Data element and coordinate algorithm-based method and device for encrypting mixed data
A technology of data encryption and data elements, applied in encryption devices with shift registers/memory, electrical digital data processing, special data processing applications, etc., can solve the problem of large packet length, high operation cost, and increased operation load and cost and other issues to achieve the effect of high safety, guaranteed safety, and reduced workload
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0055] refer to Figures 1 to 7 , discloses a hybrid data encryption method based on data elements and coordinate algorithms of the present invention. The method comprises the following steps:
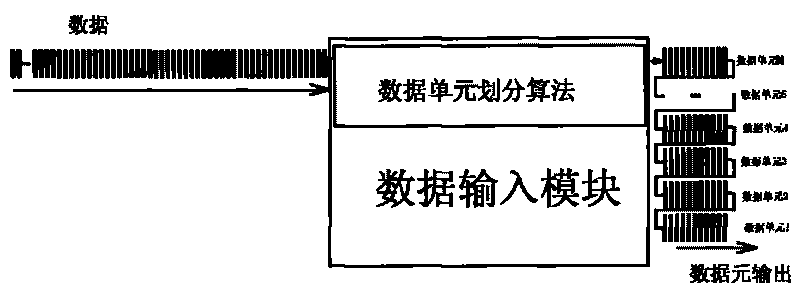
[0056] 1). Obtain the data to be encrypted through the data input module;
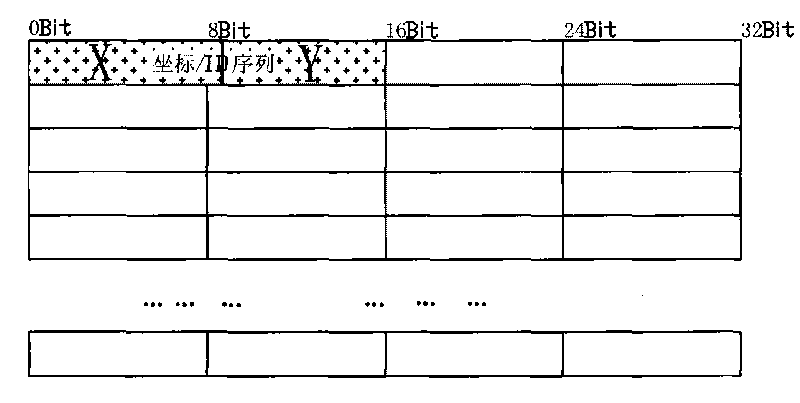
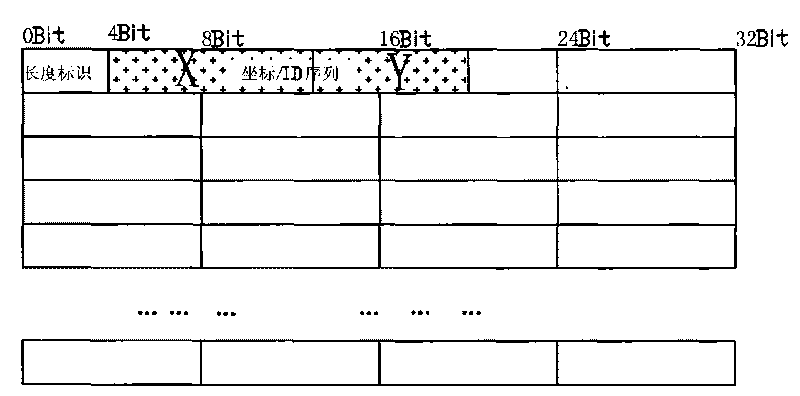
[0057]2). Data is divided into several data units, i.e. data segments; the division method includes: A. the data input stream is divided into data segments with the same fixed length unit (the length of the data segment is not limited, and can be determined according to actual needs ; Since the data part of the IP datagram of IPV4 is the longest 64KB, so it can refer to that each data segment is set to 64KB), and the remaining data less than one length unit is used as a separate data segment; B. define several Length levels (for example, 128KB, 64KB, 32KB, 12KB, 1KB, 512B, and 256B can be defined as 6-0 levels in sequence, and the definition method can be determined according to actual needs, and there is no ...
Embodiment 2
[0112] This embodiment discloses another technical solution of the present invention: a device for hybrid data encryption and decryption based on data elements and coordinate algorithms:
[0113] Such as Figure 8 As shown, the encryption device is composed of an encryption control module 10, a data input module 11, an encryption algorithm distribution module 12, an encryption algorithm database 13, an encryption module 14, a cache module 15, and a combination module 16; The control module 10 is connected, and under the centralized control of the encryption control module 10, the encryption based on the mixed algorithm of data units and coordinates is realized: during work, under the control of the encryption control module 10, the data input module 11 is responsible for obtaining the data that needs to be encrypted and performing The data unit is divided and stored, and the data unit is input into the encryption control module 10 in order; the encryption algorithm distributio...
Embodiment 3
[0117] refer to Figure 10 with Figure 11 , which is a further optimization of a device for encrypting or decrypting data based on a hybrid algorithm of data units and coordinates in the present invention. Compared with Example 2, the difference is that the encryption or decryption device also has a user private key input module; the user private key input module The module is responsible for collecting the key input by the user, and combining the key with the encrypted data to form new encrypted data after processing. When decrypting, the subsequent decryption operation is performed after the user's private key is verified first.
[0118] When implementing the method of encrypting or decrypting data with a hybrid algorithm based on data units and coordinates, the device of this embodiment can refer to Embodiment 1 for implementation, and at the same time, some steps need to be modified accordingly.
[0119] Compared with the inventive method in Embodiment 1, when the devic...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com