Detection method and device for hidden process based on virtual machine monitor
A virtual machine monitor and hidden process technology, applied in program control devices, computer security devices, instruments, etc., can solve problems such as coarse-grained detection, increased costs, and incomplete functions, and achieve high security effects
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment approach
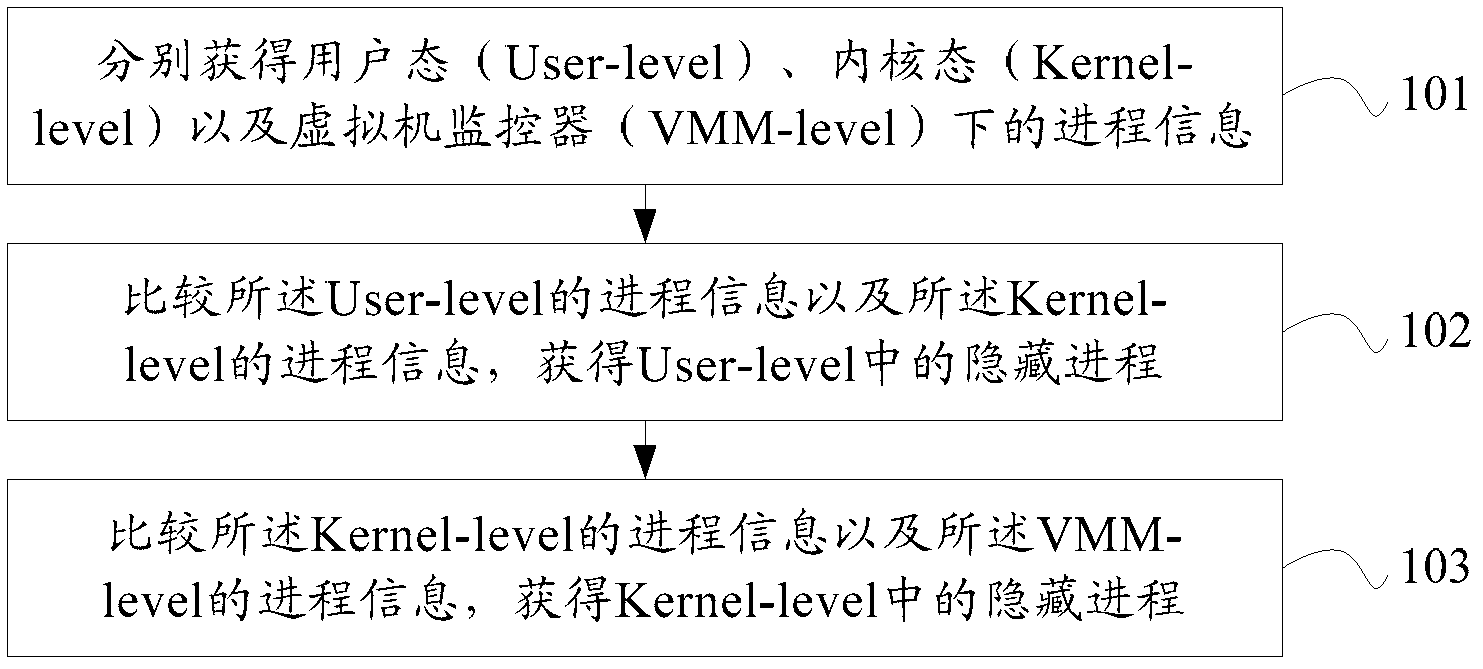
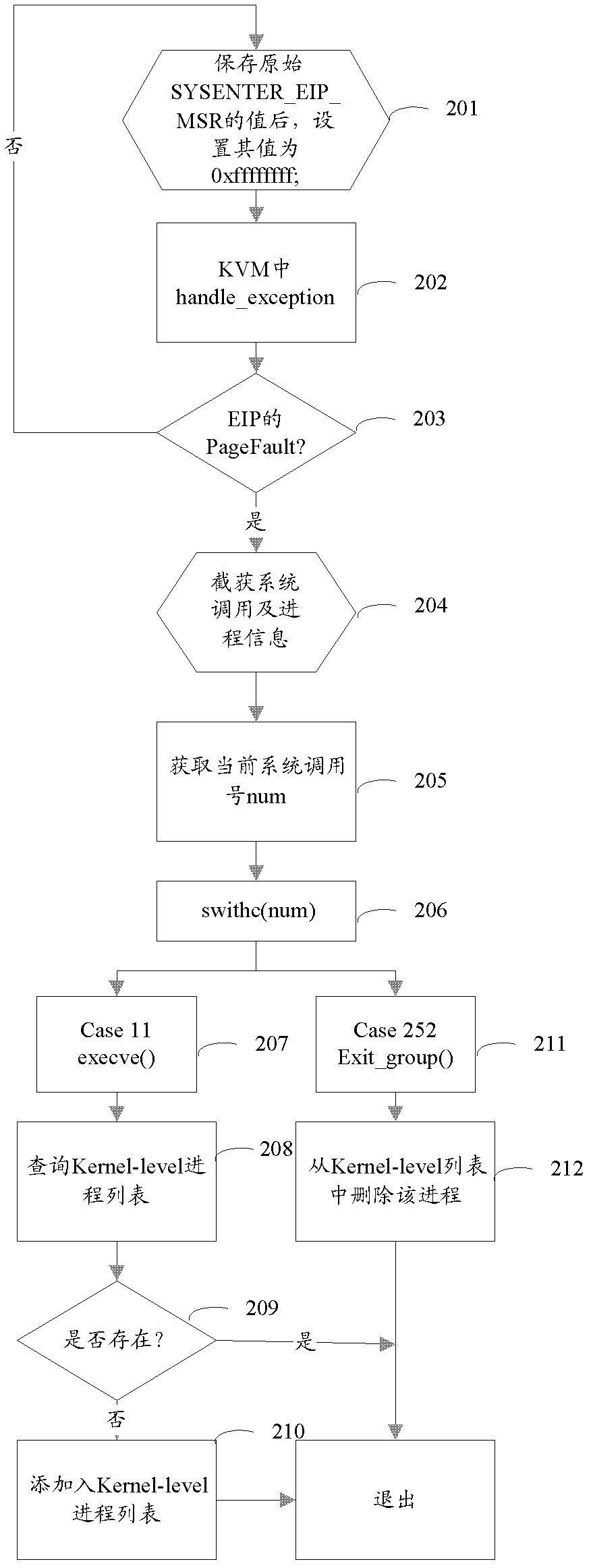
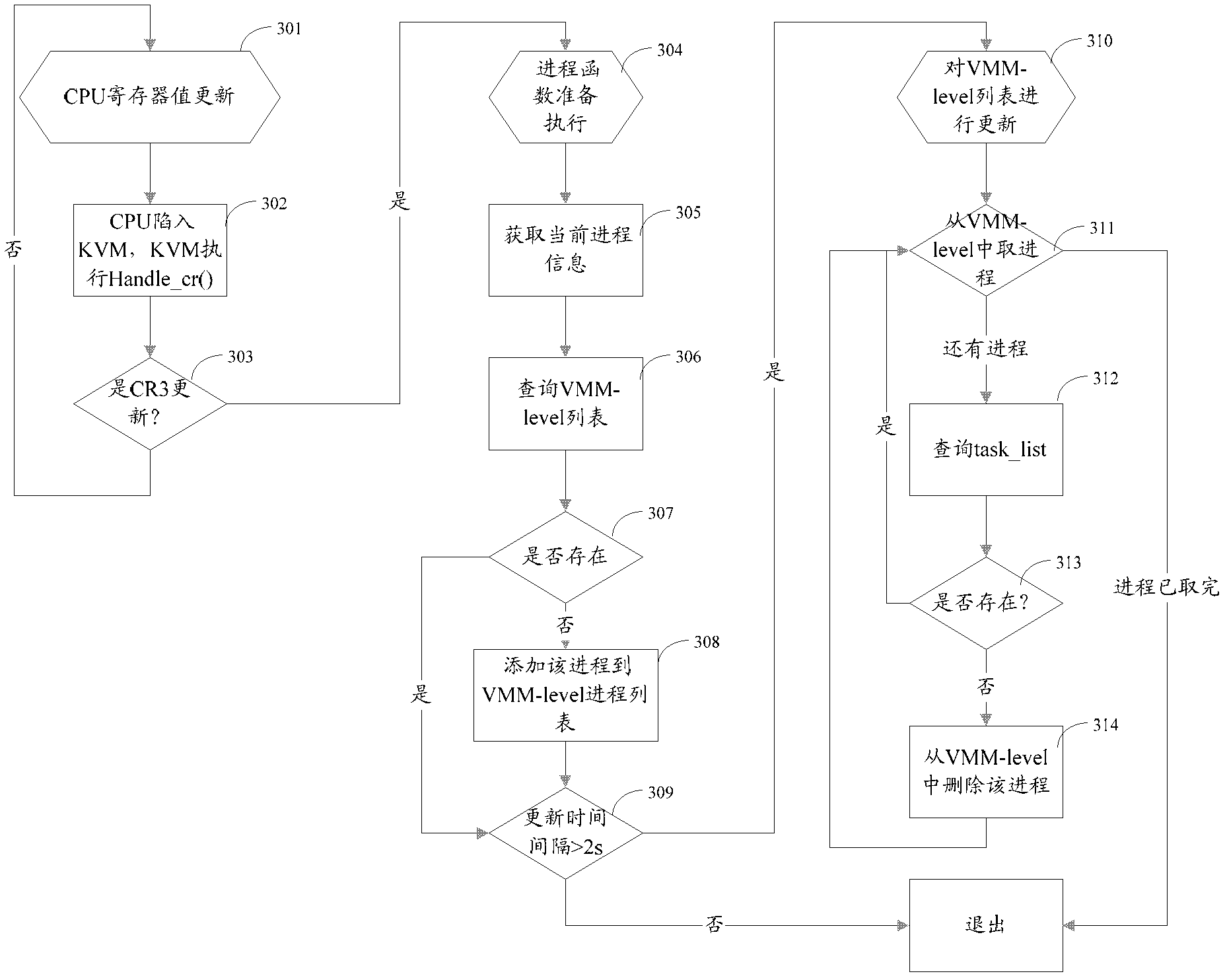
[0059] In one embodiment, the second module 702 includes a processing unit, configured to obtain a socket structure according to the socket file pointed to by the file pointer of the process, and the inet_sock data structure of the socket structure contains port to obtain the mapping information between the process and the port.
[0060] Those of ordinary skill in the art can understand that all or part of the steps for implementing the above method embodiments can be completed by program instructions and related hardware. The aforementioned program can be stored in a computer-readable storage medium. When the program is executed, it executes the steps of the above-mentioned method embodiments; and the aforementioned storage medium includes: read-only memory (ROM), random access memory (RAM), magnetic disk or optical disk and other various media that can store program codes.
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com