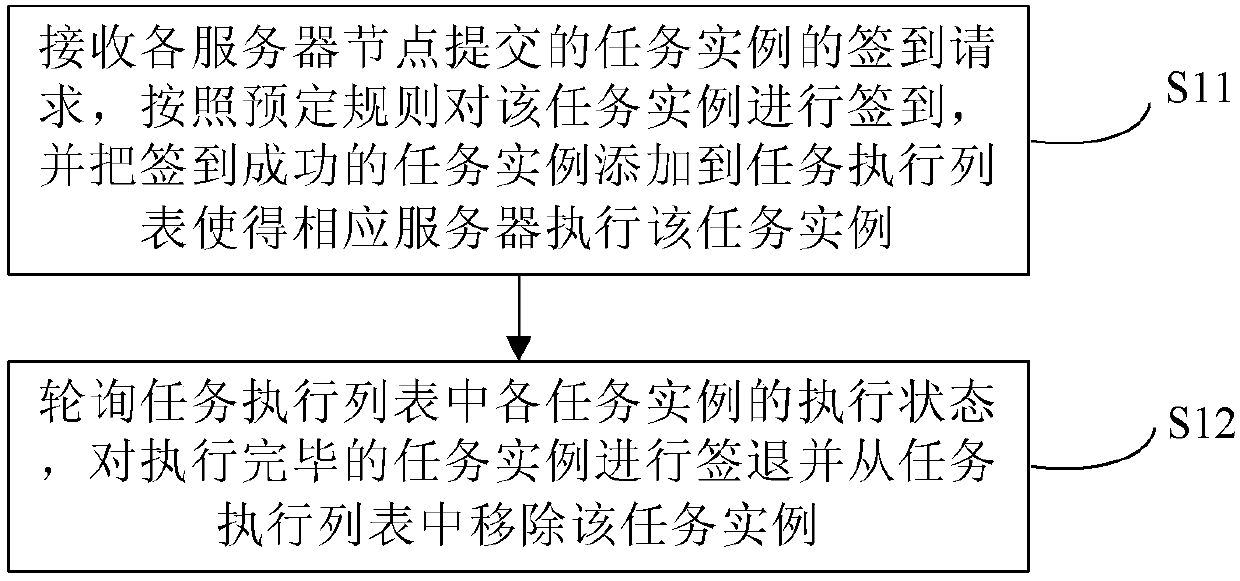
InactiveCN107918556ARealize unified configurationGuaranteed atomicityProgram initiation/switchingResource allocationBusiness developmentSingle point of failure
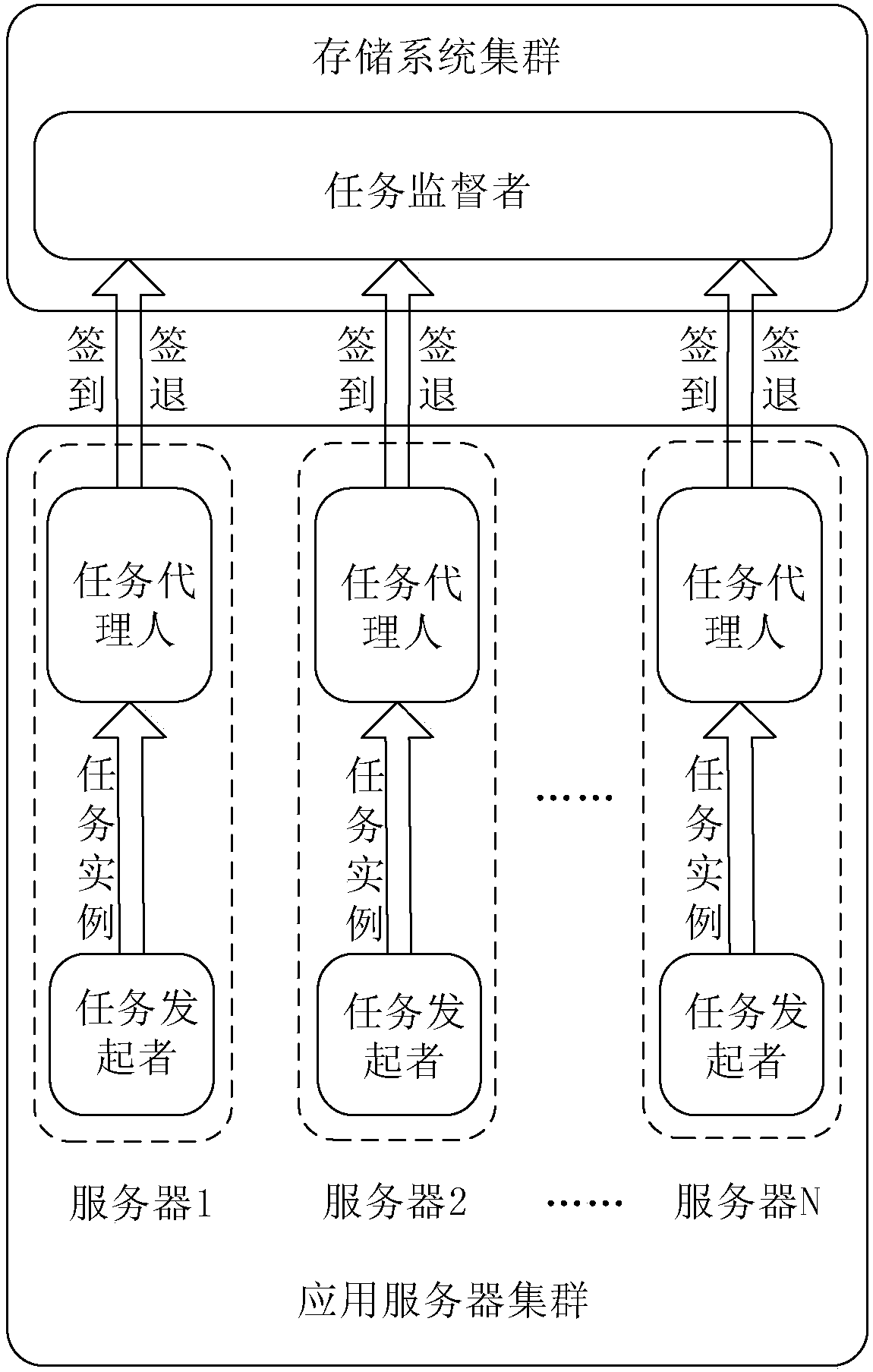
The invention provides a parallel execution method and device for a timed task on multiple servers. The uniform configuration of server nodes can be realized, limited calculation resources are fully utilized, the atomicity of a task is supported and guaranteed, operation and maintenance cost is reduced, the problem of single point failure is solved, the stagnation of service due to the single point failure is avoided, no manual intervention is required when the server crashes, the splitting of a large task is supported, application developers only need to pay attention to specific business development, and availability and expansibility are good. The parallel execution method for the timed task on the multiple servers comprises the following steps that: receiving the attendance request ofa task living example submitted by each server node, carrying out attendance on the task living example according to a preset rule, adding the task living example which is subjected to successful attendance to a task execution list to enable the corresponding server to execute the task living example; and polling the execution state of each task living example in the task execution list, signing out the task living example which finishes being executed, and removing the task living example from the task execution list.
Owner:BEIJING JINGDONG SHANGKE INFORMATION TECH CO LTD +1
Centralized service based distributed peer-to-peer network implementing method and system
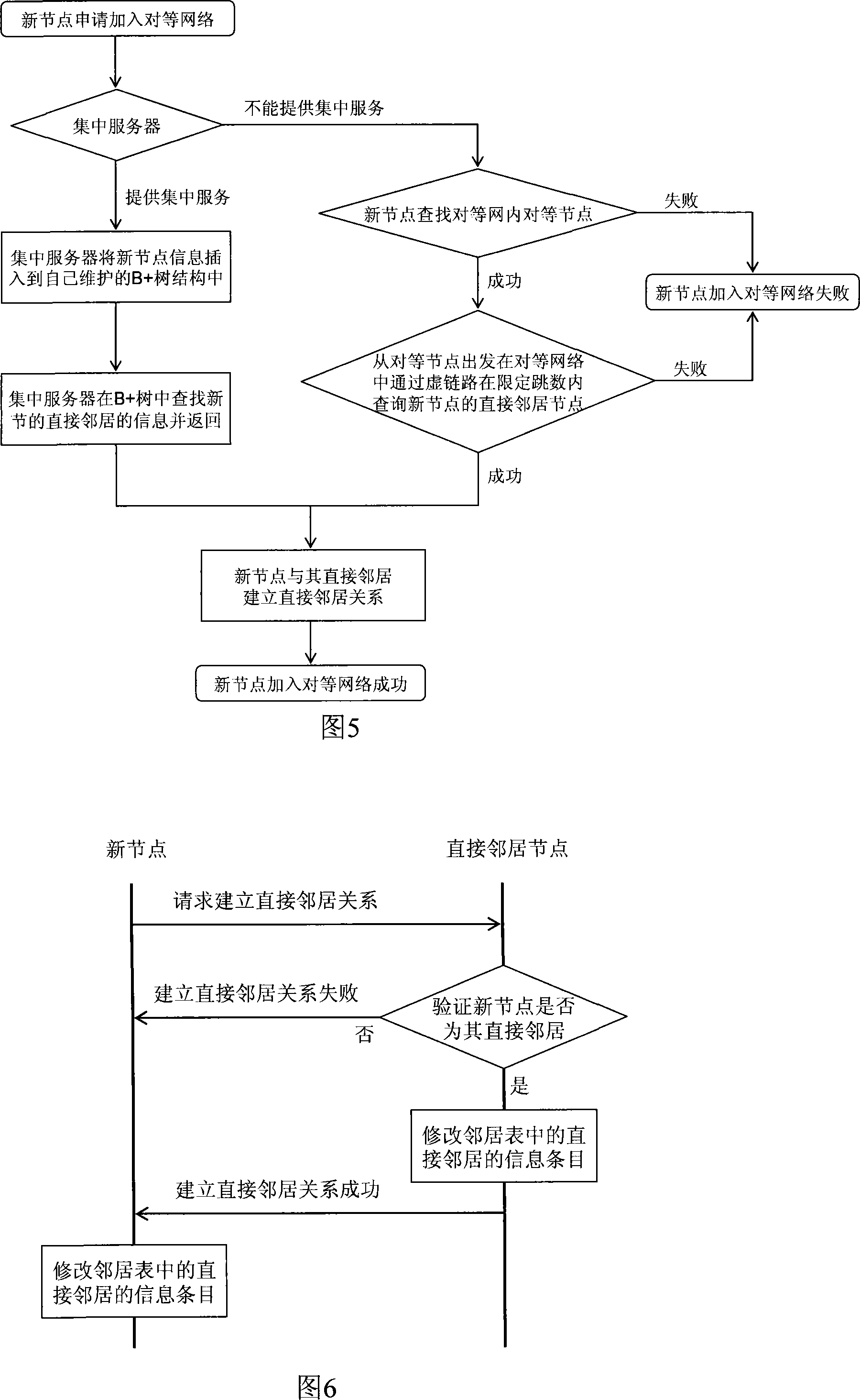
InactiveCN101179466AReduce overheadReduce the burden onLoop networksRing networkDistributed computing
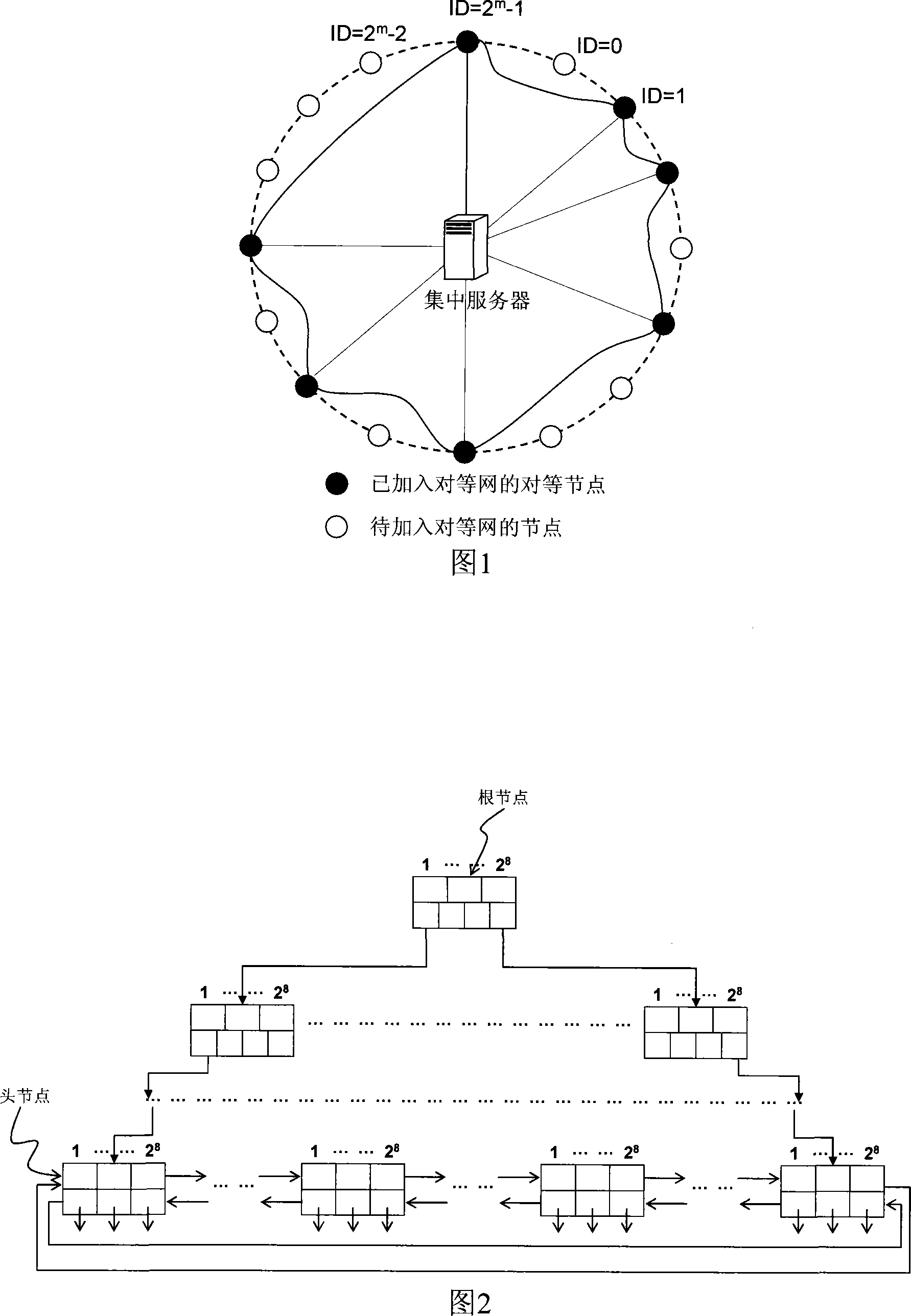
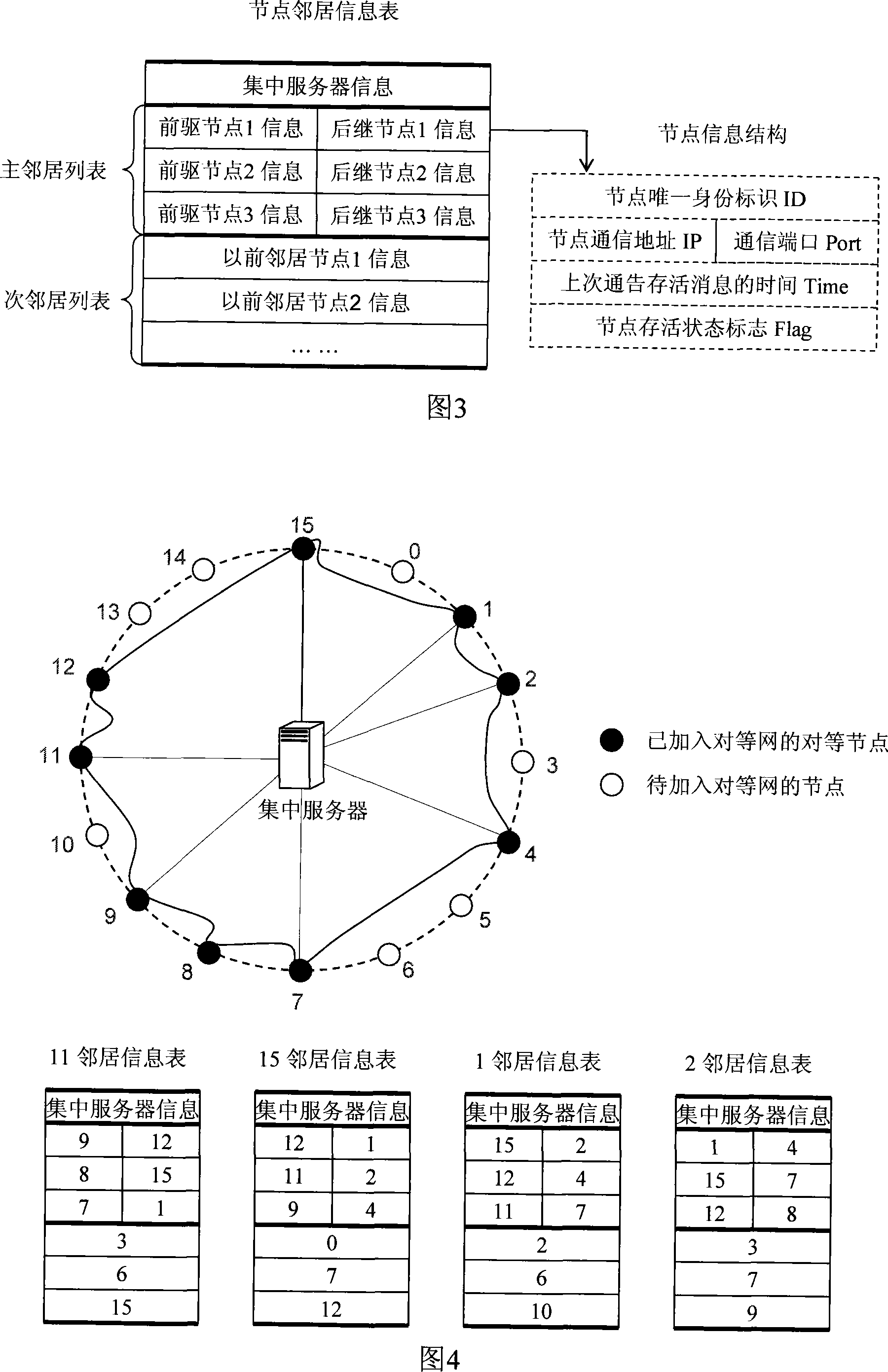
The invention relates to a distributed peer-to-peer network based on concentration service and a construction method thereof, wherein, the method includes the following steps: (1) establishing a concentration server for the peer-to-peer network, which is used for adding the peer-to-peer network for a new node and providing service for the exit of the peer-to-peer network and defining a data structure of a B plus tree for the server so as to save the information on a dynamic and variable node; (2) adopting a new node to search a direct neighbor through a concentration server or search the direct neighbor in a virtual link from a peer node and add the direct neighbor into a peer-to-peer network ; (3) applying a boundary node (a peer node with a precursor or a successor exiting from the direct neighbor) to search a direct precursor or a successor neighbor through the concentration server or search the direct precursor or the successor neighbor in the virtual link from the node, so as to maintain ring-shaped topology among the peer nodes. The invention integrates the concentration service in the distributed peer-to-peer network, thus obviously decreasing network fluctuation due to frequent entering or exiting of the node and greatly increasing the work efficiency of the peer-to-peer network.
Owner:BEIJING JIAOTONG UNIV
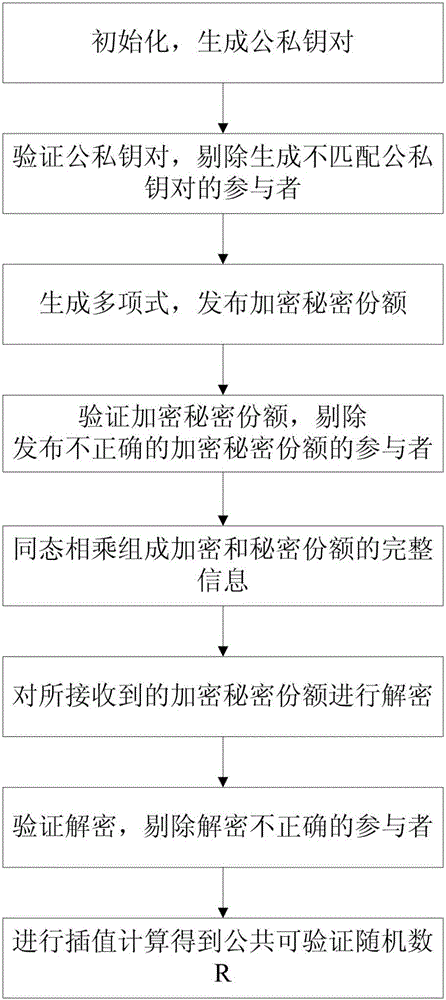
Distributed public verifiable random number generation method
InactiveCN105827402AImprove securitySolve the single point of failure problemKey distribution for secure communicationRandom number generatorsThird partyCiphertext
The invention discloses a distributed public verifiable random number generation method. A random number is generated through the cooperation of a participant, and the ciphertext is made public in the process of generating the random number so as to be verified. Unpredictability requires that the random number is private before being issued, but the public verifiability requires to discloses the information for verification, one of the main contributions of the patent is to solve the contradiction between two characters. Furthermore, the second contribution of the patent is that the trusted third party can be eliminated in the verifiable random number generation process; on one hand, the method can prevent single participant from knowing the random number result in advance, the security of the protocol is improved; on the other hand, the method is conductive to solving sing point of failure problem, and the robustness of the protocol is improved.
Owner:WUHAN UNIV OF TECH
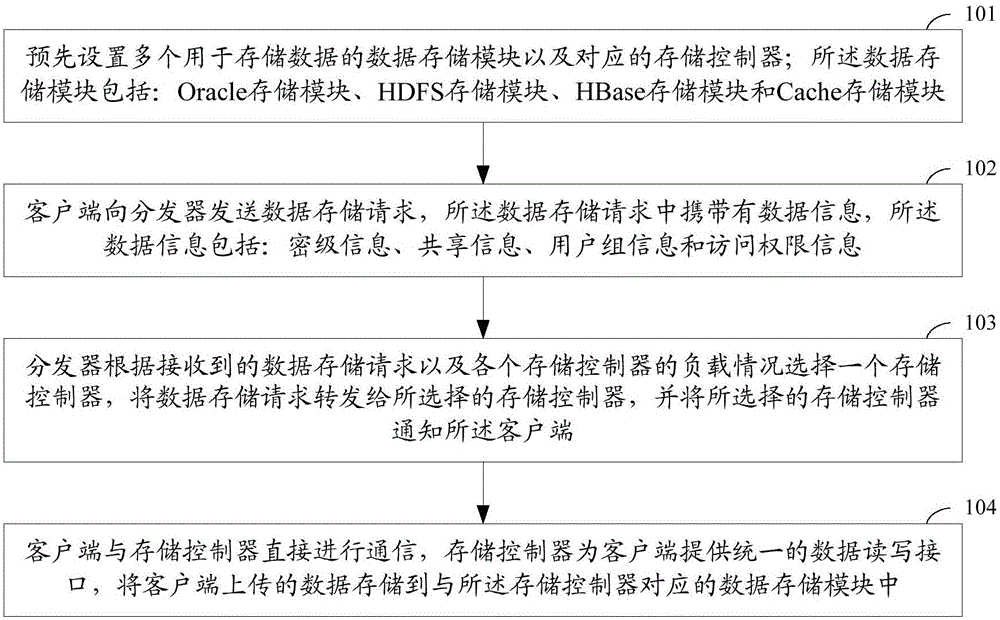
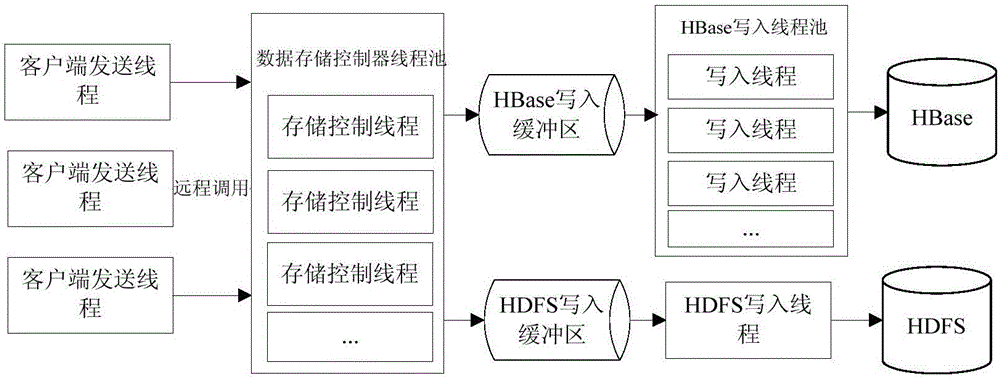
Storage method and system for target characteristic data
ActiveCN107180102AEnsure safetyReduce data storage costsDatabase distribution/replicationSpecial data processing applicationsData informationControl store
The invention provides a storage method and system for target characteristic data. The method comprises the following steps that: a plurality of data storage modules used for storing data, and corresponding storage controllers are arranged in advance; a client side sends a data storage request which carries data information to a dispatcher, wherein the data information comprises security classification information, shared information, user group information and access permission information, the data storage request is forwarded to the selected storage controller, and the selected storage controller is notified to the client side; and the client side is directly communicated with the storage controller, the storage controller provides a uniform data read-write interface for the client side, and data uploaded by the client side is stored to the data storage module corresponding to the storage controller. When the method is applied, data storage cost can be lowered, the data is uniformly managed and maintained, data safety is guaranteed, and the data can be conveniently shared and used.
Owner:BEIJING INST OF ENVIRONMENTAL FEATURES
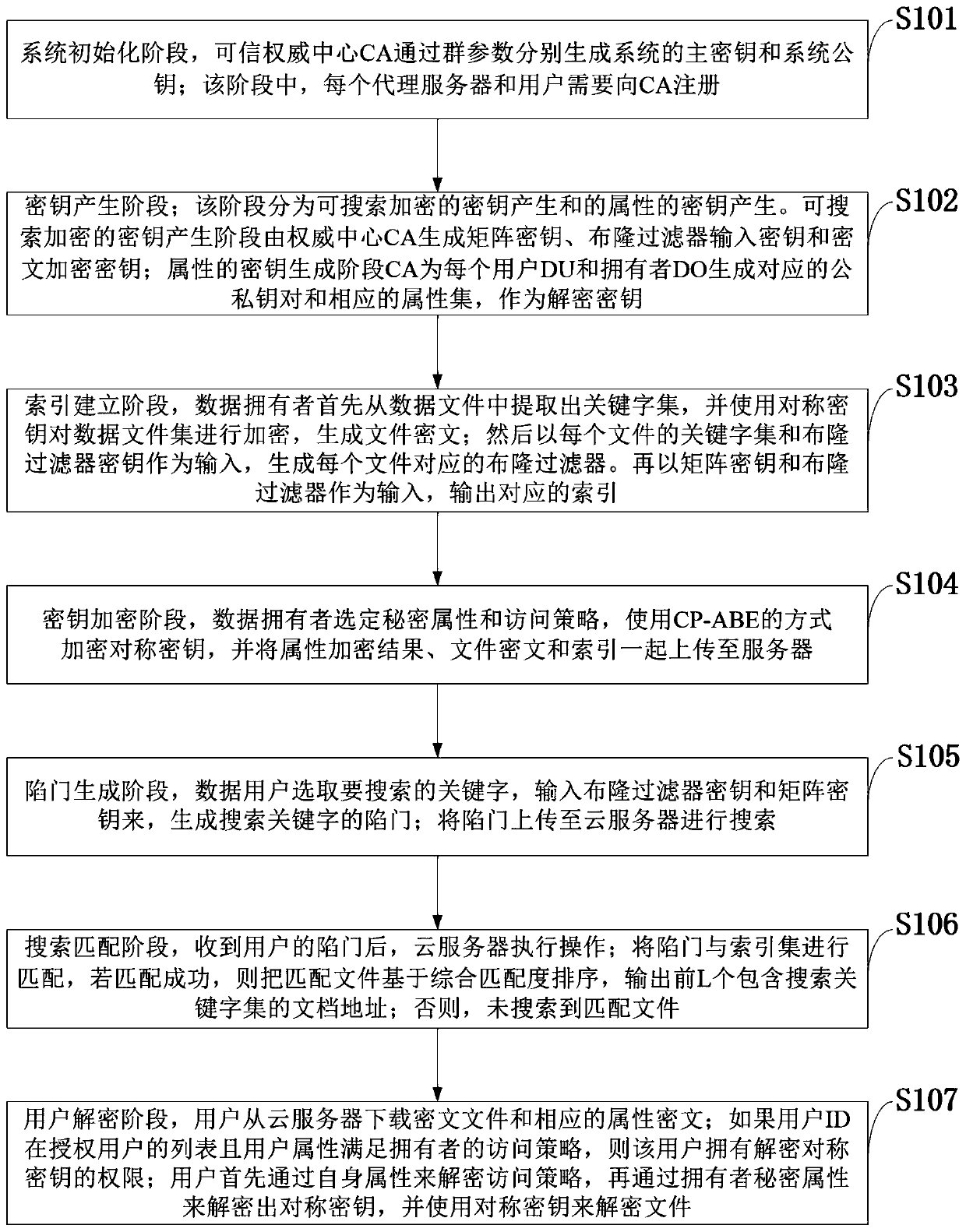
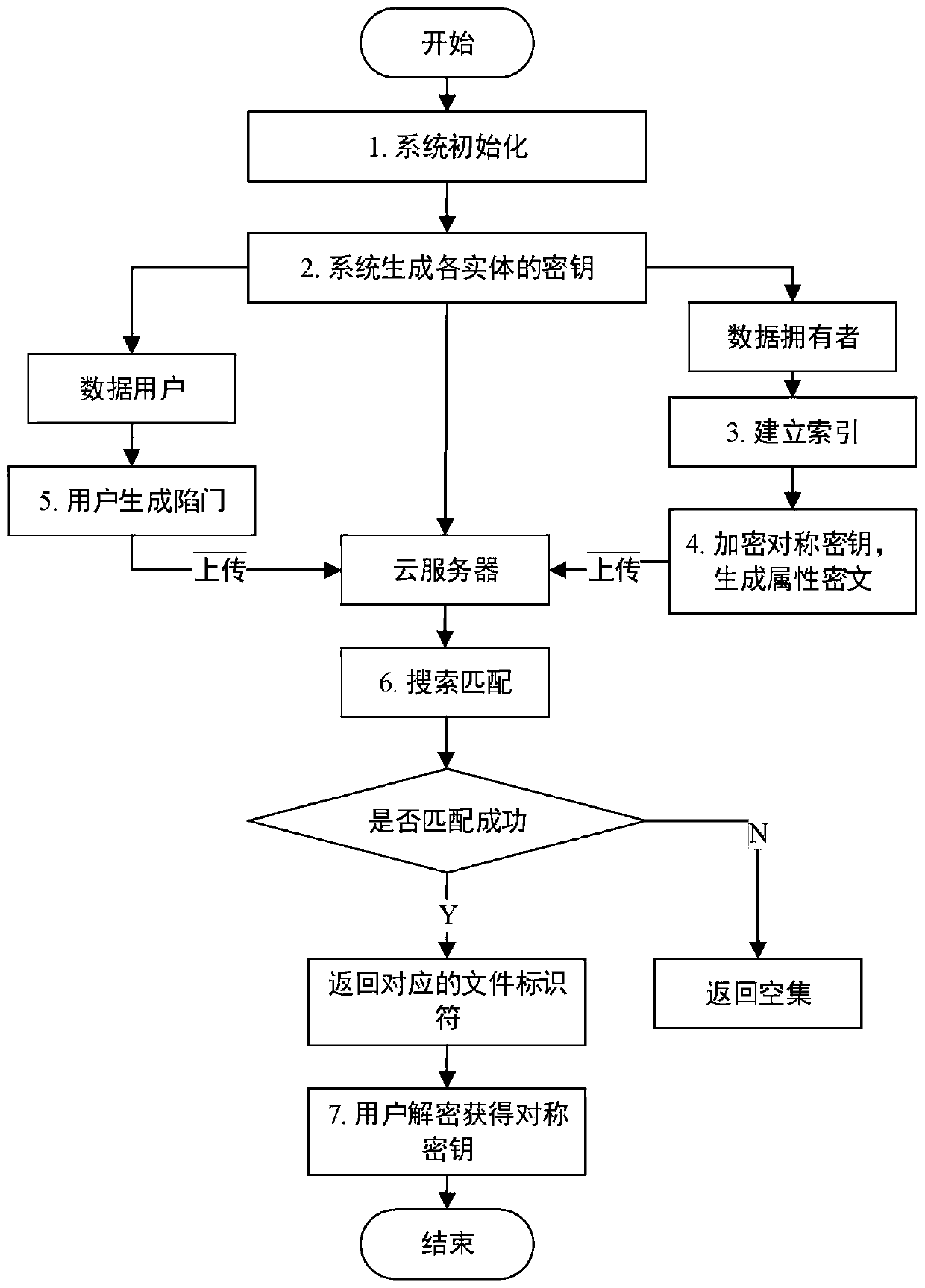
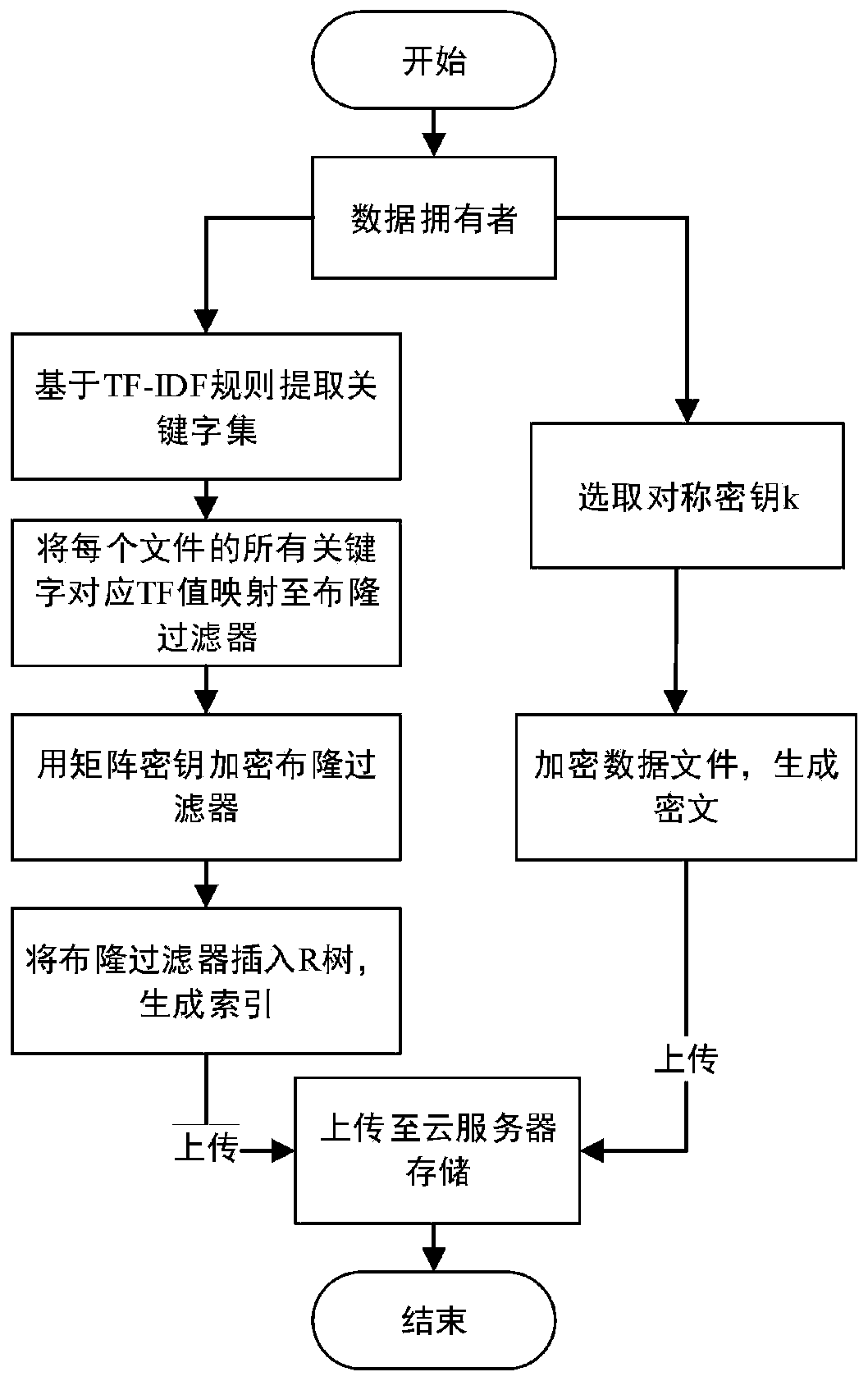
Efficient ciphertext retrieval method based on CP-ABE automatic correction and cloud computing service system
ActiveCN110138561AAvoid Frequency Guessing AttacksReduce complexityKey distribution for secure communicationPublic key for secure communicationGeneration processAccess structure
The invention belongs to the technical field of cloud computing private protection, and discloses an efficient ciphertext retrieval method based on CP-ABE automatic correction and a cloud computing service system. The method comprises the steps of storing an encrypted Bloom filter and a corresponding ciphertext file ID set in a leaf node of the R tree by combining the R tree and the Bloom filter as index structures; using the cloud server to perform the matrix positioning on the R tree according to the search trap door, and then match the encrypted Bloom filters in the leaf nodes; sorting thefiles according to the inner product result of the Bloom filter; introducing a random number in the trap door generation process, wherein different trap doors can be generated even if according to thesame keyword; performing the co-encryption by using the access structure and the owner secret attribute. According to the method, a symmetric key with a small CP-ABE encryption volume is used, so that the fine-grained access control is realized; a multi-agent server is introduced to realize the decentralization, and the collusion between the proxy servers is prevented.
Owner:XIDIAN UNIV
MIPv6 based security multicast method and steps
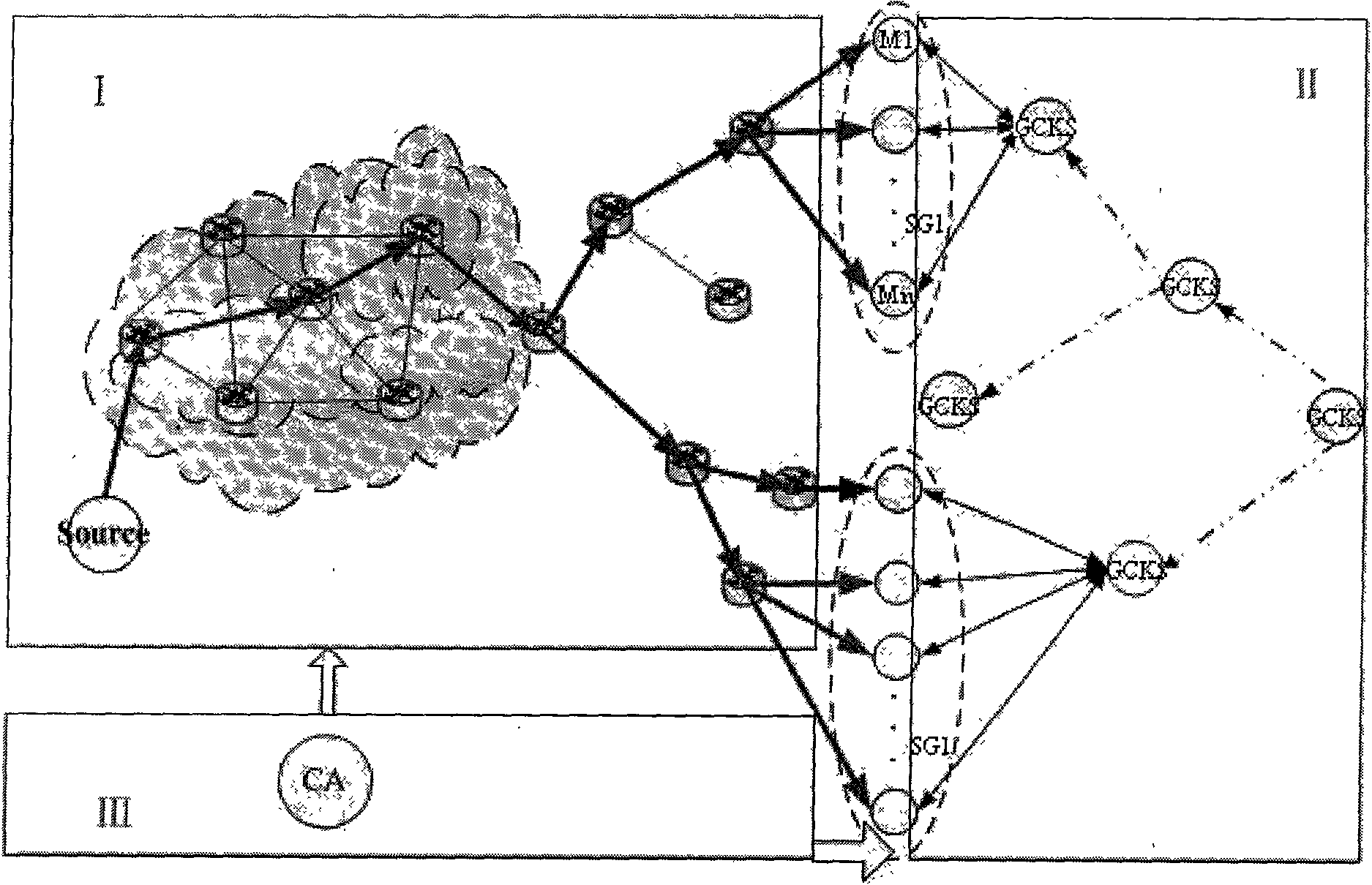
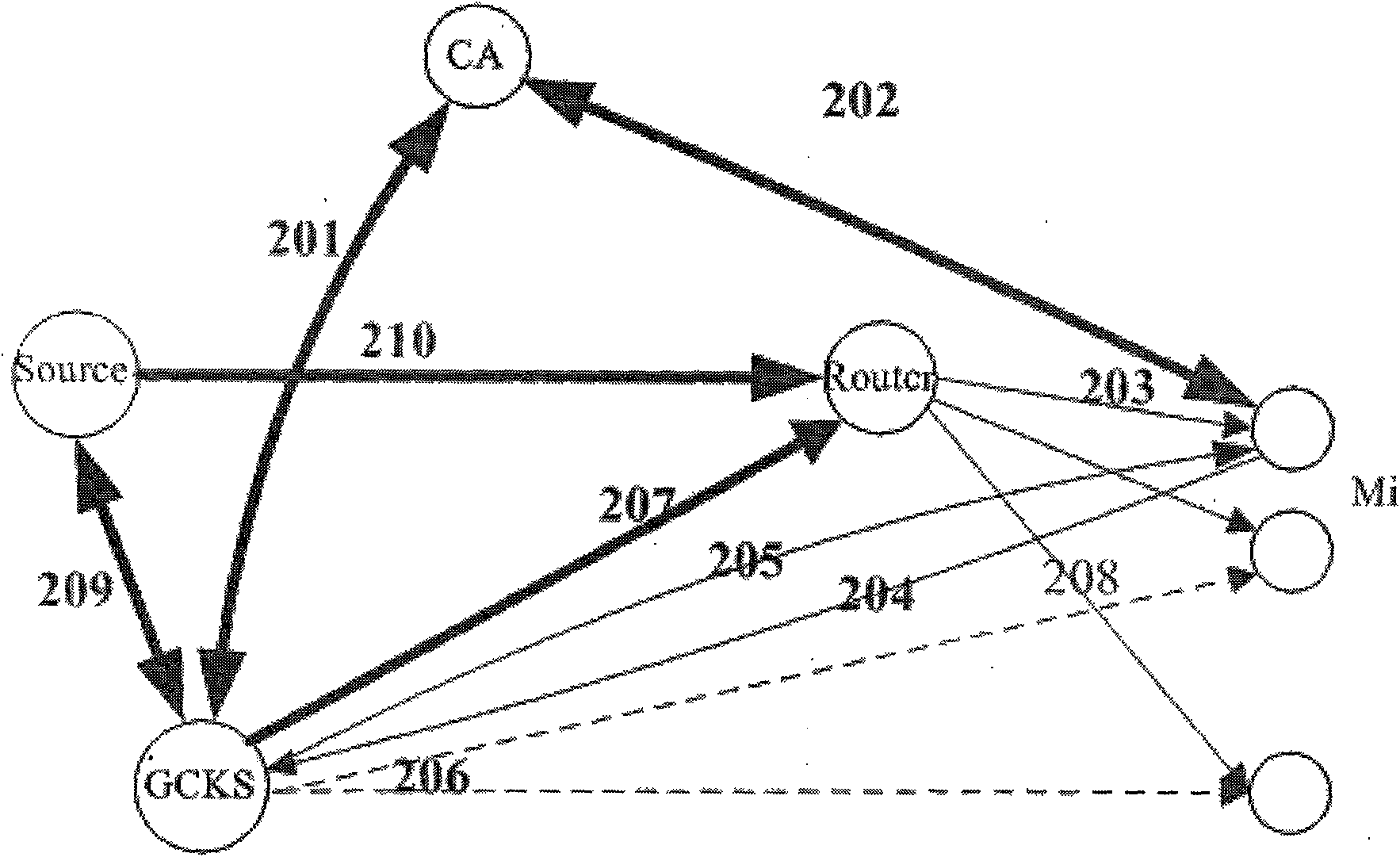
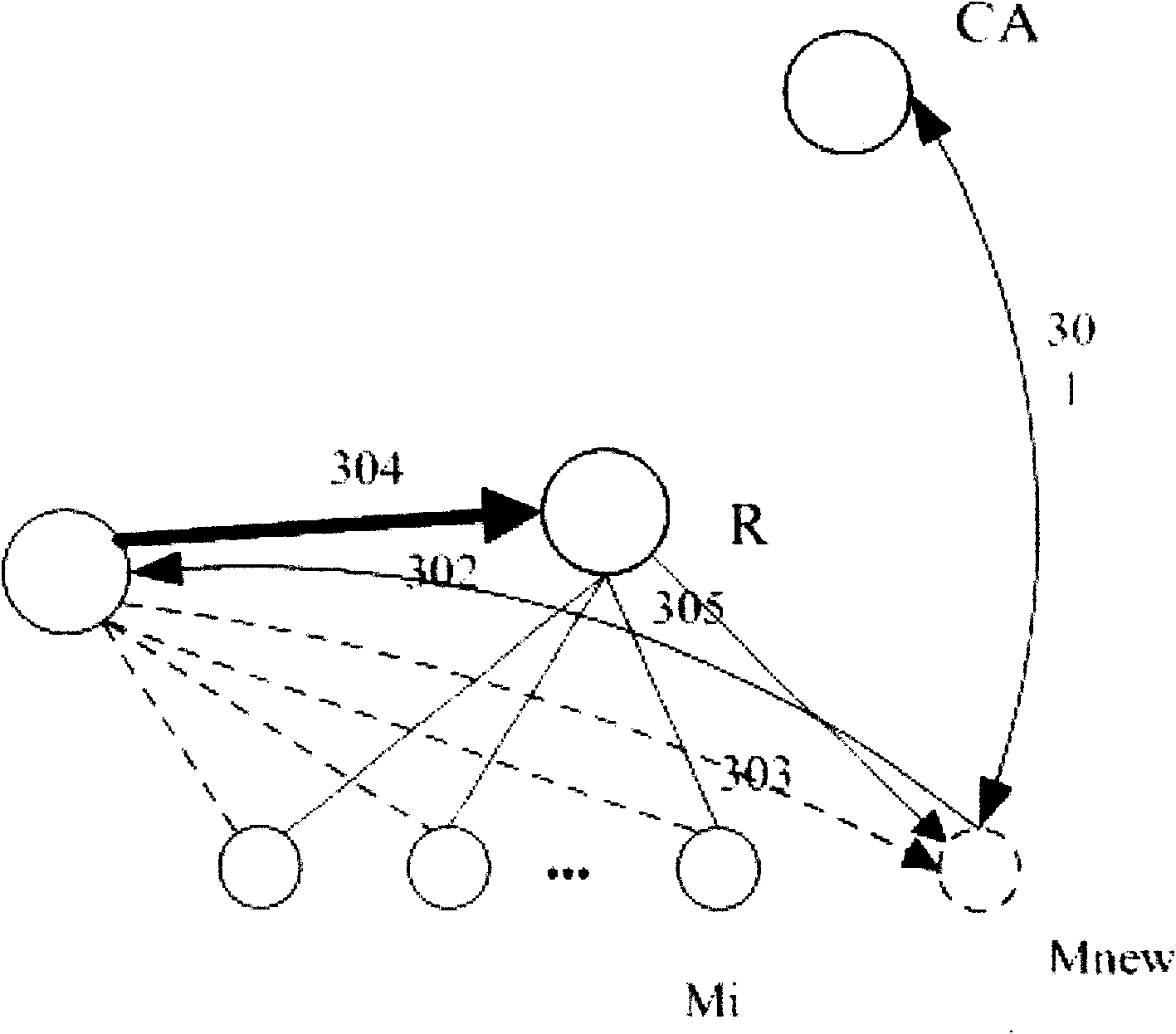
ActiveCN101588235AImprove securityReduce attackSpecial service provision for substationKey distribution for secure communicationSecurity associationNetwork packet
The invention belongs to the field of communication network security, and relates to an MIPv6 based security multicast method applied to a mobile communication network, which is characterized in that: the method comprises an authentication center 1, a group member 2, a multicast source 3 and GCKS 4, wherein the authentication center is used for authenticating the group member, the multicast source and the GCSK and distributing certificates; the GCKS is used for authenticating access registration and distributing key update messages for the group member to forward an information list of the group member 2 to an access router, is used for performing security association negotiation with the multicast source, and is used for negotiating and constructing a group key among GCKS; the multicast source 3 is used for sending a multicast data packet to the group member 2 through an intermediate router; and the group member 2 is used for acquiring the multicast data packet. The method makes that the security multicast technology can be used for actual multicast application become possible, improves the security of multicast communication, separates functions of the GCKS and the router, and can well avoid the problem of single point of failure to improve the multicast management efficiency obviously.
Owner:XIDIAN UNIV
A distributed authorization management method in the context of the Internet of Things
ActiveCN109088857ASolve the single point of failure problemUser identity/authority verificationBlockchainAuthorization
The invention discloses a distributed authorization management method under the scene of the internet of things, which adopts the block chain technology to realize the distributed right granting process. Taking advantage of the immutability of block chains, to implement resource authorization information, public audit of important information such as authorization and power transfer information, In addition, there are many users in Internet of Things applications, resource device high accessfeature, to free the device owner from the authorization process, the function of proxy authorization and revoking proxy authorization is designed, the addition of these two features is more in line with the usage scenario of the Internet of Things application, The invention adopts the block chain technology to realize the authorization of the resource service, thoroughly solves the problem of single point failure, and all the information stored on the block chain is open and transparent, the authority transfer process is recorded on the block chain, and all links of the authorization are supervised and controlled by the whole network node.
Owner:NO 15 INST OF CHINA ELECTRONICS TECH GRP +1
Resource sharing method for operation business actively participating peer-to-peer network
ActiveCN101753567AReduce trafficImprove node transmission performanceData switching networksSpecial data processing applicationsExtensibilityExclusive or
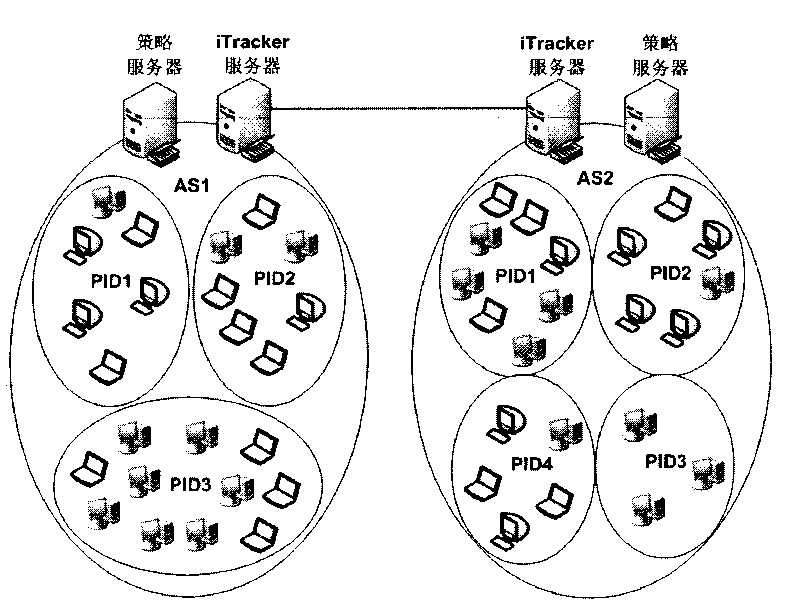
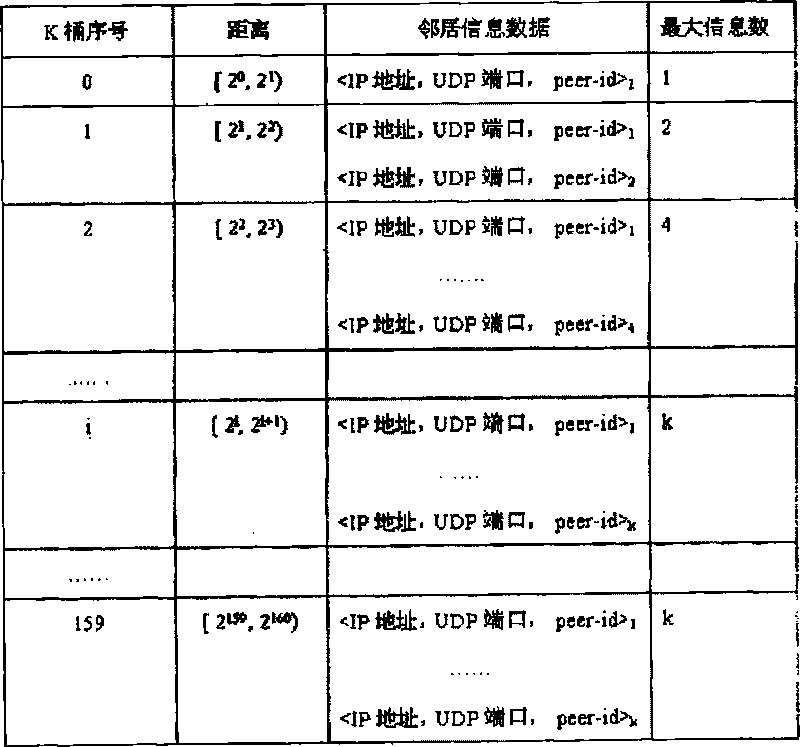
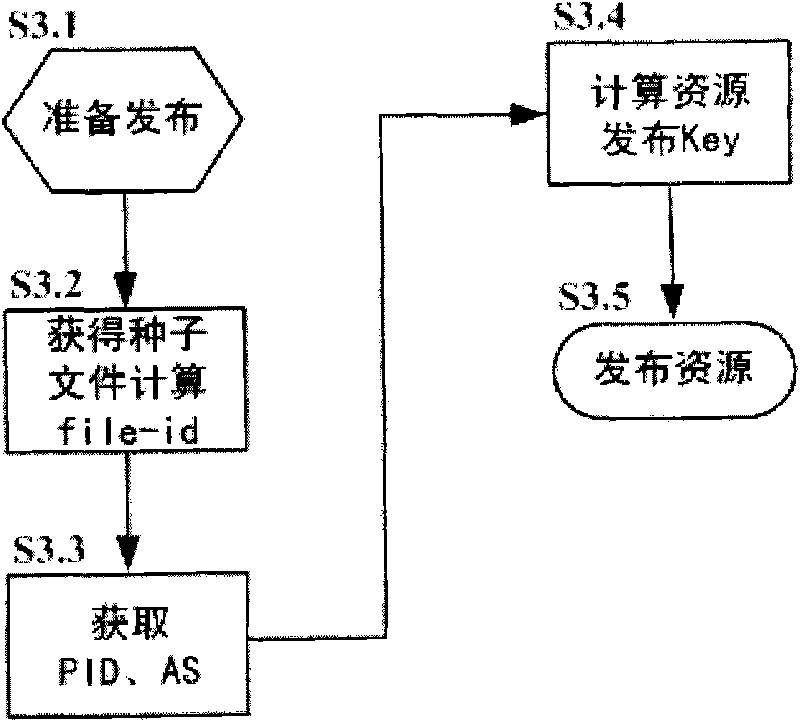
The invention provides a resource publishing method for a P4P network, which comprises the following steps of firstly, obtaining a Key value issued by a resource file at the time by an issue node according to a subordinate PID domain, a subordinate AS domain and a file-id of the issued resource file; secondly, calculating the Key value and an exclusive OR distance of peer-id of the issue node; and thirdly, finding out equivalence nodes of k nearest exclusive OR distances by the issue node as index nodes, and sending an issue message of the resource file to the index nodes by the issue node. The invention also provides a corresponding resource searching method and a strategy matrix updating method. The invention avoids the problem of single point invalidation, has the advantages of high flexibility and favorable extendibility and also avoids the bottleneck problem caused by repeatedly issuing a hot spot resource to the same position.
Owner:INST OF COMPUTING TECH CHINESE ACAD OF SCI
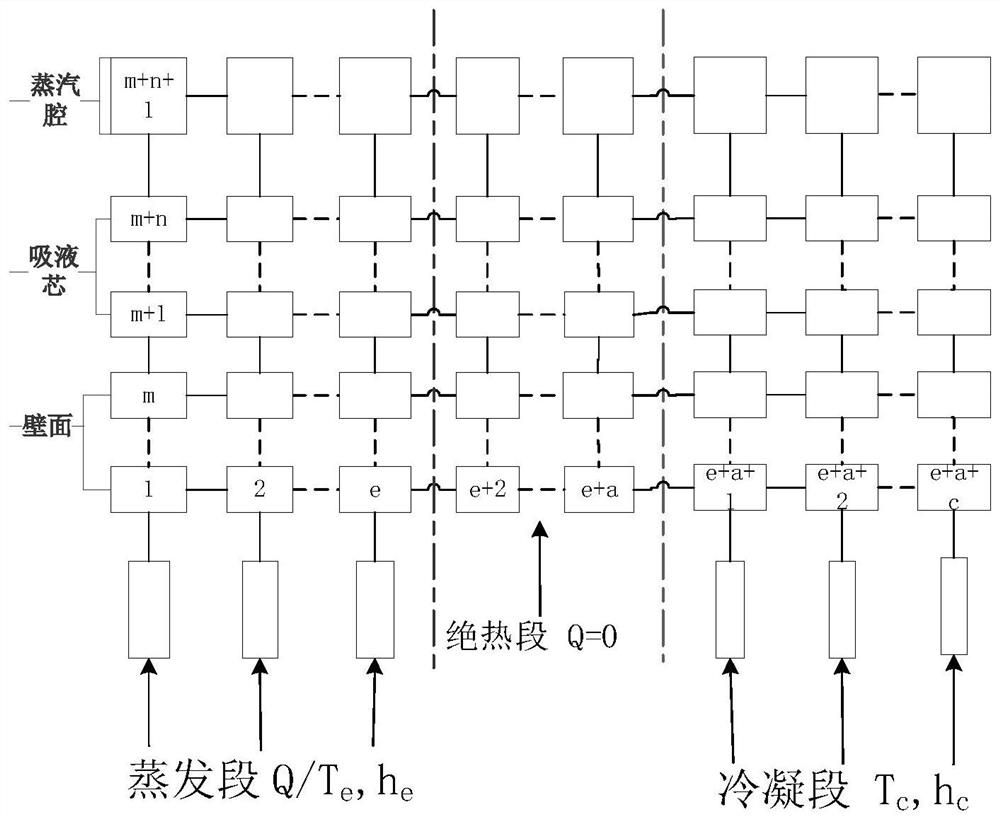
Heat transfer characteristic analysis method for heat pipe in nuclear power system
ActiveCN113434988AExcellent heat pipe parametersSolve the single point of failure problemGeometric CADNuclear energy generationEngineeringMechanical engineering
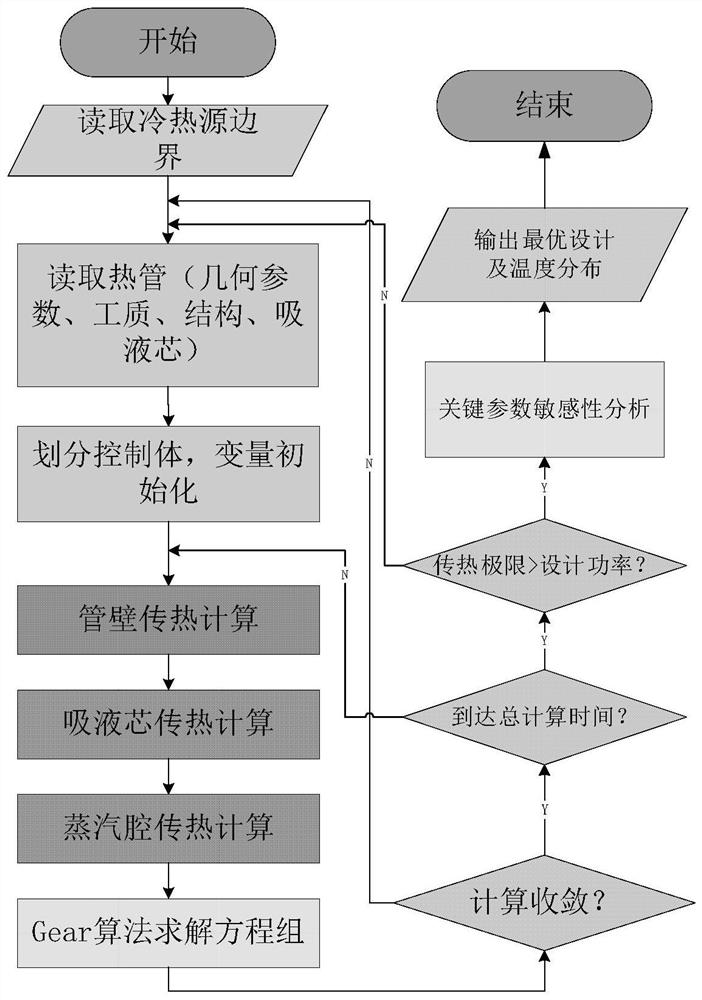
A heat transfer characteristic analysis method for a heat pipe in a nuclear power system mainly comprises the following steps that 1, inputting a heat source of the heat pipe, the working condition of a heat trap, a working medium, a structure and geometric parameters, and setting calculation time; 2, dividing the heat pipe into control bodies and carrying out initialized calculation; 3, calculating the change rate of the temperature of the pipe wall control body along with time, and considering the axial heat transfer and boundary conditions of the heat pipe; 4, calculating the change rate of the temperature of the control body in the wick along with time, ignoring convective heat transfer caused by liquid flow, and regarding the change rate as pure heat conduction; 5, calculating the change rate of the temperature of the control body in the steam cavity along with time, and simplifying continuous steam flowing into thermal resistance heat conduction; 6, solving the equation set by using a Gear algorithm, and completing calculation of all time points; 7, checking the heat transfer limit of the heat pipe and calculating equivalent thermal resistance; 8, comparing and analyzing the influence of the heat pipe key parameters on the heat transfer performance. Transient calculation and heat transfer characteristic analysis are carried out on different heat pipes, and suggestions and guidance are provided for design of a high-performance heat pipe heat exchanger in a nuclear power system.
Owner:XI AN JIAOTONG UNIV
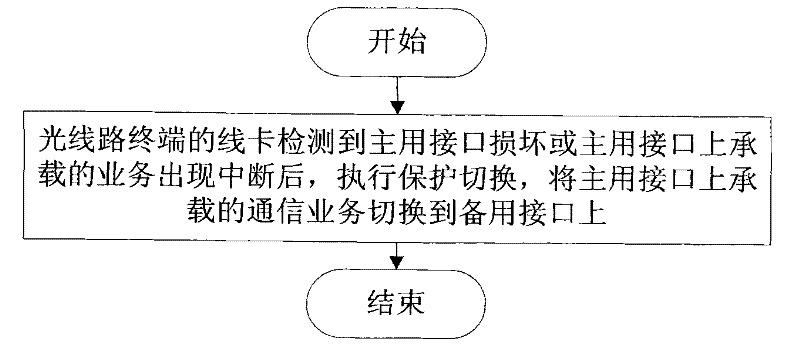
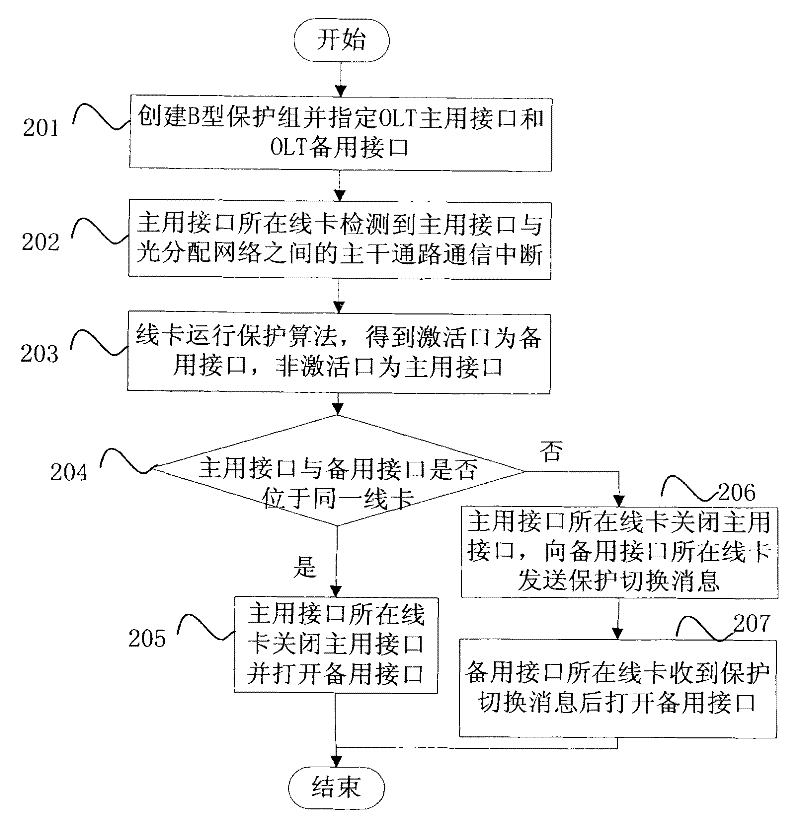
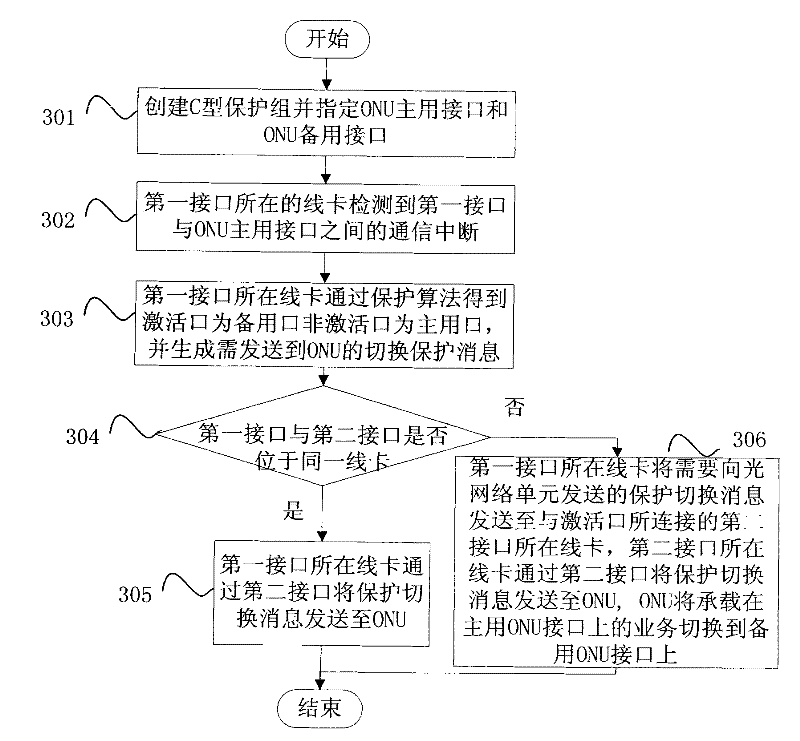
Method for realizing distributed protection and passive optical network (PON) system
ActiveCN102130717AEliminate protection switching time bottlenecksShorten recovery timeMultiplex system selection arrangementsTime-division multiplexSingle pointLine card
The invention provides a method for realizing distributed protection and a passive optical network (PON) system. The method comprises a step that: after detecting damage of a master interface or interruption of a service born on the master interface, a line card of an optical line terminal carries out protection switching to switch the communication service born on the master interface to a slave interface. According to the distributed protection method provided by the invention, a protection function of the PON is transferred to the line card from a main control switch board, and the line card performs detection alarming, operates a protection algorithm and carries out protection switching operation, so that the problem of single-point failure caused by using the unique main control switch board to realize PON protection in a centralized protection method is solved, a bottleneck for protection switching time in a centralized protection mode can be eliminated, recovery time for service protection is shortened, the service protection capacity of the optical line terminal is improved, and the requirement of an operator is further met.
Owner:ZTE CORP
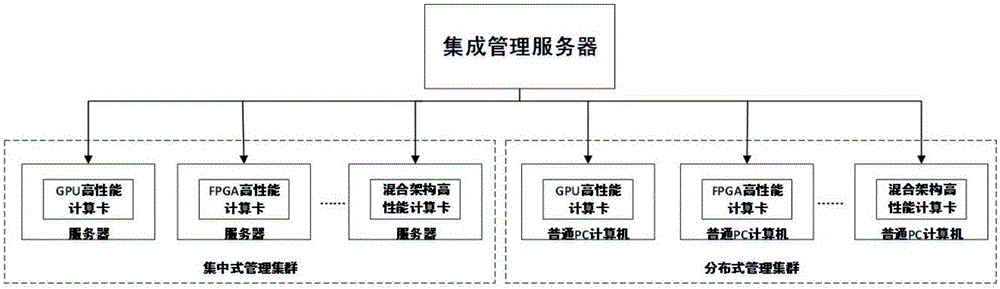
Distributed management framework based on extensible and high-performance computing and distributed management method thereof
PendingCN106803842AFlexible deploymentLow costTransmissionPerformance computingCentralized management
The invention discloses a distributed management framework based on extensible and high-performance computing and a distributed management method thereof. The distributed management framework is composed of an integrated management system, a centralized management system and a distributed management system. The integrated management system and the centralized management system are connected through a local area network. The integrated management system and the distributed management system are connected through the local area network. The centralized management system is mainly composed of multiple servers equipped with high-performance scientific computing cards. The servers manage all the scientific computing cards in a centralized way and perform unified computing. The distributed management system is composed of multiple common computers equipped with the high-performance scientific computing cards. The servers manage all the scientific computing cards in the centralized way and perform unified computing. The requirement for the single computing node and hardware is low by using distributed management so that various idle resources can be effectively utilized and the utilization rate of the common computers can be greatly enhanced.
Owner:江苏十月中宸科技有限公司
Wireless sensor network clone node identifying method based on physical channel information and credibility
ActiveCN105873085ASolve the single point of failure problemReduce overheadNetwork topologiesNetwork planningWireless sensor networkingComputer science
The invention discloses a wireless sensor network clone node identifying method based on physical channel information and credibility. The wireless sensor network clone node identifying method is used for solving the single-point invalidation problem of a clone node intensive type detecting scheme of a wireless sensor network; a witness node in a distribution type detecting scheme is not needed; the credibility is established by utilizing the physical channel information, and certain tolerance is achieved; while the clone node identifying complexity is reduced, a false alarm rate is further reduced, so that the clone node identifying precision is improved.
Owner:UNIV OF ELECTRONICS SCI & TECH OF CHINA
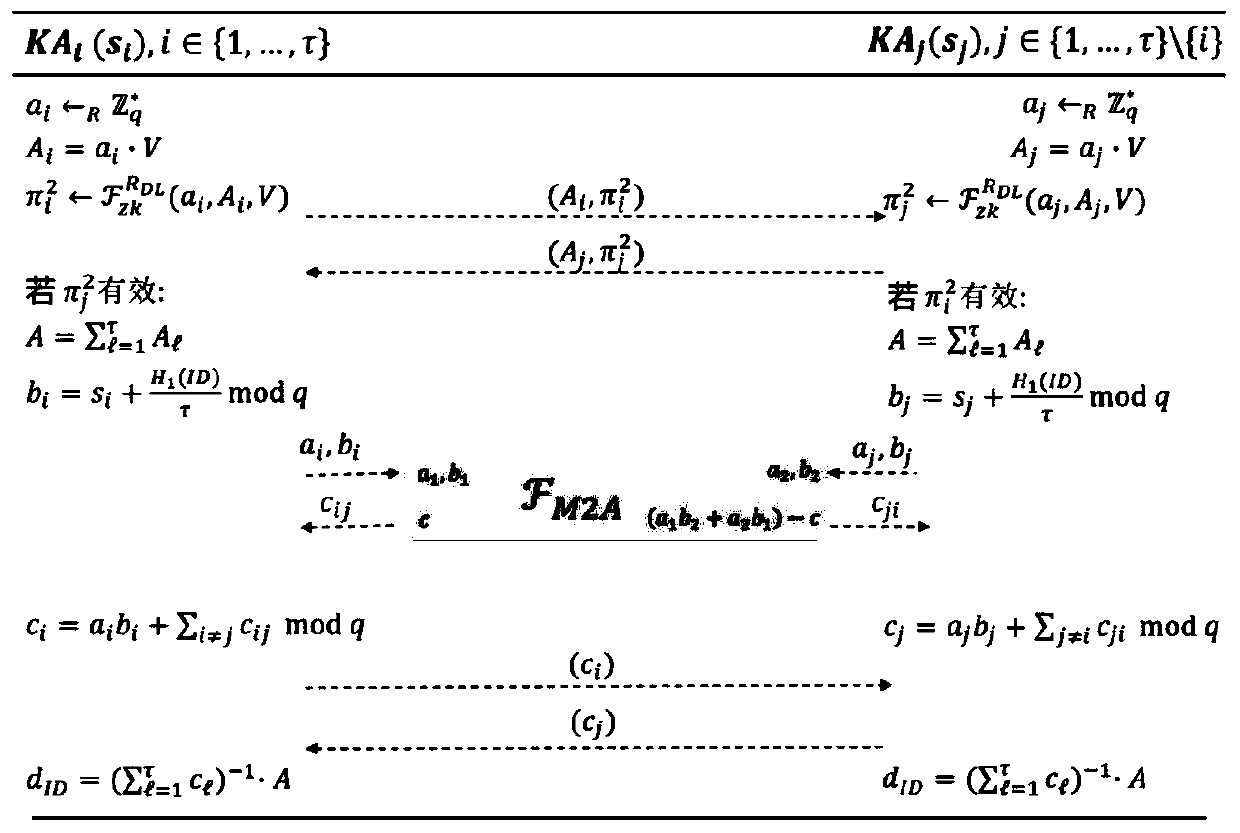
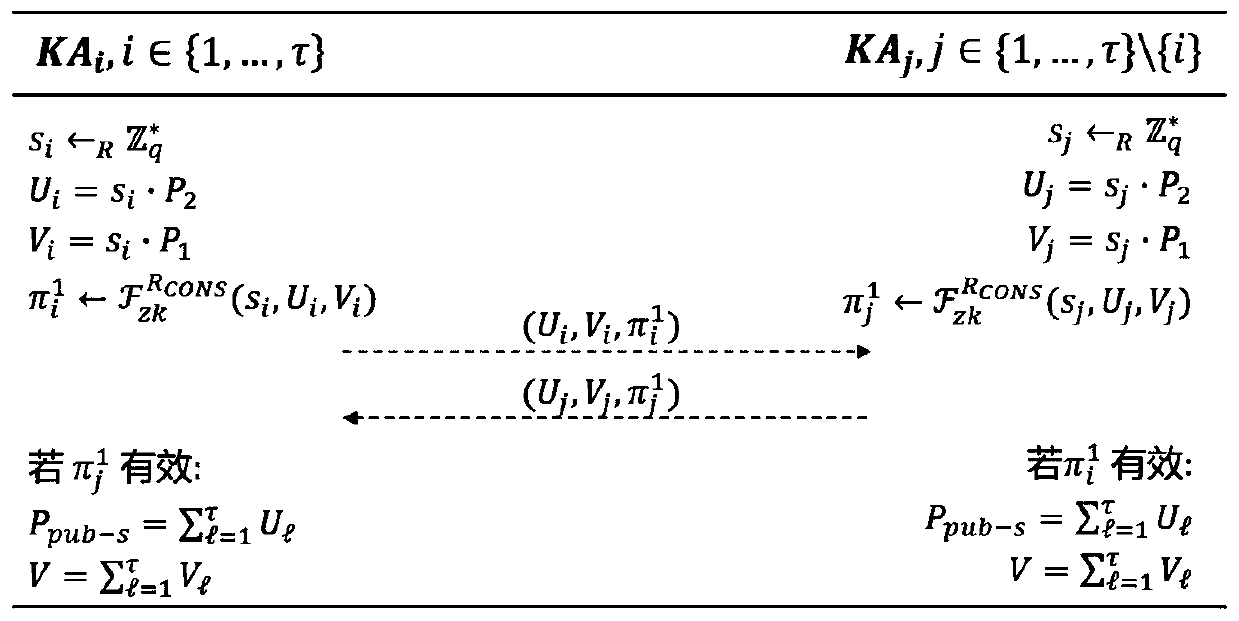
Safe and efficient SM9 multi-party key distribution method and device
ActiveCN109981269AImprove securitySolve the single point of failure problemKey distribution for secure communicationMultiple keys/algorithms usagePasswordKey distribution
The invention discloses a safe and efficient SM9 multi-party key distribution method and device. The method comprises the following steps: 1) jointly generating a system main public key by Tau participants; and 2) jointly generating a user private key by the Tau participants. According to the system, the main public key and the user private key are generated by the Tau participants in a combined mode, the system does not depend on a single KGC any more, the problem of single-point failure under a single KGC system is effectively avoided, the safety of SM9 key distribution is improved, the stability of a password system is enhanced, and the system has the advantages of being high in safety, high in efficiency and the like.
Owner:WUHAN UNIV
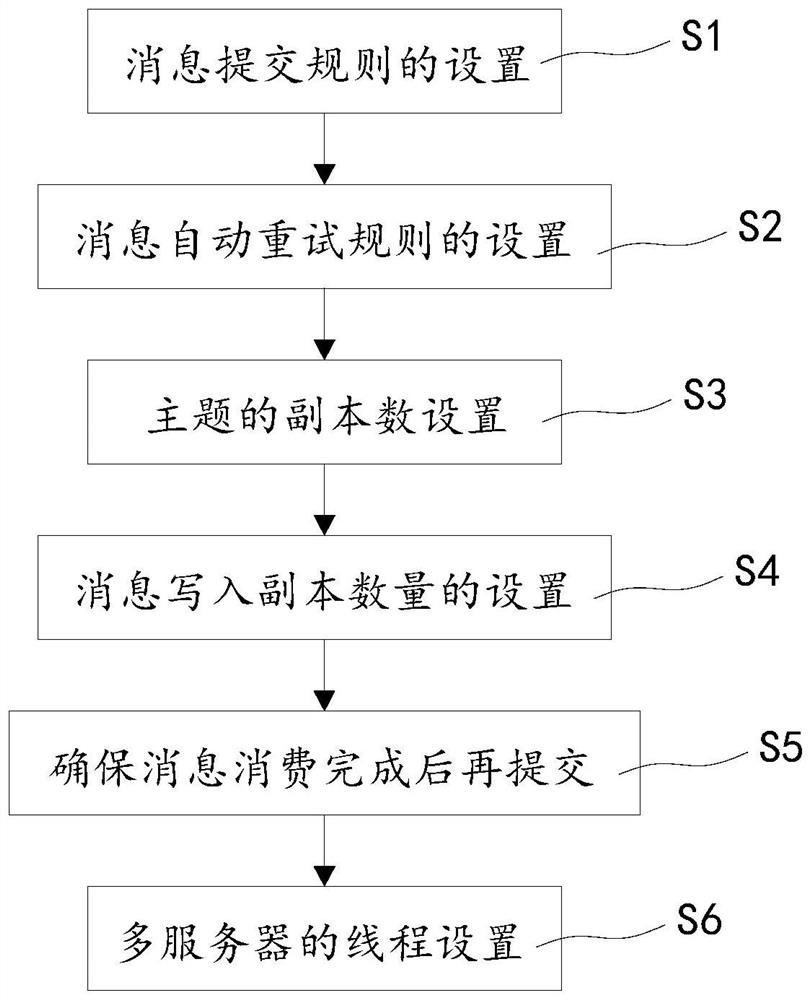
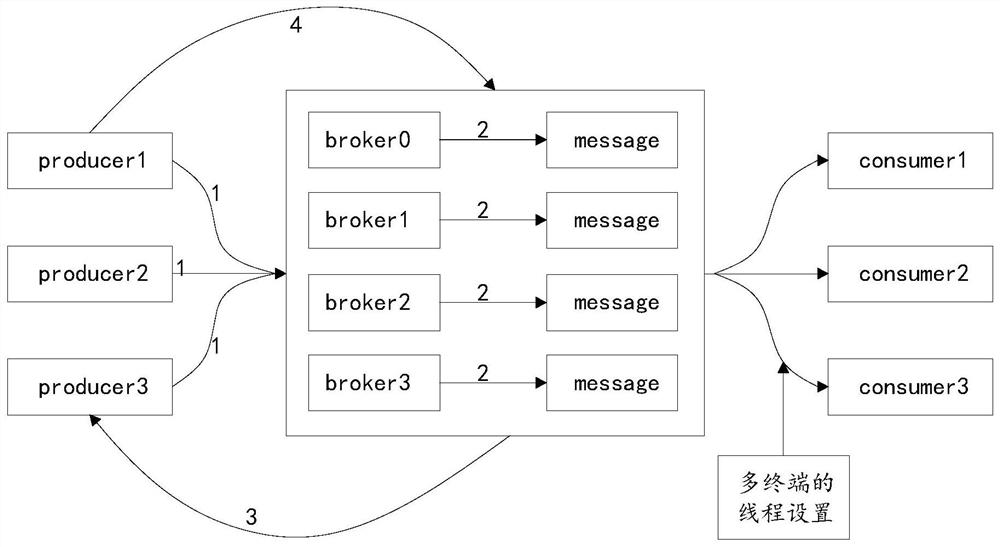
Production and consumption method based on kafka cluster
PendingCN111930538AAvoid lossEliminate volatilityInterprogram communicationRedundant hardware error correctionInformation processingData mining
The invention discloses a production and consumption method based on a kafka cluster, and relates to the technical field of information processing. The method comprises the following steps: S1, setting a message submission rule; S2, setting an automatic message retry rule; S3, setting the number of copies of the theme topic, and setting the number of copies of the theme topic to be greater than orequal to 3; S4, setting the number of message write-in copies, and ensuring that the number of copies of the topic is greater than the number of message write-in copies; S5, submitting the offset Offset after ensuring that the message consumption is finished; S6, setting threads of a plurality of servers. The method is characterized in that the partition number of multiple data topics is counted,the following formula is adopted for calculation: P / n = concurrence, P is the data of the total partition number, n is the number of servers, and concurrence is the number of threads; the method hasthe advantages that data fluctuation caused by instability of a single server is completely eradicated, and the problems of data consistency and single-point faults are solved.
Owner:银盛支付服务股份有限公司
CP-ABE access control scheme based on block chain
PendingCN111079191ASolve the single point of failure problemReduce workloadDigital data protectionTransmissionAttribute authorityAuthorization
The invention discloses a blockchain combined access control architecture based on attribute encryption. Aiming at attribute encryption based on a ciphertext strategy in a multi-authorization-center scene, the work of the authorization centers is executed by a block chain, a trust relationship between the attribute authorization centers is constructed by utilizing an intelligent contract, a key management mechanism is established, and attribute authorization, key management and attribute revocation are completed by the intelligent contract. According to the scheme, the access control process based on attribute encryption is public, transparent, more flexible and safer.
Owner:INNER MONGOLIA UNIVERSITY
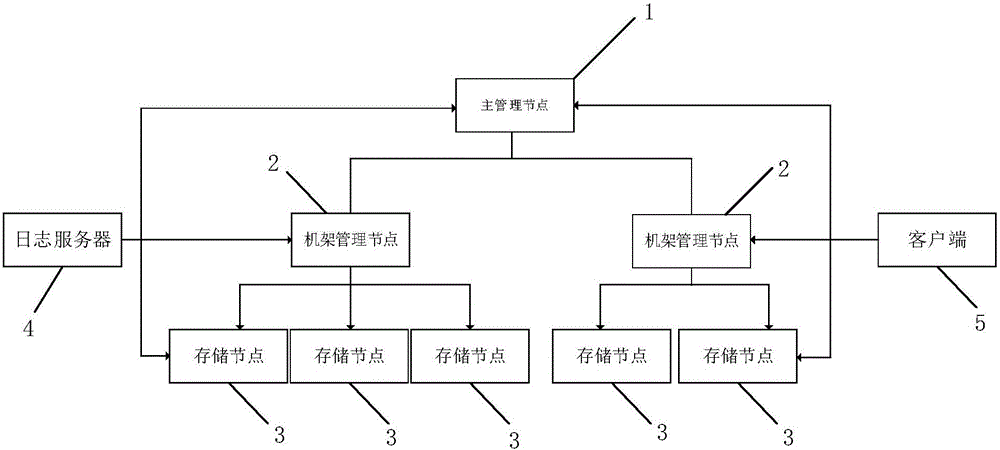
Distributed file system for cloud rendering, and construction and access methods
InactiveCN106170012AQuick operationSolve the single point of failure problemTransmissionTree shapedSingle point
The invention relates to a distributed file system for cloud rendering, and construction and access methods. The system comprises one main management node (1), multiple frame management nodes (2) and storage nodes (3), wherein the multiple frame management nodes (2) are connected with the main management node (1), each frame management node (2) is connected with the multiple storage nodes (3), the main management node (1), the frame management nodes (2) and client (5) nodes form a tree-shaped structure, the storage nodes (3) store corresponding file data blocks, the frame management nodes (2) store meta-data information of the file data blocks stored by the storage nodes (3) connected therewith, and the main management node (2) stores meta-data information of a whole file system. Compared to the prior art, the file system provided by the invention solves the problem of single-point failure and is high in stability.
Owner:SHANGHAI SHANGDA HAIRUN INFORMATION SYST +1
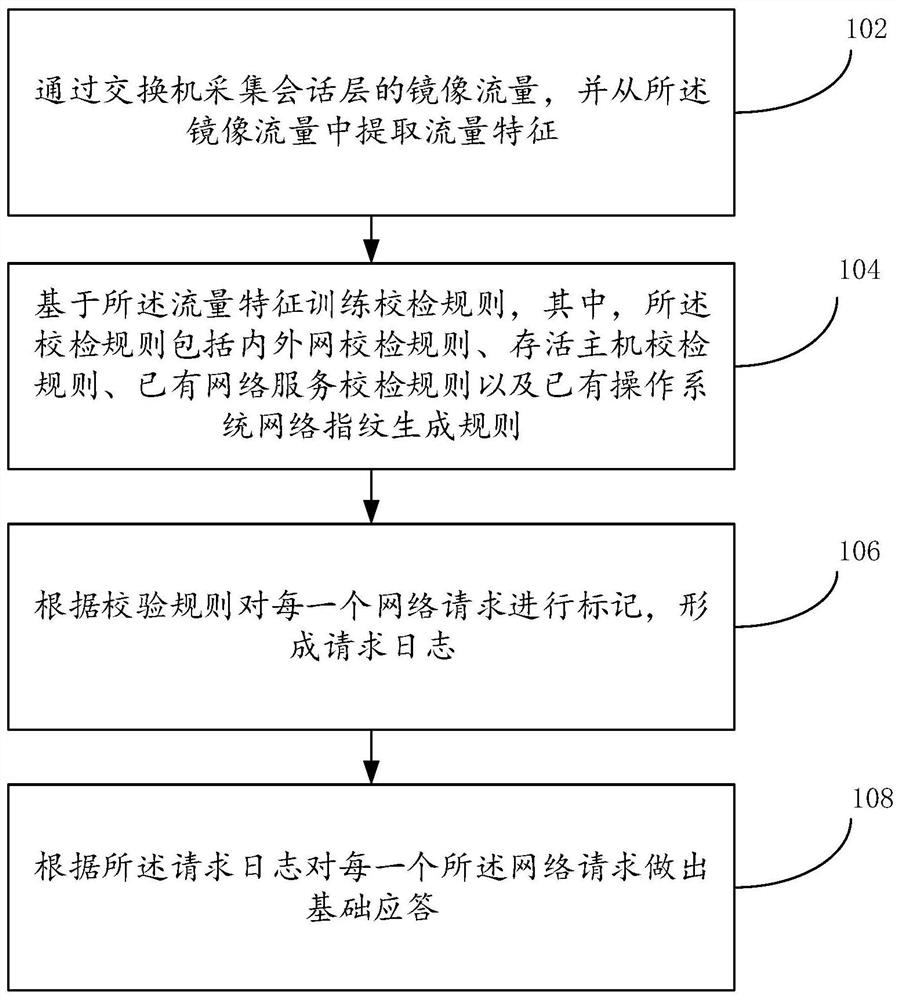
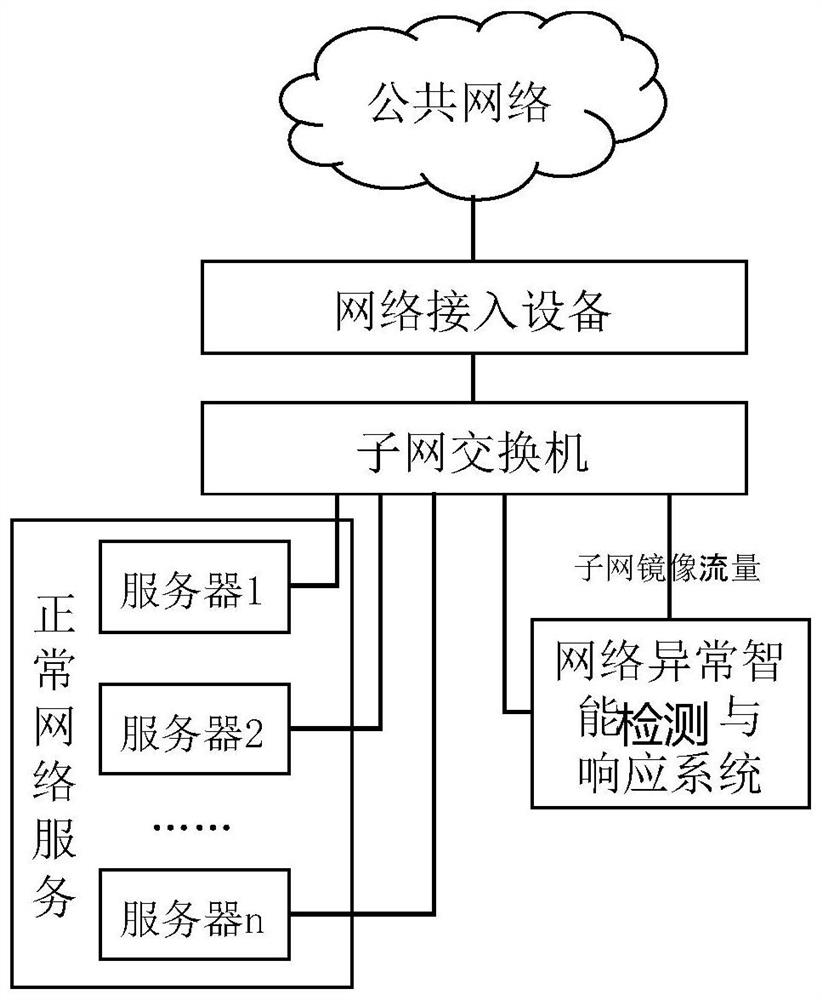
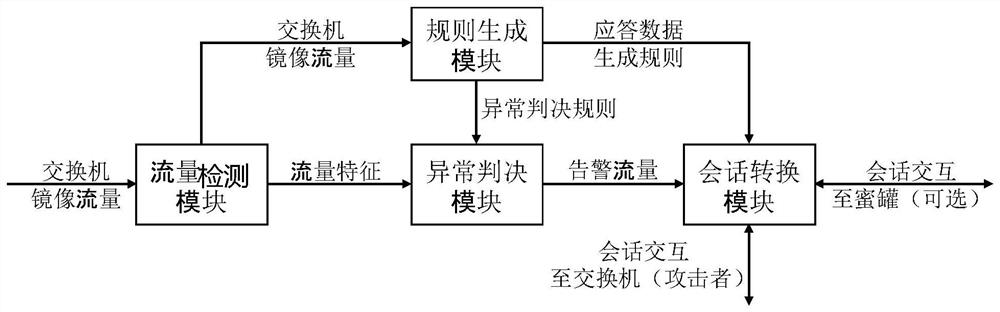
Network abnormal behavior intelligent detection and response method and device and electronic equipment
PendingCN113765846AImprove Convenience and AccuracyQuick responseTransmissionHigh level techniquesEngineeringTraffic characteristic
The embodiment of the invention provides a network abnormal behavior intelligent detection and response method and device and electronic equipment, and the method comprises the steps of collecting the mirror traffic of a session layer through a switch, and extracting a traffic feature from the mirror traffic; training verification rules based on the traffic characteristics, the verification rules including an internal and external network verification rule, a survival host verification rule, an existing network service verification rule and an existing operating system network fingerprint generation rule; marking each network request according to the verification rule to form a request log; and making a basic response to each network request according to the request log. According to the embodiment of the invention, a bypass network data detection method is adopted to realize network spoofing defense, network should be realized in a session layer, and the network defense efficiency is improved.
Owner:极客信安(北京)科技有限公司
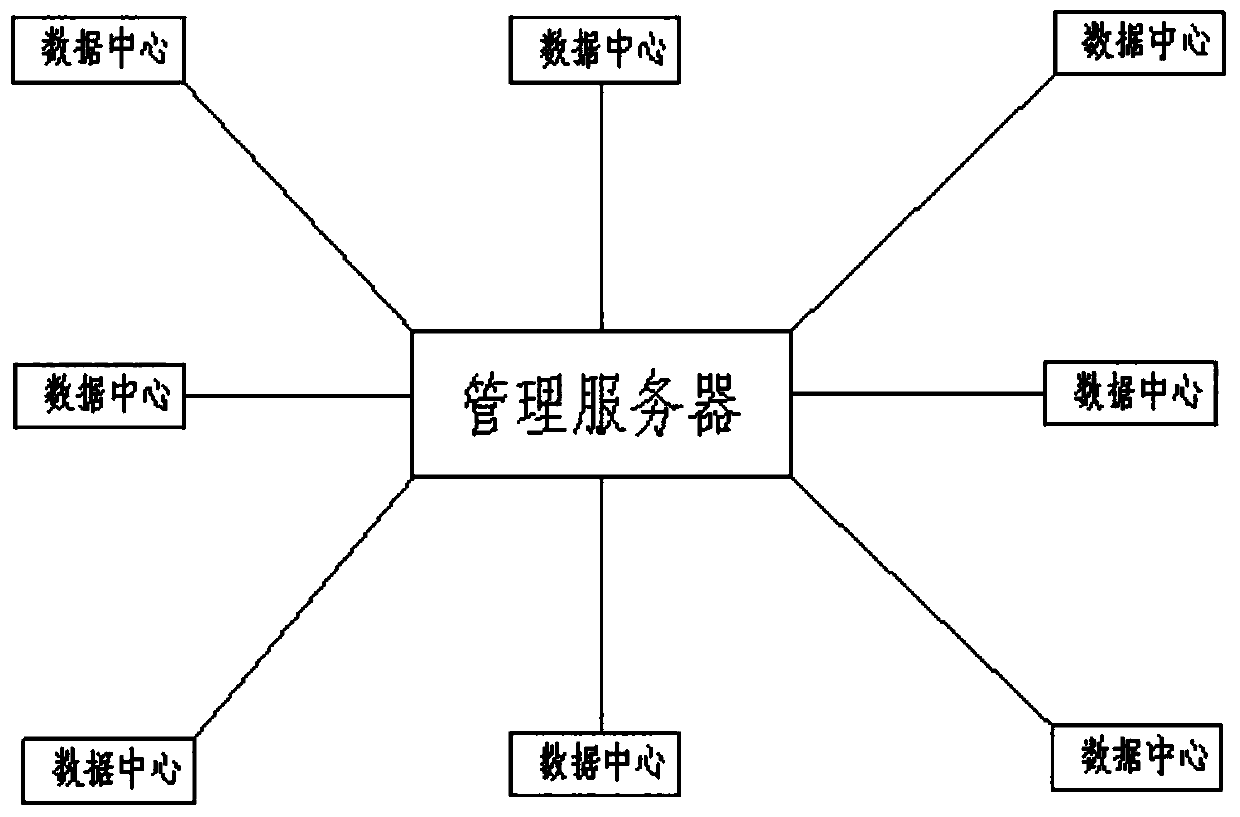
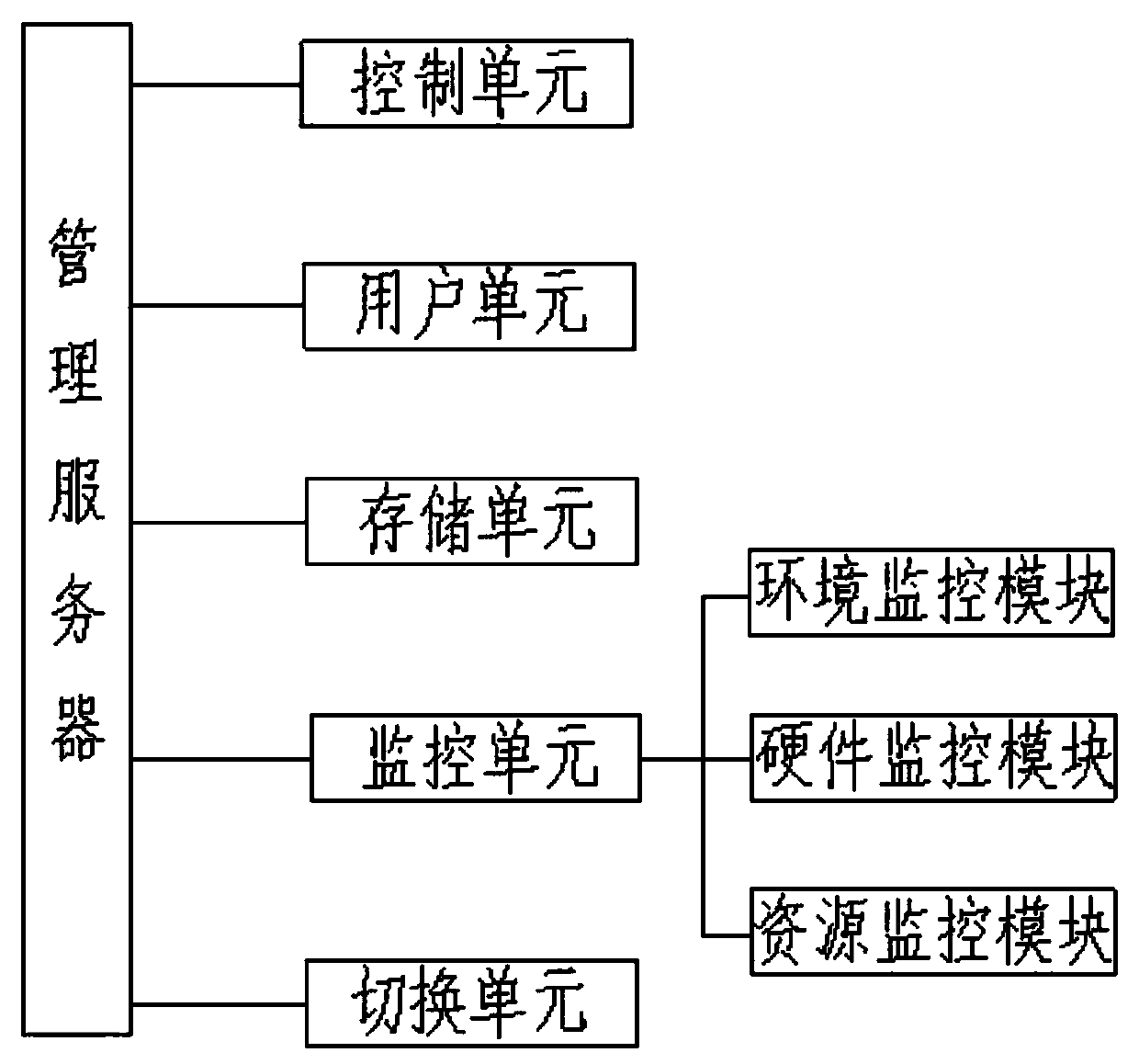
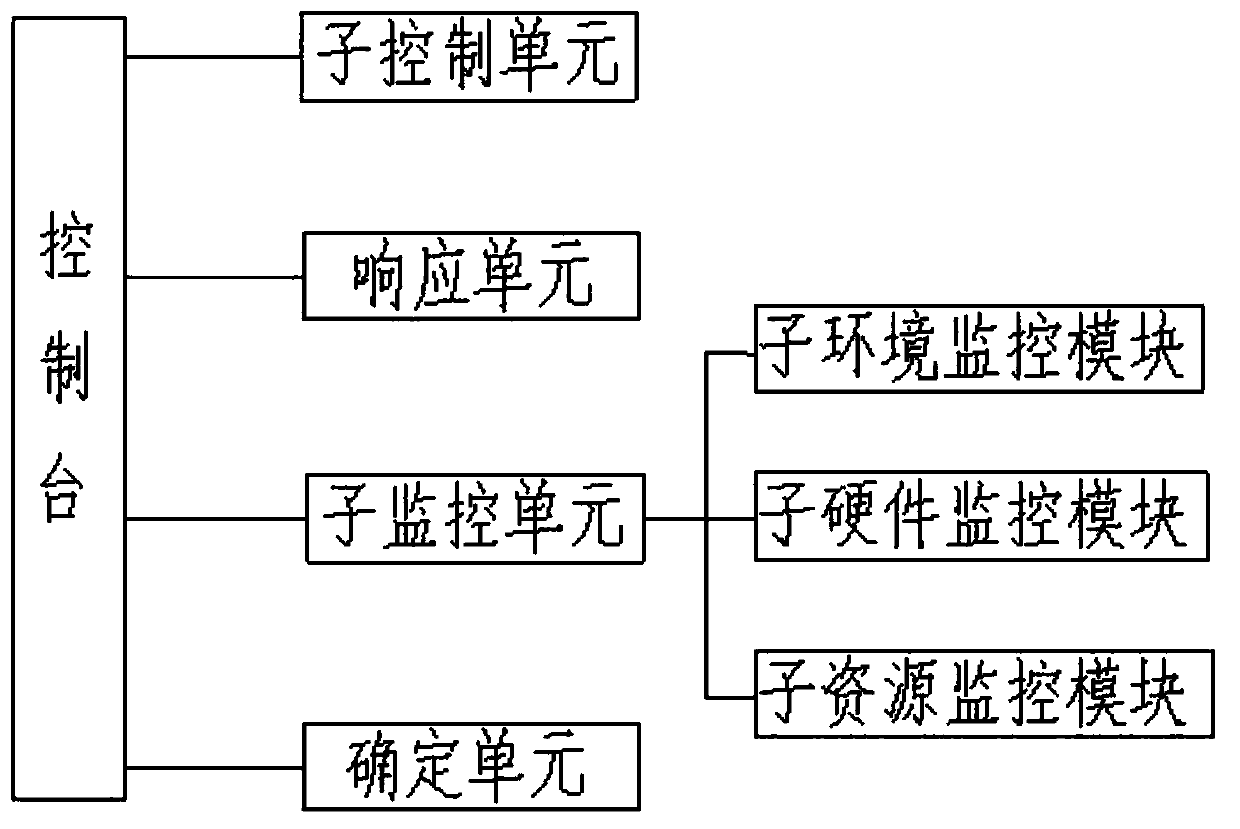
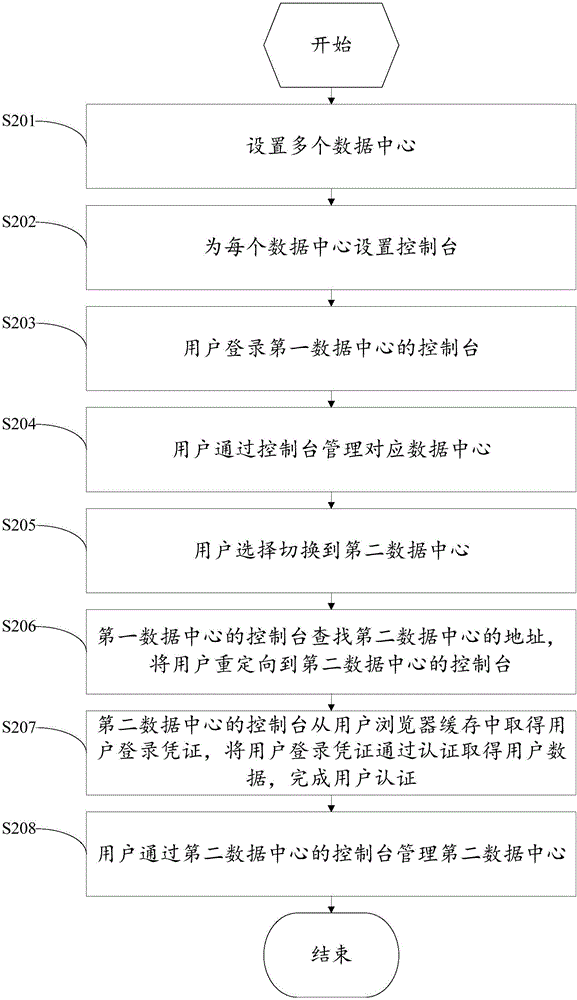
Multi-data-center online management system and management method based on Internet of Things
InactiveCN110798362AUtilization AveragingMaximize UtilizationStar/tree networksThe InternetData transmission
The invention discloses a multi-data-center online management system and method based on the Internet of Things. The online management system comprises a plurality of data centers arranged in a distributed mode, a network and a management server. Each data center is provided with a console, and a console is responsible for monitoring the environment and hardware of the corresponding data center and monitoring the resource utilization condition of each data center. The network is a data transmission medium of each data center and the management server. The management server manages a pluralityof data centers connected with the management server, monitors the environment, hardware and resource utilization conditions of the data centers, and coordinates the workload of each data center. According to the invention, each data center is provided with an independent console for management, so that the single-point fault problem and the performance bottleneck problem of the console are solved. The management server allocates the data centers for login and access according to the resource utilization rate condition in each data, the workload of each data center is coordinated, the load ofthe data centers is equalized, and the utilization rate is maximized.
Owner:HENAN VOCATIONAL COLLEGE OF WATER CONSERVANCY ANDENVIRONMENT
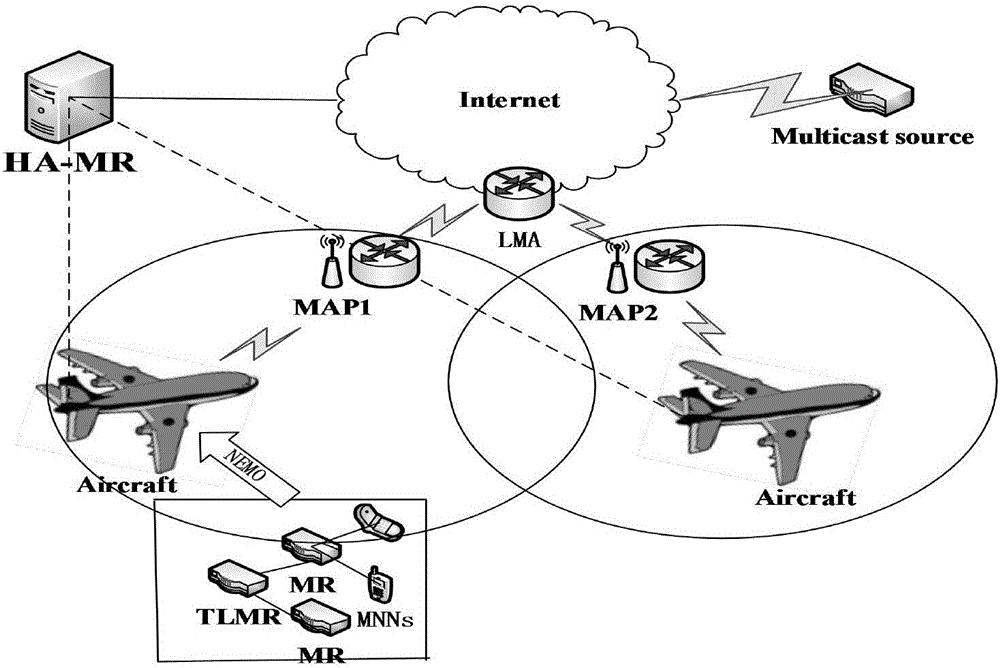
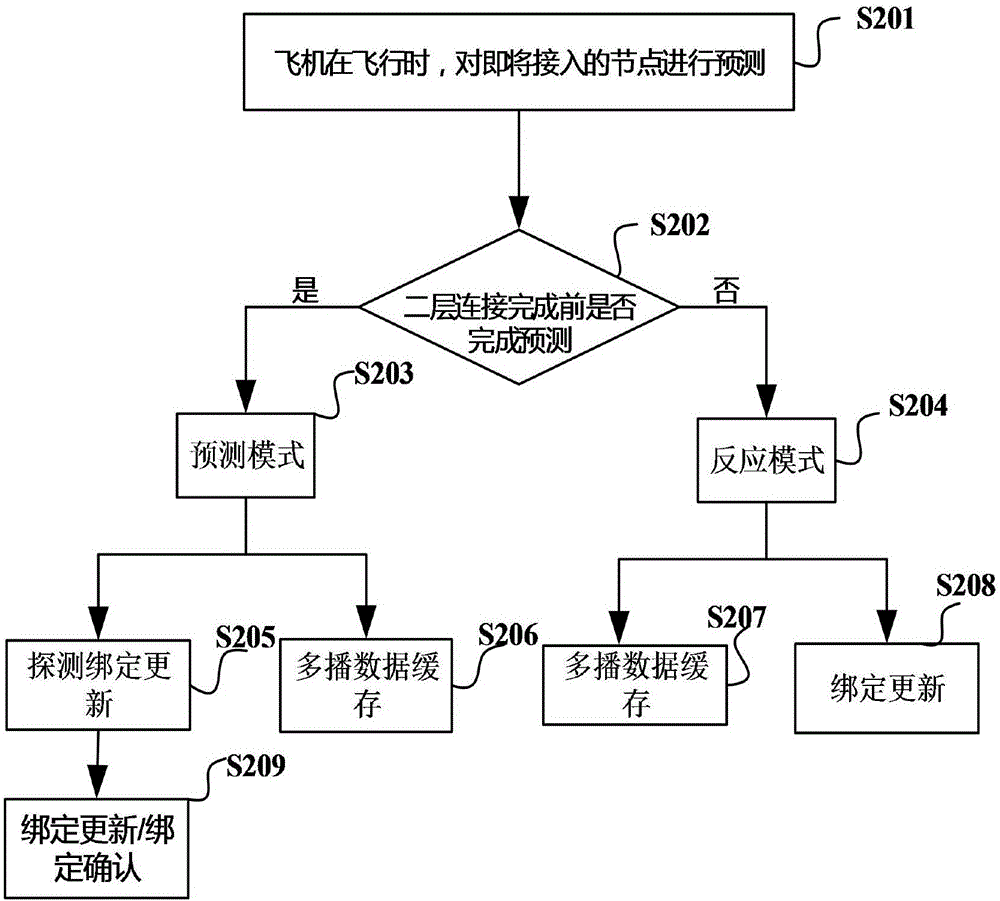
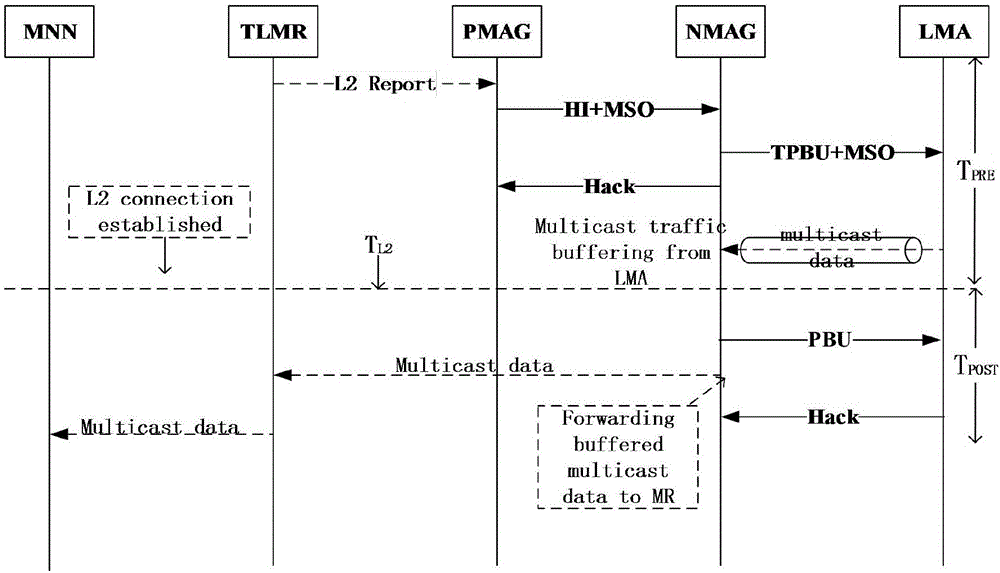
Seamless handoff mechanism for multicast service in aviation communication NEMO network
InactiveCN106792518ATroubleshoot service outagesReduce switching delayWireless commuication servicesLocation information based serviceAviationData stream
The invention discloses a seamless handoff mechanism for multicast service in an aviation communication NEMO (Network Mobility) network. In view of fixity of a flight path of an aircraft, before the aircraft accesses a next foreign domain anchor, a handoff request is sent to the anchor; a multicast agent is added to a multicast group of an aircraft node in advance, breaking of a multicast data flow during a handoff process is avoided, and seamless handoff of the aircraft node is ensured; and the handoff state of the aircraft is judged, the next to-be-accessed anchor is predicted, and a predicted handoff mechanism is carried out in advance, or otherwise, if the predicted mode fails, a handoff mechanism in a reaction mode is carried out. multicast service handoff is carried out on the aircraft node through the mentioned seamless handoff mechanism, the mobile node multicast flow continuity and the message transmission reliability are ensured, the handoff delay is reduced, the tunnel pressure is avoided, and the aviation communication process reliability is improved.
Owner:BEIJING UNIV OF POSTS & TELECOMM
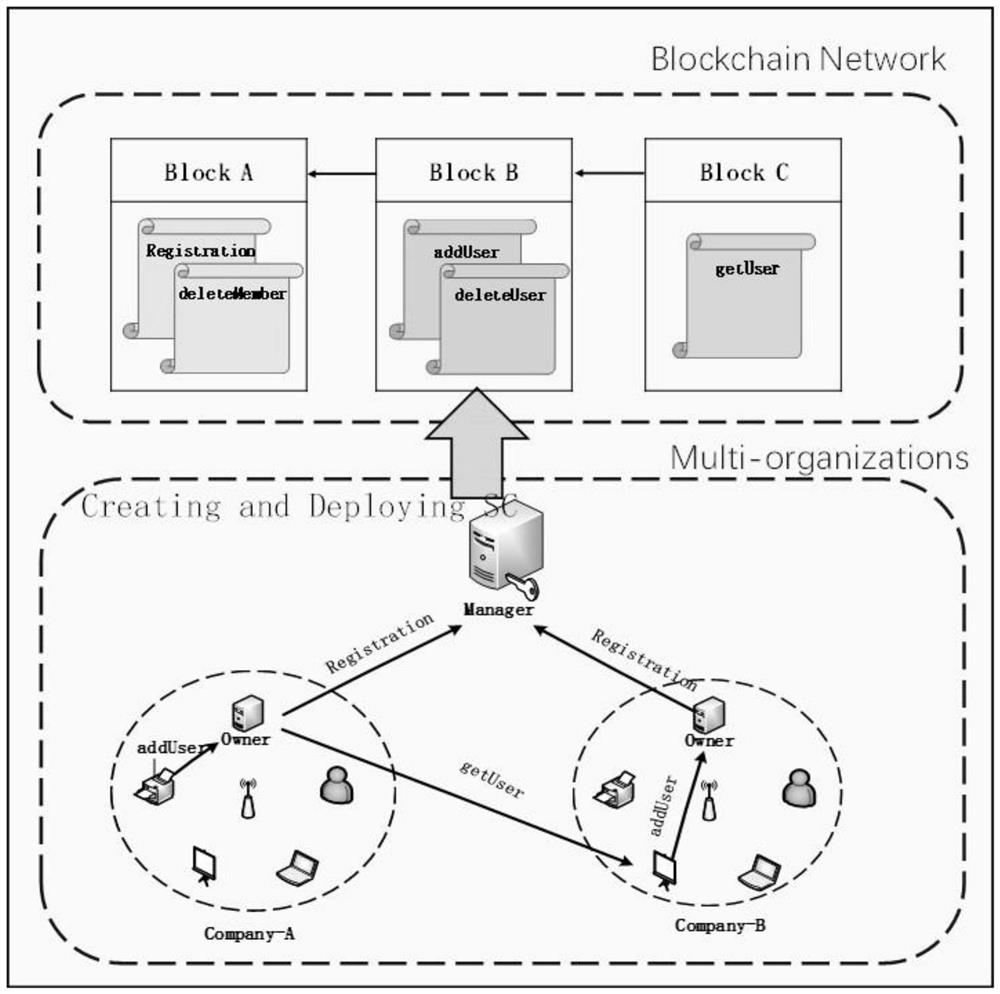
Cross-multi-organization user information access control method and device and medium
ActiveCN112329058ASolve the single point of failure problemImprove access efficiencyDatabase updatingDatabase distribution/replicationInternet privacyEngineering
The invention discloses a cross-multi-organization user information access control method and device and a medium, belongs to the technical field of Internet-of-Things access control, and aims to solve the technical problem of how to realize safe, decentralized and trustless inter-multi-organization user information access. The method comprises the following steps: initializing alliance administrator nodes; deploying the smart contract configured with the access control strategy in a blockchain network through an alliance administrator node; for each organization to join the alliance, selecting at least one server as an organization owner node of the organization, and registering each organization owner node in the blockchain network to obtain a unique account address; storing account addresses related to the organization owner nodes passing the verification into an alliance member list; enabling the organization owner node to share the user information in the organization to the blockchain network; and enabling the organization owner node to send an access request for accessing the user information in other organizations to the alliance administrator node, verifying the access request through the smart contract, and returning the corresponding user information to the organization owner node proposing the access request after the verification is passed.
Owner:QILU UNIV OF TECH
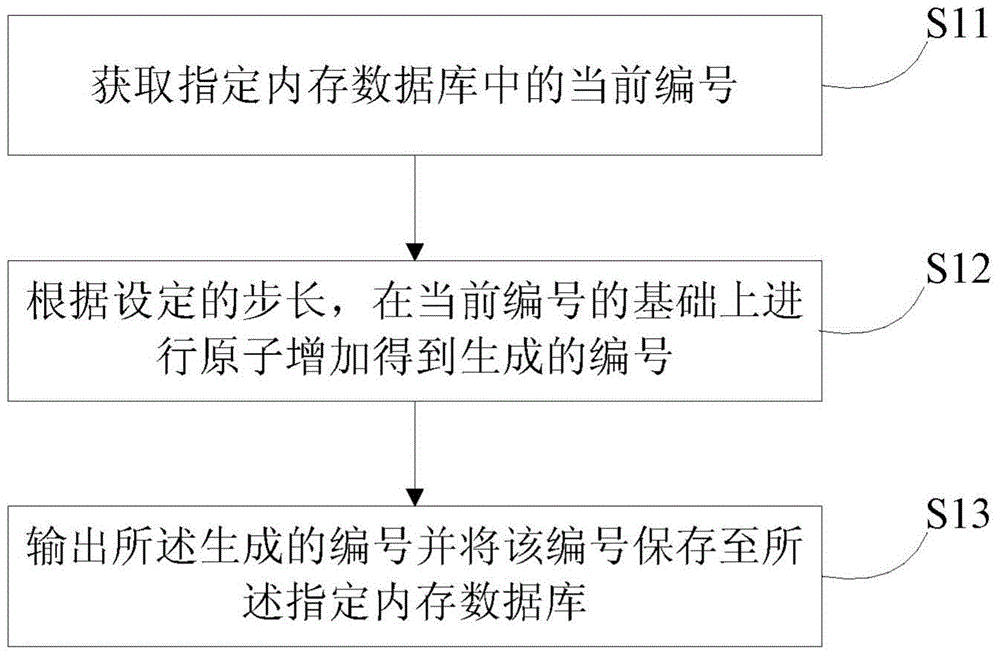
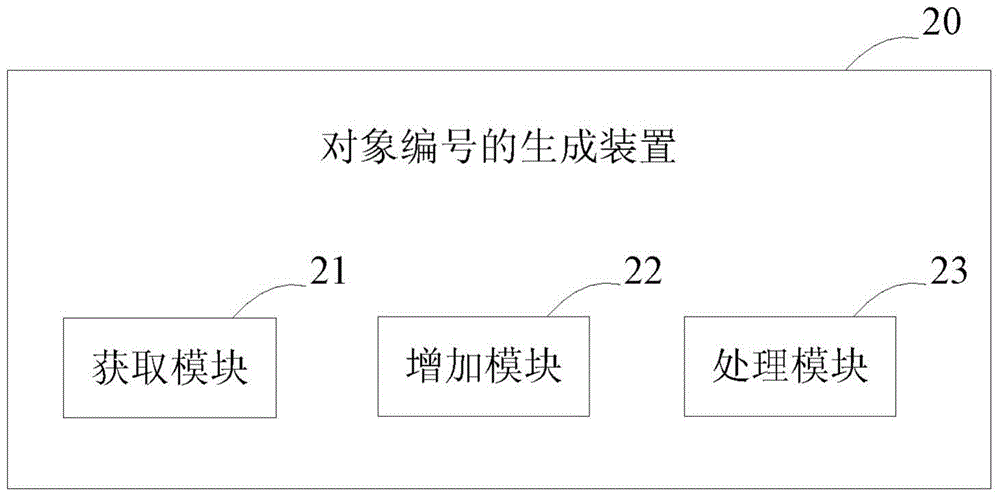
Object number generating method and device
InactiveCN104699779AImprove efficiencyImprove reliabilitySpecial data processing applicationsIn-memory databaseAlgorithm
The invention provides an object number generating method and an object number generating device. The object number generating method and the object number generating device, on the one hand, contribute to improving the discount coupon number generating efficiency and the reliability, and on the other hand, facilitate avoiding the problem of single point of failure. The object number generating method comprises the following steps: acquiring the current number in a designated memory database; regarding the memory database as a single-threaded memory database; according to the preset step length, performing atomic increase based on the current number to obtain the generated number; outputting the generated number and saving the number to the designated memory database.
Owner:BEIJING JINGDONG SHANGKE INFORMATION TECH CO LTD +1
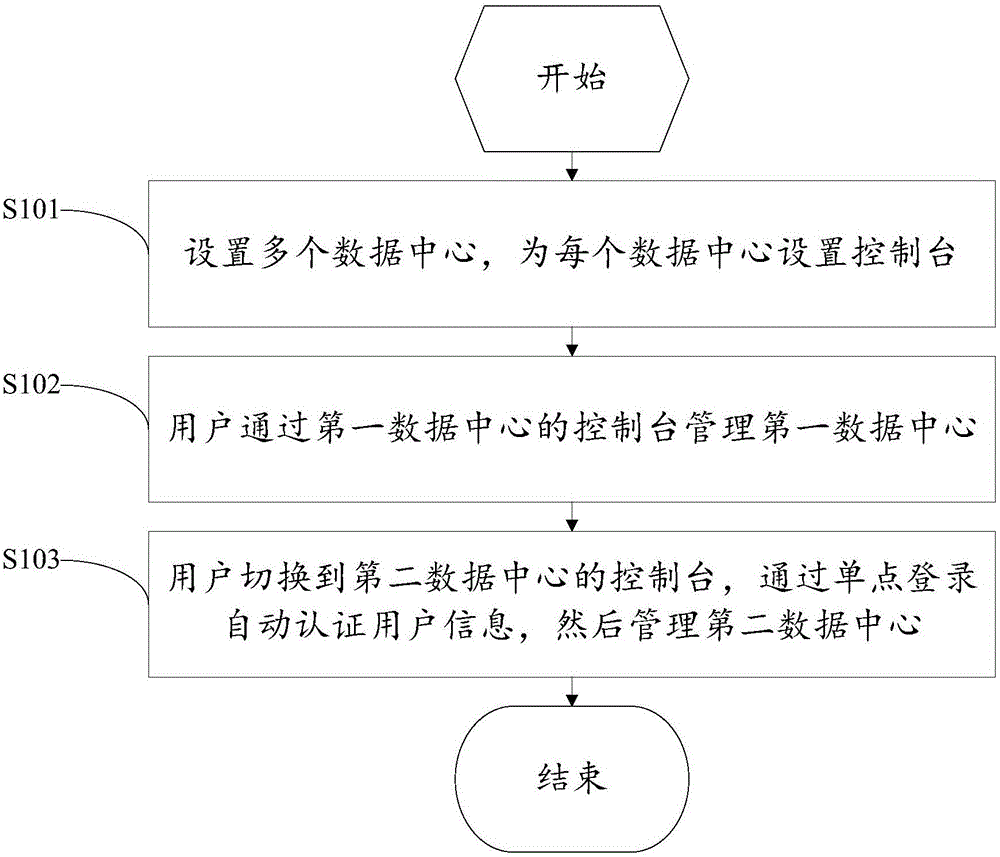
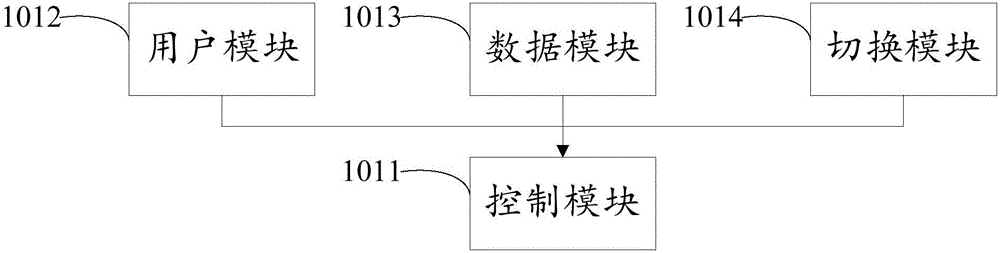
Multi-data center management method and system
InactiveCN106713356ASolve the single point of failure problemSolve performance bottlenecksTransmissionSingle point of failureComputer science
The present invention discloses a multi-data center management method and a system. The method comprises the following steps: setting multiple data centers, setting dashboard for each data center; the user using the dashboard of the first data center to manage the first data center; the user switching to the dashboard of the second data center, verifying user information automatically through single sign on, and managing the second data center. Each data center of the present invention is provided with an individual dashboard in charge of the management, which resolves the single point failure and performance bottleneck problems of the dashboard. The interaction of the dashboard and the data center service uses the intranet, which greatly improves the safety and avoids the huge cost of using special line.
Owner:CHINANETCENT TECH
Zero-trust network access system based on block chain
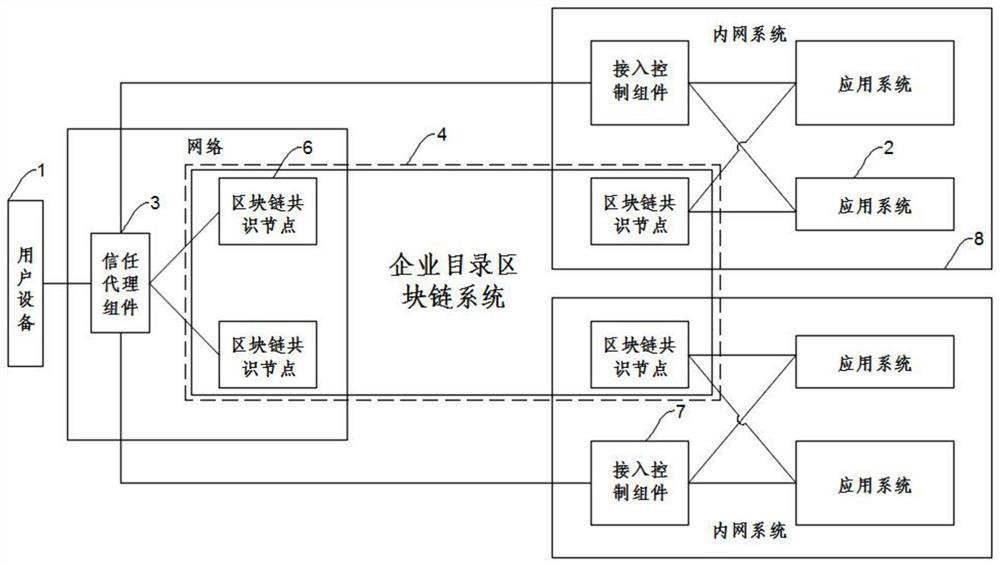
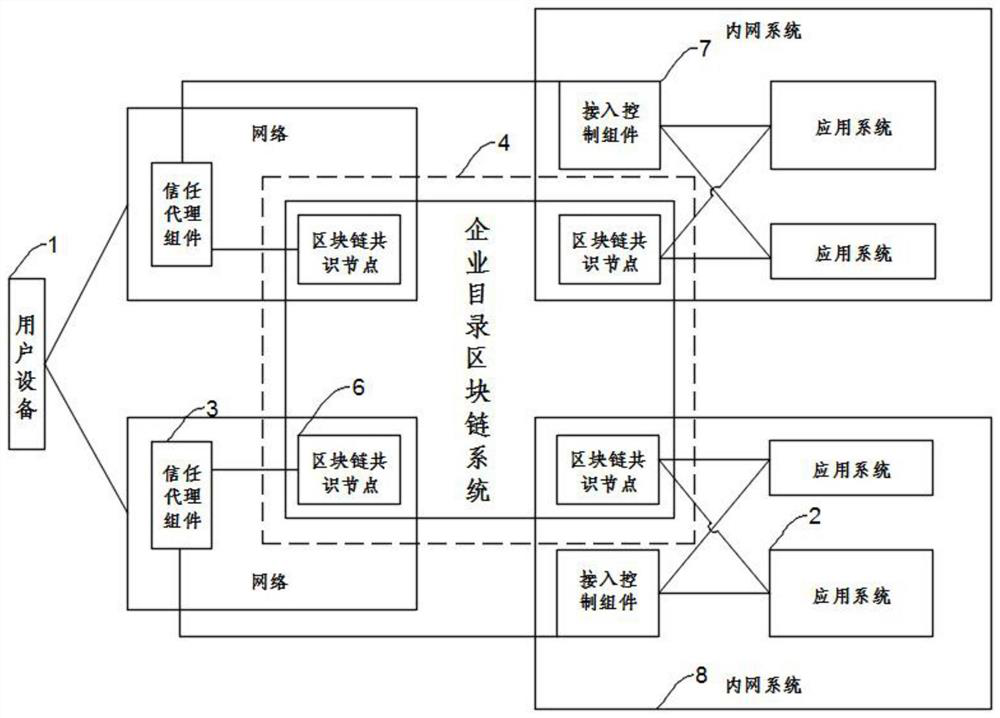
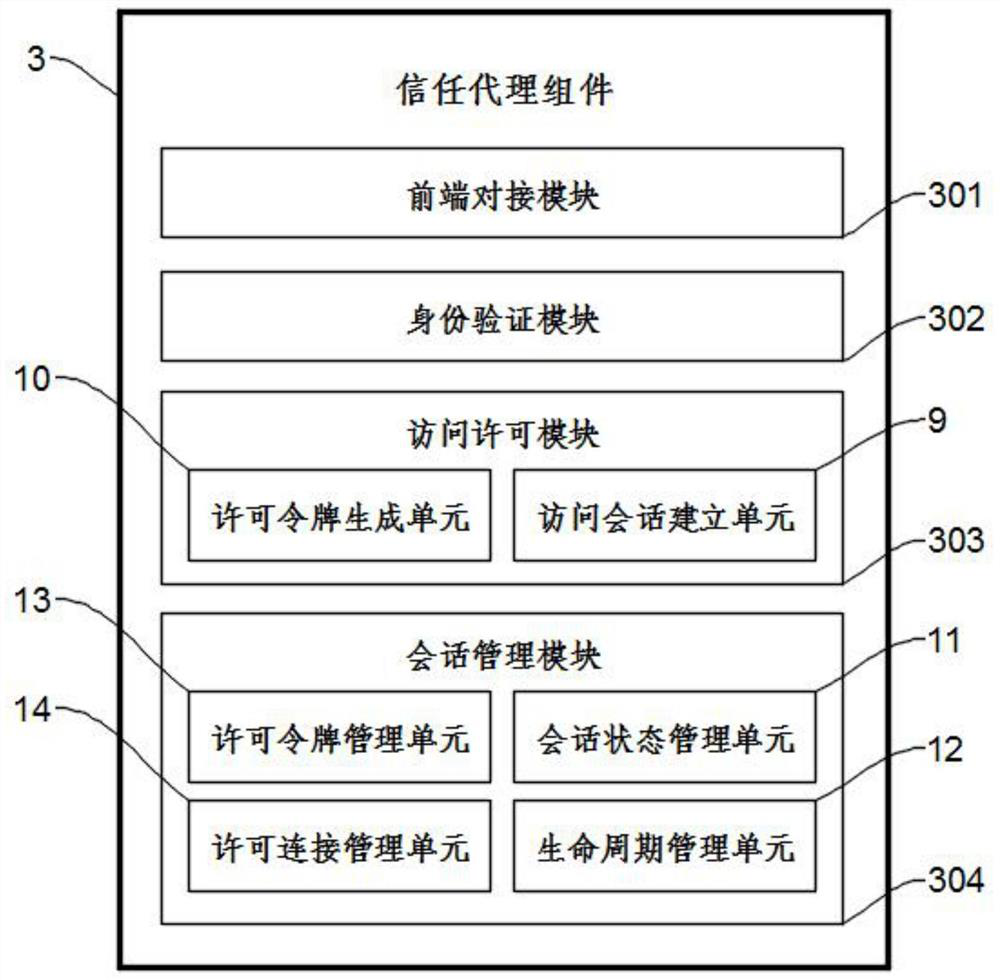
ActiveCN113051350AEnsure Security ConsistencySolve the single point of failure problemDatabase updatingDatabase distribution/replicationDirectoryData format
The invention discloses a zero-trust network access system based on a block chain, which is connected with user equipment and an application system requesting access. The system comprises a trust agent component; an access control component connected with the trust agent component, wherein one end of the access control component is connected with the trust agent component, and the other end is connected with an application system; and the access control component and the application system are arranged in a same network; an enterprise directory block chain system which is used for storing and distributing the key data accessed by the zero-trust network, and comprising a plurality of block chain consensus nodes, wherein the block chain consensus nodes are communicated with the trust agent component, the access control component and the application system. Compared with the prior art, the system has the advantages that the problem of single-point failure can be solved, the key data in network access can be timely and consistently shared and synchronously updated, the data formats and control rules are unified, and the safe and efficient integration is realized.
Owner:湖南链聚信息科技有限责任公司
Hybrid consensus method combining POW and POS
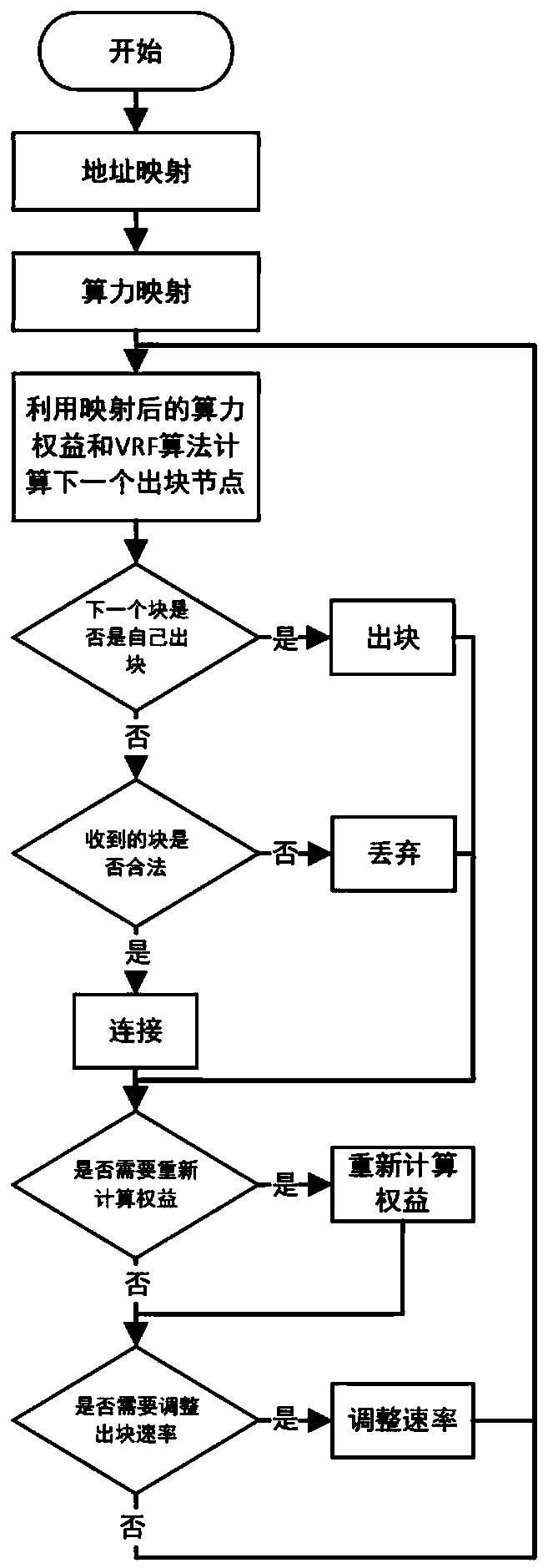
PendingCN111445241ACheating can'tSolve the single point of failure problemDatabase distribution/replicationPayment protocolsSafety propertyLogisim
The invention discloses a hybrid consensus method combining POW and POS. The consensus method comprises two block chains, a first chain adopts a POW consensus output block, a second chain adopts a POSconsensus output block based on historical data of the first chain and operates business logic, and the consensus process comprises three parts of address mapping, computing power mapping and competition output block. According to the method, the characteristics of high safety and addition without auditing of the POW algorithm are combined; the method also has the characteristics of short POS algorithm block output interval and less computing resource occupation, and can bear more business logics and provide quicker response service; on the premise of ensuring the security of the blockchain,the high efficiency of the blockchain can be ensured.
Owner:杭州泛链科技有限公司
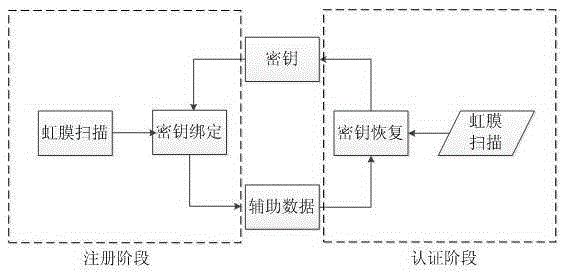
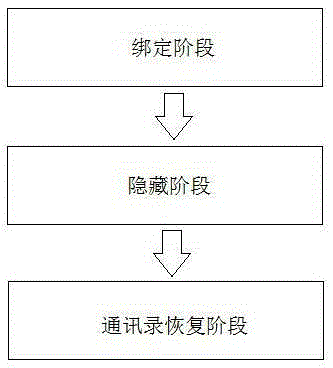
Anti-leakage cloud storage method of address list hidden in irises
The invention provides an anti-leakage cloud storage method of an address list hidden in irises. Directing at an address list in a mobile device, and combined with an iris identification technology and a cryptography data storage method, safe cloud storage of the address list is realized. The anti-leakage cloud storage method of the address list hidden in irises effectively solves the single-point failure problem and information leakage problem caused by single encryption of a file, and improves security and anti-leakage performance of cloud storage.
Owner:HUBEI UNIV OF TECH
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com