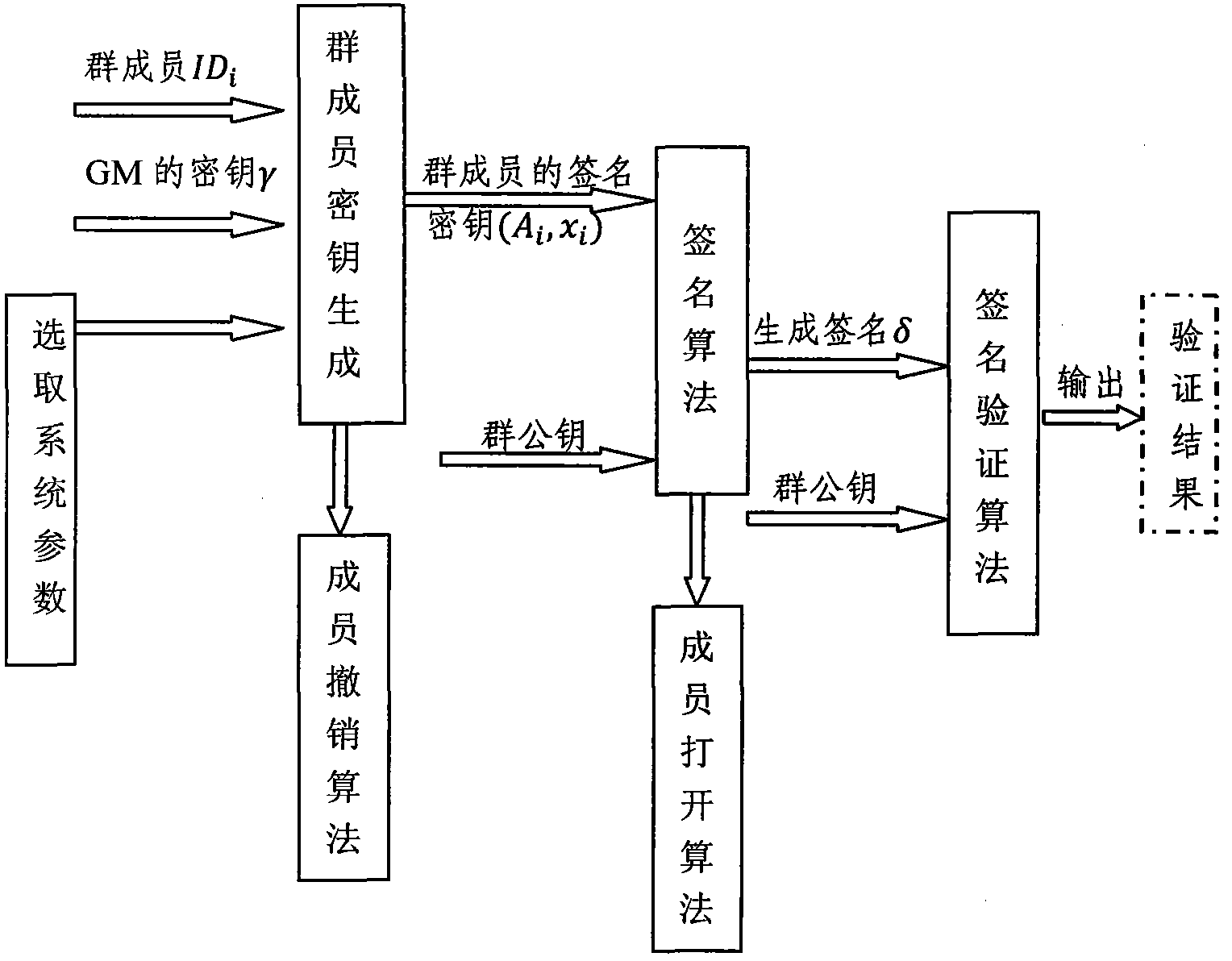
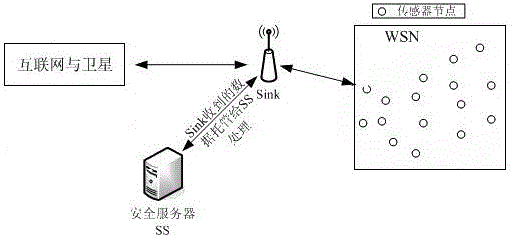
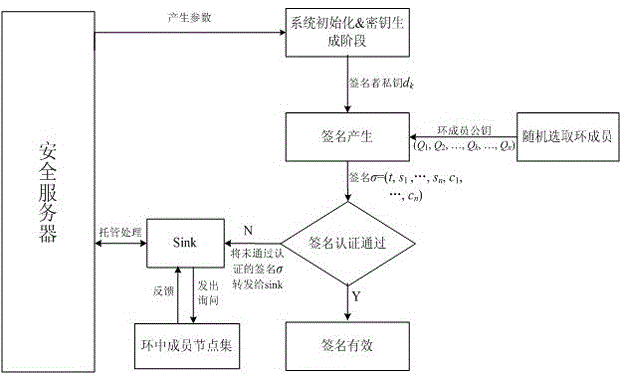
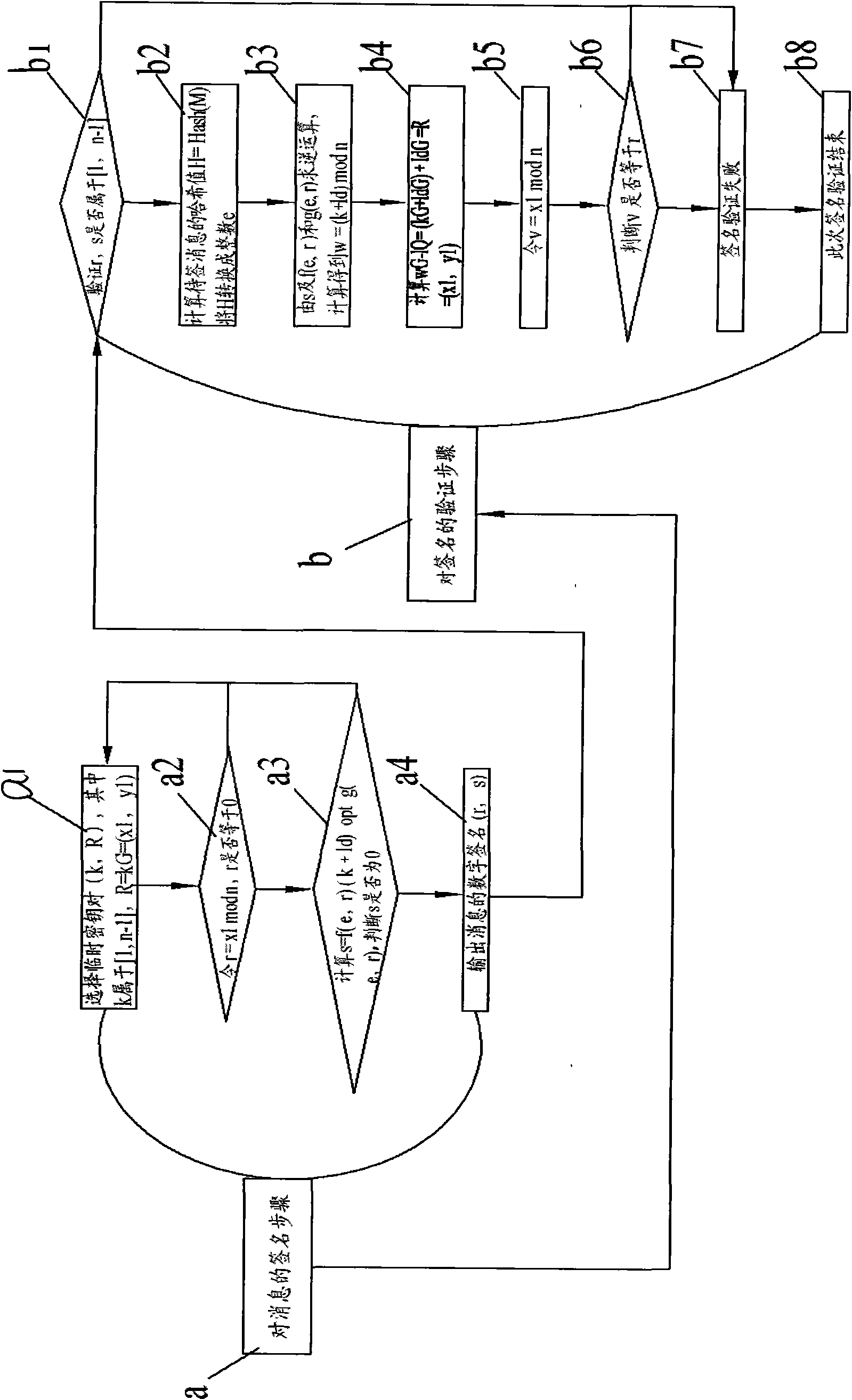
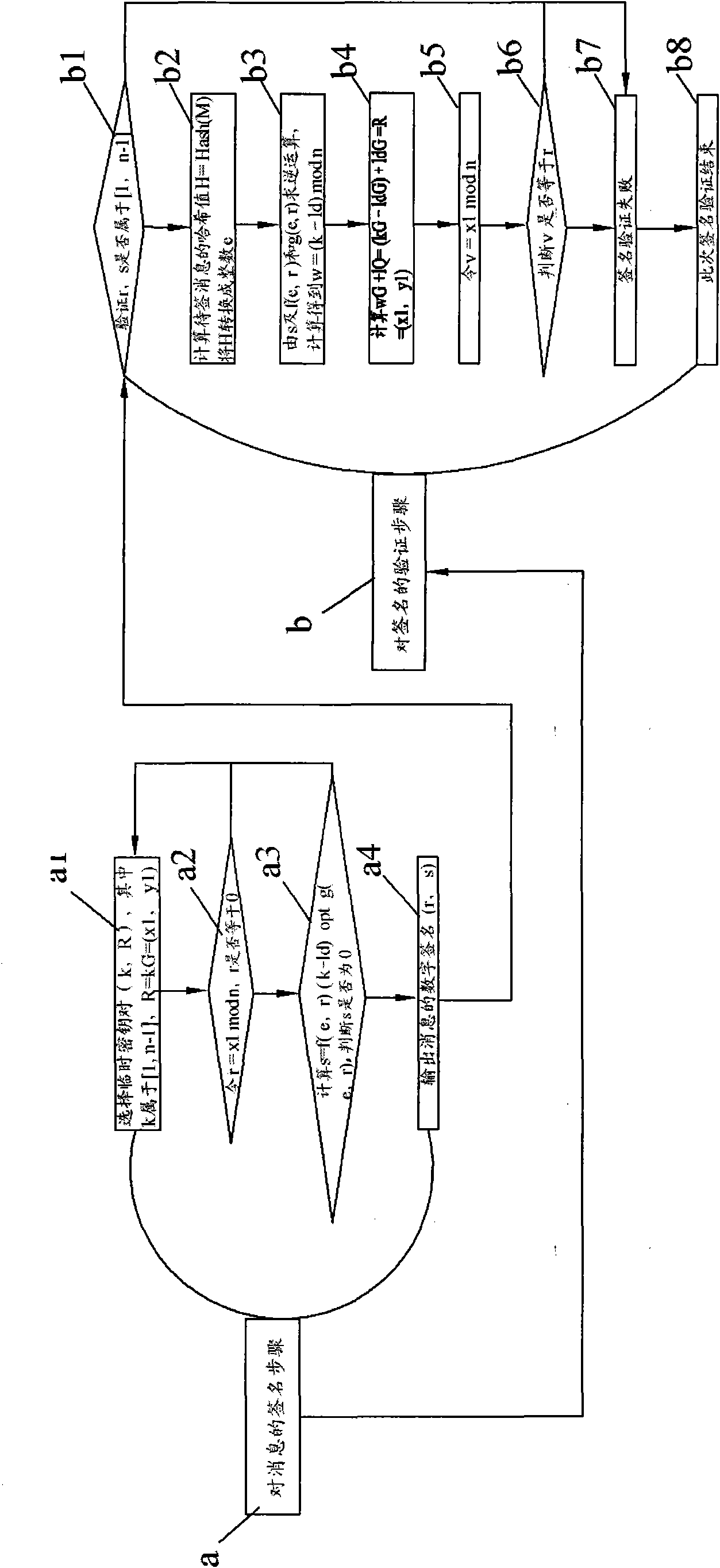
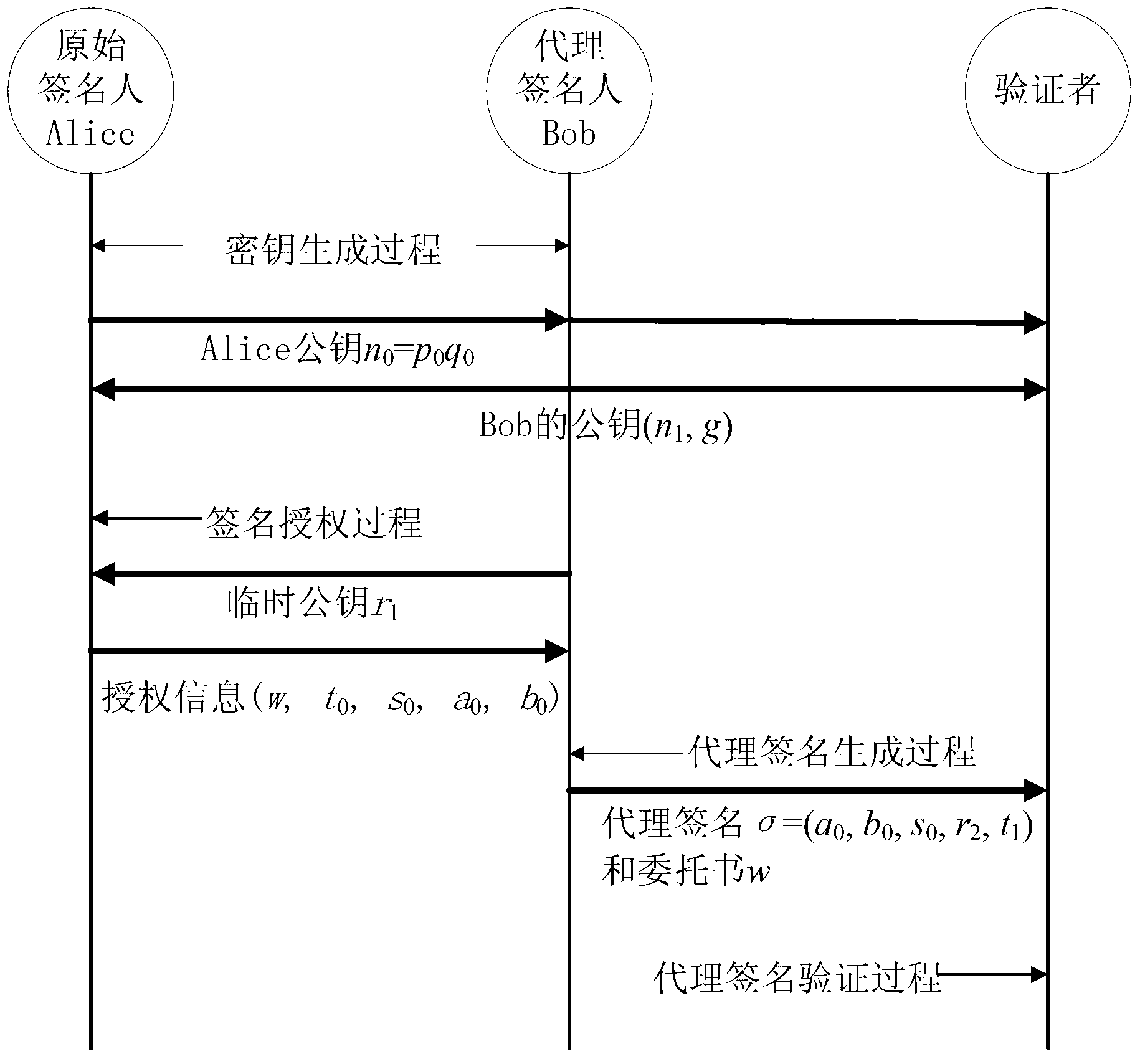
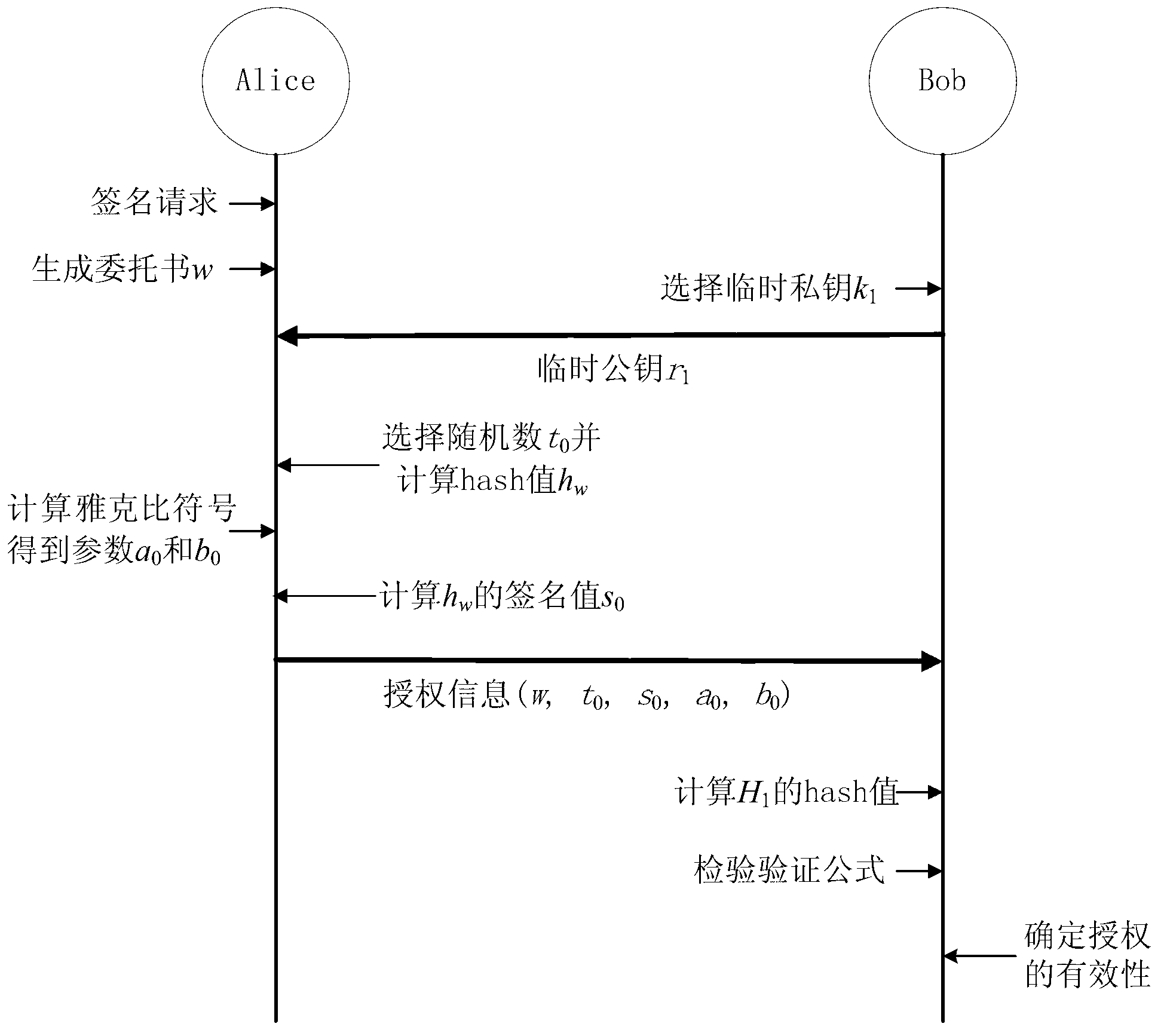
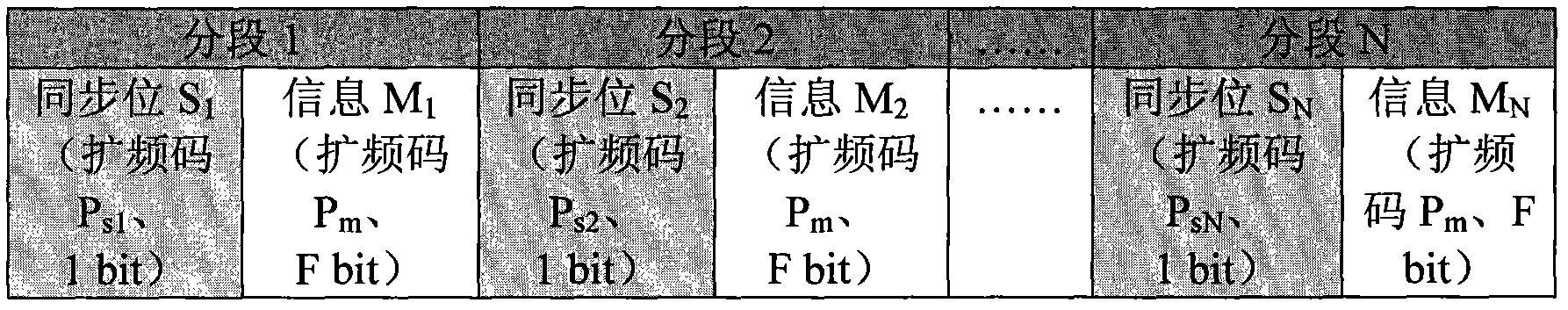
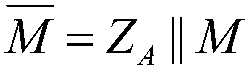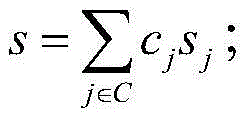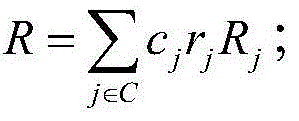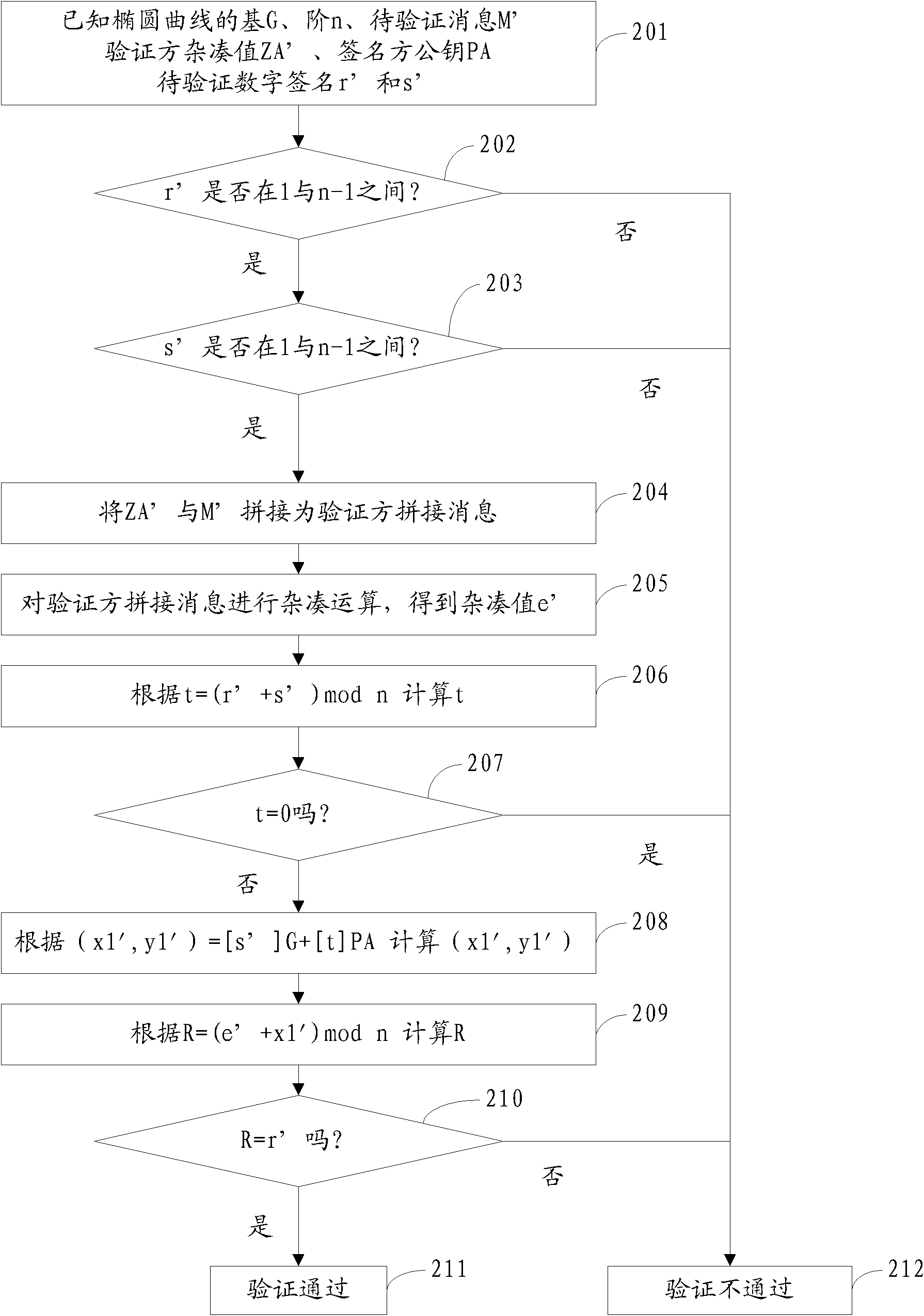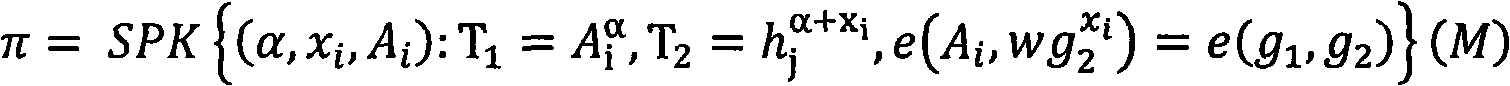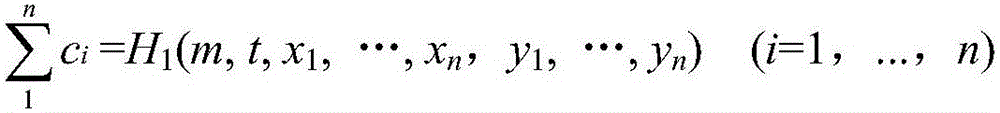Patents
Literature
219 results about "Digital Signature Algorithm" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
The Digital Signature Algorithm (DSA) is a Federal Information Processing Standard for digital signatures, based on the mathematical concept of modular exponentiation and the discrete logarithm problem. DSA is a variant of the Schnorr and ElGamal signature schemes.
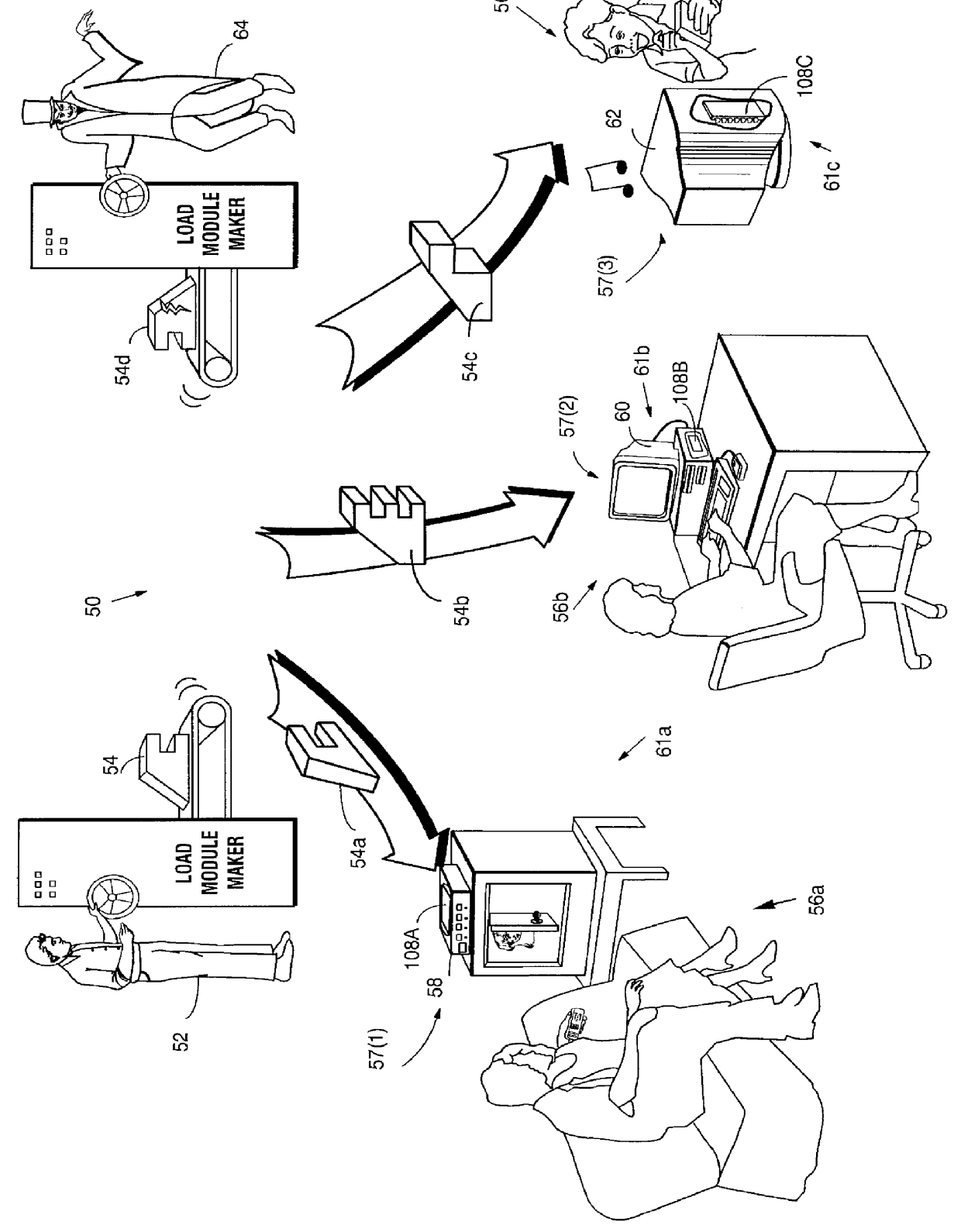
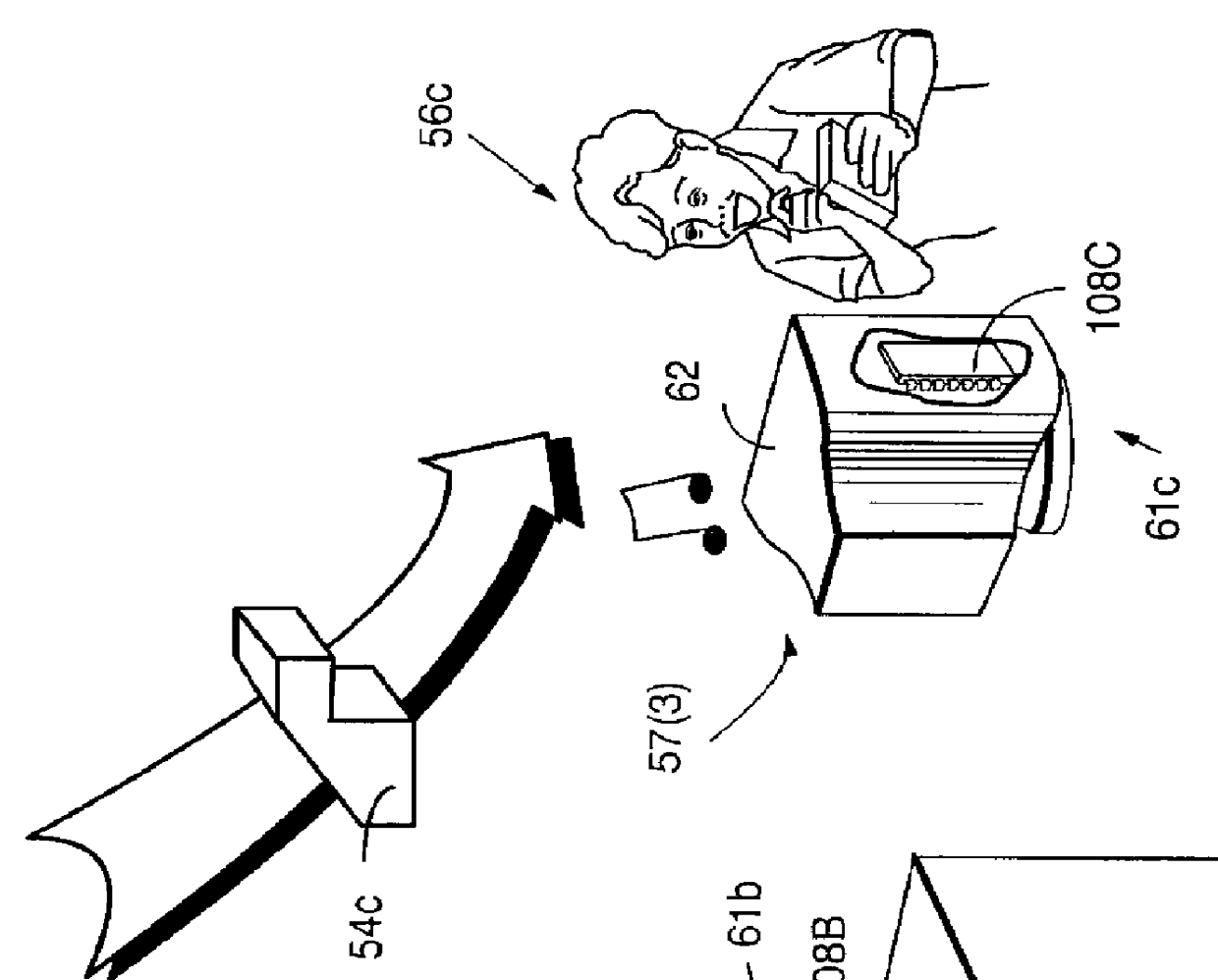
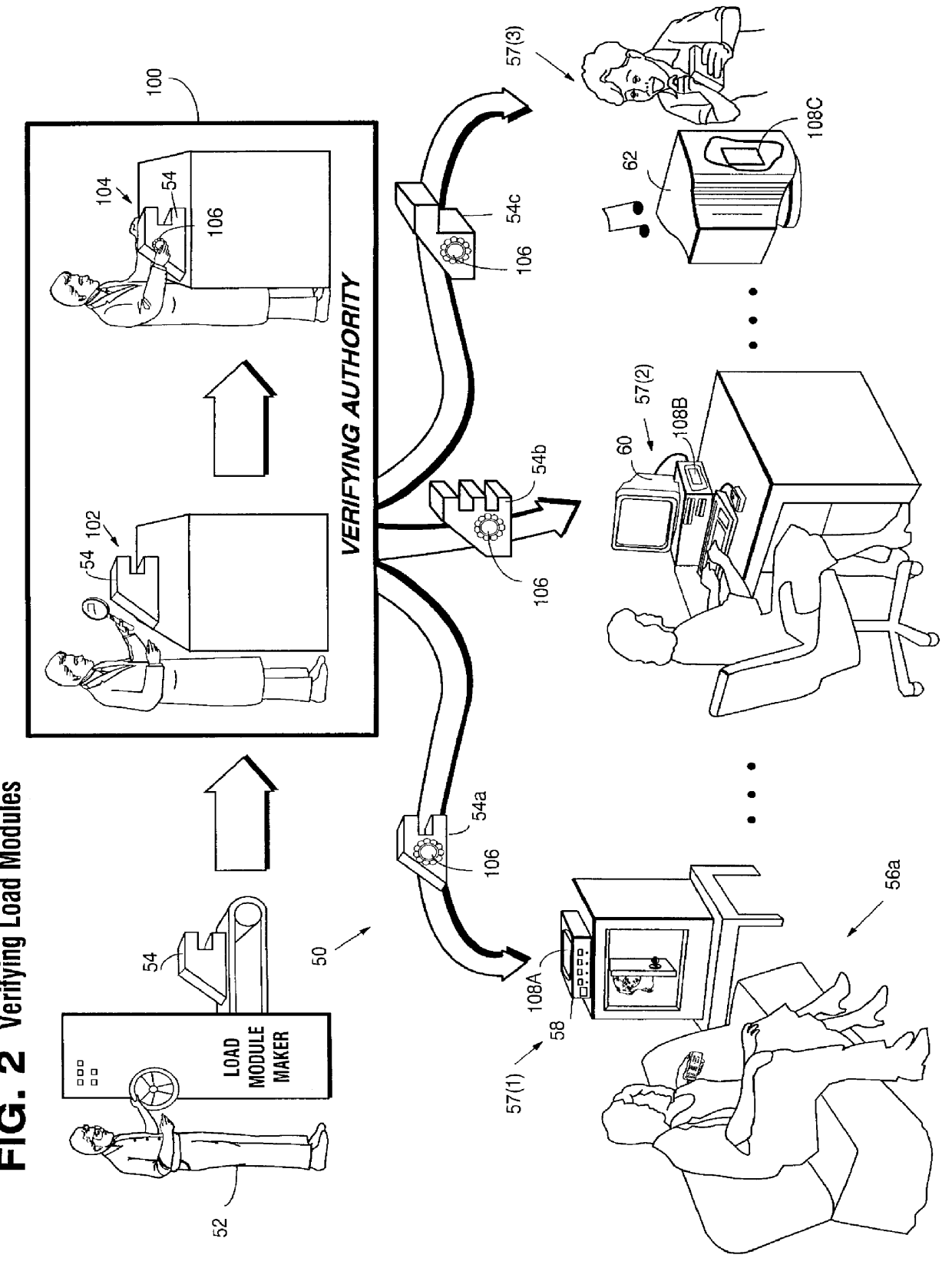
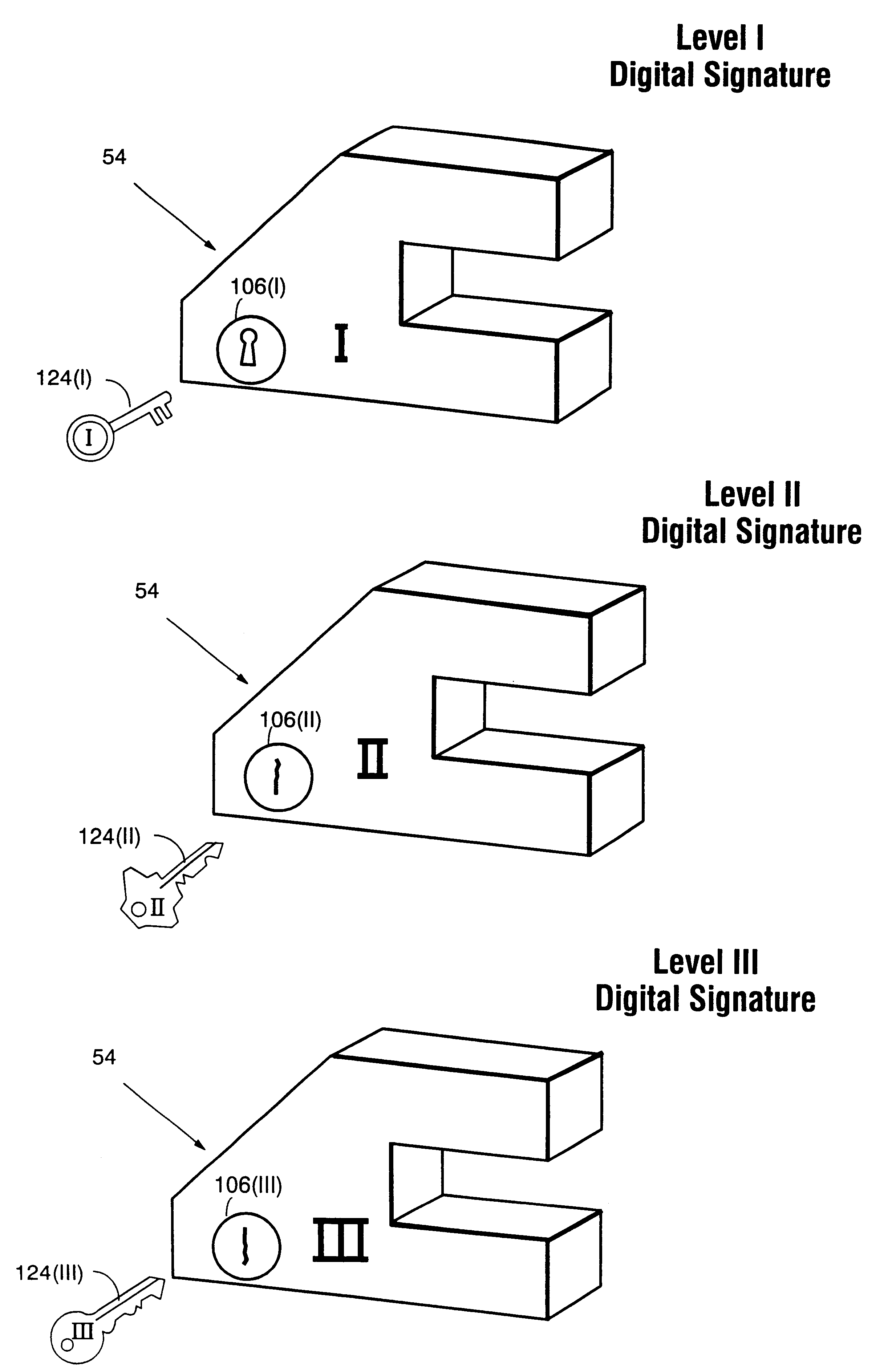
Systems and methods using cryptography to protect secure computing environments
InactiveUS6157721AProtection from disclosureSpeeding up digital signature verificationRecording carrier detailsDigital data processing detailsThird partyTamper resistance
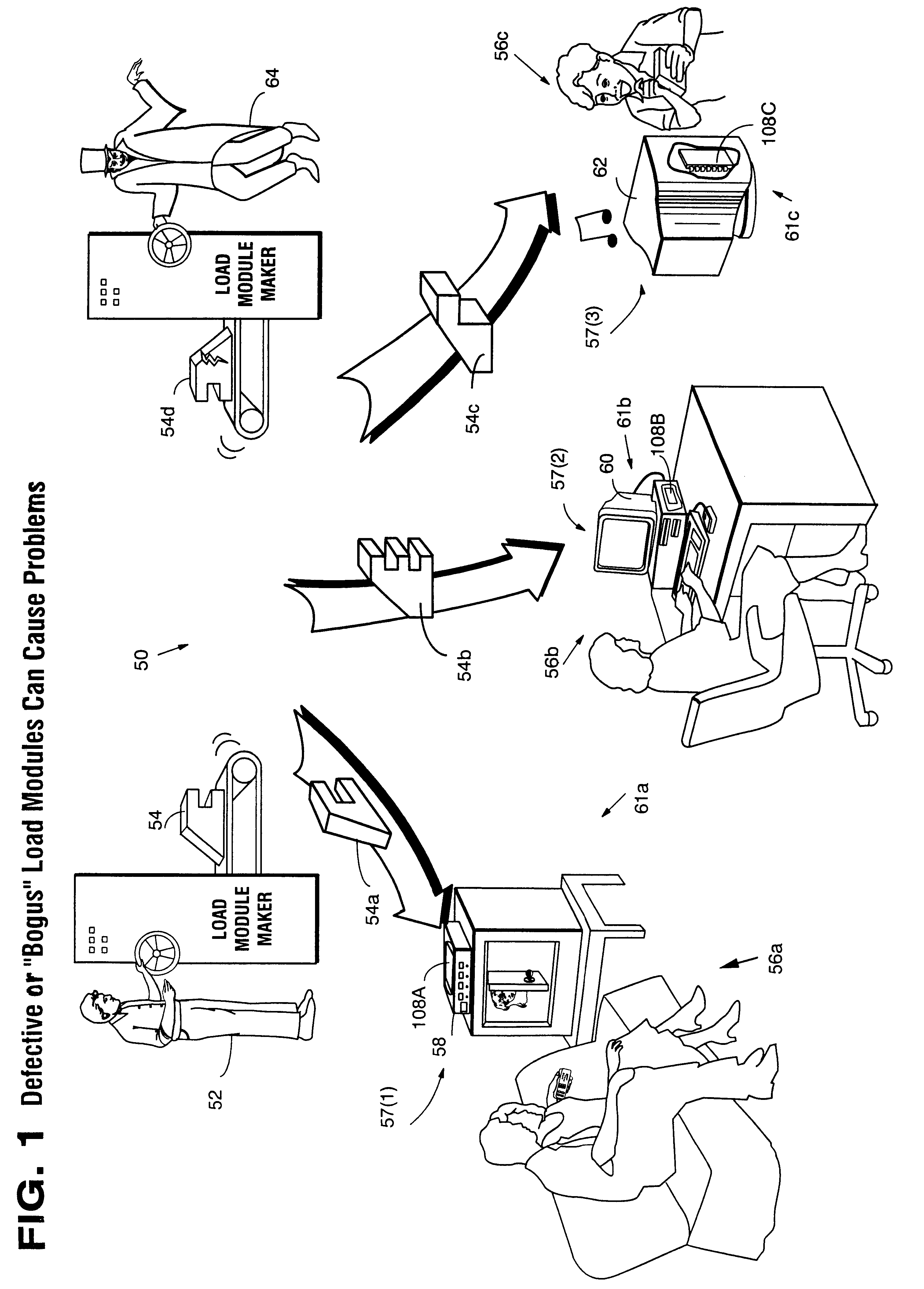
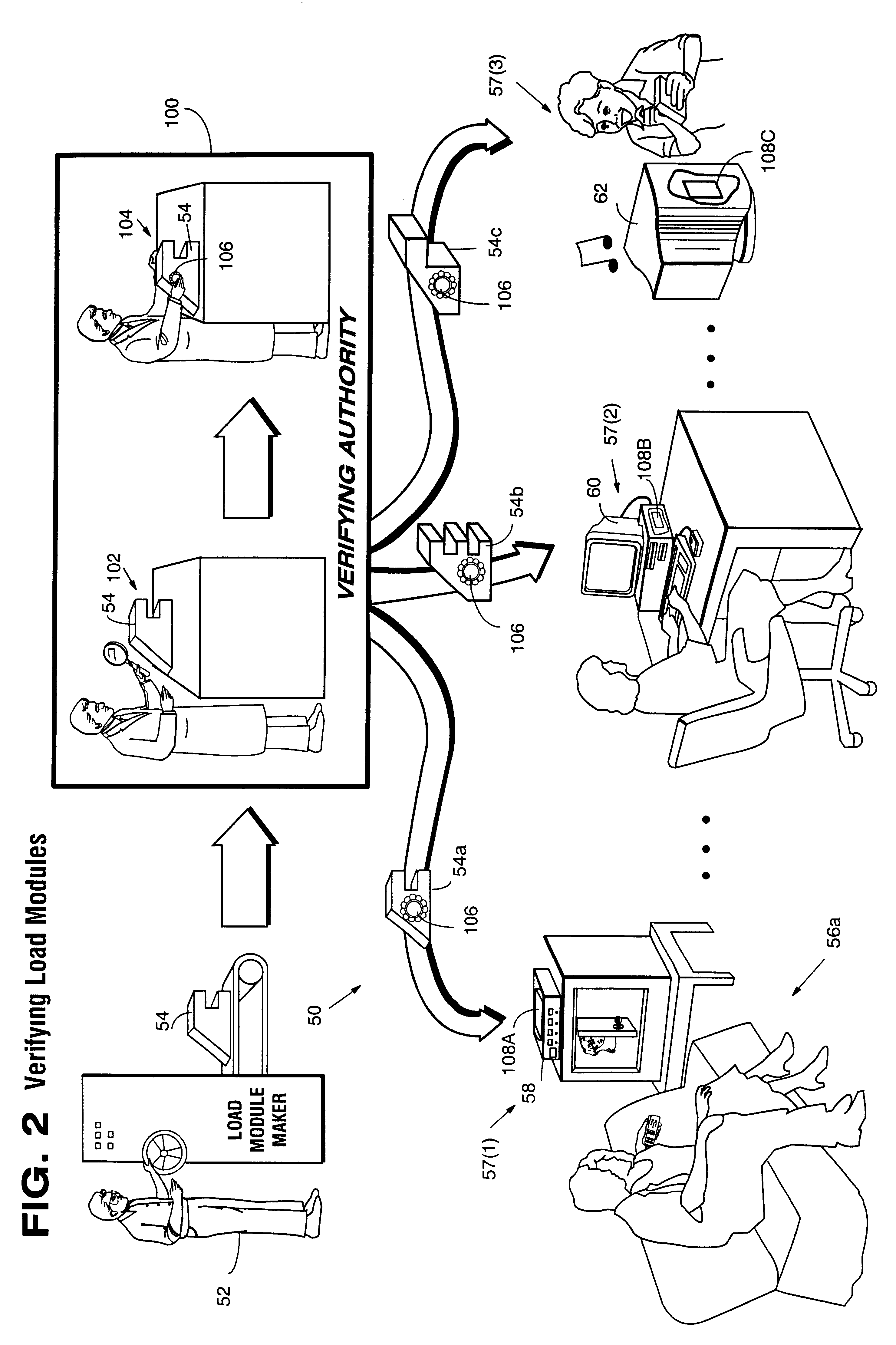
Secure computation environments are protected from bogus or rogue load modules, executables and other data elements through use of digital signatures, seals and certificates issued by a verifying authority. A verifying authority-which may be a trusted independent third party-tests the load modules or other executables to verify that their corresponding specifications are accurate and complete, and then digitally signs the load module or other executable based on tamper resistance work factor classification. Secure computation environments with different tamper resistance work factors use different verification digital signature authentication techniques (e.g., different signature algorithms and / or signature verification keys)-allowing one tamper resistance work factor environment to protect itself against load modules from another, different tamper resistance work factor environment. Several dissimilar digital signature algorithms may be used to reduce vulnerability from algorithm compromise, and subsets of multiple digital signatures may be used to reduce the scope of any specific compromise.
Owner:INTERTRUST TECH CORP
Systems and methods using cryptography to protect secure computing environments
InactiveUS6292569B1Improve connectivityComputationally orRecording carrier detailsError detection/correctionThird partyTamper resistance
Secure computation environments are protected from bogus or rogue load modules, executables and other data elements through use of digital signatures, seals and certificates issued by a verifying authority. A verifying authority-which may be a trusted independent third party-tests the load modules or other executables to verify that their corresponding specifications are accurate and complete, and then digitally signs the load module or other executable based on tamper resistance work factor classification. Secure computation environments with different tamper resistance work factors use different verification digital signature authentication techniques (e.g., different signature algorithms and / or signature verification keys)-allowing one tamper resistance work factor environment to protect itself against load modules from another, different tamper resistance work factor environment. Several dissimilar digital signature algorithms may be used to reduce vulnerability from algorithm.
Owner:INTERTRUST TECH CORP
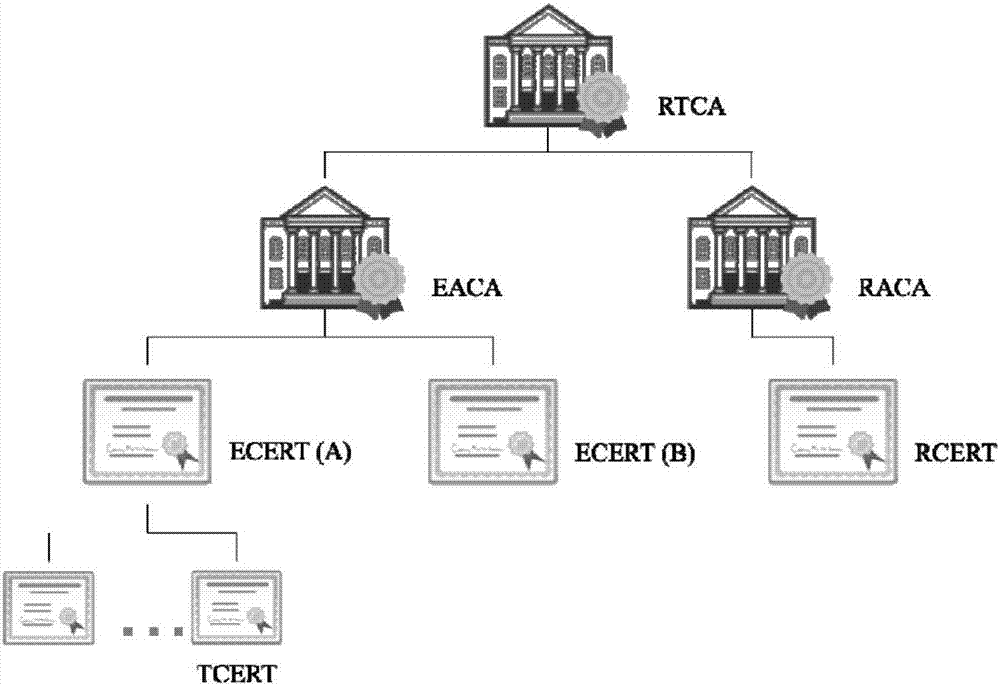
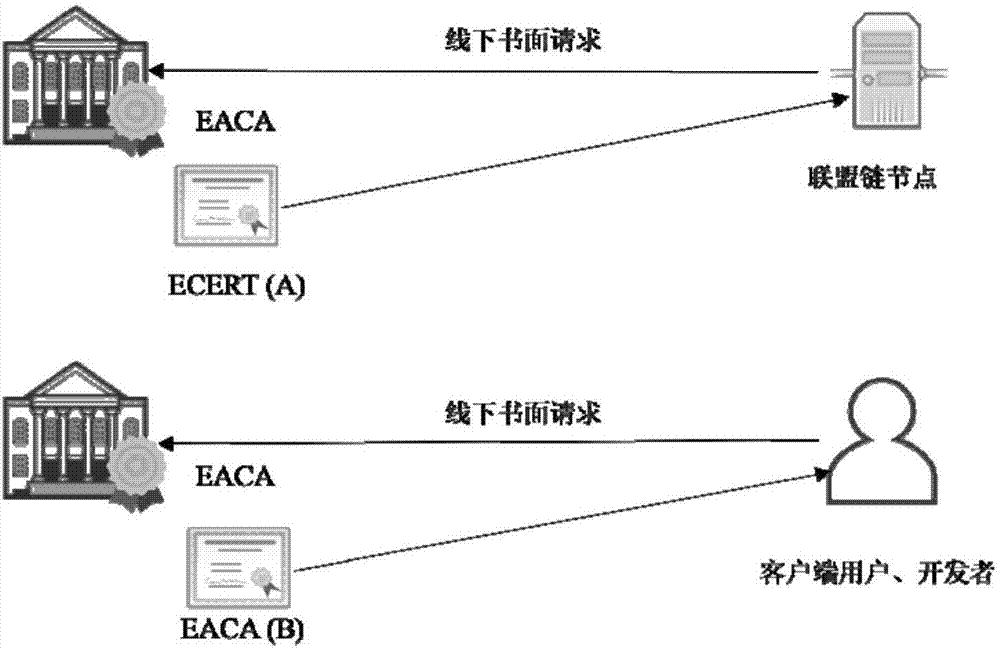
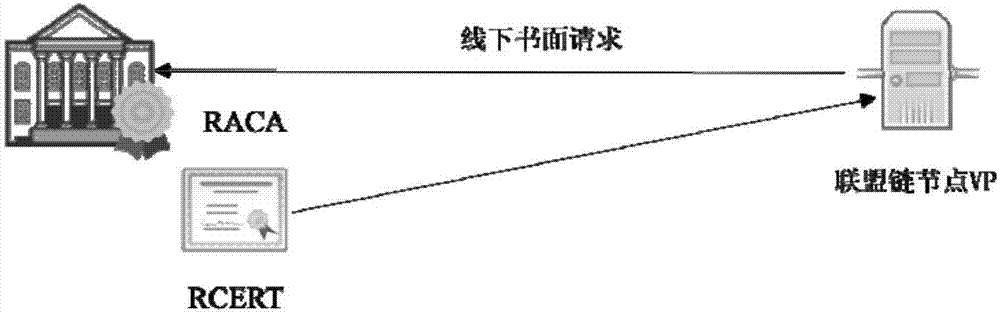
Consortium chain permission control method based on digital certificates and CA authentication system
ActiveCN107426157AProcess controlSecurityUser identity/authority verificationGranularityDigital Signature Algorithm
The invention discloses a consortium chain permission control method based on digital certificates and a CA authentication system. In a consortium chain, the enrollment control and automatic authorization of the consortium chain are realized through a layered digital certificate issuance system. The method of the invention pre-defines three kinds of permission mechanisms for respectively controlling enrollment permissions between consortium chain nodes, role permissions of the consortium chain nodes and access permissions of blockchain users. Three kinds of digital certificates including the enrollment certificate, role certificate and transaction certificate are used for respectively controlling the three permissions of node enrollment, role identification and client enrollment. An internationally accepted elliptic curve digital signature algorithm or a national crypto digital signature algorithm is used for achieving the generation of the digital certificates and secure message signature and validation, the defects of being large in permission granularity of a traditional blockchain or even having no enrollment functions and the like are overcome, the blockchain users are provided with anonymous transaction features, the security of blockchain transactions is improved, and the privacy needs of the users are met.
Owner:HANGZHOU QULIAN TECH CO LTD
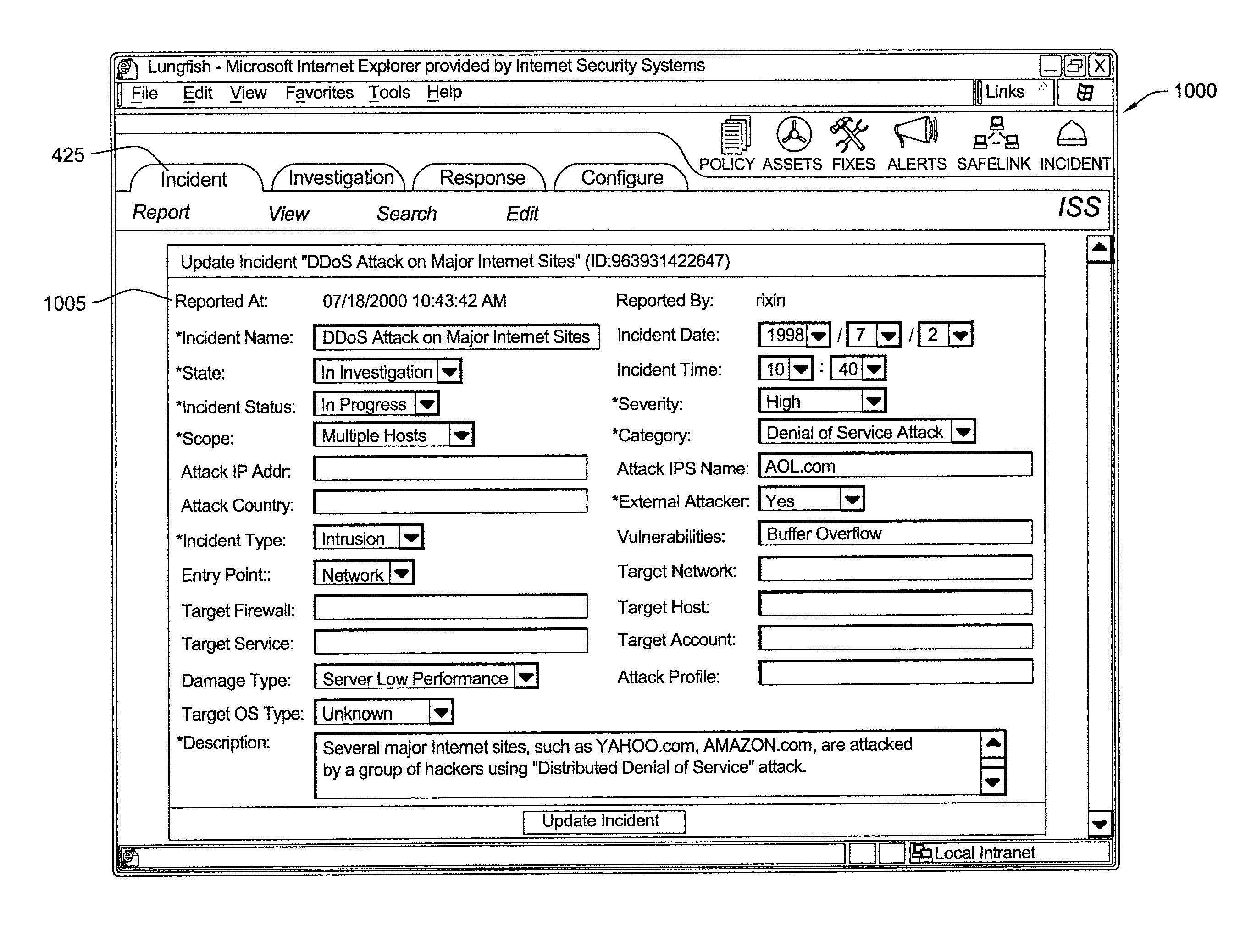
Method and System for Creating a Record for One or More Computer Security Incidents
ActiveUS20080016569A1Avoid unsafe incidentsMemory loss protectionError detection/correctionSafety management systemsDigital Signature Algorithm
A security management system can log, investigate, respond, and track computer security incidents that can occur in a networked computer system. In other words, the security management system can produce a security record of information related to the tracking of suspicious computer activity or actual computer security threats, such as denial of service attacks or other similar compromises to computers or computer networks. The security record can include, but is not limited to, date and times of computer security incidents, a name for a particular security incident, a security management system user, and a potential source of the computer security incident. The security record can be designed as a running log that saves or records all activity of a computer incident source as well as the activity of the security team responding to the computer incident source. To produce the security record, all data that relates to a computer incident and all data that relates to a computer incident response can be sent to a separate protected database, where data is protected by digital signature algorithms (DSAs).
Owner:KYNDRYL INC
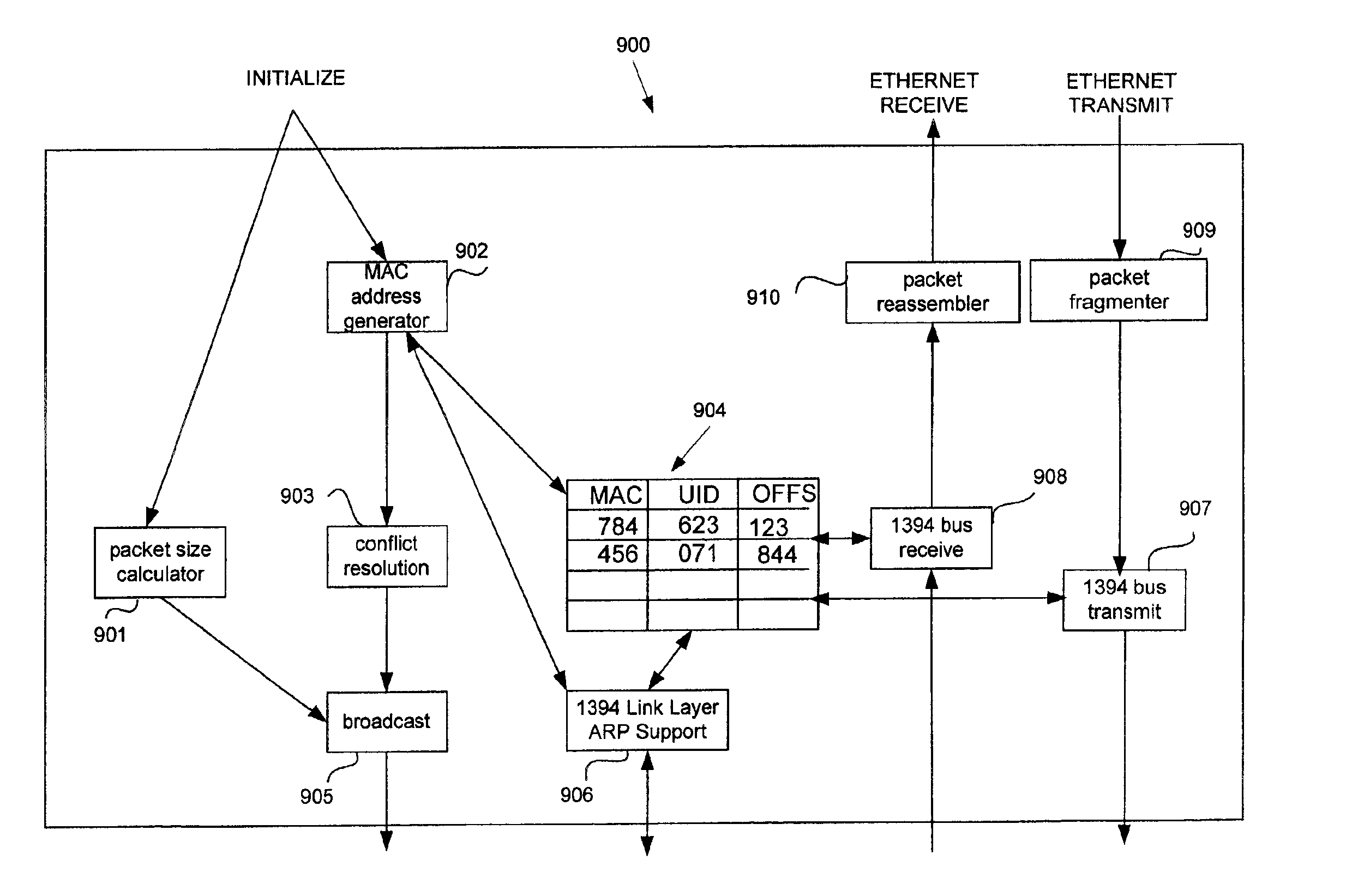
Method and apparatus for emulating ethernet functionality over a serial bus
InactiveUS6977939B2Time-division multiplexNetworks interconnectionNetwork packetDigital Signature Algorithm
The invention allows applications to transparently use a bus, such as the IEEE-1394 serial bus, as if it were an Ethernet (IEEE 802.3). In a conventional Ethernet, each node is assigned a unique 6-byte MAC address in order to receive frames addressed to it over the LAN. According to the invention, IEEE-1394 bus node identifiers are mapped to Ethernet MAC addresses using for example a digital signature algorithm. Ethernet frames are then “wrapped” into 1394 bus packets and addressed to the destination node using the hashed address. The receiver unwraps the 1394 packet and restores the Ethernet frame to its original form. An optimum packet size for transmission of Ethernet packets over the 1394 bus is selected with reference to speed topology maps in the 1394 bus nodes, and this optimum size is transmitted to bus nodes. This packet size is reported to TCP to specify the packet size, and all packets larger than that size are fragmented and reassembled at the receiving node. The protocol works transparently across networks that are linked via bridges.
Owner:MICROSOFT TECH LICENSING LLC
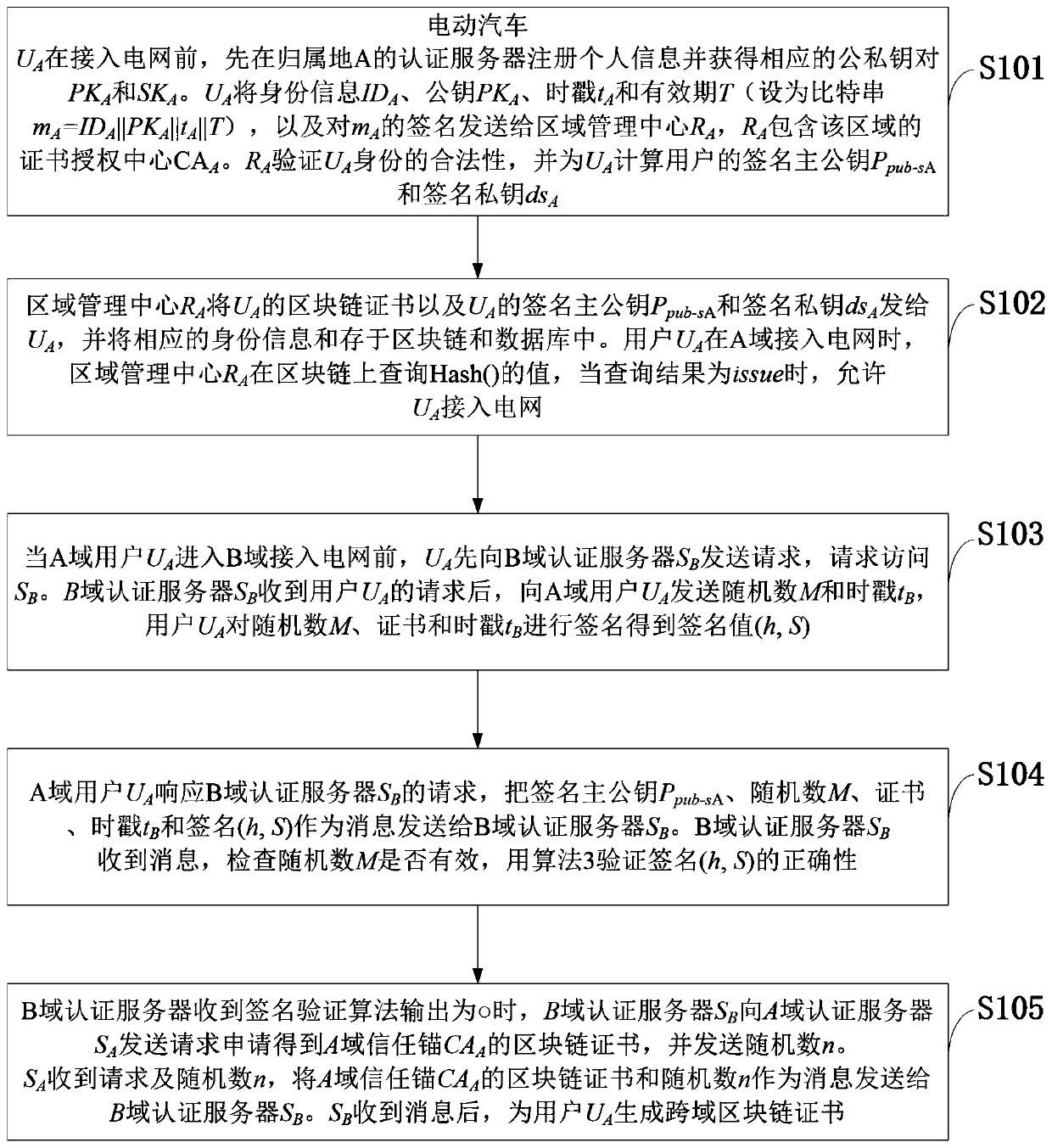
V2G network cross-domain authentication method based on alliance block chain and information data processing terminal
ActiveCN109743172AWith decentralizationAchieve traceabilityUser identity/authority verificationEngineeringElectric network
The invention belongs to the technical field of confidential or secure communication, and discloses a V2G network cross-domain authentication method based on an alliance block chain and an informationdata processing terminal. For the security threat that the electric vehicle joins a power grid V2G network, a V2G network cross-domain authentication scheme based on an alliance block chain is provided; A V2G network trust model and a system architecture are designed, and a specific scheme is described in detail. Signature and authentication of the method both adopt the latest national password standard SM9 cryptographic algorithm; The characteristic that the block chain technology is not easy to tamper is utilized, the Hash algorithm is used for verifying the certificate, and the signature and verification times of the public key algorithm are reduced, so that the efficiency is high, and the expandability is high. The introduction of the block chain technology provides a new idea and method for solving the security problem of the smart power grid. The invention provides a high-performance cross-domain authentication scheme in a V2G network by utilizing a block chain technology and anSM9 digital signature algorithm.
Owner:ELECTRIC POWER RESEARCH INSTITUTE OF STATE GRID SHANDONG ELECTRIC POWER COMPANY
Digital signature method and system based on SM2-based identity base
ActiveCN108809658AAvoid managementAvoid maintenancePublic key for secure communicationUser identity/authority verificationDigital Signature AlgorithmPublic key certificate
The invention discloses a digital signature method and a digital signature system based on an SM2-based identity base. The method firstly generates system parameters and system master, public, and private keys, and the user sends the identity identifier to the KGC for registration to obtain a signature private key, and then generates and verifies the digital signature of message M by using the signature private key. In the signature process of the invention, since a new type of user private key is generated based on the unchangeable overall architecture of the SM2 signature algorithm, the user's signature private key is generated based on the identity of the user without public key certificate, maintenance and management of the public key certificate as well as time-consuming calculation,thereby ensuring that the signature method of the invention has the characteristics such as low complexity, high security, and easy verification.
Owner:WUHAN UNIV
Two-way-security-authentication-based data downloading method and system
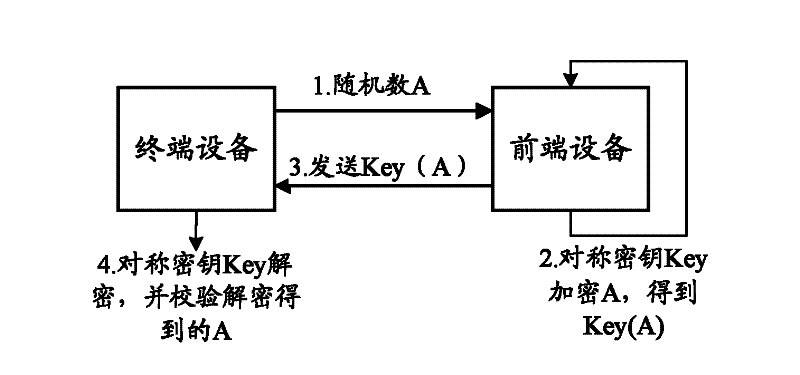
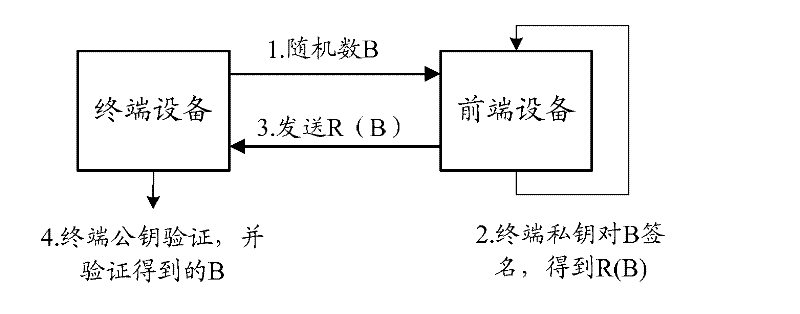
ActiveCN102413132ASolve imperfectionsProtection securityUser identity/authority verificationDigital Signature AlgorithmComputer terminal
The invention discloses a two-way-security-authentication-based data downloading method and a two-way-security-authentication-based data downloading system. The method comprises that: a first terminal verifies a second terminal through a symmetric key algorithm to acquire a first verification result; after the second terminal is determined to be a legal terminal according to the first verification result, the second terminal verifies the first terminal through an asymmetric key algorithm to acquire a second verification result; and after the first terminal is determined to be a legal terminal according to the second verification result, the second terminal downloads data which is encrypted through a digital signature algorithm to the first terminal. By the method and the system, the creation of two-way authentication channels and security downloading among different terminals can be realized, and the security and integrity of interactive data are protected.
Owner:BEIJING SUMAVISION PAYMENT TECH CO LTD
Information privacy and identity authentication method and digital signature program
InactiveCN101753311AUniversalPublic key for secure communicationUser identity/authority verificationConfidentialityCiphertext
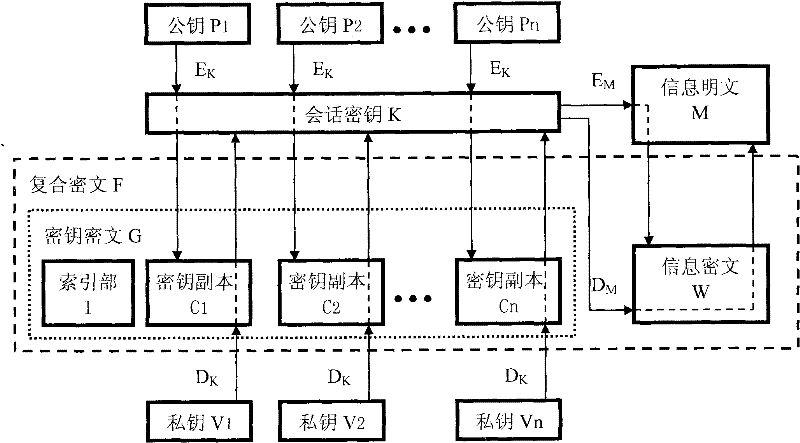
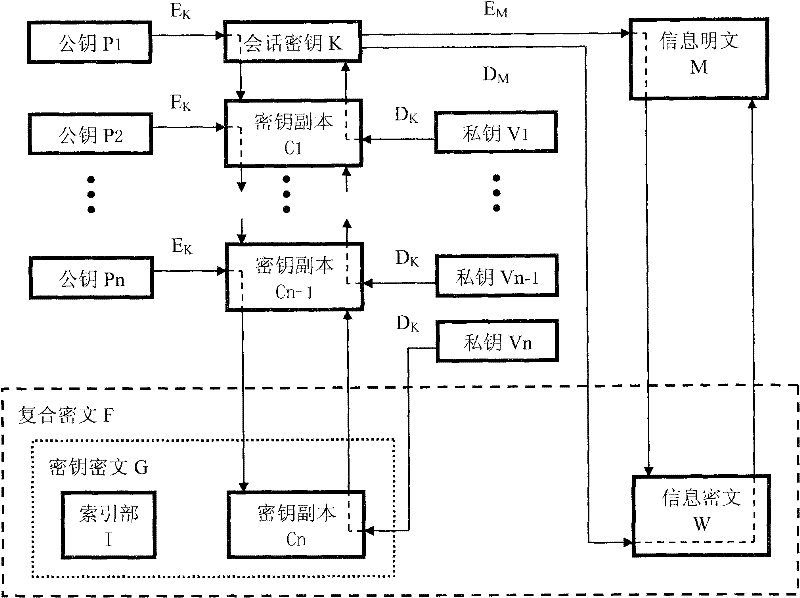
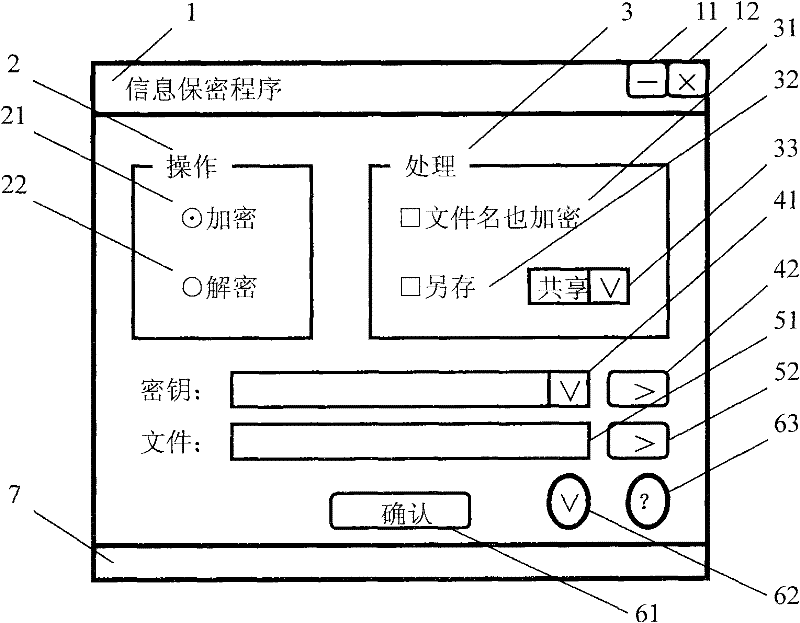
The invention provides an information privacy and identity authentication method and a digital signature program, which relate to the technical filed of computer software, network communication and information safety and are particularly used for the information privacy of instant messaging, electronic mails and file information. A symmetrical cryptographic algorithm and an unsymmetrical cryptographic algorithm are combined, and a key ciphertext and an information ciphertext form a complex ciphertext. The effect of text confidentiality and sharing is reached through the integration of effects of multiple keys, and the effect of text confidentiality interlocking is realized through the effect of the combination of multiple keys. The signature is used for challenging the response mechanism, more than two cipher devices are compatible, the effect of automatic identification distinction and / or self-customization by users can be realized, and the identity authentication is more flexible and complete. A convenient and practical data signature program is also designed, and the convenient and practical data signature program assists a target program for use and runs independently for realizing the instant signature and the instant verification on window text information.
Owner:杨筑平
Method and apparatus for calculating a multiplicative inverse of an element of a prime field
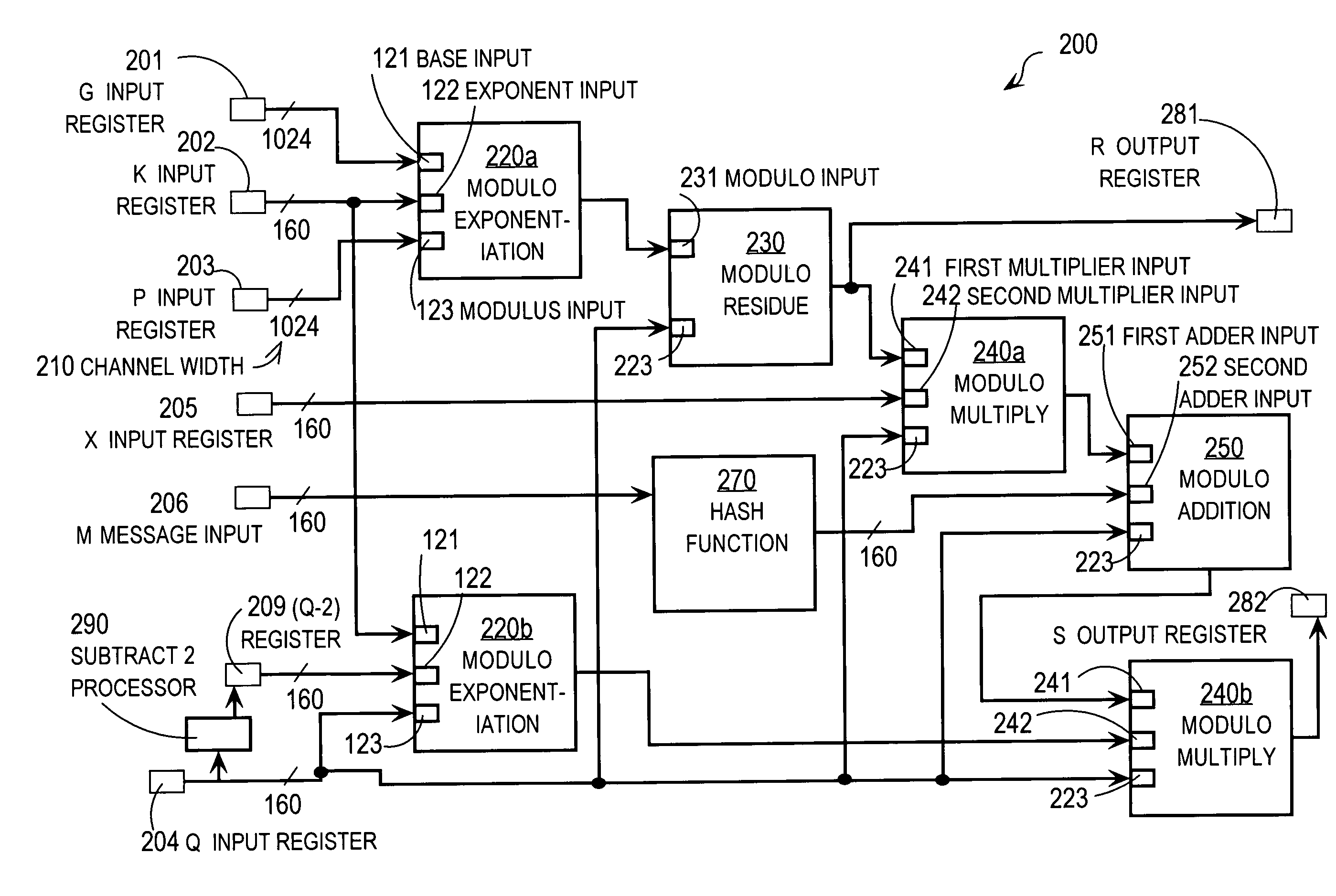
InactiveUS7191333B1Reduce areaReduce development costsDigital data processing detailsUser identity/authority verificationDigital Signature AlgorithmComputer science
Techniques for implementing a digital signature algorithm in electronic computer hardware include computing the multiplicative inverse of a particular integer modulo a prime modulus by computing a first quantity modulo the prime modulus. The first quantity substantially equals, modulo the prime modulus, the particular integer raised to a power of a second quantity. The second quantity is two less than the prime modulus. The techniques allow an integrated circuit block to compute a modulo multiplicative inverse, such as for signing and verifying digital signatures, using existing blocks of circuitry that consume considerably less area on a chip, and incur fewer developmental costs, than an implementation of an algorithm conventionally used in software.
Owner:CISCO TECH INC
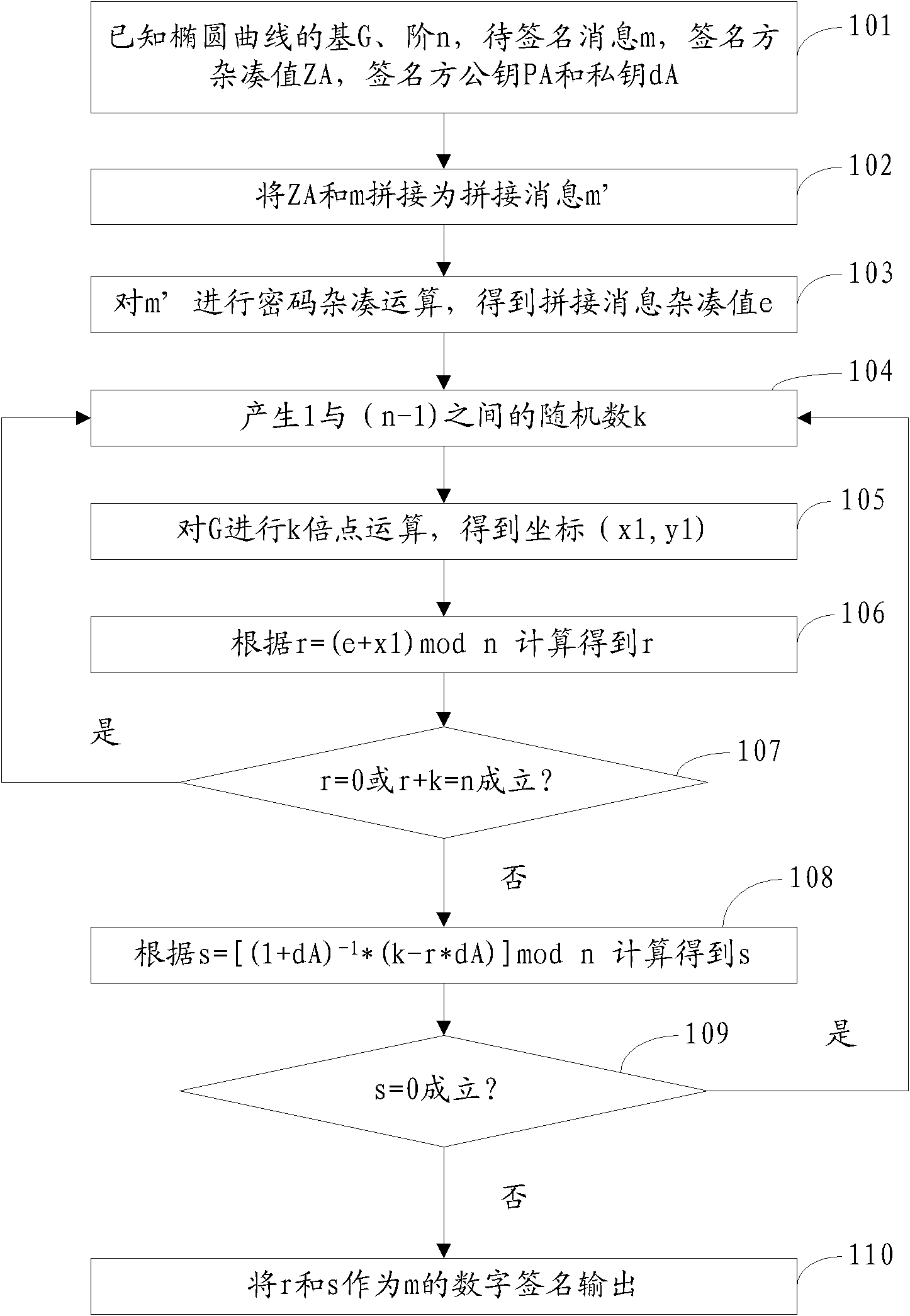
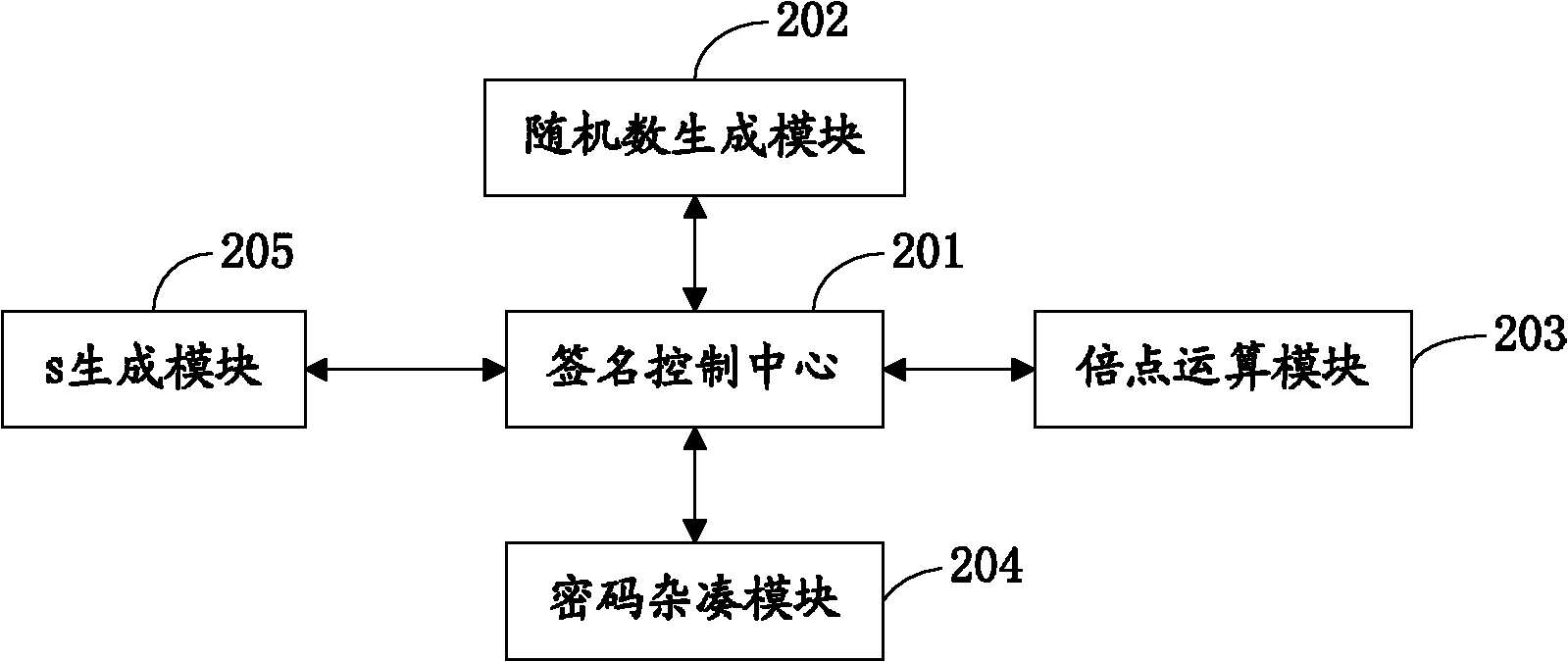
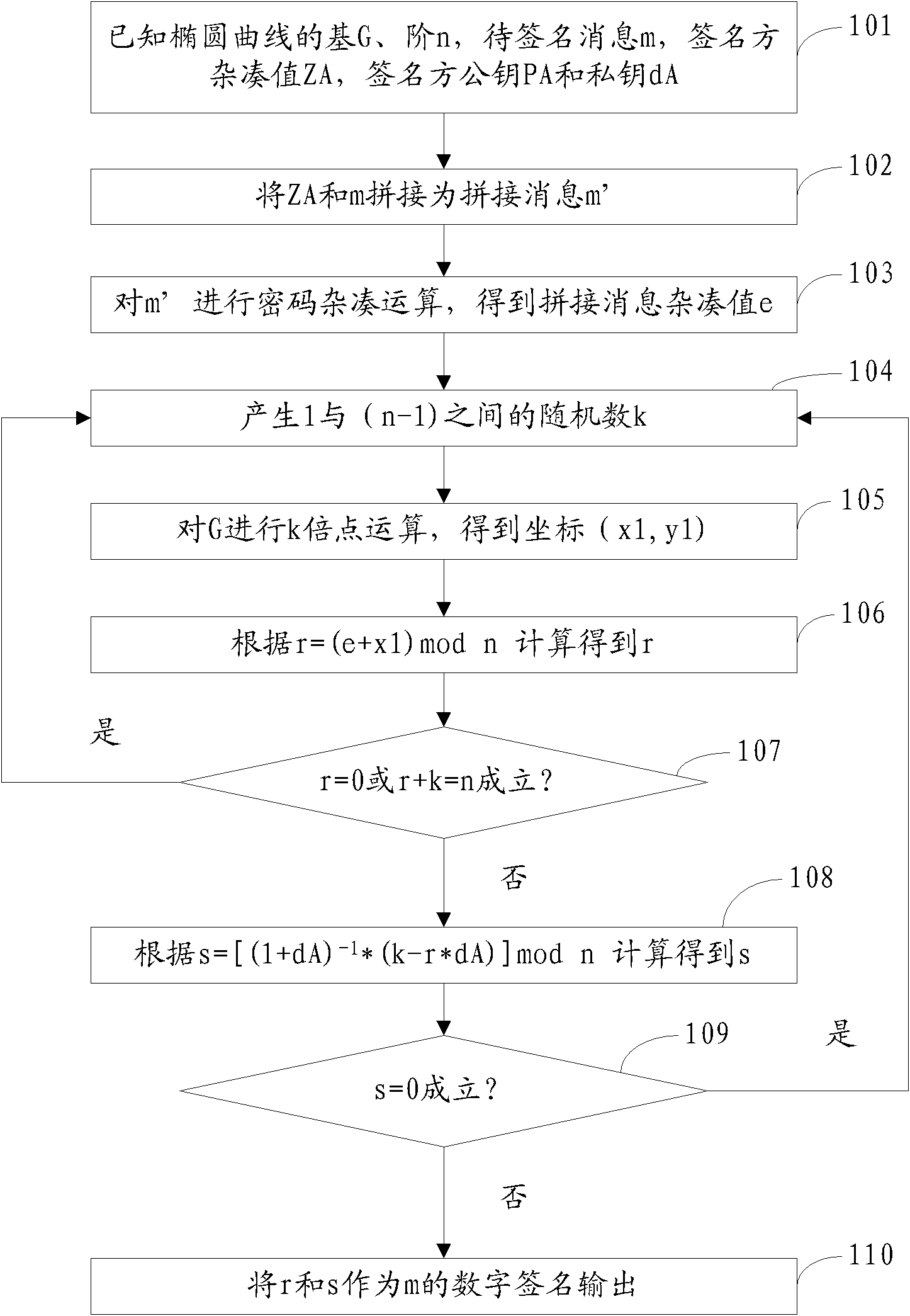
System for generating, verifying and mixing digital signatures of p-element domain SM2 elliptic curves
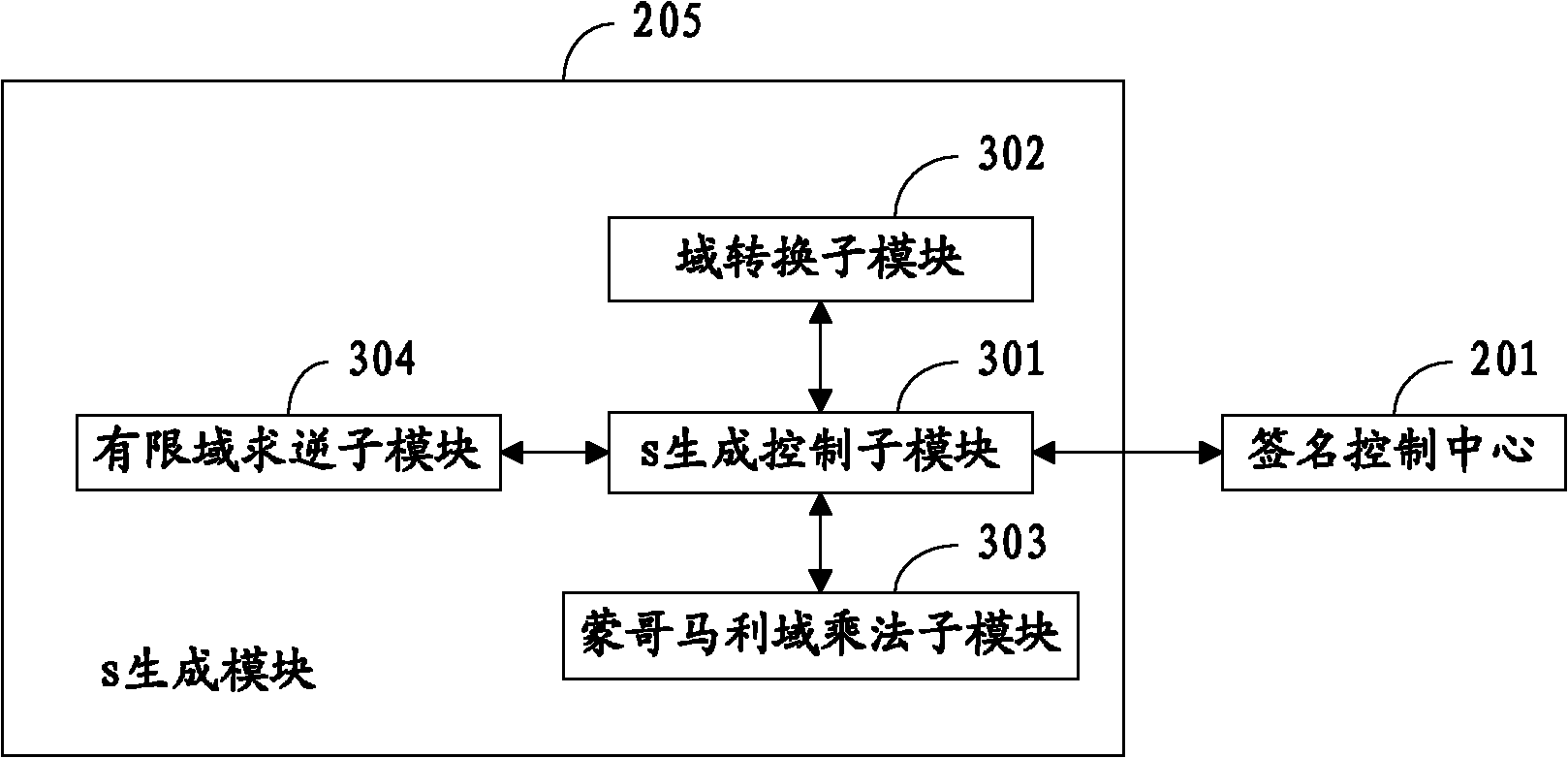
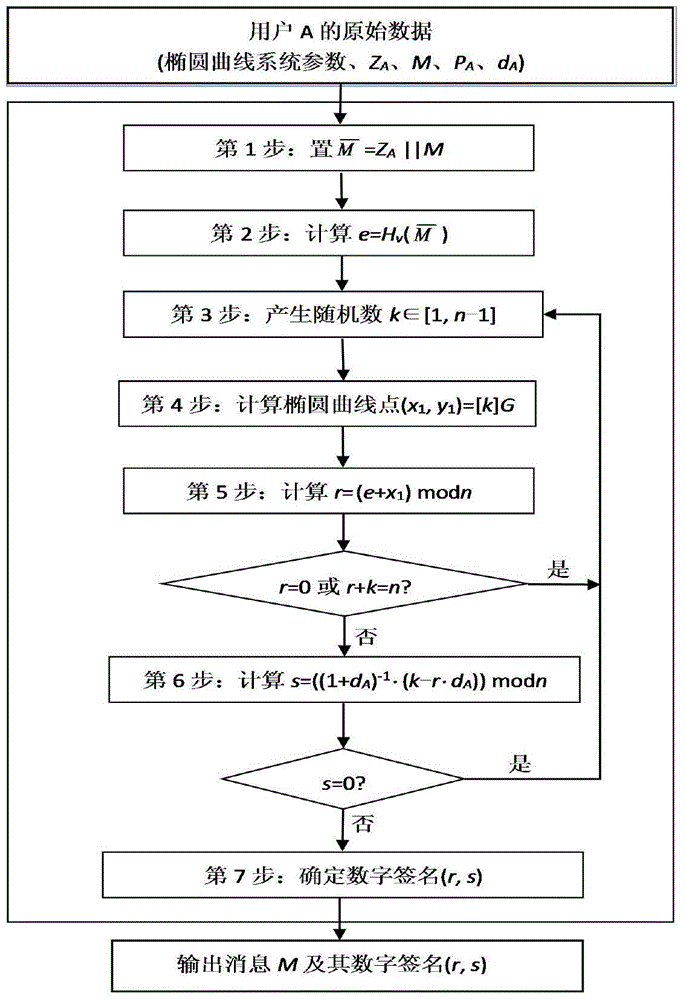
The invention relates to a system for generating, verifying and mixing digital signatures of p-element domain SM2 elliptic curves. The system functions through the following steps: m' which is obtained by combining a message (m) to be signed with a signer hash value (ZA) is sent to a password hash module; r which is obtained through r=(e+x1)mod n is sent to an s generation module; when r=0, r+k=n or s=0, a random number generation module is notified to regenerate k; r and s are used as signature control centers for output of the digital signature of m; password hash computation is performed to m' to generate the password hash module of the combined message hash value e; the random number generation module of the random number k is generated; k doubling computation is performed to the base G of an elliptic curve; the generated coordinate (x1,y1) is used as the doubling computation module of the result [k]G; and the s generation module is generated according to s=[(1+dA)<-1>*(k-r*dA)] mod n, where n is the order of the elliptic curve, and dA is the private key of the signer. According to the invention, the digital signature algorithm in the SM2 elliptic curve public-key algorithm can be achieved through hardware.
Owner:AEROSPACE INFORMATION
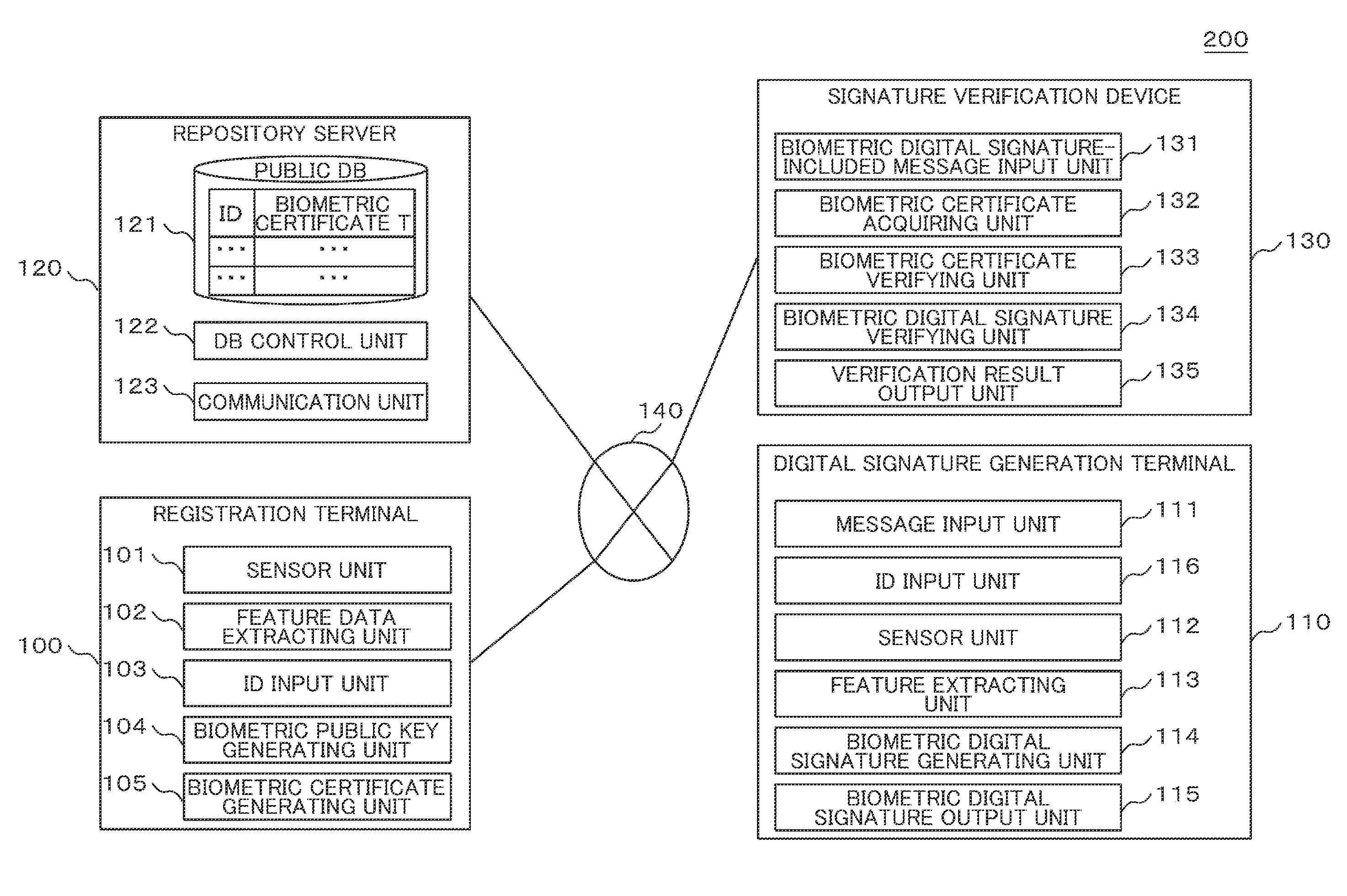
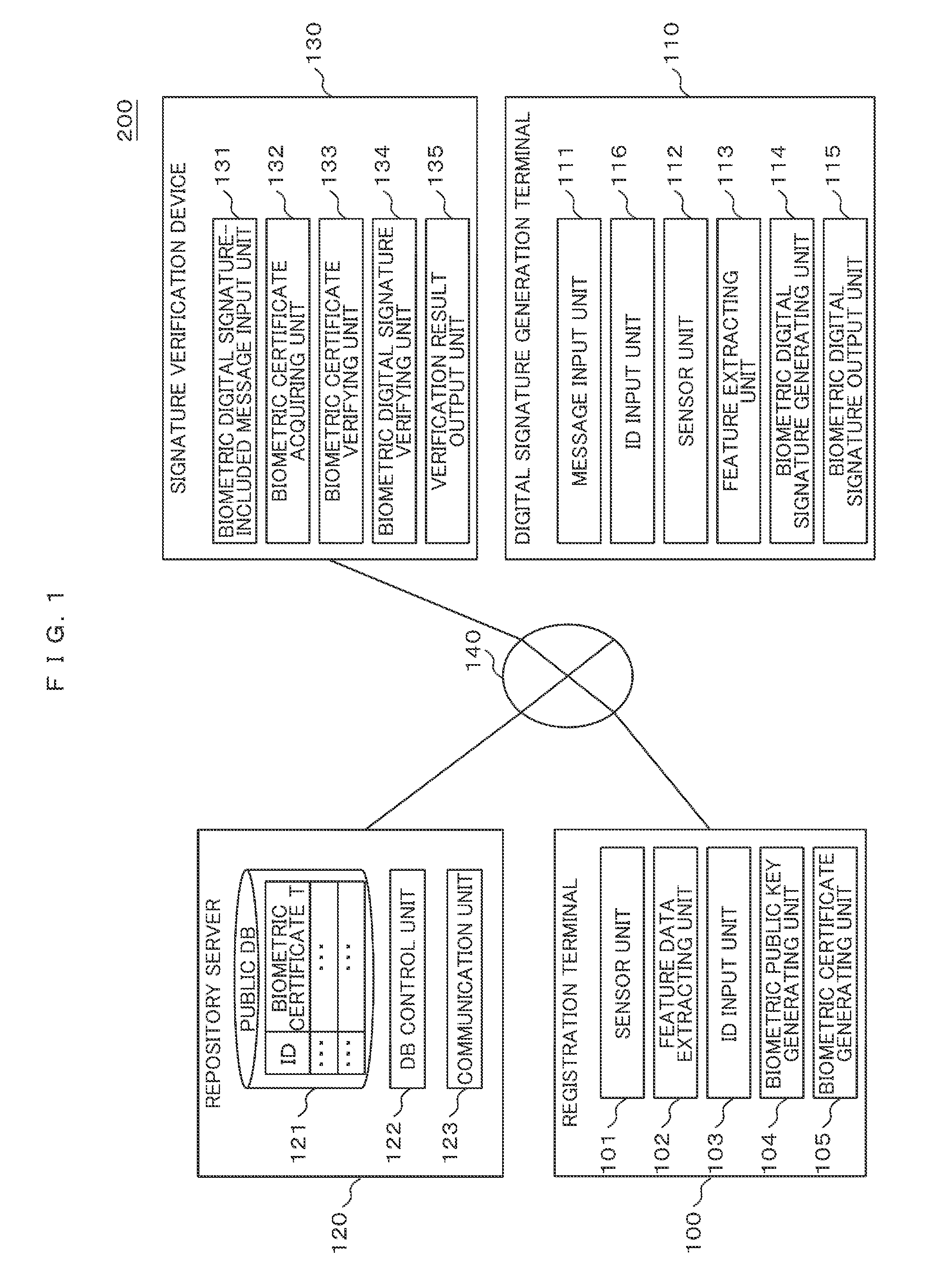
Biometric signature system, signature verification method, registration terminal, signature generation terminal, and signature verification device
ActiveUS20160094348A1Facilitate performance improvementsReduce management costsKey distribution for secure communicationUser identity/authority verificationElectronic documentDigital Signature Algorithm
A biometric signature system generates a digital signature for electronic documents using biometric information as a secret key. Registration commitment information is generated by performing expansion conversion on a predetermined secret key and embedding the resulting secret key in feature data of biometric information of a user, and a set with a corresponding public key. A pair of one-time secret and public keys is generated for digital signature feature data of the biometric information of the user, and a digital signature for a message is generated using the one-time secret key. A digital signature commitment is generated and a set of the one-time public key and the digital signature is output as the biometric digital signature. The digital signature is verified using the one-time public key. A differential secret key is calculated and a correspondence of the differential secret key, the one-time public key and the public key is verified.
Owner:HITACHI LTD
Cloud-storage data lightweight-level public auditing method with privacy protection
InactiveCN104023044AShort signature lengthSave storage spaceUser identity/authority verificationDigital data protectionOriginal dataPrivacy protection
The invention discloses a cloud-storage data lightweight-level public auditing method with privacy protection. The method comprises the steps of system initialization, signature, auditing certification, and auditing certification verification. The method uses a modified digital signature algorithm based on an elliptical curve, the security of the method depends on the discrete logarithm problem of a finite group of the elliptical curve, and the method is characterized by low signature length, small storage space and high computation speed, and is especially suitable for occasions with lightweight-level computation amount, limited storage space and high-efficiency realization. The method of the invention is simple and convenient to operate, solves the problems that cloud-storage data public auditing and present cloud-storage data are low in privacy and the completeness and accuracy of user data cannot be ensured, and ensures that original user data is not leaked out to a cloud server or a public auditor.
Owner:UNIV OF ELECTRONICS SCI & TECH OF CHINA
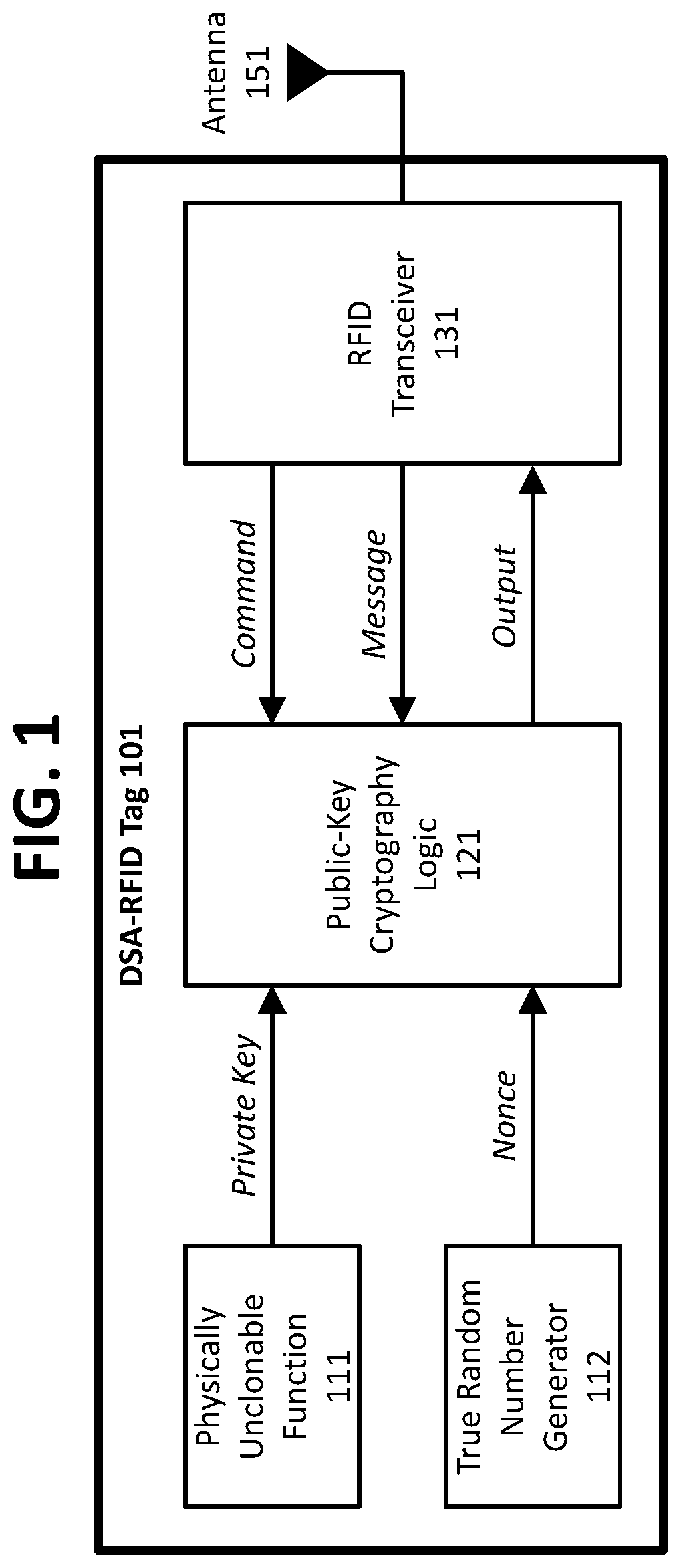
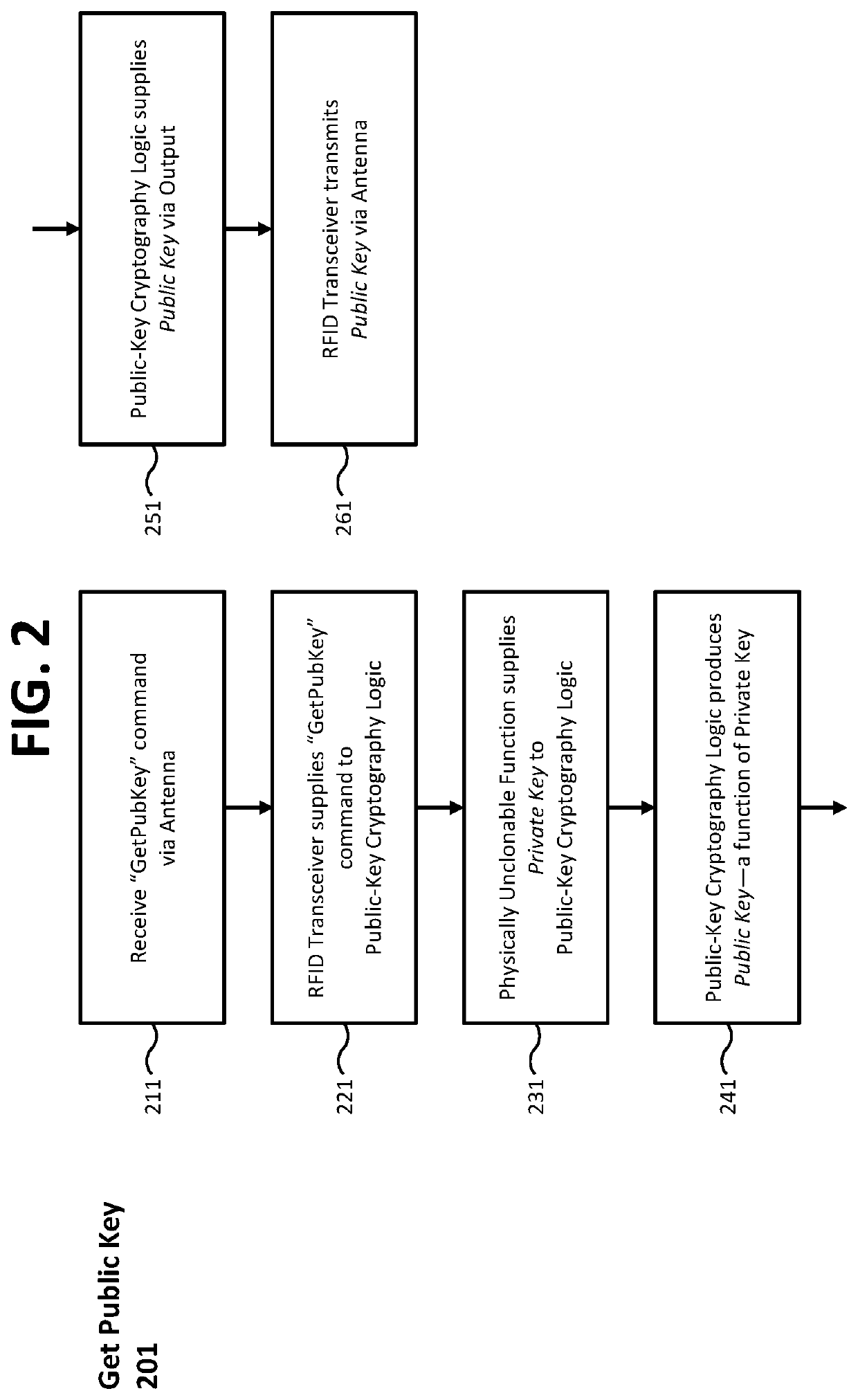
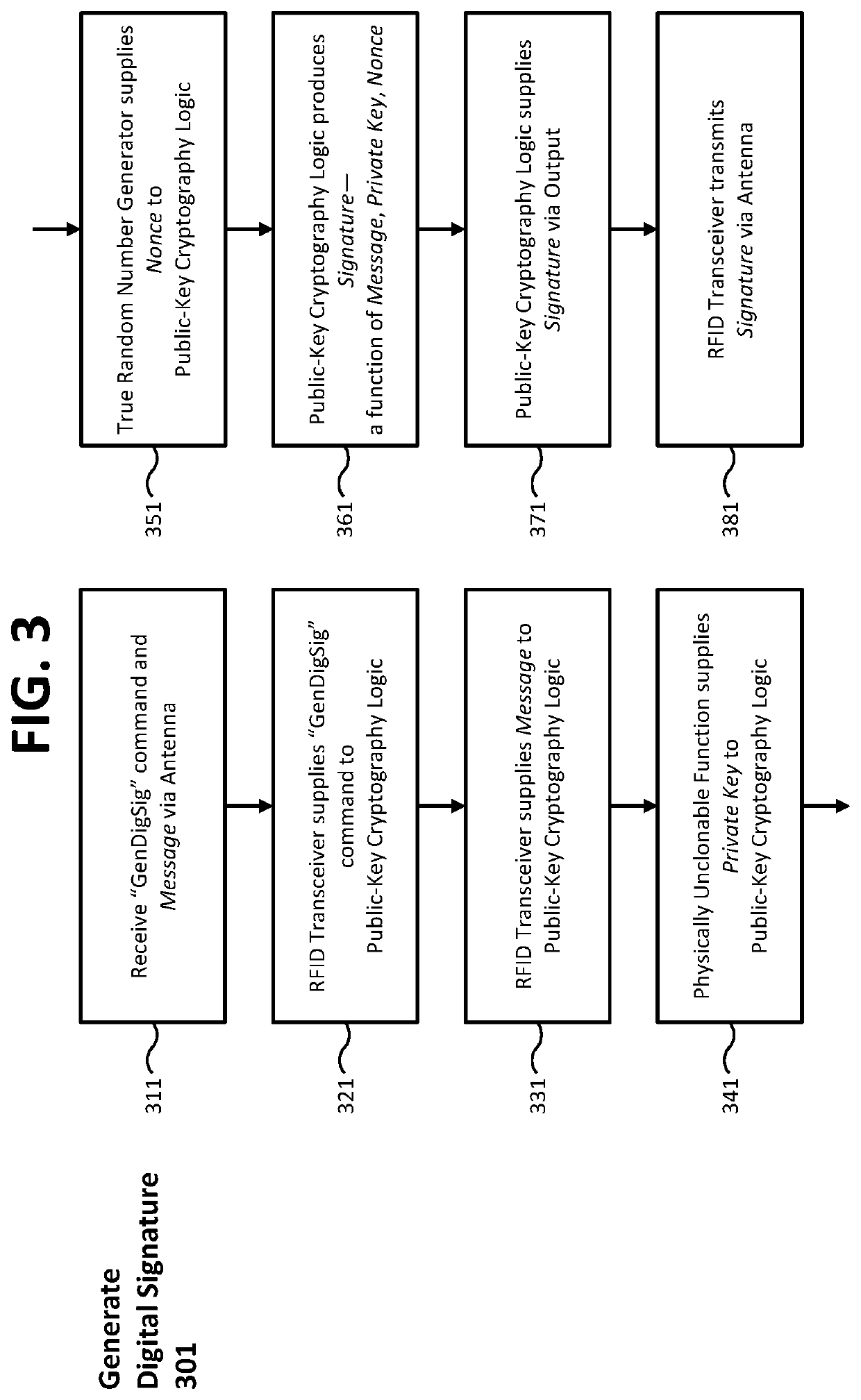
Devices, methods, and systems for cryptographic authentication and provenance of physical assets
ActiveUS10523443B1Eliminate loopholesKey distribution for secure communicationRandom number generatorsDigital Signature AlgorithmAuthentication
Authentication and provenance of physical assets may be achieved by attaching a cryptographically strong RFID tag including a physically unclonable function and public-key cryptography logic which implements a digital signature algorithm. The cryptographically strong RFID tag directly participates in a novel implementation of blockchain technology, constructing an indelible and cryptographically provable record of authenticity and provenance with a new level of trustworthiness to protect physical assets.
Owner:KLEINMAN BRUCE
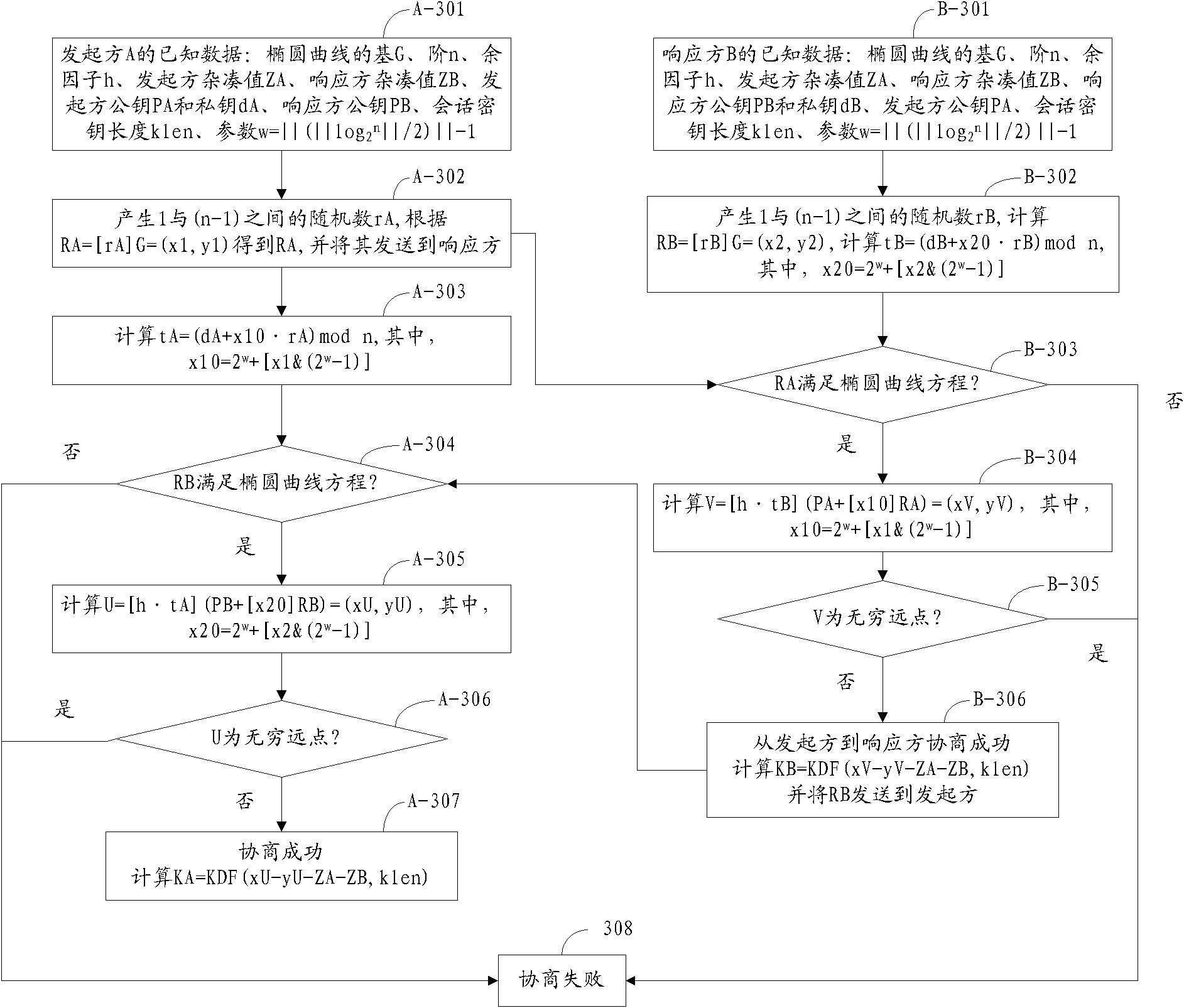
Implementation system of p-element domain SM2 elliptic curve public key cryptographic algorithm
ActiveCN102761413ARealize the generation functionPublic key for secure communicationMultiplexingKey exchange
The invention relates to an implementation system of a p-element domain SM2 elliptic curve public key cryptographic algorithm. Under the control of a master control module, the system can utilize a signature control center and a verification control center to control the implementation of a digital signature algorithm, utilize an initiator control center and a responder control center to control the implementation of a key exchange protocol, utilize an encryption party control center and a decryption party control center to control the implementation of a public key encryption algorithm, utilize an S generation module, a random number generation module, a point doubling module, a point addition module and a key derivation module to implement basic operation in the algorithm and utilize an upper-layer reelection module to implement multiplexing of the modules, thereby reducing the use of hardware resources. The implementation system disclosed by the invention can implement the p-element domain SM2 elliptic curve public key cryptographic algorithm by hardware.
Owner:AEROSPACE INFORMATION
Method of Using ECDSA with Winternitz One Time Signature
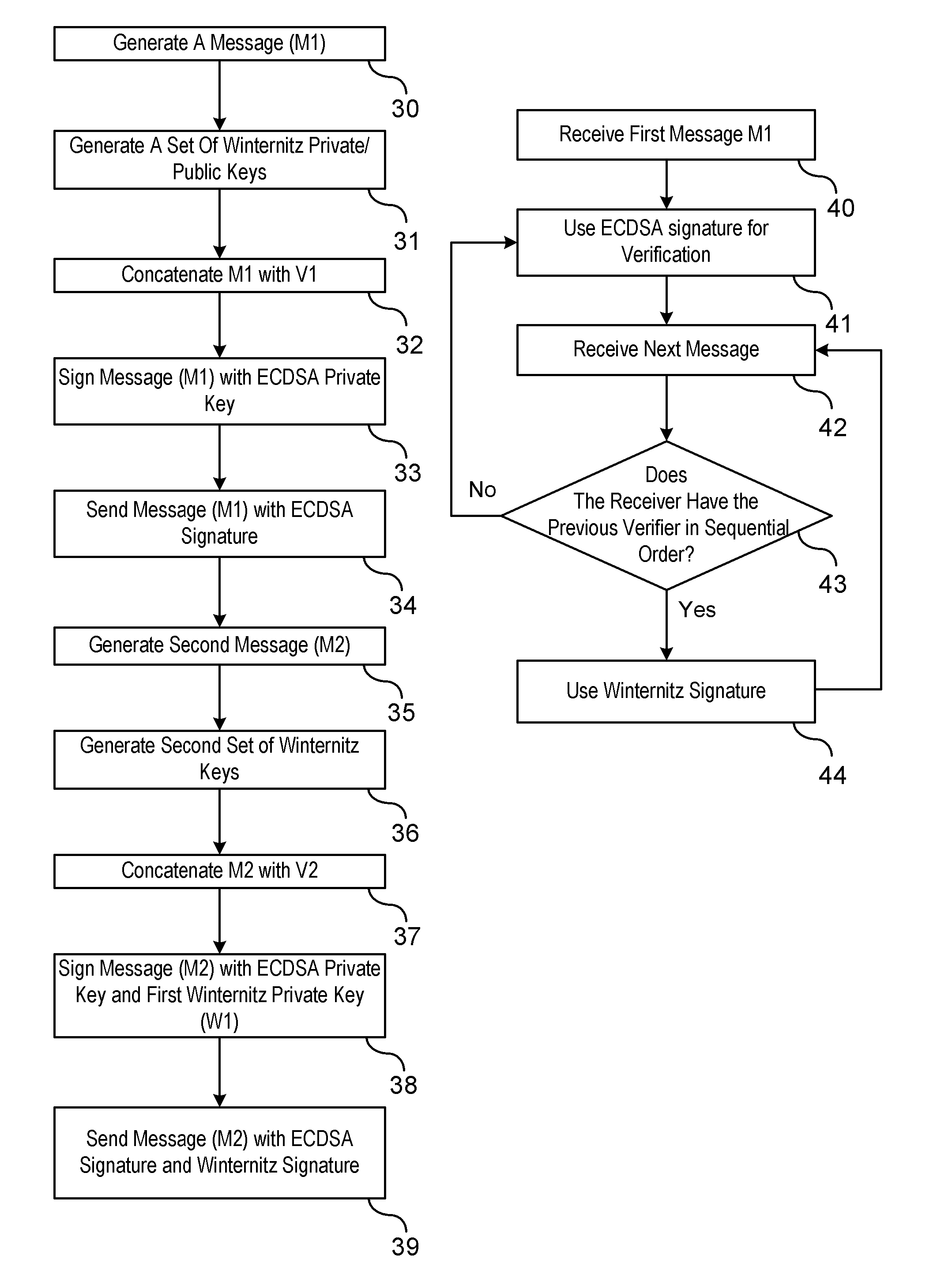
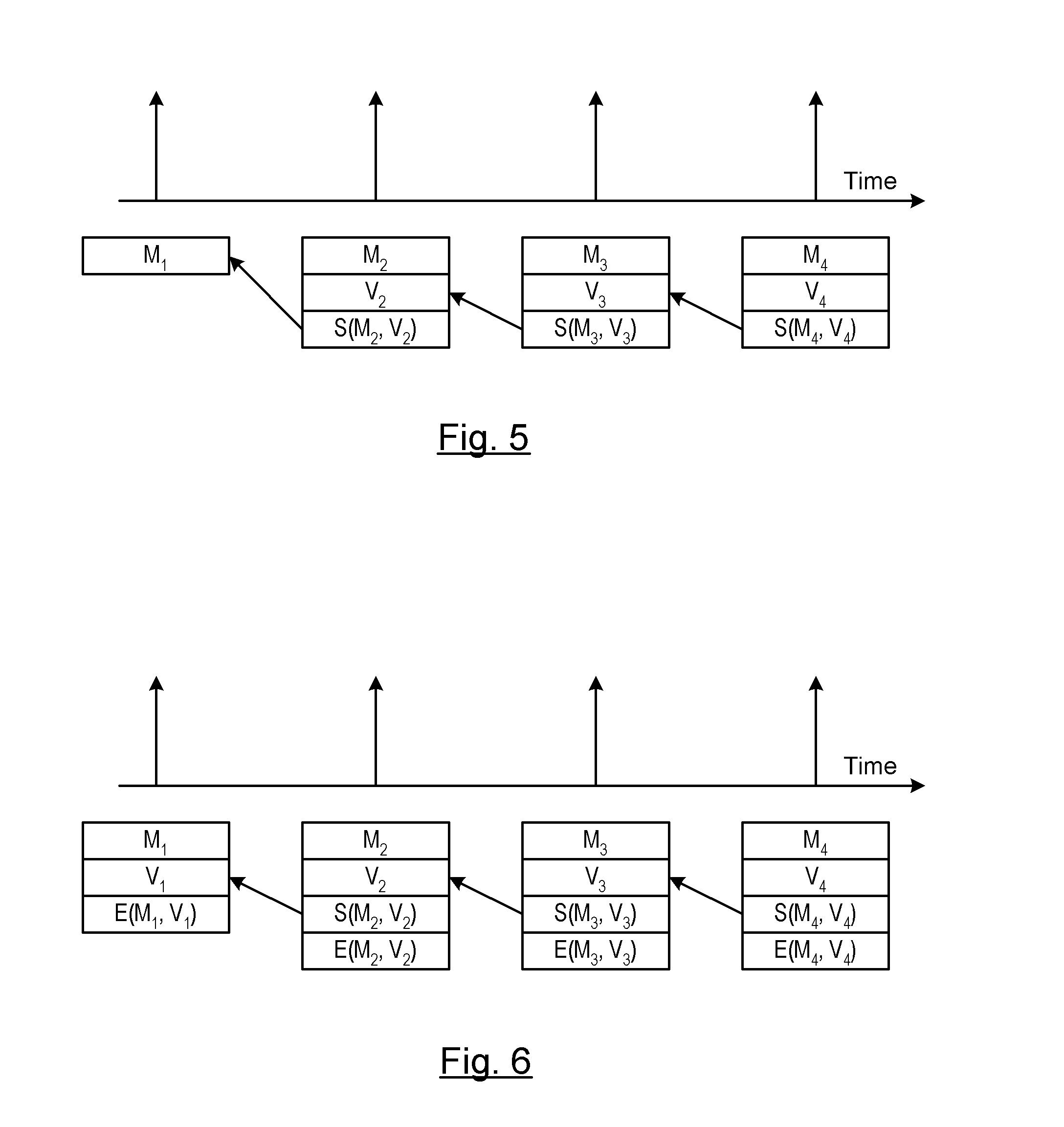
ActiveUS20110208971A1Maintain robustnessRobustnessPublic key for secure communicationUser identity/authority verificationDigital Signature AlgorithmBroadcasting
A method is provided of authenticating a digitally signed message. A chain of messages is generated. A Winternitz pair of keys is generated for each respective message. A sequence number is assigned to each of the messages. Each of the sequence numbers cooperatively identify an order of Winternitz verifiers assigned to each of the messages. A signature to a first message in the chain of messages is signed using a digital signature algorithm private key. Signatures to each of the following messages in the chain of messages are signed using both Winternitz private keys and digital signature algorithm private keys. The signed messages are broadcast from a sender to a receiver. The first signed broadcast message is authenticated at the receiver by verifying the digital signature algorithm signature. At least some of the following signed broadcast messages are authenticated at the receiver by verifying only the Winternitz signature.
Owner:GM GLOBAL TECH OPERATIONS LLC
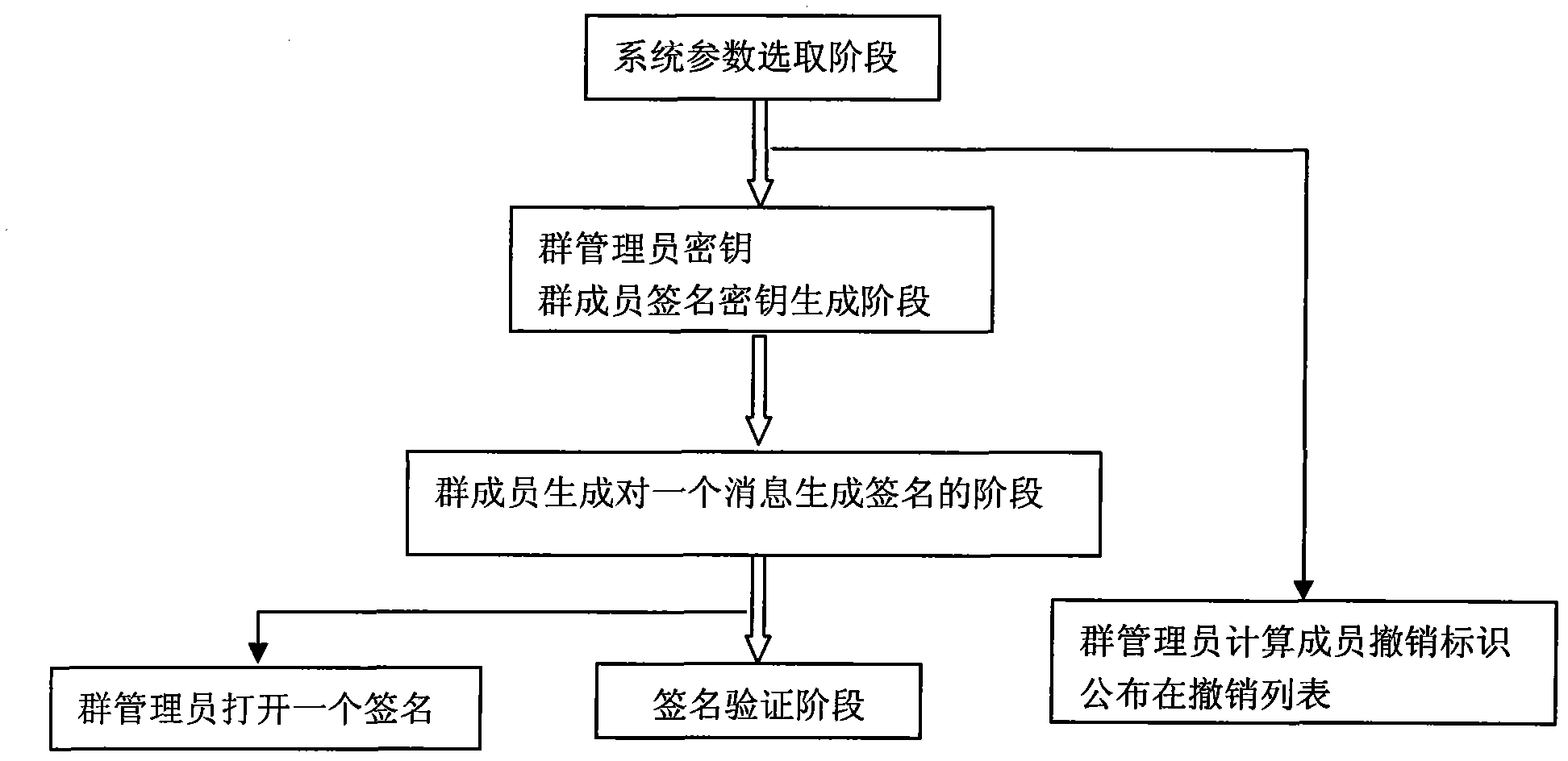
Group signature method based on elliptic curve
ActiveCN101977110ASignature length advantageComputational overhead advantagePublic key for secure communicationUser identity/authority verificationDigital Signature AlgorithmKey generation
The invention discloses a group signature method based on an elliptic curve, comprising the following six steps: 1, selecting two multiplication cyclic groups G1 and G2 with the order of p from the elliptic curve as well as a nonsingular bilinear mapping e which can map elements in the G1 and G2 into GT, namely e:G1*G2->GT; 2, operating a secret key generation algorithm by a group administrator, generating a group public key, and generating signature secrete keys for members in the groups; 3, operating a signature algorithm after members in the groups obtain corresponding signature secret keys through the secret key generation algorithm; 4, verifying the validity of signatures delta by adopting the group public key to operate a verification algorithm by a verifier; 5, as for a given signature, adopting a signature tracking algorithm to substitute revocation identification of a time slot in which the signature is generated into a revocation identification inequation, and if the inequation is true, indicating that the signature is signed by a group member corresponding to the revocation identification; and 6, in some cases, adopting a member revocation algorithm to revoke the signature qualification of some members, which requires to calculate the revocation identification of the members in corresponding time intervals and publish the revocation identification in a revocation list.
Owner:BEIHANG UNIV
Traceable anonymous authentication method based on elliptic curve
InactiveCN105812369AImprove securityPublic key for secure communicationUser identity/authority verificationRing signatureDigital Signature Algorithm
The invention discloses a traceable anonymous authentication method based on an elliptic curve. The method comprises following stages of initializing a system and generating a secrete key, generating anonymous signatures, authenticating the signatures, linking and tracing nodes. According to the method, a ring signature algorithm in a data signing process is improved; the ring signatures and the elliptic curve are combined; the linkage performance is increased; moreover, traceability to malicious nodes is provided, thus finding out the malicious nodes efficiently and accurately; the network security is improved; a critical value is unnecessary; an efficient hop-by-hop message authentication mechanism is provided; the privacy leakage problem of sending nodes in a wireless sensor network can be solved; moreover, the reality and integrity of the sent messages are ensured; and the malicious nodes can be traced if necessary.
Owner:GUANGDONG UNIV OF PETROCHEMICAL TECH
Two-dimension code electronic key implementation method based on digital signature
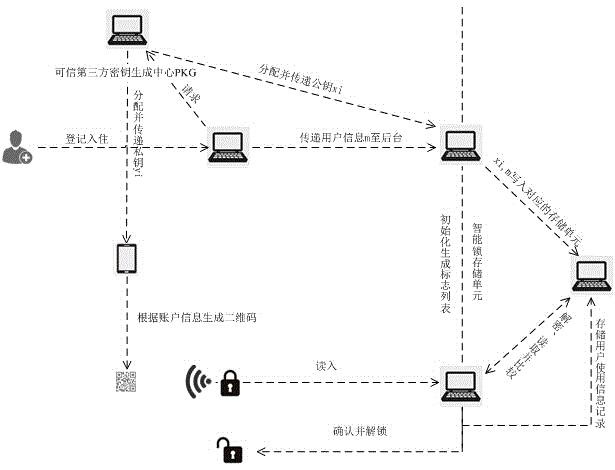
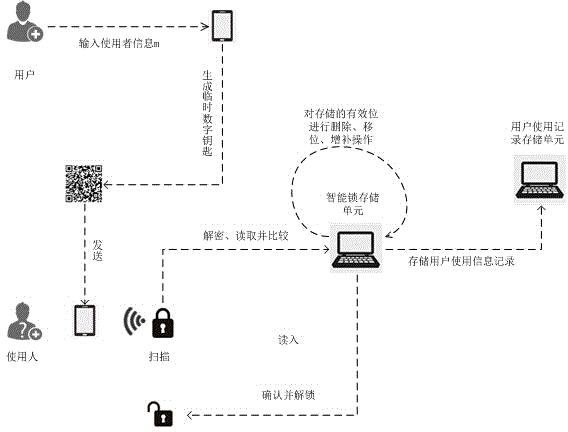
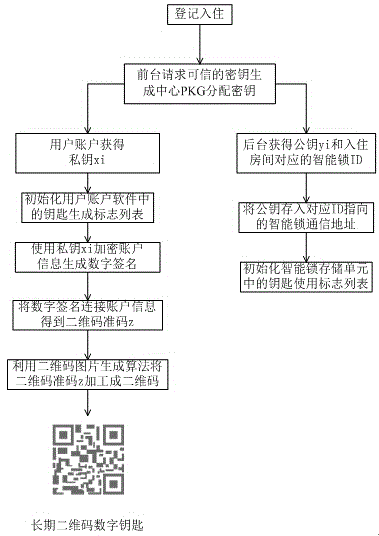
ActiveCN104933793AUniqueness guaranteedGuarantee authenticityIndividual entry/exit registersDigital Signature AlgorithmMobile device
The invention relates to a method for encoding information of a user and generating a two-dimension code digital key by adopting a digital signature technique. A mobile phone and other mobile devices are taken as carriers of the two-dimension code digital key. The method comprises steps as follows: a credible key generation center allocates a unique private / public key pair for a user account and a smart lock storage unit during starting; a digital signature algorithm is adopted, that is, a private key is used for encrypting the information of the user and a public key is used for decrypting a read-in two-dimension code sequence; the information of the user is stored and read by field. Normal use of the two-dimension code key of the user can be guaranteed, the reliability and the authenticity of the source of a generated temporary two-dimension code key can be guaranteed, meanwhile, temporary two-dimension code keys received by different people can be effectively distinguished, and the flexibility and the safety of a whole two-dimension code smart lock system are unified.
Owner:宁波飞拓电器有限公司
Mobile information system based privacy protection and encryption method
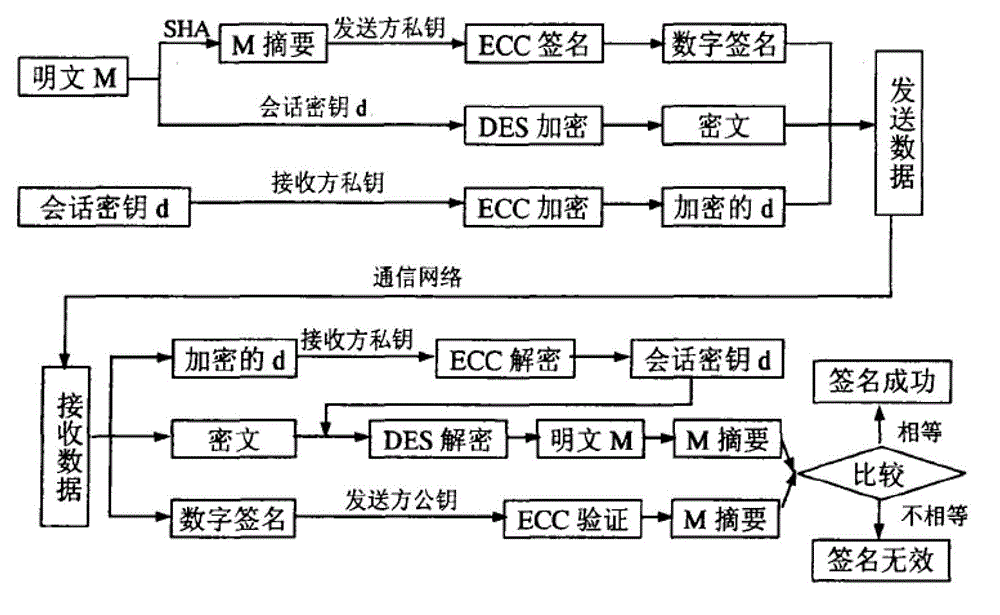
InactiveCN102946602ASolve the problem of encryption and decryption speedTroubleshoot distribution issuesEncryption apparatus with shift registers/memoriesUser identity/authority verificationError checkingPlaintext
The invention provides a mobile information system based privacy protection and encryption method. On the basis of the existing security model, a DES (data encryption standard) and ECC (error checking and correcting) based digital signature algorithm scheme is provided, the scheme has the advantages of rapid arithmetic speed and high security, and better fits the application in a wireless environment, and according to the digital signature algorithm, plaintext data is encrypted by using the DES, so that the encryption and decryption speed problem of plaintexts is solved preferably; a session key of the DES is encrypted by using an ECC algorithm, so that the problem of key distribution can be effectively solved; meanwhile, through carrying out digital signature on the digital digests of plaintexts, the identity can be identified, and a situation that whether information is changed in the process of transmission can be authenticated; and therefore, the purpose of rapid and secure mobile officing is achieved, and the authenticity, integrity, and non-repudiation of officing information are ensured.
Owner:ZHENJIANG JIANGDA KEMAO INFORMATION SYST
Method and apparatus for emulating ethernet functionality over a serial bus
InactiveUS20050157732A1Time-division multiplexNetworks interconnectionDigital Signature AlgorithmEthernet frame
Applications can transparently use a bus, such as the IEEE-1394 serial bus, as if it were an Ethernet (IEEE 802.3). In a conventional Ethernet, each node is assigned a unique 6-byte MAC address in order to receive frames addressed to it over the LAN. According to the invention, IEEE-1394 bus node identifiers are mapped to Ethernet MAC addresses using for example a digital signature algorithm. Ethernet frames are then “wrapped” into 1394 bus packets and addressed to the destination node using the hashed address. The receiver unwraps the 1394 packet and restores the Ethernet frame to its original form. An optimum packet size for transmission of Ethernet packets over the 1394 bus is selected with reference to speed topology maps in the 1394 bus nodes, and this optimum size is transmitted to bus nodes. This packet size is reported to TCP to specify the packet size, and all packets larger than that size are fragmented and reassembled at the receiving node. The protocol works transparently across networks that are linked via bridges.
Owner:MICROSOFT TECH LICENSING LLC
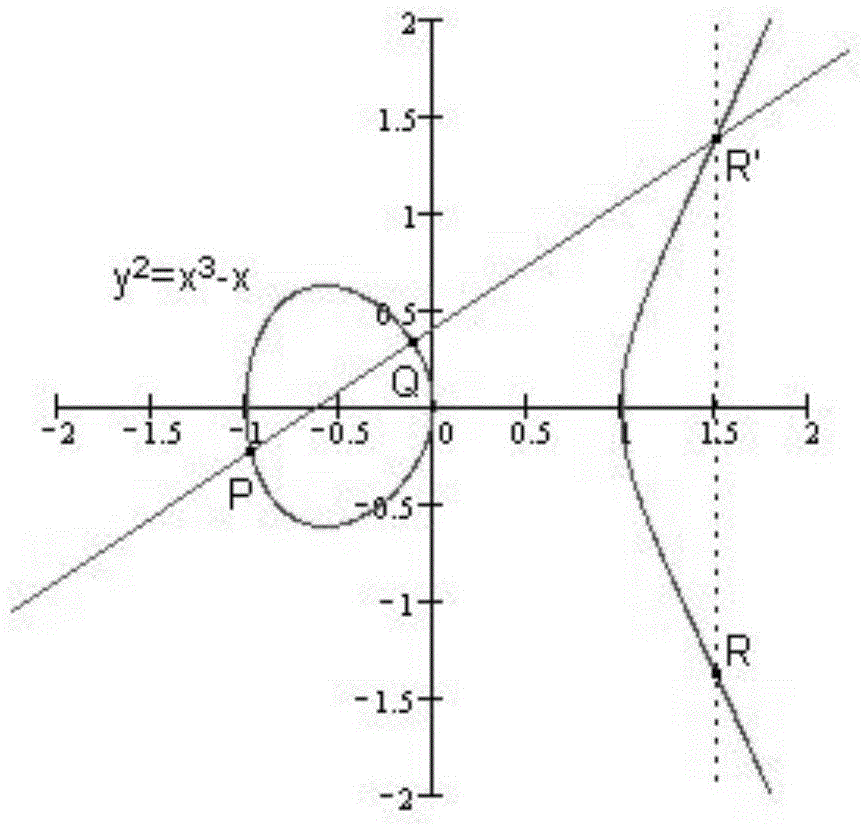
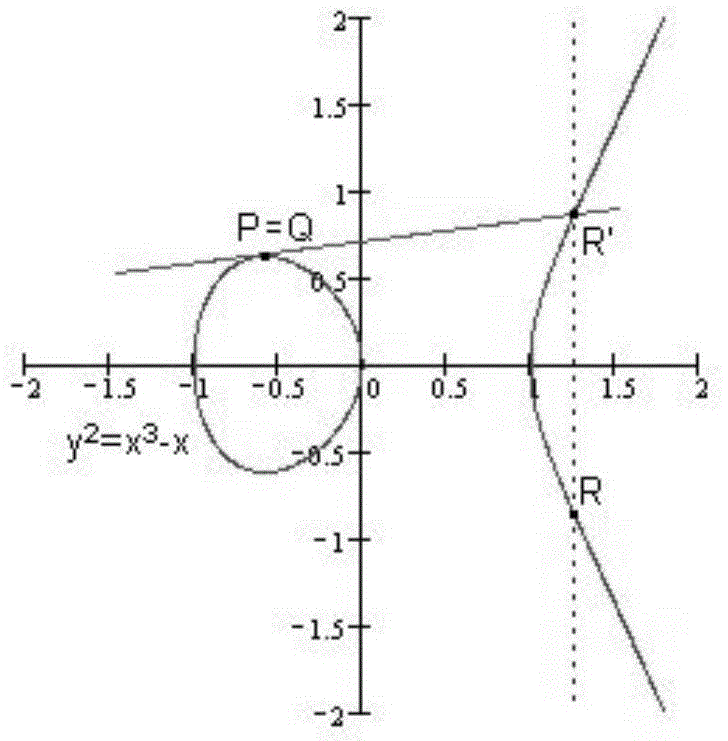
Electronic signature authentication method based on ellipse curve signature algorithm
InactiveCN101610153AShort keyCalculation speedPublic key for secure communicationUser identity/authority verificationElectronic documentInternational standard
The invention provides an electronic signature authentication method based on an ellipse curve signature algorithm, which comprises the following steps that: a user utilizes a digital signature verification algorithm in an ellipse curve cryptosystem to perform signature operation on electronic information, and embeds the signature information in a stamp frame or an interior position of a stamp electronic seal template in a digital watermark form to perform electronic signature on appointed electronic documents; and a verification party utilizes the digital signature verification algorithm in the ellipse curve cryptosystem to verify the information of the electronic signature, wherein the digital signature algorithm and the verification algorithm in the ellipse curve cryptosystem are based on an international standard ECDSA method; and twice dot product operation of the prior signature verification algorithm is changed into once dot product operation by utilizing the deformation of a signature equation of the digital signature verification algorithm in the ellipse curve cryptosystem.
Owner:AEROSPACE INFORMATION
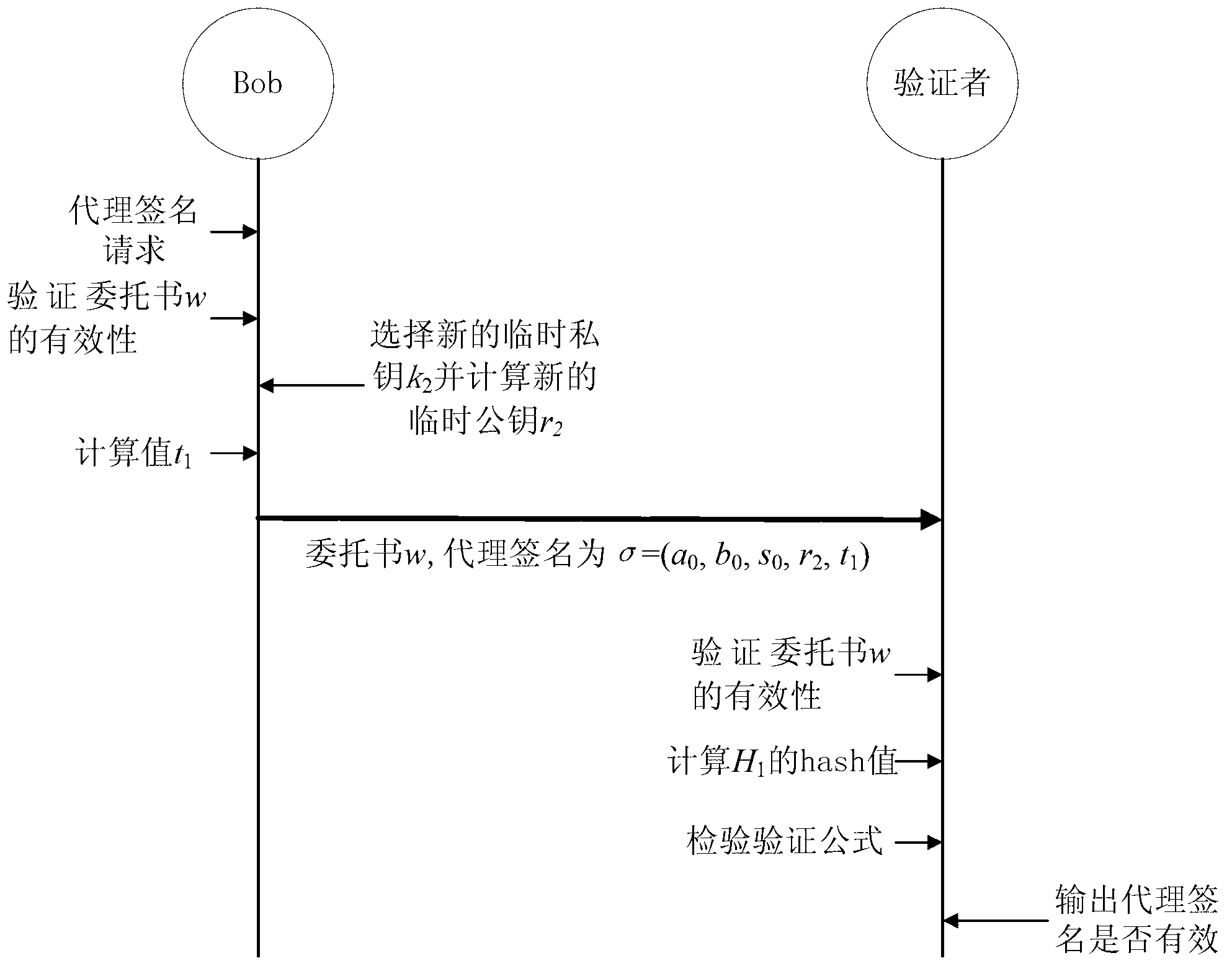
Novel procuration signature and verification method based on integer factorization problems
InactiveCN103259662AShorten the lengthSmall amount of calculationUser identity/authority verificationHash functionDigital Signature Algorithm
The invention discloses a novel procuration signature and verification method based on integer factorization problems. The novel procuration signature and verification method based on the integer factorization problems includes the steps: before a network operates, firstly generating personal public keys and private keys by original signature people and procuration signature people, and issuing the public keys; when signature requests are provided, generating authorization letters by the original signature people, and calculating signature authorization based on a chameleon hash function and an ordinary digital signature algorithm, sending the signature authorization to the procuration signature people, carrying out validity verification on the received signature authorization by the procuration signature people, if the signature authorization is effective, generating the procuration signature based on collision property of the chameleon hash function, and digital signature does not need to be carried out on information, when a verifier receives the authorization letters and the procuration signature, firstly, verifying whether the authorization letters are effective or not, after the authorization letters are verified to be effective, and then verifying validity of the procuration signature. According to the application of the novel procuration signature and verification method based on the integer factorization problems, processing efficiency of the procuration signature is high, and the length of the procuration signature is short. The novel procuration signature and verification method based on the integer factorization problems is suitable for environments such as mobile networks and the wireless networks where computing power and network bandwidth are limited.
Owner:UNIV OF ELECTRONICS SCI & TECH OF CHINA
Batch self-auditing method for cloud storage data
InactiveCN105978695AGuaranteed confidentialityVerify integrityUser identity/authority verificationCloud userCiphertext
The invention belongs to the technical field of information security, and in particular relates to a batch self-auditing method for cloud storage data. The method of the present invention mainly includes: generating a public-private key pair based on an elliptic curve digital signature algorithm, a public-private key pair of a lightweight signature algorithm, and a lightweight symmetric encryption algorithm: calculating digital signatures of multiple data files, data files Tags and ciphertexts of data files are sent to the cloud server; cloud users generate audit challenge information and send it to the cloud server; the cloud server returns the aggregated audit proof response information to the cloud user; cloud users For the response information, use the digital signature algorithm based on the elliptic curve and the symmetric encryption algorithm to verify the legitimacy of the aggregated audit proof response. The beneficial effect of the present invention is that it solves the problem of batch integrity verification of cloud storage data, enabling users to effectively verify the integrity of multiple data files at the same time.
Owner:SOUTHWEST PETROLEUM UNIV
SM2 signature algorithm security verification method based on random number unknown
ActiveCN104836670AComprehensive analysis of security capabilities against attacksGood for error injection experimentsKey distribution for secure communicationUser identity/authority verificationAttack modelValidation methods
The invention discloses an SM2 signature algorithm security verification method based on an random number unknown. The method comprises the following steps: (1) signing N+1 messages M respectively by adopting an SM2 signature algorithm, and injecting an error into every SM2 signing in order that identical errors occur in signing results s of identical set bit parts of a random number k used in every signing; (2) subtracting error signing results s in other N signing respectively from the error signing result of first signing with reference to an equation of the error signing result s of first signing to obtain an equation set, namely, a lattice attack model; and (3) solving the lattice attack model, recovering all bits of the random number k used in every signing, substituting the recovered bits into an equation for calculating corresponding signing results s to obtain a private key dA, and judging that the SM2 signature algorithm is unsafe if the private key dA is a correct private key. Through adoption of the method, the security capability of the SM2 signature algorithm in attack resistance can be analyzed more effectively and comprehensively.
Owner:INST OF SOFTWARE - CHINESE ACAD OF SCI +2
Digital signature method and system
ActiveCN104618107ALow costReduce security risksKey distribution for secure communicationUser identity/authority verificationDigital Signature AlgorithmComputer security
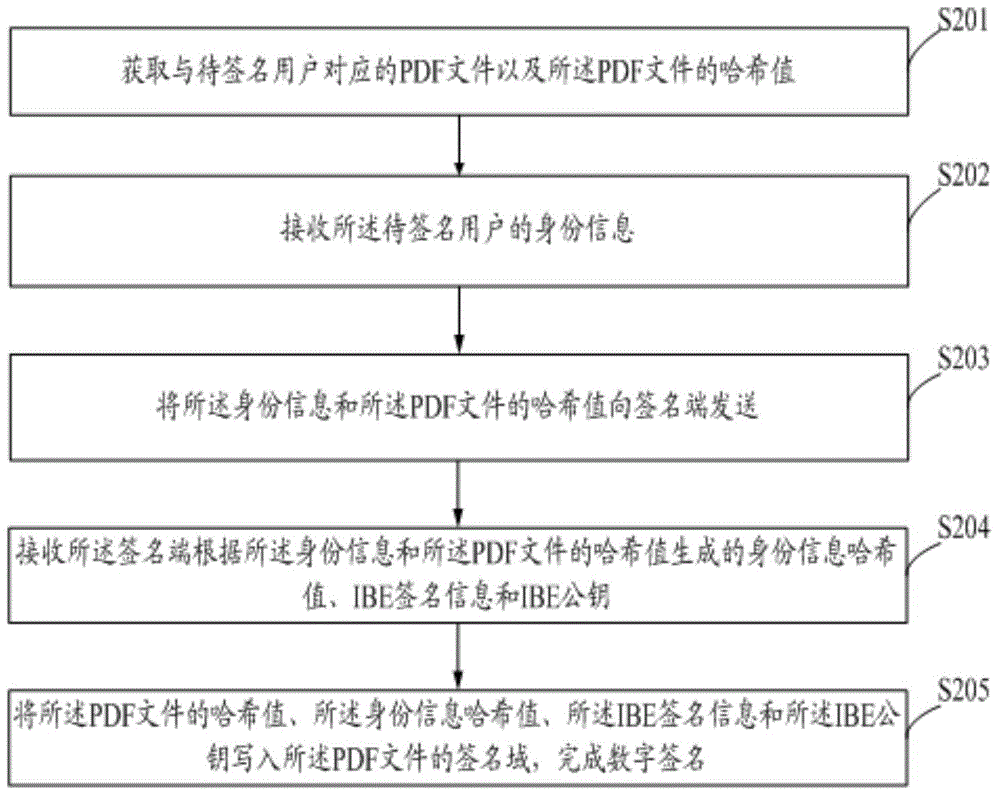
The invention discloses a digital signature method and system. The method comprises obtaining a PDF file corresponding to a to-sign user identity information and a PDF file Hash value; receiving the identity information of the to-sign user; sending the identity information and the PDF file Hash value to a signature end; receiving an identity information Hash value, IBE signature information and an IBE public key which are generated by the signature end according to the identity information and the PDF file Hash value; writing the identity information Hash value, the IBE signature information and the IBE public key into a PDF file signature domain to complete digital signature. By means of the method and the system, the digital signature can be achieved without issuing digital certificates to users, the system is convenient to operate, the signature efficiency is high, real-time IBE secret keys are generated according to user identity information, and counterfeit is difficulty, accordingly, potential safety hazards and digital signature costs can be reduced.
Owner:广东信鉴信息科技有限公司 +1
Encryption-decryption coprocessor for SOC, implementing method and programming model thereof
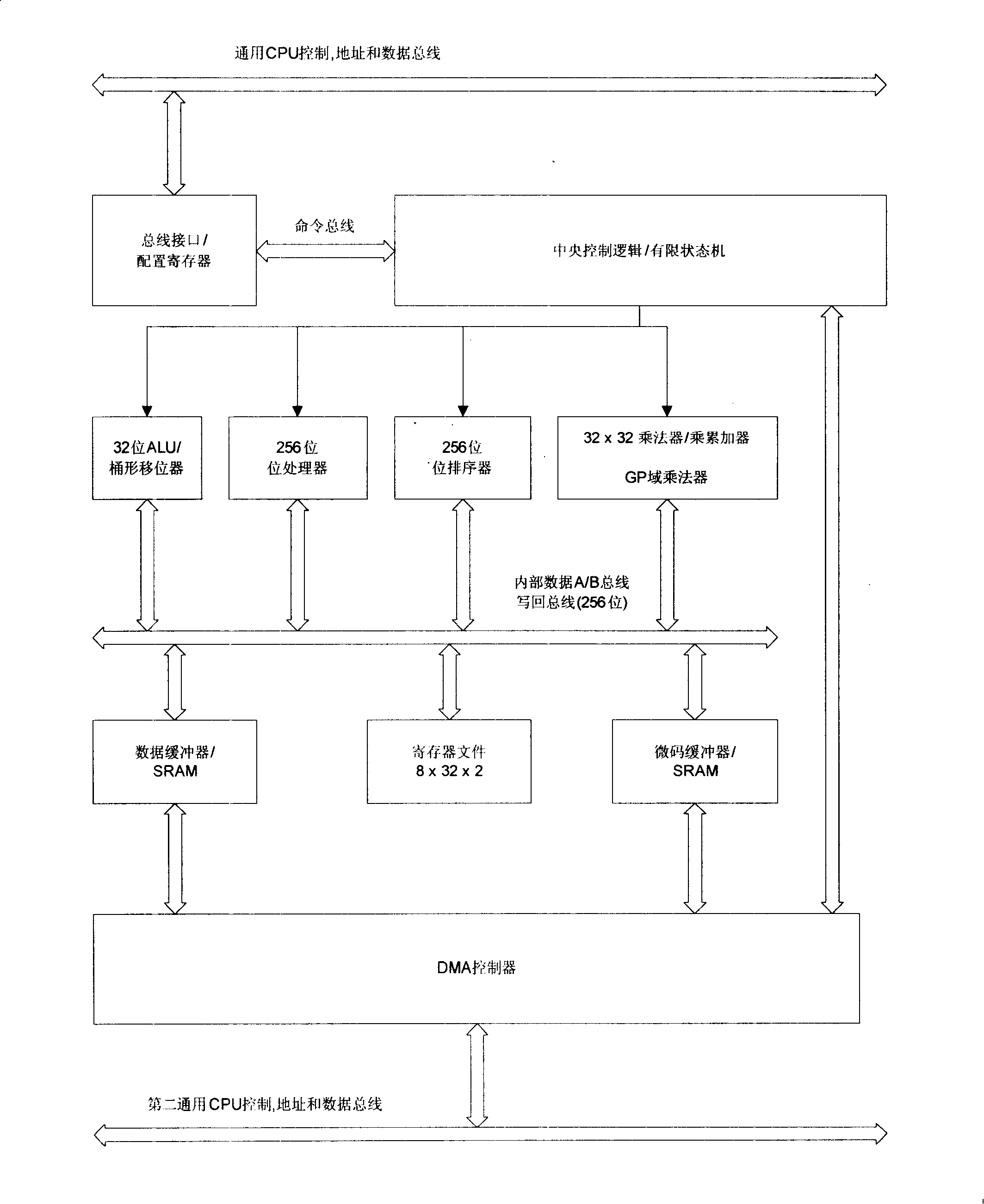
InactiveCN101201811AFlexible and economical realizationMeet the design requirementsArchitecture with single central processing unitCoprocessorData retrieval
The invention discloses a coprocessor used for decryption and encryption of an SOC, an accomplishing method and a programming model. A bus interface is connected with a general CPU bus and receives read-write order from the general CPU bus; a central control module is used for controlling the read-write order received by the bus interface and triggering the start, implementation and stop of the corresponding action of the coprocessor; a 256 bits bit processor implements the common data retrieval and hash algorithm in the encryption algorithm and the digital signature algorithm; a DMA controller is connected with a second general CPU bus and conducts data processing under the control of the central control module. The accomplishing method divides various encryption-decryption algorithms into various hardware arithmetic units which are controlled and dispatched by software. The programming model is the description of a register. The invention is more flexible and economic, can realize most known encryption-decryption algorithms and can meet the design requirements of most SOC chips.
Owner:边立剑 +1
PDF file digital signature and verification method and system
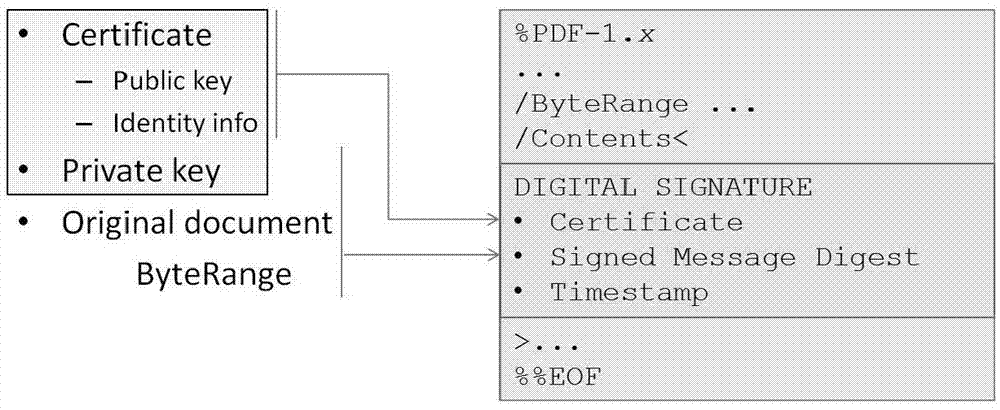
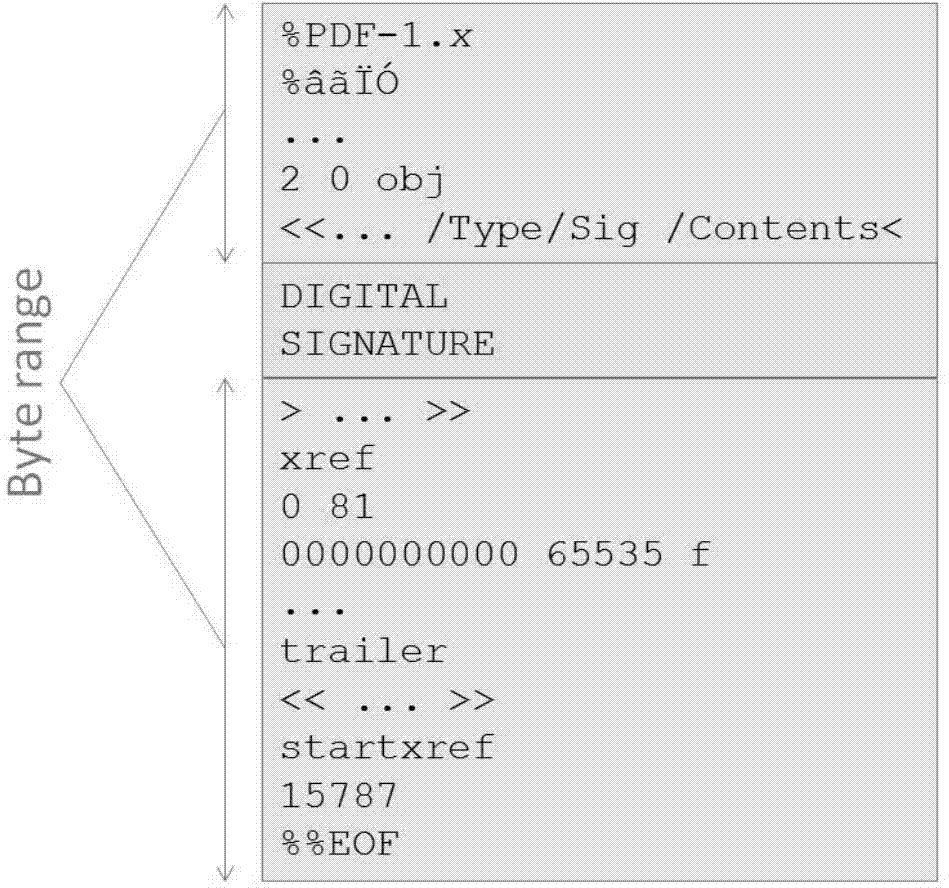
ActiveCN103617403AMeet the need to add hidden signaturesEnsure safetyUser identity/authority verificationDigital data protectionValidation methodsDigital Signature Algorithm
The invention provides a PDF file digital signature and verification method and system. The PDF file digital signature method includes the following steps of obtaining data, to be verified, of a PDF file to be signed and the data length of the data to be verified; creating the text of a digital signature according to the data to be verified and the data length; calculating a digital signature value according to the text of the digital signature, a user public key certificate and a user private secret key; writing the digital signature value into the PDF file. According to the PDF file digital signature and verification method and system, an invisible signature which can not be recognized by a client is created, data of the invisible signature can be reedited by the user, and effectiveness of the invisible signature can not be destroyed.
Owner:GUANGDONG CERTIFICATE AUTHORITY
Digital audio watermarking algorithm for copyright management
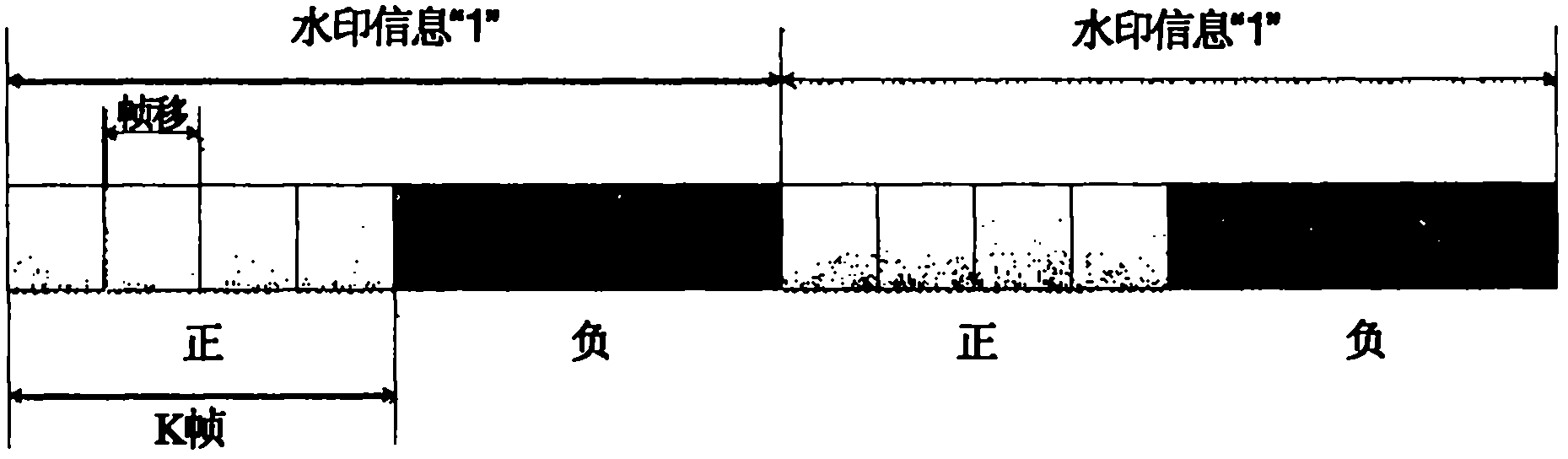
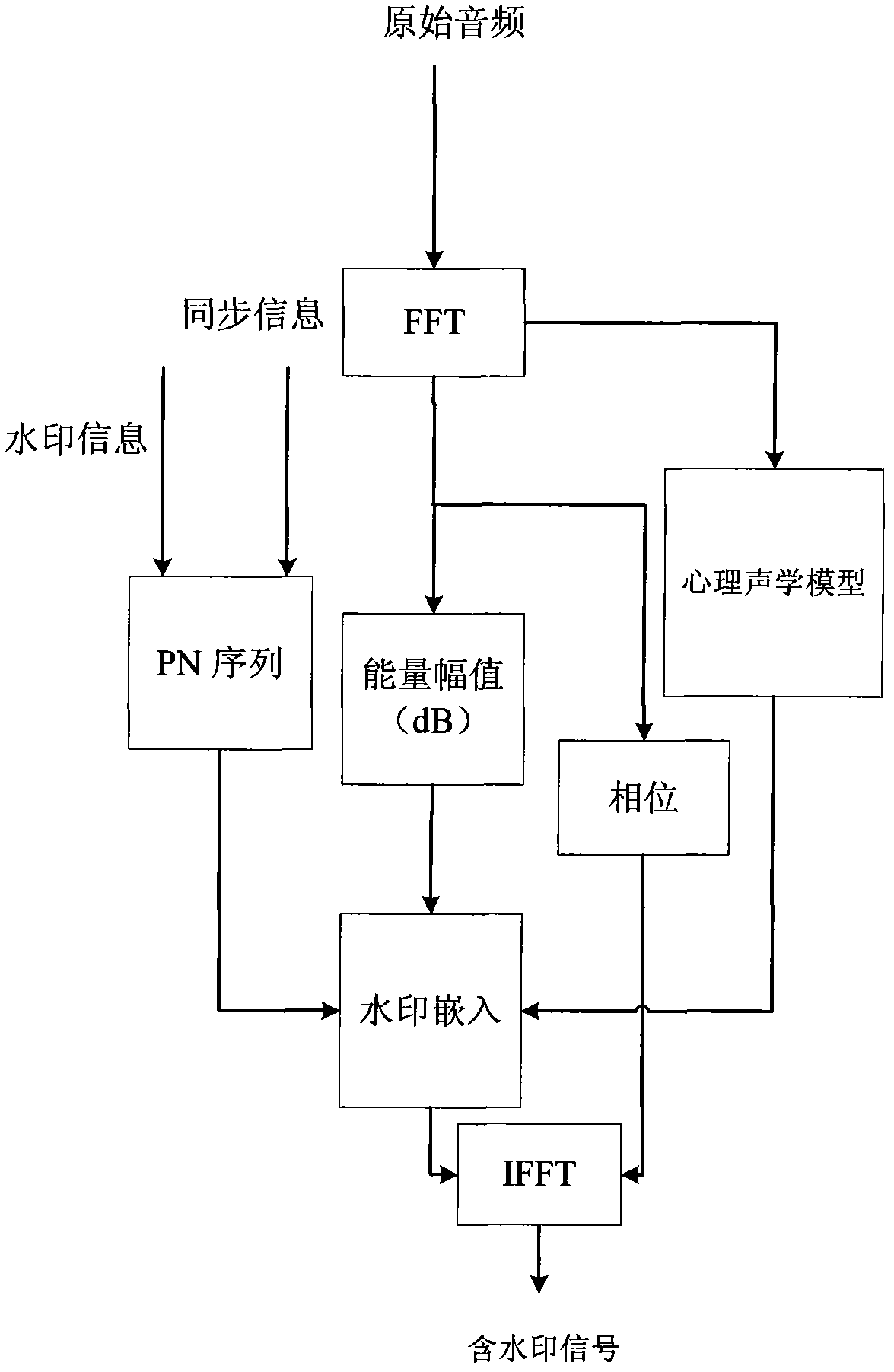
ActiveCN102074240AGuaranteed imperceptibilityImprove robustnessSpeech analysisPaymentDigital Signature Algorithm
The invention relates to a method for performing copyright management by utilizing digital audio watermarking. The method comprises the following steps: embedding a watermarking signal in a logarithm domain of the audio signal energy so that the decoding is unrelated to the amplitude; reasonably designing the frame structure of the embedded watermarking information so that the timing statistical accuracy of a de-embedded result reaches second, and the decoding time accuracy and decoding accuracy rate are not influenced under the operations of cutting, splicing and inserting other audio signals and the like; encrypting the embedded information by an RSA (Asymmetric Algorithm) digital signature algorithm so that the embedded information has security; and effectively reducing interference of the carrier audio to the watermarking information by the embedding algorithm by using the relativity of the short-time stability of the audio so as to obviously improve the success rate and accuracy rate solved by the watermarking. In the method, a digital watermarking technology is introduced to identify the audio materials in a medium library, and then the broadcast flow or audio file are decoded and analyzed to obtain the service conditions of materials, thereby acquiring copyright payment information.
Owner:INST OF ACOUSTICS CHINESE ACAD OF SCI +1
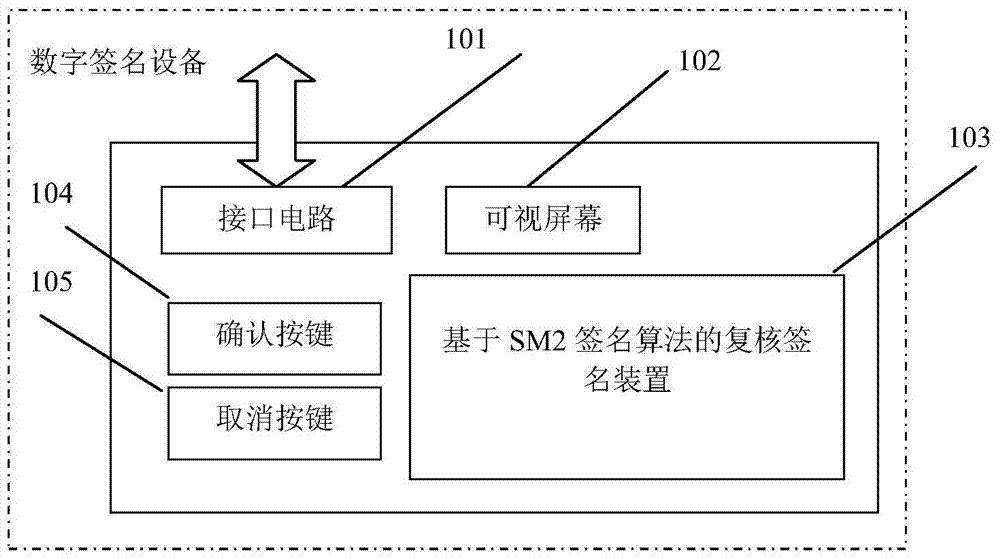
SM2 signature algorithm-based double-check signature method and digital signature equipment
ActiveCN103701598AImprove security levelImprove implementation efficiencyUser identity/authority verificationProtocol authorisationRemote controlDigital Signature Algorithm
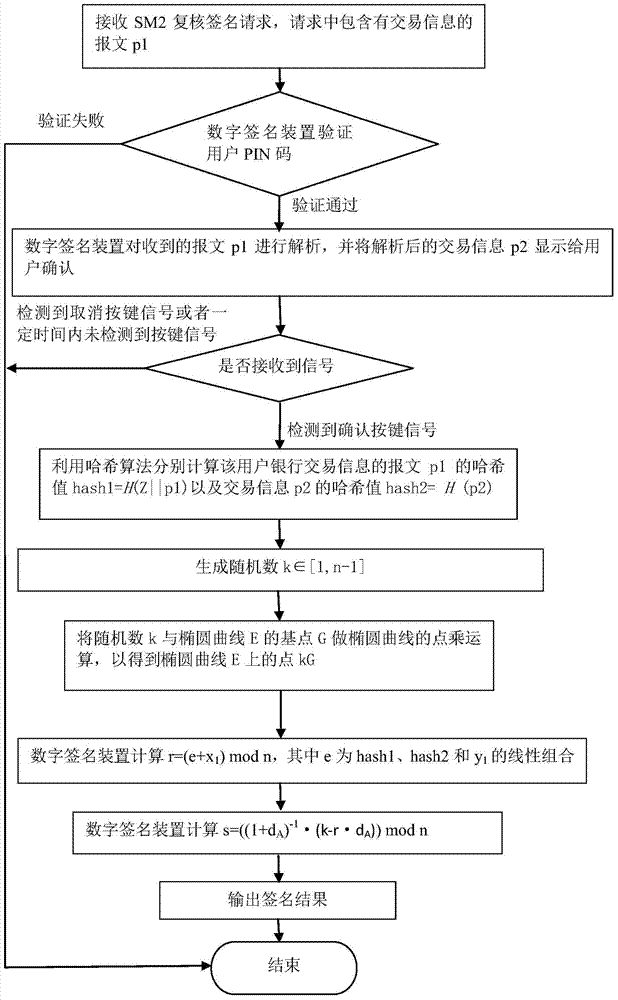
The invention discloses an SM2 signature algorithm-based double-check signature method. The method comprises the following steps: receiving an SM2 double-check signature request from a user, wherein the SM2 double-check signature request comprises a message p1 of bank transaction information of the user; analyzing the message p1 of the bank transaction information of the valid user to generate transaction information p2; displaying the analyzed transaction information p2 to the user for check and confirmation; detecting whether a confirmation signal from the user is received, if so, respectively calculating a hash value hash1=H(Z, p1) of the message p1 of the bank transaction information of the user and a hash value hash2=H(p2) of the transaction information p2 by using a hash algorithm, and generating a random number k which belongs to [1, n-1]; performing a point multiplication operation of an elliptic curve on a random number k and a base point G of the elliptic curve E to obtain a point kG on the elliptic curve E. By adopting the SM2 signature algorithm-based double-check signature method, the technical problem that user fund is stolen by online banking transaction hijacking, transaction manipulation and remote control which easily happen in the conventional method is solved.
Owner:WUHAN ARGUSEC TECH
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com