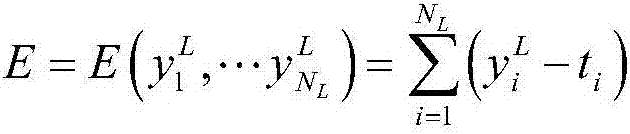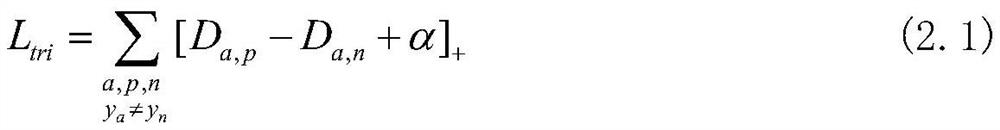Patents
Literature
4570 results about "Identification technology" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
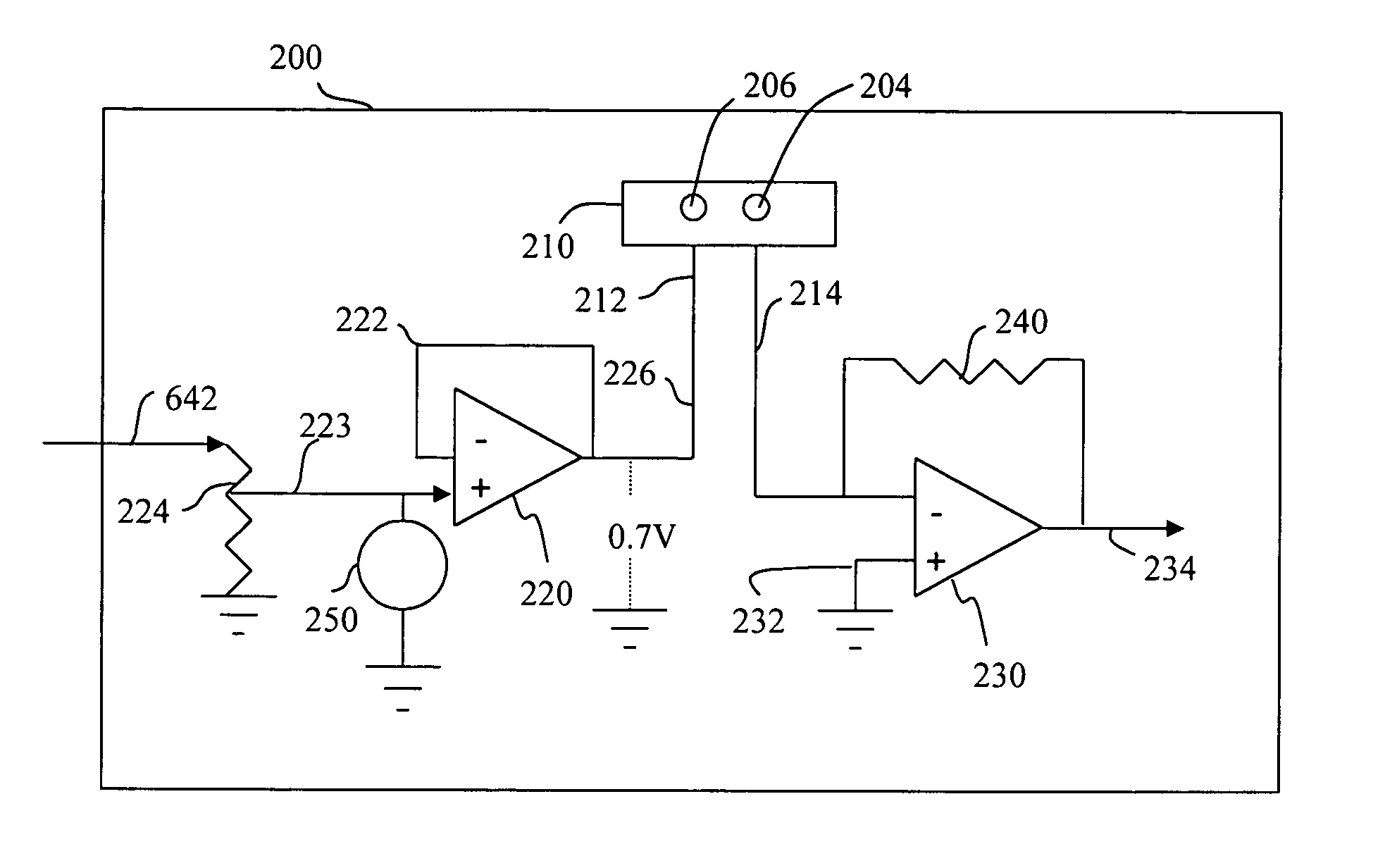
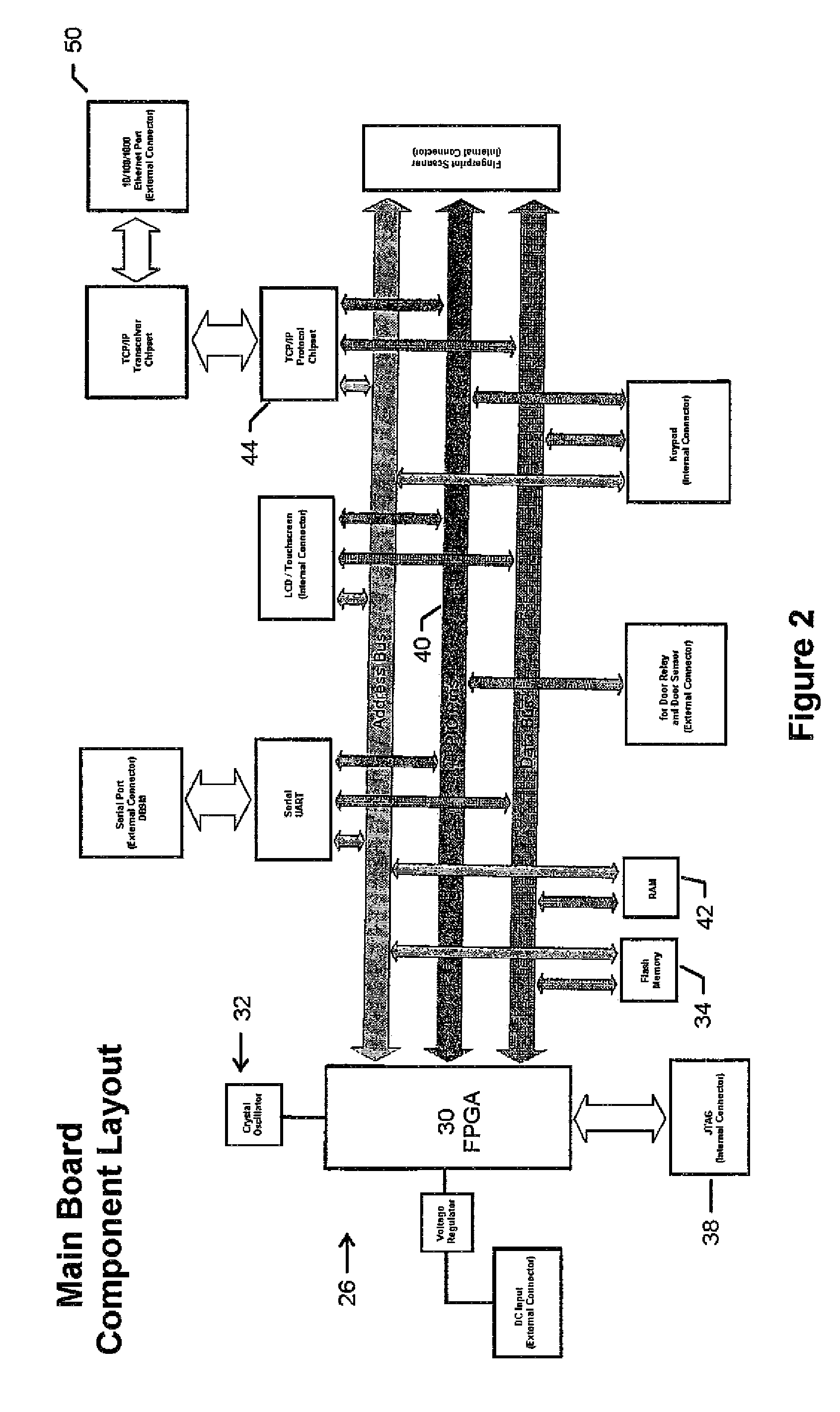
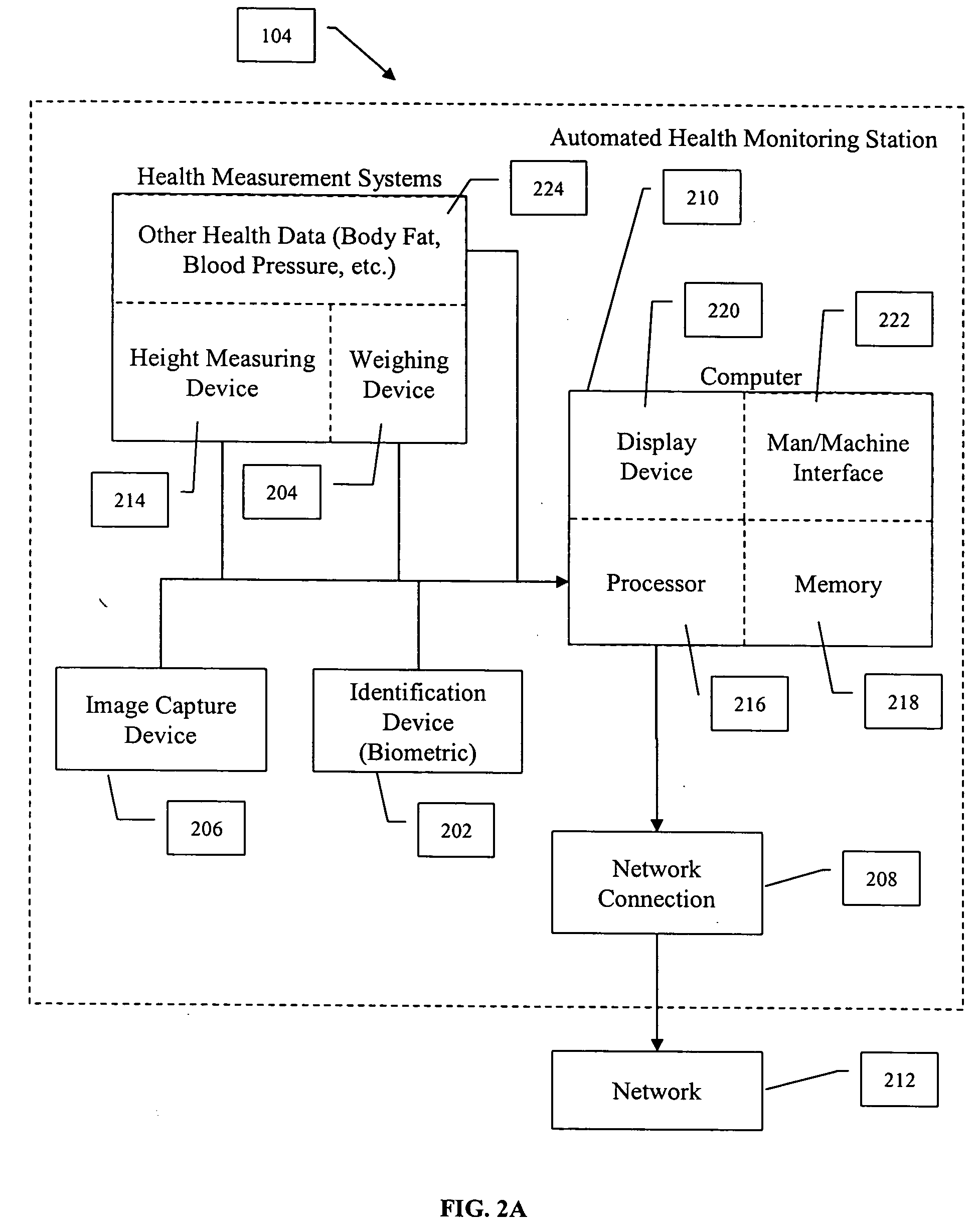
Embedded bio-sensor system
InactiveUS7125382B2Improve accuracyAccurate measurementTelemedicineEndoradiosondesGlucose sensorsConcentrations glucose
Provided is a bio-sensor system which utilizes radio frequency identification technology and which includes a remote transponder in wireless communication with an implantable passively-powered on-chip transponder. The bio-sensor system is specifically adapted to provide a substantially stable and precise sensor reference voltage to a sensor assembly that is included with the on-chip transponder. The remote transponder is also configured to remotely receive data representative of a physiological parameter of the patient as well as identification data and may enable readout of one or more of the physiological parameters that are measured, processed and transmitted by the on-chip transponder upon request by the remote transponder. The precision and stability of the sensor reference voltage is enhanced by the specific circuit architecture of the glucose sensor to allow for relatively accurate measurement of the physiological parameter such as measurement of glucose concentration by a glucose sensor without the use of a microprocessor.
Owner:JAMM TECH INC
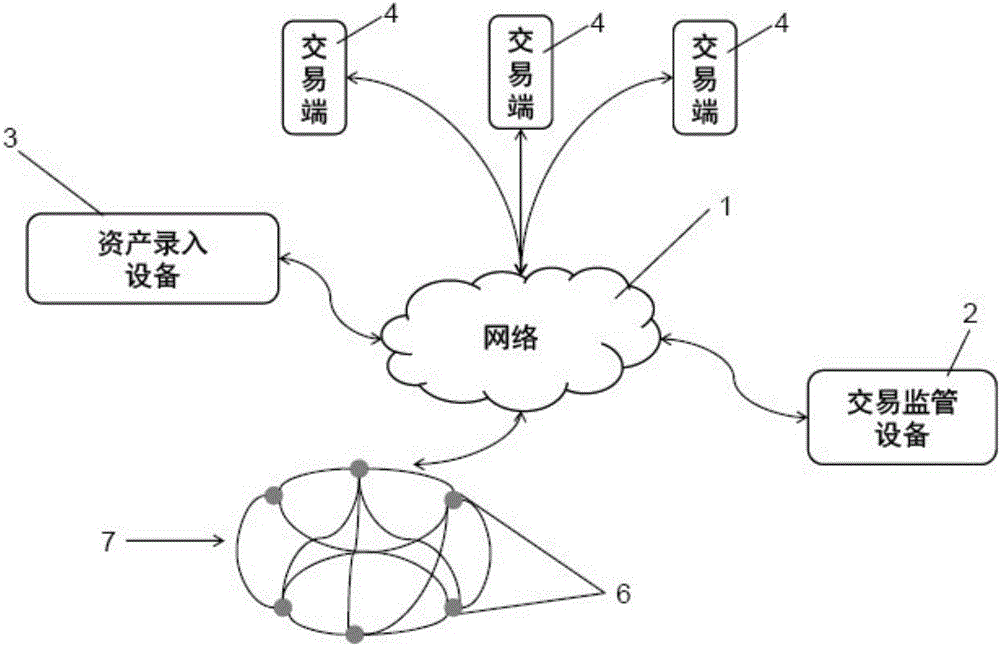
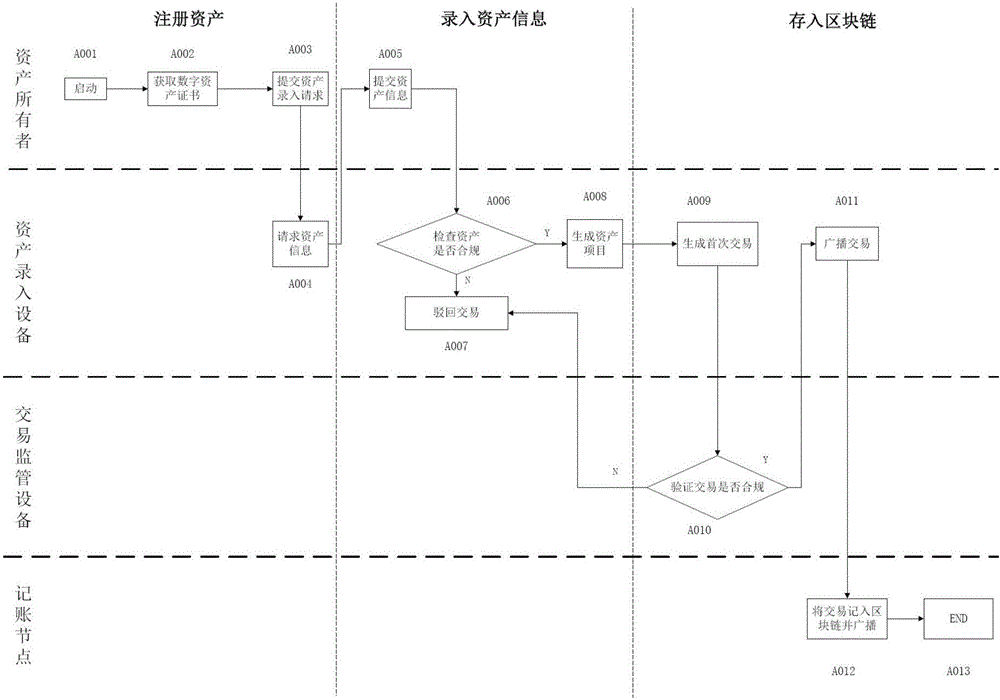
Asset transaction platform and digital certification and transaction method for assets
ActiveCN105956923AAchieve decentralizationGuarantee authenticityFinanceData synchronizationDigital identity
The present invention relates to a digital asset transaction platform, comprising an asset entry device and a distributed accounting network. An asset is validated by the asset entry device. When compliance is achieved, asset project information is generated and is input to the asset transaction platform, wherein the asset project information includes a hash value of a digital asset certificate of the asset. The distributed accounting network comprises a plurality of accounting nodes, which are connected in a point-to-point manner and each store a transaction data information general ledger which is synchronized with each other and is based on a block chain database. The asset transaction platform supports mutual transaction of at least two different types of assets. The asset transaction platform provided by the invention adopts the block chain technology and the digital identity identification technology of assets and realizes de-centralization and trusted quick transaction of various assets.
Owner:上海如鸽投资有限公司
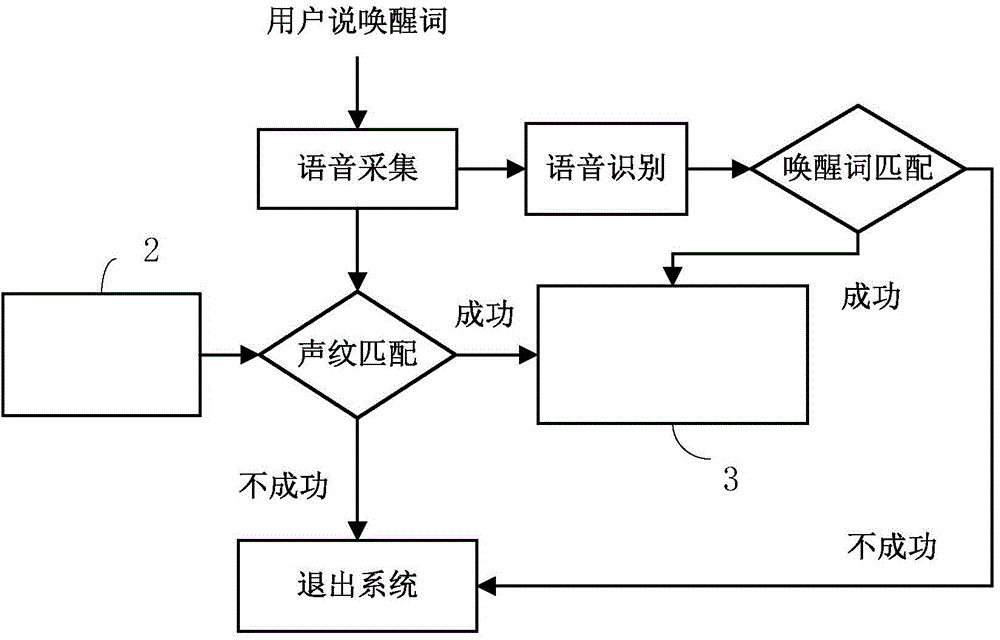
Method for personalized television voice wake-up by voiceprint and voice identification
InactiveCN104575504APersonalizedRealize TV voice wake-up functionSpeech recognitionSelective content distributionPersonalizationSpeech identification
The invention discloses a method for personalized television voice wake-up by voiceprint and voice identification, particularly a method for performing identity confirmation on a television user through voiceprint identification and controlling a television to perform personalized voice wake-up through confirmed identity and a voice identification result of user voice, and relates to voiceprint identification and voice identification technologies. A composition system comprises a voice control system (1), an information storage unit (2) and a television main controller (3) which are connected through electric signals. The method has the characteristics of short training time, very high voiceprint and voice identification speed and high identification rate. Voiceprint and voice identification can be finished by only offline training and testing, identification results do not need to be sent to a cloud server, use is convenient, and the safety of family information is guaranteed. The method also can be applied to user-personalized automatic voice channel change of the television, can be transplanted to a common high-speed DSP (digital signal processor) or chip for operation, and can be widely applied to the related fields of smart homes.
Owner:SHANGHAI NORMAL UNIVERSITY
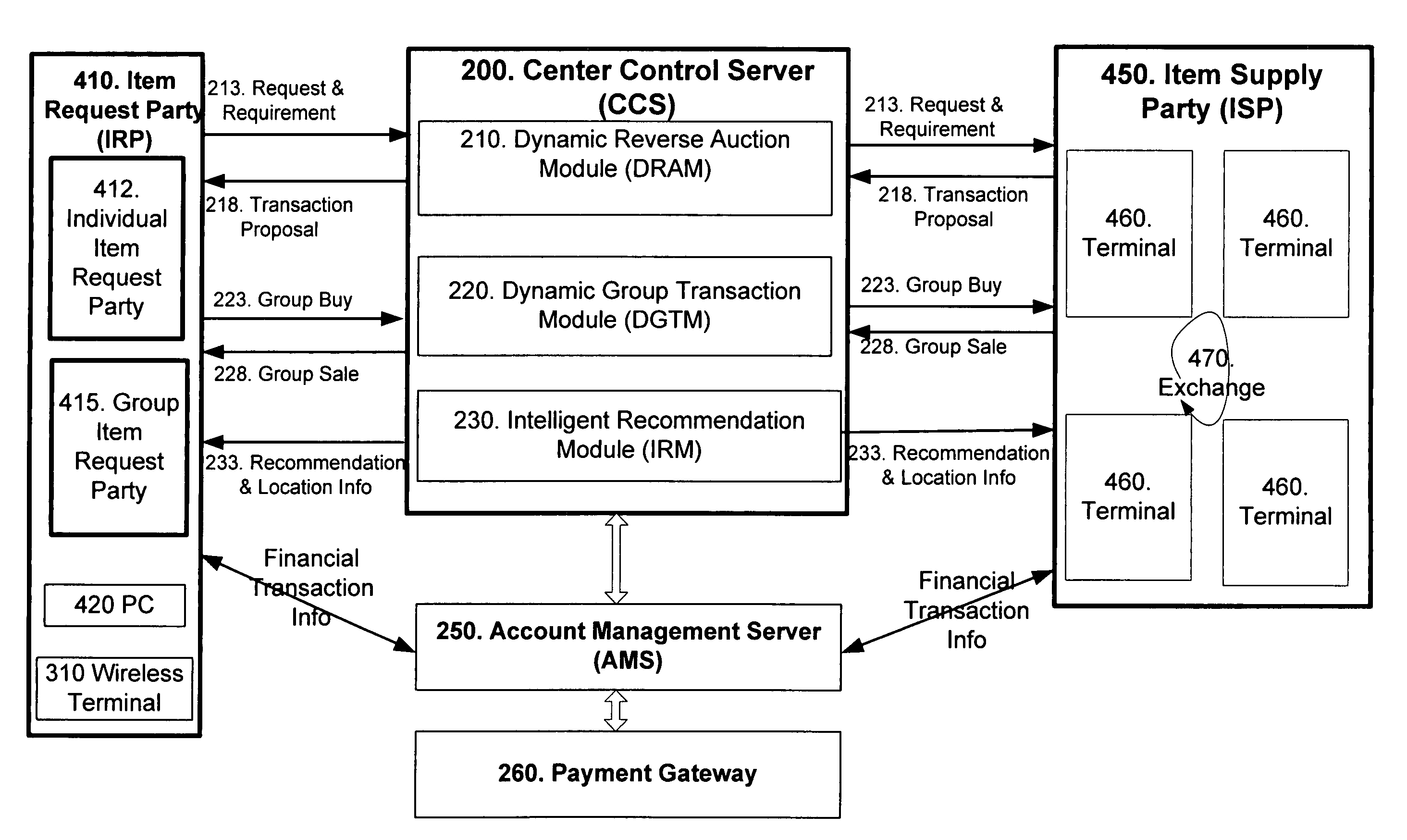
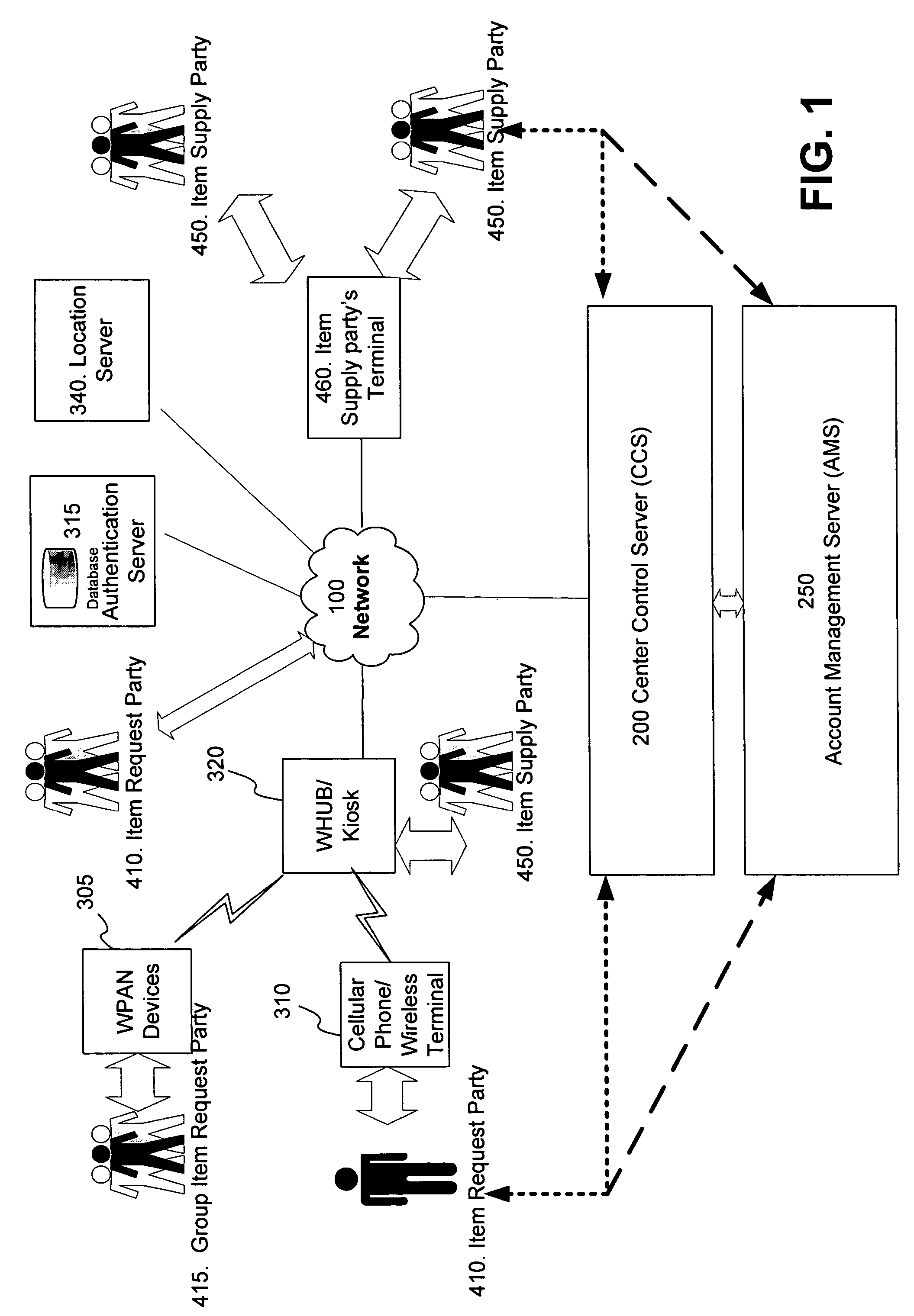
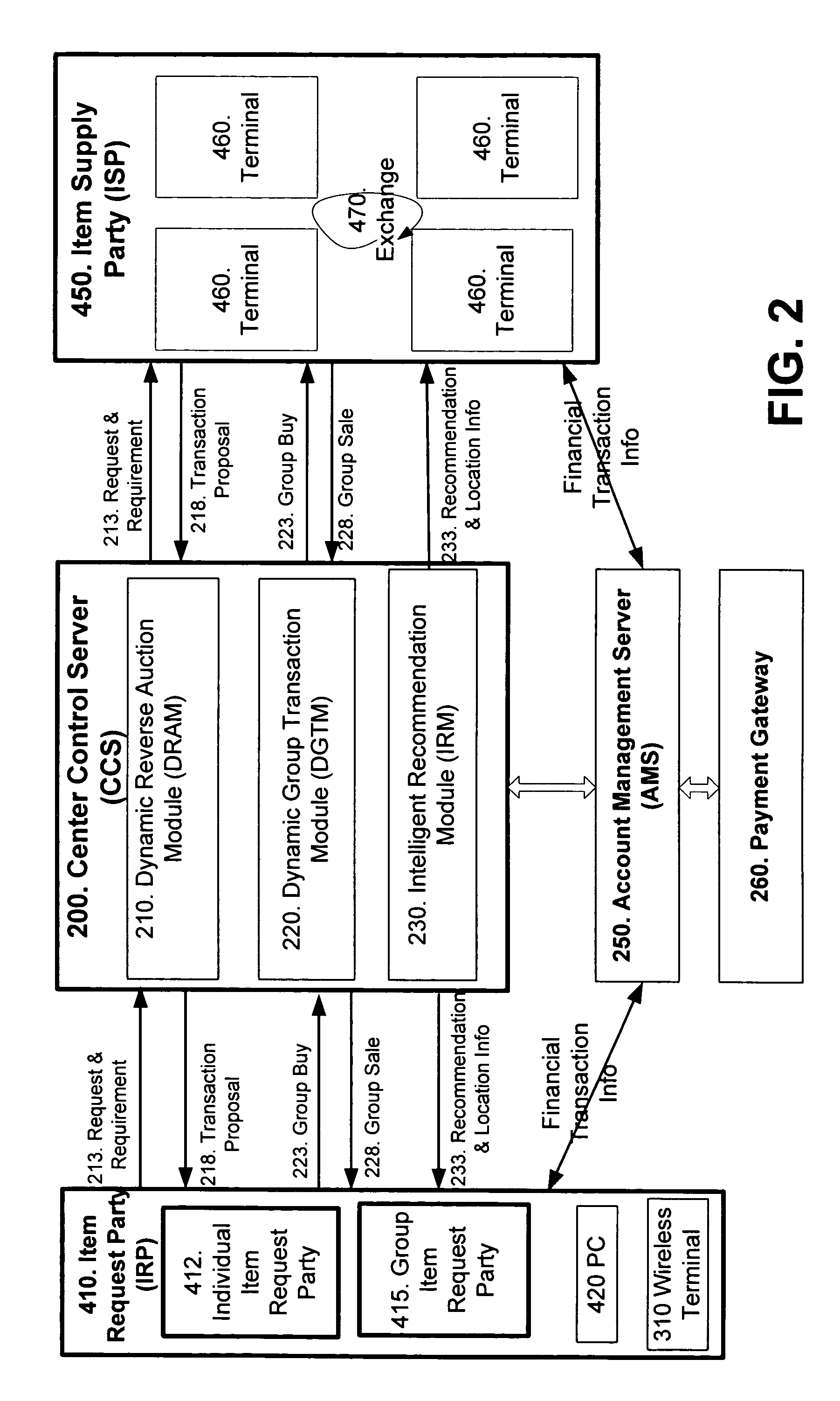
Method and system for improving client server transmission over fading channel with wireless location and authentication technology via electromagnetic radiation
InactiveUS7647024B2Facilitate communicationImprove efficiencyUnauthorised/fraudulent call preventionEavesdropping prevention circuitsAuthentication serverElectromagnetic radiation
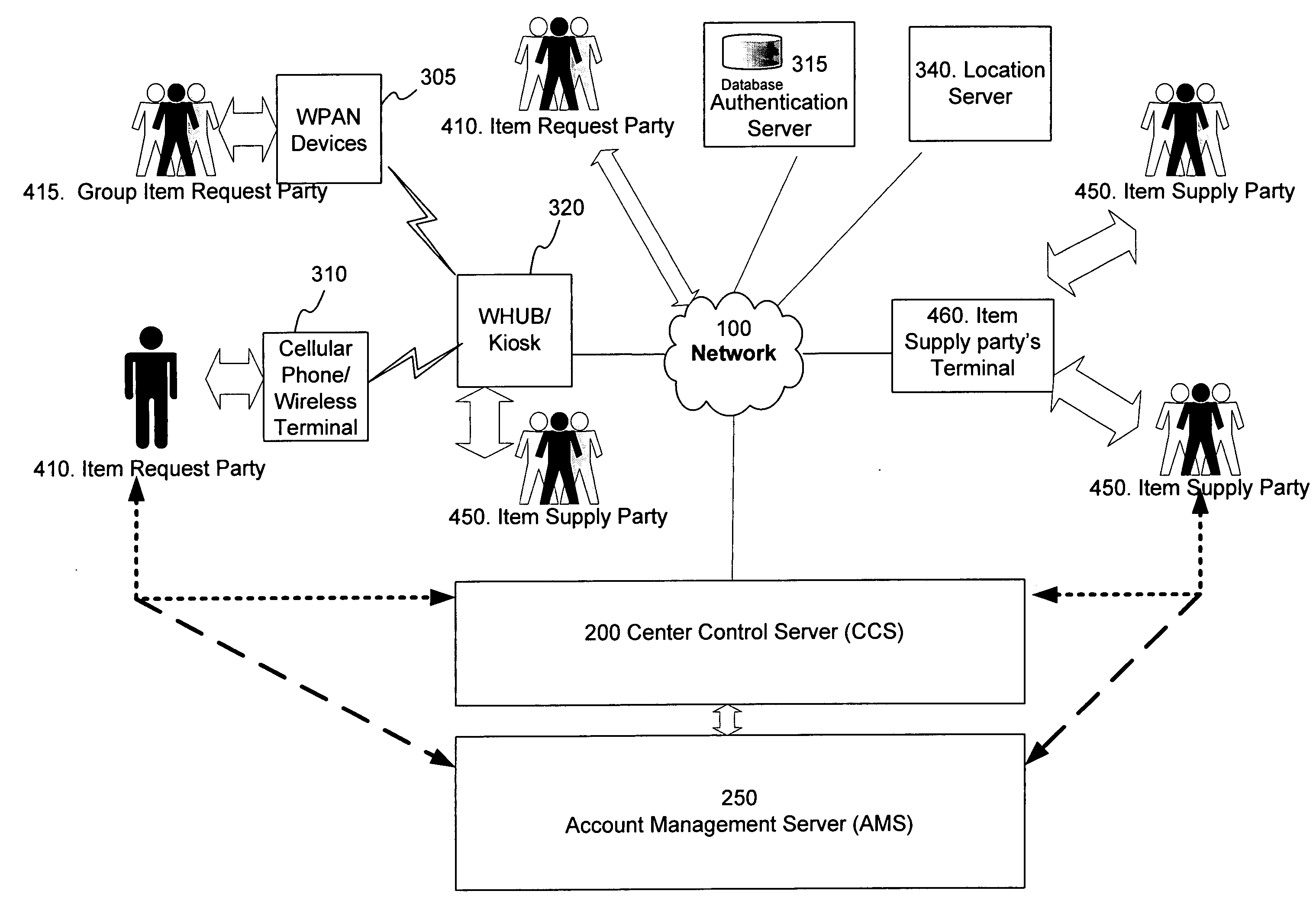
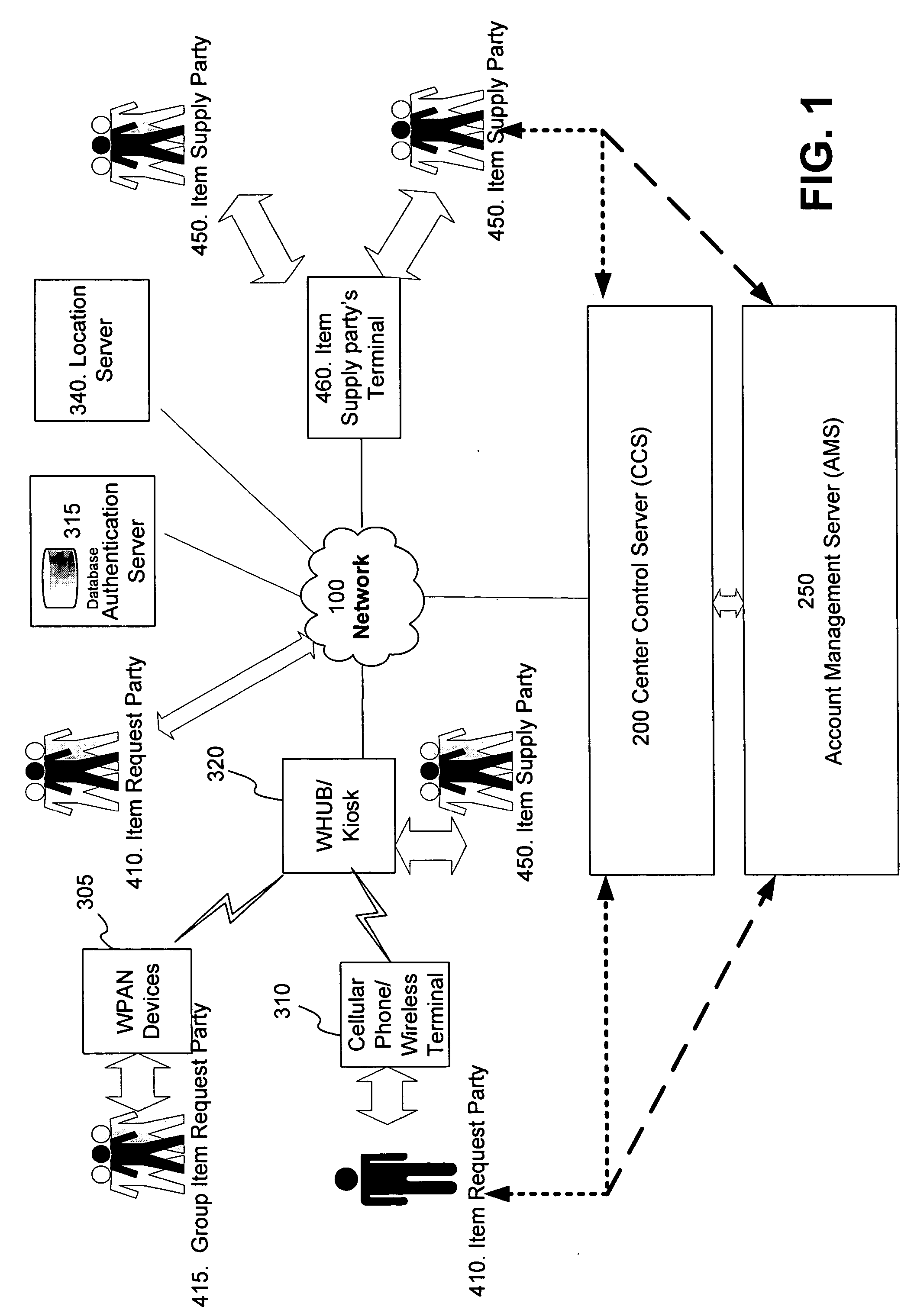
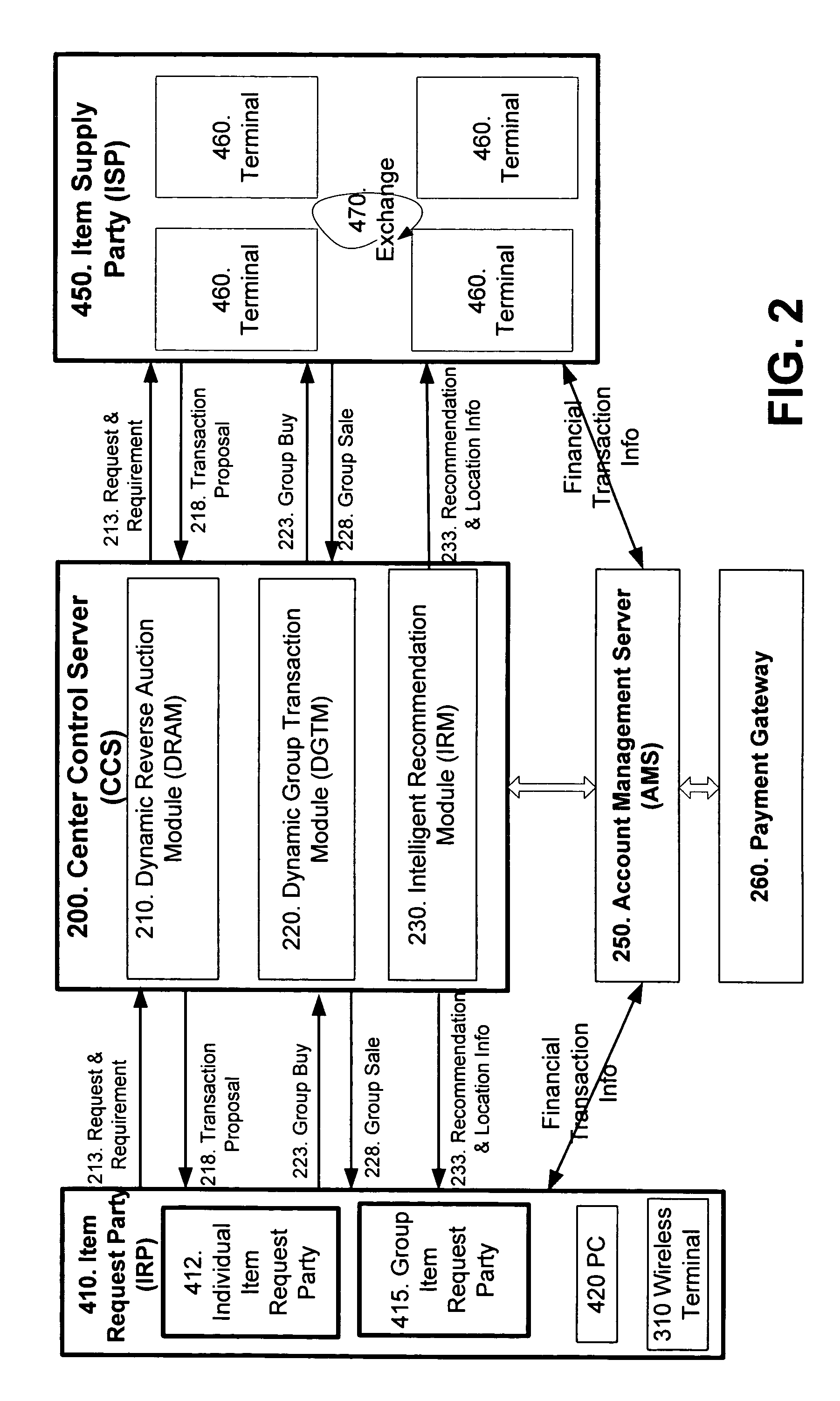
Wireless personal area network (Zigbee, Bluetooth, UWB) and wireless identification technologies (Near Field Communication (NFC), Radio Frequency Identification (RFID)) are implemented in particular client server functions and communications. Connected with an Authentication Server, a wireless HUB authenticates user identification and provides the user with access to secure data communication with a wireless terminal such as a cellular phone or a PDA. A Location Server provides user locations via methods such as RSSI, TDOA, and GPS and sends location information to a Center Control Server and the Authentication Server. With location information, the Center Control Server initiates and optimizes secure information processes and coordinates the functions of servers and user terminals.
Owner:INNOVATION SCI LLC
Method and apparatus for data entry input
ActiveUS20060190836A1Details for portable computersSpecial data processing applicationsEmbedded systemElectronic data
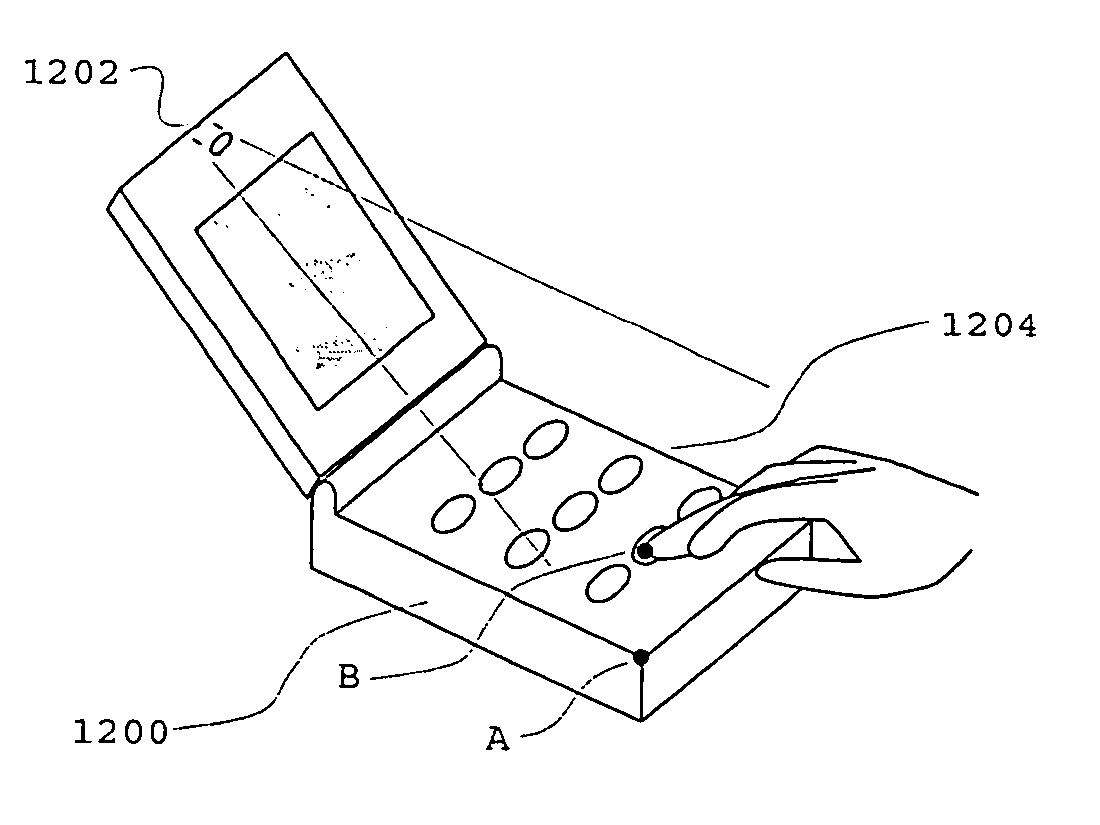
An apparatus and method of inputting data for an electronic data entry device are provided. In one embodiment, main keys on a keyboard of a device are used in which the main keys have multiple symbols or functions associated therewith, and one or more assisting keys of the device are used to select between the symbols or functions on the main keys. In a further embodiment, identification of an input object such as the particular fingers of a user that are used to actuate a key region is performed. The symbol associated with the actuated key region and the finger (or other input object) used is determined. Various types of sensors and recognition technology are implemented in order to identify fingers (or other input objects) in various embodiments.
Owner:AITECH LLC
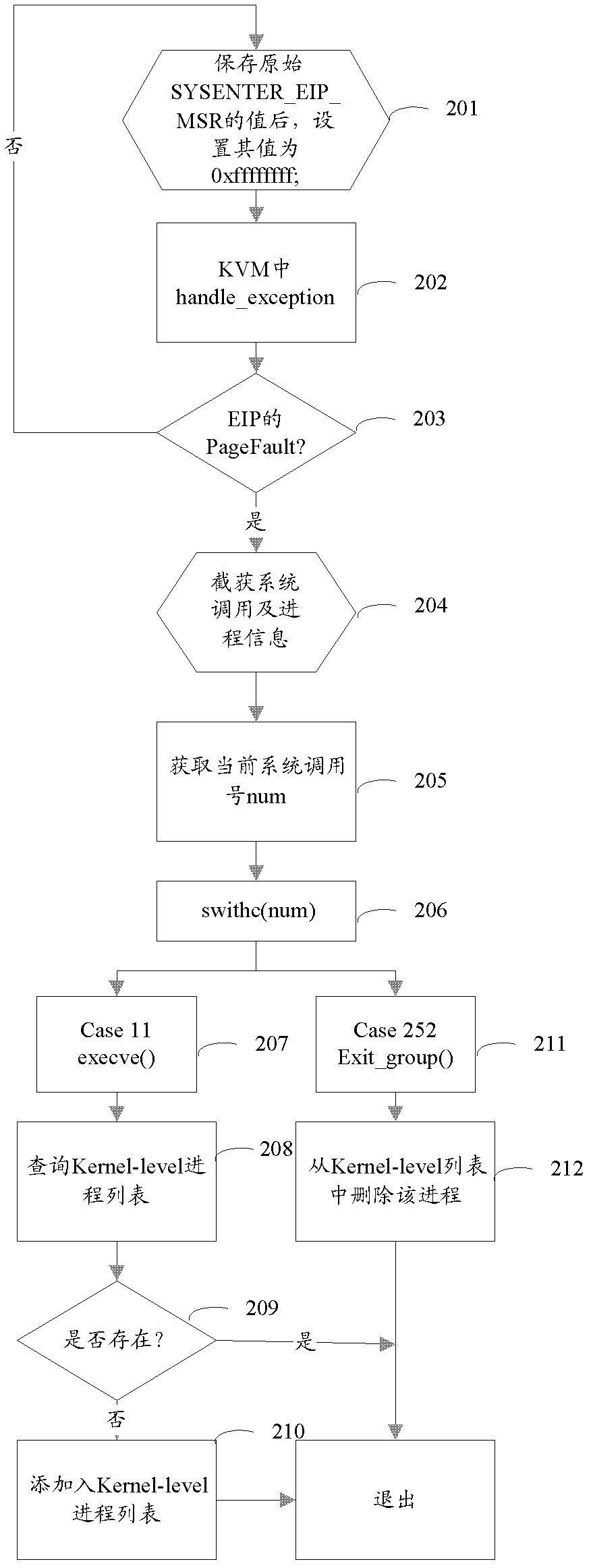
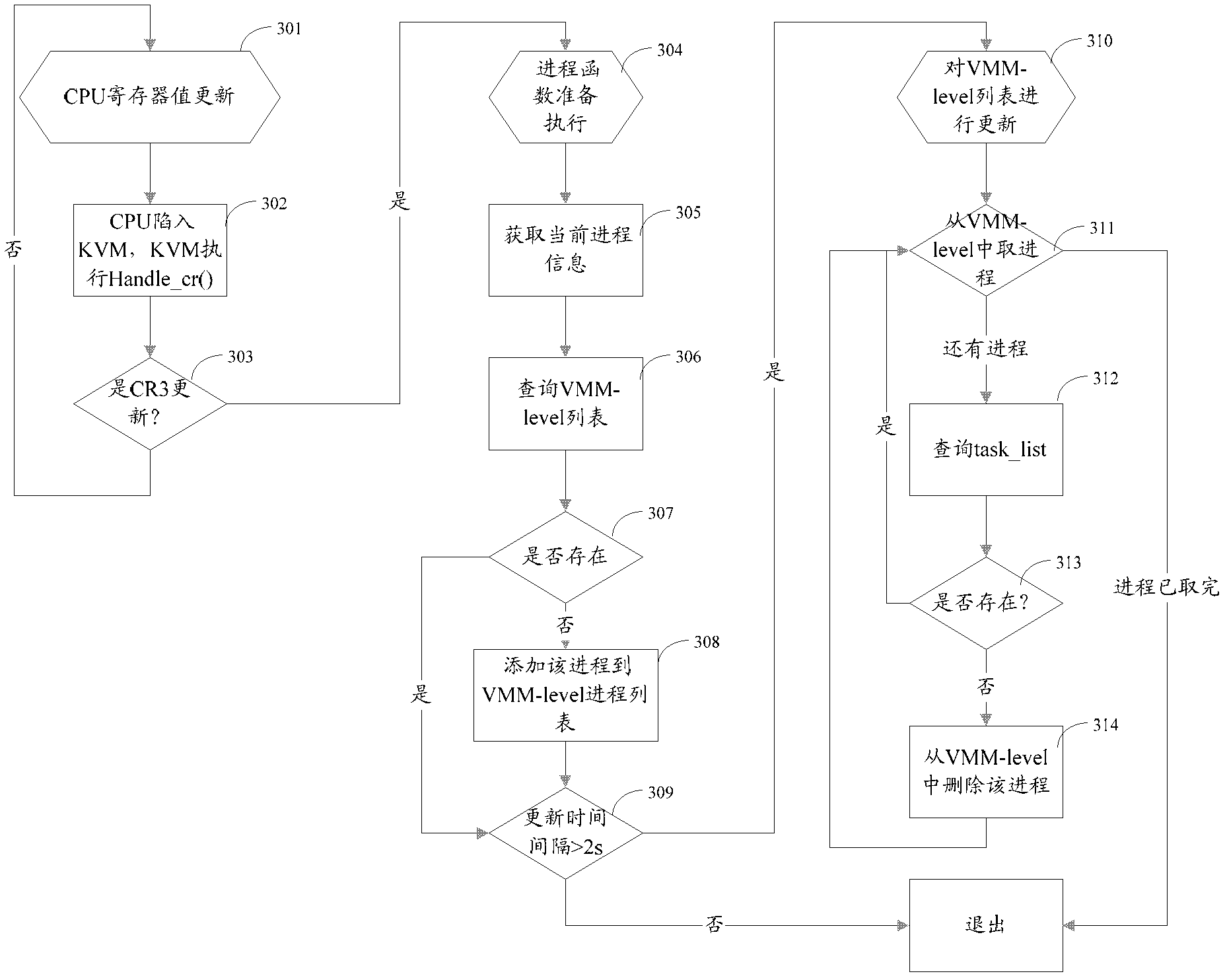
Detection method and device for hidden process based on virtual machine monitor
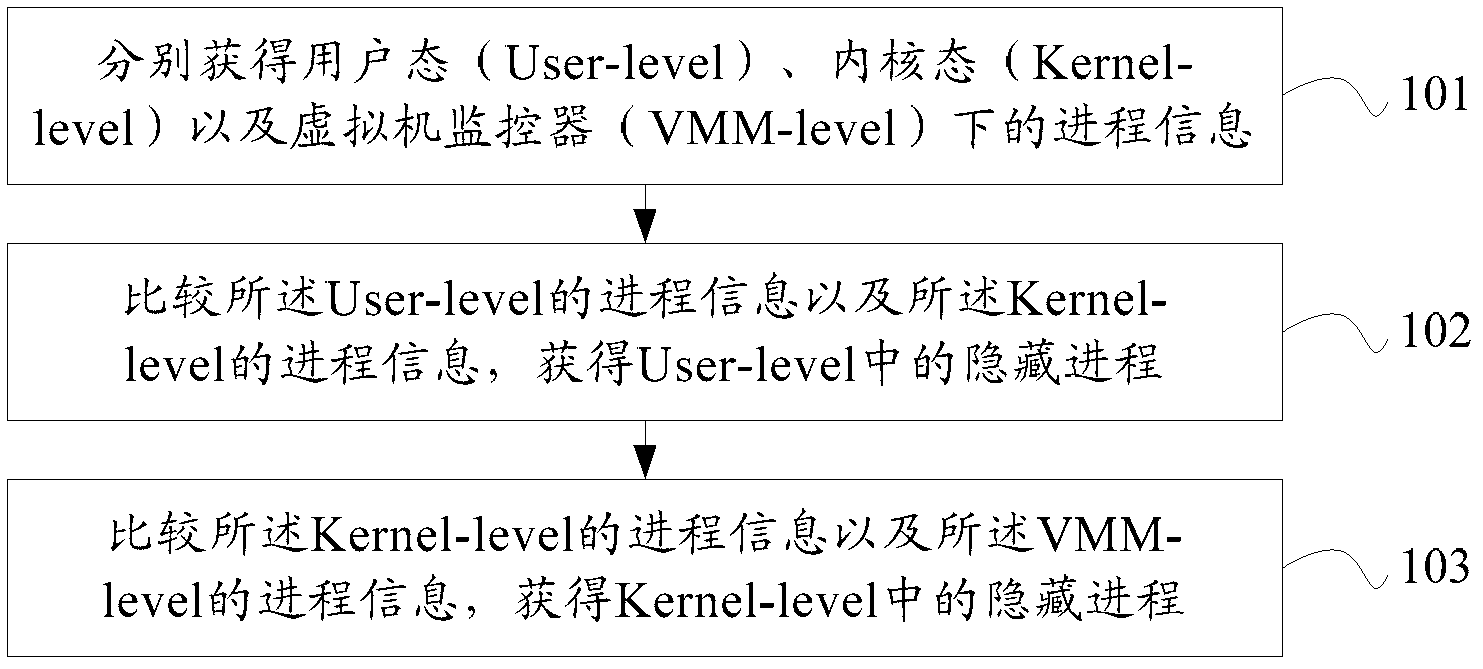
InactiveCN102521537AImprove securityDoes not affect normal operationPlatform integrity maintainanceSoftware simulation/interpretation/emulationComputer moduleProcess information
The invention provides a detection method and a device for a hidden process based on a virtual machine monitor, wherein the method comprises the steps of obtaining a user mode, a kernel mode and progress information in the virtual machine monitor; comparing the process information in the user mode with the process information in the kernel mode to obtain the hidden process in the user mode; comparing the process information in the kernel mode with the process information in the virtual machine monitor to obtain the hidden process in the kernel mode. The device comprises an acquision module, a first comparison module and a second comparison module. The scheme provided by the invention achieves multi-view hidden process detection and identification technology and provides good security for the virtual machine.
Owner:BEIHANG UNIV
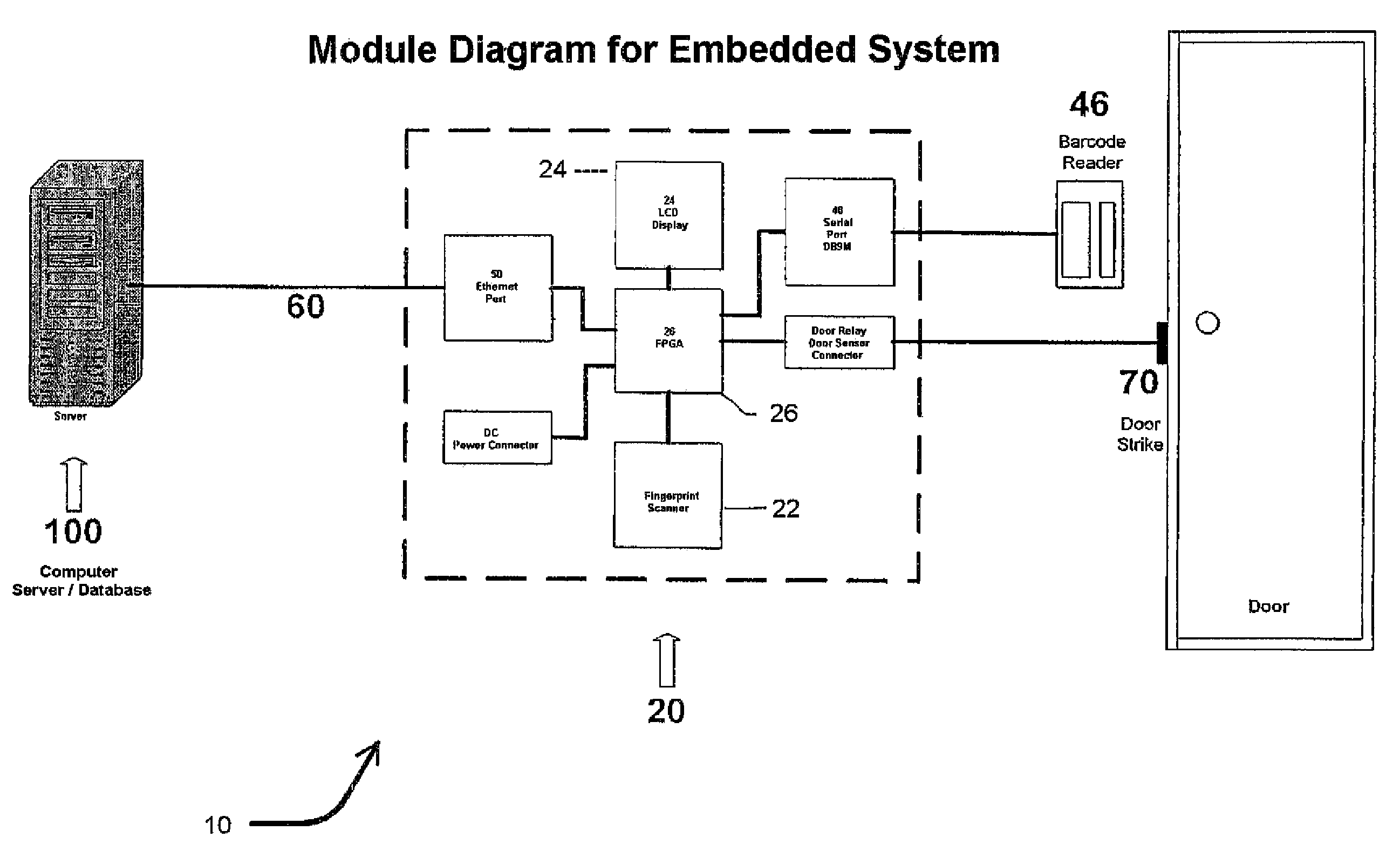
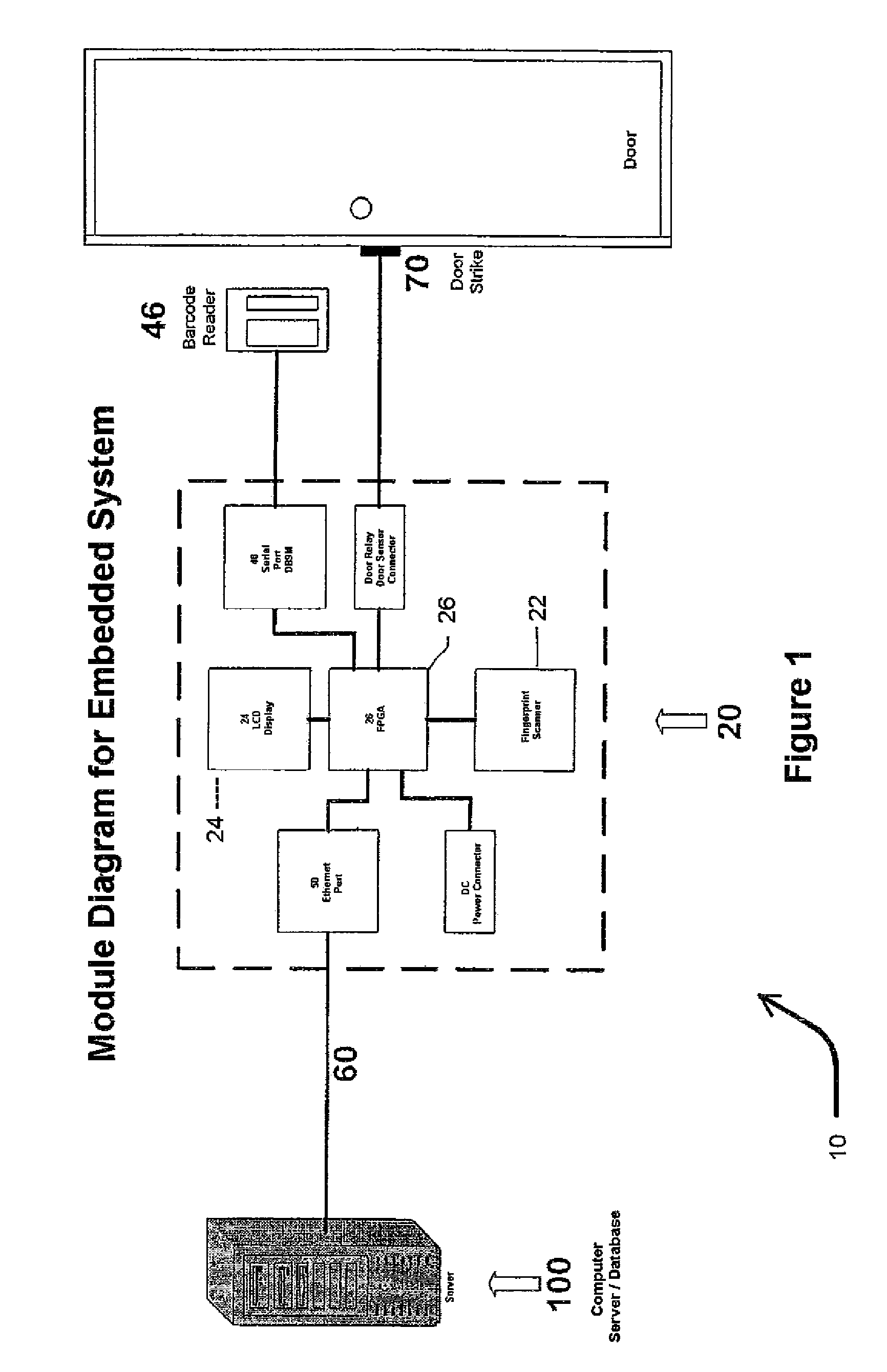
Biometric access control and time and attendance network including configurable system-on-chip (CSOC) processors with embedded programmable logic
ActiveUS7424618B2Compact efficient designCost efficient designElectric signal transmission systemsDigital data processing detailsHard disc driveHuman interaction
A biometric access control and time and attendance system comprises an integrated network including one or more remote access devices in electronic communication with a computer database. Each remote access device comprises a silicon chip based system and preferably includes a biometric input device, a liquid crystal display (LCD), computer processing capabilities based on embedded system architecture with configurable system-on-chip (CSOC) technology, and an electrical output for controlling a door lock or the like. The use of CSOC architecture in lieu of conventional personal computer technology (e.g. mother boards, hard drives, video controllers and the like) allows for a more compact and cost efficient design. A plurality of remote access devices is configured for communication with a primary computer database wherein data corresponding to biometric samples for all authorized users is stored. In an embodiment wherein the biometric input devices comprise fingerprint scanners, the devices are configured to facilitate fingerprint identification by incorporating an auto-targeting capability that enables the user to simply place his or her finger on the fingerprint scanner whereafter the system adjusts the scanned image by automatically shifting the scanned image data to a properly targeted position thereby enabling the system compare the scanned print to the biometric samples in the system's data storage memory. Auto-targeting capability eliminates the requirement for manual targeting present in systems of the background art thereby improving system performance and minimizing reliance on human interaction. The present invention contemplates the use of auto-targeting with other biometric systems, such as facial recognition and / or retinal scanning systems, or any other biometric identification technology.
Owner:PROFILE SOLUTIONS
Movement human abnormal behavior identification method based on template matching
InactiveCN101719216AGood effectThe effect is accurateCharacter and pattern recognitionVisual technologyAnomalous behavior
The invention relates to a movement human abnormal behavior identification method based on template matching, which mainly comprises the steps of: video image acquisition and behavior characteristic extraction. The movement human abnormal behavior identification method is a mode identification technology based on statistical learning of samples. The movement of a human is analyzed and comprehended by using a computer vision technology, the behavior identification is directly carried out based on geometric calculation of a movement region and recording and alarming are carried out; the Gaussian filtering denoising and the neighborhood denoising are combined for realizing the denoising, thereby improving the independent analysis property and the intelligent monitoring capacity of an intelligent monitoring system, achieving higher identification accuracy for abnormal behaviors, effectively removing the complex background and the noise of a vision acquired image, and improving the efficiency and the robustness of the detection algorithm. The invention has simple modeling, simple algorithm and accurate detection, can be widely applied to occasions of banks, museums and the like, and is also helpful to improve the safety monitoring level of public occasions.
Owner:XIDIAN UNIV
Method and system for improving client server transmission over fading channel with wireless location and authentication technology via electromagnetic radiation
InactiveUS20070123215A1Improvement of secure data communicationImprove efficiencyUnauthorised/fraudulent call preventionEavesdropping prevention circuitsAuthentication serverElectromagnetic radiation
Wireless personal area network (Zigbee, Bluetooth, UWB) and wireless identification technologies (Near Field Communication (NFC), Radio Frequency Identification (RFID)) are implemented in particular client server functions and communications. Connected with an Authentication Server, a wireless HUB authenticates user identification and provides the user with access to secure data communication with a wireless terminal such as a cellular phone or a PDA. A Location Server provides user locations via methods such as RSSI, TDOA, and GPS and sends location information to a Center Control Server and the Authentication Server. With location information, the Center Control Server initiates and optimizes secure information processes and coordinates the functions of servers and user terminals.
Owner:INNOVATION SCI LLC
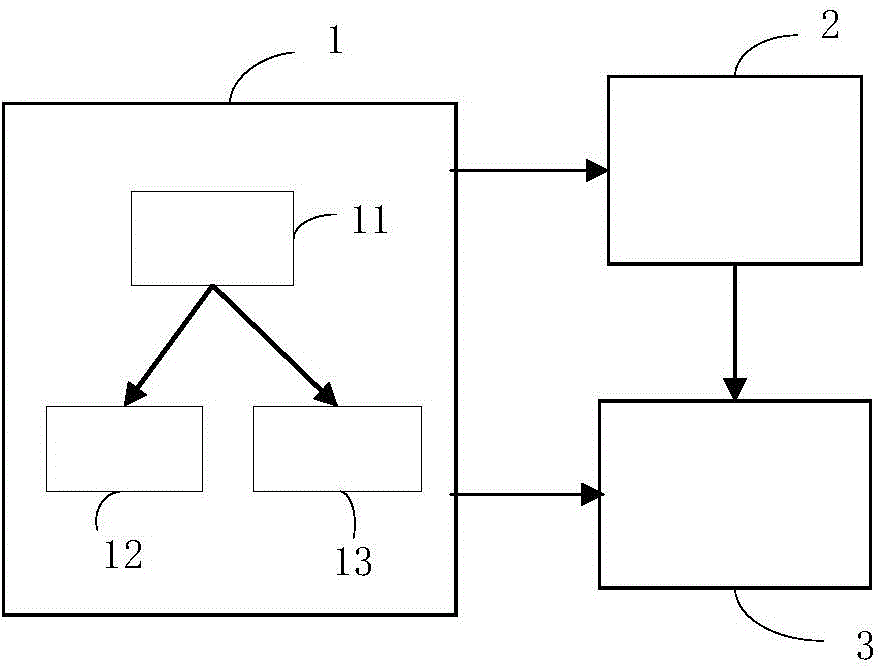
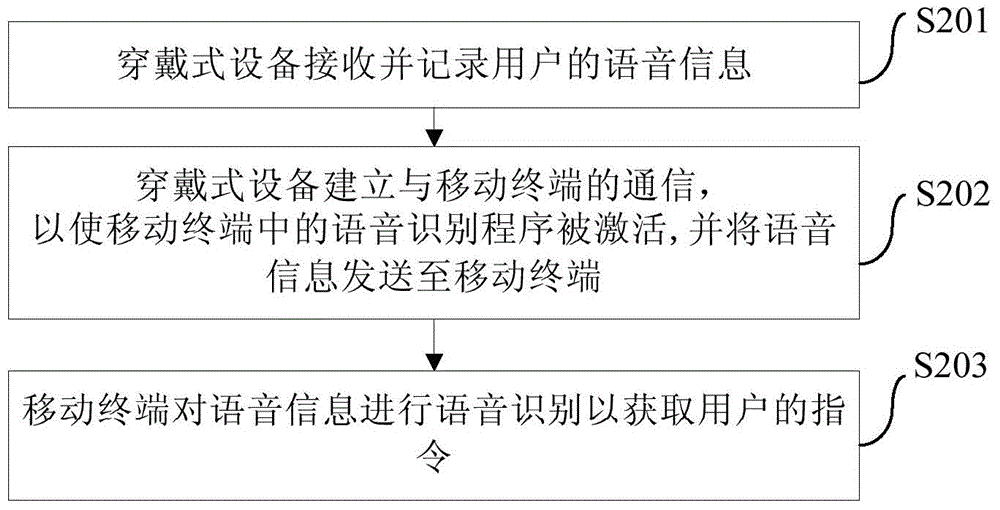
Man-machine interaction system, method and device
InactiveCN103558916AEasy to operateImprove experienceInput/output for user-computer interactionDetails for portable computersComputer terminalHuman–computer interaction
The embodiment of the invention provides a man-machine interaction system, which comprises wearing equipment and a mobile terminal, wherein the wearing equipment is used for receiving and recording voice information of users and sending the voice information to the mobile terminal after the communication is built with the mobile terminal, the mobile terminal is used for carrying out voice identification on the voice information for obtaining instructions of users. The embodiment of the invention also provides a man-machine interaction method and a man-machine interaction device. The man-machine interaction system provided by the embodiment of the invention has the advantages that the voice information of users through the wearing equipment is firstly received and recorded, in addition, after the communication is built with the mobile terminal, the voice information is sent to the mobile terminal, and then, the mobile terminal identifies the voice information through the voice identification technology for obtaining the instructions of the users, so the users do not need to take out the mobile terminal for carrying out any operation, the voice identification technology can be applied, the man-machine interaction intelligentization is realized, convenience is provided for the users, and the experience of the users is improved.
Owner:BAIDU ONLINE NETWORK TECH (BEIJIBG) CO LTD
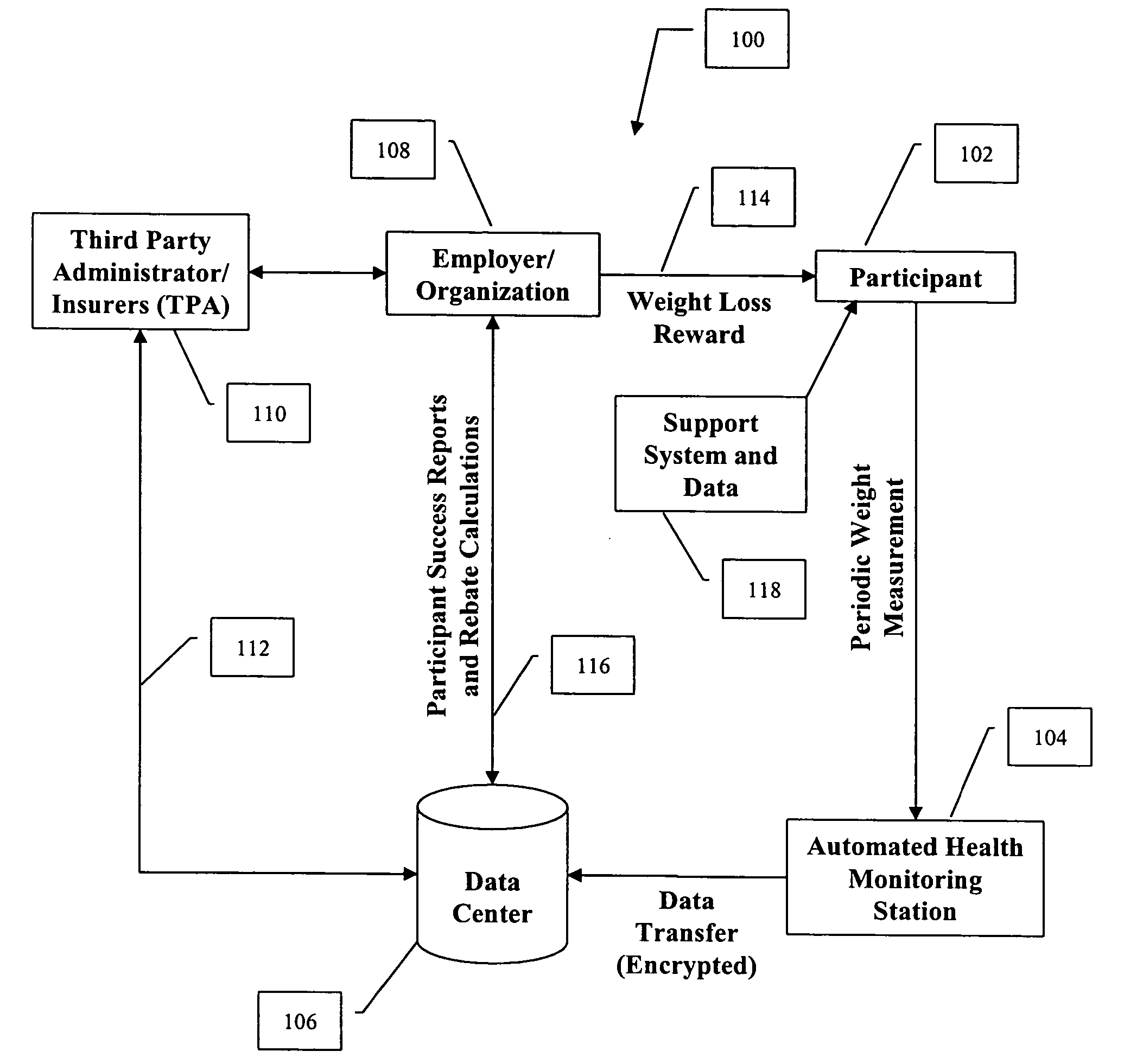
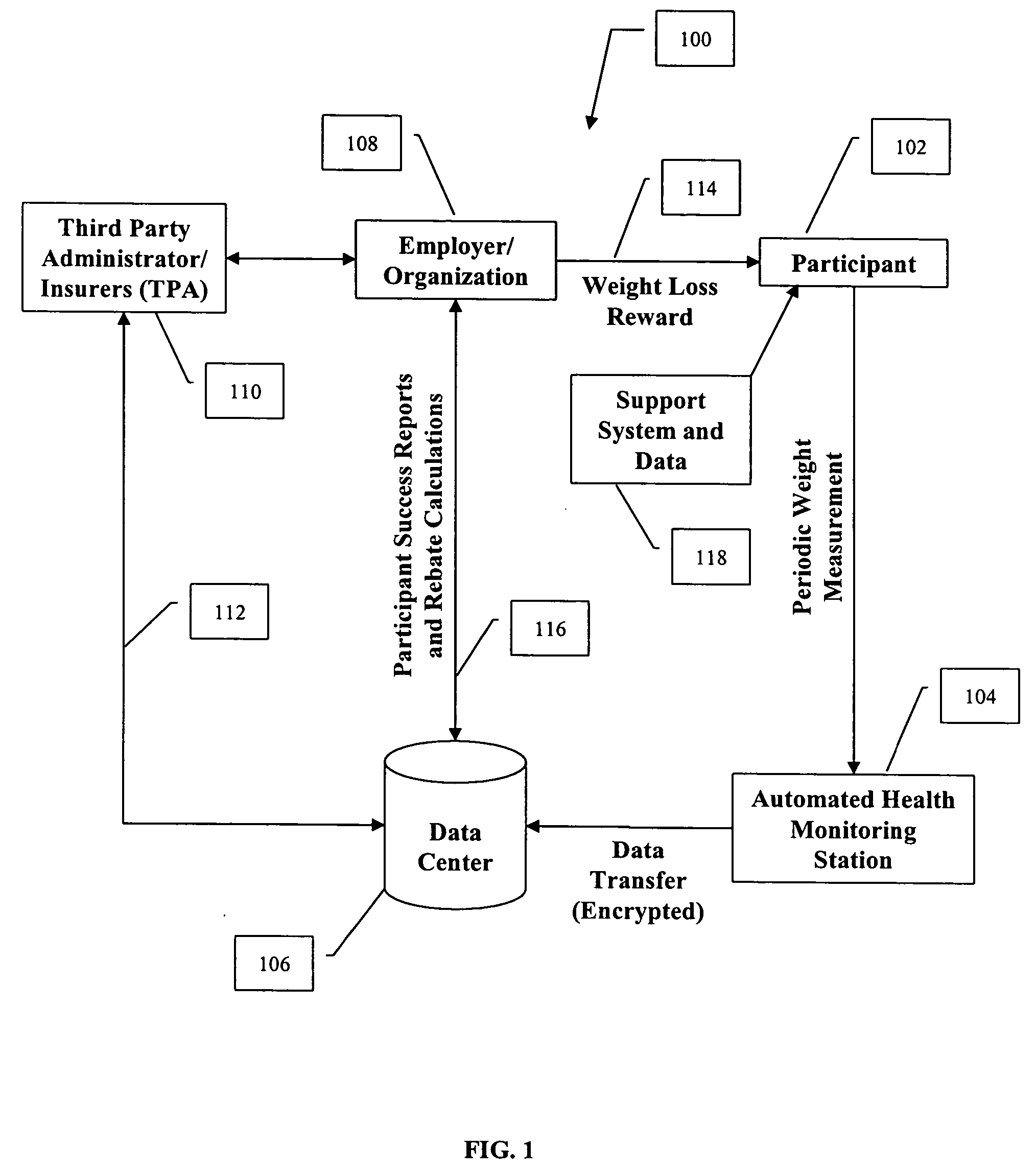
System and method for measuring and distributing monetary incentives for weight loss
ActiveUS20040131997A1Electric signal transmission systemsDigital data processing detailsData centerThe Internet
An automated identification, weight measurement and data reporting system that allows users to have their weight measured at a remote location and sent electronically to a data center. The invention can use biometric identification technology to confirm the identity of the user at the time of the measurement of the user's weight. The user's body weight may be measured via an electronic scale connected to the biometric identification device. The measurement data is then sent via a network (such as the Internet) to a central database. This secure weight measurement data is then used to offer incentives to individuals to lose weight. The more weight an individual loses, the larger the earned incentives. The invention also includes programs to measure health functions and to provide incentives to improve their health including body fat reduction, quitting smoking, reducing their blood pressure, or other health function.
Owner:INCENTAHEALTH
Vehicle remote control method based on voice command, apparatus and system thereof
InactiveCN102316162ALess likely to be safeEasy to operateSpeech recognitionTransmissionRemote controlComputer terminal
The invention, which relates to the vehicle voice control technology, discloses a vehicle remote control method based on a voice command, an apparatus and a system thereof. The method, the apparatus and the system are used to improve safety of the vehicle remote control. The vehicle remote control method based on the voice command comprises the following steps that: a communication terminal and a cloud computing platform server establish communication connection according to a sending connection control command of a user; the communication terminal receives a vehicle control voice command sent by the user and sends to the cloud computing platform server; the cloud computing platform server identifies, analyzes the vehicle control voice command by using an unspecified human voice identification technology so as to obtain the vehicle control information and return to the communication terminal; the communication terminal controls the vehicle which establishes a transmission relation with the communication terminal according to the vehicle control instruction. A scheme of the invention is suitable for carrying out remote voice intelligence control to the vehicle.
Owner:SHENZHEN VCYBER TECH
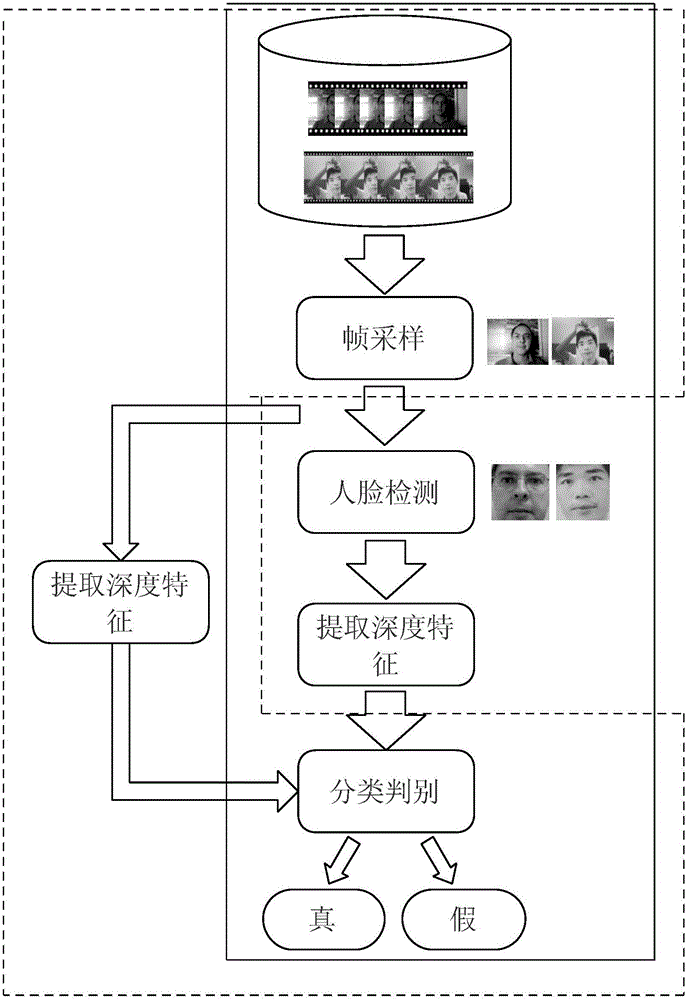
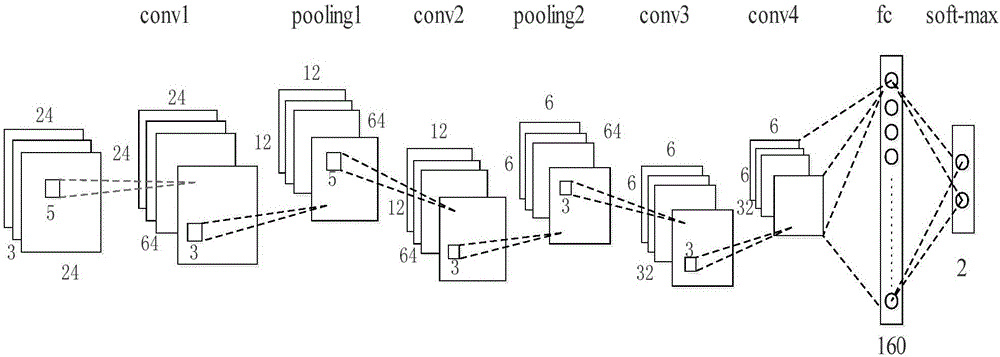
In vivo face detection method based on convolutional neural network
An in vivo face detection method based on a convolutional neural network relates to the machine learning and mode identification field, and is provided to face a cheat problem in the face identification. A conventional face identification technology is very easy to attack, the attackers frequently copy the faces of the legal users by the methods, such as the photographs, the videos, the 3D models, etc., if a face identification system can not distinguish the real faces and the fake faces effectively, the invaders can pass the face identification system very easily by the fake identities. Based on the problem, the present invention provides the in vivo face detection method based on the convolutional neural network. The convolutional neural network in the method provided by the present invention is realized based on a cuda_convnet framework, the network structure comprises four convolutional layers of two max-pooling layers, one full connection layer and one soft_max layer, and the soft_max layer comprises two nerve cells used for predicting the probability distribution of the real and fake faces.
Owner:BEIJING UNIV OF TECH
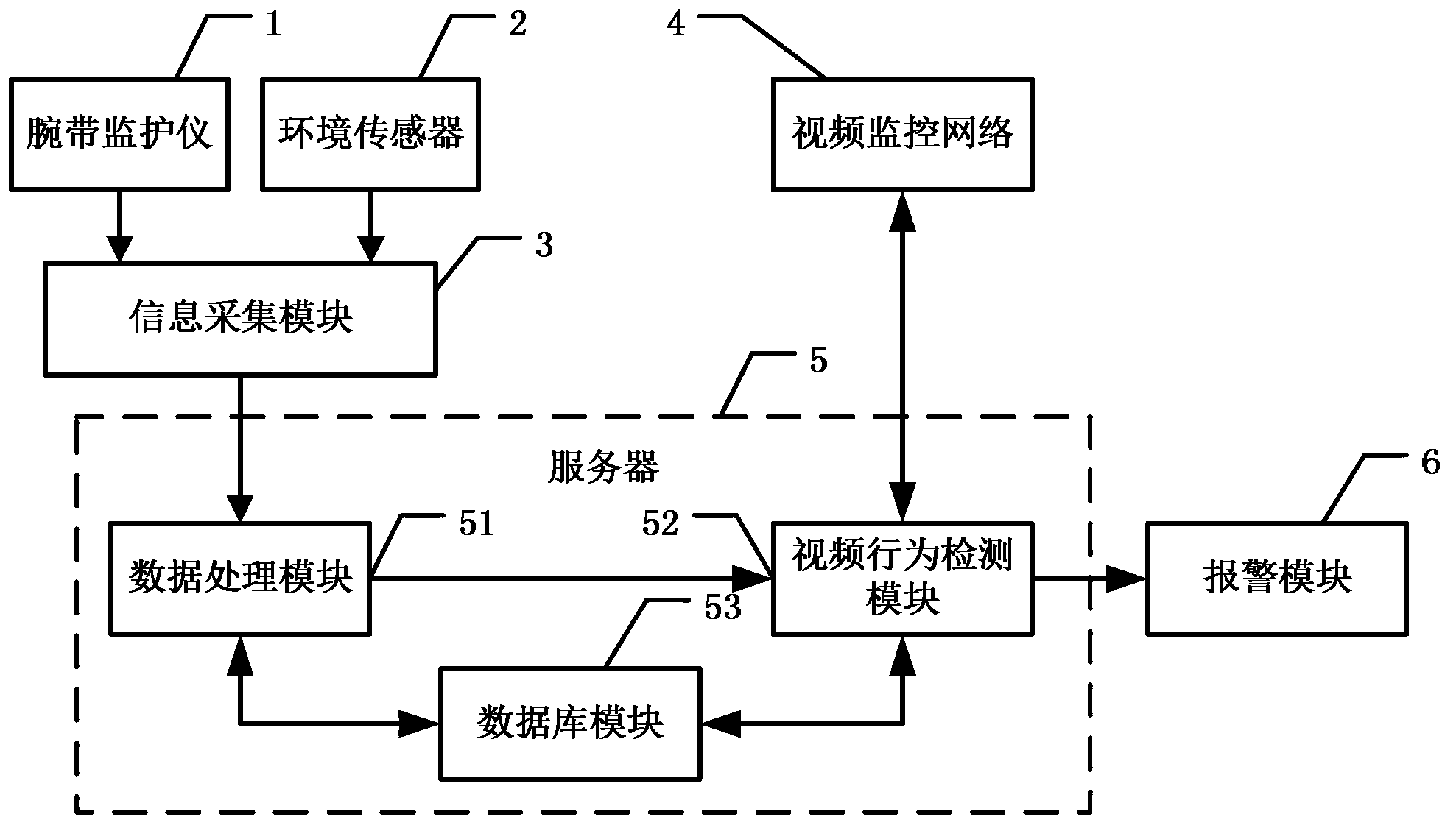
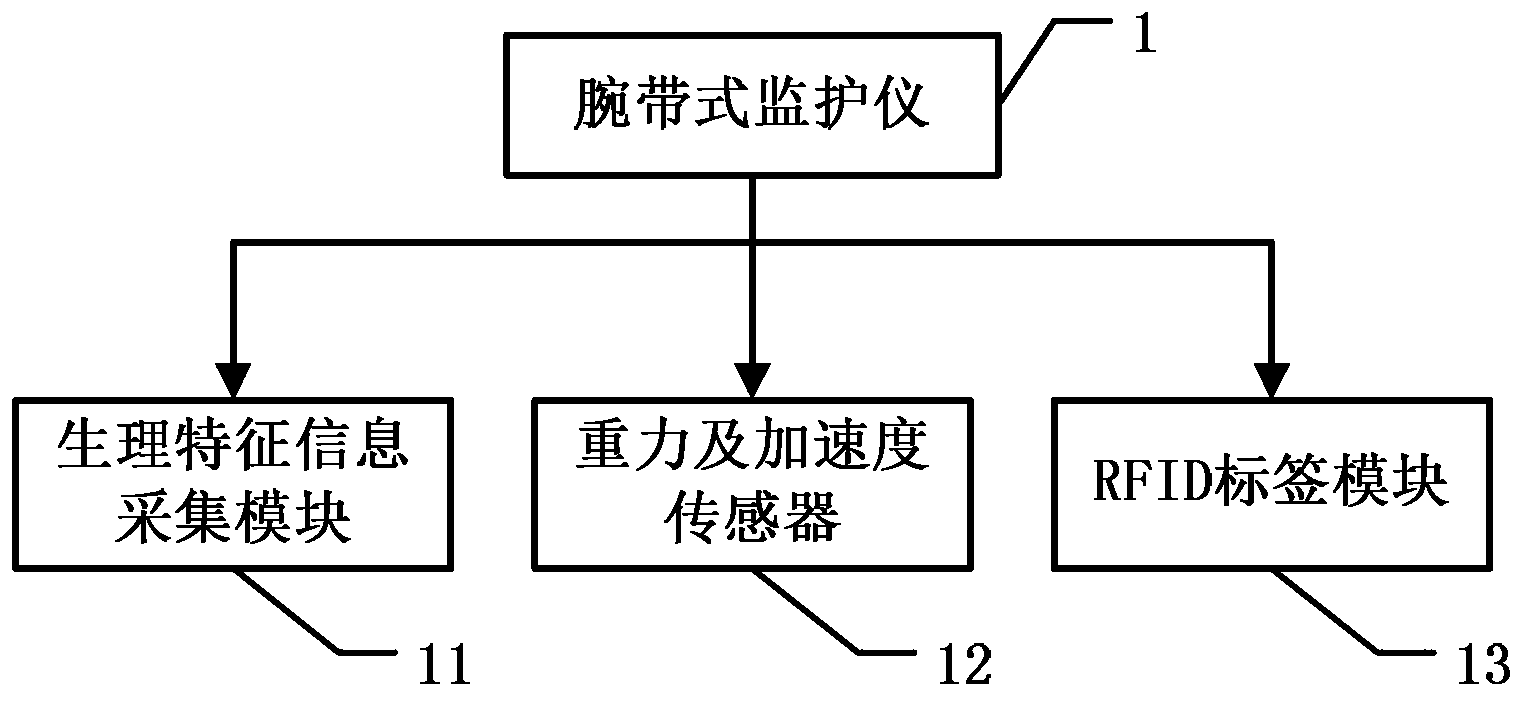
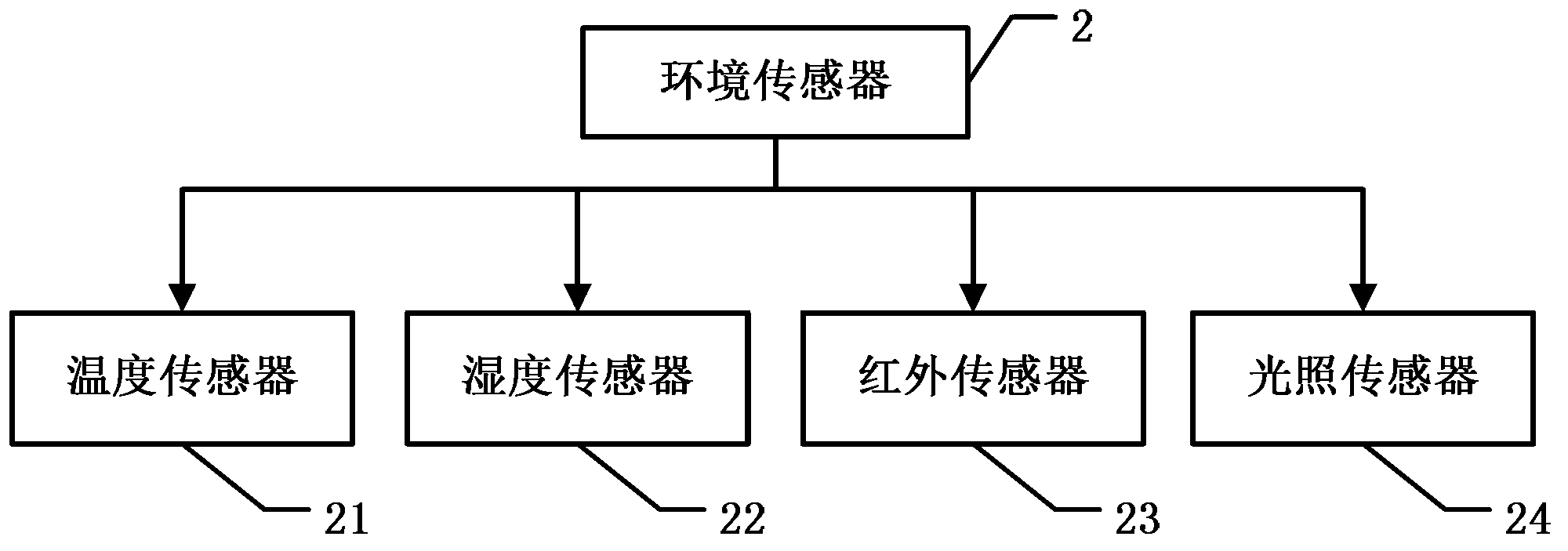
Gerocamium intelligent nursing system and method based on Internet of Things technology
InactiveCN103325080AAvoid harmDeep hurtData processing applicationsAlarmsVideo monitoringThe Internet
The invention discloses a gerocamium intelligent nursing system and method based on the Internet of Things technology. The Internet of Things technology and the behavior identification technology are combined in the gerocamium intelligent nursing system and method to monitor physiological information, attitude information and environment information of the old through a patient monitor and an environment sensor, and meanwhile, position information of the old is computed through RFID label information carried by the patient monitor. When abnormal conditions occur, a video monitoring network obtains sequence images of monitoring video of the old according to the position information of the old, behavior identification is conducted on the sequence images, and then whether dangerous situations occur or not is judged according to the behaviors of the old. By means of the grocamium intelligent nursing system and method, dual judgment is conducted when the old are in danger, danger warning accuracy is improved, and after setup is completed, the grocamium intelligent nursing system can run automatically, and therefore workload of nursing personnel is lowered and nursing quality is improved.
Owner:UNIV OF ELECTRONICS SCI & TECH OF CHINA
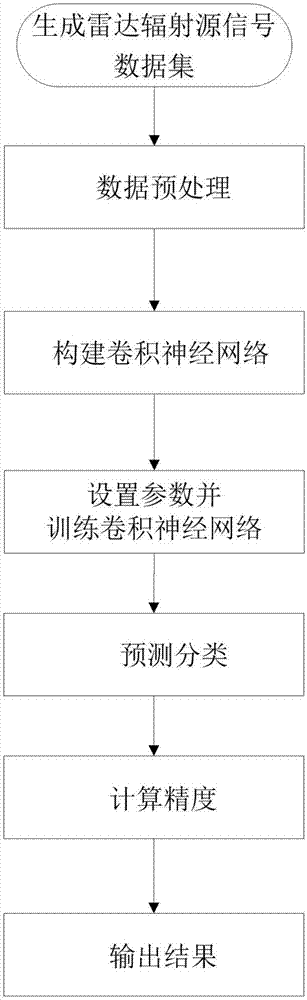
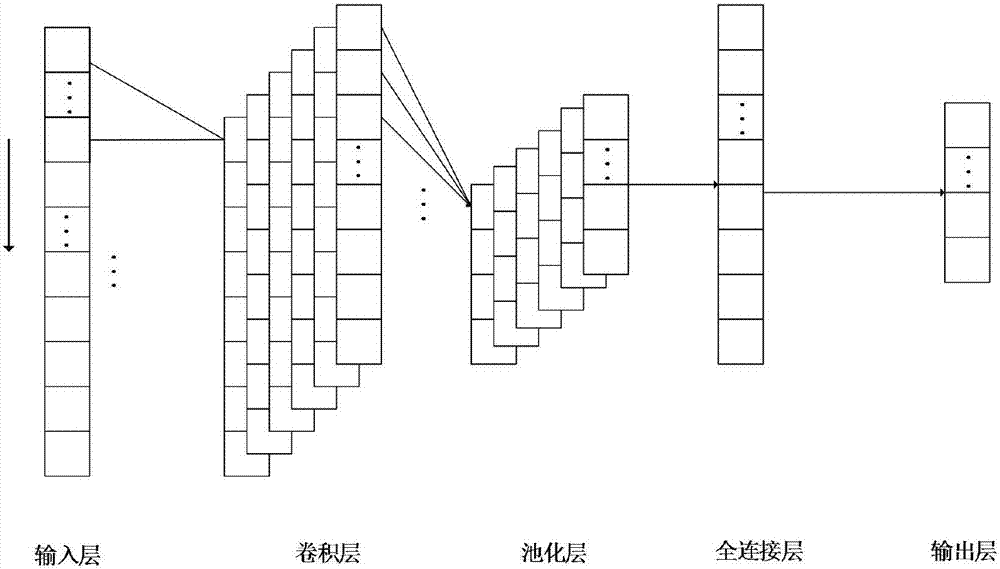
Radar radiation source signal identification method based on one-dimensional convolutional neural network
ActiveCN107220606AThe process of avoiding artificially designed featuresReduce training costWave based measurement systemsCharacter and pattern recognitionData setFeature extraction
The invention belongs to the radiation source signal identification technology field and particularly relates to a radar radiation source signal identification method based on the one-dimensional convolutional neural network. The method comprises steps that (1), a radar radiation source signal data set is generated; (2), data pre-processing is carried out; (3), the convolutional neural network is constructed; (4), parameters are set, and the convolutional neural network is trained; (5), prediction classification is carried out; (6), precision calculation is carried out; and (7), the result is outputted. The method is advantaged in that 1, a network structure of the convolutional neural network is utilized to carry out characteristic extraction of signals, and a manual characteristic design process in a traditional algorithm can be avoided; 2, signals with a signal to noise ratio lower than -10dB can be accurately identified; and 3, the method can be simply realized.
Owner:XIDIAN UNIV
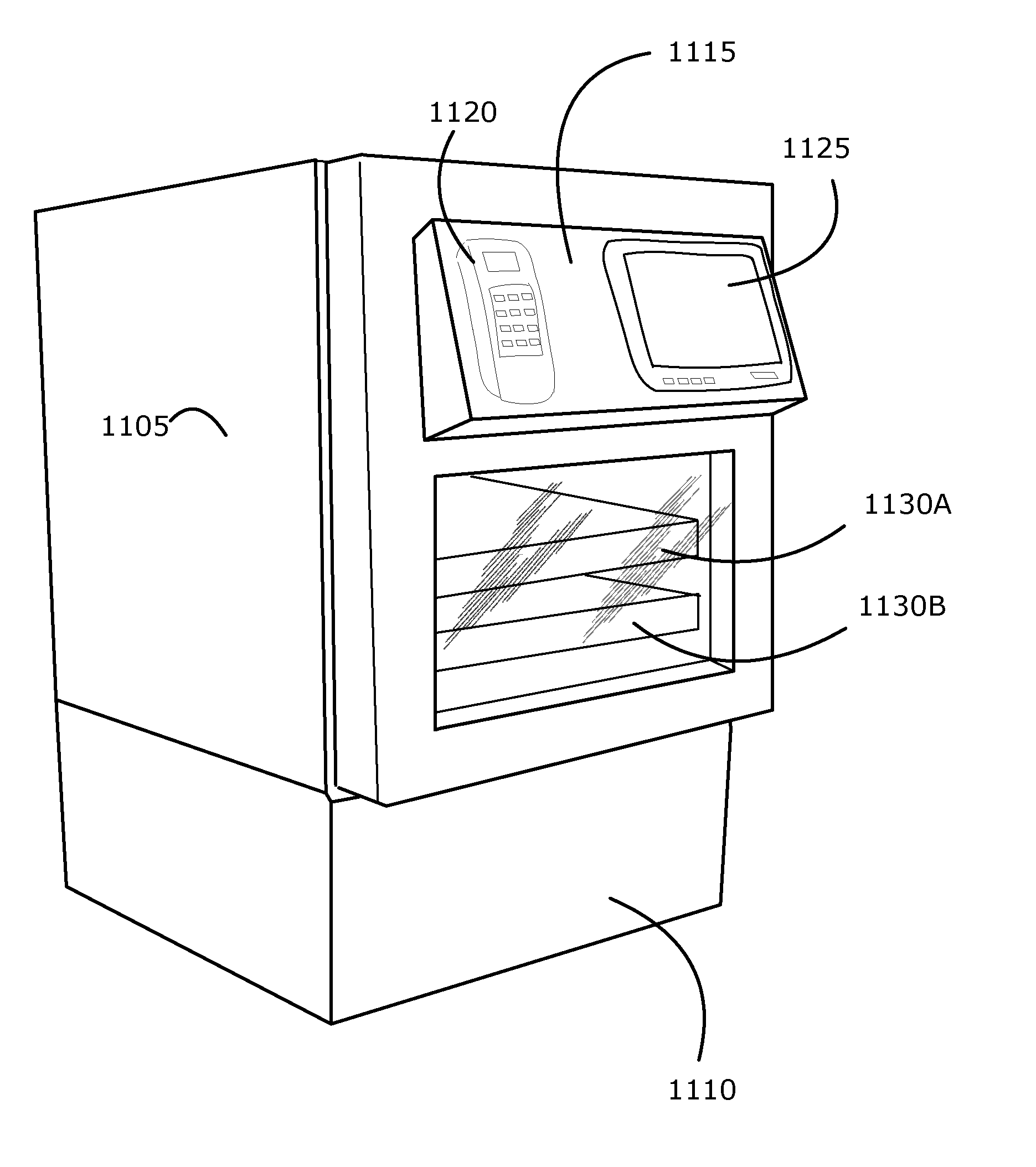
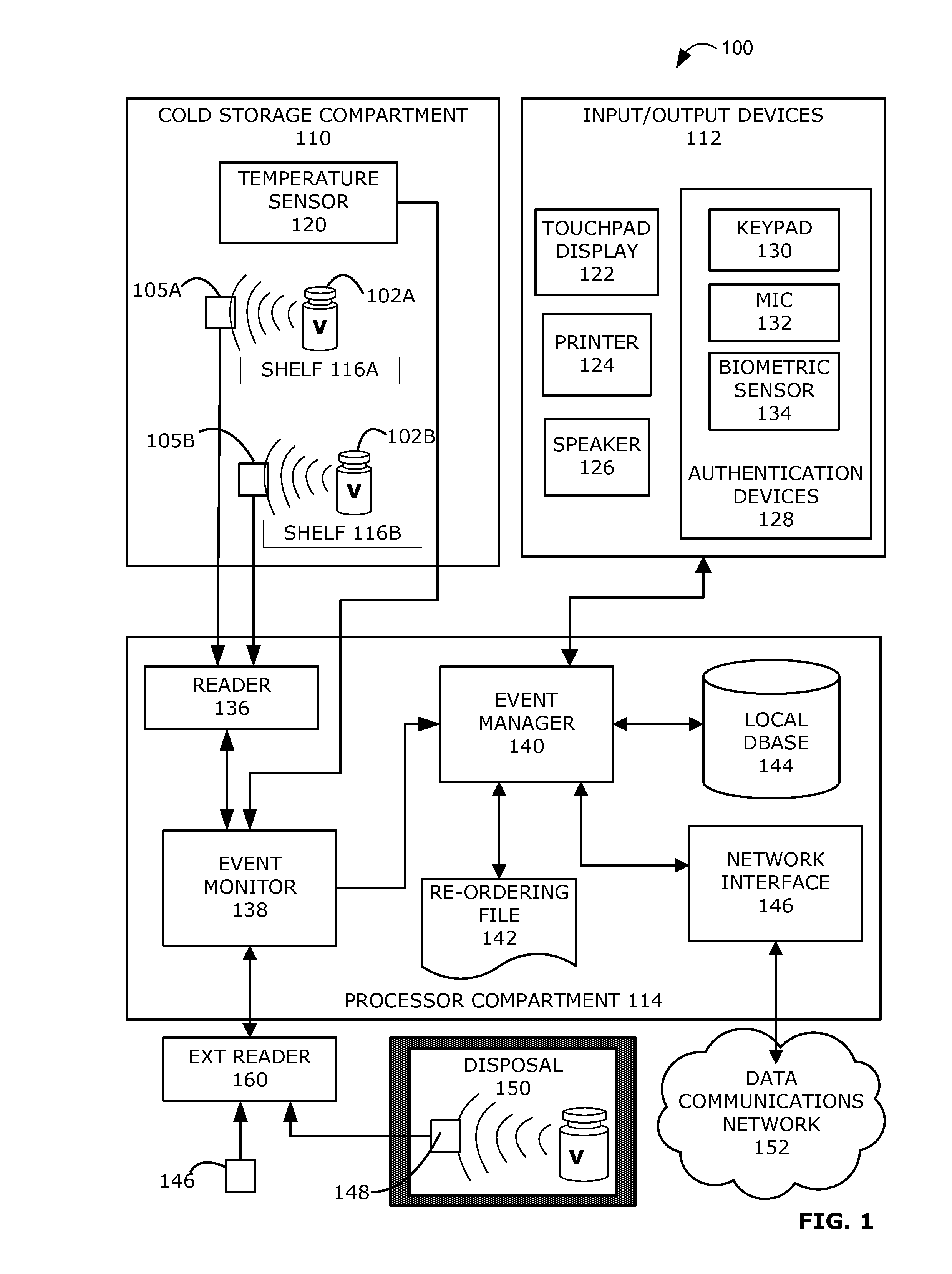
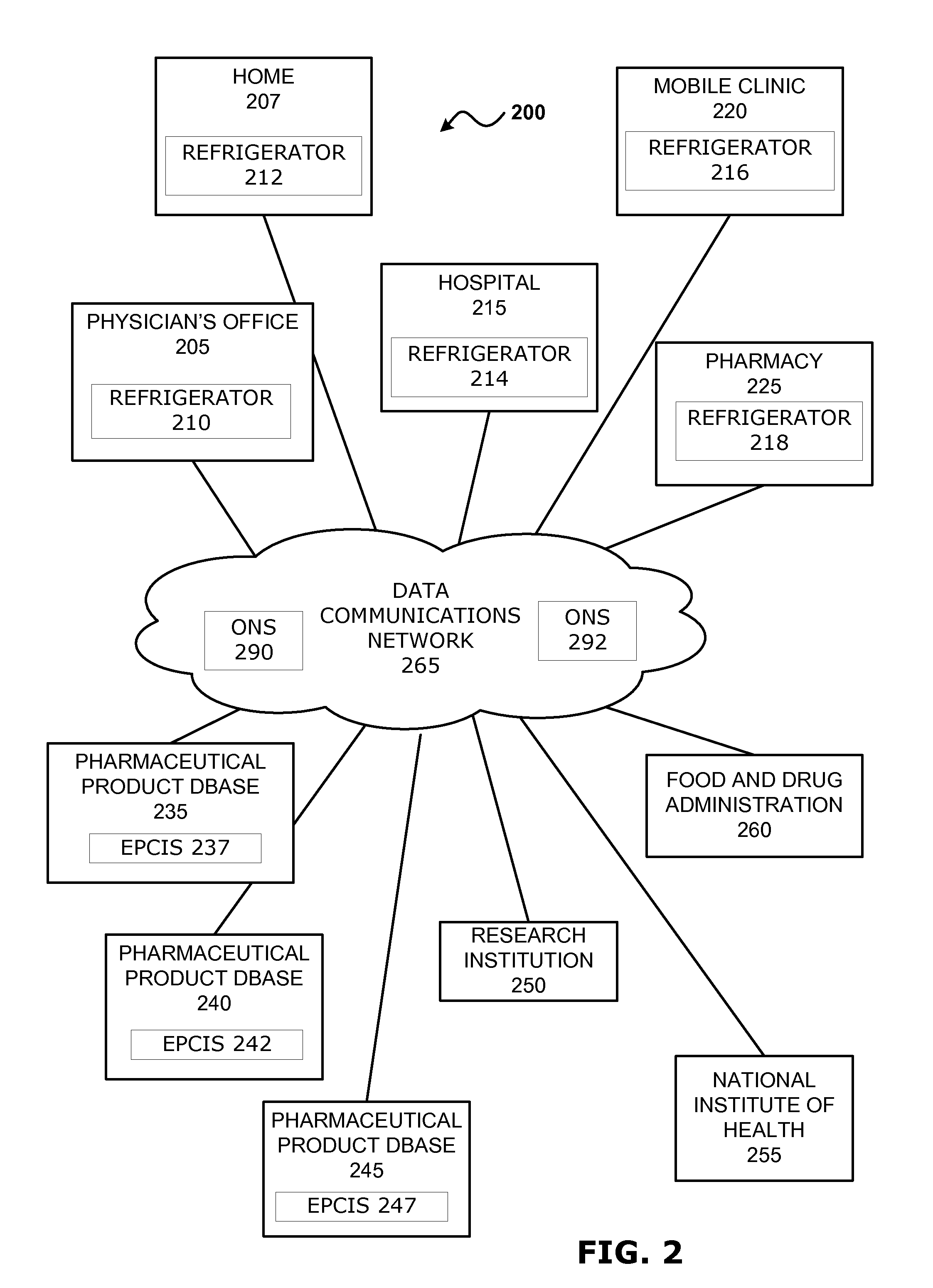
Intelligent refrigerator for storing pharmaceutical product containers
Intelligent refrigerator system for storing pharmaceutical product containers, such as vials, ampules, syringes, bottles, medication tubes, blister packs and cartons, at the point of dispensing. Embodiments of the invention use product identification technology, such as radio-frequency identification (RFID) tags and readers, to uniquely identify containers as they are added to or removed from the cold storage compartment of the refrigerator, and automatically retrieve from a local or remote database a variety of details associated with the containers and their contents, such as manufacturing data, expiration dates, time out of refrigeration, inventory levels, safety information, usage statistics, known contraindications and warnings, etc. If the details indicate that there is a problem with a particular pharmaceutical (e.g., that it is counterfeit, expired, suspect, spoiled, recalled or almost depleted), then a message or warning is automatically delivered to a human operator via an attached output device, such as a display screen, speaker or printer. Embodiments of the invention may also be configured to monitor and report temperature faults, power failures and other anomalies associated with the refrigerator or cold storage compartment.
Owner:MERCK SHARP & DOHME LLC
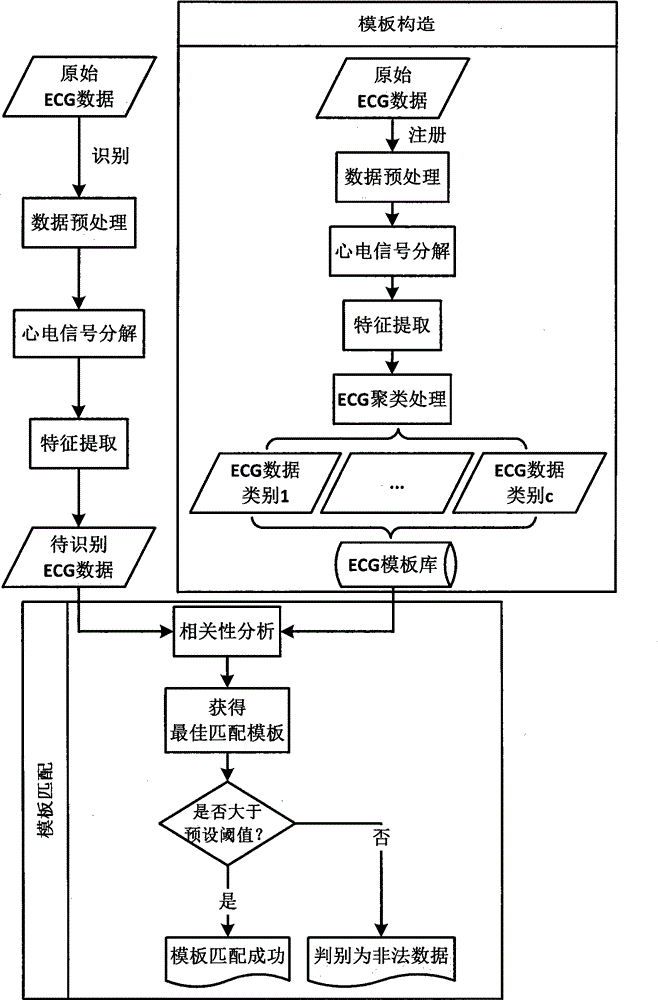
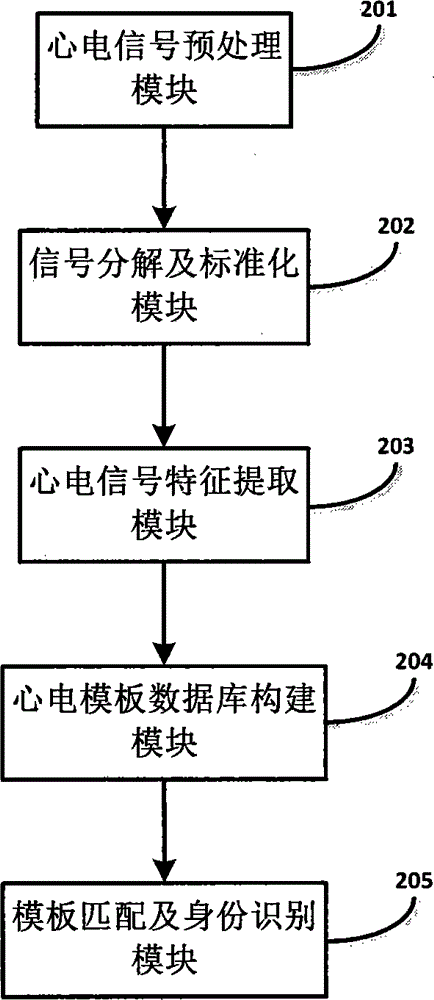
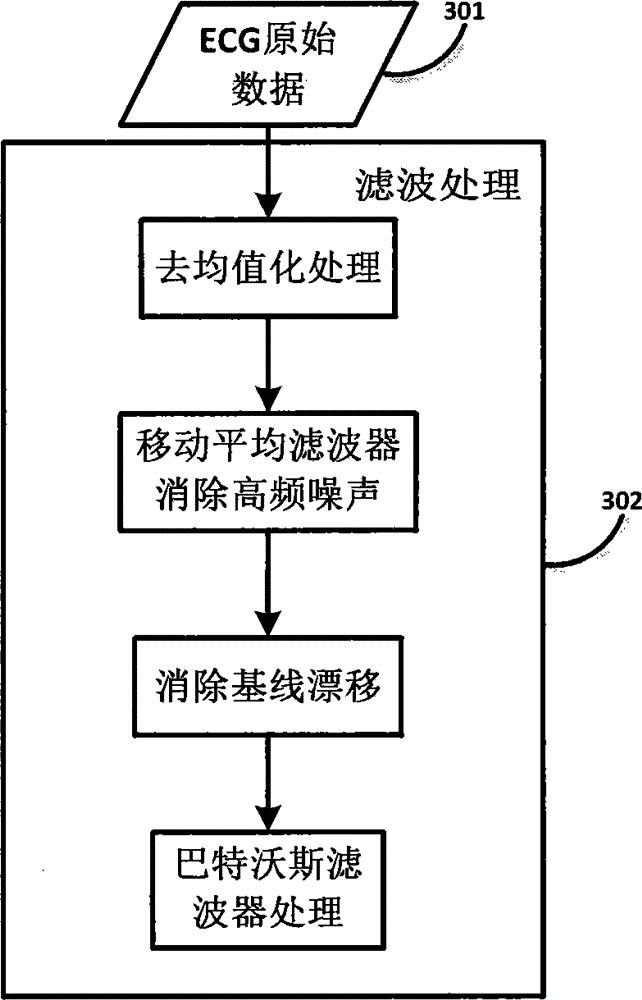
Multiple-template matching identity recognition method based on ECG (Electrocardiogram) under electrocardiogram abnormality state
ActiveCN104102915AEliminate inconsistenciesReduce time complexityCharacter and pattern recognitionDiagnostic recording/measuringEcg signalHuman body
The invention relates to a multiple-template matching identity recognition method based on an ECG (Electrocardiogram) under an electrocardiogram abnormality state, and belongs to the technical field of biological characteristic identity recognition. The ECG data of a user to be recognized is compared with the data of a registered user in a template library to obtain an identity recognition result. The key technology of the method comprises the following steps: carrying out electrocardiosignal preprocessing for eliminating noise interference; carrying out electrocardiosignal decomposition to separate an electrocardiogram waveform of each period; carrying out standardized processing for independently achieving standardization on time and amplitude scales; carrying out characteristic extraction: in the step, characteristics are extracted by wavelet transform, and clustering analysis is carried out by an ISODATA (Iterative Self-organizing Data Analysis Techniques Algorithm) so as to construct an ECC template library; and carrying out correlation analysis: in the step, correlation between ECG test data and each template is calculated, an optimal matching template is selected, and finally, an identity recognition result is obtained. The multiple-template matching identity recognition method provided by the invention utilizes the intrinsic electrocardiosignal of a human body to recognize an identity, and the ECG data under the abnormality state is considered.
Owner:SHENZHEN GRADUATE SCHOOL TSINGHUA UNIV
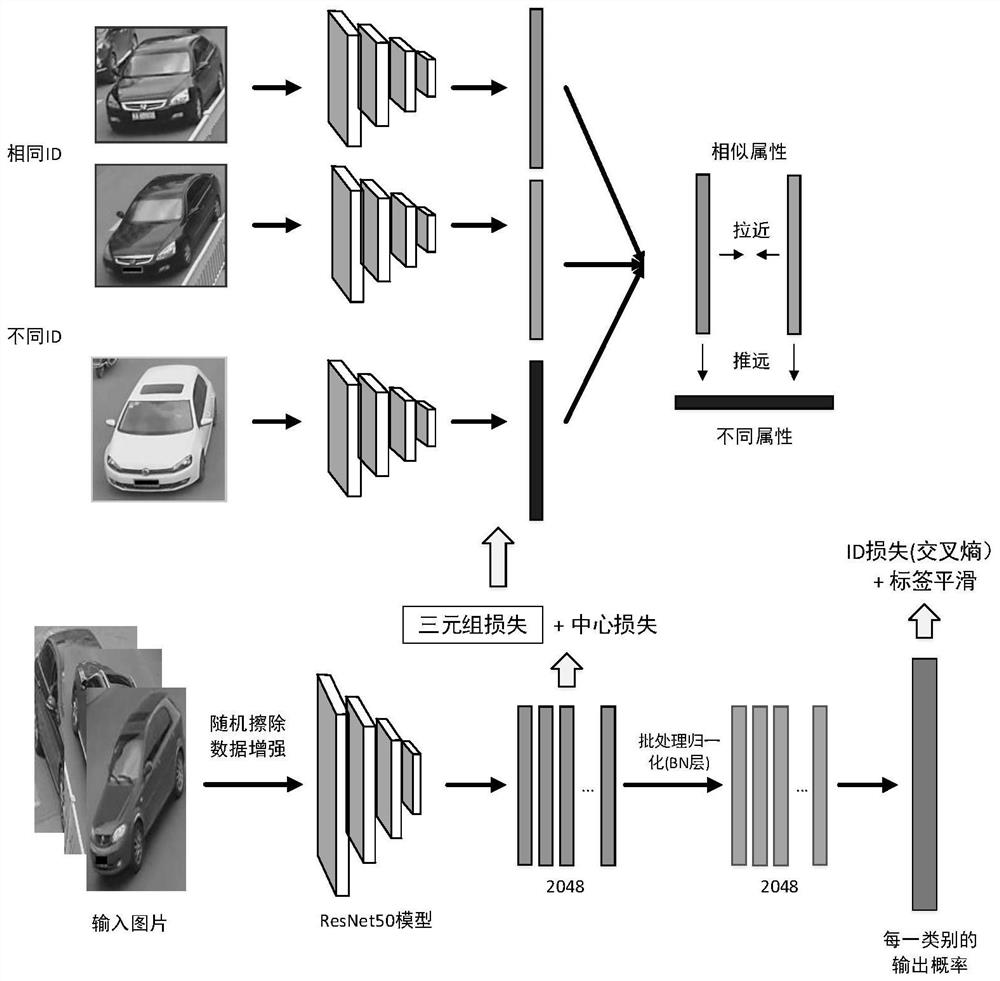
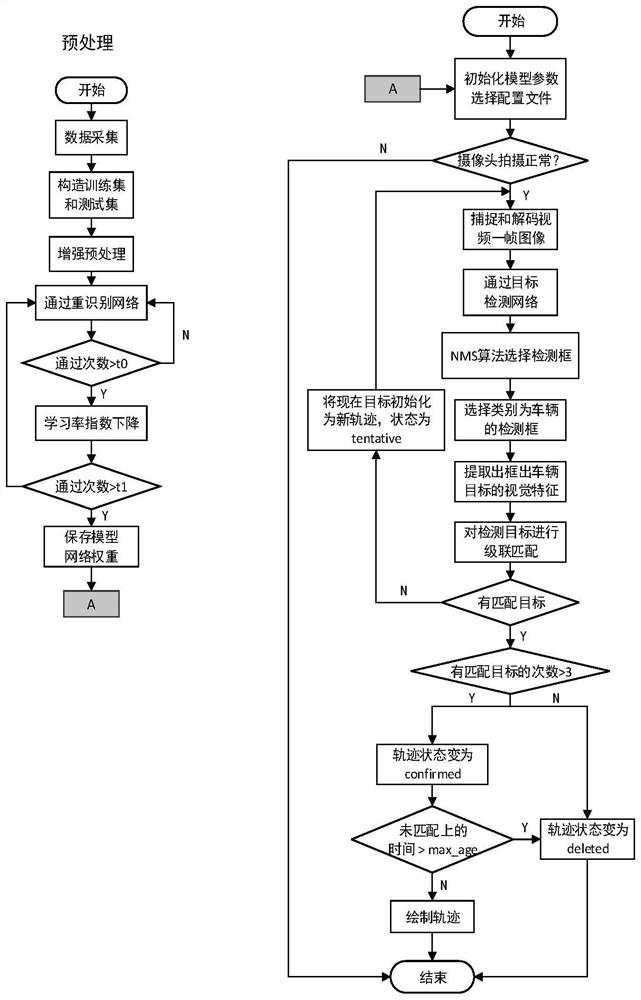
Vehicle multi-target detection and trajectory tracking method based on re-identification
InactiveCN111914664AEasy to detectRealize trajectory trackingImage enhancementImage analysisVideo monitoringVisual technology
The invention discloses a vehicle multi-target detection and trajectory tracking method based on re-identification, and belongs to the field of computer vision technology and video monitoring. The method comprises the following steps that firstly, a model capable of effectively extracting vehicle visual features on each track is trained by utilizing a vehicle re-identification technology; then, vehicle detection is carried out on each frame of image in the camera; and finally, in combination with the vehicle appearance features extracted by the re-identification model, motion prediction and visual similarity discrimination are fused, and single-camera multi-target tracking is executed, so that the driving trajectories of all matched vehicles are obtained. According to the method, multi-target matching of front and rear frames of images is successfully achieved in the aspect of tracking, the problem of tracking target shielding is effectively solved, and the appearance characteristics of the vehicle images shot by the multi-angle camera are extracted by adopting a re-identification technology aiming at the possible instability of algorithm detection performance caused by multiple visual angles and are fused into a tracking scheme, re-identification which occurs again after the tracking target is lost is achieved, and the track tracking capability is further improved.
Owner:TONGJI UNIV
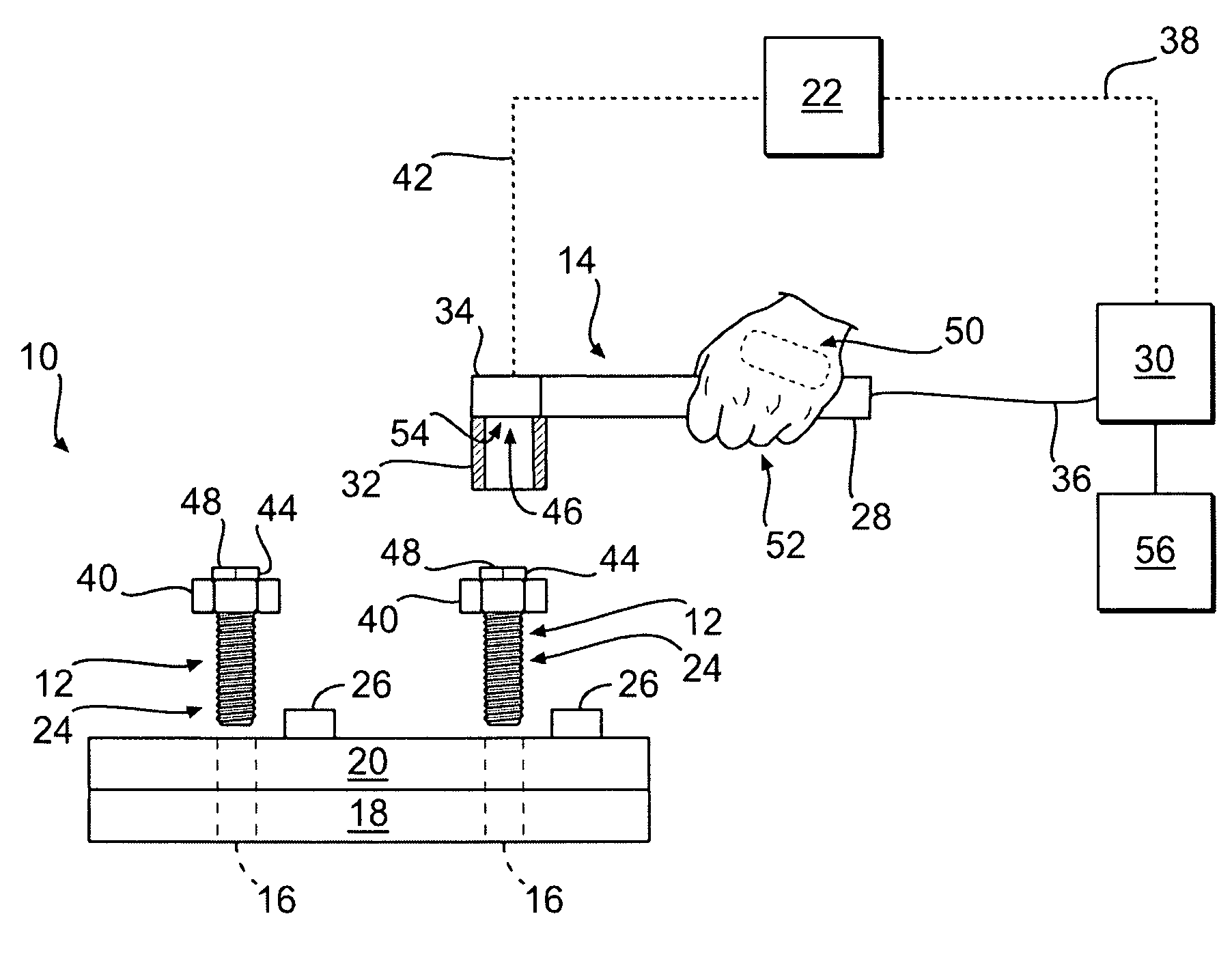
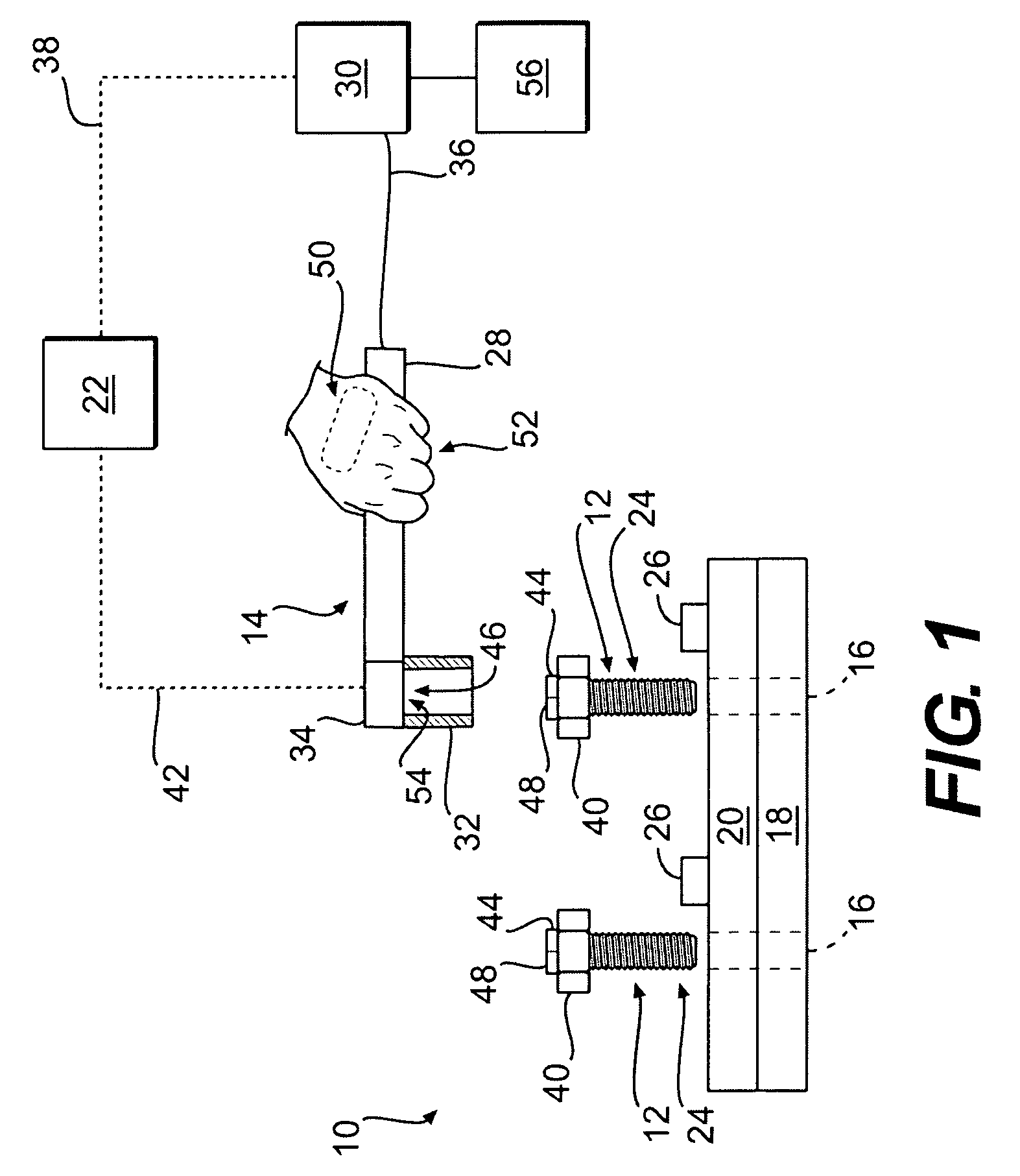
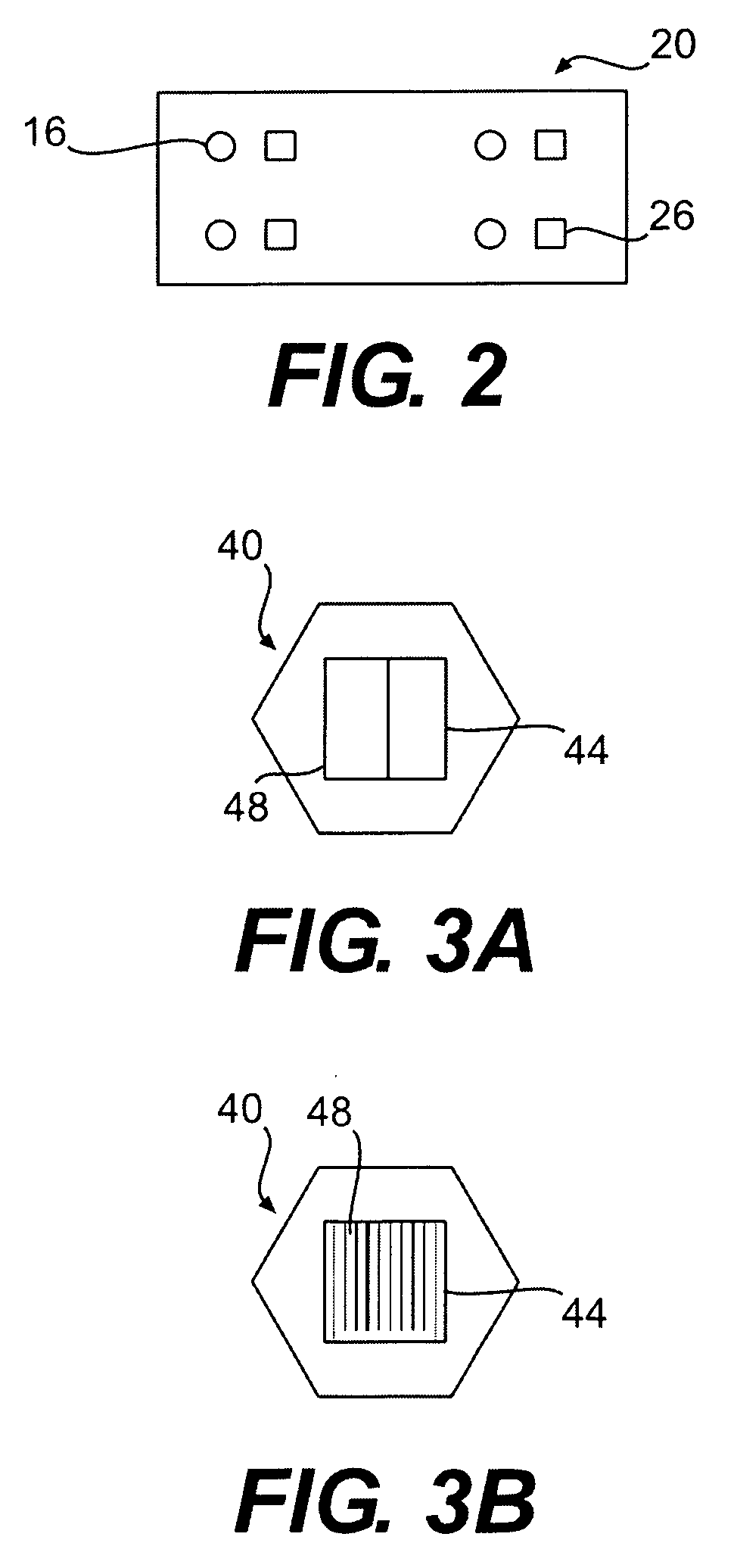
Fastener tightening system utilizing identification technology
InactiveUS20080178713A1Measurement of torque/twisting force while tighteningWork measurementSensing dataReliability engineering
In one aspect, the present disclosure is directed toward a fastener tightening system. The system has a tightening tool configured to apply a torque to a fastener. Additionally, the system has a fastener data storage device located on the fastener and configured to store data related to the associated fastener. The system further has at least one component data storage device located on a component receiving the fastener to store data related to a tightening process. A data sensor is also included and is configured to sense data stored on the fastener data storage device and the at least one component data storage device. The system also has a controller configured to regulate operation of the tightening tool based on the sensed data and the sensed parameter.
Owner:CATERPILLAR INC
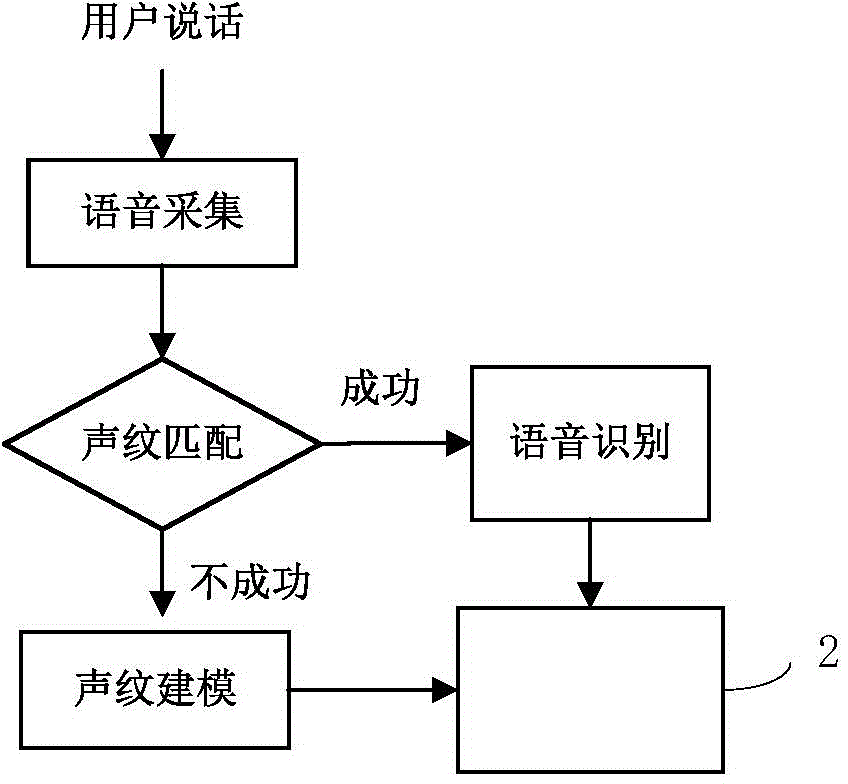
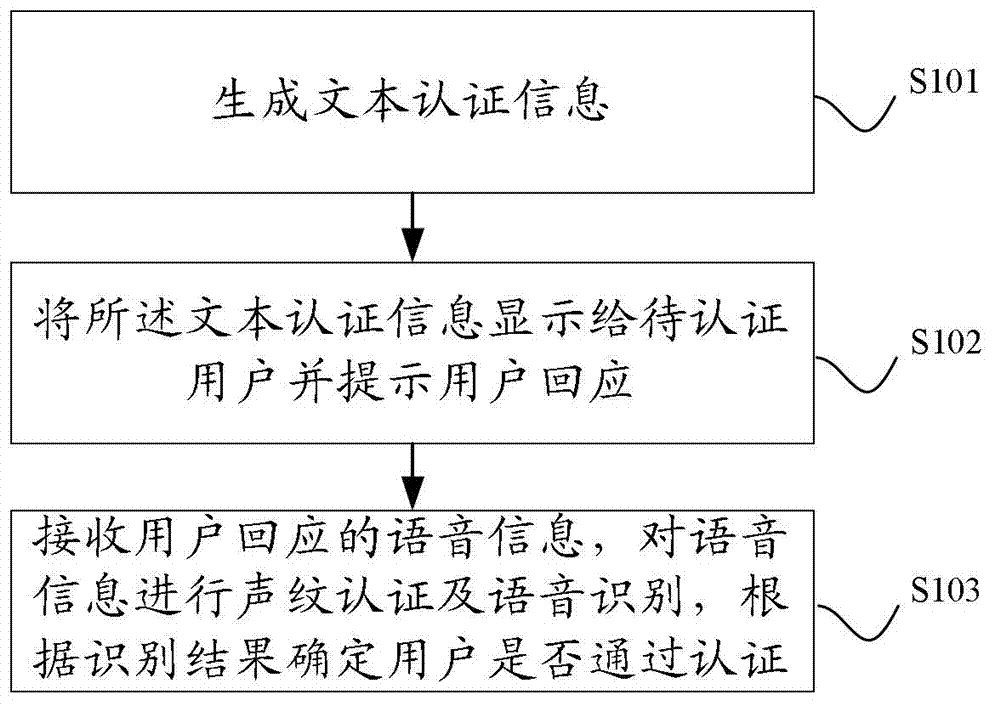
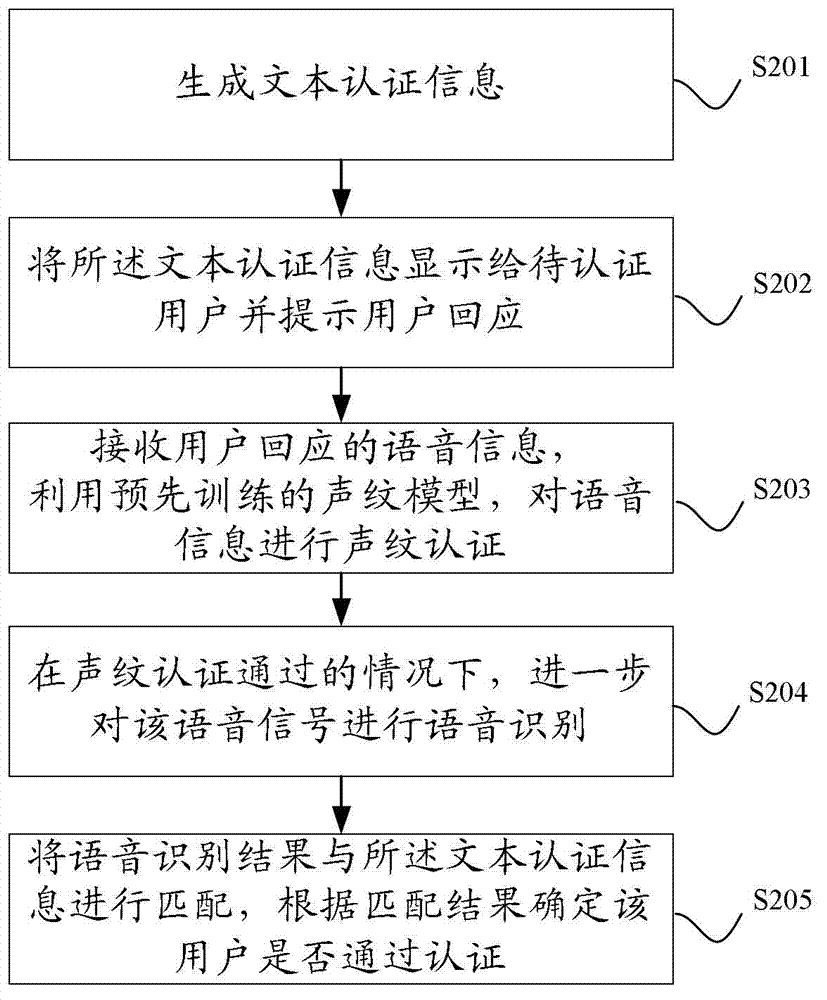
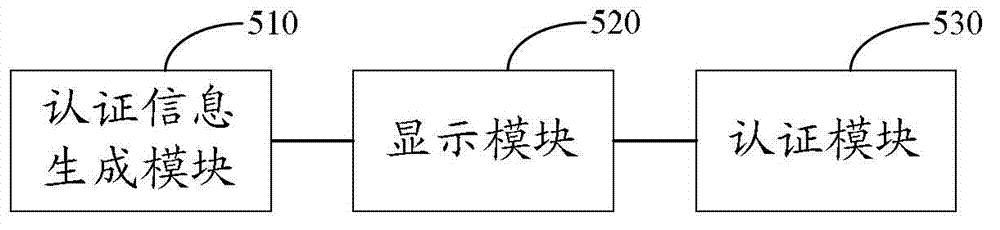
Authentication method and device based on voice
InactiveCN102737634AAvoid safety hazardsAvoid Recording SpoofingSpeech recognitionSpeech identificationSpeech sound
The invention discloses an authentication method and device based on a voice. The authentication method based on a voice comprises the following steps: generating text authentication information; displaying the text authentication information to a user to be authenticated and prompting the user to make a response; and receiving response voice information of the user, performing voiceprint authentication and voice identification on the voice information, and judging whether the user passes the authentication according to an identification result. According to the technical scheme provided by the embodiment of the invention, a voiceprint authentication technology is combined with the voice identification technology; therefore, the identity of the user can be determined through voiceprint authentication, and the user can make a response to the instantly generated authentication information; whether the content of the response voice information of the user conforms to the generated authentication content is judged through voice identification, so that record cheating can be effectively avoided; and the potential safety hazard of the conventional single voiceprint identification technology is avoided.
Owner:BAIDU ONLINE NETWORK TECH (BEIJIBG) CO LTD
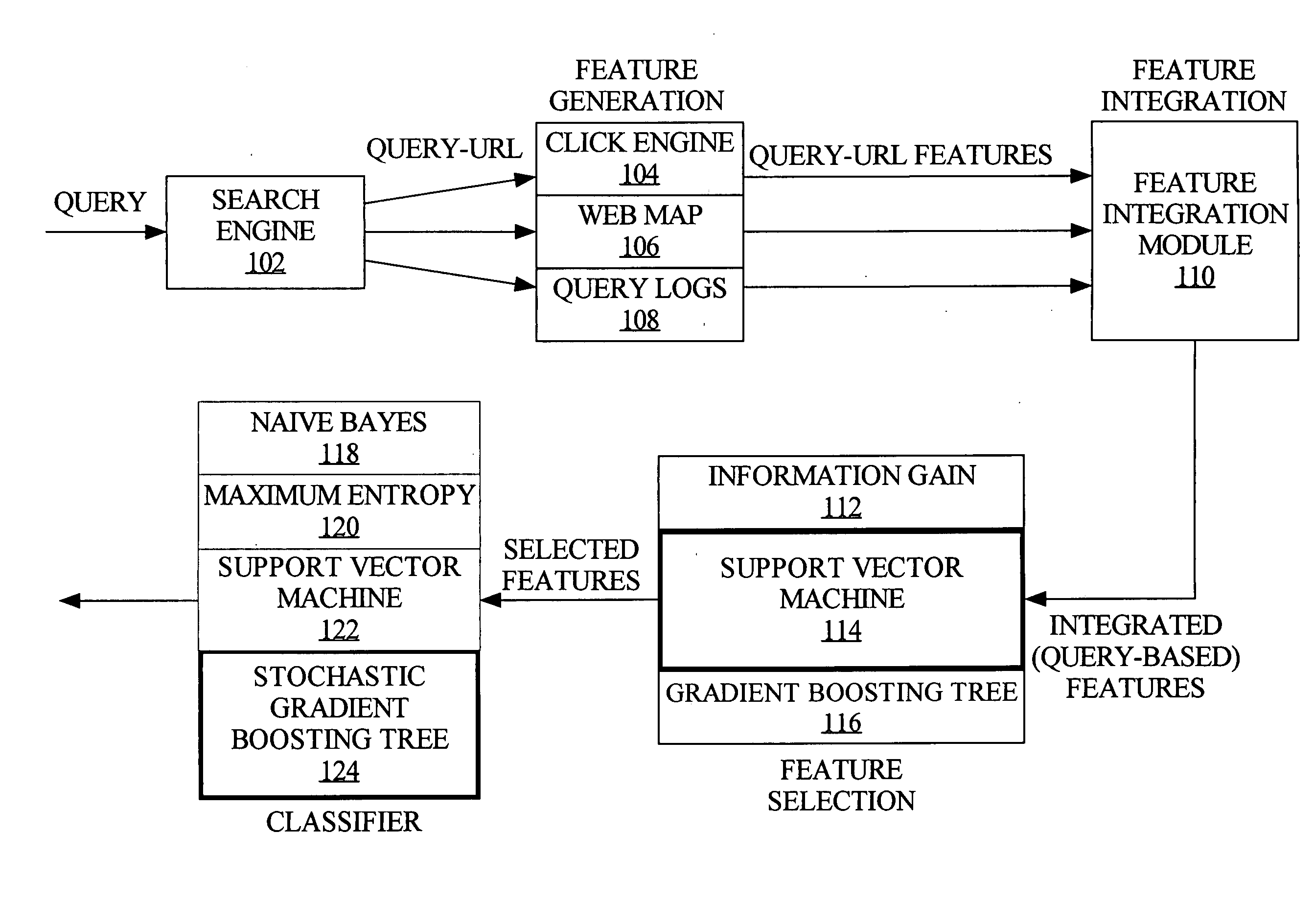
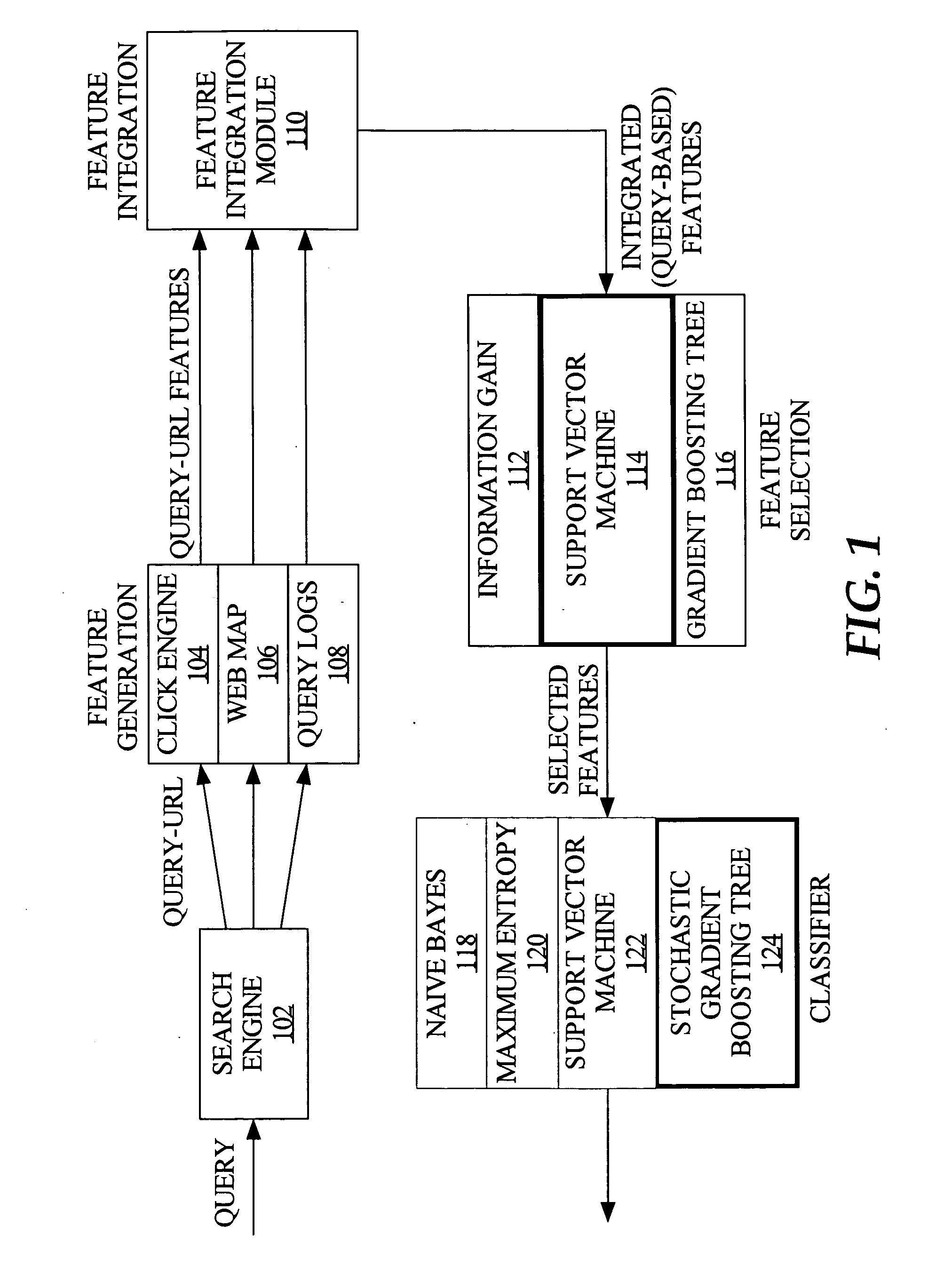
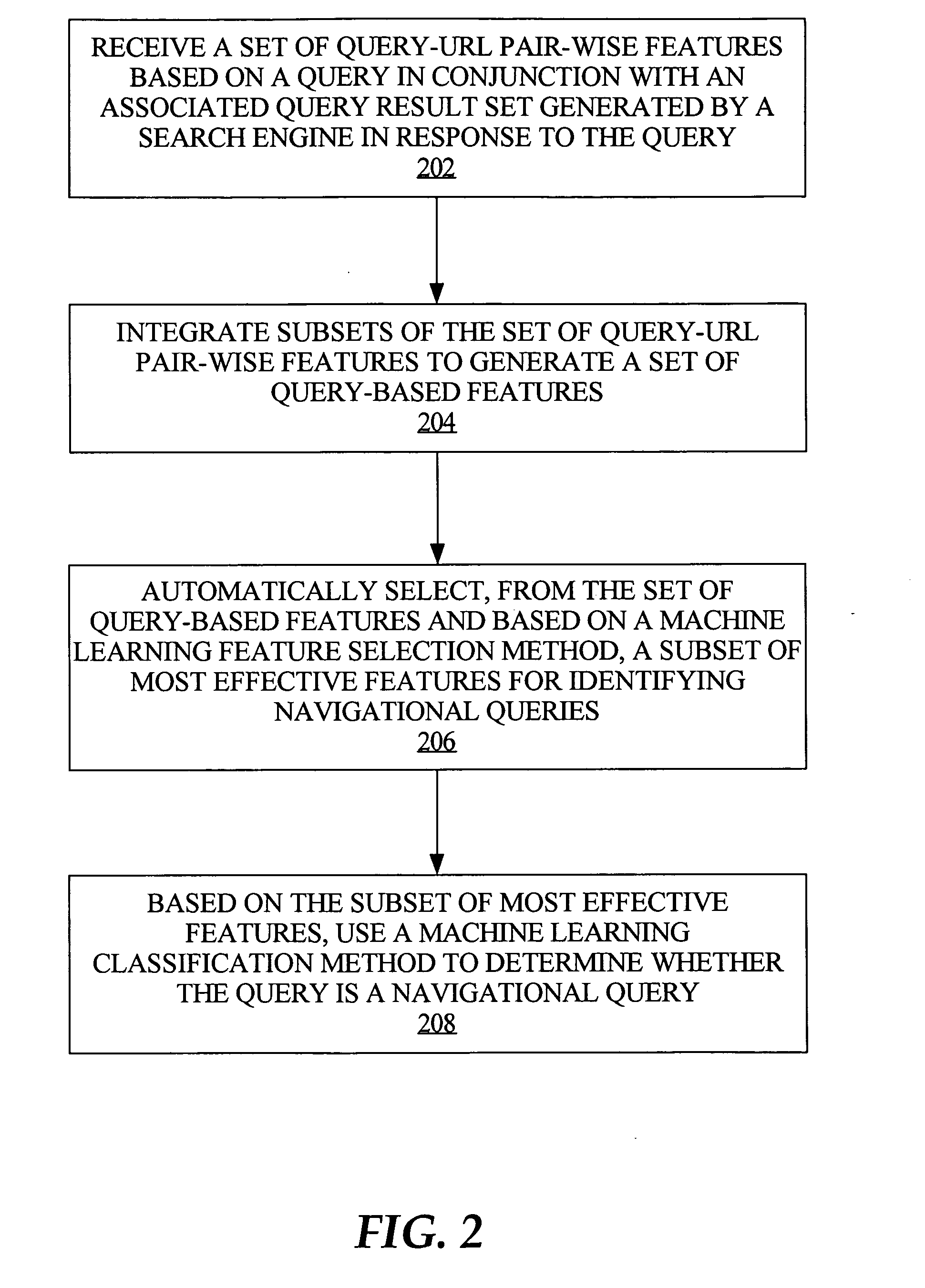
Techniques for navigational query identification
InactiveUS20080059508A1Web data indexingDigital data processing detailsThree levelSupport vector machine
To accurately classify a query as navigational, thousands of available features are explored, extracted from major commercial search engine results, user Web search click data, query log, and the whole Web's relational content. To obtain the most useful features for navigational query identification, a three level system is used which integrates feature generation, feature integration, and feature selection in a pipeline. Because feature selection plays a key role in classification methodologies, the best feature selection method is coupled with the best classification approach to achieve the best performance for identifying navigational queries. According to one embodiment, linear Support Vector Machine (SVM) is used to rank features and the top ranked features are fed into a Stochastic Gradient Boosting Tree (SGBT) classification method for identifying whether or not a particular query is a navigational query.
Owner:R2 SOLUTIONS
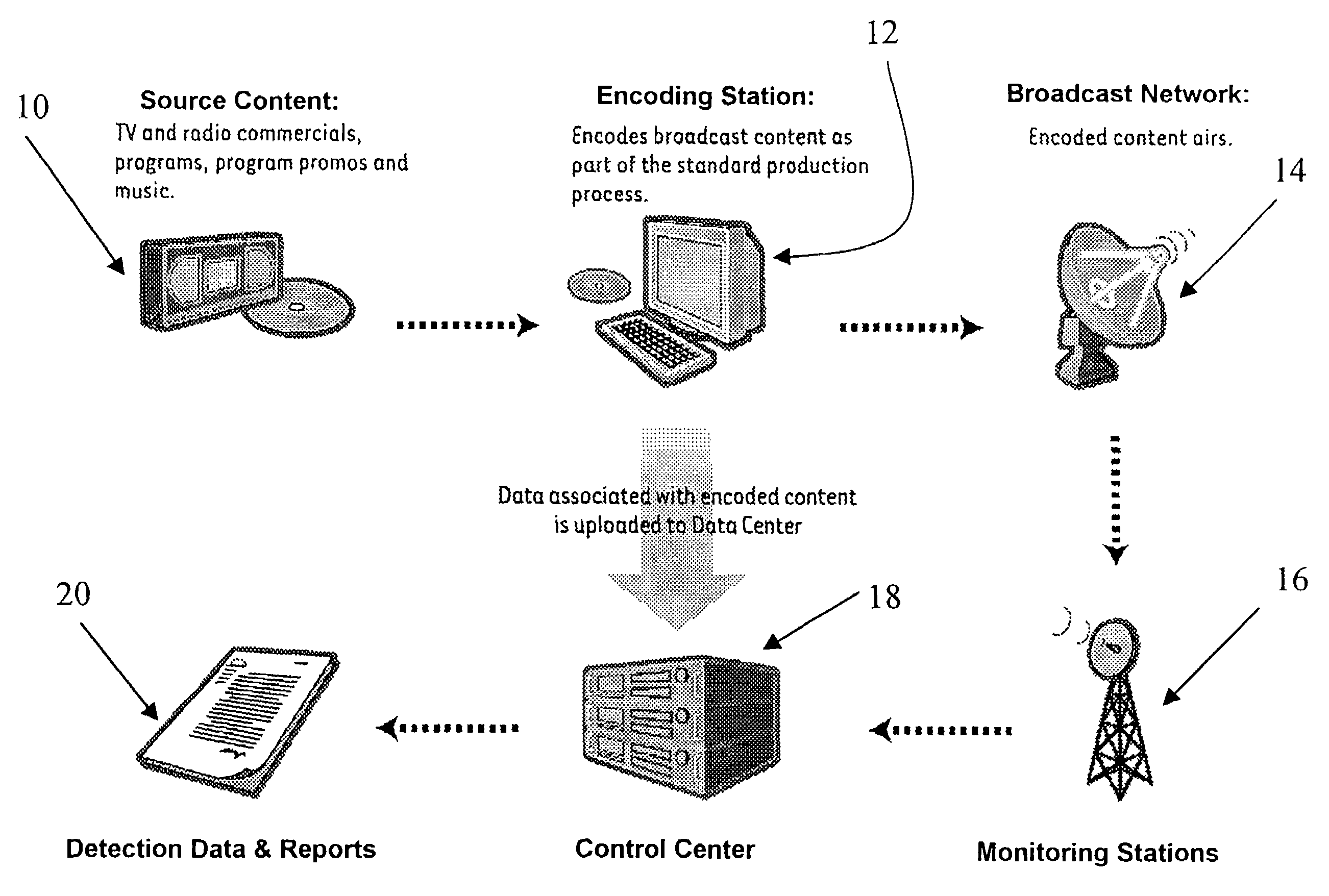
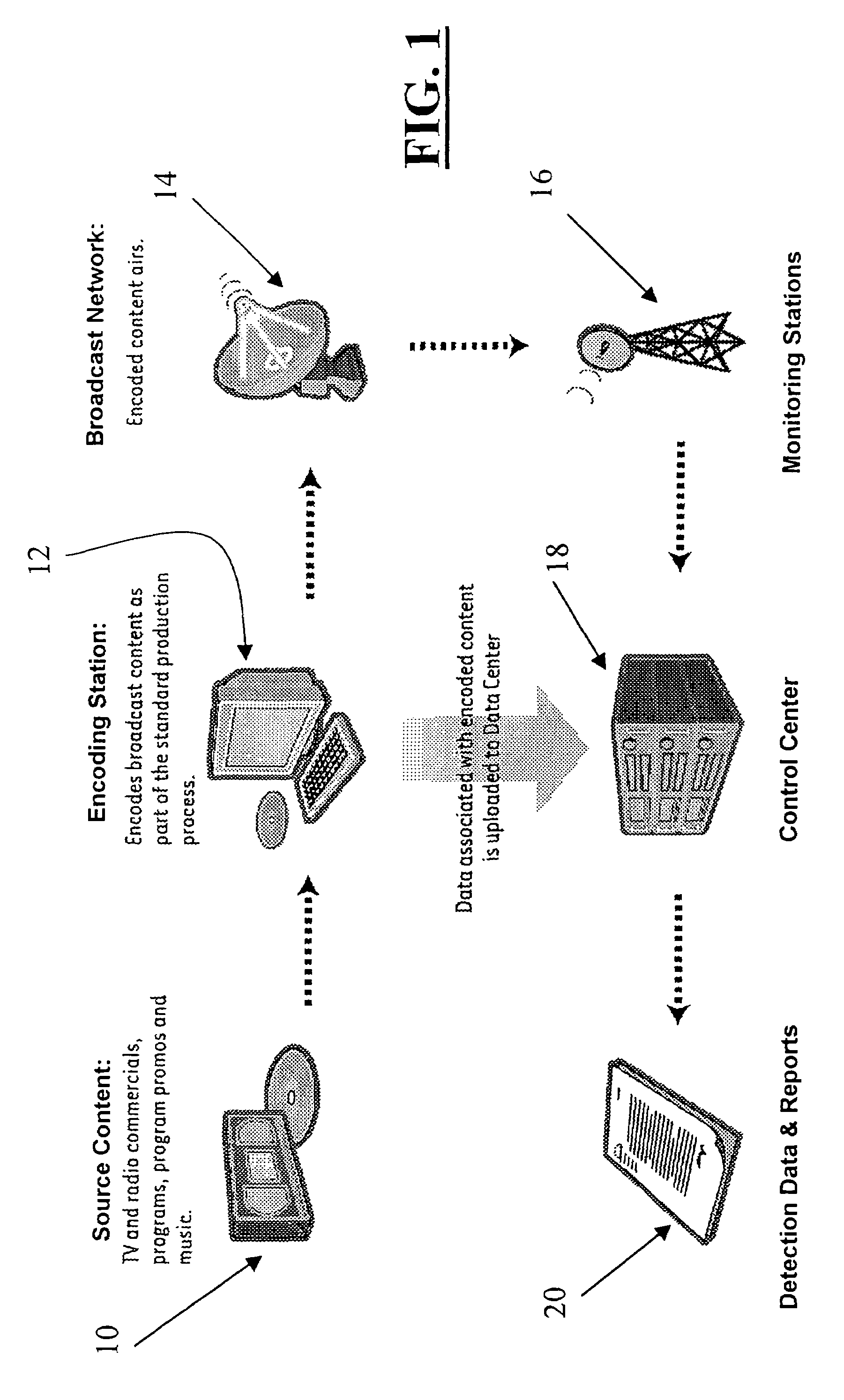
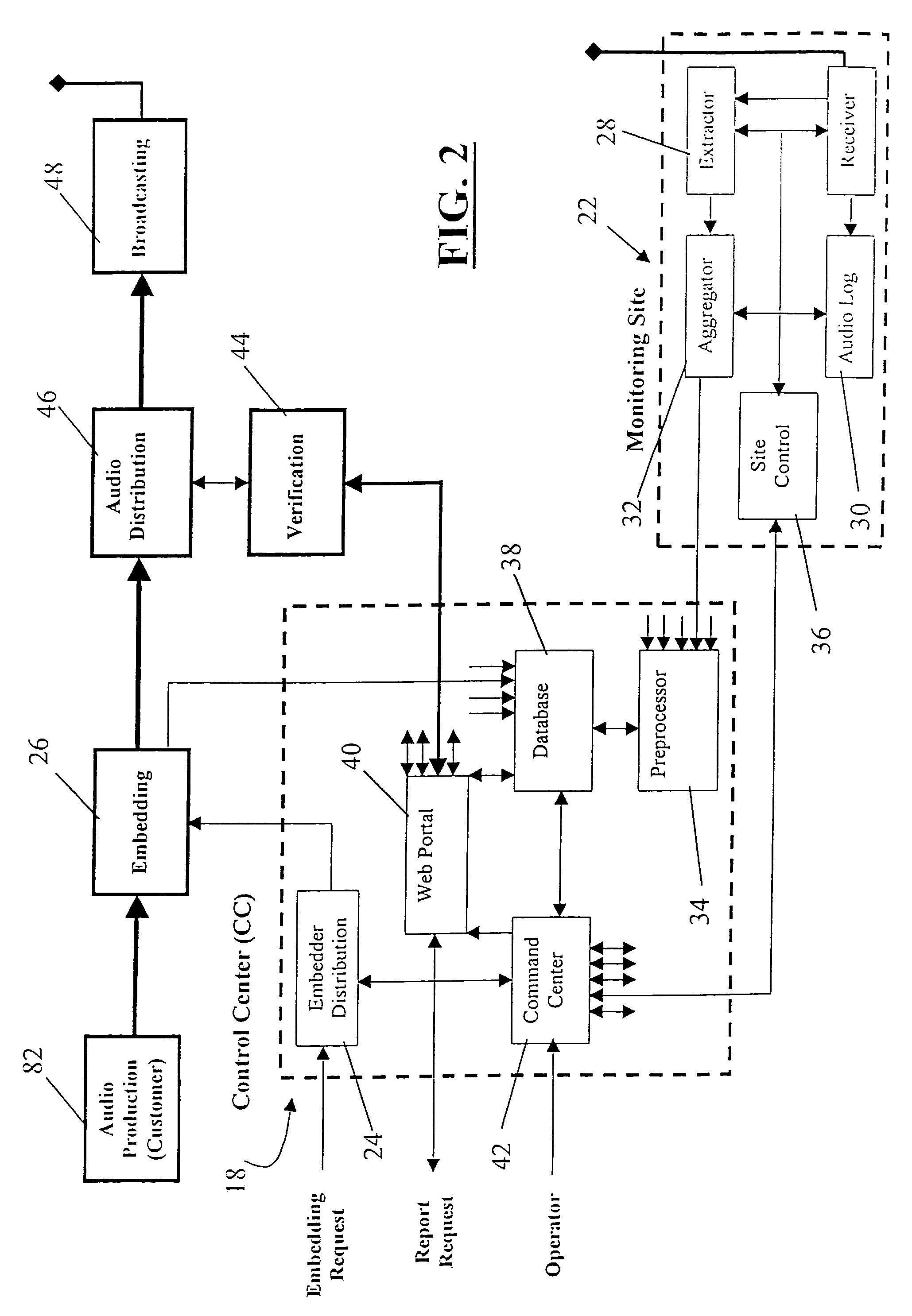
Media monitoring, management and information system
ActiveUS7788684B2Easy to monitorImprove accuracyBroadcast systems characterised by watermarksUser identity/authority verificationMonitoring systemBusiness requirements
Systems and methods are provided for monitoring transmissions of media content (such as audio and audiovisual content) in order to obtain independent and objective data regarding the use of specific media content recordings or works within the transmissions. Processing and reporting of such data is provided in various ways to serve a variety of business needs. Methods for employing content identification technology to efficiently and automatically obtain reliable, accurate, and precise monitoring data are also disclosed. Various information products and services based on such monitoring systems are proposed.
Owner:IP ACQUISITIONS LLC
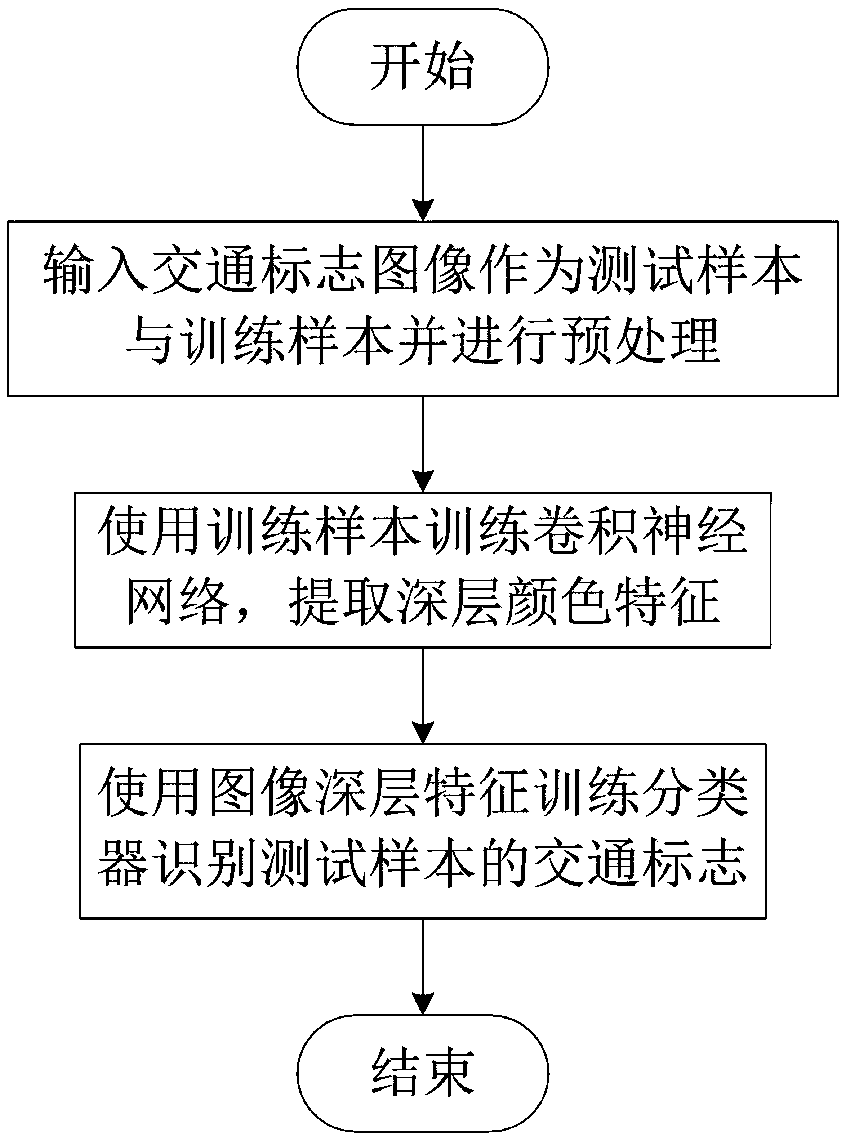
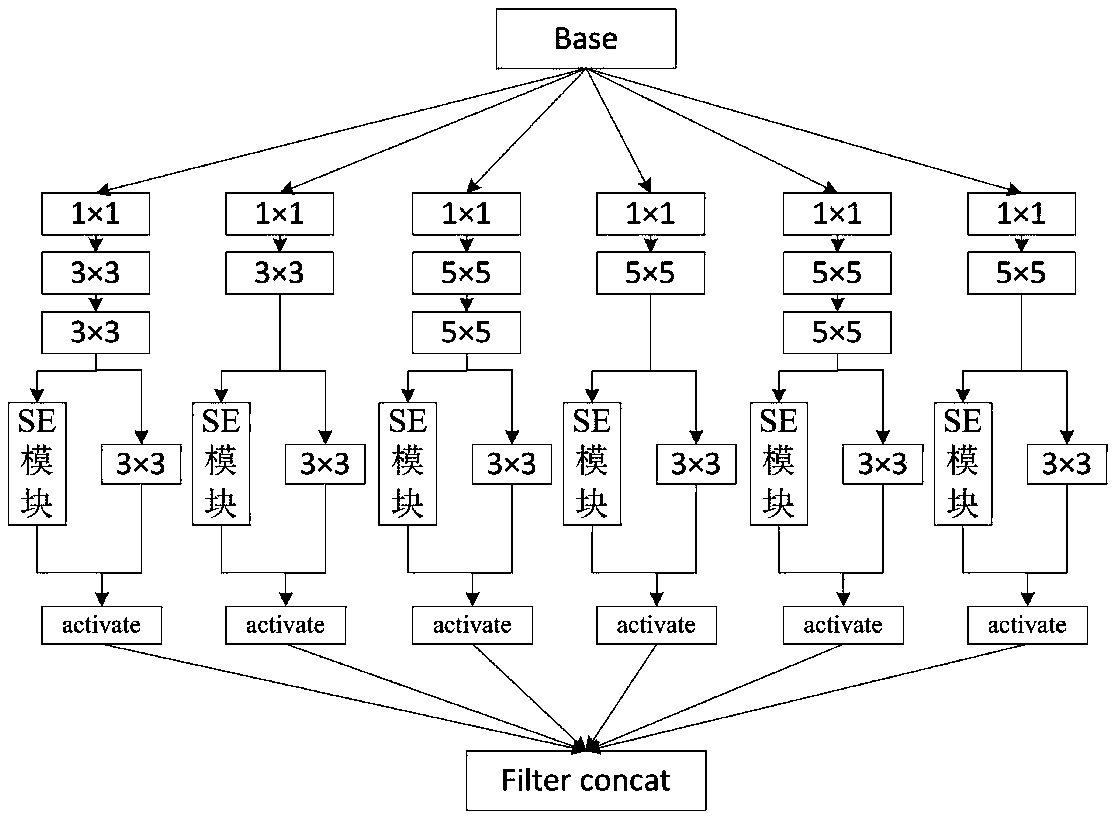
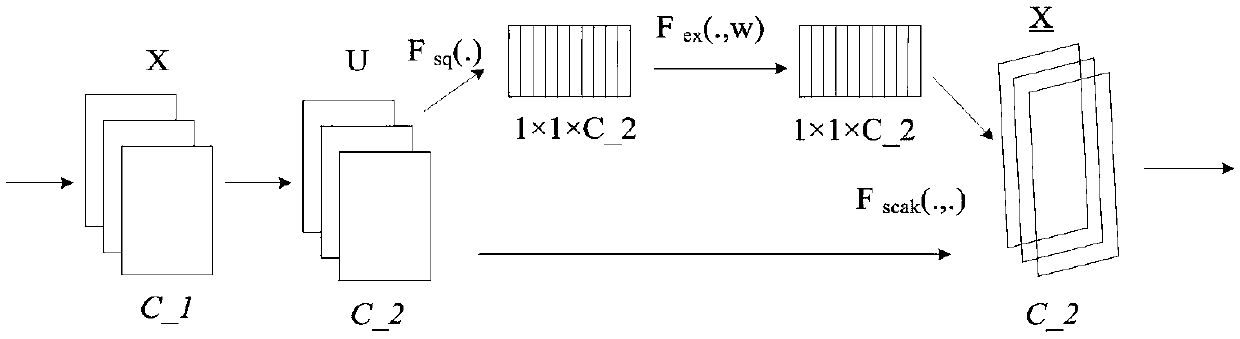
A traffic sign deep learning mode identification method
InactiveCN108710826AImprove accuracyThin Structure ParametersCharacter and pattern recognitionTraffic sign recognitionNerve network
The invention discloses a traffic sign deep learning mode identification method. The method includes the following steps: pretreatment is performed on a test sample and, a training sample of a trafficsign image, a residual deep learning network based on the multiscale characteristic weight operation fusion of a convolution nerve network is designed, the characteristic is automatically extracted by the network in order to eliminate the artificial trace mainly through training, and identification is performed on the traffic sign test sample by using a deep color characteristic trained classifier. The image characteristic weight operation combining with the multiscale convolution fusion network is applied to the traffic mode identification technology, the training efficiency of the network is substantially improved, and the problem that the accuracy and the real-time performance are not ideal, the network structure is complex, the training time is long, the stability and the robustness are bad encountered in the traffic sign identification method can be effectively solved. The image recognition accuracy of the trained network in 43 kinds of traffic signs reaches 97%.
Owner:YANSHAN UNIV
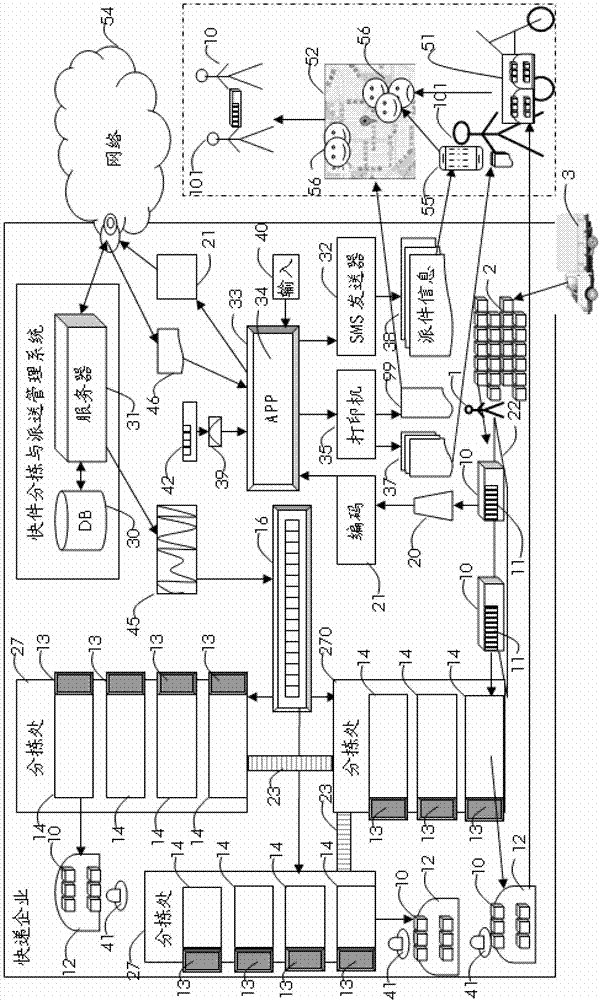
Express sorting and delivering system and method
The invention discloses an express sorting and delivering system and a method thereof. The system and the method are capable of fast sorting expresses and designing an optimal delivering scheme by using a bar-code recognition technology, a computer technology and a mechanical automation technology. In one embodiment, the information of the recipient and the coding of the express bar-code are stored in a system database in an associated way; the association of the receiving address with the delivering area ID, the guide plate ID and the sorting slide delivery port ID is established by an application program; a server searches the express coding to confirm the receiving address and issues a swing instruction to a power device controller of a multi-path guide plate so that the related guide plates swing to form a slope shape; the express slides downward and forward along the guide plate by a continuous transport device and finally falls into a holding basket below the delivery port, wherein one delivery port is provided with a plurality of holding baskets, the use sequence numbers of which can be changed by a basket changing switch; the holding baskets can be carried in the delivering vehicles, and the deliverers are capable of contacting the recipients orderly and fast delivering the expresses with the help of the delivering list and the printout of the optimal delivering route as well as a smart phone.
Owner:张革伕
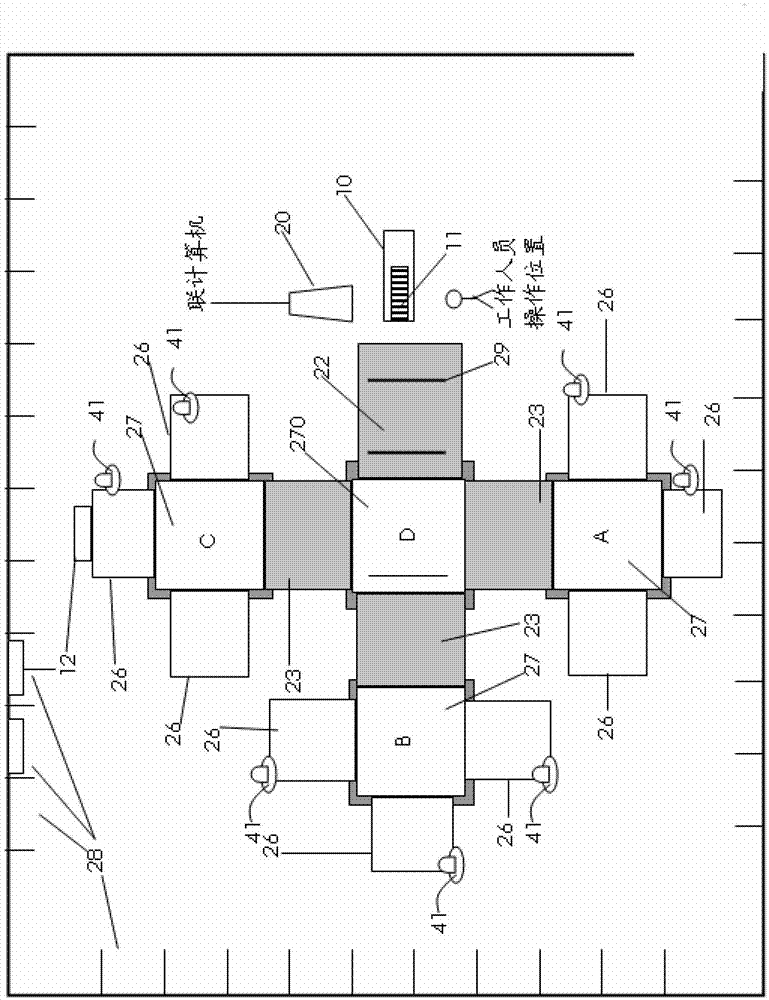
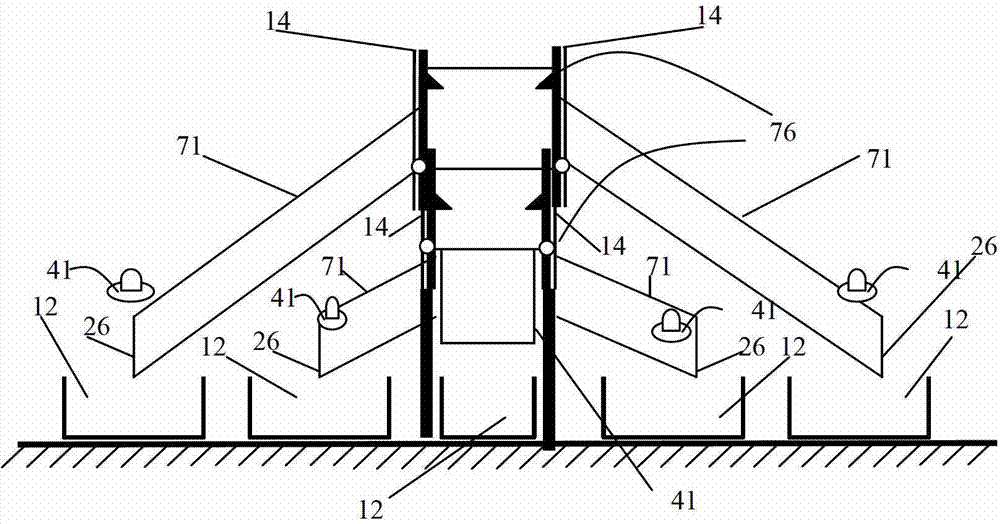
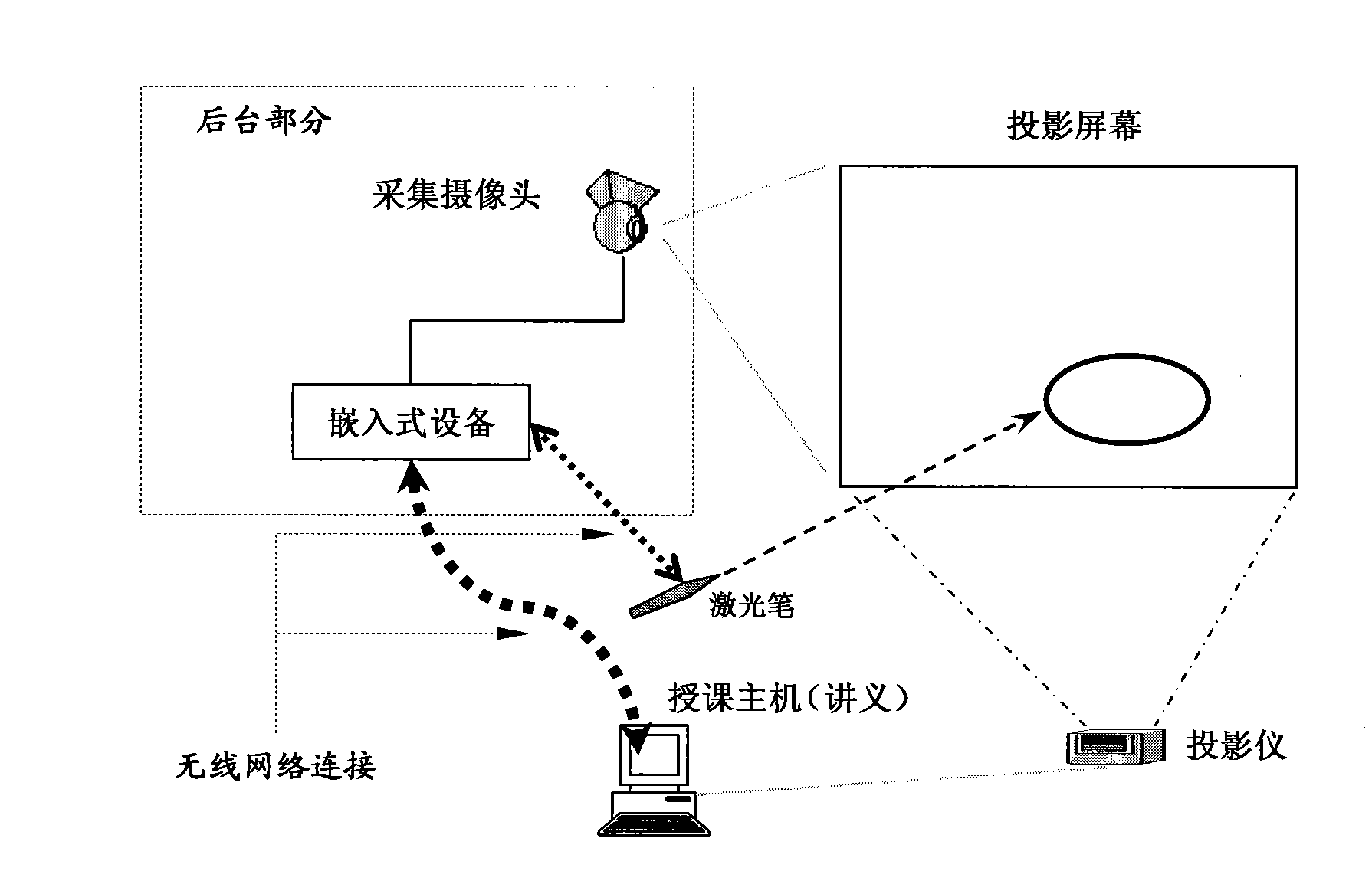
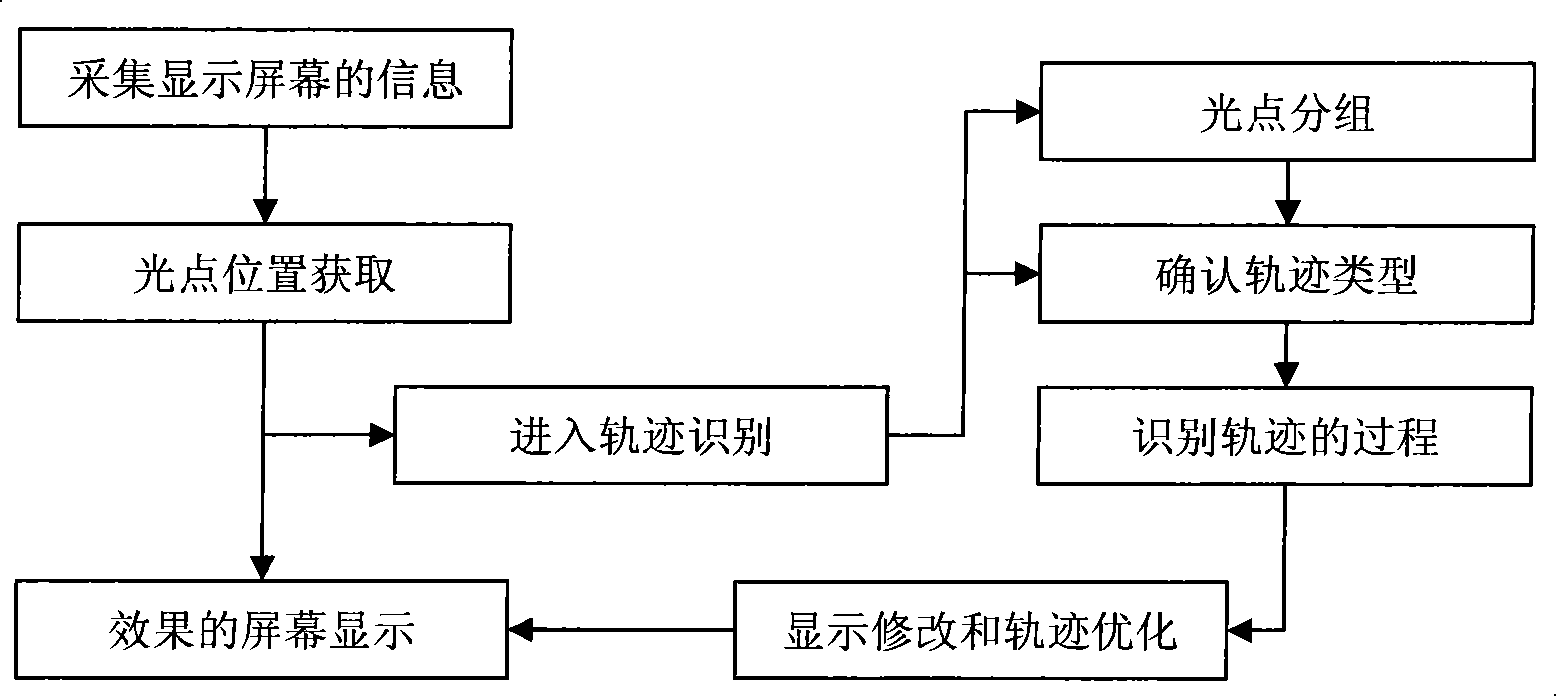
Laser pen indication and luminescent spot track recognizing method
InactiveCN101251784ATeaching continuity and freedomProduce wear and tearReadingCharacter and pattern recognitionLight spotComputer vision
The present invention discloses a laser pen indicating and light spot trajectory identification method which belongs to the interactive reorganization technical field. Step 1, according to laser pen indicating information, a user obtains video information of a display screen from a video input device; step 2, an embedded device extracts light spots from the acquired video information, and determines the positions of the light spots after a de-noising process; step 3, the position coordinates of the light spots are transmitted to a computer which controls a target screen; step 4, according to the position coordinates of the light spots, the computer which controls the target screen recognizes the light spot trajectory; with the specific light spot information, the trajectory information indicated by the user is obtained; when the recognition is succeeded, step 5 is carried out; step 5, after the trajectory recognition is succeeded, the trajectory of the recognition result of the original trajectory is optimized, so that a new trajectory is obtained; the optimized result is displayed with visually optimized effect on the target screen to replace the indication effect of the step 3. The method can be applied in various interactive recognition display circumstances so as to carry out highly effective light spot analysis and trajectory recognition.
Owner:SHANGHAI JIAO TONG UNIV
Augmented reality messaging system and method based on multi-factor recognition
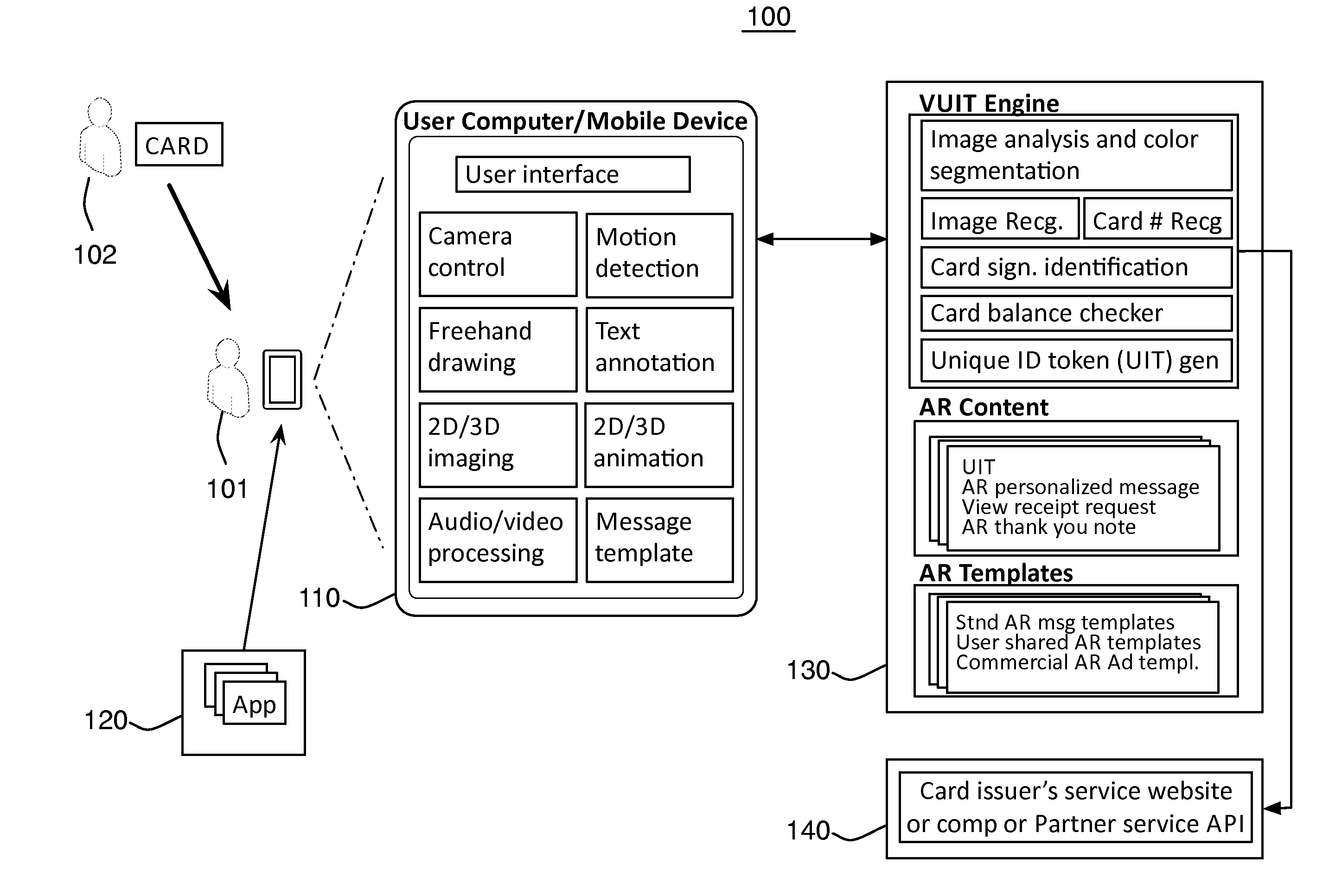
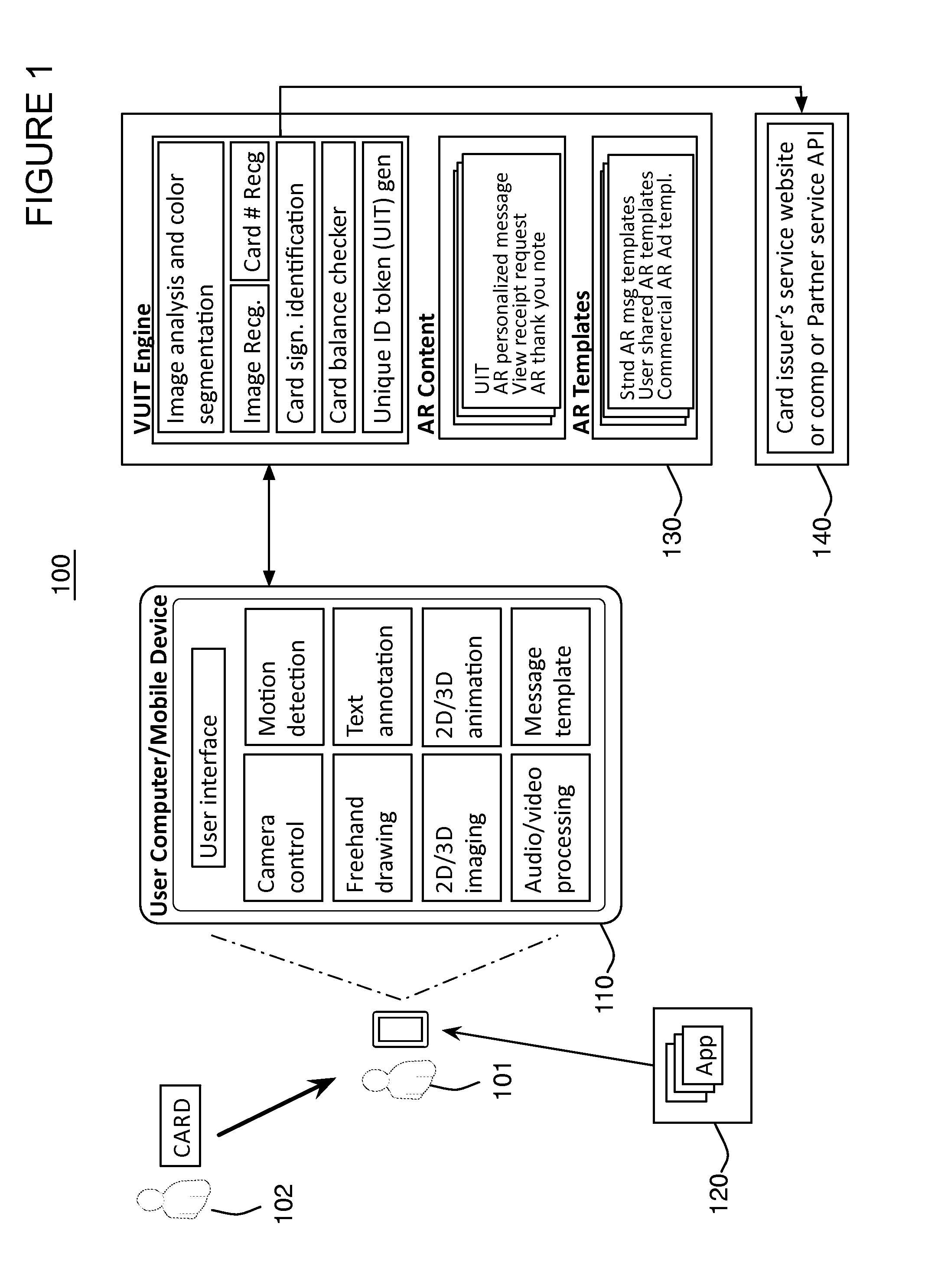
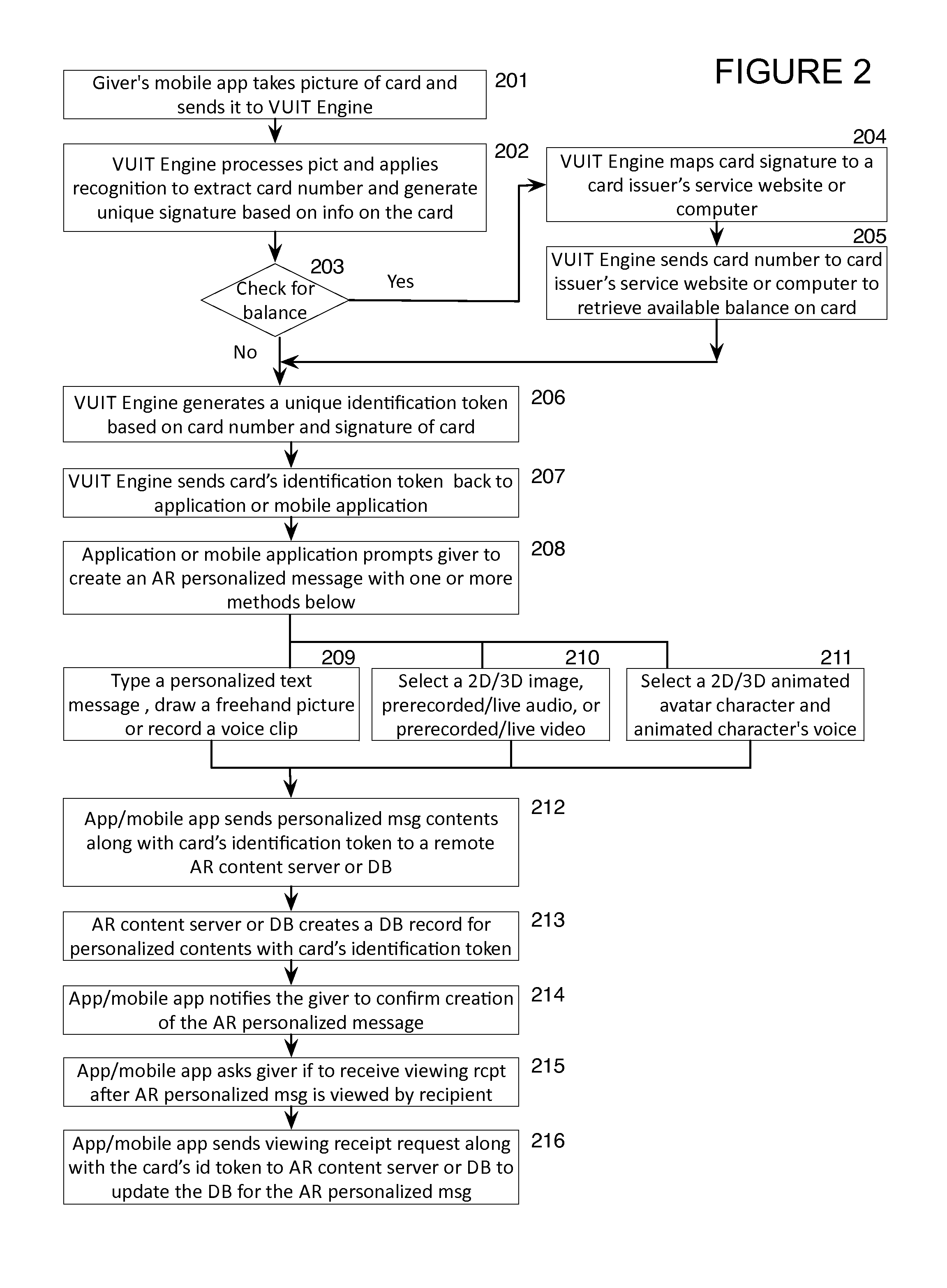
ActiveUS20140076965A1Accurate and reliable processPayment architectureWireless commuication servicesPersonalization3d image
Enables creating, displaying, and managing augmented reality (AR) messages linked to objects that display or contain identifiable information such as codes, including card products / prepaid card products, etc. Applies multi-factor recognition technology to process an object / card having a unique code. May utilize an application on a mobile device / computer, to capture an image of the object, recognize the signature of the object, convert the code into alphanumeric digits and generate a Unique Identification Token (UIT). The application can create a personalized AR message, e.g., text, 2D / 3D image, freehand drawing, animation, video, audio, avatar character, or any combination, optionally enhanced with pre-made templates. The completed message is stored in a remote database with the UIT. The recipient of the object / card uses the application and captures an image of the object or card image with code, triggering the message experience that may display account balance information and targeted advertising.
Owner:BECOREST WILLIAM +1
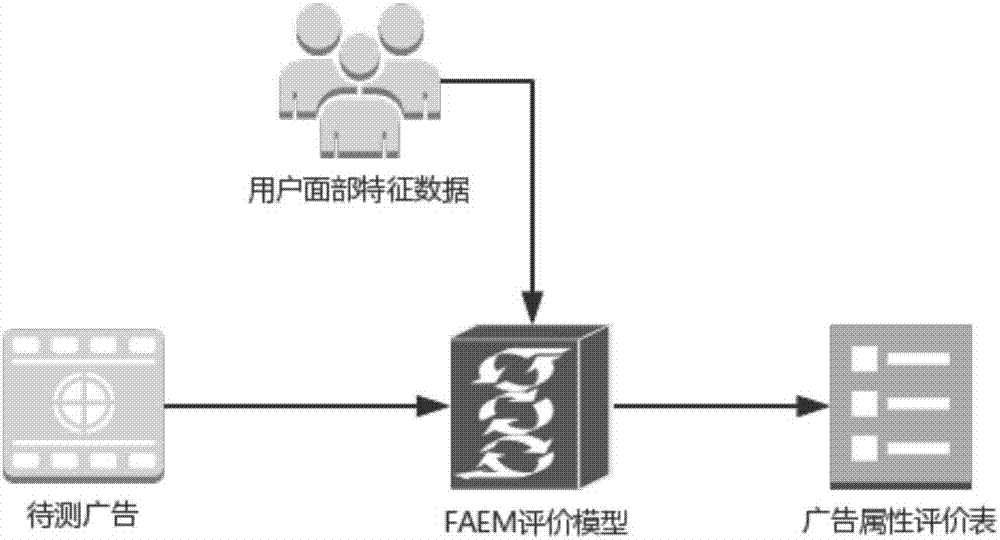
Advertisement injecting effect evaluation and intelligent push decision method based on face identification and big data analysis
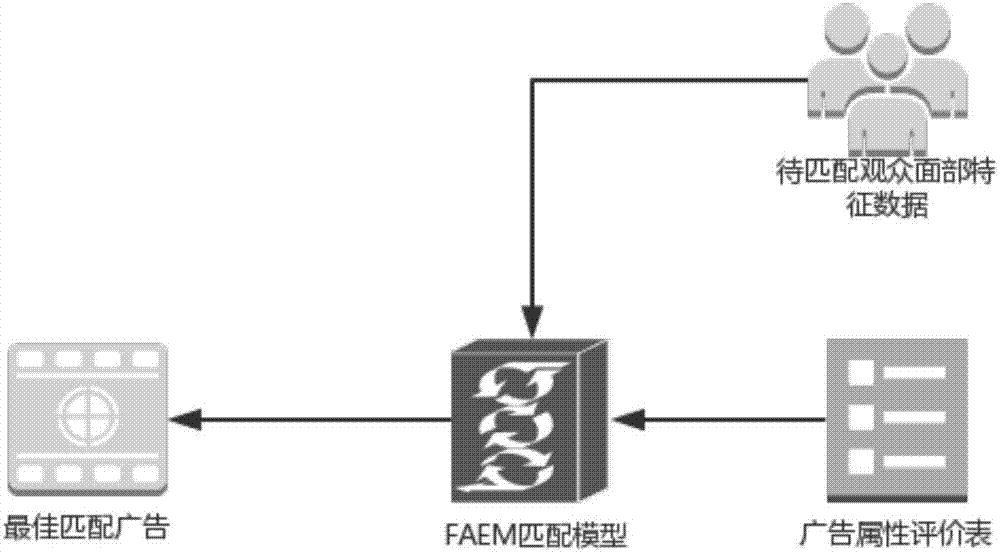
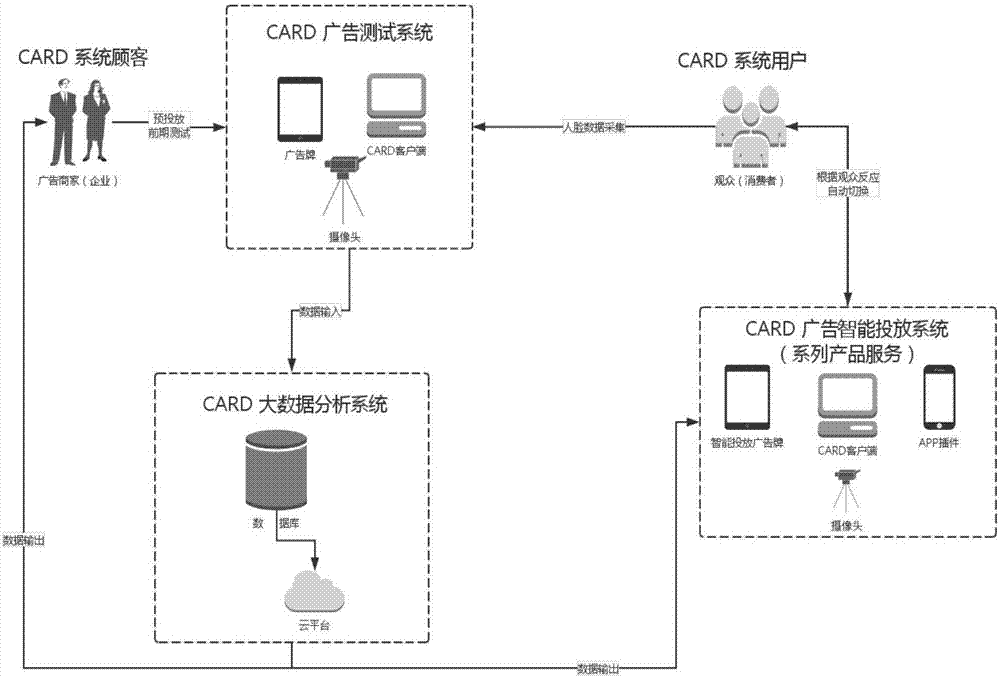
The invention discloses an advertisement injecting effect evaluation and intelligent push decision method based on face identification and big data analysis. The advertisement injecting effect evaluation and intelligent push decision method comprises a face identification technology is employed to obtain face feature data of the audience group, and the data is introduced into an advertisement injecting effect evaluation module as parameters, and is used for quantifying the advertisement injecting effect; furthermore, historical data is stored in a database, a data analysis system can carry out further analysis, the analysis result can be provided for the advertiser as an injecting decision reference, and can also be provided for the advertising agency who can carry out reasonable bidding and charging on the advertising position. At the same time, an FAEM matching algorithm is employed to match the advertisement played at present with audience face feature data at present, and advertisement push is carried out in dependence on the matching result. According to the invention, accurate evaluation of the advertisement injecting effect can be given out scientifically and objectively, and advertisements can be injected selectively and intelligently in dependence on audiences of the advertisements.
Owner:杨伊迪
Biometrics-based device for detecting indentity of people and identification
InactiveCN101669824AReduce work intensityReduce error ratePerson identificationCharacter and pattern recognitionFace detectionProcess module
The invention discloses a biometrics-based device for detecting identity of people and identification, which comprises an omni-directional vision sensor used for acquiring the facial image of an ID card holder, an ID card reader used for reading the photograph information in a bulit-in chip of the second-generation ID card and a microprocessor used for comparing whether the facial photograph imagestored in the built-in chip of the second-genration ID card and the facial images acquired by the omni-directional vision sensor are consistent or not, wherein the microprocessor comprises a data module used for reading photograph image in the ID card, a first facial detecting module, a first facial feature extraction module, a panoramicpicture reading module, a second facial detecting module, animage expanding module, a second facial feature extraction module, an identity detecting module for the biological feature of people and the ID card and a decision-layer voting and processing module.The device adopts biometrics identification technology, can greatly improve the efficiency for validating the ID card, and reduce the working strength and error rate of office personnels.
Owner:ZHEJIANG UNIV OF TECH
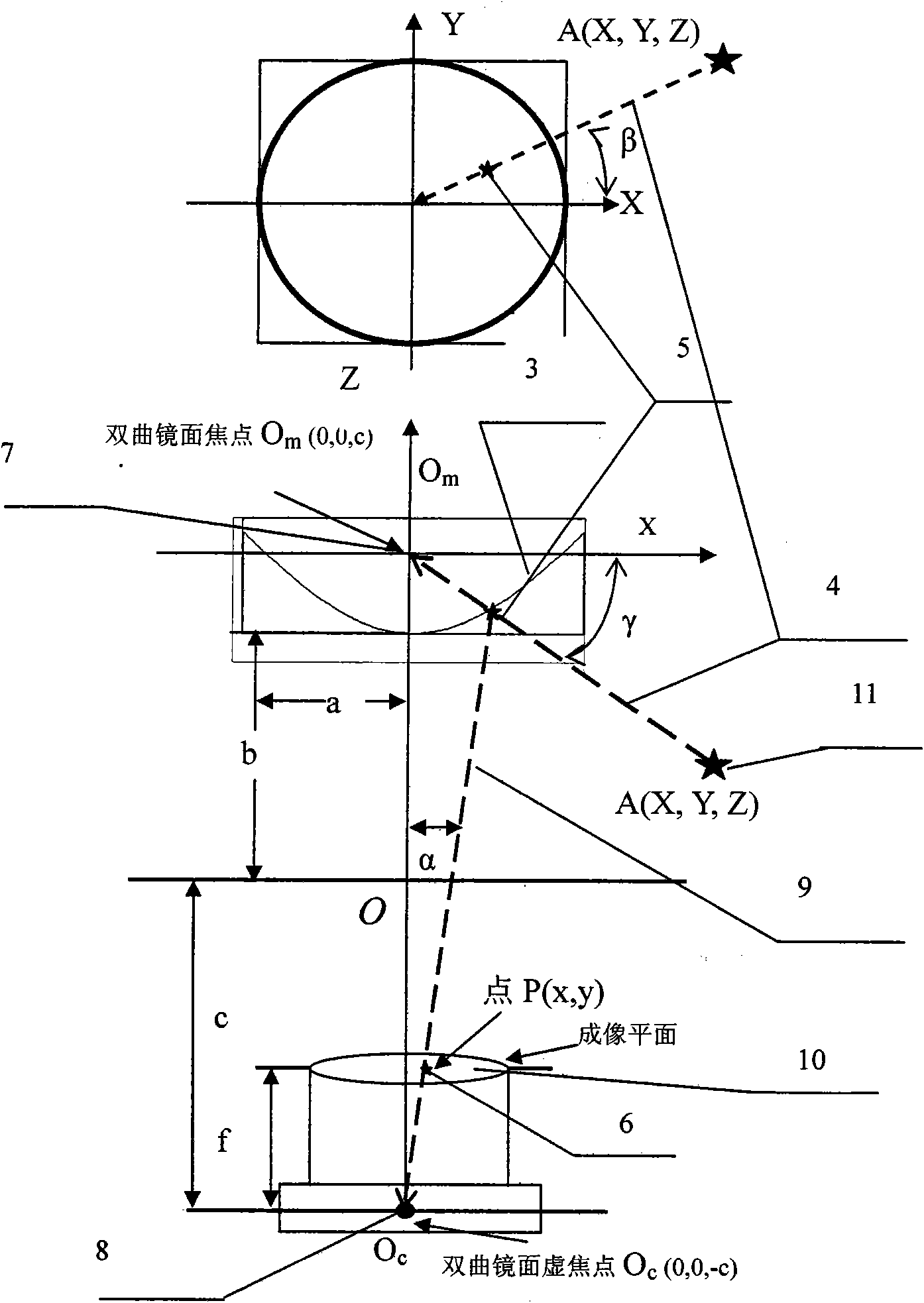
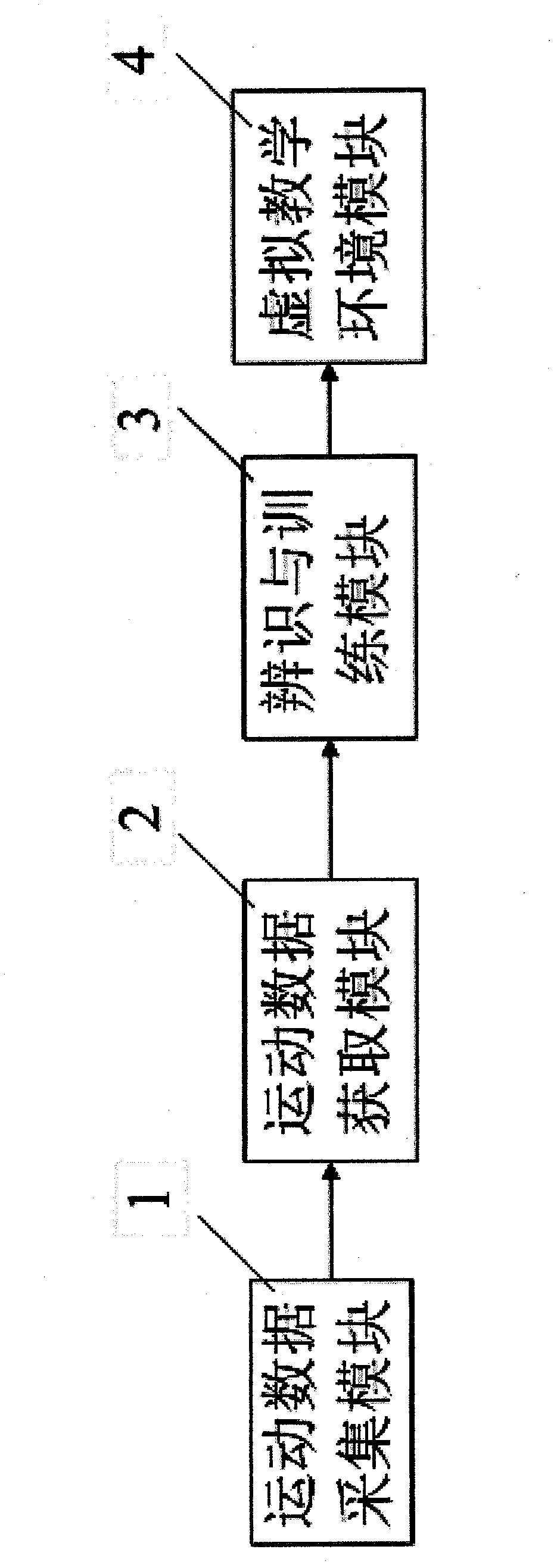
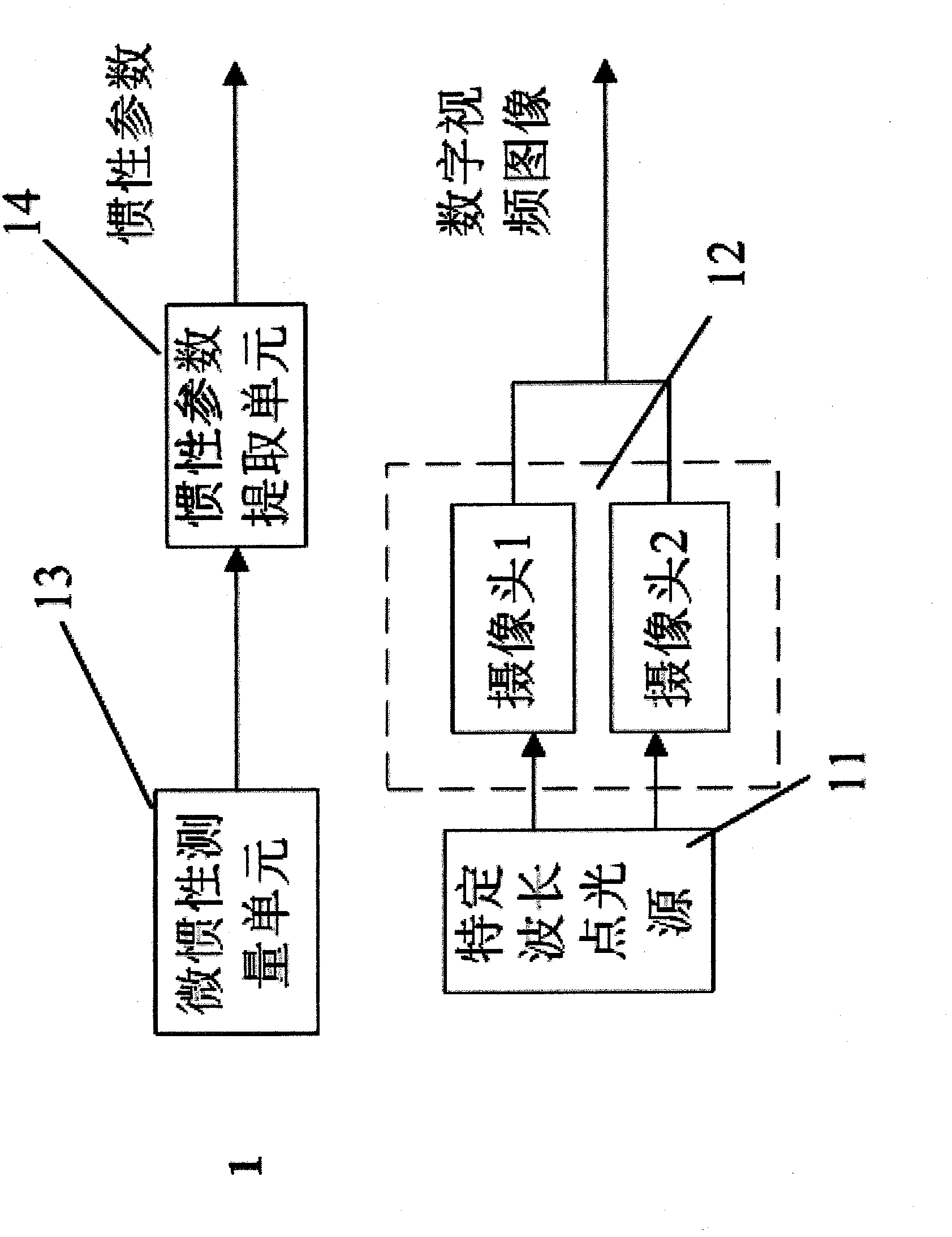
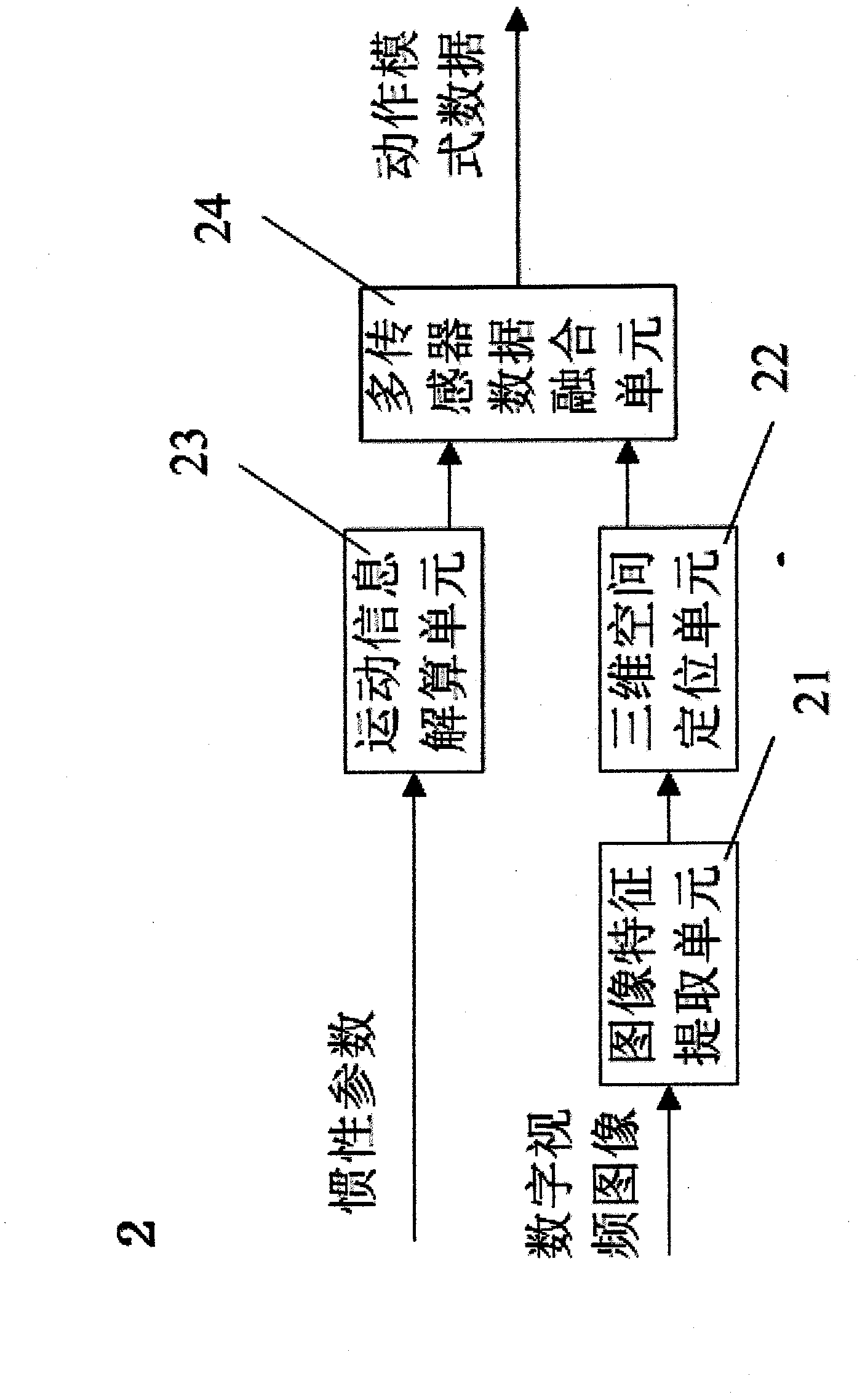
Physical education teaching auxiliary system based on motion identification technology and implementation method of physical education teaching auxiliary system
InactiveCN102243687ASolve the problem of poor authenticitySolution rangeCharacter and pattern recognitionSport apparatusData acquisitionData acquisition module
The invention provides a physical education teaching auxiliary system based on a motion identification technology and an implementation method of the physical education teaching auxiliary system. The system is applicable to a personal computer (PC) or an embedded host. The system comprises a movement data collection module, a movement data acquisition module, an identification and training module and a virtual teaching environment module. The device is characterized in that: a micro-inertia measurement unit and an inertia parameter extraction unit are arranged in the movement data collection module; and a movement information resolving unit transmits data which is output by the inertia parameter extraction unit to a multi-sensor data fusion unit for resolving. The movement situation of a target is reflected comprehensively in an inertia tracking mode and an optical tracking mode, so a tracking range is effectively expanded, measurement accuracy is improved, and the problems that the integral information of the target cannot be acquired in the inertia tracking mode, complicated movement identification cannot be performed and sensitivity is poor are solved. A brand new teaching mode is provided for physical education teaching, and a physical education teaching method is digitalized, multi-media and scientifically standardized.
Owner:ANHUI COSWIT INFORMATION TECH
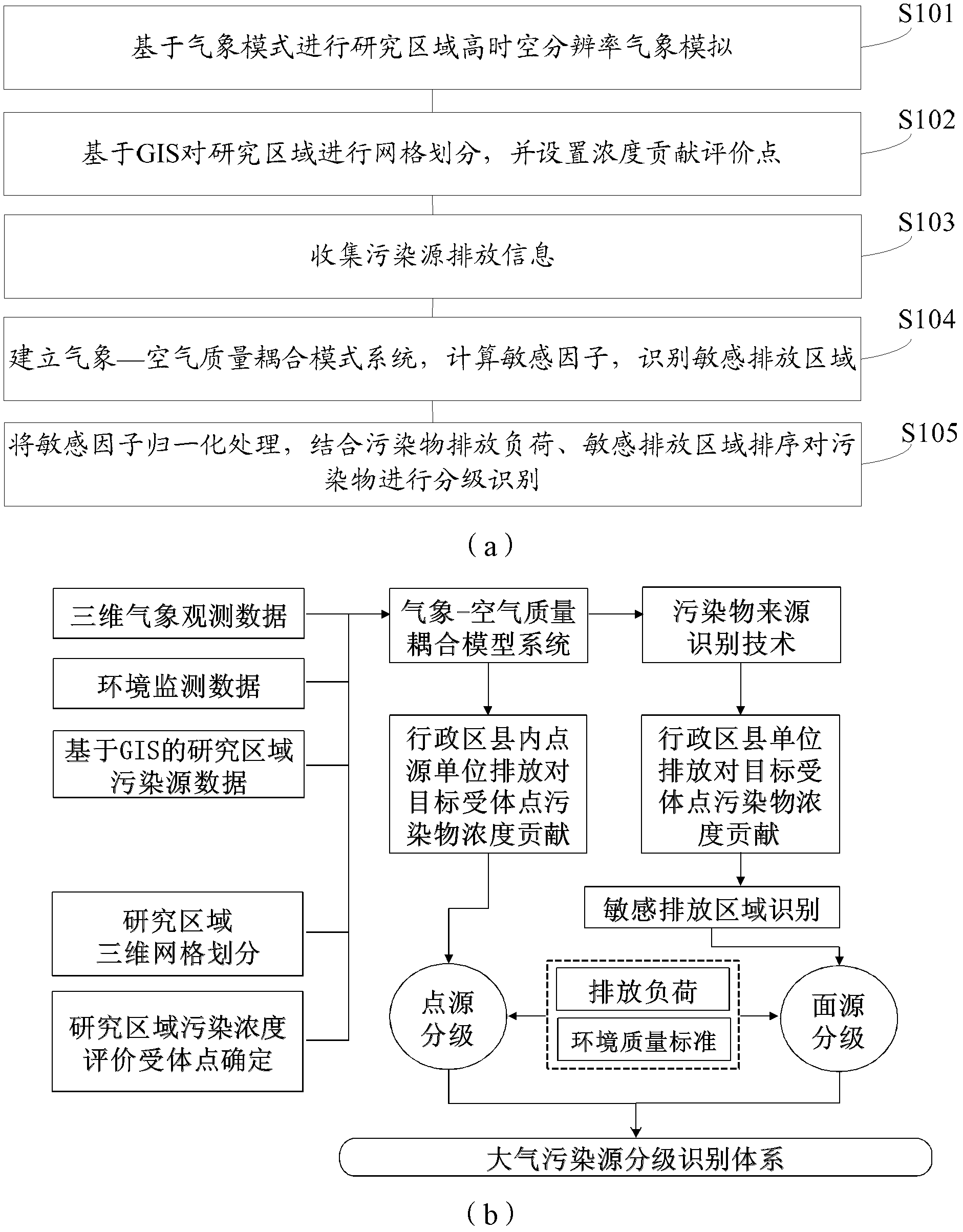
Atmospheric pollution source grading method based on pollutant source identification technology
ActiveCN102628852AReduce air quality concentrationImprove emission reduction efficiencyMaterial analysisTemporal resolutionCoupling system
The invention provides an atmospheric pollution source grading method based on a pollutant source identification technology. The atmospheric pollution source grading method based on a pollutant source identification technology belongs to the technical field of atmospheric environment planning management, and prevention and control of pollution. The atmospheric pollution source grading method based on a pollutant source identification technology comprises the following steps of carrying out high spatio-temporal resolution meteorological simulation of a researched area based on a meteorological model, carrying out grid division of the researched area based on the geographic information system (GIS), arranging concentration contribution evaluation points, collecting pollution source discharge information, building a weather-air quality model coupled system, computing a sensitive factor, identifying sensitive discharge areas, carrying out unitization processing of the sensitive factor, and carrying out grading identification of pollution sources according to pollutant discharge loads and the order of the sensitive discharge areas. The invention aims at providing the atmospheric pollution source grading method based on a pollutant source identification technology so that the evaluation and quantitative grading of sensibility of atmospheric pollution sources are realized and an effective technical support for scientific pollutant-discharge reduction is provided.
Owner:BEIJING UNIV OF TECH
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com