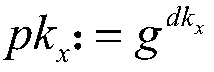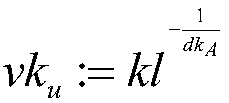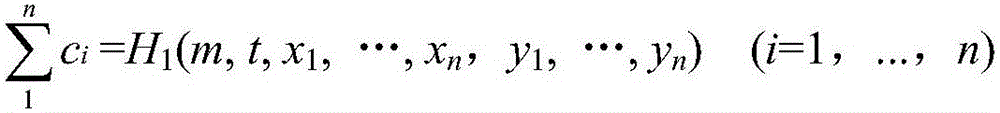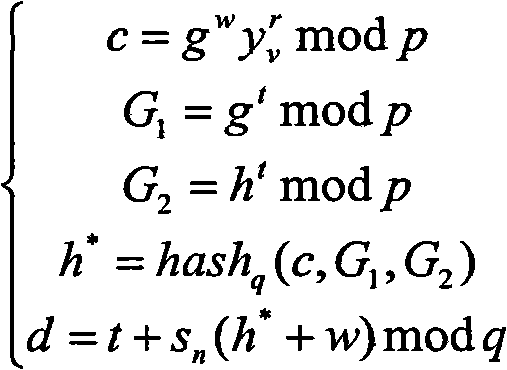Patents
Literature
197 results about "Ring signature" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
In cryptography, a ring signature is a type of digital signature that can be performed by any member of a group of users that each have keys. Therefore, a message signed with a ring signature is endorsed by someone in a particular group of people. One of the security properties of a ring signature is that it should be computationally infeasible to determine which of the group members' keys was used to produce the signature. Ring signatures are similar to group signatures but differ in two key ways: first, there is no way to revoke the anonymity of an individual signature, and second, any group of users can be used as a group without additional setup. Ring signatures were invented by Ron Rivest, Adi Shamir, and Yael Tauman, and introduced at ASIACRYPT in 2001. The name, ring signature, comes from the ring-like structure of the signature algorithm.
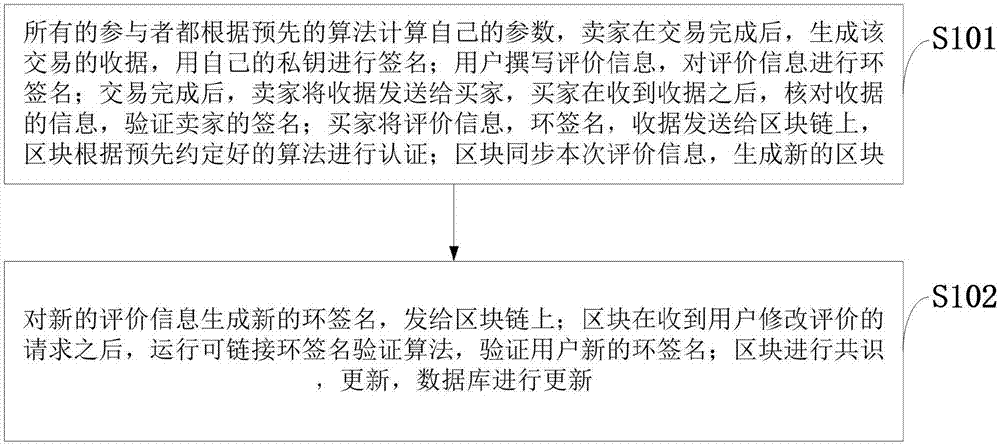
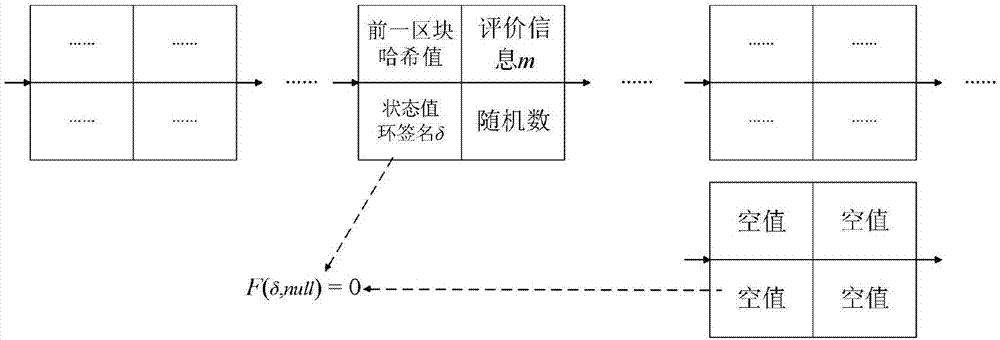
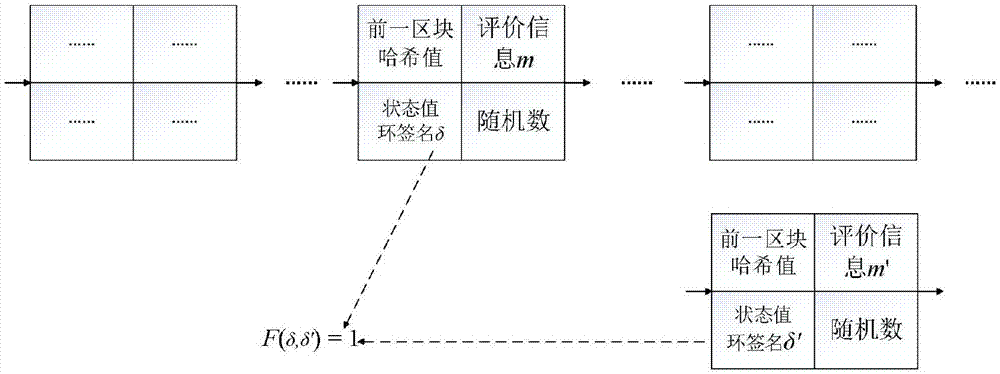
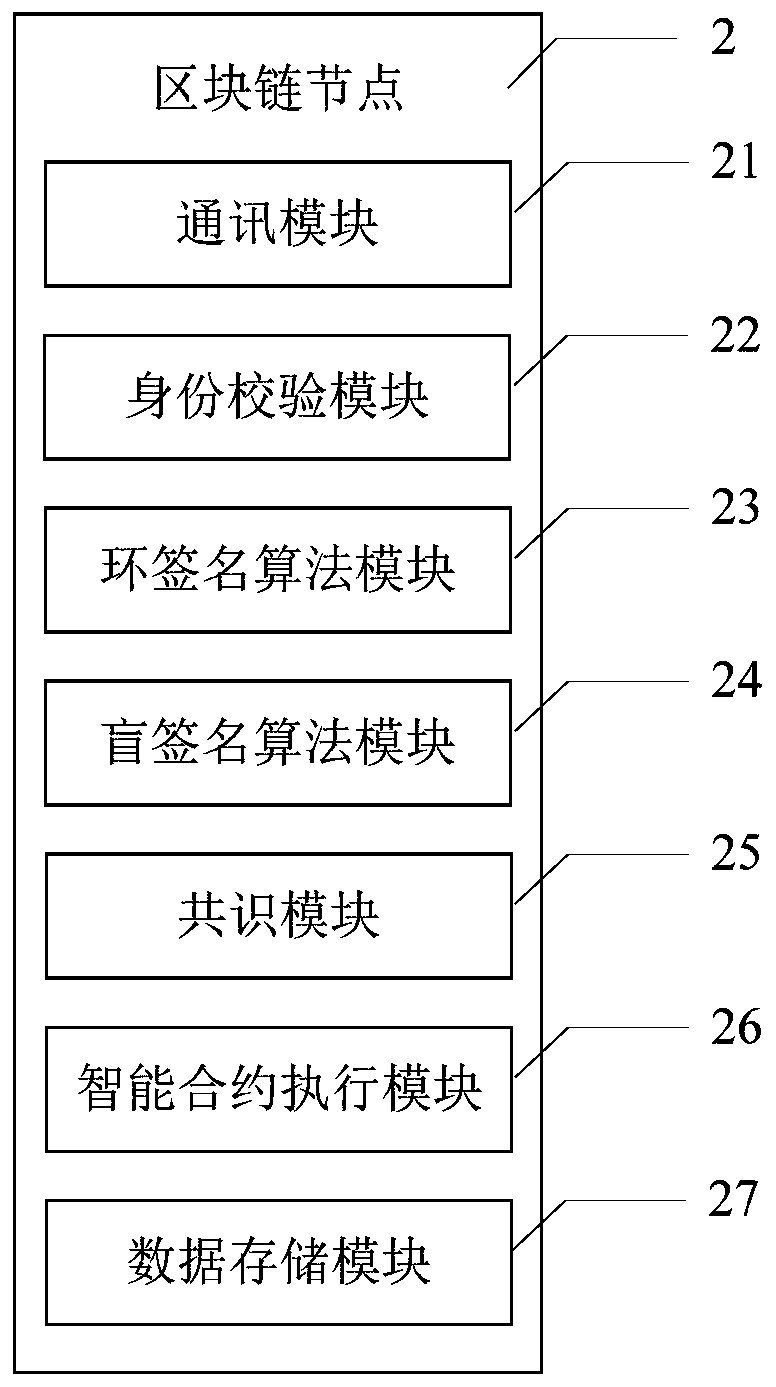
Modifiable reputation evaluation system and method based on block chain, and electronic payment system
ActiveCN107967557AAvoid injusticeGuaranteed transaction privacyFinanceDigital data protectionRing signatureE-commerce
The invention belongs to the e-commerce technology field and discloses a modifiable reputation evaluation system and method based on a block chain, and an electronic payment system. A receipt from a seller is received by a user, the signature of the seller in the receipt is verified, and the evaluation information is generated; after verification is completed, a ring signature of the evaluation information is generated by the user, and the ring signature is sent to the block chain; the receipt and the ring signature of the user are verified by the block chain; a database is updated after the block is generated; a new signature is acquired by the user through a signature algorithm, and the new signature is sent to the block chain; validity of the signature is verified by the block chain, and whether the two signatures are completed by the same user is determined; a pointer corresponding to the block of a previous message is modified after verification completion, the previous message ismarked as invalid, and the previously-revoked information is replaced by the block of the message. The method is advantaged in that on the condition that user anonymity and transaction non-tamperability are guaranteed, integrity and openness of the evaluation information are guaranteed, and reliability of the evaluation information is guaranteed.
Owner:XIDIAN UNIV
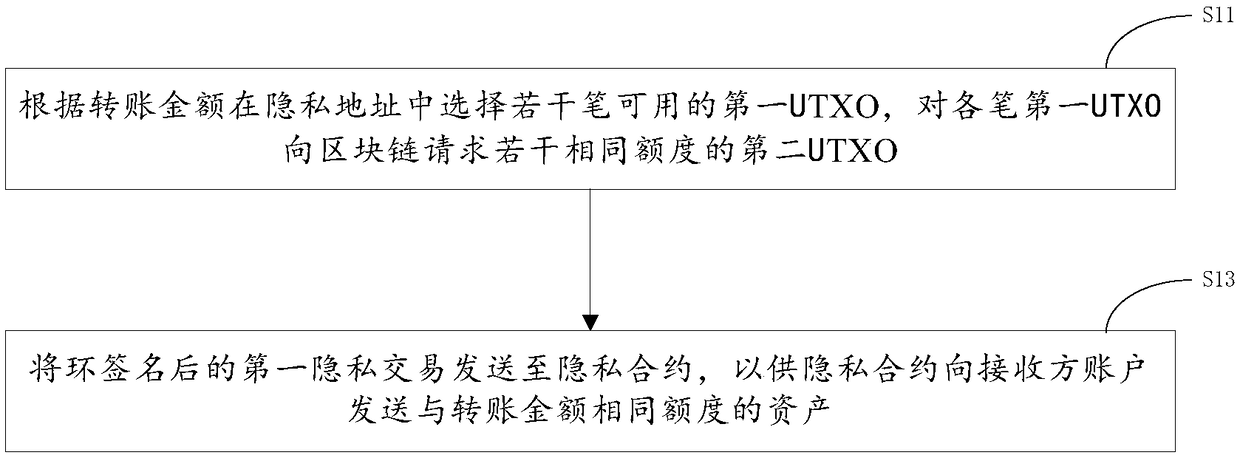
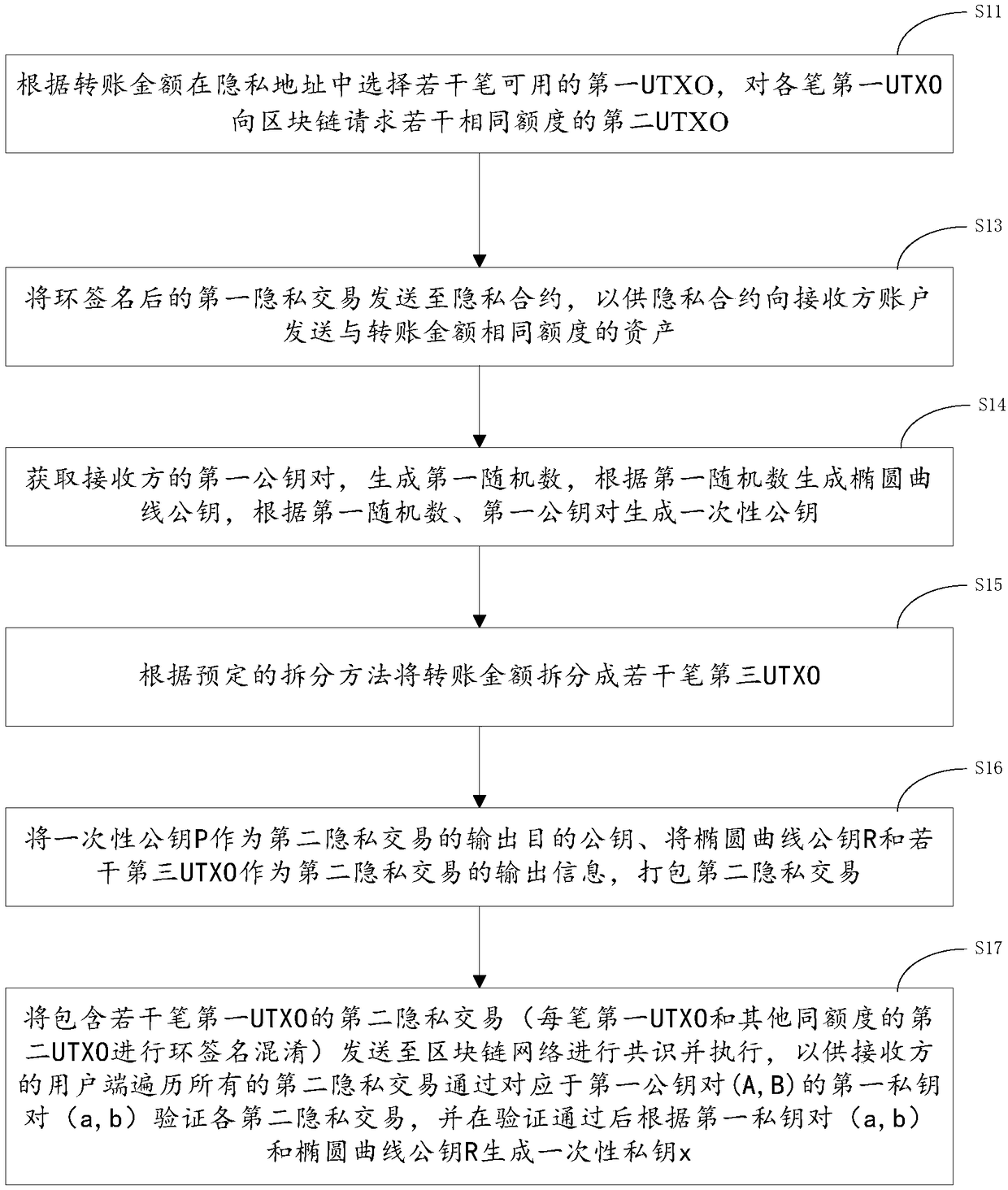
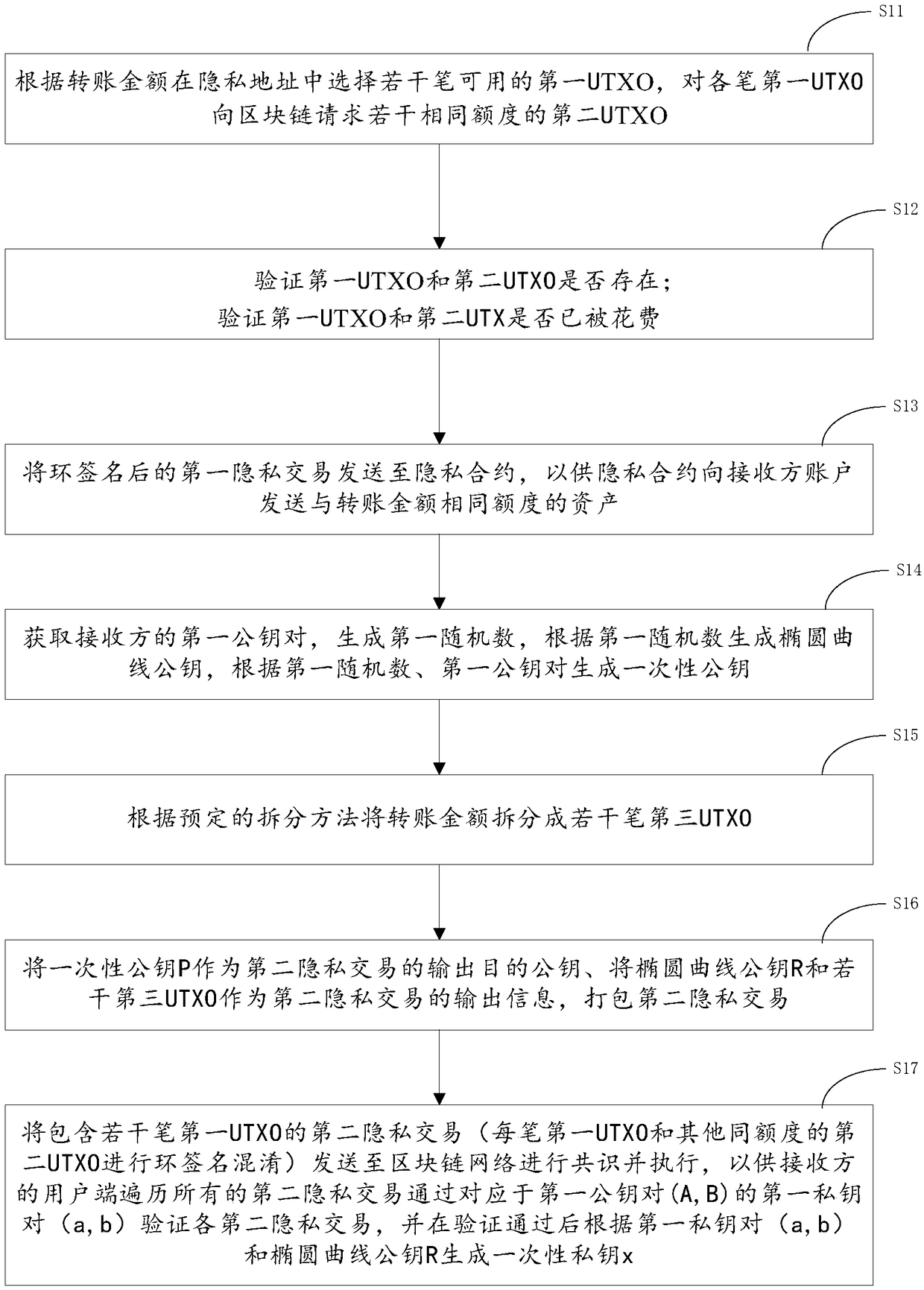
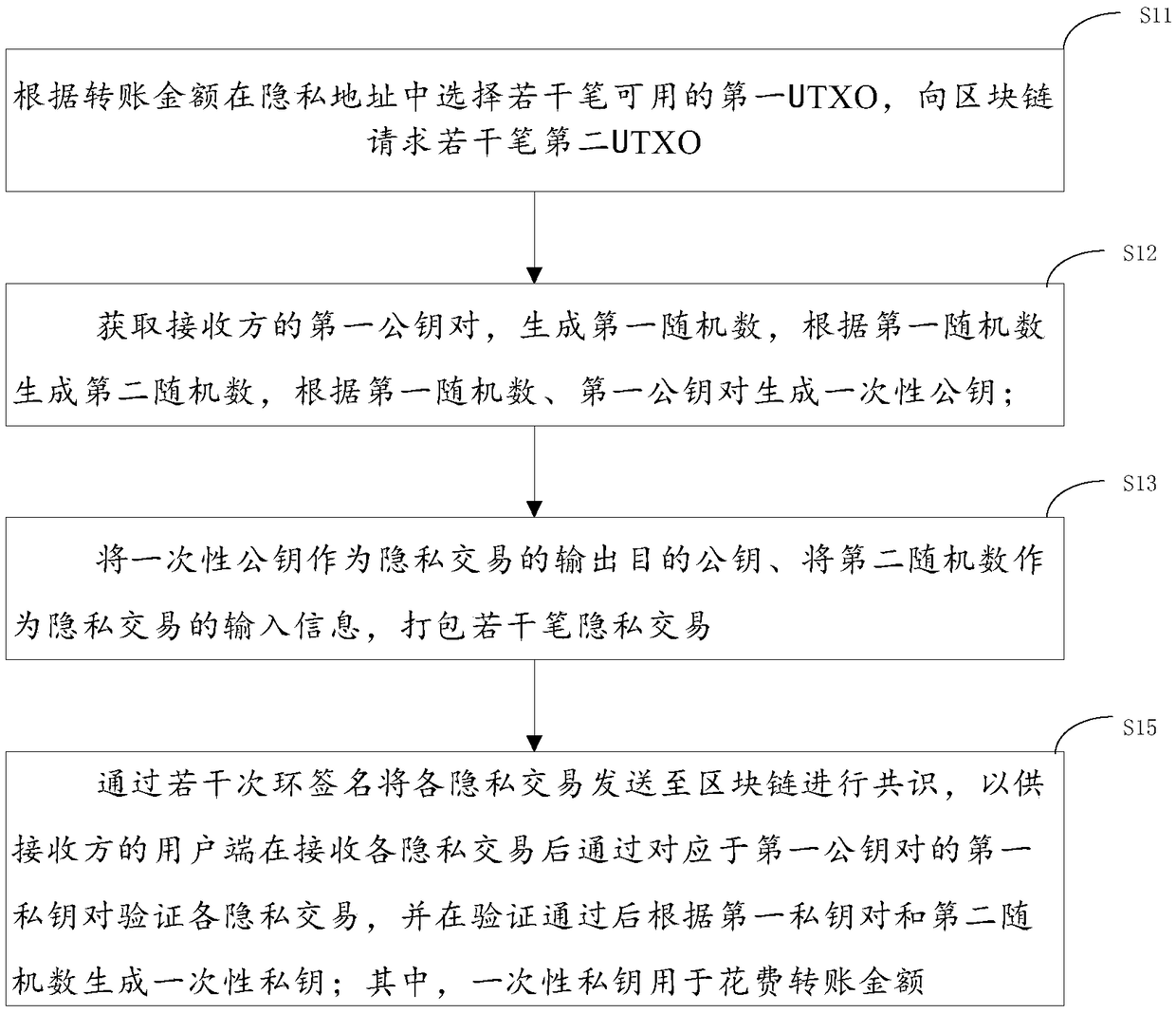
Privacy transaction method, system and device
PendingCN109034800AFree circulationTransaction realizationAnonymous user systemsPublic accountRing signature
The invention provides a privacy transaction method, a system and a device. The method comprises the following steps: selecting a plurality of available first UTXOs in a privacy address according to atransfer amount; requesting a plurality of second UTXOs with the same quota from a block chain for each of the first UTXOs; selecting a plurality of available first UTXOs in the privacy address according to the transfer amount; and selecting a second UTXO with the same quota from the block chain. Wherein each of the second UTXOs is used for ring signature confusion of UTXOs of transfer transactions; the ring-signed first privacy transaction is sent to a privacy agreement for the privacy agreement to send assets of the same amount as the transfer amount to a recipient account. The ring-signedfirst privacy transaction is sent to a privacy agreement for the privacy agreement to send assets of the same amount as the transfer amount to a recipient account. The device ensures that the sender in the privacy transaction process is not traced through ring signature and confusion technology, and the invention realizes the transaction from UTXO model to account model, so that the block chain system can freely flow in the public account and the privacy account.
Owner:HANGZHOU FUZAMEI TECH CO LTD
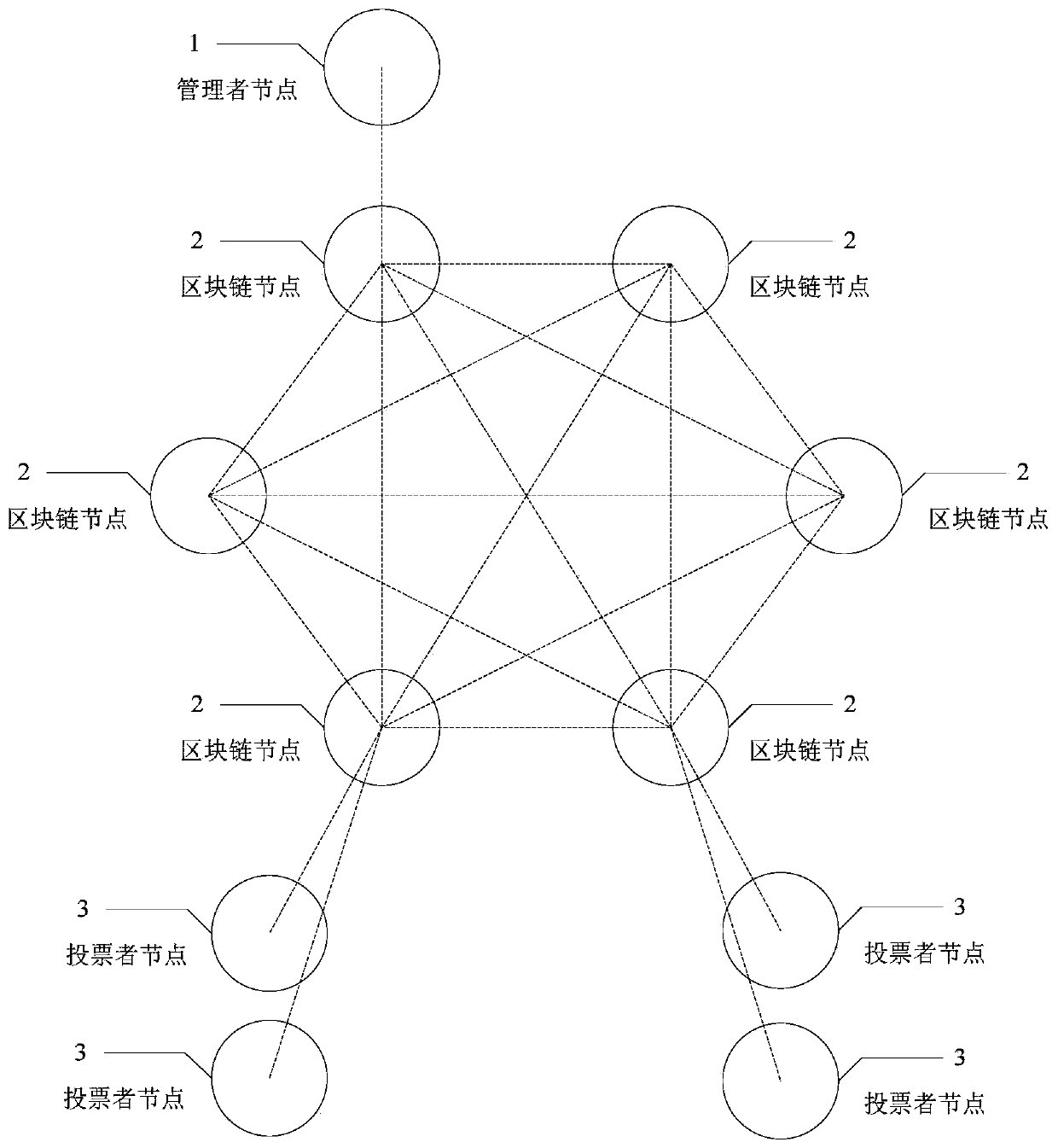
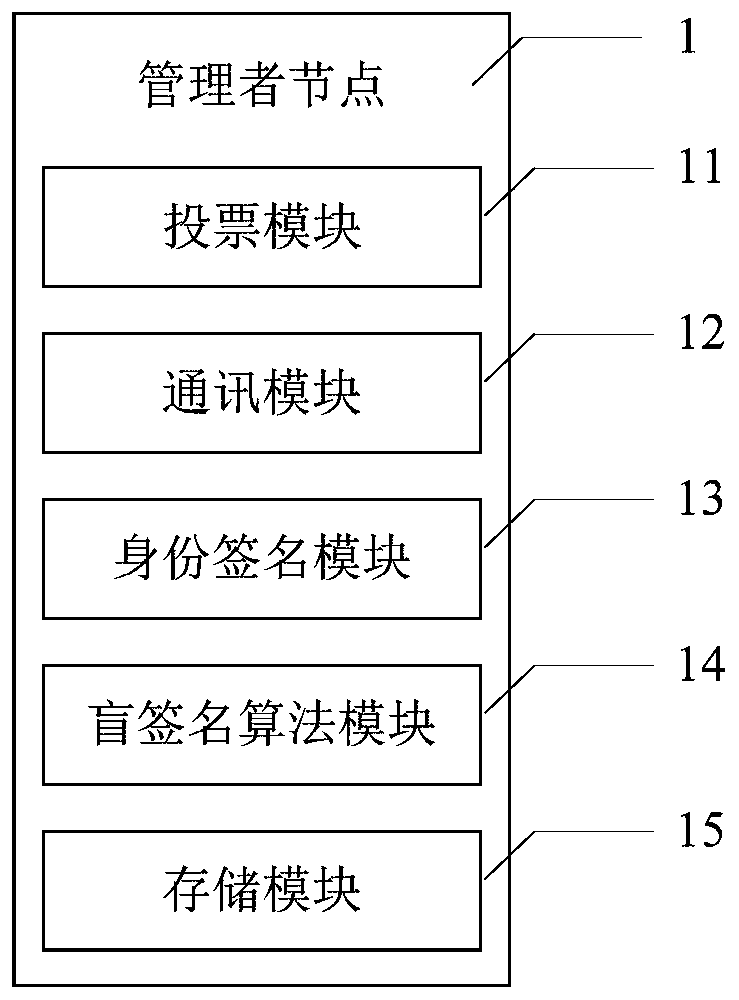
Blockchain anonymous voting system and method
ActiveCN110391911ASolve human cheatingSolve machine failureKey distribution for secure communicationFinanceRing signatureBlind signature
The invention provides a blockchain anonymous voting system and method. A voting system is realized by using a block chain; voting logic is put into an intelligent contract for operation; voting datacan be publicized and transparentized; a centralized node does not exist, even if a single node fault occurs, the overall operation of the system is not influenced;, the voting data in the blockchaincan be tampered by any person, and moreover, by introducing cryptographic technologies such as blind signature and ring signature into the blockchain, details such as identity information and voting intention of voters are hidden on the premise of ensuring the openness and legality of necessary voting data, so that the effect of protecting the privacy of users is achieved.
Owner:INDUSTRIAL AND COMMERCIAL BANK OF CHINA
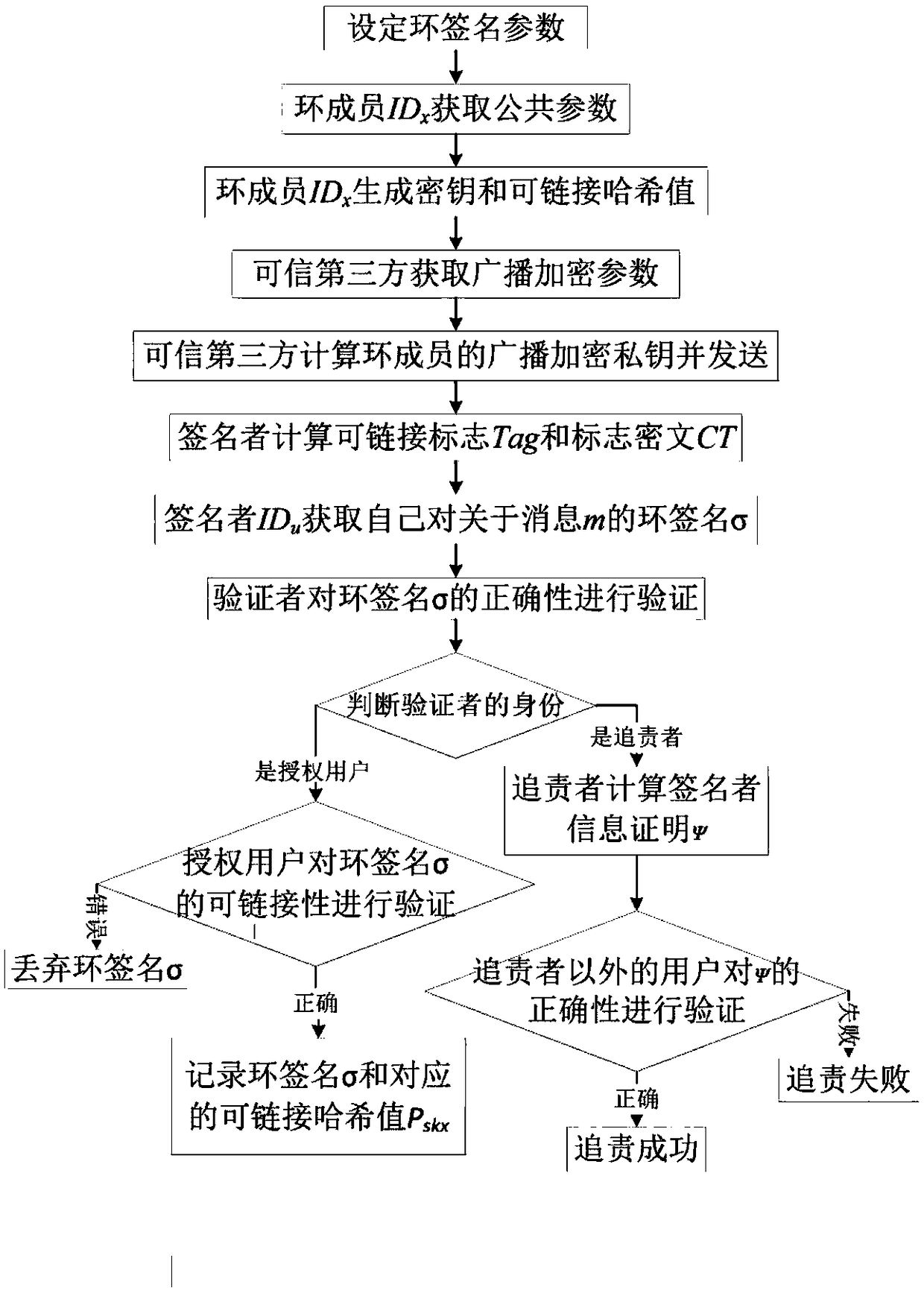
Linkable ring signature method based on anonymous broadcast encryption
ActiveCN109257184ASolve the problem of freely specifying chainable verifiersSolve the problem of anonymityUser identity/authority verificationBlockchainRing signature
The invention provides a linkablering signature method based on anonymous broadcast encryption, aiming at widening the application range of the linkable ring signature and improving the safety of thelinking verifier.The implementation method comprises following steps: setting ring signature parameters;a ring member IDx gets the public parameter; thering member IDx generates a key and a linkable hash value PKskx. The trusted third party obtains broadcast encryption parameters and calculates broadcast encryption private key SKIDx of ring member IDx. The signer calculates a linkable flag Tag anda flag ciphertext CT and obtains a ring signature sigma of the message m. The verifier verifies the correctness of the ring signature sigma; judging the identity of the verifier; an authorized user verifies the linkability of ring signature sigma; an obtainer calculates the signer information to prove Psi. The verifier verifies the correctness of Psi. The invention can be used for a transaction scene under a block chain which needs permission to judge whether the transaction scene can be linked or not.
Owner:XIDIAN UNIV
Traceable anonymous authentication method based on elliptic curve
InactiveCN105812369AImprove securityPublic key for secure communicationUser identity/authority verificationRing signatureDigital Signature Algorithm
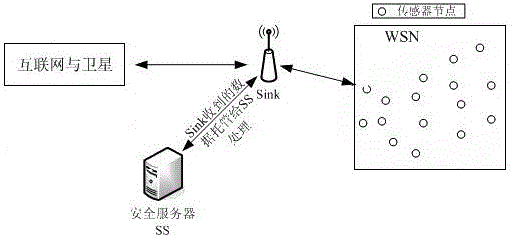
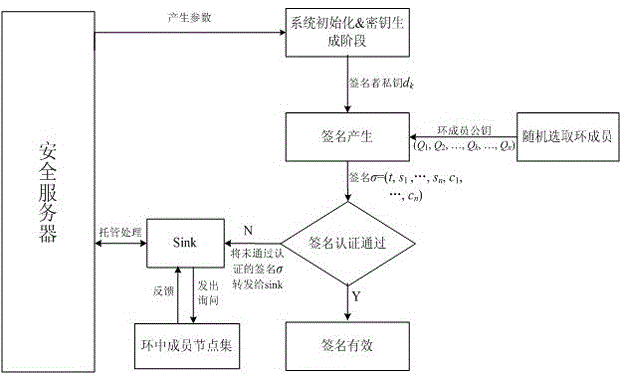
The invention discloses a traceable anonymous authentication method based on an elliptic curve. The method comprises following stages of initializing a system and generating a secrete key, generating anonymous signatures, authenticating the signatures, linking and tracing nodes. According to the method, a ring signature algorithm in a data signing process is improved; the ring signatures and the elliptic curve are combined; the linkage performance is increased; moreover, traceability to malicious nodes is provided, thus finding out the malicious nodes efficiently and accurately; the network security is improved; a critical value is unnecessary; an efficient hop-by-hop message authentication mechanism is provided; the privacy leakage problem of sending nodes in a wireless sensor network can be solved; moreover, the reality and integrity of the sent messages are ensured; and the malicious nodes can be traced if necessary.
Owner:GUANGDONG UNIV OF PETROCHEMICAL TECH
Internet of Vehicles privacy protection trust model based on block chain
ActiveCN110300107AAddress privacy concernsResolve trust issuesUser identity/authority verificationRing signaturePrivacy protection
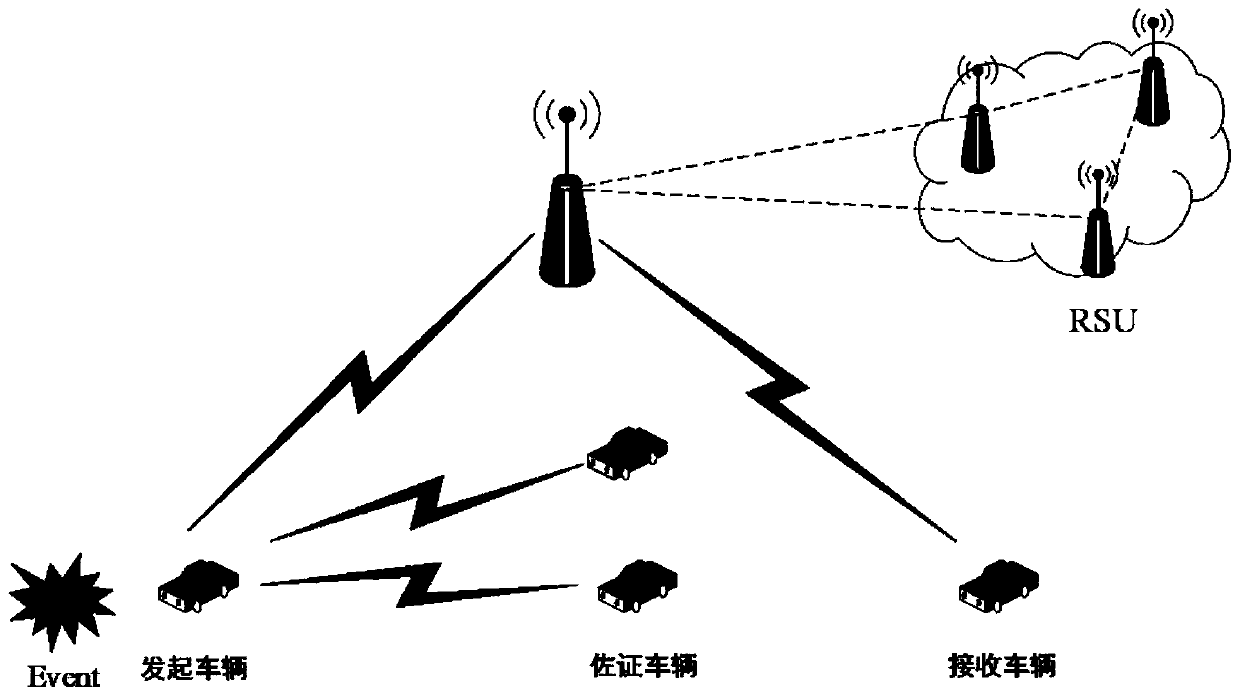
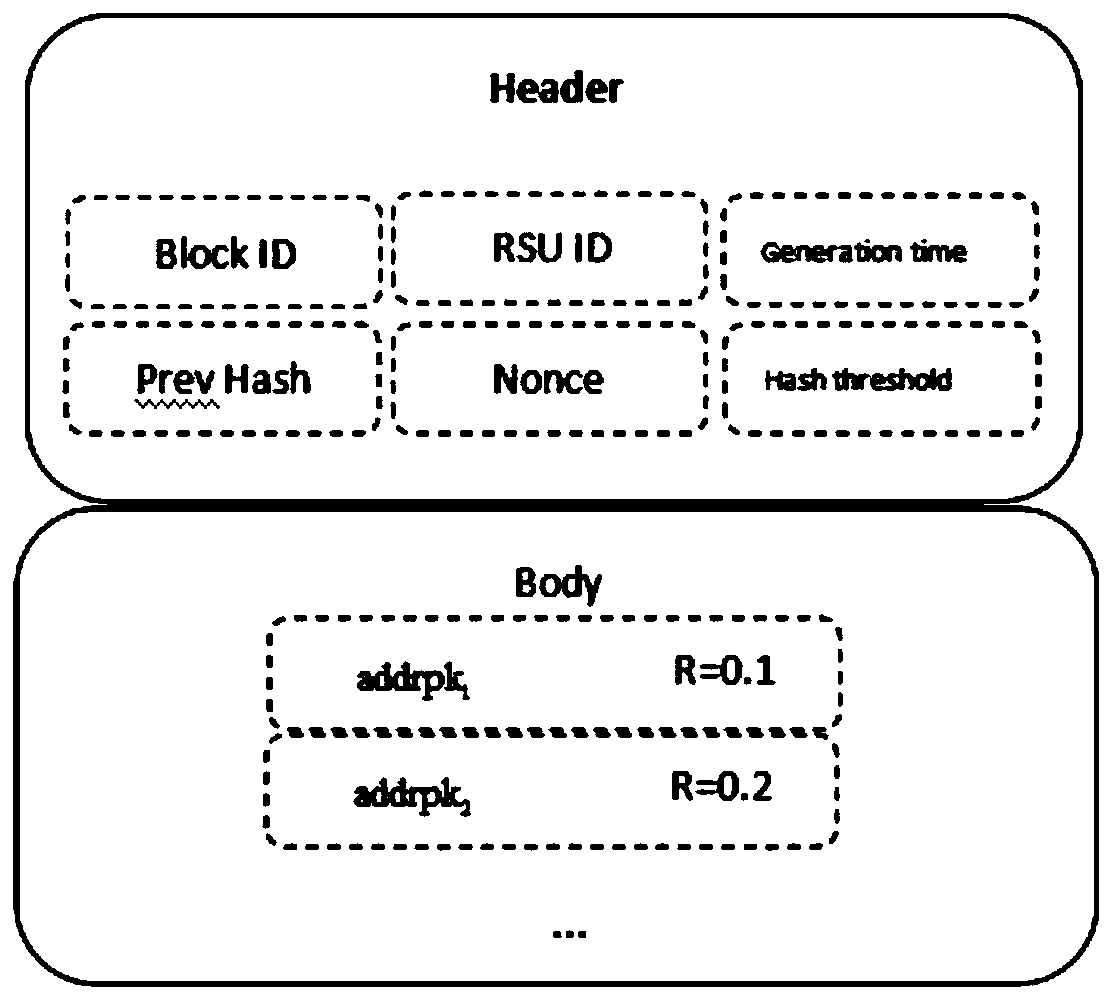
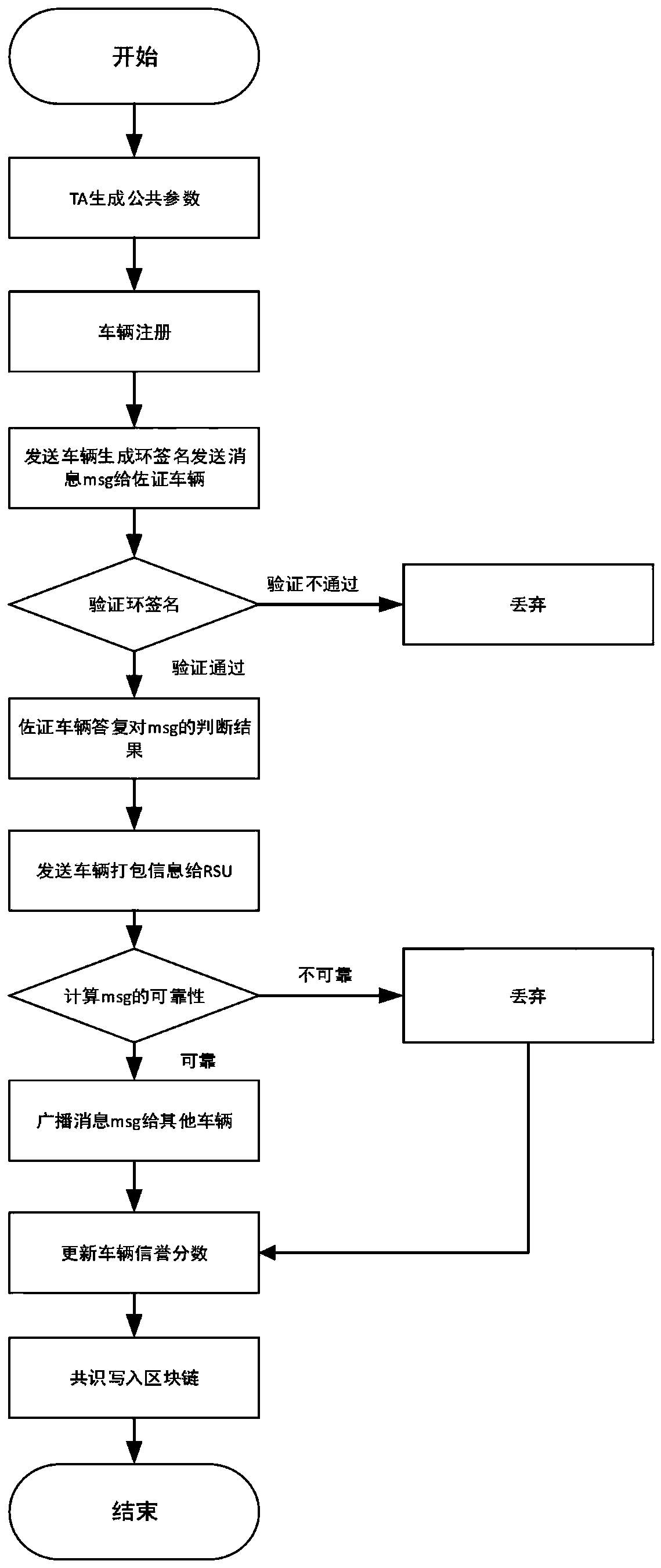
The invention provides an Internet of Vehicles privacy protection trust model based on a block chain. Vehicles on the road generate and broadcast messages through the vehicle-mounted ad hoc network toshare surrounding traffic information so as to improve the traffic efficiency and safety. However, due to the untrusted network environment of the vehicle-mounted ad hoc network, the privacy of the vehicle is easy to expose, and whether the received message is reliable cannot be judged. The message is anonymously sent by the vehicle through the ring signature technology, so that the vehicle is prevented from being tracked by a malicious vehicle. Messages sent by the vehicle are evaluated and screened through a reputation evaluation mechanism based on the block chain technology, and forged information in the messages is filtered. Based on the characteristics of the block chain, it is guaranteed that the vehicle reputation is not maliciously tampered, real-time synchronous updating of the vehicle reputation is achieved, and the safety and usability of the vehicle-mounted ad hoc network are further improved.
Owner:NANJING UNIV OF POSTS & TELECOMM
Ring signature method for anonymizing information based on multivariate public key cryptography
InactiveCN102006165AFix bugs that are no longer safeImprove efficiencyPublic key for secure communicationUser identity/authority verificationRing signatureCryptosystem
The invention discloses a ring signature method for anonymizing information based on multivariate public key cryptography, comprising the following steps: generating system parameters, generating a secret key, generating the ring signature and verifying the ring signature. The ring signature method based on the traditional cryptosystem is subjected to security threat under the quantum computer while the ring signature method based on the multivariate public key cryptosystem solves the problem that the existing ring signature systems are insecure under the quantum computation. The method has the advantages of security and high computing efficiency.
Owner:XIAN UNIV OF TECH
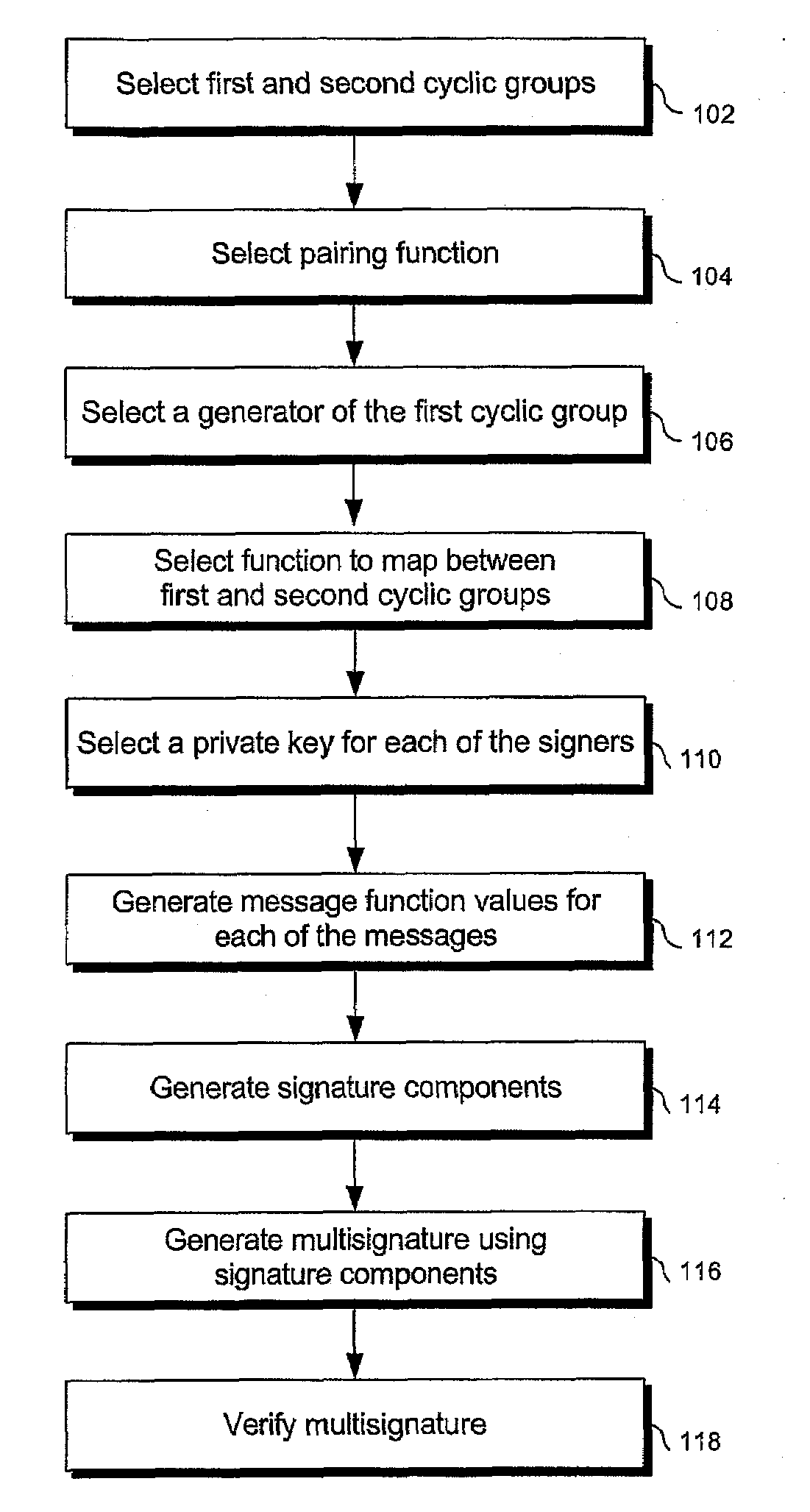
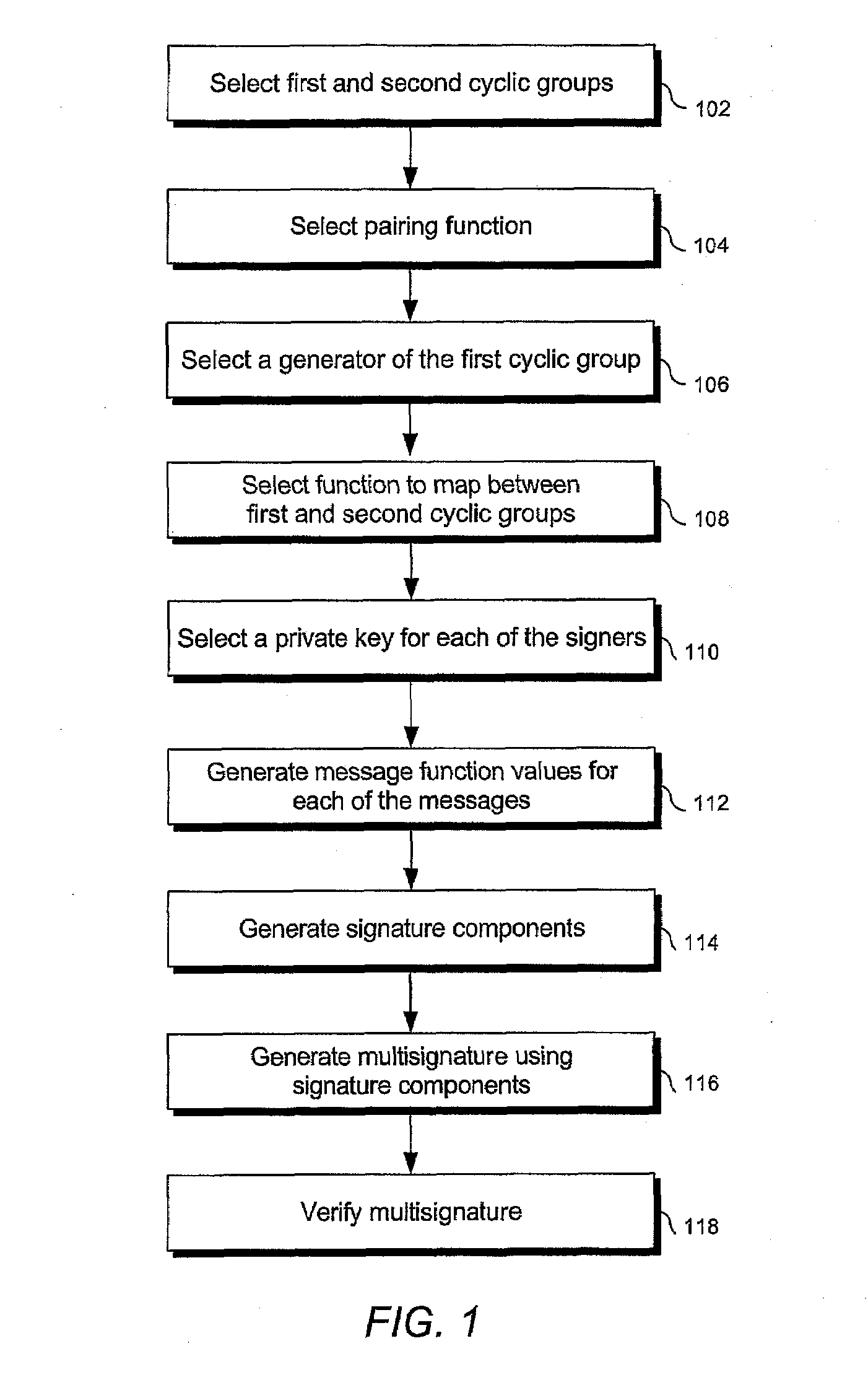
Signature schemes using bilinear mappings
InactiveUS20080178005A1User identity/authority verificationCoding/ciphering apparatusRing signatureMultisignature
Methods and systems are provided for generating and verifying signatures of digital messages communicated between signers and verifiers. Using bilinear mappings, such as Weil or Tate pairings, these methods and systems enable generation and verification of efficient multisignatures, identity-based ring signatures, hierarchical proxy signatures, and hierarchical online / offline signatures.
Owner:NTT DOCOMO INC
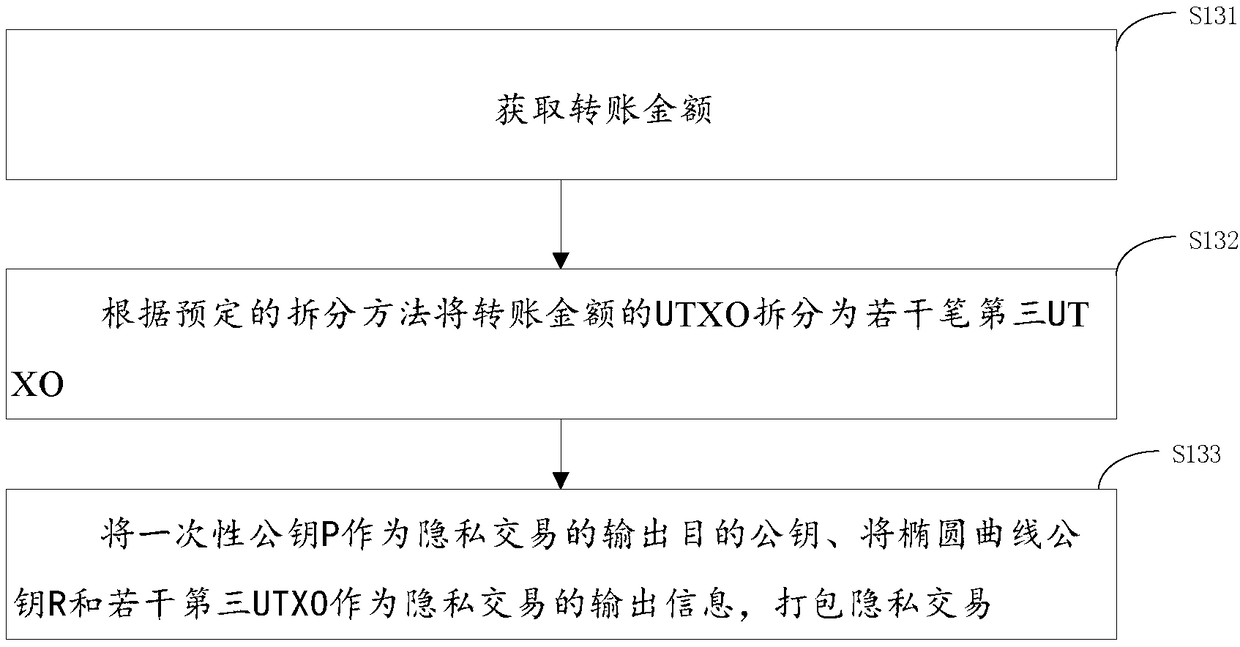
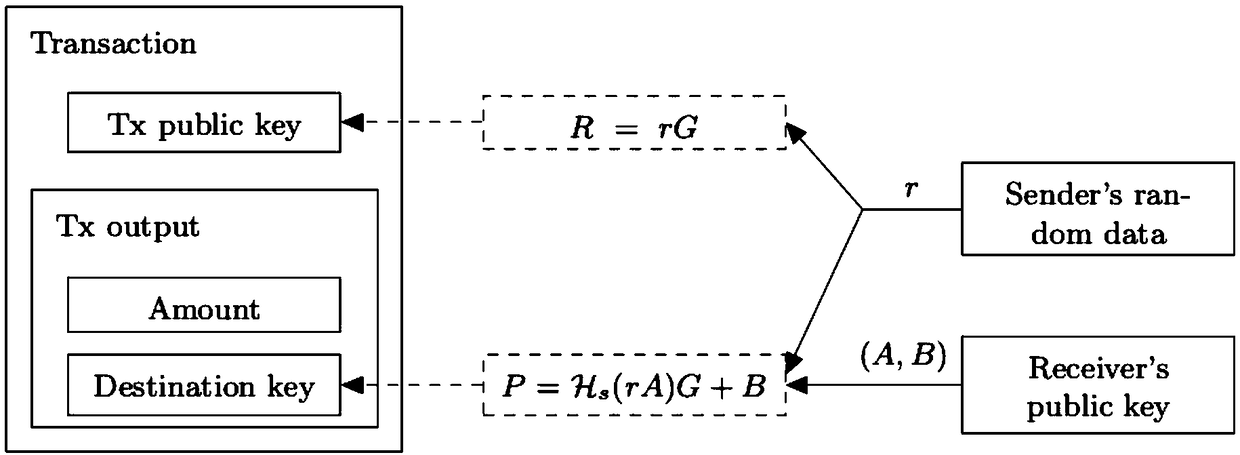
Privacy transaction method and system, device and storage medium
PendingCN109087099AGuarantee informationEasy accessPayment circuitsAnonymous user systemsRing signatureFinancial transaction
The invention provides a privacy transaction method and a system, a device and a storage medium. The method comprises: selecting a plurality of available first UTXOs in a privacy address according toa transfer amount, and requesting a plurality of second UTXOs from a block chain; selecting a plurality of available first UTXOs in the privacy address according to the transfer amount; acquiring a first public key pair of a receiver, generating a first random number, generating a second random number according to the first random number, and generating a one-time public key according to the firstrandom number; taking the one-time public key as the output destination public key of the privacy transaction, taking the second random number as the output information of the privacy transaction, and packaging a plurality of privacy transactions; each of the privacy transactions being sent to a block chain network for consensus through a plurality of ring signatures. The invention ensures the related information of the sender and the receiver by using the ring signature technology and the one-time target address, thereby realizing the unconnectedness and untraceability of the transaction.
Owner:HANGZHOU FUZAMEI TECH CO LTD
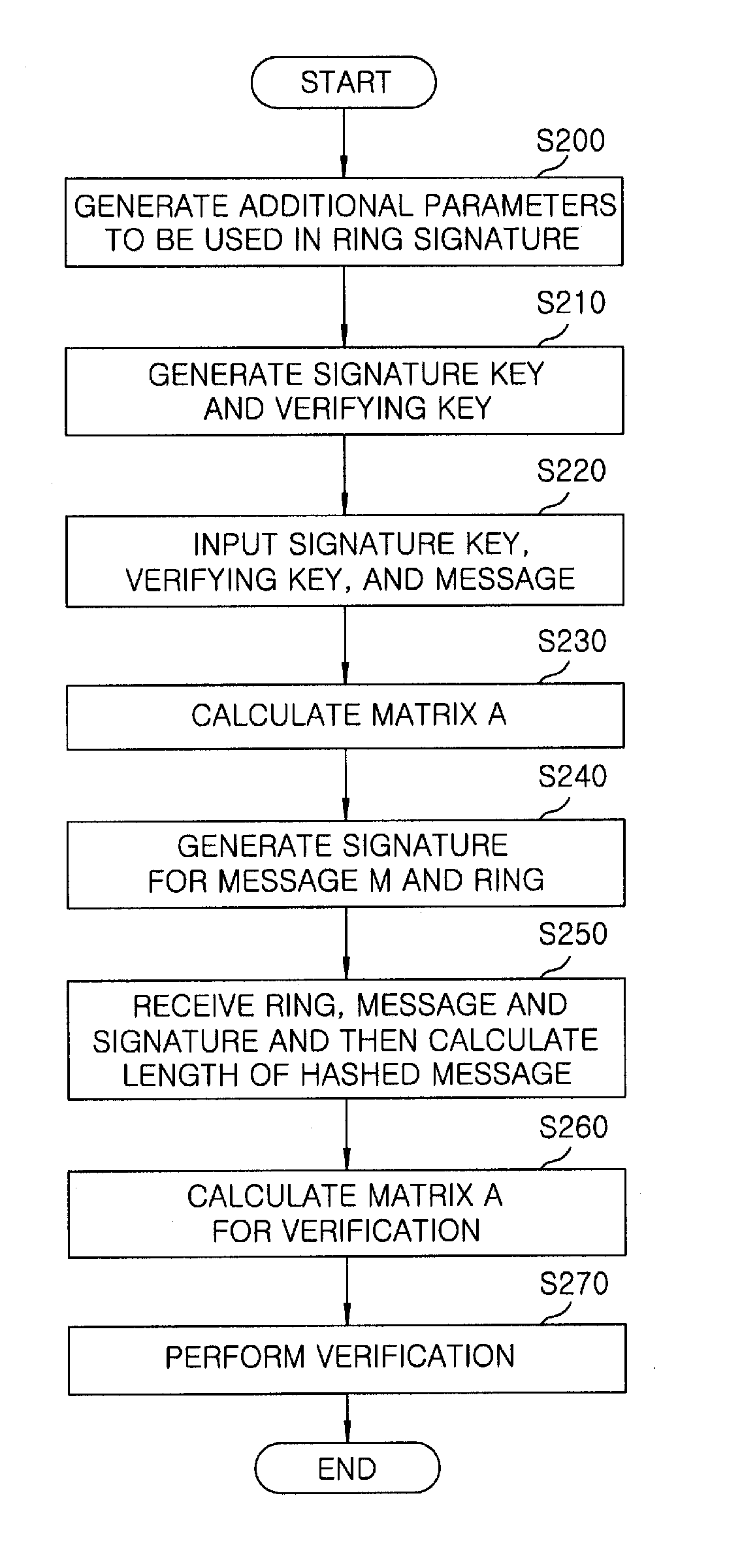
Lattice-based ring signature method
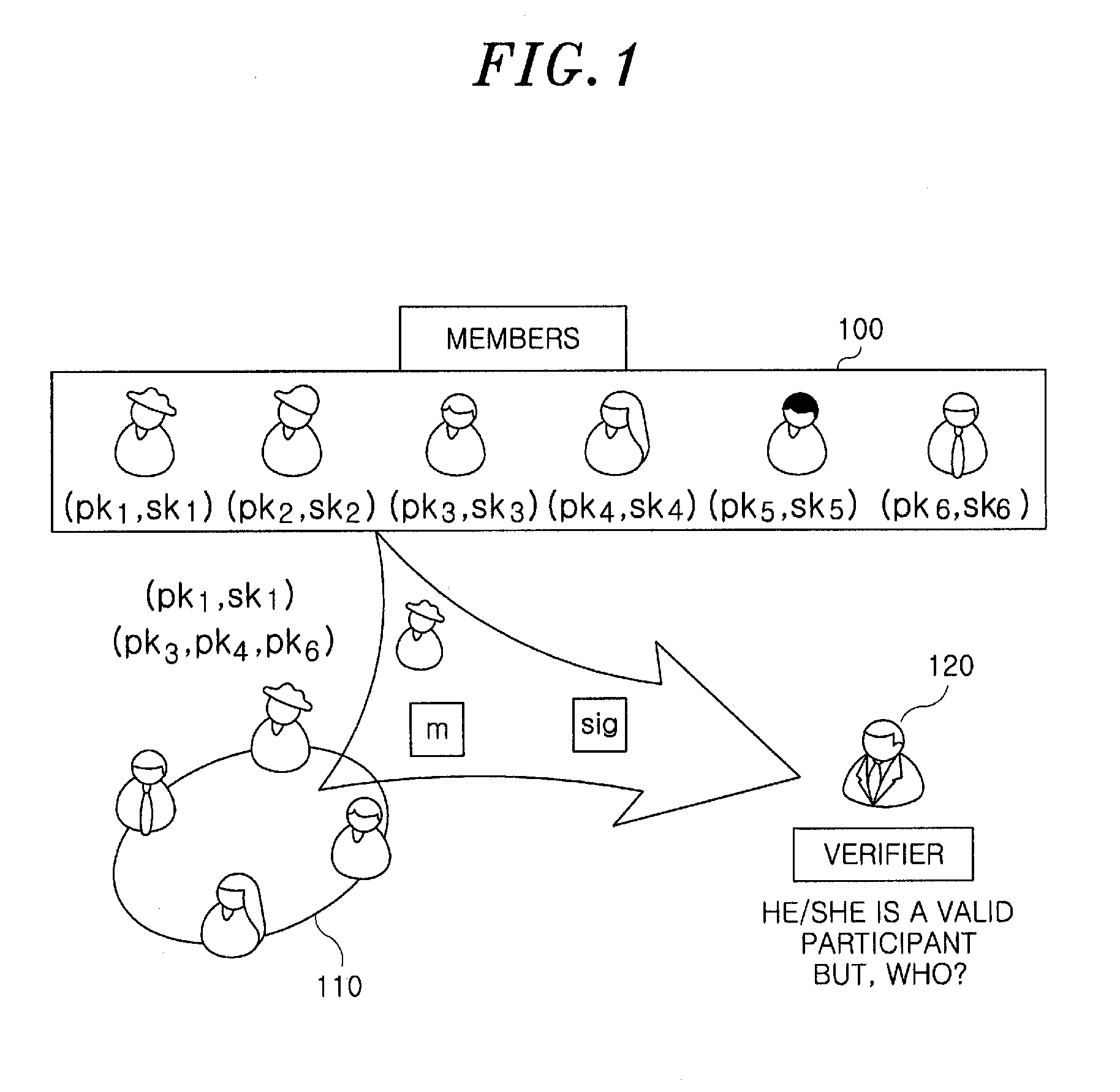
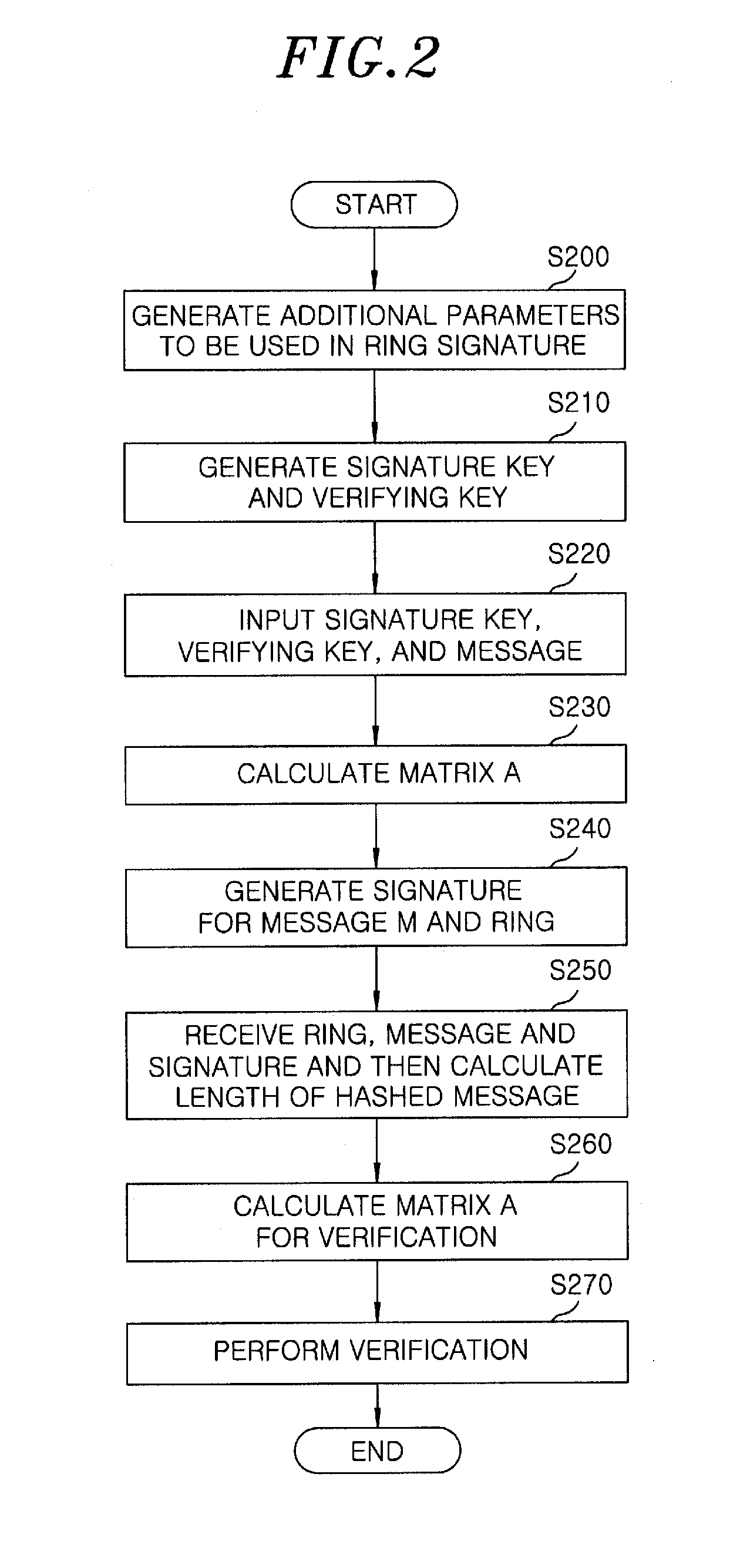
InactiveUS20120166808A1Security configurationImprove securityUser identity/authority verificationDot matrixRing signature
A lattice-based ring signature method includes generating a dimension, a bound, a length of a hashed message, a Gaussian parameter and an open parameter, which are parameters necessary for a ring signature. Further, the lattice-based ring signature method includes generating a signature key and a verifying key for a user who construct a ring by using the parameter necessary for the ring signature. Furthermore, the lattice-based ring signature method generating a signature for a message and the ring by using the signature key and the verifying key.
Owner:ELECTRONICS & TELECOMM RES INST
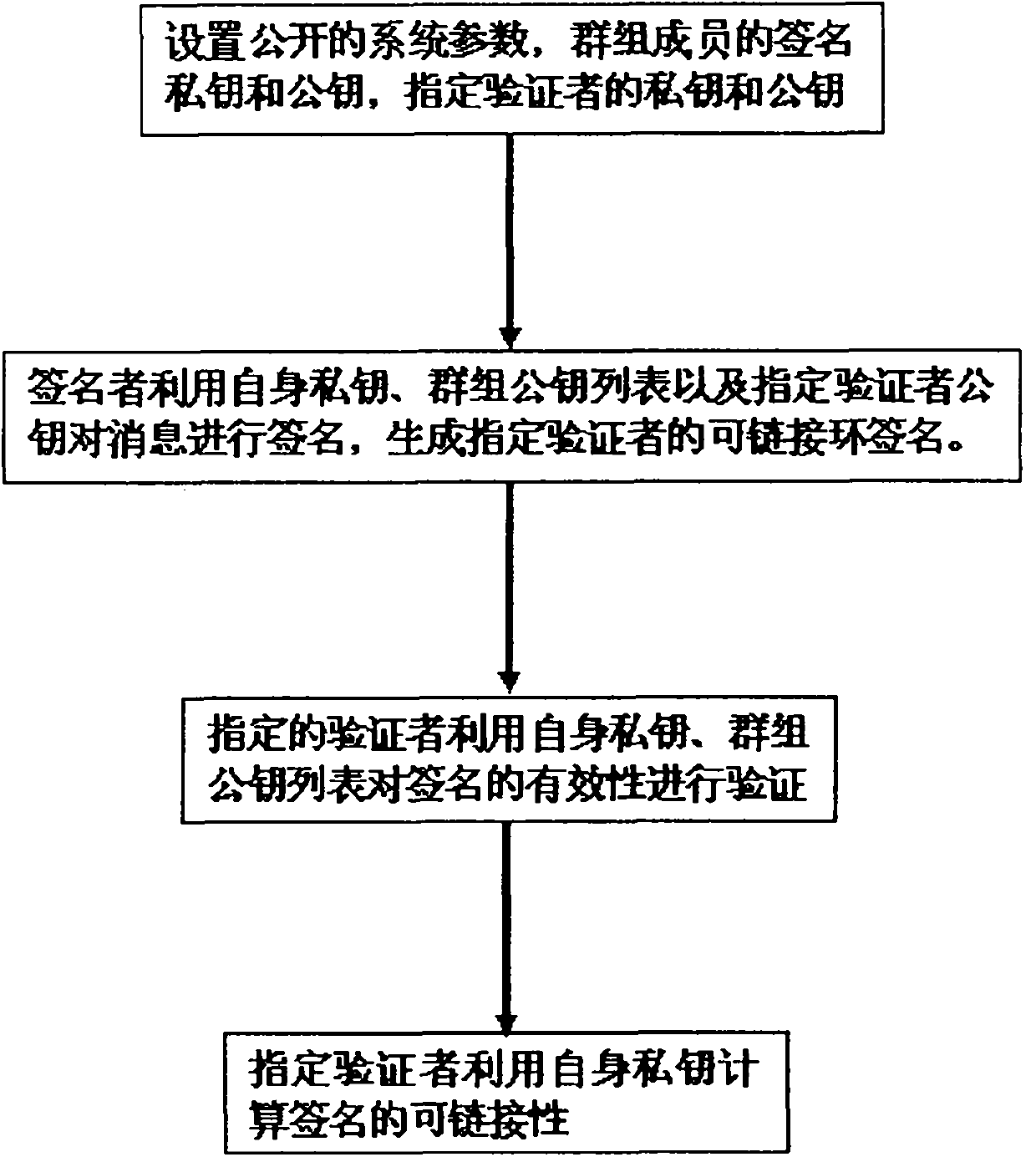
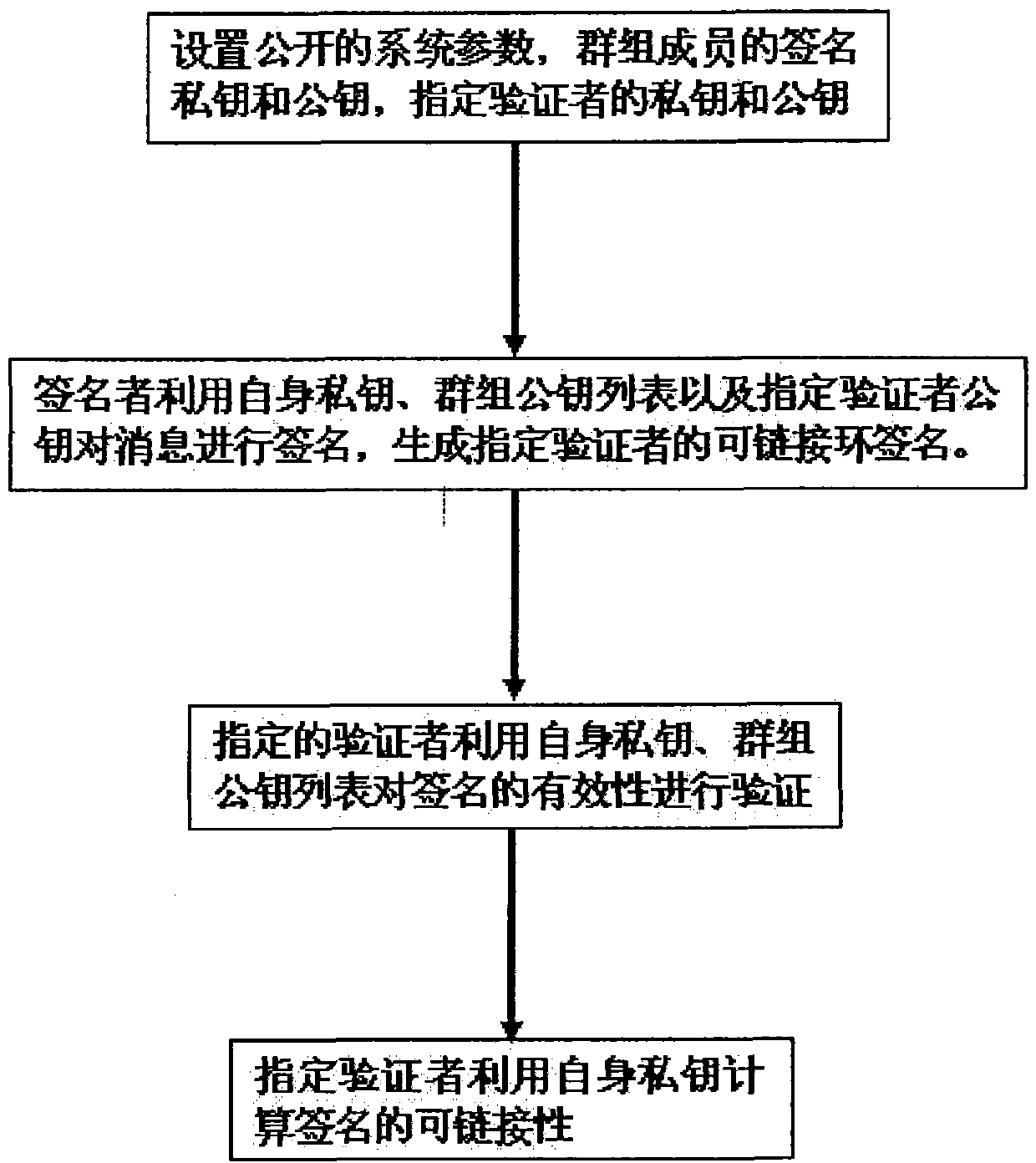
Linkable ring signature method based on appointed verifier
InactiveCN102377565AImprove efficiencyKey distribution for secure communicationPublic key for secure communicationRing signatureElectronic cash
The invention relates to a linkable ring signature method based on an appointed verifier. In the method, a non-interactive zero-knowledge proof technology is adopted, and a linkable ring signature based on the appointed verifier is realized under the hypothesis of the difficulty in a bilinear Diffie-Hellamn problem. According to the invention, the problems that no linkable ring signature method based on the appointed verifier is available in the prior art and the linkable ring signature cannot be used to solve the problem of receipt-freeness in electronic-cash and electronic voting are solved.
Owner:陈国敏 +1
Blockchain-based anonymous information transmission method and device, and readable storage medium
ActiveCN108768992ARealize transmissionRealize anonymous transmissionUser identity/authority verificationInformation transmissionRing signature
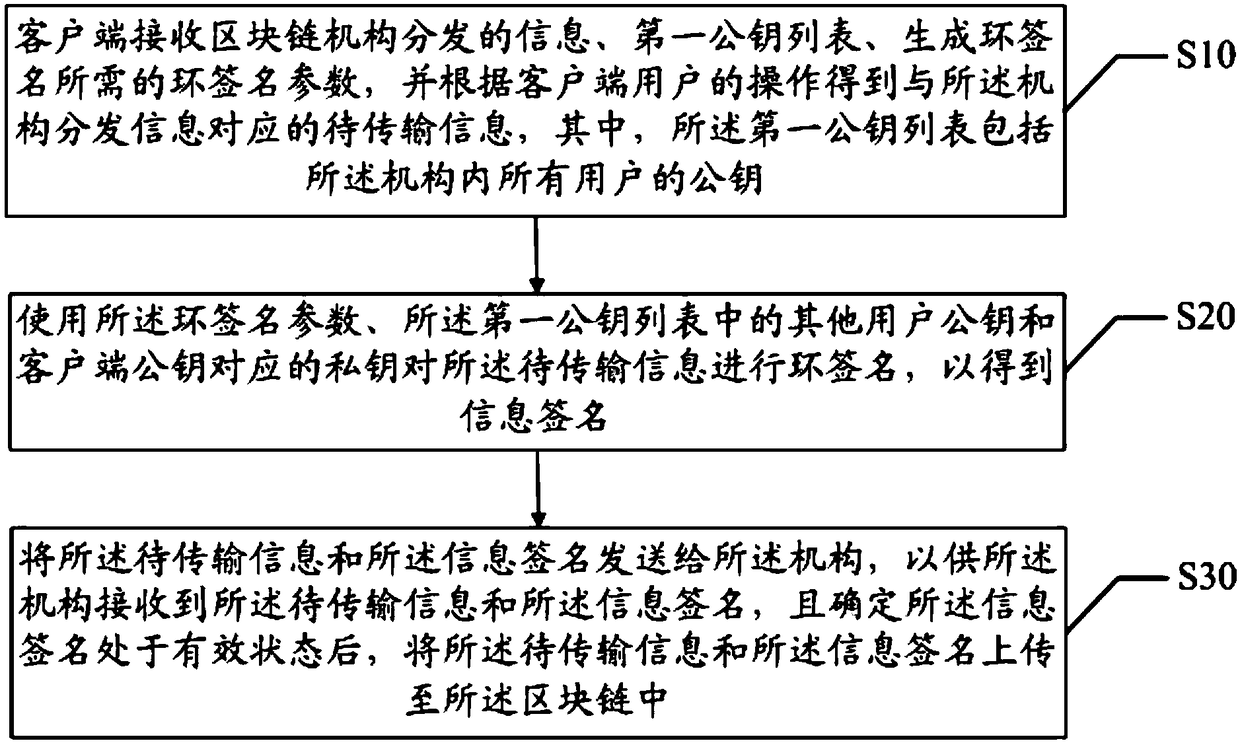
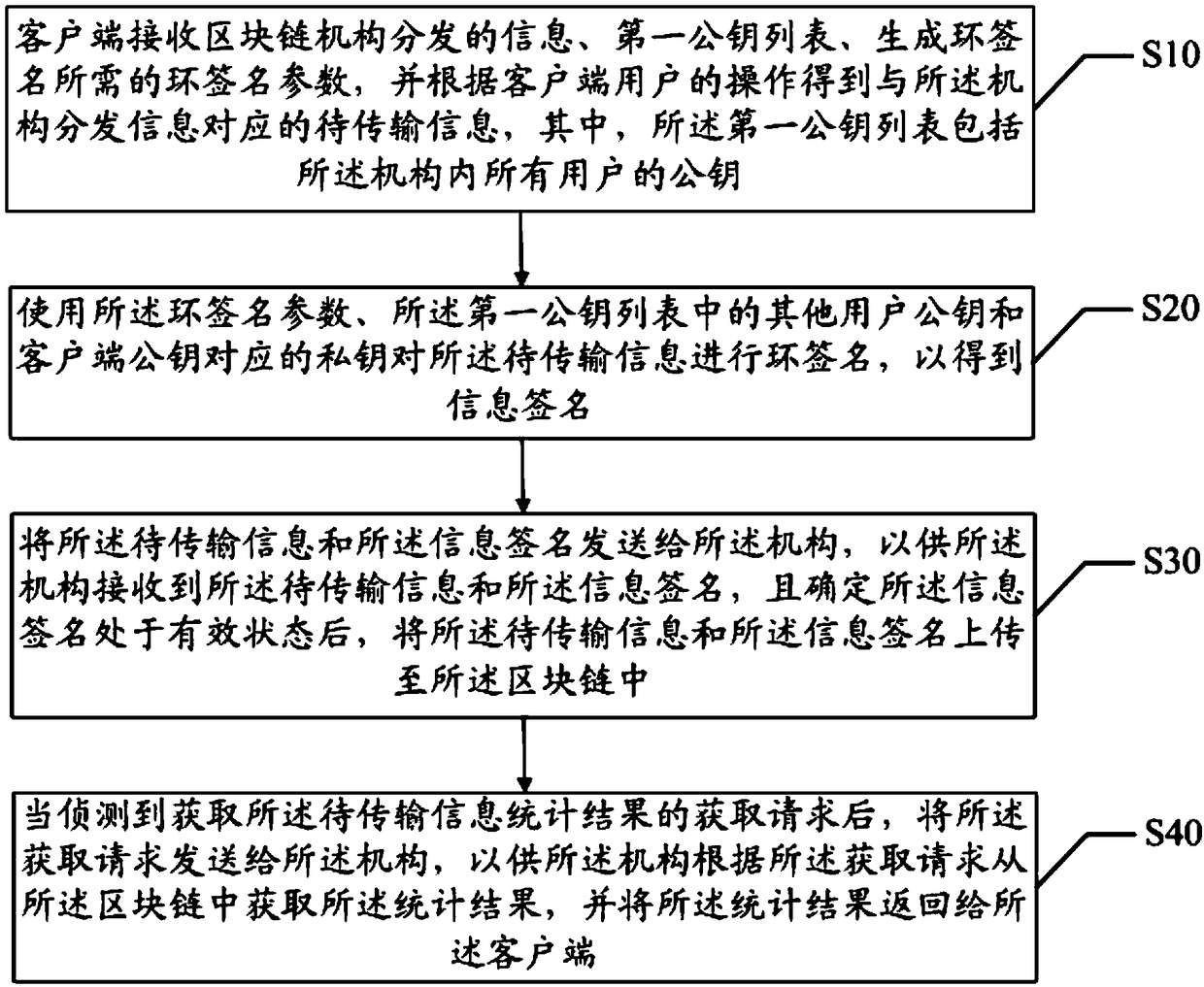
The invention discloses a blockchain-based anonymous information transmission method and device, and a readable storage medium. The method comprises the following steps: receiving, by a client, information distributed by a blockchain mechanism, a first public key list and a ring signature parameter required for generating a ring signature, and obtaining information to be transmitted correspondingto the information distributed by the mechanism according to the operation of a user of the client; performing ring signature on the information to be transmitted by using the ring signature parameter, other user pubic keys in the first public key list and a private key corresponding to the public key of the client to obtain an information signature; and sending the information to be transmitted and the information signature to the mechanism, so that the mechanism, receives the information to be transmitted and the information signature and uploads the information to be transmitted and the information signature to a blockchain after determining that the information signature is in an effective state. By adoption of the blockchain-based anonymous information transmission method and device disclosed by the invention, the anonymous information transmission is realized; and by writing the information to be transmitted and the corresponding information signature into the blockchain, the non-tampering of the information to be transmitted is achieved by the characteristics of the blockchain.
Owner:WEBANK (CHINA)
Encryption and signature schemes using message mappings to reduce the message size
ActiveUS20060159259A1Computationally efficientBandwidth-reduced ring signaturePublic key for secure communicationUser identity/authority verificationComputer hardwareRing signature
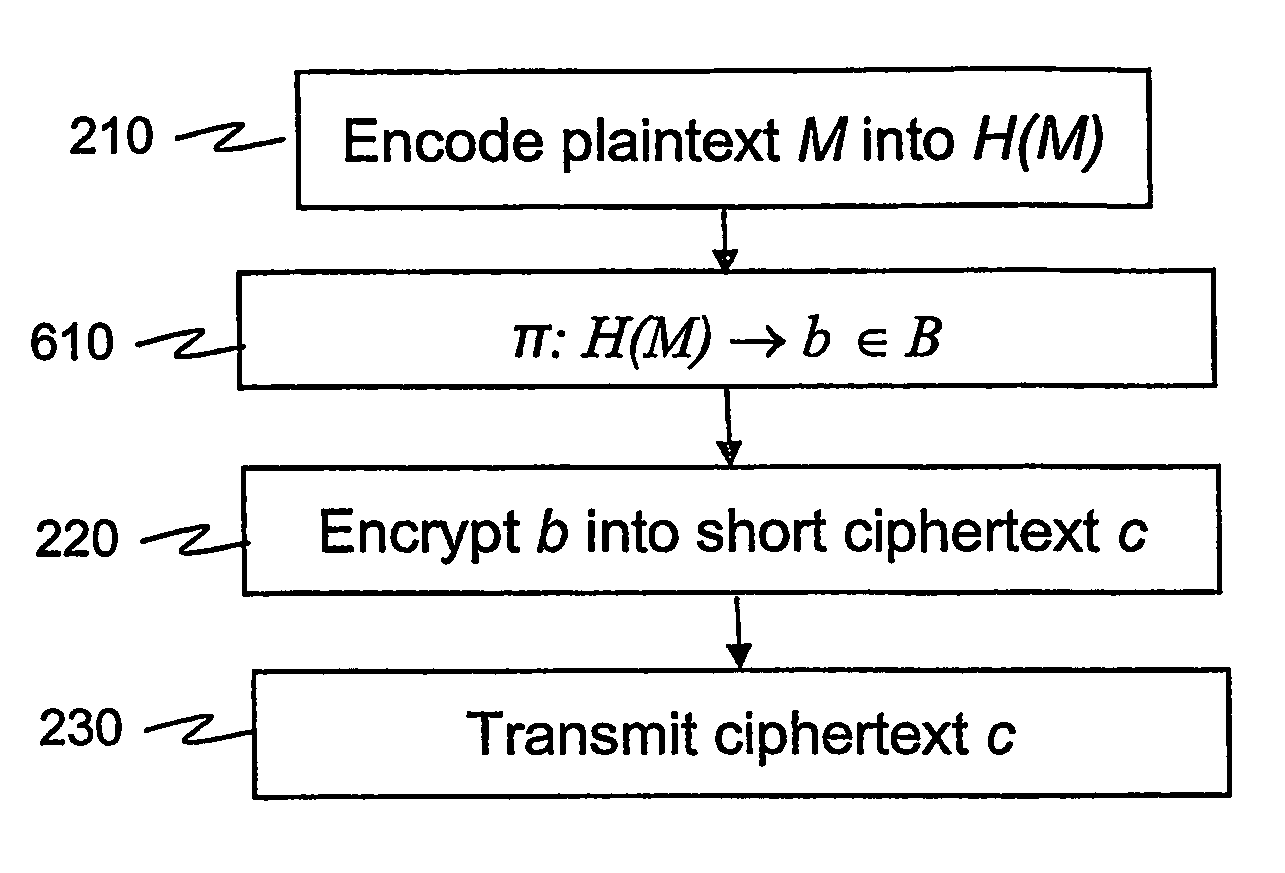
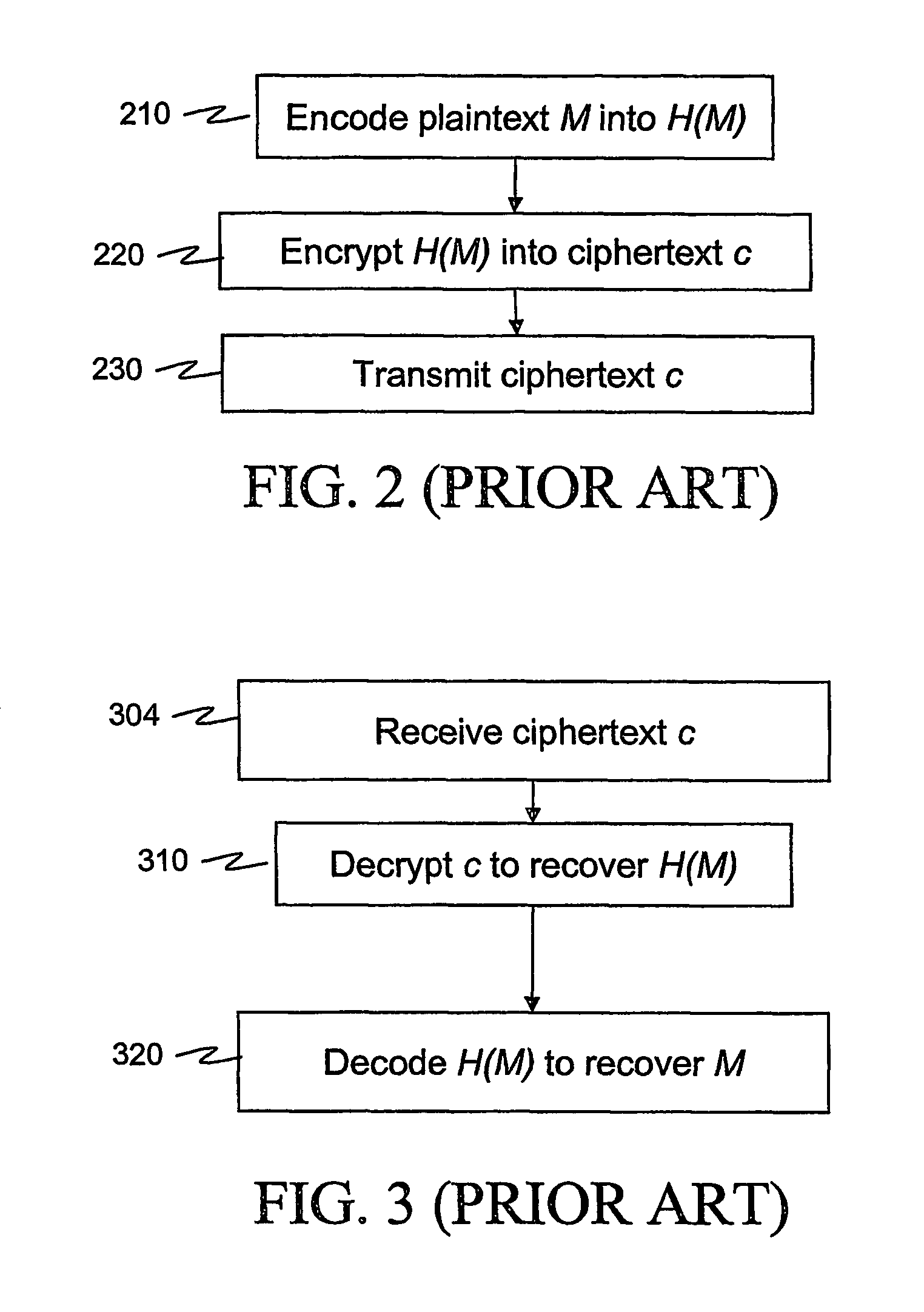
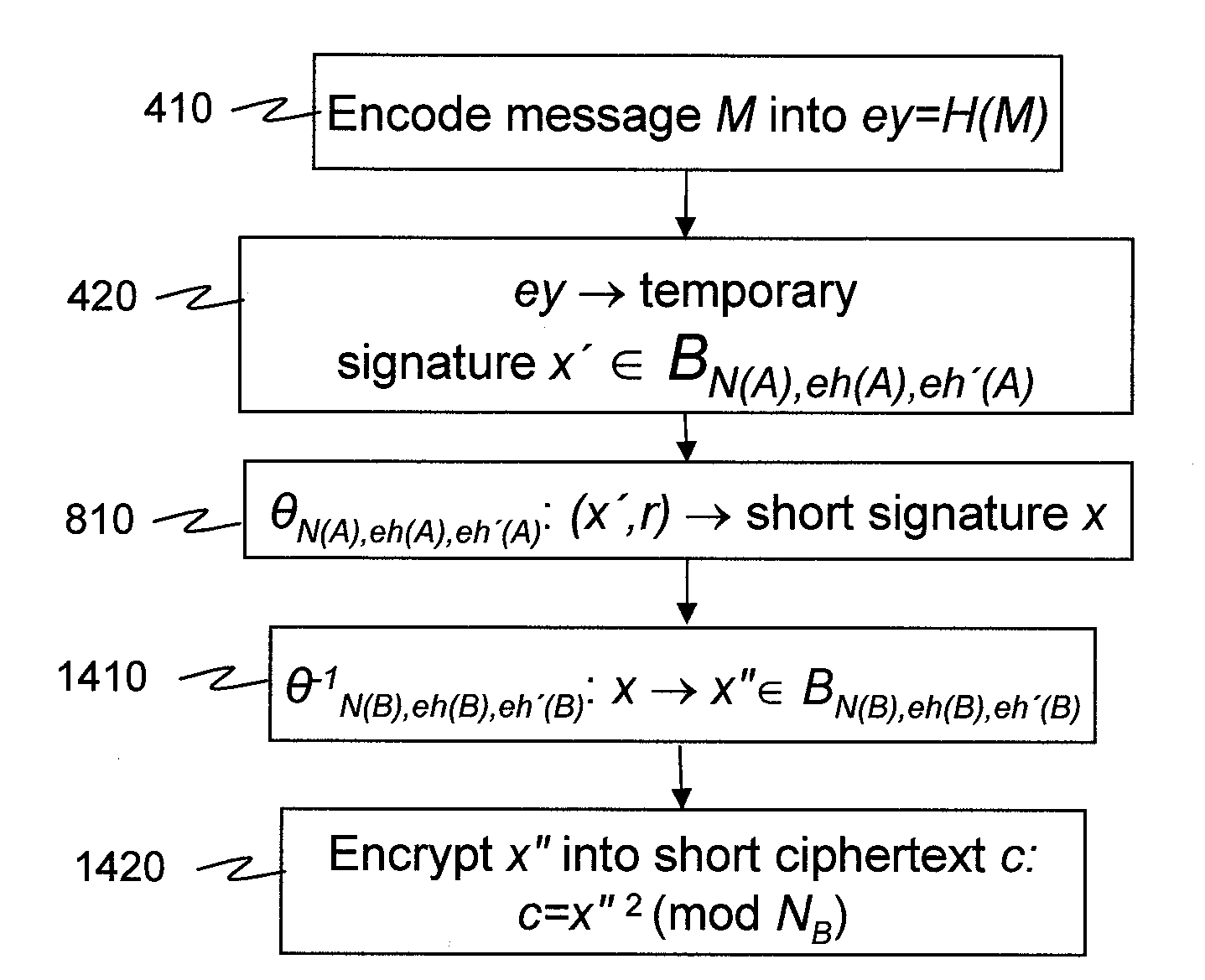
According to some embodiments of the invention, a message is processed before encryption so that the encryption method generates a short ciphertext. The message processing can be viewed as a mapping (610) that maps the message into another message that generates the short ciphertext. The mapping is reversible at least if the (possibly encoded) message (H(M)) is in a restricted set, e.g. a set [0,h?] of short messages. In some embodiments of the present invention, short signatures are provided by mapping the signature into a short signature. The mapping (810) is reversible at least if the original message (H(M)) used to generate the signature is short. Signcryption, aggregate signature, and ring signature outputs are also shortened.
Owner:NTT DOCOMO INC
Anti-adaptive attack alliance chain consensus method based on Byzantine fault tolerance
ActiveCN110289966APrevent Adaptive AttacksKeep aliveUser identity/authority verificationByzantine fault toleranceRing signature
An anti-adaptive attack alliance chain consensus method based on Byzantine fault tolerance comprises the following steps: constructing an anonymous sorting master selection algorithm based on ring signatures, and selecting a potential proposor PP from all consensus nodes in an alliance chain network in a concealed manner; enabling a potential proposor PP to construct a proposal block, sign the proposal block and broadcast the proposal block to the alliance chain network; enabling the consensus node to verify the received proposal block, vote the proposal block passing the verification based on a threshold signature, and broadcast a voting result in the alliance chain network; if a consensus node receives a legal threshold signature of the proposal block within a predetermined time, enabling the proposal block to complete the consensus; and enabling all nodes in the alliance chain network to store the blocks completing the consensus. The method has the advantages that the system overhead is reduced, the expandability is improved, the safety is higher, the system activity can be effectively ensured before and after proposal, and the support is provided for a high-availability Byzantine system.
Owner:西安周盘汇通科技有限公司
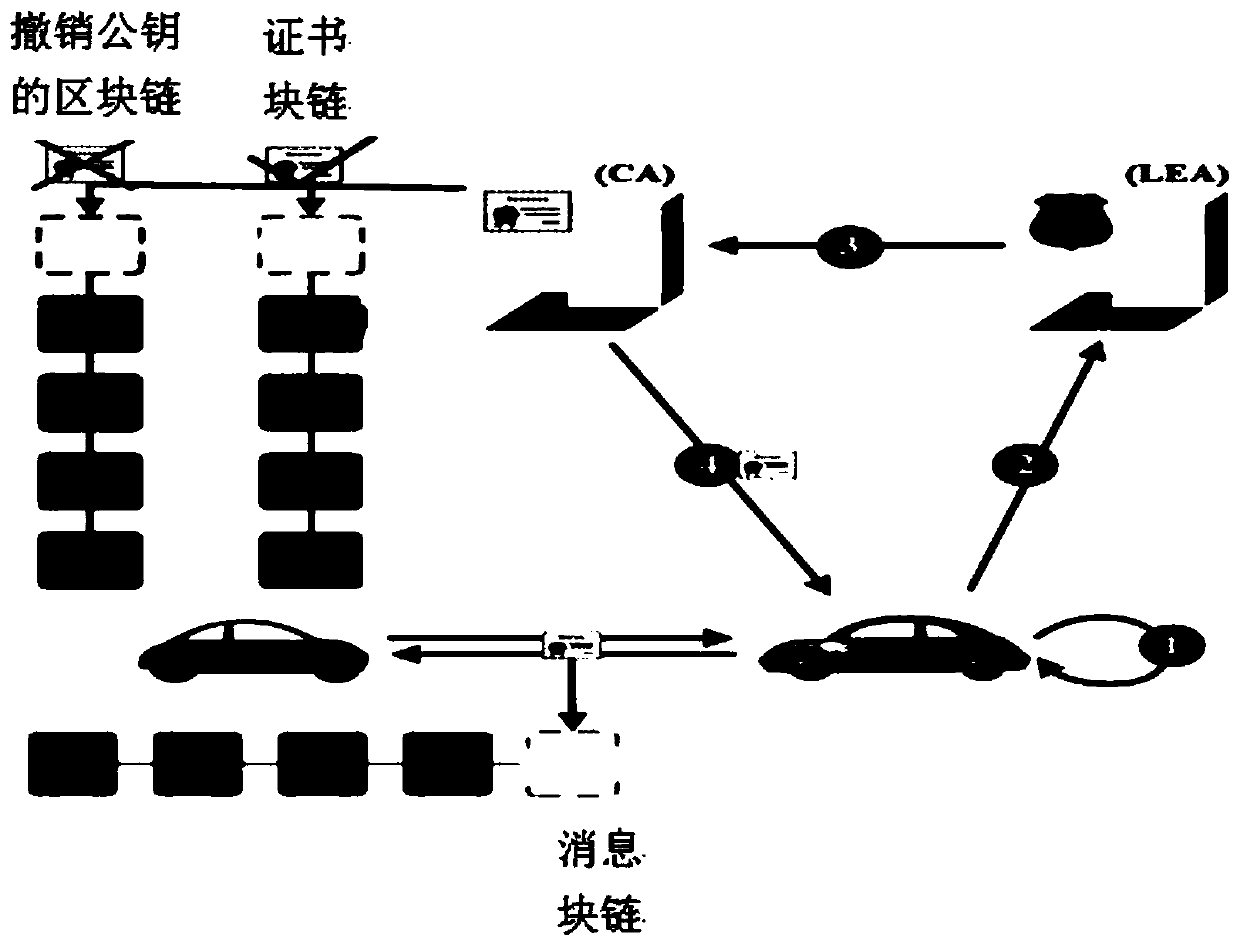
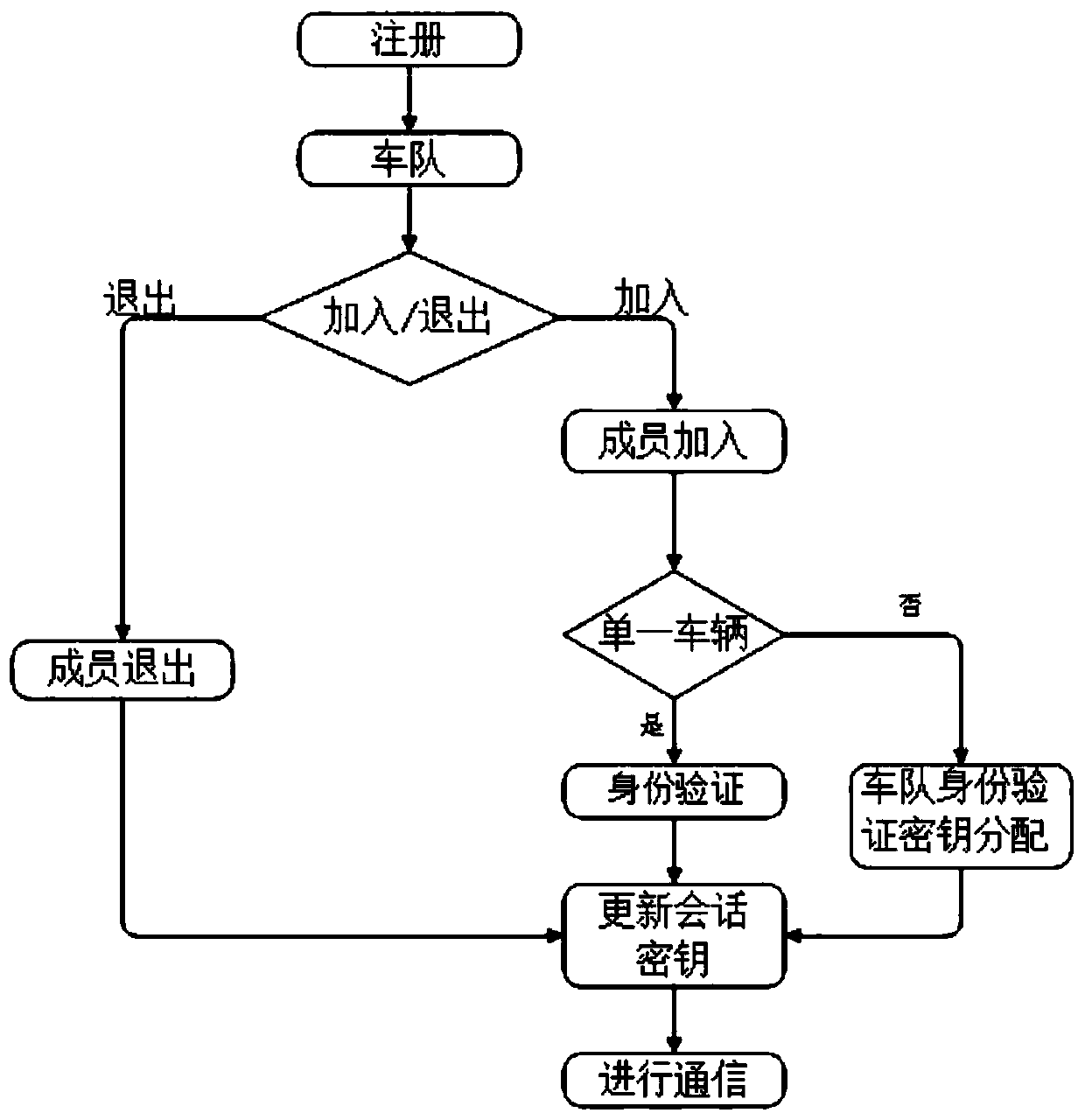
Motorcade safety management system and method based on ring signature and vehicle management platform
ActiveCN109698754AEnsure safetyPrevent leakageKey distribution for secure communicationPublic key for secure communicationSafety management systemsRing signature
The invention belongs to the technical field of Internet of Vehicles, and discloses a motorcade safety management system and method based on ring signatures, and a vehicle management platform. identity-based ring signatures are performed on the identities of motorcade members on the basis of an elliptic curve. Hiding and public key updating are conducted on identities of motorcade members throughthe elliptic curve, the block chain and the ring signatures, the identities of the message senders are authenticated, and session keys are updated; the block chain is utilized to publish a public keycertificate and a reputation value of the vehicle; The vehicle inquires the public key, the public key validity and the current reputation value of the surrounding vehicles through the roadside unit,so that the addition of malicious vehicles is avoided; Updating of the public key can prevent information from being intercepted and tampered by malicious vehicles when the private key of the user issubjected to security threats. The privacy of registered users and the privacy of motorcade members are effectively prevented from being leaked, and the communication safety of the members in the motorcade is ensured.
Owner:XIAN UNIV OF POSTS & TELECOMM
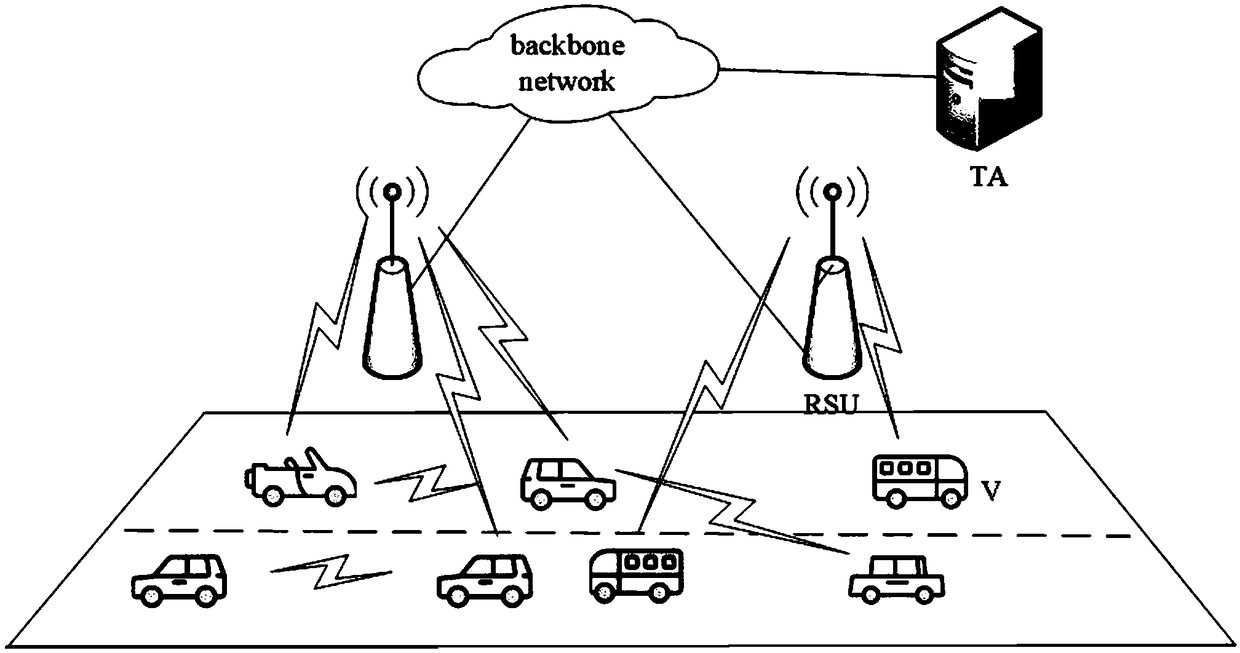
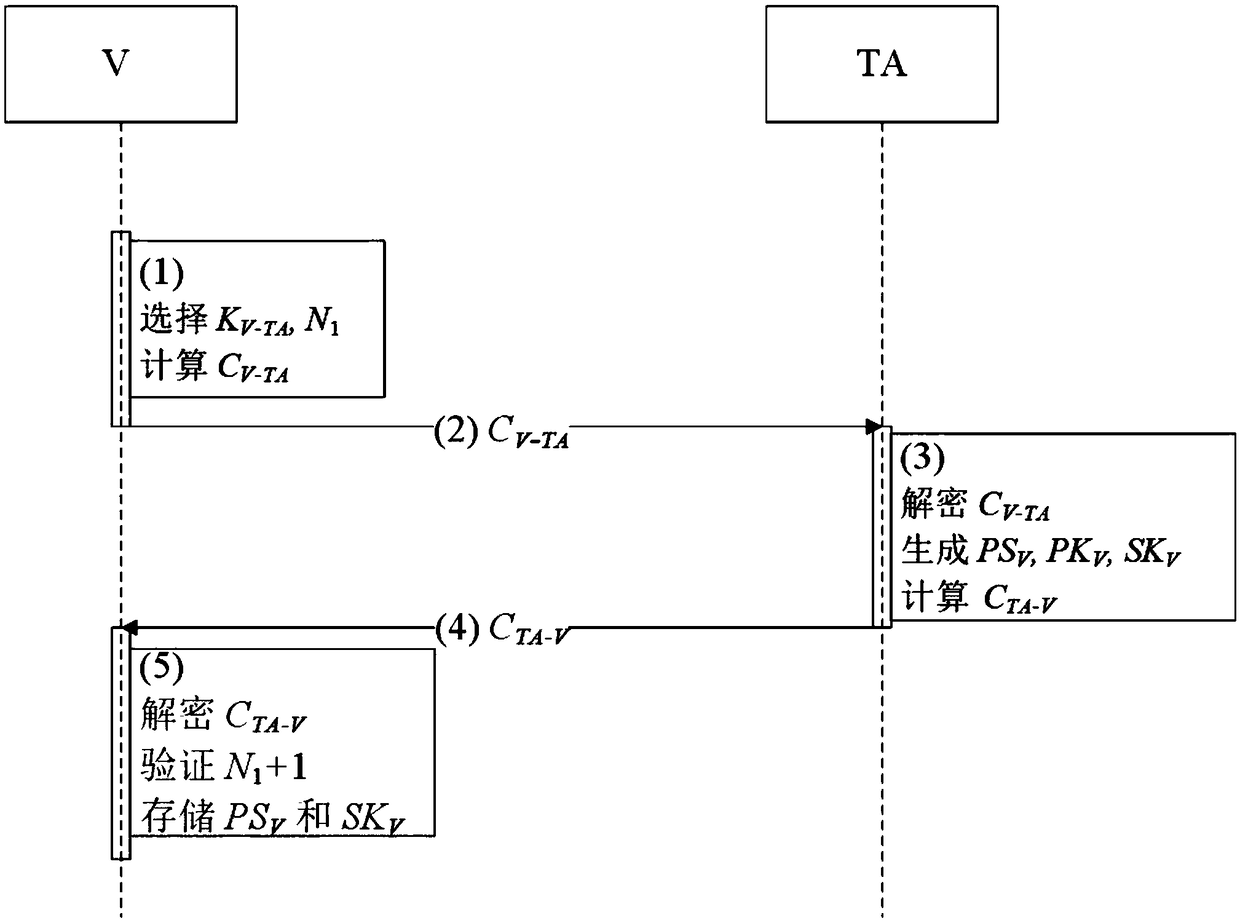
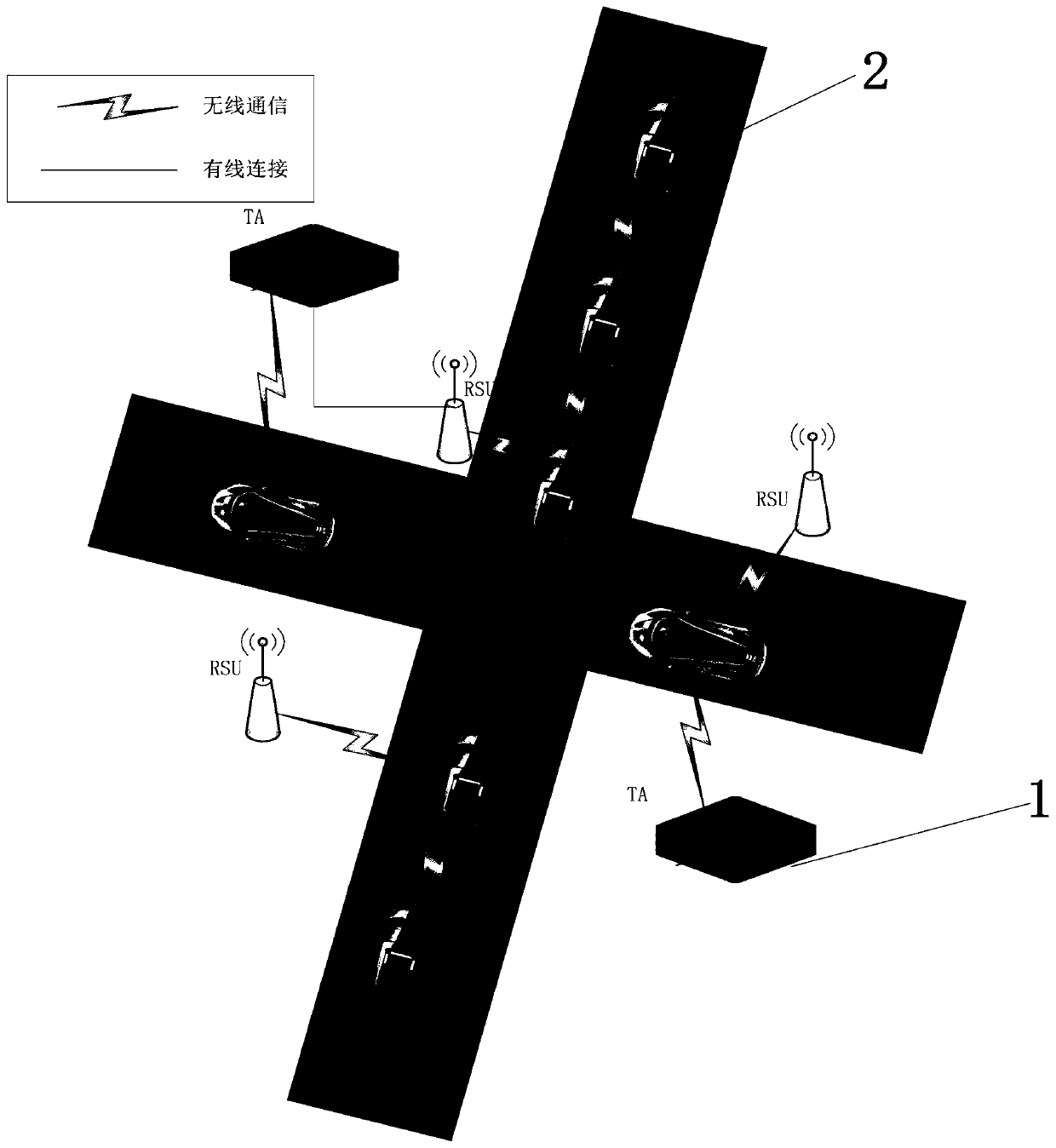
Vehicle-mounted-network anonymous-communication system based on ring signature and method
ActiveCN109412816AProtect privacy and securityGuarantee authentication efficiencyUser identity/authority verificationSecurity arrangementThird partyCommunications system
The invention relates to the technical field of network security, and provides a vehicle-mounted-network anonymous-communication system based on ring signature. The system includes a third-party trustinstitution, road side units and vehicles. The invention also provides a method of using the above system for vehicle-mounted-network anonymous-communication. The third-party trust institution firstly publishes public parameters, then the vehicles and the road side units apply for registration to the third-party trust institution, the third-party trust institution issues pseudonyms and public andprivate keys for the vehicles, and issues public and private keys and initial pseudonym ring members for the road side units, and then states of the vehicles in a vehicle-mounted network are monitored; and initial accessing authentication is carried out with a road side unit RSU if a vehicle accesses the vehicle-mounted network for the first time, and switching accessing authentication is carriedout with a road side unit RSU' if the vehicle does out access the vehicle-mounted network for the first time, and two-way authentication is carried out under assistance of a road side unit if a vehicle Vi is ready to communicate with a vehicle Vj. The system and the method integrate pseudonym certificate and group signature technology, and can fully protect privacy safety of communicators on thepremise of ensuring authentication efficiency.
Owner:NORTHEASTERN UNIV
Trusted LBS service protocol implementation method based on privacy protection
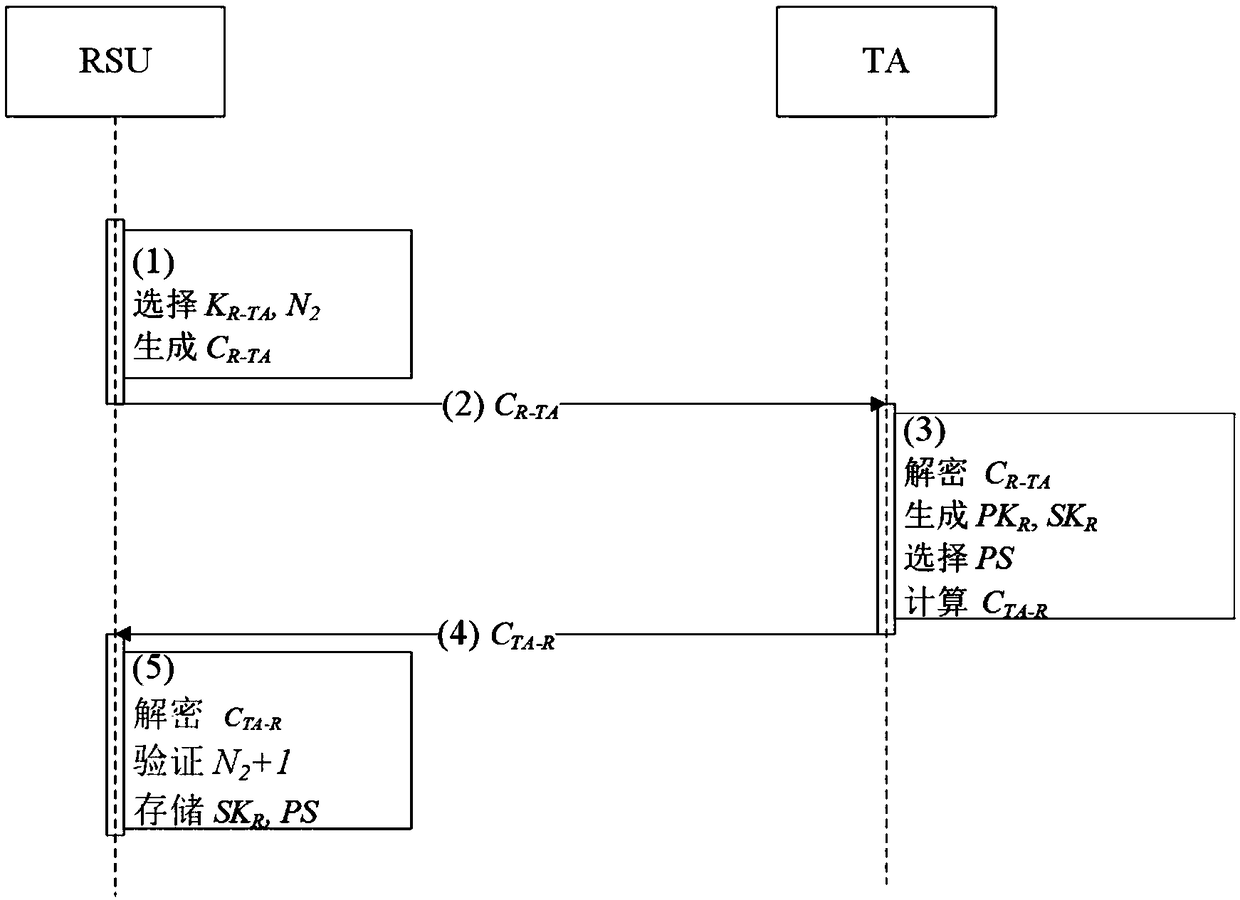
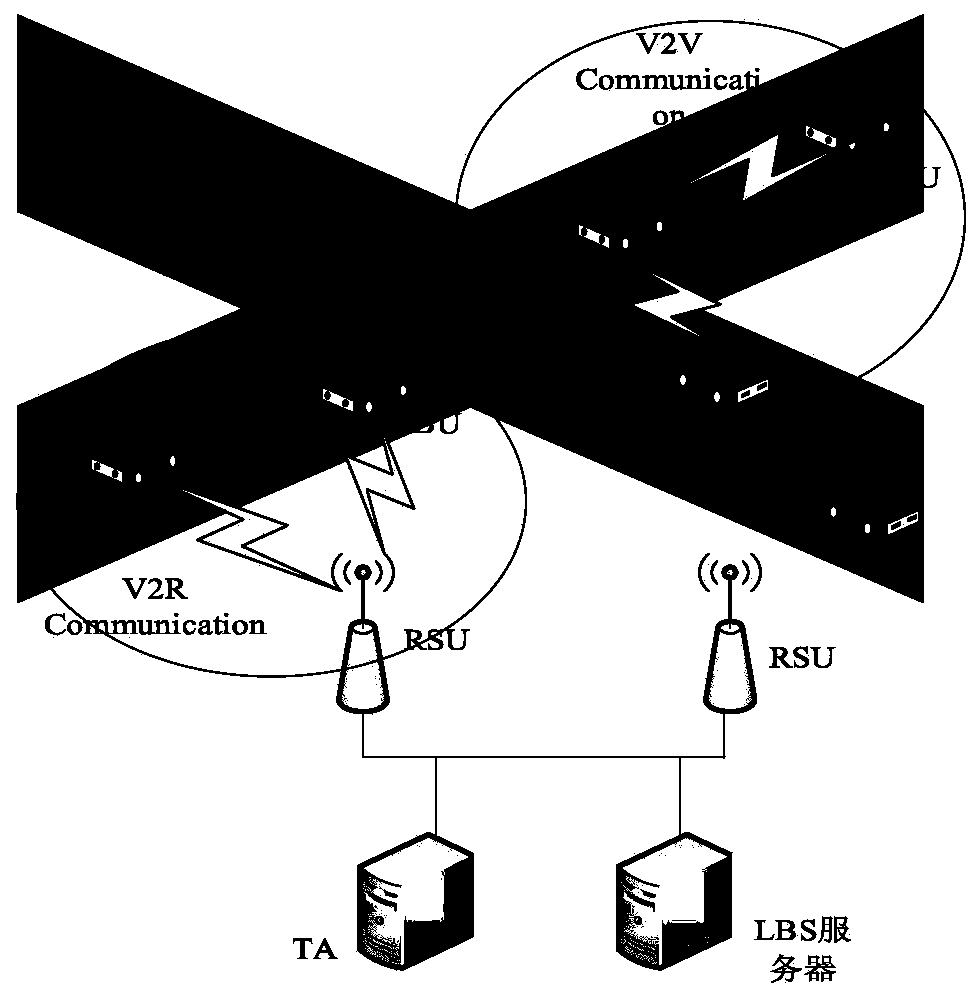
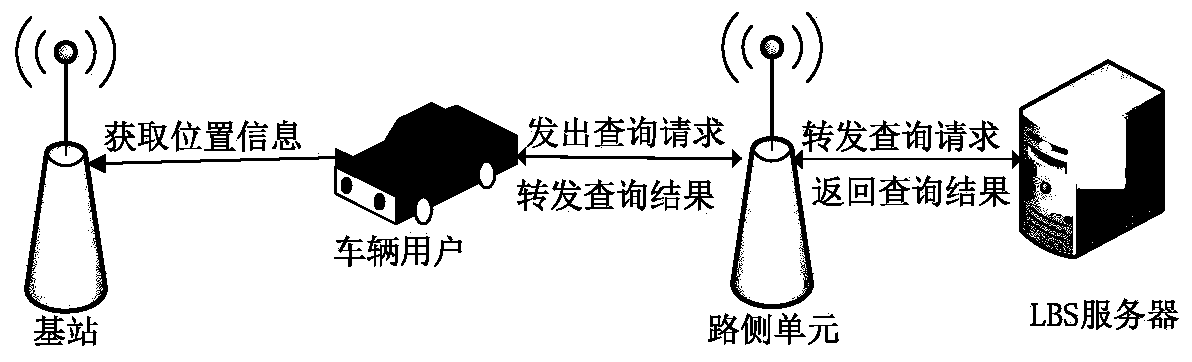
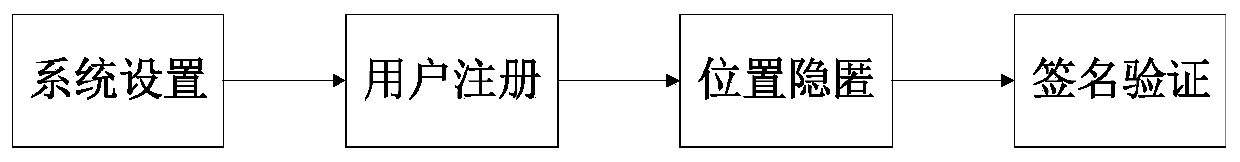
ActiveCN111083098APrevent leakageProve identityUser identity/authority verificationService protocolRing signature
The invention provides a trusted LBS service protocol implementation method based on privacy protection, and belongs to the technical field of Internet of Vehicles security. According to the technicalscheme, the trusted LBS protocol implementation method based on privacy protection comprises the four steps of system setting, user registration, position hiding and signature verification. The beneficial effects of the invention are as follows: bidirectional trusted communication between a vehicle user and an LBS server in an Internet of Vehicles LBS environment is realized, position concealmentand identity concealment are generated through cooperation of an OBU, the LBS and the TA, position concealment of the LBS server by the OBU is achieved, meanwhile, identity authentication of the OBUis achieved, and the adopted certificateless ring signature scheme is more suitable for the Internet of Vehicles environment and has unconditional anonymity and unforgeability.
Owner:NANTONG UNIVERSITY
Privacy ensured brokered identity federation
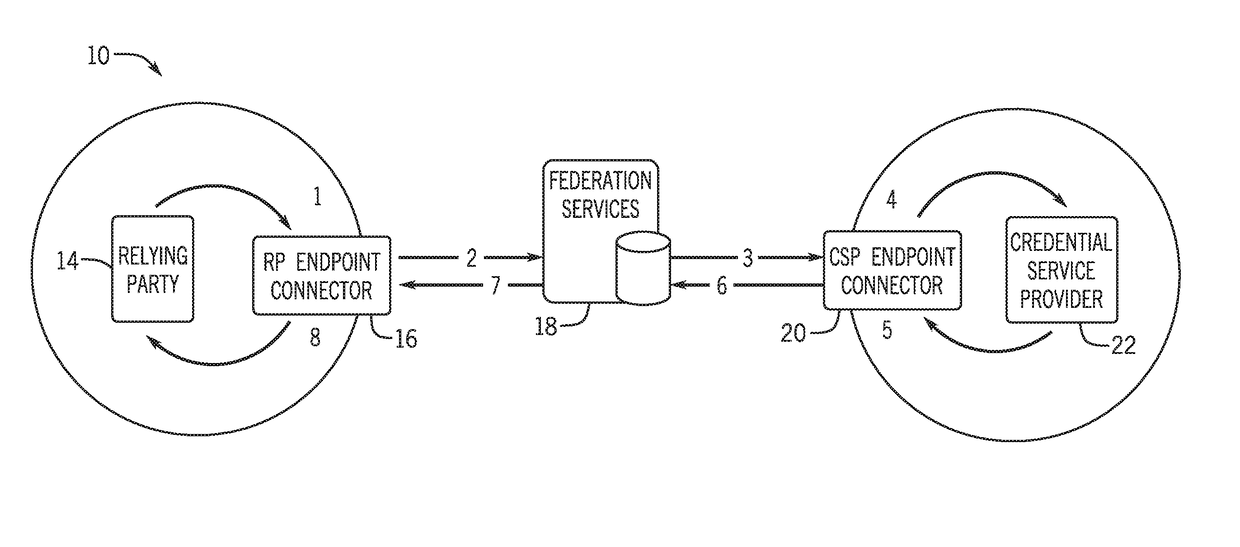
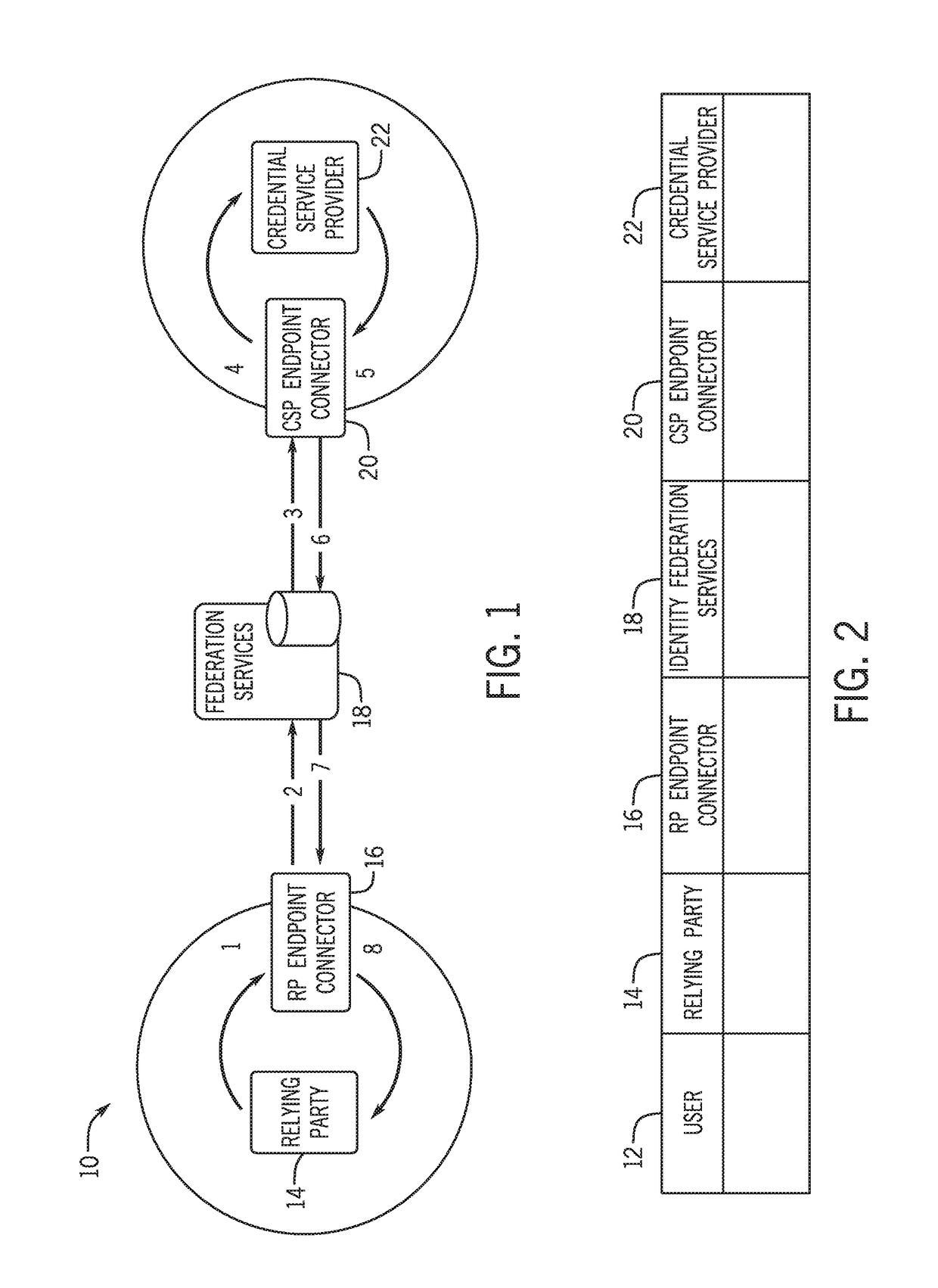
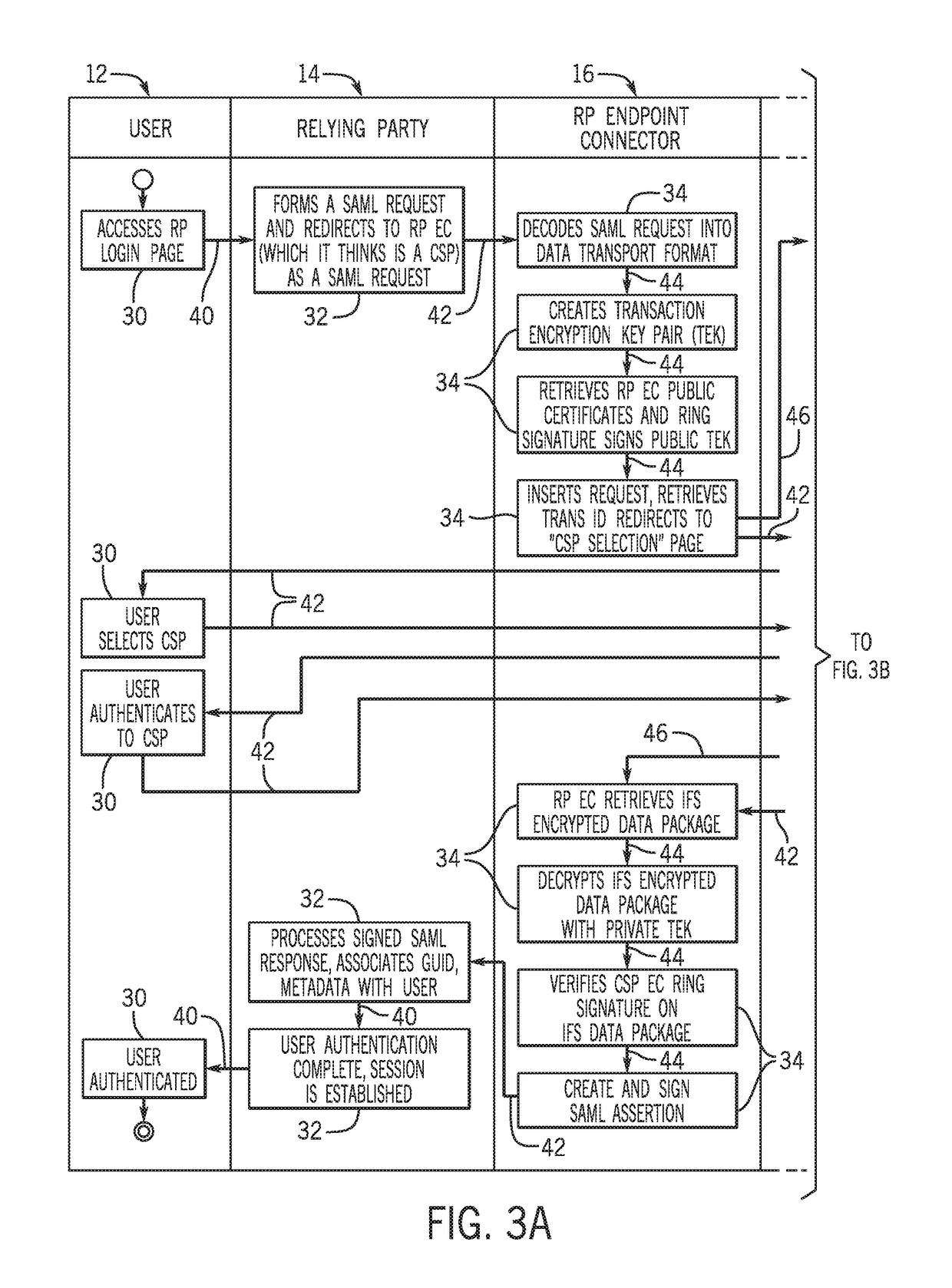
ActiveUS20180234409A1Ensuring privacyUser identity/authority verificationInternet privacyService provision
A system, method, apparatus, and computer program product for a privacy ensured brokered identity federation system. The privacy ensured brokered identity federation system connects a user in a brokered identity federation environment that blinds relying parties (RP) from credential service providers (CSP), blinds CSPs from RPs, and blinds a user's identity and data from the federation middleware hubs. The system utilizes ring signatures to attest to CSPs that a valid RP of the federation is making a request. The process utilizes CSP ring signatures to assure RPs that a valid CSP of the federation has provided a response. The process utilizes per transaction encryption keys created by the RP to ensure the federation has no access to data messages. It can further ensure that only the correct RP can decrypt a CSP response.
Owner:AVALANCHE CLOUD
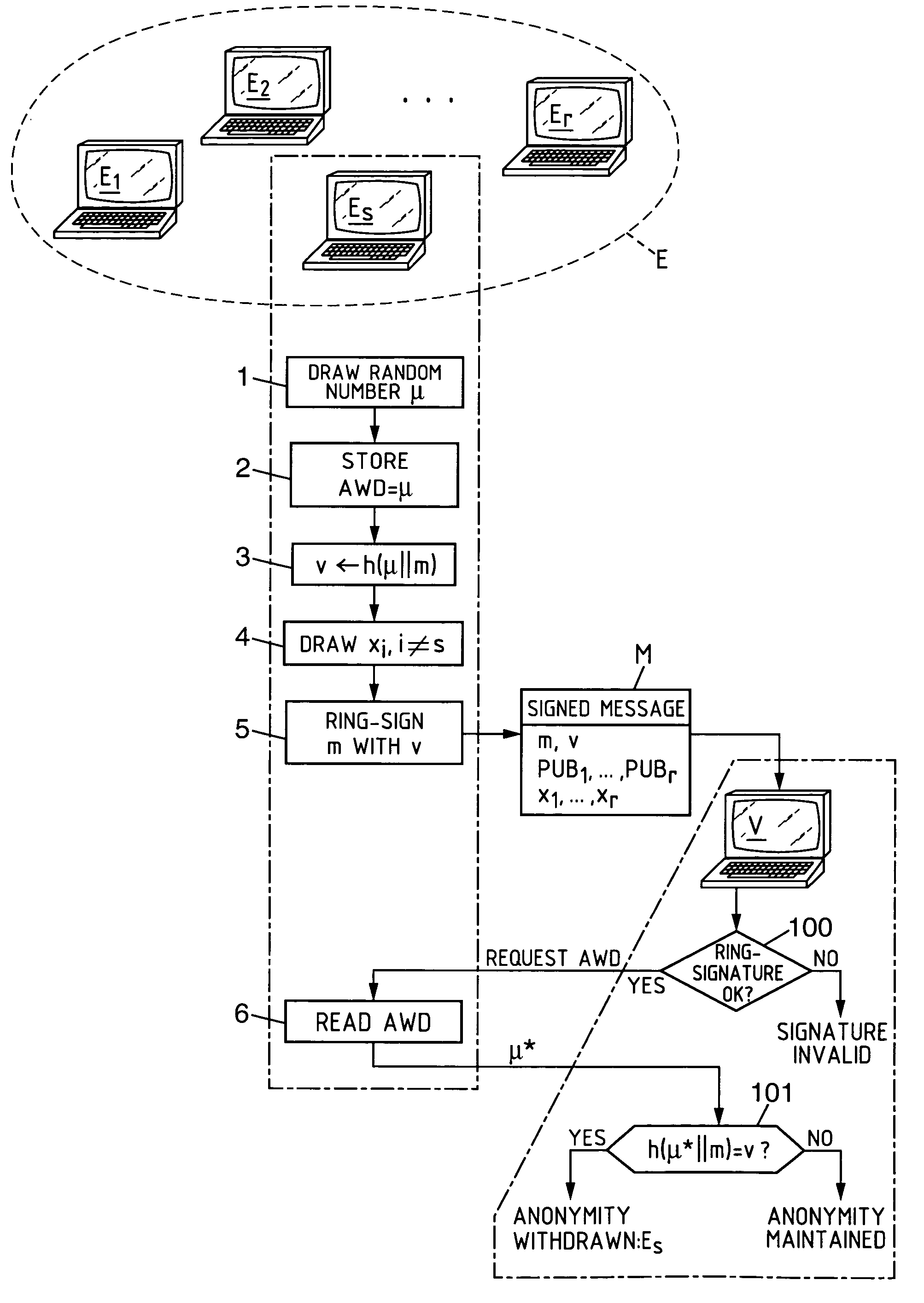
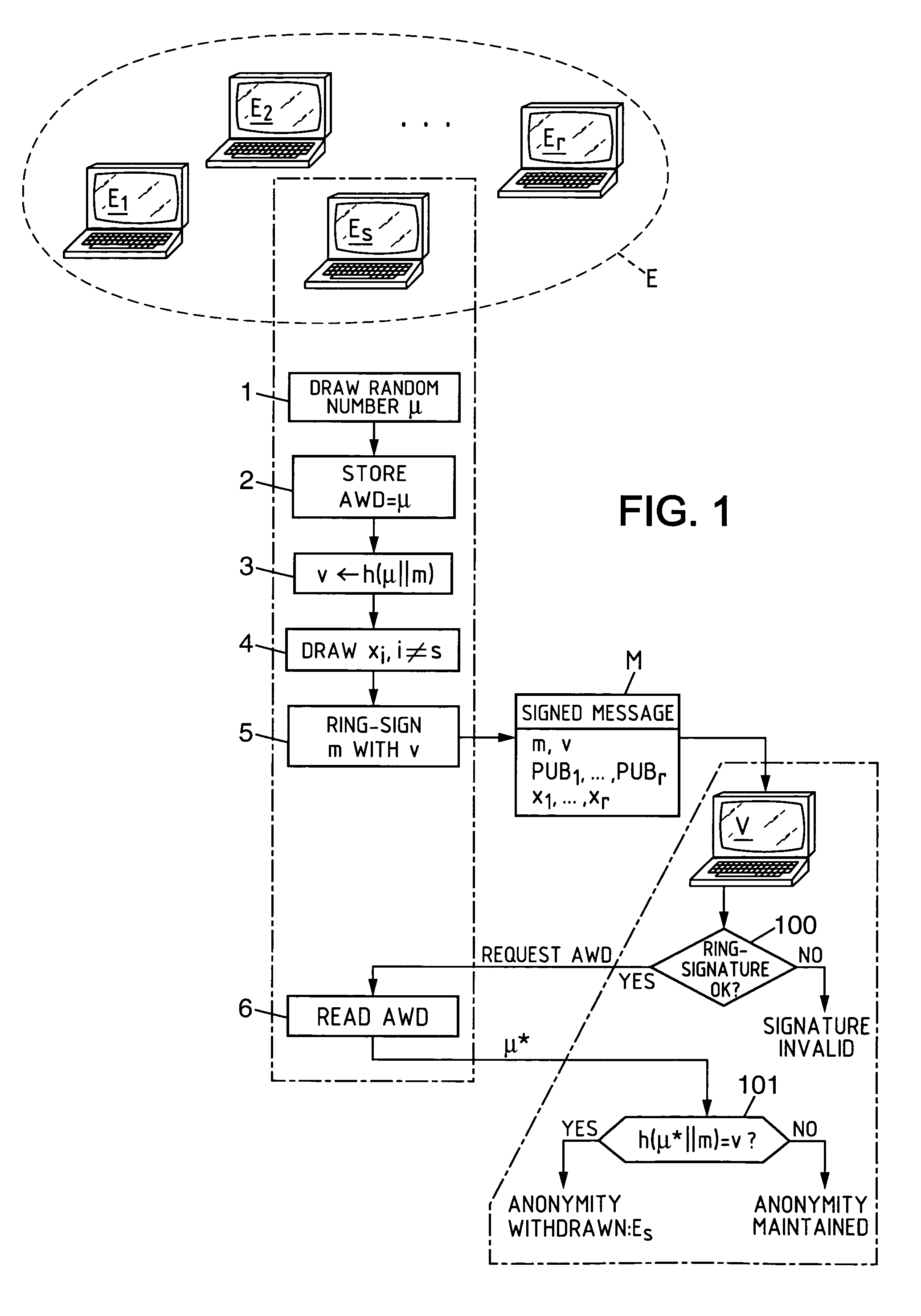
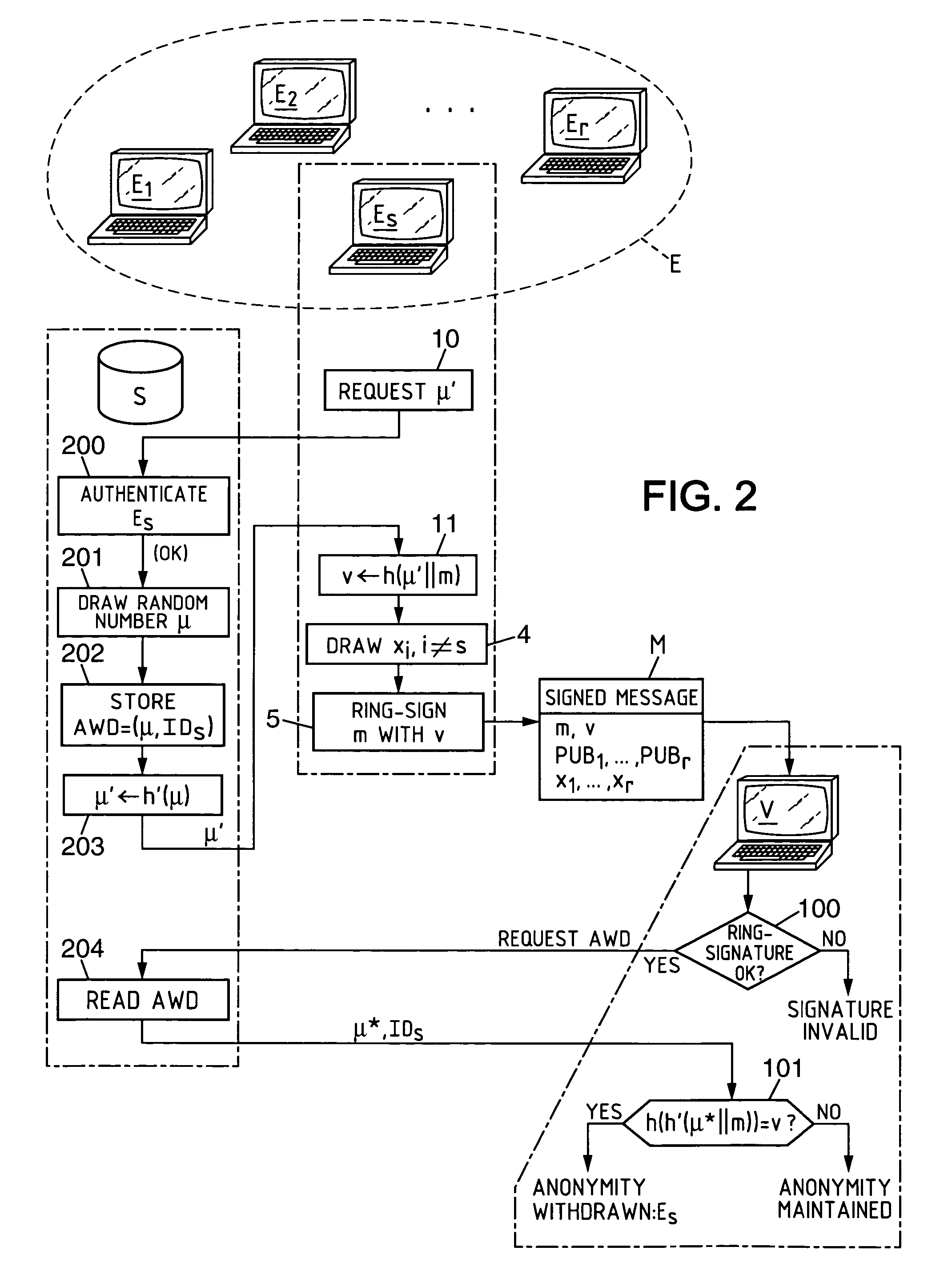
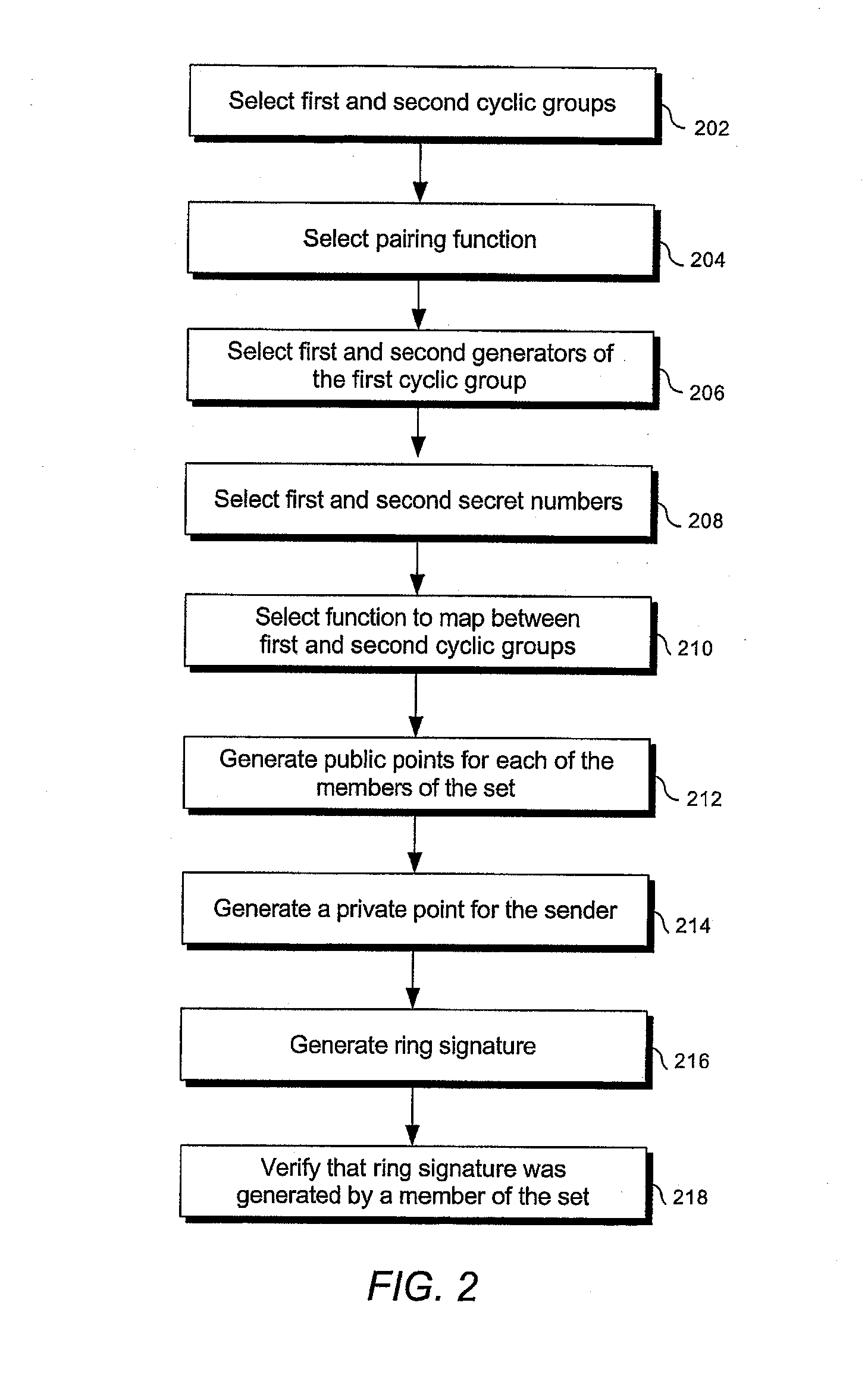
Electronic group signature method with revocable anonymity, equipment and programs for implementing the method
A ring-signature scheme is adapted so that at least one of the variability parameter values used is an identity trace of the anonymous signatory, determined as a function of anonymity withdrawal data stored and held secret by an anonymity withdrawal entity in connection with an identification of the anonymous signatory. This provides a subsequent controlled capacity of withdrawing the anonymity of the signatory, either by an authority, or by the signatory himself.
Owner:FRANCE TELECOM SA
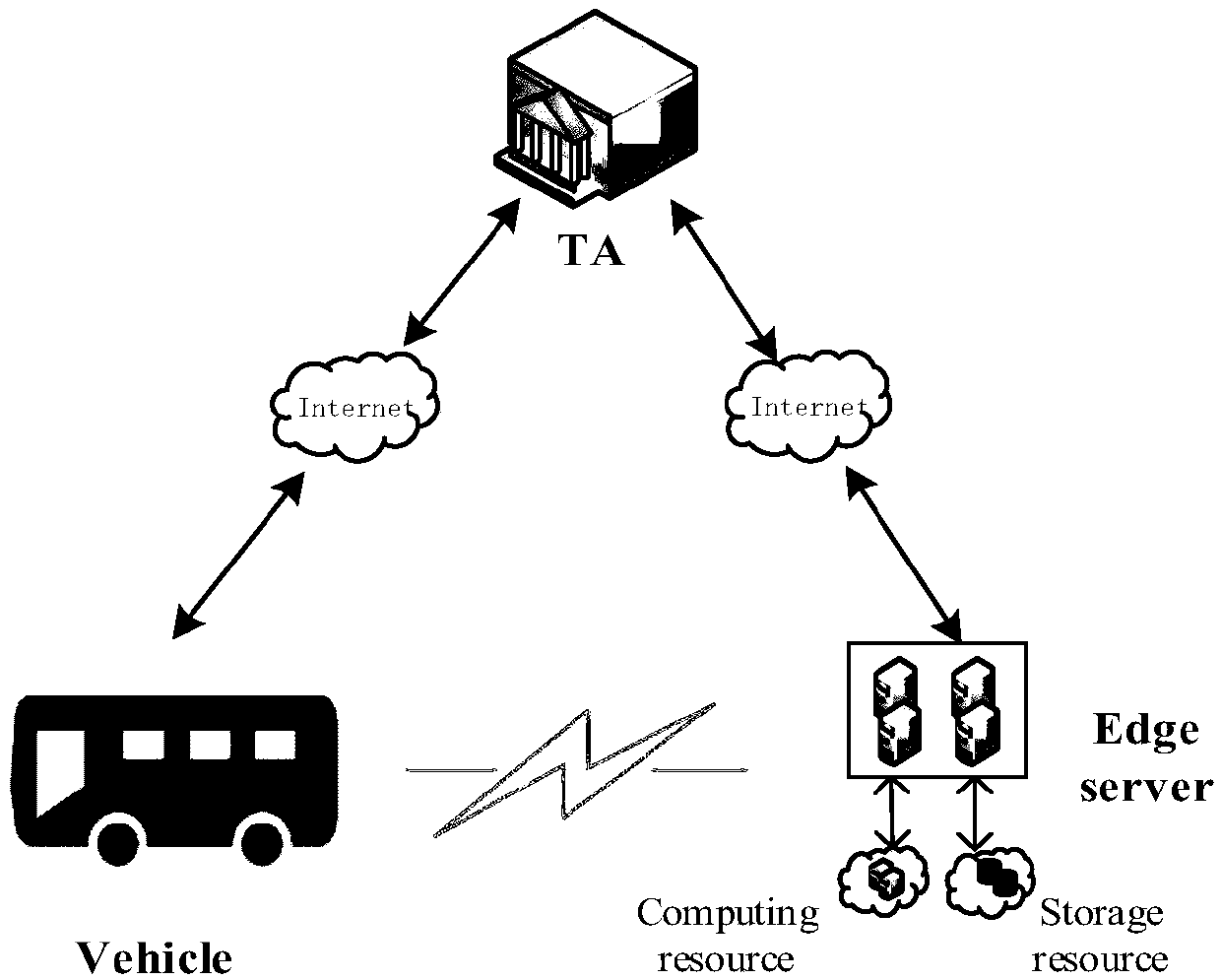
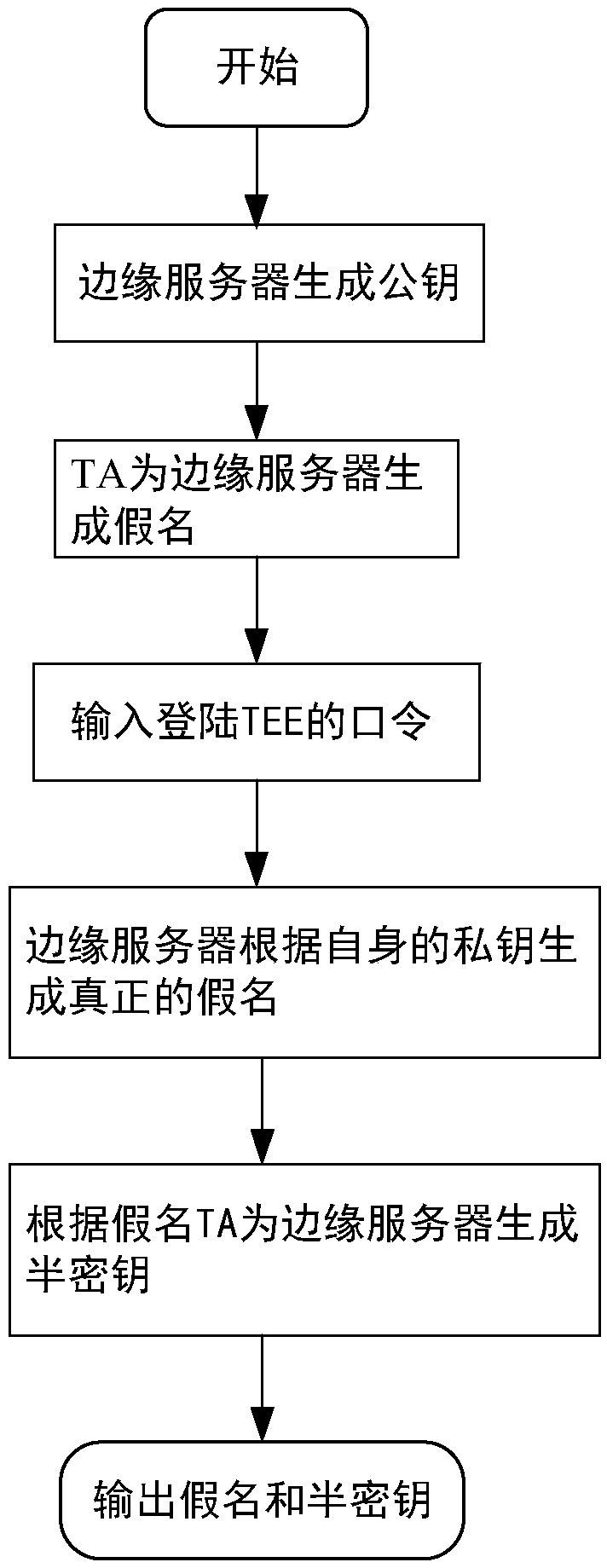
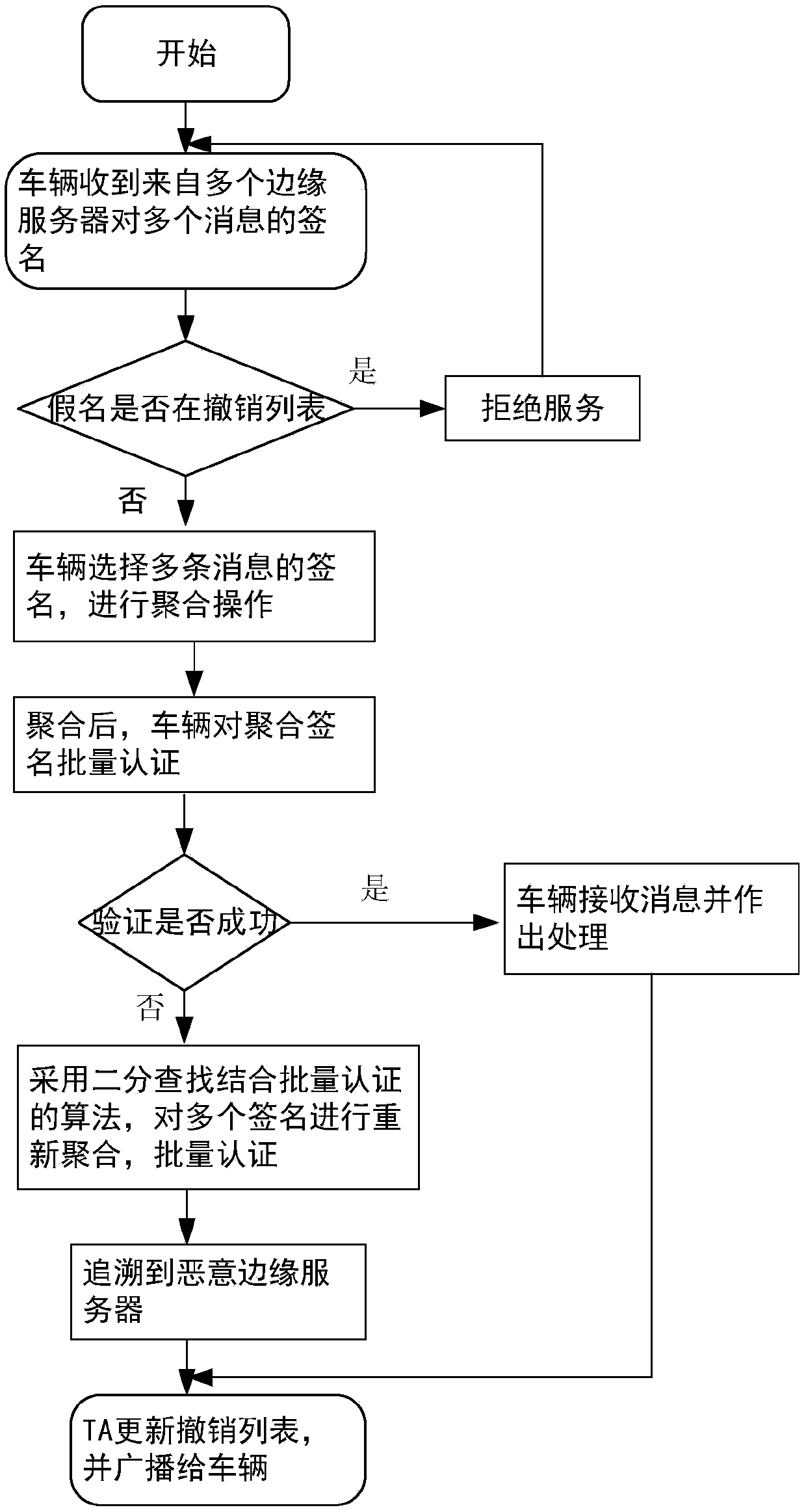
A message authentication method between an unmanned vehicle and a multi-mobile edge computing server
ActiveCN109005538ARealize privacy protectionReduce resource consumptionKey distribution for secure communicationUser identity/authority verificationEdge serverEdge computing
A message authentication method between an unmanned vehicle and a multi-mobile edge computing server is disclosed. The steps are system parameter generation, pseudonym generation for a mobile edge computing server and semi-key extraction, and authentication of a message between the mobile edge computing server and the vehicle. The step comprises: the vehicle migrates a large number of calculationor stored tasks to the mobile edge computing server, the mobile edge computing server performs ring signature on the message, and the vehicle authenticates the message in batch. The invention introduces the edge computing into the traditional vehicle-mounted ad hoc network, and the vehicle can migrate the computing or storage tasks to the edge server to execute instead of sending them to the cloudend for centralized processing. In the signature part of the invention, ring signature is combined with pseudonym, and the application of ring signature effectively protects the privacy of mobile edge computing server and traces the malicious mobile edge computing server through pseudonym.
Owner:ANHUI UNIVERSITY
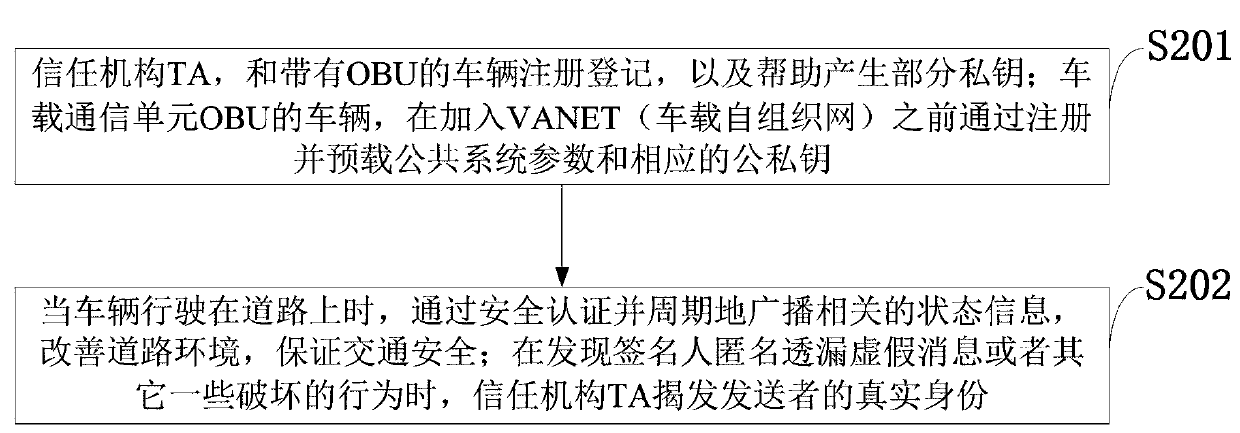
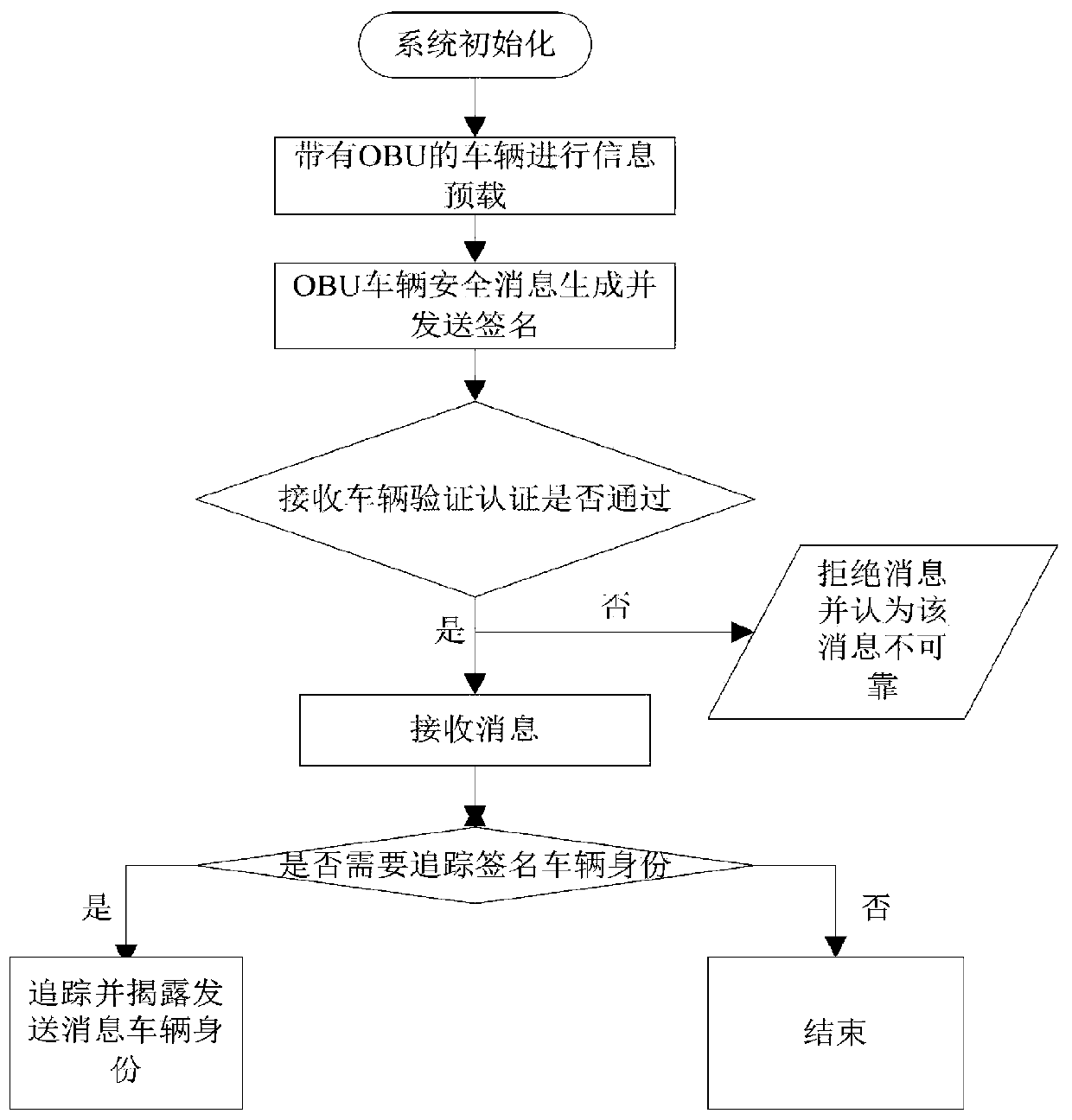
Vehicle-mounted network anonymous authentication system and method based on ring signature and vehicle communication platform
ActiveCN109802956ARealize communicationAuthentication securityUser identity/authority verificationCommunications securityRelevant information
The invention belongs to the technical field of vehicle communication security, and discloses a vehicle-mounted network anonymous authentication system and method based on a ring signature, and a vehicle communication platform. The trust mechanism and the vehicle with the OBU are registered to generate a part of private keys; A vehicle of the OBU is registered and preloaded with public system parameters and corresponding public and private keys before being added into the vehicle-mounted ad hoc network. When the vehicle runs on a road, related state information is periodically broadcasted after safety certification; And when the signer finds that the signer anonymously leaks the false message or the behavior that the signer is damaged, the trust mechanism uncovers the real identity of thesender. According to the invention, the certificateless public key cryptosystem and the ring signature are combined to form the certificateless ring signature, so that anonymity and unforgeability aremet, and meanwhile, security authentication is met; A traceable algorithm is formed by adding related information to effectively solve the problem that when a signer anonymity leaks false messages orother destructive behaviors, identity tracking and revocation are carried out according to the received messages.
Owner:XIAN UNIV OF POSTS & TELECOMM
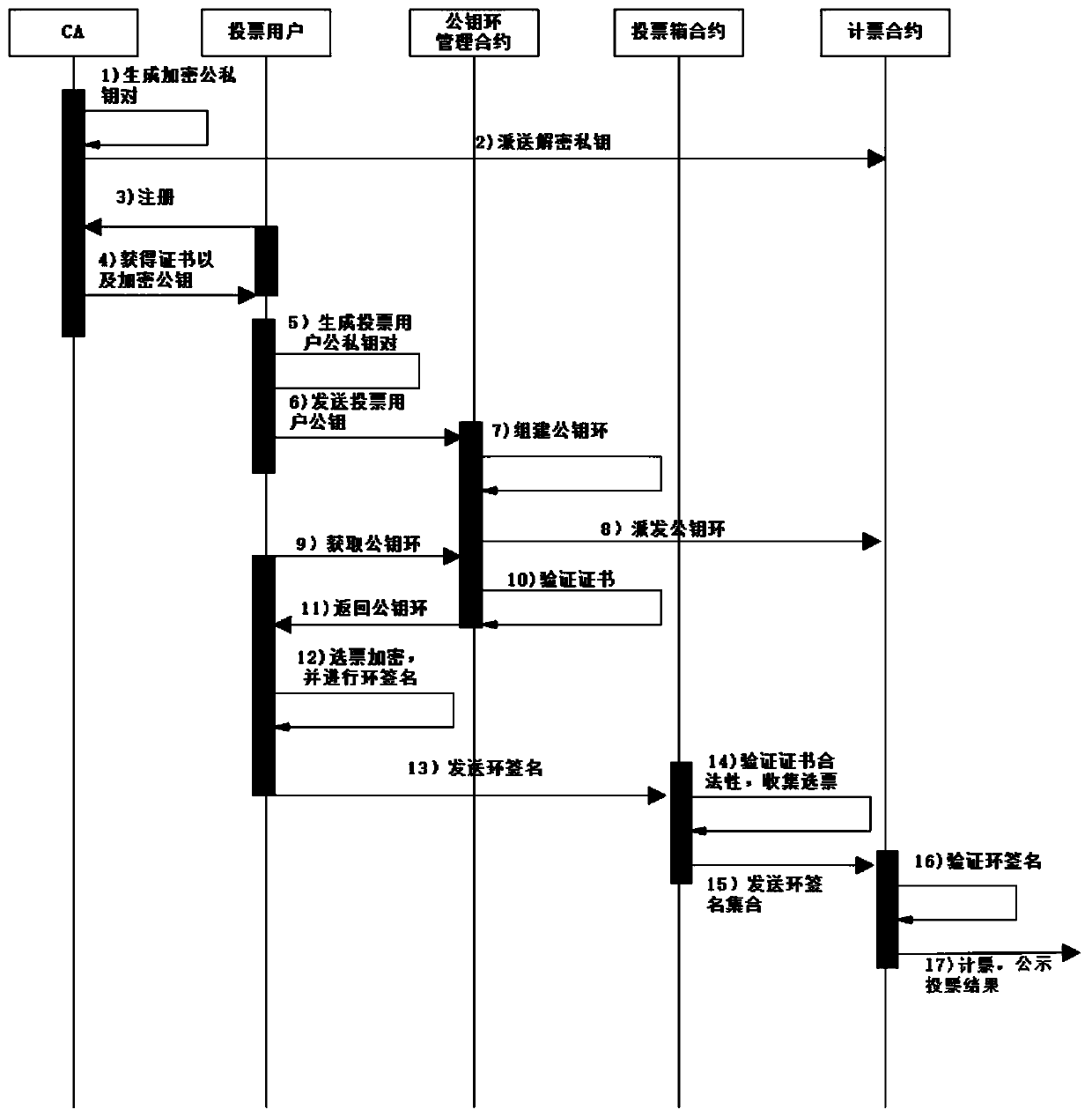
Anonymous electronic voting method based on alliance block chain
ActiveCN110572267AEnsure safetyGuaranteed reliabilityVoting apparatusUser identity/authority verificationRing signatureSmart contract
The invention discloses an anonymous electronic voting method based on an alliance block chain technology. A new anonymous voting method is designed by combining an alliance block chain technology andan existing ring signature algorithm. Based on the alliance block chain, the system has an admission mechanism, and only voters who are authenticated by the CA mechanism and acquire certificates havevoting qualification, so that the legality of the voters is ensured; the ring signature algorithm is adopted to ensure the anonymity of the votes, the votes subjected to ring signature are collectedthrough an intelligent contract and then sent to the vote counting contract, and the relevance of voter information and the votes is isolated. According to the method provided by the invention, the anonymity of voting is ensured, voters and voting information are thoroughly isolated through the vote collection contract, the whole voting process and the voting result are recorded in the block chain, the voting information is public, transparent and verifiable, and the anonymous voting function of the alliance block chain is realized.
Owner:BEIJING UNIV OF TECH
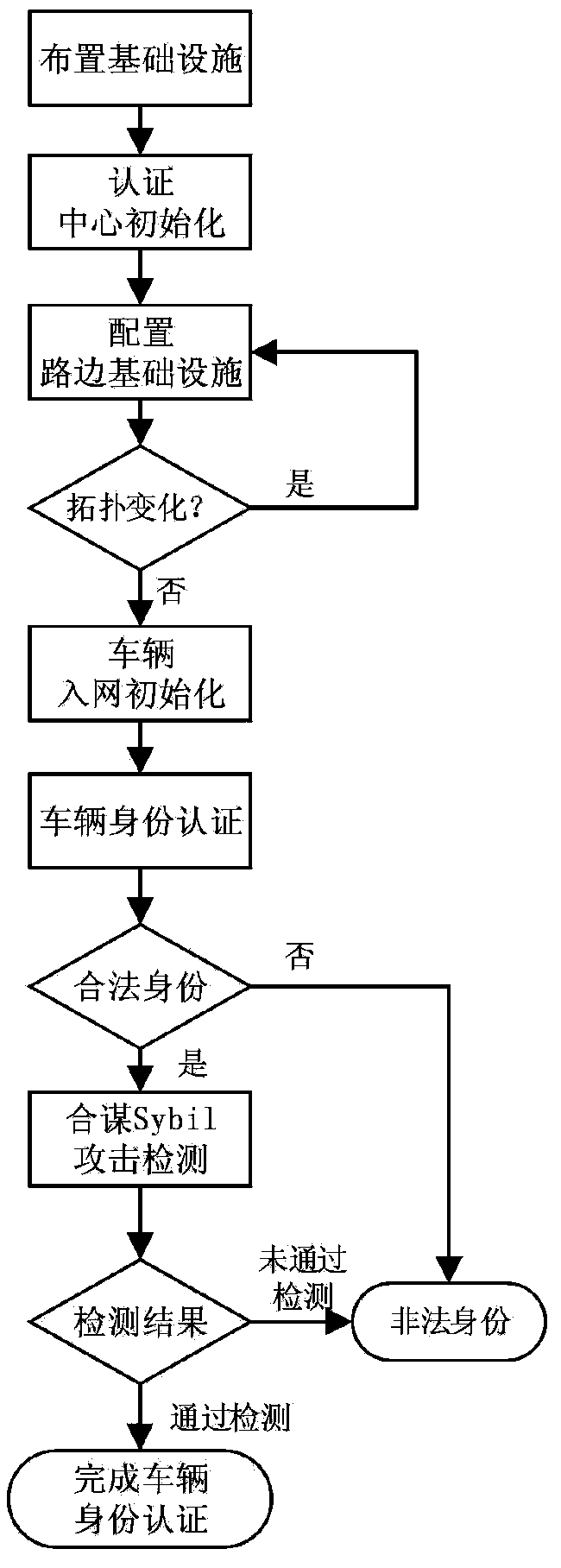
Location privacy based ring signature method in Internet of vehicles
The invention relates to a location privacy based ring signature method in the Internet of vehicles, belongs to the field of vehicle identity authentication in the Internet of vehicles, and aims at solving the problem in detecting collusive Sybil attacks. Path information of a vehicle is used as identity information of the vehicle, the path information contains location privacy information of the vehicle, and location privacy information is protected in the ring signature method. Compared with a present Sybil attack detection method, the vehicle identity authentication method provided by the invention can make vehicles independent from each other, protect the location privacy of the vehicles, and detect the novel collusive Sybil attack existing in the Internet of vehicles in real time.
Owner:JIANGSU UNIV
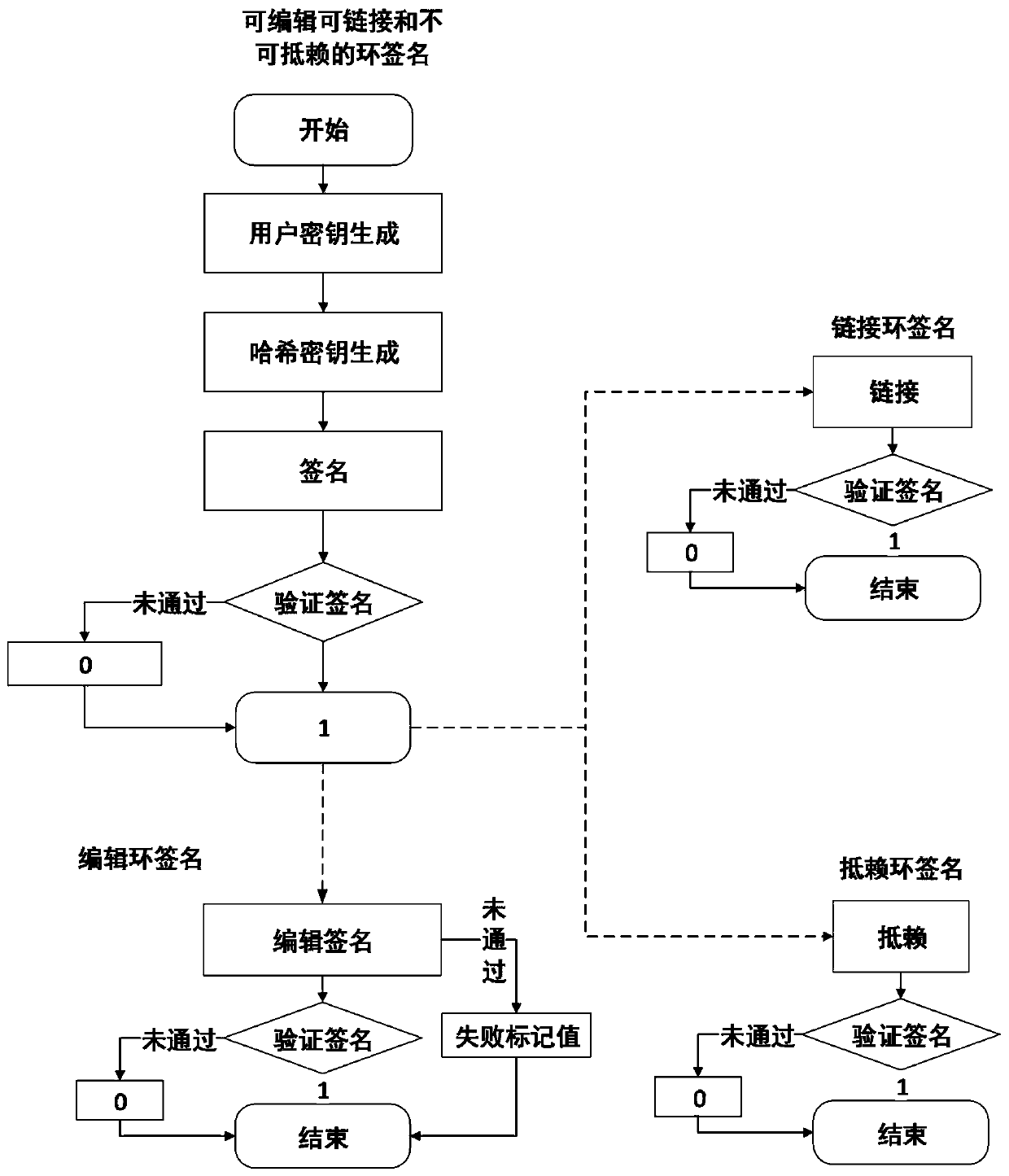
Editable, linkable and non-repudiation ring signature method
ActiveCN110071812APrivacy is not abusedAchieve traceabilityUser identity/authority verificationRing signaturePrivacy protection
The invention discloses an editable, linkable and non-repudiation ring signature method, belongs to the field of network security, and solves the problems of difficulty in revocation of a ring signature, difficulty in tracing identity information of a malicious user, capability of being authenticated by the signature after being edited, no privacy protection, no flexible authentication mechanism and the like in the prior art. The method is used for sequentially carrying out system initialization, user key generation, hash key generation and signature and providing conditional revocation identity privacy, editable and non-repudiation ring signatures. After the signature is edited, if the signature is required to be edited and whether the signature can be linked or repudiated is judged, thesignature is verified respectively, and after the verification is passed, the signature is edited and whether the signature can be linked or repudiated and the like is judged to be used for providingidentity privacy capable of being revoked, editable and non-repudiated ring signatures.
Owner:UNIV OF ELECTRONICS SCI & TECH OF CHINA
Signature schemes using bilinear mappings
ActiveUS20080133926A1User identity/authority verificationCoding/ciphering apparatusRing signatureMultisignature
Methods and systems are provided for generating and verifying signatures of digital messages communicated between signers and verifiers. Using bilinear mappings, such as Weil or Tate pairings, these methods and systems enable generation and verification of efficient multisignatures, identity-based ring signatures, hierarchical proxy signatures, and hierarchical online / offline signatures.
Owner:NTT DOCOMO INC
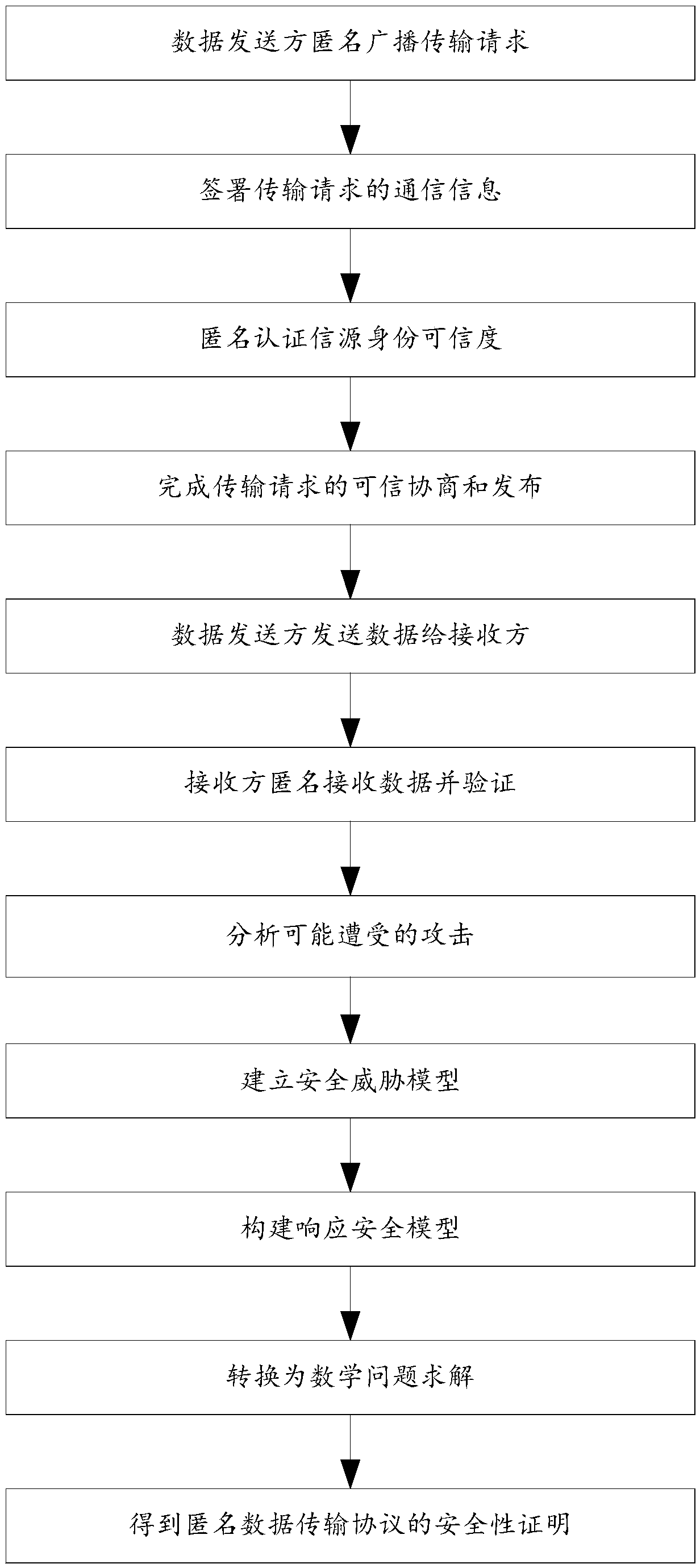
A block chain anonymous transport protocol based on ring signature
ActiveCN109104284AImprove securityImprove communication transmission efficiencyUser identity/authority verificationTransmission protocolRing signature
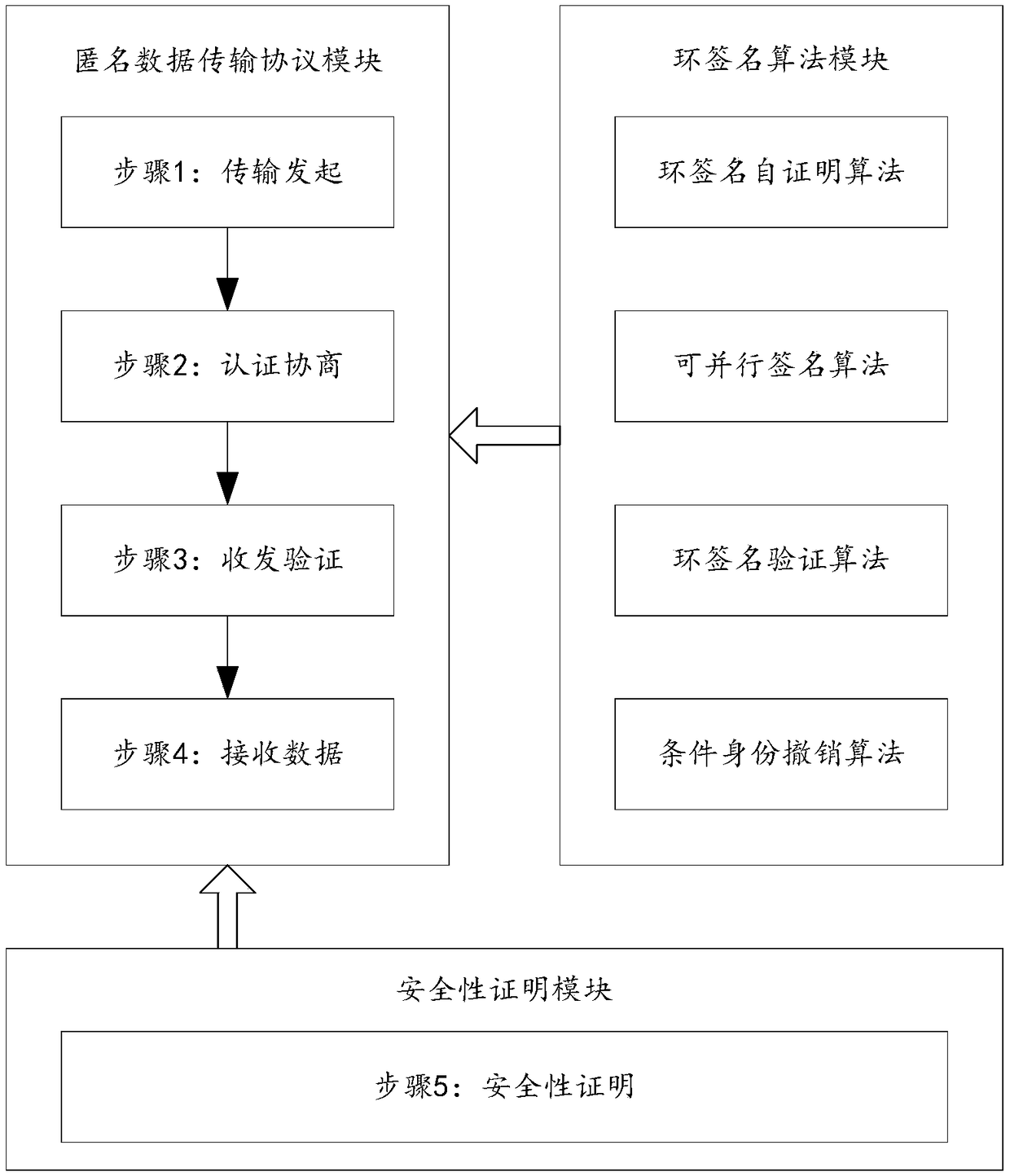
The invention discloses a block chain anonymous transmission protocol based on ring signature, belonging to the technical field of network security. The method comprises steps of 1,anomynously broadcasting a transmission request by a data sender; 2, signing the communication information of the transmission request, anonymously authenticating the trustworthiness of the information source identity of the data sender, obtaining the trustworthiness mechanism and parameters of the transmission request, and issuing the transmission request; 3, the data sender broadcasts and transmits data accordingto the negotiation mechanism and parameters of the step 2; 4, anonymously receiving, verifying and restoring the content of the data by the receiver; Step 5: proving the security of the anonymous datatransfer protocol. The invention solves the problems of poor transmission efficiency and low transmission security of the data transmission protocol on the existing block chain, as well as low sourcereliability and data security of the sending and receiving sides on the block chain, and the invention also solves the problems of low transmission efficiency and low transmission security of the data transmission protocol on the existing block chain.
Owner:SICHUAN UNIV
Identity-based threshold ring signature method
InactiveCN102684885AImprove securityPublic key for secure communicationUser identity/authority verificationRing signatureComputer security
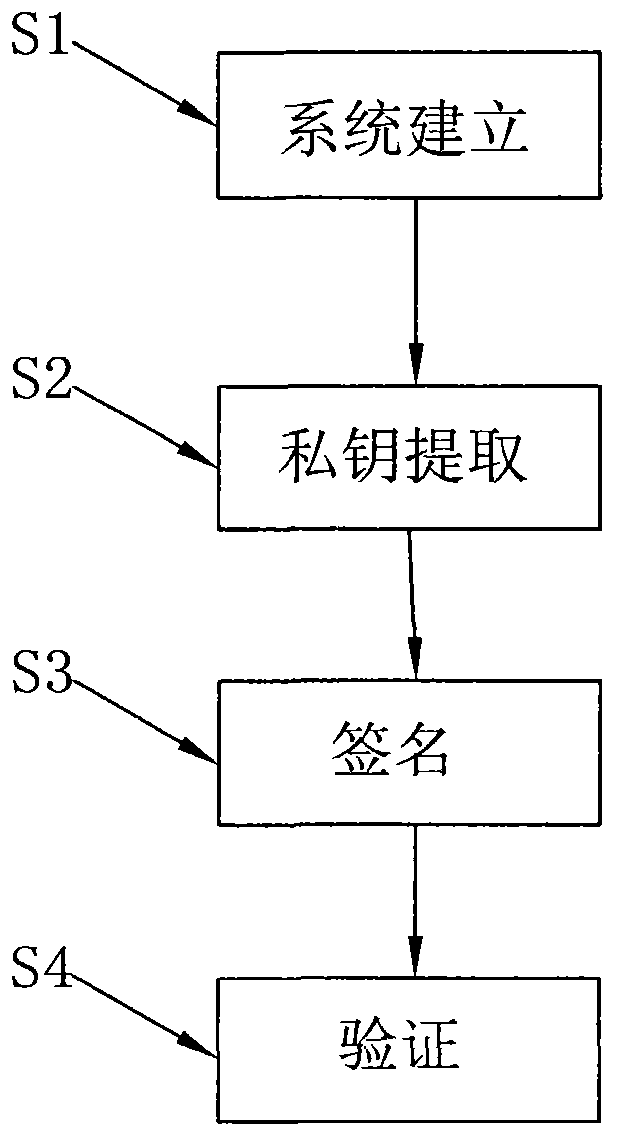
An identity-based threshold ring signature method comprises the following steps: (1), system establishment; (2), private key extraction; (3), signature; and (4), verification. The method provided by the invention is established under a standard model and has better security compared with a scheme designed under a random predictive model.
Owner:孙华 +4
Encryption and signature schemes using message mappings to reduce the message size
ActiveUS20100008496A1Computationally efficientBandwidth-reduced ring signatureKey distribution for secure communicationPublic key for secure communicationRing signatureCiphertext
According to some embodiments of the invention, a message is processed before encryption so that the encryption method generates a short ciphertext. The message processing can be viewed as a mapping (610) that maps the message into another message that generates the short ciphertext. The mapping is reversible at least if the (possibly encoded) message (H(M)) is in a restricted set, e.g. a set [0,h″] of short messages. In some embodiments of the present invention, short signatures are provided by mapping the signature into a short signature. The mapping (810) is reversible at least if the original message (H(M)) used to generate the signature is short. Signcryption, aggregate signature, and ring signature outputs are also shortened.
Owner:NTT DOCOMO INC
Method and device for generating and verifying linkable ring signature in block chain
ActiveCN110009349AUser identity/authority verificationPayment protocolsArray data structureRing signature
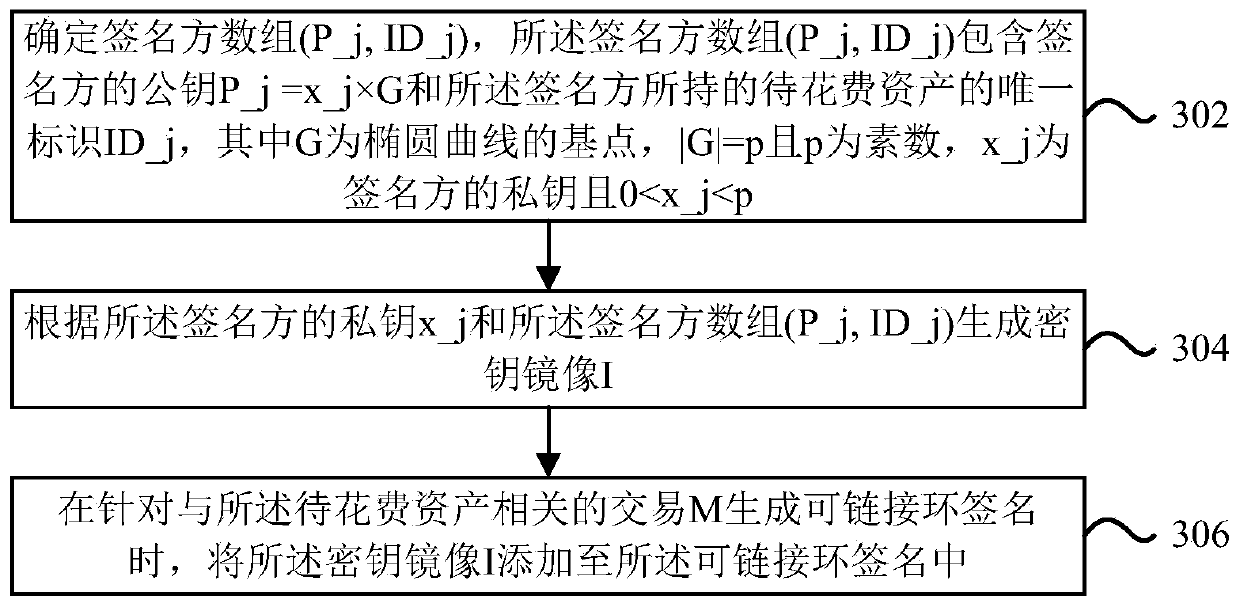
One or more embodiments of the invention provide a method and a device for generating and verifying a linkable ring signature in a block chain. The method may include: determining a signer array (P_j,ID_j), the signer array (P_j, ID_j) comprising a public key P_j of a signer and a unique identifier ID_j of an asset to be spent held by the signer, G being a base point of an elliptic curve, | G | =p and p being a prime number, x_j being a private key of the signer and 0 <x_j<p; generating a key image I according to the private key x_j of the signer and the signer array (P_j, ID_j); and when alinkable ring signature is generated for the transaction M related to the asset to be spent, adding the key mirror image I to the linkable ring signature.
Owner:ADVANCED NEW TECH CO LTD
Ring signature method for anonymizing information based on multivariate polynomial
InactiveCN102006166AFix bugs that are no longer safeImprove efficiencyPublic key for secure communicationUser identity/authority verificationRing signatureCryptosystem
The invention discloses a ring signature method for anonymizing information based on multivariate polynomial, comprising the following steps: generating system parameters, generating a secret key, generating the ring signature and verifying the ring signature. The ring signature method based on the traditional cryptosystem is subjected to security threat under the quantum computer while the ring signature method based on the multivariate public key cryptosystem solves the problem that the existing ring signature systems are insecure under the quantum computation. The method has the advantagesof security and high computing efficiency.
Owner:XIAN UNIV OF TECH
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com