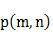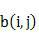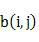Patents
Literature
618 results about "SIMPLE algorithm" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
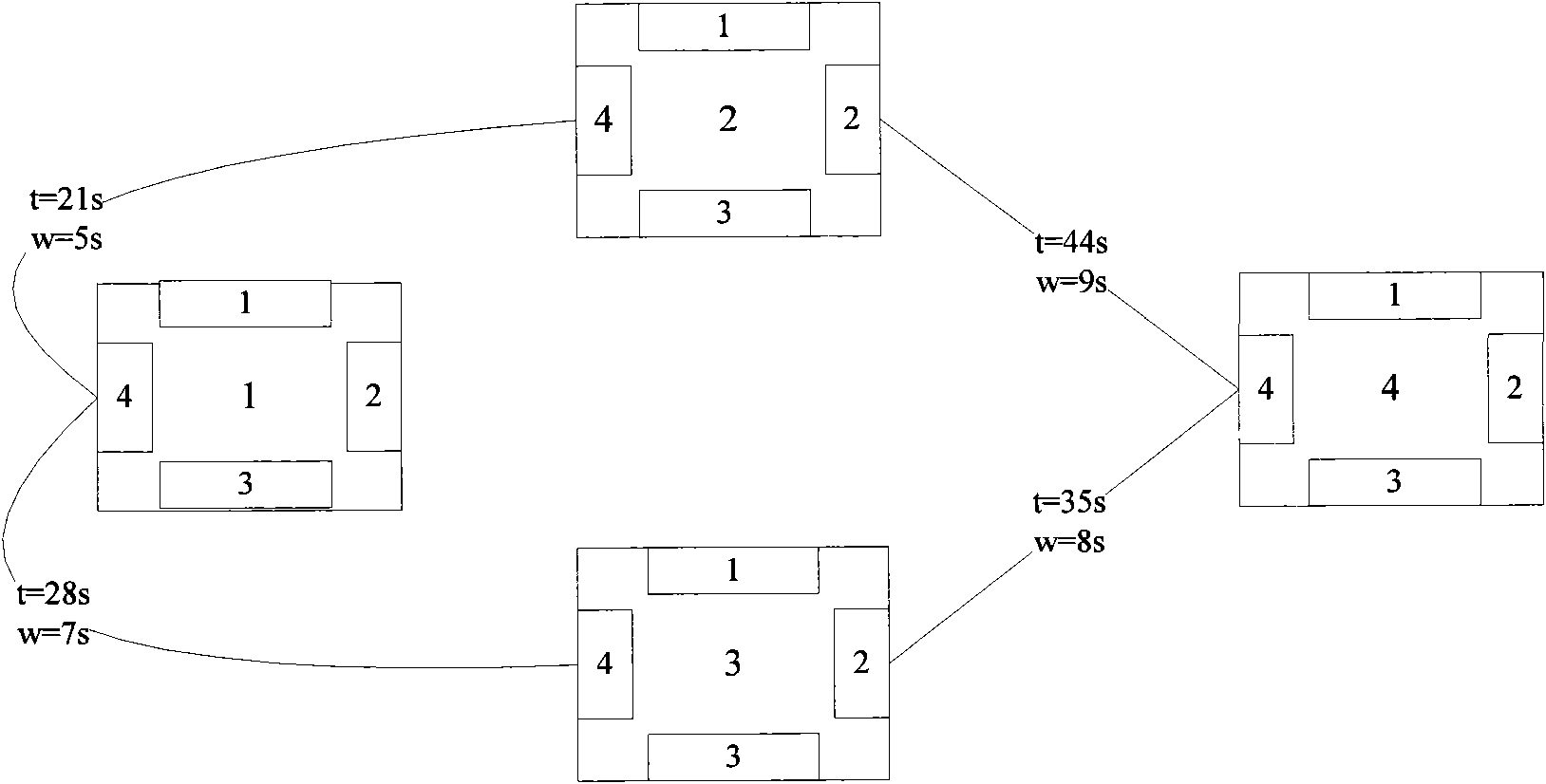
In computational fluid dynamics (CFD), the SIMPLE algorithm is a widely used numerical procedure to solve the Navier-Stokes equations. SIMPLE is an acronym for Semi-Implicit Method for Pressure Linked Equations.
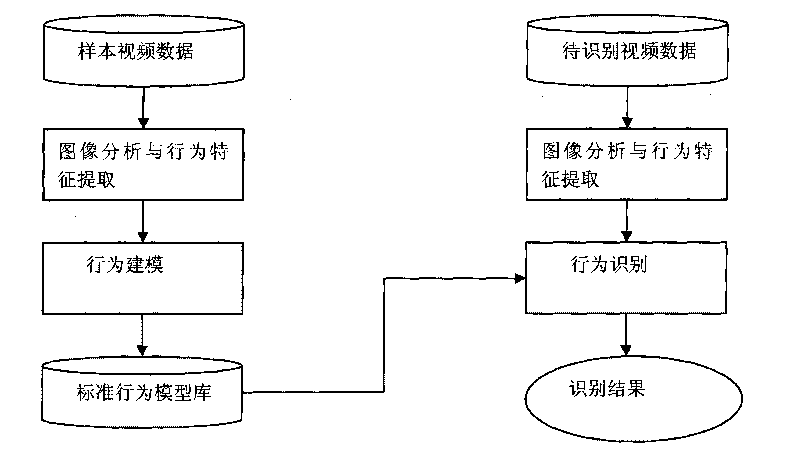
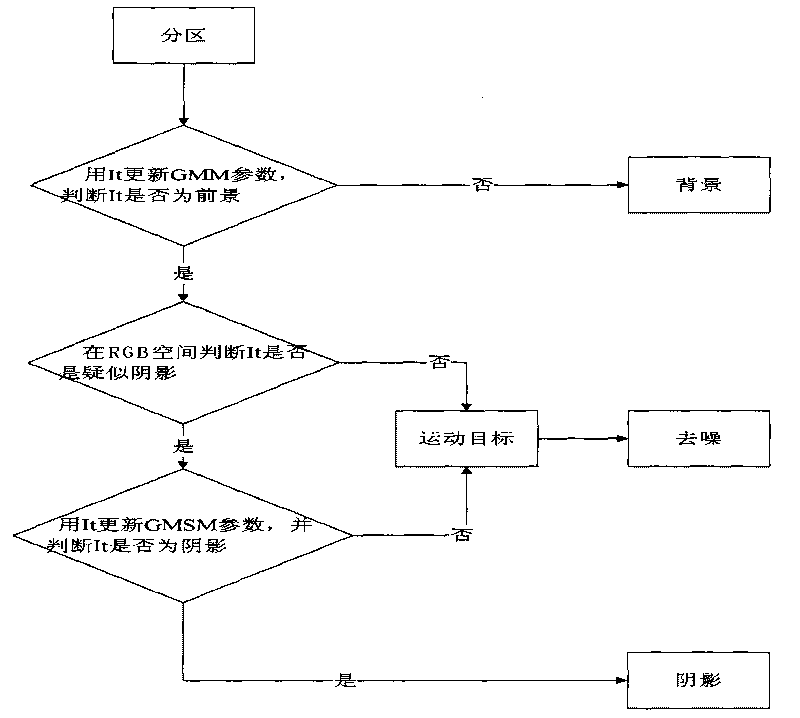
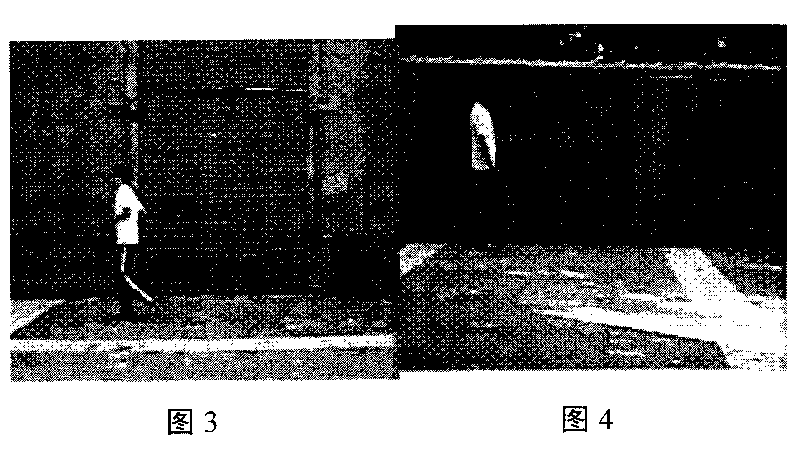
Movement human abnormal behavior identification method based on template matching
InactiveCN101719216AGood effectThe effect is accurateCharacter and pattern recognitionVisual technologyAnomalous behavior
The invention relates to a movement human abnormal behavior identification method based on template matching, which mainly comprises the steps of: video image acquisition and behavior characteristic extraction. The movement human abnormal behavior identification method is a mode identification technology based on statistical learning of samples. The movement of a human is analyzed and comprehended by using a computer vision technology, the behavior identification is directly carried out based on geometric calculation of a movement region and recording and alarming are carried out; the Gaussian filtering denoising and the neighborhood denoising are combined for realizing the denoising, thereby improving the independent analysis property and the intelligent monitoring capacity of an intelligent monitoring system, achieving higher identification accuracy for abnormal behaviors, effectively removing the complex background and the noise of a vision acquired image, and improving the efficiency and the robustness of the detection algorithm. The invention has simple modeling, simple algorithm and accurate detection, can be widely applied to occasions of banks, museums and the like, and is also helpful to improve the safety monitoring level of public occasions.
Owner:XIDIAN UNIV
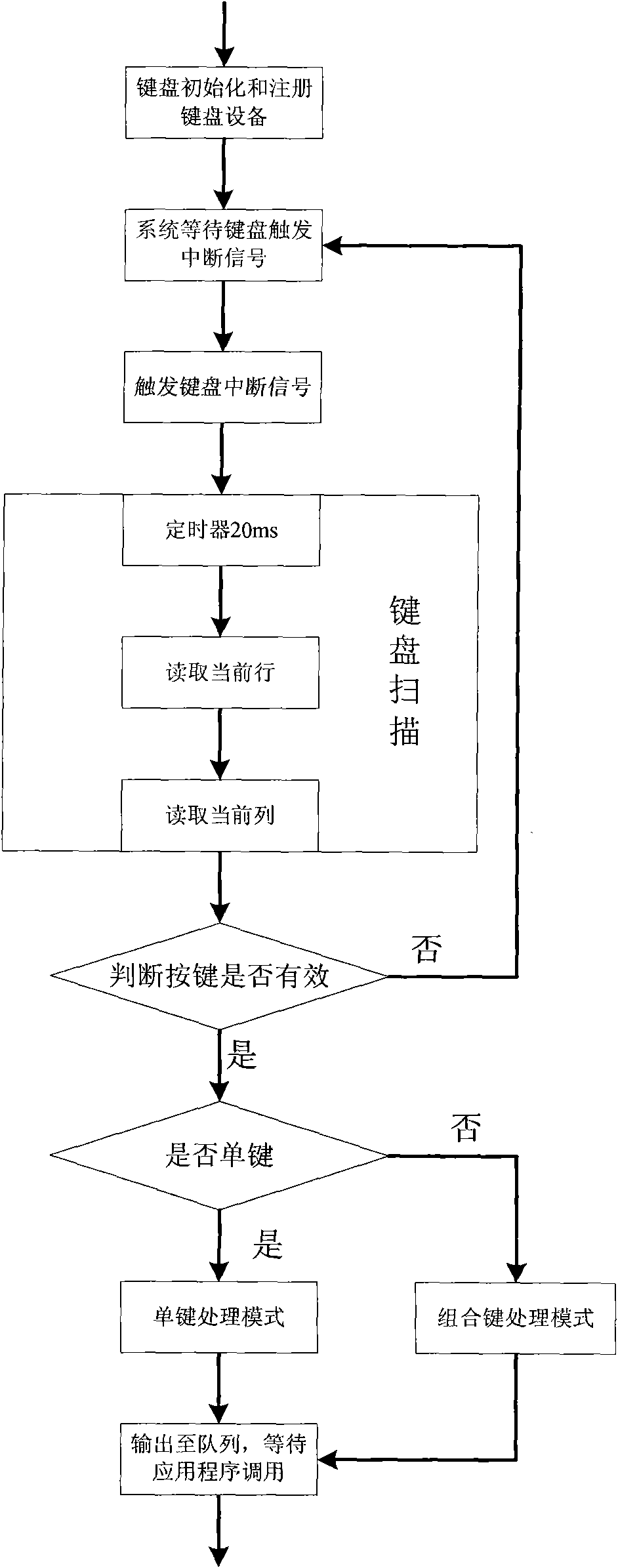
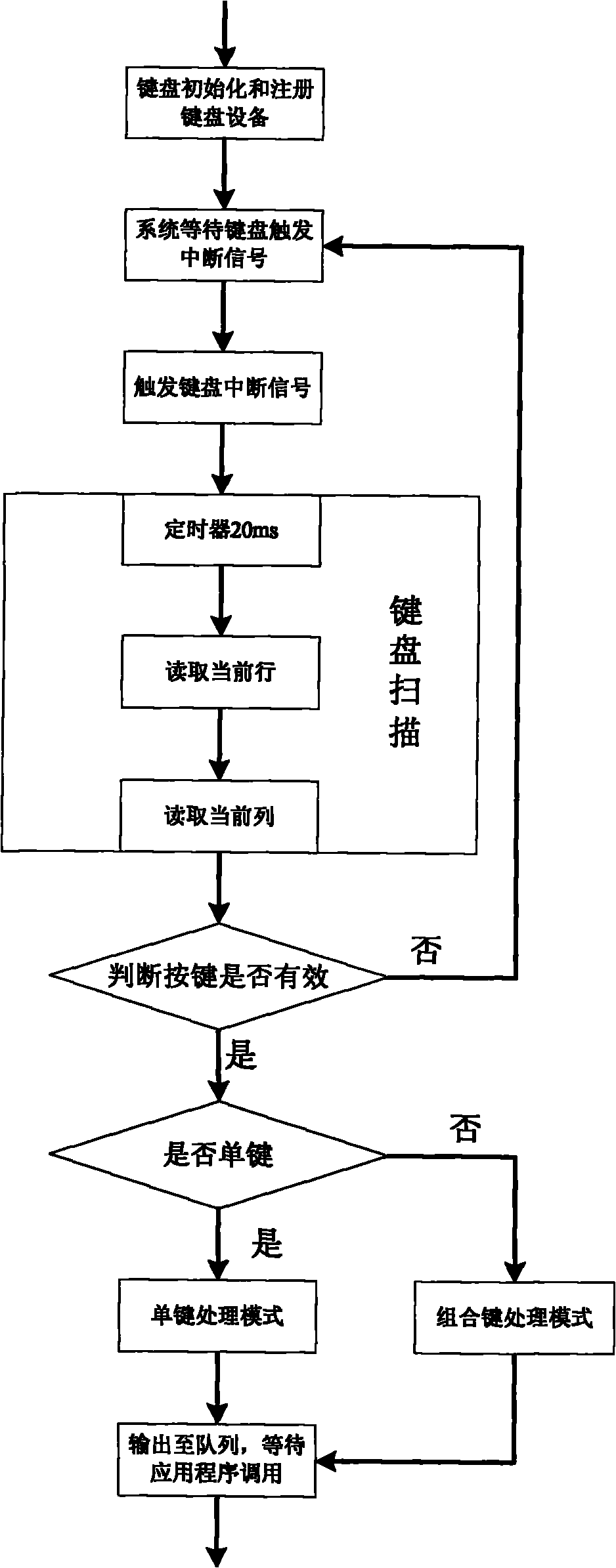
Method for fast scanning and positioning of matrix keyboard
ActiveCN101840268AAvoid level instabilityAvoid jitterInput/output for user-computer interactionTerminal equipmentFast scanning
The invention discloses a method for fast scanning and positioning of a matrix keyboard, which relates to a method for the fast scanning and positioning of the matrix keyboard in the field of controlling an embedded system, and is particularly suitable for designing the matrix keyboard of an embedded terminal device. The method comprises the following steps of: initializing a keyboard device and registering the keyboard device; waiting for the keyboard to trigger an interruption signal by a system; triggering a keyboard interruption signal; responding to the interruption signal by the system; performing keyboard scanning; judging whether keys are effective; and outputting a keyboard key value to a queue, and waiting for an application program to read the key value. The method can effectively avoid instable and dithering levels of the matrix keyboard because of per se mechanical properties, improves the accuracy of the scanning and the positioning of the matrix keyboard, and has the characteristics of simple algorithm, steady performance, high control accuracy and the like.
Owner:NO 54 INST OF CHINA ELECTRONICS SCI & TECH GRP
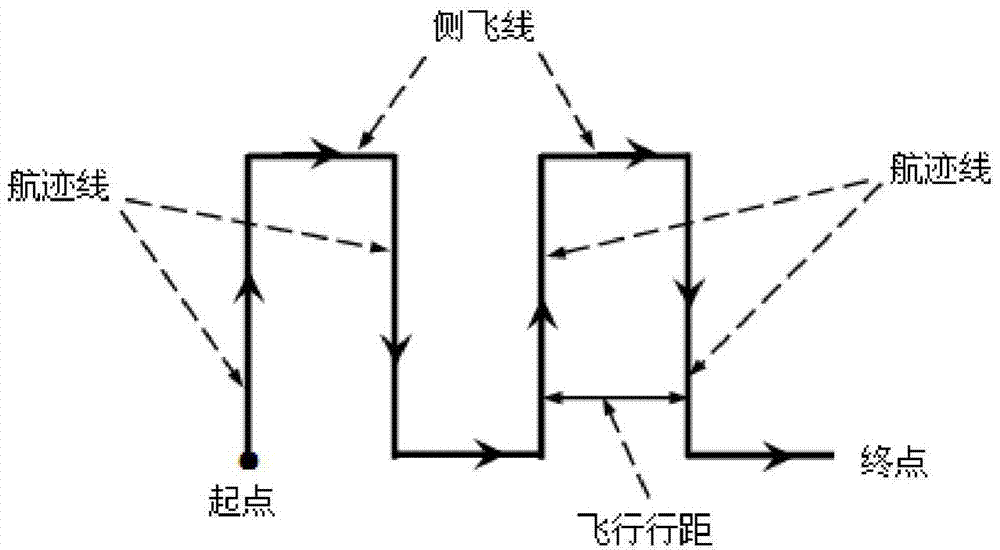
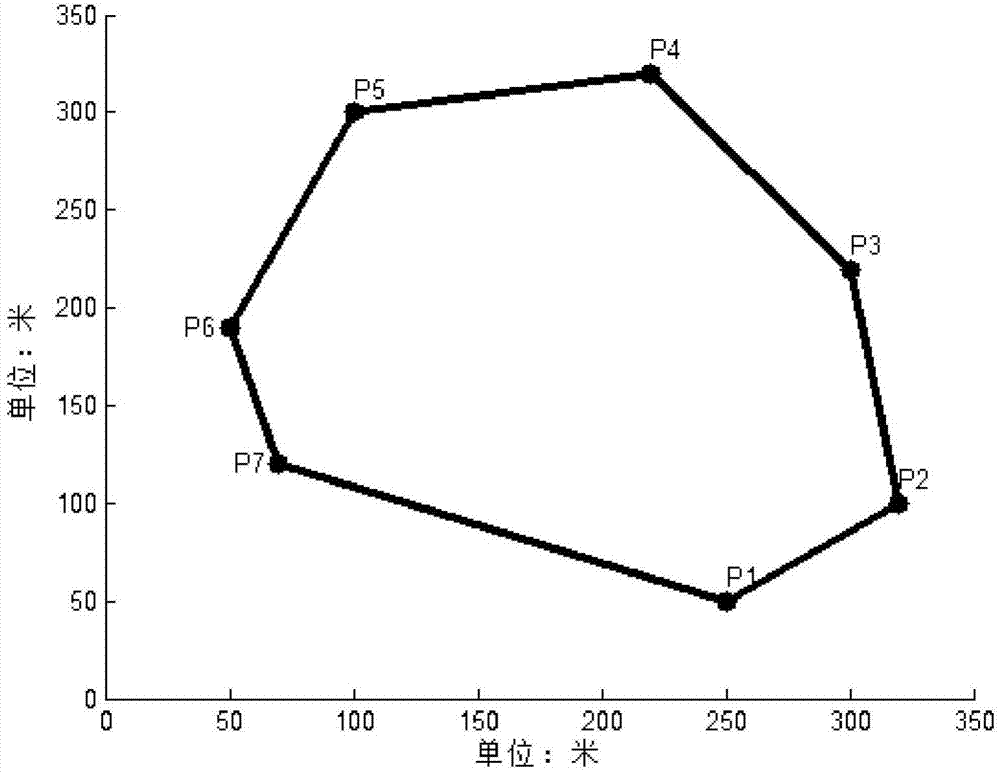
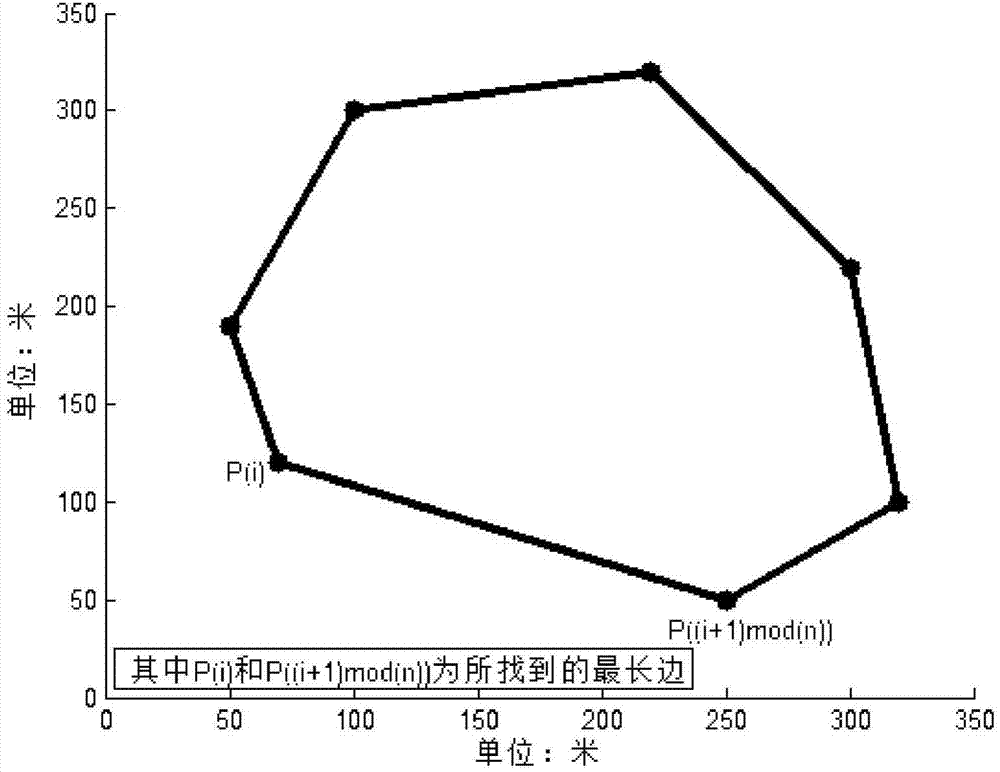
Computer-based convex polygon field unmanned aerial vehicle spraying operation route planning method
ActiveCN104503464AAccurate operationPrecision SprayingPosition/course control in three dimensionsArray data structureUncrewed vehicle
The invention discloses a computer-based convex polygon field unmanned aerial vehicle spraying operation route planning method. The method includes the steps: firstly, solving a linear equation of each edge of a polygon; secondly, finding out the longest edge of the polygon; thirdly, respectively solving the distance from each endpoint of a field boundary to the longest point, and finding out the point farthest from the longest edge; fourthly, selecting a group of equidistant parallel lines parallel to the longest edge between the longest edge and the farthest point; fifthly, solving two intersections of each parallel line and the field boundary and storing result sets into corresponding groups; sixthly, connecting the two intersections of each parallel line and the polygon into a line segment, and then cutting off the parts, located outside the field operation area, of the group of parallel lines so as to obtain a group of parallel line segments located in the field operation area; finally, planning out a route. The method is simple algorithm and good in universality, efficiency of unmanned helicopters for executing spraying operation to irregular fields can be improved, and energy consumption of flight is lowered.
Owner:CENT SOUTH UNIV
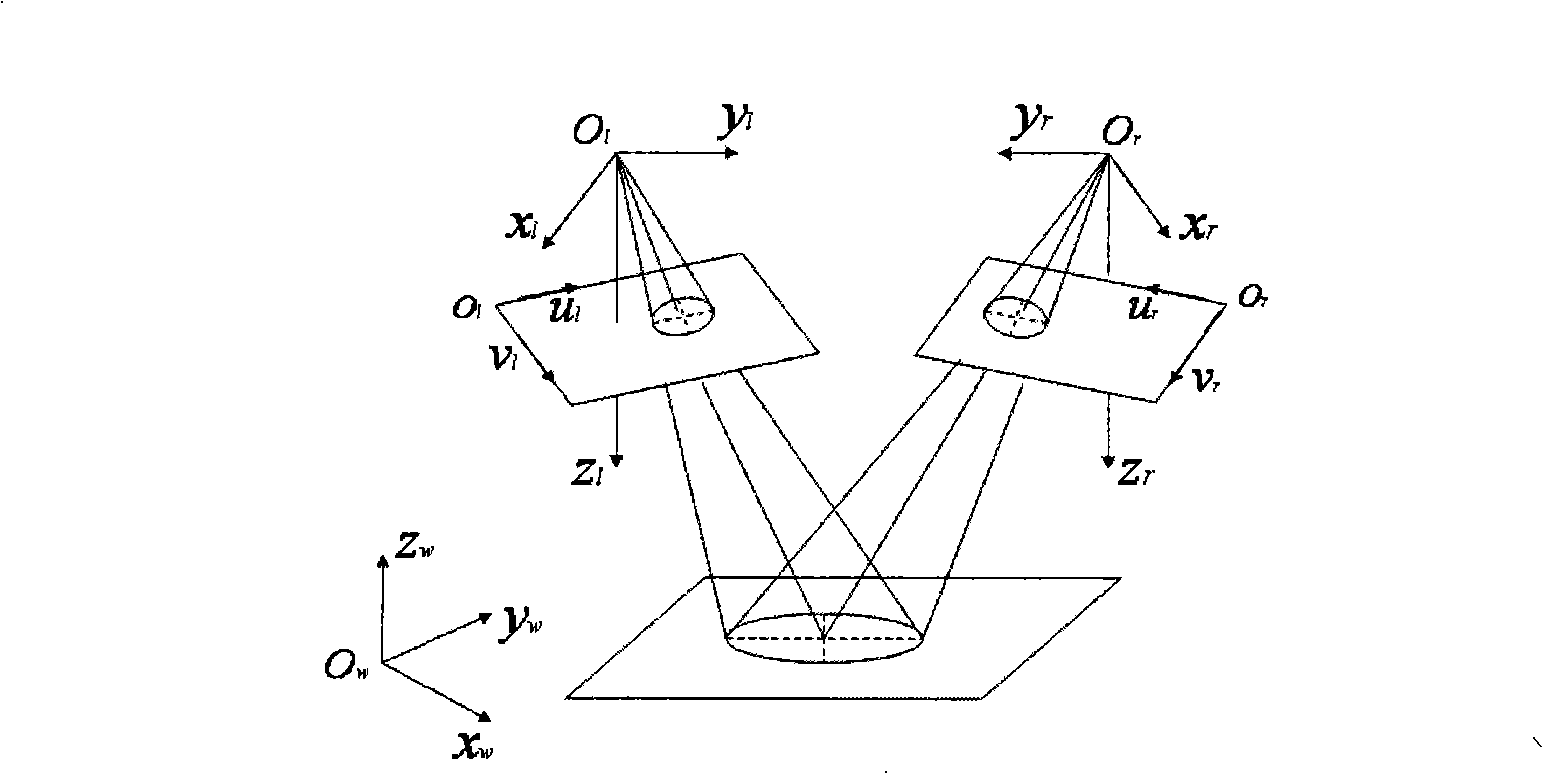
Spatial circular geometric parameter binocular stereo vision measurement method
InactiveCN101261115APrecise sub-pixel precisionSmall amount of calculationBiological neural network modelsUsing optical meansBinocular stereoVisual perception
The invention discloses a spatial circle geometrical parameter dual-eye solid visual measurement method suitable for non-contact type online measurement of the spatial circle geometrical parameter of an industrial product, aiming at overcoming the existing problems of low measurement precision, slow measurement speed and low automation degree. The method is divided into a calibrating stage, an image processing stage and a spatial circle fitting stage. A neural network technique is firstly adopted to carry out the calibration of a camera; a dual-camera is utilized to carry out the extraction of sub-pixel image edges of the spatial circle, a simple algorithm is developed based on the image gray gradient distribution characteristic so as to realize the match of edge points, the practical 3D spatial coordinates of the circle edges are then obtained, and the geometrical parameters of the spatial circle comprise radius, position of center of circle and orientation of the plane where the spatial circle is arranged are gained by the fitting of the spatial circle with corresponding mathematical geometrical knowledge. The spatial circle geometrical parameter dual-eye solid visual measurement method has fast image processing speed and high automation degree, and has relative measurement error of the spatial circle of superior to plus or minus 0.6% when the plane where the spatial circle is arranged has an angle of about 50 DEG with the image plane.
Owner:JILIN UNIV
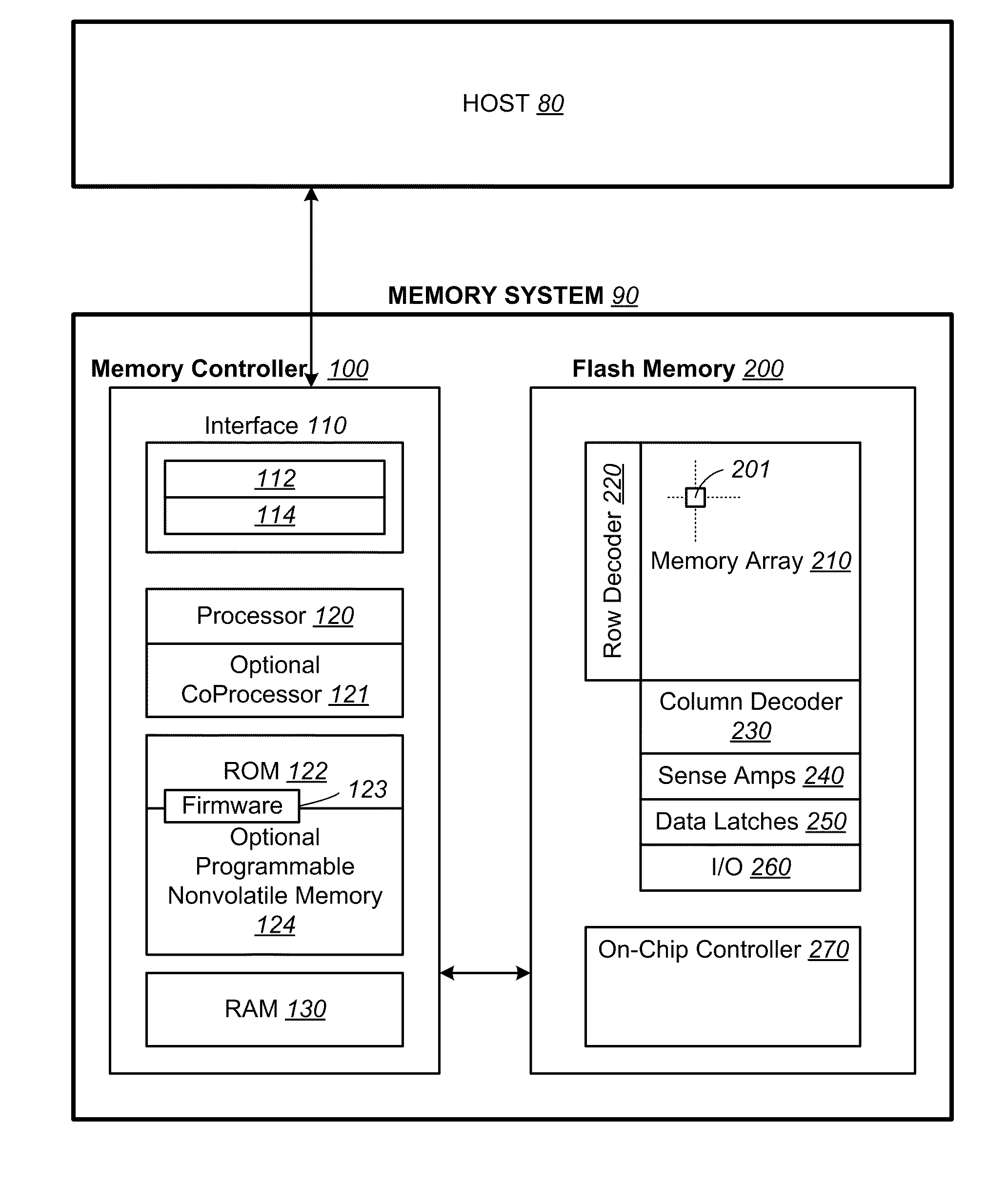
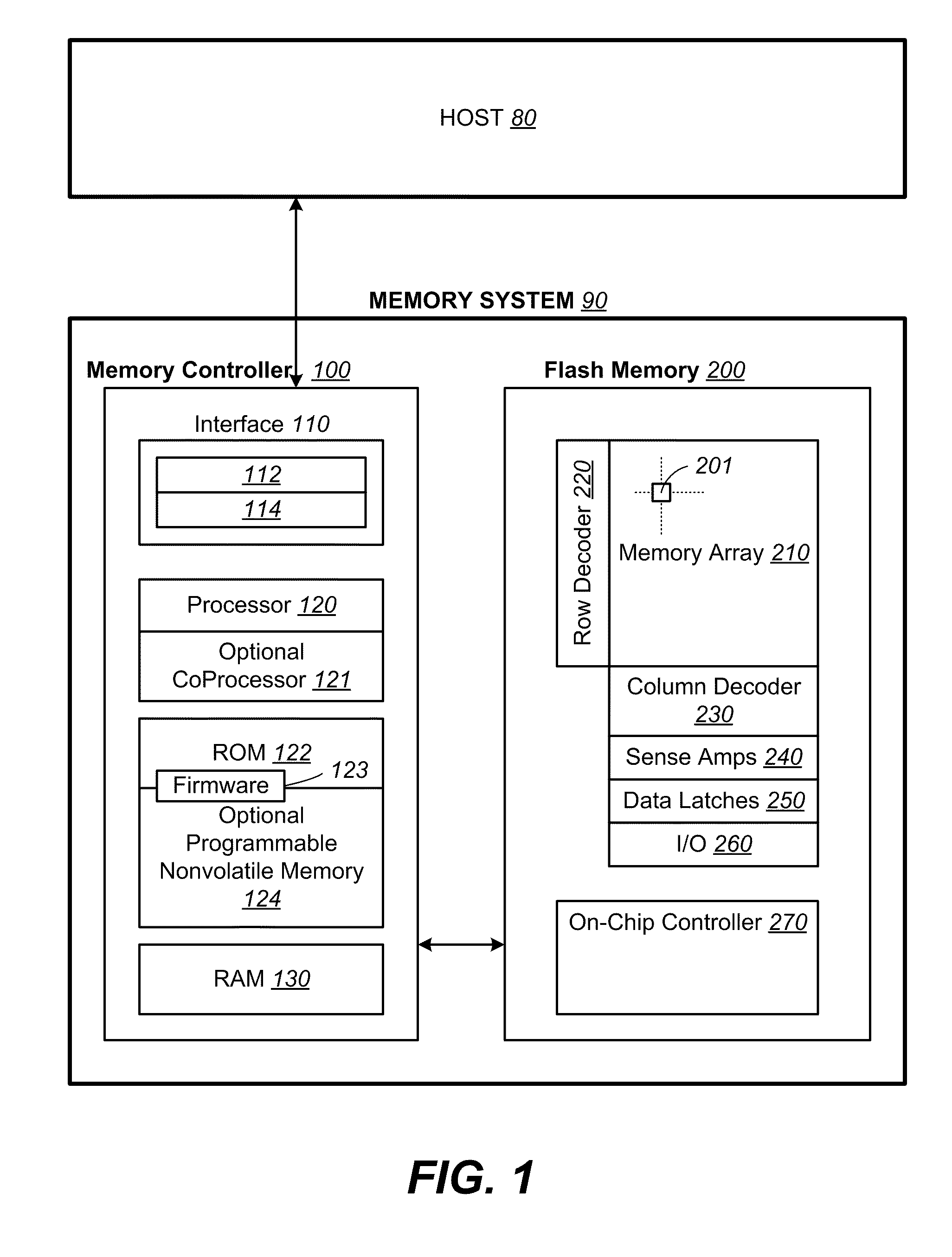
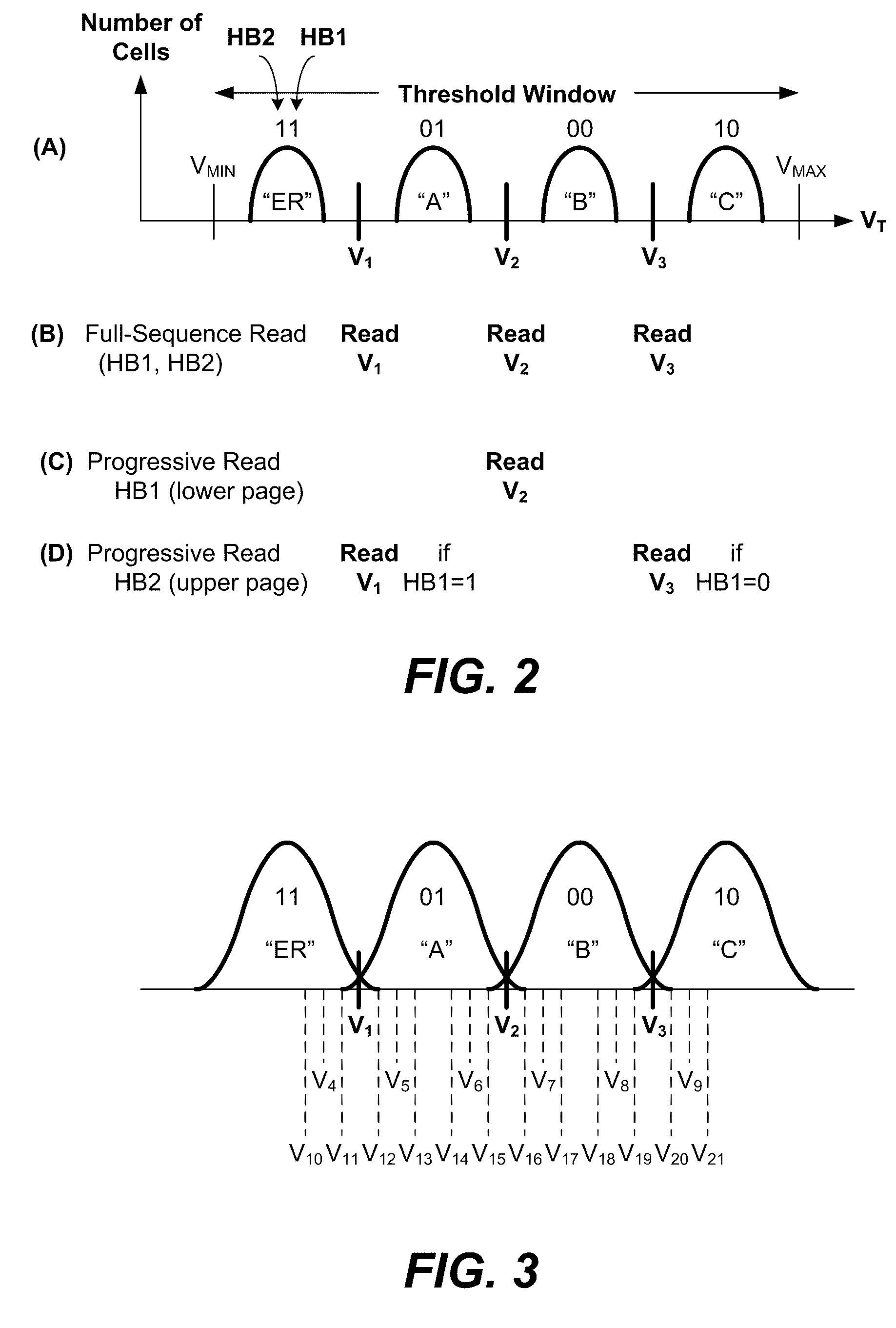
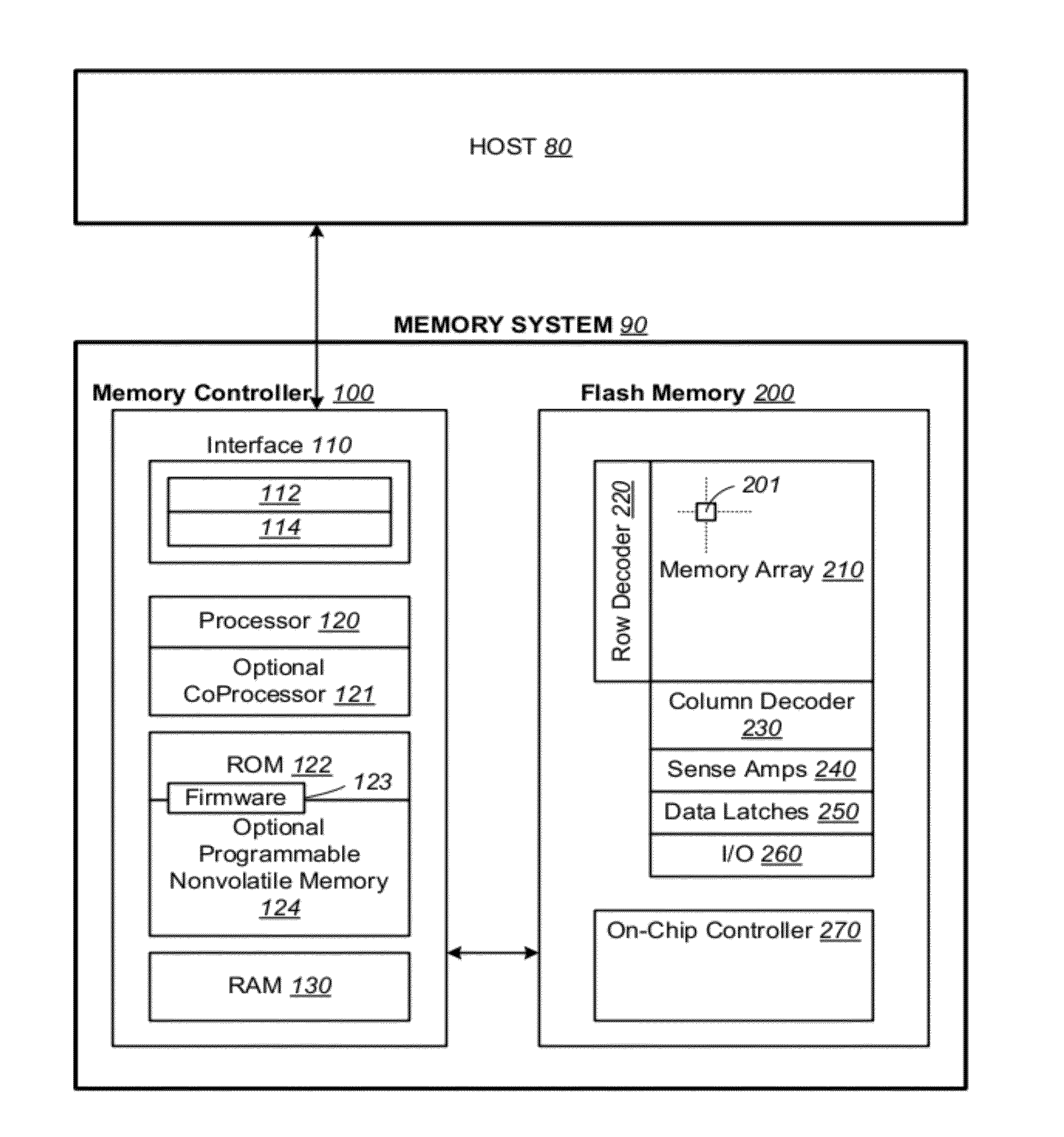
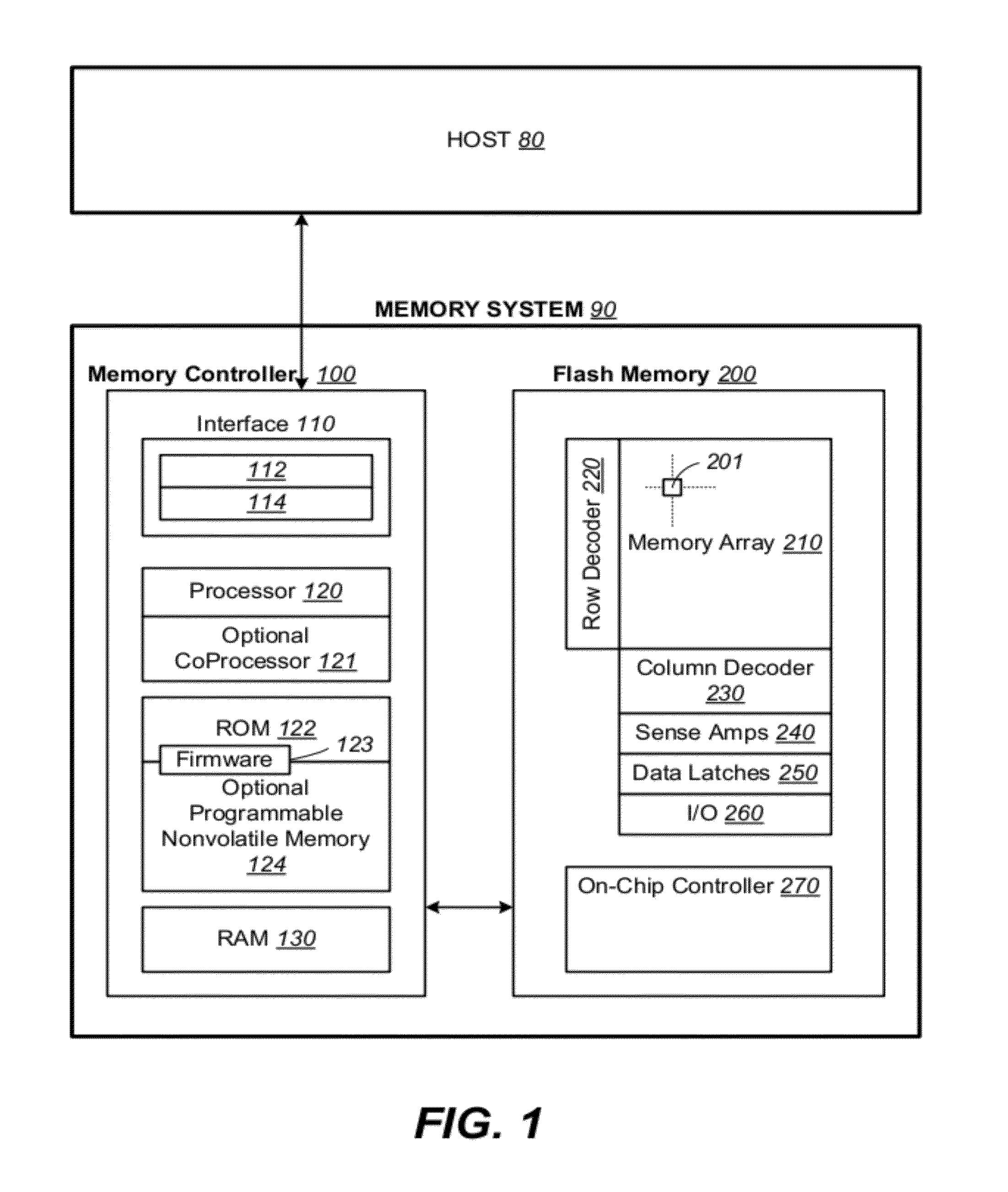
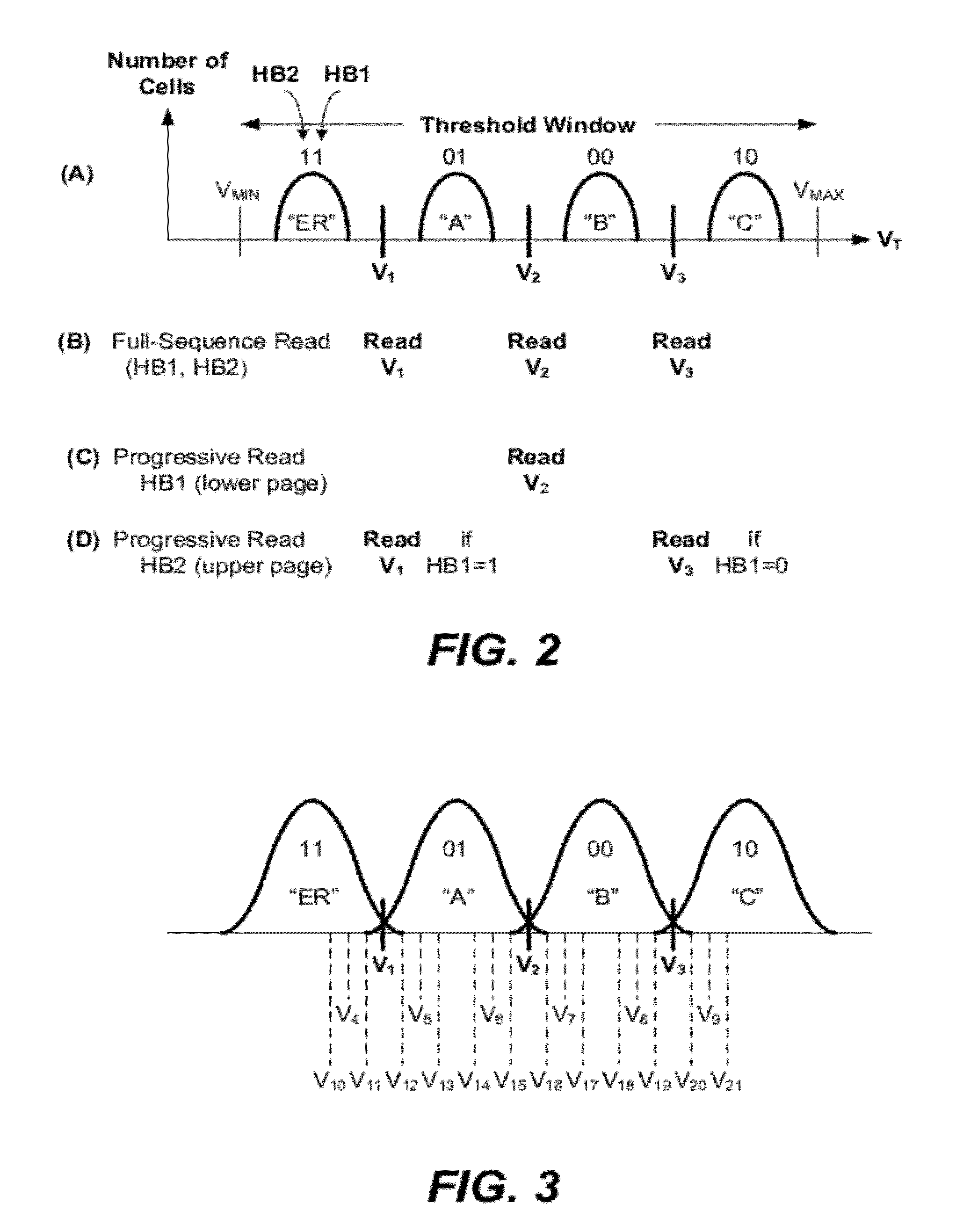
Non-volatile memory and methods with reading soft bits in non uniform schemes
ActiveUS8099652B1Increasing digital circuit requiredImprove reading speedError detection/correctionRead-only memoriesImage resolutionComputer science
A non-volatile memory has its cells' thresholds programmed within any one of a first set of voltage bands partitioned by a first set of reference thresholds across a threshold window. The cells are read at a higher resolution relative to a second set of reference thresholds so as to provide additional soft bits for error correction. The reference thresholds of the second set are set up to be non-uniformly distributed on the threshold window so as to provide higher resolution at designated regions. At the same time they are conducive to be read in groups for soft bits to be read bit-by-bit systematically with a simple algorithm and read circuit and using a minimum of data latches. This is accomplished by relaxing the requirement that the first set of reference threshold is a subset of the second set and that the resulting soft bits are symmetrically distributed about the hard bits.
Owner:SANDISK TECH LLC
Multisource information fusion method in evidence high-conflict environment
InactiveCN101996157ASimple structureSimple processCharacter and pattern recognitionSpecial data processing applicationsInformation integrationMutual support
The invention discloses a multisource information fusion method in an evidence high-conflict environment, which comprises the following steps of: determining the mutual support degree of evidences according to evidence distances, further calculating the relative discount factor of each evidence by taking a characteristic vector corresponding to the maximum characteristic value of a evidence support degree matrix pattern as a weighting vector of the evidence, wherein the evidence with the maximum weighing coefficient is a key evidence; and discounting each evidence information, and fusing the information of multisource sensor data by using the D-S (Dempster / Shafer) rule so as to increase the accuracy and precision of a monitoring proposition judgment under an evidence high-conflict status.The method can effectively eliminate the uncertainties of multisource information, increase the accuracy of information evaluation and overcome the limitation that correct evaluation results can not be acquired by using the traditional D-S evidence theory under the evidence high-conflict status, and has the advantages of simple algorithm, high convergence rate and the like.
Owner:SHANDONG UNIV OF SCI & TECH
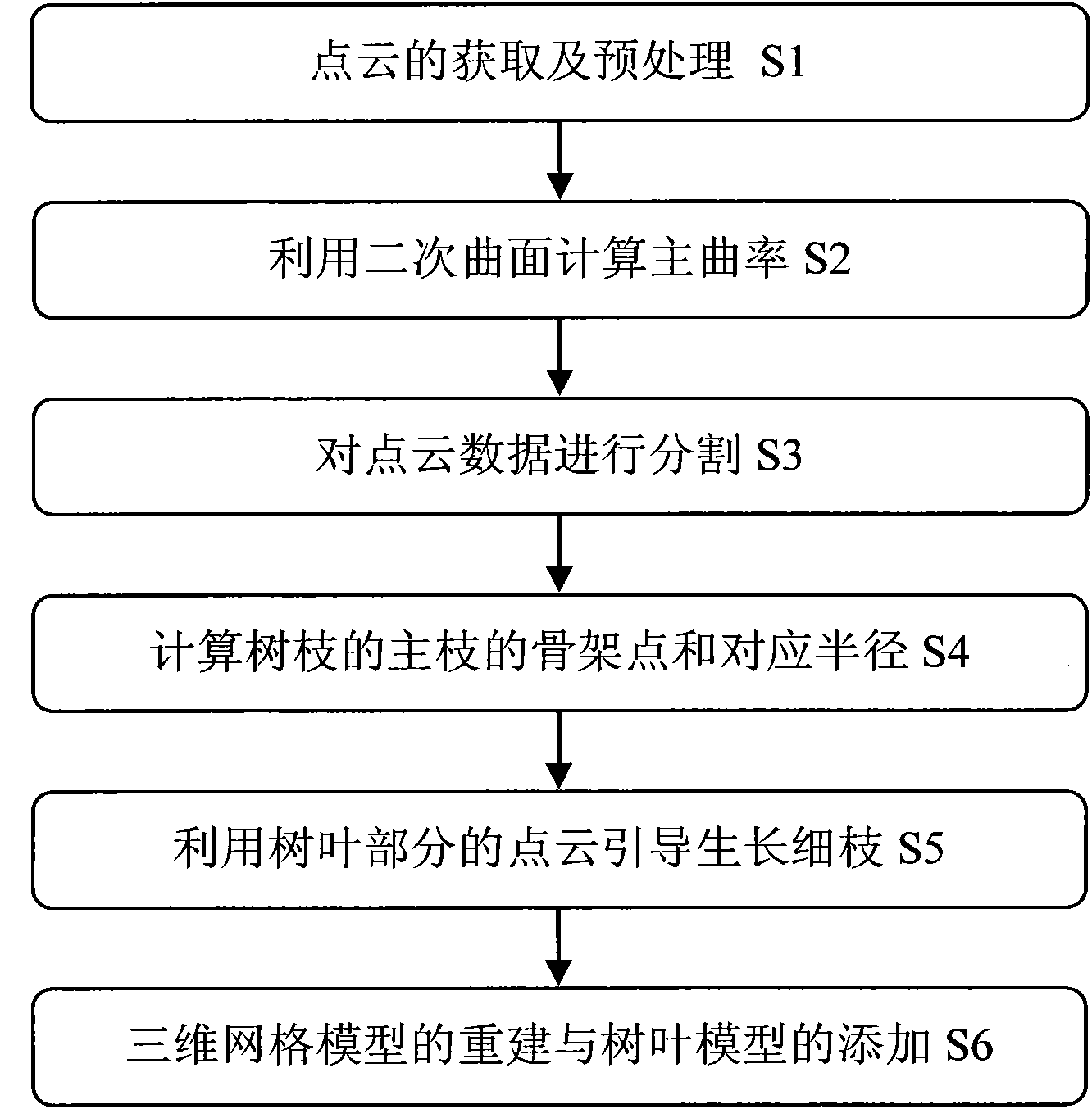
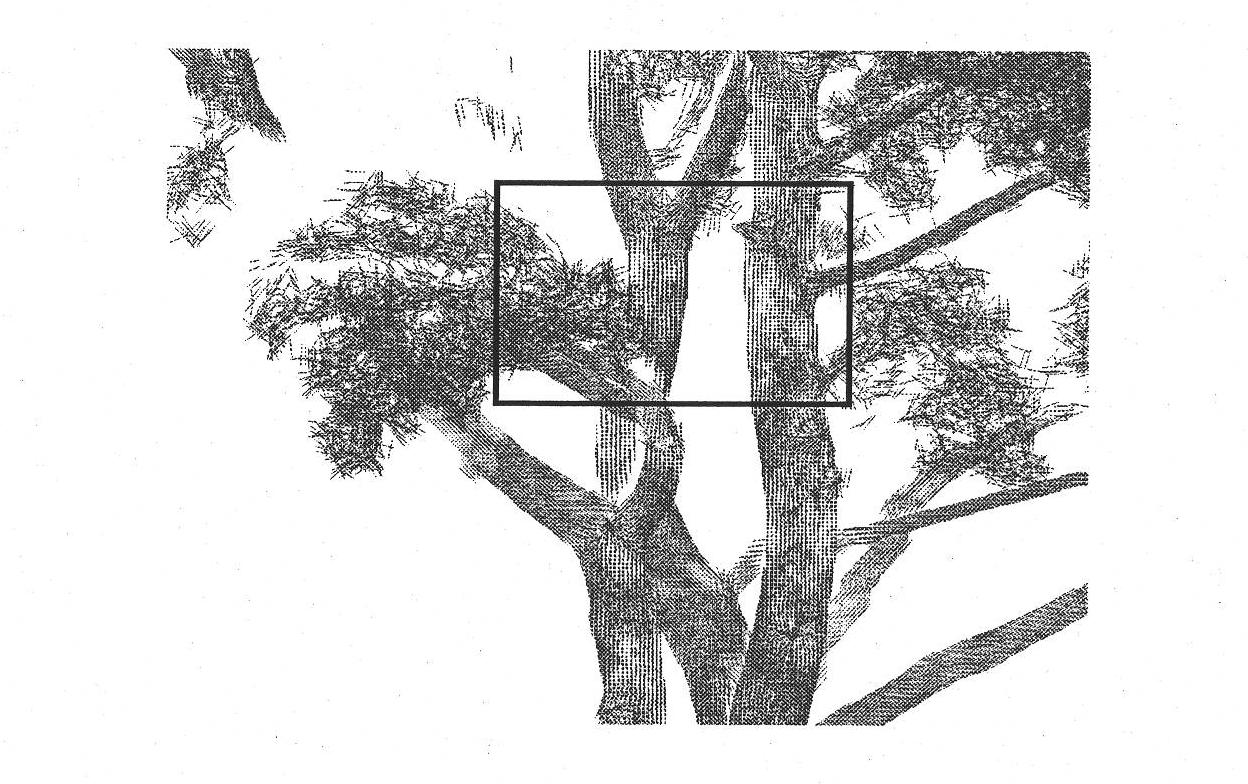
Three-dimensional model reconstruction method of tree point cloud data based on partition and automatic growth
InactiveCN101887596AReduce human interactionEasy to operate3D modellingLaser scanningReconstruction method
The invention relates to a three-dimensional model reconstruction method of tree point cloud data based on partition and automatic growth, comprising the following steps: preprocessing; estimating the main curvature of point cloud; partitioning data according to the main curvature; calculating a framework of a principal branch of branches by the partitioned point cloud belonging to a branch part;leading from the framework of the principal branch of the branches to generate twigs of the branches by the partitioned point cloud belonging to a leaf part; and generating a branch mesh model and adding a leaf model at the ends of the twigs of the branches. In the method, the three-dimensional reconstruction model which is faithful to original entities can be obtained by means of the scanning data of a laser scanner; the reconstruction model of the tree point cloud data can be obtained based on data partition and growth of the twigs of the branches, thus the method has simple algorithm and accurate calculation result; and the calculation result has important application value in the fields such as virtual reality, computer games, natural scene simulation, urban landscape design, film production, three-dimensional reconstruction of trees, agriculture and forestry measurement and the like.
Owner:INST OF AUTOMATION CHINESE ACAD OF SCI
Method of transmitting data stream including multi-path sections
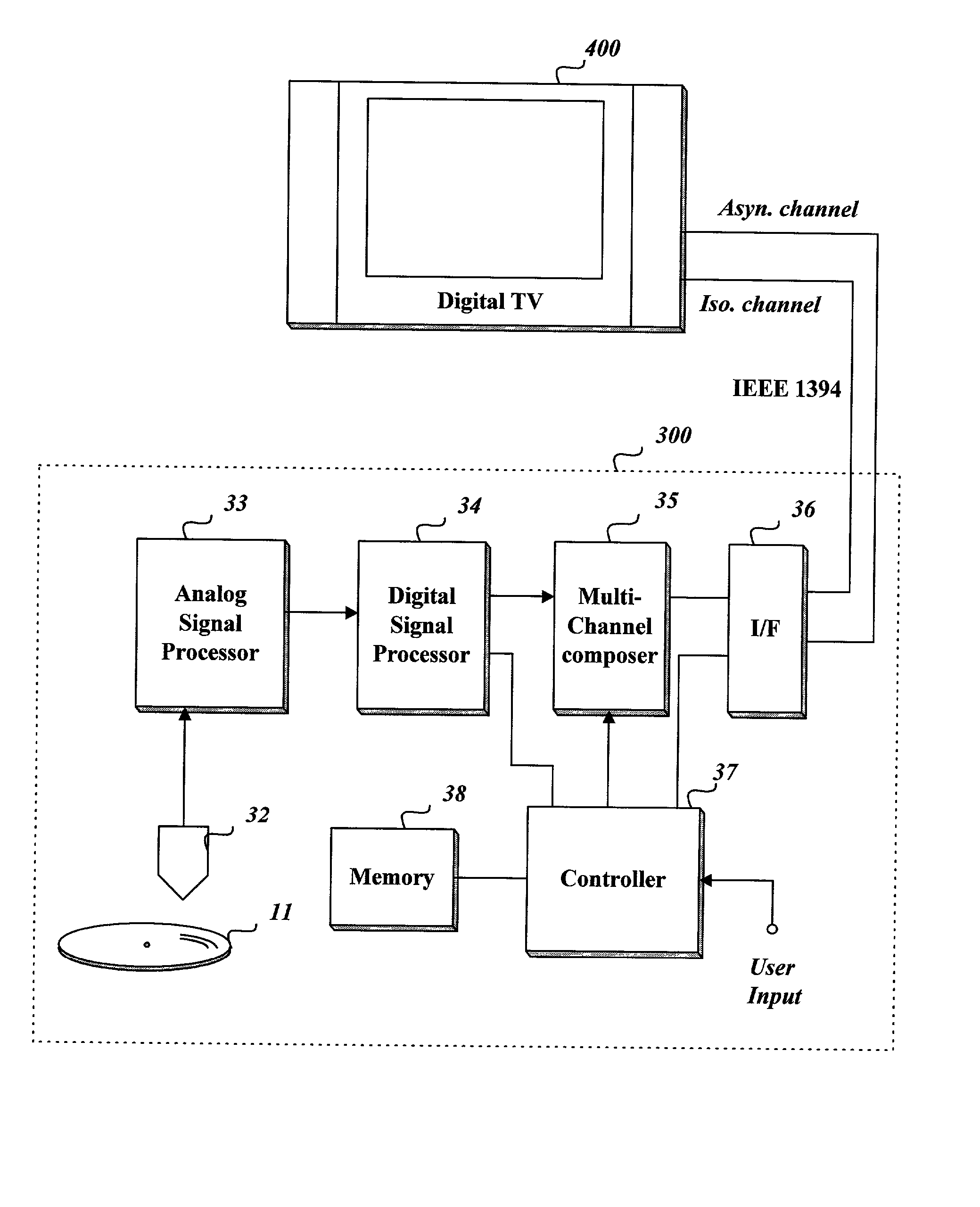
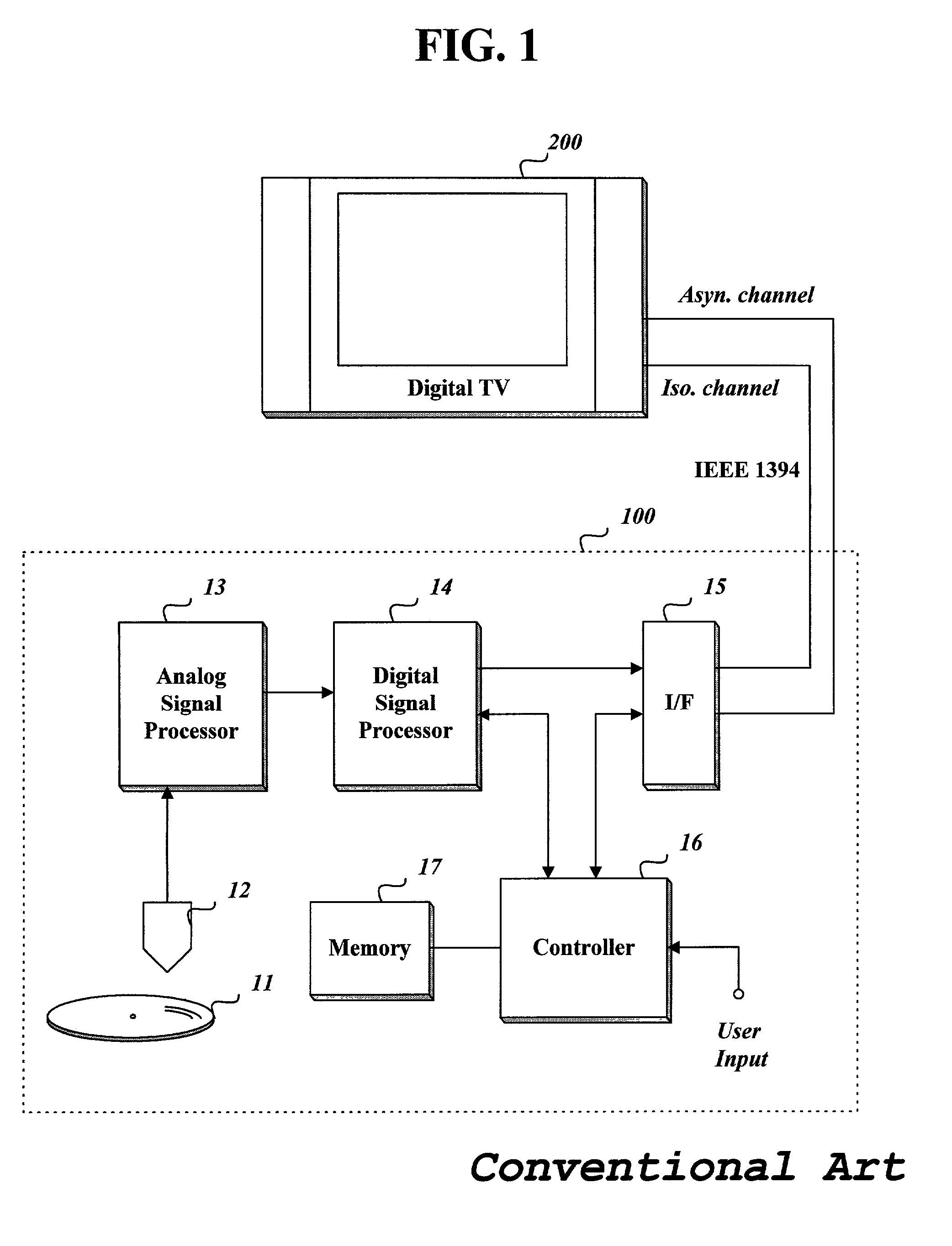
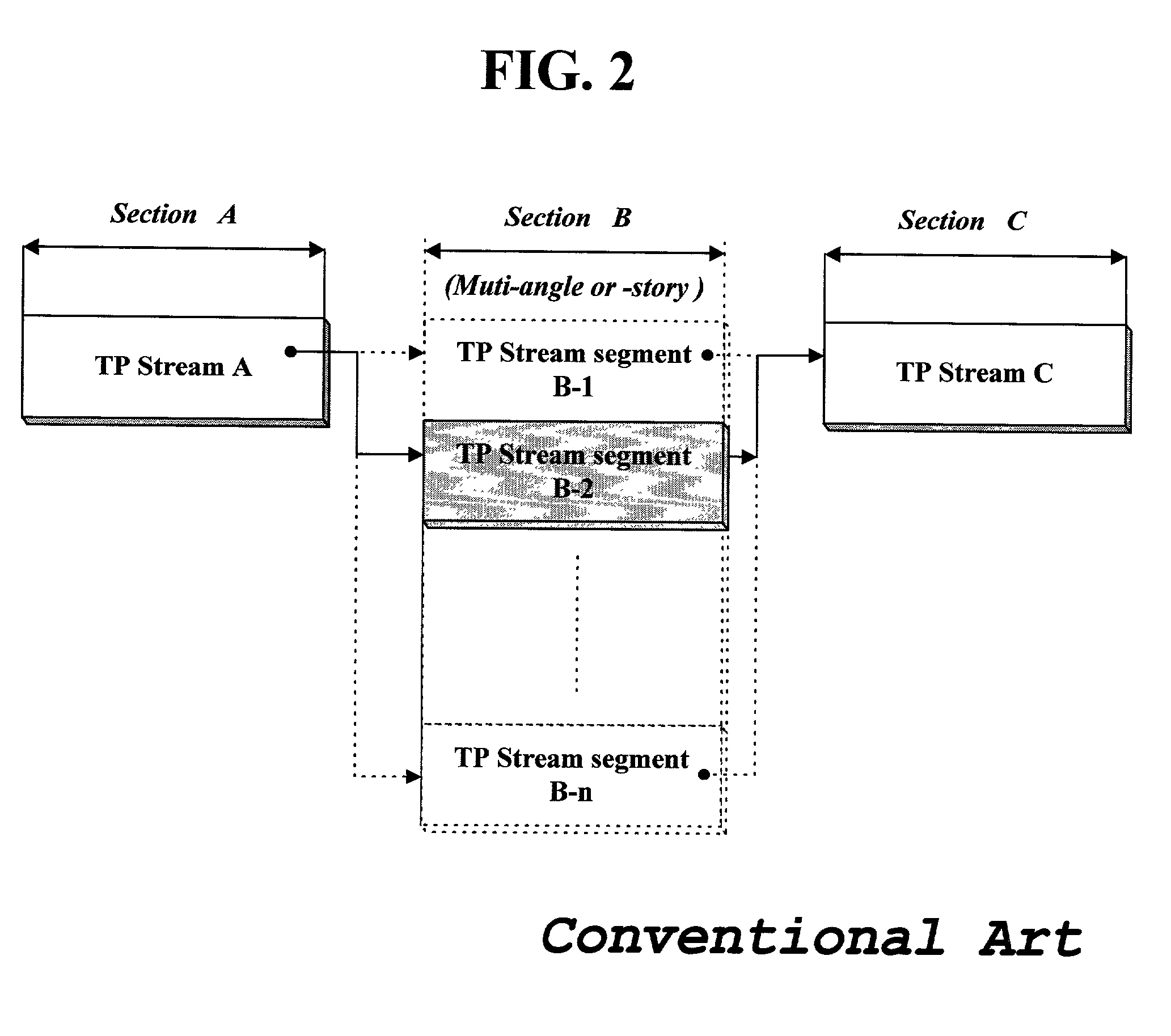
InactiveUS20020097981A1Television system detailsRecord information storageData streamDigital interface
The present invention relates to a method of transmitting data stream including multi-path data stream sections to a connected digital television. This data stream transmitting method checks the number of maximum multiple paths of data streams recorded in a recording medium when a reproduction is requested, copies an uni-path stream section read from the recording medium so that the number of total same stream sections is equal to a target number which is determined based on the maximum number, assigns each stream section to a virtual channel to form multi-channel streams, and transmits the multi-channel streams to an outer device through a digital interface. Through this data stream transmitting method, it is possible to transmit an angle- or story-based stream segment a viewer wants to view among multi-path stream so that the stream of the selected angle or story may be presented seamlessly at the borders between neighboring stream sections by very simple algorithm.
Owner:LG ELECTRONICS INC
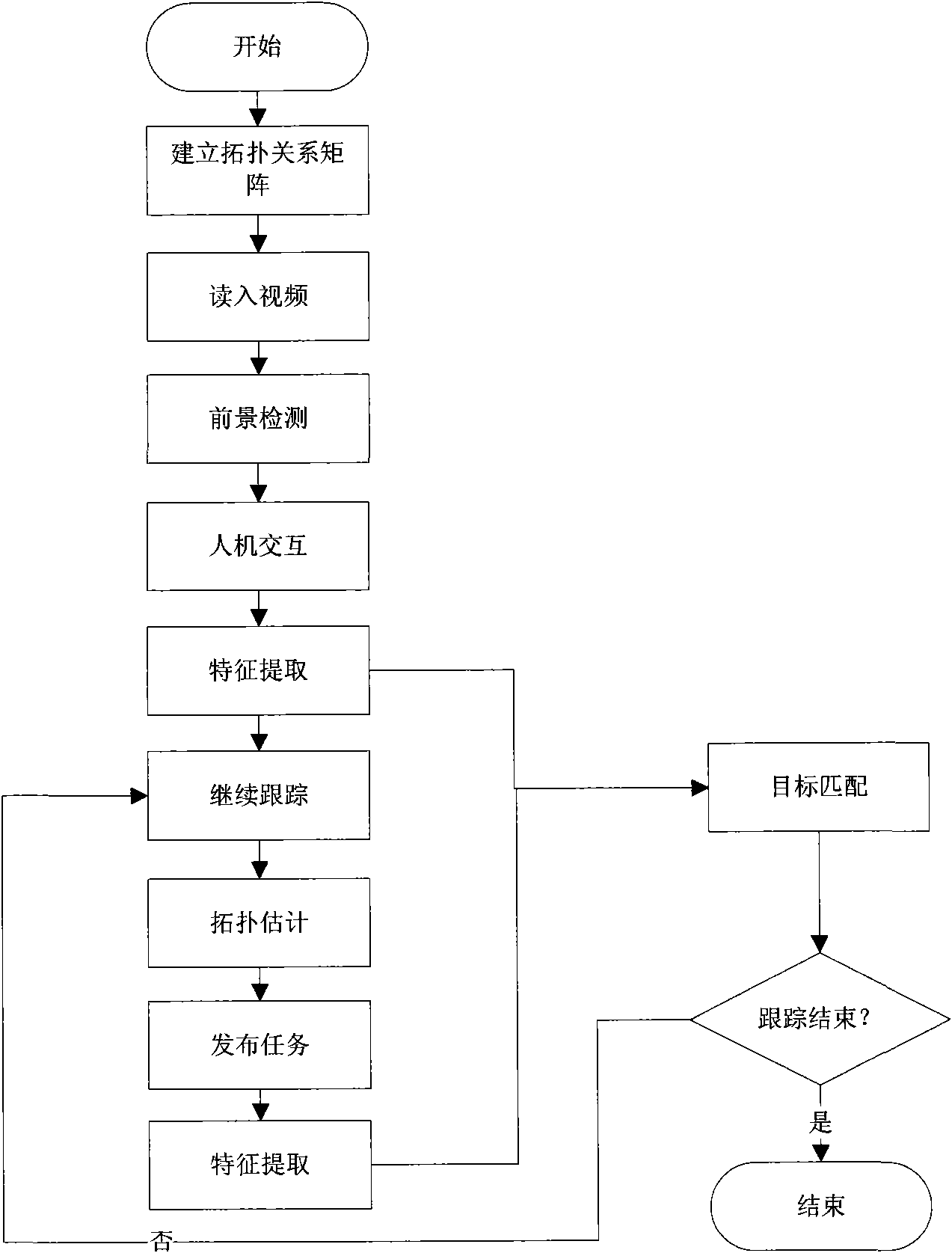
Non-overlapping visual field multiple-camera human body target tracking method
InactiveCN101616309AExact matchHigh precisionImage analysisCharacter and pattern recognitionHuman bodyMulti camera
The invention relates to a non-overlapping visual field multiple-camera human body target tracking method, in particular to a method for carrying out target matching and tracking in multi-camera videos of a non-overlapping visual field under the condition of known topological relation among multiple cameras, comprising the following steps: firstly, establishing a topological relation matrix among multiple cameras, then extracting a foreground image of a pedestrian target followed by selecting a tracking target in the visual range of a certain camera by a human-machine interaction interface, using a mixed Gaussian model to extract the appearance characteristics of the target, comprising colour histogram characteristic and UV colour characteristic, in the whole tracking process, adopting a tree structure to manage tracking task, using Bayesian model to estimate overall similarity, and searching for the optimal matching target according to the overall similarity. The invention has the advantages of high precision, simple algorithm, easy realization, strong instantaneity and the like, and can provide a new real-time and reliable method for multi-camera target recognition and tracking.
Owner:SHANGHAI JIAO TONG UNIV
Keyframe extracting method and system for monitoring system videos
InactiveCN103810711AReduce redundant dataReduce storageImage analysisClosed circuit television systemsMonitoring systemComputer science
The invention provides a keyframe extracting method and system for monitoring system videos. The method comprises the following steps of (a) utilizing a background differencing method to extract keyframe sequences including movement objects in the videos; (b) calculating the similarity degree of every two adjacent frames in the keyframe sequences based on a joint histogram, extracting keyframes with the similarity degree smaller than a threshold value and adding the keyframes into a keyframe set; (c) judging whether mark numbers of every two adjacent keyframes in the keyframe set are smaller than a certain interval or not, deleting the keyframes with small information entropies and updating the keyframe set if the mark numbers are smaller than the certain interval. By utilizing the keyframe extracting method and system for monitoring the system videos, the keyframes including the movement objects can be extracted from a large amount of monitored videos by using a simple algorithm, redundant data in the keyframe sequences are remarkably decreased, and the storage amount of video data are remarkably decreased.
Owner:ZHENGZHOU RIXING ELECTRONICS
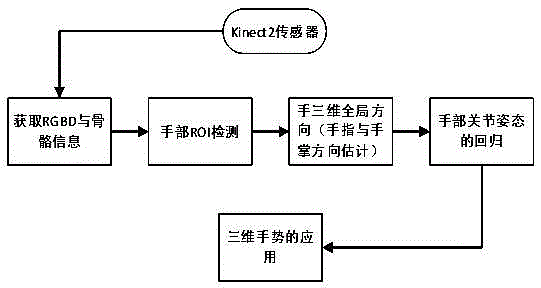
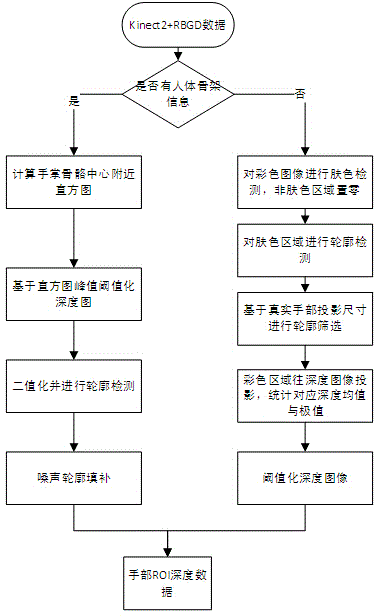
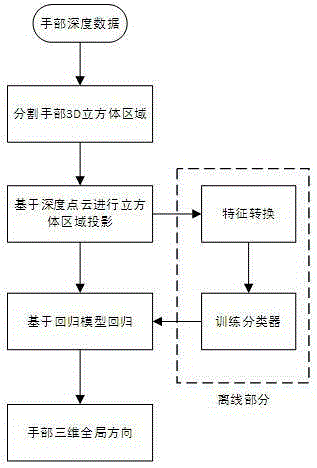
Three-dimensional gesture estimation method and three-dimensional gesture estimation system based on depth data
ActiveCN105389539AGood practical valueThe estimate is reasonableCharacter and pattern recognitionFeature extractionHand parts
The invention discloses a three-dimensional gesture estimation method and a three-dimensional gesture estimation system based on depth data. The three-dimensional gesture estimation method comprises the following steps of S1, performing hand region of interest (ROI) detection on photographed data, and acquiring hand depth data, wherein the S1 comprises the processes of (1), when bone point information can be obtained, performing hand ROI detection through single bone point of a palm; (2) when the bone point information cannot be obtained, performing hand ROI detection in a manner based on skin color; S2, performing preliminary estimation in a hand three-dimensional global direction, wherein the S2 comprises the processes of S21, performing characteristic extracting; S22, realizing regression in the hand global direction according to a classifier R1; and S3, performing joint gesture estimation on the three-dimensional gesture, wherein the S3 comprises the processes of S31, realizing gesture estimation according to a classifier R2; and S32, performing gesture correction. According to the three-dimensional gesture estimation method and the three-dimensional gesture estimation system, firstly cooperation of two manners is utilized for dividing hand ROI data; afterwards estimation in the hand global direction is finished according to a regression algorithm based on hand ROI data dividing; and finally three-dimensional gesture estimation is realized by means of the regression algorithm through utilizing the data as an aid. The three-dimensional gesture estimation method and the three-dimensional gesture estimation system have advantages of simple algorithm and high practical value.
Owner:UNIV OF ELECTRONICS SCI & TECH OF CHINA
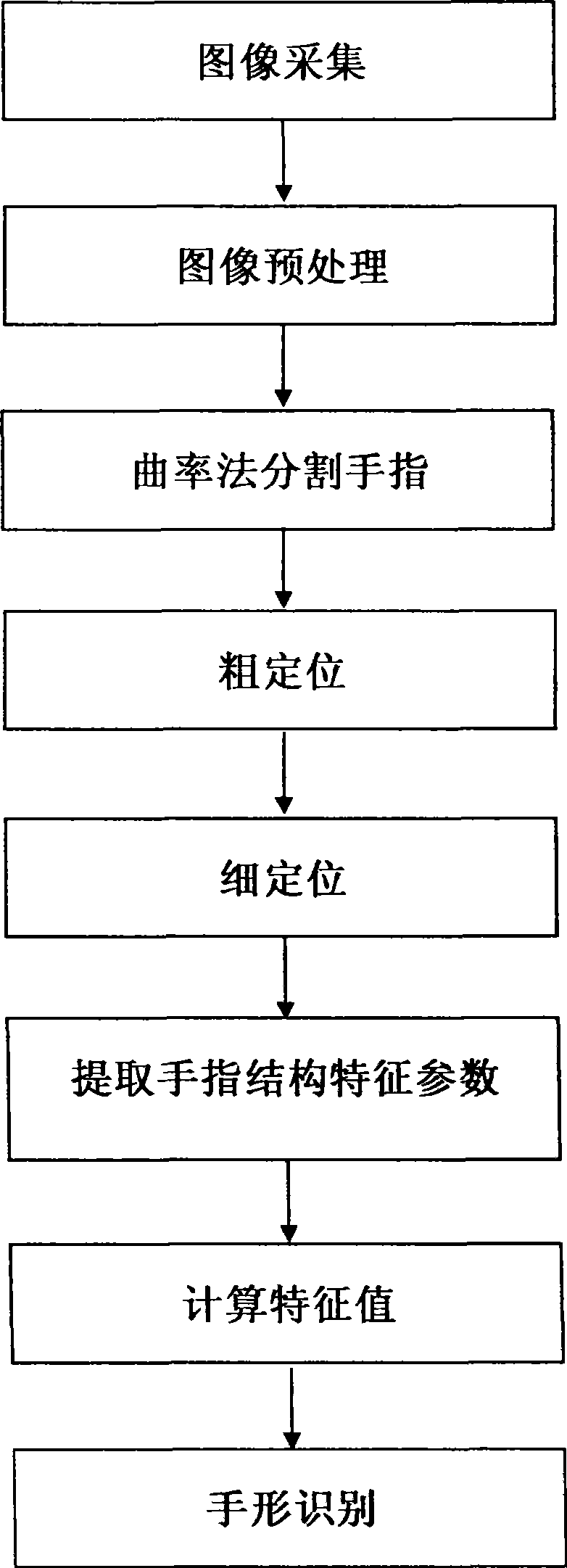
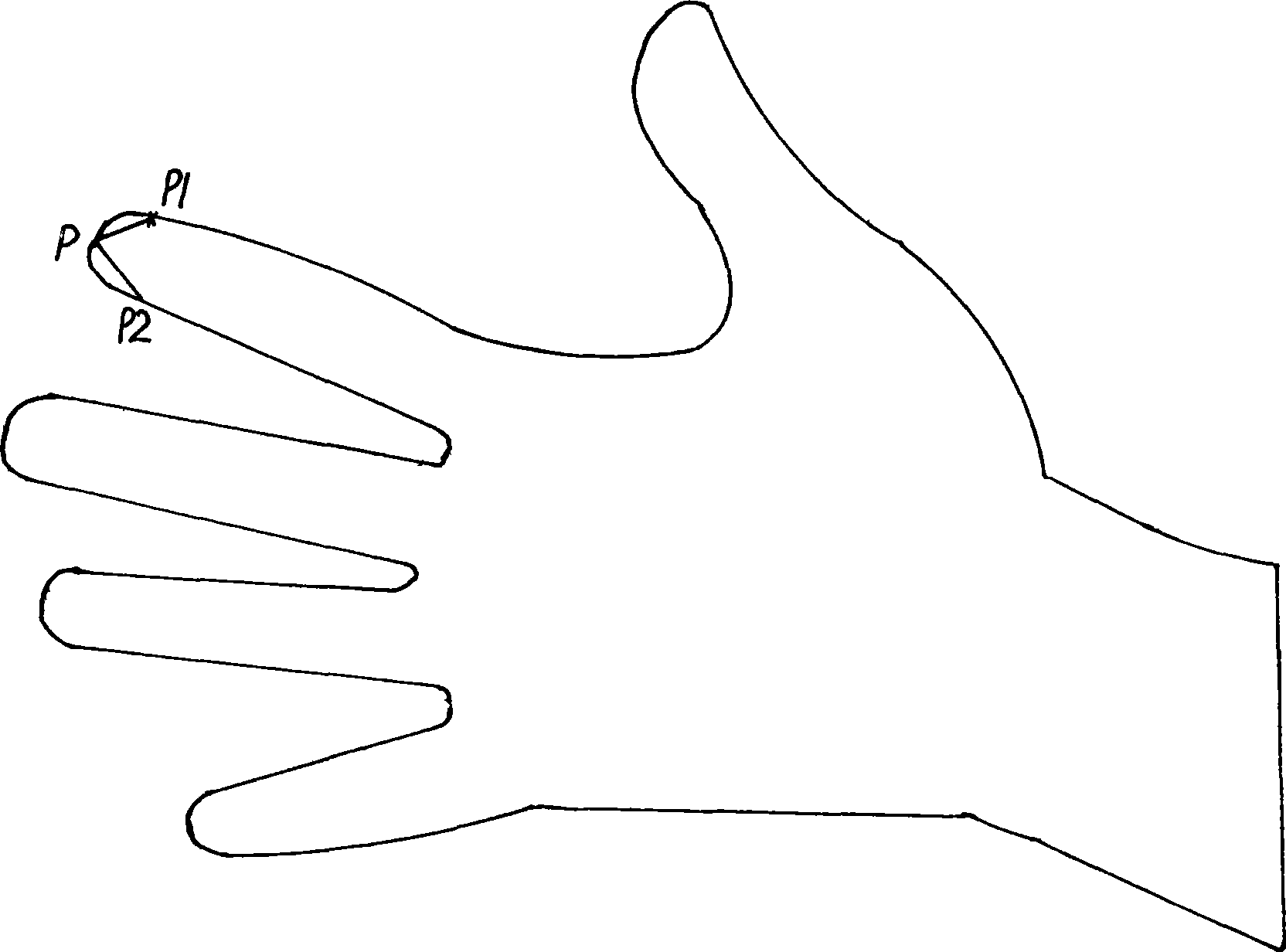
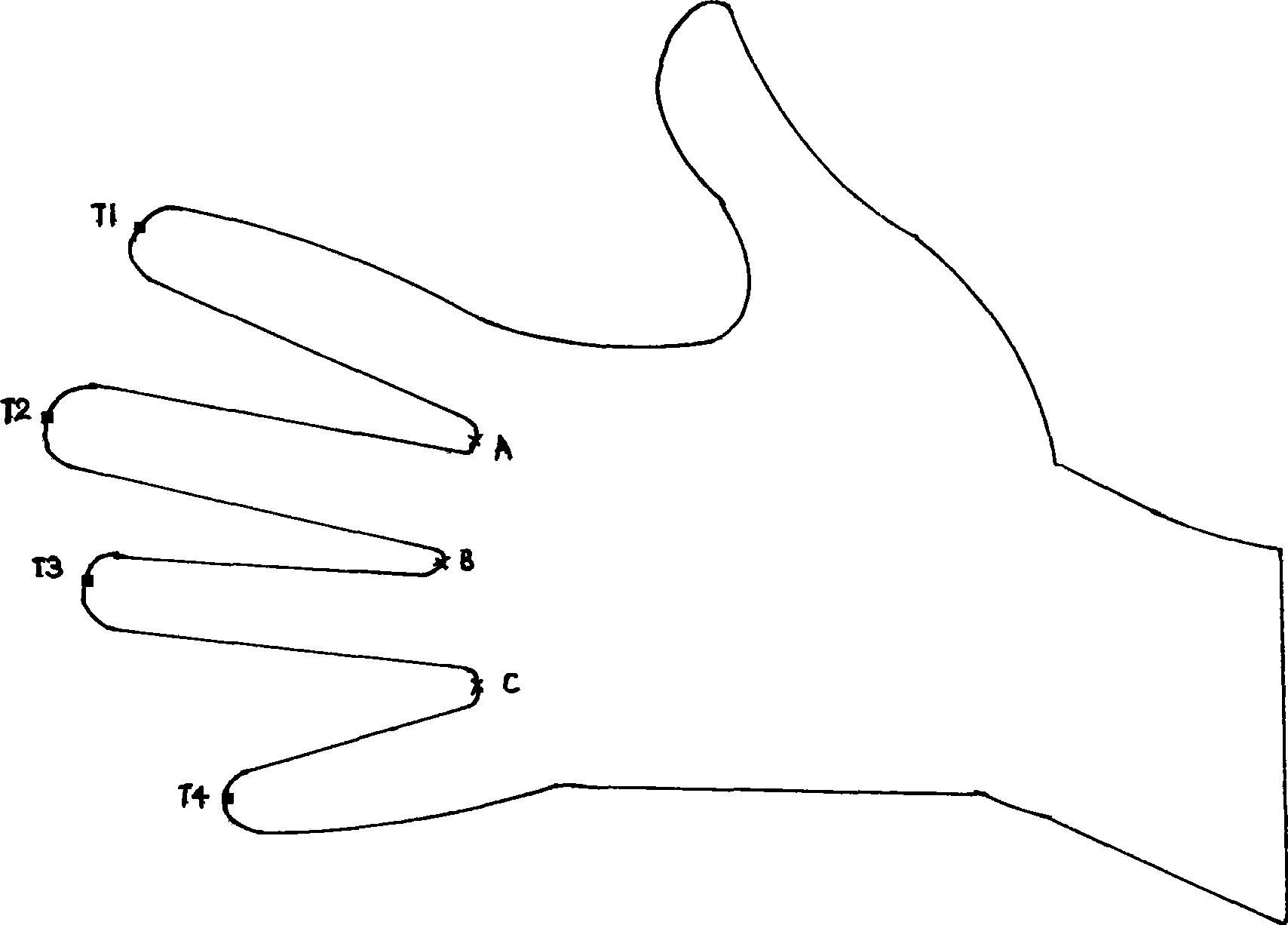
Hand shape recognition method
InactiveCN101470800ALow costWork fasterCharacter and pattern recognitionFeature vectorCharacteristic point
The invention discloses a personal identity identification method based on hand shapes, which adopts an imaging device to obtain human hand images, and obtaining personal character description through computer analyzing and processing, and achieving personal identity identification. The concentrate implementation step comprises the following steps: firstly, adopting an imaging device to obtain hand shape images, secondly, extracting hand shape outlines on the hand shape images, thirdly, extracting hand shape characteristic points according to the hand shape outlines, fourthly, forming hand shape characteristic vectors according to the hand shape characteristic points, fifthly, matching hand shape characteristics according to the hand shape characteristic vectors. The personal identity identification method is mainly characterized in of simple algorithm, high received degree of a tester and stable performance, which is easy to achieve multi-modality identification. The personal identity identification method is particularly suitable for the occasions of a gate inhibition and the like.
Owner:SHENYANG POLYTECHNIC UNIV
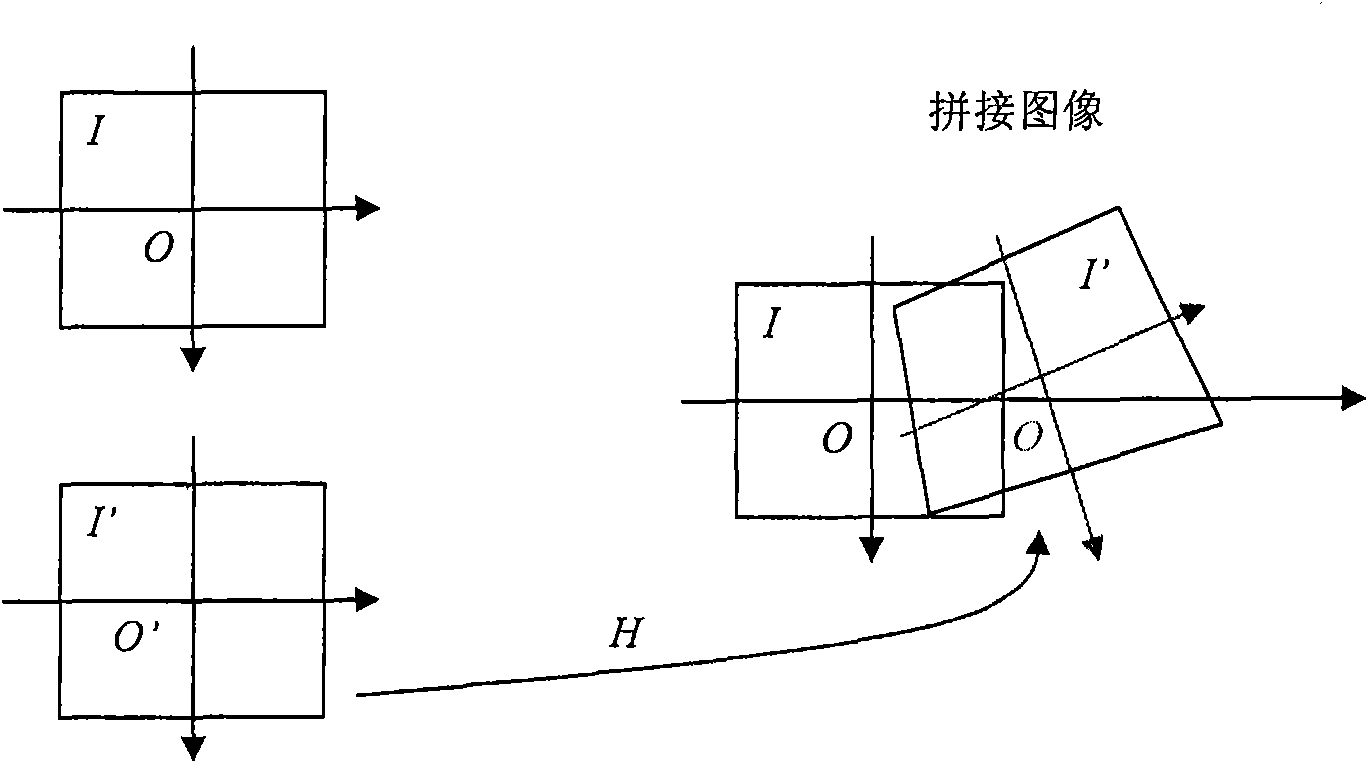
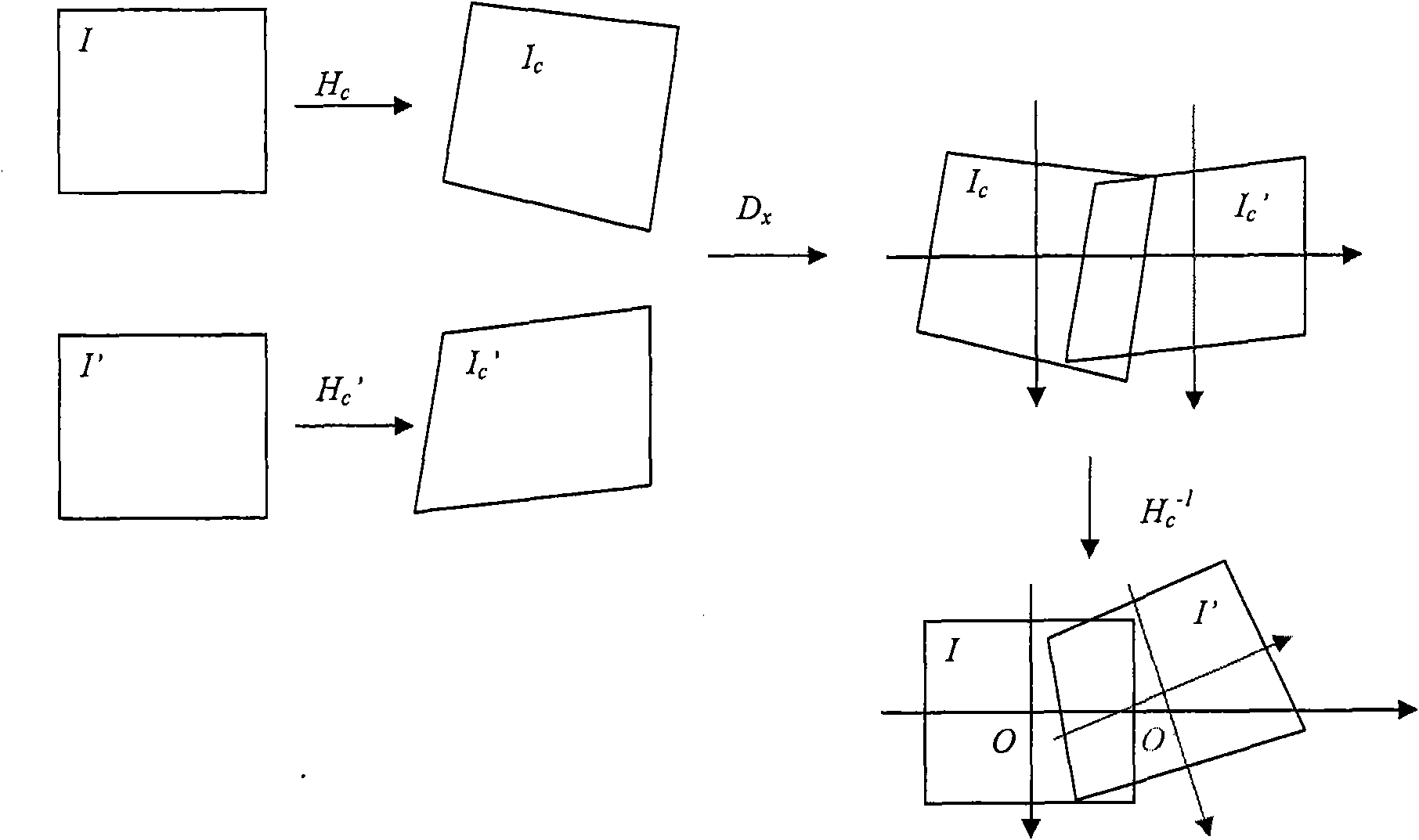
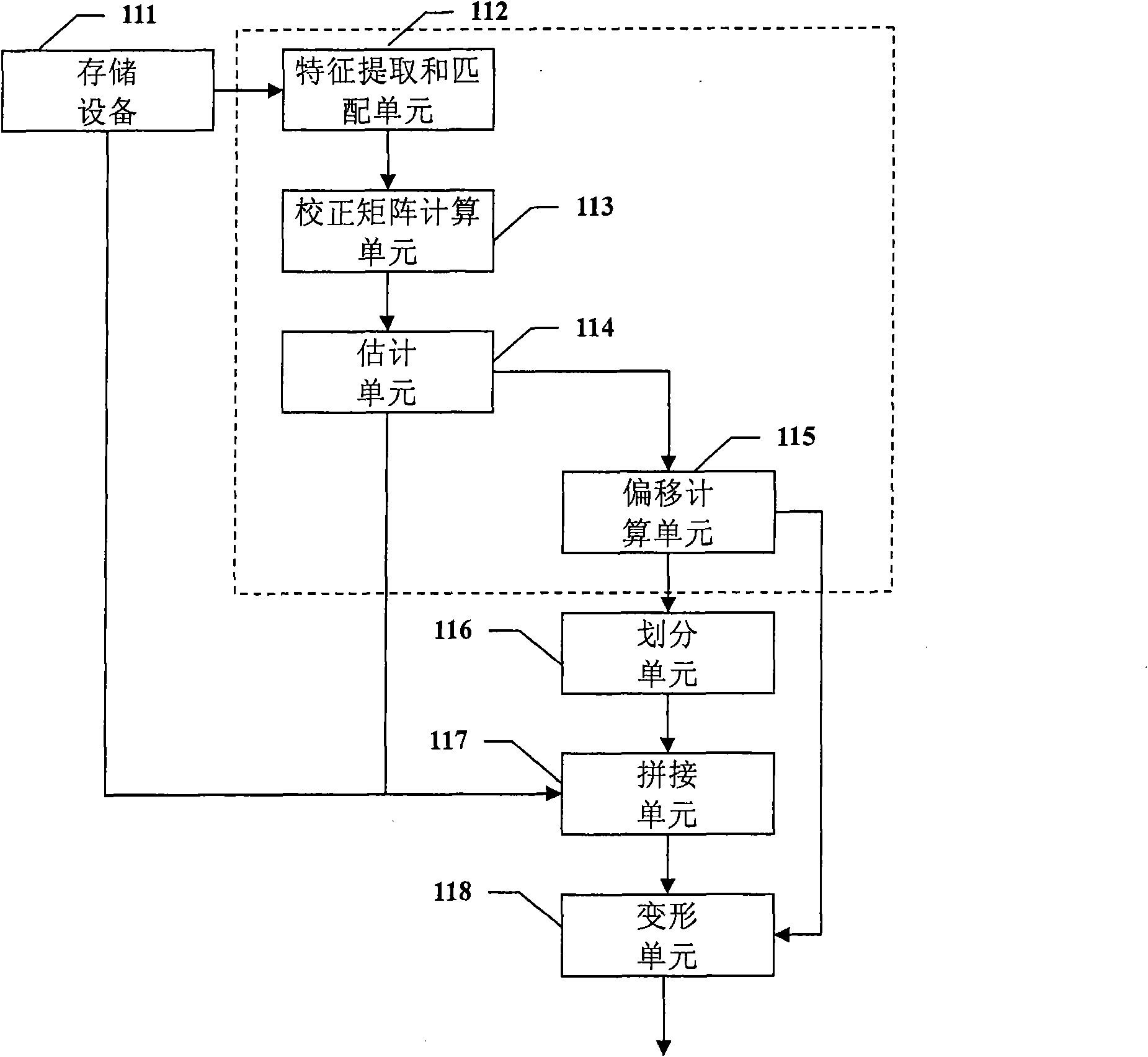
Image splicing method and equipment
InactiveCN101923709AHigh speedEliminate visual inconsistenciesTelevision system detailsImage enhancementVisual perceptionImage splicing
The invention discloses an image splicing method and image splicing equipment which are used for splicing an image rapidly and do not reduce the quality of the spliced image. The method comprises the following steps of: determining a quilt between a first image and a second image; dividing pixels of the first image and the second image into a foreground pixel and a background pixel; splicing the foreground pixel of the first image and the second image based on the quilt; and deforming the background pixel and enabling the background pixel to be fused with the spliced foreground pixel. The method has the characteristics of simple algorithm and high speed. Layered splicing is adopted, and background deformation adapts to the foreground pixel splicing, therefore the inconsistency of vision is eliminated and the quality of image splicing is high.
Owner:NEC (CHINA) CO LTD
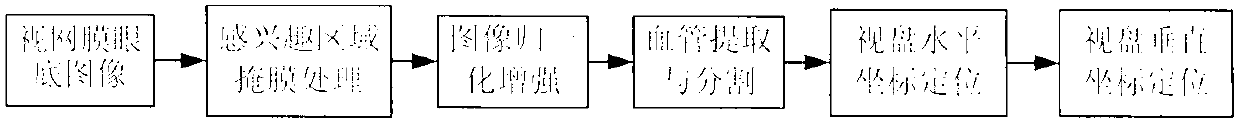
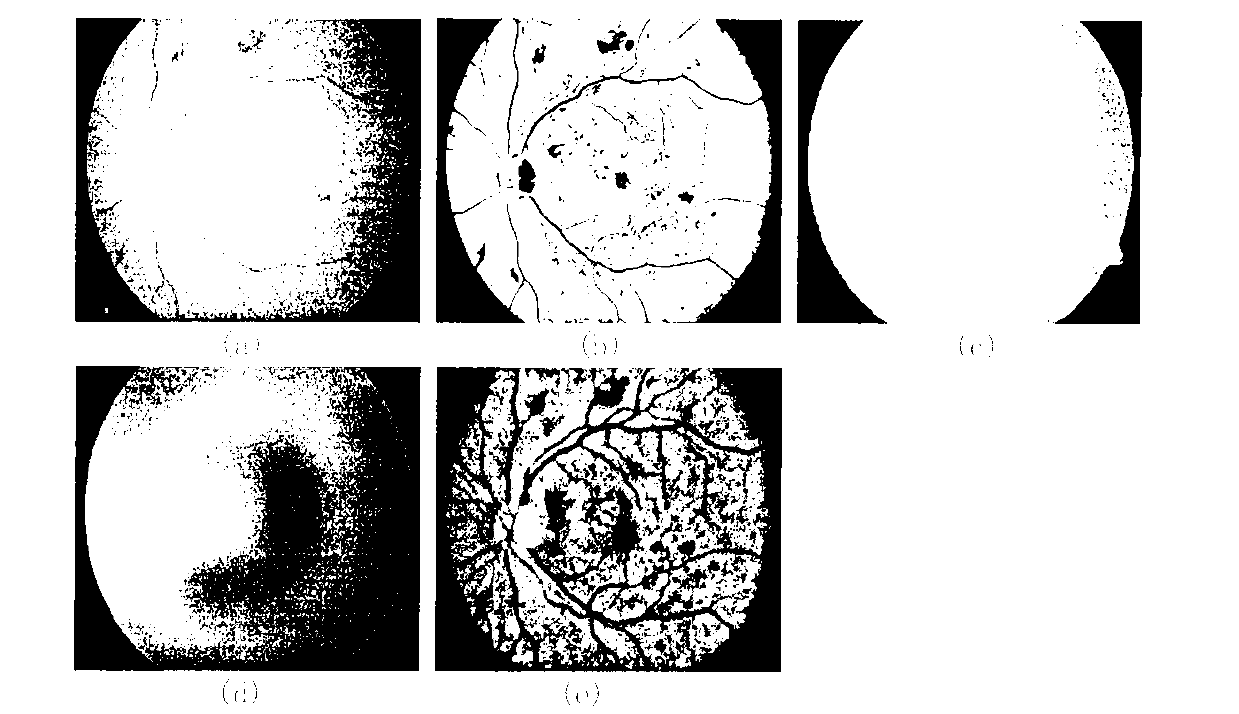
Optic disc projection location method synthesizing vascular distribution with video disc appearance characteristics
InactiveCN102842136AImprove accuracySuppress non-vascular pixelsImage enhancementImage analysisVertical projectionHysteresis
The invention discloses an optic disc projection location method synthesizing vascular distribution with video disc appearance characteristics, which comprises the following steps of: (1) extracting an interest retina fundus image region by use of a mask operation; (2) carrying out normalization enhancement on a fundus image based on an image observation model; (3) achieving extraction and segmentation of the fundus image by using a non-vascular structure inhibition operator and combining with a hysteresis multi-threshold processing technology; (4) setting a vertical window of double main blood vessel width to slide on a blood vessel segmentation image along the horizontal direction and calculating a vascular distribution degree D(x) at each horizontal position x to obtain a distribution degree curve of a horizontal projection, wherein the minimum value point of the curve is determined to be optic disc horizontal coordinate xod; (5) setting a rectangular window side length of which is equal to the optic disc diameter to slide up and down at the horizontal coordinate xod, estimating local region brightness IN(xod, y) and edge gradient information gN(xod, y) respectively, drawing a vertical projection curve reflecting a change of a characteristic value f(y)=IN(xod, y)*gN(xod, y), wherein a maximum value point of the curve is optic disc vertical coordinate yod. The method has a simple algorithm, a high success rate and excellent robustness.
Owner:XIANGTAN UNIV
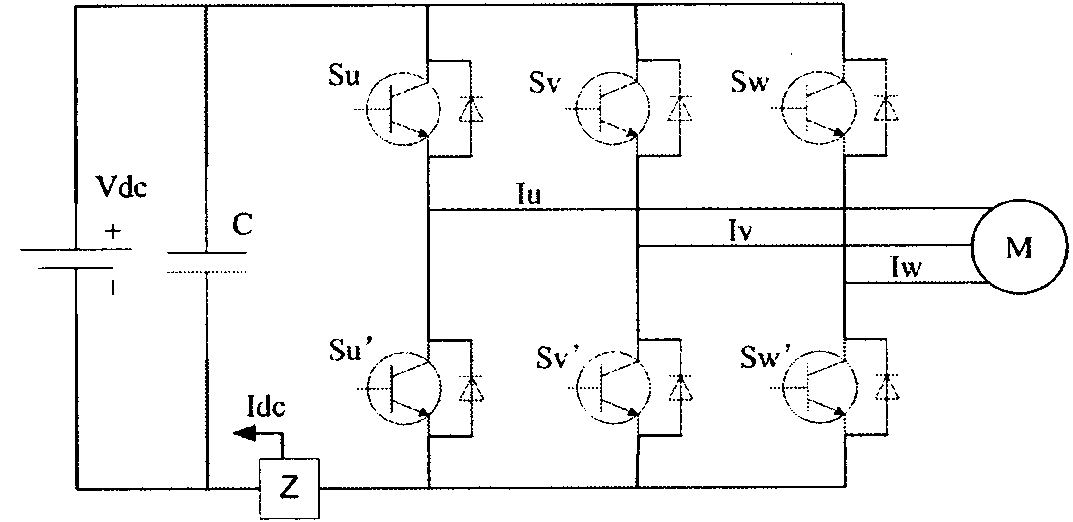
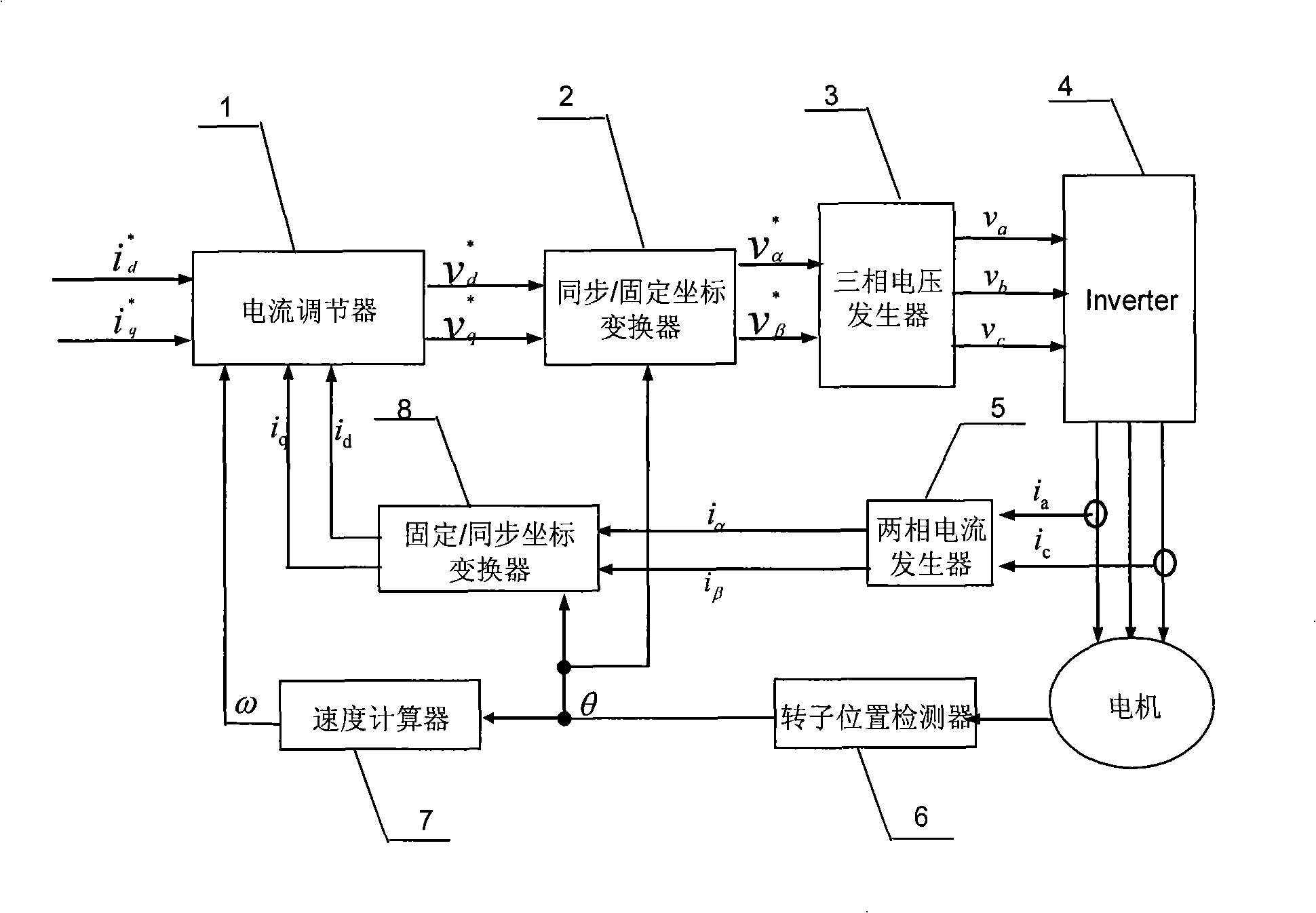
Method for reconstructing phase current of electromotor
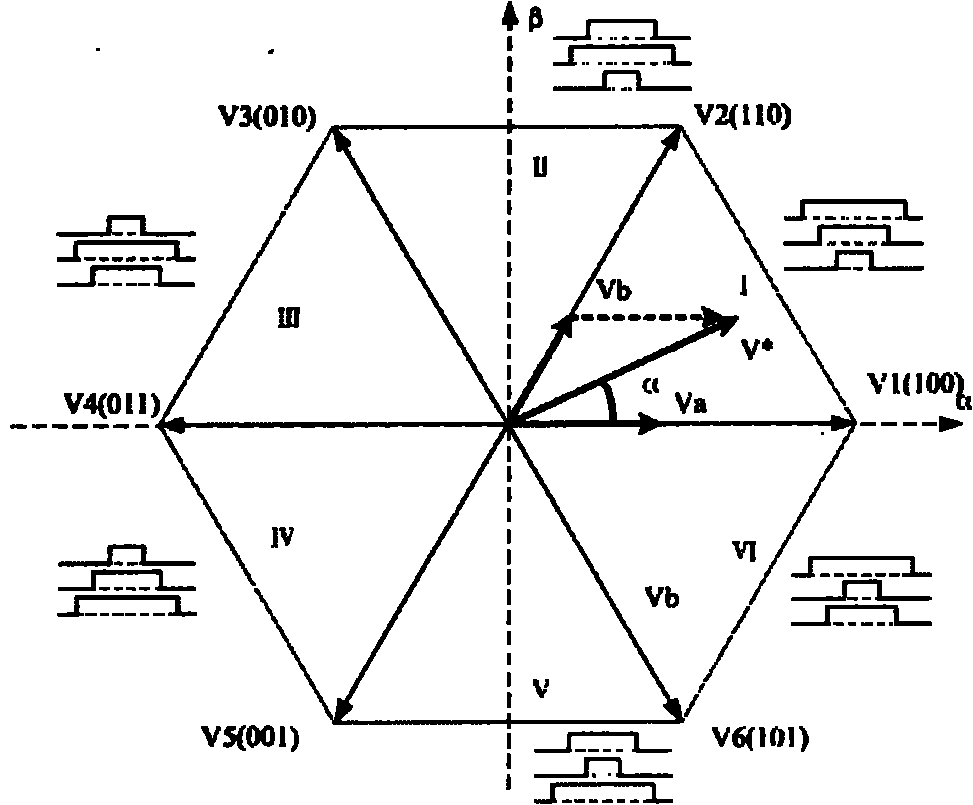
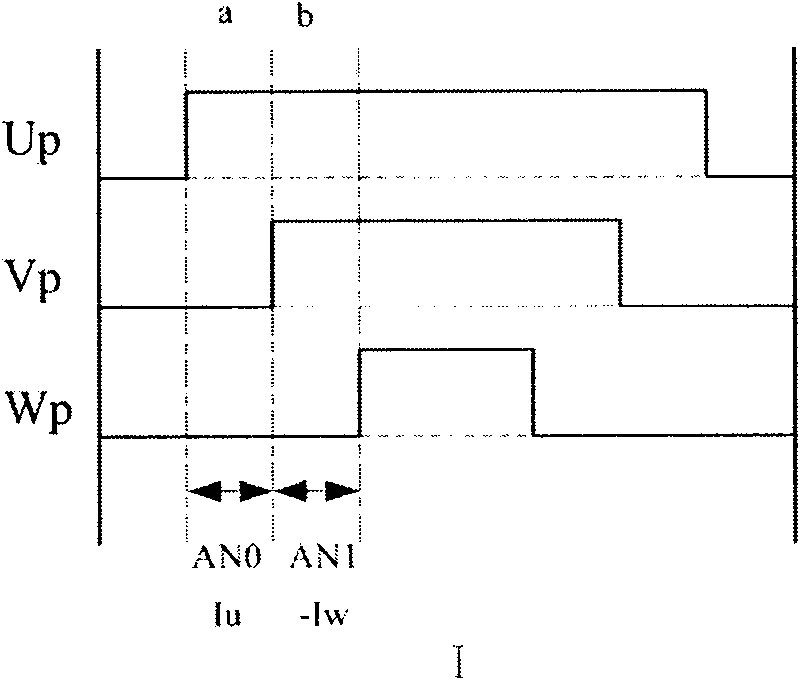
ActiveCN101917157AAvoid distortionReduce occupancyElectronic commutation motor controlVector control systemsPhase currentsLow speed
The invention provides a method capable of reconstructing a three-phase current of an electromotor in full range at any time when the electromotor is driven by a space vector pulse-width modulation mode, which has simple algorithm, high university and relatively good control effects. In the method, an asymmetrical pulse-width modulation (PWM) mode is used for modulation, modulation vectors in a non-observation area are decomposed and one of the decomposed vectors has at least two different non-zero basic space vectors of which the continuous action time is longer than or equal to the action time of a minimal vector in a PWM period; and thus, the non-observation areas are avoided in a space vector PWM process , and the full-time and full-range three-phase current reconstruction and detection of the electromotor are realized, in particular vector distortion is avoided when the electromotor is controlled to be at a low speed. Moreover, the method has the advantages of greatly improving reliability, obviously reducing cost, along with simple algorithm, small code occupation and little increase of current harmonics.
Owner:东元总合科技(杭州)有限公司
Vibration monitoring structure and method based on optical fiber polarized light time domain reflection sense
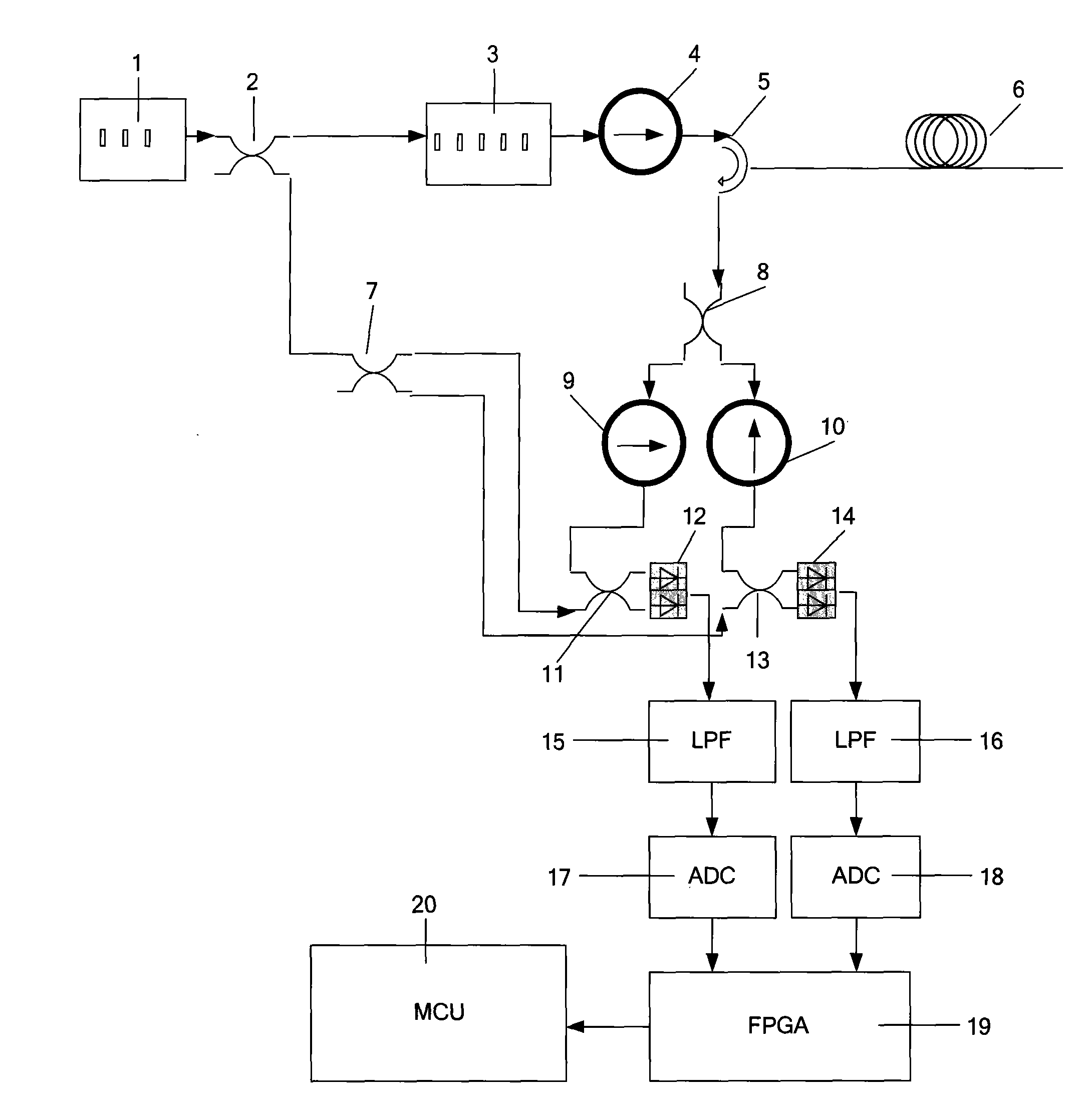
InactiveCN101639379AWith anti-electromagnetic interferenceCorrosion resistantSubsonic/sonic/ultrasonic wave measurementUsing wave/particle radiation meansFrequency spectrumLow-pass filter
The invention relates to a vibration monitoring structure based on optical fiber polarized light time domain reflection sense, comprising a laser (1), a first coupler (2), a second coupler (7), a third coupler (8), a fourth coupler (11), a fifth coupler (13), an acoustic optical modulator (3), a polarizer (4), a circulator (5), a sensing optical fiber (6), a first analyzer (9), a second analyzer (10), a first detector (12), a second detector (14), a first low-pass filter (15), a second low-pass filter (16), a first analog-to-digital converter (17), a second analog-to-digital converter (18), anFPGA (19) and a microprocessor MCU (20); the method comprises the following steps: measuring the changes of the polarization state of each optical fiber section with time according to a plurality ofmeasurements, combining Fourier transformation technology to obtain frequency spectrum information, and analyzing the frequency spectrum information to obtain vibration information. Compared with theprevious method which is adopted by a POTDR system and carries out iteration operation on polarization state, the method has the advantages of simple algorithm and small data operation and greatly reduces monitoring time and cost of the system.
Owner:NANJING UNIV
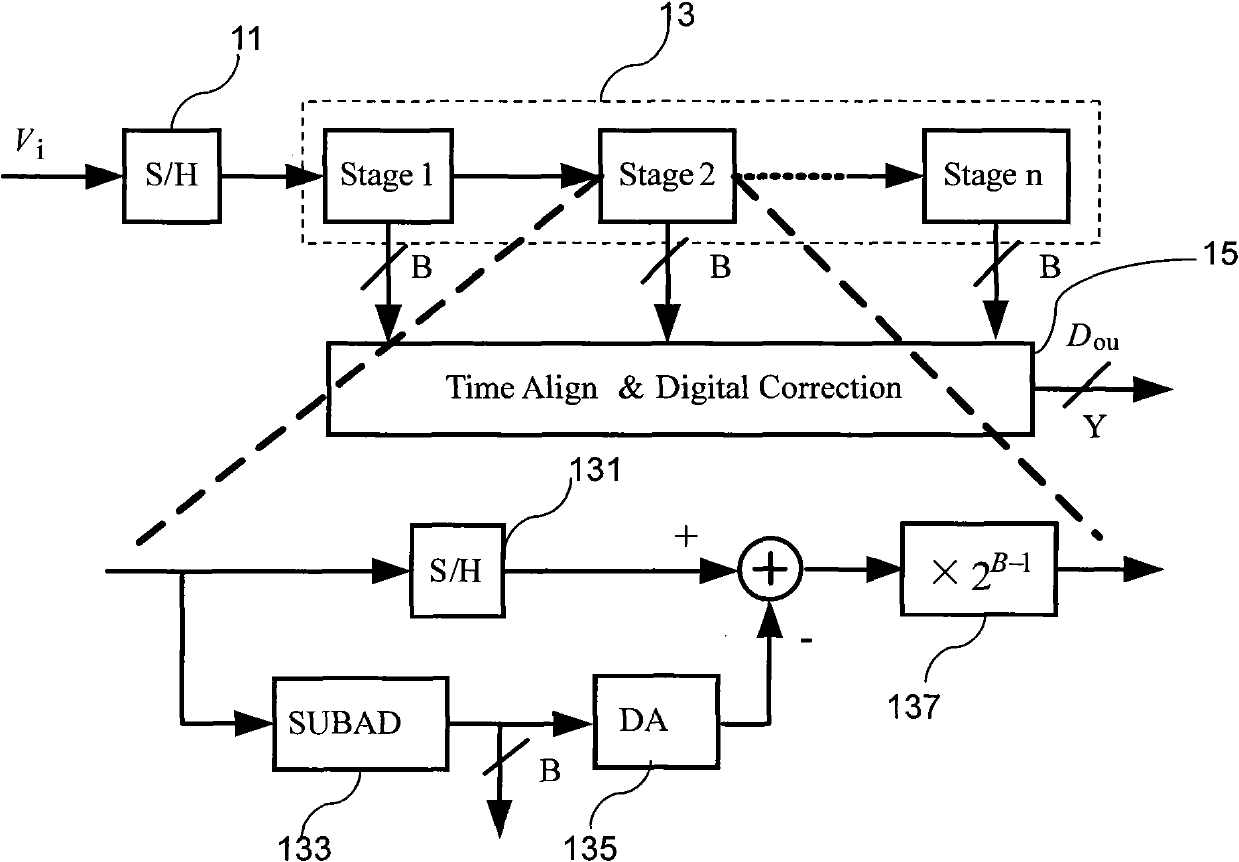
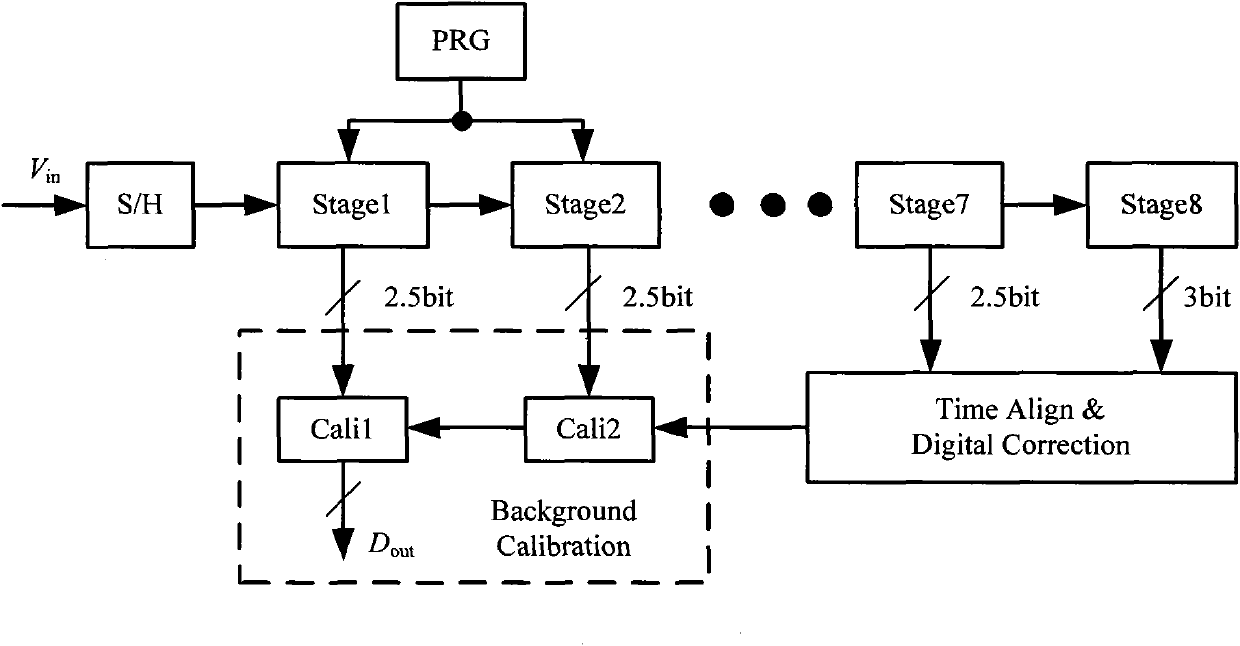
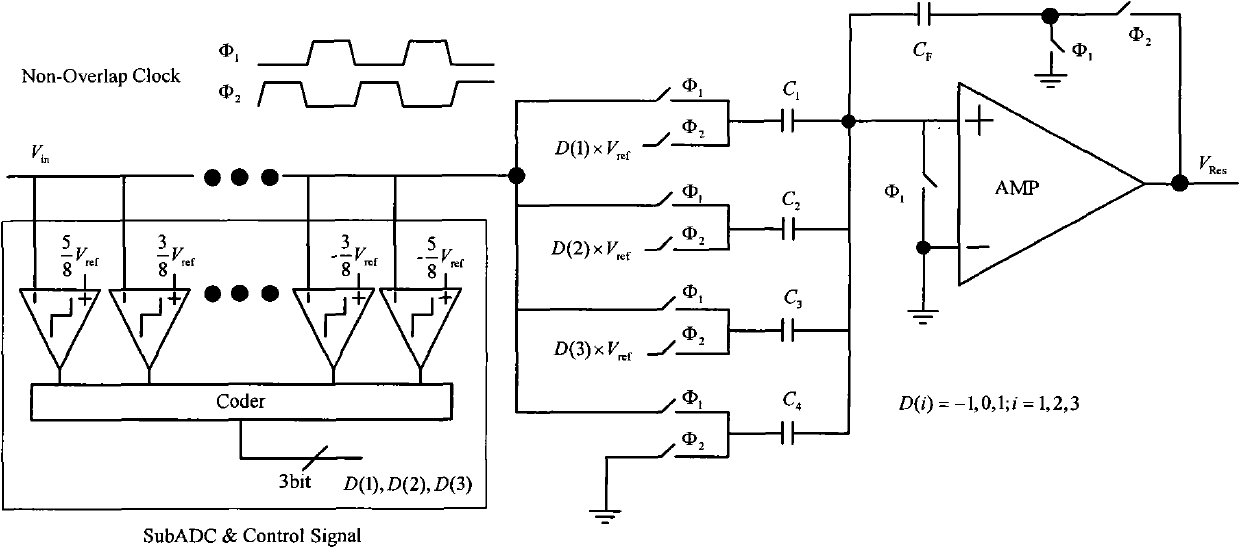
Digital background calibration circuit
InactiveCN102025373AReduce areaReduce design difficultyAnalogue-digital convertersAnalogue/digital conversion calibration/testingDigital down converterSecondary stage
The invention discloses a digital background calibration circuit used for a high-speed and high-precision pipelined analog-to-digital converter. The digital background calibration circuit comprises a pseudo random number generator, pipelined circuits with calibration functions and a digital background calibration engine. Based on the structure of the traditional pipelined analog-to-digital converter, a primary-stage pipelined circuit and a secondary-stage pipelined circuit are modified in the circuit disclosed in the invention to realize the injection of random signals and the digital background calibration engine is used to associate the random signals so as to realize the real-time extraction and compensation of error information, thereby avoiding the influence of irrational factors of the traditional pipelined analog-to-digital converter (such as capacitor mismatching, limitations of operational amplifier gains and the like) on the conversion precision of the analog-to-digital converter. The technology can lower the design difficulty of an analog circuit and ensure the performance of a system. At the same time, because of the simple algorithm and the low implementation complexity, the calibration circuit can be used to effectively reduce the area of the chip and lower the power consumption of the system, thereby being especially applicable to a high-speed system.
Owner:FUDAN UNIV
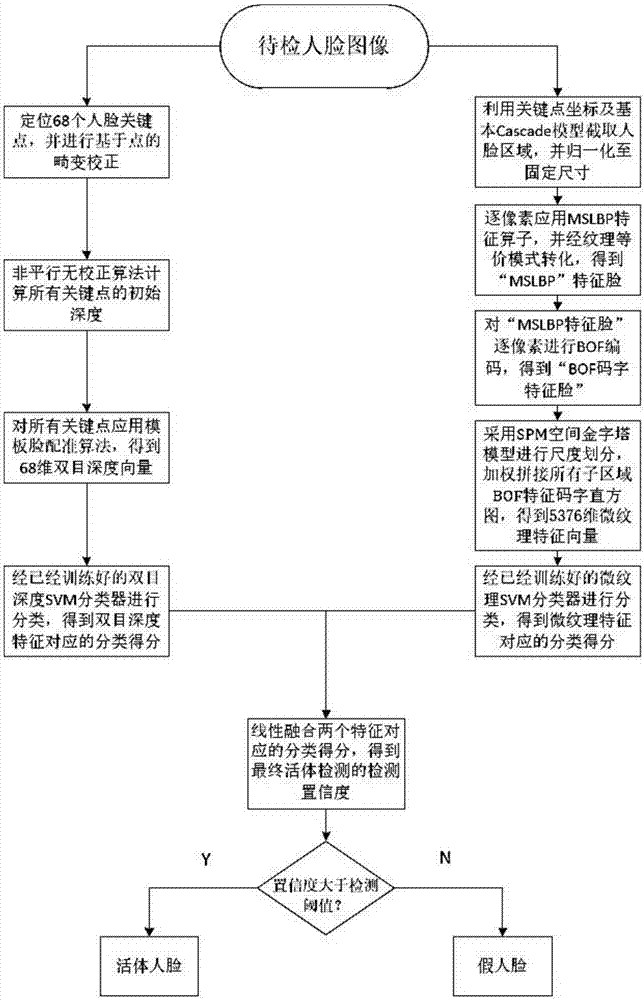
Binocular vision depth feature and apparent feature-combined face living body detection method
The present invention provides a binocular vision depth feature and apparent feature-combined face living body detection method. The method includes the following steps that: step 1, a binocular vision system is established; step 2, a face is detected through the binocular vision system, so that a plurality of key points can be obtained; step 3, a binocular vision depth feature and a classification score corresponding to the binocular vision depth feature are obtained; step 4, a complete face area is intercepted from a left image, the complete face area is normalized to a fixed size, and a local binary pattern (LBP) feature is extracted so as to be adopted as an apparent feature descriptor; step 5, a face living body detection score corresponding to a micro-texture feature is obtained; and step 6, the classification score corresponding to the binocular vision depth feature obtained in the step 3 and the face living body detection score corresponding to the micro-texture feature obtained in the step 5 are fused in a decision-making layer, so that whether an image to be detected is a live body can be judged. The binocular vision depth feature and apparent feature-combined face living body detection method of the invention has the advantages of simple algorithm, high operation speed, high precision and the like. With the method adopted, a new and reliable method can be provided for living body face detection.
Owner:SHANGHAI JIAO TONG UNIV
User interface device
InactiveUS20100194713A1Improve accuracyInput/output processes for data processingComputer visionComputer science
A user interface device detects a fingertip placed on an imaging range. The imaging range is located or arranged so that a user inserts and place a hand along a predetermined direction. A device detects a tip area corresponding to the fingertip from the imaging range. The device determines whether the detected tip area is a finger or not. The determination can be performed by evaluating a size of the tip area, for example, whether the width is in an appropriate range or not. If the tip area is verified as a finger, a position of the fingertip is calculated. According to the device, it is possible to determine whether it is a finger or not by using a relatively simple algorithm. As a result, it is possible to eliminate objects other than finger and to provide sufficient accuracy for detecting the fingertip.
Owner:DENSO CORP
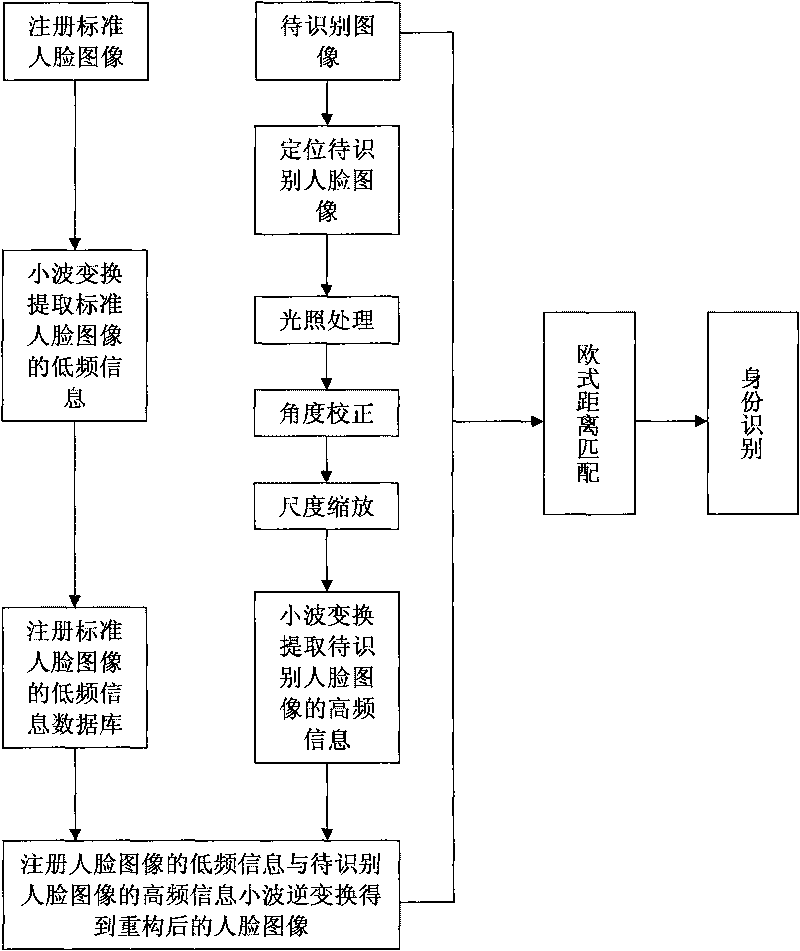
Image cross reconstruction-based single-sample registered image face recognition method
InactiveCN101739546AEasy accessSave storage spaceCharacter and pattern recognitionSingle sampleIdentity recognition
The invention discloses an image cross reconstruction-based single-sample registered image face recognition method. The method adopting the image cross reconstruction realizes the personal identity authentication by computer analysis and processing, and particularly comprises the following steps: registering low-frequency information of standard face images in a face database; acquiring a front image of a face to be recognized; extracting high-frequency information of the image of the face to be recognized; performing the image cross reconstruction on the high-frequency information of the image of the face to be recognized and the low-frequency information of the registered face images; and finally, performing matching judgment on the fused images and the image of the face to be recognized to realize the identity recognition. The image cross reconstruction-based single-sample registered image face recognition method has the advantages of small space of the database registering the face information, simple algorithm, short recognition time, high recognition rate and the like.
Owner:SHENYANG POLYTECHNIC UNIV
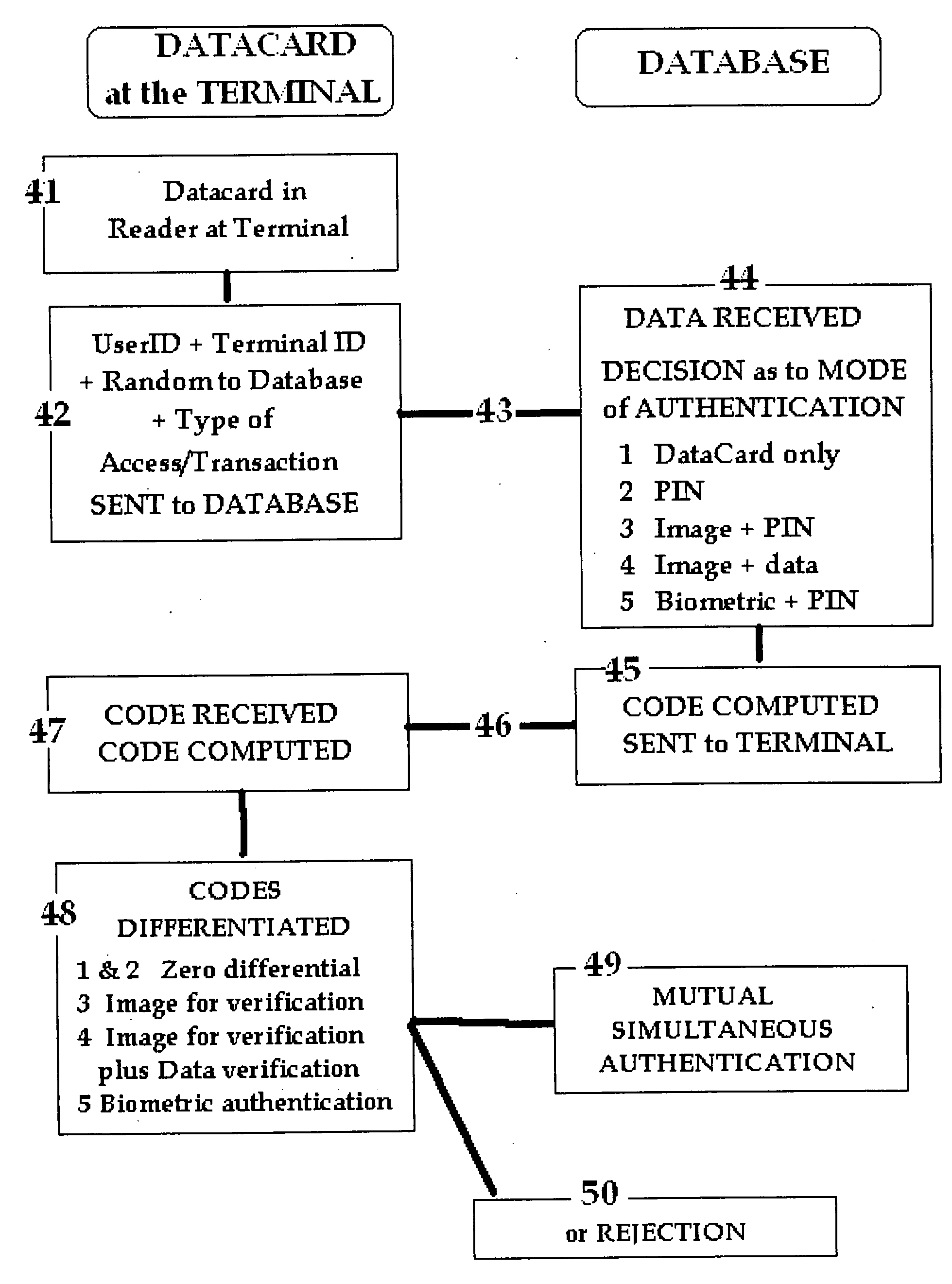
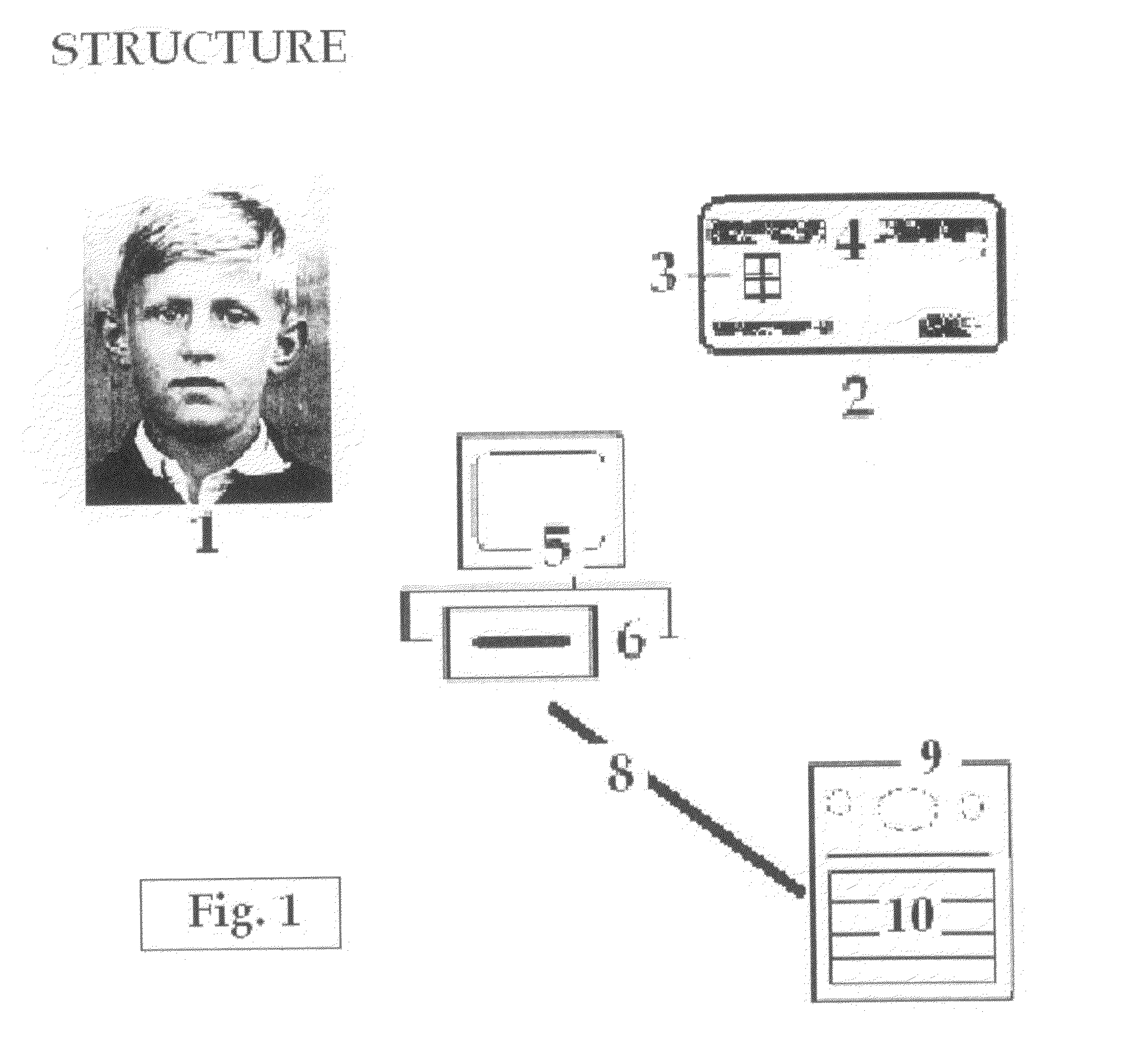
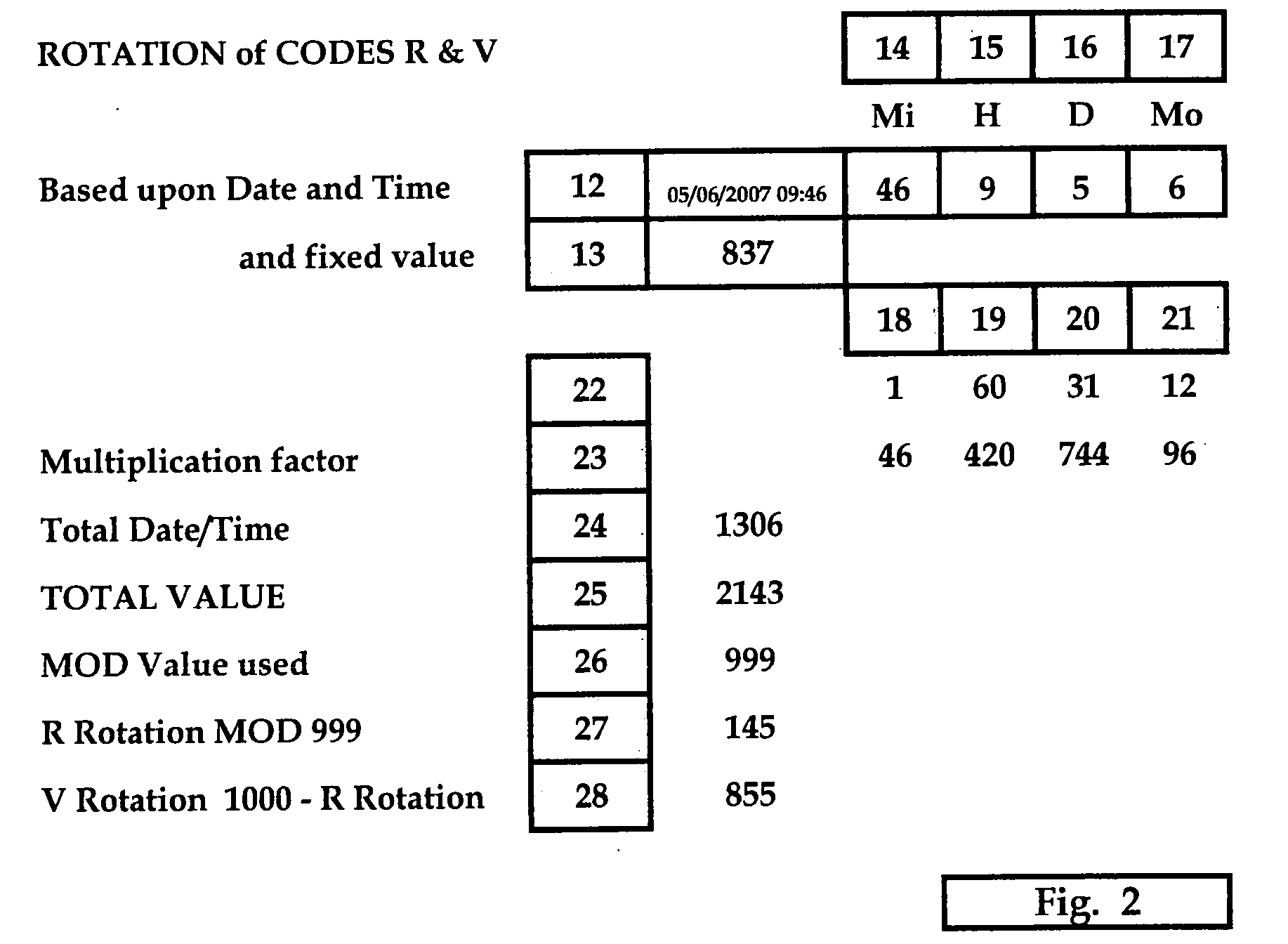
Integrated systems for simultaneous mutual authentication of database and user
InactiveUS20080313726A1Enhanced security and protectionSimple and inexpensiveDigital data processing detailsUser identity/authority verificationSource Data VerificationUser authentication
In the field of user authentication, the present invention provides an integrated system for the mutual authentication of a system database and a registered user with a view to increasing the security of remote authentication and the prevention of “phishing / man-in-the-middle” attacks, by one of several alternative means including Code matching, PIN verification, Image reproduction and recognition, Signature and personal data verification, DNA verification and Biometric verification, in each case by means of the differential between variable Codes computed at the database from data recorded for that user and at a remote terminal from replicate data retrieved from a data carrying device. The Codes are derived from the recorded data and a simple algorithm such that the Codes are not predicable.
Owner:GARDNER RICHARD MERVYN
Method for detecting and classifying glass defects based on machine vision
InactiveCN102305798AFast operationHigh precisionMaterial analysis by optical meansMachine visionClassification methods
The invention relates to a method for detecting and classifying glass defects based on machine vision. The method comprises the following steps of: extracting a defect area in a picture provided by a camera (linear scanning) by Canny edge detection to obtain a minimum connected domain of the defects; processing a target area according to a filter and a W characteristic which are provided by the method; defining nine kinds of characteristic modes, scanning the minimum connected domain according to rows and columns, and counting the emerging frequency of the nine kinds of characteristic modes in a sample; and judging the types of the defects (bubbles are used as hollow defects, and impurities are used as solid defects) on the basis of the emerging frequency. Compared with the prior art, themachine-vision-based method has the advantages of simple algorithm, quick operation speed, high accuracy and the like, and a new reliable method is provided for the detection of the glass defects.
Owner:SHANGHAI JIAO TONG UNIV
Network structure topology layout method and network management device
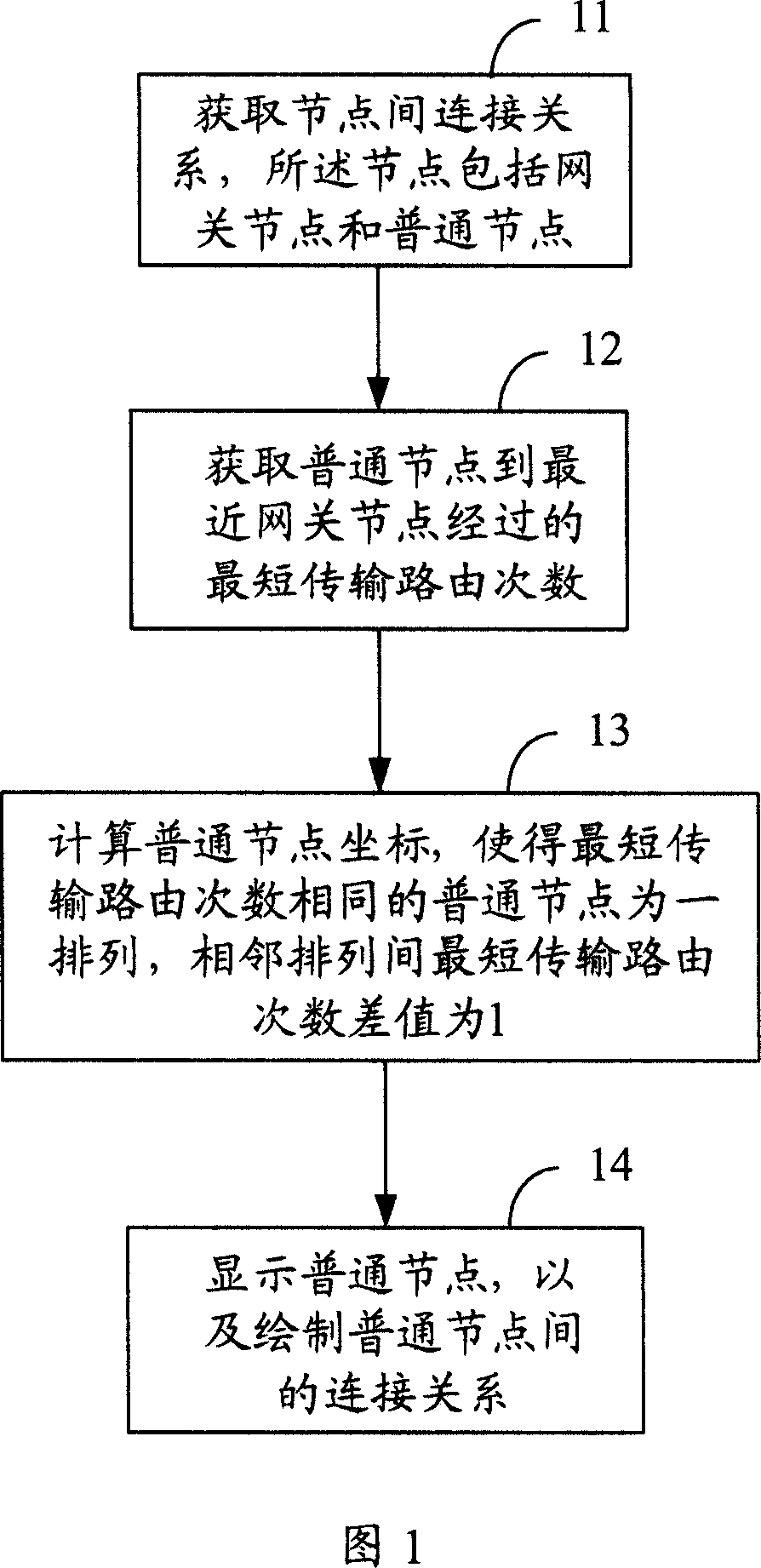
InactiveCN101035023AImprove layout speedImprove stabilityElectromagnetic transmissionData switching networksClear LayerNetwork structure
The invention provides a network topology layout method and the network management device thereof. And the method comprises: obtaining connection relation between nodes, where the nodes include common nodes and gateway nodes; according to the connection relation, obtaining numbers of times of shortest path routing from common nodes to the nearest gateway nodes; calculating node coordinates and making the common nodes with the same number of times of shortest path routing compose an array, where the difference value between the numbers of times of shortest path routing between the adjacent arrays is equal to 1; displaying the common nodes and drawing the connection relation between the common nodes. And the invention has the advantages of simple algorithm, low cost, and clear layers of network topology and clear network topology.
Owner:HUAWEI TECH CO LTD
Method suitable for low-speed switched reluctance motor without position sensor
The invention discloses a method suitable for a low-speed switched reluctance motor without a position sensor, which belongs to the technical field of control of the switched reluctance motors. The method is as follows: taking the switched reluctance motor as a control object, injecting high frequency pulses into a non-conduction phase, detecting the differences between rising slopes and descending slopes of three-phase current during the whole period, filtering the discrete differences, and then forming three envelope lines respectively, thereby being capable of determining the position of a rotor according to cross points of the envelope lines due to the special relationship between the envelope lines and inductance, calculating other positions according to the rotational speed and further realizing the normal running of the motor and the adjustable control of a turn-on angle and a turn-off angle. The method has simple algorithm and flexible control, only the phase current needs to be detected, and the affects of counter potential are simultaneously eliminated, thereby improving the accuracy of position estimation to a greater extent.
Owner:NANJING UNIV OF AERONAUTICS & ASTRONAUTICS
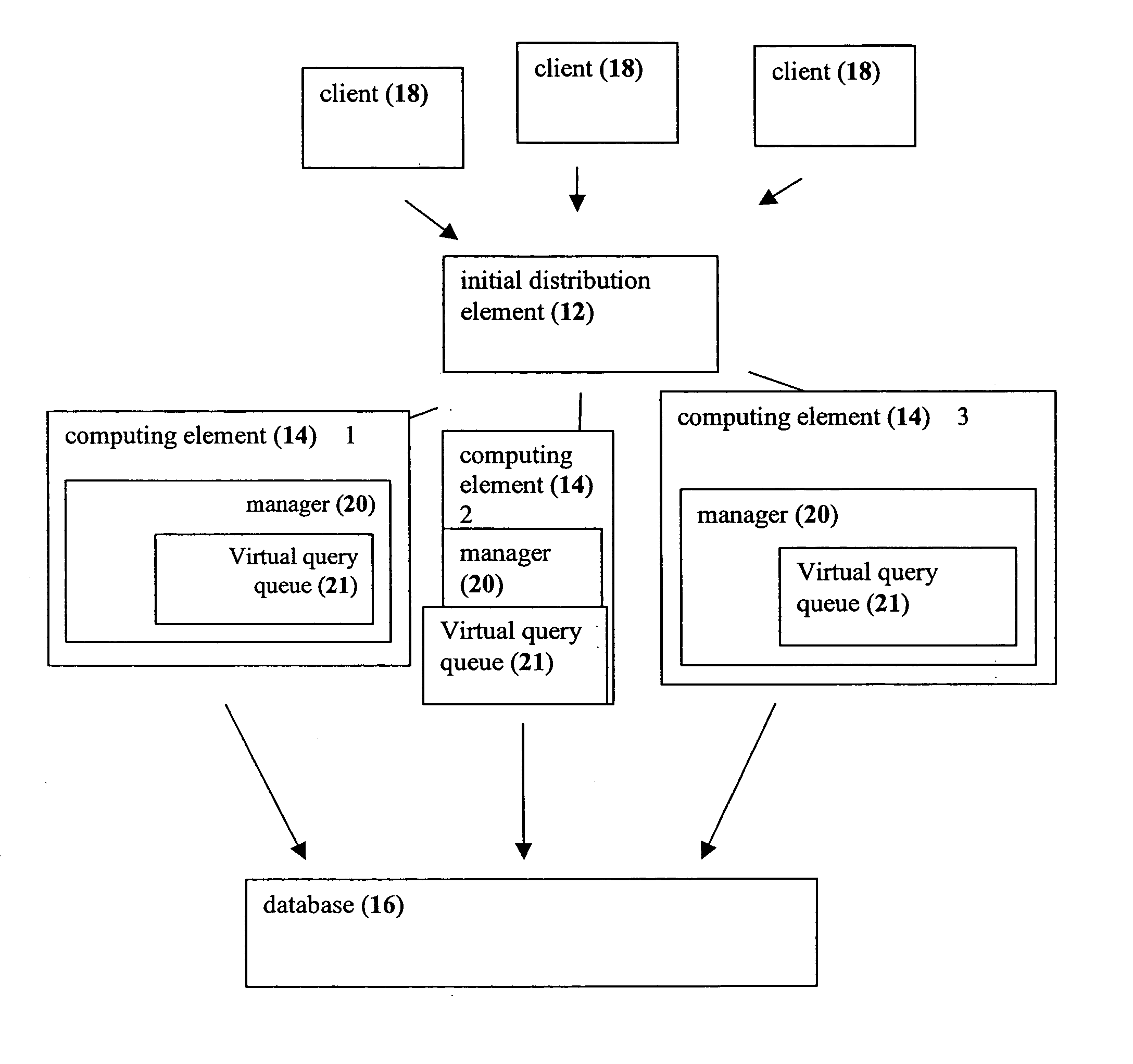
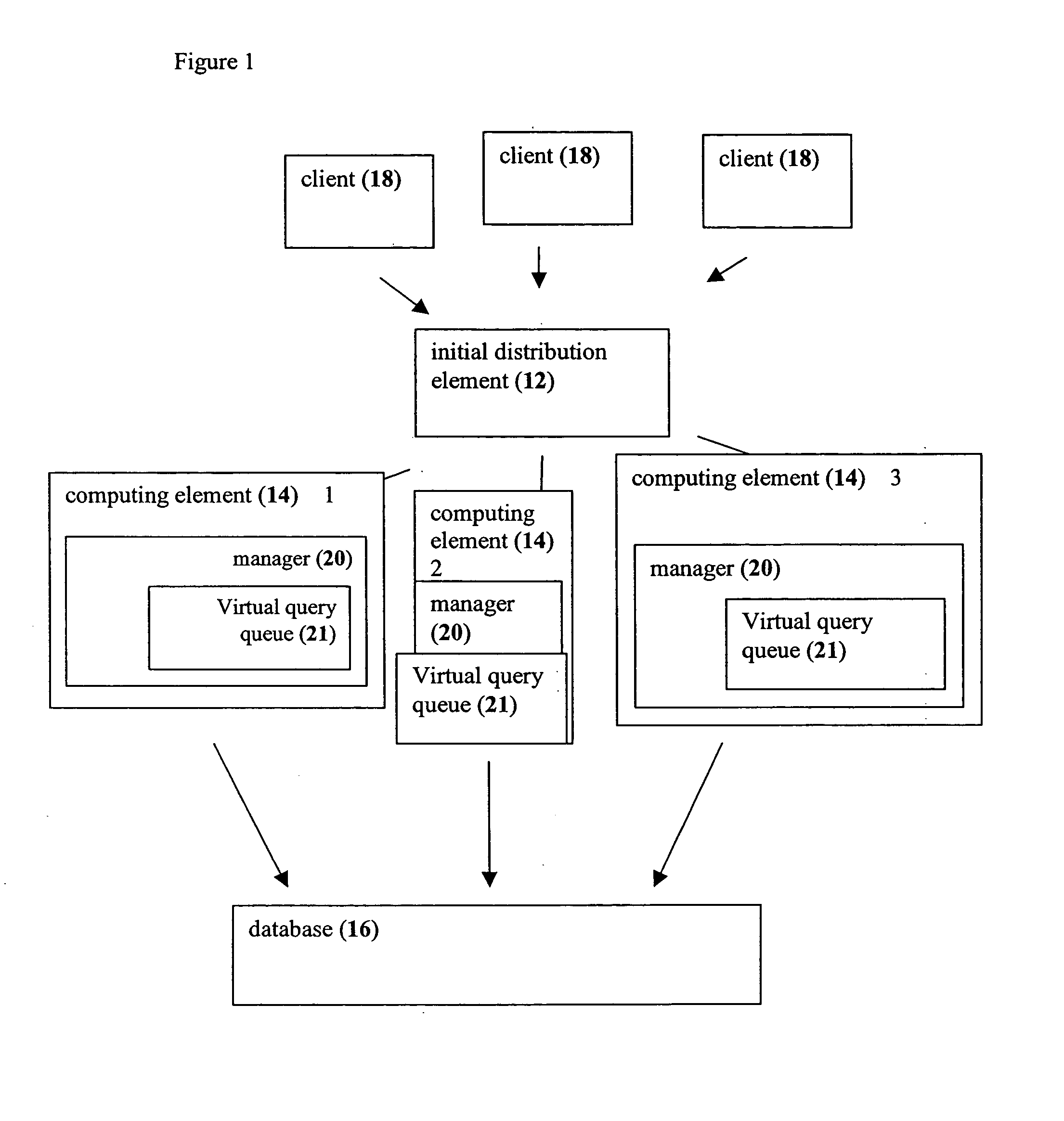
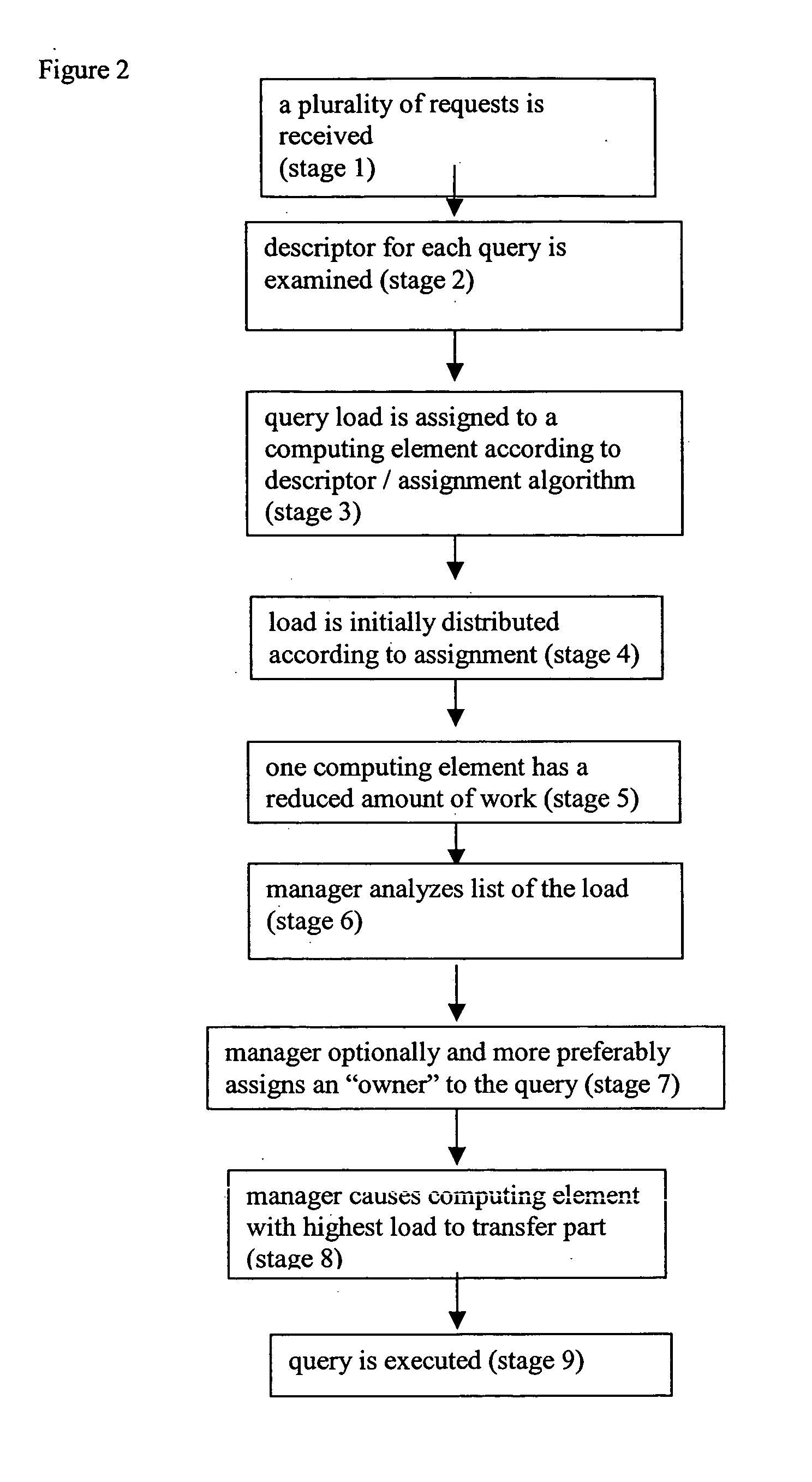
System and method for load balancing in database queries
InactiveUS20050021511A1Reduce in quantityReduce the numberDigital data information retrievalDigital data processing detailsDatabase queryLoad Shedding
A system and method in which query load balancing process is performed in a cluster of middle-tier computing elements according to the load on at least one, but more preferably a plurality, of the computing elements of the group, this by passing pointers to queries between machines with information or processes pertinent to the query. Optionally the balancing may be carried out in two stages. The first stage performed rapidly, preferably implemented as a hardware device such as a switch for example in which a plurality of queries is distributed to a plurality of computing elements according to at least one descriptor attached to each query or a simple algorithm is used. The second stage preferably performed as above by at least one computing element of the group, but may optionally be performed by a plurality of such elements. Alternatively, the second stage may be performed by a separate computer.
Owner:KCI LICENSING INC +1
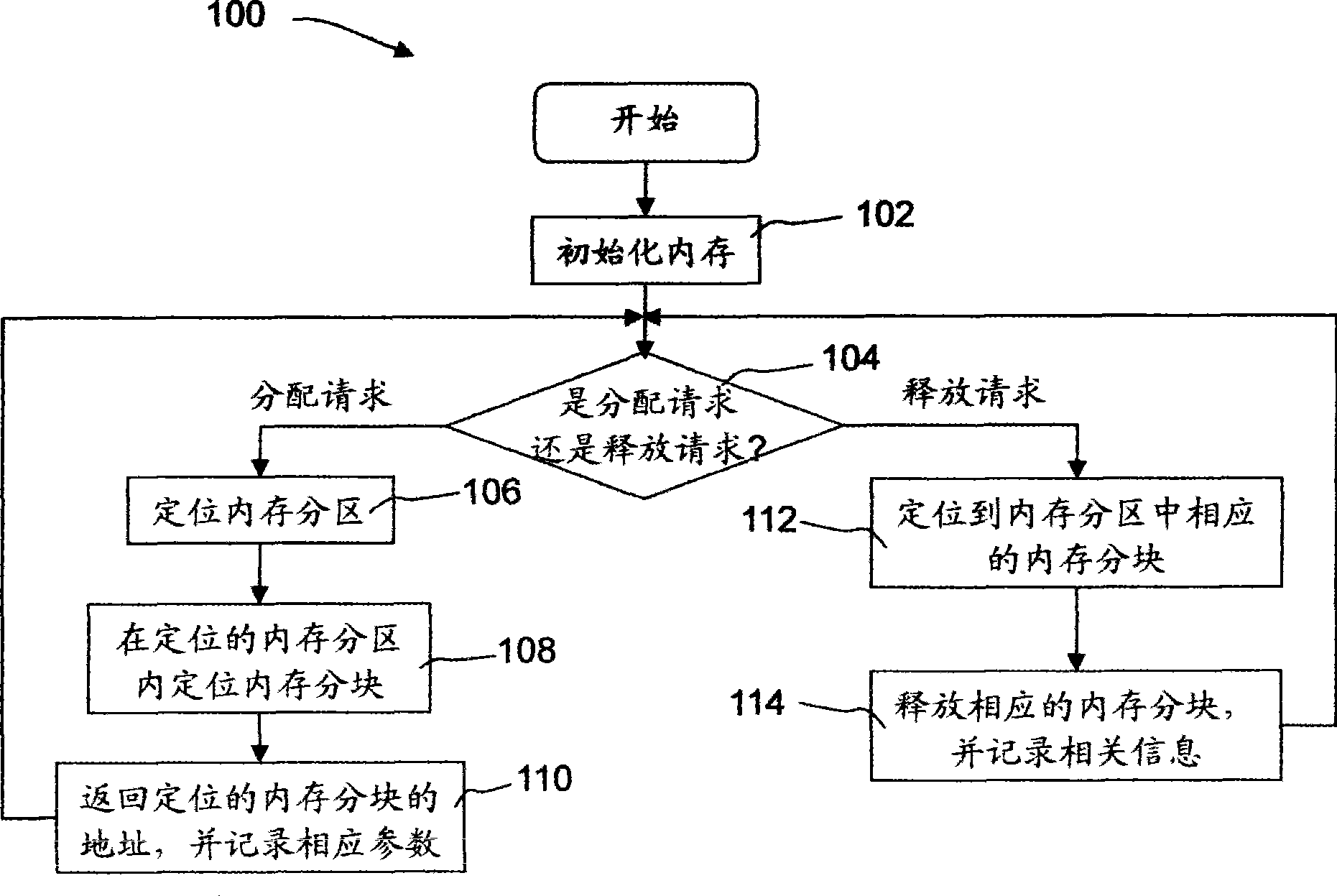
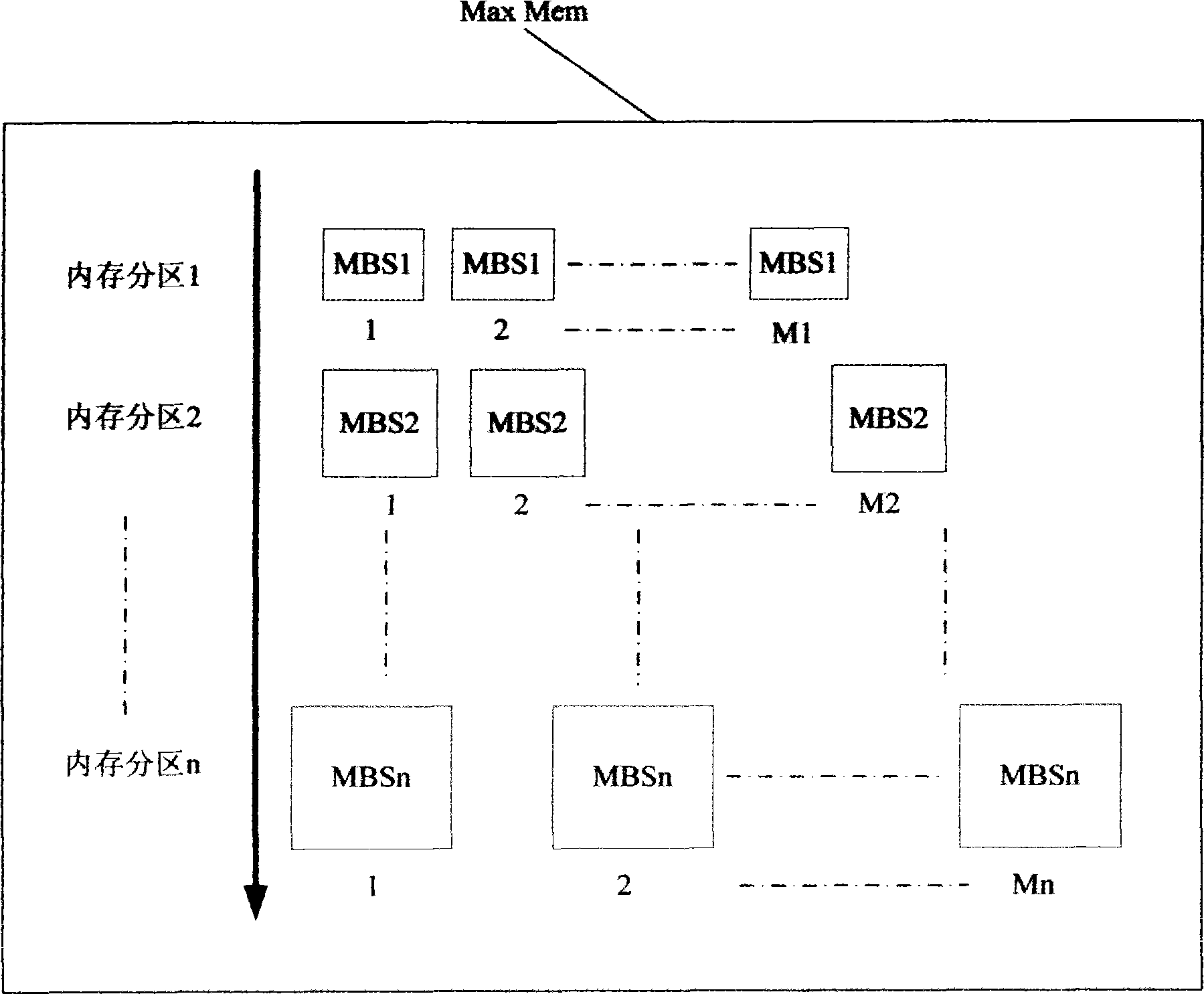
Internal memory management method
InactiveCN101499034AReal-timeAchieve reliabilityMemory adressing/allocation/relocationInternal memoryDistributed memory
The invention discloses a memory management method applicable for an embedded system, comprising steps of: providing a memory area with a certain volume; dividing a memory area into a plurality of memory branch areas and unit memory blocks; when it is necessary to provide memory, distributing the unit memory block greater than needed memory for use. The memory management method related to the invention uses a memory layout aiming at the embedded system, distributing memory via simple algorithm in a high effect manner and detecting whether memory error occurs.
Owner:VIMICRO CORP
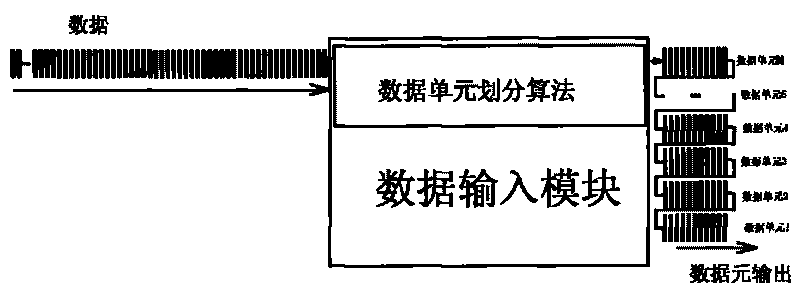
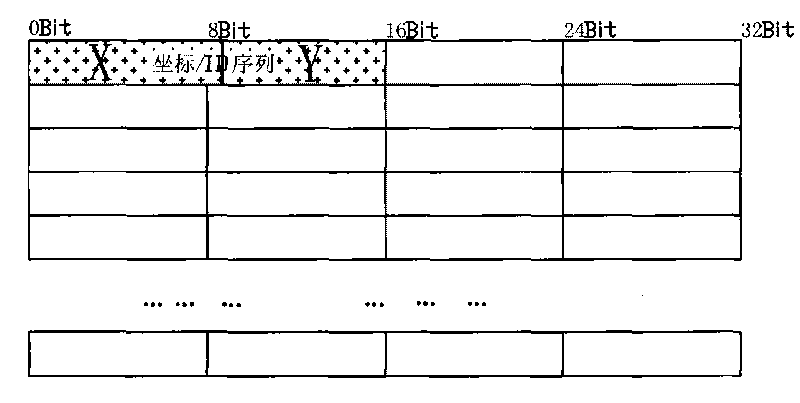
Data element and coordinate algorithm-based method and device for encrypting mixed data
InactiveCN101692636AImprove securityDiversity guaranteedEncryption apparatus with shift registers/memoriesSpecial data processing applicationsComputer hardwareHybrid type
The invention relates to the field of data encryption, and discloses a method and a device for encrypting by performing data element division on data, performing coordinate distribution on each data element and adopting different algorithms and keys. The device is characterized in that: the security guarantee of the data does not depend on the complexity of a certain encryption algorithm or the length of a key for encrypting any more. By introducing various custom simple algorithms which cannot be predicted outside and mixing various different encryption algorithms to encrypt the same document, the advantages of the algorithms are effectively integrated, the computational load and cost for encrypting are greatly reduced, and the method and the device have significant beneficial effects and technical progress.
Owner:广东宽提科技有限公司
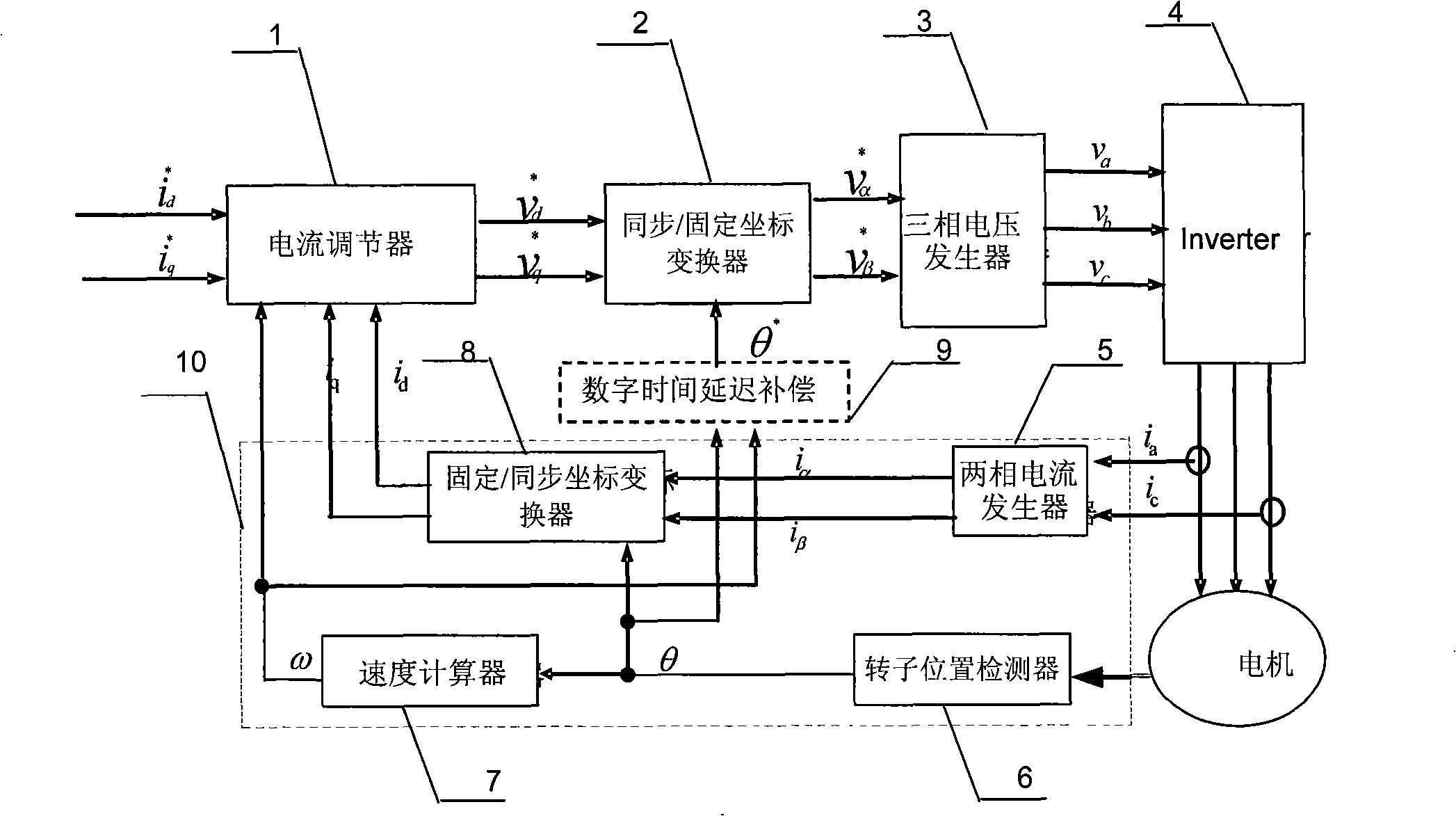
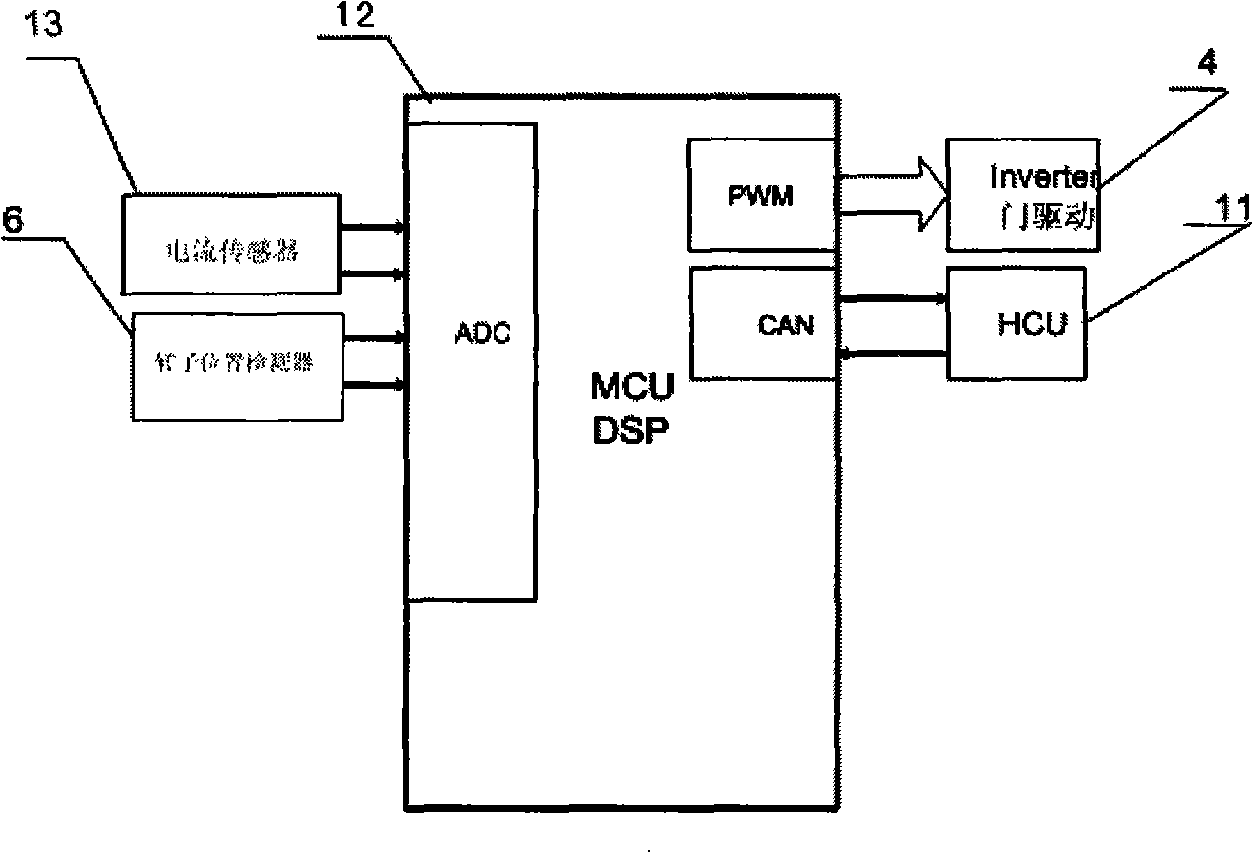
Method for compensating time delay during controlling whole digital AC motor and control device thereof
The present invention discloses a time delay compensation method in the full-digital AC motor control and a full-digital AC motor control device. In the technical proposal, the delay compensation method ignores the influence of amplitude error and only compensates the phase error. A functional module is added into the full-digital AC motor control device in the prior art for time delay compensation so as to implement the method. The method adopts a quite simple algorithm, and overcomes the problems of poor dynamic performance and instability of the current regulator in the control which requires high controlling performance of the motor or high-speed operation.
Owner:CHERY AUTOMOBILE CO LTD
Non-Volatile Memory And Methods With Asymmetric Soft Read Points Around Hard Read Points
ActiveUS20120166913A1Improve reading speedReduce energy consumptionRead-only memoriesError correction/detection using block codesImage resolutionComputer science
A non-volatile memory has its cells' thresholds programmed within any one of a first set of voltage bands partitioned by a first set of reference thresholds across a threshold window. The cells are read at a higher resolution relative to a second set of reference thresholds so as to provide additional soft bits for error correction. The reference thresholds of the second set are set up to be non-uniformly distributed on the threshold window so as to provide higher resolution at designated regions. At the same time they are conducive to be read in groups for soft bits to be read bit-by-bit systematically with a simple algorithm and read circuit and using a minimum of data latches. This is accomplished by relaxing the requirement that the first set of reference threshold is a subset of the second set and that the resulting soft bits are symmetrically distributed about the hard bits.
Owner:SANDISK TECH LLC
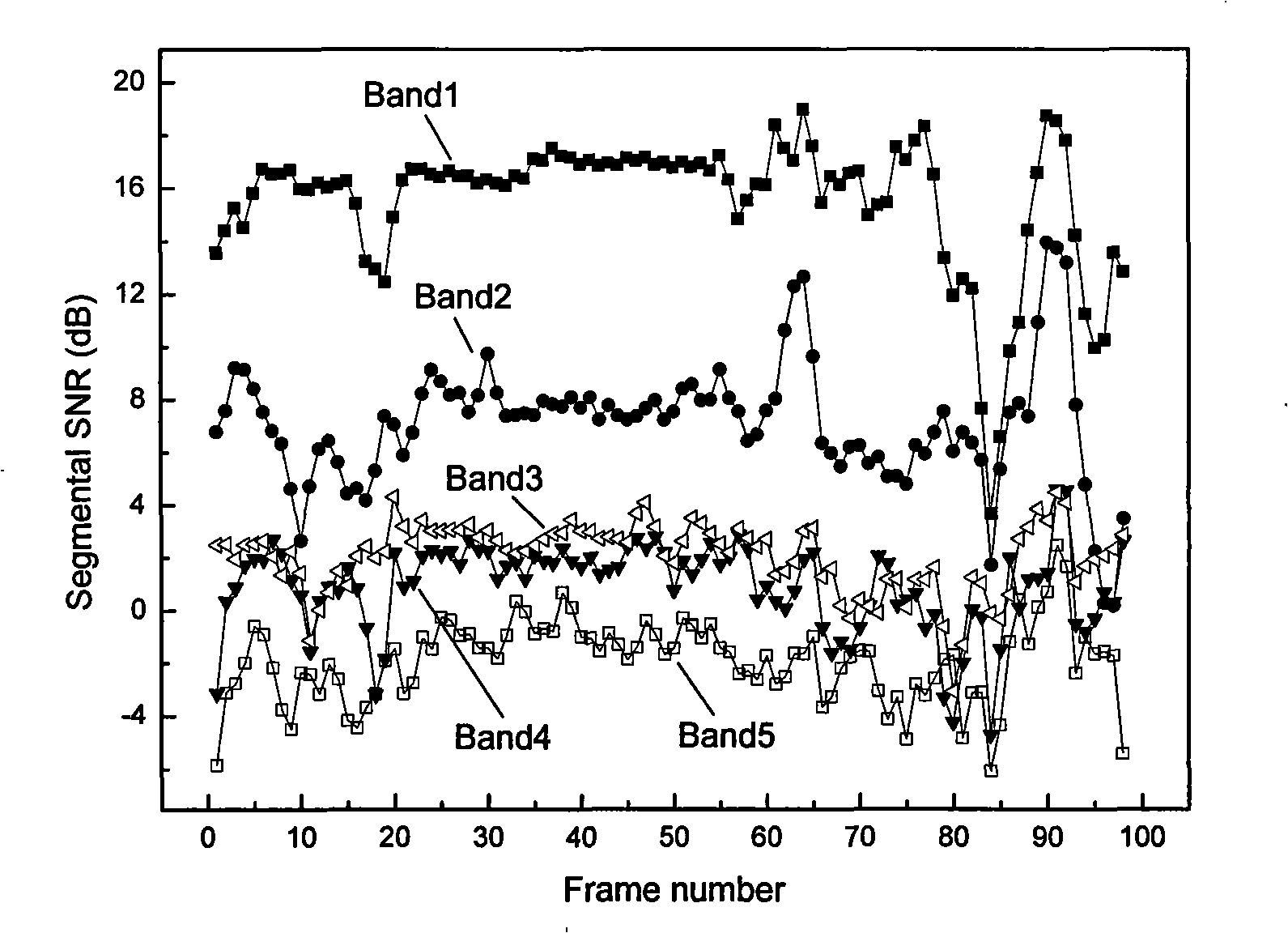
Non-air conduction speech reinforcement method based on multi-band spectrum subtraction
InactiveCN101320566ABroad application prospectsBroad marketing valueSpeech analysisMulti bandFrequency spectrum
The present invention discloses a non-air conduction speech enhancement method based on a multi-band spectral subtraction. Because of the noise in the radar-based non-air conduction speech is always colored and no uniform influence on the speech signals within the whole range of the frequency spectrum, the method divides the speech frequency spectrum in a targeted manner into five sections without overlapping; simultaneously, each section is provided with an individual spectral subtraction coefficient, so as to achieve the effectiveness and pertinence of the algorithm. The embodiment proves the non-air conduction speech enhancement method can effectively compensate the weakness of low pertinence in the traditional speech enhancement method; moreover, the method has the advantages of highly efficient implementation, simple algorithm and obvious effect. Therefore, the method has higher practical value and application prospects.
Owner:FOURTH MILITARY MEDICAL UNIVERSITY
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com