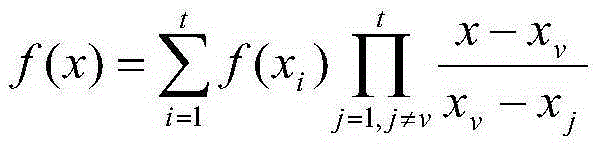Anti-leakage cloud storage method of address list hidden in irises
A cloud storage and address book technology, applied to electrical components, transmission systems, etc., to reduce the probability of data loss, protect user privacy, and achieve the effect of multi-cloud anti-leakage security storage
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0032] The following is a detailed description of the program process in conjunction with the accompanying drawings, mainly based on the embodiments of this program, and describes the core process of the program. Under the premise of no innovative work, all implementation steps of this program are carried out by those skilled in the art. scope of protection.
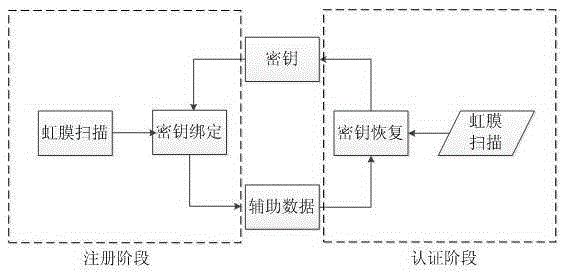
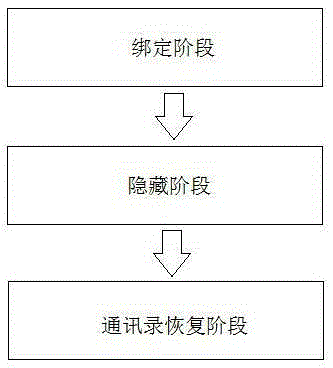
[0033] Such as figure 2 , Step 1: Binding stage, this step is used for the user to register when the plan is executed for the first time and for the user to update the address book during the use of the plan.
[0034] Step 1.1 collects the iris; this method uses the existing iris recognition technology to collect the iris. First, the iris of the user is scanned by using the camera of the mobile device to obtain an iris image P. The iris image P is normalized, positioned and enhanced to obtain the biometric feature C.
[0035] Step 1.2 binds the address book; this method is based on traditional key binding systems suc...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com