Location privacy based ring signature method in Internet of vehicles
A technology of ring signature and Internet of Vehicles, which is applied in the field of vehicle identity authentication in the Internet of Vehicles, can solve the problems of inability to achieve independent vehicle authentication, low feasibility, waste of computing and communication resources, etc., and achieve the effect of protecting the privacy of vehicle location.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0033] The present invention will be further described below in conjunction with the accompanying drawings and implementation examples.
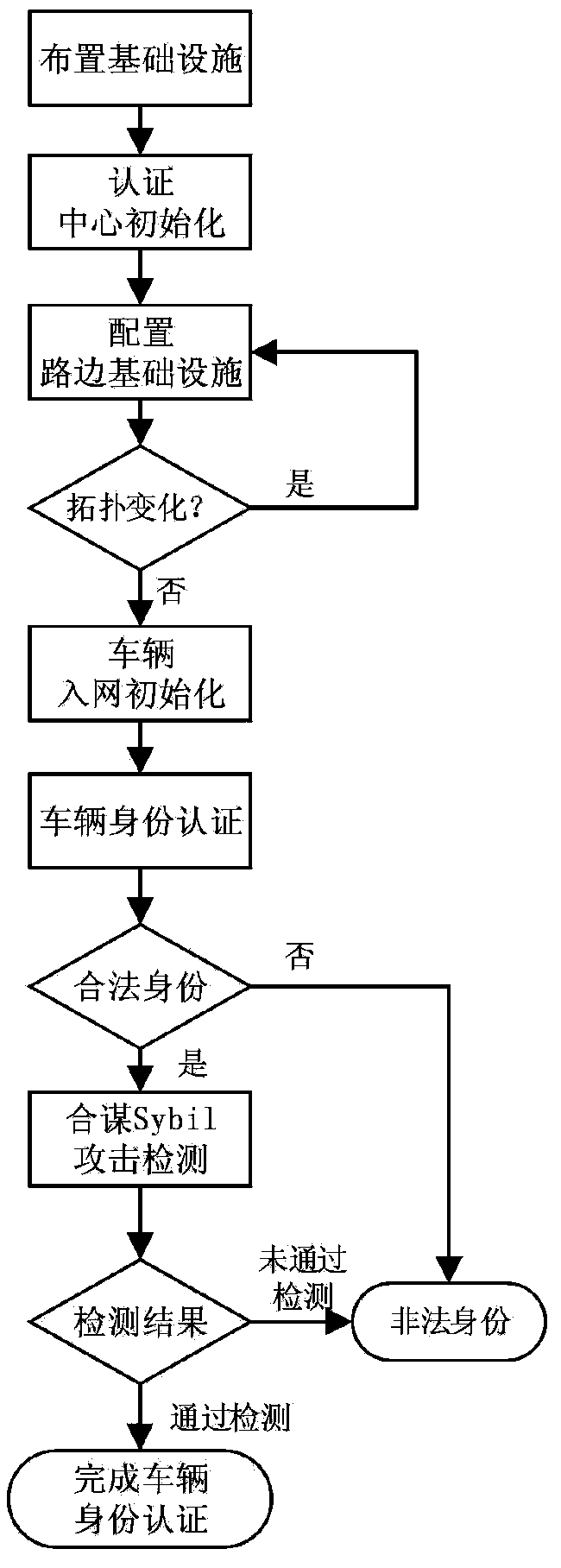
[0034] figure 1 It is a flow chart of the ring signature method based on location privacy in the Internet of Vehicles of the present invention, including the following steps:
[0035] (1) Arrange roadside infrastructure RSU at intersections using greedy algorithm.
[0036] Choose whether to arrange RSU (roadside infrastructure) according to the traffic flow at the intersection. RSU is only arranged at the intersection, and the intersection where RSU is arranged needs to meet the following two conditions: 1) Within the communication range of the RSU that is twice the distance from the intersection 2) In the intersections without RSUs, the product K=F*B of the traffic volume F of the intersection and the distance R of the nearest RSU to the intersection is the largest.
[0037] (2) Initialize the authentication center TA, the initialization ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com