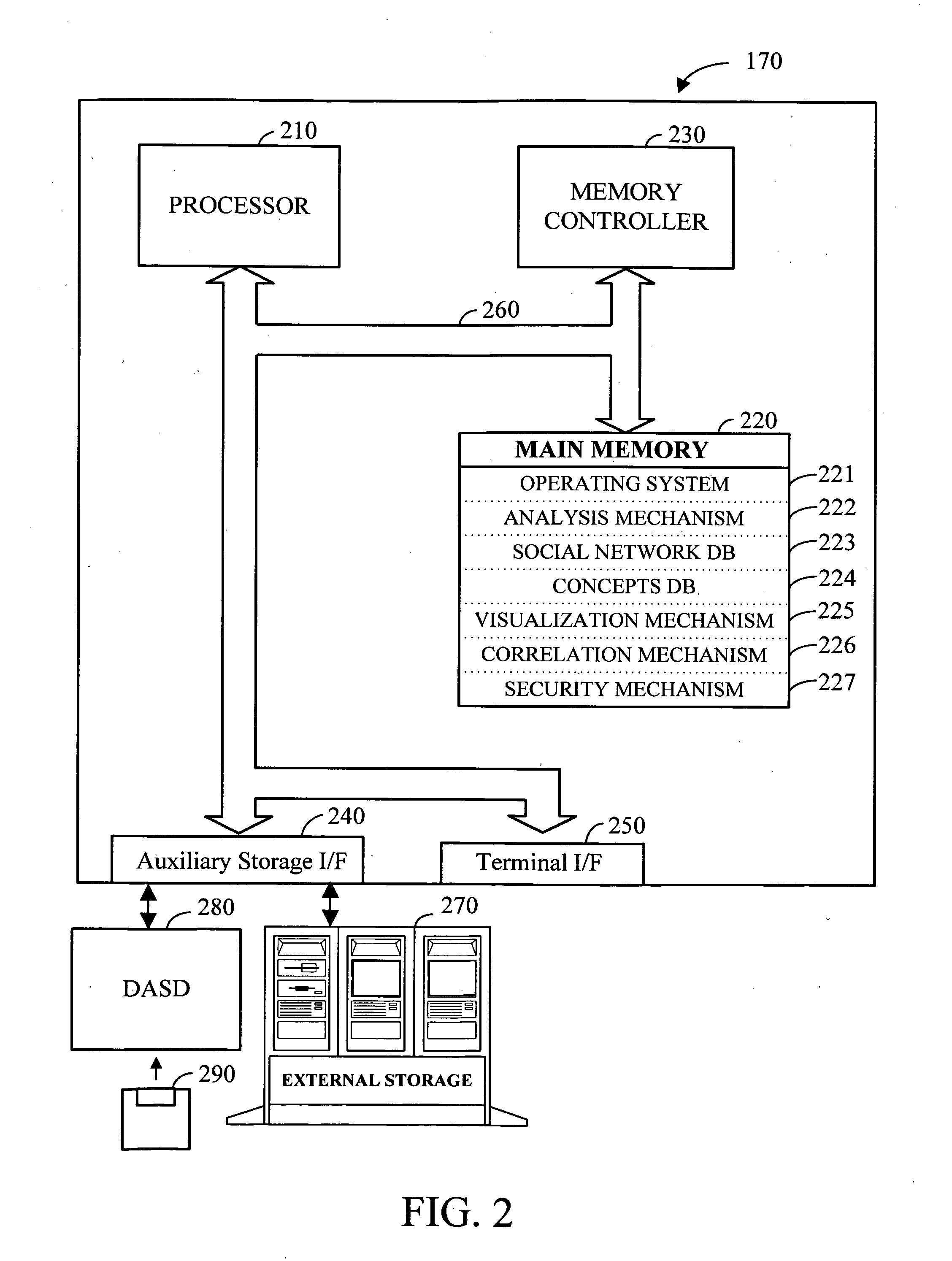
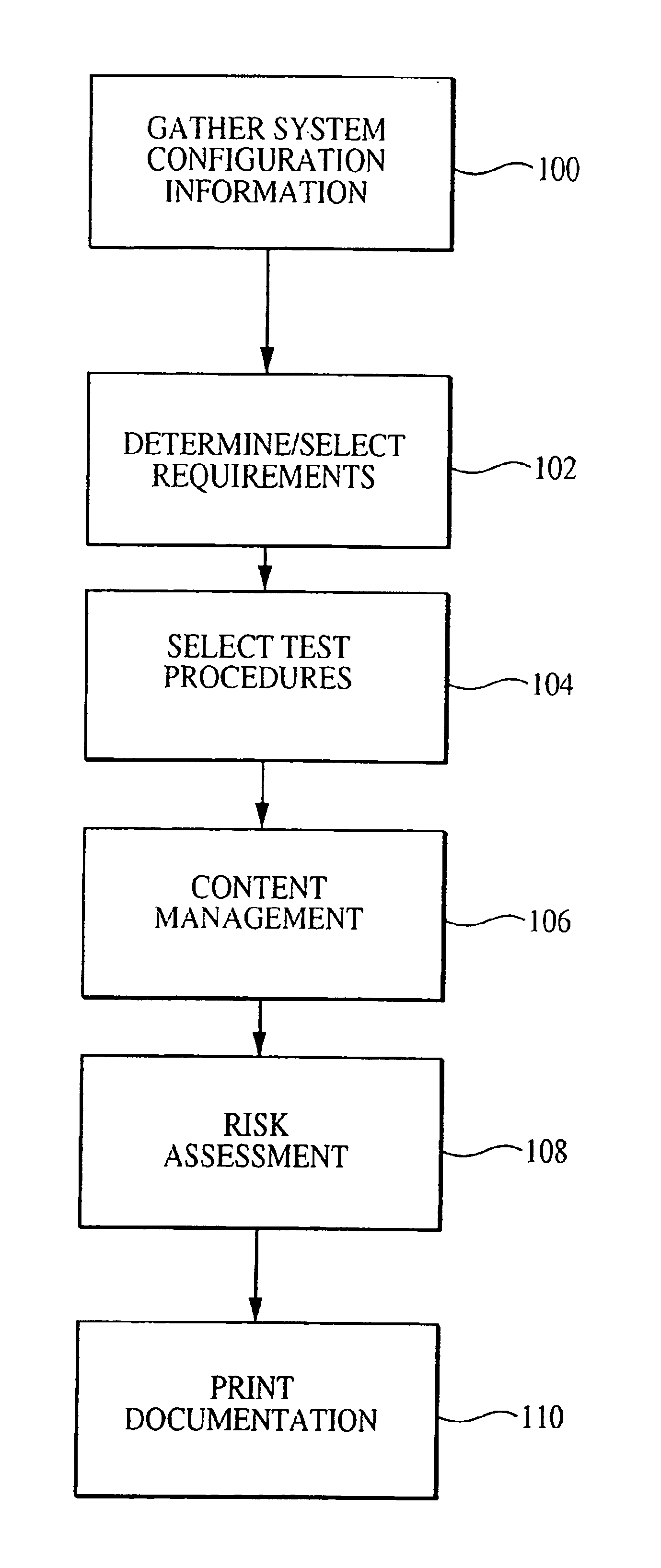
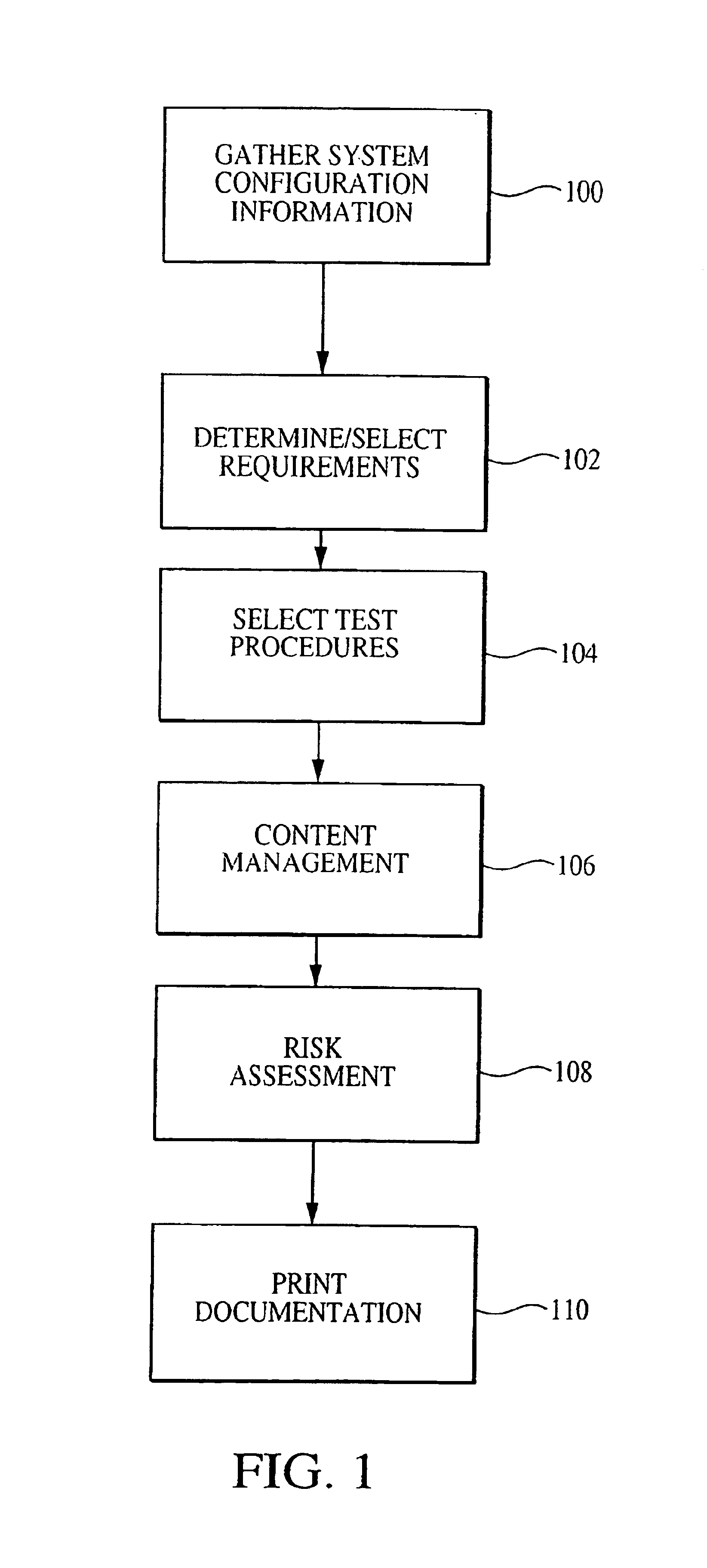
Patents
Literature
3213 results about "Data element" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
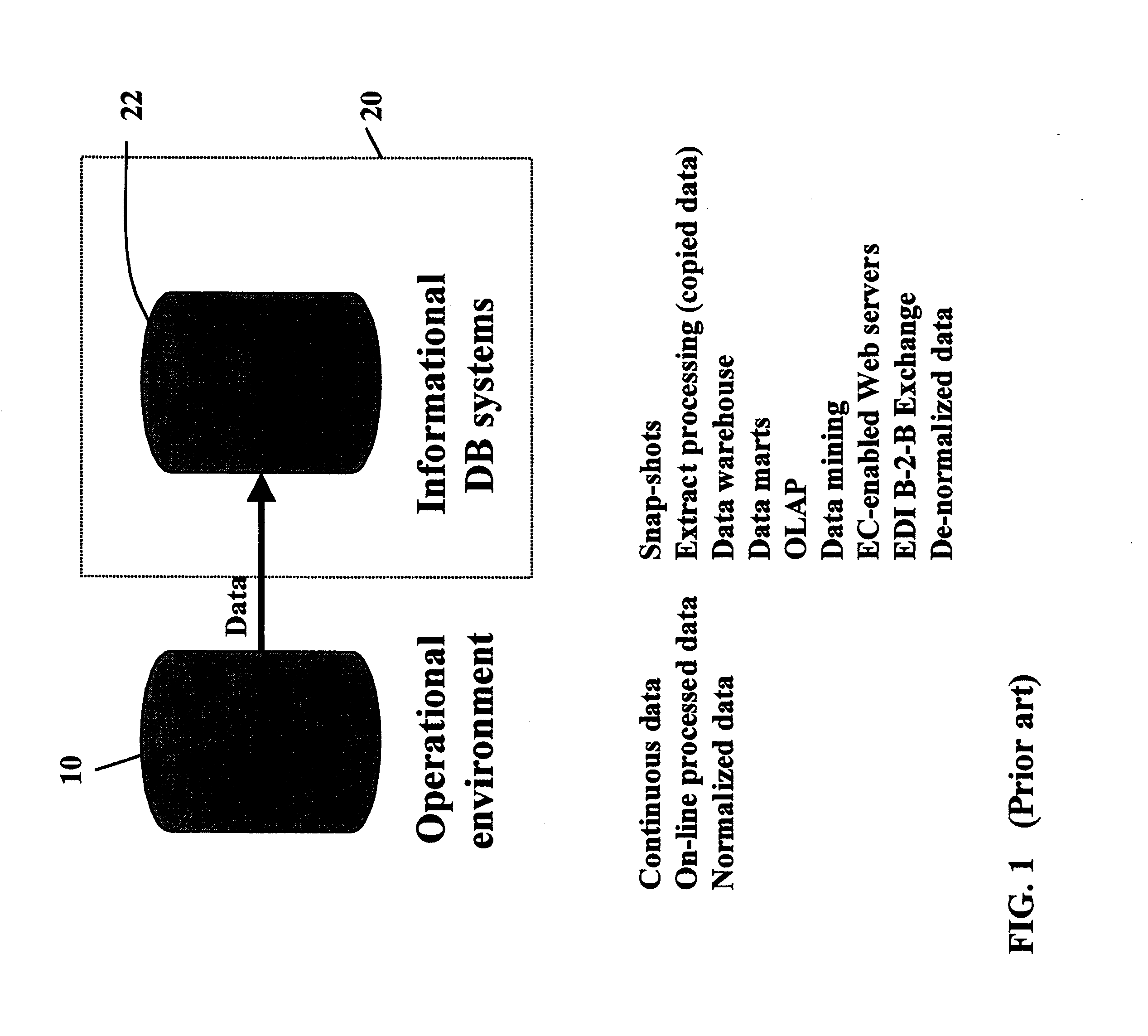
In metadata, the term data element is an atomic unit of data that has precise meaning or precise semantics. Data elements usage can be discovered by inspection of software applications or application data files through a process of manual or automated Application Discovery and Understanding. Once data elements are discovered they can be registered in a metadata registry.
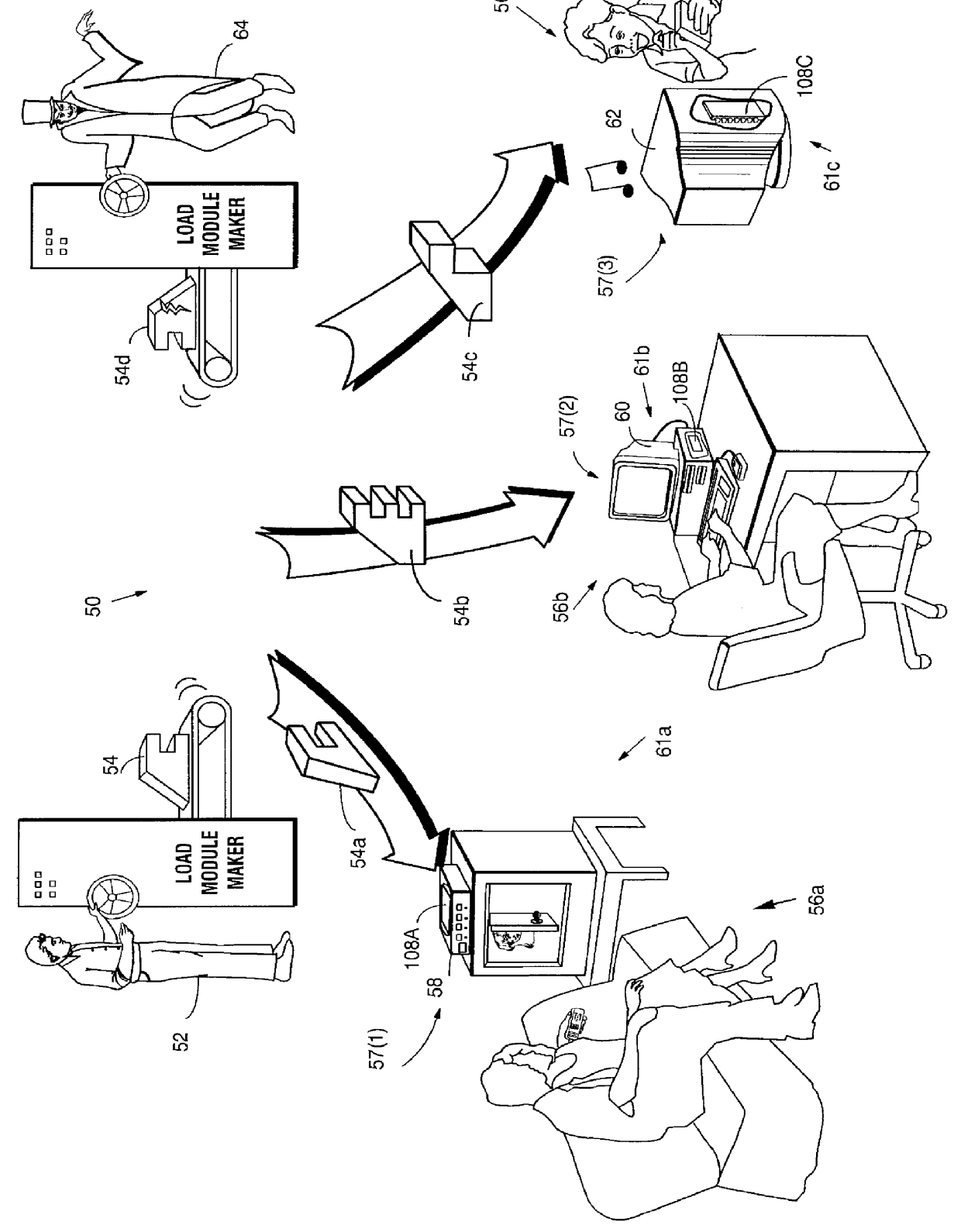
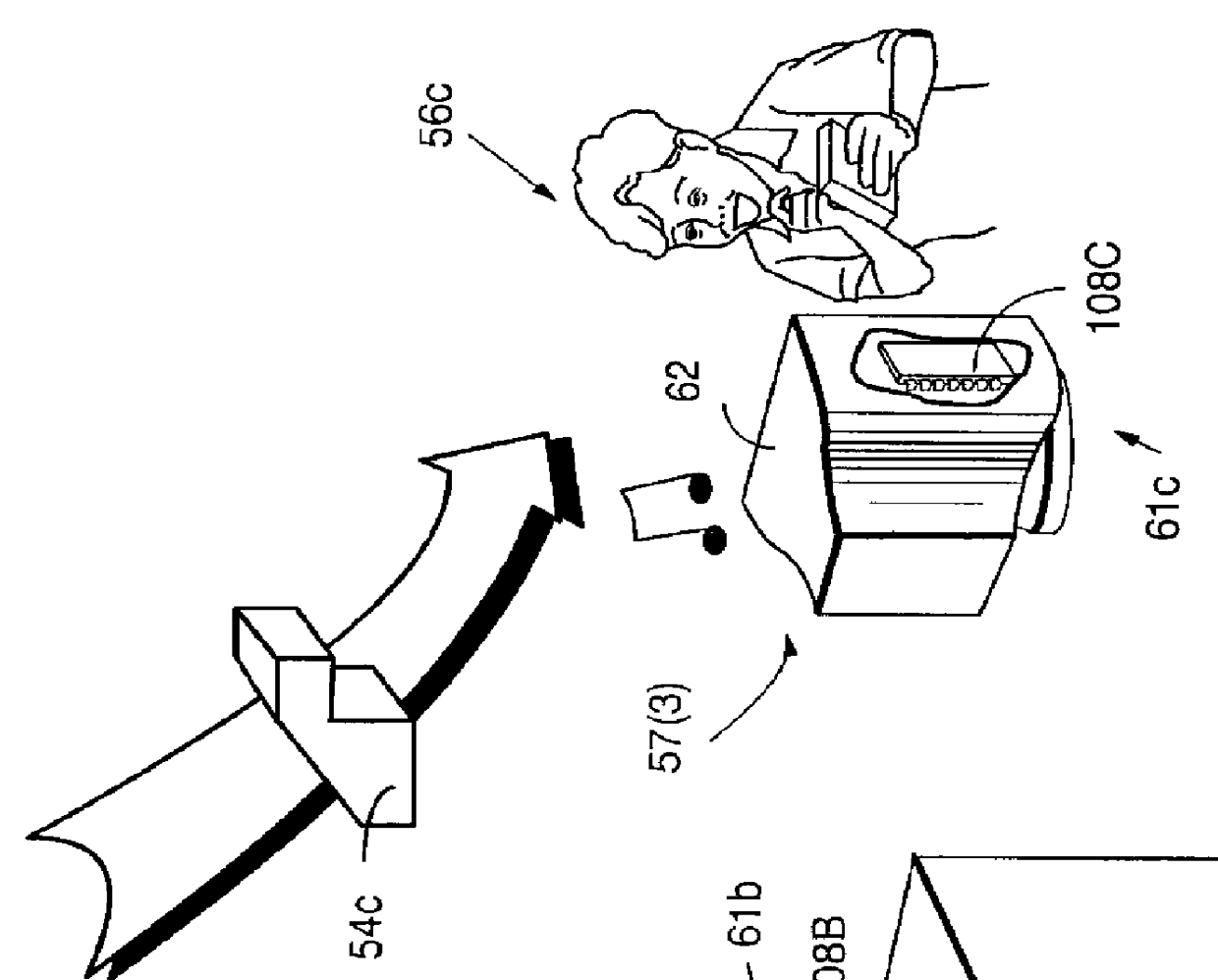
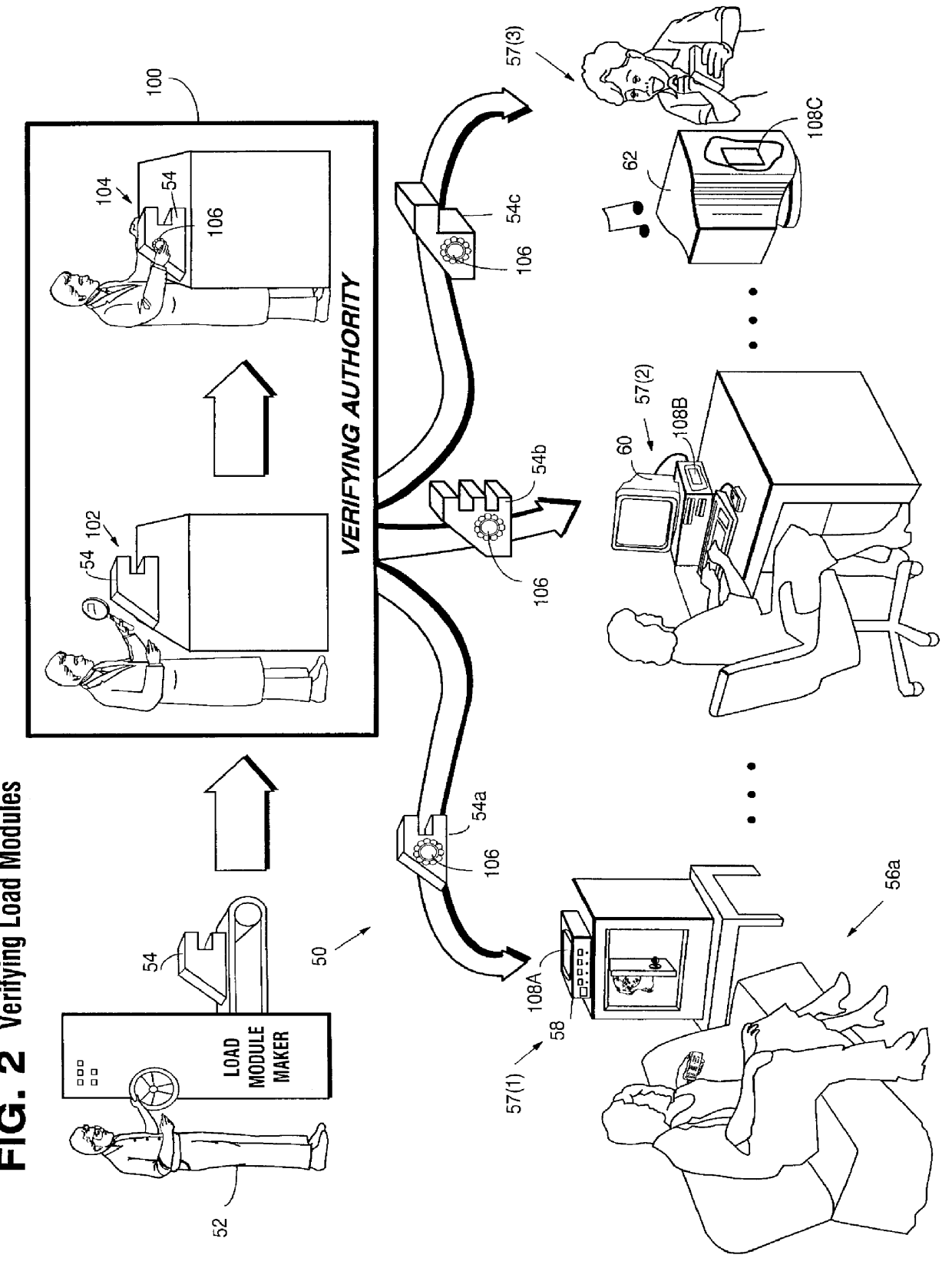
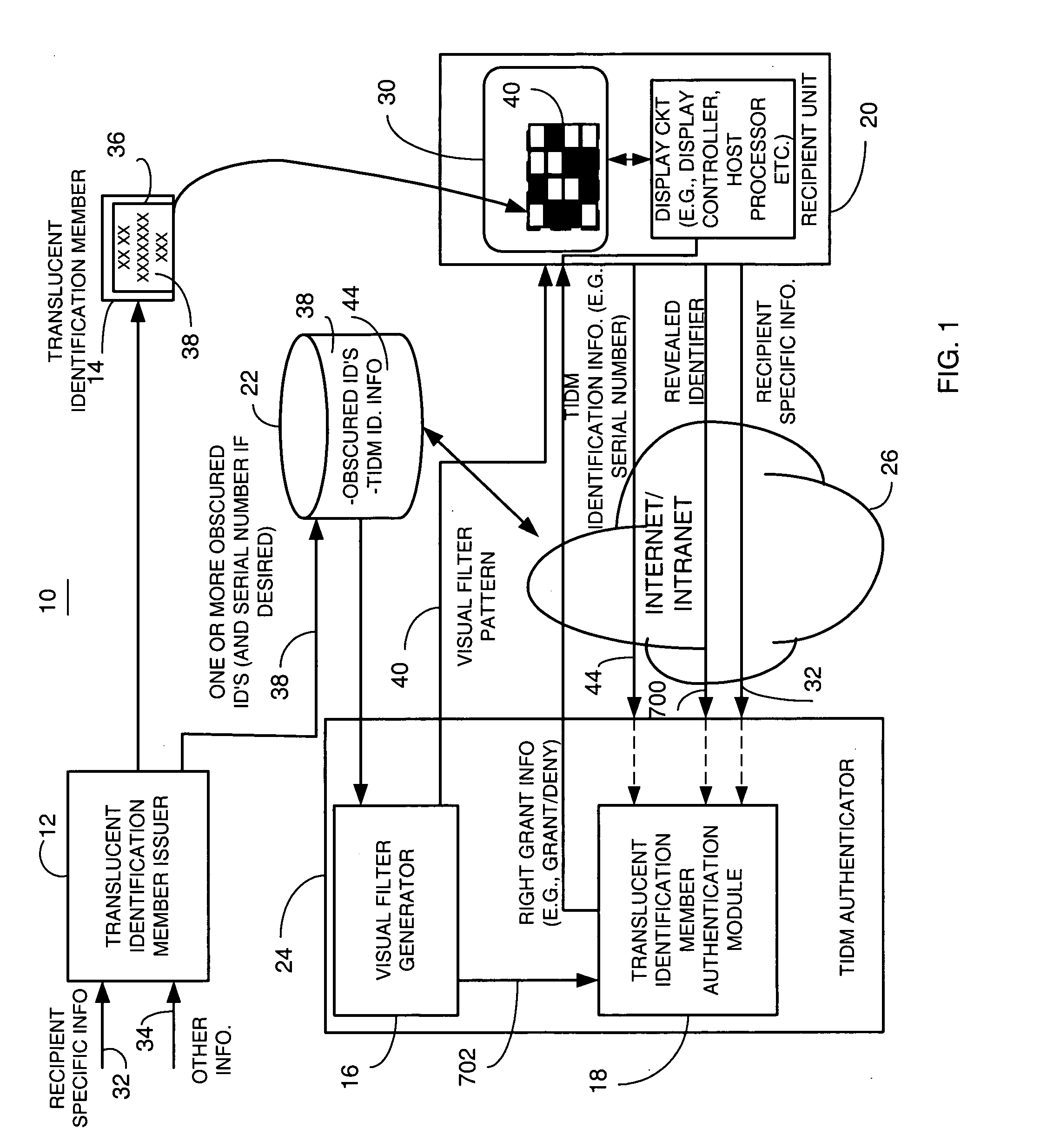
Systems and methods using cryptography to protect secure computing environments
InactiveUS6157721AProtection from disclosureSpeeding up digital signature verificationRecording carrier detailsDigital data processing detailsThird partyTamper resistance
Secure computation environments are protected from bogus or rogue load modules, executables and other data elements through use of digital signatures, seals and certificates issued by a verifying authority. A verifying authority-which may be a trusted independent third party-tests the load modules or other executables to verify that their corresponding specifications are accurate and complete, and then digitally signs the load module or other executable based on tamper resistance work factor classification. Secure computation environments with different tamper resistance work factors use different verification digital signature authentication techniques (e.g., different signature algorithms and / or signature verification keys)-allowing one tamper resistance work factor environment to protect itself against load modules from another, different tamper resistance work factor environment. Several dissimilar digital signature algorithms may be used to reduce vulnerability from algorithm compromise, and subsets of multiple digital signatures may be used to reduce the scope of any specific compromise.
Owner:INTERTRUST TECH CORP
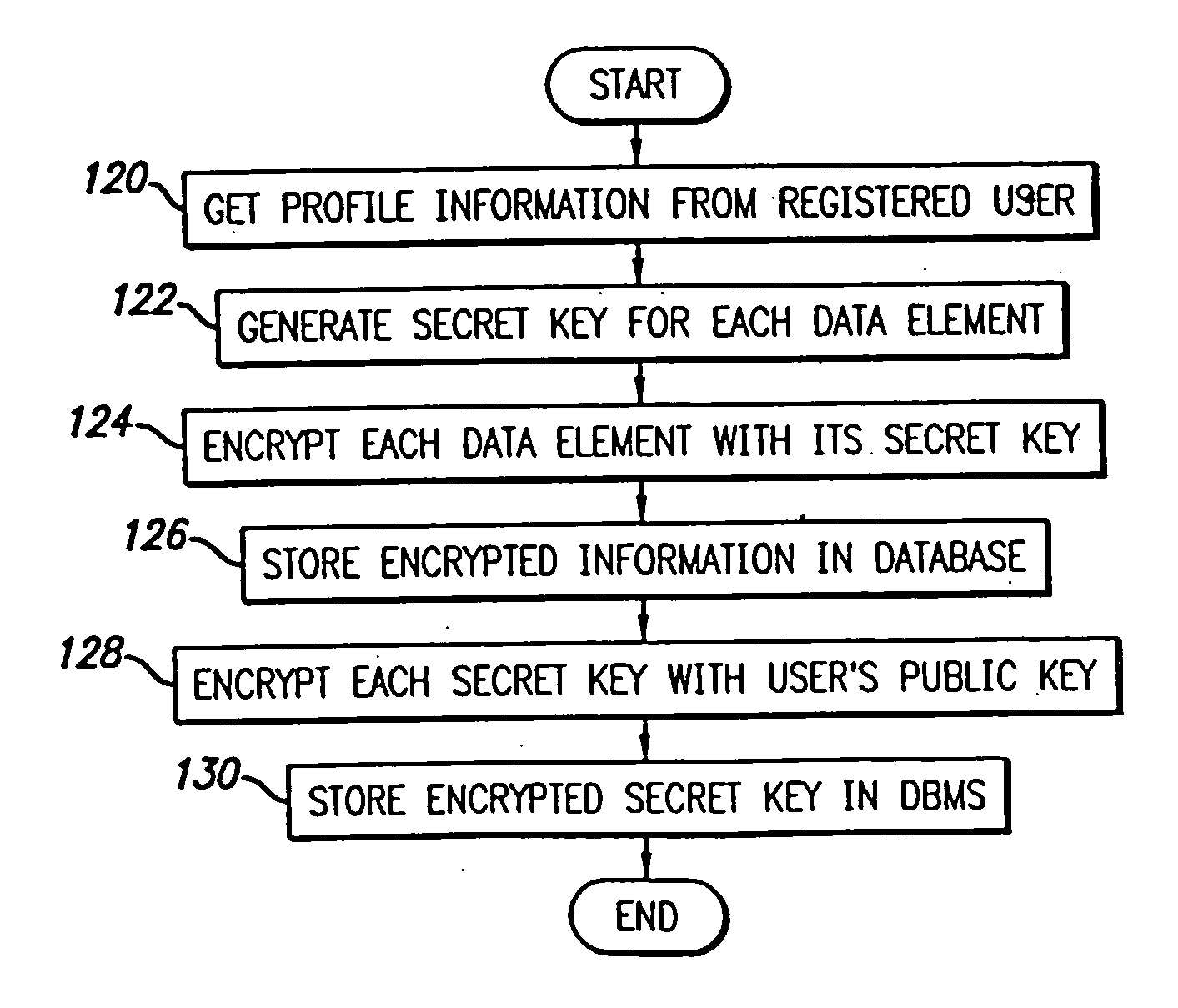
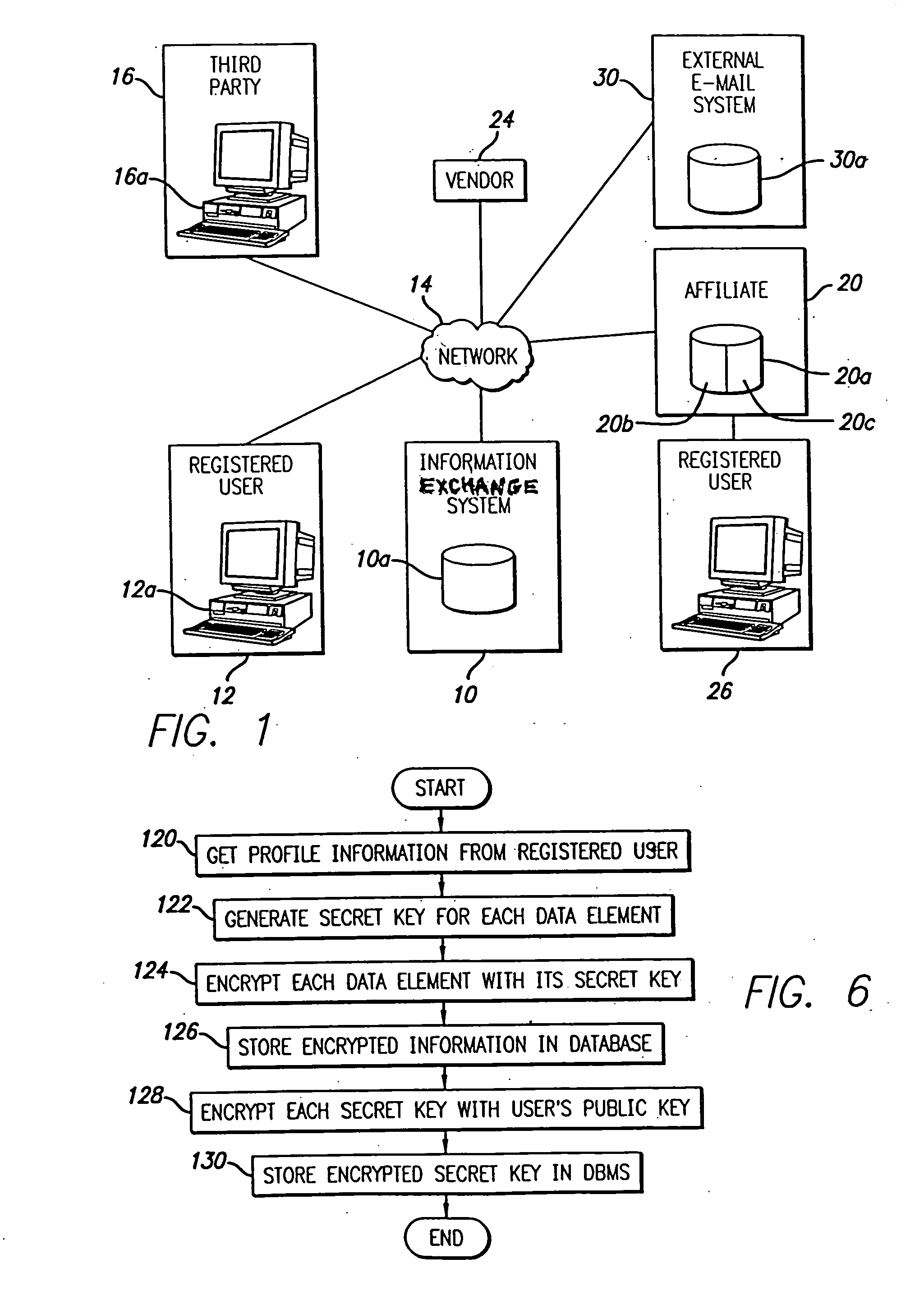
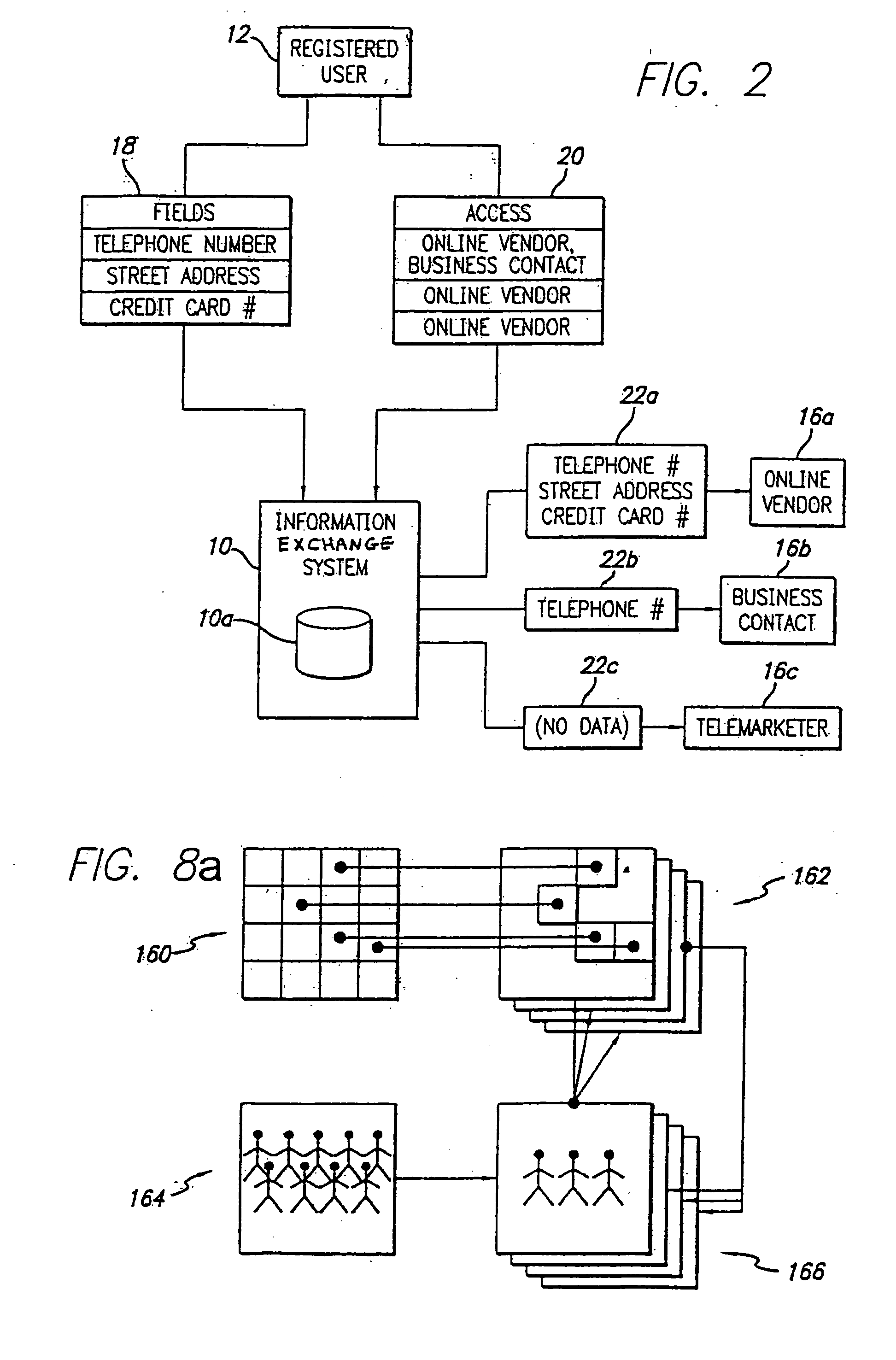
System and method for selective information exchange
InactiveUS20050192008A1Avoid accessComputer security arrangementsRadio/inductive link selection arrangementsTime informationThe Internet
A system and method for providing users with granular control over arbitrary information that allows for selective, real-time information sharing in a communications network such as the Internet is provided. In a network including a plurality of network devices operated by a plurality of users, a real-time information exchange system for sharing user profile information between respective users includes a database management system connected to the network. The database management system, which may be distributed across the network, stores the user profile information for a plurality of registered users of the information exchange system The user profile information includes a plurality of data elements, each data element having an associated one of the plurality of registered users. Each data element has an associated group of users to whom access to the data element has been granted, and users not included in the associated group of users are denied access to the data element. Each registered user may selectively control the granting and denying of access to each of its associated data elements by other respective user, on an element-by-element, and user-by-user basis. Further, each registered user may dynamically create its own data fields.
Owner:DESAI NIMESH +5
Method and apparatus for the management of data files
InactiveUS6263330B1Easy retrievalEasy accessData processing applicationsTelemedicineMedical recordData file
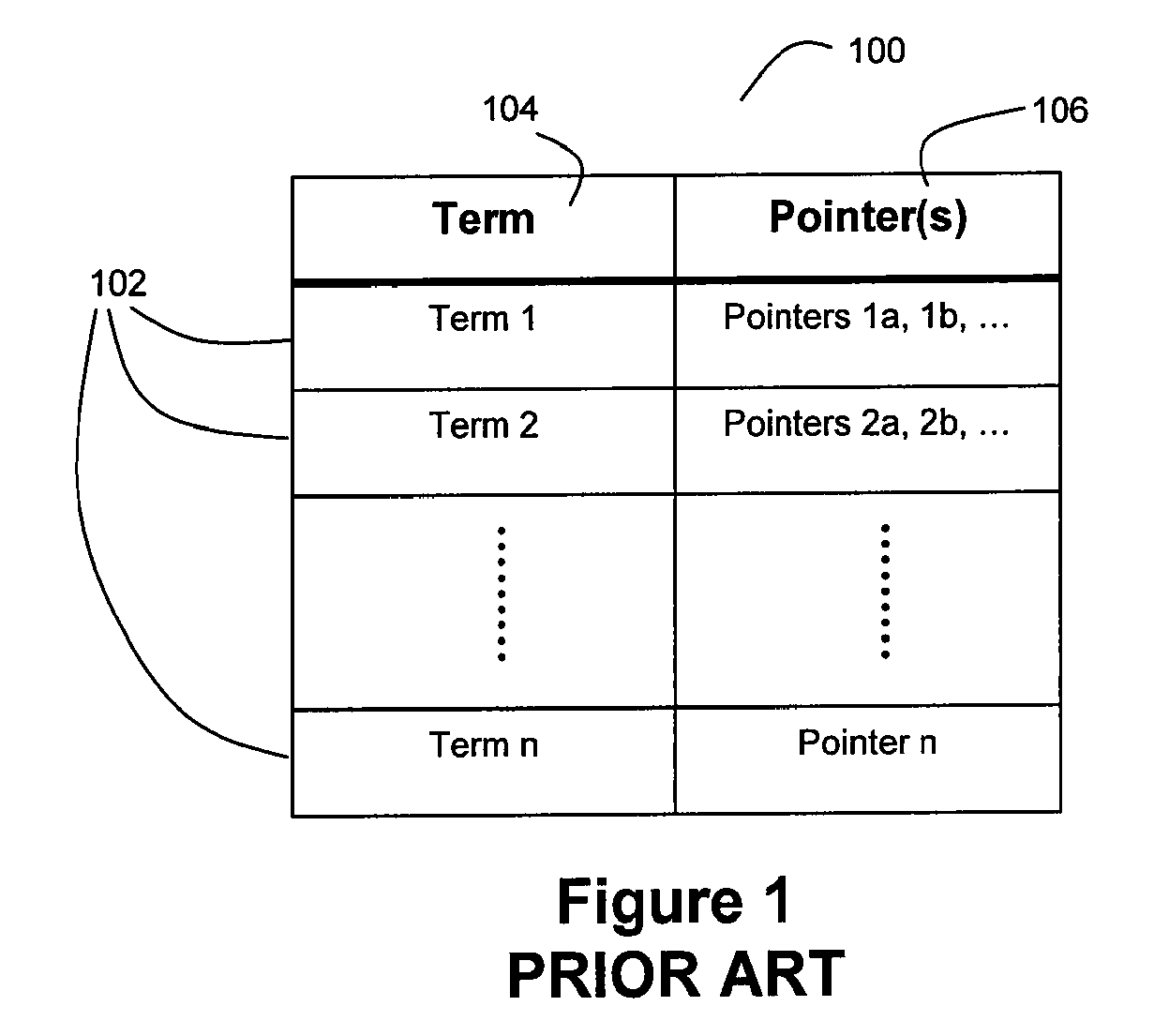
The present invention provides a network system for storage of medical records. The records are stored in a database on a server. Each record includes two main parts, namely a collection of data elements containing information of medical nature for the certain individual, and a plurality of pointers providing addresses or remote locations where reside other medical data for that particular individual. Each record also includes a data element indicative of the basic type of medical data found at the location pointed to by a particular pointer. This arrangement permits a client workstation to download the record along with the set of pointers which link the client to the remotely stored files. The identification of the basic type of information that each pointer points to allows the physician to select the ones of interest and thus avoid downloading massive amounts of data where only part of that data is needed at that time. In addition, this record structure allows statistical queries to be effected without the necessity of accessing the data behind the pointers. For instance, a query can be built based on keys, one of which is the type of data that a pointer points to. The query can thus be performed solely on the basis of the pointers and the remaining information held in the record.
Owner:BESSETTE LUC
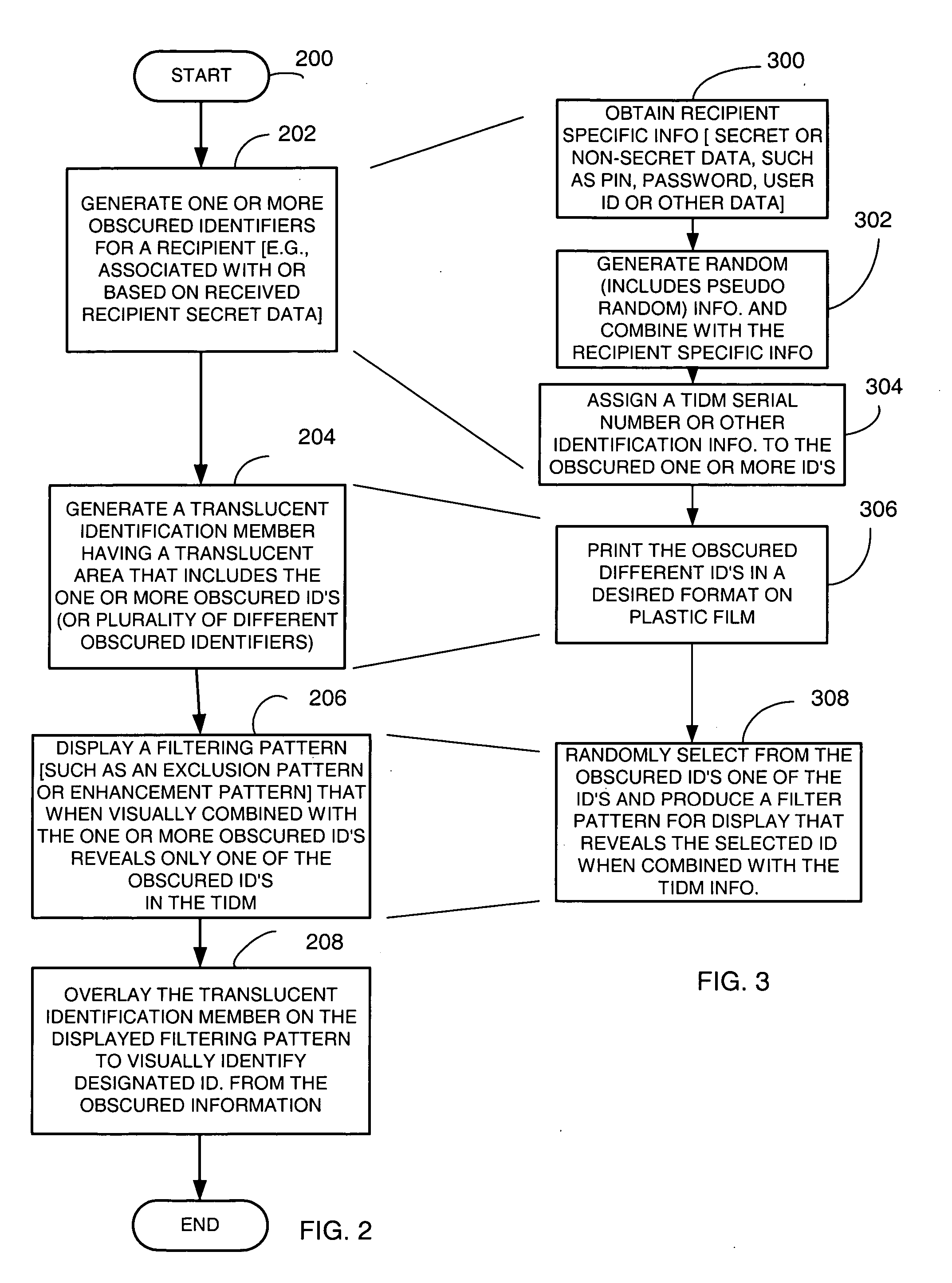
Method, software and apparatus for saving, using and recovering data
InactiveUS6016553ADigital data information retrievalInput/output to record carriersOperational systemOriginal data
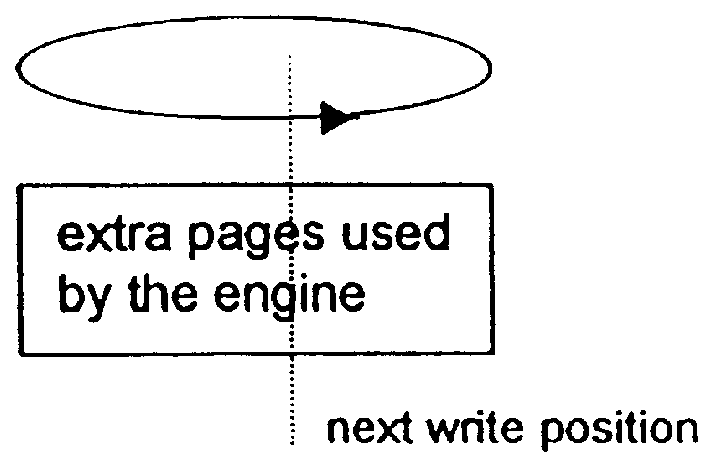
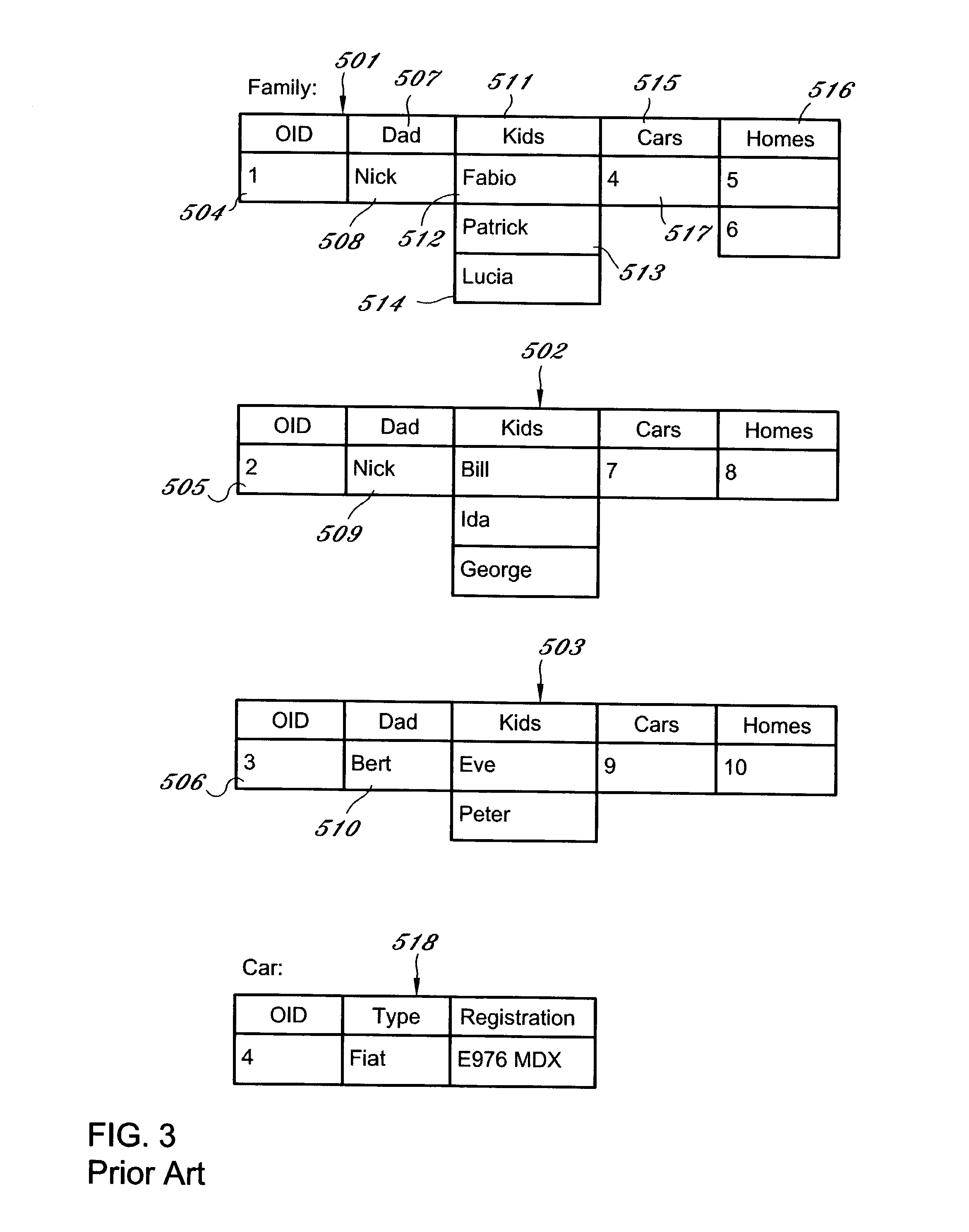
A method and apparatus for reverting a disk drive to an earlier point in time is disclosed. Changes made to the drive are saved in a circular history buffer which includes the old data, the time it was replaced by new data, and the original location of the data. The circular history buffer may also be implemented by saving new data elements into new locations and leaving the old data elements in their original locations. References to the new data elements are mapped to the new location. The disk drive is reverted to an earlier point in time by replacing the new data elements with the original data elements retrieved from the history buffer, or in the case of the other embodiment, reads to the disk are mapped to the old data elements stilled stored in their original locations. The method and apparatus may be implemented as part of an operating system, or as a separate program, or in the controller for the disk drive. The method and apparatus are applicable to other forms of data storage as well. Also disclosed are method and apparatus for providing firewall protection to data in a data storage medium of a computer system.
Owner:POWER MANAGEMENT ENTERPRISES
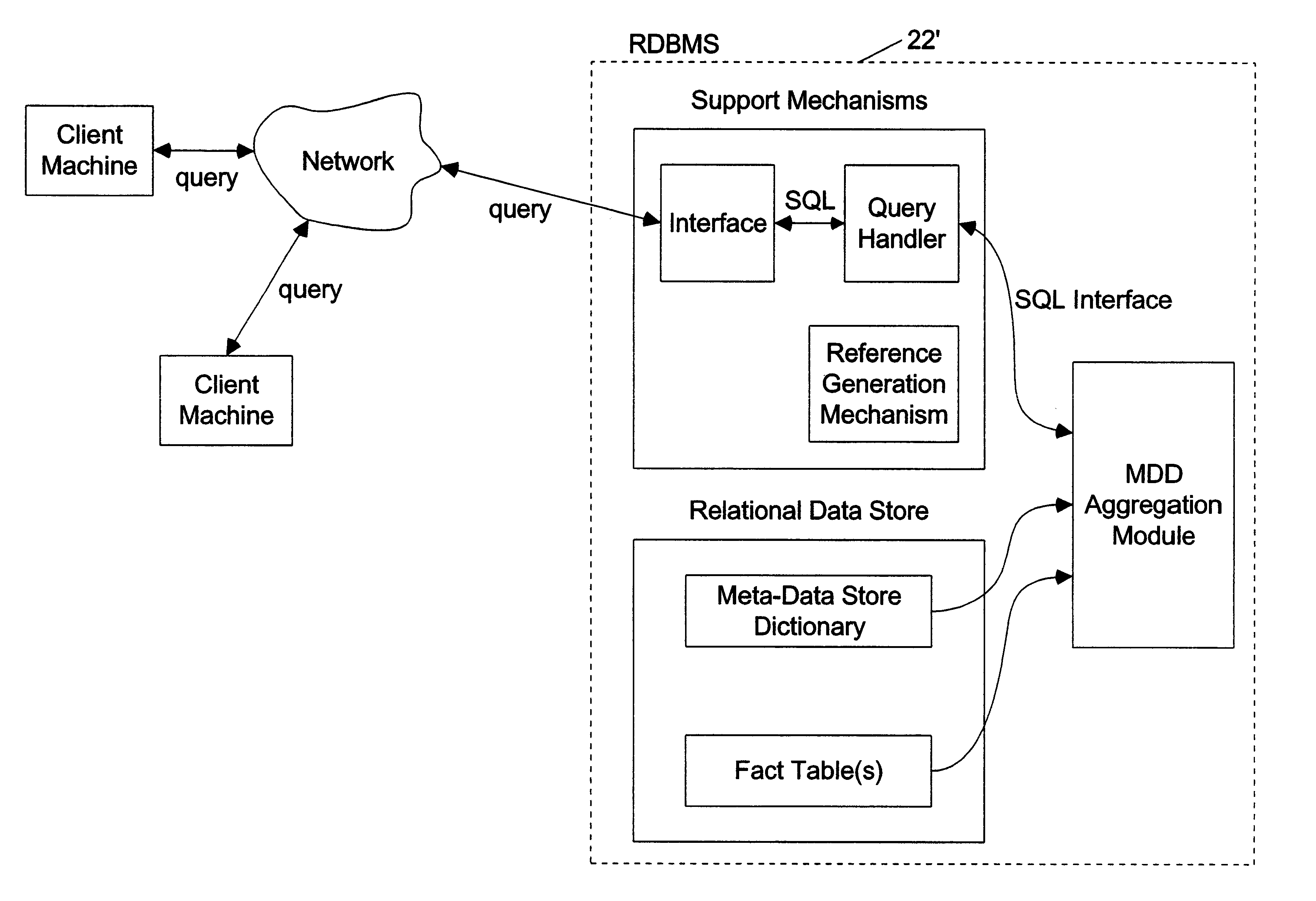
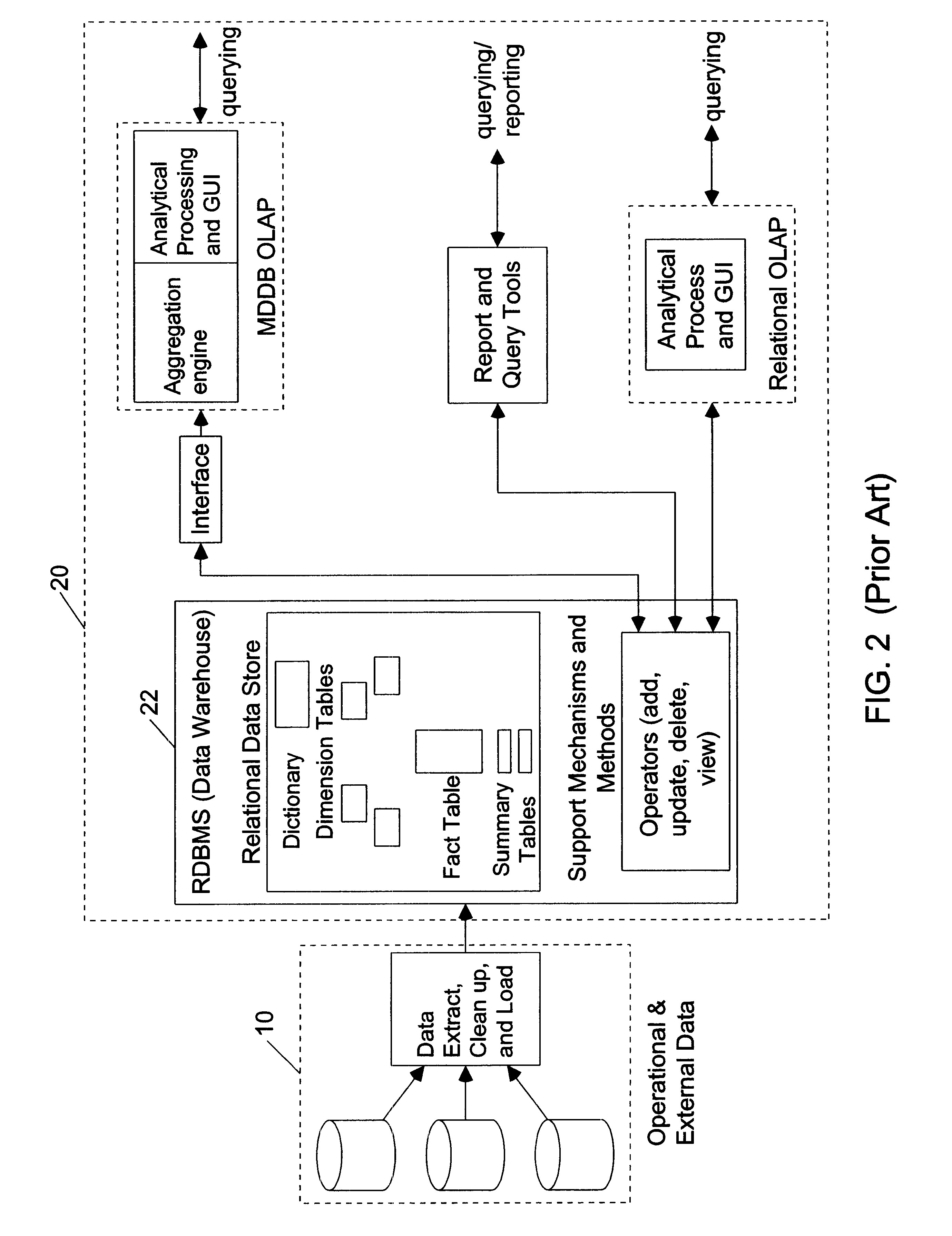
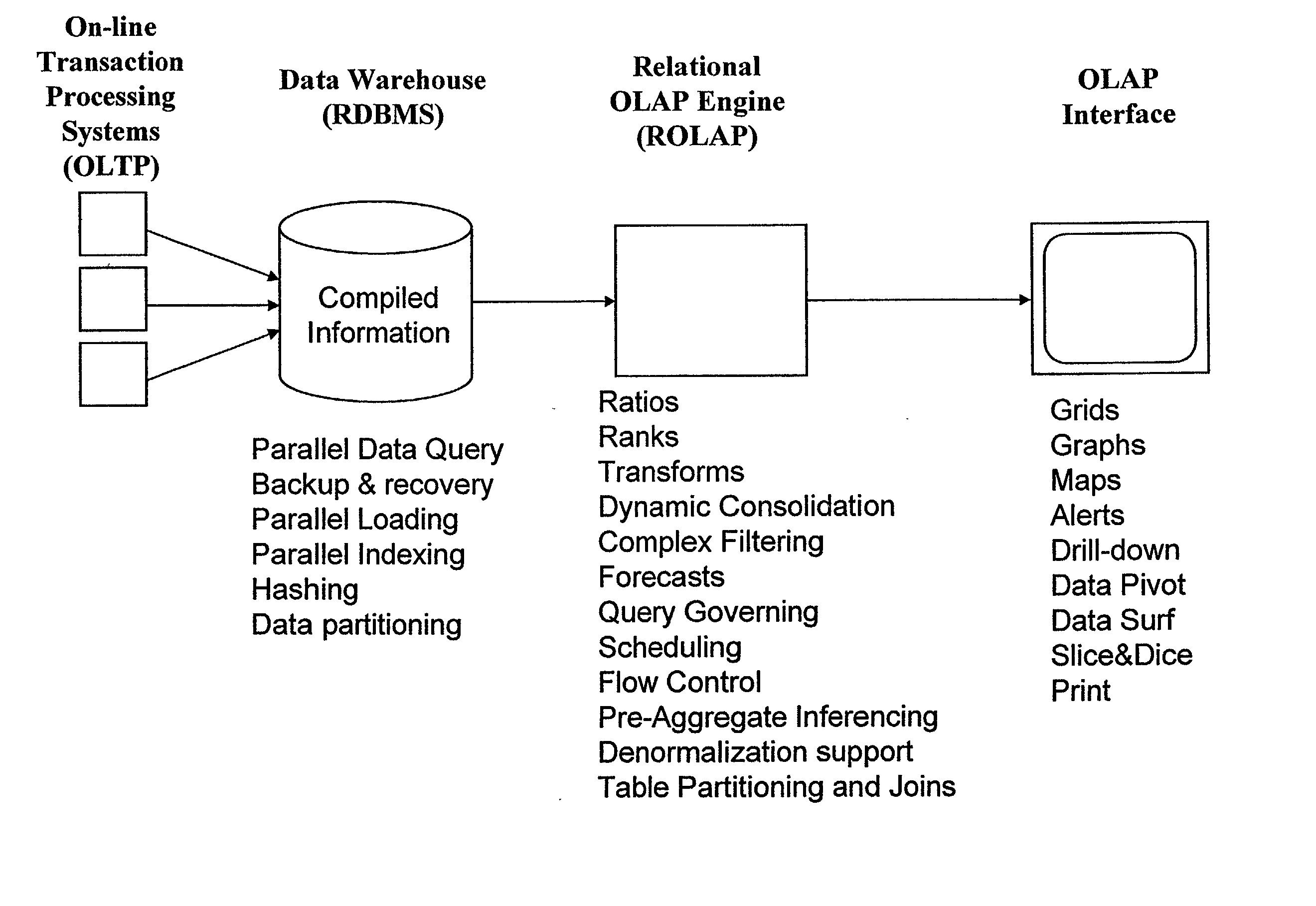
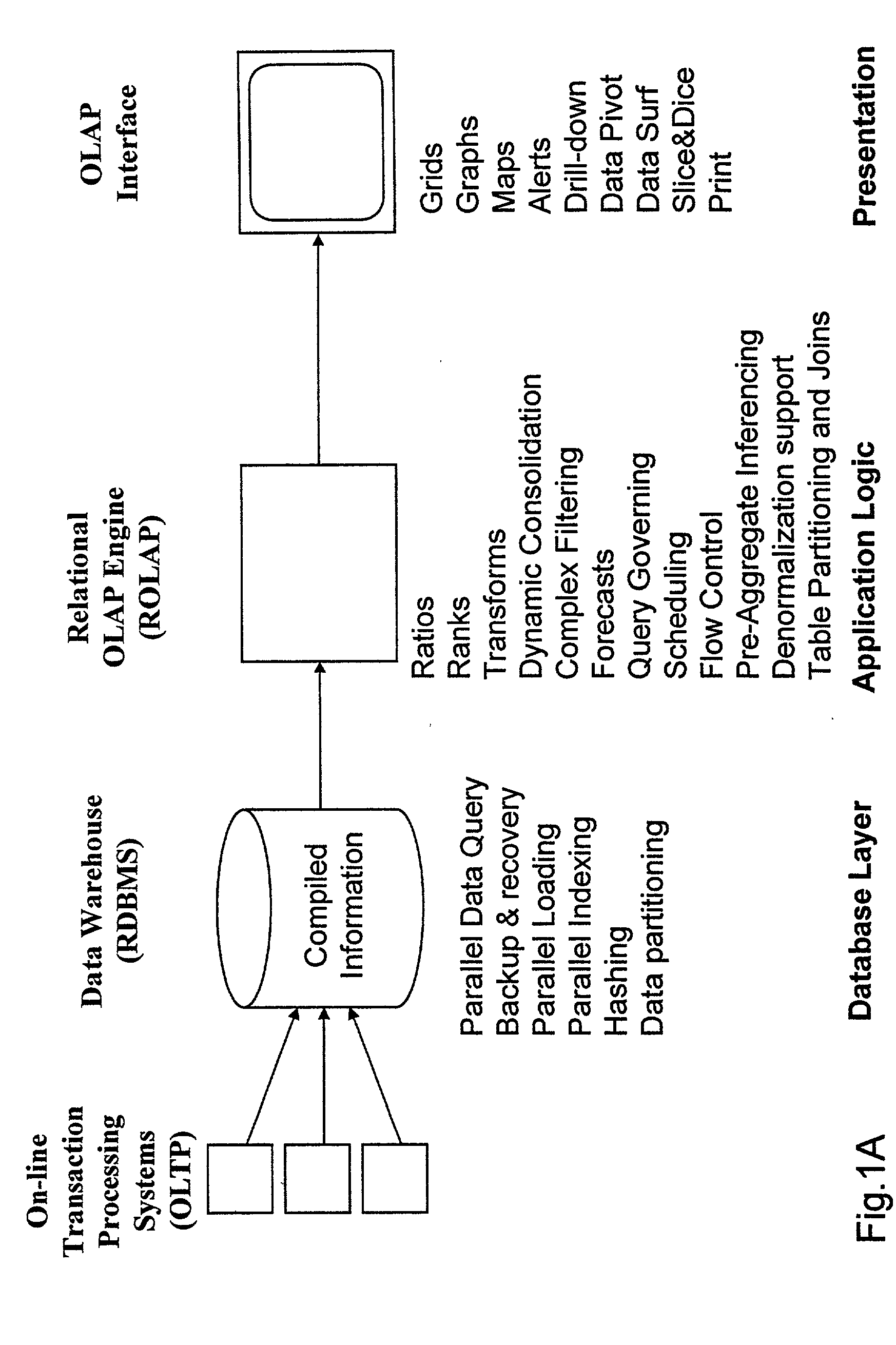
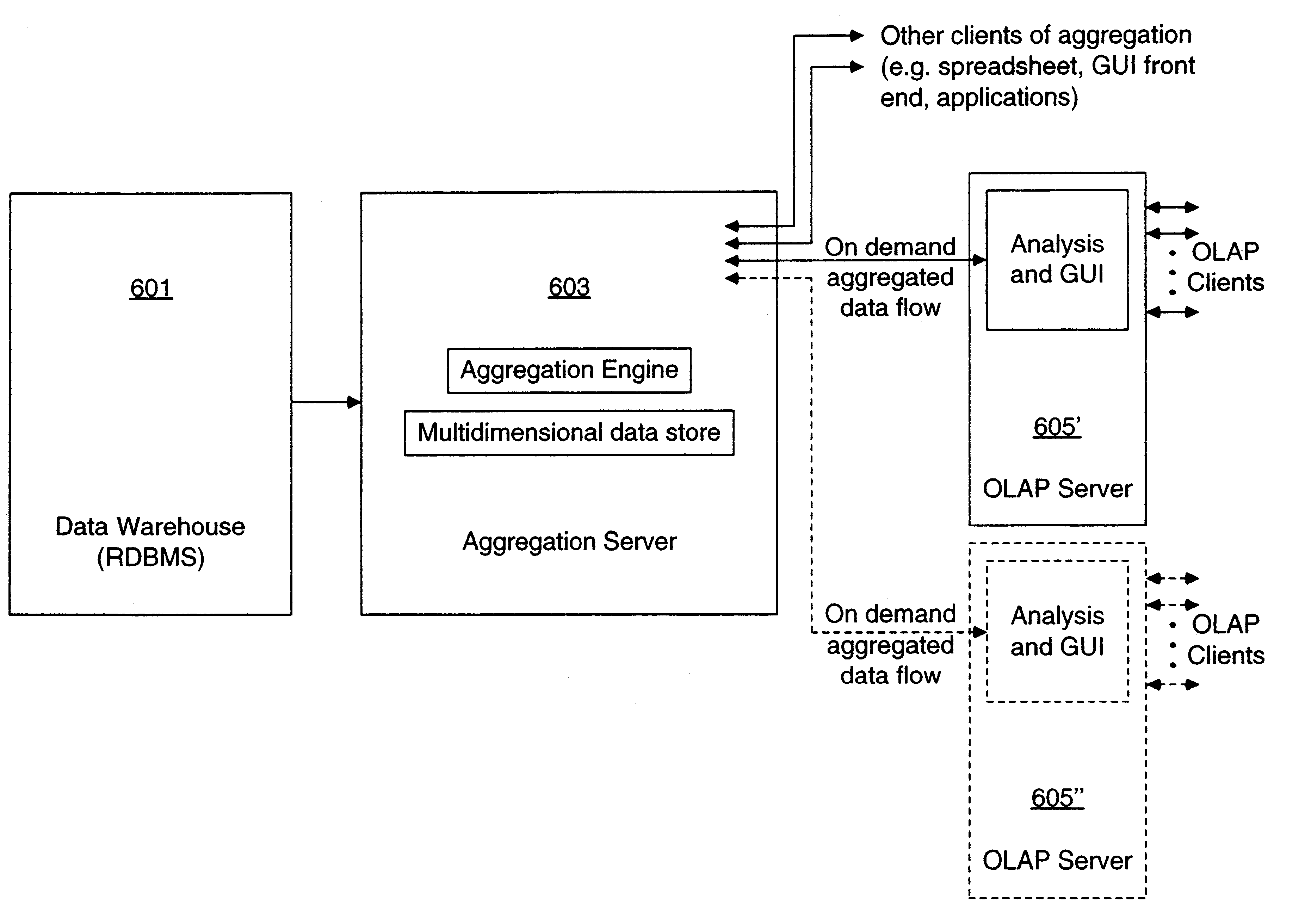
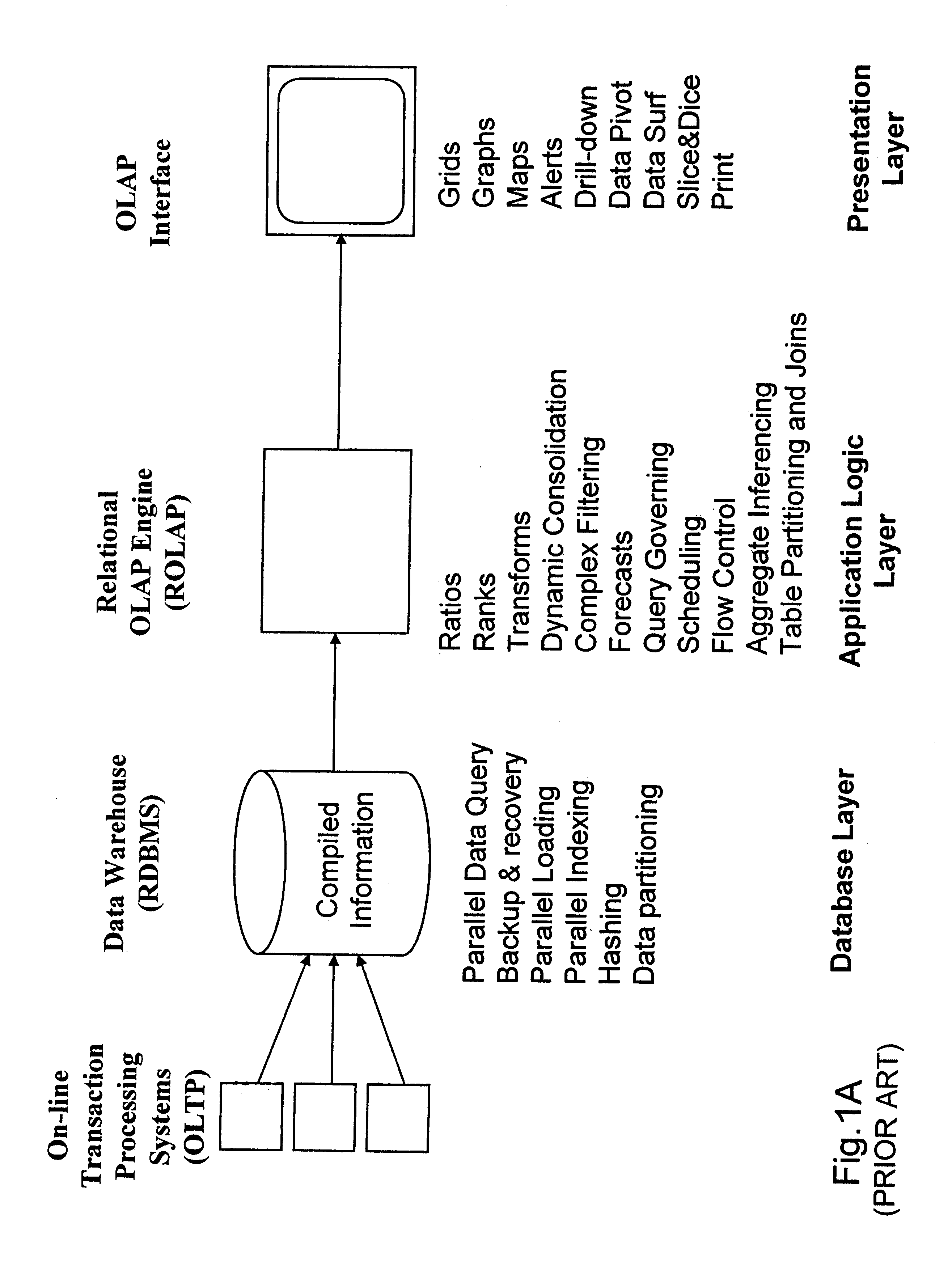
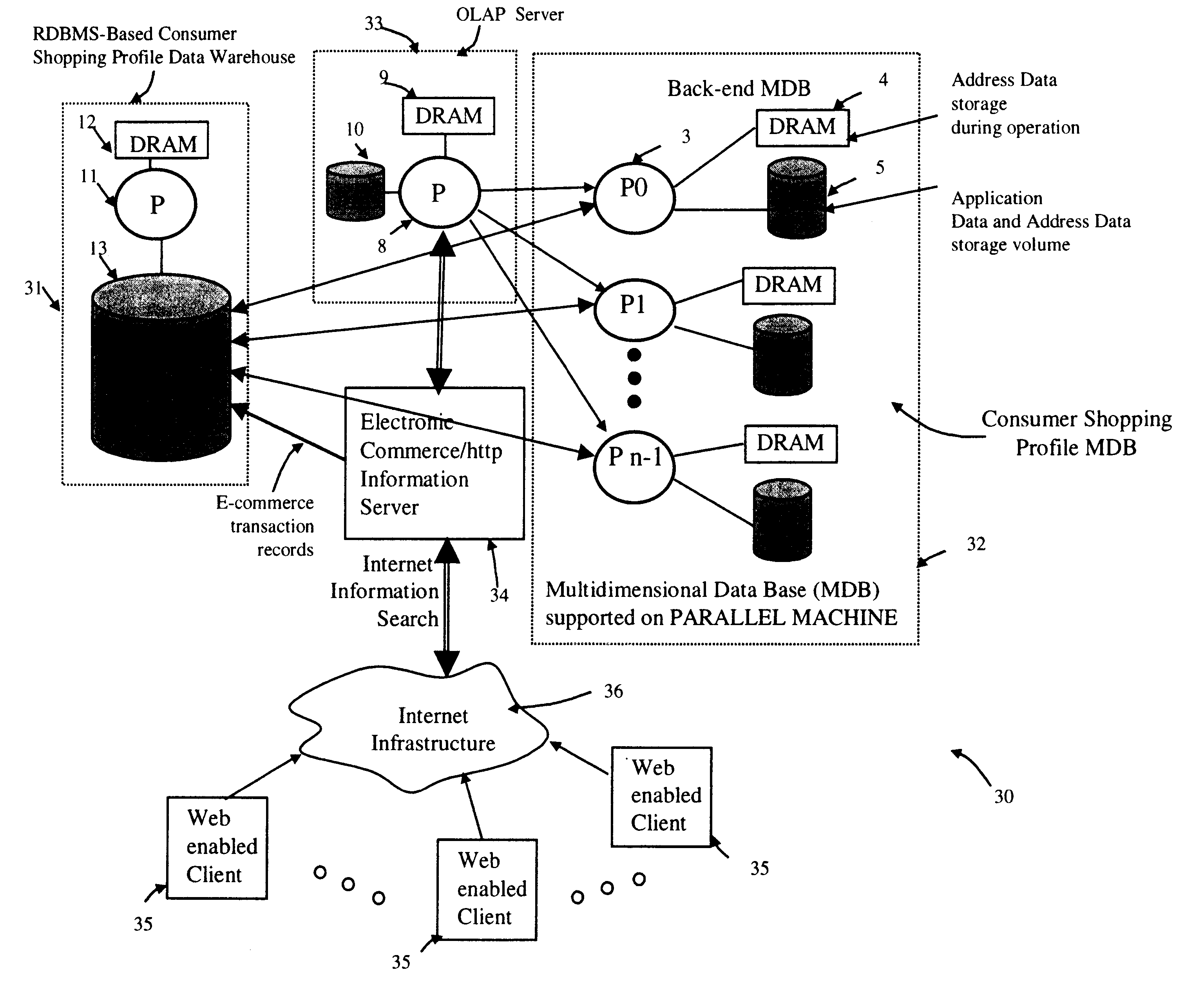
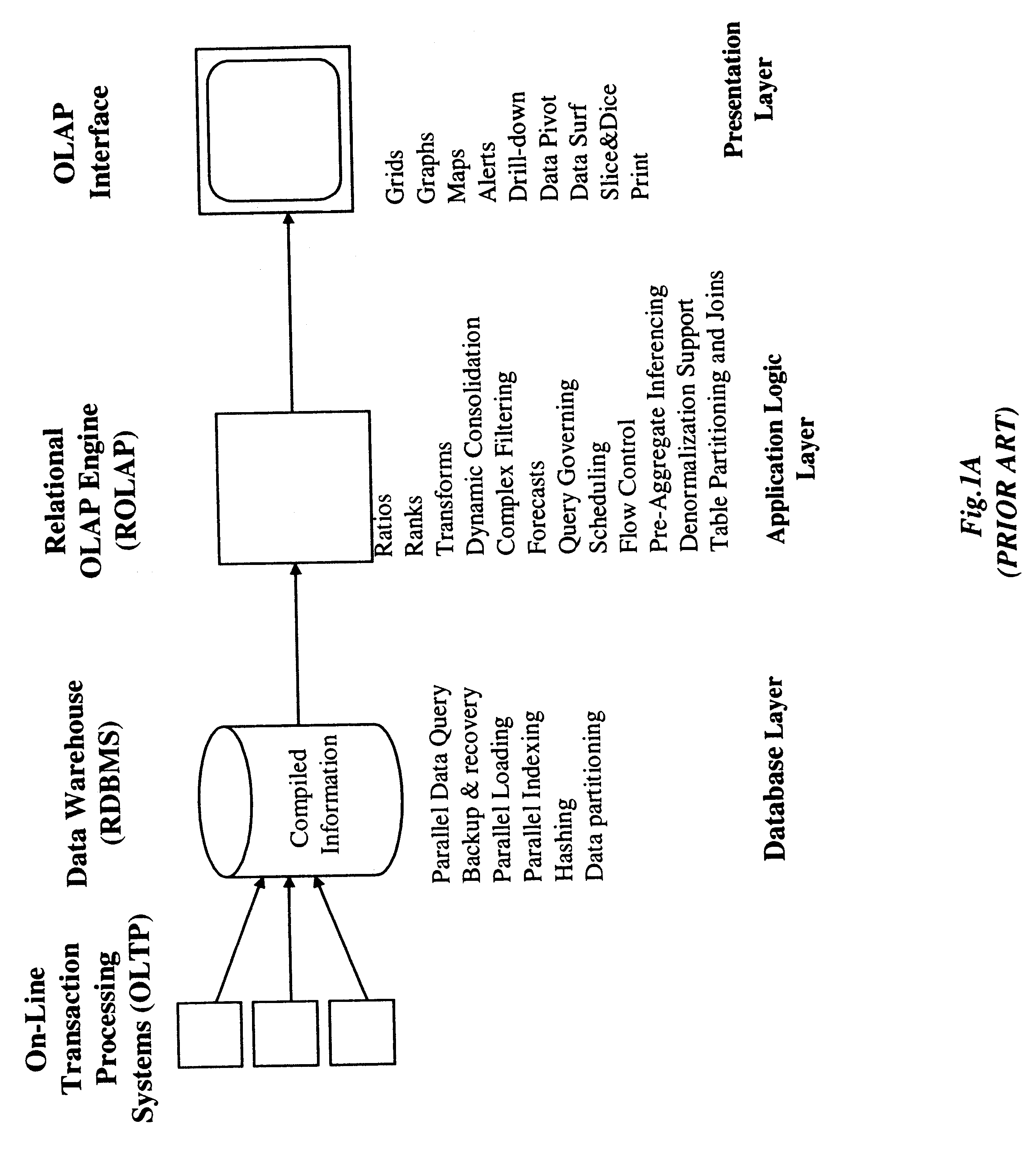
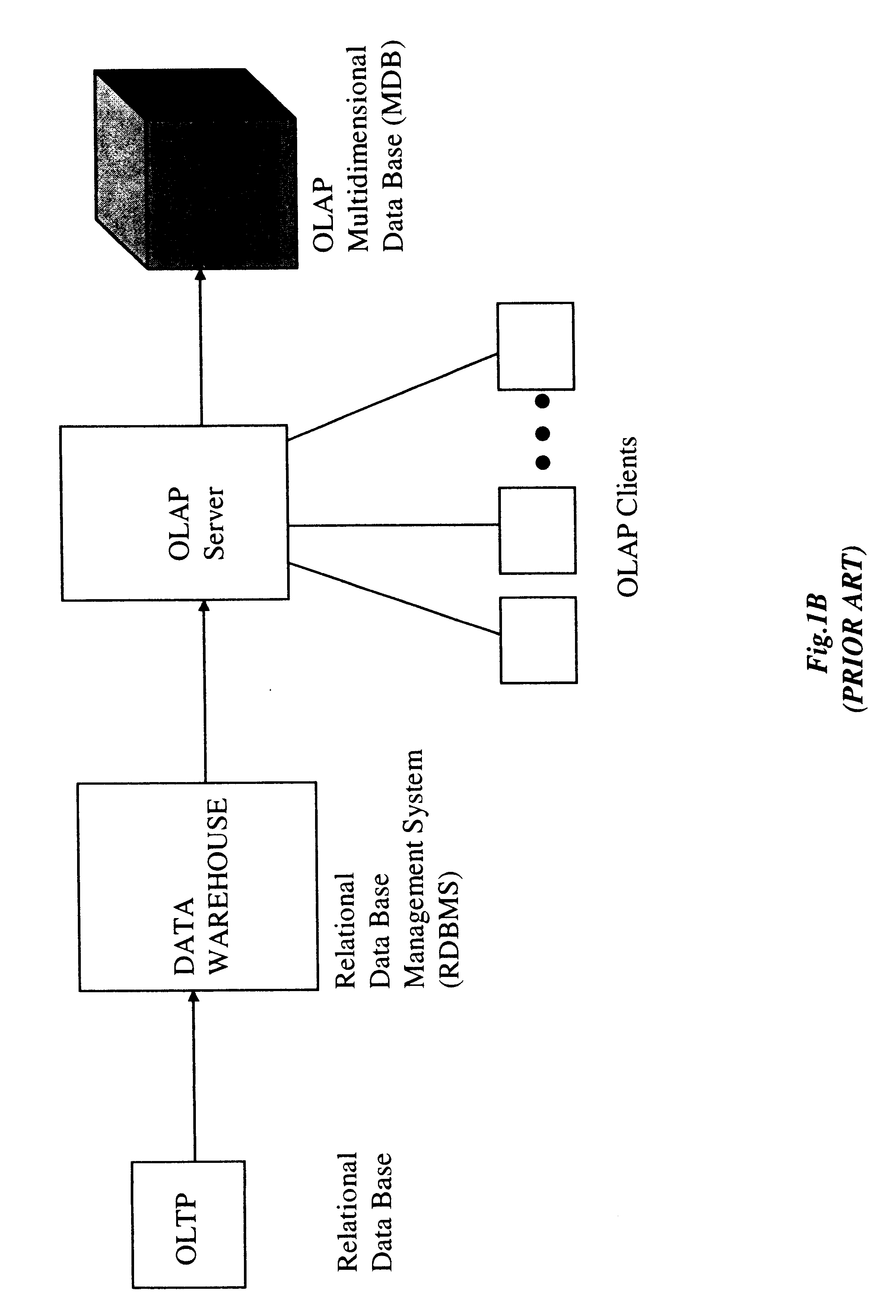
Relational database management system having integrated non-relational multi-dimensional data store of aggregated data elements
InactiveUS6385604B1Increase performanceDecrease timeData processing applicationsGlass fibre drawing apparatusOn line analytical processingUsability
Improved method of and apparatus for joining and aggregating data elements integrated within a relational database management system (RDBMS) using a non-relational multi-dimensional data structure (MDD). The improved RDBMS system of the present invention can be used to realize achieving a significant increase in system performance (e.g. [deceased] decreased access / search time), user flexibility and ease of use. The improved RDBMS system of the present invention can be used to realize an improved Data Warehouse for supporting on-line analytical processing (OLAP) operations or to realize an improved informational database system or the like.
Owner:MEC MANAGEMENT LLC +1
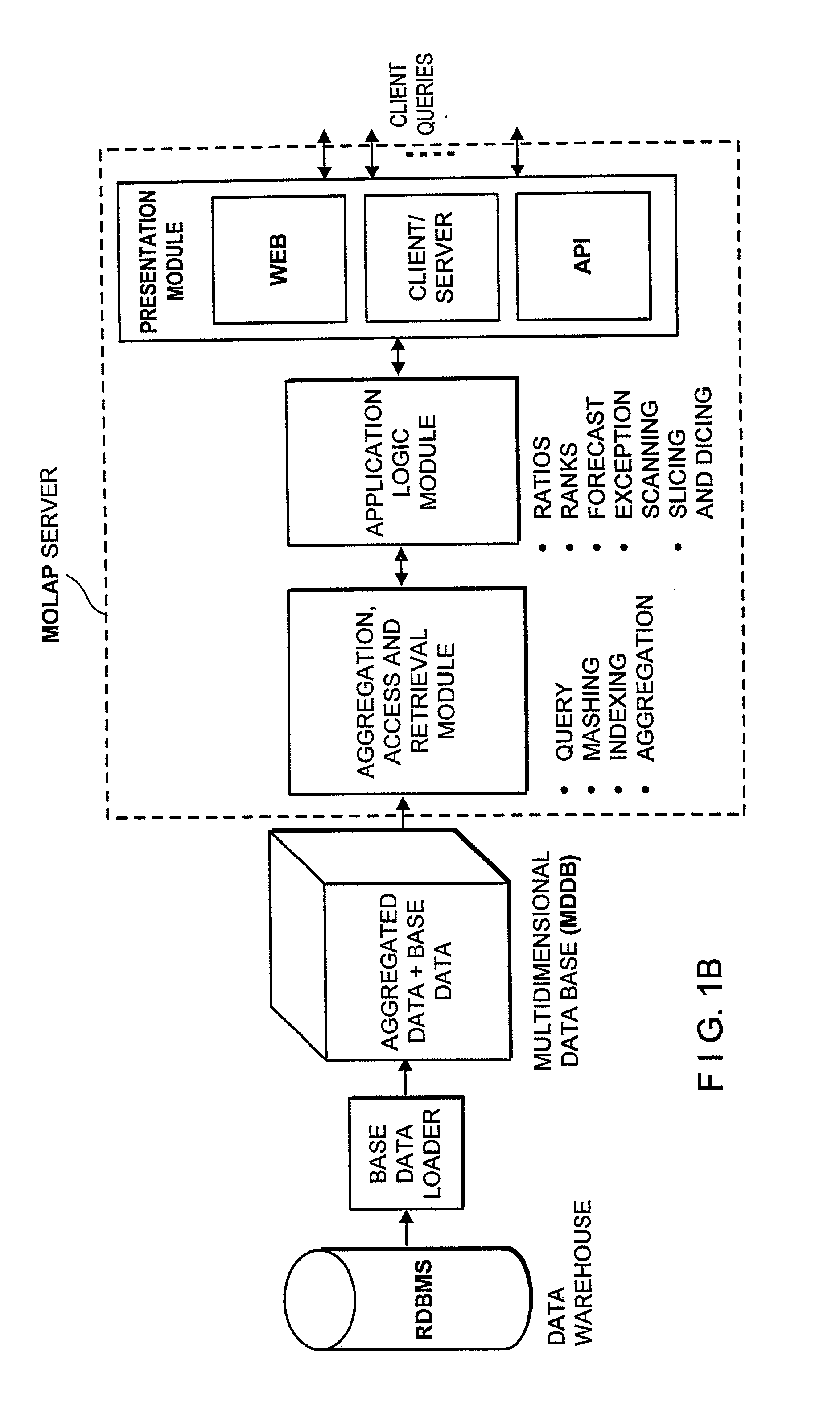
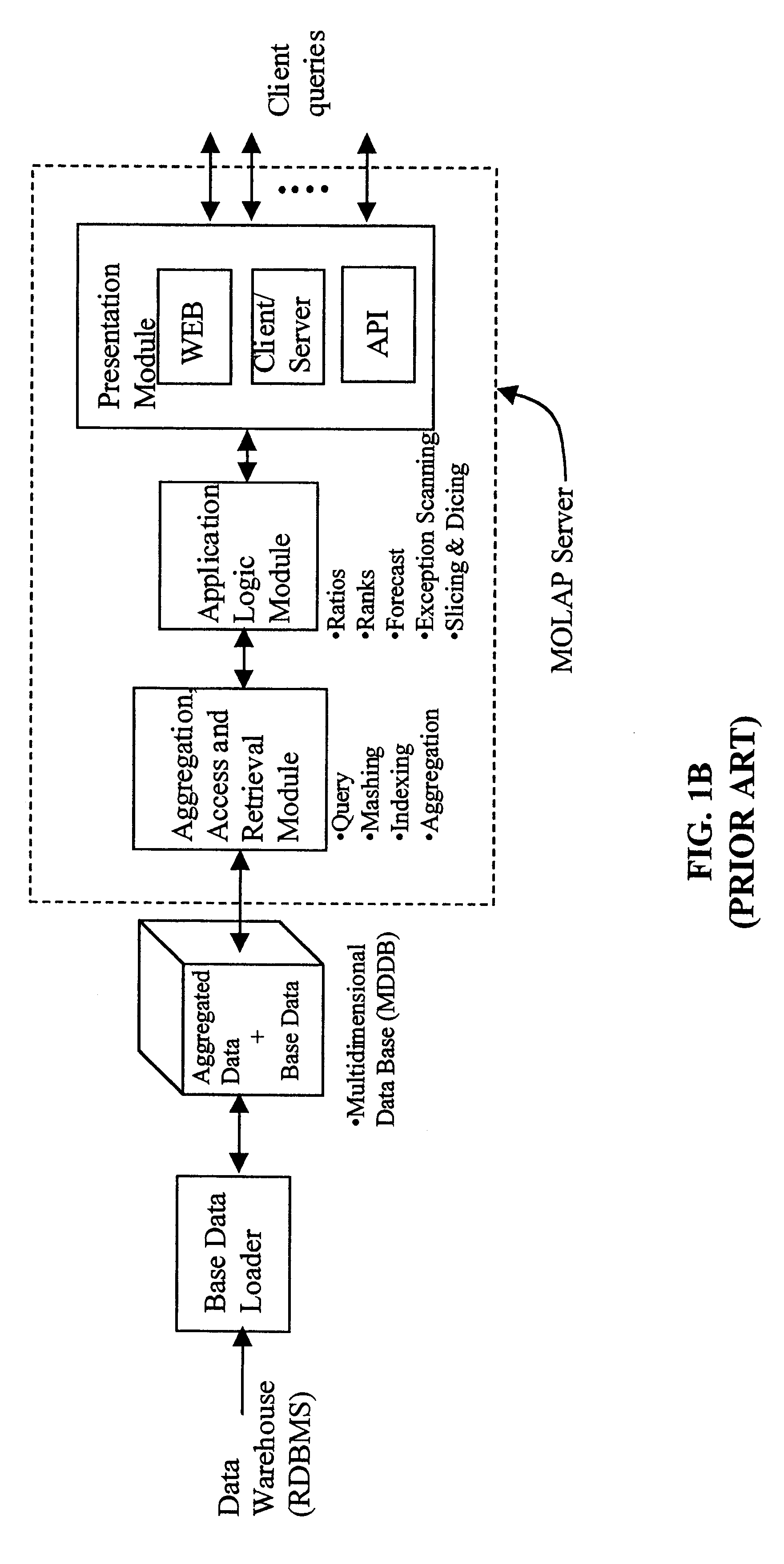
Data aggregation server for managing a multi-dimensional database and database management system having data aggregation server integrated therein
InactiveUS20020029207A1Reduce the burden onImprove system performanceData processing applicationsDigital data processing detailsData aggregatorThe Internet
Improved method of and apparatus for aggregating data elements in multidimensional databases (MDDB). In one aspect of the present invention, the apparatus is realized in the form of a high-performance stand-alone (i.e. external) aggregation server which can be plugged-into conventional OLAP systems to achieve significant improments in system performance. In accordance with the principles of the present invention, the stand-alone aggregation server contains a scalable MDDB and a high-performance aggregation engine that are integrated into the modular architecture of the aggregation server. The stand-alone aggregation server of the present invention can uniformly distribute data elements among a plurality of processors, for balanced loading and processing, and therefore is highly scalable. The stand-alone aggregation server of the present invention can be used to realize (i) an improved MDDB for supporting on-line analytical processing (OLAP) operations, (ii) an improved Internet URL Directory for supporting on-line information searching operations by Web-enabled client machines, as well as (iii) diverse types of MDDB-based systems for supporting real-time control of processes in response to complex states of information reflected in the MDDB. In another aspect of the present invention, the apparatus is integrated within a database management system (DBMS). The improved DBMS can be used to realize achieving a significant increase in system performance (e.g. deceased access / search time), user flexibility and ease of use. The improved DBMS system of the present invention can be used to realize an improved Data Warehouse for supporting on-line analytical processing (OLAP) operations or to realize an improved informational database system, operational database system, or the like.
Owner:YANICKLO TECH LIABILITY +1
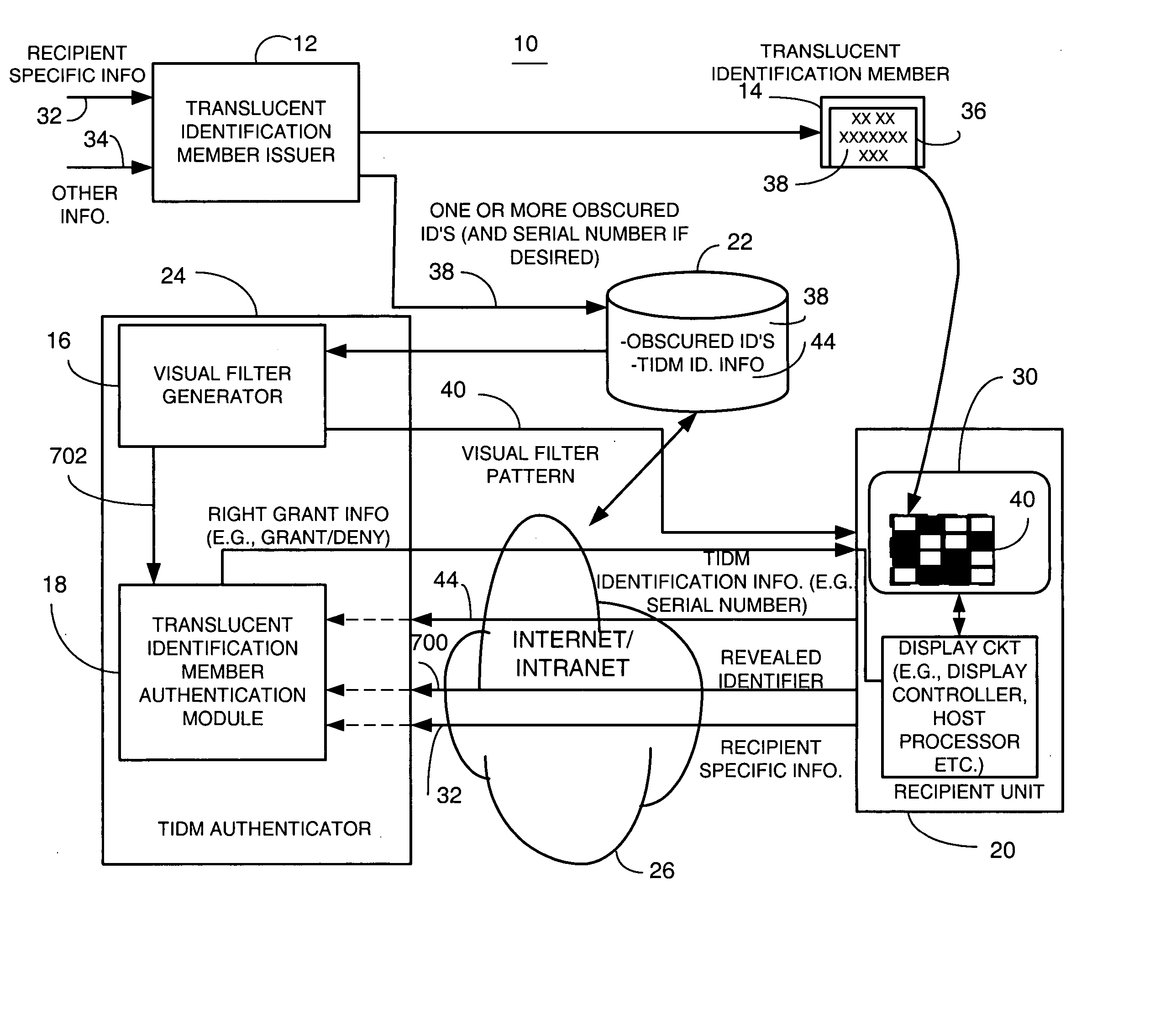
Method and apparatus for providing authentication using policy-controlled authentication articles and techniques
A method and apparatus provides first or second factor authentication by providing selectability of a plurality of second factor authentication policies associated with a second factor authentication article. The first or second factor authentication article includes authentication information, such as a plurality of data elements in different cells or locations on the authentication article, which can be located by using corresponding location information. The method and apparatus provides second factor authentication based on the first or second factor authentication article by enforcing at least one of the plurality of selected authentication policies.
Owner:ENTRUST
Representation of data records
ActiveUS7461077B1Easy to browseConsistent interfaceDigital data information retrievalSpecial data processing applicationsData sourceDisplay device
A computerized method for representing a data record comprising: querying a data source to obtain data selected from the group consisting of a data element in a record, and metadata concerning the record; presenting in a display a record handle for manipulation of the record; presenting in the display a data item wherein the data item is a list of data items or a reference to another record; and, optionally, presenting on the display the metadata above the data item. In some embodiments, the method includes the step of retrieving one or more heterogeneous records from a plurality of databases for display and manipulation. The invention is also a grid control programmed to implement a disclosed method and is a computer-readable medium having computer-executable instructions for performing a disclosed method. The invention links the grid control of the invention with automatic query generation using hierarchical data schema trees. Both the trees and the grid records represent relational foreign keys as extra reference columns. In the grid control, these reference columns are additional embedded record handles.
Owner:MUSICQUBED INNOVATIONS LLC
System and method for restoring a computer system after a failure
InactiveUS20020049883A1Memory adressing/allocation/relocationInternal/peripheral component protectionOperational systemOriginal data
A method and apparatus for reverting a disk drive to an earlier point in time is disclosed. Changes made to the drive are saved in a circular history buffer which includes the old data, the time it was replaced by new data, and the original location of the data. The circular history buffer may also be implemented by saving new data elements into new locations and leaving the old data elements in their original locations. References to the new data elements are mapped to the new location. The disk drive is reverted to an earlier point in time by replacing the new data elements with the original data elements retrieved from the history buffer, or in the case of the other embodiment, reads to the disk are mapped to the old data elements stilled stored in their original locations. The method and apparatus may be implemented as part of an operating system, or as a separate program, or in the controller for the disk drive. The method and apparatus are applicable to other forms of data storage as well. Also disclosed are method and apparatus for providing firewall protection to data in a data storage medium of a computer system.
Owner:NORTONLIFELOCK INC
Method, system, and computer program product for customer-level data verification
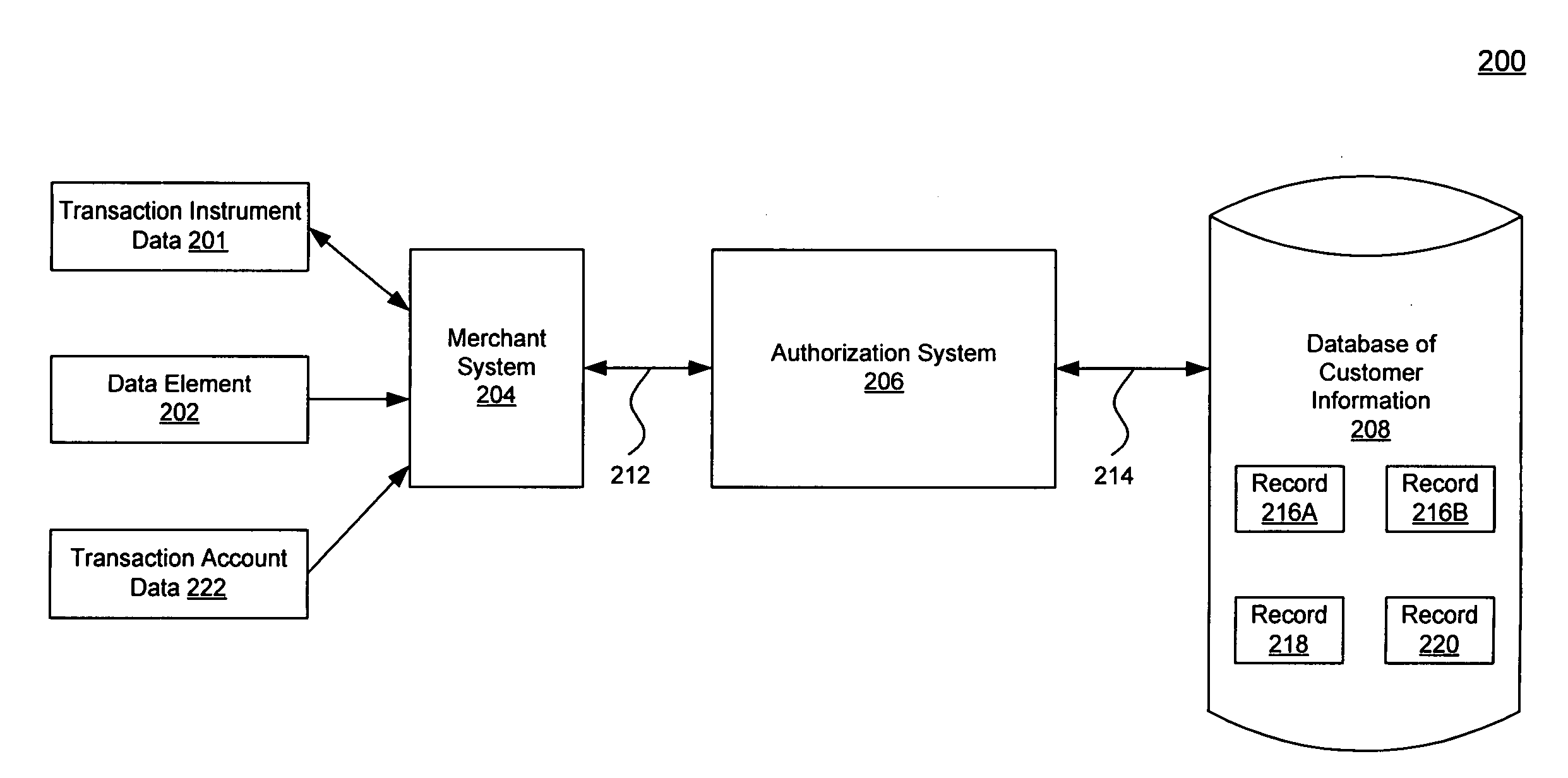
ActiveUS20070284433A1Improve accuracyReduce error rateComplete banking machinesFinanceData validationSource Data Verification
A system, method, and computer program to reduce incorrectly declined transactions and improve risk calculation accuracy by reducing error probability during fraud detection. The tool first receives at least one data element as well as transaction account data and / or financial transaction instrument data. Then a customer is determined from a first record associated with the transaction account data and / or financial transaction instrument data. A record search is performed to identify at least one additional record associated with the customer. Finally, the data element is compared to the information contained in the additional record to create a comparison result that verifies a customer address. The comparison result may be used as an input to transaction risk calculations. The comparison result may also be provided to a merchant system and / or merchant for use in a decision-making process, for example, to verify customer identity.
Owner:LIBERTY PEAK VENTURES LLC
Apparatus and method for message-centric analysis and multi-aspect viewing using social networks
ActiveUS20060173957A1Data switching by path configurationMultiple digital computer combinationsReference modelMulti aspect
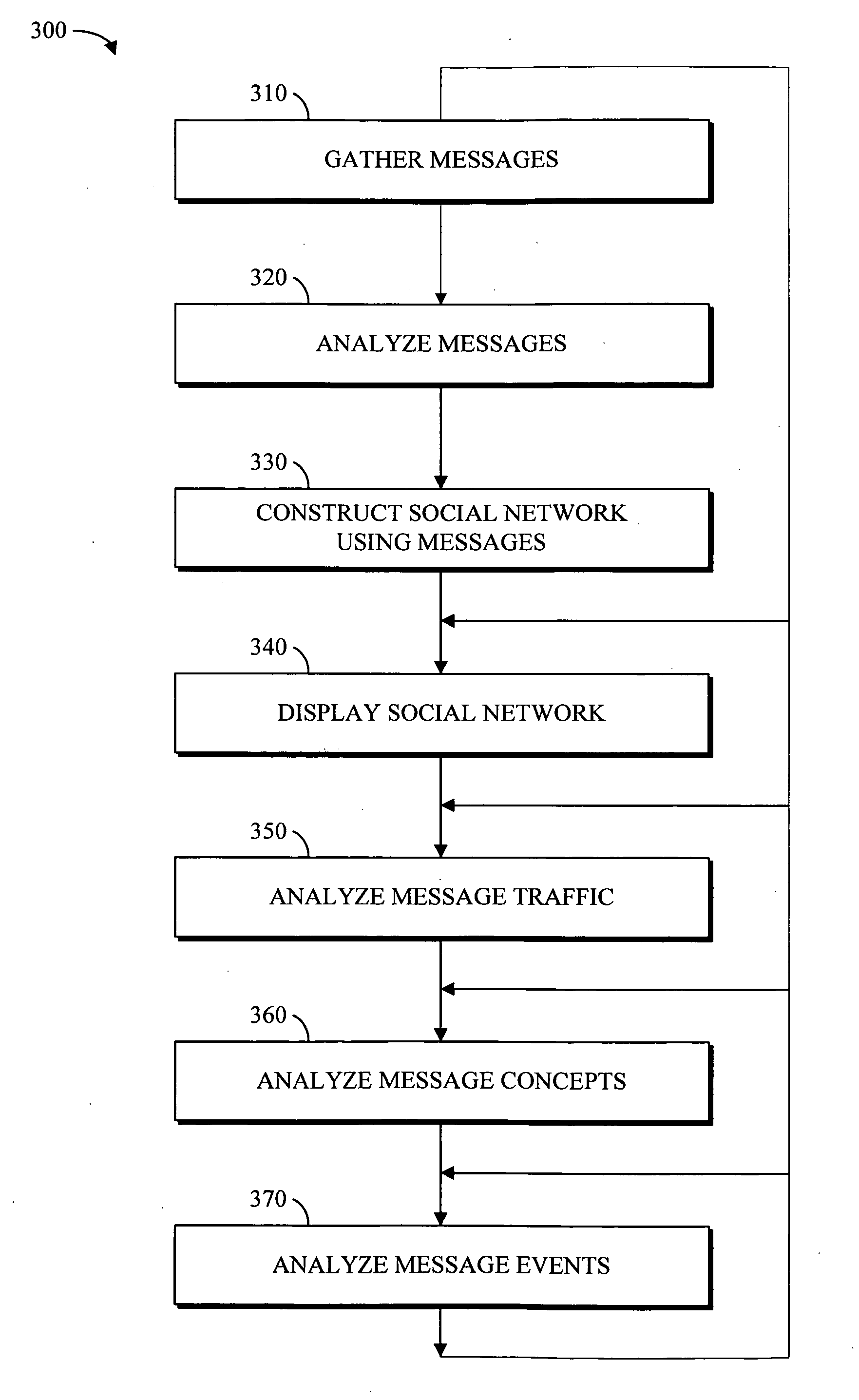
Electronic data files are broadly characterized as “messages” and a social network is constructed by analyzing one or more messages exchanged between various entities. Additionally, messages from structured and / or unstructured data stores are correlated using one or more common / related data elements from two or more messages. Further, the social network and the concepts contained in the exchanged messages (i.e. semantic network) can be visualized using a series of multi-aspect viewing tools. Finally, in conjunction with the social network and the semantic network, a message network based on the chronological relationship of the messages (event network) can be constructed to analyze and visualize how the messages relate to each other in a time-based reference model. Once visualized, the relationship of the concepts contained in the messages as well as the relationship between the entities and the timing involved in the exchange of messages can be analyzed for desired information.
Owner:NUIX NORTH AMERICA
Enhanced system, method and medium for certifying and accrediting requirements compliance utilizing robust risk assessment model
InactiveUS6983221B2Enhances and facilitates security risk assessmentsFinanceError detection/correctionComputer-aidedGoal system
Owner:TELOS CORP
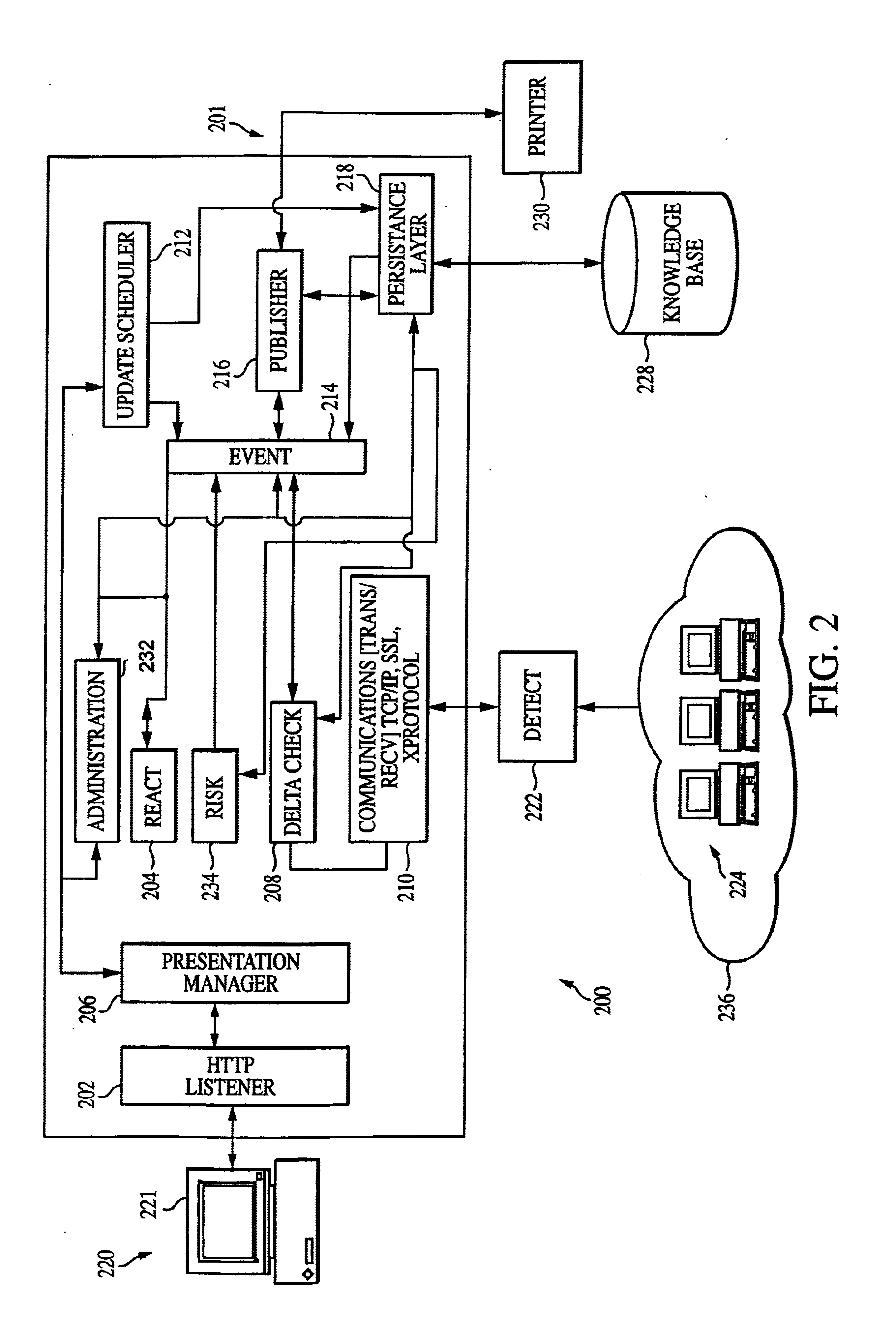
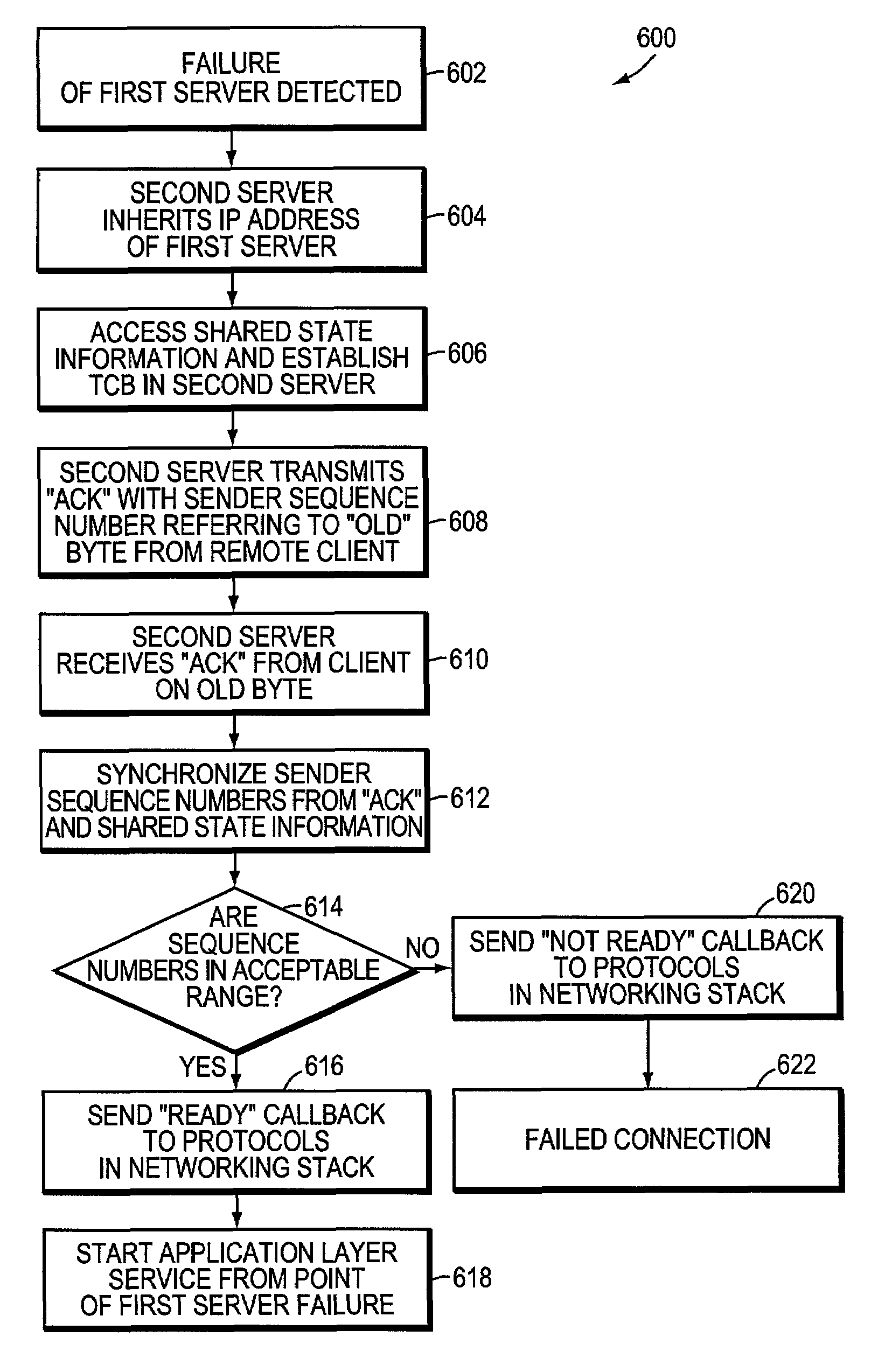
System and method for transparent takeover of TCP connections between servers
A system and a method for transparent takeover (or failover) of a remote client TCP connection from a first server in a cluster of interconnected servers to a second server provides the storing of shared state information relative to the connection on each involved server and using of the shared state information to reestablish the connection on the second server. A message using a sequence number to refer to a previously transmitted data element (such as a byte) is sent by the second server and a received client acknowledgement (ACK) of that sequence number, or a higher one, is used to synchronize the server's data packet transmission sequence number with the ACK-transmitted sequence number. If synchronization is successful, then the connection is restarted on the second server from the point of termination / failure on the first server.
Owner:MICRO FOCUS SOFTWARE INC
Query language for unstructed data
InactiveUS20150019530A1Digital data information retrievalDigital data processing detailsRDF query languageUnstructured data
A system and methods are provided for interactive construction of data queries. One method comprises: generating a query based upon a plurality of user-identified data items, wherein the user-identified data items are data items representing desired results from a query, and wherein information related to the user-identified data items is included in a “given” clause of the query, assigning received input data to a hierarchical set of categories, presenting to a user a plurality of new query results, wherein the plurality of new query results are determined by scanning the received input data to find data elements in the same hierarchical categories as those in the “given” query clause and not in the same hierarchical categories as those of an “unlike” clause of the query, receiving from the user an indication as to whether each query result of the presented plurality of new query results is a desirable query result, adding query results indicated by the user as desirable to the “given” clause of the query, adding query results indicated by the user as undesirable to the “unlike” clause of the query, evaluating a metric indicative of the accuracy of the query, and responsive to a determination that the query achieves a predetermined threshold level of accuracy, storing the query.
Owner:COGNITIVE ELECTRONICS INC
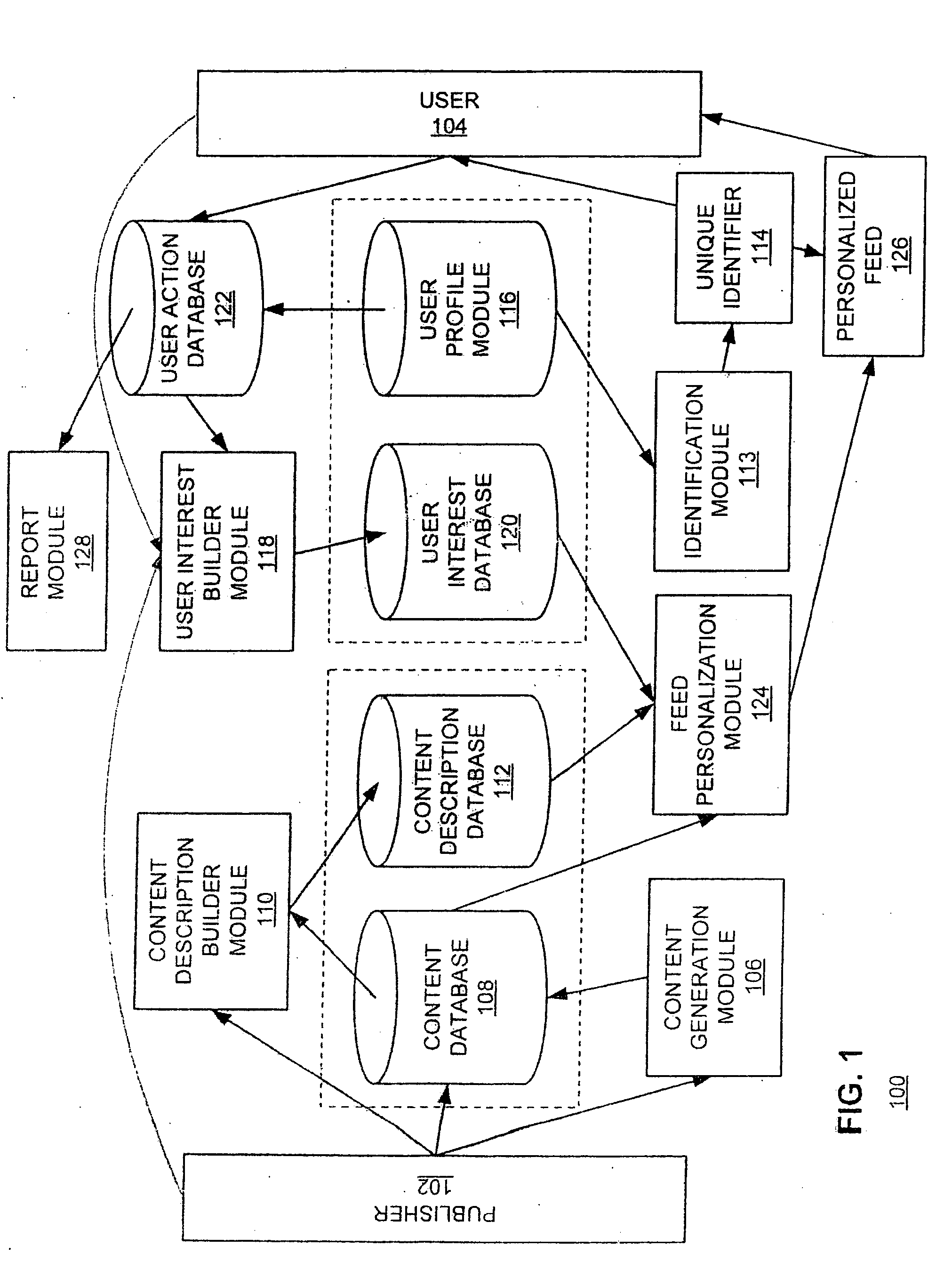
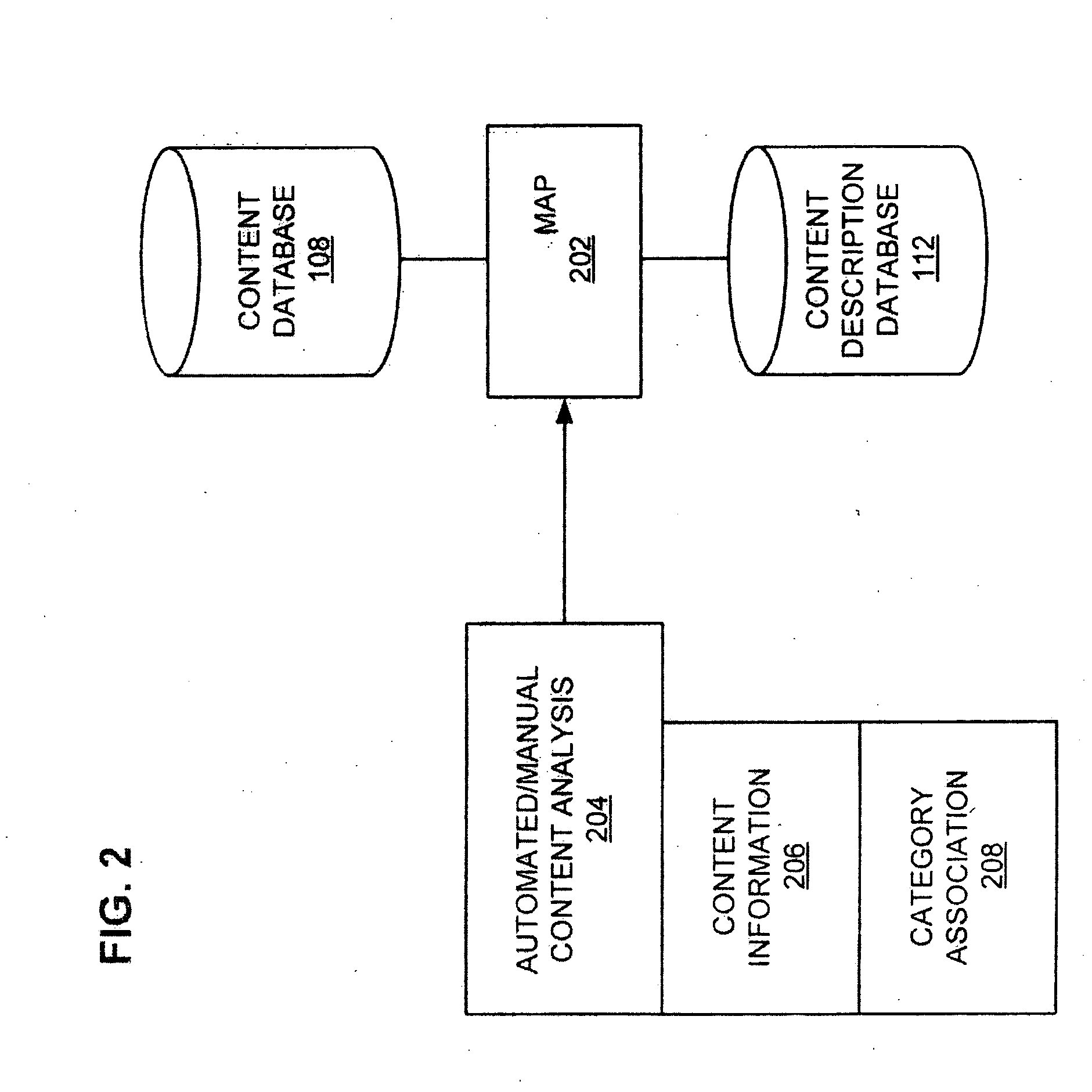
Data extraction for feed generation
ActiveUS20060167860A1Quick assemblyDigital data processing detailsMultiple digital computer combinationsTemplate matchingUnstructured data
A system (and a method) automatically generates a feed from structured or unstructured data. The system identifies a resource having two or more data elements. The resource is matched with a pre-defined template. The pre-defined template is structured for a feed and includes a plurality of fields. The system extracts data elements from the two or more data elements of the resources. Each extracted data element corresponds to a field or the plurality of fields in the pre-defined template. Each extracted data element is then merged into the corresponding field or the plurality of fields in the pre-defined template to generate the feed.
Owner:SIMPLEFEED
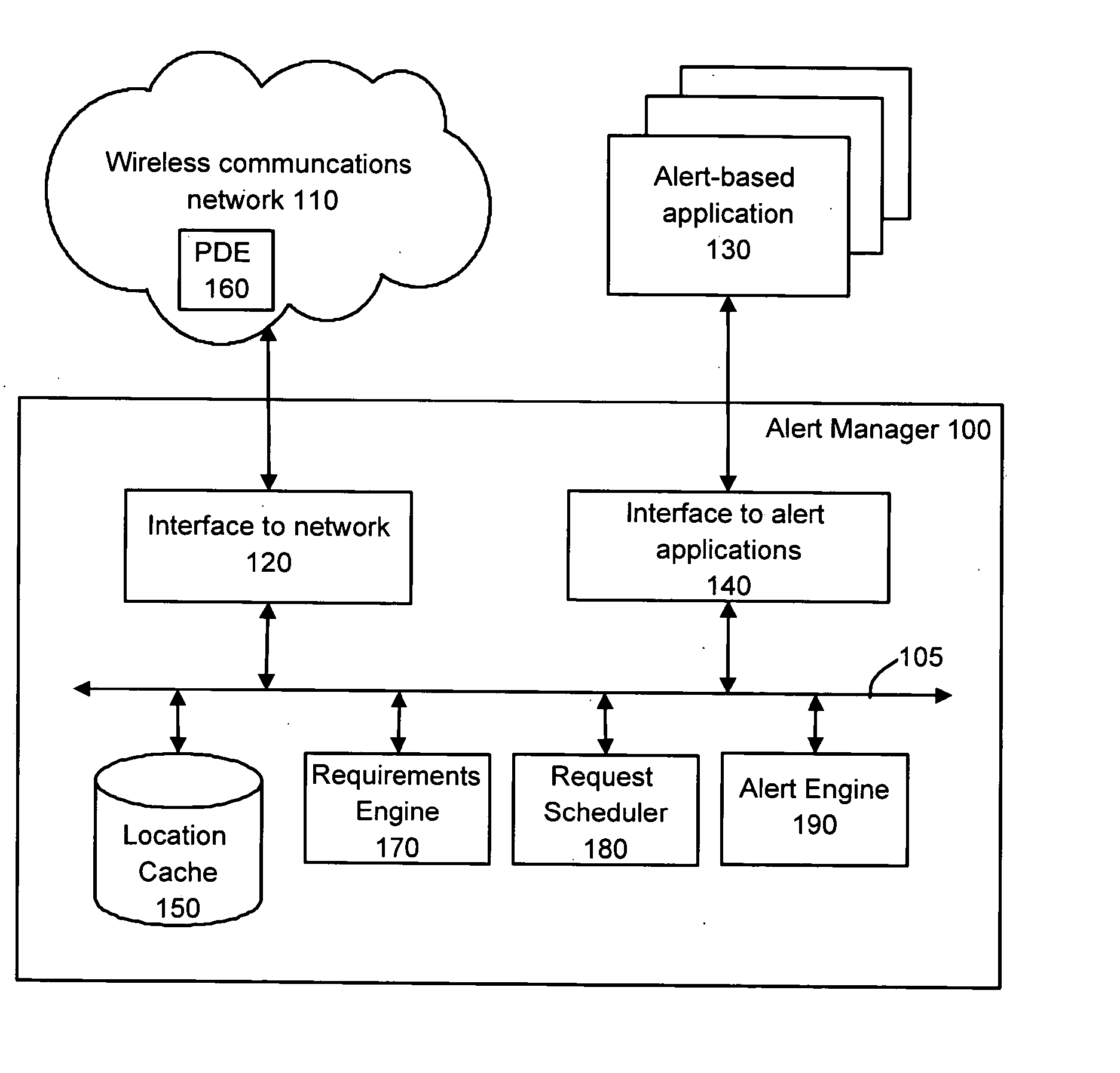
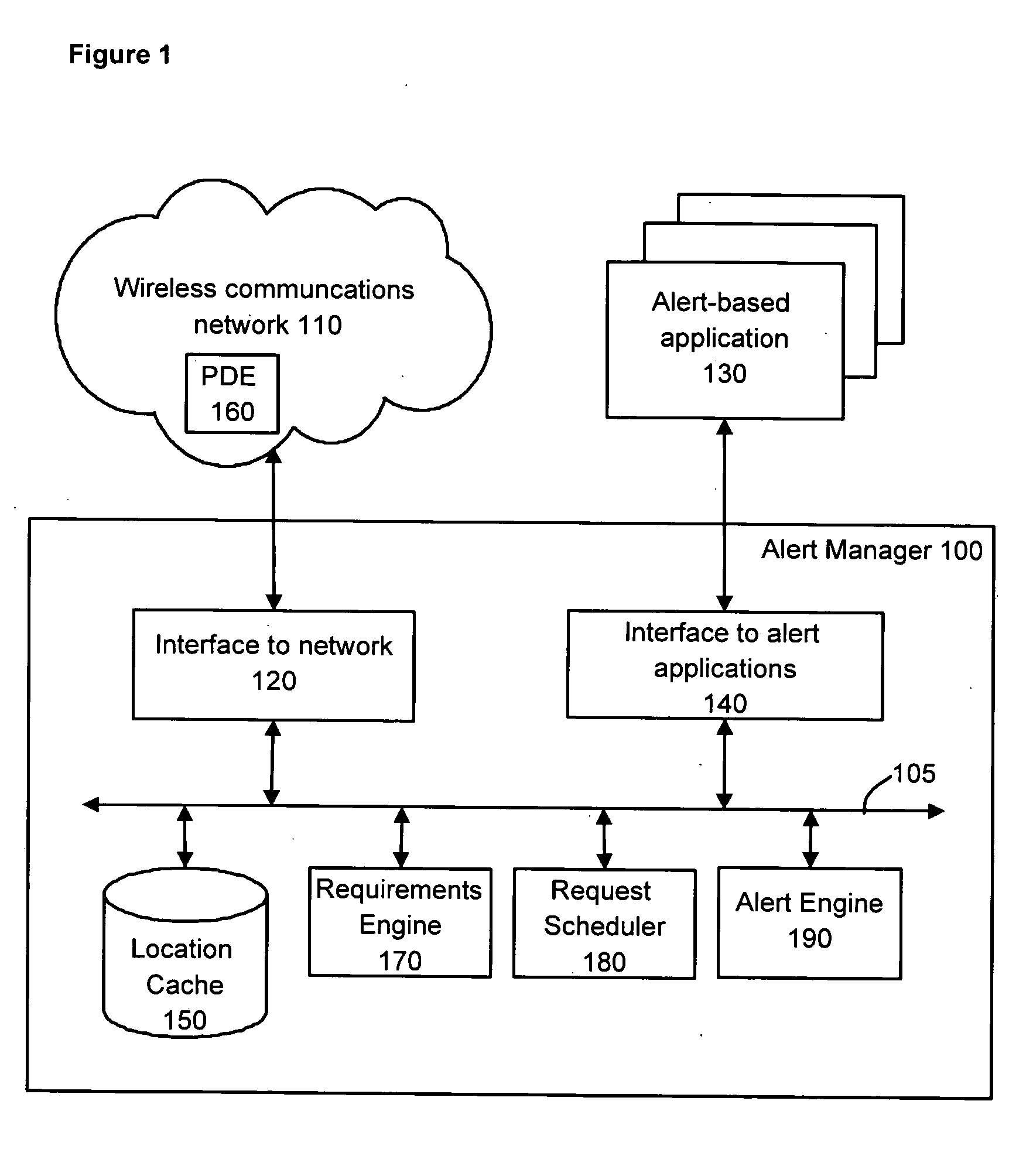
System for providing alert-based services to mobile stations in a wireless communications network
InactiveUS20050043037A1Radio/inductive link selection arrangementsLocation information based serviceTelecommunicationsMobile station
System for providing alert-based communication services for which corresponding alert conditions to be met by mobile stations are defined. The system includes an alert engine capable of firing alerts associated with the alert-based communication services if location data regarding the mobile stations is indicative of the mobile stations meeting the alert conditions corresponding to the alert-based communication services. A requirements engine is provided for determining an expected earliest future time at which at least one alert condition is capable of being met by a particular mobile station and outputting a data element indicative of a requirement to obtain updated location data about the particular mobile station in advance of the expected earliest future time. Also provided is a scheduler for receiving expiry times data indicative of a plurality of expiry times relating to respective location requests, processing the expiry times data for determining an order for servicing the location requests by positioning determining equipment (PDE) at least in part on a basis on the expiry times of the location requests and an output for interfacing with the PDE, allowing it to service the location requests according to the order determined.
Owner:SMITH MICRO SOFTWARE LLC
SIMD datapath coupled to scalar/vector/address/conditional data register file with selective subpath scalar processing mode
InactiveUS6839828B2Not compromise SIMD data processing performanceReduce consumptionRegister arrangementsDigital data processing detailsProcessor registerOperation mode
There is provided a processor designed to operate in a plurality of modes for processing vector and scalar instructions. Register files are each for storing scalar and vector data and address information. A parallel vector unit, coupled to the register files, includes functional units configurable to operate in a vector operation mode and a scalar operation mode. The vector unit includes an apparatus for tightly coupling the functional units to perform an operation specified by a current instruction. Under a vector operation mode, the vector unit performs, in parallel, a single vector operation on a plurality of data elements. The operations performed on the plurality of data elements are each performed by a different functional unit of the vector unit. Under a scalar operation mode, the vector unit performs a scalar operation on a data element received from the register files in a functional unit within the vector unit.
Owner:INTEL CORP
Method and apparatus for indexing and searching content in hardcopy documents
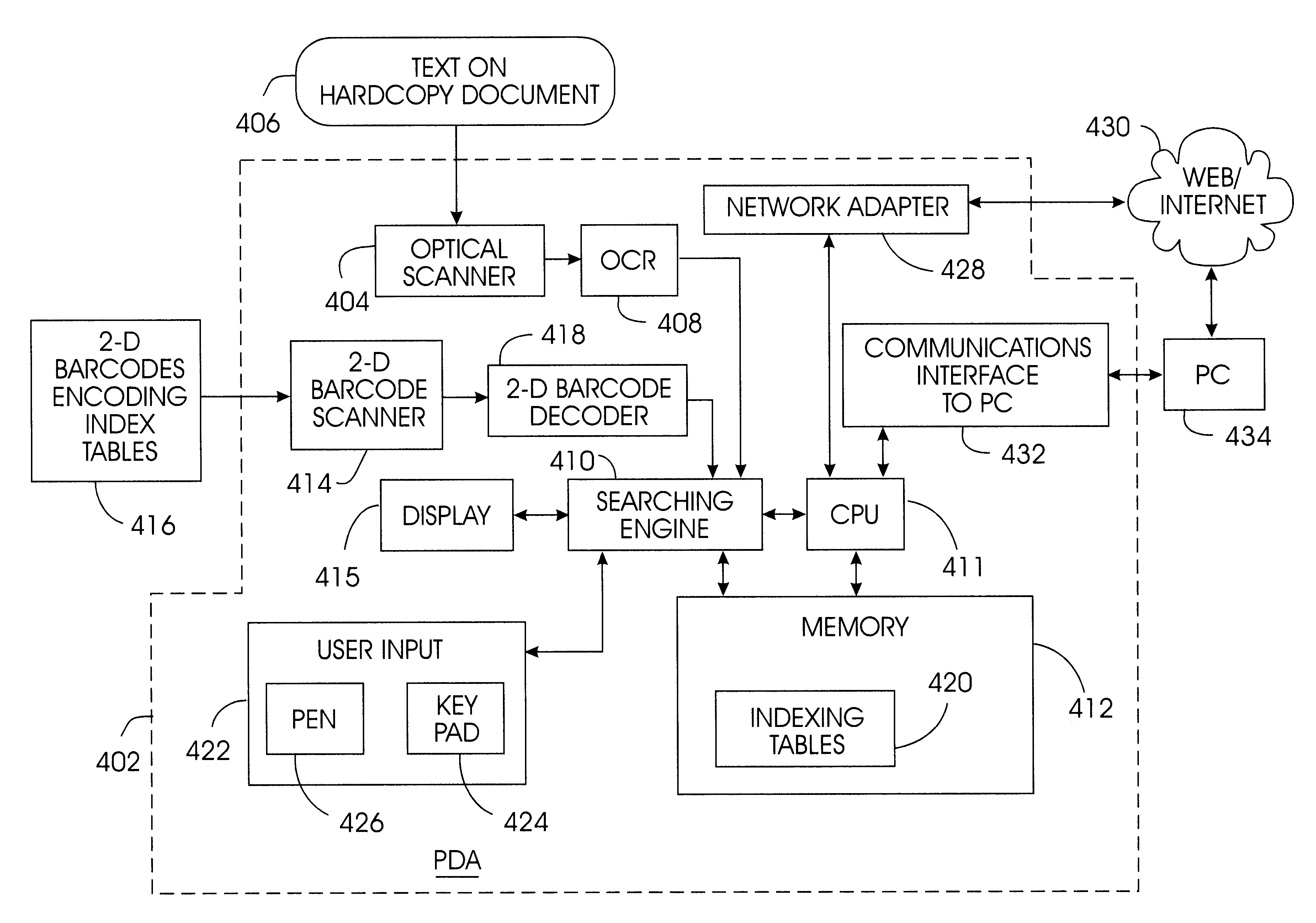
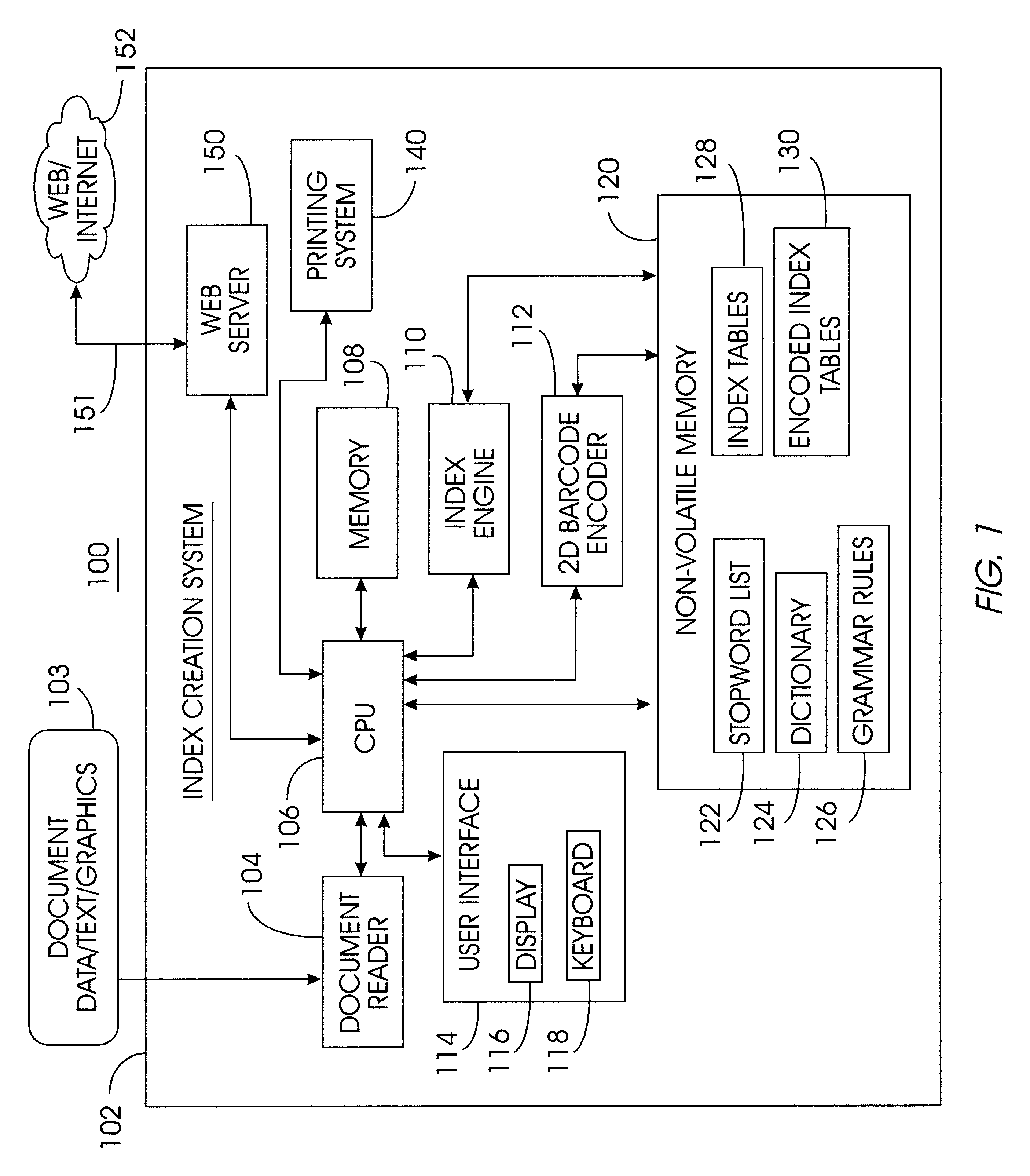
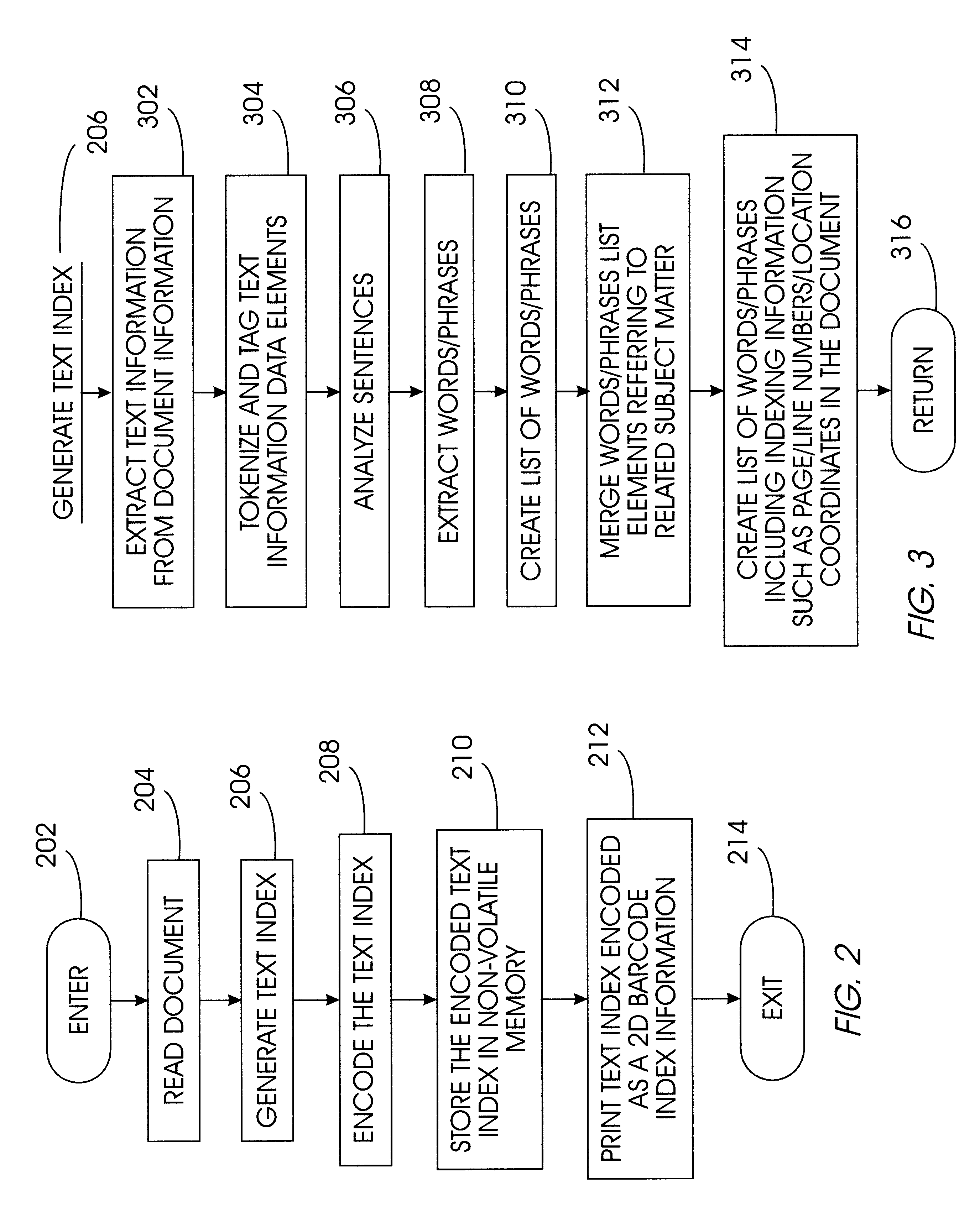
InactiveUS6546385B1More informationSmall volumeData processing applicationsDigital data processing detailsBarcodeThe Internet
A method and apparatus for indexing and searching content in a hardcopy document utilizes a searching assistant computing device (402) with an index table (420) stored in memory (412). The index table (420) is created in memory by scanning a 2-D barcode from a hardcopy document or alternatively by downloading indexing information from a web page via the Internet (430). A search engine (410) in the searching assistant (402) searches the index table (420) to locate a data element found in the content of the hardcopy document. The indexing information corresponding to the data element is displayed to a user as part of the search results to indicate the location of the data element in the hardcopy document.
Owner:IBM CORP
Stand-alone cartridge-style data aggregation server providing data aggregation for OLAP analyses
InactiveUS6434544B1Improve system performanceQuick searchData processing applicationsMulti-dimensional databasesData aggregatorThe Internet
An improved method of and apparatus for aggregating data elements in multidimensional databases (MDDB) realized in the form of a high-performance stand-alone (i.e. external) aggregation server which can be plugged-into conventional OLAP systems to achieve significant improvements in system performance. In accordance with the principals of the present invention, the stand-alone aggregation server contains a scalable MDDB and a high-performance aggregation engine that are integrated into the modular architecture of the aggregation server. The stand-alone aggregation server of the present invention can uniformly distributed data elements among a plurality of processors, for balanced loading and processing, and therefore is highly scalable. The stand-alone aggregation server of the present invention can be used to realize (i) an improved MDDB for supporting on-line analytical processing (OLAP) operations, (ii) an improved Internet URL Directory for supporting on-line information searching operations by Web-enabled client machines, as well as (iii) diverse types of MDDB-based systems for supporting real-time control of processes in response to complex states of information reflected in the MDDB.
Owner:INTELLECTUAL VENTURES ASSETS 114 LLC +1
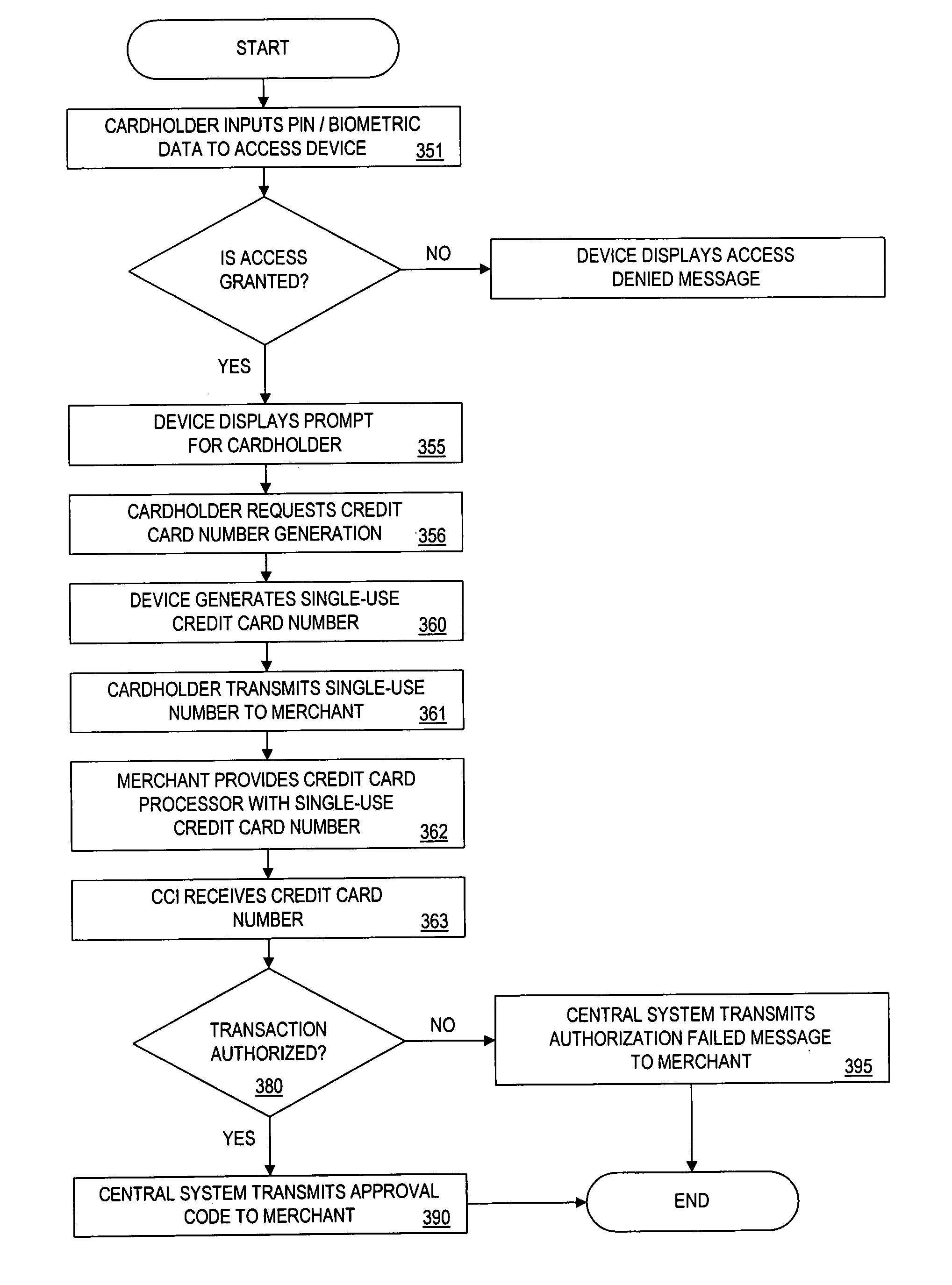
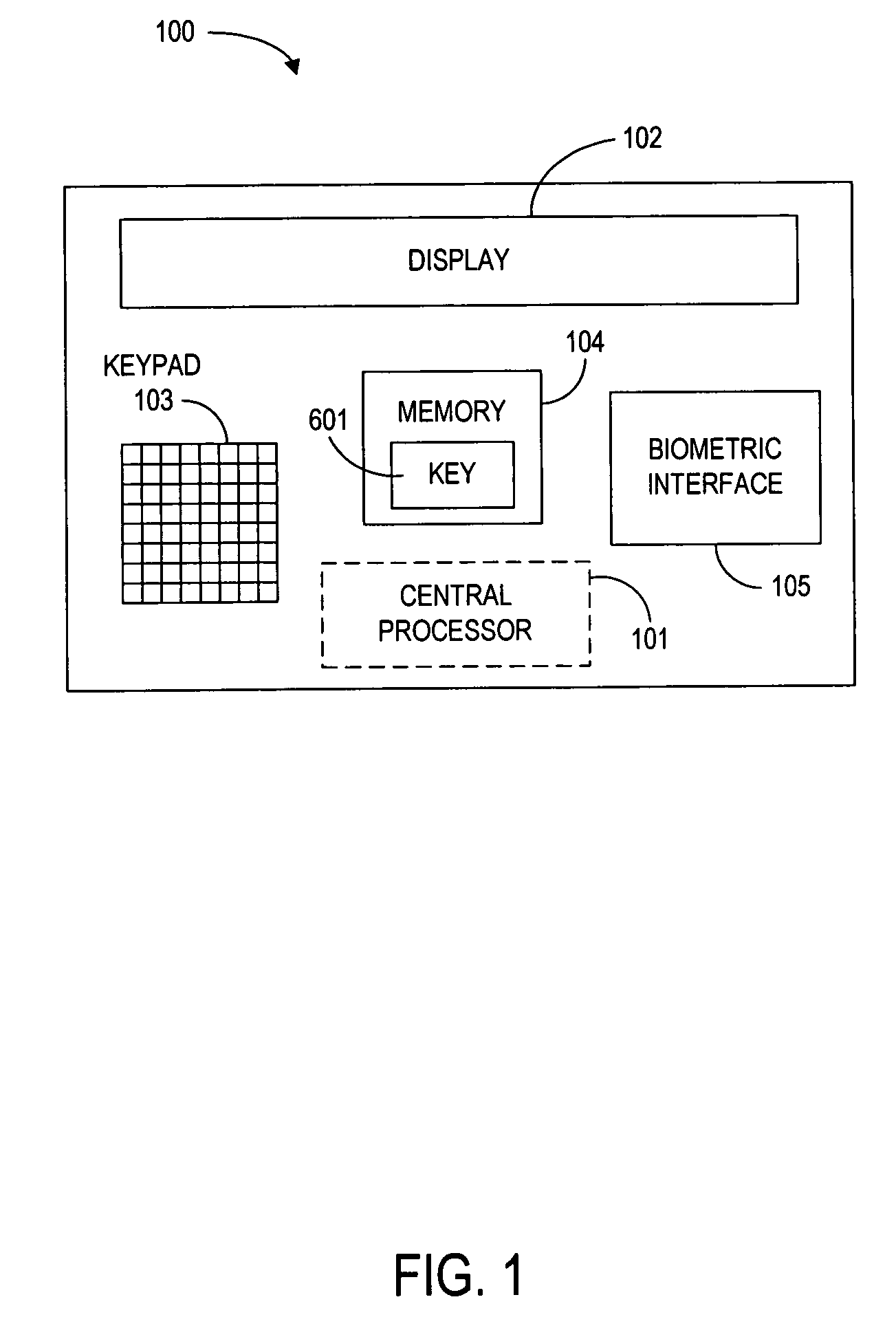
Method and device for generating a single-use financial account number
InactiveUS7177835B1Improve security levelReduce riskFinanceCredit schemesFinancial transactionData element
Owner:PAYPAL INC +1
Remote authentication and transaction signatures
InactiveUS20110258452A1Simple ideaUser identity/authority verificationPayment architecturePersonalizationSmart card
The invention provides a method, apparatus, computer readable medium and signal which allows the usage of devices containing PKI private keys such as PKI-enabled smart cards or USB sticks to authenticate users and to sign transactions. The authenticity of the user and / or the message is verified. Furthermore the operation (authentication and / or signing) occurs without the need for an application to have some kind of a direct or indirect digital connection with the device containing the private key. In addition the operation occurs without the need for the PKI-enabled device containing the private key (e.g. a PKI smart card or USB stick) to either support symmetric cryptographic operations or to have been personalized with some secret or confidential data element that can be read by a suitable reader.
Owner:ONESPAN NORTH AMERICA INC
Method of and system for managing multi-dimensional databases using modular-arithmetic based address data mapping processes on integer-encoded business dimensions
InactiveUS6408292B1Improve performanceFast knowledge discoveryData processing applicationsMulti-dimensional databasesData warehouseThe Internet
An improved method of and a system for managing data elements in a multidimensional database (MDB) supported upon a parallel computing platform using modular-arithmetic based address data mapping (i.e. translation) processes on integer-encoded business dimensions. The parallel computing platform has a plurality of processors and one or more storage volumes for physically storing data elements therein at integer-encoded physical addresses in Processor Storage Space (i.e. physical address space in the one or more storage volumes associated with a given processor). The location of each data element in the MDB is specified in MDB Space by integer-encoded business dimensions associated with the data element. A data loading mechanism loads the integer-encoded business dimensions and associated data elements from a data warehouse. The address data mapping mechanism performs a two part address mapping processing. The first step maps the integer-encoded business dimensions associated with each data element to a given processor identifier (which uniquely identifies the processor amongst the plurality of processors of the parallel computing platform). The second step maps the integer-encoded business dimensions associated with each data element into an integer-encoded physical data storage address in Processor Storage Space associated with the processor identified by the processor identifier generated in the first mapping step. The mapping performed in this second step is based upon size of the integer encoded business dimensions. The data management mechanism manages the data elements stored in the storage volumes using the integer-encoded data storage addresses generated during the two-part address data mapping process. The use of modular-arithmetic functions in the two-part address data mapping mechanism ensures that the data elements in the MDB are uniformly distributed among the plurality of processors for balanced loading and processing. The present invention can be used to realize (i) an improved MDB for supporting on-line analytical processing (OLAP) operations, (ii) an improved Internet URL Directory for supporting on-line information searching operations by Web-enabled client machines, as well as (iii) diverse types of MDB-based systems for supporting real-time control of processes in response to complex states of information reflected in the MDB.
Owner:MEC MANAGEMENT LLC +1
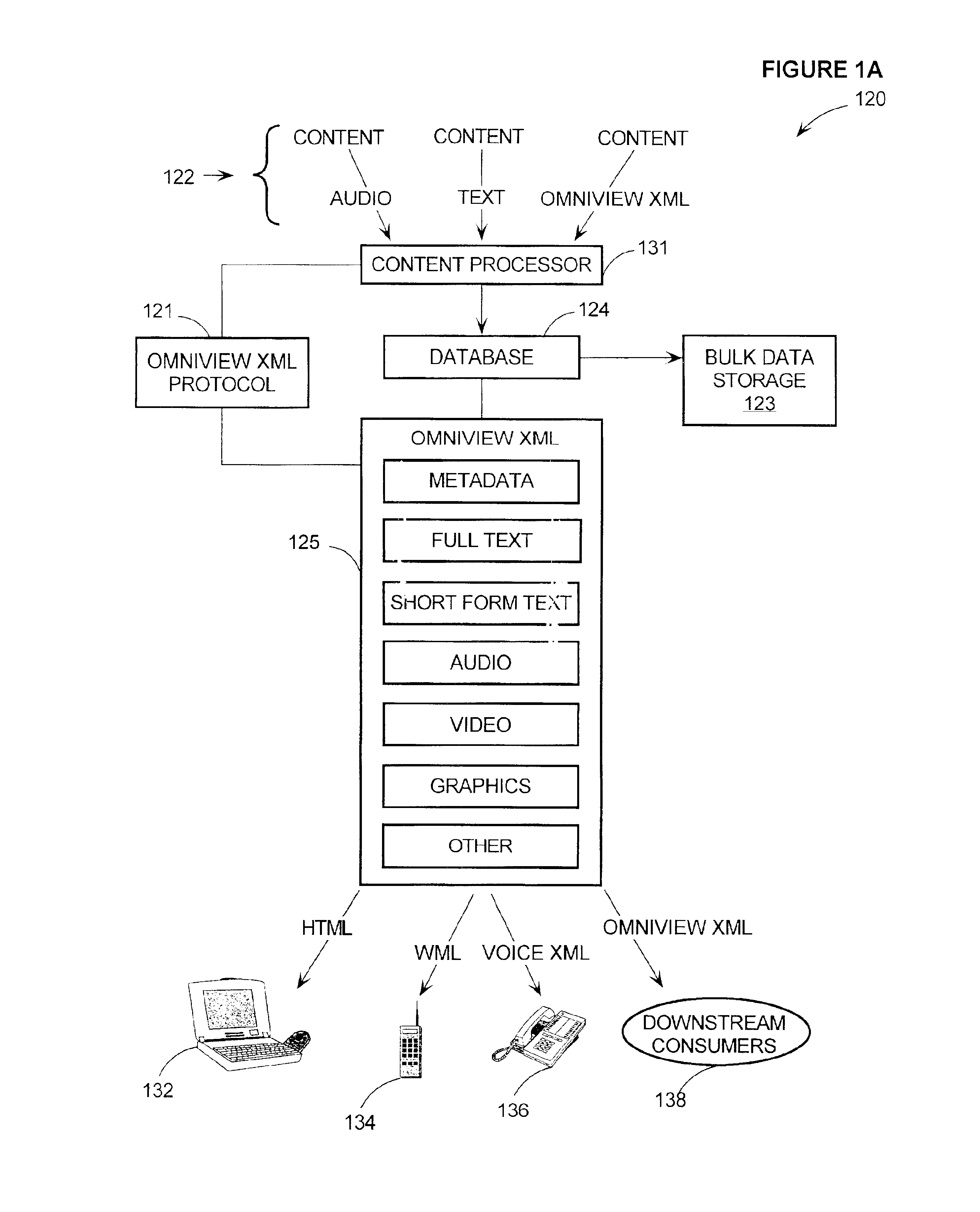
System and method for construction, storage, and transport of presentation-independent multi-media content
InactiveUS7028252B1Increase contentEnsure consistencyData processing applicationsAutomatic exchangesCompositional dataExtensible markup
Owner:ORACLE INT CORP
System and method for extended media retention
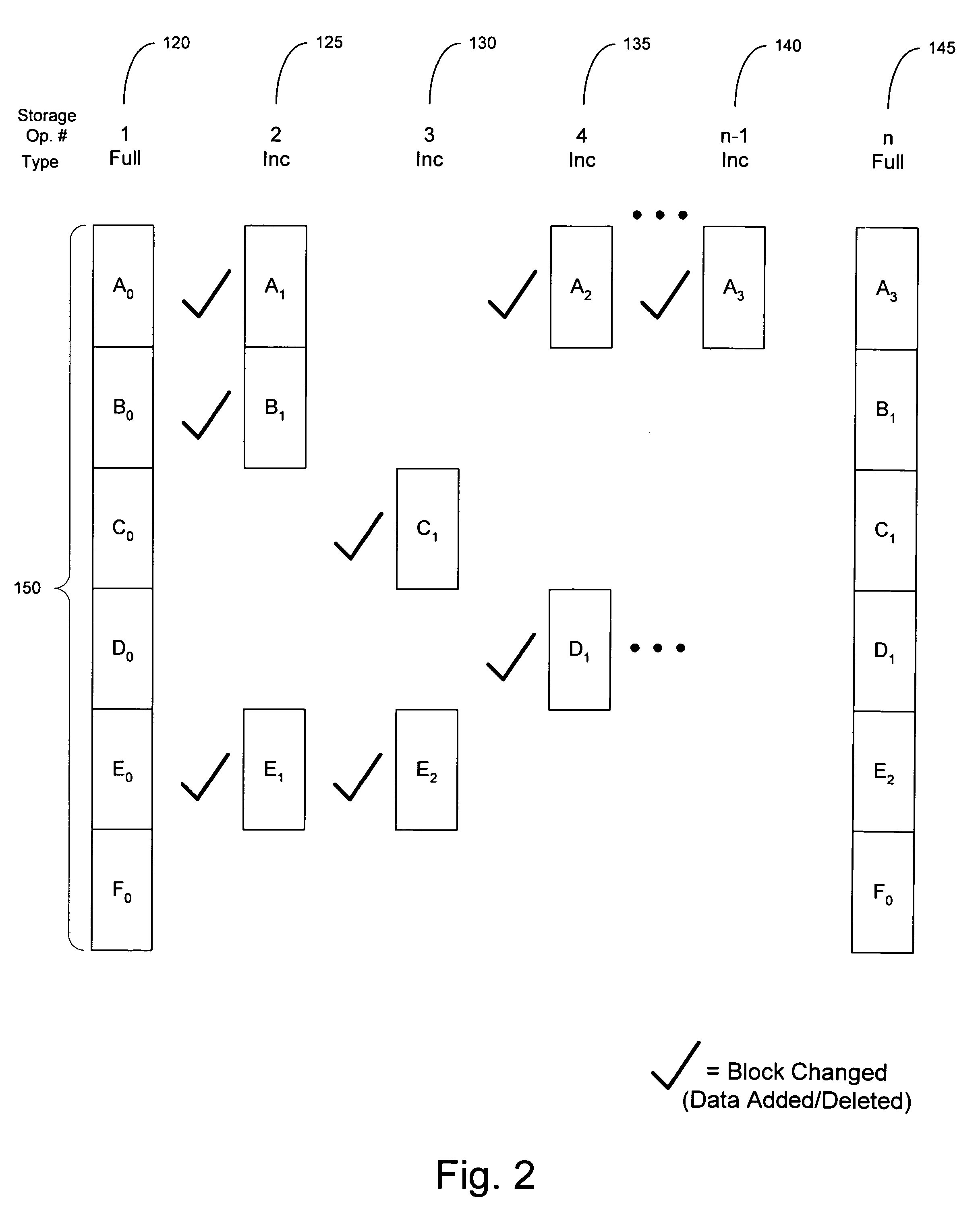
ActiveUS7596586B2High retention rateData processing applicationsInput/output to record carriersData setData element
Owner:COMMVAULT SYST INC
Mobile stamp creation and management for digital communications
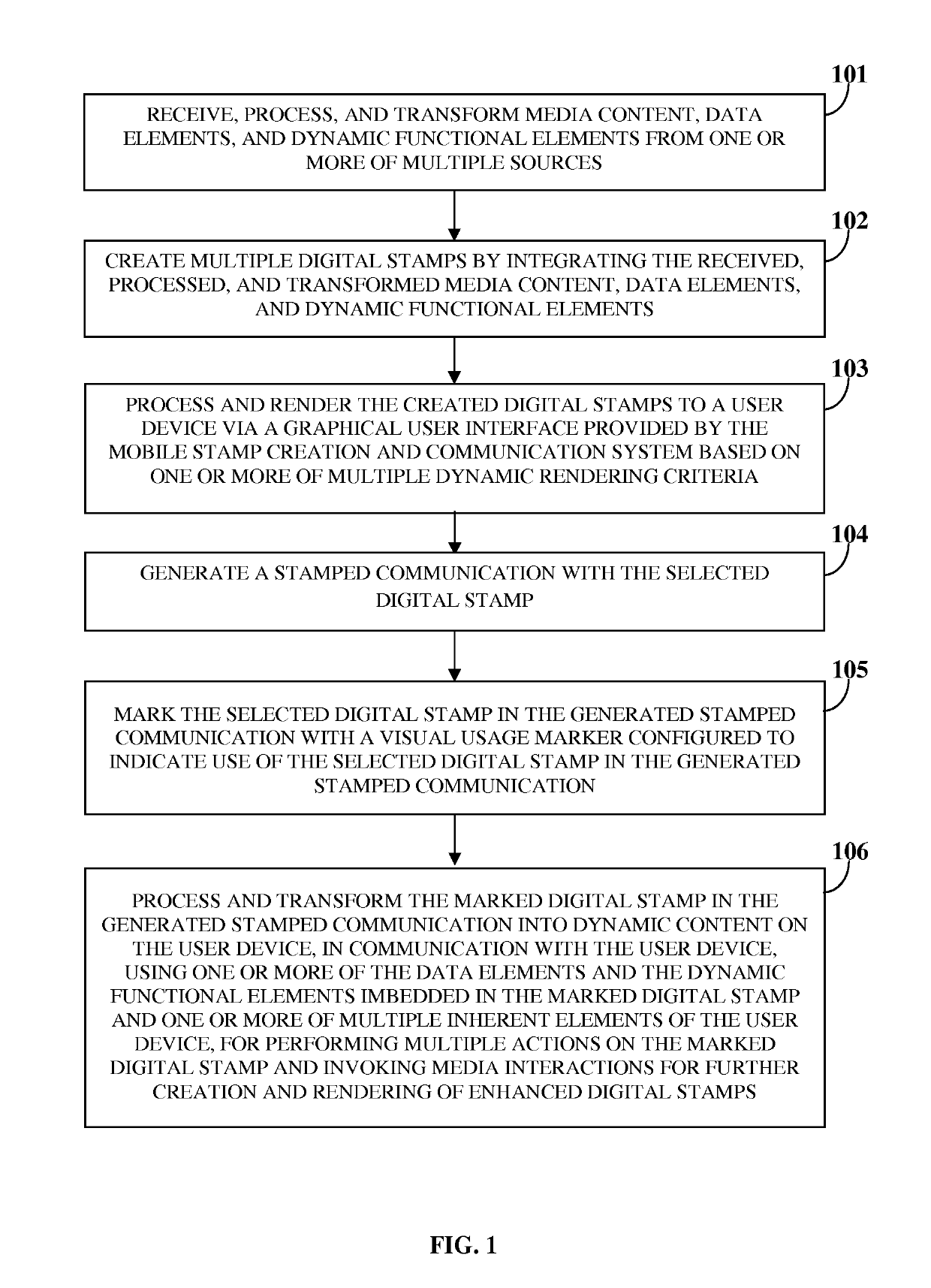
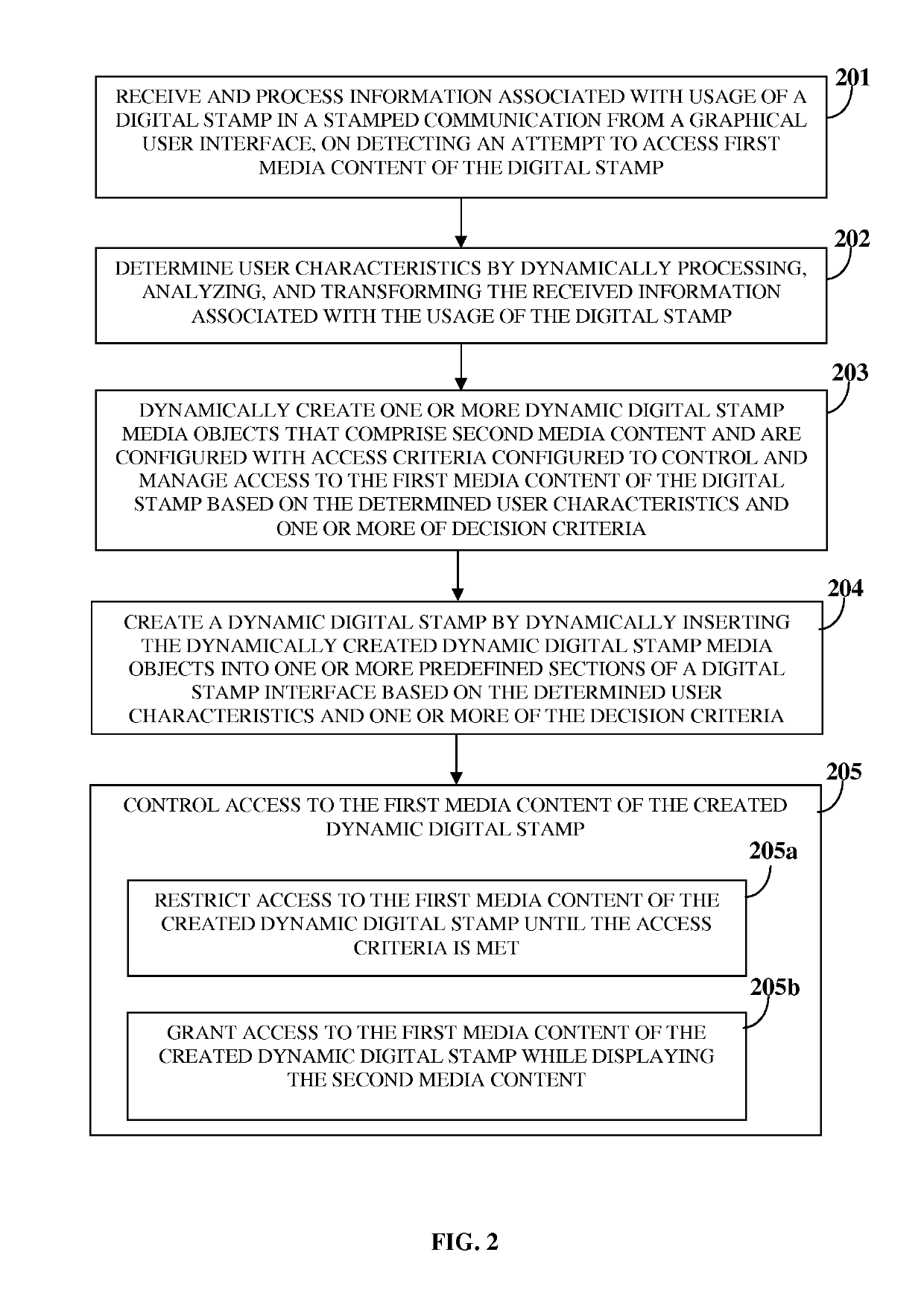
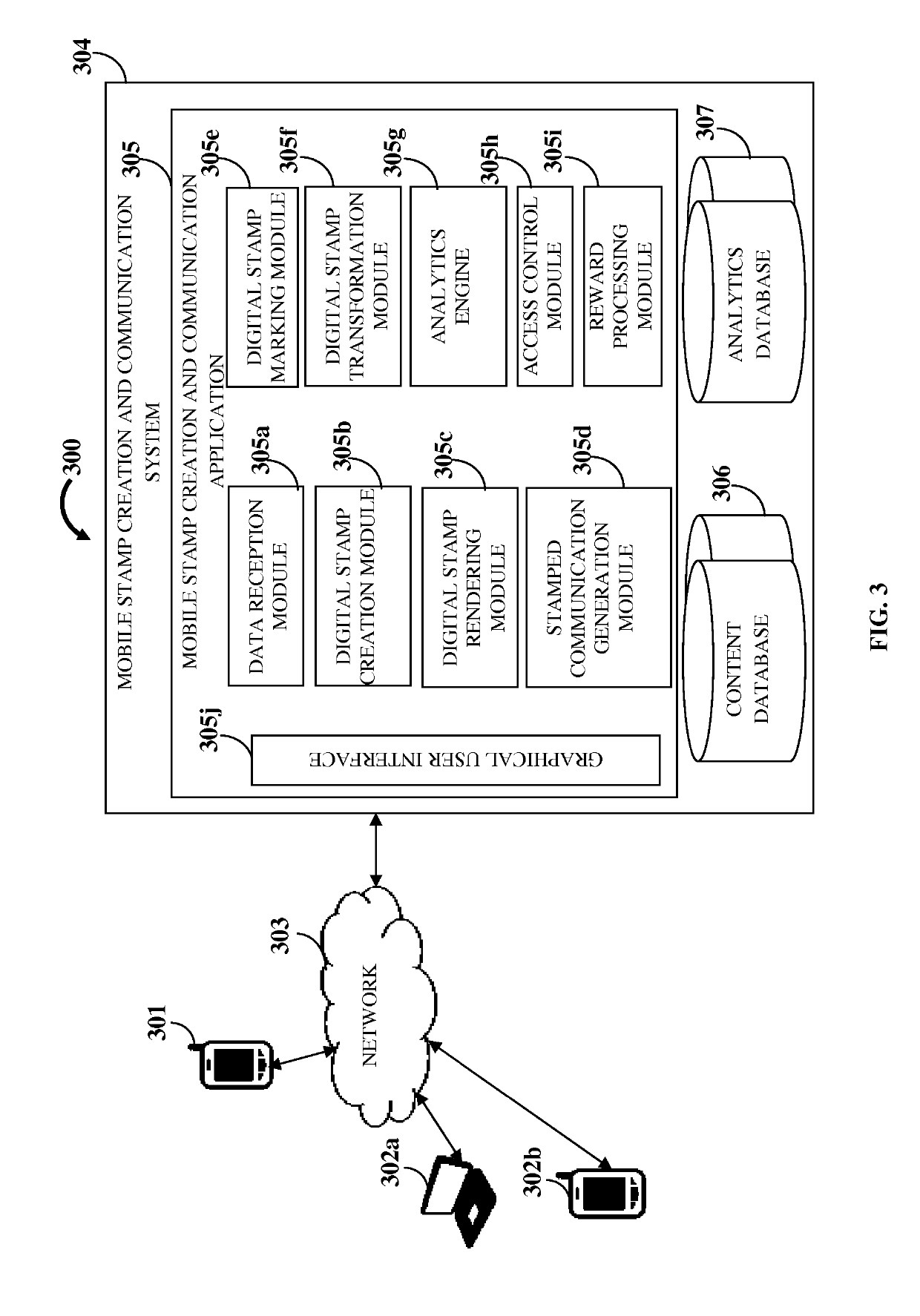
A computer implemented method and a mobile stamp creation and communication system (MSCCS) dynamically creates, renders, and transforms a digital stamp for a stamped communication and media interactions. The MSCCS creates digital stamps by integrating media content, data elements, and dynamic functional elements received from multiple sources. The MSCCS renders the digital stamps to a user device for user selection based on dynamic rendering criteria, generates a stamped communication with the selected digital stamps, and marks the selected digital stamps with a visual usage marker that indicates use of the selected digital stamps in the stamped communication. The MSCCS transforms the marked digital stamps into dynamic content on the user device using data elements and functional elements imbedded in the marked digital stamps and inherent elements of the user device for performing actions on the marked digital stamps and invoking media interactions for creation and rendering of enhanced digital stamps.
Owner:LETT RS
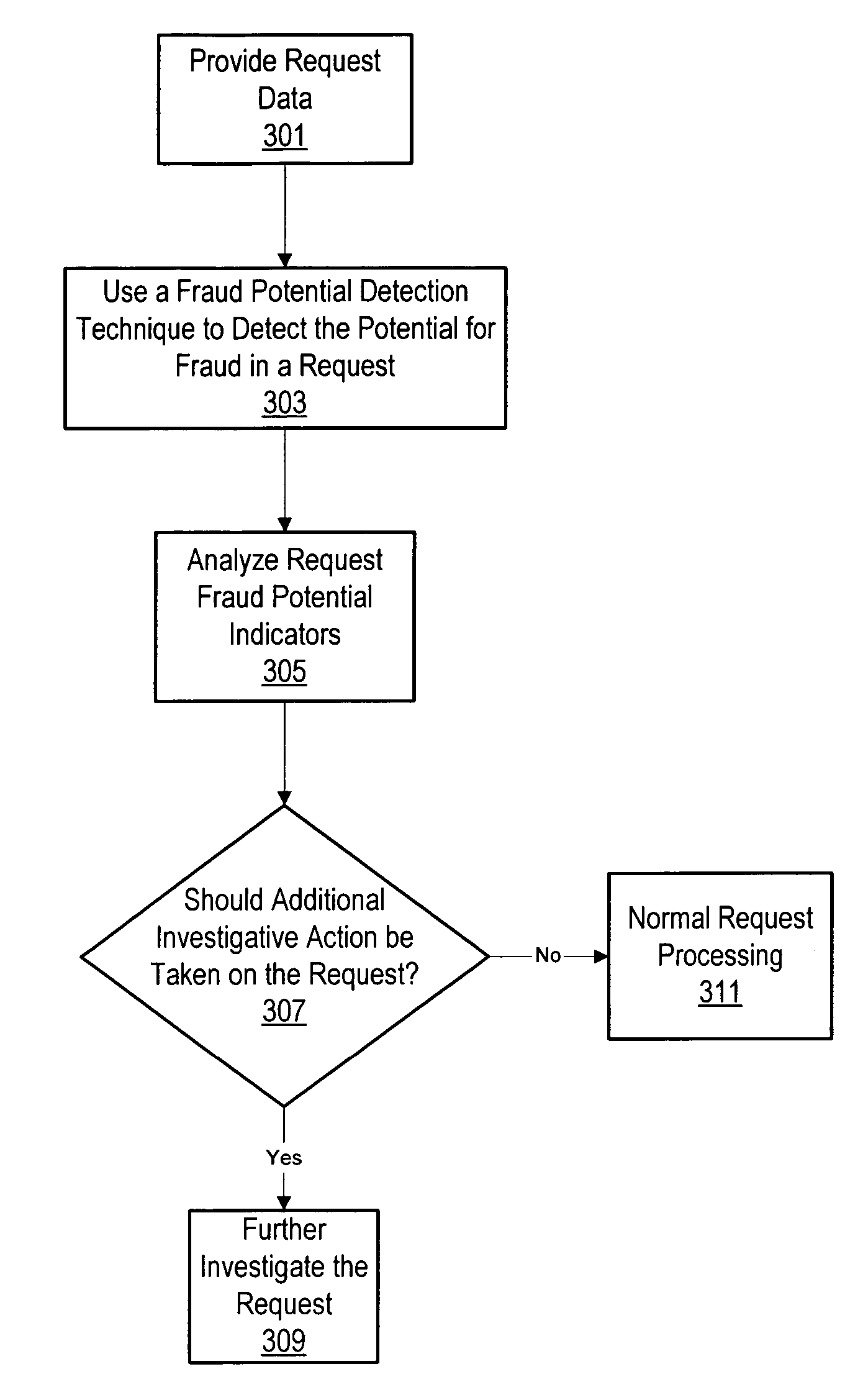
Systems and methods for assessing the potential for fraud in business transactions
InactiveUS20050108063A1High and lower potentialFinanceTelephonic communicationData elementData science
Methods and systems are provided for assessing the potential for fraud of an insurance claim. In some embodiments, request data may be provided to a computer system. In some embodiments, at least one fraud potential indicator may be assessed to the request data from at least one comparison of at least one request data element to at least one fraud model. In some embodiments, a fraud potential indicator may be an estimate of the potential for fraud in an insurance claim. In some embodiments, at least one fraud potential indicator for request data may be assessed based on at least one comparison of at least one request data element to additional insurance data. Some embodiments may include assessing at least one fraud potential indicator for request data based on at least one fraud potential indicator.
Owner:COMP SCI A OF NV
System and method for providing a callback cloud
ActiveUS20130054684A1Avoid the needIncrease contactDigital data information retrievalReservationsSession managementMedia type
A system for providing a callback cloud, comprising an application server operated by a callback cloud service provider, a media server, a session management server, an interaction manager, and an intent analysis engine. The application server receives registrations from callback providers unaffiliated with the callback service provider. The application server is adapted to receive callback requests from users, comprising a specific callback provider from whom a callback is requested, when a requested callback should be made, and allowable media types. The application server directs the callback request to the interaction manager, and the interaction manager sends data elements pertaining to the request to the intent analysis engine and receives therefrom data elements pertaining to the callback request determined based on an analysis of the requester's intent. The interaction manager directs the session management server to initiate a callback, and the session management server provides signaling to the media server to conduct the callback.
Owner:VIRTUAL HOLD TECH
Obfuscating sensitive data while preserving data usability
InactiveUS20090132419A1Computer security arrangementsSecuring communicationConfidentialityData field
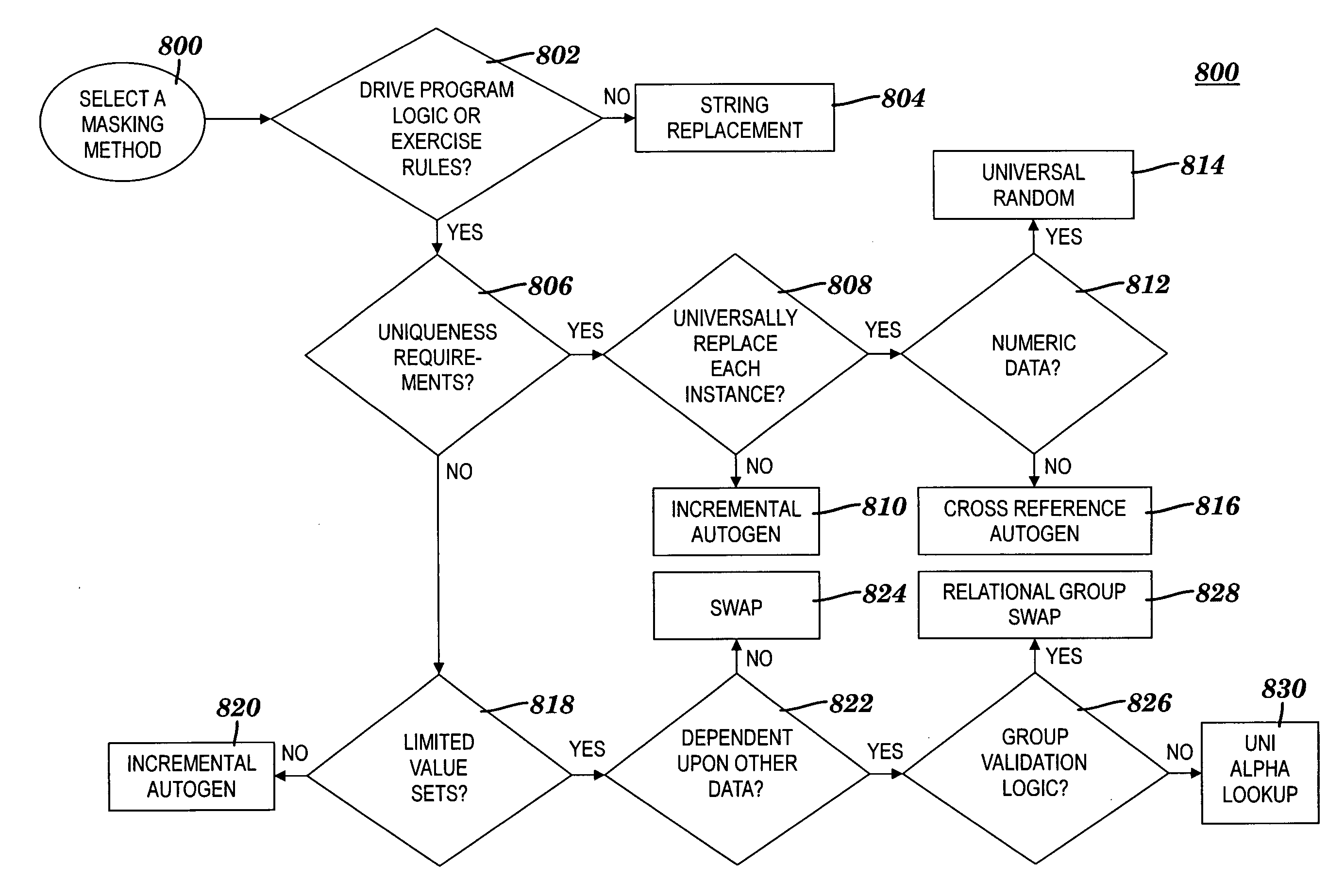
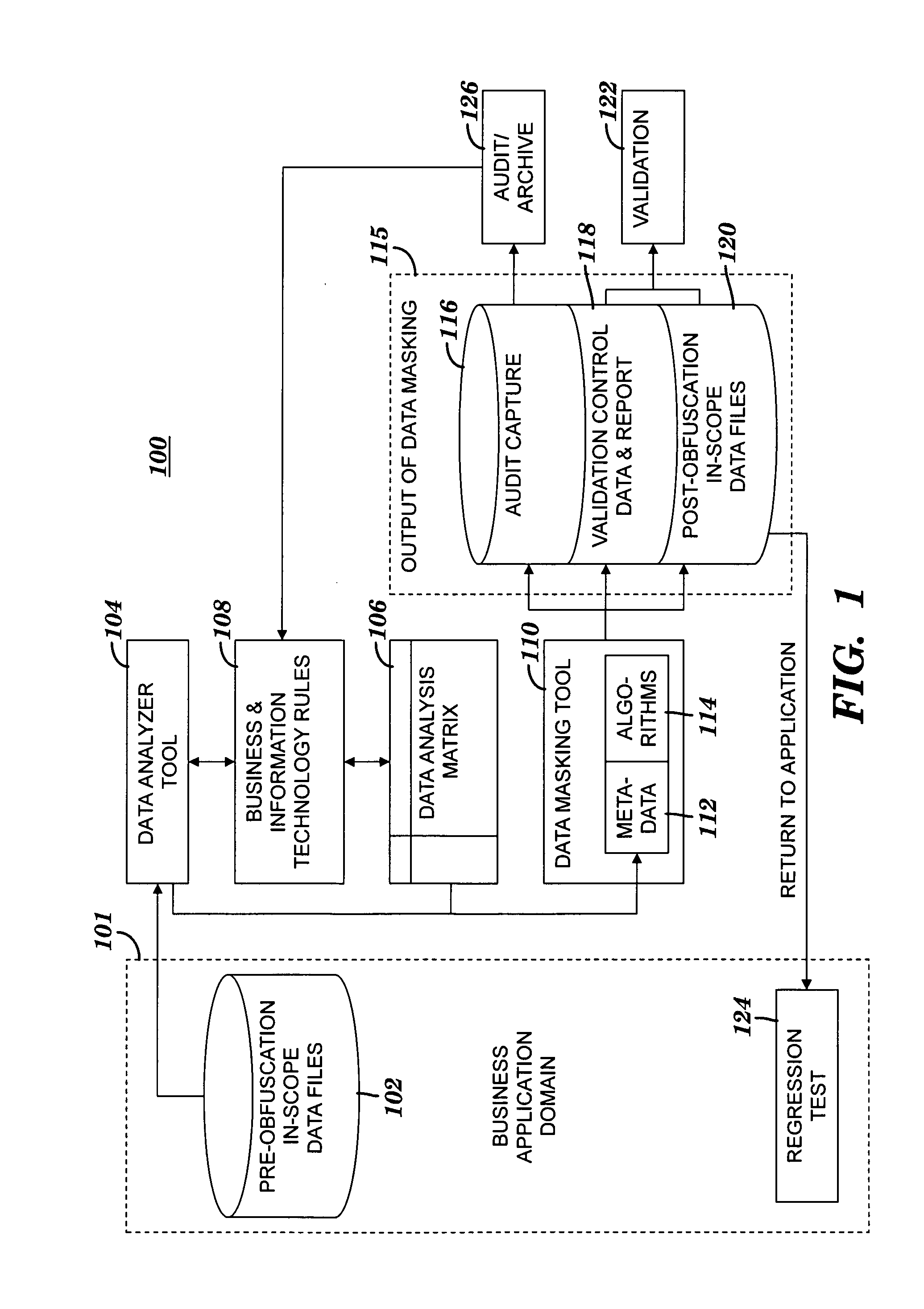
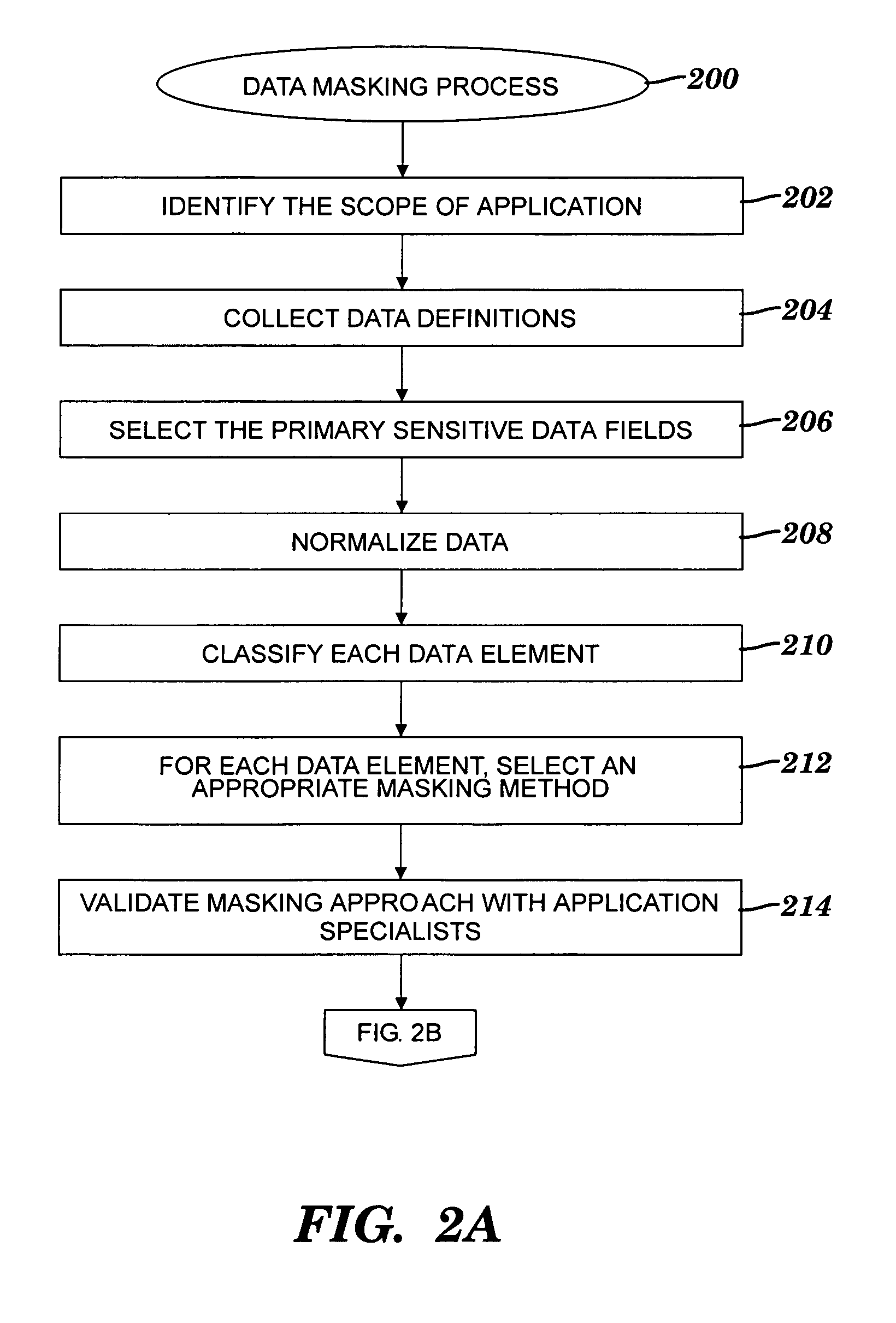
A method and system for obfuscating sensitive data while preserving data usability. The in-scope data files of an application are identified. The in-scope data files include sensitive data that must be masked to preserve its confidentiality. Data definitions are collected. Primary sensitive data fields are identified. Data names for the primary sensitive data fields are normalized. The primary sensitive data fields are classified according to sensitivity. Appropriate masking methods are selected from a pre-defined set to be applied to each data element based on rules exercised on the data. The data being masked is profiled to detect invalid data. Masking software is developed and input considerations are applied. The selected masking method is executed and operational and functional validation is performed.
Owner:IBM CORP
System and method for patient-worn monitoring of patients in geographically dispersed health care locations
InactiveUS7321862B2Minimizing adverse eventsMinimize complicationsPhysical therapies and activitiesComputer-assisted treatment prescription/deliveryMonitoring systemEmergency medicine
A patient-worn monitoring system and method for geographically dispersed health care locations. A patient-worn monitoring system comprises a network, a body-worn monitoring station, a monitoring station server, a remote command center, and a rules engine. The network comprises a first sub-network and a second sub-network. The body-worn monitoring station comprises monitoring equipment. The body worn monitoring station monitors data elements from a patient assigned to a health care location and sends monitored data elements to a monitoring station server via the first sub-network. The monitoring station server receives the monitored data elements from the body worn monitoring station and relays the monitored data elements to the remote command center via the second sub-network. The remote command center receives the monitored data elements from the monitoring station server, associates the monitored data elements with the patient assigned to the health care location, accesses patient data elements indicative of a medical condition associated with the patient, and establishes a patient-specific rule associated with the patient. The rules engine selects data elements from the monitored data elements and the patient data elements associated with the patient and applies the patient-specific rule to the selected data elements continuously and simultaneously. A determination is made whether the patient-specific rule for the patient has been contravened. An alert is issued from the remote command center in the event the patient-specific rule for the patient has been contravened.
Owner:VISICU
Method and System for High Performance Data Metatagging and Data Indexing Using Coprocessors
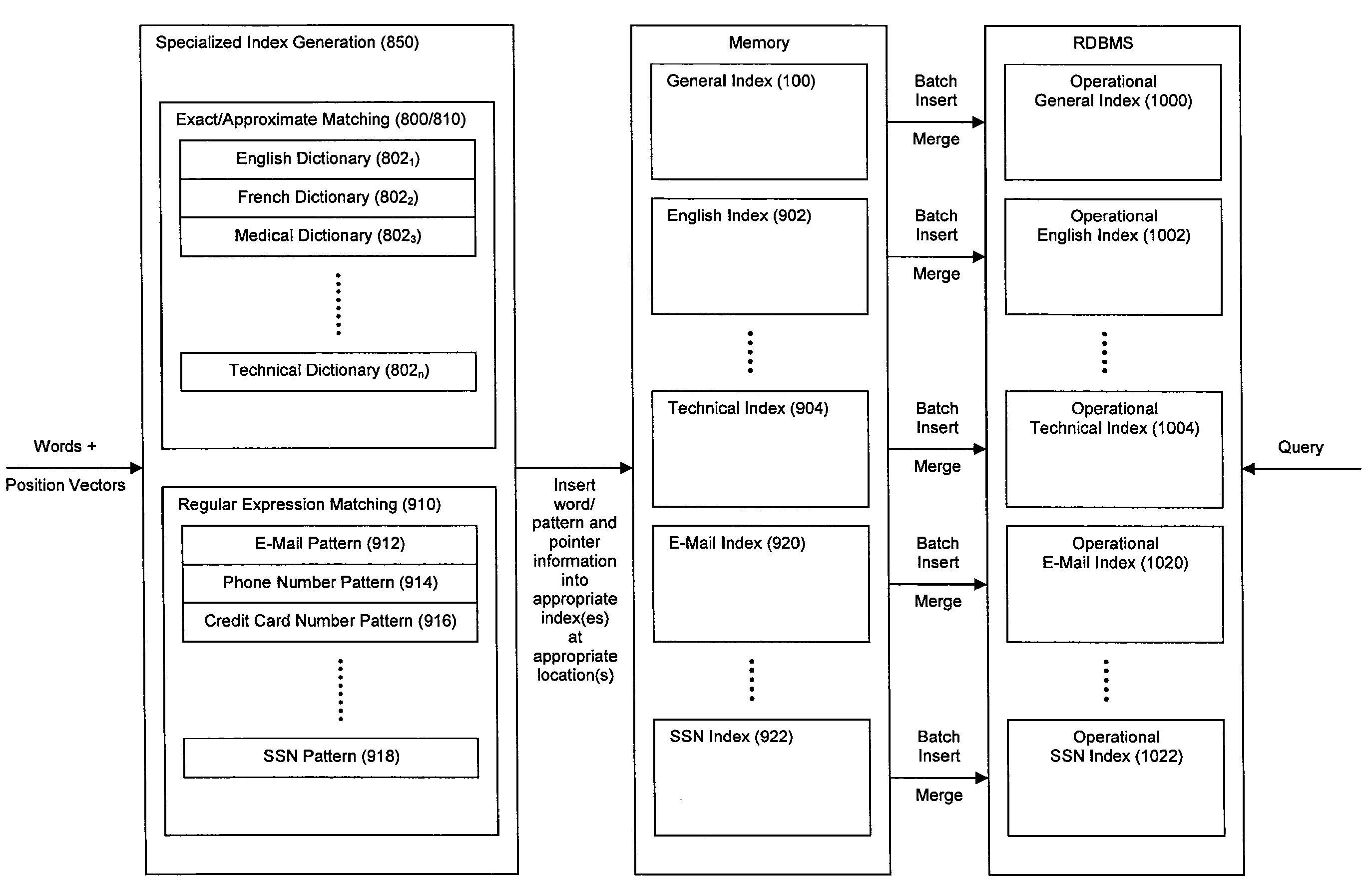
ActiveUS20080114725A1Robust and high performance data searchingHigh indexWeb data indexingFile access structuresData streamCoprocessor
Disclosed herein is a method and system for hardware-accelerating the generation of metadata for a data stream using a coprocessor. Using these techniques, data can be richly indexed, classified, and clustered at high speeds. Reconfigurable logic such a field programmable gate arrays (FPGAs) can be used by the coprocessor for this hardware acceleration. Techniques such as exact matching, approximate matching, and regular expression pattern matching can be employed by the coprocessor to generate desired metadata for the data stream.
Owner:IP RESERVOIR
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com